Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Alternative program" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
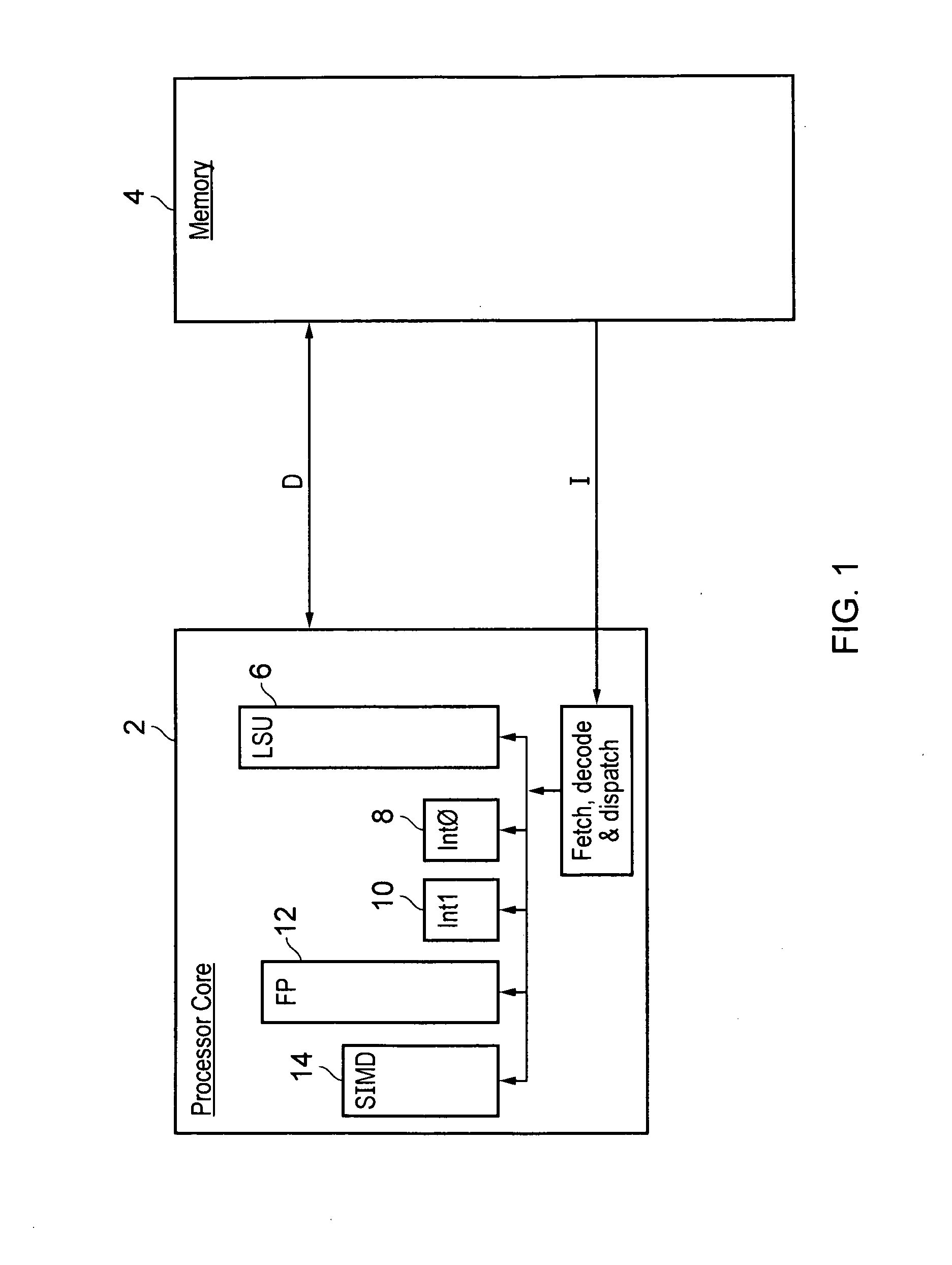
Method and apparatus for performing unit testing of software modules with use of directed automated random testing
A method and apparatus for performing unit testing of software modules uses a novel directed automated random testing approach that advantageously combines automated extraction of the interface of a program with its external environment using static source code parsing; automatic generation of a test driver for this interface that advantageously performs random testing to simulate the most general environment the program can operate in; and dynamic analysis of how the program behaves under random testing and automatic generation of new test inputs to direct systematically the execution along alternative program paths. Together, these techniques constitute a directed automated random testing approach (DART). With DART, testing can be performed completely automatically on any program that compiles without the need to write any test driver or harness code. During testing, DART detects standard errors such as program crashes, assertion violations, and non-termination conditions.
Owner:LUCENT TECH INC
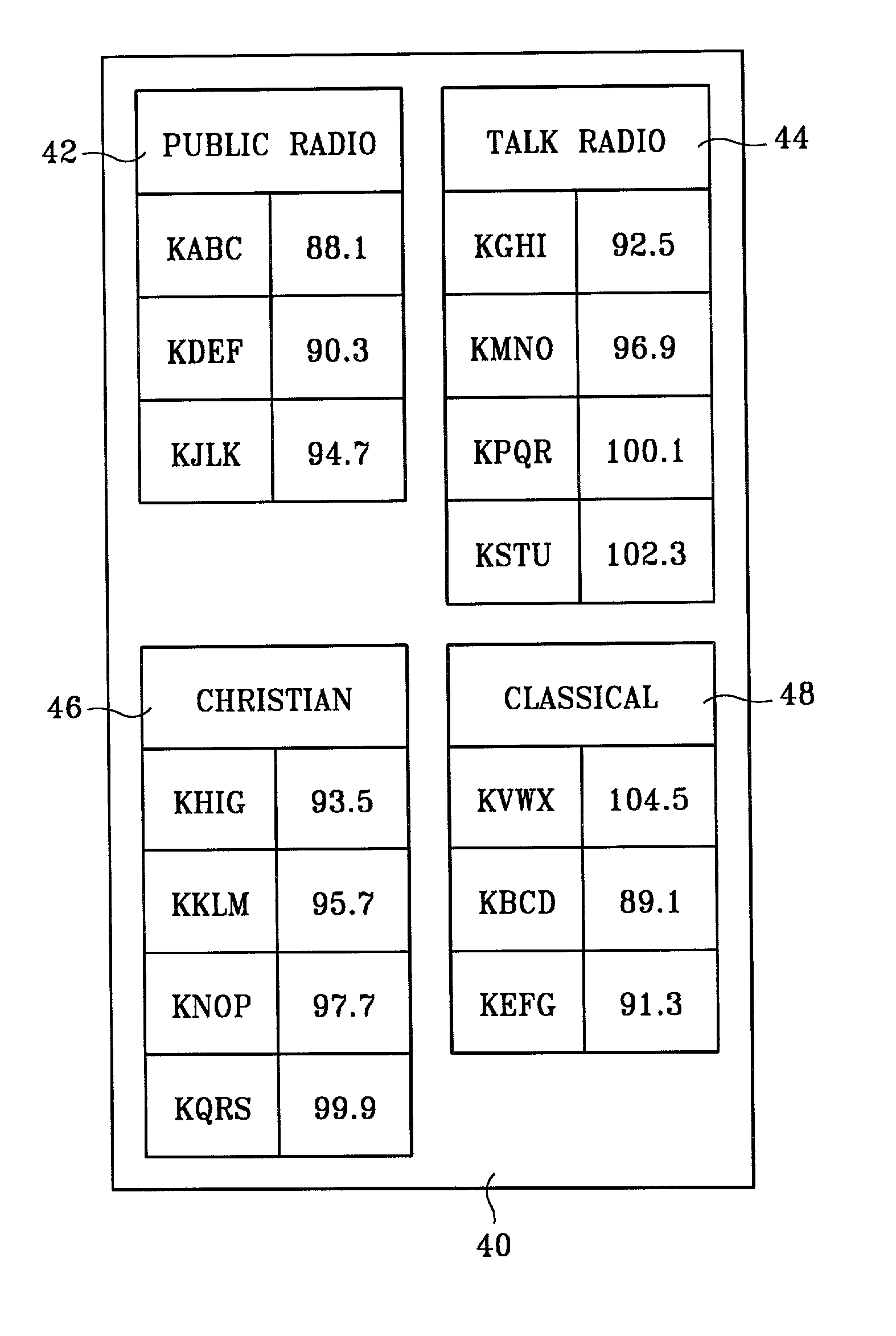
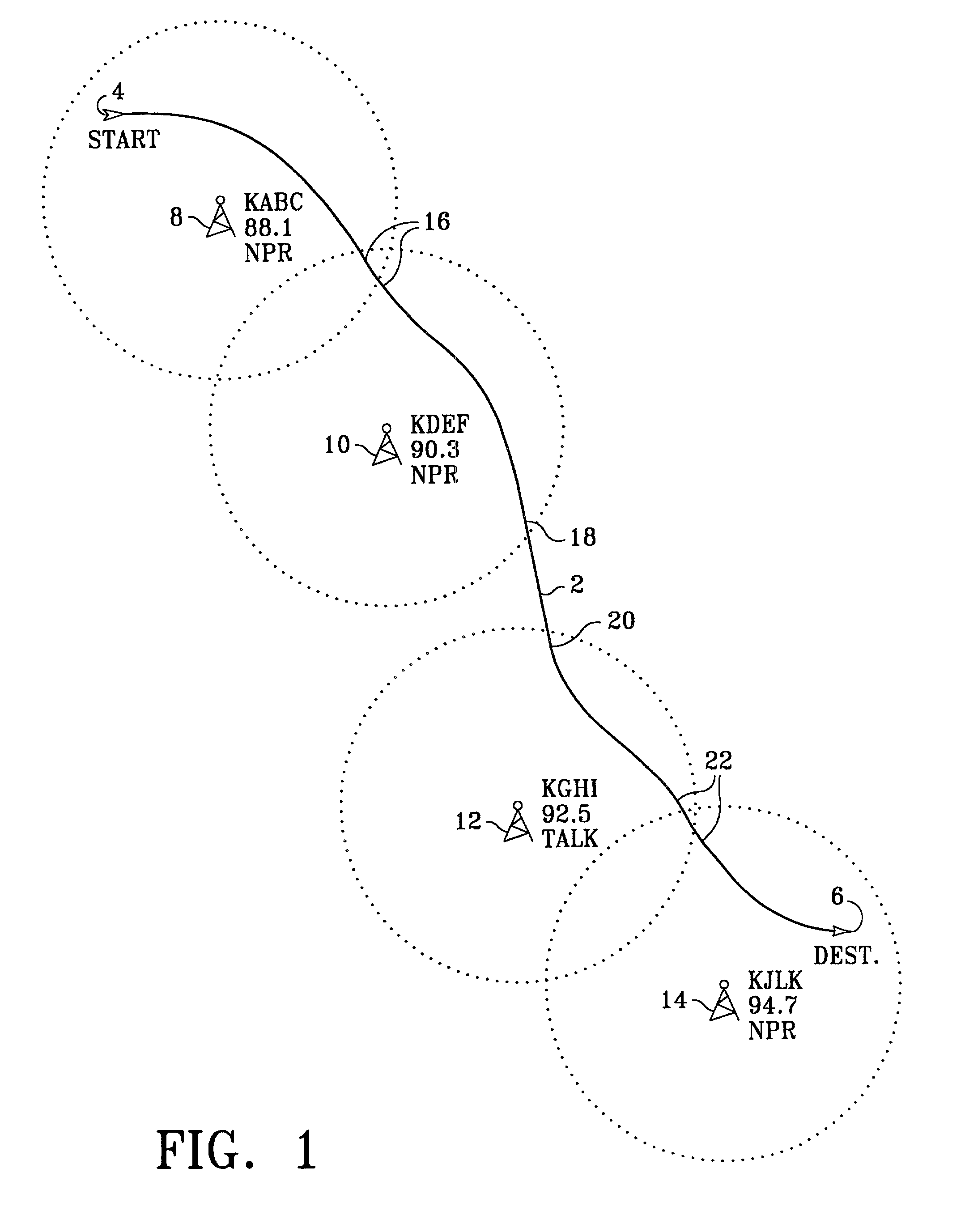
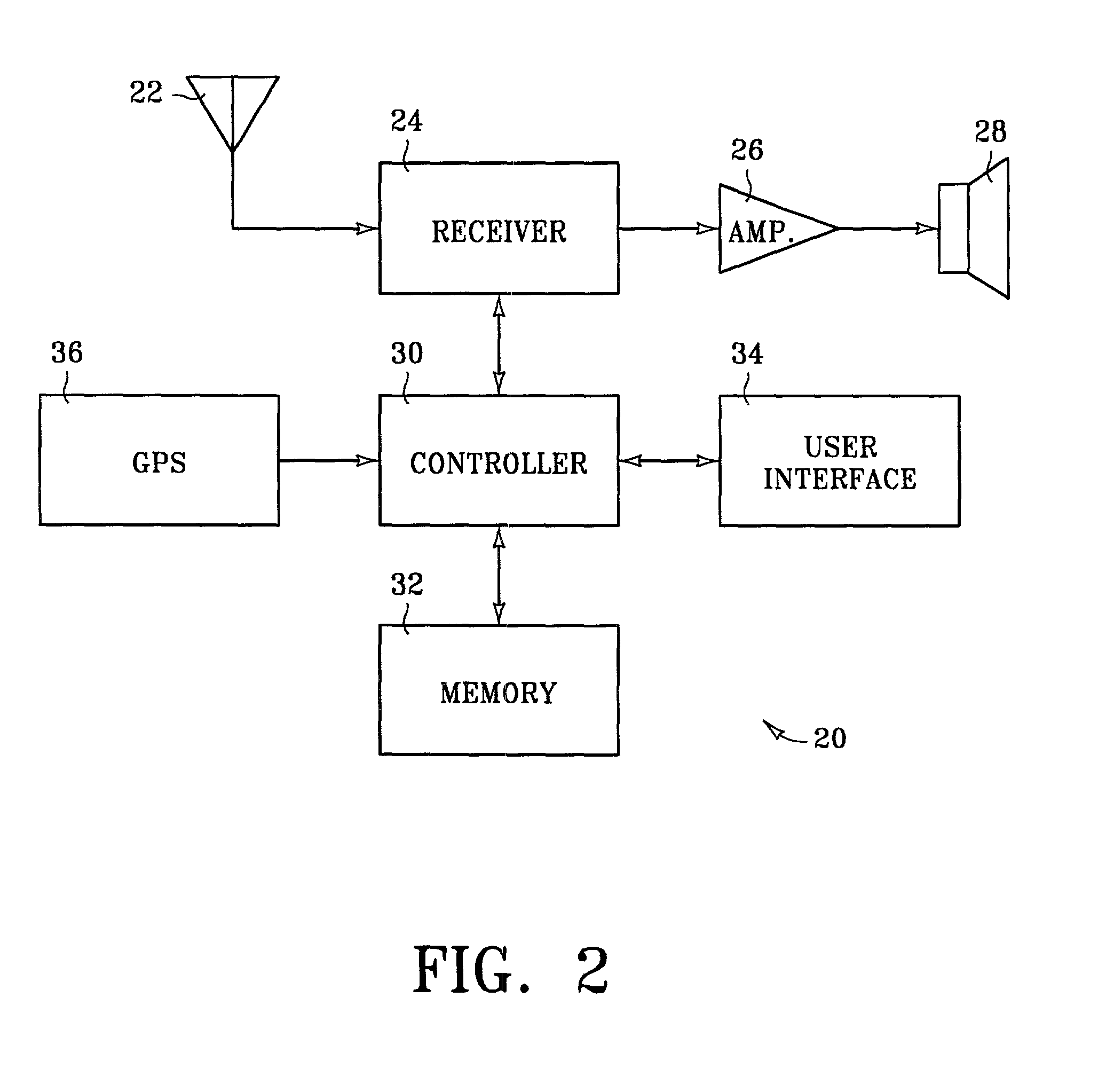
Selection of radio station based on preferred program content
InactiveUS20030032399A1Resonant circuit detailsPlural information simultaneous broadcastGeolocationAlternative program
A method and apparatus for selecting radio stations for reception based on a preferred program content. A list of radio station identifiers is stored in a memory and organized according to program content specifiers. When a presently received signal fades, the memory is searched for an alternate radio station with similar program content. If none is available, a prioritized list of alternative program content preferences is accessed and used to index other preferred radio stations for searching. In one embodiment, radio station geographic location information is stored in the memory, and the searching operation considers both program content preference and geographic proximity. The memory can be manually programmed, pre-programmed, updated by subscription, or programmed over-the-air by radio transmission. In one embodiment, a global positioning system receiver is employed to provide instantaneous radio location information.
Owner:HEWLETT PACKARD DEV CO LP
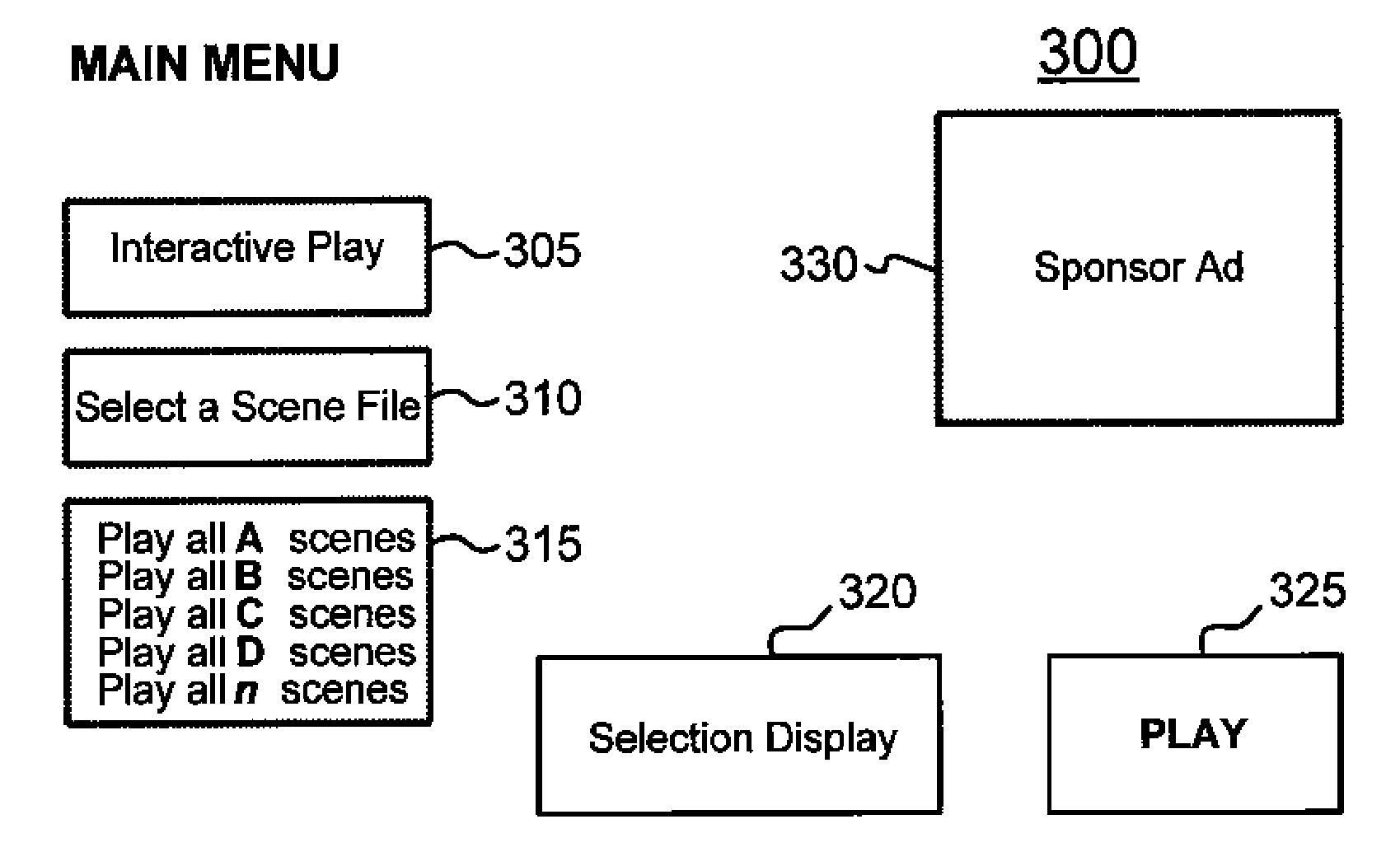
Methods of enhancing media content narrative
InactiveUS20070220583A1Improve video experienceTelevision system detailsElectronic editing digitised analogue information signalsComputer graphics (images)Display device
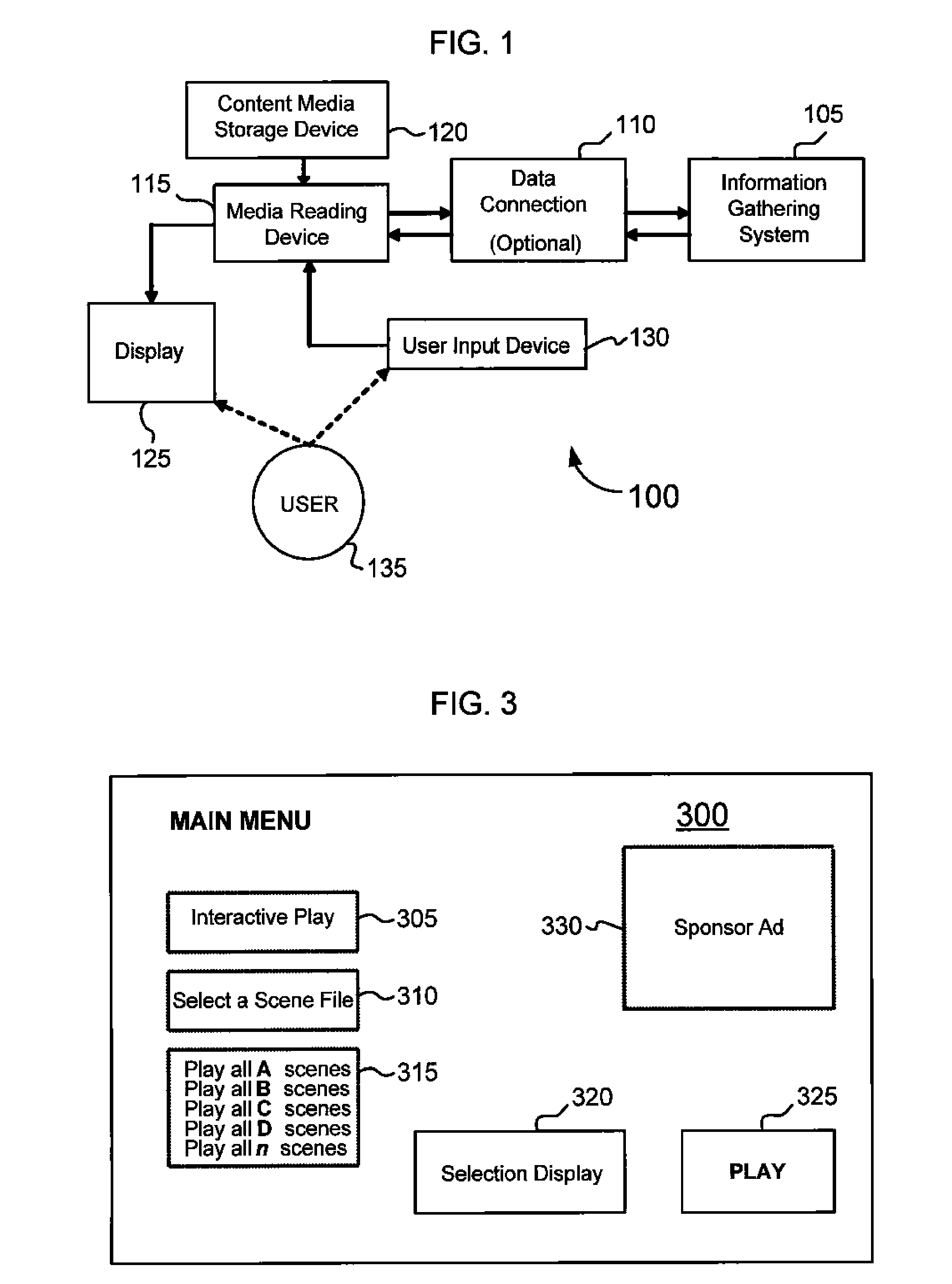
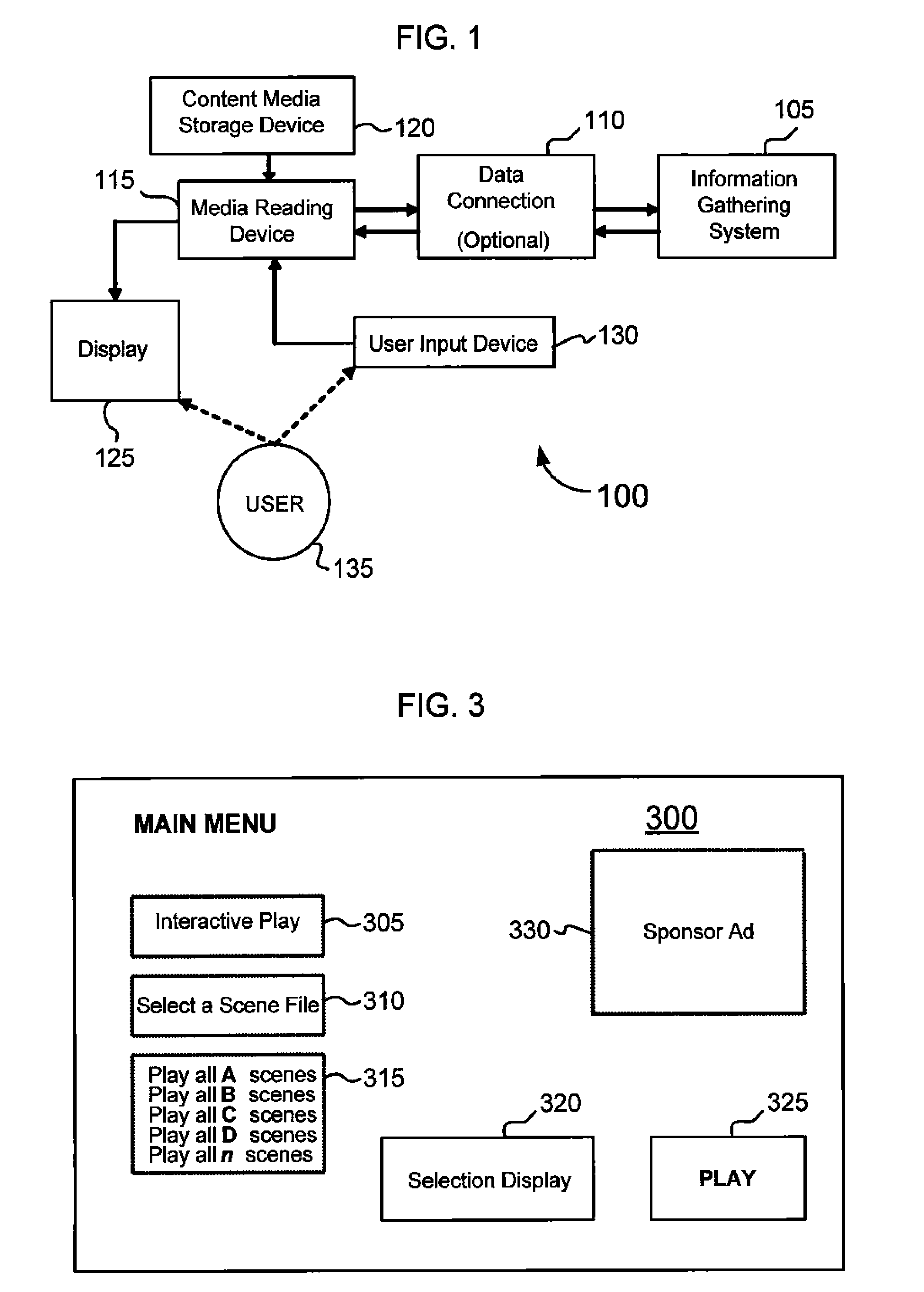
In a method of enhancing a viewer's experience of a video program, a plurality of selectable alternative video program scenes are provided for a video program being viewed on a display. The selectable alternative program versions are pre-rendered video scenes. A user is prompted to select at least one of the selectable alternative video program scenes for viewing.
Owner:INTENSION
Methods of enhancing media content narrative
ActiveUS7669128B2Improve video experienceTelevision system detailsElectronic editing digitised analogue information signalsComputer graphics (images)Display device
In a method of enhancing a viewer's experience of a video program, a plurality of selectable alternative video program scenes are provided for a video program being viewed on a display. The selectable alternative program versions are pre-rendered video scenes. A user is prompted to select at least one of the selectable alternative video program scenes for viewing.
Owner:INTENSION
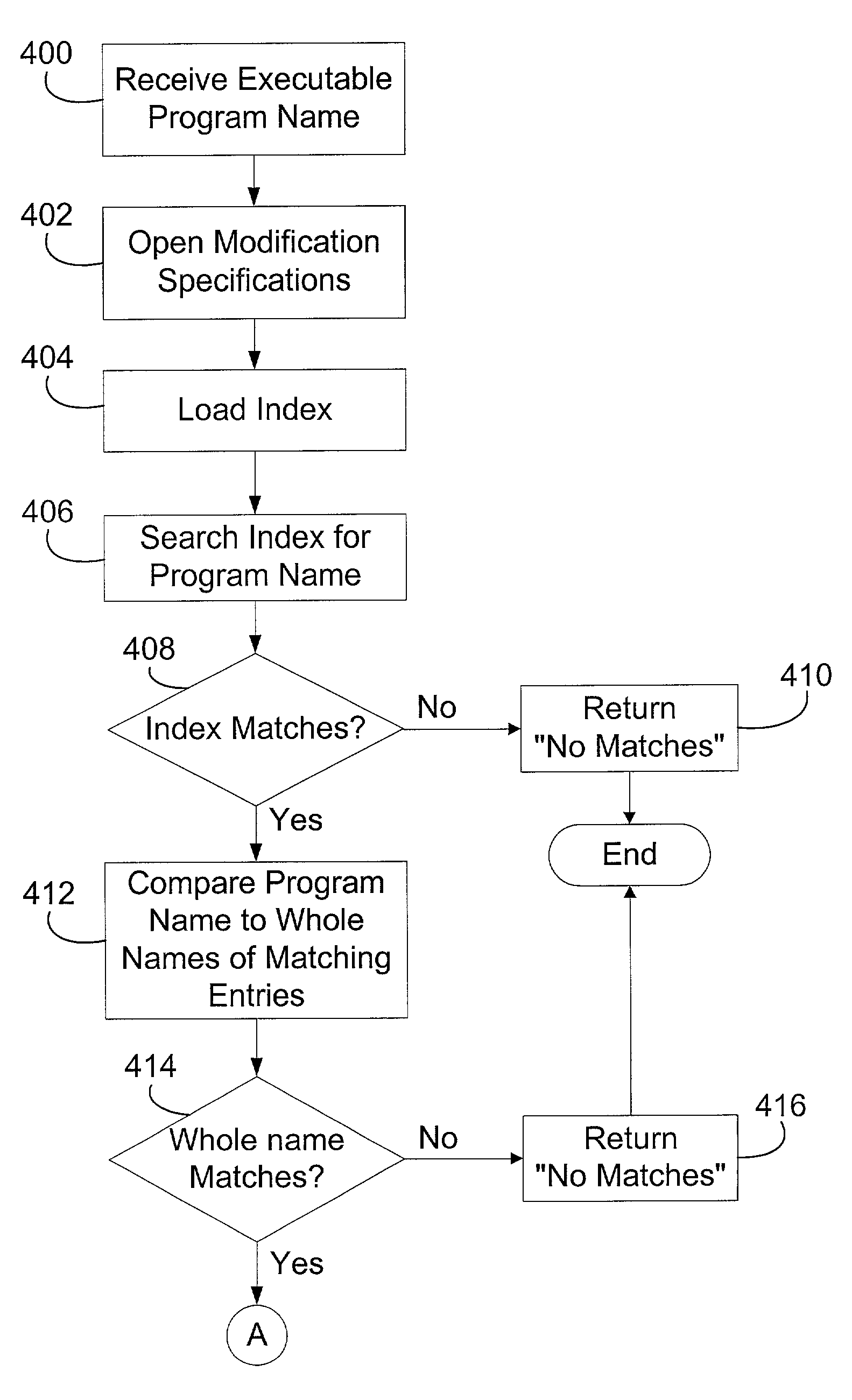
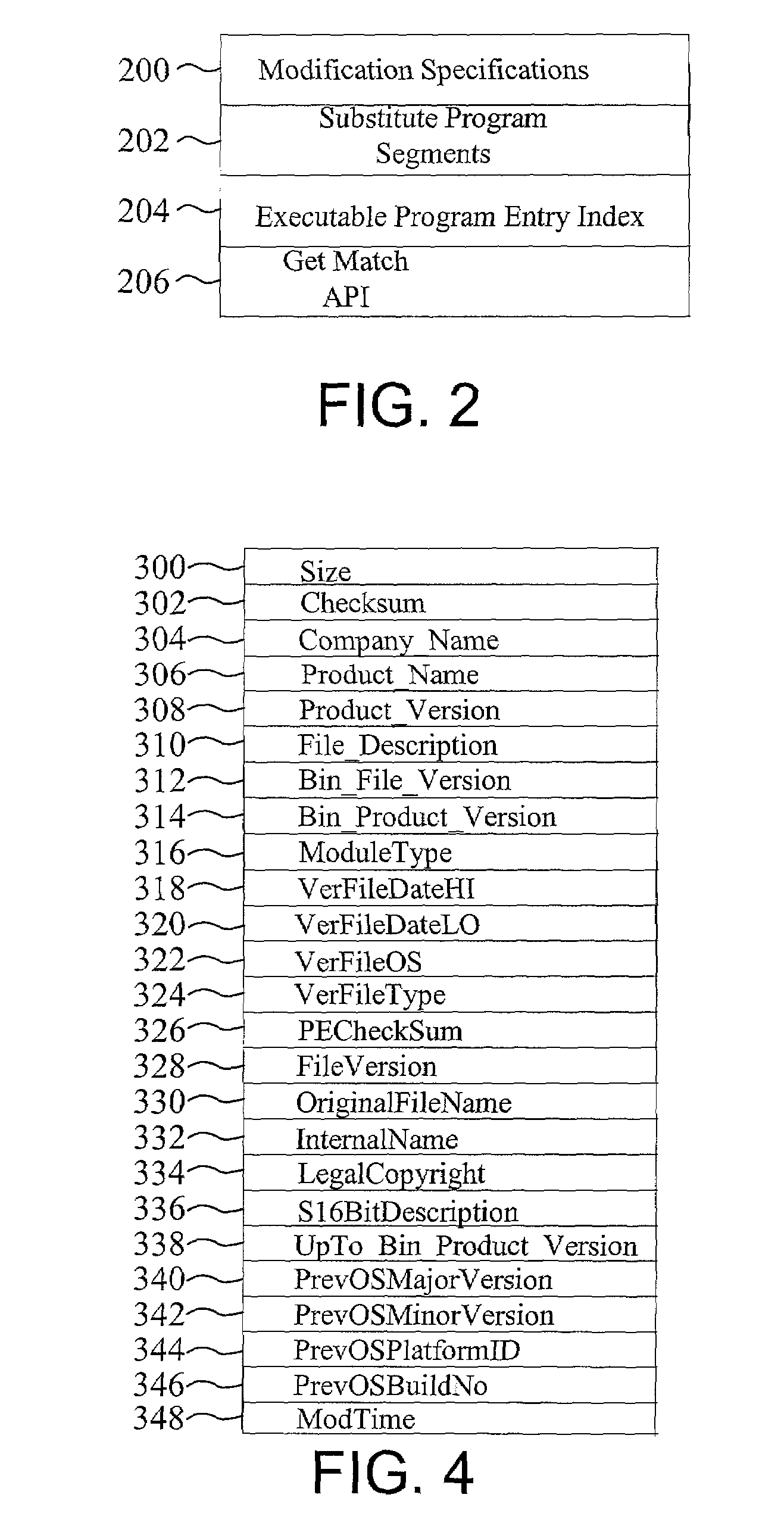
Computer system utility facilitating dynamically providing program modifications for identified programs
InactiveUS7191436B1Easy to optimizeQuick checkData processing applicationsSpecific program execution arrangementsProgramming languageInformation type
A program modification database and method for identifying a candidate entry within the correction database for a particular executable program are disclosed. The program modification database provides a general depository of program changes, referred to herein as substitute program segments, and a set of executable program entries containing program matching criteria and corresponding program changes. The program modification database includes an index. Each entry in the index includes a piece of identifying information for a referenced, corresponding executable program entry. The program modification database architecture is applicable to any type of program segment information for modifying either instruction code or data values within a program. The types of information, within a program matching criteria, taken from an executable program file used to identify a corresponding executable program entry within the program modification database are selectable on an individual basis from an extensible set of executable program information types.
Owner:MICROSOFT TECH LICENSING LLC
Selection of radio station based on preferred program content
InactiveUS7369825B2Resonant circuit detailsPlural information simultaneous broadcastAlternative programGeolocation
Owner:HEWLETT PACKARD DEV CO LP
Method for processing communal locks
InactiveUS6986003B1Reducing hardware utilizationShort response timeMemory adressing/allocation/relocationUnauthorized memory use protectionMulti processorAlternative program
Multi-processor computer systems with multiple levels of cache memories are slowed down in trying to process software locks for common functions. This invention obviates the problem for the vast majority of transactions by providing an alternate procedure for handling so-called communal locks differently from ordinary software locks. The alternative procedure is not used for ordinary (non communal software lock) data and instruction transfers. The function of the CSWL (Communal SoftWare Lock) is actually accomplished at a specific cache to which an individual CSWL is mapped to, rather than sending the lock to the requesting process, which also enhances efficiency.
Owner:UNISYS CORP
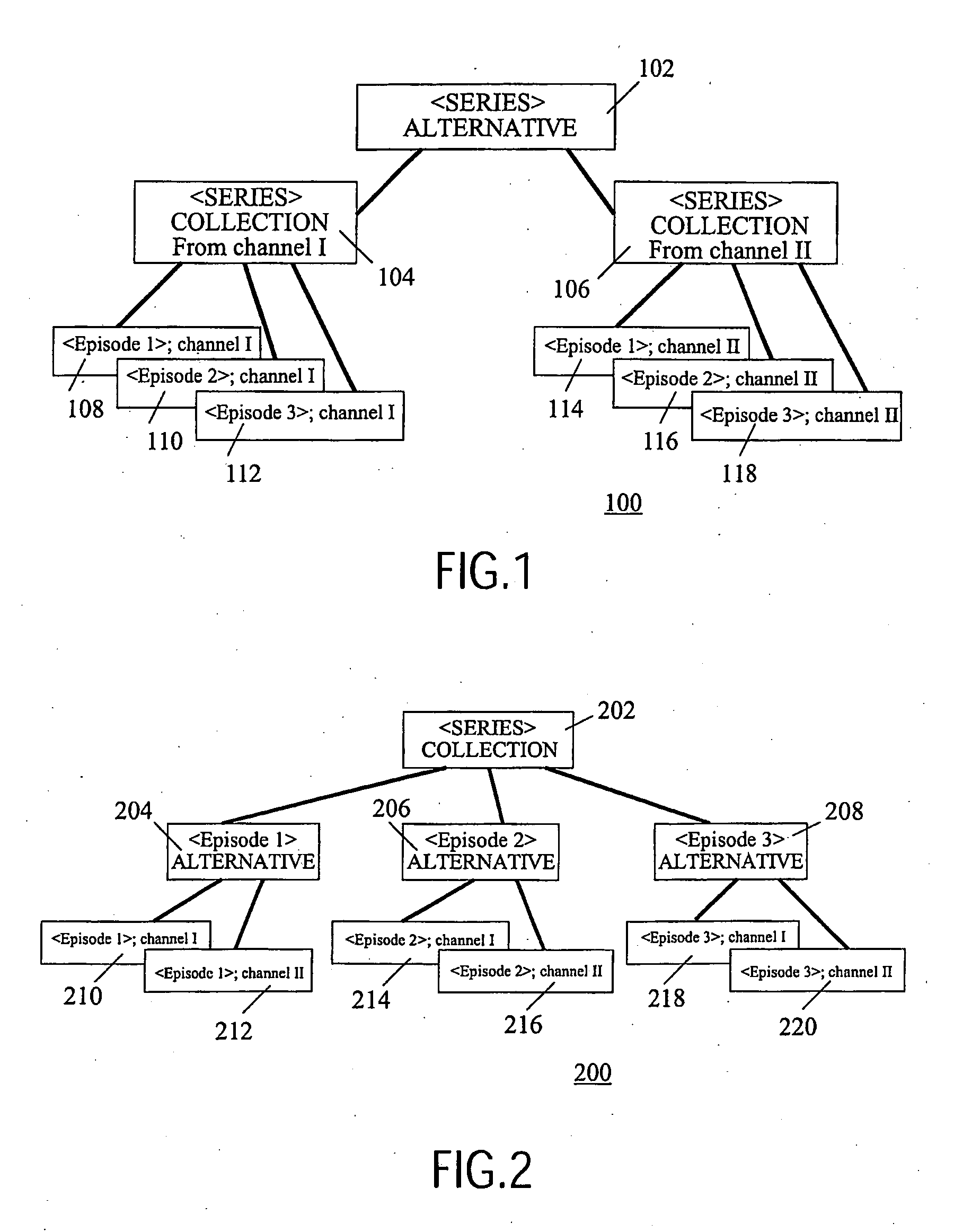
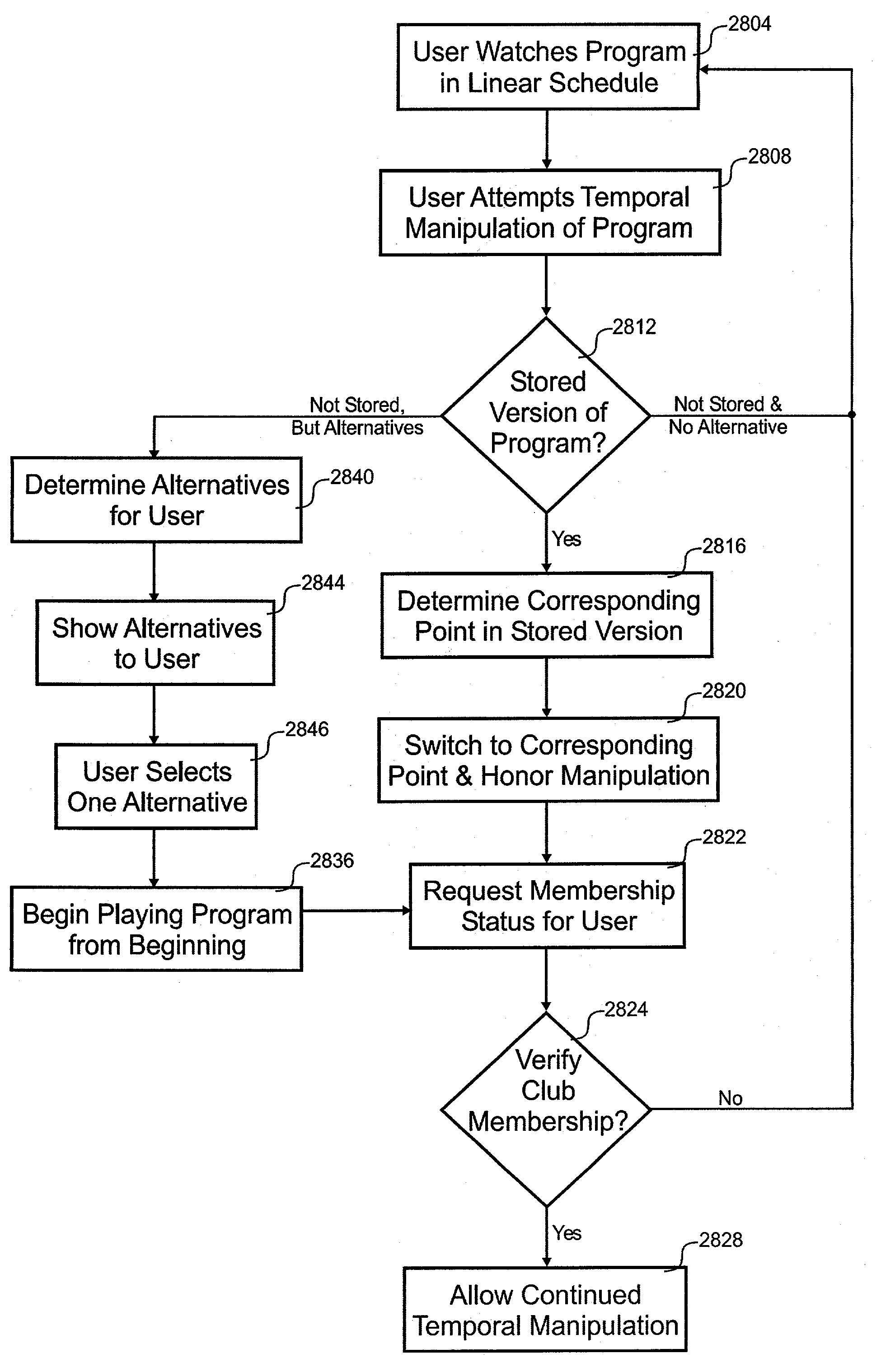
Alternative Program Source Avoids Dvr Scheduling Conflict
InactiveUS20080152315A1Minimizing conflictGood choiceTelevision system detailsColor television detailsAlternative programDistributed computing
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
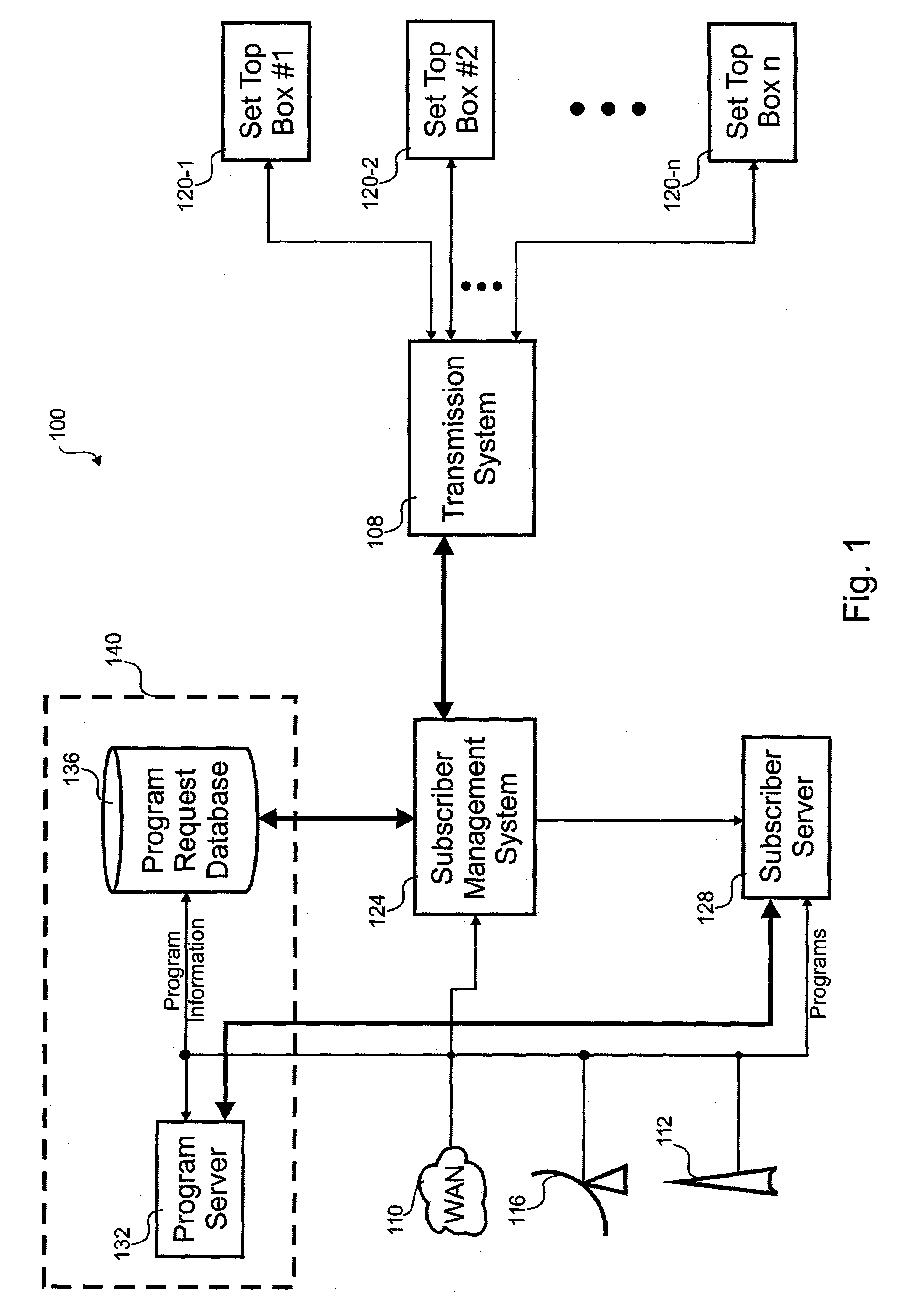
Program guide environment
ActiveUS7779439B2Television system detailsColor television signals processingContent distributionAlternative program
According to the invention, a method for suggesting alternative content for a video service in a content distribution system is disclosed. In one step, it is detected when a user stops viewing a program associated with a content provider. Alternative programs associated with the content provider are determined without considering content from other providers. Those alternative programs are presented to the user.
Owner:STARZ ENTERTAINMENT GROUP
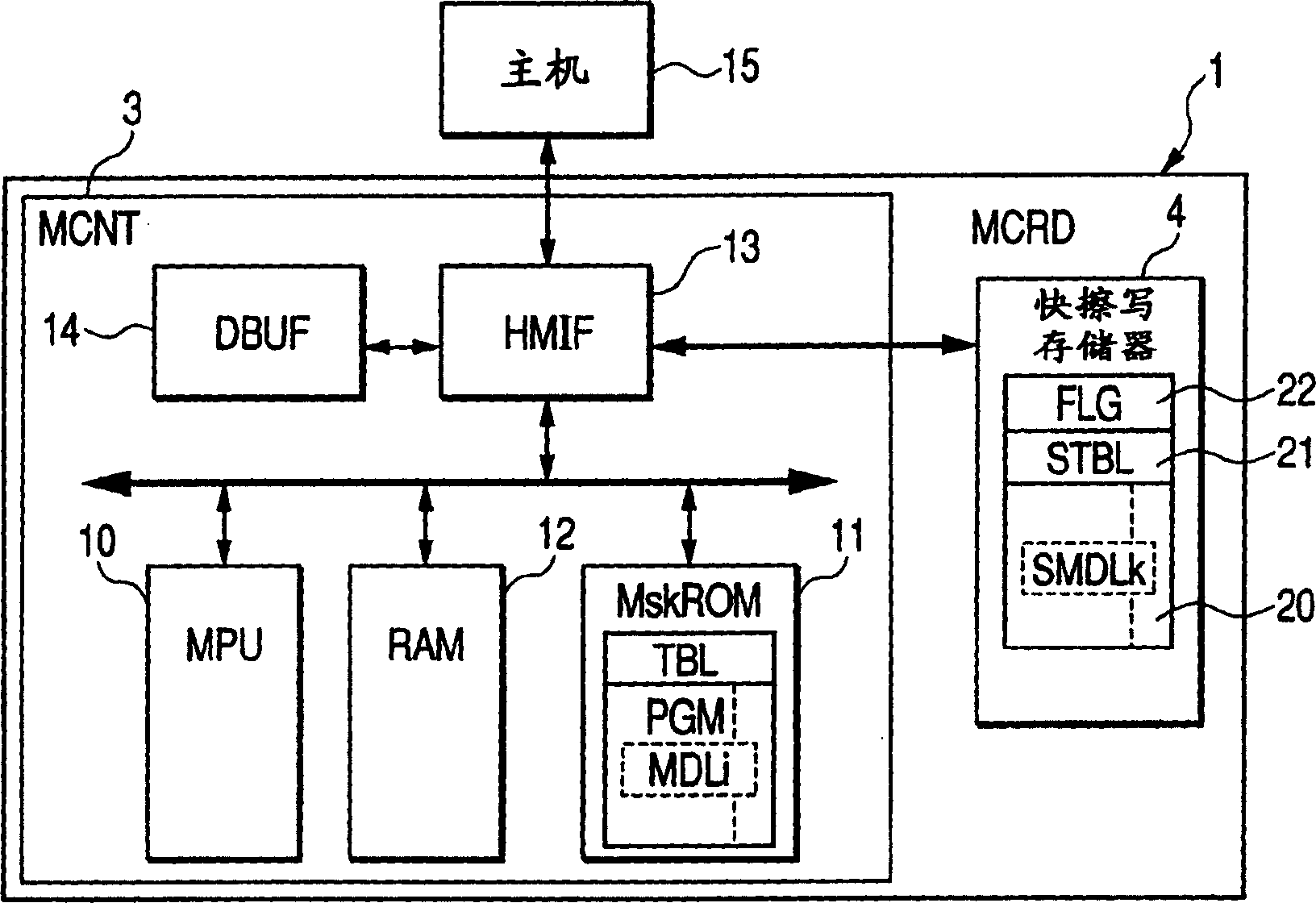
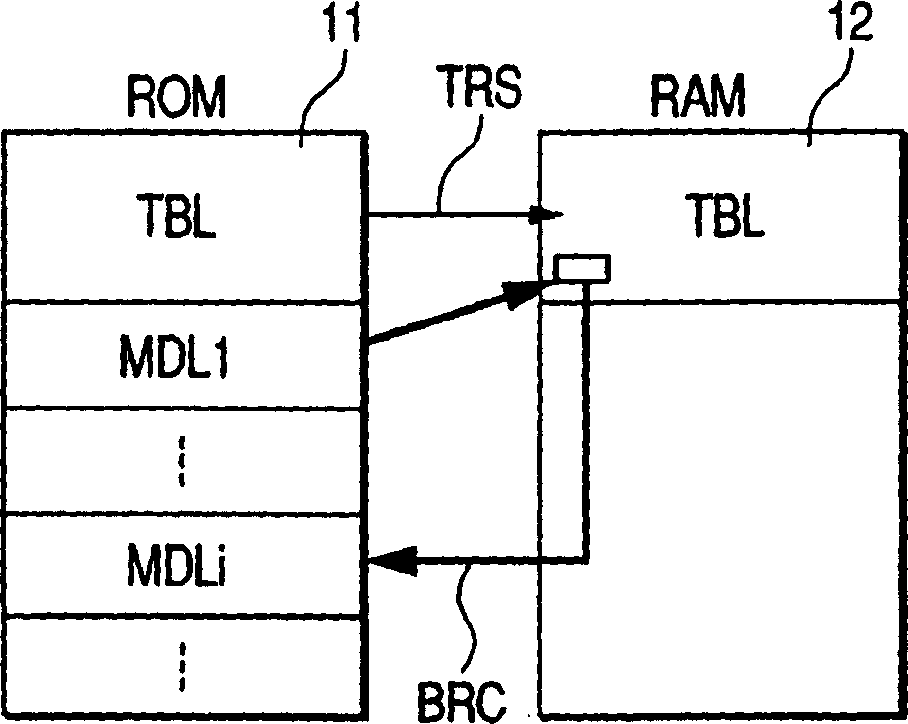
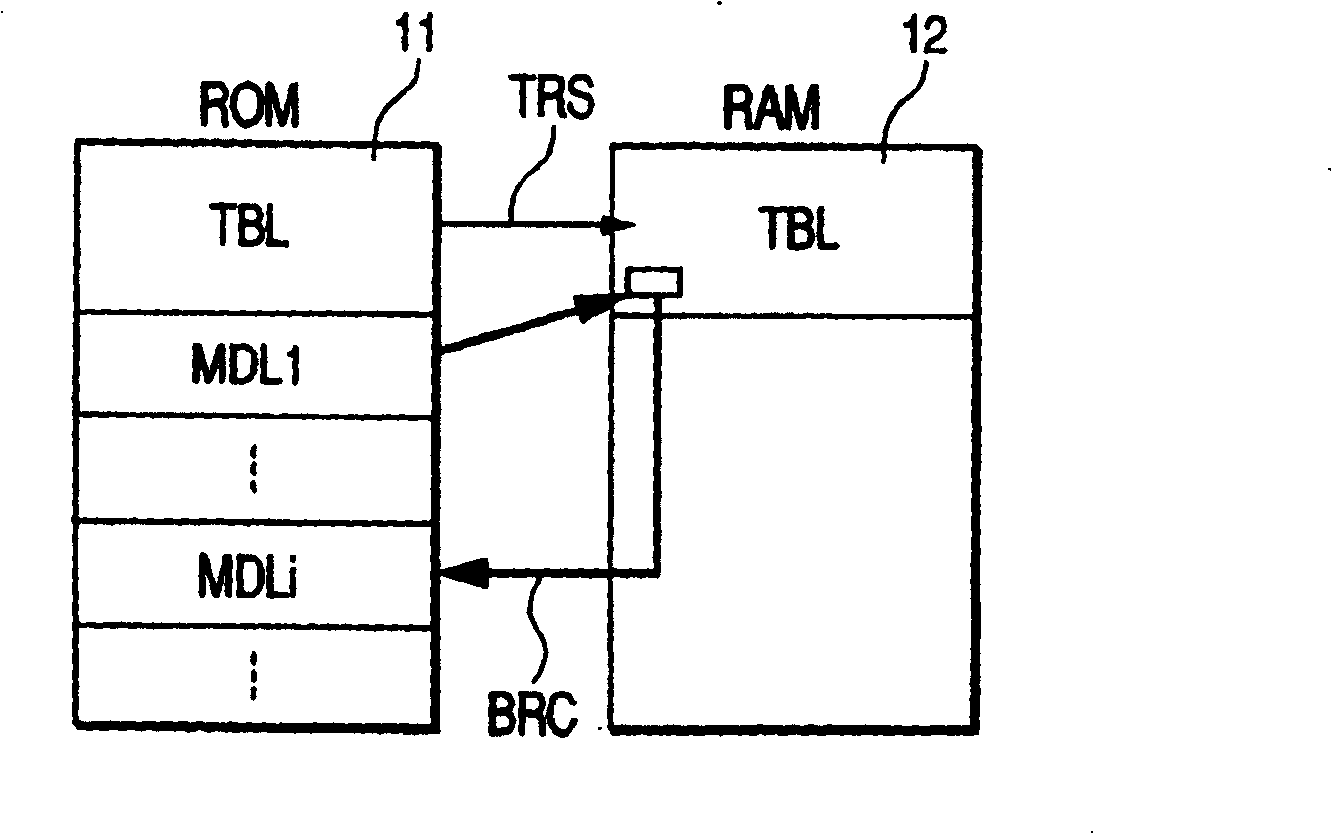
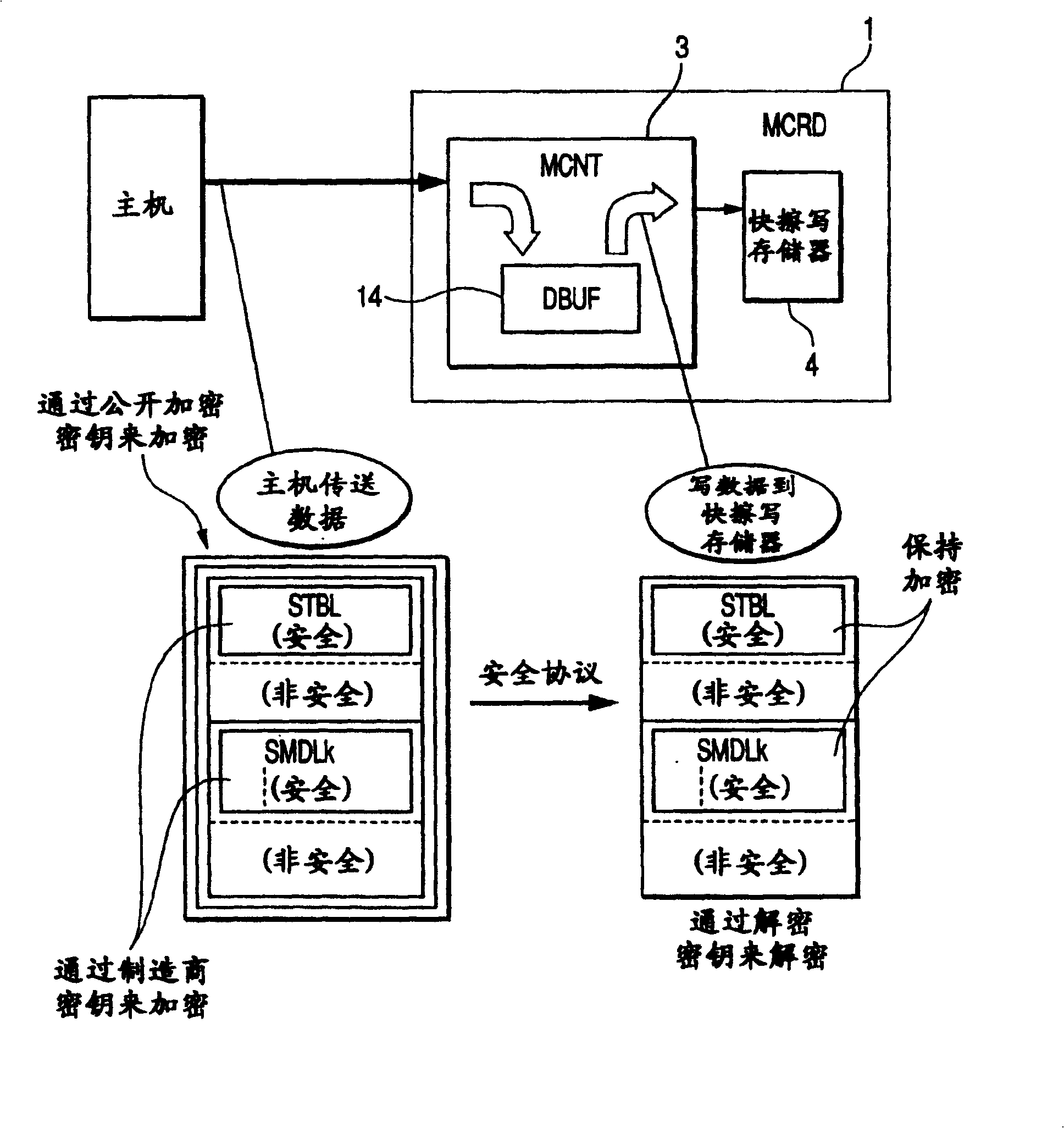
Nonvolatile memory apparatus
InactiveUS20050259465A1Leak preventionAvoid replacementRead-only memoriesUnauthorized memory use protectionPower-on resetAnalysis data
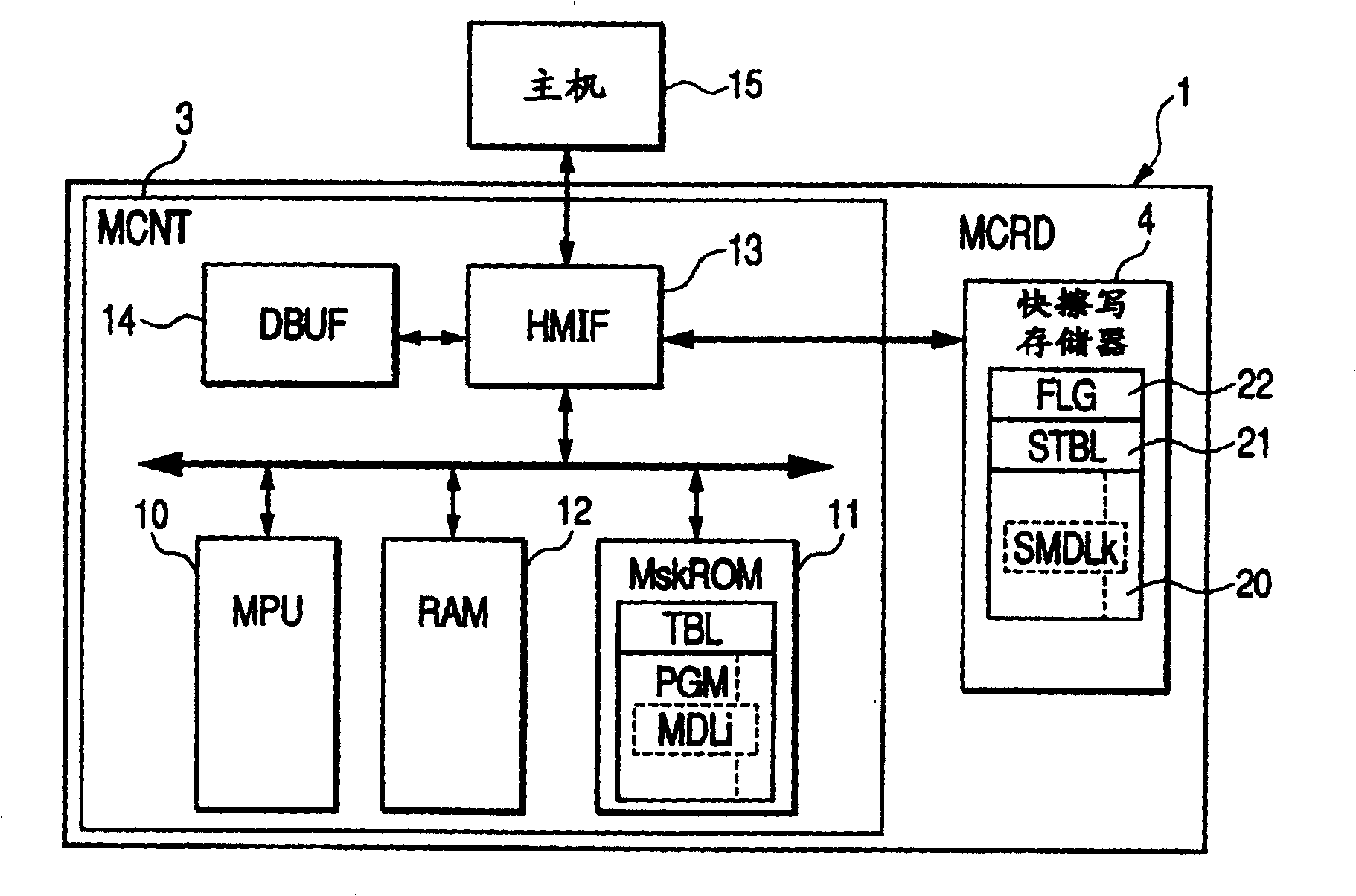
In technology for enabling the replacement of part of an operating program of a controller by a modified program on a nonvolatile memory, the present invention prevents tampering and leak of storage information within the nonvolatile memory and the controller. At power-on reset, an encrypted alternative program, if present, is transferred from a nonvolatile memory to a volatile memory, and decrypted when actually executed. A long wait is not required until data processing by a data processor is enabled after the exit from the reset processing. Since the alternative program once decrypted is held in the volatile memory so as to be reusable, it does not need to be decrypted each time it is executed. Since the alternative program is encrypted, even if the nonvolatile memory is physically separated from the controller to illegally dump the alternative program, it is difficult to analyze the data.
Owner:RENESAS TECH CORP
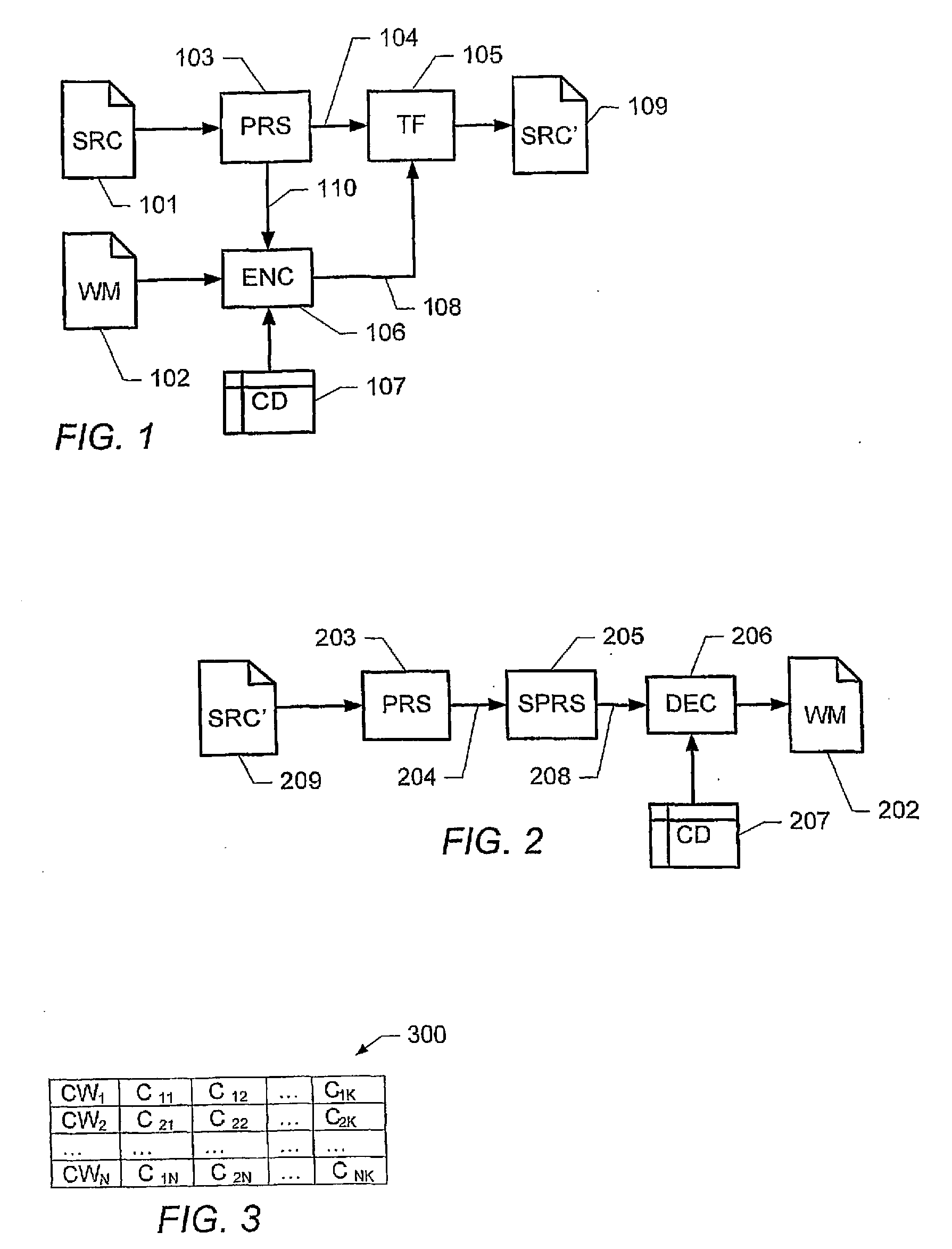
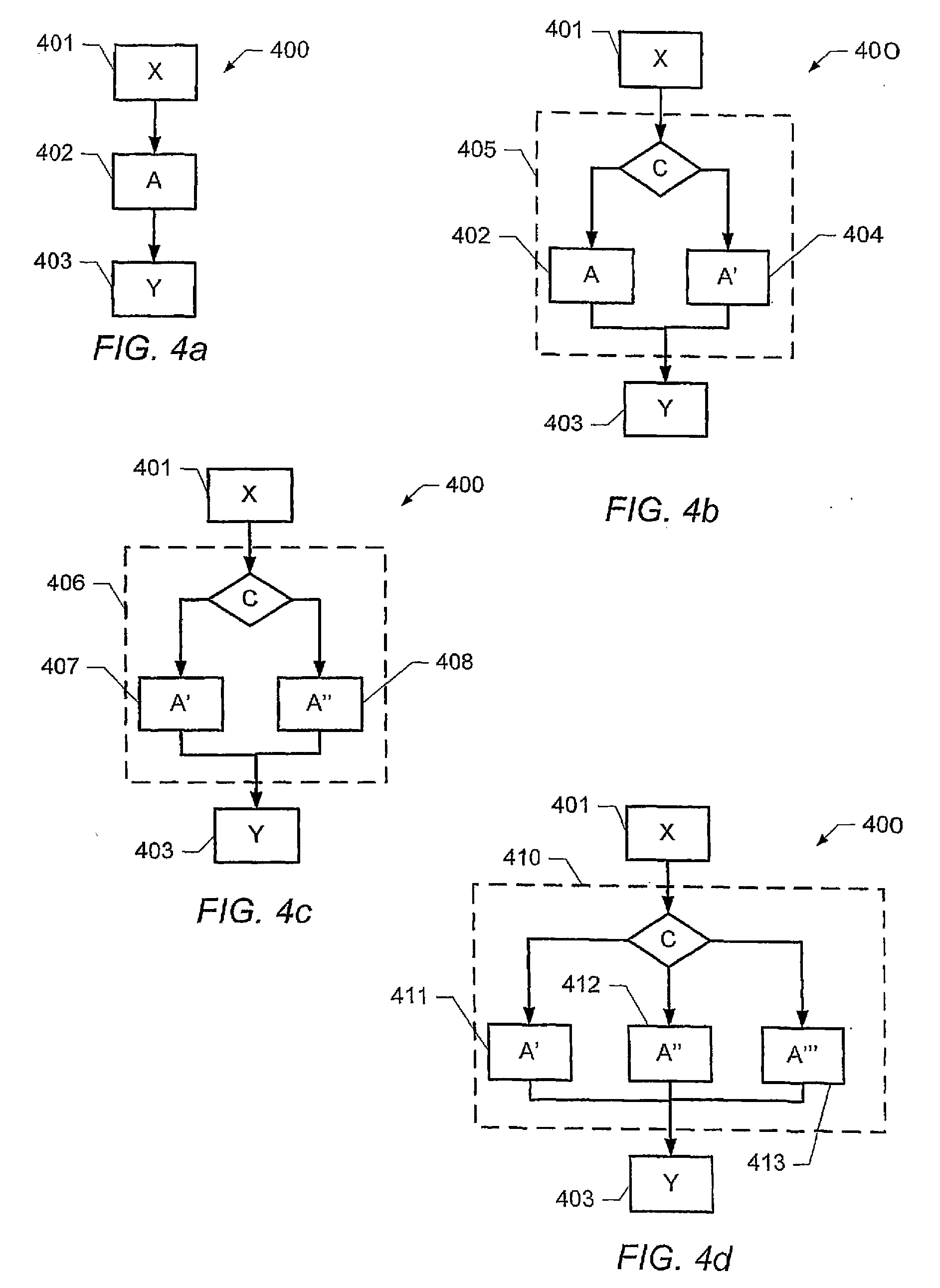
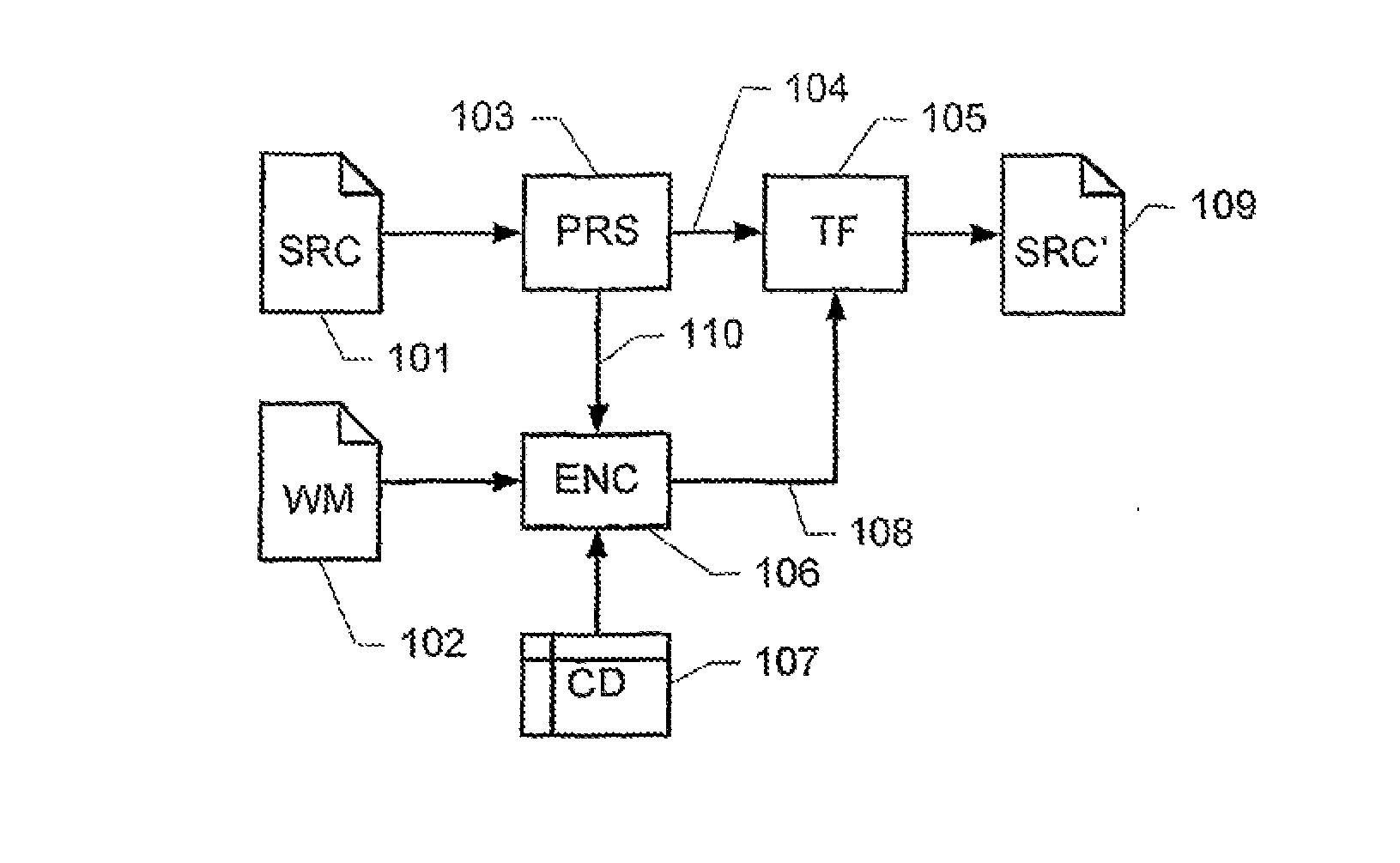
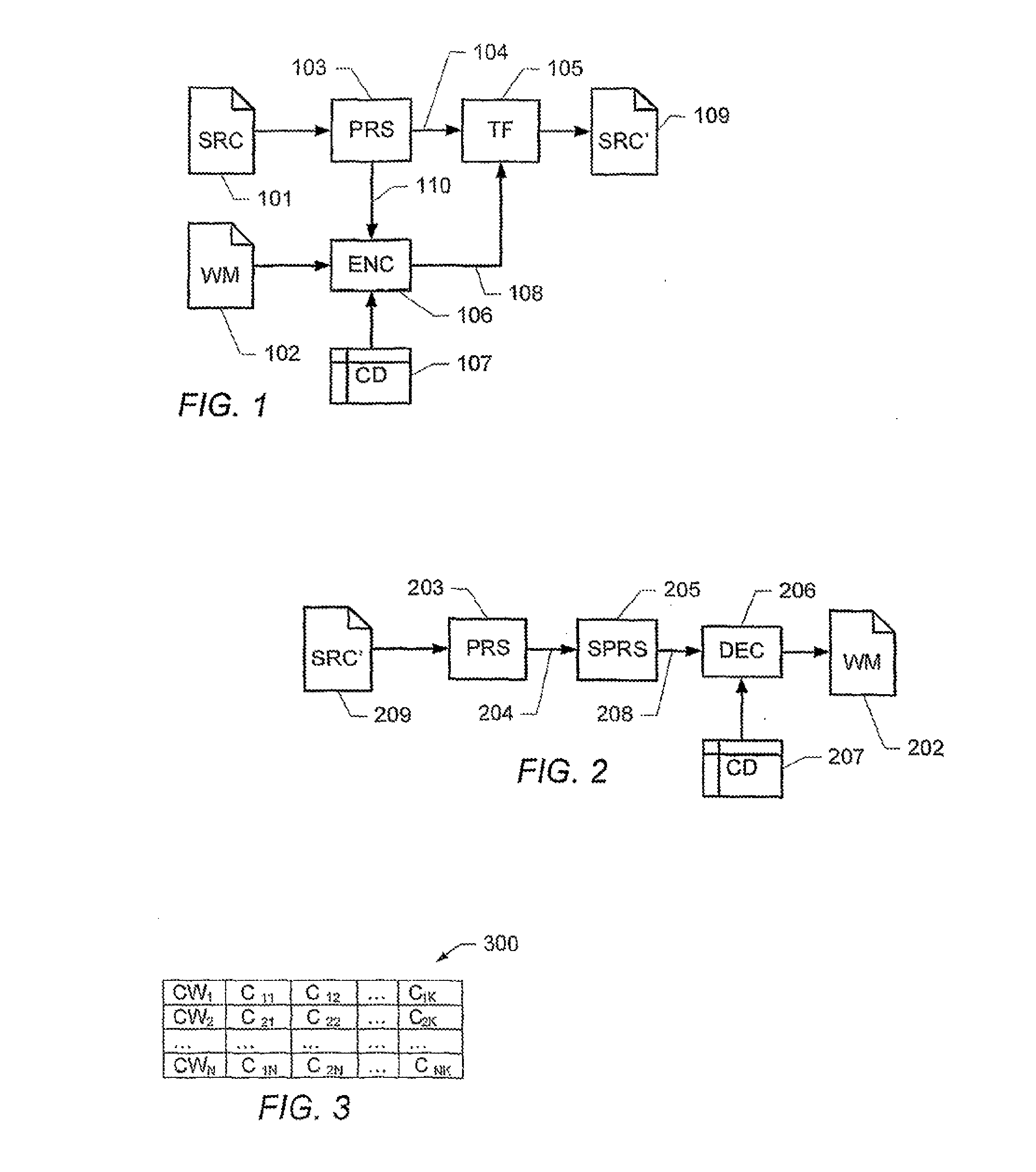
Watermarking computer program code
ActiveUS20090254752A1Efficient software implementationReasonable overheadDigital data processing detailsUser identity/authority verificationData processing systemAlternative program
A method of embedding information in a computer program code, including a plurality of program statements. The method comprises: inserting a conditional program statement in the computer program code, the conditional program statement including a condition and a plurality of alternative program statements, the conditional program statement being adapted to cause a data processing system to evaluate said condition and, responsive to a result of said evaluating step, to selectively execute one of said plurality of alternative program statements; wherein said condition is indicative of at least a part of said information; and wherein the plurality of alternative program statements are adapted to cause the computer program code to produce the same program output irrespective of which of said alternative program statements is executed.
Owner:TELEFON AB LM ERICSSON (PUBL)
Nonvolatile memory apparatus
InactiveCN1707446APrevent tamperingPrevent leakageRead-only memoriesUnauthorized memory use protectionAnalysis dataAlternative program
Among the techniques for realizing replacement of part of the controller's working program by modifying the program on the nonvolatile memory, the present invention prevents tampering and leakage of stored information in the nonvolatile memory and the controller. At power-on reset, if an encrypted alternative program exists, it is transferred from the non-volatile memory to the volatile memory and decrypted when it is actually executed. There is no need to wait for a long time until the data processing of the data processor is allowed after exiting from the reset processing. Since the substitute program once decrypted is held in volatile memory for re-use, it does not need to be decrypted each time it is executed. Since the substitute program is encrypted, it is difficult to analyze the data even if the nonvolatile memory is physically separated from the controller to illegally dump the substitute program.
Owner:RENESAS ELECTRONICS CORP
Intelligent upgrading method and system for program
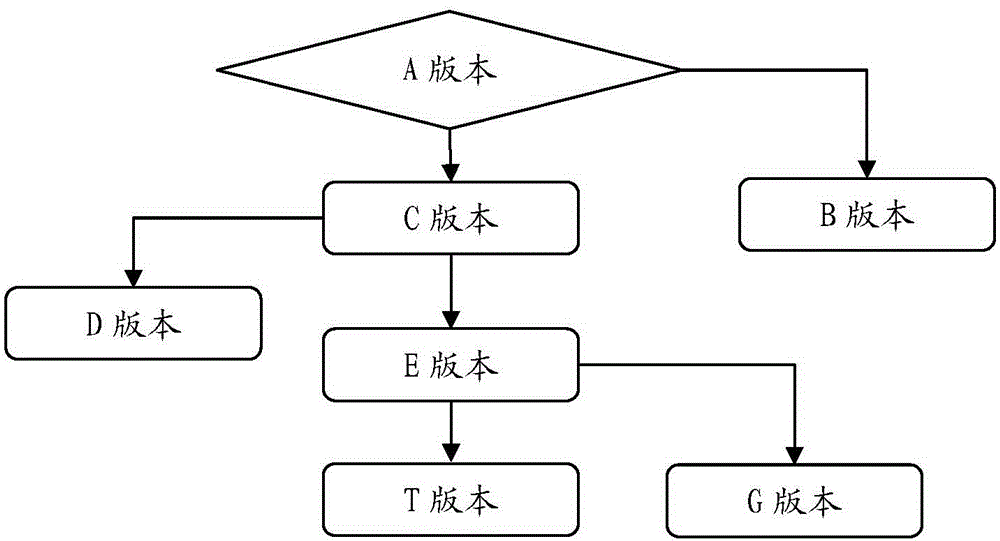
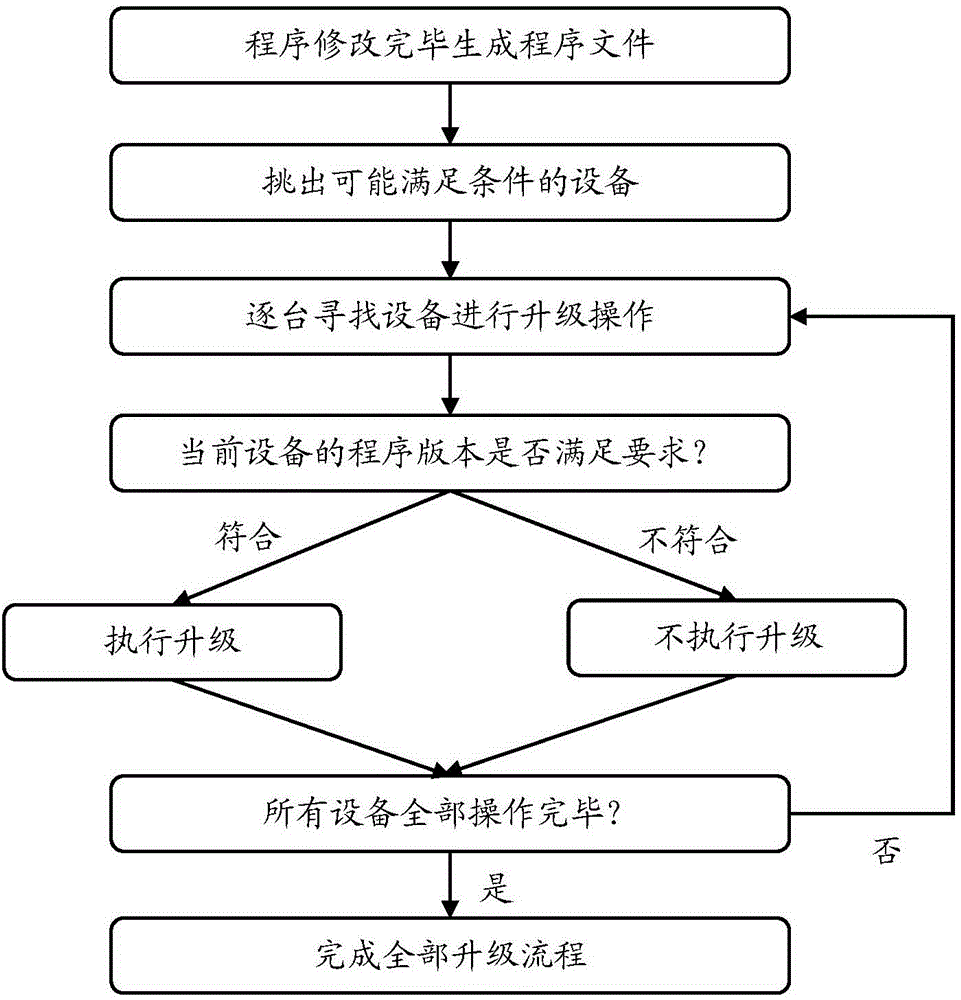
InactiveCN104407897ASimplify the manual judgment processImprove upgrade efficiencyProgram loading/initiatingAlternative programSoftware engineering
The invention provides an intelligent upgrading method for a program. The method comprises the following steps: 1, inserting a piece of field data at a file header of an original program file to generate an amended program file, wherein the field data comprises integrated check, file type, total number of alternative program version numbers, lengths of the alternative program version numbers, version numbers of alternative program versions, total number of upgrading program version numbers, lengths of upgrading program version numbers and version numbers of upgrading program versions; 2, downloading the amended program file to equipment; 3, receiving and storing the amended program file by the equipment, and analyzing the field data; 4, judging whether one alternative version meets the requirement on upgrading through the field data, executing cover upgrading if the requirement is met, and otherwise, giving up the upgrading. The invention also provides an intelligent upgrading system for the program. The efficiency and the reliability of the upgrading are greatly improved.
Owner:XIAMEN YAXON NETWORKS CO LTD
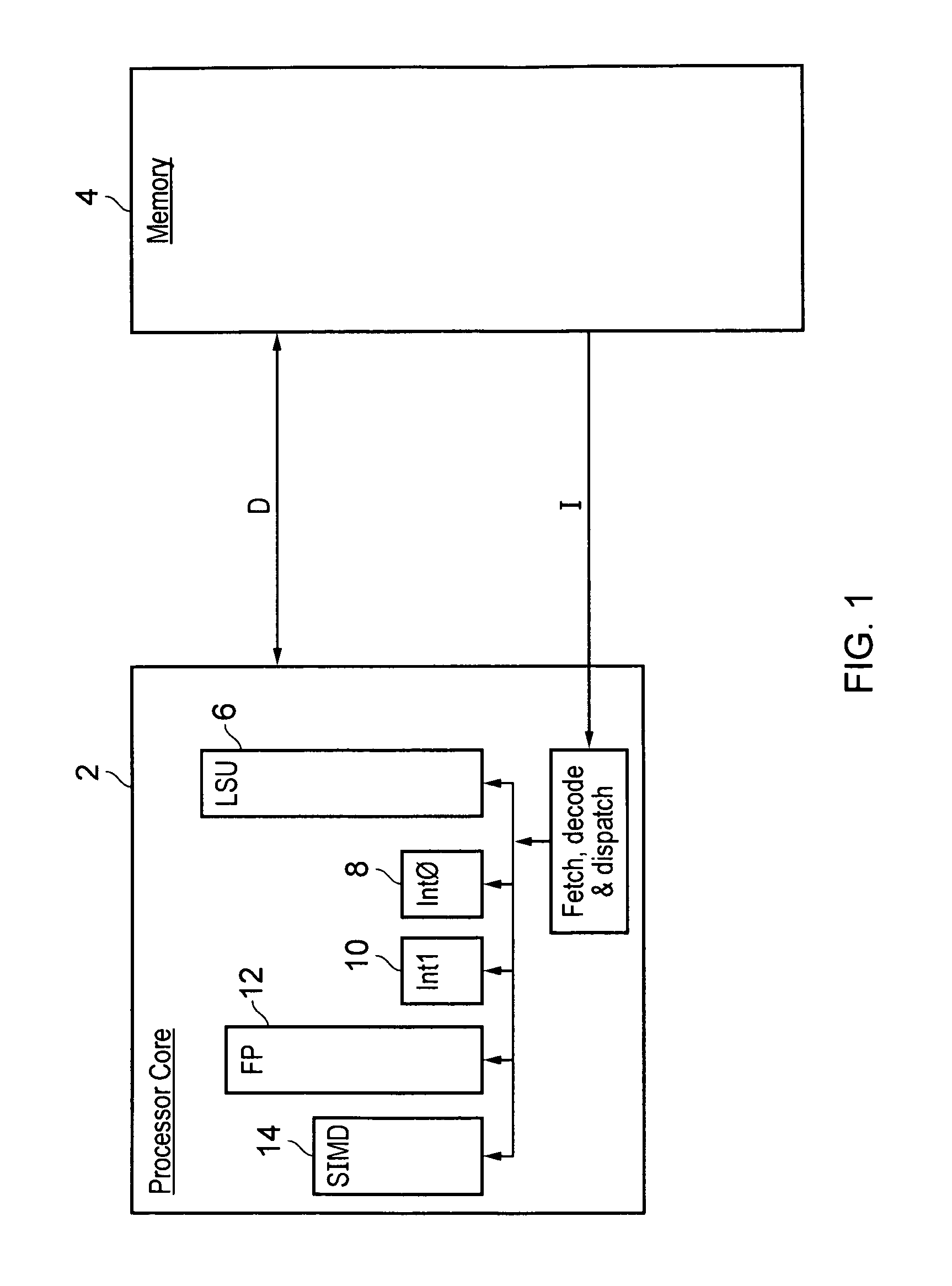
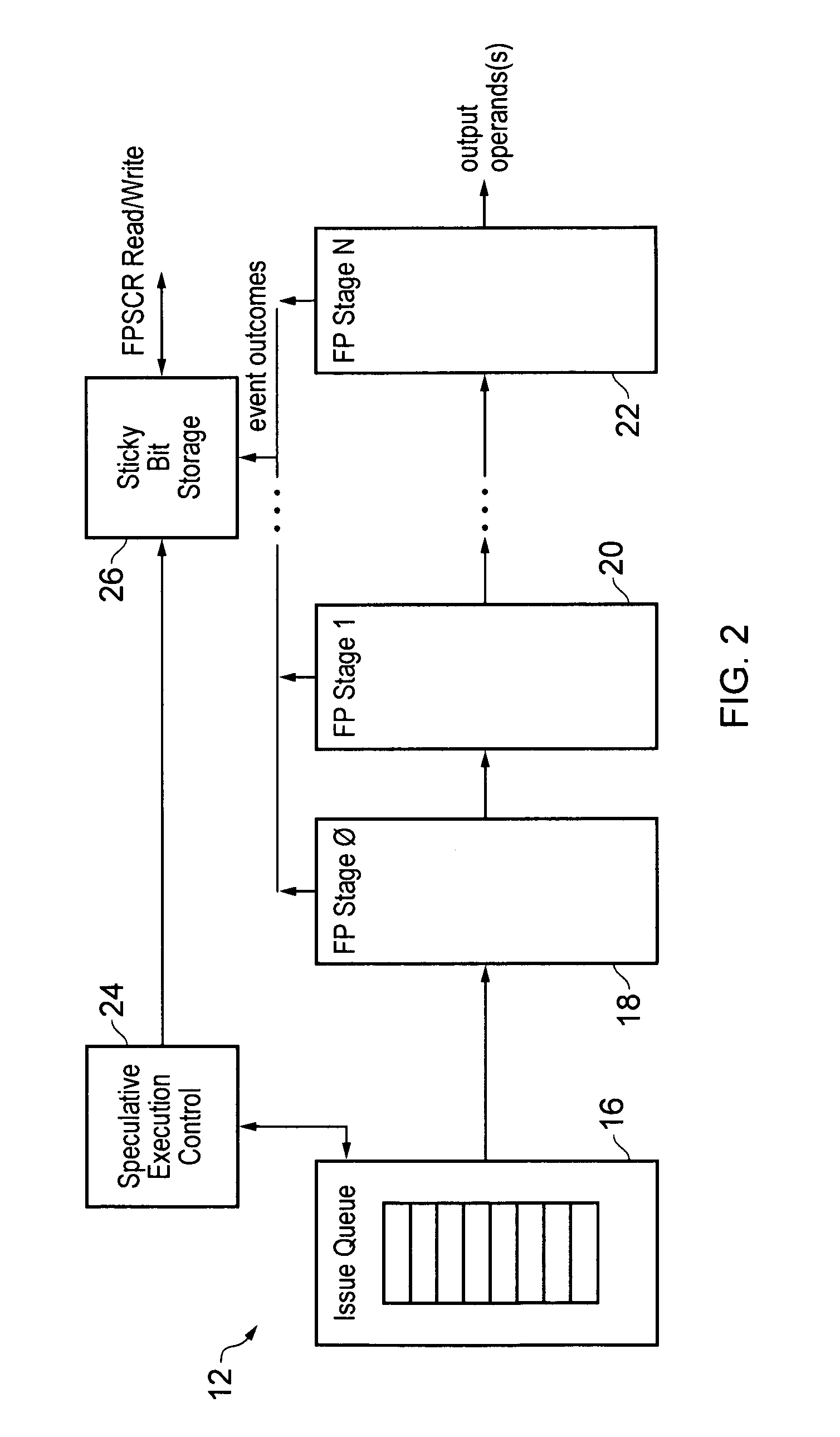
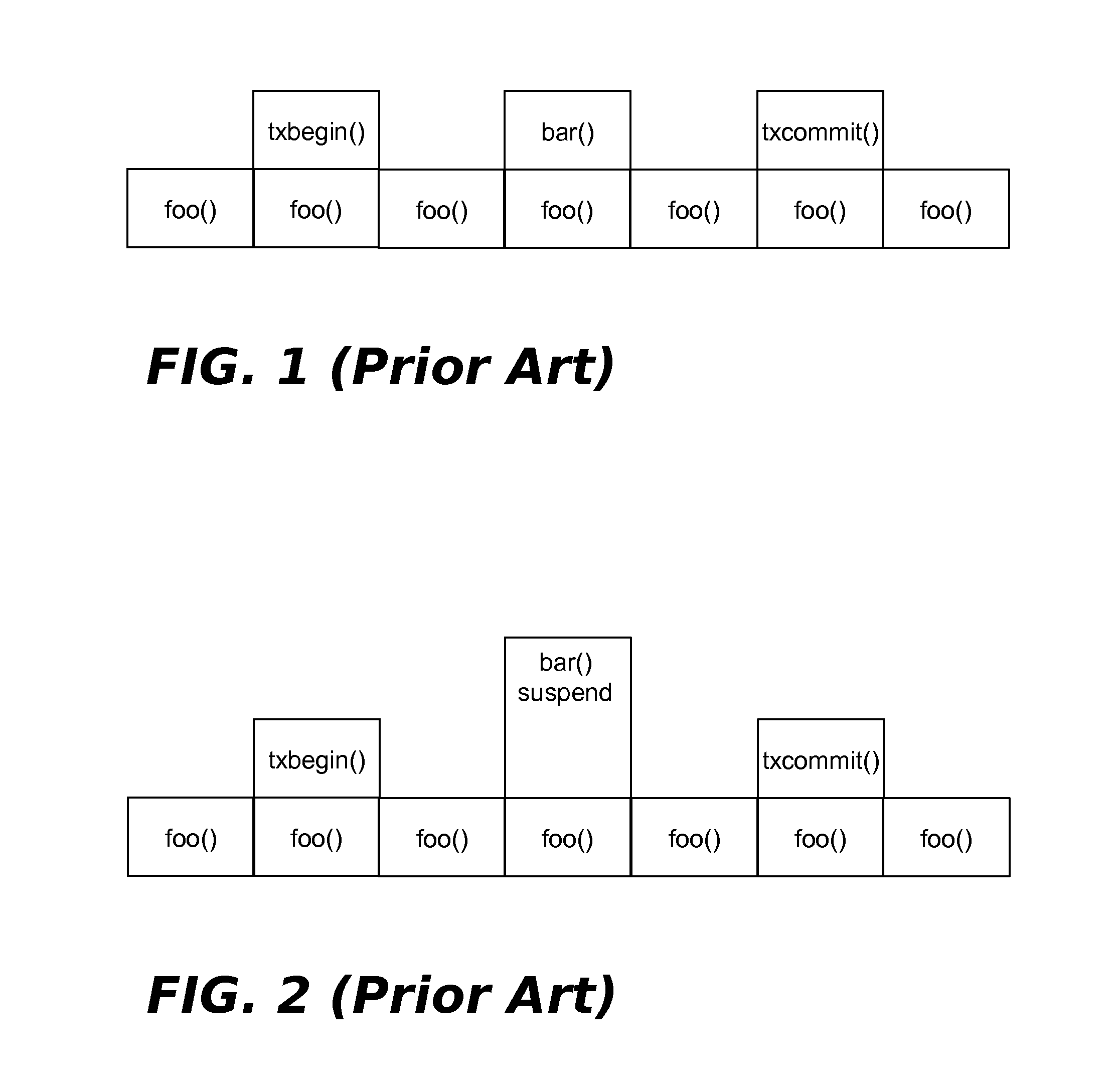
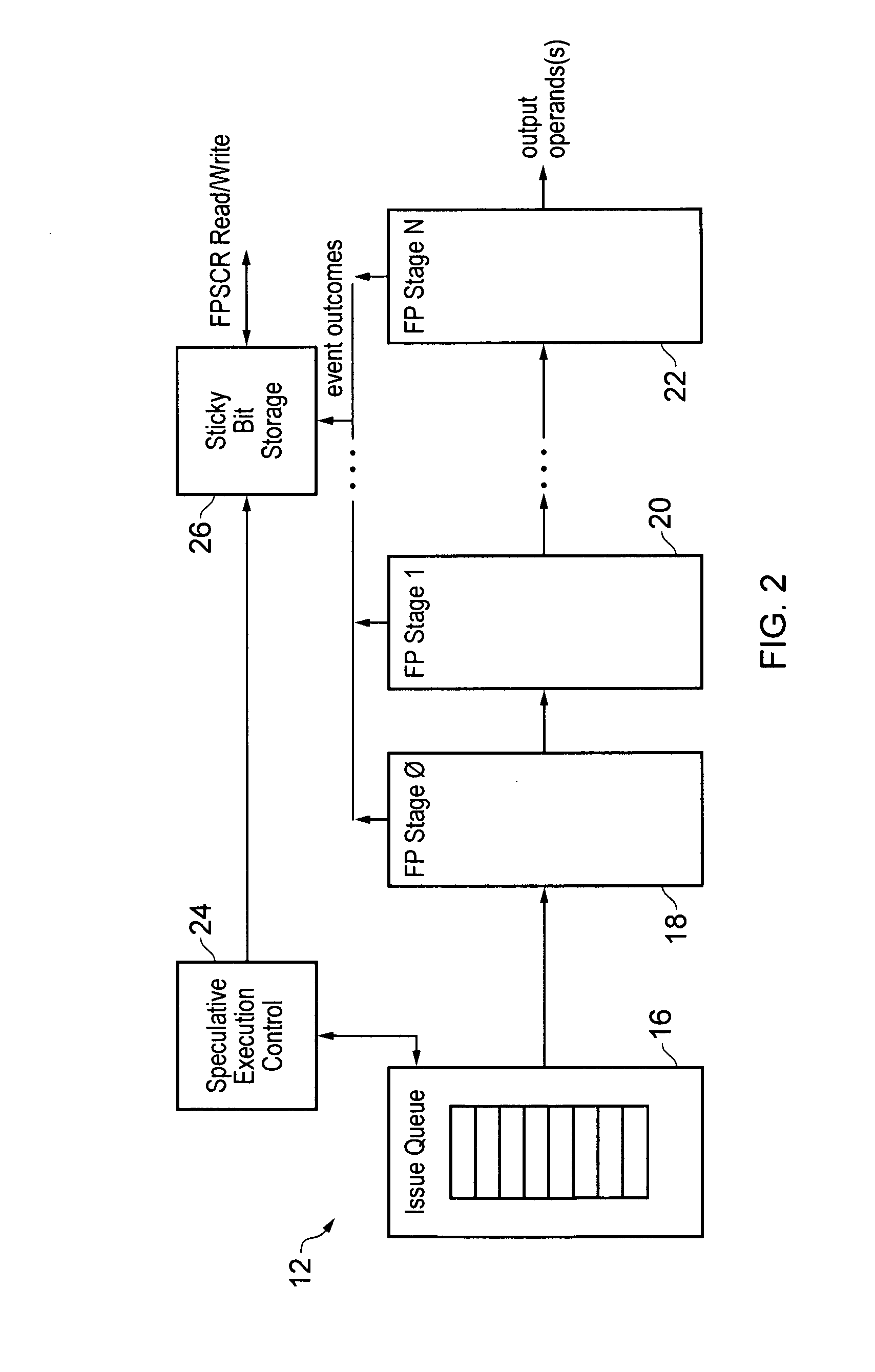
Sticky bit update within a speculative execution processing environment
ActiveUS9311087B2General purpose stored program computerConcurrent instruction executionSpeculative executionProgram instruction
Owner:ARM LTD
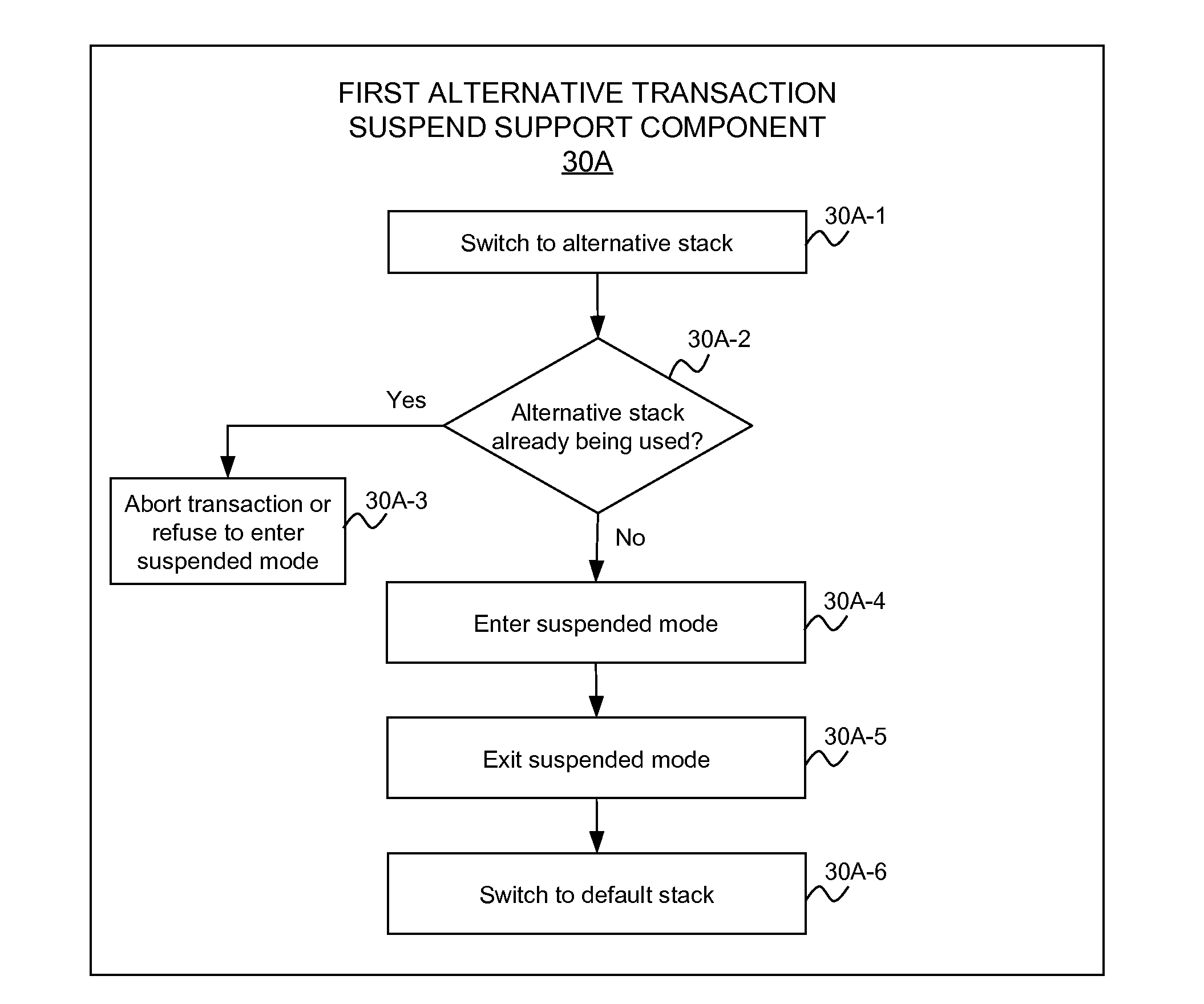
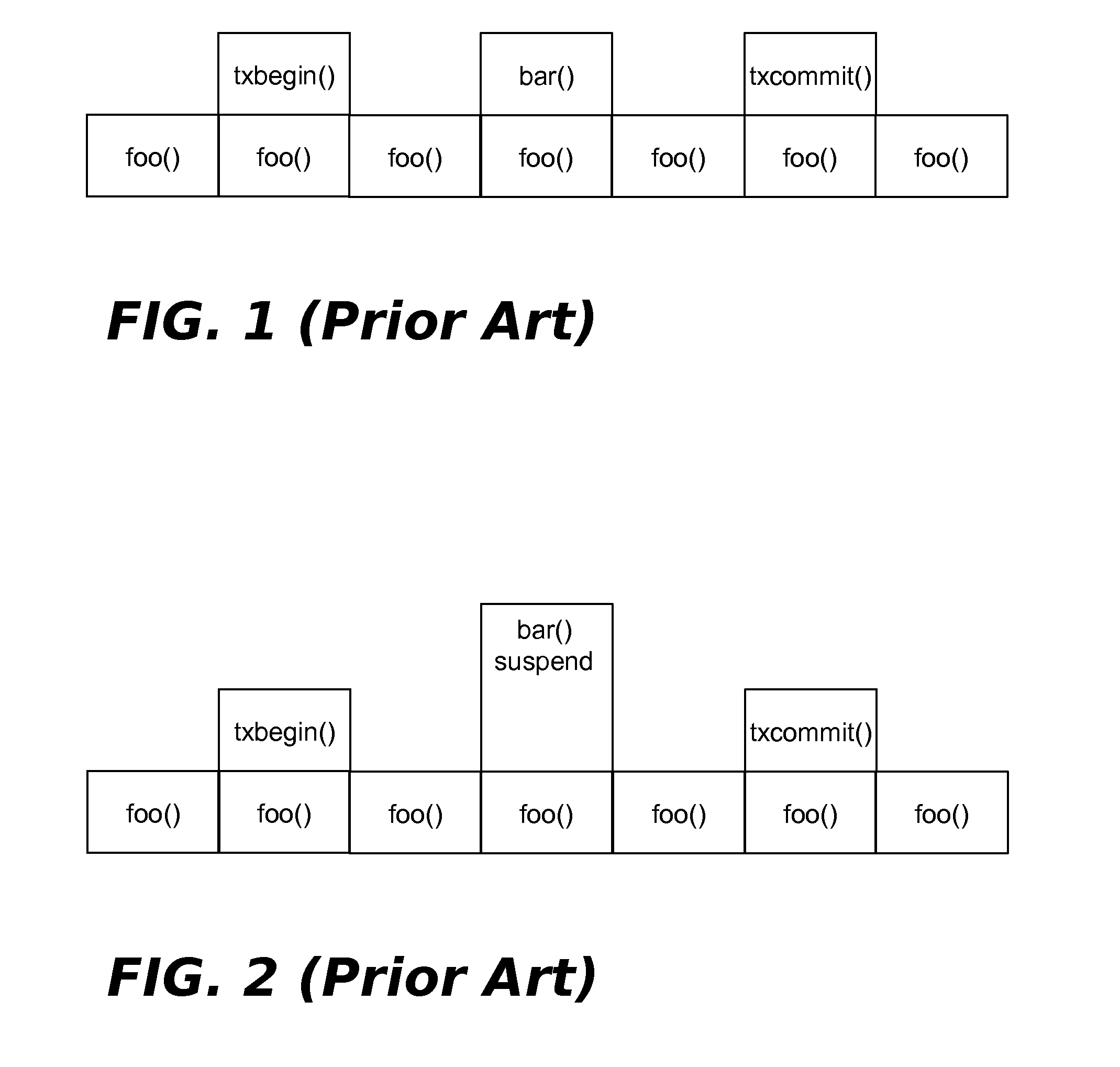
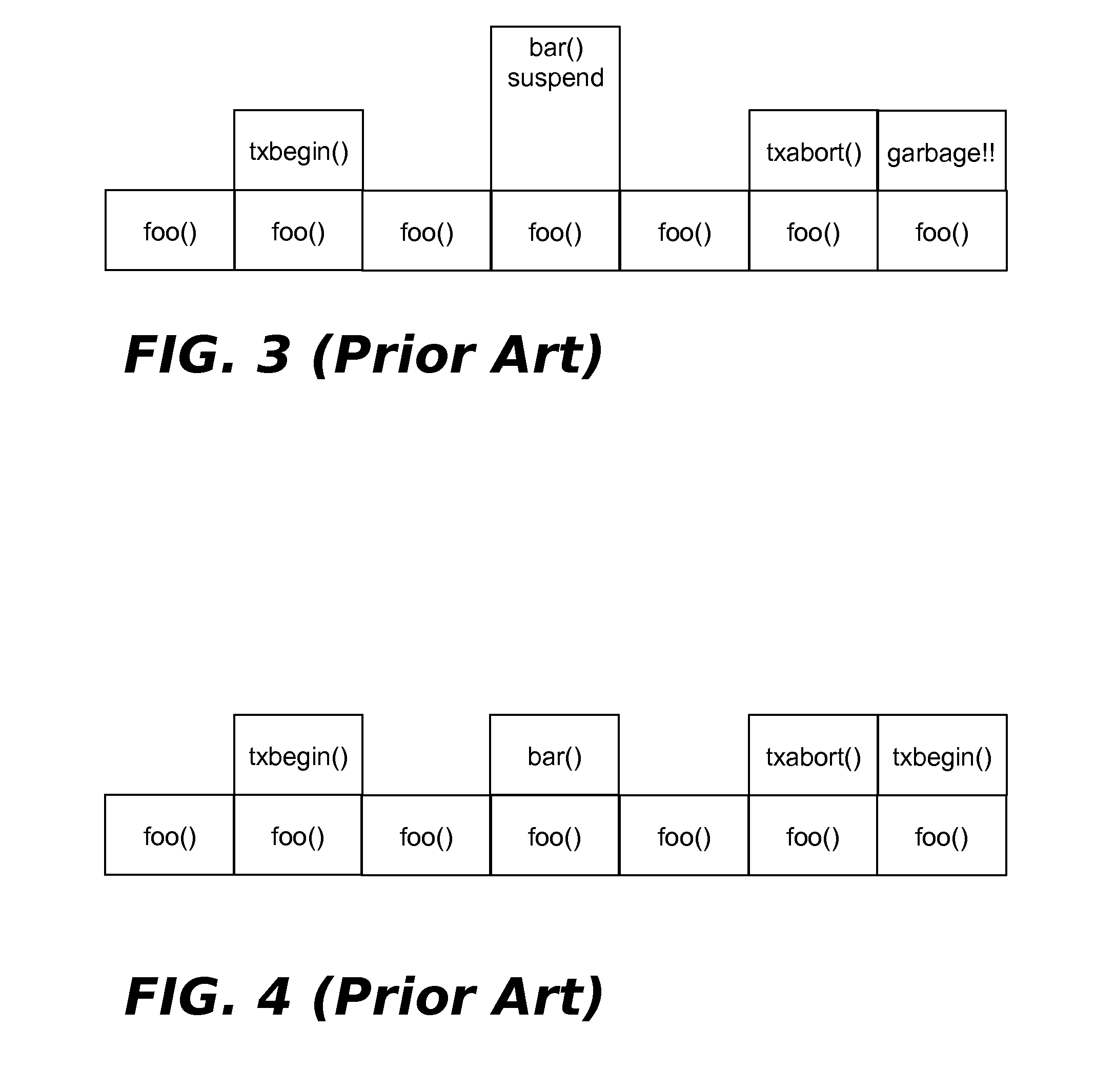
Suspending Transactional-Memory Transactions Without Stack Corruption
InactiveUS20160085549A1Error detection/correctionDigital computer detailsAlternative programTransactional memory
A technique for suspending transactional memory transactions without stack corruption. A first function that begins a transactional memory transaction is allocated a stack frame on a default program stack, then returns. Prior to suspending the transaction, or after suspending the transaction but prior to allocating any suspended mode stack frames, either of the following operations is performed: (1) switch from the default program stack to an alternative program stack, or (2) switch from a default region of the default program stack where the first function's stack frame was allocated to an alternative region of the default program stack. Prior to resuming the transaction, or after resuming the transaction but prior to allocating any transaction mode stack frames, either of the following operations is performed: (1) switch from the alternative program stack to the default program stack, or (2) switch from the alternative stack region to the default stack region.
Owner:IBM CORP
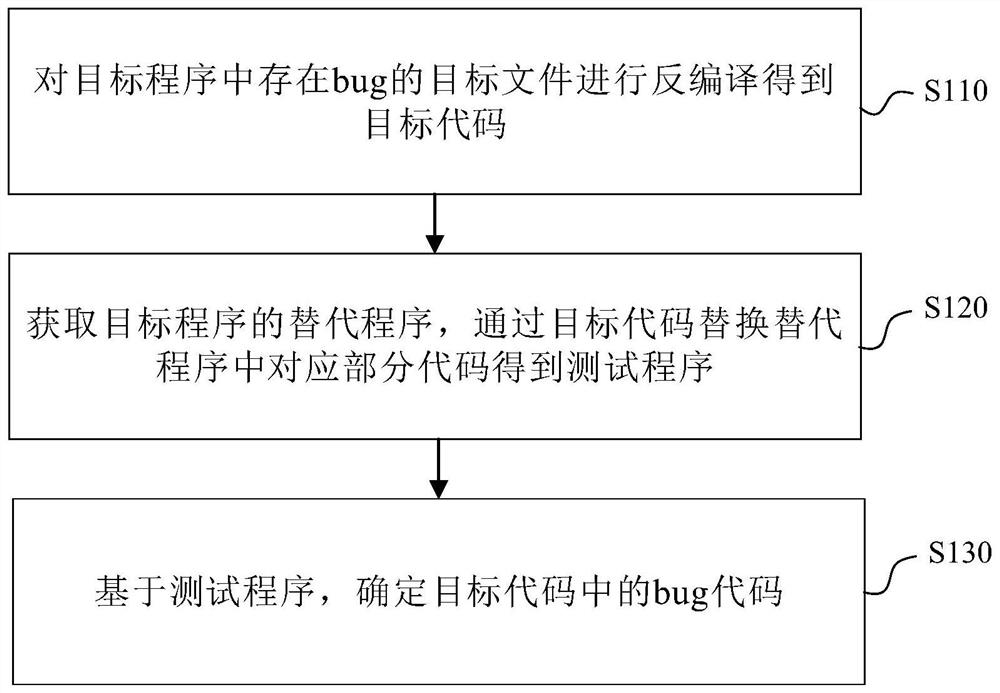
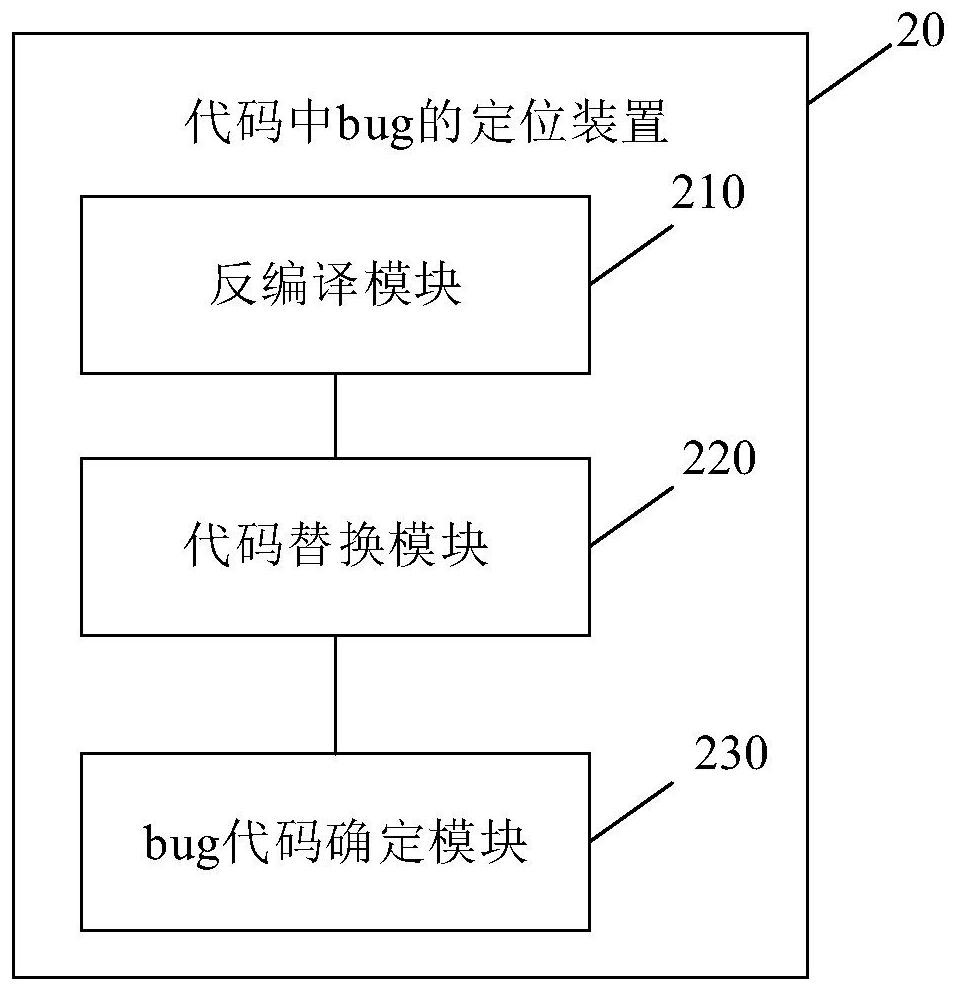
Method and device for positioning bug in code, electronic equipment and readable storage medium
ActiveCN111897711AEasy to useDecompilation/disassemblySoftware testing/debuggingSoftware engineeringAlternative program
The embodiment of the invention provides a method and device for positioning a bug in a code, electronic equipment and a readable storage medium. The method comprises the following steps: decompilinga target file with bug in a target program to obtain a target code; obtaining a replacement program of the target program, and replacing a corresponding part of codes in the replacement program with the target code to obtain a test program; and determining a bug code in the target code based on the test program. Based on this scheme, a test program is obtained by replacing a code with a bug into acode of an alternative program; the bug code is determined by debugging the test program, so that the bug code is determined under the condition that the code of the target program is not subjected to open source, a basis can be provided for modifying the determined bug code to repair the bug, and normal use of a user is guaranteed.
Owner:CCB FINTECH CO LTD
Watermarking computer program code
ActiveUS8458476B2Reasonable overheadDigital data processing detailsUser identity/authority verificationData processing systemAlternative program
A method of embedding information in a computer program code, including a plurality of program statements. The method comprises: inserting a conditional program statement in the computer program code, the conditional program statement including a condition and a plurality of alternative program statements, the conditional program statement being adapted to cause a data processing system to evaluate said condition and, responsive to a result of said evaluating step, to selectively execute one of said plurality of alternative program statements; wherein said condition is indicative of at least a part of said information; and wherein the plurality of alternative program statements are adapted to cause the computer program code to produce the same program output irrespective of which of said alternative program statements is executed.
Owner:TELEFON AB LM ERICSSON (PUBL)
Firmware code execution method, memory storage device and memory control circuit unit
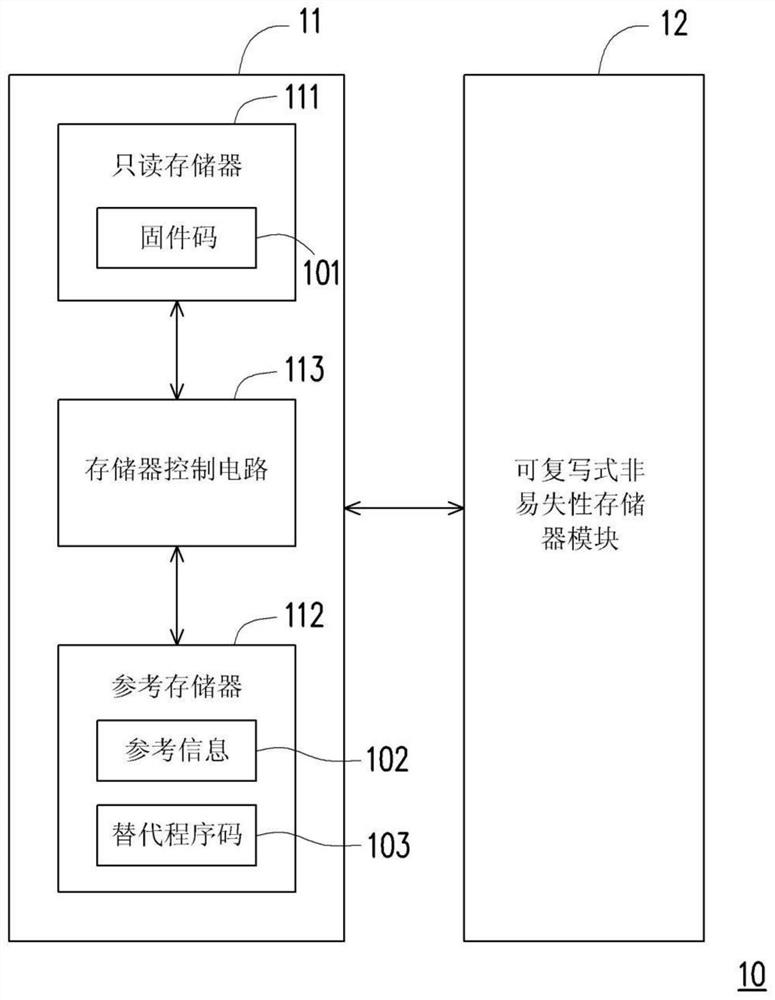
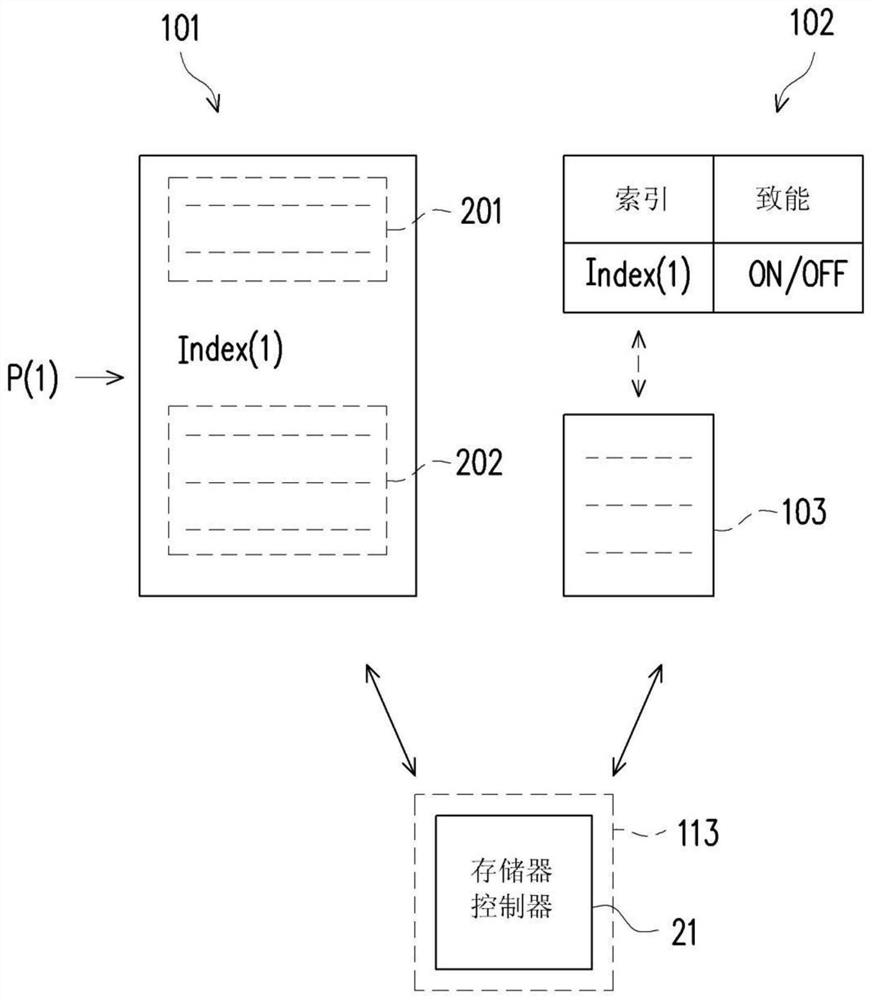
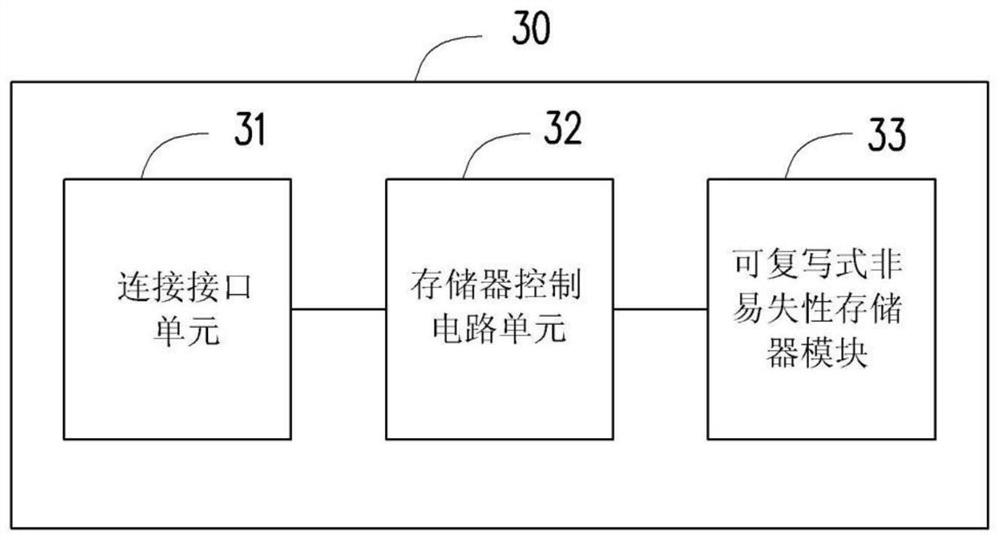
PendingCN111949321AExtended service lifeIncrease elasticityRead-only memoriesBootstrappingAlternative programControl circuit
The invention provides a firmware code execution method, a memory storage device and a memory control circuit unit. The method comprises the following steps: executing a firmware code in a read-only memory; after executing the first part of the firmware code, querying reference information in a reference memory according to index information in the firmware code; and determining to continue to execute the second part of the firmware code or switch to execute the alternative program code in the reference memory according to the reference information so as to finish the startup program. Therefore, the use flexibility of the memory storage device (or the memory control circuit unit) can be improved, and / or the service life of the memory storage device (or the memory control circuit unit) canbe prolonged.
Owner:PHISON ELECTRONICS
Nonvolatile memory apparatus
InactiveCN100428187CPrevent tamperingPrevent leakageRead-only memoriesUnauthorized memory use protectionPower-on resetAnalysis data
Owner:RENESAS ELECTRONICS CORP
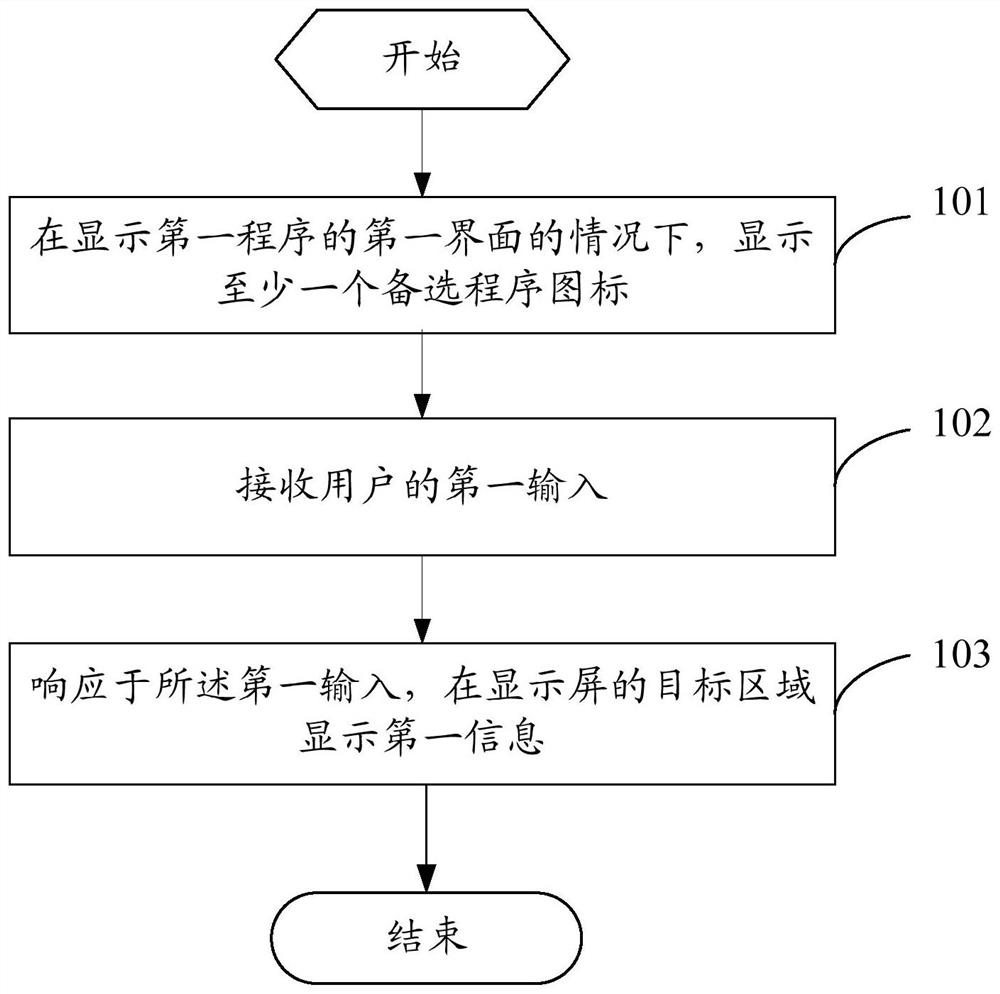
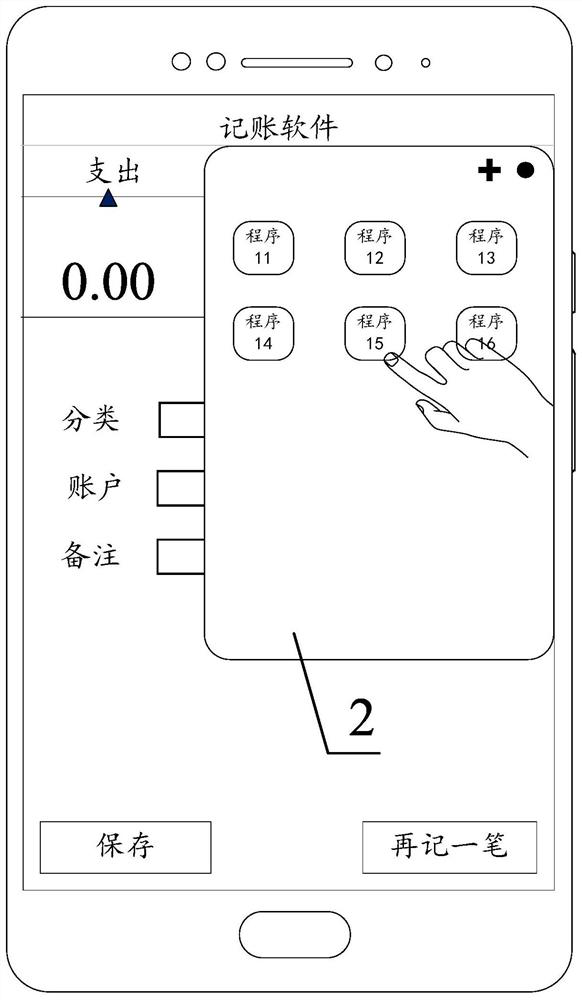
Information acquisition method and device, electronic equipment and readable storage medium
PendingCN114237451AImprove acquisition efficiencyImprove search efficiencyExecution for user interfacesInput/output processes for data processingComputer hardwareSoftware engineering
The invention discloses an information acquisition method and device, electronic equipment and a readable storage medium, and belongs to the technical field of computers. The method comprises the steps that under the condition that a first interface of a first program is displayed, at least one alternative program icon is displayed, and the at least one alternative program icon is a program icon associated with the first program; receiving a first input of a user; and in response to the first input, displaying first information in a target area of a display screen, the first information being information in a target program, and a target program icon corresponding to the target program being an icon in the at least one alternative program icon.
Owner:VIVO MOBILE COMM CO LTD
Preparation of nano-aluminum powder ink for inkjet printers by emulsification dispersion method
A method for preparing nano-aluminum powder ink for ink-jet printers by emulsification and dispersion method. According to a certain mass ratio, nano-aluminum powder, ethanol, and isopropanol are blended in a container, and the above blended solution is uniformly emulsified and dispersed by high-speed emulsification equipment After a certain dispersion time, add the dispersant to the blend solution in three batches during the emulsification and dispersion process. Add the above emulsion one at a time, and then continue to emulsify the above emulsion for 1.5~3 hours to obtain the nano-aluminum powder ink for inkjet printers with excellent performance. The method of the present invention is applied to the production of thin-film solar cells. The production process is simple and the production cost is low. The thin-film solar cells produced are natural and low-pollution, and the price is reduced. They are suitable for portable electronic products and are very competitive energy substitutes in the future. The program has potential extremely broad practicability and market promotion prospects.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Suspending Transactional-Memory Transactions Without Stack Corruption
InactiveUS20160085548A1Error detection/correctionDigital computer detailsParallel computingAlternative program
A technique for suspending transactional memory transactions without stack corruption. A first function that begins a transactional memory transaction is allocated a stack frame on a default program stack, then returns. Prior to suspending the transaction, or after suspending the transaction but prior to allocating any suspended mode stack frames, either of the following operations is performed: (1) switch from the default program stack to an alternative program stack, or (2) switch from a default region of the default program stack where the first function's stack frame was allocated to an alternative region of the default program stack. Prior to resuming the transaction, or after resuming the transaction but prior to allocating any transaction mode stack frames, either of the following operations is performed: (1) switch from the alternative program stack to the default program stack, or (2) switch from the alternative stack region to the default stack region.
Owner:IBM CORP
Sticky bit update within a speculative execution processing environment
ActiveUS20140181485A1Digital computer detailsConcurrent instruction executionSpeculative executionProgram instruction
A data processing apparatus 2 supports speculative execution and the use of sticky bits. A different version of a sticky bit is associated with each segment of the speculative program flow. The segments of the program flow are separated by speculation nodes corresponding to program instructions which may be followed by a plurality of different alternative program instruction serving as the next program instruction. When a speculation node is resolved, then the segments separated by that speculation node are merged and the sticky bit values for those two segments are merged.
Owner:ARM LTD
Processing method of nano-aluminum powder ink for sol-gel type inkjet printer
The invention discloses a processing method of nano-aluminum powder ink for a sol-gel type inkjet printer. Mix and stir aluminum isopropoxide and deionized water for 1 hour to hydrolyze, add nitric acid at intervals to form a white transparent alumina sol for later use; gradually add nano-aluminum powder to the above sol-gel according to a certain mass ratio and mix it with a stirring device Disperse the above blended sol-gel evenly, add the dispersant in batches during the dispersion process, add polypropylene butyral to the above sol-gel in batches, and then continue to stir the above sol-gel solution, that is A sol-gel type nano-aluminum powder ink for an ink-jet printer with excellent performance is obtained. The method of the present invention is applied to the production of thin-film solar cells with simple production process and low manufacturing cost; the produced thin-film solar cells are natural, low-pollution, lower in price, suitable for portable electronic products, and are highly competitive energy substitutes in the future The program has potential extremely broad practicability and market promotion prospects.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Suspending transactional-memory transactions without stack corruption
InactiveUS9594589B2Error detection/correctionTransaction processingAlternative programTransactional memory
A technique for suspending transactional memory transactions without stack corruption. A first function that begins a transactional memory transaction is allocated a stack frame on a default program stack, then returns. Prior to suspending the transaction, or after suspending the transaction but prior to allocating any suspended mode stack frames, either of the following operations is performed: (1) switch from the default program stack to an alternative program stack, or (2) switch from a default region of the default program stack where the first function's stack frame was allocated to an alternative region of the default program stack. Prior to resuming the transaction, or after resuming the transaction but prior to allocating any transaction mode stack frames, either of the following operations is performed: (1) switch from the alternative program stack to the default program stack, or (2) switch from the alternative stack region to the default stack region.
Owner:IBM CORP
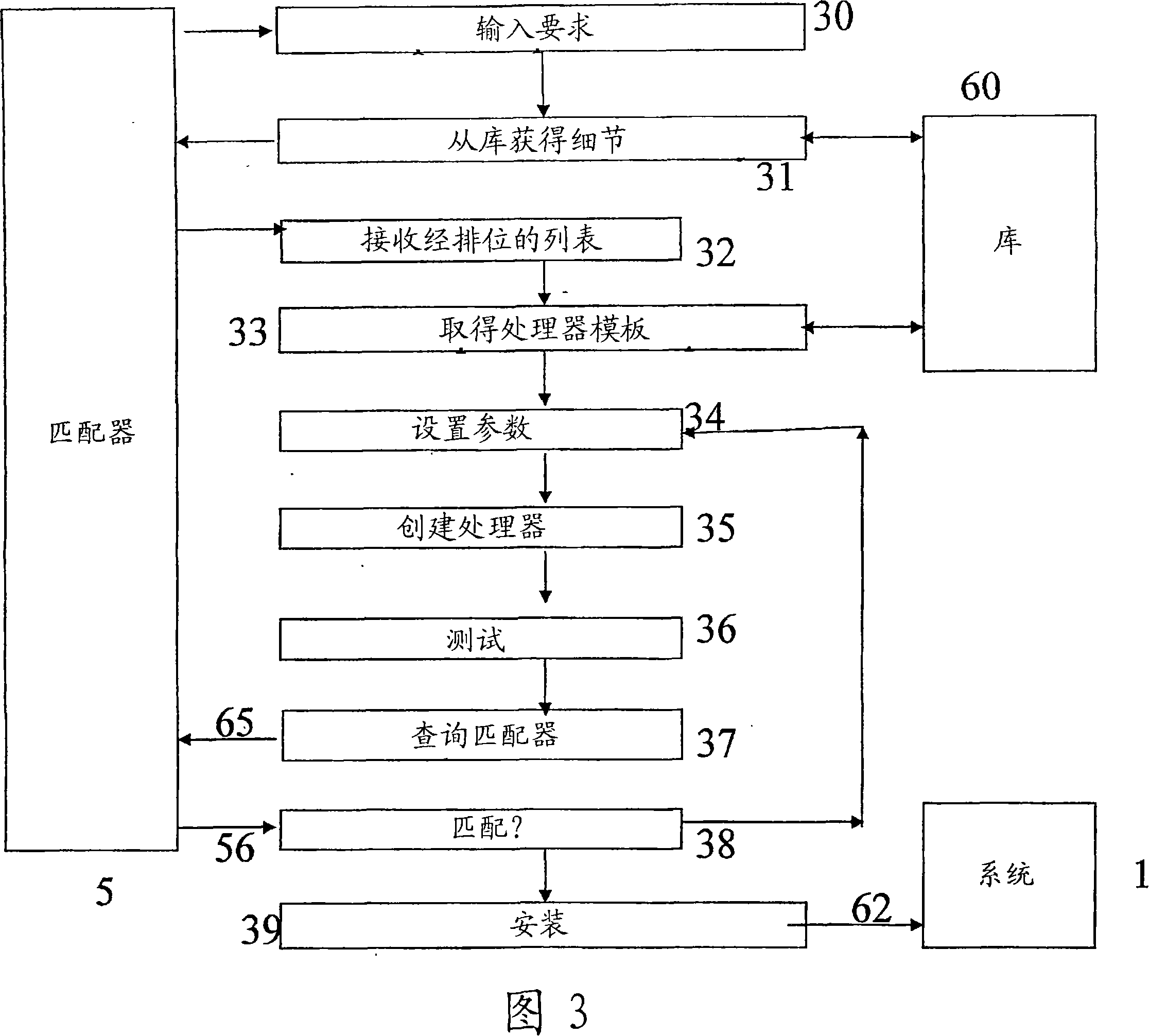
Monitoring computer-controlled processes
The performance of a computer-controlled system (1) operating under the control of a first process (2), is monitored (4) by comparison (5) with a predetermined set of requirements (15, 25), to identify whether the performance of the system (1) meets the predetermined requirements. If the performance does not meet those requirements, an alternative program (22) may be selected, or generated from program elements stored in a library (60), to replace the current controller process (2).
Owner:BRITISH TELECOMM PLC
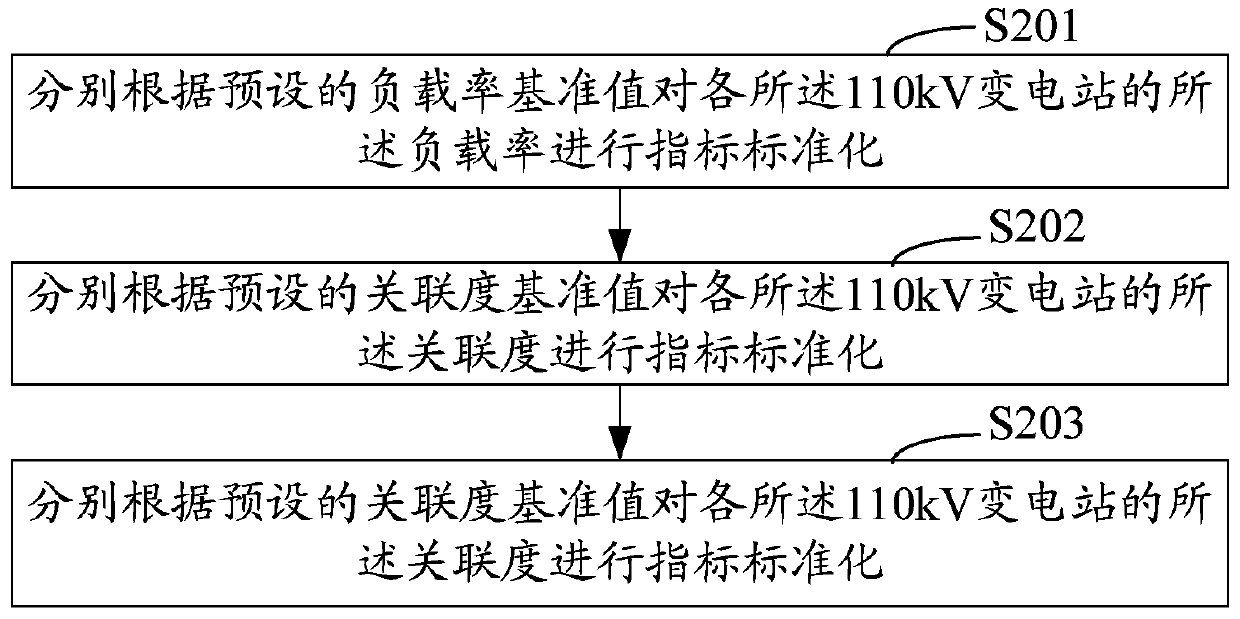
Site Selection Method and System for 110kv Substation
ActiveCN104820954BImprove selection efficiencyGuaranteed reliabilityData processing applicationsSpecial data processing applicationsTransformerLine rate
A method and system for site selection of a 110kV substation, the method comprising the steps of: separately obtaining the main transformer capacity, load rate, total capacity of the installed distribution transformers, interval utilization ratio, 10KV line overload rate, 10KV line non-transferable rate, 10KV line trunk overlength rate; respectively determine the correlation degree of each 110kV substation according to the main transformer capacity and the distribution transformer total capacity; Index standardization; combining the 10KV line overload rate, 10KV line non-transfer rate, 10KV line trunk overlength rate, and the load rate, correlation degree, and interval utilization rate after standardization of indicators, determine the coordination of the site selection plan corresponding to each 110kV substation degree; select the site corresponding to the site selection scheme with the highest degree of coordination as the final site, which can improve the coordination of medium-voltage distribution network operation while ensuring the reliability of the distribution network.
Owner:GUANGDONG POWER GRID CO LTD +1
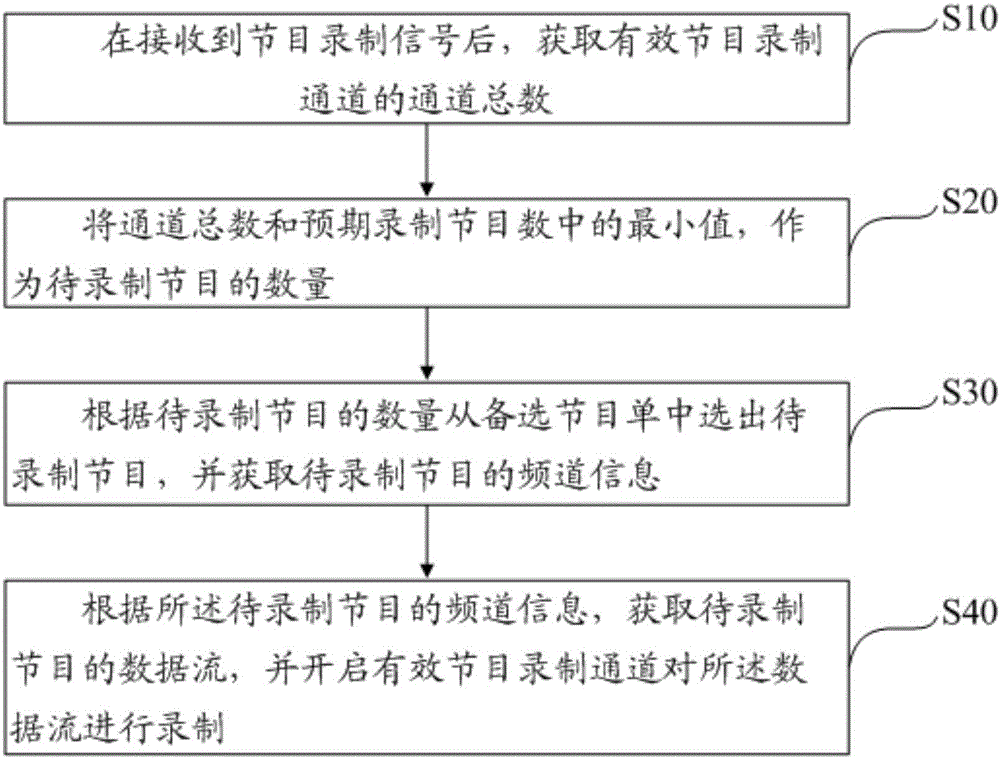
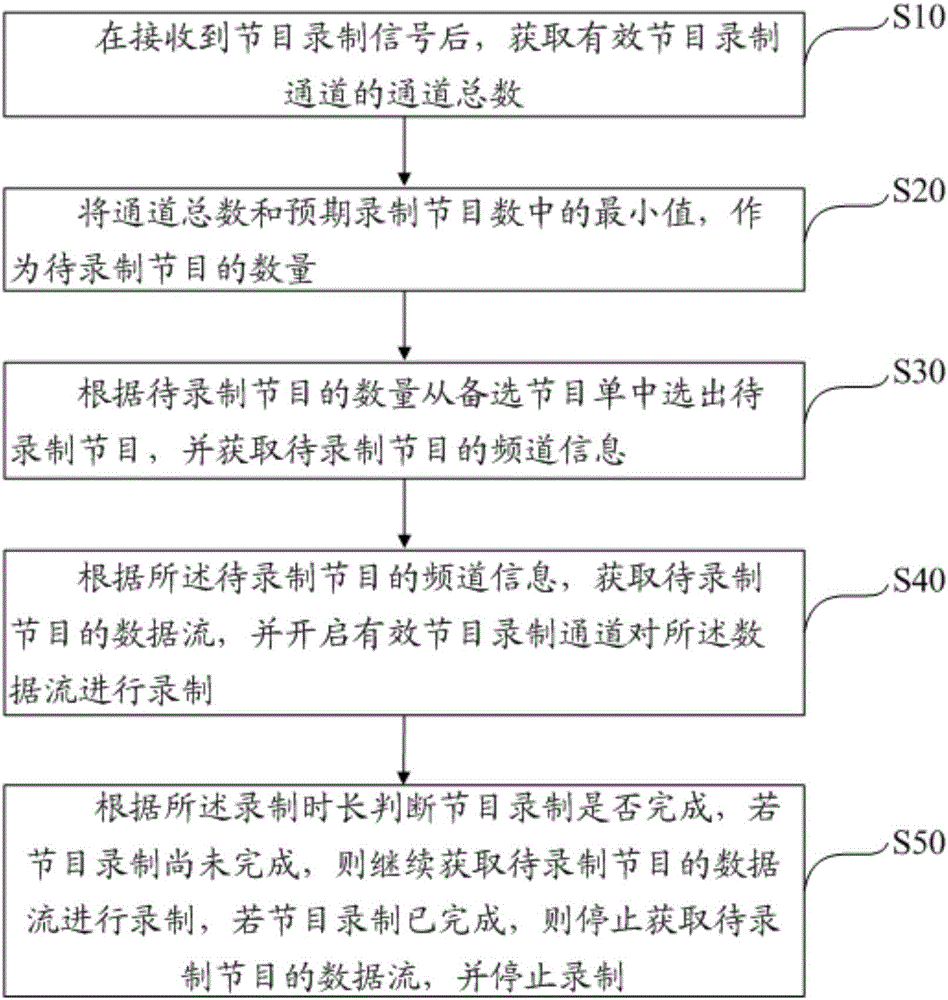
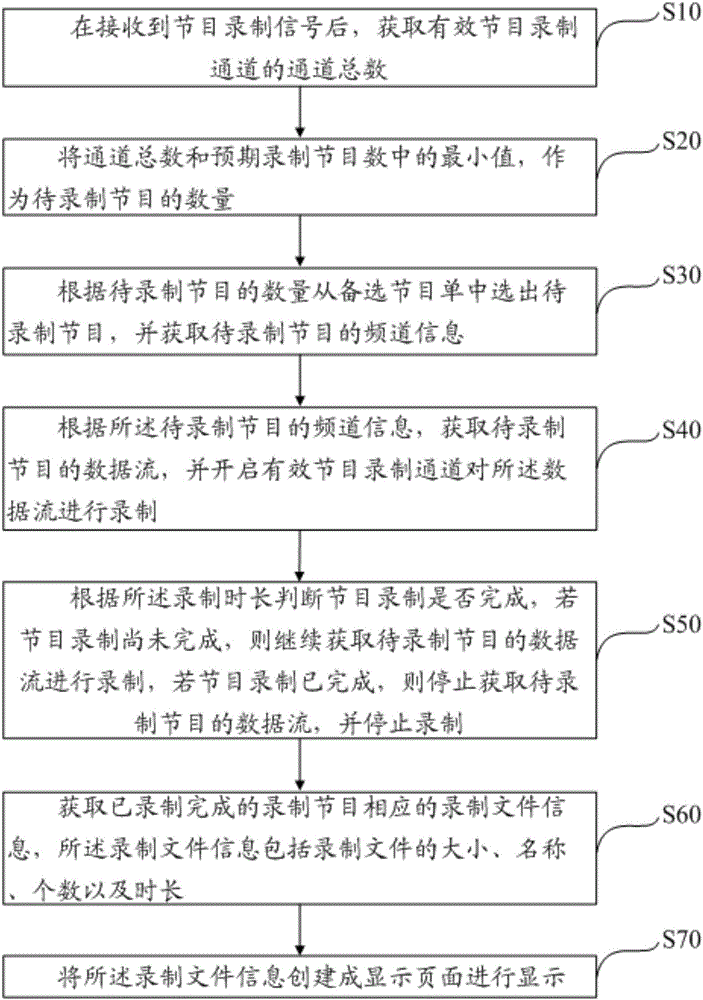
Program recording method and device
InactiveCN106851383AEasy to watchImprove experienceSelective content distributionData streamAlternative program
The invention discloses a program recording method. The program recording method comprises the steps of after a program recording signal is received, obtaining the total channel number of effective program recording channels; taking the minimum value of the total channel number and the expected program recording number as the number of to-be-recorded programs; selecting the to-be-recorded programs from an alternative program list according to the number of to-be-recorded programs and obtaining channel information of the to-be-recorded programs; and obtaining data streams of the to-be-recorded programs according to the channel information of the to-be-recorded programs and starting the effective program recording channels to record the data streams. According to the scheme, different programs are recorded according to the number of the to-be-recorded programs and recording demands of a user for different programs; the problem that the favorite programs cannot be watched timely due to the difference between personal time of the user and the program playing time is solved; the user can watch the favorite programs conveniently at any time; and the user experience is good. The invention also discloses a program recording device.
Owner:SHENZHEN TCL DIGITAL TECH CO LTD
A TV that can make automatic channel selection decisions
ActiveCN102487437BAvoid controversyTelevision system detailsColor television detailsAlternative programDecision taking
The invention provides a television set capable of automatically making a channel selection decision. The television set comprises a channel selection switch, a reception unit, a channel selection decision storage unit, a determination unit, a random selection unit, a frequency point obtaining unit and a playing unit. The random selection unit is used for carrying out random selection on program numbers stored in the channel selection decision storage unit as well as sending an obtained program number to the frequency point obtaining unit. According to the television set capable of automatically making a channel selection decision in the invention, after a channel selection decision function of the television set is started, a program number can be randomly selected from a plurality of alternative program numbers to carry out playing, so that disputes of television program selection for playing between watchers can be solved.
Owner:深圳华康创展科技控股集团有限公司
Method for quickly inputting program codes
PendingCN110928551AEasy to rememberIncrease typing speedCode compilationObject codeSoftware engineering
The invention discloses a method for quickly inputting a program code, which belongs to the field of computer programs and comprises the following steps: 1, writing an alternative program; 2, writingthe replacement source code and the replacement target code into a replacement program replacement database; 3, obtaining a replacement target code; 4, programming in the replacement program by usingthe replacement target code; 5, running an alternative program to replace the alternative target code with the alternative source code; and 6, outputting an alternative source code program. Accordingto the method, the substitution program is pre-programmed by a programmer, then the substitution program is operated, the substitution target code is used for programming in the substitution program,and the length of the substitution target code is smaller than that of the substitution source code, so that the programmer memorizes the substitution target code conveniently, the program code inputspeed is increased, and code input errors are reduced.
Owner:山东省国土测绘院
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com