Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52 results about "Organizational hierarchy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
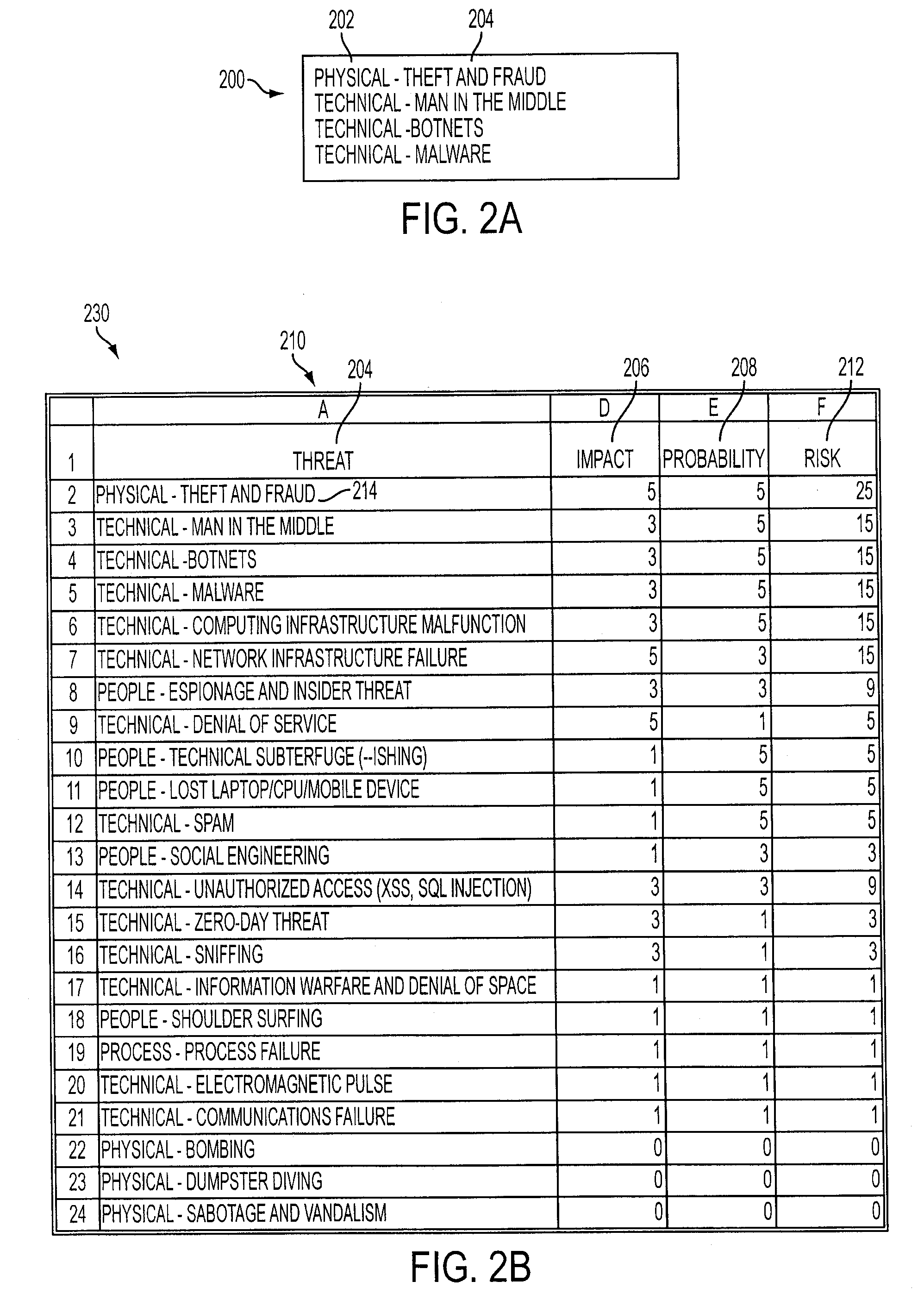
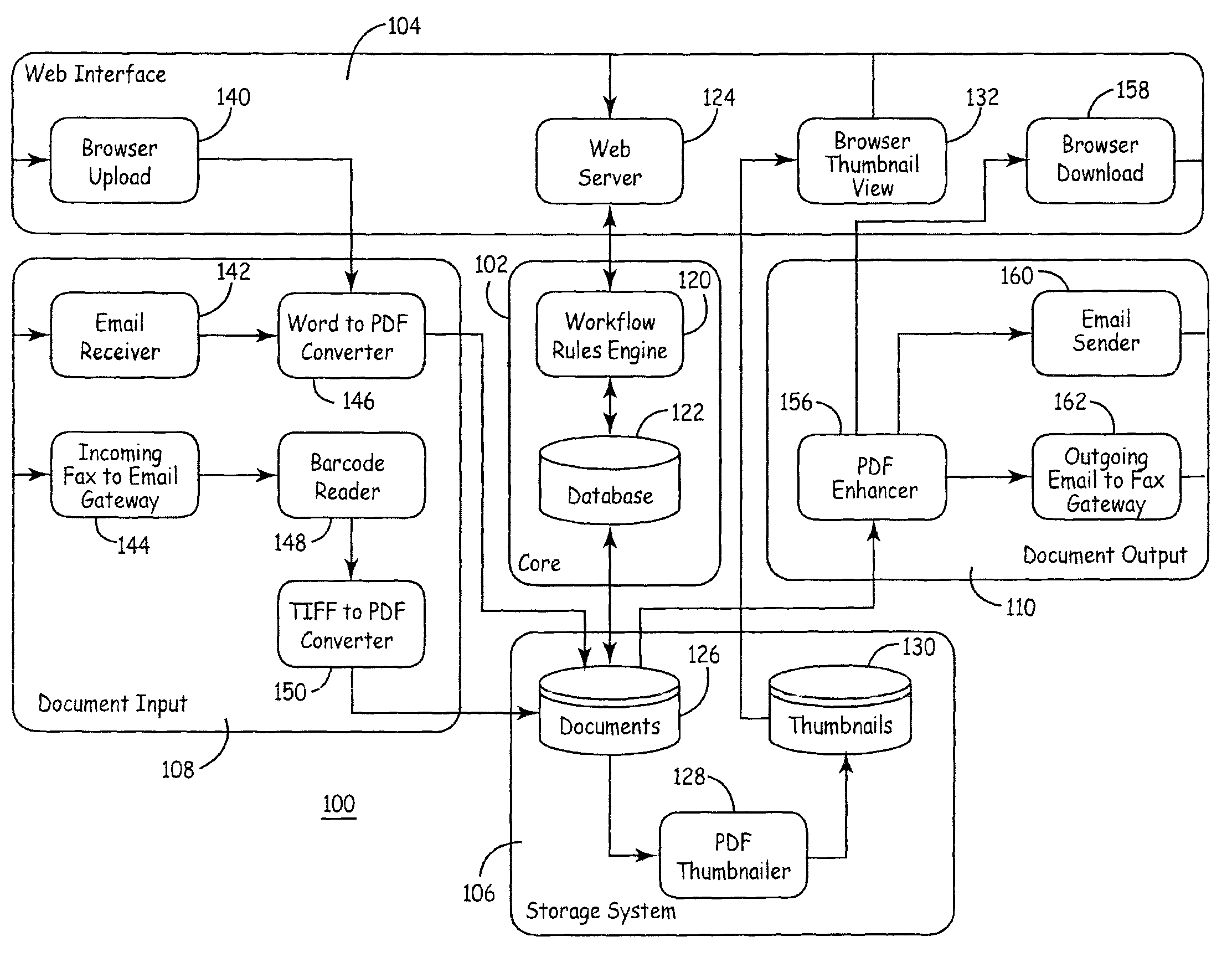
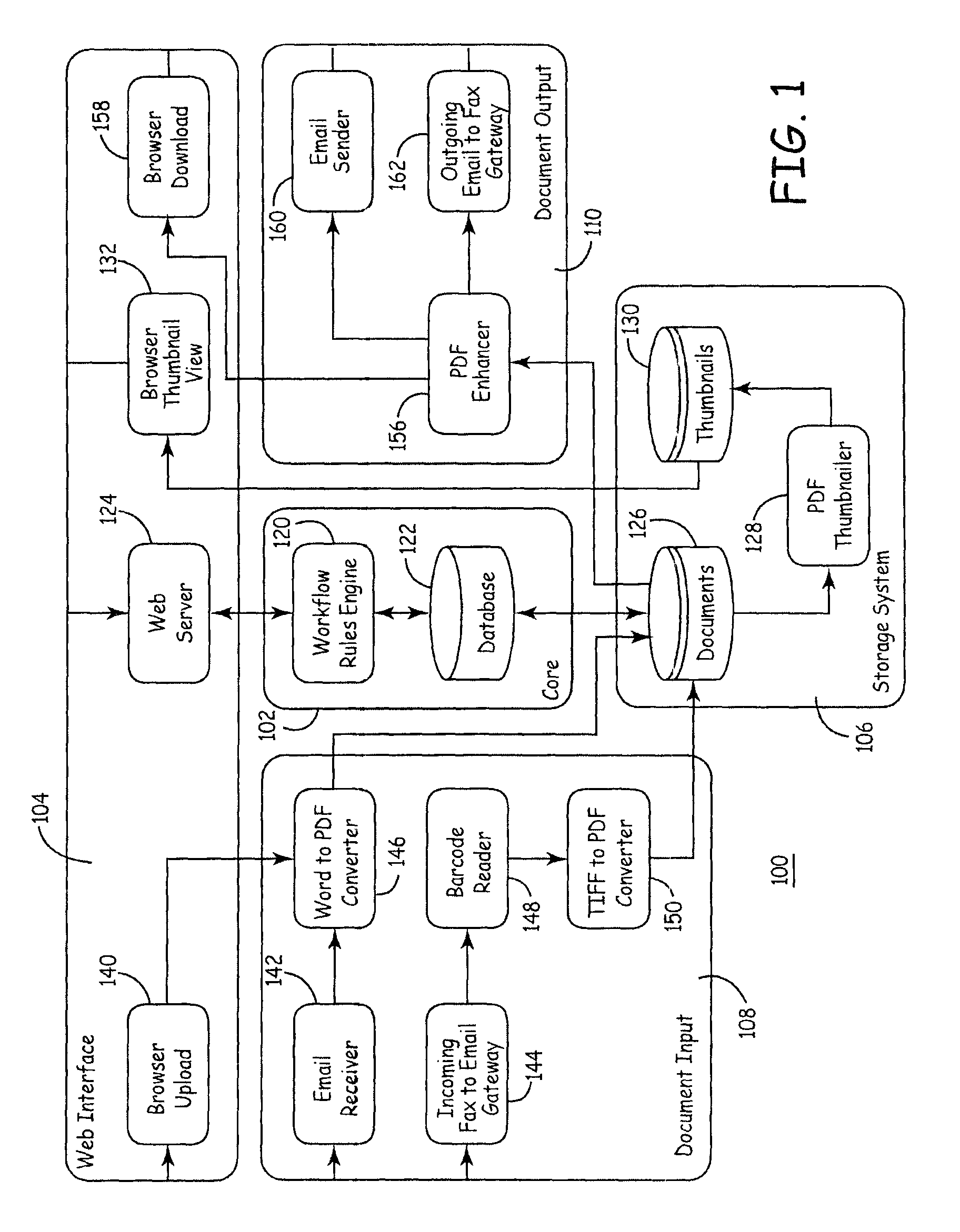
Systems and Methods for Infinite Information Organization
InactiveUS20070208685A1Special data processing applicationsMetadata based other databases retrievalDistributed Computing EnvironmentDepth level
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system. A method of displaying digital asset of a distributed computing system according to an organization specified by the end-user of a client includes: receiving an organization semantic having at least one depth level from an end-user of the client, the organization semantic specifying at least one attribute of a digital asset identification tag; and displaying, to the end-user of the client, on a virtual computing element the digital assets of the distributed computing system that substantially match the organization semantic defined by the end-user, without reference to a pre-existing organizational hierarchy of the distributed computing environment.
Owner:IRON MOUNTAIN INCORPORATED
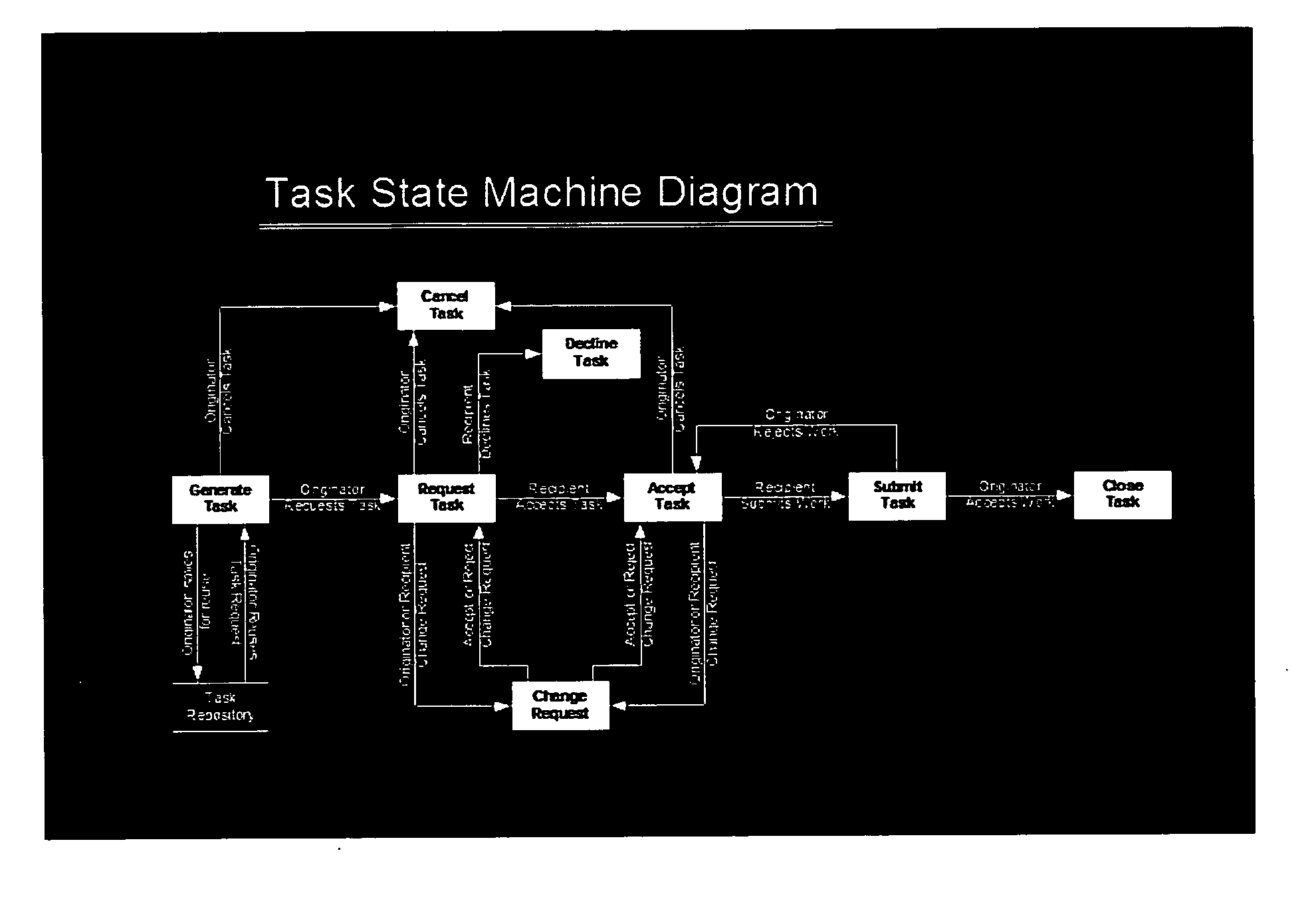
Organizationally interactive task management and commitment management system in a matrix based organizational environment
InactiveUS20050159968A1Easy to modifyBig advantageSpecial data processing applicationsVisibilityGraphics
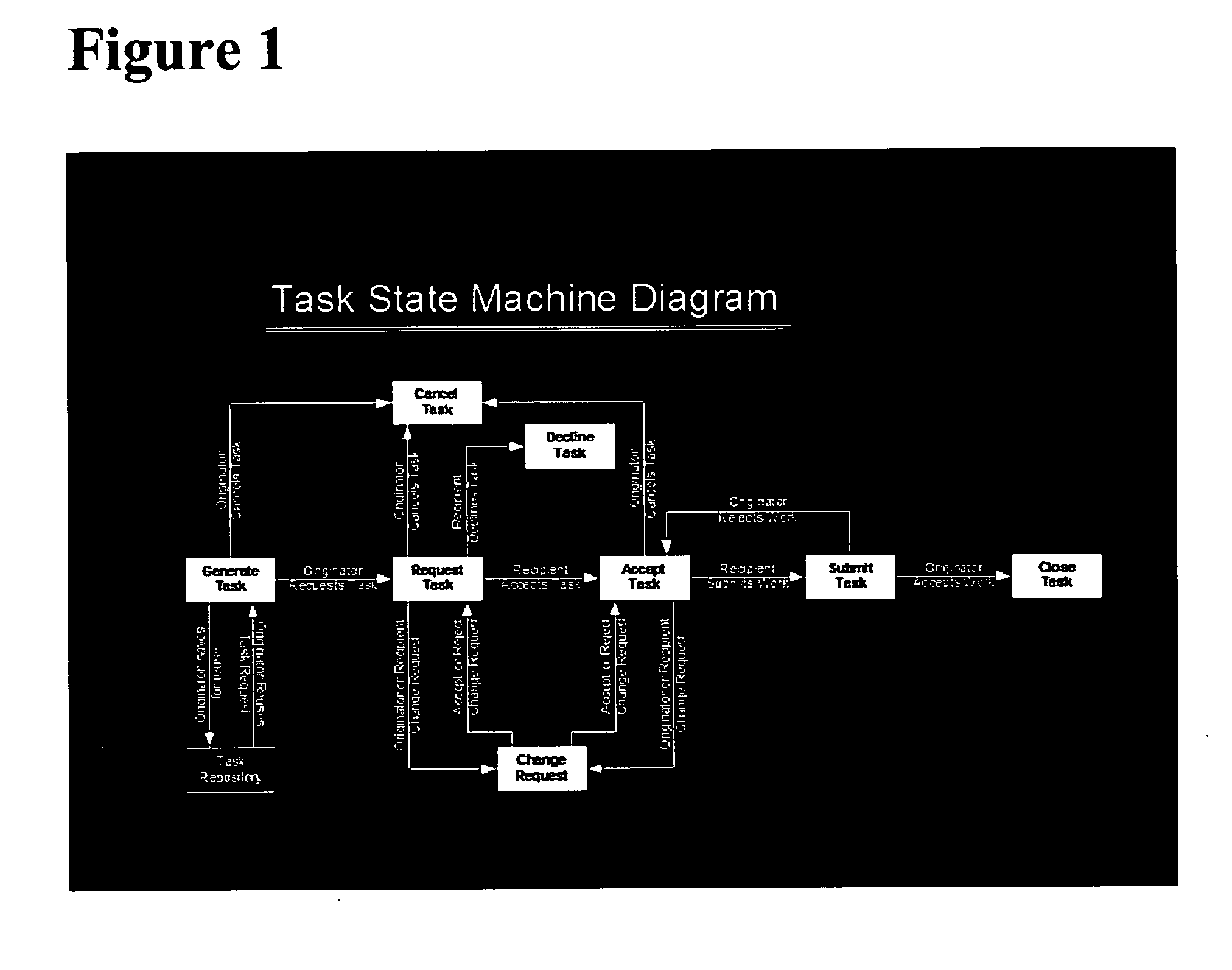
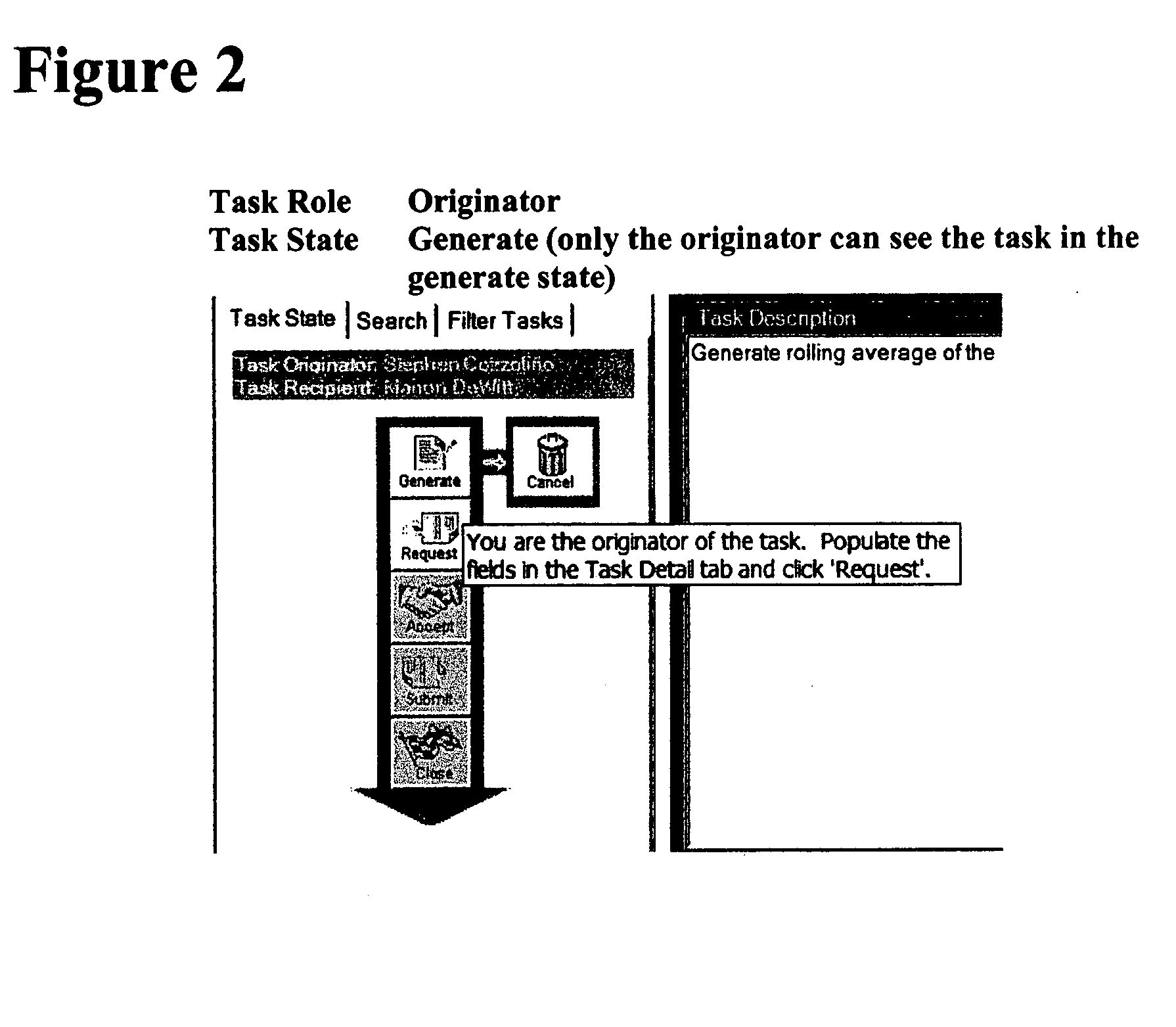
A task management and commitment management system installed enterprise wide in a matrix based organizational environment allows one-on-one interaction between an Originator and a Recipient in defining a task which is a part of a complex project. A graphically oriented software system incorporates the rules of interaction based on a task state machine diagram. The graphical interface uses Task Role and Task State to display appropriate buttons which may be activated to generate a task as an Originator, request a task of a Recipient, who may review the task, and accept it, decline it or modify it. After the task definition is accepted by the Originator and the Recipient, the Recipient completes the work required by the task and submits it to the Originator. The Originator reviews the submitted work and may accept it so that the Originator can close the task. If the Originator is not pleased with the submitted work, he may request rework of the task by the Recipient. All these interactions between the Originator and the Recipient at every stage are recorded by the system software and are visible to anyone who is in the upward, inline management of the organizational hierarchy. Inline managers can observe all the interactions of an employee on one or more matrix based projects and evaluate employee performance, providing accurate assessment. The visibility of every aspect of task interaction allows rapid modification of related tasks. The repository of all tasks from all employees provides first hand content for the performance appraisal, creates a task transaction repository for business process managers to mine for new efficiencies, archives indisputable evidence for a compliance audit, and provides a means to communicate information up inline management ranks.
Owner:COZZOLINO STEPHEN
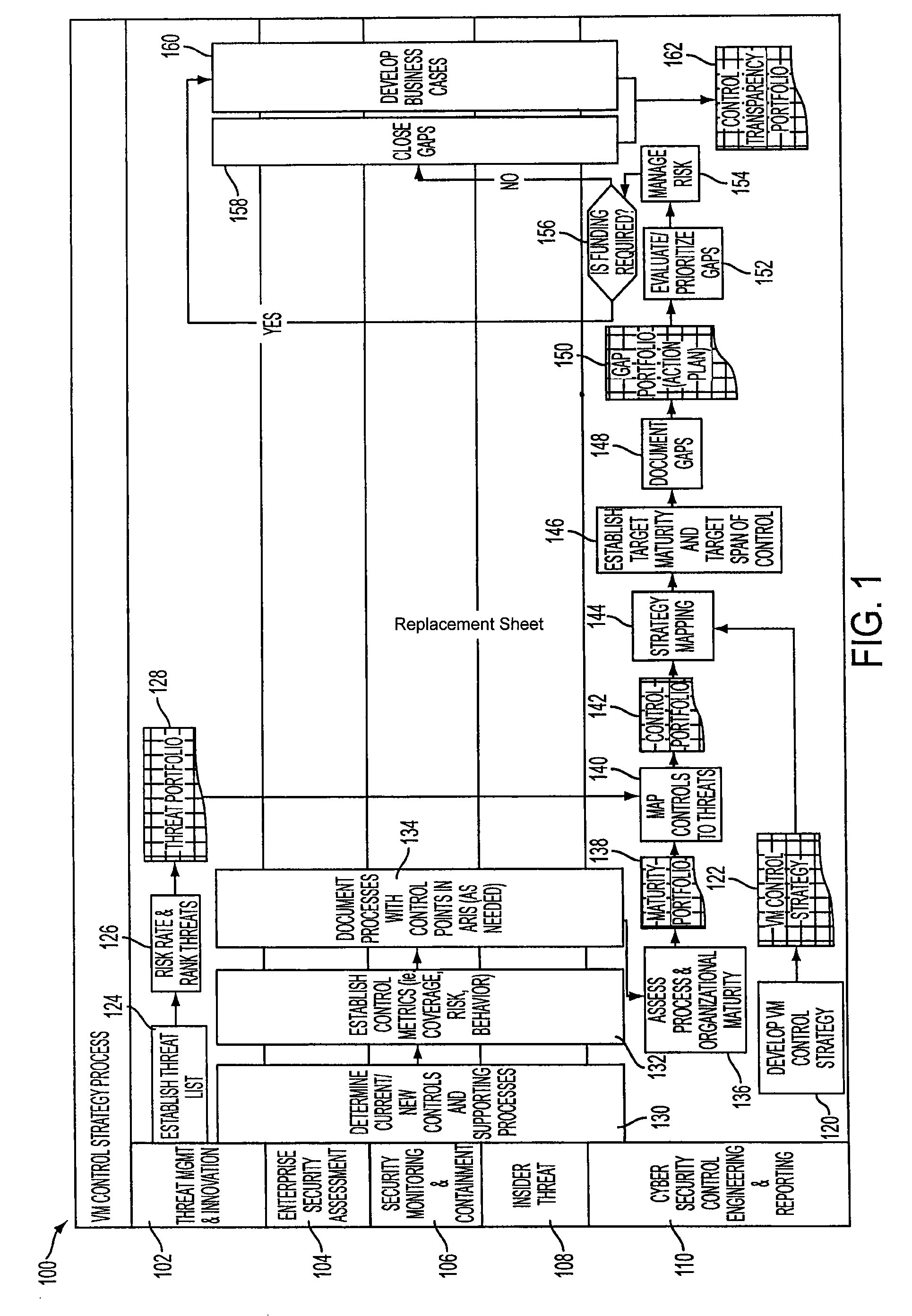
Control automation tool
ActiveUS20100199352A1Memory loss protectionDigital data processing detailsProgram planningAction plan
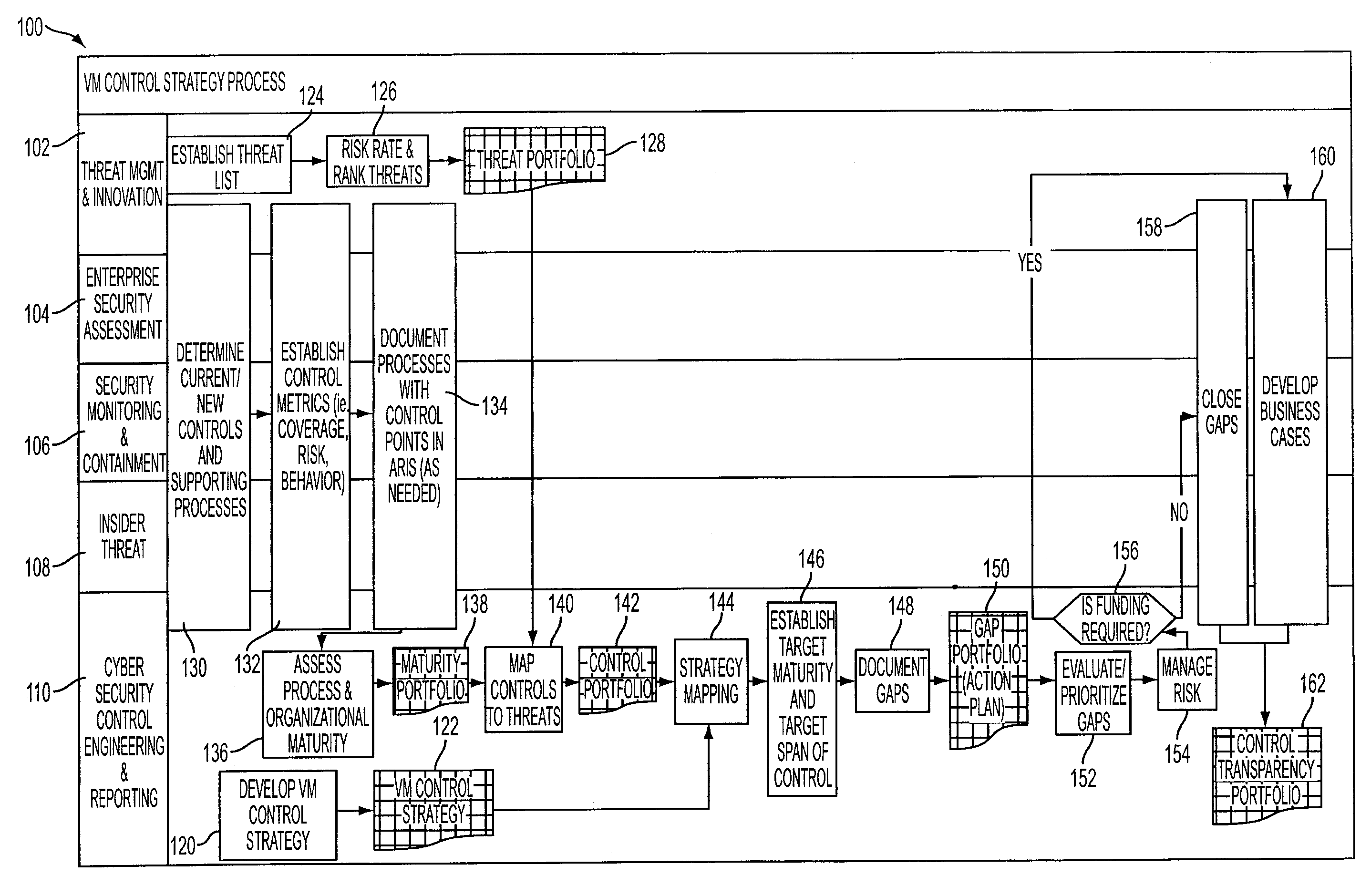
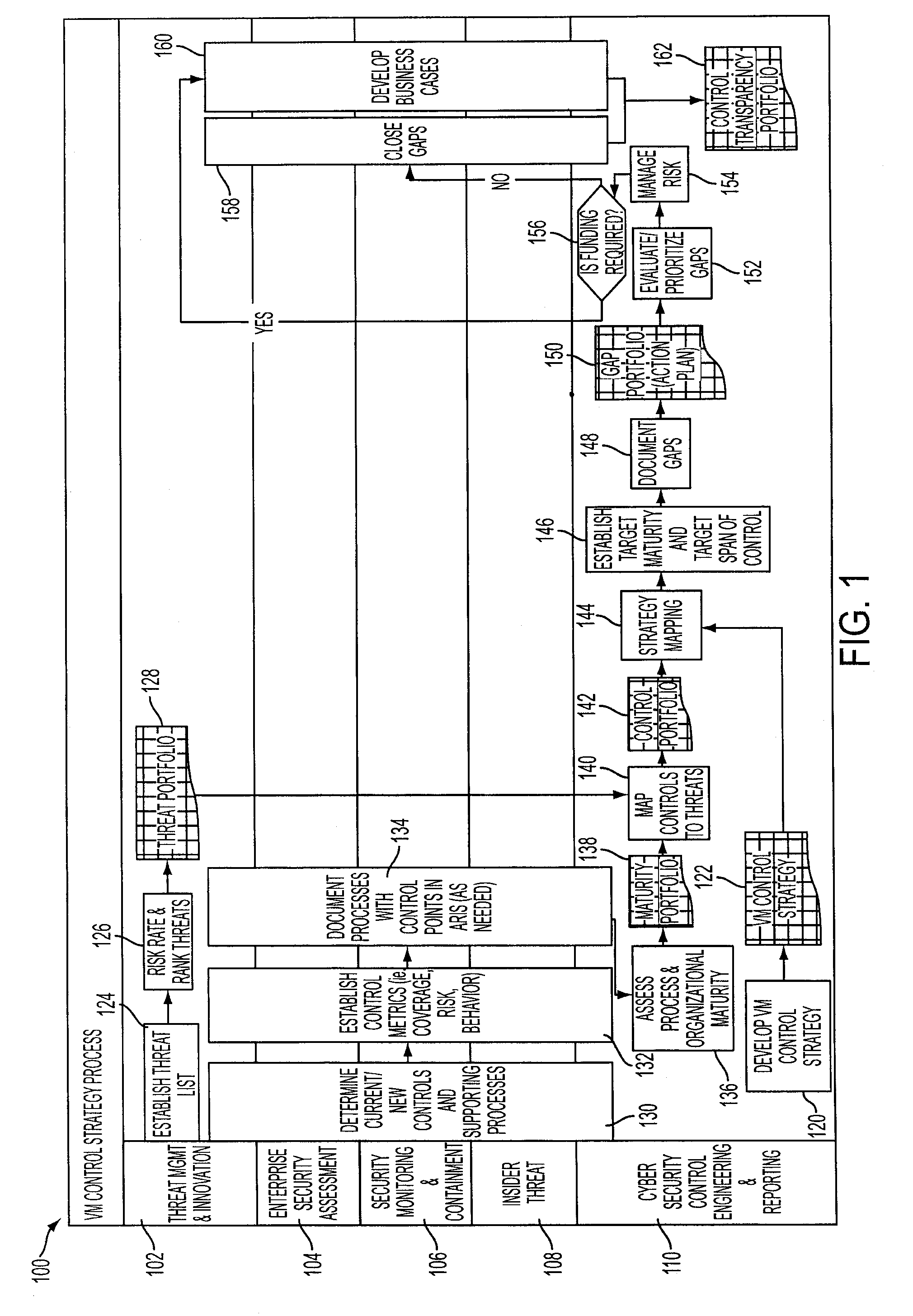
A control automation tool (“CAT”) is configured for supporting discrete management of controls and their corresponding metrics. The control automation tool includes a software application connected with, stored on, and executed by one or more relational, closed-loop data repositories and computer systems. The use and maturation of a control within an organization depends on management of operational performance and expenses, which the CAT assists through lean project management, effective implementation of action plans and financial functions. Further, people resources, organizational hierarchy and access management functions are used to support mapping of controls arranged by organizational unit and support access permissions that are consistent with appropriate data management. The CAT also provides transparency and meaning to control and metric status and relevant data regarding controls and their associated metrics and is configured for ease of control and metric management via the CAT interface.
Owner:BANK OF AMERICA CORP
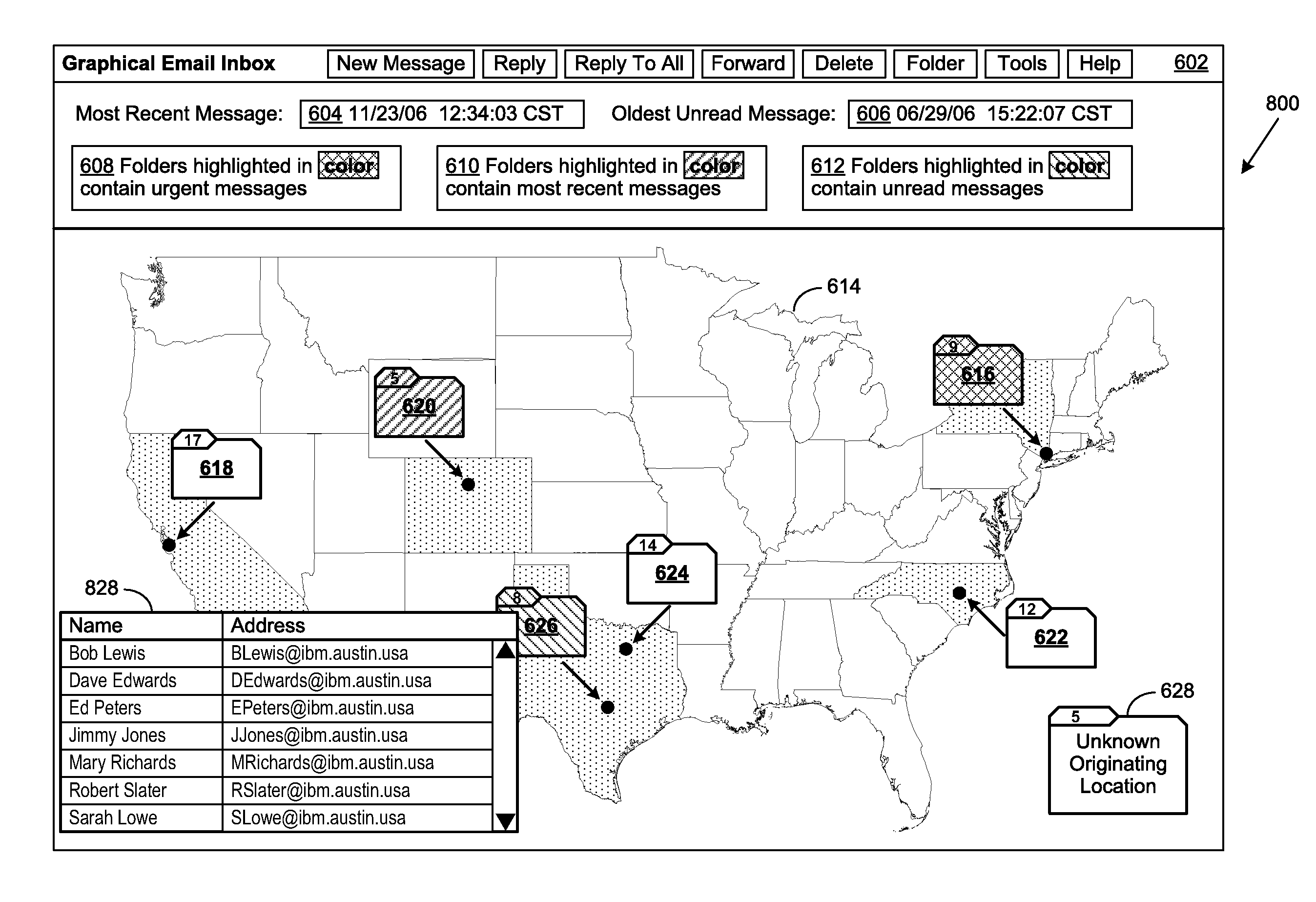
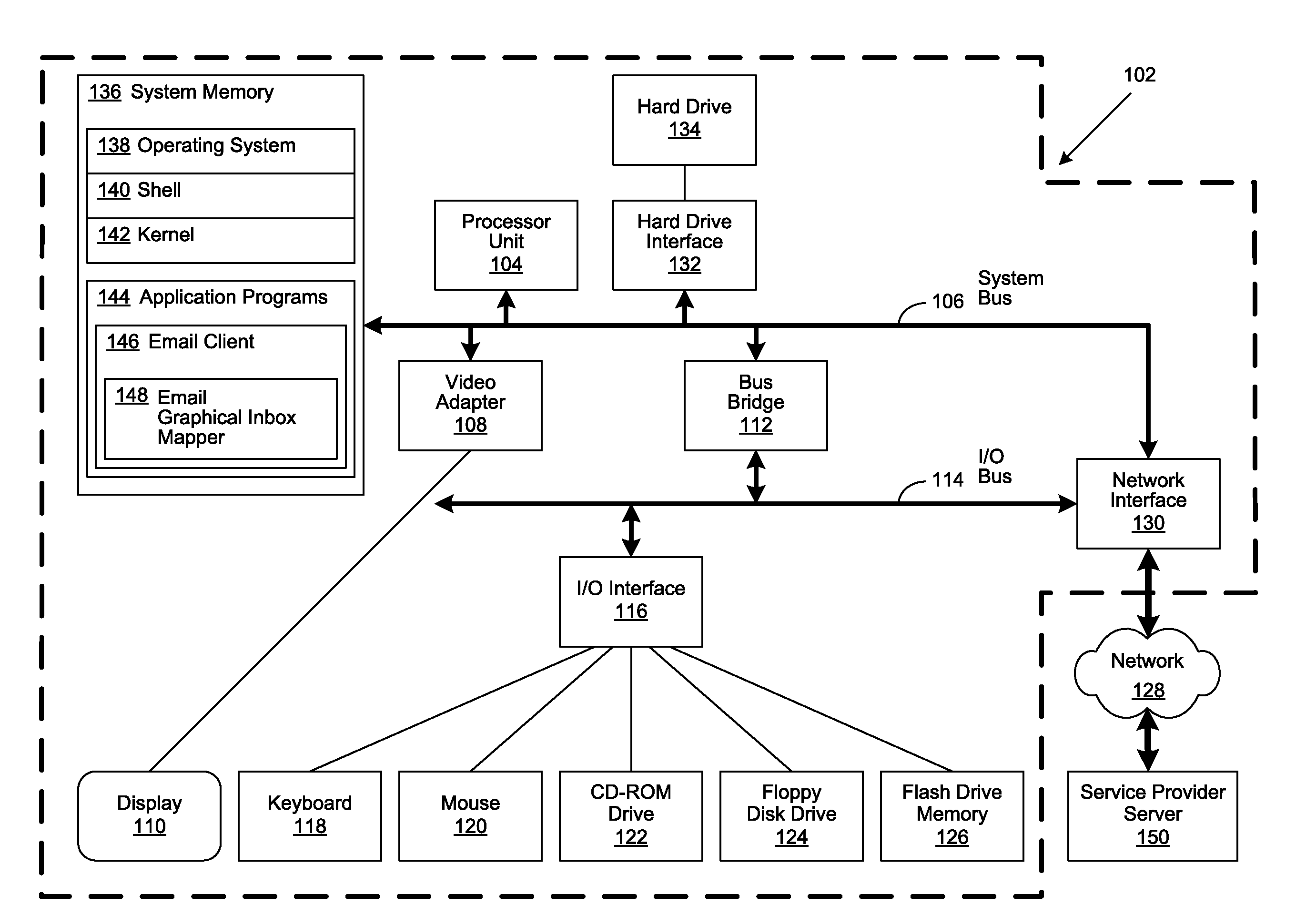
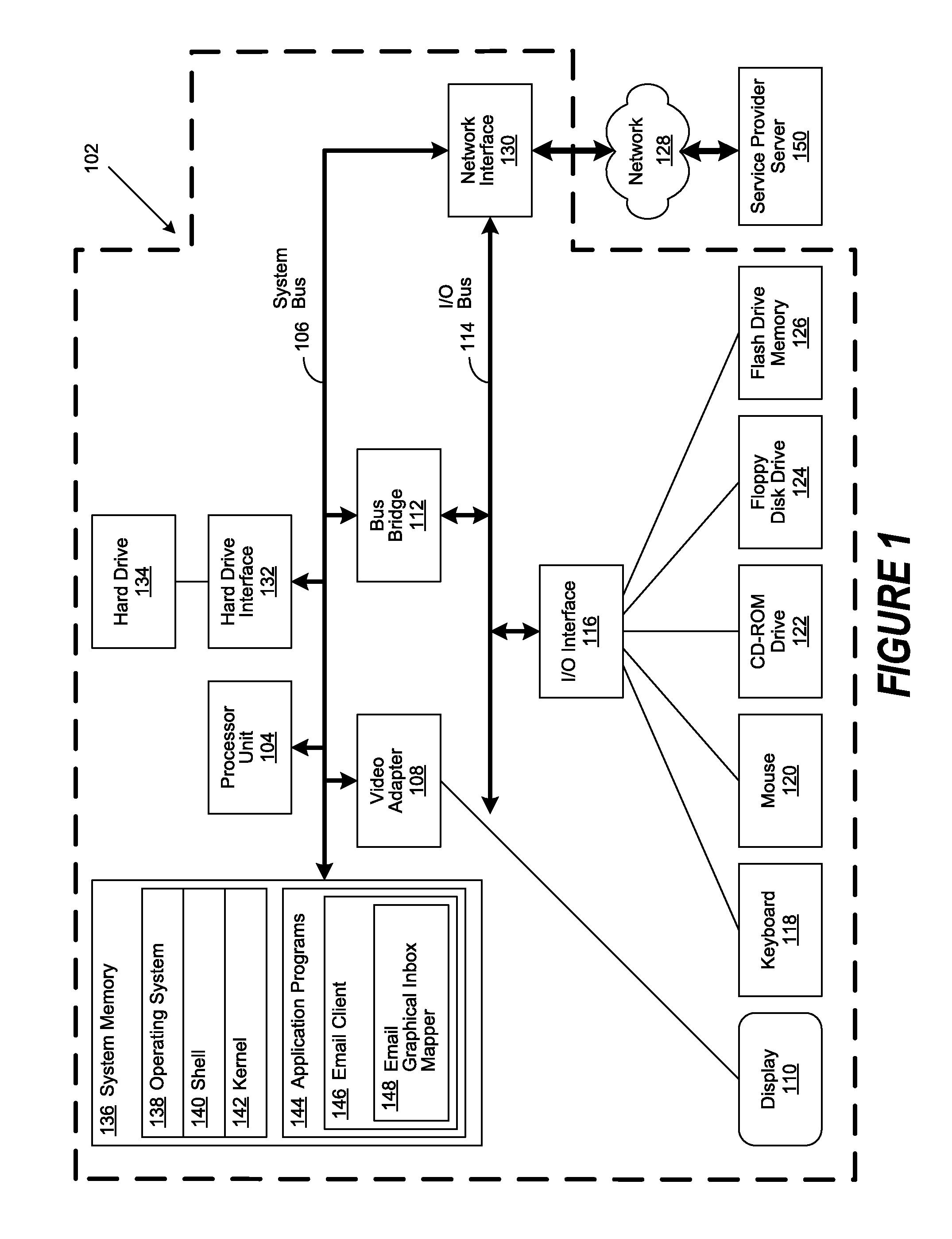
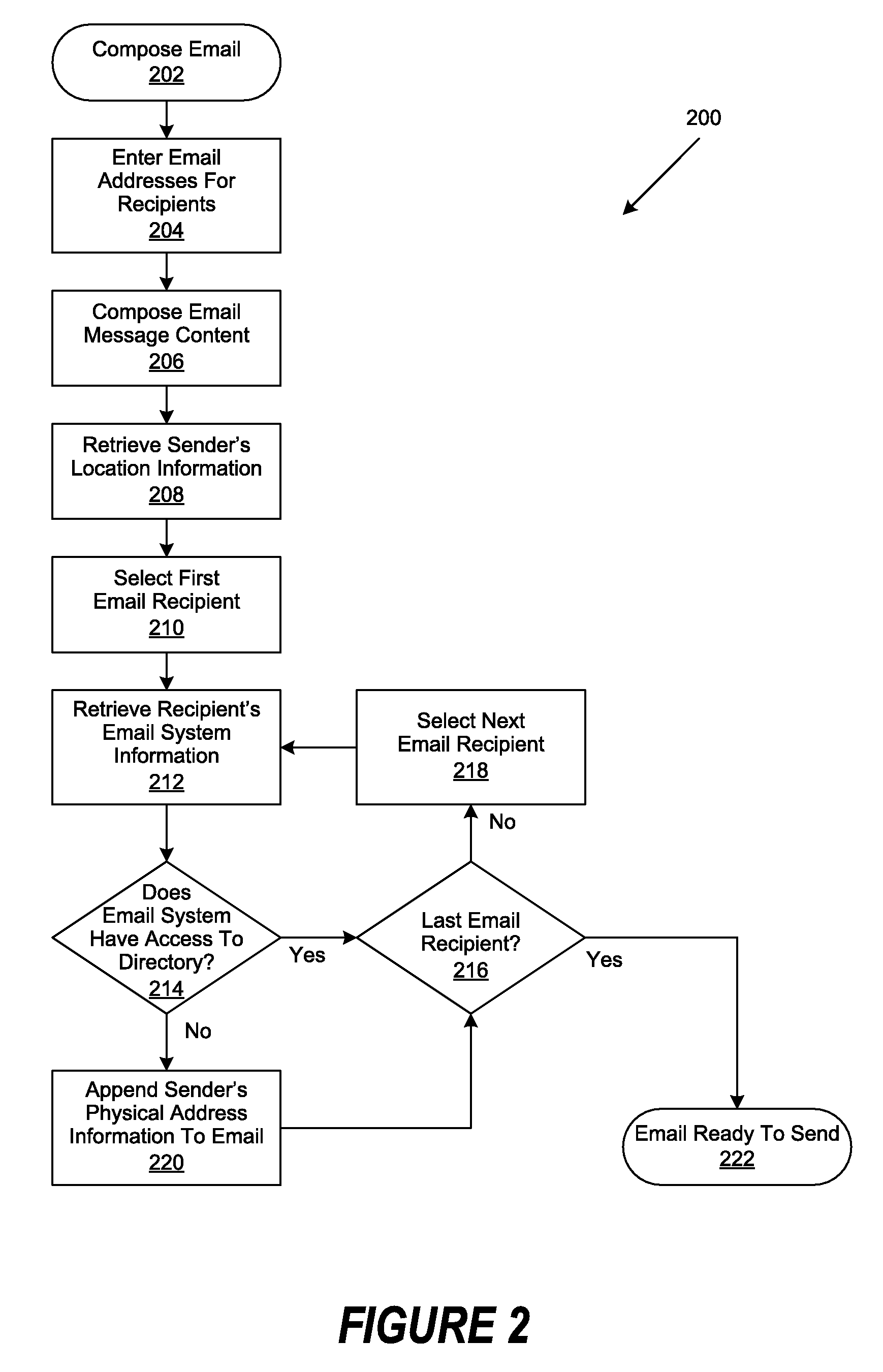
Geographical Email Presentation
ActiveUS20080168347A1Multiple digital computer combinationsInput/output processes for data processingGraphicsClient-side
An email content management method, system and program are provided for mapping a plurality of received electronic mail (email) messages to a plurality of predetermined graphical representations of an email Inbox. Predetermined sender and originating information is associated with an email. When the email is received by the recipient, the associated sender and originating information is used to map the email to a graphical Inbox depicting the email's originating location. Once mapped, the corresponding email graphical Inbox is represented in a graphical display, such as the user interface of an email client. Graphical Inboxes can be represented as subsets of a geographical map or depict an organizational hierarchy chart. Status information related to the received email messages is generated and display attributes are applied to their corresponding email graphical Inboxes.
Owner:SNAP INC
Method and system for providing communication context specific formality control
InactiveUS20080126481A1Reduce frustrationIncrease speedMultiple digital computer combinationsData switching networksProfessional relationshipGeolocation
A system for automatically providing different levels of formality controls in a communication is disclosed, in which a formality level is determined based on a current communication context. The formality level is used to enable an appropriate level of automatic checking of the communication contents. The determination of a formality level for a communication may be based on any specific context information regarding the participants and / or contents of a communication. including but not limited to the relative positions of participants within an organizational hierarchy (“organizational distance”), the professional relationships of the participants (e.g. service provider to client / customer), the frequency of communications between participants, the geographic locations of participants, the number of previous errors in the communication contents, configurable participant preferences, express communication settings by participants, etc. The determined formality level may be used to enable any specific type or level of automatic message contents checking, including but not limited to various types and levels of spell checking (e.g. location specific spell checking), grammar checking, acronym substitution, cultural filtering, etc. The disclosed system may determine organisational distances based on the contents of user directories, such as lightweight directory access protocol (LDAP) directories.
Owner:IBM CORP
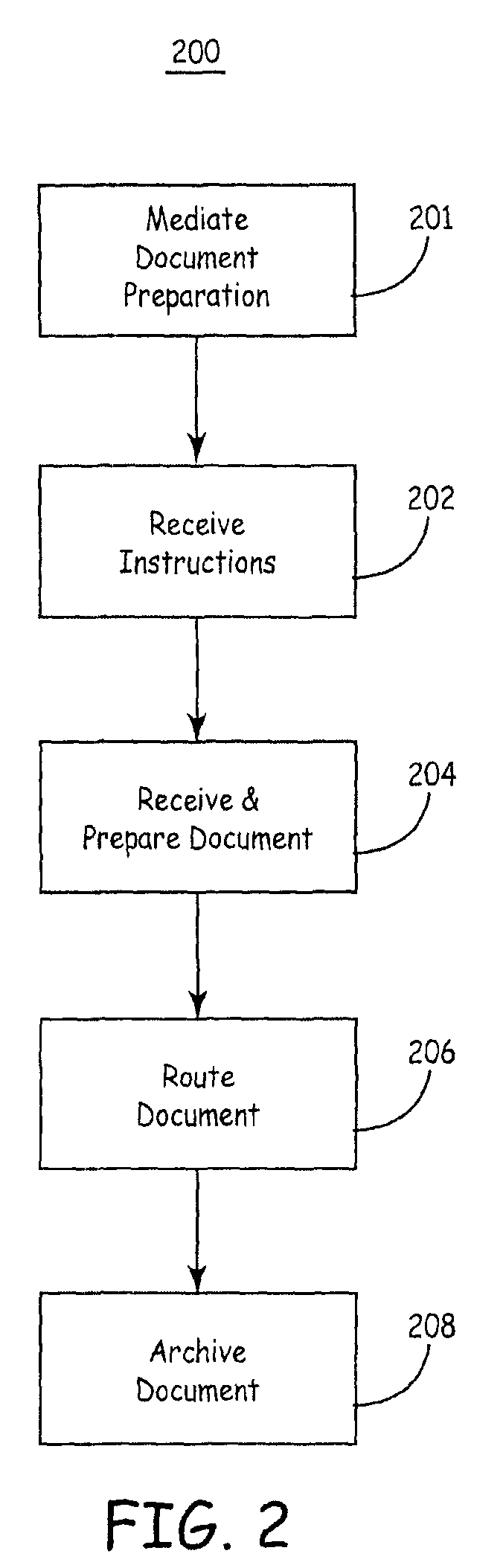
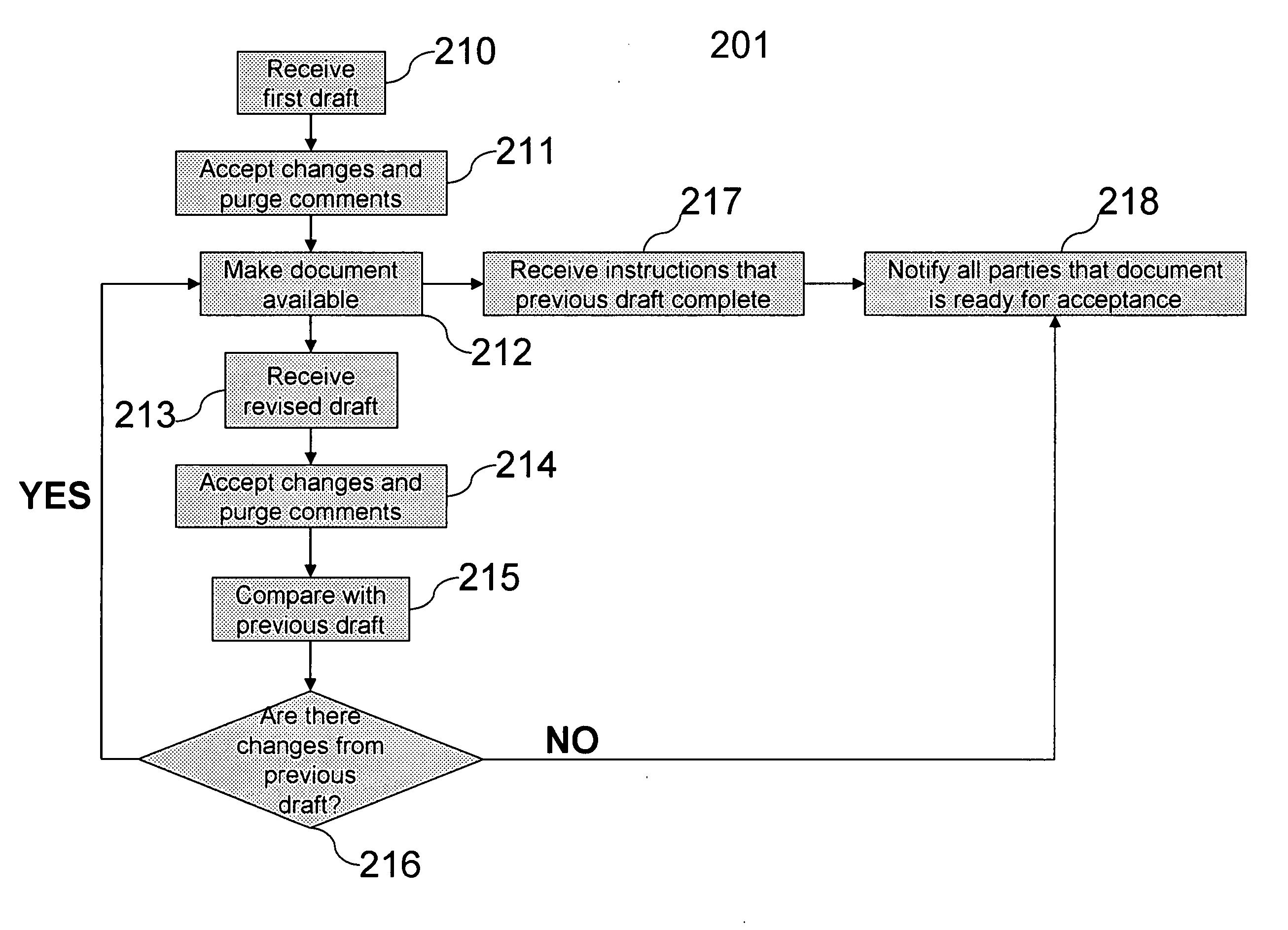
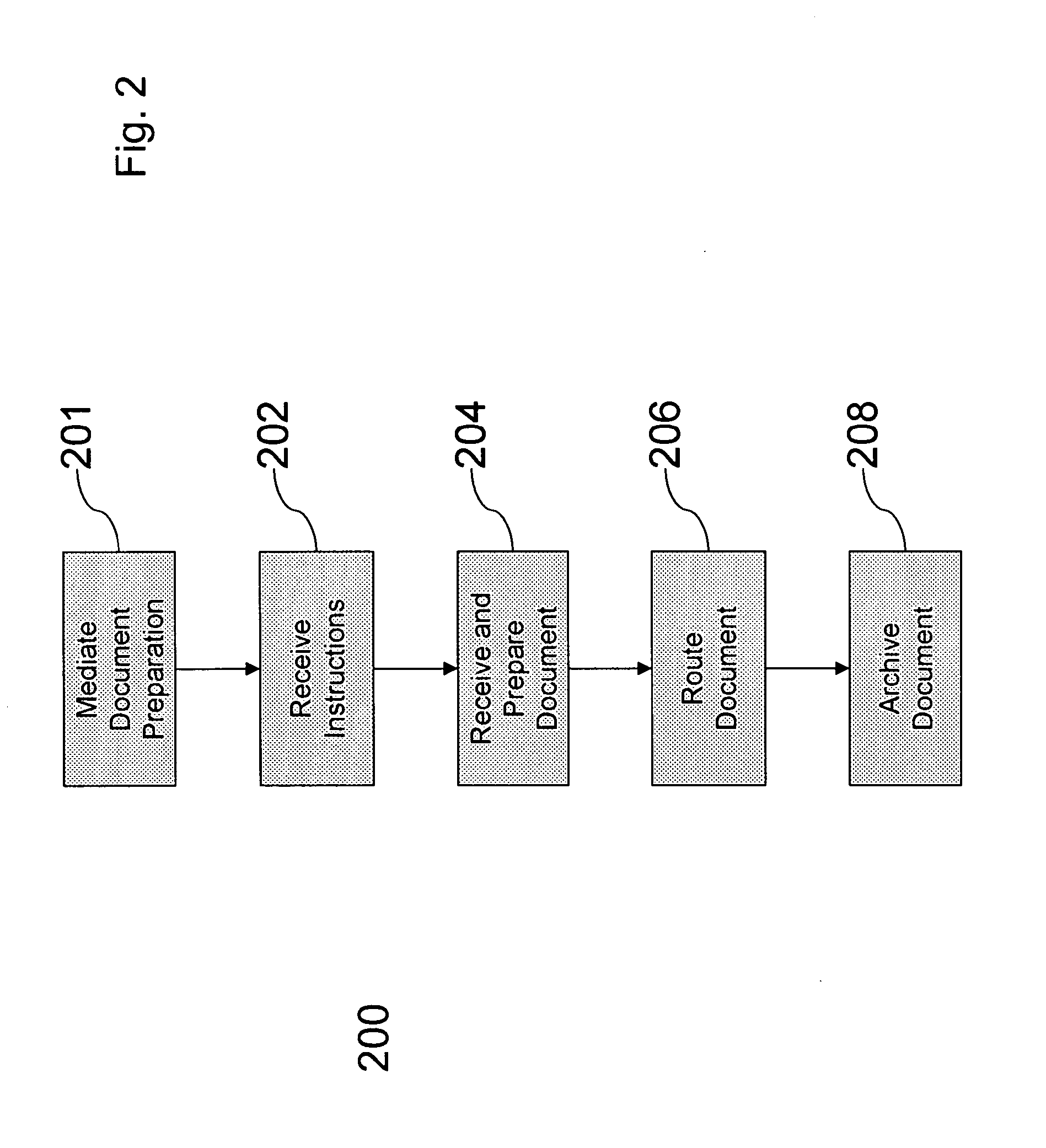
Automatic document exchange with archiving capability
ActiveUS7895166B2Digital data processing detailsSpecial data processing applicationsOperational systemDocument preparation
The exchange of documents for execution can be performed efficiently using an automated system that routes and archives documents. The system may facilitate the exchange of drafts between parties by highlighting changes of the current draft with respect to the previous draft. Documents may be conveniently archived for efficient document storage and access by providing one or more central archive databases accessible through a shared network to a plurality of organizations. The operating system of the database may provide systematic access to individuals associated with an organization with the privilege to access documents according to a specific organizational hierarchy. Routing and archiving documents may be accomplished through a central exchange server.
Owner:ADOBE SYST INC
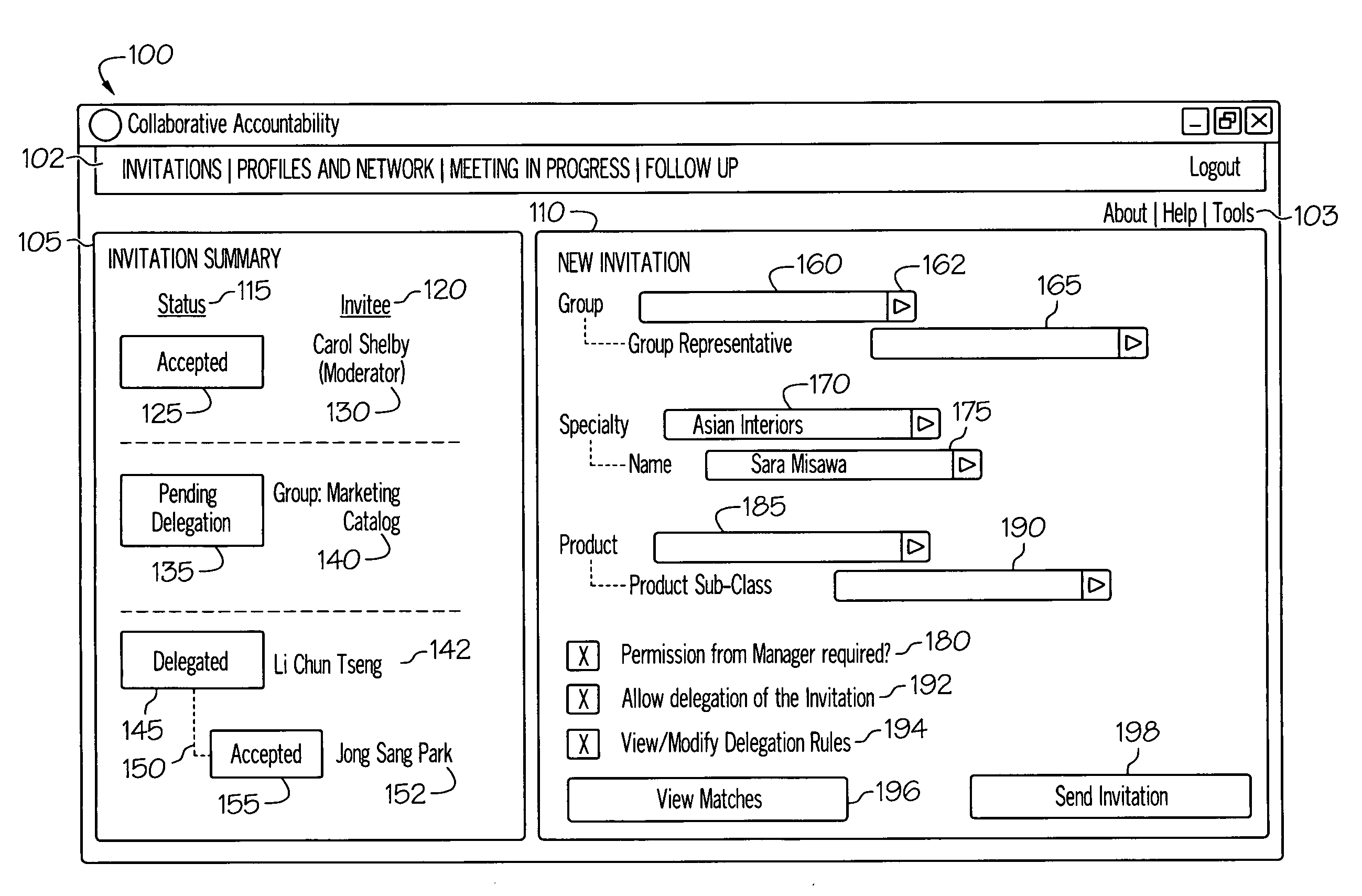
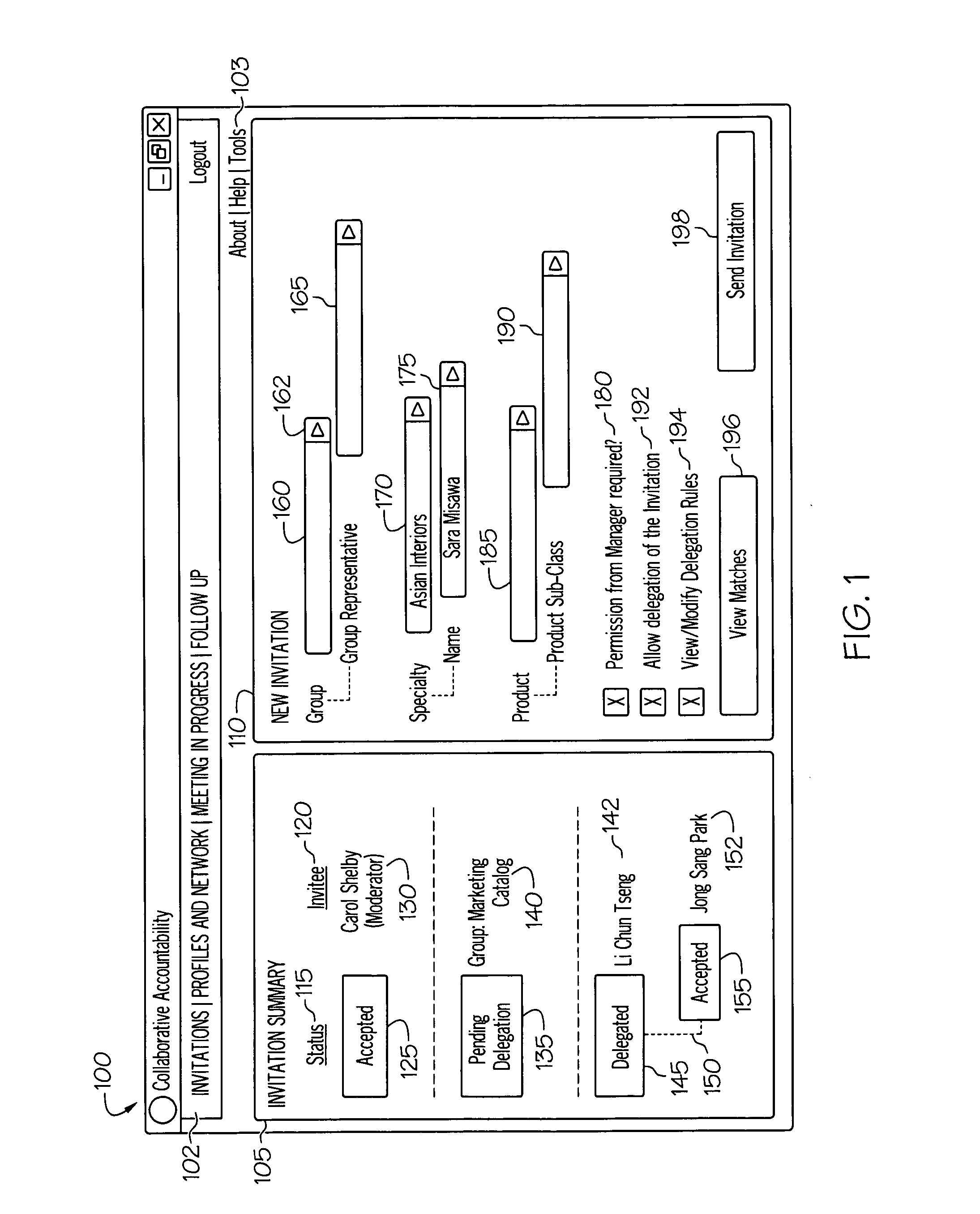
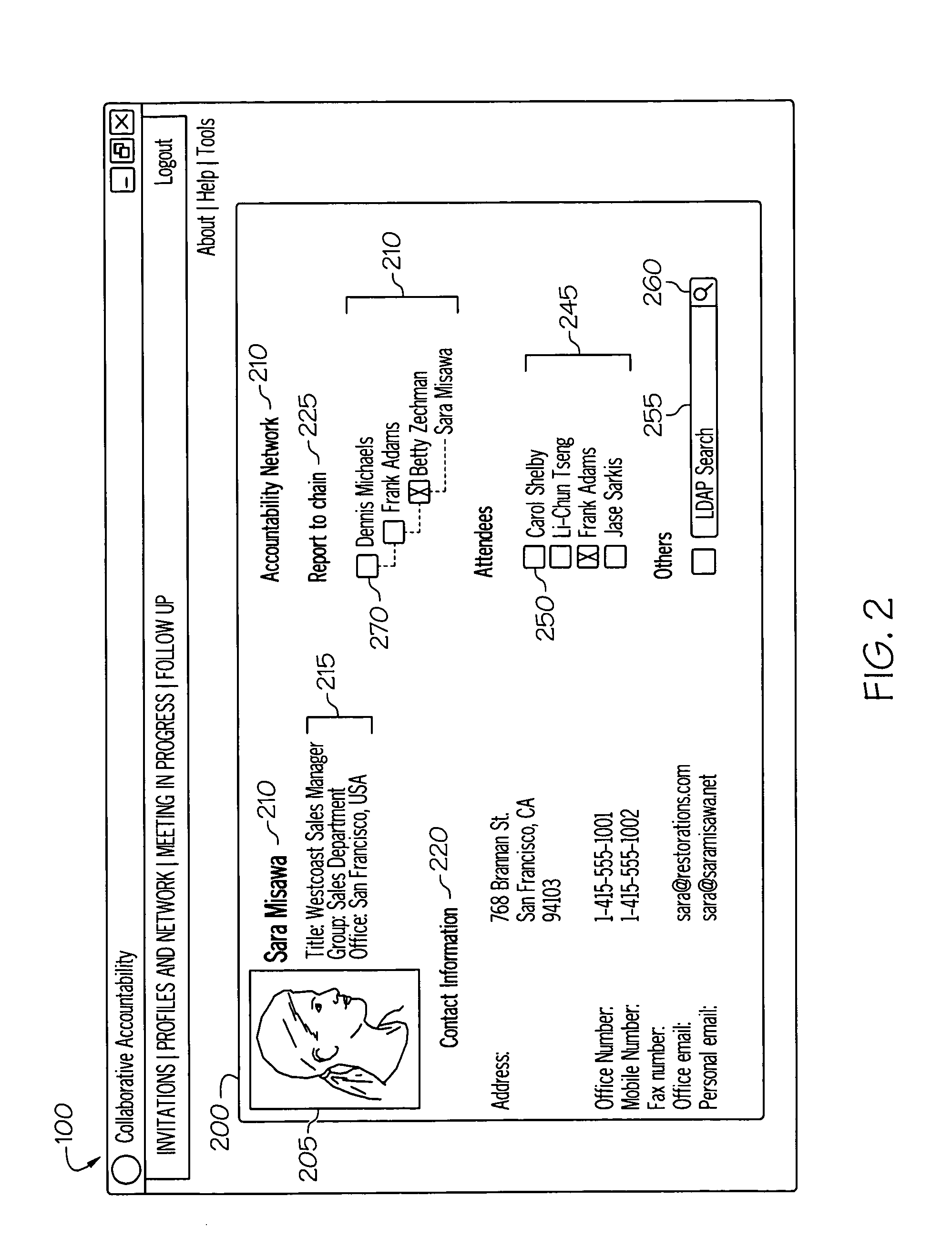
Collaborative accountability in meeting workflow
InactiveUS20090259718A1Multiple digital computer combinationsOffice automationComputer programWorkflow
A computer program product provides collaborative accountability in meeting workflows by including appropriate notification and endorsement of workflow events by an accountability network which includes supervisors in an organizational hierarchy. Workflow events may include invitations to attend meetings, delegations of those invitations, meeting attendance, and action items generated within meetings.
Owner:IBM CORP
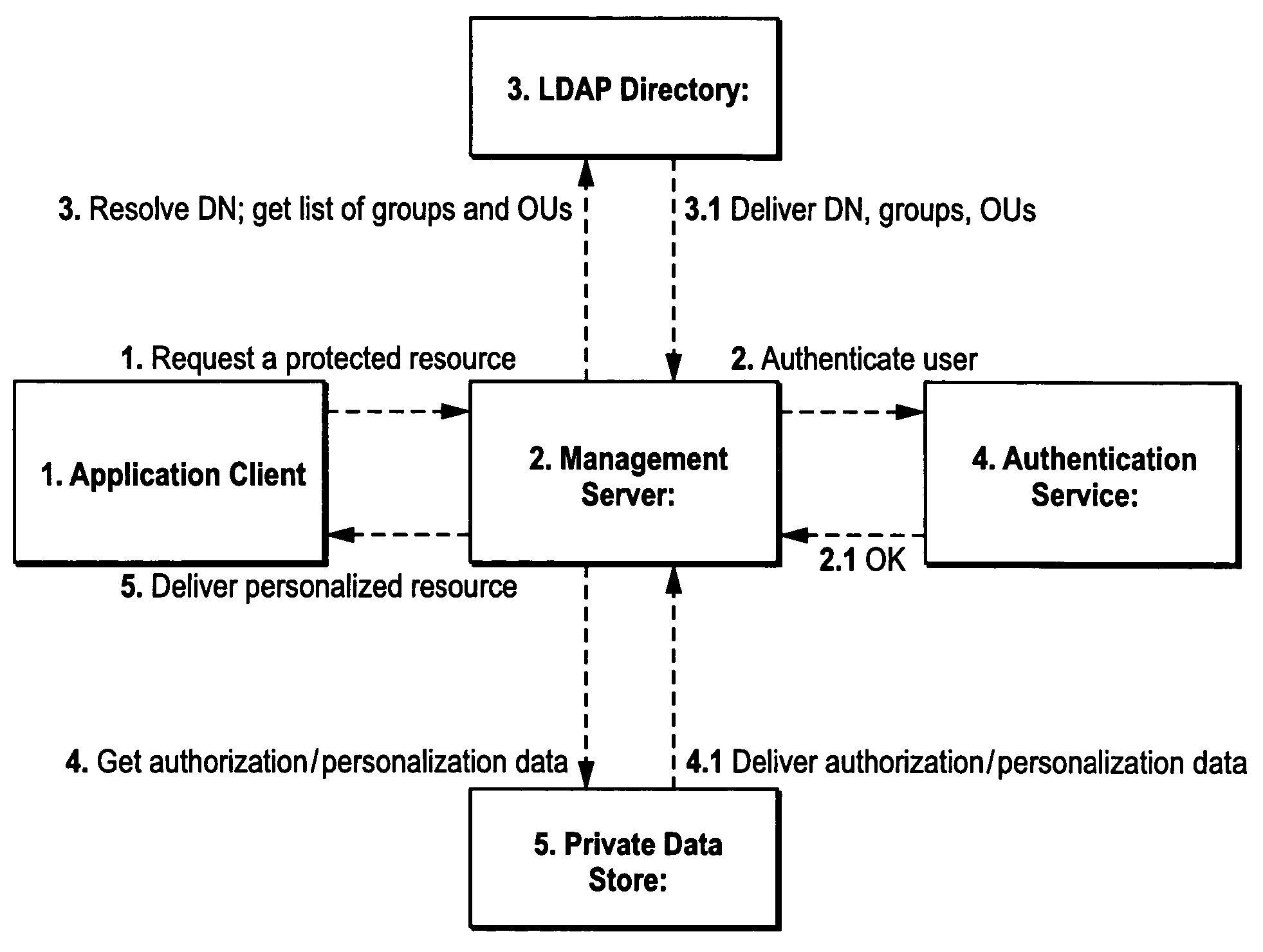
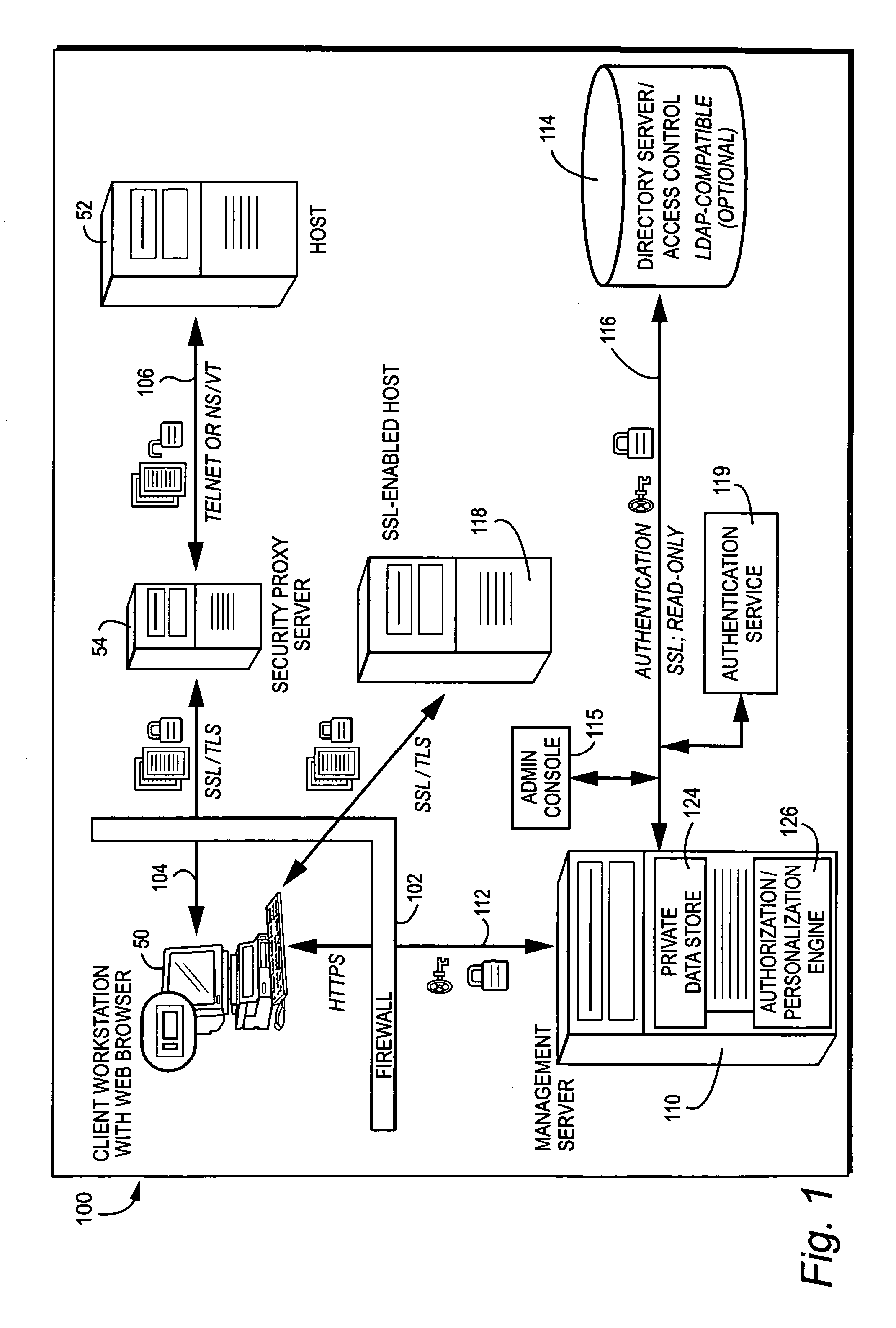
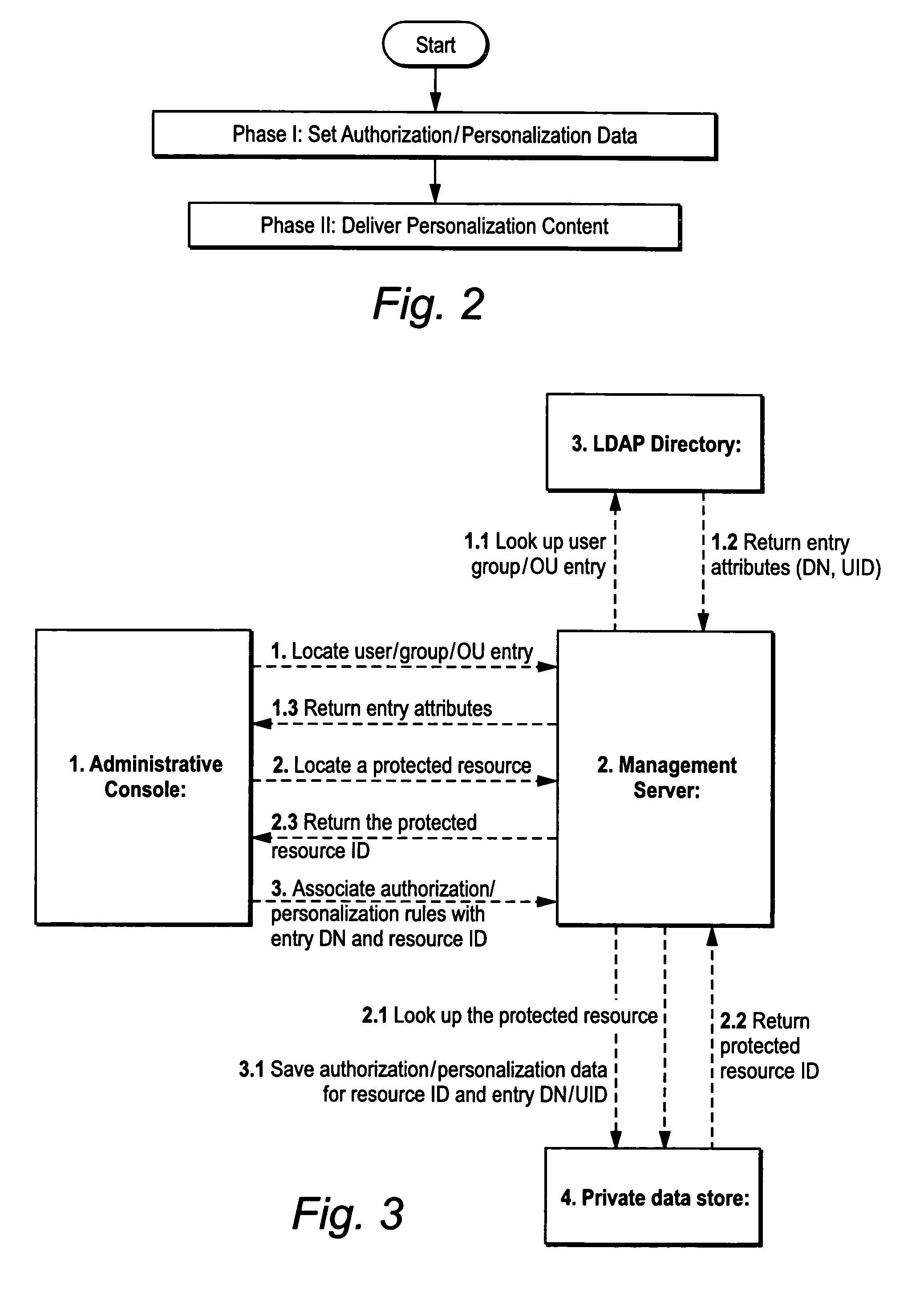
Utilizing LDAP directories for application access control and personalization
ActiveUS7571180B2Save processing resourcesAddressing slow performanceData processing applicationsDigital data processing detailsPersonalizationComputerized system
Lightweight LDAP Access Control for authorization and personalization integrates with a directory service for defining sessions for users and groups without requiring read access or modification to directory schemas. In one exemplary illustrative non-limiting implementation, authorization / personalization data is stored in a private data store outside of the LDAP directory (e.g., on a management or other server). When a user attempts to log on to the computer system, the LDAP directory is queried for a list of associated groups and / or organizational units in the normal way. To compute a resulting set of authorization / personalization rules applicable to the user, an entity (.e.g., the management or other server) traverses the organizational hierarchy of the directory groups / OU's, overriding the inherited attributes with explicitly associated ones. Integration with existing user / group / organization unit infrastructures is provided while avoiding the need to deploy additional user / group databases. In one example arrangement, an LDAP directory is queried for the list of groups and OUs during user logon. There is no need to replicate user / group directory data in a private data store of the Management Server. This improves performance and eliminates the need to synchronize data between the directory and the private data store of the Management Server. To compute the resulting set of authorization / personalization rules applicable to a user, the Management Server traverses the organizational hierarchy of directory groups / OUs, overriding the inherited attributes with the explicitly mapped ones. This minimizes the amount of administrative work for restricting access to protected resources for individuals. In many cases, users will simply inherit authorization / personalization data from the group / OUs they are members of.
Owner:ATTACHMATE
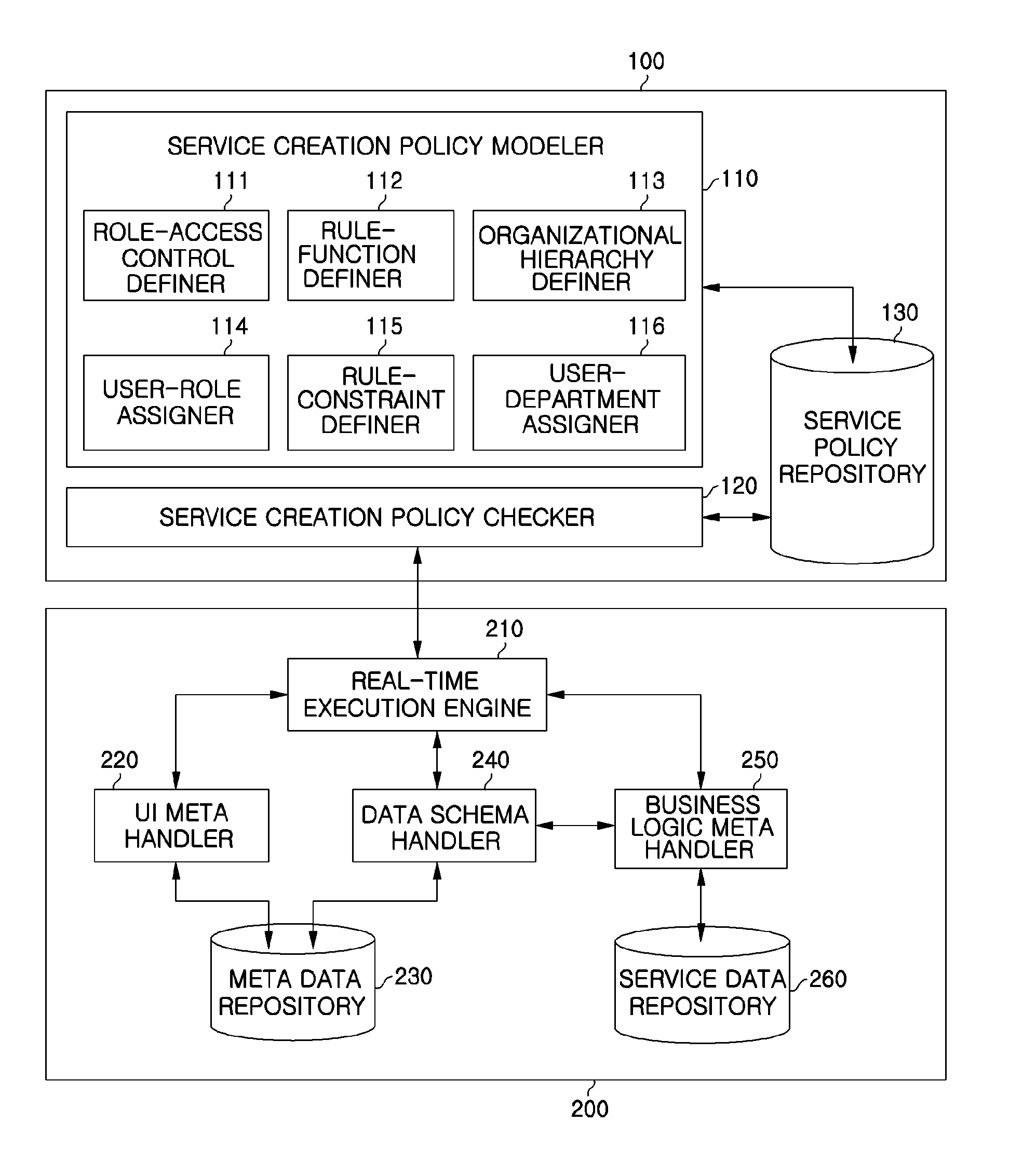
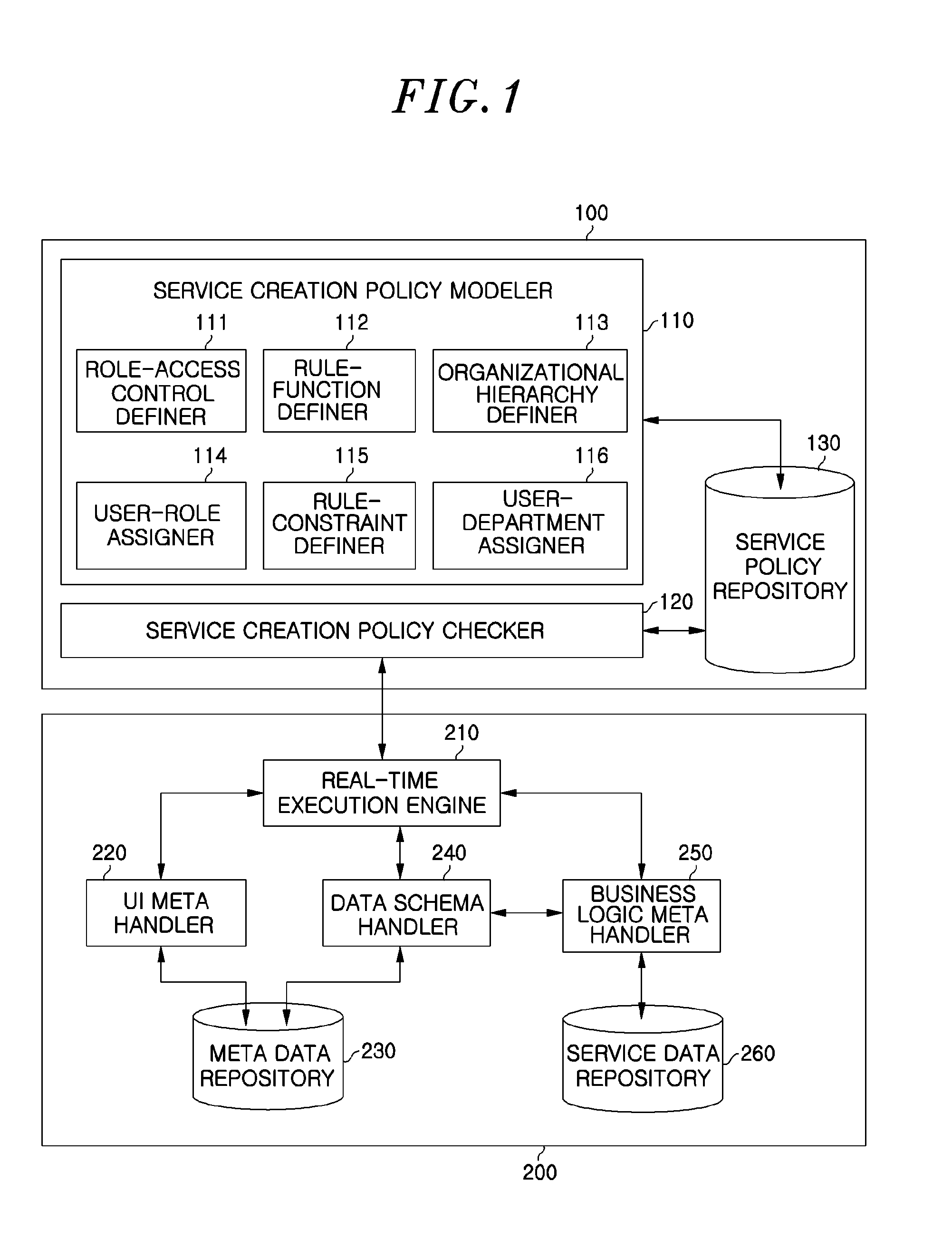
Method and apparatus for delivering application service using pre-configured access control corresponding to organizational hierarchy
InactiveUS20130111562A1Digital data processing detailsComputer security arrangementsWorld Wide WebService use
A method for delivering an application service defines an organizational hierarchy, defines an expanded role graph by mapping the organizational hierarchy to an authority structure in the form of a role graph, and defines a service creation policy based on authority information of each role depending on the expanded role graph. The method then creates a software service based on the defined authority information of each role.
Owner:ELECTRONICS & TELECOMM RES INST
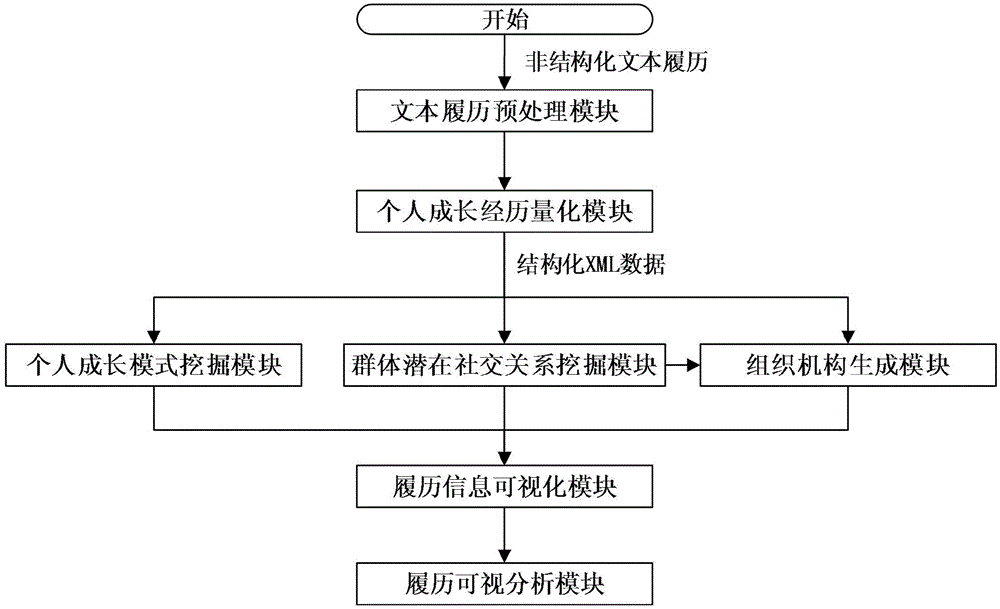
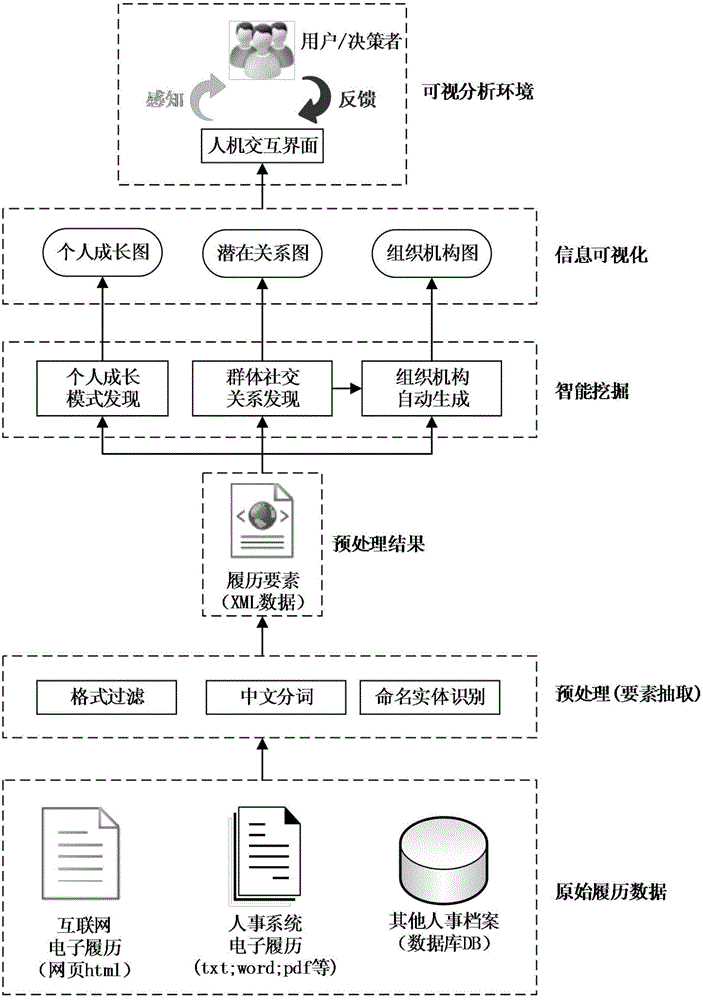
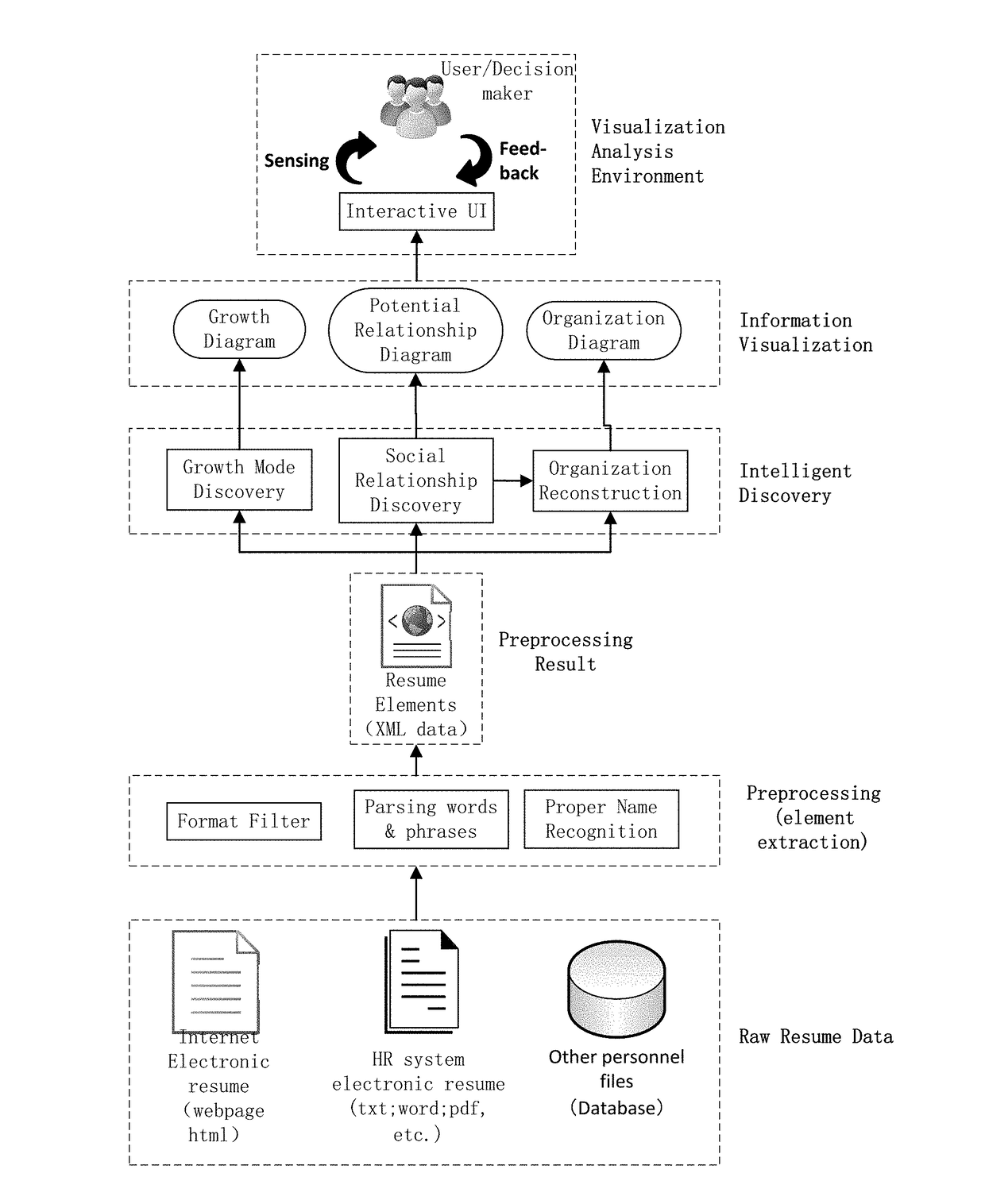
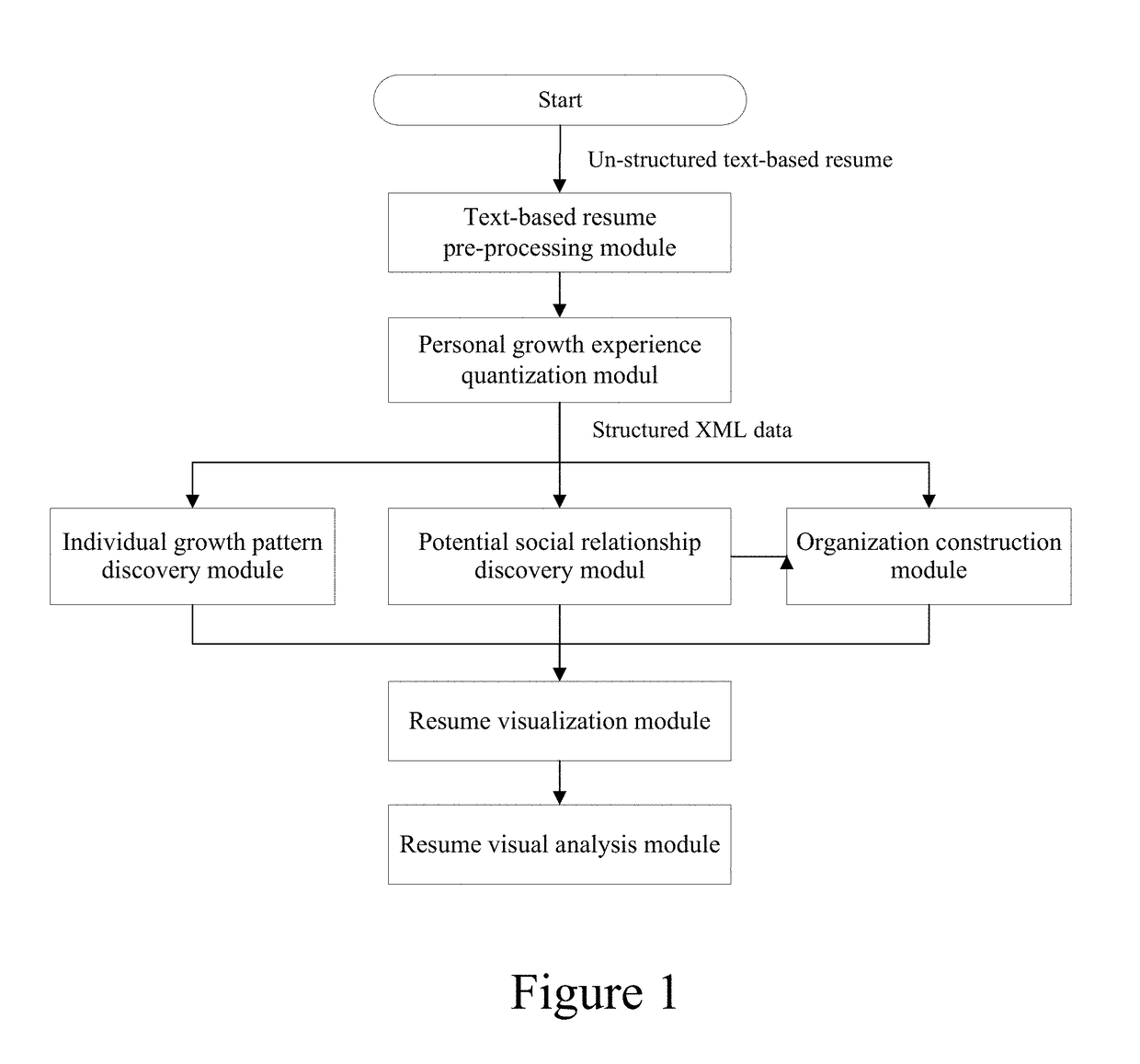
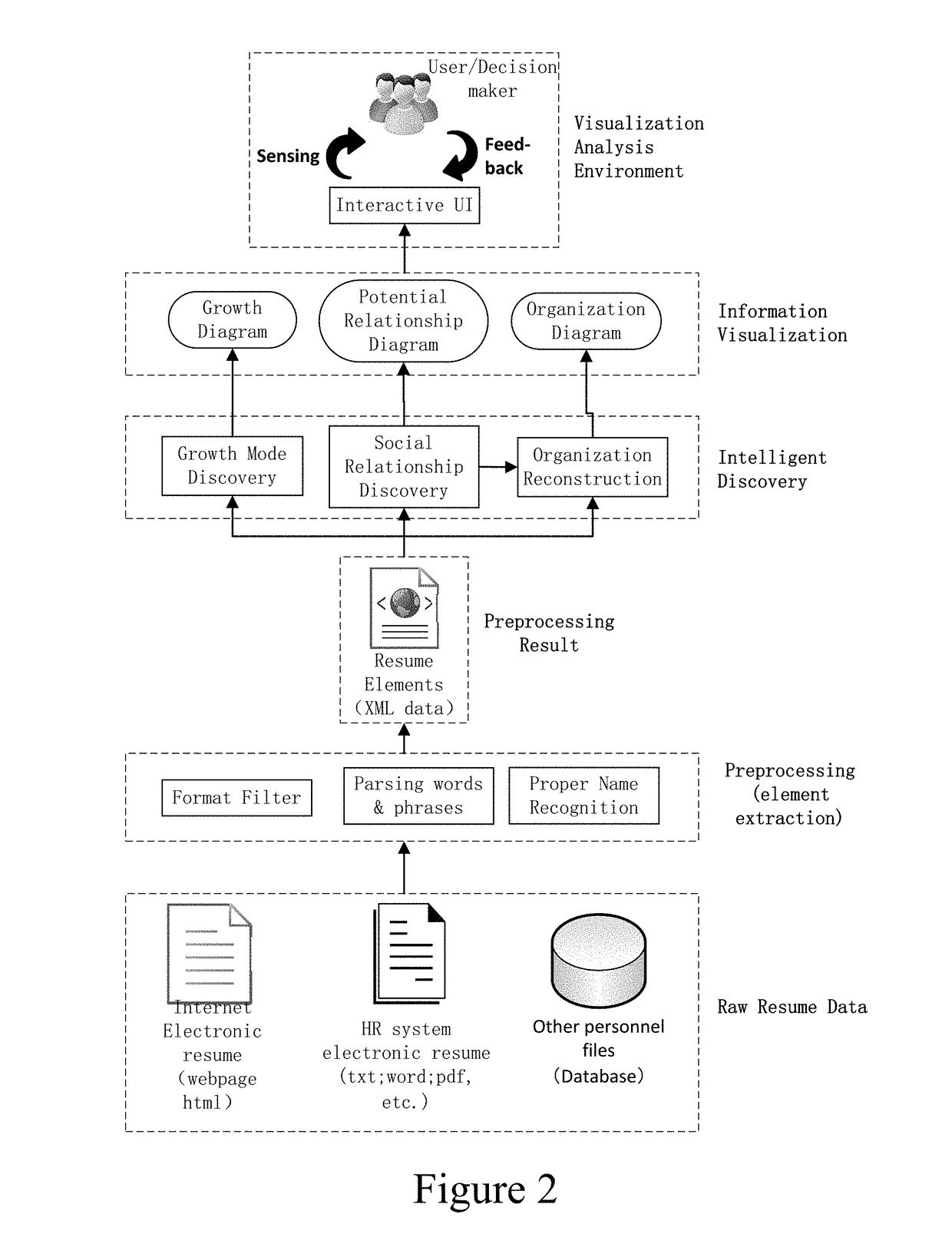
Information visualization method and intelligent visual analysis system based on text curriculum vitae information
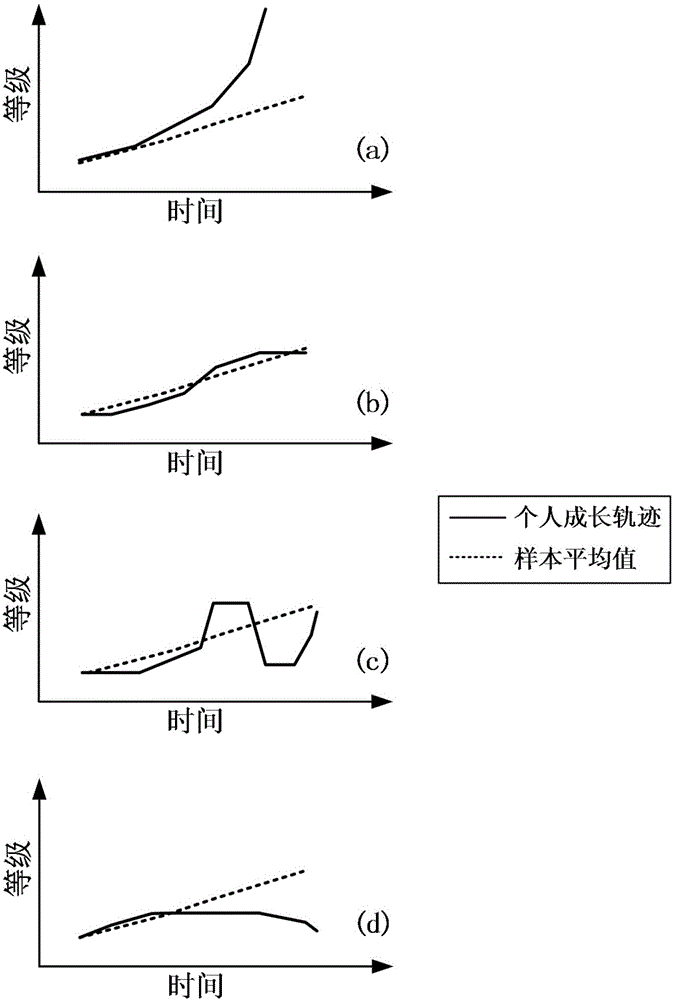
ActiveCN104318340AMeet unified processing needsNatural language data processingResourcesData dredgingInformation visualization techniques
The invention discloses an information visualization method and an intelligent visual analysis system based on text curriculum vitae information. The method comprises the following steps: (1) experience level quantization calculation is performed on experience information in each piece of text curriculum vitae information to obtain growth trajectory sequence data, and the data is visualized; (2) the growth trajectory sequence data of multiple pieces of text curriculum vitae information is selected for correlation calculation to obtain the potential social relation between text curriculum vitaes, and the potential social relation is visualized on a social network; and (3) curriculum vitaes with unit intersection are converted into the organizational hierarchy of corresponding persons in the unit based on the potential social relation between the curriculum vitaes, and the organizational hierarchy is visualized in an organization. Through data mining and the information visualization technology, the spatio-temporal growth experience of a person represented by a curriculum vitae can be obtained, the potential social relation between persons can be found, and the organizational hierarchy of the persons can be restored, thus obtaining the deep cognition of the group growth model and the social relation.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
System and method for managing an instant messaging community
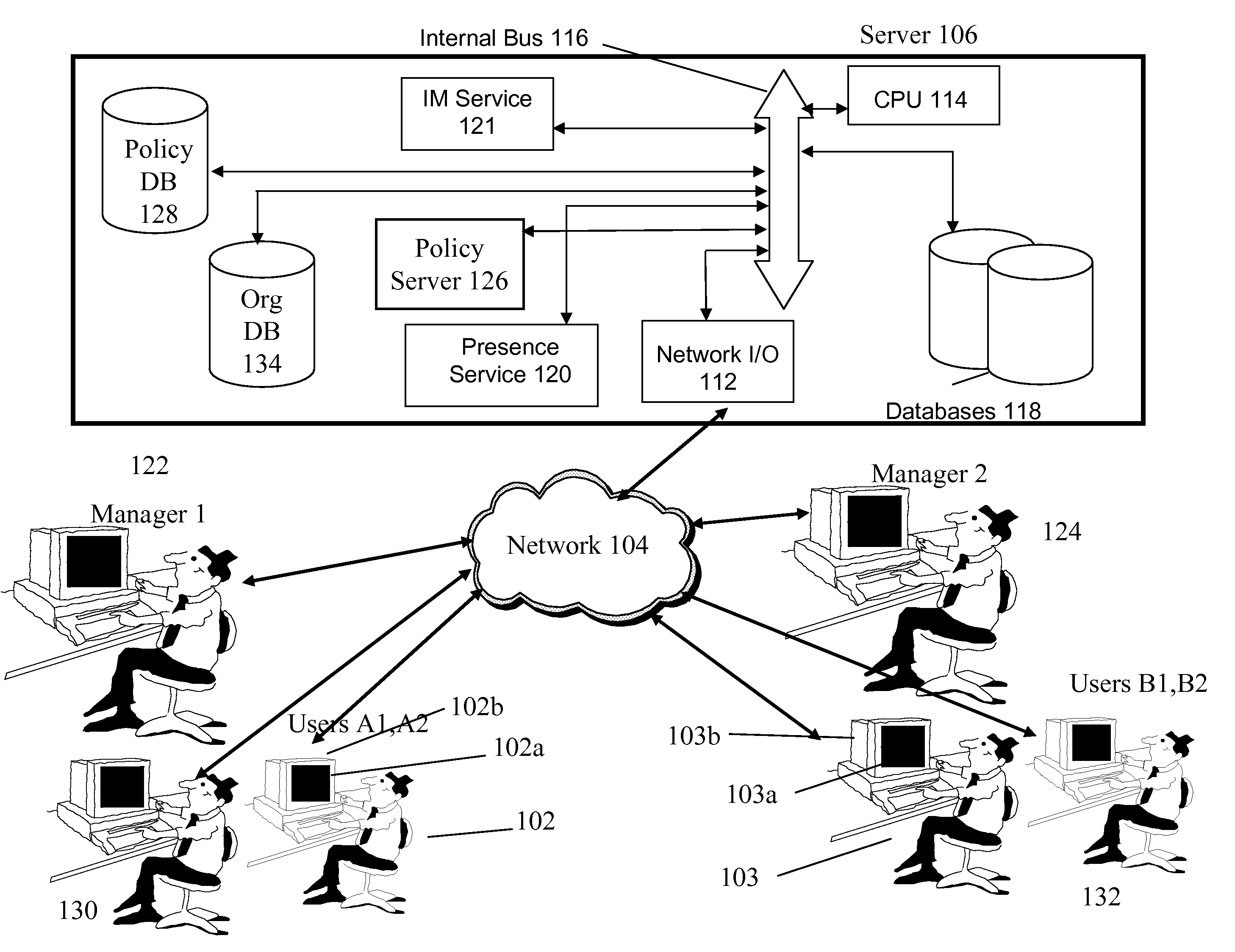
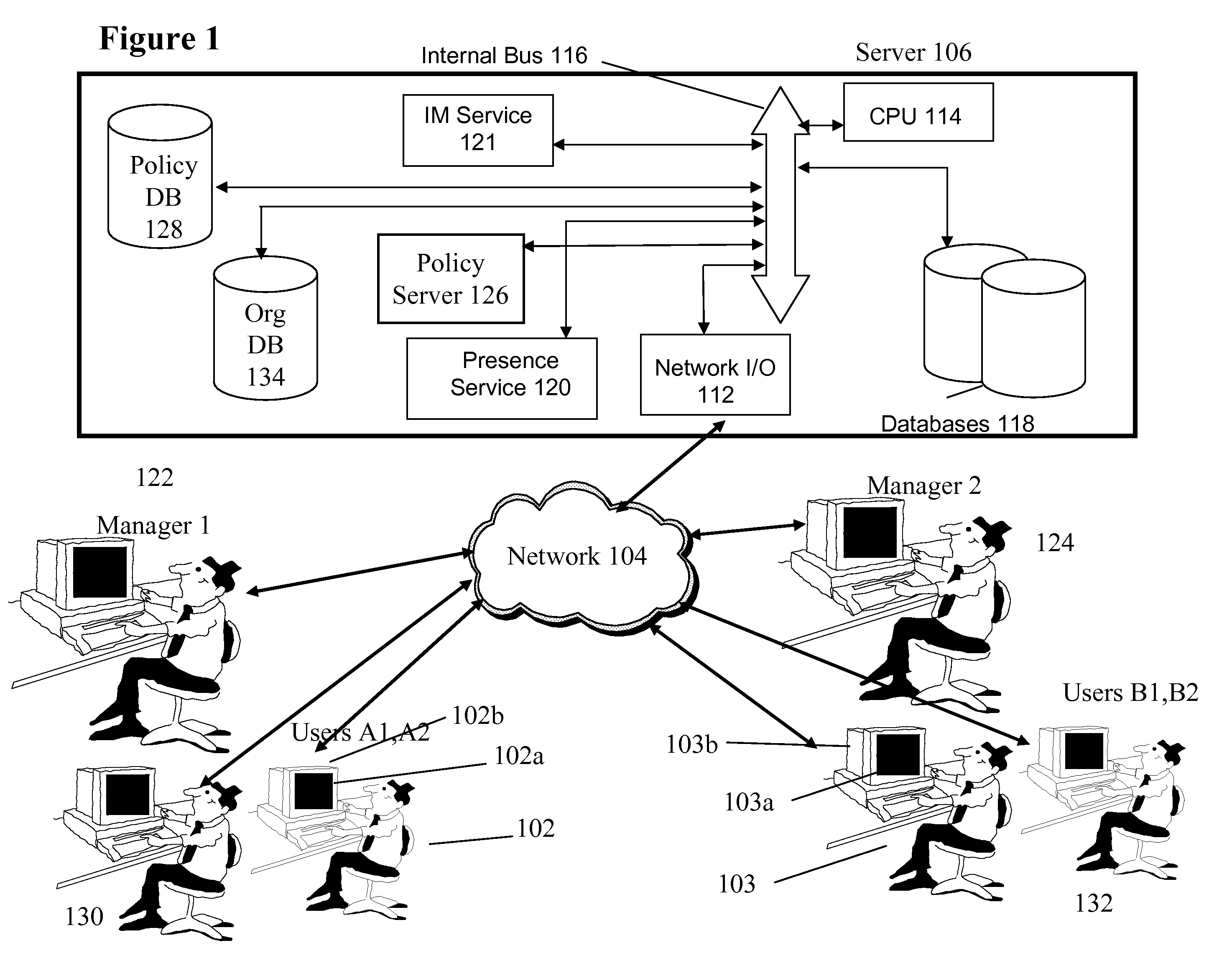
InactiveUS20090049135A1Multiple digital computer combinationsData switching networksMessage passingDirected acyclic graph
A system and method exploits organizational distances associated with an organizational hierarchy in a directed acyclic graph to both affect behavior in instant messaging systems, as well as to modify behavior (presence, IM, availability, who can get to the IM user) based on the reporting relationships that exist in an organization. One part of the invention is in exploiting a directed acyclic graph for the purposes of controlling instant messaging behavior for an individual, a team or a community. This is accommodated by abstracting organizational reporting relationships. The reporting relationships that exist in LDAP are used to enforce top-down rules which determine actions that motivate a change in behavior for instant messaging users across the organization. Such actions are not possible to motivate in conventional art. Conventional art relies on rules that a specific user manually builds, and do not consider capabilities around hierarchical imposition, not a reporting team / group / organizational. The present invention may force a change in behavior for a plurality of instant messaging users based on reporting relationships.
Owner:IBM CORP
System and method for corporate-wide policy management
InactiveUS20060143194A1Easy retrievalDigital data processing detailsAnalogue secracy/subscription systemsEase of AccessOrganizational hierarchy
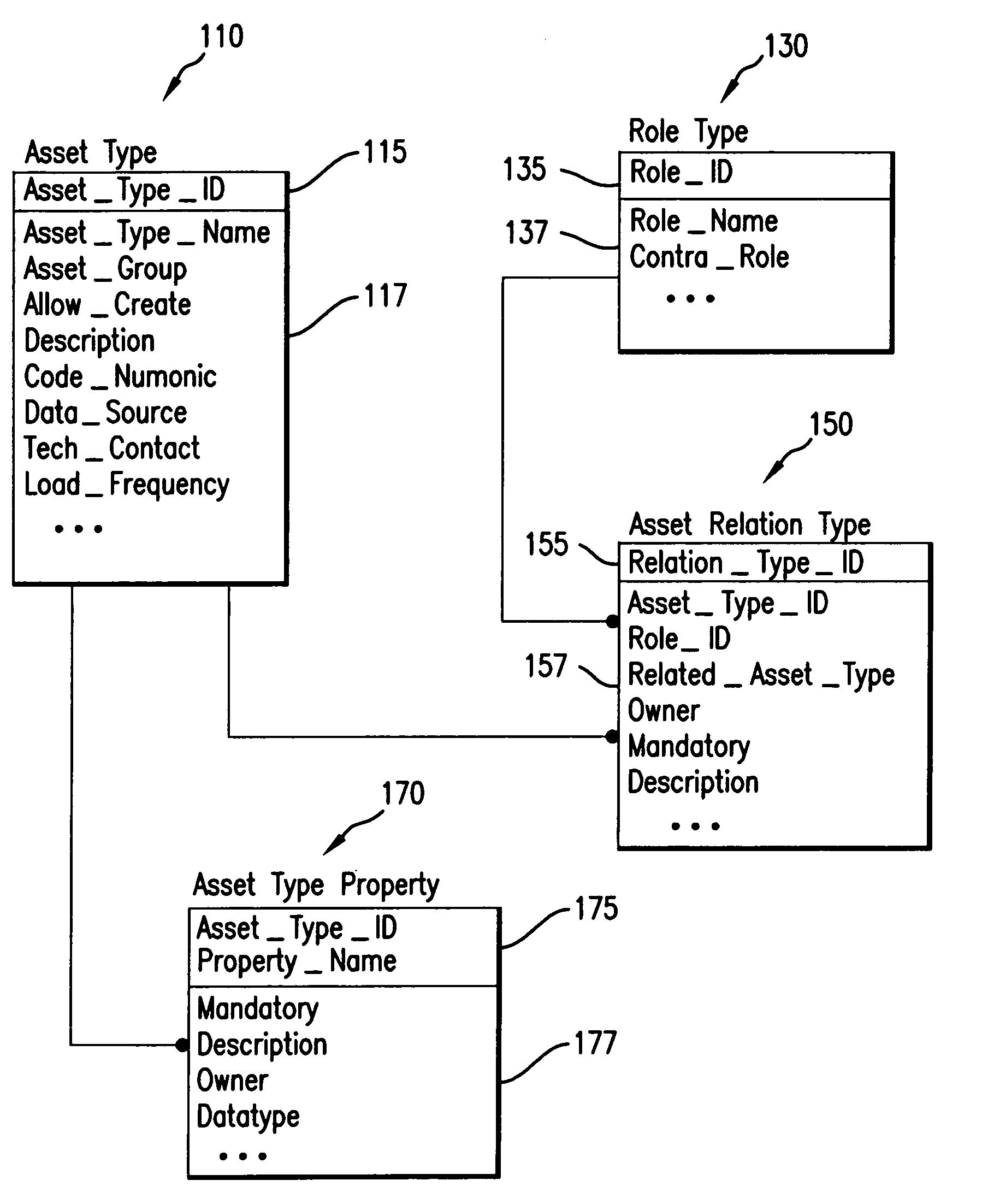
An organization asset database (ADb) is described that contains a complete, up-to-date, secure, and easily accessible inventory of the organization's assets. Each asset is mapped onto a structure that represents the organizational hierarchy of the organization, which provides for multiple levels of accountability for each asset. Each asset has one or more roles in relation to other assets in the ADb and has one or more entitlements in relation to other assets in the ADb. The relationship between assets ensures that the ADb is complete and up-to-date and allows for easy filtering and retrieval of the information contained in the ADb.
Owner:BARCLAYS CAPITAL INC
Method for recommending enterprise documents and directories based on access logs
InactiveUS20110197166A1Digital data processing detailsSpecial data processing applicationsDocumentation procedureBookmarking
Systems and methods recommend documents or directories in an enterprise context by analyzing use proximity in the organizational hierarchy to find similar users. Evidence may be used from different sources to gage the degree of interest a user may have in a document. Such pieces of evidence may include viewing page thumbnails, viewing the document online, or printing, saving, or bookmarking the document. To make managing these different sources of evidence from users related by different degrees tractable, a model may be created where evidence values decay by different amounts over time and are combined with different weights. Additionally, these systems and methods also can make use of the directory structure of the document space to recommend directories as well as individual documents.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Automatic document exchange with archiving capability
ActiveUS20070192275A1Digital data processing detailsSpecial data processing applicationsOperational systemPaper document
The exchange of documents for execution can be performed efficiently using an automated system that routes and archives documents. The system may facilitate the exchange of drafts between parties by highlighting changes of the current draft with respect to the previous draft. Documents may be conveniently archived for efficient document storage and access by providing one or more central archive databases accessible through a shared network to a plurality of organizations. The operating system of the database may provide systematic access to individuals associated with an organization with the privilege to access documents according to a specific organizational hierarchy. Routing and archiving documents may be accomplished through a central exchange server.
Owner:ADOBE INC
Geographical email presentation
ActiveUS8195748B2Multiple digital computer combinationsInput/output processes for data processingContent managementUser interface
An email content management method, system and program are provided for mapping a plurality of received electronic mail (email) messages to a plurality of predetermined graphical representations of an email Inbox. Predetermined sender and originating information is associated with an email. When the email is received by the recipient, the associated sender and originating information is used to map the email to a graphical Inbox depicting the email's originating location. Once mapped, the corresponding email graphical Inbox is represented in a graphical display, such as the user interface of an email client. Graphical Inboxes can be represented as subsets of a geographical map or depict an organizational hierarchy chart. Status information related to the received email messages is generated and display attributes are applied to their corresponding email graphical Inboxes.
Owner:SNAP INC
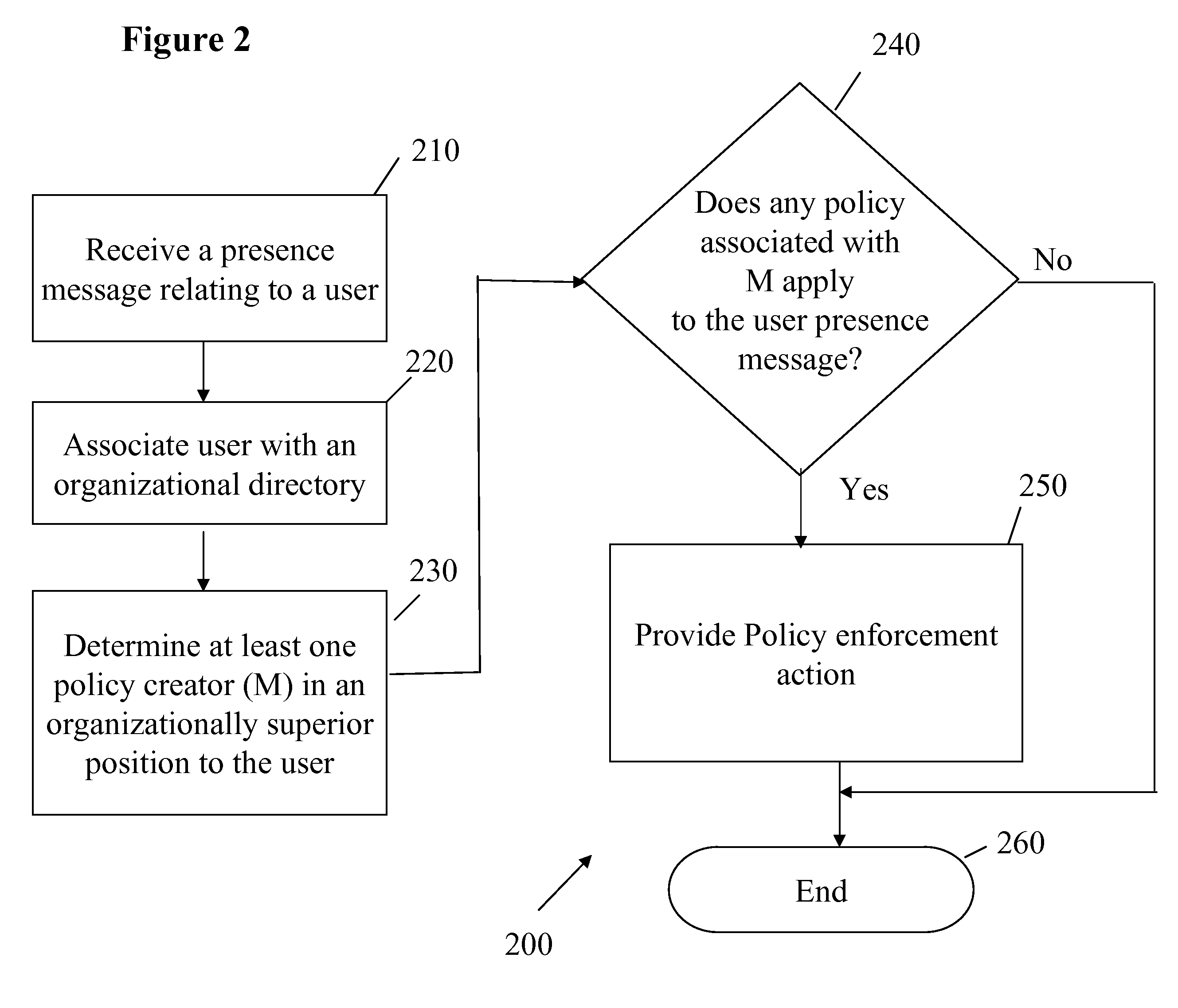
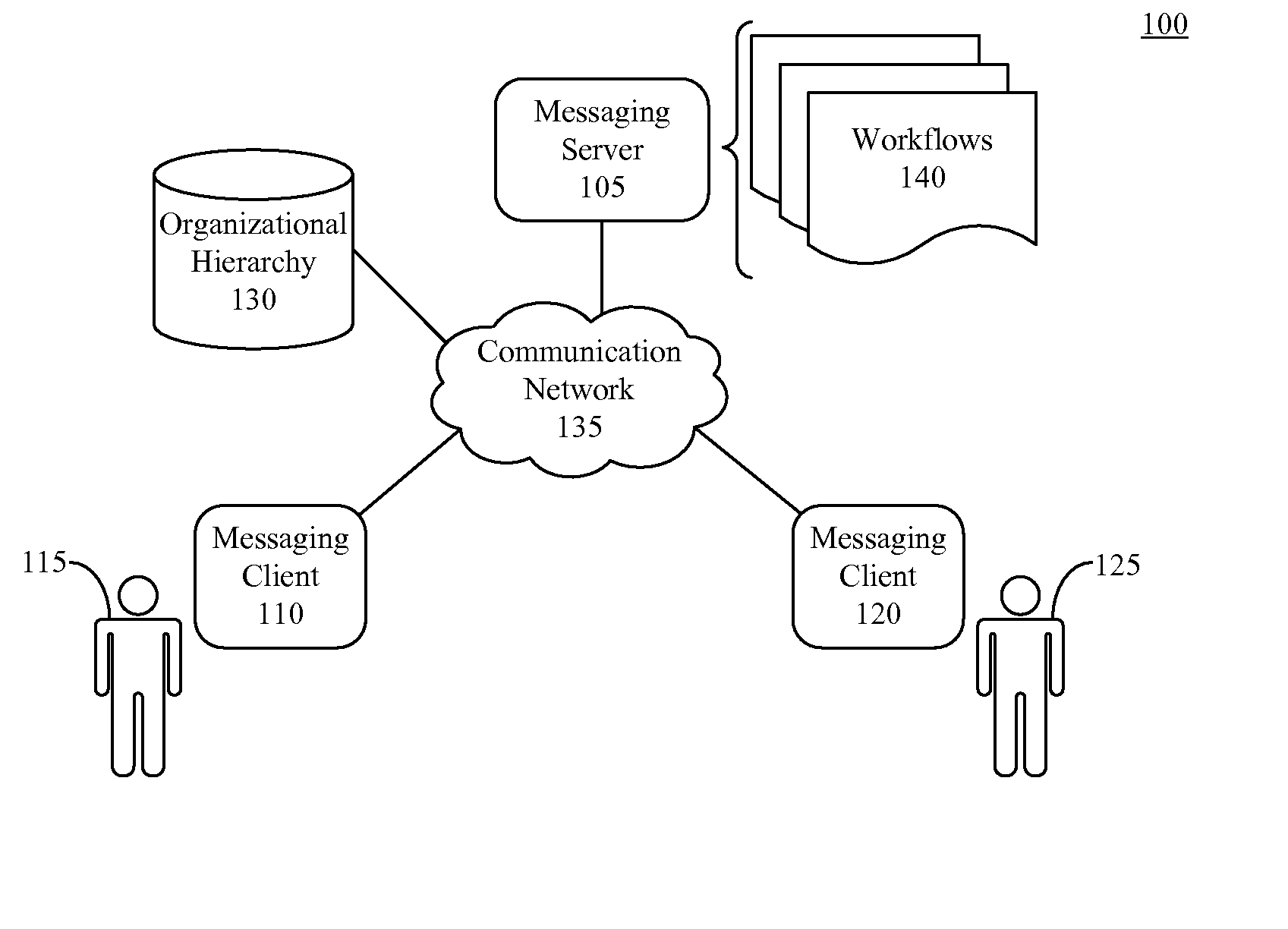
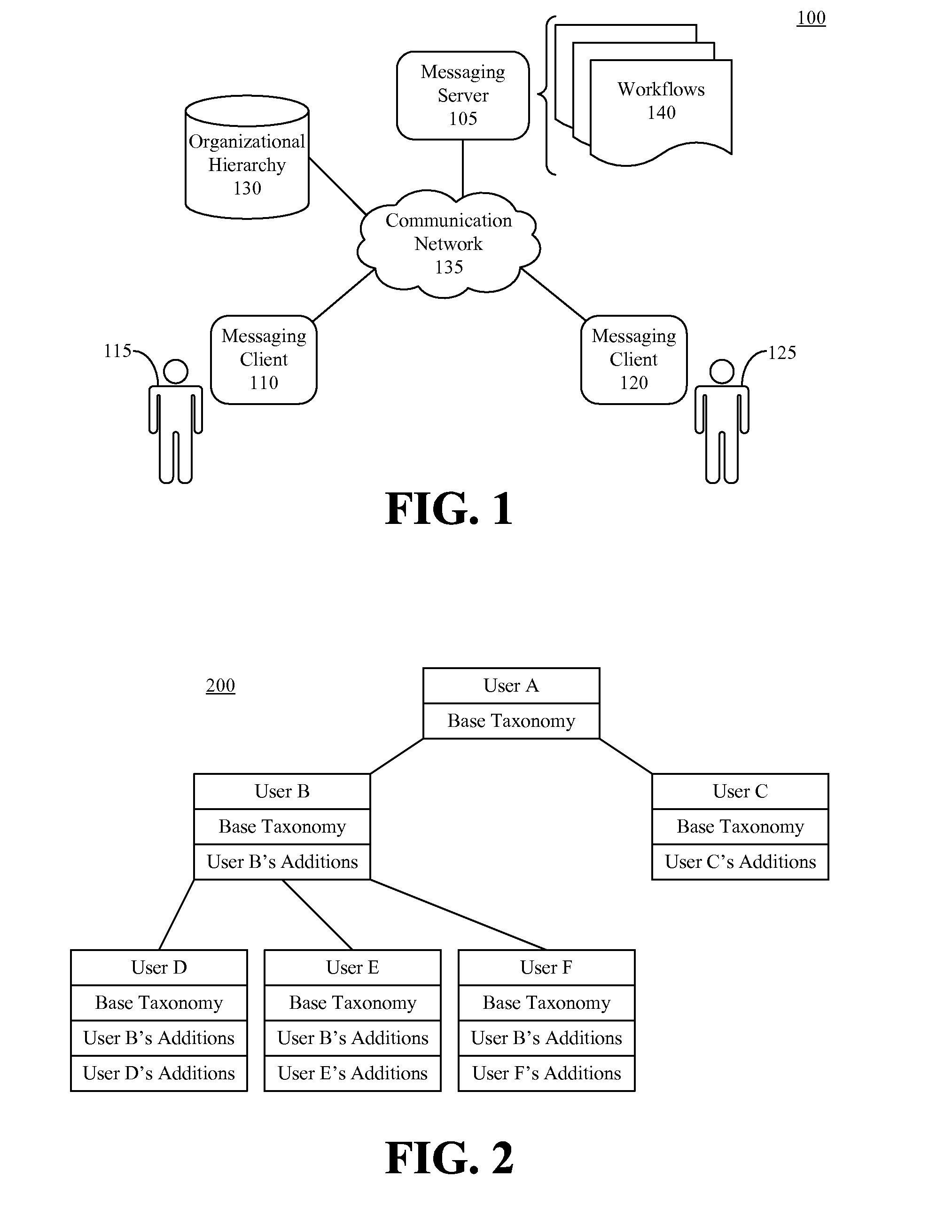
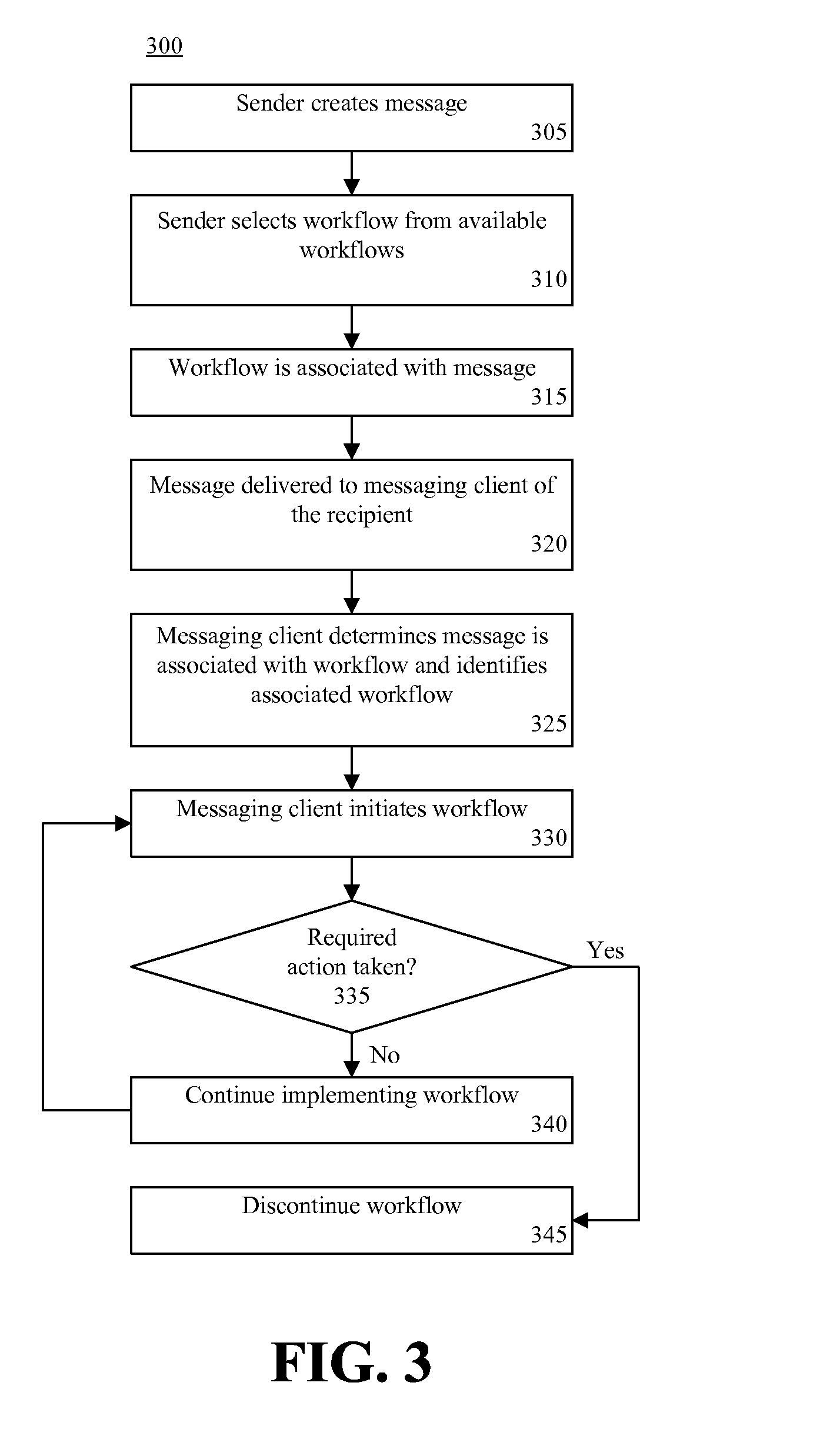
Modifying Behavior in Messaging Systems According to Organizational Hierarchy
InactiveUS20080133571A1Multiple digital computer combinationsSpecial data processing applicationsComputer scienceDistributed computing
The behavior of a messaging system can be modified. A message from a sender can be received. A determination can be made that the message is associated with a workflow. A position of the sender within an organizational hierarchy can be identified. The workflow associated with the message can be initiated according to the position of the sender.
Owner:IBM CORP
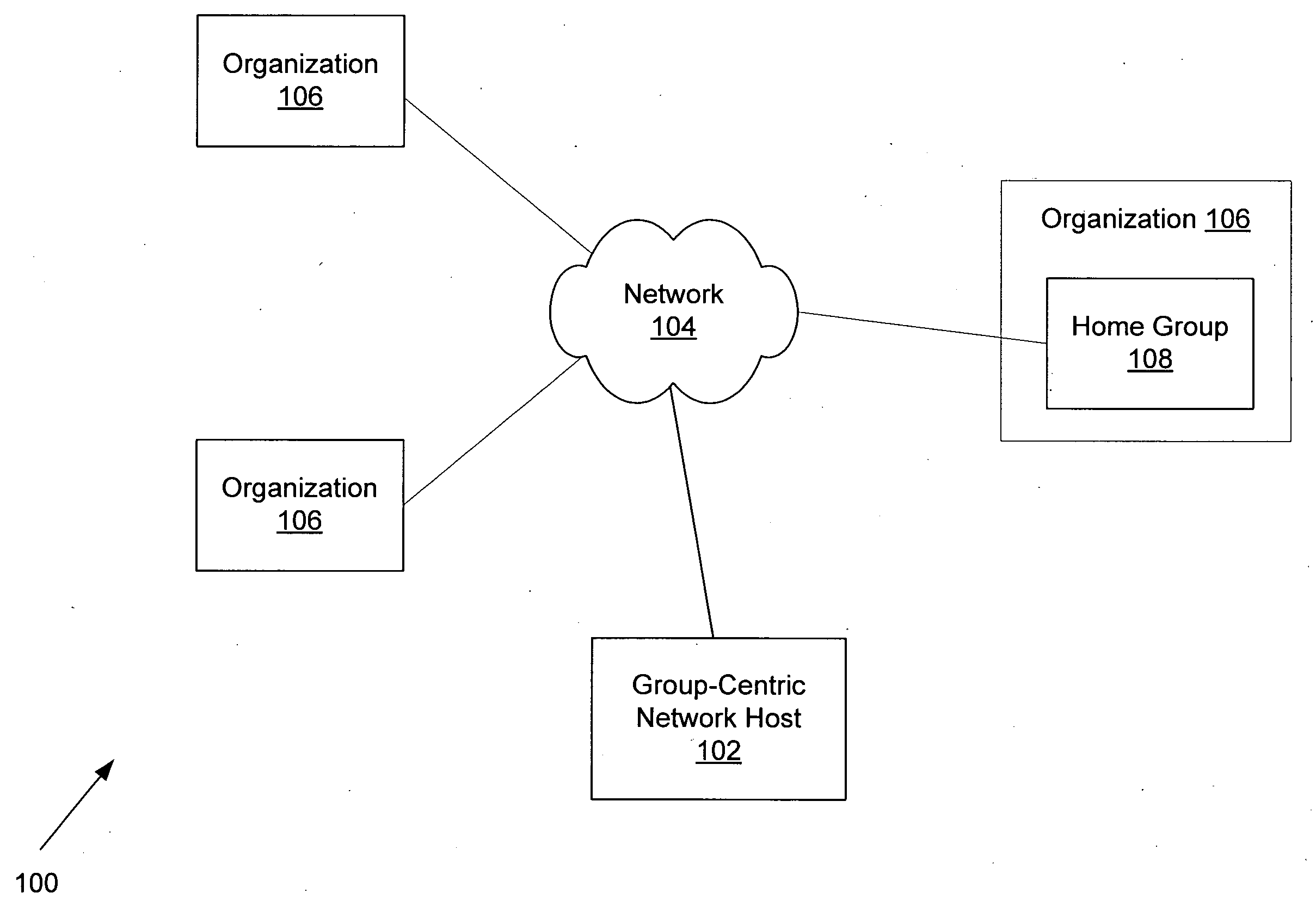
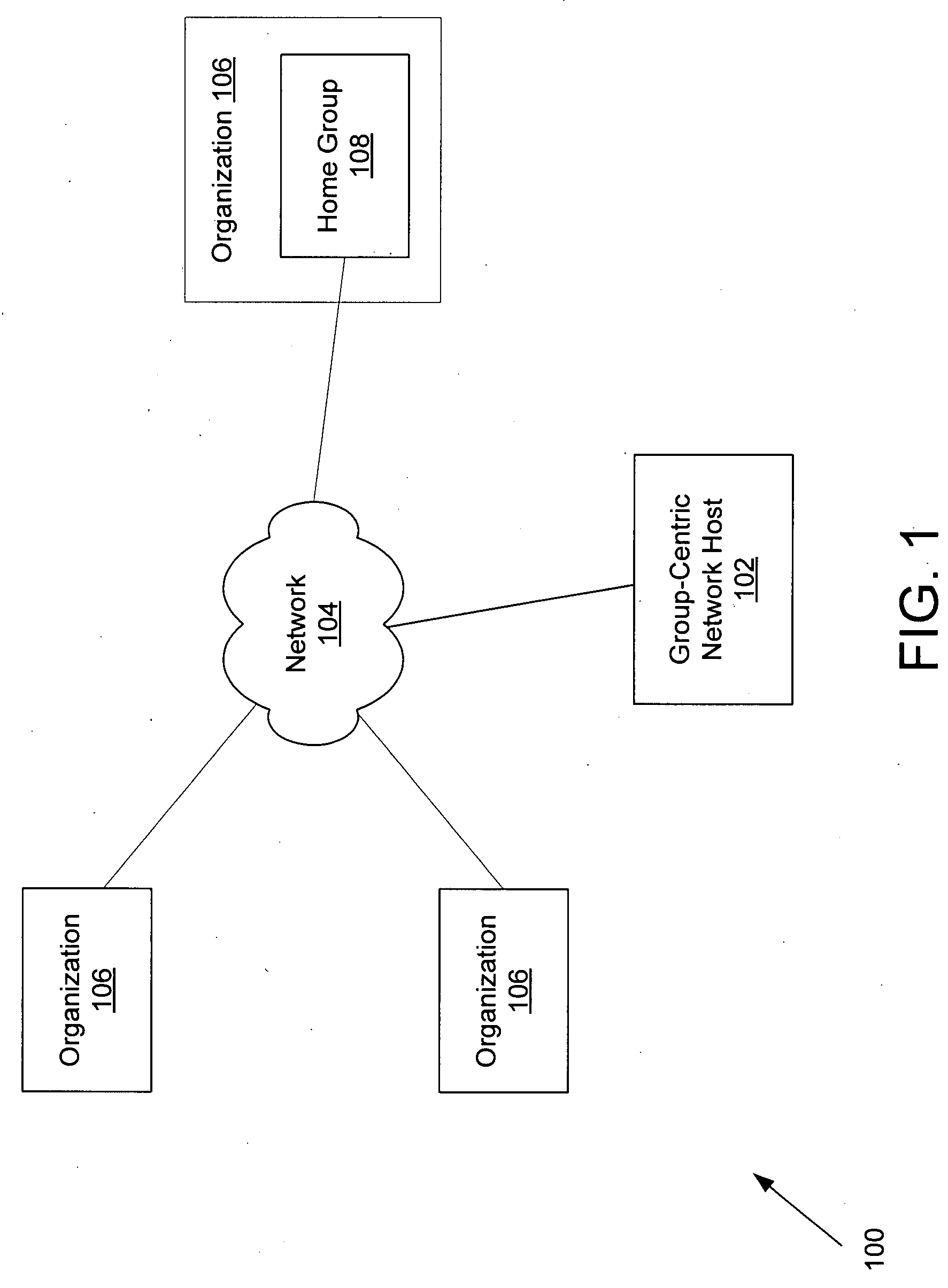
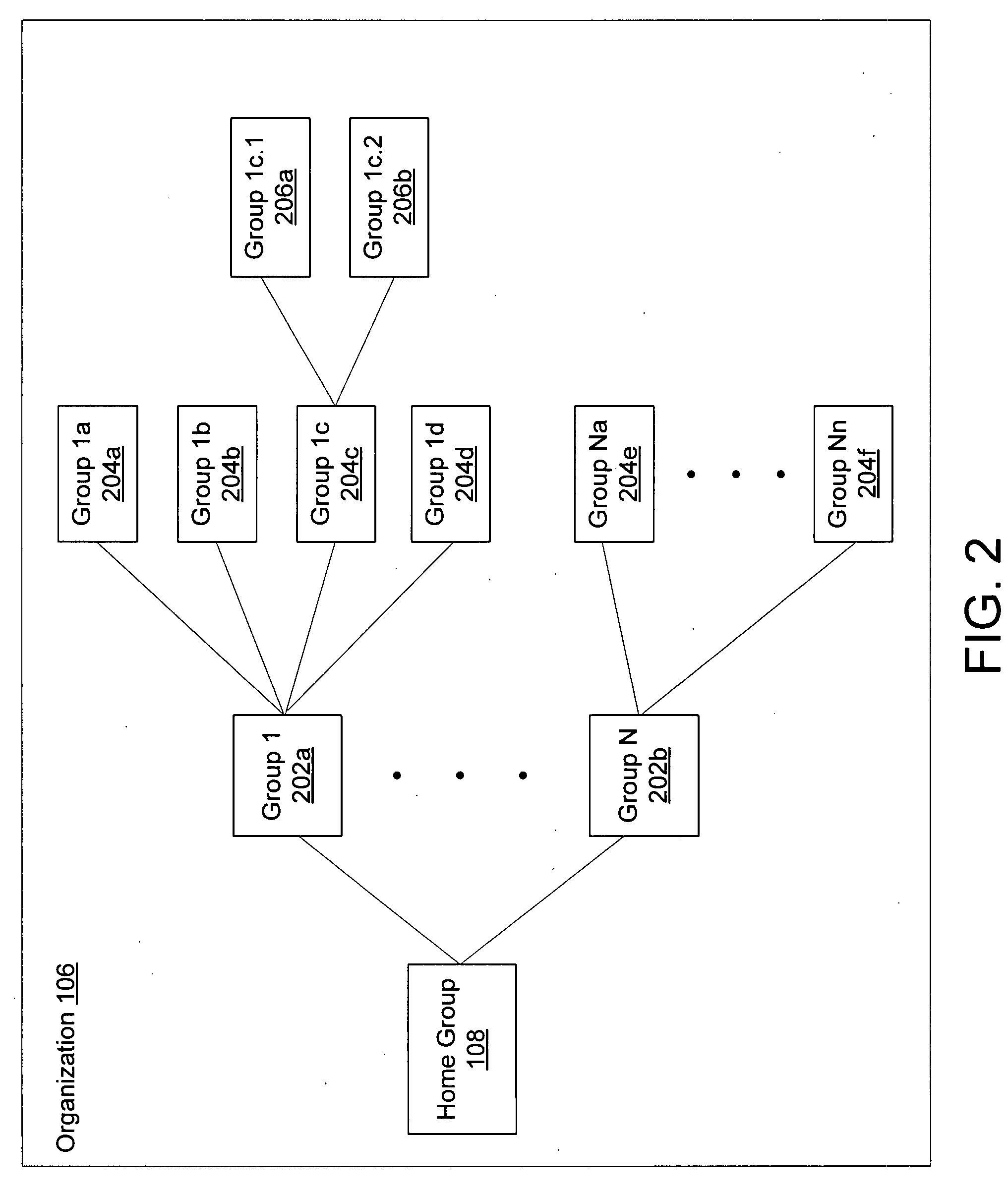
Creation of organizational hierarchies in a group-centric network via handshake mechanisms
InactiveUS20080205295A1Data switching by path configurationOffice automationHandshakeComputer security
Exemplary systems and methods for creating organizational hierarchies in a group-centric network are provided. In exemplary embodiments, a request to establish a new group within an organization on the group-centric network is received by the group-centric network host. The group-centric network host then determines if the request if from an authorized individual, such as a leader of a home group representing the organization. If the request is not from an authorized individual, at least one message-based handshake through which one or more relationships of the new group may be activated is performed.
Owner:CARR & FARRELL LLP +1
Information visualization method and intelligent visual analysis system based on text curriculum vitae information
InactiveUS20170200125A1Deep knowledgeOvercomes drawbackNatural language data processingOffice automationSocial internet of thingsData science
The present invention discloses an information visualization method and an intelligent visual analytics system for visualizing information in text resume. The method includes: 1) conducting quantitative calculation on experience data for each text resume to obtain a growth trajectory sequence and visualizing such sequence; 2) selecting the growth trajectory sequence from multiple resumes to conduct associative analysis to obtain potential social relationships between resumes, and creating visualization for a latent social network; 3) based on the potential social relationships, converting personnel overlapping in a common work place into an organization hierarchy, and visualizing such organization hierarchy. The present invention uses data mining and information visualization techniques to obtain a person's temporal growth experience, to identify potential social relations among people, and to reconstruct the organization hierarchy of personnel, which achieves deeper understanding of personnel growth patterns and social relationships.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Computer-implemented method and system for automated patentability and/or design around claim charts with context associations
ActiveUS9454731B1Readily annotatingEasy to navigateNatural language data processingPower supply for data processingHyperlinkThumbnail
A system correlates intellectual property analyzes, for example, patent claim charts, with respect to analyzed intellectual property and a target product or other intellectual property. Analyzes are stored to enable searching and / or creating reports over multiple analyzes. Units of the analysis are associated with a context, inherited, e.g., from the intellectual property document's assignment to a relative role within organizational hierarchy; and associated with a context derived from the analysis itself. The analysis and respective documents and / or targets of the analysis can be searched / retrieved / analyzed from the hierarchical analysis, the context analysis, and / or the content of the analysis. This obviates the need to store each analysis as a separate document. The target or annotations may be visually represented by an item such as a thumbnail or hyperlink, and the system automatically associates the item with the appropriate application program.
Owner:LEE EUGENE M
Control automation tool
A control automation tool (“CAT”) is configured for supporting discrete management of controls and their corresponding metrics. The control automation tool includes a software application connected with, stored on, and executed by one or more relational, closed-loop data repositories and computer systems. The use and maturation of a control within an organization depends on management of operational performance and expenses, which the CAT assists through lean project management, effective implementation of action plans and financial functions. Further, people resources, organizational hierarchy and access management functions are used to support mapping of controls arranged by organizational unit and support access permissions that are consistent with appropriate data management. The CAT also provides transparency and meaning to control and metric status and relevant data regarding controls and their associated metrics and is configured for ease of control and metric management via the CAT interface.
Owner:BANK OF AMERICA CORP
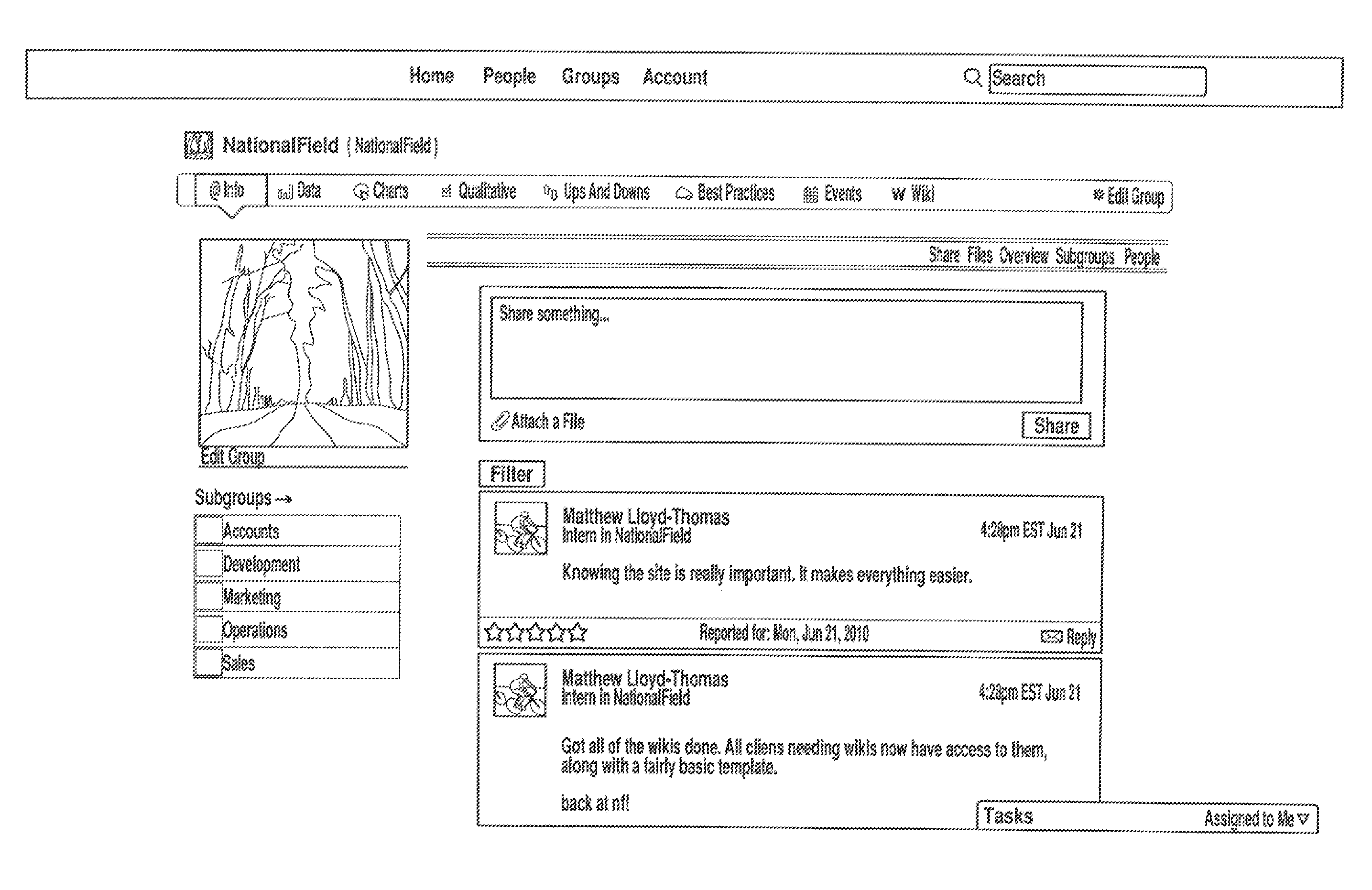
Hierarchical social network system
InactiveUS20120036209A1Save organization timeMultiple digital computer combinationsOffice automationSocial webOrganizational hierarchy
A social network system with an organizational hierarchy established to include a main group with at least one subgroup reporting to the main group. At least one of the one subgroup has field users reporting to the subgroup. Each subgroup has multiple subgroup users while the main group at the apex of the hierarchy has at least one main group user. A server is provided that receives messages from the field users and subgroup users. The field user- and subgroup-messages are communicated to a wireless device associated with the main group user while a first subgroup user receives on a wireless device messages from first subgroup field users on a wireless device. The server employs communication permissions for the organization hierarchy that limit the information to which a member of the organization hierarchy is able to receive based on the role filled by an organization hierarchy member.
Owner:NAT FIELD
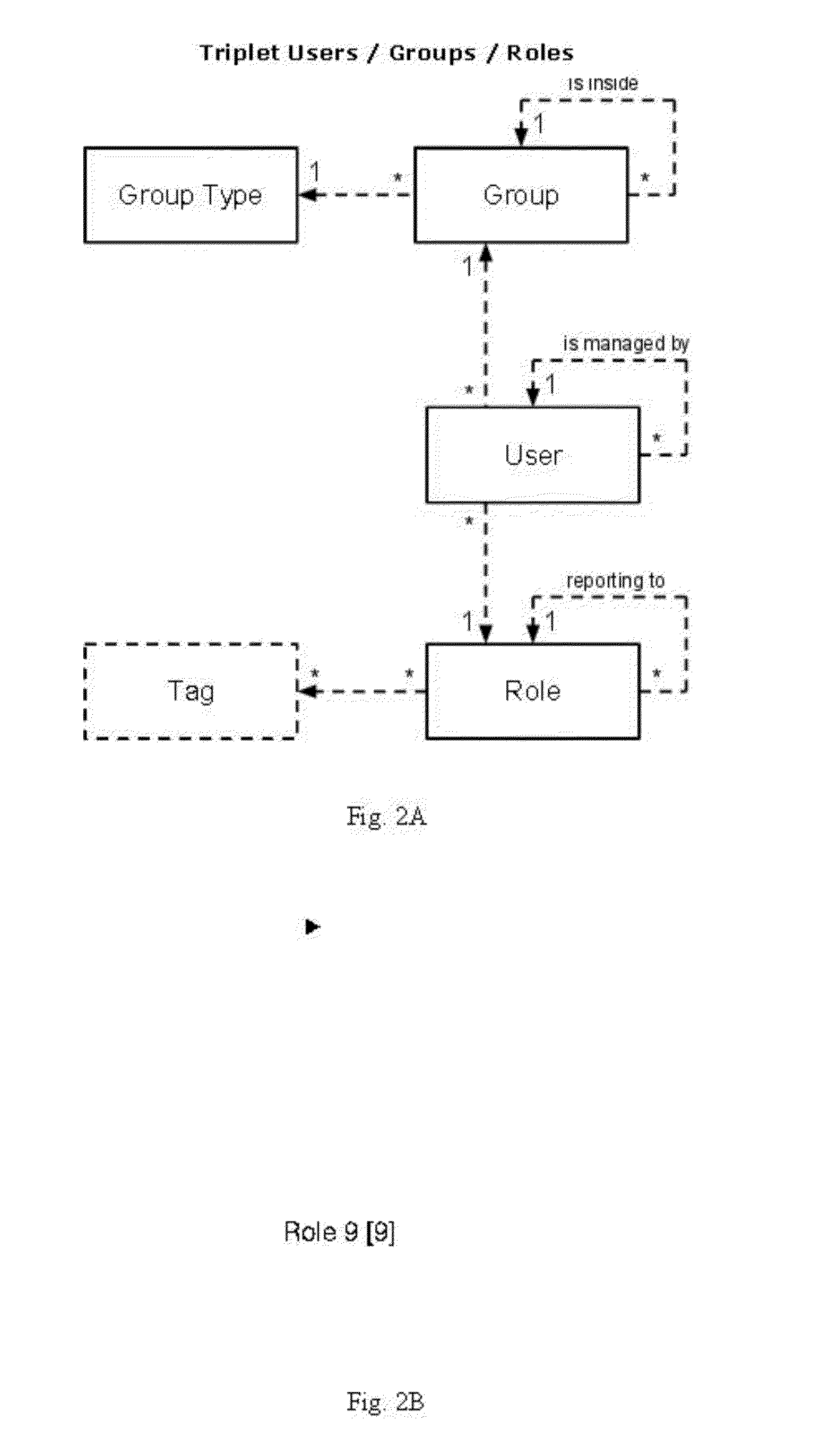
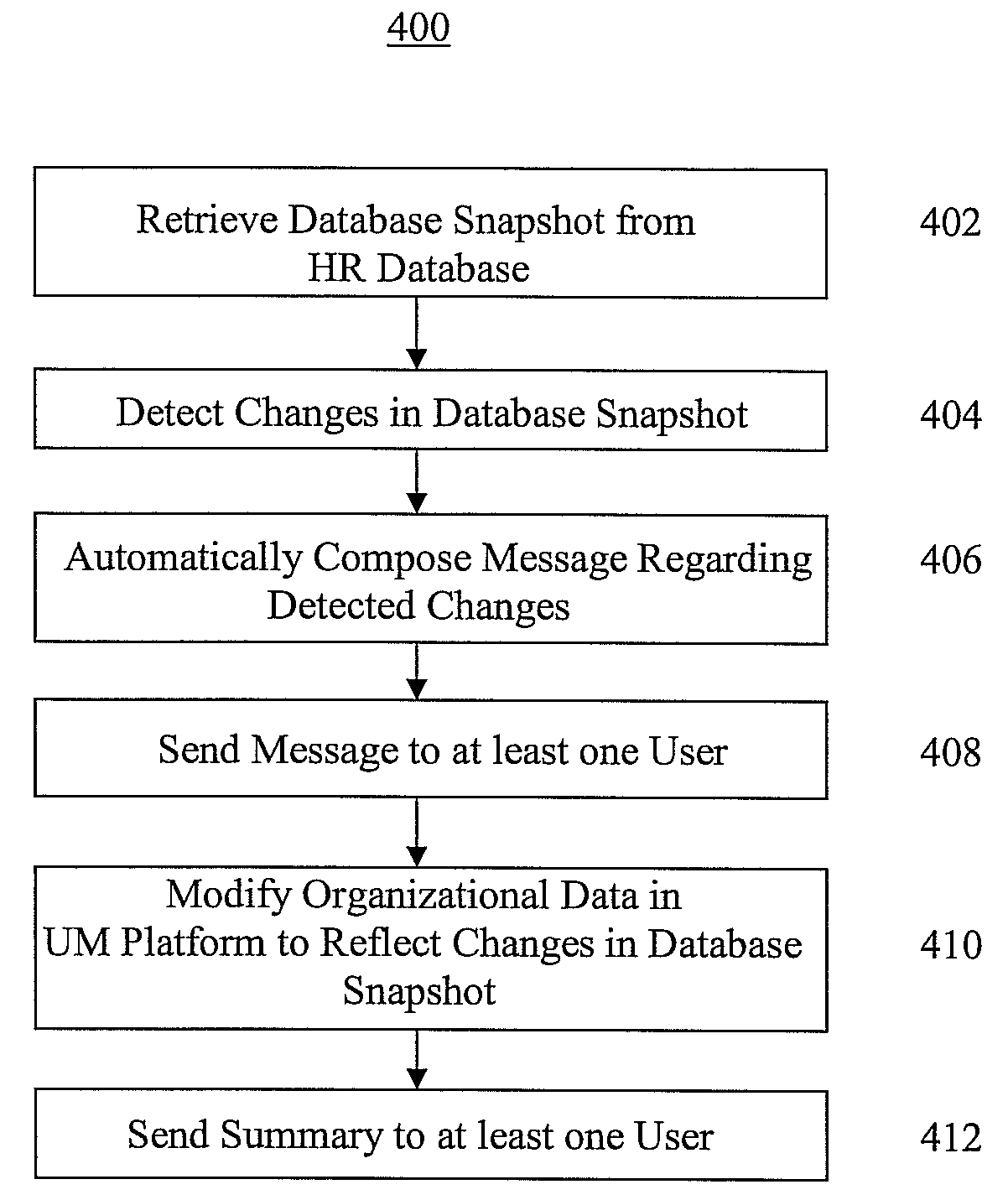
Method and System for Managing Changes in Organizational Data in Unified Messaging Systems
ActiveUS20100153340A1Digital data information retrievalDigital data processing detailsResource informationClient-side
A method and system for automatically managing changes to organizational data in a unified messaging (UM) platform are disclosed. A database snapshot is retrieved from a client human resources database. The database snapshot includes human resources information organized in an organizational hierarchy. A change is detected in the database snapshot from a previous database snapshot, and organizational data in the UM platform is automatically modified to reflect the detected change in the database snapshot. When the change is detected in the database snapshot, it is possible for the UM platform to automatically compose and send a message to at least one user associated with the change including potential modifications of the organization data. The organizational data in the UM platform can then be modified only in response to receiving approval of the potential modifications of the organizational data from at least one user associated with the change.
Owner:AT&T INTPROP I L P
System and method for corporate-wide policy management
InactiveUS7644089B2Digital data processing detailsAnalogue secracy/subscription systemsDatabaseOrganizational hierarchy
An organization asset database (ADb) is described that contains a complete, up-to-date, secure, and easily accessible inventory of the organization's assets. Each asset is mapped onto a structure that represents the organizational hierarchy of the organization, which provides for multiple levels of accountability for each asset. Each asset has one or more roles in relation to other assets in the ADb and has one or more entitlements in relation to other assets in the ADb. The relationship between assets ensures that the ADb is complete and up-to-date and allows for easy filtering and retrieval of the information contained in the ADb.
Owner:BARCLAYS CAPITAL INC
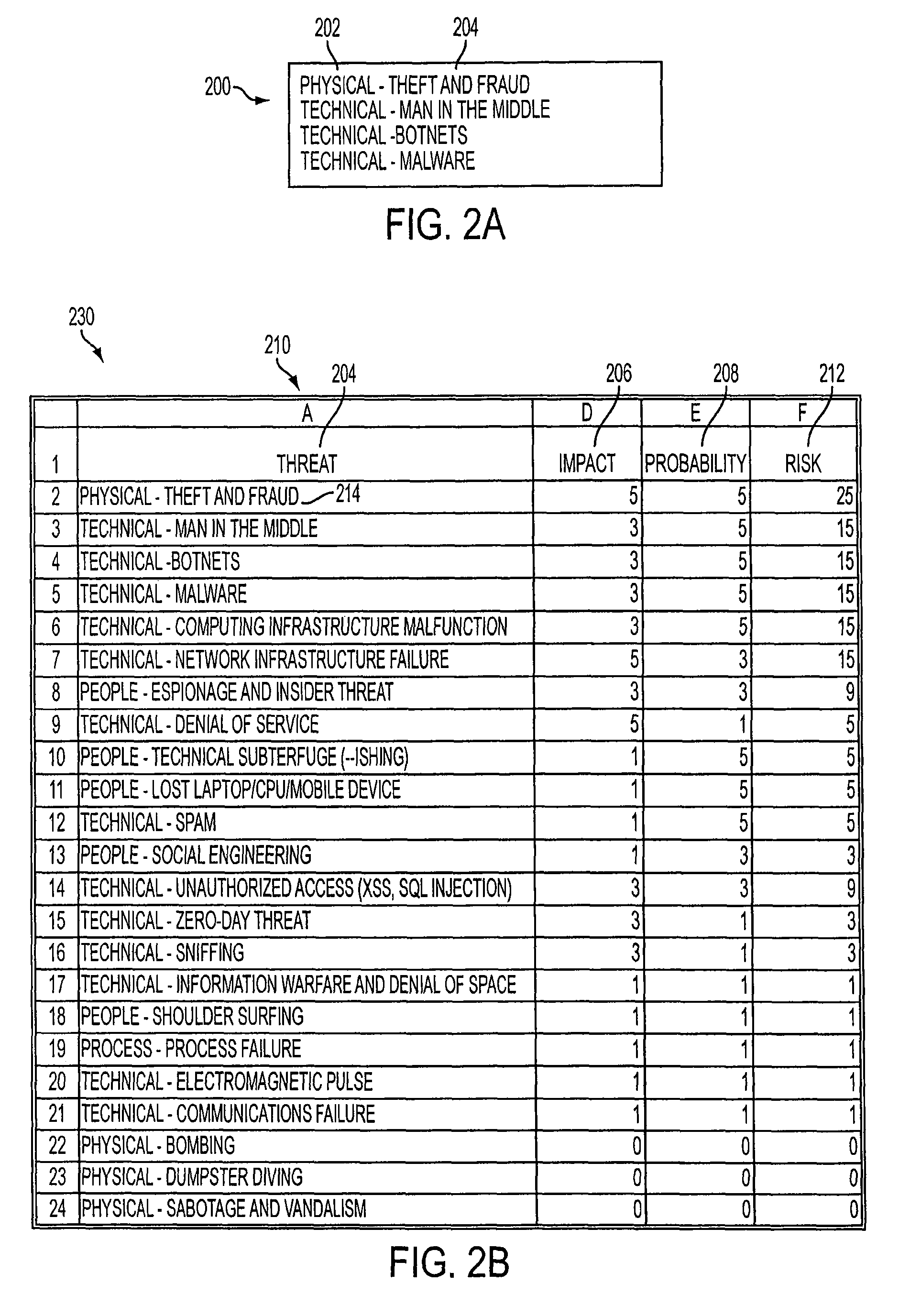
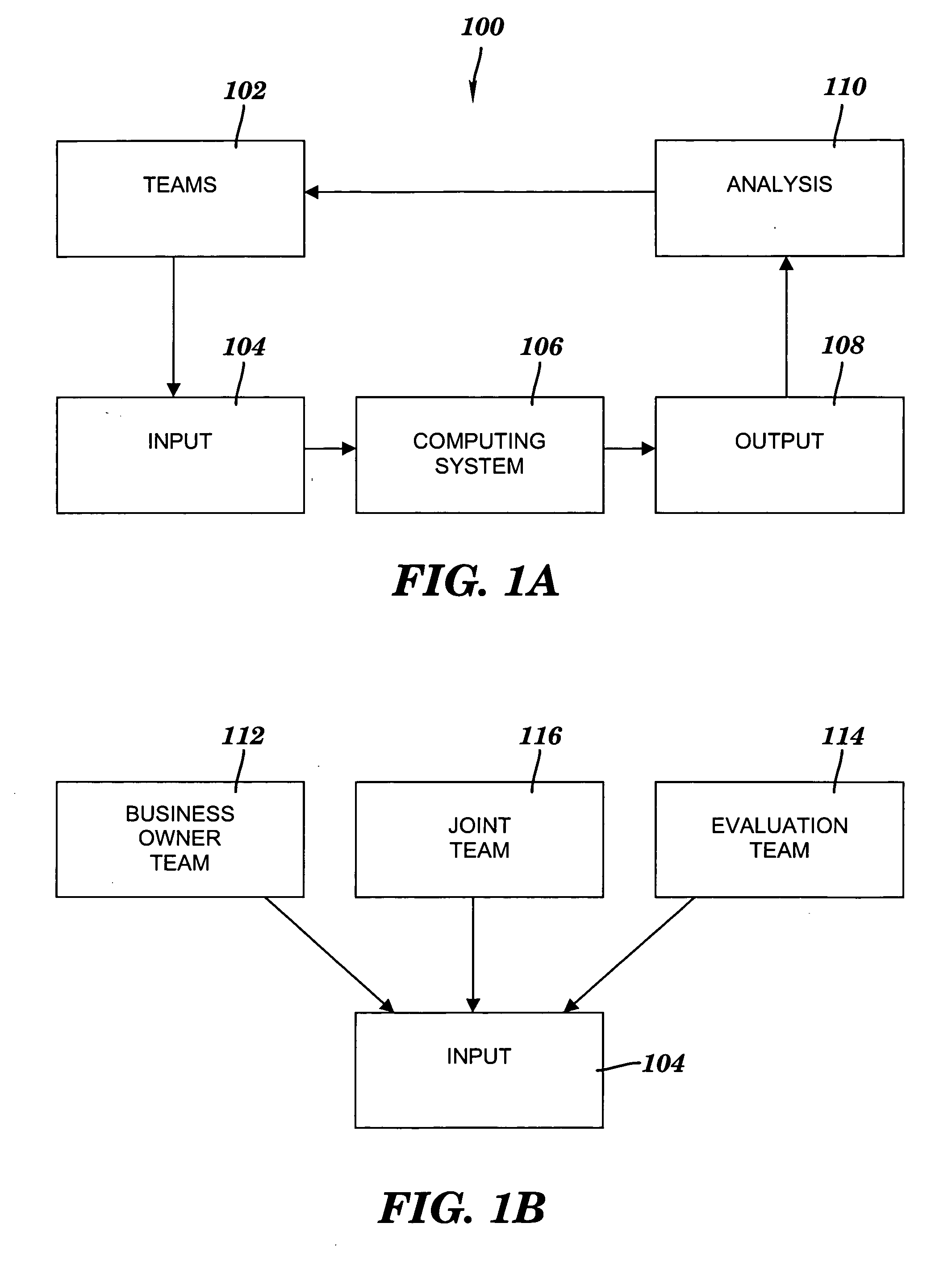
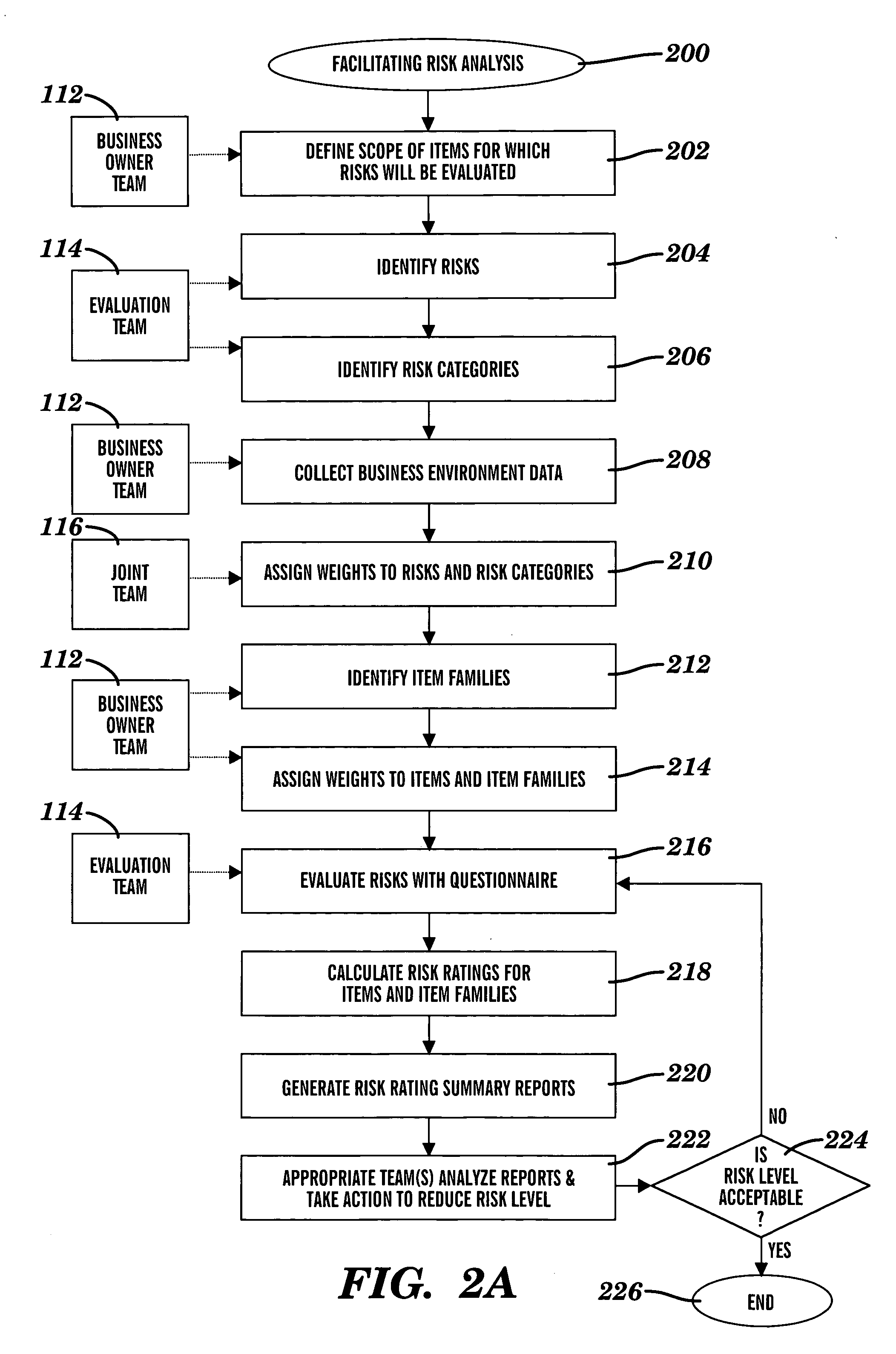
Method and system for facilitating analysis of risks
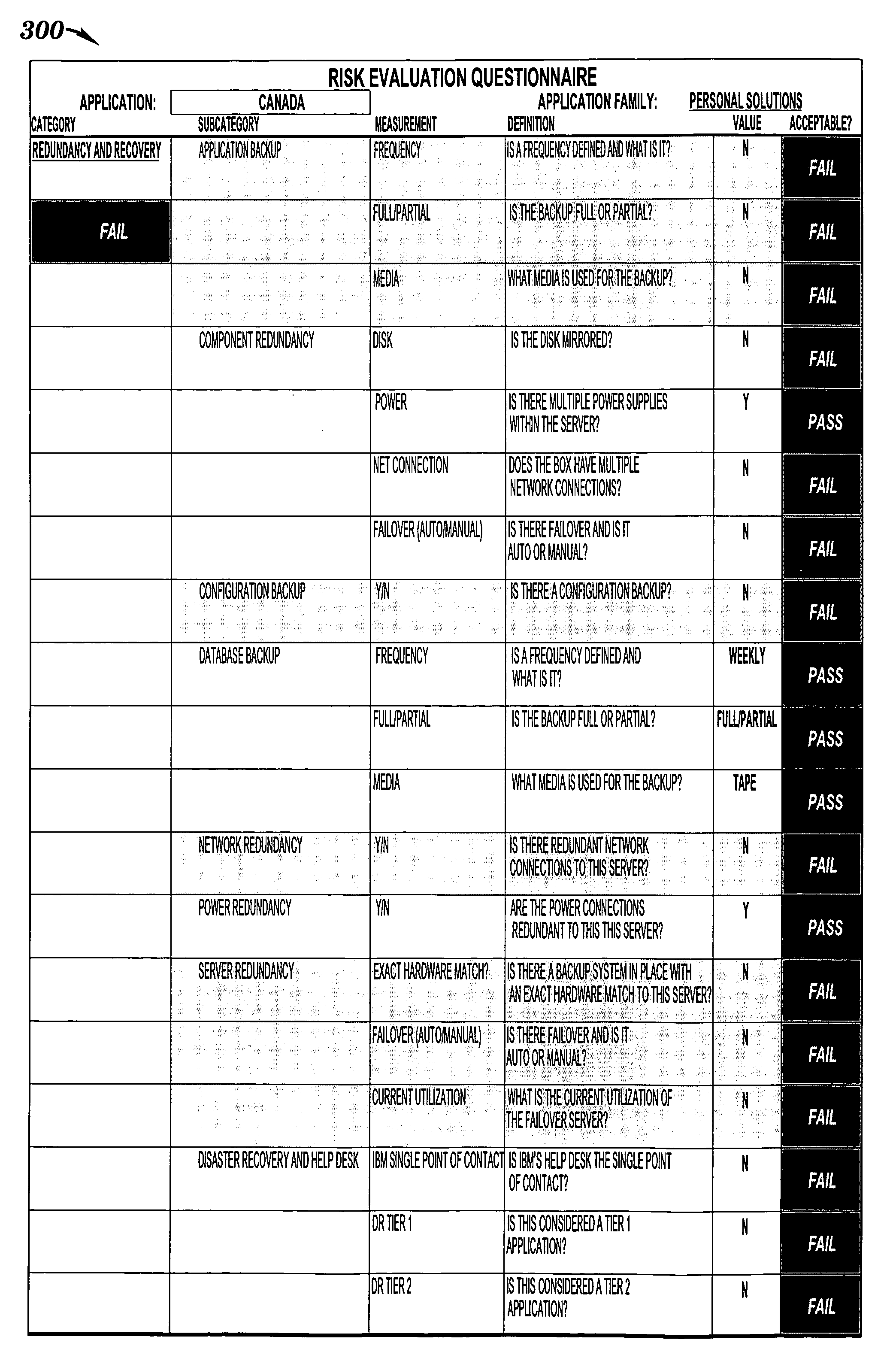
InactiveUS20060247957A1Facilitates analysis of riskFacilitate risk analysisFinanceSpecific program execution arrangementsRisk ratingRisk evaluation
A method and system for facilitating analysis of risks. Items, families of items, risks, sub-categories of risks, and categories of risks are weighted. Items are related to each other by a common business function. The risks are associated with each item. For each item, each associated risk is evaluated to determine whether the risk is mitigated. Risk ratings associated with the items or families are calculated using at least risk evaluations and weights assigned to risks and items. The risk ratings are summarized in selectable views which are based on the sub-categories or categories, and which are to be analyzed by wide-ranging levels in a business organizational hierarchy.
Owner:SERVICENOW INC
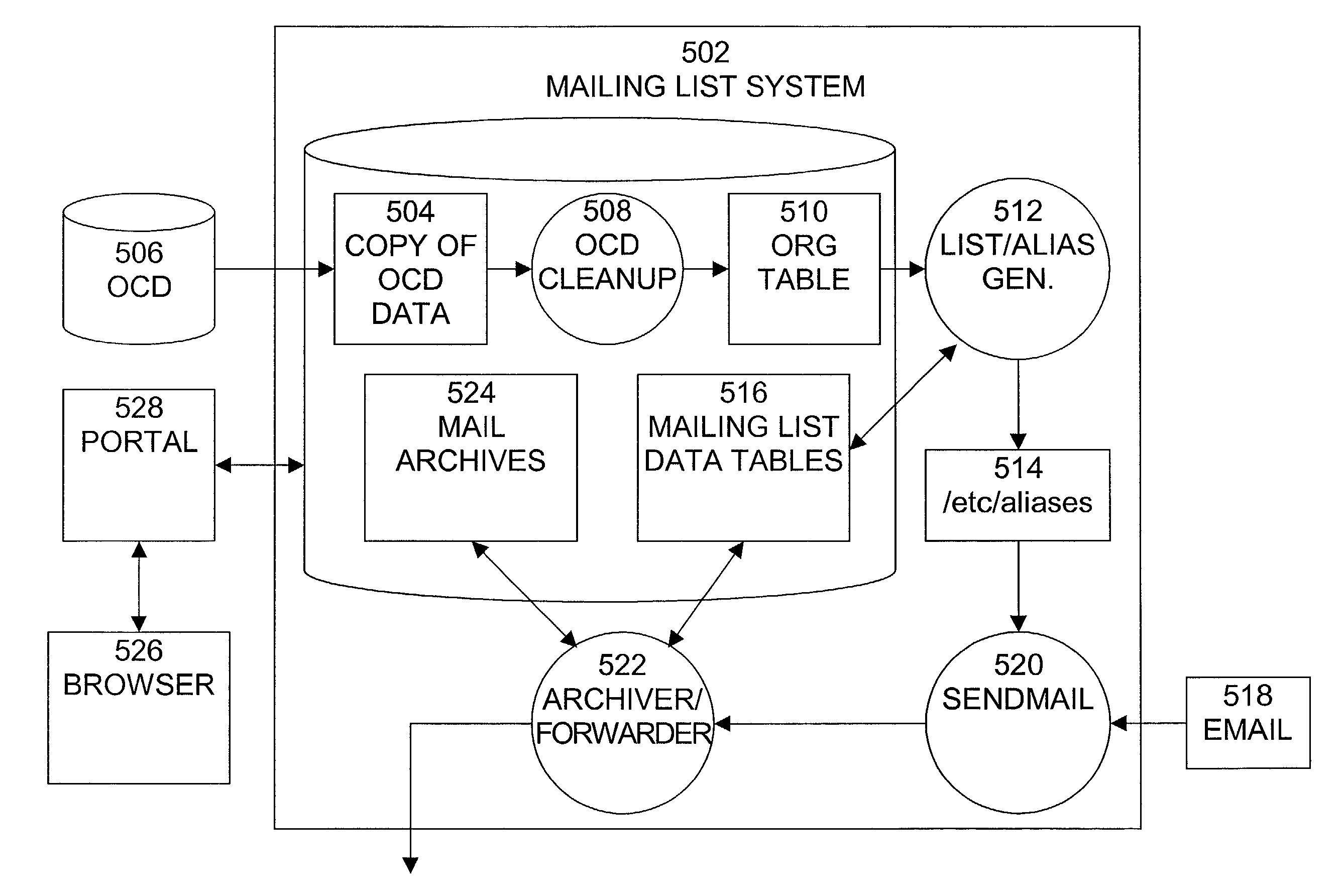
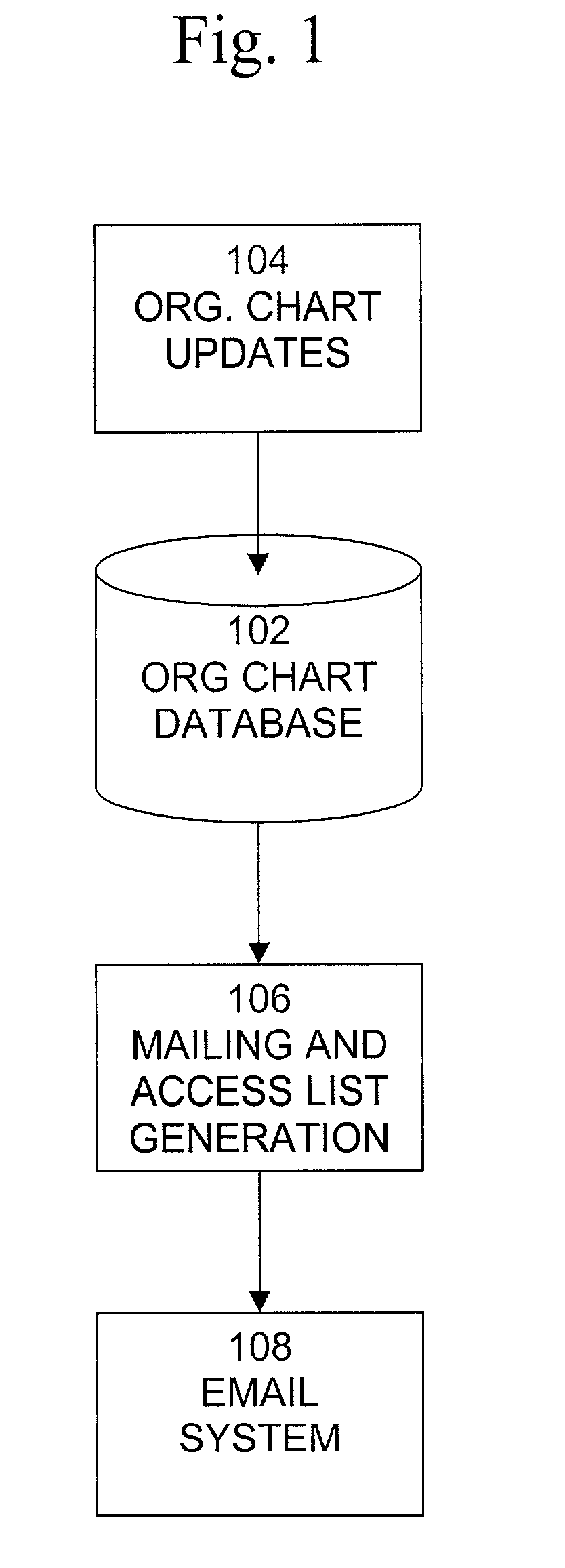
Hierarchical org-chart based email mailing list maintenance
InactiveUS7734696B2Digital data processing detailsMultiple digital computer combinationsMailing listEmail address
The present invention is a system, method, and computer program product that provides the capability by which changes in an organization can be automatically reflected in the organization's mailing lists and access lists. The email messaging system comprises a mailing list generator operable to receive information relating to an organizational hierarchy and generate from the received information a plurality of mailing lists, at least some of the mailing lists relating to a member of the organizational hierarchy to whom at one other member of the organizational hierarchy reports and an archiver / forwarder operable to receive an email message including an address identifying at least one of the plurality of mailing lists, access the mailing list to obtain email addresses for members of the mailing list, and send the email message to the obtained email addresses.
Owner:ORACLE INT CORP
Data federation with industrial control systems
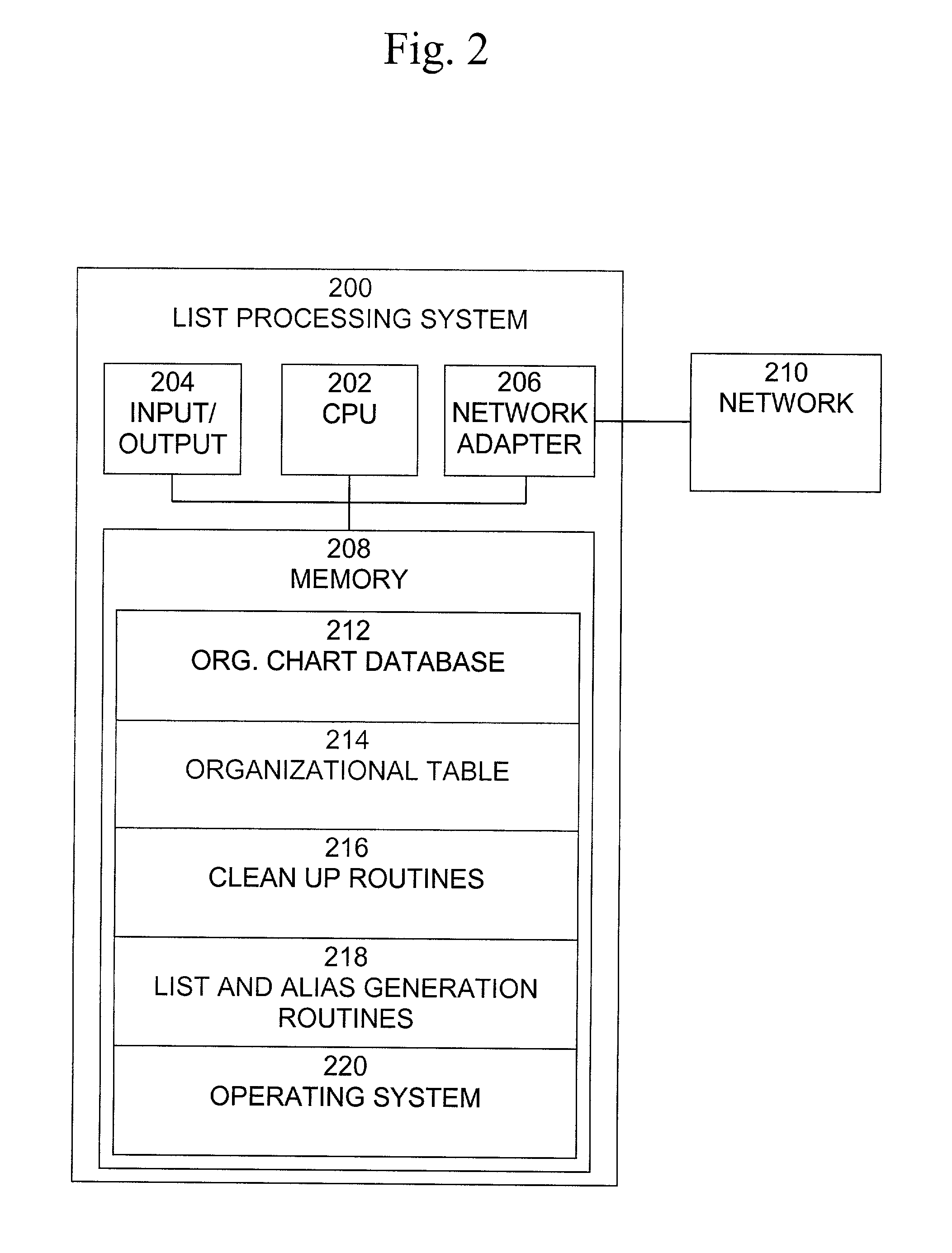
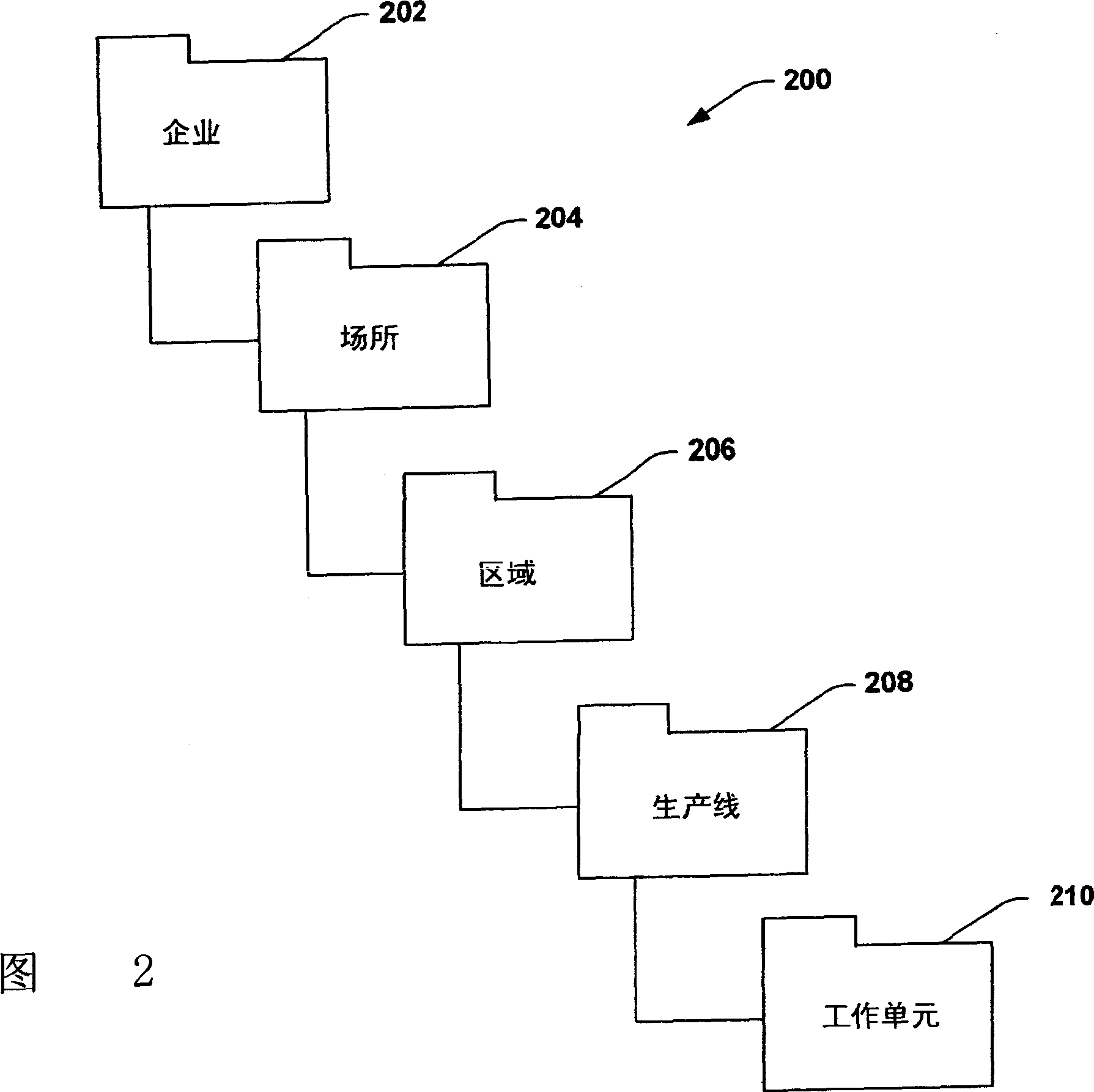
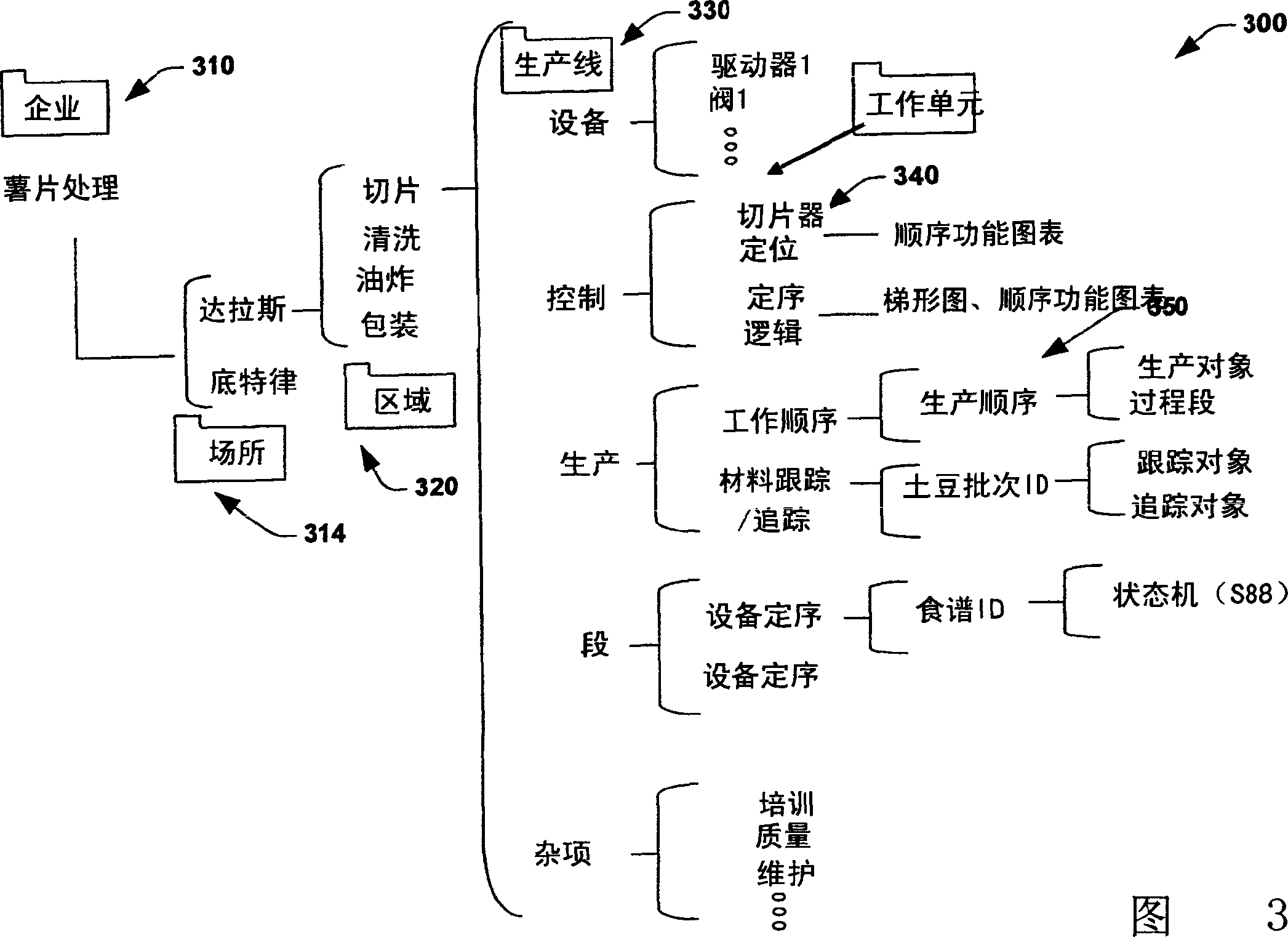
InactiveCN1952815ARealize distributed deploymentHierarchical databasesTotal factory controlProgrammable logic controllerData exchange
An organizational model of a hierarchical system can be distributed across various elements of an enterprise. Such elements include representations of the system that are maintained on higher-level business servers and other representations that serve control elements of the system such as programmable logic controllers and / or other industrial control components. In one aspect, an industrial automation system is provided. The system includes at least one controller to instantiate a portion of an organizational hierarchy. A communications component in the controller interacts with at least one other portion of the organizational hierarchy to facilitate data exchange and control between various components of an enterprise.
Owner:ROCKWELL AUTOMATION TECH
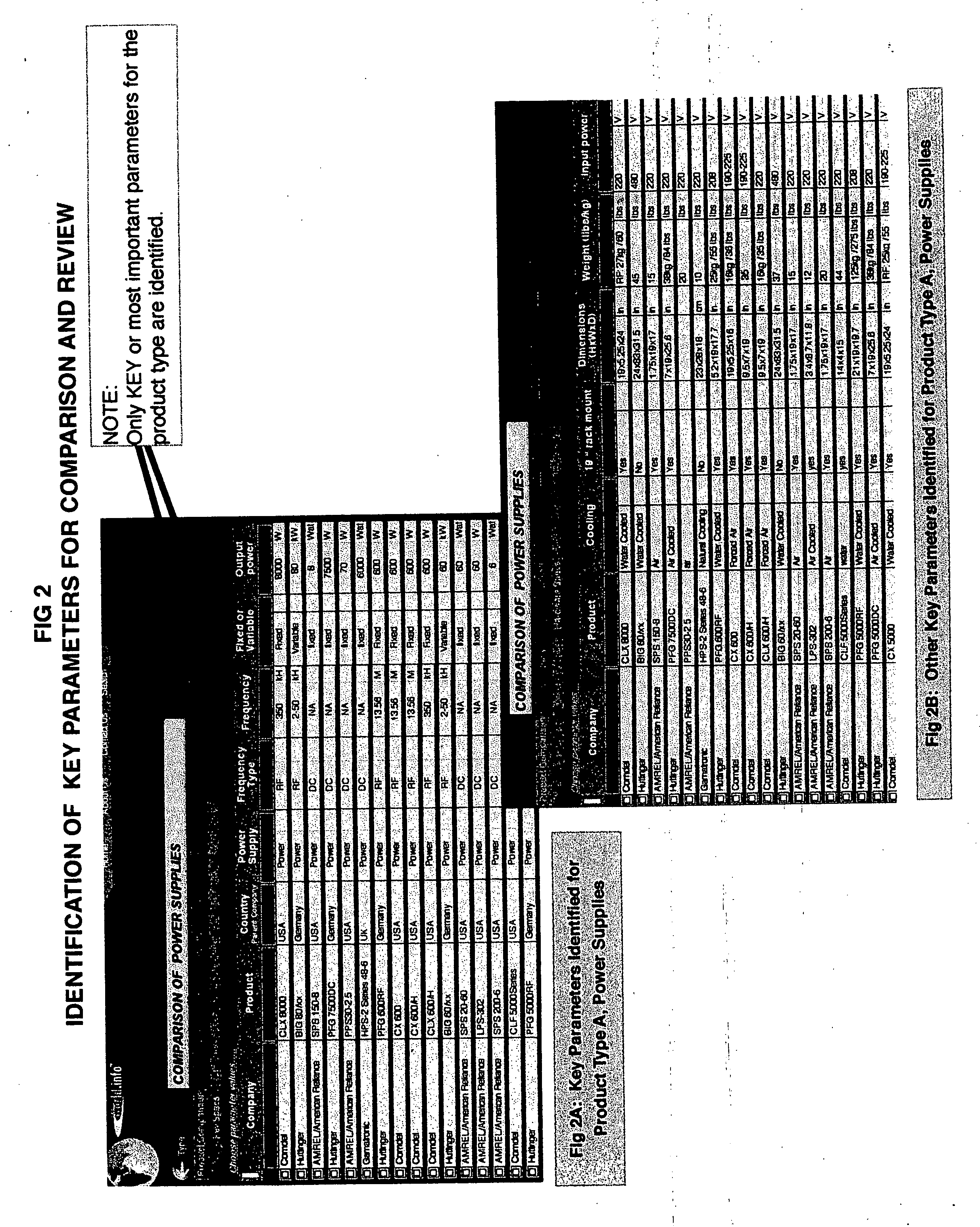
System and method for organization and display of data using identification of key data for comparison and analysis
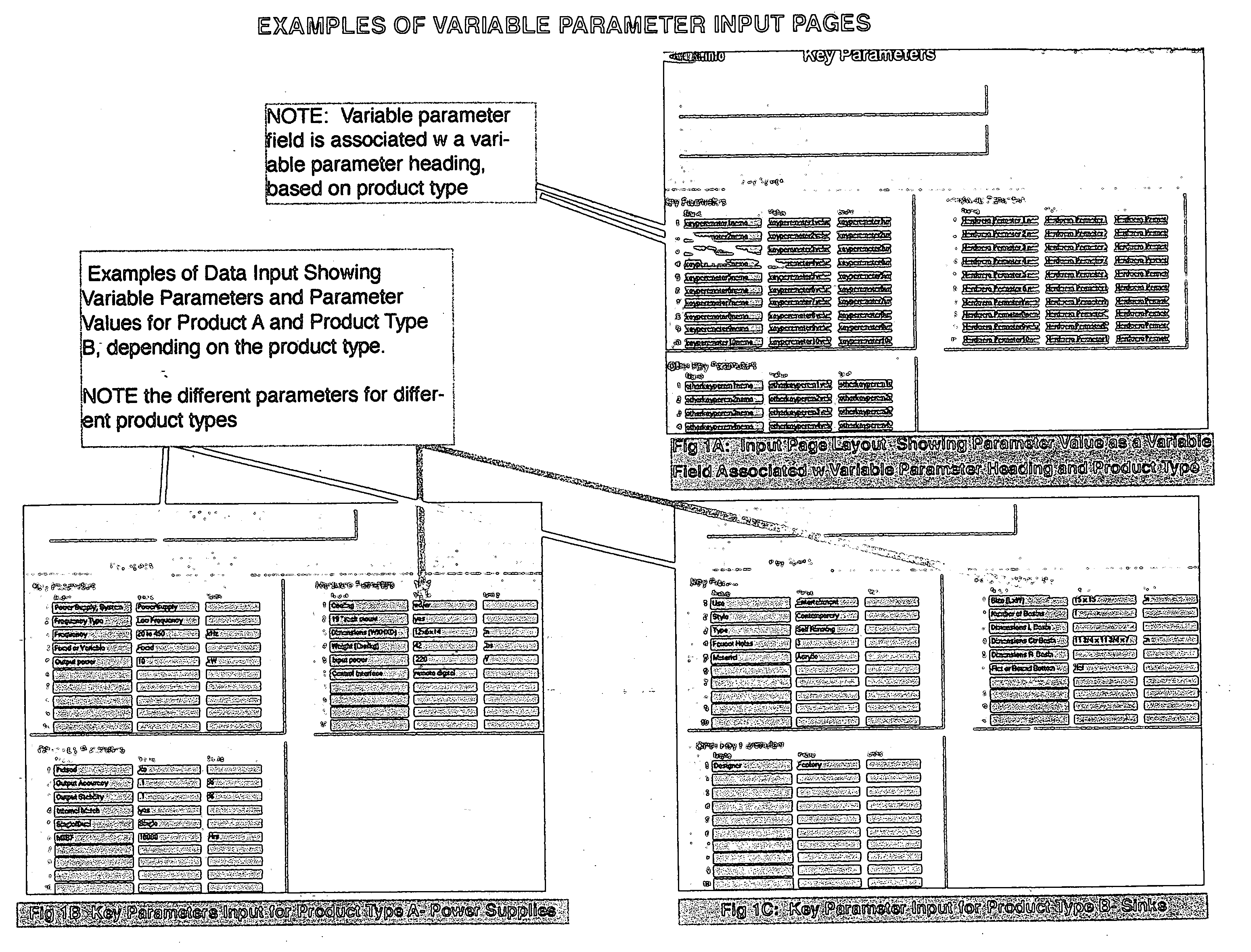
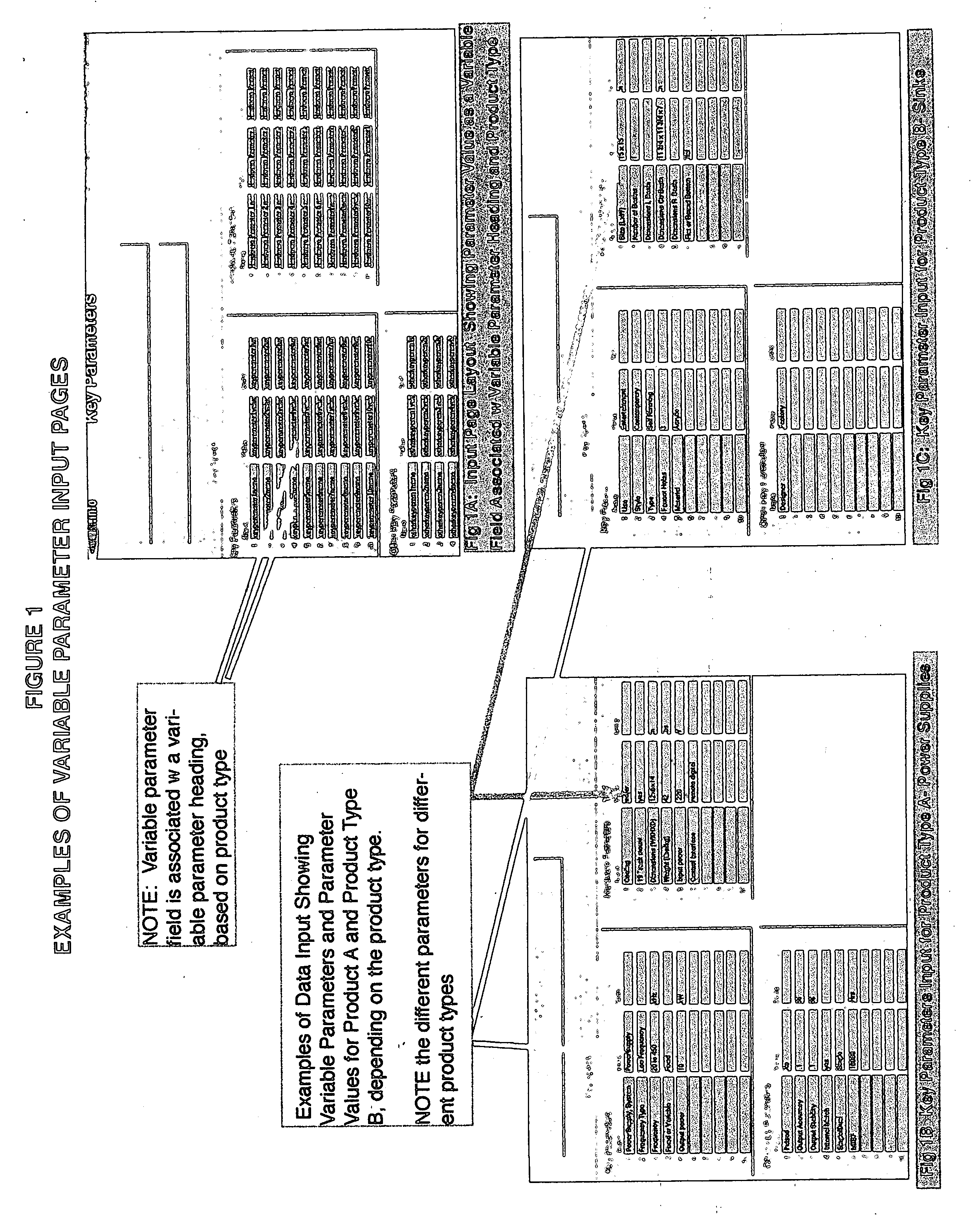
The use of computer technology and the internet to quickly locate, view, compare, and select marketable products or other data arranged according to selected Key Parameters. The growth of the internet has exceeded the capacity of existing technologies and business methods to allow business and consumer users to sort through a vast sea of data. Variable Field Names expressed as Key Parameters builds upon the simple concept of organizational hierarchy, and enables the manipulation of data in a specific manner through the internet to the marketplace, in which all conceivable products, whatever their use or country of manufacture, can be located, reviewed, compared, and selected for purchase. The invention uses a hierarchy-based software system that will allow the computer user to search and find required data directly. This invention is a system and method of identifying, selecting and displaying Key or most important attributes or parameters associated with each product Type. The user will no longer waste time sifting through search results that are not germane to his needs or are outside the needs of his current search.
Owner:SCHECHINGER DIANE +1
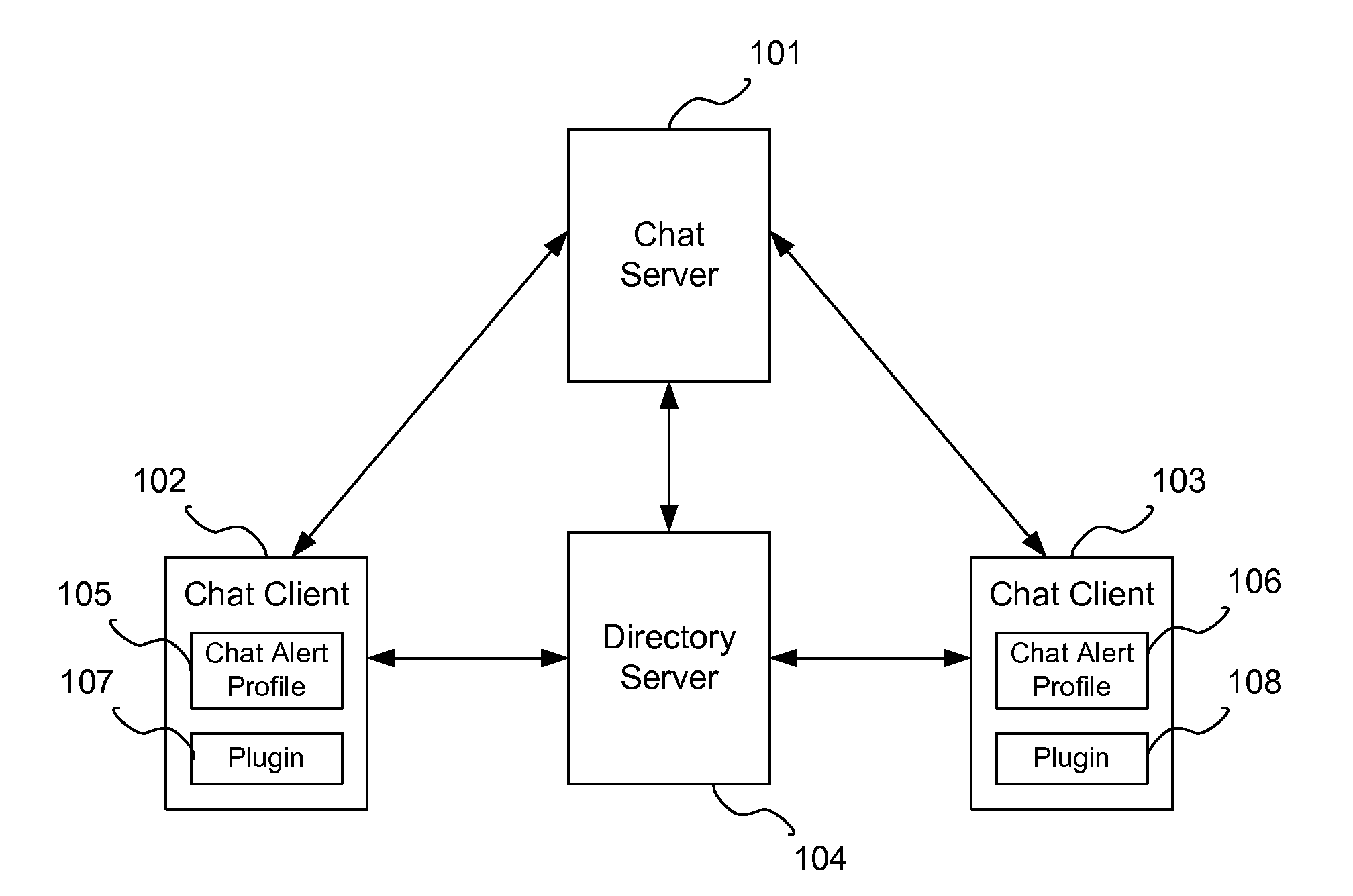
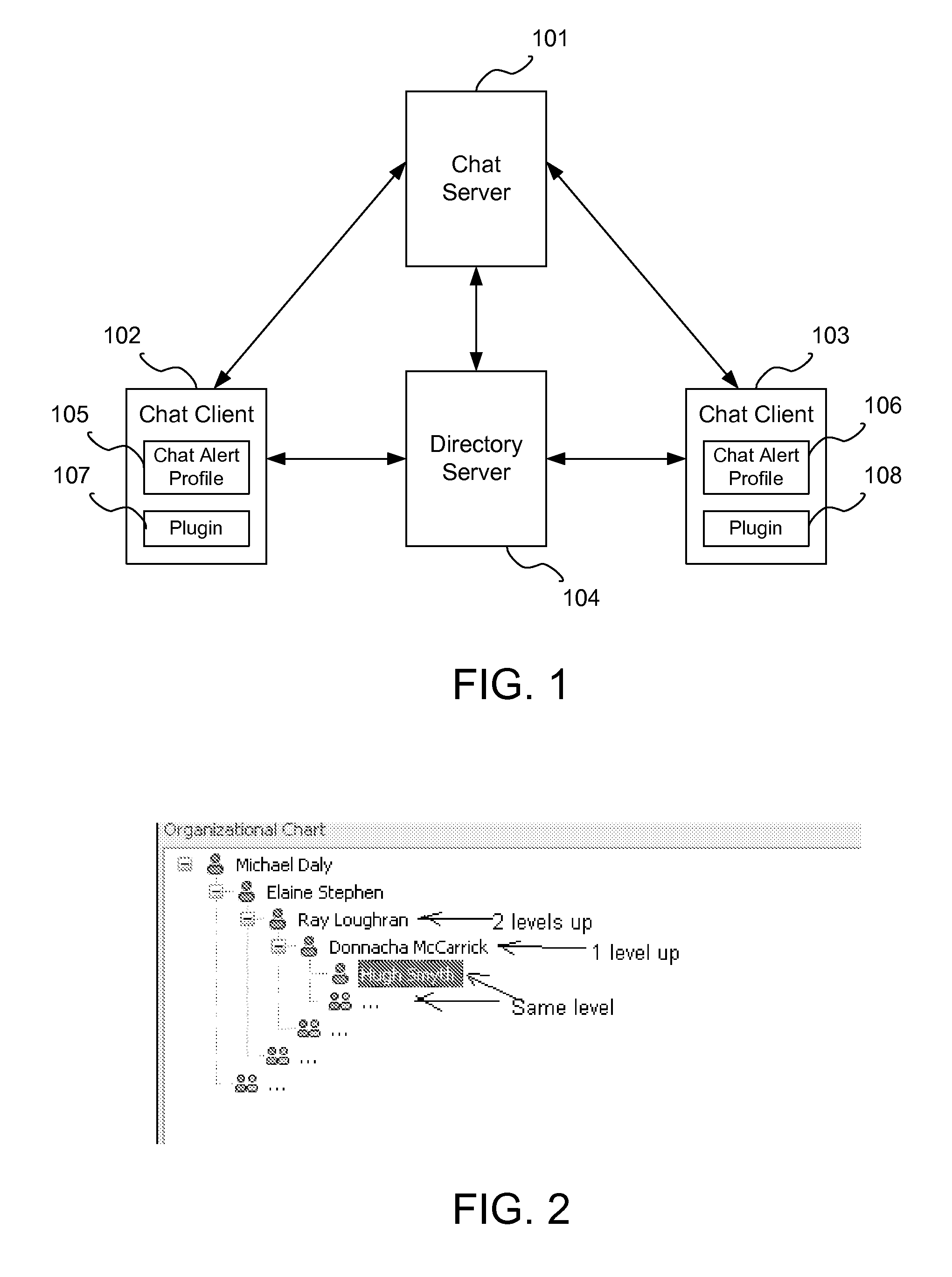
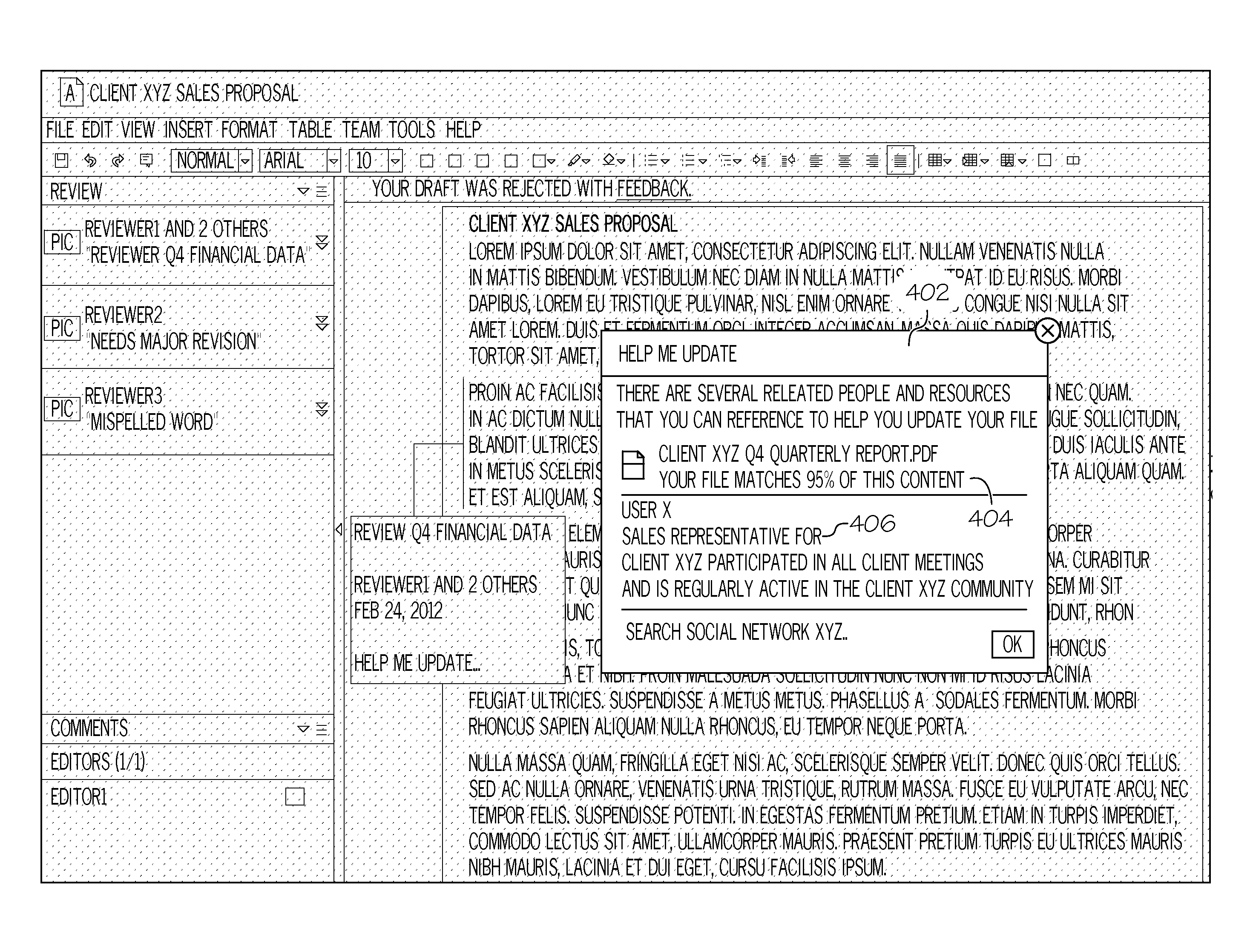
System and method to prioritize chat alerts based on an organizational hierarchical chain
In a chat alert method and system, a chat user creates alert profiles that include the requestor's level in an organizational hierarchy as a parameter and the alert type for the level. When a chat client receives a chat request from a requester for a receiver, the chat client determines if there is a chat alert profile that matches the requestor's level. If so, then an alert is issued to the receiver according to the matching chat alert profile. Optionally, the chat alert profile sets an alternate alert system, where if the receiver does not respond to the request within a specified time, an alert is sent using the alternate alert system. Chat requests from requesters higher up in the reporting chain can be highlighted for the receiver. The receiver can then prioritize the chat requests that he / she receives and respond to them in a timely fashion.
Owner:IBM CORP
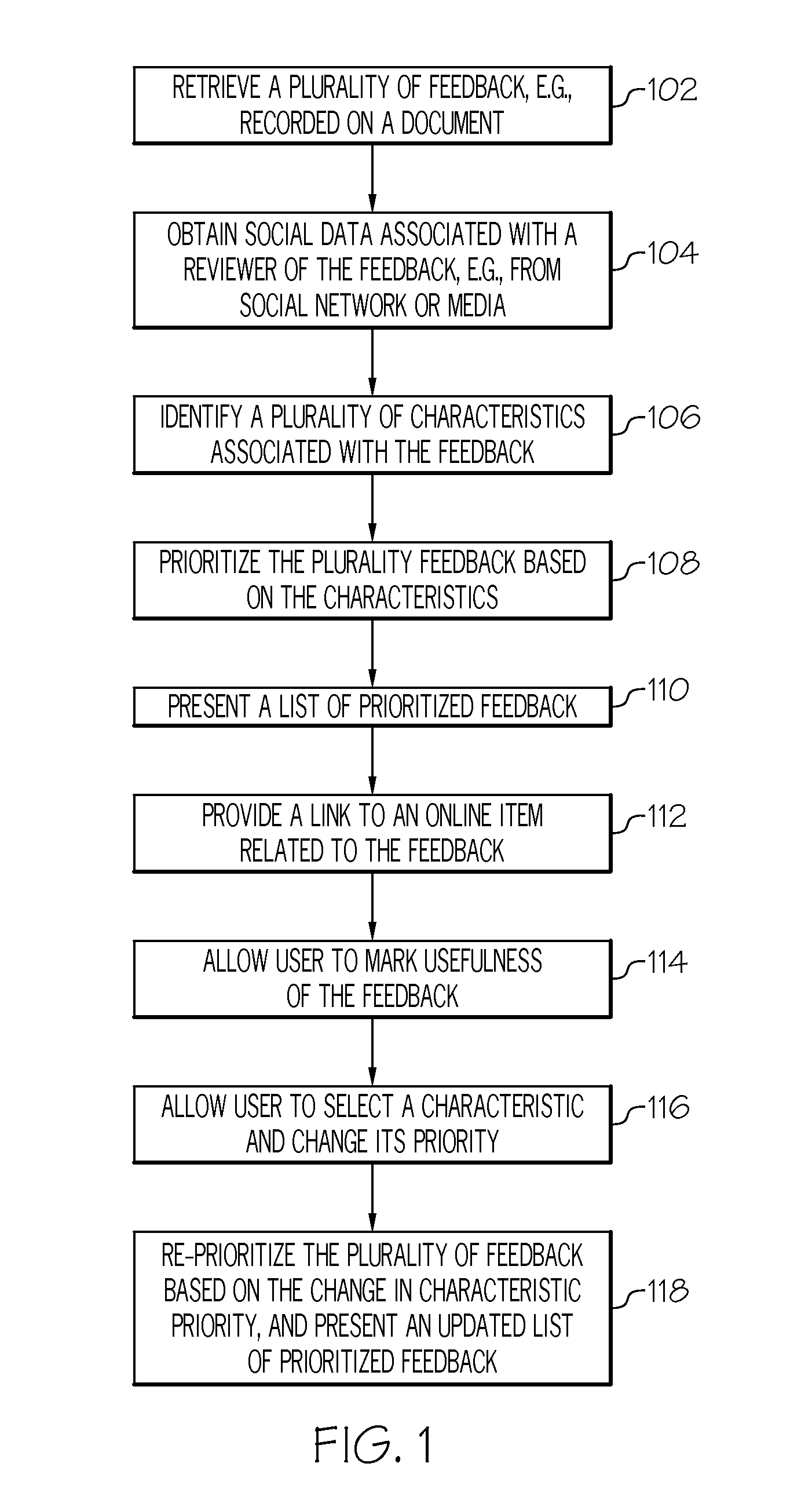
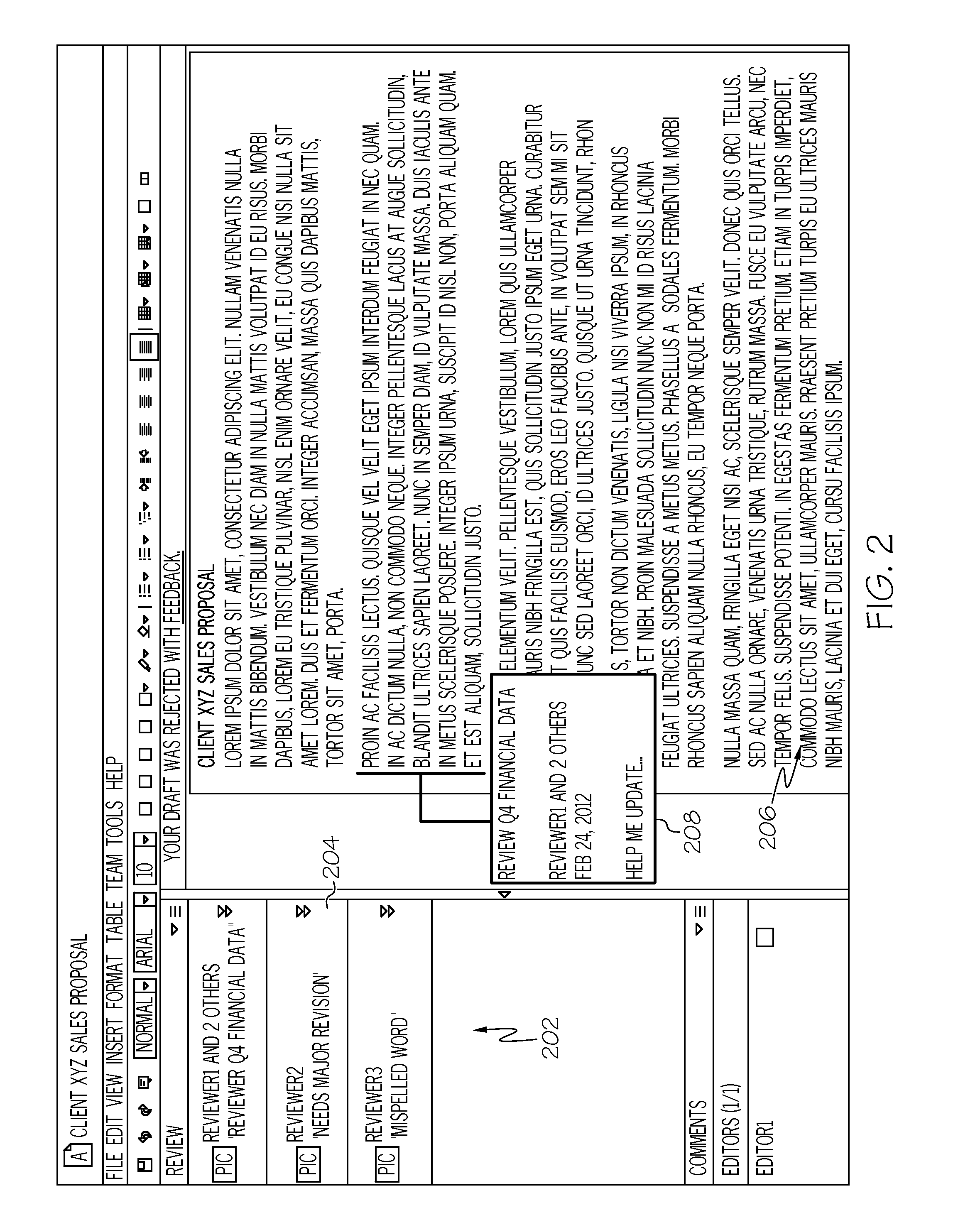
Using social data to assist editors in addressing reviewer feedback in a document review workflow
ActiveUS20160041973A1Digital data processing detailsSpecial data processing applicationsDocumentation procedureWorkflow
Presenting a reviewer feedback of a document, one aspect, may comprise retrieving a plurality of feedback on a document, each feedback having an associated reviewer who provided the feedback. Social data associated with the reviewer of the feedback may be obtained. A plurality of characteristics associated with the feedback may be identified, at least some of the characteristics identified based on the social data. The characteristics may include at least the associated reviewer's position in an organization hierarchy, the reviewer's expertise, frequency of the feedback, impact of the feedback, and usefulness of the feedback. The plurality of feedback may be prioritized based on the plurality of characteristics, and a list of prioritized feedback may be presented via a user interface.
Owner:IBM CORP
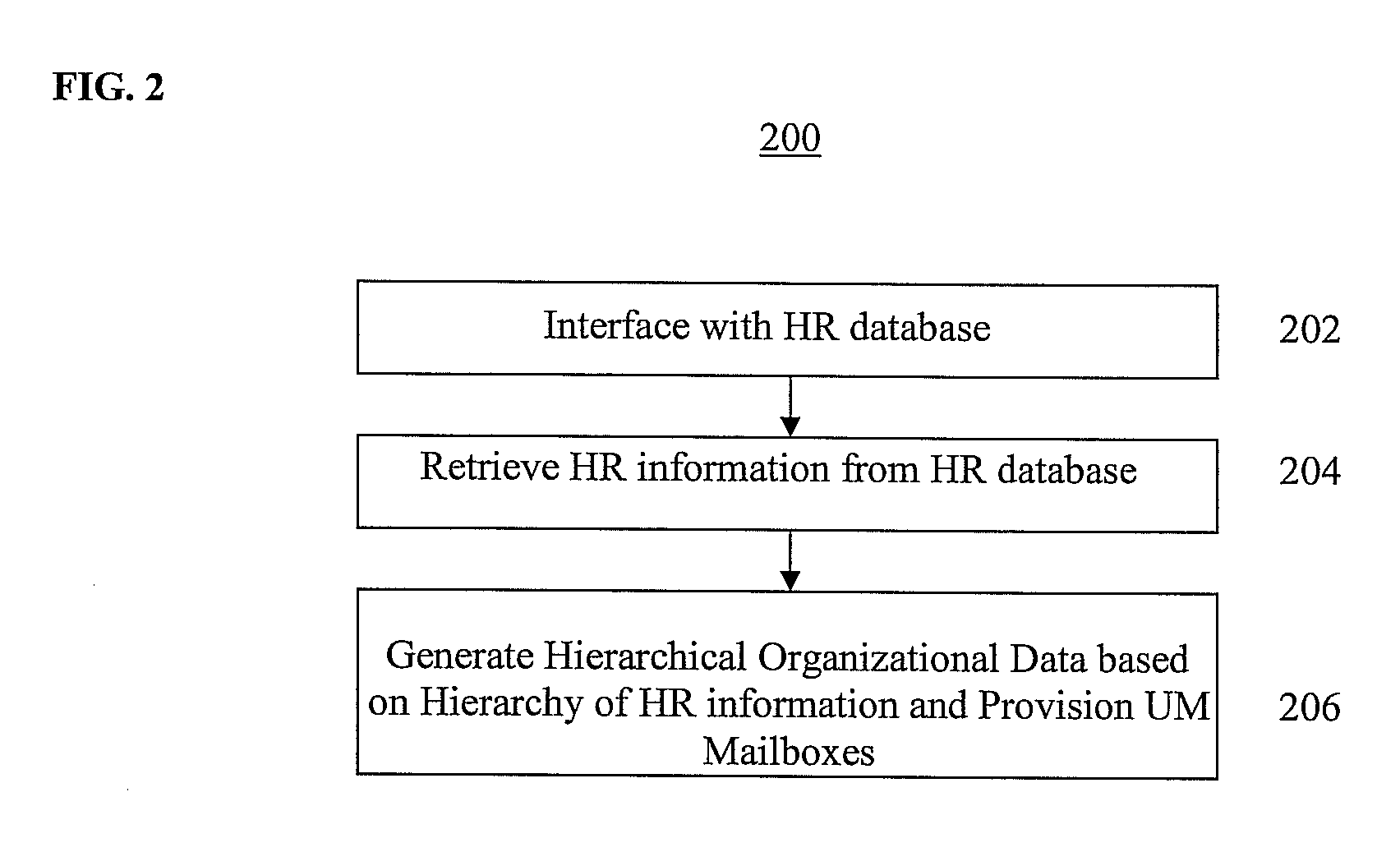
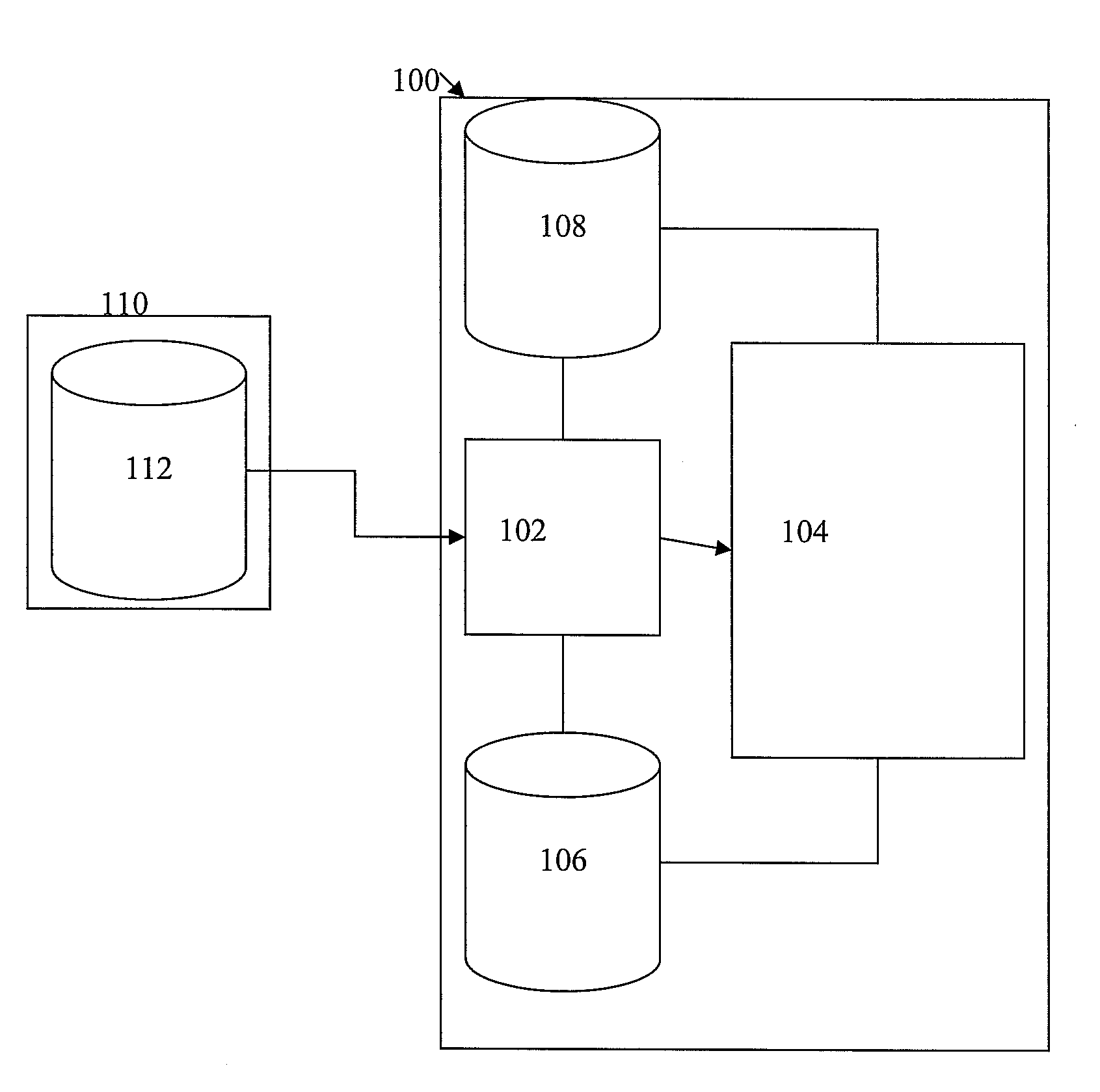
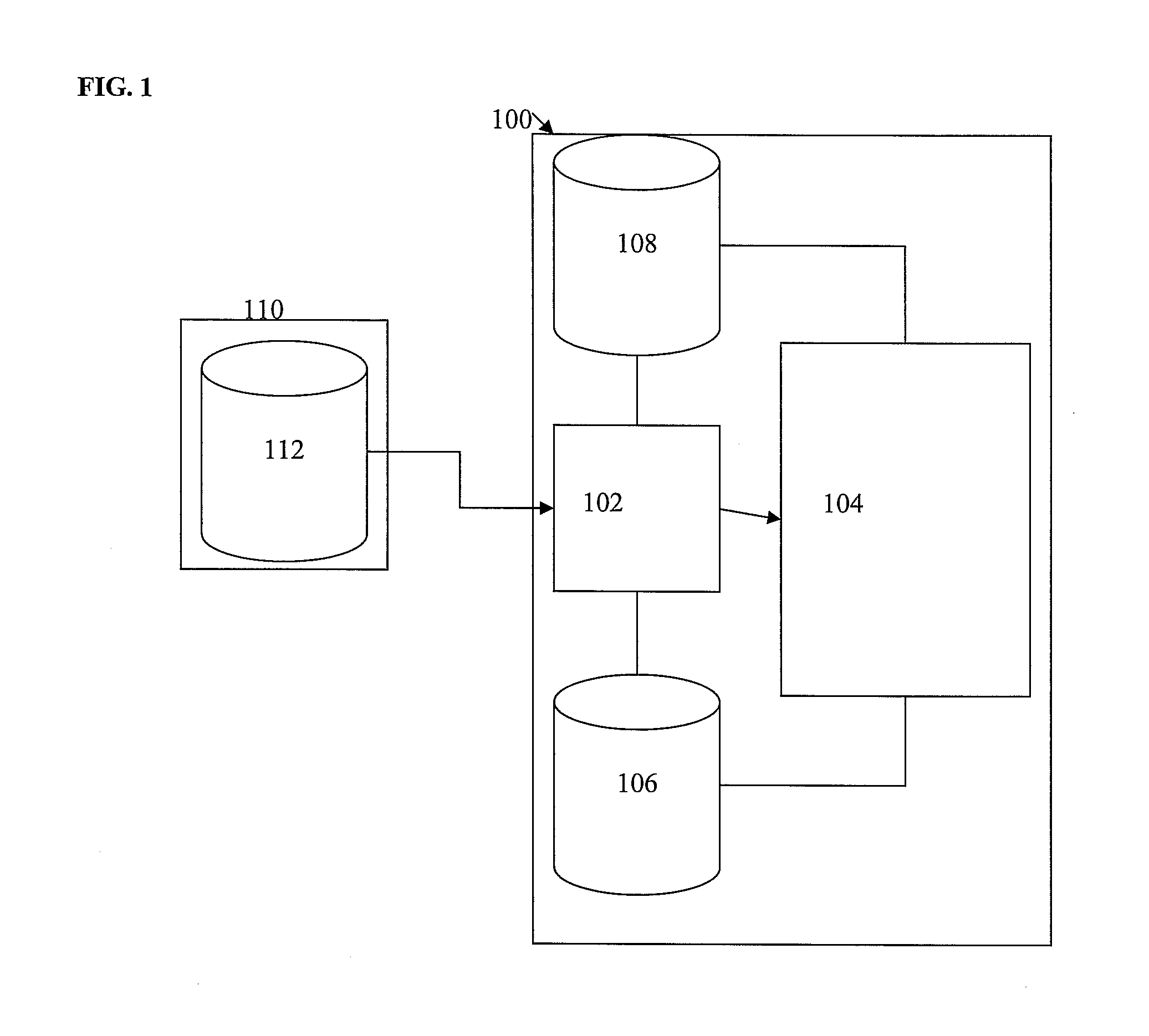
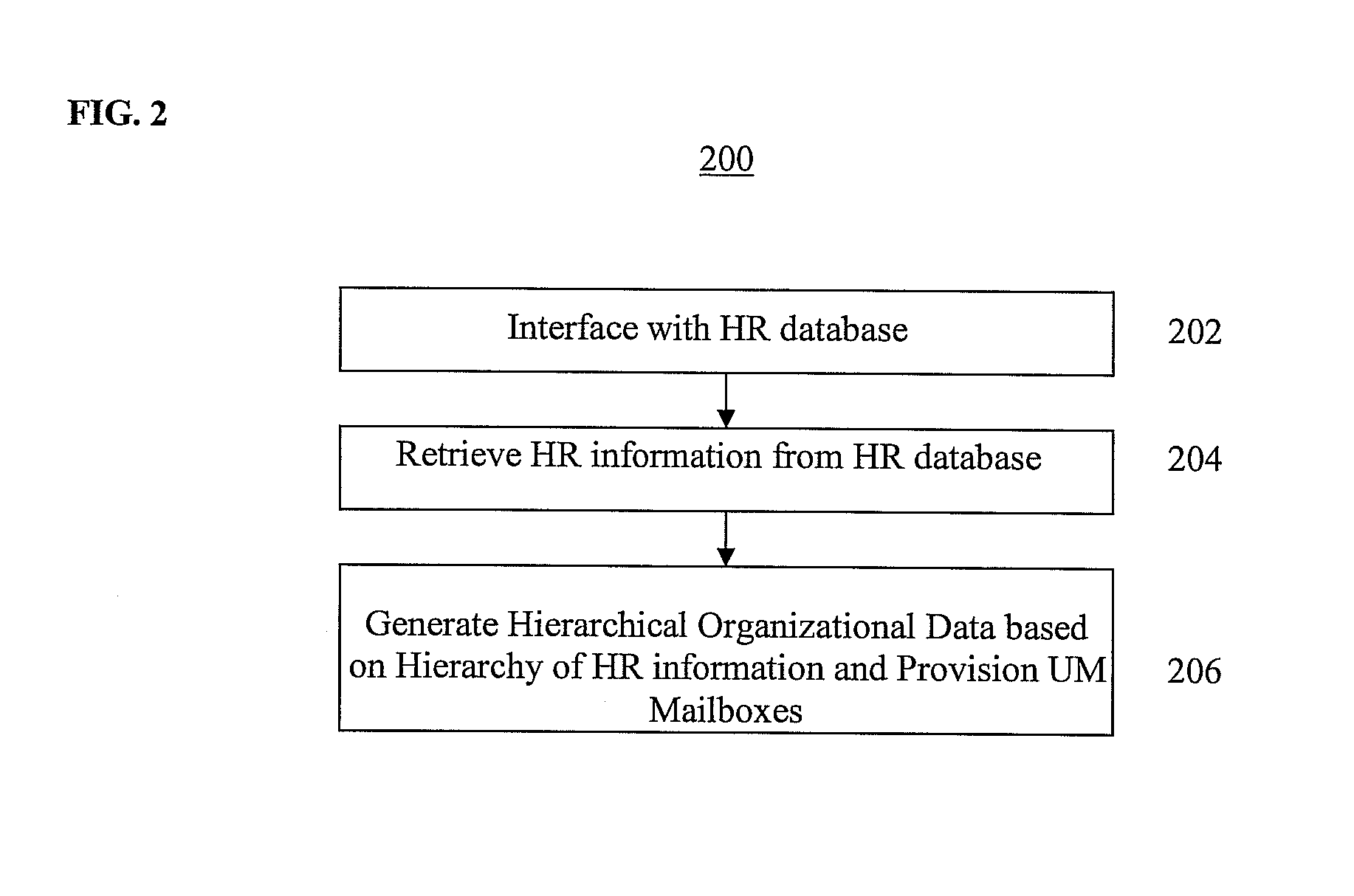
Method and System for Automatically Defining Organizational Data in Unified Messaging Systems
ActiveUS20100153455A1Digital data processing detailsData switching networksResource informationClient-side
A method and system for automatically defining and provisioning organizational data in a unified messaging (UM) platform are disclosed. An adapter in a unified messaging platform connects to at least one client human resources database. Human resources information that is organized in an organizational hierarchy is retrieved from the human resources database, and hierarchical organizational data is automatically generated in the UM platform based on the organizational hierarchy of the human resources information retrieved from the human resources database. UM mailboxes are provisioned to messaging centers in the UM platform based on the hierarchical organizational data.
Owner:AT&T INTPROP I L P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com