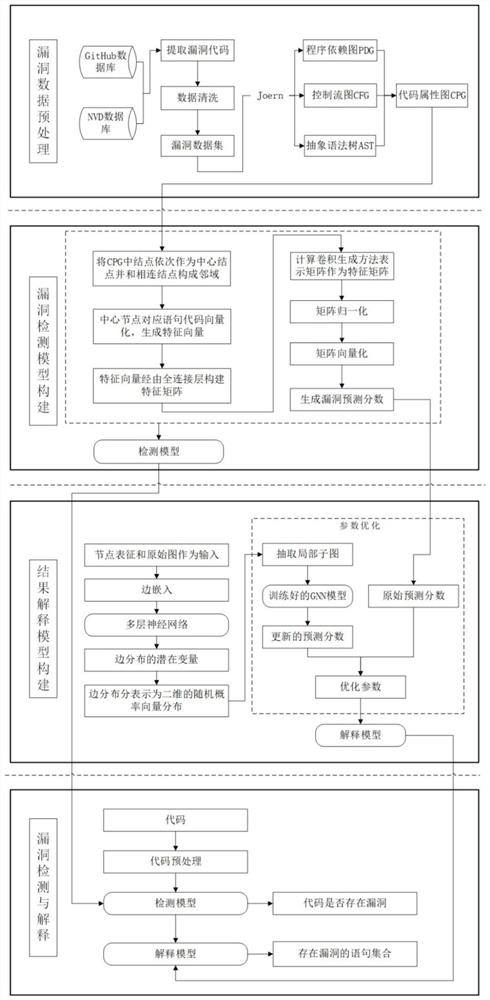
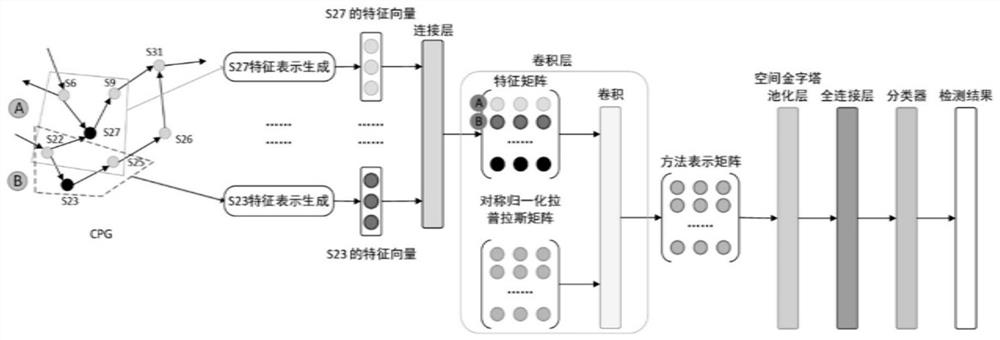
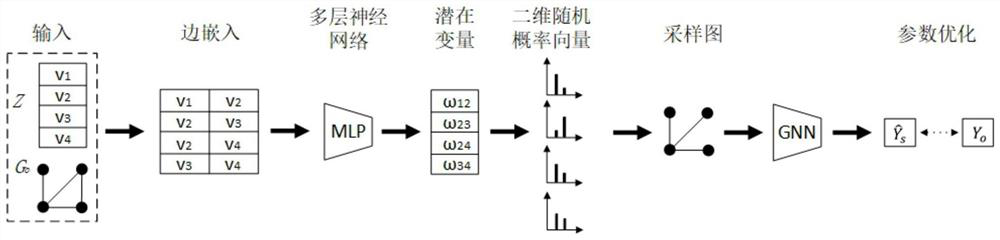
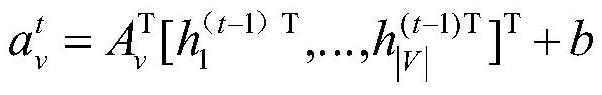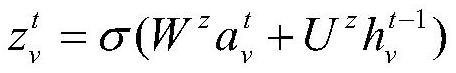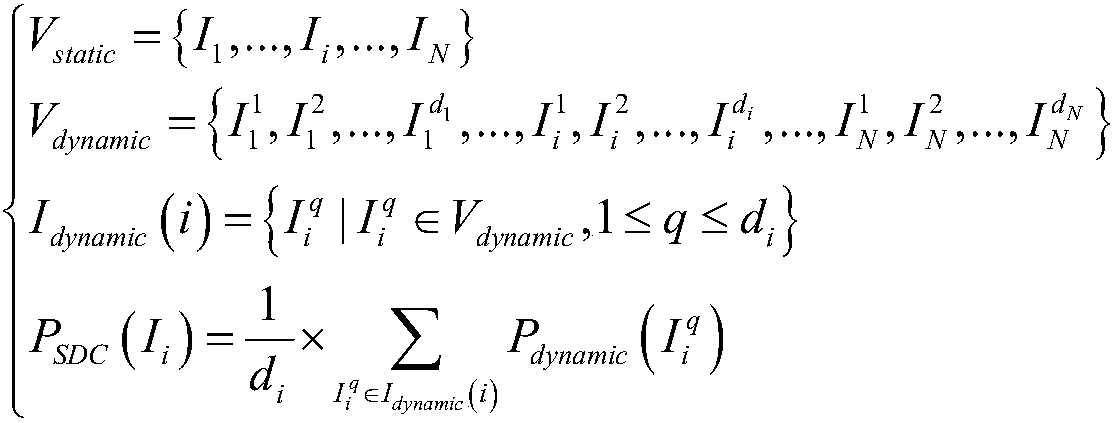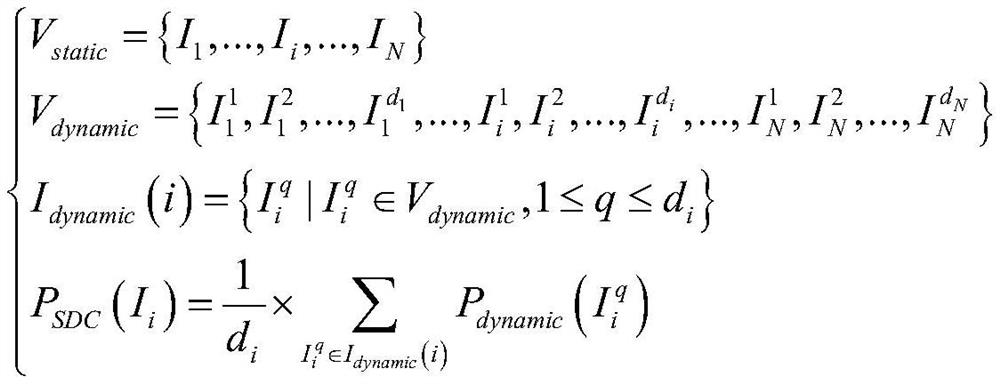Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Vulnerability prediction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network device vulnerability prediction
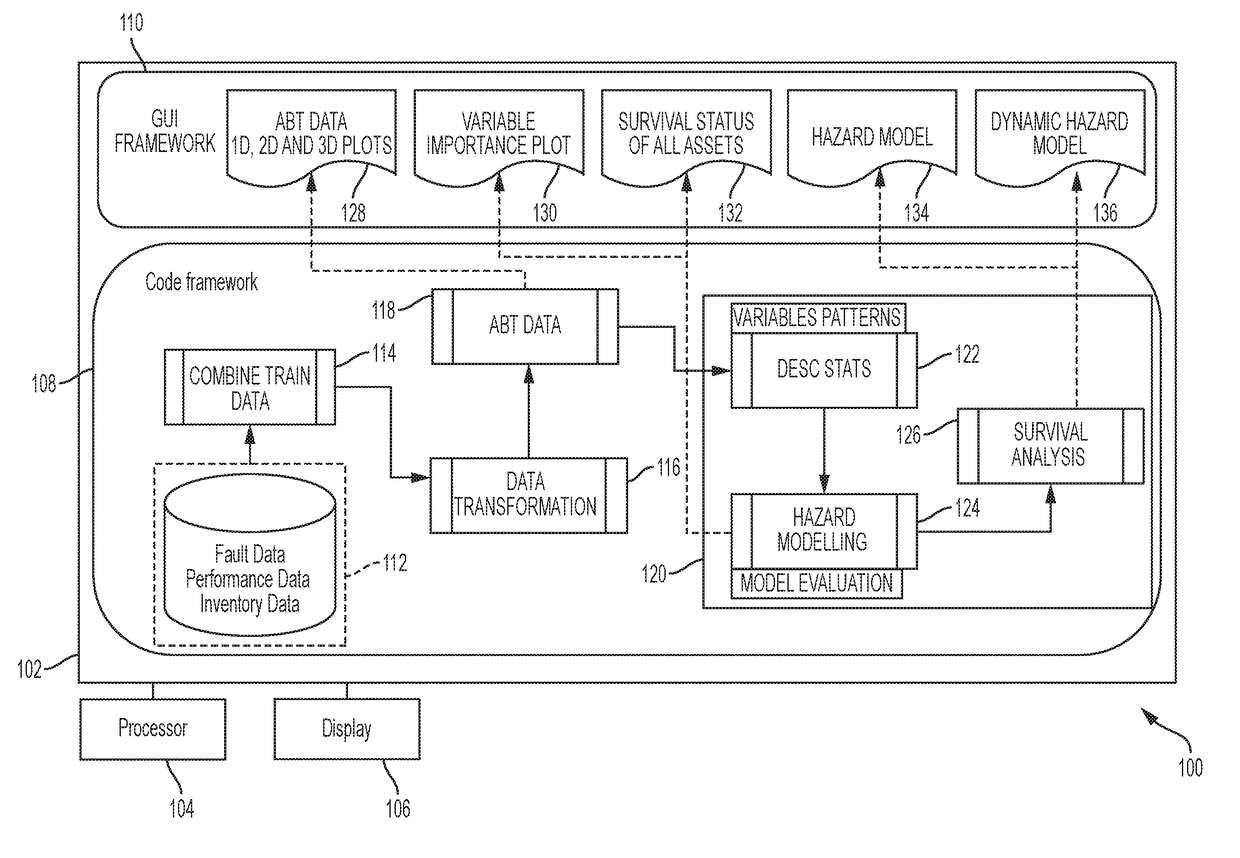
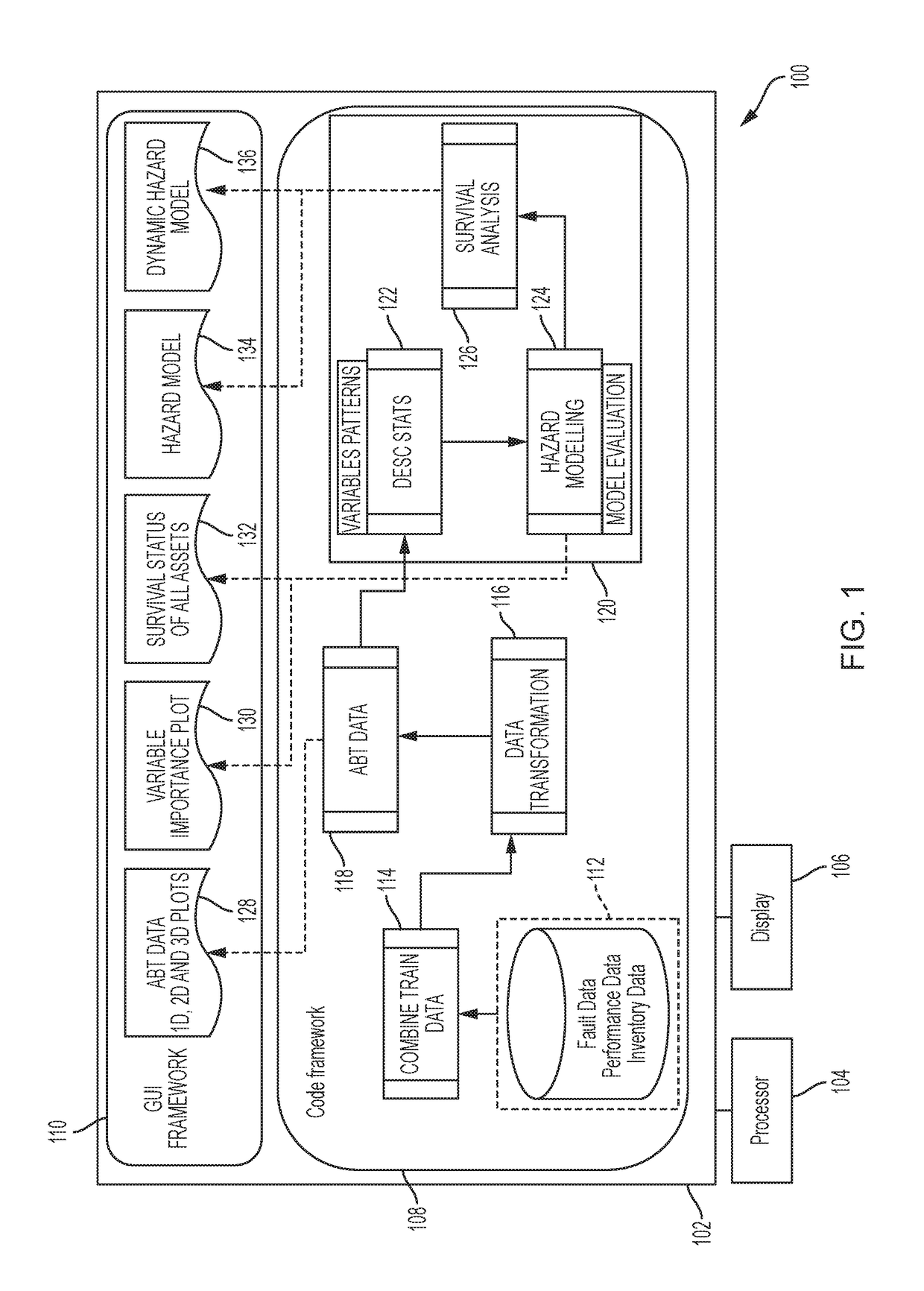
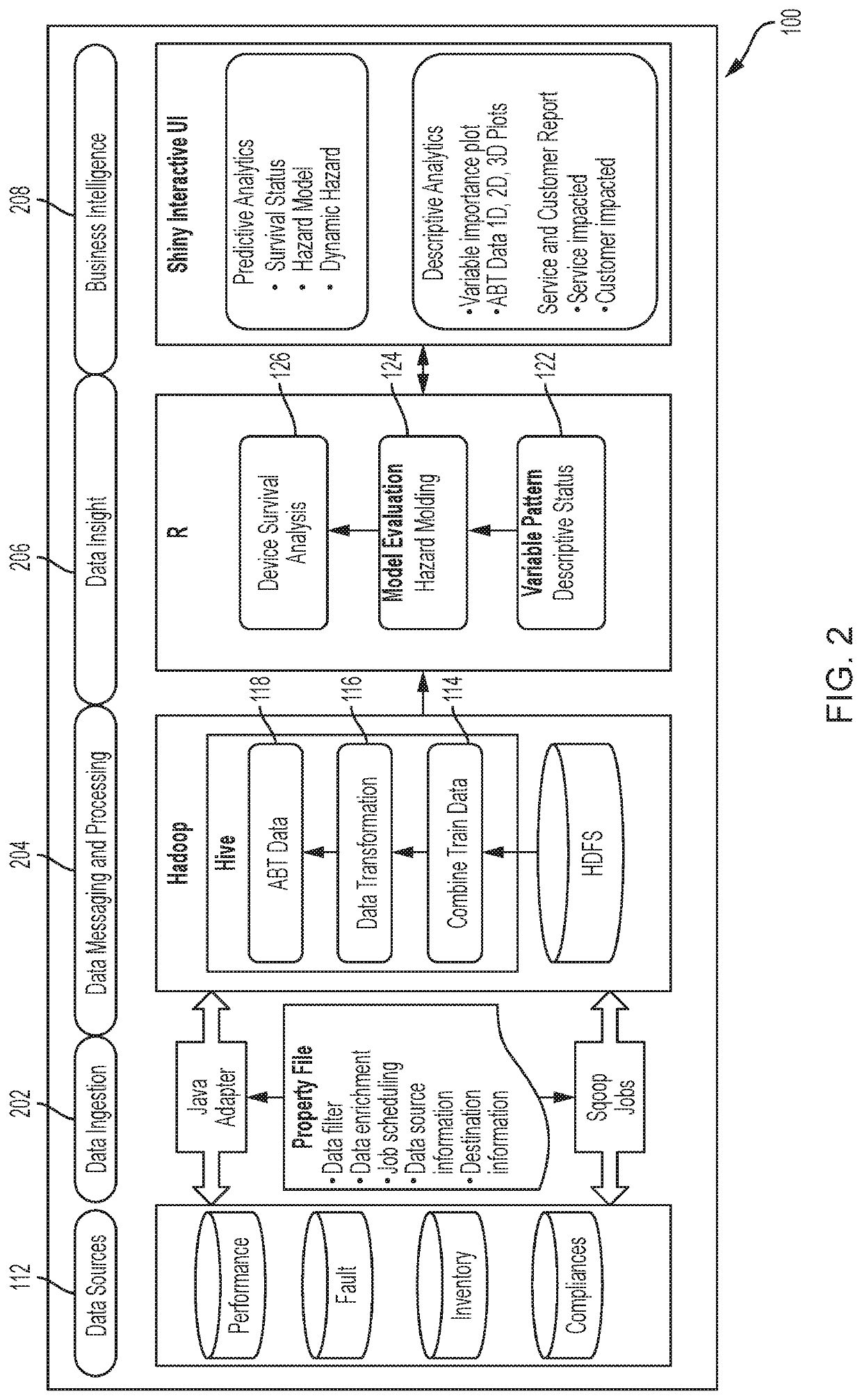
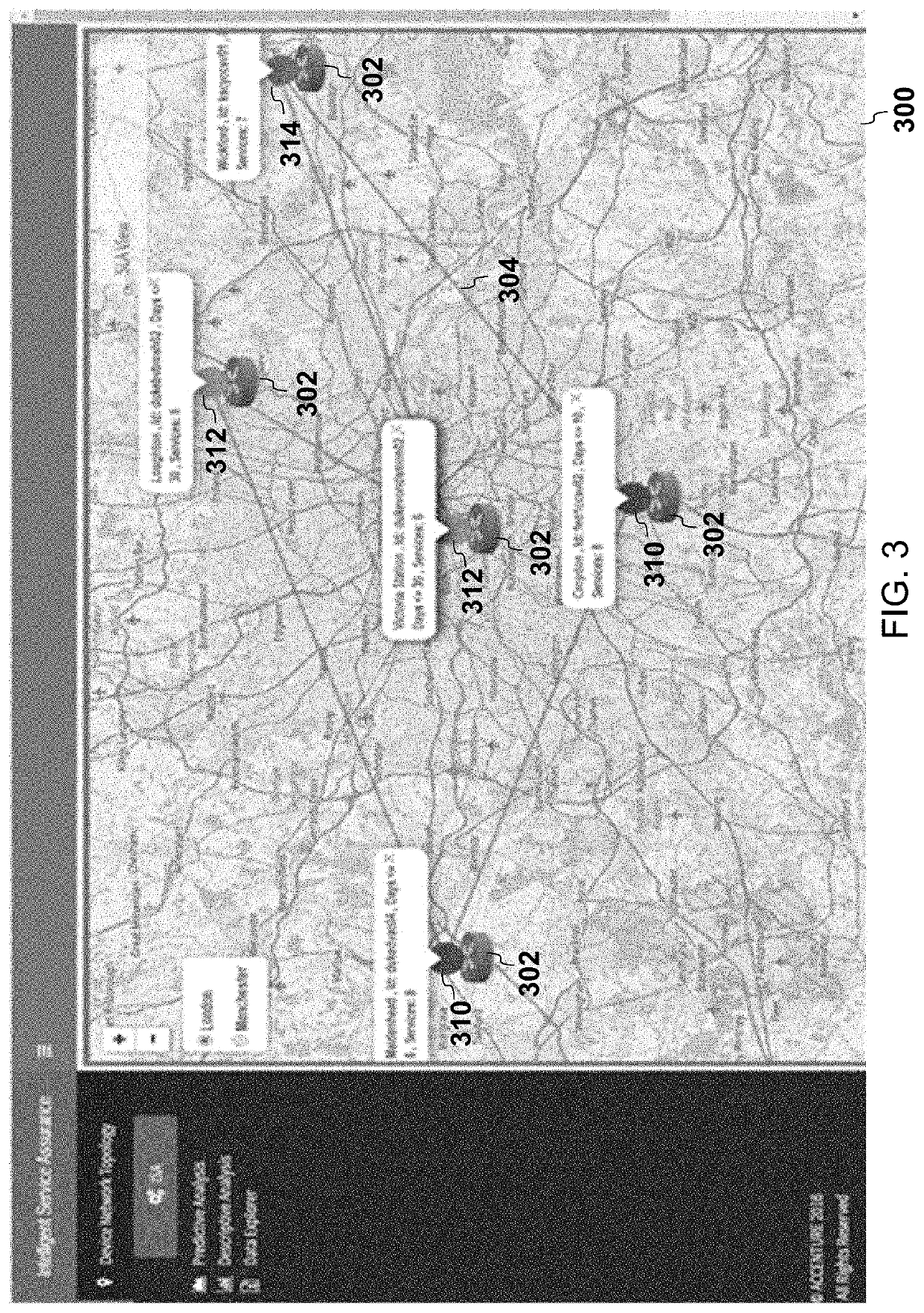
The vulnerability of network devices may be predicted by performing a survival analysis on big data. A prediction algorithm may be built by considering historical data from heterogeneous data sources. The operating state of the network devices on a network may be predicted. The services potentially affected by a predicted outage may be determined and displayed. Alternatively or in addition, the number of clients potentially affected by a predicted outage may be determined and displayed.
Owner:ACCENTURE GLOBAL SOLUTIONS LTD
Intelligent contract multi-vulnerability detection method and system based on source code graph representation learning
PendingCN113360915AAvoid loss of structural featuresImprove accuracySoftware testing/debuggingPlatform integrity maintainanceAlgorithmTheoretical computer science
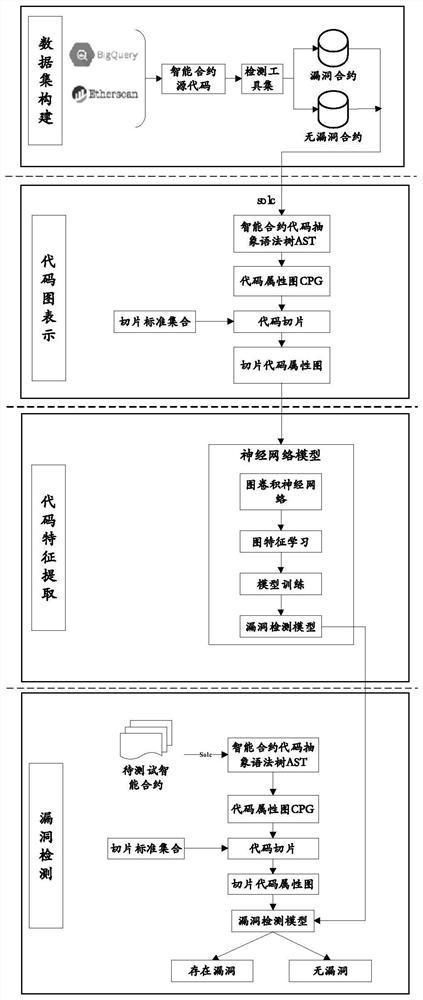
The invention discloses an intelligent contract multi-vulnerability detection method and system based on source code graph representation learning, and the method comprises the steps: carrying out representation of an intelligent contract source code through a function granularity code attribute graph in combination with an abstract syntax tree and semantic information of an intelligent contract; and according to grammatical features of different types of vulnerabilities of the intelligent contract, defining a slicing criterion, using a program slicing technology to carry out noise reduction on the intelligent contract graph representation, carrying out feature extraction in combination with a gated graph neural network, and carrying out vulnerability prediction based on the extracted features. The method has the advantages that the intelligent contract source code is represented by combining multiple graph structures, and grammar and semantic information and a context structure of the code are fully reserved; noise codes irrelevant to vulnerability detection are removed by using a program slicing technology, so that the detection accuracy is improved; the features of various vulnerabilities are automatically learned based on the gated graph neural network, the application range and the detection efficiency of vulnerability detection are improved, and the detection cost is reduced.
Owner:YANGZHOU UNIV
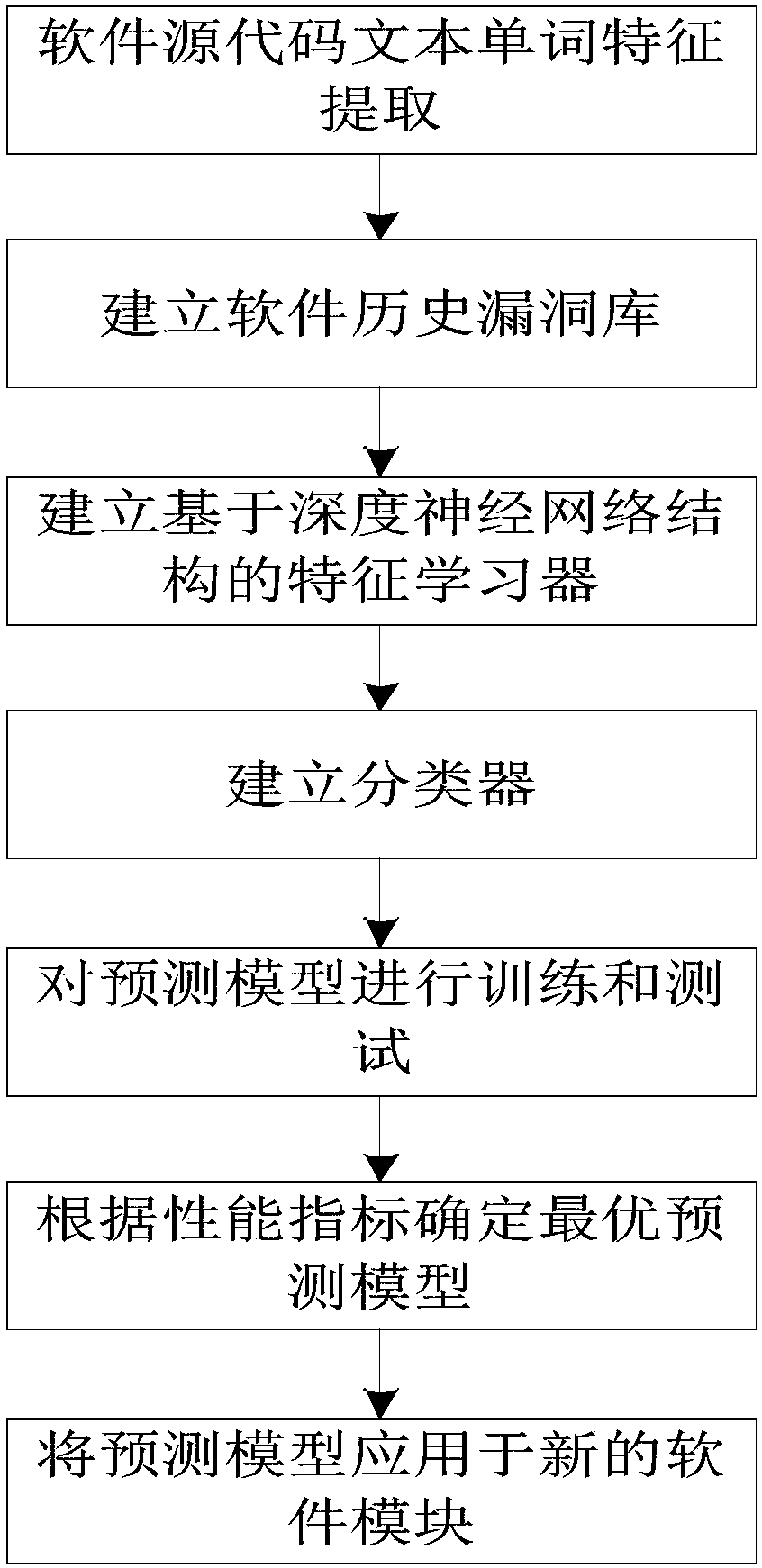
Text deep learning-based software security vulnerability prediction method
PendingCN108549817AHigh precisionImprove performance indicatorsNatural language data processingPlatform integrity maintainanceLearning basedTheoretical computer science
The invention discloses a text deep learning-based software security vulnerability prediction method, which learns features and knowledge from a historical software source code text by adopting a deepneural network model and a shallow machine learning algorithm, and can be used for predicting security vulnerabilities in new software source codes. According to the method, structural features in the features of the software source code text are learnt by adopting the deep neural network model; by taking the learnt features as inputs of a classifier, the classifier is subjected to training adjustment; an optimal vulnerability prediction model is obtained; and the method is used for vulnerability prediction of new software modules of software.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
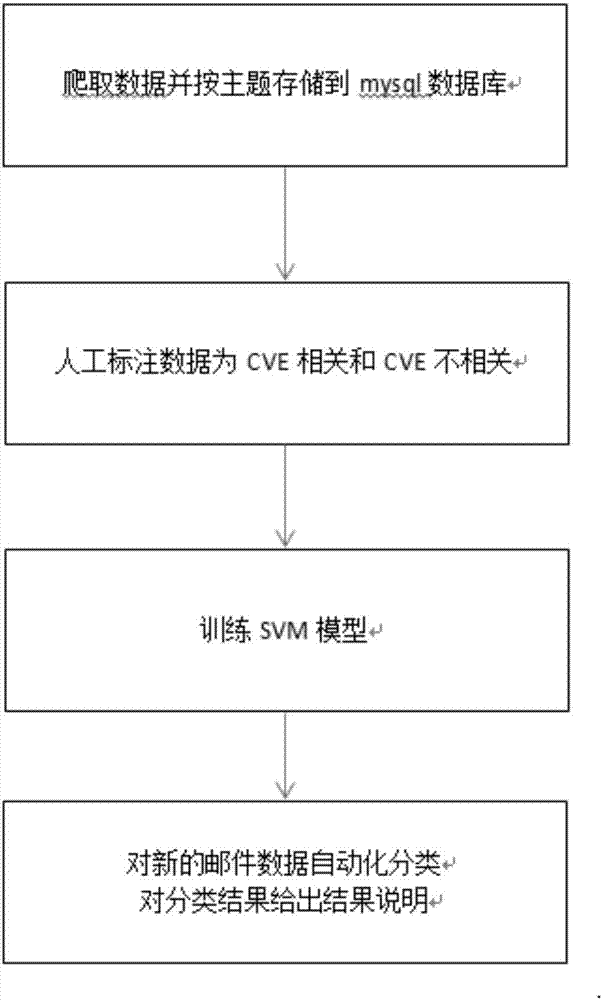
Linux-Kernel associated CVE (Common Vulnerabilities and Exposures) intelligent prediction method based on machine learning
InactiveCN107194260AFully automatedWeb data indexingPlatform integrity maintainanceWeb sitePredictive methods
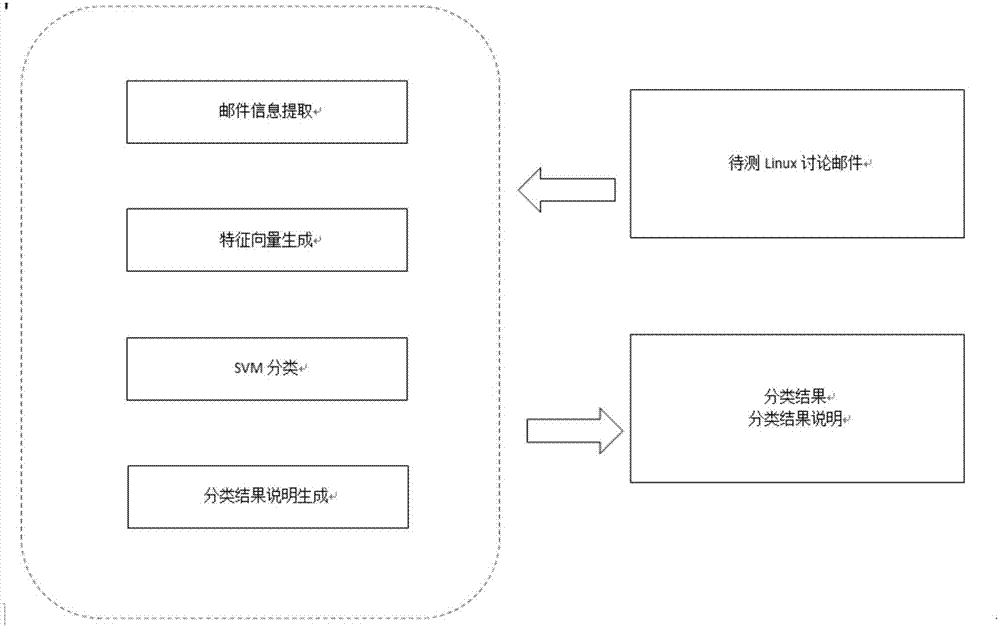
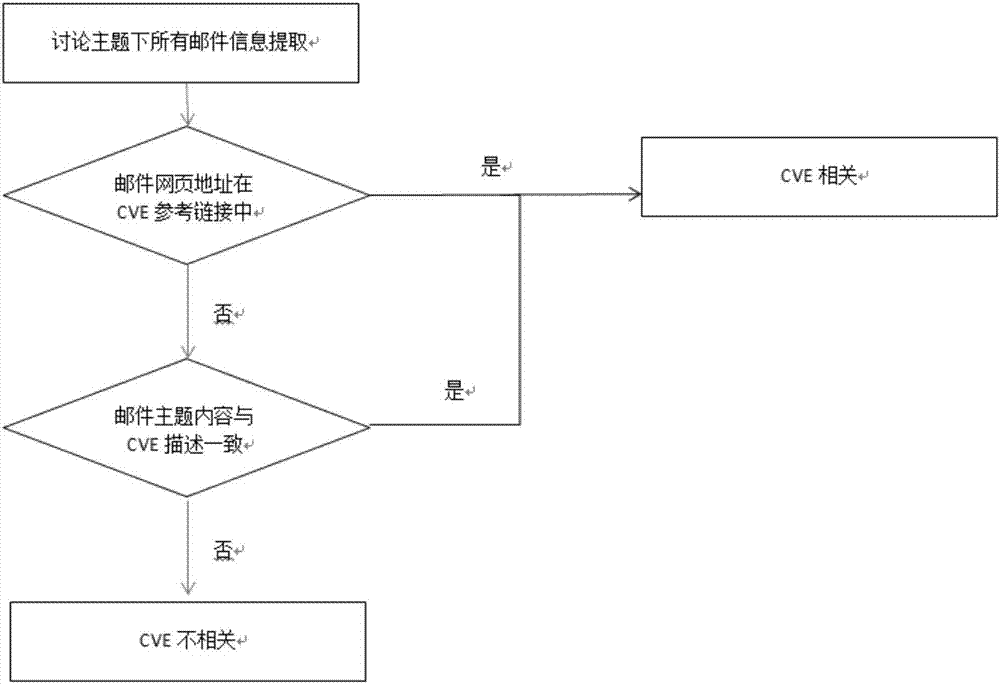
The invention discloses a Linux-Kernel associated CVE (Common Vulnerabilities and Exposures) intelligent prediction method based on machine learning. The method comprises the following steps that: 1) from a Linux discussion mail data publishing website, crawling the data of a set time period, carrying out classified storage according to themes by mail titles; 2) labeling the crawled data, i.e., labeling a discussion theme as CVE association and CVE non association according to the contents of the discussion theme and CVE description contents; 3) randomly extracting multiple pieces of sample data labeled as CVE association and multiple pieces of sample data labeled as CVE non association, and utilizing a machine learning algorithm to train to obtain a CVE vulnerability prediction model; and 4) utilizing the CVE vulnerability prediction model to automatically predict new mail data to obtain the prediction result and the result explanation of the mail data. By use of the method, possible vulnerability information in a kernel can be found as early as possible, a detailed explanation for a judgment result that the vulnerability may be caused is given for reference.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Seed optimization method based on vulnerability prediction model
InactiveCN114117454AImprove effectivenessEasy to digSoftware testing/debuggingPlatform integrity maintainanceAlgorithmData mining
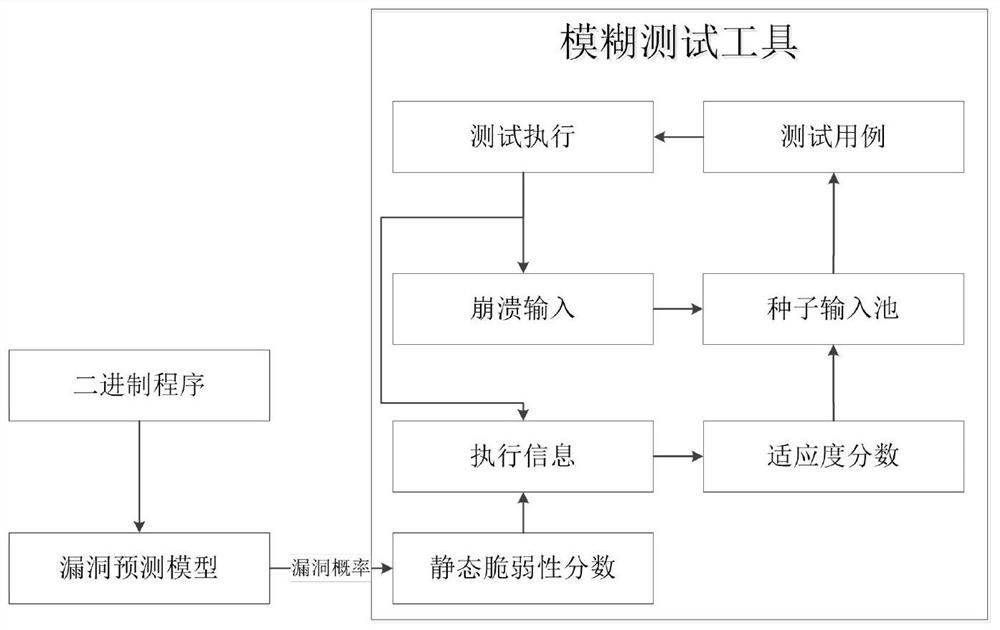
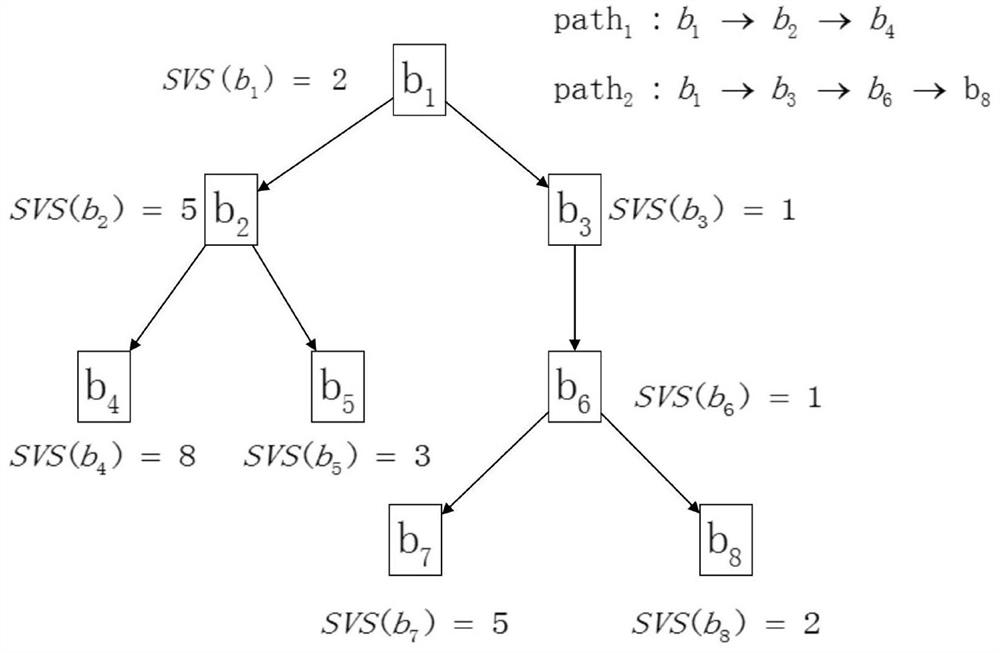
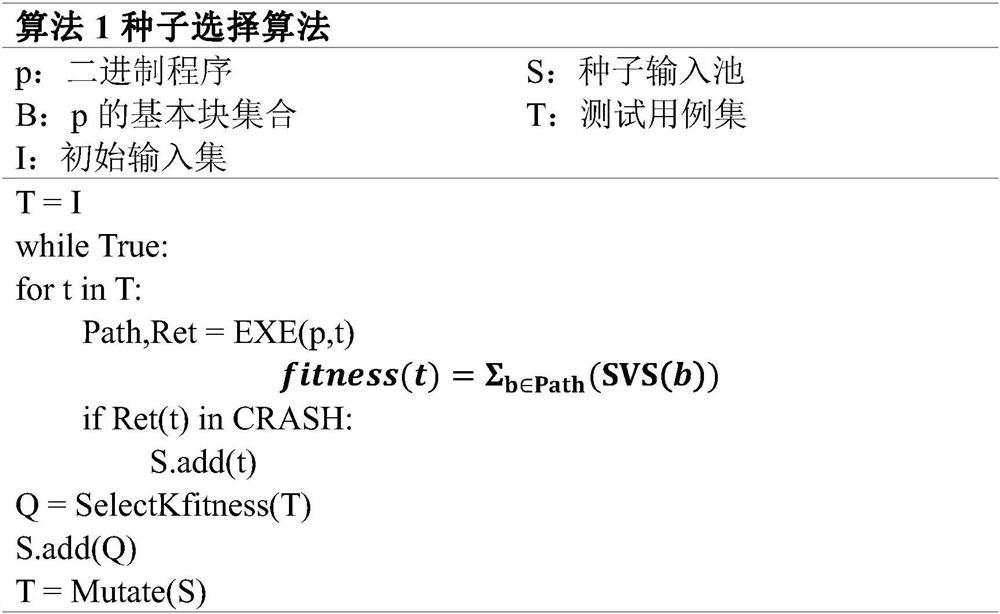
The invention discloses a seed optimization method based on a vulnerability prediction model, and the method comprises the steps: building the vulnerability prediction model, enabling the vulnerability prediction model to be used for predicting the vulnerability of a function in a target program, achieving the seed optimization through the screening of seeds, and tracking the execution information of the target program through a dynamic binary detection method, and calculating a static vulnerability score SVS according to the vulnerability probability obtained by the vulnerability prediction model, and storing the test case with the score higher than a certain threshold in a seed input pool. The test cases are selected by using a seed selection strategy and stored in a seed input pool, and executed test cases capable of causing collapse are also stored in the seed input pool. Next generation inputs of the seed input pool are generated by mutating the inputs in the seed input pool. According to the method, the vulnerability prediction probability of the basic block of the target program is fully considered, effective variation aiming at the target program is favorably realized, the effectiveness of the test case is improved, and vulnerabilities are more easily mined.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP +2
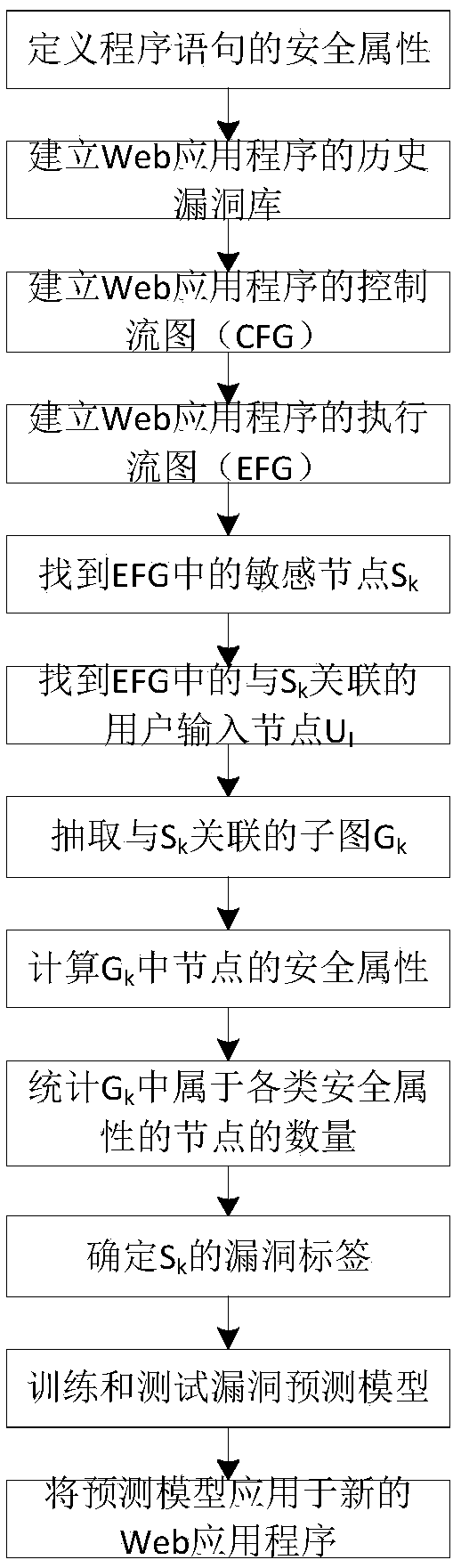
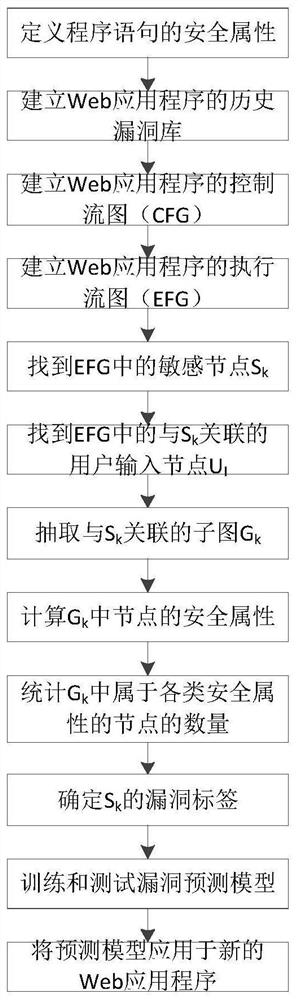
A Web application security vulnerability prediction method based on execution flow graph
ActiveCN109101820APredicting Vulnerability LocationsPlatform integrity maintainanceNODALProgram slicing
The invention discloses a Web application security vulnerability prediction method based on an execution flow graph. The execution flow graph EFG is constructed according to the data dependency relationship and the control dependency relationship of the Web application; a sub-graph is extracted from the EFG with the node Sk where the security sensitive statement is located as an end point and theuser inputs node UI associated with the Sk as a starting point, and a metric element is extracted for each sub-graph; the concrete value of the metric element of the sub-graph is taken as the input and the Sk vulnerability of the corresponding sub-graph is taken as the output, the vulnerability prediction model is constructed, so as to realize the security vulnerability prediction of Web application. The invention comprises a judging node on the extraction of the metric element, and the workload is greatly reduced compared with the analysis of the program slice directly.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
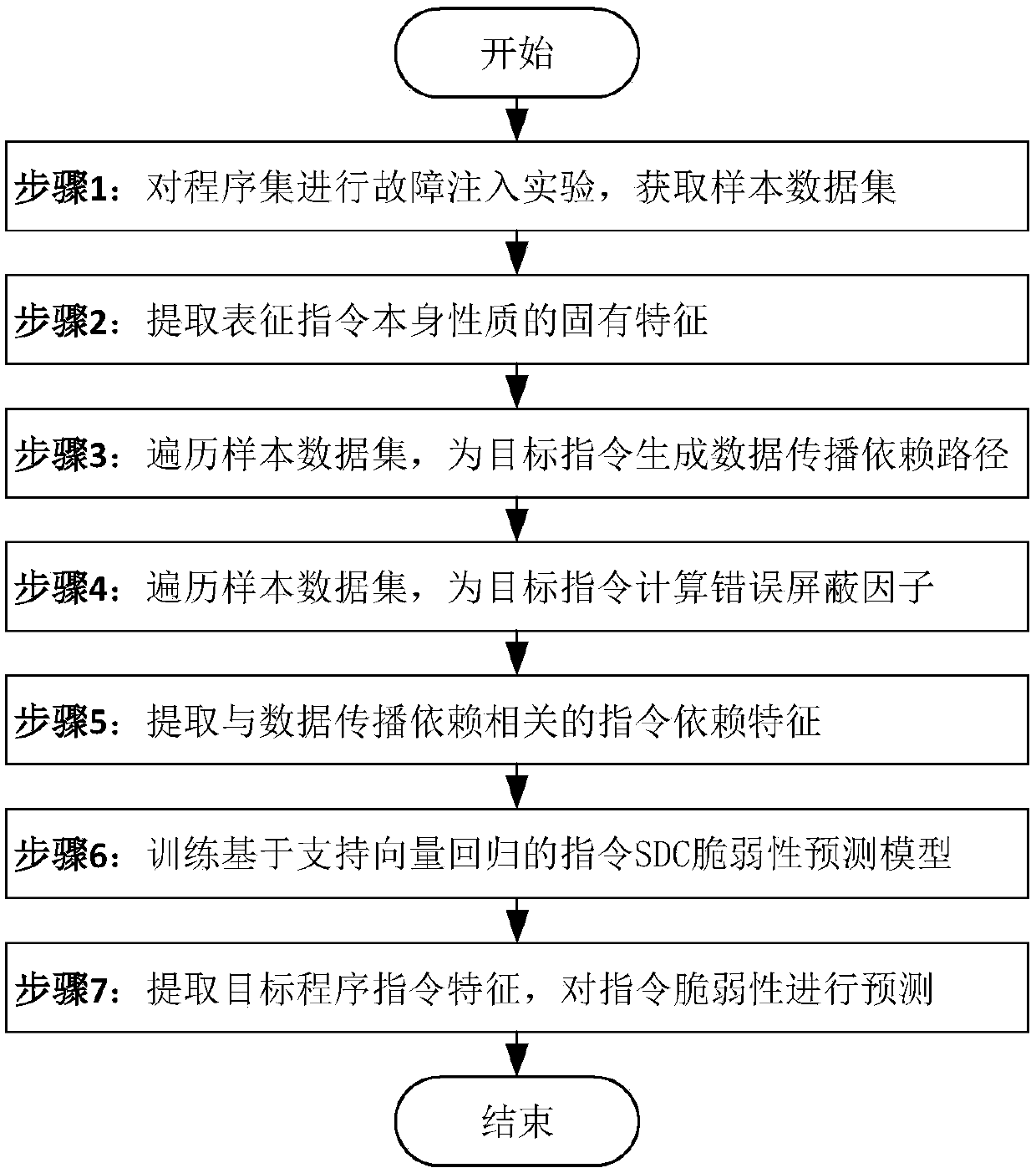
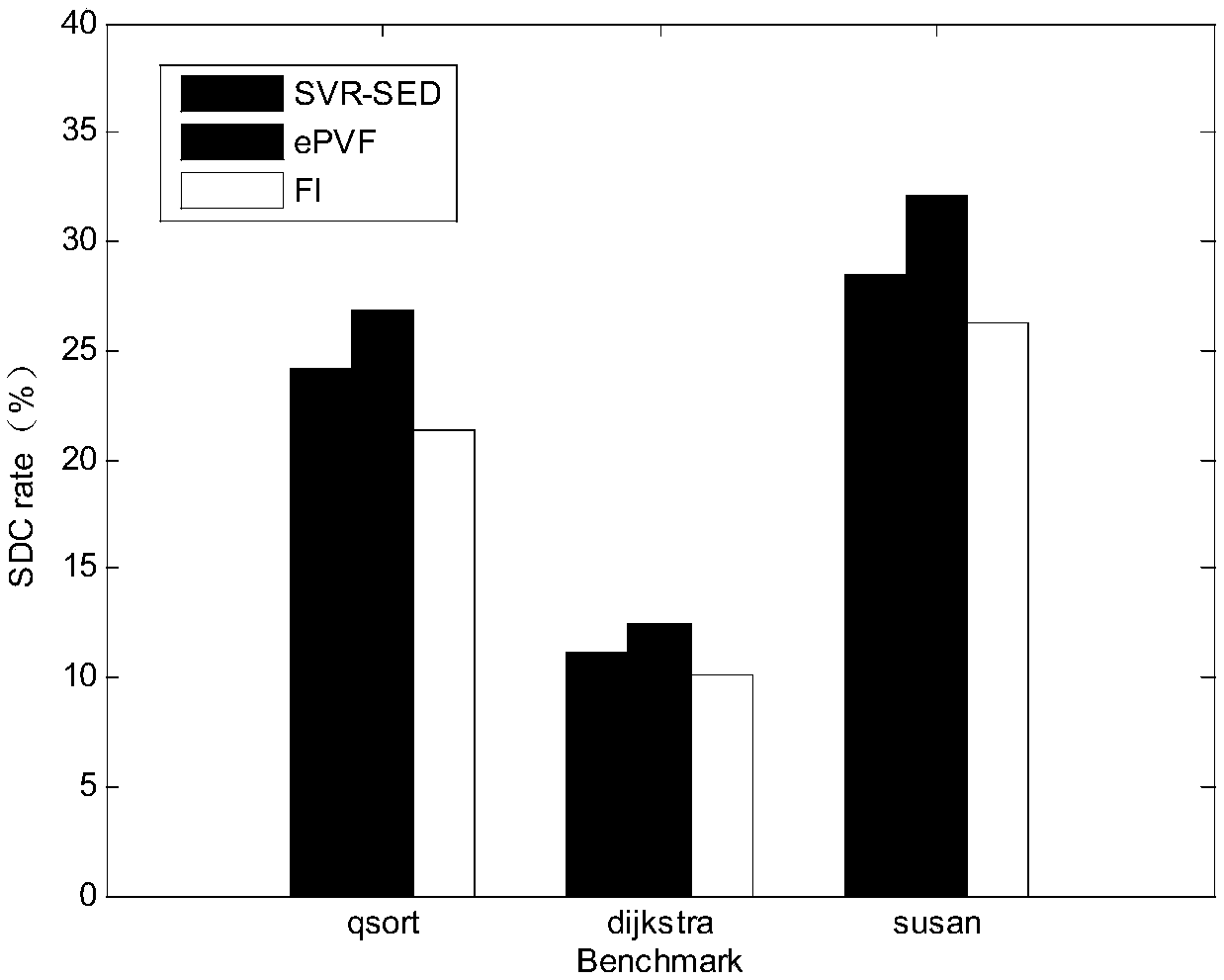
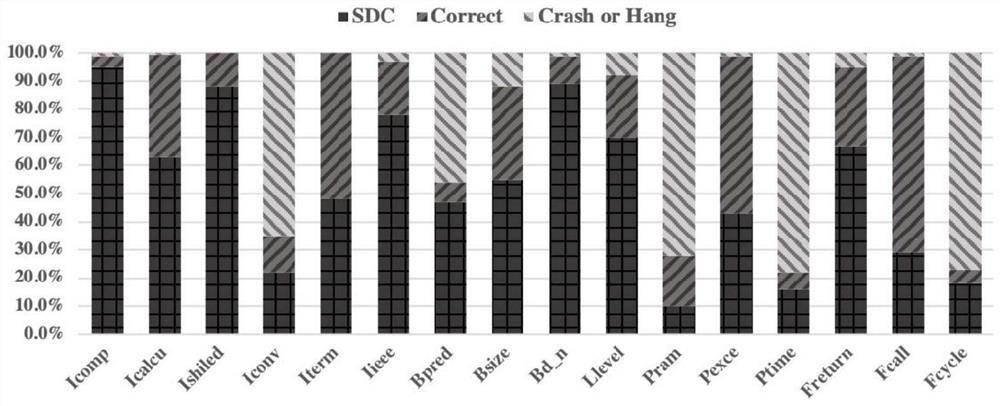
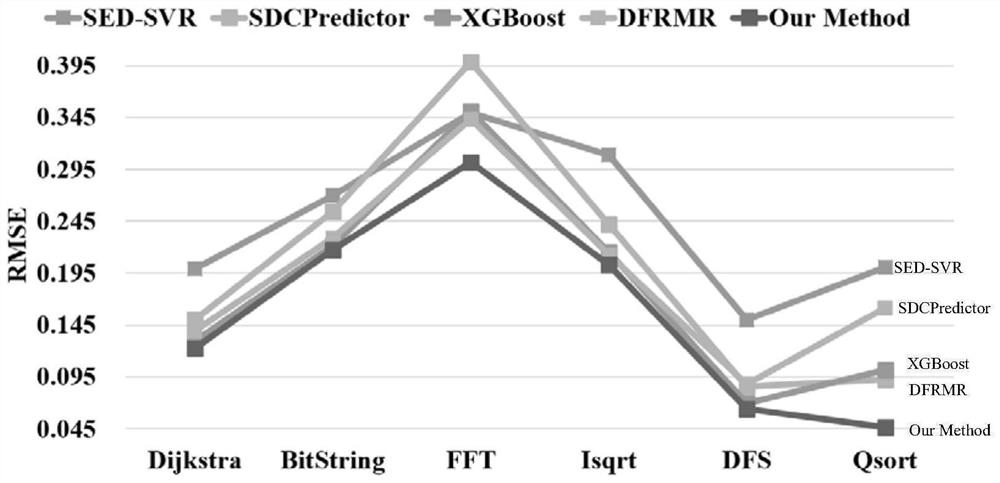
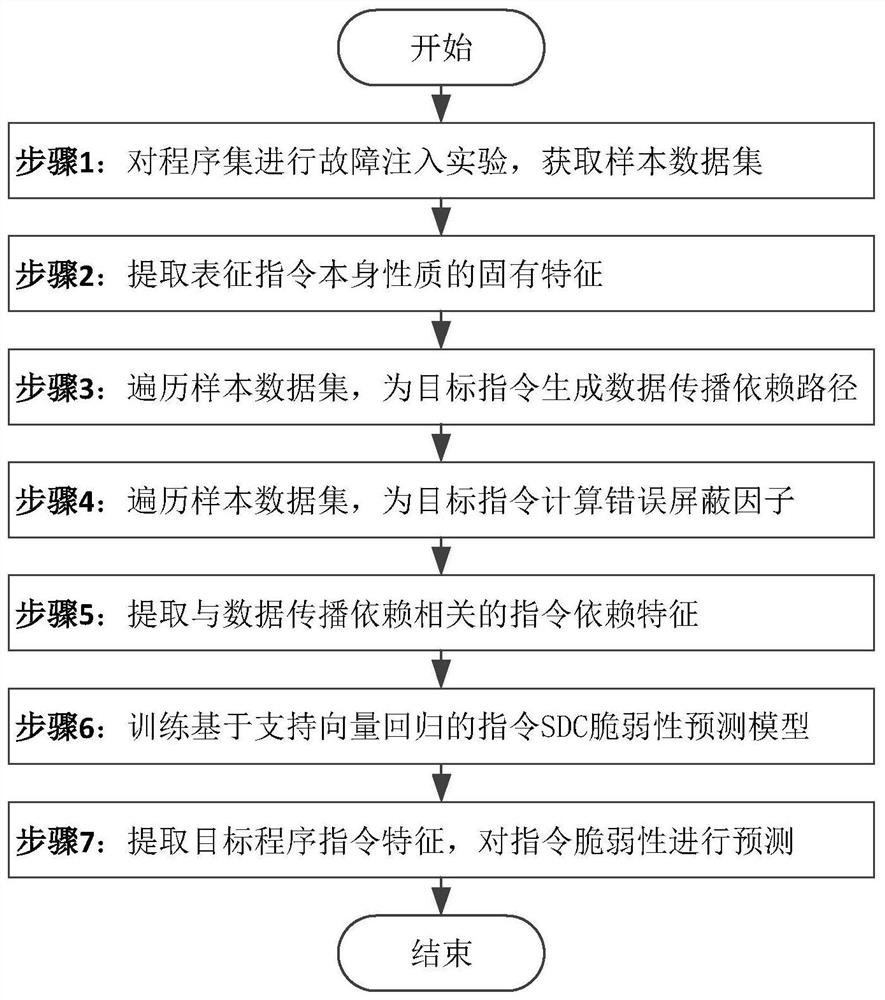
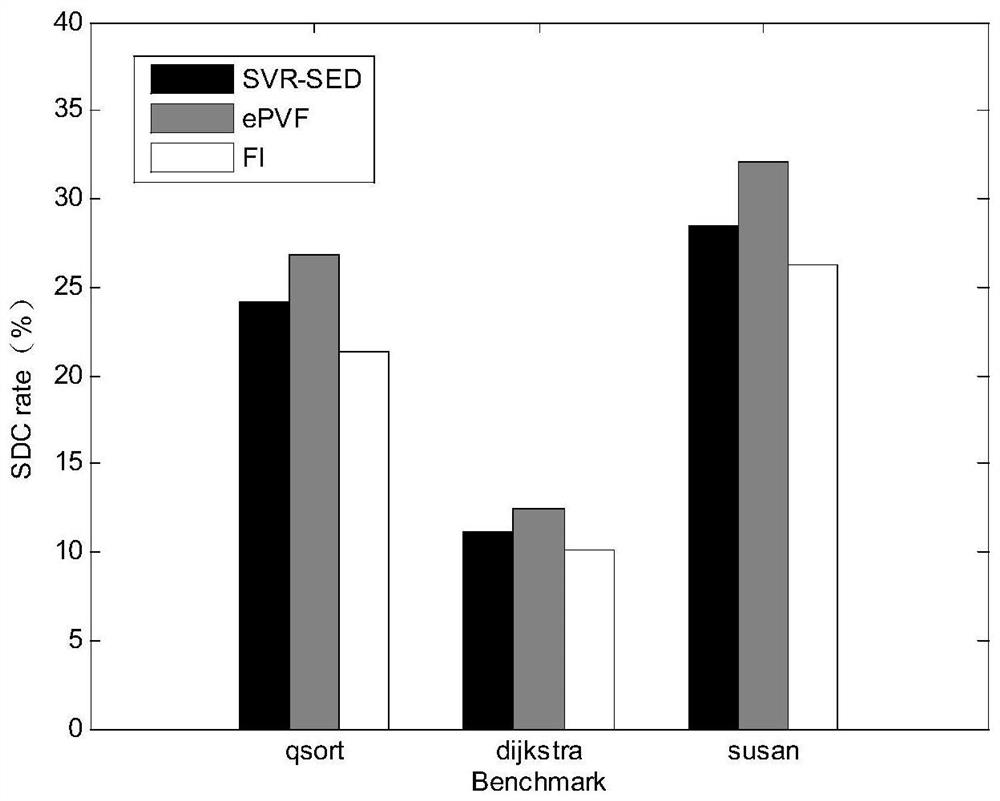
Method for predicting vulnerability of instruction SDC (Silent Data Corruption) based on support vector regression
ActiveCN108334903AImprove accuracyImprove generalization abilityCharacter and pattern recognitionProgram instructionData set
The invention discloses a method for predicting vulnerability of an instruction SDC (Silent Data Corruption) based on support vector regression. The method comprises the following steps: 1, carrying out a fault injection experiment on a program set to acquire a sample data set; 2, extracting inherent features characterizing the nature of the instruction; 3, transversing the sample data set, and generating a data propagation dependence path for a target instruction; 4, transversing the sample data set, and calculating fault screening factors for the target instruction; 5, extracting dependencyfeatures of the instruction relevant with data propagation dependence; 6, training a vulnerability prediction model of the instruction SDC based on the support vector regression; and 7, extracting thefeatures of the target program instruction, and predicting the vulnerability of the instruction. The method has the advantages of high prediction accuracy, and low performance overhead; and moreover,the method also can be effectively applied to predicting the vulnerability of the instruction SDC after the program is affected by transient faults.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
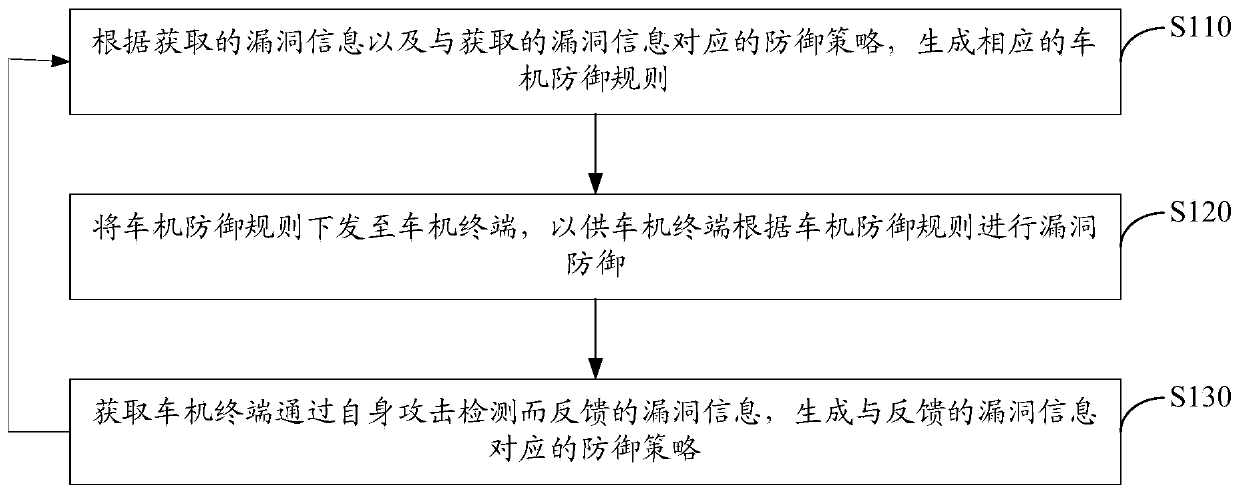
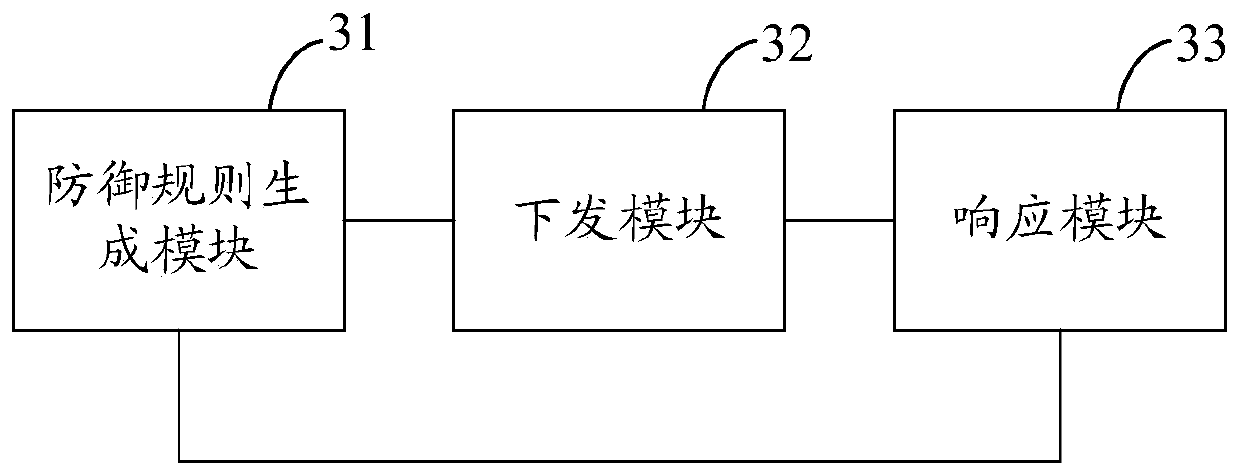
Safety protection method and device for vehicle-mounted system
PendingCN111447167ARealize security protectionImprove the protective effectPlatform integrity maintainanceTransmissionIn vehicleVulnerability prediction
The invention discloses a safety protection method and device for a vehicle-mounted system. The method comprises the following steps: S1, generating a corresponding vehicle machine defense rule according to acquired vulnerability information and a defense strategy corresponding to the acquired vulnerability information; S2, issuing the vehicle machine defense rule to a vehicle machine terminal, sothat the vehicle machine terminal performs vulnerability defense according to the vehicle machine defense rule; S3, acquiring vulnerability information fed back by the vehicle-mounted terminal through self-attack detection, and generating a defense strategy corresponding to the fed-back vulnerability information, and further executing the step S1. According to the scheme, vulnerability prediction, defense of the predicted vulnerability, attack detection of the terminal and quick response to attack detection of the terminal can be realized; loophole prediction is provided for the other terminal according to loophole detection and response results of the terminal, circulation is carried out in sequence, and a complete protection ecological cycle for the vehicle-mounted system is formed, sothat safety protection of the vehicle-mounted system can be integrally realized in multiple directions, and an excellent protection effect is achieved.
Owner:BEIJING QIHOO TECH CO LTD
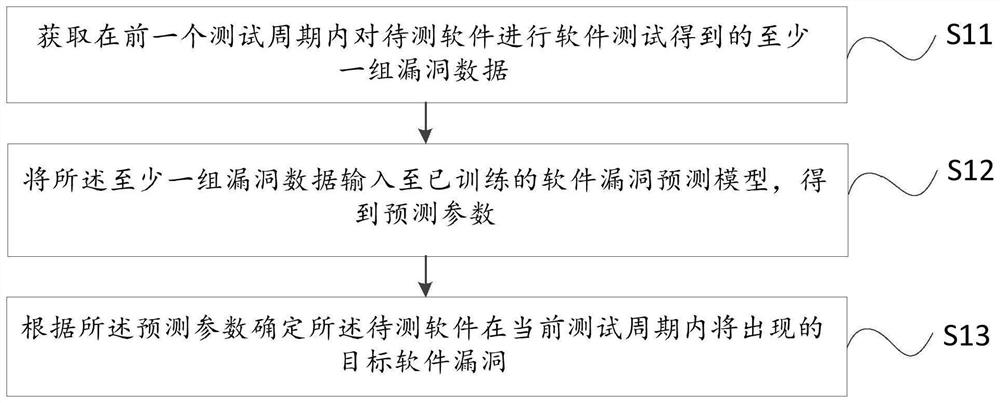
Software vulnerability prediction method and device, computer equipment and storage medium
PendingCN112417463APrediction helpsTest helpsCharacter and pattern recognitionSoftware testing/debuggingTest efficiencyData mining
Embodiments of the invention relate to a software vulnerability prediction method and apparatus, a computer device and a storage medium. The method comprises the steps of obtaining at least one groupof vulnerability data obtained by performing a software test on to-be-tested software in a previous test period; inputting the at least one group of vulnerability data into a trained software vulnerability prediction model to obtain prediction parameters, the prediction parameters at least comprising a plurality of software vulnerabilities and the probability of occurrence of each software vulnerability of the to-be-tested software; and according to the prediction parameter, determining a target software vulnerability to occur in the to-be-tested software in the current test period, so that the possible vulnerability can be specifically and emphatically tested according to the prediction result of the model in the later software test process, and the software test efficiency and effect areimproved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD
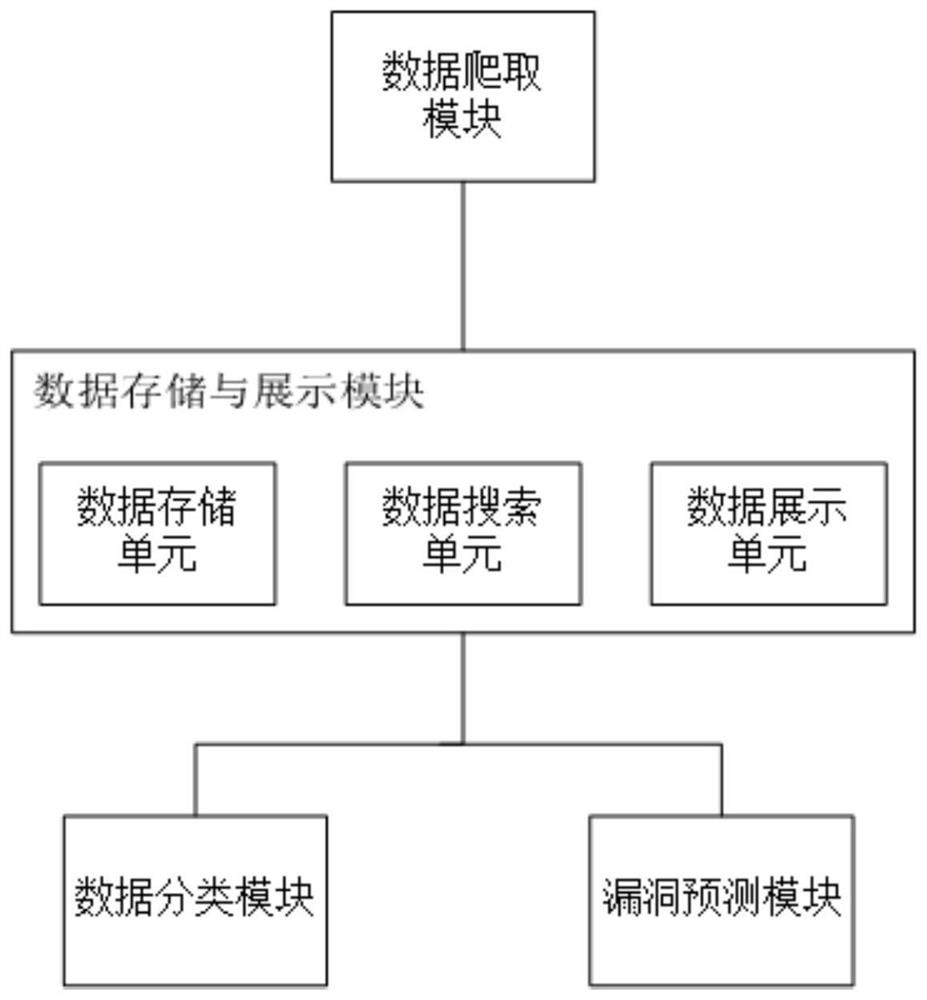
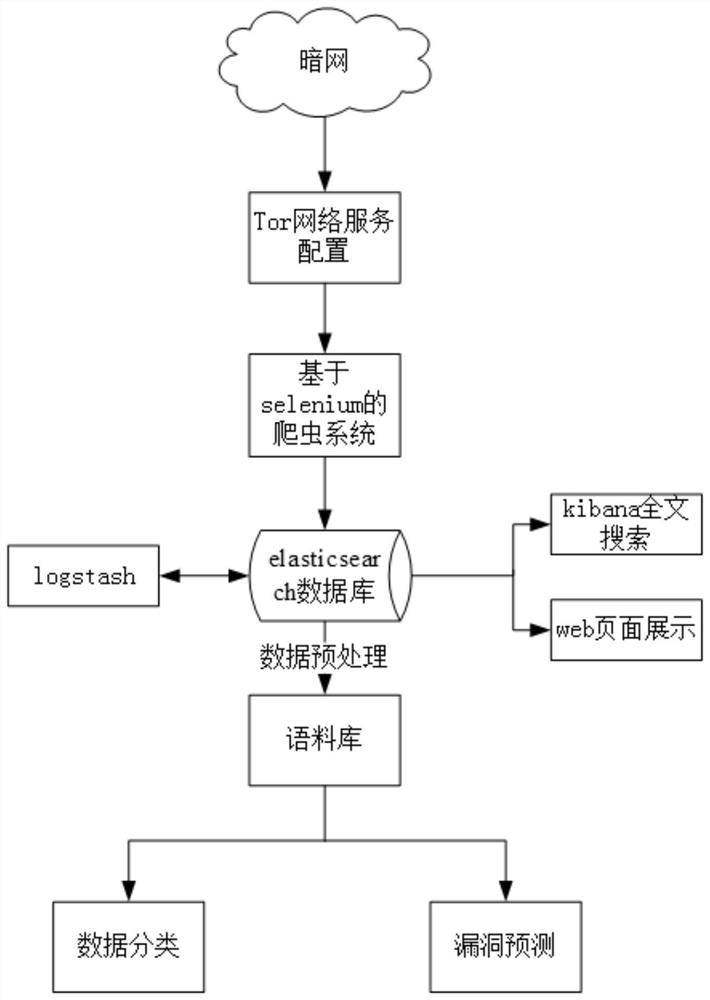
Dark network threat prediction system based on machine learning
InactiveCN112202788APrevent Zero-Day VulnerabilitiesUnderstand the purposeMachine learningTransmissionFull text searchData display
Owner:SHANGHAI JIAO TONG UNIV
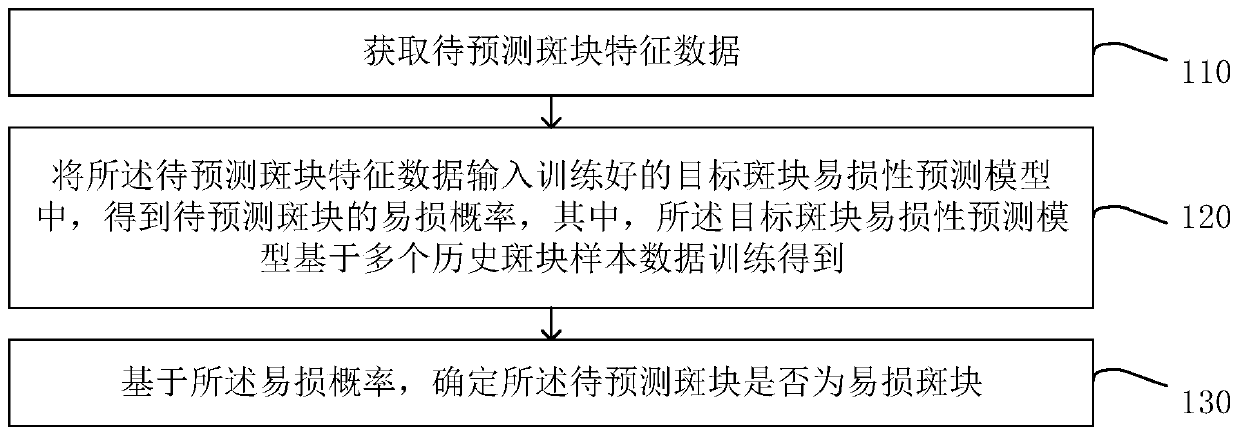
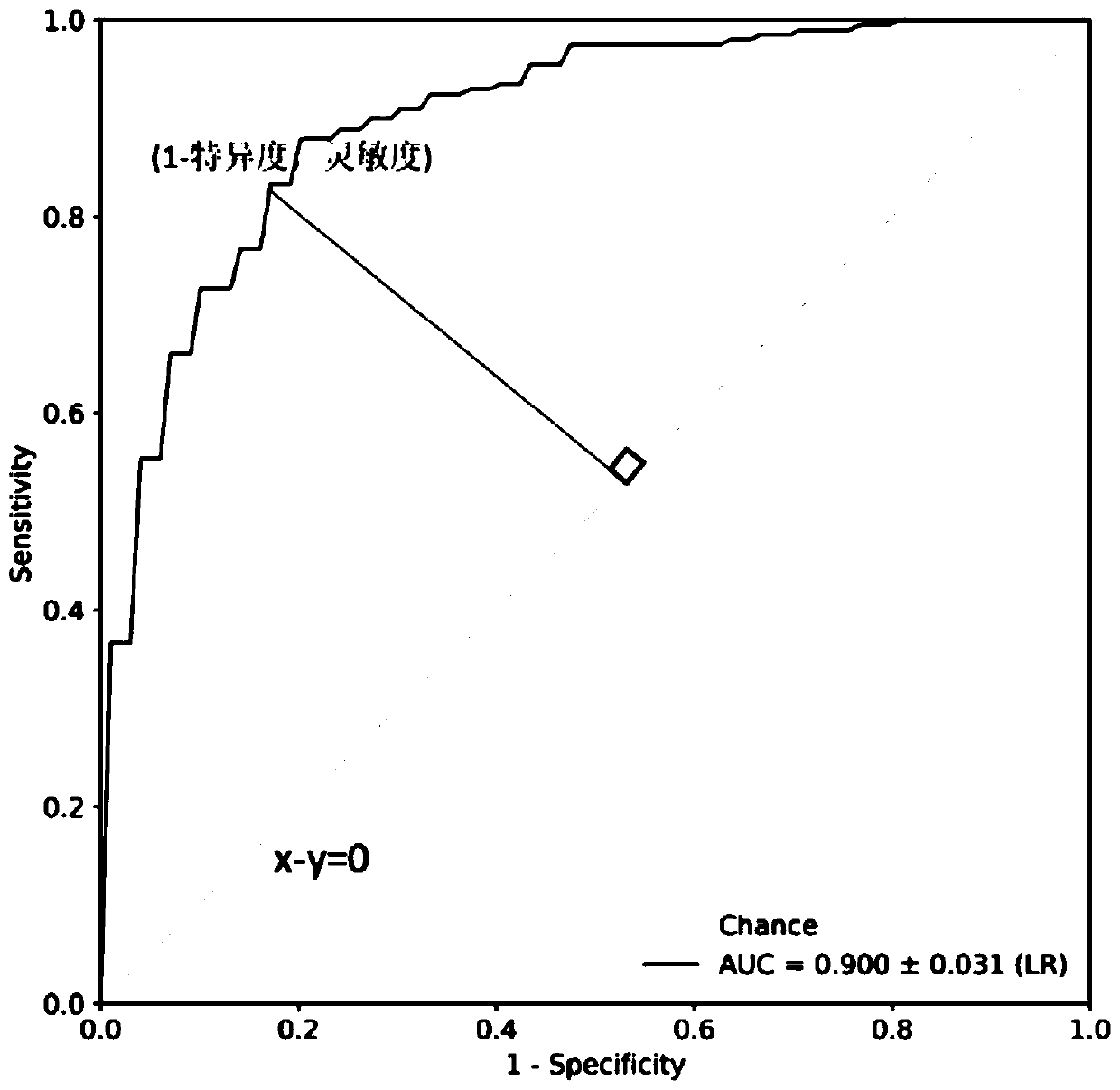
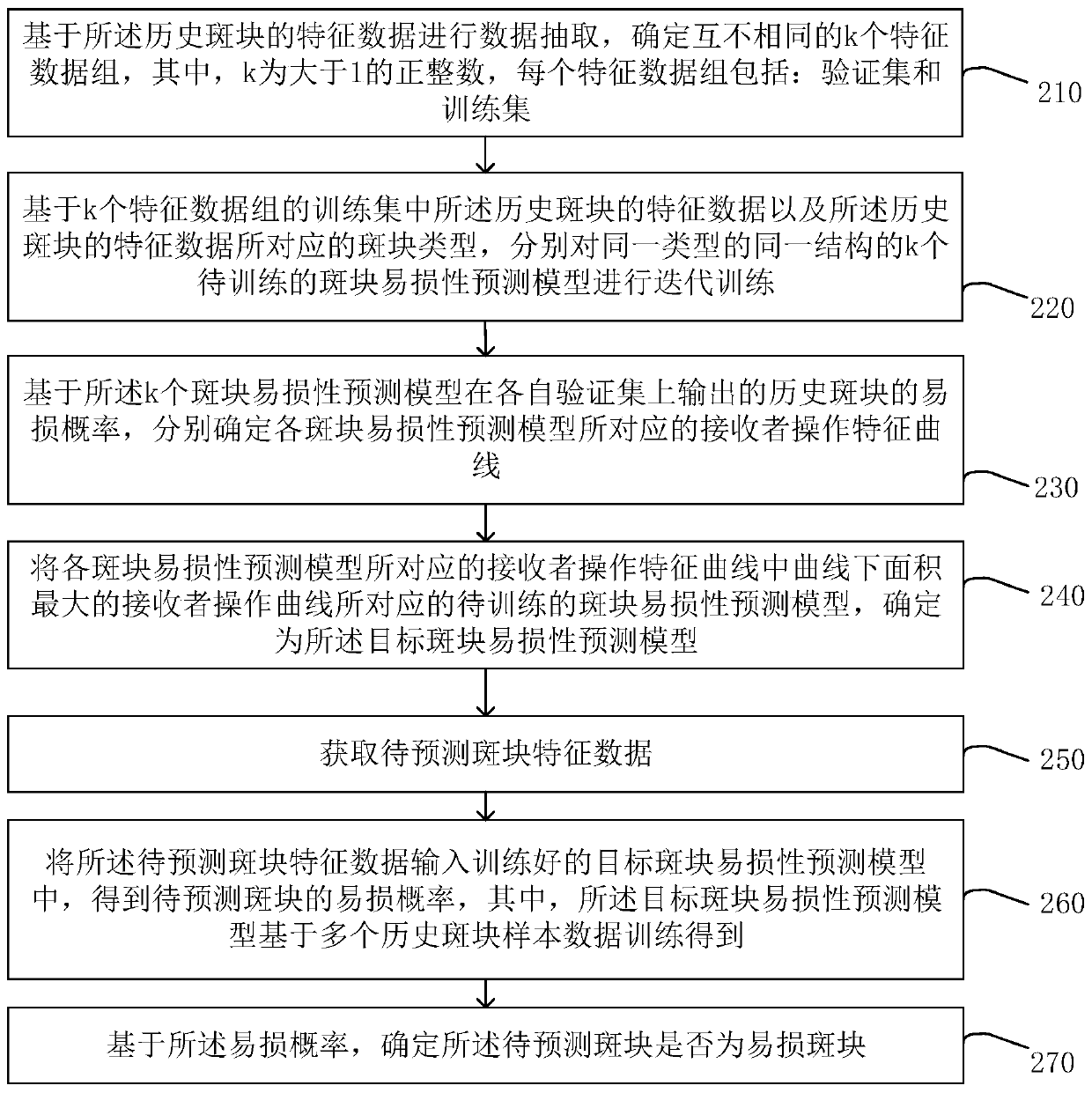
Plaque vulnerability prediction method and device, equipment and storage medium
PendingCN111583260AVulnerability is effectiveAccurate predictionImage enhancementImage analysisVulnerable plaqueEngineering
The embodiment of the invention discloses a plaque vulnerability prediction method and device, equipment and a storage medium. The method comprises the following steps: acquiring feature data of a to-be-predicted plaque; inputting the to-be-predicted plaque feature data into a trained target plaque vulnerability prediction model to obtain a vulnerability probability of the to-be-predicted plaque,with the target plaque vulnerability prediction model being obtained by training based on a plurality of historical plaque sample data; and determining whether the to-be-predicted plaque is a vulnerable plaque based on the vulnerable probability. Therefore, the probability that the plaque is a vulnerable plaque can be accurately and effectively predicted by using a non-invasive method.
Owner:FUWAI HOSPITAL CHINESE ACAD OF MEDICAL SCI & PEKING UNION MEDICAL COLLEGE +1
Power distribution network toughness improvement strategy based on environmental data prediction
PendingCN113962461AImprove the effect of early warningAccurate analysisForecastingDesign optimisation/simulationData predictionVulnerability prediction
The invention relates to a power distribution network toughness improvement strategy based on environmental data prediction. Comprehensive environment data prediction analysis is carried out on the operation condition of a power distribution network and vulnerable links of the power distribution network are predicted, so that the early warning capability of disaster risks is improved; a power distribution network vulnerability prediction model based on environmental data pre-judgment is established, and the fault rate prediction level is improved; a power distribution network fault bearing capacity evaluation method based on environmental data is provided, and a power distribution network fault bearing capacity evaluation method is provided; the influence of ice disaster on the toughness of a power distribution network is reflected by using the change of system performance, and a power distribution network toughness evaluation model is established; the invention aims at implementing planning and scheduling measures for improving the toughness of a power distribution network in a catastrophe defense stage and a post-disaster recovery stage, and further provides a power distribution network toughness improvement strategy under environmental data pre-judgment. According to the invention, the toughness of a power distribution network is comprehensively improved in a disaster process and a post-disaster process through coordination and cooperation of active defense before a fault occurs and fault recovery after disaster.
Owner:FUSHUN POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER SUPPLY +1
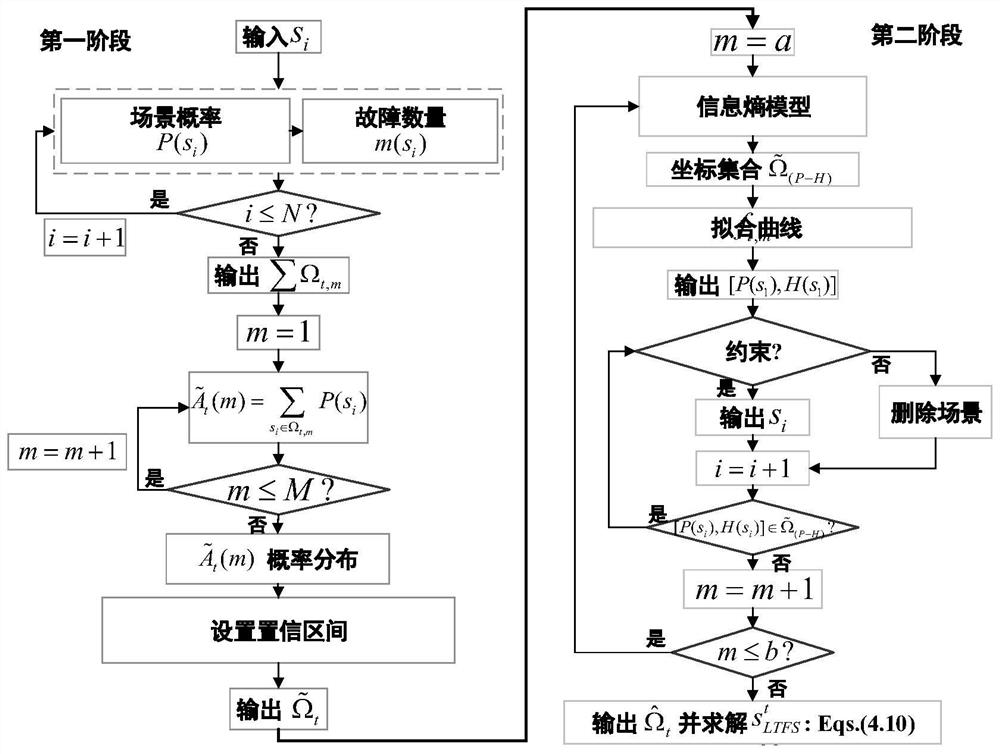
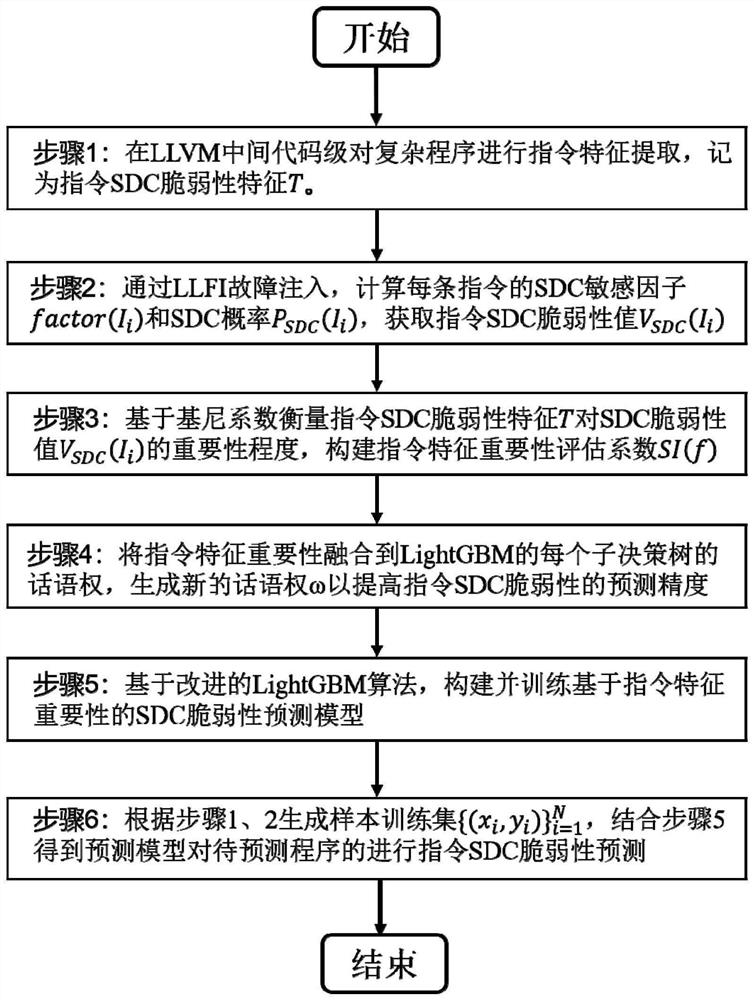
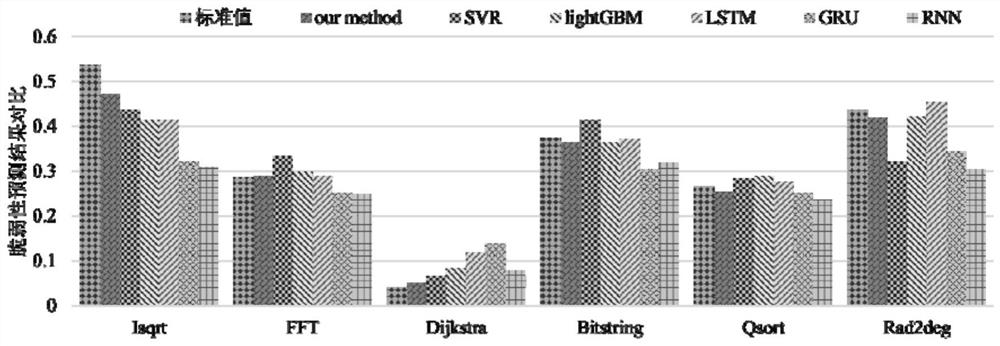
SDC vulnerability prediction method based on instruction feature importance
PendingCN114511015AReduce consumptionImprove learning accuracyCharacter and pattern recognitionData classFeature extraction
The invention discloses an SDC vulnerability prediction method based on instruction feature importance. The method comprises the following steps: performing instruction feature extraction on a complex program; random fault injection is carried out on the complex program, and an instruction SDC vulnerability value is obtained; measuring the importance degree of the instruction SDC vulnerability feature T to an SDC vulnerability value based on a Gini coefficient, and constructing an instruction feature importance evaluation coefficient; the instruction feature importance is fused into the discourse right of each sub-decision tree of LightGBM, and a new discourse right omega is generated to improve the prediction precision of the instruction SDC vulnerability. Based on an improved LightGBM algorithm, constructing and training an SDC vulnerability prediction model based on instruction feature importance; and performing instruction SDC vulnerability prediction on the to-be-predicted program by the obtained final SDC vulnerability prediction model. Compared with other methods, the method has higher vulnerability prediction precision, can effectively reduce memory consumption and calculation cost, can be applied to standard data types and mixed data types, and has the advantages of light weight, high interpretation and the like.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
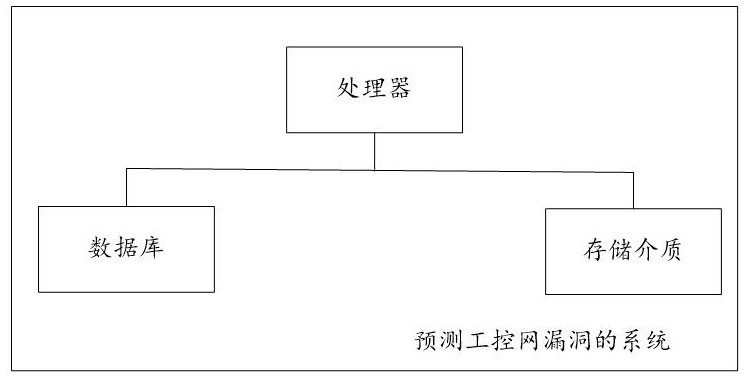
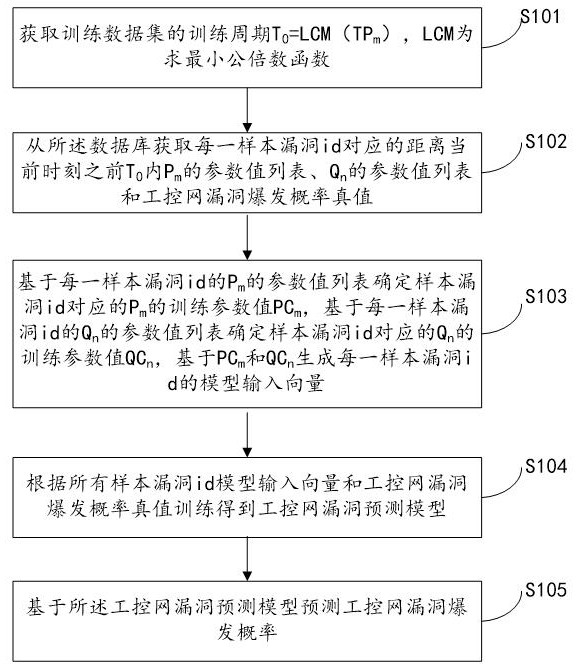
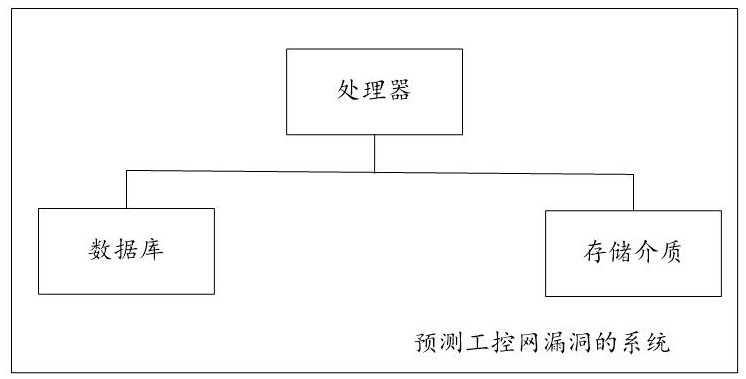
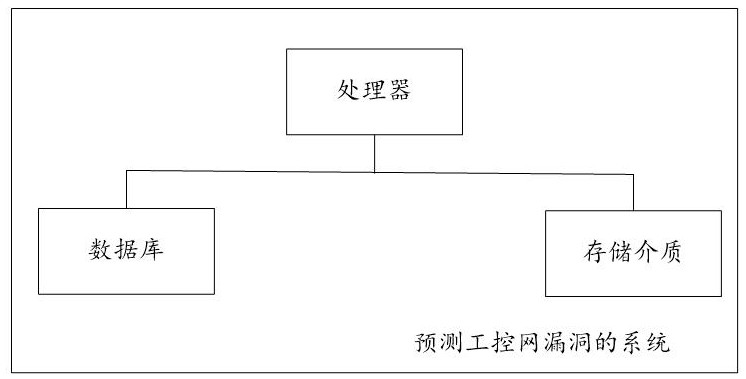
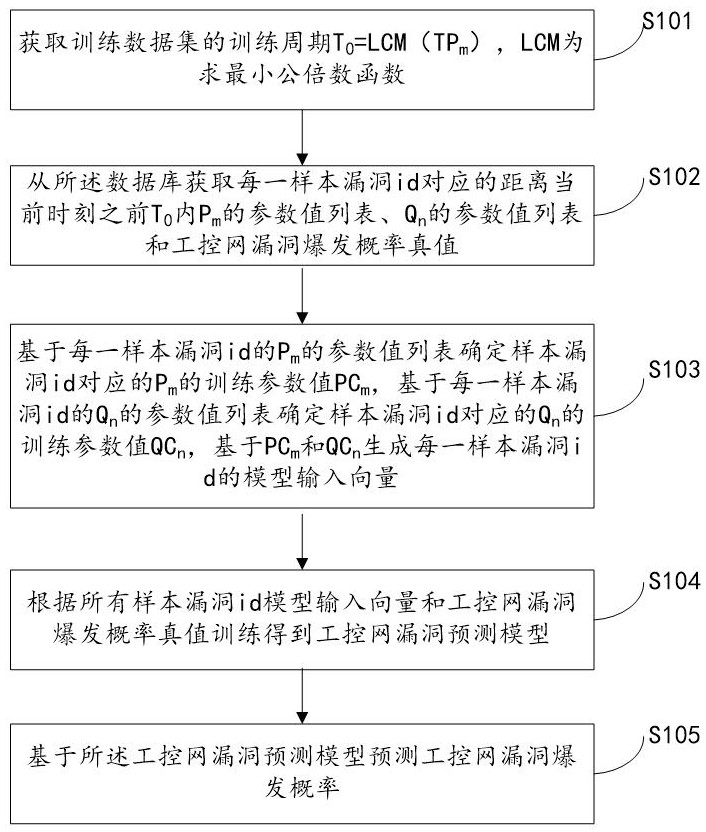
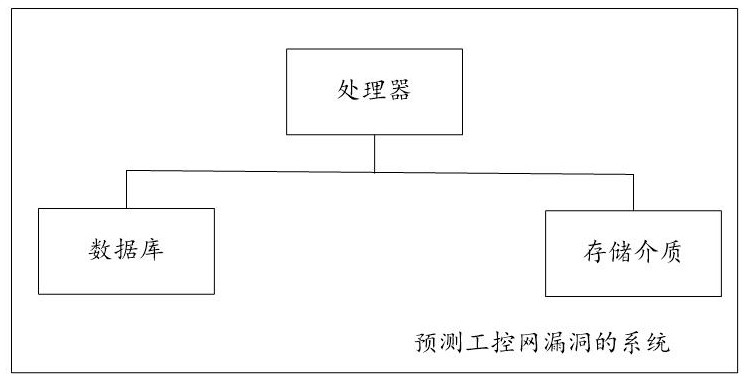
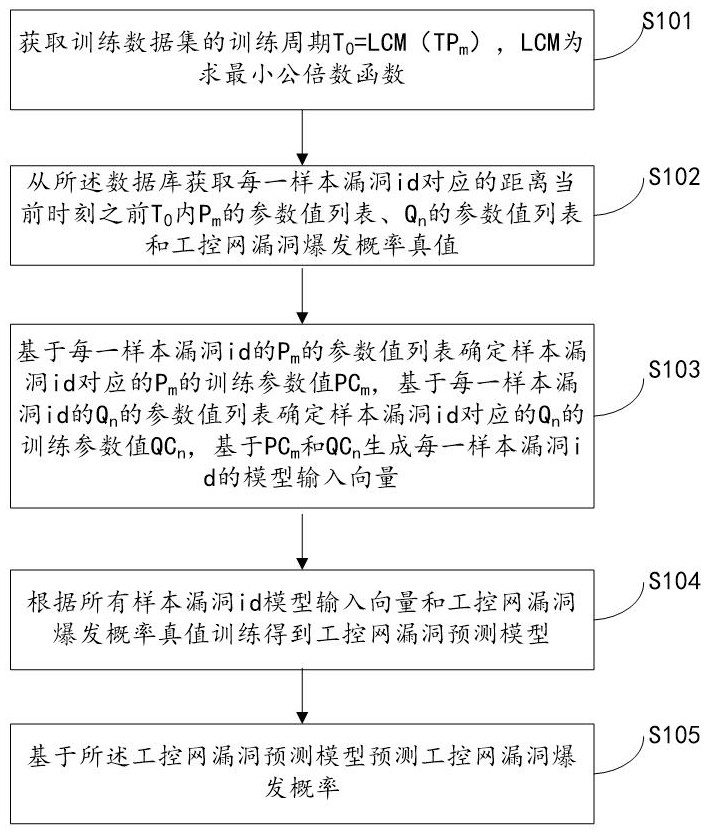
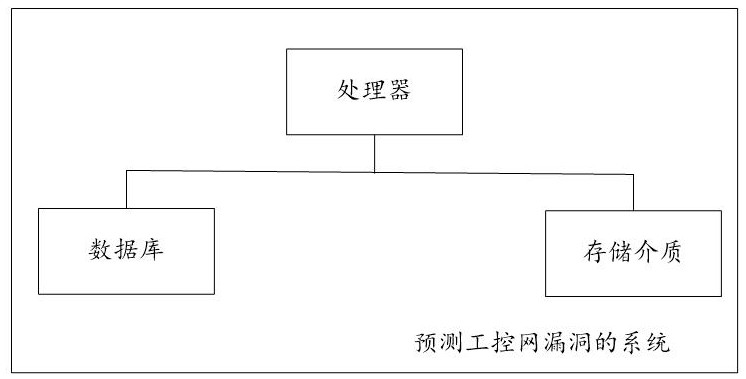
A system for predicting industrial control network vulnerabilities based on Internet and industrial control network vulnerability parameters
ActiveCN113792300BWidely used valueImprove securityCharacter and pattern recognitionNatural language data processingThe InternetEngineering
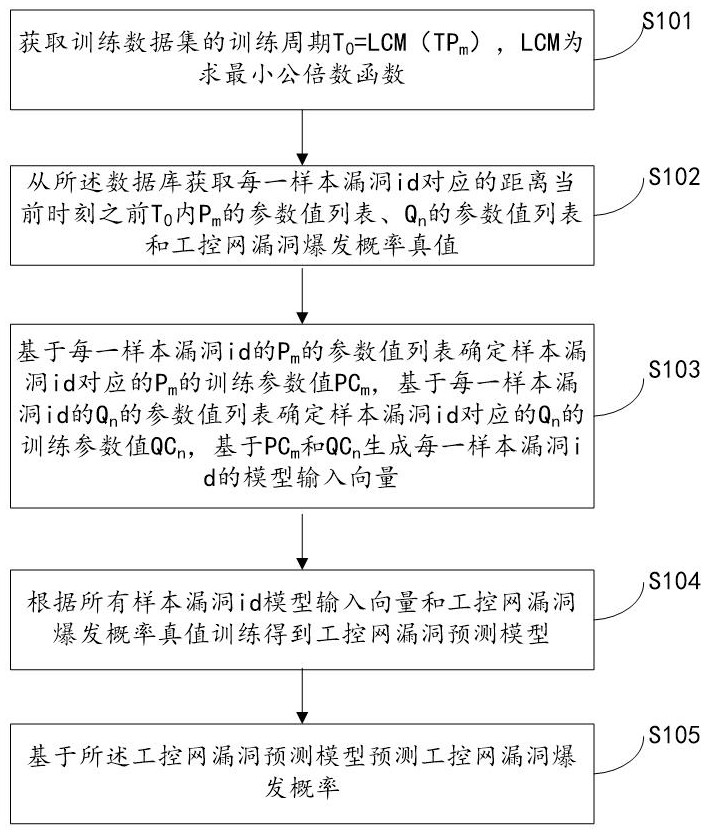
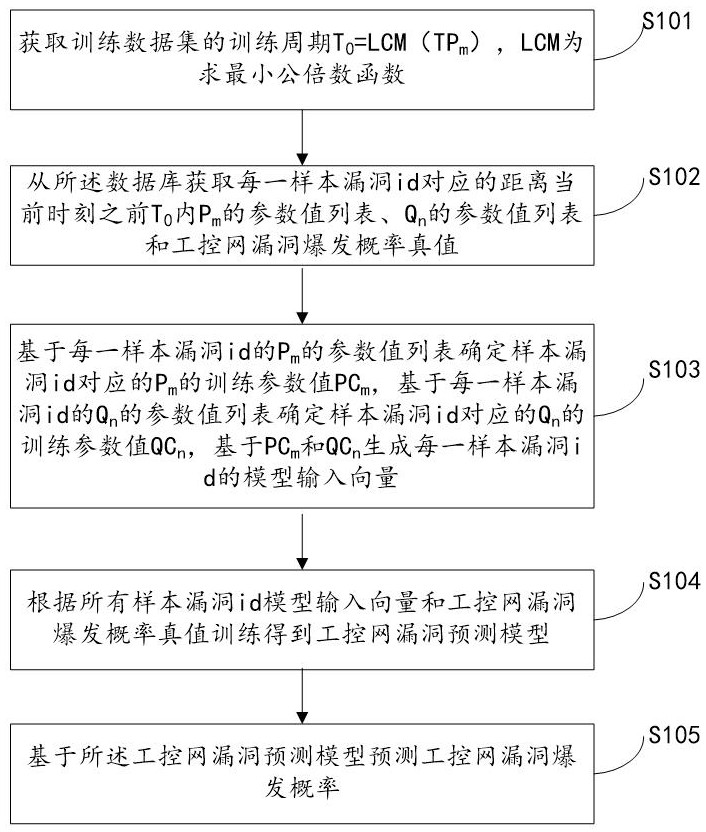
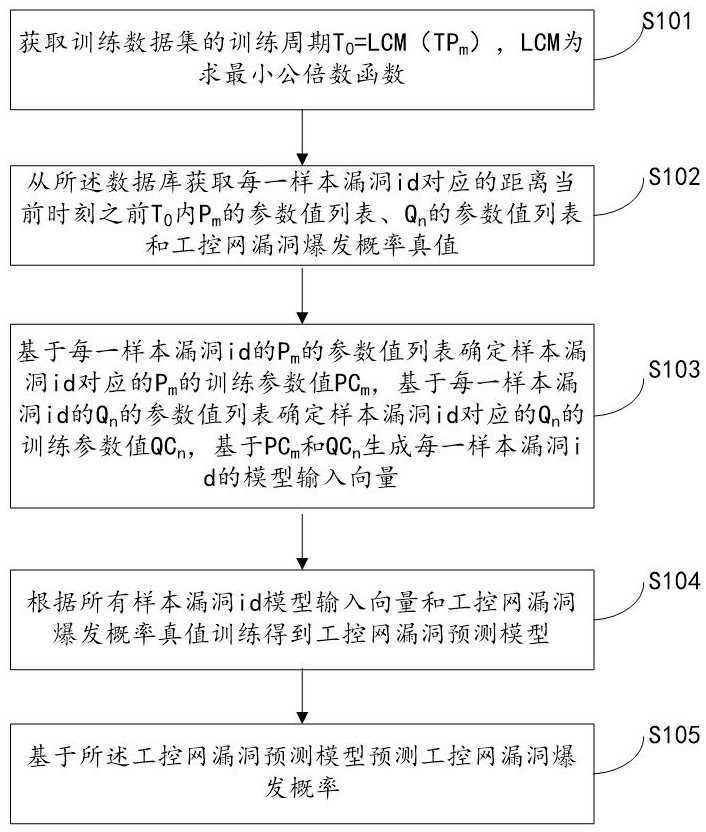
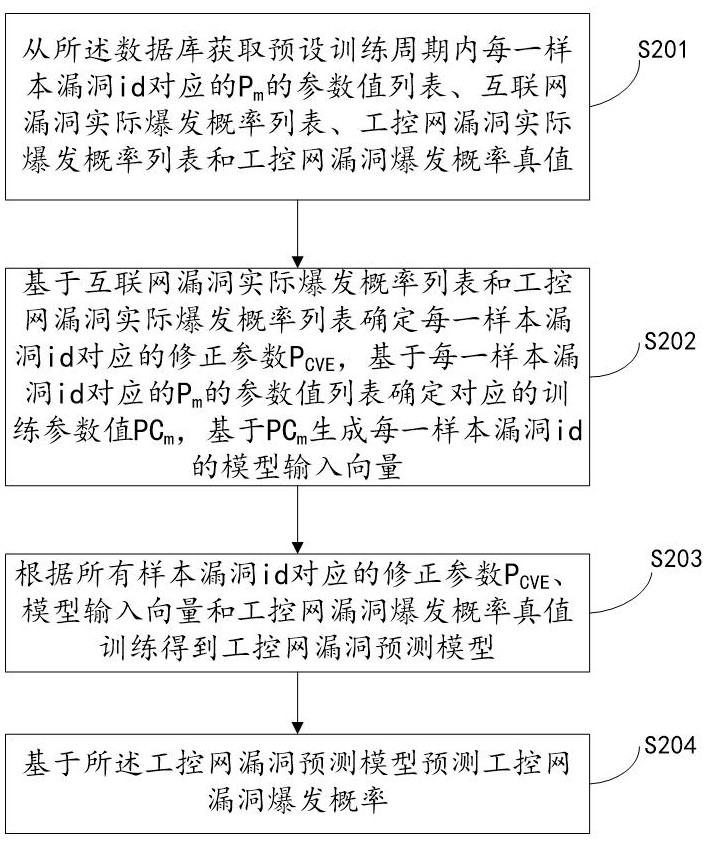
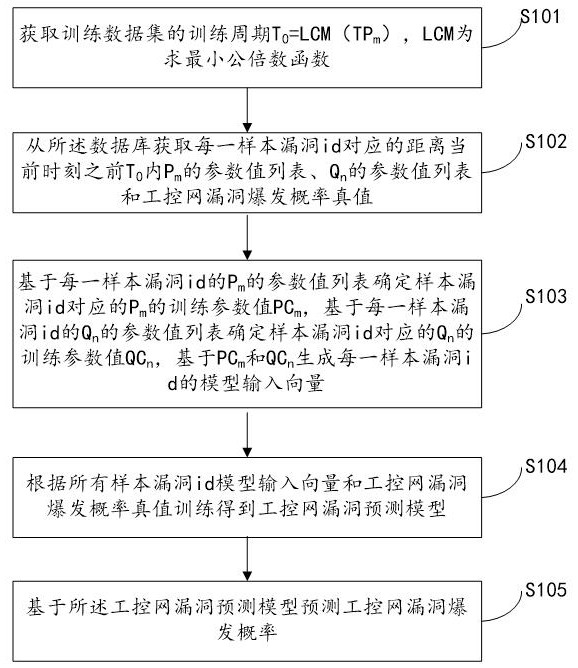
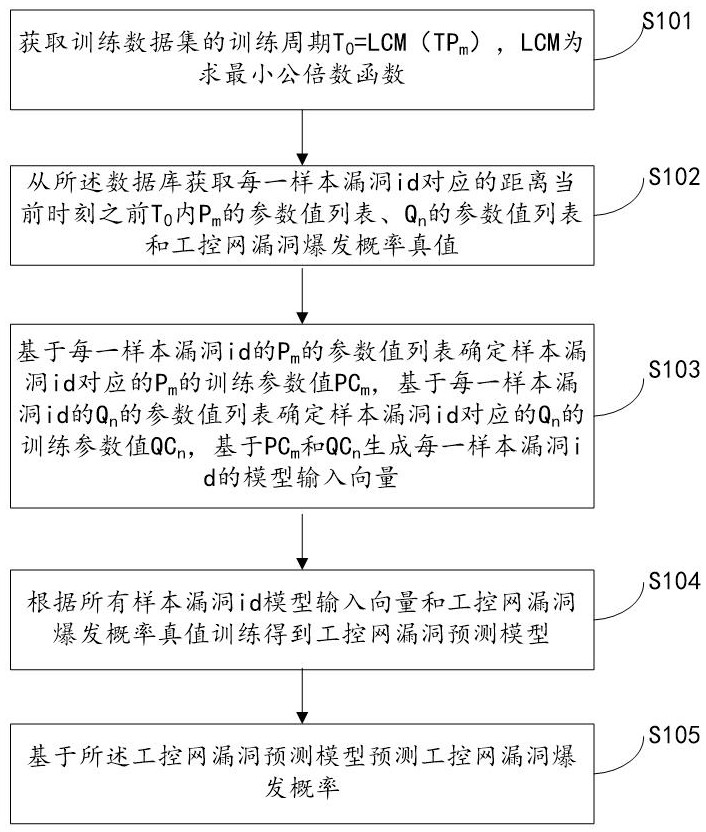
The present invention relates to a system for predicting the vulnerability of the industrial control network based on the Internet and the vulnerability parameters of the industrial control network, realizing step S101, obtaining the training period T of the training data set 0 =LCM(TP m ); step S102, obtaining from the database the distance T before the current moment corresponding to each sample vulnerability id 0 Inner P m A list of parameter values for , Q n Parameter value list and industrial control network vulnerability outbreak probability true value; Step S103, determine P m The training parameter value PC m and Q n The training parameter value QC n , PC-based m and QC n Generate the model input vector of each sample vulnerability id; step S104, obtain the industrial control network vulnerability prediction model according to all sample vulnerability id model input vectors and the true value training of the industrial control network vulnerability outbreak probability; step S105, predict based on the industrial control network vulnerability prediction model Explosion probability of industrial control network vulnerabilities. The invention can quickly and accurately predict the outbreak probability of loopholes in the industrial control network and improve the security of the industrial control network.
Owner:山东云天安全技术有限公司
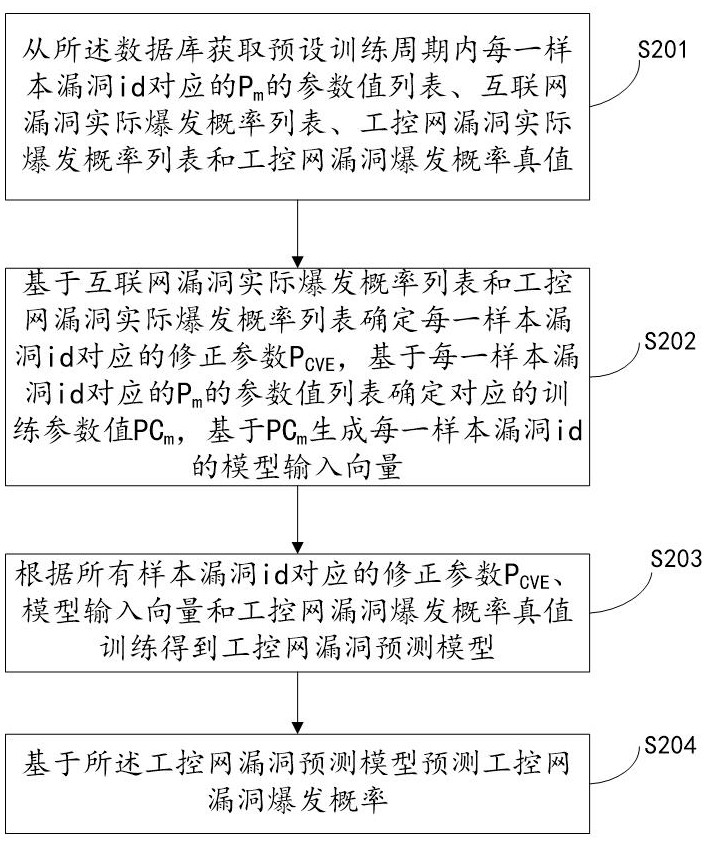
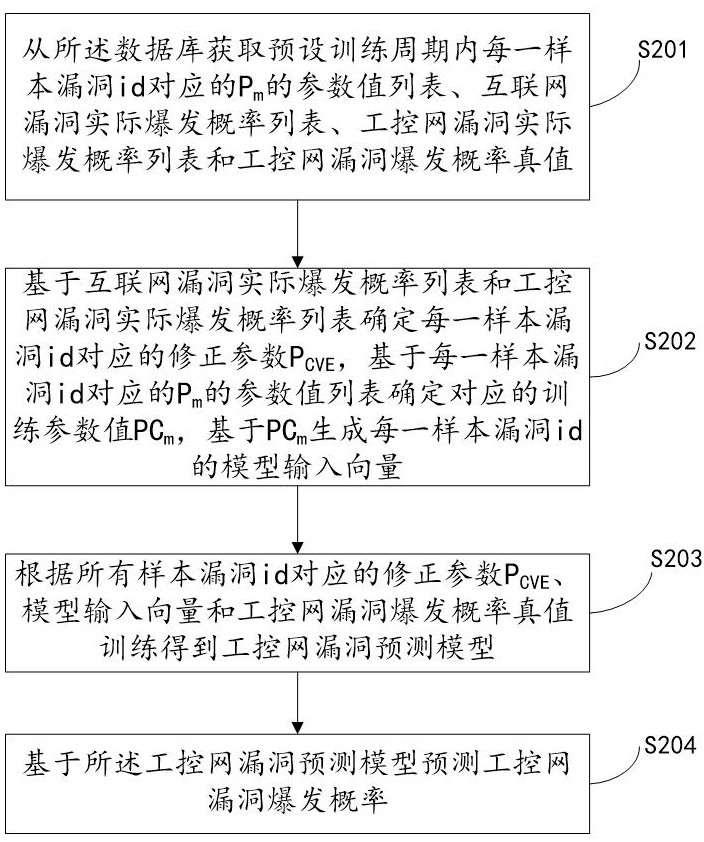
System for predicting industrial control network vulnerabilities based on correction parameters
ActiveCN114021149AFairly technologically advancedQuite practicalPlatform integrity maintainanceThe InternetEngineering
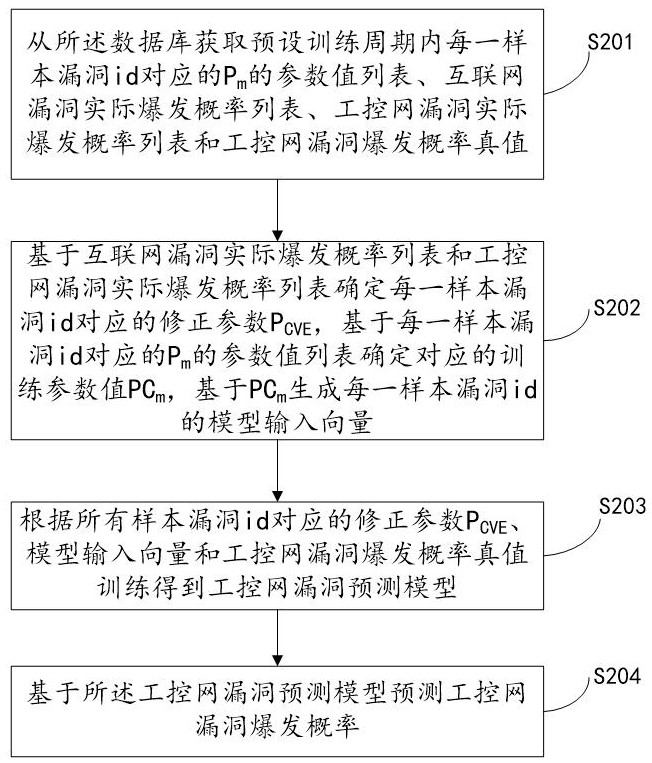
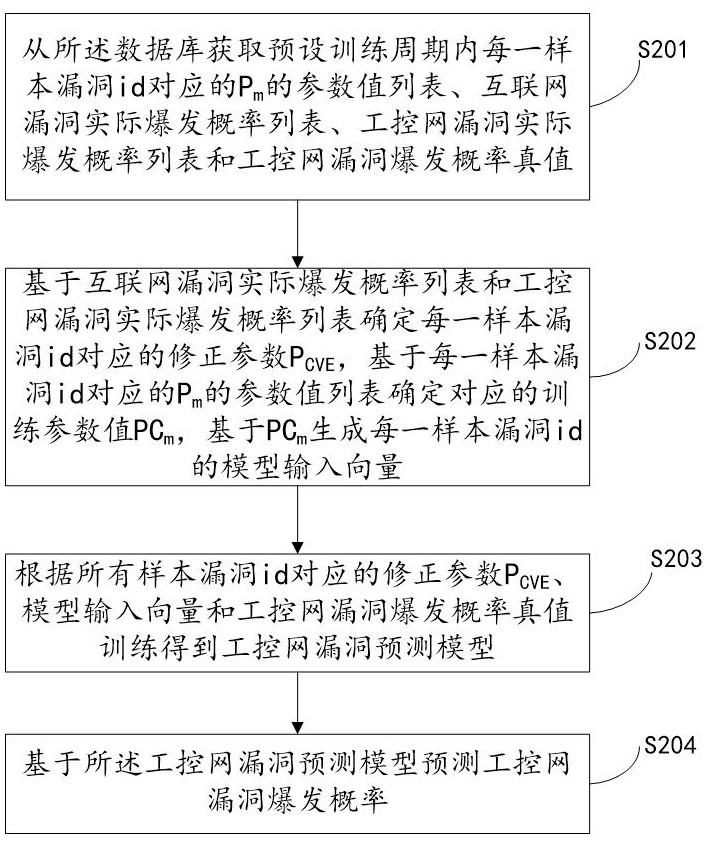
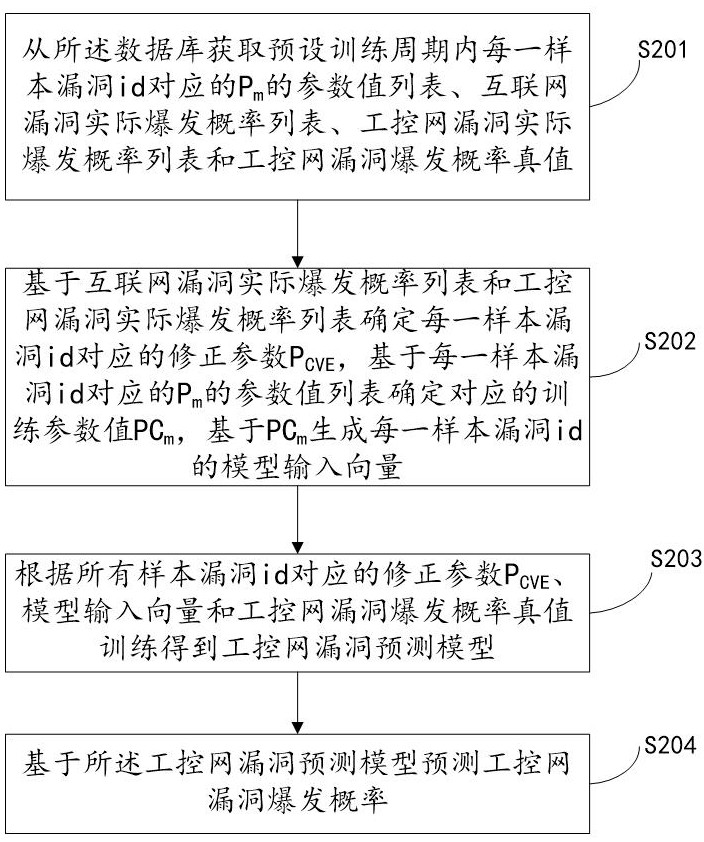
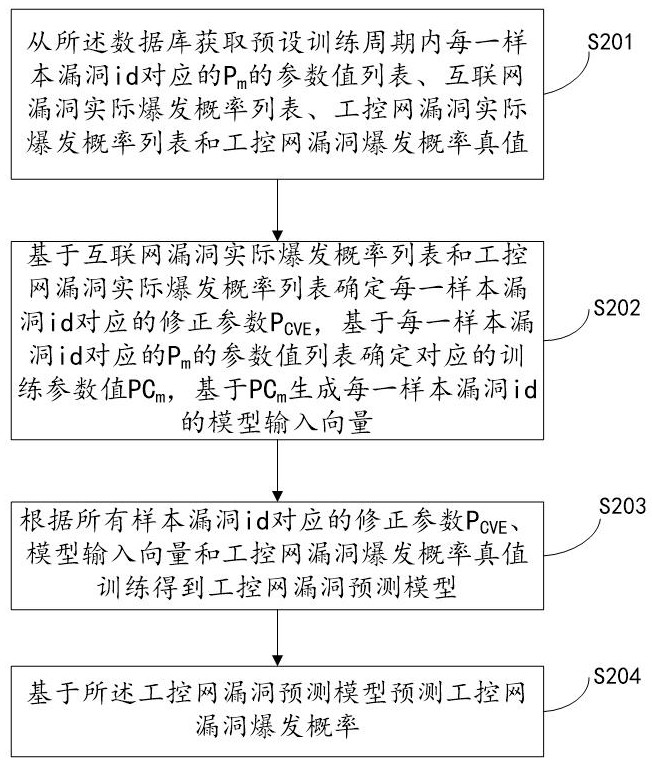
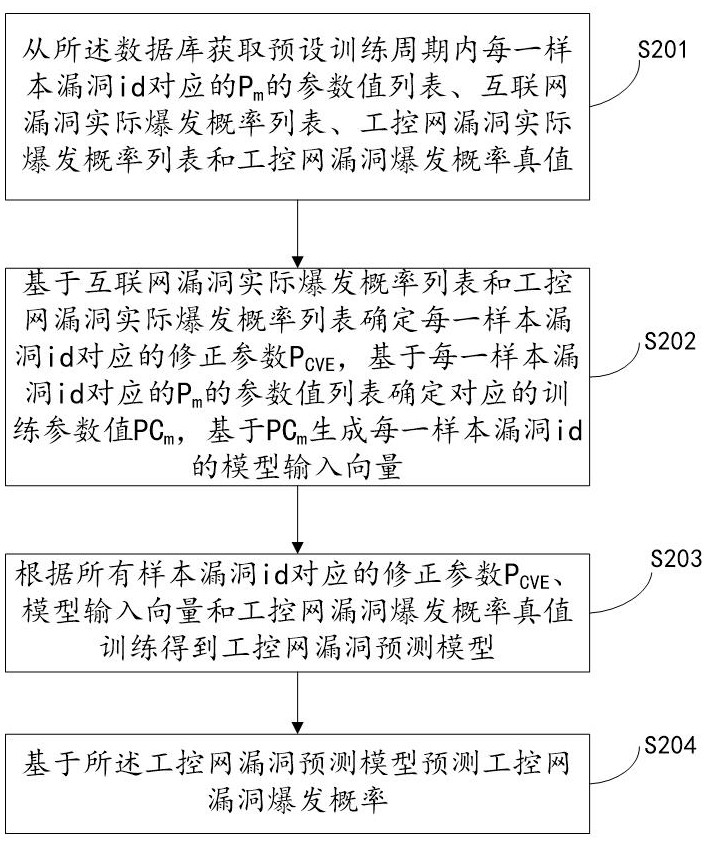
The invention relates to a system for predicting industrial control network vulnerabilities based on correction parameters, which is implemented by the following steps: S201, acquiring a parameter value list of Pm corresponding to each sample vulnerability id in a preset training period, an internet vulnerability actual outbreak probability list, an industrial control network vulnerability actual outbreak probability list and an industrial control network vulnerability outbreak probability true value from a database; s202, determining a correction parameter PCVE corresponding to each sample vulnerability id, determining a corresponding training parameter value PCm, and generating a model input vector of each sample vulnerability id based on the PCm; s203, training to obtain an industrial control network vulnerability prediction model according to the correction parameters PCVE corresponding to all the sample vulnerability id, the model input vector and the industrial control network vulnerability burst probability true value; and S204, predicting an industrial control network vulnerability outbreak probability based on the industrial control network vulnerability prediction model. According to the invention, the vulnerability outbreak probability of the industrial control network can be quickly and accurately predicted, and the safety of the industrial control network is improved.
Owner:山东云天安全技术有限公司
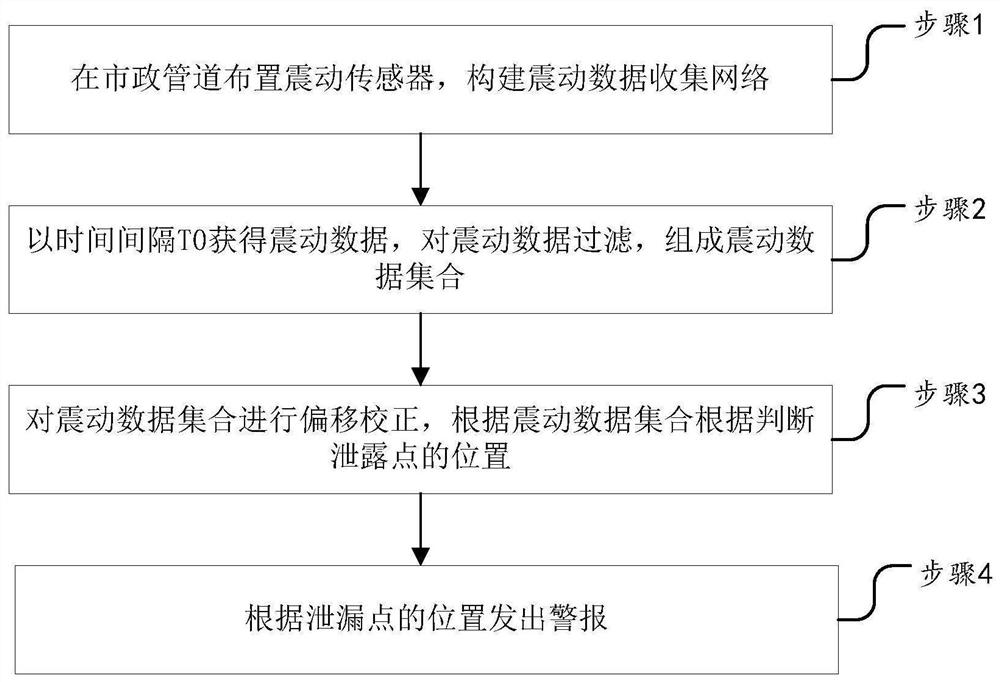
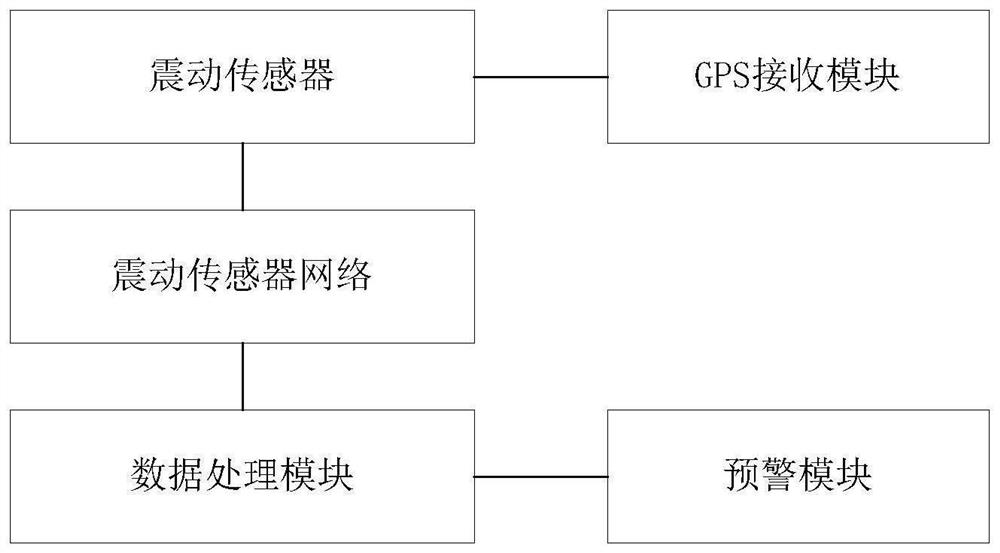
Municipal pipeline vulnerability prediction and early warning method and system
PendingCN113945337ADisadvantages of Avoiding Vulnerability AlertsAccurate Vulnerability PredictionDetection of fluid at leakage pointPipeline systemsData setFalse alarm
The invention discloses a municipal pipeline vulnerability prediction and early warning method which comprises the steps of arranging a vibration sensor on a municipal pipeline, constructing a vibration data collection network, obtaining vibration data at a time interval T0, filtering the vibration data, forming a vibration data set, performing offset correction on the vibration data set, and judging the position of the leakage point according to the vibration data set, and giving an alarm according to the position of the leakage point. The defects of traditional municipal pipeline vulnerability early warning based on pressure and flow are avoided, for example, the defects that an existing pipeline needs to be subjected to invasive transformation, the false alarm rate is large and the response is slow are overcome, and accurate vulnerability prediction of the municipal pipeline is achieved.
Owner:GUANGDONG ZHONGQIANG CONSTR ENG
System for predicting industrial control network vulnerability based on N-gram
ActiveCN114021150AFairly technologically advancedQuite practicalPlatform integrity maintainanceThe InternetIndustrial Internet
The invention relates to a system for predicting industrial control network vulnerabilities based on N-gram, which is implemented by the following steps: S601, removing industrial Internet stop words in Sore based on an industrial Internet stop word bank, and segmenting the Sore at the positions of the industrial Internet stop words to generate corresponding text fragment sequences; step S602, performing preset N-gram word segmentation processing on each Frei, and performing combination and duplicate removal on segmented words of all the Frei of each Sret to obtain a corresponding segmented word vector FBe; step S603, combining and de-duplicating the segmented words in all the FBe to obtain a segmented word set FC, and determining the number of the segmented words of the FC as the dimension of one-hot coding; step S604, performing one-hot coding on the word segmentation vector FBe based on the dimension of one-hot coding, and obtaining an original feature parameter value of each Sret; and step S605, training based on the original characteristic parameter value of Sre to obtain an industrial control network vulnerability prediction model, and predicting the vulnerability outbreak probability of the industrial control network. According to the invention, the vulnerability outbreak probability of the industrial control network can be quickly and accurately predicted, and the safety of the industrial control network is improved.
Owner:山东云天安全技术有限公司
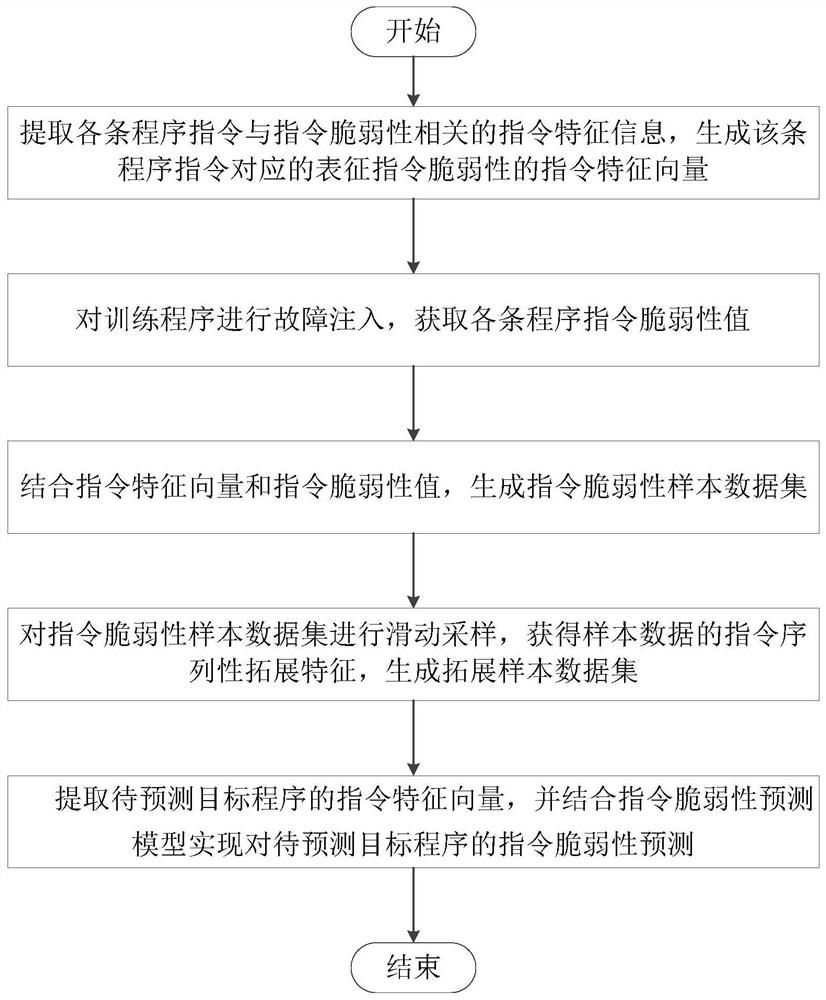
Instruction vulnerability prediction method and system based on deep random forest
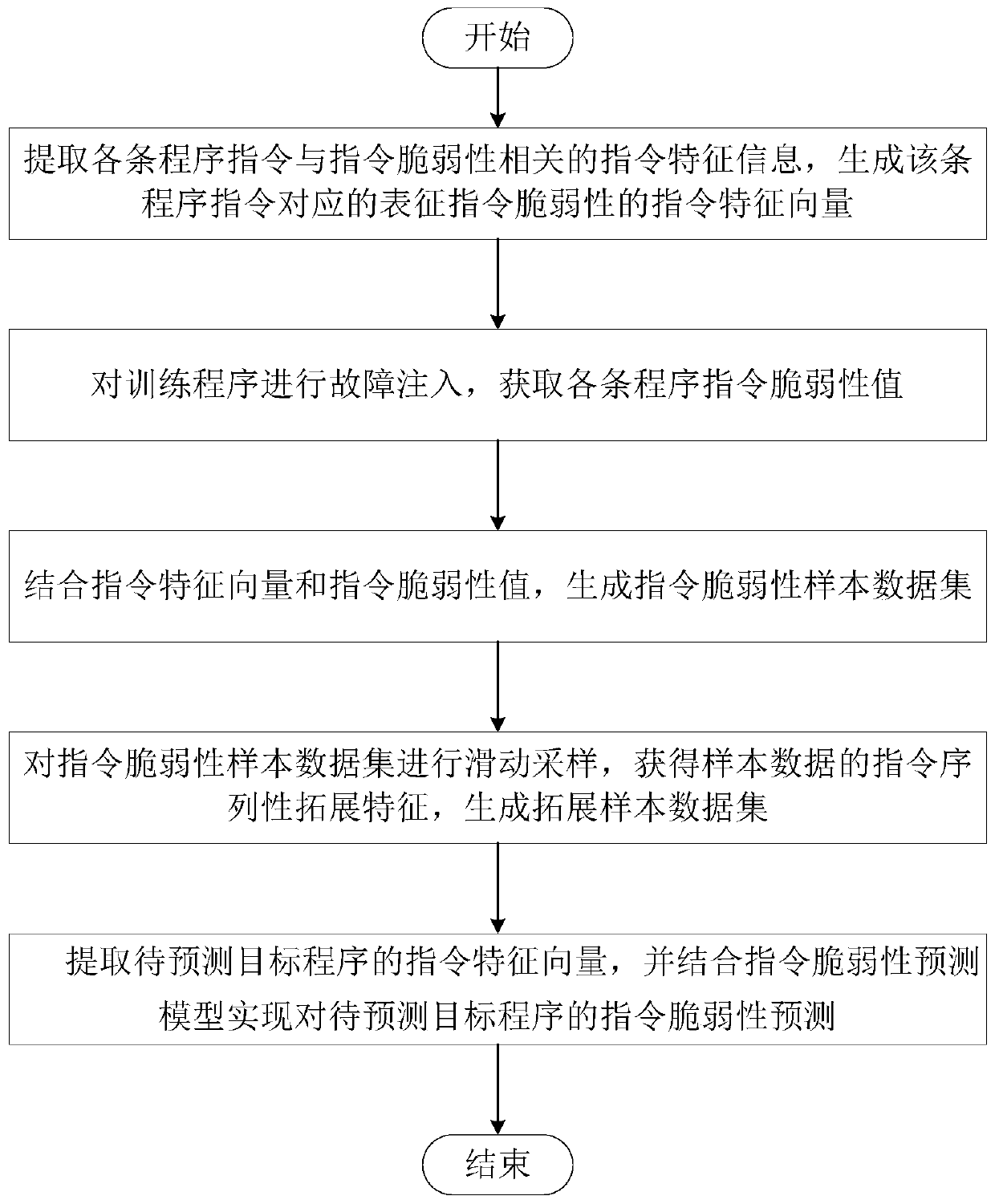
ActiveCN111159011AReflect vulnerabilityImprove forecast accuracySoftware testing/debuggingMachine learningData setProgram instruction
The invention discloses an instruction vulnerability prediction method and system based on a deep random forest, and the method comprises the steps: extracting the instruction feature information, related to the instruction vulnerability, of each program instruction, and generating an instruction feature vector representing the instruction vulnerability; performing fault injection on the trainingprogram to obtain a vulnerability value of each program instruction; generating an instruction vulnerability sample data set in combination with the instruction feature vector and the instruction vulnerability value; performing sliding sampling on the instruction vulnerability sample data set through a sliding window to generate an extended sample data set; constructing and training an instructionvulnerability prediction model based on the deep random forest; and extracting an instruction feature vector of the to-be-predicted target program, and combining the instruction feature vector with the instruction vulnerability prediction model to realize instruction vulnerability prediction of the to-be-predicted target program. The system is used for realizing the method. The method is high inprediction accuracy, low in demand for a sample set and less in required manual adjustment work, and can be effectively applied to prediction of instruction vulnerability after a program is affected by an instantaneous fault.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
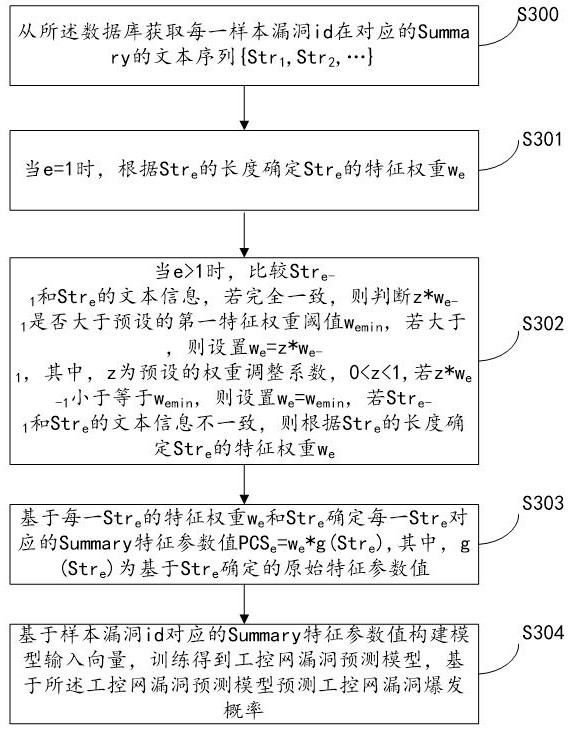
System for predicting industrial control network vulnerabilities based on Summary length features
ActiveCN114021151AWidely used valueImprove securityPlatform integrity maintainanceEngineeringThresholding
The invention relates to a system for predicting industrial control network vulnerabilities based on Summary length features, and the method comprises the implementation steps: S300, obtaining a text sequence {Str1, Str2,...} of each sample vulnerability id in the corresponding Summary; s301, when e is equal to 1, determining the feature weight we of the Sre according to the length of the Sre; Step S302, when e is greater than 1, comparing the text information of the Stre-1 and the text information of the Stre; if the two are consistent, judging whether z * we-1 is larger than a preset first feature weight threshold value wemin or not; if yes, setting w = z * we-1; if z * we-1 is smaller than or equal to wemin, setting wee to be equal to wemin; if the text information of the Stre-1 is inconsistent with the text information of the Stre, determining a feature weight we of the Stre according to the length of the Stre; step S303, based on the feature weight we of each Stre and the Stre, determining a Summary feature parameter value corresponding to each Stre; and step S304, training based on the Summary feature parameter value corresponding to the sample vulnerability id to obtain an industrial control network vulnerability prediction model to predict an industrial control network vulnerability outbreak probability. According to the invention, the vulnerability outbreak probability of the industrial control network can be quickly and accurately predicted, and the safety of the industrial control network is improved.
Owner:山东云天安全技术有限公司
Network device vulnerability prediction
The vulnerability of network devices may be predicted by performing a survival analysis on big data. A prediction algorithm may be built by considering historical data from heterogeneous data sources. The operating state of the network devices on a network may be predicted. The services potentially affected by a predicted outage may be determined and displayed. Alternatively or in addition, the number of clients potentially affected by a predicted outage may be determined and displayed.
Owner:ACCENTURE GLOBAL SOLUTIONS LTD
Docker mirror image scanning method based on static analysis
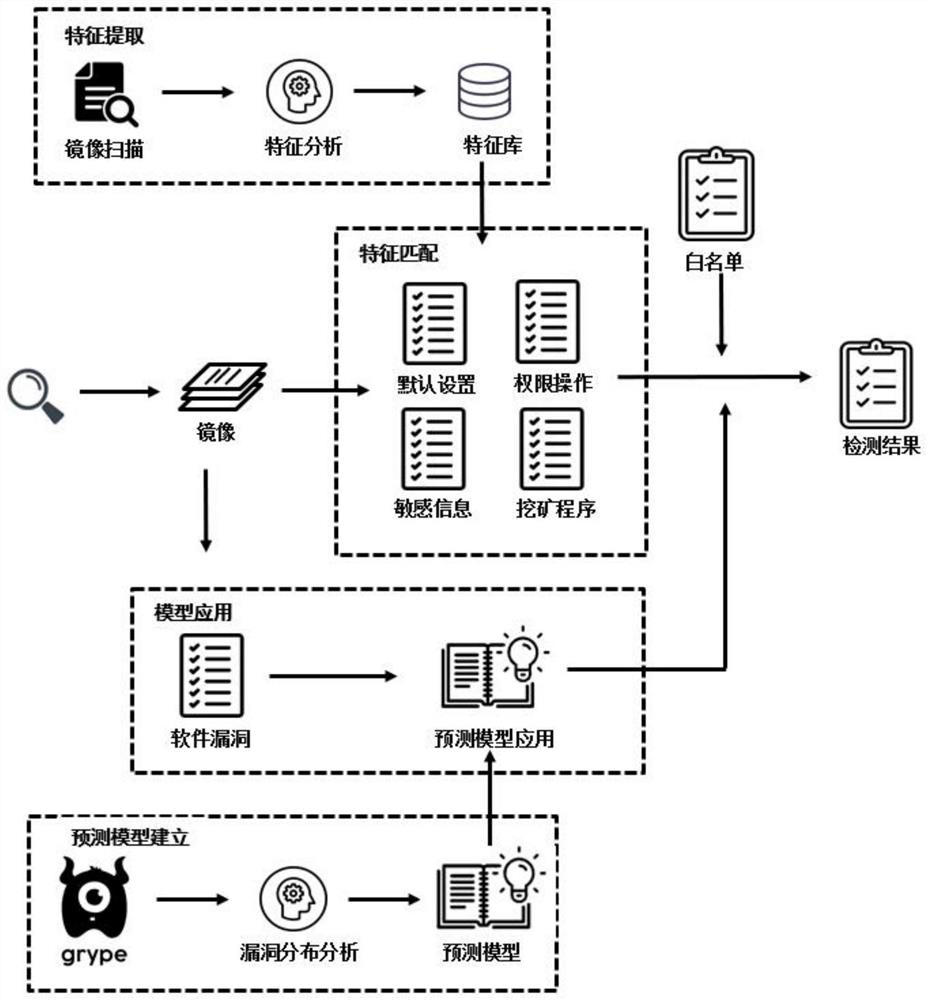
PendingCN114564719AValid scanFully reflect the security situationPlatform integrity maintainanceComputer graphics (images)Algorithm
The invention discloses a Docker mirror image scanning method based on static analysis, and the method comprises the steps: carrying out the feature extraction of a large number of Docker mirror image construction historical records through a manual analysis method, building a safety feature library, carrying out the feature matching of a to-be-detected mirror image according to the safety feature library, and detecting the safety problem of the mirror image according to the feature information and a white list mechanism. Meanwhile, the number of software vulnerabilities in the mirror image is detected through a mirror image scanning tool, function fitting is conducted according to a scatter diagram of time distribution, a vulnerability prediction model is established, finally, the safety problem of the Docker mirror image is comprehensively analyzed through information of the software vulnerabilities and the scatter diagram, and a mirror image scanning result is fed back. According to the method, mirror image software vulnerabilities are analyzed in combination with a mirror image scanning tool and a self-defined scanning method, the mirror image scanning tool analyzes the mirror image software vulnerabilities, function fitting is carried out according to a vulnerability number distribution scatter diagram, and a mirror image vulnerability prediction model is established.
Owner:ZHEJIANG UNIV
A system for predicting industrial control network vulnerabilities based on summary word segmentation features
ActiveCN114021148BWidely used valueImprove securityPlatform integrity maintainanceData miningFeature parameter
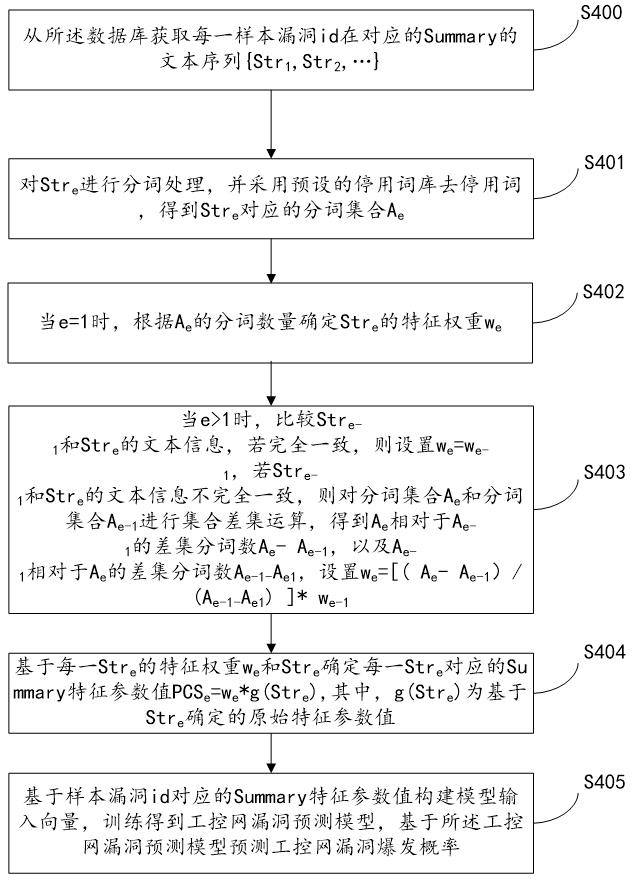
The present invention relates to a system for predicting industrial control network vulnerabilities based on summary word segmentation features, and implements step S400, acquiring the text sequence of each sample vulnerability id in the corresponding summary; step S401, comparing Str e Process to get the corresponding word segmentation set A e ; Step S402, when e=1, according to A e The number of participles determines Str e The feature weight w e ; Step S403, when e>1, compare Str e‑1 and Str e , if they are exactly the same, set w e =w e‑1 , if it is not completely consistent, then the participle set A e and participle set A e‑1 Perform the set difference operation to get A e relative to A e‑1 The number of difference participles A e ‑A e‑1 , and A e‑1 relative to A e The number of difference participles A e‑1‑ A e1 , set w e =[(A e ‑A e‑1 ) / (A e‑1‑ A e1 )]*w e‑1 ; Step S404, determine each Str e Corresponding summary characteristic parameter values; step S405, training to obtain an industrial control network vulnerability prediction model, and predicting the industrial control network vulnerability outbreak probability. The present invention can quickly and accurately predict the industrial control network vulnerability outbreak probability and improve the security of the industrial control network.
Owner:山东云天安全技术有限公司
System for Predicting Vulnerabilities of Industrial Control Network Based on Modified Parameters
ActiveCN114021149BWidely used valueImprove securityPlatform integrity maintainanceThe InternetData mining
The present invention relates to a system for predicting loopholes in industrial control networks based on correction parameters, which implements step S201, obtaining P corresponding to each sample loophole id in a preset training period from a database. m The parameter value list, the actual outbreak probability list of Internet vulnerabilities, the actual outbreak probability list of industrial control network vulnerabilities and the true value of the industrial control network vulnerability outbreak probability; step S202, determine the correction parameter P corresponding to each sample vulnerability id CVE , to determine the corresponding training parameter value PC m , PC-based m Generate a model input vector for each sample vulnerability id; step S203, modify the parameter P according to all sample vulnerability ids CVE , training the model input vector and the true value of the vulnerability outbreak probability of the industrial control network to obtain the vulnerability prediction model of the industrial control network; step S204 , predicting the outbreak probability of the vulnerability of the industrial control network based on the vulnerability prediction model of the industrial control network. The invention can quickly and accurately predict the outbreak probability of loopholes in the industrial control network and improve the security of the industrial control network.
Owner:山东云天安全技术有限公司
System for predicting industrial control network vulnerability based on Internet and industrial control network vulnerability parameters
ActiveCN113792300AWidely used valueImprove securityCharacter and pattern recognitionNatural language data processingData setThe Internet
The invention relates to a system for predicting industrial control network vulnerabilities based on Internet and industrial control network vulnerability parameters. The implementation steps are as follows: S101, obtaining a training period T0 = LCM (TPm) of a training data set; S102, acquiring a parameter value list of Pm, a parameter value list of Qn and an industrial control network vulnerability burst probability true value corresponding to each sample vulnerability id within T0 before the current moment from a database; S103, determining a training parameter value PCm of the Pm and a training parameter value QCn of the Qn, and generating a model input vector of each sample vulnerability id based on the PCm and the QCn; S104, training according to all sample vulnerability id model input vectors and an industrial control network vulnerability burst probability true value to obtain an industrial control network vulnerability prediction model; and S105, predicting the vulnerability outbreak probability of the industrial control network based on the industrial control network vulnerability prediction model. According to the method, the vulnerability outbreak probability of the industrial control network can be quickly and accurately predicted, and the safety of the industrial control network is improved.
Owner:山东云天安全技术有限公司
System for predicting industrial control network vulnerabilities based on bitmap
ActiveCN114021147AFairly technologically advancedQuite practicalPlatform integrity maintainanceData miningFeature parameter
The invention relates to a system for predicting industrial control network vulnerabilities based on bitmap, and the method comprises the implementation steps: S501, determining a Summary cycle detection window TK based on a preset training cycle; step S502, taking Be as the a bit information in the TK, obtaining the detection window information TKe of the e period, and determining the feature weight we of Be based on the bit change in Be and TKe; step S503, on the basis of the feature weight we of each Be and the Summary text Stry, determining a Summary feature parameter value corresponding to each Summary text; and step S504, constructing a model input vector based on the Summary feature parameter value corresponding to the sample vulnerability id, training to obtain an industrial control network vulnerability prediction model, and predicting an industrial control network vulnerability outbreak probability based on the industrial control network vulnerability prediction model. According to the invention, the vulnerability outbreak probability of the industrial control network can be quickly and accurately predicted, and the safety of the industrial control network is improved.
Owner:山东云天安全技术有限公司
A Vulnerability Prediction Method of Instruction SDC Based on Support Vector Regression
ActiveCN108334903BImprove accuracyImprove generalization abilityCharacter and pattern recognitionProgram instructionData set
The invention discloses an instruction SDC vulnerability prediction method based on support vector regression, the steps are as follows: step 1, perform fault injection experiments on the program set, and obtain a sample data set; step 2, extract the inherent characteristics representing the nature of the instruction itself; step 3. Traversing the sample data set to generate a data propagation dependency path for the target instruction; Step 4, traversing the sample data set to calculate the error masking factor for the target instruction; Step 5, extracting the dependency features of the instruction related to the data propagation dependency; Step 6, Train the instruction SDC vulnerability prediction model based on support vector regression; step 7, extract the target program instruction features, and predict the instruction vulnerability. This method has high prediction accuracy and low performance overhead, and can be effectively applied to the prediction of instruction SDC vulnerability after the program is affected by a transient fault.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Instruction vulnerability prediction method and system based on deep random forest
ActiveCN111159011BReflect vulnerabilityImprove forecast accuracySoftware testing/debuggingMachine learningProgram instructionData set
The invention discloses a method and system for predicting instruction vulnerability based on deep random forest. The method includes: extracting instruction feature information related to each program instruction and instruction vulnerability, and generating instruction feature vectors representing instruction vulnerability; training program Perform fault injection to obtain the vulnerability value of each program instruction; combine the instruction feature vector and instruction vulnerability value to generate an instruction vulnerability sample data set; perform sliding sampling on the instruction vulnerability sample data set through a sliding window to generate an extended sample data set ; Construct and train an instruction vulnerability prediction model based on deep random forest; extract the instruction feature vector of the target program to be predicted, and combine the instruction vulnerability prediction model to realize the instruction vulnerability prediction of the target program to be predicted. The system is used to implement the above method. The invention has high prediction accuracy, low demand for sample sets and less manual adjustment work, and can be effectively applied to the prediction of instruction vulnerability after a program is affected by a transient fault.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
A Web Application Security Vulnerability Prediction Method Based on Execution Flow Graph
ActiveCN109101820BPredicting Vulnerability LocationsPlatform integrity maintainanceWeb applicationProgram slicing
The invention discloses a web application security loophole prediction method based on the execution flow graph. According to the data dependency and control dependency of the web application, the execution flow graph EFG is constructed; the node S where the security-sensitive statement is located is extracted from the EFG k as the end point, with S k The associated user input node U I is the subgraph of the starting point, and extracts the metric element for each subgraph; the specific value of the metric element of the subgraph is used as input, and the S corresponding to the subgraph is k With or without vulnerabilities as the output, a vulnerability prediction model is constructed to realize the prediction of web application security vulnerabilities. The invention includes judgment nodes in the extraction of metric elements, and compared with directly analyzing program slices, the workload is greatly reduced.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Context-aware interpretable vulnerability detection system and method
PendingCN114817930AAchieve collective interpretationReverse engineeringPlatform integrity maintainanceGeneration processLocal optimum
The invention discloses a context-aware interpretable vulnerability detection system, which comprises the following steps of: extracting vulnerability codes through an open source database to construct a first code attribute graph, constructing a detection model according to the first code attribute graph, performing code representation on vulnerability code statements, generating vulnerability prediction scores, and constructing an interpretation model according to the vulnerability prediction scores. And constructing a second code attribute graph, detecting a to-be-detected vulnerability code according to the second code attribute graph, finally outputting a local optimal sub-graph as a vulnerability detection result for interpretation, and parameterizing an interpretation generation process by an interpretation model by adopting a multi-layer neural network to realize collective interpretation of a plurality of instances. The invention correspondingly provides a context-aware interpretable vulnerability detection method.
Owner:YANGZHOU UNIV
System for predicting industrial control network vulnerabilities based on Summary word segmentation features
ActiveCN114021148AWidely used valueImprove securityPlatform integrity maintainanceEngineeringArtificial intelligence
The invention relates to a system for predicting industrial control network vulnerabilities based on Summary word segmentation features. The implementation steps are as follows: S400, obtaining a text sequence of each sample vulnerability id in a corresponding Summary; step S401, processing the Stre to obtain a corresponding word segmentation set Ae; step S402, when e = 1, determining a feature weight we of Sret according to the word segmentation number of Ae; Step S403, when e is greater than 1, comparing Stre-1 with Stre; if the two are fully consistant, setting we = we-1; if the are not completely consistent, performing set difference set operation on the word segmentation set Ae and the word segmentation set Ae-1 to obtain a difference set word segmentation number Ae-Ae-1 of the Ae relative to the Ae-1 and a difference set word segmentation number Ae-1-Ae1 of the Ae-1 relative to the Ae, and setting we = [(Ae-Ae-1) / (Ae-1-Ae1)] * w <we-1 >; step S404, determining a Summary characteristic parameter value corresponding to each Stre; and S405, training to obtain the industrial control network vulnerability prediction model, and predicting the vulnerability outbreak probability of the industrial control network. According to the invention, the vulnerability outbreak probability of the industrial control network can be rapidly and accurately predicted, and the security of the industrial control network is improved.
Owner:山东云天安全技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com