Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
145 results about "Internal link" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An internal link is a type of hyperlink on a webpage to another page or resource, such as an image or document, on the same website or domain. Hyperlinks are considered either "external" or "internal" depending on their target or destination. Generally, a link to a page outside the same domain or website is considered external, whereas one that points at another section of the same webpage or to another page of the same website or domain is considered internal.
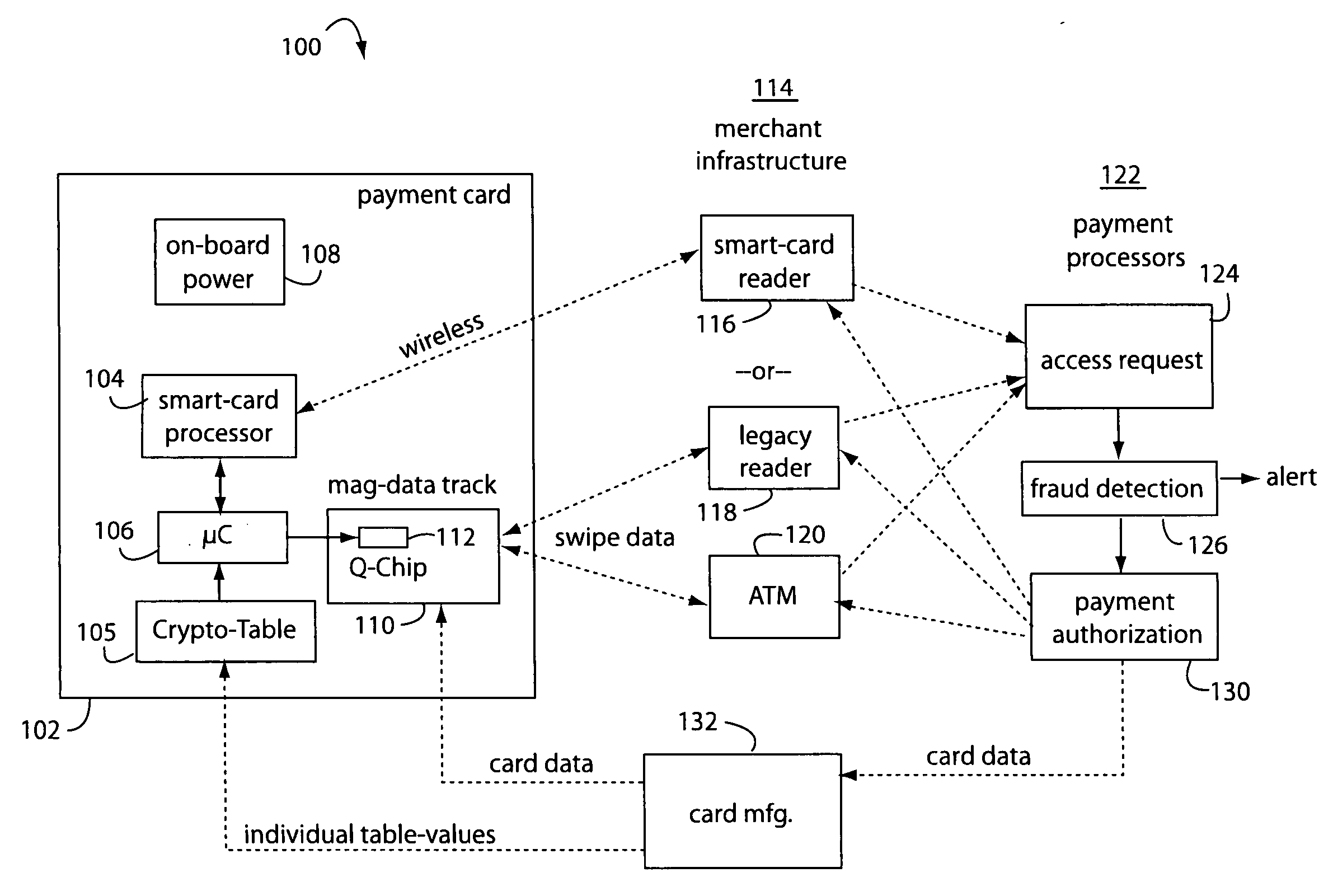
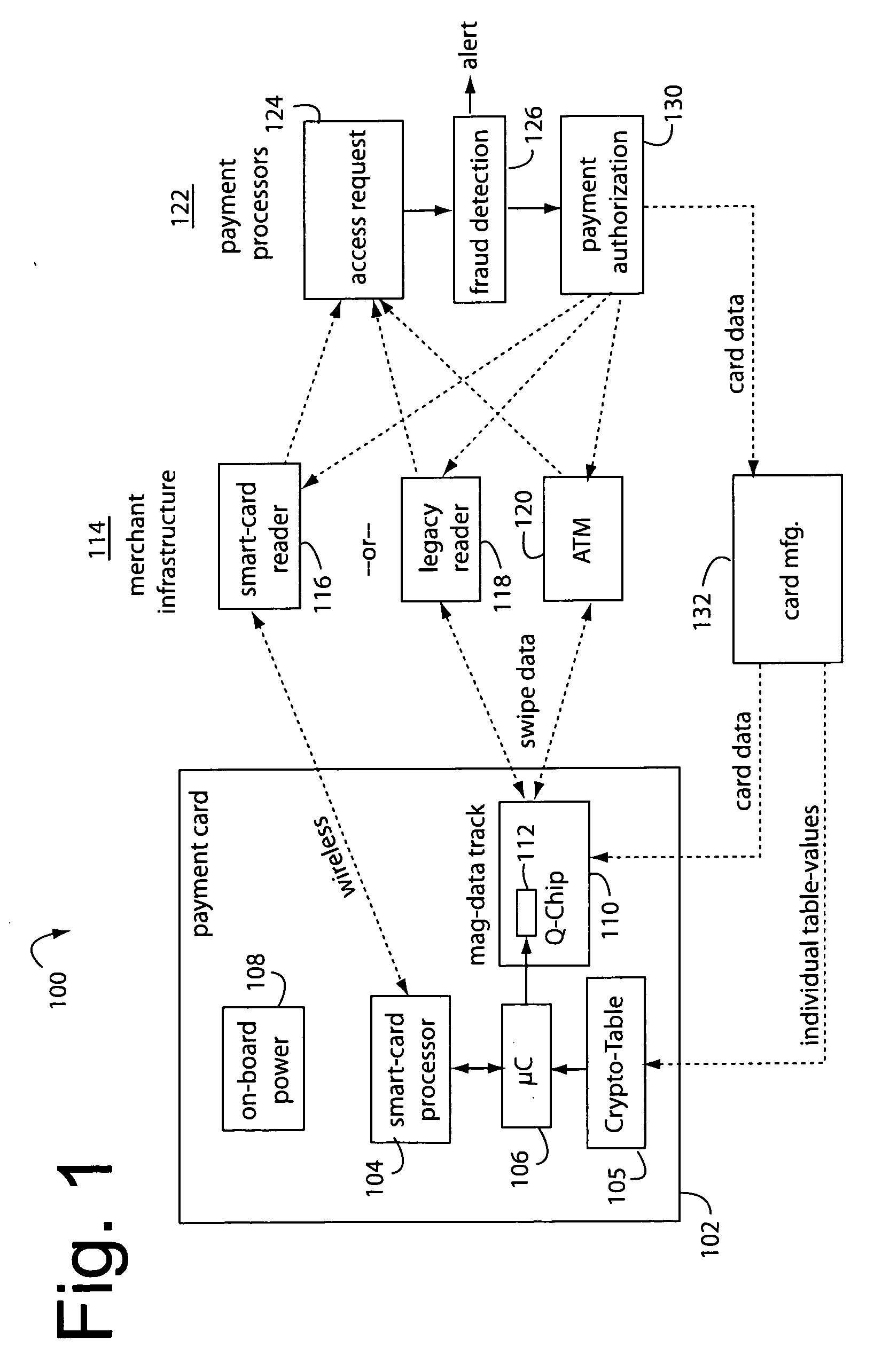
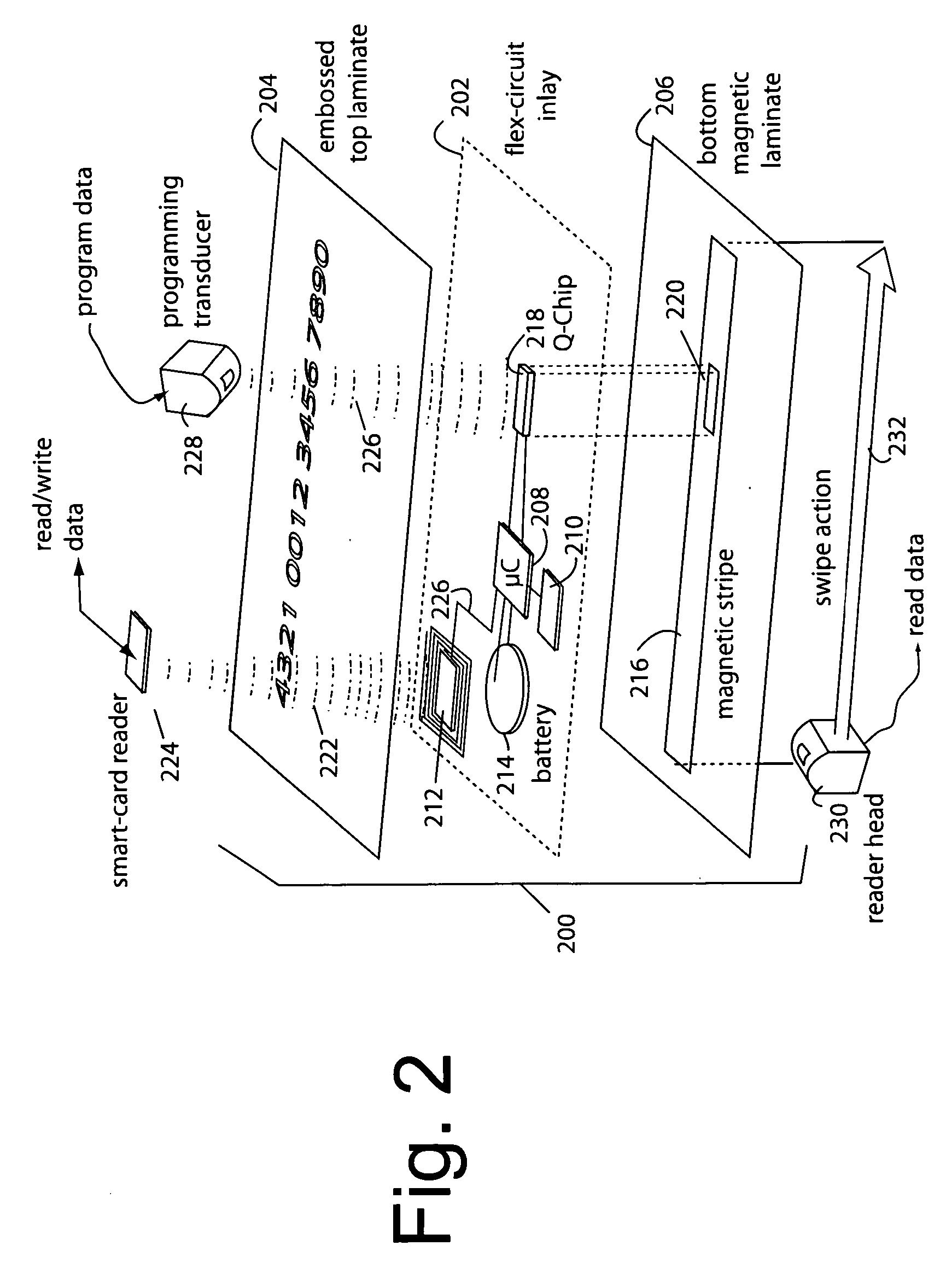
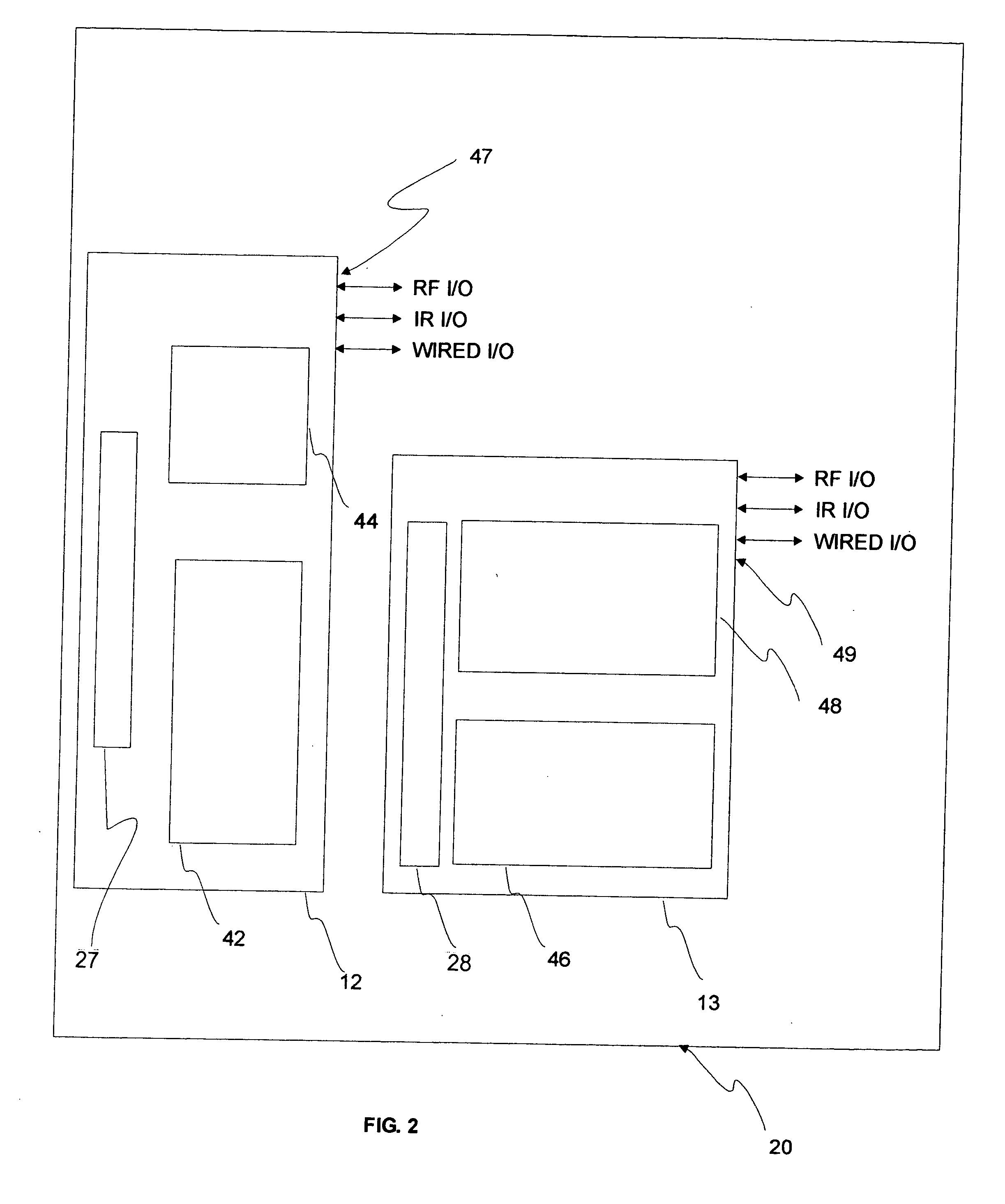
Contact/contactless and magnetic-stripe data collaboration in a payment card
InactiveUS20060287964A1Reduce loss due to fraudDebit schemesMarketingComputer hardwareData collaboration
A method of providing a magnetic-stripe type payment card with coupons and micropayment authorizations provides an internal link on a payment card between a contact / contactless processor and a MEMS magnetic device. This communicates information received from a contact / contactless payments infrastructure to be presented to a magnetic stripe payments infrastructure as specially recorded data bits written by the MEMS magnetic device in a magnetic stripe track.
Owner:FITBIT INC
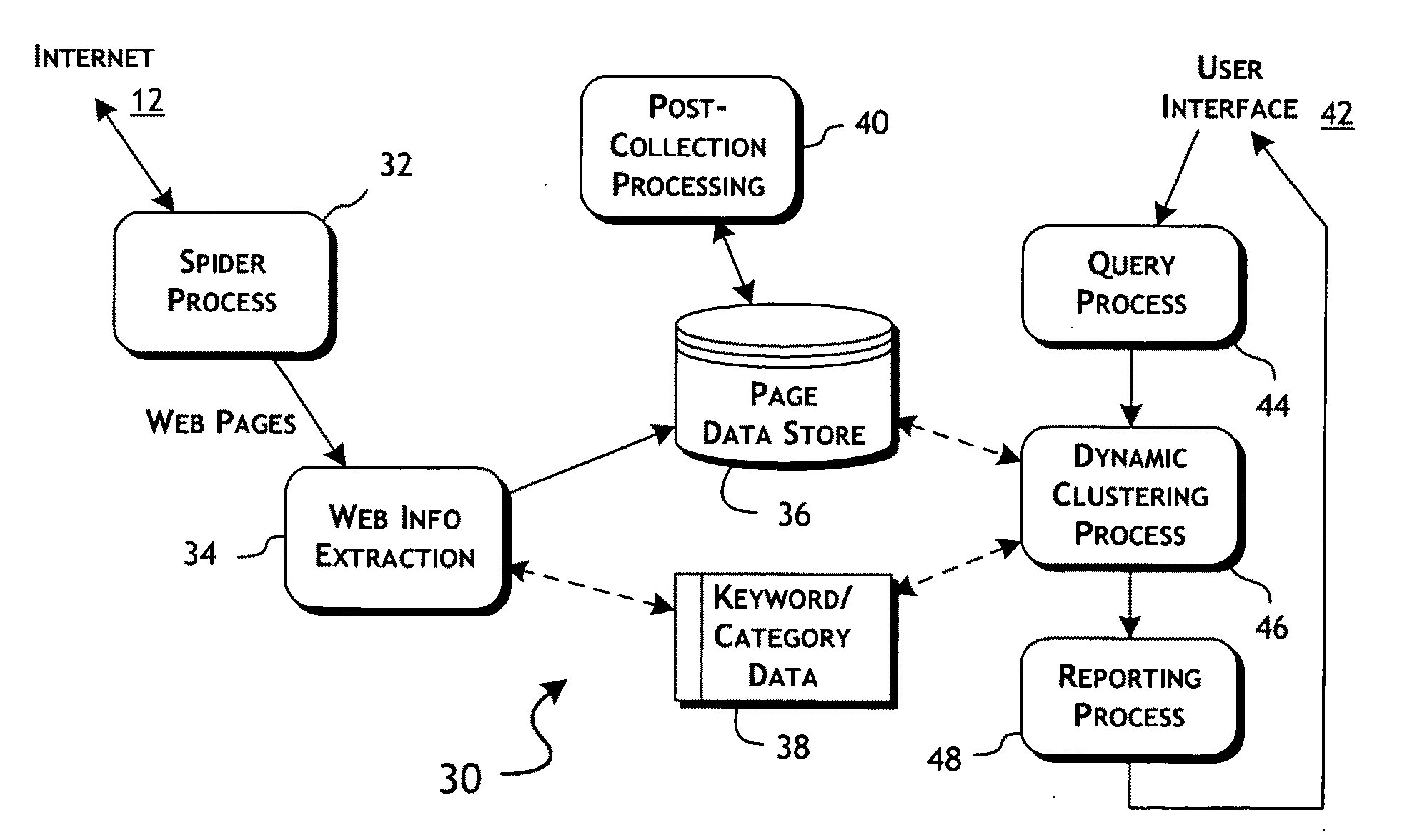
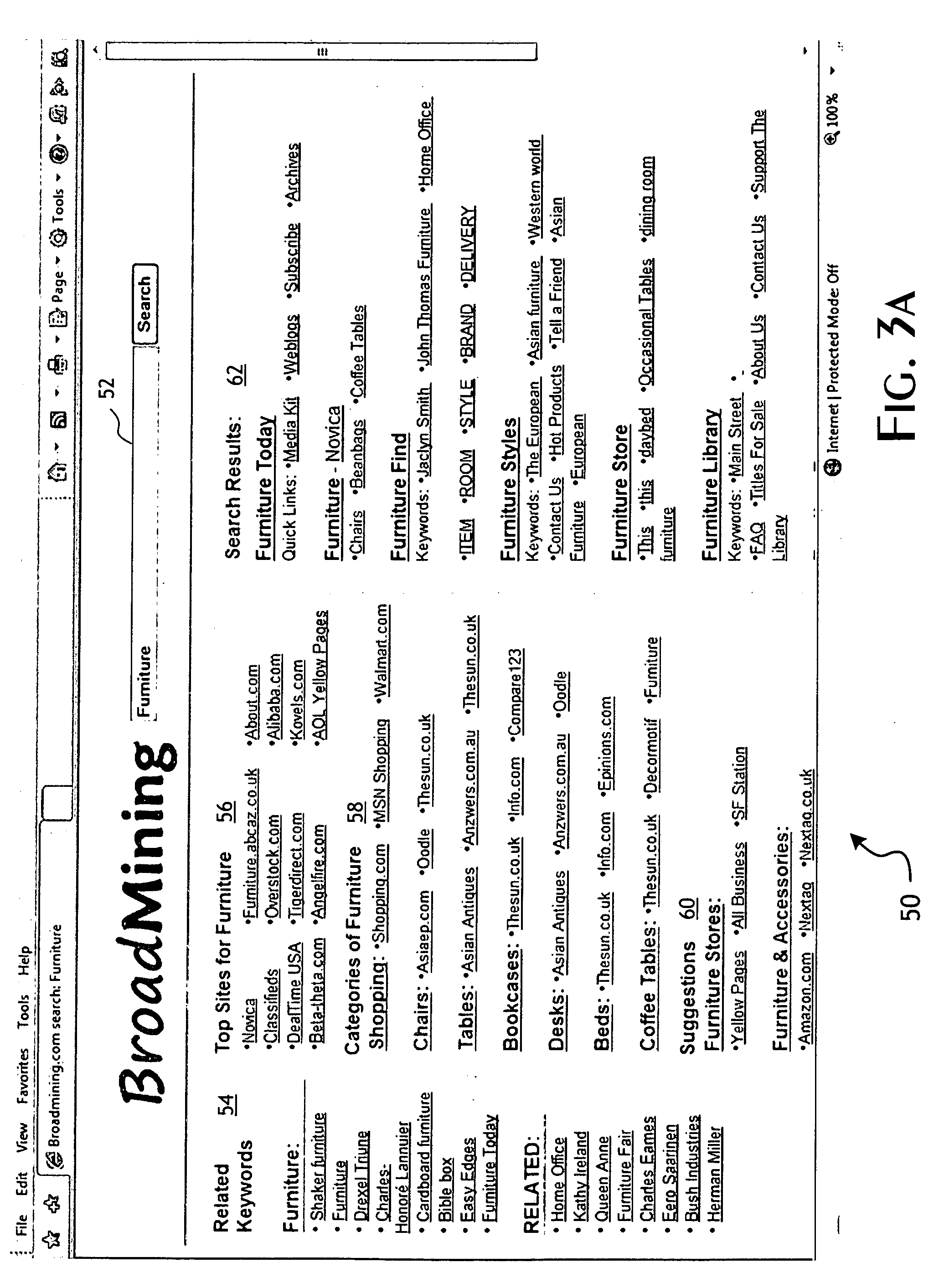
System and methods for automatic clustering of ranked and categorized search objects
InactiveUS20100131563A1Great cognitive valueGreat relevanceDigital data information retrievalDigital data processing detailsFrequency of occurrenceInternal link
A search results page includes multiple search lists generated by multiple clustering operations applied to an initial match set of documents selected based on a user query. A first result list is constructed by clustering a top-n set of documents by primary domain address and sorting based on extrinsic ranking factors such that the first list includes a ranked and ordered list of primary domain linked anchor text. A second result list is constructed by clustering the top-n set of documents based on a unified ranked occurrence of keywords within the top-n set of documents. The generated second list contains a plurality of cluster class references with each of the cluster class reference including a ranked ordered sub-list of the keywords occurring within the top-n set of documents and respectively associated with the cluster class reference, each of the keywords of the ranked ordered sub-lists including linking references to a corresponding one of the top-n set of documents. A third result list is constructed by clustering the top-n set of documents based on a ranked frequency of occurrence of internally linked anchor texts. The generated third result list includes the top-n set of the internally linked anchor texts and respective ranked and ordered sub-lists of linking references to primary domain Web-pages containing the corresponding one of the internally linked anchor texts.
Owner:YEBOL CORP
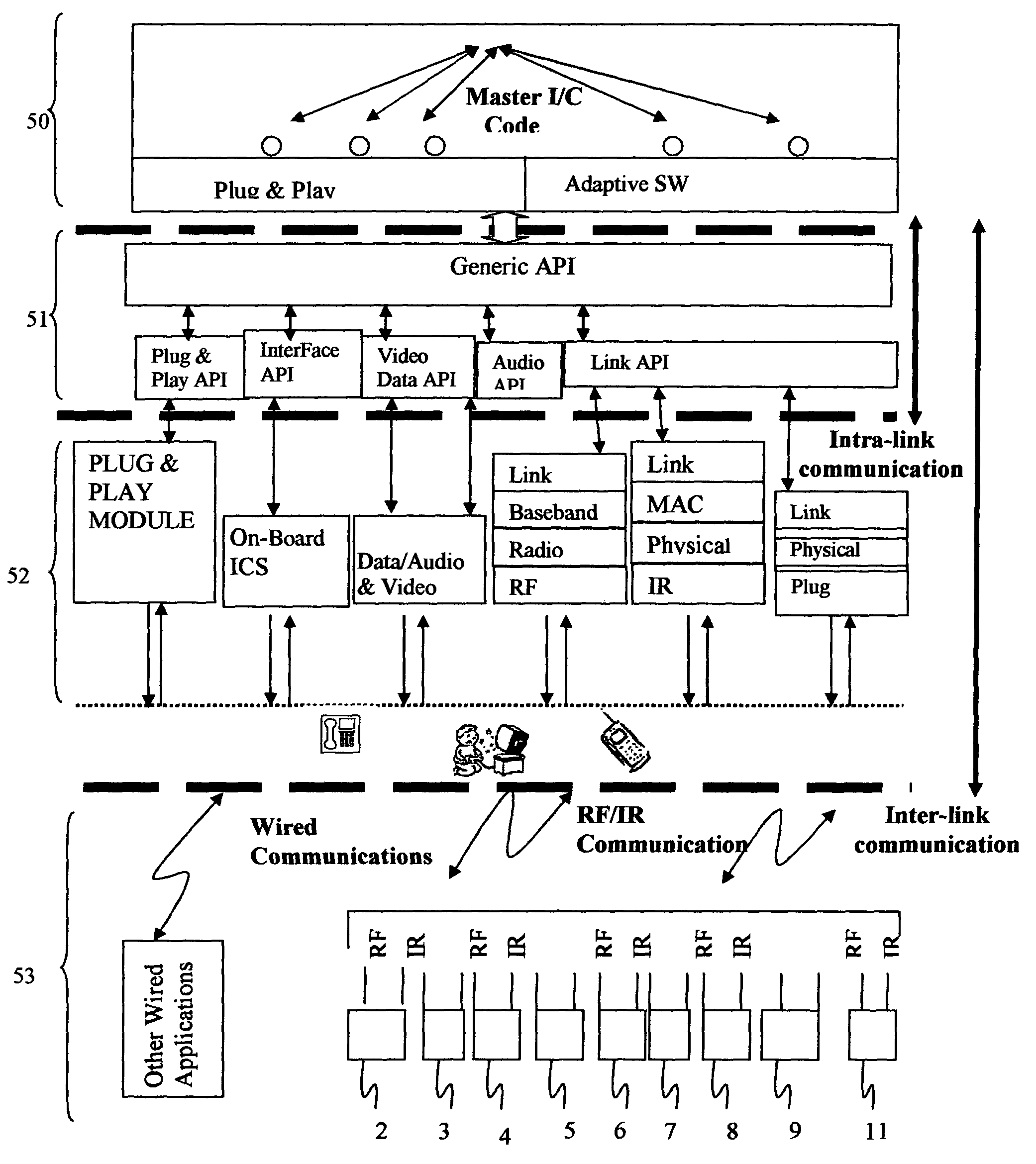
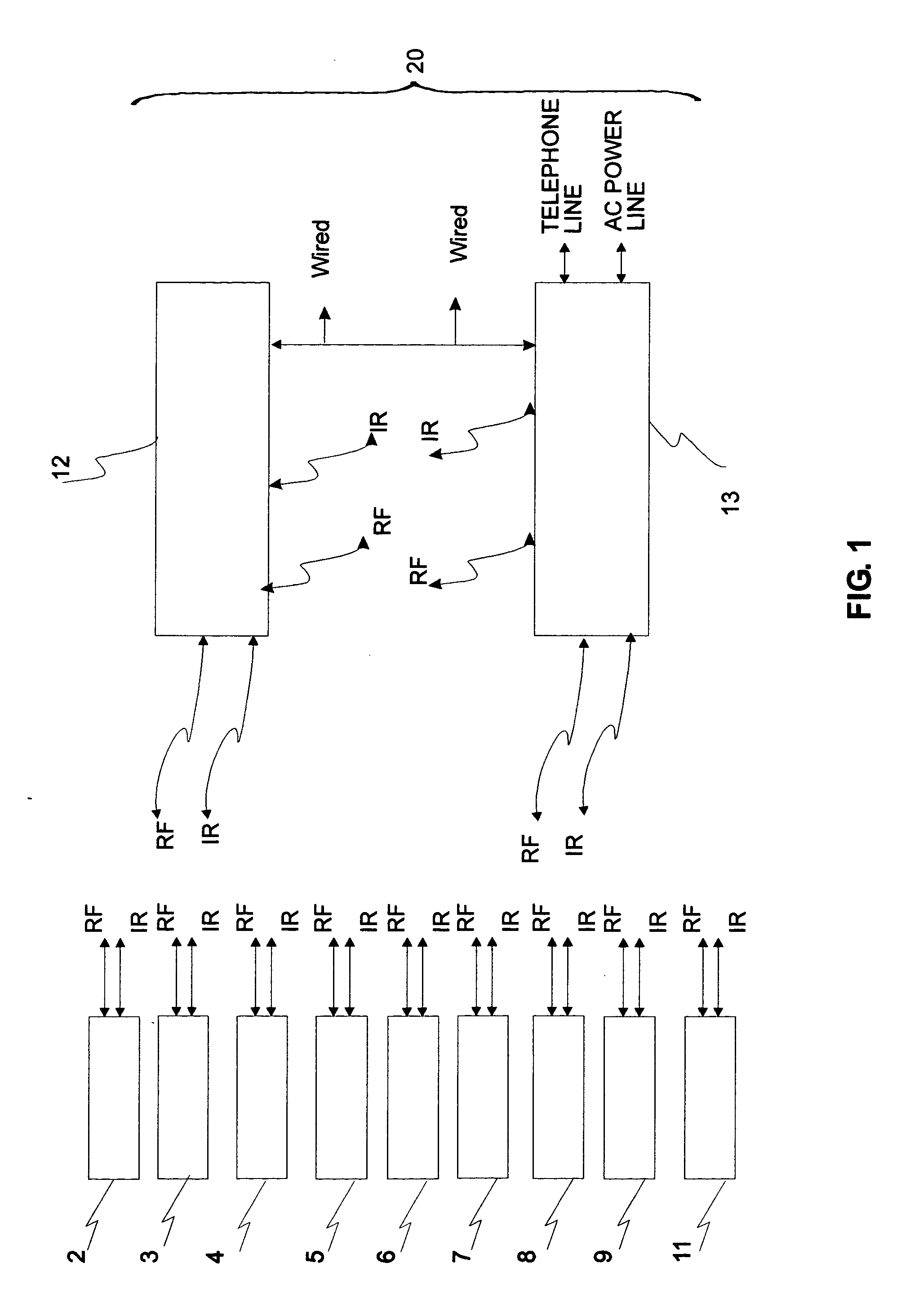
Communications, command, and control system with plug-and-play connectivity
InactiveUS20050054289A1Function increaseCordless telephonesTransmission systemsInformation processingInteroperability
A modular communications, command, and control system with plug-and-play connectivity, utilizing configurable independent base stations and portable handsets that preferably have similar components and functionality so as to be interoperable. The system utilizes an open system interconnection architecture preferably having fully integrated layers permitting inter-operability with adaptive applications and inter / intra-linking with external appliances and / or apparatuses. Optionally, the system may be utilized to perform extended information handling / processing, networking, personal assistance, industrial, commercial, medical, military, and / or security functions.
Owner:SALAZAR JOE ANDREW MR
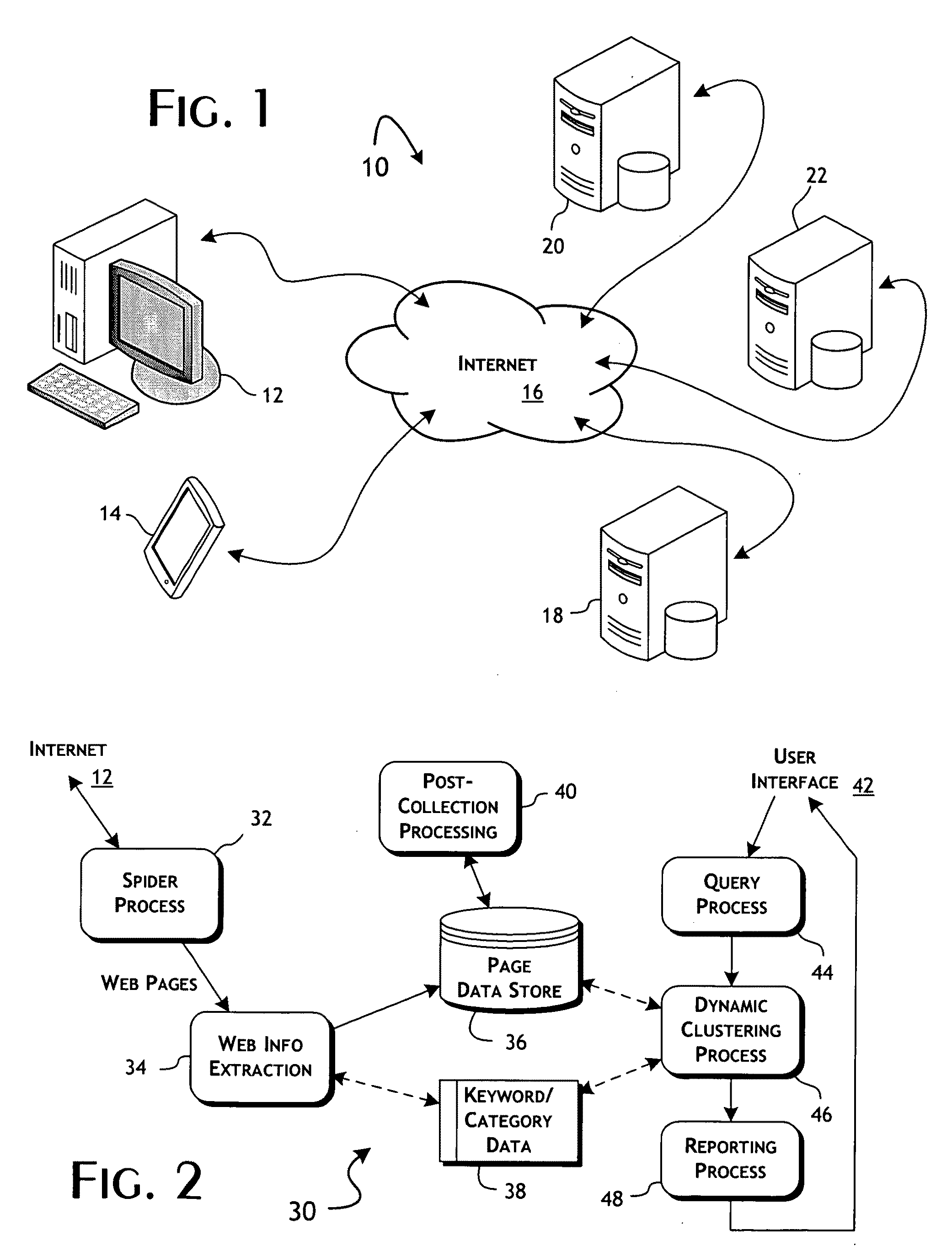
Computer method and apparatus for collecting people and organization information from Web sites
ActiveUS6983282B2Efficient and accurate in its taskData processing applicationsWeb data indexingWeb siteUnique identifier
Computer processing method and apparatus for searching and retrieving Web pages to collect people and organization information are disclosed. A Web site of potential interest is accessed. A subset of Web pages from the accessed site are determined for processing. According to types of contents found on a subject Web page, extraction of people and organization information is enabled. Internal links of a Web site are collected and recorded in a links-to-visit table. To avoid duplicate processing of Web sites, unique identifiers or Web site signatures are utilized. Respective time thresholds (time-outs) for processing a Web site and for processing a Web page are employed. A database is maintained for storing indications of domain URLs, names of respective owners of the URLs as identified from the corresponding Web sites, type of each Web site, processing frequencies, dates of last processings, outcomes of last processings, size of each domain and number of data items found in the last processing of each Web site.
Owner:ELIYON TECH CORP
High-Availability Networking with Intelligent Failover
InactiveUS20080215910A1Improve usabilityPrevent misidentificationData switching networksRedundant hardware error correctionFailoverOSI model
Methods and systems for maintaining high-availability in a computer network using intelligent failover are presented. In a network switch running an OSI model layer-2 or higher protocol on its external links, the protocol state information is monitored to determine failover status of the link to avoid identifying external link failures due to link flapping. One such protocol is the spanning tree protocol. Additionally, flexibility in failover is provided using configurable triggers to define external failure events. The triggers initiate a link drop of one or more internal links of the network switch in response to an external failure event. The link drops, in turn, initiate failover of an attached computing device to a redundant link through a network interface teaming / failover arrangement whereby the computing device switches to an alternative network interface accessing the network through a redundant path. Failover can be selective depending upon VLAN and trunking configurations.
Owner:AVAYA INC
Filtering approach for network system alarms
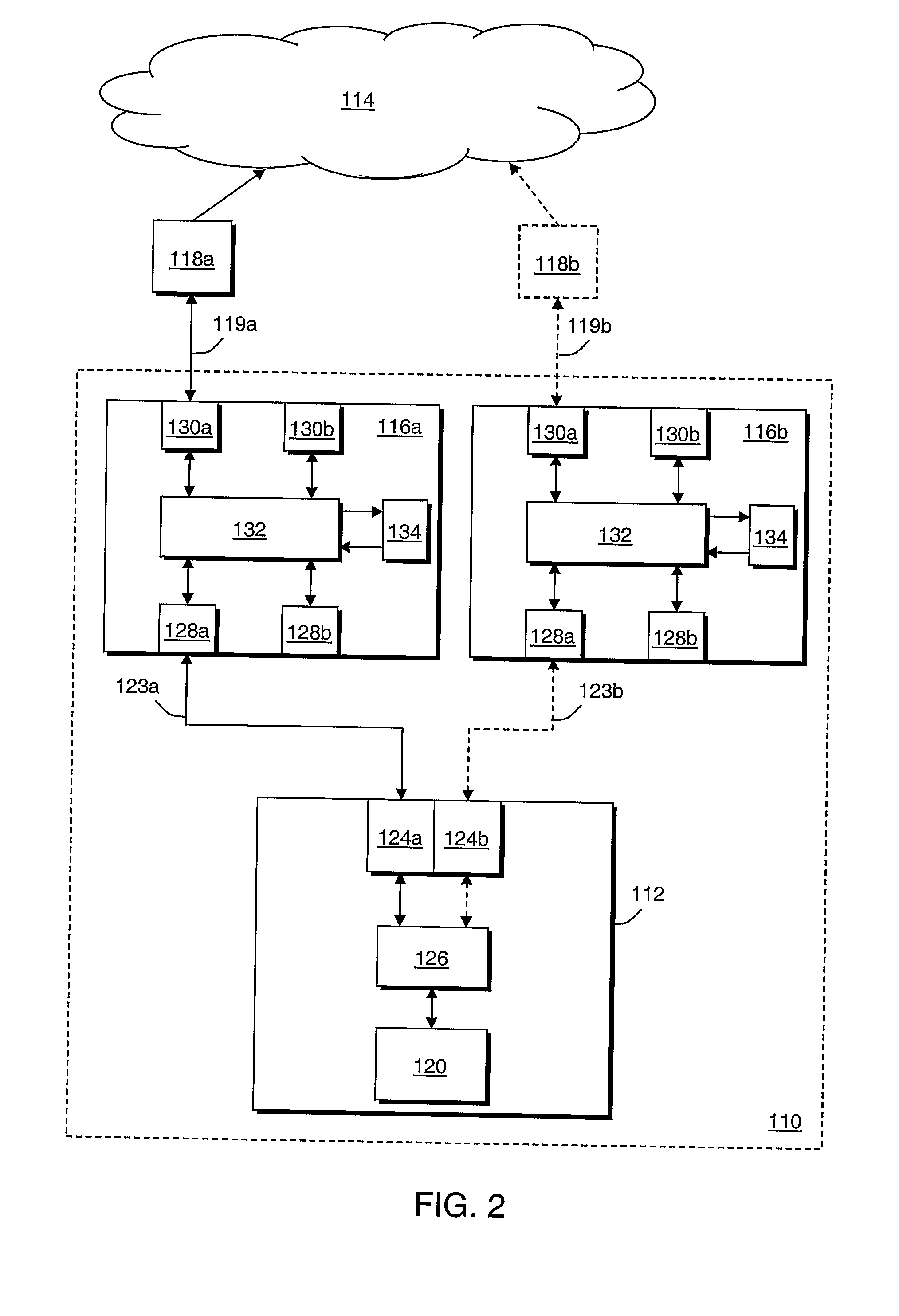
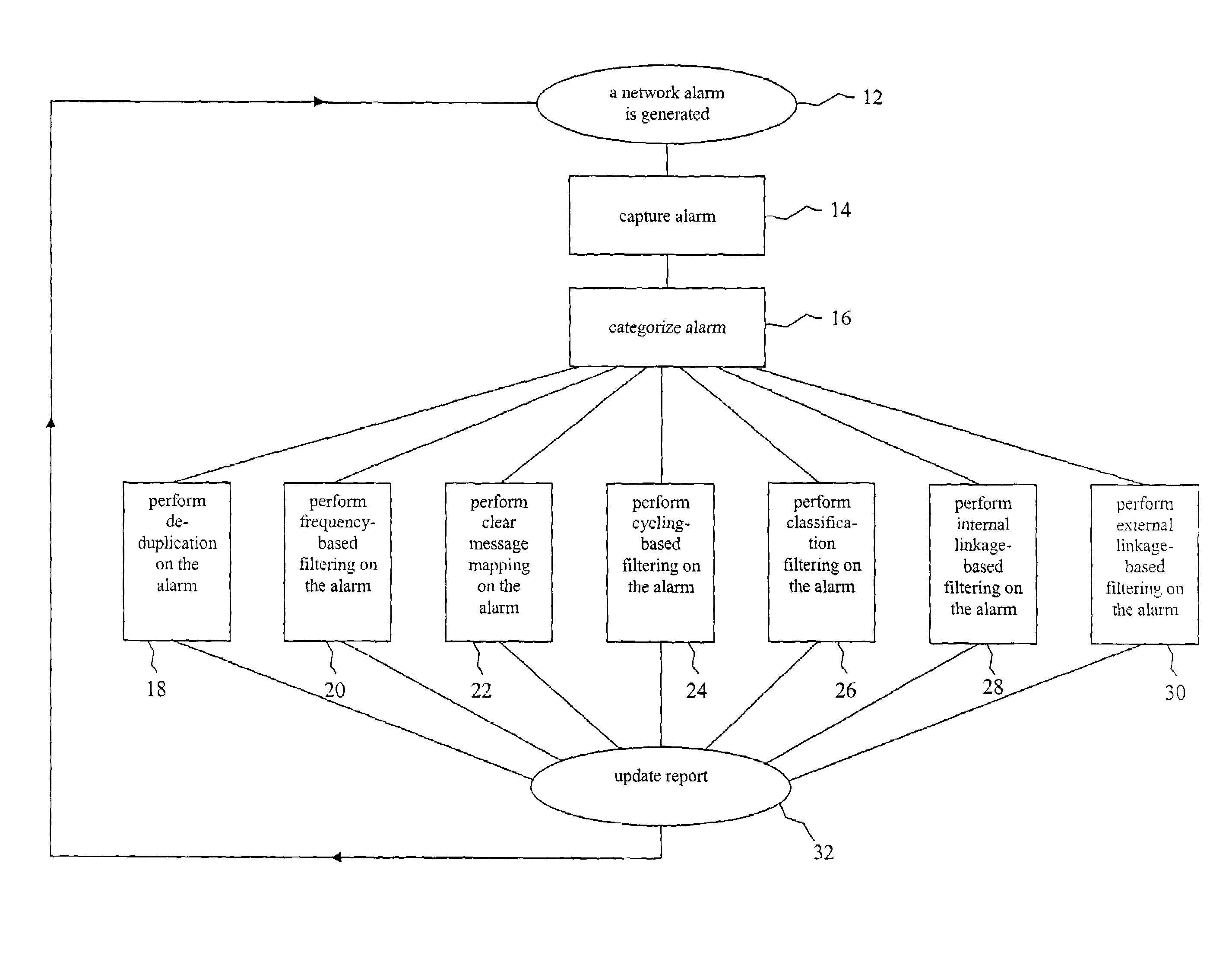
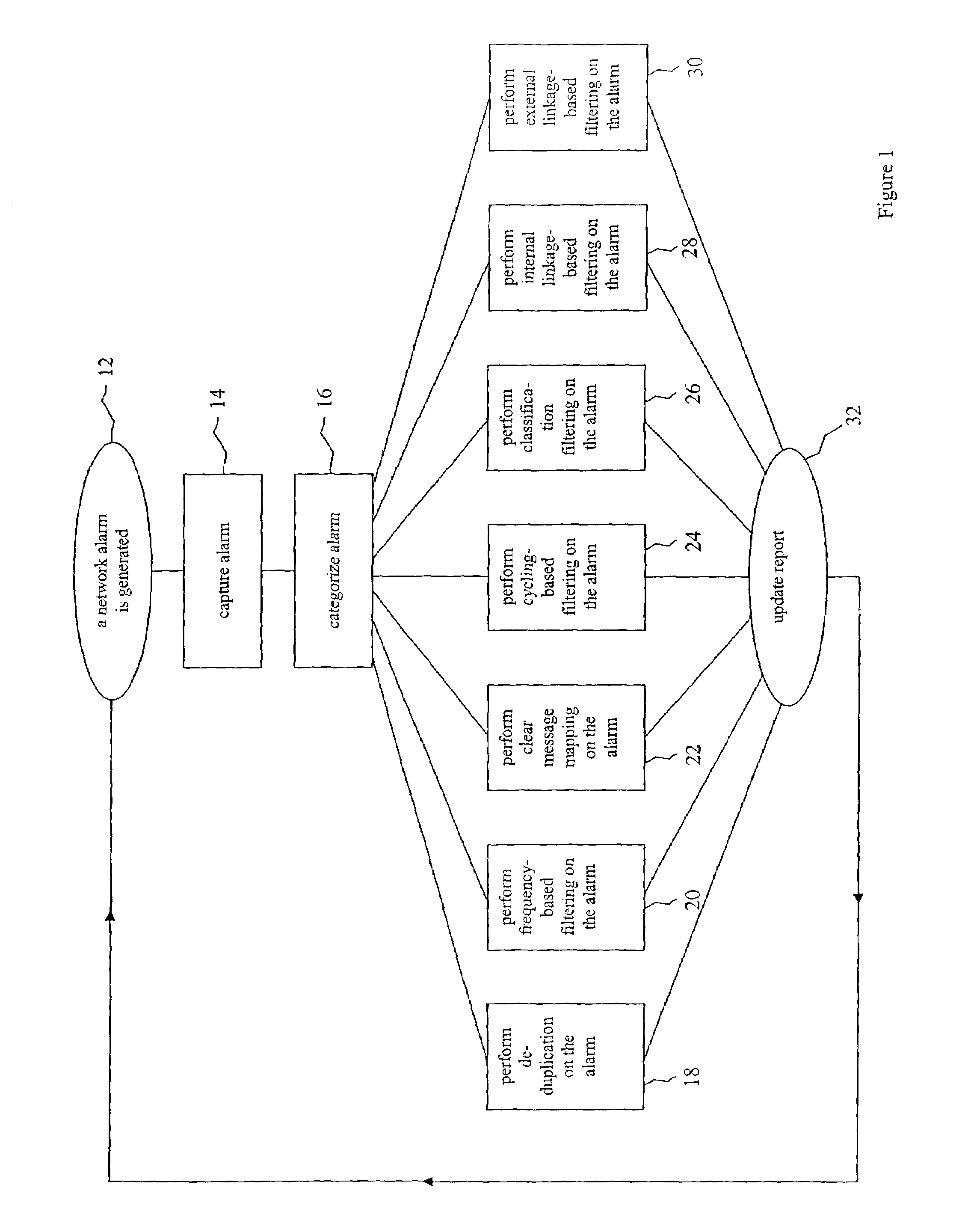
A method for creating an updateable report representing the alarm status of a network. Network alarms are categorized based on the source and type of alarm, the alarms are placed in a filtering system based on source and type, selected alarms are replaced with alarm representations, and a report is updated with alarm representations. The filtering system comprises non-temporal, temporal, and linkage-based filtering. Non-temporal filtering includes de-duplication, clear message mapping, and classification. Temporal filtering includes frequency-based and cycling-based filtering. Linkage-based filtering includes internal linkage-based and external linkage-based filtering. The network can comprise the interconnected networks of an enterprise or of a single domain of an enterprise. The domain can comprise a business domain or operating system domain. The network can comprise a group of client computers connected to a server computer. The report can be displayed on a computer screen or can be sent to another location for further processing.
Owner:T MOBILE INNOVATIONS LLC
Bendable display apparatus and supporting device
ActiveUS9874048B1Efficient solutionDigital data processing detailsCasings with display/control unitsGear driveDisplay device
Owner:FIRST DOME
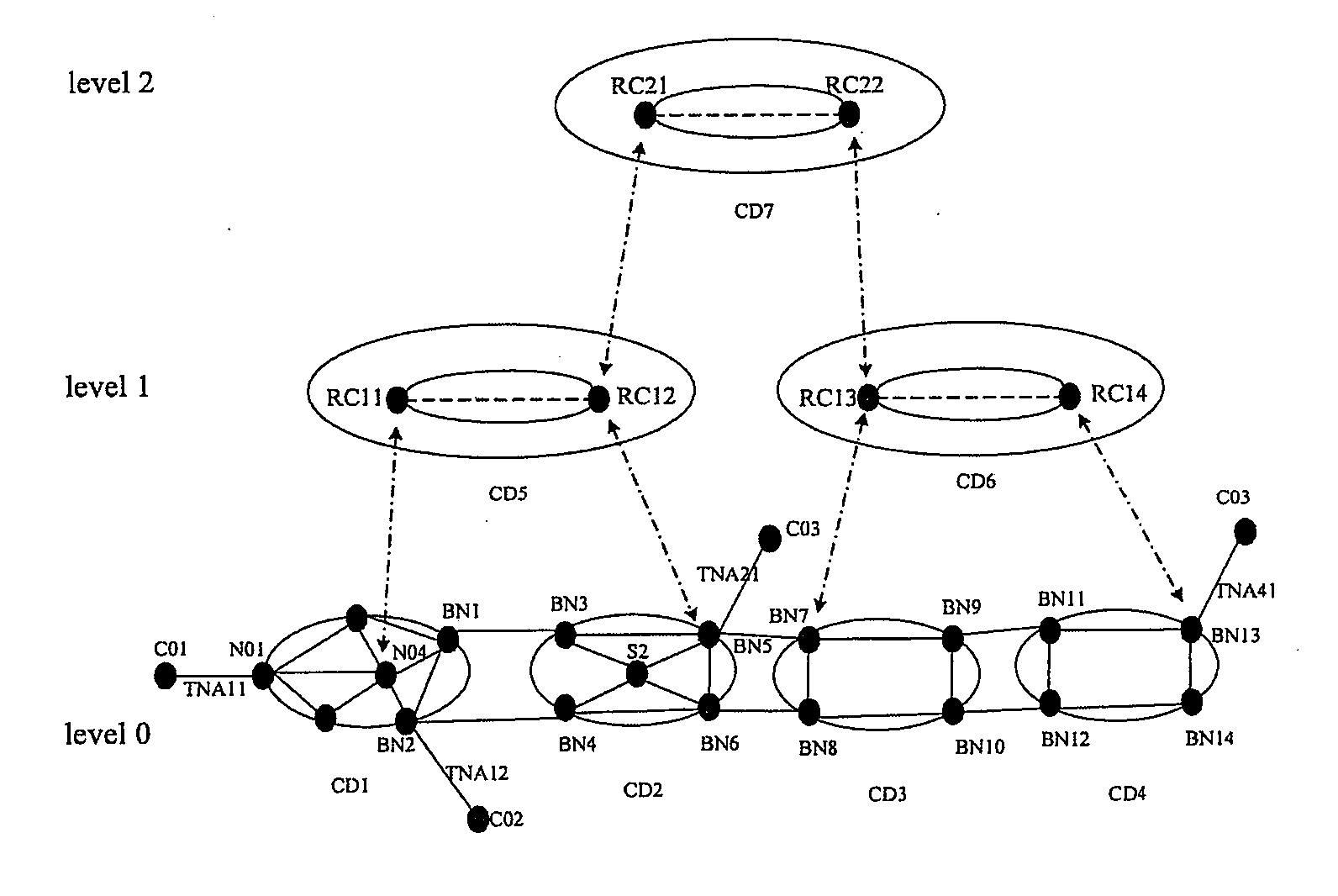
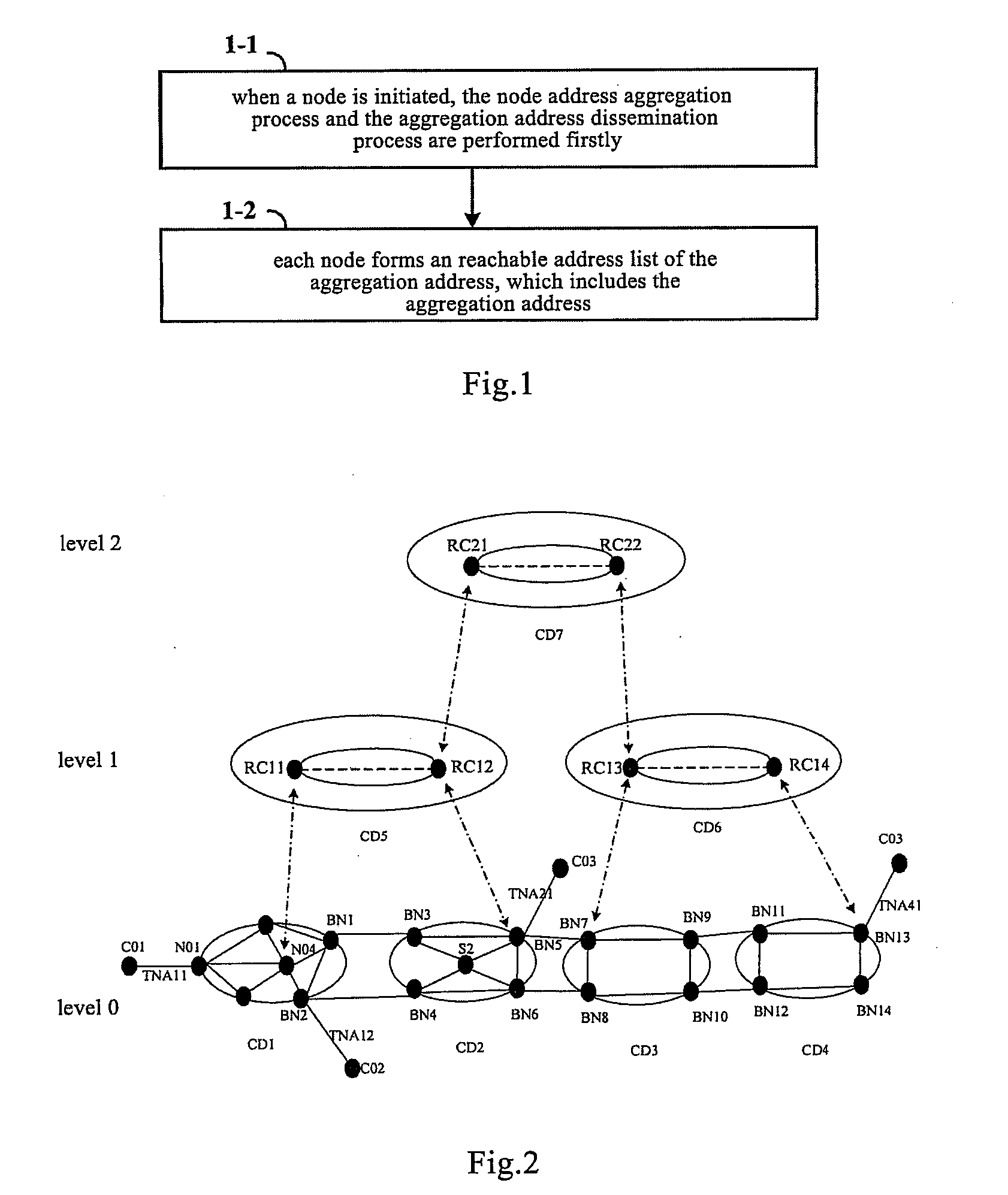
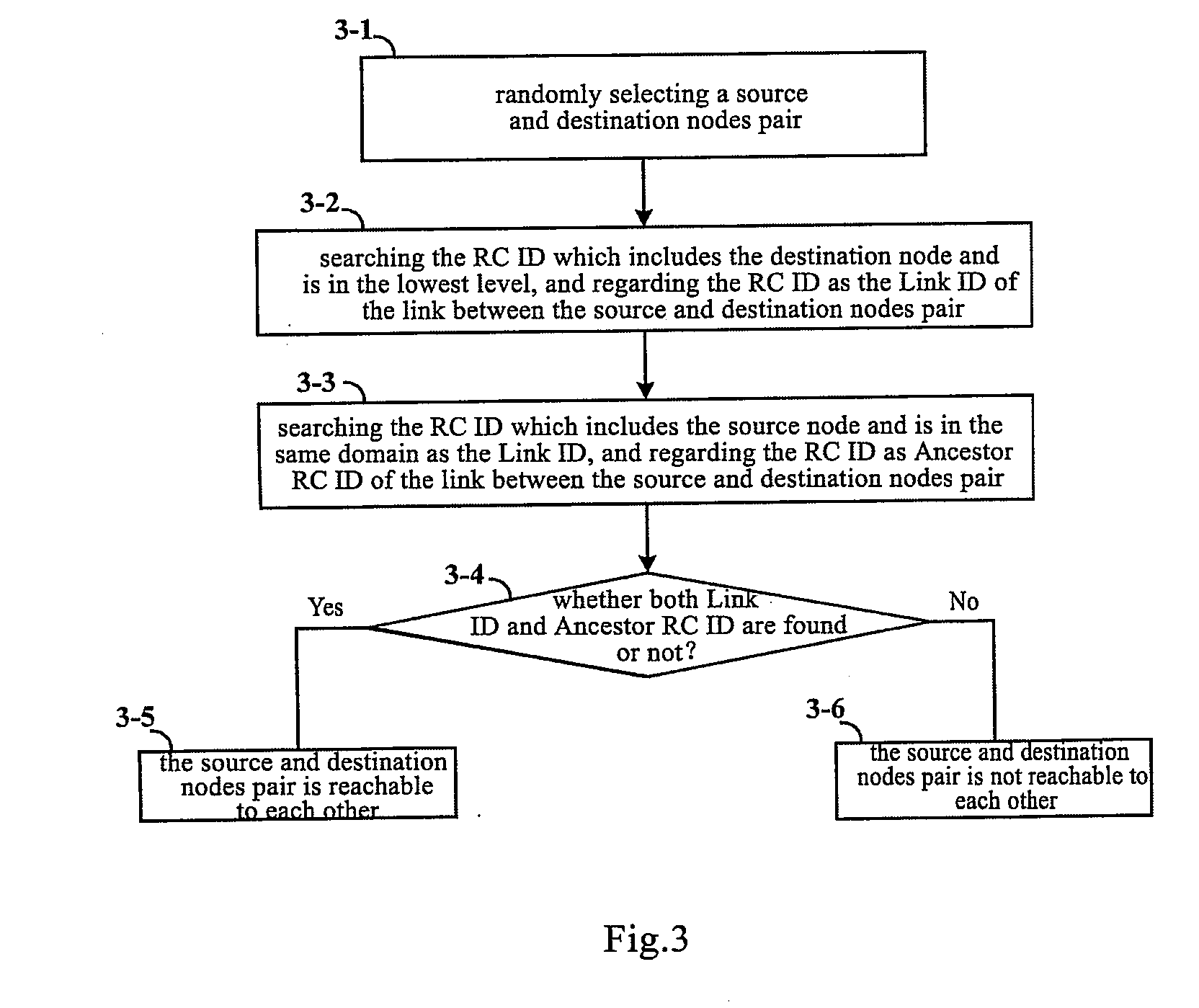
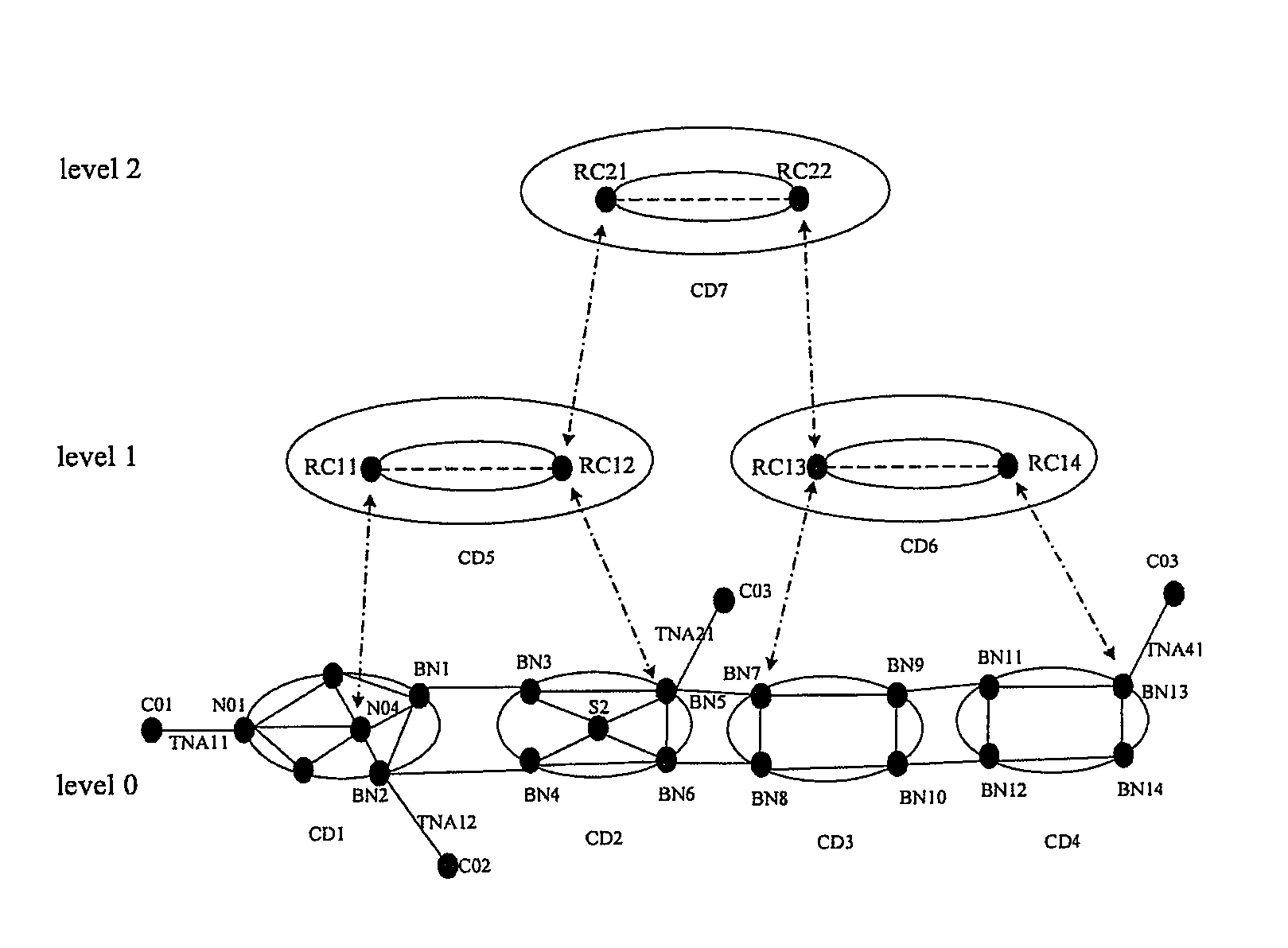
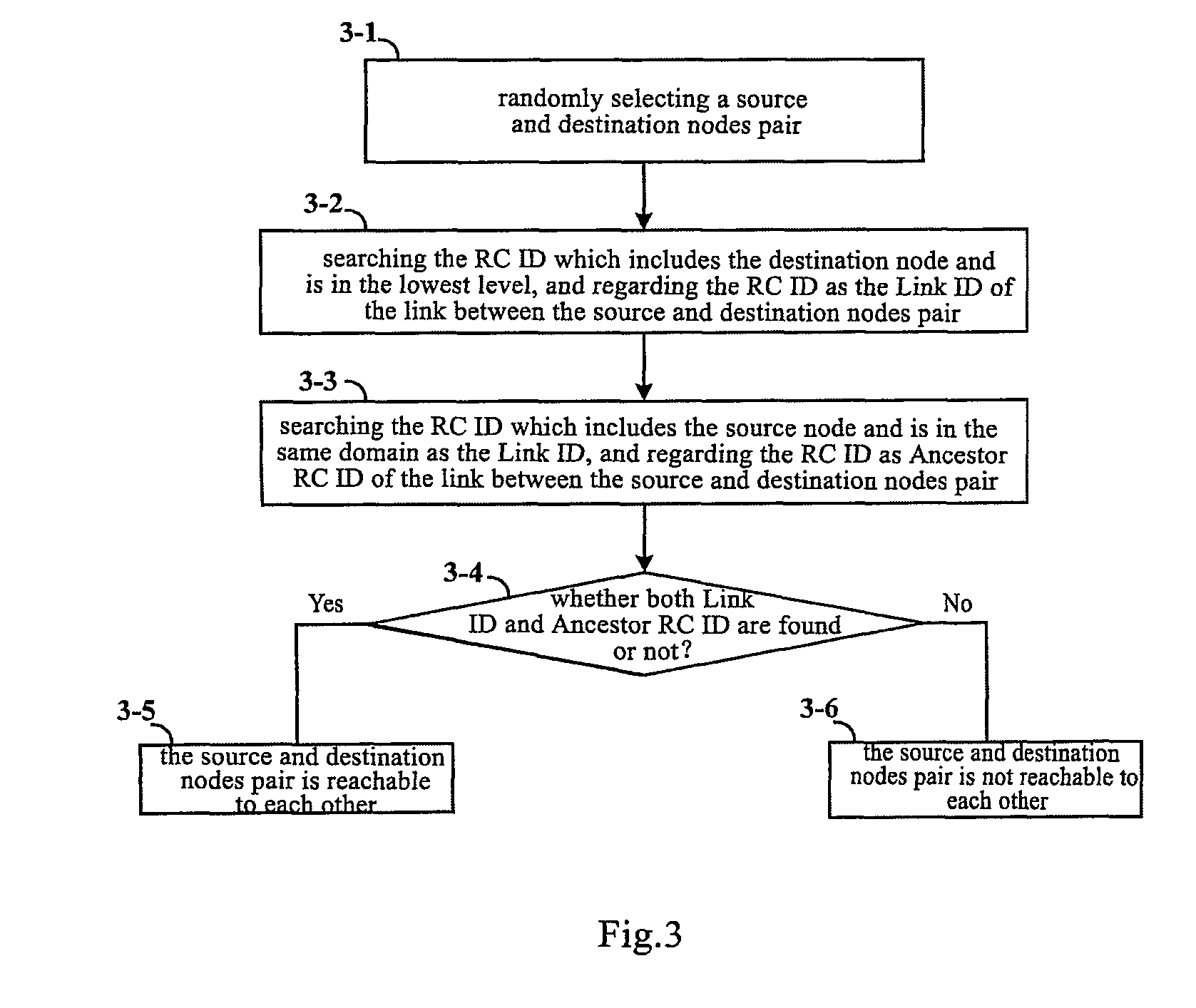
Method for identifying node reachability, method for identifying whether a link is an external link, method for calculating a routing, and method for disseminating node address information
ActiveUS20070160039A1Multiplex system selection arrangementsData switching by path configurationReachabilityInformation Dissemination
The present invention discloses a method for identifying node reachability, a method for identifying a link, a method for calculating a routing, and a method for disseminating node address information. In the method of the node address information dissemination, when the network is initiated, each node in the automatically switched optical network performs a node address aggregation process and an aggregation address dissemination process, and obtains and stores the aggregation address respectively. Therefore, any node in the network may judge whether the node and another node in the network are reachable to each other, and may further calculate the routing between the source and destination nodes pair. Moreover, the present invention also may determine whether any traffic engineering link in the multi-level ASON network is an external link or an internal link.
Owner:HUAWEI TECH CO LTD
Bendable display apparatus and supporting device
ActiveUS9874906B1Efficient solutionDigital data processing detailsMulti-purpose toolsEngineeringInternal link
Owner:FIRST DOME
Non-blocking destination-based routing networks
InactiveUS7898957B2Simple designFAC will be greatly simplifiedError preventionTransmission systemsLink weightThe Internet
Owner:THE HONG KONG UNIV OF SCI & TECH
Automatic maintenance of a distributed source tree (DST) network
In one embodiment, an automatically maintained, distributed source tree (DST) network has a plurality of fully connected internal nodes. One or more internal nodes may be connected to one or more external nodes. A first internal node synchronizes its link-state database with another internal node by sending and receiving respective Reduced Sequence Number Packet-Data-Units (PDUs) (RSNPs). An RSNP includes summary information for link-state packets (LSPs) (1) originated by the first internal node, (2) received by the first internal node from the other internal node, and (3) received from and / or originated by external nodes. If an internal link fails, then the corresponding end-nodes may recover and maintain automatic DST operation by entering either relay-mode or switch-mode operation. In relay-mode operation, an end-node tunnels packets to the other end-node via an intermediary node. In switch-mode operation, an intermediary node is selected to forward packets from one end-node to the other end-node.
Owner:WSOU INVESTMENTS LLC +1
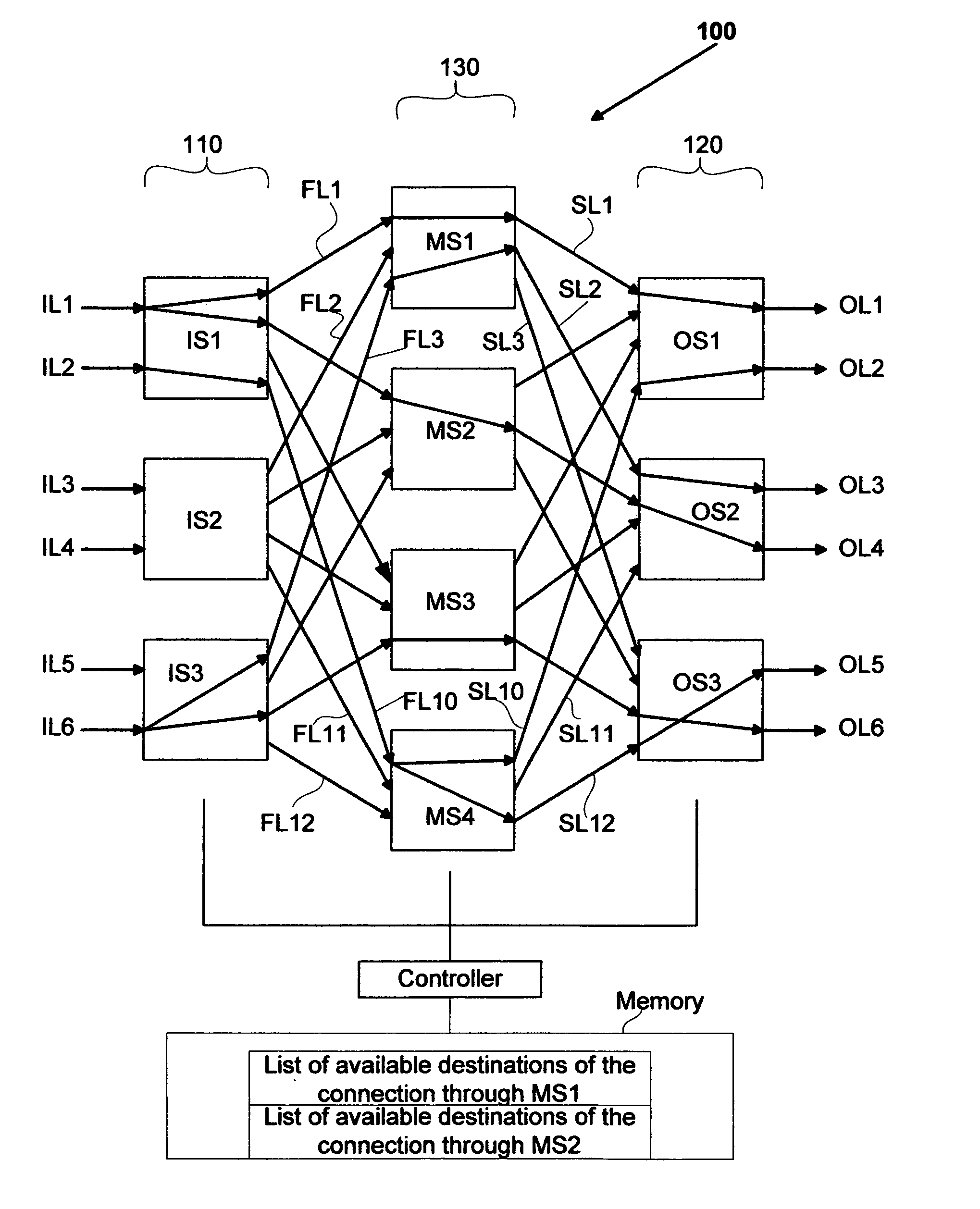
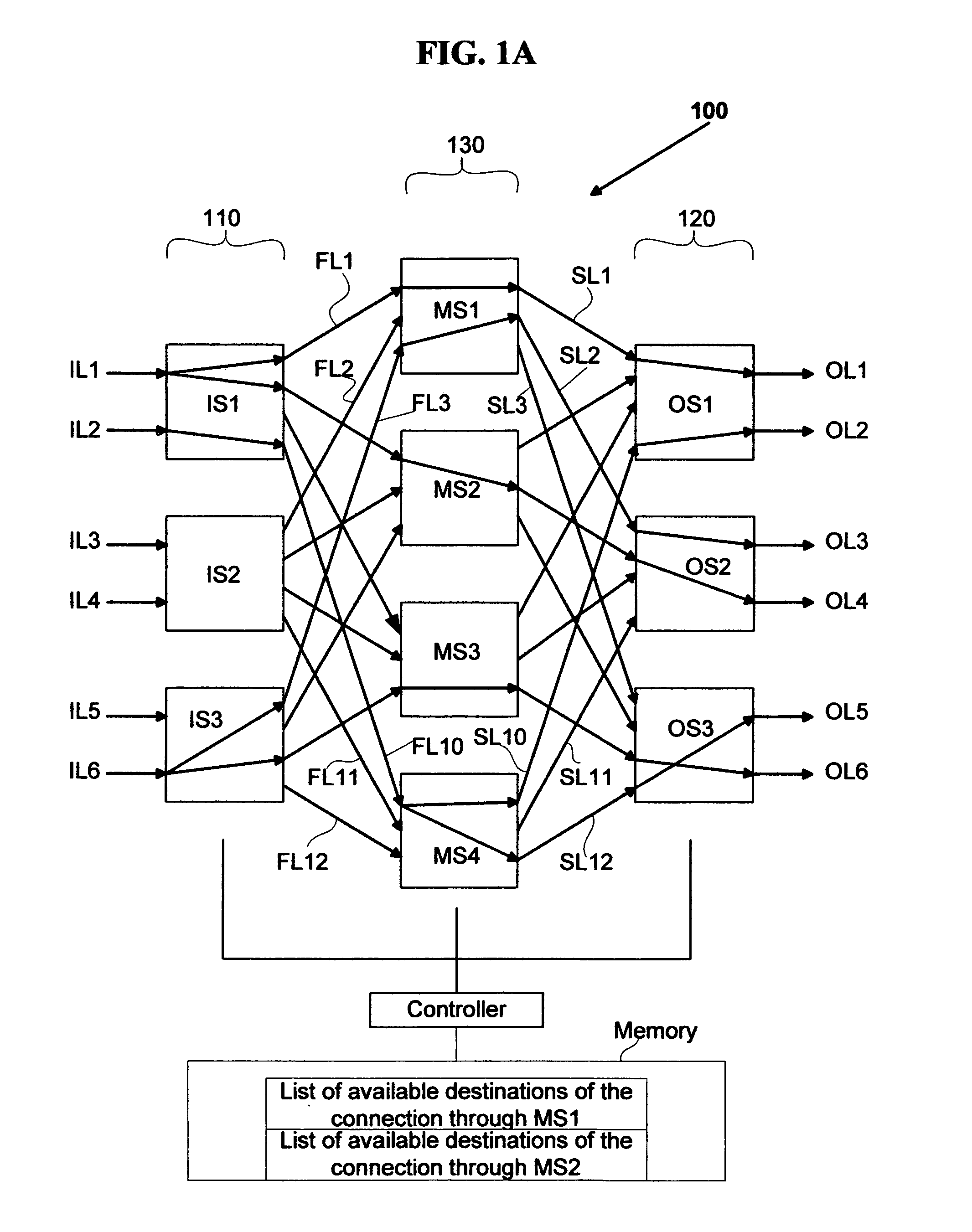
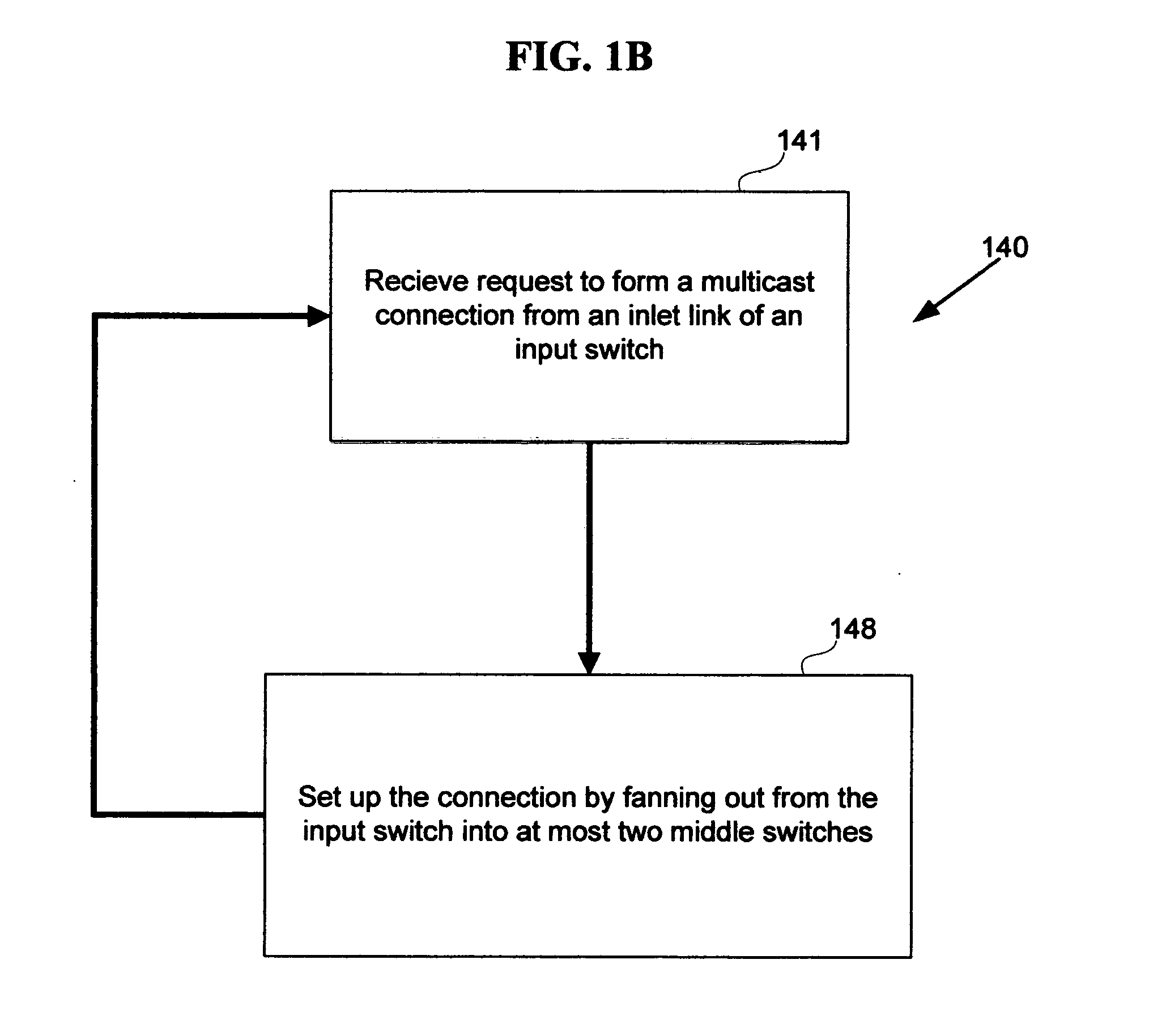
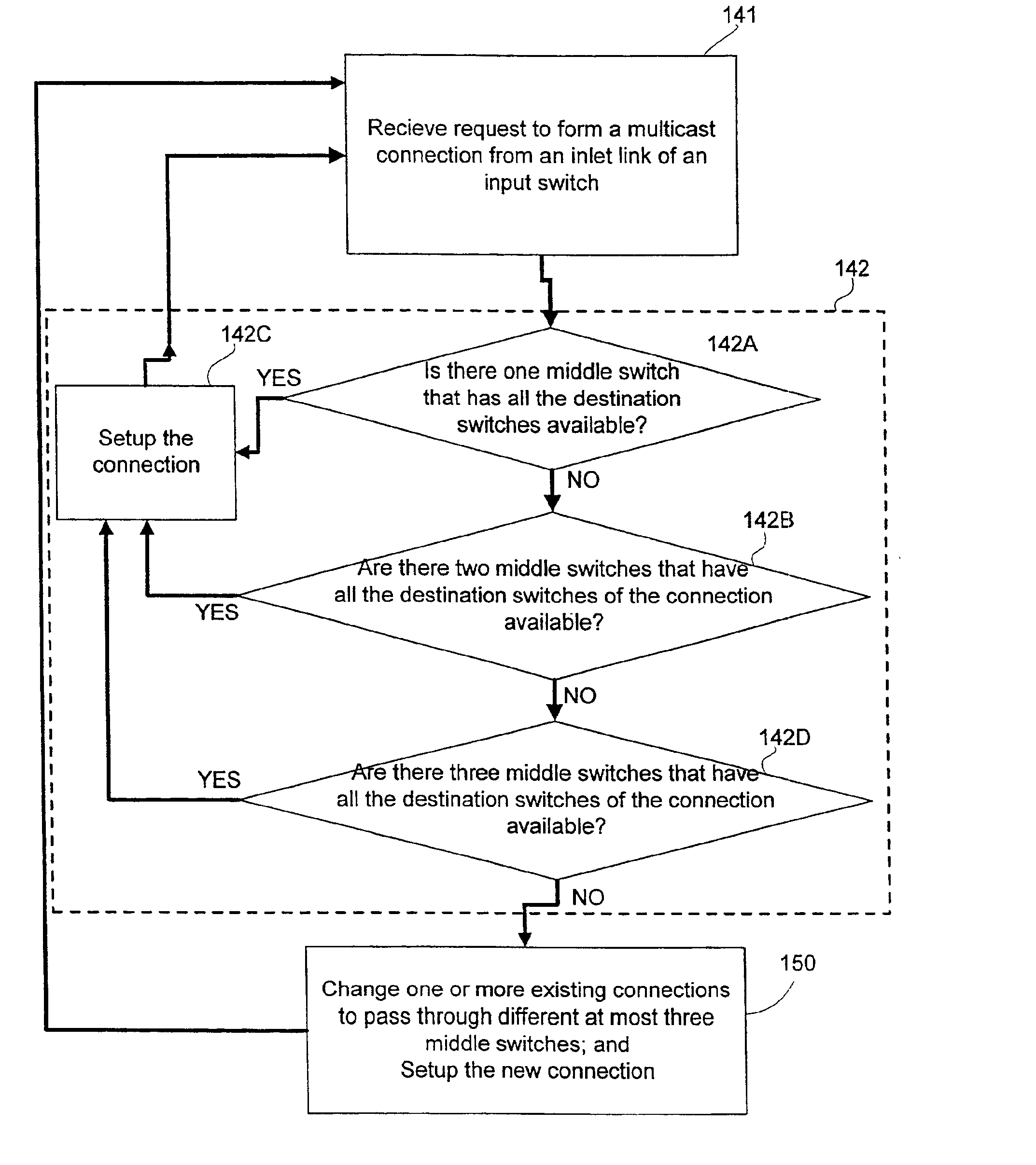
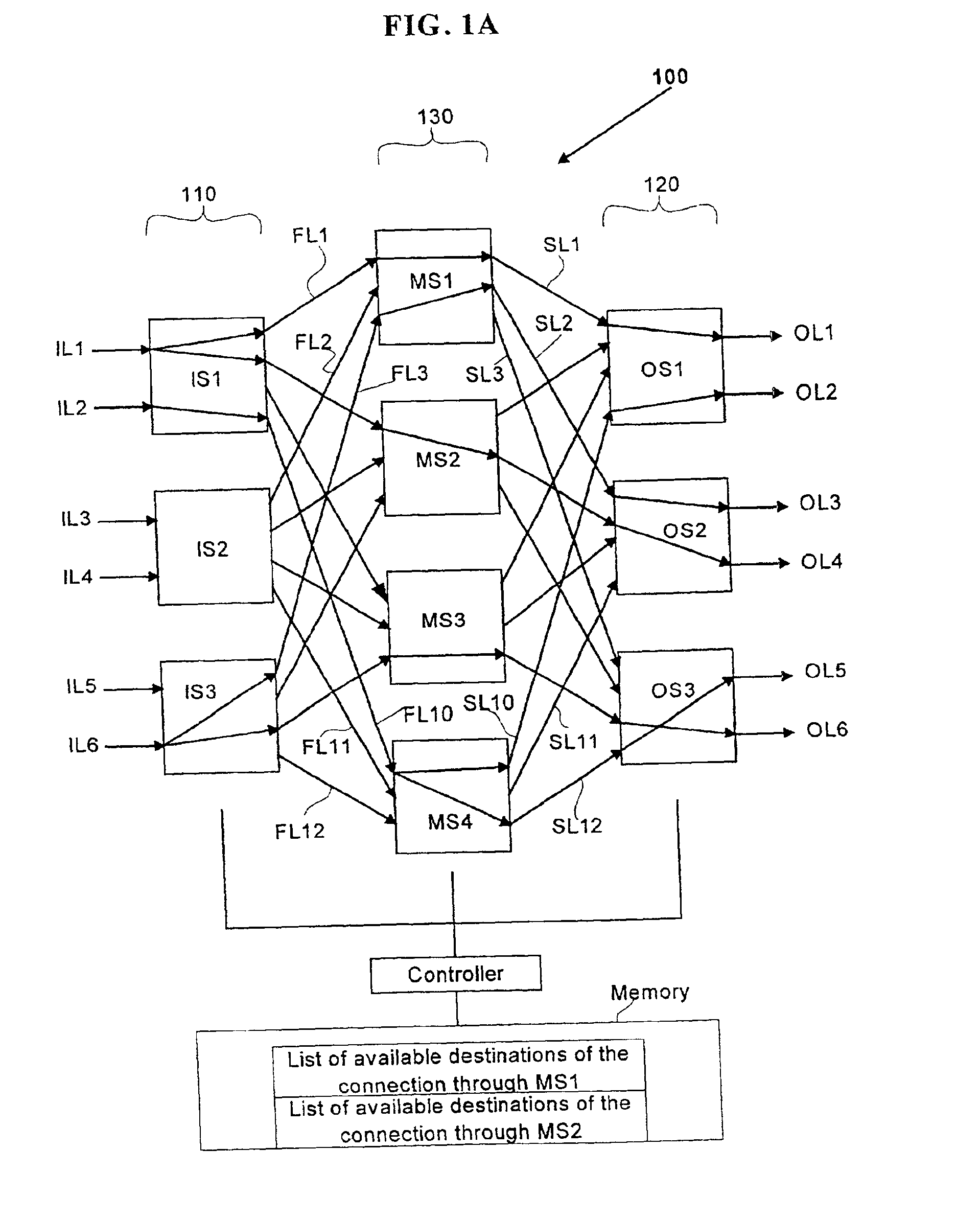
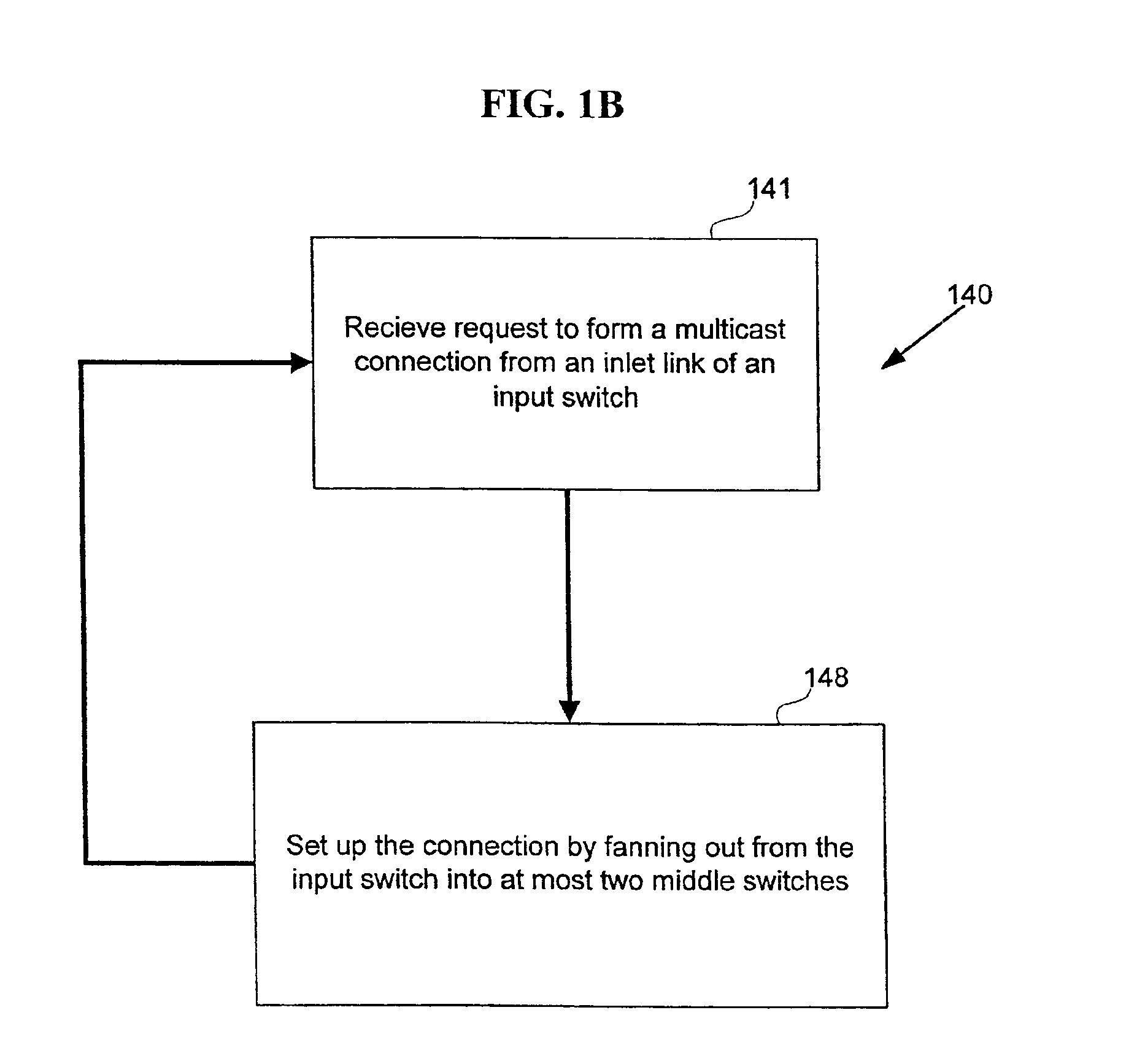
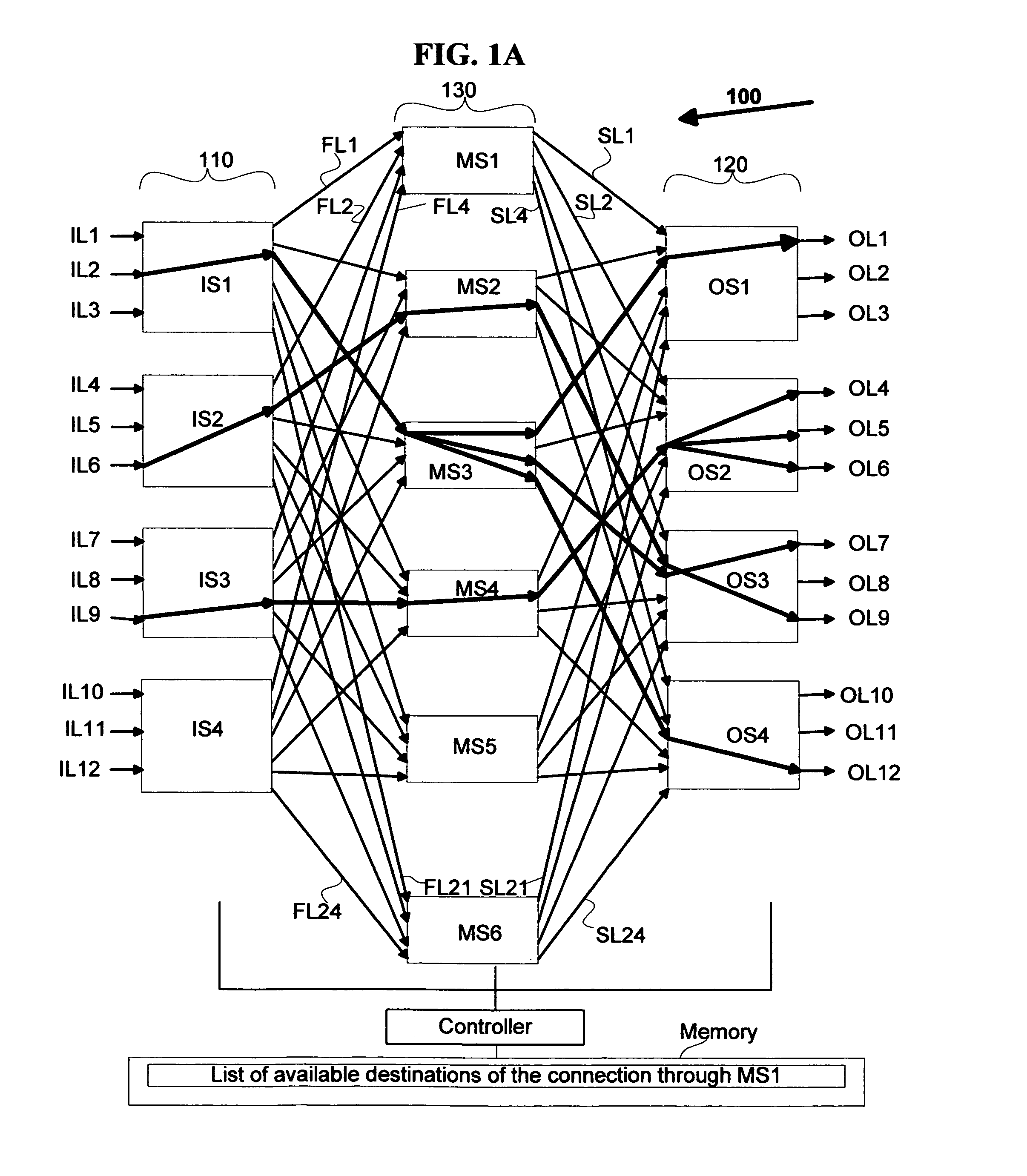
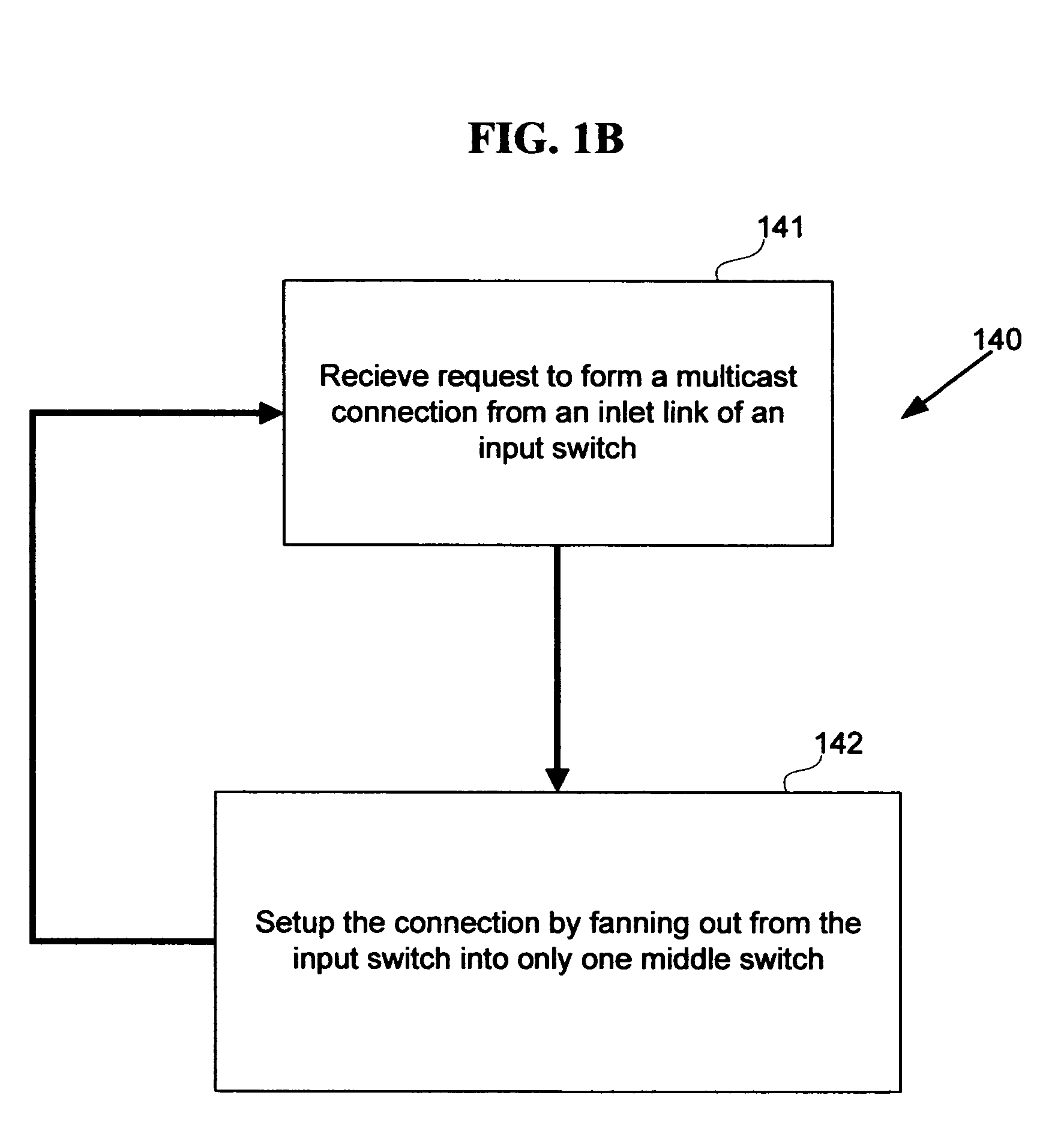
Strictly nonblocking multicast multi-stage networks
InactiveUS6868084B2Multiplex system selection arrangementsElectronic switchingThree stageEngineering
A three-stage network is operated in strictly nonblocking manner in accordance with the invention includes an input stage having r1 switches and n1 inlet links for each of r1 switches, an output stage having r2 switches and n2 outlet links for each of r2 switches. The network also has a middle stage of m switches, and each middle switch has at least one link connected to each input switch for a total of at least r1 first internal links and at least one link connected to each output switch for a total of at least r2 second internal links, where m≧2*n1+n2−1. In one embodiment, each multicast connection is set up through such a three-stage network by use of at most two switches in the middle stage. When the number of inlet links in each input switch n1 is equal to the number of outlet links in each output switch n2, and n1=n2=n, a three-stage network is operated in strictly nonblocking manner in accordance with the invention if m≧3*n−1. Also in accordance with the invention, a three-stage network having more middle switches than 2*n1+n2−1 is operated in strictly nonblocking manner even if some multicast connections are set up by using more than two middle switches as long as each connection has available links into at least two middle switches and there are always at least n1−1 unused links from each input switch to middle switches, after each connection is set up.
Owner:TEAK TECH
Track comprised or internal and external links
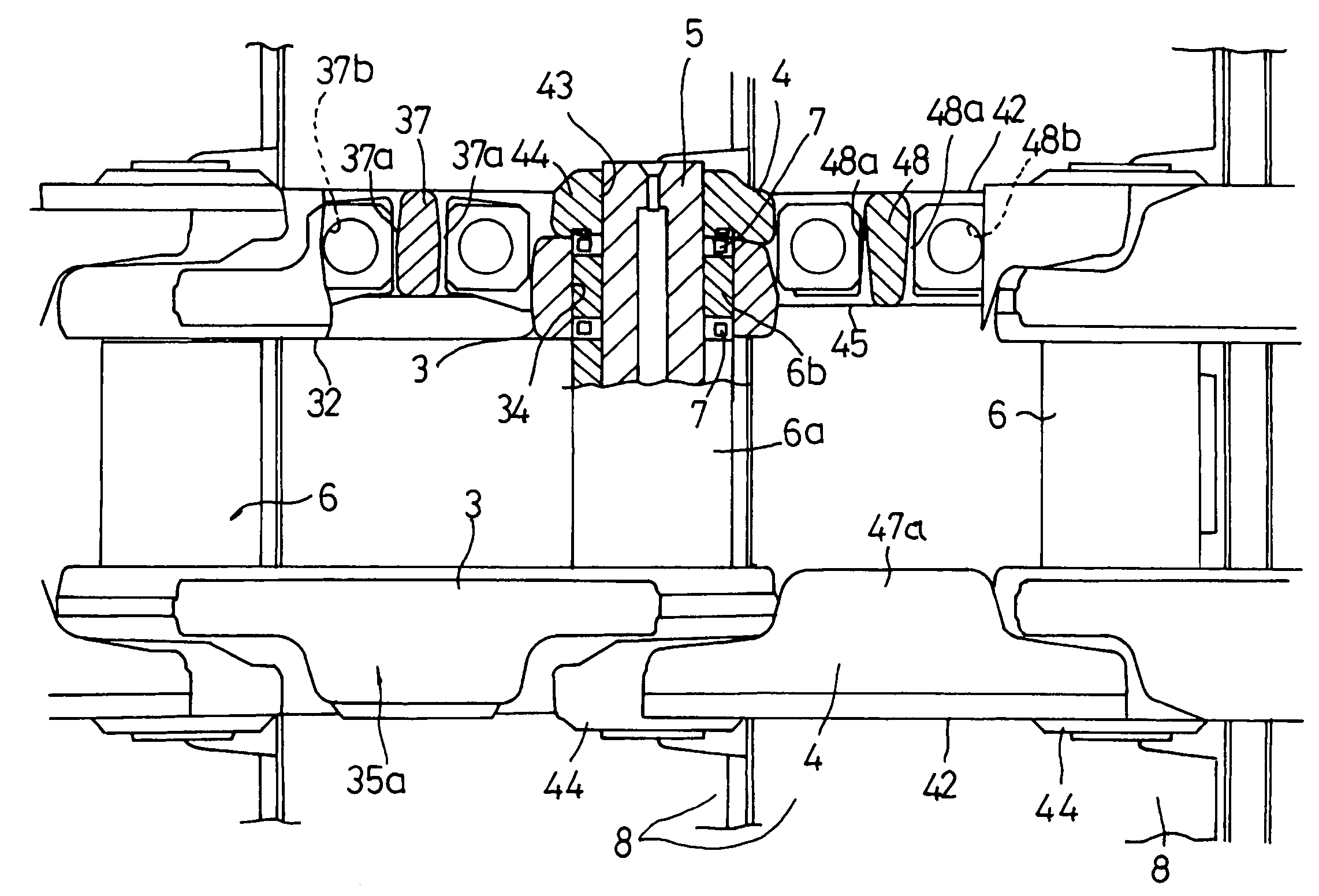
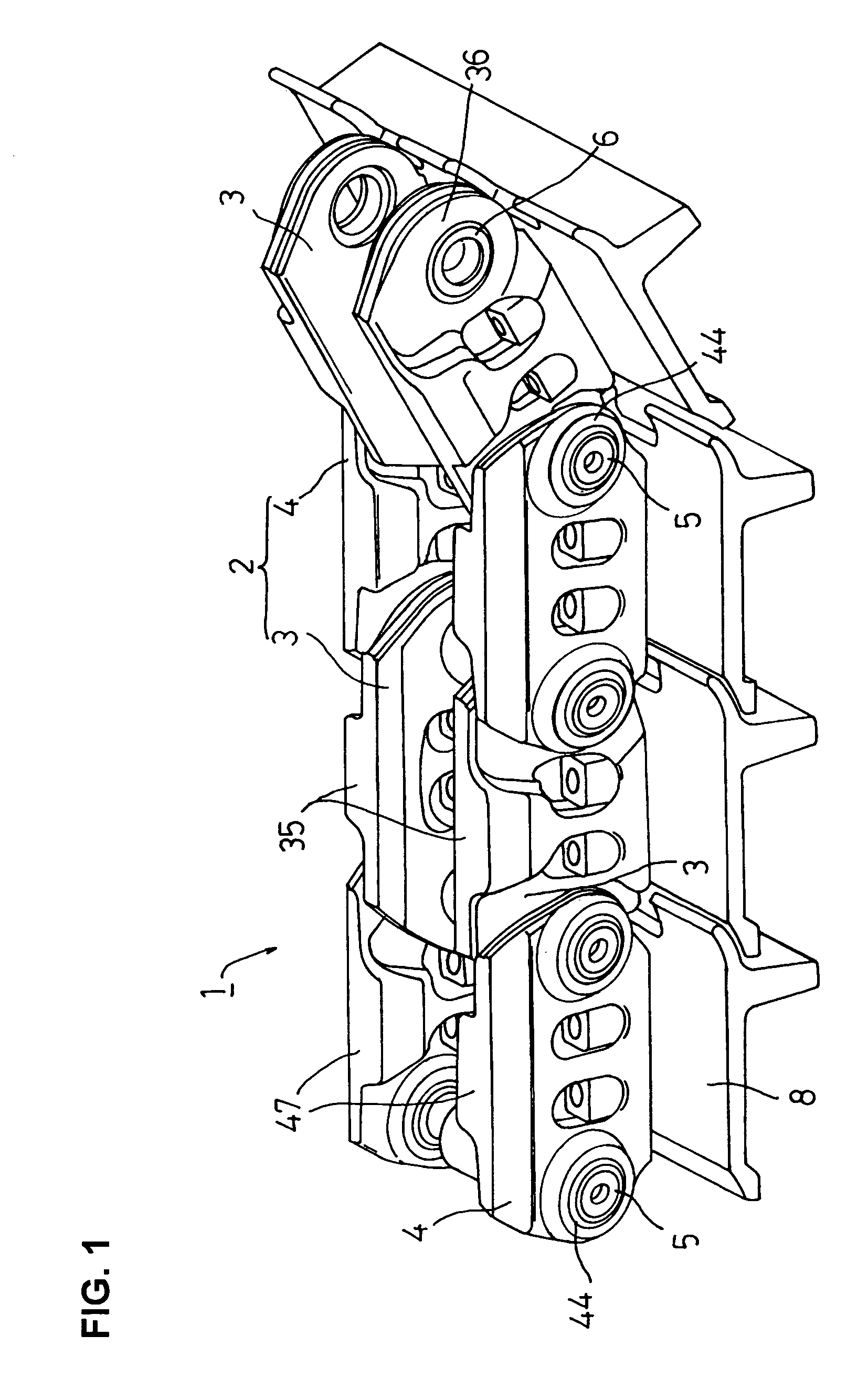
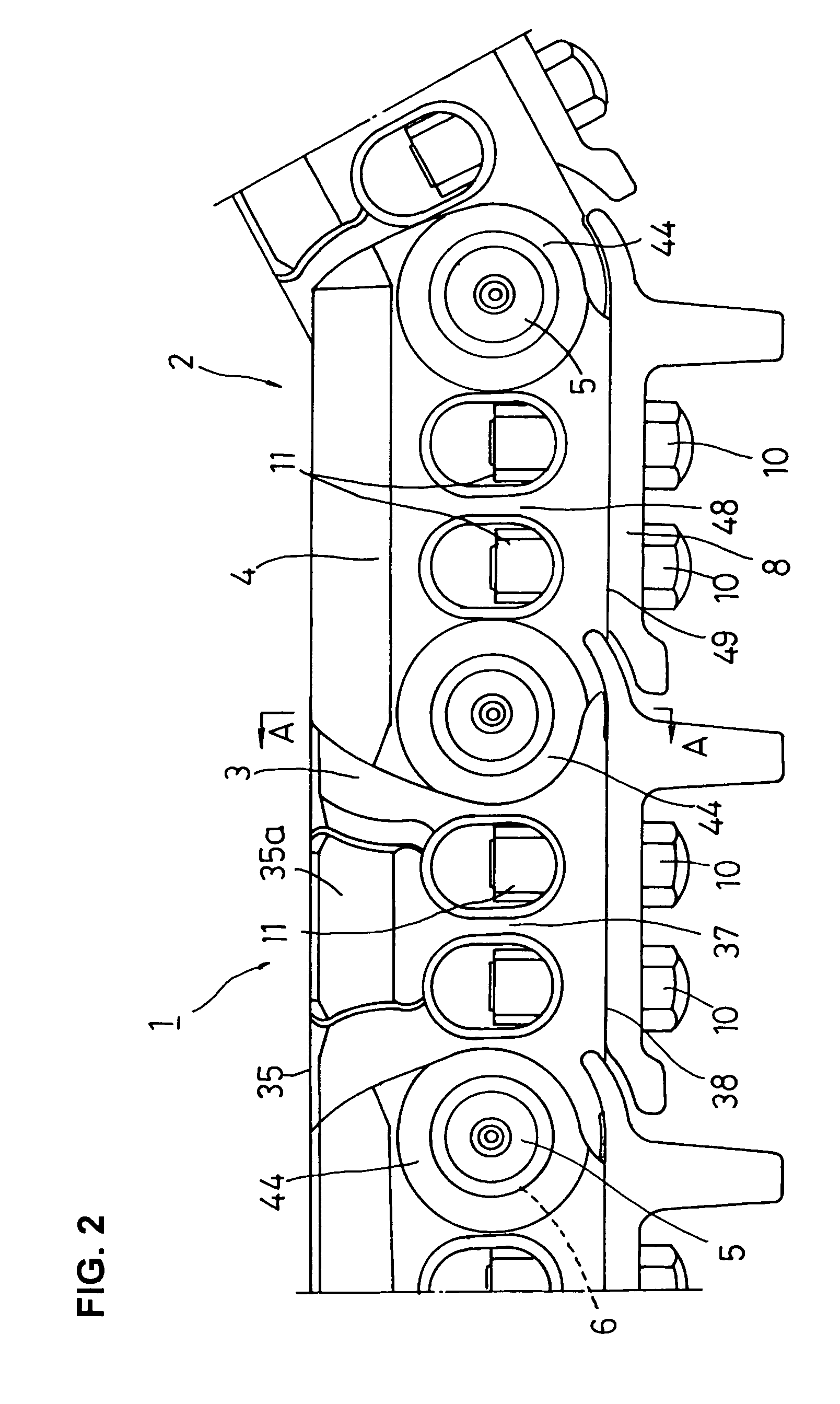
InactiveUS7661774B2Avoid stress concentrationFlexible cuttingGearingTilling equipmentsEngineeringSprocket
In a track with a rotatable bushing which is brought into engagement with a sprocket of a track-type vehicle, it is intended that strength is enhanced rationally by link functionality sharing and by combination of such assigned functional tasks for achieving further improvements in rotatable bushing function. To this end, a first bolt insertion hole provided in a track shoe mount surface of an external link and a second bolt insertion hole provided in a track shoe mount surface of an internal link are arranged on the same straight line, and a straight line connecting the first bolt insertion hole and the second bolt insertion hole is situated at a position more interior than a contact plane of the external link and internal link.
Owner:KOMATSU LTD
Ad Hoc network functional layer structure and route method for supporting multi-speed rate transmission
InactiveCN1645863ASupport multi-rate transmission capabilityImprove throughputData switching networksWireless communicationProtocol overheadLow speed
The method includes following steps: through adding sub-layer functional unit in local route between network layer and data link layer, the route figured out by network layer is optimized; the route contains multi high speed short link divided up from a low speed long distance link; these short links build up new route to transmit data and support multi speed transmission; meanwhile the sub-layer of local route also needs to renew the internal link state table and neighboring node state table in order to provide message parameter for next optimization of route.
Owner:XIDIAN UNIV
Track
InactiveUS20080164756A1Avoid stress concentrationFlexible cuttingGearingTilling equipmentsEngineeringSprocket
In a track with a rotatable bushing which is brought into engagement with a sprocket of a track-type vehicle, it is intended that strength is enhanced rationally by link functionality sharing and by combination of such assigned functional tasks for achieving further improvements in rotatable bushing function. To this end, a first bolt insertion hole provided in a track shoe mount surface of an external link and a second bolt insertion hole provided in a track shoe mount surface of an internal link are arranged on the same straight line, and a straight line connecting the first bolt insertion hole and the second bolt insertion hole is situated at a position more interior than a contact plane of the external link and internal link.
Owner:KOMATSU LTD
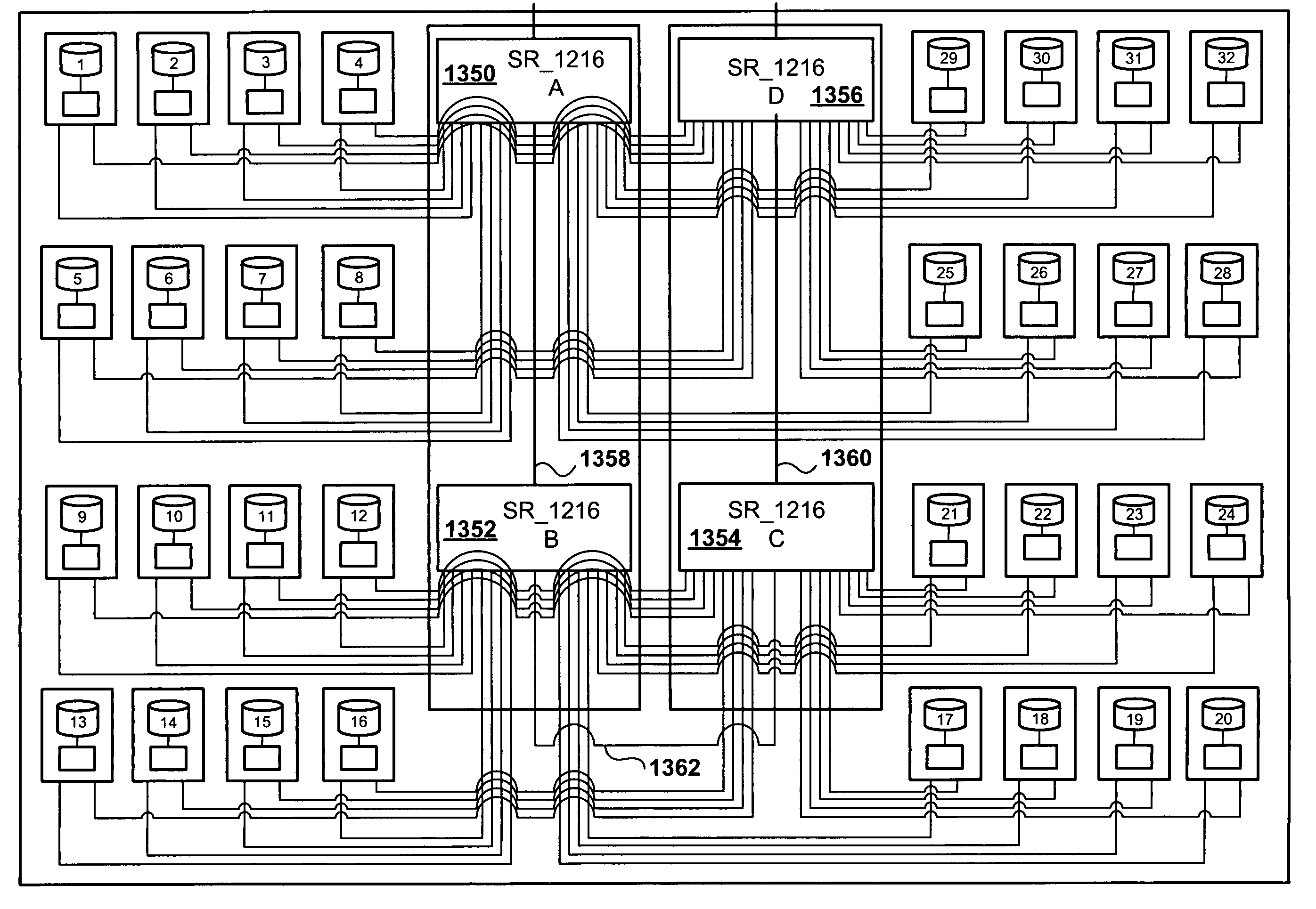
Integrated-circuit implementation of a storage-shelf router and a path controller card for combined use in high-availability mass-storage-device shelves that may be incorporated within disk arrays
ActiveUS7353321B2Eliminates cumulative node delay problemHigh operating requirementsInput/output to record carriersError detection/correctionMass storageNetwork Communication Protocols
An integrated circuit implementing a storage-shelf router used alone, or in combination with other storage-shelf routers, and in combination with path controller cards, to interconnect the disks within a storage shelf or disk array to a high-bandwidth communications medium, such as an FC arbitrated loop, through which data is exchanged between the individual disk drives of the storage shelf and a disk-array controller. A set of interconnected storage-shelf routers within a storage shelf can be accessed through a single port of an FC arbitrated loop or other high-bandwidth communications medium. Because, in one implementation, eight storage-shelf routers can be interconnected within a storage shelf to provide highly available interconnection of sixty-four disk drives within the storage shelf to an FC arbitrated loop via a single FC-arbitrated-loop port, a single FC arbitrated loop including a disk-array controller, may interconnect 8,000 individual disk drives to the disk-array controller within a disk array. The storage-shelf router can serve to translate FC-based communications protocols into one or more communication protocols appropriate to the internal links, providing for use of less expensive, non-FC-compatible disk drives within the storage shelf.
Owner:SIERRA LOGIC
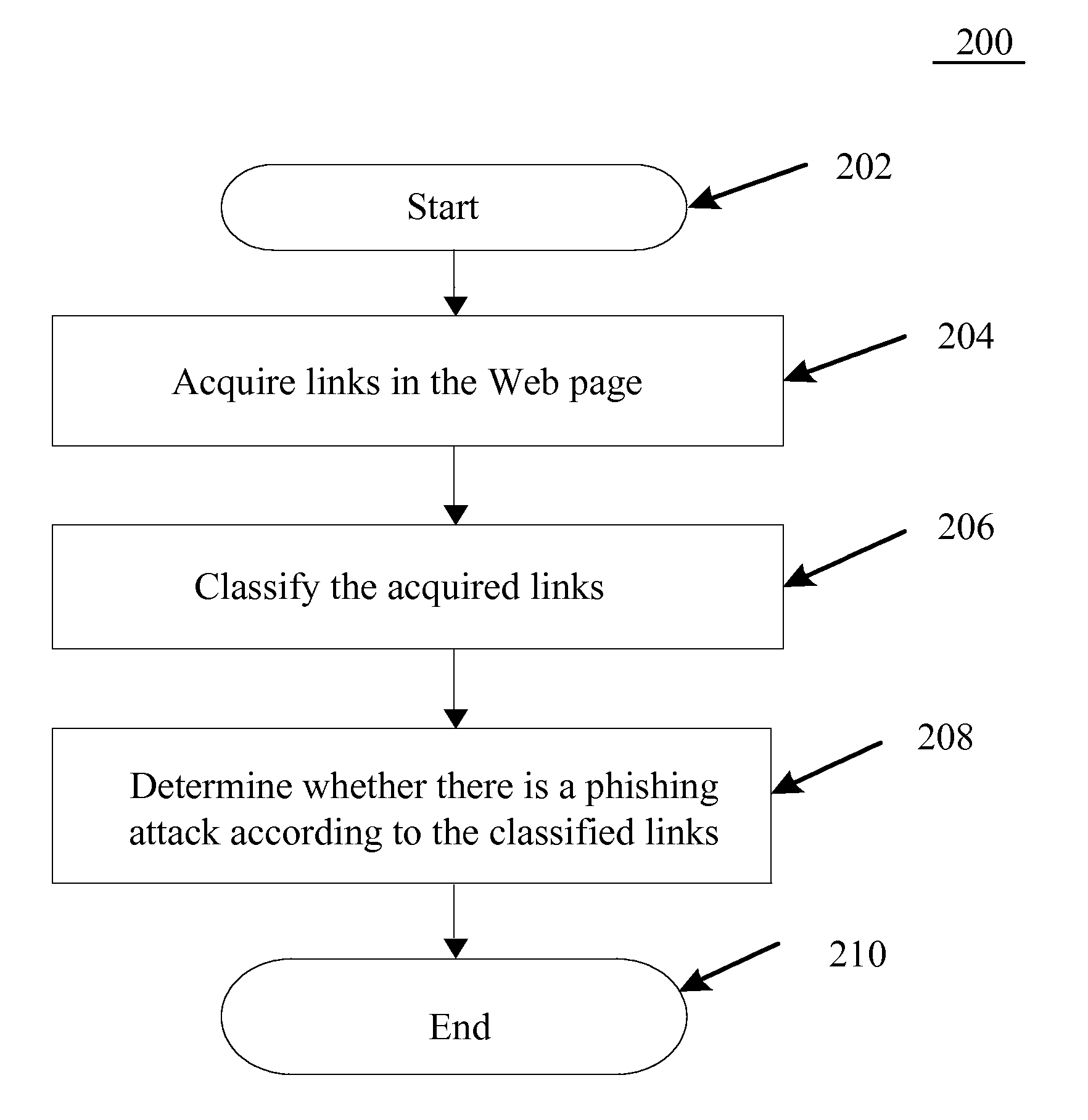
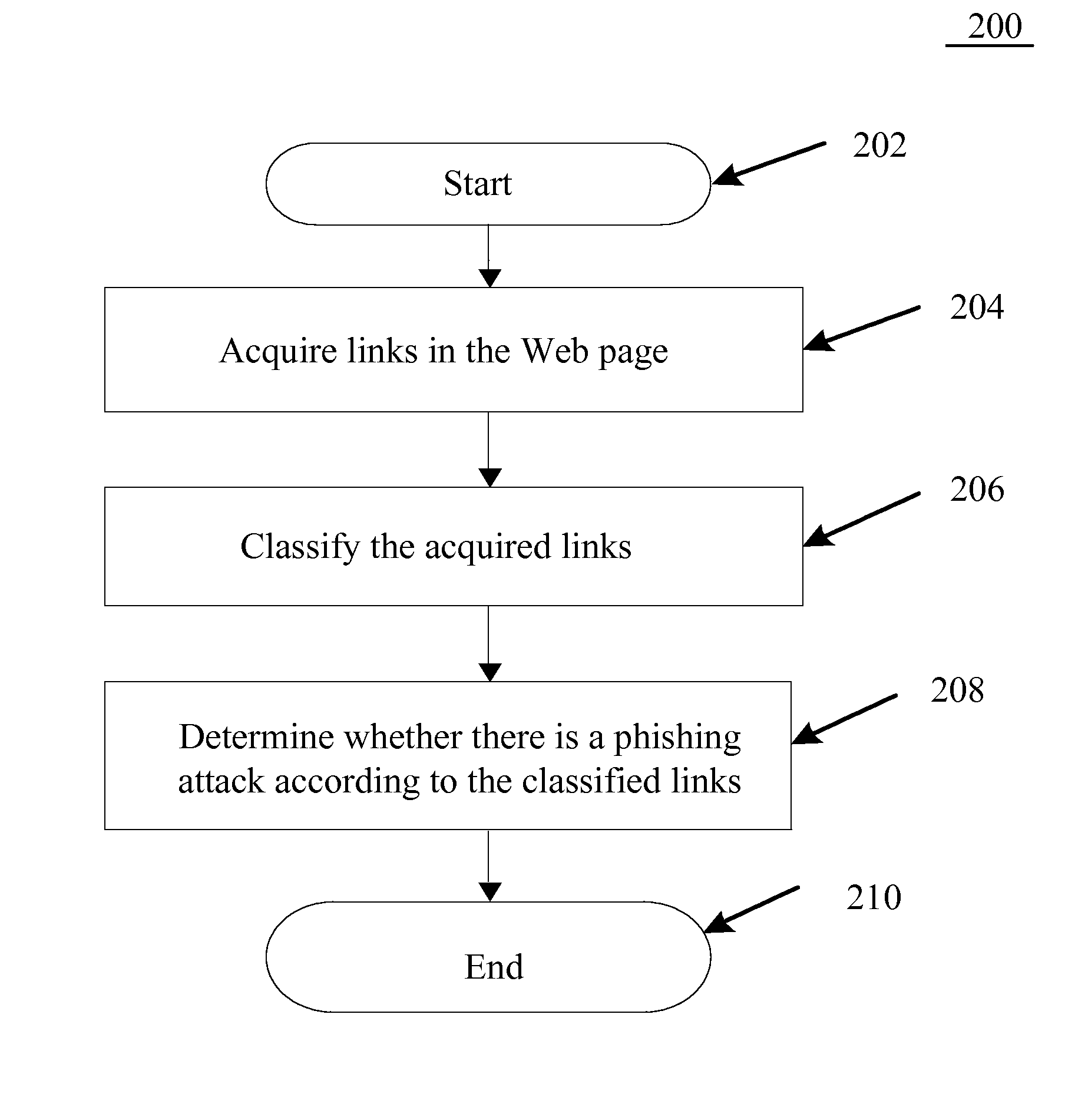
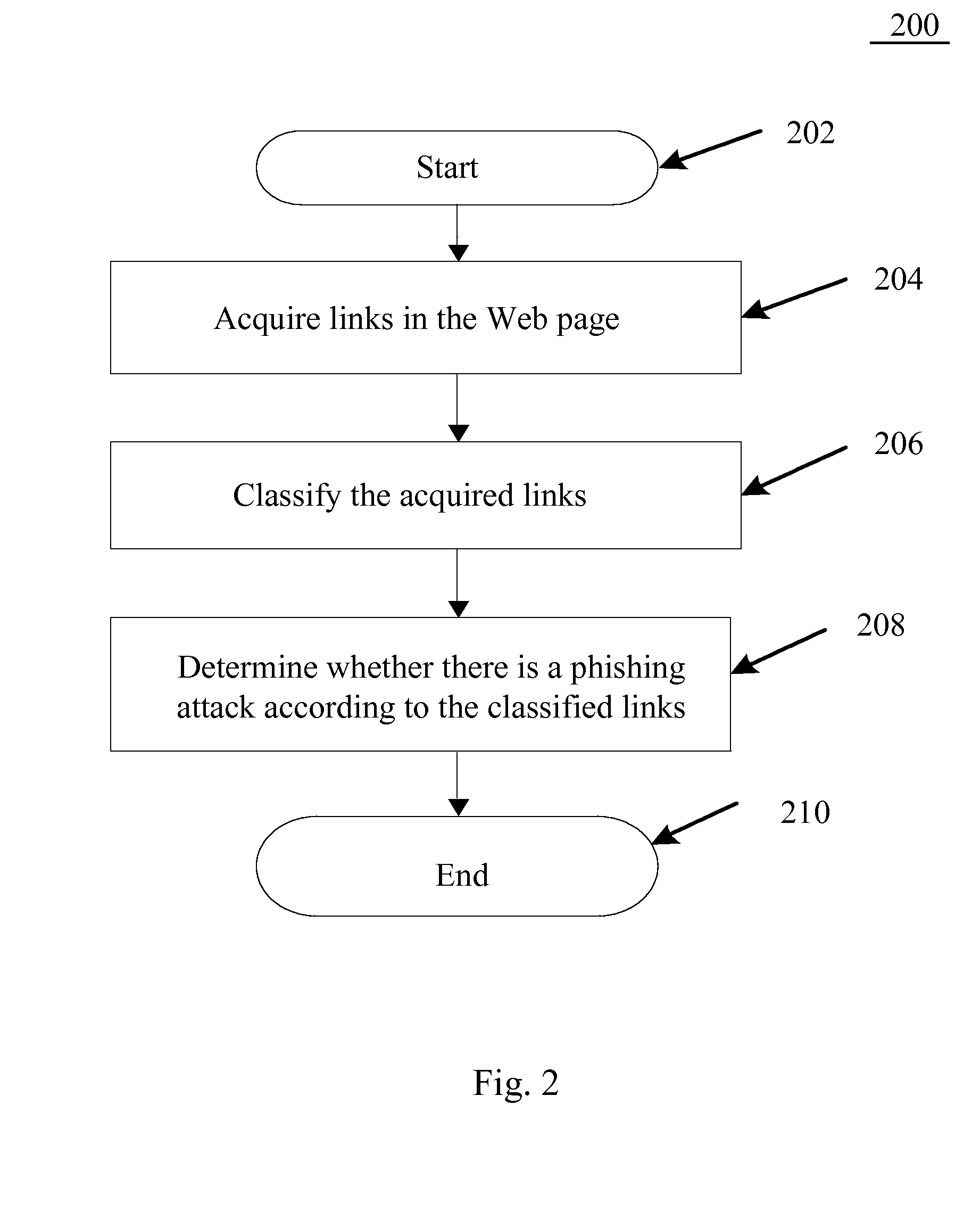
Method and System for Preventing Phishing Attacks
InactiveUS20130031627A1Prevent unnecessary losses causedAvoid attackMemory loss protectionError detection/correctionWeb siteInternal link
A method, system and program product for preventing phishing attacks, wherein the method comprises: acquiring links in a Web page; classifying the acquired links according link types; and determining whether a phishing attack exists according to the classified links, wherein the links are classified into two types: internal links belonging to the same domain as the address of the Web page, and external links belonging to a different domain from the address of the Web page. By carrying out the method or system according to the above one or more embodiments of the present disclosure, since it is first detected whether a Web page is a fake website of a phishing attack before displaying the reproduced Web page to the user and the user is warned upon detecting a fake website, unnecessary losses due to phishing attacks can be prevented.
Owner:BEIJING PIANRUOJINGHONG TECH CO LTD
Rearrangeably nonblocking multicast multi-stage networks
InactiveUS20050117573A1Multiplex system selection arrangementsElectronic switchingThree stageMulticast network
A rearrangeably nonblocking multicast network in accordance with the invention includes an input stage having r1 switches and n1 inlet links for each of r1 switches, an output stage having r2 switches and n2 outlet links for each of r2 switches. The network also has a middle stage of m switches, and each middle switch has at least one link connected to each input switch for a total of at least r1 first internal links and at least one link connected to each output switch for a total of at least r2 second internal links, where m≧n1+n2. The network has all multicast connections set up such that each multicast connection passes through at most two middle switches to be connected to the destination outlet links. When the number of inlet links in each input switch n1 is equal to the number of outlet links in each output switch n2, and n1=n2=n, a three-stage network is operated in rearrangeably nonblocking manner in accordance with the invention, where m≧2*n. Also in accordance with the invention, a three-stage network having m>n1+n2 is operated in rearrangeably nonblocking manner even if some multicast connections are set up using more than two middle switches as long as each connection has available links into at least two middle switches.
Owner:TEAK TECH
Track having rotatable bushing and link for the same
In a track with a rotatable bushing which is brought into engagement with a sprocket of a track-type vehicle, it is intended that strength is enhanced rationally by link functionality sharing and by combination of such assigned functional tasks for achieving further improvements in rotatable bushing function. To this end, a track link comprises a combination of an external link and an internal link; a coupler pin hole is provided through the external link; a bushing hole is provided through the internal link, and the thickness dimension of a bushing hole formation part of the internal link is made greater than that of a coupler pin formation part of the external link.
Owner:KOMATSU LTD
Method for monitoring novel words on Internet
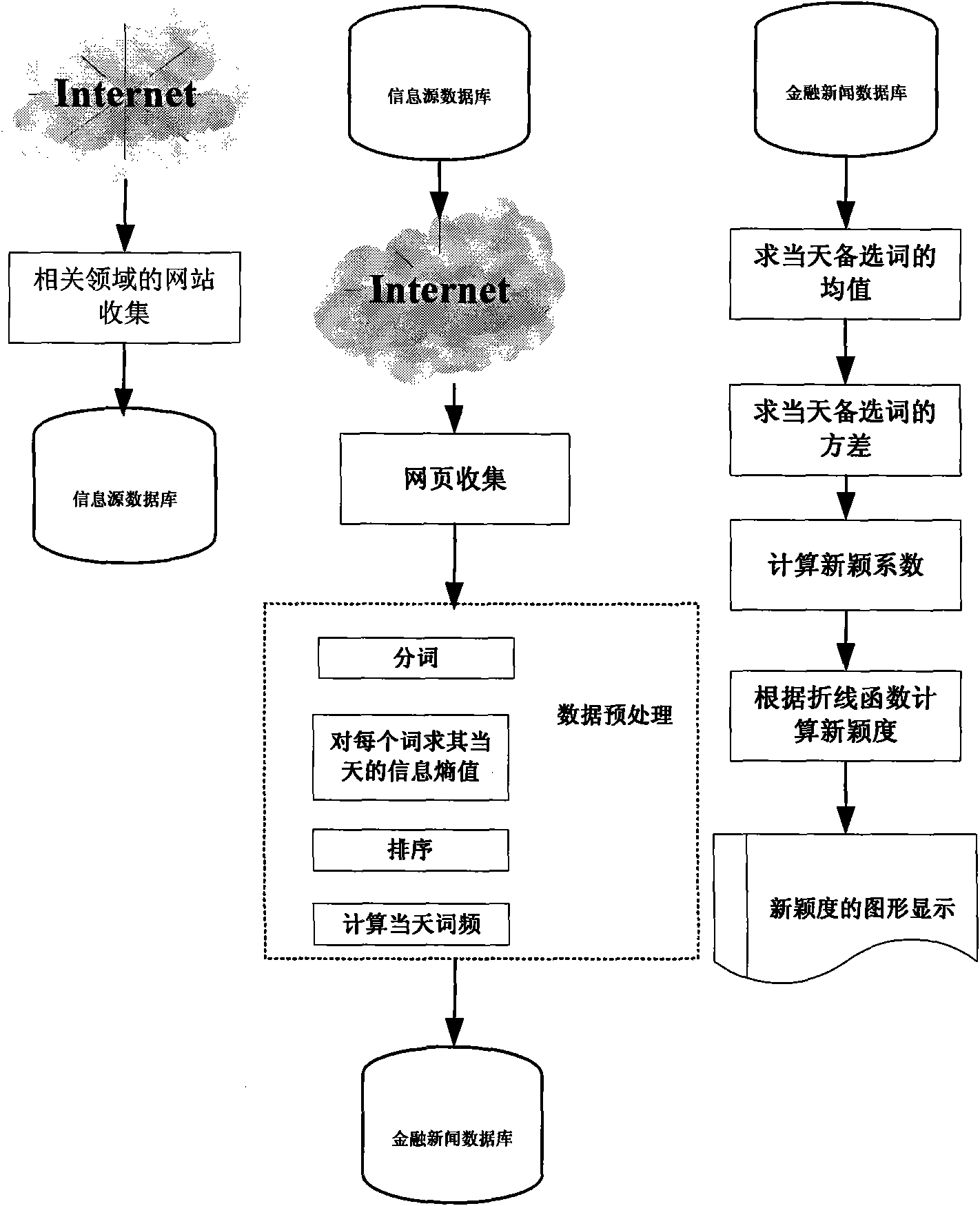
InactiveCN101645066AImprove the efficiency of discovering new topic informationAlarm is accurateSpecial data processing applicationsNatural language processingHome page
The invention discloses a method for monitoring novel words on Internet and belongs to the field of Internet information mining. The method comprises the following steps: acquiring all articles of thesame day on home pages and subpages of all subordinates directed to by all internal links of the home pages according to a target information source collection; subjecting the articles to word segmentation, assigning weight for each word in each article, using top a words having the largest weight as alternative novel words of the article, and using the number of a plurality of articles as the freq of an alternative novel word on the same day when the word is an alternative novel word of the articles at the same time; calculating the novelty coefficients n of the alternative words according to the records of the freq of the alternative novel words in b days; and determining novelties theta according to the novelty coefficients and determining an alternative novel word as a novel word of the same day when the novelty of the word is greater than a novelty threshold thetat. The method of the invention can effectively find the novel word of the same day and direct the practice for findingand monitoring Internet information.
Owner:PEKING UNIV
System and method providing permission based access to automotive computers
A Link device has a processor connected to an internal Link bus, a non-transitory memory, a digital device ID, one or both of firmware or software executing from non-transitory media, a first communication port enabled to communicate with a vehicle bus coupling computerized devices in a vehicle, and a second communication port enabled to communicate with one or more digital devices external to the vehicle. The firmware or software enables the Link device to communicate with the vehicle bus, and to accomplish a variety of tasks including pulling data from data stores in the vehicle and operating specific vehicle functions, and wherein the firmware or software manages communication with the one or more external digital devices, accepting only requests for cooperation with the Link device using the unique device ID with a request that is cryptographically secure.
Owner:AUTOMATIC LABS
Strictly nonblocking multicast multi-split linear-time multi-stage networks
InactiveUS20050053061A1Multiplex system selection arrangementsElectronic switchingThree stageIntermediate stage
A three-stage network is operated in strictly nonblocking manner in accordance with the invention includes an input stage having r1 switches and n1 inlet links for each of r1 switches, an output stage having r2 switches and n2 outlet links for each of r2 switches. The network also has a middle stage of m switches, and each middle switch has at least one link connected to each input switch for a total of at least r1 first internal links and at least one link connected to each output switch for a total of at least r2 second internal links, if m≧s*MIN(n1,n2) where s=2 when r2=[9,11], s=3 when r2=[25,48], s=4 when r2=[49,99], s=5 when r2=[100,154], s=6 when r2=[155,224], and s=7 when r2=[225,278]. In one embodiment, each multicast connection is set up through such a three-stage network by use of at most s middle stage switches. When the number of input stage r1 switches is equal to the number of output stage r2 switches, and r1=r2=r, and also when the number of inlet links in each input switch n1 is equal to the number of outlet links in each output switch n2, and n1=n2=n1 a three-stage network is operated in strictly nonblocking manner in accordance with the invention if m≧s*n where s=2 when r=[9,11]; s=3 when r=[25,48]; s=4 when r=[49,99]; s=5 when r=[100,154]; s=6 when r=[155,224]; and s=7 when r=[225,278]. In one embodiment, each multicast connection is set up through such a three-stage network by use of at most s middle stage switches.
Owner:TEAK TECH
Rearrangeably nonblocking multicast multi-stage networks
InactiveUS6885669B2Multiplex system selection arrangementsElectronic switchingThree stageMulticast network
A rearrangeably nonblocking multicast network in accordance with the invention includes an input stage having r1 switches and n1 inlet links for each of r1 switches, an output stage having r2 switches and n2 outlet links for each of r2 switches. The network also has a middle stage of m switches, and each middle switch has at least one link connected to each input switch for a total of at least r1 first internal links and at least one link connected to each output switch for a total of at least r2 second internal links, where m≧n1+n2. The network has all multicast connections set up such that each multicast connection passes through at most two middle switches to be connected to the destination outlet links. When the number of inlet links in each input switch n1 is equal to the number of outlet links in each output switch n2, and n1=n2=n, a three-stage network is operated in rearrangeably nonblocking manner in accordance with the invention, where m≧2*n. Also in accordance with the invention, a three-stage network having m>n1+n2 is operated in rearrangeably nonblocking manner even if some multicast connections are set up using more than two middle switches as long as each connection has available links into at least two middle switches.
Owner:TEAK TECH
Method for identifying node reachability, method for identifying whether a link is an external link, method for calculating a routing, and method for disseminating node address information
ActiveUS7782798B2Multiplex system selection arrangementsData switching by path configurationTraffic capacityReachability
Owner:HUAWEI TECH CO LTD
Strictly nonblocking multicast linear-time multi-stage networks
InactiveUS20050063410A1Multiplex system selection arrangementsTime-division multiplexTelecommunicationsThree stage
A three-stage network is operated in strictly nonblocking manner in accordance with the invention includes an input stage having r1 switches and n1 inlet links for each of r1 switches, an output stage having r2 switches and n2 outlet links for each of r2 switches. The network also has a middle stage of m switches, and each middle switch has at least one link connected to each input switch for a total of at least r1 first internal links and at least one link connected to each output switch for a total of at least r2 second internal links, where m≧└{square root}{square root over (r2)}┘*MIN(n1,n2) when └{square root}{square root over (r2)}┘ is >1 and odd, or when └{square root}{square root over (r2)}┘=2, m≧(└{square root}{square root over (r2)}┘−1)*MIN(n1,n2) when └{square root}{square root over (r2)}┘ is >2 and even, and m≧n1+n2−1 when └{square root}{square root over (r2)}┘=1. In one embodiment, each multicast connection is set up through such a three-stage network by use of only one switch in the middle stage. When the number of input stage r1 switches is equal to the number of output stage r2 switches, and r1=r2=r, and also when the number of inlet links in each input switch n1 is equal to the number of outlet links in each output switch n2, and n1=n2=n, a three-stage network is operated in strictly nonblocking manner in accordance with the invention where m≧└{square root}{square root over (r)}┘*n when └{square root}{square root over (r)}┘ is >1 and odd, or when └{square root}{square root over (r)}┘=2, m≧(└{square root}{square root over (r)}┘)*n when └{square root}{square root over (r)}┘is >2 and even, and m≧2*n−1 when └{square root}{square root over (r)}┘=1. Also in accordance with the invention, a three-stage network having middle switches m≧x*MIN(n1,n2) for 2≦x≦└{square root}{square root over (r2)}┘ is operated in strictly nonblocking manner when the fan-out of each multicast connection is ≦x.
Owner:TEAK TECH
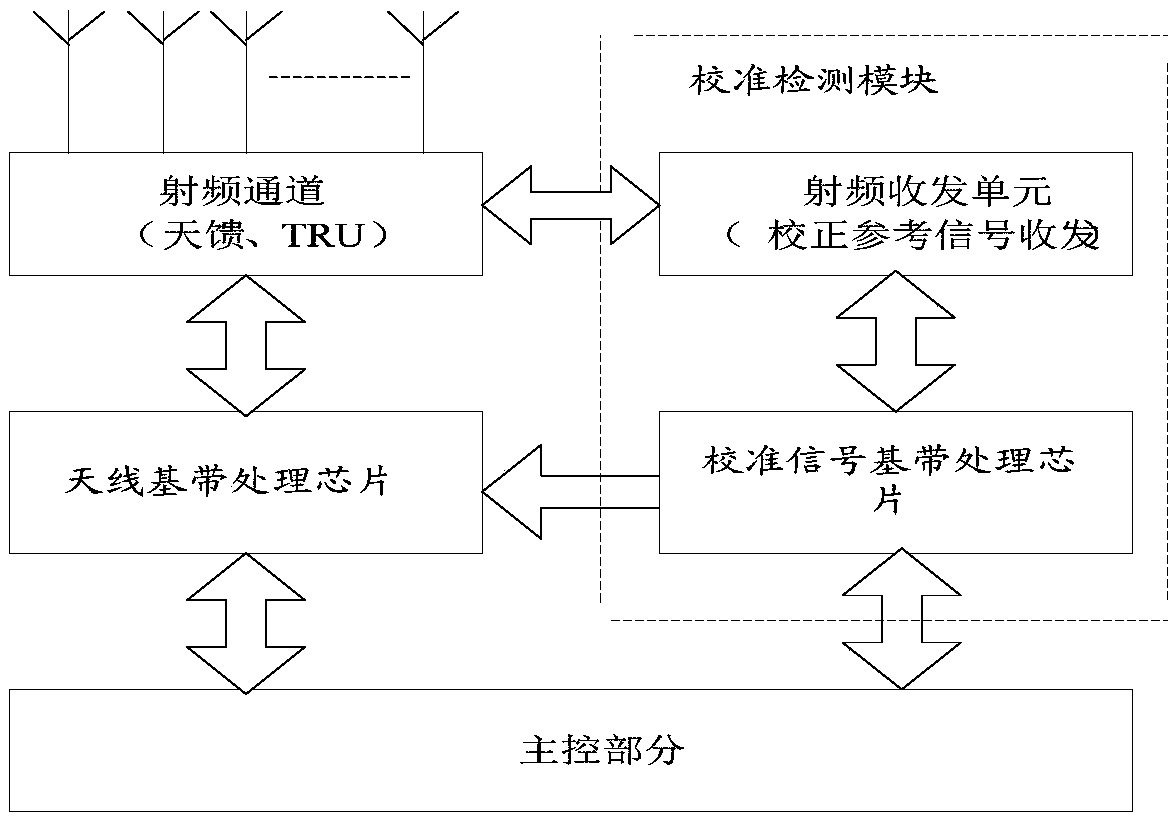
Active array antenna calibration system, method, apparatus, and active array antenna system
PendingCN109088679AExpand coverageIncrease coverageTransmitters monitoringReceivers monitoringPower splitTransceiver
An active array antenna calibration system, a method, an apparatus, and an active array antenna system are provided. The calibration system includes a calibration cable,a power splitting and combininglink and a calibration detection module. The calibration detection module comprises a calibration signal baseband processing chip and a radio frequency transceiver unit connected with the calibration signal baseband processing chip. The calibration cable is respectively connected with the transceiver links of each transceiver radio frequency single board and collects calibration signals of the transceiver links of each transceiver radio frequency single board. The power splitting and combining link is connected with the calibration cable and the calibration detection module, and the calibration signal collected by the calibration cable is sent to the calibration signal baseband processing chip, and the calibration signal baseband processing chip performs calibration processing. Or the original signal is sent to the antenna baseband processing chip of each RF single board, and the antenna baseband processing chip performs calibration processing. The invention realizes the self-calibration function of the multi-channel antenna array through the internal link of the equipment, thereby optimizing the antenna coverage range and the effect.
Owner:COMBA TELECOM SYST CHINA LTD
Method applied to FCoE (Fiber Channel over Ethernet) networking and used for optimizing FSPE (Fiber Shortest Path First) protocol and switchboards
The invention provides a method applied to FCoE (Fiber Channel over Ethernet) networking and used for optimizing an FSPE (Fiber Shortest Path First) protocol and switchboards. The method is applied to an FCoE networking system comprising a plurality of switchboards; when one of the switchboards is a local-end switchboard, the other switchboards are opposite-end switchboards of the local-end switchboard; and the method comprises the following steps of: receiving HLO SW_ILS (Hello Switch Internal Link Services) messages from the opposite-end switchboards by the local-end switchboard, and searching whether neighbor state machines corresponding to the opposite-end switchboards are established in the local-end switchboard according to domain identifiers (ID) of the opposite-end switchboards carried in the HLO SW_ILS messages; and if the neighbor state machines are not established, establishing the neighbor state machines corresponding to the opposite-end switchboards to finish a neighbor discovery process of the opposite-end switchboards. By adopting the method and the switchboards, the neighbor switchboards of the switchboards in an FCoE network can be discovered by the switchboards in the FCoE network.
Owner:NEW H3C TECH CO LTD
Preventing Phishing Attacks
ActiveUS20130031628A1Prevent unnecessary losses causedAvoid attackMemory loss protectionError detection/correctionWeb siteWeb page
A method, system and program product for preventing phishing attacks, wherein the method comprises: acquiring links in a Web page; classifying the acquired links according link types; and determining whether a phishing attack exists according to the classified links, wherein the links are classified into two types: internal links belonging to the same domain as the address of the Web page, and external links belonging to a different domain from the address of the Web page. By carrying out the method or system according to the above one or more embodiments of the present disclosure, since it is first detected whether a Web page is a fake website of a phishing attack before displaying the reproduced Web page to the user and the user is warned upon detecting a fake website, unnecessary losses due to phishing attacks can be prevented.
Owner:AWEMANE LTD
Non-Blocking Destination-Based Routing Networks
InactiveUS20070076615A1Simple designFAC will be greatly simplifiedError preventionTransmission systemsTraffic capacityLink weight
A route computation algorithm, a load-balancing scheme inside a router for making a hop-by-hop routing network (such as the Internet) nonblocking are described in this patent. The output of the route computation algorithm includes a set of link weights that determine the paths of the hop-by-hop routing network. The route computation algorithm and the load-balancing scheme also determine the ingress and egress traffic constraints at each edge router such that as long as the traffic entering and leaving the network does not exceed the constraints, none of the internal links will ever have traversing traffic more than its link capacity. The network is thus non-blocking internally. This greatly simplifies flow admission control and allows hard QoS to be supported inside the network.
Owner:THE HONG KONG UNIV OF SCI & TECH
Network element with redundant switching matrix
InactiveUS6914879B1Less hardwareLow costError preventionTransmission systemsInternal linkComputer science
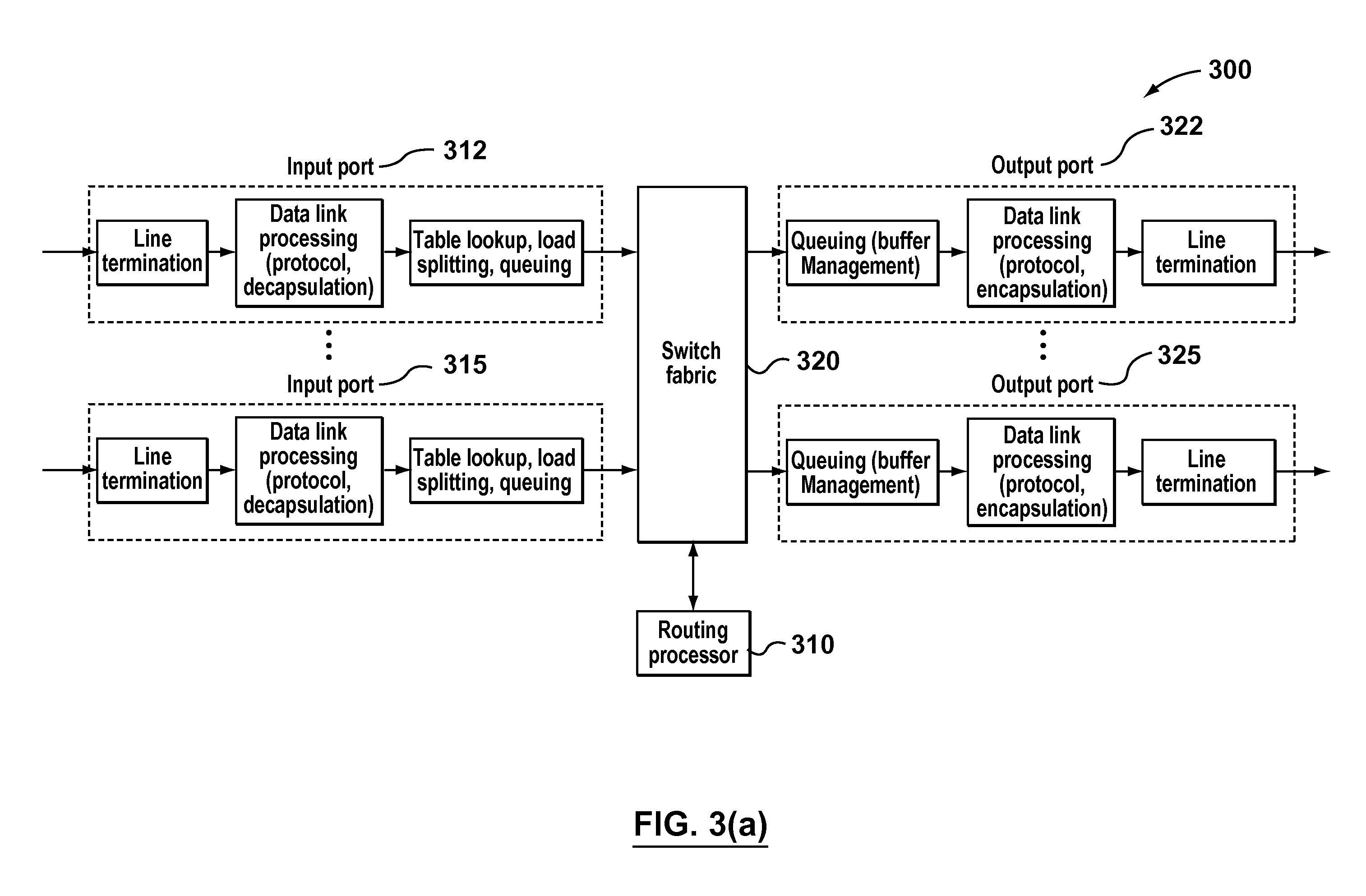
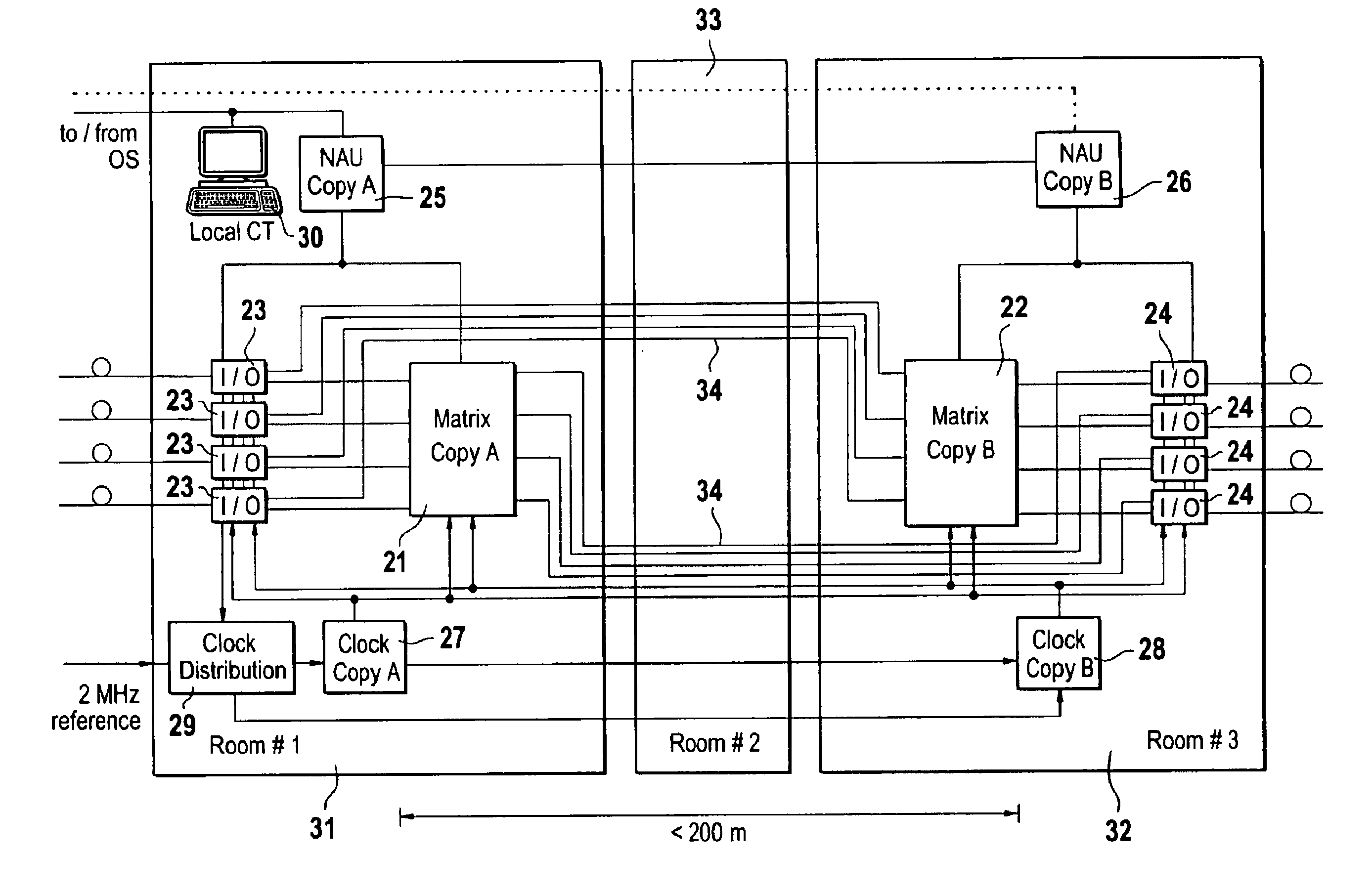
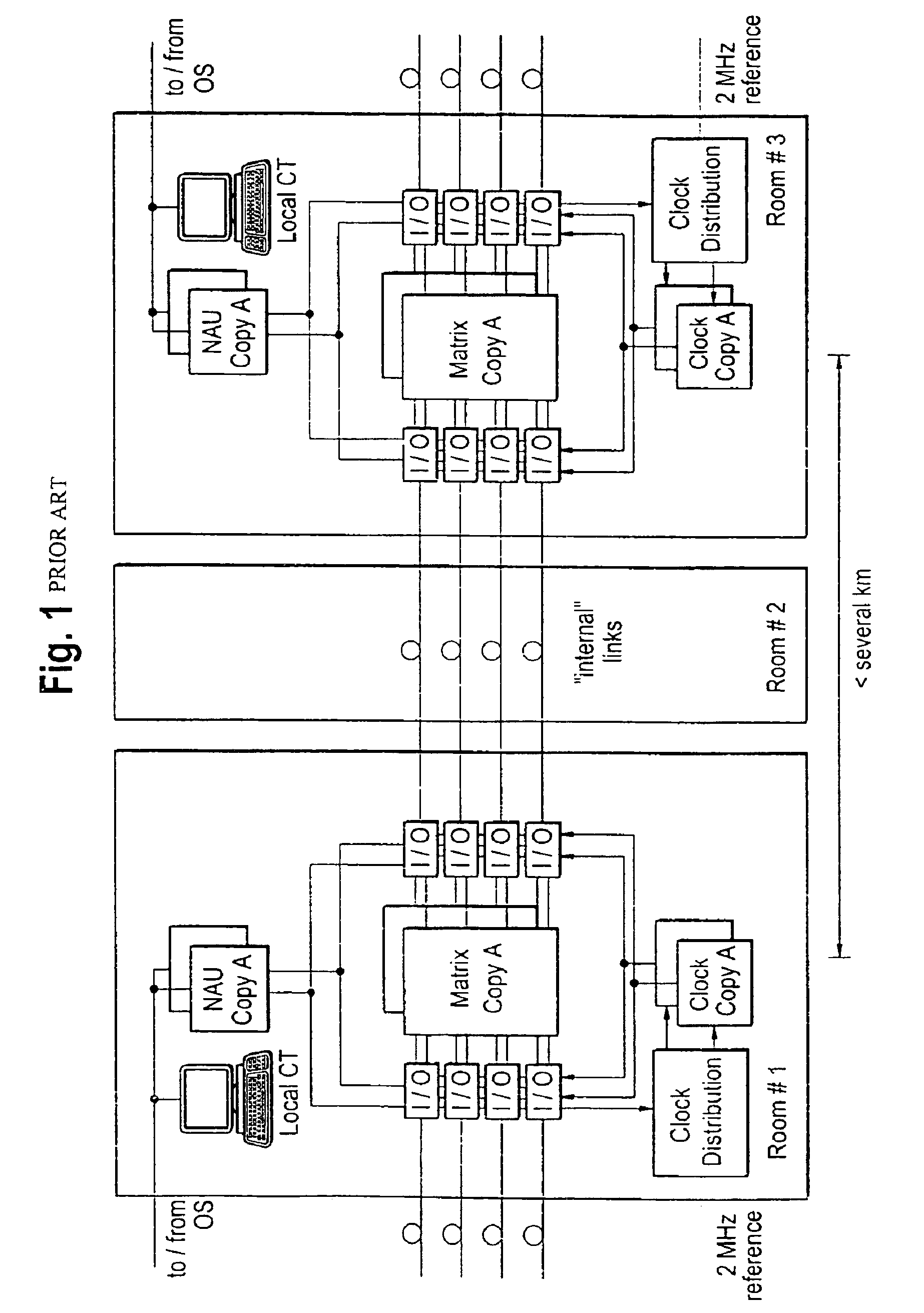
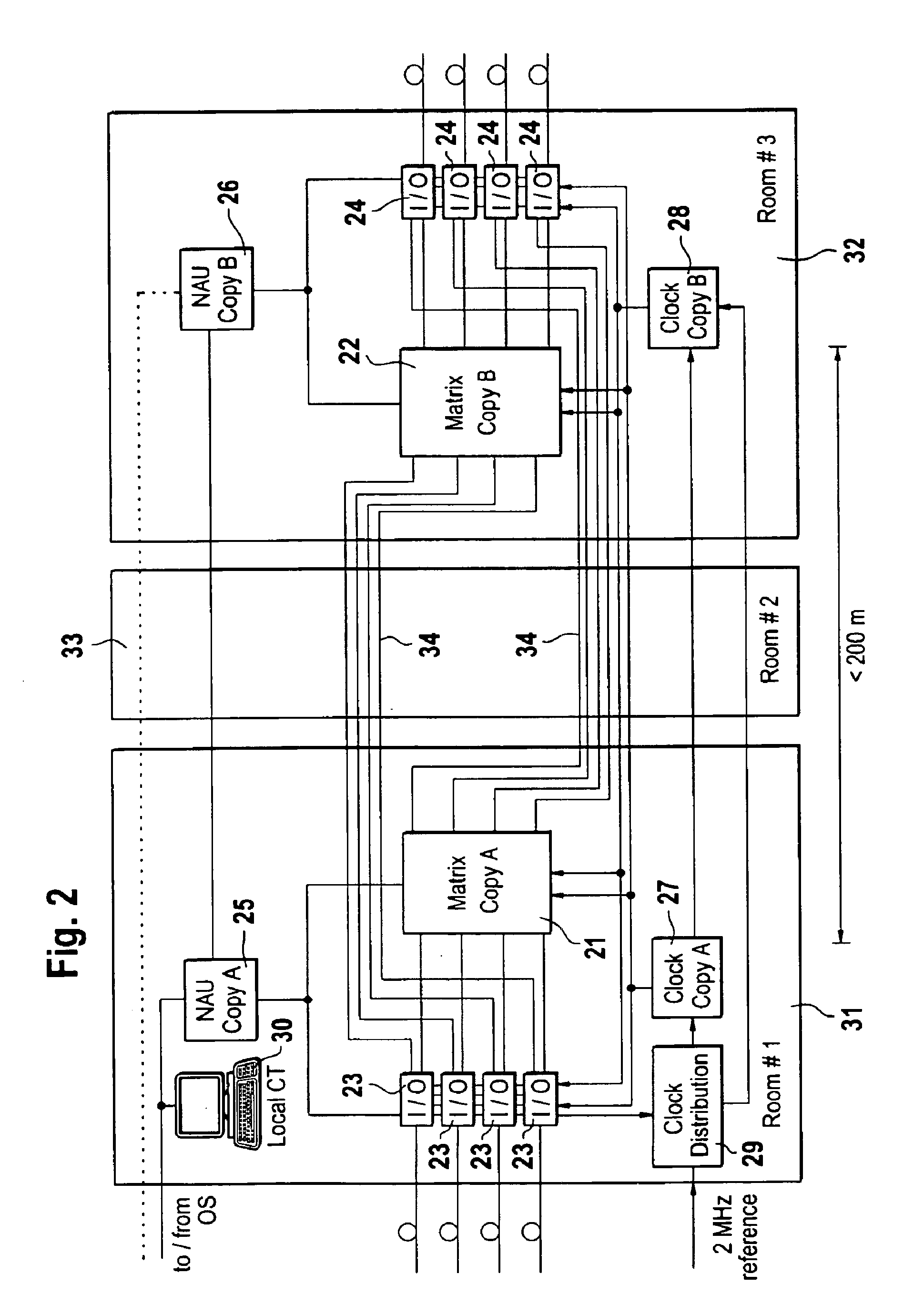
Network elements such as digital crossconnects are provided with a 1:1 redundancy of, among other things, the switching matrix in order to maintain their functionality in the event of a hardware failure. Against disasters such as fires, explosions, or floods in which all equipment in a room is destroyed, the redundancy used in prior-art network elements can afford no protection.To remedy this, the two switching matrices (21, 22), which are present anyhow, are installed in separate rooms (31, 32), i.e., a single network element is divided between two rooms. To this end, the interface modules (23, 24) are divided into two groups, and each of the groups is assigned to a respective one of the switching matrices. A respective one of the switching matrices and a respective one of the groups of interface modules are arranged in, e.g., a cabinet or rack so as to form a unit, and the units are interconnected by simple internal links (34) such that both switching matrices (21, 22) are connected to all interface modules (23, 24).
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com