Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Open code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Open Location Code (OLC) is a geocode system for identifying an area anywhere on the Earth.
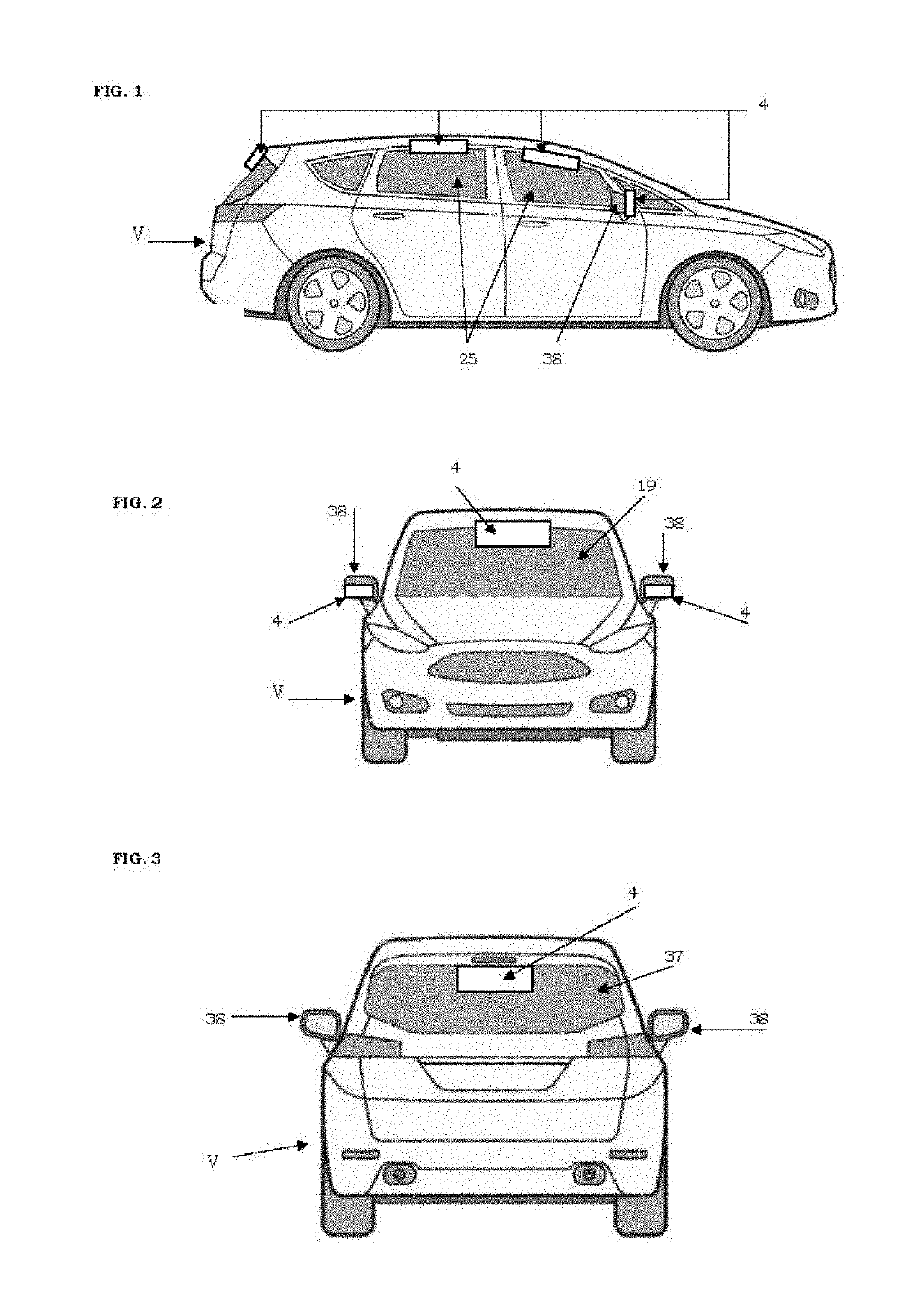
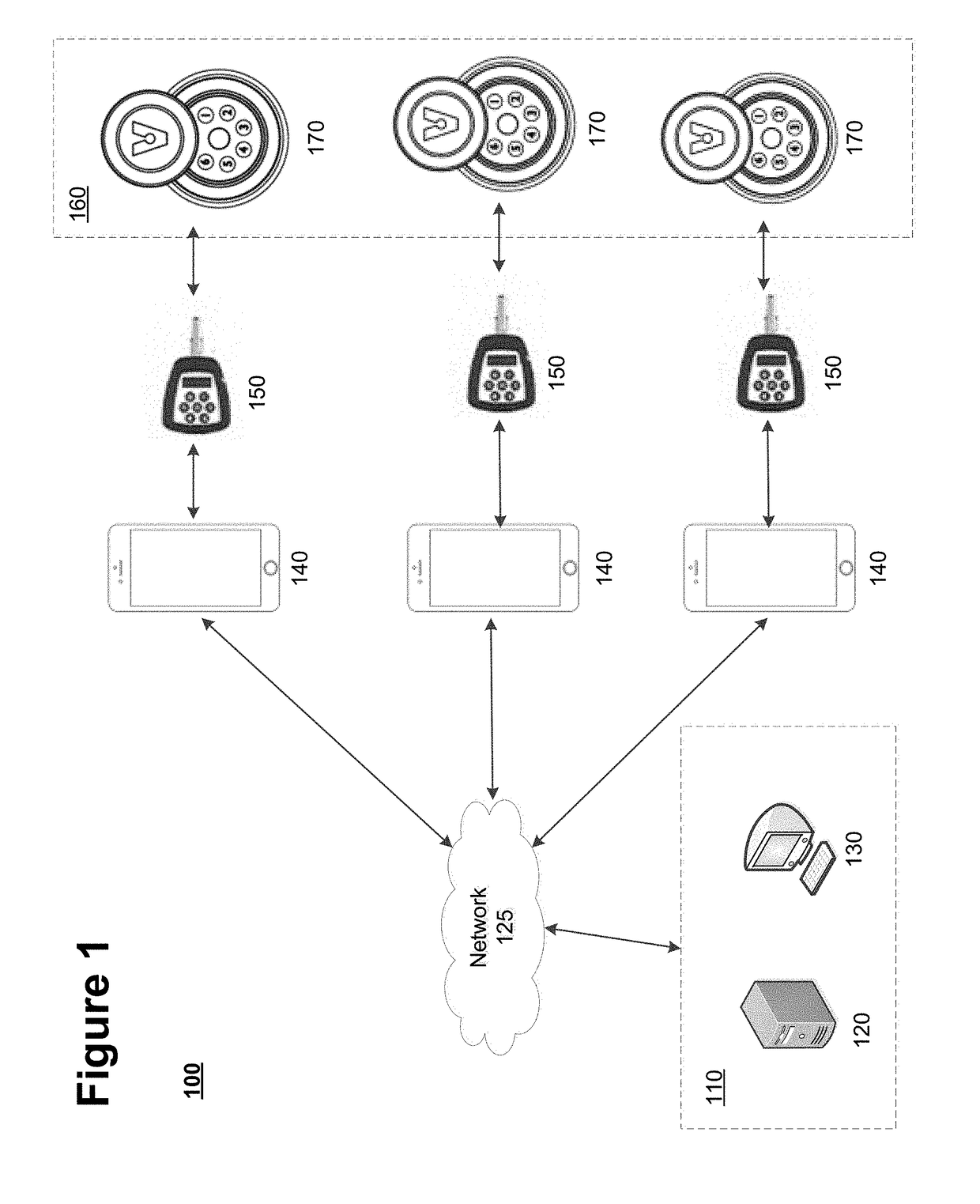
Alarm, safety device and device for expelling attackers for motor vehicles
ActiveUS10507793B1Stay safeImprove abilitiesAcoustic signal devicesAnti-theft devicesMobile vehicleDriver/operator
An alarm, safety device and device for expelling attackers for vehicles, to protect the vehicle and its occupants when stopped, parked or moving, containing a sound alarm, a lighting alarm, a surveillance camera inside the vehicle for face recognition of a non-authorized driver, a remote system for sending information to the police authority, having a smoke release system, surveillance cameras and sensors installed within boxes at external locations of the vehicle. The surveillance cameras monitor the external activity of the vehicle, the images as received by the cameras being analyzed in real time by an internal processing center, provided with an artificial intelligence processor, processing those images by a public domain algorithm, trained for recognizing violence-related objects, wherein the images are processed and transformed into data matrices which are submitted to a neural open code network, for recognizing the presence of violence-related objects in the hands of a person in or near the vehicle.
Owner:DE MOURA PARTIKA FELIPE BORIS
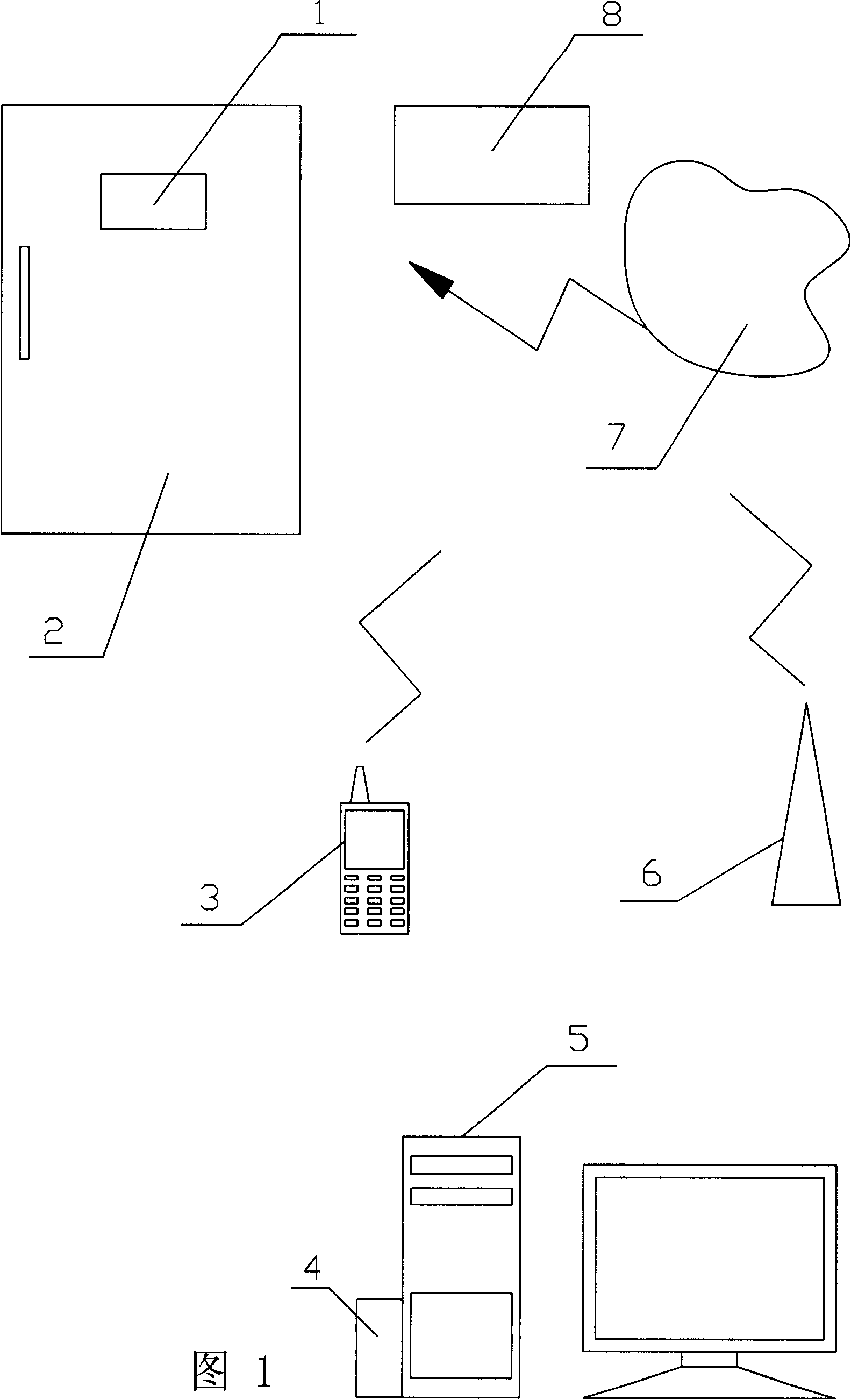
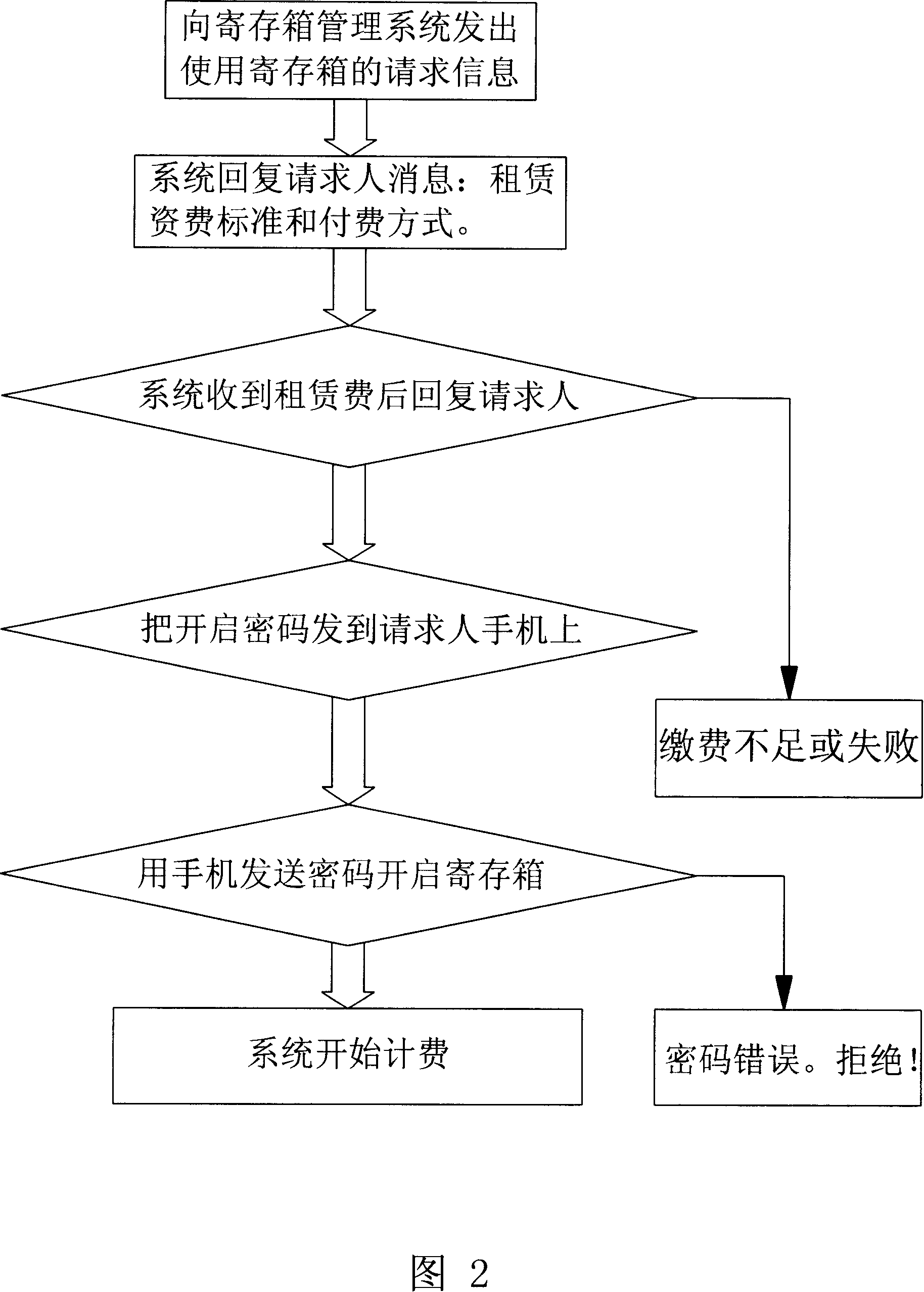
A system and method for mobile phone control register
InactiveCN101123654AShorten the timeImprove the efficiency of delivering goodsTelephonic communicationLogistics managementControl system
The present invention relates to a system and a method for controlling a safe box used in logistics and e-business activities. In a method for controlling the safe box with a cell phone, the unlock system of the safe box is connected with the network, the opening code of the safe box is in the management and control of a safe box management system, and safe box users can apply a safe box and open the safe box by the cell phone. The present invention efficiently utilizes handheld mobile terminals carried with people, and the safe box users transmit the opening code to the safe box unlock system to open the safe box.
Owner:孙学群
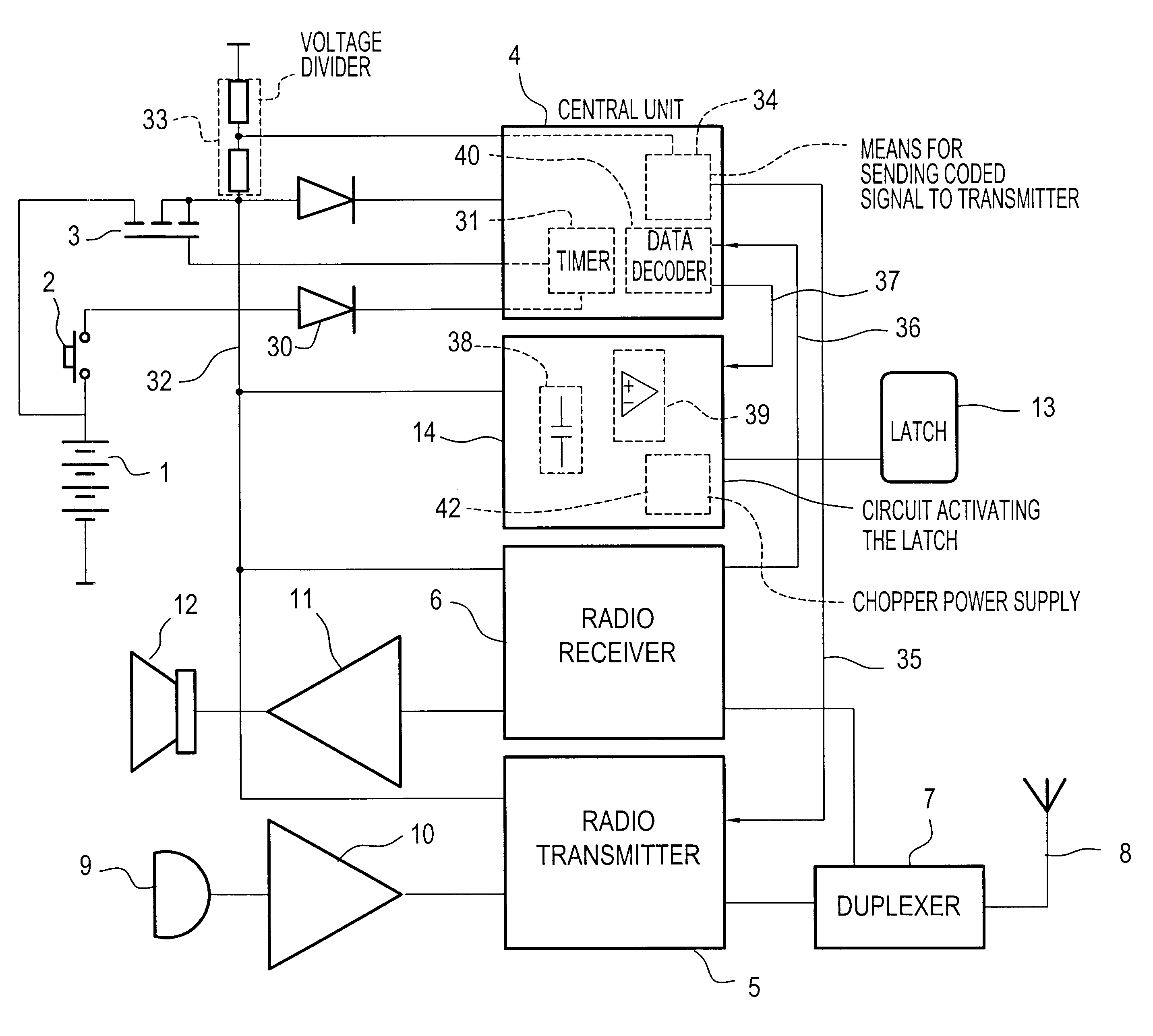
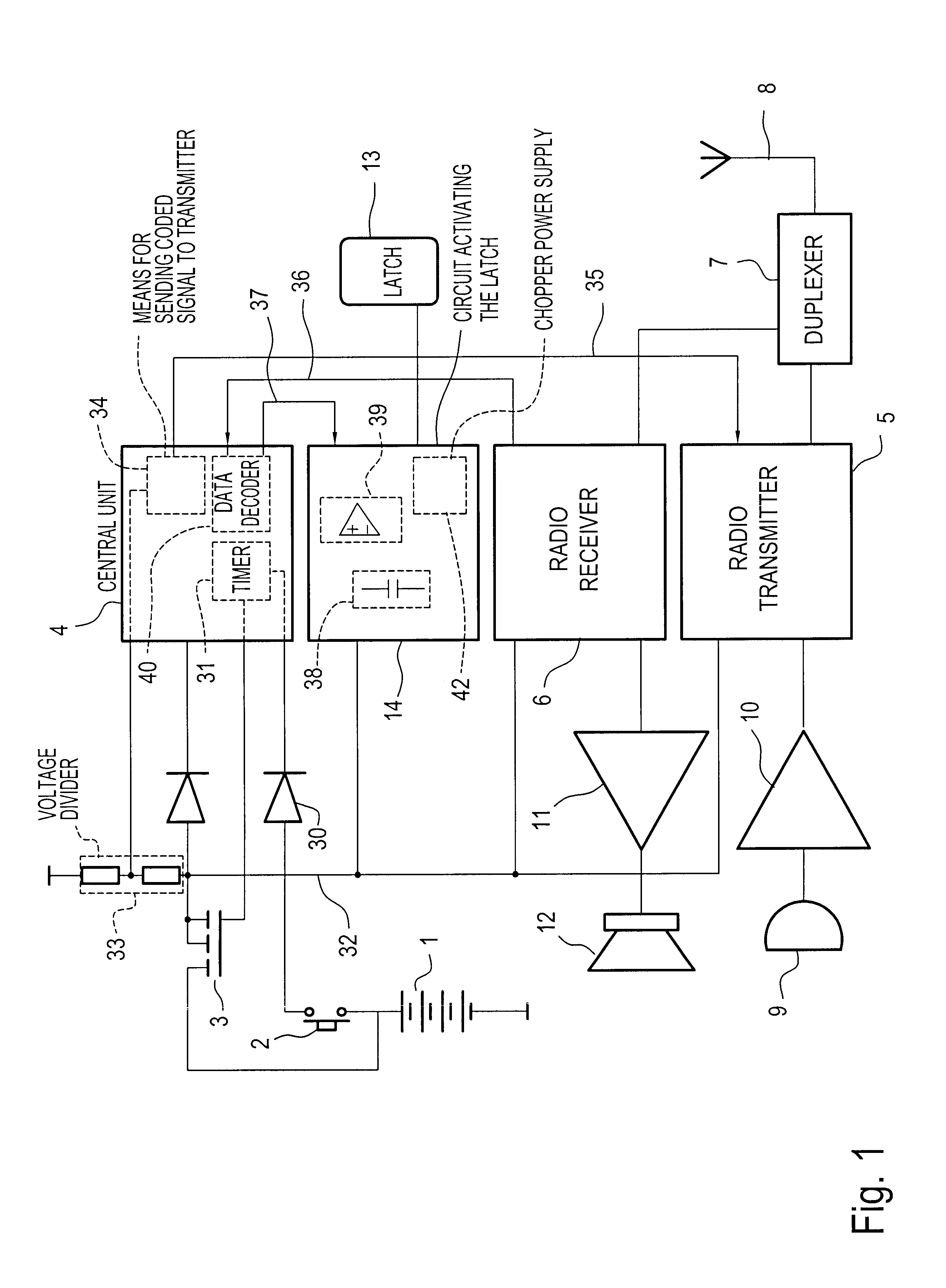
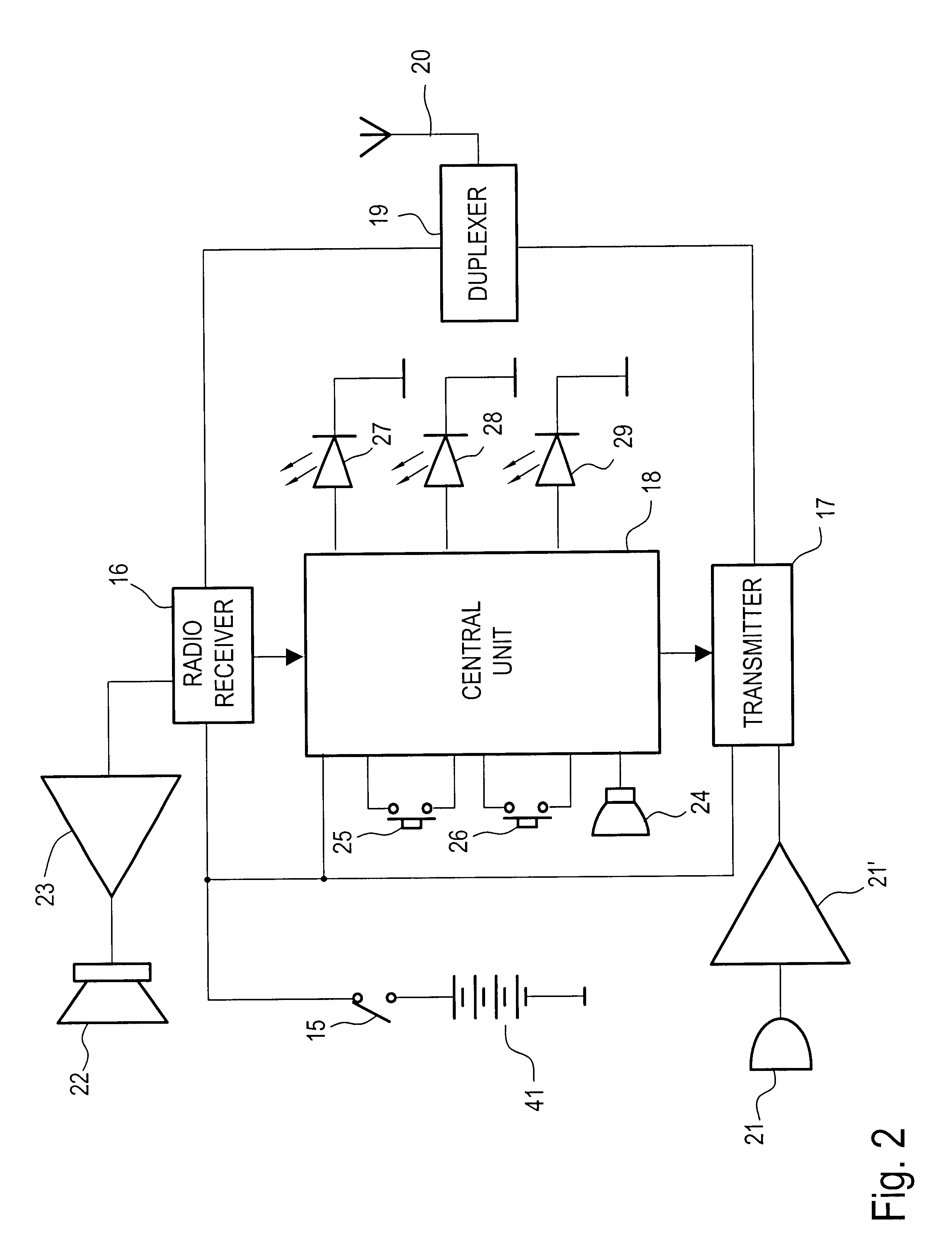
Wireless door intercom
InactiveUS6256479B1Low costQuality improvementUnauthorised/fraudulent call preventionEavesdropping prevention circuitsElectricityRadiotransmitter
A door intercom for a dwelling, the intercom comprising a street panel and an indoor set, the street panel being provided with a call button and being connected to an electric latch fitted to a door of the dwelling, the street panel including a radio transmitter and receiver, means for recognizing a latch-opening code received by the receiver, a stand-alone electrical power supply, and means for activating the electric circuit of the latch. The street panel also includes means for controlling electricity consumption firstly to put the street panel in a standby state in which its electricity consumption is practically zero while waiting for the call button to be pressed, and secondly to put it in an active state enabling a sound link to be established with the indoor set, and enabling the electric circuit of the latch to be activated when the latch-opening code is recognized, and the means for activating the electric circuit of the latch have the necessary amount of electrical energy available.
Owner:COMPTOIR FR DE LINTERPHONE
Method of free no-repeater mobile communication
InactiveCN101540960AIncomparable superiorityLifestyle changesNetwork topologiesBroadcast service distributionMobile phoneEthernet communication
The invention relates to a method of free no-repeater mobile communication. A method that a radio signal is directly transmitted and received between mobile phones is adopted, and the mobile communication between a mobile phone and a mobile phone, a mobile phone and a computer and two or more parties of users between computers is realized without handshaking and relay service from telecom operators. The communication method can be call ethernet communication for short; the ethernet communication well solves the problem of information asymmetry, is like the seventh sense organ of a person, and enables the person to remotely sense the identity information and other any information willingly disclosed by other persons or the unit at the distance of a plurality of meters, hundreds of meters and even a plurality of kilometers; both the individual and the unit can issue the own information to the space ranged from a plurality of kilometers to a dozen kilometers around to provide for searching and sensing for other persons; and each user has one open code or code name, and even if you are strangers, you can also send a short message or call him or her in the remote place for greeting.
Owner:周向进
Strong discrimination method of enciphered mode by public key cryptographic algorithm
InactiveCN1658553APrevent eavesdroppingEasy to managePublic key for secure communicationUser identity/authority verificationCommunications securityRelevant information
This invention discloses a strong distinguishing method adopting open code key calculation encryption mode. The process is:found wireless chain-channel, the identifier sends the identification request to the user, and return the identification information to the server, the server find the user open code key and the information integrality code key from the database to found the dialog with the user, the server and the user produce the random numbers, encode the open code key for each other, decode the code key through the identifier, compare self random number with the random number changed by the opposite side and judge whether the identification is successful. Repeat this process for three times, and the server and the user calculate the whole identification and exchange integrality value through encoding and decoding code key and the information integrality code key and the relative information. The identifier judges whether the identification is successful, decides whether the user can get into the network and realizes the online communication of users and the broadcasting of the base station. The strong points are that it realizes the insurance of the identification of the user and the server and the safety of the communication.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
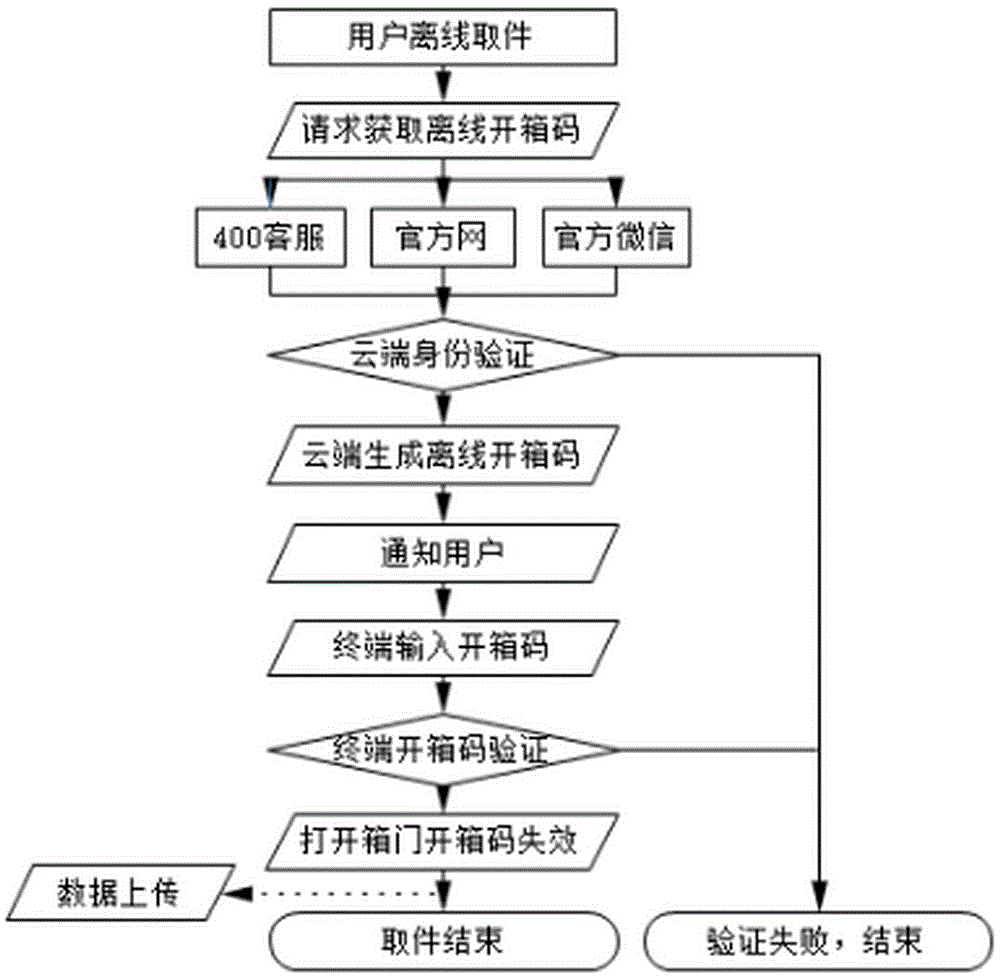
Offline box opening method of intelligent storage cabinet
InactiveCN104637185AReduce workloadSolve the problem that cannot be taken outData processing applicationsApparatus for meter-controlled dispensingUser inputComputer terminal
The invention discloses an offline box opening method of an intelligent storage cabinet. The method includes: a user requests to acquire an offline box opening code; a cloud server performs identity authentication; after the identity authentication is passed, the cloud server generates the offline box opening code and transmits the offline box opening code to a user; the user inputs the offline box opening code into an intelligent storage cabinet terminal, and a box door is opened after the verification of the offline box opening code is passed. By the offline box opening method, workload of manual processing by staff is reduced, and the problem that express cannot be taken out due to the misoperation of the user.
Owner:CHENGDU WOLAILA GRID INFORMATION TECH
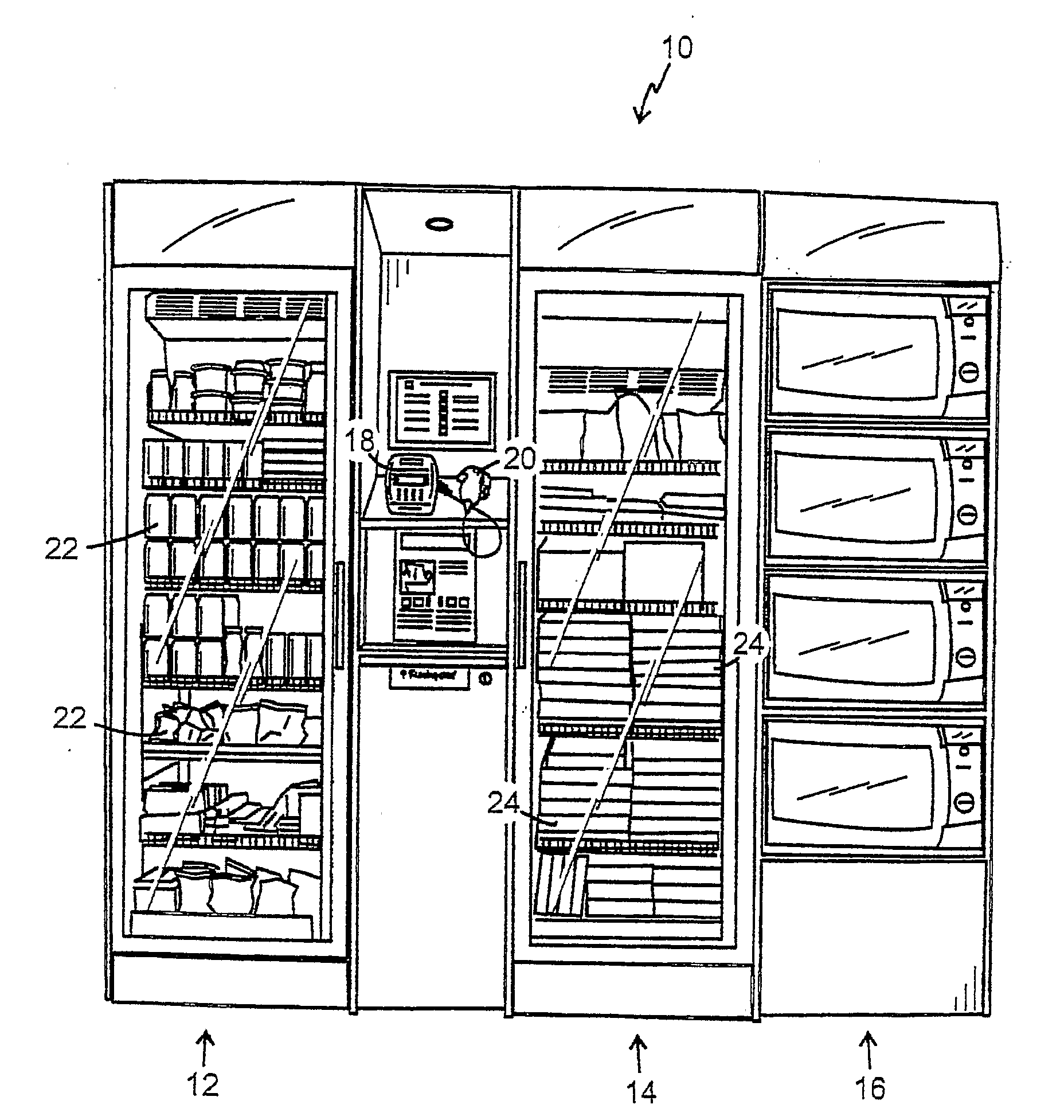
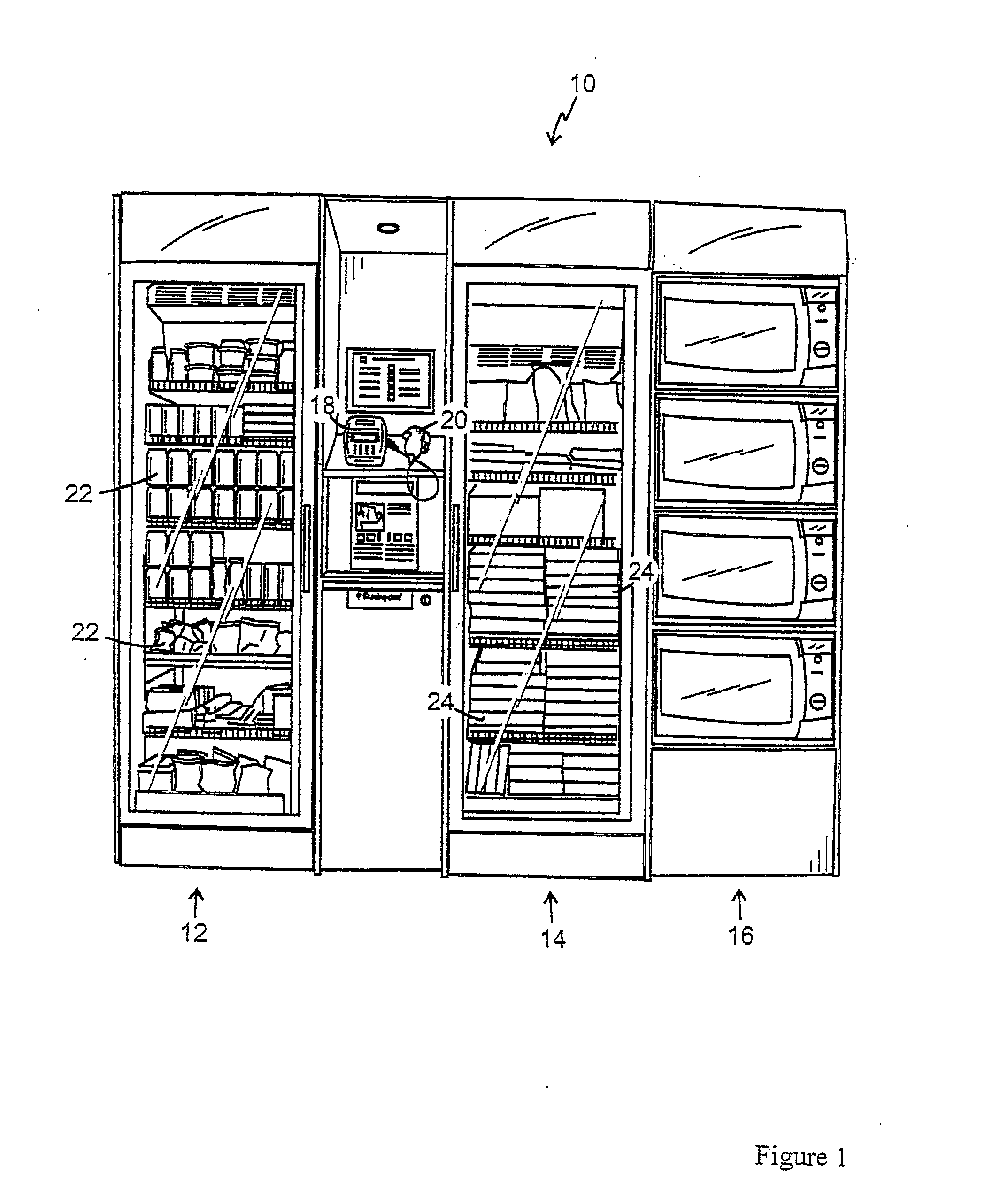
Storage-Cabinet and Method for Selling Frozen and/or Refrigerated Goods From Such a Locked Storage-Cabinet
InactiveUS20090094127A1Avoid buyingControlling coin-freed apparatusCash registersTransaction dataEngineering
The invention is related to a storage cabinet (12, 14or at least one of refrigerated and frozen goods (22, 24) for sale through that the cabinet door opens via entering of a door opening code in a payment terminal (18) with scanning equipment (20) for reading of codes which identify said goods (22, 24). The goods which are purchased by lifting them out of the cabinet (12, 14) are scanned with the scanning equipment (20) and are debited to a purchasing account associated with the door opening code. The cabinet is locked when the cabinet door closes. Further the cabinet rests (12, 14) on a weighing device (30). If a predetermined difference between the scanned goods' (22, 24) weight and the cabinet's (12, 14) weight occurs, the weight difference is registered in a transaction data file associated with the door opening code, wherein loss of goods (22, 24) is registered on a known purchasing account.
Owner:ENQVIST ANDERS
Stream media content downloading method based on data characteristic
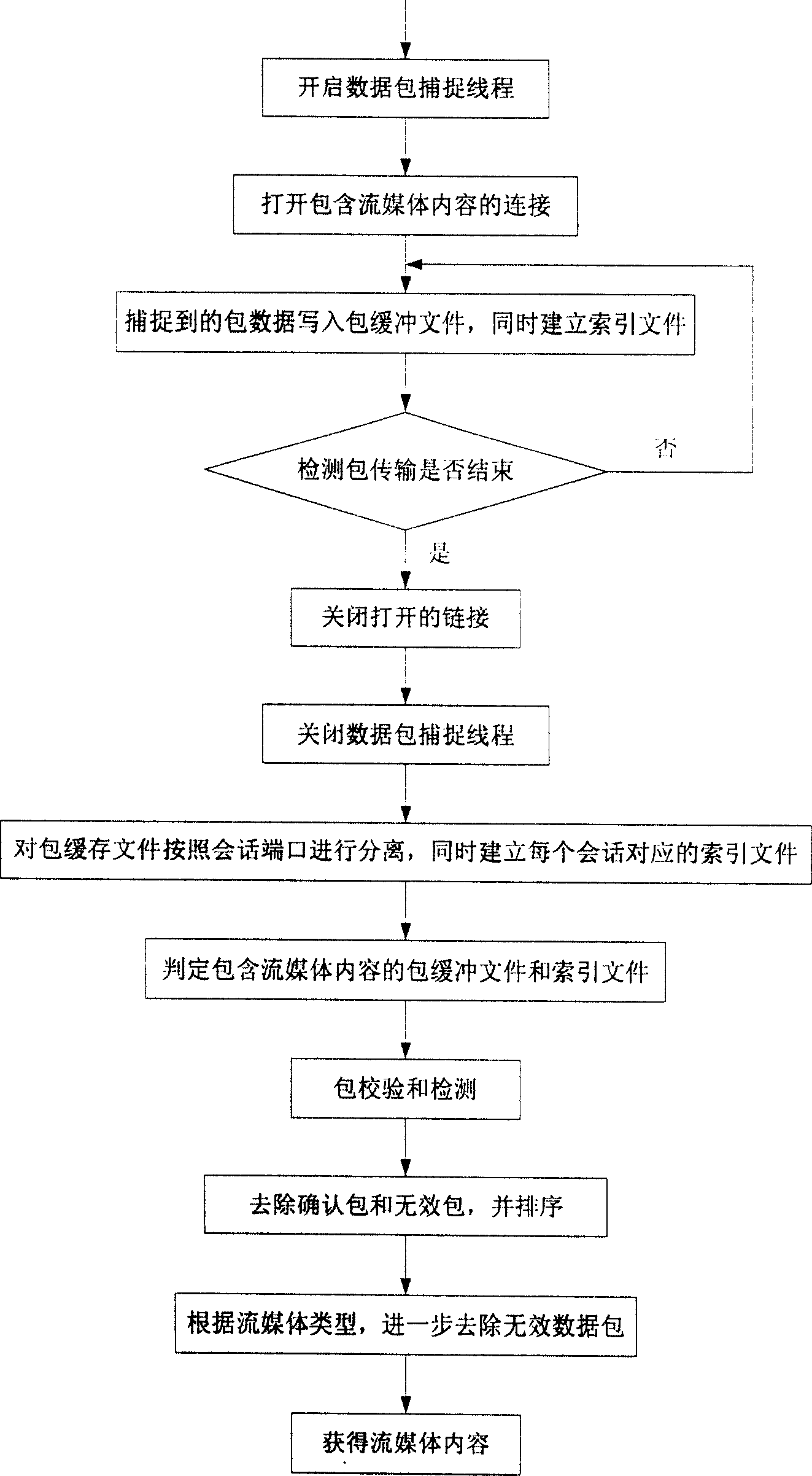
InactiveCN101155122AReduce performanceSolve the problem of not being able to downloadData switching networksComputer hardwareData stream
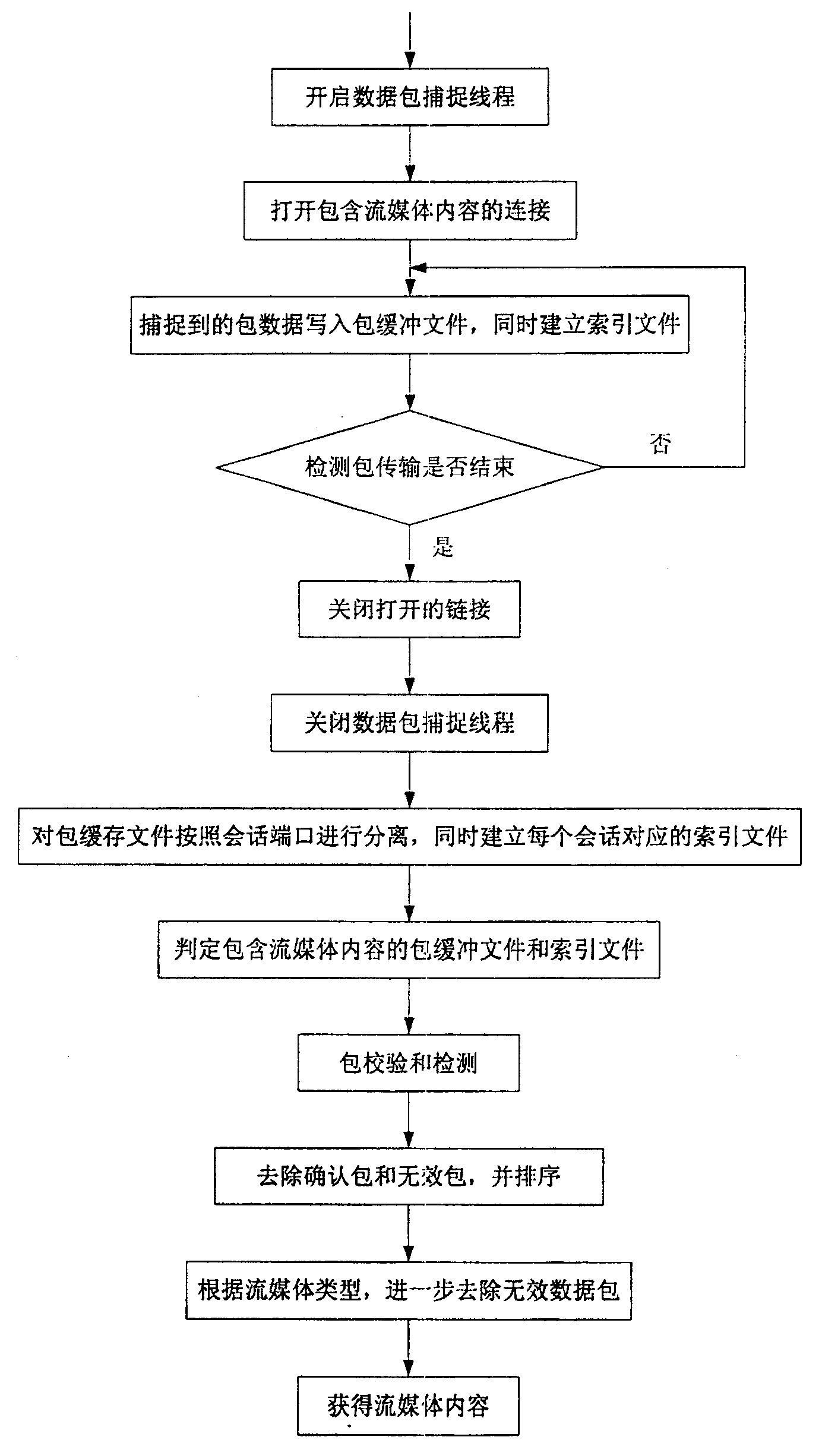
The invention relates to a downloading method of stream media content based on data character, comprising: starting data package seizing wire; opening the link address containing video content and buffer memorizing the seized data package in the form of binary data stream in a buffer file. The buffer file is read and a number of conversational files are separated based on the conversation terminal. On the basis of the size of the conversational file and the opening code of the media content in the said file, the said conversational file is determined whether the media content is in the conversational file or not, and the conversational file without the media content is deleted. The data packages in the conversational file are read in turn based on the conversation index file and the retransmission package and error package are deleted on the basis of the sequence number and affirm number in the data package, and then the effective media data package is ordered and stored in the new media content file. Only page address with media content is provided to accurately download the required media content without reducing the website performance of stream media.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Defense withdrawing and arranging electronic lock control system and external and internal opening control method
InactiveCN104746965ANo interferenceRealize automatic disarmNon-mechanical controlsElectric permutation locksControl systemEngineering
The invention discloses a defense withdrawing and arranging electronic lock control system and external and an internal opening control method. The system comprises a fingerprint electronic lock part arranged on a door and an out-door early warning and alerting part arranged outside the door. The fingerprint electronic lock part comprises a fingerprint door lock, an open-close travel switch, a lock-use radio transmitting and receiving circuit, a lock-use micro processor circuit and a lock-use power supply circuit. The open-close travel switch is connected with the lock-use radio transmitting and receiving circuit through the lock-use micro processor circuit, is arranged in the fingerprint door lock, and is used for detecting an open-close state of a lock. When the fingerprint door lock is in a correct fingerprint unlocking state, a defense withdrawing code signal is transmitted by the lock-use radio transmitting and receiving circuit. When the fingerprint door lock is in an unlocking state, a radio door opening code signal is transmitted by the lock-use radio transmitting and receiving circuit. When the fingerprint door lock is in a locked state, a radio door closing code signal is transmitted by the lock-use radio transmitting and receiving circuit. The defense withdrawing and arranging electronic lock control system and the external and internal opening control method have the advantages that the utilization is safe, the operation is convenient and fast, the security and protection effect is good, and defense withdrawing and defense arranging can be automatically achieved.
Owner:陈宏乔
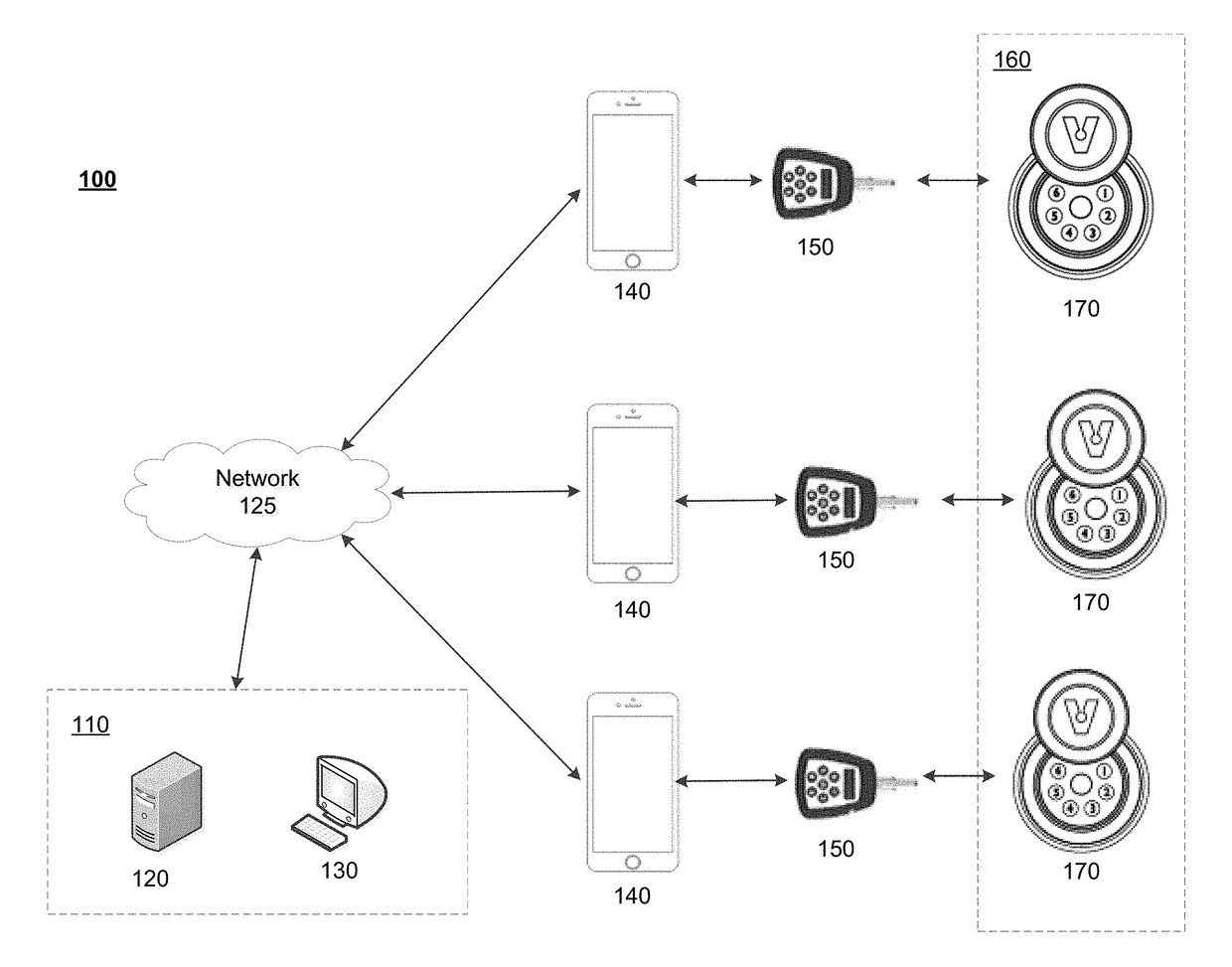
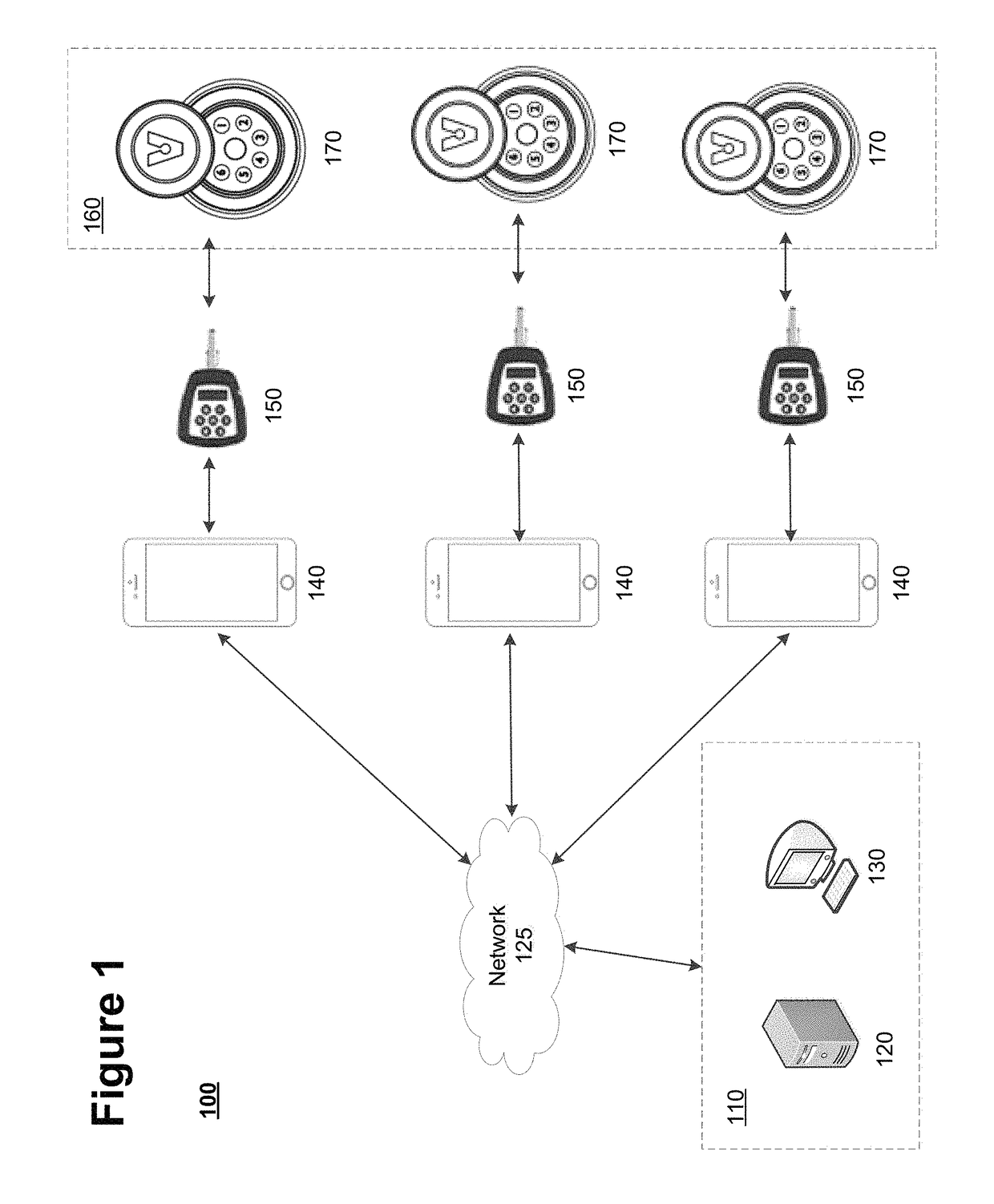
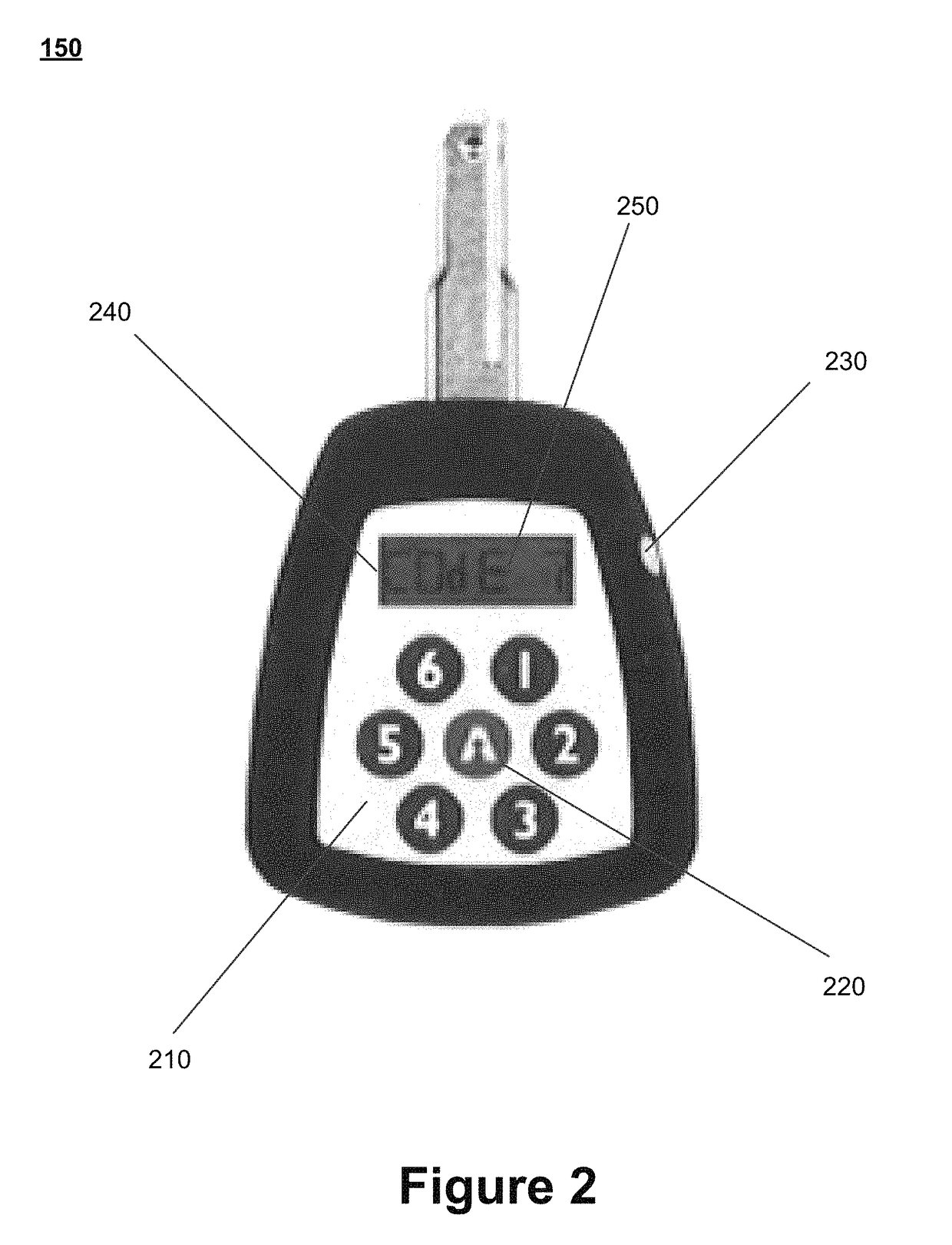
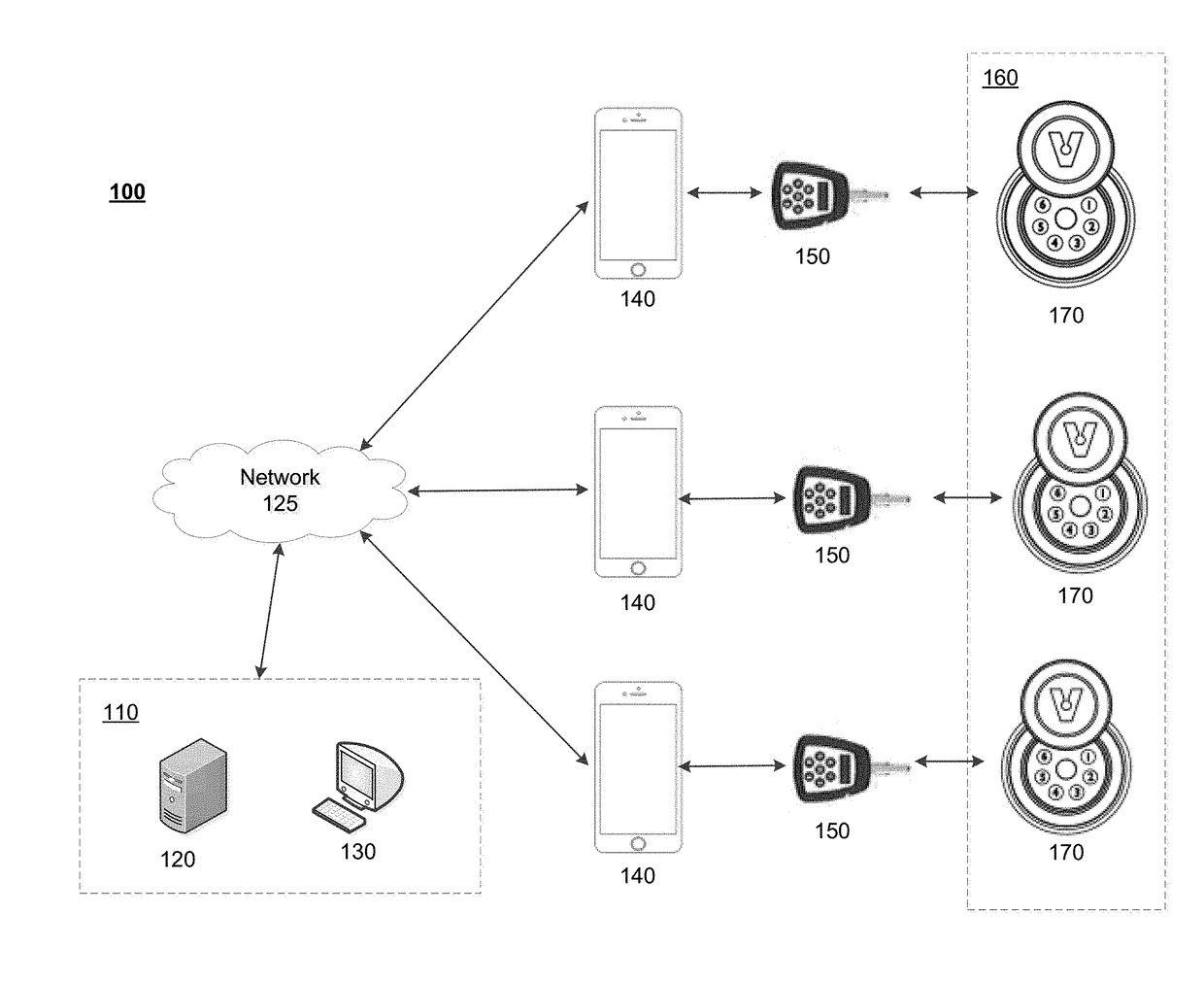
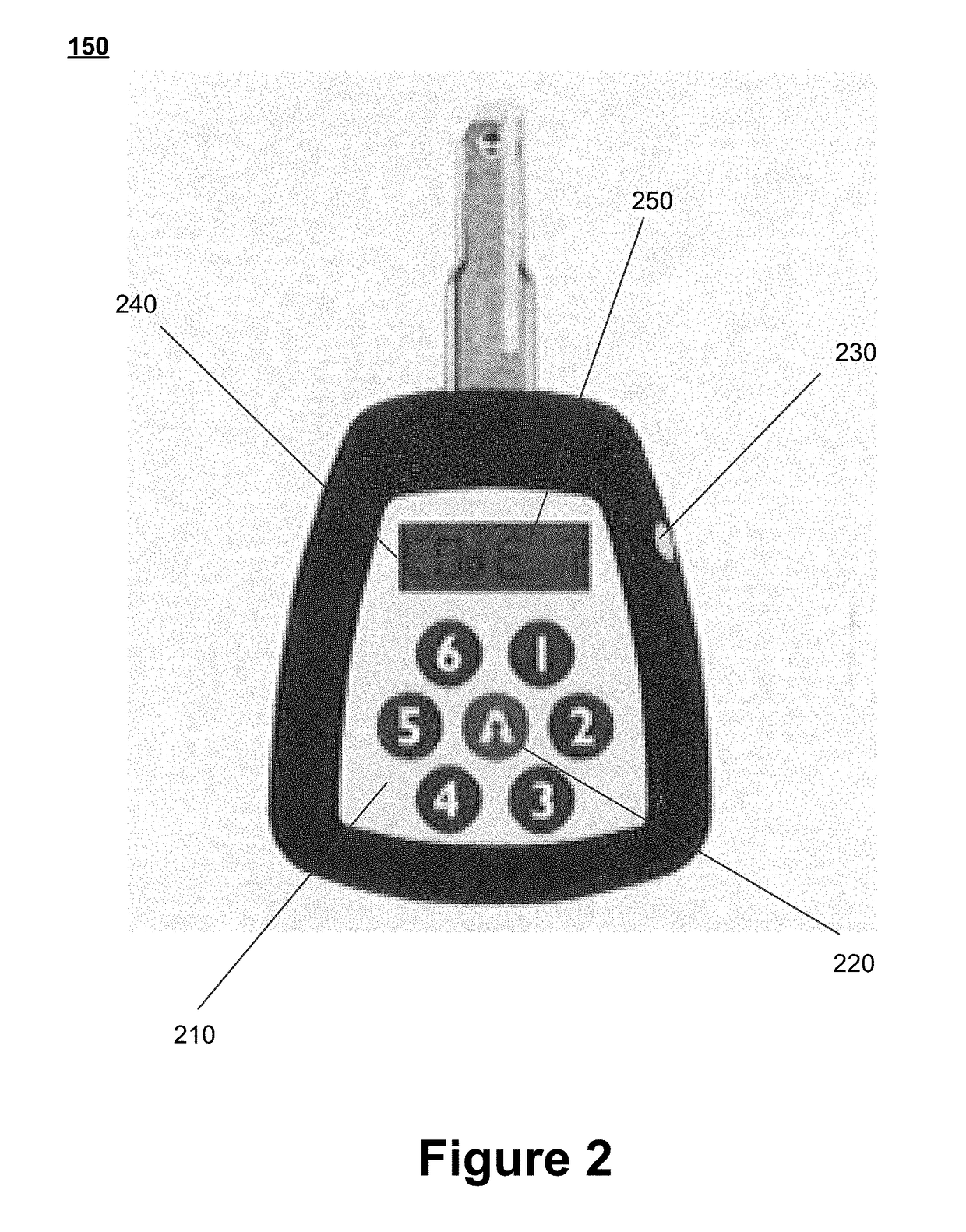
Systems and methods for remote access rights and verification
ActiveUS9984524B2Increase the number ofAvoid energyChecking time patrolsDigital data authenticationControl systemNetwork operations center
An access control system is provided that enables a network operations center to manage and control access to a plurality of remote sites and to verify servicing of the remote sites. Individuals in possession of electronic programmable keys can be provided opening codes to activate their keys while in the field, and to enable the keys to access one or more electronic locks located at the remote sites. Usage information associated with the utilization of the electronic programmable keys at the remote sites is stored on the electronic programmable keys. A lock attendance code is generated by the keys to verify attendance at the remote locations. The lock attendance codes are then transmitted to the network operations center where they are decoded to verify servicing of the remote sites.
Owner:ACSYS HLDG LTD
Systems and methods for remote access rights and verification
ActiveUS20170213406A1Increase the number ofAvoid energyChecking time patrolsDigital data authenticationControl systemNetwork operations center
An access control system is provided that enables a network operations center to manage and control access to a plurality of remote sites and to verify servicing of the remote sites. Individuals in possession of electronic programmable keys can be provided opening codes to activate their keys while in the field, and to enable the keys to access one or more electronic locks located at the remote sites. Usage information associated with the utilization of the electronic programmable keys at the remote sites is stored on the electronic programmable keys. A lock attendance code is generated by the keys to verify attendance at the remote locations. The lock attendance codes are then transmitted to the network operations center where they are decoded to verify servicing of the remote sites.
Owner:ACSYS HLDG LTD
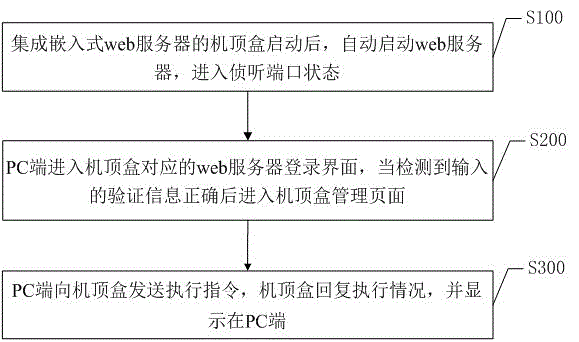
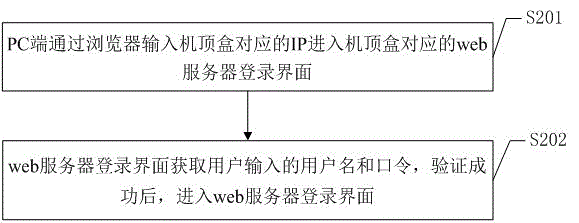
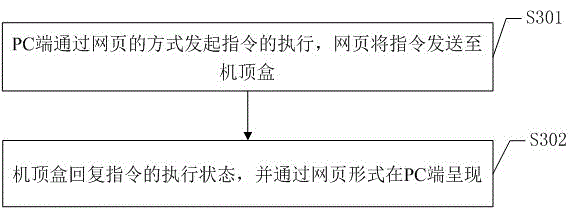
Method and system for debugging set-top box based on embedded web
InactiveCN106534130AEasy maintenanceEasy to upgradeTransmissionSelective content distributionWeb serviceEmbedded system
The invention discloses a method and system for debugging a set-top box based on an embedded web. The method comprises the following steps: automatically starting a web server to enter a listening port state after the set-top box integrated with the embedded web server is started; enabling a PC to enter a corresponding web server log-in interface of the set-top box and then enter a set-top box management page when it is detected that input verification information is correct; enabling the PC to send to the set-top box an execution instruction, and enabling the set-top box to return an execution state and display the execution state on the PC. The method can debug the set-top box through the network by using the PC without the need of welding a special interface on the set-top box so as to save production cost. All the debugging work is carried out in the set-top box, which is beneficial to the maintenance and upgrading of the set-top box. It is safer than an open code debugging method to control the debugging instruction via the network.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Chitinase gene of pea bean and its amino-acid squence of coded product
InactiveCN1597963AStrong resistanceIncreased chitinase activityHydrolasesGenetic engineeringBiotechnologyIntein
The invention relates to a bean chitinase gene and the aminophenol sequence of its coded product, relating to a new gene sequence. It has a registered number AY357300 in GenBank, 1088bp long, where T, C, G and A are 232 (21.3%), 330 (30.3), 276 (25.4%) and 276 (23.0%), respectively, there is a starting codon ATG at 7bp site, there is a terminating codon TGA at 988bp site, and there is a poly (A) additional signal at 1008bp and 1082bp sites, respectively. It has no intron but complete 981bp-long open code read frame, coding 327 aminophenols. Its coded product has molecular weight of 35.3kD and equipotential point pI at 7.93. The invention separates a chitinase gene from bean genome, enlarges plant anti-fungal disease gene resources, thus providing richer excellent gene candidates for gene engineering of resisting plant diseases and insect pests and improving plant variety.
Owner:HARBIN NORMAL UNIVERSITY
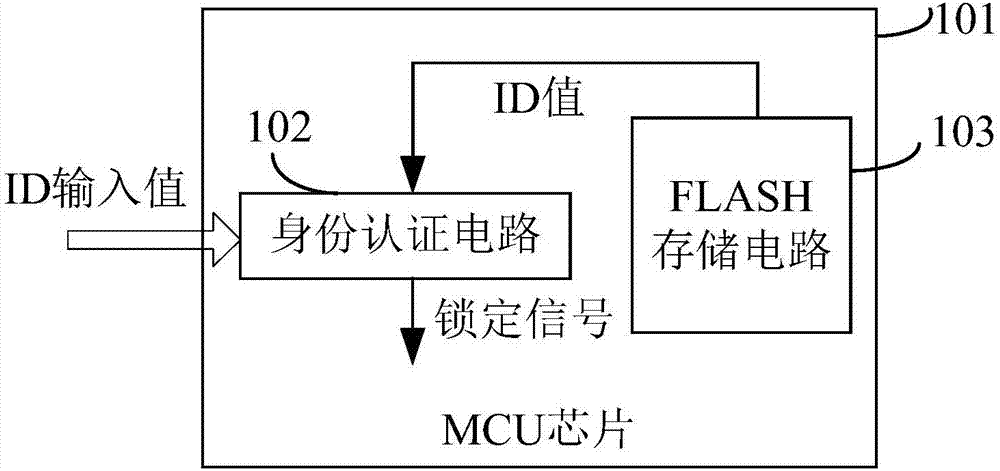
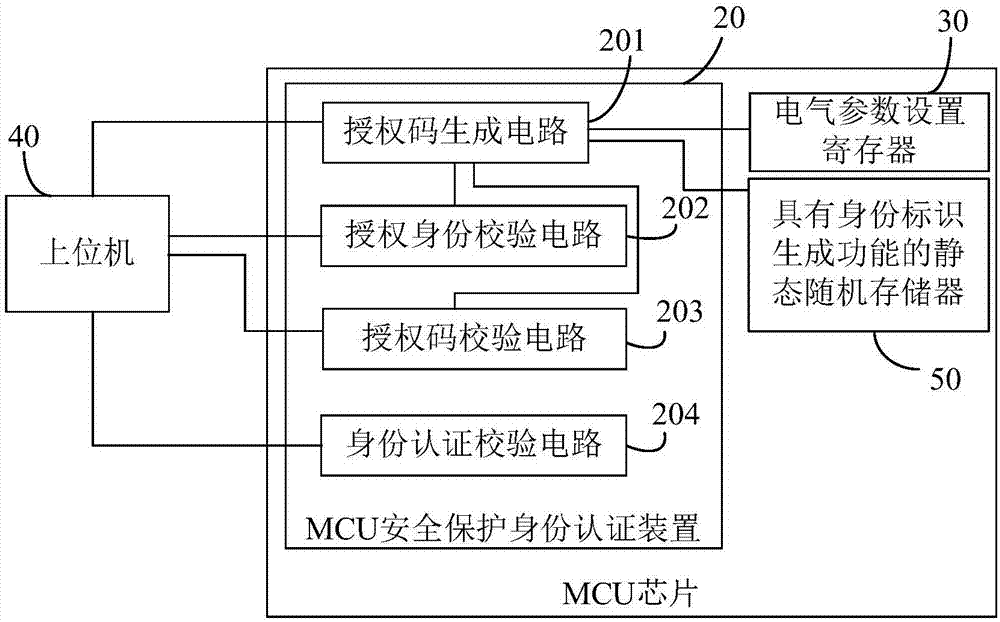
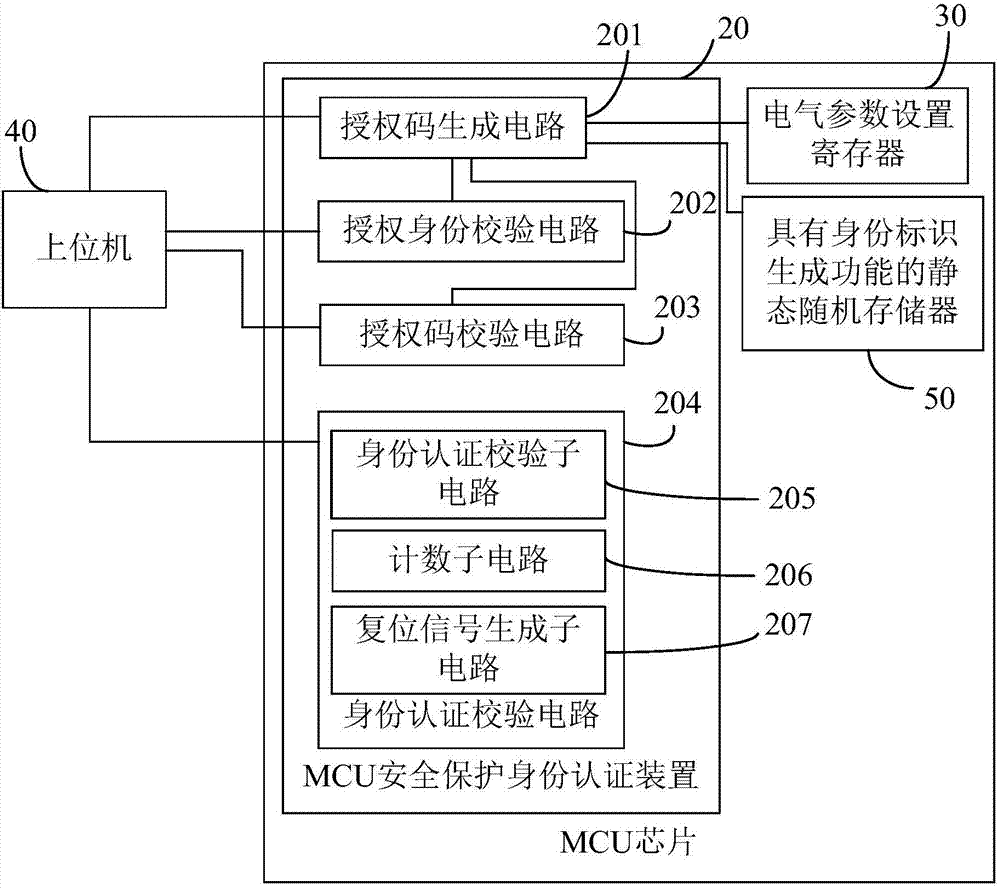
MCU security protection identity authentication device and method
ActiveCN107977568AInternal/peripheral component protectionDigital data authenticationStatic random-access memoryProcessor register
The invention provides an MCU security protection identity authentication device and method, and relates to the technical field of computer chip security. An authorization code generation circuit in the device generates an authentication code according to a value of an electrical parameter setting register or a value of a static random access memory with an identity identification generation function or a combination of the two values; an authorization identity checking circuit receives an authorization opening code sent by an upper computer and checks the authorization opening code; the authorization code generation circuit sends the authentication code to the upper computer after the authorization identity checking circuit checks the authorization opening code successfully; the authorization code checking circuit receives an authorization check code sent by the upper computer, checks the authorization check code according to the authorization code, and sends an authorization code checking success instruction to the upper computer after checking the authorization check code successfully; and the identity authentication checking circuit receives an identity authentication code sentby the upper computer and checks the identity authentication code to generate an authentication result in order to determine whether an MCU chip can be normally operated or locked according to the authentication result.
Owner:RENESAS SEMICON DESIGN BEIJING CO LTD
Gasoline motor car anti-theft system
InactiveCN1668006AIncrease the difficultyBig oil supply difficultyAnti-theft devicesUser identity/authority verificationOpen codeAnti theft
This invention is composed of a remote controller, an executor, its antenna and a control program, among which, the remote controller is carried by a car legal user, the executor and an electric gasoline pump are integrated in an oil tank, the executor antenna is mounted outside of the oil tank, a control chip is on the CB in the remote controller and executor, a control program is stored in the control chip. The remote controller emits an identifying code and last time stored lock-open code, the executor identifies the identity and compares the two codes to turn on the working circuit of the pump, generates a new control code and sends it to the remote controller together with the identify code and encodes the new control code to new comparing code to be stored, the new control code is encoded to new lock-open code and stored after the controller identifies the identity
Owner:时国庆
Receiving method and device of drone delivery, storage medium and express box
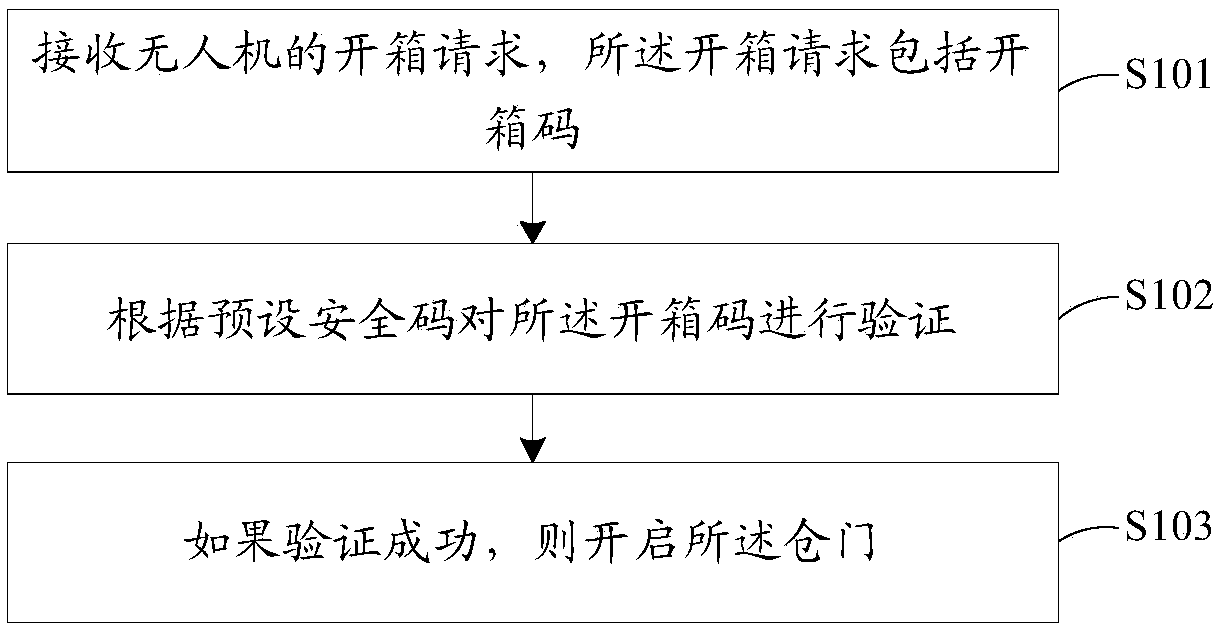
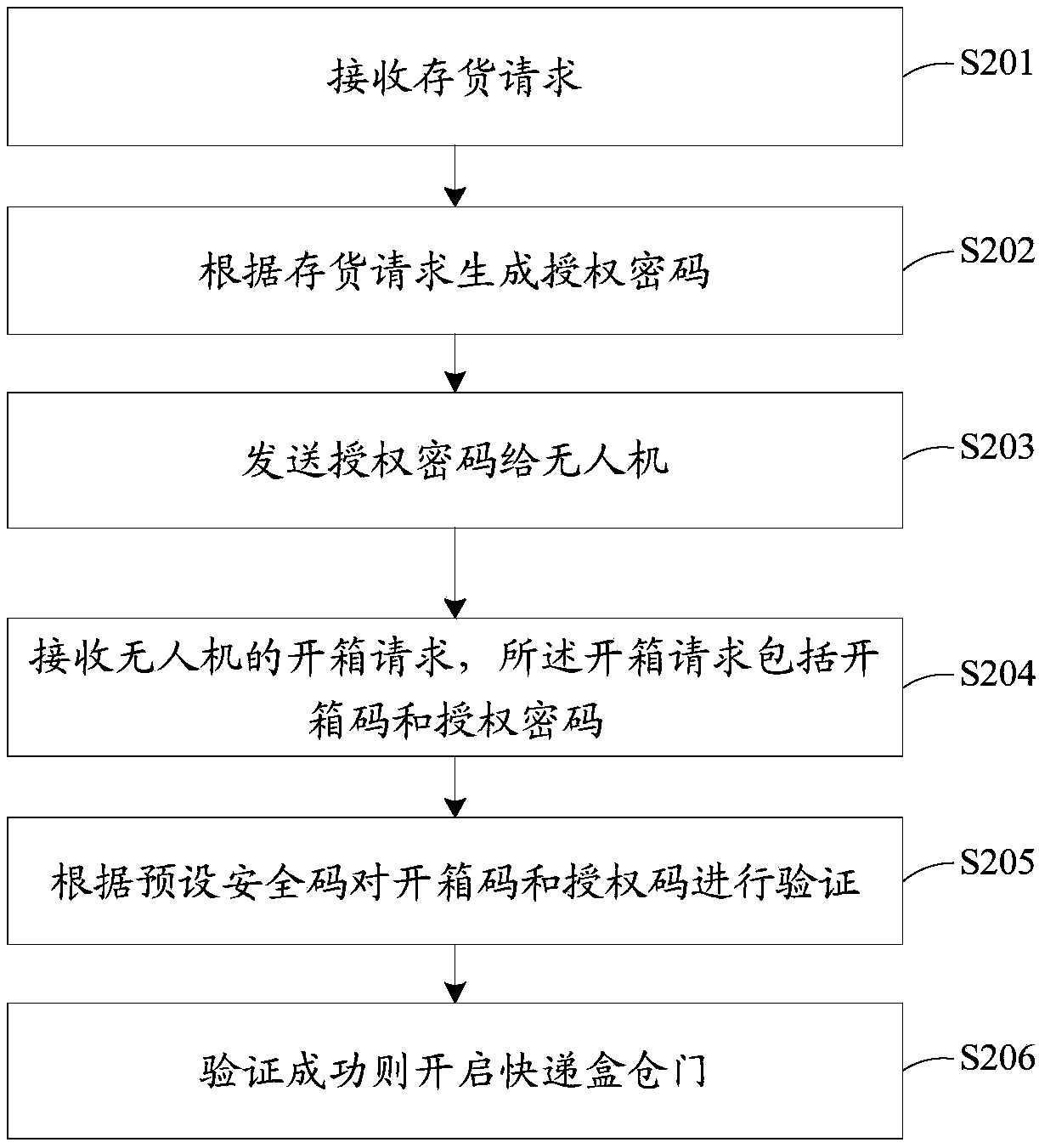
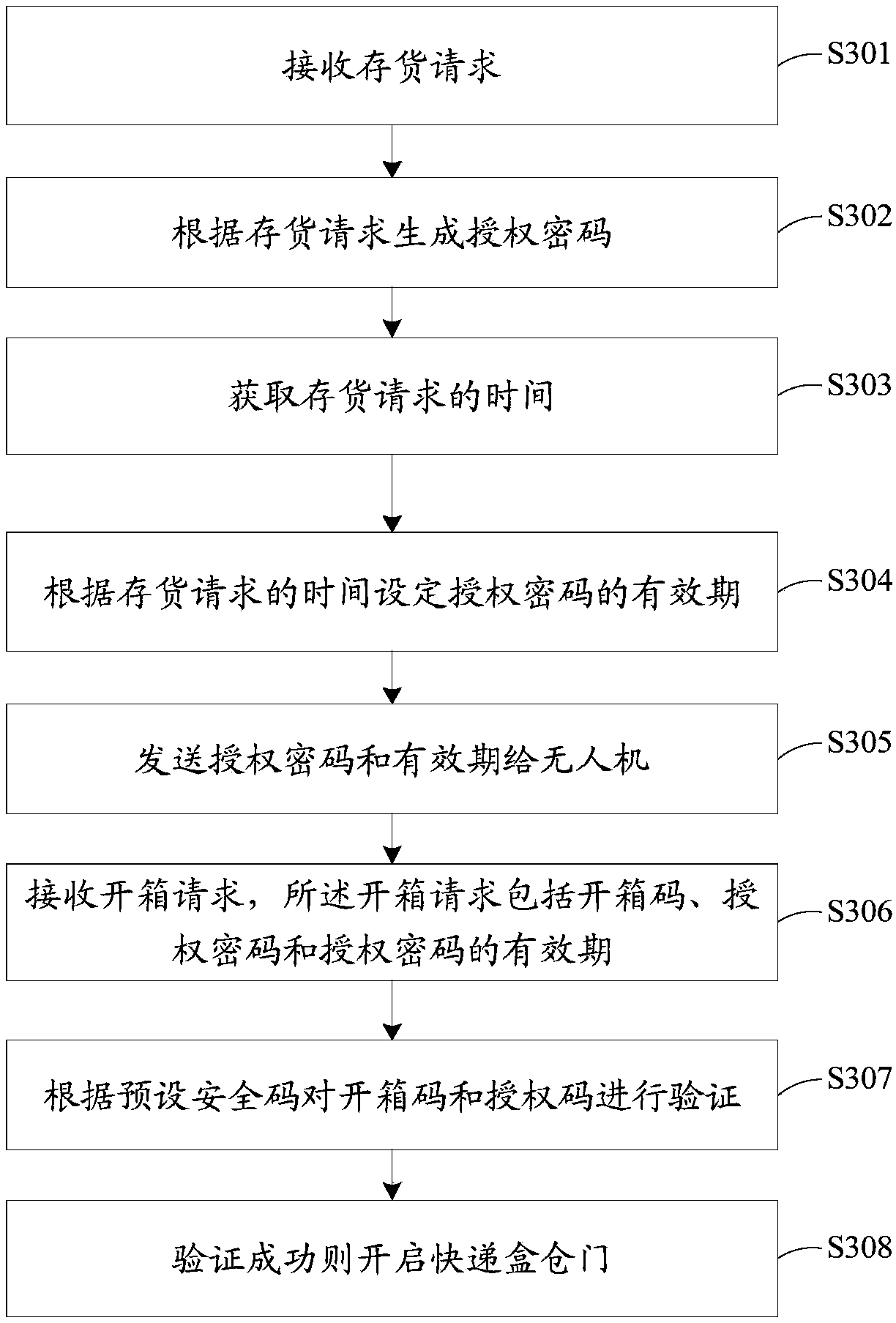
InactiveCN109345728ASave delivery timeConvenient receiving experienceApparatus for meter-controlled dispensingComputer scienceOpen code
The embodiment of the invention discloses a receiving method and device of drone delivery, a storage medium, and an express box. The receiving method of the drone delivery is applied to the express box comprising a door. The method comprises the following steps: receiving a box opening request of a drone, wherein the box opening request comprises a box opening code; verifying the box opening codeaccording to a preset security code; and opening the door if the verification is successful. According to the receiving method of drone delivery, the drone automatically delivers express goods directly to the express box owned by a user without the user going to a designated receiving place or a public express cabinet to collect the express goods, and the drone needs to verify the box opening codesent by the drone before delivering the goods. Thus, the drone is prevented from sending a wrong express box, and the safety performance of the express box owned by the user is improved.
Owner:SHENZHEN HIVE BOX TECHNOLOGY CO LTD
Two-dimensional code scanning method and mobile terminal
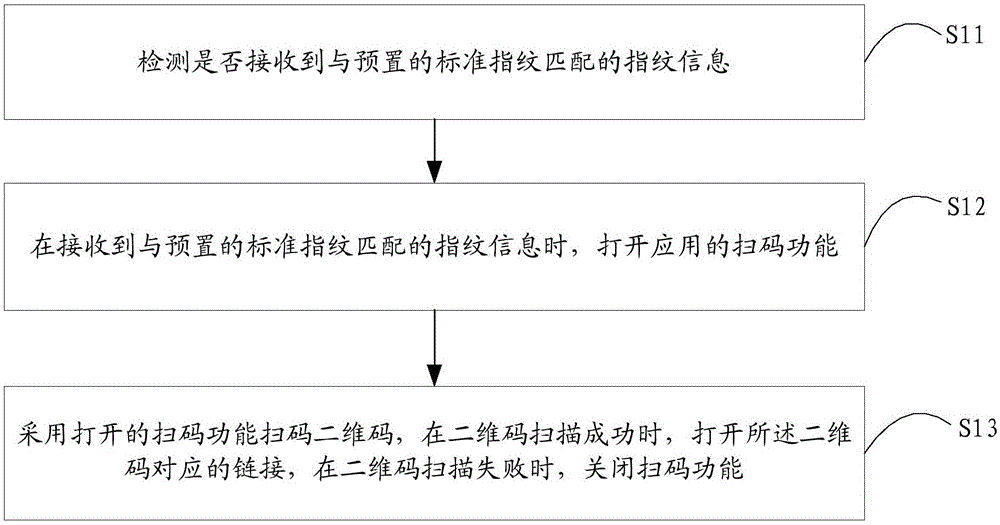
ActiveCN106709392AEasy to operateImprove operational efficiencyInput/output processes for data processingSensing by electromagnetic radiationComputer terminalOpen code
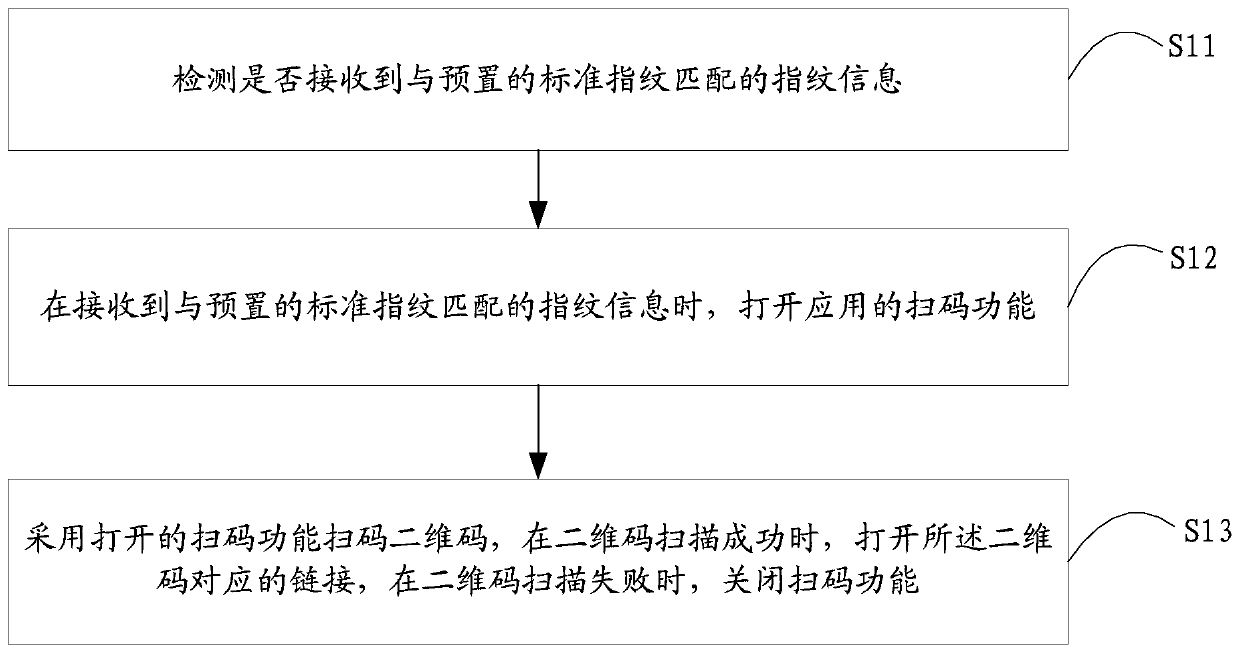
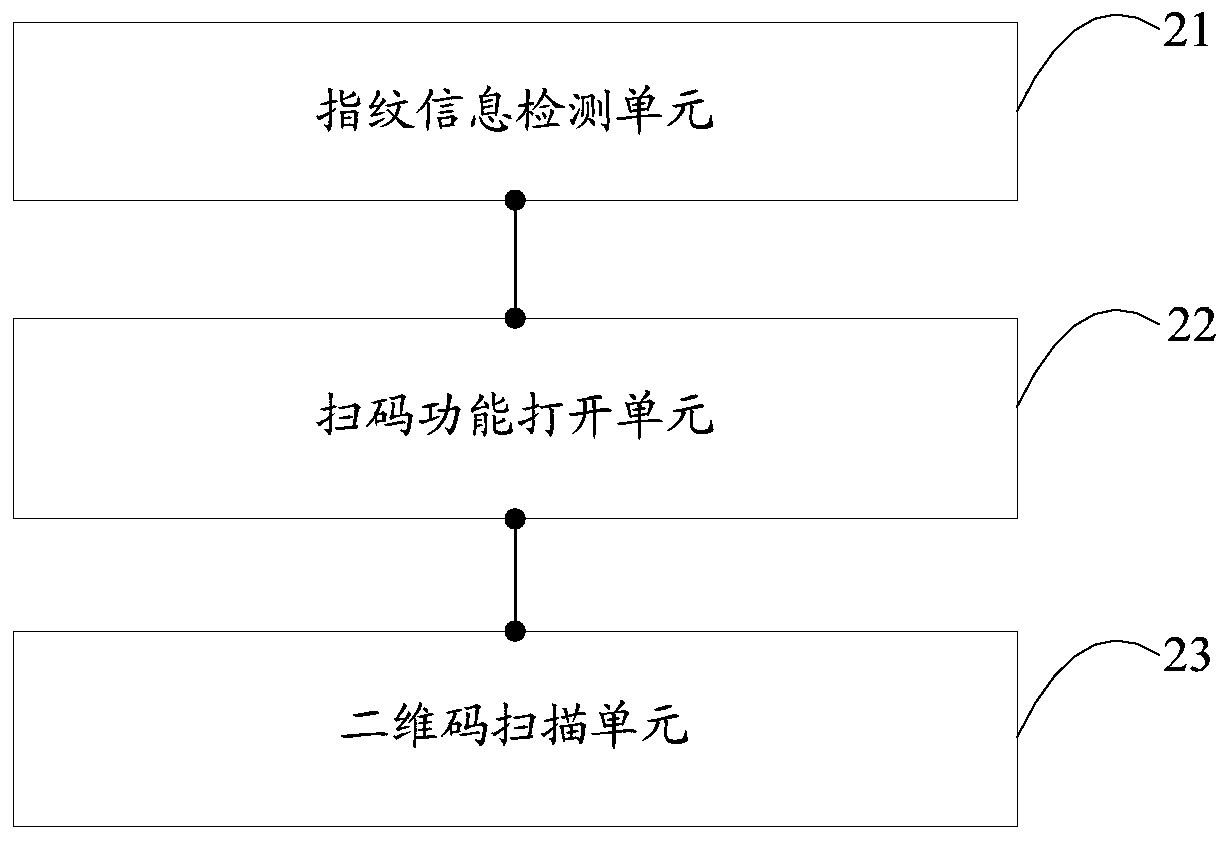
The invention is suitable for the field of mobile terminals, and provides a two-dimensional code scanning method and a mobile terminal. The method comprises the steps that whether fingerprint information matched with a preset standard fingerprint is received is detected; when the fingerprint information matched with the preset standard fingerprint is received, the code scanning function of an application is opened; and a two-dimensional code is scanned by using the opened code scanning function, a link corresponding to the two-dimensional code is opened when scanning of the two-dimensional code is successful, and the code scanning function is closed when scanning of the two-dimensional code fails. With application of the method, the operation steps can be simplified and the operation efficiency can be enhanced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
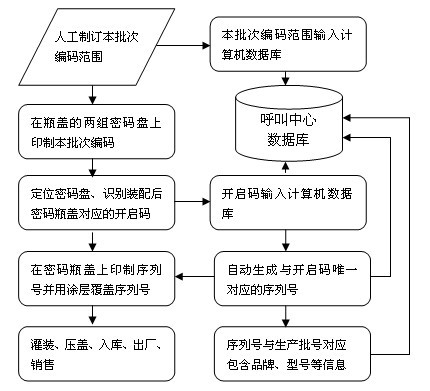
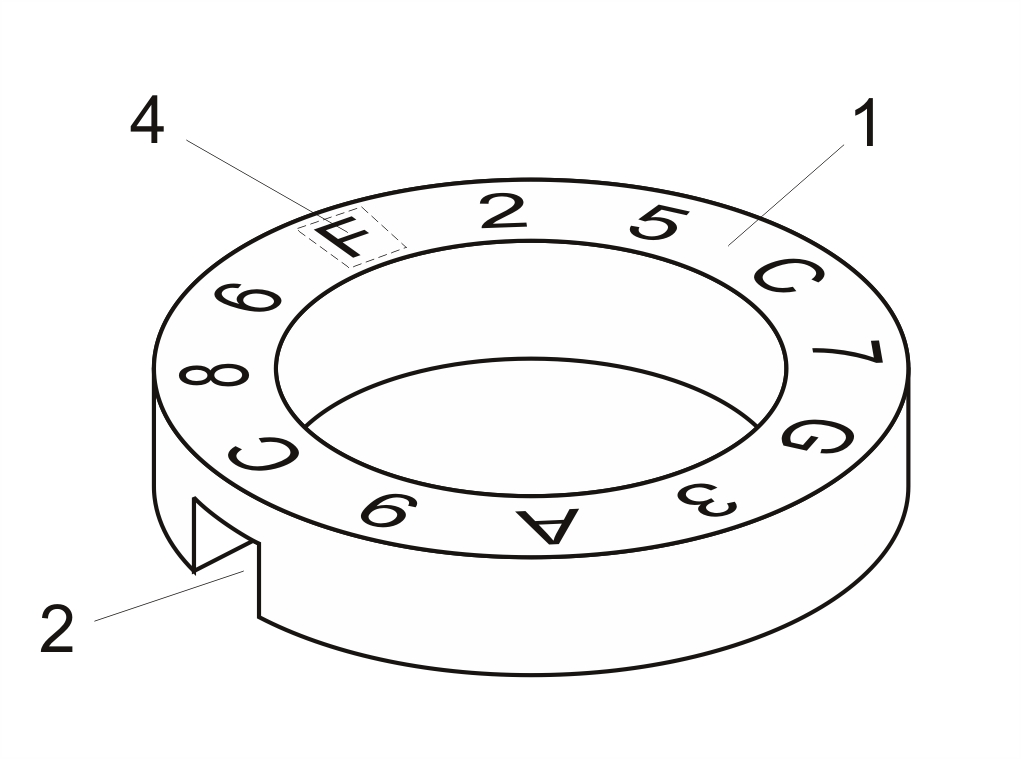
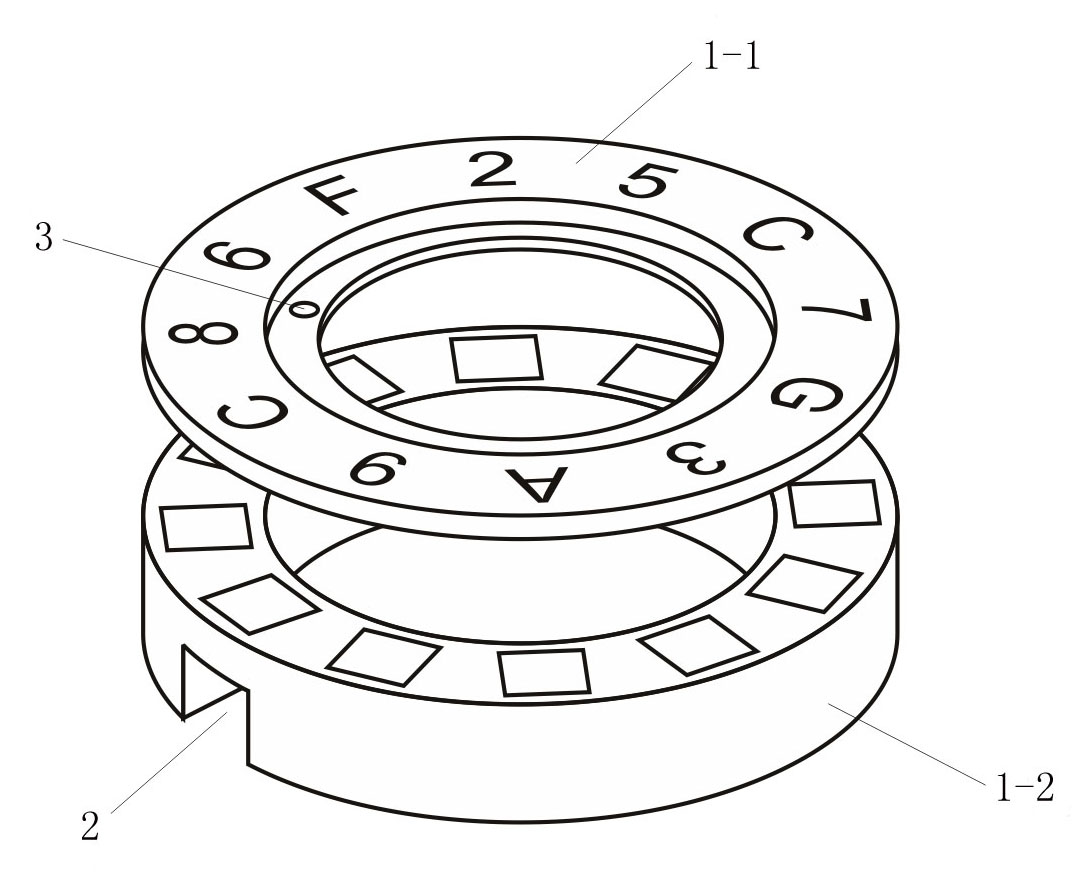
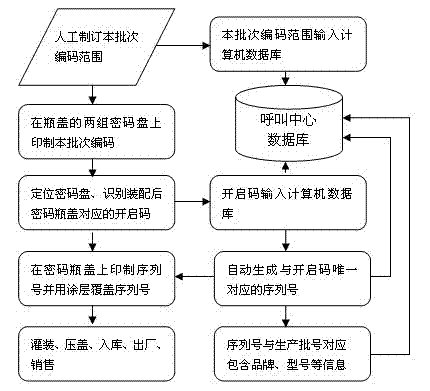
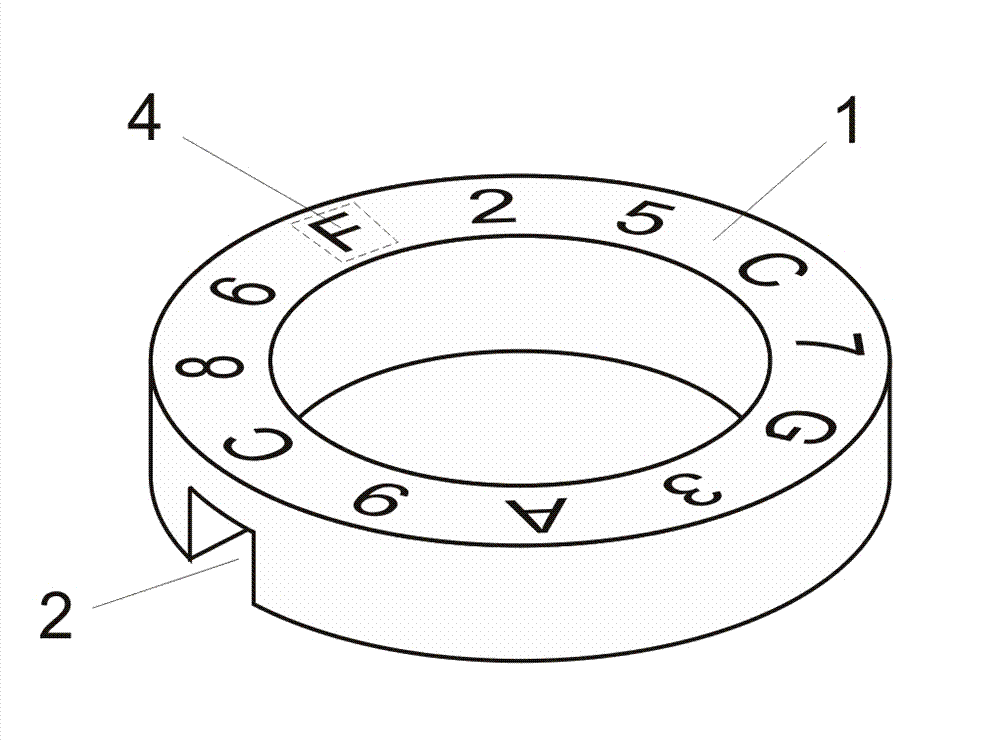
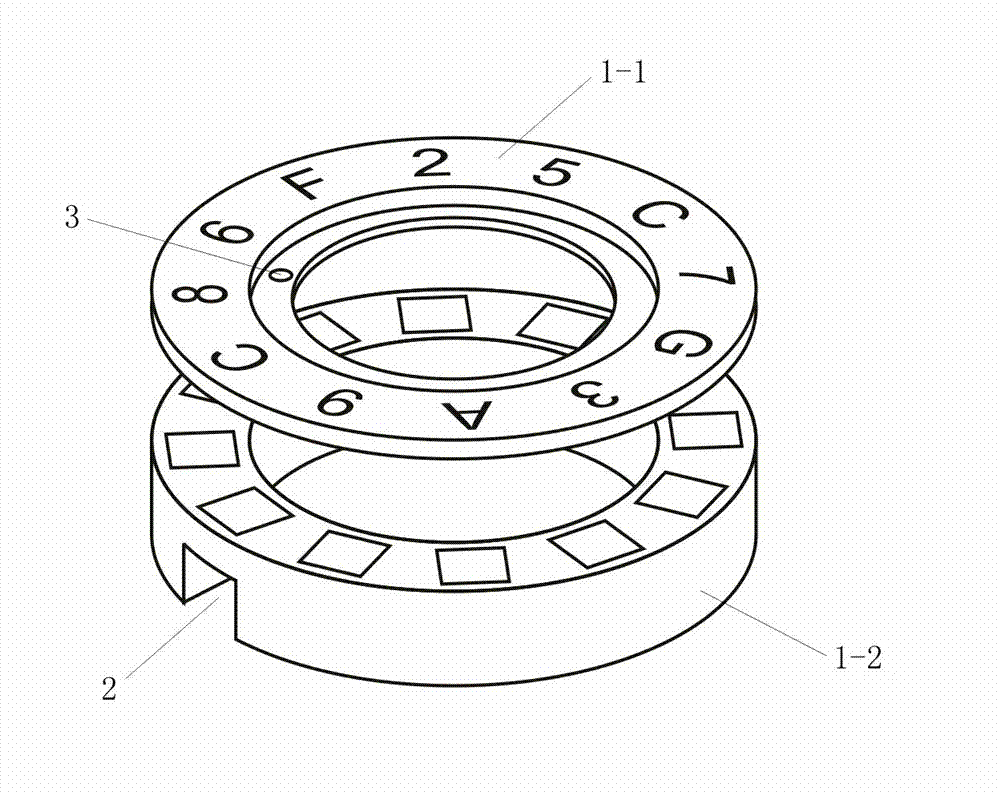
Intelligent coding and identification method for password bottle caps
The invention discloses an intelligent coding and identification method for password bottle caps, which comprises random organization and printing mode for a code group on a password disk, and automatic positioning of the password disk and automatic identification of the opening code group. From the process of printing the code group on the password disk to the process of positioning the passworddisk and identifying the opening codes, the opening codes corresponding to the password disk are always kept in a secret state, an opening code for opening a corresponding password disk has higher randomicity and randomness, and automatic mechanical and electronic means is adopted to realize positioning and identification to radically solve a plurality of problems of a method of manually recording corresponding opening codes in the prior art. When the method is adopted for manufacturing the password bottle caps, the production efficiency is greatly improved, and a phenomenon that the passwordbottle caps wrongly correspond to the opening codes is radically avoided.
Owner:成都拓成工业产品设计有限公司
Method for controlling electronic safe and cabinet opening by telephone and dedicated apparatus thereof
InactiveCN1920229AImprove securityEasy to useElectric permutation locksMicrocontrollerRemote control
The invention relates to a control method used to open electric strong box with telephone, wherein the invention is characterized in that: the single chip of control circuit will continuously detect the input signal of dual-voice receiving circuit connected to the telephone line, to detect the user open code of user via the telephone line and dual-voice receiving circuit, to compare the user open code with the preset open code of memory; if it is right, the single chip outputs execute signal to the executor of electric strong box, to open the strong box; if it is wrong, the single chip will not output execute signal to the executor to open the electric strong box; therefore, the user can use the common voice telephone or mobile phone to open the code lock of electric box, to realize remote control, with simple structure.
Owner:陈国庆
Anti-counterfeiting technology and operation method
InactiveCN101017564AAvoid enteringPrevent entry into the marketTelephonic communicationCommerceMarket placeComputer science
This invention relates to one anti-false technique and its operation method, which is characterized by the following: the technique is composed of key code lock, code management structure and code management structure to get the credit and path of the code, wherein, the method comprises the following steps: a, according to the credit bill through code management structure to get the path and management structure to get open codes; b, the management structure feeds back codes accordingly; c, getting the codes to check the product.
Owner:唐忠华
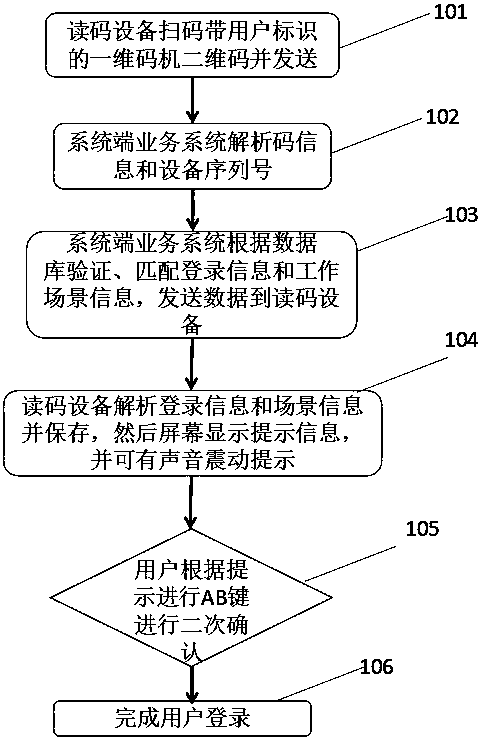
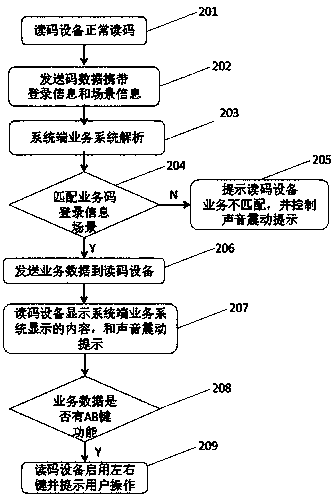
Code reading device and method based on system end business analysis
InactiveCN108280380AAchieve arbitrary controlRealize the display effectSensing by electromagnetic radiationSoftware engineeringOpen code
The invention discloses a code reading device and method based on system end business analysis. With the code reading device and method based on the system end business analysis, data accuracy can beguaranteed in different work scenarios and environments so that effective data check is conducted; through the code reading device, login and logout functions and a scene selection function can be completed by an existing user identifying an one-dimensional code or a two-dimensional code with no need for customers to increase additional bar code customization cost; the system end business analysisis capable of realizing arbitrary control and display of the code reading device with business not relying on the code reading device; an analysis system is configured with service scenarios and implements scenario selection so as to realize one point deployment multi-point execution. Furthermore, the system can also be configured by enterprises according to the business to achieve needs of different scenarios, such as work statistics and performance appraisal, and the open code reading device based on the system end business analysis has a wide range of application scenarios in many industries.
Owner:HANGZHOU LINKHEALTH TECH CO LTD
Access personnel management system and method compatible with existing IC card access control
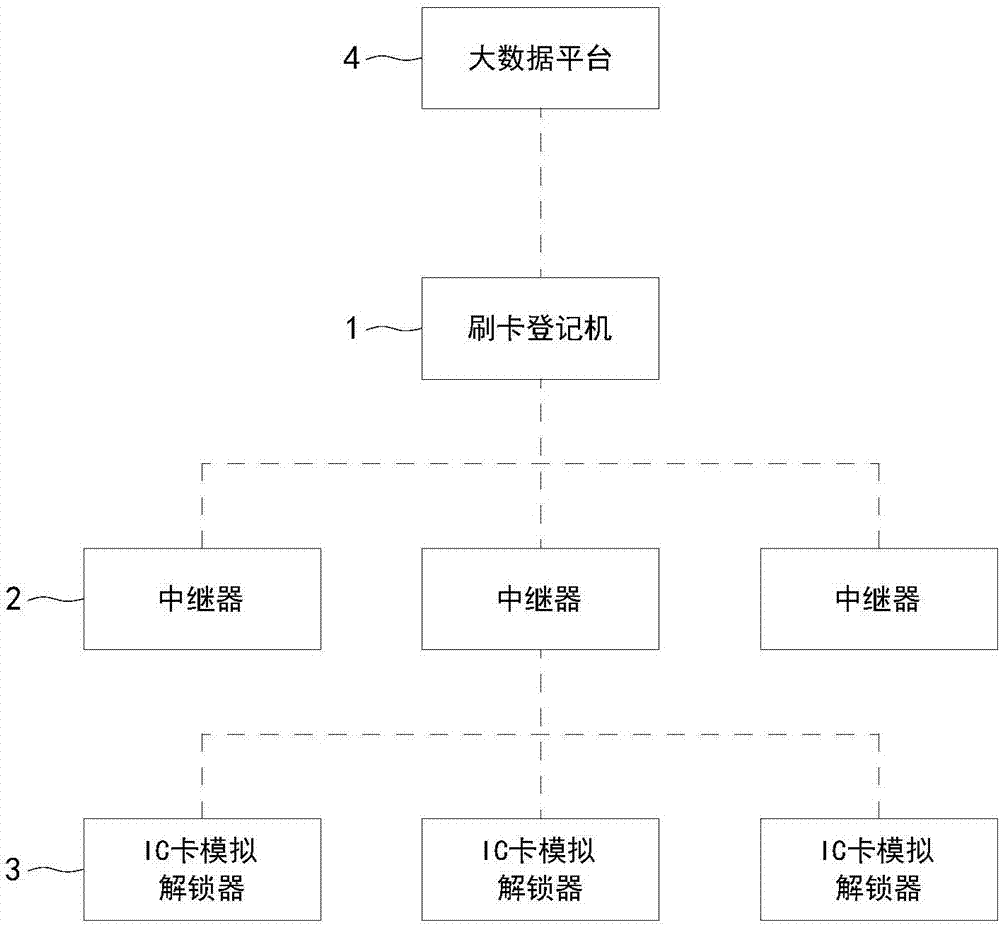
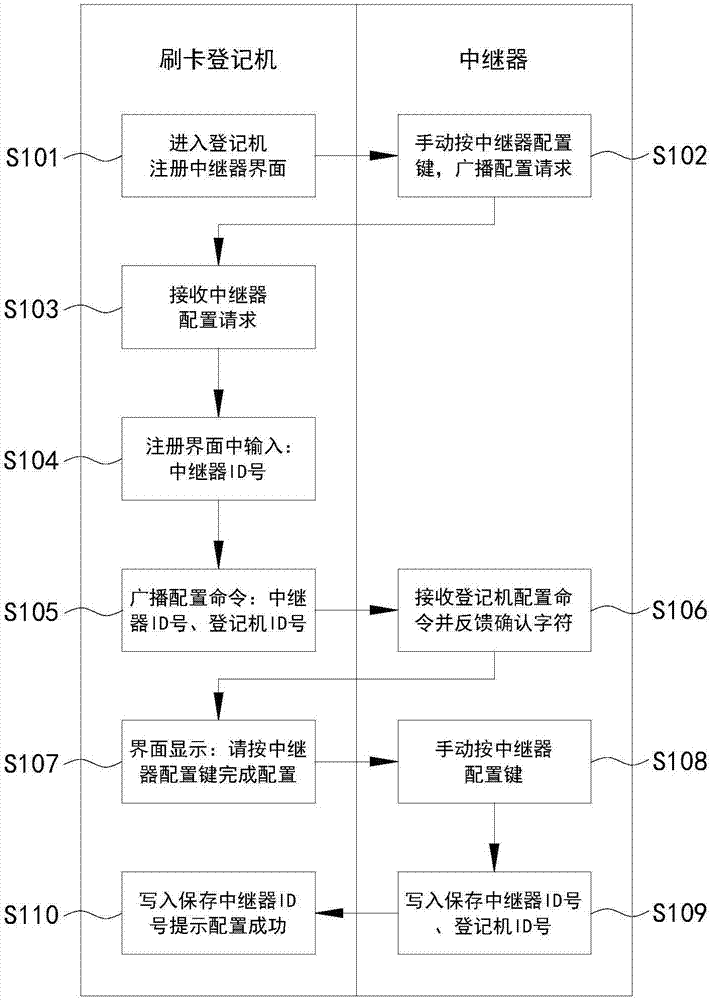
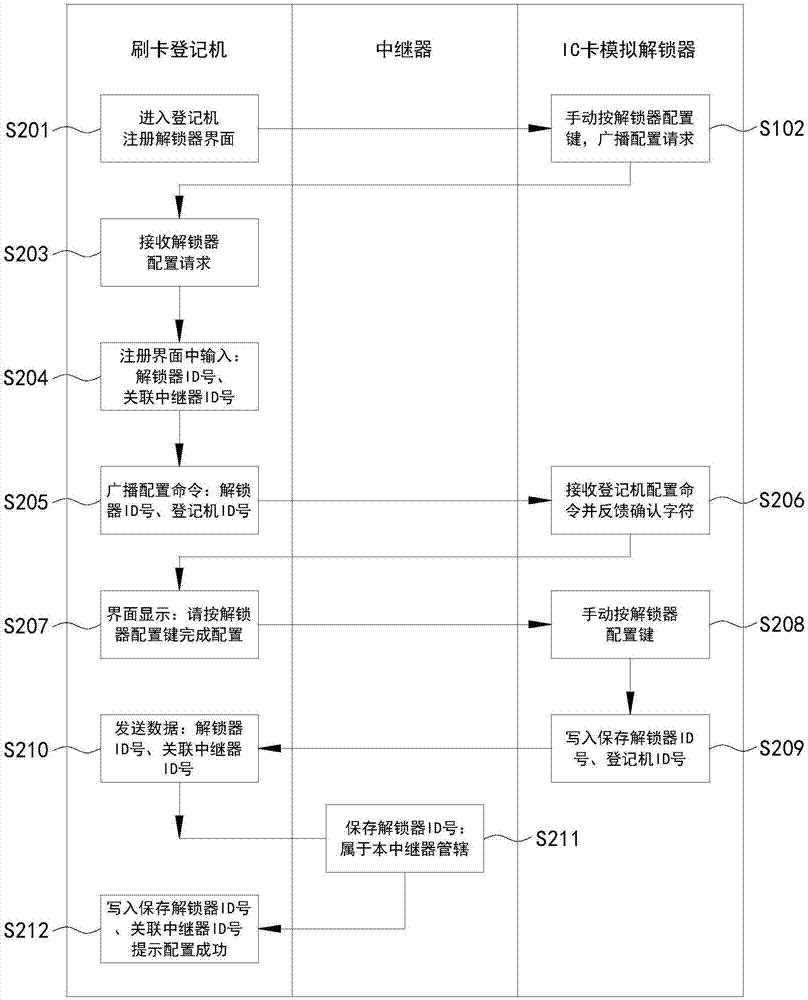
InactiveCN107358695AReduce usageReduce lossIndividual entry/exit registersInduction zoneManagement system
The invention relates to an access personnel management system compatible with original IC card access control. The system includes a card swiping register and an IC card simulation unlocker installed at an original IC card access control induction zone, the card swiping register is used for collecting and registering user identity information, setting an opening code, and binding or unbinding the user identity information, the opening code and an IC card simulation unlocker number, the IC card simulation unlocker is used for collecting the opening code, sending the collected opening code and the IC card simulation unlocker number simultaneously to the card swiping register for verification, and sending simulated authorized IC card information to the IC card access control after passing the verification to unblock the IC card access control, and reporting the door opening integrated information after successful unblocking. Without destroying or refitting the original IC card access control, a system for real-time recording of access personnel identity and time during card swiping entry is added on the basis of the original IC card access control to meet the supervision requirements, and also the refitting cost and time can be eliminated.
Owner:ZHEJIANG TENDENCY TECH
Stream media content downloading method based on data characteristic
InactiveCN100593928CSolve the problem of not being able to downloadFix download issuesData switching networksComputer hardwareData stream
The invention relates to a downloading method of stream media content based on data character, comprising: starting data package seizing wire; opening the link address containing video content and buffer memorizing the seized data package in the form of binary data stream in a buffer file. The buffer file is read and a number of conversational files are separated based on the conversation terminal. On the basis of the size of the conversational file and the opening code of the media content in the said file, the said conversational file is determined whether the media content is in the conversational file or not, and the conversational file without the media content is deleted. The data packages in the conversational file are read in turn based on the conversation index file and the retransmission package and error package are deleted on the basis of the sequence number and affirm number in the data package, and then the effective media data package is ordered and stored in the new media content file. Only page address with media content is provided to accurately download the required media content without reducing the website performance of stream media.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Remote-control unlocking type decoding proof type electronic security lock for vehicle
InactiveCN101042782ASimple structurePrevent decoding car theftTransmission systemsAnti-theft devicesRemote controlElectronic security
This invention relates to one remote lock open de-coding automobile and anti-smash electron lock, which comprises remoter receive circuit and de-coding circuit, wherein, decoding circuit and anti-rob control circuit, lock open control circuit are connected and the lock open circuit and anti-rob control circuit and lock part are connected; the function restore circuit and the decode circuit are connected and the lock close execution circuit is connected to the anti-rob control circuit, and lock part; in opening lock, remoter orderly sends out two series of open codes signals to decode circuit for identification, decoding, judgment and testing and sending the correct signal into open control circuit; the circuit control lock fulfills opening to prevent decoding anti-theft incidence.
Owner:史会桐
Lock
ActiveCN101929273AImprove reliabilitySituation improvement of layout promotionKeysLock casingsEngineeringSteel ball
The invention relates to a lock, in particular to a secondary key lock. The lock comprises a lock body, a lock core, inner cylinders with notches, a code distinguishing chip and a lock core pin or clutch bolt. The improvement of the lock is that: the code distinguishing chip is improved into an axial normally-open code distinguishing chip. A driving device and a lock opening control member are respectively arranged in the lock, wherein the driving device is used for driving the code distinguishing chip, and the lock opening control member is controlled by the code distinguishing chip; the code distinguishing action of the code distinguishing chip is indirectly driven by the driving device through a spring; the driving device is a torsion driving device or a key insertion driving device comprising a line-tooth key; and the lock opening control member is a rigid lock core pin or / and clutch bolt. Further improvement of the lock is that: one or more rows of inner cylinders are radially arranged. The lock consisting of the key insertion driving device, the clutch bolt and a positioning steel ball can be applied to a lock set requiring accurate positioning.
Owner:马学文
Multi-dimensional heterogeneous big data relationship identification and authentication method and system
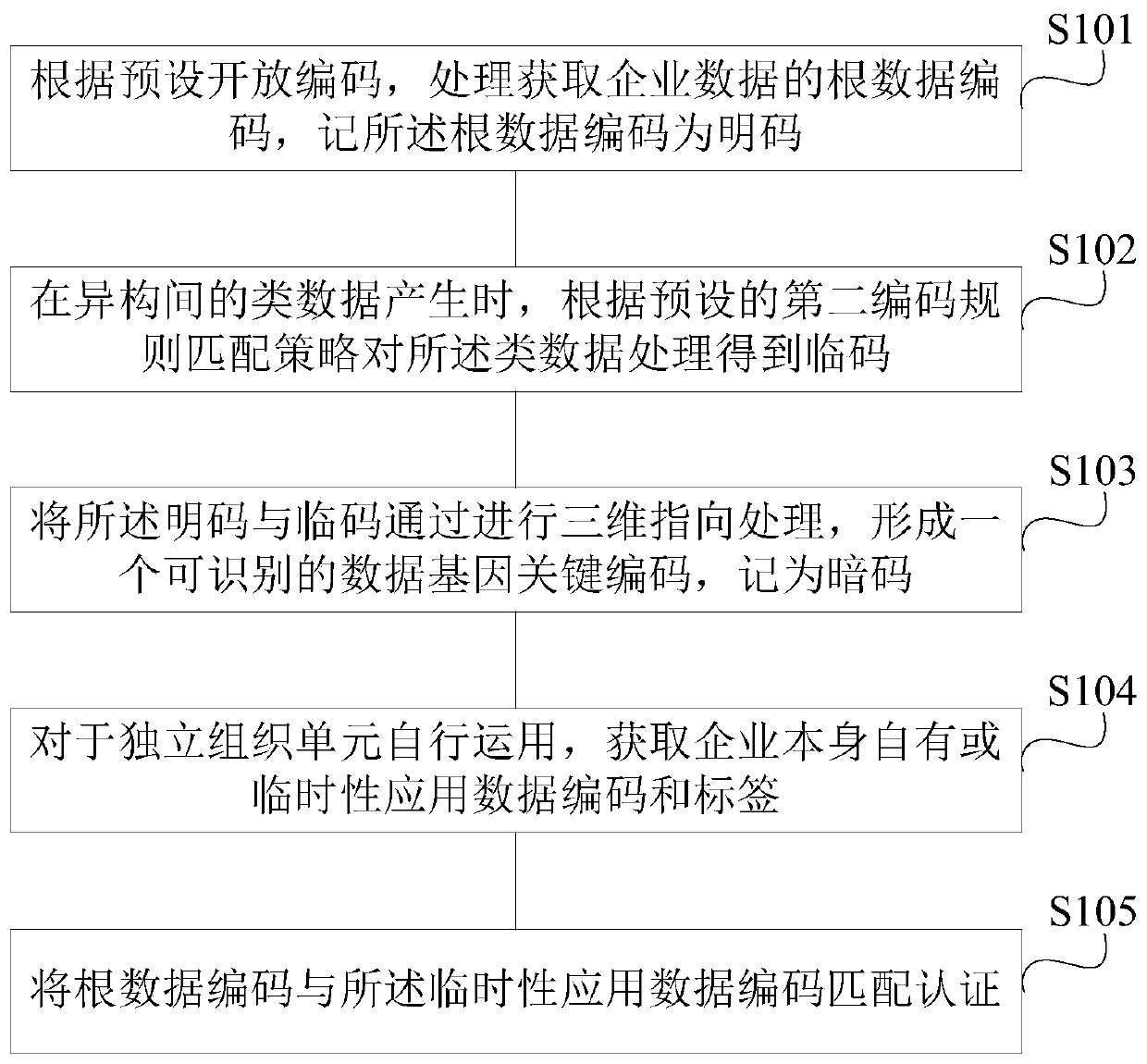
The invention is applicable to the technical field of big data matching, and provides a multi-dimensional heterogeneous big data relationship identification and authentication method, which comprisesthe following steps: processing and acquiring a root data code of enterprise data according to a preset open code, and recording the root data code as a plain code; when the class data between the isomerism are generated, processing the class data according to a preset second coding rule matching strategy to obtain an adjacent code; performing three-dimensional pointing processing on the plain code and the adjacent code to form an identifiable data gene key code, and recording the data gene key code as a secret code; for independent organization unit self-use, obtaining own or temporary application data codes and labels of the enterprise; the root data code is matched with a temporary application data code for authentication. The invention correspondingly provides a multi-dimensional heterogeneous big data relationship identification and authentication system. Therefore, the method can effectively meet the intelligent application in big data, block chains, Internet of Things and artificial intelligence generated between Internet online heterogeneous software functions, between data, between information and the like.
Owner:今天誉讯(北京)科技有限公司
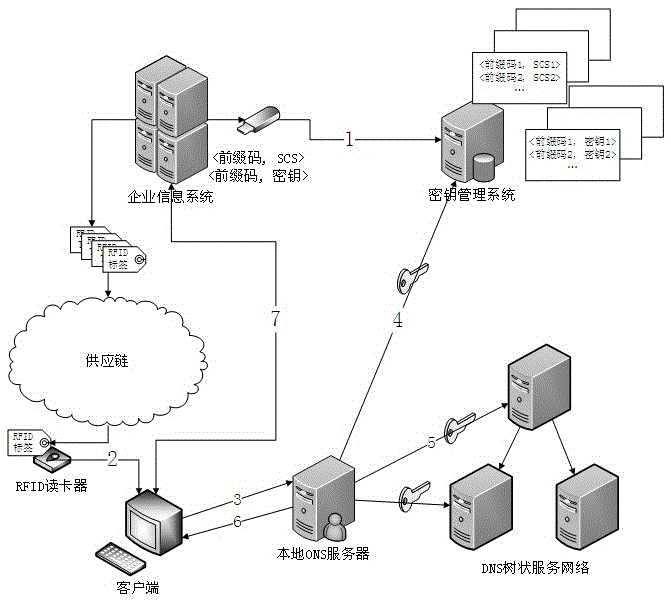
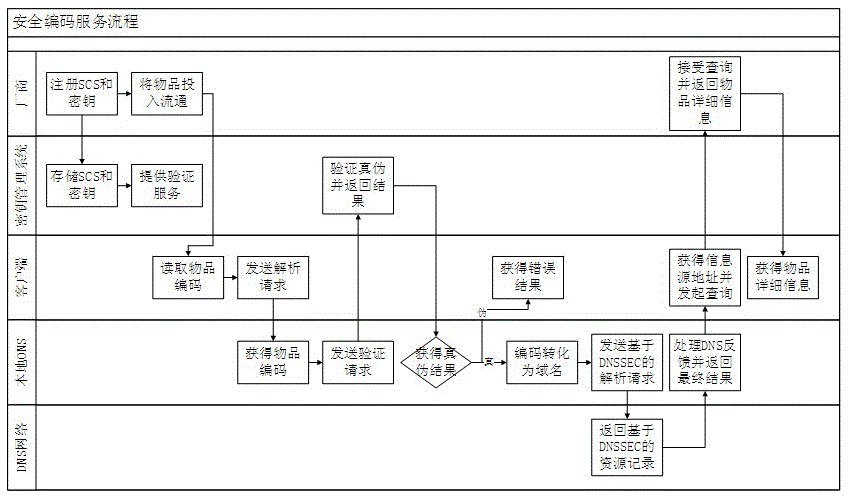
A method of providing security protection for item identification and its analysis service
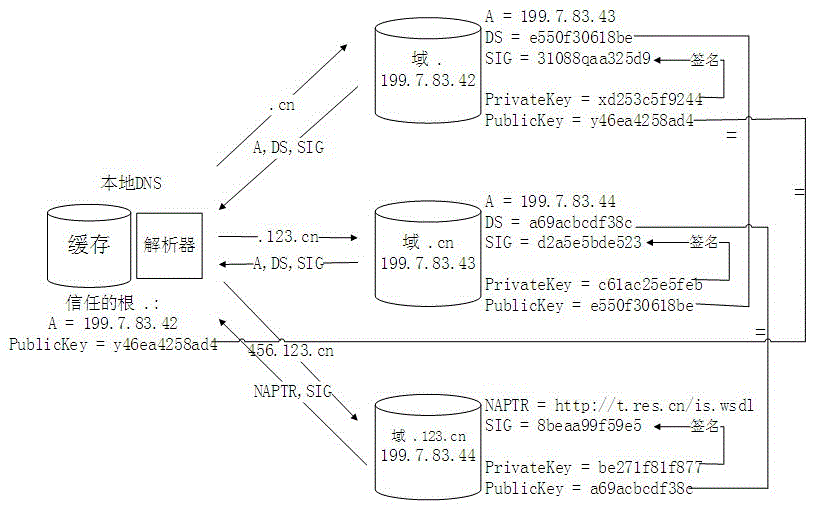
The invention belongs to the technical field of an Internet of Things information system, and particularly relates to a method for providing safety protection for item identification and an item resolution service. The method ensures that the item identification in Internet of Things can not be easily forged, and the effect that a resource address returned by the item resolution service is safe and credible is guaranteed. A mode of a safety extended code is used for encrypting the item identification, and custom configuration can be conducted on part of parameters in a strategy by a manufacturer according to product space sensitiveness, required safety levels and other factors. A safety coding strategy and a secret key are registered in a unified secret key management system by the manufacturer, and the secret key management provides an open coding authentication service. After an item is put in circulation, a user owning the item can authenticate authenticity of the item through the open coding authentication service, the resolution service protected by DNSSEC is transferred to acquire a safe and credible item detailed information source, and then detailed information of the item is acquired.
Owner:FUDAN UNIV
Two-dimension code scanning method and mobile terminal
ActiveCN106709392BEasy to operateImprove operational efficiencyInput/output processes for data processingSensing by electromagnetic radiationComputer terminalDimensional modeling
The invention is suitable for the field of mobile terminals, and provides a two-dimensional code scanning method and a mobile terminal. The method comprises the steps that whether fingerprint information matched with a preset standard fingerprint is received is detected; when the fingerprint information matched with the preset standard fingerprint is received, the code scanning function of an application is opened; and a two-dimensional code is scanned by using the opened code scanning function, a link corresponding to the two-dimensional code is opened when scanning of the two-dimensional code is successful, and the code scanning function is closed when scanning of the two-dimensional code fails. With application of the method, the operation steps can be simplified and the operation efficiency can be enhanced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Remote control system and remote control method
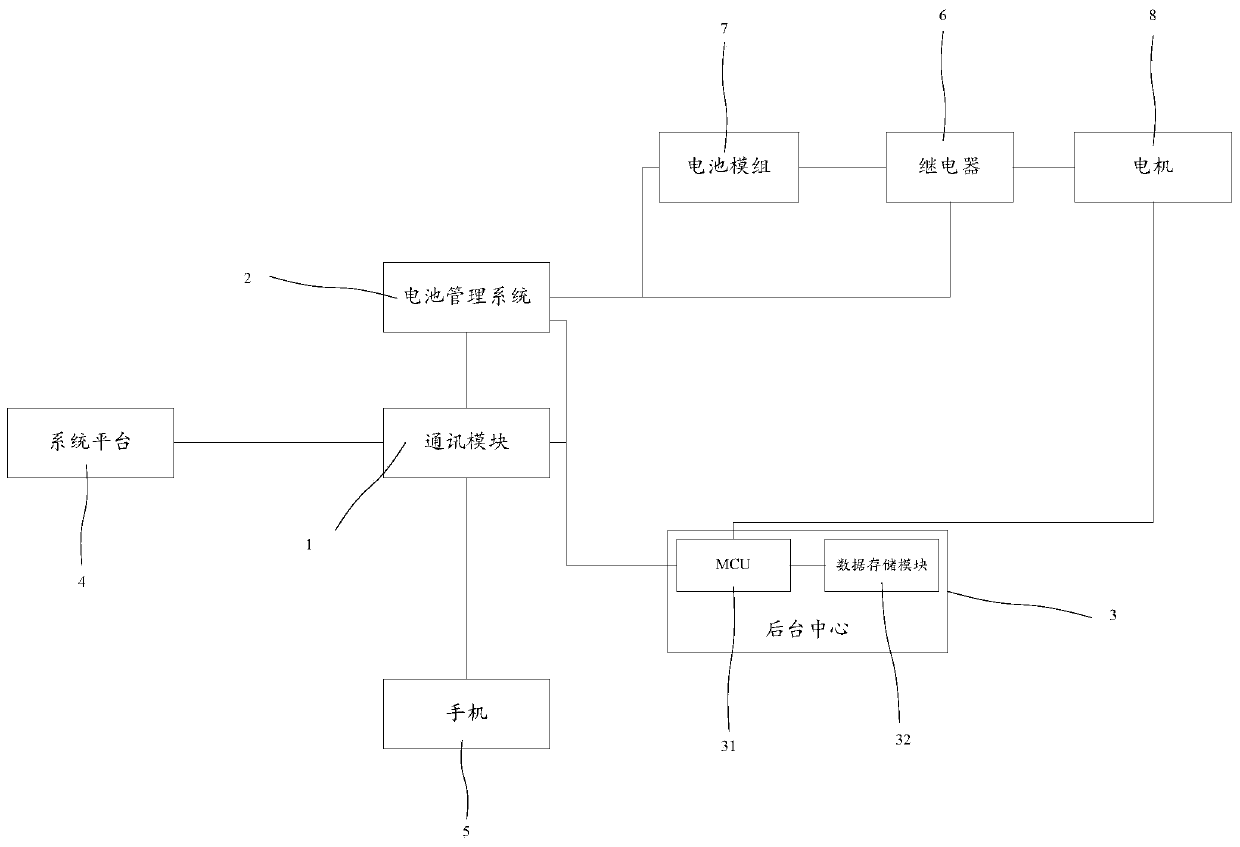
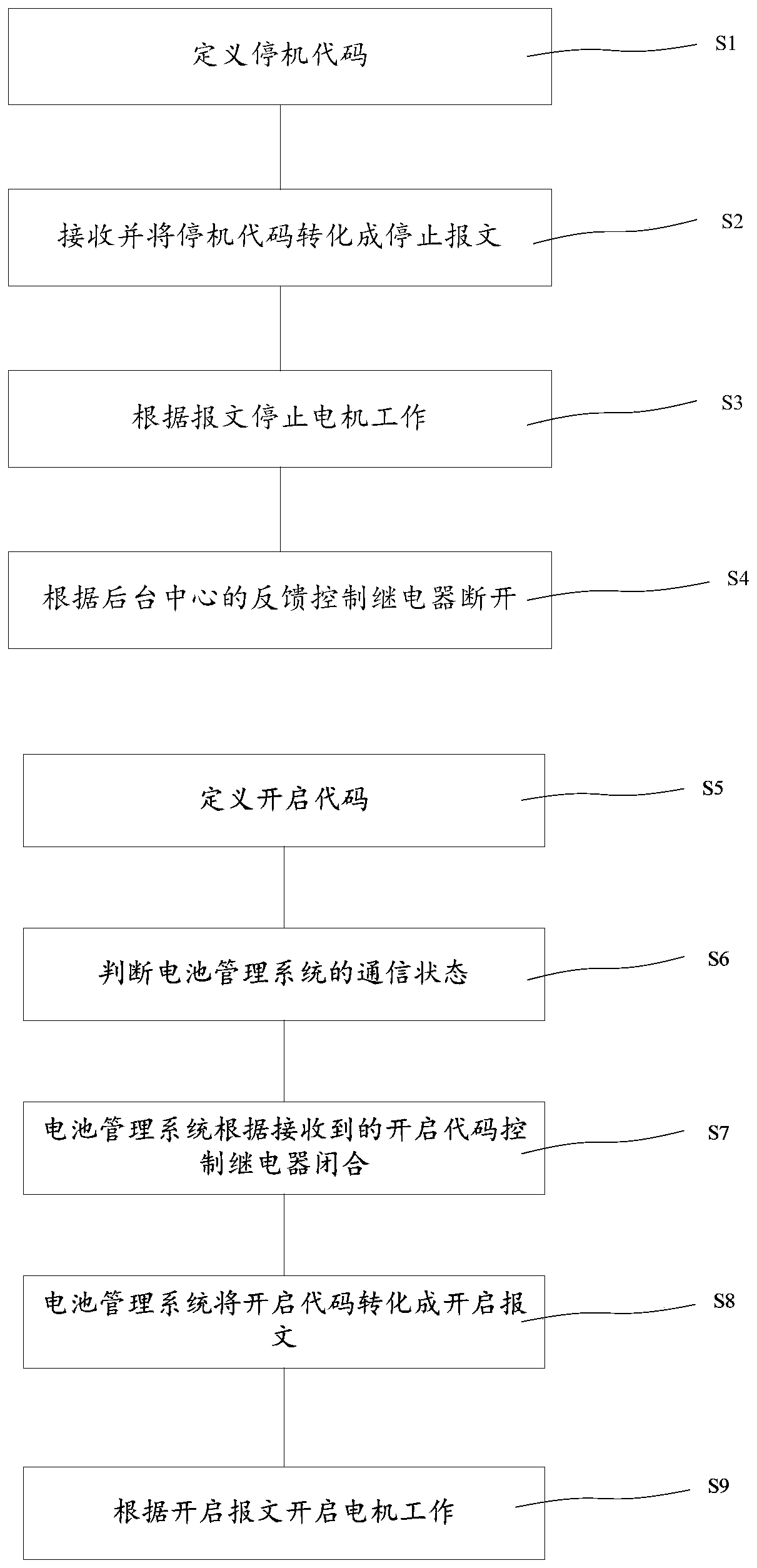
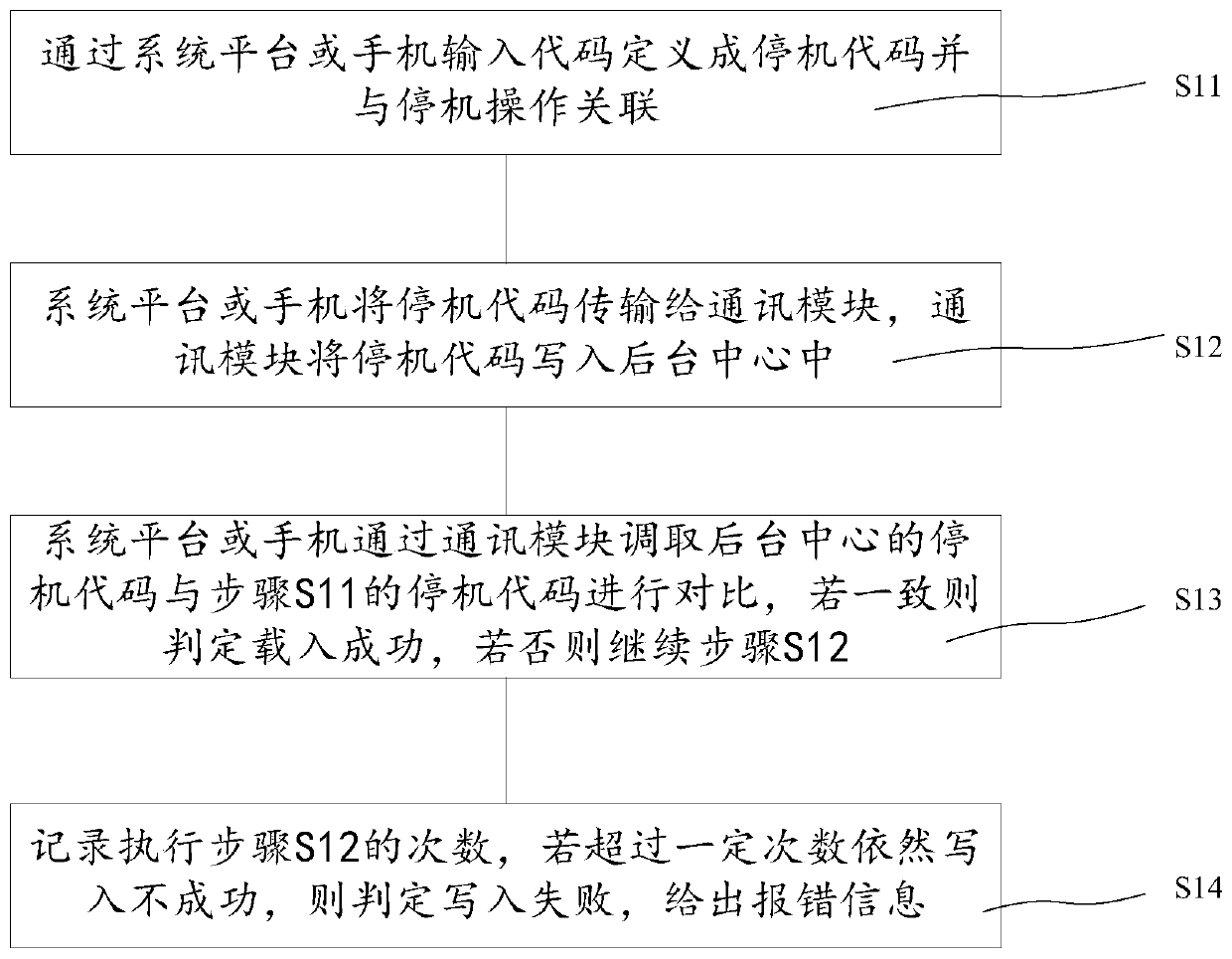
InactiveCN110225080ASave spaceReduce learning costsSubstation equipmentTransmissionStopped workStart stop
The invention discloses a remote control system, which comprises a battery management system, a background center, a mobile terminal, a relay, a battery module and a motor, and is characterized in that the remote control method comprises a remote closing method and a remote opening method, and the remote closing method comprises the following steps: 1, defining a shutdown code; 2, receiving the shutdown code and converting the shutdown code into a shutdown message; 3, stopping working of the motor according to the message; 4, controlling the relay to be disconnected according to feedback of the background center; the remote opening method comprises the following steps: 5, defining an opening code; 6, judging the communication state of the battery management system; 7, enabling the batterymanagement system to control the relay to be closed according to the received starting code; 8, enabling the battery management system to convert the starting code into a starting message; and 9, starting the motor to work according to the starting message. According to the invention, the learning cost of start-stop operation is reduced, a system platform or a mobile terminal is adopted for operation, and the space of the high-altitude operation vehicle is greatly saved.
Owner:GEM WUHAN URBAN MINE RECYCLING IND PARK DEV +1
Intelligent coding and identification method for password bottle caps
The invention discloses an intelligent coding and identification method for password bottle caps, which comprises random organization and printing mode for a code group on a password disk, and automatic positioning of the password disk and automatic identification of the opening code group. From the process of printing the code group on the password disk to the process of positioning the passworddisk and identifying the opening codes, the opening codes corresponding to the password disk are always kept in a secret state, an opening code for opening a corresponding password disk has higher randomicity and randomness, and automatic mechanical and electronic means is adopted to realize positioning and identification to radically solve a plurality of problems of a method of manually recording corresponding opening codes in the prior art. When the method is adopted for manufacturing the password bottle caps, the production efficiency is greatly improved, and a phenomenon that the passwordbottle caps wrongly correspond to the opening codes is radically avoided.
Owner:成都拓成工业产品设计有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com