Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "Return statement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, a return statement causes execution to leave the current subroutine and resume at the point in the code immediately after the instruction which called the subroutine, known as its return address. The return address is saved by the calling routine, today usually on the process's call stack or in a register. Return statements in many languages allow a function to specify a return value to be passed back to the code that called the function.
Interactive search engine
Owner:META PLATFORMS INC
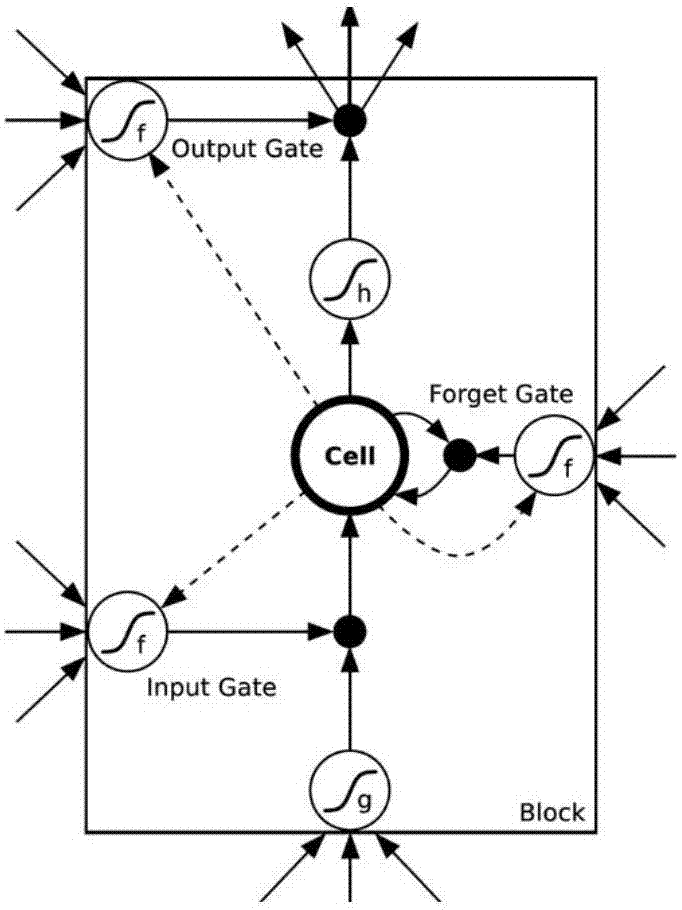
Statement classification method and system, electronic equipment, refrigerator and storage medium
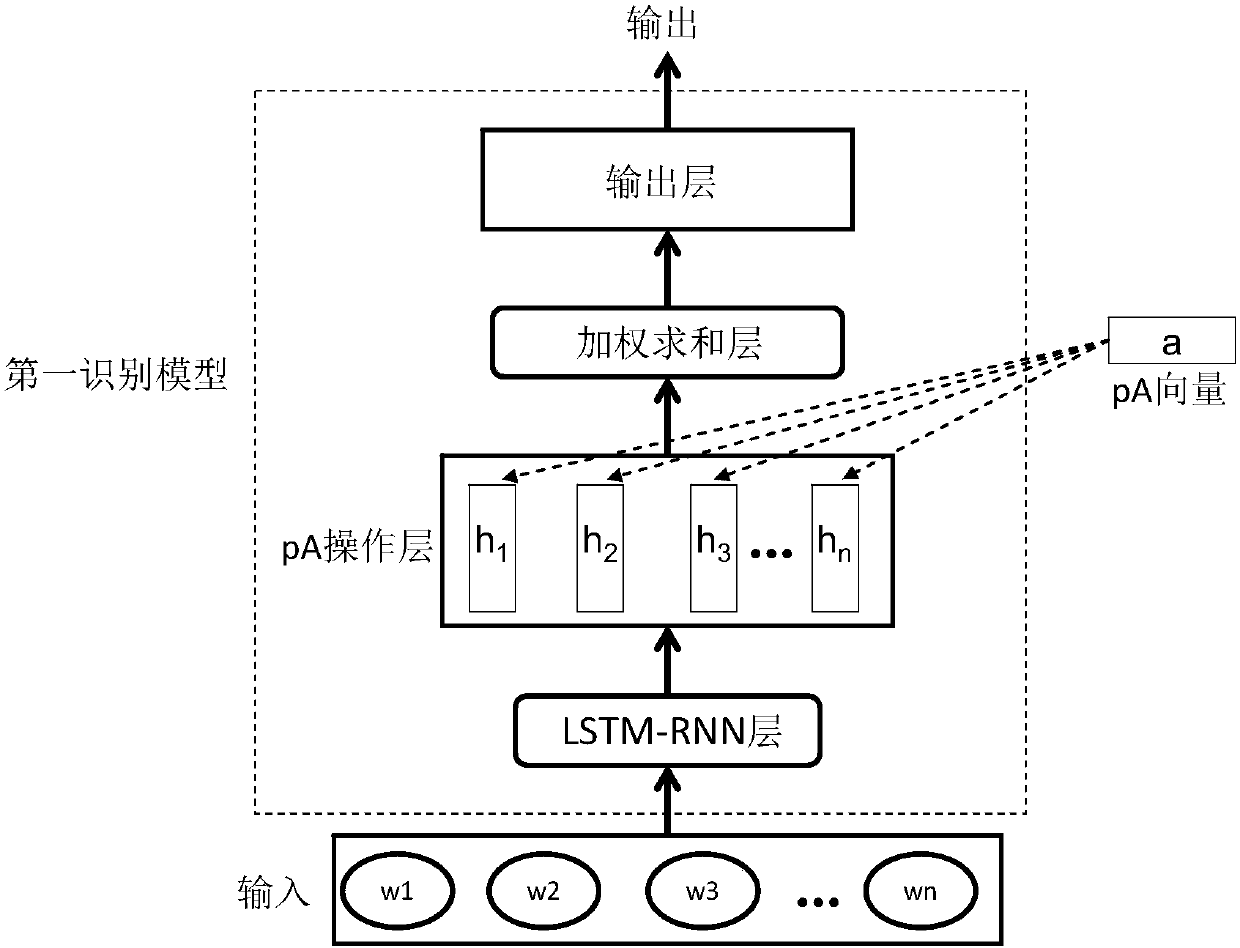
ActiveCN107229684AImprove accuracyImprove experienceSpecial data processing applicationsNeural learning methodsPart of speechShort-term memory
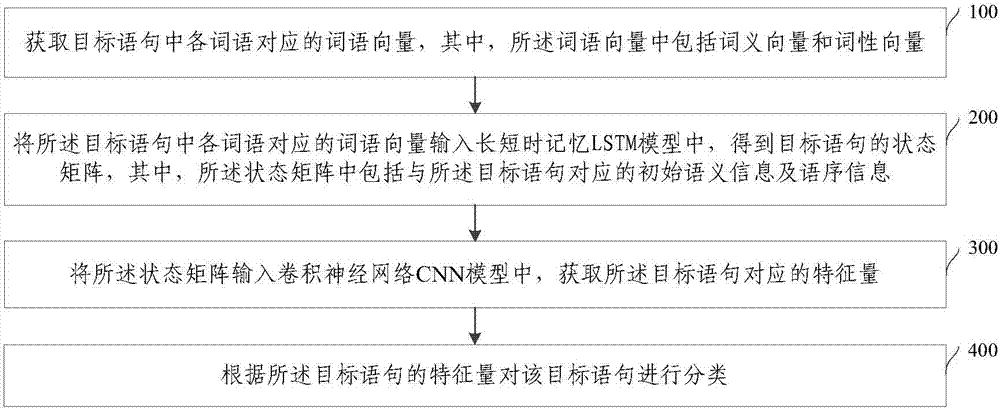
The invention provides a statement classification method and system, electronic equipment, a refrigerator and a storage medium. The statement classification method comprises the following steps of: obtaining a word vector corresponding to each word in a target statement, wherein the word vector comprises a word meaning vector and a part-of-speech vector; inputting the word vector corresponding to each word in the target statement into a long / short-term memory LSTM model so as to obtain a state matrix of the target statement, wherein the state matrix comprises initial semantic information and word order information corresponding to the target statement; inputting the state matrix into a convolutional neural network CNN model so as to obtain a characteristic quantity corresponding to the target statement; and classifying the target statement according to the characteristic quantity of the target statement. According to the method, the correctness of statement classification and statement type recognition can be improved and the user experience can be enhanced.
Owner:HEFEI MIDEA INTELLIGENT TECH CO LTD
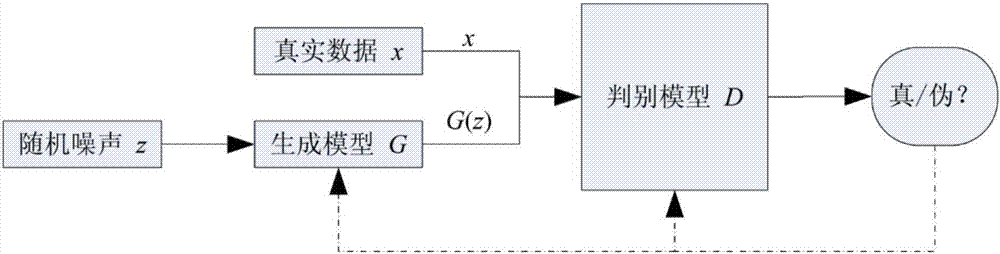
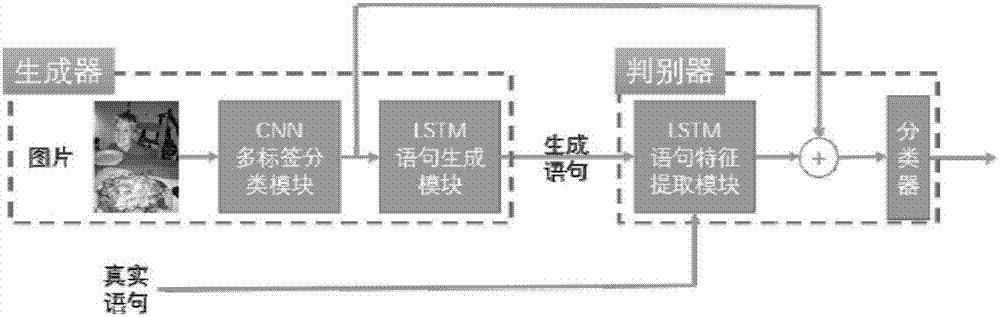
Method for image automatic text annotation based on generative adversarial networks
InactiveCN107330444AValid descriptionEasy retrievalCharacter and pattern recognitionSpecial data processing applicationsDiscriminatorPattern recognition
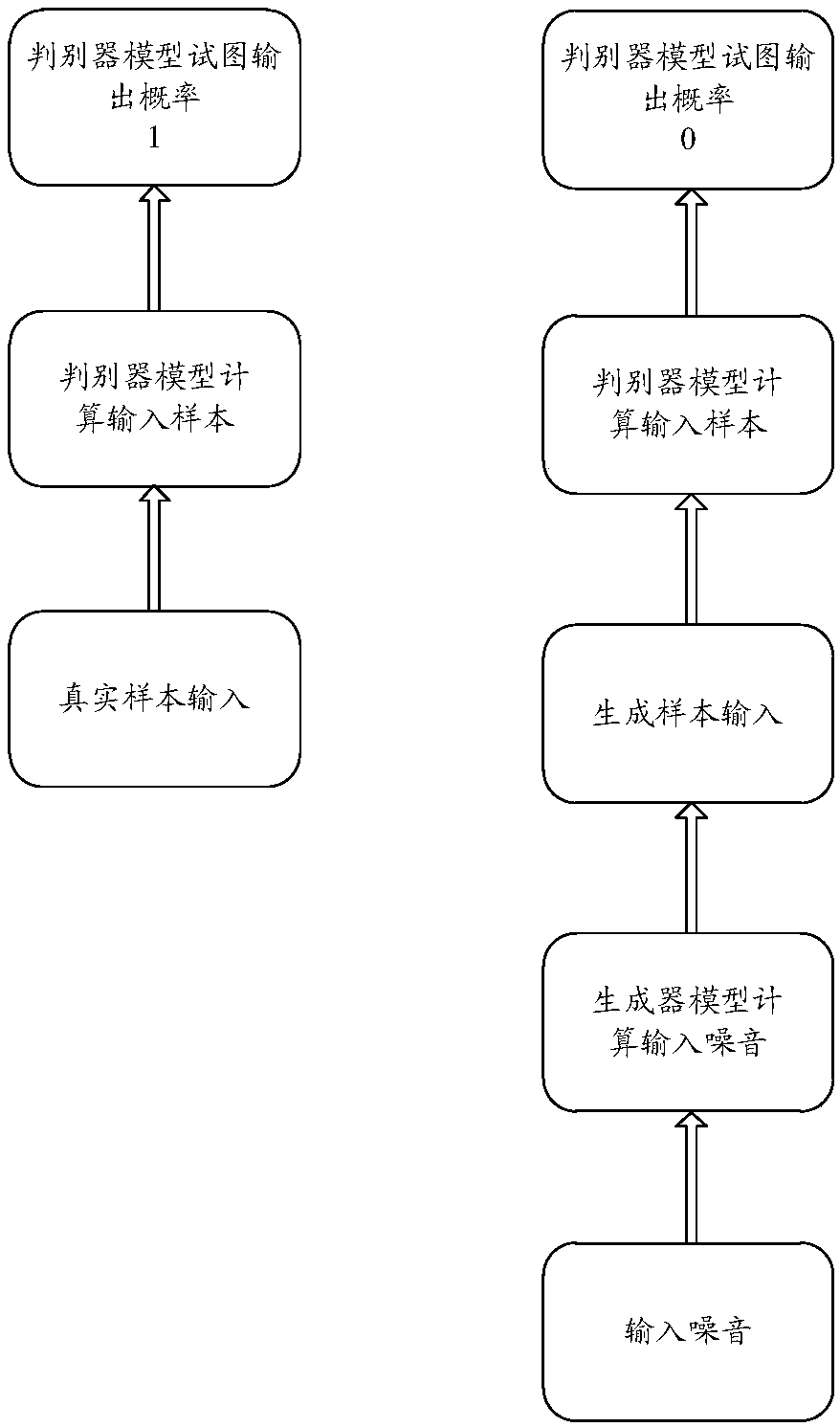
The invention discloses a method for image automatic text annotation based on generative adversarial networks, which comprises the steps of generating false statements by a generator, rebuilding a discriminator at the same time, and inputting the generated statements and real statements into the discriminator to train until the discriminator cannot discriminate the real statements and the generated statements. The method disclosed by the invention changes a problem that sentences are rigid and inflexible in CNN-RNN image automatic statement annotation, and enables the generated sentences to be more accurate, more natural and more diversified. The generated statements can face more complex scenes in reality and more conform to language expression means annotation images of the human, thereby having more extensive applications in practice.
Owner:SUZHOU UNIV OF SCI & TECH
Translation model-based training and translation methods and apparatuses, and storage medium
ActiveCN108304390AImprove accuracyRealize linkageNatural language translationSemantic analysisNatural language processingReturn statement
Embodiments of the invention disclose translation model-based training and translation methods and apparatuses, and a storage medium. The training method comprises the steps of inputting a source statement to a translation model, thereby obtaining a target statement output by the translation model; determining the fidelity of the target statement to the source statement; by taking the target statement and a reference statement as inputs of a judger model and taking the fidelity as an output of the judger model, training the performance of calculating the similarity between the target statementand the reference statement by the judger model; outputting the similarity between the target statement and the reference statement by using the judger model; and by taking the source statement as aninput of the translation model, taking the target statement as an output of the translation model and taking the similarity as a weight coefficient, training the performance of outputting the corresponding target statement according to the input source statement by the translation model.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for realizing non-barrier automatic psychological consult by adopting computer
InactiveCN101799849AEasy accessImprove scalabilitySpecial data processing applicationsReturn statementNatural language
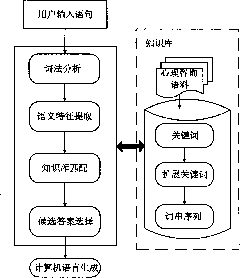
The invention discloses a method for realizing non-barrier automatic psychological consult by adopting a computer, relating to a psychological consult technology and solving the problems of unavailable independent operation, consult and monitoring without real-time feedback, consult results without duly feedback, psychological consult files without establishment of overall process of consult and therapy, and weak expansibility of traditional psychological consultant adjuvant therapy equipment. A process of the method comprises the steps of: A, carrying out extraction of key words, expansion key words and work string sequence on input natural language statements; B, carrying out semantic matching, wherein the semantic matching comprises key words matching, expansion key words matching and word string sequence matching, and if certain matching in the semantic matching exceeds a threshold value, the matching is judged to be successful, or else, information incapable of being answered is output; and C, carrying out conversation management and outputting return statement, wherein the conversation management comprises rehearsal, a content reflection technology and conversation context management. The invention can be used independently or mutually compensated with a psychological consultant, which makes up the deficiency of the psychological consultative organization to some extent.
Owner:HARBIN INST OF TECH
Statement generation method and system
ActiveCN107451109AMeet the need for quick responseMeet the need for quick response to technical issuesText processingSpecial data processing applicationsReal-time dataReturn statement
The invention provides a statement generation method, which comprises the following steps that: obtaining a target statement element, wherein the target statement element is generated in a way that the statement element used for displaying real-time data is customized in a statement generation template, and the statement generation template can customize a development statement; on the basis of the target statement element, obtaining real-time data to be displayed; and injecting the obtained real-time data to be displayed into the target statement element so as to generate a target statement used for displaying the real-time data to be displayed. The invention also provides a statement generation system, a computer readable medium and a computer system.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Answer extraction method and system based on deep learning
InactiveCN107729468AEffectively foundAdd filter functionWeb data indexingNatural language data processingReturn statementExtraction methods
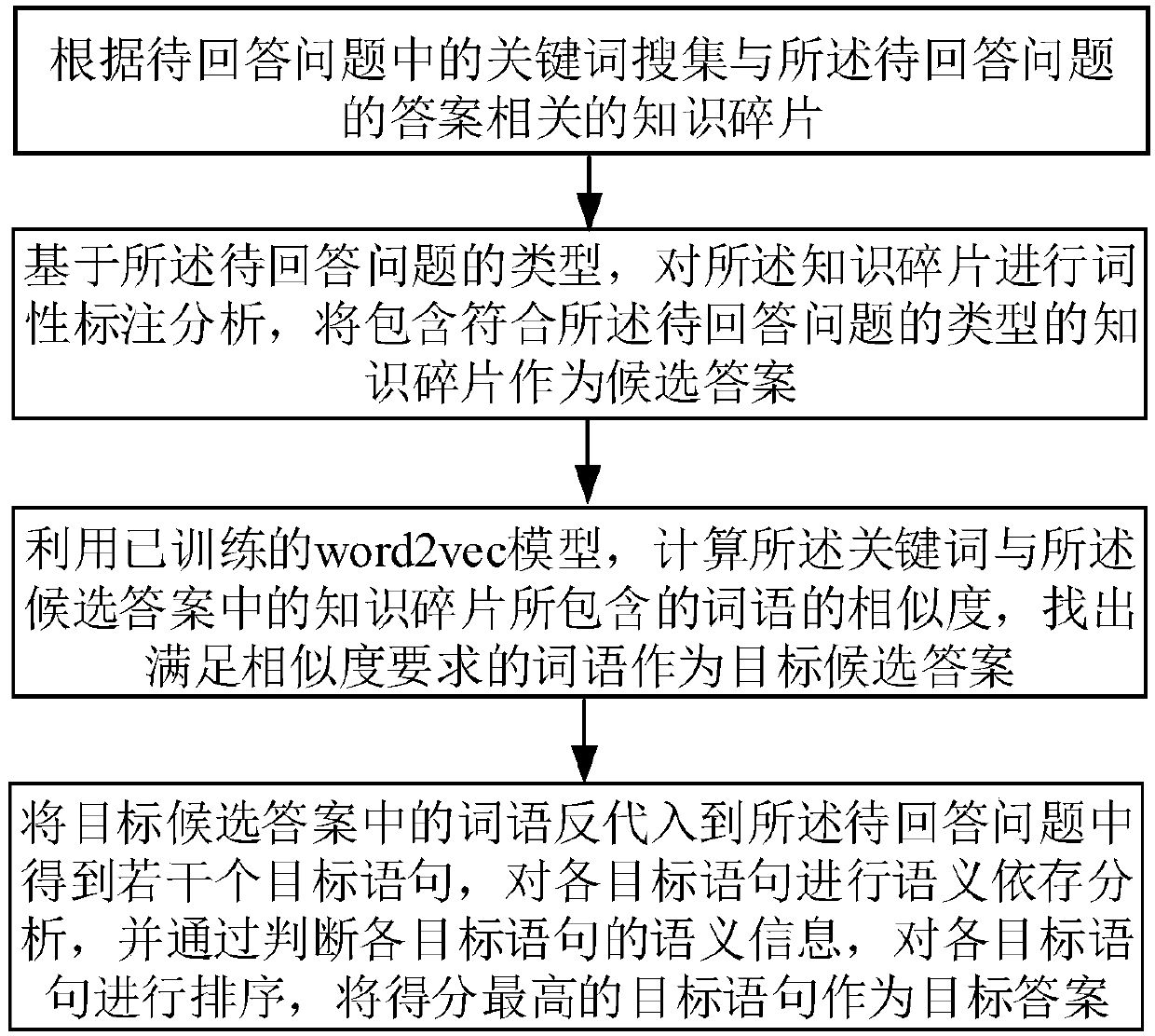
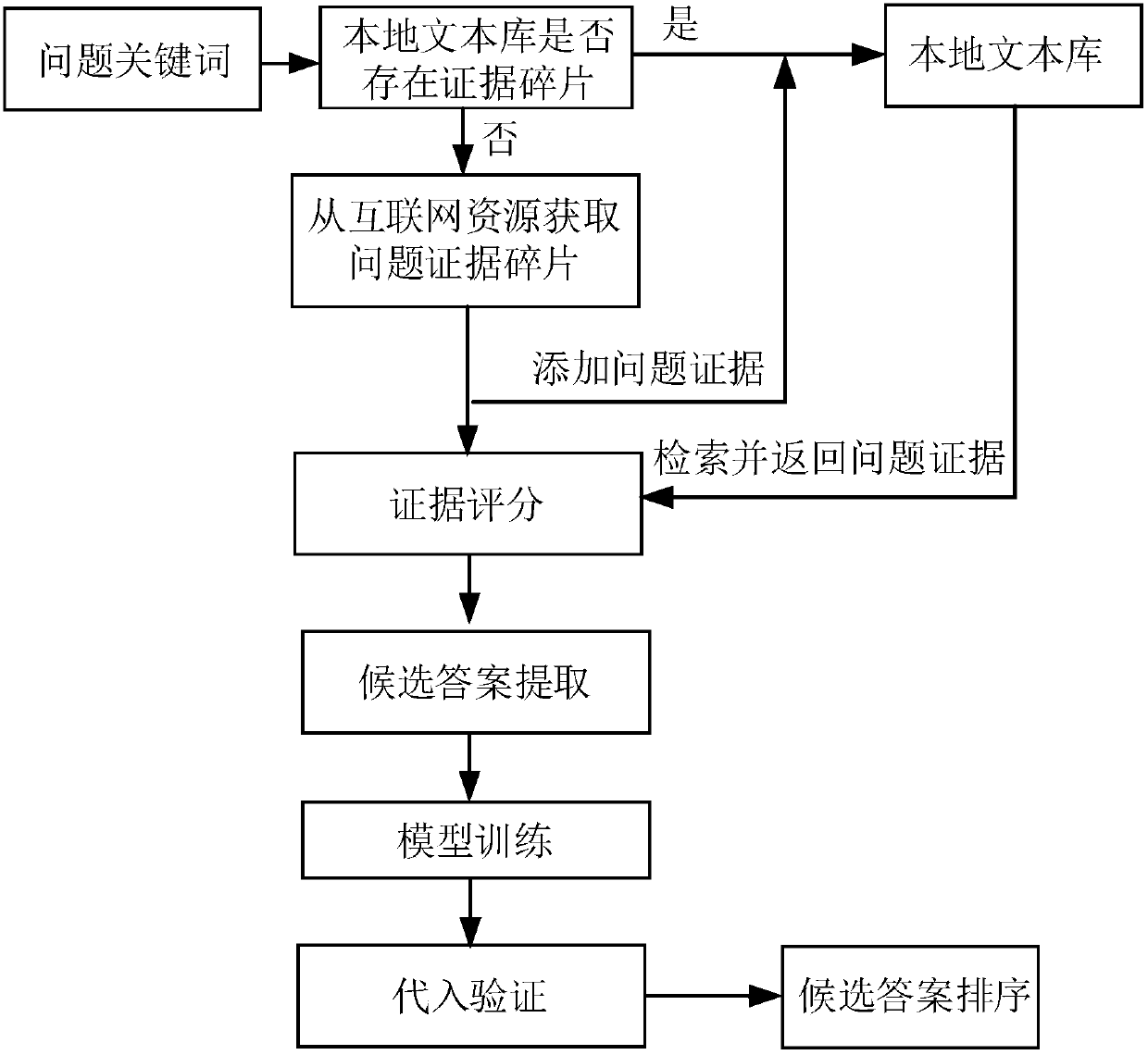
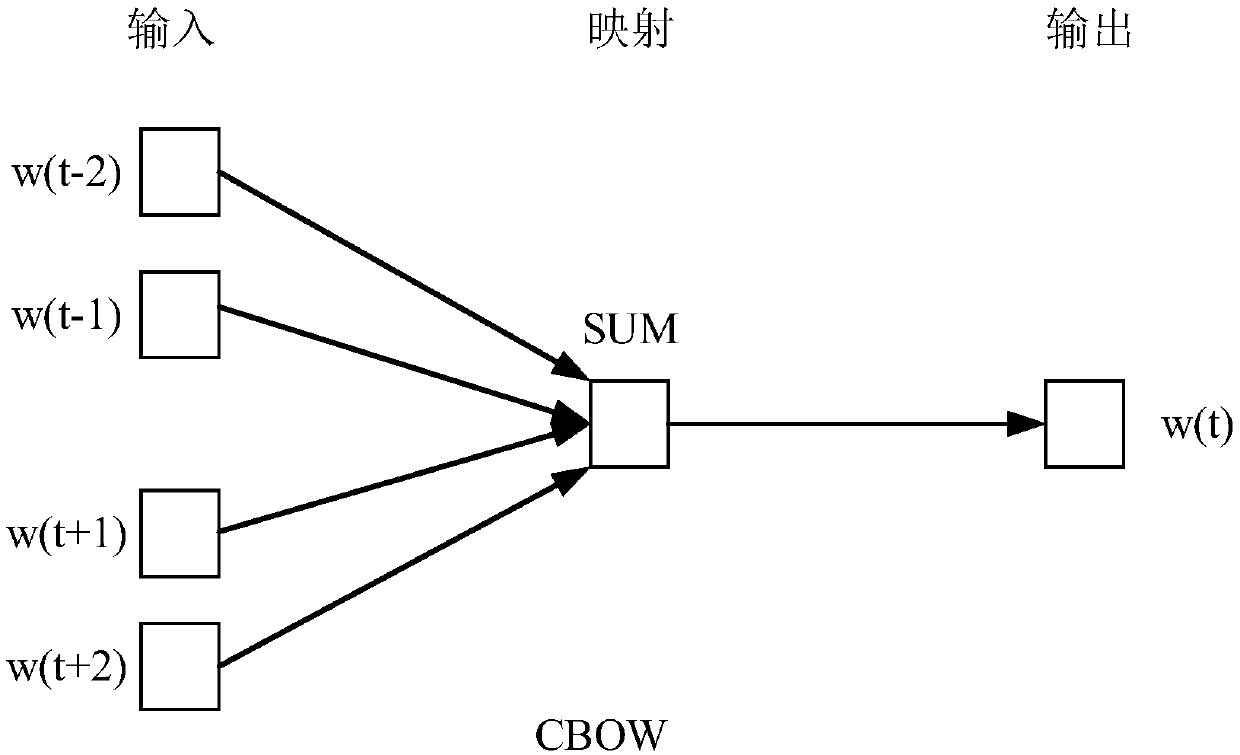
The invention discloses an answer extraction method and system based on deep learning. wherein an implementation of the method includes the steps of collecting knowledge fragments related to the answer of a question to be answered according to keywords in the question to be answered; based on the type of the question to be answered, analyzing the part-of-speech tagging of the knowledge fragment, and using the knowledge fragment containing the type of the question to be answered as a candidate answer; using the trained word2vec model to calculate the similarity between the keywords and words contained in the knowledge fragment in the candidate answer, and finding words that meet the similarity requirements as target candidate answers; substituting the words in the target candidate answers into the question to be answered to obtain a number of target statements, sorting each target statement by judging semantic information of each target statement, and using the target statement with thehighest score as the target answer. Through the extraction method and system, the answers of multiple words with higher similarity can be found, thereby improving the accuracy of the system.
Owner:HUAZHONG UNIV OF SCI & TECH
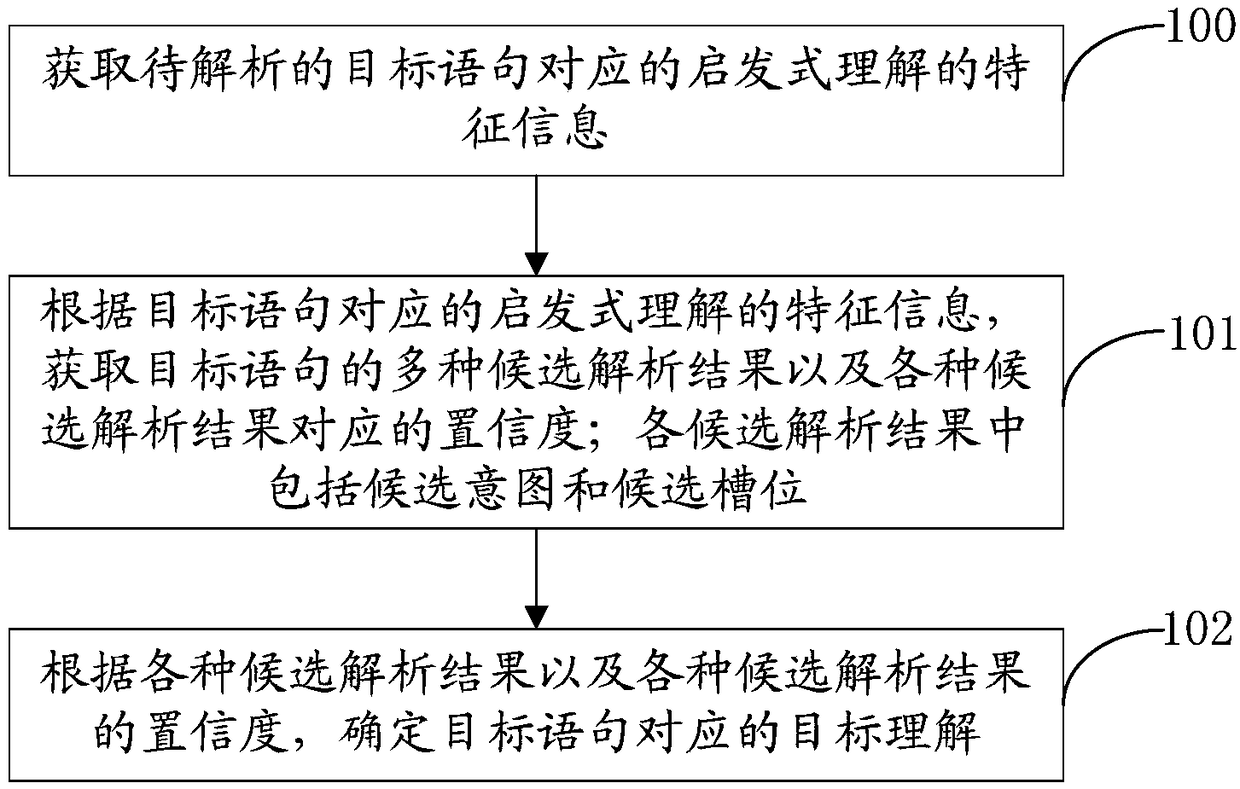
Statement analysis method and apparatus, computer device and readable medium
ActiveCN108549656AAccurate understandingImprove accuracySemantic analysisSpecial data processing applicationsReturn statementTheoretical computer science
The invention provides a statement analysis method and apparatus, a computer device and a readable medium. The method comprises the steps of obtaining feature information of heuristic understanding corresponding to a to-be-analyzed target statement; according to the feature information of the heuristic understanding corresponding to the to-be-analyzed target statement, obtaining multiple candidateanalysis results of the target statement and confidence degrees corresponding to various candidate analysis results, wherein each candidate analysis result comprises a candidate intention and a candidate slot position; and according to the candidate analysis results and the corresponding confidence degrees, obtaining target understanding corresponding to the target statement. According to the statement analysis scheme, even in a cold-start stage with insufficient training data resources, the feature information of the heuristic understanding corresponding to the target statement can be obtained, thereby realizing accurate understanding of the target statement. Moreover, a template in a fixed format can be prevented from being used for performing statement identification, so that the technical defect of poor statement understanding accuracy caused by weak template generalization capability can be avoided and the statement analysis accuracy and efficiency can be effectively improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
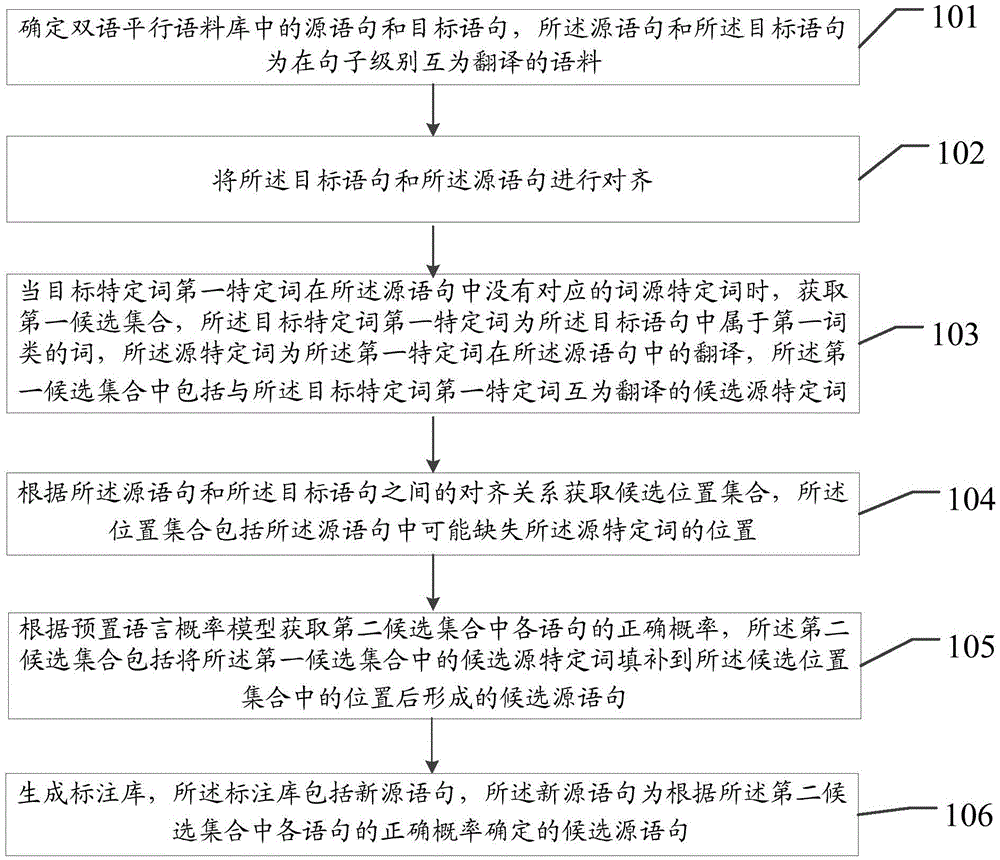
Annotation library generation method and annotation library generation device
ActiveCN106815215AReduce consumptionNatural language translationSpecial data processing applicationsPart of speechReturn statement
An embodiment of the invention discloses an annotation library generation method and an annotation library generation device. The method includes: aligning a target statement and a source statement, mutually translated in sentence level, in a bilingual parallel corpus; if a first specific word, belonging to a first word class, in the target statement has no corresponding source specific word in the source statement, acquiring a first candidate set which includes candidate source specific words in mutual translation relation with the first specific word; acquiring a candidate position set according to the alignment relation between the source statement and the target statement, wherein the candidate position set includes positions of possibly lost source specific words in the source statement; acquiring the correct probability of each statement in a second candidate set according to a preset language probability model, wherein the second candidate set includes candidate source statements formed by filling of the candidate source specific words in the first candidate set to the positions of the candidate position set; generating an annotation library which includes candidate source statements determined according to the correct probability of statement in the second candidate set.
Owner:HUAWEI TECH CO LTD
A Chinese text proofreading method based on a knowledge graph
ActiveCN109918640AAvoid dependenceImprove recallEnergy efficient computingSpecial data processing applicationsReturn statementKnowledge graph
The invention discloses a Chinese text proofreading method based on a knowledge graph. Firstly, an entity extraction technology is used for extracting to obtain an entity in a text statement, and thenaccording to a matching result of the entity and a relation rule, a syntactic semantic error type is searched and discovered in a knowledge graph. According to the method, dependence on a large-scaleword library can be avoided, and semantic proofreading is conducted on texts from the three aspects of wrongly written characters, component deletion and definition contradiction. Compared with an existing Chinese automatic proofreading system, the proofreading method has high recall ratio for proofreading various semantic errors in the limited field. The method can effectively improve the accuracy and recall ratio of text proofreading, and is helpful for text workers to improve the text quality.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
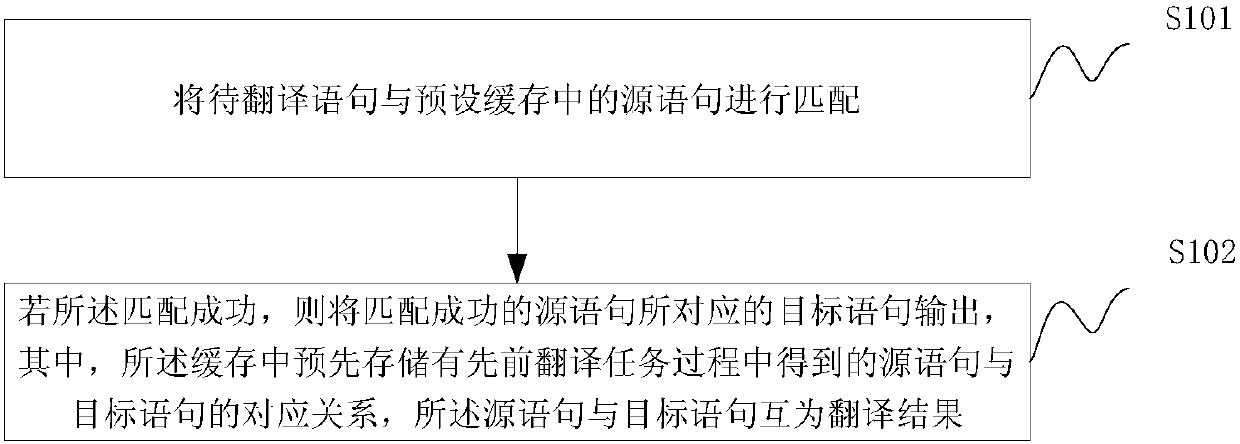
Translation method and system
InactiveCN107943794ANatural language translationSpecial data processing applicationsNatural language processingReturn statement
The invention discloses a translation method and system, which is used for improving translation efficiency. The translation method provided by an embodiment of the invention comprises the steps of matching a to-be-translated statement with a source statement in a preset cache; if the matching succeeds, outputting a target statement corresponding to the successfully matched source statement, wherein a corresponding relationship between the source statement obtained in a previous translation task process and the target statement is pre-stored in the cache, and the source statement and the target statement are translation results for each other.
Owner:ALIBABA GRP HLDG LTD
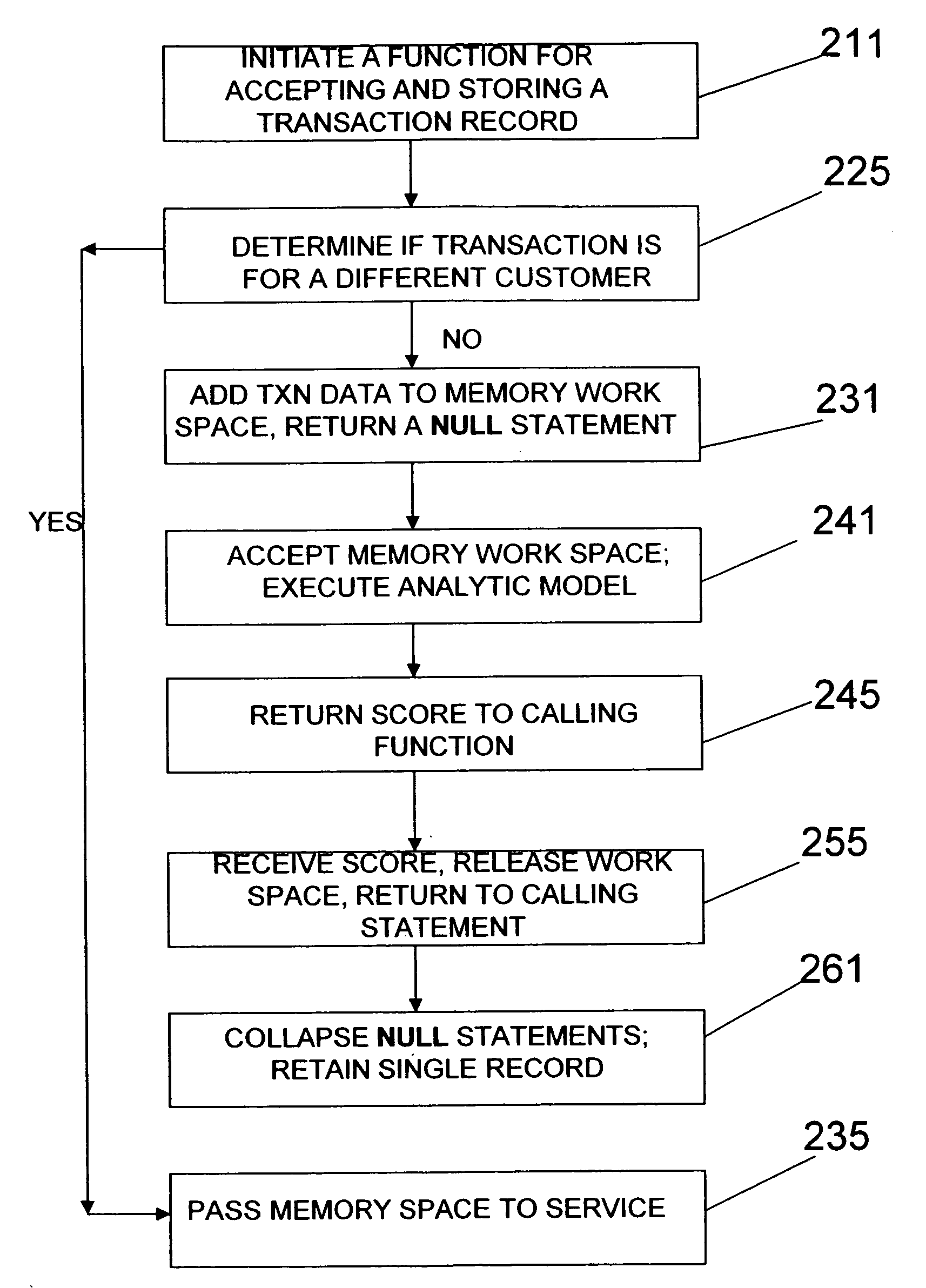
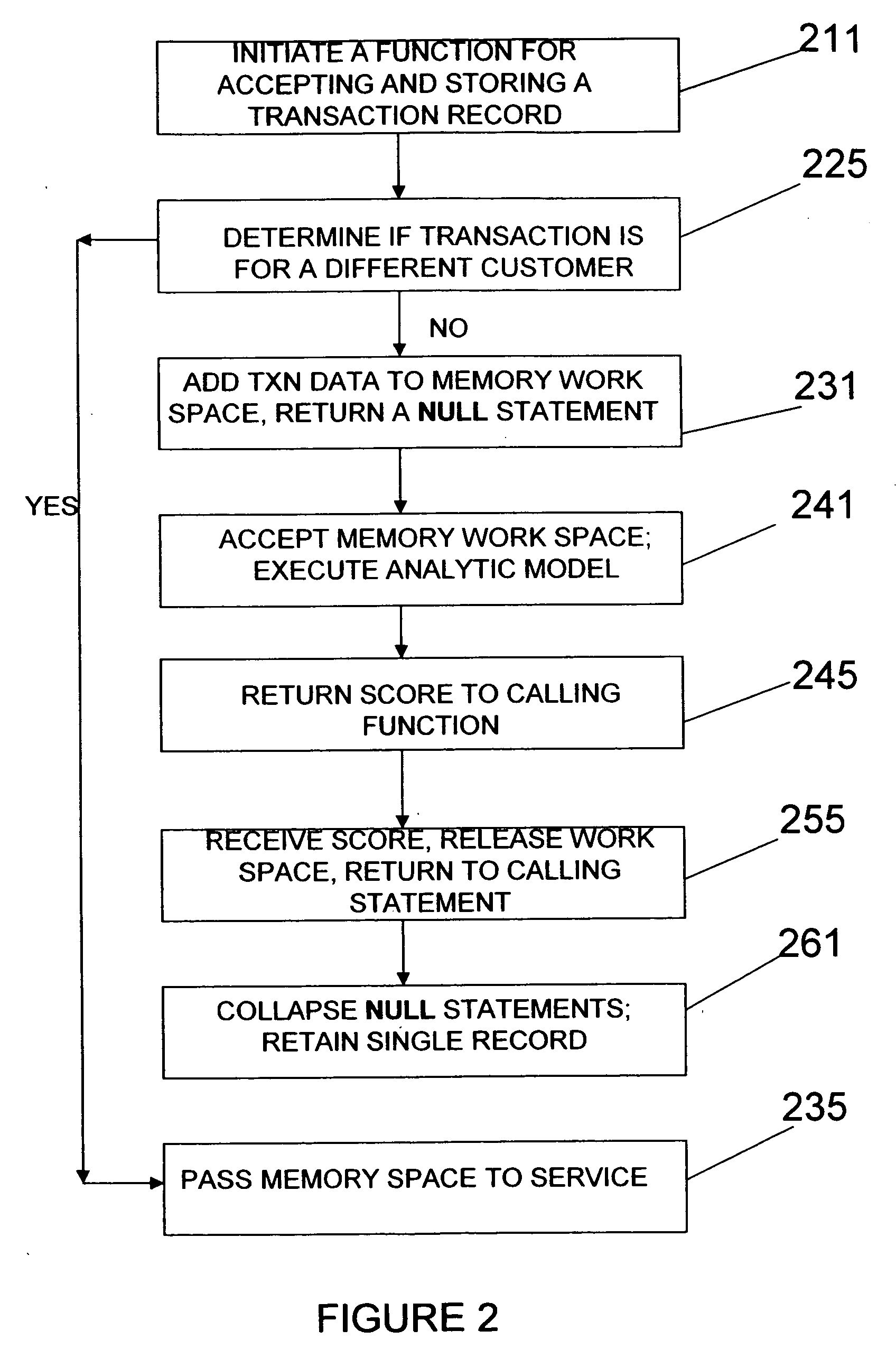
Method and system for executing data analytics on a varying number of records within a RDBMS using SQL
InactiveUS20060178982A1Minimal system overheadProduce the customer score quickly and simplyFinanceRelational databasesAnalytic modelReturn statement
Scoring and detecting anomalies in a dynamic number of transaction records within a relational database management system by initiating a function for accepting and storing a transaction record in the relational database management system; This function and the analytics are integral to the RDBMS, as distinguished from extracting the data and passing the data to a separate application external to the RDBMS. The function determines if the transaction is for a different individual then a previous transaction or for the same individual. If the transaction is not for a different individual, adding the new transaction data to a memory work space and returning a NULL statement, otherwise passing the memory work space to a service. In the next step the memory workspace is accepted and an analytic model is executed to produce a score, and return the score to a calling function. This score is received at the calling function, the memory work space for the individual is released, and the score is returned to the calling statement. All of the NULL statements are collapsed and a single record is retained for the individual. This record contains the score, that is, a buying preference or pattern, a travel pattern, a calling pattern, a maintenance prediction, a risk score, or a credit score, by way of illustration.
Owner:IBM CORP
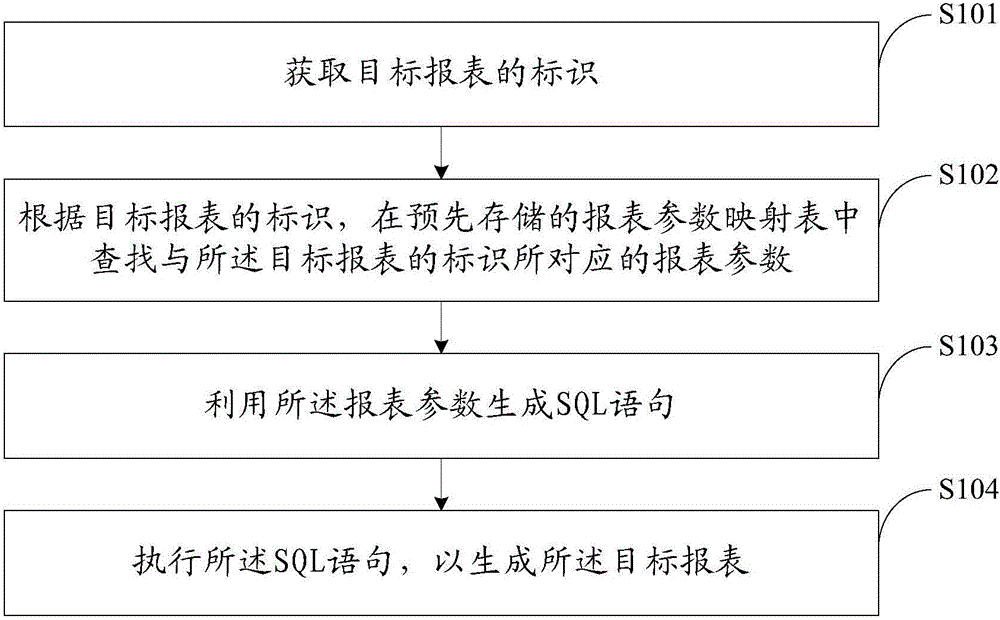
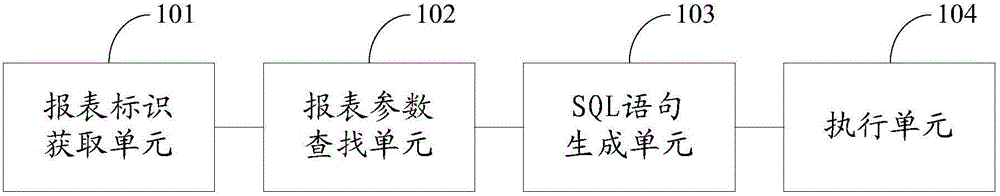
Statement generation method and device
InactiveCN105843784AShorten development timeImprove development efficiencyText processingSpecial data processing applicationsReturn statementSQL
The embodiment of the invention discloses a statement generation method and device, and improves statement development efficiency. The method comprises the following steps: obtaining the identifier of a target statement; according to the identifier of the target statement, looking up a statement parameter corresponding to the identifier of the target statement from a pre-stored statement parameter mapping table; utilizing the statement parameter to generate a SQL (Structured Query Language) statement; and executing the SQL statement to generate the target statement.
Owner:BANK OF CHINA
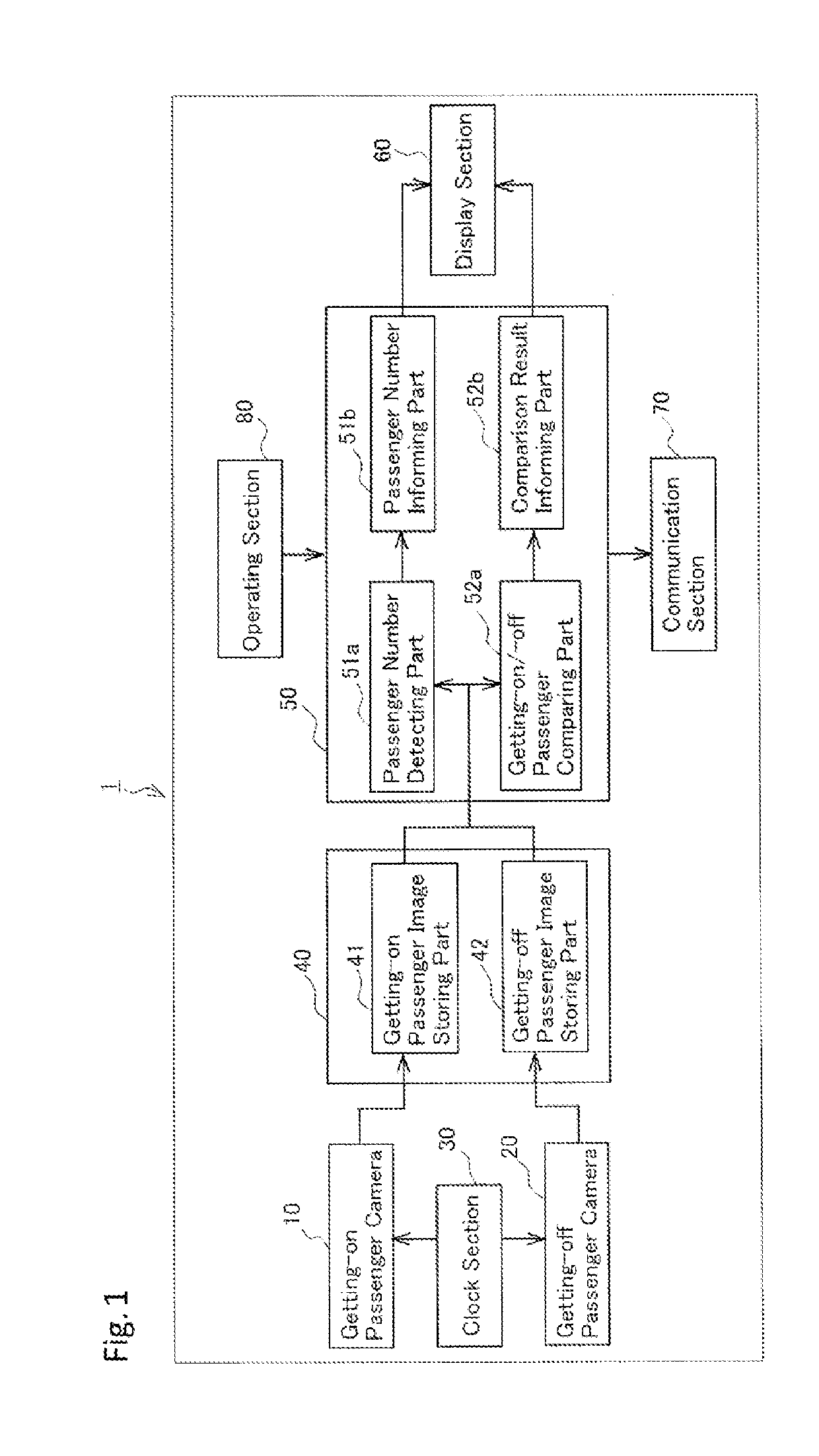
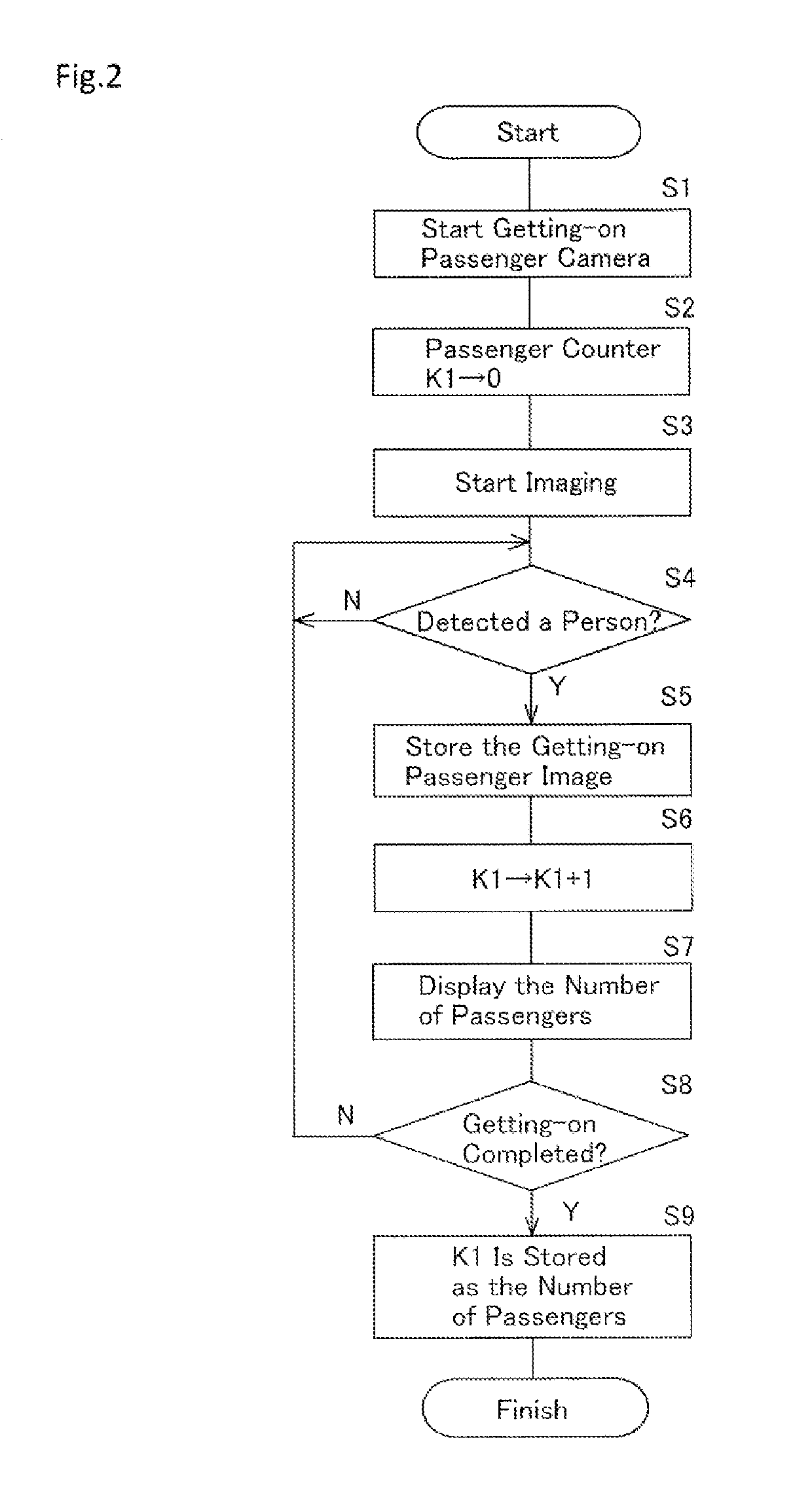
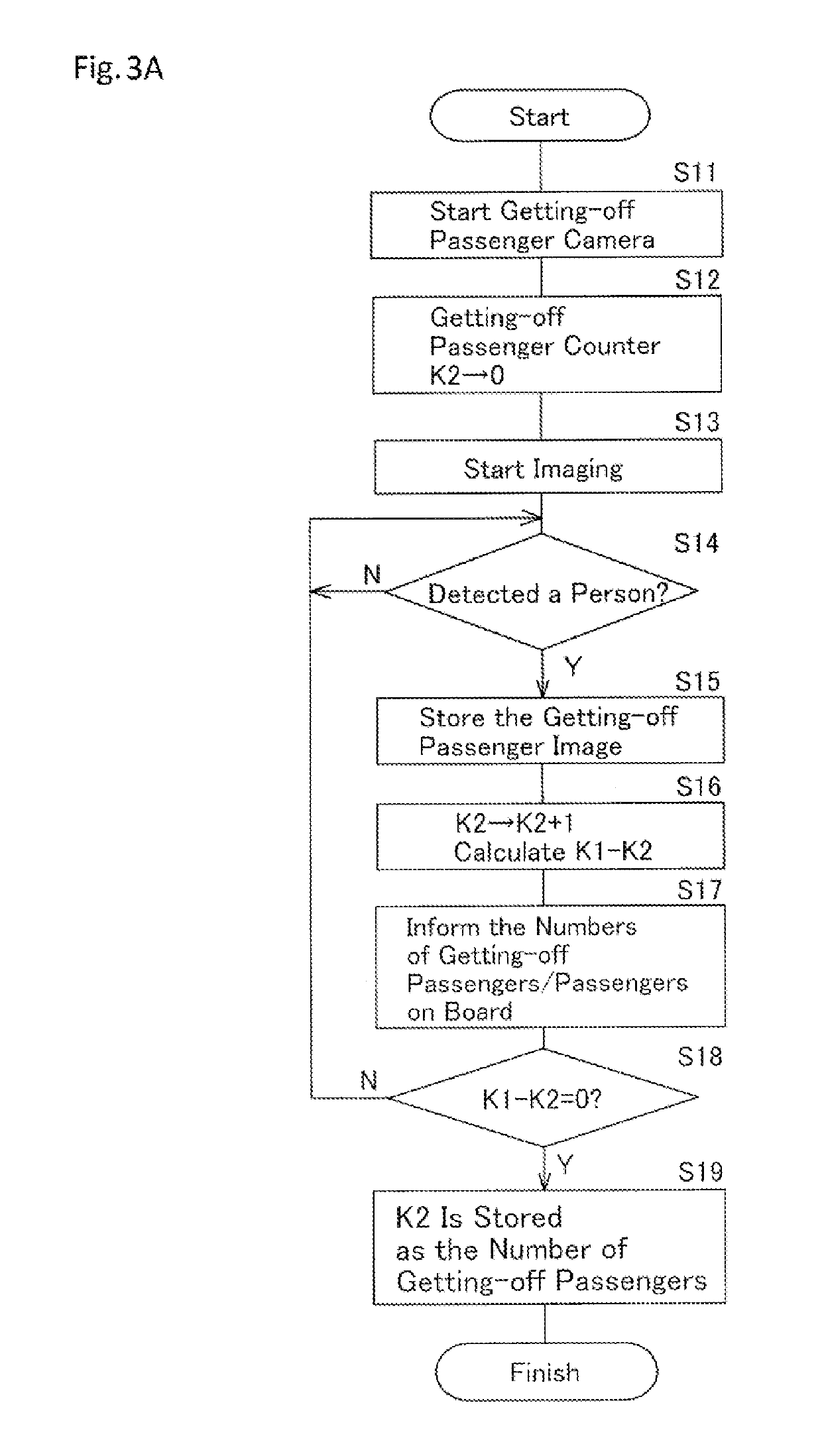
Passenger management apparatus and passenger management method
InactiveUS20190114563A1Precise managementAvoid differentImage enhancementImage analysisReturn statementEngineering
Owner:SUBARU CARBELL CO LTD
Control method for Flash memory on-line programming
InactiveCN101409106AGuaranteed stabilityOnline programming convenienceRead-only memoriesReturn statementGeneric programming
The invention discloses an on-line programming control method of a Flash memory, comprising erasing operation and read-in operation. The method is characterized in that machine codes of operation statements and return statements of the Flash memory in the period of adding high pressure are preset in an RAM. The operation statements include the statement for writing interrupt identification in a status register so as to start a corresponding command, as well as the statement for judging the completion of a wait command; and in the processes of erasing operation and writing operation, program operation is carried out when the period of adding high pressure turns to the RAM. The invention separates the instable factors caused in the period of adding high pressure from the erasing and writing operations of the Flash memory, and the control method has universality and convenient programming and ensures the on-line programming stability of the Flash memory.
Owner:SUZHOU UNIV
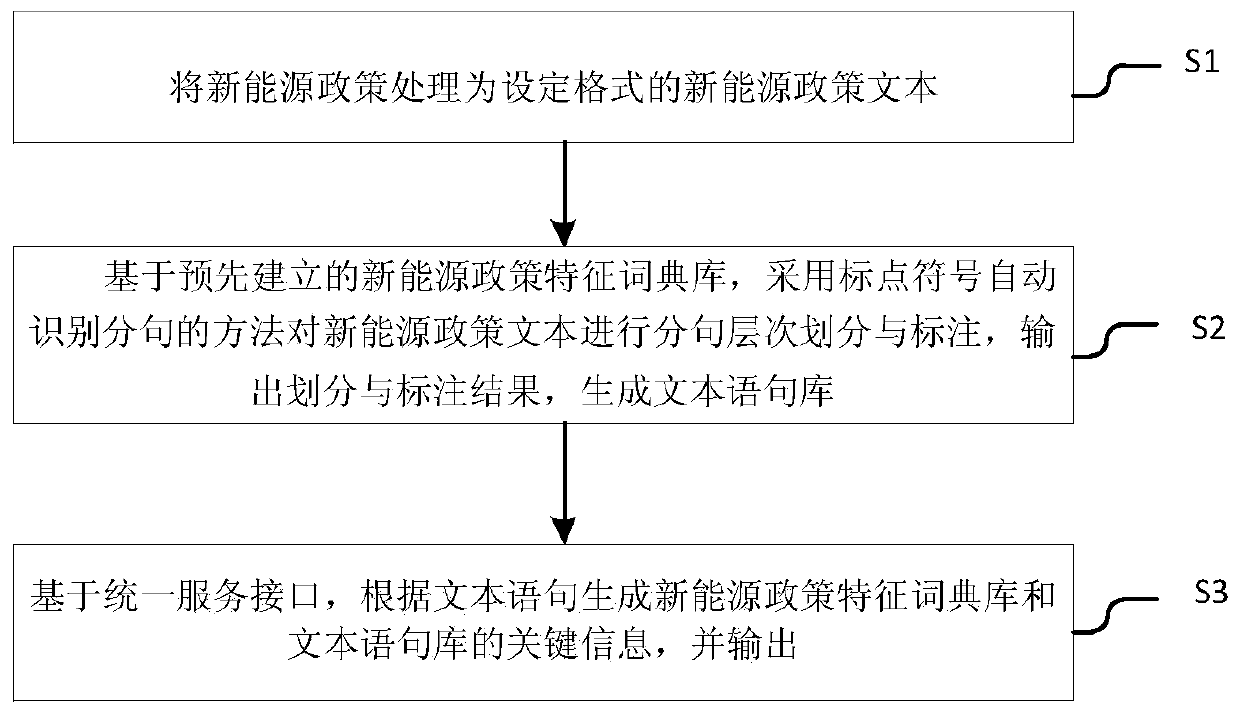
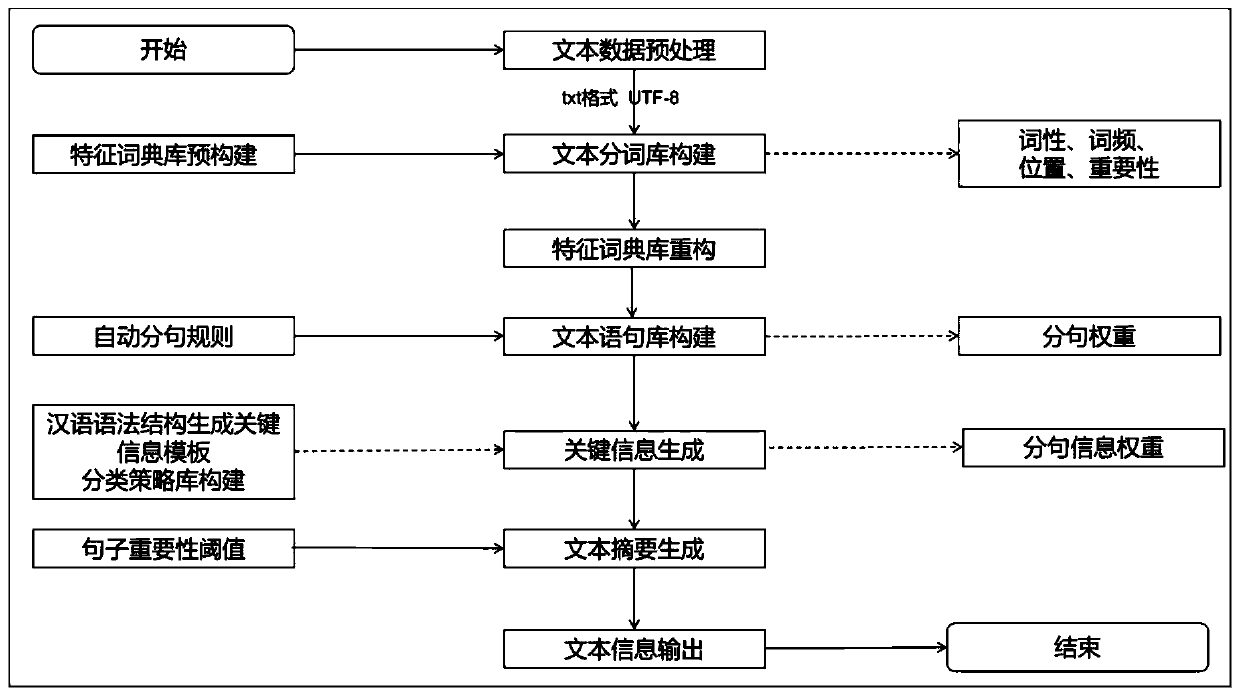
A new energy policy information extraction method and system
PendingCN109766416AAchieve distinctionAchieve splitSpecial data processing applicationsSemantic tool creationReturn statementNew energy
The invention provides a new energy policy information extraction method and system. The method is characterized by processing a new energy policy into a new energy policy text in a set format; basedon a pre-established new energy policy feature dictionary library, using a punctuation symbol automatic identification sentence division method to perform sentence division and marking on the new energy policy text, outputting a division and marking result, and generating a text sentence library; and based on a unified service interface, generating key information of a new energy policy feature dictionary library and a text statement library according to the text statement and outputting the key information.
Owner:CHINA ELECTRIC POWER RES INST +2
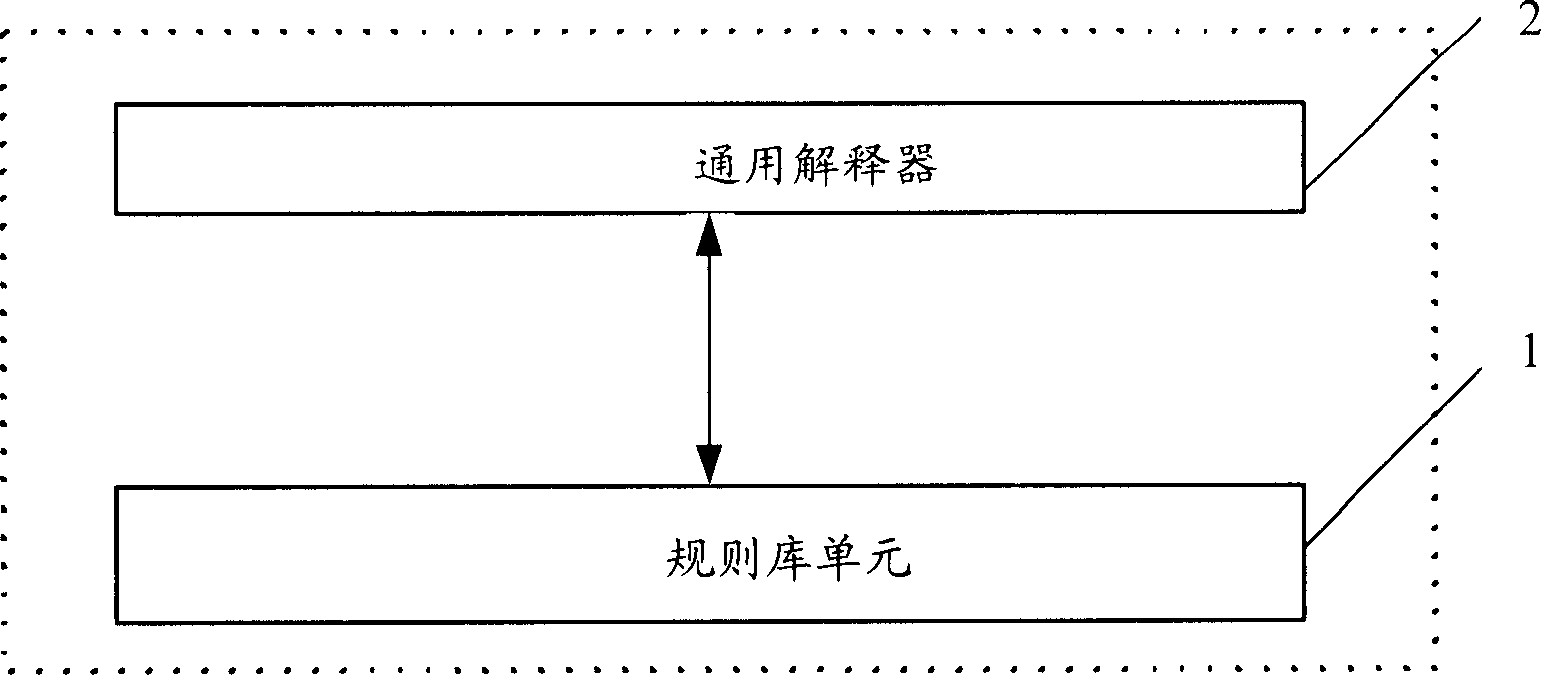
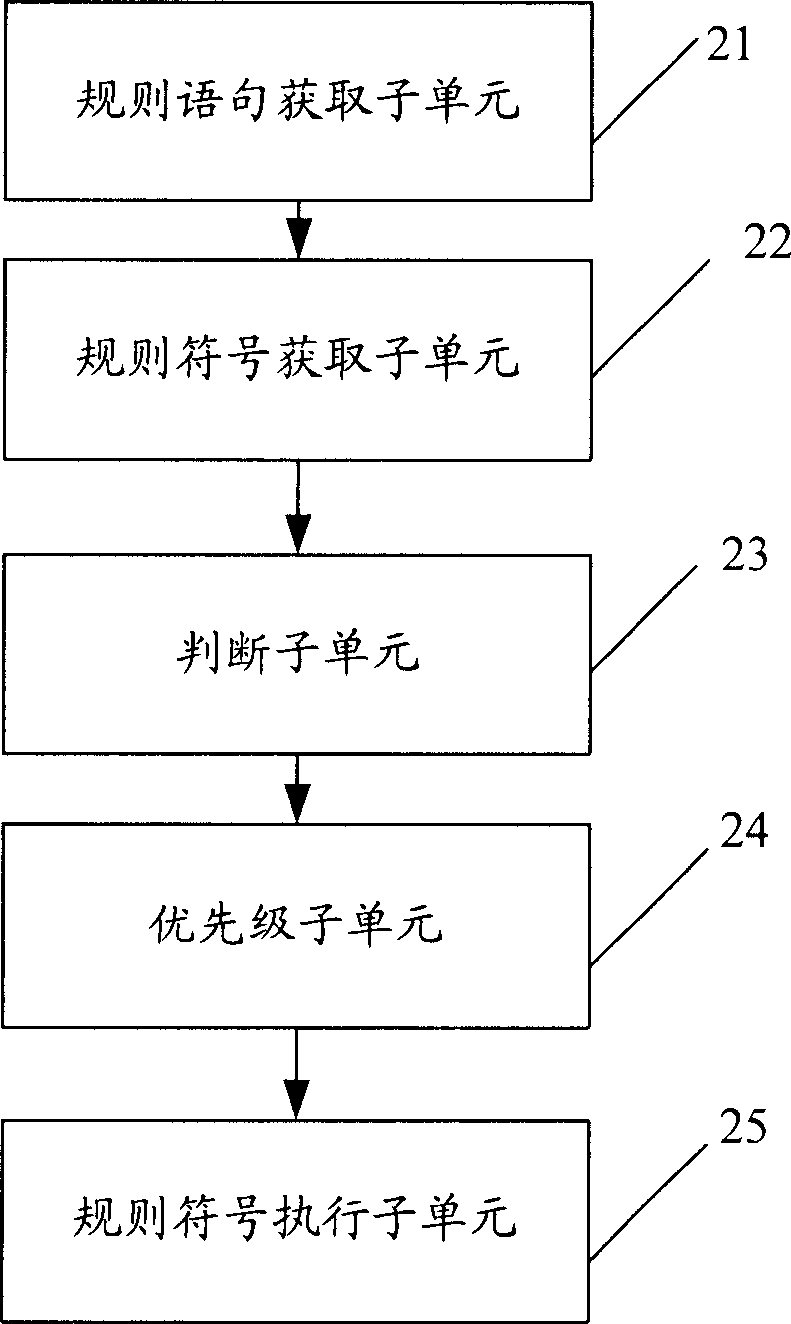
Protocol message analytic method and protocol message analytic system
ActiveCN1735091AShort upgrade cycleReduce the difficulty of analysisTransmissionReturn statementAnalysis method
This invention provides a analysis method and system for protocol information composed of some IEs. Wherein, the method comprises following steps: 1) dividing and selecting a set rule signs for control action from all logic control actions used in protocol analysis process, the control action comprises: positioning IE position, connecting and uniting IE, calculating, deciding and outputting the IE; 2) generating a general explainer to recognize the said rule signs; 3) setting rule database unit according to a exact protocol; 4) when receiving the bit stream, the said explainer reads rule statement from rule database, executes every control action set by rule sign, and completes the analysis. When the protocol changes, it needs just to modify the rule database unit instead of the said explainer; thereby, the invention decreases modification time and analysis difficulty.
Owner:DATANG MOBILE COMM EQUIP CO LTD
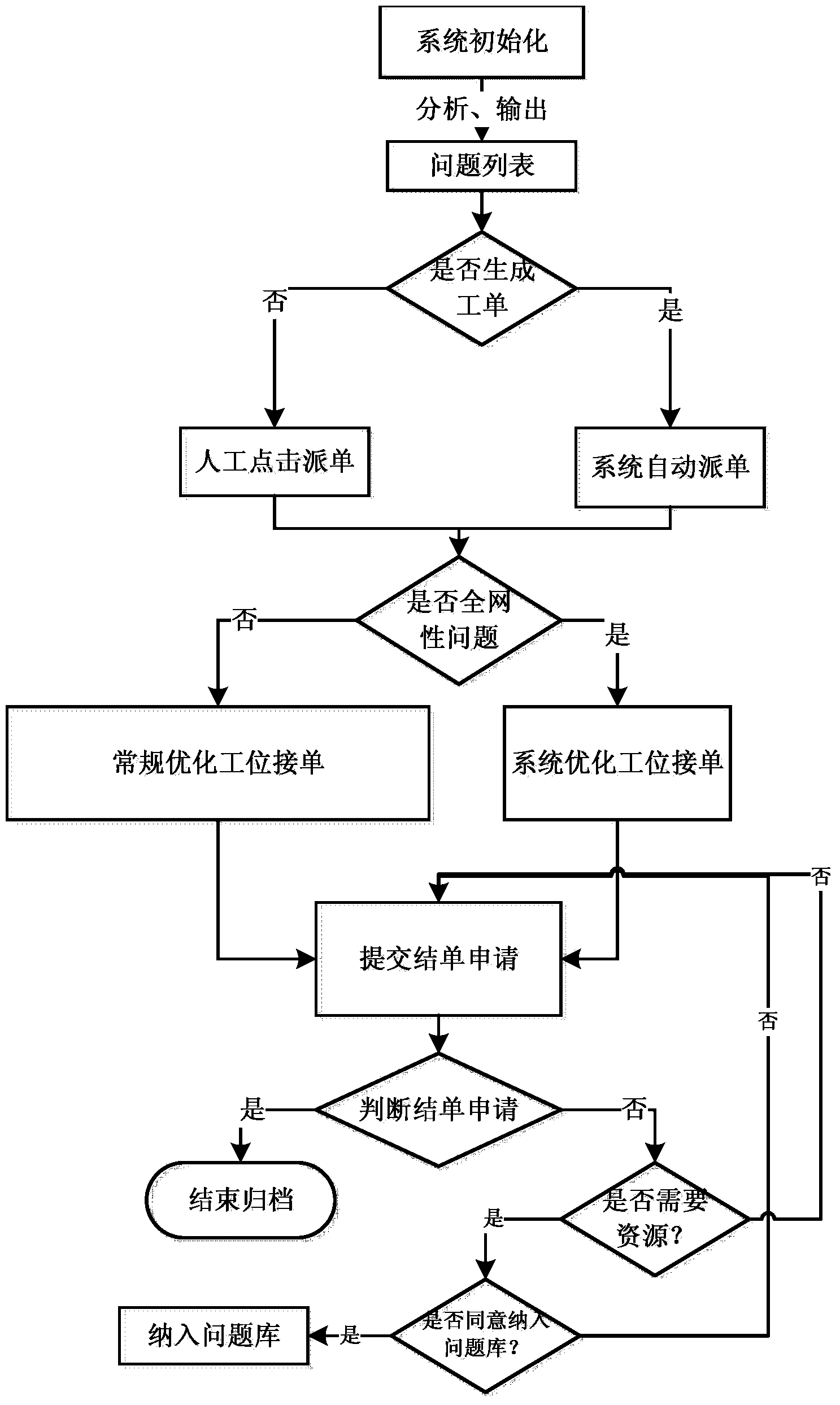
Full-automatic closed-loop control method of wireless network work order
ActiveCN104270787AQuality improvementImprove efficiencyInstrumentsWireless communicationReturn statementData source
The invention discloses a full-automatic closed-loop control method of a wireless network work order. Source data are collected from an underlying data source through Hadoop and are classified and calculated through a preset classification algorithm, index values of the source data are obtained, then the index values are compared with a preset threshold value to obtain problem data, the problem data meeting the order sending condition generate a work order, the work order is stored in a work order table, a big data system and an electronic operation and maintenance system carry out order sending, order statement and filing on the work order in the work order table respectively, and therefore the closed-loop control over the full work order sending, shifting and settlement process is achieved. Thus, the operating quality and efficiency of the wireless network are improved, and meanwhile work accuracy and objectivity are ensured.
Owner:四川公用信息产业有限责任公司
Determining whether method of computer program is a validator
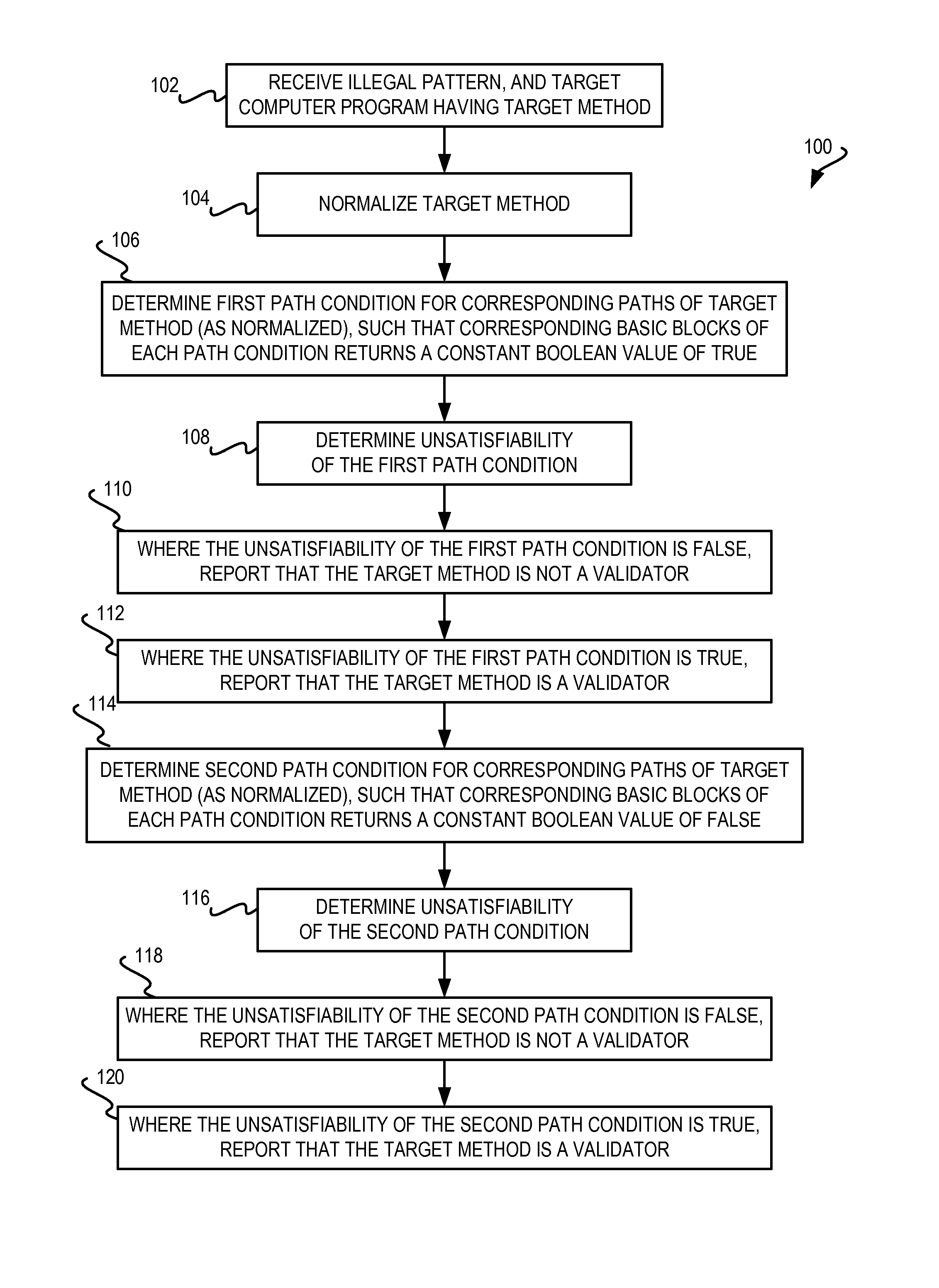
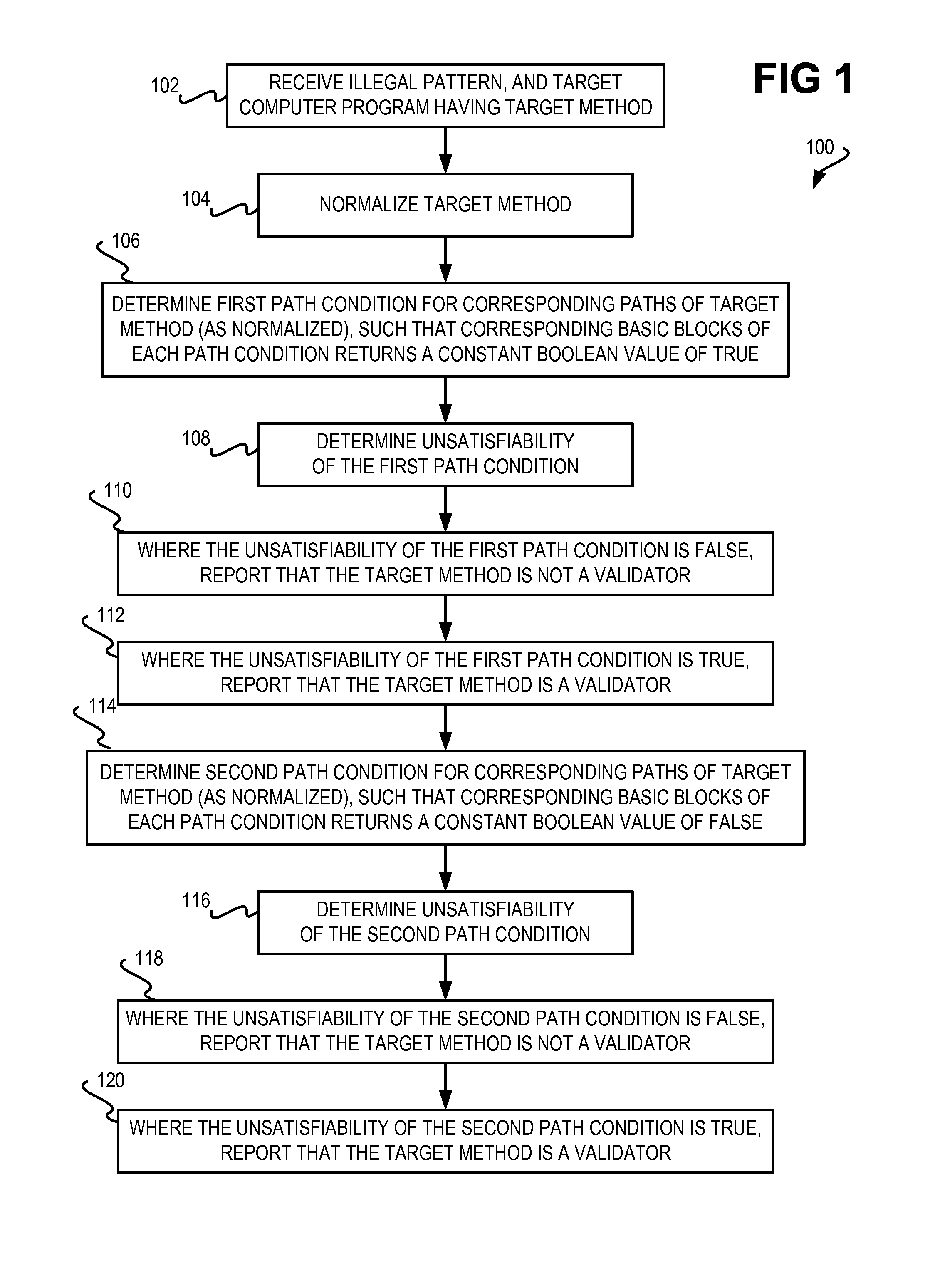
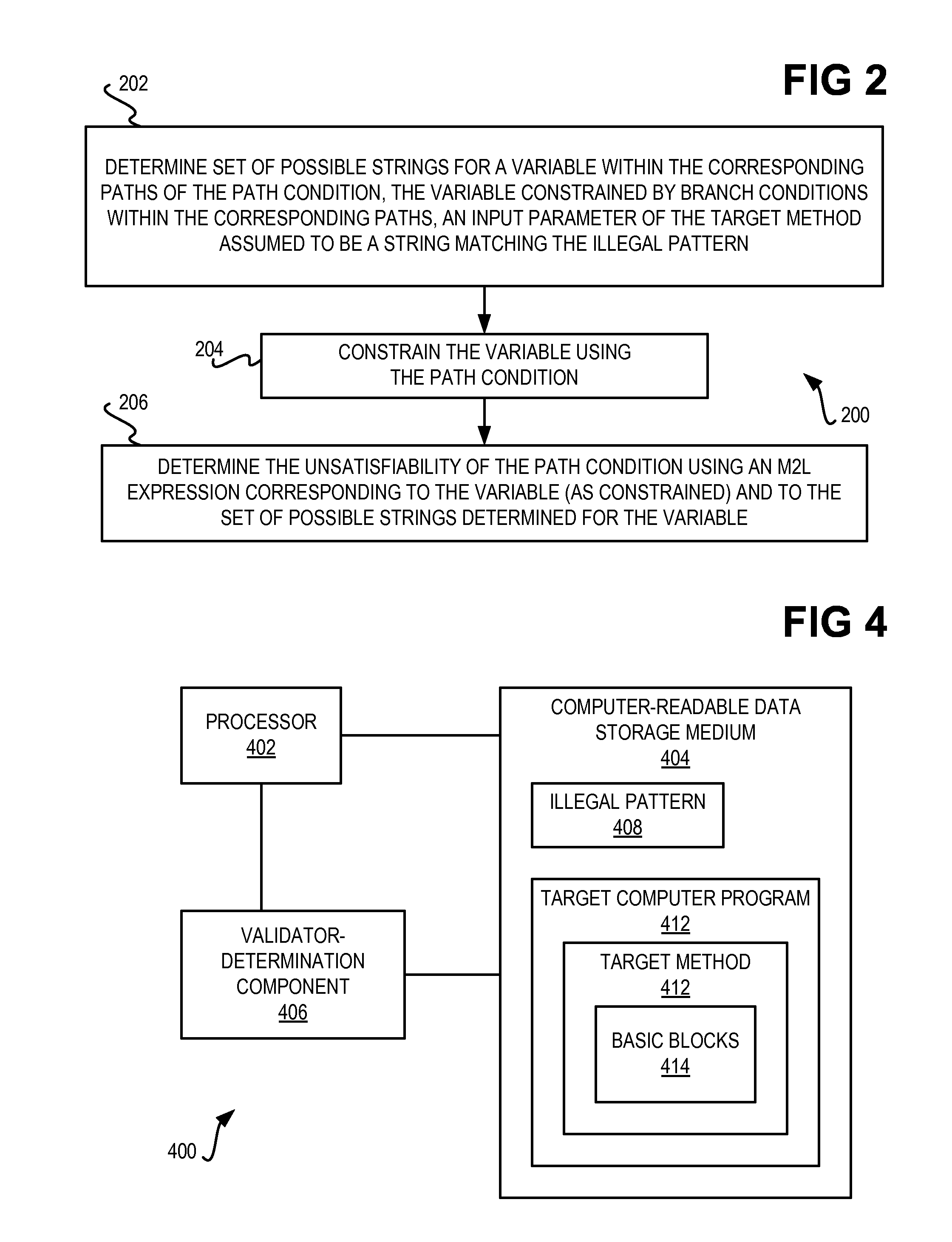
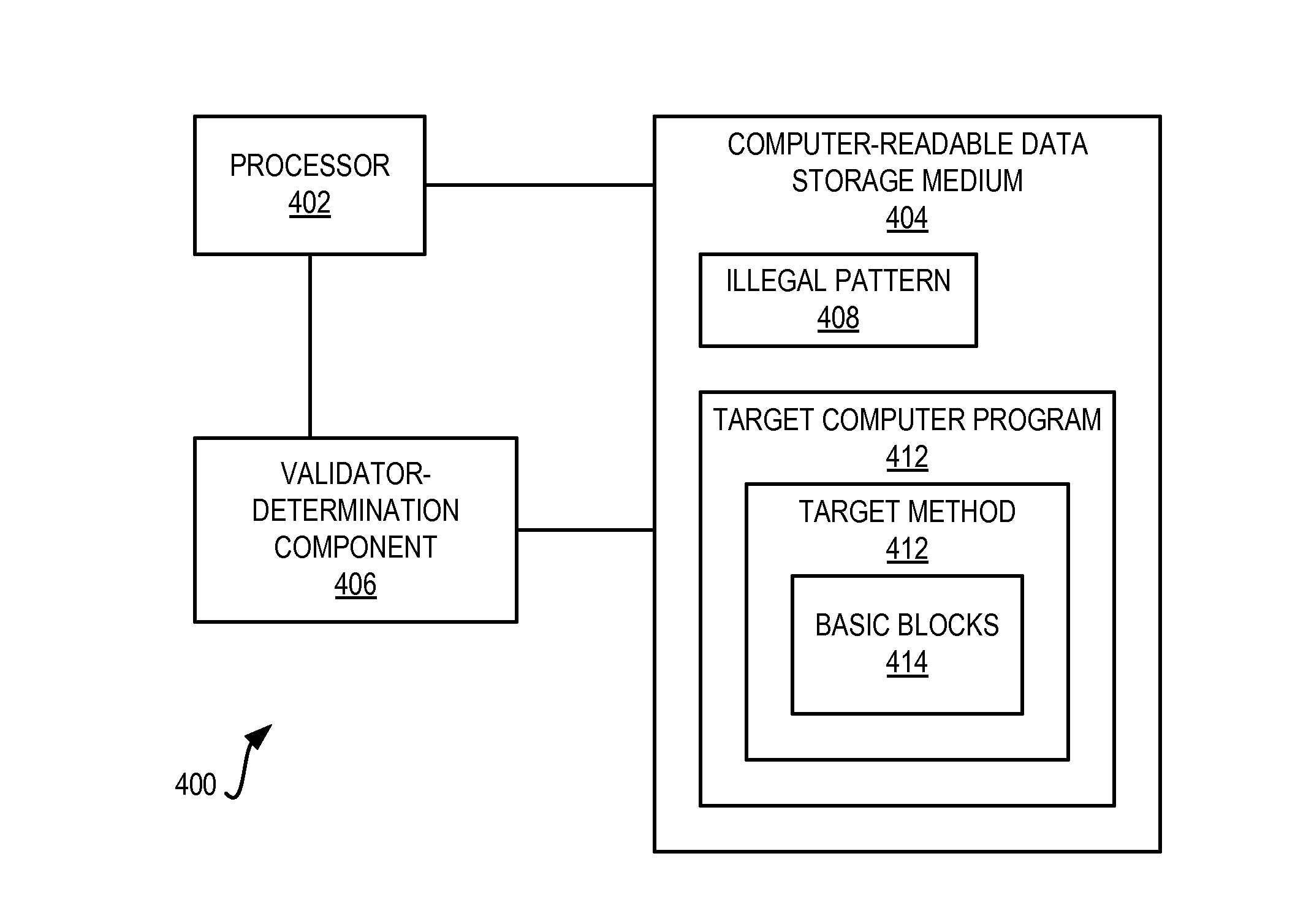
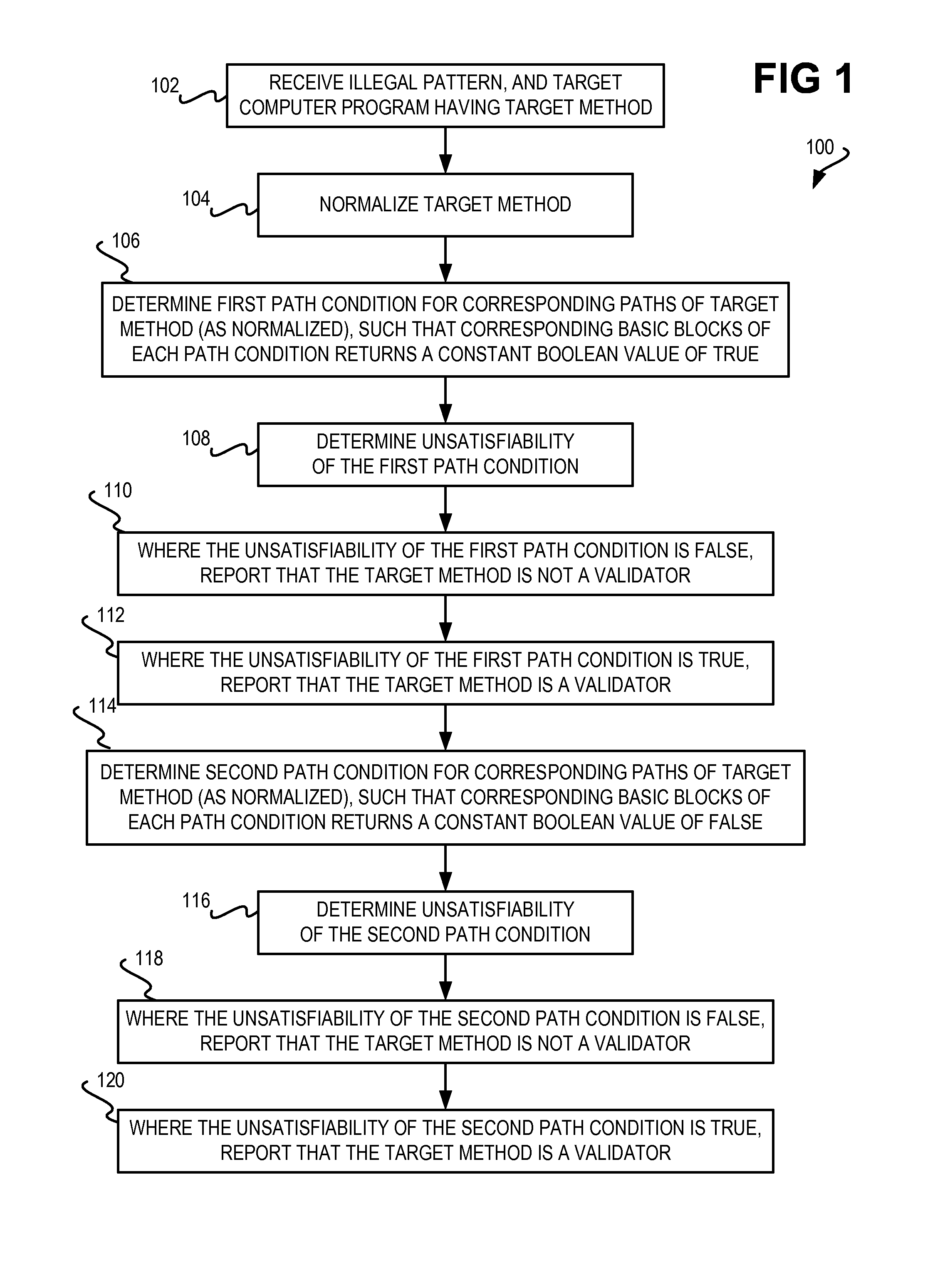
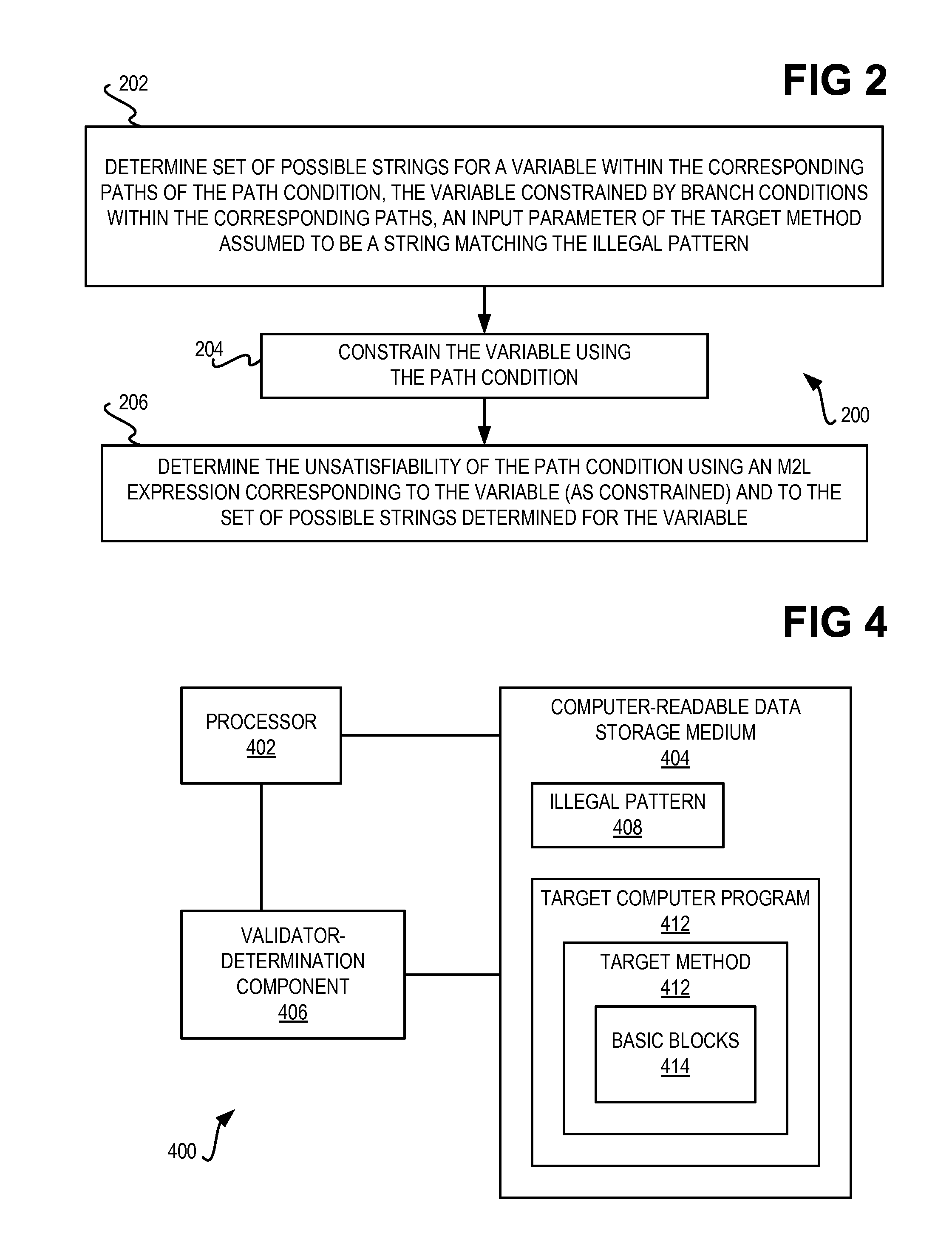
InactiveUS20120131669A1Constant valueMemory loss protectionUser identity/authority verificationReturn statementTruth value
An illegal pattern and a computer program having a method are received. The method has one or more return statements, and a number of basic blocks. The method is normalized so that each return statement of the target method relating to the illegal pattern returns a constant Boolean value. A first path condition and a second path condition for one or more corresponding paths is determined such that one or more corresponding basic blocks return a constant Boolean value of true for the first path condition and a constant Boolean value of false for the second path condition. An unsatisfiability of each path condition is determined using a monadic second-order logic (M2L) technique. Where the unsatisfiability of either path condition is false, the method is reported as not being a validator. Where the unsatisfiability of either path condition is true, the method is reported as being a validator.
Owner:IBM CORP
Determining whether method of computer program is a validator
InactiveUS8365281B2Memory loss protectionUser identity/authority verificationTruth valueReturn statement
An illegal pattern and a computer program having a method are received. The method has one or more return statements, and a number of basic blocks. The method is normalized so that each return statement of the target method relating to the illegal pattern returns a constant Boolean value. A first path condition and a second path condition for one or more corresponding paths is determined such that one or more corresponding basic blocks return a constant Boolean value of true for the first path condition and a constant Boolean value of false for the second path condition. An unsatisfiability of each path condition is determined using a monadic second-order logic (M2L) technique. Where the unsatisfiability of either path condition is false, the method is reported as not being a validator. Where the unsatisfiability of either path condition is true, the method is reported as being a validator.
Owner:IBM CORP
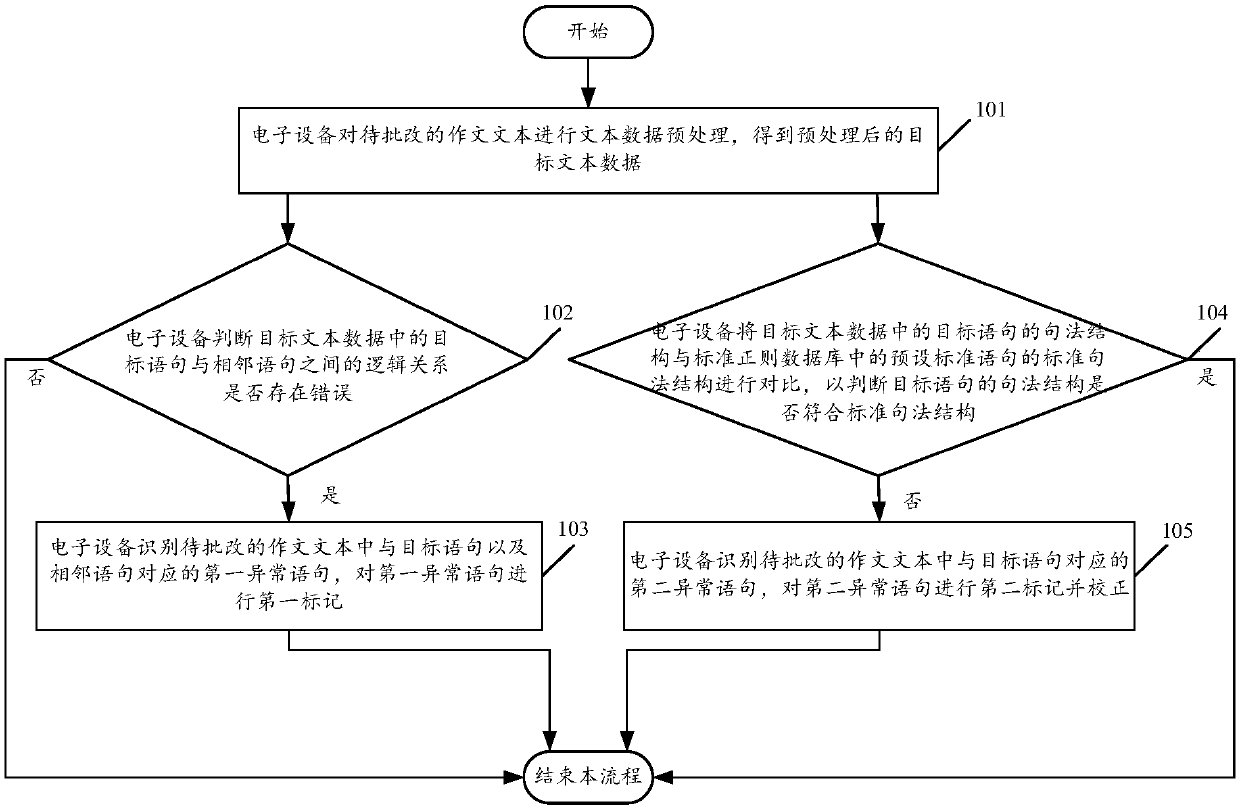
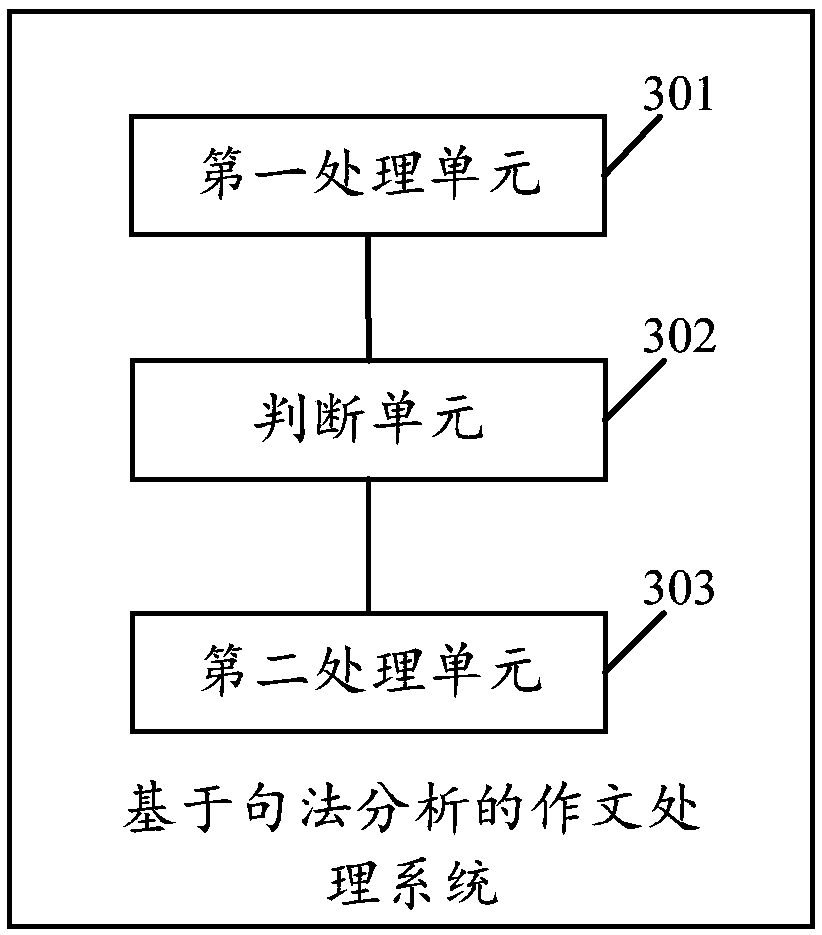
Composition processing method and system based on syntactic analysis
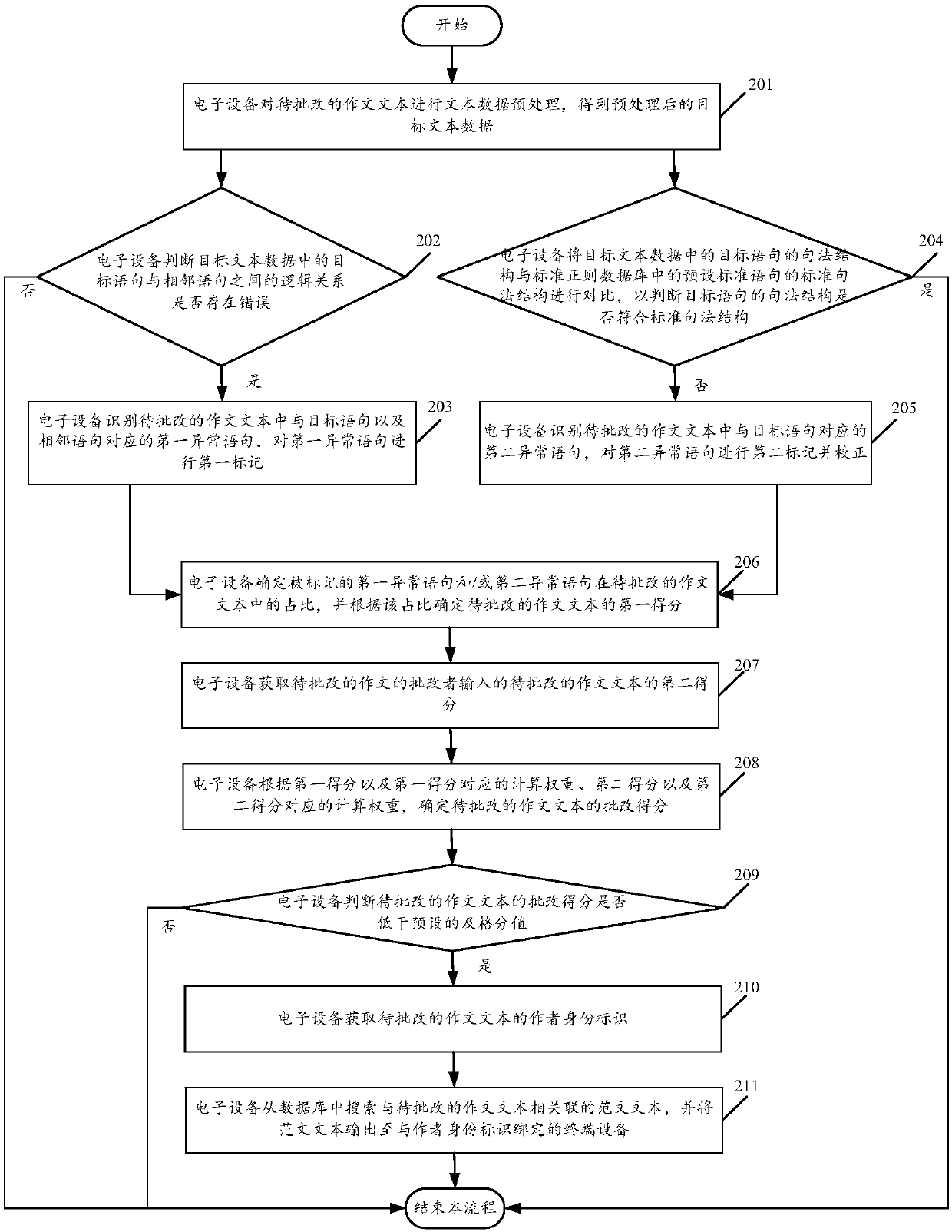
PendingCN109614623AImprove correction efficiencyReduce workloadDigital data information retrievalNatural language data processingReturn statementGrammatical error
The invention discloses a composition processing method and system based on syntactic analysis, and the method comprises the steps: carrying out the text data preprocessing of a composition text to becorrected, and obtaining the preprocessed target text data; judging whether an error exists in a logic relation between a target statement and an adjacent statement in the target text data or not, ifyes, identifying a first abnormal statement corresponding to the target statement and the adjacent statement in the composition text to be corrected, and performing first marking on the first abnormal statement; and / or comparing the syntactic structure of the target statement in the target text data with a standard syntactic structure of a preset standard statement in a standard regular databaseto judge whether the syntactic structure of the target statement conforms to the standard syntactic structure or not; if not, identifying a second abnormal statement corresponding to the target statement in the composition text to be corrected; and the second abnormal statement is marked and corrected, so that the grammatical error in the composition can be automatically corrected, and the composition correction efficiency is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
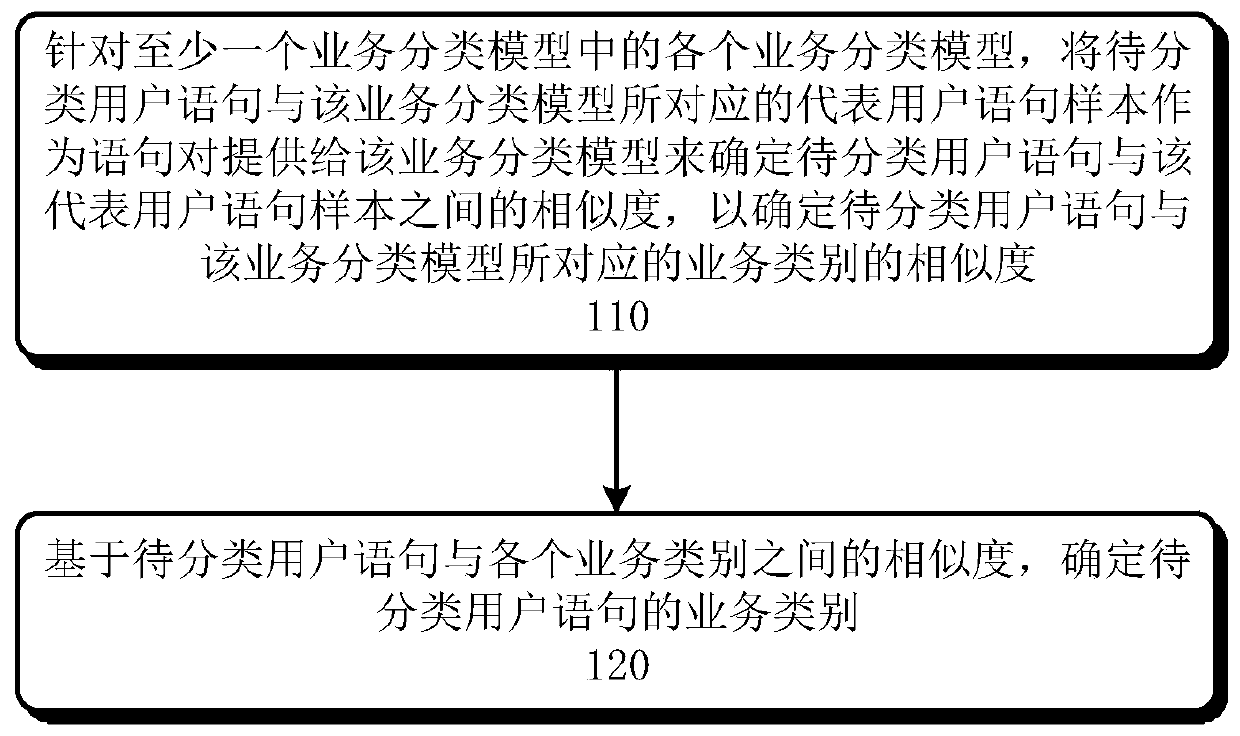
Method and device for classifying services based on at least one service classification model
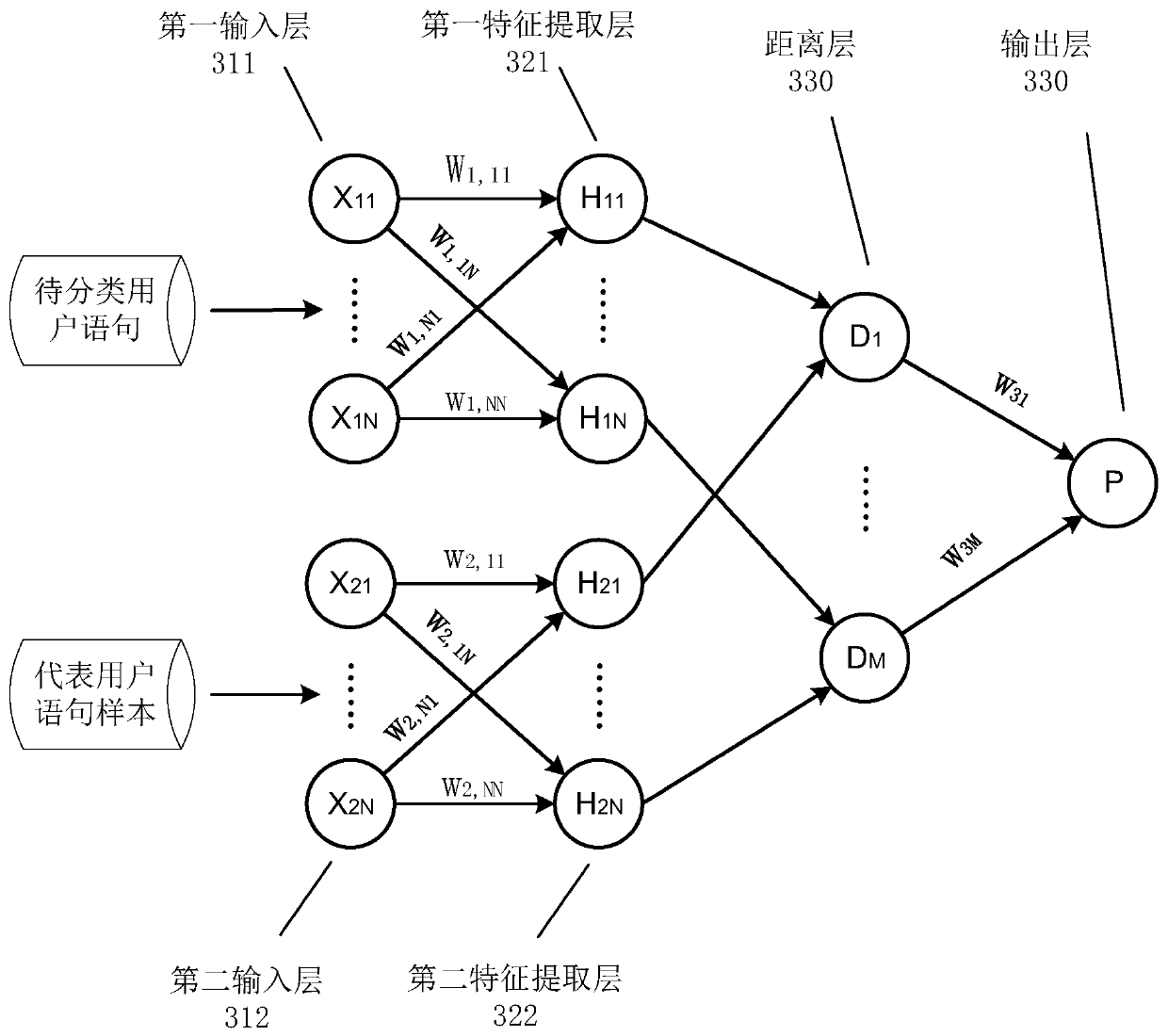
ActiveCN110046648AAvoid classification failureImprove accuracyCharacter and pattern recognitionReturn statementClassification methods
Owner:ADVANCED NEW TECH CO LTD
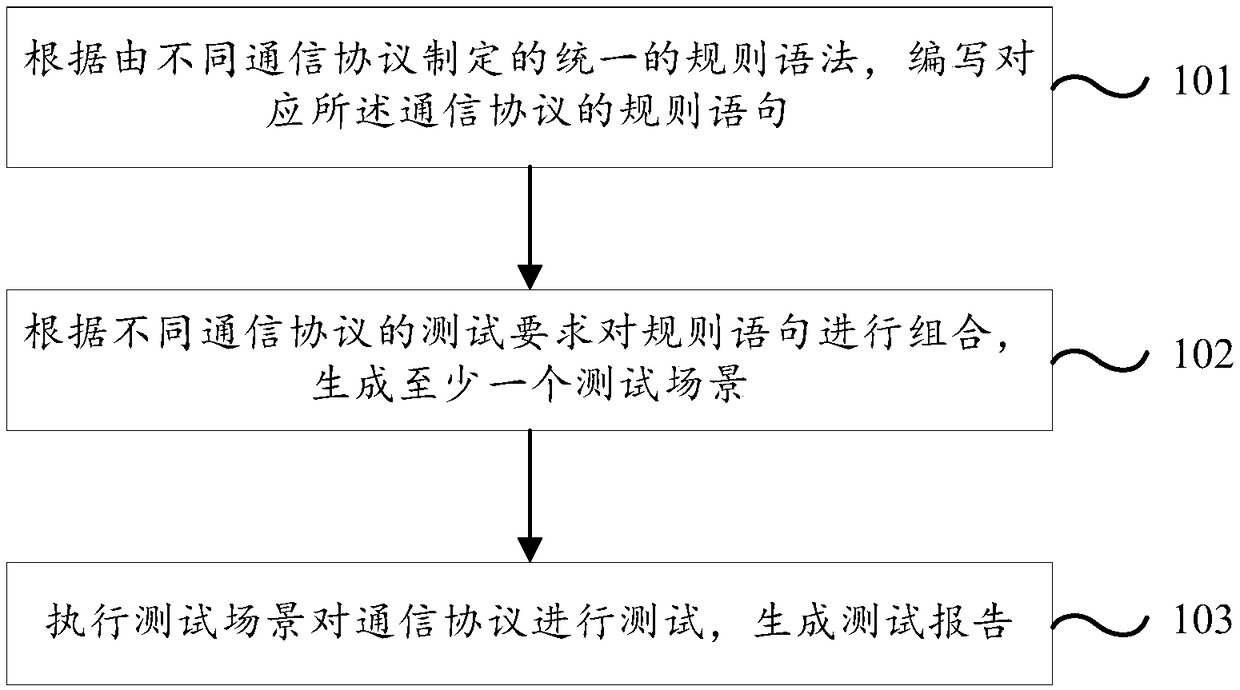
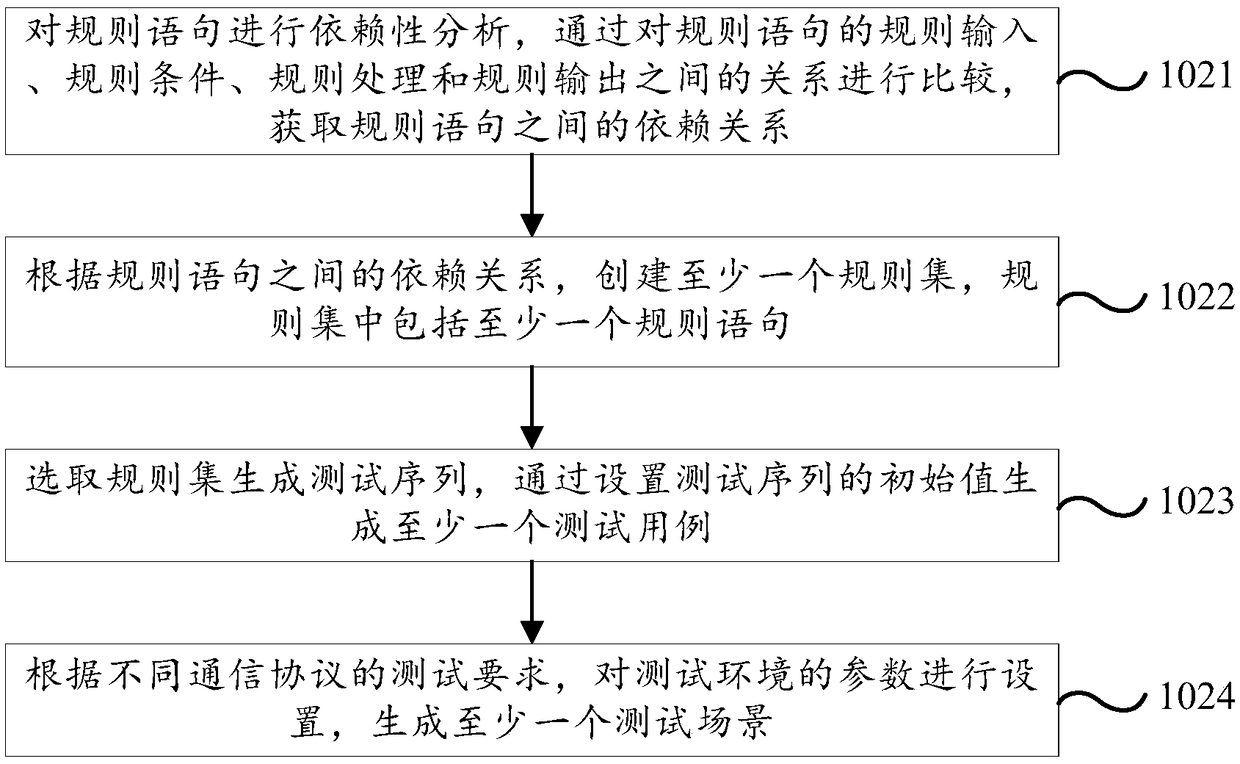
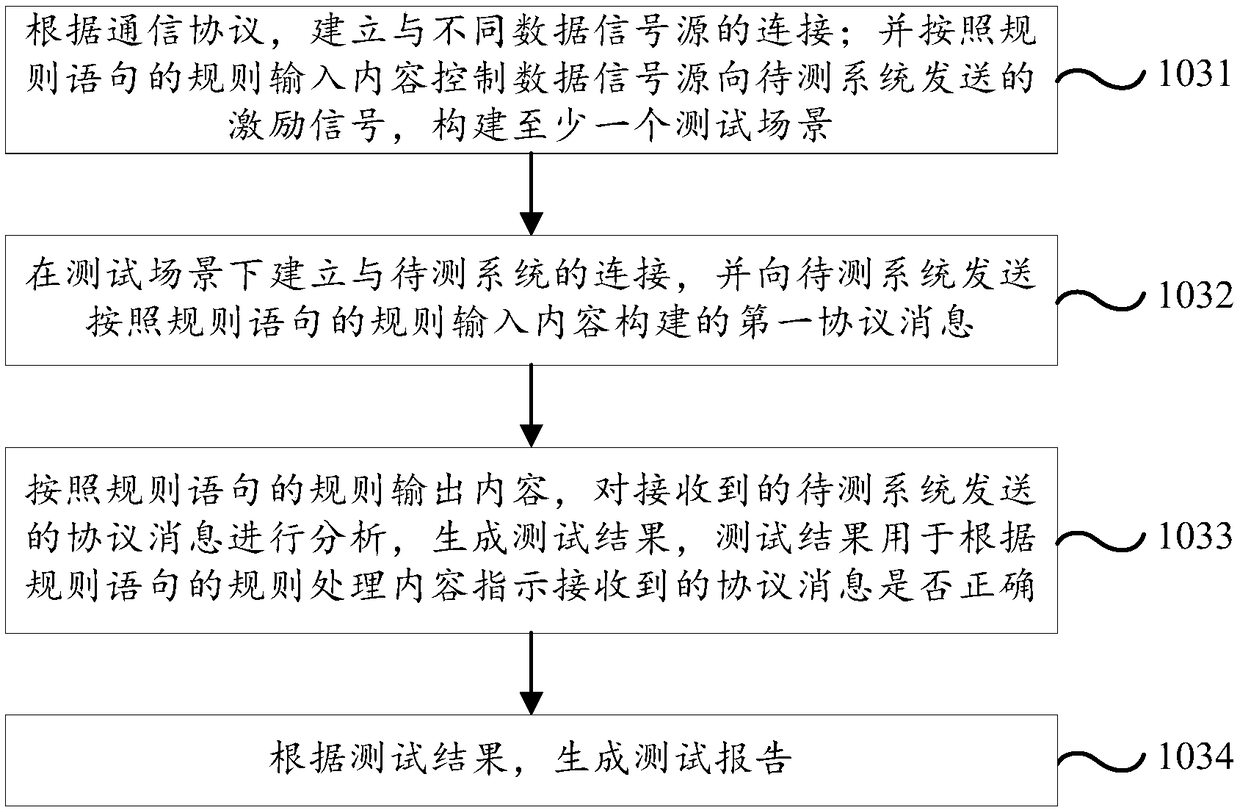
Software testing method and testing platform
ActiveCN109491919ASimplify the process of writing test casesAvoid the problems of developing different test toolsSoftware testing/debuggingComputer hardwareReturn statement
The invention discloses a software testing method and a testing platform, and the method comprises the steps: compiling rule statements corresponding to communication protocols according to unified rule grammar formulated by different communication protocols; combining the rule statements according to test requirements of different communication protocols to generate at least one test scene; executing the test scene to test the communication protocol, and generating a test report. Any communication protocol can be converted into a plurality of rule statements in a user-defined format, a plurality of test scenes are generated on the basis of the rule statements according to the test requirements of different communication protocols, and the specified test scenes are operated to complete thetest of the communication protocol. Therefore, in the whole test process, not only is the process of compiling the test case by a tester simplified, but also the generality of encoding and decoding and protocol message receiving and transmitting processing of different communication protocols is integrated, and the problem that different test tools are developed for different communication protocols is avoided.
Owner:中电科西北集团有限公司
Synchronous termination method and system of wide area fault recording
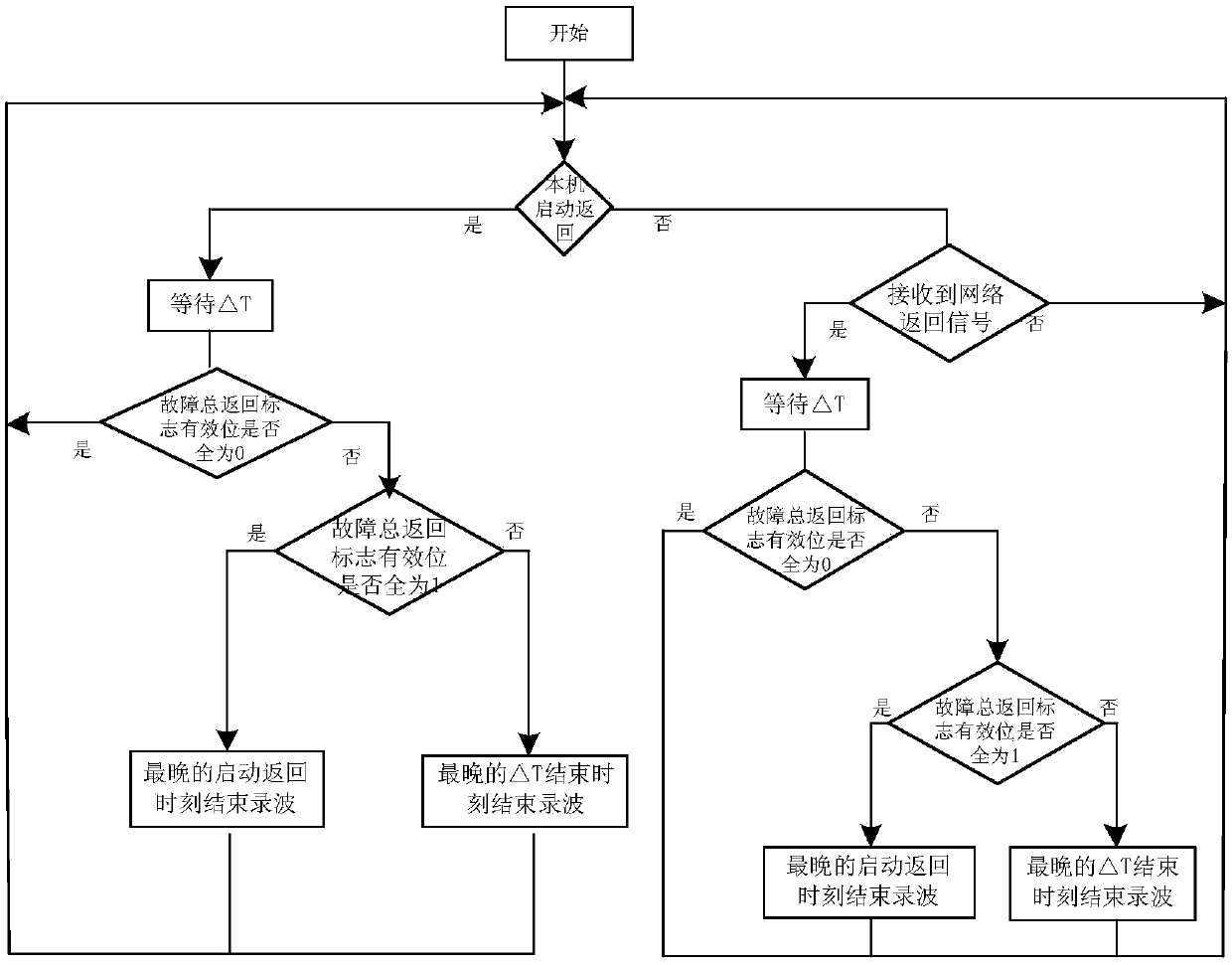
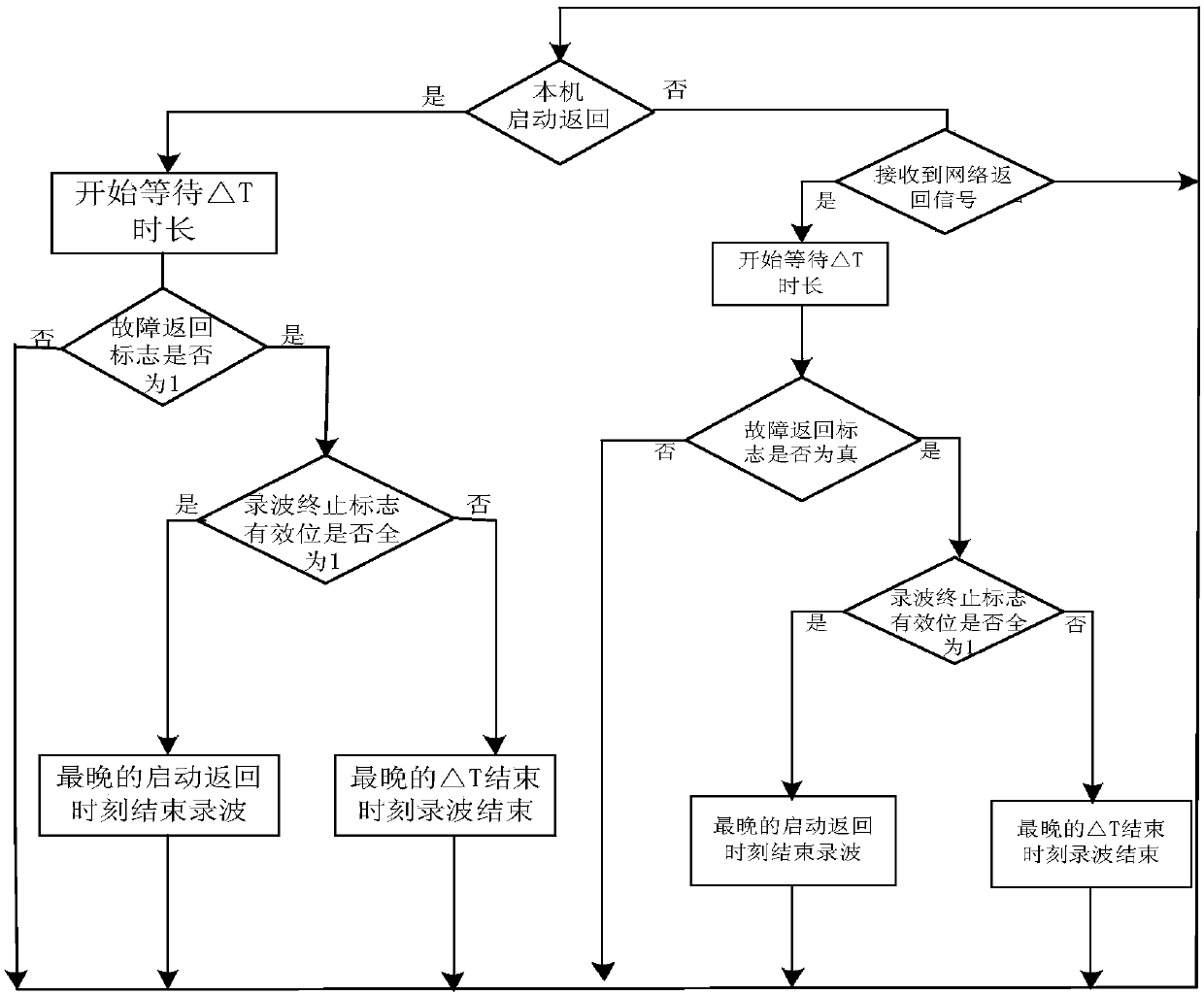
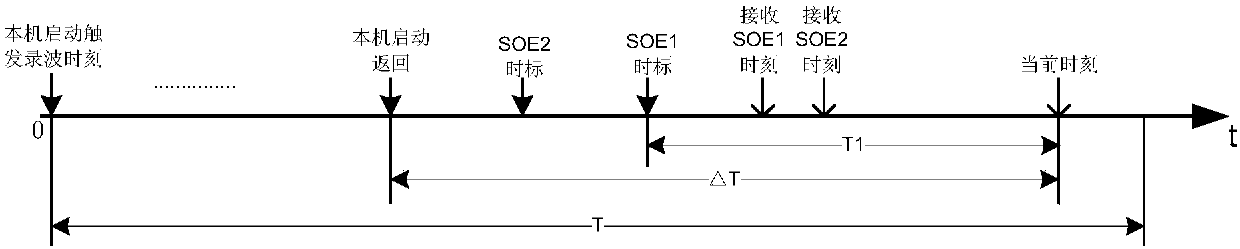
ActiveCN107769880ALow real-time requirementsEnsure faults are coveredElectrical testingTime-division multiplexNon real timeComplete data
The invention discloses a synchronous termination method and system of wide area fault recording. Fault recording devices are arranged in each substation in the system and are grouped according to a power supply system structure, and the devices in the same group are accessed to a satellite timing system and are connected via a communication network for communication. The method comprises the following steps: after the fault recording devices are started or return, sending starting signals or return signals to the other devices in the same group, and when the fault recording devices return orreceive network return signals, starting to wait for a time length delta T; marking the effective positions 1 according to the return state of the fault recording devices in the group during the waiting; if the effective positions are all 1 after the waiting, terminating the recording at the latest return moment in the return signals in the group; and if not all effective positions are 1, terminating the recording at the latest return moment of the delta T in the group. According to the synchronous termination method and system, synchronous communication can be achieved by using the constructed non-real-time E1 network, the synchronous termination of wide area fault recording can be achieved, and more complete data support is provided for the system fault analysis.
Owner:NR ELECTRIC CO LTD +1
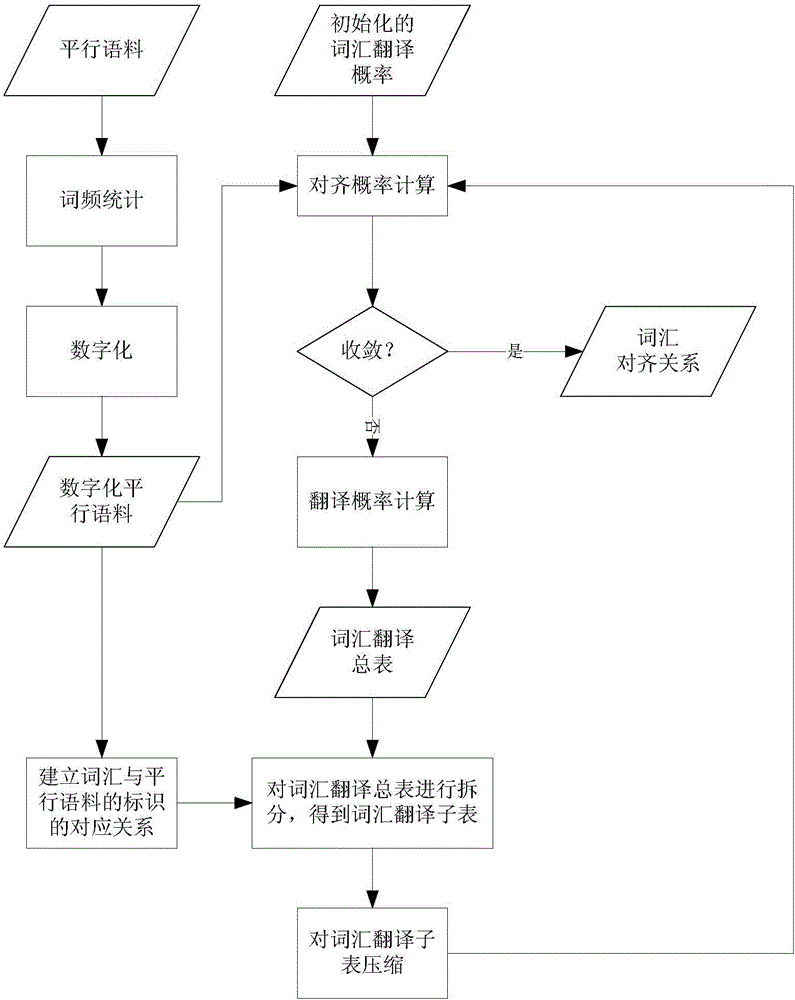
Word alignment training method, machine translation method and system
ActiveCN107436865ANatural language translationSpecial data processing applicationsReturn statementMachine translation system
The application discloses a word alignment training method, a machine translation method and system for increasing the efficiency of word alignment training. The application provides a word alignment training method comprising following steps: determining a vocabulary translation general table of multiple parallel corpus, wherein the vocabulary translation general table comprises the translation probability of a word of a source statement to a word of a target statement in the parallel corpus; splitting the vocabulary translation general table to obtain multiple vocabulary translation sub-tables, wherein the vocabulary translation sub-table comprises the translation probability of at least one word of a source statement to a word of a target statement in the parallel corpus; on the basis of the vocabulary translation sub-tables, determining the alignment relationship between words in the source statement and words in the target statement in the parallel corpus.
Owner:阿里巴巴(中国)网络技术有限公司
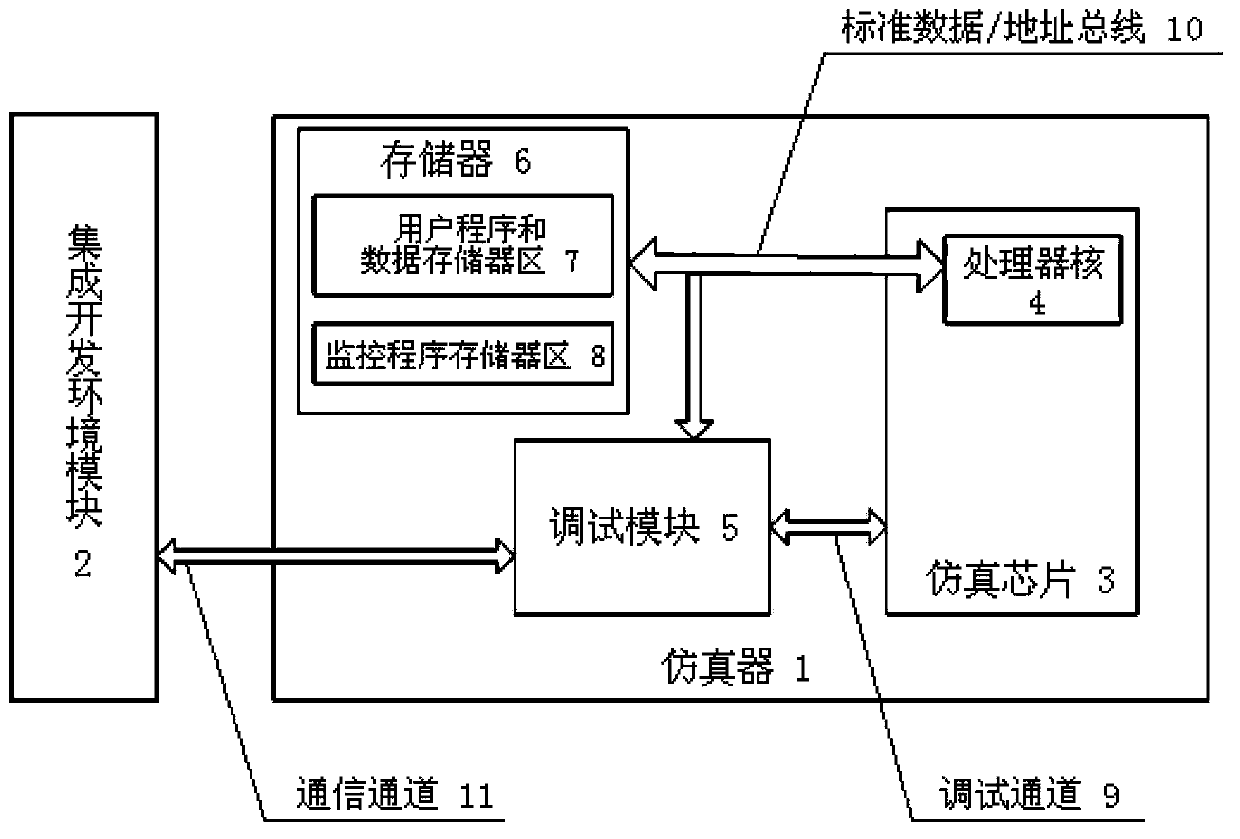
Emulator with program counter value settable
InactiveCN103677953AIncreased development complexityIncrease development costsSoftware simulation/interpretation/emulationReturn statementProgram Efficiency
The invention discloses an emulator with the program counter value settable. The emulator comprises an emulation chip, a debugging module and a storage. A user program and data storage area and a monitoring program storage area are arranged inside the storage. The debugging module controls the emulation chip to be in a monitoring mode or in a user mode, and in the monitoring mode, the emulation chip is controlled to execute a program at the position of a corresponding address in the monitoring program storage area, wherein a PC value correcting monitoring program is stored in the monitoring program storage area. When a return statement of the PC value correcting monitoring program is executed, the current PC value automatically becomes an address value stored in a stack. Under the situation that a processor core of the emulation chip does not support PC value instruction writing, the emulator can still provide the debugging function of correcting PC values; the user program debugging efficiency is improved, meanwhile, the dependence of emulation debugging function realization on the functions of the processor core is lowered, the development complexity and the cost of the emulation chip are lowered, and the universality of emulator design is improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
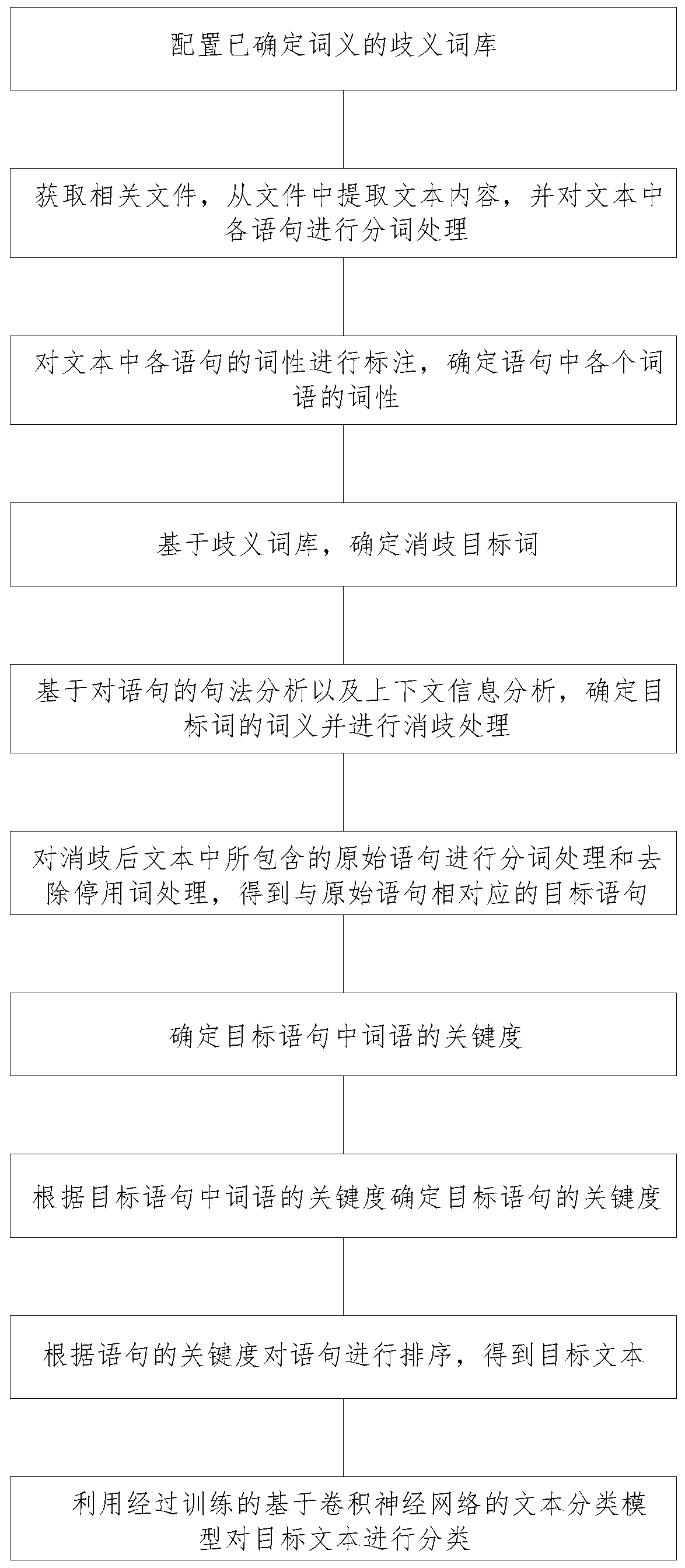
Text classification method based on word sense disambiguation convolutional neural network
InactiveCN110321434AOptimize classification methodImprove classification efficiencyNatural language data processingText database queryingPart of speechReturn statement
The invention discloses a text classification method based on a word sense disambiguation convolutional neural network. The method comprises the following steps of configuring an ambiguous word bank with determined word senses; obtaining a related file, extracting text content from the file, and performing word segmentation processing on each statement in the text; determining the part-of-speech of each word in the statement; determining a disambiguation target word; determining the meaning of the target word and performing disambiguation processing; performing word segmentation processing andstop word removal processing on original statements contained in the disambiguated text to obtain target statements corresponding to the original statements; determining the criticality of words in the target statement; determining the criticality of the target statement; sorting the statements according to the criticality of the statements to obtain a target text; and utilizing the trained textclassification model based on the convolutional neural network to classify the target text. According to the method, text classification can be carried out based on the word sense disambiguation convolutional neural network, the text classification method is optimized, the text classification efficiency and the text classification accuracy are improved, and time and labor are saved.
Owner:厦门美域中央信息科技有限公司
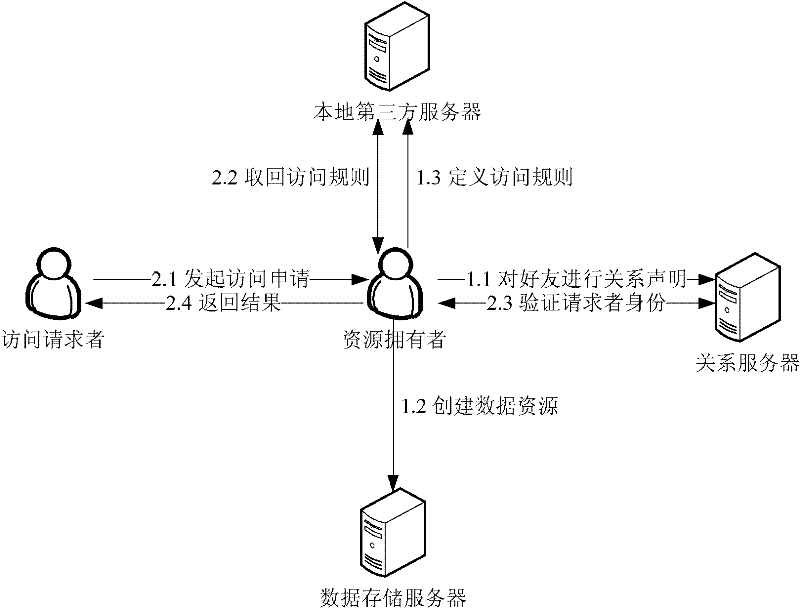
Social network user identity authentication method based on relation statement
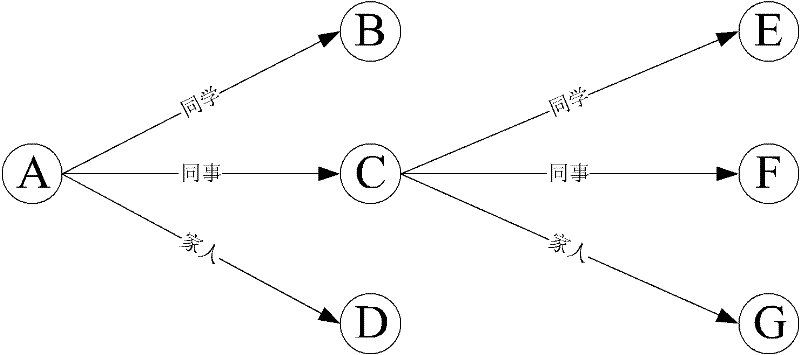
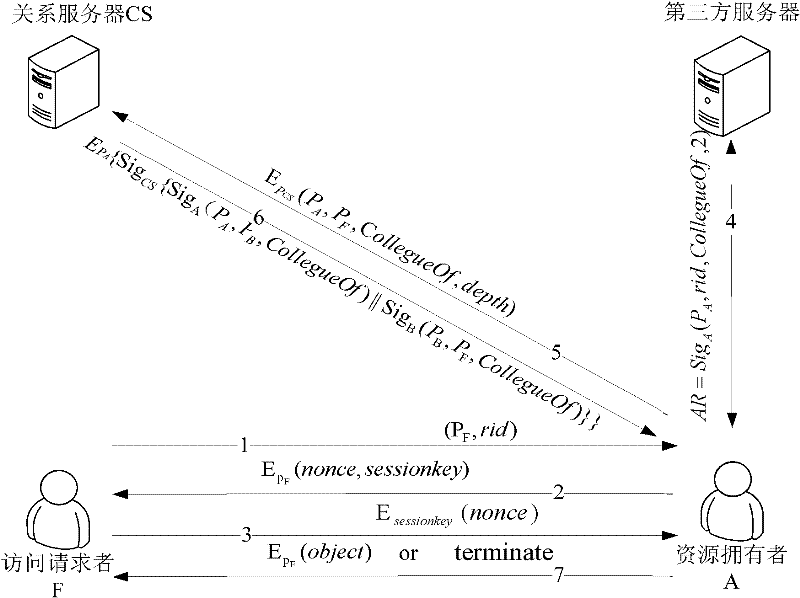
ActiveCN102035846BFit social characteristicsThe path is firm and crediblePublic key for secure communicationUser identity/authority verificationReturn statementSocial network
The invention discloses a social network user identity authentication method based on a relation statement, comprising the following three steps of: 1. issuing a relation statement; 2. defining an access rule; and 3. implementing relation authentication. A user determines the relation type between the user and a friend by issuing the relation statement to the direct-relation friend of the user; arelation server builds a relation path for the user according to the relation statement issued by the user; because each level of relation is signed by a relation statement publisher, the reliabilityof the level of relation can be effectively guaranteed so as to integrally improve the reliability of the relation path. The method is simple and convenient for operation and convenient for verification and has better practical value and wide application prospect in the technical field of network security.
Owner:BEIHANG UNIV
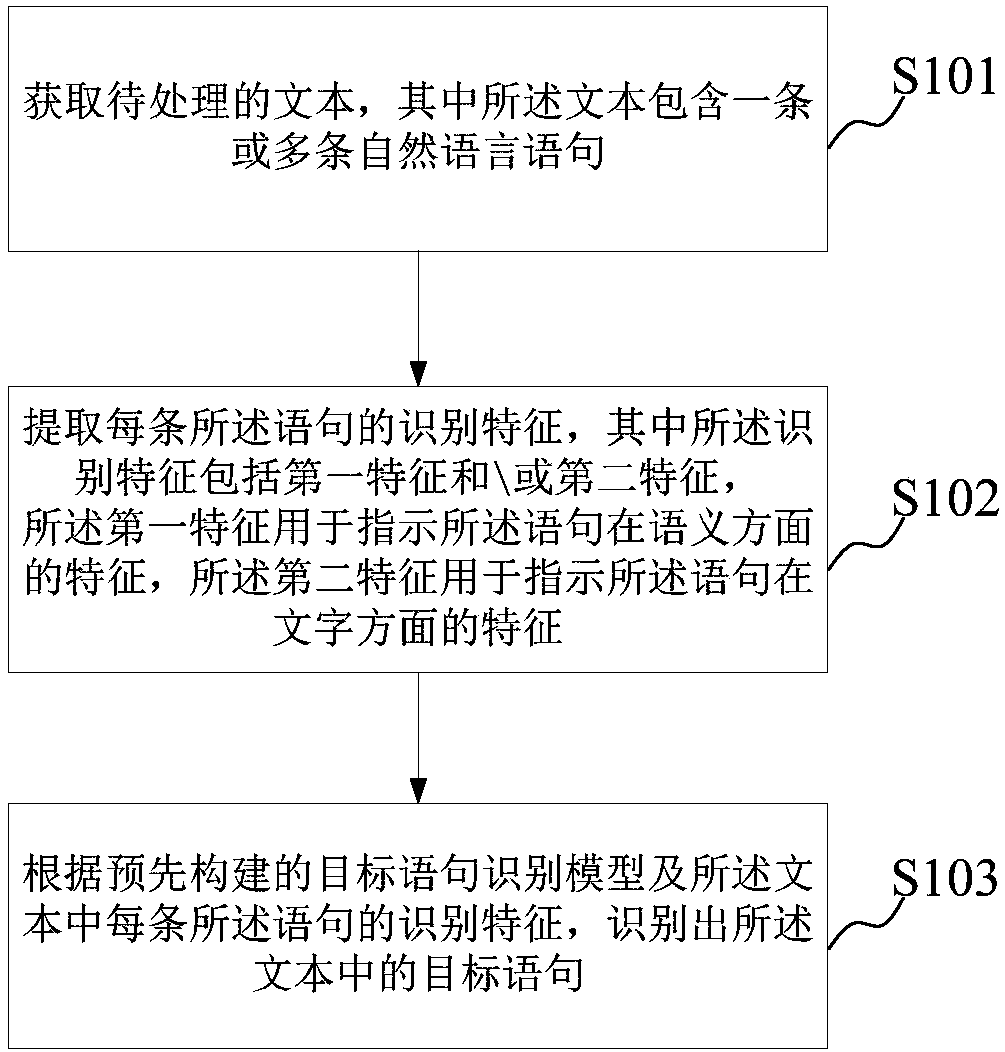
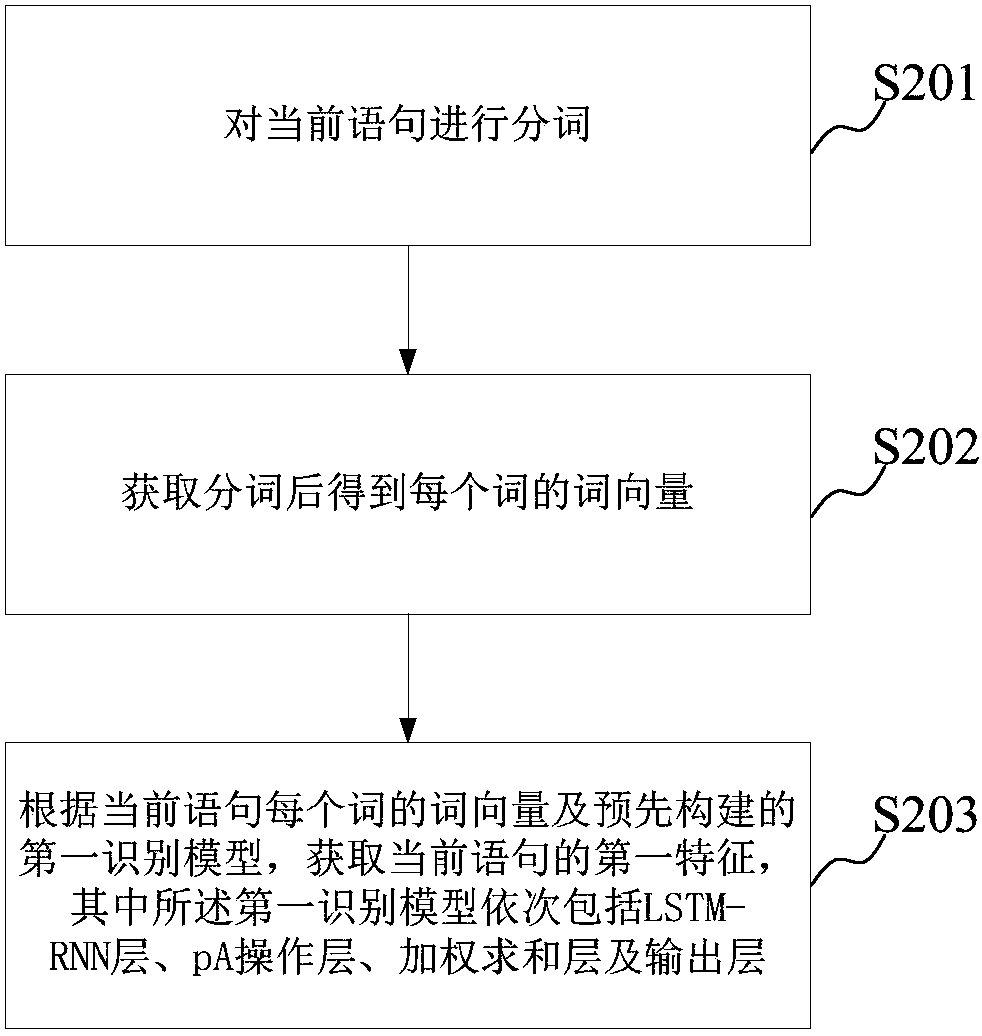
Target statement identification method and device
ActiveCN107783958AImprove recognition efficiencyThe recognition result is objectiveSemantic analysisSpecial data processing applicationsReturn statementHuman language
The embodiment of the invention provides a target statement identification method and device. The method includes the steps of obtaining to-be-processed text which includes one or a plurality of natural language statements; extracting recognition features of each statement, wherein the recognition features include a first feature and / or a second feature, the first feature is used for indicating features of the statement in the semantic aspect, and the second feature is used for indicating features of the statement in the text aspect; and identifying target statements in the text according to aprebuilt target statement recognition model and the recognition features of each statement in the text. According to the target statement identification method and device, statements belongs to the target statements (such as graceful statements) can be automatically found, and thus target statement identification efficiency is greatly improved; meanwhile, the identification standard is based on objective features and models, so that identification results are objective, and thus the subjectivity problem during manual identification is solved.
Owner:IFLYTEK CO LTD
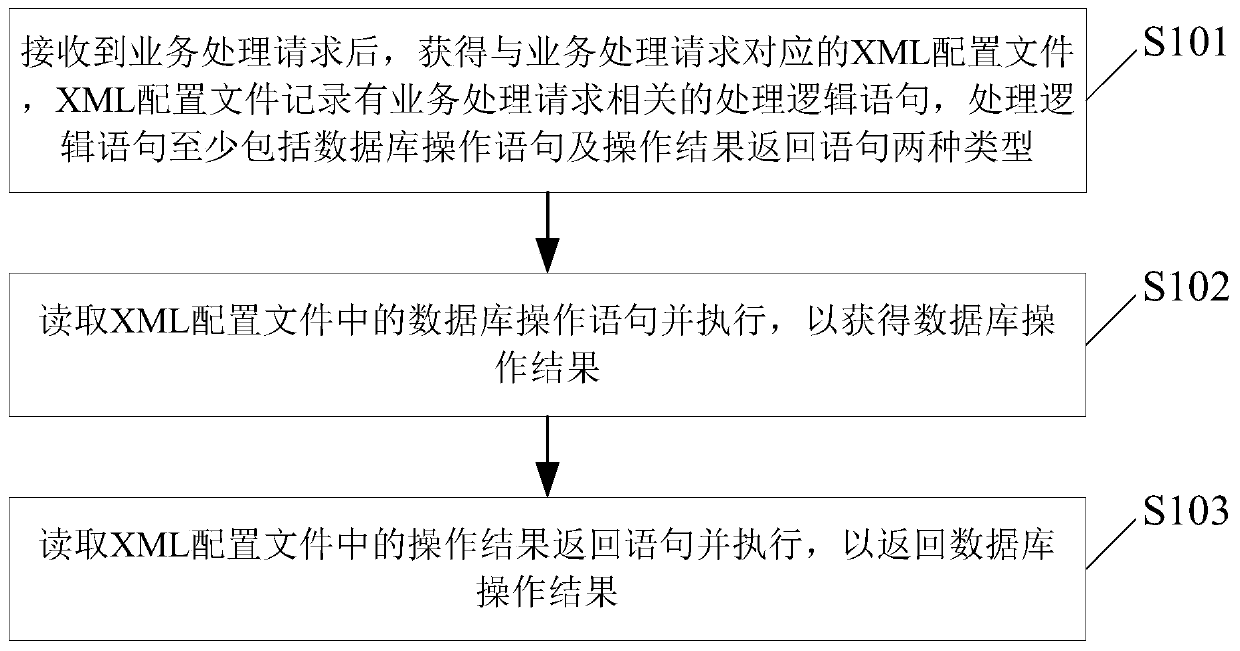
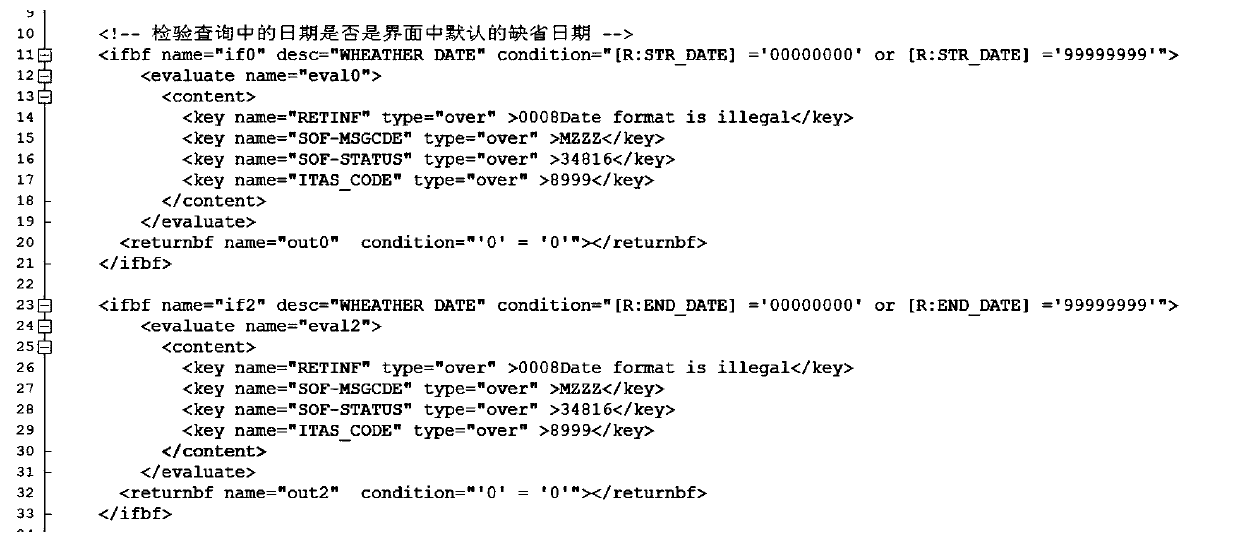
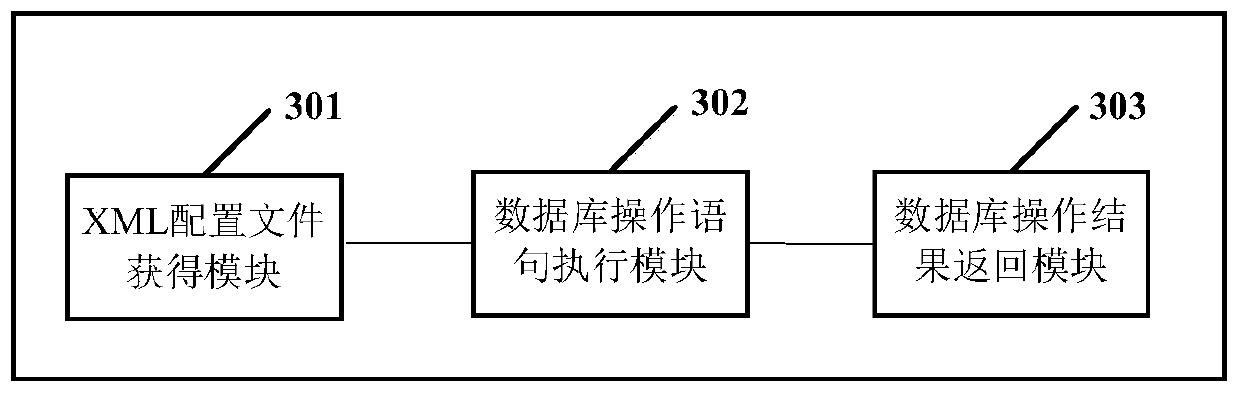
Database operation method and device
The invention provides a database operation method and device. The method comprises the following steps: receiving a service processing request; obtaining an XML configuration file corresponding to the service processing request, wherein a processing logic statement related to the service processing request is recorded in the configuration file, the processing logic statement at least comprises two types of a database operation statement and an operation result return statement; and reading and executing the database operation statement in the XML configuration file to obtain a database operation result, and reading and executing an operation result return statement in the XML configuration file to return the obtained database operation result. Compared with an existing mode of performingdatabase operation by using a JAVA file, the JAVA file is not used, the database operation statement is recorded in the XML configuration file, and the execution efficiency of the XML configuration file is superior to that of the JAVA file, so that the execution efficiency of the method and the device is higher than that of an existing database operation mode.
Owner:BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com