Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42results about How to "Prevent illegal access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
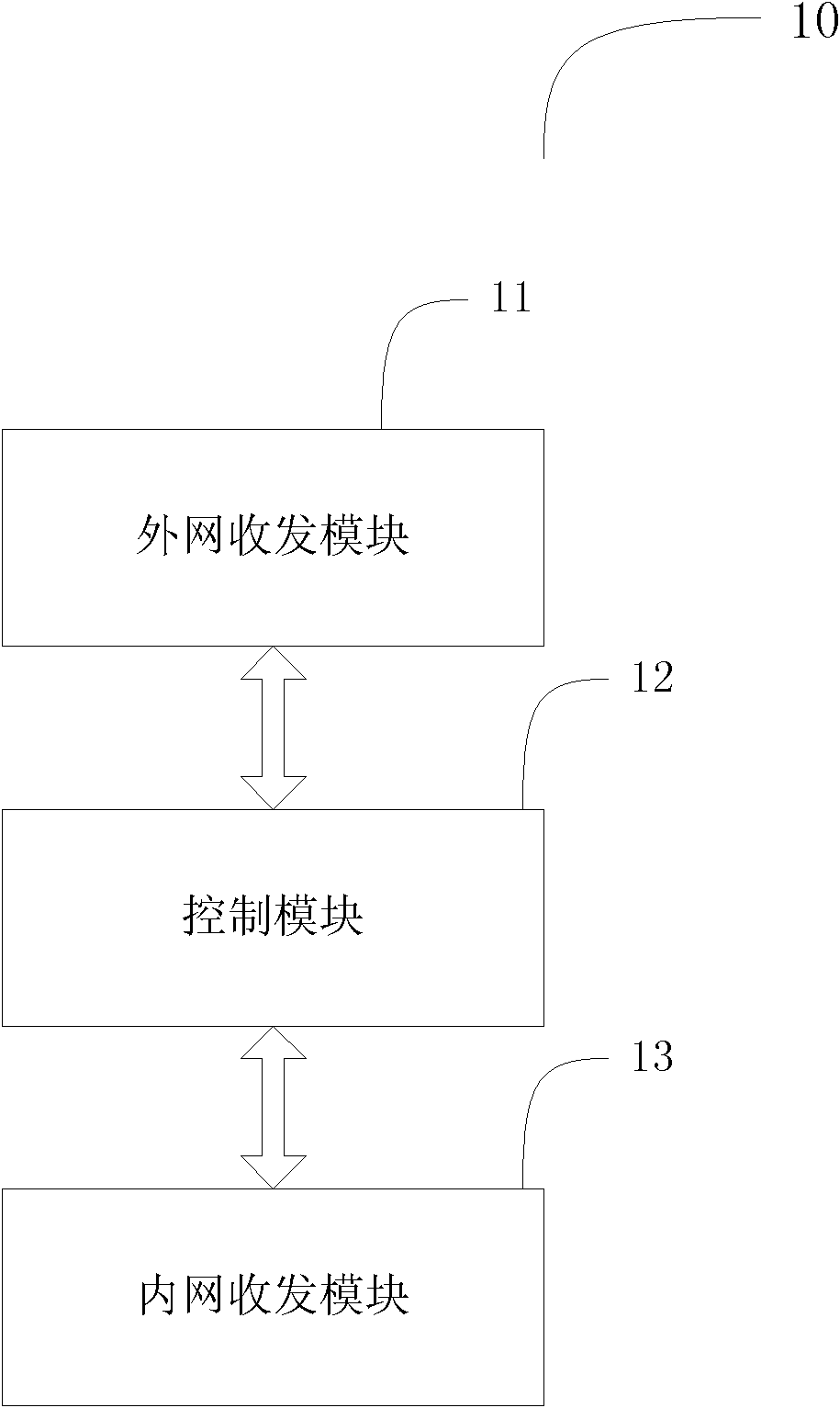
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
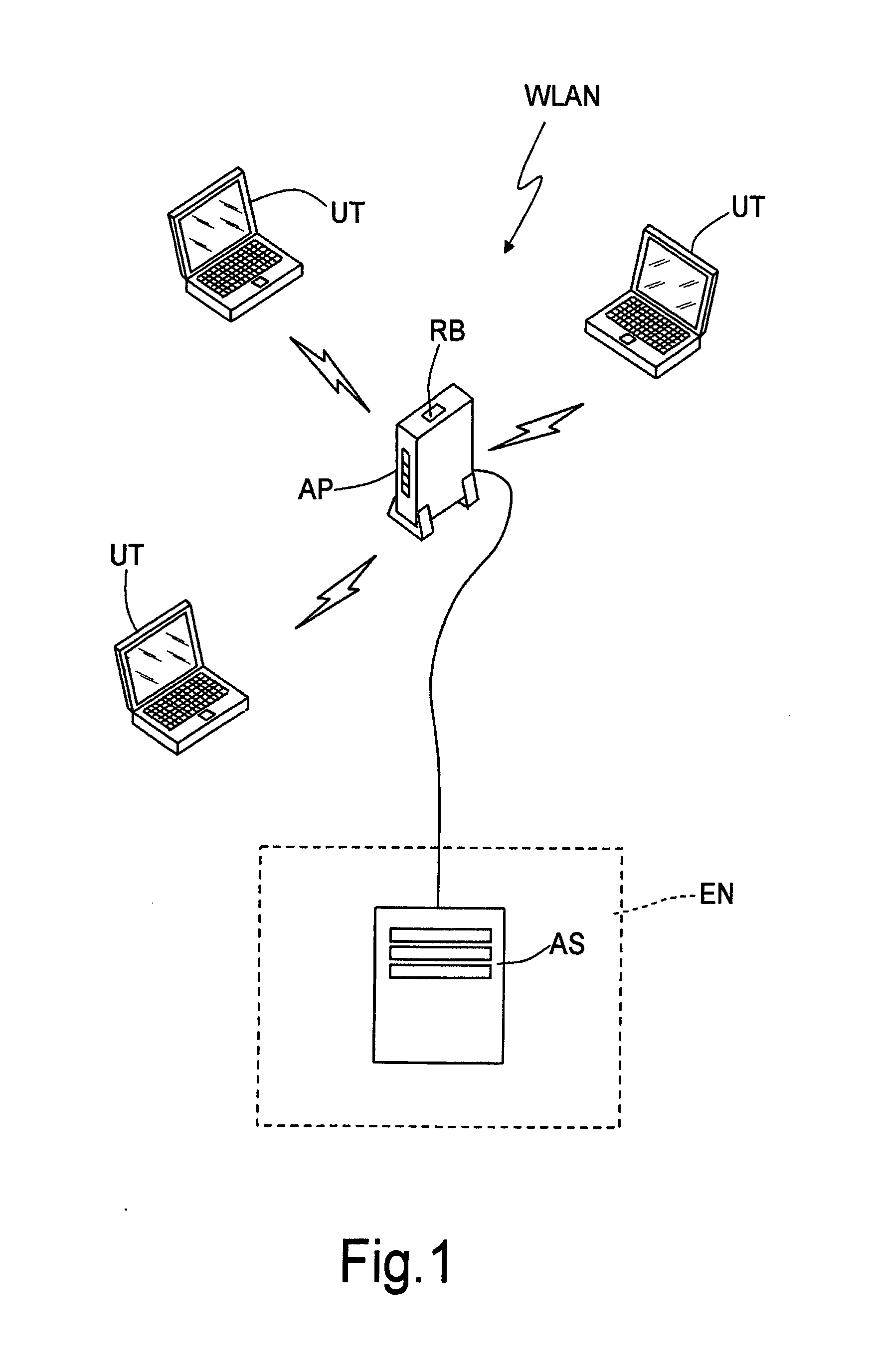
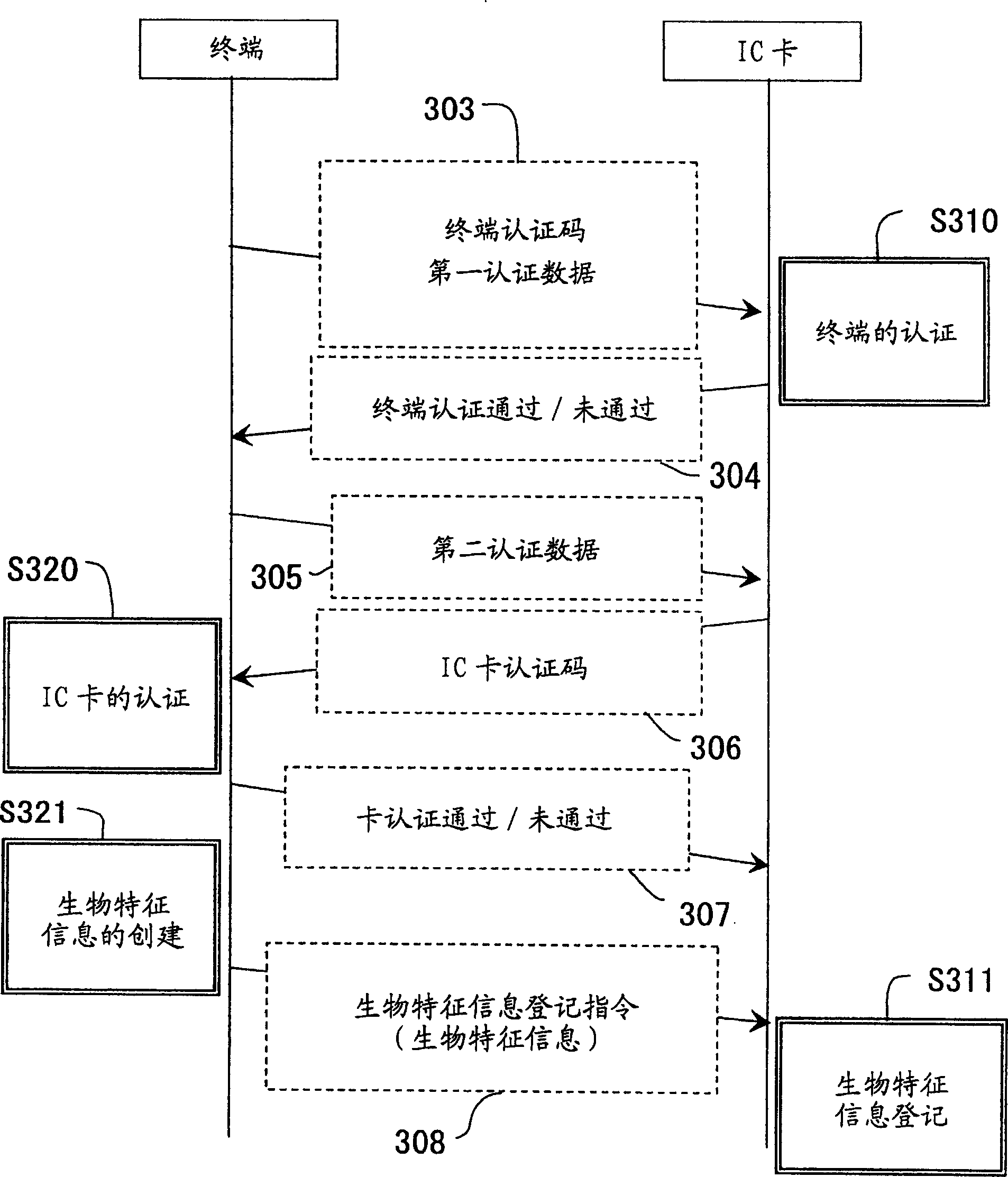
Method for Enrolling a User Terminal in a Wireless Local Area Network
ActiveUS20070263577A1Prevent illegal accessSimplify procedureUnauthorised/fraudulent call preventionEavesdropping prevention circuitsLocal area networkRegistered user
Owner:TELECOM ITALIA SPA
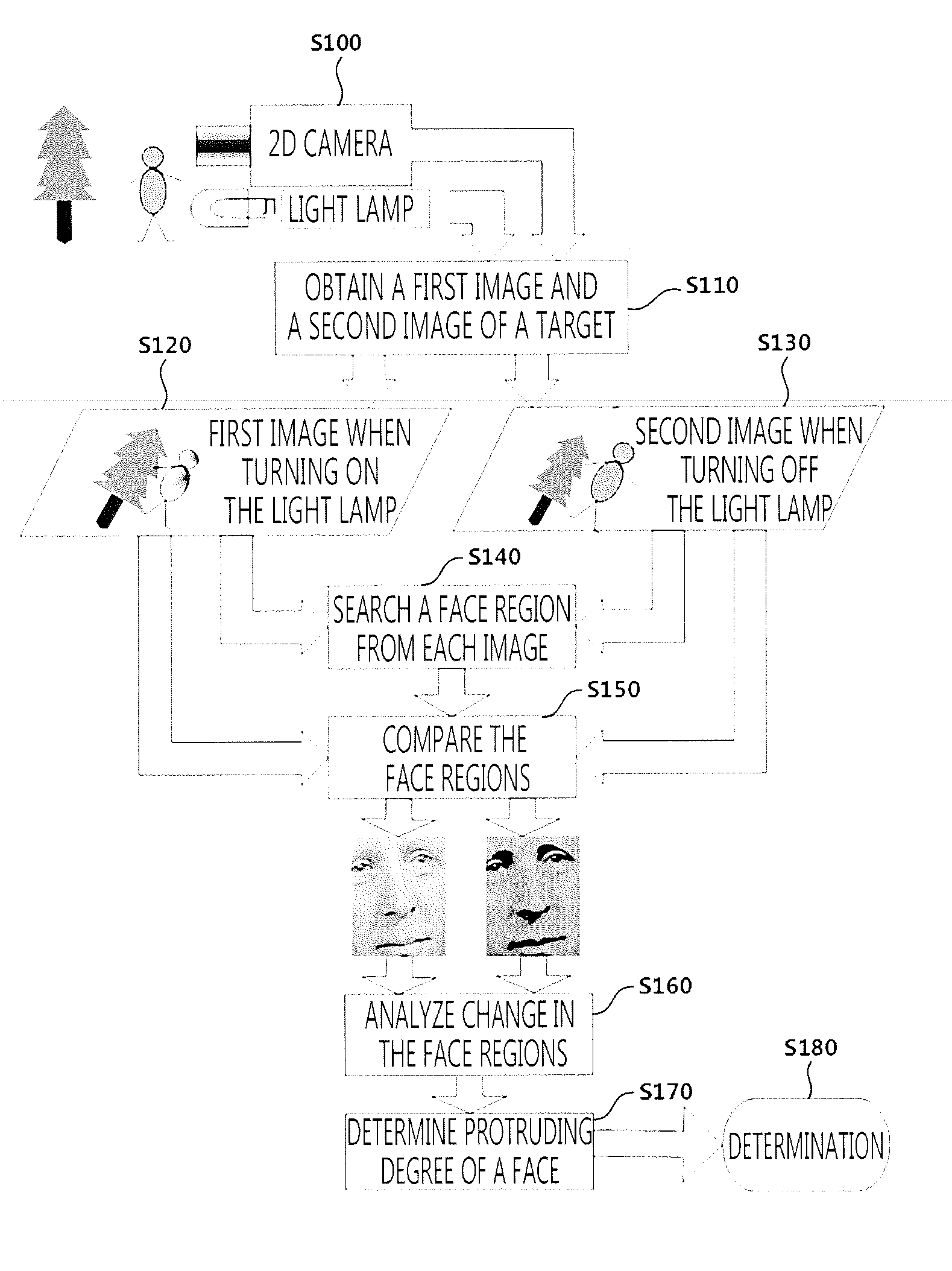
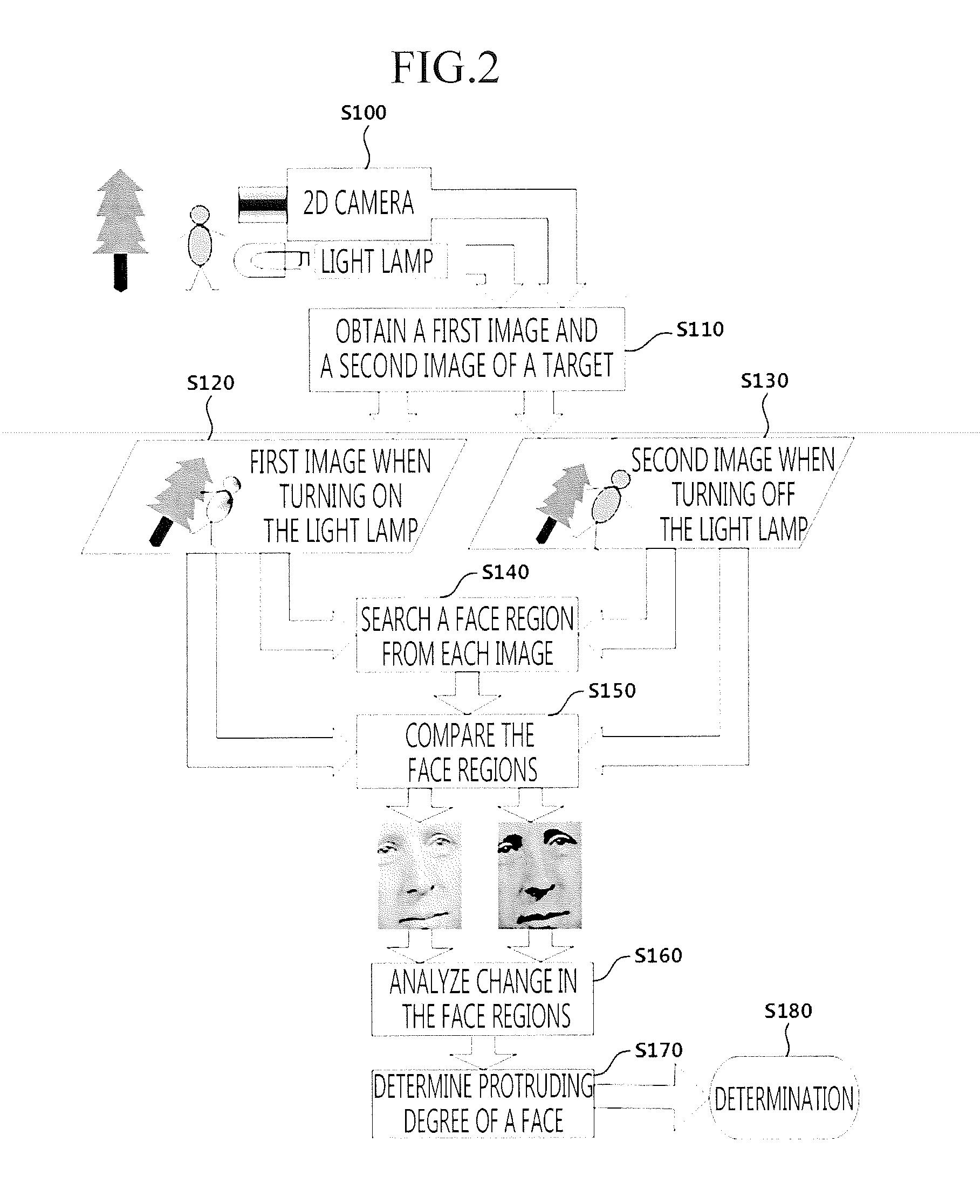
Method and apparatus for recognizing a protrusion on a face
ActiveUS20120140091A1Prevent illegal accessEasily detectTelevision system detailsImage enhancementComputer visionComputer graphics (images)
Owner:S1 CORP
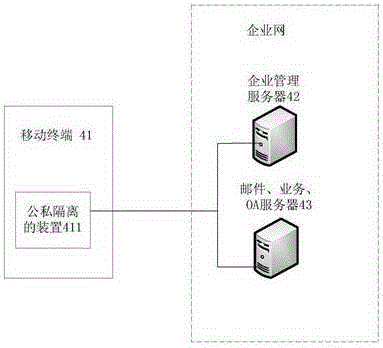
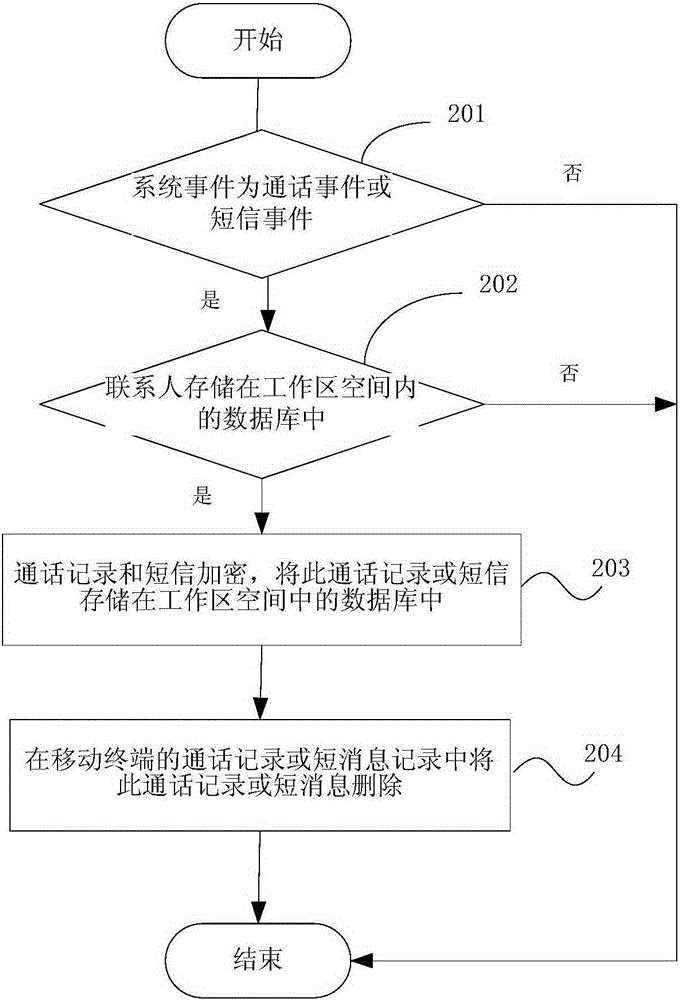
Public and private isolation method and device
ActiveCN103647784AProtection applicationProtect dataDigital data protectionTransmissionMonitoring systemComputer terminal
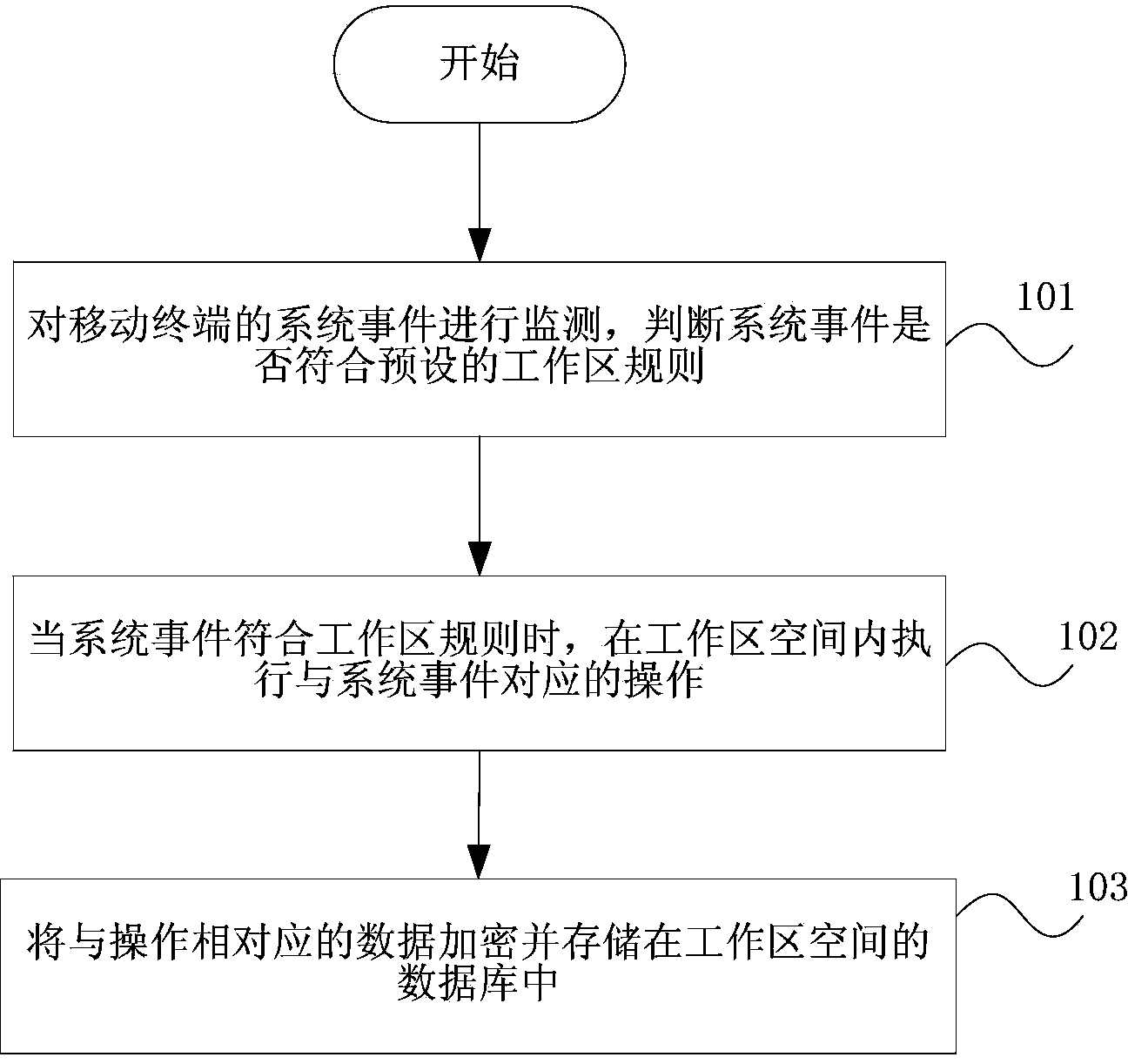
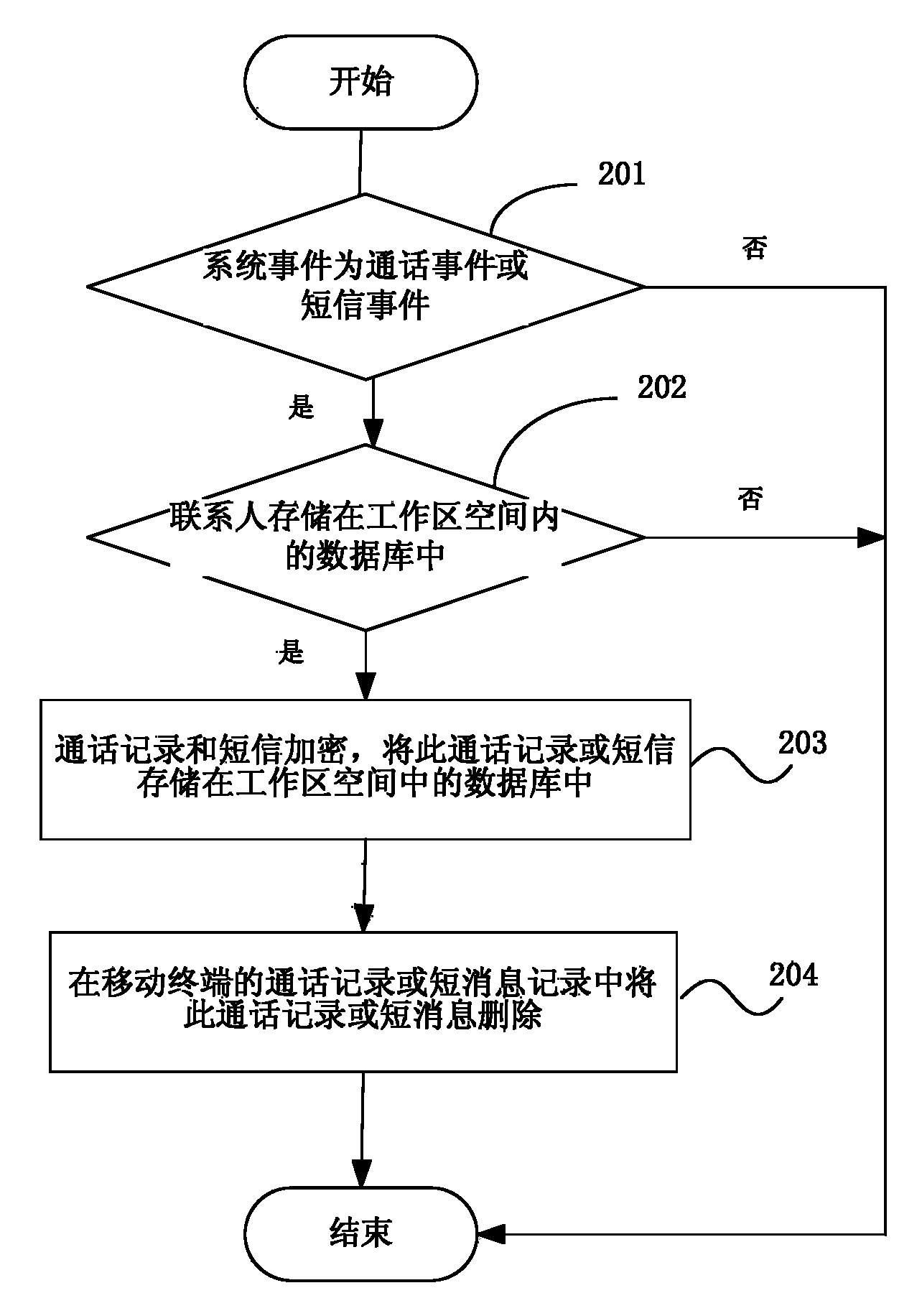
The invention discloses a public and private isolation method and device. The method includes monitoring system events on a mobile terminal, judging whether the system events accord with a preset working area rule, executing operation corresponding to the system events in the working area space on yes judgment and encrypting and storing data corresponding to the operation in a database of the working area space. According to the public and private isolation method and device, a safe independent working area is built on the mobile terminal, all working data are stored in a protected safe area, personal applications cannot visit enterprise data, the enterprise data are prevented from being stored illegally by the personal applications, IT departments can well protect enterprise applications and the enterprise data, indistinctive personal application experience is provided for workers, and the dual purpose effect is achieved.
Owner:BEIJING QIHOO TECH CO LTD
Method for realizing secure access of data in hard disk
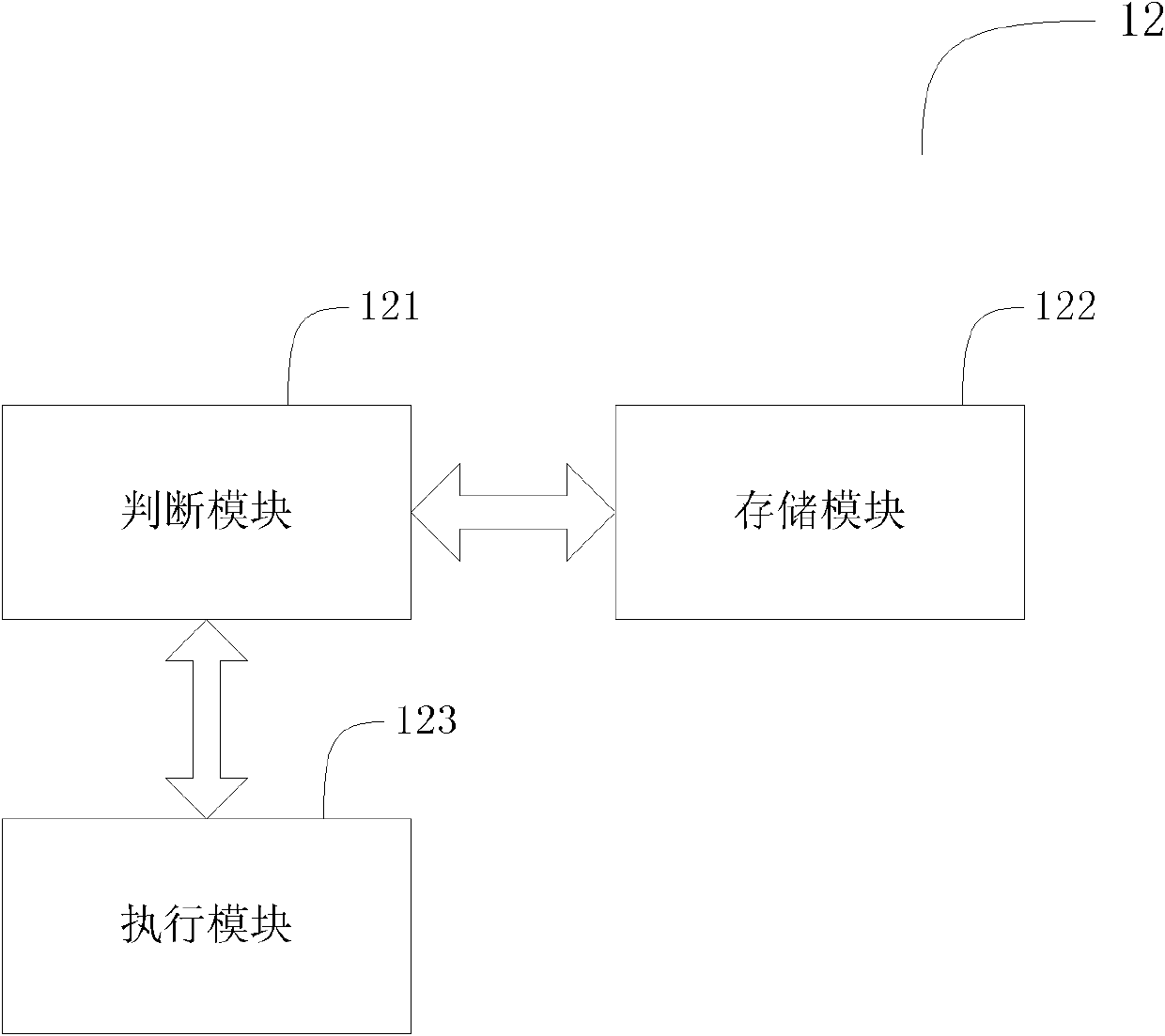
ActiveCN102508792ARealize active defenseImplement proactive alertsUnauthorized memory use protectionDigital data protectionPasswordSecret code
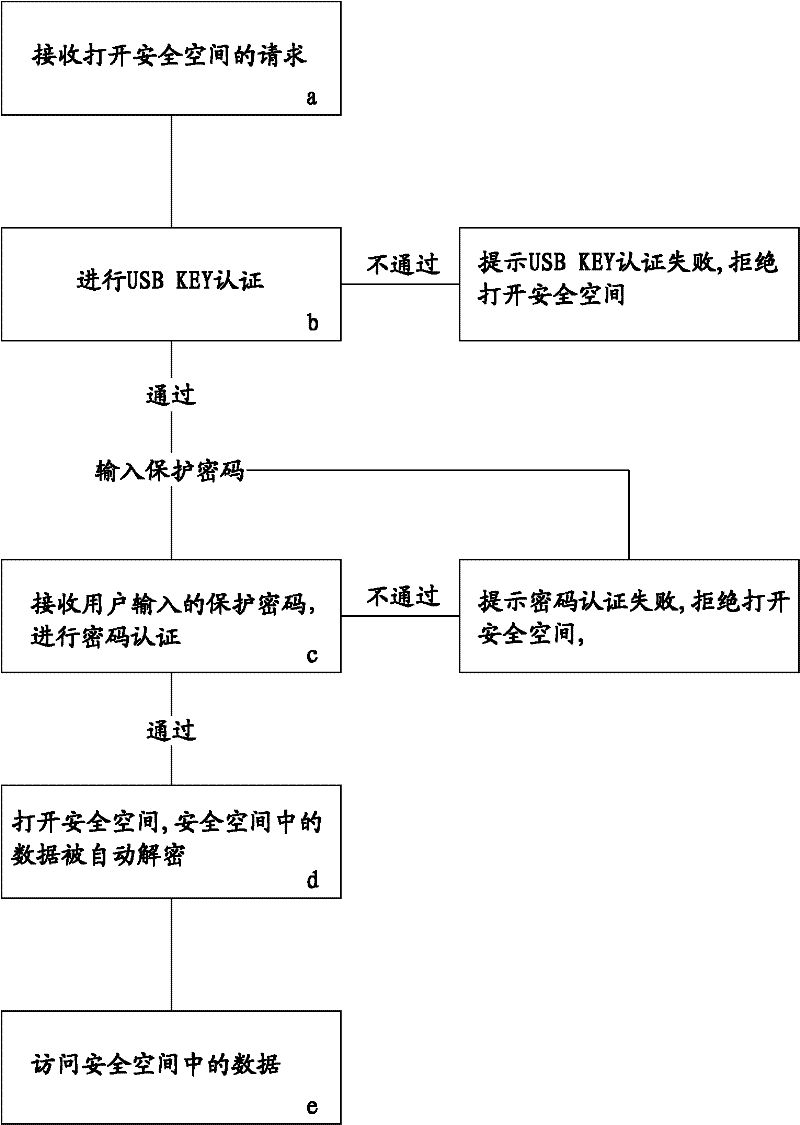
The invention discloses a method for realizing secure access of data in a hard disk. The method is realized by the following steps: establishing a secure space on the hard disk and monitoring the secure space; automatically encrypting the data written in the secure space; associating the secure space with a USBKEY; and setting protection passwords required for opening the secure space. When the data in the secure space is accessed, USBKEY authentication and passwords authentication are carried out in sequence, the secure space can be opened only after the double authentication; and when the situation that the data in the secure space is accessed but the secure space is not opened is monitored, whether the USBKEY authentication passes or not is checked, if not, the accessing is blocked, and a preset ISMG (internet short message gateway) or / and an instant communication port is / are used for sending an alarm information to a user. In the invention, by virtue of the double authentication and the monitoring on the secure space, the secret-divulging risk is reduced, the effects of safety, rapidness and easiness in use are achieved, and the active defense and active alarming are also realized, therefore, the safety is improved to the maximum extent.
Owner:GUANGZHOU SHINE TECH
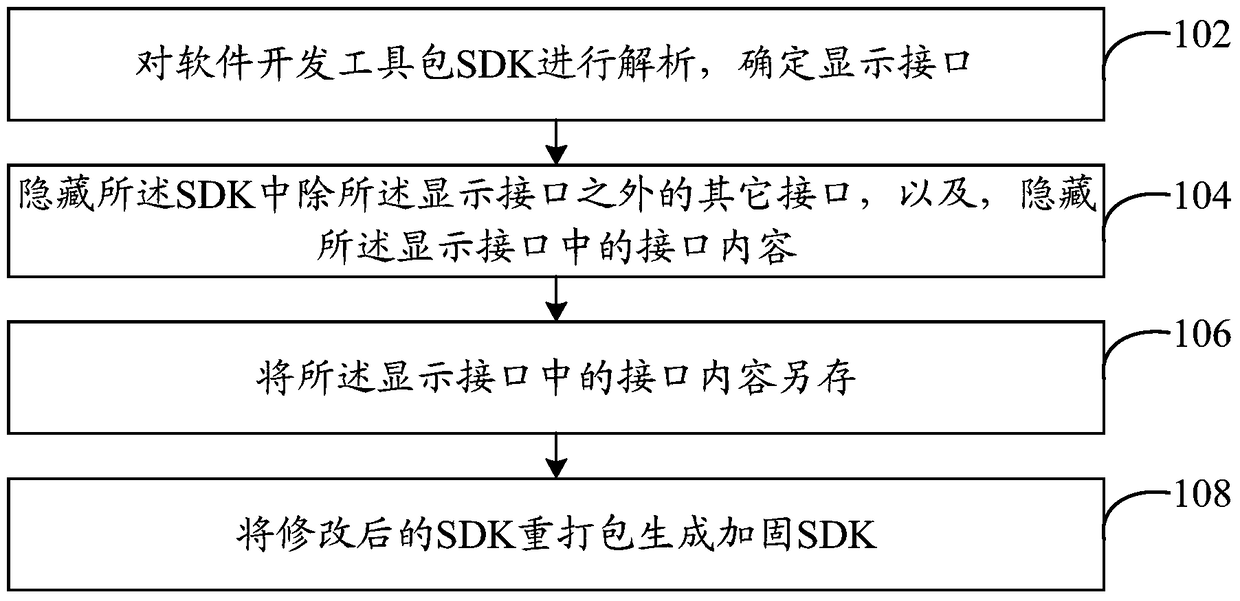
Software hardening method and system
ActiveCN105760721AAchieve protectionPrevent illegal accessPlatform integrity maintainanceProgram/content distribution protectionSoftware developmentComputer engineering
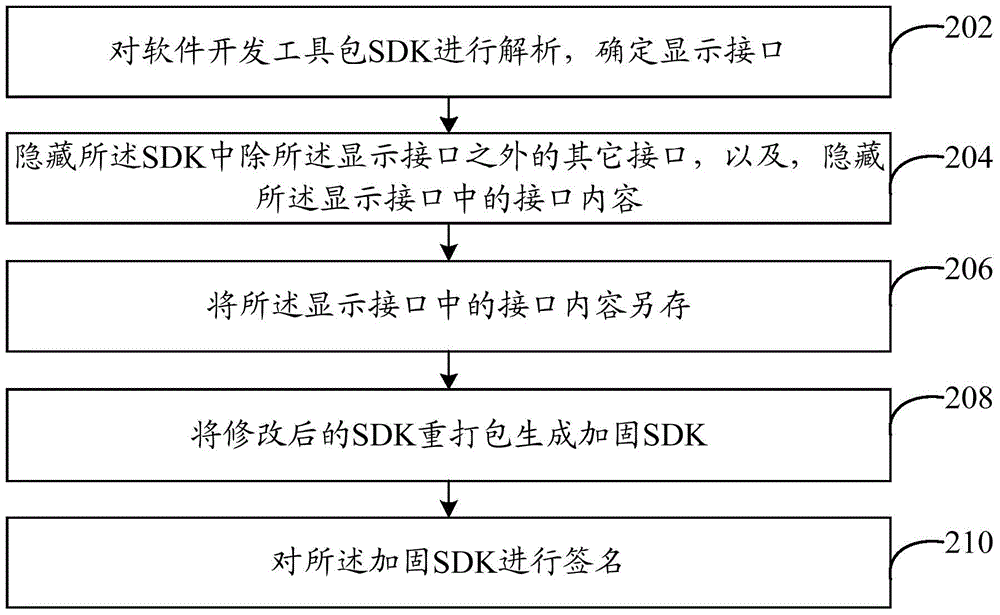
The invention discloses a software hardening method and system. The method comprises the steps of analyzing a software development kit (SDK), and determining a display port; hiding other ports, except the display port, in the SDK, and hiding the port content in the display port; saving the port content in the display port in another place so as to acquire the corresponding port content from the another place when the display port is called; repackaging the corrected SDK to generate a hardened SDK. By the adoption of the method and system, software protection is achieved, software safety is improved, and the rights of developers and users are protected.
Owner:BEIJING QIHOO TECH CO LTD
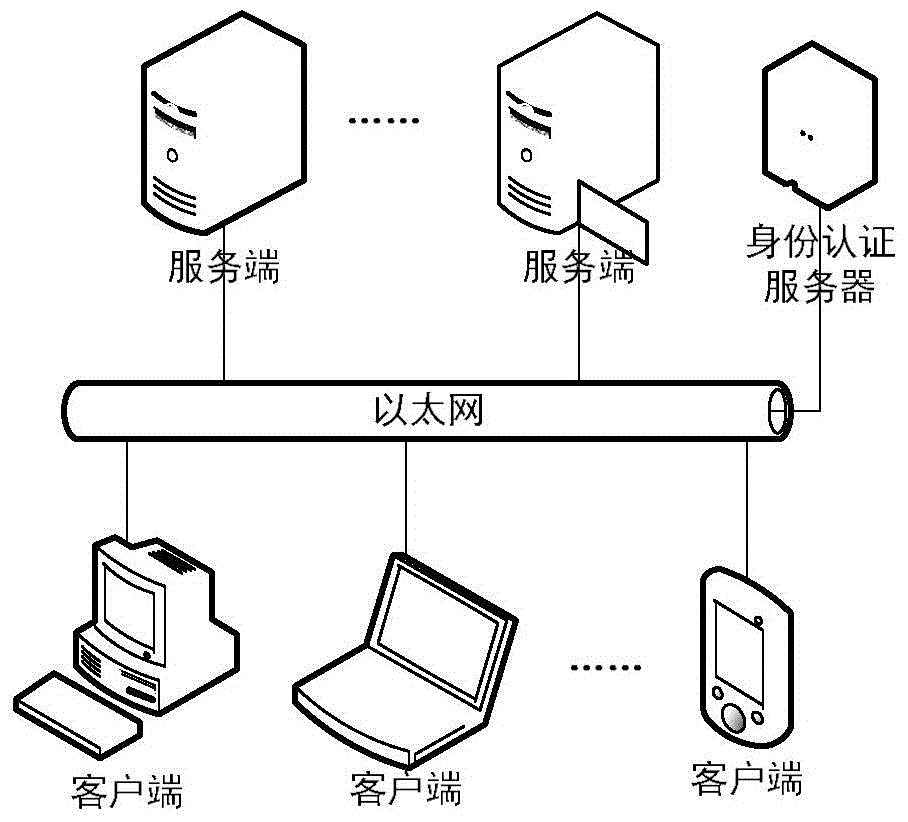
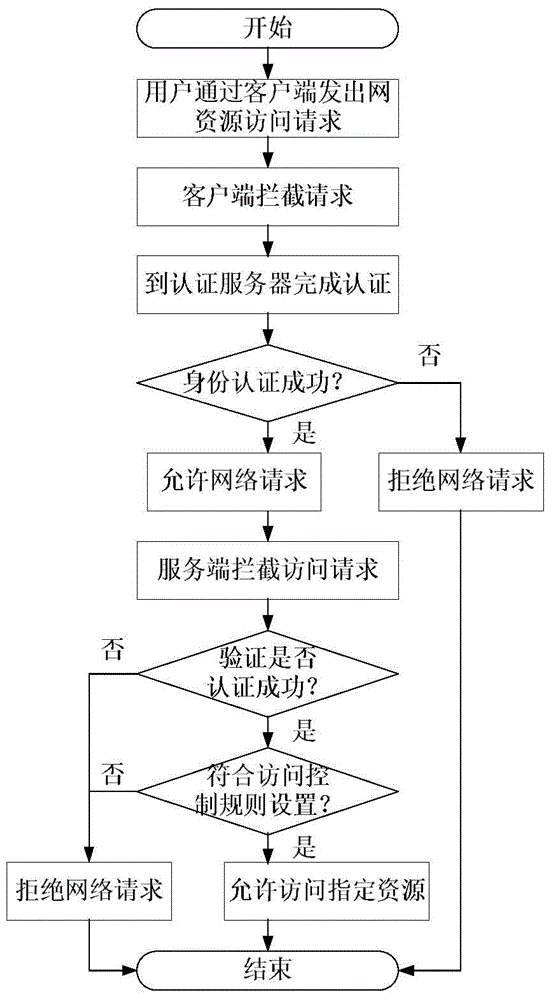
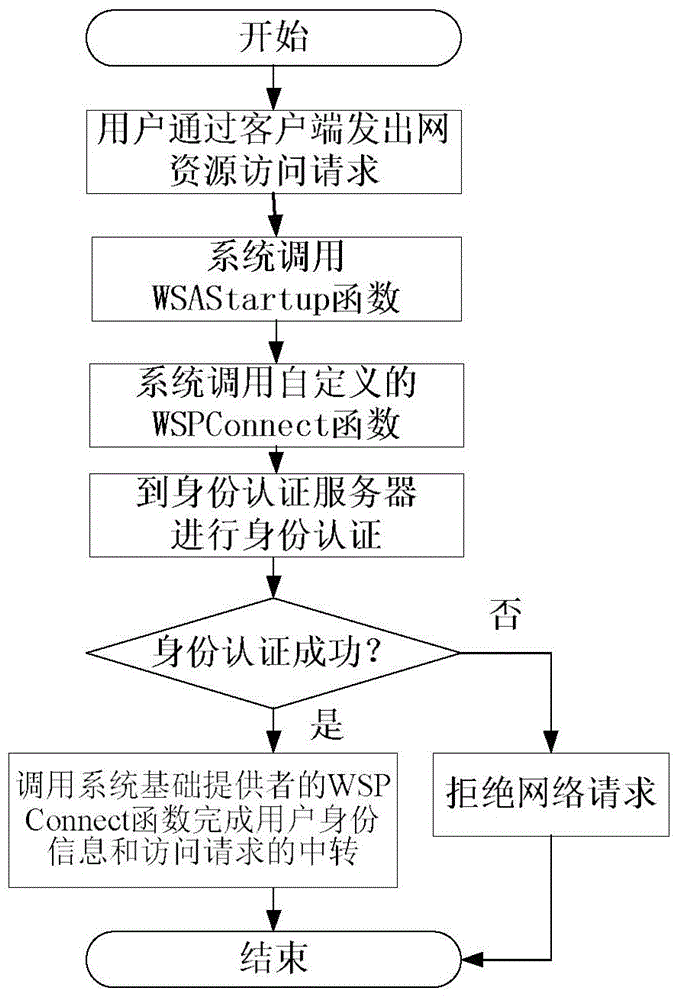
Network-resource-access control method based on identity authentication and data-packet filtering technology
InactiveCN103607374AAccess protectionImplement access controlTransmissionThird partyNetwork connection
The invention discloses a network-resource-access control method based on identity authentication and a data-packet filtering technology. A network access request is filtered at a network-resource-access requesting client and a server side and a network request initiated by a user is intercepted at the client and the user is required to complete identity authentication; after the authentication succeeds, the client forwards user identify information and the access request to the server side; and the server side intercepts the network request and verifies whether the request passes the identify authentication and if so, the user is allowed to access specified network resources. Through SPI programming interfaces provided by Windows Sockets, one layer is inserted into Socket to filter network data packets so that an objective of filtering network connection requests is realized; a third-party identity authentication system is used in combination to realize functions such as identity authentication and the like through interfaces provided by the third-party identity authentication system. The network-resource-access control method based on the identity authentication and the data-packet filtering technology combines the network-resource-access request with user identity authentication so that fine-grit network-resource access can be realized.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
Biometric authentication device, biometric information authentication method
InactiveCN1758266AReduce the number of illegal attacksPrevent leakageAcutation objectsCharacter and pattern recognitionThird partyComputer terminal
Owner:FUJITSU LTD +1
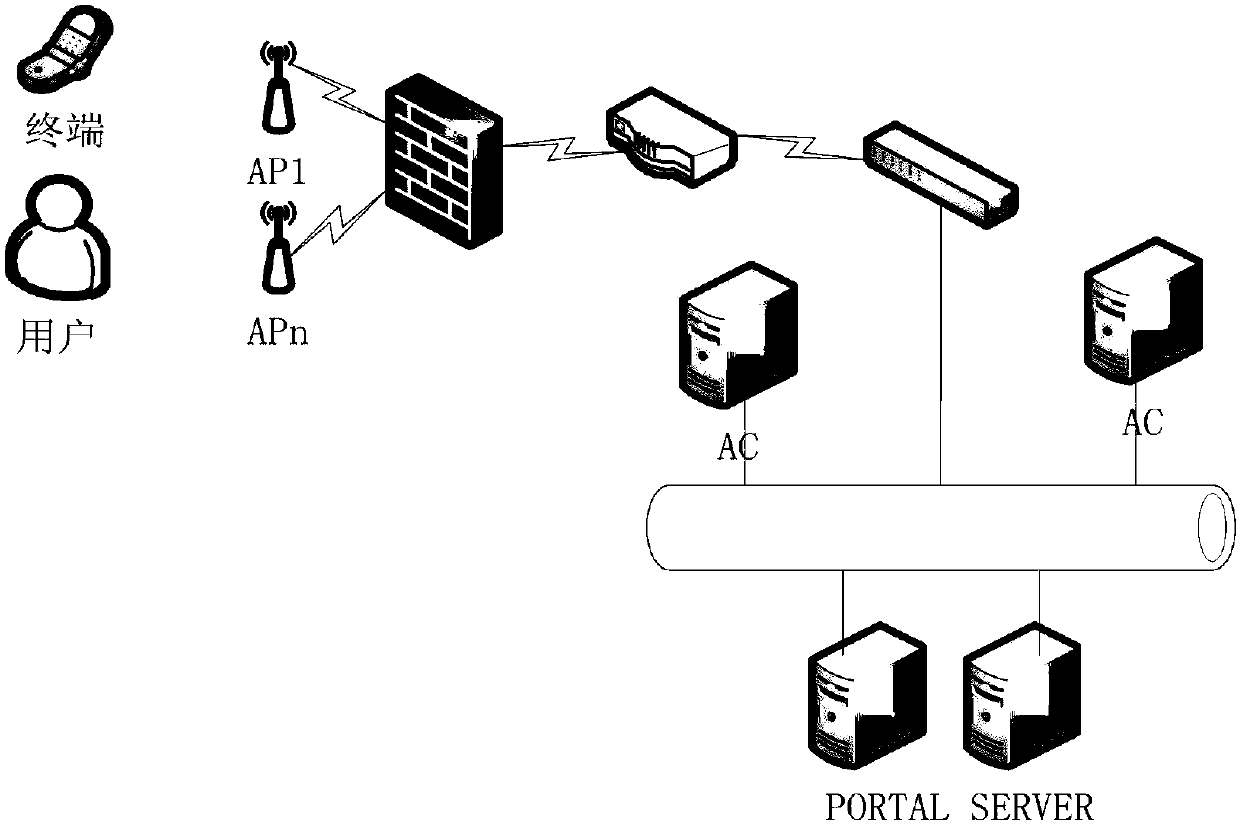
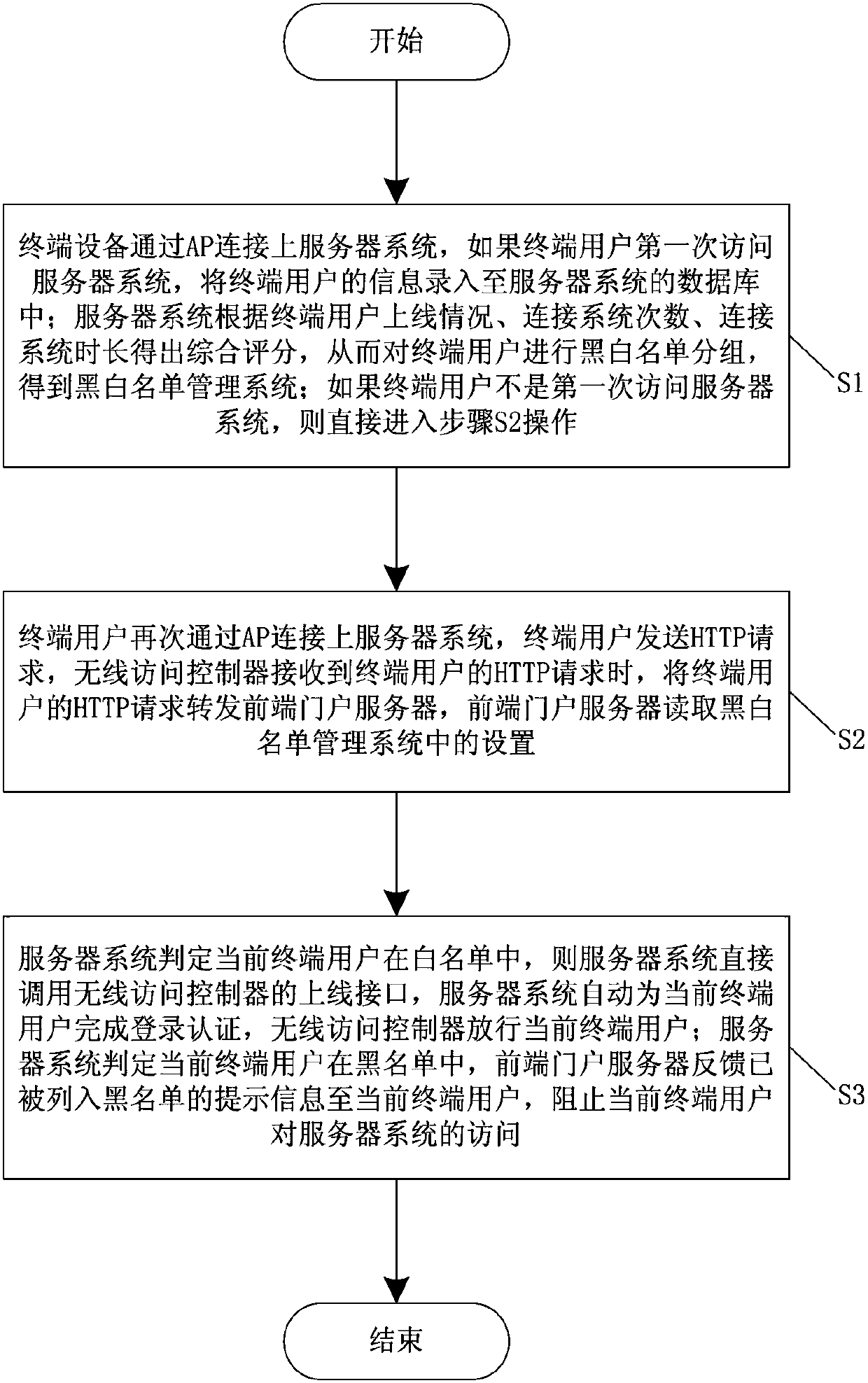
Method for implementing AC black list and white list control based on portal protocol
ActiveCN108040031APrevent illegal accessPromote constructionNetwork topologiesTransmissionComputer securityLocal area network
The invention relates to a black list and white list control method, and particularly relates to a method for implementing AC black list and white list control based on a portal protocol. By performing black list and white list grouping on terminal users to obtain a black list and white list management system, judging whether the current terminal user is within the black list, the current terminaluser can be automatically presented from accessing a server system, the system can effectively prevent illegal access, malicious destruction and access of the terminal user with intentional script injection to the system, the system can effectively and intelligently filter and intercept the terminal users, and provide guarantee for urban security. The method plays an important role in the construction of the entire wireless local area network, and can effectively and intelligently filter and intercept the terminal users, and provide guarantee for urban security. The system automatically monitors the basic information of on-line terminal users, effectively controls the online behaviors of the terminal users for a long time, lays the foundation for the construction of smart cities, and greatly improves the construction of urban wireless local area networks.
Owner:ANHUI SUN CREATE ELECTRONICS
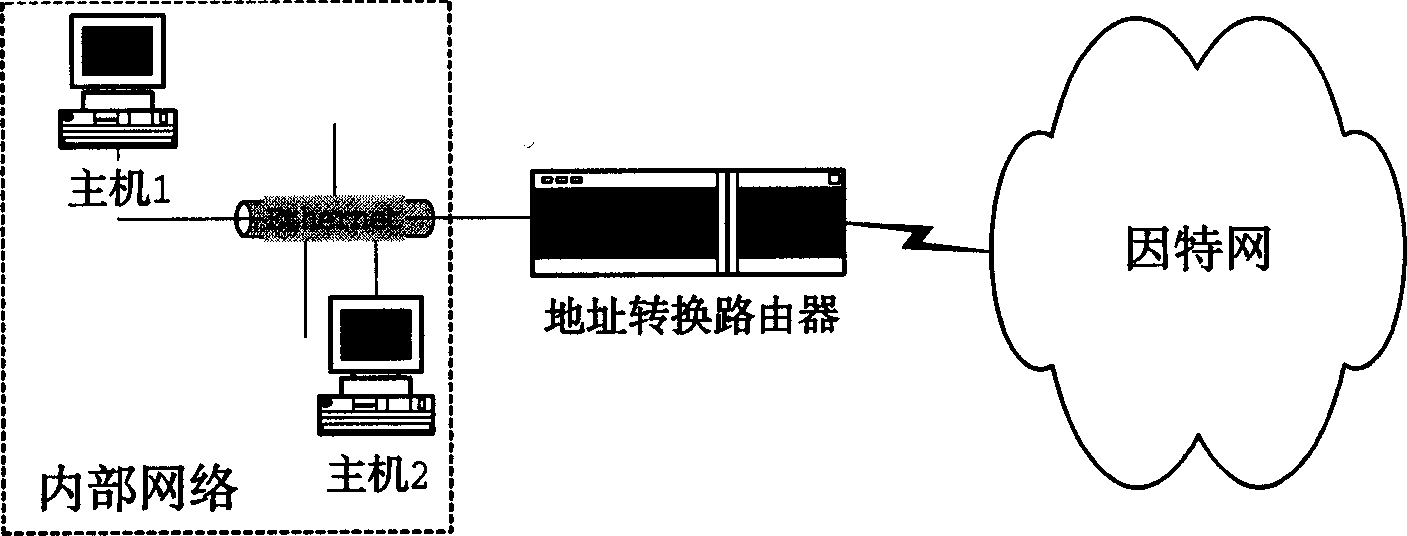
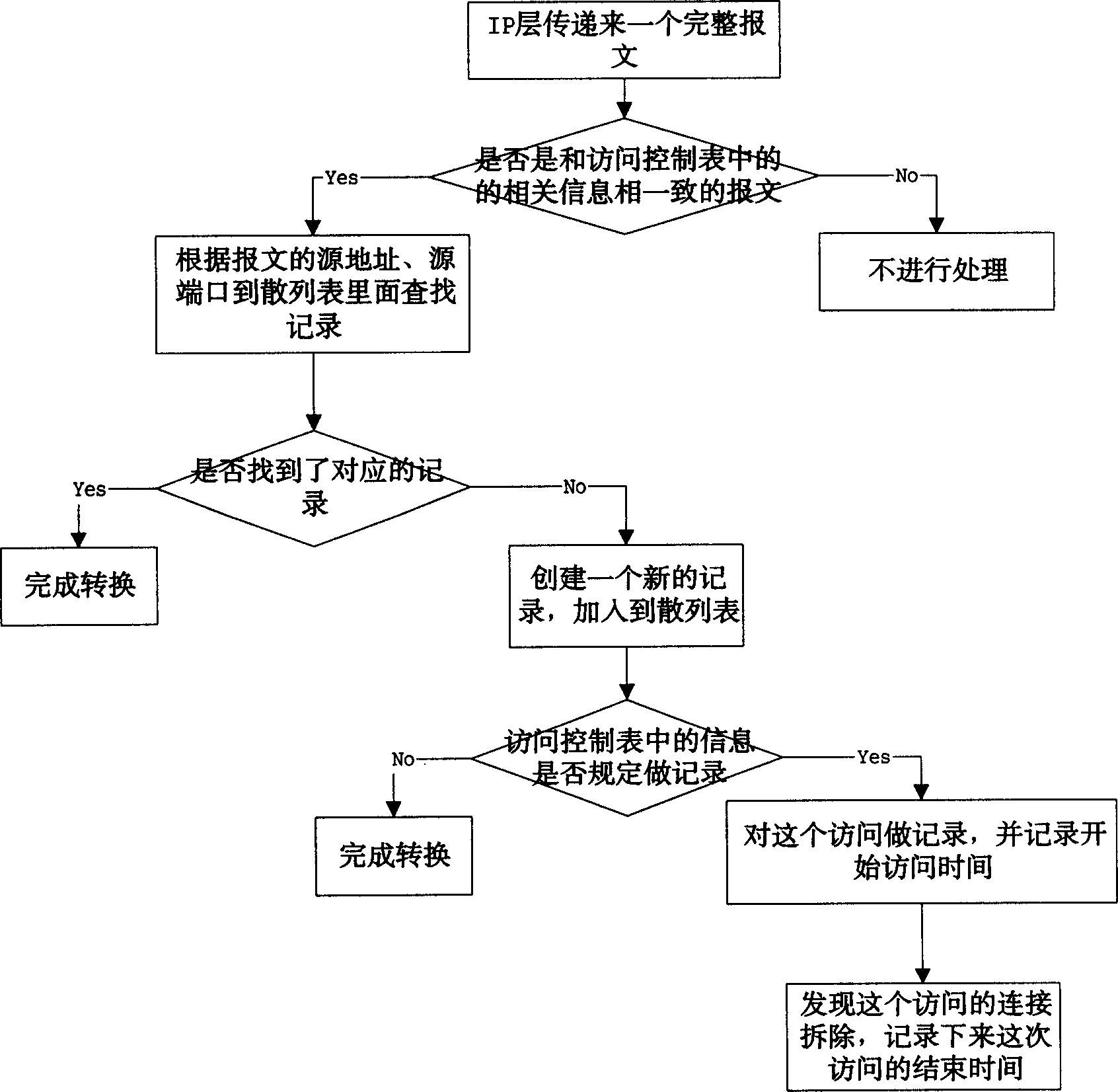
Method for recording access of address changeover users in data transmission process
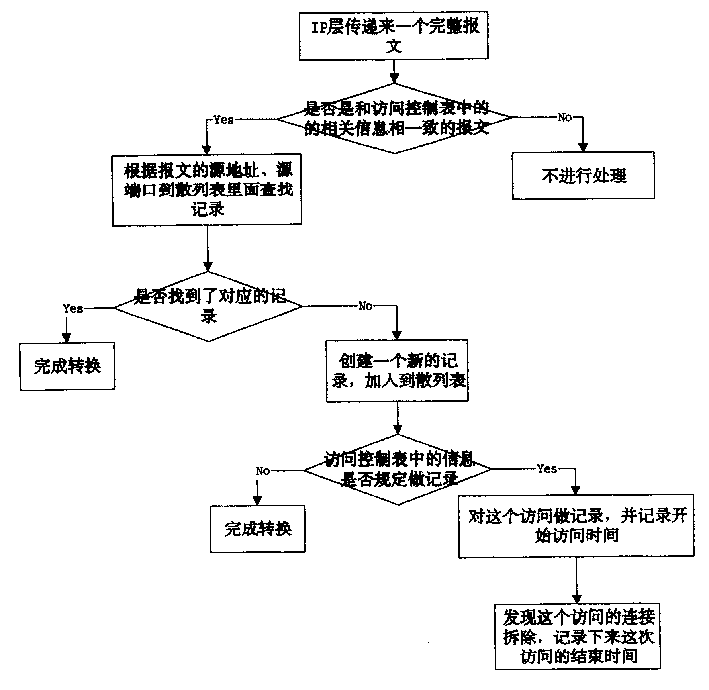
InactiveCN1474570APrevent illegal accessSolve the problem that it is not easy to track usersSecuring communicationStart timeAccess time
This invention relates to a method for registering access of address conversion users in data transmission. This invention first of all sets a message information register hash table at initialization, sets up access control table of each host to compare the information contained in the message and in the access control table not register if they are different or if all information is the same, acorresponding register of the said message is recalled from the hash table according to the source and destination ports to finish the address conversion or add the received message information into the hash table to make judgement to the messages, then register them and finish address conversion to register the access time finally.
Owner:HUAWEI TECH CO LTD
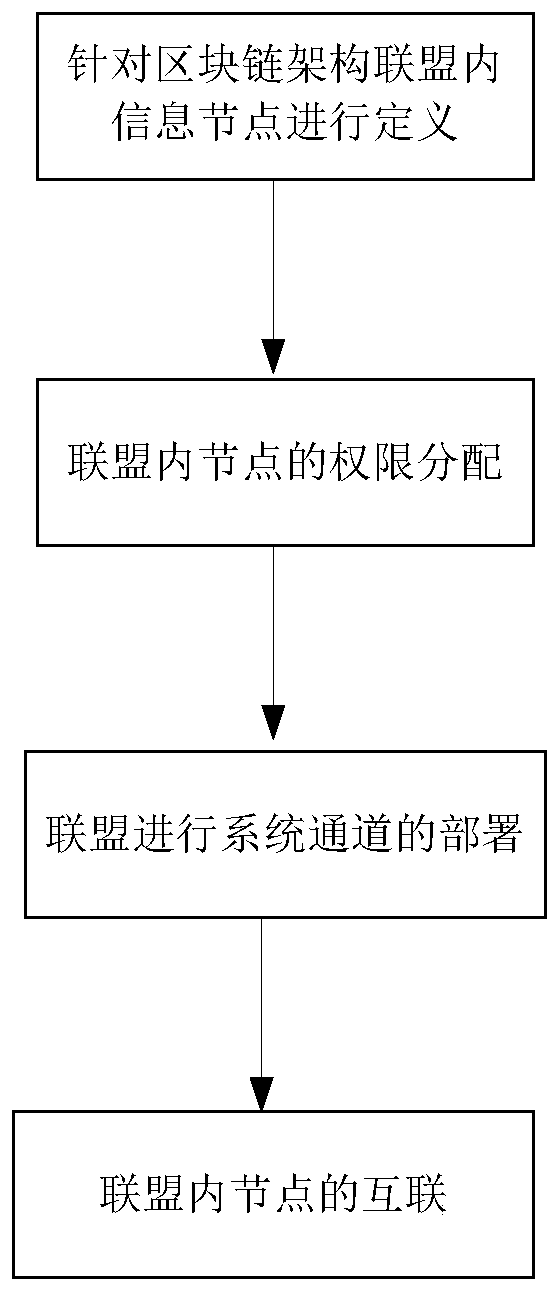
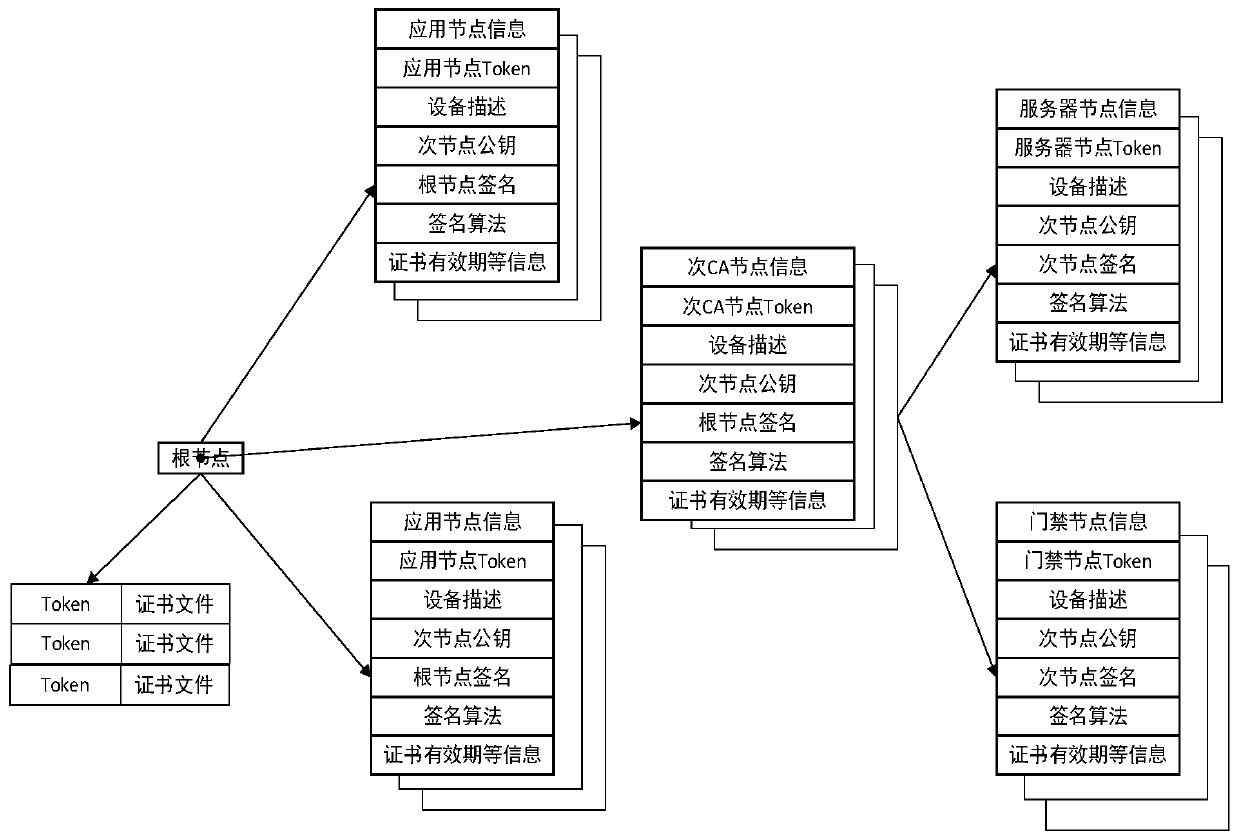
Access control identification system information node interconnection method based on blockchain architecture
ActiveCN111383378AGuarantee normal establishmentAvoid illegal acquisitionDigital data protectionIndividual entry/exit registersData accessInterconnection
The invention relates to an access control identification system information node interconnection method based on a blockchain architecture. Compared with the prior art, the method irons out the defect that numerous child nodes in an access control management system are difficult to connect by utilizing a blockchain technology. The method comprises the following steps: defining information nodes in a blockchain architecture alliance; performing authority distribution of nodes in the alliance; enabling the alliance to deploy a system channel; and performing the interconnection of nodes in the alliance. According to the invention, the member and channel management of the blockchain alliance is realized by using the digital certificate; the data separation and limitation of members to data channel access are adopted to achieve data mutual access of alliance members, it is guaranteed that the alliance members cannot obtain excessive information except service correlation, and the establishment of information node data circulation channels under data isolation and data access channel mutual isolation is guaranteed.
Owner:合肥鼎方信息科技有限公司
Temporary passenger access control self-service registration device and control system thereof
PendingCN113920633AAvoid enteringImprove practicalityIndividual entry/exit registersBurglar alarmControl systemPedestrian
The invention discloses a temporary passenger access control self-service registration device and a control system thereof. The temporary passenger access control self-service registration device comprises a pedestrian area and a driving area, the pedestrian area comprises two electric blocking doors and three first stand columns, and one side of the first stand column located at one edge position is fixedly provided with an in-entrance registration plate; one side of the first stand column located at the other edge position is fixedly provided with a going-out identification mechanism, the vehicle running area comprises two vehicle handrails and four second stand columns, one side of each vehicle handrail is provided with a rising and falling adjusting mechanism, and the opposite sides of the two second stand columns located at the middle position are each fixedly provided with an identification camera. According to the temporary guest access control self-registration device and the control system thereof, the identification module can complete information self-registration of temporary guests, so that the situation that manual intervention is needed to complete entry of the temporary guests is avoided, the practicability of the access control system is improved, meanwhile, follow-up screening work on personnel circulation is facilitated, and the safety and practicability of the access control system are improved.
Owner:湖南云脸智联科技有限公司
Language independent login
InactiveUS8752164B2Safe and secureEasy to mergeElectric signal transmission systemsDigital data processing detailsLanguage independenceComputer science
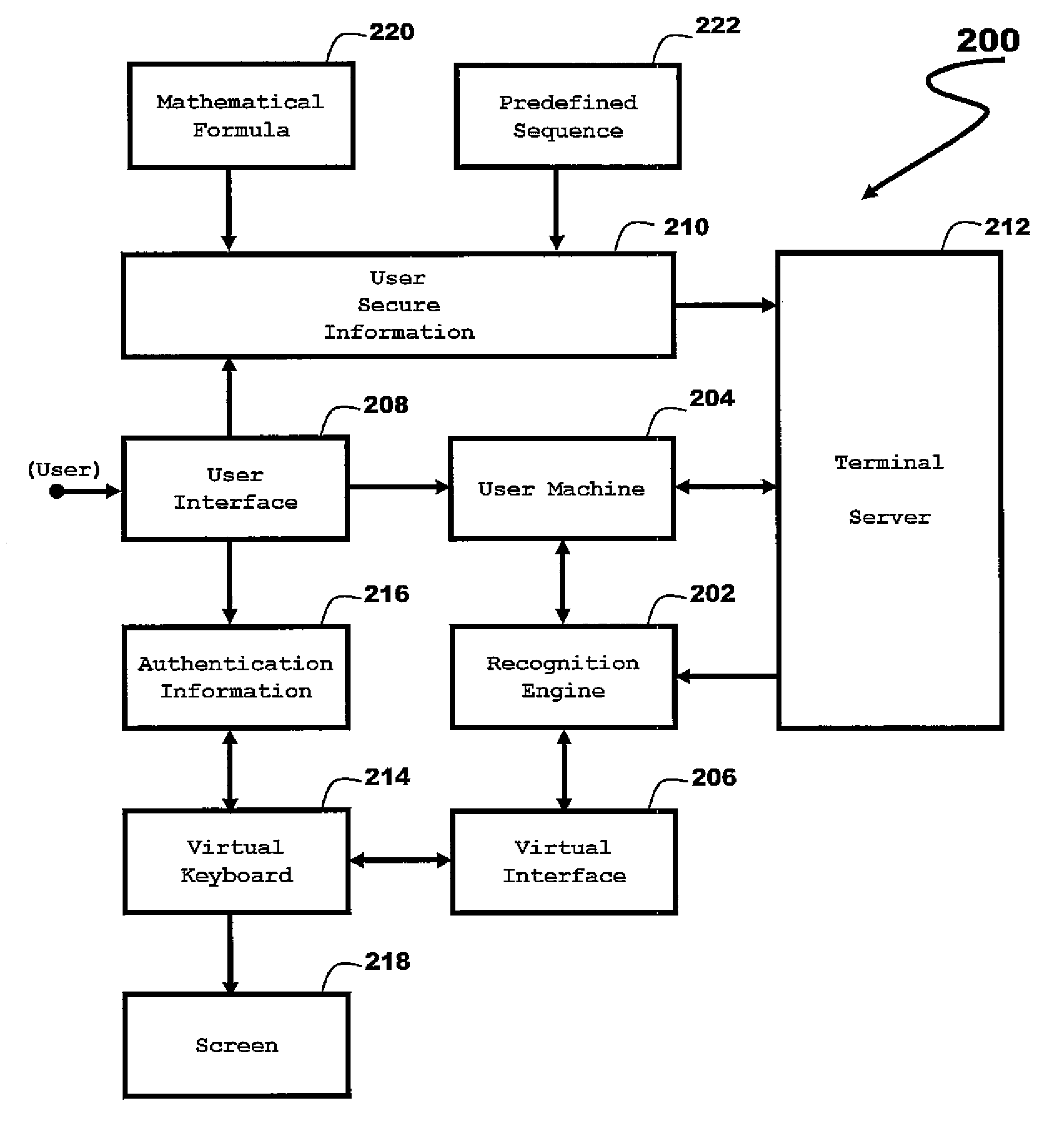
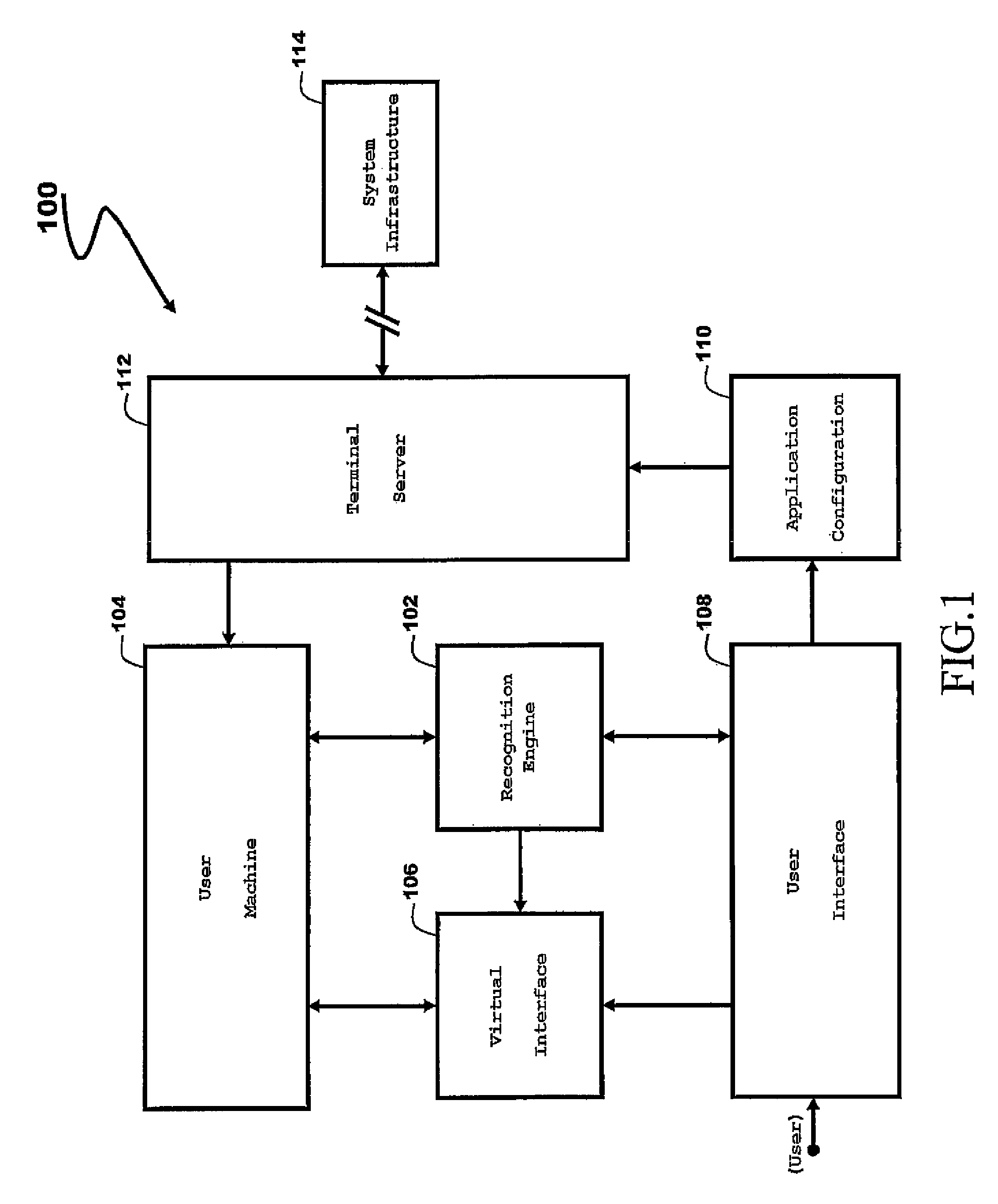
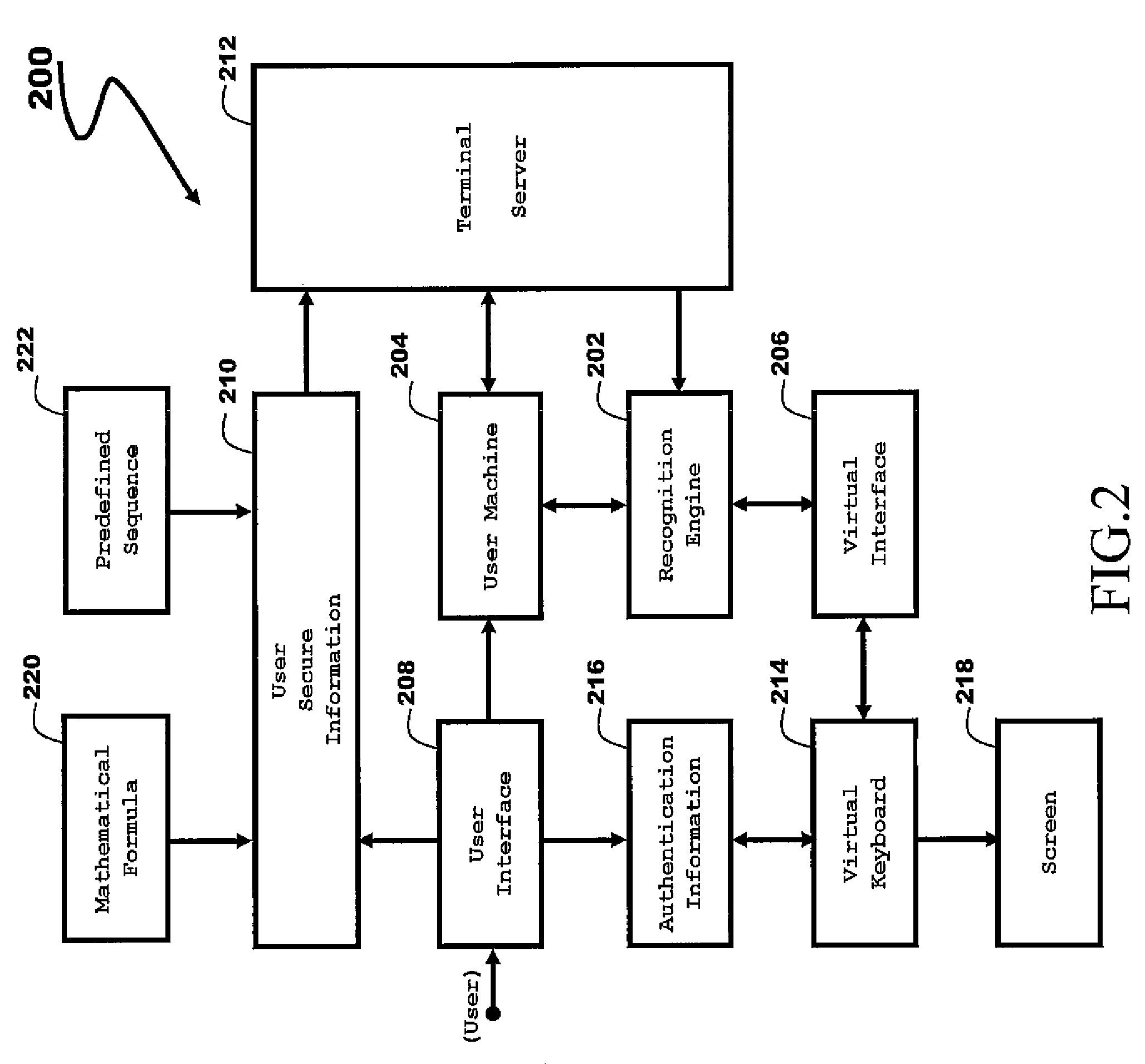
The present invention prevents illegitimate access to a user computing machine. A method in accordance with an embodiment includes: setting an authentication routine in the user computing machine; generating a virtual keyboard on the user computing machine; entering a user identification through the virtual keyboard, the user identification being entered according to a virtual keyboard form factor; comparing the entered user identification with a secure user identification previously stored in the user computing machine; and validating the user access to the user computing machine if a match occurs, otherwise denying access.
Owner:IBM CORP
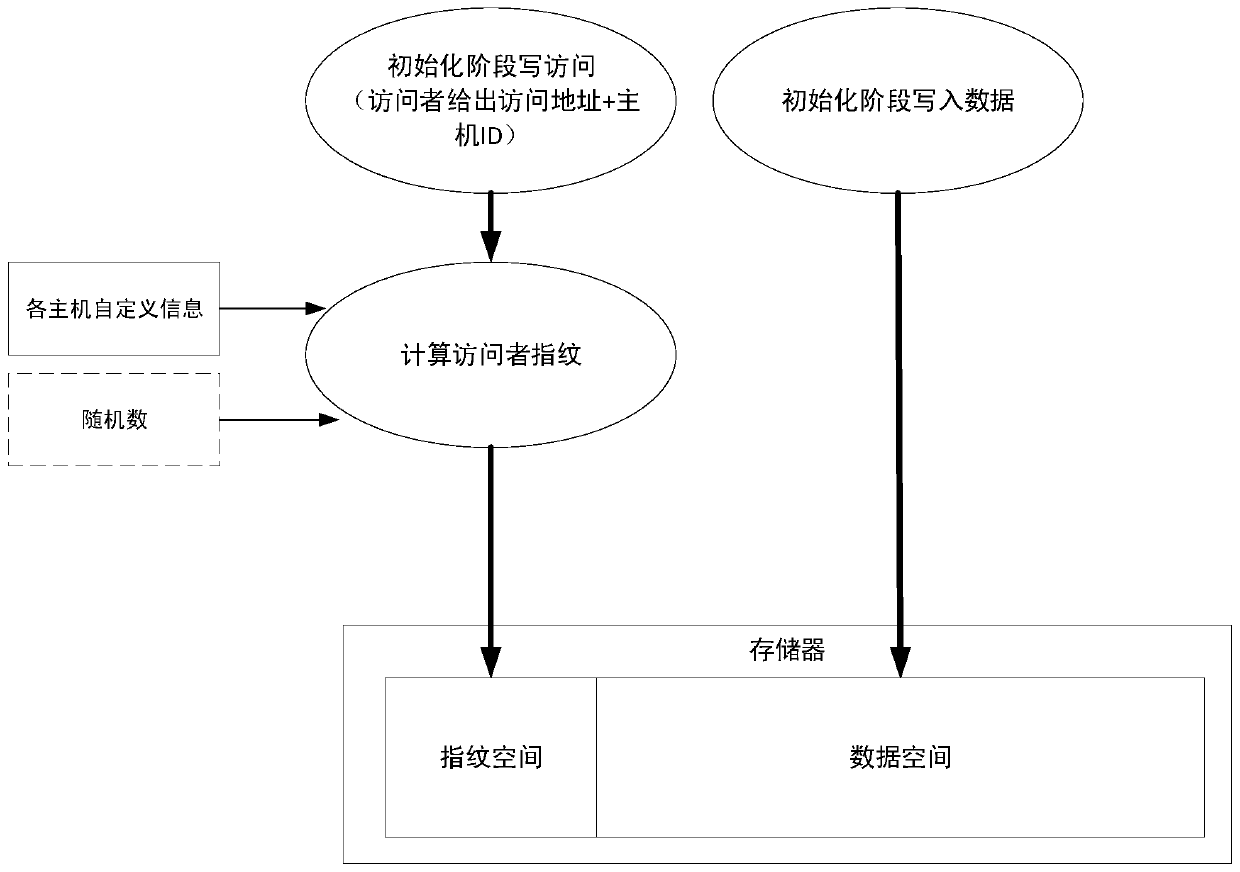
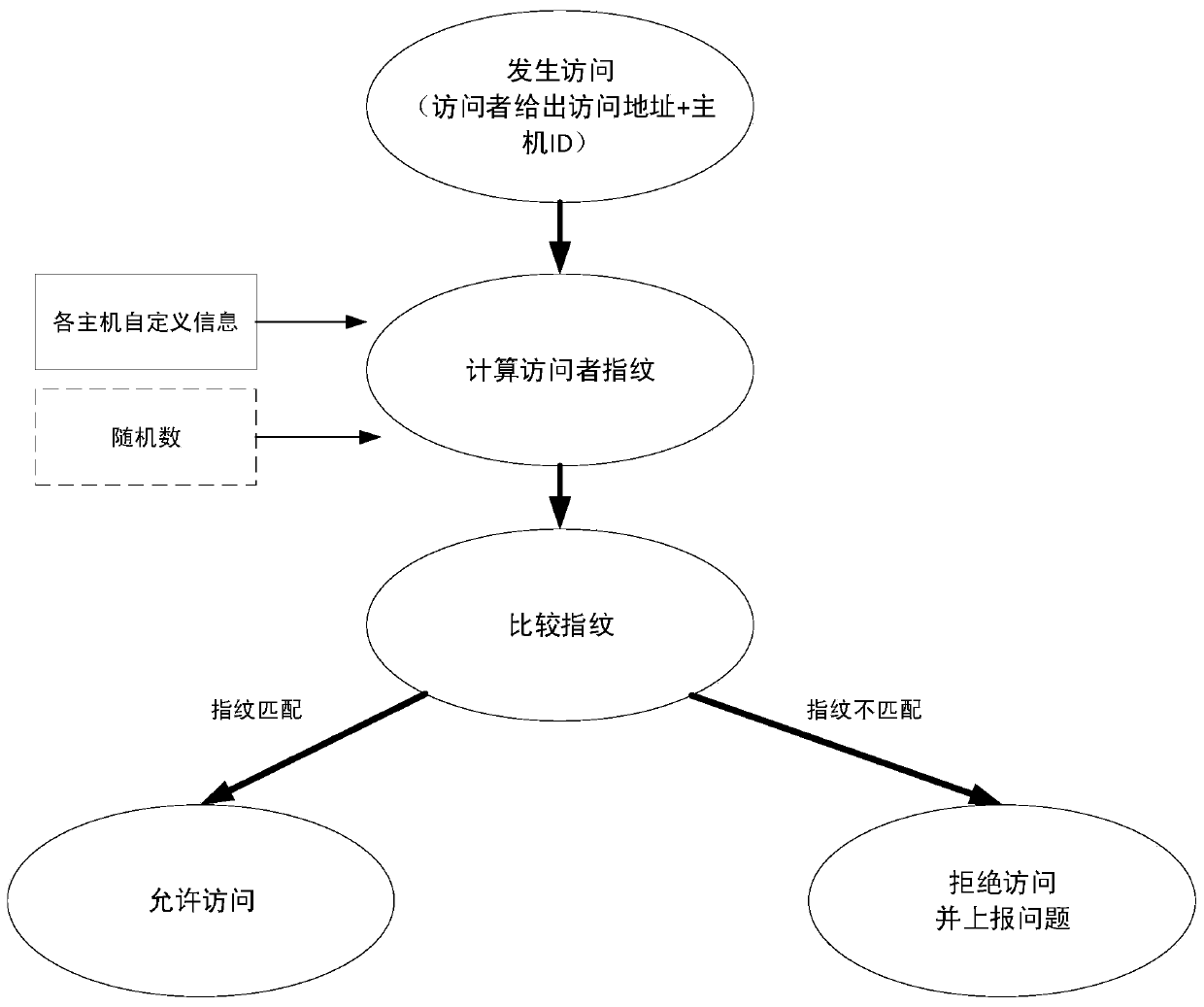
Multi-host shared storage system and data integrity protection method
InactiveCN110443070AImprove integrityPrevent illegal readingDigital data protectionInternal/peripheral component protectionData integrityData access
The invention discloses a multi-host shared storage system and a data integrity protection method. The fingerprint for the data is calculated according to the feature information of the data owner system, the address information needing to be stored and the like, and the fingerprint and the data are written into the storage medium together. Therefore, in the data access process, whether the fingerprint information corresponds to the original fingerprint information or not can be judged on the basis of the system identity of the system corresponding to the visitor, the provided address and other information, and therefore the integrity of data is protected between different systems. Particularly, since in the data access process, fingerprint matching needs to be carried out on the system requested to be accessed in advance, illegal access can be prevented and the system sending the abnormal data access request can be reported in time when fingerprint mismatching is judged, traceabilityis achieved, illegal reading and tampering of data can be detected and prevented, integrity of data between different systems is protected, and data safety is greatly enhanced.
Owner:NANJING SEMIDRIVE TECH CO LTD
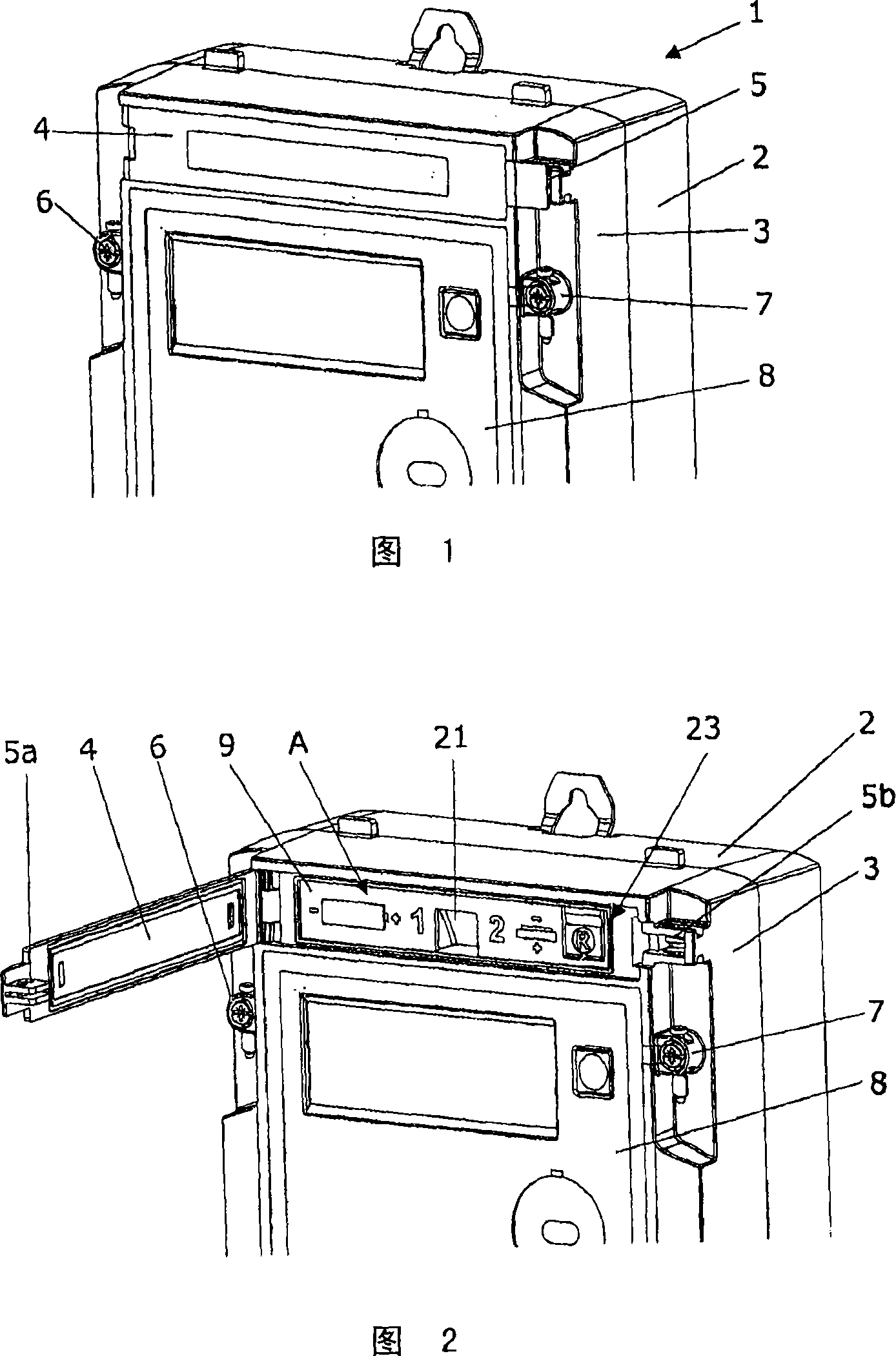
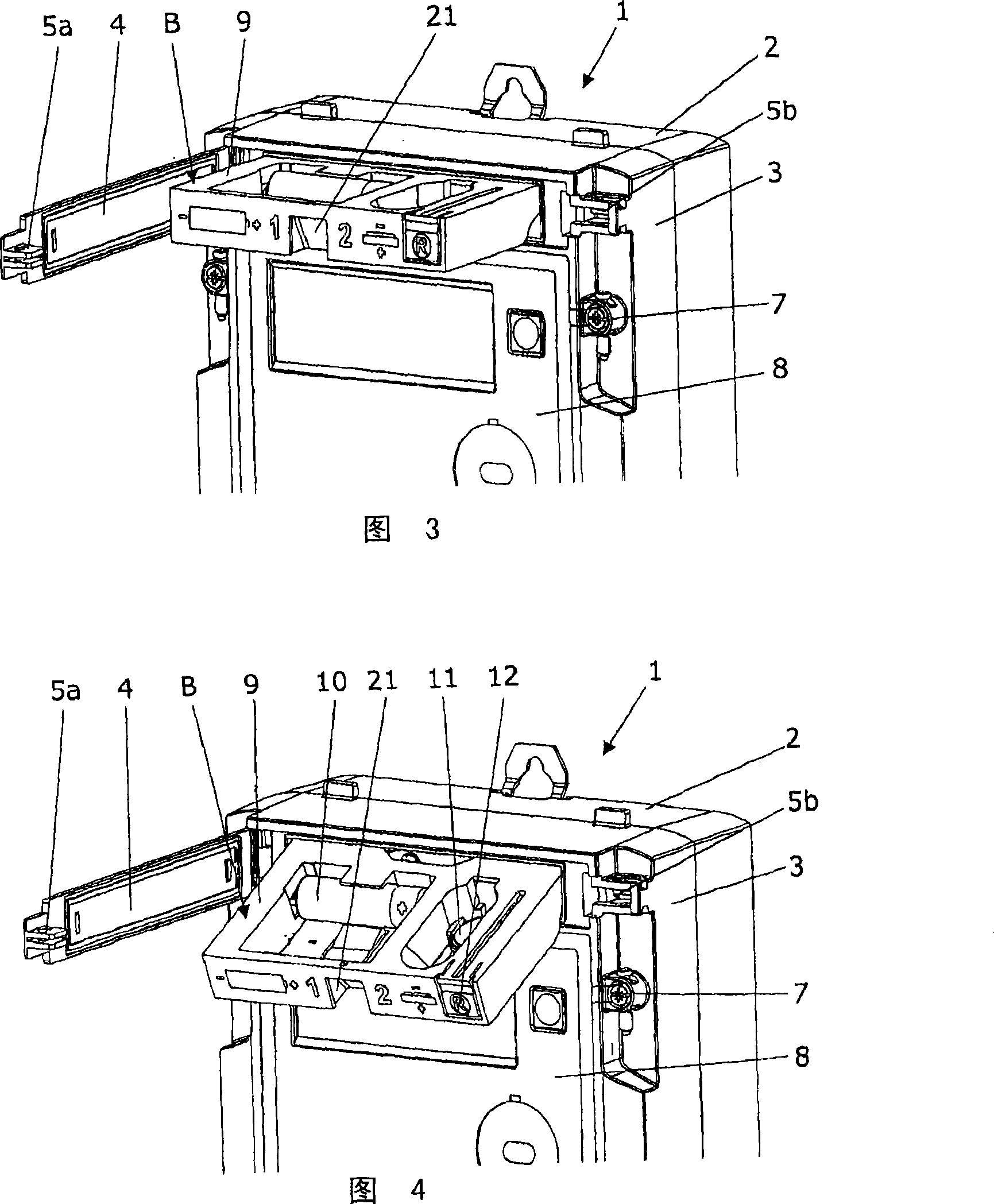
Functional unit for an electrical or electronic appliance
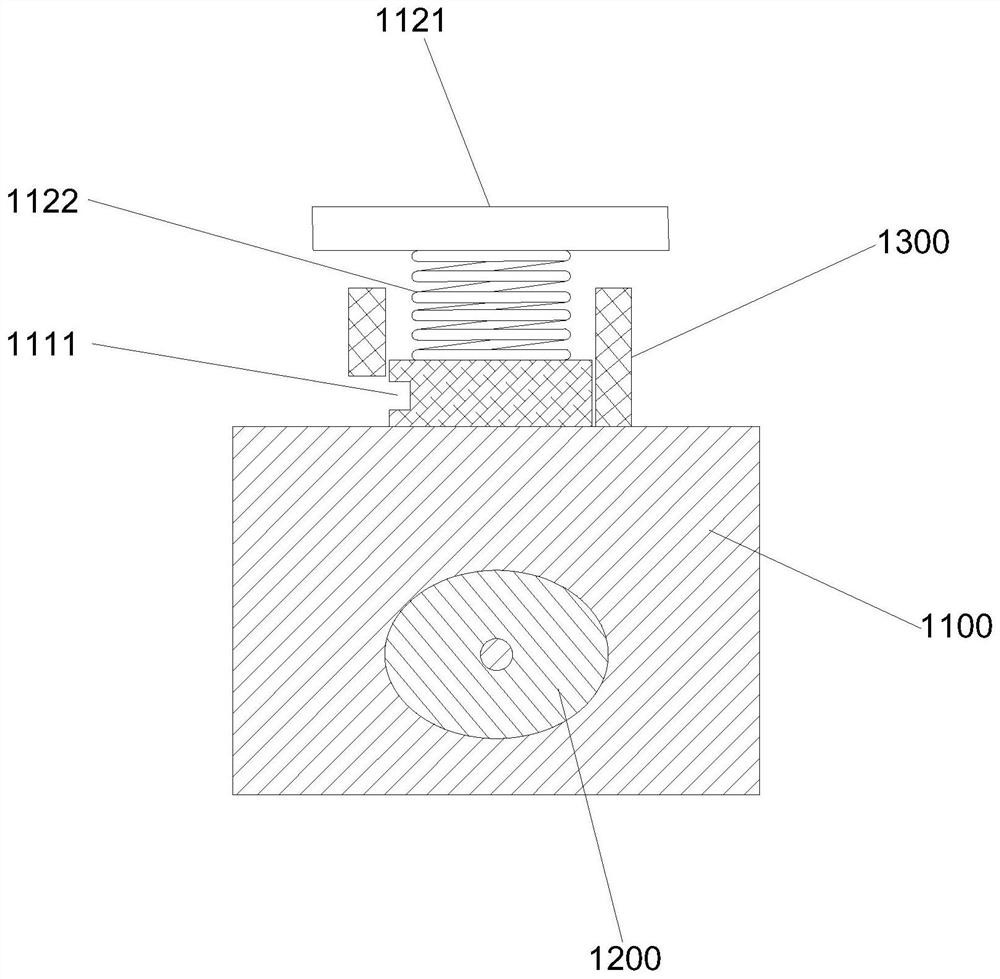
InactiveCN101238377AEliminate potential hazardsPrevent illegal accessCasings/cabinets/drawers detailsTime integral measurementEngineeringElectronic instruments
Unit has batteries (10, 11) and a button (12) including spring clips in an operating position of the unit. The batteries and the button are free from the spring clips in a service position (B) of the unit. The unit inaccessibly covers the spring clips in the operating position and in the service position. The unit is arranged in an operating condition of the apparatus and is reverse operated to handle the batteries and the button.
Owner:兰迪斯+盖尔股份有限公司
Network access method and system for autonomous cloud in autonomous network
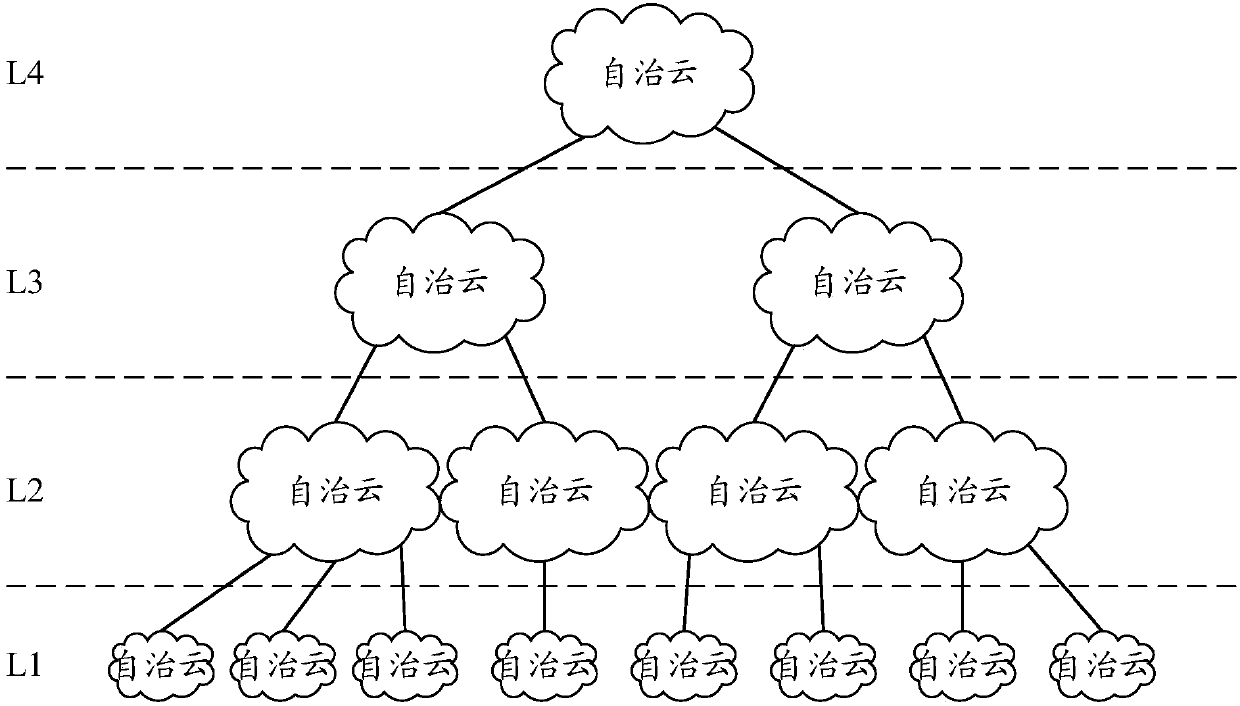
ActiveCN109728982AEasy to manageStable rateData switching by path configurationAccess methodNetwork method
The embodiment of the invention provides a network access method and system for an autonomous cloud in an autonomous network. The autonomous network comprises a plurality of autonomous clouds distributed layer by layer, in each autonomous cloud, a main control server and a micro-cloud server access to a switching network, a terminal sub-control server and a terminal access to another switching network, and a boundary sub-control server and a boundary router access to a third switching network; the method comprises the following steps: the (N-1)th layer of autonomous cloud accesses the network;the boundary router of the (N-1)th layer of autonomous cloud sends a network access configuration command to the main control server of the (N-1)th layer of autonomous cloud, so that the main controlserver of the Nth layer of autonomous cloud accesses the (N-1)th layer of autonomous cloud;; and the boundary router of the (N-1)th layer of autonomous cloud sends a network access configuration command to the main control server of the Nth layer of autonomous cloud, so that the main control server of the (N-1)th layer of autonomous cloud accesses the Nth layer of autonomous cloud;. According tothe embodiment of the invention, the stability, safety and manageability of the autonomous network are improved, and the stable operation of the autonomous network is ensured.
Owner:BEIJING QIANTANG NETWORK TECH
A professional ability big data knowledge graph data access management method and system
ActiveCN114547423BReduce lossesPrevent illegal accessDigital data authenticationText database queryingDatabase serverData access
The invention provides a data access management method and system for professional ability big data knowledge graph data, including a server receiving a user's access request for professional ability big data knowledge graph data from an intranet; The intranet access database; the server processes the intranet access database, and obtains the N-level nodes in its parent node for each leaf node; the server receives the user's access request from the external network to the professional ability big data knowledge graph data, and the server determines the The leaf node accessed by the user from the external network this time; determine whether the leaf node accessed from the external network falls within the scope of the N-level node domain; when the leaf node accessed from the external network does not fall into the N-level node domain When it is within the range, the server determines that the user account is abnormal, and terminates the user's access to the professional ability big data knowledge graph.
Owner:杜江波
A method and device for public-private isolation
ActiveCN103647784BProtect dataPrevent illegal accessDigital data protectionTransmissionMonitoring systemComputer terminal
The invention discloses a public and private isolation method and device. The method includes monitoring system events on a mobile terminal, judging whether the system events accord with a preset working area rule, executing operation corresponding to the system events in the working area space on yes judgment and encrypting and storing data corresponding to the operation in a database of the working area space. According to the public and private isolation method and device, a safe independent working area is built on the mobile terminal, all working data are stored in a protected safe area, personal applications cannot visit enterprise data, the enterprise data are prevented from being stored illegally by the personal applications, IT departments can well protect enterprise applications and the enterprise data, indistinctive personal application experience is provided for workers, and the dual purpose effect is achieved.
Owner:BEIJING QIHOO TECH CO LTD
Pole-mounted circuit breaker switch structure
ActiveCN112701006AEasy accessSimple structureHigh-tension/heavy-dress switchesAir-break switchesStructural engineeringArc extinction
A pole-mounted circuit breaker switch structure is disclosed in the invention, and comprises a connecting sleeve and a connecting column, a first binding post and a second binding post are arranged on the connecting sleeve and the connecting column respectively, the connecting column is connected into the connecting sleeve in a sliding mode and is in clearance fit with the connecting sleeve, the connecting sleeve is a cylinder with one end open, an isolation spring is arranged at the bottom of the connecting sleeve, one end of the connecting column is extruded to the isolation spring, the other end of the connecting column extends out of the connecting sleeve, and the second binding post can extrude the isolation spring along with the connecting column to be communicated with the first binding post; a second positioning hole is formed in one side of the connecting column, and a release is inserted into the second positioning hole to position the connecting column; and at least the connecting column is made of a ceramic material. According to the device, the generation space of the arc can be greatly reduced, the generation time of the arc is greatly shortened, and the arc extinguishing effect and reliability are improved.
Owner:DONGFANG ELECTRONICS +1
Image processing method and image processing device
InactiveCN1708095APrevent illegal accessPrevent leakageComputer security arrangementsOther printing apparatusImaging processingRadiology
Provided is an image processing method that uses an image processing device to receive image data and one or more reference information that is referred to when performing processing on the image data, performs processing corresponding to the reference information on the received image data, and performs processing corresponding to the reference information based on the received reference. The information is used to determine the confidentiality level of the image data to be processed, the processing to be executed is determined based on the result of the determination, and the determined processing is executed.
Owner:SHARP KK
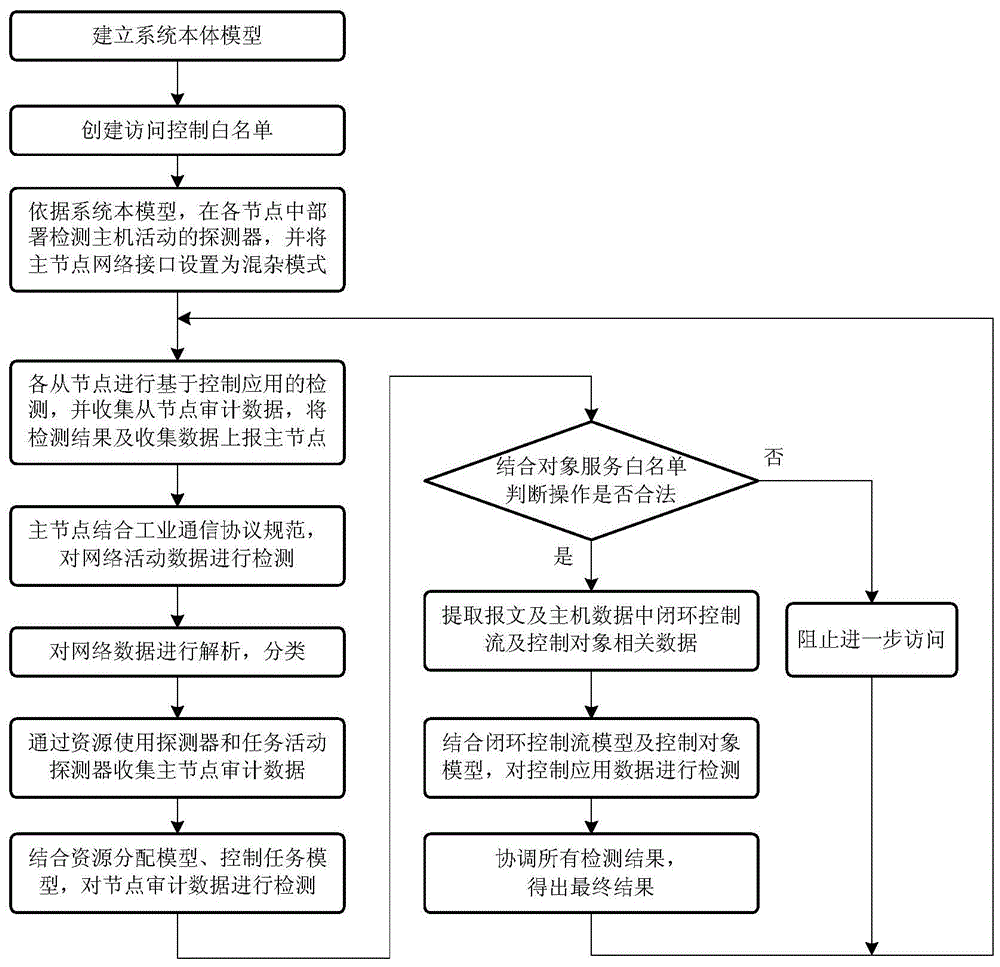
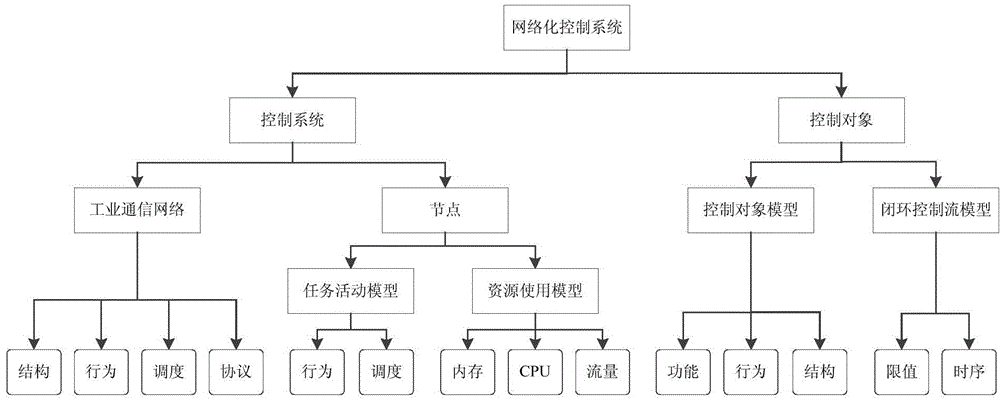
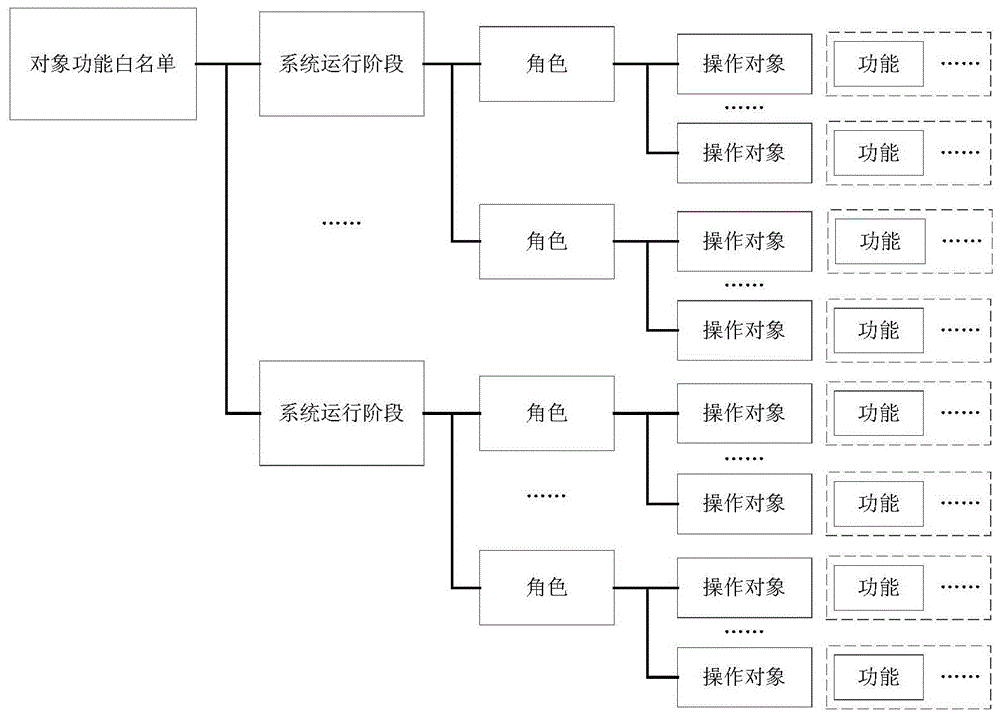
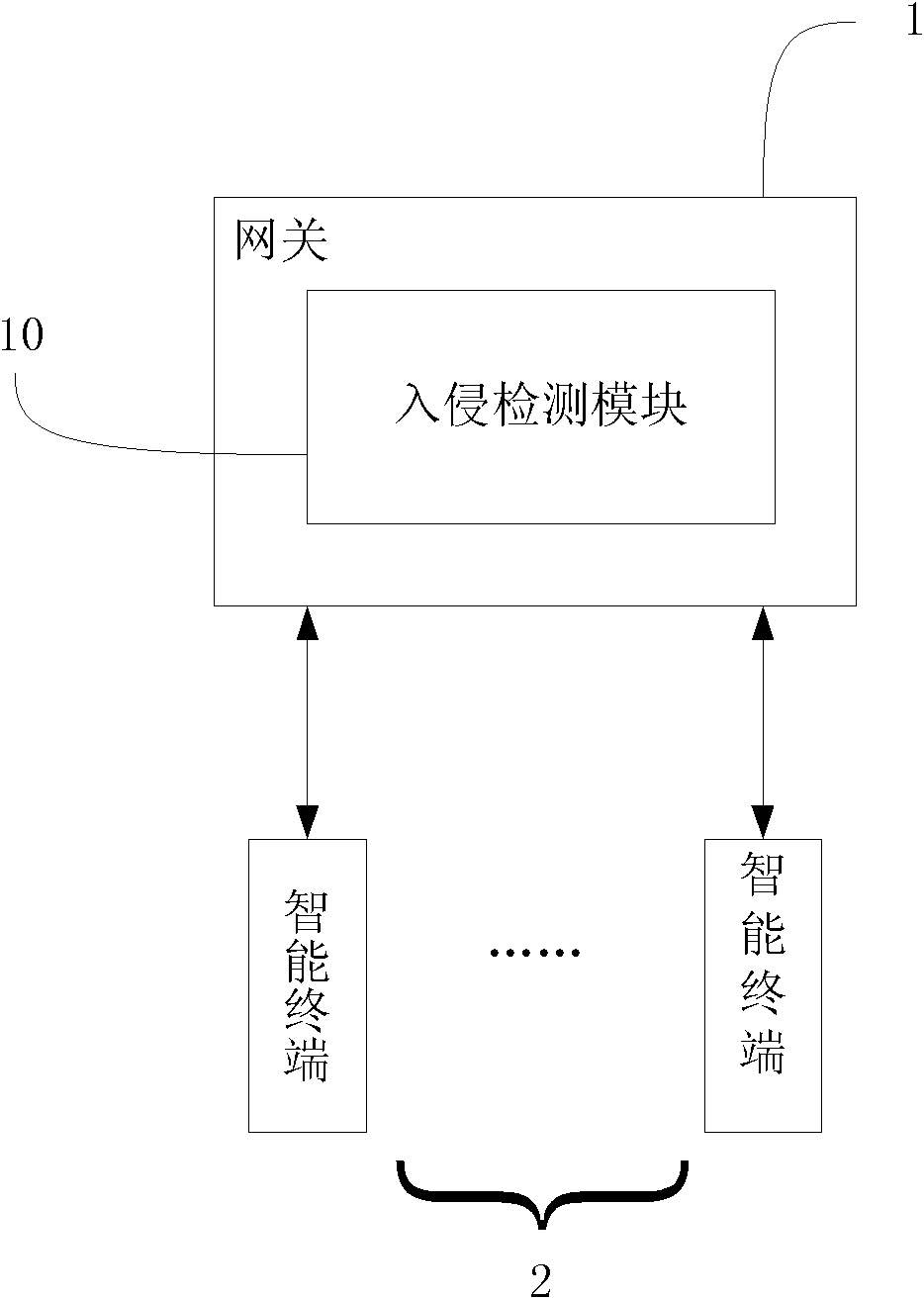
Intrusion detection method and system for networked control system based on ontology model
ActiveCN103716203BReal-time intrusion detectionEfficient Intrusion DetectionData switching networksNetwork activityNetwork model
Owner:HUAZHONG UNIV OF SCI & TECH
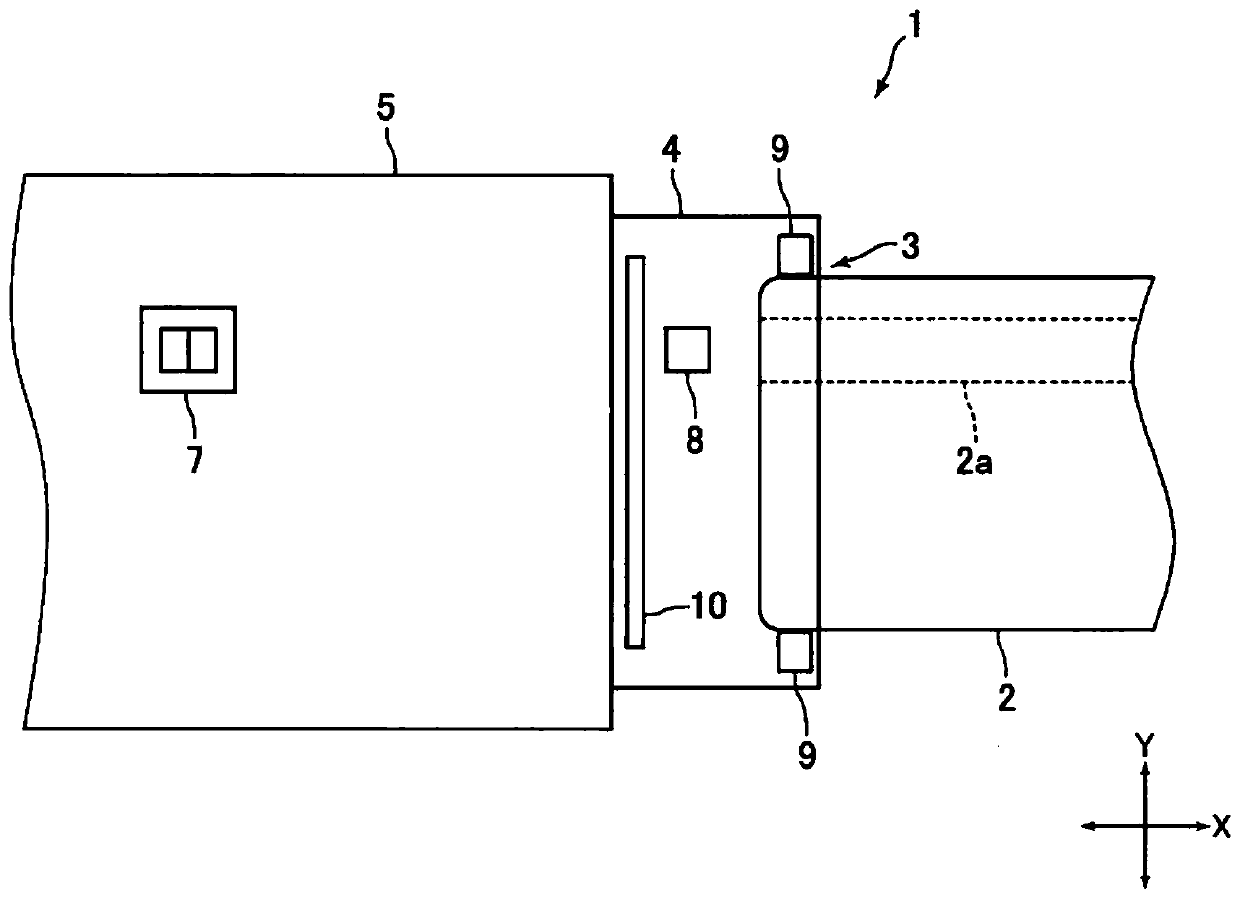
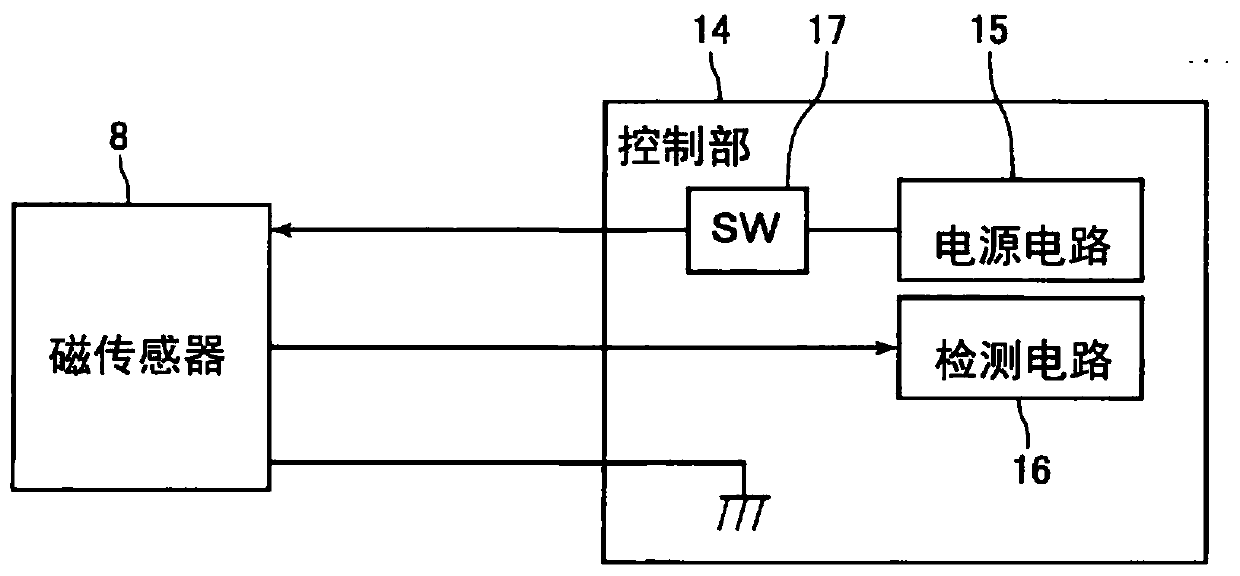
Card reader and method for controlling card reader
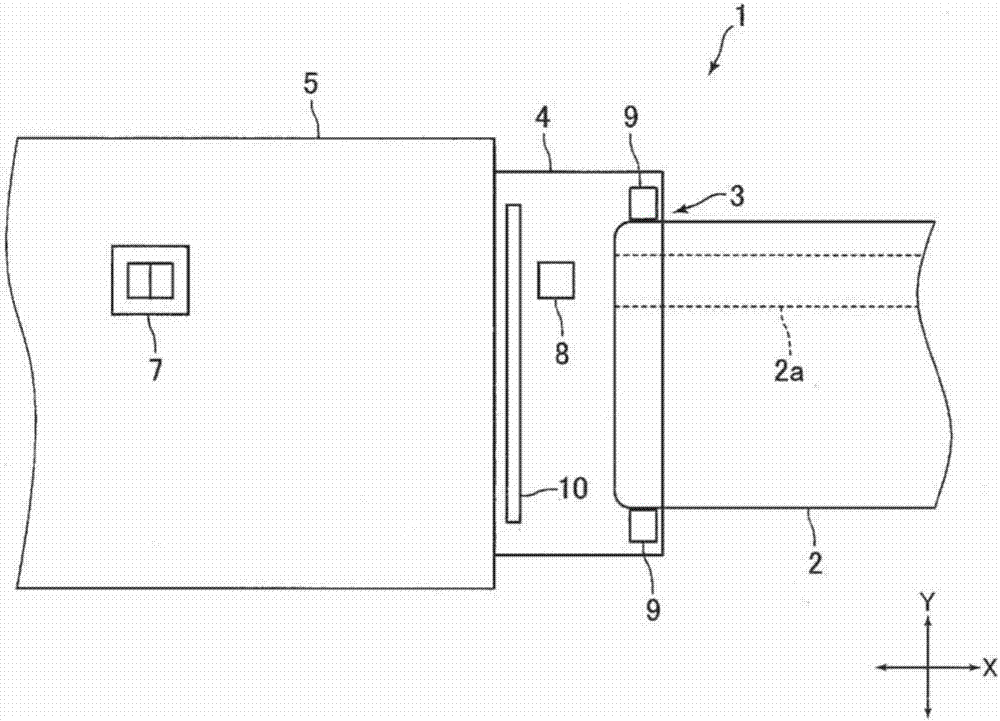
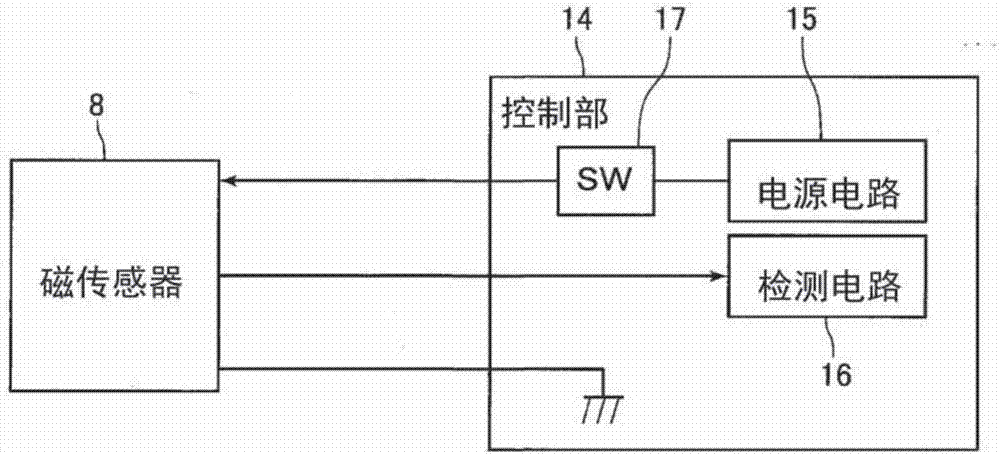
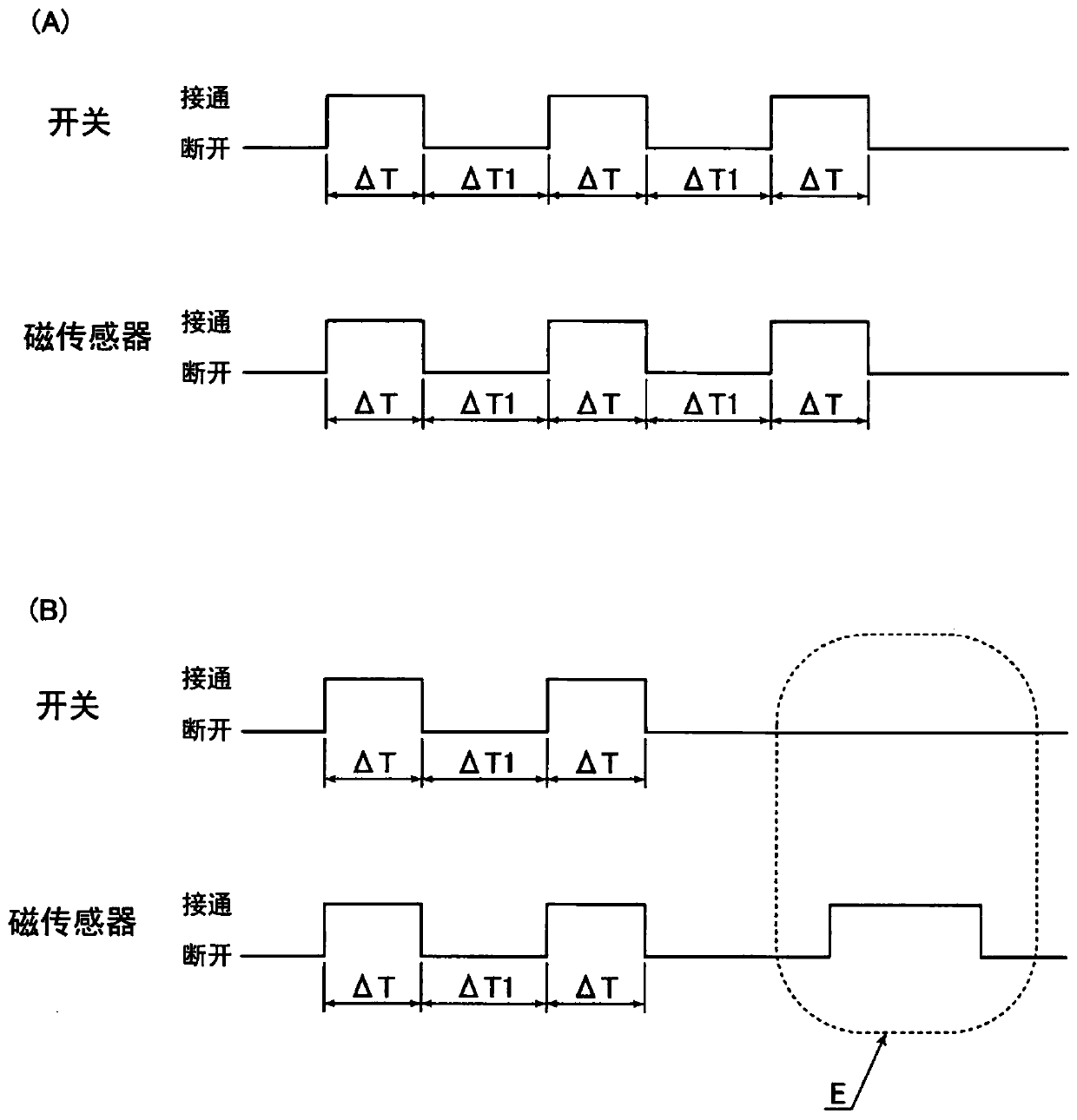
ActiveCN107077583APrevent illegal accessLow costRecord information storageDigital recordingComputer scienceControl unit
Provided is a card reader with which the illegitimate acquisition of magnetic information by a criminal can be prevented even when it is possible to determine whether magnetic data has been recorded on the magnetic stripe on a card that has been inserted from a card insertion port, and with which the cost can be reduced, and a method for controlling the card reader. This card reader is equipped with a magnetic sensor (8) for detecting whether magnetic data has been recorded on the magnetic stripe of a card, and a control unit (14) that supplies power to the magnetic sensor (8) and receives an input of an output signal from the magnetic sensor (8). The magnetic sensor (8) outputs an output signal when power is supplied from the control unit (14). When the card transit time is defined as the time from when a recording region for magnetic data recorded on the magnetic stripe on a card inserted into the card insertion port begins to pass by the magnetic sensor (8) until the time when the recording region finishes passing by, the control unit (14) supplies power to the magnetic sensor (8) for a first supply time that is shorter than the card transit time.
Owner:SANKYO SEIKI MFG CO LTD
Method for recording access of address changeover users in data transmission process
InactiveCN1225877CPrevent illegal accessSolve the problem that it is not easy to track usersSecuring communicationStart timeAccess time
This invention relates to a method for registering access of address conversion users in data transmission. This invention first of all sets a message information register hash table at initialization, sets up access control table of each host to compare the information contained in the message and in the access control table not register if they are different or if all information is the same, a corresponding register of the said message is recalled from the hash table according to the source and destination ports to finish the address conversion or add the received message information into the hash table to make judgement to the messages, then register them and finish address conversion to register the access time finally.
Owner:HUAWEI TECH CO LTD
Intelligent Internet of things and its control method
ActiveCN103227988BPrevent illegal accessEnsure safetyNetwork topologiesTransmissionInternet privacyEngineering
Owner:青岛顶腾工业科技有限公司
Vocational ability big data knowledge graph data access management method and system
ActiveCN114547423AReduce lossesPrevent illegal accessDigital data authenticationText database queryingDatabase serverData access
The invention provides a vocational ability big data knowledge graph data access management method and system. The vocational ability big data knowledge graph data access management method comprises the steps that a server receives an access request of a user for vocational ability big data knowledge graph data from an intranet; the server records an intranet access user identifier and a leaf node to form an intranet access database; the server processes the intranet access database, and N-level nodes in father nodes of each leaf node are obtained for each leaf node; the server receives an access request of a user for vocational ability big data knowledge graph data from an extranet, and the server determines a leaf node accessed by the user from the extranet at this time; judging whether the leaf node accessed by the external network falls into the N-level node domain range or not; and when the leaf node accessed by the external network does not fall into the N-level node field range, the server judges that the account of the user is abnormal, and terminates the access of the user to the vocational ability big data knowledge graph.
Owner:杜江波
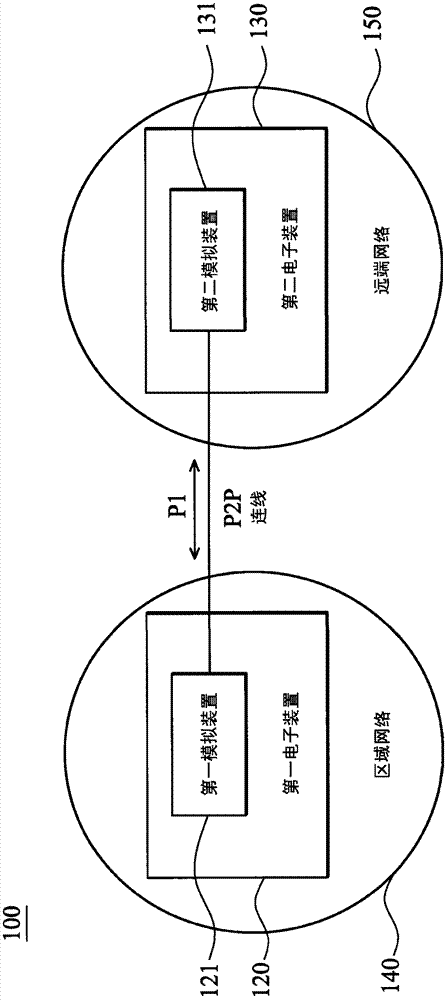
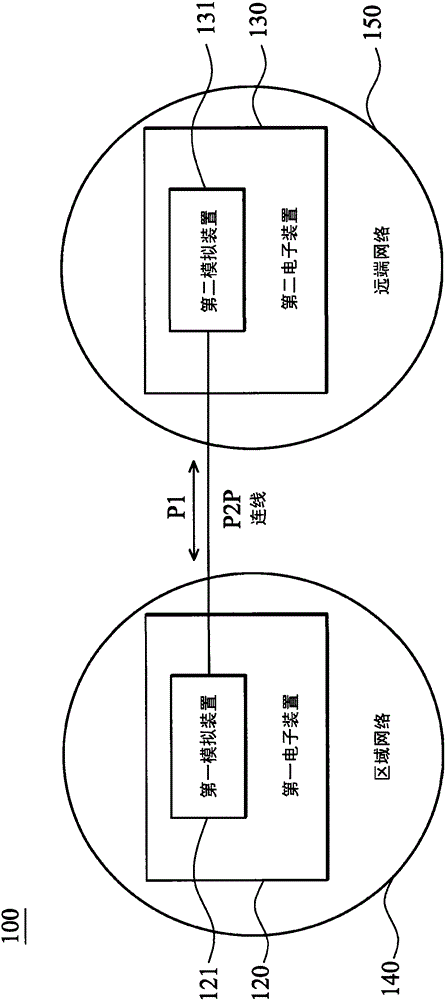
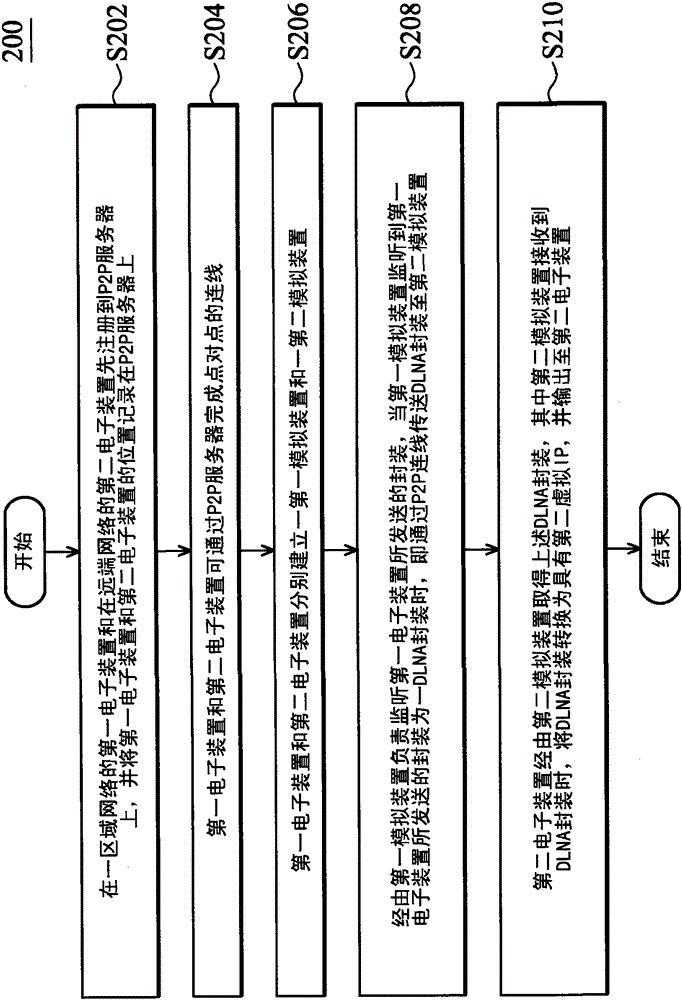
DLNA (digital living network alliance) packaging and transmitting method and system
ActiveCN102957684AAvoid illegal accessPrevent illegal accessTransmissionArea networkDigital Living Network Alliance
The invention discloses a DLNA (digital living network alliance) packaging and transmitting method and system. The method is suitable for transmitting to a remote network, and comprises the following steps that: the connection between a first electronic device of an area network and a second electronic device of a remote network is completed through a server; a first analog device and a second analog device are respectively established in the first electronic device and the second electronic device; the first analog device monitors a package sent by the first electronic device, and when the first analog device monitors that the package sent by the first electronic device is a DLNA packet package, the DLNA package is transmitted to the second analog device through a connecting wire; and the second electronic device obtains the DLNA package through the second analog device. According to the invention, users can access data of home networks in an external network at any time; networks are integrated by using a point-to-point architecture, so that gateways do not become a bottleneck of the scale growth of home networks; and through network authentication, a situation that unauthorized devices illegally access data of home networks can be avoided.
Owner:ACER INC
Cross- segment multimode network management device of ancient books protection case system
InactiveCN107124724AAddressing coverage issuesSolve the problem of adjacent relay interferenceNetwork traffic/resource managementTransmissionWireless mesh networkNetwork management
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
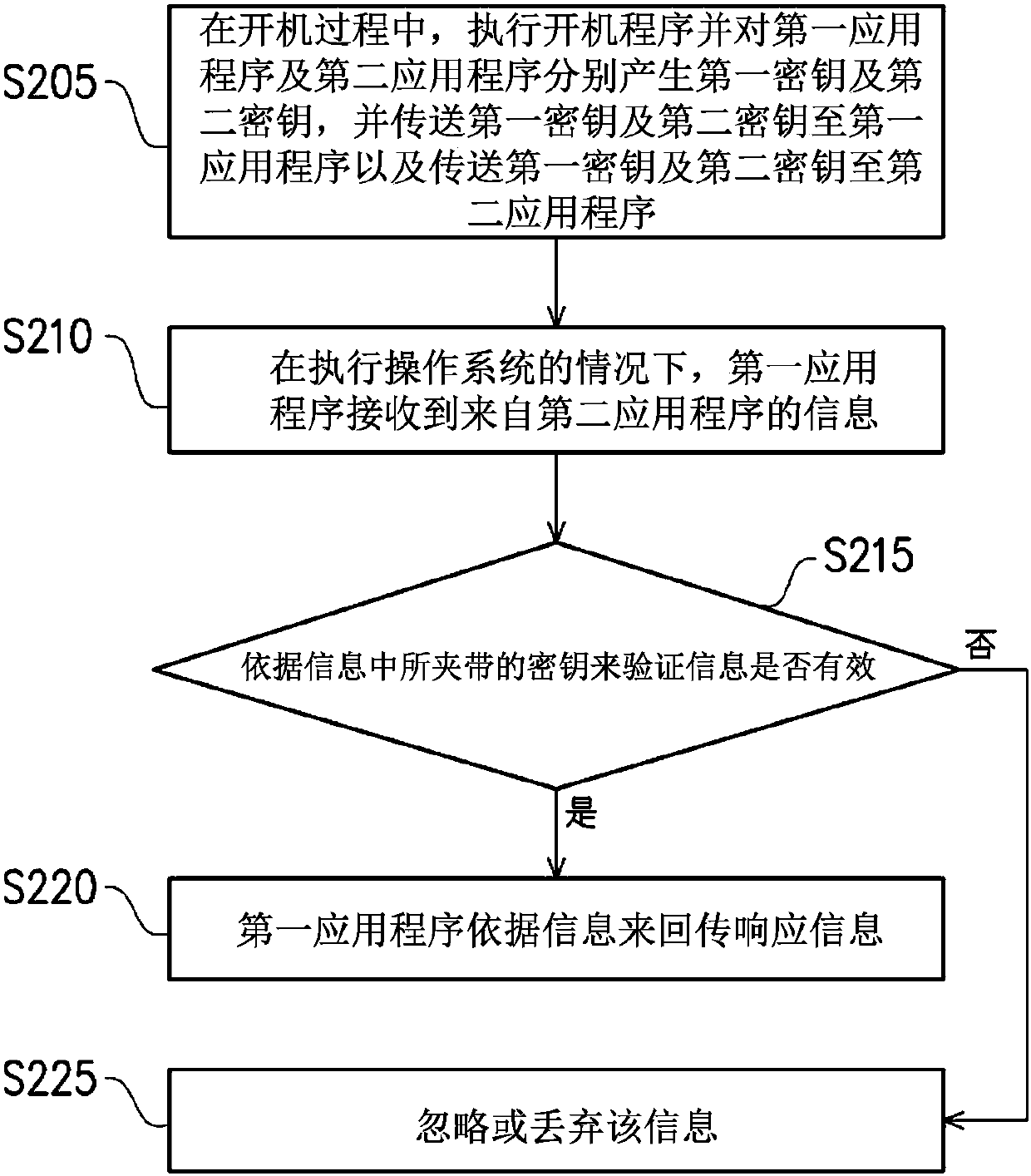
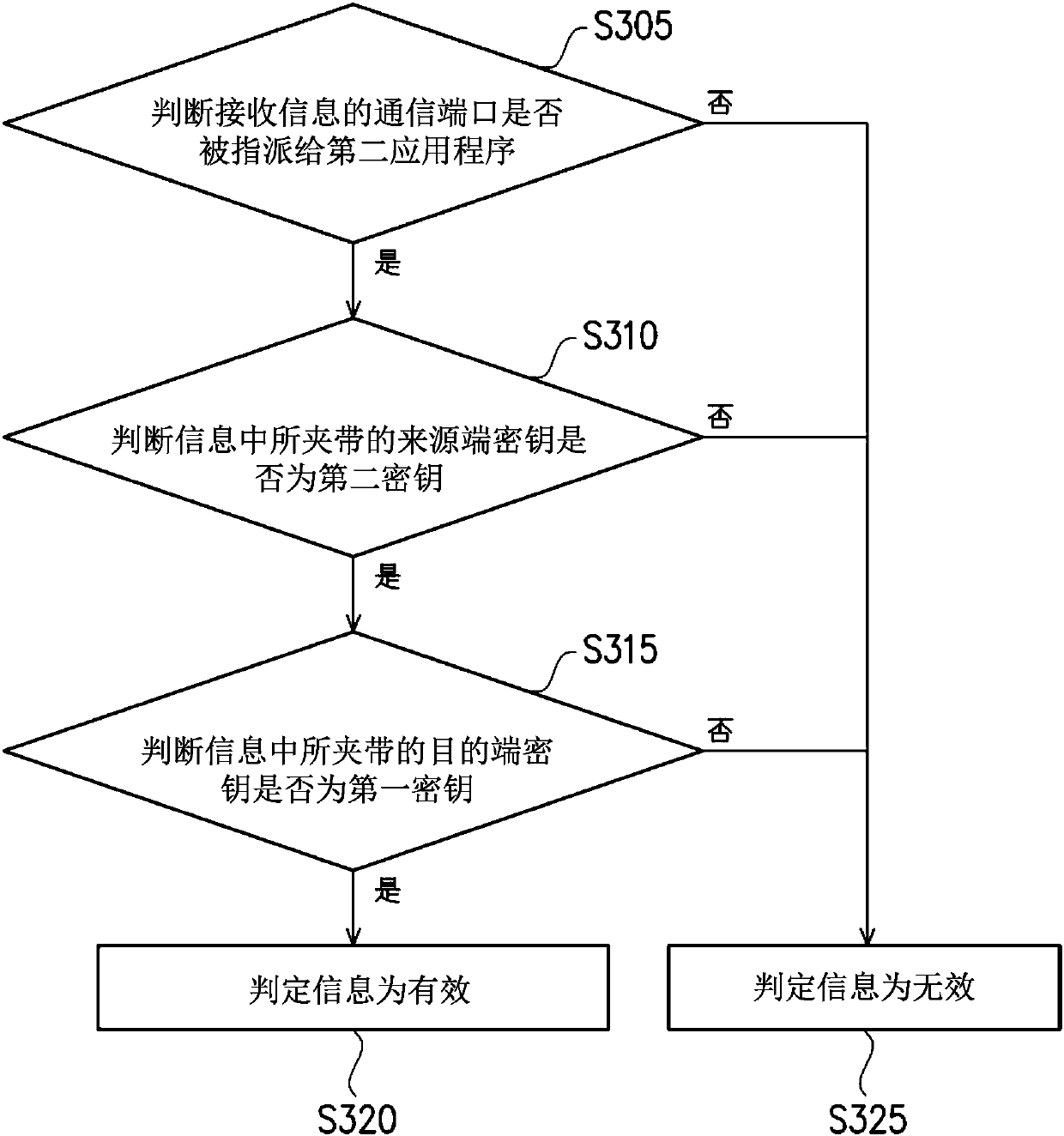
Communication hub and method for verifying message among applications thereof
ActiveCN107783846APrevent illegal accessInterprogram communicationOperational systemApplication software
The invention relates to a communication hub and a method for verifying a message among applications thereof. In a start-up process, a processor uses a start-up program to generate a secret key for afirst and second application separately and transmits all the secret keys to the first and second applications, so that each of the applications carries corresponding at least one secret key when performing message transfer. After entering an operating system, when the first application receives a message from the second application, whether the message is valid is verified according to the secretkey carried in the message. When the message is judged to be valid, the first application passes back response information according to the message. When the message is judged to be invalid, the message is neglected or discarded. According to the communication hub, in the start-up process, a corresponding secret key is given to each of the applications, and the secret keys are utilized to performverification during message transfer among the applications, thereby preventing illegal access of malicious programs. In addition, a communication port of each application can be matched for verification, thereby further enhancing security.
Owner:WISTRON NEWEB
Digital living network alliance encapsulation delivery method and system
The invention discloses a DLNA (digital living network alliance) packaging and transmitting method and system. The method is suitable for transmitting to a remote network, and comprises the following steps that: the connection between a first electronic device of an area network and a second electronic device of a remote network is completed through a server; a first analog device and a second analog device are respectively established in the first electronic device and the second electronic device; the first analog device monitors a package sent by the first electronic device, and when the first analog device monitors that the package sent by the first electronic device is a DLNA packet package, the DLNA package is transmitted to the second analog device through a connecting wire; and the second electronic device obtains the DLNA package through the second analog device. According to the invention, users can access data of home networks in an external network at any time; networks are integrated by using a point-to-point architecture, so that gateways do not become a bottleneck of the scale growth of home networks; and through network authentication, a situation that unauthorized devices illegally access data of home networks can be avoided.
Owner:ACER INC
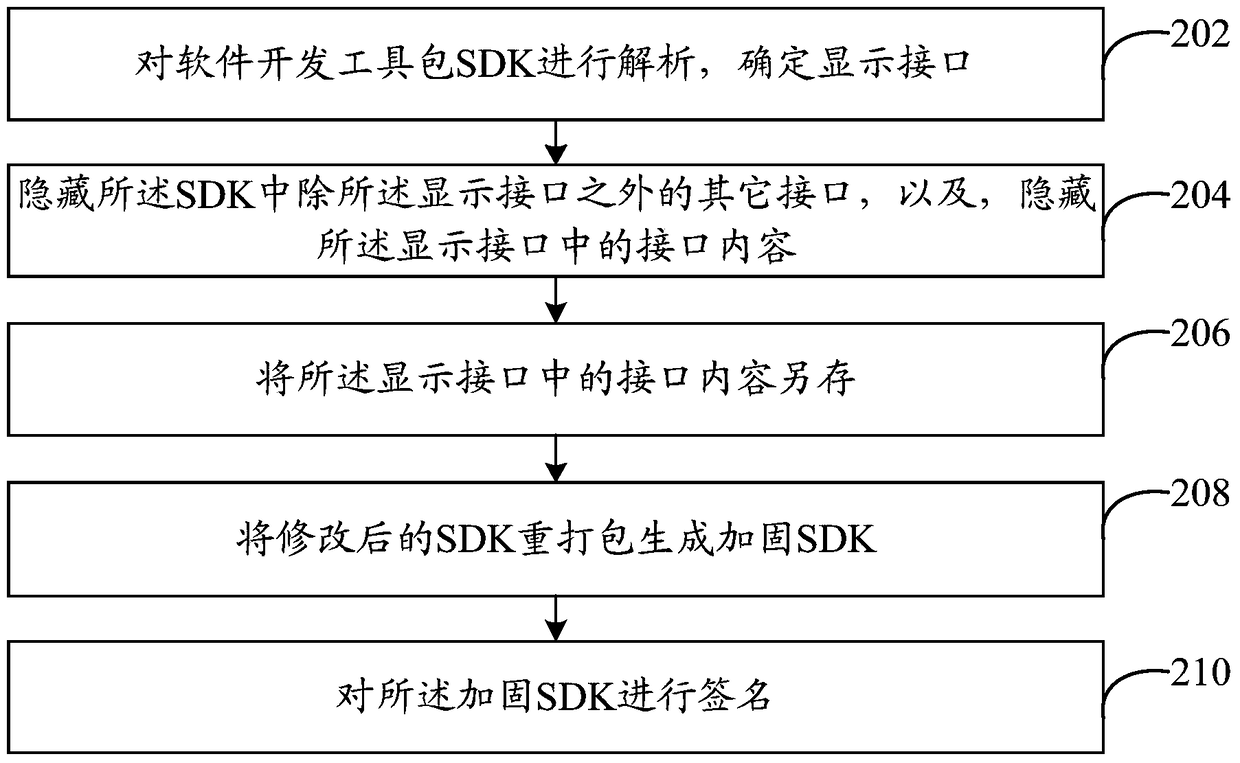
A software reinforcement method and system
ActiveCN105760721BAchieve protectionImprove securityPlatform integrity maintainanceProgram/content distribution protectionSoftware engineeringSoftware development
The invention discloses a software hardening method and system. The method comprises the steps of analyzing a software development kit (SDK), and determining a display port; hiding other ports, except the display port, in the SDK, and hiding the port content in the display port; saving the port content in the display port in another place so as to acquire the corresponding port content from the another place when the display port is called; repackaging the corrected SDK to generate a hardened SDK. By the adoption of the method and system, software protection is achieved, software safety is improved, and the rights of developers and users are protected.
Owner:BEIJING QIHOO TECH CO LTD
Card reader and control method of card reader
ActiveCN107077583BPrevent illegal accessLow costRecord information storageDigital recordingEmbedded systemElectrical and Electronics engineering
The invention provides a card reader and a control method of the card reader. The card reader can detect whether magnetic data is recorded in the magnetic stripe of the card inserted from the card insertion port, prevent criminals from obtaining magnetic information illegally, and reduce the cost. The card reader has: a magnetic sensor (8) for detecting whether magnetic data is recorded in the magnetic strip of the card; and a control unit that supplies power to the magnetic sensor (8) and receives an input of an output signal of the magnetic sensor (8) (14), if the magnetic sensor (8) is supplied with power from the control unit (14), it outputs an output signal. When the recording area of the magnetic data recorded in the magnetic stripe of the card inserted from the card insertion port starts to pass through the magnetic sensor (8) and the time until the end of passing through is set as the card passing time, the control unit (14) sends a signal to the magnetic sensor (8). ) power supply for a first supply time shorter than the card passing time.
Owner:SANKYO SEIKI MFG CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com