A software reinforcement method and system
A technology of software and software development tools, applied in the field of security, can solve the problems of deepening the degree of threat, endangering users, and many security threats, so as to prevent illegal acquisition, improve security, and achieve the effect of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
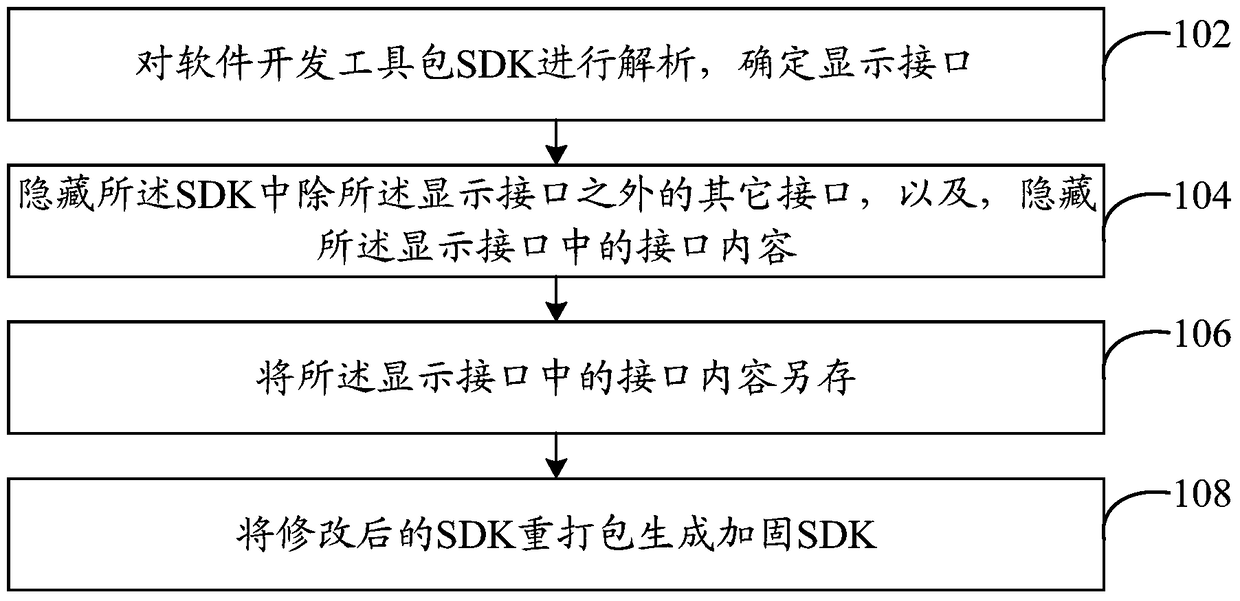
[0025] Reference figure 1 , Shows a flowchart of the steps of a software hardening method in the first embodiment of the present invention. In this embodiment, the software hardening method may include:
[0026] Step 102: Analyze the software development kit SDK to determine the display interface.
[0027] Software Development Kit, SDK, Software Development Kit: Generally, it is a collection of development tools used by software engineers to build application software for specific software packages, software frameworks, hardware platforms, operating systems, etc.
[0028] The SDK can be distributed to users along with the installation package of the corresponding application software. At present, when the SDK is distributed to the user along with the installation package of the corresponding application software, all interfaces in the SDK and the content in the interface are exposed Out of (show). In this embodiment, according to the application software or the interface actually r...
Embodiment 2
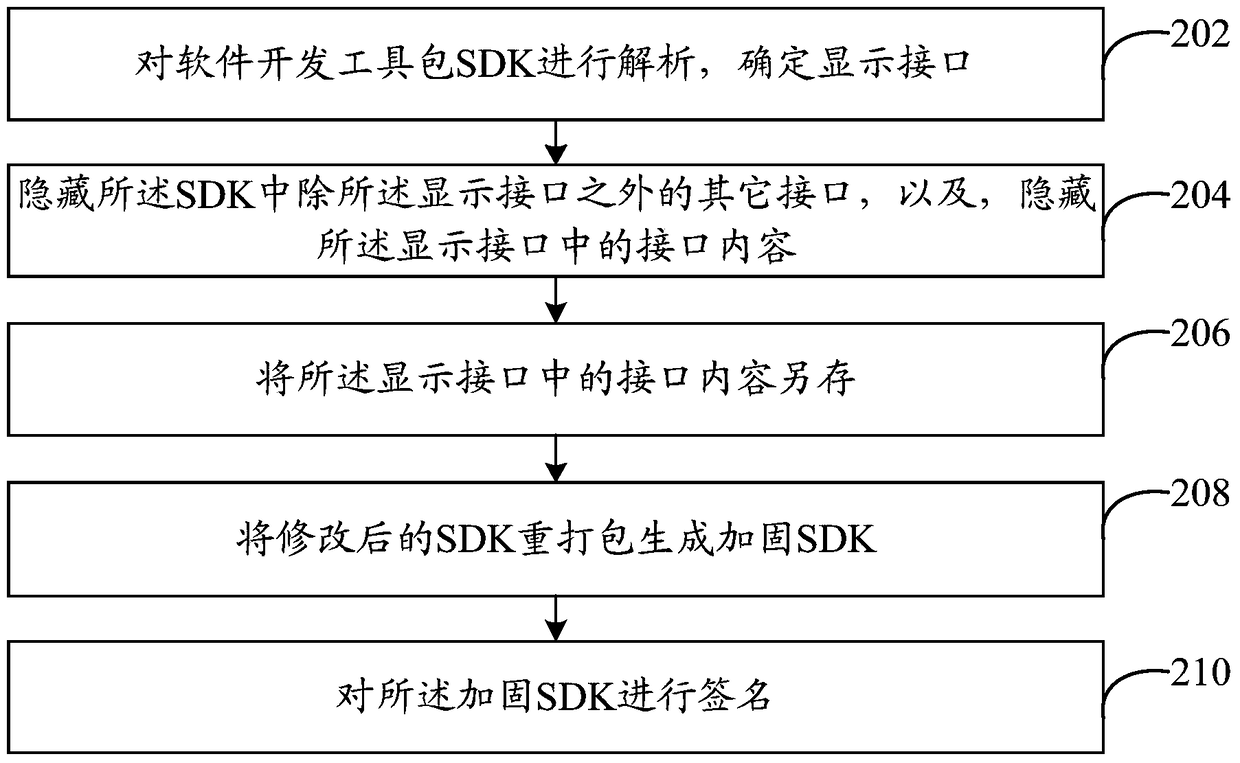
[0037] Reference figure 2 , Shows a flowchart of the steps of a software hardening method in the second embodiment of the present invention. In this embodiment, the software hardening method can be but not limited to being applied to the Android system, and the method can specifically include:
[0038] Step 202: Analyze the software development kit SDK to determine the display interface.
[0039] In this embodiment, the display interface may be determined according to the type of service to be executed; wherein there is at least one display interface. For example, for a certain application software, according to the type of business to be executed, the interfaces to be used can be determined as: program initialization interface, order query interface, and order generation interface, then the program initialization interface and order query interface in the SDK can be used The order generation interface is determined as the display interface, so as to be provided for the user to c...
Embodiment 3
[0057] Based on the same inventive concept as the above method embodiment, refer to image 3 , Shows a structural block diagram of a software reinforcement system in the third embodiment of the present invention. In this embodiment, the software reinforcement system includes:
[0058] The parsing module 302 is used to analyze the software development kit SDK and determine the display interface.
[0059] The first hiding module 304 is used to hide other interfaces in the SDK except the display interface.
[0060] The second hiding module 306 is used to hide the interface content in the display interface.
[0061] The save as module 308 is configured to save the interface content in the display interface separately, so as to obtain the corresponding interface content from the save location when the display interface is called.
[0062] The generating module 310 is used to repackage the modified SDK to generate a reinforced SDK.
[0063] It can be seen that in this embodiment, only the dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com