Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
240 results about "Method access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An access method is a software component, operating system service or network interface that handles the storage/retrieval and sending/receipt of data. Access methods provide an application programming interface (API) for programmers to perform these services, which rely on low-level, specialized instructions.
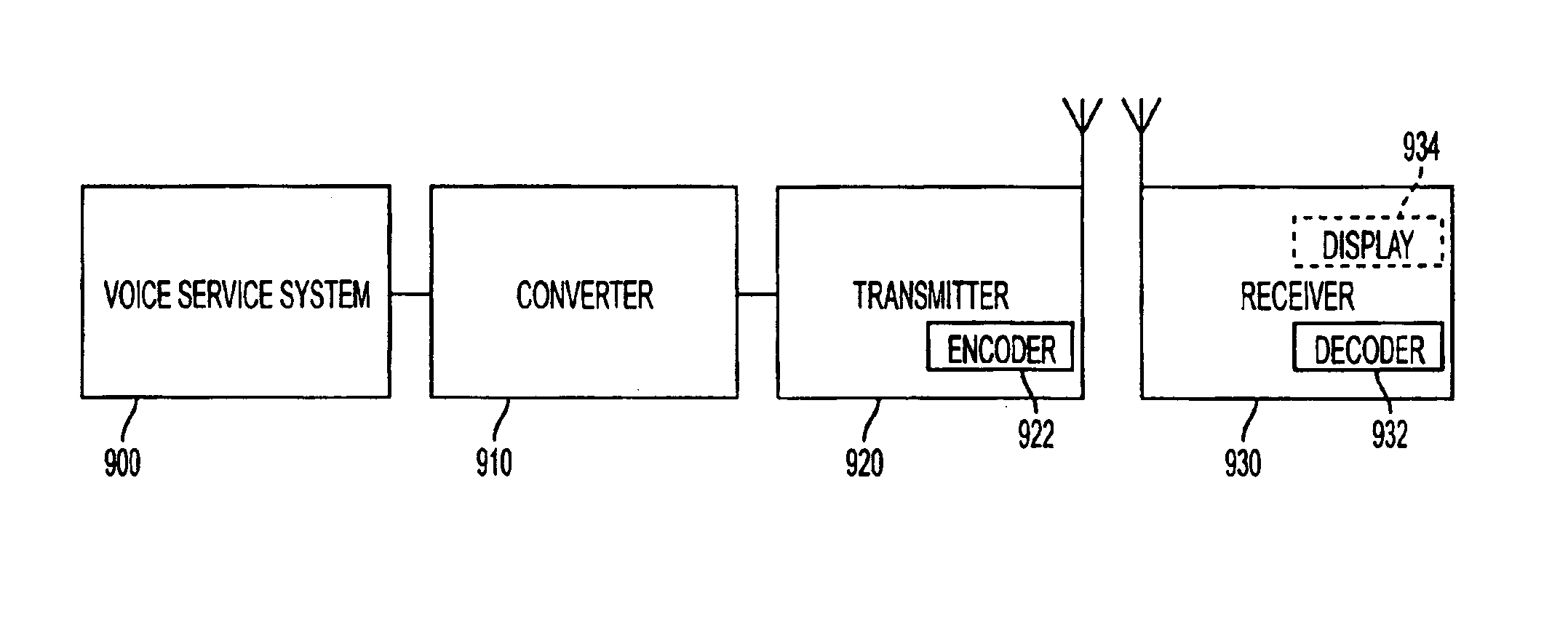
System and method for the creation and automatic deployment of personalized, dynamic and interactive voice services, including deployment through personalized broadcasts
InactiveUS6964012B1Convenient transactionProvide informationBroadcast systems characterised by addressed receiversBroadcast-related systemsPersonalizationBroadcasting
Owner:MICROSTRATEGY
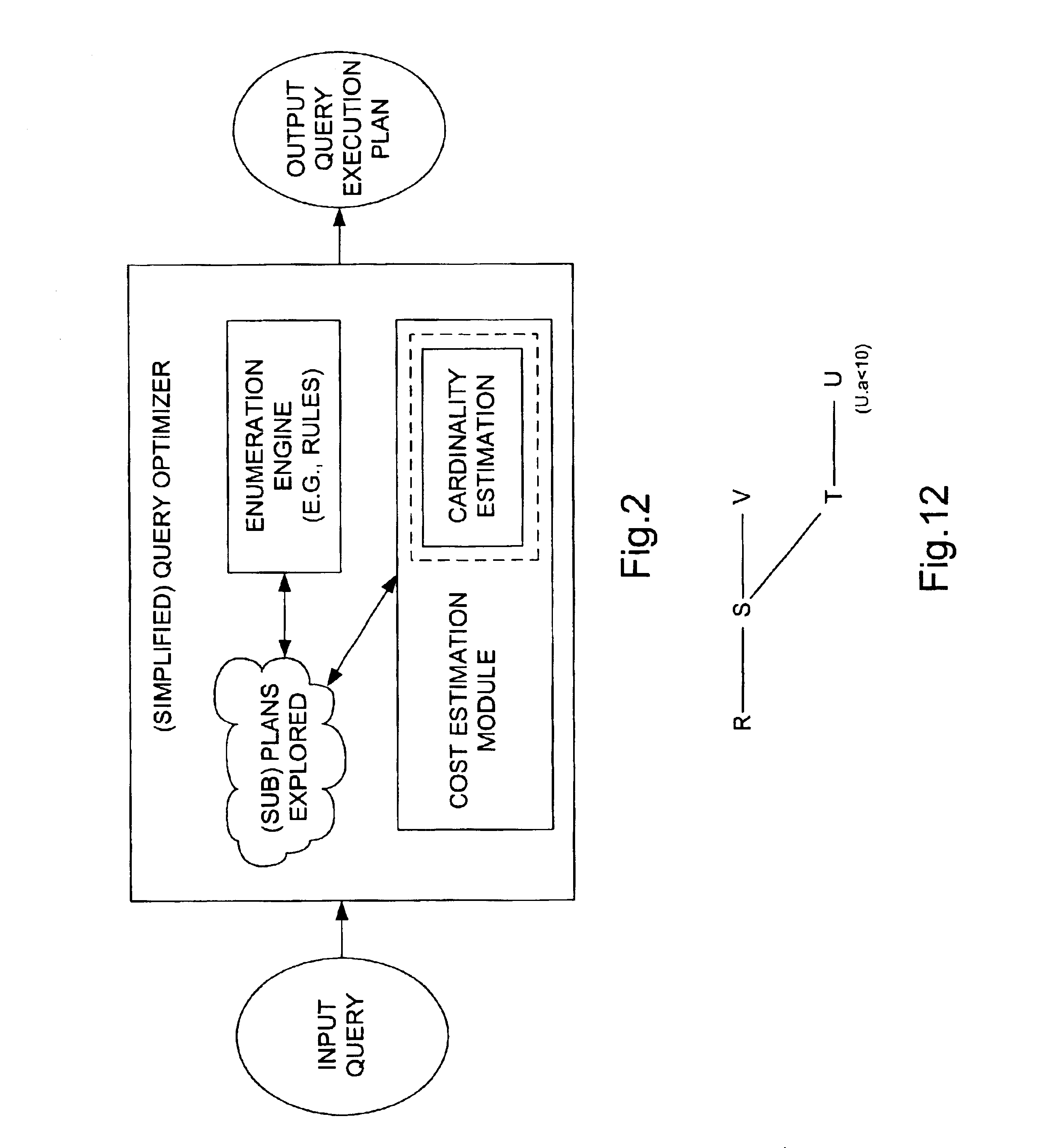
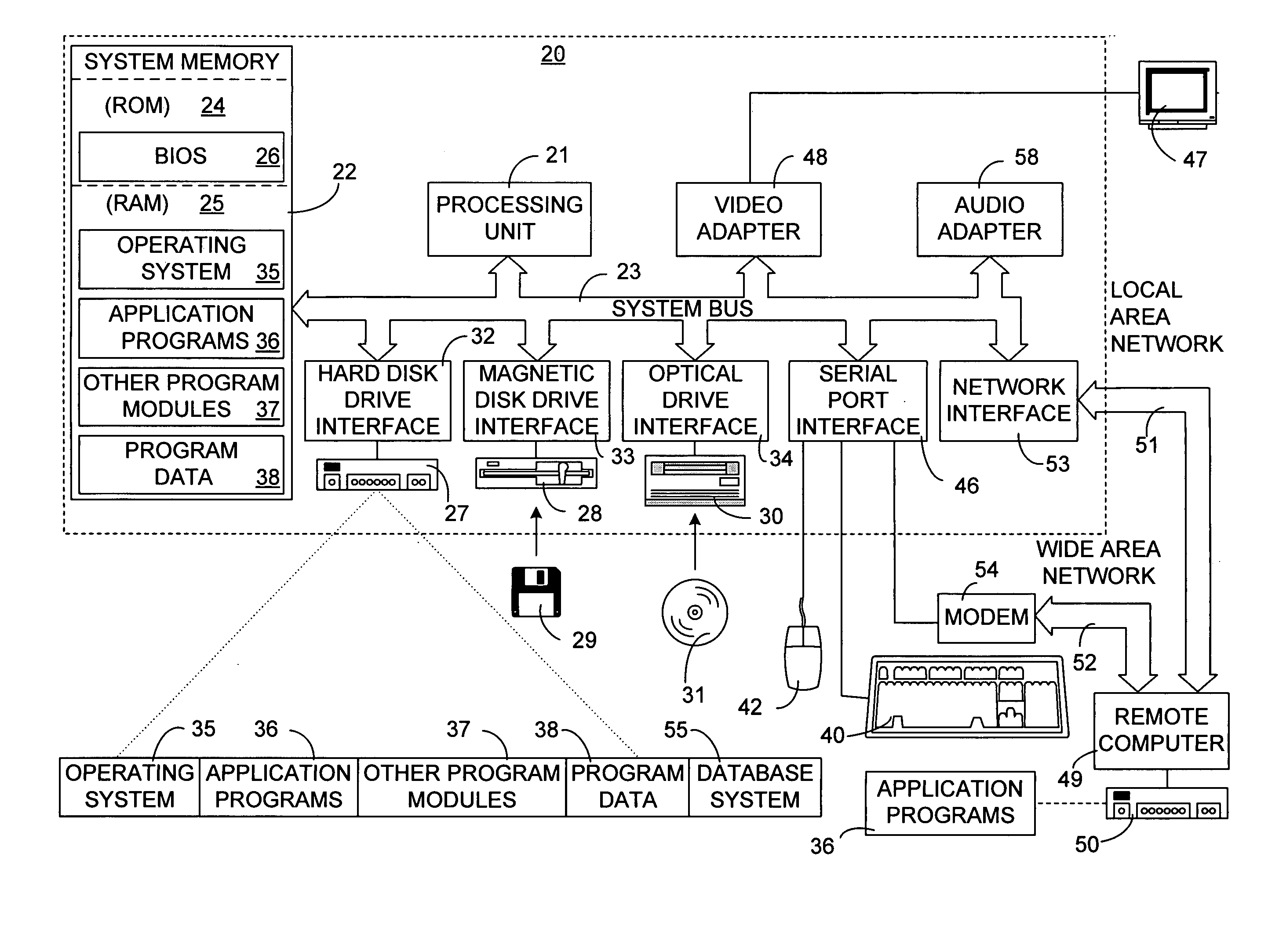
Method and apparatus for exploiting statistics on query expressions for optimization
ActiveUS6947927B2Improve accuracyData processing applicationsDigital data information retrievalQuery planExecution plan
A method for evaluating a user query on a relational database having records stored therein, a workload made up of a set of queries that have been executed on the database, and a query optimizer that generates a query execution plan for the user query. Each query plan includes a plurality of intermediate query plan components that verify a subset of records from the database meeting query criteria. The method accesses the query plan and a set of stored intermediate statistics for records verified by query components, such as histograms that summarize the cardinality of the records that verify the query component. The method forms a transformed query plan based on the selected intermediate statistics (possibly by rewriting the query plan) and estimates the cardinality of the transformed query plan to arrive at a more accurate cardinality estimate for the query. If additional intermediate statistics are necessary, a pool of intermediate statistics may be generated based on the queries in the workload by evaluating the benefit of a given statistic over the workload and adding intermediate statistics to the pool that provide relatively great benefit.
Owner:MICROSOFT TECH LICENSING LLC
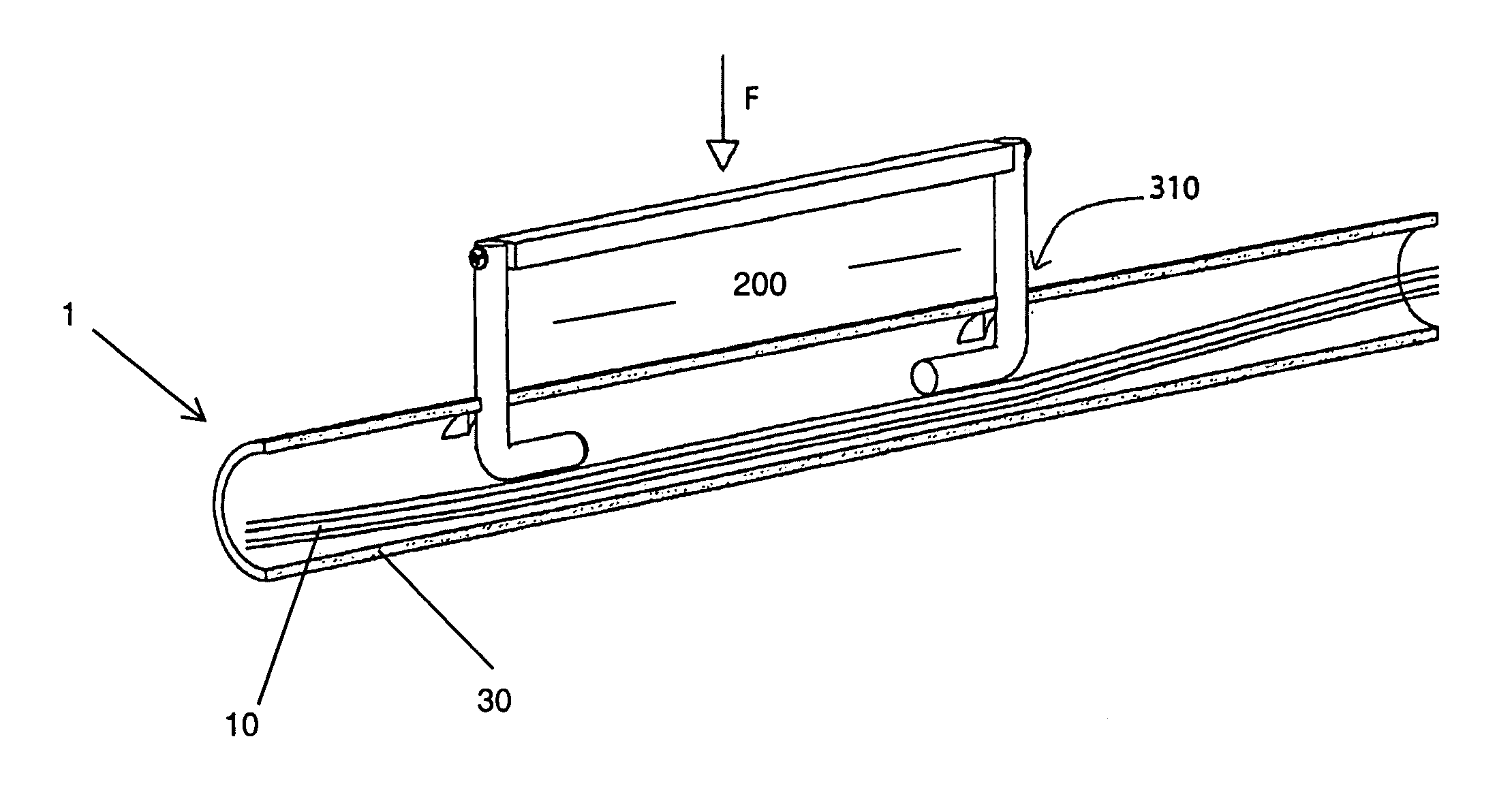
Method for accessing optical fibers within a telecommunication cable
Disclosed is a method accessing one or more optical fibers in a telecommunication cable in a way that considerably reduces the risk of damaging the optical fibers. To avoid inadvertent damage caused by a cutting tool, the method includes moving optical fibers and / or micromodules away from the area on the cable that is to be cut.
Owner:DRAKA COMTEQ BV
Method for delivering tailored asset information to a device
InactiveUS20080086685A1Digital computer detailsInput/output processes for data processingGraphicsGraphical user interface
A method and system for delivering tailored asset information to a device are disclosed. According to one embodiment, a method accesses a database comprising information from a first reporting source about an asset and information from a second reporting source about the asset. A pre-defined user selectable criteria is then utilized to select portions of the information from the first reporting source and the information from the second reporting source. A tailored asset information report is then generated, wherein the tailored asset information report comprises the pre-defined portions of the information about the asset. In so doing, a layout of the tailored asset information report is provided based on a graphical user interface (GUI).
Owner:TRIMBLE INC
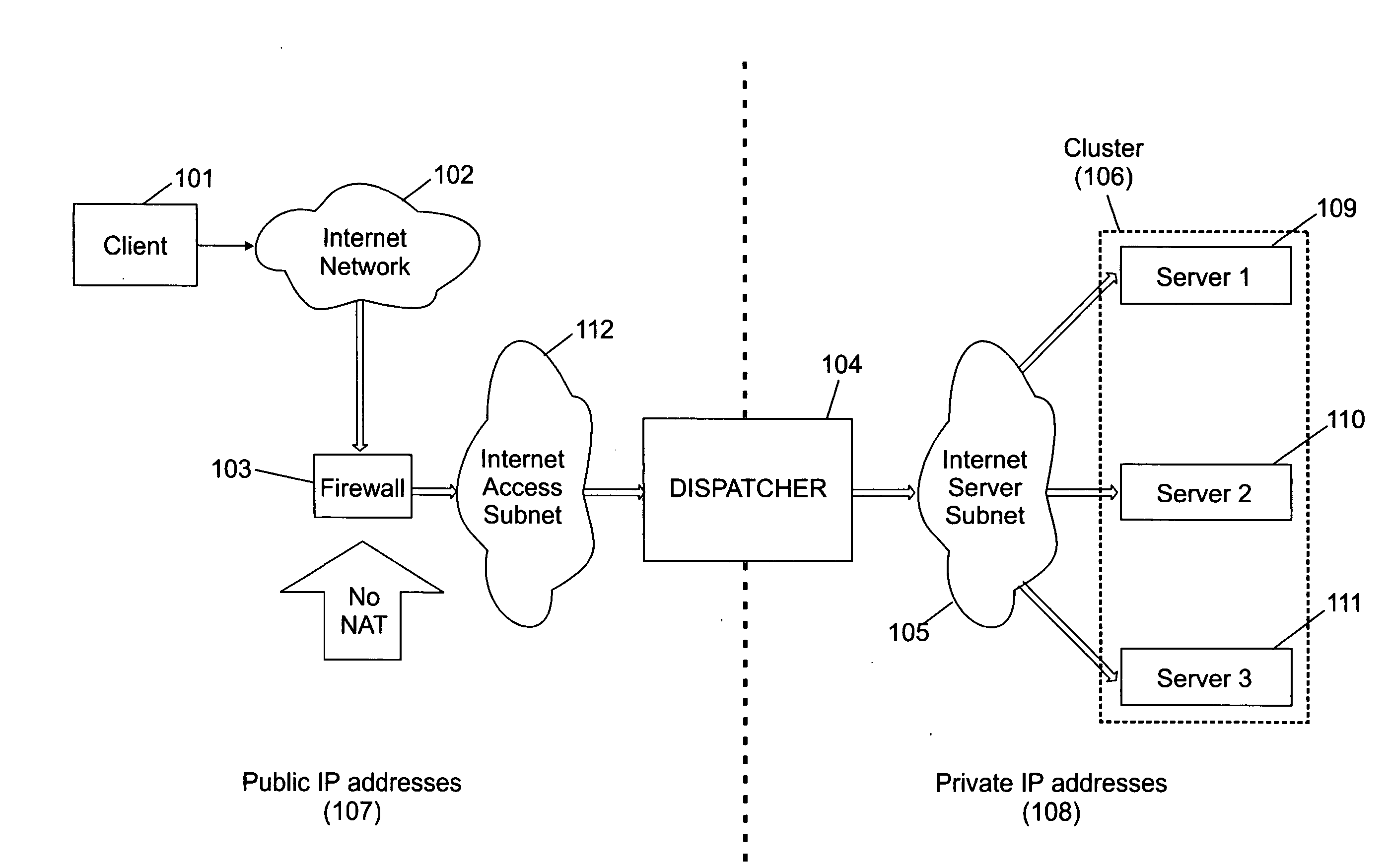
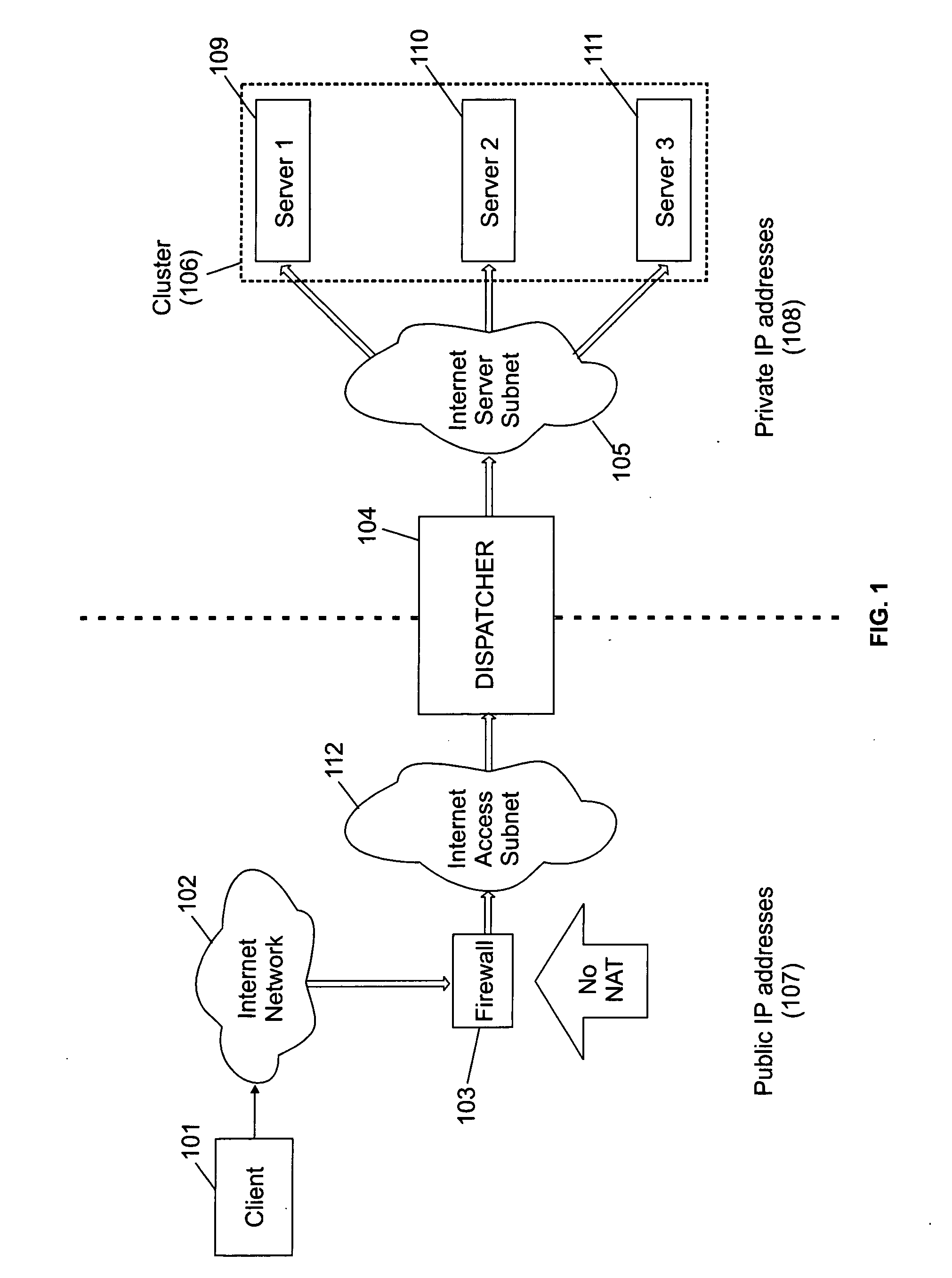
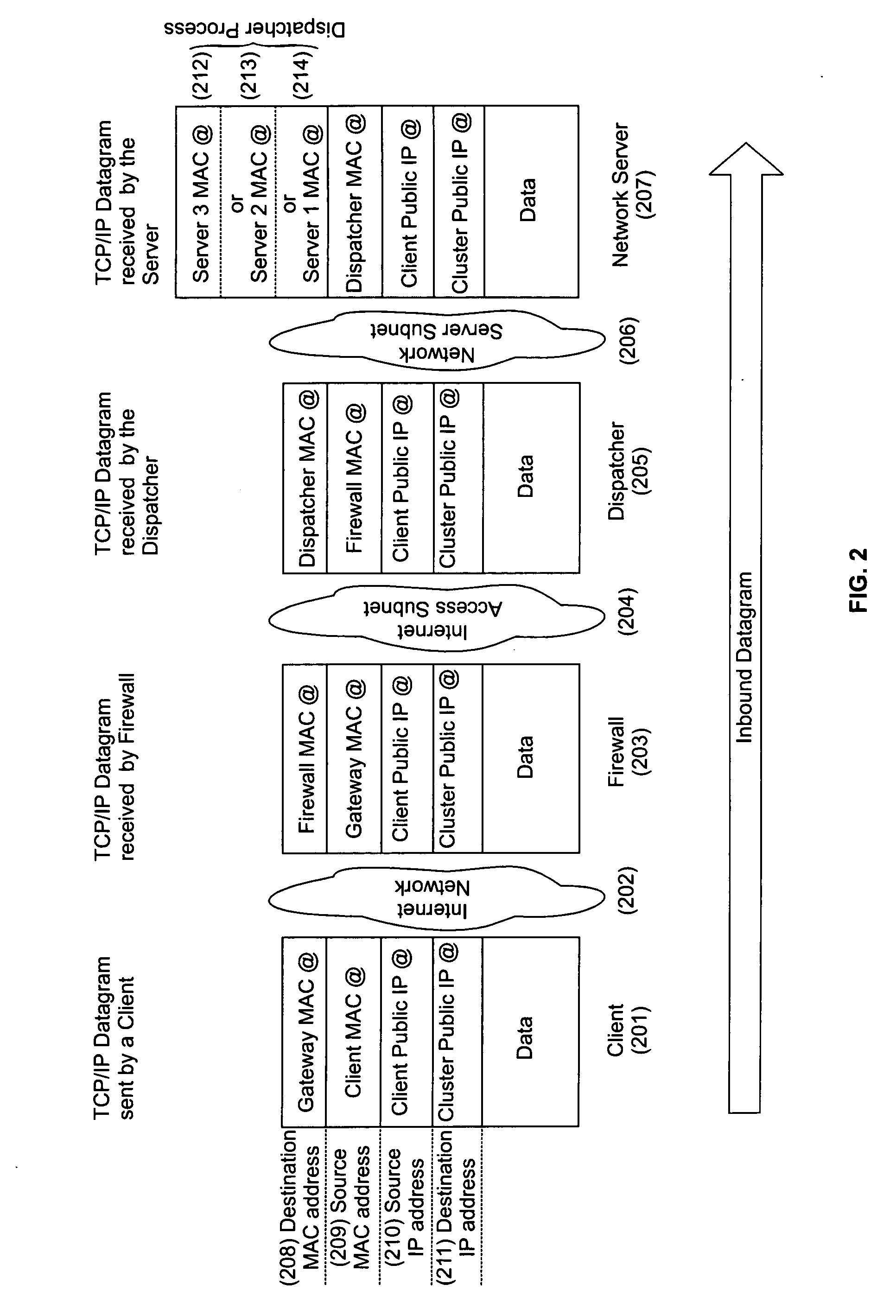
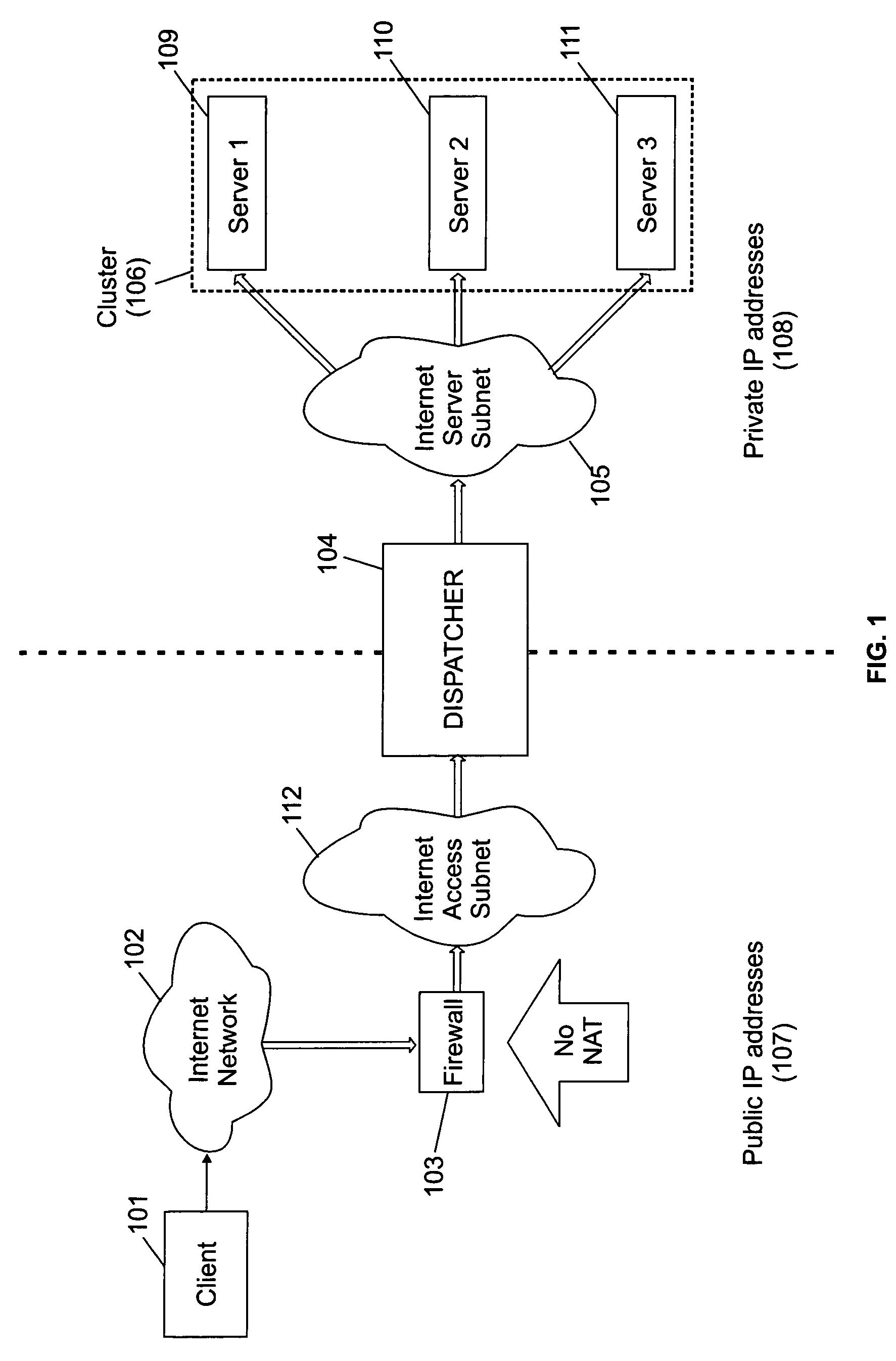
System and method for accessing clusters of servers from the internet network
InactiveUS20050005006A1Multiprogramming arrangementsMultiple digital computer combinationsAccess routePrivate network
A cluster system and method accesses from an internet network, a network server within one or a plurality of clusters, each cluster being identified by a single cluster public Internet Protocol (IP) address. The cluster system has a plurality of network servers organized in one of a plurality of clusters and a network load balancer system for selecting a destination network server in a cluster. Each cluster has one or a plurality of identical network servers, the network load balancer system being connected on one hand to an access routing device and on another hand to the plurality of network servers through a private network server subnet. The method includes the steps of at initialization time, on each network server defining, as a non-advertising alias, in an interface table, the public IP address of each cluster to which the network server belongs, and upon reception, by the network load balancing system, of a datagram having an IP header including a destination IP address field and a medium access control (MAC) header including a destination MAC address field, selecting a destination network server within the cluster corresponding to the cluster public IP address identified in the destination IP address field of the datagram IP header, replacing the destination medium access control (MAC) address field of the datagram MAC header by the MAC address of the selected destination network server, and sending the datagram through the private network server subnet, using the MAC address of the selected destination network server. Upon reception, by the destination network server, of the datagram sent by the network load balancing system, the MAC address in the destination MAC address field of the datagram MAC header is identified as being the MAC address of the selected destination network server, and the IP datagram is processed if the identified cluster public IP address in the destination IP address field of the datagram IP header, is defined as a non-advertising alias in the interface table of the destination network server.
Owner:IBM CORP
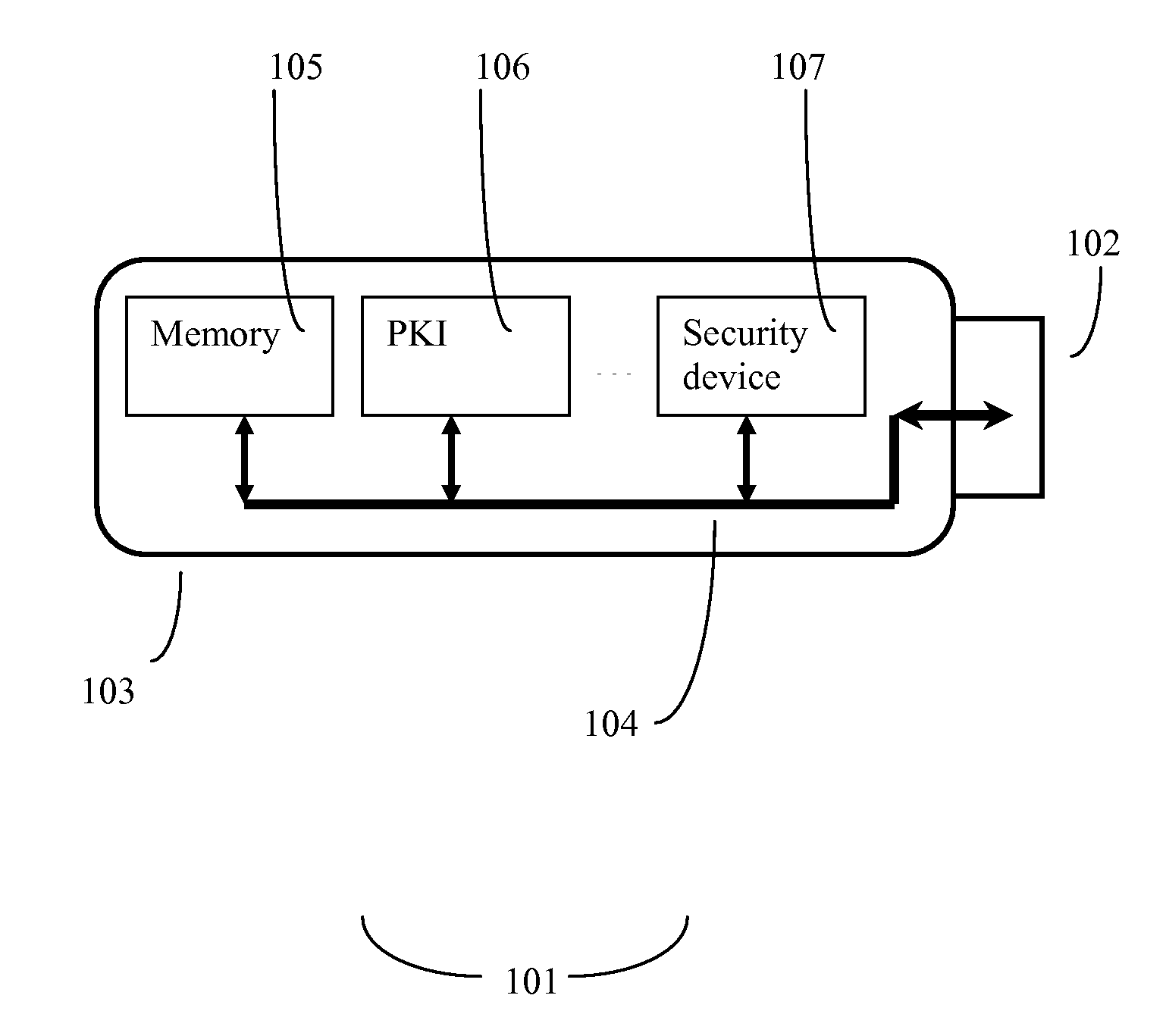
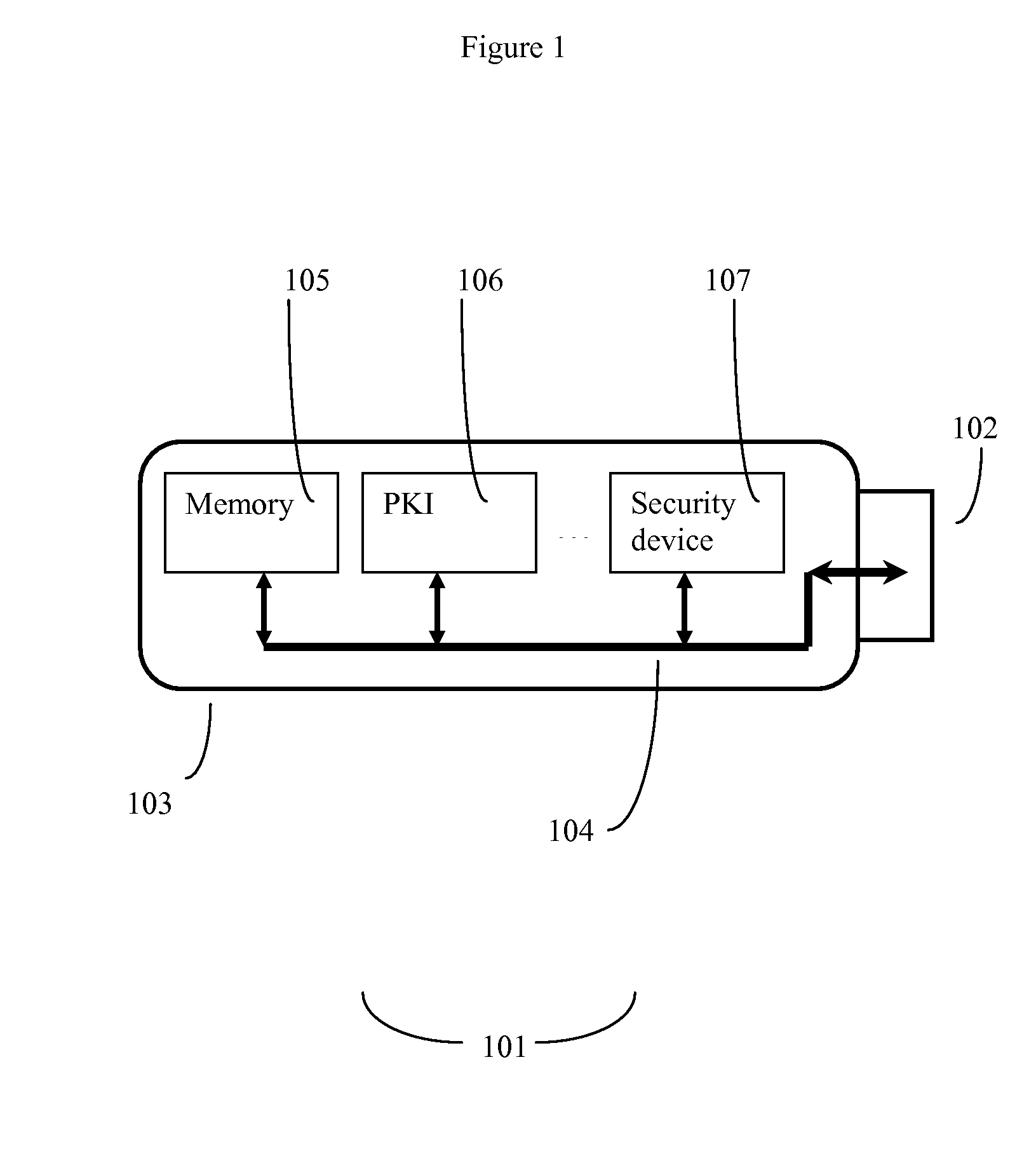
System and Method for Providing a Multifunction Computer Security USB Token Device
InactiveUS20090049307A1User identity/authority verificationInternal/peripheral component protectionUSB hubThe Internet
The invention discloses a small token device, ideally about the size of a key, which can plug into the USB interface of a host computer, which need not be fully trusted, and handle a variety of different security functions. The device is capable of serving as a secure USB hub, and thus can function on a host computer that only has one available USB port. Among the multiple functions that the device can perform include communicating through the internet in a secure manner, storing data in a secure manner, and access secure information through public key (PKI) methods. The invention also allows secure USB peripherals to maintain security while being hooked up to either a non-secure host computer or other non-secure USB peripherals.
Owner:AUTHENEX
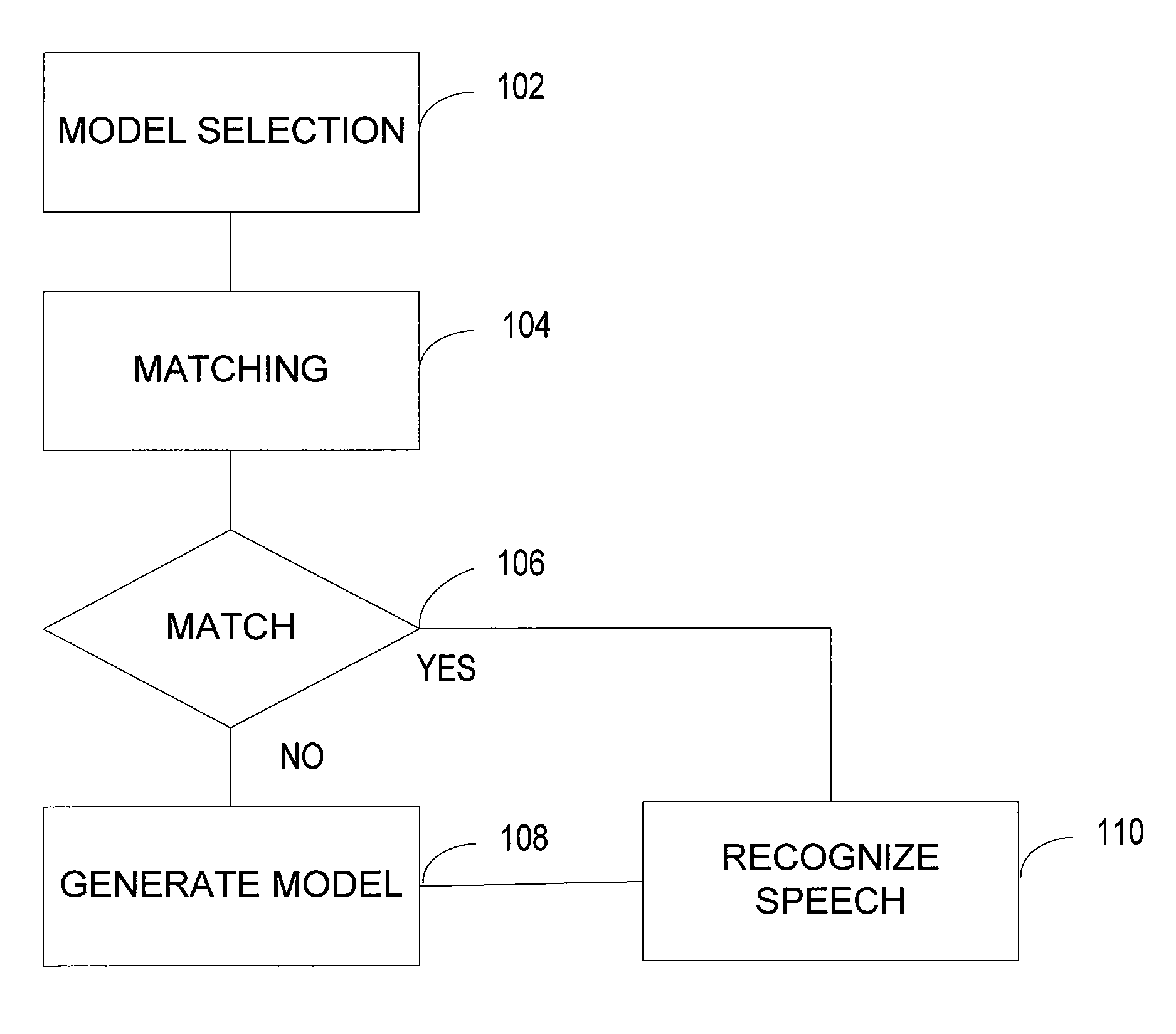
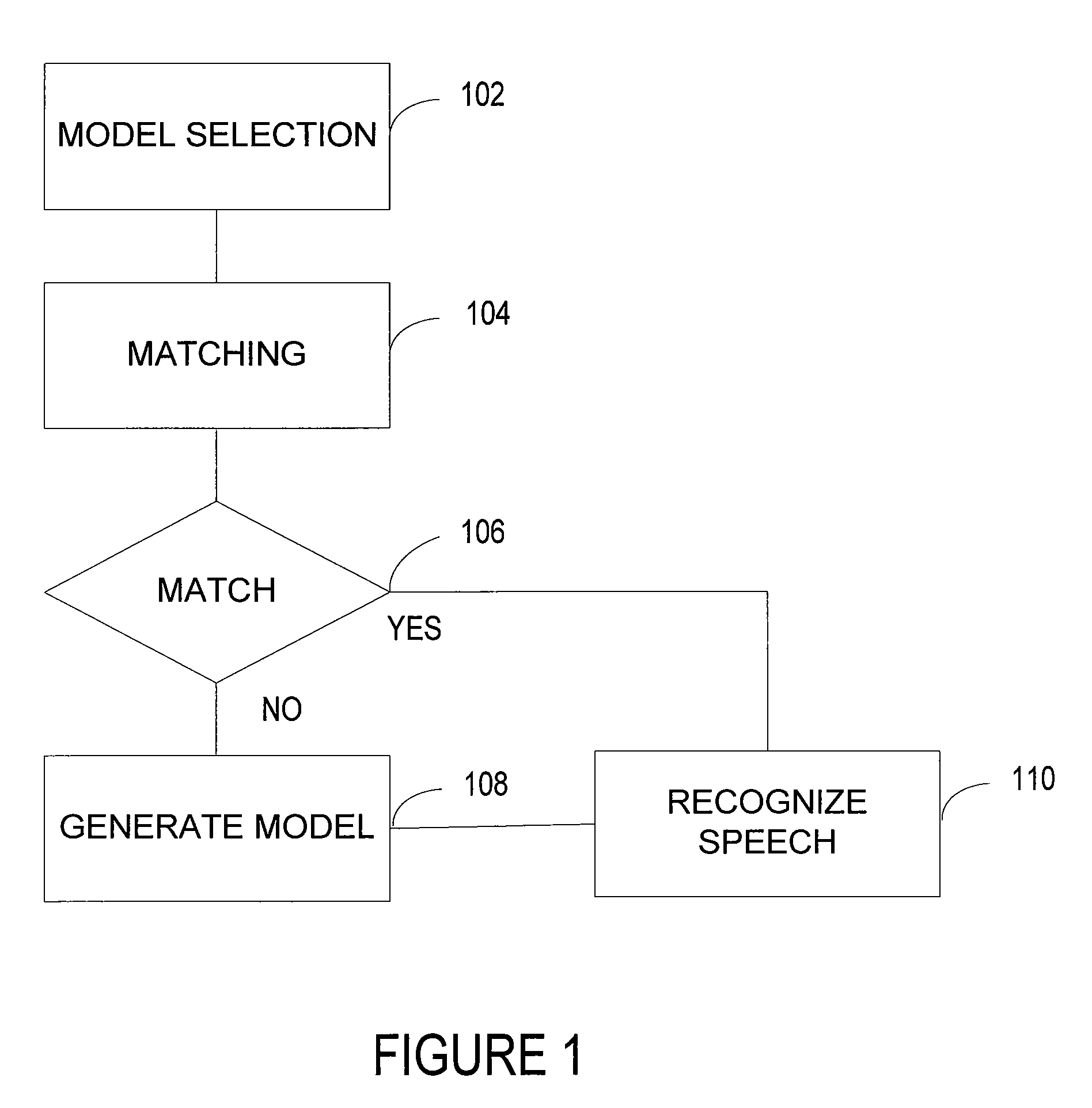
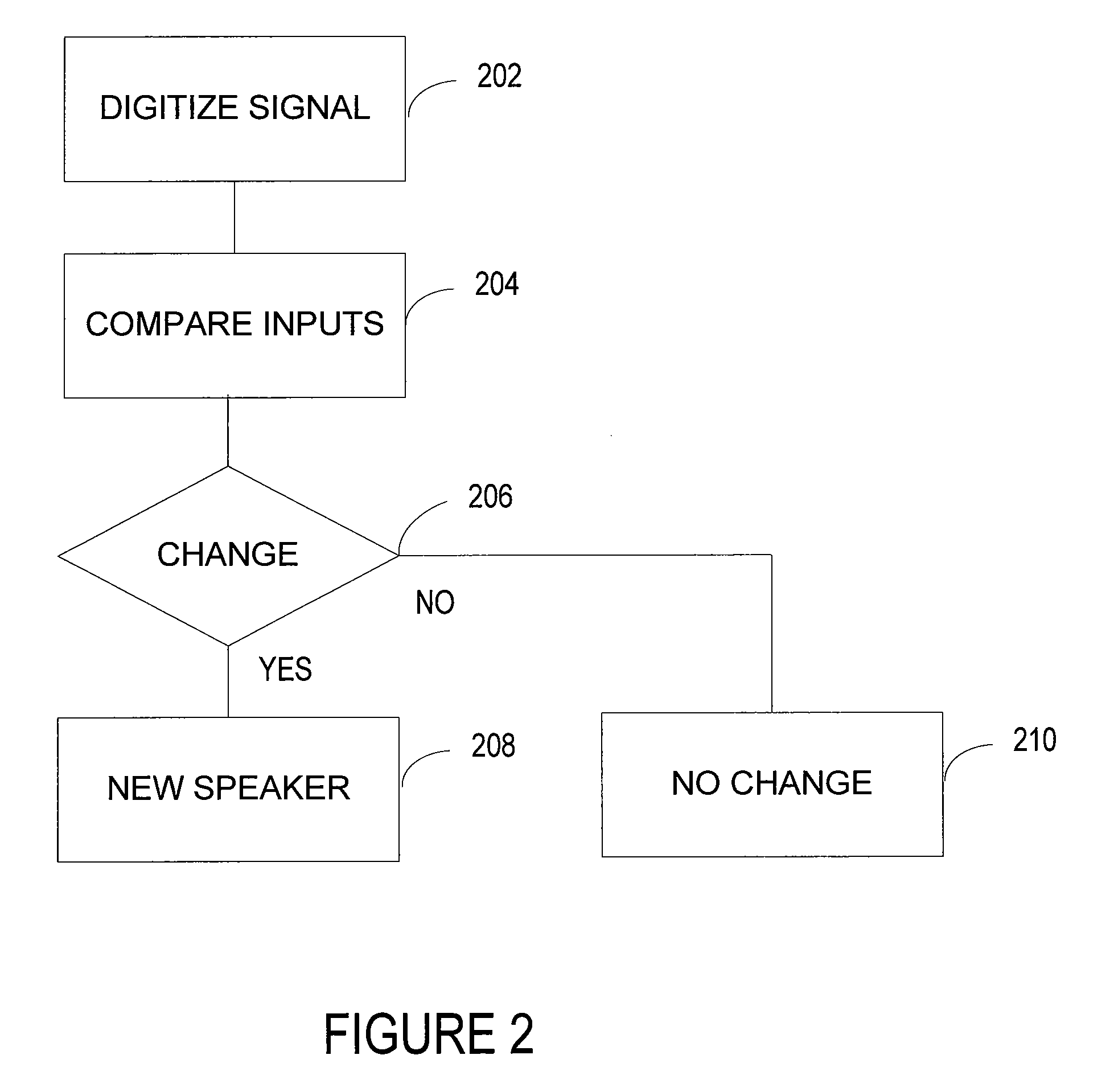
Speaker recognition system
A method automatically recognizes speech received through an input. The method accesses one or more speaker-independent speaker models. The method detects whether the received speech input matches a speaker model according to an adaptable predetermined criterion. The method creates a speaker model assigned to a speaker model set when no match occurs based on the input.
Owner:NUANCE COMM INC
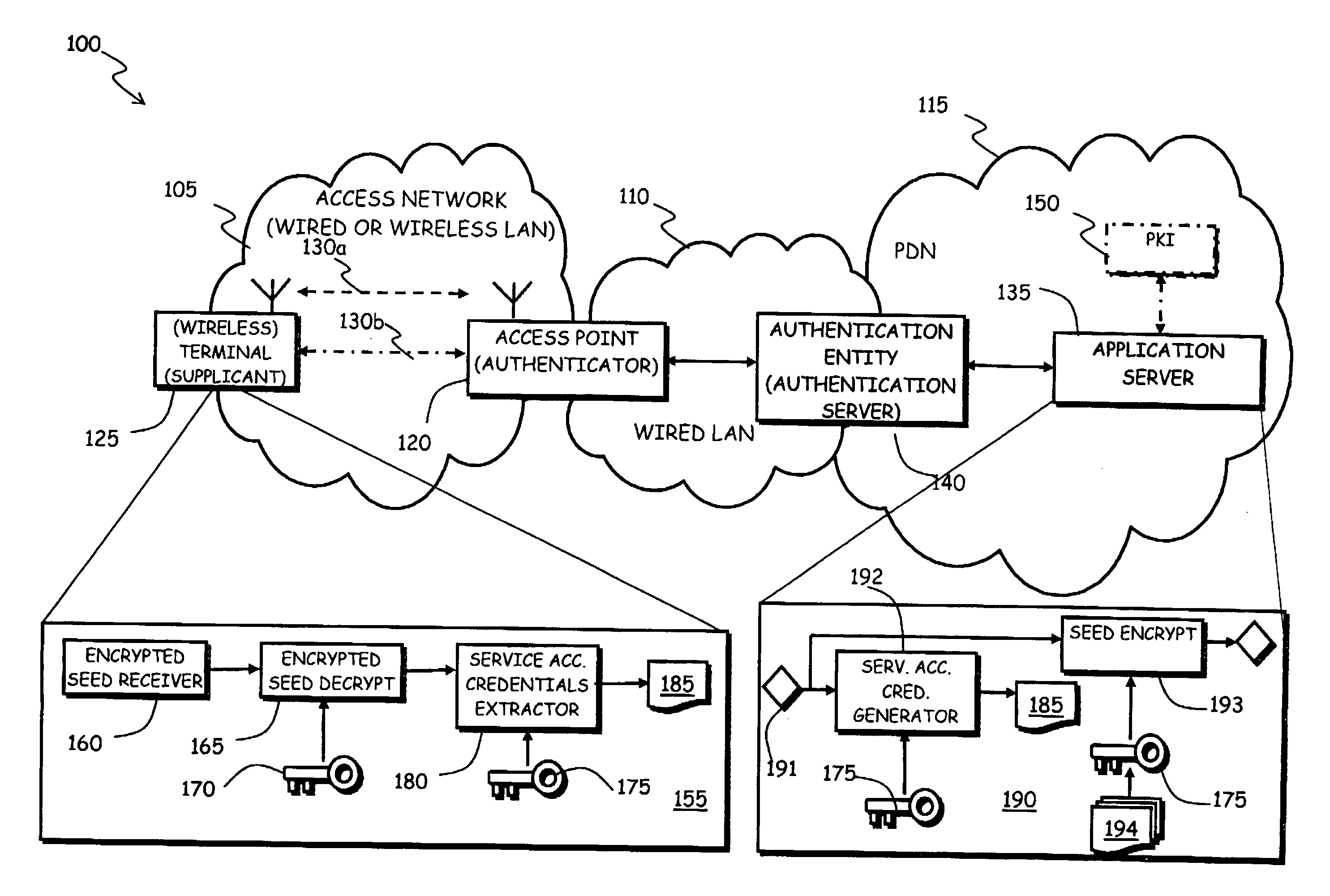
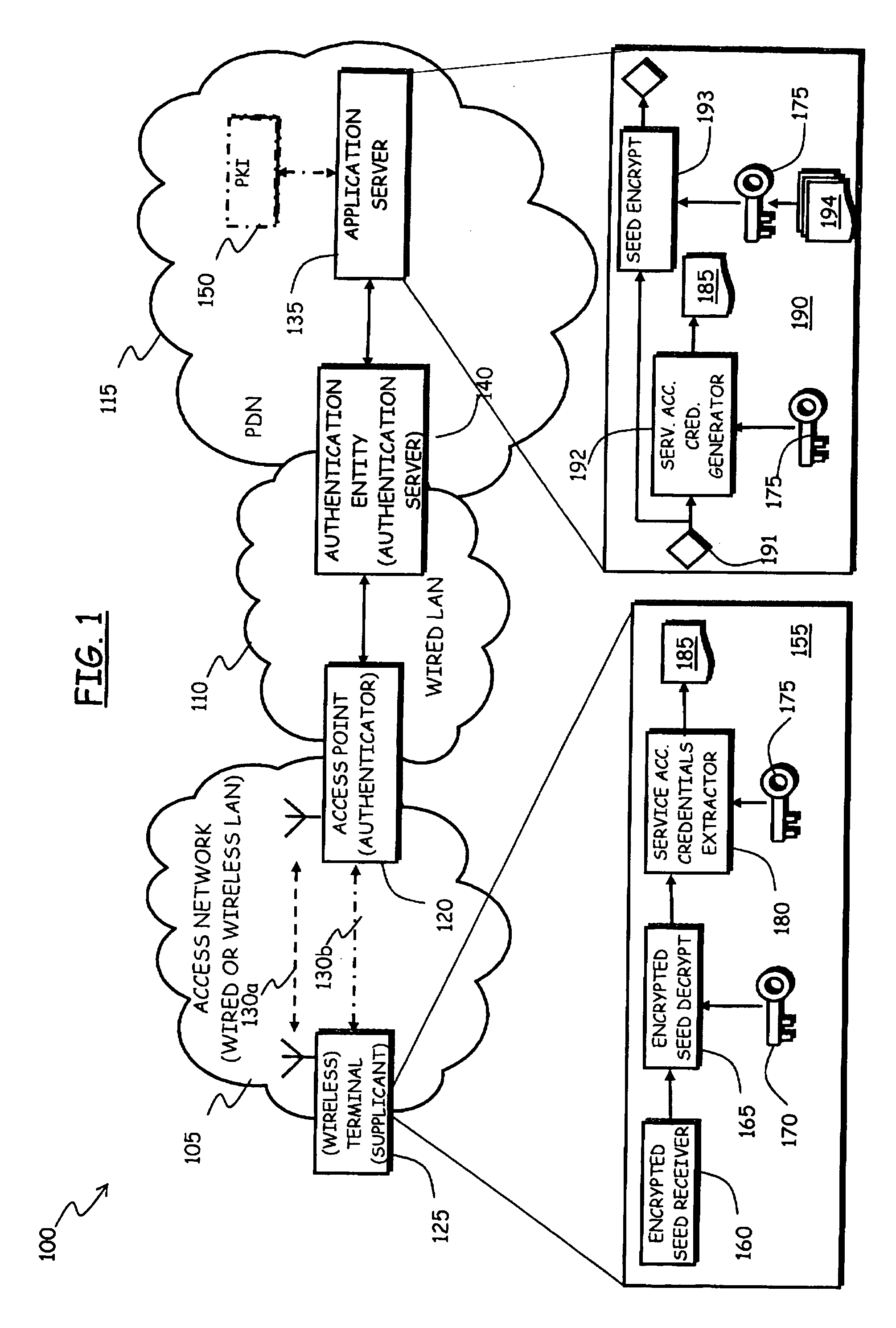
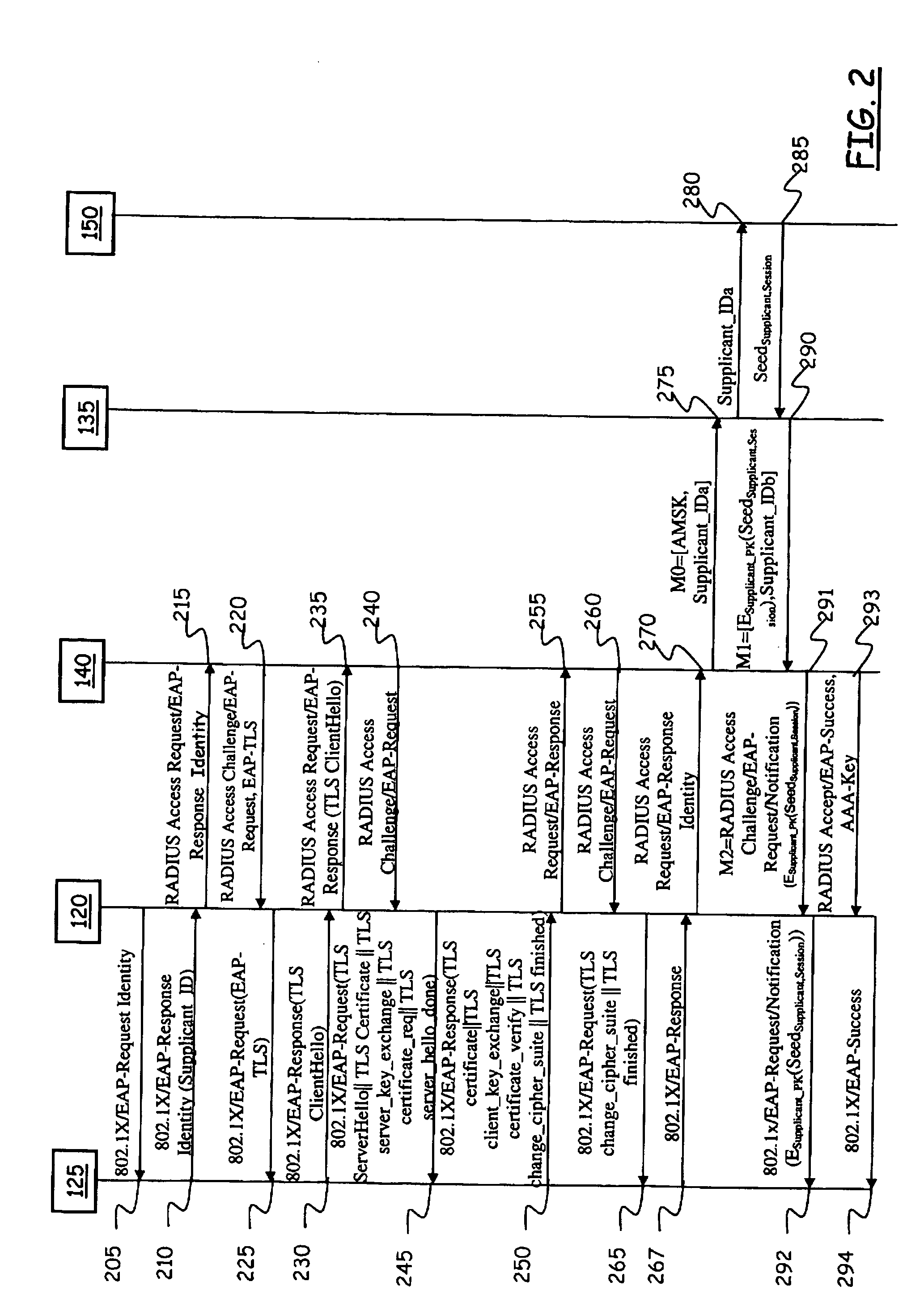
Method and System for Automated and Secure Provisioning of Service Access Credentials for On-Line Services to Users of Mobile Communication Terminals
InactiveUS20090158032A1Easy to implementSimplifying credential managementSecret communicationSecuring communicationEnd userMethod access
In a communications network including at least one authentication entity adapted to authenticating a network access requestor in order to conditionally grant thereto access to the communications network, wherein the authenticating is based on public key cryptography, a method for automatically provisioning the network access requestor with service access credentials for accessing an on-line service offered by an on-line service provider accessible through the communications network. The method includes: during the authenticating the network access requestor, having an authentication entity request to the on-line service provider the generation of the service access credentials; at the on-line service provider, generating the service access credentials, encrypting the service access credentials by exploiting a public encryption key of the network access requestor and providing the encrypted service access credentials to the authentication entity; and having the authentication entity cause the network access requestor to be provided with the encrypted service access credentials.
Owner:TELECOM ITALIA SPA +1
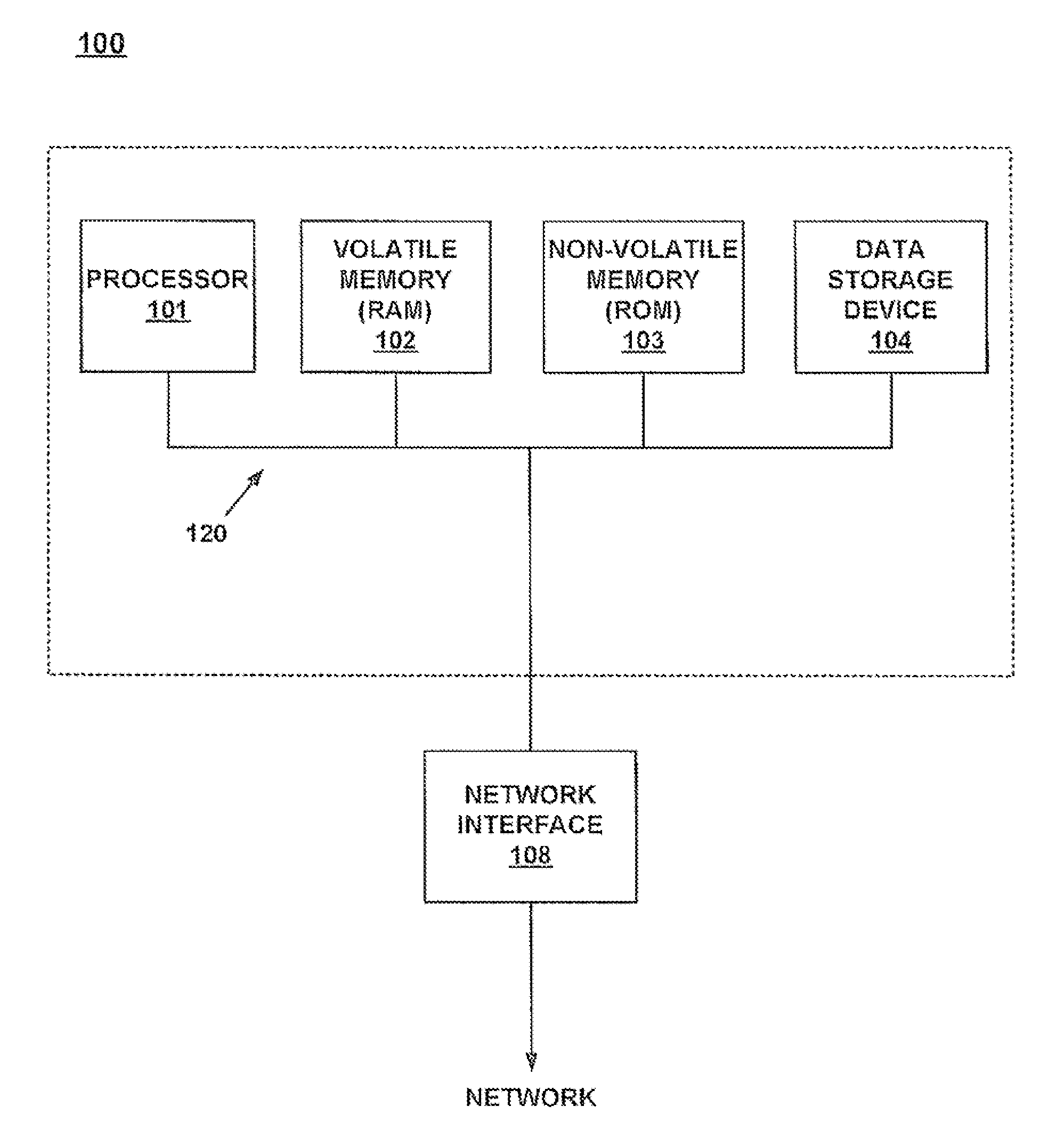
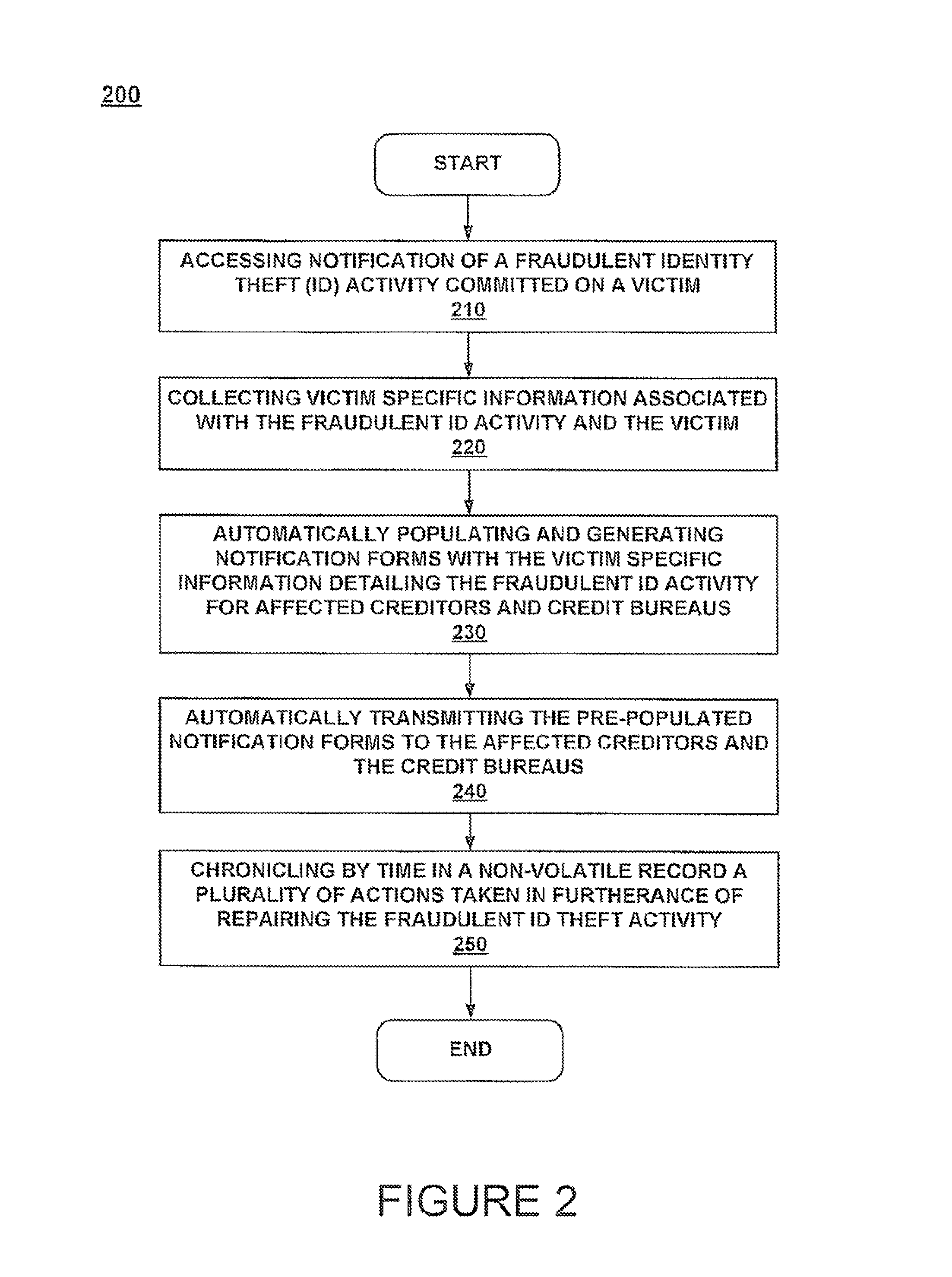
Method and system for automatically repairing a fraudulent identity theft incident
InactiveUS8938399B1Combat allegationTime-consume processFinanceComputer security arrangementsIdentity theftMethod access
A method and system for automatically repairing identity theft under computer control. In one embodiment, a method is disclosed for repairing identity theft. The method accesses notification of a fraudulent identity theft incident committed on a victim. The method collects victim specific information that is associated with the fraudulent identity theft incident and the victim. Then, the method automatically populates and generates notification forms with the victim specific information. The populated notification forms detail the fraudulent identity theft incident for affected creditors and credit bureaus. Then, the method automatically transmits the notification forms to the affected creditors, credit bureaus, law enforcement agencies, and any other required entities. The method then chronicles by time in a non-volatile record all the actions taken in furtherance of repairing the fraudulent identity theft incident.
Owner:HERMAN EDWARD S
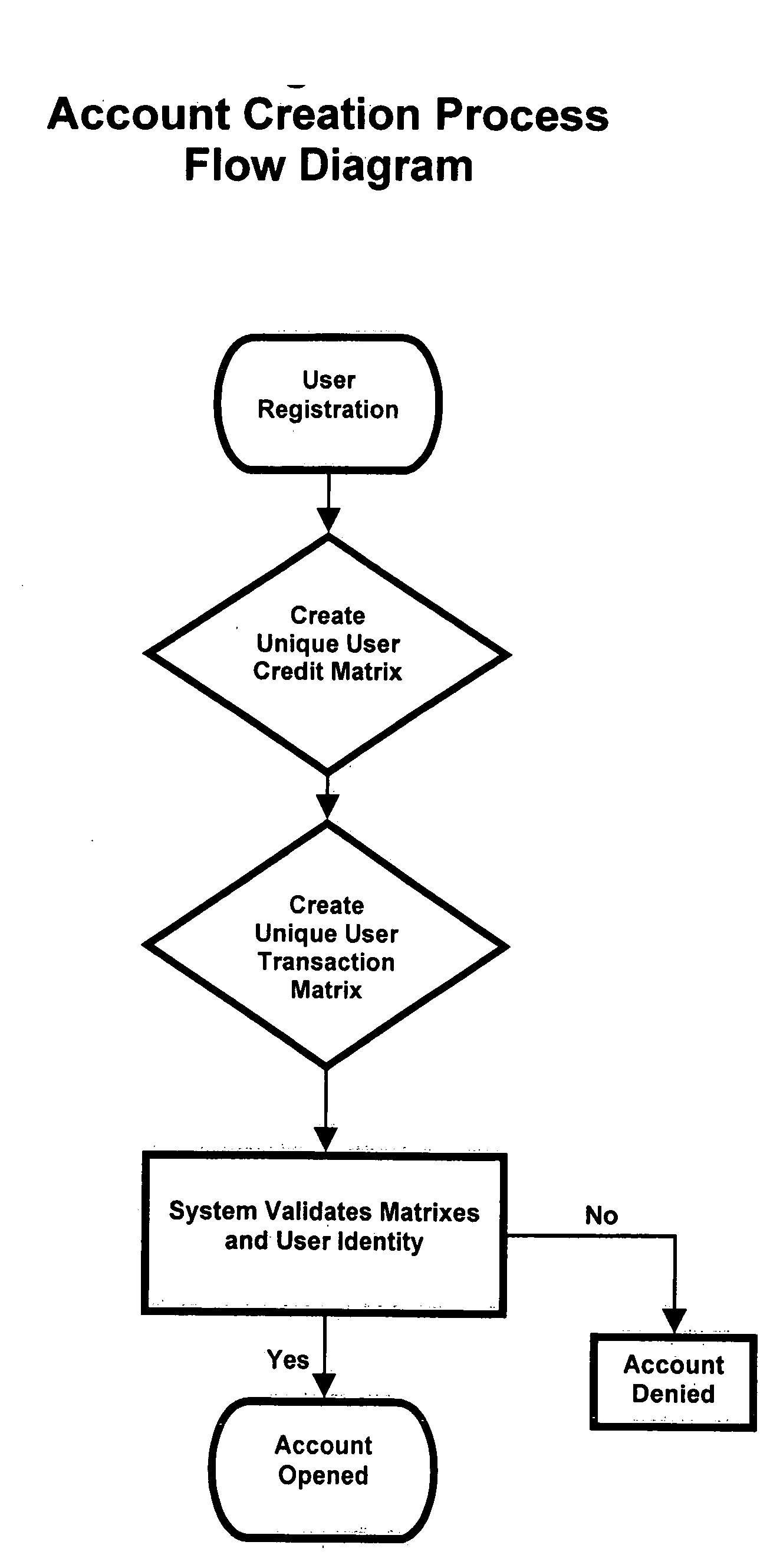
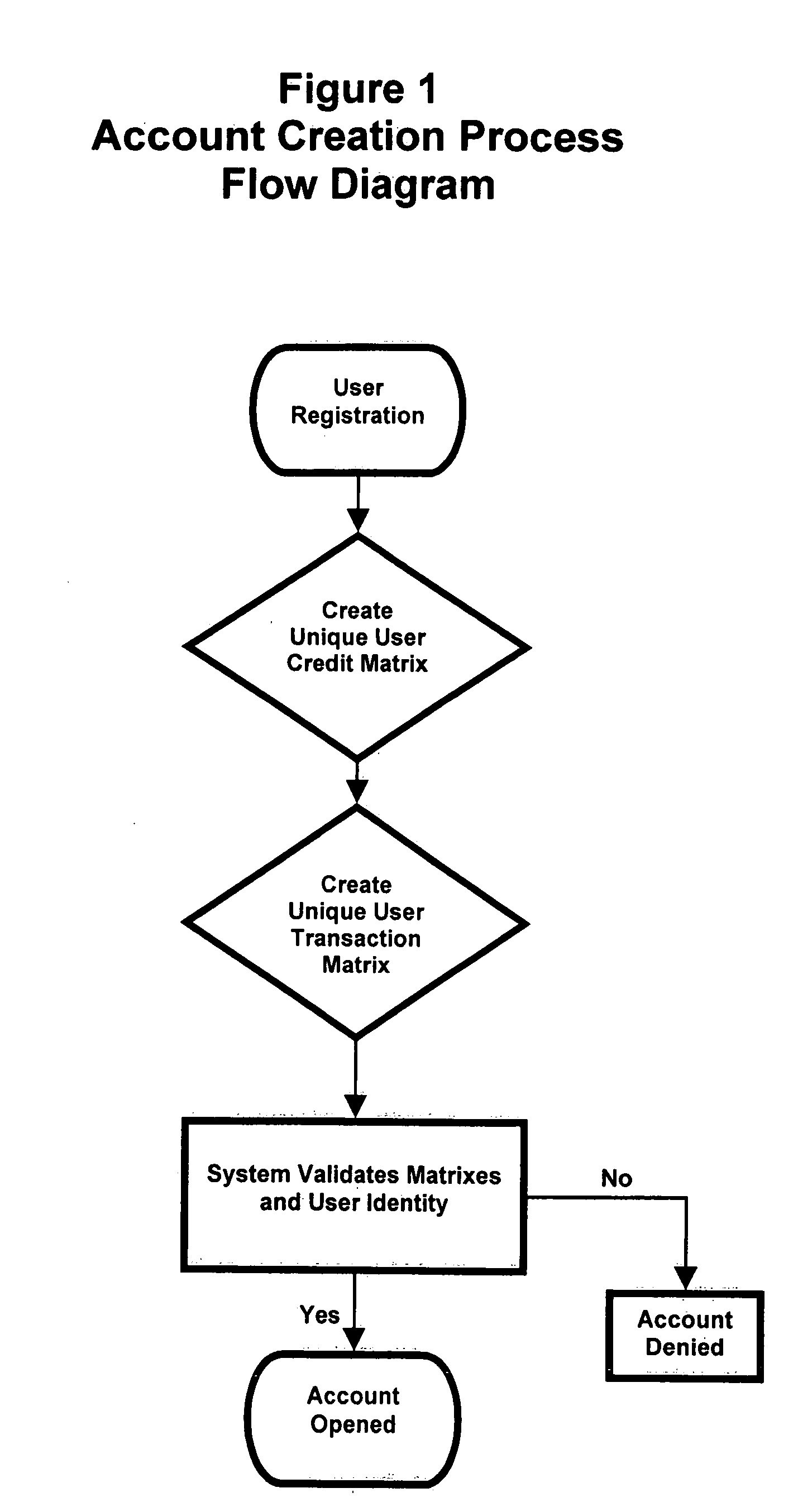
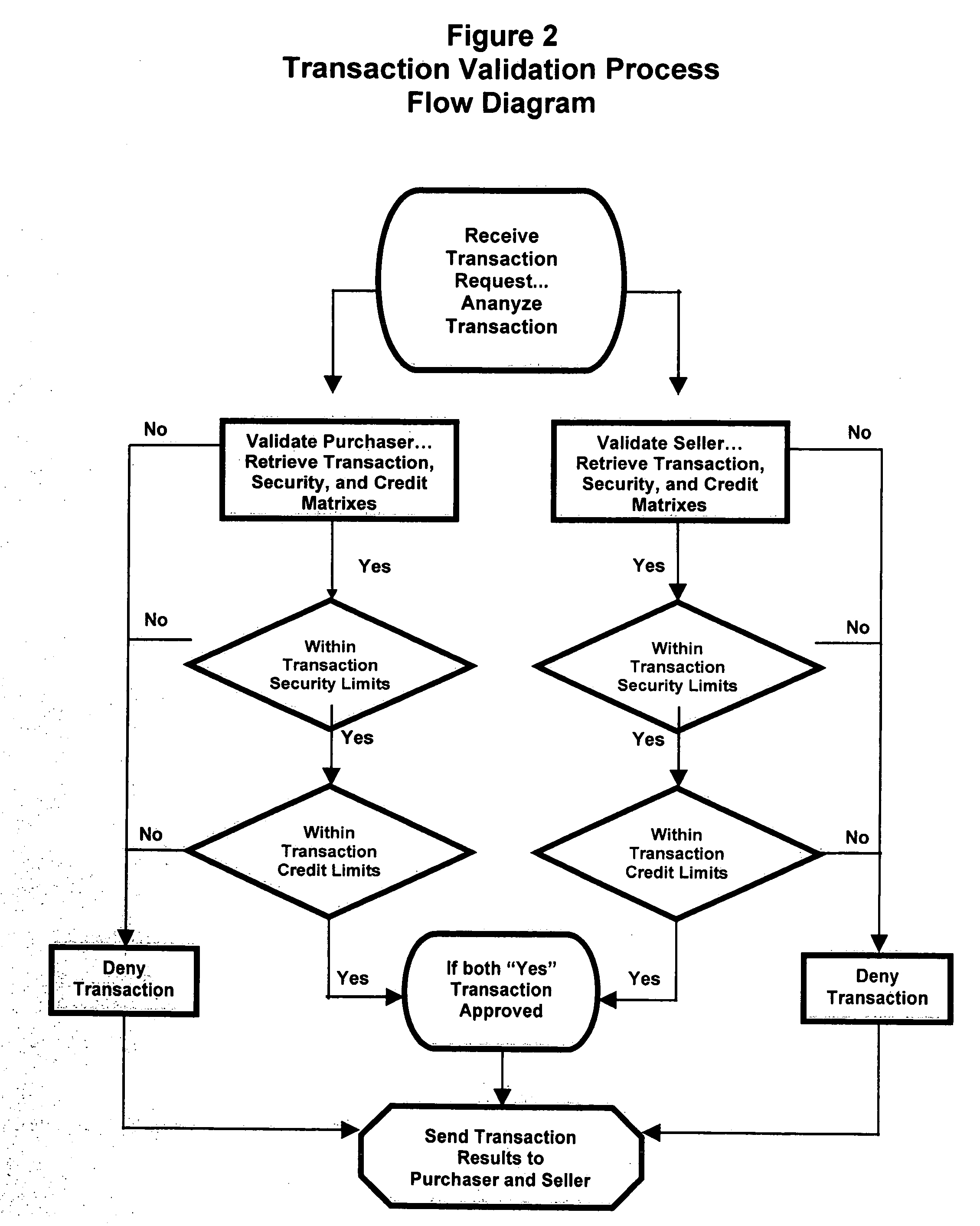
Mobile payment and accounting system with integrated user defined credit and security matrixes
InactiveUS20080255993A1Improve securityFinanceProtocol authorisationThe InternetFinancial transaction
A platform that accommodates financial transactions and is accessible via mobile phone networks, Internet and traditional methods is linked to user defined credit and security matrixes. Credit risk tolerance factors consider the qualifications, characteristics, and profile of counterparties. Security risk tolerance factors consider the user's willingness to use a particular financial platform in an environment where abuse, fraud, theft, and other security factors are of concern. In both cases the user creates matrixes that describe risk tolerance and financial transactions must successfully pass through the filters designed by the user. The system can be used alone or linked to bank accounts, credit and debit accounts, etc. This provides a higher level of security and risk control in a mobile or Web-based environment. By giving customers way to control risk, use of new electronic methods of payment and other financial transactions can be accommodated in a more comfortable, secure, and efficient manner.
Owner:BLINBAUM JACQUES
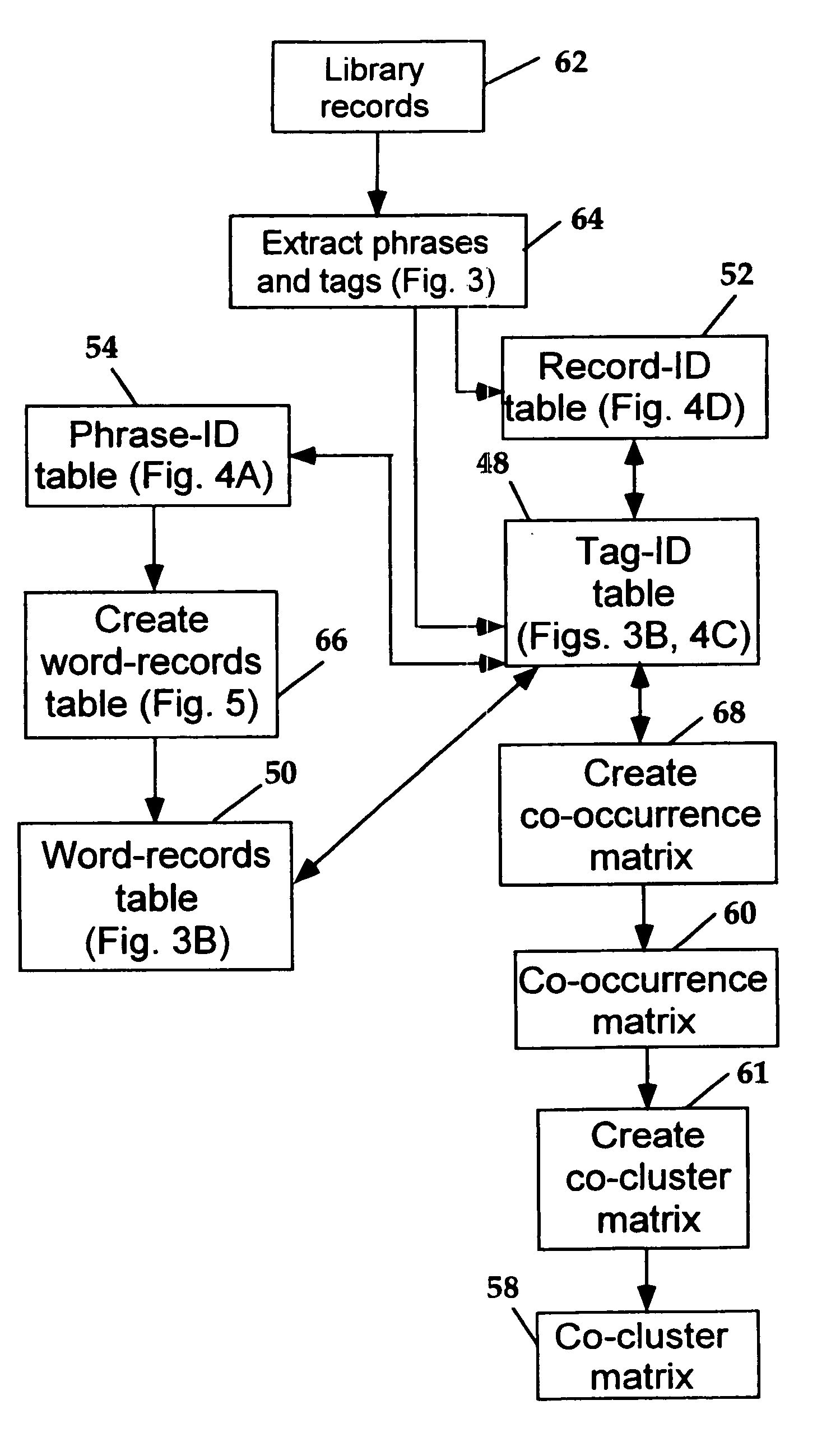
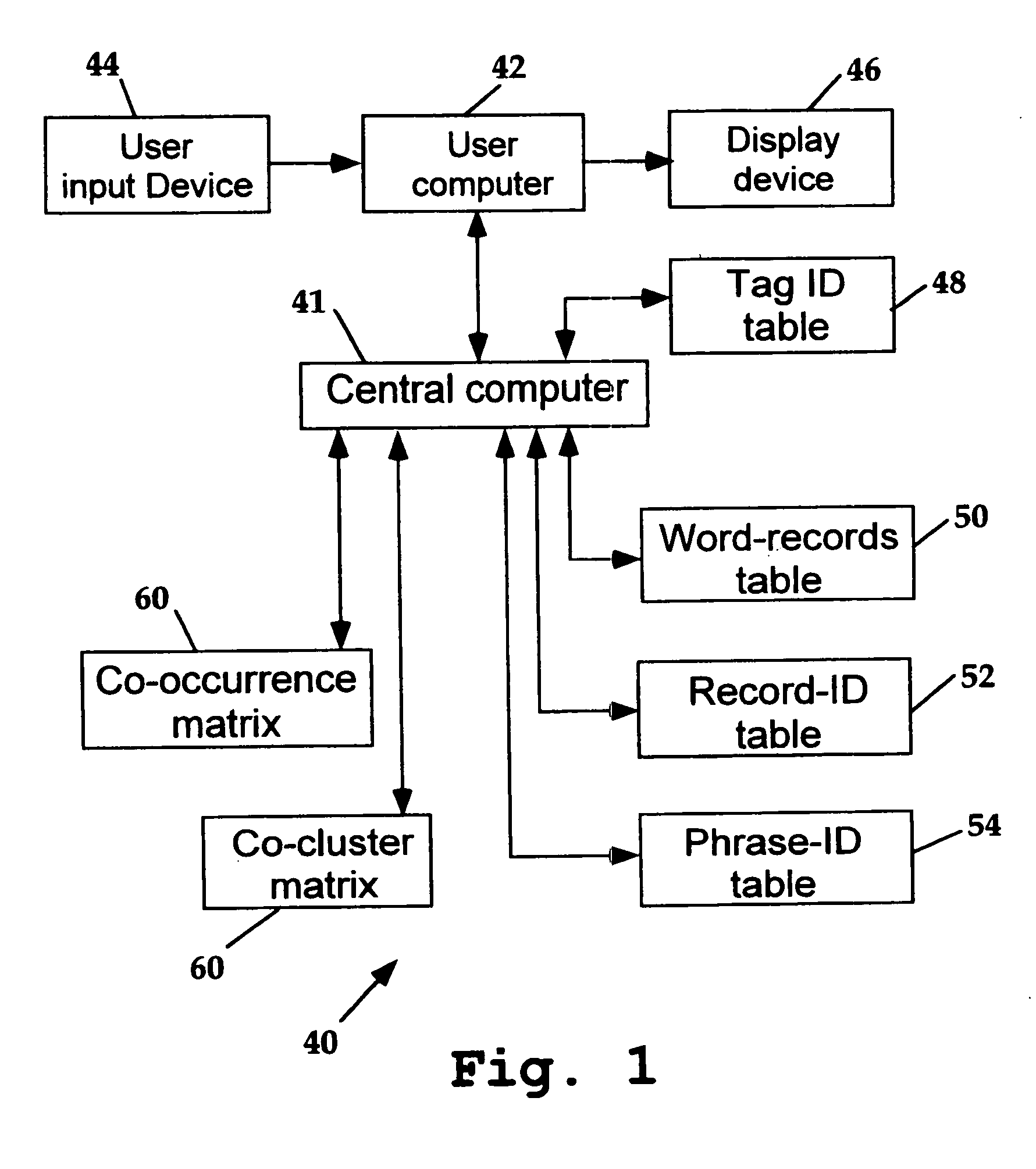
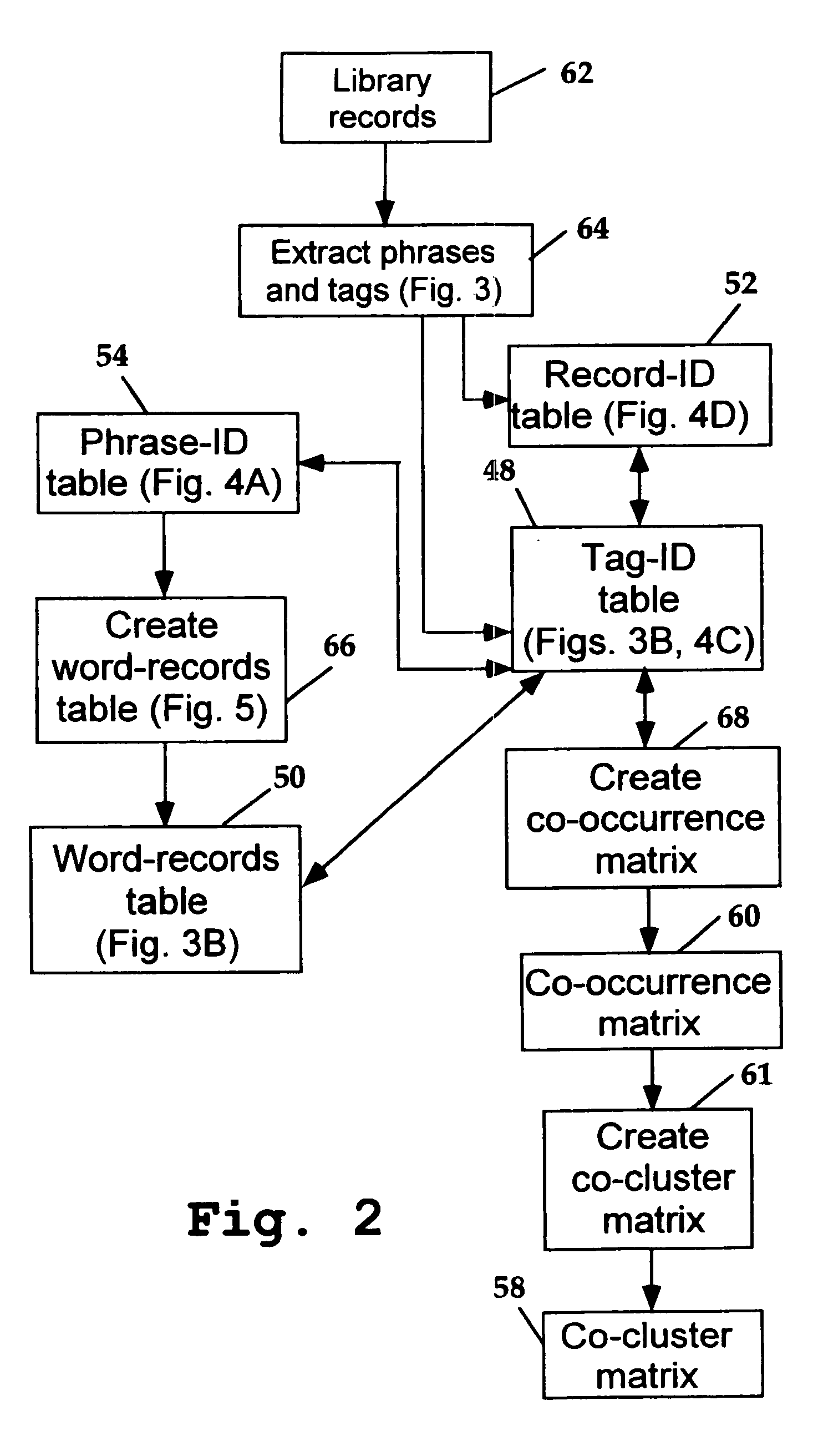
Database system and method for retrieving records from a record library
InactiveUS20060259475A1Special data processing applicationsMetadata based other databases retrievalTable (database)Electronic form
Disclosed are a computer-readable code, system and method for retrieving one or more records stored in electronic form in a library of records. The program that executes the method accesses a database table to identify, from user-generated information, one or more phrases likely to be contained in or associated with a record of interest, and from these phrase(s), identifies one or more phrase-related tags. The program uses the one or more tags so identified to find, independent of user input, test tags associated with those already identified, and to present to the user the number of records associated with the test tags, allowing the user to find records based on the inclusion of known tags and associated phrases.
Owner:WORD DATA
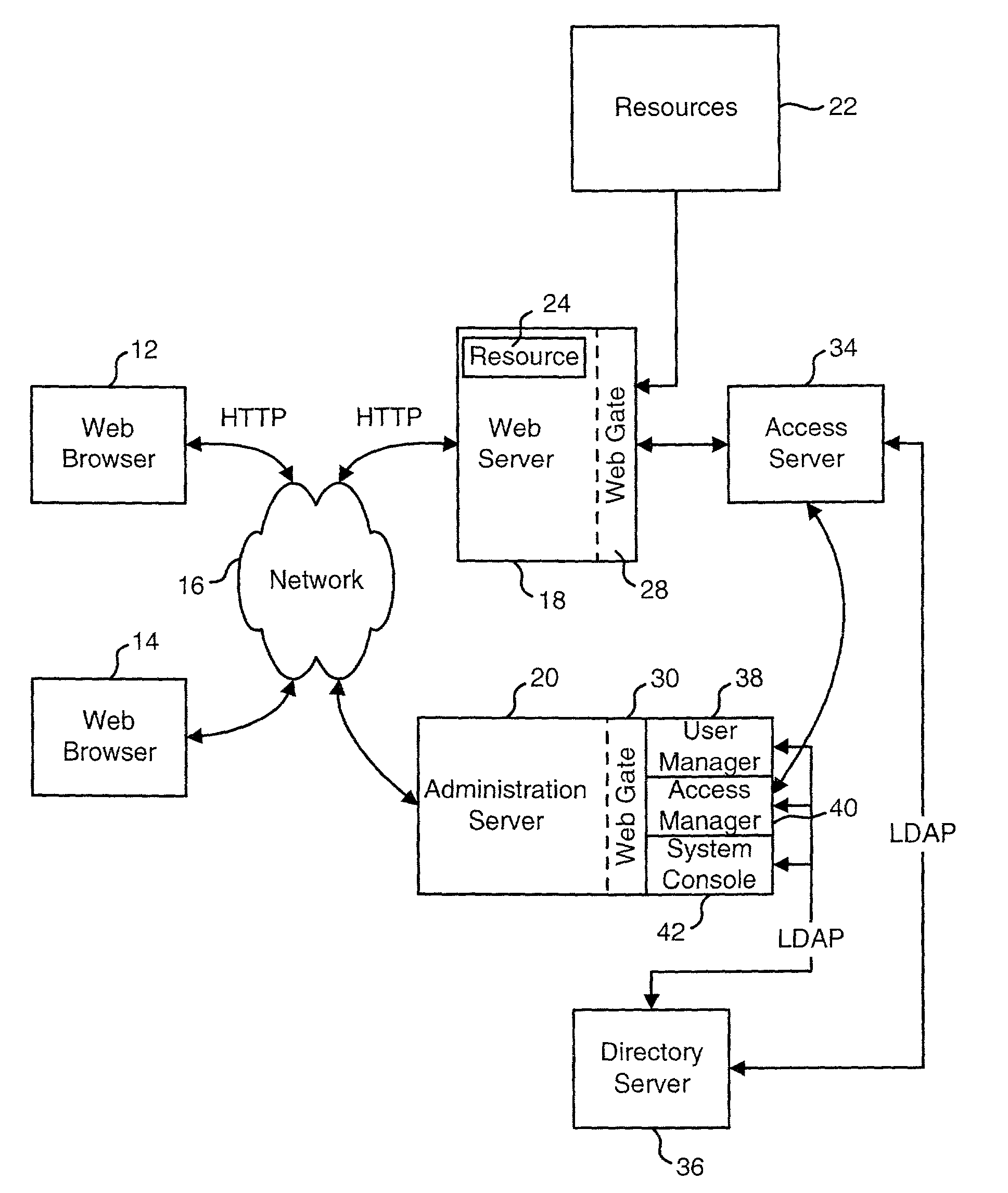
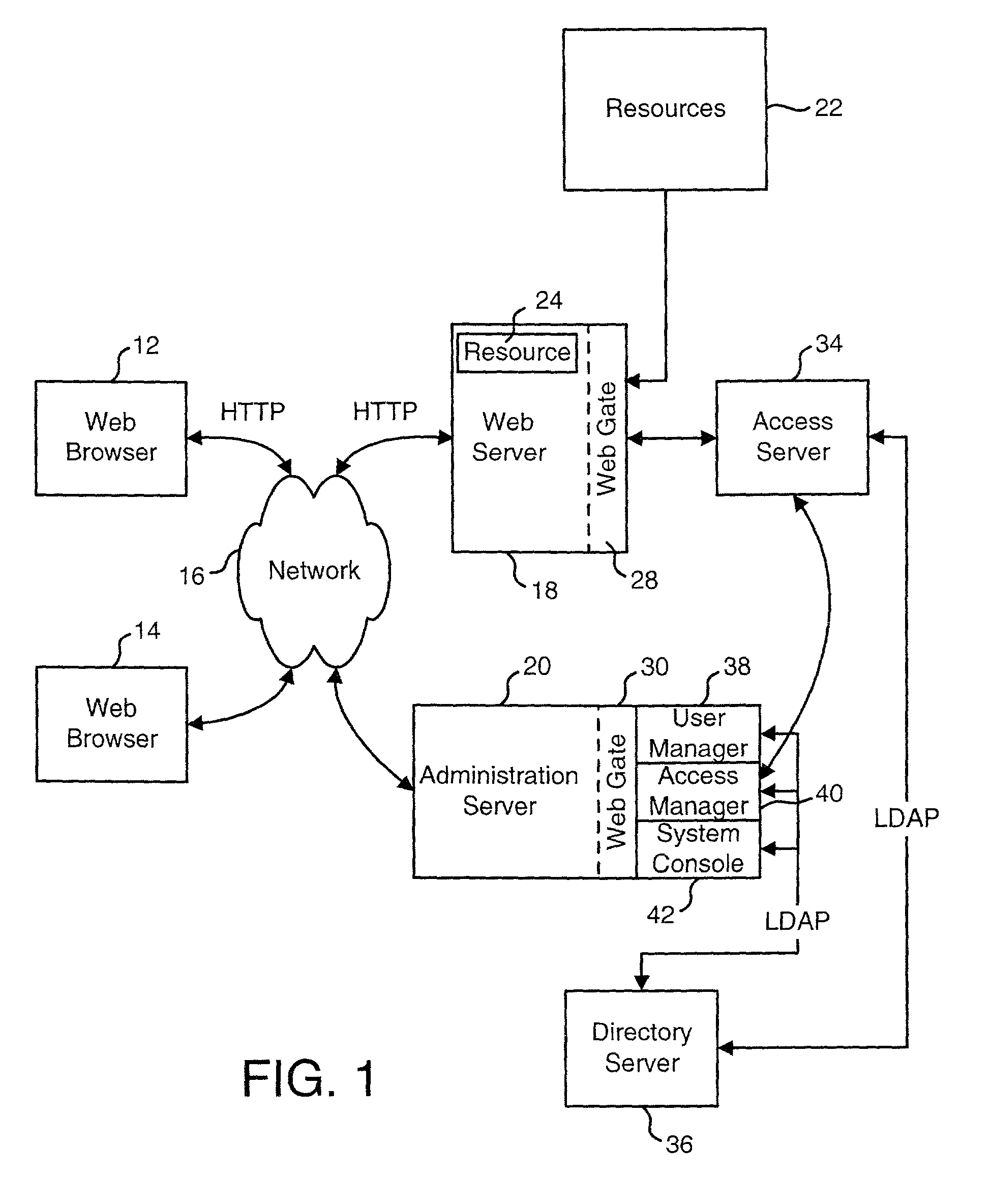
Systems and methods for testing whether access to a resource is authorized based on access information
ActiveUS7464162B2Random number generatorsUser identity/authority verificationGraphicsGraphical user interface
The Access Tester allows an administrator, or any other authorized user, to determine who or what entities have access to a resource, whether a particular individual or set of individuals have access to a resource under certain conditions and whether the authorization rules associated with a resource operate as intended. In one embodiment, an administrator uses a graphical user interface to enter access information. Exemplar access information includes one or more URLs identifying the resource(s), one or more request methods, one or more IP addresses, date and time restrictions, and an identification of one or more users. The Access Tester determines whether the identified users are authorized to access the resource(s) associated with the URL(s) using the request methods, during the date and time provided.
Owner:ORACLE INT CORP
System and method for enabling DTMF detection in a VoIP network
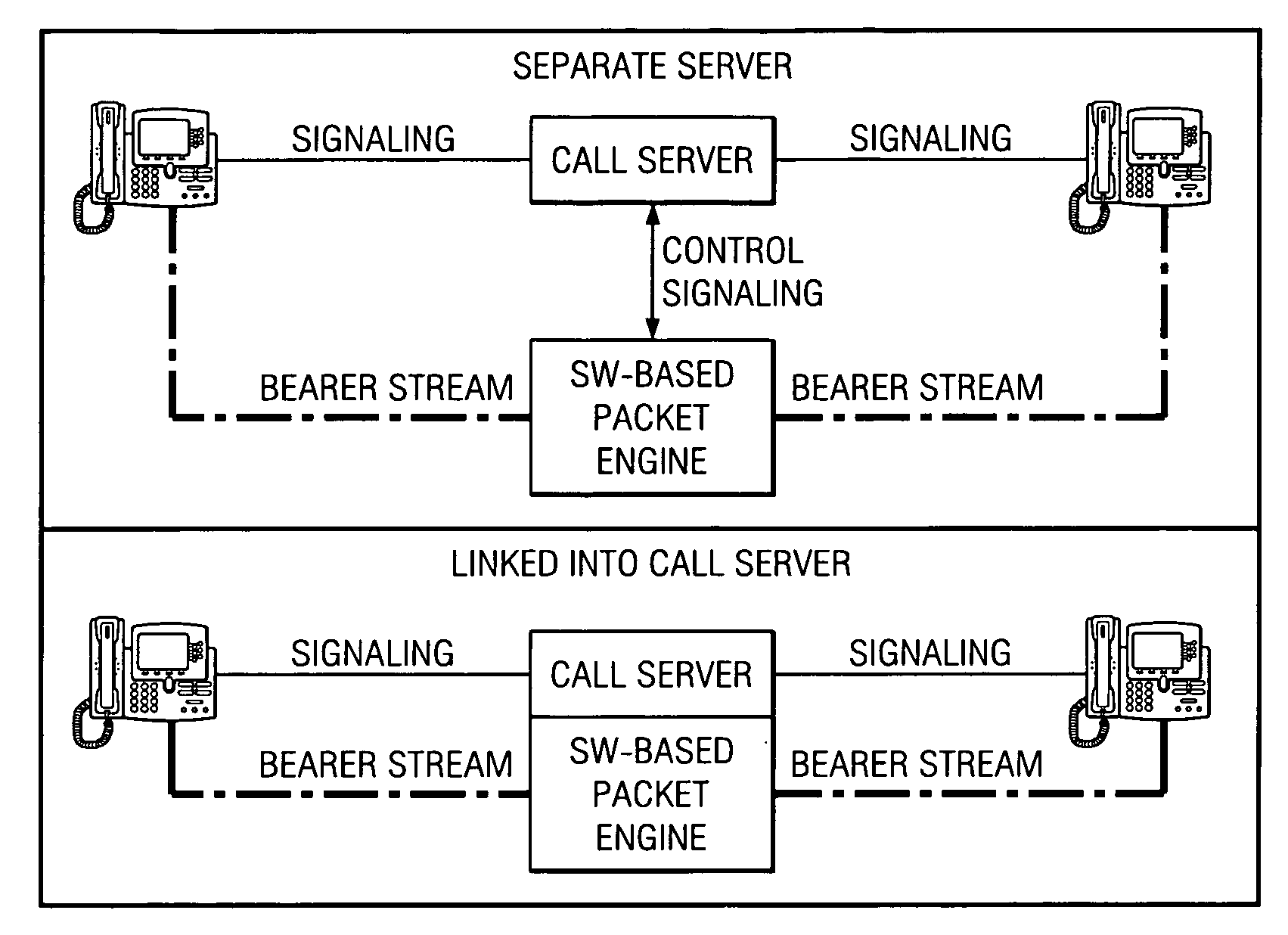
ActiveUS20070206735A1Automatic call-answering/message-recording/conversation-recordingData switching by path configurationTelecommunicationsMethod access
A method, mobile terminal, and system for selectively establishing an outgoing caller ID on a mobile terminal served by a wireless network, for identifying a line called on a mobile terminal, and for directing a call from a mobile terminal to a network subscriber based on accessed information of the subscriber in the subscriber's network.
Owner:TANGO NETWORKS
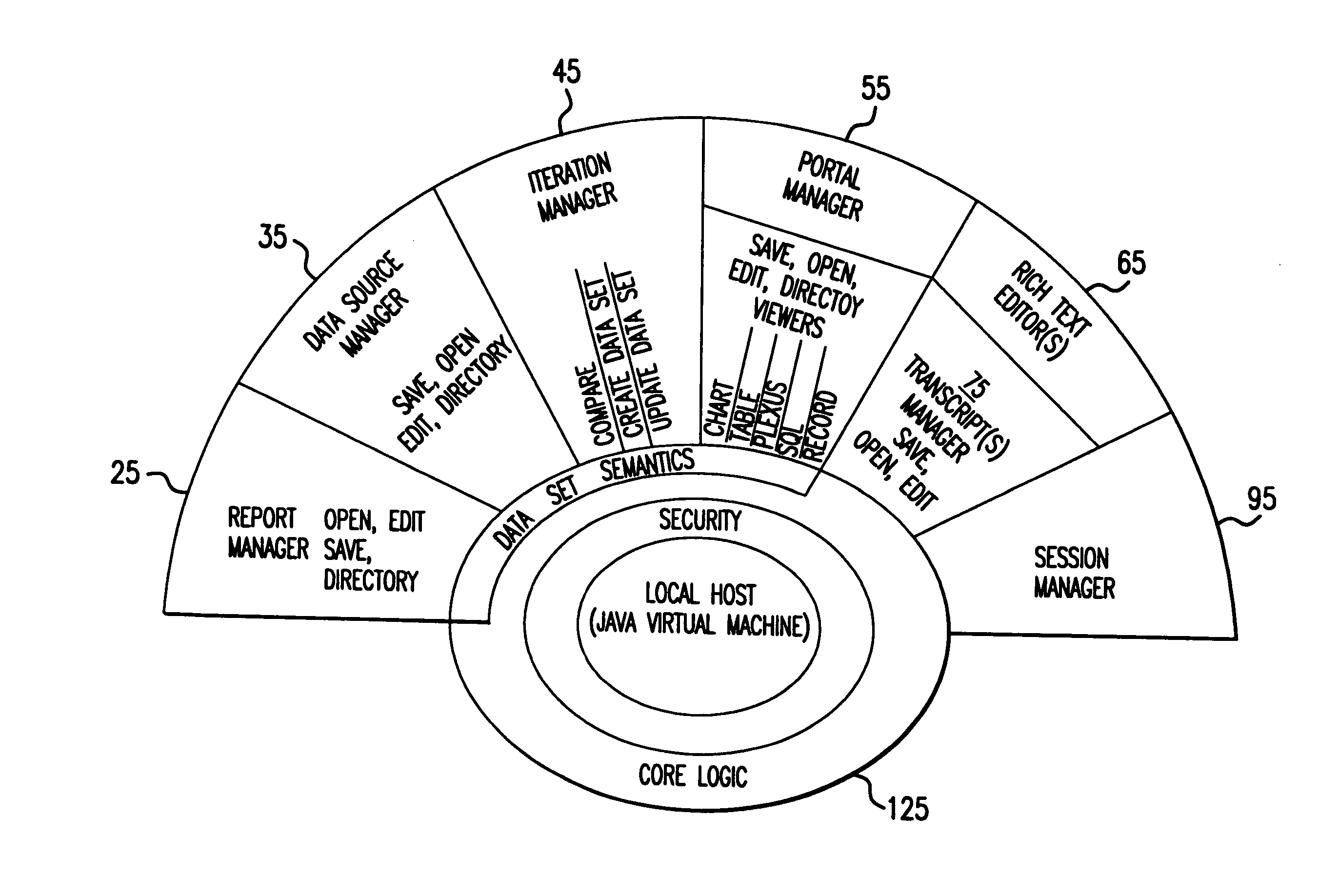
System and method for data quality management and control of heterogeneous data sources
ActiveUS20070150562A1Simpler and efficient to useSave user time necessaryDigital computer detailsImage data processing detailsData setData analysis system
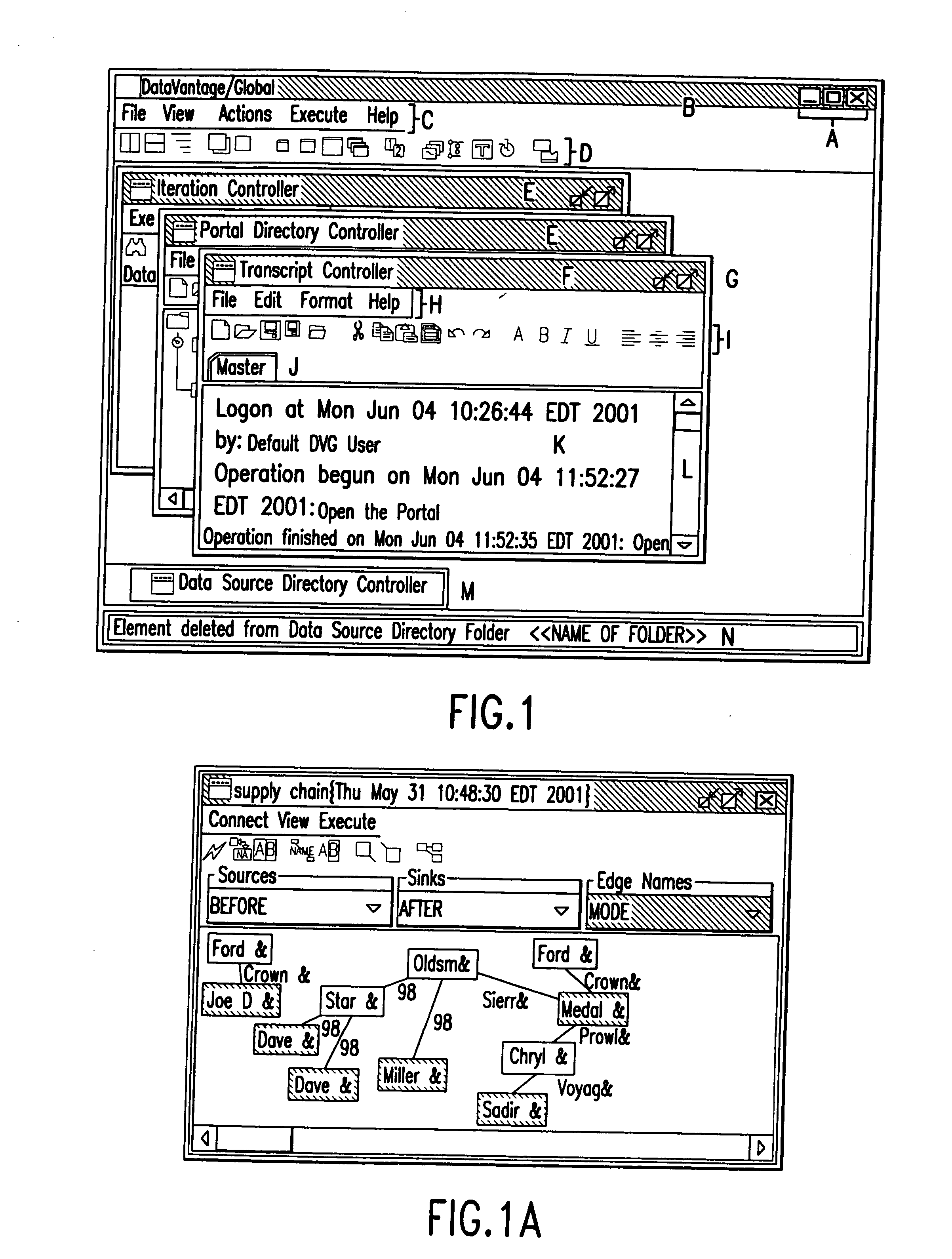
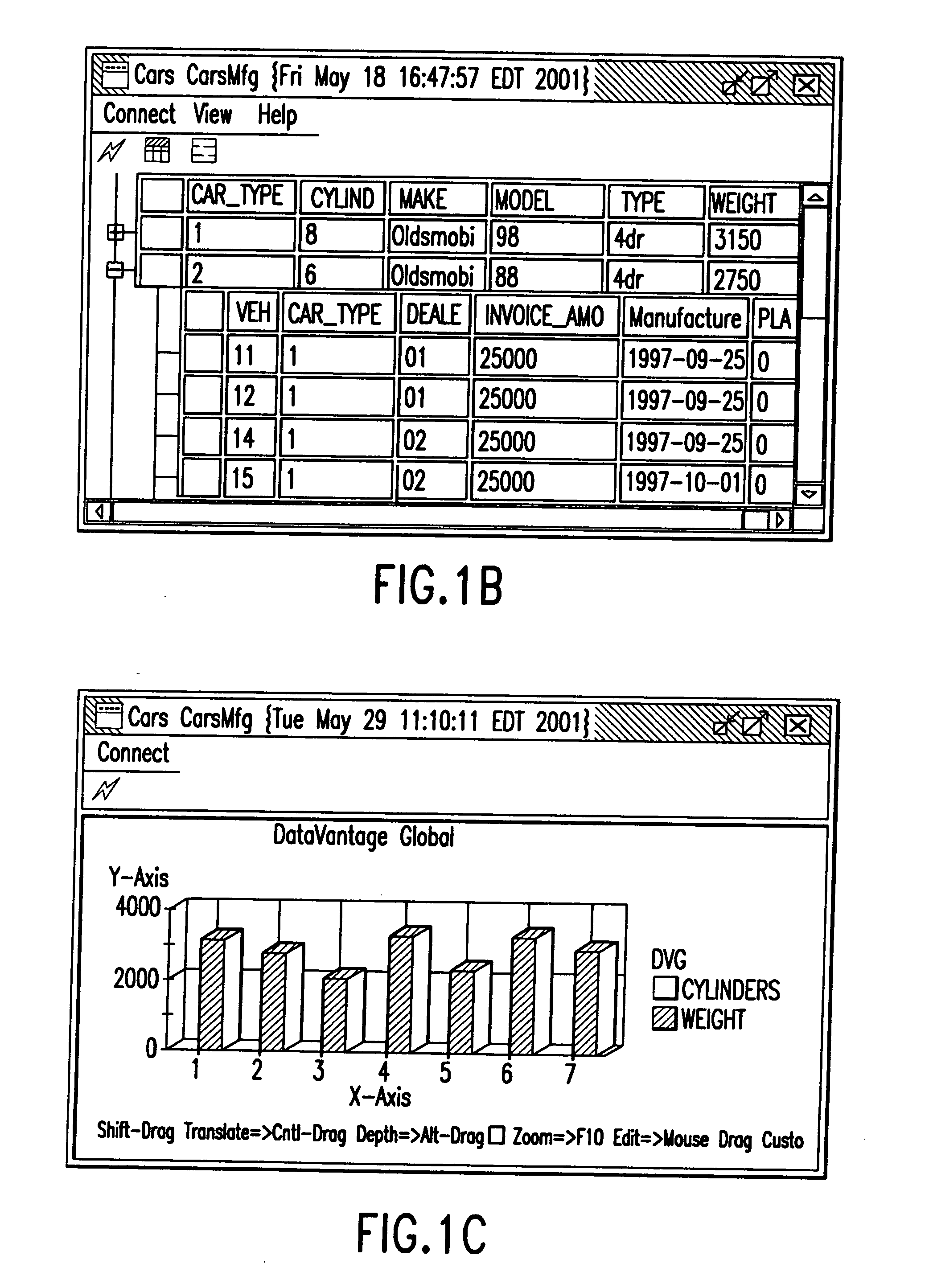
System and method for data quality management and control of heterogeneous data systems. In a preferred embodiment, the system functions as a resource management tool that simplifies the process of managing data systems. More specifically, the system provides connections to source data systems, allows users to view data structures and enables simple management and manipulation of data contained within possibly heterogeneous data systems. The system utilizes an advanced graphical user interface, which allows users to access and manage systems using a simple point and click methodology. The system uses portals, which are tools that collect, visualize, analyze and directly edit data sets associated with different data sources. In another aspect, the system keeps track of its operational status, allowing users to automatically reproduce in one logon session work done in the previous session, without the need to replicate previous data analysis. Various additional features of the system and methods are disclosed and illustrated.
Owner:DIRECT COMP RESOURCES
Design, creation, and delivery of personalized message/audio-video content
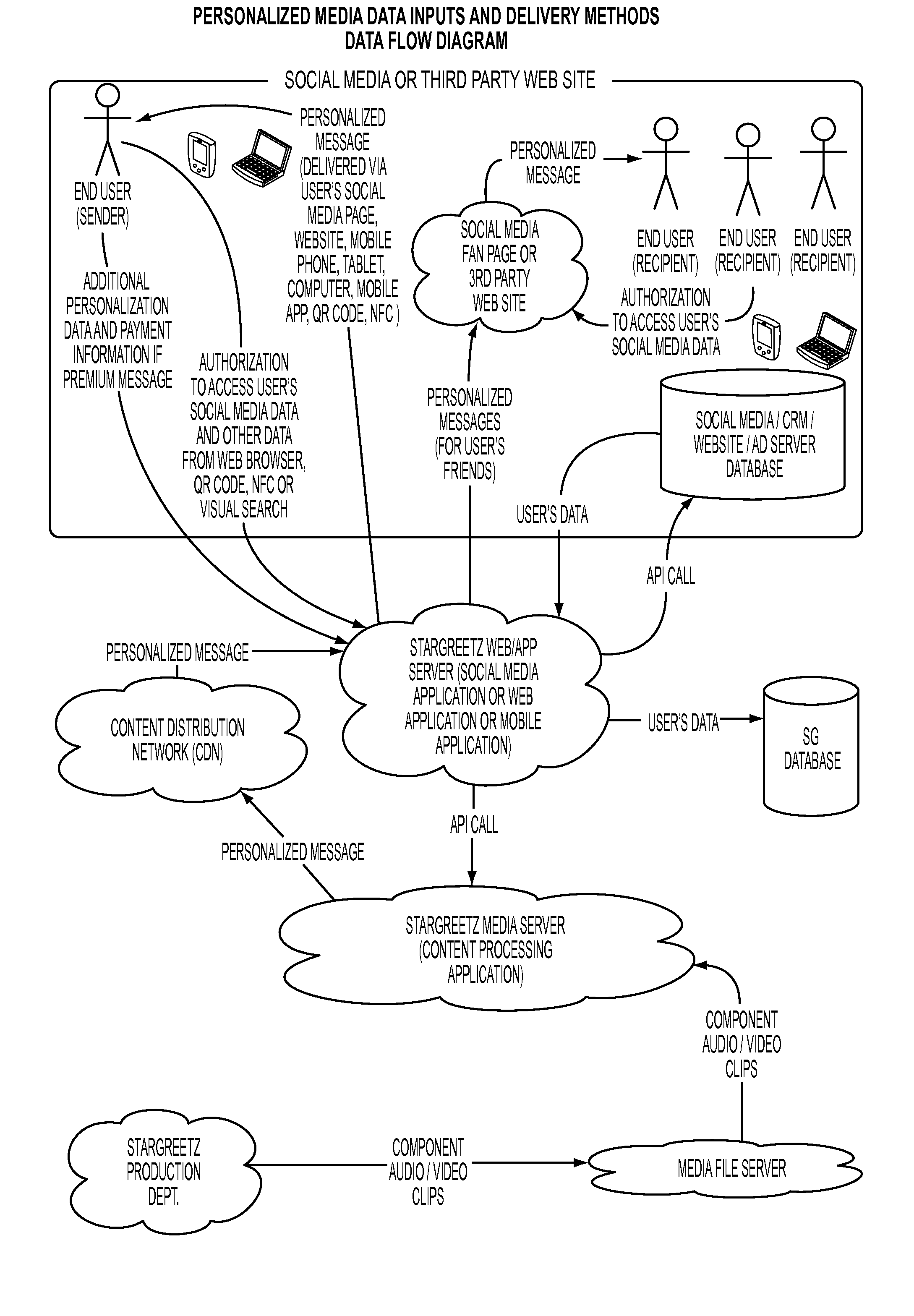
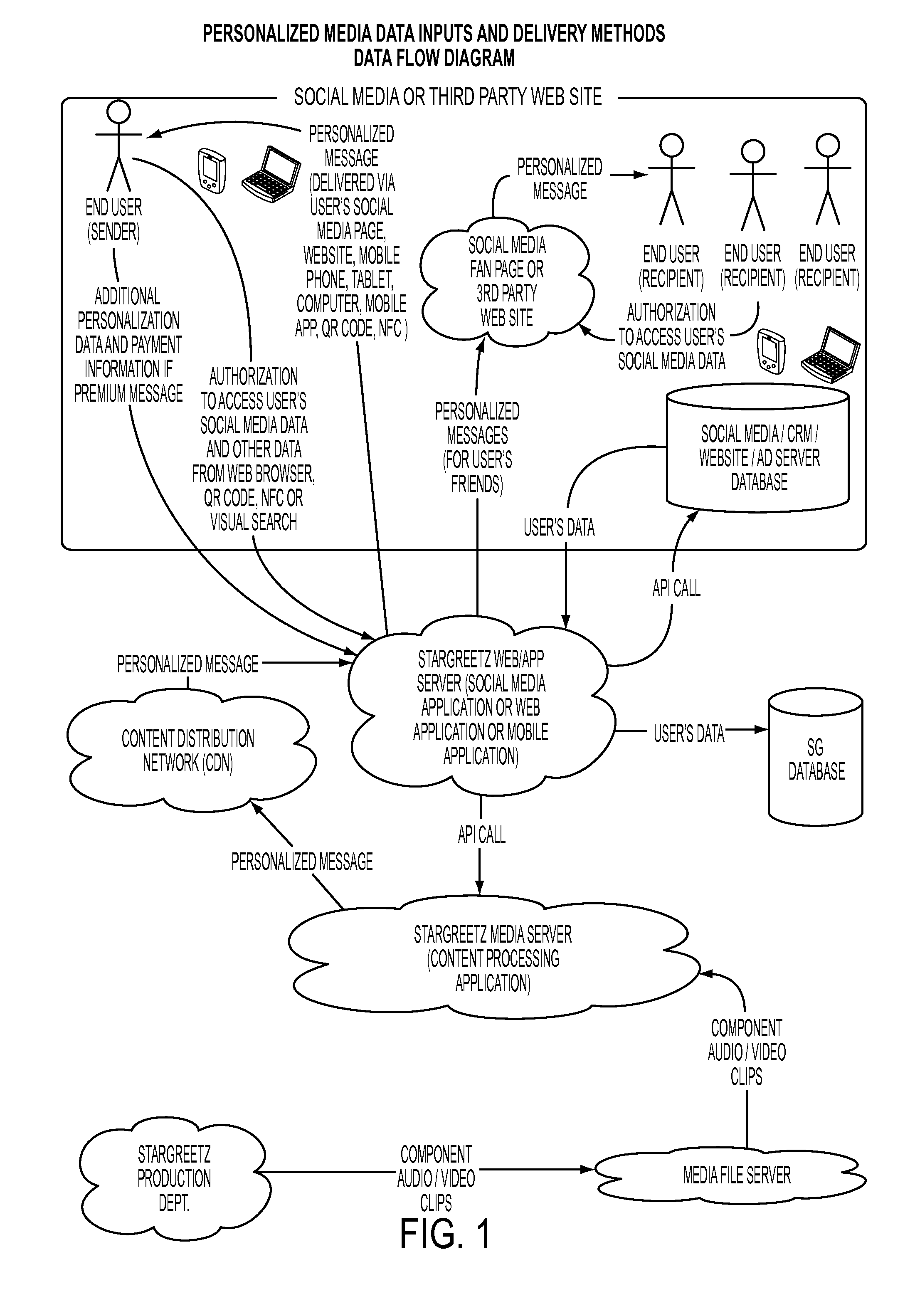
A computer implemented system and method for retailers, brands, manufacturers, service providers, and resellers to deliver personalized messages based on a script about their products to an end user. The end user data has been collected via end user input, a social media database containing user input, a CRM database query based on end user information, cookies and browser header from the end user net surfing, and second and third party data providers, etc. The system and method via a web application server accesses and stores the end user data. A media server retrieves the data and with a content management system having product templates defined by the script, accesses the media file server and processes the media clips to generate a personalized message. A content distribution network relays the personalized message to the web application server which delivers the personalized message to the end user.
Owner:STARGREETZ
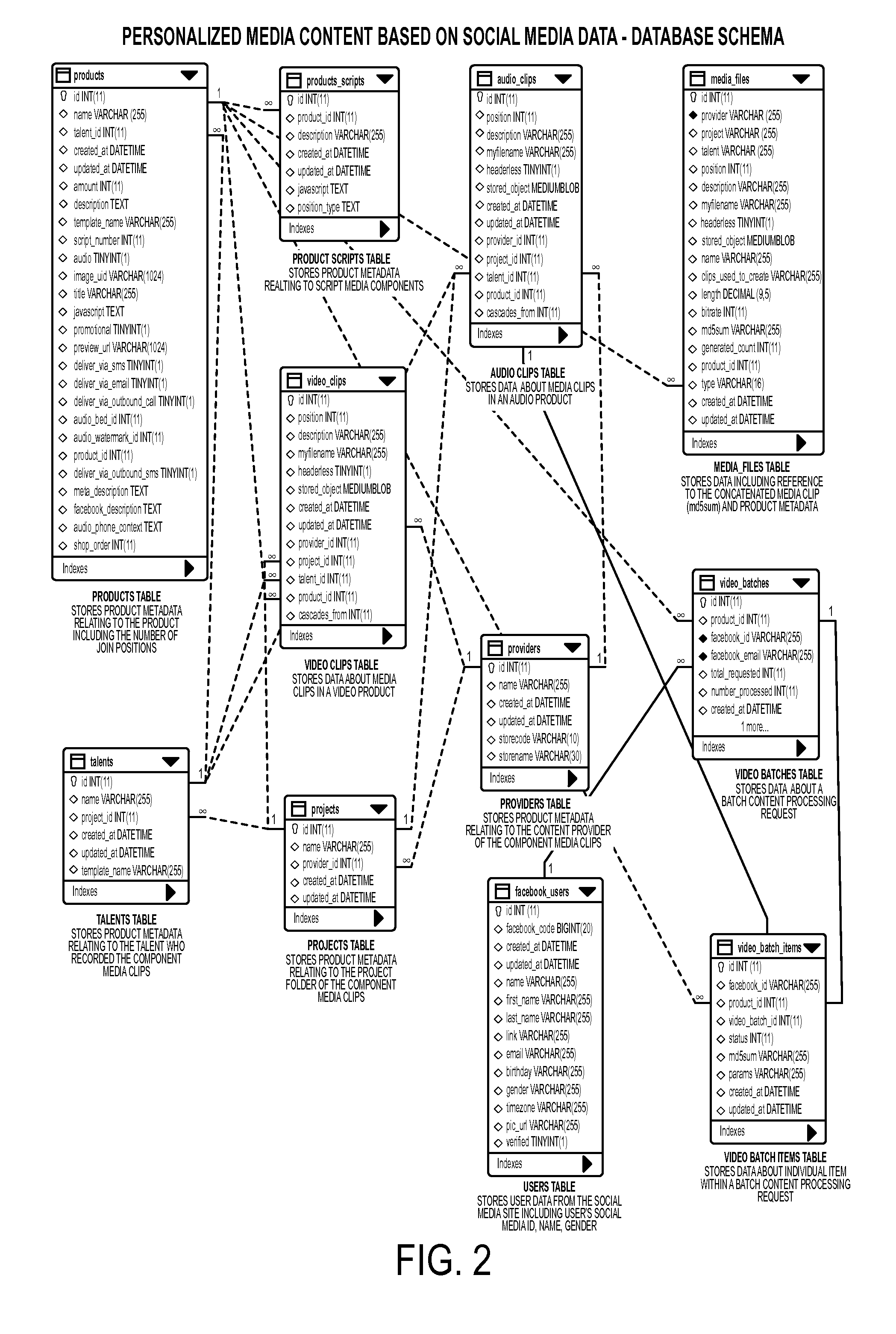
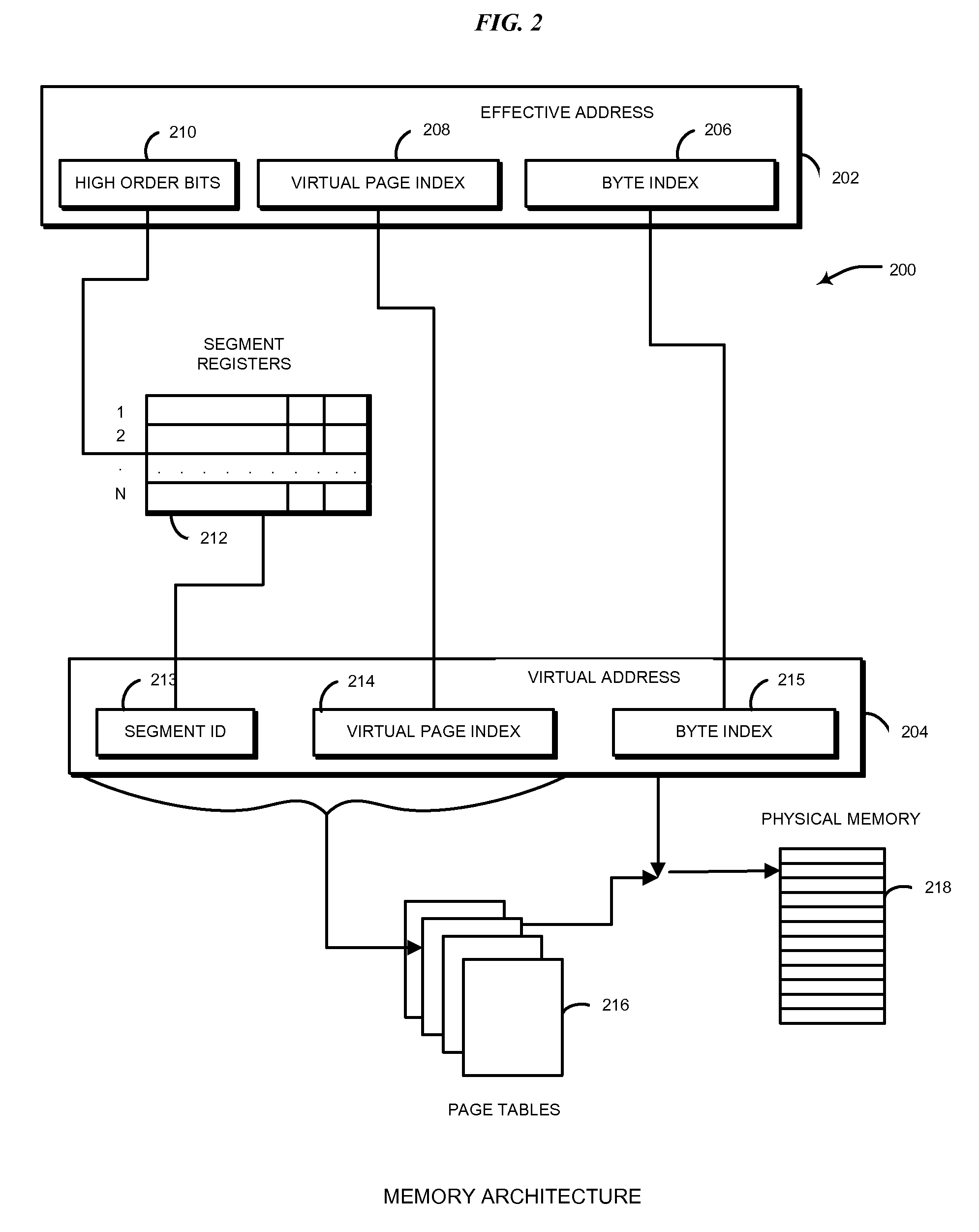
Virtual memory management
InactiveUS7930515B2Memory architecture accessing/allocationMemory systemsPhysical addressVirtual memory management
A method for managing a virtual memory system configured to allow multiple page sizes is described. Each page size has at least one table associated with it. The method involves maintaining entries in the tables to keep track of the page size for which the effective address is mapped. When a new effective address to physical address mapping needs to be made for a page size, the method accesses the appropriate tables to identify prior mappings for another page size in the same segment. If no such conflicting mapping exists, it creates a new mapping in the appropriate table. A formula is used to generate an index to access a mapping in a table.
Owner:INT BUSINESS MASCH CORP
System and method for data quality management and control of heterogeneous data sources
InactiveUS7251693B2Simpler and efficient to useSave user time necessaryDigital data processing detailsDigital computer detailsData setData system
System and method for data quality management and control of heterogeneous data systems. In a preferred embodiment, the system functions as a resource management tool that simplifies the process of managing data systems. More specifically, the system provides connections to source data systems, allows users to view data structures and enables simple management and manipulation of data contained within possibly heterogeneous data systems. The system utilizes an advanced graphical user interface, which allows users to access and manage systems using a simple point and click methodology. The system uses portals, which are tools that collect, visualize, analyze and directly edit data sets associated with different data sources. In another aspect, the system keeps track of its operational status, allowing users to automatically reproduce in one logon session work done in the previous session, without the need to replicate previous data analysis. Various additional features of the system and methods are disclosed and illustrated.
Owner:DIRECT COMP RESOURCES
System and method for accessing clusters of servers from the internet network
InactiveUS7454489B2Multiprogramming arrangementsMultiple digital computer combinationsAccess routePrivate network
A cluster system and method accesses from an internet network, a network server within one or a plurality of clusters, each cluster being identified by a single cluster public Internet Protocol (IP) address. The cluster system has a plurality of network servers organized in one of a plurality of clusters and a network load balancer system for selecting a destination network server in a cluster. Each cluster has one or a plurality of identical network servers, the network load balancer system being connected on one hand to an access routing device and on another hand to the plurality of network servers through a private network server subnet. The method includes the steps of at initialization time, on each network server defining, as a non-advertising alias, in an interface table, the public IP address of each cluster to which the network server belongs, and upon reception, by the network load balancing system, of a datagram having an IP header including a destination IP address field and a medium access control (MAC) header including a destination MAC address field, selecting a destination network server within the cluster corresponding to the cluster public IP address identified in the destination IP address field of the datagram IP header, replacing the destination medium access control (MAC) address field of the datagram MAC header by the MAC address of the selected destination network server, and sending the datagram through the private network server subnet, using the MAC address of the selected destination network server. Upon reception, by the destination network server, of the datagram sent by the network load balancing system, the MAC address in the destination MAC address field of the datagram MAC header is identified as being the MAC address of the selected destination network server, and the IP datagram is processed if the identified cluster public IP address in the destination IP address field of the datagram IP header, is defined as a non-advertising alias in the interface table of the destination network server.
Owner:INT BUSINESS MASCH CORP
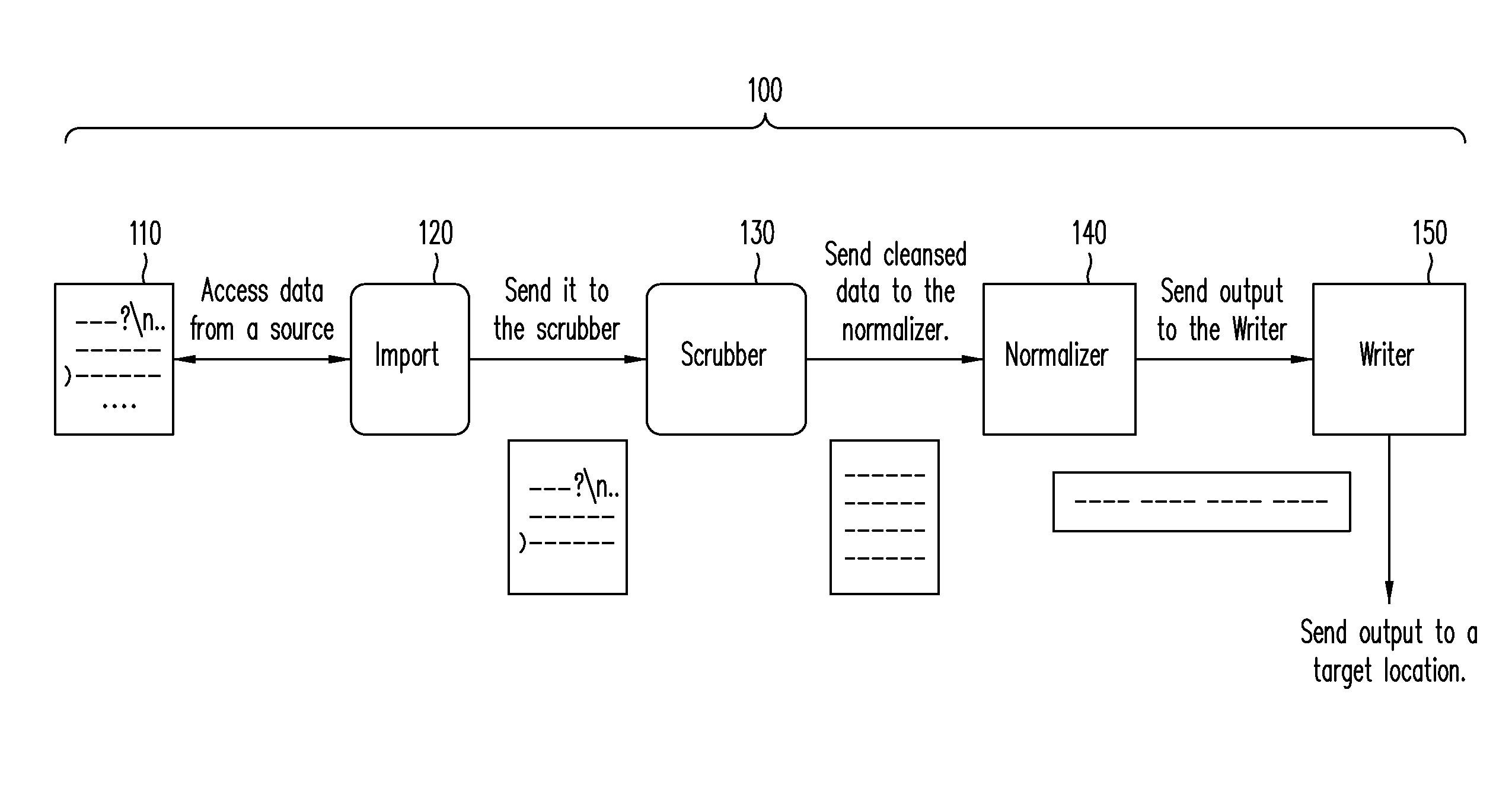
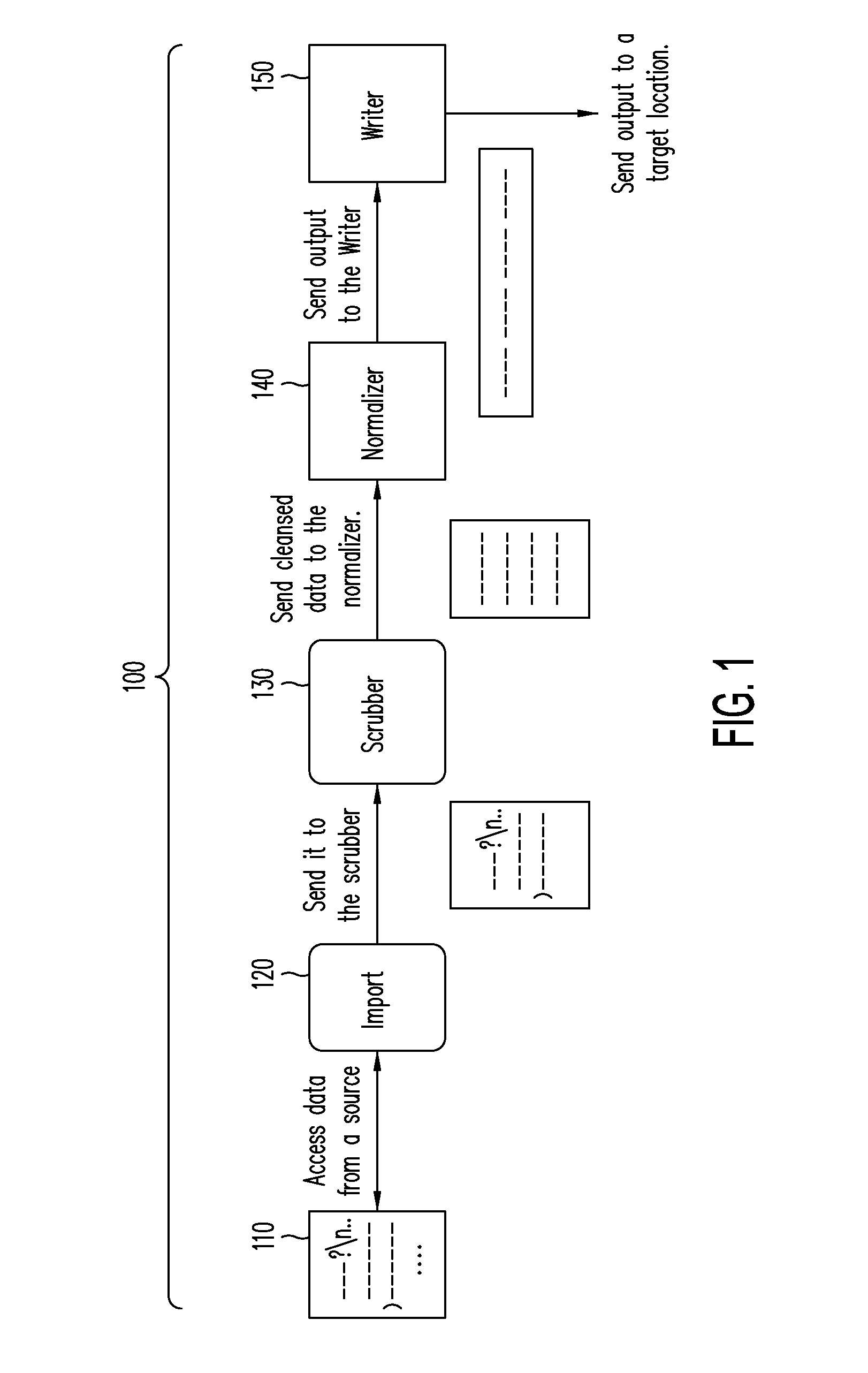
Constructing a data adaptor in an enterprise server data ingestion environment
The present disclosure involves a method of ingesting data in an enterprise server environment. A configuration file is accessed. The configuration file specifies a blueprint for constructing a data adaptor that includes a data adaptor source, a data adaptor sink, and a data adaptor channel coupled between the data adaptor source and the data adaptor sink. The data adaptor is constructed based on the configuration file. Via the data adaptor, data is retrieved from a first entity. Also via the data adaptor, the retrieved data is written to a second entity different from the first entity. The accessing, the constructing, the retrieving, and the writing are performed by one or more electronic processors.
Owner:EBAY INC
Method and apparatus for system monitoring and maintenance
InactiveUS7702435B2Vehicle testingMultiplex system selection arrangementsComputer scienceSystem monitoring
A method and an apparatus provide intelligent monitoring and maintenance of a system. The method according to one embodiment accesses data relating to functional components of the system; extracts parameter information for functional components of the system, the step of extracting parameter information including performing inferential processing and trend recognition of the data using previous knowledge about the system, and simulating performance of the system using models of the system and previous knowledge about the system; identifies new information about the system present in extracted parameter information; and provides the new information to the step of extracting parameter information, to be used as previous knowledge.
Owner:HONEYWELL INT INC
Method to Access Storage Device Through Universal Serial Bus
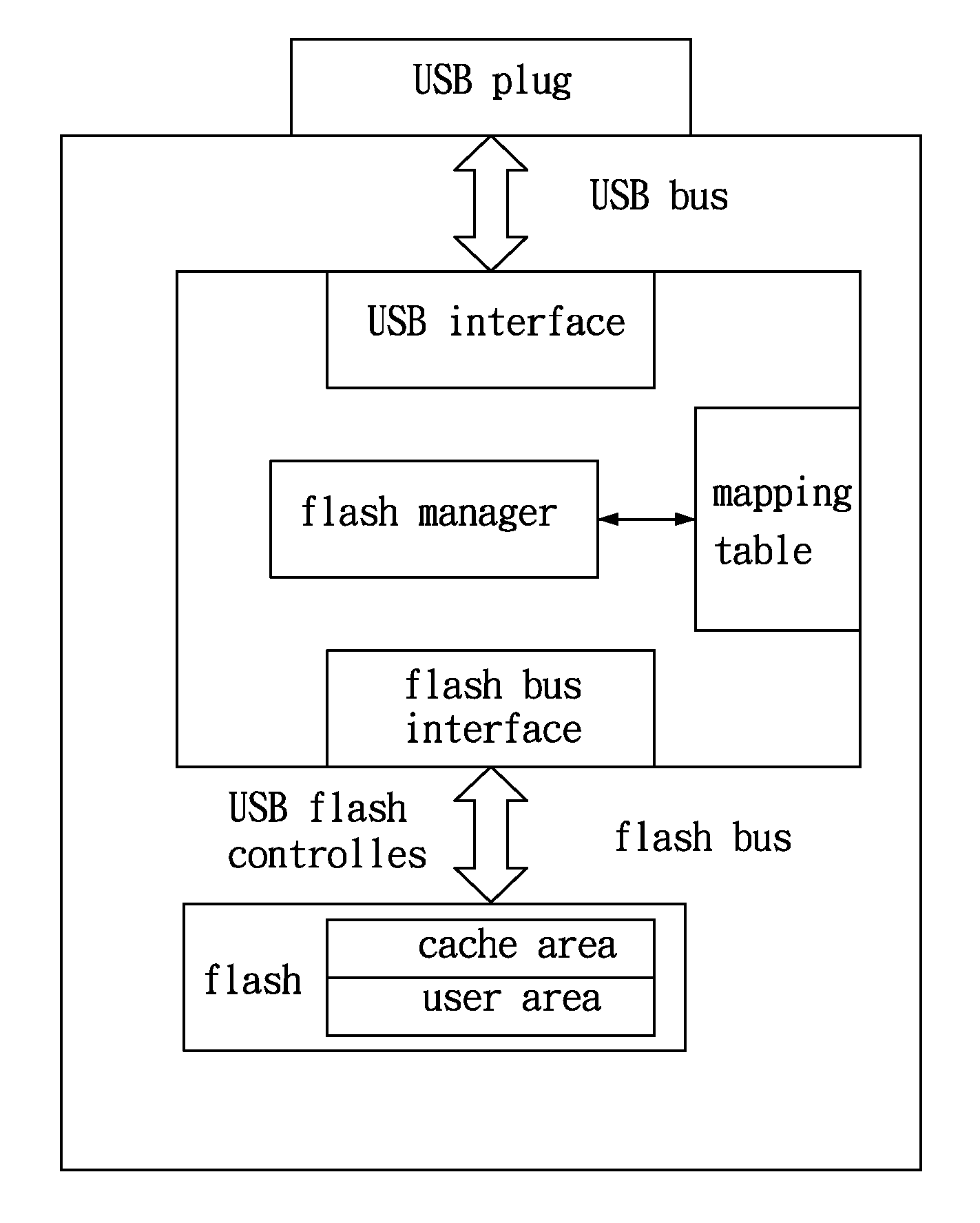
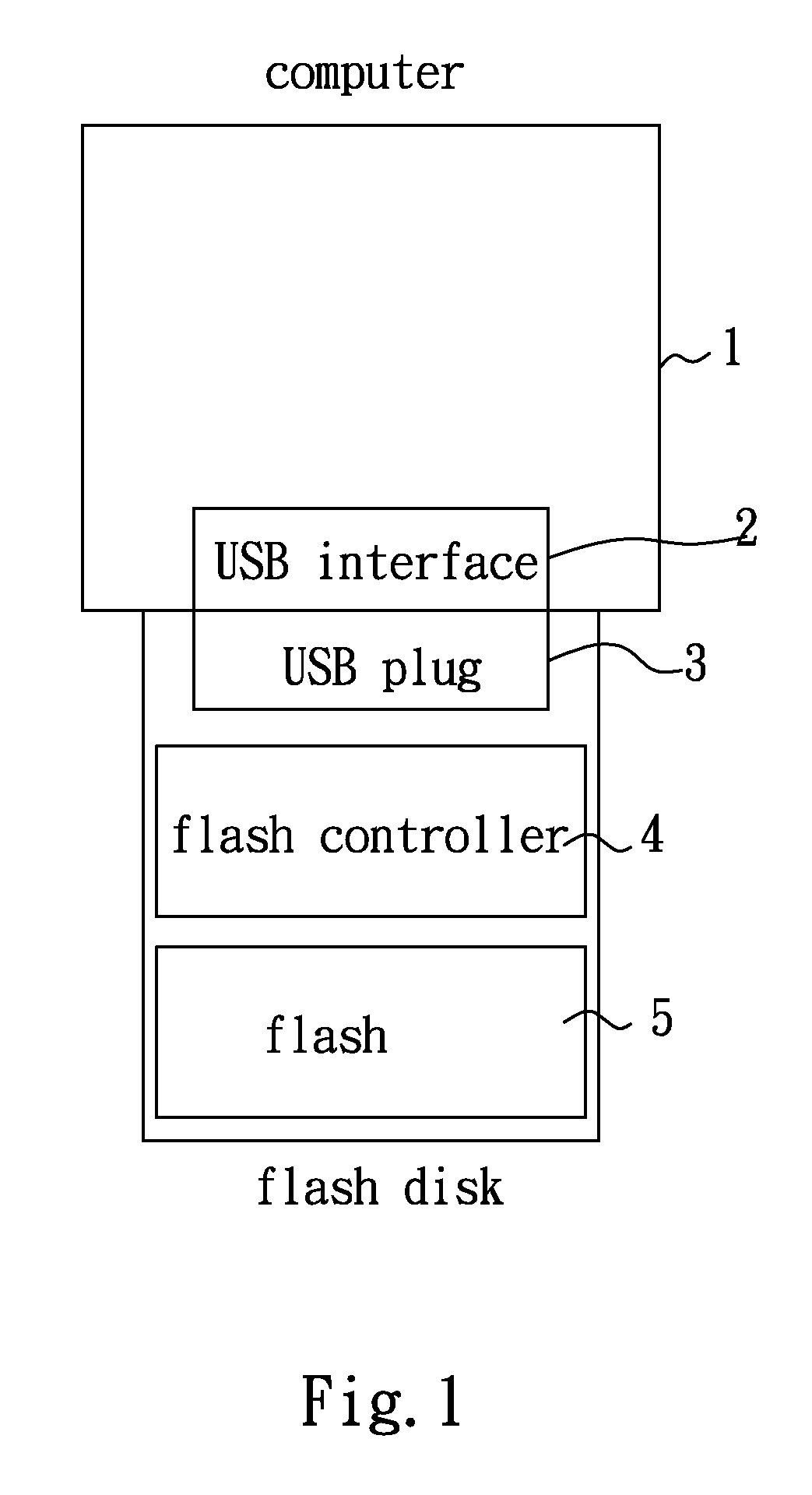
InactiveUS20080276037A1Reduce time consumptionLess timeMemory adressing/allocation/relocationInput/output processes for data processingFile systemFlash memory controller
A method accessing a flash memory storage device through universal serial bus (USB) of the present invention includes a flash controller and a flash memory, wherein the method includes connecting the storage device to a USB interface of an electronic device; outputting a plurality of accessing instructions to the flash controller via the electronic device; deciding which data is needed to be temporarily saved in a cache memory and a priority of the accessing instructions according to the characteristic of the file system and the content of preceding instructions of the flash controller; and writing the data temporarily saved in the cache memory into the flash memory according to the priority of the flash controller. The objective of the method of the present invention is to enhance the operation efficiency of the storage device.
Owner:ALCOR MICRO CORP
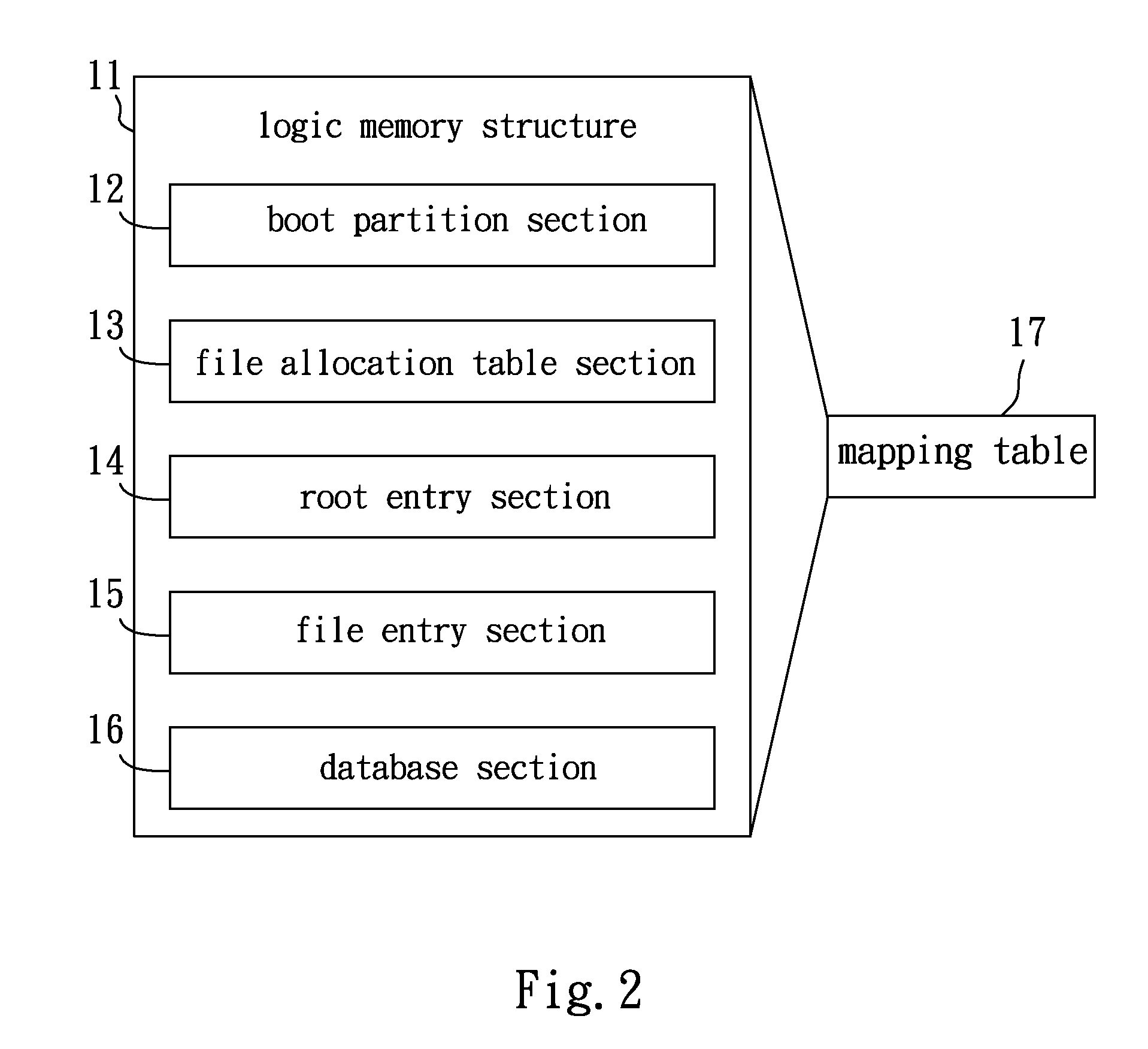
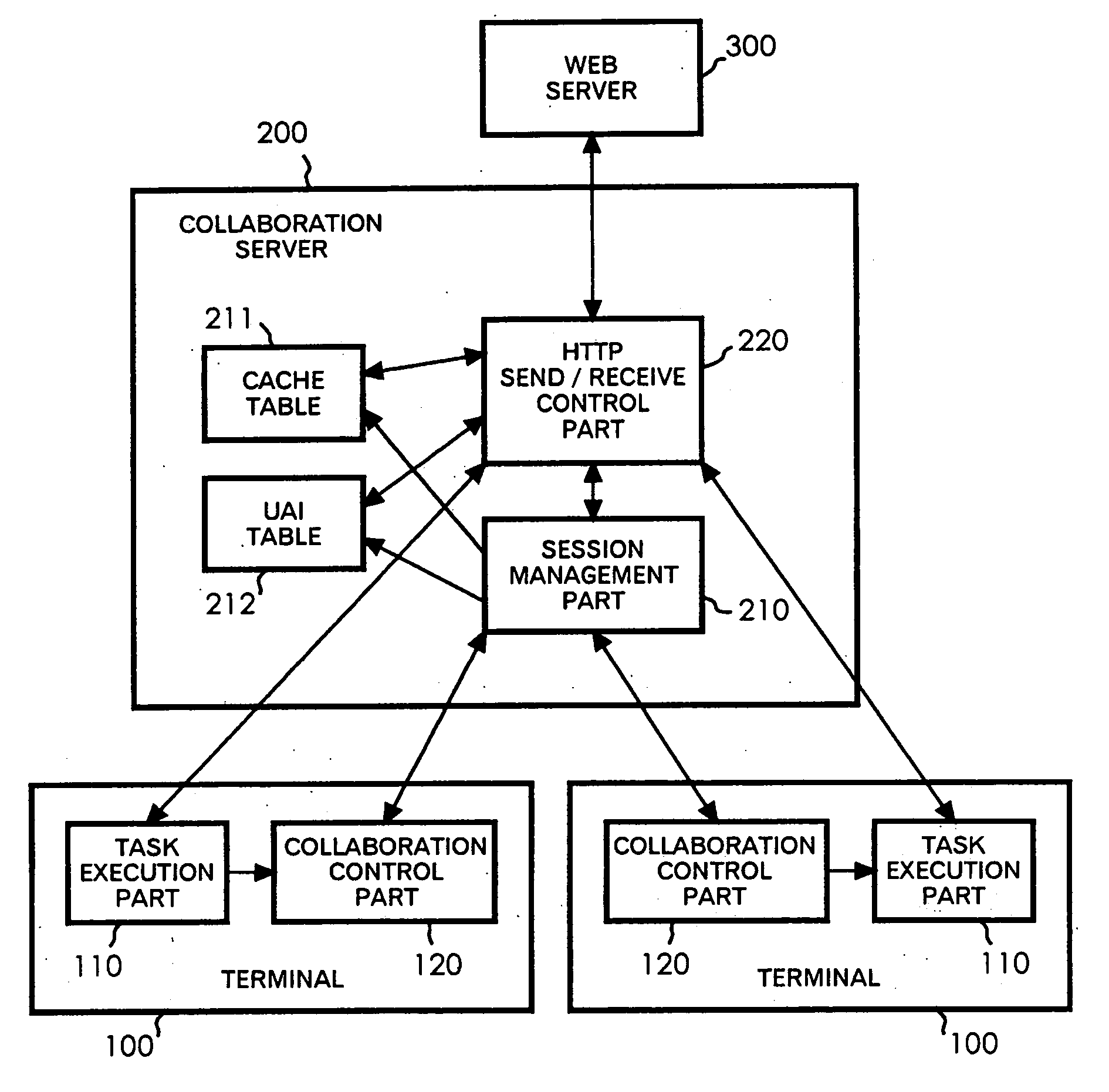
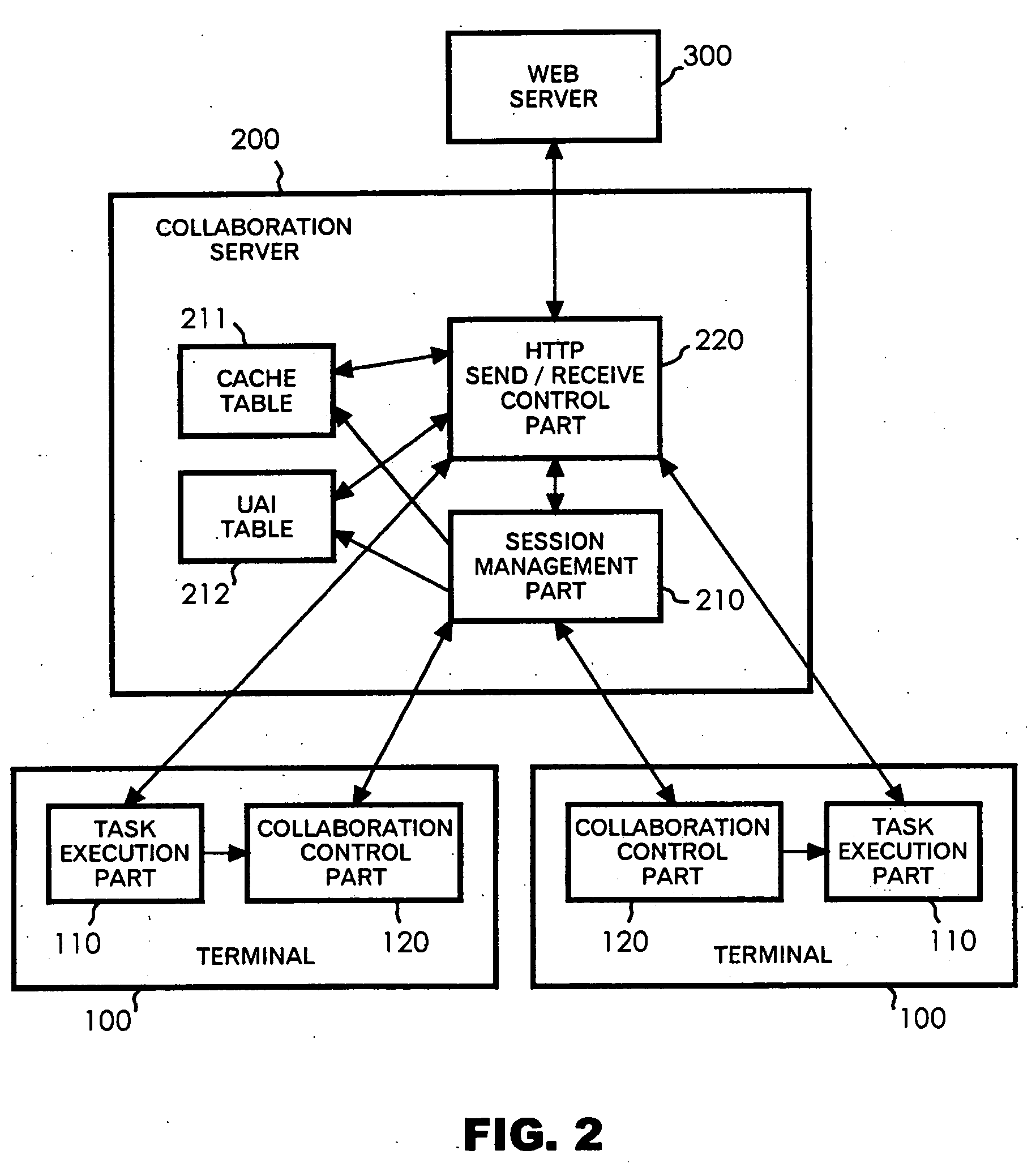
Collaboration server, collaboration system, and session management method
InactiveUS20050198204A1Special service provision for substationUser identity/authority verificationSession managementAuthorization
Access control in a collaboration system is realized, in which, even when only particular one of users working together has access permission to a resource, the other users are allowed to access the resource under certain conditions. The collaboration system includes multiple terminals 100 exchanging data through a network to perform collaborative work, and a collaboration server 200 that acquires a resource in response to a request from each terminal 100 and sends the resource to the terminal 100. When an access request for an access-controlled resource is made from a user terminal 100 not having the access permission to the resource, the collaboration server 200 uses access authorization of a session owner to the resource to acquire the resource.
Owner:IBM CORP
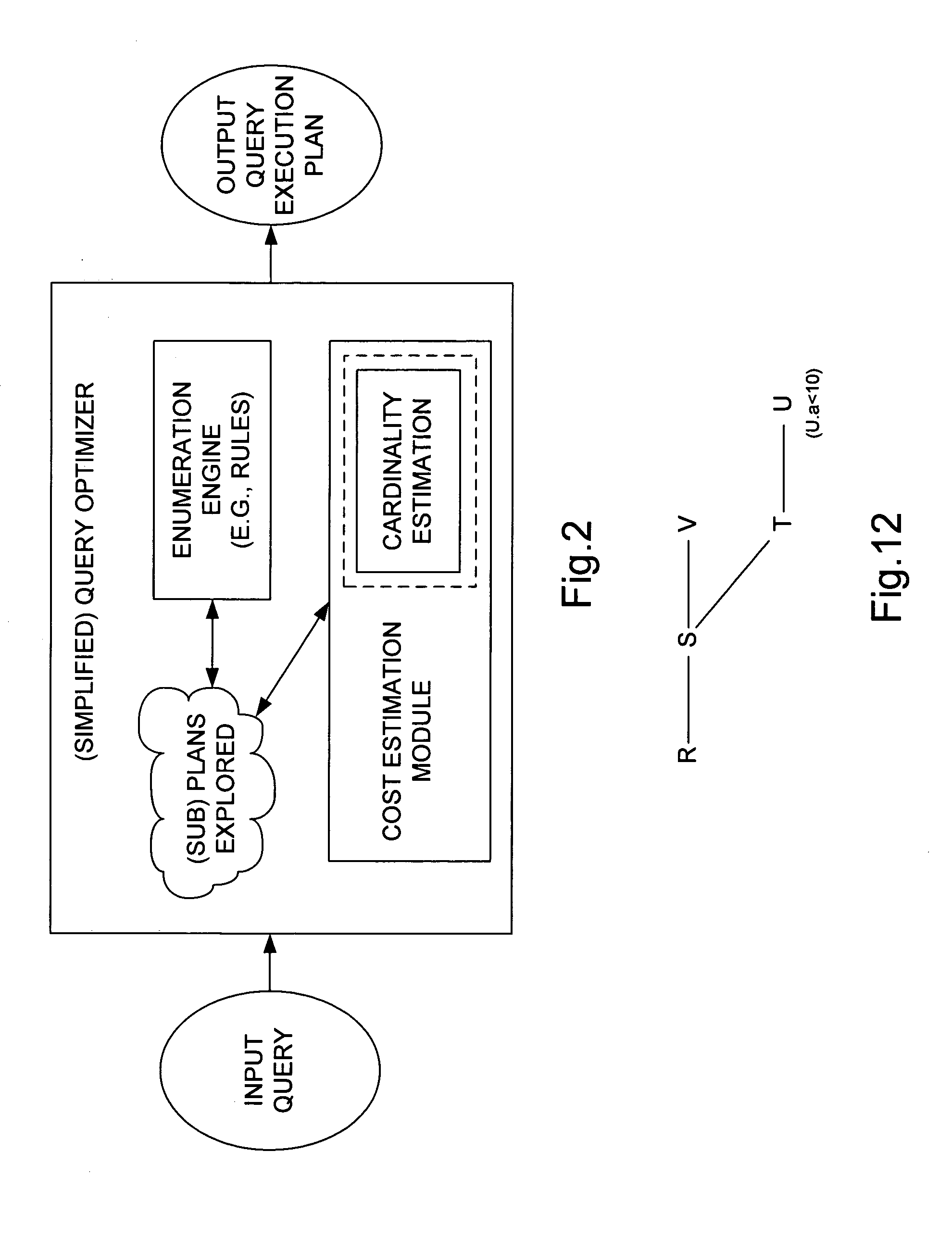
Method and apparatus for exploiting statistics on query expressions for optimization
InactiveUS20050267877A1Improve accuracyData processing applicationsDigital data information retrievalQuery planExecution plan
A method for evaluating a user query on a relational database having records stored therein, a workload made up of a set of queries that have been executed on the database, and a query optimizer that generates a query execution plan for the user query. Each query plan includes a plurality of intermediate query plan components that verify a subset of records from the database meeting query criteria. The method accesses the query plan and a set of stored intermediate statistics for records verified by query components, such as histograms that summarize the cardinality of the records that verify the query component. The method forms a transformed query plan based on the selected intermediate statistics (possibly by rewriting the query plan) and estimates the cardinality of the transformed query plan to arrive at a more accurate cardinality estimate for the query. If additional intermediate statistics are necessary, a pool of intermediate statistics may be generated based on the queries in the workload by evaluating the benefit of a given statistic over the workload and adding intermediate statistics to the pool that provide relatively great benefit.
Owner:MICROSOFT TECH LICENSING LLC
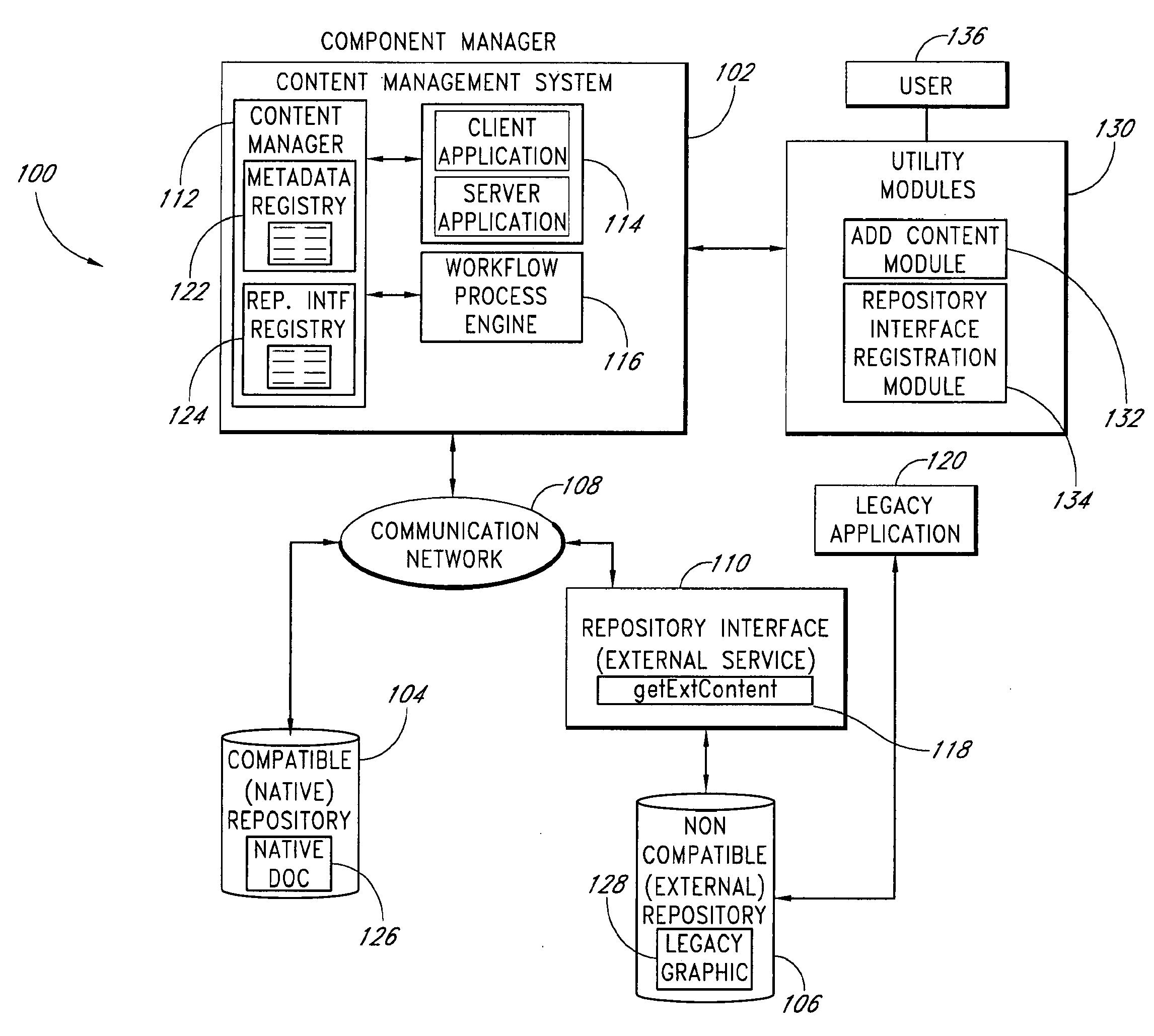
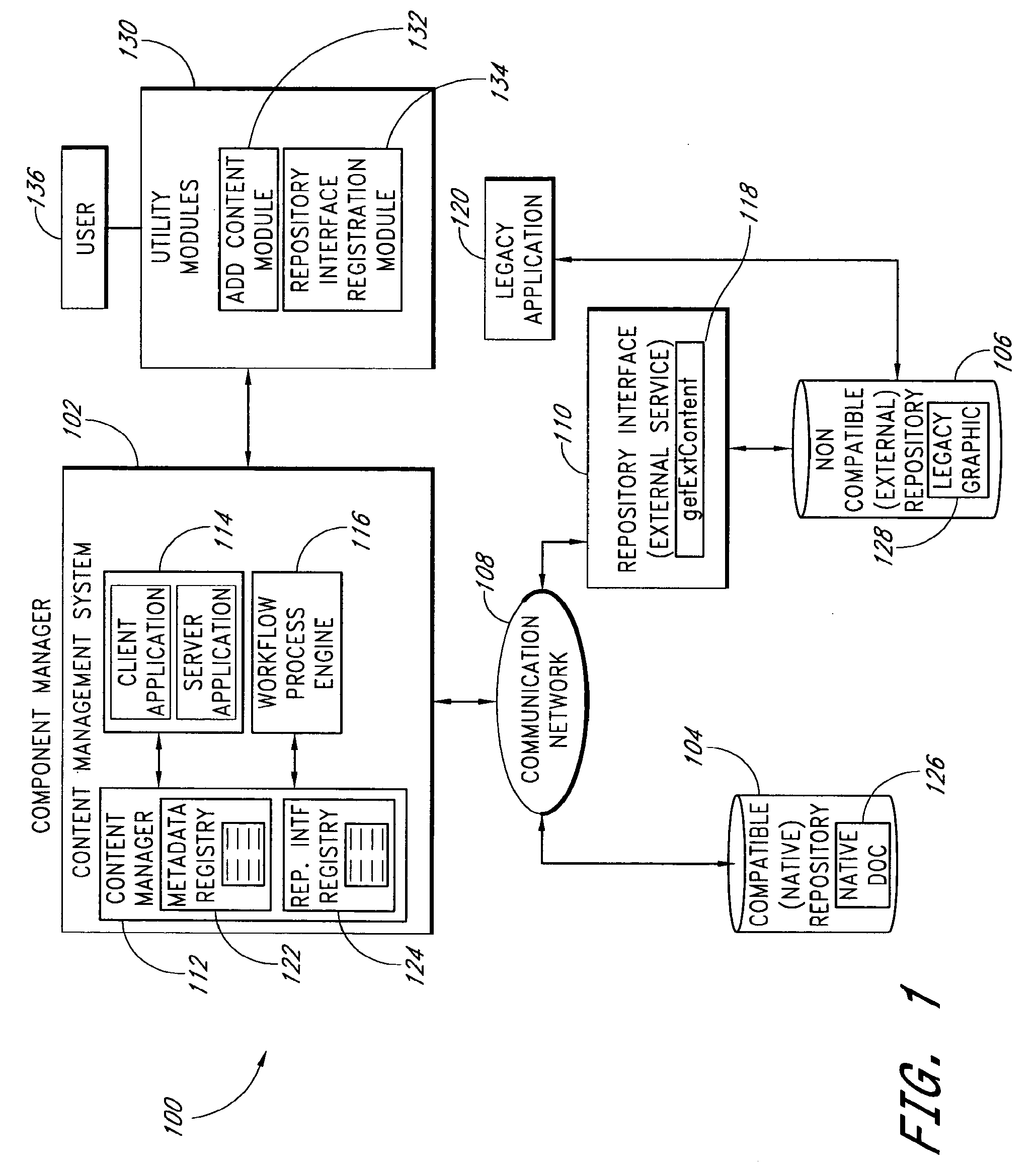
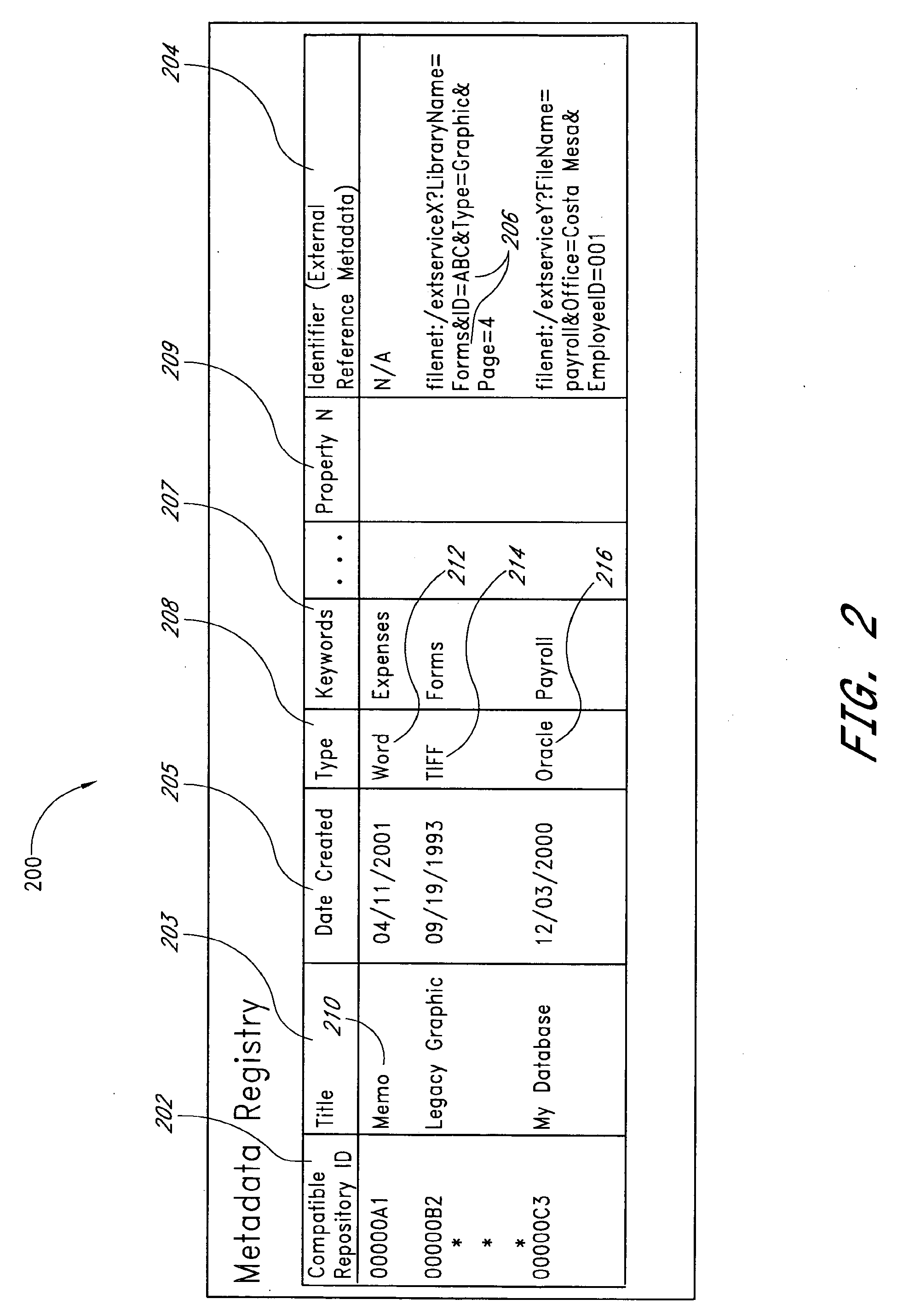
System and method for accessing non-compatible content repositories
InactiveUS20090077043A1Easy to deployImprove access capabilitiesDigital data processing detailsOffice automationContent managementMetadata registry
Systems and methods access non-compatible content repositories that are not natively accessible to a content management system. A metadata registry maintains metadata about content stored in both compatible and non-compatible repositories. For content in a non-compatible repository, the metadata indicates a repository interface capable of accessing the non-compatible repository. The content manager communicates with the repository interfaces to access the content in non-compatible repositories. The content manager may receive a request for content in a non-compatible repository, refer to the metadata registry to select a repository interface to employ, transmit a request for the requested content to the selected repository interface, and receive the requested content from the repository interface. A repository interface registry maintains information about available repository interfaces. Entries may be added to either the metadata registry and the repository interface registry, thus allowing the systems and methods to be extended to be able to access additional non-compatible repositories.
Owner:INT BUSINESS MASCH CORP
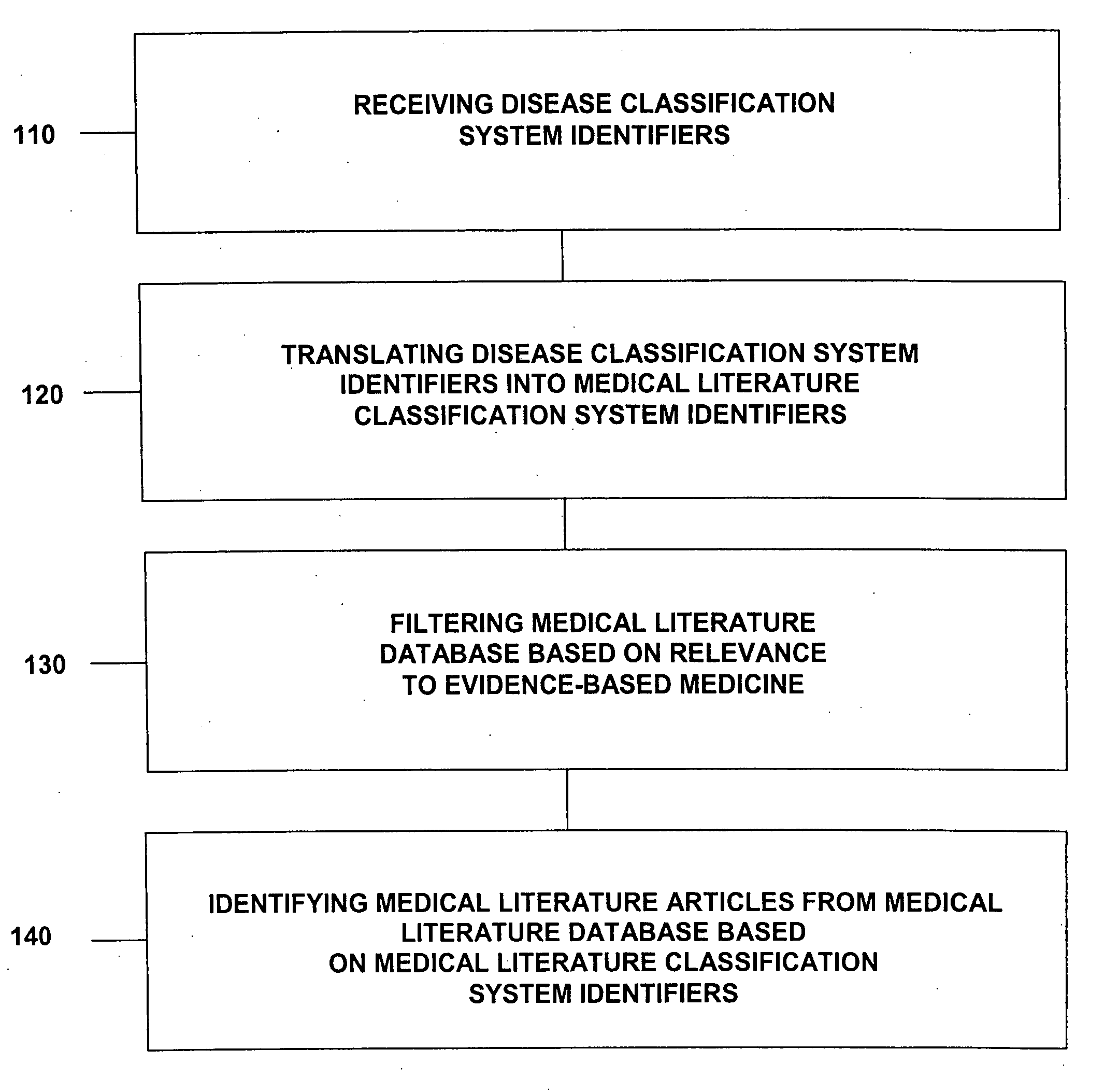
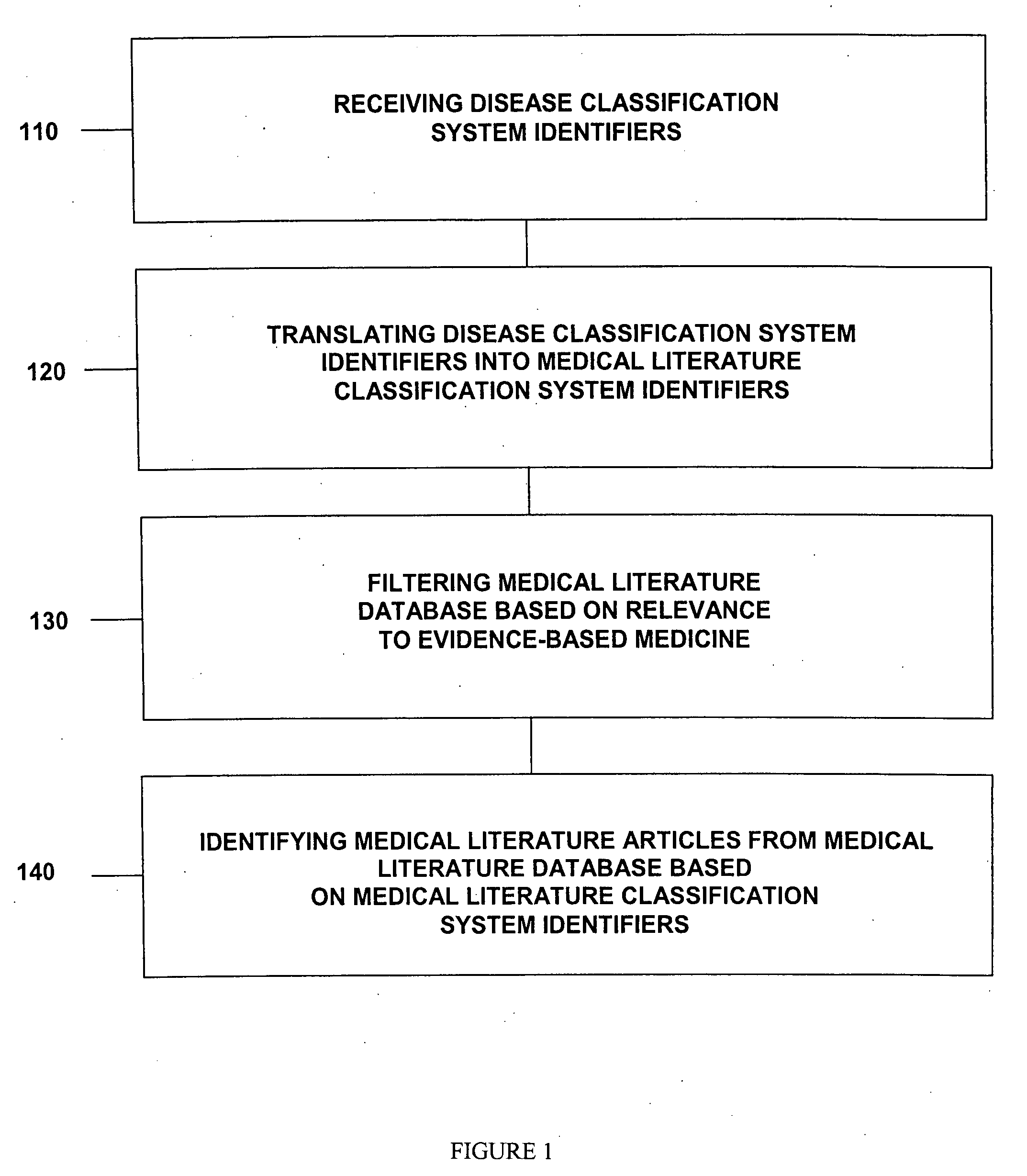
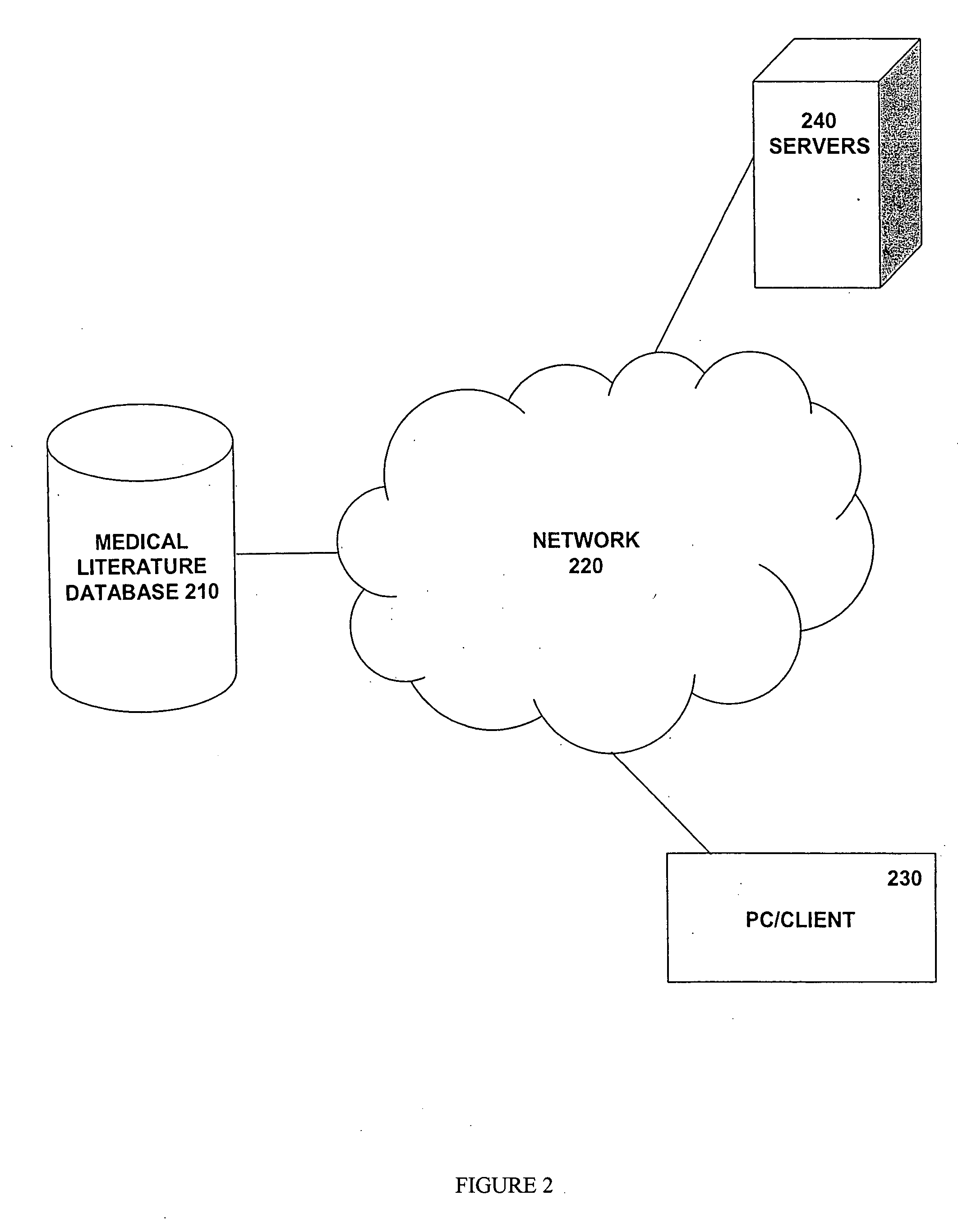
Medical literature database search tool
This invention provides a method of identifying clinically relevant, evidence based medical literature on diseases and their treatment to physicians, nurses and other healthcare personnel. This method accesses a medical literature database that is then searched using a medical literature classification system identifier for a disease integrated with an evidence based medicine search filter. In conjunction with identifying the evidence based medical literature, a database of articles selected and reviewed by experts that concern the disease is also searched. The results of both searches are then displayed to the user. This invention can be implemented through the use of an encoded computer readable medium.
Owner:COGENT MEDICINE
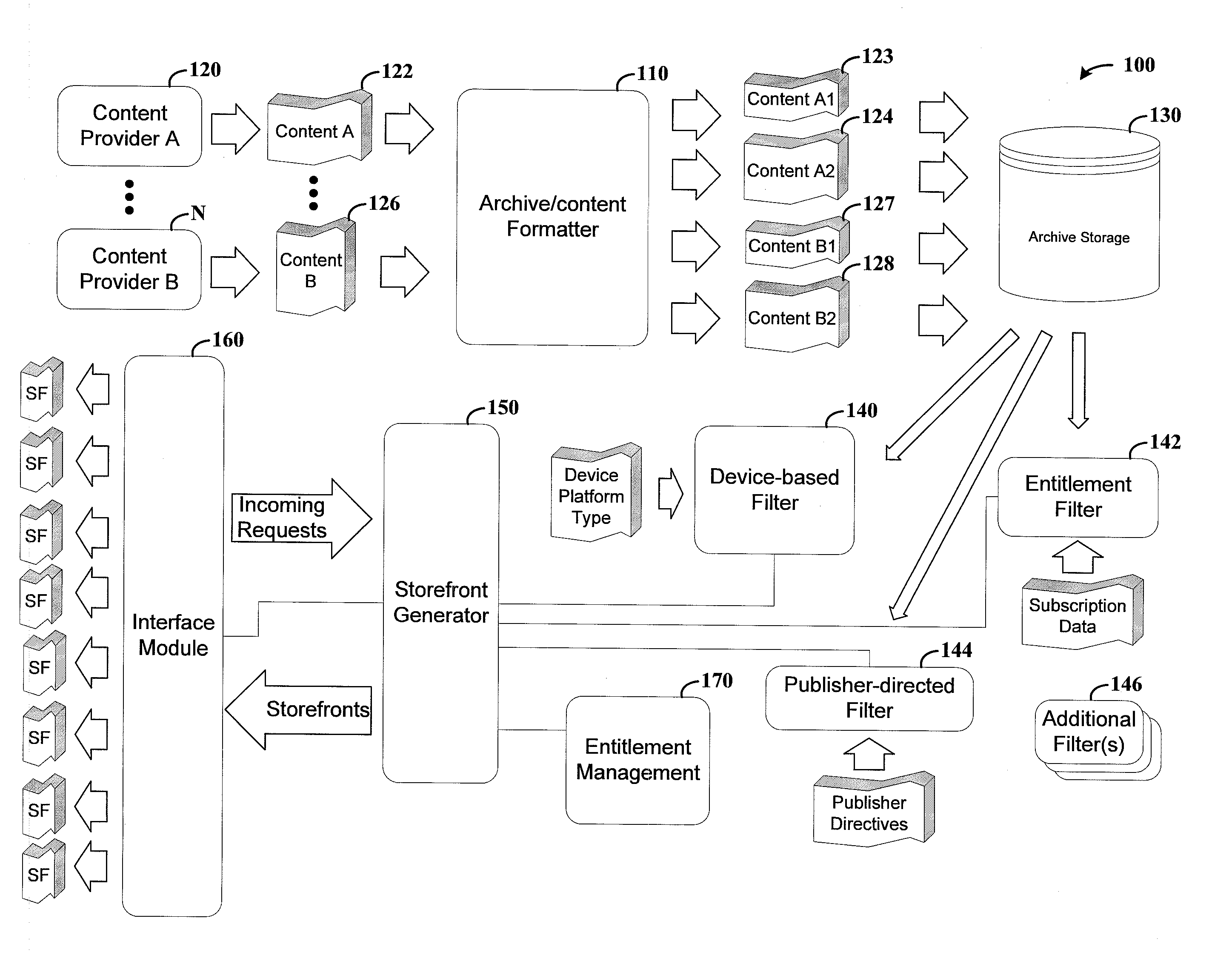
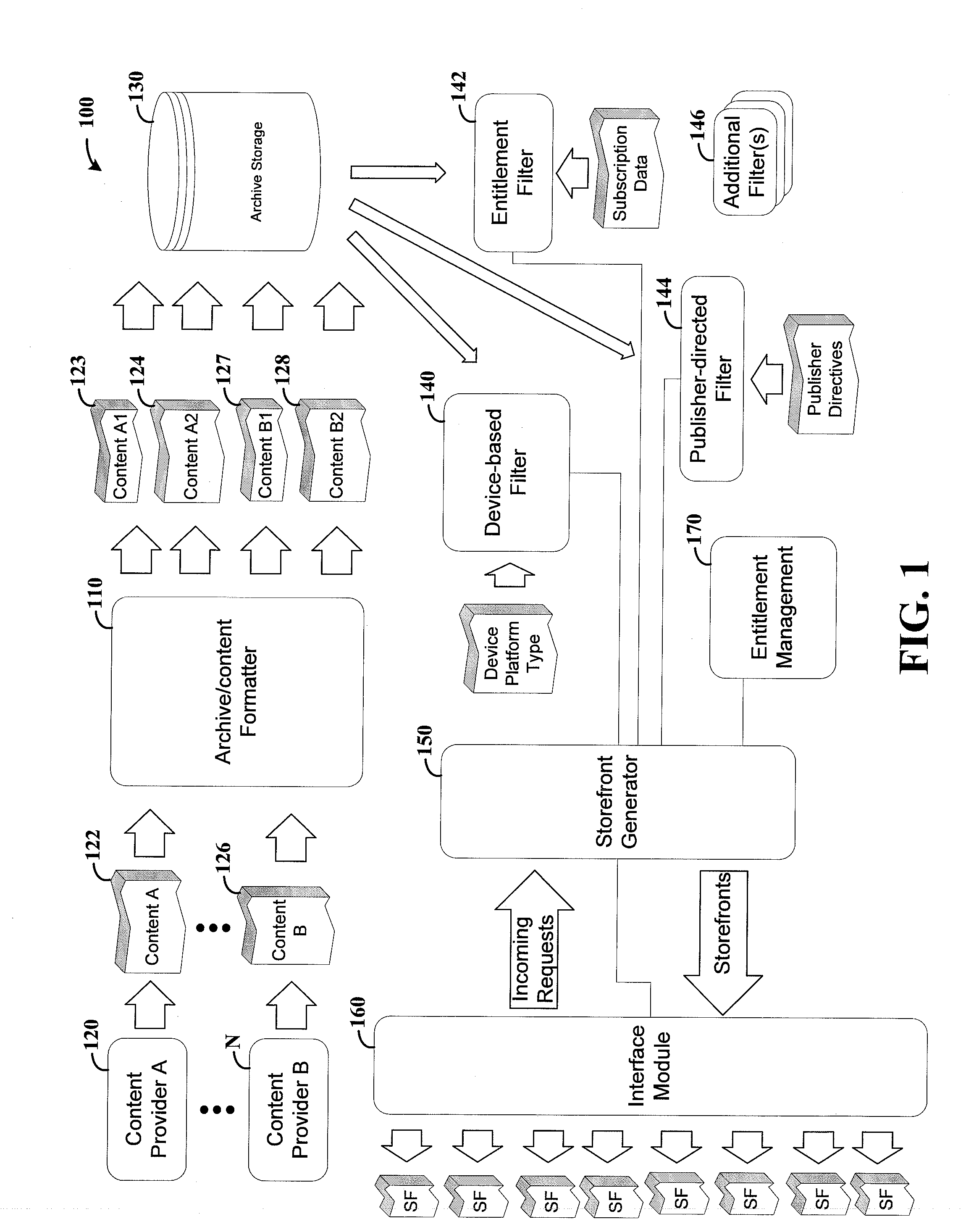
Media content device, system and method
ActiveUS20120317482A1Reduce deliveryEasy to demonstrateInput/output for user-computer interactionDigital data protectionUser deviceWorld Wide Web
Access is provided for different types of media content provided by disparate publishers, and in formats corresponding to operating characteristics of respective user devices. As consistent with one or more example embodiments herein, media content access is filtered for users requesting access via different user devices, based upon characteristics of the device to which the access is provided, user subscription data and publisher-specific criteria. A user-specific storefront interface is generated for each of a multitude of users, based upon the filtering. Each storefront interface indicates media content that can be displayed at the device to which access is requested, and identifies media content to which the user does and does not have subscription access. The user-specific storefront interfaces are presented at respective user devices, and media content is delivered to each device in response to selections made via the user-specific storefront interfaces.
Owner:APPLE INC
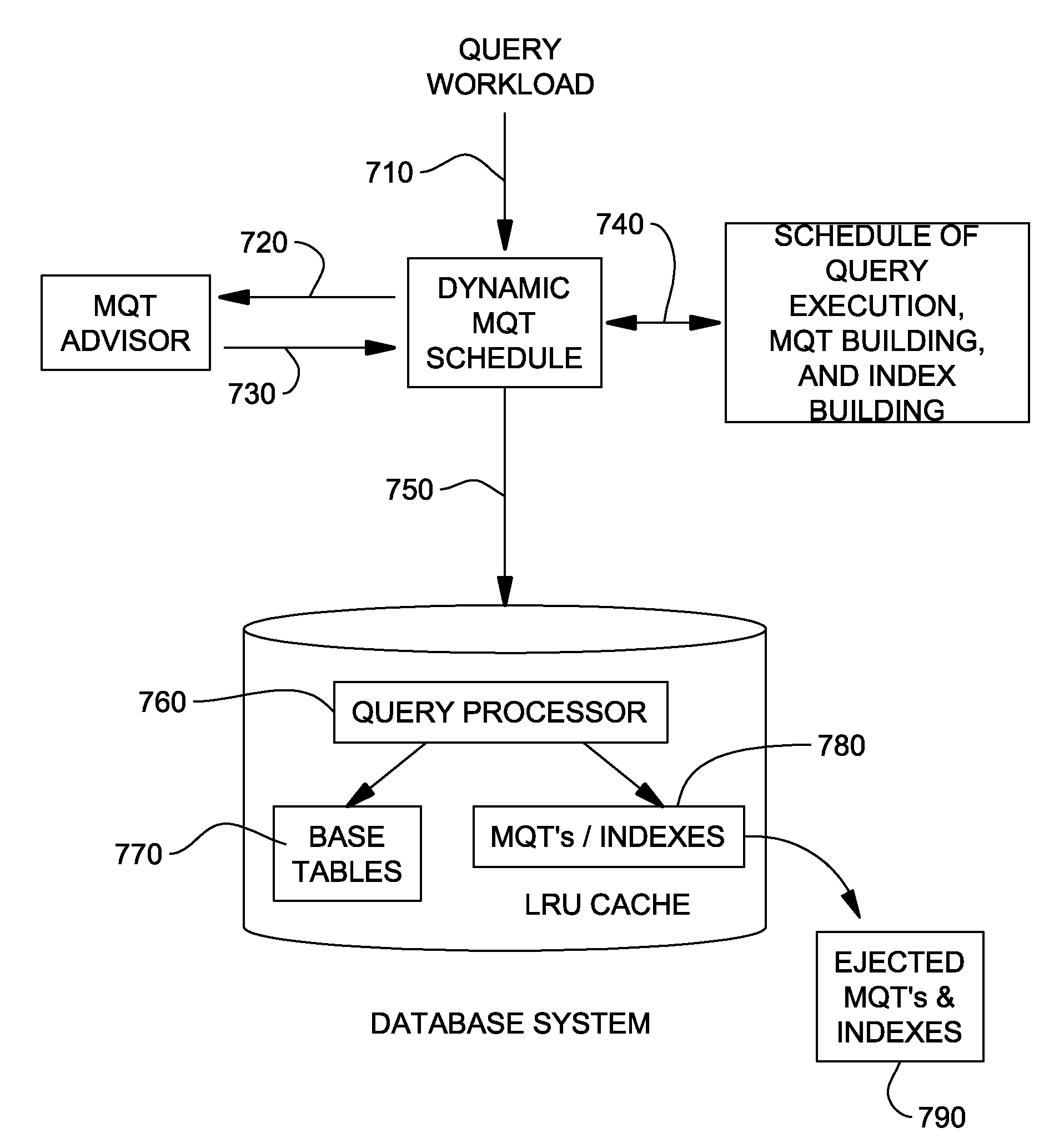
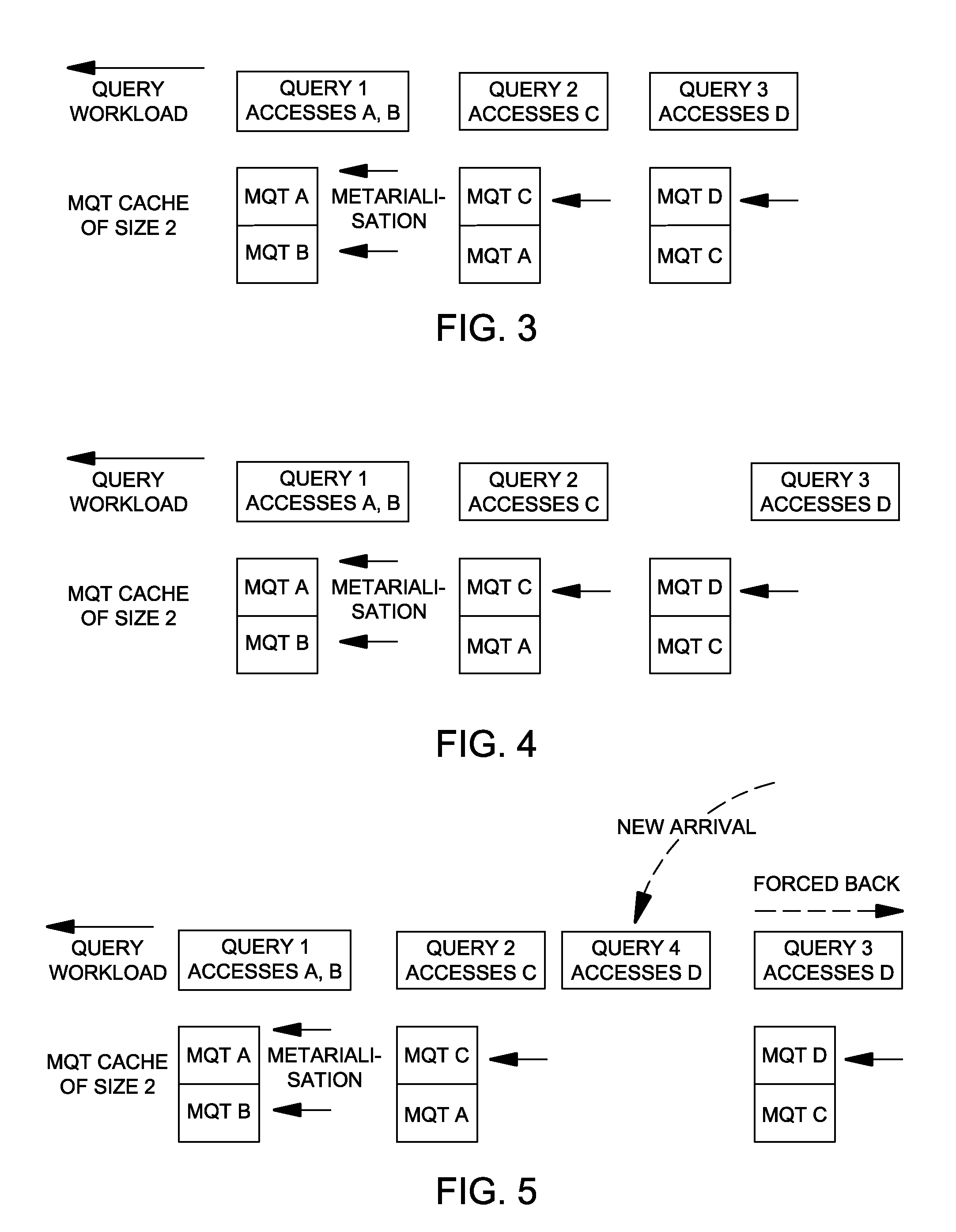
Automated and dynamic management of query views for database workloads
InactiveUS20080177700A1Reduce processing costsDigital data processing detailsSpecial data processing applicationsDynamic managementWorkload
The embodiments of the invention provide a method, program storage device, etc. for automated and dynamic management of query views for database workloads. More specifically, a method begins by executing queries, which includes accessing a set of data tables for each of the queries. During the executing of the queries, the method accesses a required data table from a cache if the required data table is present in the cache and creates the required data table if the required data table is not present in the cache. The accessing of the required data table from the cache has a lower processing cost than accessing the required data table from a base table. Also during the executing of the queries, created data tables are stored in the cache, wherein one or more of the created data tables are removed from the cache when the cache becomes full.
Owner:IBM CORP
Device and method to enforce security tagging of embedded network communications
InactiveUS20150135271A1Digital data processing detailsMultiple digital computer combinationsNetwork communicationMethod access
Owner:GM GLOBAL TECH OPERATIONS LLC
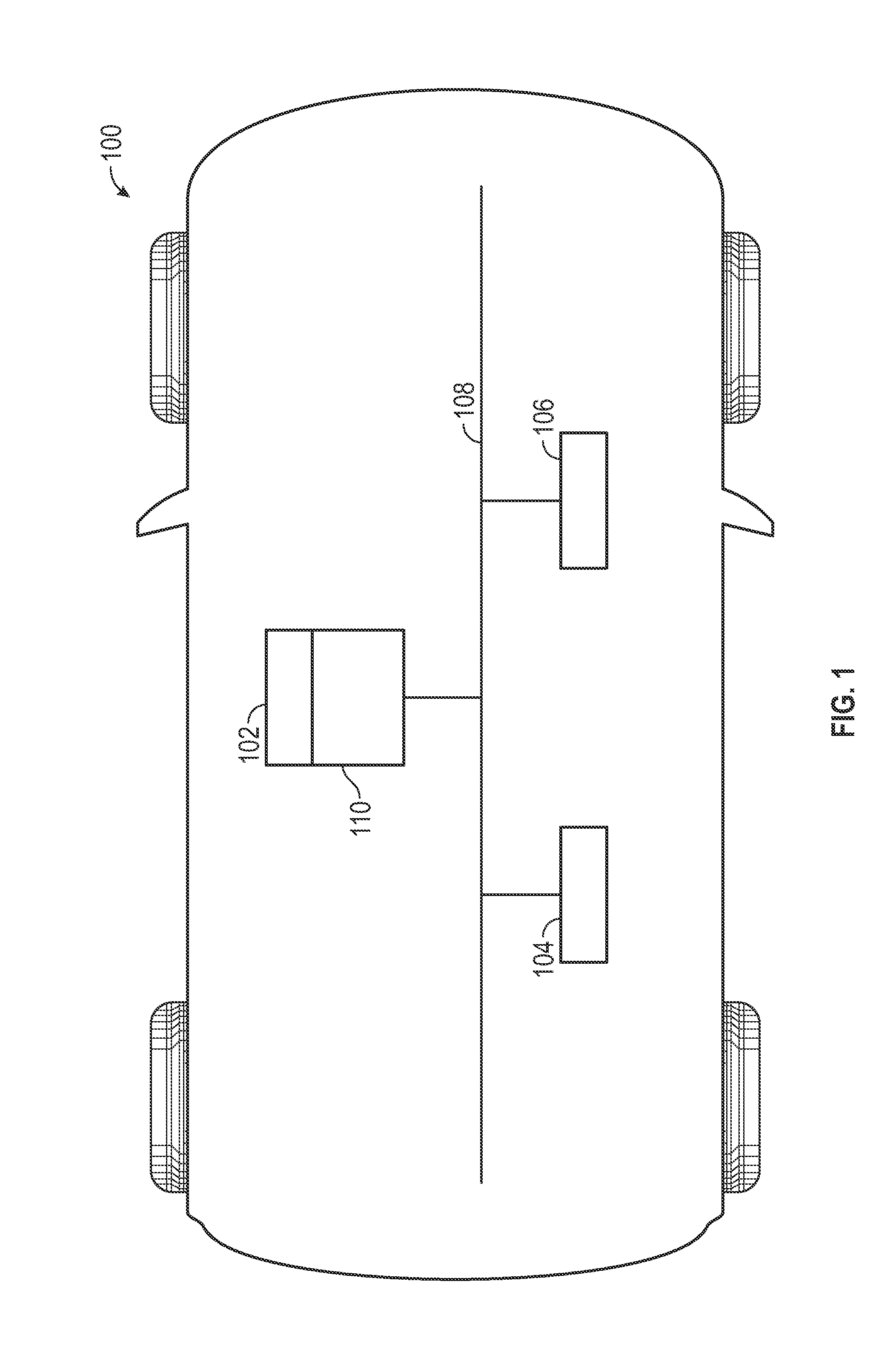
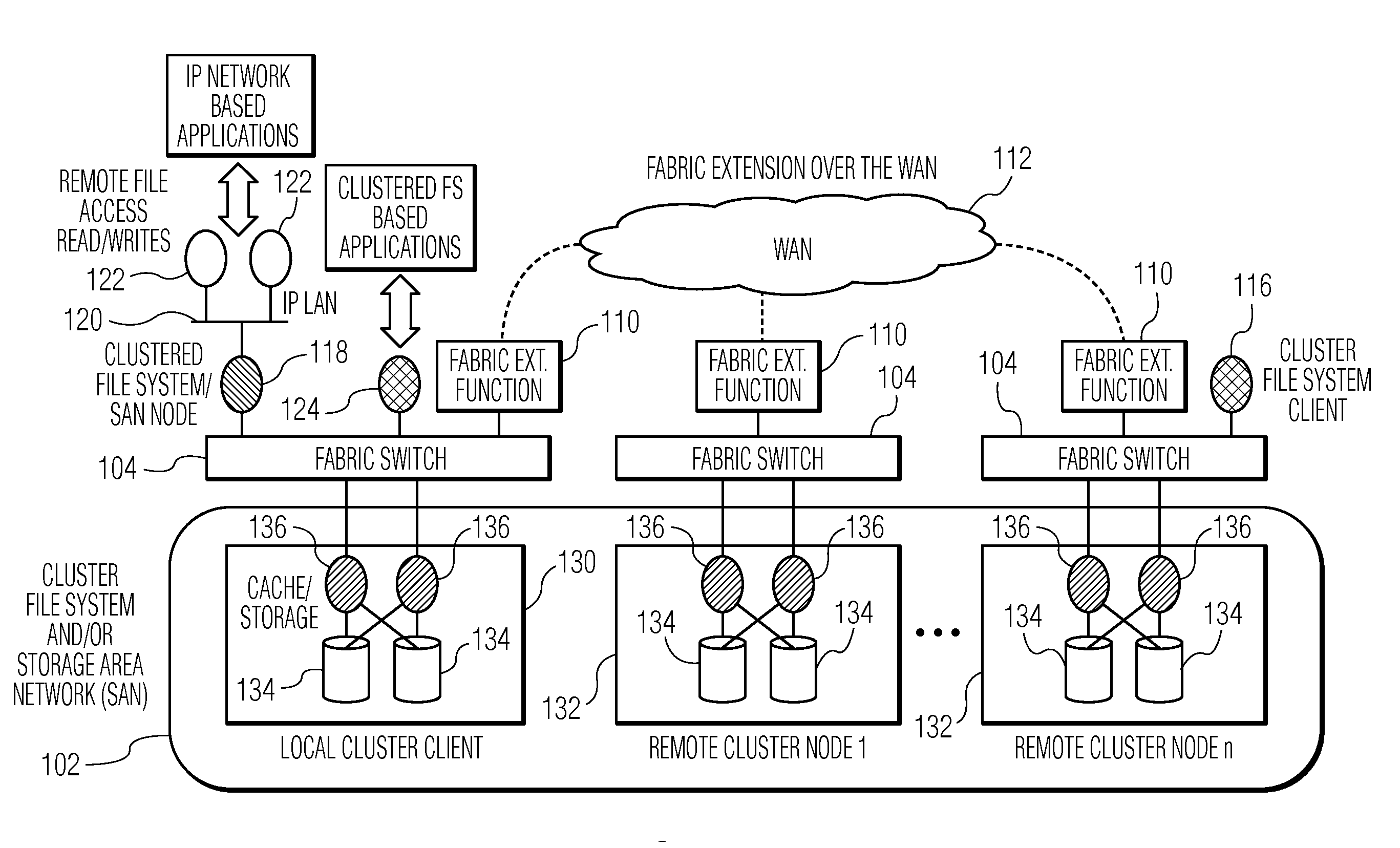
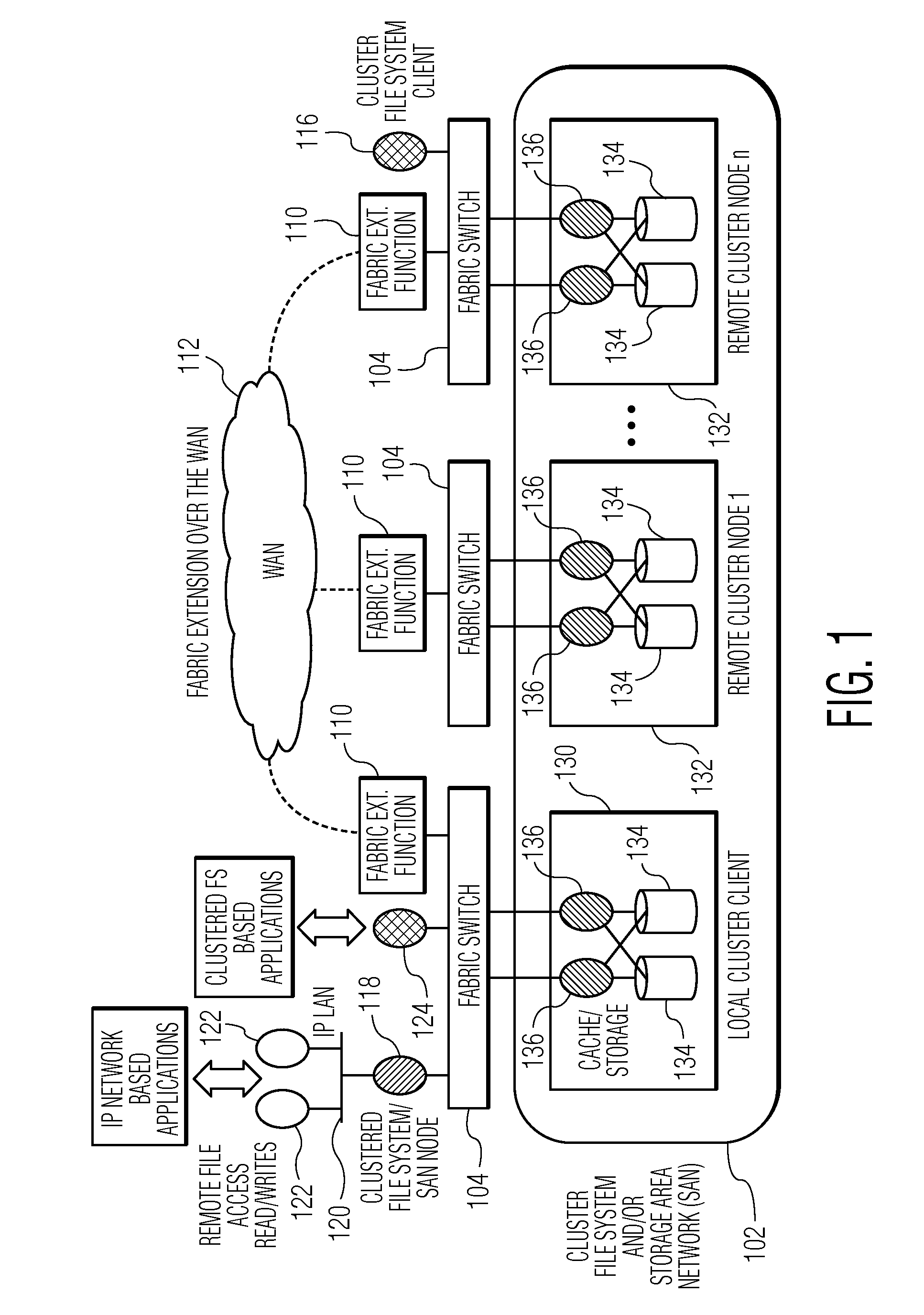
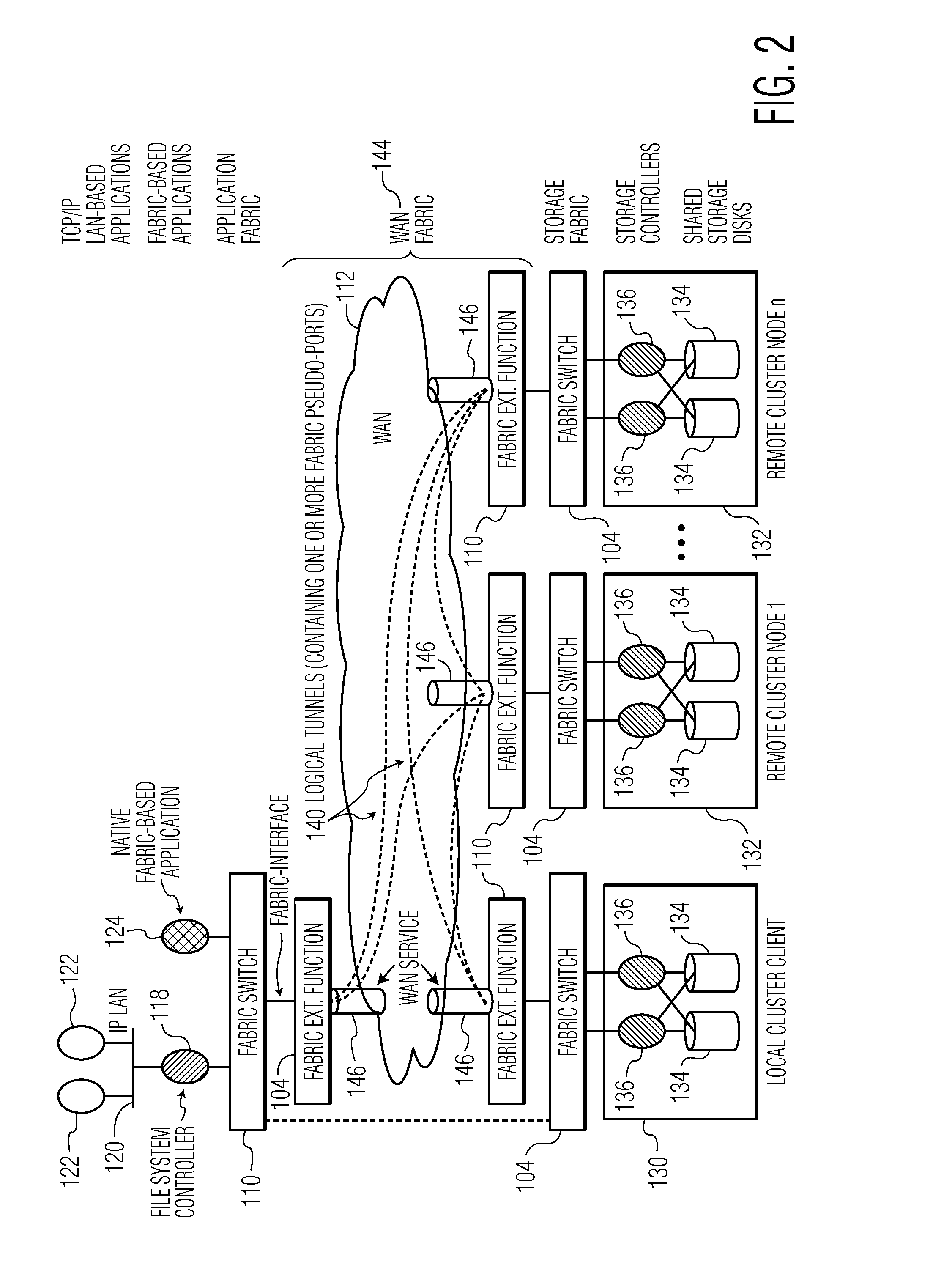
Methods and systems for accessing remote digital data over a wide area network (WAN)
ActiveUS20150334034A1Hybrid transportMultiple digital computer combinationsDigital dataLAN switching
Systems and methods accessing remote digital data over a wide area network (WAN) are disclosed. In an embodiment, a network device is disclosed. The network device includes a local area network (LAN) switching fabric physical interface configured to communicate according to a LAN switching fabric protocol, a WAN physical interface configured to communicate according to a WAN protocol, and a fabric extension function configured to map LAN switching fabric interfaces to pseudo-ports, map pseudo-ports to WAN interfaces, and transmit LAN fabric datagrams received at the LAN switching fabric physical interface from the WAN physical interface via a mapped pseudo-port and a corresponding WAN interface.
Owner:BAY MICROSYSTEMS INC
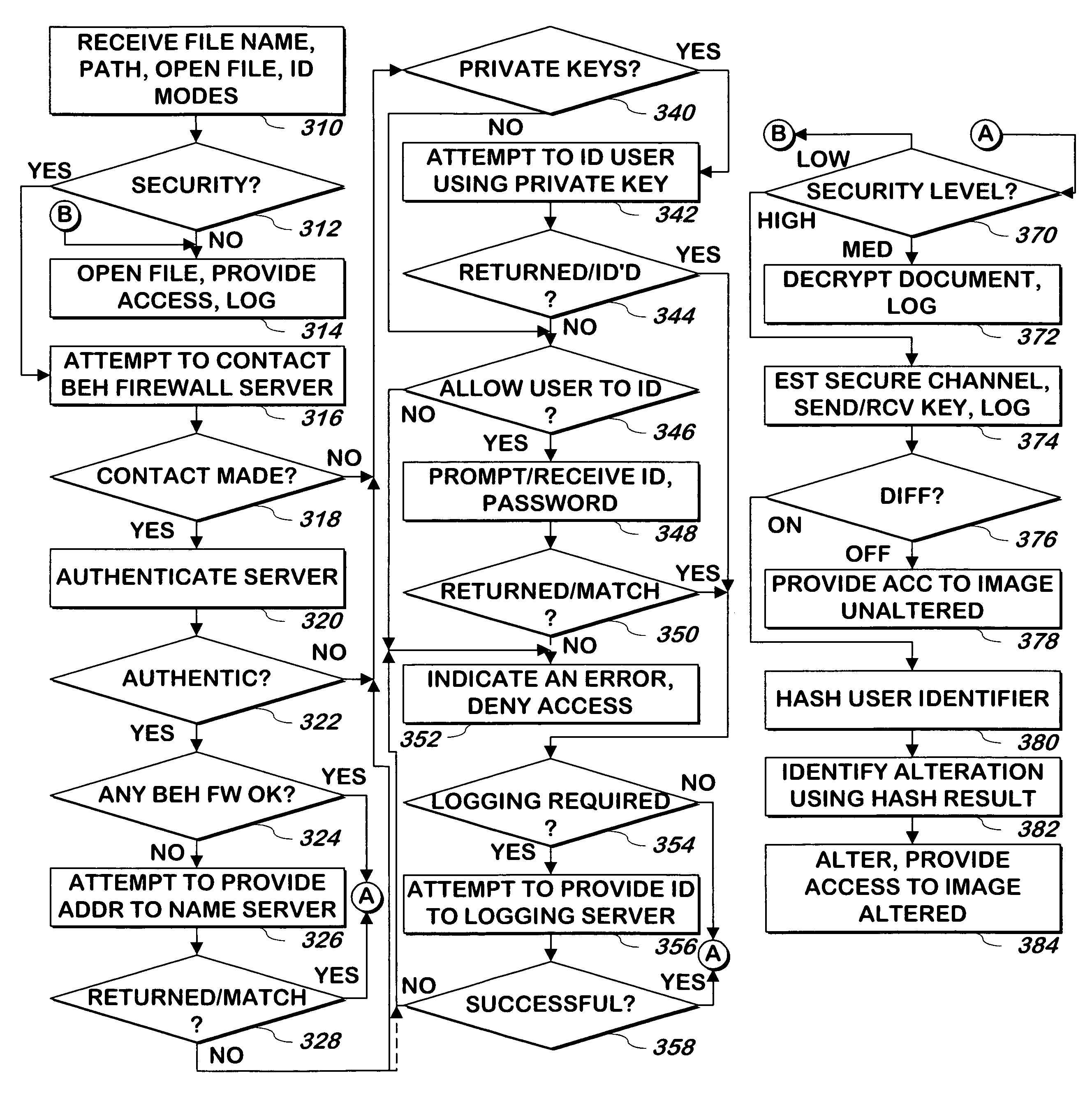
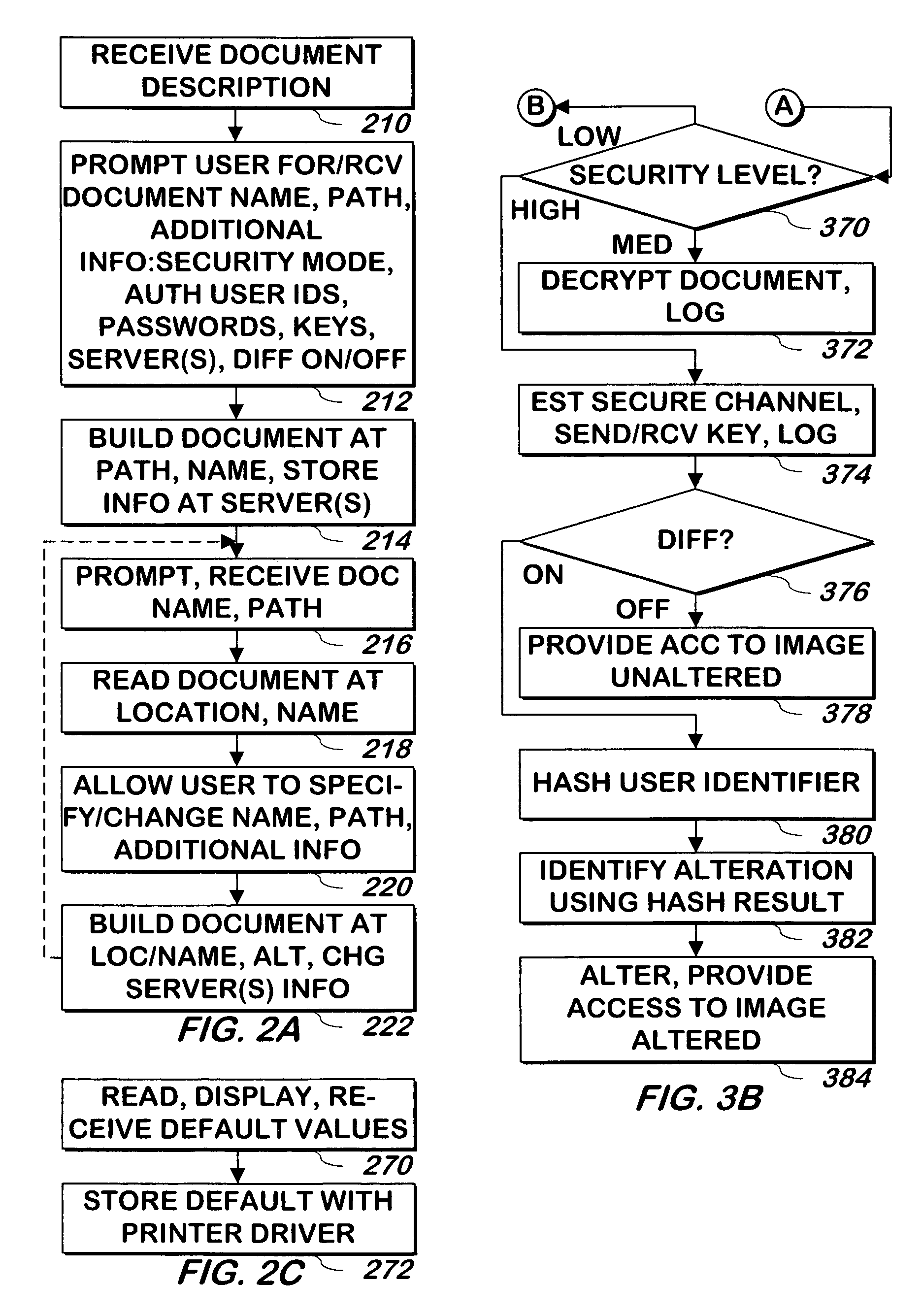
System and method for providing document security, access control and automatic identification of recipients
ActiveUS7660798B1Digital data processing detailsMultiple digital computer combinationsElectronic documentMedia access control
A system and method attempts to access a portable electronic document using different methods depending on whether the user attempting access is in front of, or behind, a firewall.
Owner:ADOBE SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com