Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103results about How to "Network security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
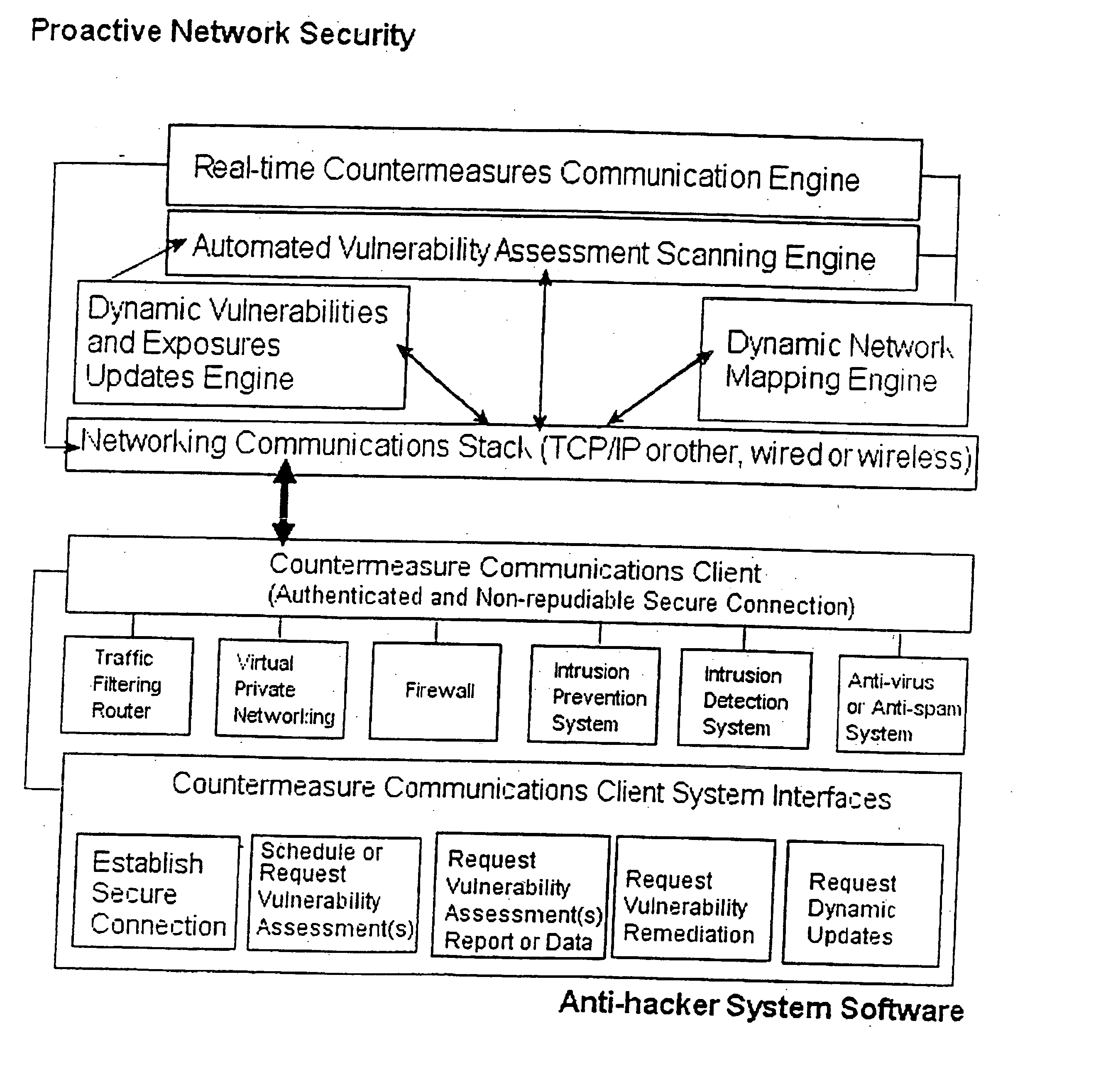
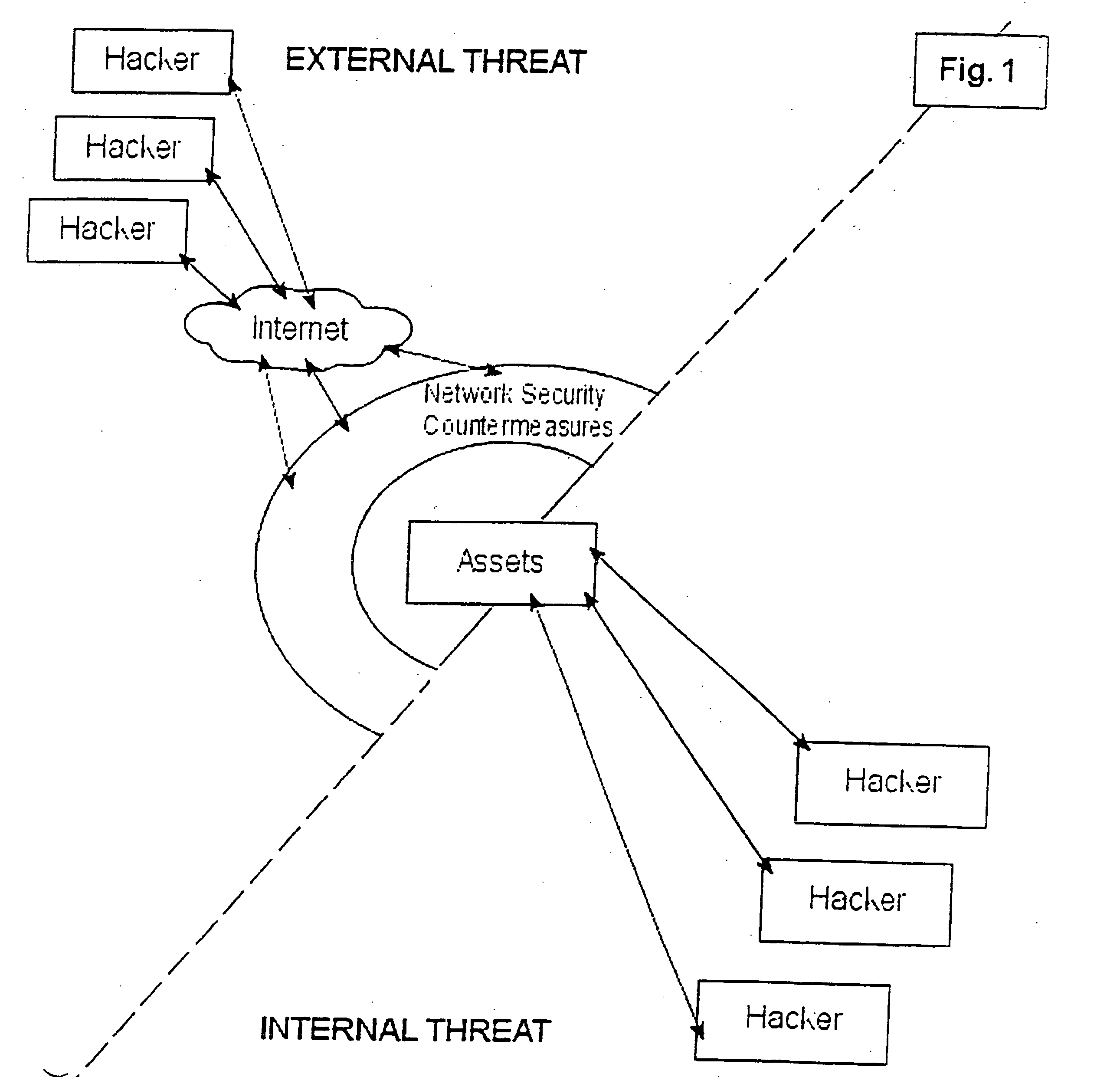
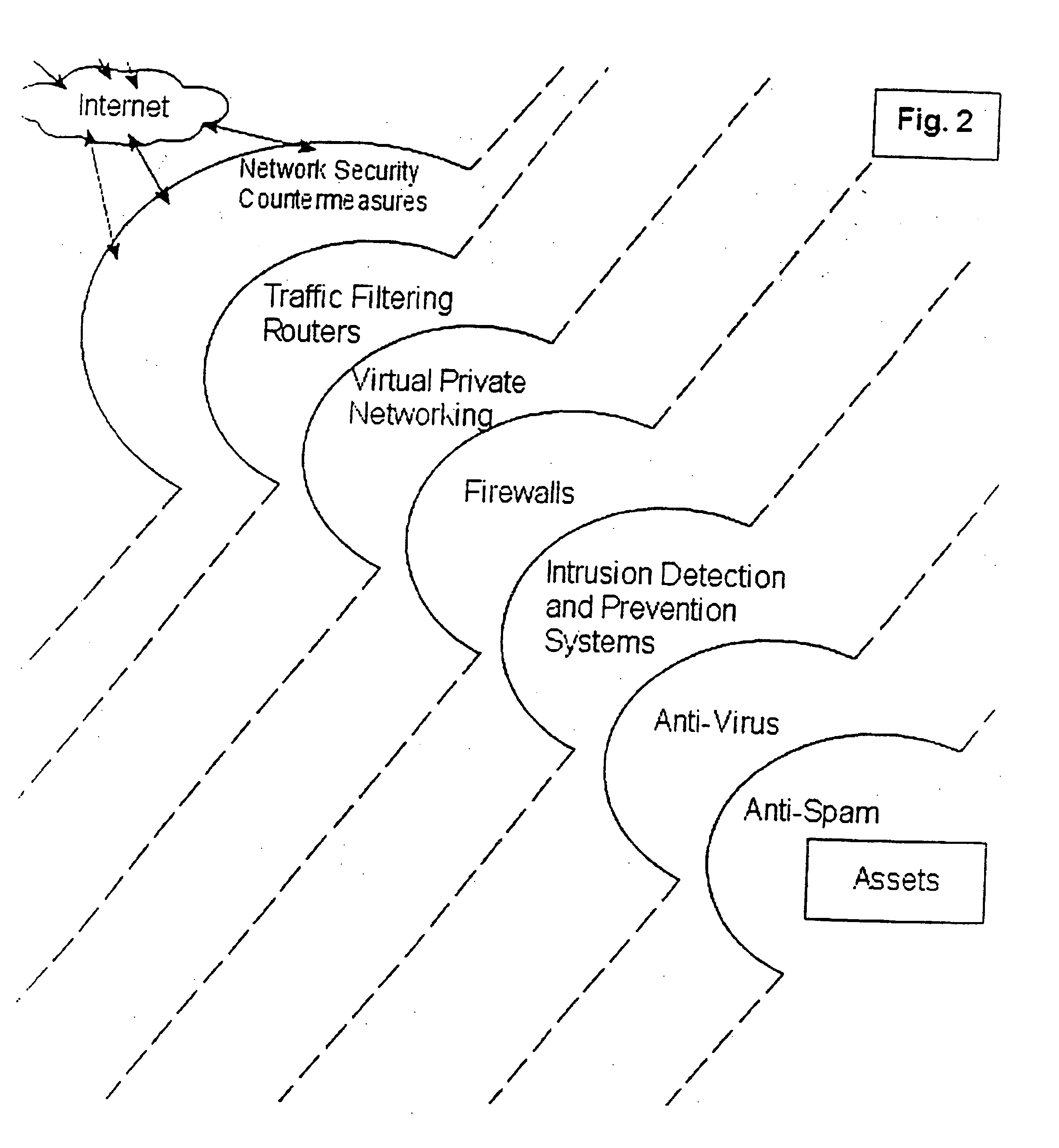
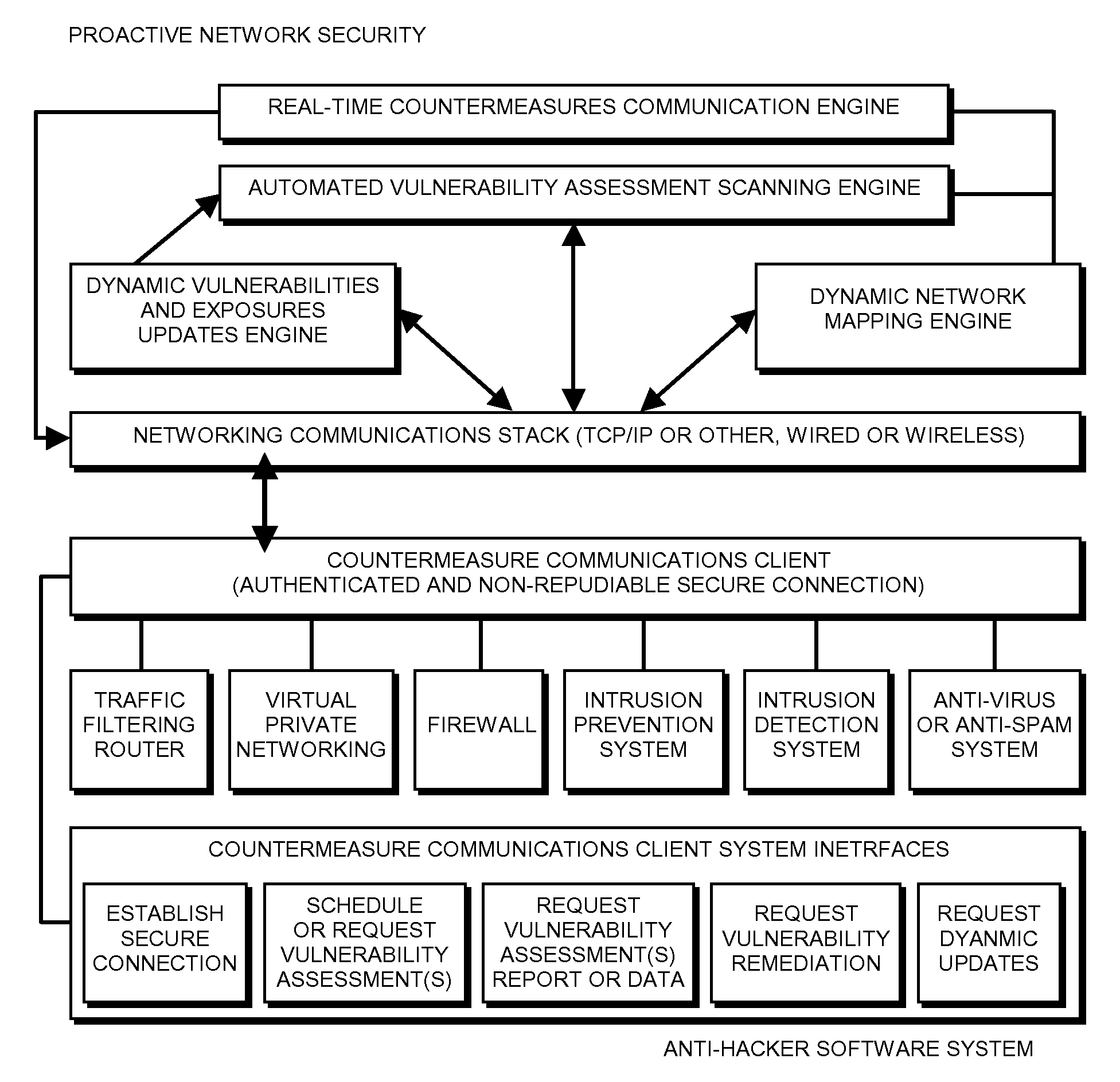
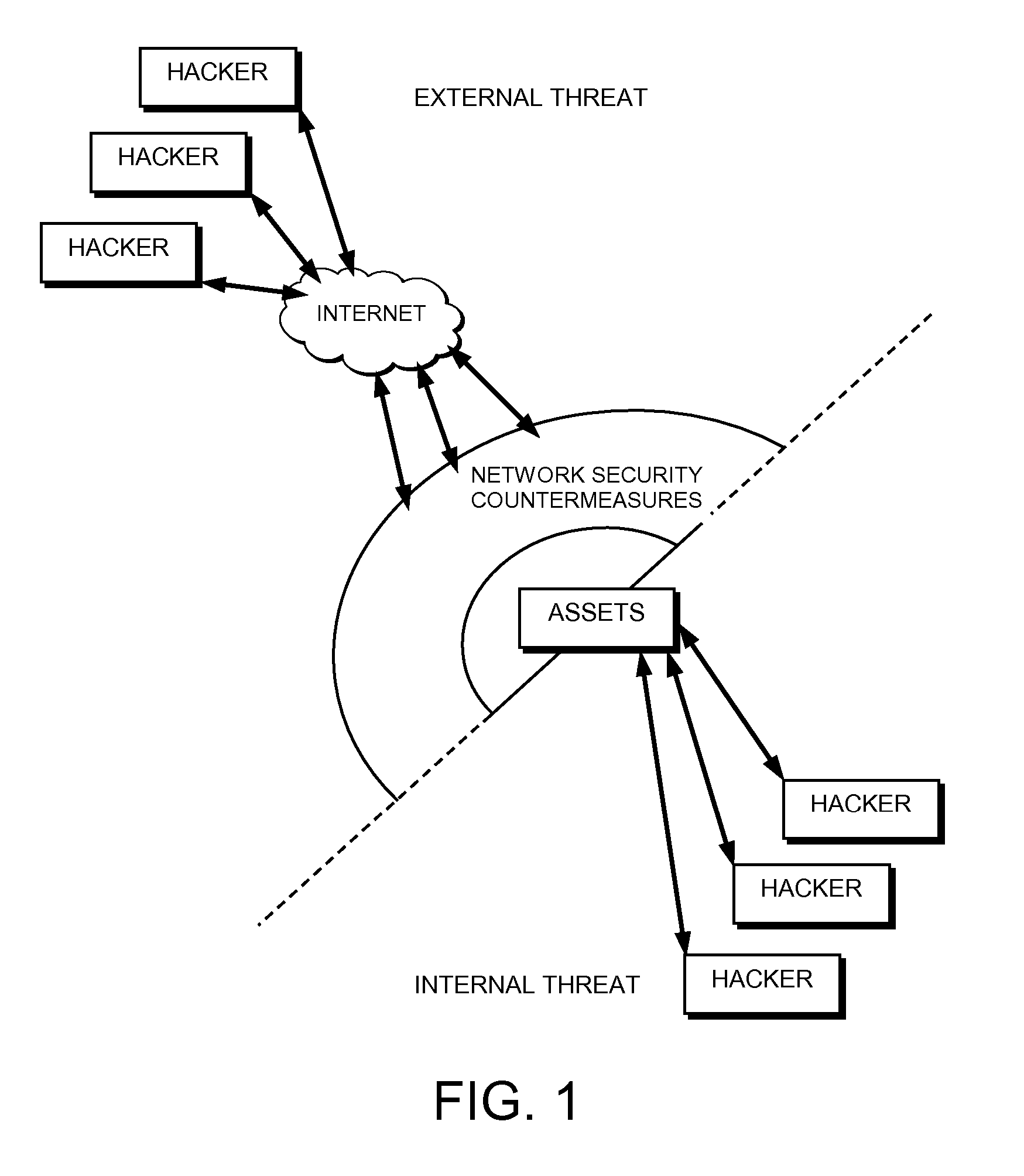
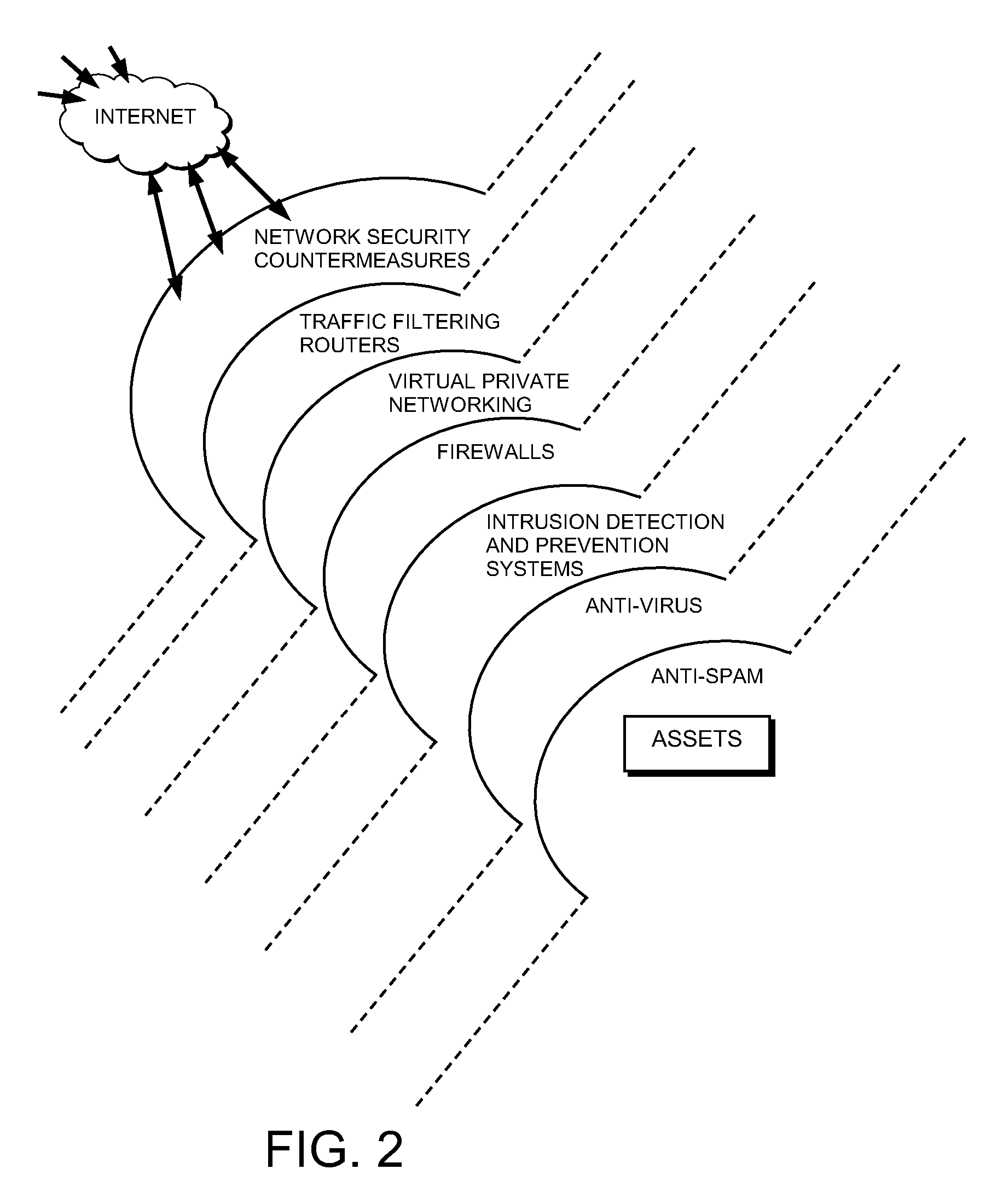
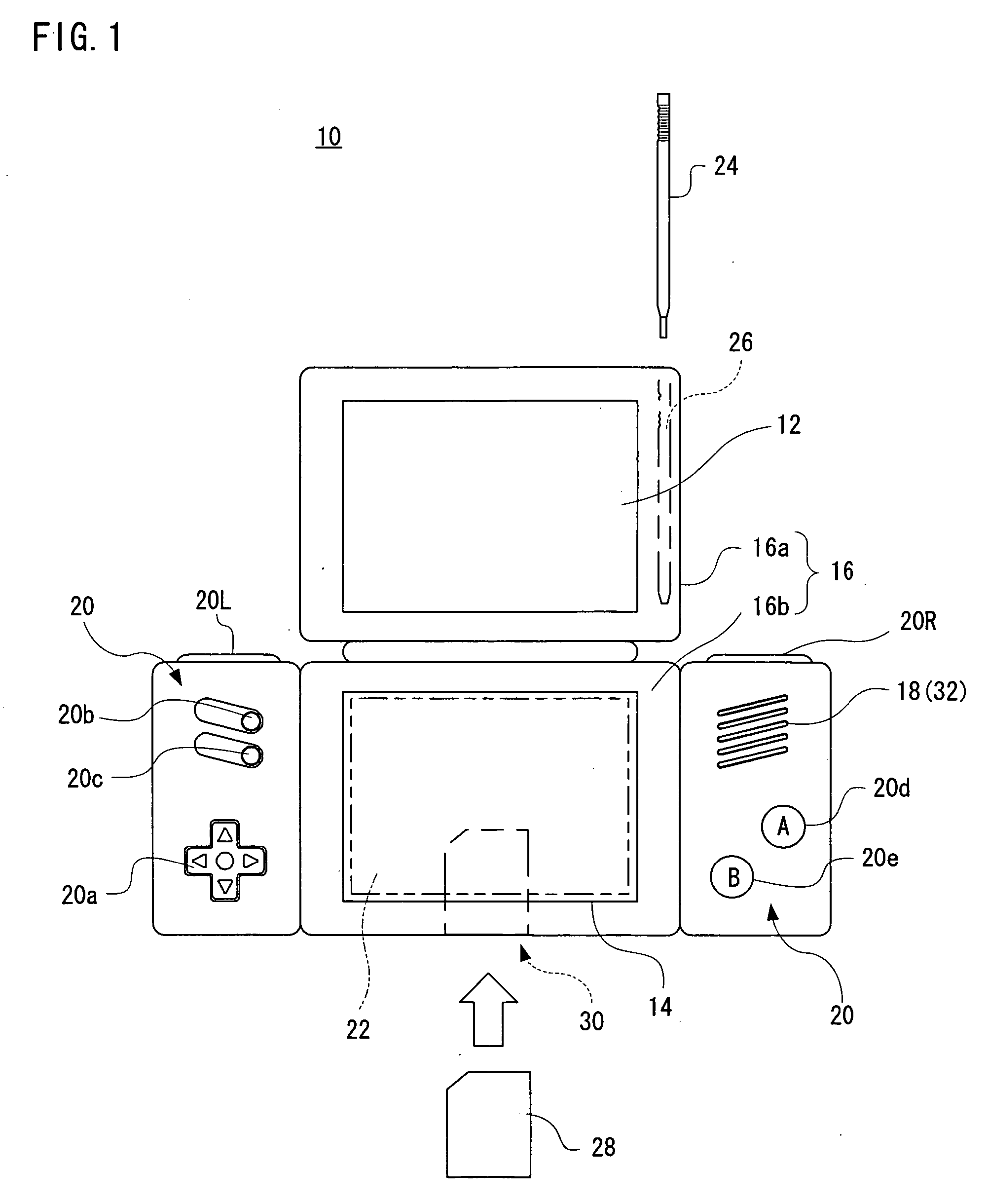
Proactive network security system to protect against hackers
InactiveUS20050044418A1Reduce riskEasily manageMemory loss protectionDigital data processing detailsCountermeasureCommon Vulnerabilities and Exposures
A proactive network security system to protect against hackers for the proactive automated defense against hackers by automatically finding, reporting, communicating with countermeasures about and removing the common vulnerabilities and exposures (CVEs) that they exploit.
Owner:NETSHIELD CORP
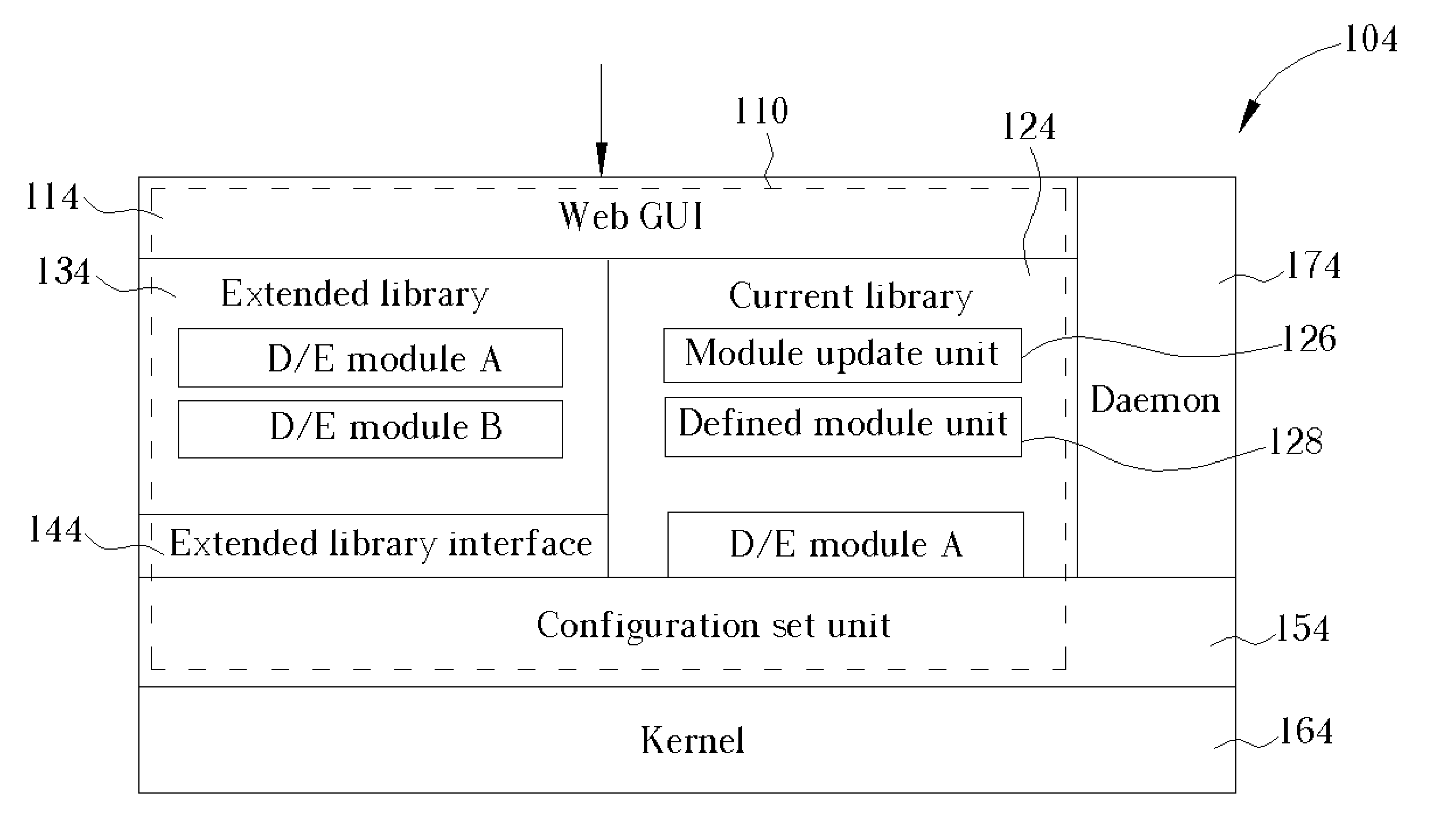
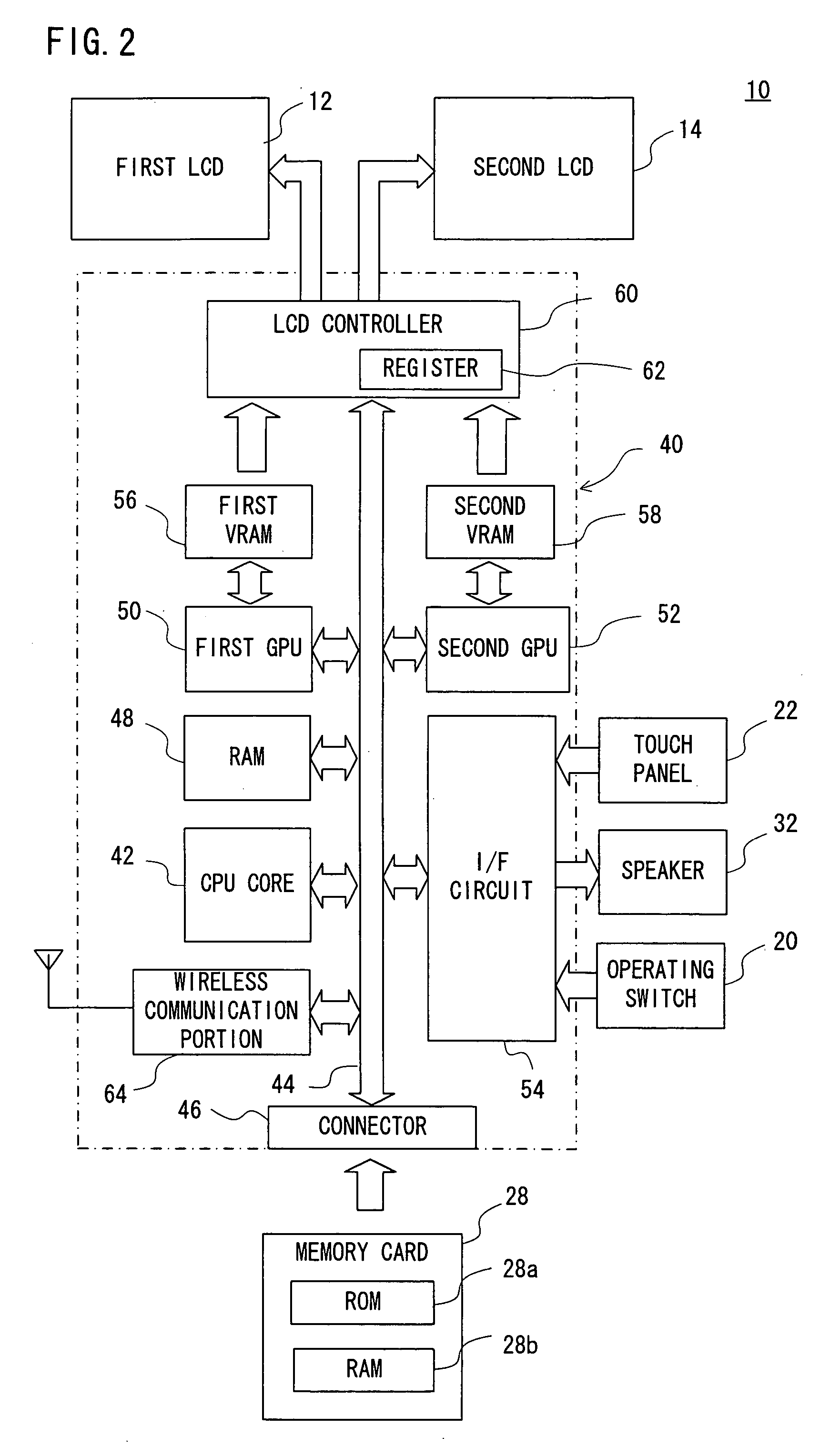
System for actively updating a cryptography module in a security gateway and related method
InactiveUS20050149746A1Time expendedImprove operational efficiencyDigital data processing detailsUser identity/authority verificationComputer scienceIpsec protocol
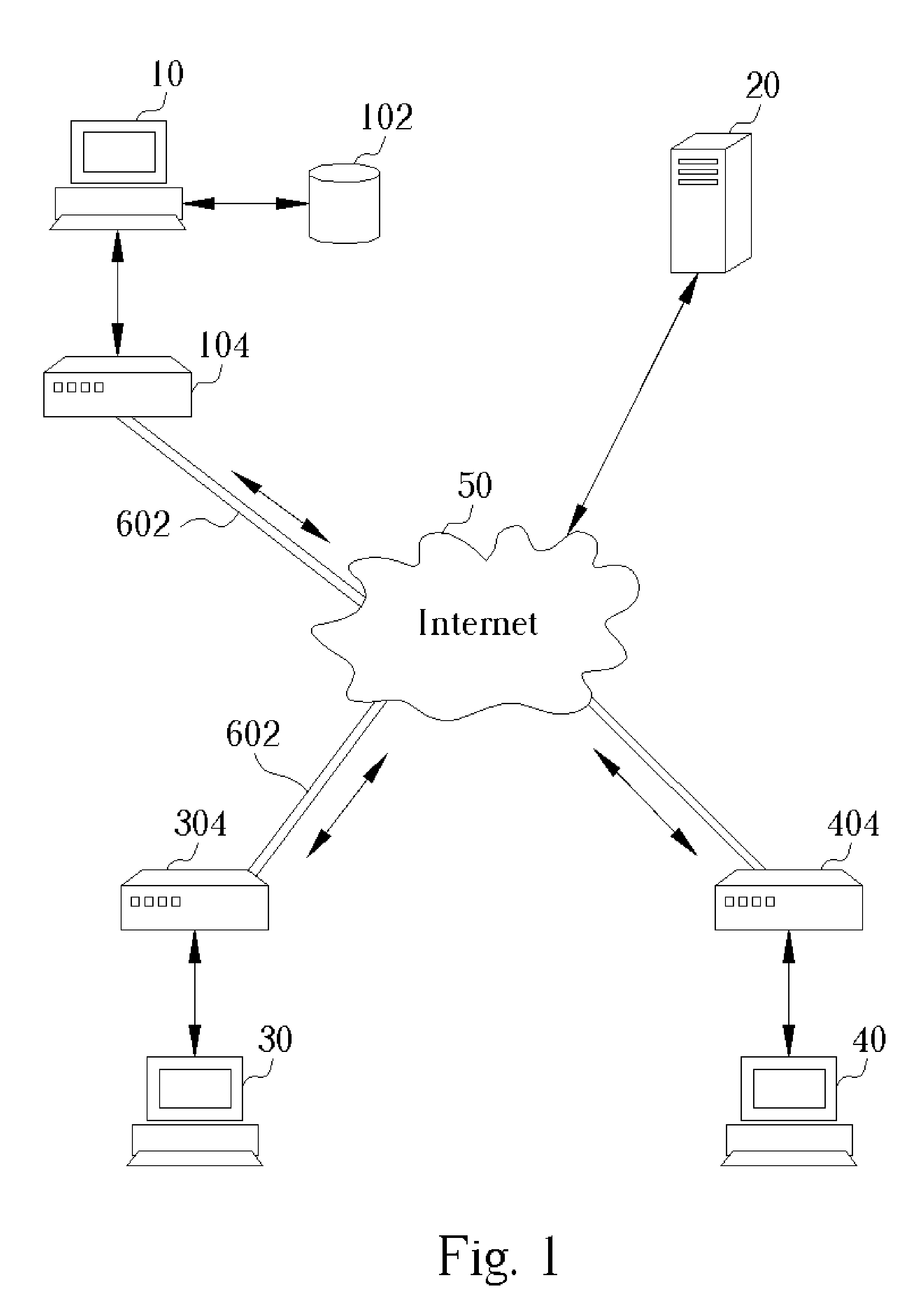
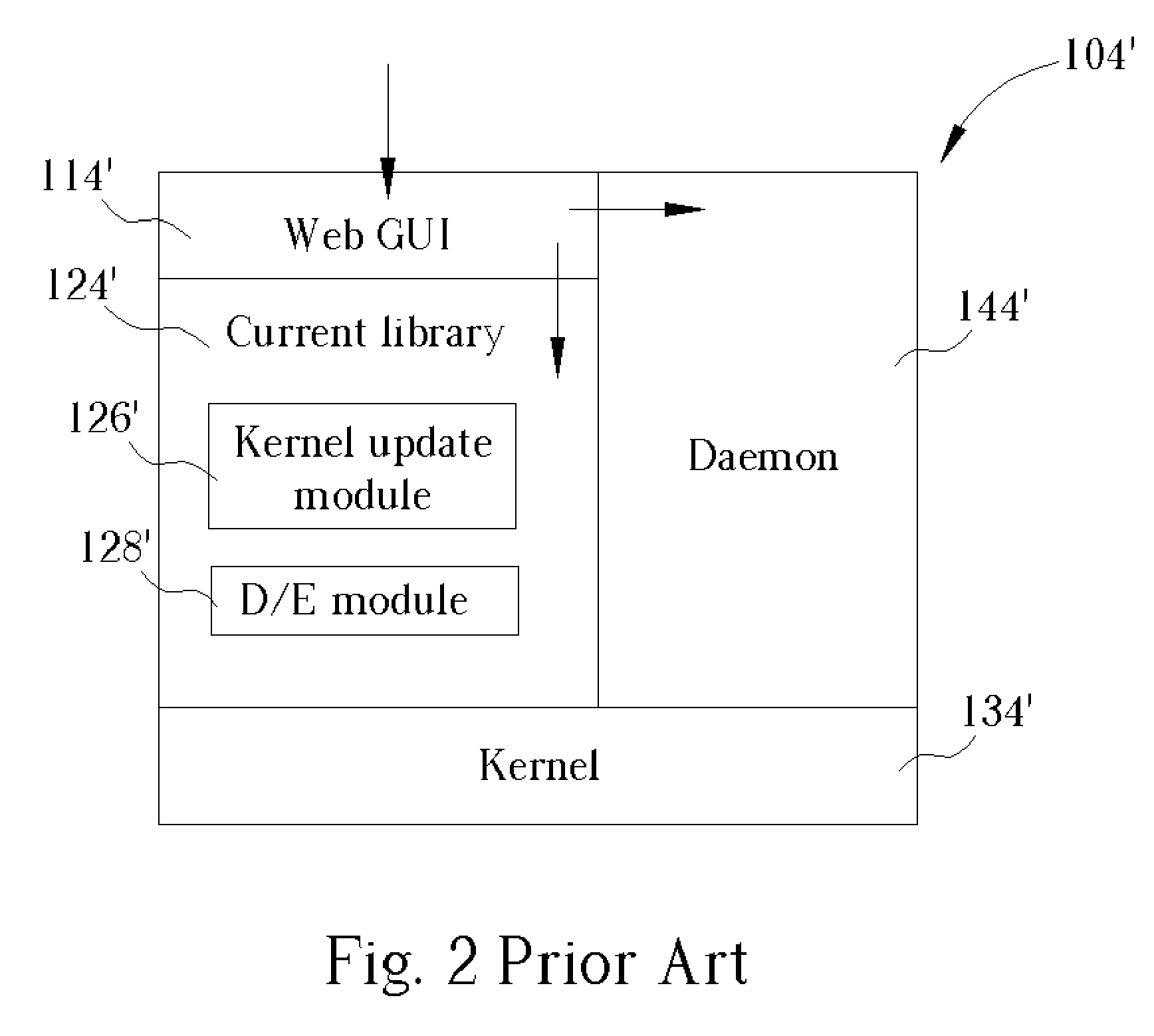
A system for actively updating a cryptography module in a security gateway and related method is used in a security gateway, such as a VPN gateway according to an IPSEC protocol, which is connected between at least one user computer system and a network system. The system includes a Web GUI, a module update unit, a defined module unit, and an extended library. A user can easily update or add decryption / encryption modules into the extended library of the gateway through the Web GUI and the module update unit instead of updating the decryption / encryption modules along with the entire kernel firmware. This can reduce the setting time, increase the efficiency of operation, reduce the maintenance cost, and promote the expansion of decryption / encryption modules of the gateway so that network transmission can become much safer.
Owner:ICP ELECTRONICS
Security protocol model for ubiquitous networks
InactiveUS20070118879A1Network securityEasy to useDigital data processing detailsUser identity/authority verificationSingle pointUbiquitous network
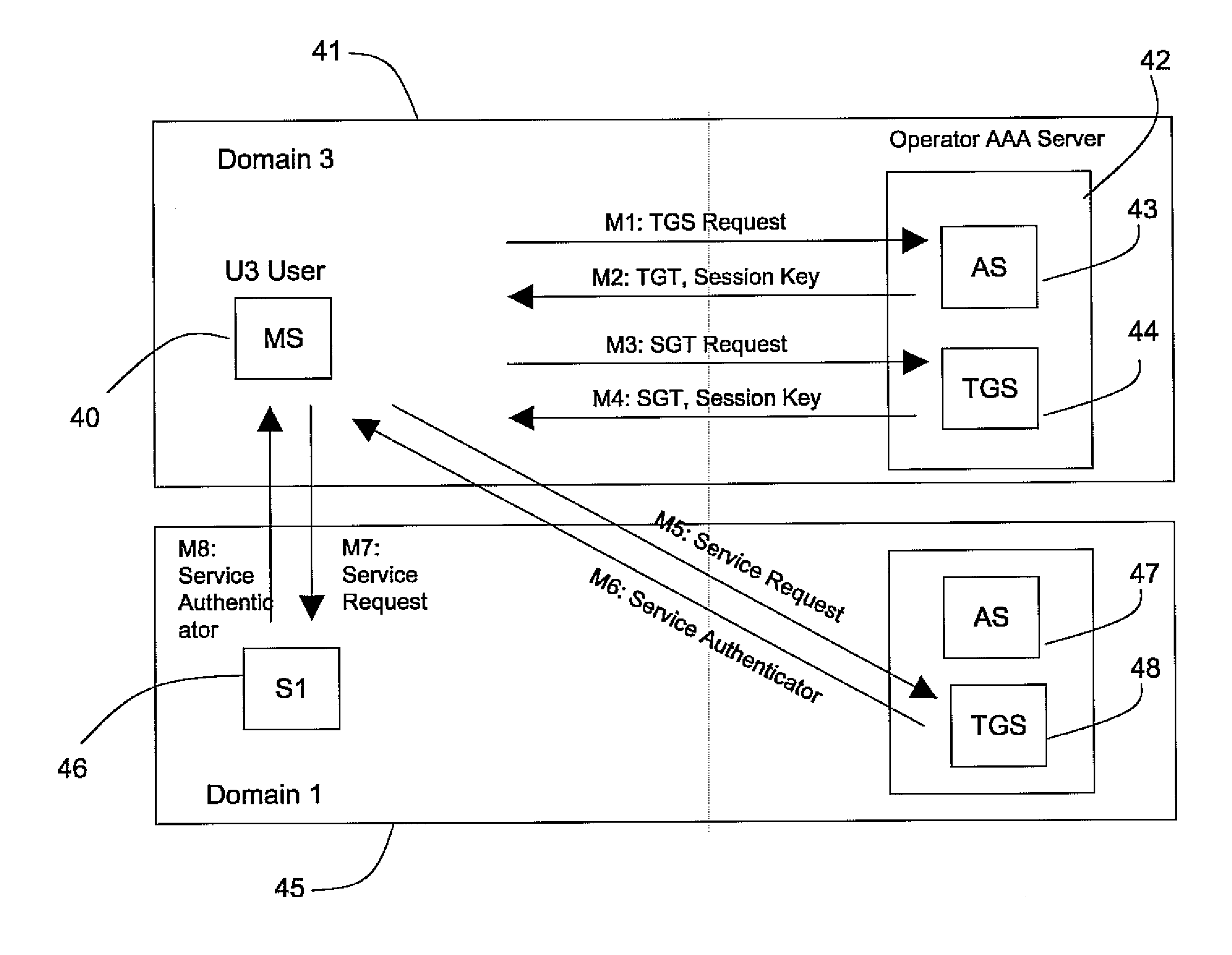
Gaining secure access to a ubiquitous network by detecting a user joining one particular network domain of the ubiquitous network, authenticating the joined user by employing symmetric key authentication together with a single sign-on mechanism, and allowing the authenticated user to access one or more other network domains of the ubiquitous network based upon the authenticating for the one particular network domain.
Owner:LG ELECTRONICS INC
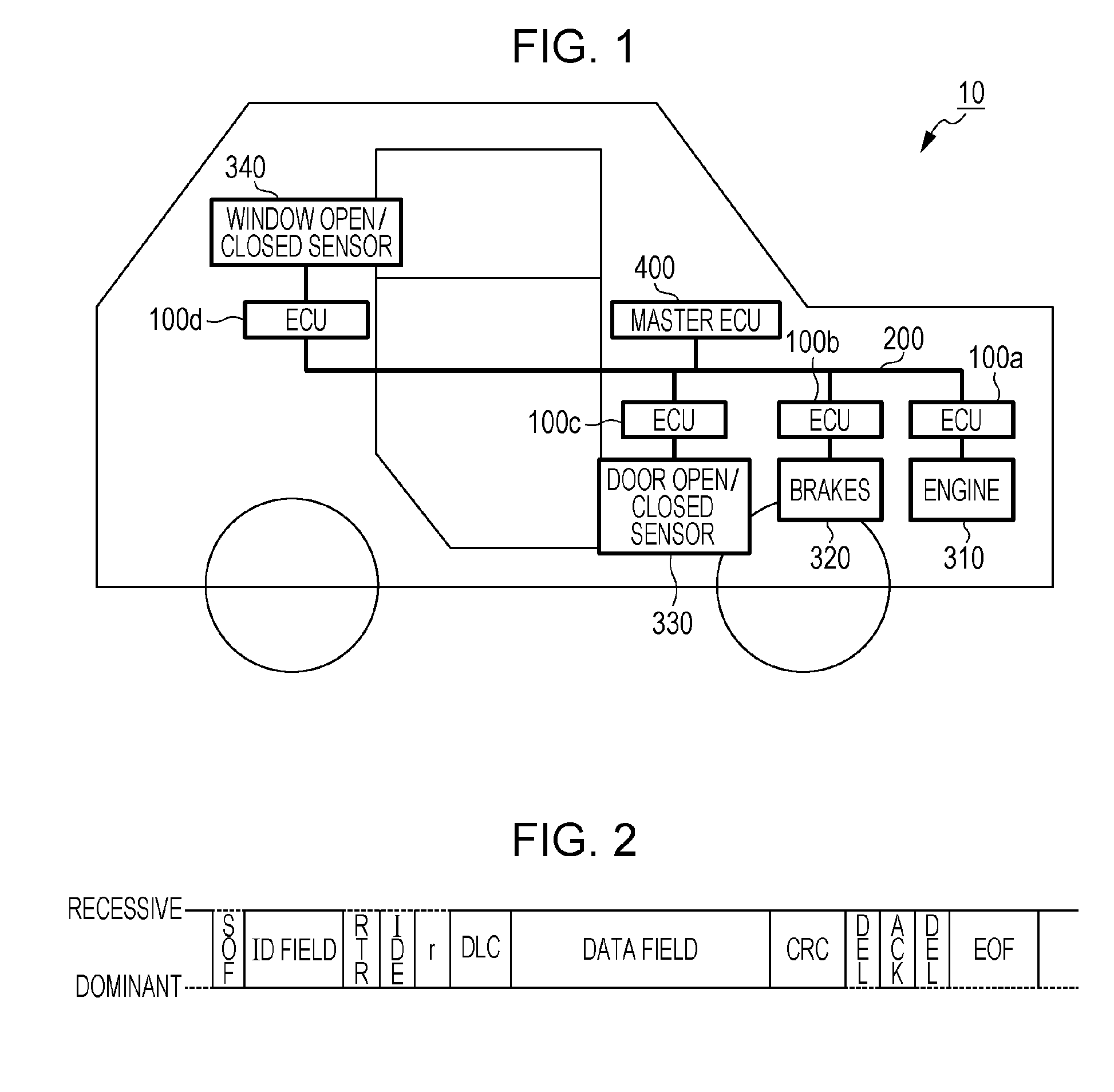
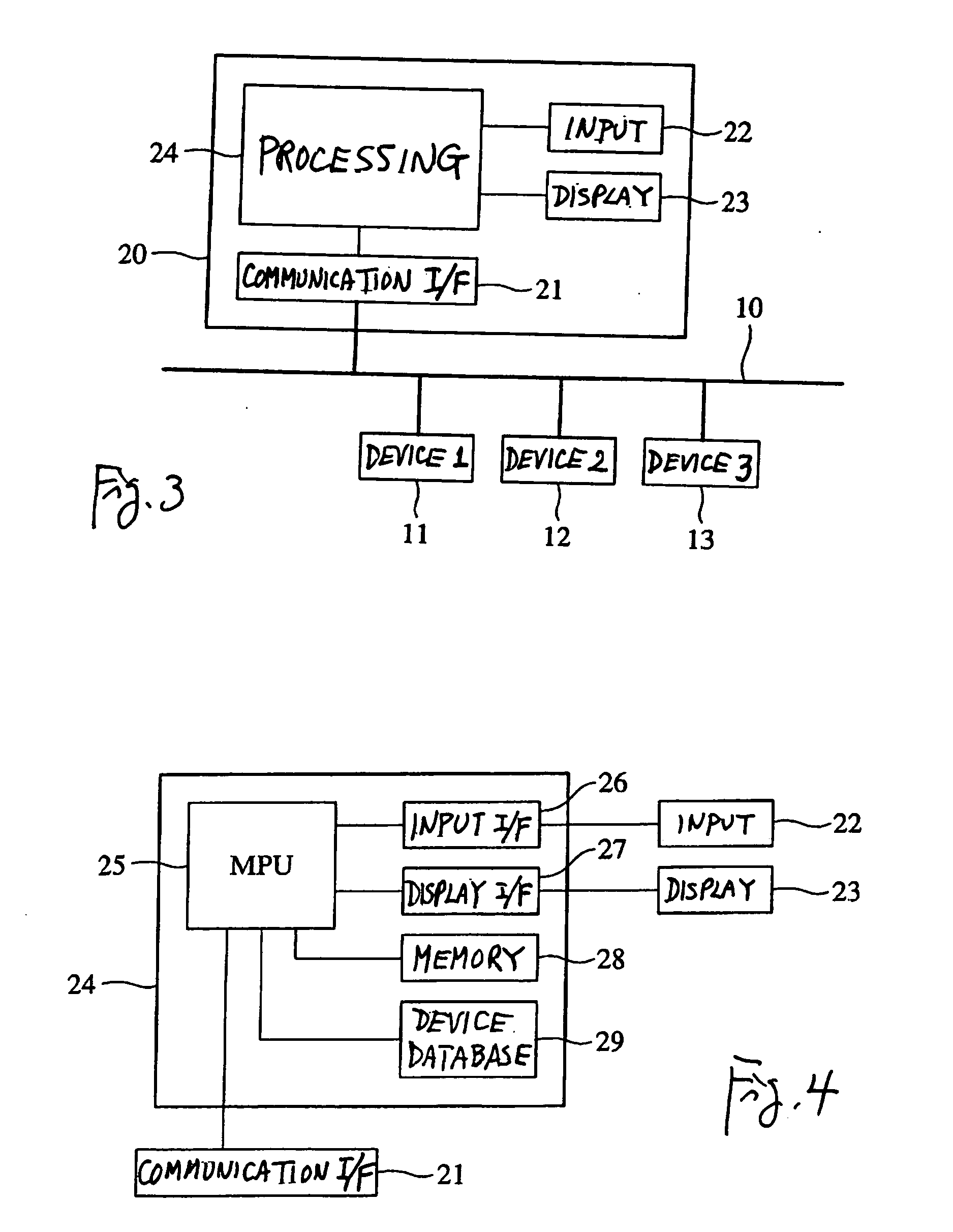
Vehicle-Mounted Network System
InactiveUS20130227650A1High processing loadReduce processing loadDigital data processing detailsElectric testing/monitoringComputer scienceCommunication device
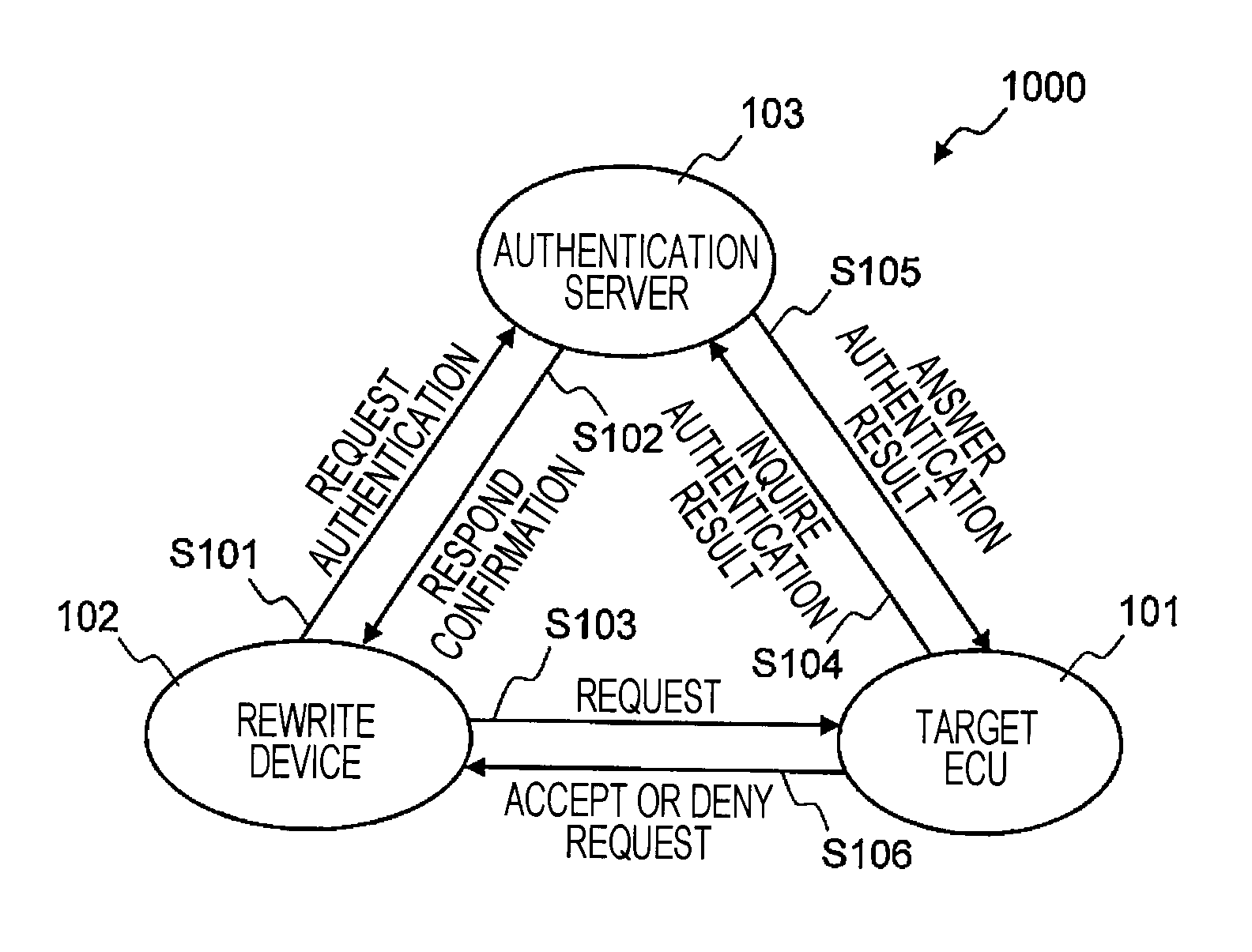
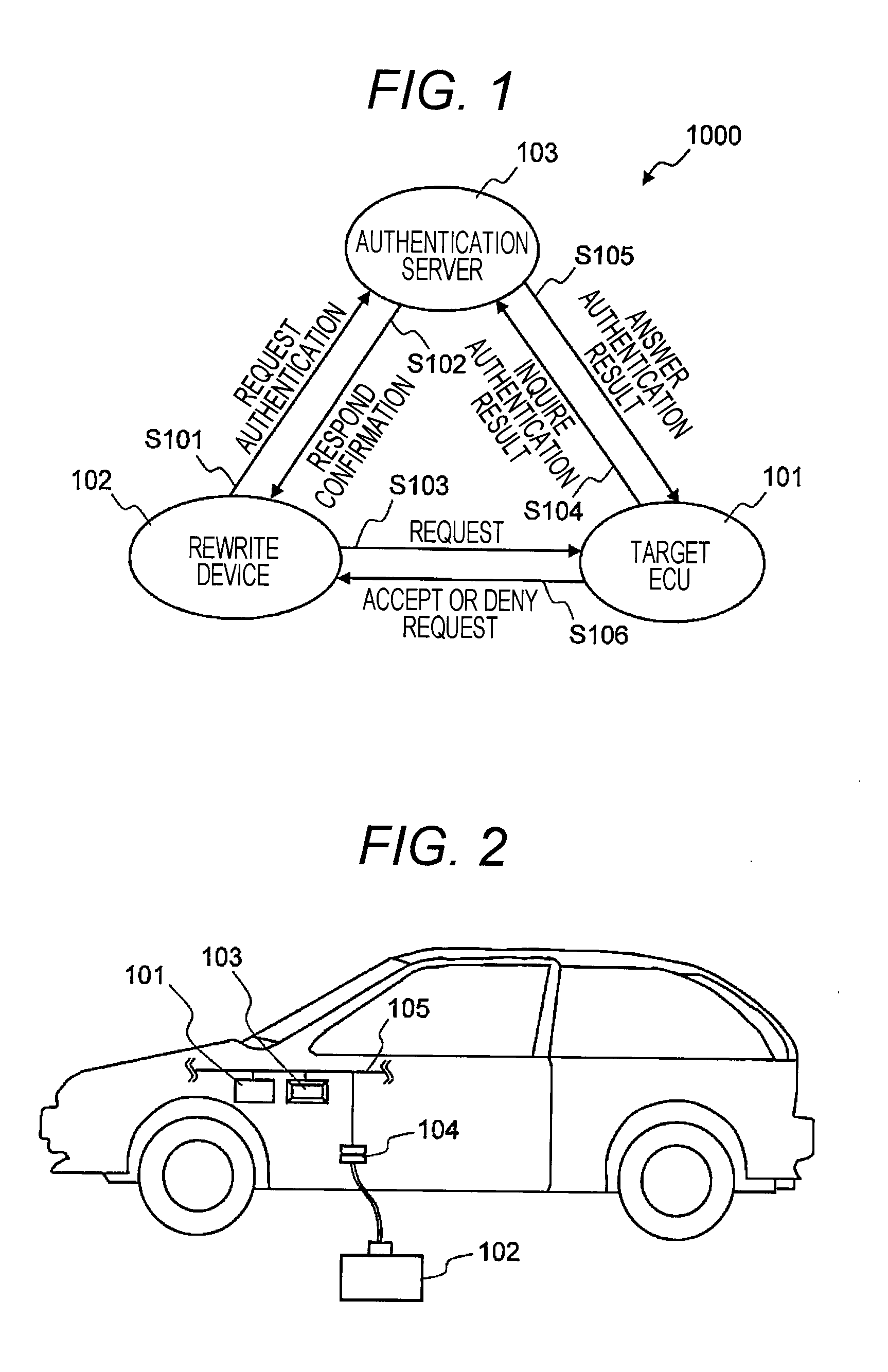
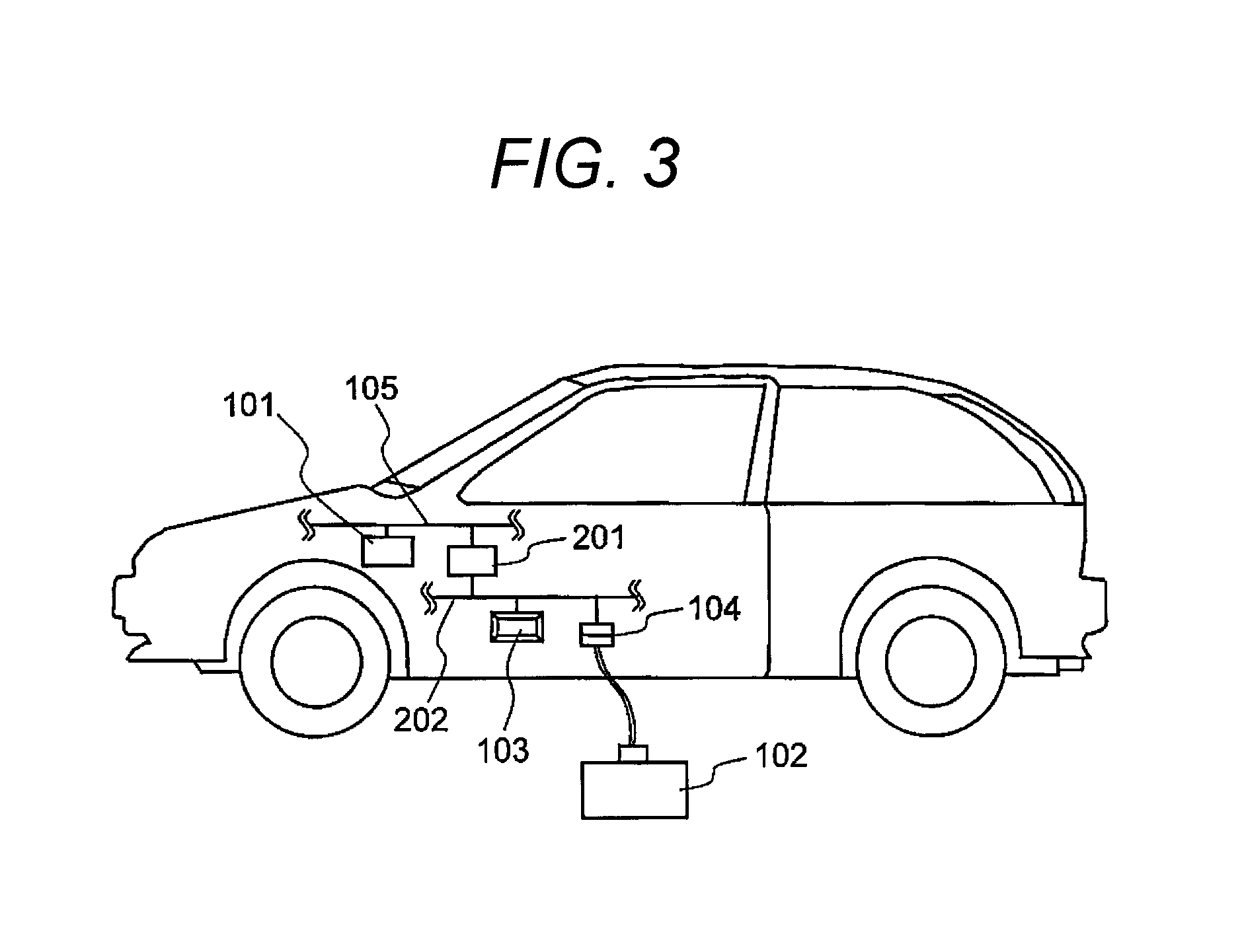
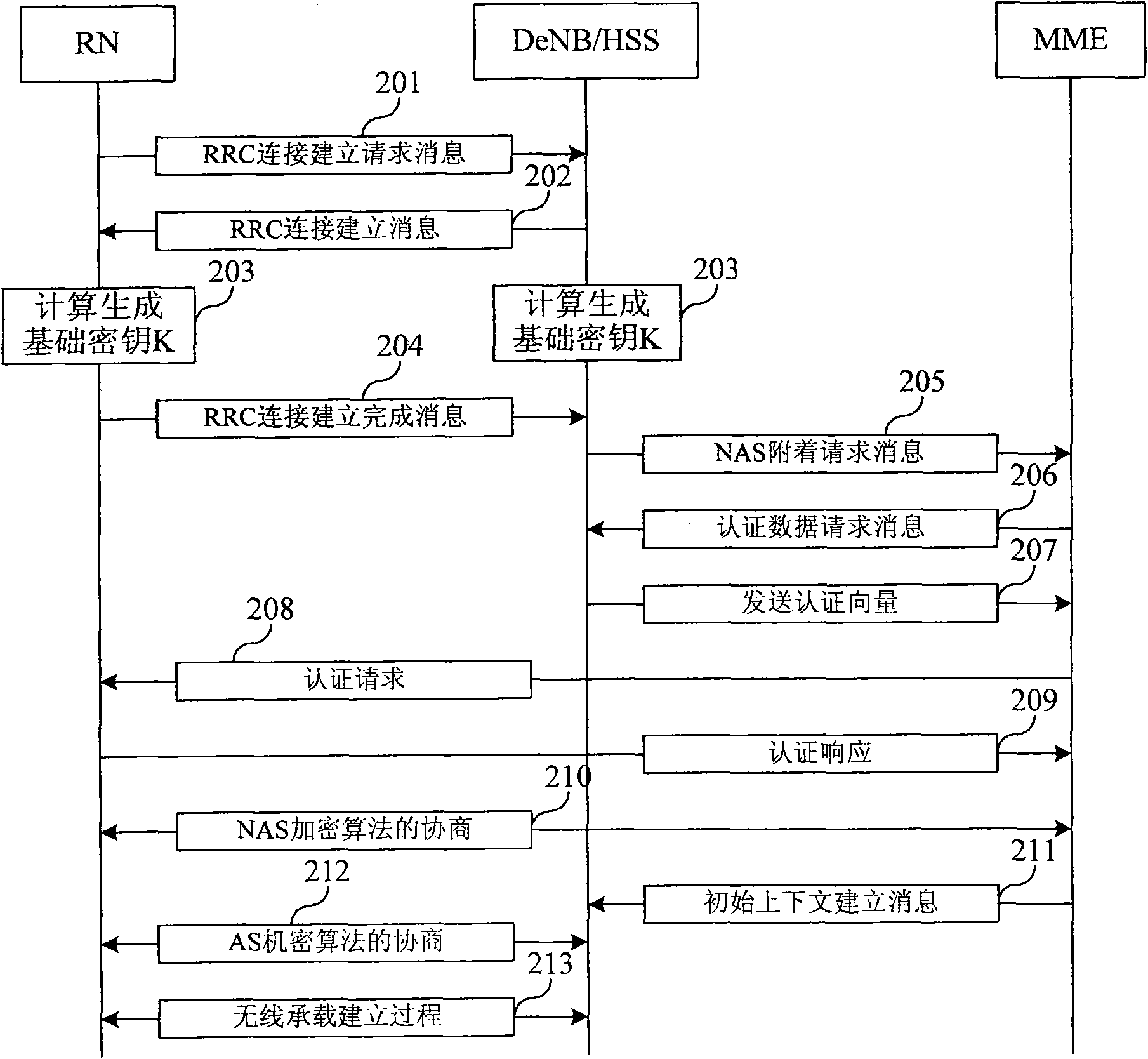
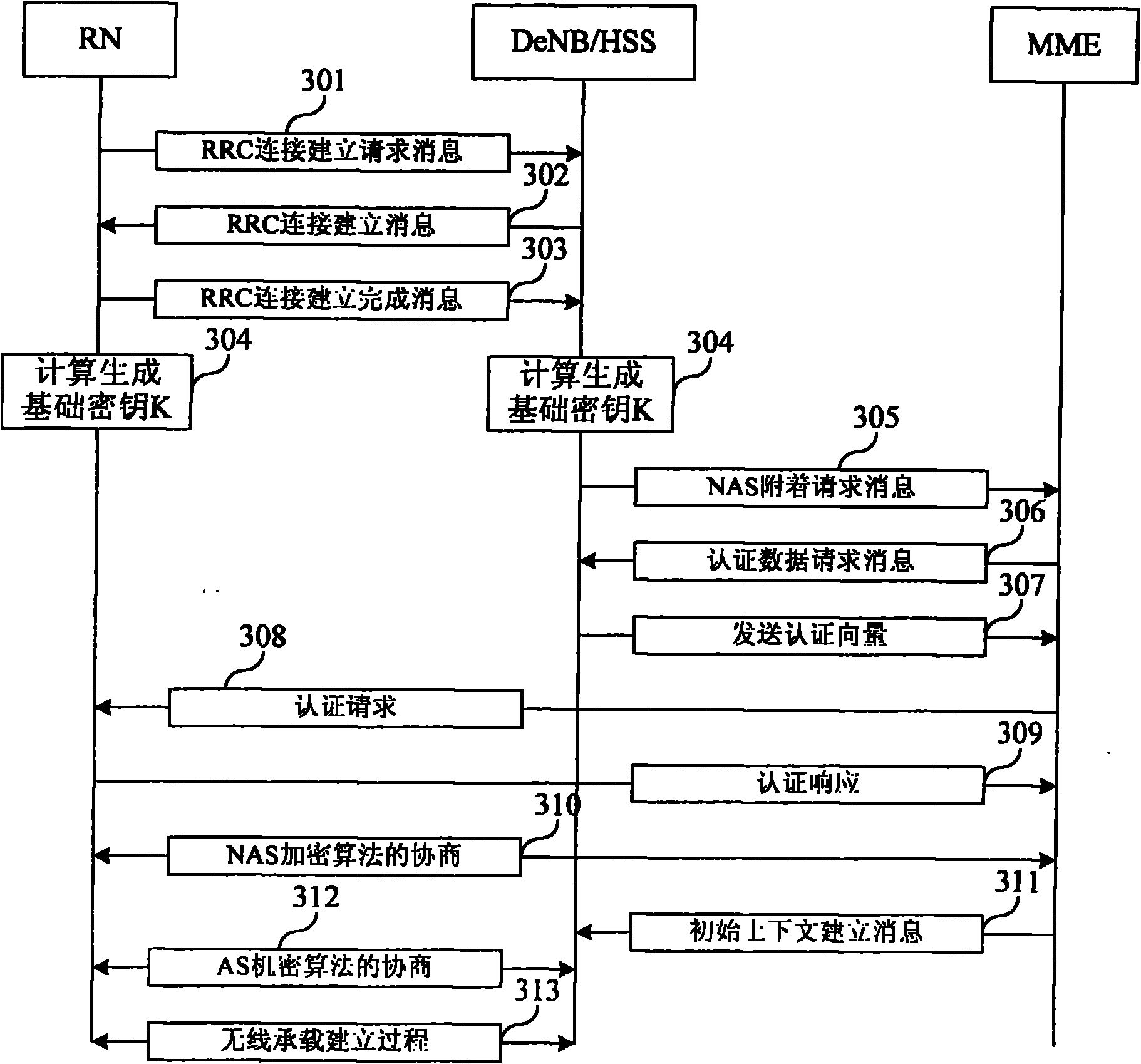
Provided is a method capable of enhancing security of a vehicle-mounted network while reducing processing loads in each vehicle-mounted control device.In a vehicle-mounted network system according to the present invention, a communication device issuing a read request or a write request on data held in the vehicle-mounted control device is previously authenticated by an authentication device (see FIG. 1).
Owner:HITACHI AUTOMOTIVE SYST LTD
Proactive network security systems to protect against hackers
InactiveUS20080005784A1Improve abilitiesIncrease probabilityDigital data processing detailsHardware monitoringCountermeasureCommon Vulnerabilities and Exposures
A proactive network security system to protect against hackers for the proactive automated defense against hackers by automatically finding, reporting, communicating with countermeasures about and removing the common vulnerabilities and exposures (CVEs) that they exploit.
Owner:NETCLARITY
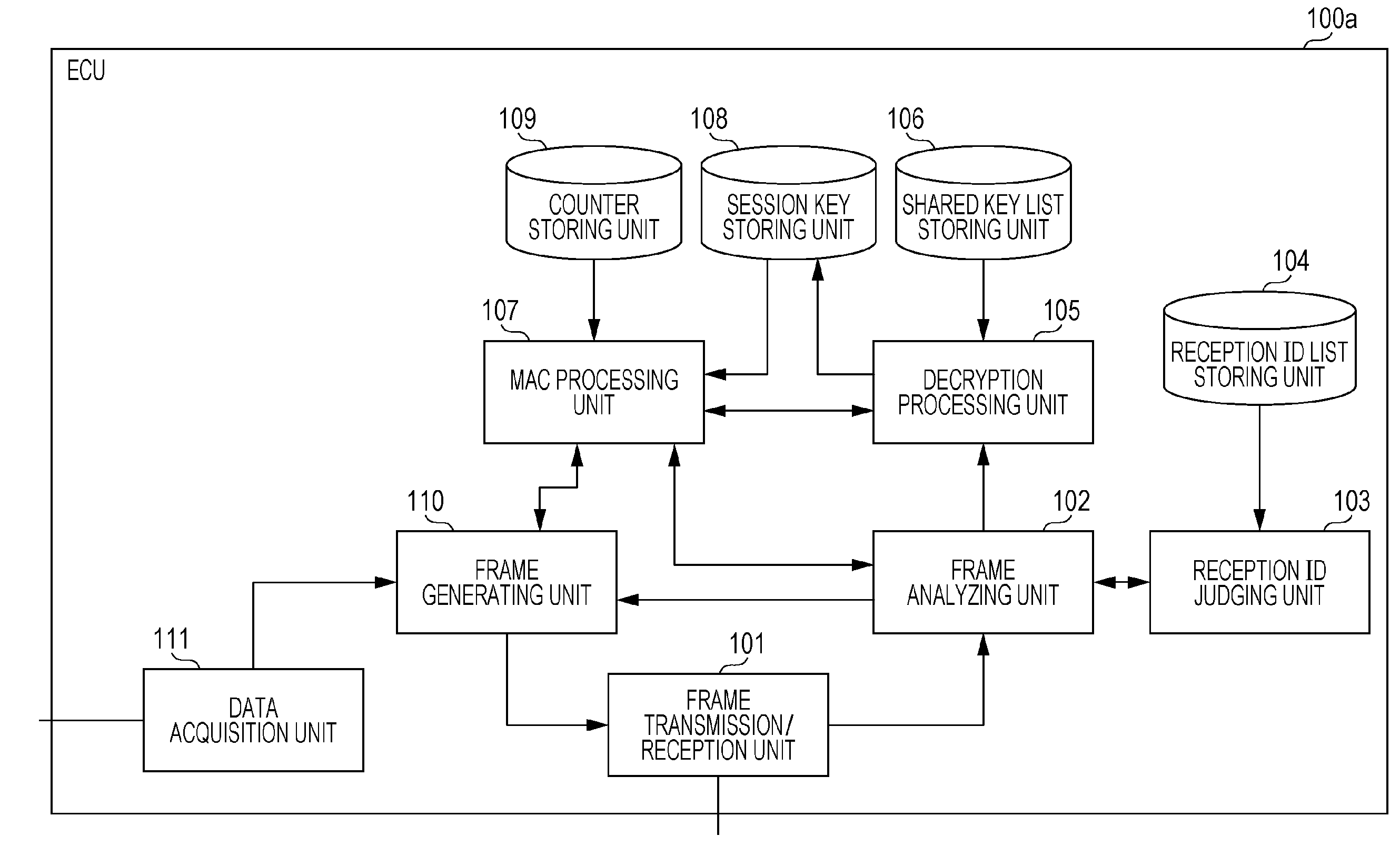
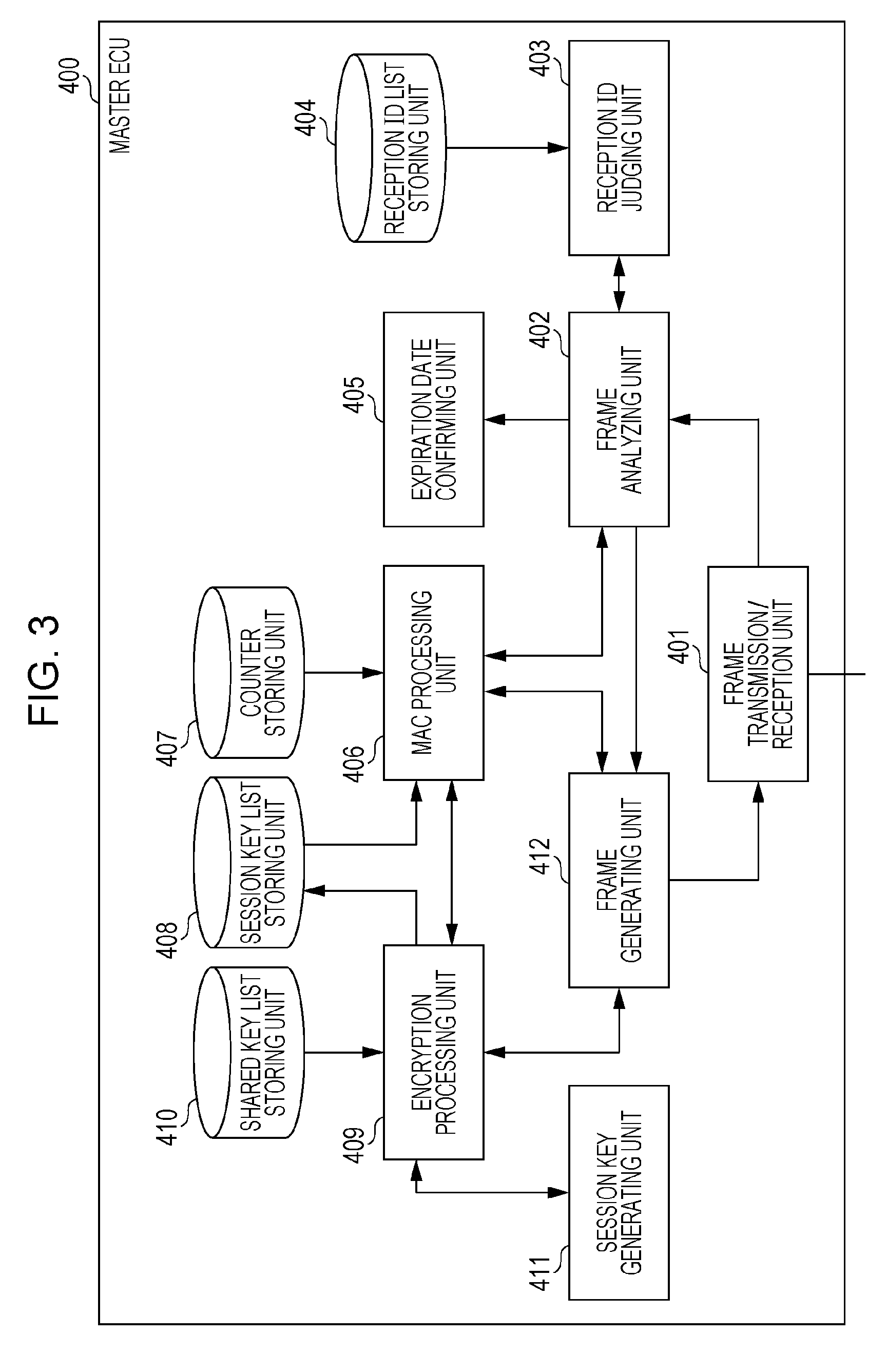
Key management method used in encryption processing for safely transmitting and receiving messages
ActiveUS20160315766A1Network securityEnsure safetyKey distribution for secure communicationElectric vehicle charging technologyIn vehicleNetworked system
Provided is a key management method to secure security in an onboard network system having multiple electronic control units storing a shared key. In the key management method of the onboard network system including multiple electronic units (ECUs) that perform communication by frames via a bus, a master ECU stores a shared key to be mutually shared with one or more ECUs. Each of the ECUs acquire a session key by communication with the master ECU based on the stored shared key, and after this acquisition, executes encryption processing regarding a frame transmitted or received via the bus, using this session key. In a case where a vehicle in which the onboard network system is installed is in a particular state, the master ECU executes inspection of a security state of the shared key stored by the ECU or the like.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
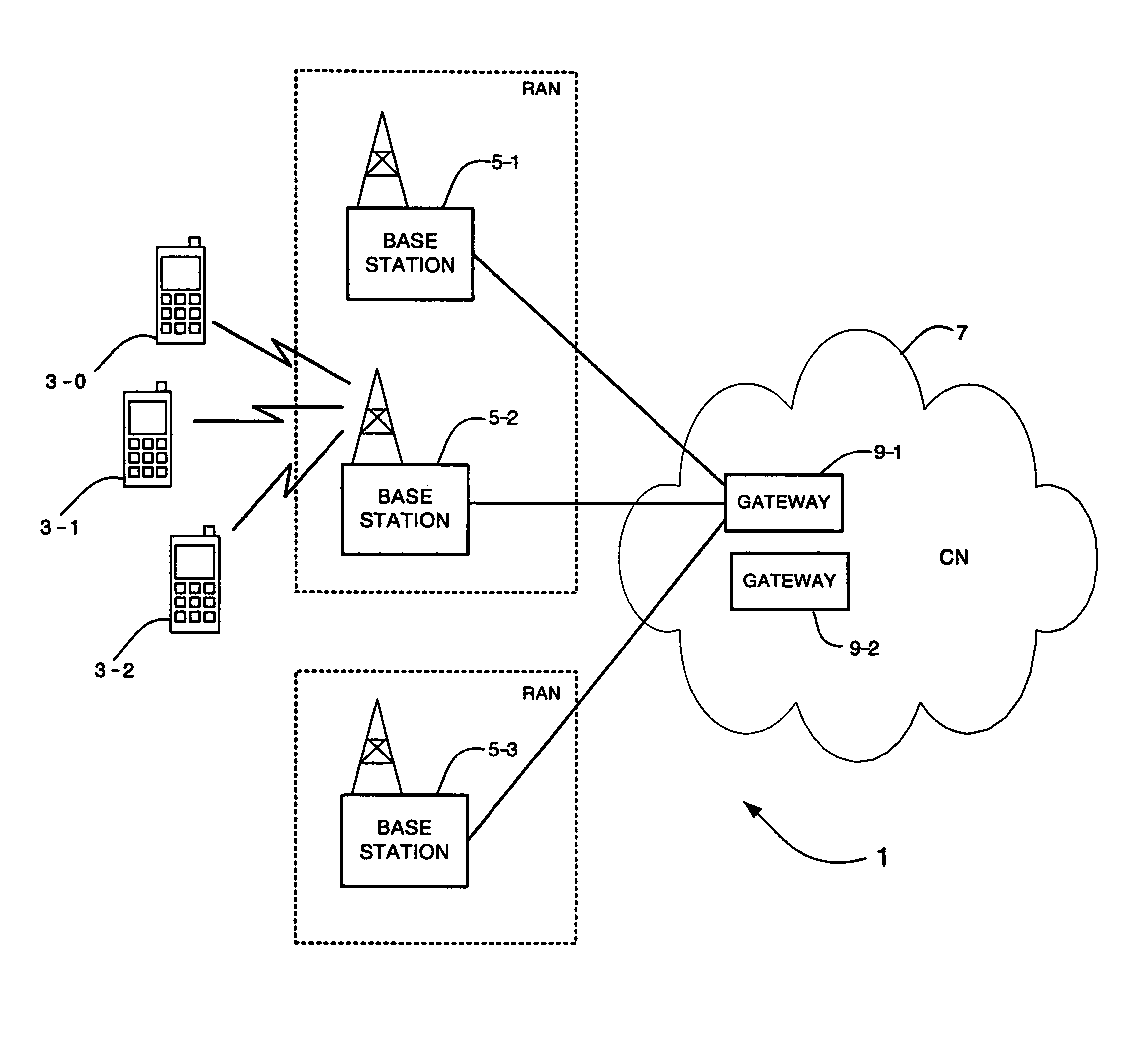
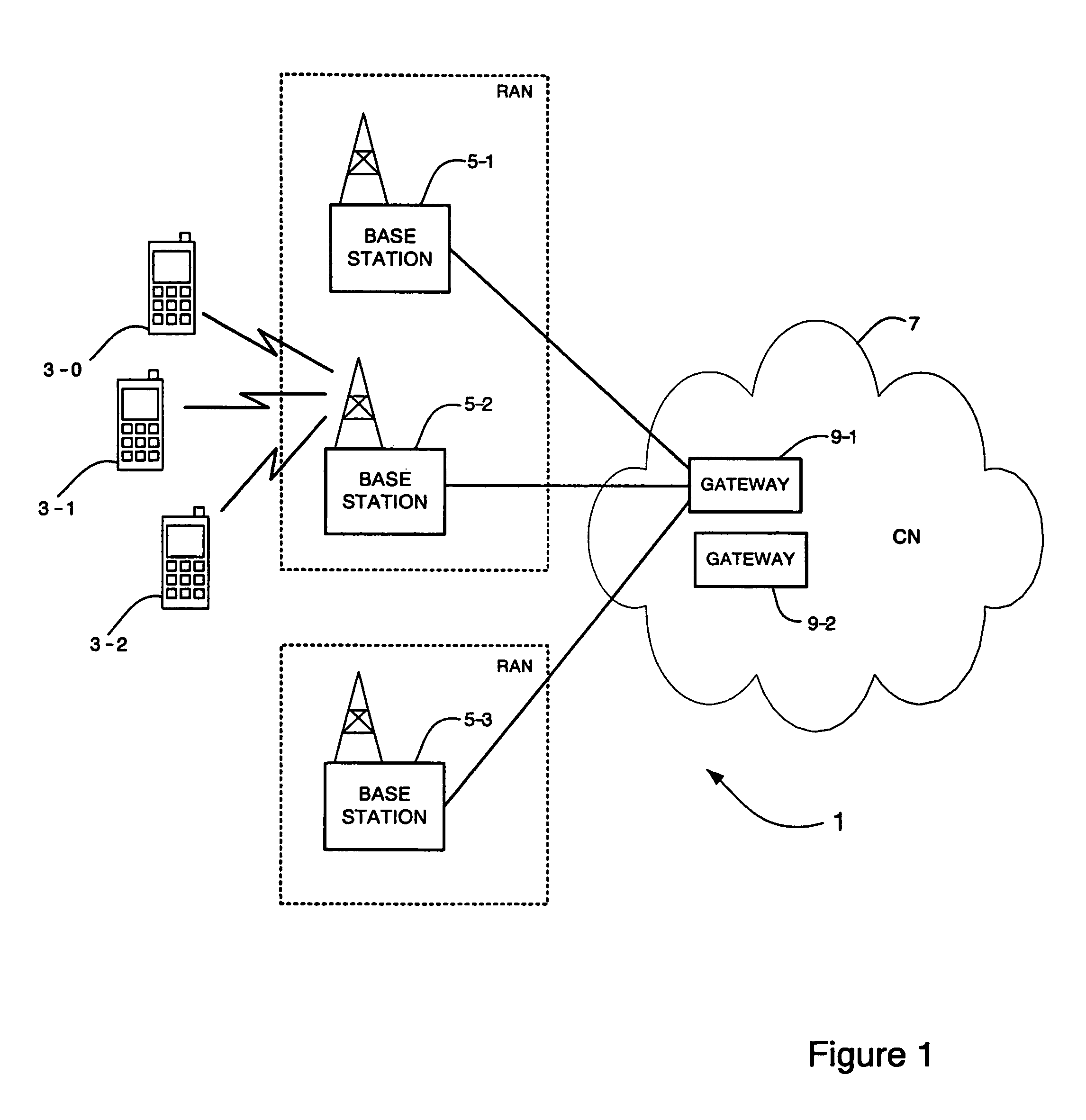
System and method for selection of security algorithms
ActiveUS20100263021A1Information obtainedFast connection setTransmissionSpecial data processing applicationsUser deviceSecurity policy
There is described a method and apparatus for managing security for a connection between a user device and a communications network comprising at least one base station and a core network. In one embodiment, the method includes receiving at the core network security capability information for the user device connecting to the communications network. Security capability information for the base station is then obtained from memory or from the base station itself. The security capability information for the user device and the security capability information for the base station is then processed in the core network to select a security policy for a connection between the user device and the base station and the selected security policy is transmitted to the base station.
Owner:LENOVO INNOVATIONS LTD HONG KONG
Control system and method for controlling system
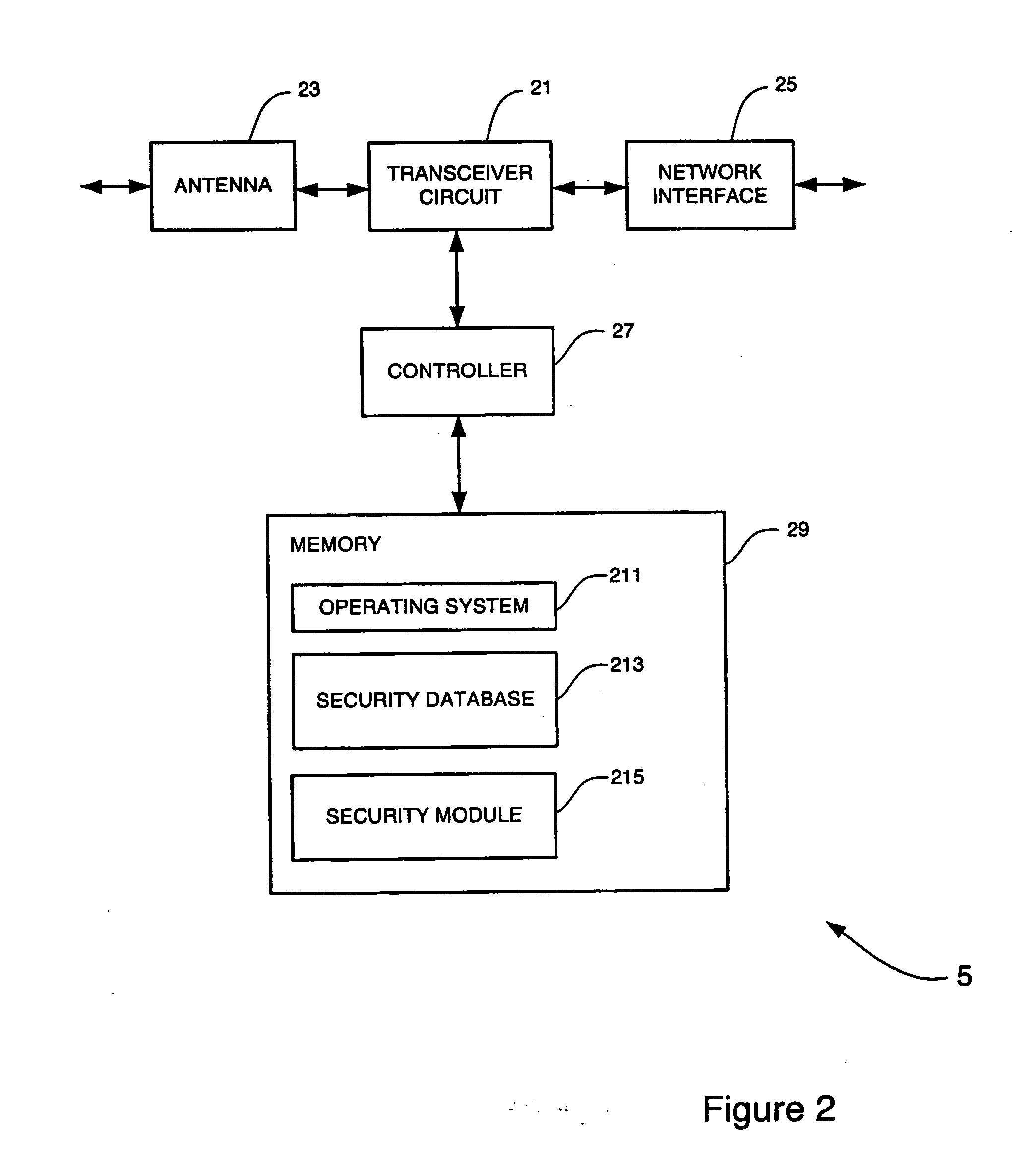
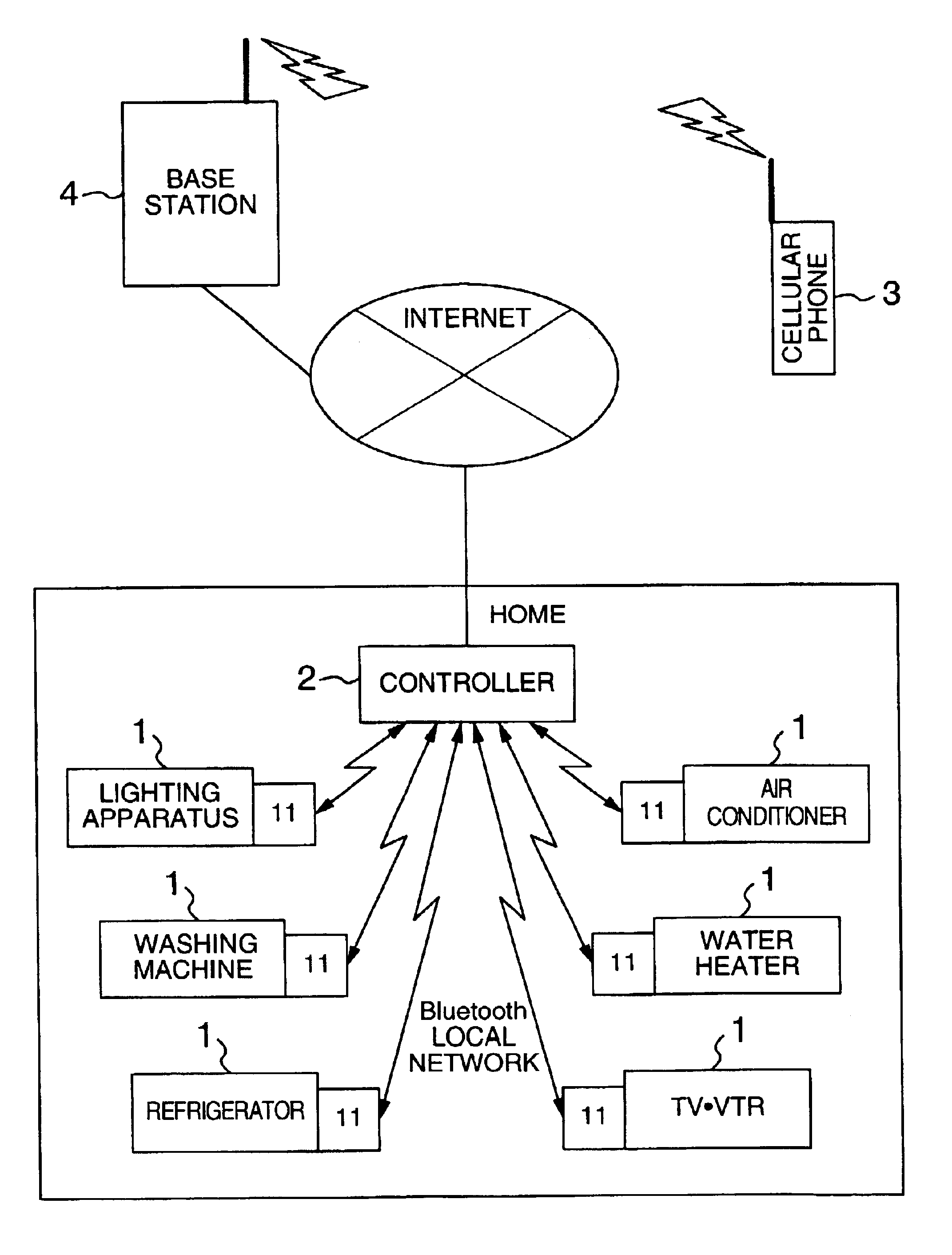
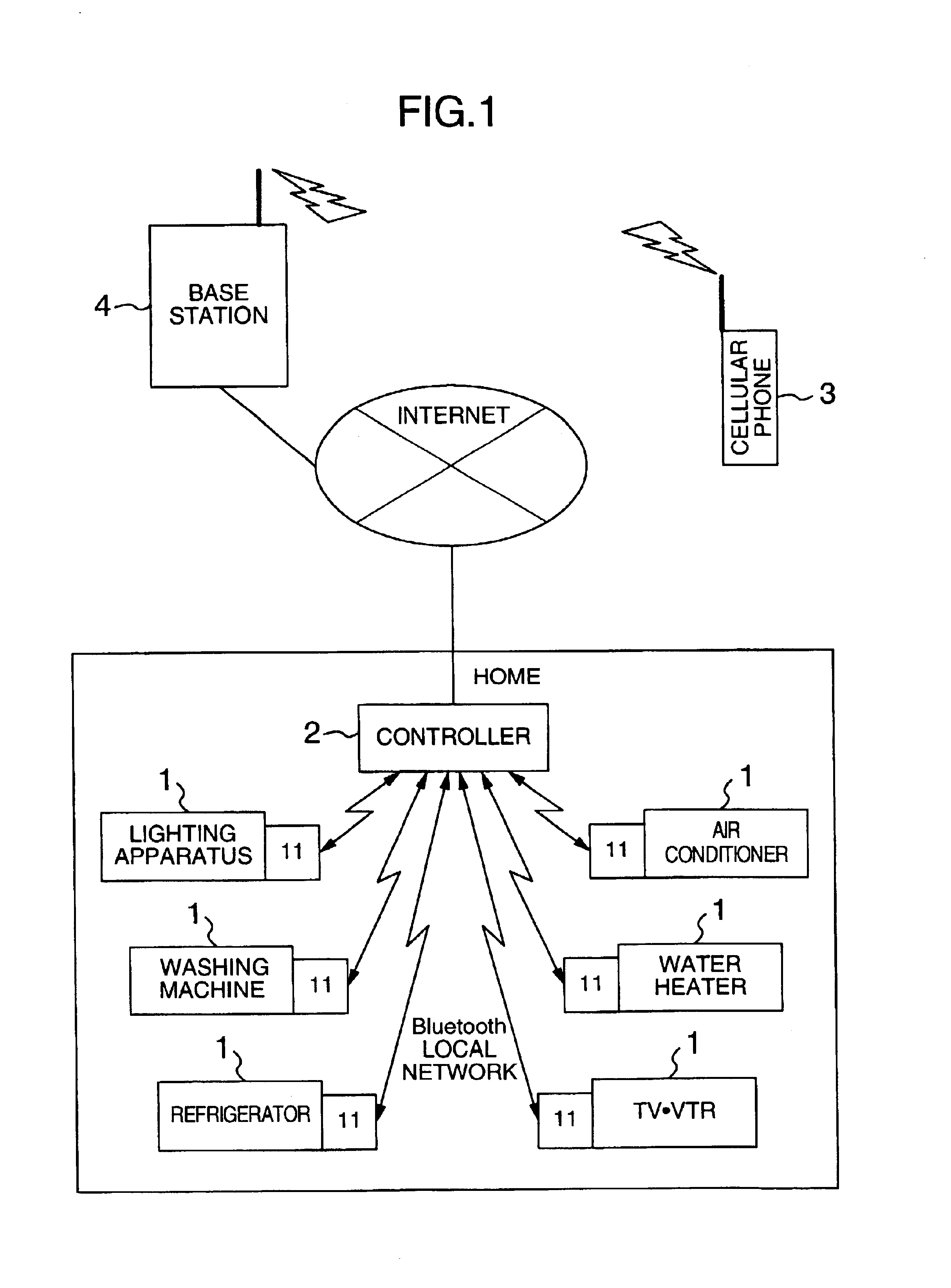
ActiveUS6919790B2Reduce loadEasy to operateElectric signal transmission systemsMultiple keys/algorithms usageControl systemPassword
A controller has a unit that stores therein a password specified by a user for each home electric appliance connected to a home network; a unit that, when a home-electric-appliance operation-request message is received, determines whether the message entry location is inside or outside the home; a unit that sends a password request message if it is determined as a result of the determination that the message entry location is outside the home; and a unit that, upon receiving a password in response to the request, determines if the received password matches the password of the controlled home electric appliance that is stored. The controller executes the operation of the home electric appliance connected to the home network only when the passwords match, thus preventing an unauthorized user outside the home from operating the home electric appliances at home.
Owner:HITACHI LTD
Method and system for acquiring information of machine type communication user equipment
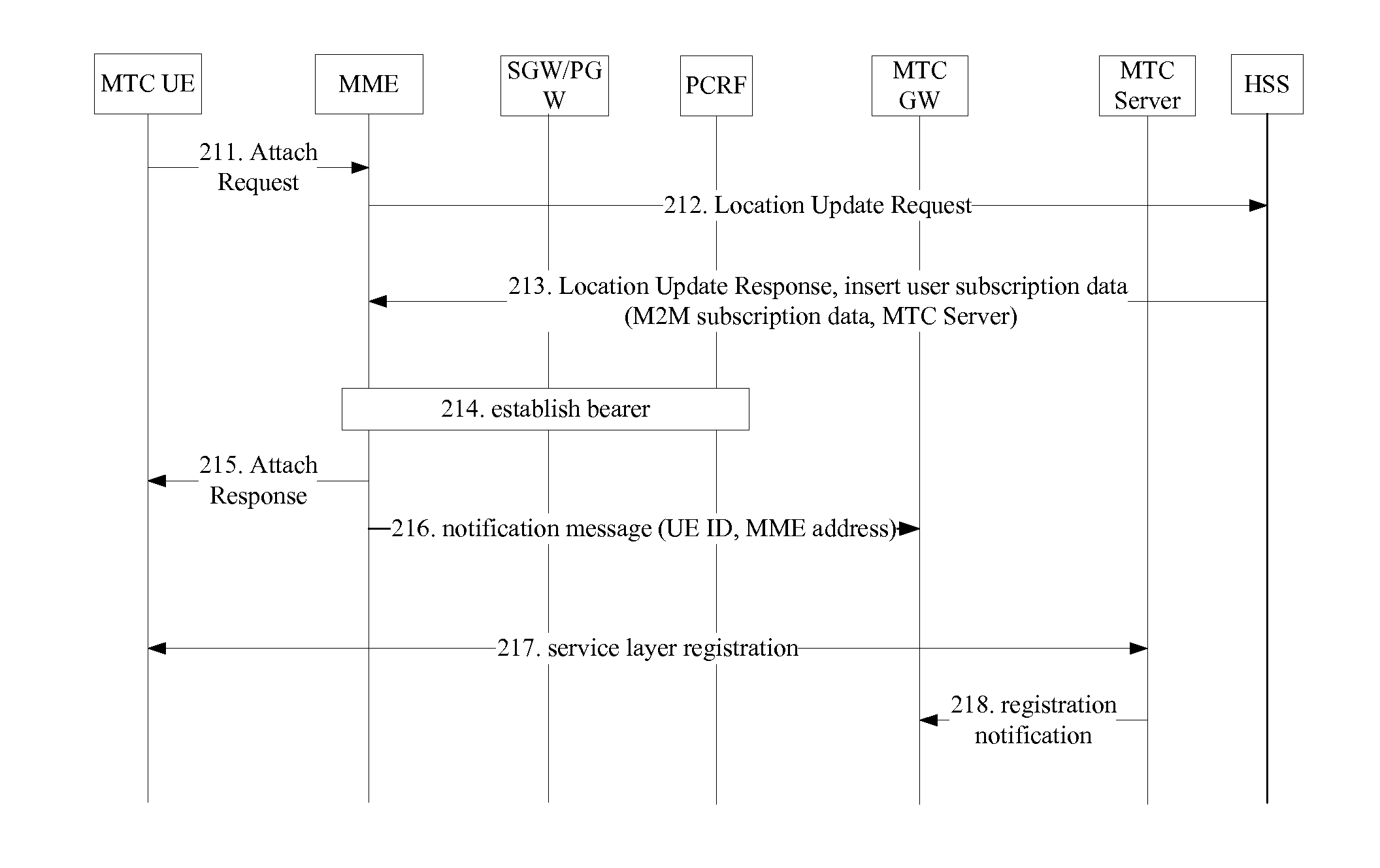
ActiveUS20120220326A1Network securitySolve the real problemRadio transmissionMachine-to-machine/machine-type communication serviceMobility managementUser equipment
A method and a system for acquiring information of Machine Type Communication (MTC) user equipment (UE) are provided. The method comprises the steps of: an MTC GateWay (MTC GW) acquiring the information of the MTC UE which currently requests to attach to a network or has attached to a network from a mobility management network element; the MTC GW sending the information of the MTC UE acquired from the mobility management network element to an MTC Server. The method and the system can control the MTC UE in real time and intelligently.
Owner:ZTE CORP
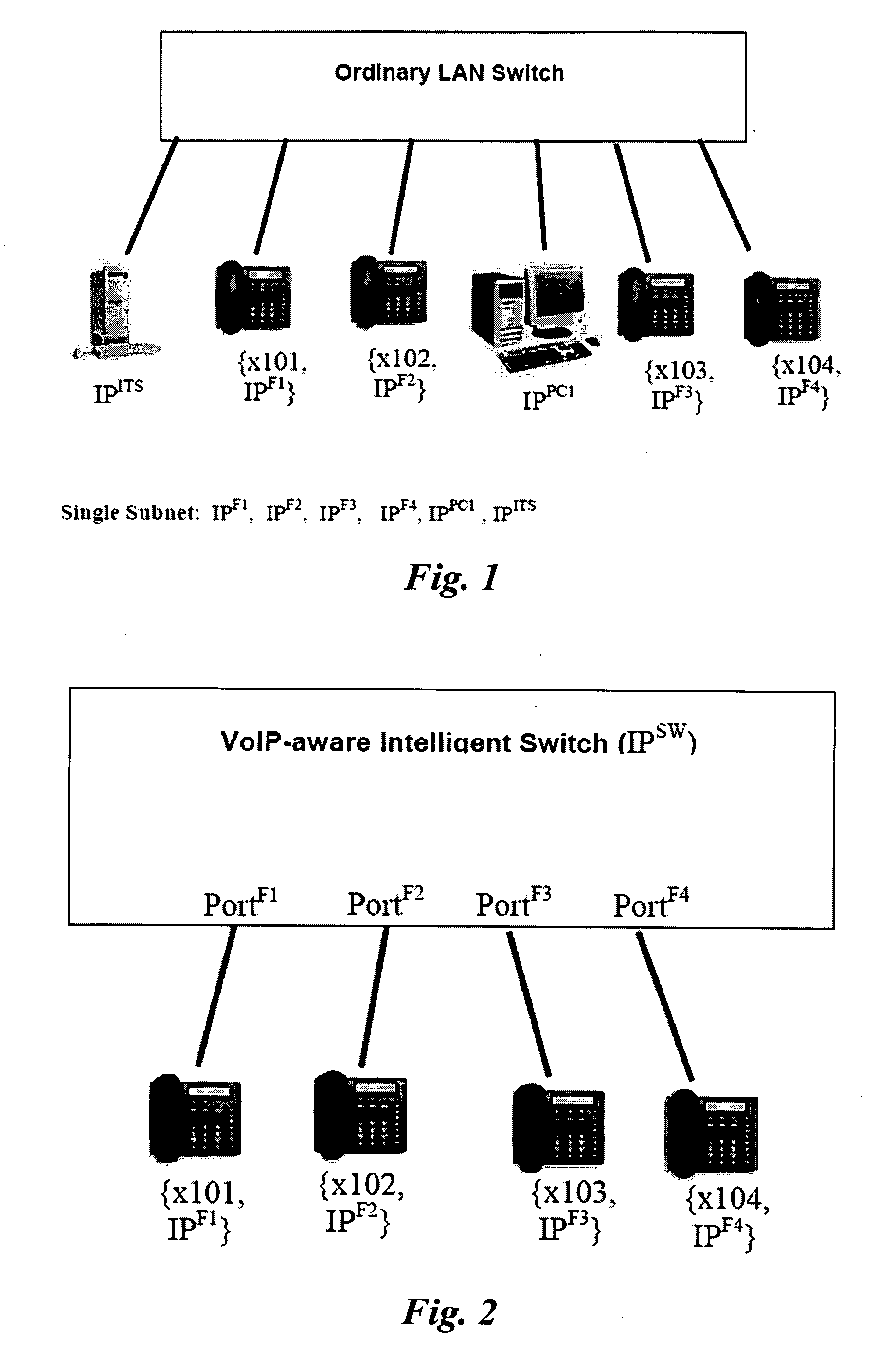
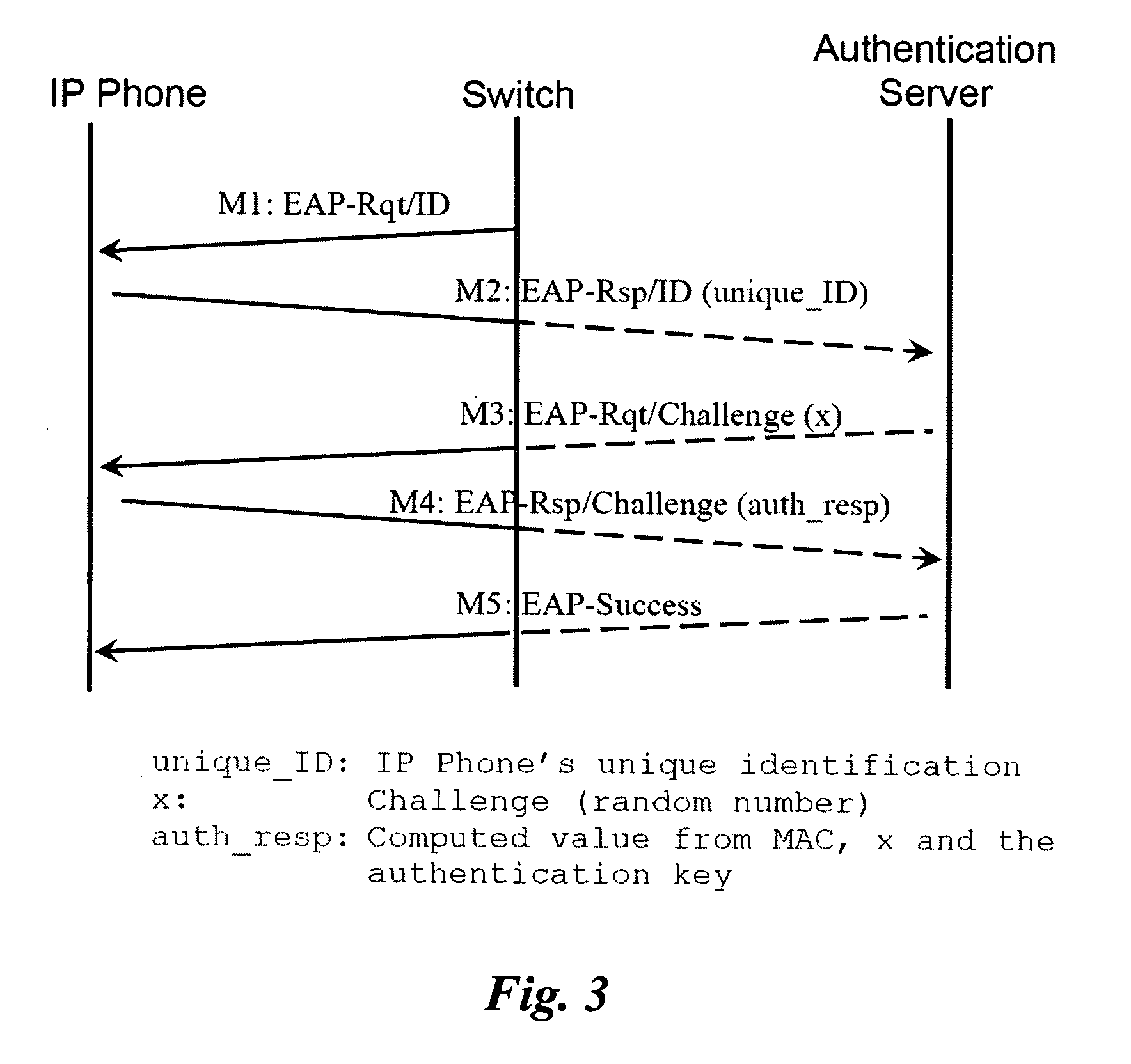
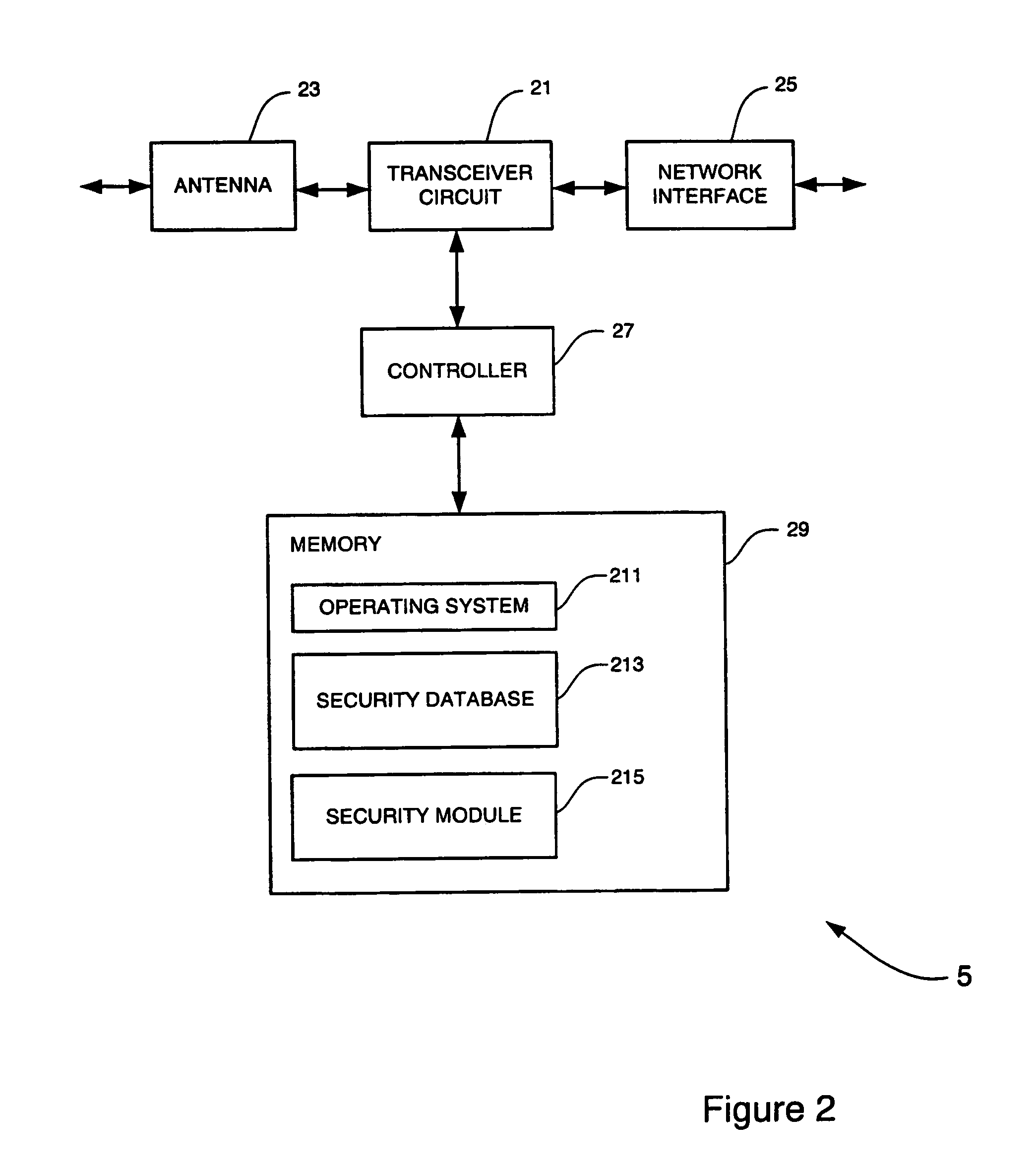
Authentic device admission scheme for a secure communication network, especially a secure IP telephony network
ActiveUS20070044141A1Network securityDigital data processing detailsUser identity/authority verificationSecure communicationMAC address
An admission scheme for a communication network comprising the step of:—a) acquiring and storing the MAC address of a device on admitting the device to the communication network, b) checking the source MAC address of a data packet before said data packet is admitted into the communication network, and c) admitting a data packet into the communication network only if the MAC address is registered with the communication network.
Owner:HONG KONG APPLIED SCI & TECH RES INST
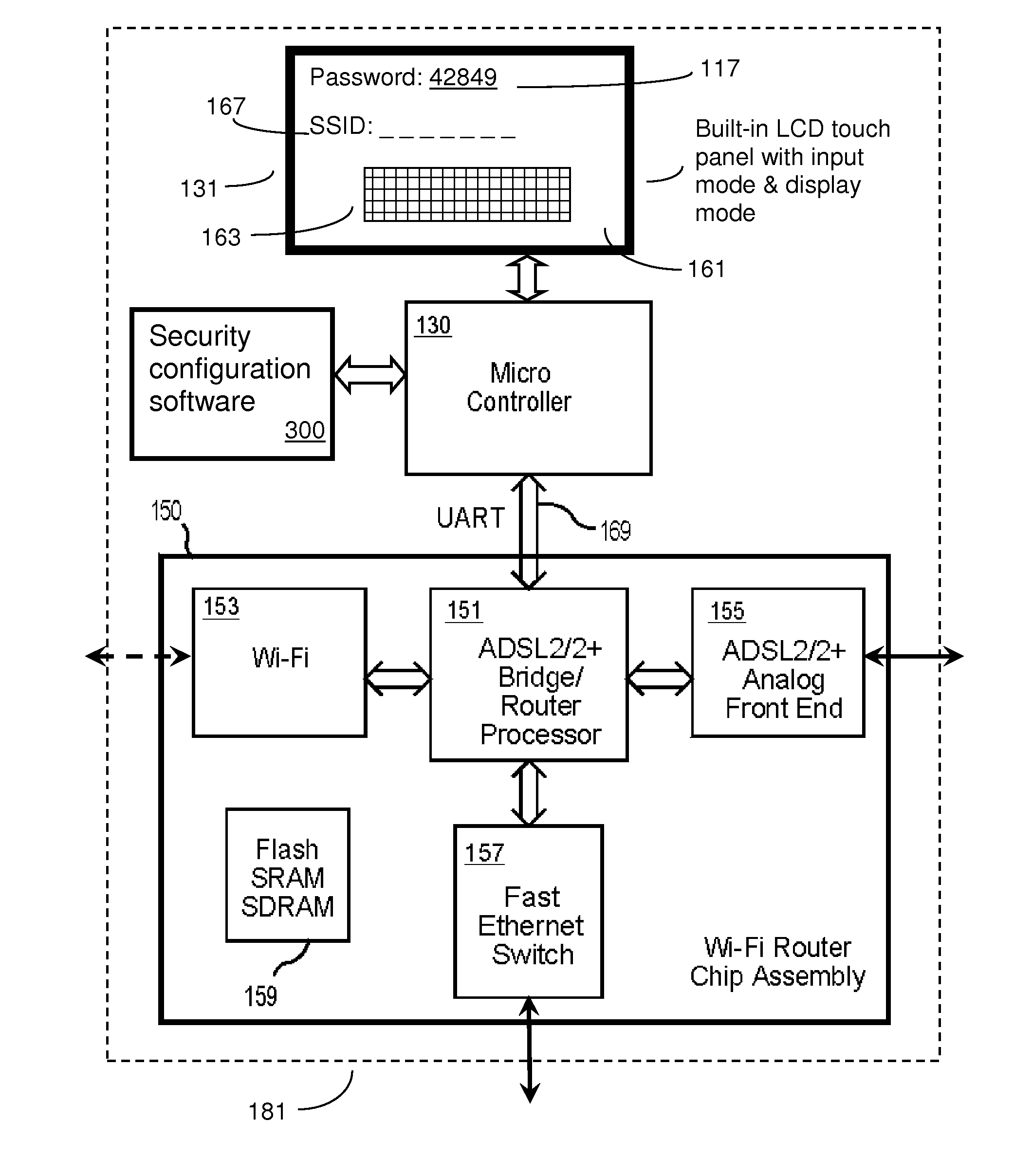
Wi-fi router with integrated touch-screen and enhanced security features
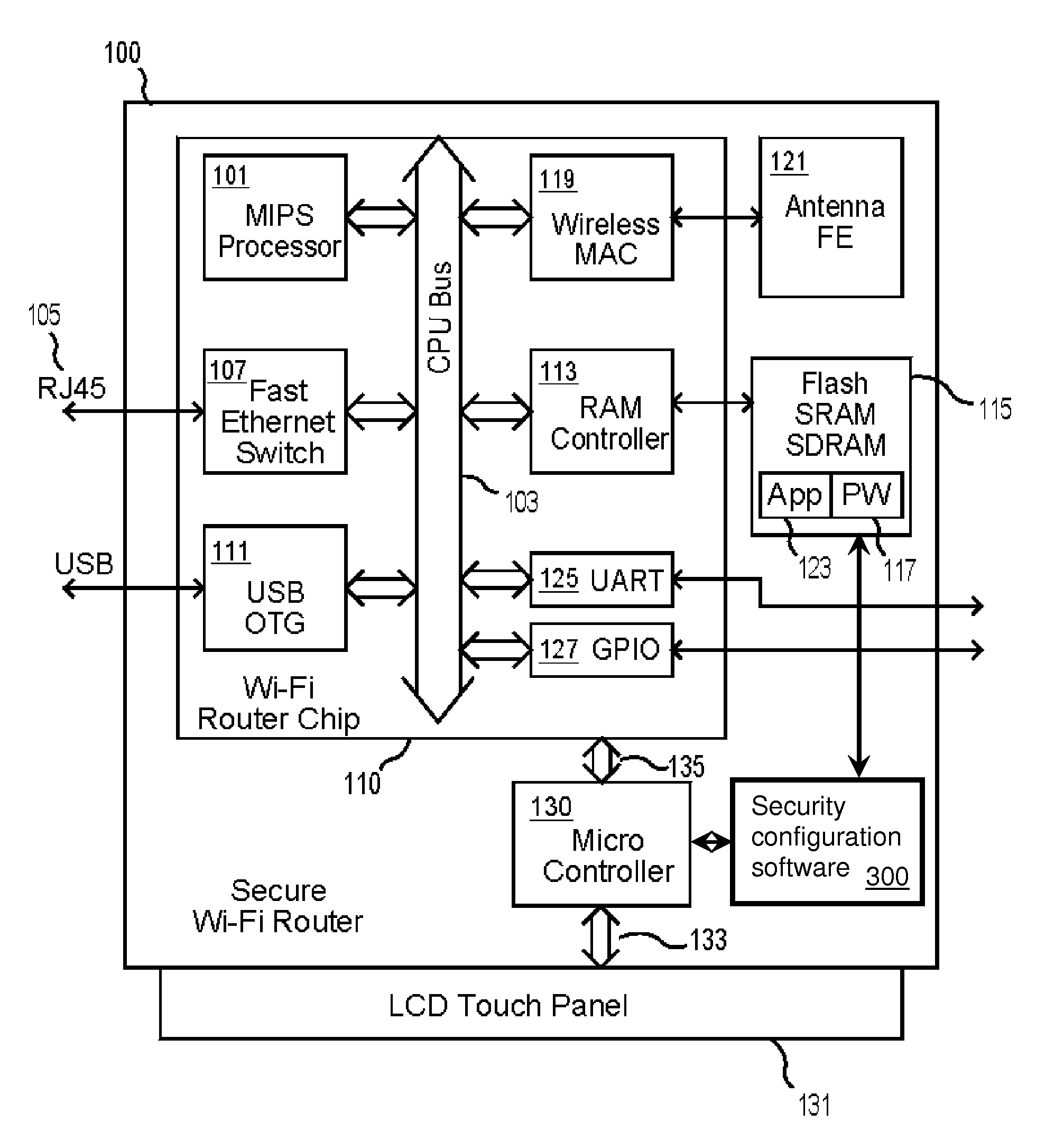
ActiveUS20120239916A1Easy to reconfigureNetwork securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsWi-FiPassword
A Wi-Fi router with an integrated configuration touch-screen, and method to use this integrated touch screen to provide enhanced security features. The Wi-Fi router, which has a wired or optical network interface, may be factory pre-configured with hard to anticipate passwords and encryption codes, thus making even its default Wi-Fi settings difficult to attack. Besides displaying interactive menus on the touch-screen, the router may also generate touch sensitive dynamic alphanumeric virtual keypads to enable administrators to interact with the device without the need of extra computers or software. Inexperienced administrators secure in the knowledge that they may access and change even difficult to remember security settings at any time through the built-in touch-screen controller and simplified user interface, are encouraged to set up secure Wi-Fi systems. The device may optionally include security software that, upon touch of a button, can provide new randomized or otherwise obfuscated router settings.
Owner:SECURIFI INC
Method and apparatus for remote management of a monitoring system over the internet
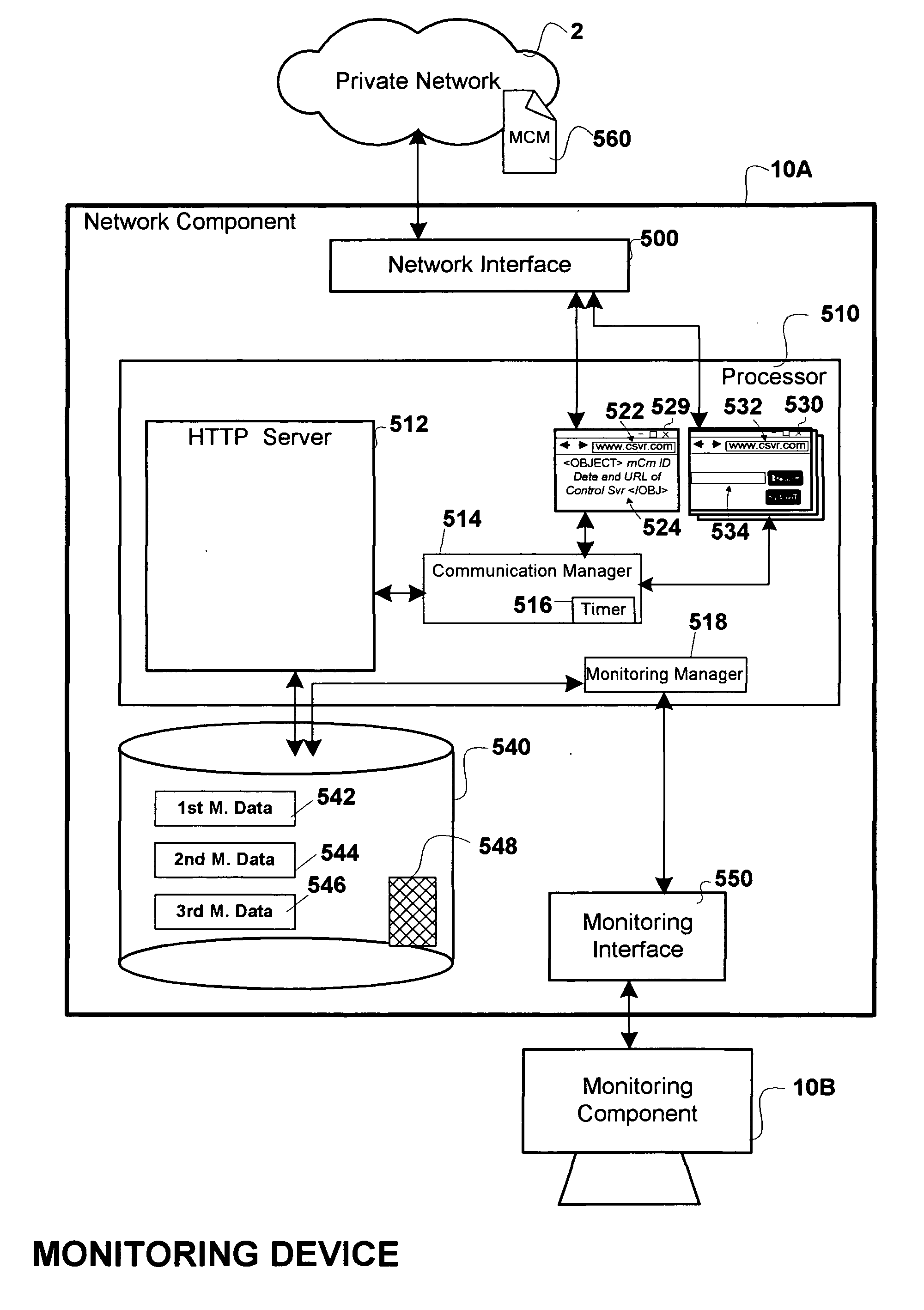
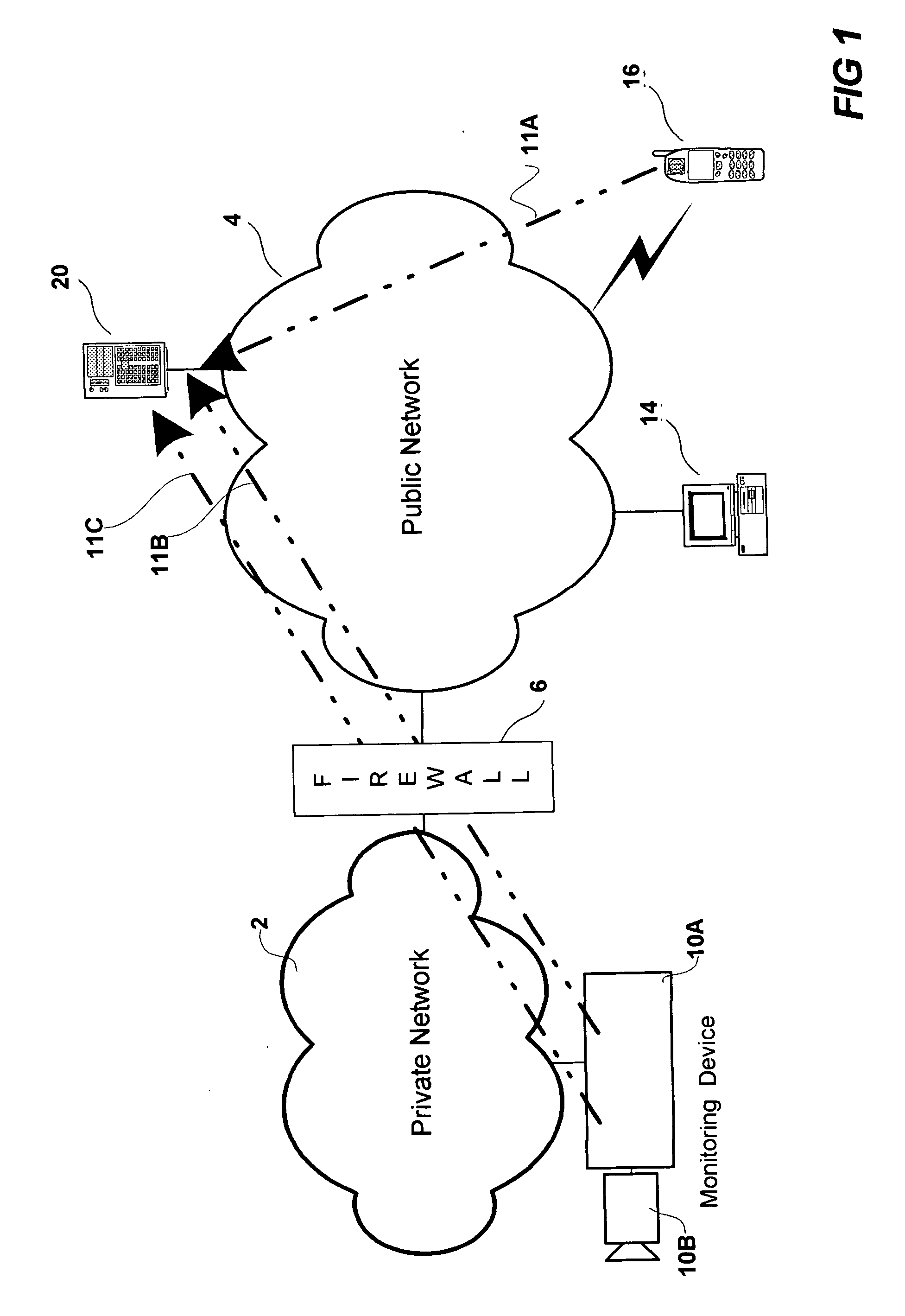
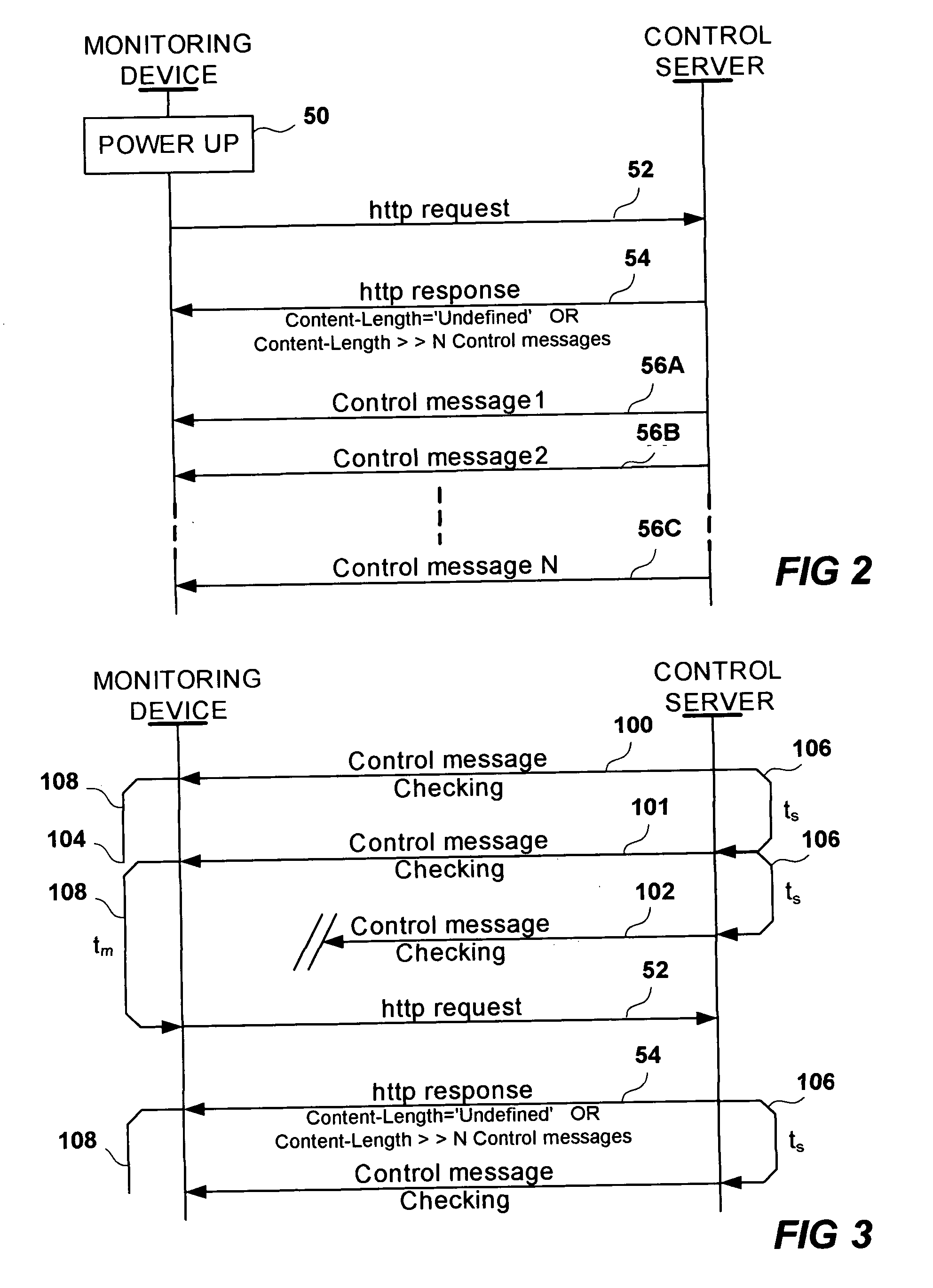
InactiveUS20060173997A1Balance network loadLess loadDigital computer detailsTransmissionPathPingPrivate network
A Monitoring system and a method in a monitoring system comprising a public network, a private network, an access limiting device arranged to limit the access of the private network from the public network, and a control server connected to the public network. The monitoring system further comprises a monitoring device connected to the private network and being arranged to send an HTTP request to the control server. The control server being arranged to send a HTTP response to the monitoring device in response to the HTTP request, wherein the HTTP header's ‘Content-Length’ field of the HTTP response is not defined or wherein the HTTP header's ‘Content-Length’ field is set to a number that is large enough to enable transport of a plurality of future control messages as part of an over time stretched HTTP response resulting in an open path from the control server to the monitoring device through the access limiting device and wherein the control server is arranged to send control messages to the monitoring device via said open path.
Owner:AXIS
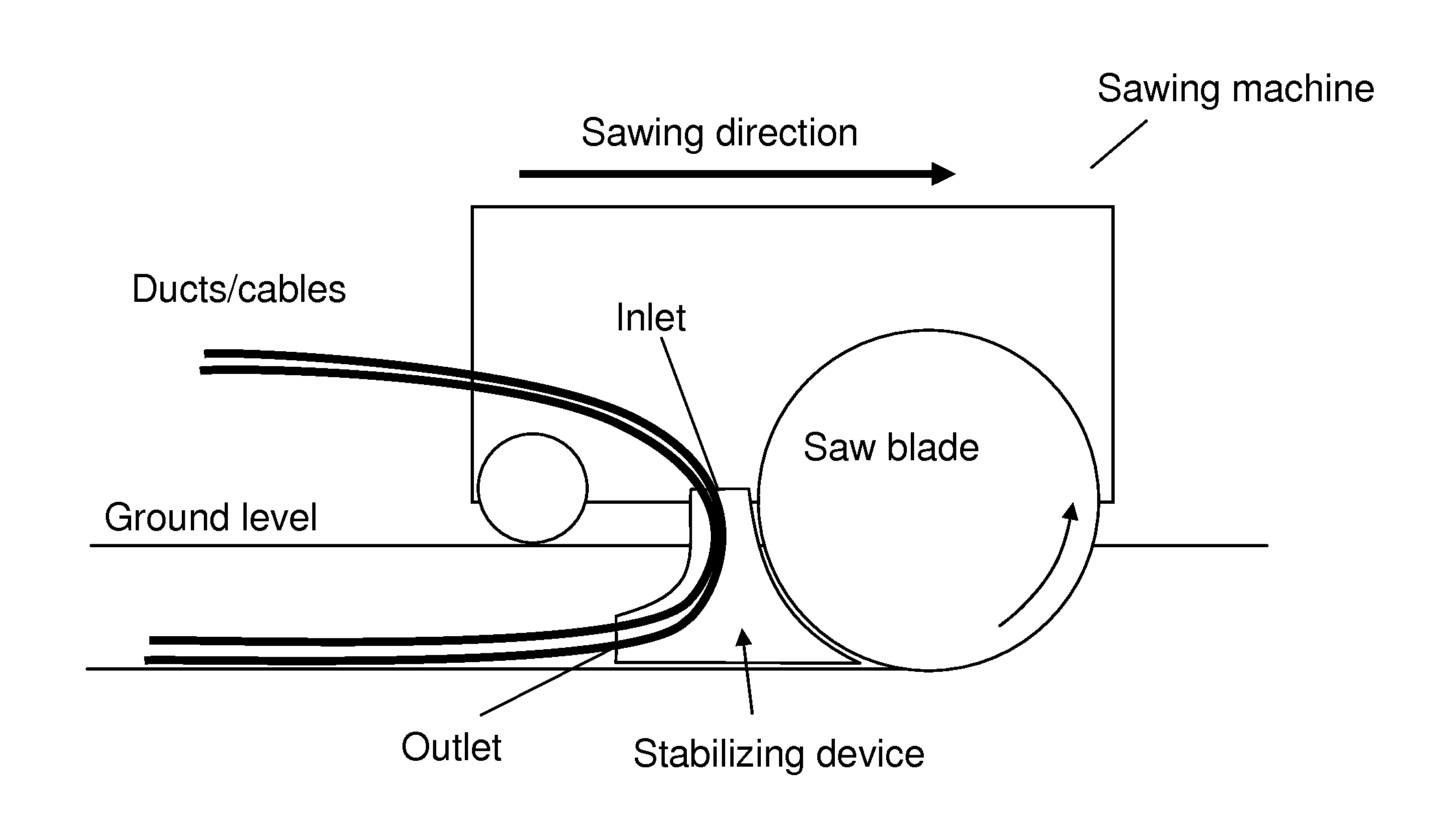
Method for placing at least one duct/communication cable below a road surface in an area
ActiveUS20130294839A1Low costNetwork securitySoil-shifting machines/dredgersFoundation engineeringEngineeringRoad surface
Owner:GUSTAVSSON CONNY MR +2
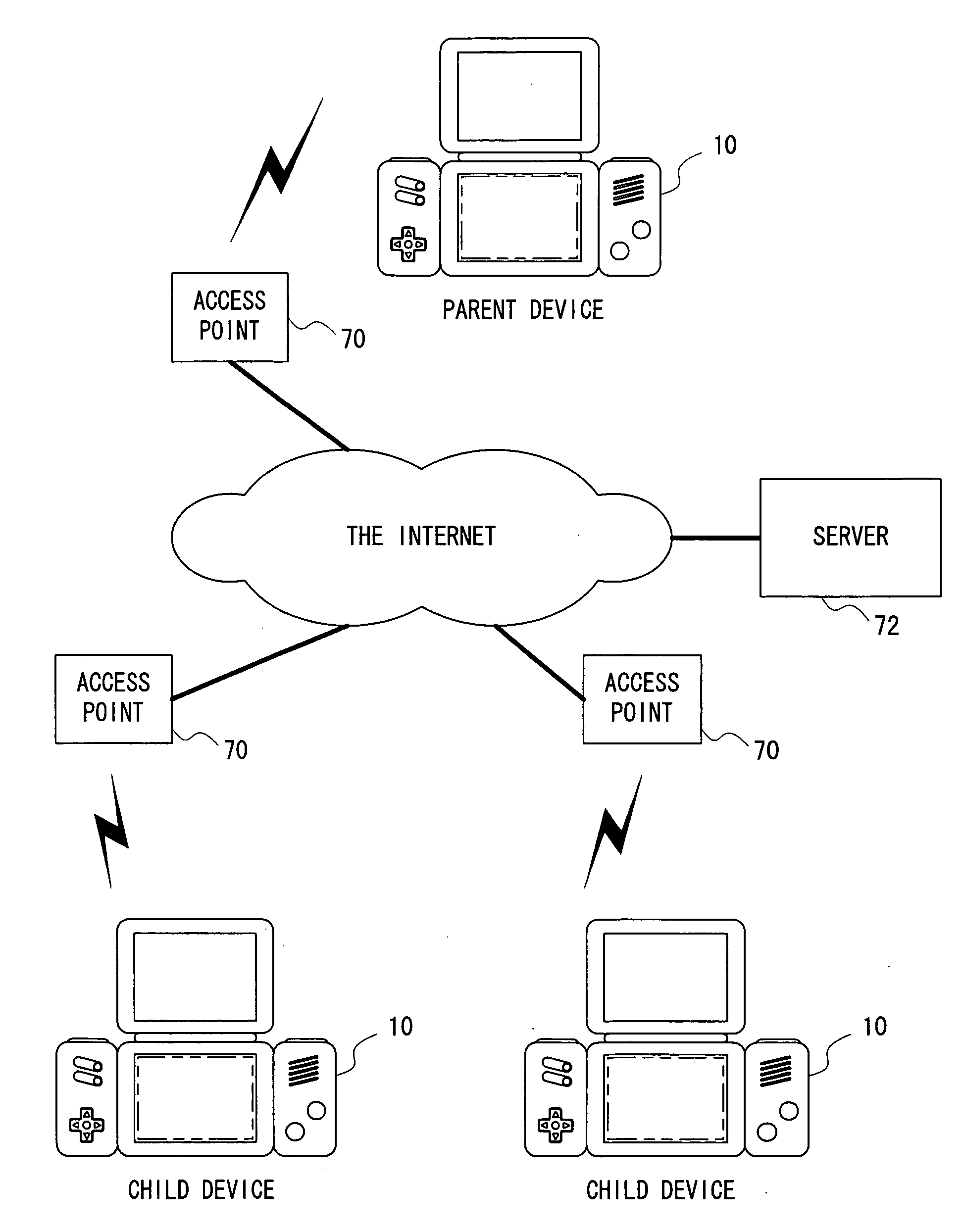
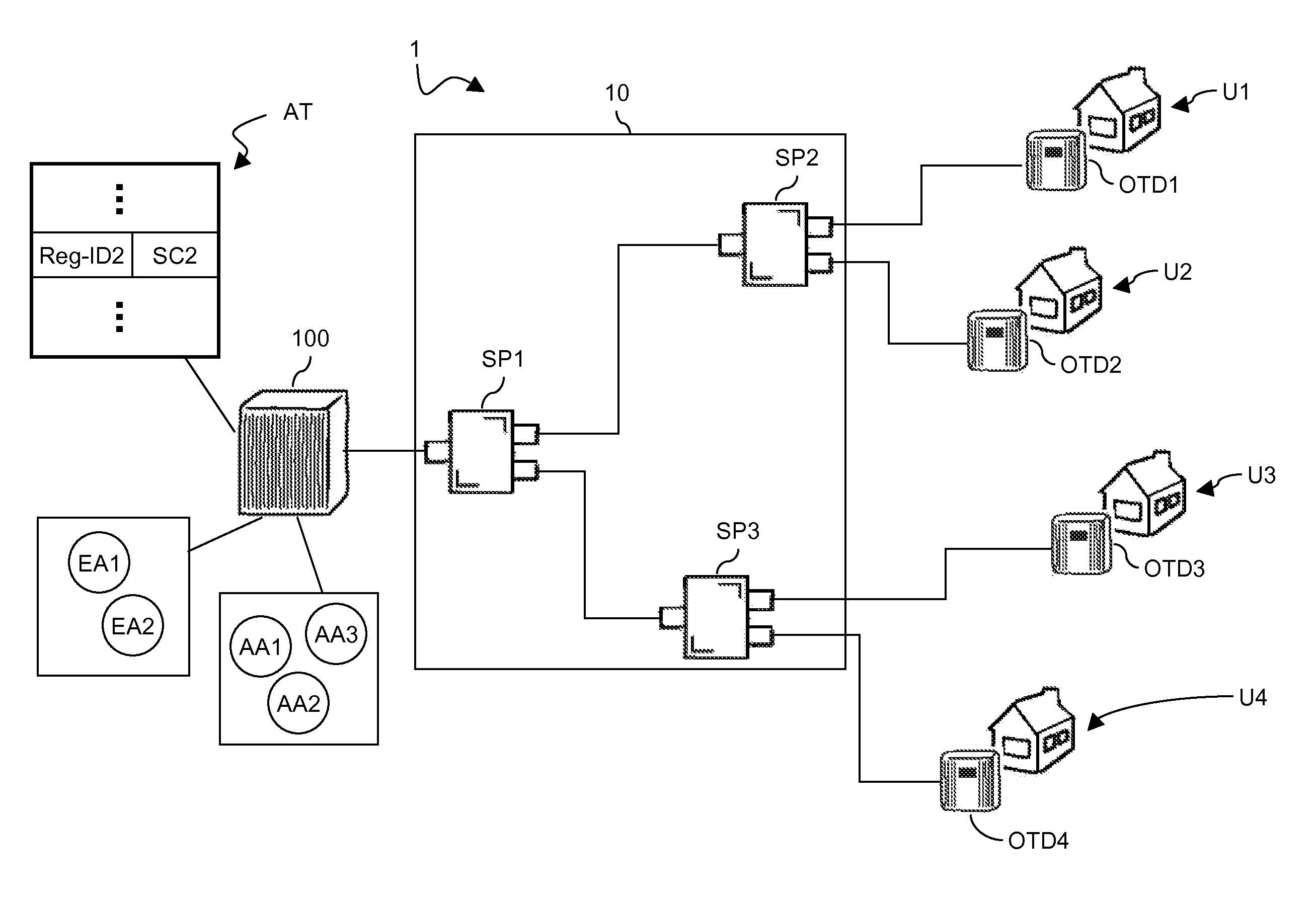
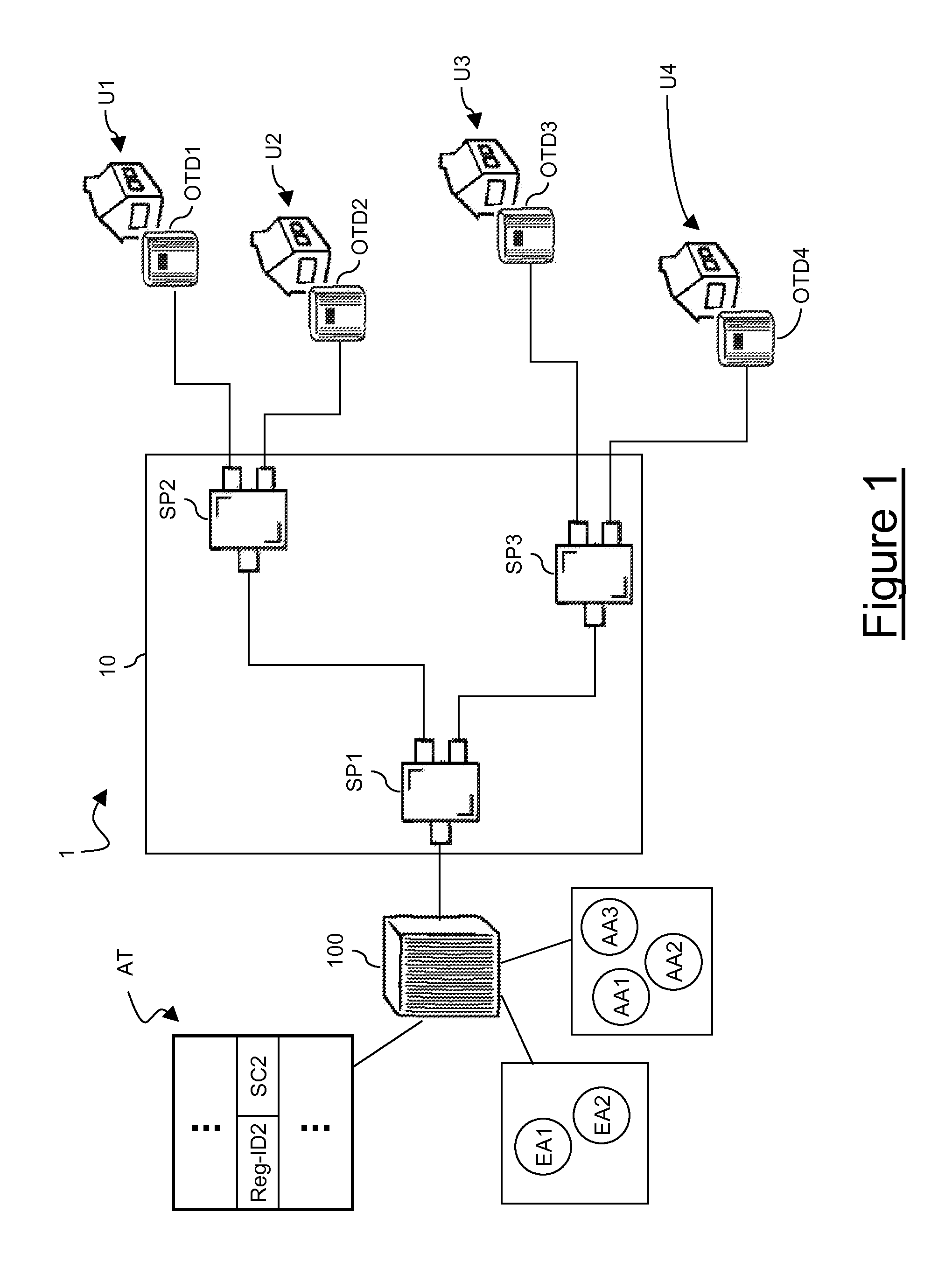
Communication game system, game apparatus, server, storage medium storing a program, and game control method
ActiveUS20060252548A1Increase rangeNetwork securityData processing applicationsTelephonic communicationShortest distanceThe Internet
A communication game system includes a plurality of game apparatuses which are able to wirelessly communicate with each other. Each of the game apparatus registers identifying information of an opponent obtained by a short-distance wireless communication or by user's input in a friend list. Thereafter, the game apparatus connects to the Internet, and inquires server, etc. whether or not it is possible to communicate with the opponent in the friend list over a network. If it is possible to communicate, the game apparatus obtains an address of the opponent to make a network communication. In a case that a still another opponent being connected to its own apparatus exists, when other game apparatus makes a connection, its own game apparatus transmits their identifying information to introduce the communicating opponents to each other. The game apparatuses introduced to each other make a communication over a network, and add the identifying information of the opponents to the friend list, if necessary.
Owner:NINTENDO CO LTD
Method for Increasing Security in a Passive Optical Network
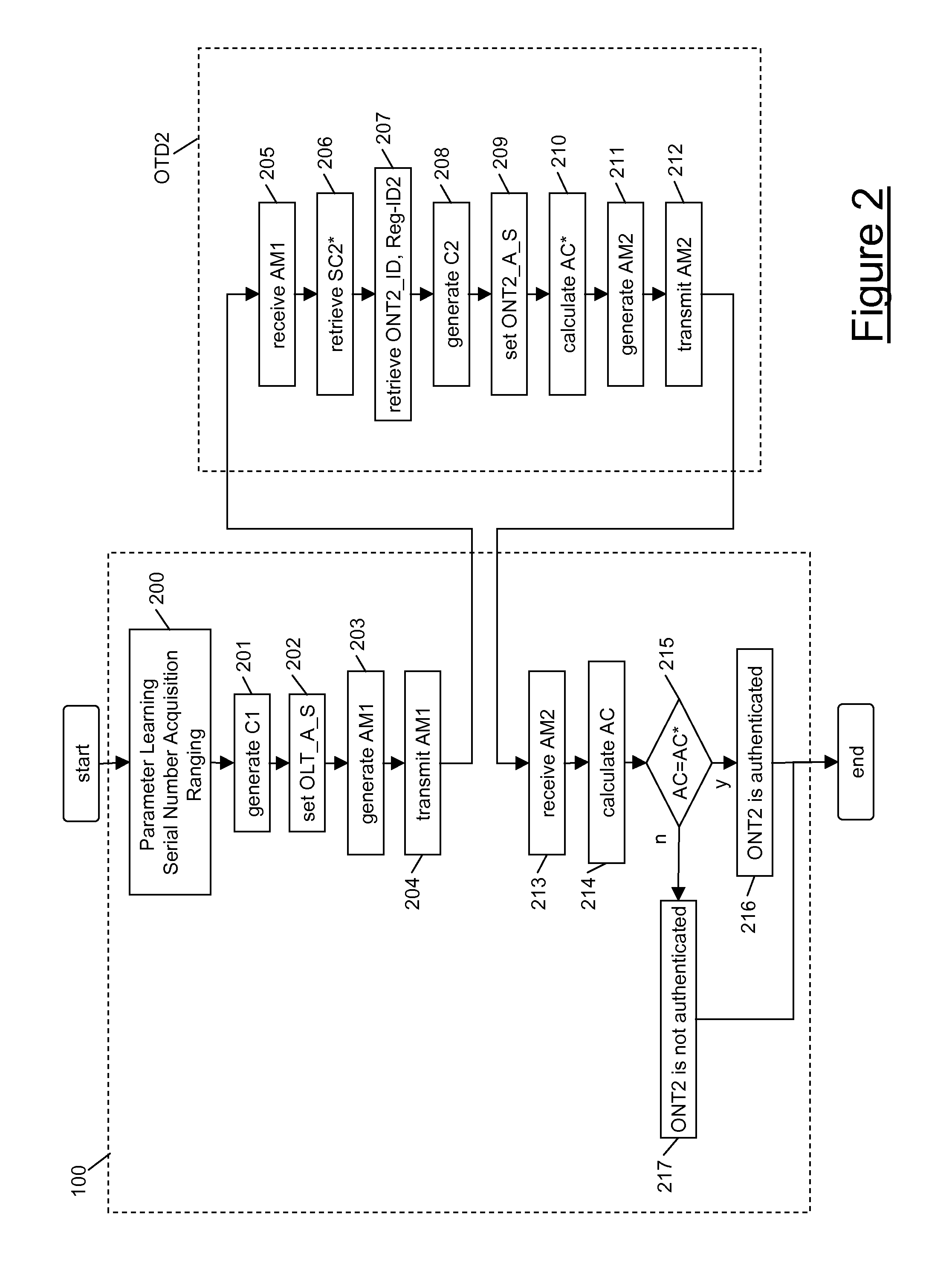
ActiveUS20110214160A1Network securityImprove securityMultiplex system selection arrangementsDigital data processing detailsSecret codeTerminal equipment
A method for security in a passive optical network is disclosed. The method includes, at an optical line termination (OLT): detecting an optical termination device and establishing a connection with the device; generating a first authentication message including a first random number; and transmitting the first authentication message through the established connection. At the optical termination device, the method may include: receiving the first authentication message; calculating a first authentication code by using the first random number and a secret code stored at the device; and generating and transmitting to the OLT a second authentication message including the first authentication code. The method may further include, at the OLT: receiving the second authentication message; calculating a second authentication code by using the first random number and a secret code stored at the OLT; and authenticating the optical termination device if the first authentication code matches the second authentication code.
Owner:TELECOM ITALIA SPA
Automatic loan administration system
InactiveUS20020120557A1Reduce riskNetwork securityFinanceSpecial data processing applicationsAutomatic controlEngineering
An automatic financing administration system of this invention is provided. In the automatic financing administration system of this invention, the roles of provider and user of loans are integrated and all participants in a financing operation are made members of a group. The financing transactions in said financing group are conducted in a computerized network automatically. Limitations in number of member, amount per transaction and existing term of a financing group are selectively decided. An automatic financing administrative system is able to automatically control the financing transactions of an unlimited plurality of financing groups.
Owner:SHACOM COM
Radio node network-accessing method and system as well as relay node
ActiveCN102158860ANetwork securityConnection managementSecurity arrangementAccess networkAccess method
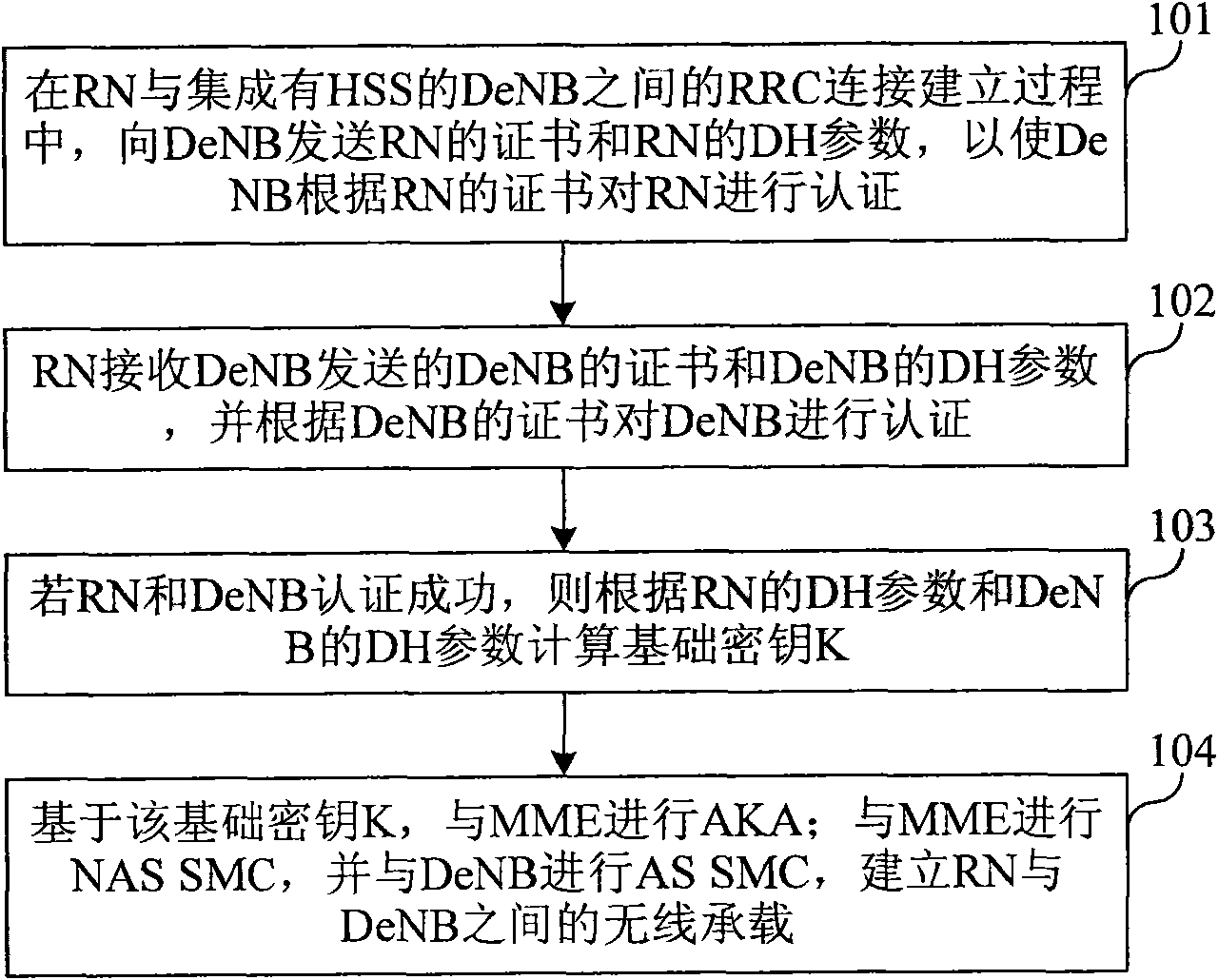
The embodiment of the invention relates to a radio node network-accessing method and system as well as a relay node. In the radio node network-accessing method and system as well as the relay node in the embodiment of the invention, through carrying a certificate in a message interacted between the relay node and a donor base station or home subscriber server or mobile management entity, authentication between the relay node and the donor base station or home subscriber server or mobile management entity is carried out; and through a DH (Diffie-Hellman) parameter between the relay node and the donor base station or home subscriber server or mobile management entity, a shared key similar to a key when user equipment accesses network is calculated, and finally, a radio bearer between the relay node and the donor base station is established, therefore, the authentication method based on the certificate when the relay node accesses the network is realized, and the relay node at the network side accesses the network more safely.
Owner:HUAWEI TECH CO LTD
Risk evaluation support device, program product and method for controlling safety network risk evaluation support device
InactiveUS20060038688A1Accurately carry-outEasy to learnSafety arrangmentsComputer controlOutput deviceRisk evaluation
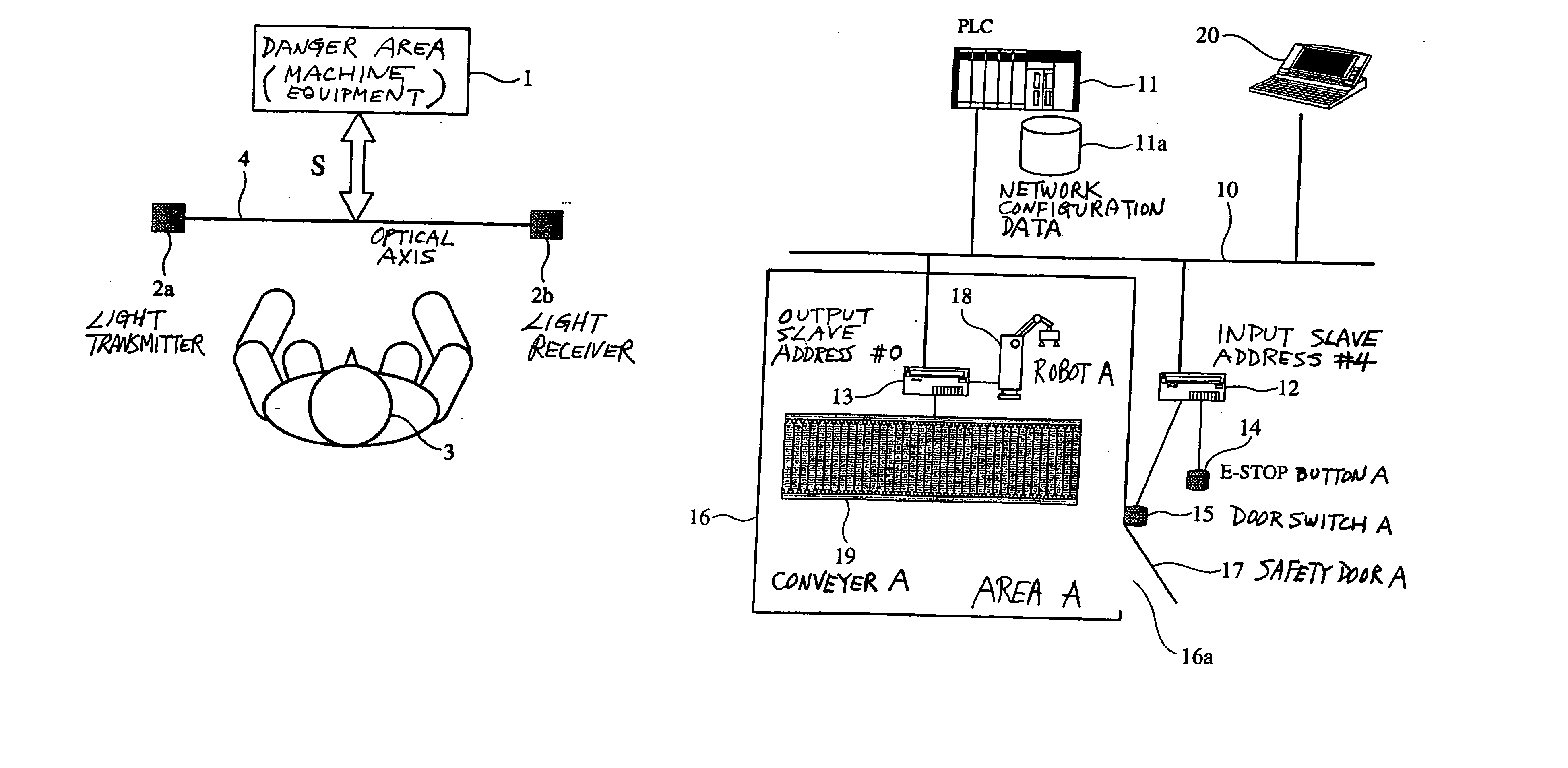
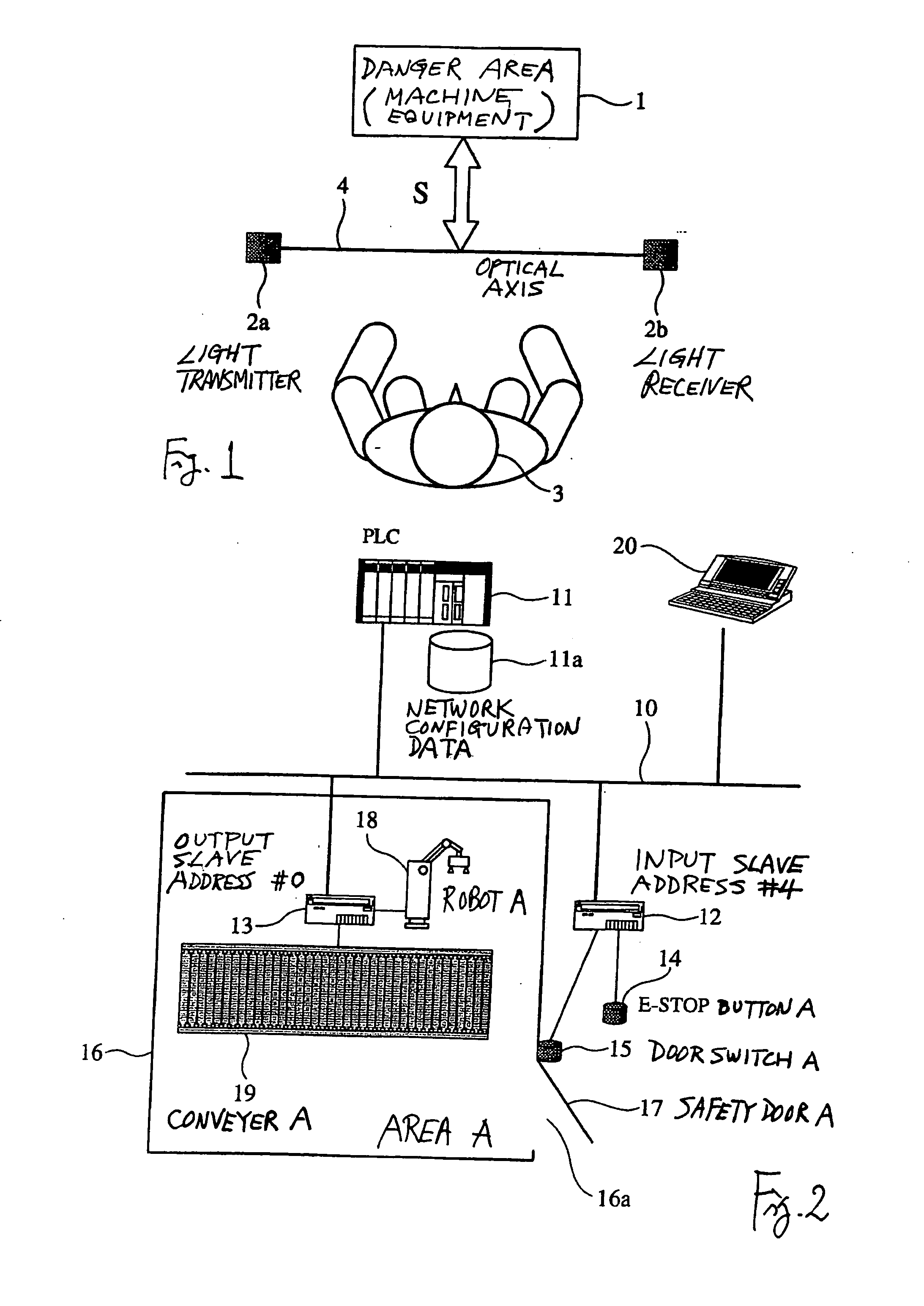
A risk evaluation support device is used for a safety network which serves to cause an output device to make a controlled device operable based on a detection signal outputted from an input device when the input device detects a safety condition. The support device creates a parameter setting table for correlating a danger source with the input and output devices and a PLC for risk evaluation based on configuration data of the safety network obtained through a communication part and device data on devices obtained from a component database. Operating data for the safety network are obtained according to conditions provided by the parameter setting table and a current risk evaluation value for the danger source is calculated based on the obtained operating data. The calculated risk evaluation value is outputted to a display part.
Owner:ORMON CORP
System and method for selection of security algorithms
ActiveUS8949927B2Improve trustNetwork securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser deviceSecurity policy
Owner:LENOVO INNOVATIONS LTD HONG KONG
Method of establishing routing path of sensor network for improving security and sensor node for implementing the same
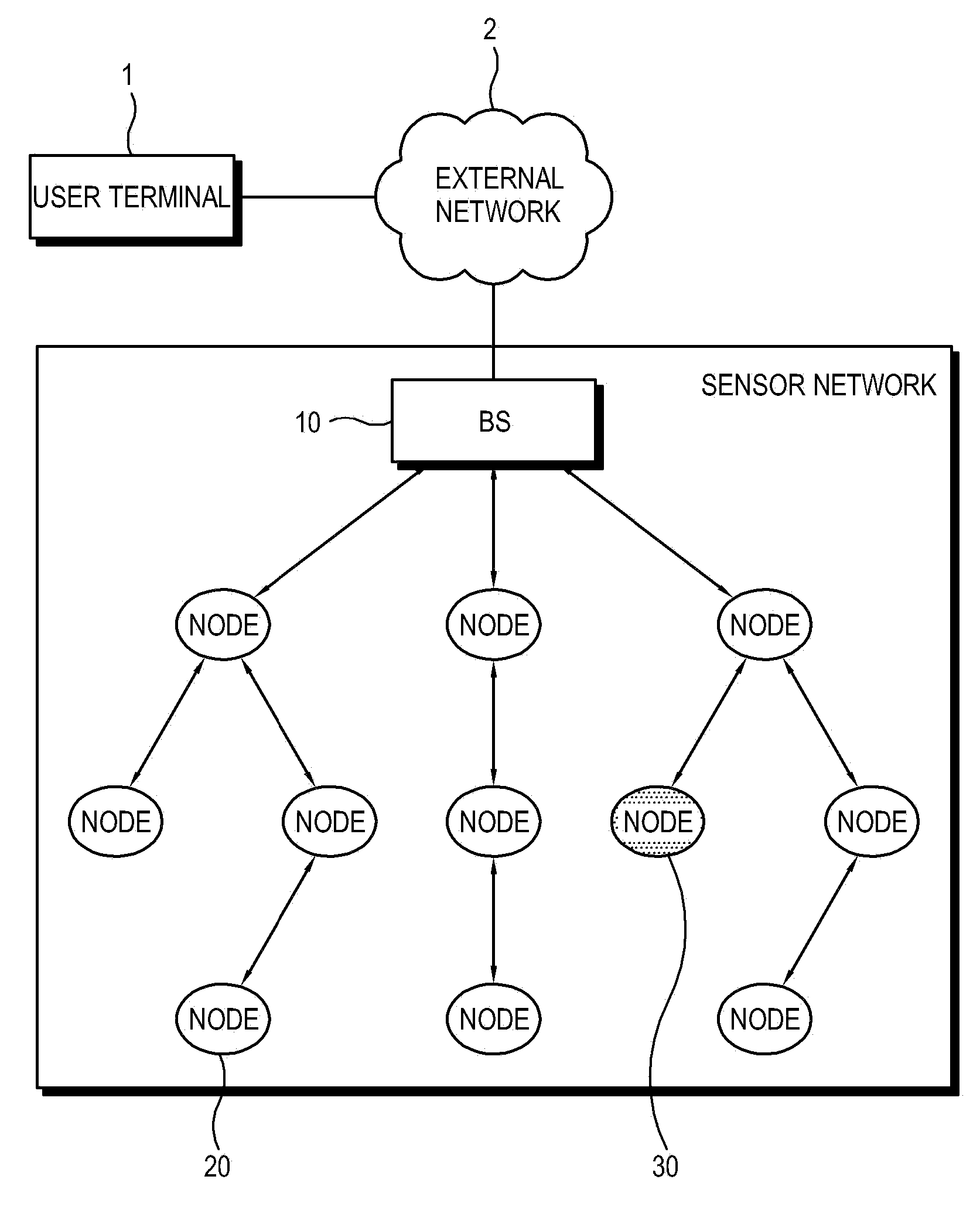
InactiveUS20100183153A1Increase probabilityNetwork securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSensor nodeDistributed computing
Disclosed herein is a method of establishing the routing path of a sensor network and a sensor node for implementing the method. Each of a plurality of sensors belonging to a sensor network is assigned a key index and a key corresponding to the key index. The sensor node acquires information about key indices possessed by sensor nodes existing on a candidate routing path. The sensor node selects a final routing path from among a plurality of candidate routing paths using the information about the key indices. Accordingly, the present invention can implement a sensor network having improved security.
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
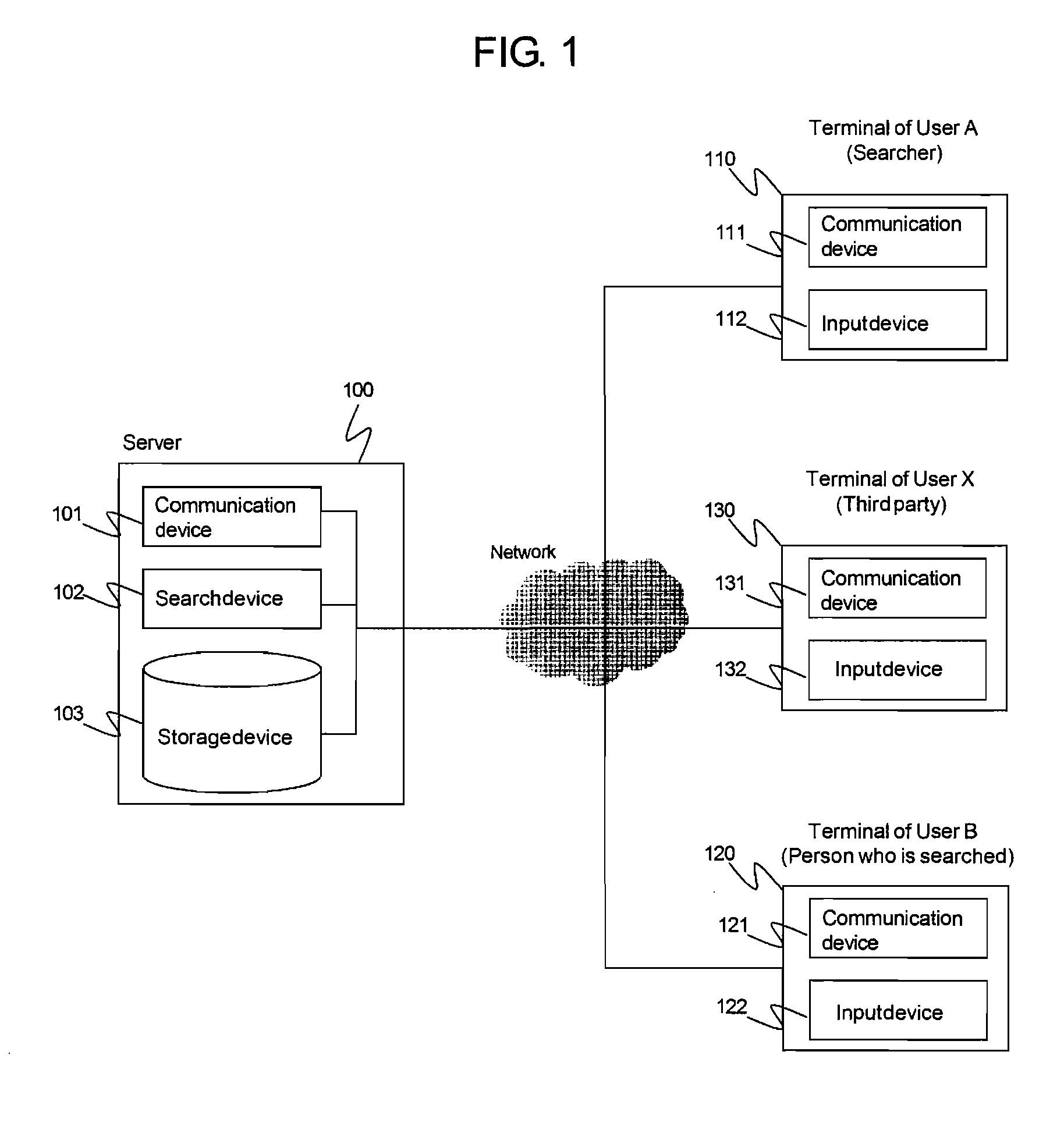
Terminal device and system for searching personal information
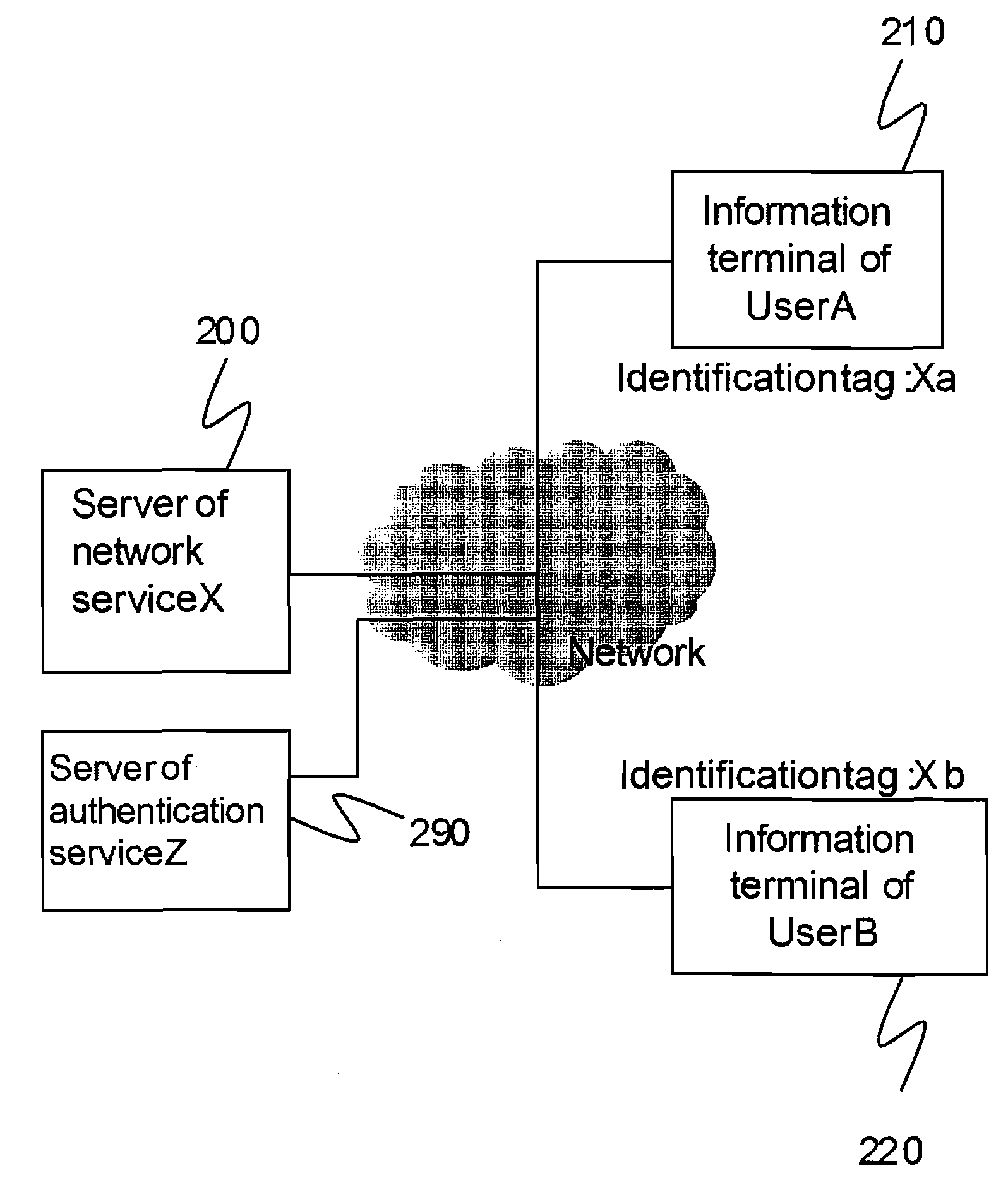
InactiveUS20100023510A1Network securityEliminate effectiveDigital data information retrievalDigital data protectionTerminal equipmentComputer science
An information terminal of a user B who permits a user A to search the person B calculates a calculation result G(Pa′, Pb) by using information Pa′ related to the user A and information Pb of the user B, both Pa′ and Pb being stored in the information terminal of the user B and transmits to a server the calculation result G(Pa′, Pb). Further, the information terminal of the user B receives trust information expressing that Pb is authenticated and calculates a calculation result F(Pb) and transmits to the server. The information terminal of the user A calculates G(Pa, Pb′) and transmits it to the server. When the server receives G(Pa, Pb′) from the information terminal of the user A, the server searches G(Pa′, Pb) which matches G(Pa, Pb′) and the search result with F(Pb) to the information terminal of the user A. The information terminal of the user A calculates F(Pb′) and compares it with F(Pb) which is sent by the server.
Owner:RIPPLEX
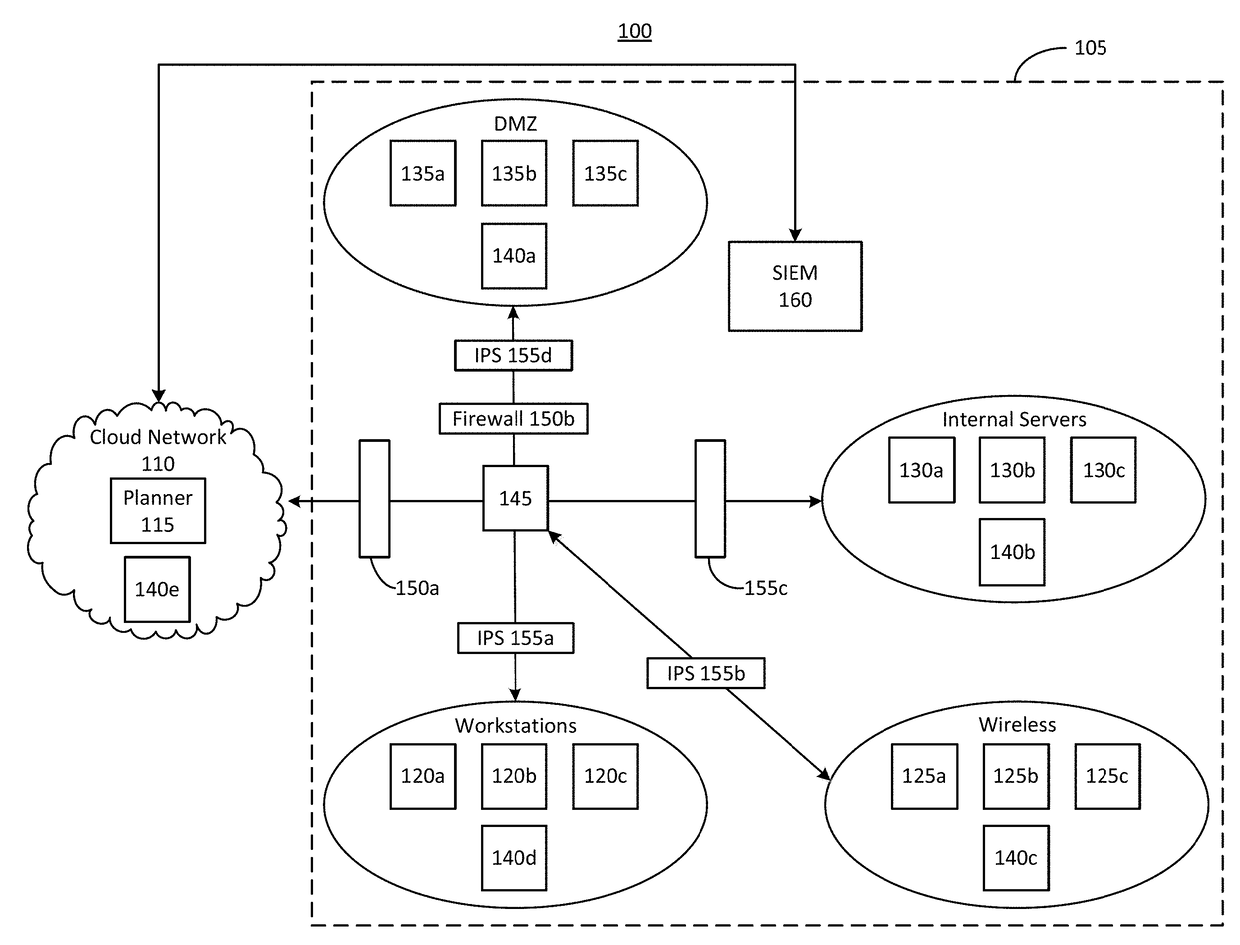
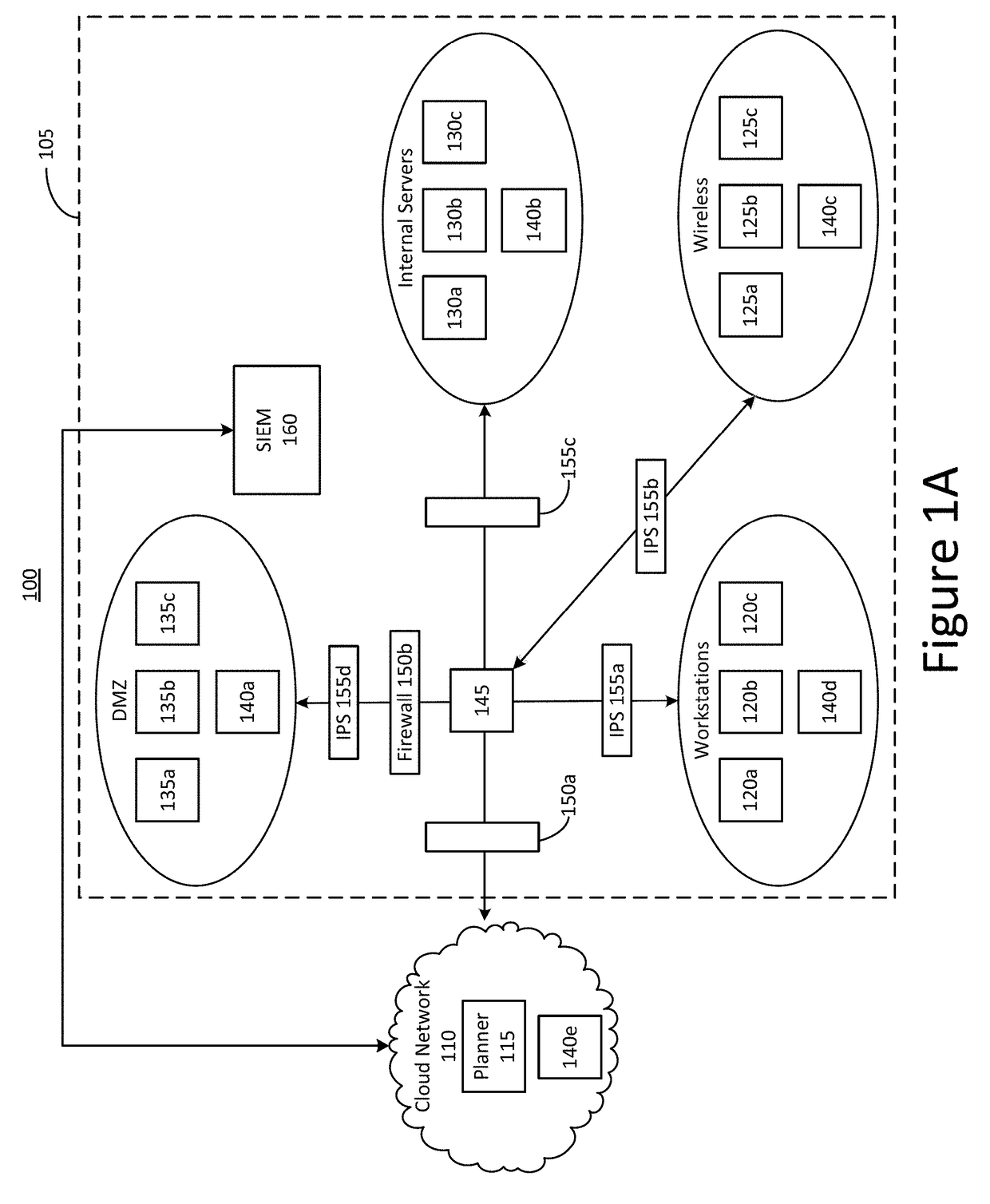
Systems and methods for attack simulation on a production network
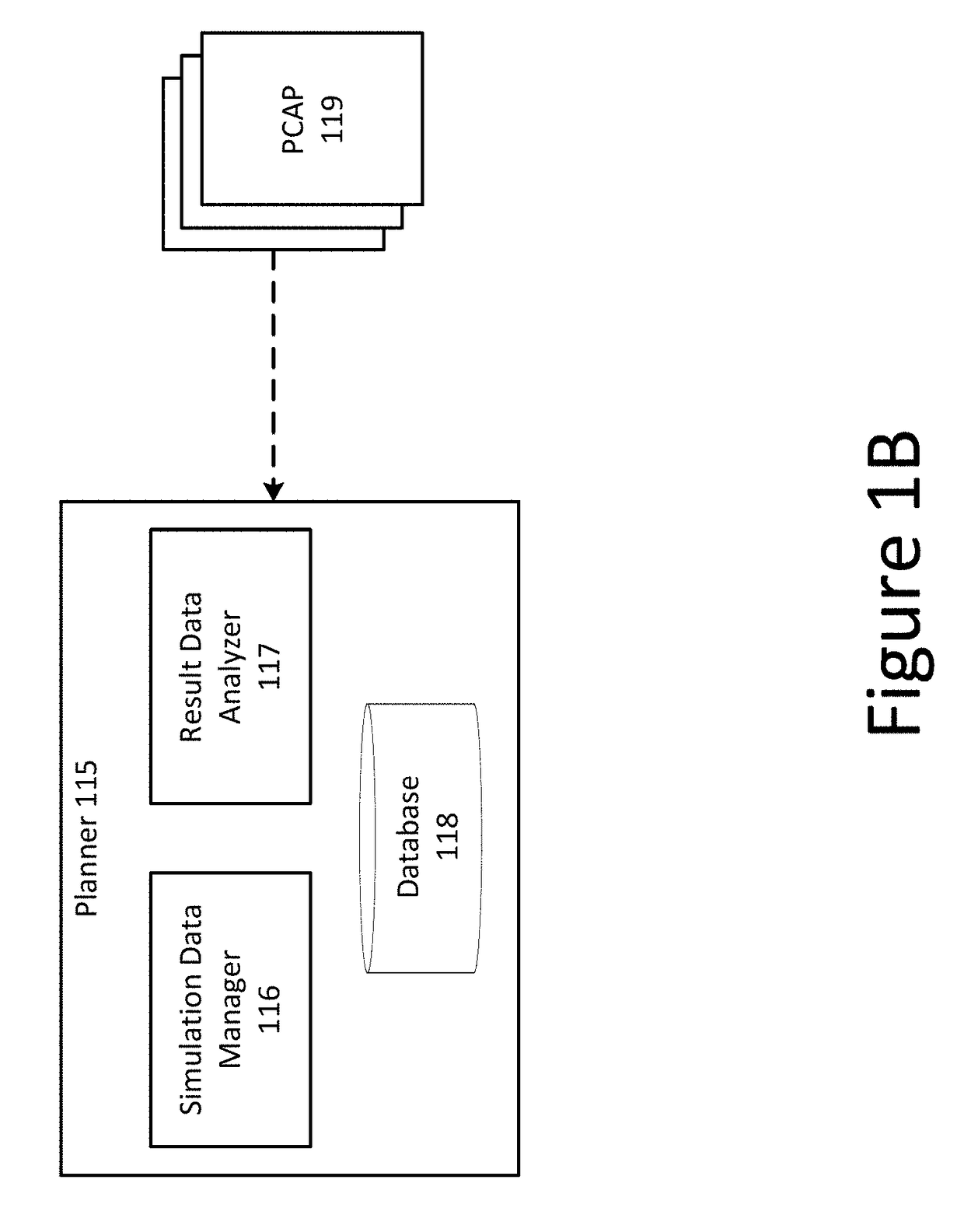
The disclosure is directed towards systems and methods for improving security in a computer network. The system can include a planner and a plurality of controllers. The controllers can be deployed within each zone of the production network. Each controller can be configured to assume the role of an attacker or a target for malicious network traffic. Simulations of malicious behavior can be performed by the controllers within the production network, and can therefore account for the complexities of the production network, such as stateful connections through switches, routers, and other intermediary devices. In some implementations, the planner can analyze data received from the controllers to provide a holistic analysis of the overall security posture of the production network.
Owner:GOOGLE LLC
Multi-website shopping cart system and the method for the same
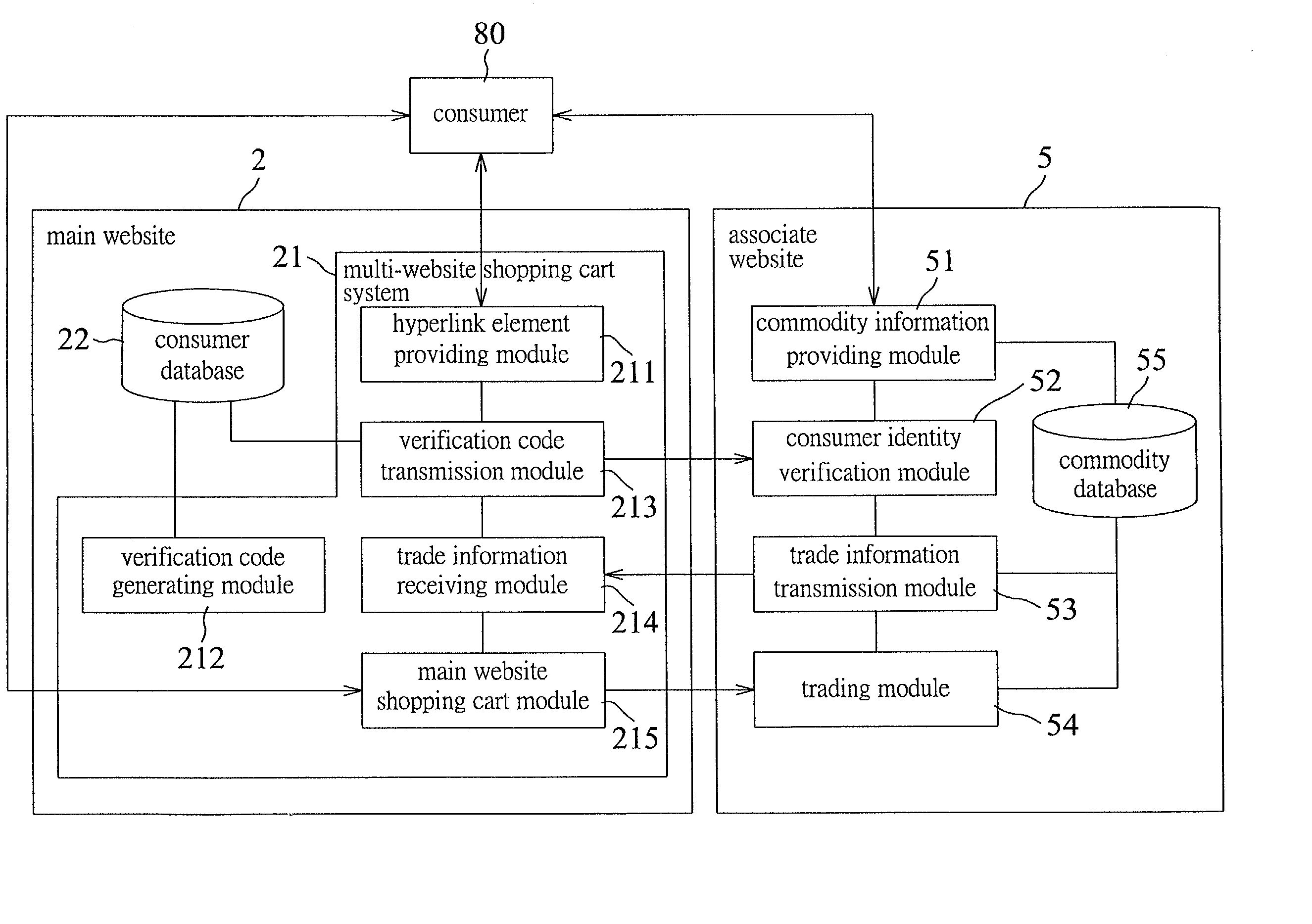
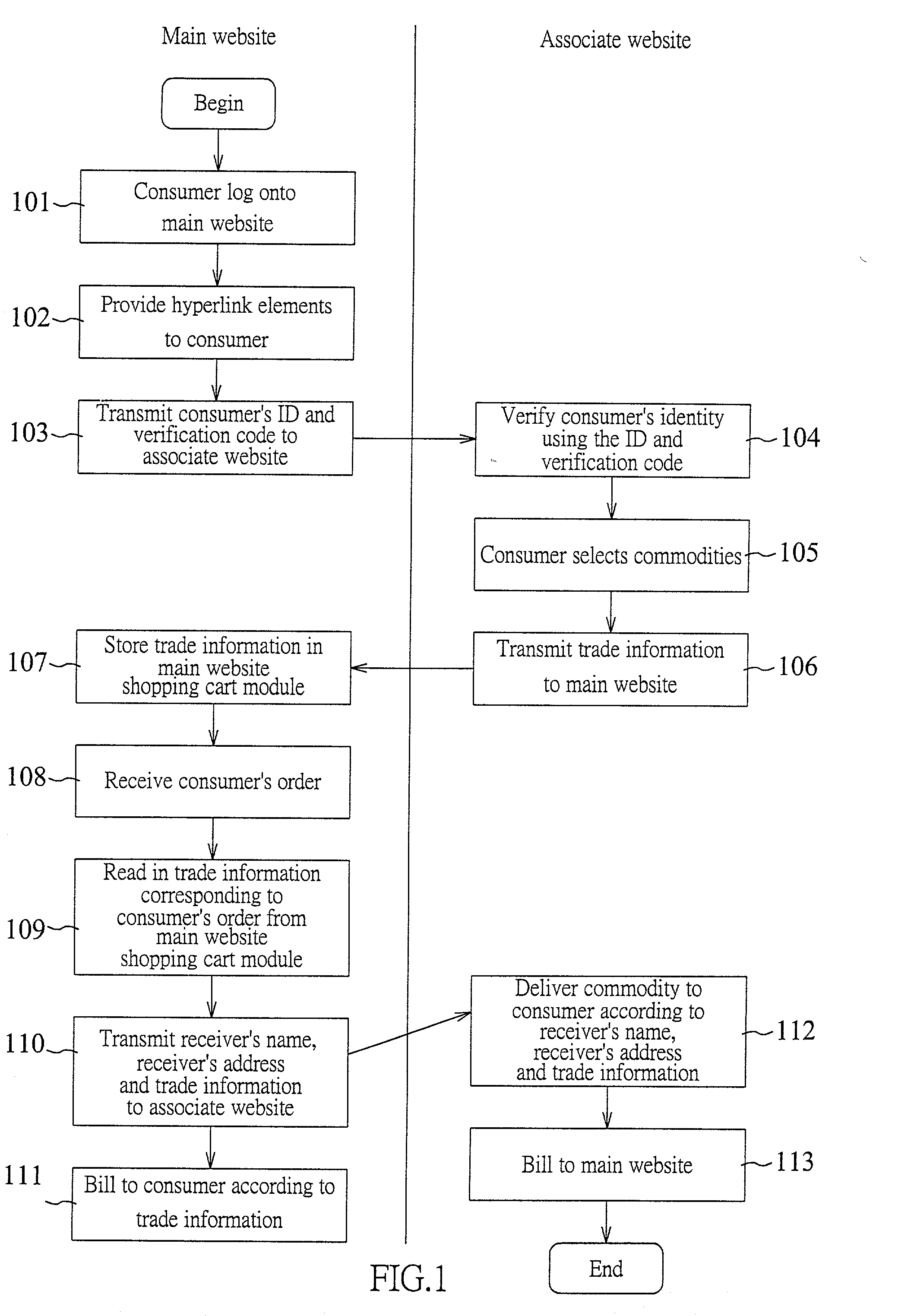
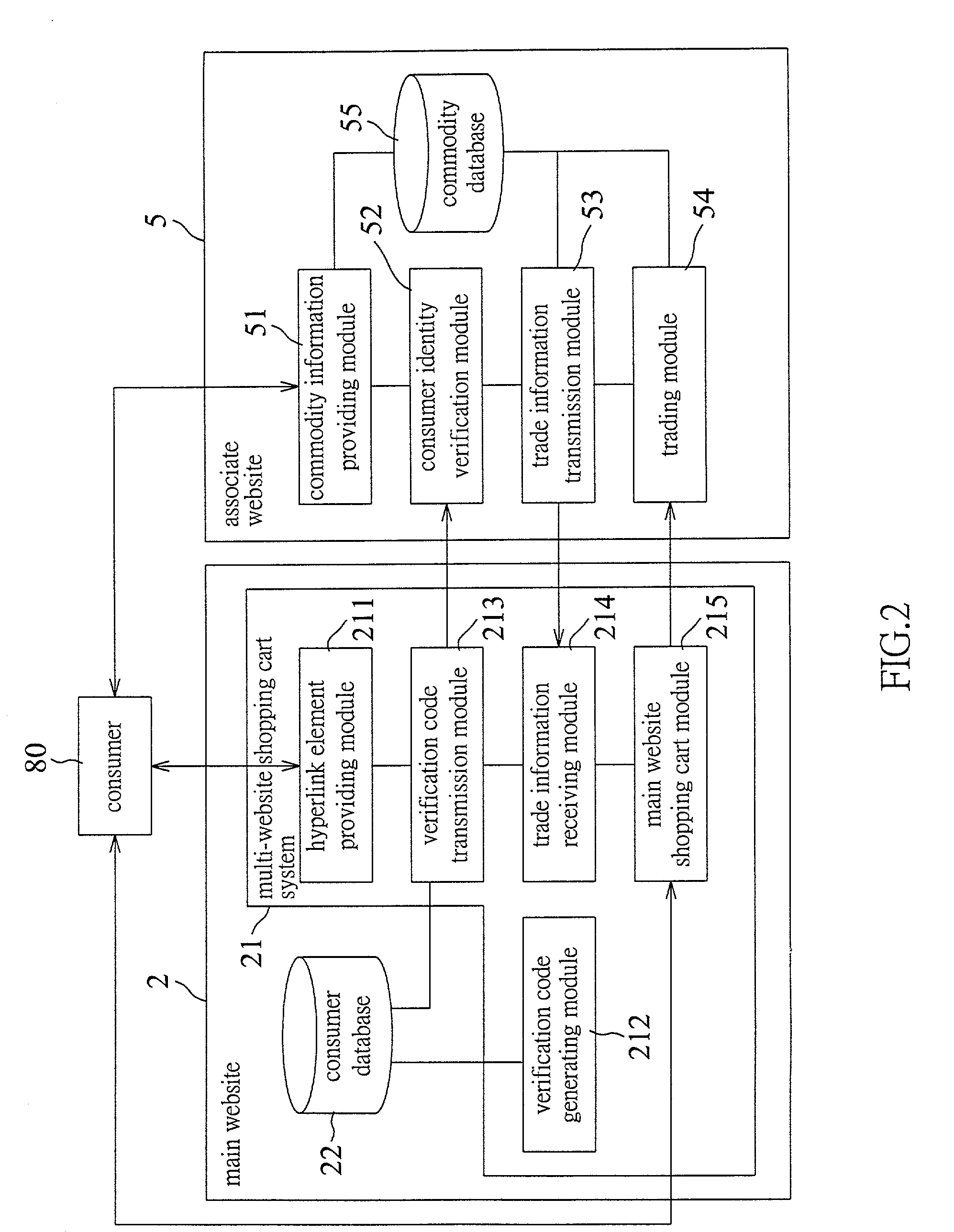
InactiveUS20020133429A1Reduce riskHigh network trading securityBuying/selling/leasing transactionsSpecial data processing applicationsHyperlinkCart
The invention discloses a multi-website shopping cart implementation method, which uses a main website to provide consumers a hyperlink element linking to an associate website. When a consumer selects the hyperlink element, the main website will transmit the ID of the consumer and the verification code to the associate website so as to verify the identity of the consumer. When the consumer wants to purchase a particular commodity sold at the associate website, the main website will receive trade information transmitted from the associate website and thereby charge to the consumer. Finally, the main website places an order to the associate website and provides the name and the address of the receiver to the associate website. With the trade information, the name and the address of the receiver, the associate website sends out the commodity. The invention also discloses a multi-website shopping cart system to implement the above method.
Owner:BUYSELL ASIA
Method and apparatus for providing a private communication system in a public switched telephone network
InactiveUSRE44577E1Network securityImprove securityMultiplex system selection arrangementsSpecial service provision for substationPrivate communicationCommunications system
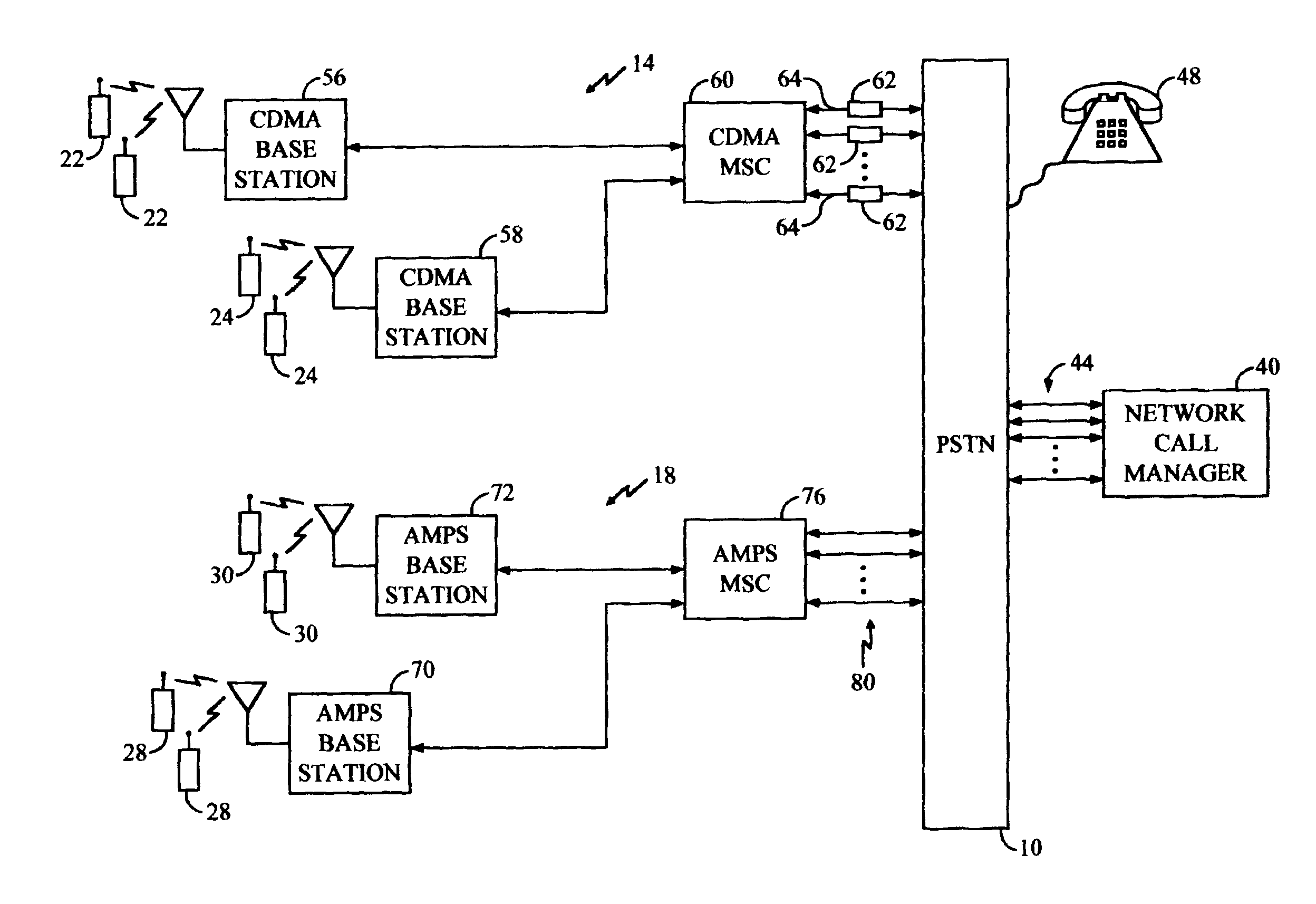
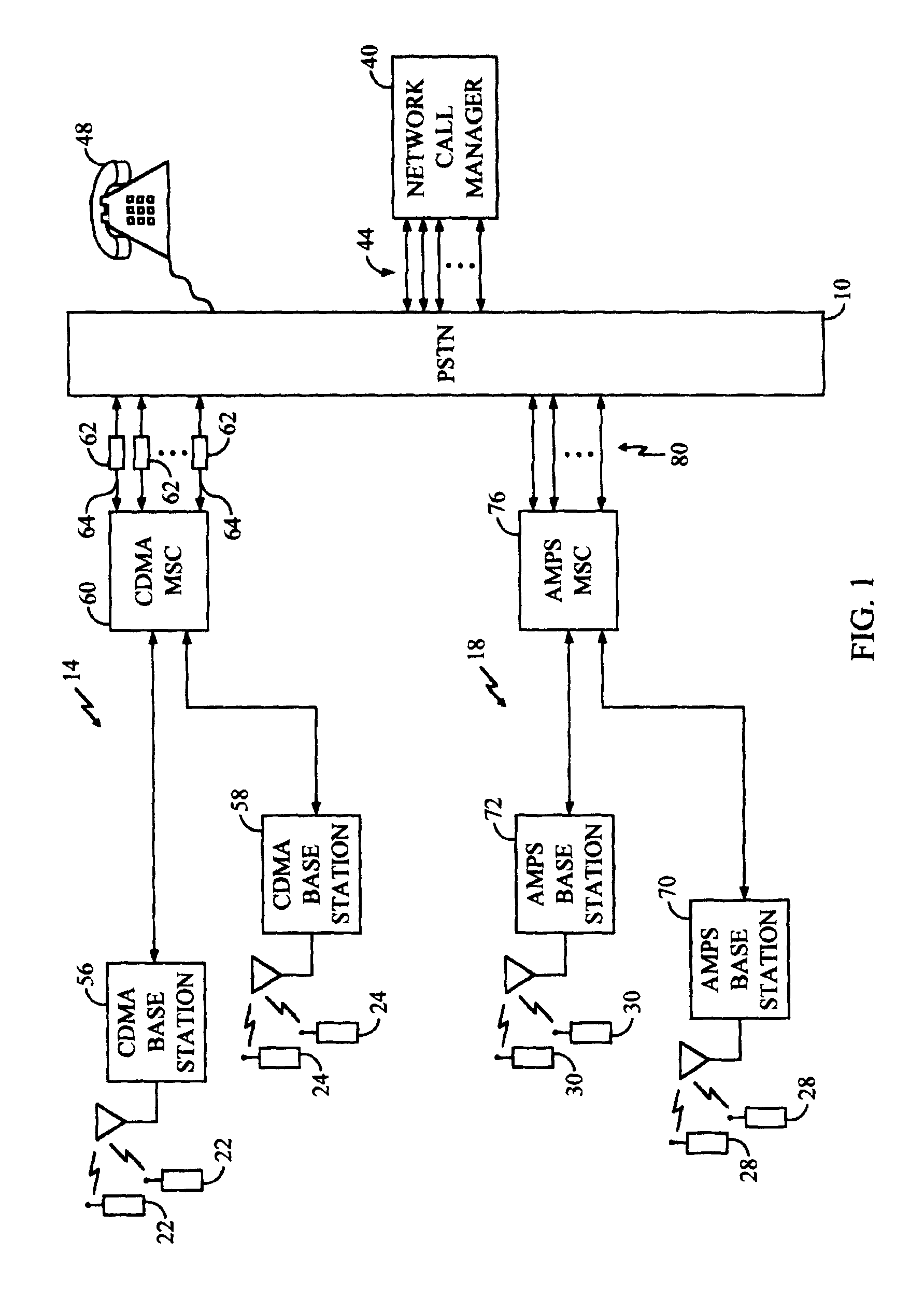
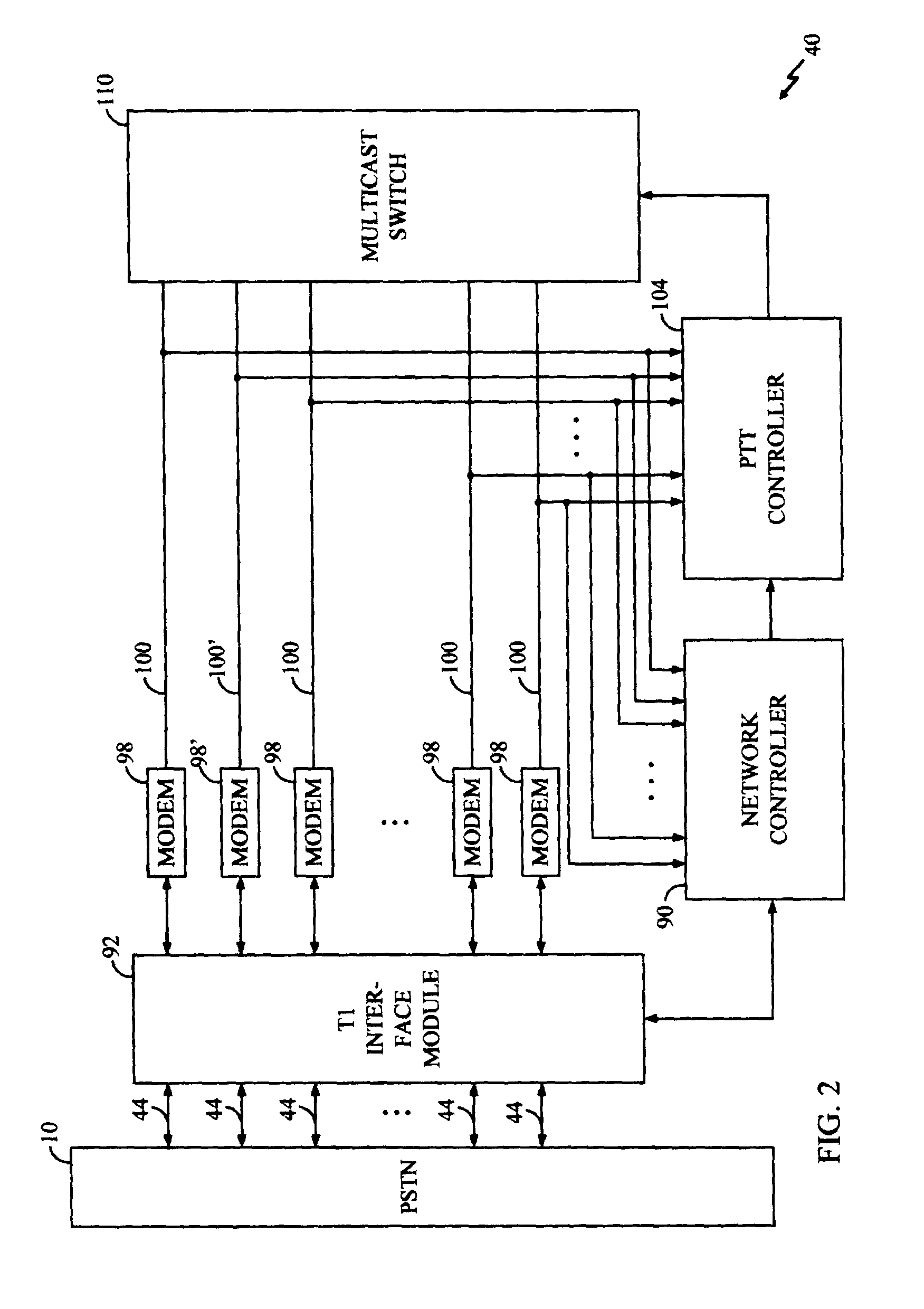
A private communication network through which a plurality of member users communicate using the public switched telephone network (PSTN) is disclosed herein. Each member user utilizes either a modified land line telephone directly connected to PSTN, or uses a modified mobile telephone operatively coupled to the PSTN through a wireless communication system. The private communication network includes network call manager having a telephone network interface for establishing a telephone connection with each of a plurality of telephone lines of the PSTN. Each of the plurality of telephone lines is associated with one of the plurality of member users. The network call manager further includes a switch matrix, coupled to the telephone network interface, for providing an information signal received from an active member user over a selected telephone line to the remaining non-active member users. A network call manager controller identifies the active member user the basis of push-to-talk (PTT) request signals received from the member users'telephones over the plurality of telephone lines. The telephone set of each member user will typically be capable of both standard telephone operation as well as of PTT operation over the private communication network. The security of the PTT private network may be enhanced by configuring each telephone set for encryption of all such reverse link transmissions, as well as for corresponding decryption of the forward link information from the active member user.
Owner:QUALCOMM INC
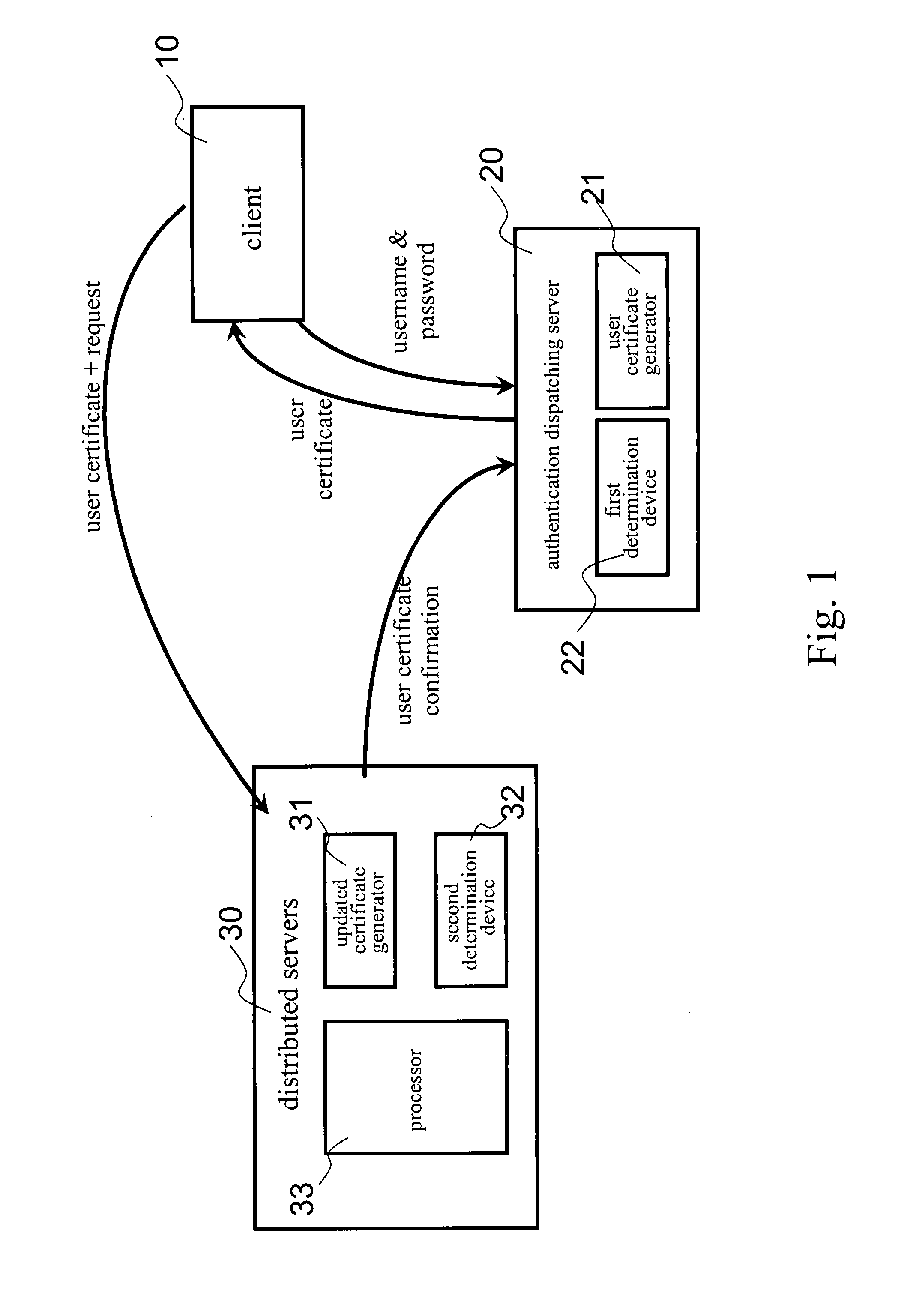
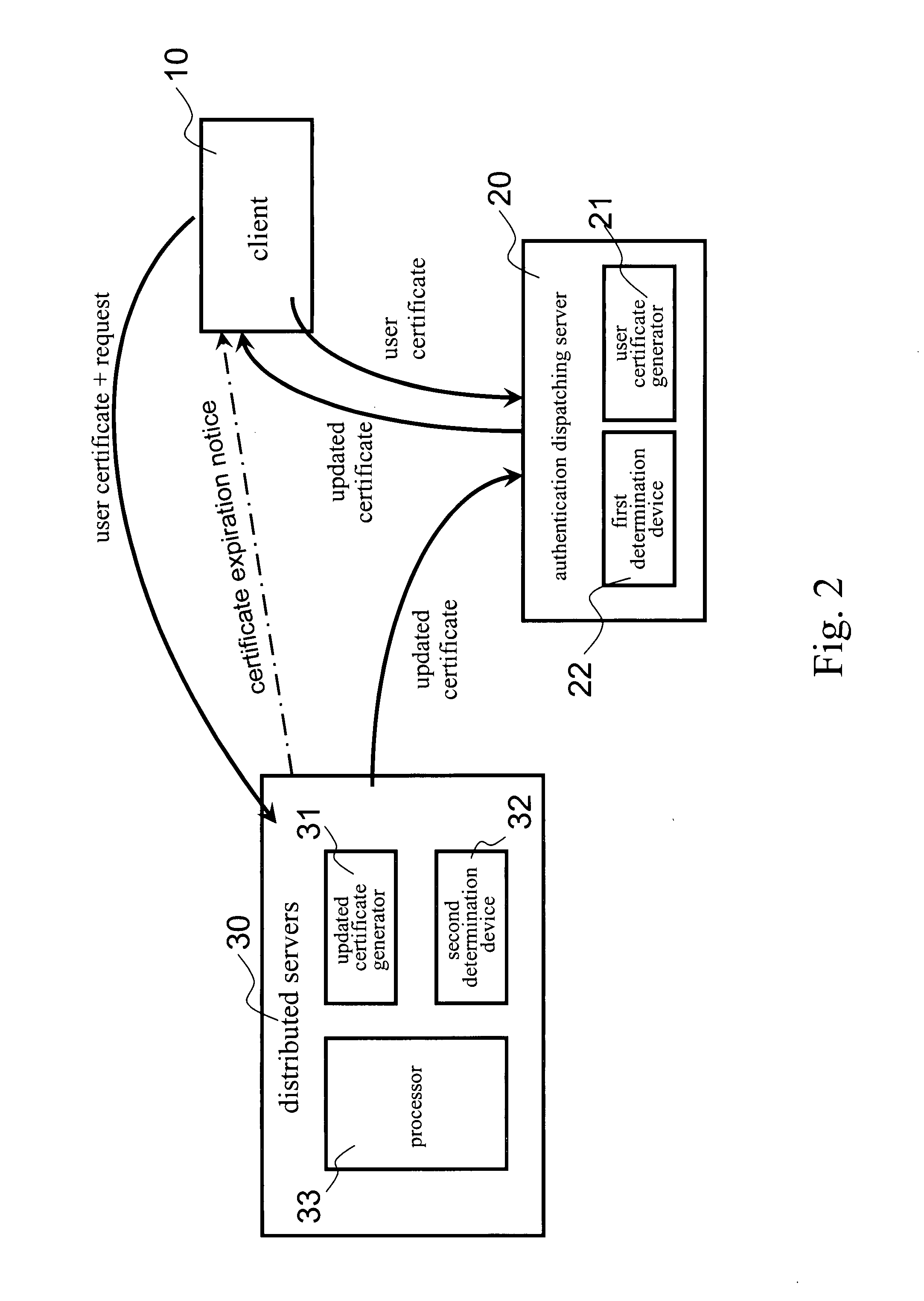
Network data security system and protecting method thereof
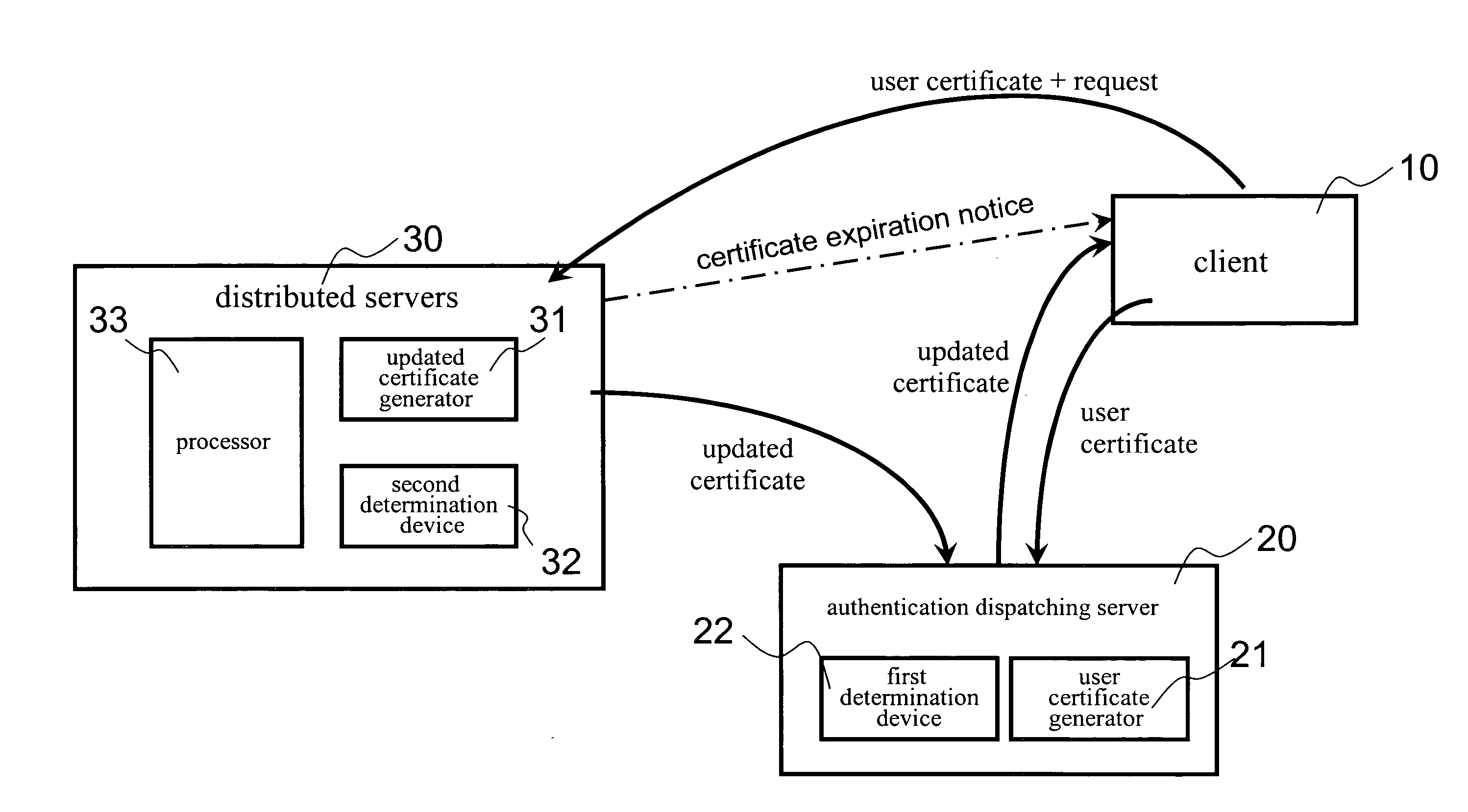
InactiveUS20080222412A1Network securityEnsure safetySecuring communicationDistributed serversClient-side
The invention presents a network data security system and a protecting method applied in network data transmission. Meanwhile the network data security system includes a client, an authentication dispatching server and a number of distributed servers. The authentication dispatching server includes a first determination device and a user certificate generator; and each distributed server includes a second determination device, a second user certificate generator and a processor. The method for protecting data of the present invention introduces the authentication dispatching server providing the client with a user certificate in a valid period of time and further introduces an updated certificate mechanism for preventing the user certificate from being stolen and further preventing network data from being let out.
Owner:KINGHOOD TECH
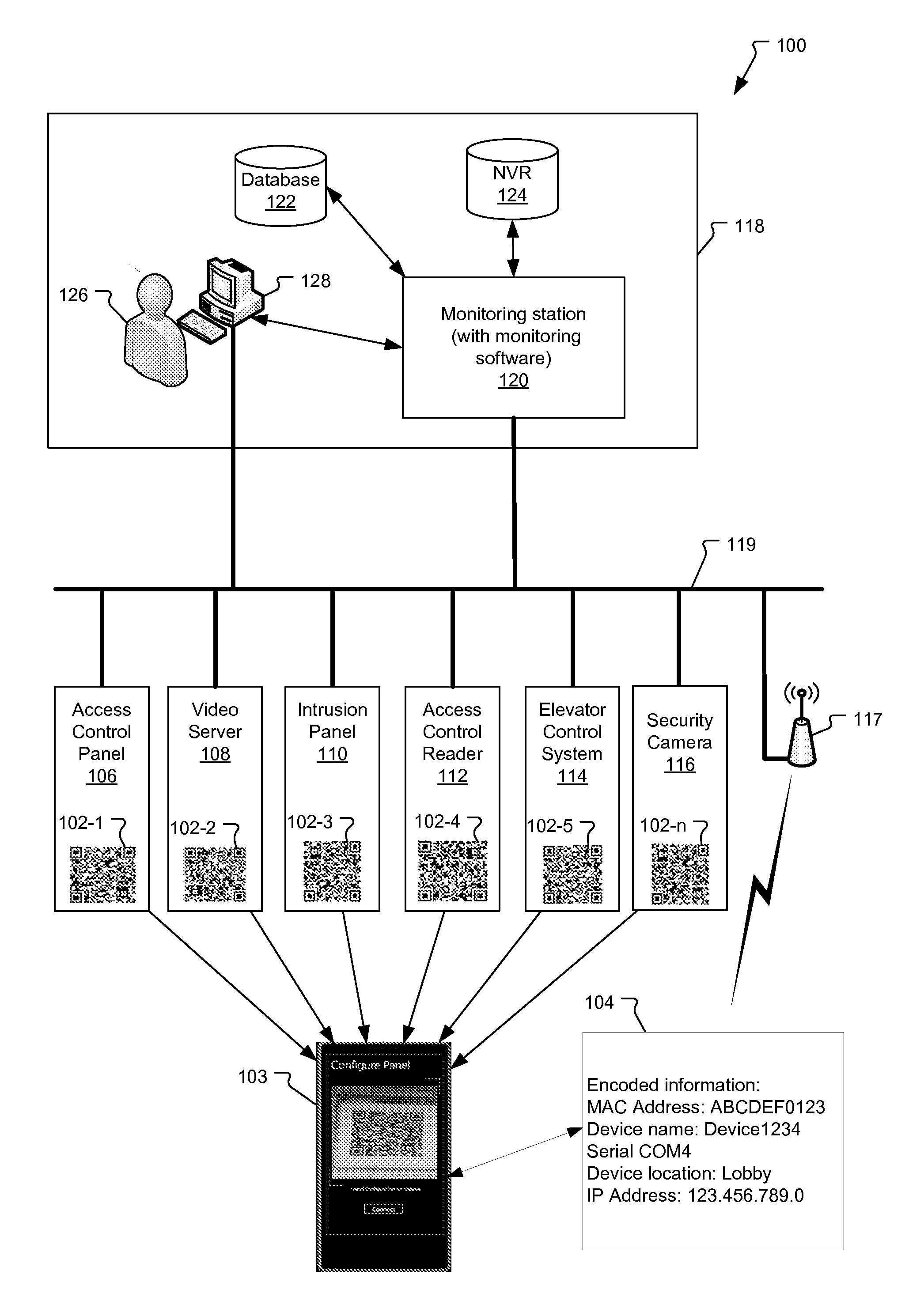
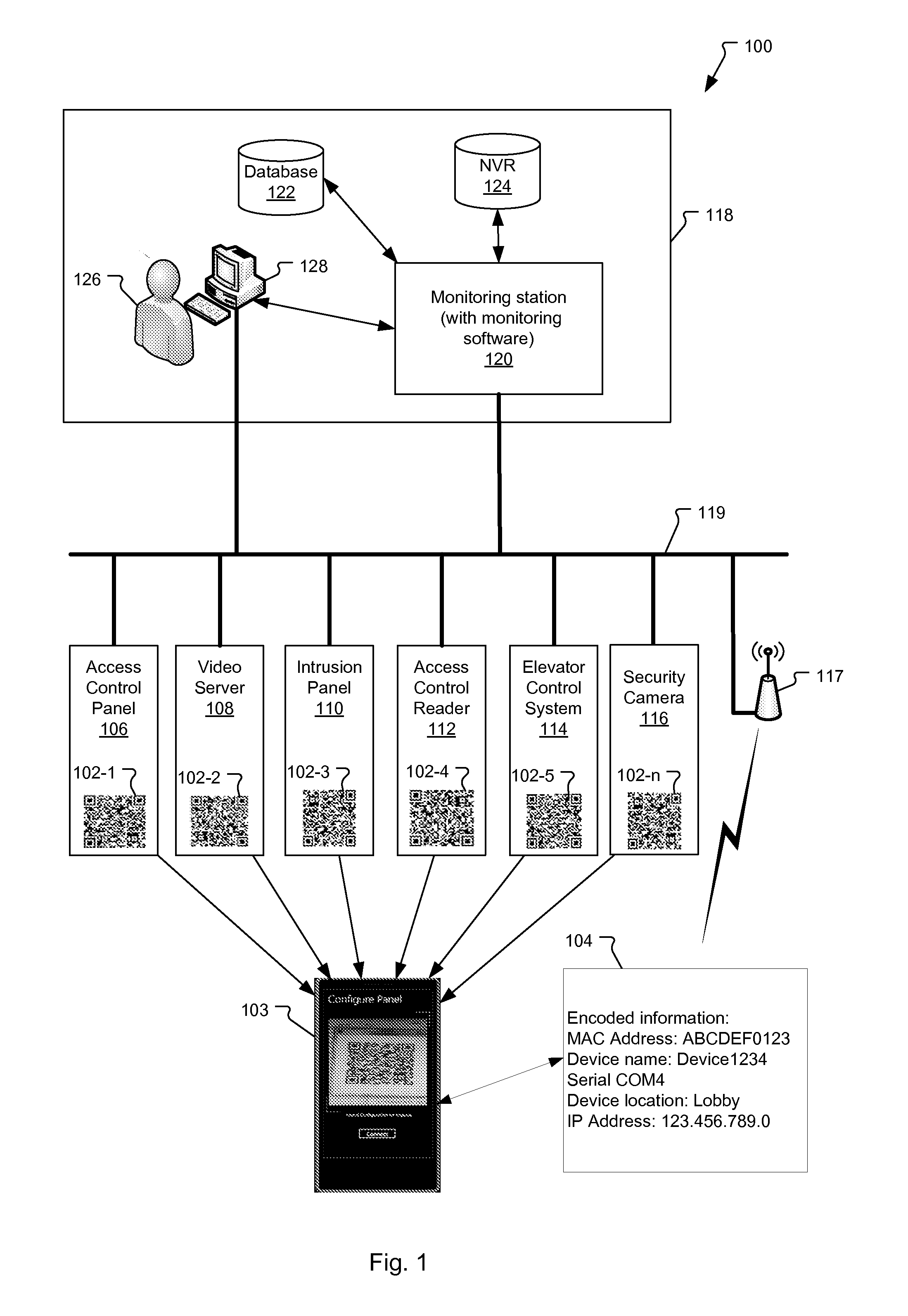
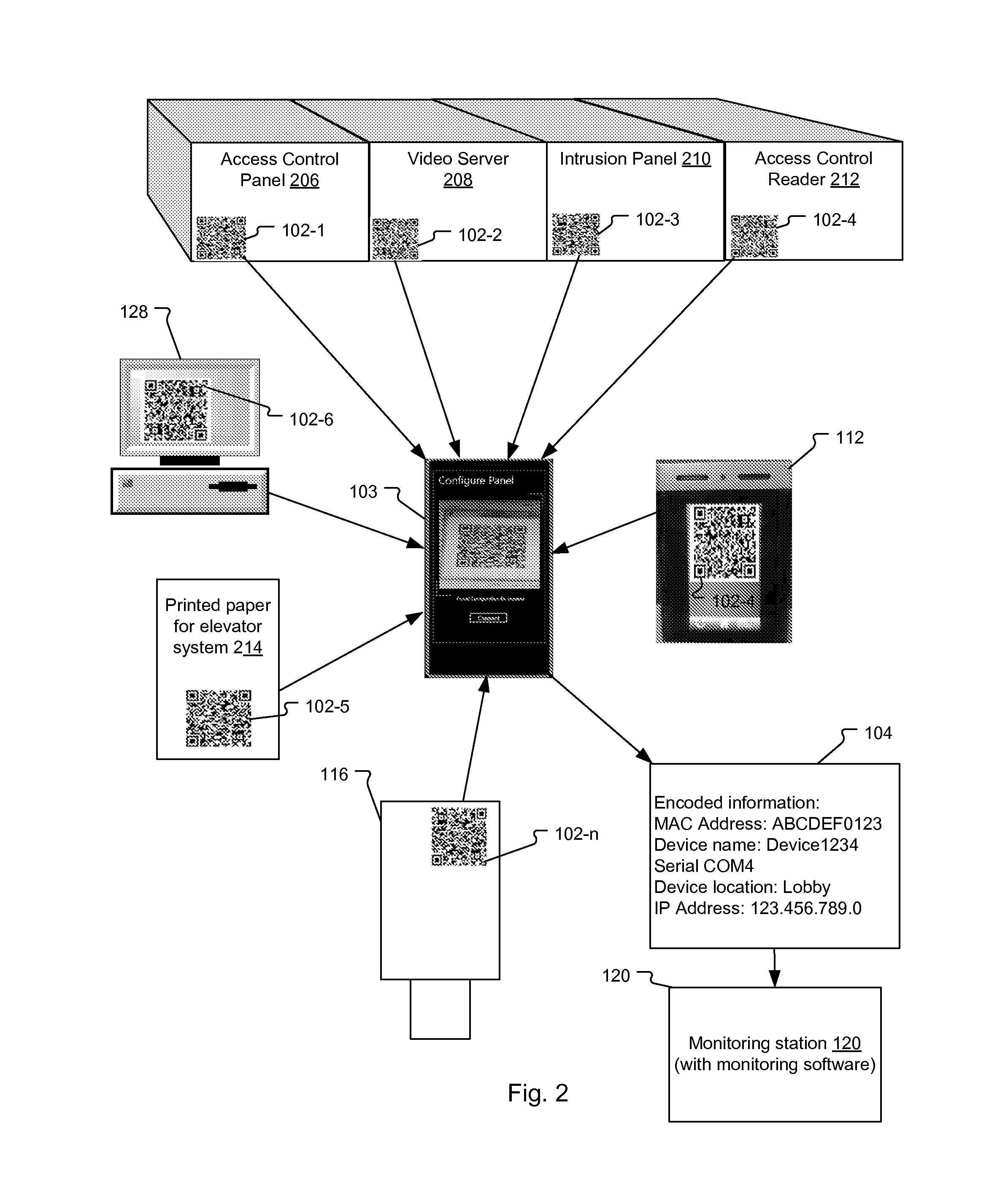
Configuration of Security Devices Using Spatially-Encoded Optical Machine-Readable Indicia
ActiveUS20140218164A1Network securityProgramme controlElectric signal transmission systemsSpatial encodingMobile computing
A method and system for configuring security devices on a security network. A mobile computing device reads spatially-encoded optical machine-readable indicia, decodes the indicia, and extracts encoded configuration information for the security devices. The configuration information from the indicia is then transmitted to a monitoring station, which uses the configuration information to configure communication with the security devices on the security network.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
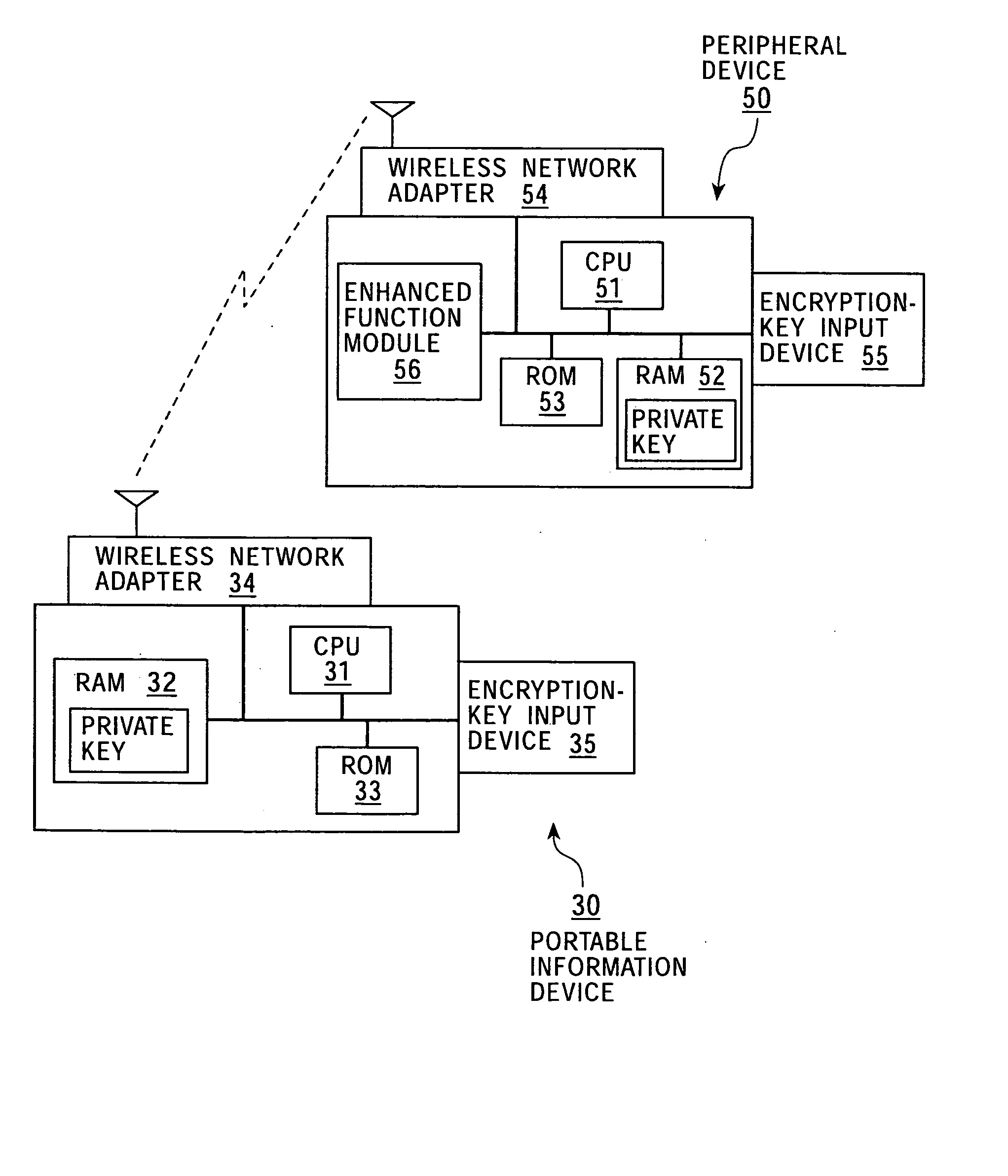
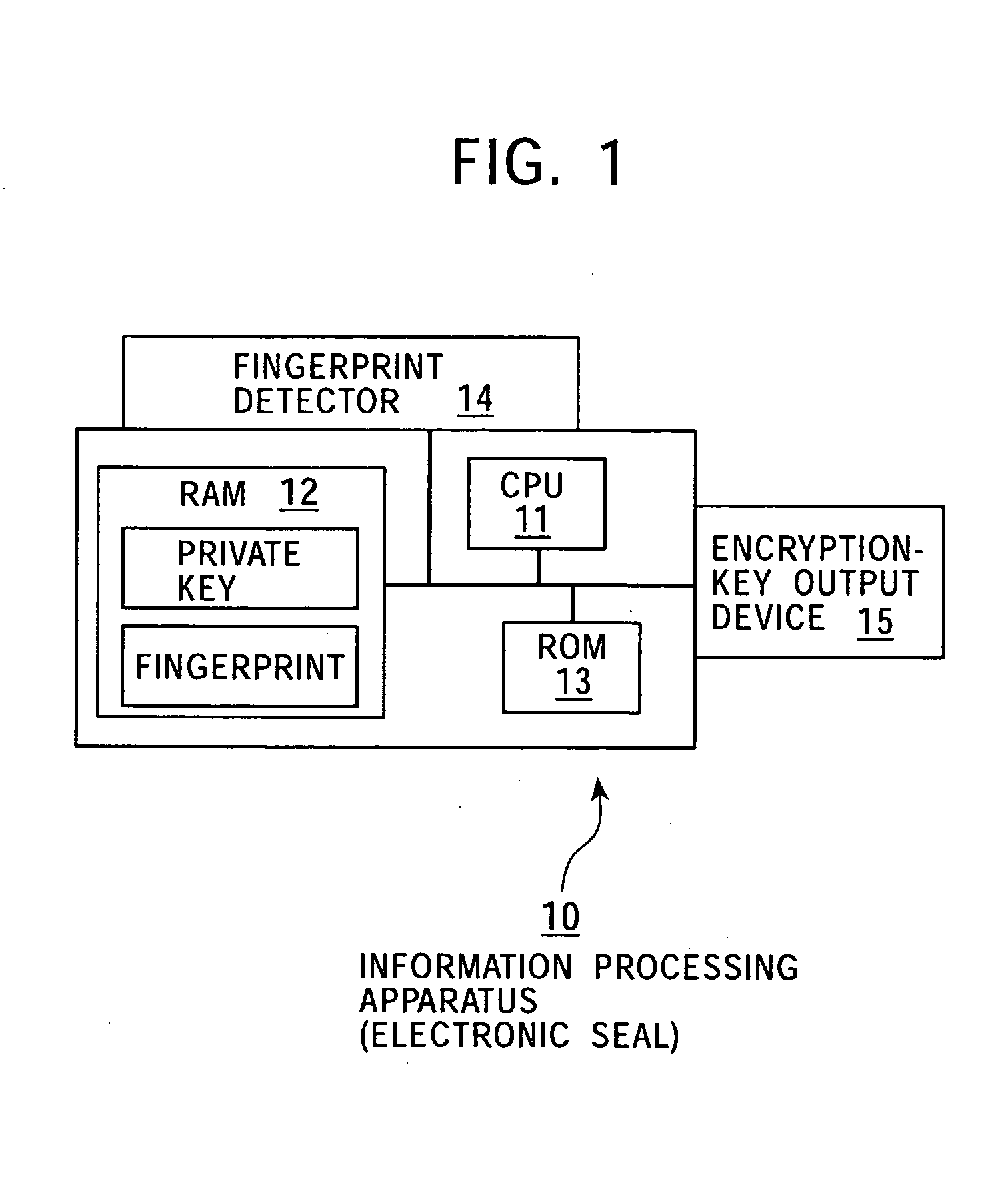
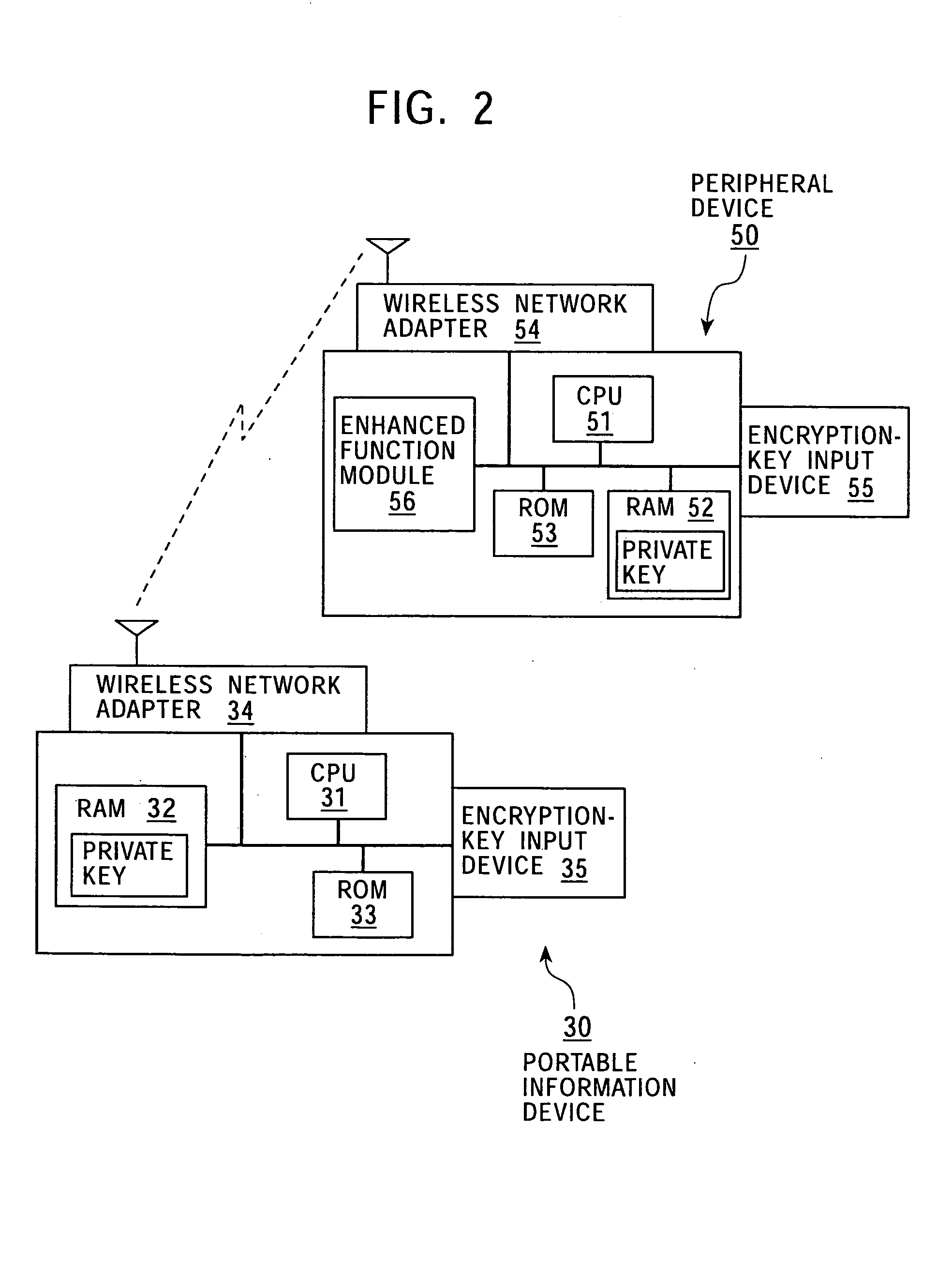
Information processing apparatus and method, and storage medium
InactiveUS20050081035A1Ensure safetyNetwork securityData processing applicationsUser identity/authority verificationInformation processingInformation device
A secure connection between the main unit of a portable information device and a peripheral device via a wireless network is ensured by using an electronic seal that makes it possible to transmit an encryption key to the portable information terminal and the peripheral device thereof by an operation which is analogous to “seal affixing” by a user confirmed as an authorized user. For example, user confirmation is performed by an authentication technology using biometric information, such as “fingerprint authentication”. After the portable information terminal and the peripheral device thereof perform mutual recognition, they can perform secure mutual communication via a wireless network, etc., by using the encryption key provided via the electronic seal.
Owner:SONY CORP
Method and system for file-system based caching
InactiveUS20060129657A1Improve efficiencyImprove securityDigital data information retrievalDigital data processing detailsFile systemFile size
A method and system for file-system based caching can be used to improve efficiency and security at network sites. In one set of embodiments, the delivery of content and storing content component(s) formed during generation of the content may be performed by different software components. Content that changes at a relatively high frequency or is likely to be regenerated between requests may not have some or all of its corresponding files cached. Additionally, extra white space may be removed before storing to reduce the file size. File mapping may be performed to ensure that a directory within the cache will have an optimal number of files. Security at the network site may be increased by using an internally generated filename that is not used or seen by the client computer. Many variations may be used is achieving any one or more of the advantages described herein.
Owner:OPEN TEXT SA ULC
Method and system for secure block acknowledgment (block ack) with protected mac sequence number
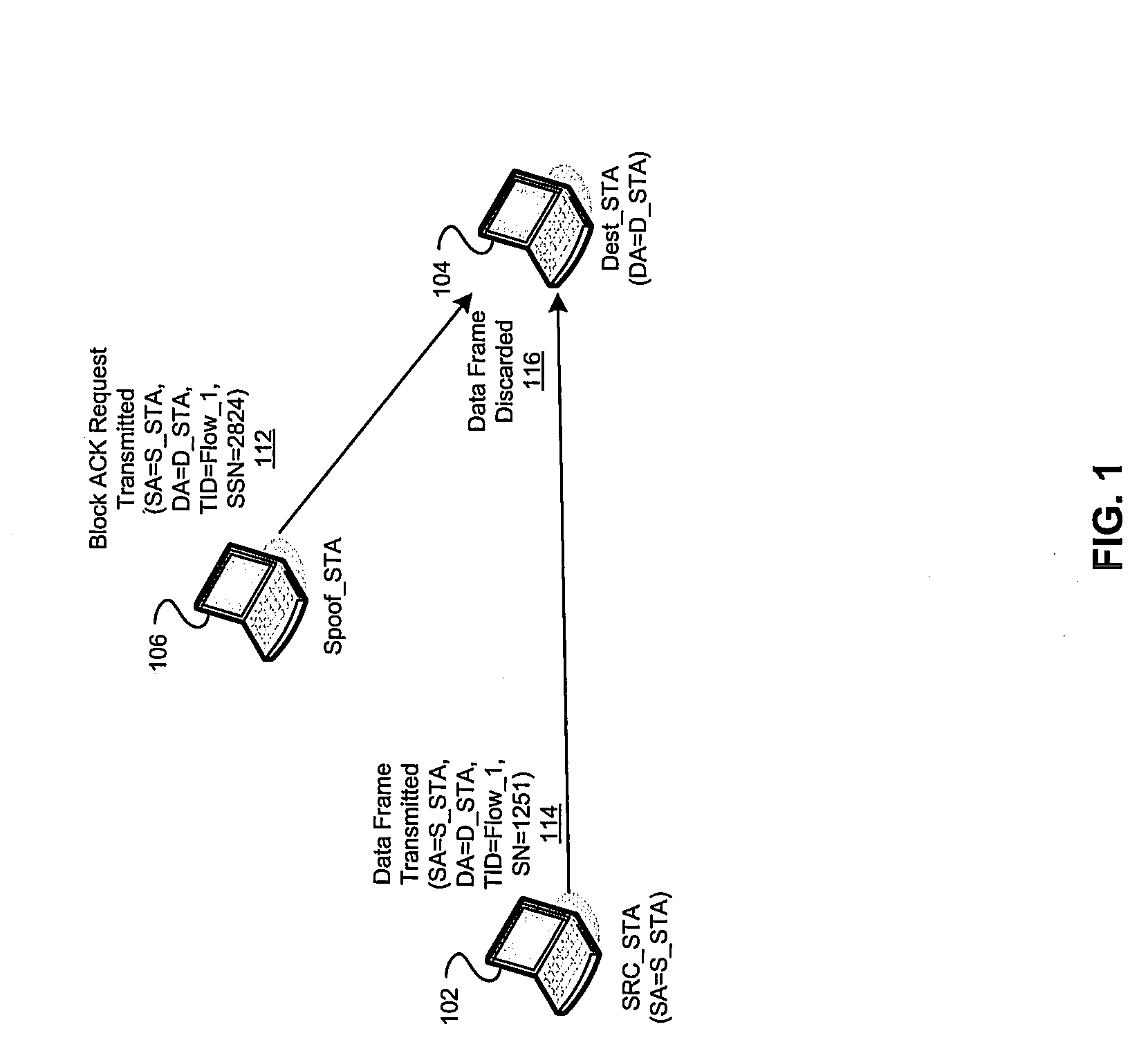
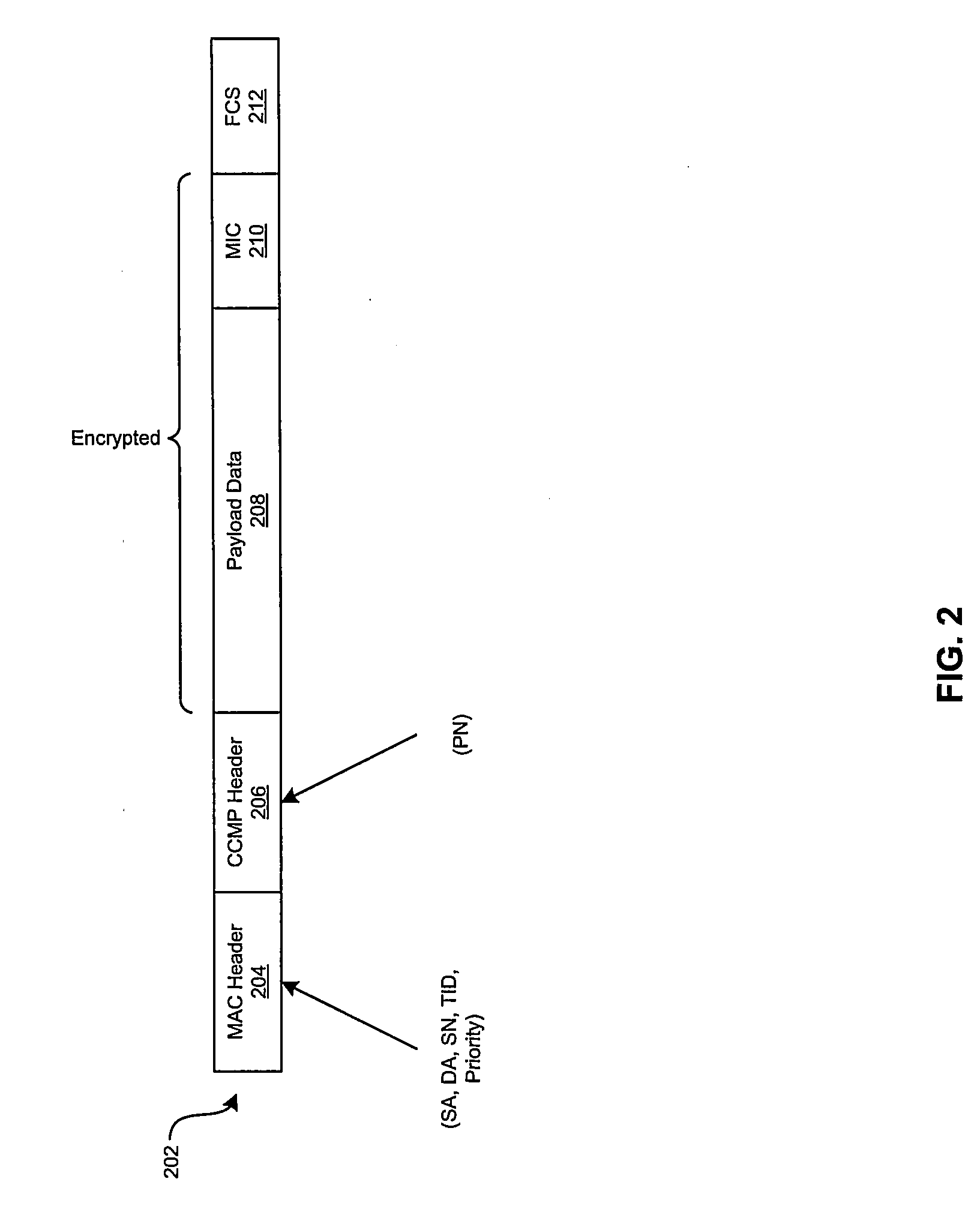
ActiveUS20090235066A1Network securityNetwork topologiesSecurity arrangementComputer hardwareProtocol data unit
Aspects of a method and system for protected MAC sequence numbers, as well as secure block acknowledgment (block ACK) with protected MAC sequence number are presented. In one aspect of the system a communicating station (STA) may protect the sequence number (SN) field portion of transmitted protocol data units (PDUs), for example data MAC layer PDUs (MPDUs), or frames. In another aspect of the system, starting sequence number (SSN) information communicated via control frames, such as block acknowledgment request (BAR) and block acknowledgment (BA) frames, may be protected. In another aspect of the system, communicating STAs may exchange management frames to enable the protection of SN information in data MPDUs and / or the protection of SSN values in control MPDUs.
Owner:AVAGO TECH INT SALES PTE LTD
Wi-Fi router with integrated touch-screen and enhanced security features
ActiveUS8555047B2Easy to reconfigureNetwork securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsWi-FiSecurity software
A Wi-Fi router with an integrated configuration touch-screen, and method to use this integrated touch screen to provide enhanced security features. The Wi-Fi router, which has a wired or optical network interface, may be factory pre-configured with hard to anticipate passwords and encryption codes, thus making even its default Wi-Fi settings difficult to attack. Besides displaying interactive menus on the touch-screen, the router may also generate touch sensitive dynamic alphanumeric virtual keypads to enable administrators to interact with the device without the need of extra computers or software. Inexperienced administrators secure in the knowledge that they may access and change even difficult to remember security settings at any time through the built-in touch-screen controller and simplified user interface, are encouraged to set up secure Wi-Fi systems. The device may optionally include security software that, upon touch of a button, can provide new randomized or otherwise obfuscated router settings.
Owner:SECURIFI INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com