Context-aware interpretable vulnerability detection system and method
A vulnerability detection and context technology, applied in the field of context-aware interpretable vulnerability detection system, can solve the problems of low accuracy of vulnerability detection, providing explanations, and not considering control dependencies, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
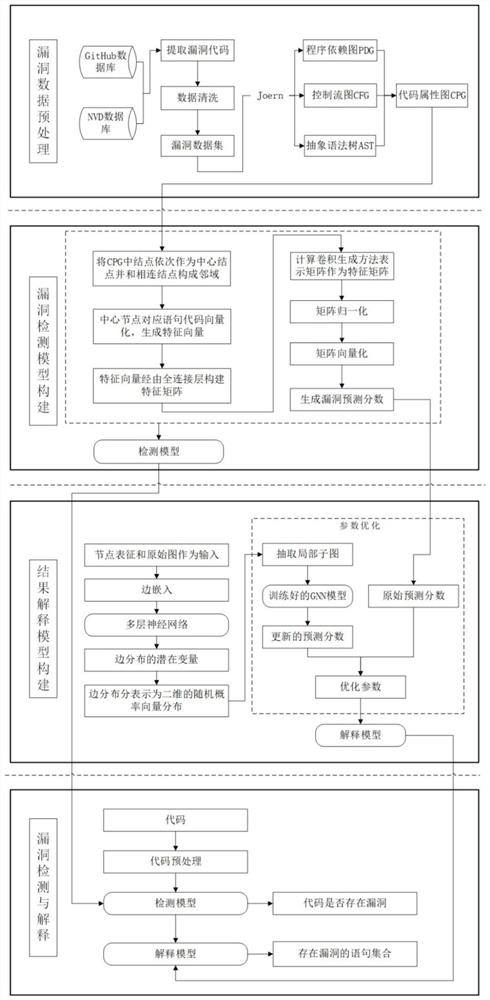
[0049] see figure 1 As shown, a context-aware interpretable vulnerability detection system provided by this embodiment includes a vulnerability data preprocessing module, a vulnerability detection model building module, a result interpretation model building module, and a vulnerability detection and interpretation module;
[0050] The vulnerability data preprocessing module is used to extract the vulnerability code from the vulnerability database to construct the vulnerability data set, and convert the vulnerability data set constructed by the vulnerability code into the first code attribute map;
[0051] The vulnerability data preprocessing module includes acquisition unit, representation unit, and synthesis unit:
[0052] The collection unit is used to collect vulnerability data from the vulnerability database NVD, including detailed information such as vulnerability types, collect code sets that may have vulnerabilities from the open source code repository GitHub, and prepr...
Embodiment 2
[0089] see figure 1 As shown, corresponding to the context-aware interpretable vulnerability detection system of Embodiment 1, Embodiment 2 provides a context-aware interpretable vulnerability detection method, which includes the following steps:
[0090] 1) Extracting the vulnerability code from the vulnerability database to construct a vulnerability dataset, and converting the vulnerability code constructing the vulnerability dataset into a first code attribute map;
[0091] 1.1) Collect vulnerability data from the vulnerability database NVD, including detailed information such as vulnerability types, collect code sets that may have vulnerabilities from the open source code repository GitHub, and preprocess the vulnerability data extracted from the database. Extract it, remove the redundant information in the data and extract the vulnerability function, clean the vulnerability data, and finally obtain the vulnerability data set;
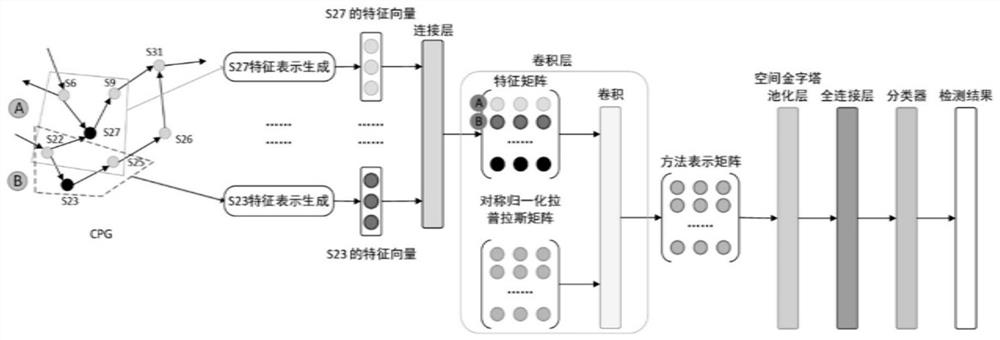
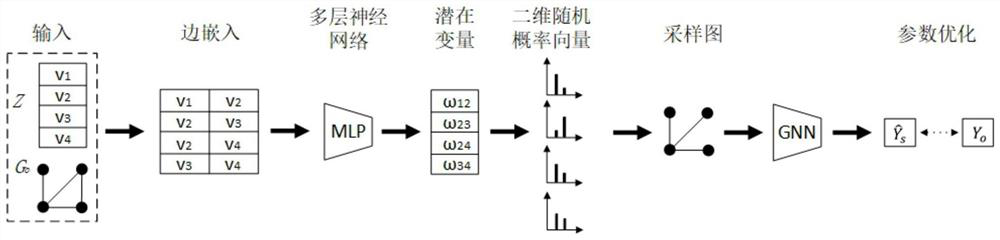
[0092] 1.2) Perform code representation on ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com