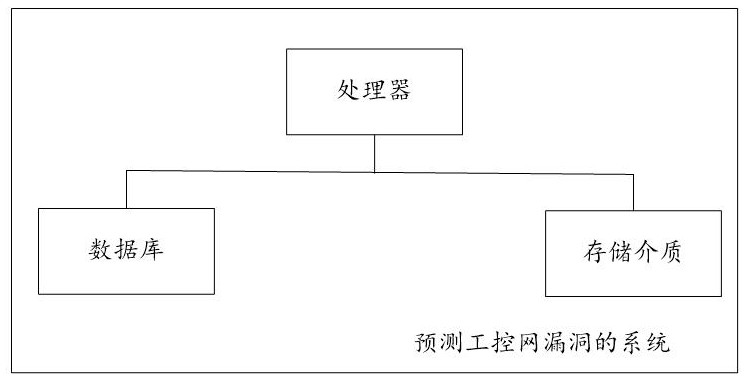
System for Predicting Vulnerabilities of Industrial Control Network Based on Modified Parameters
A technology for correcting parameters and loopholes, applied in the computer field, can solve problems such as the inability to guarantee the security of industrial control networks, and achieve the effect of improving security and stability and making extensive use of value.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] The computer program stored in the storage medium includes a first computer program, and when the processor executes the first computer program, the following steps are implemented:
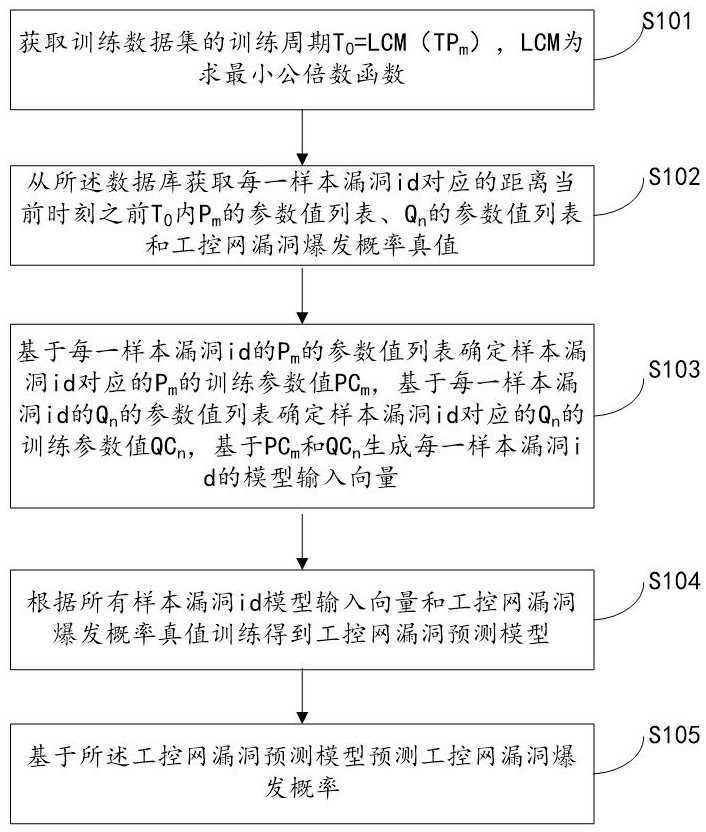
[0036] Step S101, obtaining the training period T of the training data set 0 =LCM(TP m ), LCM is the least common multiple function.
[0037] Due to different P m and Q n There is a big difference in the update cycle of the model. If the sliding window is directly used to select training parameters, many parameters will not change within a certain period of time, wasting computing resources, and has little significance for model training. Therefore, in this embodiment, TP is selected. m The LCM is used as the training period port. It should be noted that, since the update period of the Internet vulnerability characteristic parameters is much larger than the update period of the industrial control network vulnerability characteristic parameters, only the update period of the Internet vu...
Embodiment 2
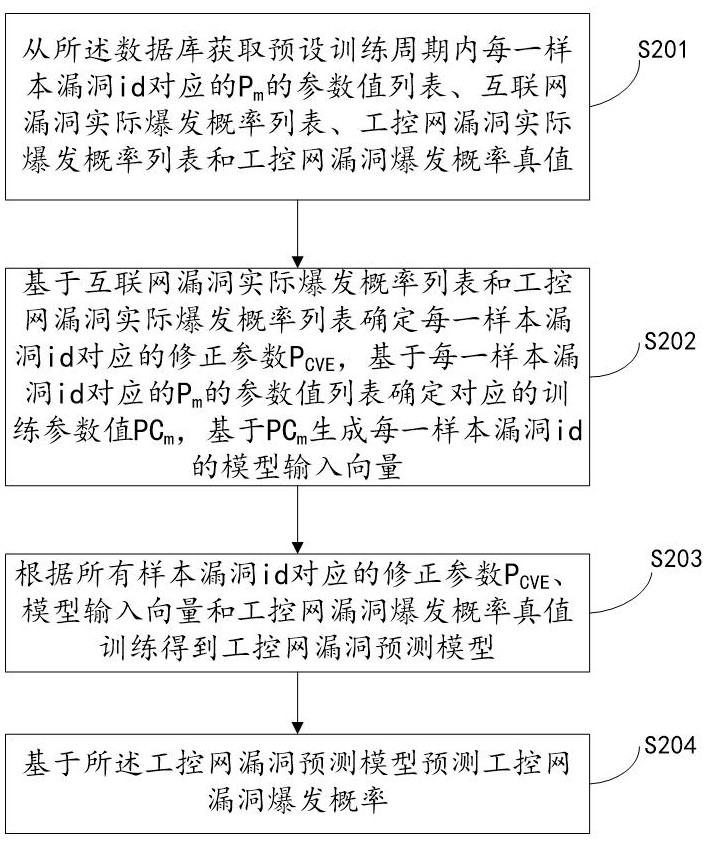
[0063] It should be noted that there are many Internet vulnerability characteristic parameters, which are easy to obtain. However, in some application scenarios, limited by various factors such as the scale of the industrial control network, it may not be possible to obtain enough characteristic parameters of the industrial control network to train the industrial control network. Vulnerability prediction model. However, since the trend of the outbreak of the same vulnerability in the industrial control network is consistent with the overall trend of the Internet outbreak, there is a correlation. Therefore, based on the correlation between the industrial control network and the Internet vulnerability outbreak, combined with the characteristic parameters of the Internet vulnerability, the probability of the outbreak of the industrial control network vulnerability can be calculated. predict.
[0064] Specifically, the computer program stored in the storage medium includes a secon...
Embodiment 3
[0093] The computer program stored in the storage medium includes a third computer program, and when the processor executes the third computer program, the following steps are implemented:
[0094] Step S300, obtain the text sequence {Str of each sample vulnerability id in the corresponding Summary from the database 1 ,Str 2 ,…}, Str e is the text of the Summary corresponding to the e-th update cycle, and the value of e ranges from 1 to infinity.
[0095] Step S301, when e=1, according to Str e The length of Str is determined e The feature weight w e .
[0096] Through step S301, each Str can be e Set the corresponding initial feature weights.
[0097] Step S302, when e>1, compare Str e-1 and Str e If the text information is completely consistent, then judge z*w e-1 Is it greater than the preset first feature weight threshold w emin , if greater than, set w e =z*w e-1 , where z is the preset weight adjustment coefficient, 0e-1 less than or equal to w emin , then ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com