A Web Application Security Vulnerability Prediction Method Based on Execution Flow Graph
A web application and vulnerability technology, applied in the field of network security, can solve problems such as heavy workload and not intuitive enough, and achieve the effect of small generation and calculation workload and intuitive expression
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
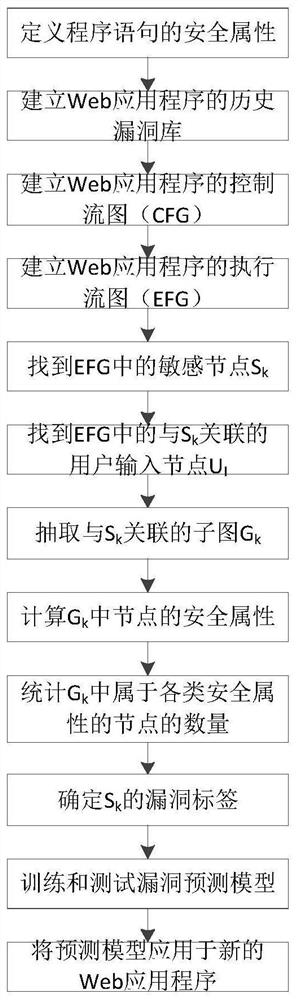
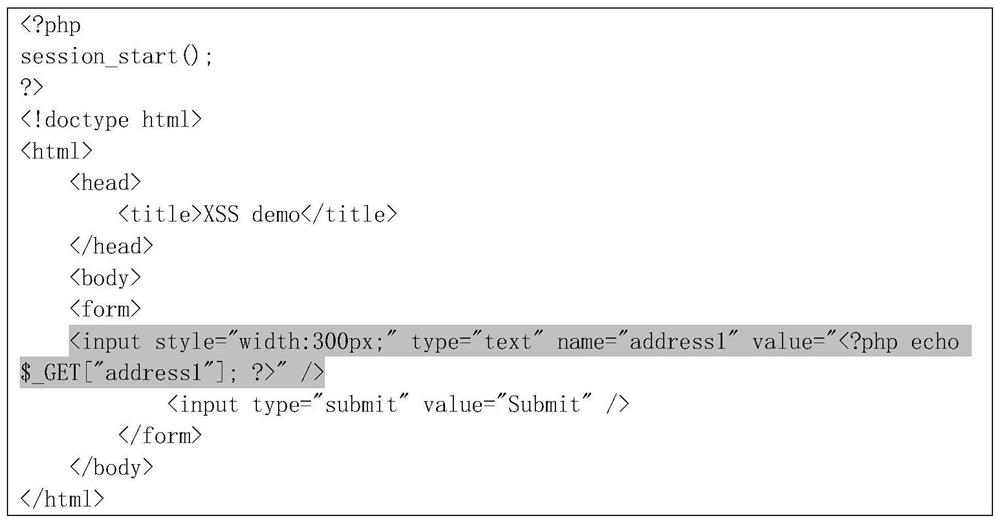
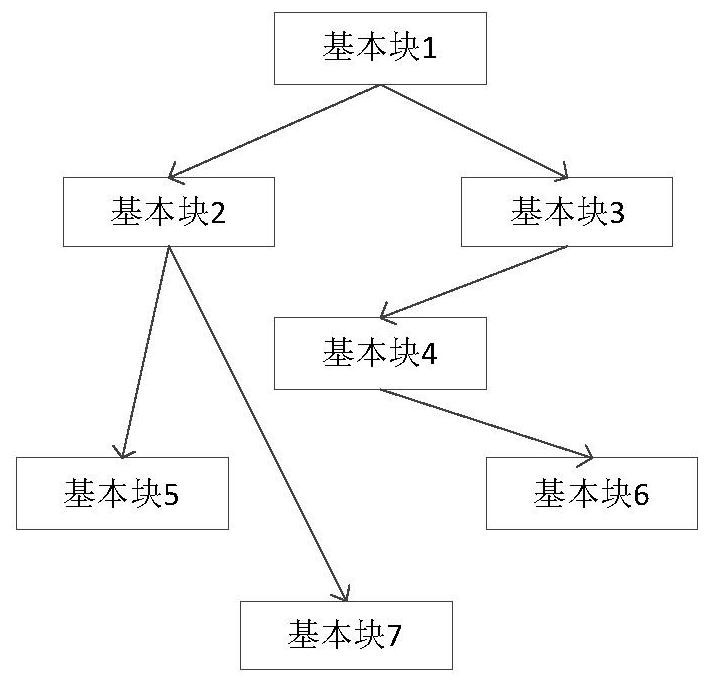
[0041] The present invention provides a web application security loophole prediction method based on the execution flow graph. The basic idea is: combine the data dependency graph and the control dependency graph to construct the execution flow graph EFG of the program; extract security-sensitive statements from the EFG Where the node S k as the end point, with node S k The associated user input node U I is the subgraph of the starting point, and extracts the metric element for each subgraph; the specific value of the metric element of the subgraph is used as input, and the S corresponding to the subgraph is k With or without vulnerabilities as the output, a vulnerability prediction model is constructed to realize the prediction of web application security vulnerabilities.
[0042] Such as figure 1 As shown, the method includes the following steps:
[0043] Step 1. Define the security attribute of the program statement.
[0044] Describe various security properties relate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com