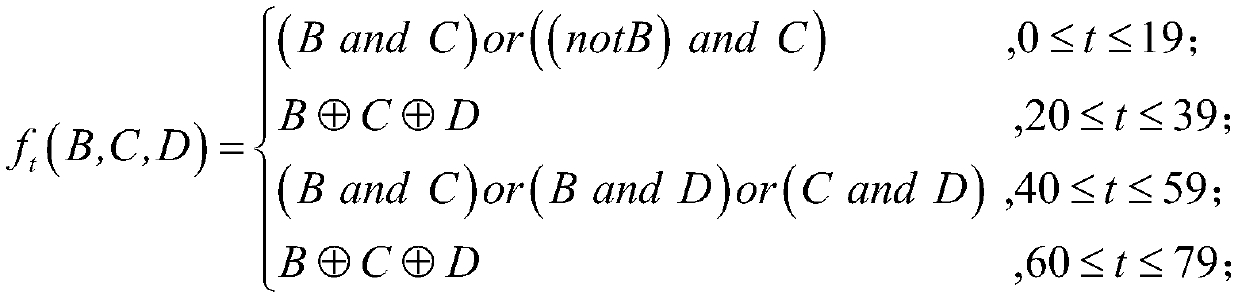Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54 results about "SHA-1" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard.
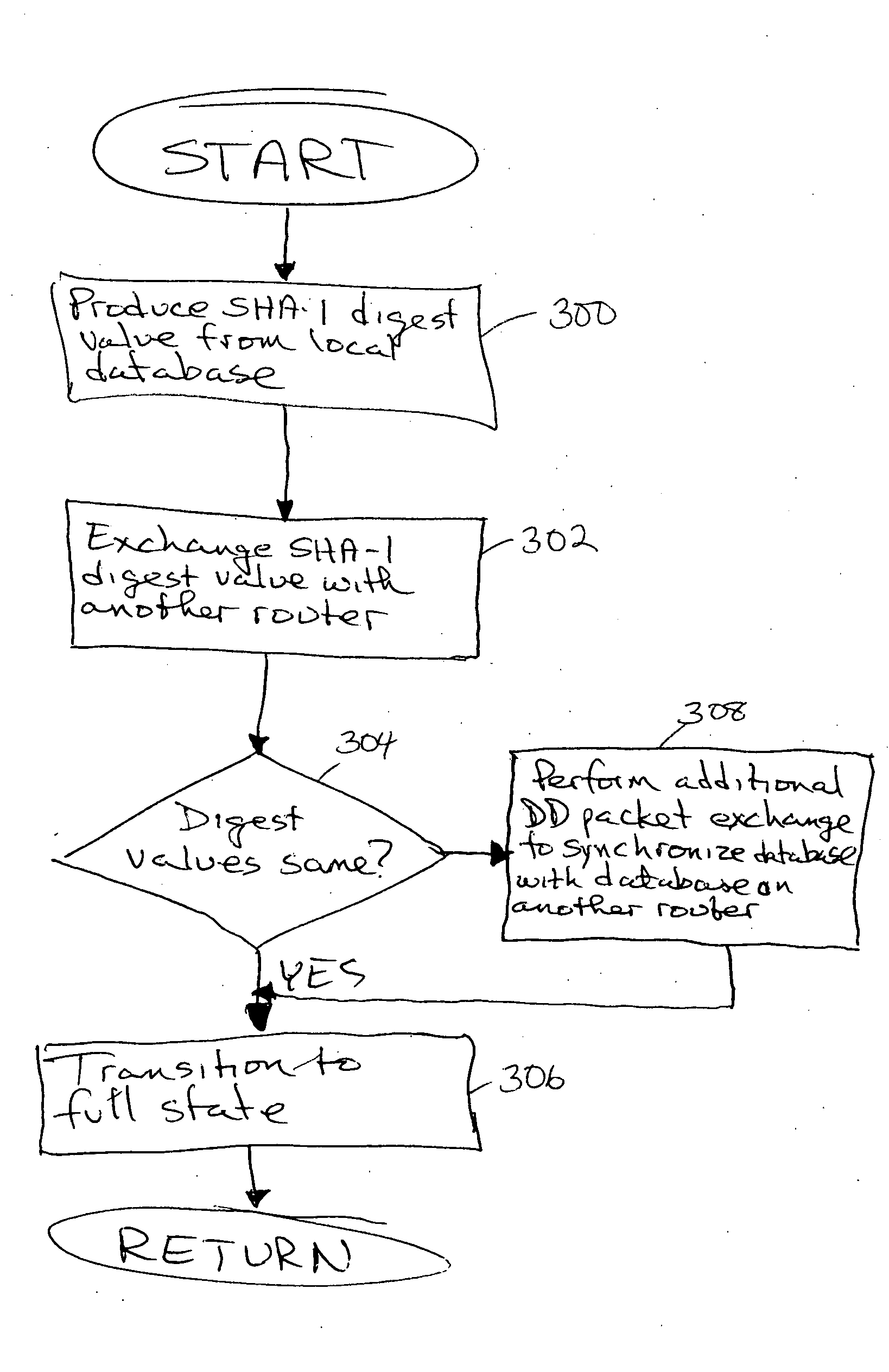
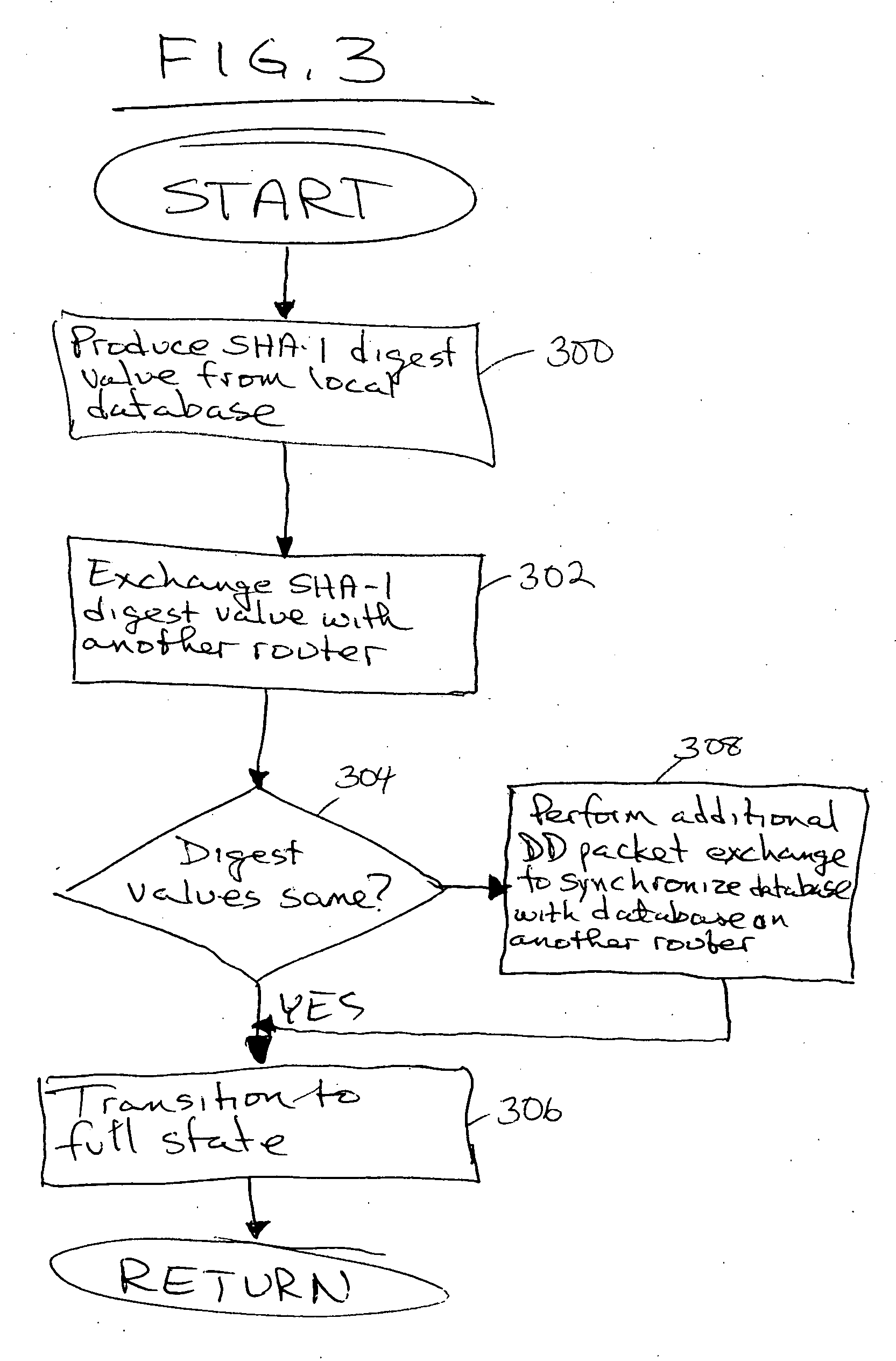
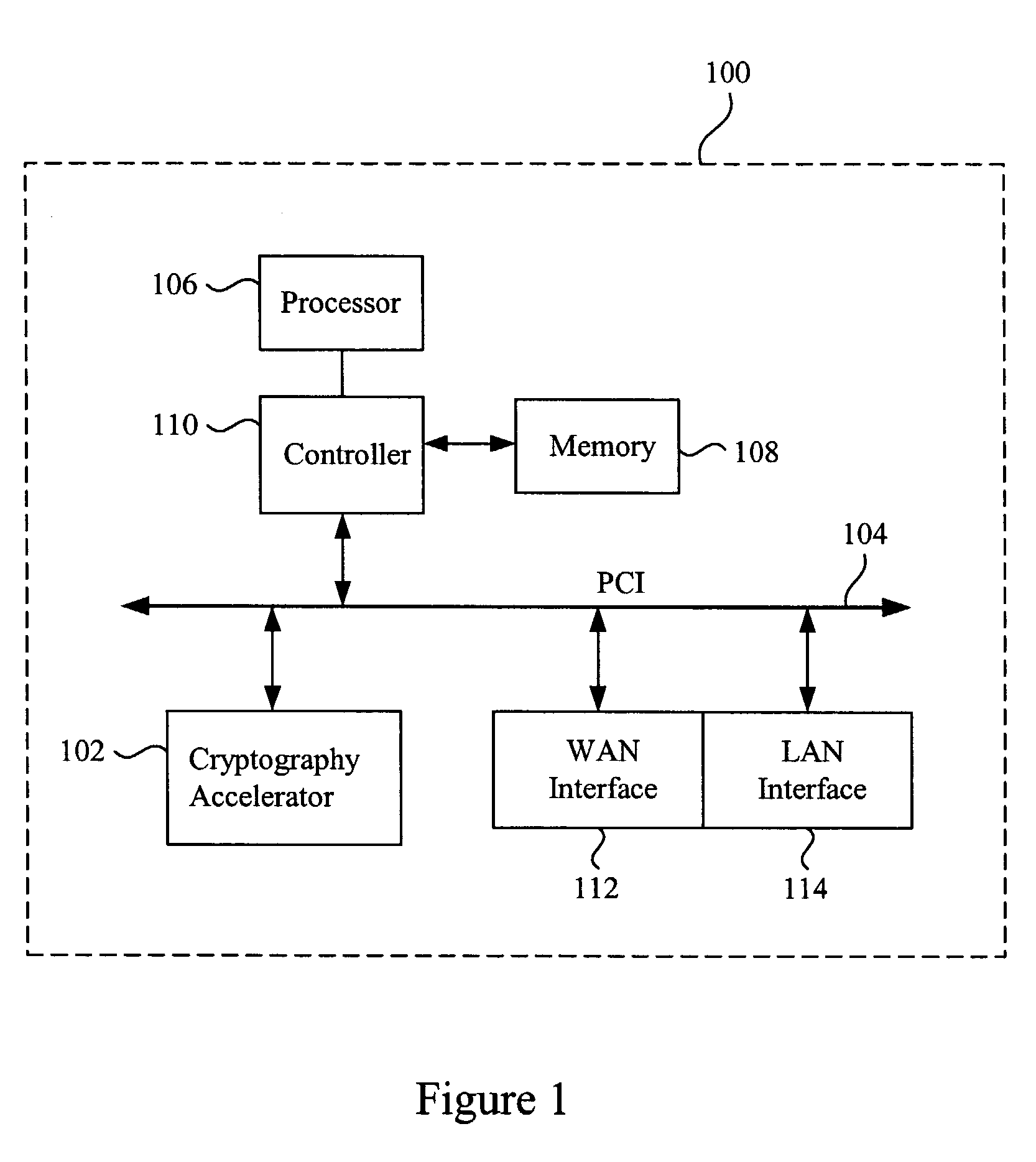
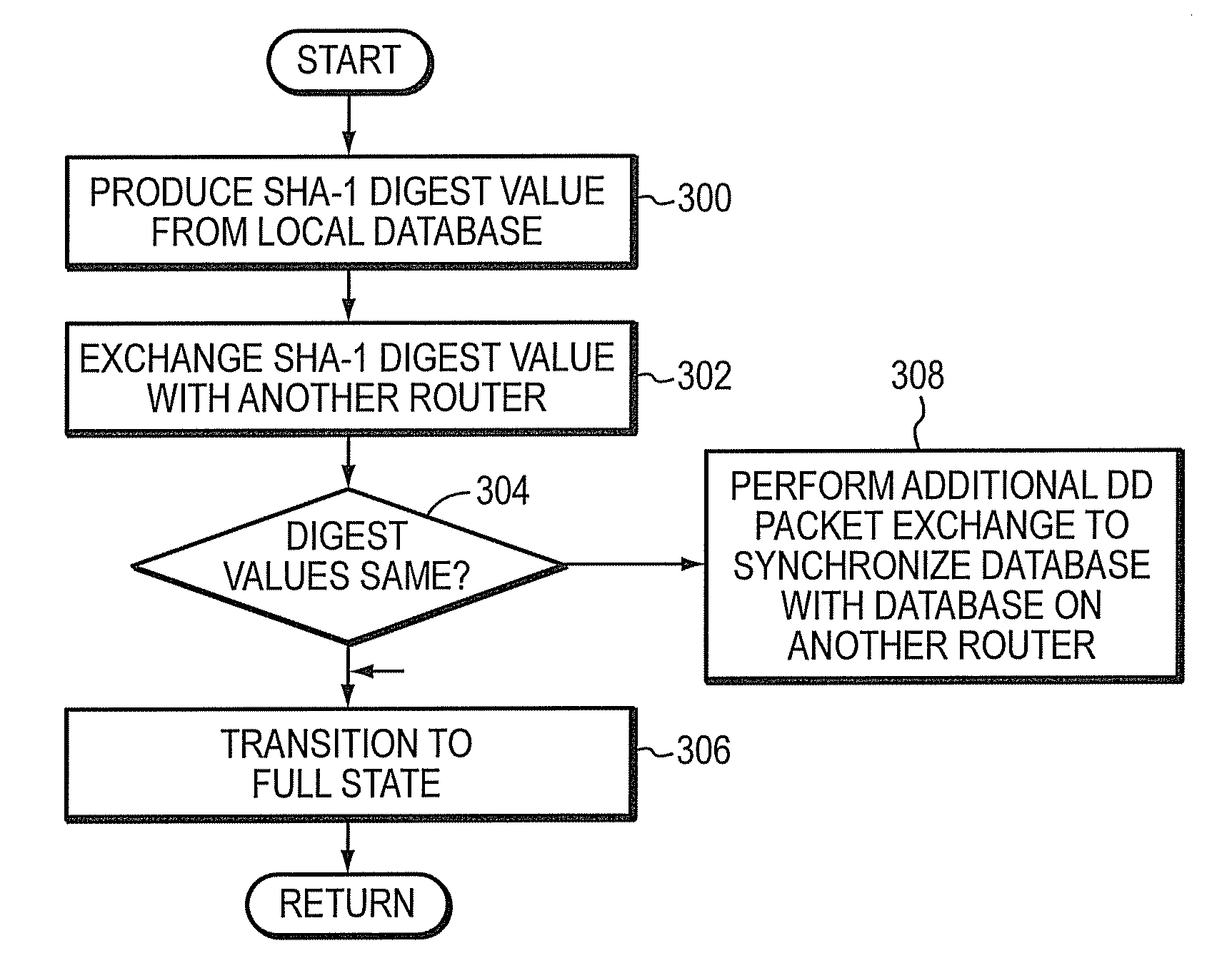
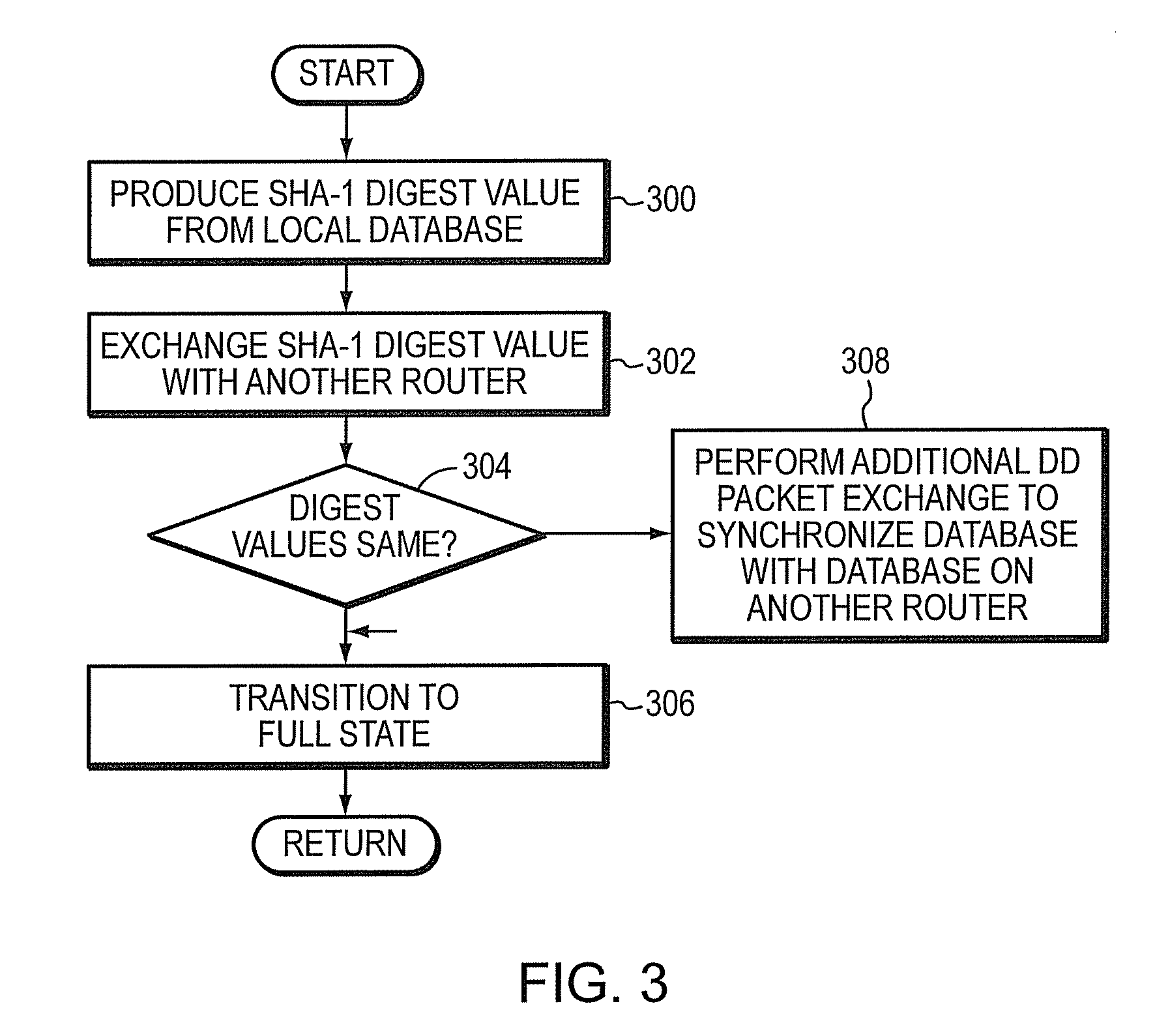
Method and apparatus to minimize database exchange in OSPF by using a SHA-1 digest value
The present invention provides a method of determining whether database located on a first router is synchronized with the database located on a second router by performing a hash function on the values contained in a link state database to derive a SHA-1 digest value. In an embodiment, the digest value is based on LSA type. The digest value is exchanged initially during a database description packet swap between the first router and second router. If the digest values are the same, the databases are already synchronized. The routers thus skip the database description packet exchange of LSAs in the database and go directly to FULL state, indicating full synchronization between databases on the first and second router and announcing adjacency to each other. If the digest differs, normal database description packet exchange is performed as specified in OSPF.
Owner:CISCO TECH INC
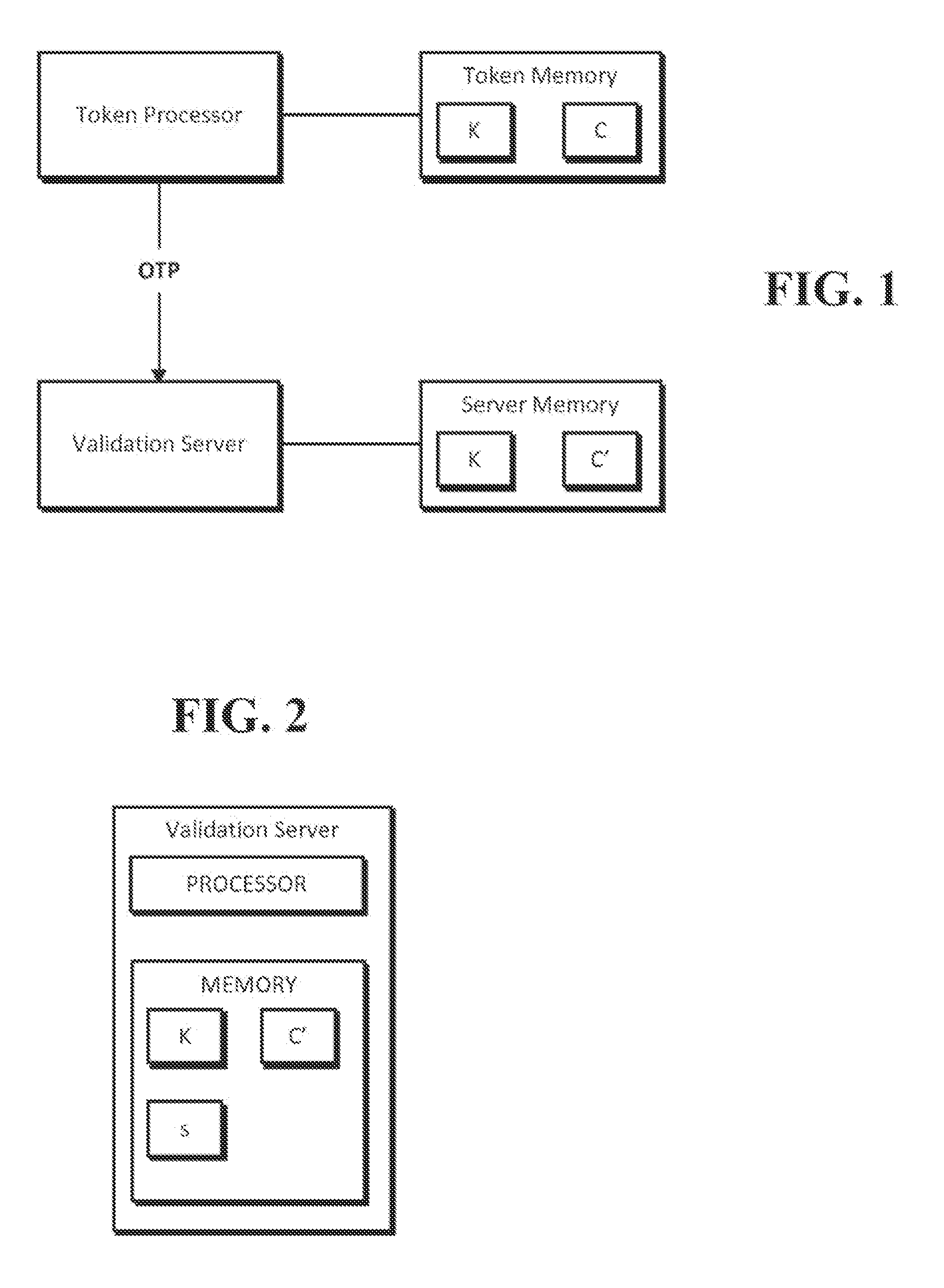
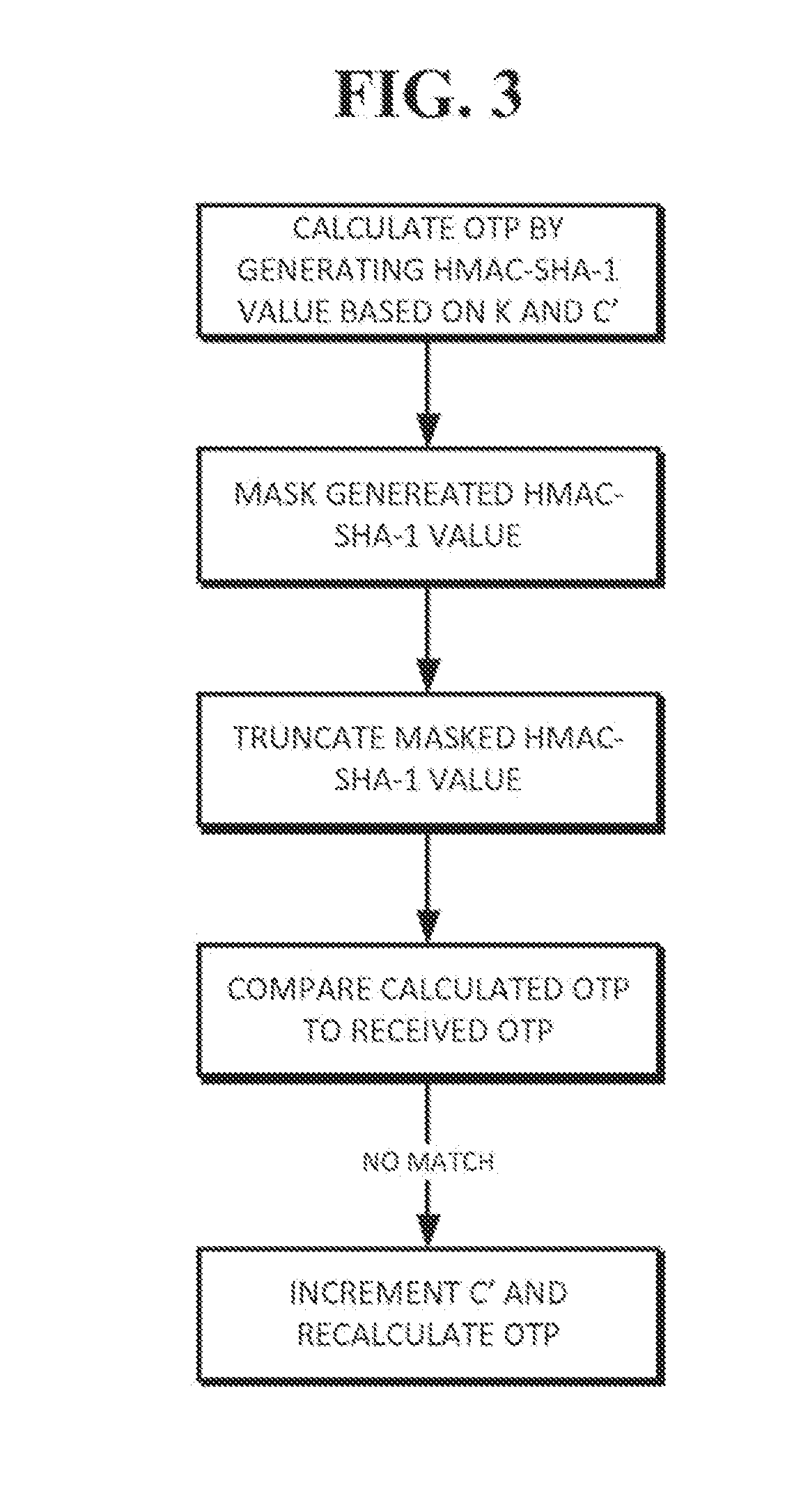
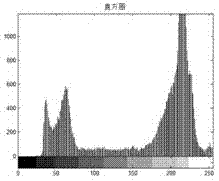
One time password
ActiveUS20090313687A1Public key for secure communicationVolume/mass flow measurementComputer hardwareOne-time password
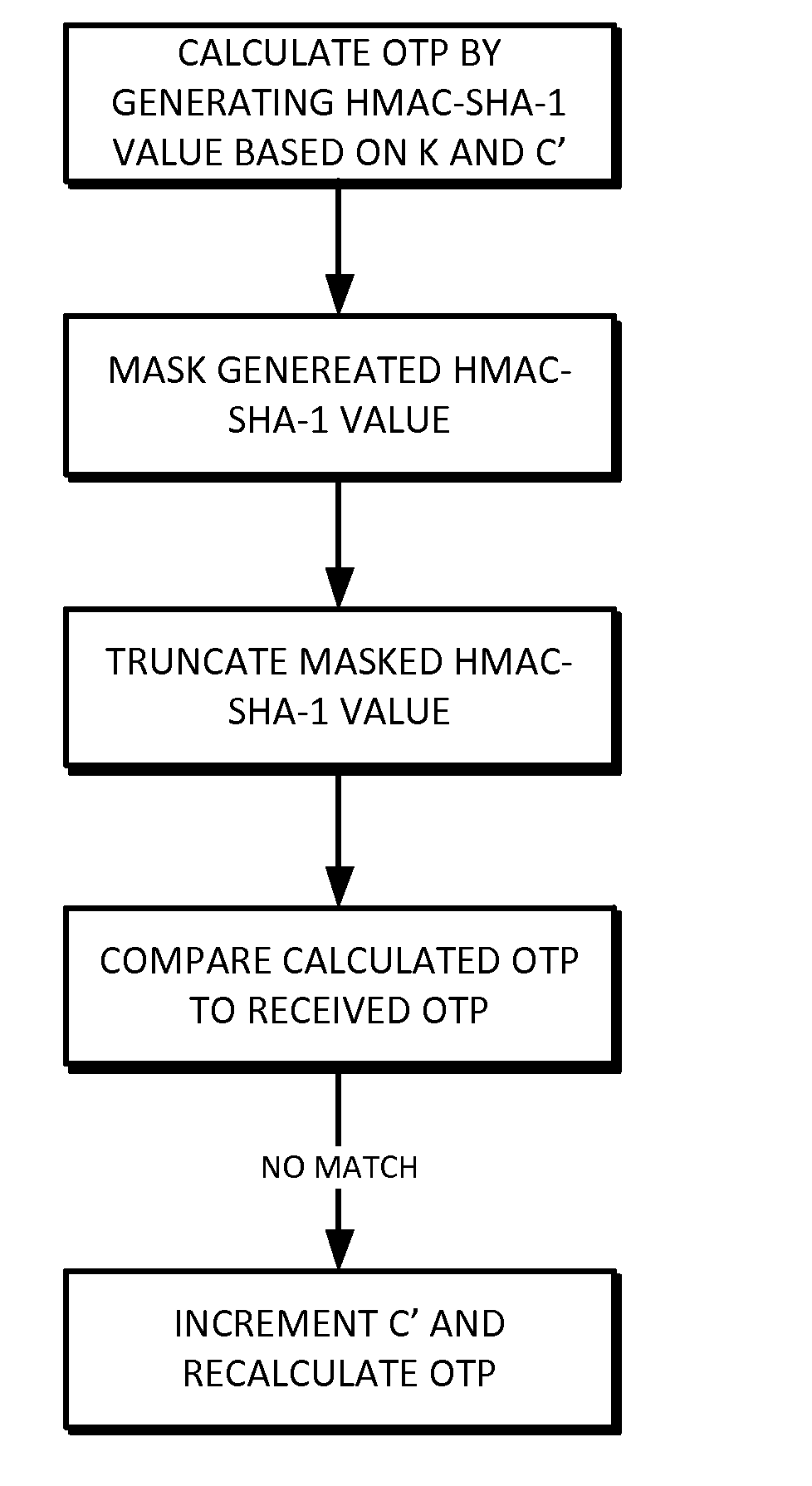
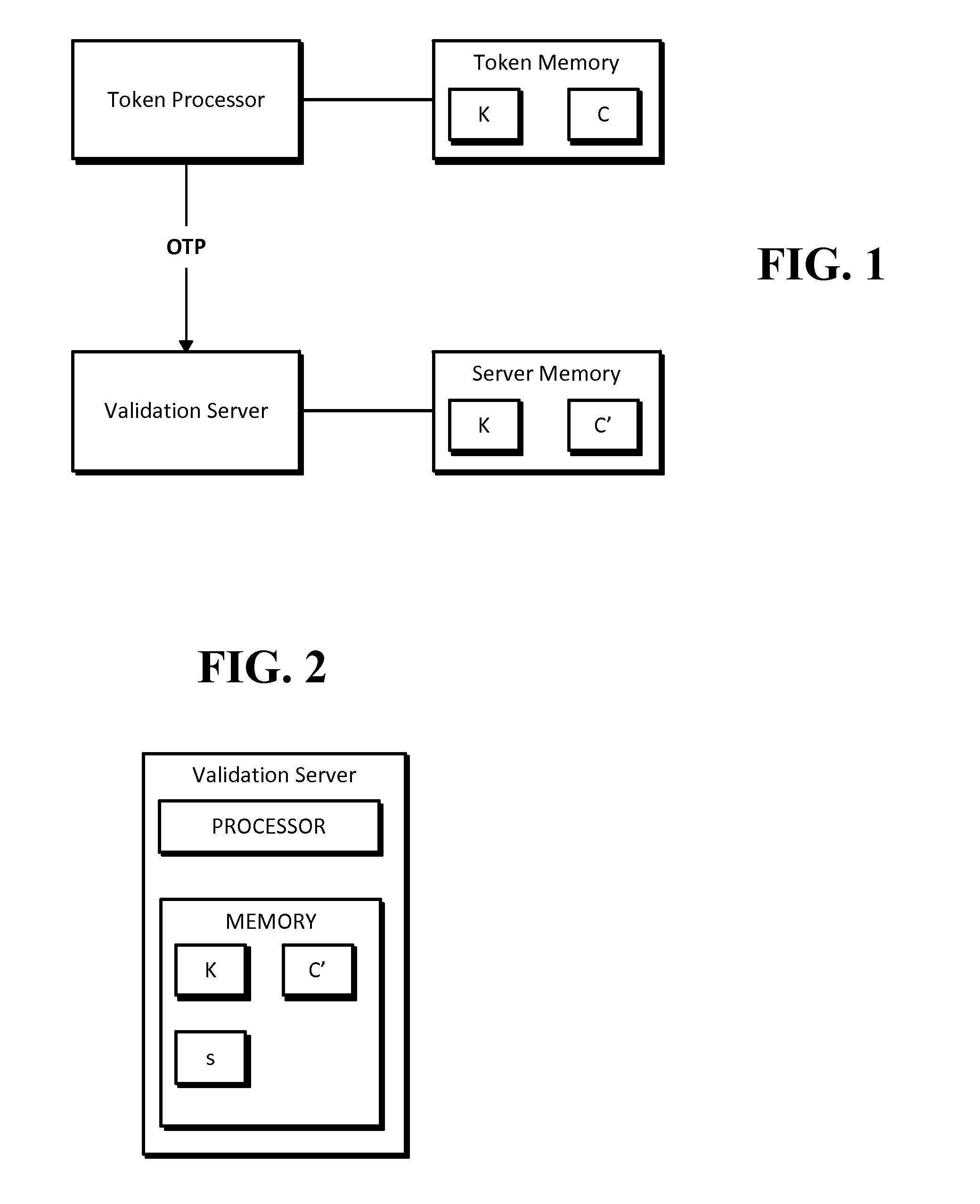
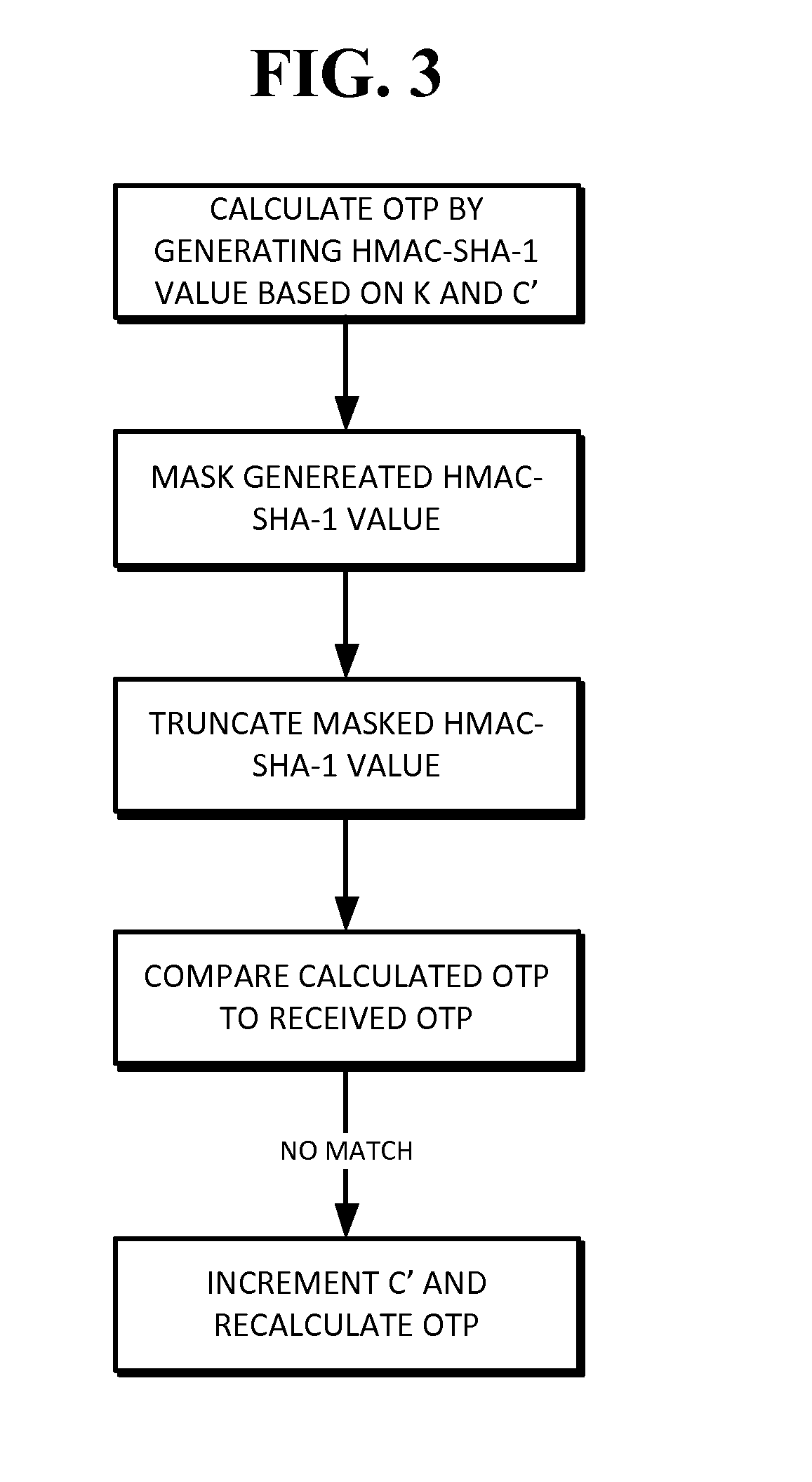
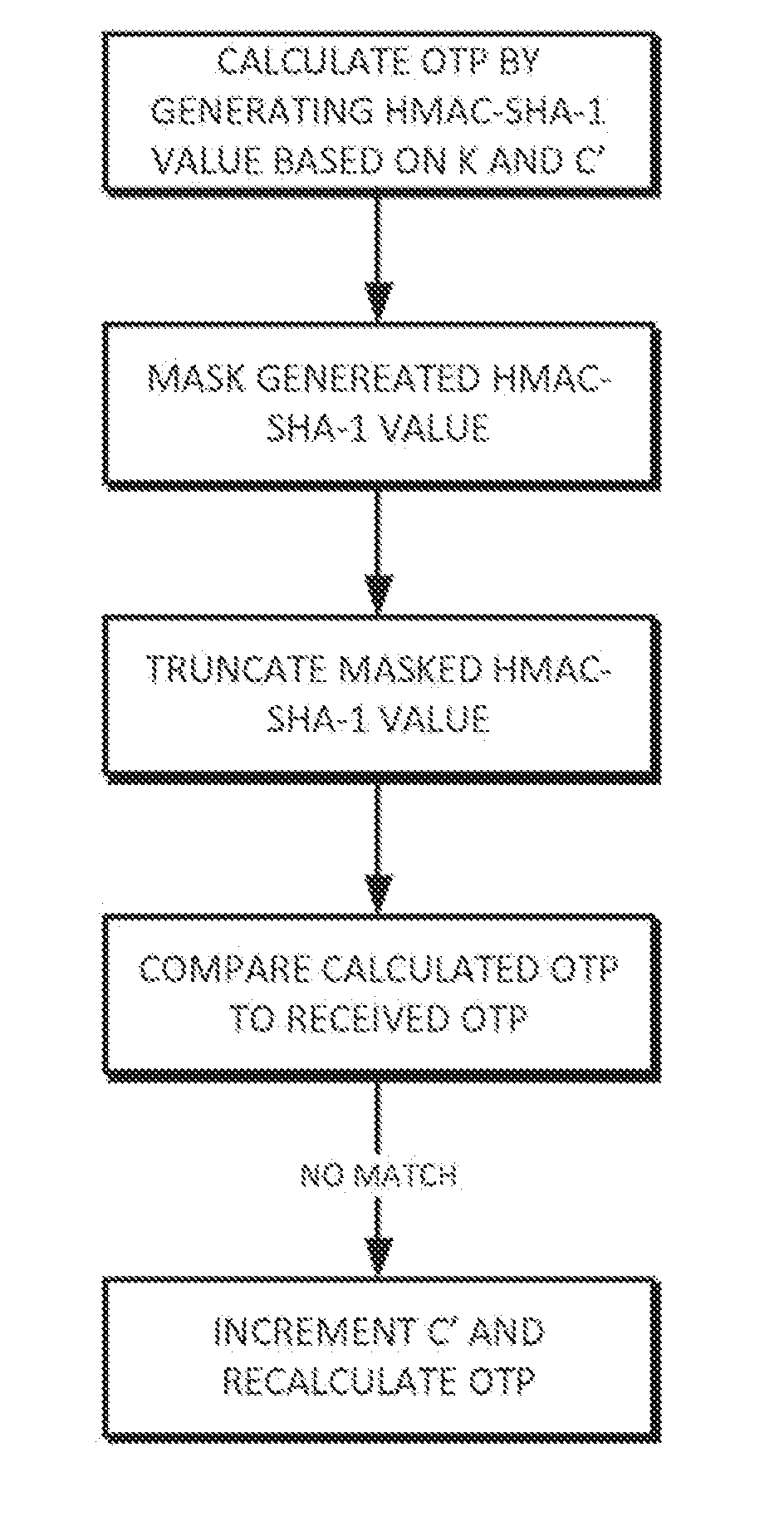
A token calculates a one time password by generating a HMAC-SHA-1 value based upon a key K and a counter value C, truncating the generated HMAC-SHA-1 value modulo 10̂Digit, where Digit is the number of digits in the one time password. The one time password can be validated by a validation server that calculates its own version of the password using K and its own counter value C′. If there is an initial mismatch, the validation server compensate for a lack of synchronization between counters C and C′ within a look-ahead window, whose size can be set by a parameter s.
Owner:SYMANTEC CORP
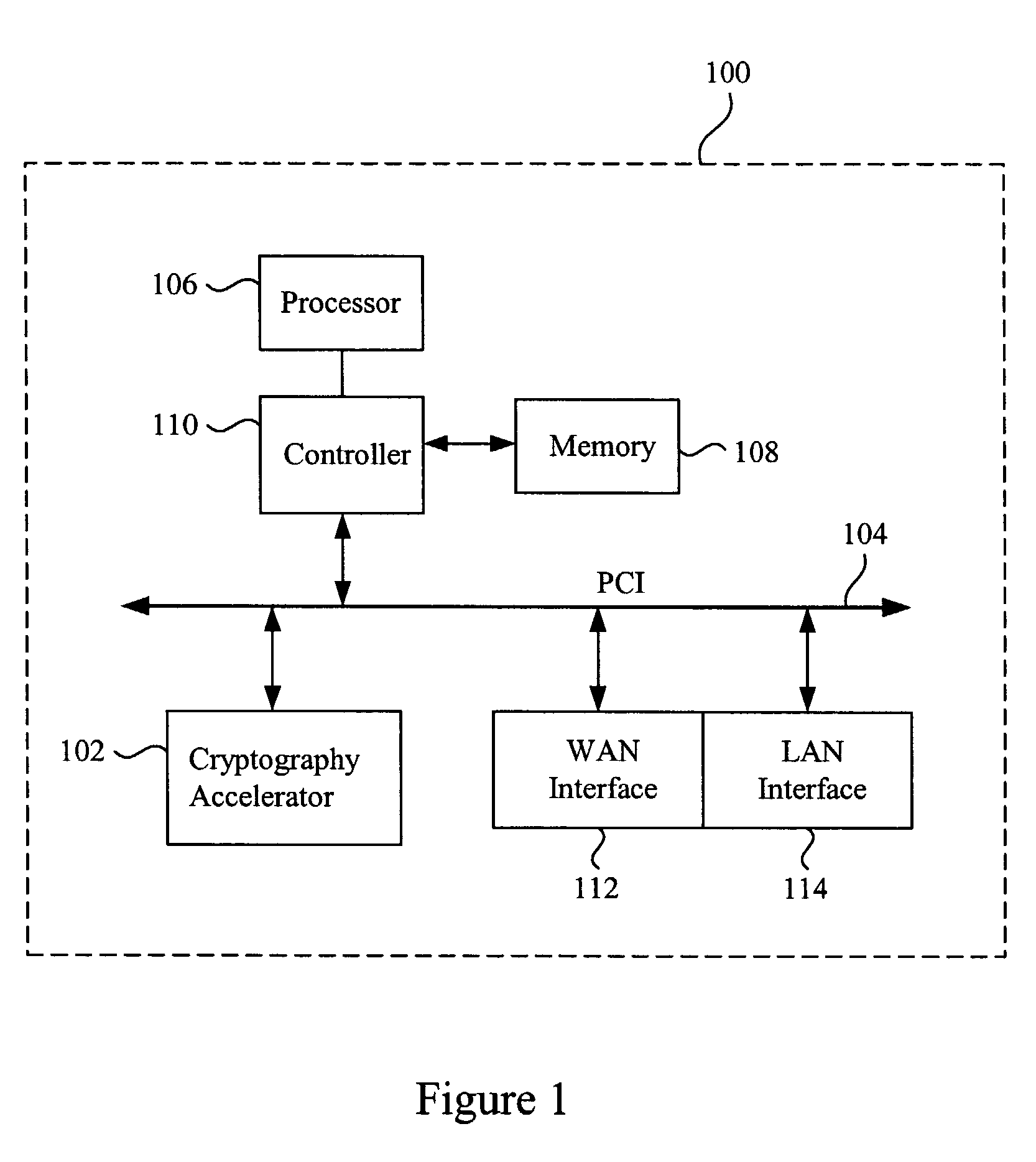
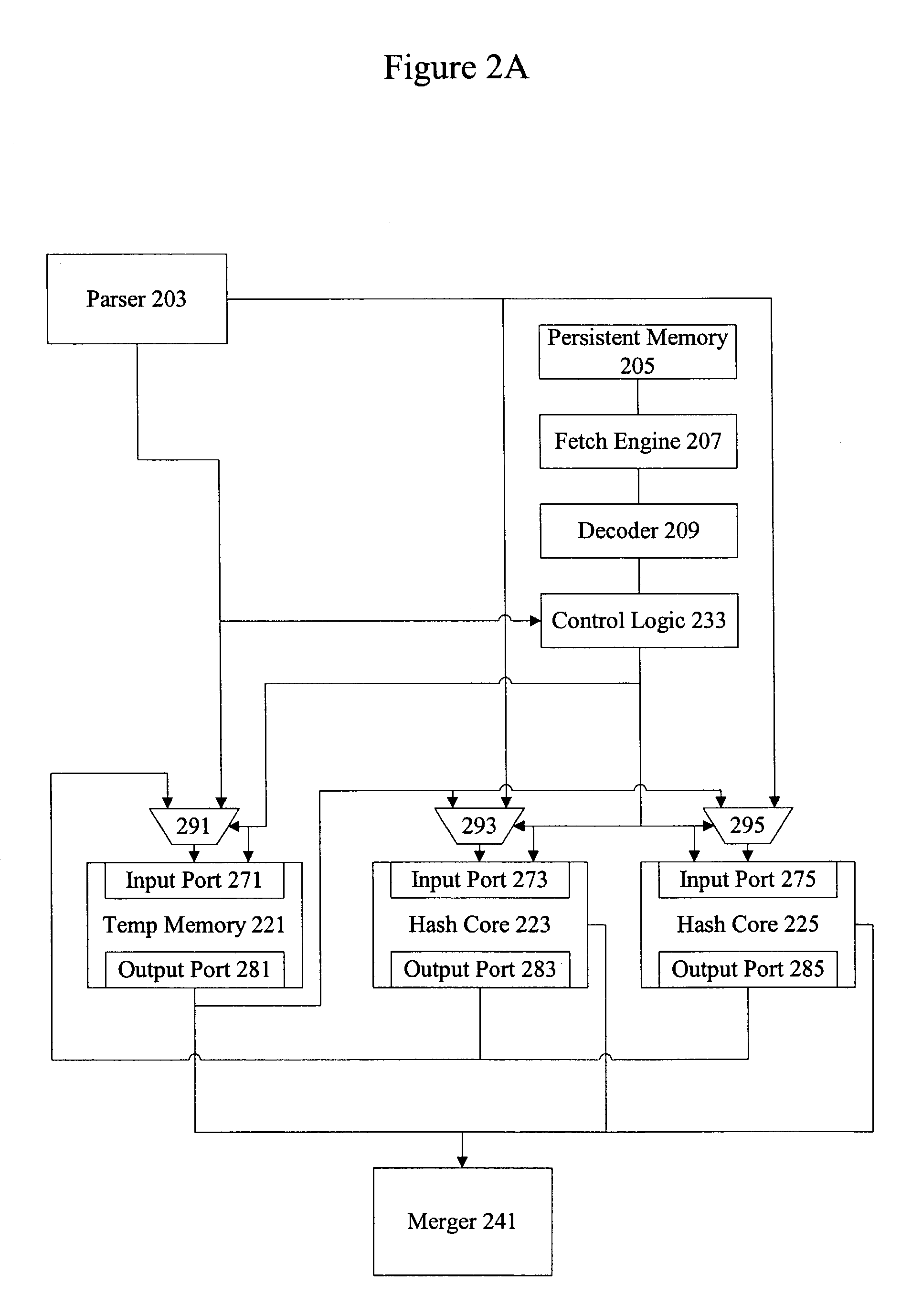
Methods and apparatus for performing hash operations in a cryptography accelerator
ActiveUS20030185391A1User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic accelerator
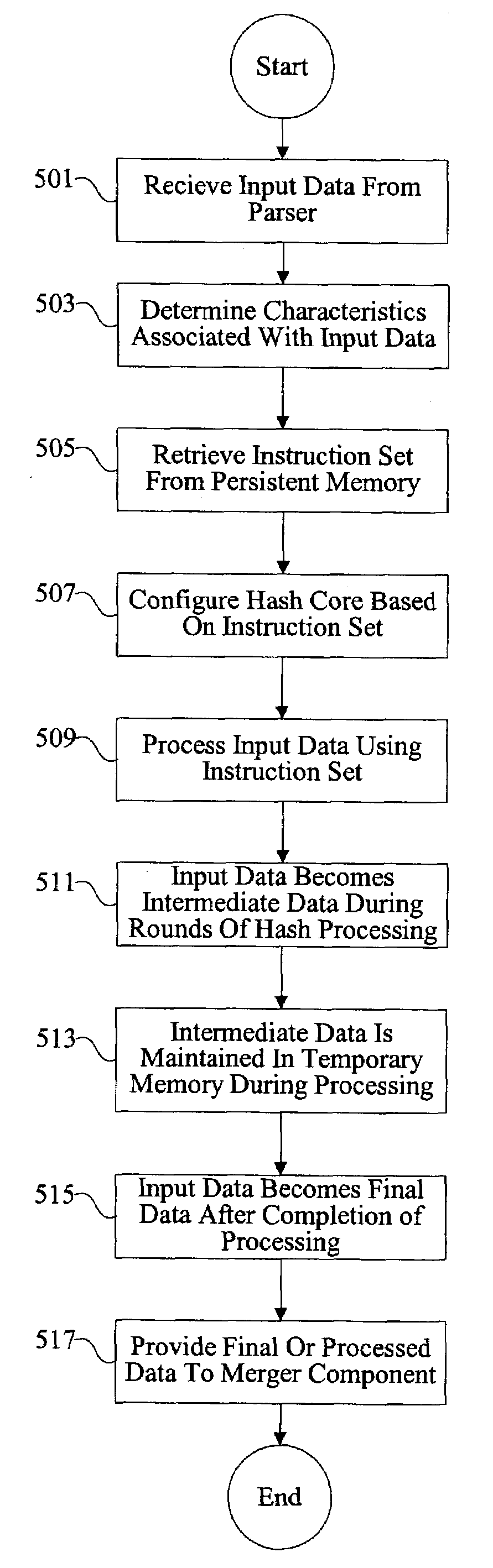
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
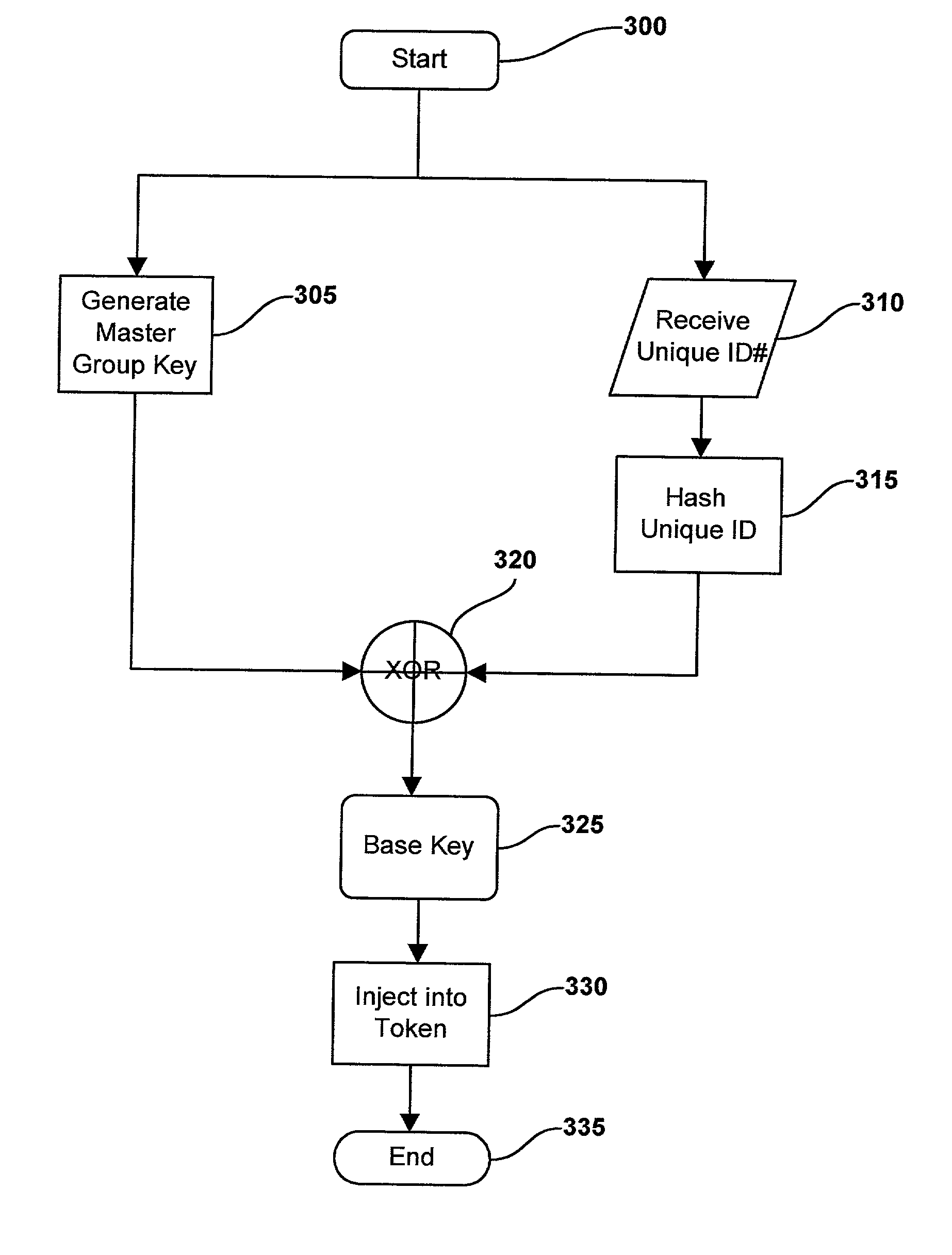
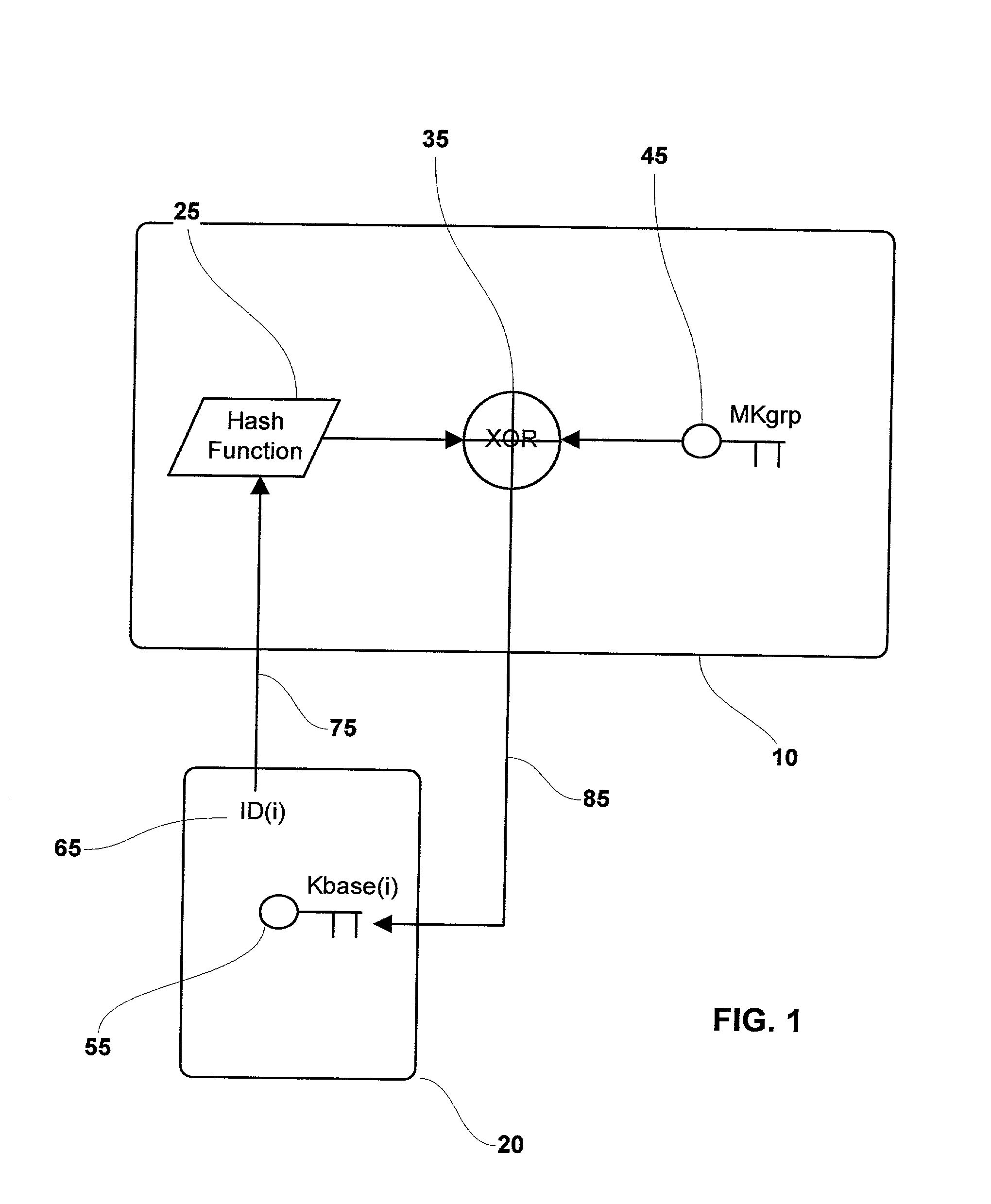
System and method for performing mutual authentications between security tokens
InactiveUS20030145203A1Key distribution for secure communicationUser identity/authority verificationData processing systemGeneration process
This patent describes a data processing system and method for performing mutual authentications between two security tokens by generation of a common cryptographic key. The common cryptographic key is generated using unique identifiers associated with each security token that diversify a common master key. The generation process incorporates a message digest function such as SHA-1 and an XOR operator to arrive at the common symmetric key.
Owner:ACTIVCARD
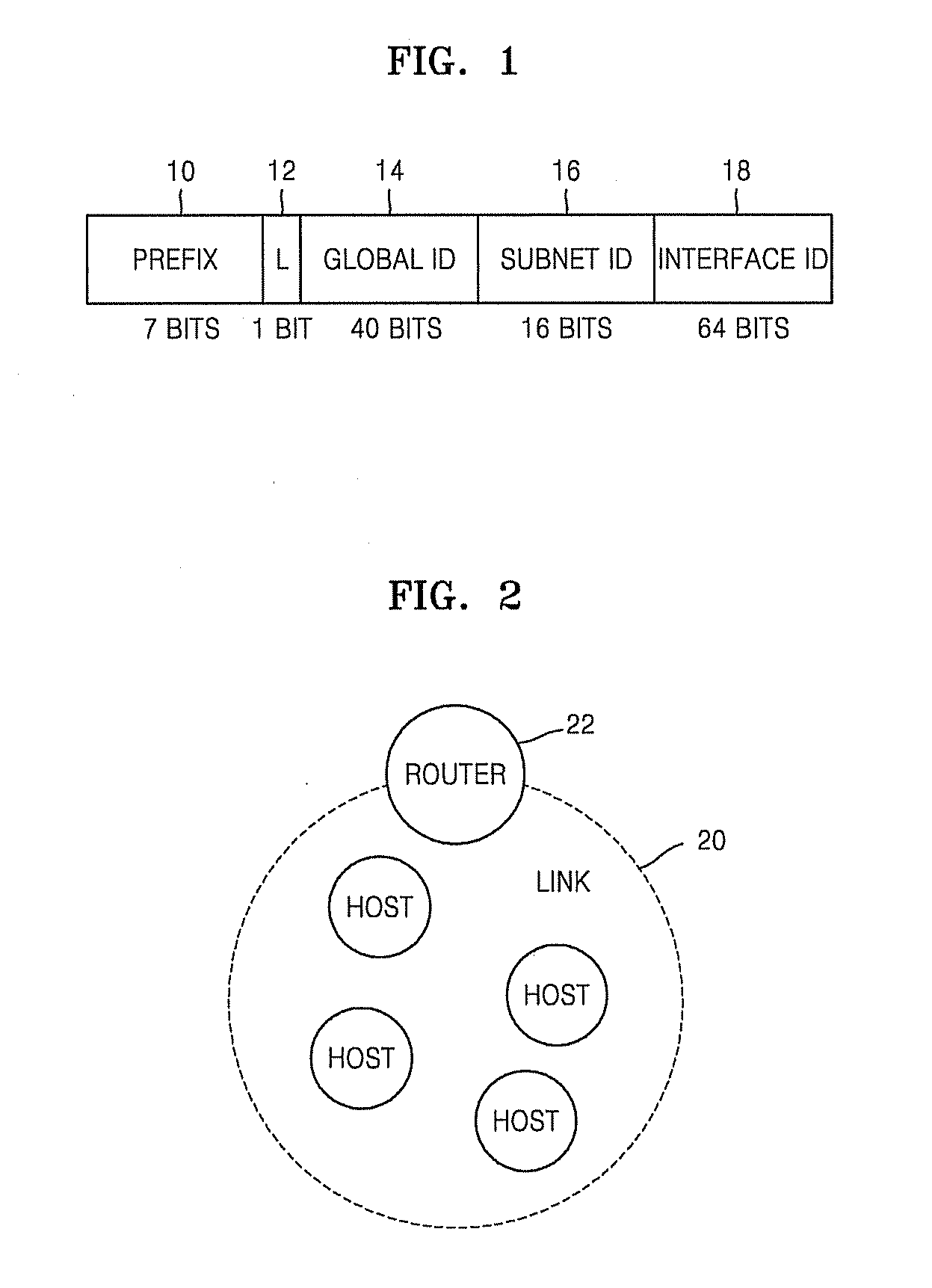
Method and apparatus for generating ipv6 unique local address
A method and apparatus for generating an IPv6 unique local address (ULA) are provided. The method includes generating a 64-bit first value using unique information on a UPnP device used by a router; generating a modified 64-bit EUI-64 using unique information on an interface device used by the router; generating a 128-bit second value by concatenating the 64-bit first value and the modified EUI-64; generating a 160-bit third value by applying SHA-1 to the 128-bit second value; and generating a global ID by extracting 40 bits from the 160-bit third value. A global ID is generated using unique information on an UPnP device and an interface device and the IPv6 ULA is generated using the global ID, thereby generating the IPv6 ULA having uniqueness in an entire IPv6 address system without an NTP.
Owner:SAMSUNG ELECTRONICS CO LTD
Accelerating cryptographic hash computations
ActiveUS7599489B1General purpose stored program computerComputation using non-denominational number representationExecution unitBit-length
Provided is an apparatus and method for accelerating cryptographic hash computations. For example, in a cryptographic hash computation such as SHA-1, multiple execution units in a processor can process loosely coupled data. Specifically, after preprocessing a message with a particular bit length and parsing the padded message into multiple blocks, a first execution unit can begin processing the blocks for a message schedule computation. While the first block is processed, the first execution unit produces a partial result for the computation of the compression function in the second execution unit. By simultaneously processing the blocks on multiple execution units, the cryptographic hash computation performance can improve.
Owner:ORACLE INT CORP
Methods and apparatus for performing hash operations in a cryptography accelerator
ActiveUS7400722B2User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic accelerator
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
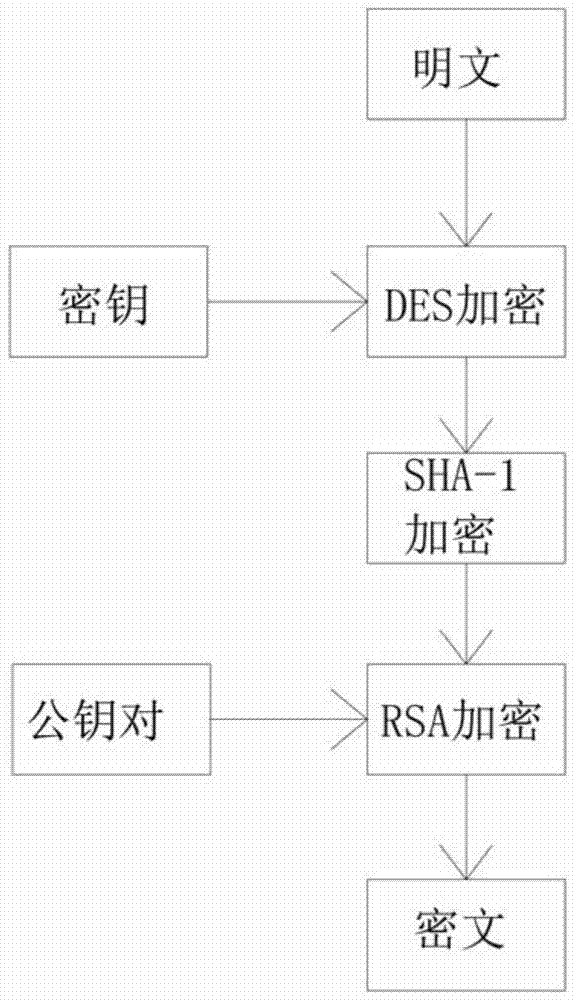
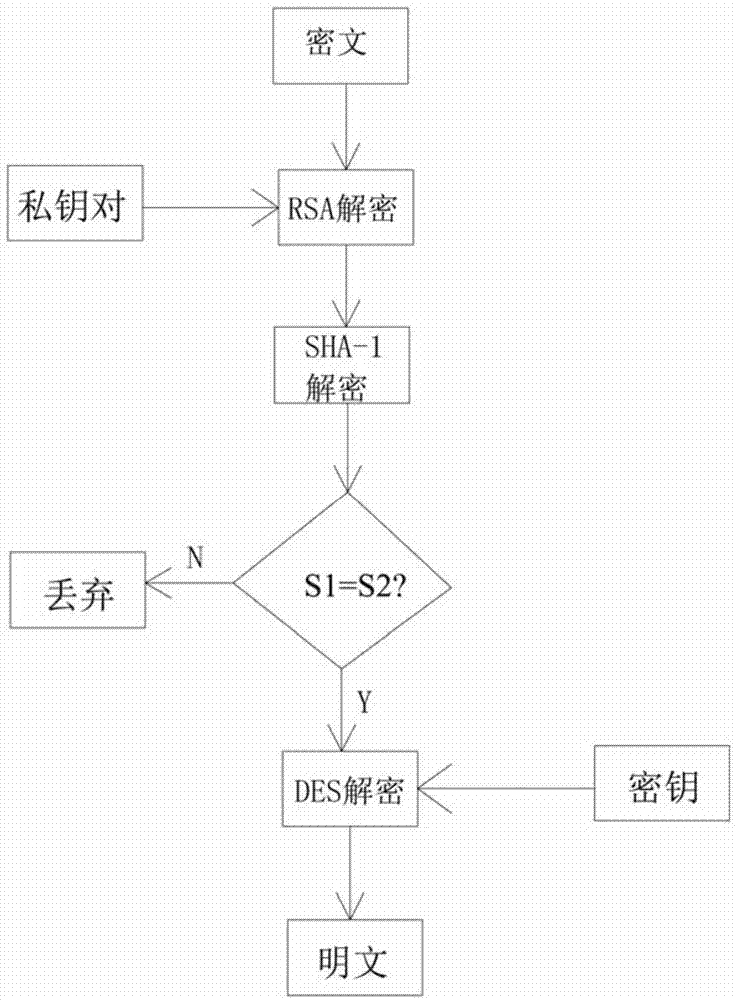
Communication data encryption and decryption method based on DES (Data Encryption Standard), RSA and SHA-1 (Secure Hash Algorithm) encryption algorithms
ActiveCN103684794AImprove securityAvoid harmPublic key for secure communicationUser identity/authority verificationDigital signatureCiphertext
The invention discloses a communication data encryption and decryption method based on DES (Data Encryption Standard), RSA and SHA-1 (Secure Hash Algorithm-) encryption algorithms. The communication data encryption and decryption method based on DES, RSA and SHA-1 encryption algorithms comprises the following steps: 1, generating data to be encrypted for sending; 2, encrypting the data to be sent for the first time, namely performing block DES encryption; 3, performing SHA-1 encryption algorithm to the data which has been encrypted for the first time to generate abstract content; 4, encrypting the data encrypted by SHA-1 and the abstract by a RSA encryption public key received by a receiving end; 5, sending cryptograph; 6, receiving the cryptograph by the receiving end and decrypting the cryptograph by an own private key for the first time; 7, authenticating the received data; 8, performing DES decryption to the data which has been authenticated, and reading the data content. The communication data encryption and decryption method based on DES, RSA and SHA-1 encryption algorithms utilizes different characteristics of the three encryption algorithms, and respectively encrypts a message to be sent by DES, RSA and SHA-1 encryption algorithms, so that the encrypted message for communication is much safer, and a digital signature is achieved for ensuring that the received message is the original message sent by a sending end without tampering.
Owner:SOUTH CHINA UNIV OF TECH
One time password
ActiveUS8087074B2Public key for secure communicationVolume/mass flow measurementComputer hardwareOne-time password
Owner:SYMANTEC CORP
One Time Password
ActiveUS20120096535A1Public key for secure communicationVolume/mass flow measurementComputer hardwareOne-time password
A token calculates a one time password by generating a HMAC-SHA-1 value based upon a key K and a counter value C, truncating the generated HMAC-SHA-1 value modulo 10̂Digit, where Digit is the number of digits in the one time password. The one time password can be validated by a validation server that calculates its own version of the password using K and its own counter value C′. If there is an initial mismatch, the validation server compensate for a lack of synchronization between counters C and C′ within a look-ahead window, whose size can be set by a parameter s.
Owner:GEN DIGITAL INC
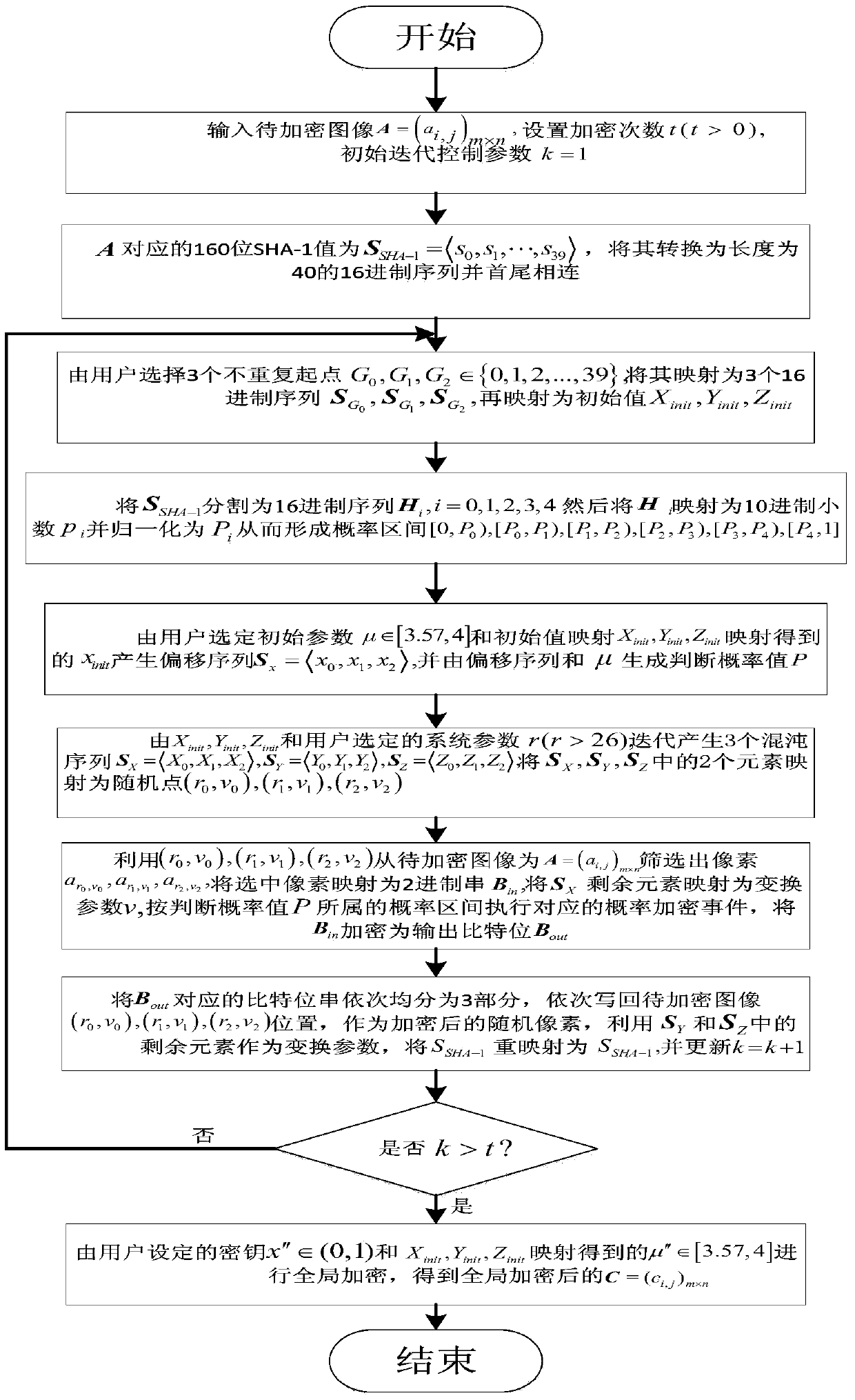
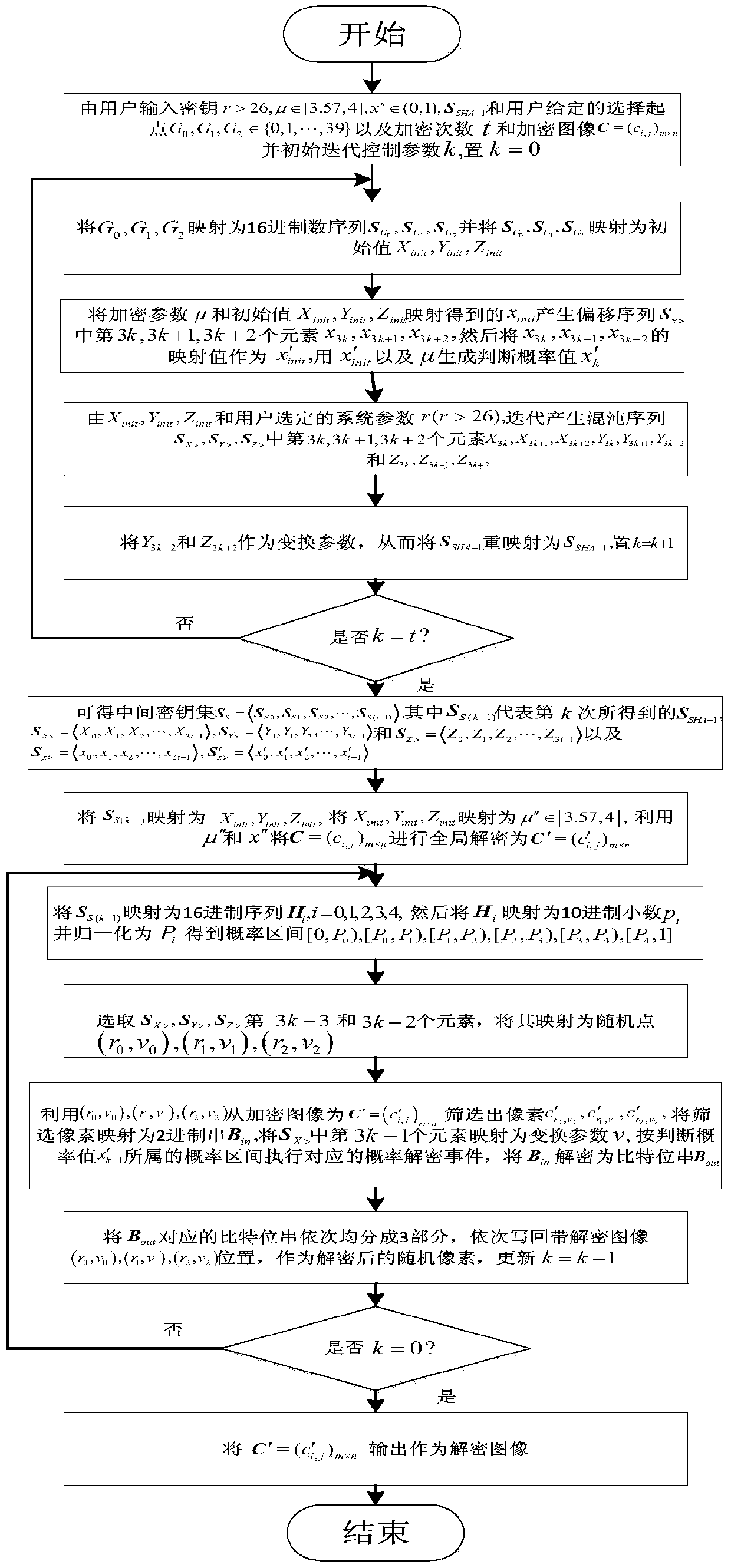
Image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping
ActiveCN103929563AIncrease the number of replacements generatedEnsure safetySecuring communicationPictoral communicationComputer hardwareCoupling
The invention provides an image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping. An SHA-1 value of an image to be encrypted and encryption parameters selected by a user are combined to serve as a secret key, generalized Henon mapping is driven to randomly disturb the initial position, the counting-off interval and the counting-off direction of Joseph traversal mapping used for position point permutation, so that different encryption images and encryption parameters correspond to different position point permutation processes in essence; coupling of all the encryption steps is enhanced, different encryption processes are started according to different images to be encrypted, so that selective plain text attacks are effectively resisted, and the image encryption and decryption method has large secret key space and is easy to implement and low in cost.
Owner:江苏瀚洋精工科技有限公司
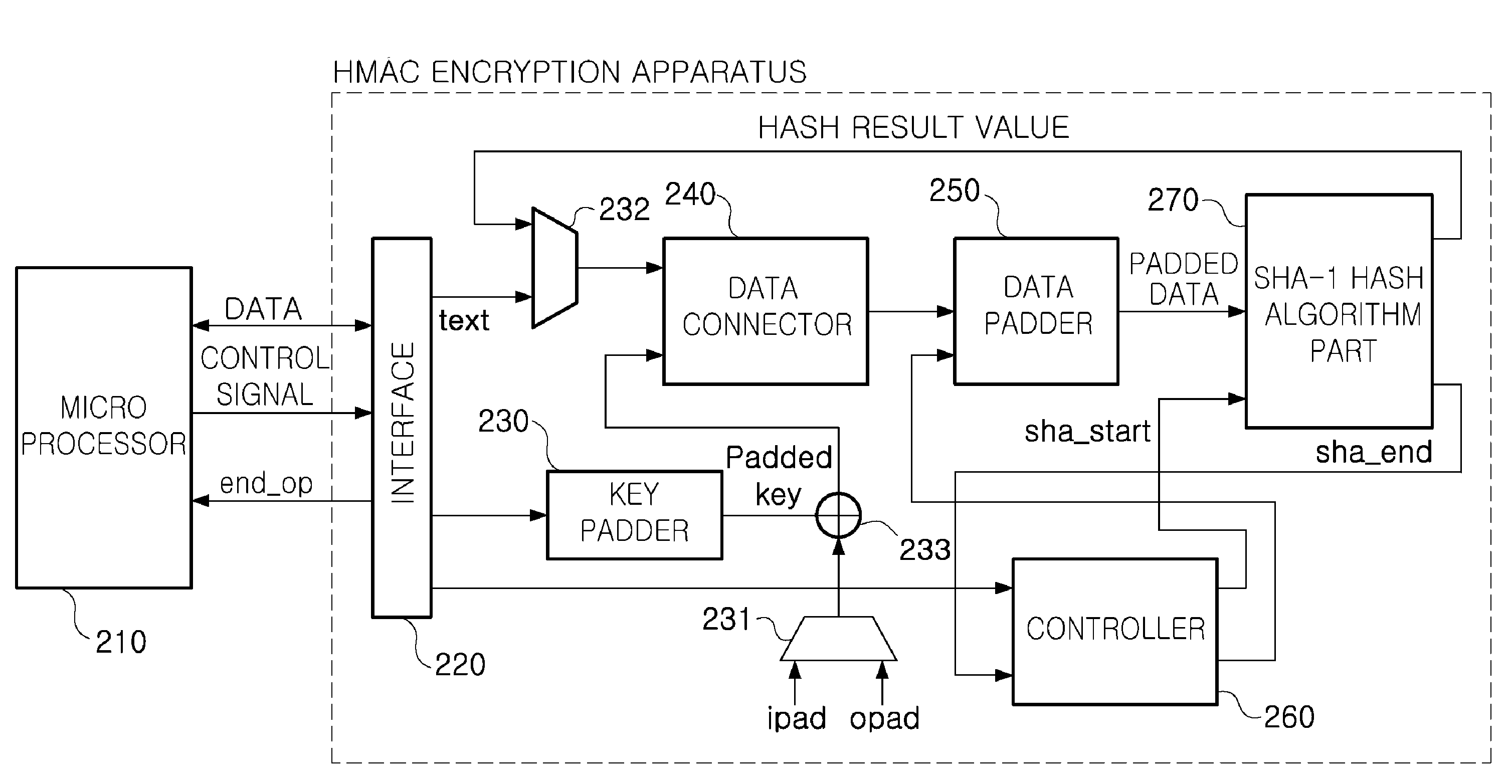
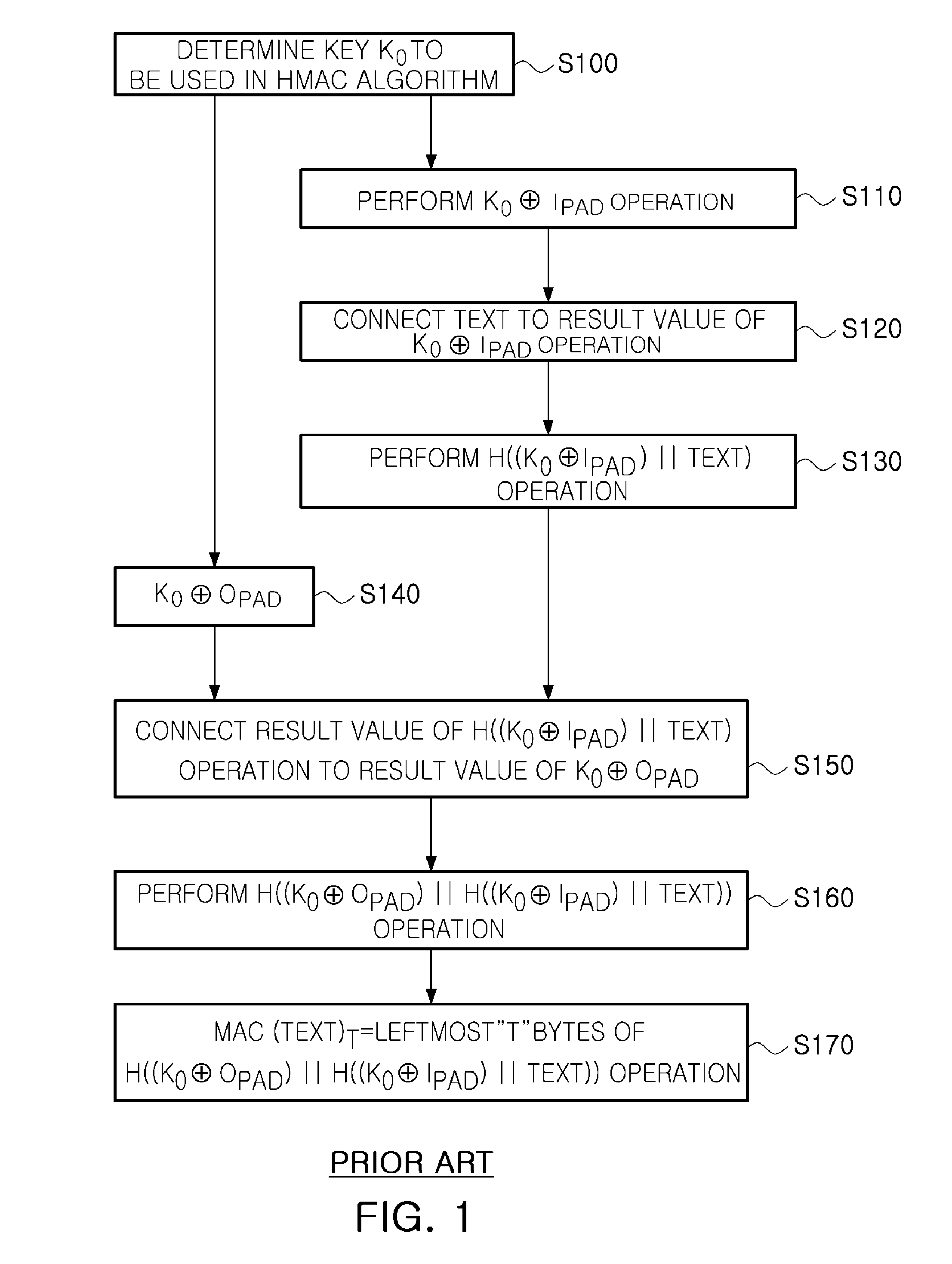
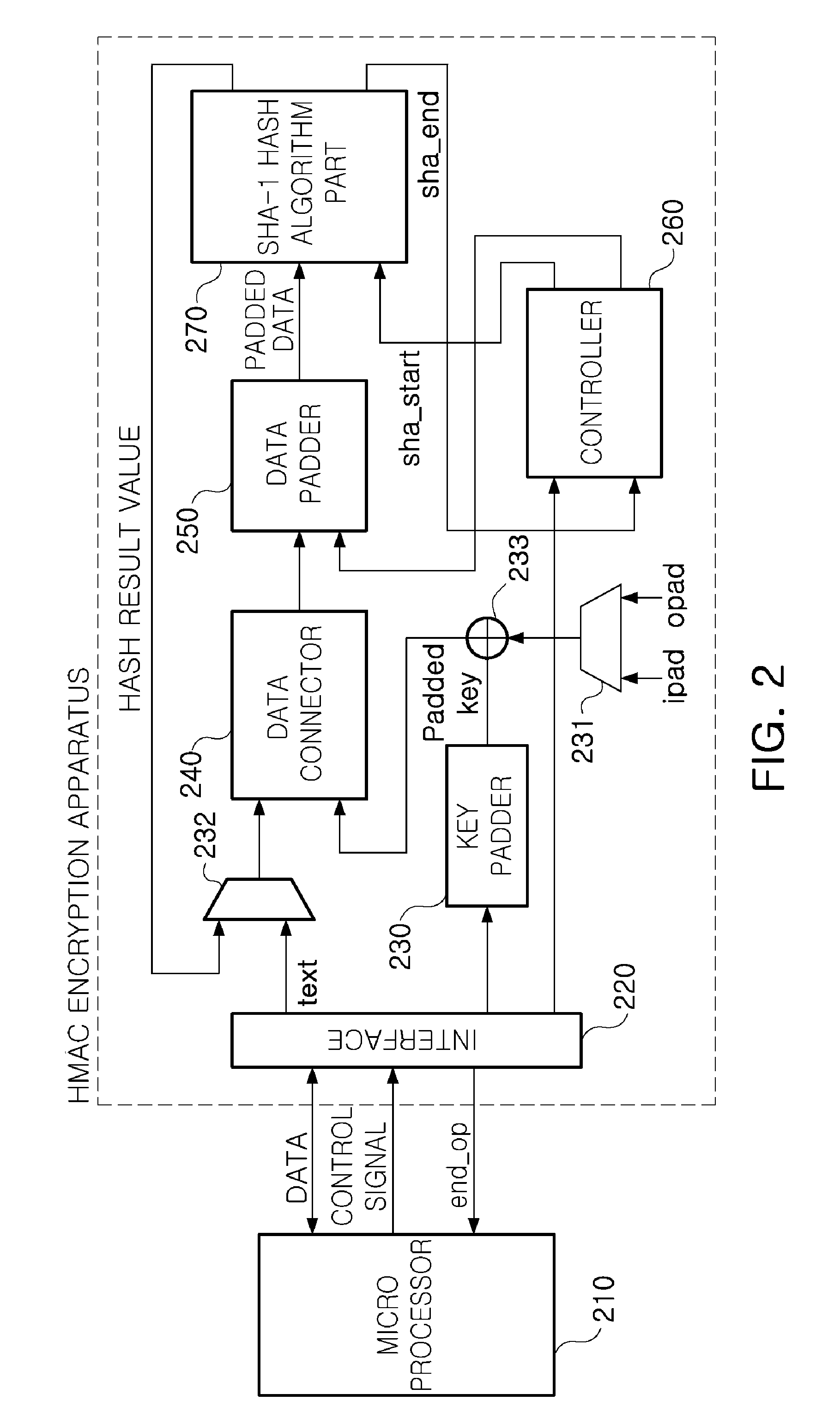
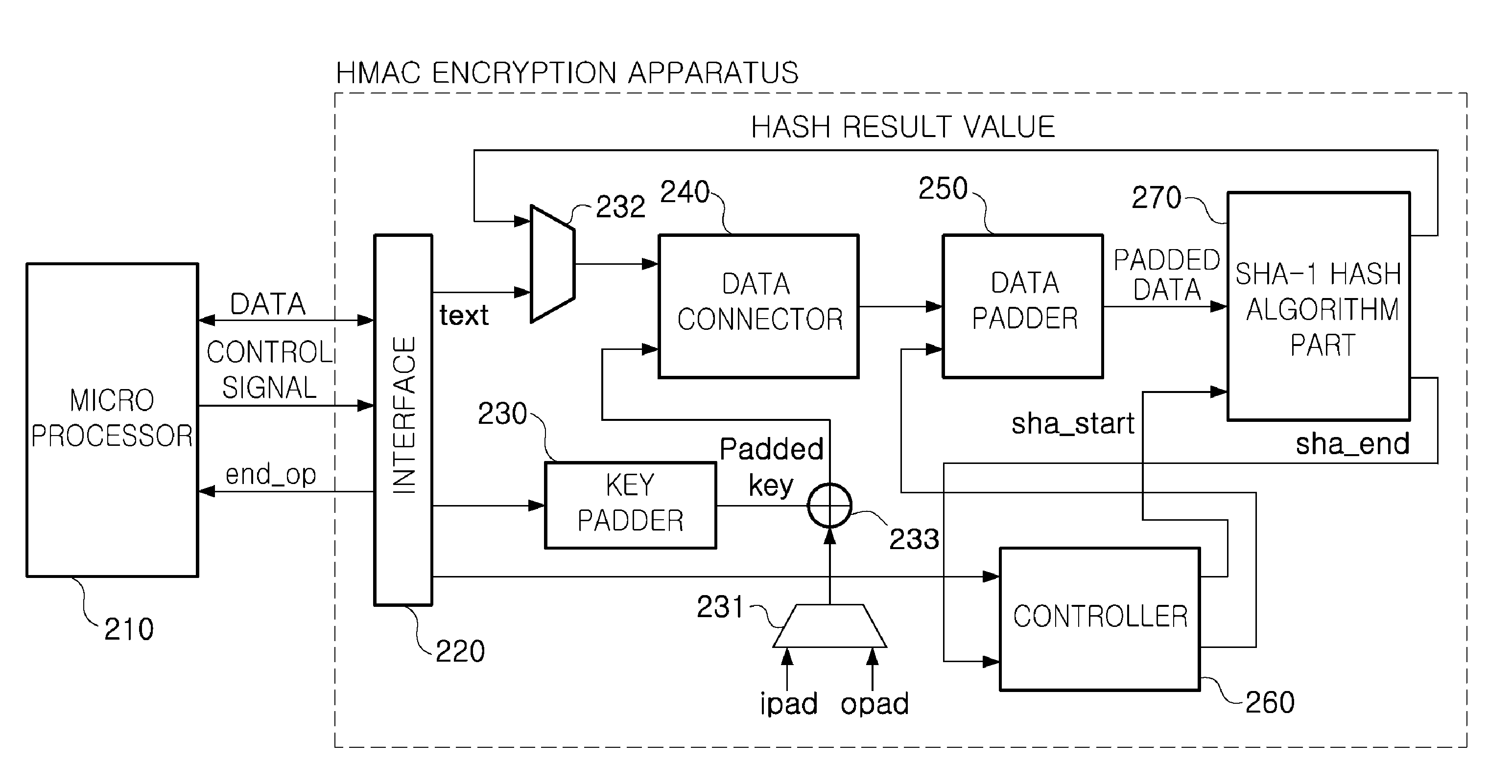
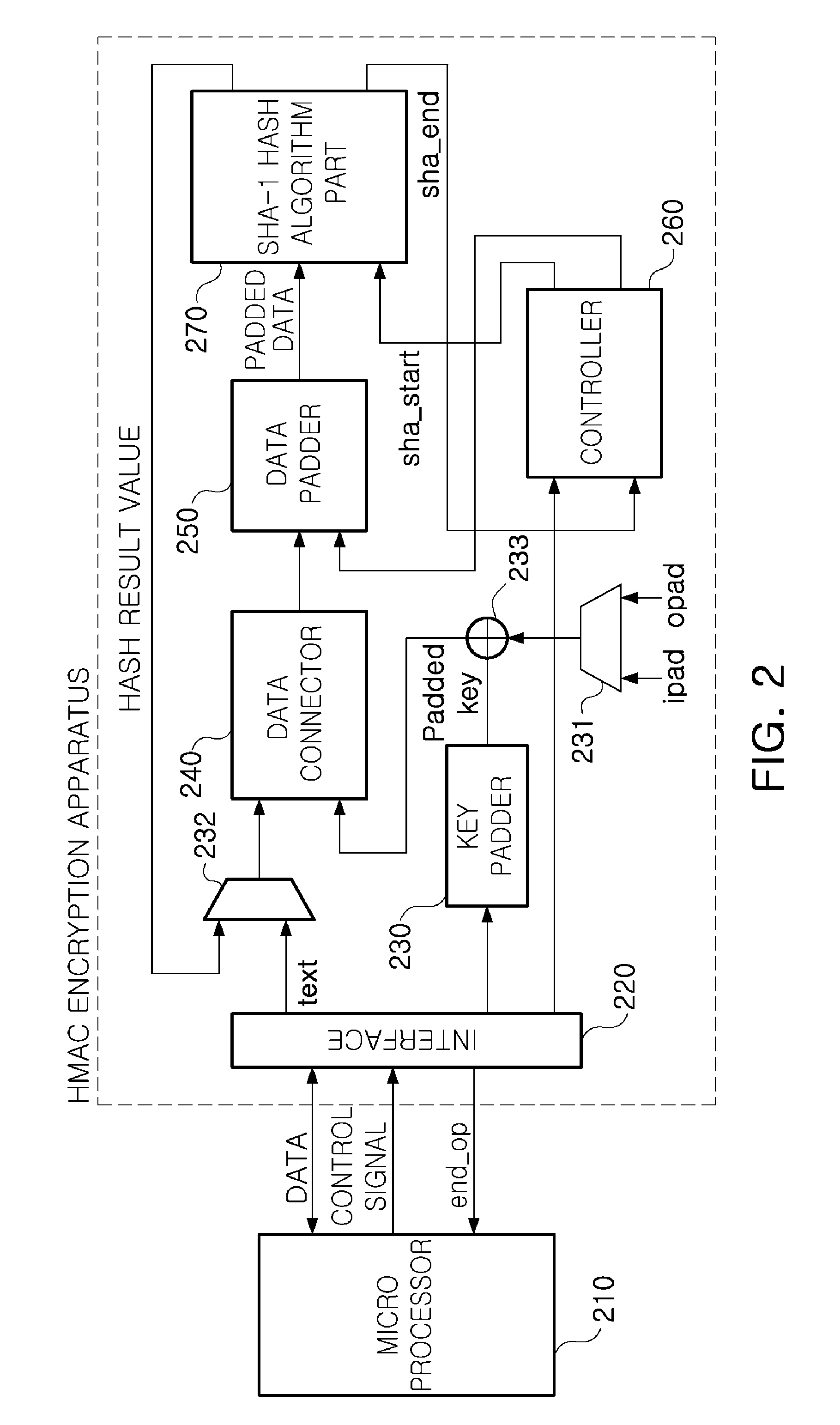
Low power hmac encryption apparatus
InactiveUS20100031052A1Privacy protectionReduce power consumptionDigital data processing detailsUser identity/authority verificationData connectionHash-based message authentication code
There are provided a low power SHA-1 hash algorithm apparatus having a low power structure and optimized to a trusted platform module (TPM) applied to a mobile trusted computing environment and a low power keyed-hash message authentication code (HMAC) encryption apparatus using the low power SHA-1 hash algorithm apparatus, the HMAC encryption apparatus including: a key padder padding key data for HMAC algorithm; an XOR operator XOR operating the padded key data and a padding constant; a data connector connecting a text to be encrypted, to data obtained by the XOR operating; a data padder padding the connected data; an SHA-1 hash algorithm part performing an SHA-1 hash algorithm on the padded data; a data selector selecting and applying one of a result of the SHA-1 hash algorithm and the text to be encrypted, to the data connector; and a controller controlling operations of the key padder, data connector, and data padder, a sequence of performing a hash algorithm of the SHA-1 hash algorithm part, and storing an operation result to read data required for performing an encryption operation and store data with memory.
Owner:ELECTRONICS & TELECOMM RES INST
Image encryption and decryption method based on probability interval division and dynamic probability events
ActiveCN105577354AIncrease tight couplingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPattern recognitionProbabilistic encryption
The invention provides an image encryption and decryption method based on probability interval division and dynamic probability events. The method comprises steps of during encryption, firstly mapping secret key parameters and SHA-1 values of to-be-encrypted images to different probability encryption sections; carrying out random screening on to-be-encrypted pixels based on the secret key parameters and the SHA-1 values; and executing and writing different probability encryption events into corresponding pixel positions according to the probability sections where the probability encryption events fall. In order to improve safety, an SHA-1 value remapping process is added for dividing the probability sections, screening the to-be-encrypted pixels and carrying out stochastic disturbance on encryption; and by adding an overall situation encryption process related to SHA-1 update values and user secret keys, performance of an image encryption algorithm is enhanced. The method also comprises steps of during decryption, firstly recovering encrypted parameters; then finishing overall decryption; and at last executing inverse decryption operation on randomly screened pixels. Compared with the prior art, different pixels and secret keys correspond to different encryption processes, so the method is highly safe.
Owner:SHAANXI NORMAL UNIV
Instruction and logic to provide SIMD secure hashing round slice functionality
ActiveUS8924741B2Single instruction multiple data multiprocessorsInstruction analysisExecution unitOperand
Instructions and logic provide SIMD secure hashing round slice functionality. Some embodiments include a processor comprising: a decode stage to decode an instruction for a SIMD secure hashing algorithm round slice, the instruction specifying a source data operand set, a message-plus-constant operand set, a round-slice portion of the secure hashing algorithm round, and a rotator set portion of rotate settings. Processor execution units, are responsive to the decoded instruction, to perform a secure hashing round-slice set of round iterations upon the source data operand set, applying the message-plus-constant operand set and the rotator set, and store a result of the instruction in a SIMD destination register. One embodiment of the instruction specifies a hash round type as one of four MD5 round types. Other embodiments may specify a hash round type by an immediate operand as one of three SHA-1 round types or as a SHA-2 round type.
Owner:INTEL CORP
Modified SHA-1 hash algorithm
InactiveCN101872338AImprove efficiencyImprove securityTransmissionComplex mathematical operationsMessage processingMessage passing
The invention relates to a modified SHA-1 hash algorithm. The existing SHA-1 harsh algorithm has low security. The invention firstly adds a 1, a plurality of 0 and a 64-bit binary string after the information to be processed, then enlarges and groups the information, so the original 512-bit group is changed into a 1024-bit group and a register value is initialized; then a main cycle is utilized to sequentially process each group, the main cycle totally has four operations, and each operation contains logical function and compression function processing; and finally, after the processing of all the groups is completed, 160-bit message digest is output, and when the message digest is transferred, the message to be transferred is added with a safety hashed value. Through the algorithm of the invention, the original SHA-1 algorithm has more safety on message processing, and through modifying the logical function expression and the compression function logical structure of the algorithm, the efficiency of the SHA-1 algorithm is improved.
Owner:HANGZHOU DIANZI UNIV
System and method for reducing memory requirements of firmware
ActiveUS7603562B2Reduce memory requirementsUser identity/authority verificationDigital computer detailsMD5Unique identifier
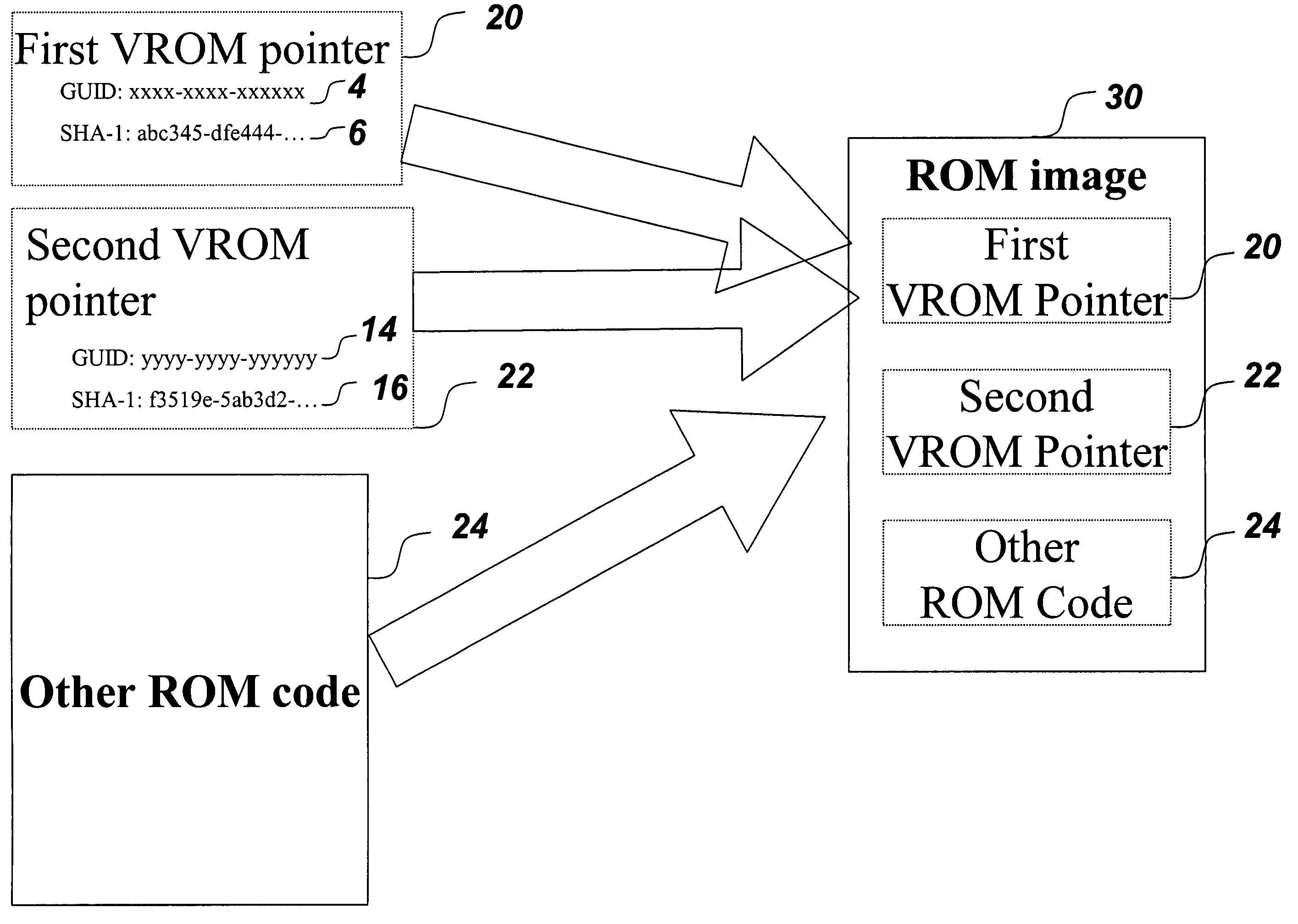
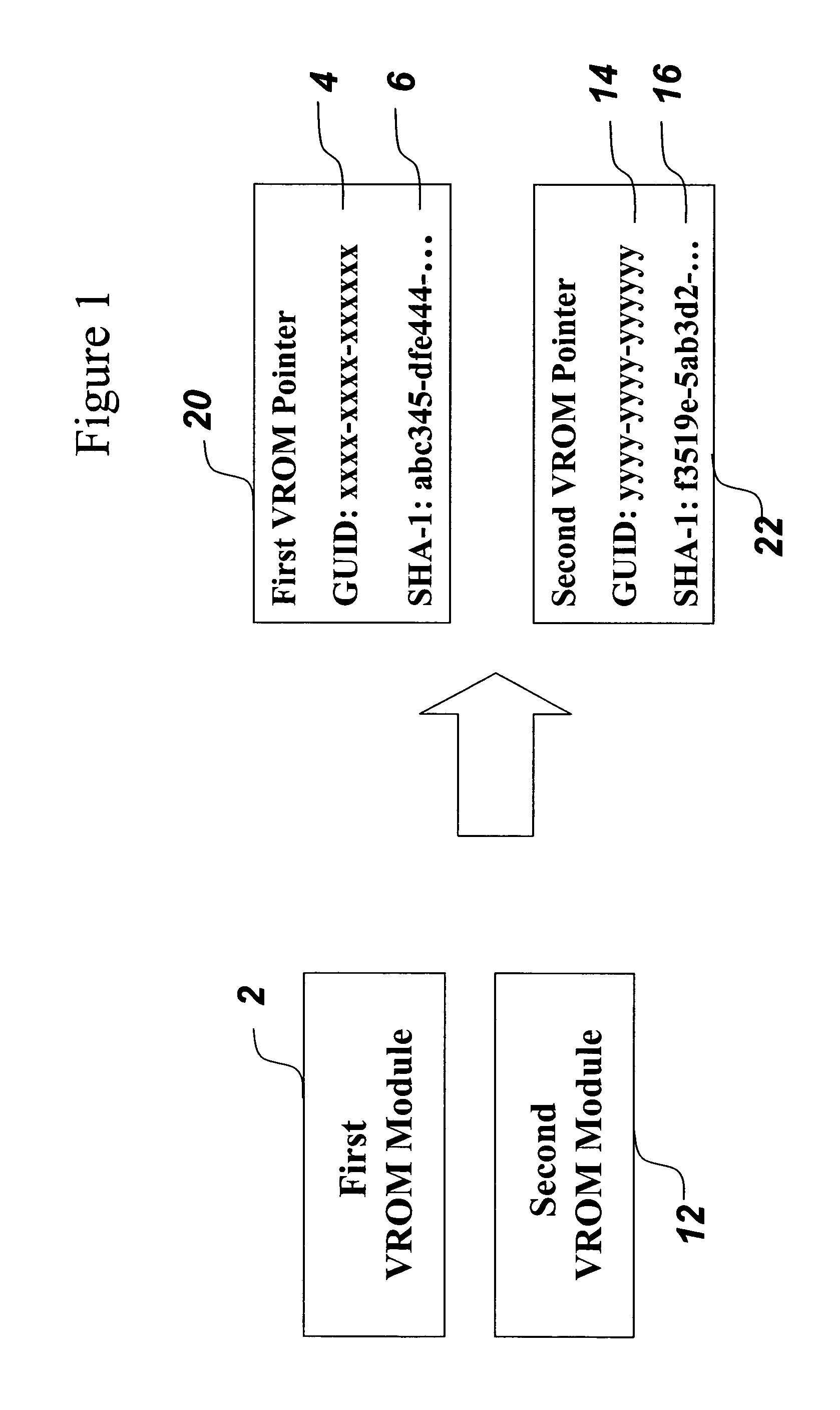
A mechanism for making increased amounts of firmware available to a computer pre-boot is discussed. To increase the amount of firmware available pre-boot, a design decision is made during the build process as to which segments of the firmware need to be placed on the ROM part and which segments of the firmware can be located elsewhere. The segments of the firmware that are stored remotely from the ROM are referred to as “virtual ROM modules”. Each of the virtual ROM modules is assigned a generated unique identifier, and a “message digest” is constructed for each module using an algorithm such as MD5 or SHA-1. In the software build of the ROM image, the message digest-unique identifier pair created for each Virtual ROM module is used as a logical pointer for the virtual module. Additionally, a search path variable is placed into the ROM image in non-volatile storage. The search path provides for one or more locations in which to look for the Virtual ROM modules, and may be updated at a later point in time.
Owner:INSYDE SOFTWARE CORP
Low power HMAC encryption apparatus
InactiveUS8086864B2Reduce power consumptionDigital data processing detailsUser identity/authority verificationData connectionHash-based message authentication code
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus to Implement Dual Hash Algorithm
InactiveUS20080123841A1Easy to processEffective calculationReliability increasing modificationsUser identity/authority verificationAlgorithmProcessor register
An apparatus arranged to accept digital data as an input and to process the data according to one of either the Secure Hash Algorithm (SHA-1) or Message Digest (MD5) algorithm to produce a fixed length output word. The apparatus includes a plurality of rotational registers for storing data, one of the registers arranged to receive the input data, and data stores for initialization of some of the plurality of registers according to whether the SHA-1 or MD5 algorithm is used. The data stores include fixed data relating to SHA-1 and MD5 operation. Also included is a plurality of dedicated combinatorial logic circuits arranged to perform logic operations on data stored in selected ones of the plurality of registers.
Owner:STMICROELECTRONICS ASIA PACIFIC PTE
A sliding block repeating data deleting method based on edge calculation
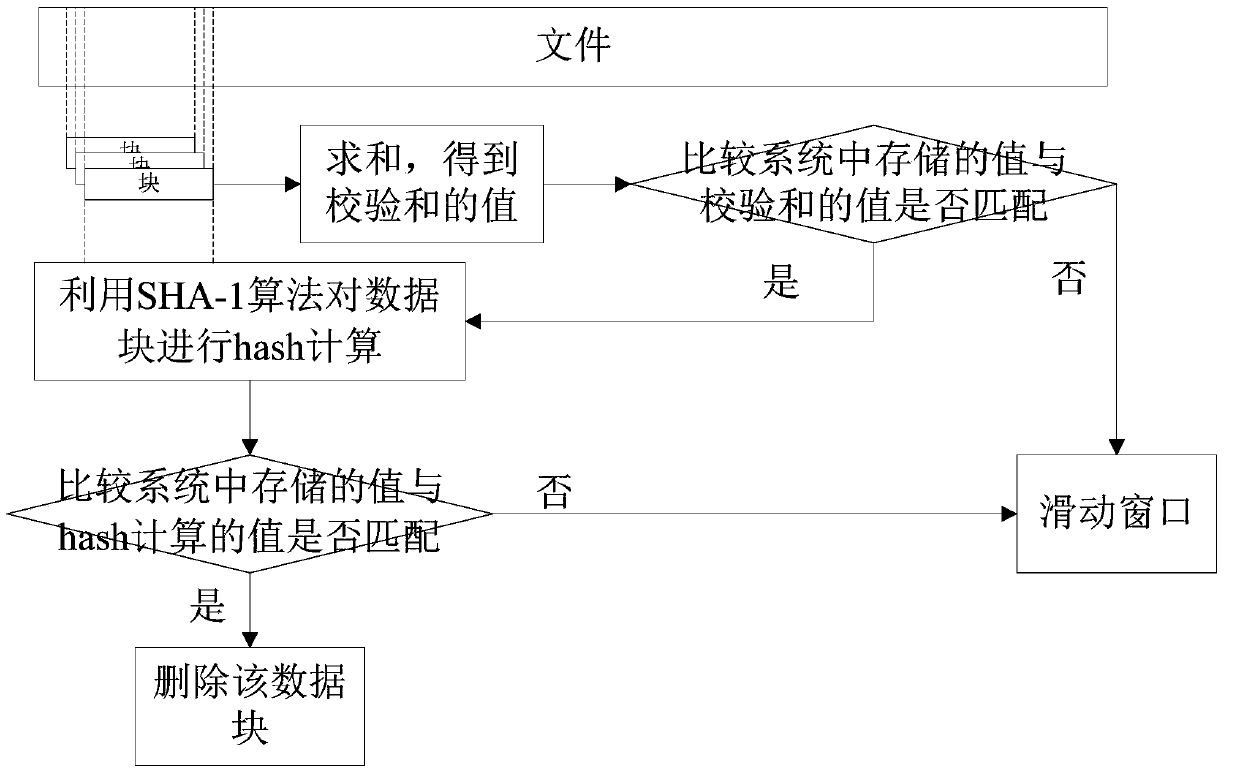
InactiveCN109684284AGood delete effectDelete has little effectDigital data information retrievalSpecial data processing applicationsSlide windowGranularity
The invention belongs to the technical field of data deduplication, and particularly relates to a sliding block duplication data deletion method based on edge calculation, which comprises the following steps: calculating the summation of each overlapped block of a file object according to an Rsync summation check function and a sliding window to obtain the value of a check sum; Comparing, for eachblock, the value of the checksum to a previously stored value; If the value of the checksum is matched with the value stored in advance, comparing the calculated hash value of the SHA-1 with a previously stored value so as to carry out redundancy detection, and deleting a data block represented by the same data if the same data is detected; According to the sliding block repeated data deleting technology based on edge computing, the problems that traditional data de-duplication is poor in granularity and high in cost are solved, the defect that inserting and deleting of data are sensitive isovercome. A check method, a weak check detection method and a thought of manually setting the size of a window are added on the basis of an SHA algorithm 1, so that a better duplicate removal effect is achieved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Communication data encryption and decryption method based on BBS, RSA and SHA-1 encryption algorithm
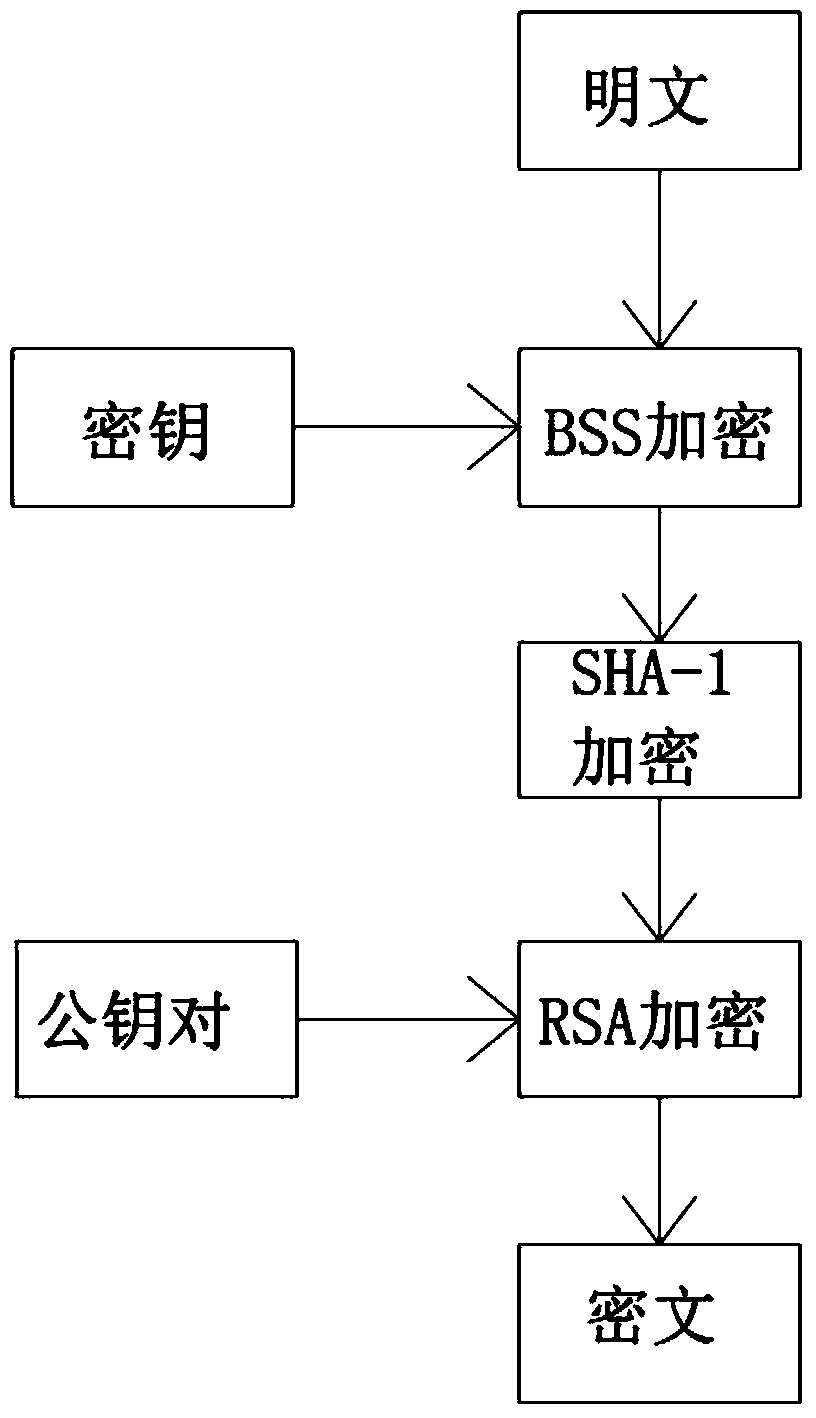
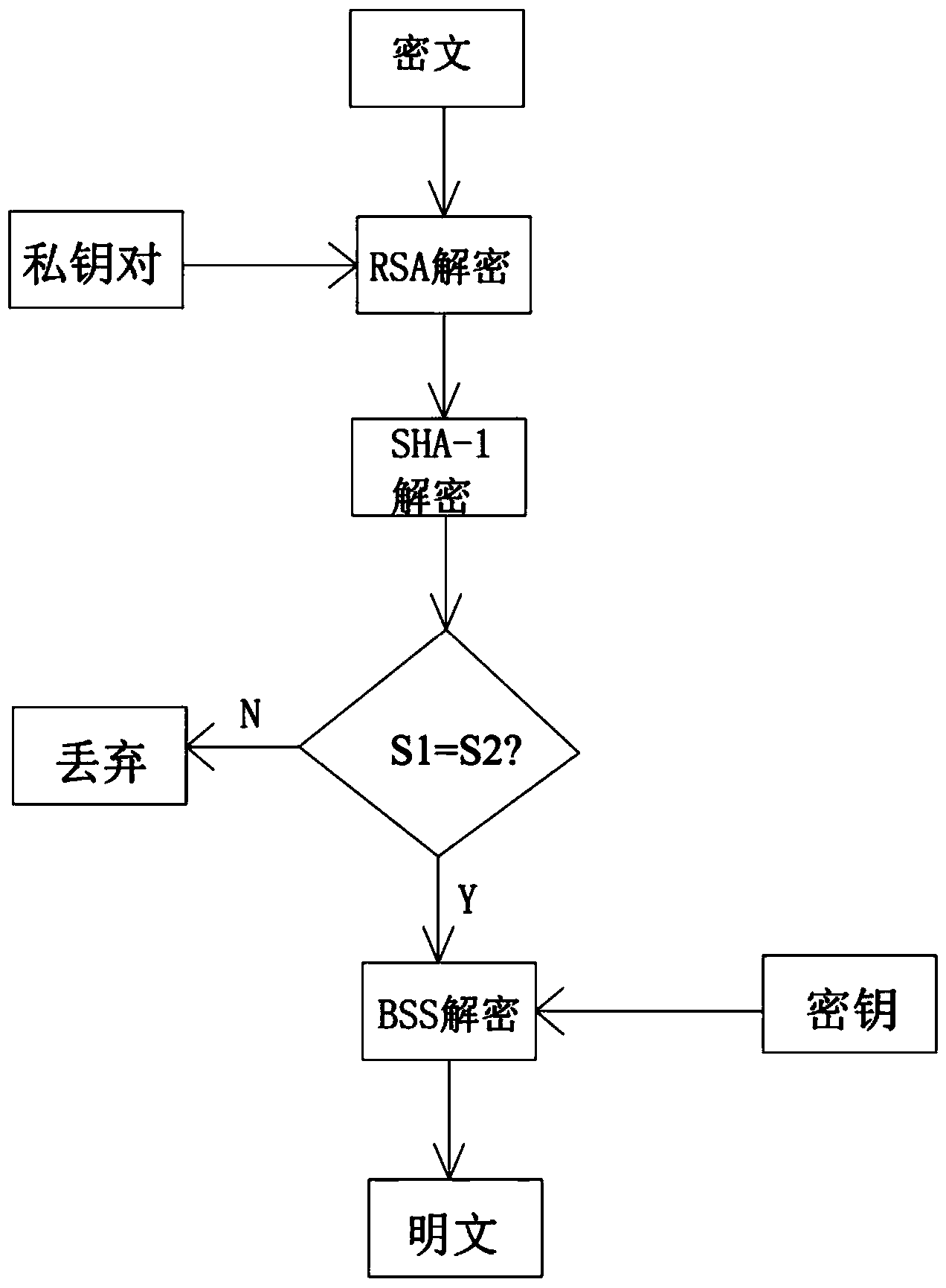
ActiveCN103731270AImprove securityAvoid harmPublic key for secure communicationUser identity/authority verificationDigital signatureCiphertext
The invention discloses a communication data encryption and decryption method based on BBS, RSA and an SHA-1 encryption algorithm. The communication data encryption and decryption method comprises the steps that 1) data to be encrypted and sent are generated; 2) the data to be sent are encrypted for the first time, that is, BBS encryption is carried out on the data to be sent; 3) the data encrypted for the first time generate abstract contents through the SHA-1 encryption algorithm; 4) the data encrypted through the SHA-1 and an abstract are encrypted through an RSA encryption public key provided by a receiving end; 5) cryptograph is sent; 6) the cryptograph is received by the receiving end and is decrypted for the first time through the private key of the receiving end; 7) identity authentication is carried out on the received data; 8) BSS decryption is carried out on the data after the identity authentication, and the content of the data is read. The different characteristics of the three encryption algorithms are utilized, messages to be sent are encrypted through the BBS, the SHA-1 and the RSA algorithm, the encrypted messages for communication are safer, digital signatures are achieved, and it is guaranteed that the received messages are initial messages sent by a sending end and are not tampered.
Owner:SOUTH CHINA UNIV OF TECH
Method and apparatus to minimize database exchange in OSPF by using a SHA-1 digest value
Owner:CISCO TECH INC
Methods and apparatus performing hash operations in a cryptography accelerator
InactiveUS20090028326A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareCryptographic accelerator
Methods and apparatus are provided for implementing a cryptography accelerator for performing operations such as hash operations. The cryptography accelerator recognizes characteristics associated with input data and retrieves an instruction set for processing the input data. The instruction set is used to configure or control components such as MD5 and SHA-1 hash cores, XOR components, memory, etc. By providing a cryptography accelerator with access to multiple instruction sets, a variety of hash operations can be performed in a configurable cryptographic accelerator.
Owner:AVAGO TECH INT SALES PTE LTD
Neural network weight synchronization based lightweight key negotiation method
InactiveCN101141248AReduce computing requirementsFast executionKey distribution for secure communicationPublic key for secure communicationNerve networkOperand
A neural network weight value synchronization-based lightweight key consultation method of which two neural networks with the same input perceptions are interacted, namely, the continuous renew of the weight value vector output, so as to realize the weight value of two neural networks. Based on the traditional random number generator LFSR and Hash algorithm SHA 1, the perception neural network is discretized and extended to the multilayered model, while the synchronic property of weight value is unchanged. Thus, the synchronic weight value can be mapped to the conversation key, which means the key coordination and renew can be applied. The utility model provides a synchronic lightweight key coordination method which is based on the neural network weight value and suitable to flush-type environment. Such method is provided with low operand and low computing resource requirement.
Owner:ZHEJIANG UNIV OF TECH
Method and device for hashing onto points of an elliptic curve
Hashing onto elements of a group, in particular onto points of an elliptic curve. An input message is run through a “regular” hashing algorithm, such as e.g. SHA-1 and MD5, and used as a scalar in multiplication with an element of the group. The result is necessarily also an element of the group. An advantage is that the security of the hashing algorithm is the same as that of the underlying “regular” hashing algorithm. Also provided is a device.
Owner:THOMSON LICENSING SA
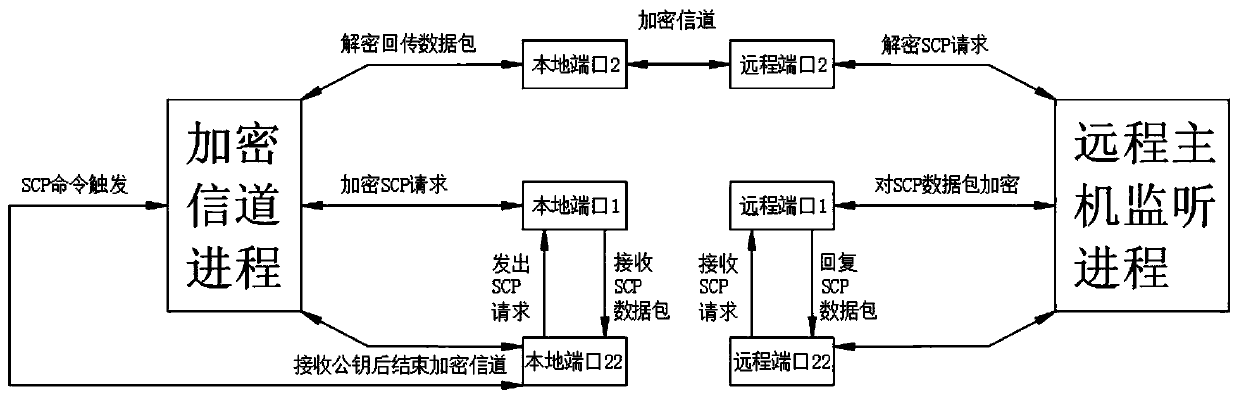
Ssh-based data security protection method and device
PendingCN109981257ARisk of Denying AttacksEasy to buildKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey exchangeMan-in-the-middle attack
The invention belongs to the technical field of data security and encryption, relates to an ssh-based data security protection method and device. The method comprises the following steps: establishingan encryption channel using a one-time password, storing a used six-bit short password in a remote host in advance in the form of a configuration file to generate a secret key, configuring the one-time six-bit short password, and using SHA-1 value of the short password to encrypt an encrypted channel by using an ECC algorithm, encrypting a secret key, transmitting the secret key to a client through the encrypted channel, transmitting the secret key, deploying a plurality of one-time passwords, completing the deployment of the secret key, and setting password-based ssh remote login protection; using the encryption channel to protect key exchange, so that the risk of man-in-the-middle attacks is blocked to a great extent. The encryption channel is established based on the Linux upper portforwarding function, establishment is easy and the reliability is high, the one-time key can defend password attacks based on password blasting and password guessing, and the safety of the encryptionchannel is improved.
Owner:HONGQIN (BEIJING) TECHNOLOGY CO LTD
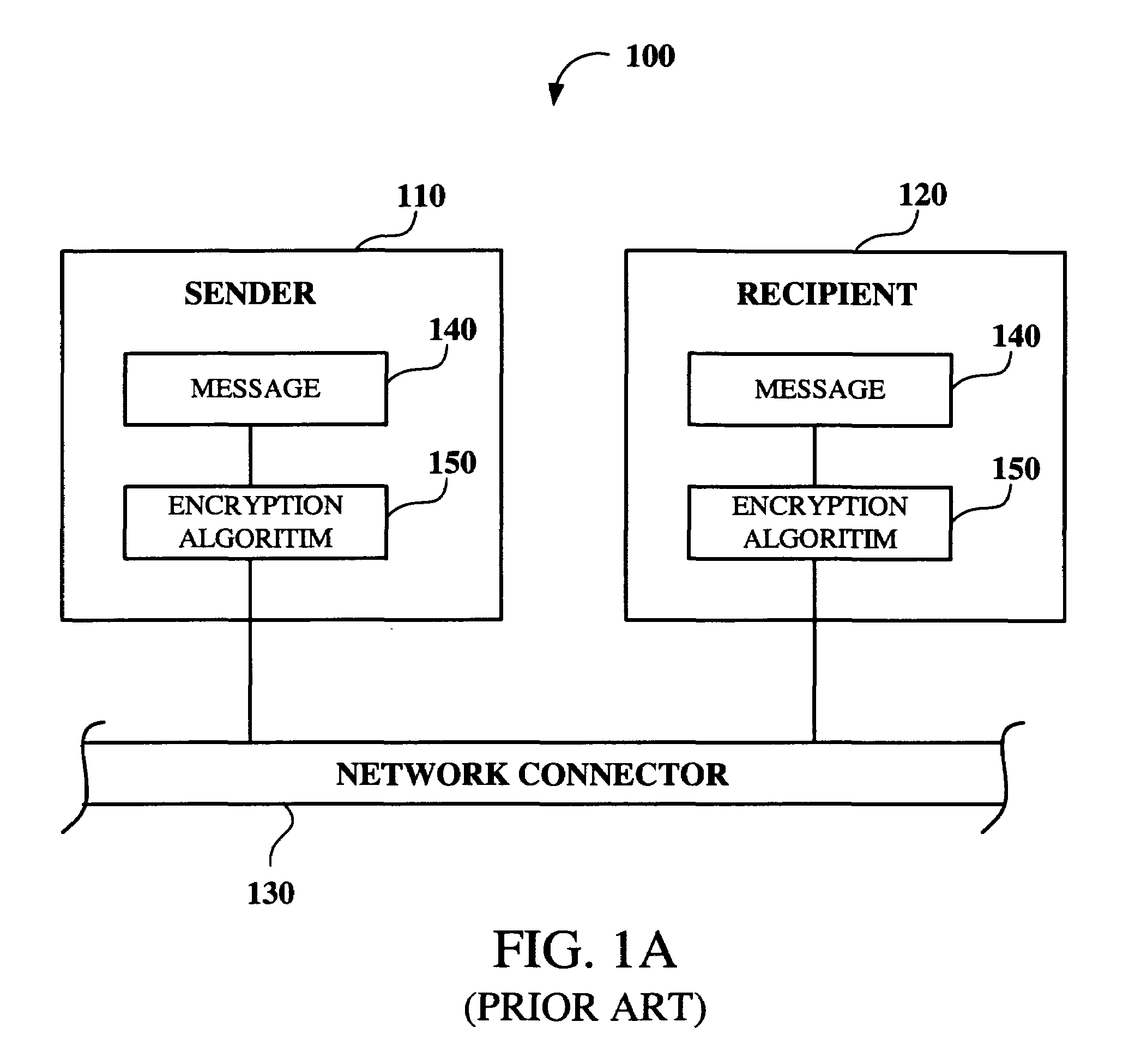
Seasoning for meat canned products
The invention relates to a seasoning for meat canned products. The seasoning consists of dill seeds 2 parts, cinnamon 1 part, amomum fruits 0.5 part, pepper 2 parts, elecampane 1 part, xiang sha 1 part, netmeg 1 part, anise 0.5 part, white pepper 0.5 part, angelica root 0.5 part, tsaoko amomum fruits 0.5 part, clove 1 part, fennel 0.5 part, galangal 1 part and rhizome kaempferiae 0.5 part. The seasoning can be utilized to made pork, beef, chicken and the like into delicious, tasty, nutritional and healthy sausages, ham sausages, blood sausage and other meat canned products.
Owner:杨建民
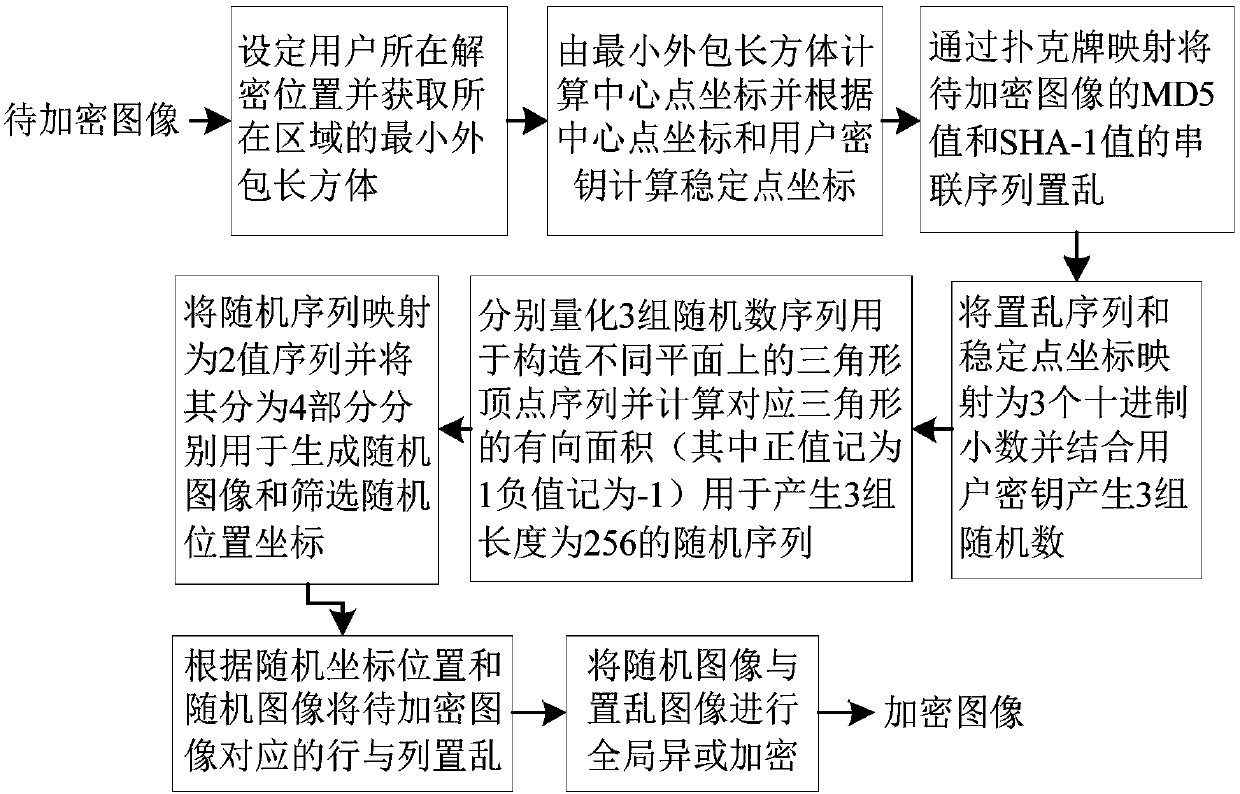
Image encryption method for decryption area limitation using directed area and poker mapping
ActiveCN108174053AImprove securityImprove impact resistanceEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsComputer hardwarePlaintext
The invention provides an image encryption method for decryption area limitation using a directed area and poker mapping. The method is characterized in that firstly, a stable point of the minimum epiboly is obtained through the minimum epiboly of a decryption position, a random triangle is generated through the stable point, an MD5 value and an SHA-1 value of an image to be encrypted, and a userkey, and intermediate encryption parameters are generated through the direction area of the triangle; an initial value and parameter values of chaotic mapping are generated through the intermediate encryption parameters, and the chaotic mapping is driven to generate a random image with the same size as the image to be encrypted; and poker mapping scrambling and overall xor encryption are carried out on randomly selected lines and rows of the image to be encrypted through the chaotic mapping and the random image, so that an encrypted image is generated. Compared with the conventional method, the method provided by the invention has the advantages that the decryption area is limited, so that the encrypted image can only be decrypted within a specific range; and plain text attributes and therandom image are introduced, so that encryption steps for the different encrypted images are different, and the safety is further improved.
Owner:SHAANXI NORMAL UNIV
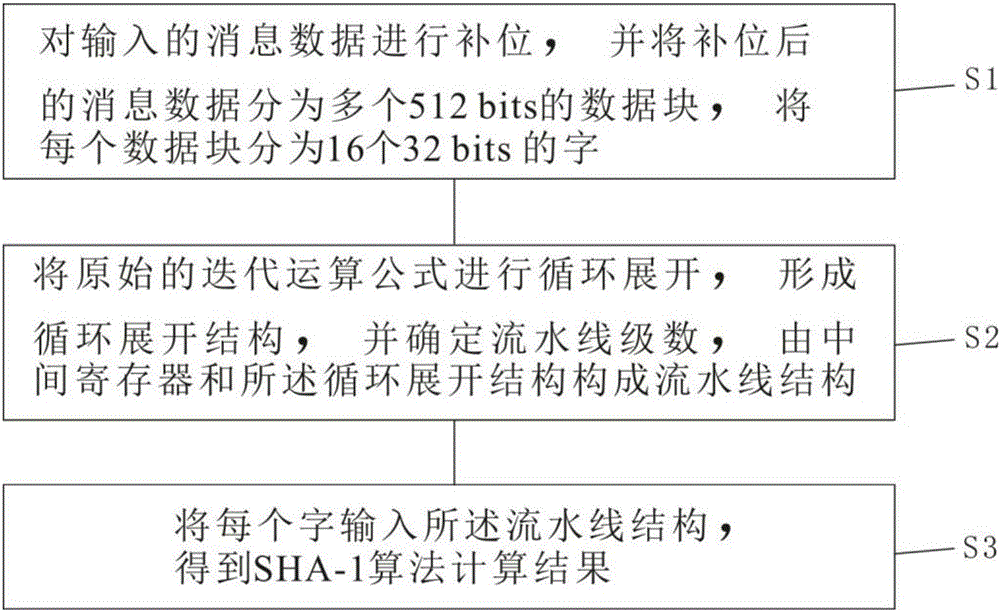
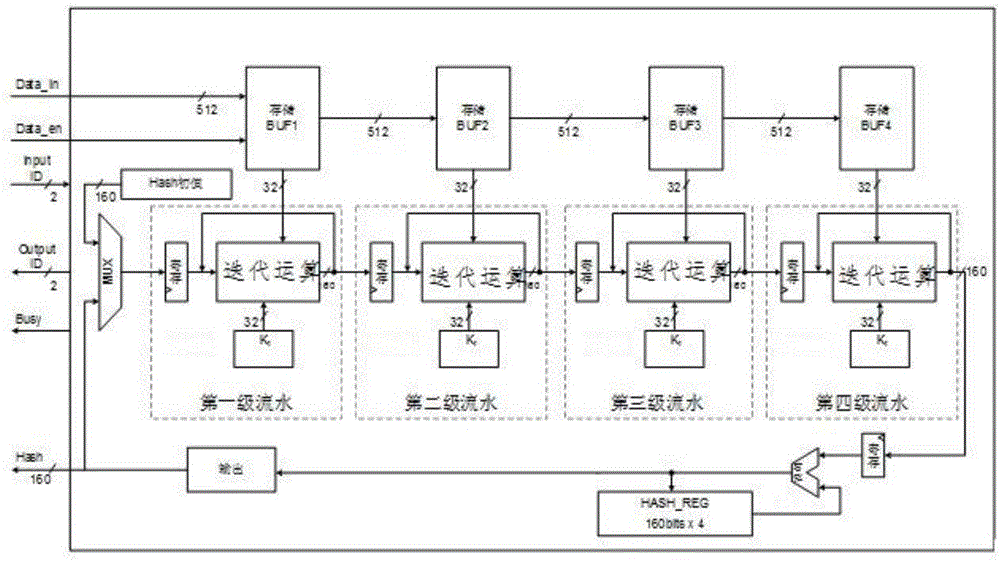
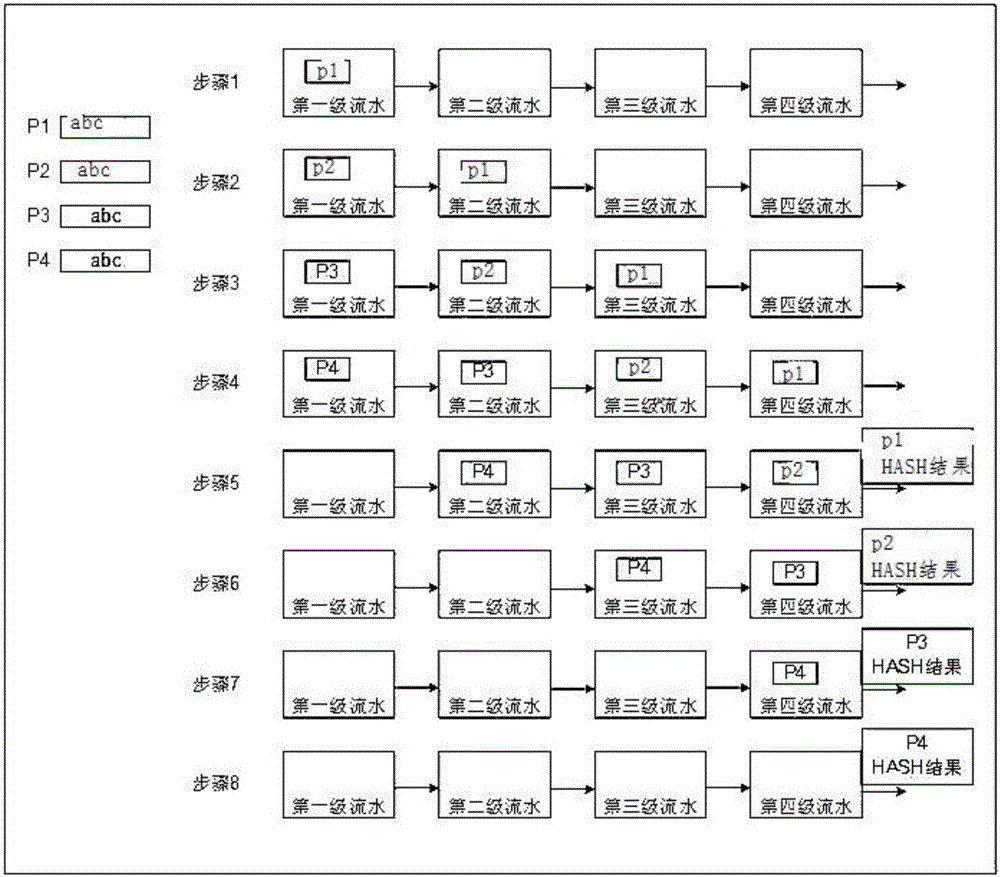
High-throughput SHA-1 (Secure Hash Algorithm) based on FPGA
InactiveCN106100825AReduce clock cyclesCalculation speedEncryption apparatus with shift registers/memoriesProcessor registerCritical path method
The invention provides a high-throughput SHA-1 (Secure Hash Algorithm) based on an FPGA. The method comprises the steps of S1, judging whether length of input message data exceeds 512 bits or not; S2, carrying out bit compensation on the message data until the length is integer multiples of the 512 bits if the length of input message data exceeds 512 bits; S3, segmenting the message data after bit compensation into multiple data blocks, wherein each data block is 512 bits, and segmenting each data block into 16 characters, wherein each character is 32 bits; S4, carrying out loop unrolling on an original iteration operation formula, thereby forming a loop unrolling structure; S5, determining pipeline series, and forming a pipeline structure by an intermediate register and the loop unrolling structure; and S6, inputting each character into the pipeline structure, thereby obtaining a SHA-1 calculation result. According to the algorithm, the iteration operation is simplified, an intermediate variable is added, therefore, a key path is shortened, and a calculation speed is improved. Moreover, through adoption of a pipeline processing mode, the data processing quantity is increased, and the throughput is improved.
Owner:SHENZHEN FORWARD IND CO LTD
Data document on-demand synchronization method based on enterprise cloud disk
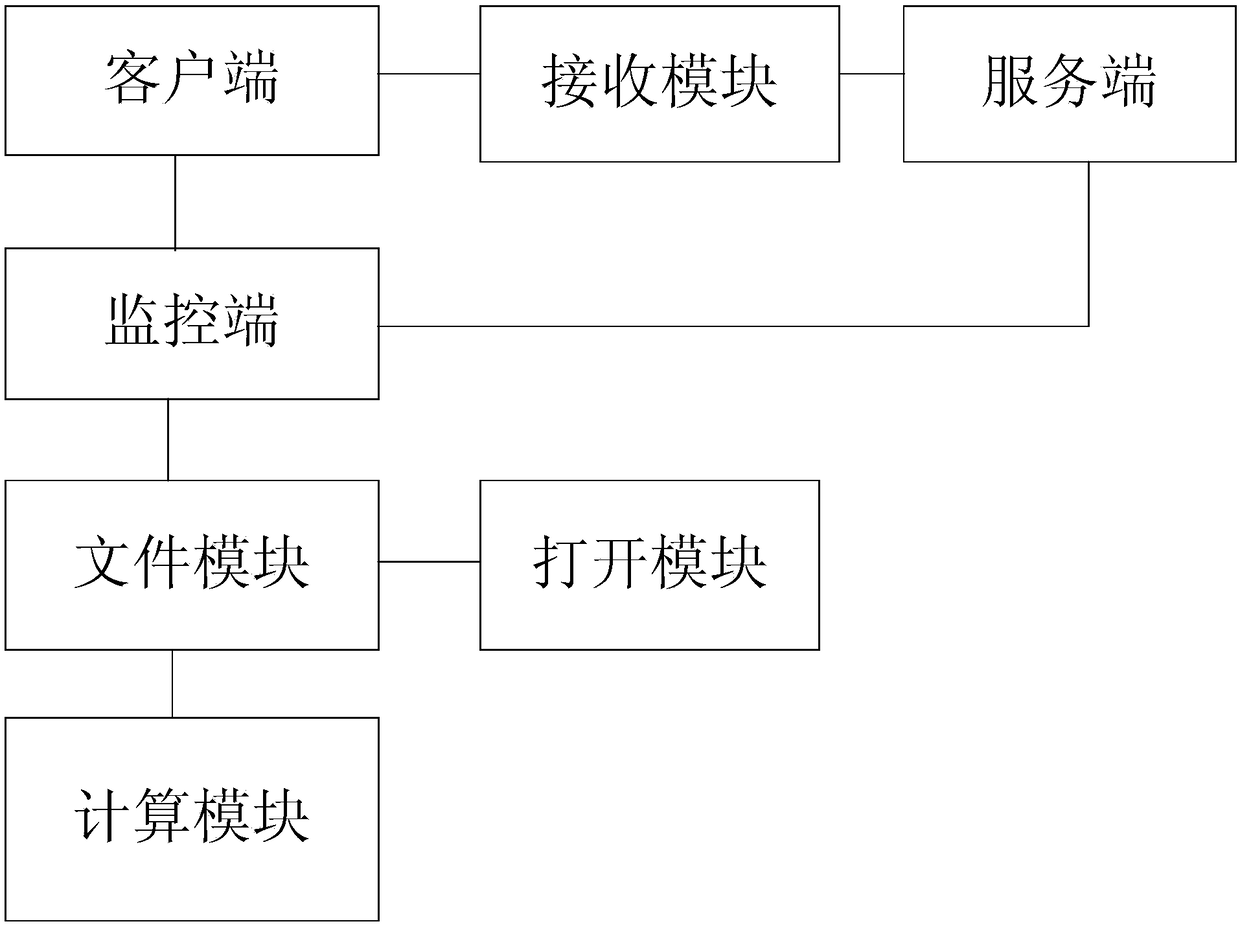
InactiveCN108415911ARealize synchronous sharingAchieve protectionSpecial data processing applicationsTime changesFile size
The invention discloses a data document on-demand synchronization method based on an enterprise cloud disk, which comprises the following steps: a step 1: allowing a client to monitor whether a directory file in a file module changes in real time through a monitoring terminal, and going to a step 3 if the file size or the modification time changes in the director, otherwise, going to a step 2; thestep 2, determining if the content of the directory file in the file module changes or not, going to a step 4 if so, otherwise, going to a step 5; the step 3, calculating the SHA 1 value of the filethrough the calculation module, and going to the step 5; the step 4, creating a synchronous uploading task, transmitting the file to a server end, and going to the step 5. The invention can effectively strengthen the storage and control of the data of the enterprise, save the storage space of a local client of the enterprise cloud disk, prevent data leakage, has a wide application range, and is convenient to use.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Method of game update
This invention discloses one green game update method, which comprises the following steps: game servo end send files SHA-1 property value; using formula to compare game customer end file SHA-1 value and next value; checking whether matching, if not, customer end requires of update through WEB based on HTTP agreement; decompressing game files download and putting the files onto WINDOWS system fold; then extracting the decompressed files value and tests whether matching with game servo end.
Owner:成都金山互动娱乐科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
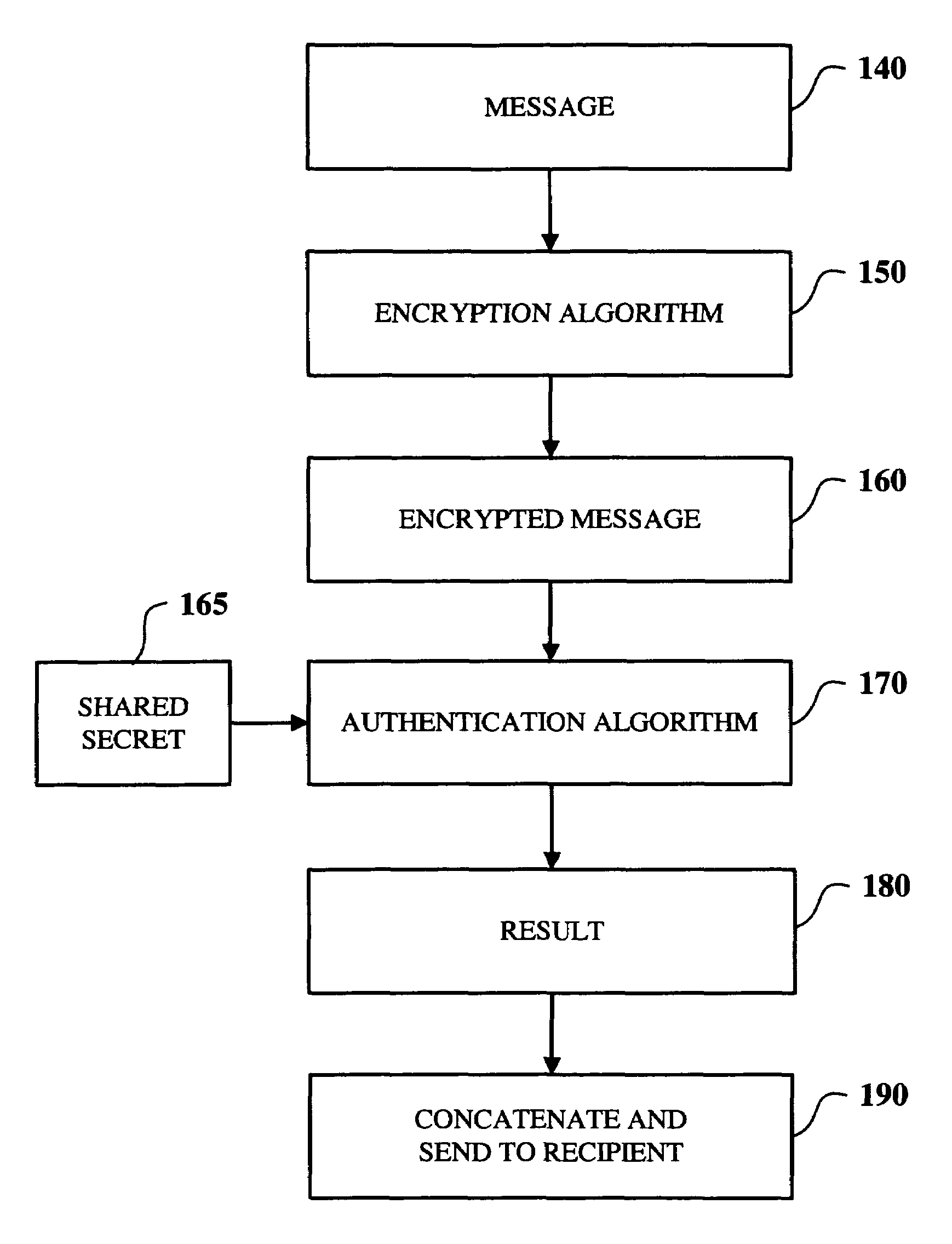
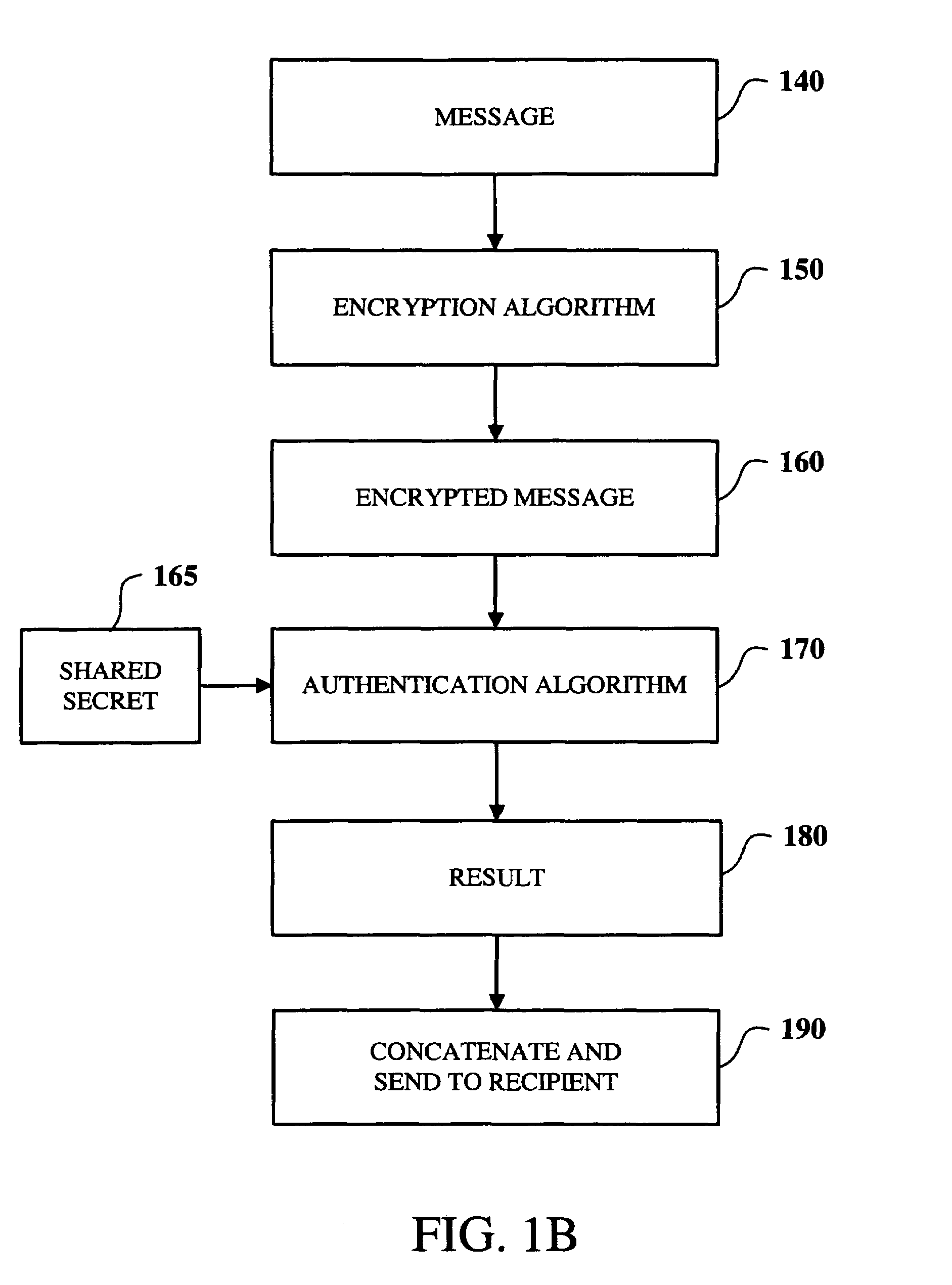
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com