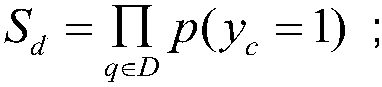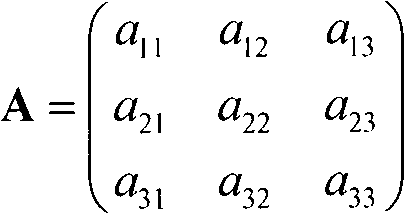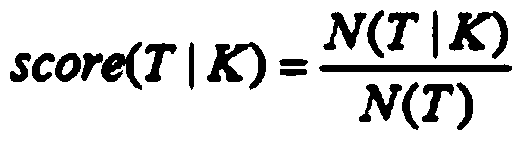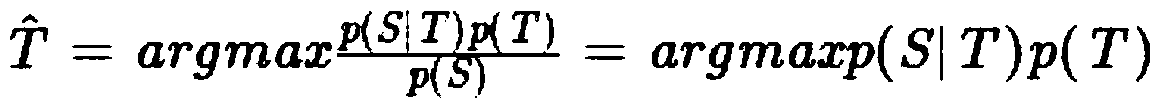Patents
Literature
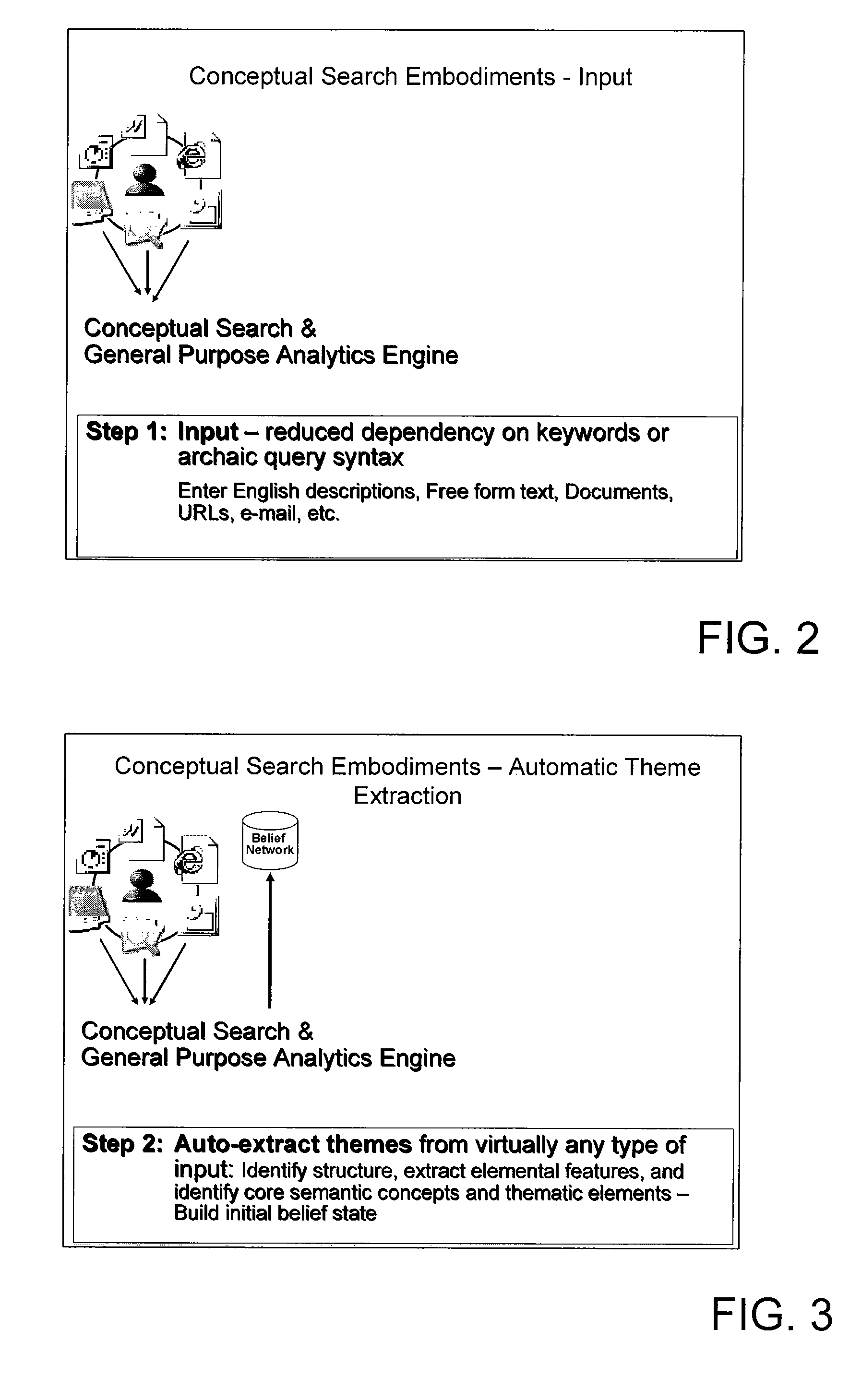
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
100 results about "Contextual Associations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In learning and memory, associations made to environmental or internal conditions during learning or memorization. In perception and communication, environmental conditions that affect such aspects as perceptual accuracy, comprehension, or meaning.
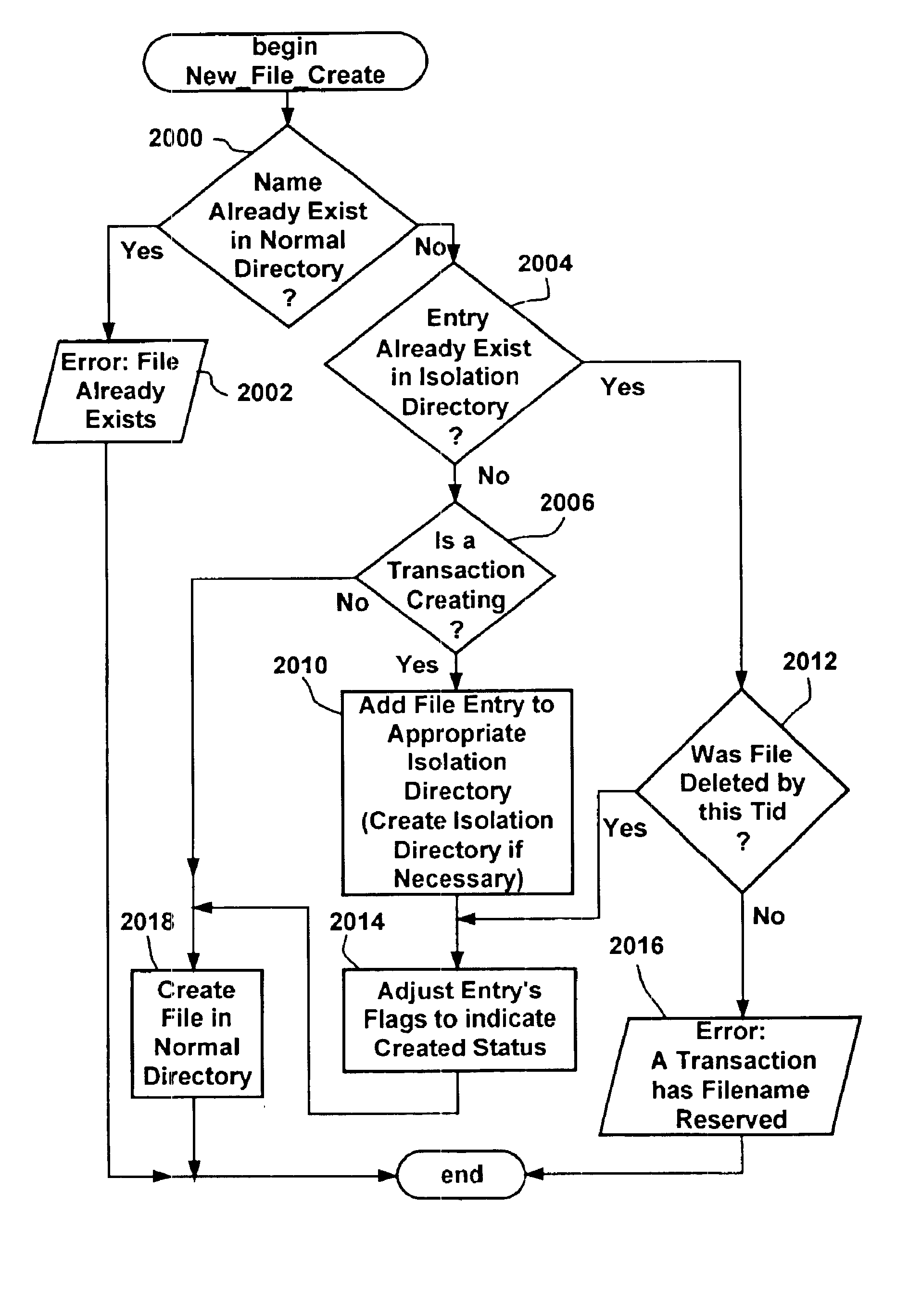
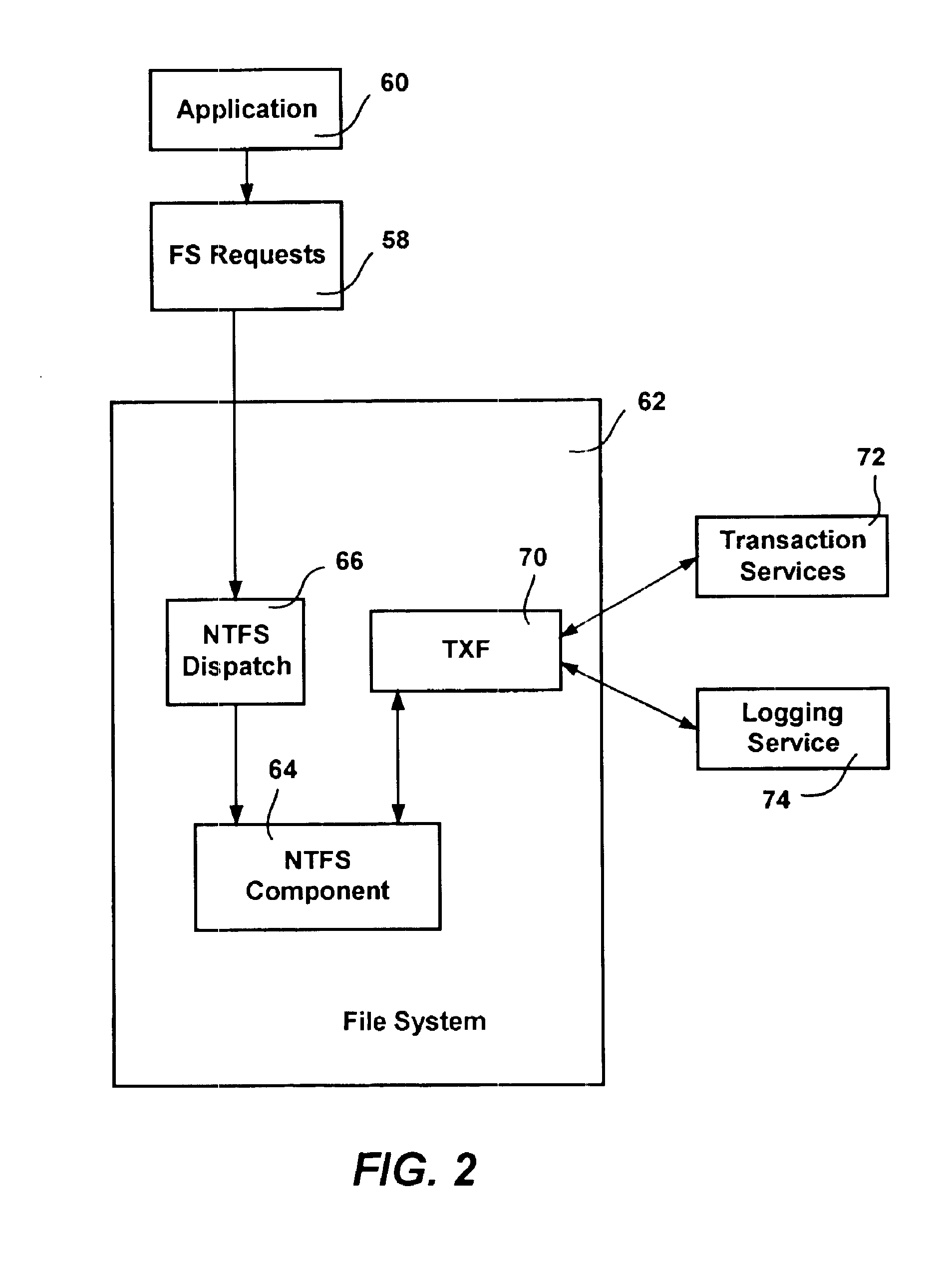
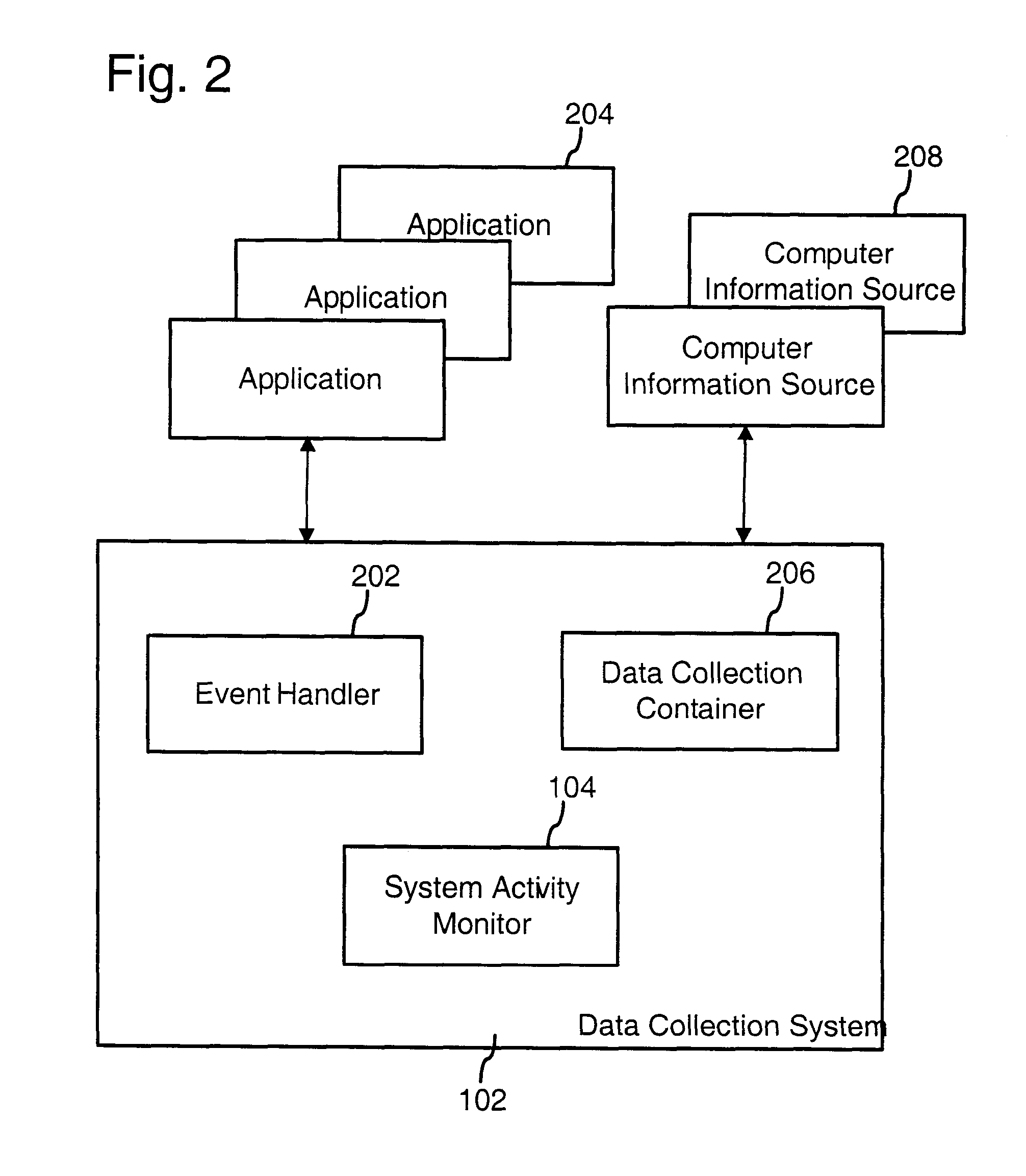
Transactional file system
InactiveUS6856993B1Easy to implementMultiple operationData processing applicationsDigital data information retrievalFile systemApplication software
A transactional file system wherein multiple file system operations may be performed as transaction. An application specifies that file system-related operations should be handled in a transaction, and is given a file handle associated with a transaction context. For file system requests associated with a transaction context, a file system component manages operations consistent with transactional behavior. The component provides data isolation by providing multiple file versions such that transactional readers do not receive changes until after the transaction commits and the reader reopens the file. The component handles namespace logging operations in a multiple-level log that facilitates logging and recovery. Page data is logged separate from the main log, with signatures establishing whether pages were fully flushed to disk. Namespace isolation via isolation directories allows a transaction to see its operational effects but not effects of other uncommitted transactions. Transactions over a network are facilitated.
Owner:MICROSOFT TECH LICENSING LLC
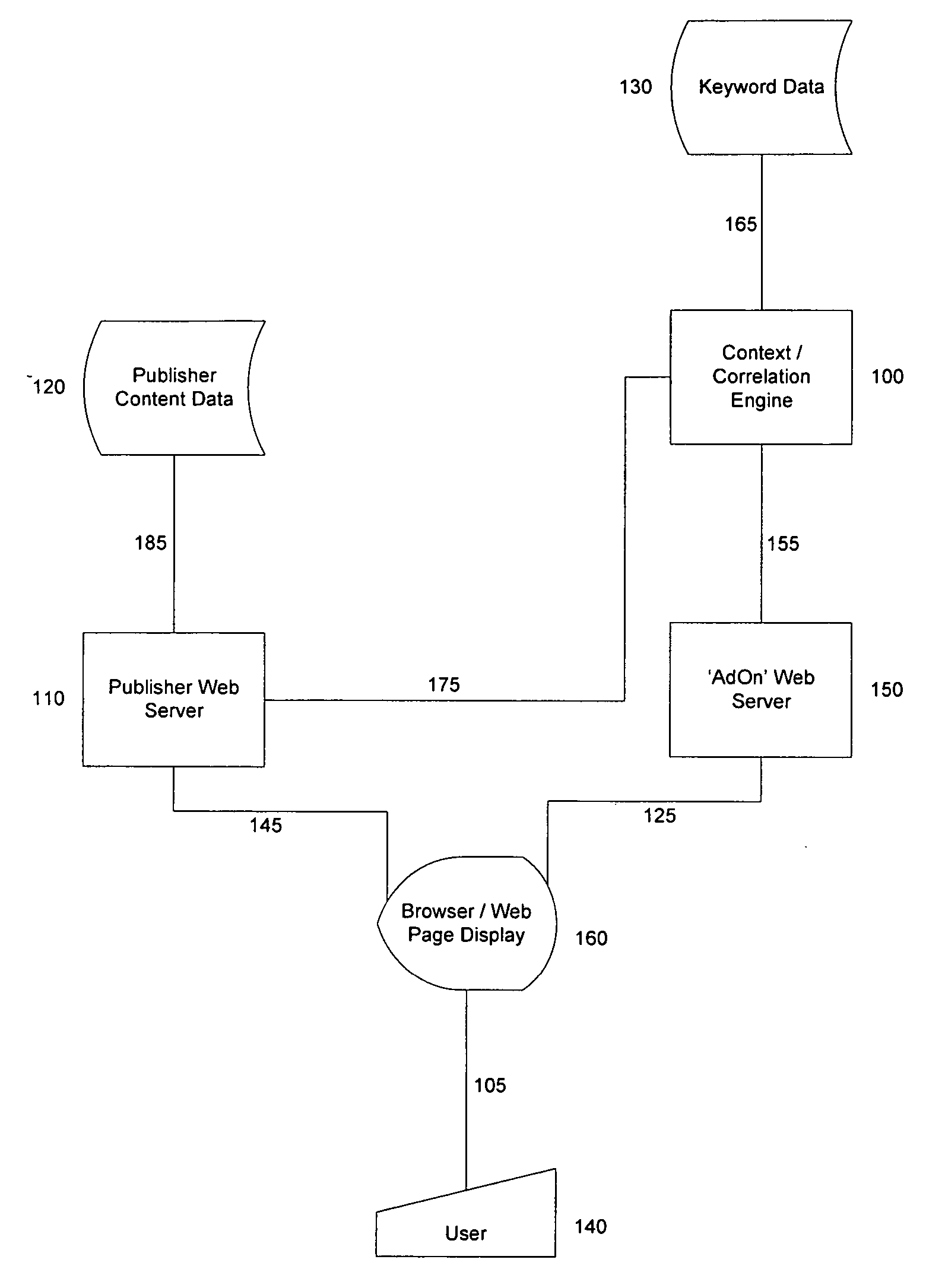
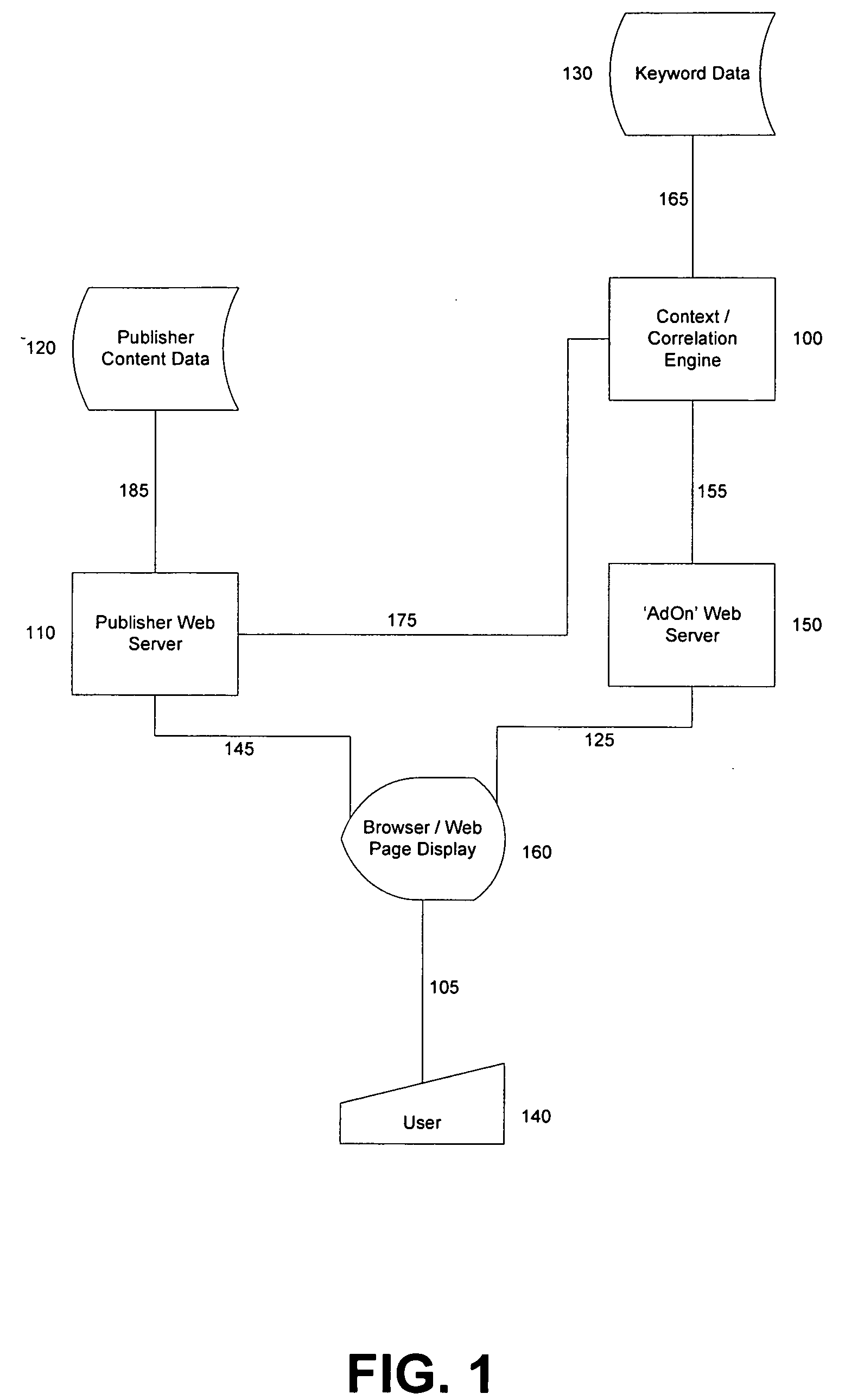
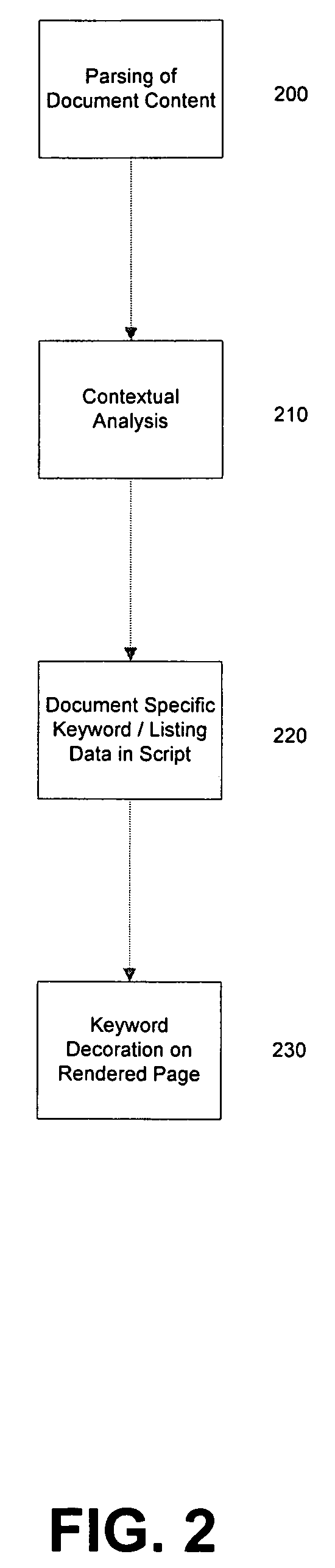
System and method for contextual correlation of web document content
InactiveUS20050262428A1Website content managementSpecial data processing applicationsPaper documentDocument preparation
An exemplary system and method for contextually correlating web page document text is disclosed as comprising inter alia: a context engine for analyzing at least a portion of web page document content in order to identify textual components therein as correlation candidates; and a correlation engine for marking-up or otherwise identifying textual components in association with related keywords and / or link destinations. Disclosed features and specifications may be variously controlled, adapted or otherwise optionally modified to improve correlation and / or embedded markup of web page document content for any application or operating environment. Exemplary embodiments of the present invention generally provide enhanced online searching and advertising capabilities.
Owner:MYGEEK COM
Method and apparatus for semiotic correlation
InactiveUS7912701B1Increase speedEasy to useNatural language analysisSemantic analysisComputerized systemDocument preparation
A method for a computer system includes receiving an input source comprising a plurality of sentences, determining a set of semiotic relationships from the plurality of sentences, performing a contextual correlation in response to the set of semiotic relationships and in response to an ideas index to determine a reduced set of semiotic relationships from the set of semiotic relationships, omparing the reduced set of semiotic relationships to each of a plurality of semiotic relationships associated with a set of documents to determine comparison values, determining a reduced set of documents from the set of documents in response to the comparison values, and outputting portions of the reduced set of documents to a user.
Owner:VIRTUALSYNAPTICS INC
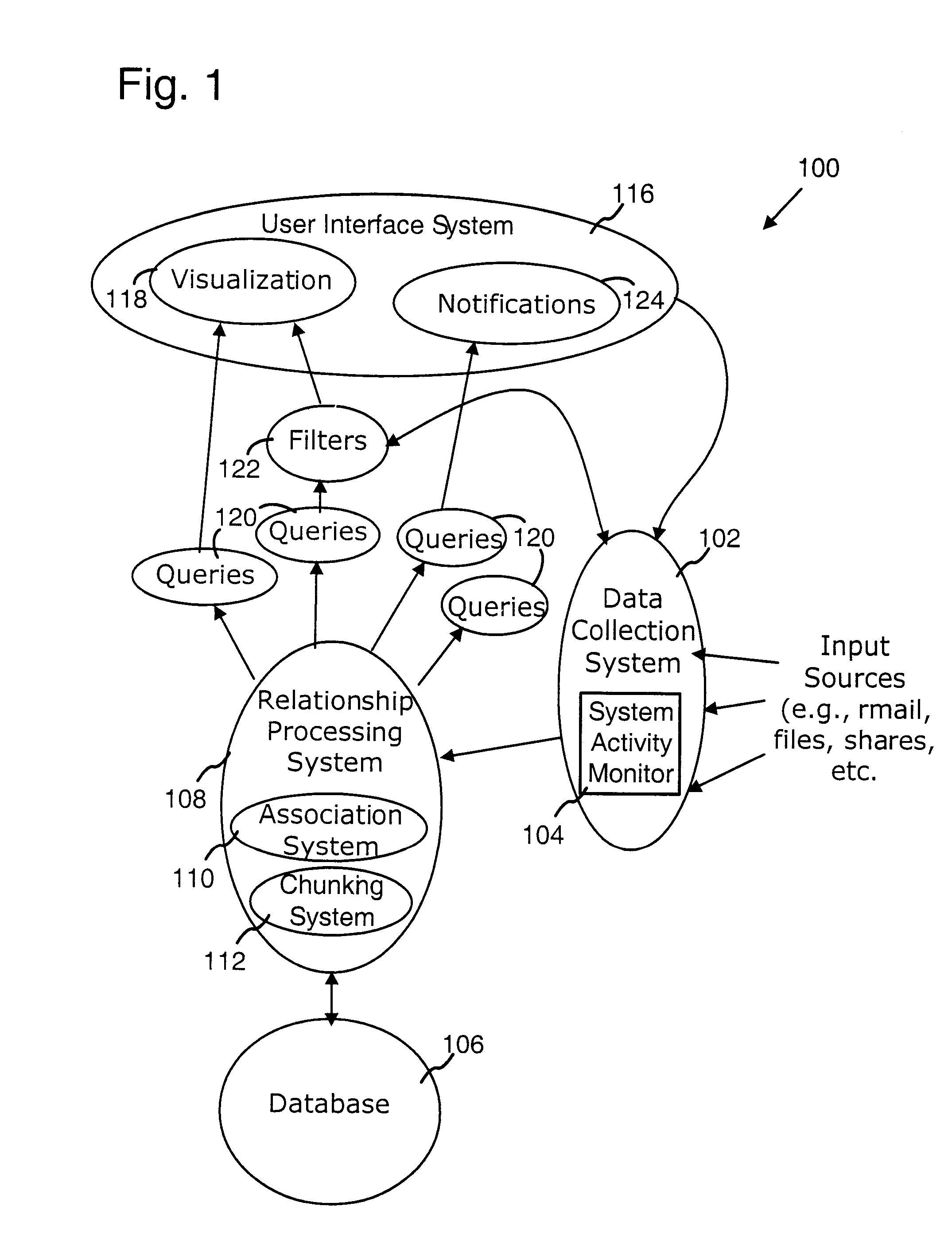
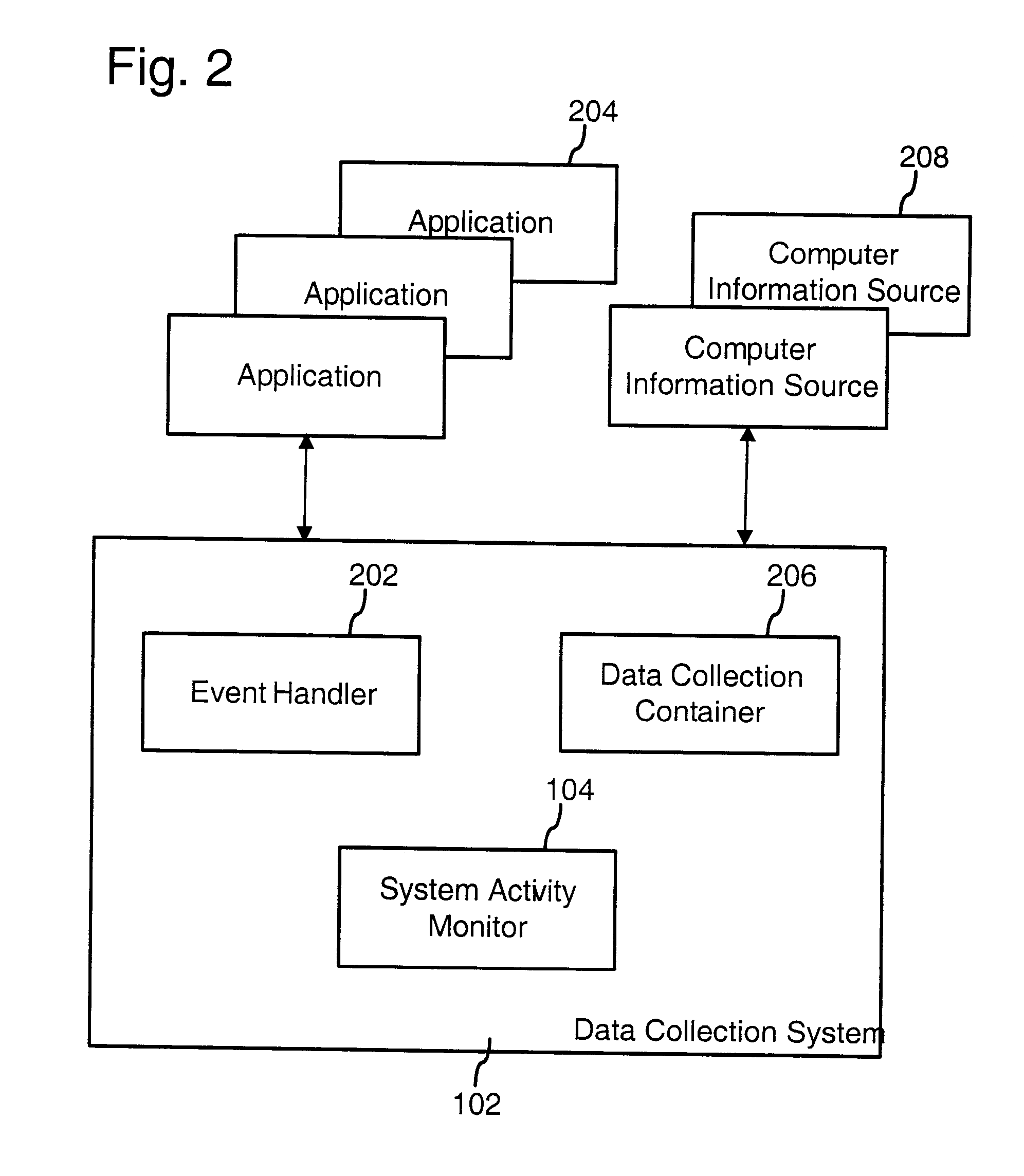
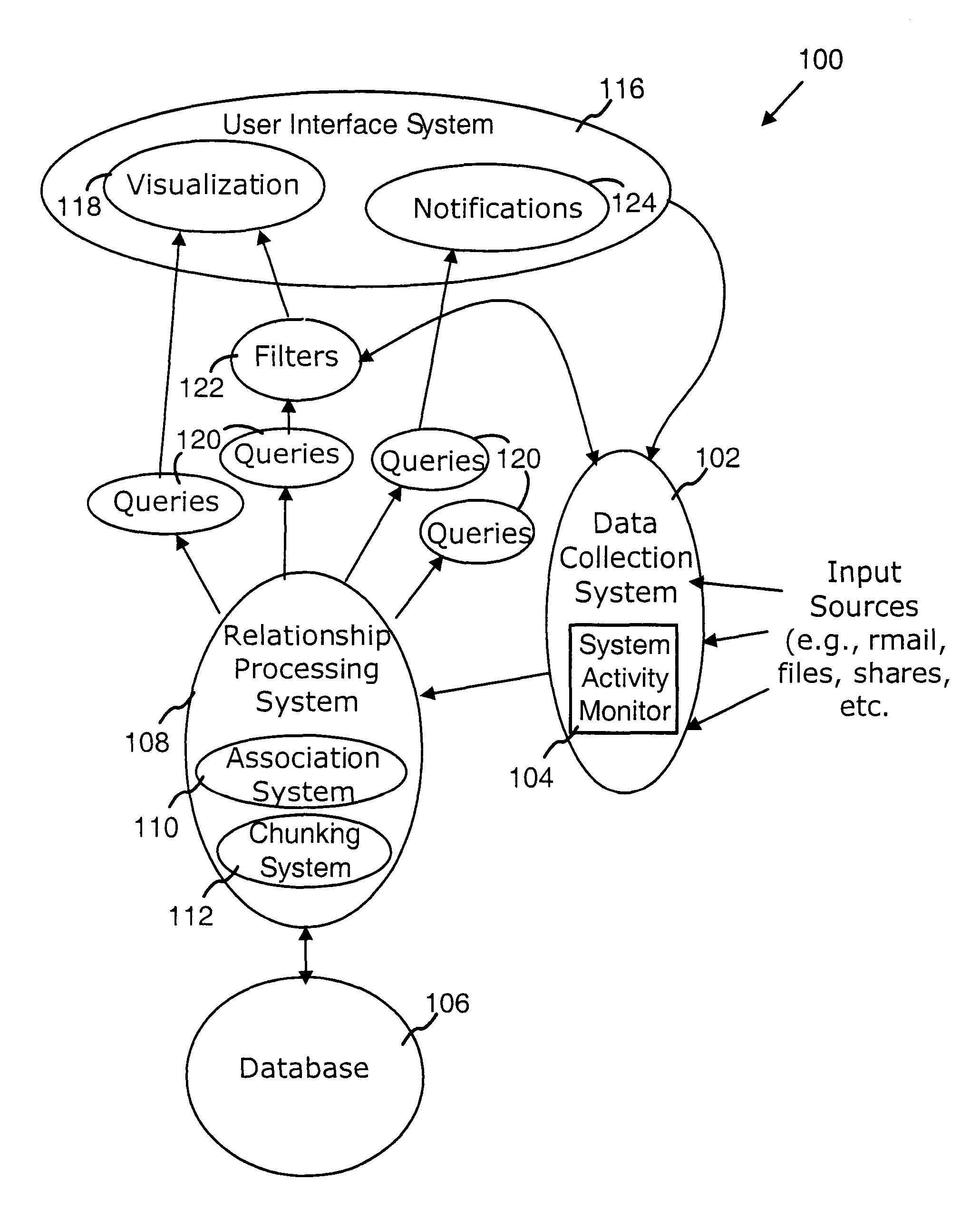
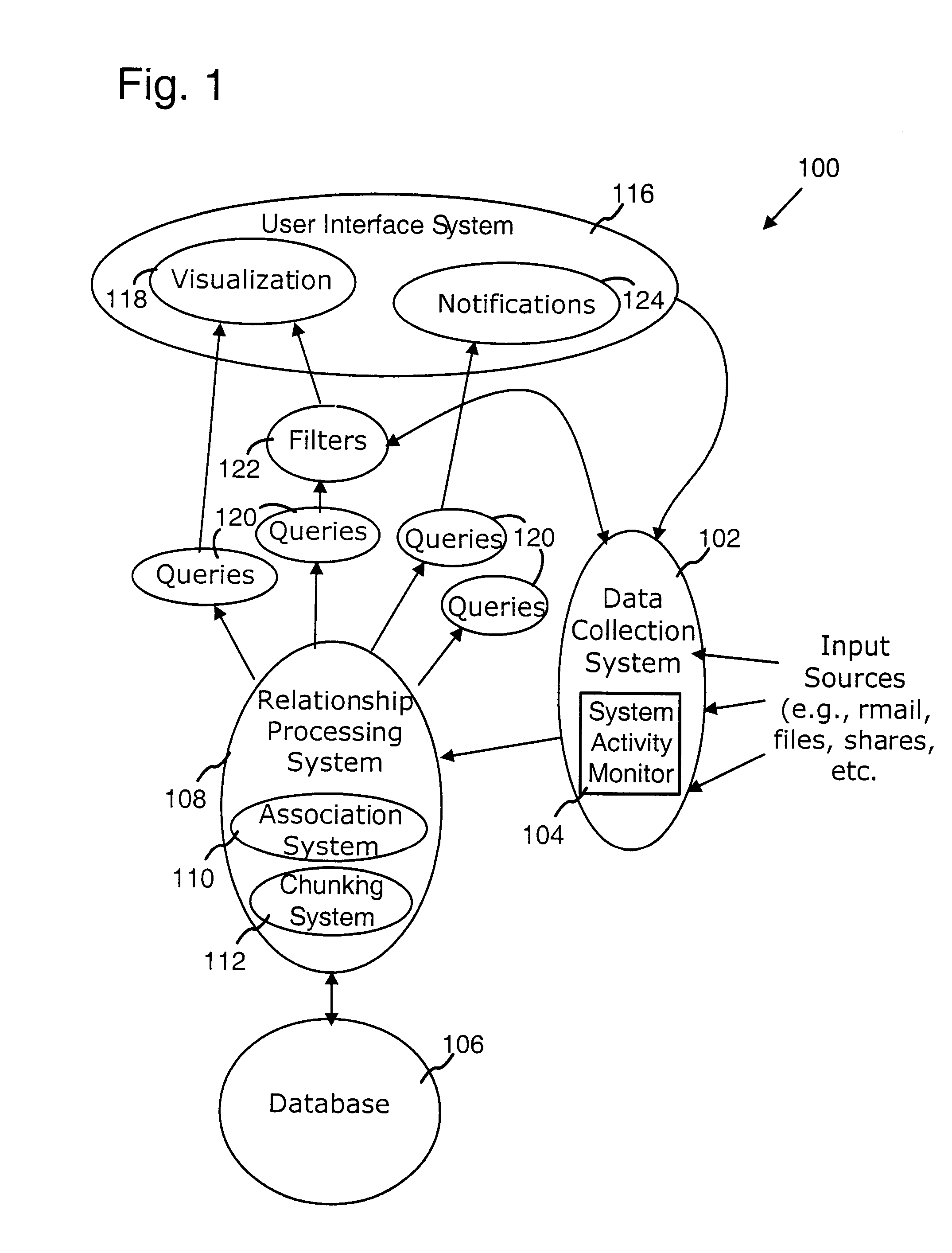
Computer system architecture for automatic context associations
InactiveUS20080222170A1Digital data processing detailsOffice automationComputer usersBehavioral analytics
A computer system models human memory by deriving associations between objects, events, and the context of the computer user or users. These associations can be dynamically generated, changing depending on the behavior of the user and context. Examples of areas in which this system can be used include time management (e.g., a calendar that presents time-based groupings of objects), people management (e.g., use analysis of user communications to rank importance of people to the user, groupings, and associations between people / groups and other objects such as documents, email), and general computer management (e.g., use analysis of user behavior to identify important objects and objects that are related to a current focus and context of the computer user).
Owner:MICROSOFT TECH LICENSING LLC
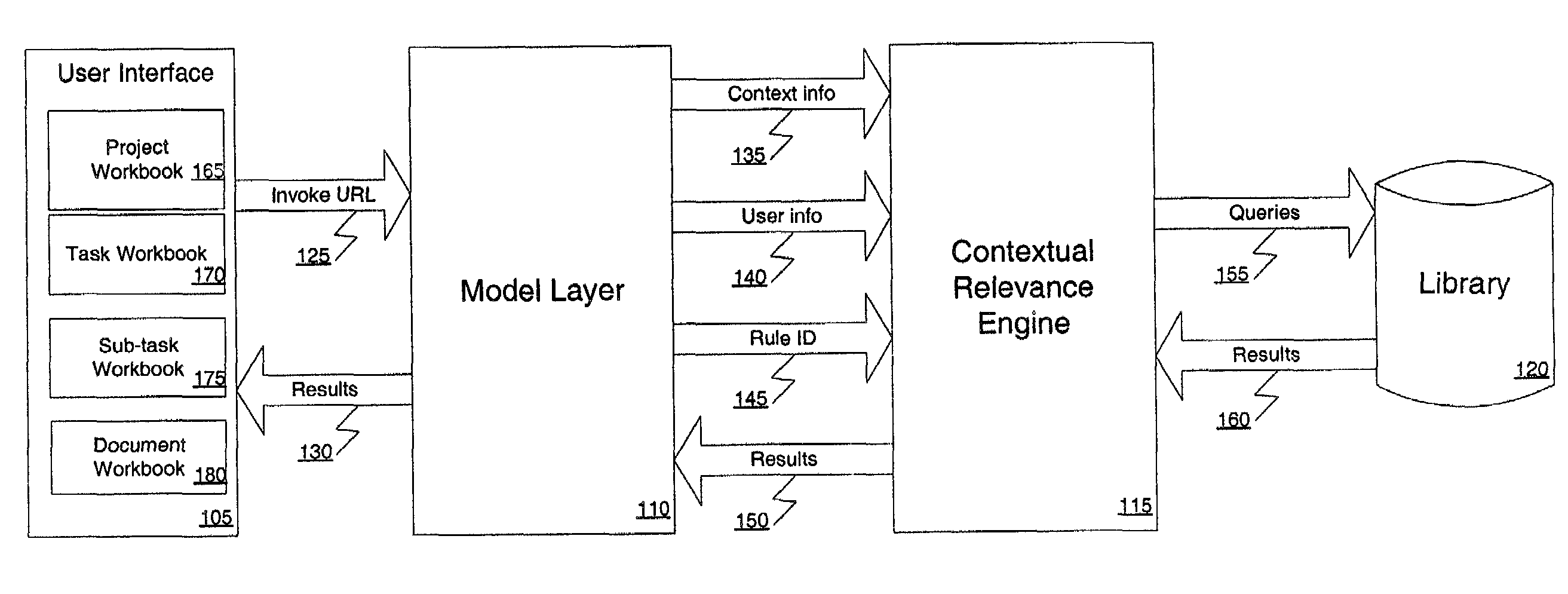
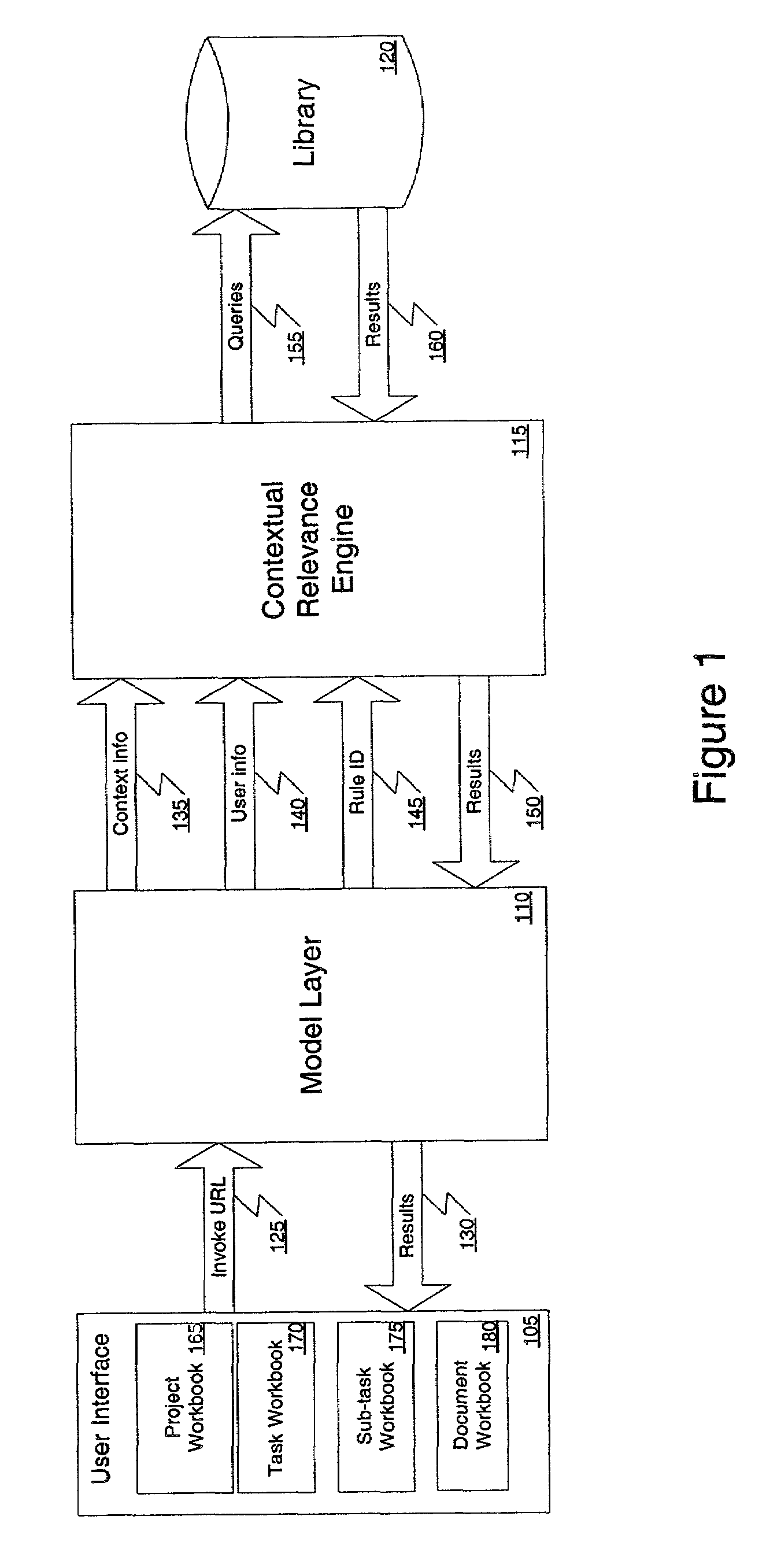
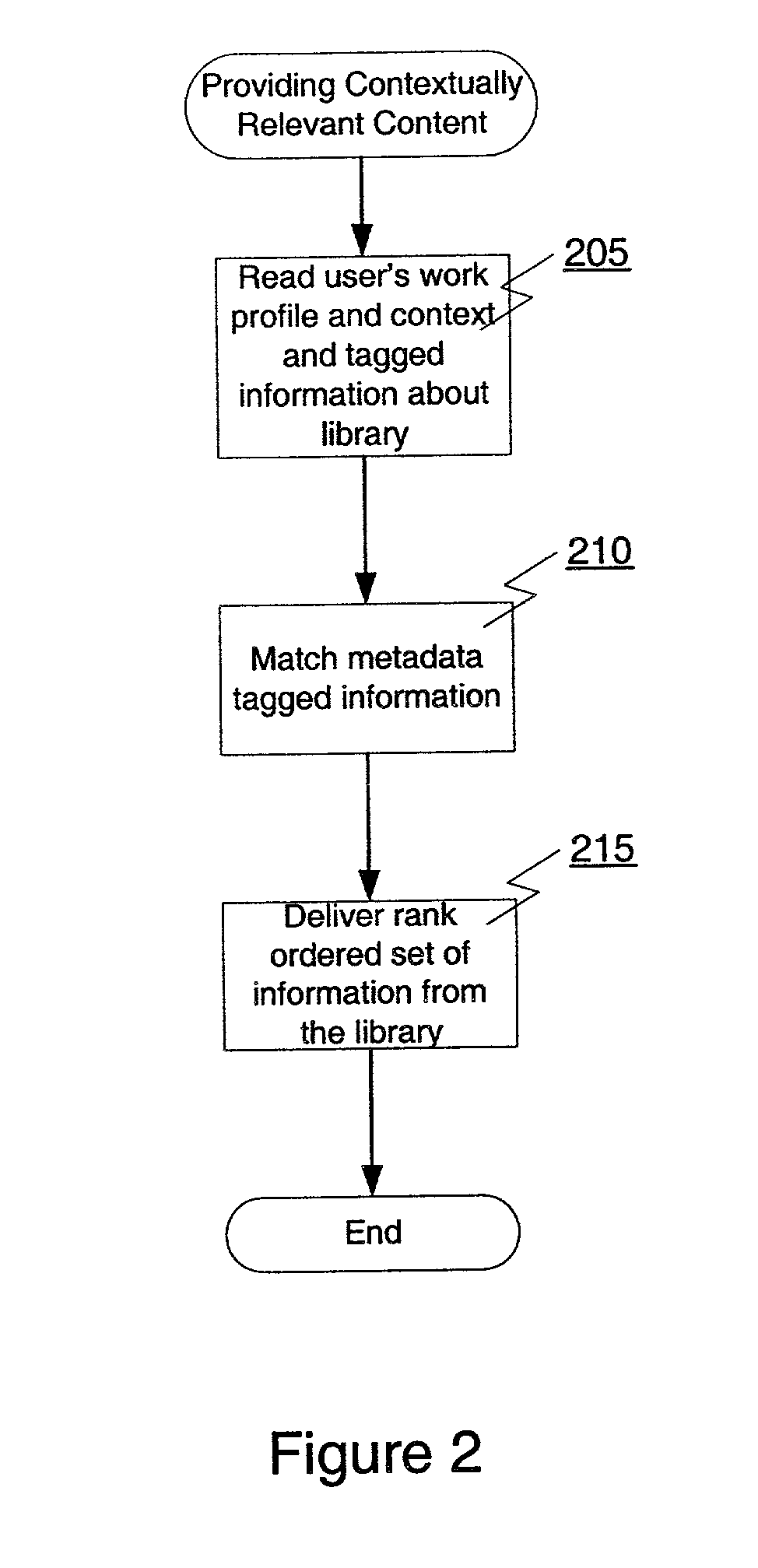
Contextual relevance engine and knowledge delivery system
ActiveUS7139757B1Metadata text retrievalData processing applicationsInformation repositoryLibrary science
A method and apparatus are described for providing a user with contextually relevant content from a library of information. According to one embodiment of the present invention, metadata tagged information about a user's work profile and working context, and content within a library of information are read. The metadata tagged information about content within the library of information to metadata tagged information about one or more of the user's work profile, the user's working context, or other content within the library of information is matched using one or more programmable rules. A rank ordered set of the most contextually relevant content from the library of information is then delivered to the user based on the matching of the metadata tagged information.
Owner:EMMPERATIVE INC +1
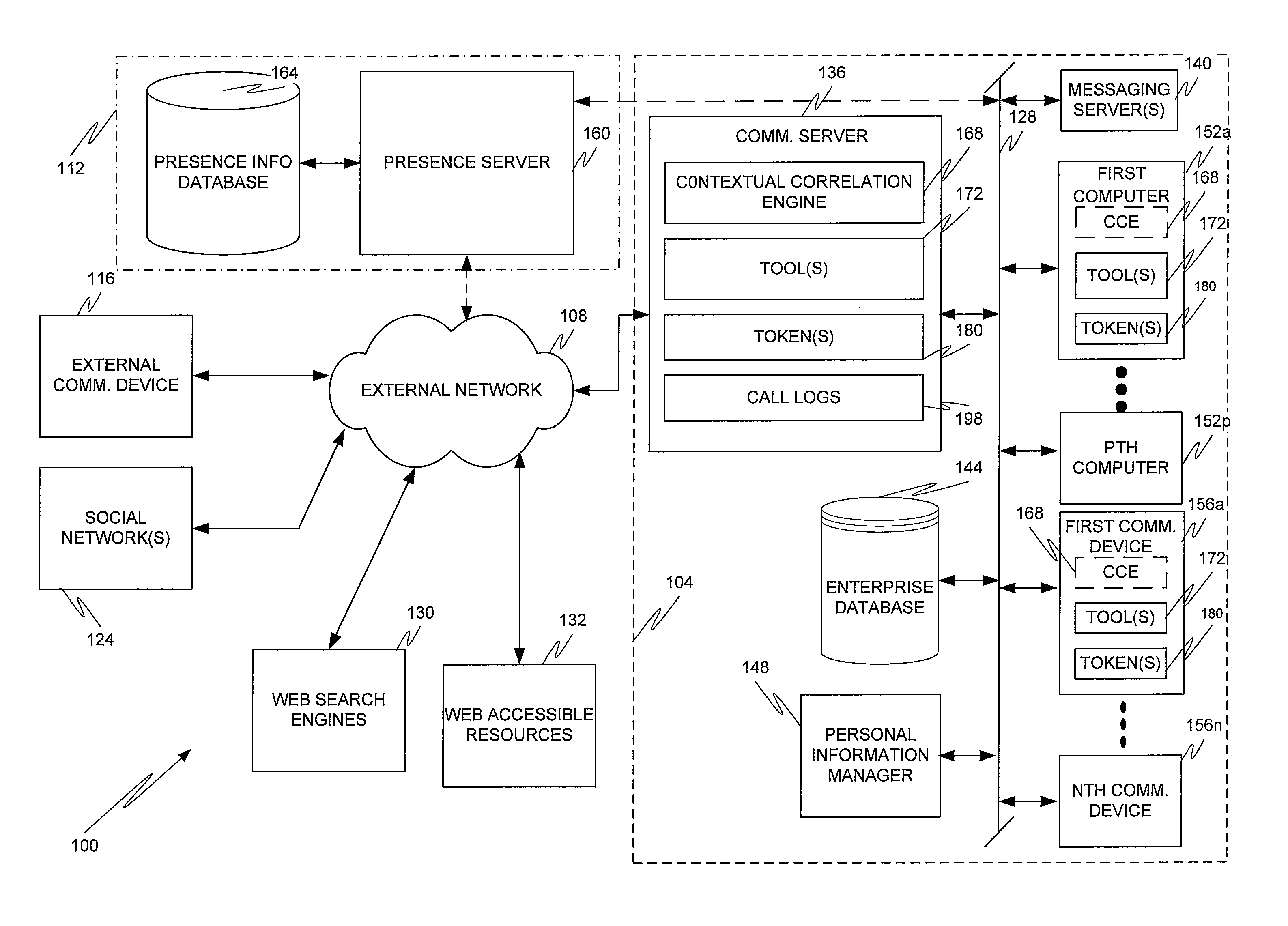
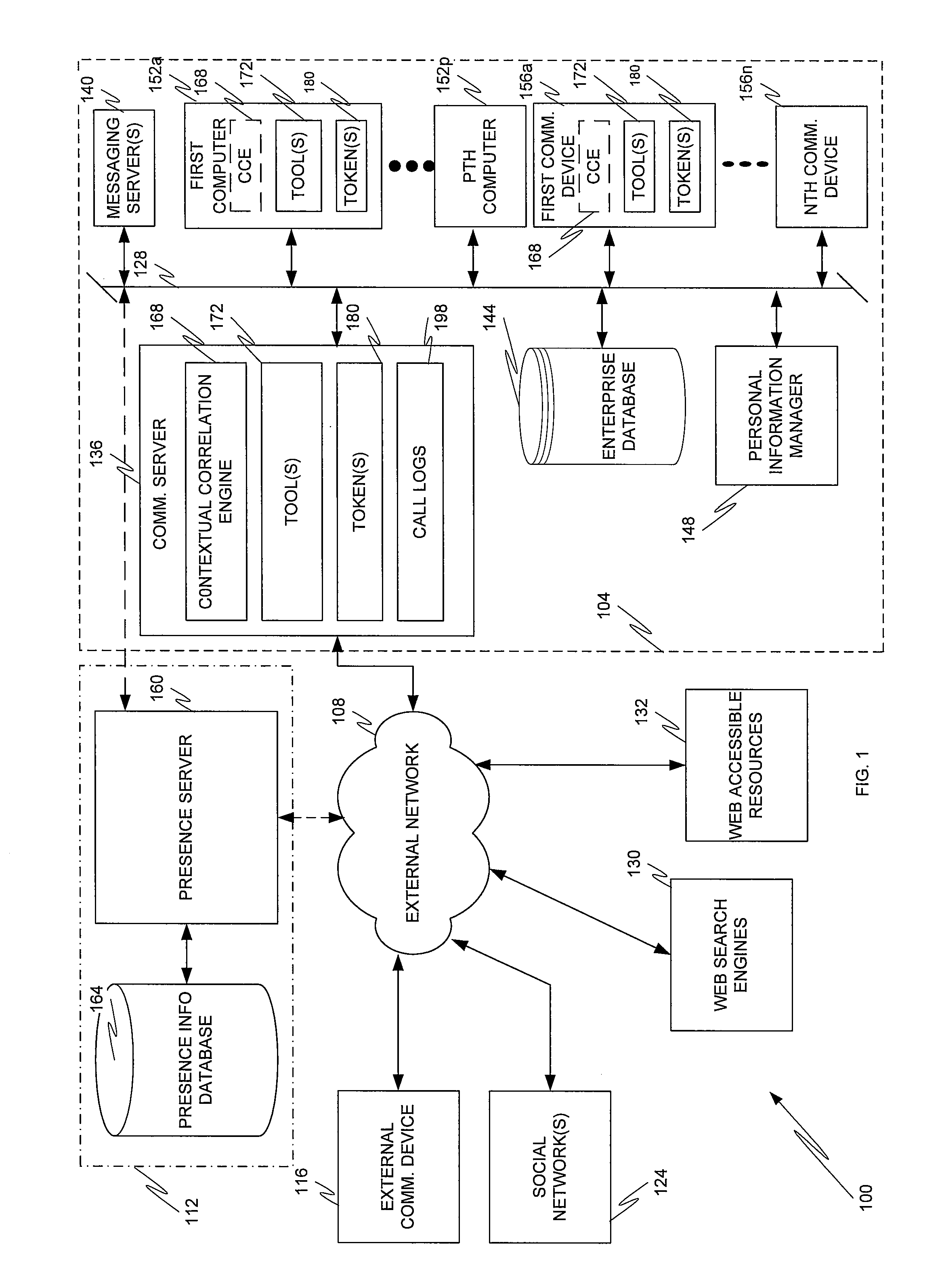
Contextual correlation engine
InactiveUS20110209159A1Quickly and conveniently locate and launchImprove abilitiesMetadata text retrievalDigital data processing detailsCommunications systemApplication software
Embodiments of the present invention are directed to a communication system that provides various automated operations, including linking applications and metadata across computational devices, using a stimulus to automatically find and launch associative and / or contextual materials and / or information required to conduct a work session without manually having to locate and launch each of these materials and / or information, and, by monitoring user behavior, creating and maintaining tokens defining the state of an instance of a workflow for later workflow resumption.
Owner:AVAYA INC
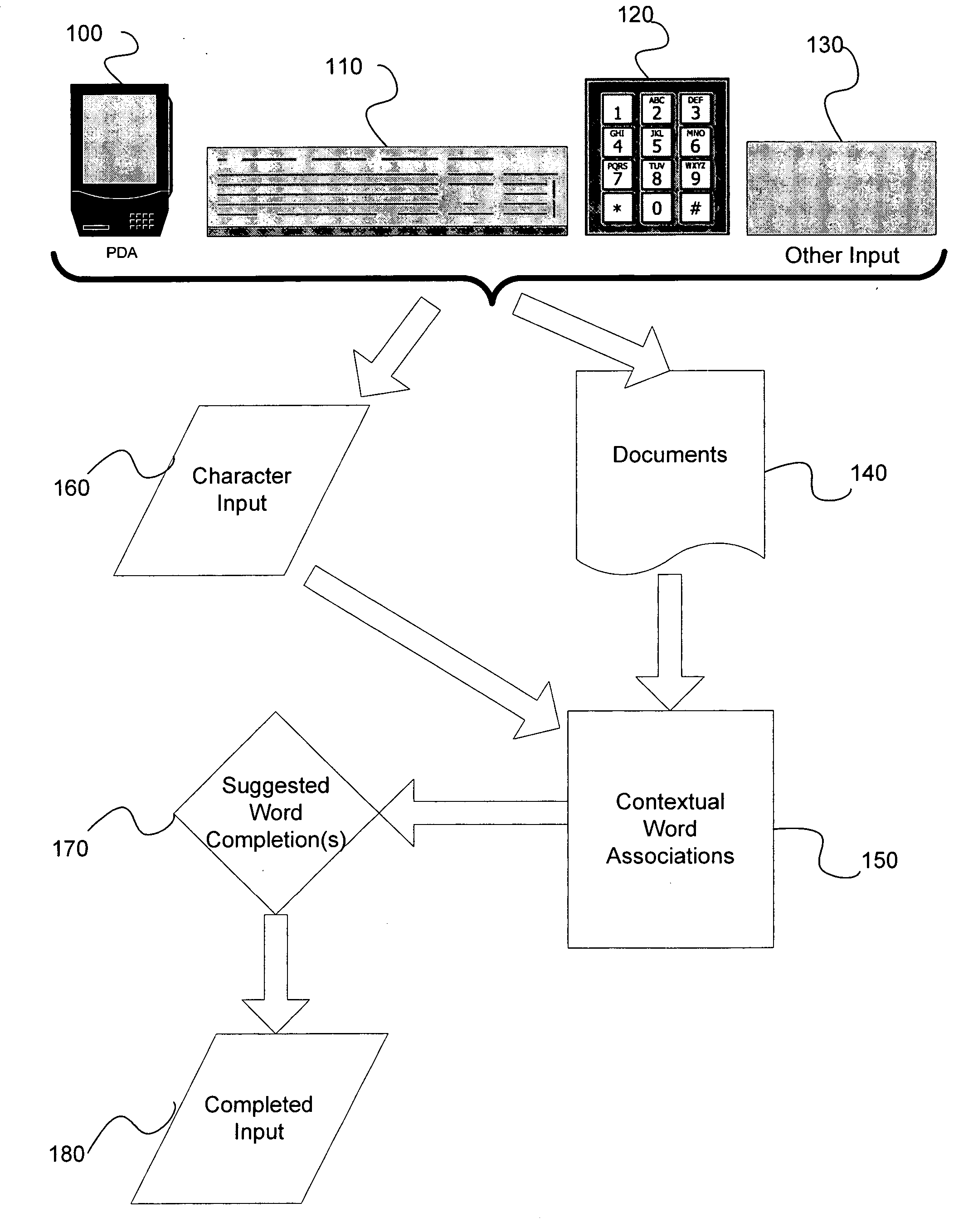
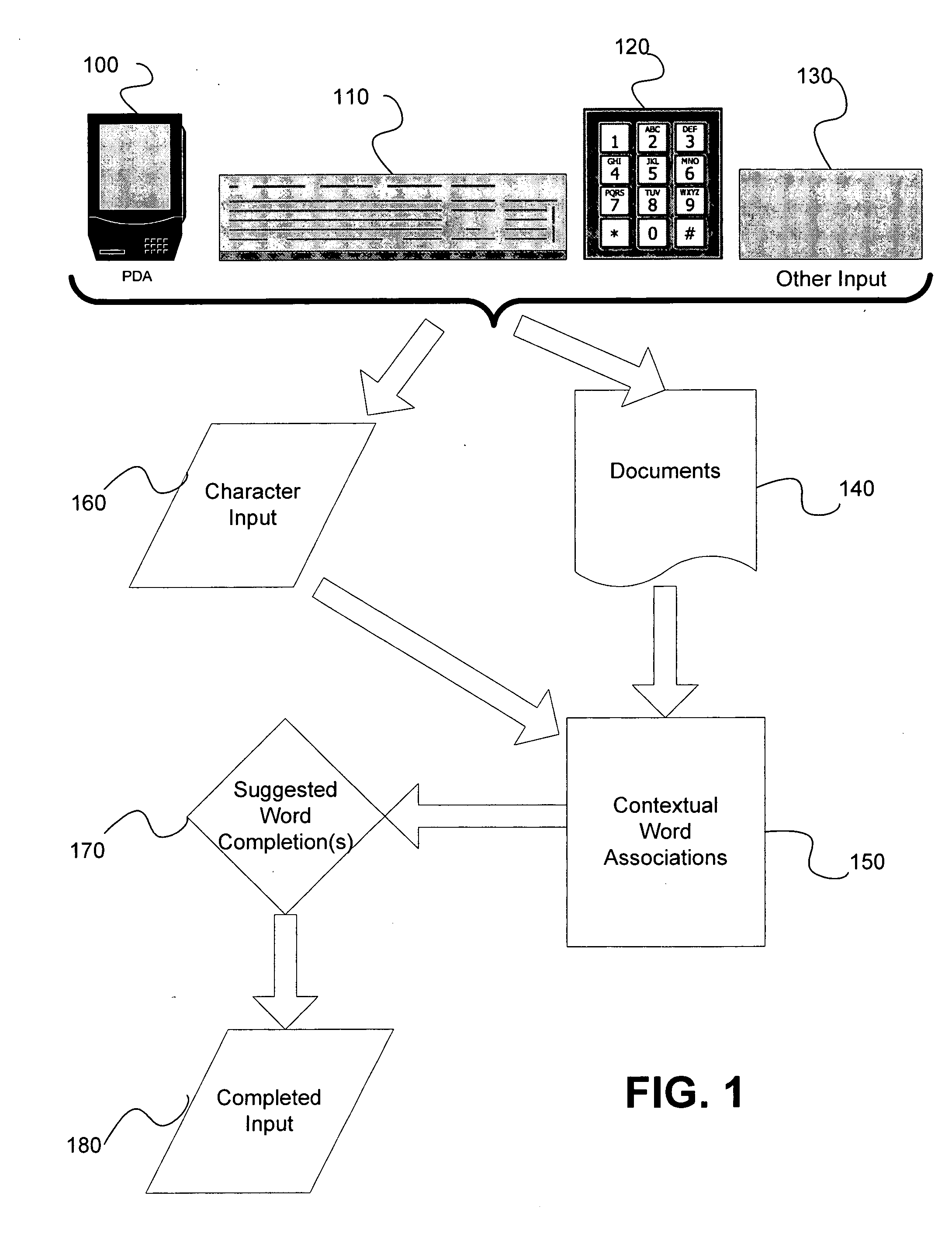
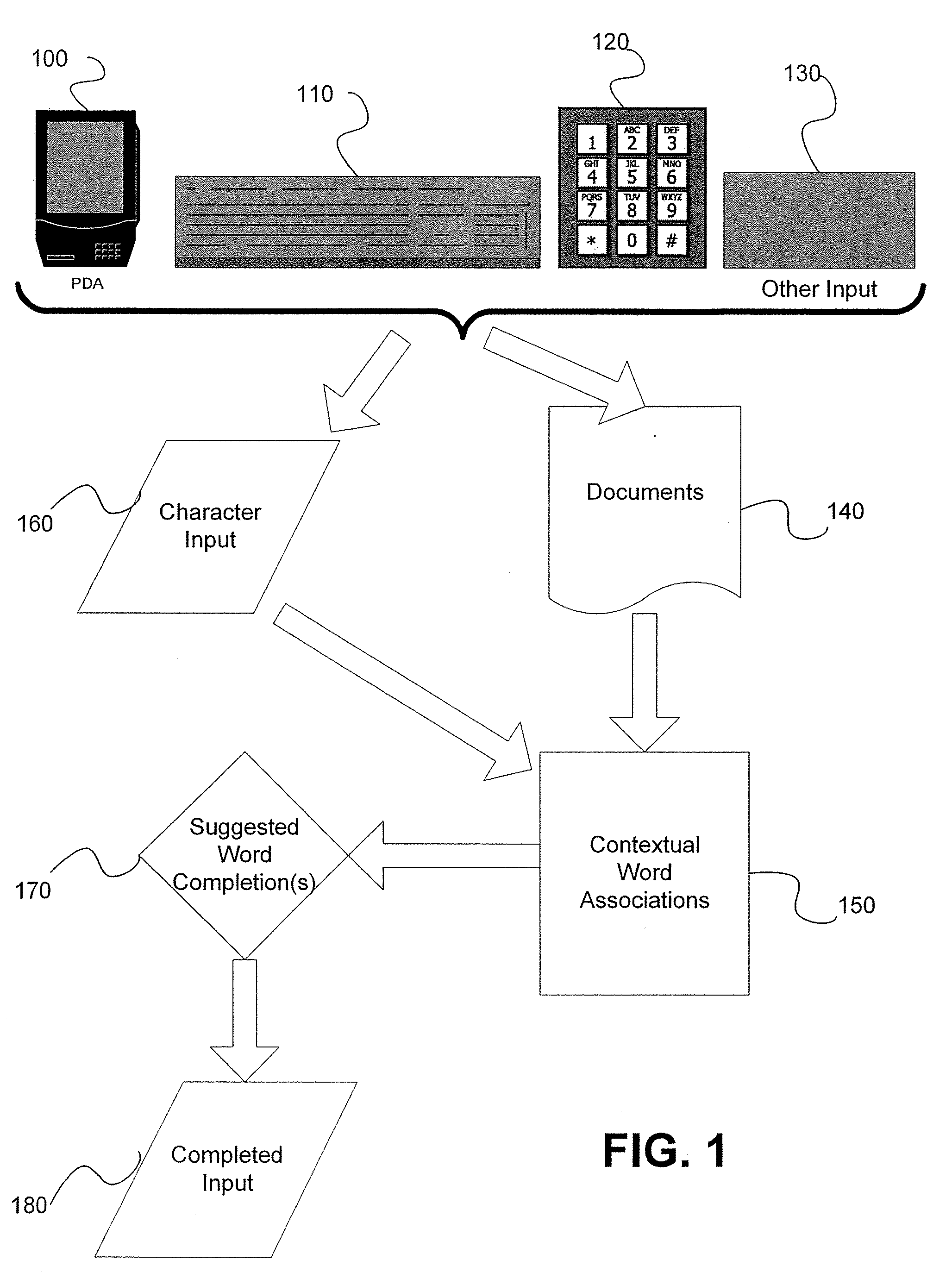
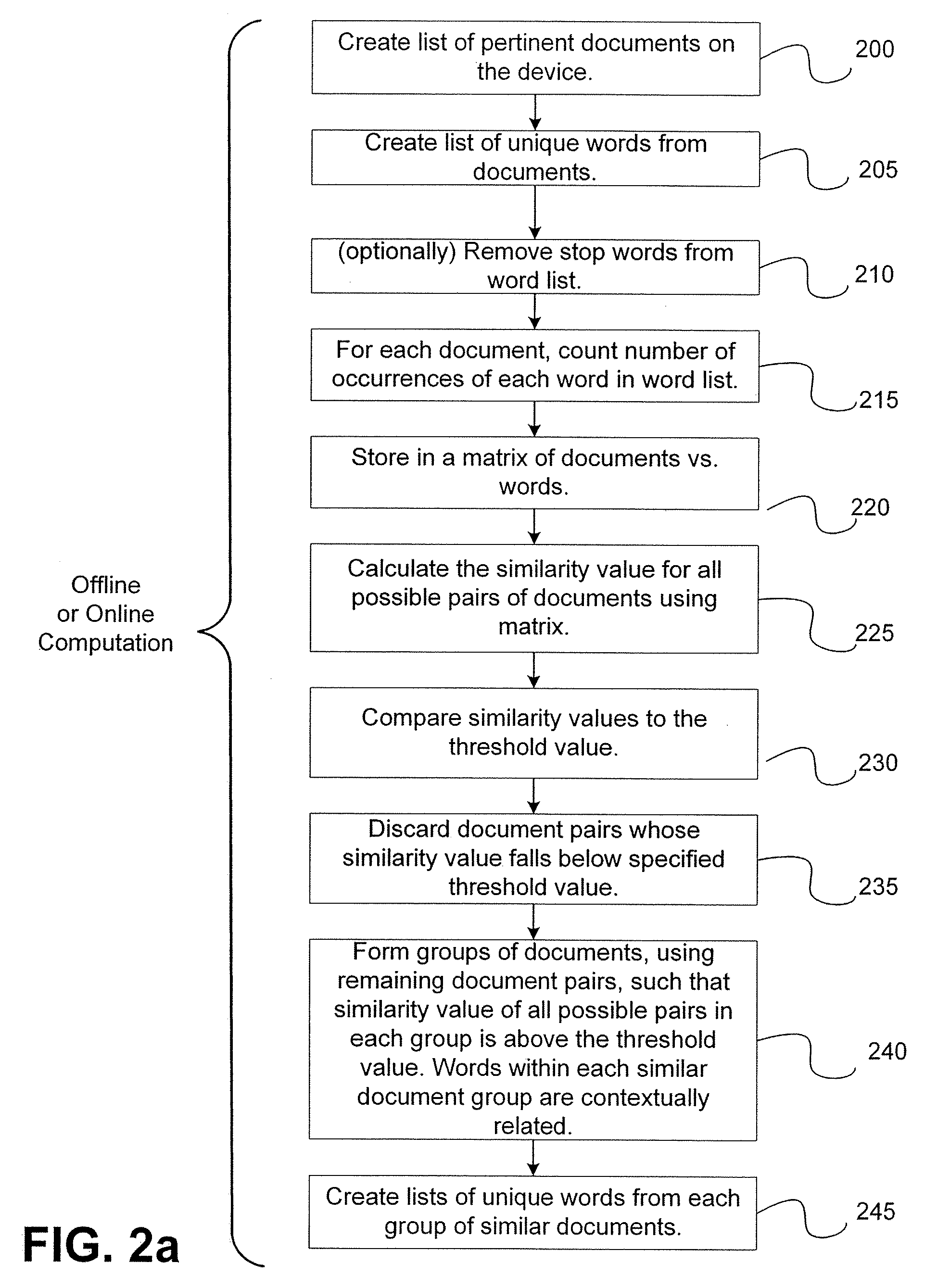
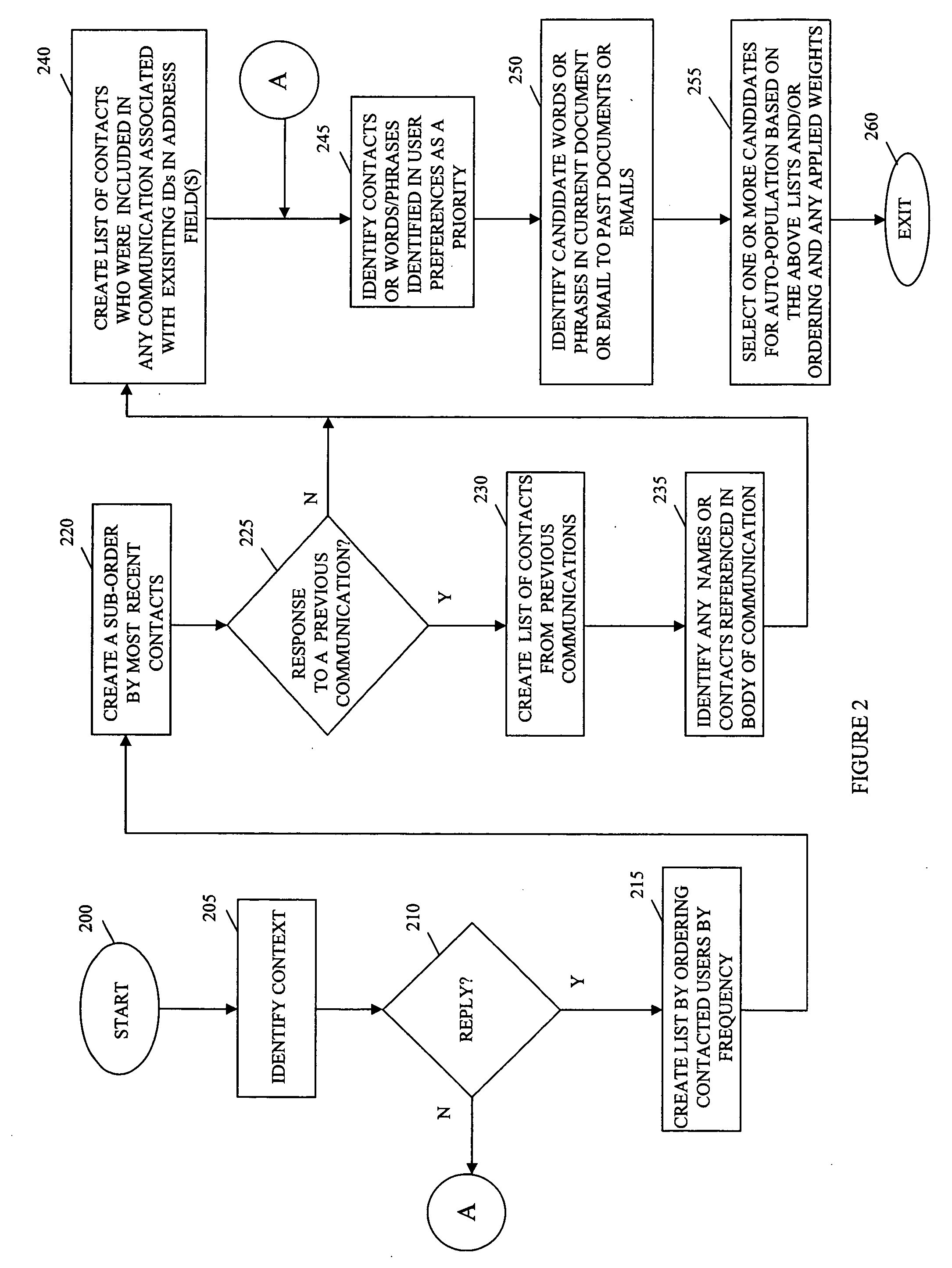
Automatic dynamic contextual data entry completion system
InactiveUS20060167872A1Room for improvementUser is requiredDigital data processing detailsNatural language data processingCo-occurrencePaper document
A method, performed in a character entry system, for interrelating character strings so that incomplete input character strings can be completed by a selection of a presented character string involves computing contextual associations between multiple character strings based upon co-occurrence of character strings relative to each other in documents present in the character entry system, in response to inputting of a specified threshold of individual characters, identifying at least one selectable character string from among the computed contextual associations that can compete the incomplete input character string in context; and providing the identified at least one selectable character string to a user for selection.
Owner:MOUNTECH IP LLC
Generating next user prompts in an intelligent online personal assistant multi-turn dialog
InactiveUS20180052885A1Improve identityDigital data information retrievalSemantic analysisDialog systemUser input
Systems and methods for generating prompts for further data from a user in a multi-turn interactive dialog. Embodiments improve searches for the most relevant items available for purchase in an electronic marketplace via a processed sequence of user inputs and machine-generated prompts. Question type prompts, validating statement type prompts, and recommendation type prompts may be selectively generated based on whether a user query has been sufficiently specified, user intent is ambiguous, or a search mission has changed. Detection of a new dominant object denotes search mission change. Contextual associations between prompts and user replies are maintained, but a search mission change results in previous context data being disregarded. Prompts can be directed to unspecified knowledge graph dimensions based on data element association strength values, relative data element positions and depths in the knowledge graph, and generated following a predetermined order of data element knowledge graph dimension types.
Owner:EBAY INC
Automatic dynamic contextual data entry completion system
InactiveUS20060217953A1Natural language data processingSpecial data processing applicationsPaper documentContext data
Owner:MOUNTECH IP LLC
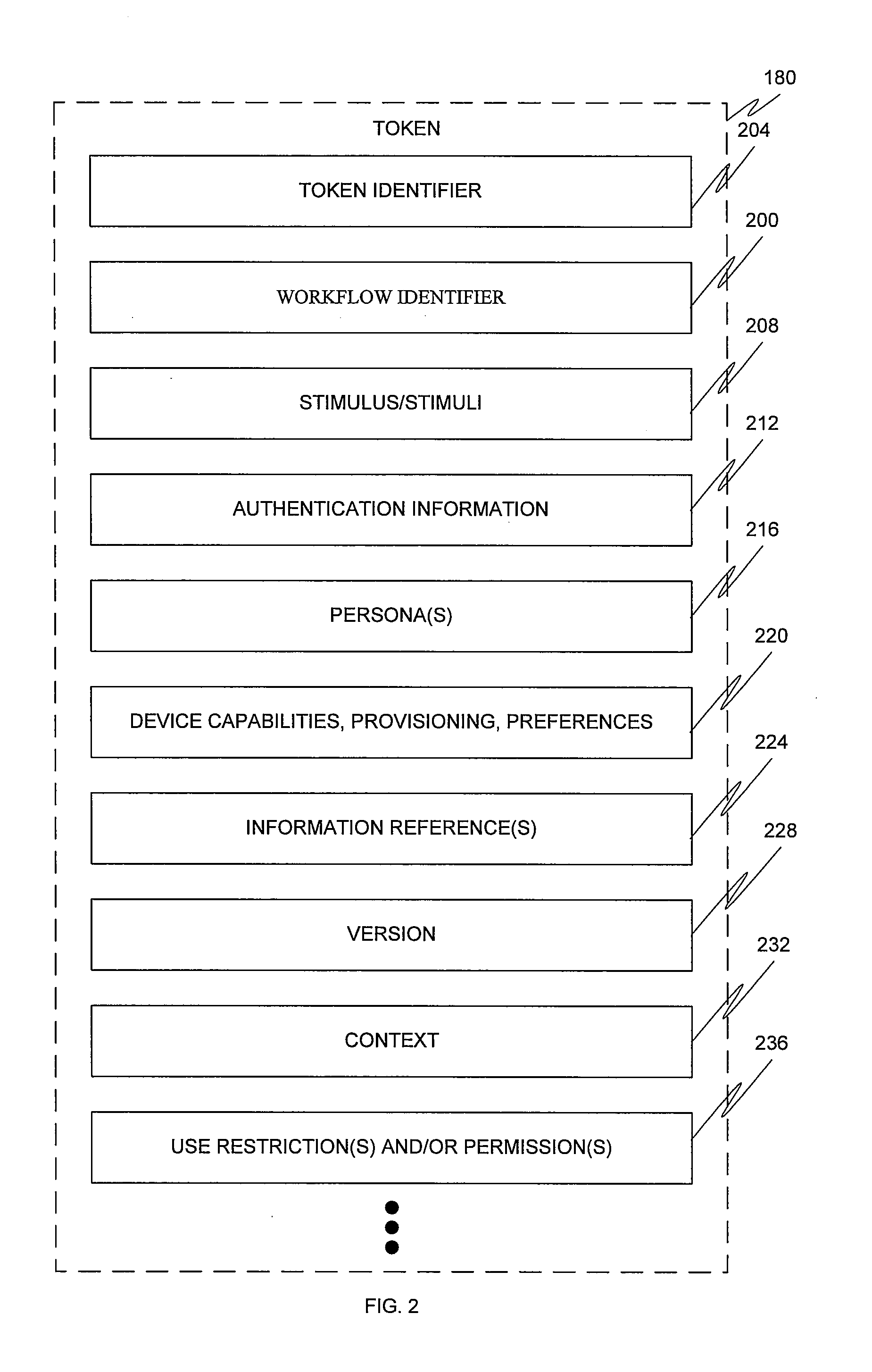
Method of Authentication by Token
ActiveUS20150172283A1Easy to useLimitation on frequencyDigital data processing detailsMultiple digital computer combinationsUnique identifierAuthorization
A method is provided for authentication by token for accessing a service from a terminal. The method includes, on receipt of a service access authorization request including at least one unique identifier of the terminal, steps of determining a network access context of the terminal; checking validity of the service access rights, including at least checking an access right associated with the network access context of the terminal; and, if the access rights are valid, generating a valid authentication token on the basis of the unique identifier of the terminal and the network access context, and transmitting the token to the terminal.
Owner:ORANGE SA (FR)
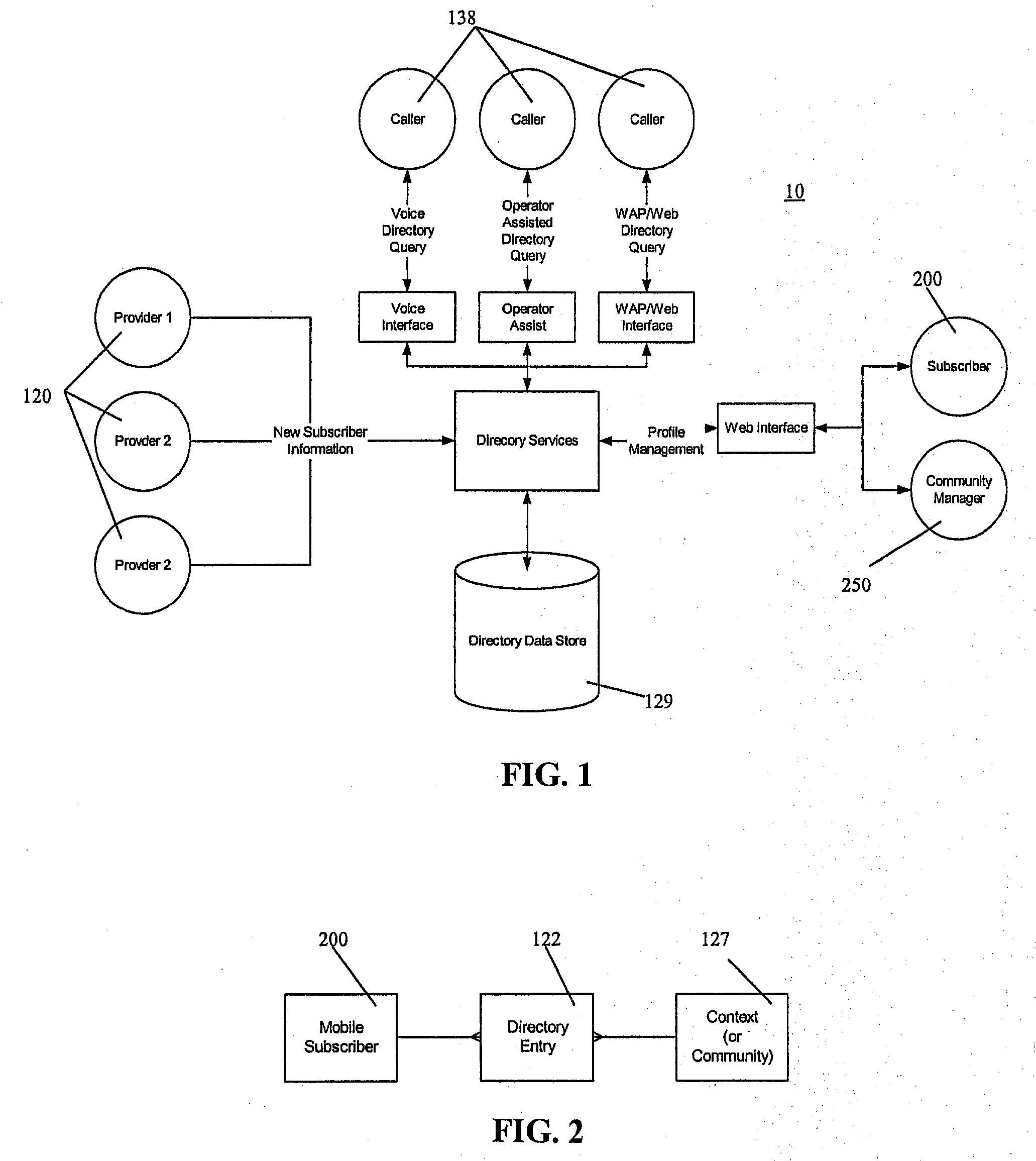
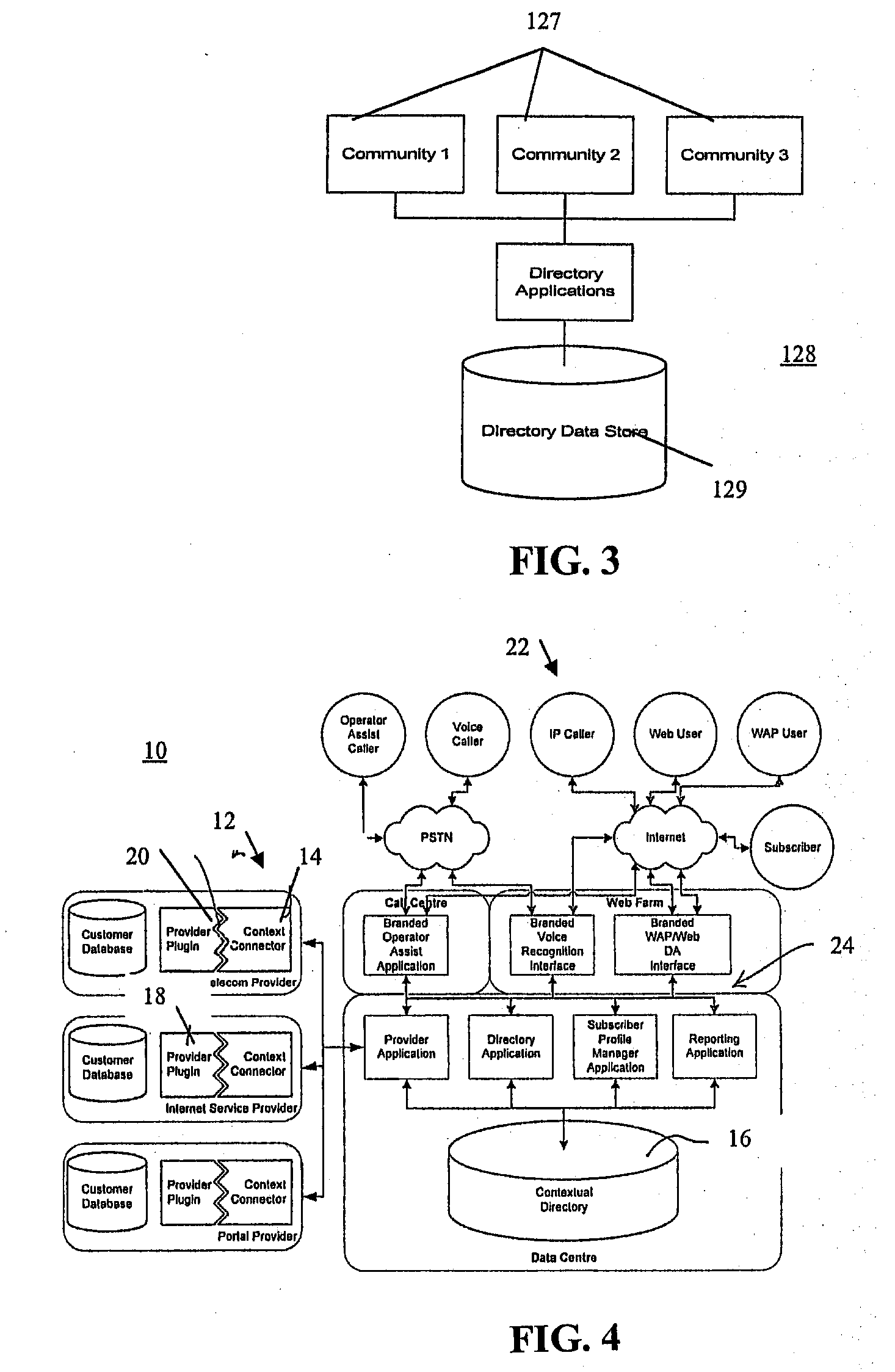
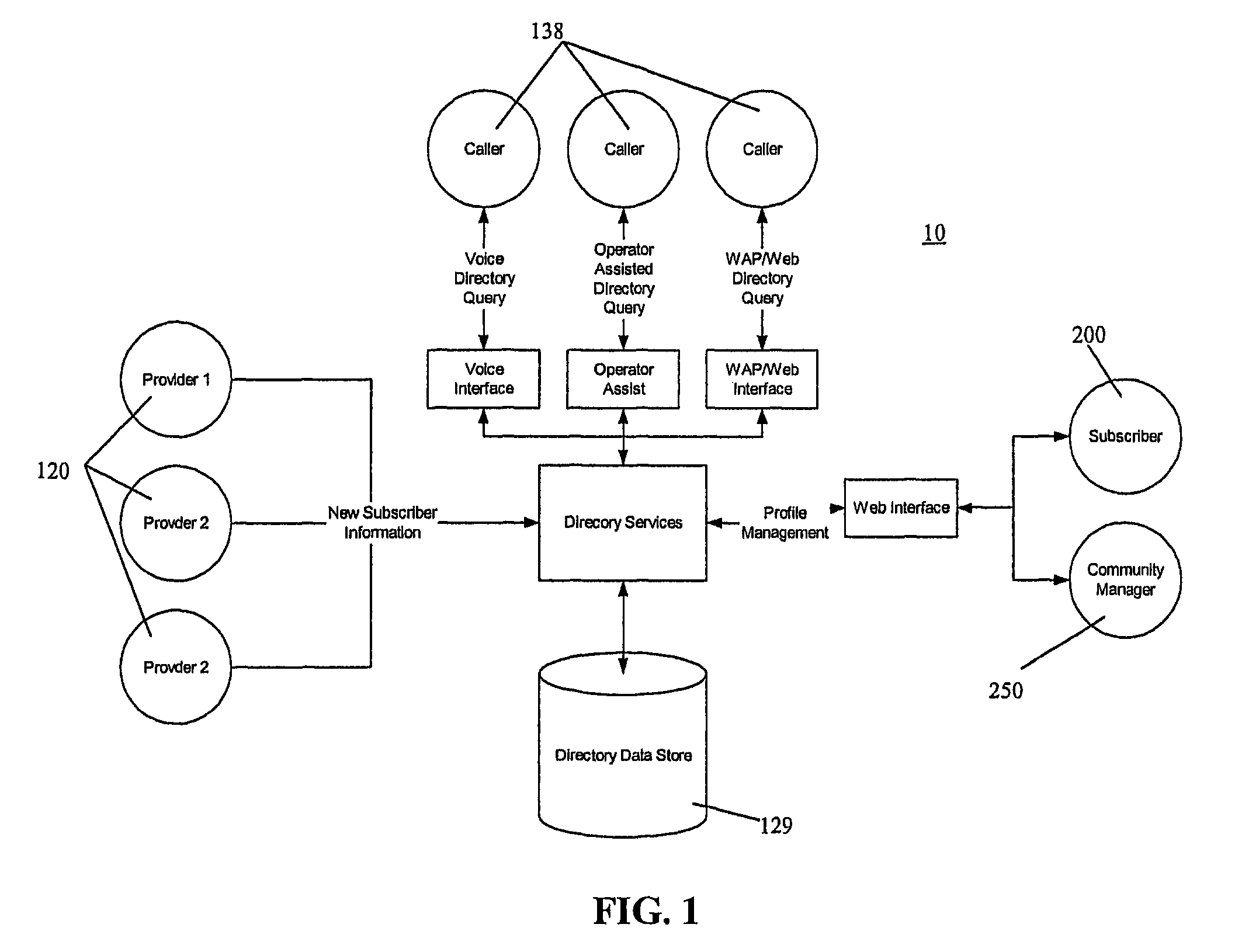
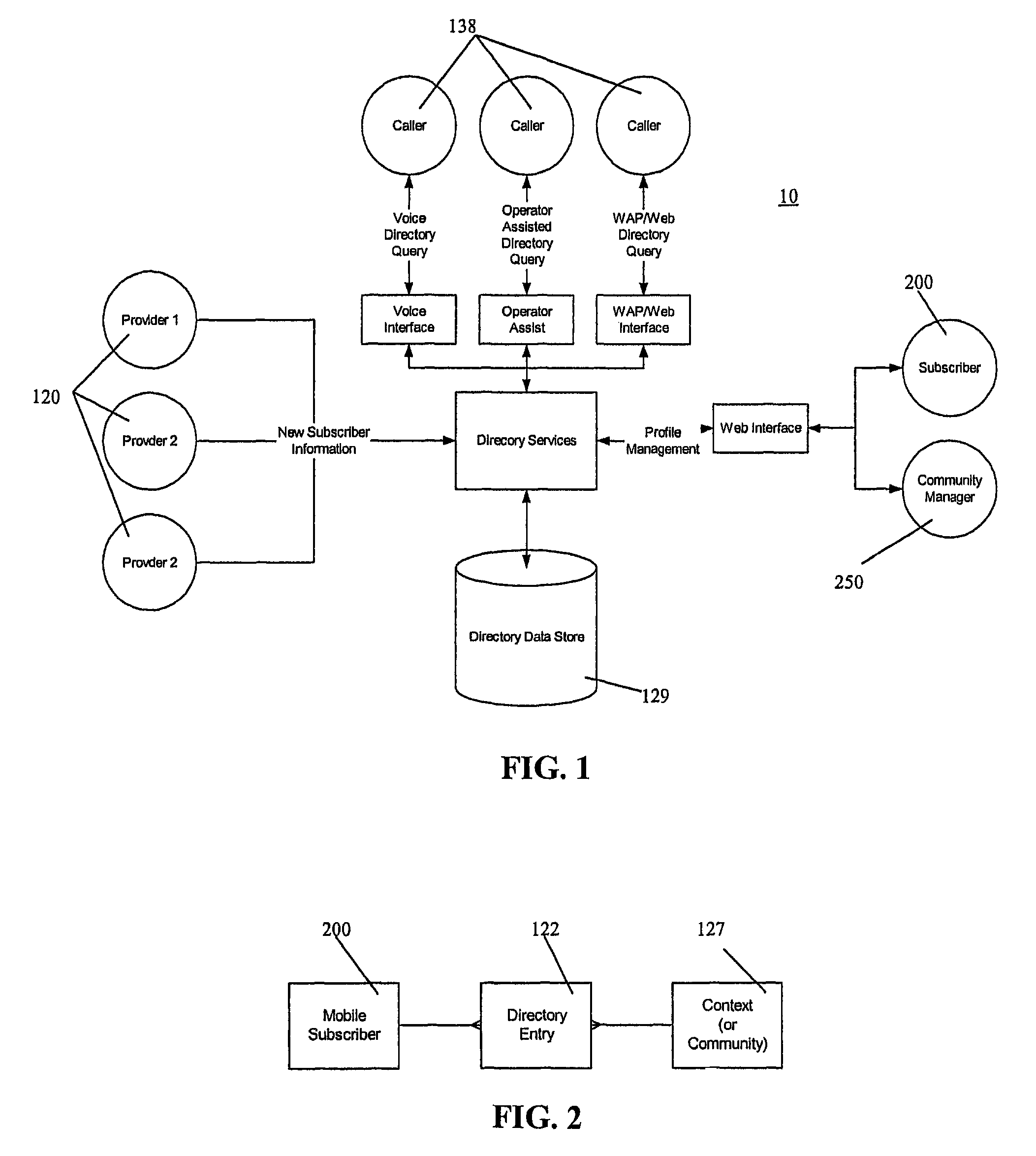
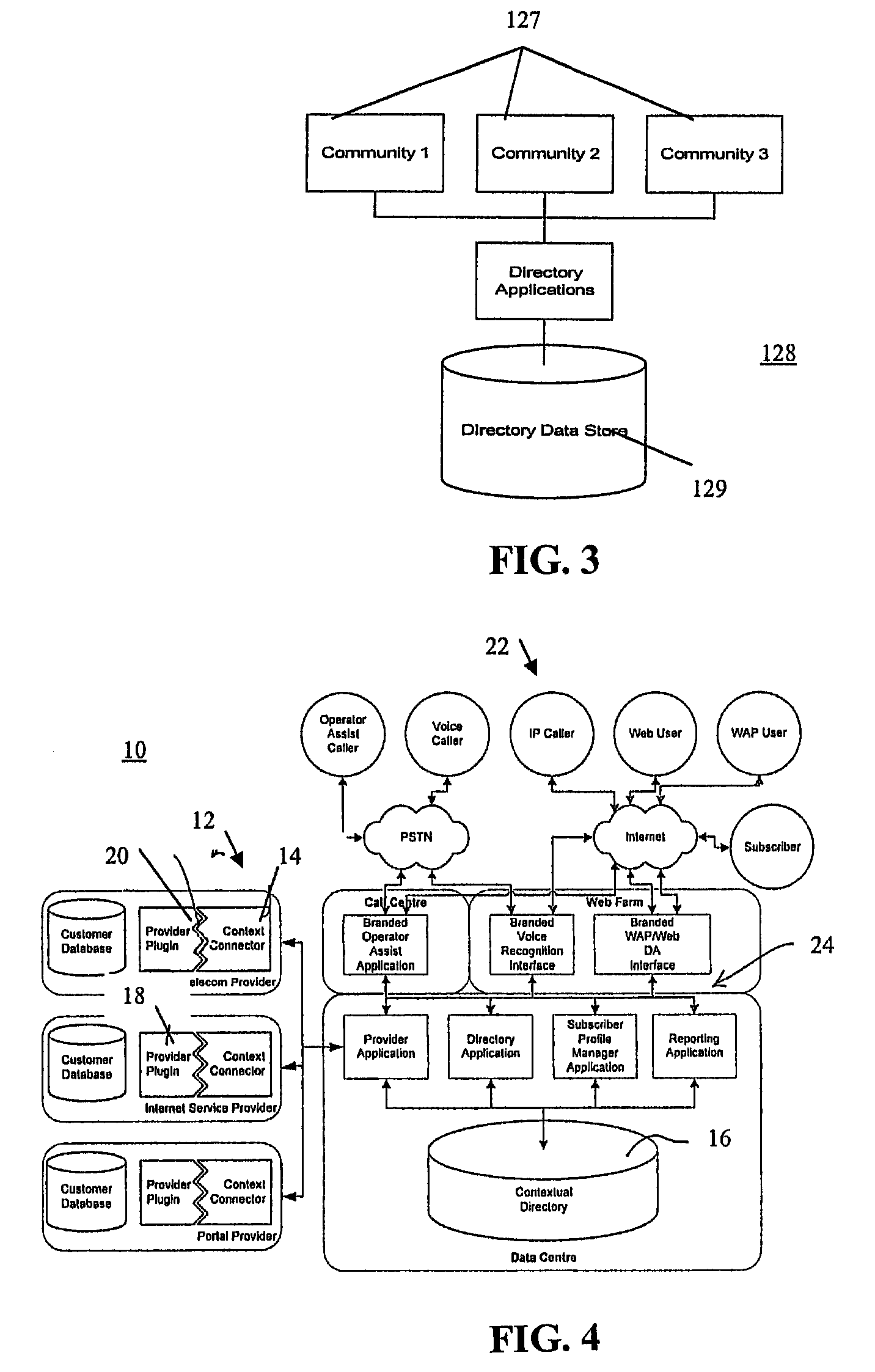
Communication connectivity via context association, advertising sponsorship, and multiple contact databases
InactiveUS20080319823A1Shifted burdenLosing control of privacyTelephone data network interconnectionsAccounting/billing servicesData centerCall routing
Communication connectivity via context association is provided by associating targeted subscriber contact information with a key at a subscriber database. At a data center, the keys are associated with unique characteristics or aliases (contexts) of the subscribers, thereby facilitating context searching. A caller initiates a connection to a subscriber by providing a subscriber's context. The context is located and associated key identified. The key is resolved in the subscriber database, and the call routed. Use of the key allows subscriber connectivity without revealing, to the caller or to the data center, sensitive contact information. Through a caller database, call initiation occurs by subscriber alias identification in a caller's communication device; thereby foregoing inclusion of sensitive contact information within the caller's communication device. Communication connectivity can be advertiser sponsored, with advertisements accompanying messages selected by matching profile information of targeted subscribers with participating advertiser provided profile information of desired targeted subscribers.
Owner:WALMART APOLLO LLC
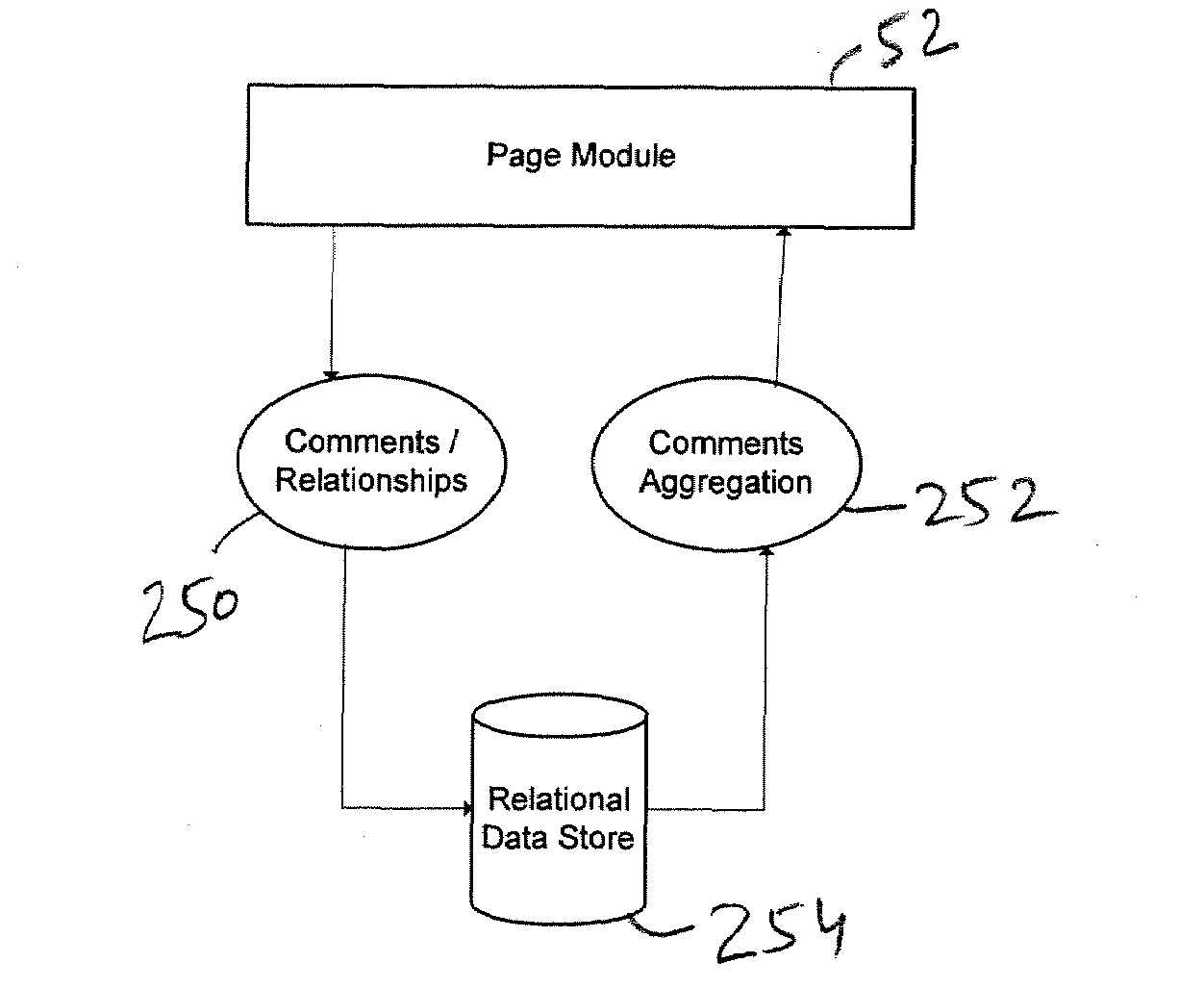
Systems and methods for comments aggregation and carryover in word pages
InactiveUS20090043814A1Easy to integrateImprove user interactionMetadata multimedia retrievalNatural language data processingContextual AssociationsMultimedia
Owner:R2 SOLUTIONS
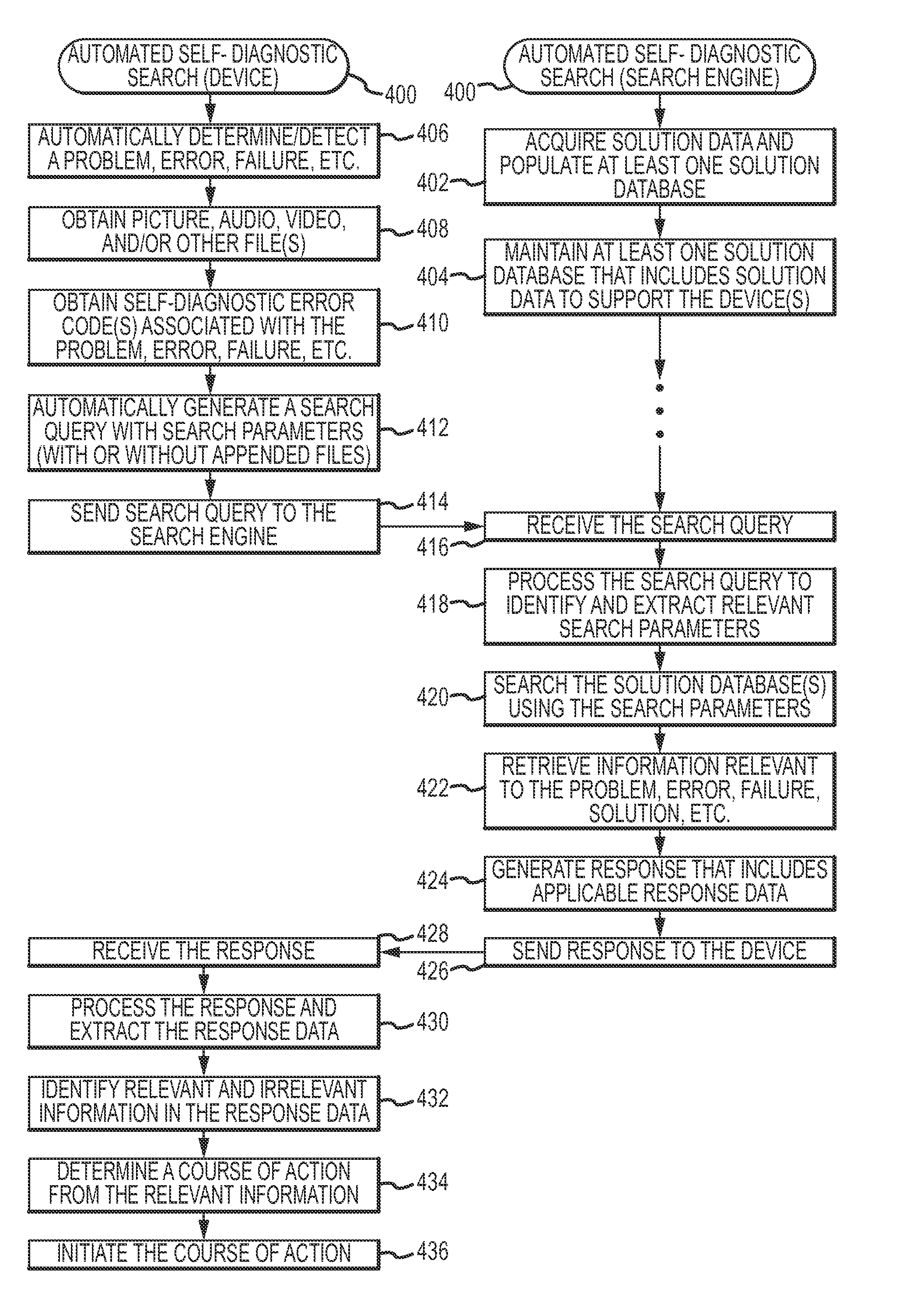
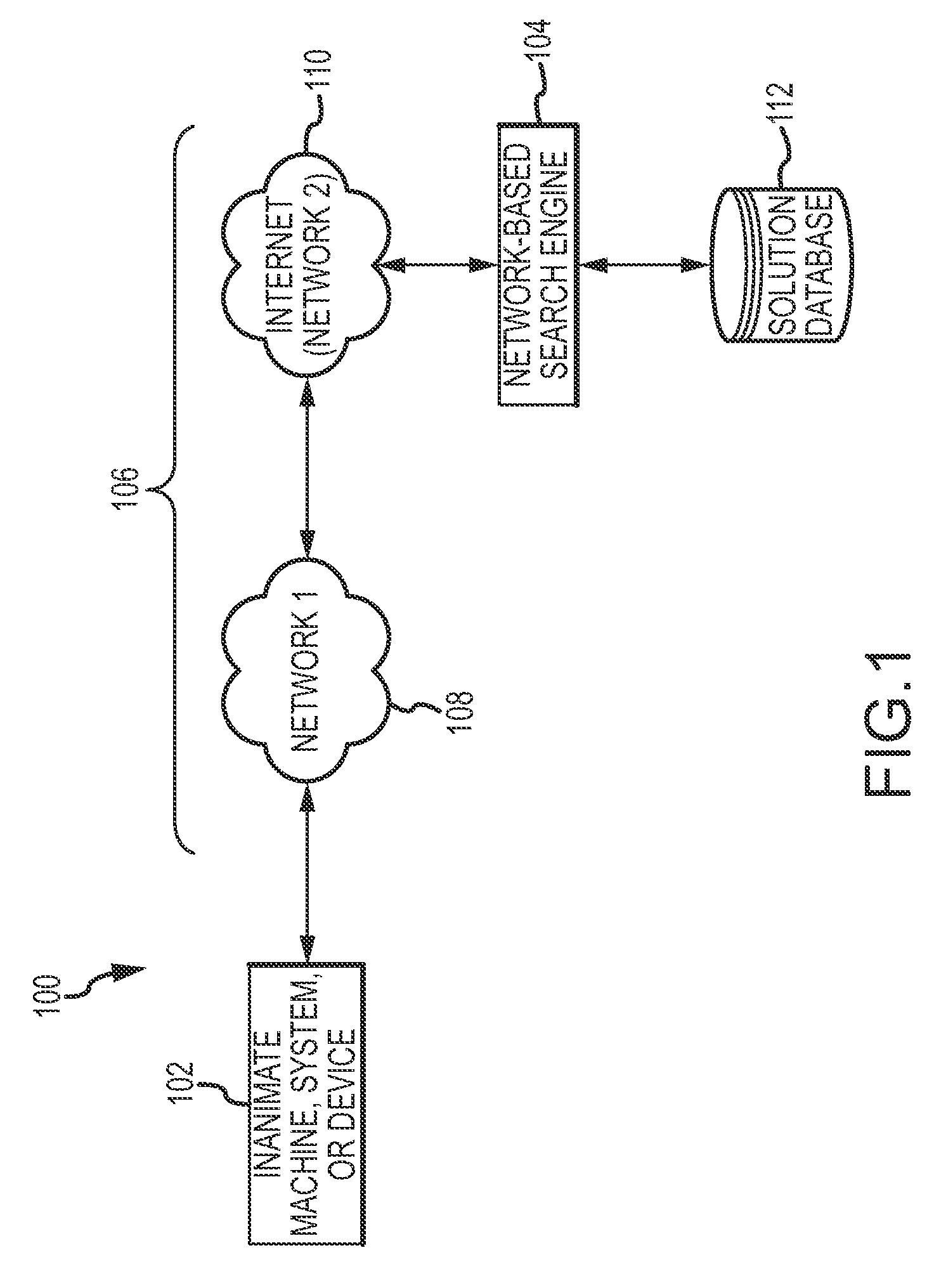
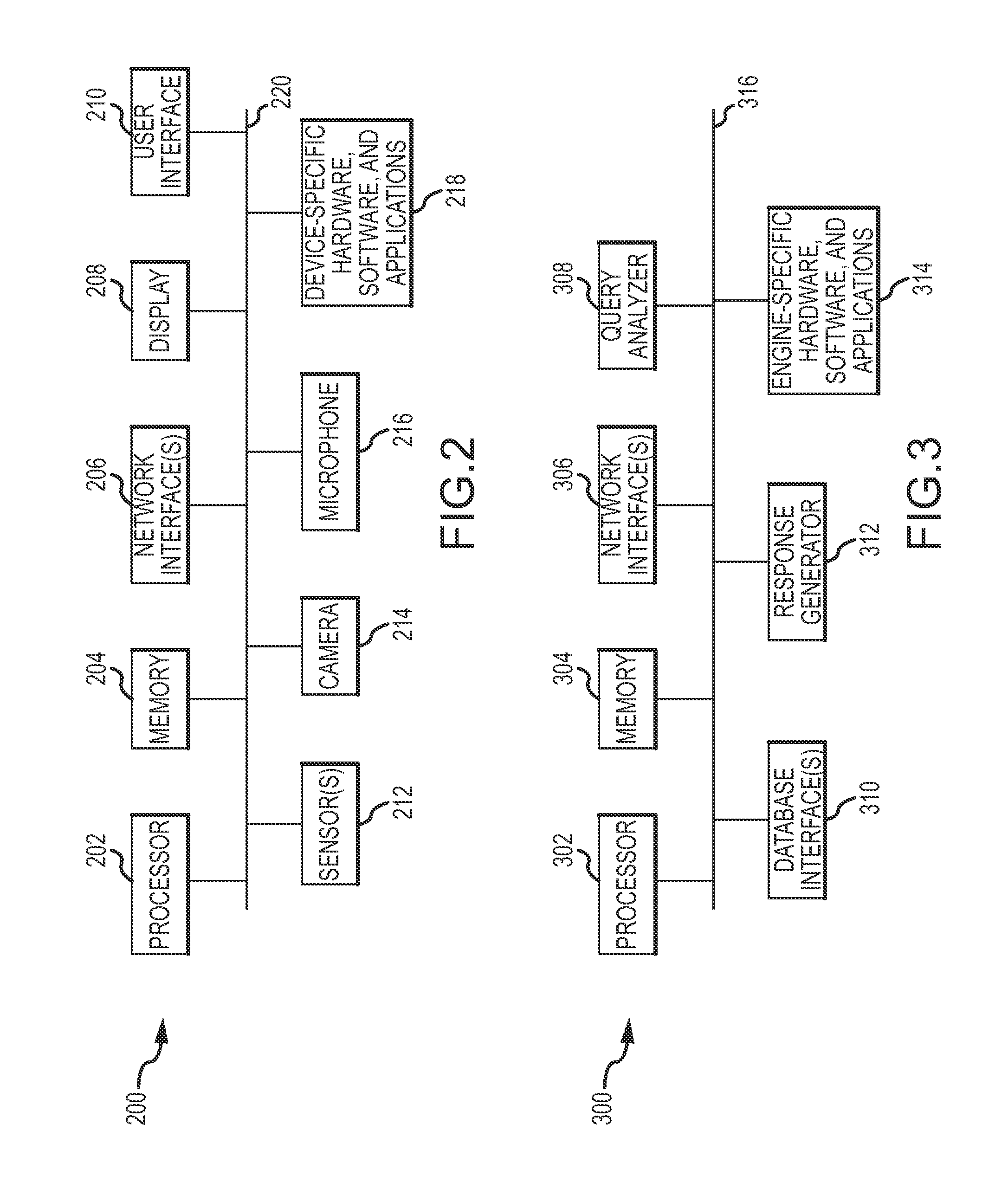
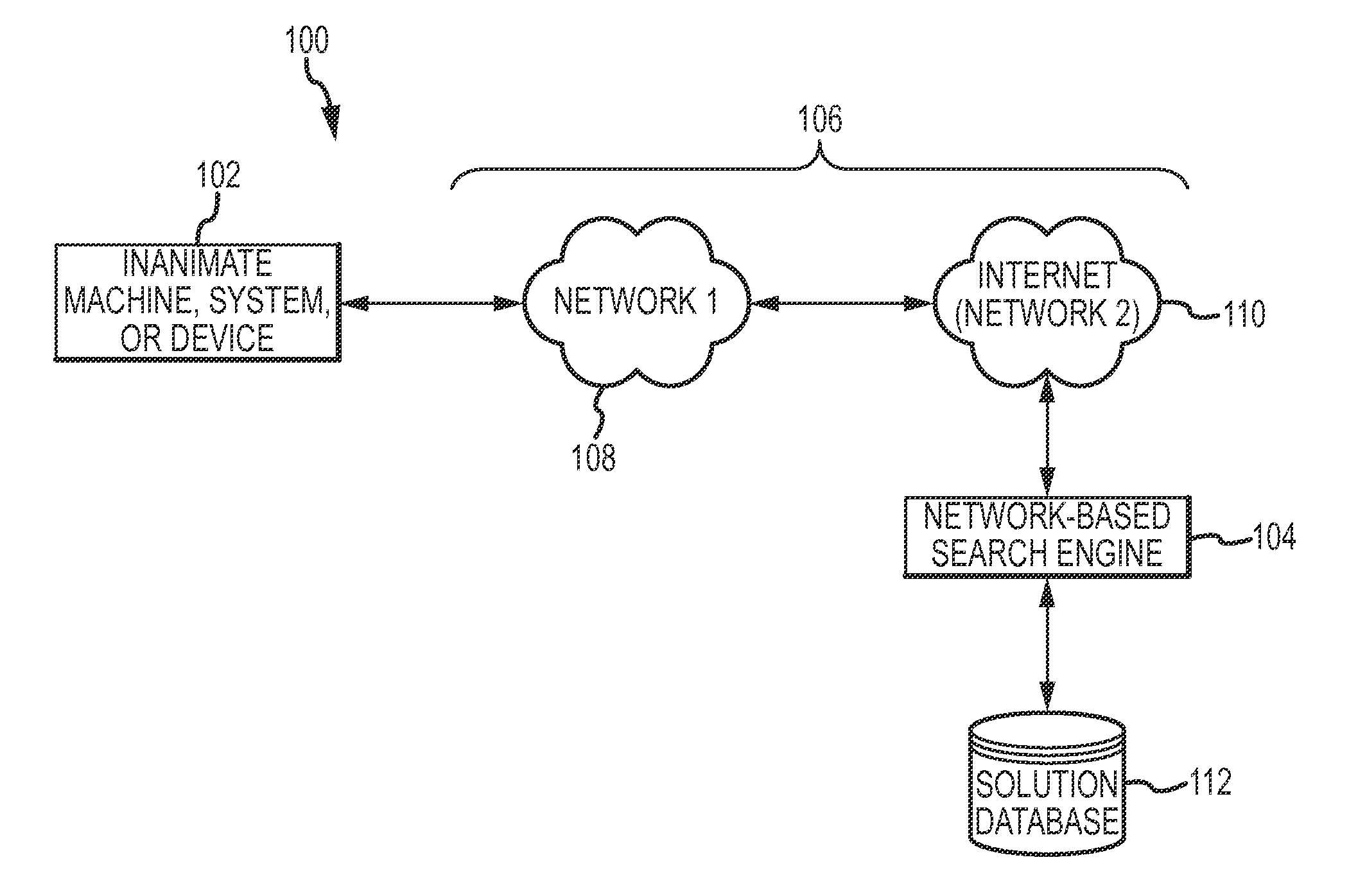
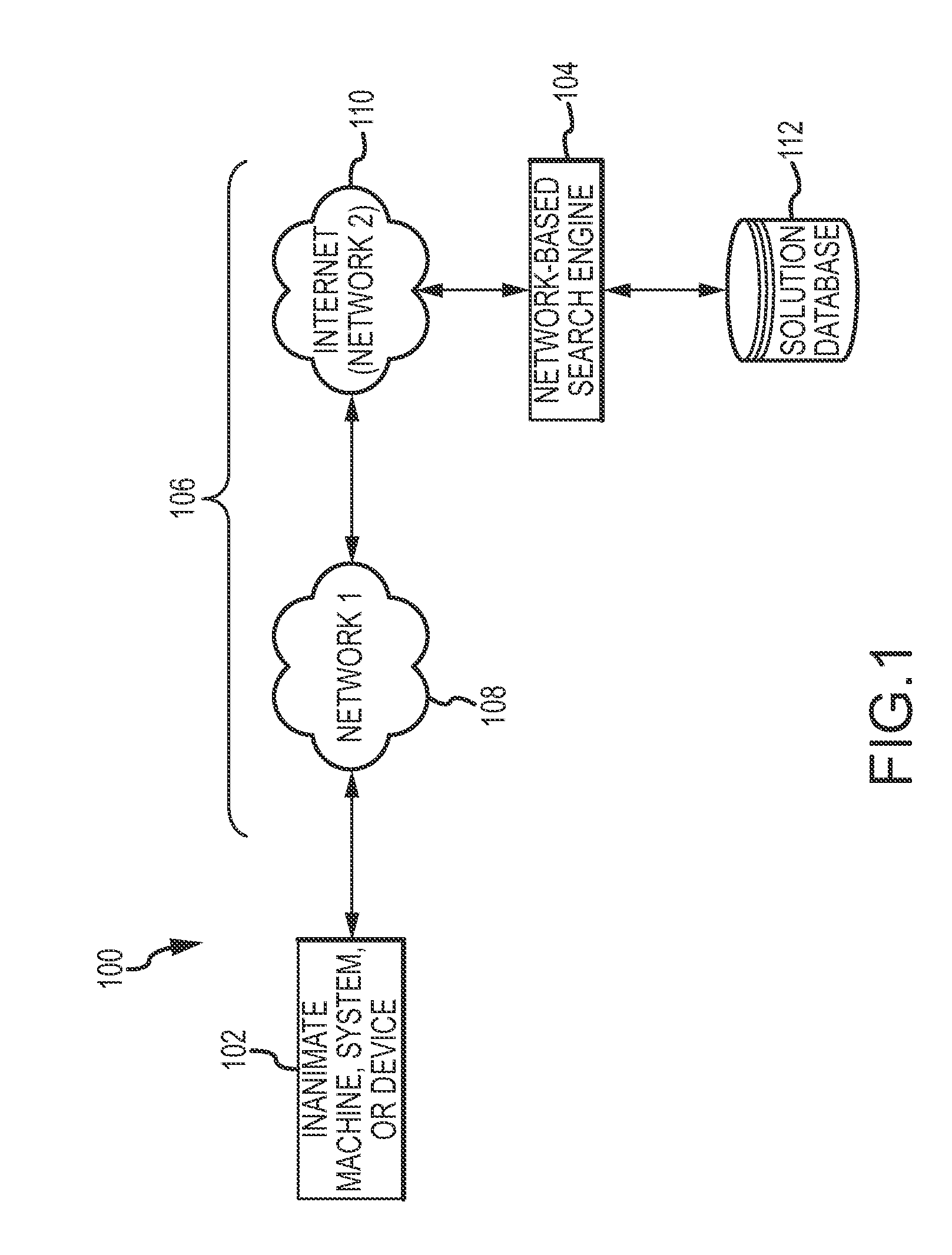
Automated searching for solutions to support self-diagnostic operations of web-enabled devices
ActiveUS8543562B2Digital data information retrievalDigital data processing detailsRelevant informationCourse of action
An automated diagnostic system is presented here. The system includes a network-enabled device, a remote network-based search engine, and a data communication network to facilitate data communication between the network-enabled device and the remote network-based search engine. The device automatically detects a problem, error, or failure associated with its operation, and automatically sends a corresponding search query to the remote network-based search engine. The search engine receives the search query and, in response to the search query, searches for relevant information pertaining to the problem, error, or failure, and sends a corresponding response to the network-enabled device. The response includes response data having some contextual association with the solution. The device receives the response, processes at least some of the response data to determine a course of action, and initiates that course of action.
Owner:DISH NETWORK TECH INDIA PTE LTD
System and method for read-ahead enhancements
InactiveUS20060165289A1Character and pattern recognitionNatural language data processingDocumentation procedureData field
A method and system is provided for analyzing potential repeatable values for placement into a data field based on user-defined criteria and includes analyzing relationships between documents for the purpose of correlating sender and receiver information into a context to more accurately populate type-ahead functions in repeatable data fields. Threaded messages are typically limited to those messages that are responses to responses or responses to an original message and are usually denoted by terms such as, for example, “forwarded” or “reply to” and where the history of the previous related message is included in the most recent message. However, the invention now expands correlation into non-thread related documents to achieve a higher correlation rate. The expanded documents may be any previous email or associated documents of a sender or receiver, including any documents defined by user criteria. In the case of stand-alone applications such as word processors, any user associated document, as defined by user criteria may be included in a contextual association for purposes of type-ahead analysis.
Owner:KYNDRYL INC
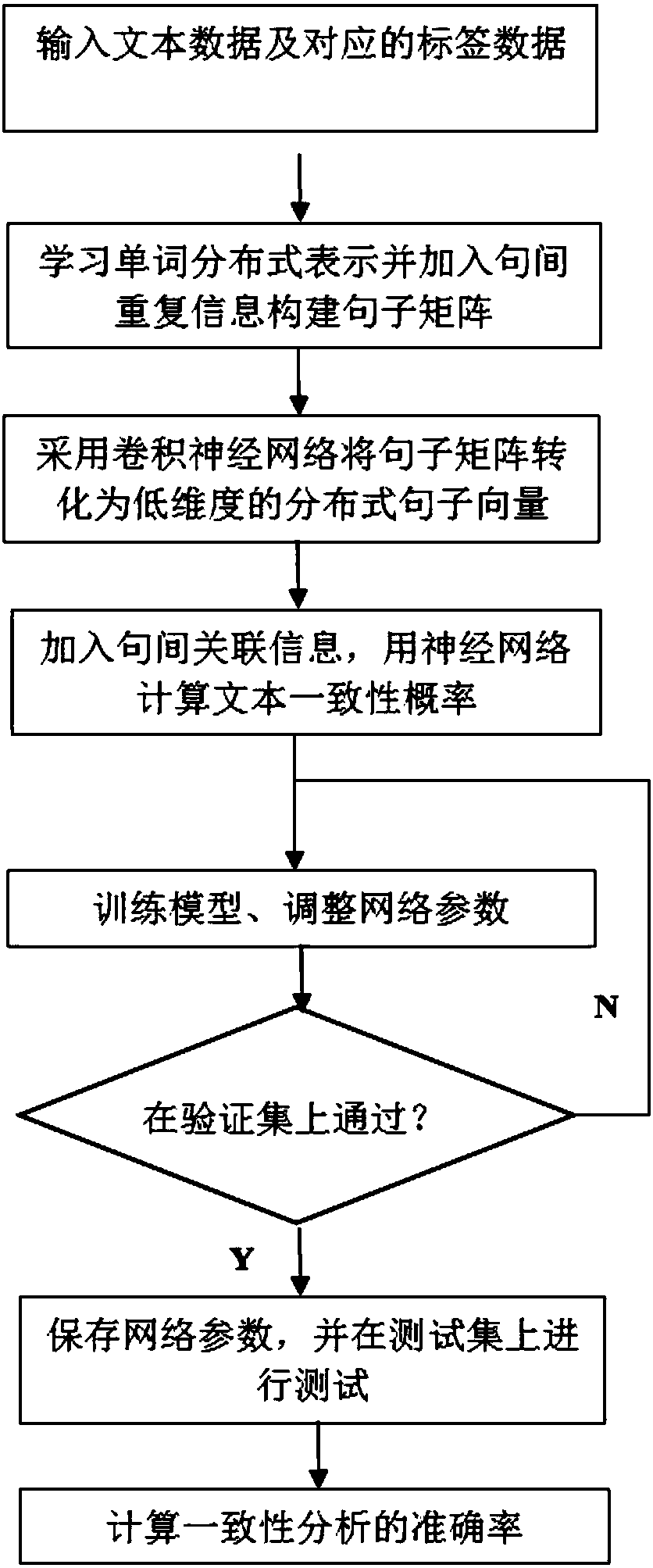
Deep neural network-based text consistency analysis method
ActiveCN107766324AGood effectReduce mistakesSemantic analysisCharacter and pattern recognitionNerve networkFeature extraction
The invention discloses a deep neural network-based text consistency analysis method. After a section of text is input, a distributed method is adopted to translate each word in sentences into vectorsto form distributed sentence matrices, the words repeatedly appearing in the adjacent sentences are counted, and repeated information of the adjacent sentences is added through a manner of expandingdimensionality of the matrices; a convolutional neural network is utilized to learn distributed representations of the sentences, and important features of logic, semantics, syntax and the like in thesentences are extracted to form sentence vectors; and similarity degrees between the adjacent sentence vectors are calculated to add context association contents, finally, a neural network is continuously trained, and probability of text consistency is output. The method is characterized in that complex artificial feature extraction operations do not need to be carried out, external resources arealso not relied on, and compared with existing consistency analysis technology, the method provided by the invention has a great improvement in an accuracy rate, and has a better practical value.
Owner:ZHEJIANG UNIV
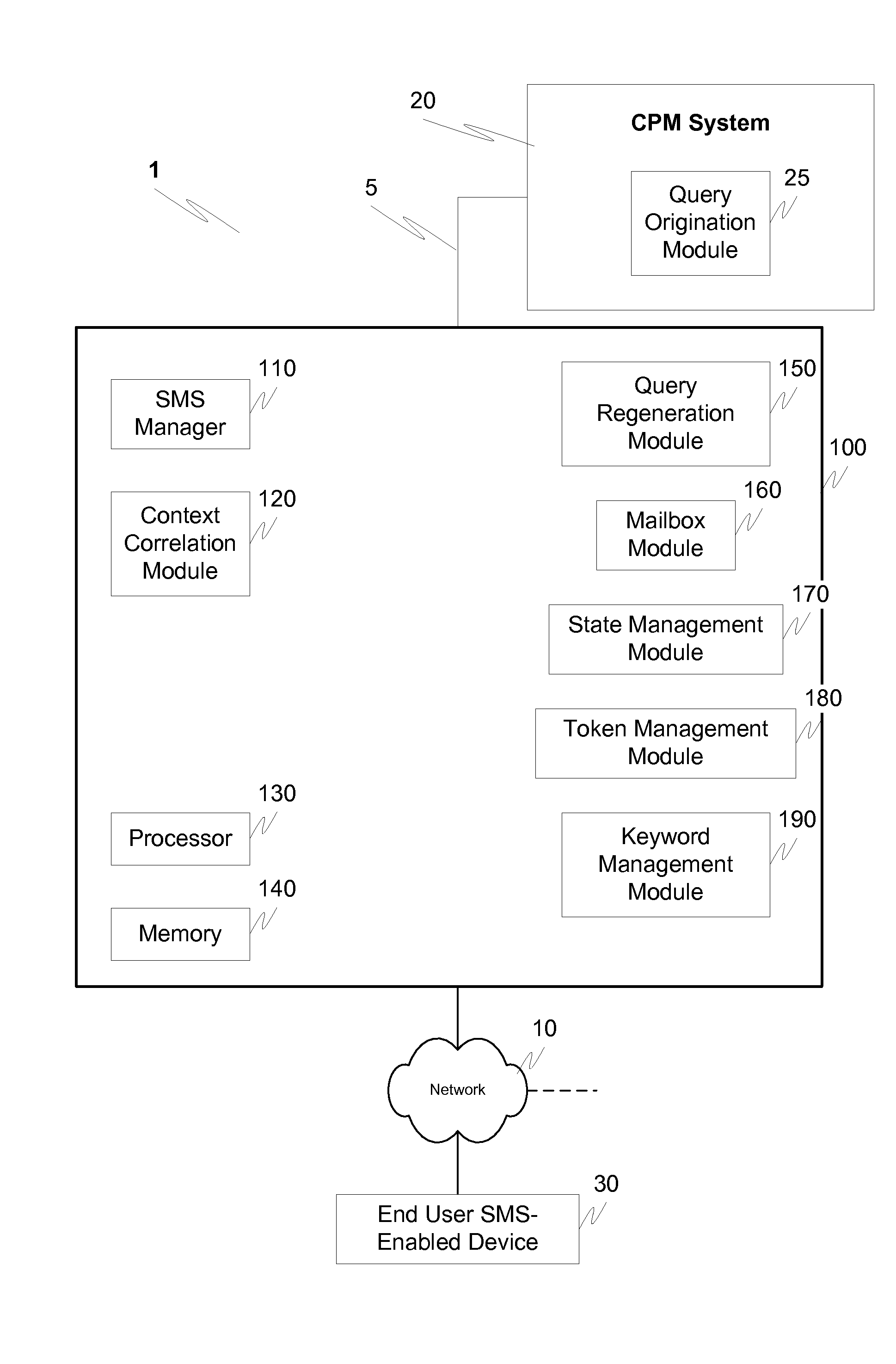
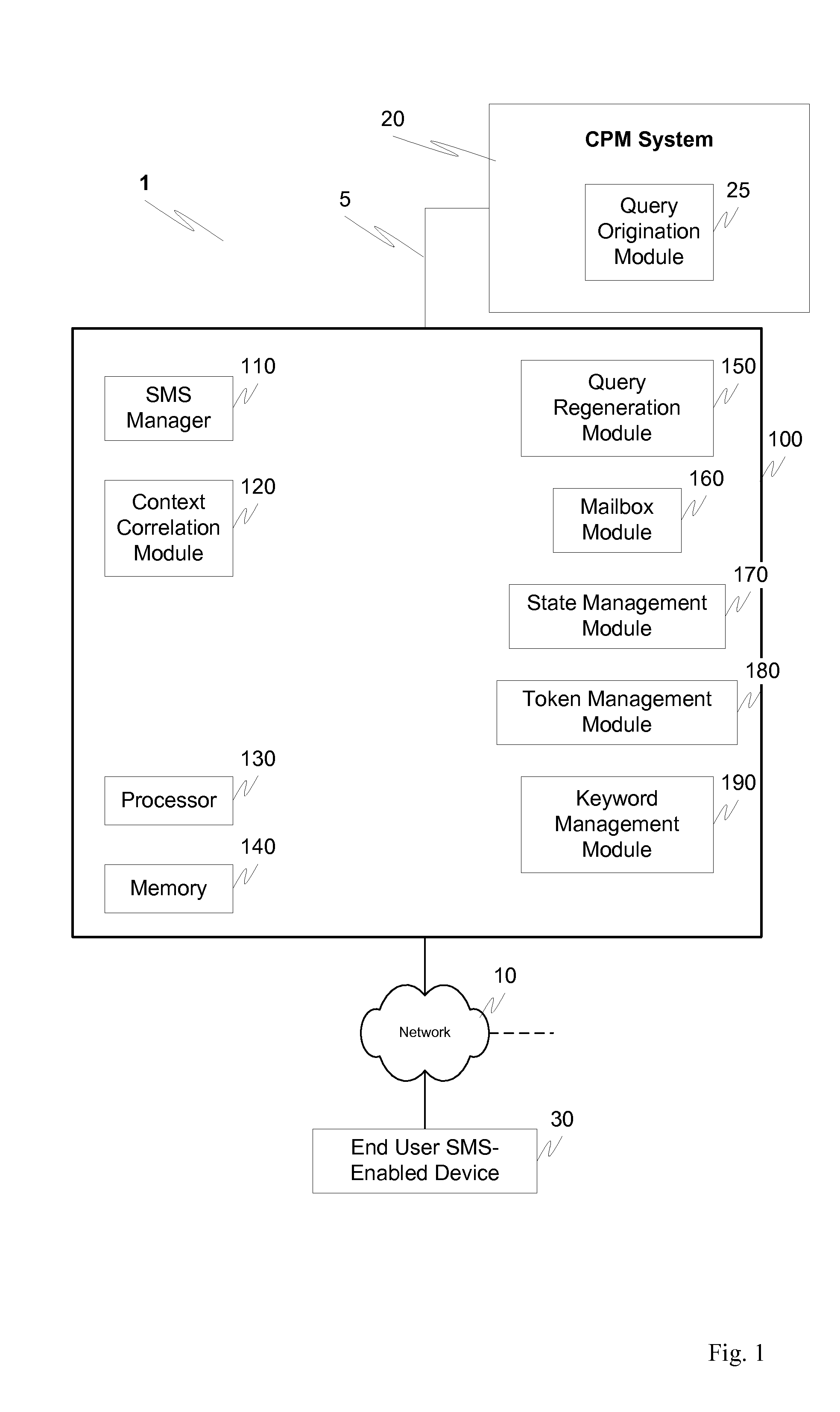
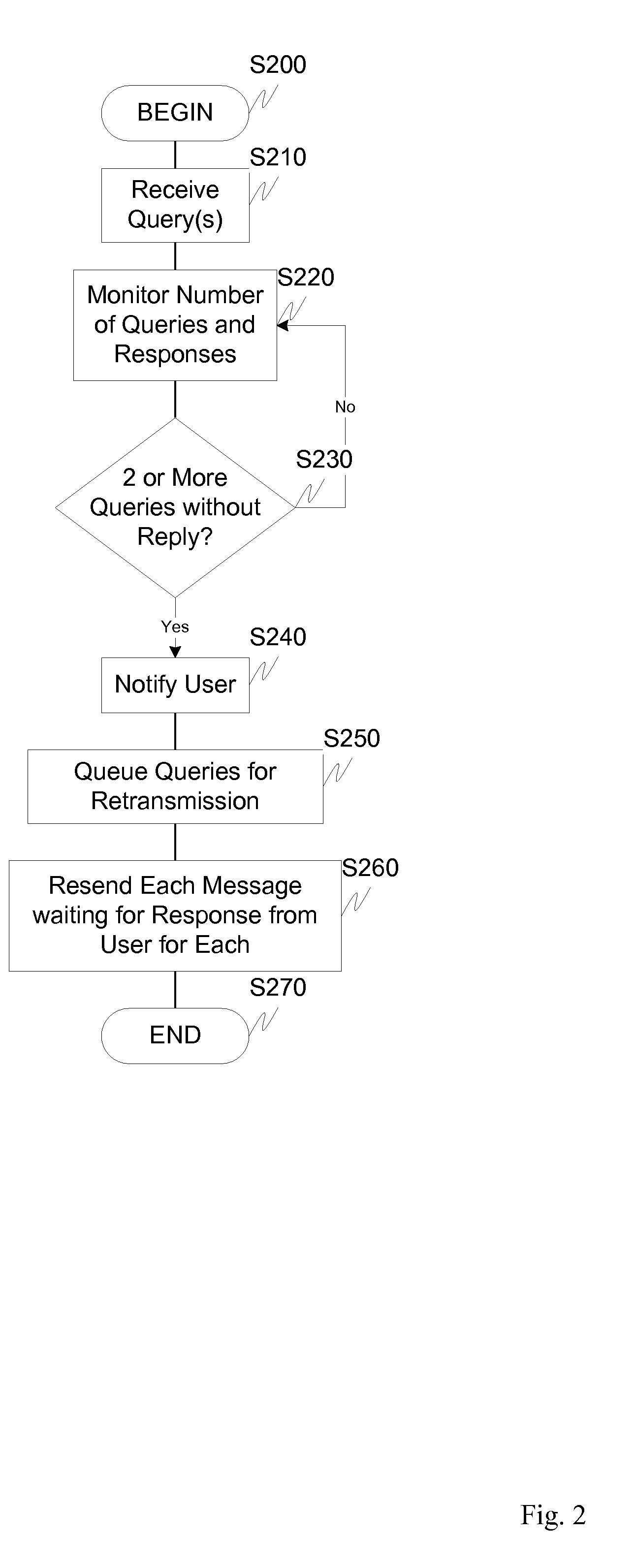
Associating system requests with SMS user responses
ActiveUS20100088302A1Error preventionNetwork traffic/resource managementUser needsShort Message Service
A messaging system can initiate a communication with one or more users through via cell phone text messages, for example using the short message service protocol. These systems often need a way to correlate user responses with system requests or queries. This problem can present challenges because the email mailbox metaphor used by cell phone user interfaces generally allows users to reply to any previously sent messages, but no message context is automatically supplied. A system that may send multiple messages to a user needs a mechanism by which the system can correlate a user-sent response to one of potentially many system-sent requests or queries. Context correlation to resolve ambiguities can be based on one or more of a dialog-based solution, a token-based solution and a keyword-based solution.
Owner:AVAYA INC
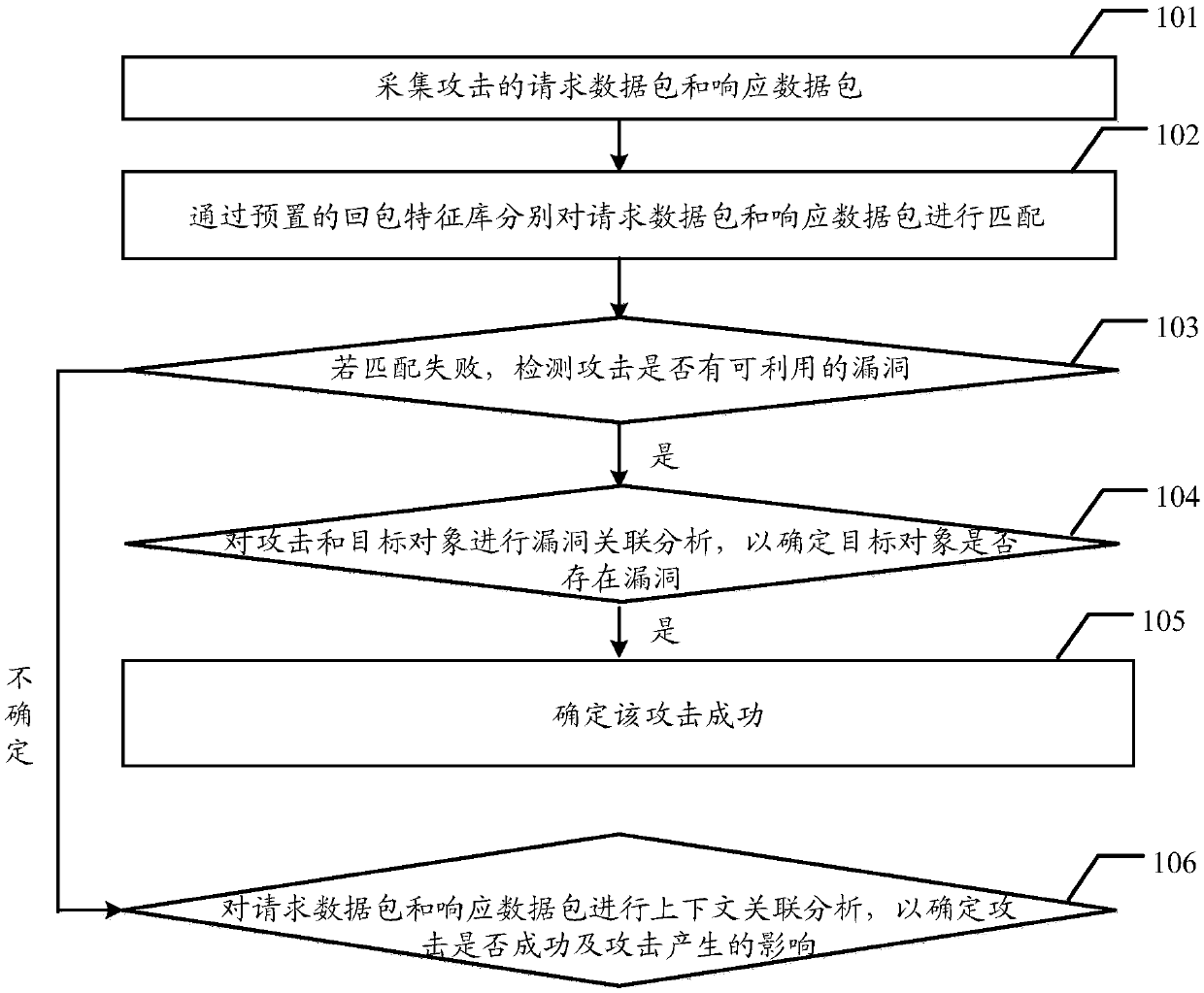
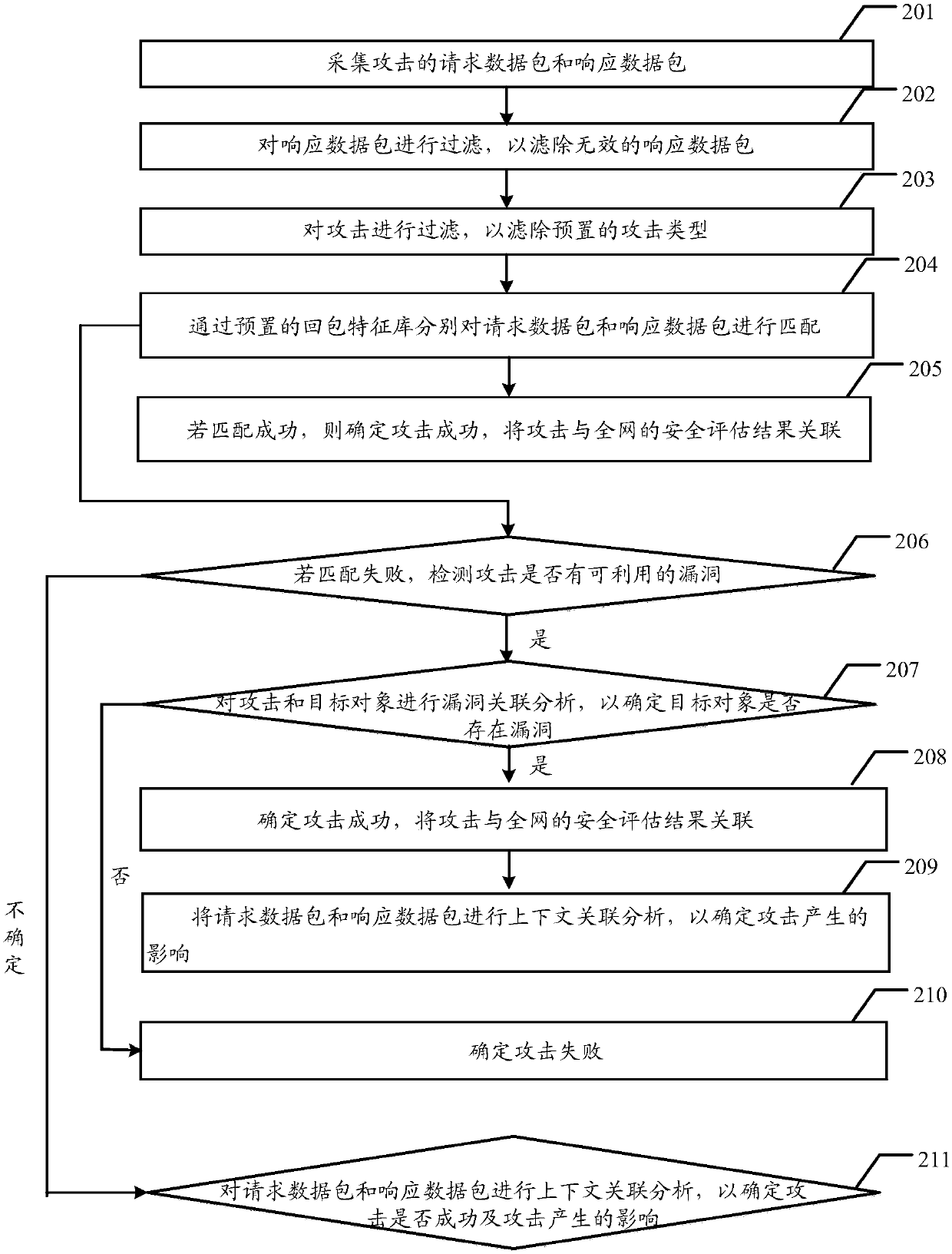
Method and system for detecting attacks in events
The embodiment of the invention discloses a method and system for detecting attacks in events for effectively detecting the attacks and improving the success rate and accuracy of attack detection. Themethod in the embodiment of the invention comprises the following steps: collecting a request data packet and a response data packet of attack; separately matching the request data packet and the response data packet by a preset packet return feature library; in the case of matching failure, detecting whether the attack has available vulnerability; if the detection result is yes, performing vulnerability correlation analysis on the attack and the target object to determine whether the target object has vulnerability; if the target object has the vulnerability, determining attack success; andif the detection result is undetermined, performing context correlation analysis on the request data packet and the response data packet to determine whether the attack is successful and the influencegenerated by the attack. The embodiment of the invention further discloses a system for detecting attacks in events for improving the success rate and accuracy of attack detection.
Owner:SANGFOR TECH INC
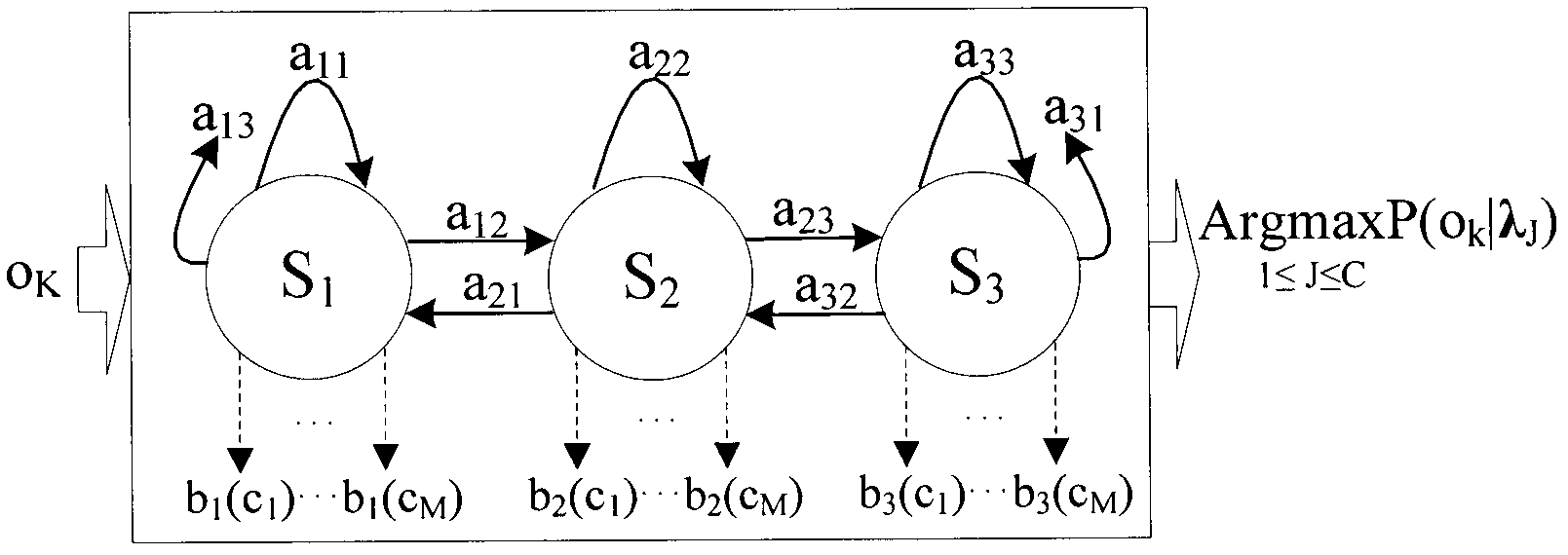
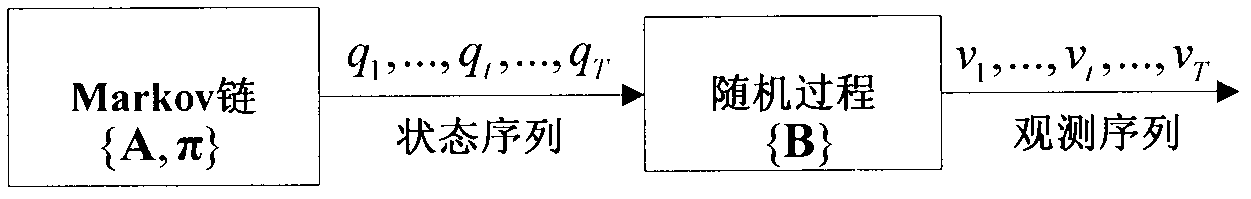
Hidden Markov model based method for detecting assembler instruction level vulnerability
InactiveCN101923618AAccurate identificationImprove detection efficiencyPlatform integrity maintainanceProgramming languageHide markov model
The invention relates to a hidden Markov model based method for detecting assembler instruction level vulnerabilities, belonging to the technical field of information security. The method comprises the following steps of: (1) constructing a vulnerability instruction library (VIL); (2) respectively selecting a plurality of executable programs with the vulnerability as training data of the vulnerability for each vulnerability in the vulnerability instruction library by aiming at all the vulnerabilities in the vulnerability instruction library constructed in the step (1); (3) obtaining assembler instruction segments of the training data of each vulnerability in the vulnerability instruction library; (4) obtaining a numerical code sequence of the training data; (5) sequentially obtaining a parameter lambda r=(Ar, Br, pi r) of the corresponding hidden Markov model of each vulnerability in the vulnerability instruction library; and (6) recognizing the vulnerability of an executable program to be detected. Compared with the prior art, the hidden Markov model based method for detecting the assembler instruction level vulnerability has the following advantages of establishing a model for the assembler instruction with context correlation and recognizing vulnerability characteristics by using the HMM (Hidden Markov Model) for the first time, increasing vulnerability detection efficiency and reducing error report rate and missing report rate.
Owner:中国航天科技集团公司第七一0研究所 +1
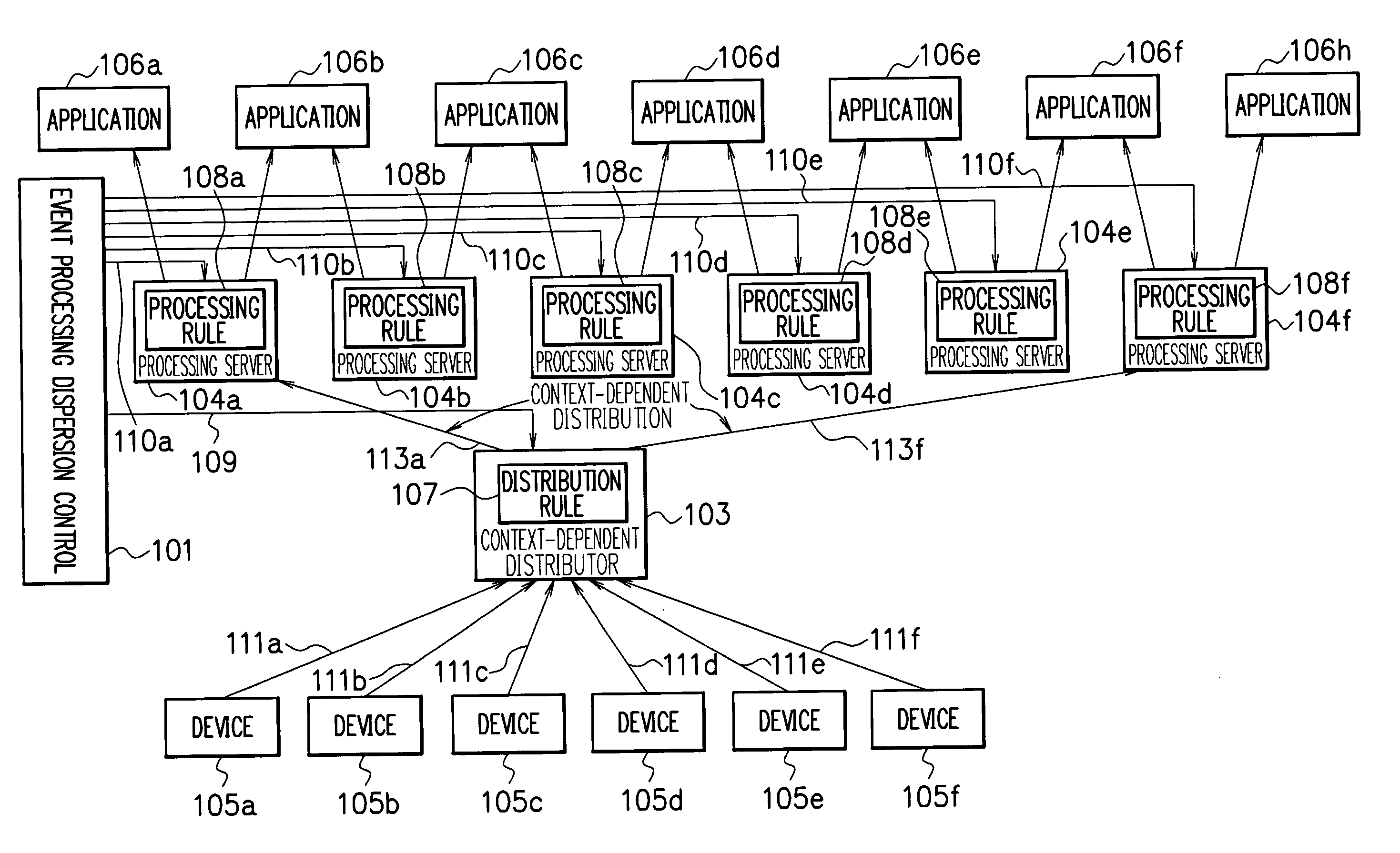
Load distribution system, and event processing distribution control apparatus, and an event processing distribution control program
ActiveUS20060230077A1Digital data processing detailsMultiprogramming arrangementsDistribution controlLoad distribution
In a load distribution system, a plurality of processing servers are installed and a context-dependent distributor is arranged in a stage before the processing servers such that a distribution rule is set to the distributor to appropriately distribute an event to an associated processing server, the event being necessary for the server to execute a processing rule set thereto. To achieve the processing distribution in a system of this type, a plurality of processing servers are disposed and an event processing distribution control unit sets event processing rules to the respective processing servers for individual applications. The distribution controller sets a distribution rule associated with context of an event to a distributor so that the event is distributed to an associated server beforehand designated to process the event. This makes it possible to accomplish load distribution for the processing servers.
Owner:NEC CORP
Computer-implemented method and system for automated patentability and/or design around claim charts with context associations
ActiveUS9454731B1Readily annotatingEasy to navigateNatural language data processingPower supply for data processingHyperlinkThumbnail
A system correlates intellectual property analyzes, for example, patent claim charts, with respect to analyzed intellectual property and a target product or other intellectual property. Analyzes are stored to enable searching and / or creating reports over multiple analyzes. Units of the analysis are associated with a context, inherited, e.g., from the intellectual property document's assignment to a relative role within organizational hierarchy; and associated with a context derived from the analysis itself. The analysis and respective documents and / or targets of the analysis can be searched / retrieved / analyzed from the hierarchical analysis, the context analysis, and / or the content of the analysis. This obviates the need to store each analysis as a separate document. The target or annotations may be visually represented by an item such as a thumbnail or hyperlink, and the system automatically associates the item with the appropriate application program.
Owner:LEE EUGENE M
Automated searching for solutions to support self-diagnostic operations of web-enabled devices
ActiveUS20120130968A1Digital data information retrievalDigital data processing detailsRelevant informationCourse of action
An automated diagnostic system is presented here. The system includes a network-enabled device, a remote network-based search engine, and a data communication network to facilitate data communication between the network-enabled device and the remote network-based search engine. The device automatically detects a problem, error, or failure associated with its operation, and automatically sends a corresponding search query to the remote network-based search engine. The search engine receives the search query and, in response to the search query, searches for relevant information pertaining to the problem, error, or failure, and sends a corresponding response to the network-enabled device. The response includes response data having some contextual association with the solution. The device receives the response, processes at least some of the response data to determine a course of action, and initiates that course of action.
Owner:DISH NETWORK TECH INDIA PTE LTD
Computer system architecture for automatic context associations
InactiveUS8069186B2Digital data processing detailsOffice automationComputer usersDocumentation procedure
A computer system models human memory by deriving associations between objects, events, and the context of the computer user or users. These associations can be dynamically generated, changing depending on the behavior of the user and context. Examples of areas in which this system can be used include time management (e.g., a calendar that presents time-based groupings of objects), people management (e.g., use analysis of user communications to rank importance of people to the user, groupings, and associations between people / groups and other objects such as documents, email), and general computer management (e.g., use analysis of user behavior to identify important objects and objects that are related to a current focus and context of the computer user).
Owner:MICROSOFT TECH LICENSING LLC
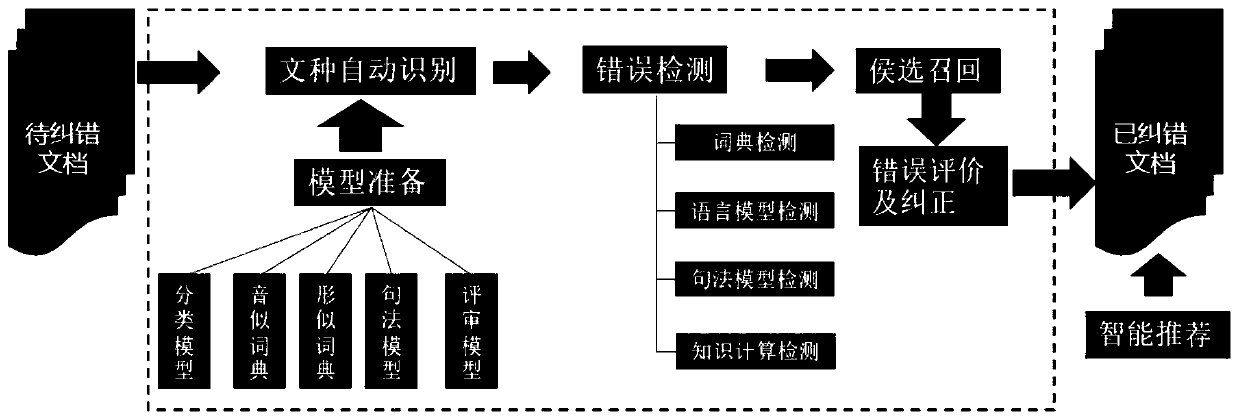
Official document error correction method
InactiveCN111090986AImprove error correction performanceAuthoritativeSemantic analysisCharacter and pattern recognitionText recognitionText detection
The invention discloses an official document error correction method, which comprises the following steps of: a text detection step: carrying out text recognition model training by utilizing machine learning, and classifying document texts into notification, report, approval, notification, letter, conference summary and ask-for-leave types; an error detection step: making word segmentation througha Chinese word segmentation device, detecting errors from the aspects of word granularity and word granularity, integrating suspected error results of the two types of granularity detection, to forma suspected error position candidate set; using a bidirectional character-level N-gram LM deep learning model for scoring characters in sentences, regarding the position with the low score as a position to be corrected, conducting dictionary word checking on the position to be corrected and context combinations, and when all the combinations cannot be found in a dictionary, regarding the combinations as wrong characters and added into a wrong position candidate set. According to the scheme, auditing requirements such as row text specifications, incomplete contents, unknown questions, grammar error correction, smoothness detection, context association and the like are combined, the characteristics are used for innovating, reconstructing and combining the existing technical scheme, and the error correction effect of the enterprise electronic official document can be effectively improved through tests.
Owner:FUJIAN YIRONG INFORMATION TECH +2
Method and device for controlling access security
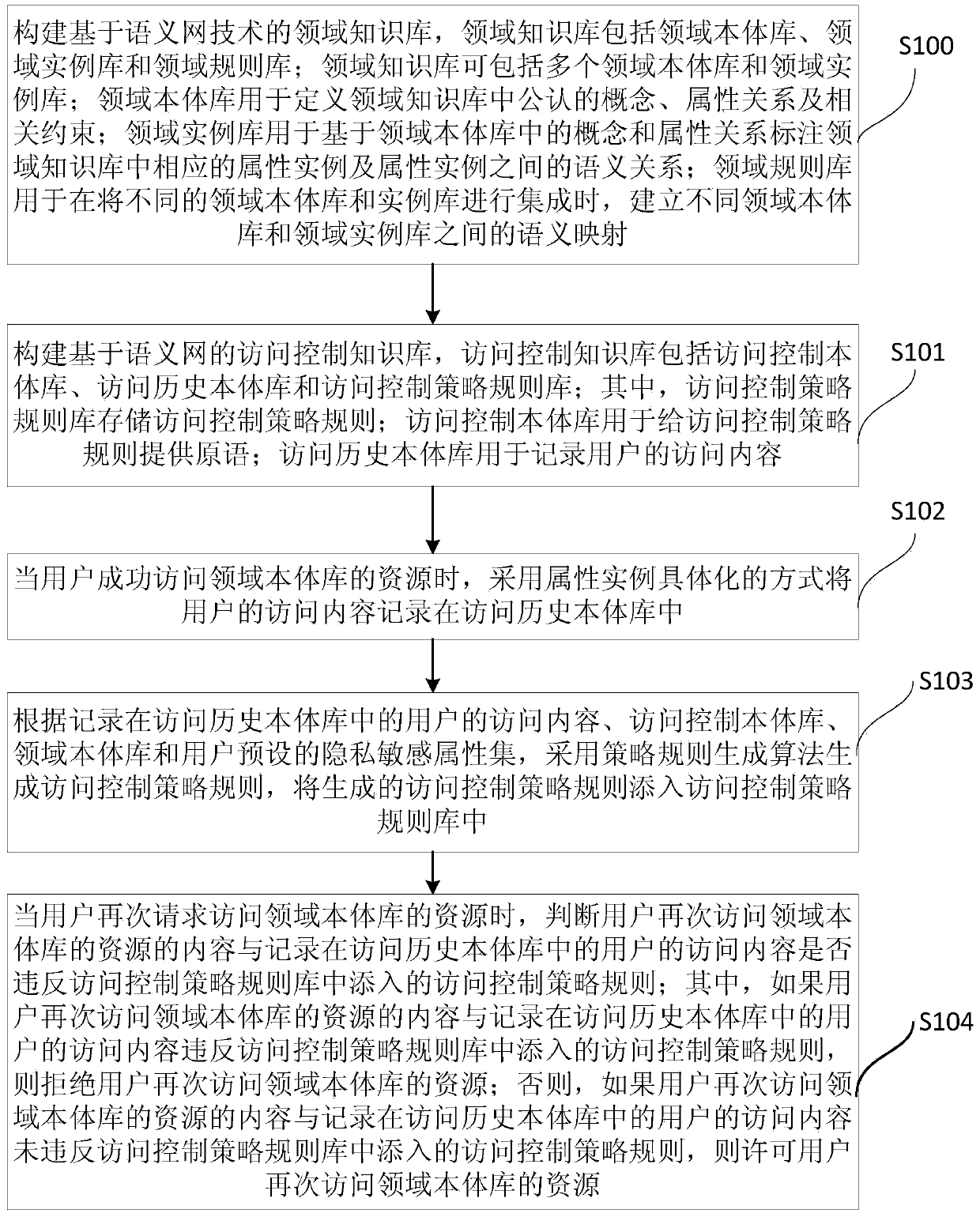
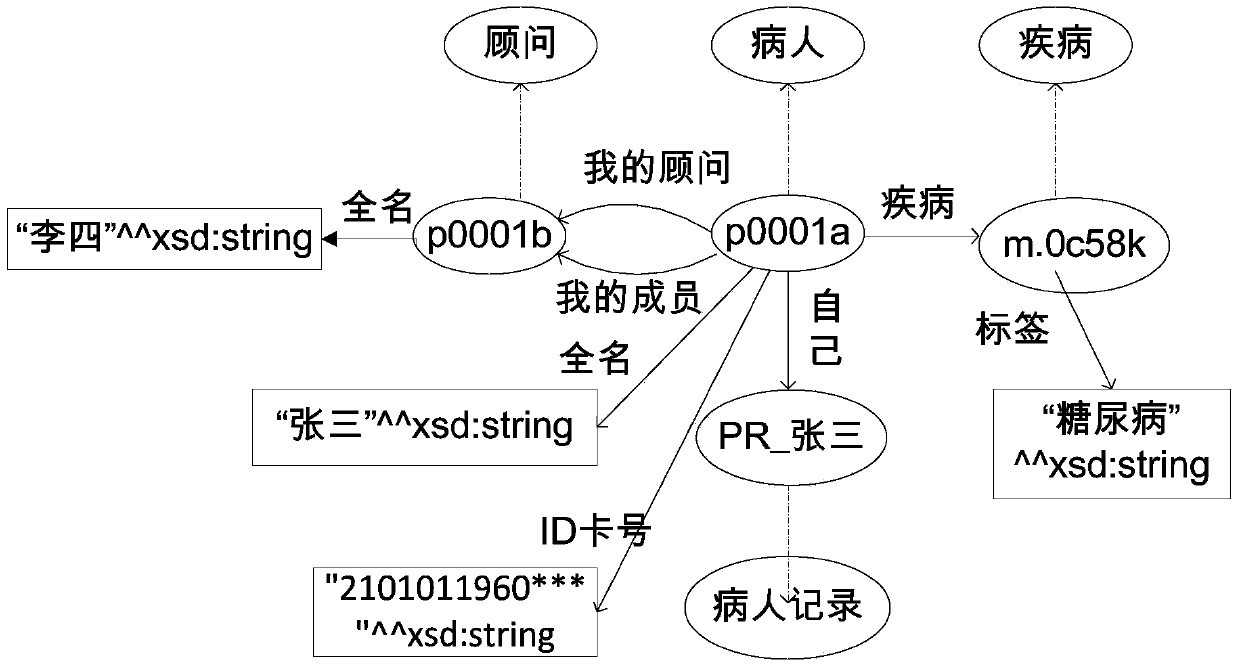
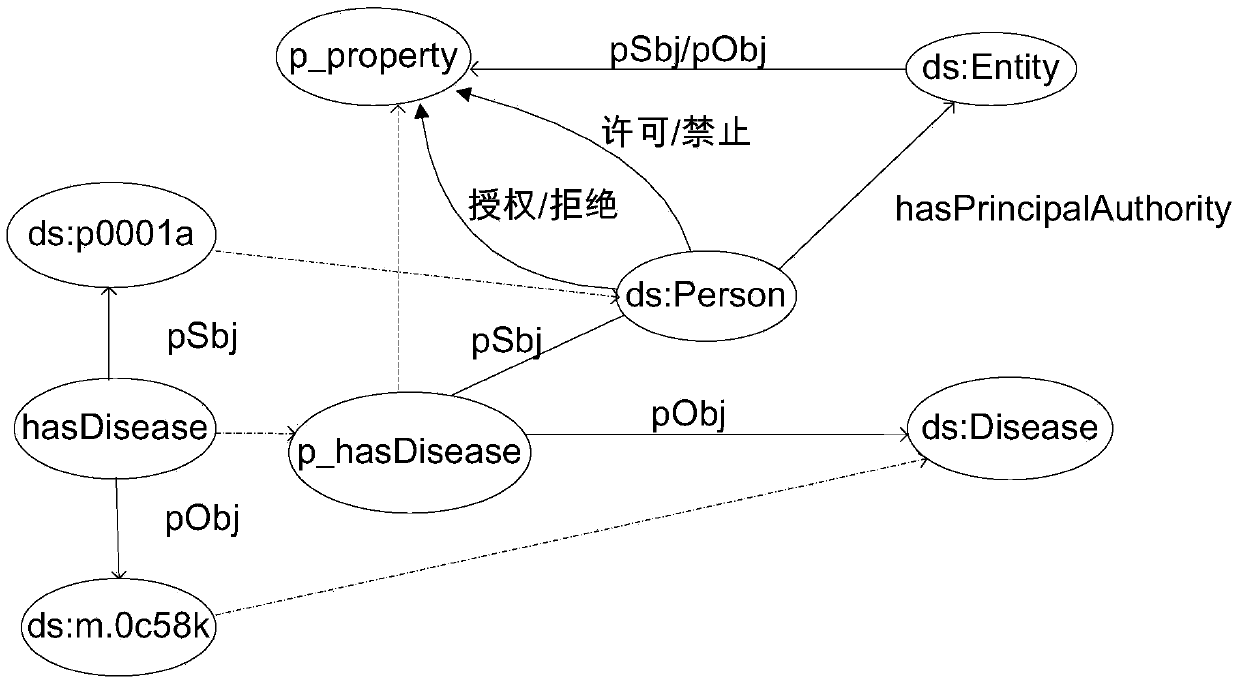
ActiveCN103745161AIncrease flexibilityImprove robustnessDigital data protectionTransmissionAccess historyA domain
The invention provides a method and a device for controlling access security, wherein the method comprises the steps of establishing semantic web technology-based domain knowledge bases (including a domain ontology base, a domain example base and a domain rule base) and access control knowledge bases (including an access control ontology base, an access history ontology base and an access control policy rule base), when a user succeeds in accessing resources in the domain knowledge bases, recording the historical contents accessed by the user by an attribute example embodying method and generating an access control policy rule simultaneously, when the same user requests for accessing to the resources in the domain knowledge bases again, determining whether the access content of the user at the present time and the historical content accessed by the user previously break the made access policy rule, and if breaking the made access policy rule, rejecting the access request of the user at the present time, otherwise, allowing the access request of the user at the present time. The method and the device can be used for solving the security and privacy disclosure problems caused by context linkage between the contents accessed a plurality of times by the same user.
Owner:NEUSOFT CORP
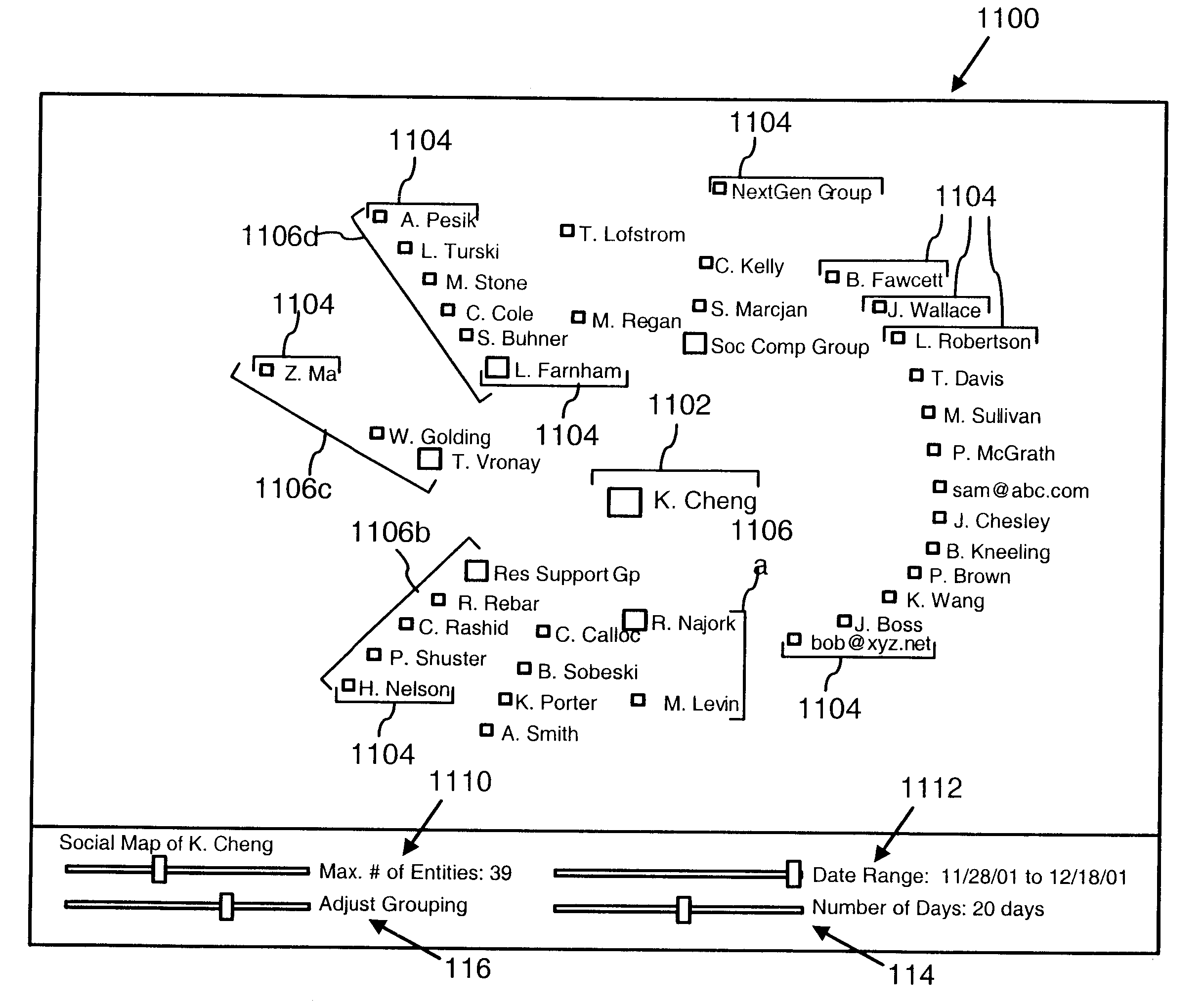
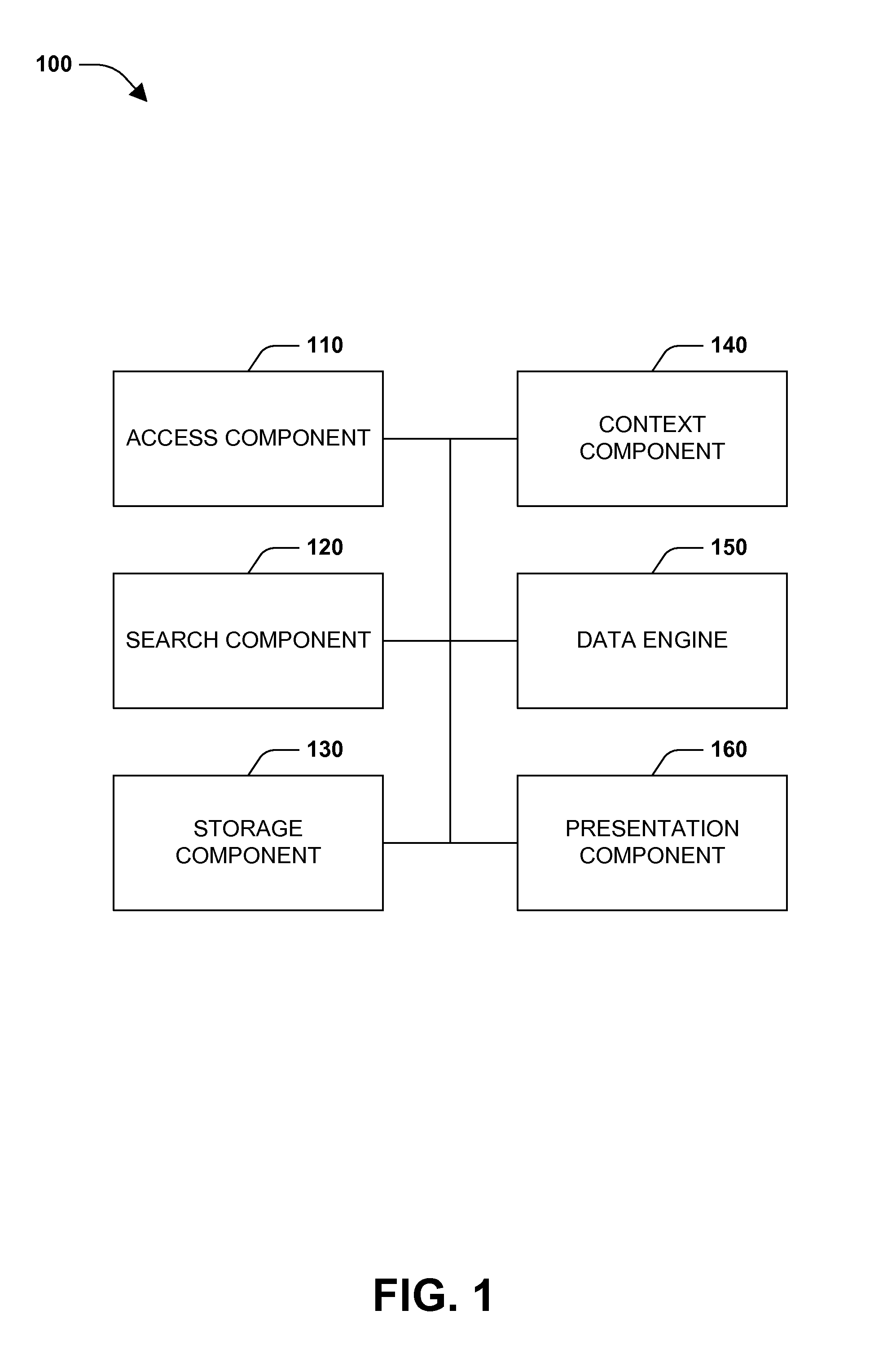
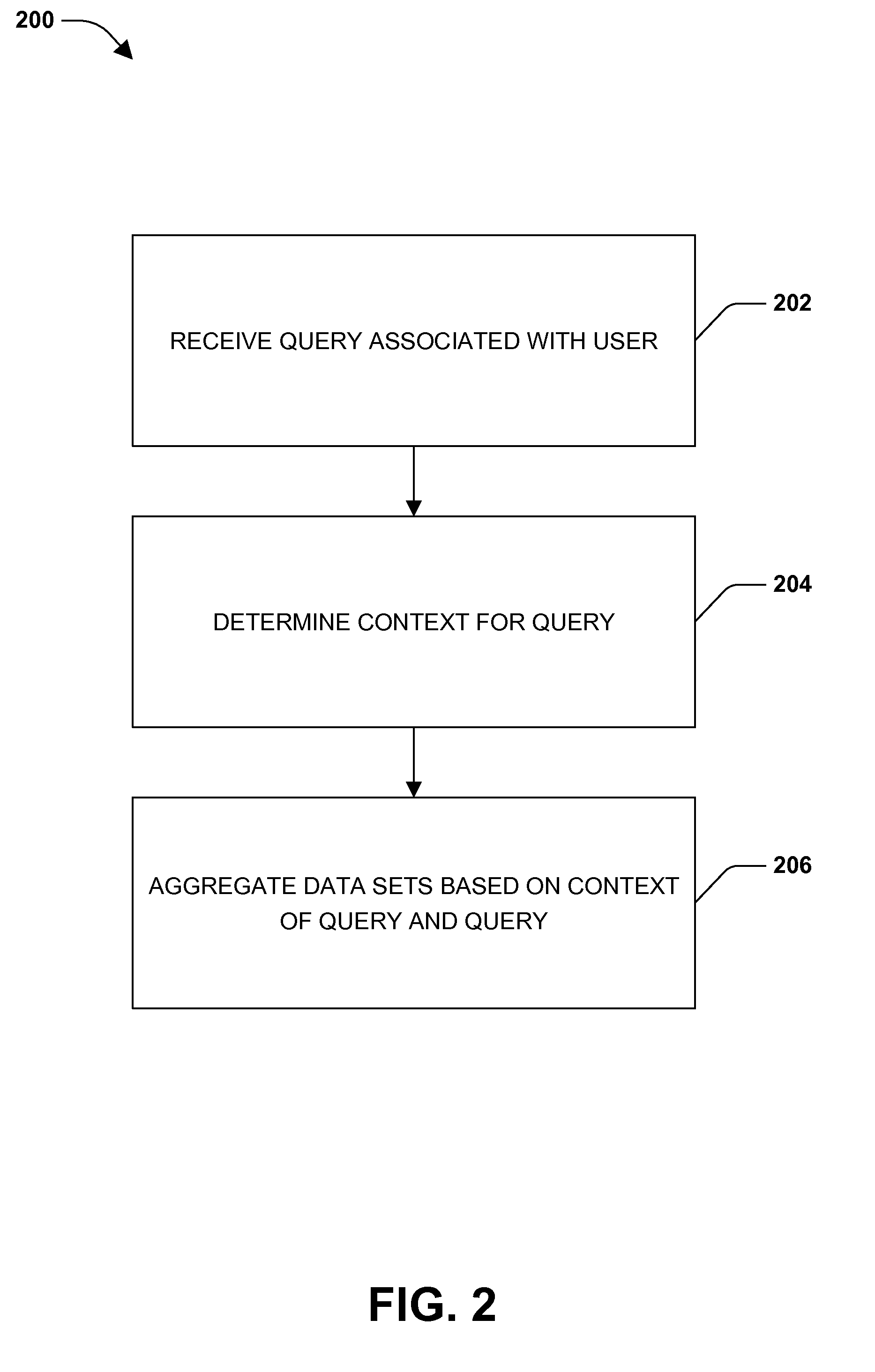
Context association
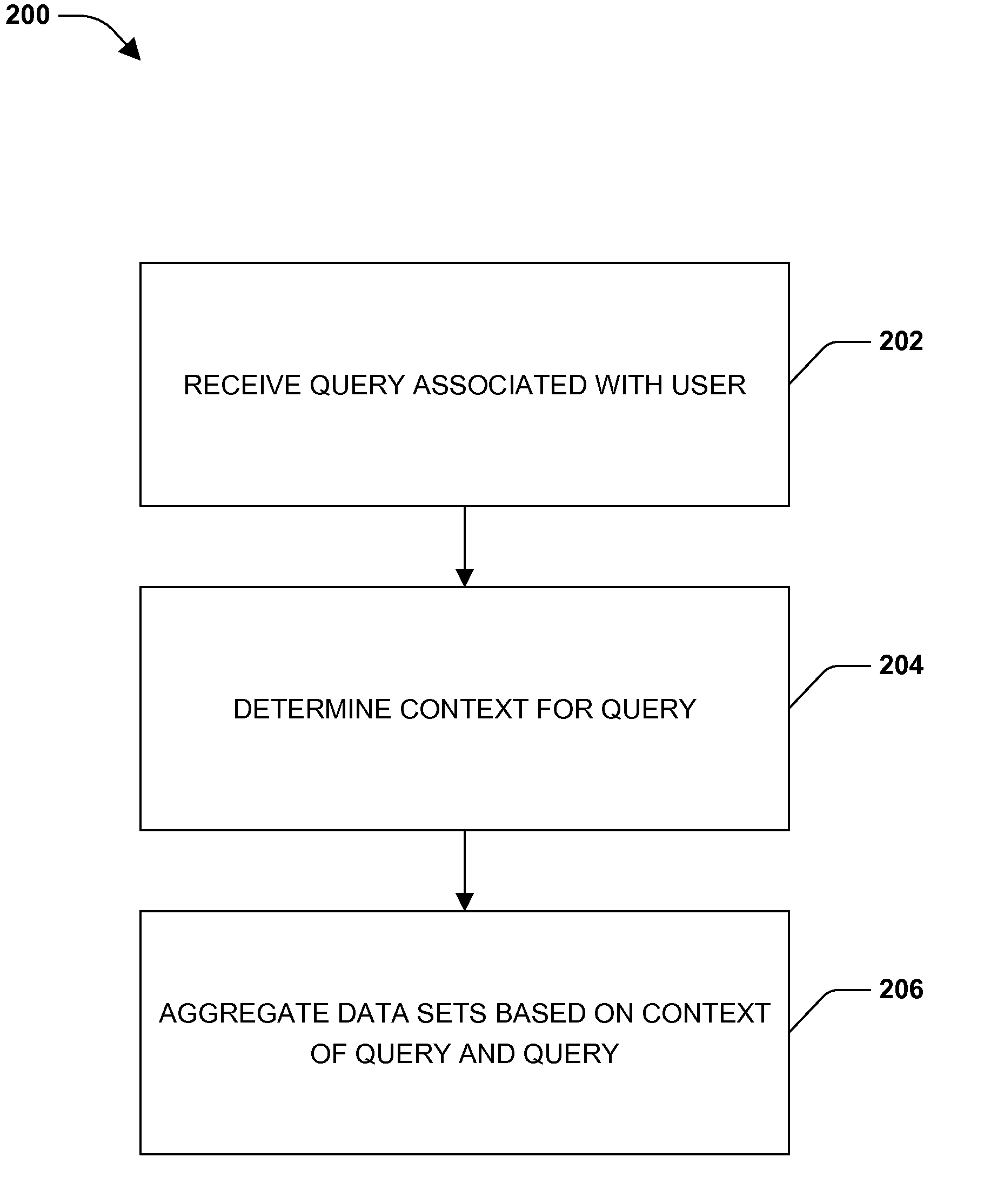
InactiveUS20150134675A1Well formedDigital data information retrievalDigital data processing detailsSocial mediaData set
One or more embodiments of techniques or systems for search context association are provided herein. Search context association can include search filtering and / or search expansion. For example, when a query is submitted, data or data sets can be filtered to narrow a search or expanded such that additional data sets or queries are included. Data or data sets can be aggregated, filtered, or expanded based on a context of the query. A context can include user characteristics, environmental factors, social media factors, route based characteristics, or destination based characteristics. As an example, when a new product (e.g., a new mobile phone) is released, limited quantities may be available. Users may be directed to different retailers or stores based on inventory levels, length of lines (which may be determined using social media among other things), distance, and the like.
Owner:WELLS FARGO BANK NA
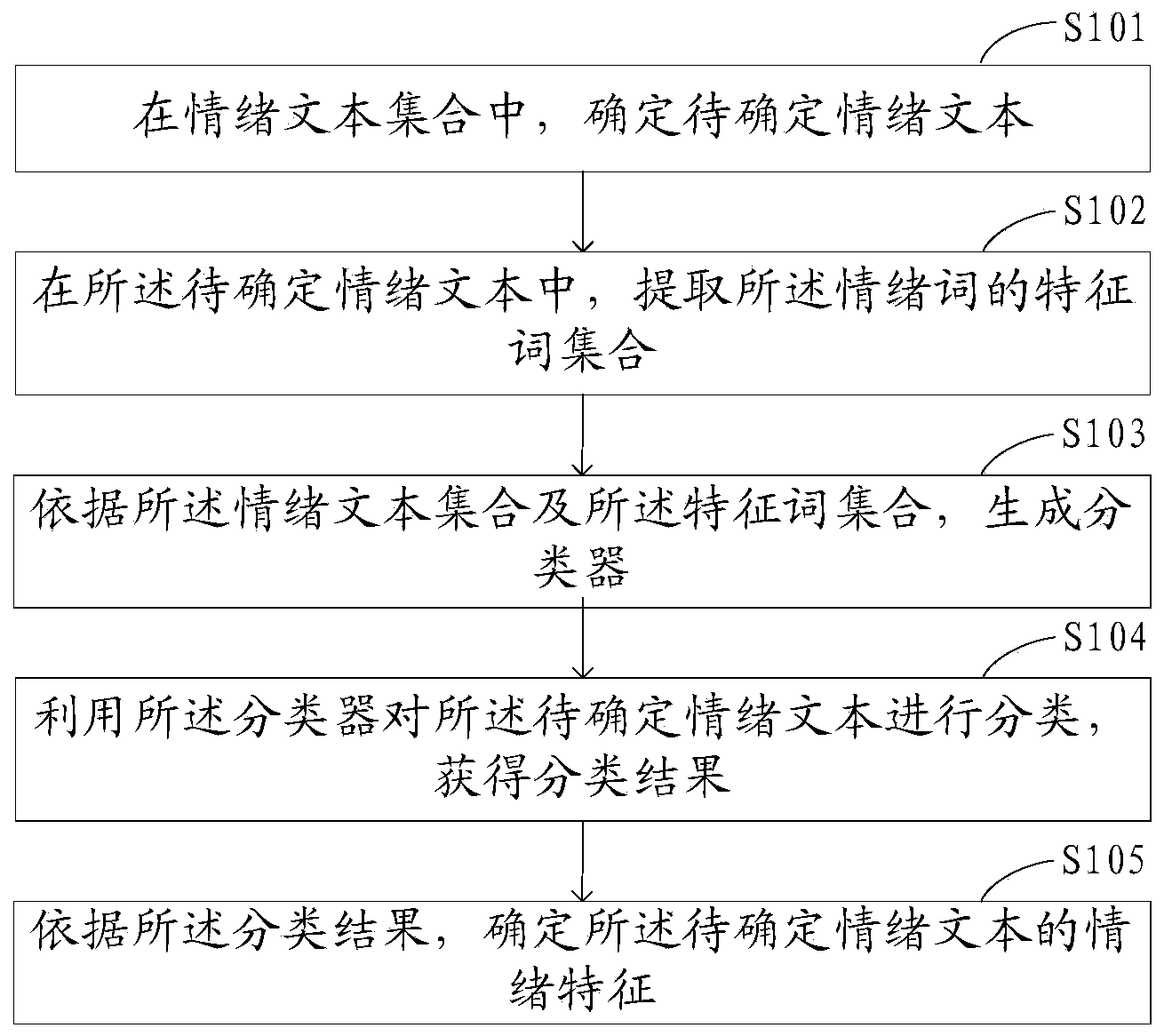
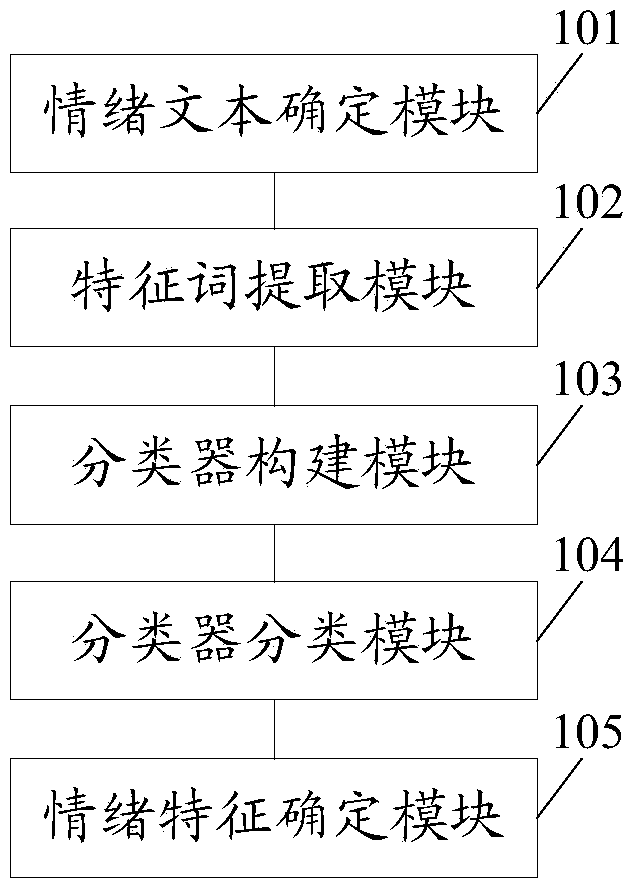
Method and device for determining emotional characteristics of emotional texts
InactiveCN104346326AImprove accuracySpecial data processing applicationsContextual AssociationsClassification result
The invention provides a method and a device for determining emotional characteristics of emotional texts. The method comprises the following steps: extracting characteristic word set of emotional words in determined emotional texts; constructing a classifier according to an emotional text set and the characteristic word set; classifying the emotional texts to be determined by utilizing the classifier so as to obtain a classification result; determining whether the emotional characteristic of the emotional texts to be determined is emotion occur or emotion hide according to the classification result. The determined characteristic word set comprises characteristic words with context correlation characteristics, and the characteristic words are used for constructing the classifier, so that the constructed classifier fully takes into consideration the influences of the context on the emotional expression; compared with the manner of simply and mechanically determining the emotional characteristics by utilizing the emotional words in the prior art, the method and the device provided by the invention have the effect of greatly improving the correctness of the determination.
Owner:SUZHOU UNIV
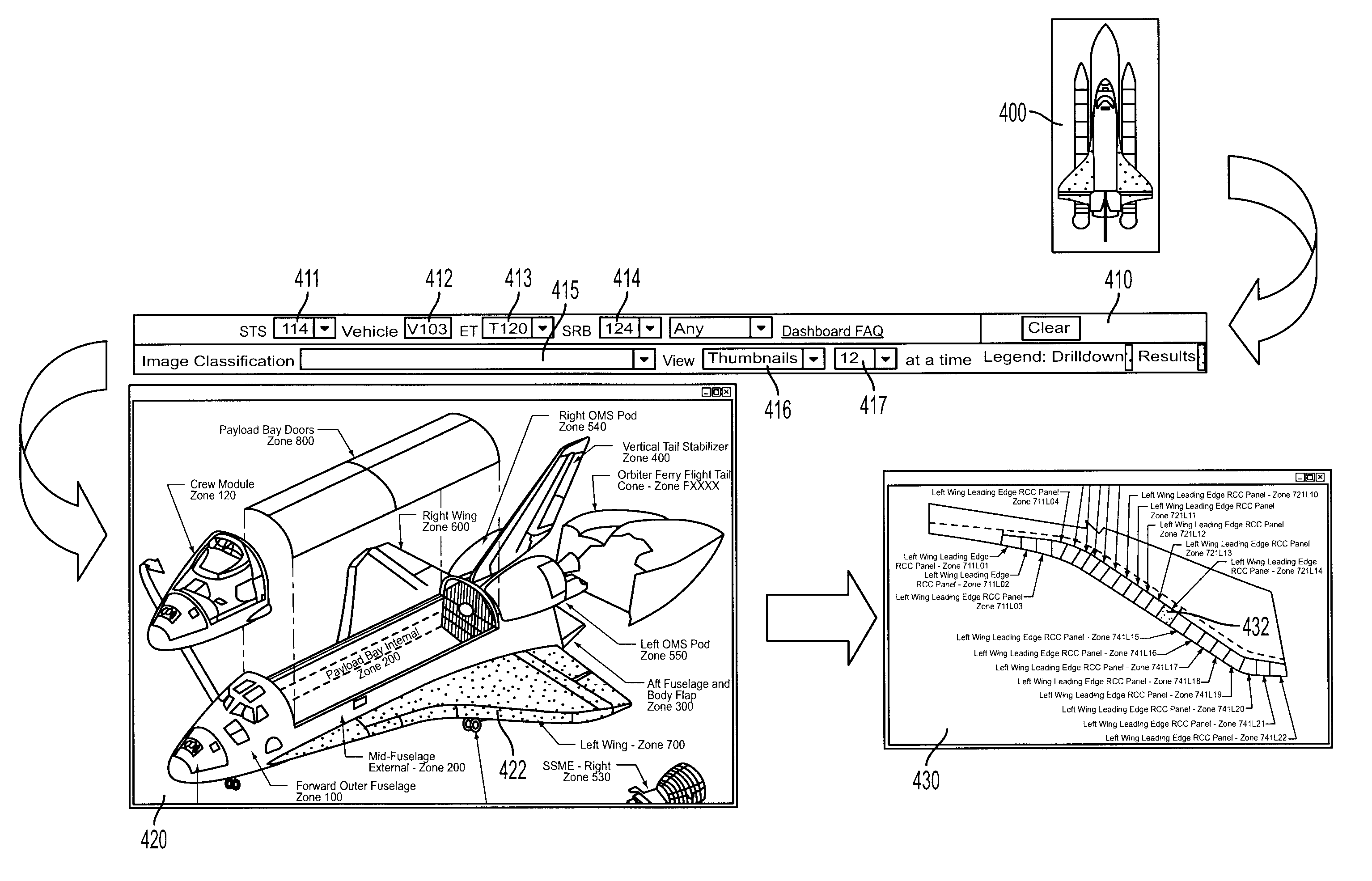
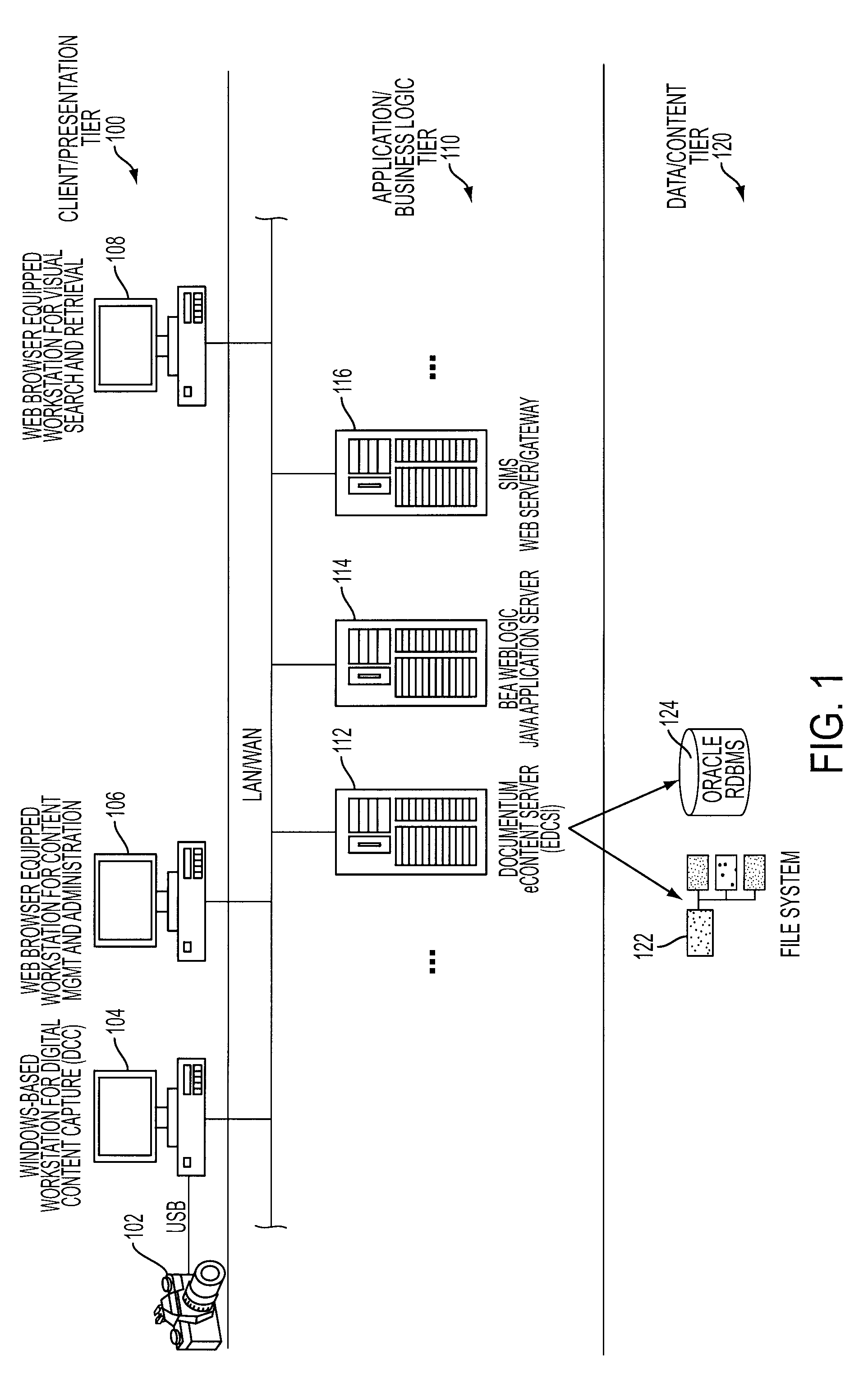
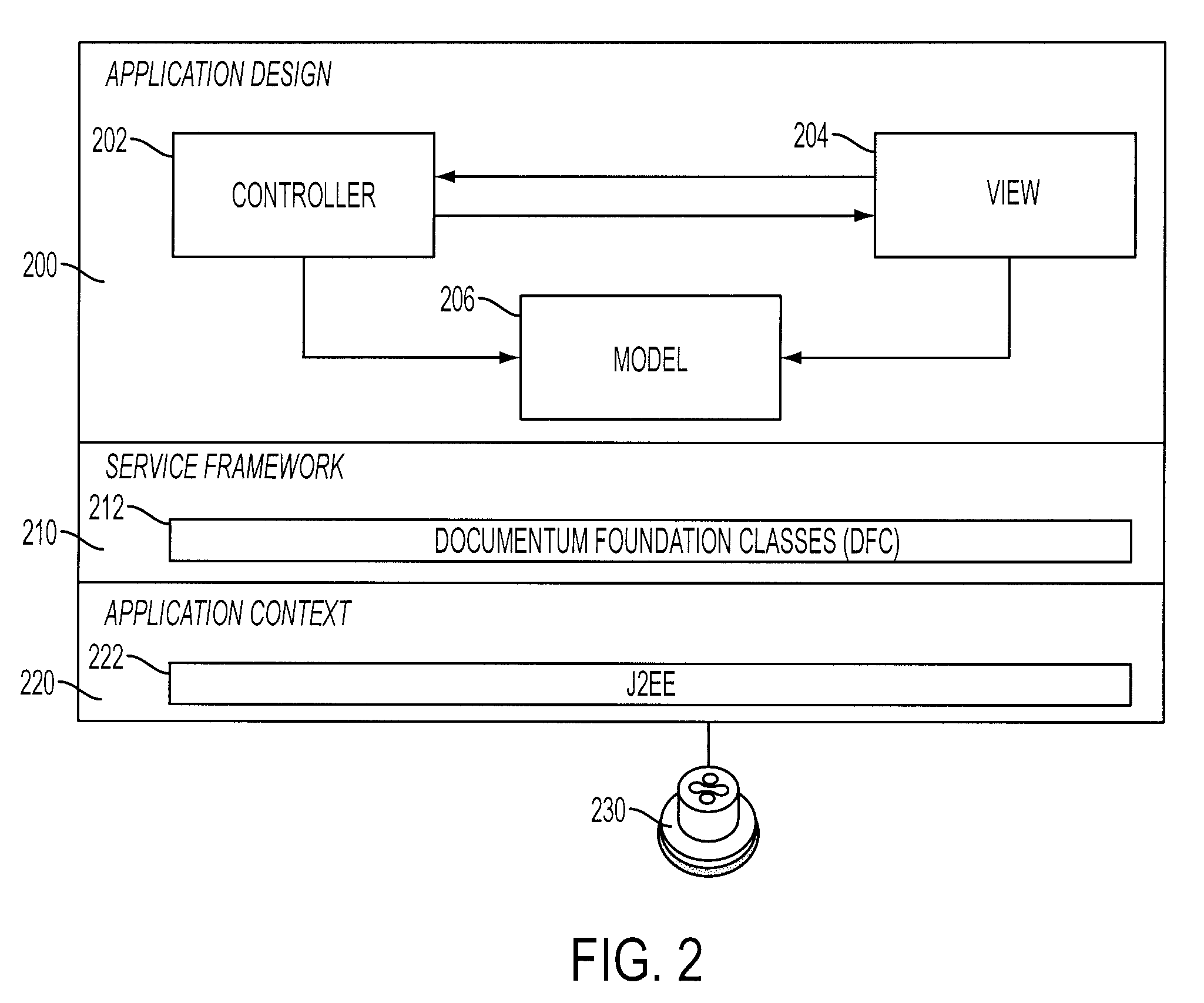
Image and information management system
InactiveUS7295719B2Simple and reliable interfaceEasy to useData processing applicationsCharacter and pattern recognitionGraphicsSearch filter
A system and methods through which pictorial views of an object's configuration, arranged in a hierarchical fashion, are navigated by a person to establish a visual context within the configuration. The visual context is automatically translated by the system into a set of search parameters driving retrieval of structured data and content (images, documents, multimedia, etc.) associated with the specific context. The system places “hot spots”, or actionable regions, on various portions of the pictorials representing the object. When a user interacts with an actionable region, a more detailed pictorial from the hierarchy is presented representing that portion of the object, along with real-time feedback in the form of a popup pane containing information about that region, and counts-by-type reflecting the number of items that are available within the system associated with the specific context and search filters established at that point in time.
Owner:UNITED SPACE ALLIANCE
Communication connectivity via context association, advertising sponsorship, and multiple contact databases
InactiveUS7899173B2Easy to identifyEasy to findTelephone data network interconnectionsAccounting/billing servicesFunctional connectivityTelecommunications
Communication connectivity via context association is provided by associating targeted subscriber contact information with a key at a subscriber database. At a data center, the keys are associated with unique characteristics or aliases (contexts) of the subscribers, thereby facilitating context searching. A caller initiates a connection to a subscriber by providing a subscriber's context. The context is located and associated key identified. The key is resolved in the subscriber database, and the call routed. Use of the key allows subscriber connectivity without revealing, to the caller or to the data center, sensitive contact information. Through a caller database, call initiation occurs by subscriber alias identification in a caller's communication device; thereby foregoing inclusion of sensitive contact information within the caller's communication device. Communication connectivity can be advertiser sponsored, with advertisements accompanying messages selected by matching profile information of targeted subscribers with participating advertiser provided profile information of desired targeted subscribers.
Owner:WALMART APOLLO LLC
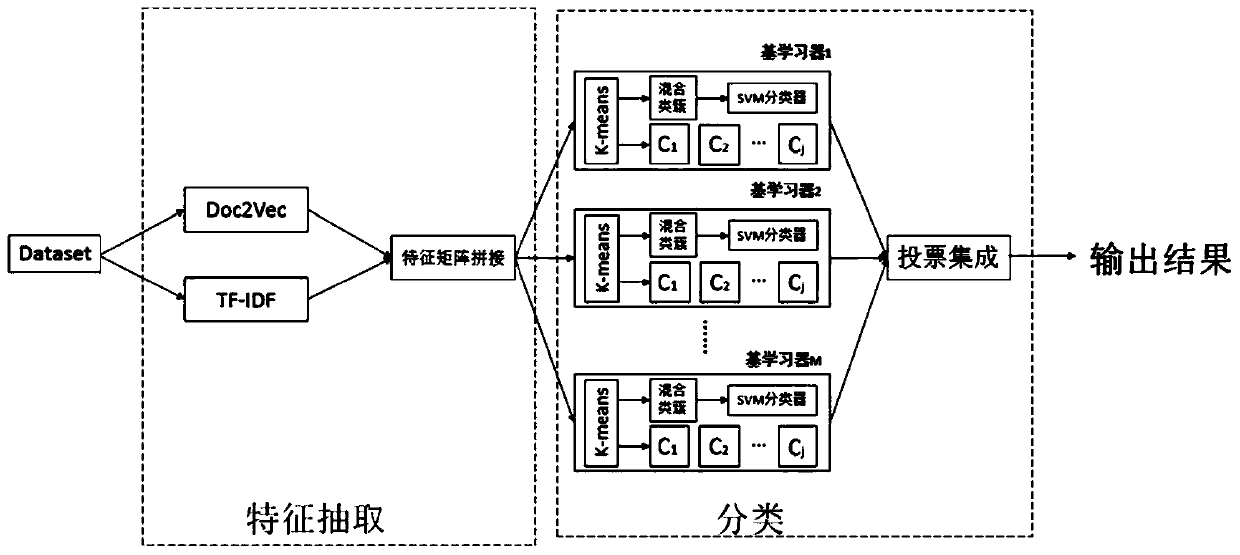
Malicious code detection method and system
ActiveCN111143842AImprove accuracyImprove completenessCharacter and pattern recognitionPlatform integrity maintainanceData setAlgorithm
The invention discloses a malicious code detection method and system, and the method comprises the steps: S1, enabling a Windows API action sequence in an operation process of each malicious code to serve as a text with a context relation, and respectively carrying out the feature extraction through TF-IDF and Doc2vec; s2, after a TF-IDF feature matrix and a Doc2vec feature matrix are obtained respectively, splicing the features extracted by the TF-IDF and the Doc2vec, and obtaining a feature matrix of the malicious code after dimensionality reduction; s3, constructing an integrated classification improved model based on clustering, classifying the data set by adopting a plurality of base learners; and S4, in a prediction stage, respectively inputting the samples into the nearest single class cluster / SVM classifier in each base learner, outputting a prediction class, and finally according to a voting principle, taking the class occupying the majority in the learner output classes as afinal prediction class. According to the method, the TF-IDF and the Doc2vec are combined, the API frequency in the malicious code action sequence is considered, the context association of the action sequence is also considered, and the malicious code detection accuracy is improved.
Owner:GUANGZHOU UNIVERSITY
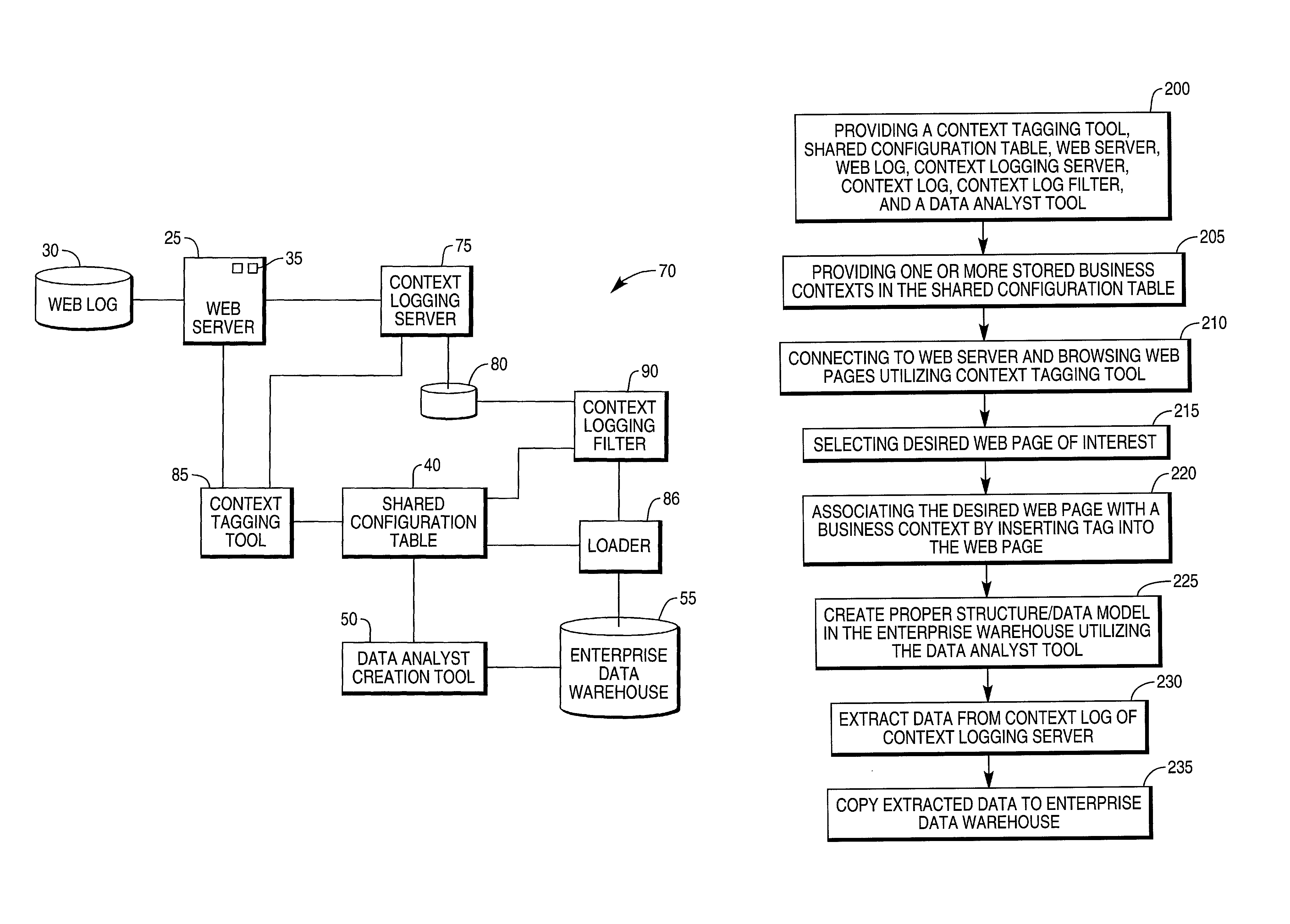
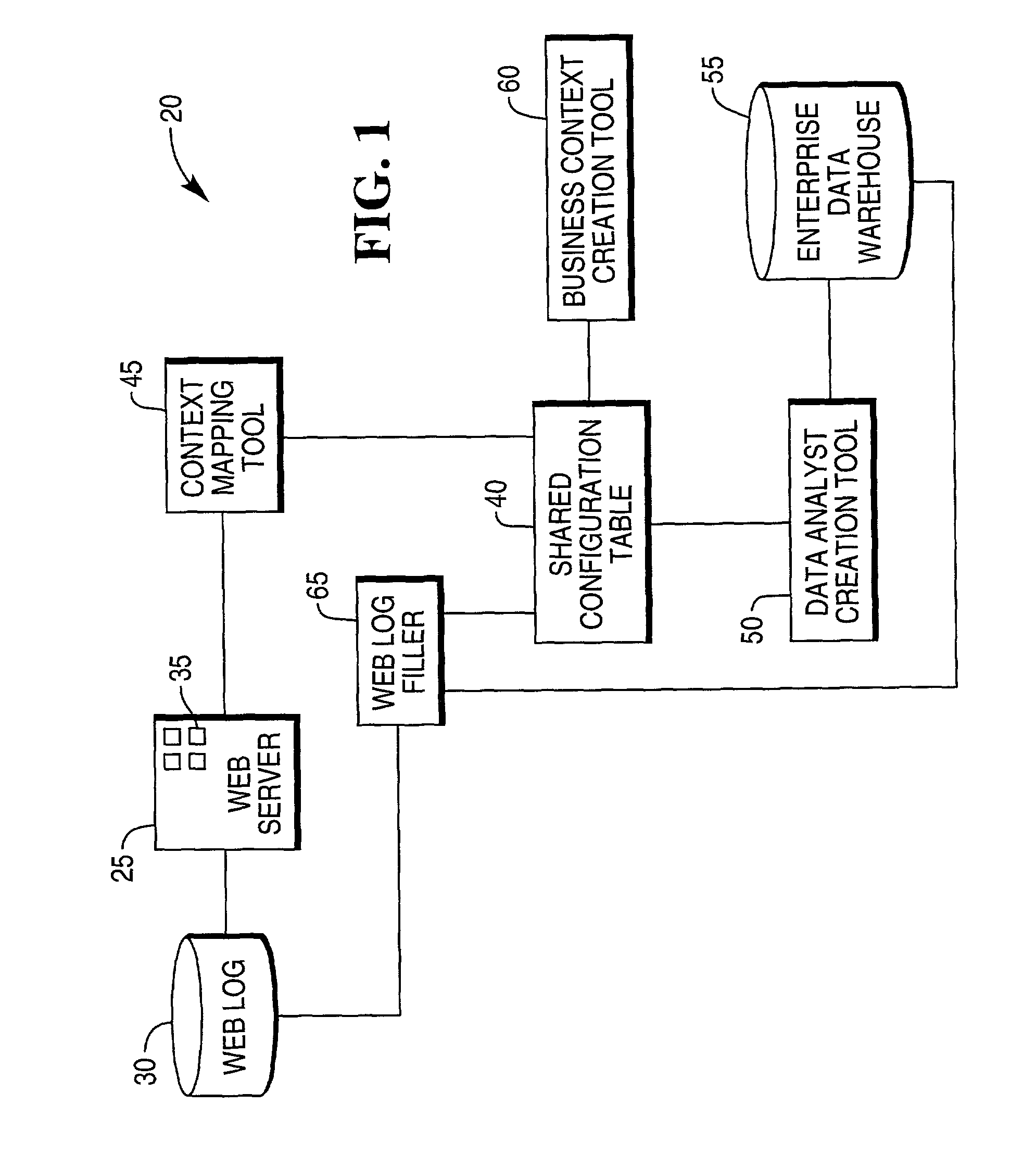
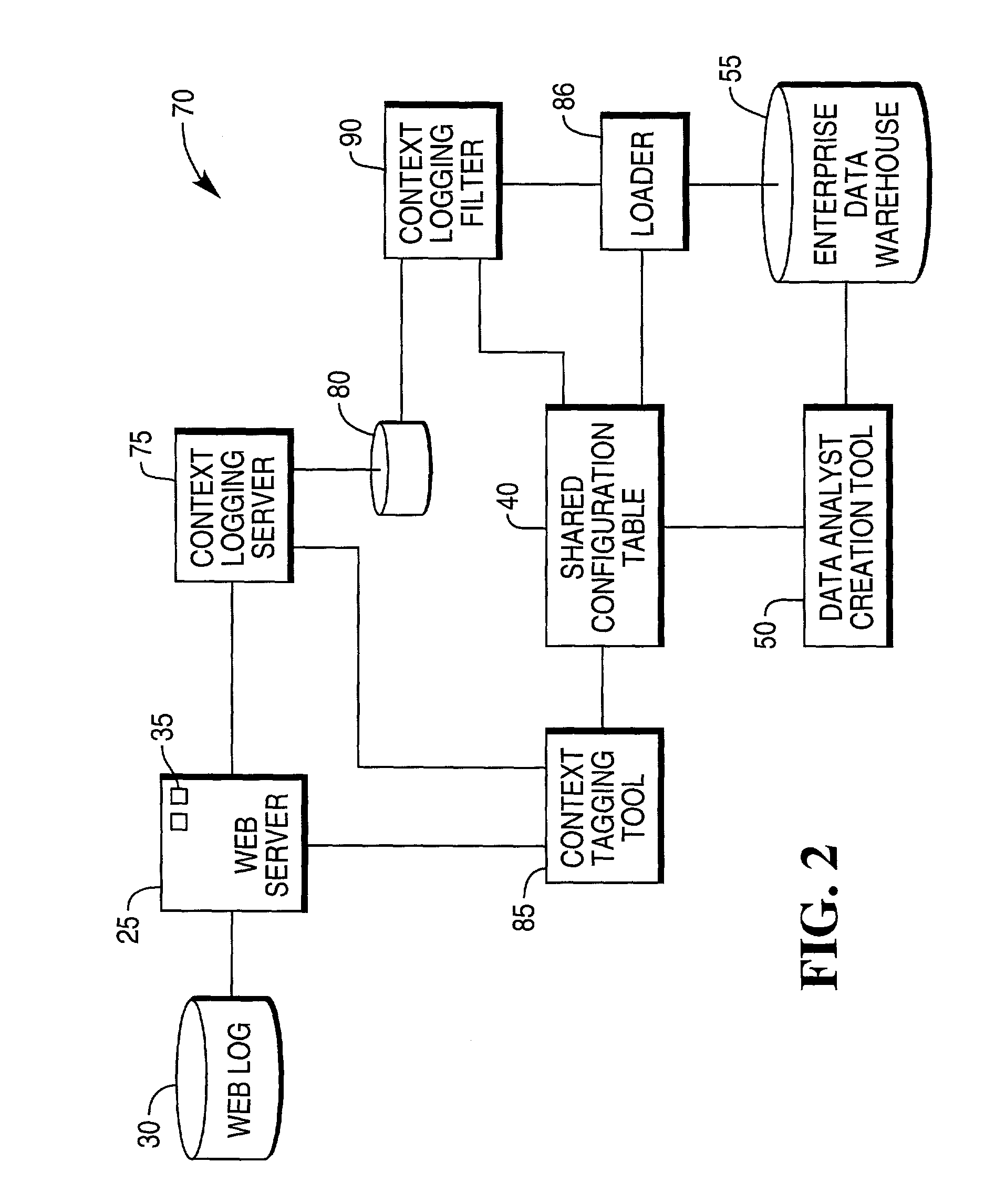
System for capturing a business context of a user's interaction with a website and method for the same
ActiveUS8280873B1Digital data information retrievalDigital data processing detailsData warehouseWeb service
The present invention relates to a system for capturing a business context of a user's interaction with a website. The system has a web server containing web pages and a web log. A web log filter extracts data from the web log associated with the address associated with the business context. A data analysis creation tool is in communication with a shared configuration table in the enterprise data warehouse, wherein the data analysis creation tool has executable instructions for creating a logical data model for mapping the extracted data to the enterprise data warehouse. A method for the same is also provided.
Owner:TERADATA US
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com