Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Minimal user interaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
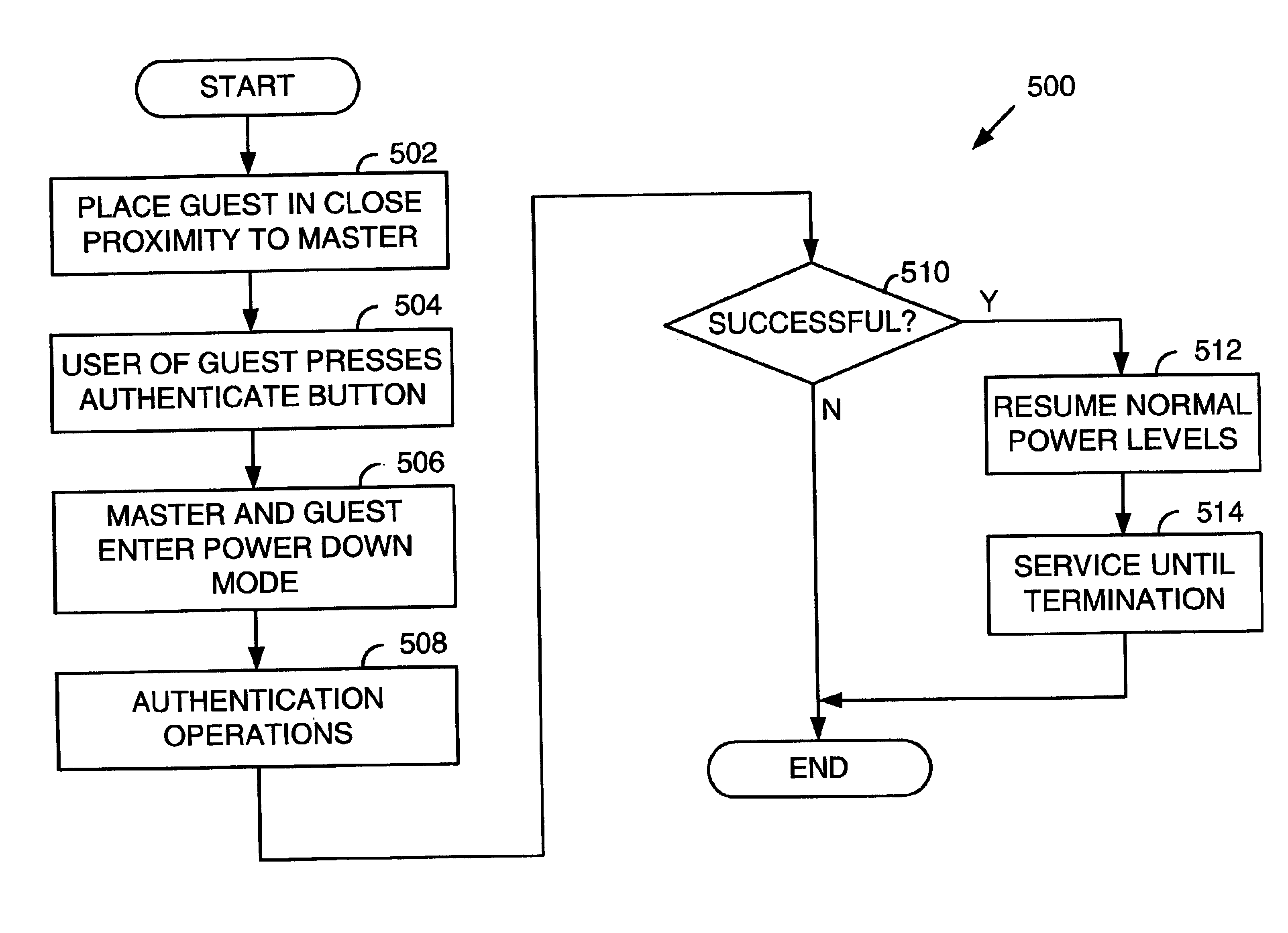
Wireless device authentication at mutual reduced transmit power
InactiveUS6928295B2Avoid difficult choicesReduce transmit powerEnergy efficient ICTPower managementTraffic capacityPower mode
A system and method for facilitating the authentication of wireless devices in an environment with multiple wireless networks. A user wishing to join an operating wireless network can bring his wireless device within close physical proximity, for example, less than one meter, of a device in the network that he wishes to join. The user then presses an authenticate button, which causes both devices to enter a low transmission power mode. In such case, the devices are only capable of operation within the close proximity. Being in low power mode will diminish the possibility of eavesdropping on the authentication process. Power down mode also reduces the amount of message traffic in the area and saves scarce power and processing resources at the nodes, which are now out of range. Authentication then takes place in low power mode and once completed, both devices resume normal power levels and continue communicating normally.
Owner:AVAGO TECH INT SALES PTE LTD
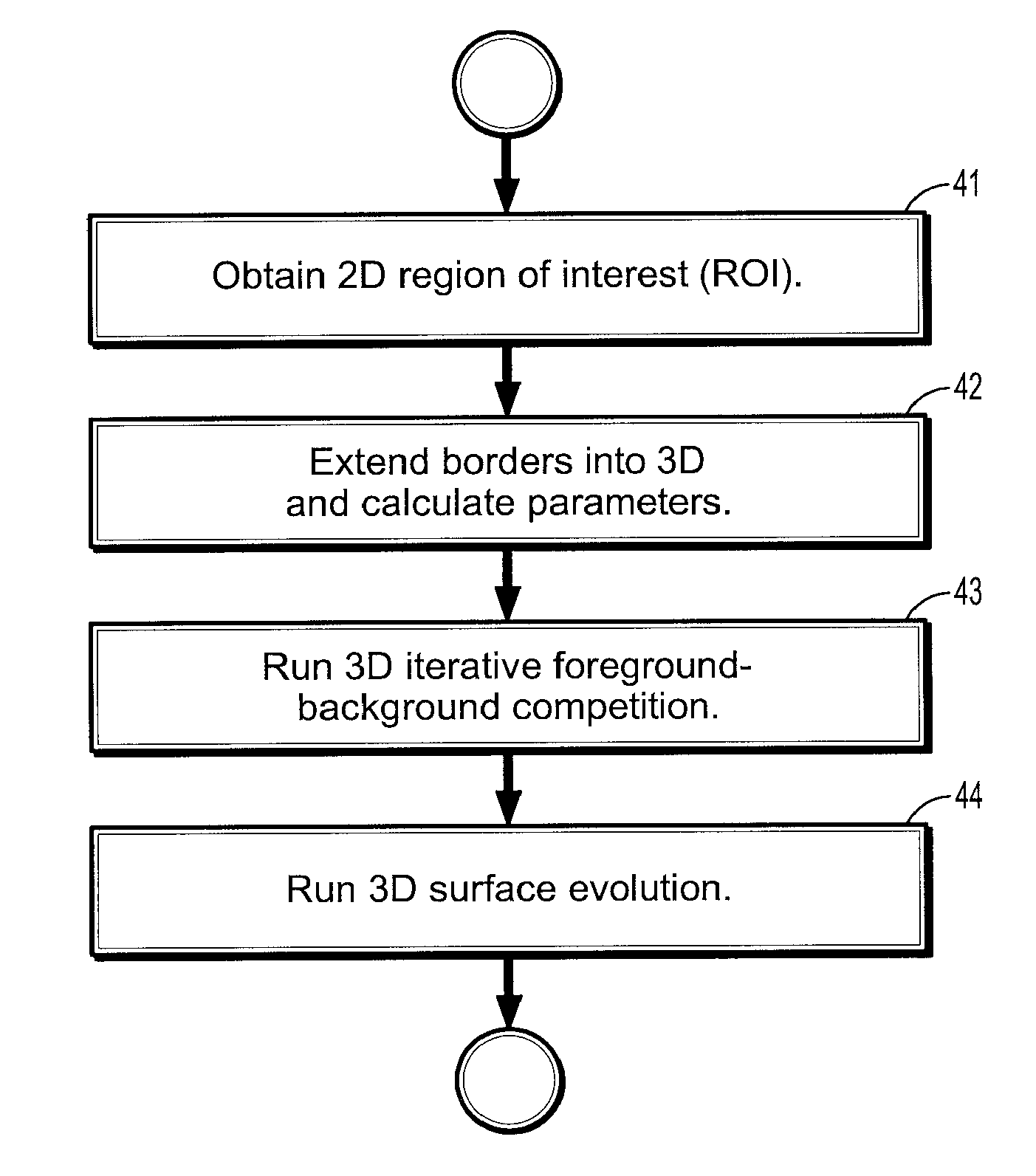
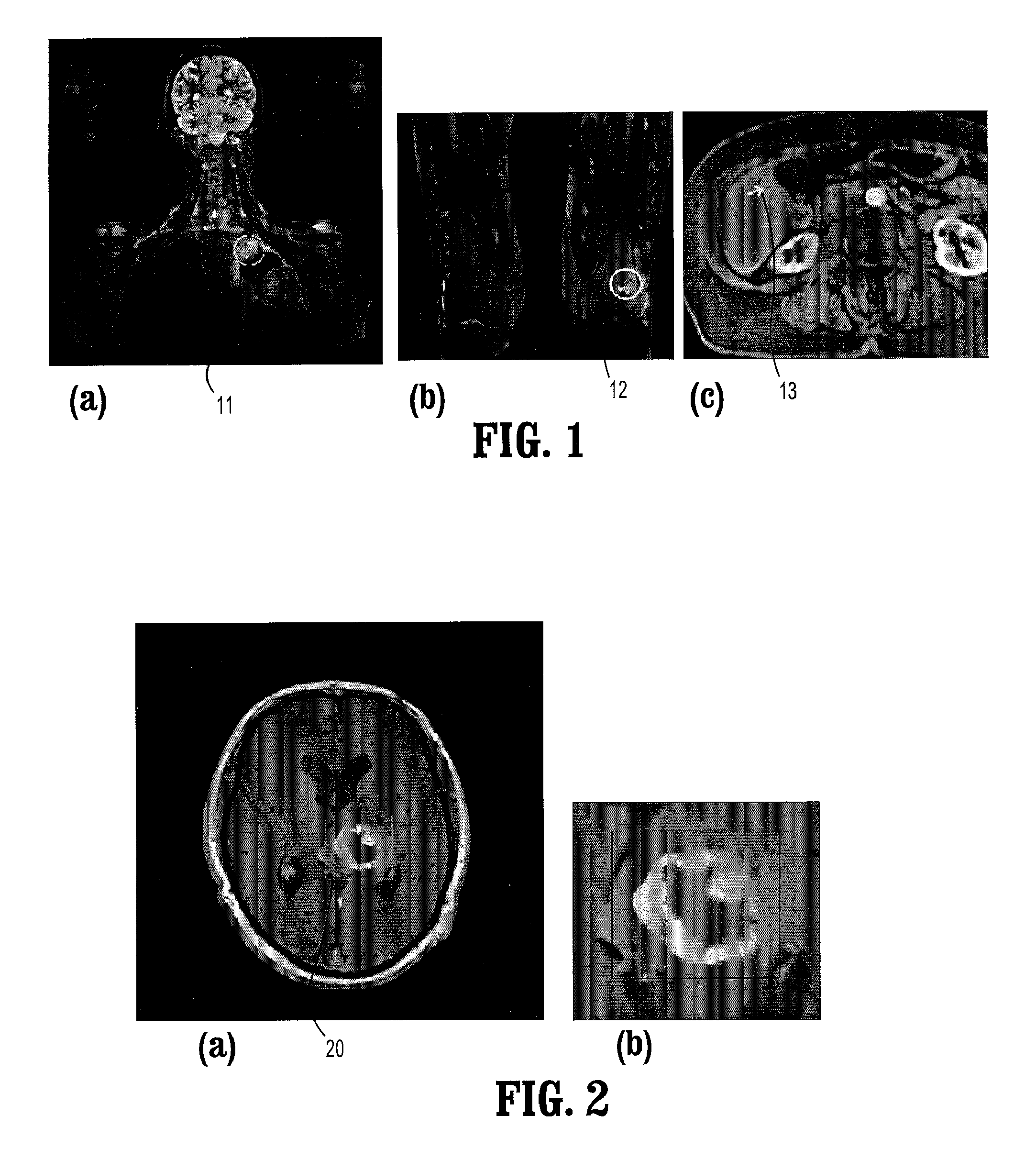
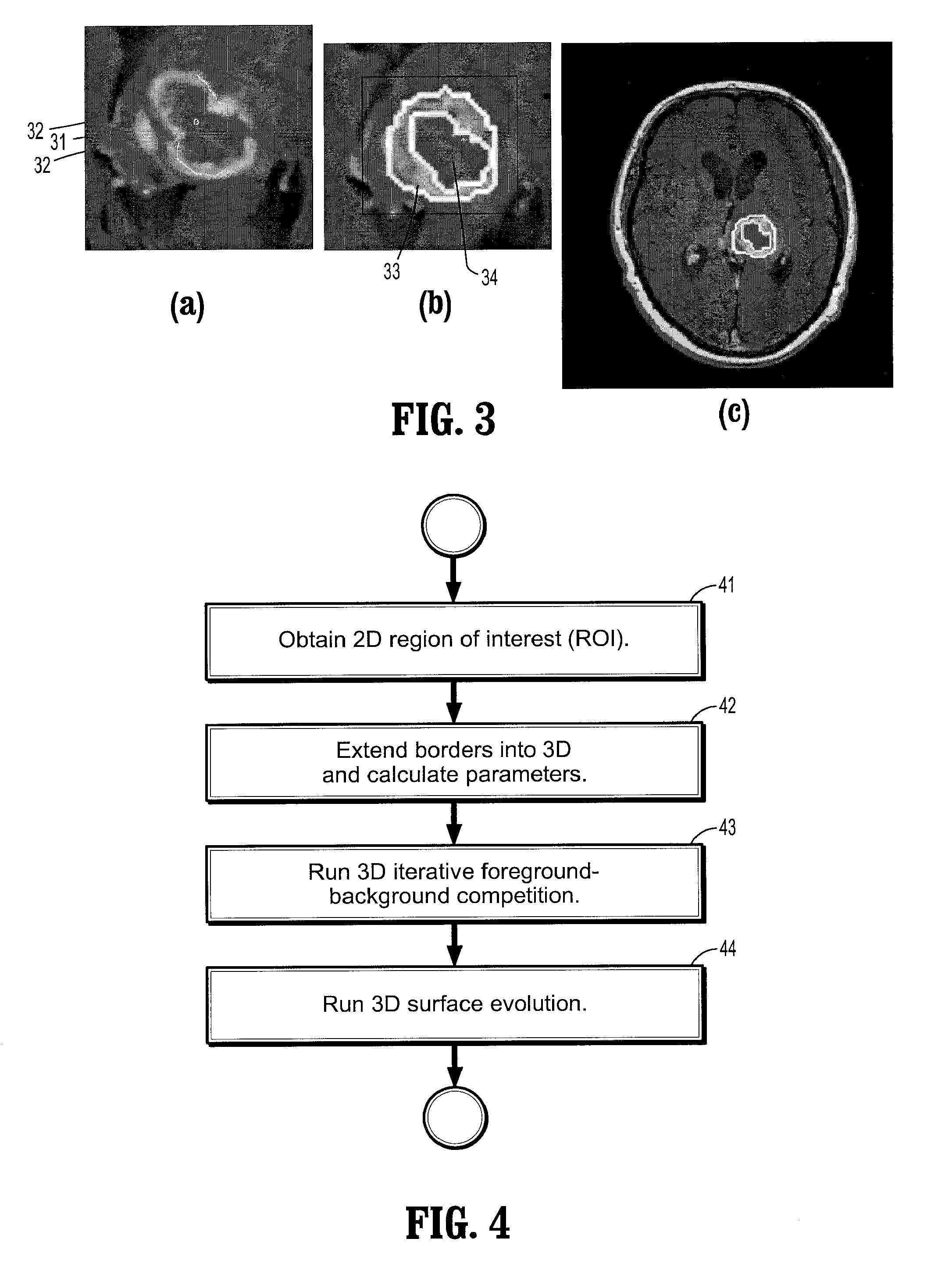
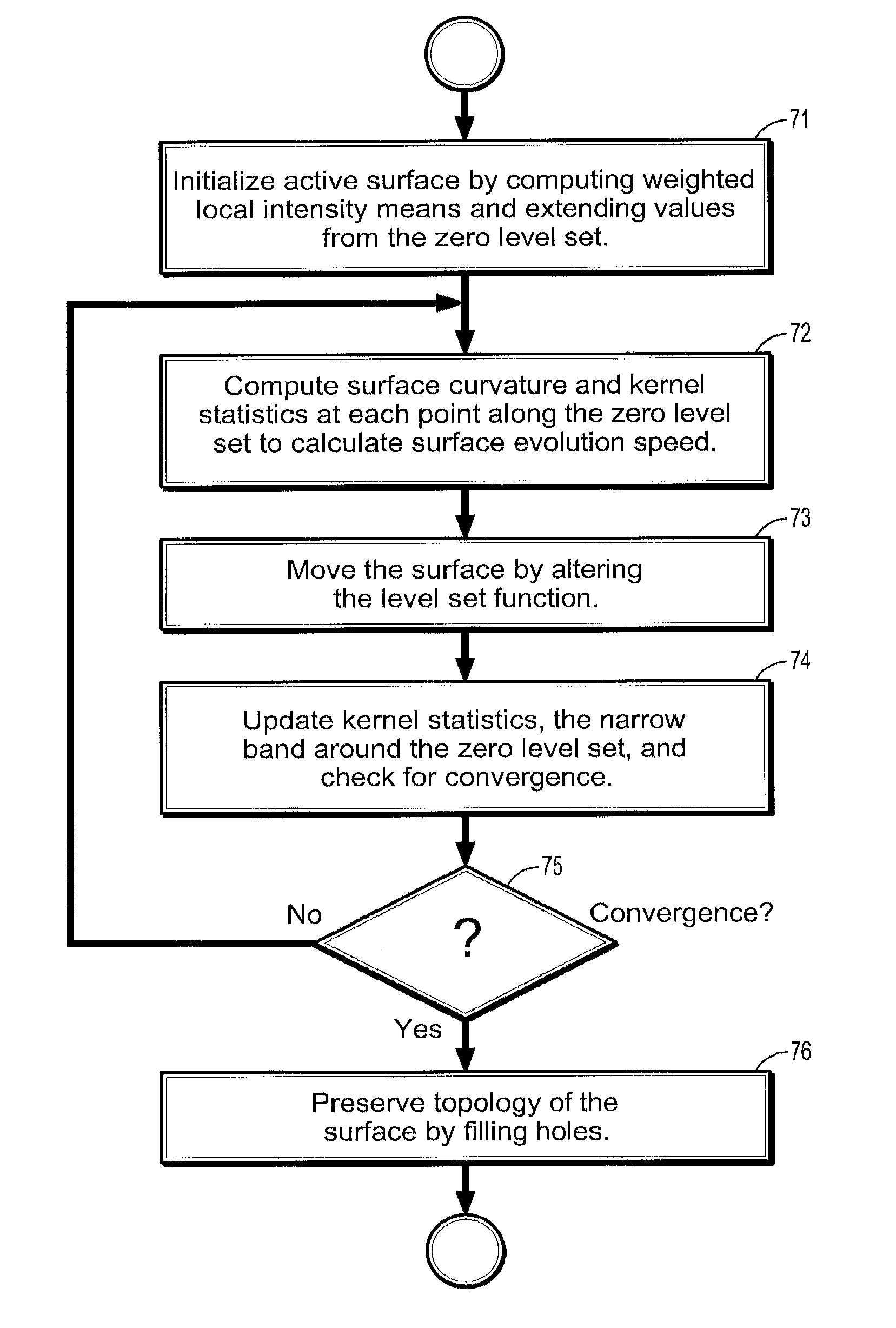
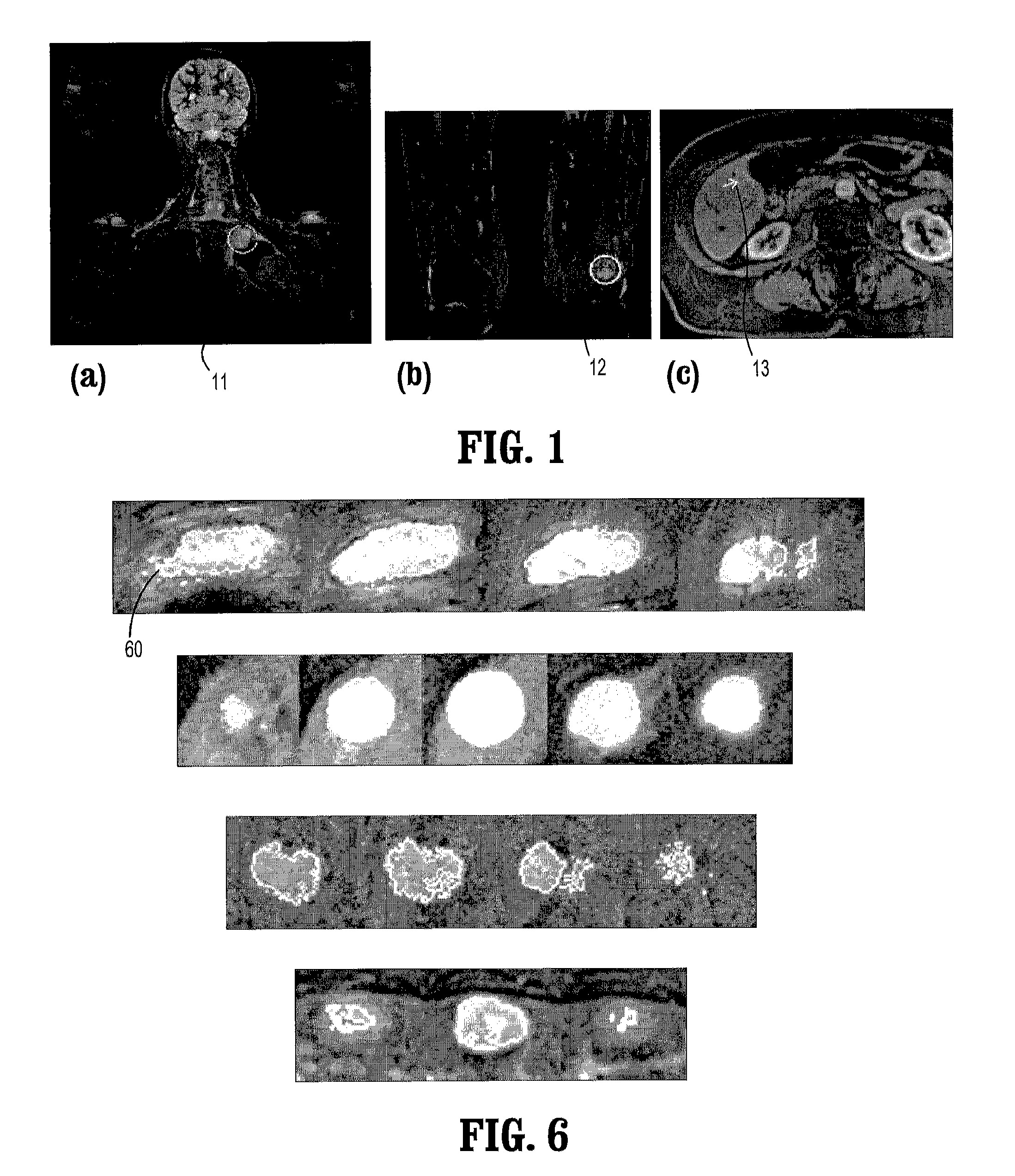
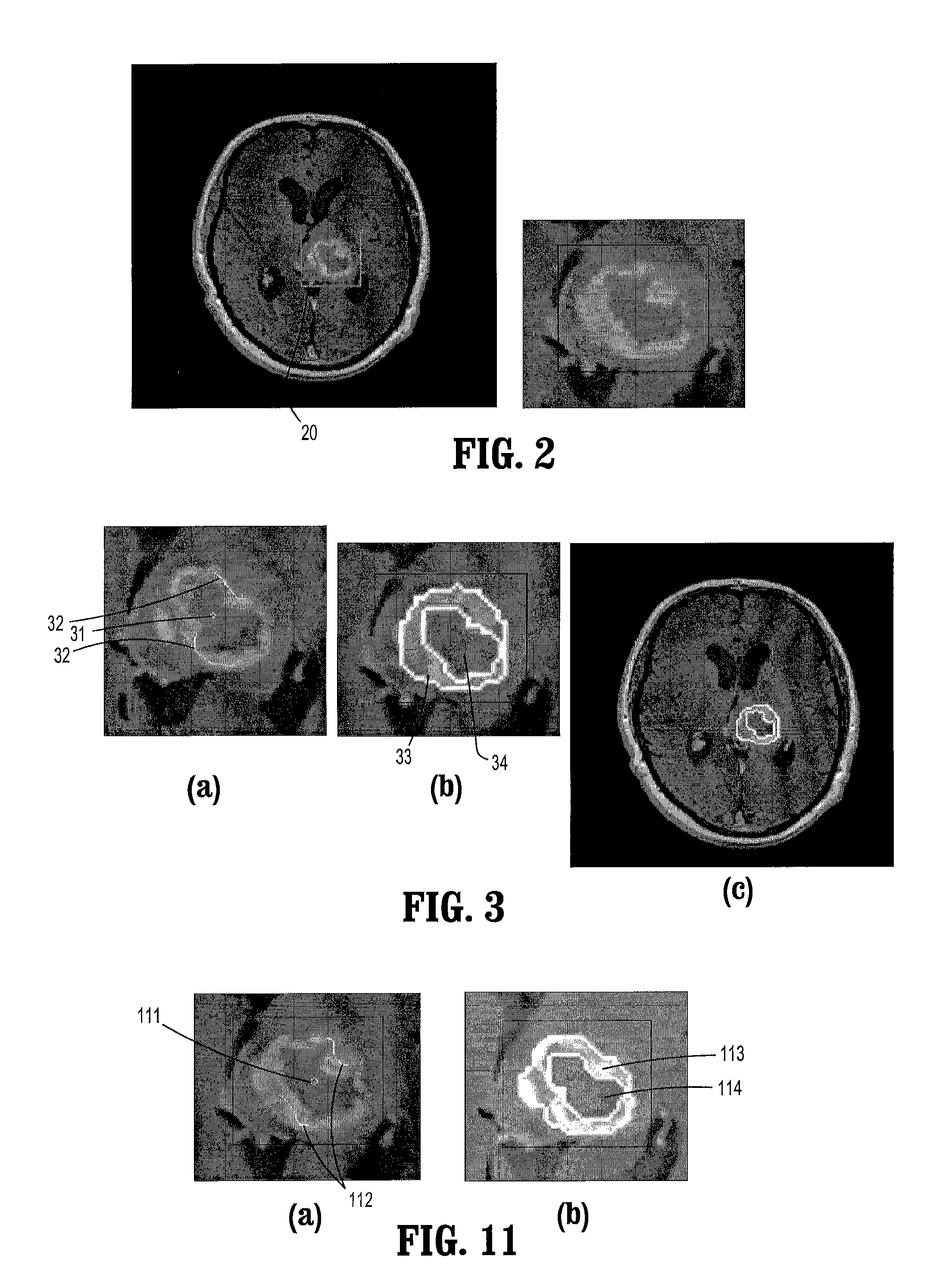
System and Method for Lesion Segmentation in Whole Body Magnetic Resonance Images
InactiveUS20080260221A1The result is accurateMinimal user interactionImage enhancementImage analysisWhole body mriVoxel
A method for lesion segmentation in 3-dimensional (3D) digital images, includes selecting a 2D region of interest (ROI) from a 3D image, the ROI containing a suspected lesion, extending borders of the ROI to 3D forming a volume of interest (VOI), where voxels on the borders of the VOI are initialized as background voxels and voxels in an interior of the VOI are initialized as foreground voxels, propagating a foreground and background voxel competition where for each voxel in the VOI, having each neighbor voxel in a neighborhood of the voxel attack the voxel, and, if the attack is successful, updating a label and strength of the voxel with that of the successful attacking voxel, and evolving a surface between the foreground and background voxels in 3D until an energy functional associated with the surface converges in value, where the surface segments the suspected lesion from the image.
Owner:SIEMENS HEALTHCARE GMBH
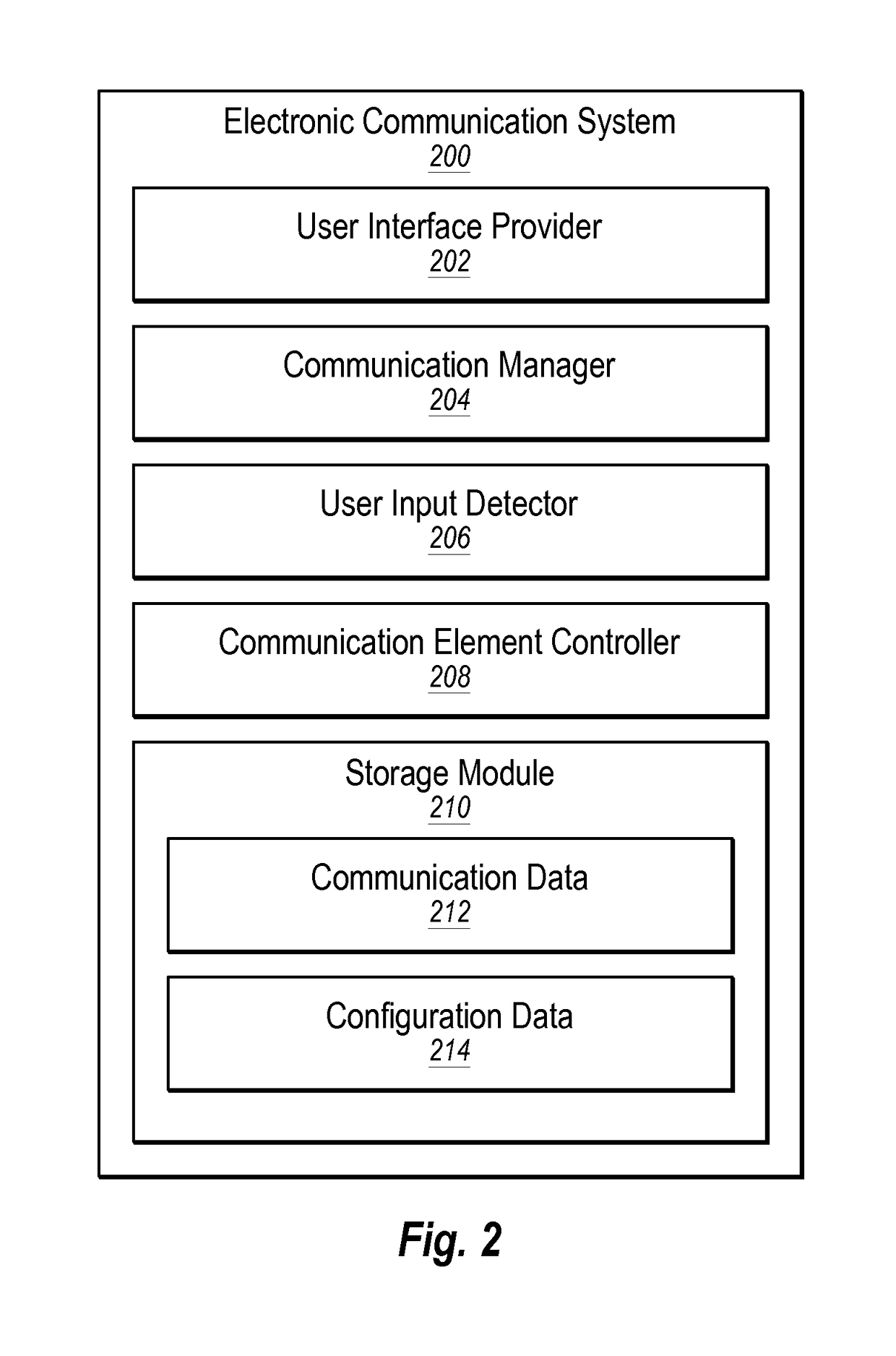
Configurable electronic communication element
ActiveUS20150268826A1Facilitate communicationEasy to configureData switching networksInput/output processes for data processingElectronic communicationAnimation
One or more embodiments of the disclosure include an electronic communication system that allows a user to select, configure, and send an electronic communication element to another user. For example, an electronic communication element can include a symbol, icon, animation, sound, and / or other elements that can be sent via an electronic communication. In particular, one or more embodiments of the electronic communication system allow a user to configure the electronic communication element to send a customized message to another user with the configured communication element.
Owner:META PLATFORMS INC
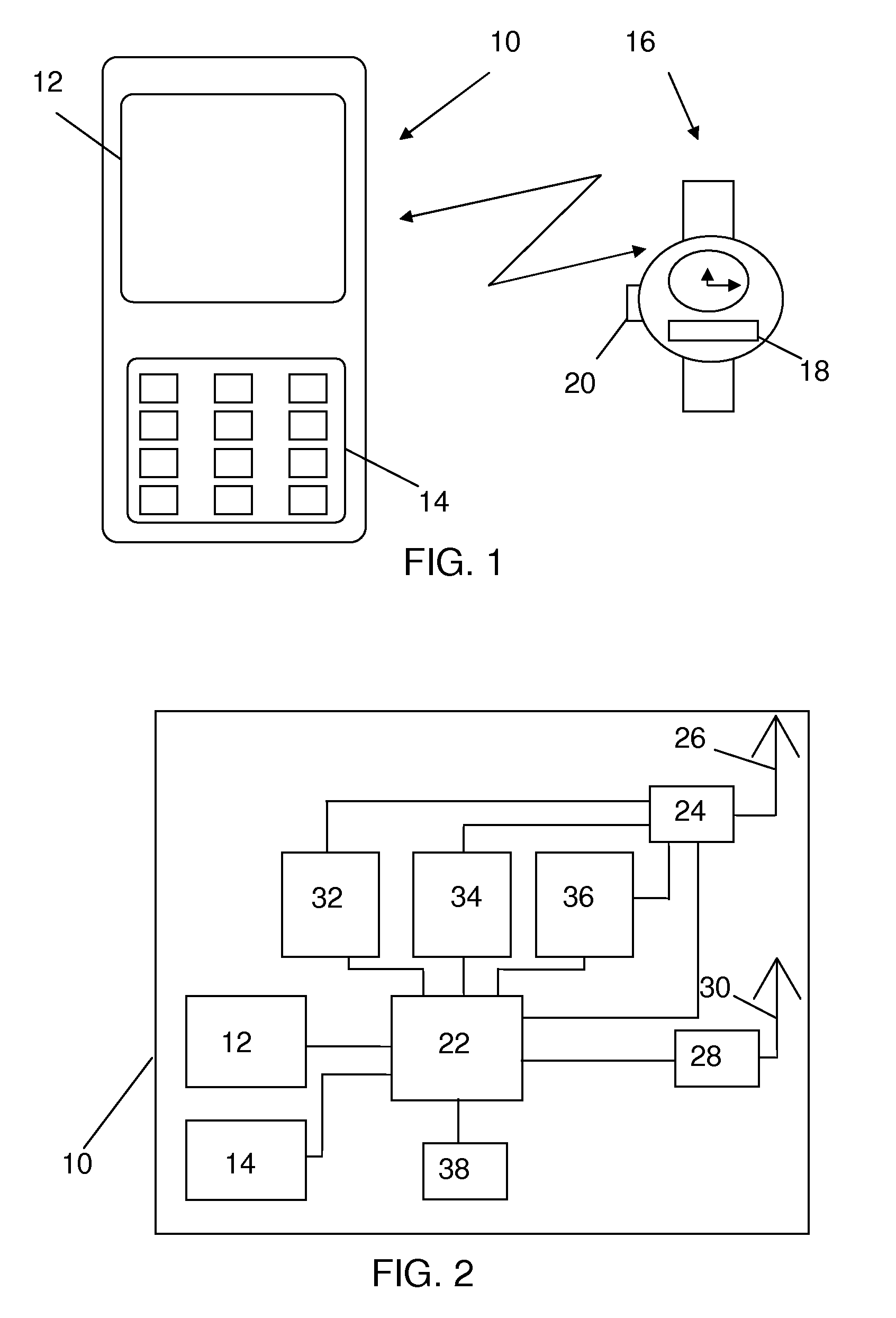
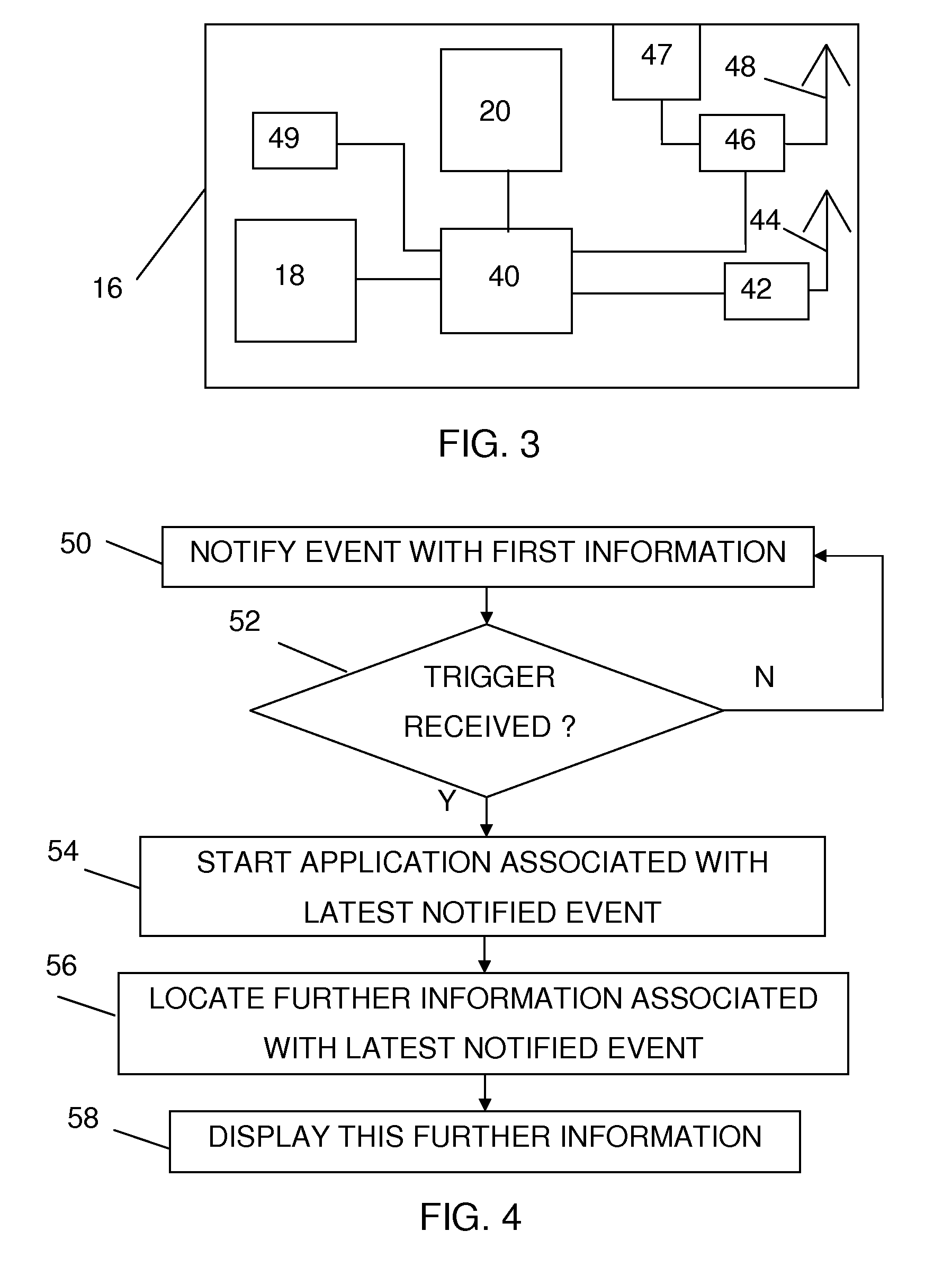
Continued transfer or streaming of a data file after loss of a local connection
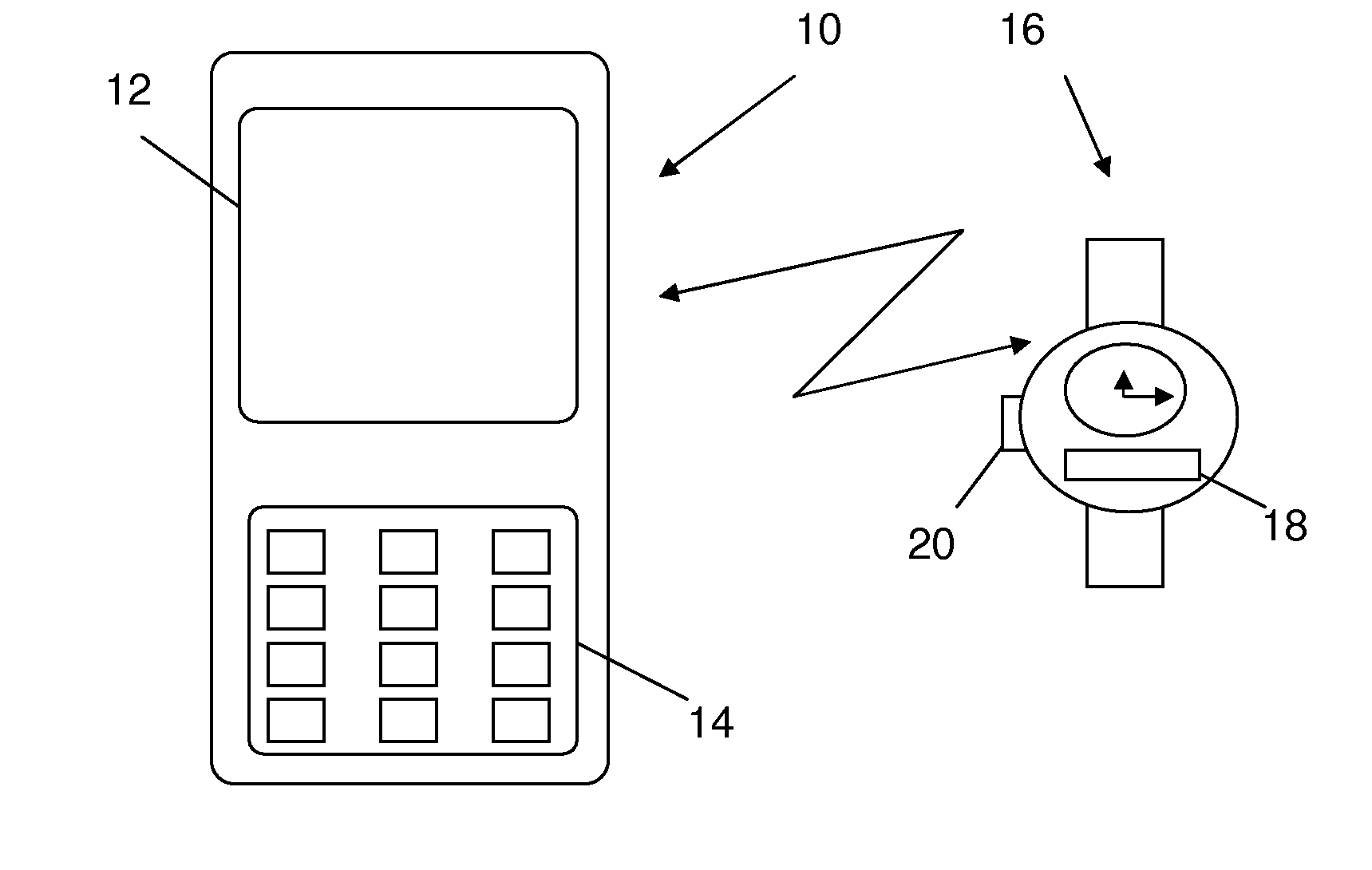
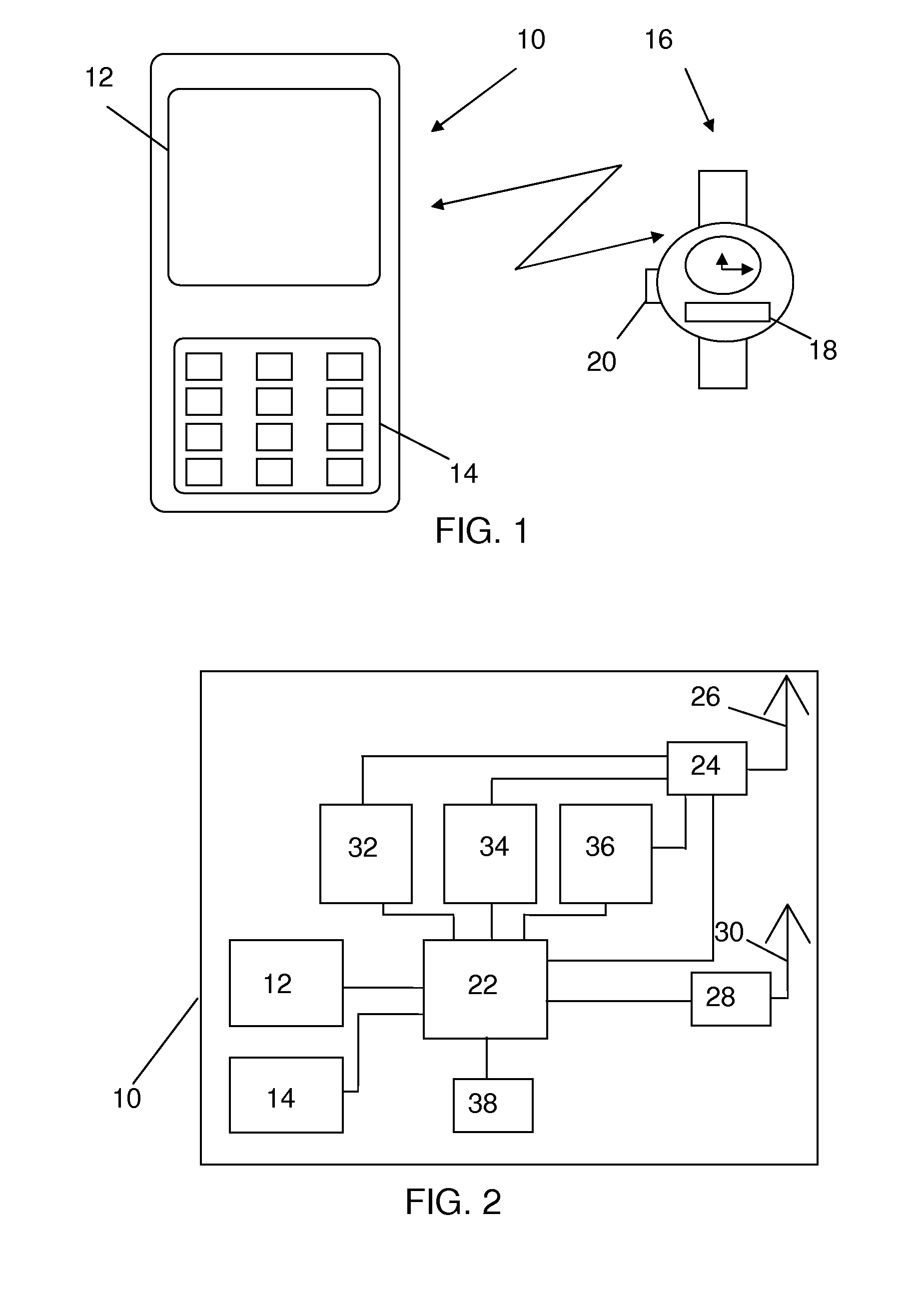
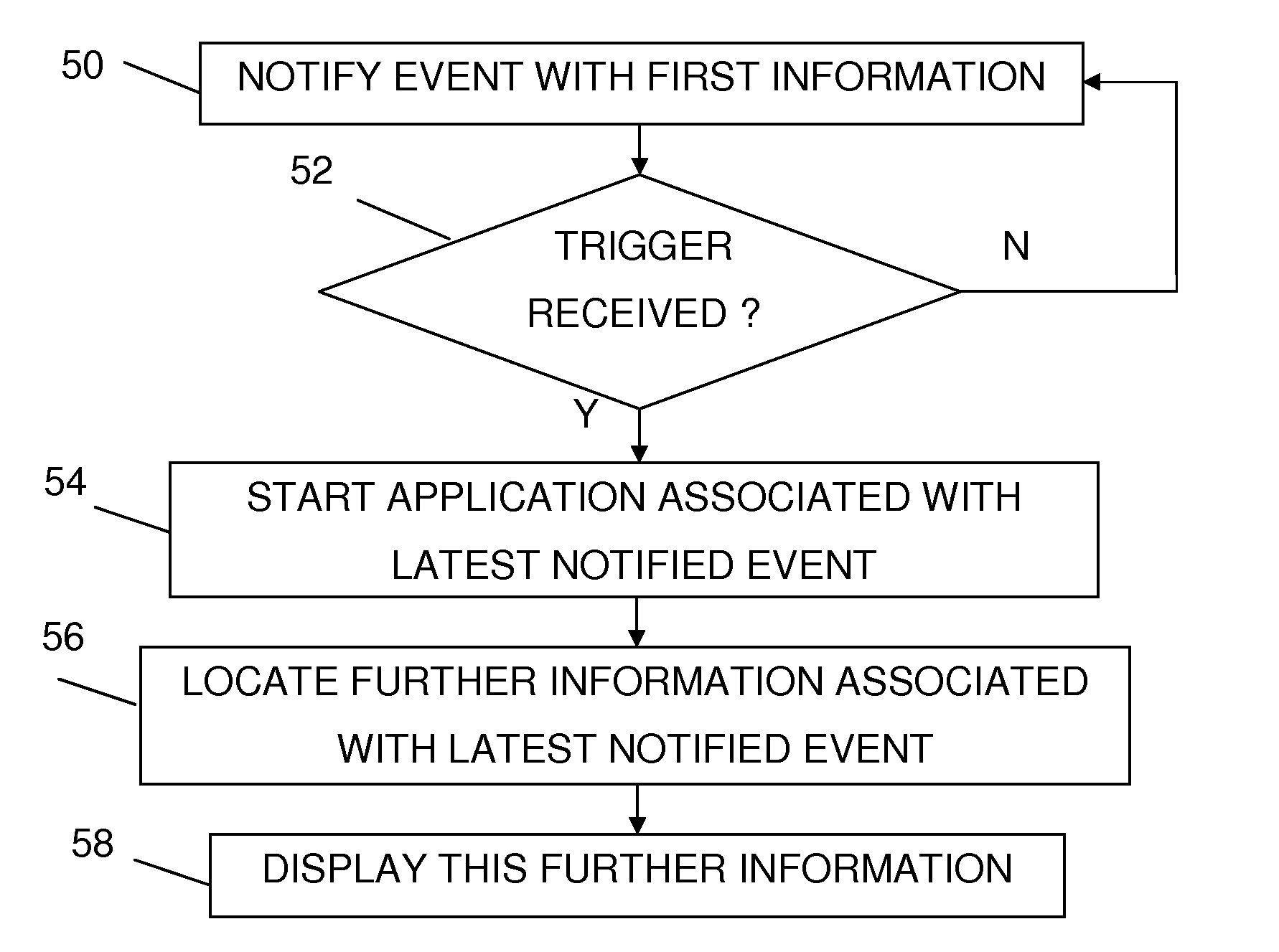
ActiveUS20080070612A1Optimize locationMinimal user interactionSubstation equipmentRadio transmissionTelecommunicationsDisplay device
A central portable communication device can display further information related to first information received in an associated local portable communication. The associated local portable communication device may receive and present the first information, and may send, in dependence of a selection made by a user, a request for displaying the further information in the central portable communication device via a local link. The central portable communication device may receive the request, automatically retrieve further information based on the request, and display the additional information on a display.
Owner:SONY CORP
Continued transfer or streaming of a data file after loss of a local connection
ActiveUS7809406B2Optimize locationMinimal user interactionFrequency-division multiplex detailsTime-division multiplexTelecommunicationsData file
A central portable communication device can display further information related to first information received in an associated local portable communication. The associated local portable communication device may receive and present the first information, and may send, in dependence of a selection made by a user, a request for displaying the further information in the central portable communication device via a local link. The central portable communication device may receive the request, automatically retrieve further information based on the request, and display the additional information on a display.
Owner:SONY CORP
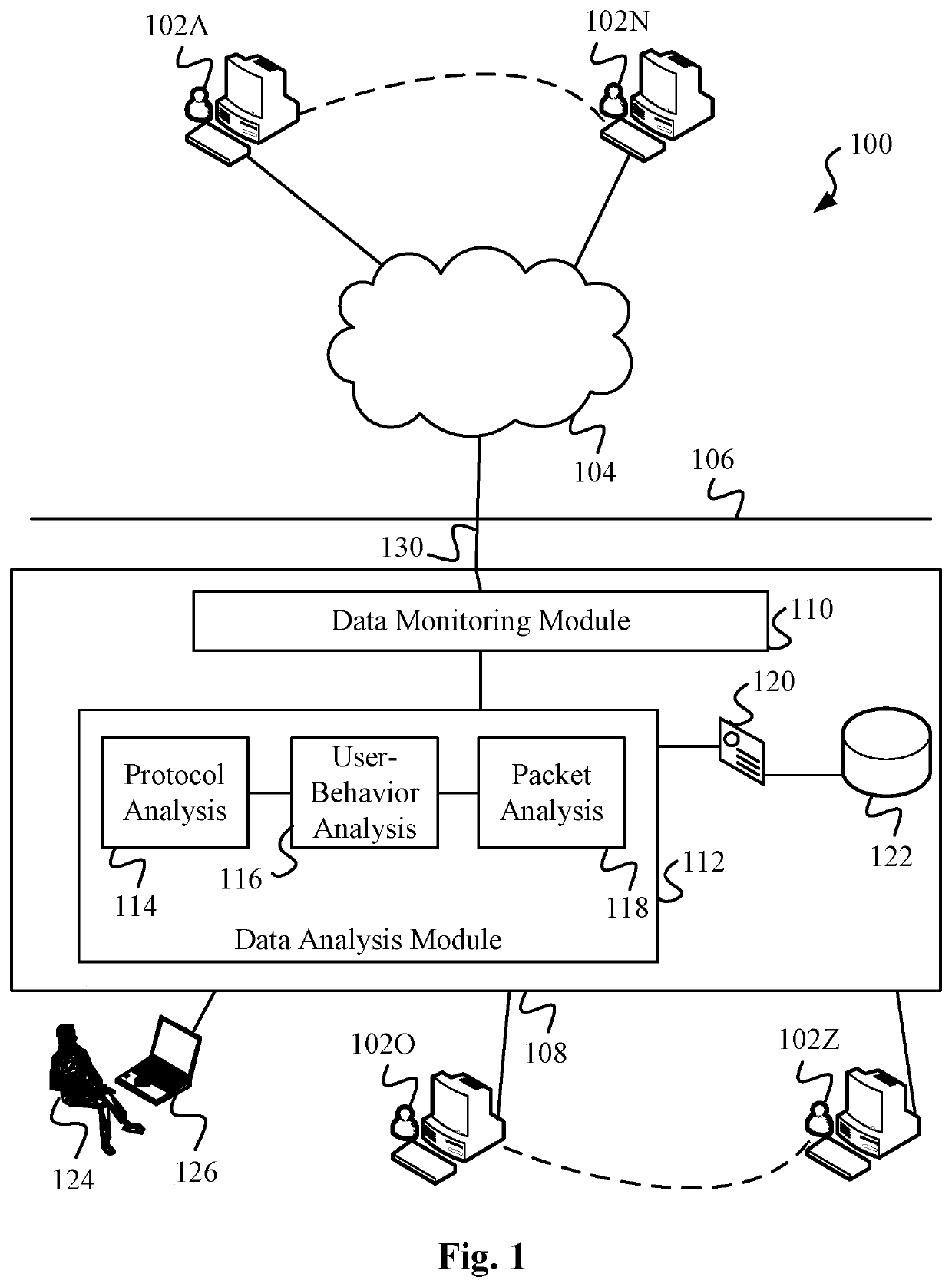
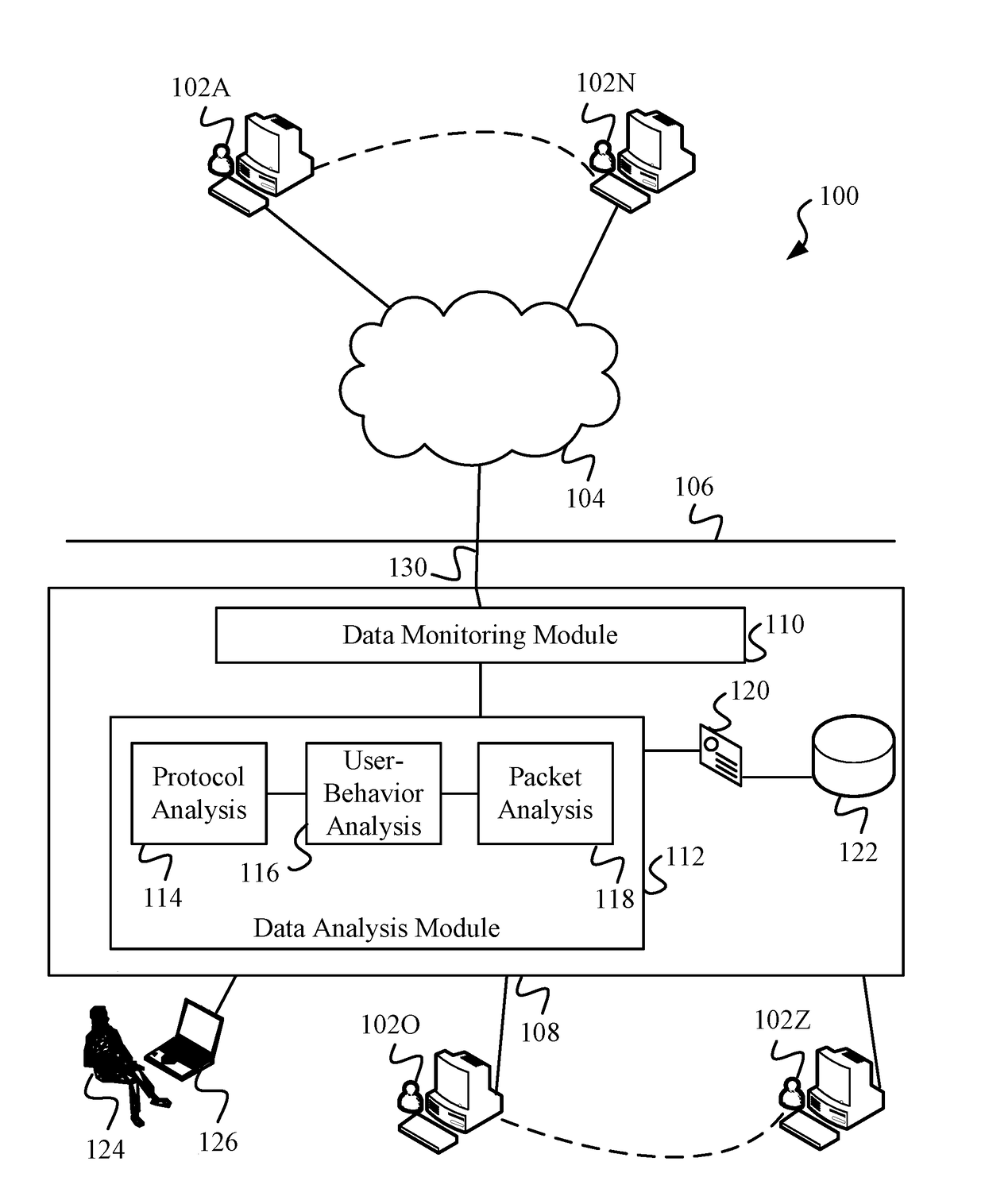
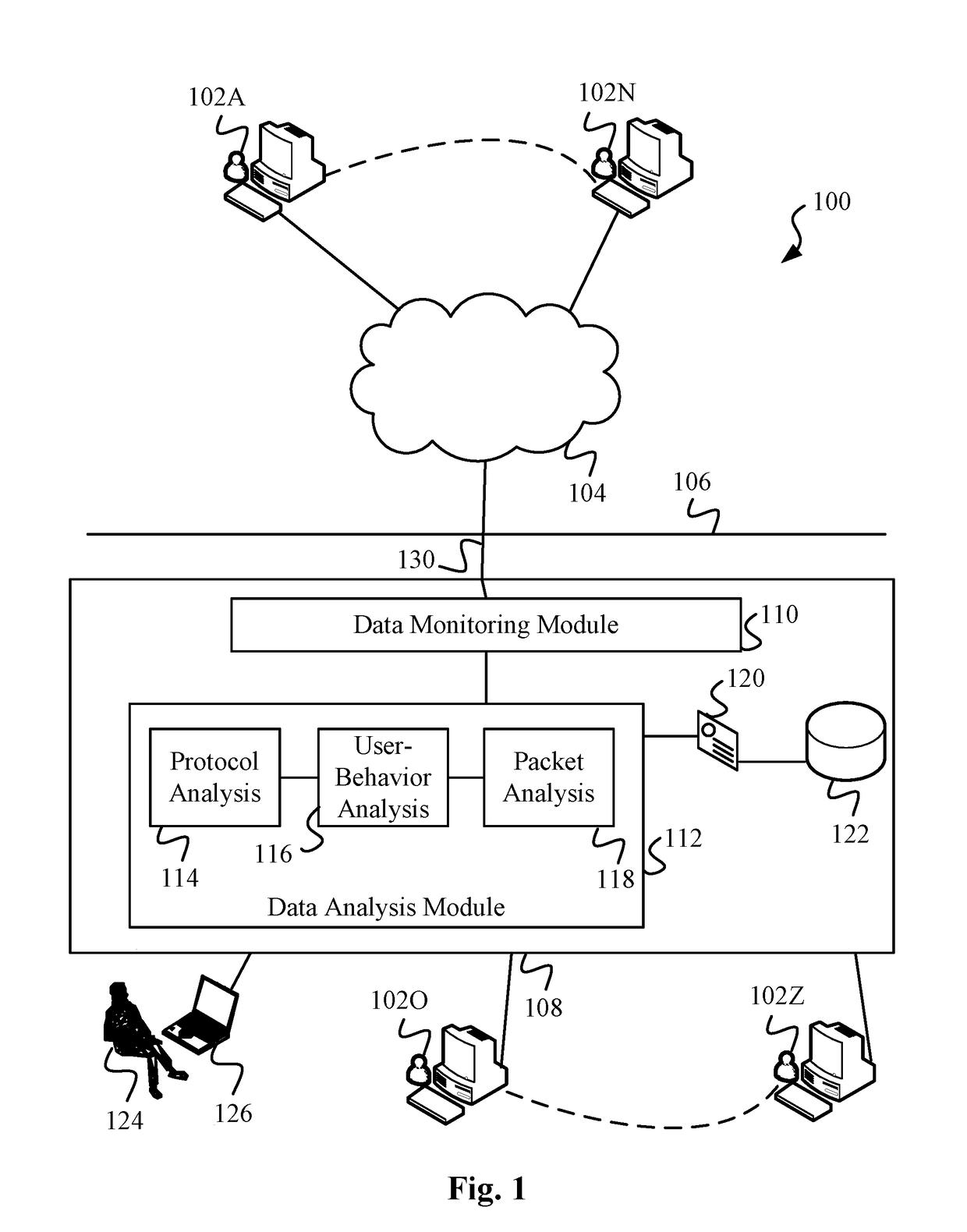
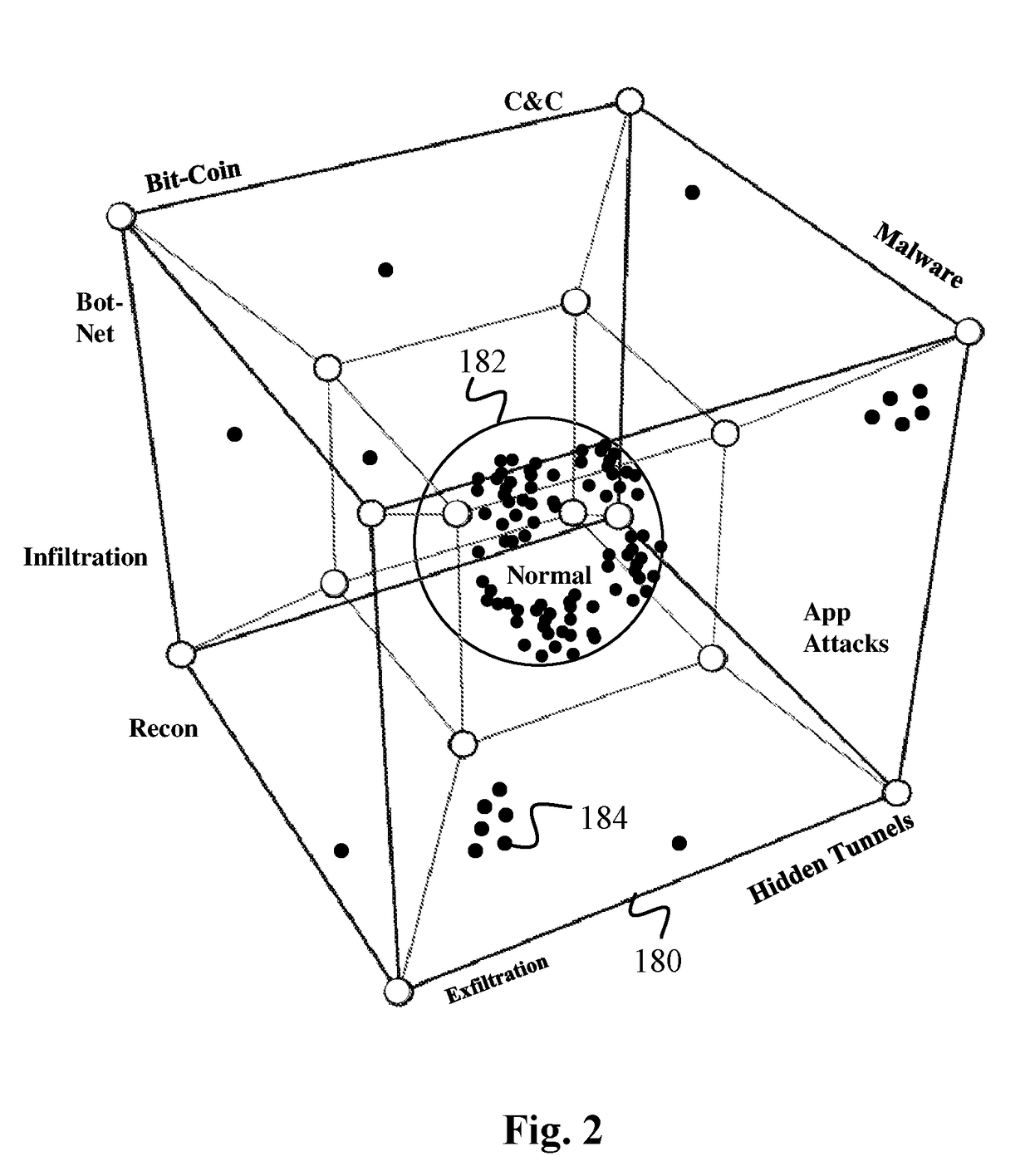
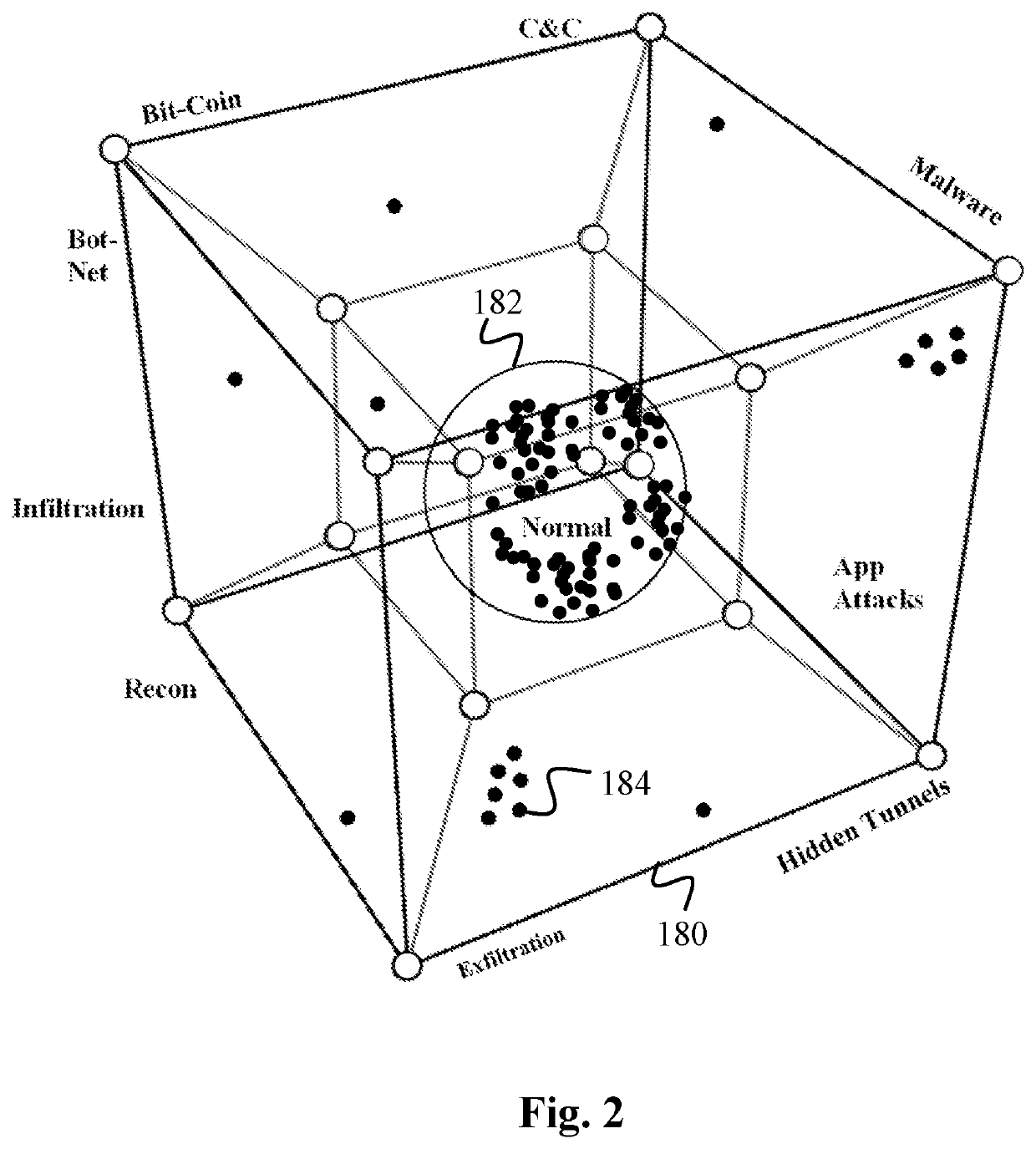
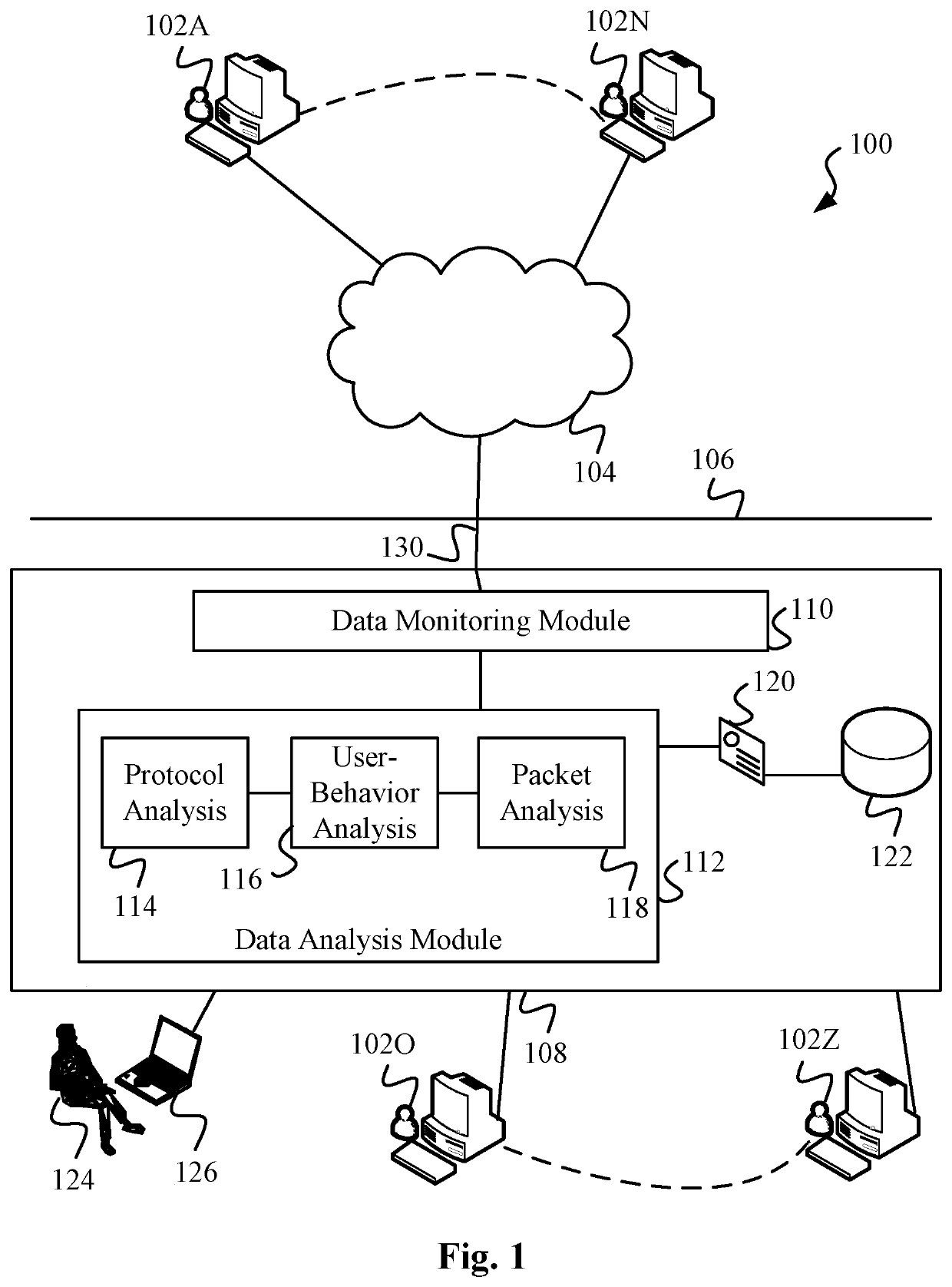
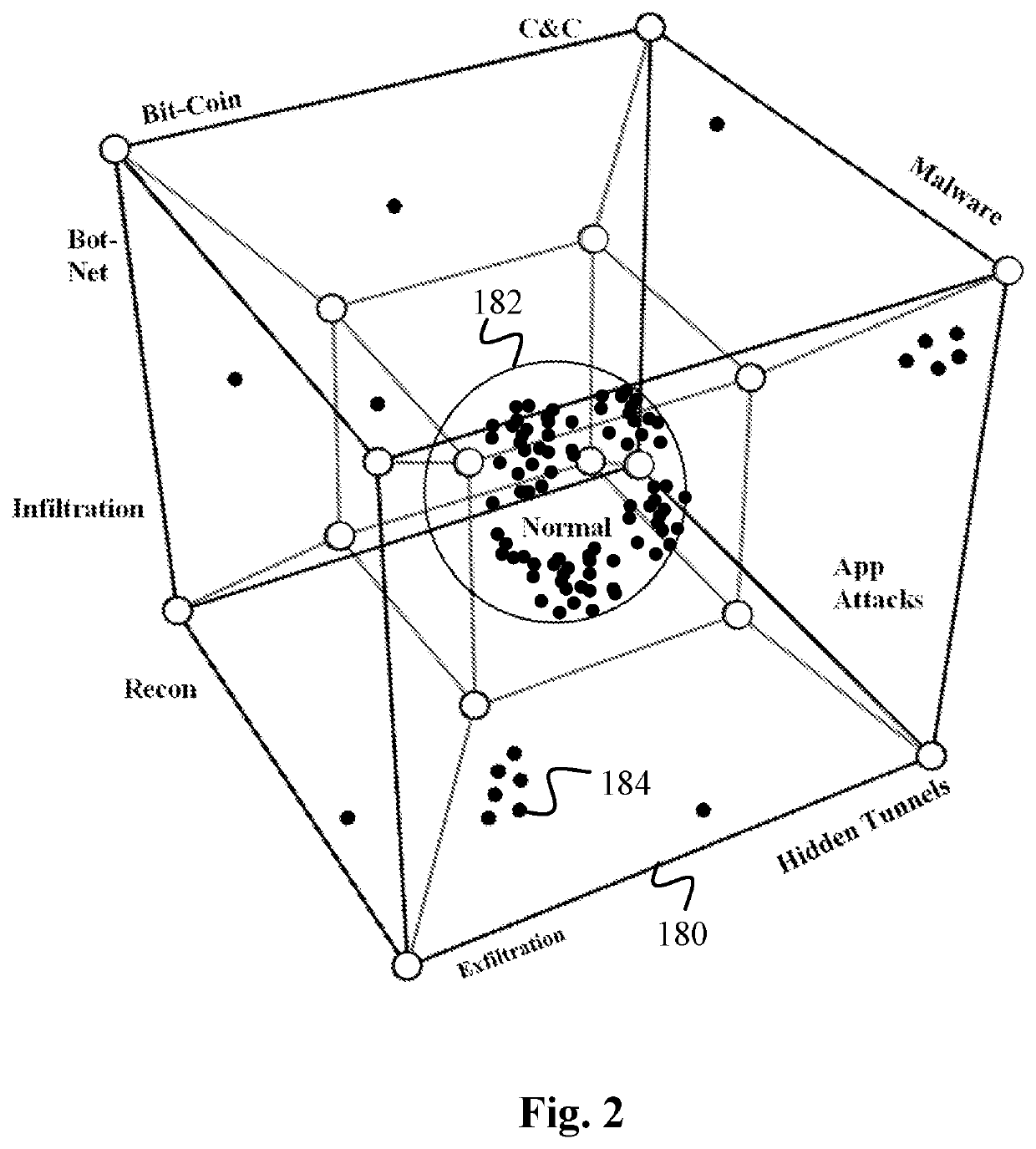
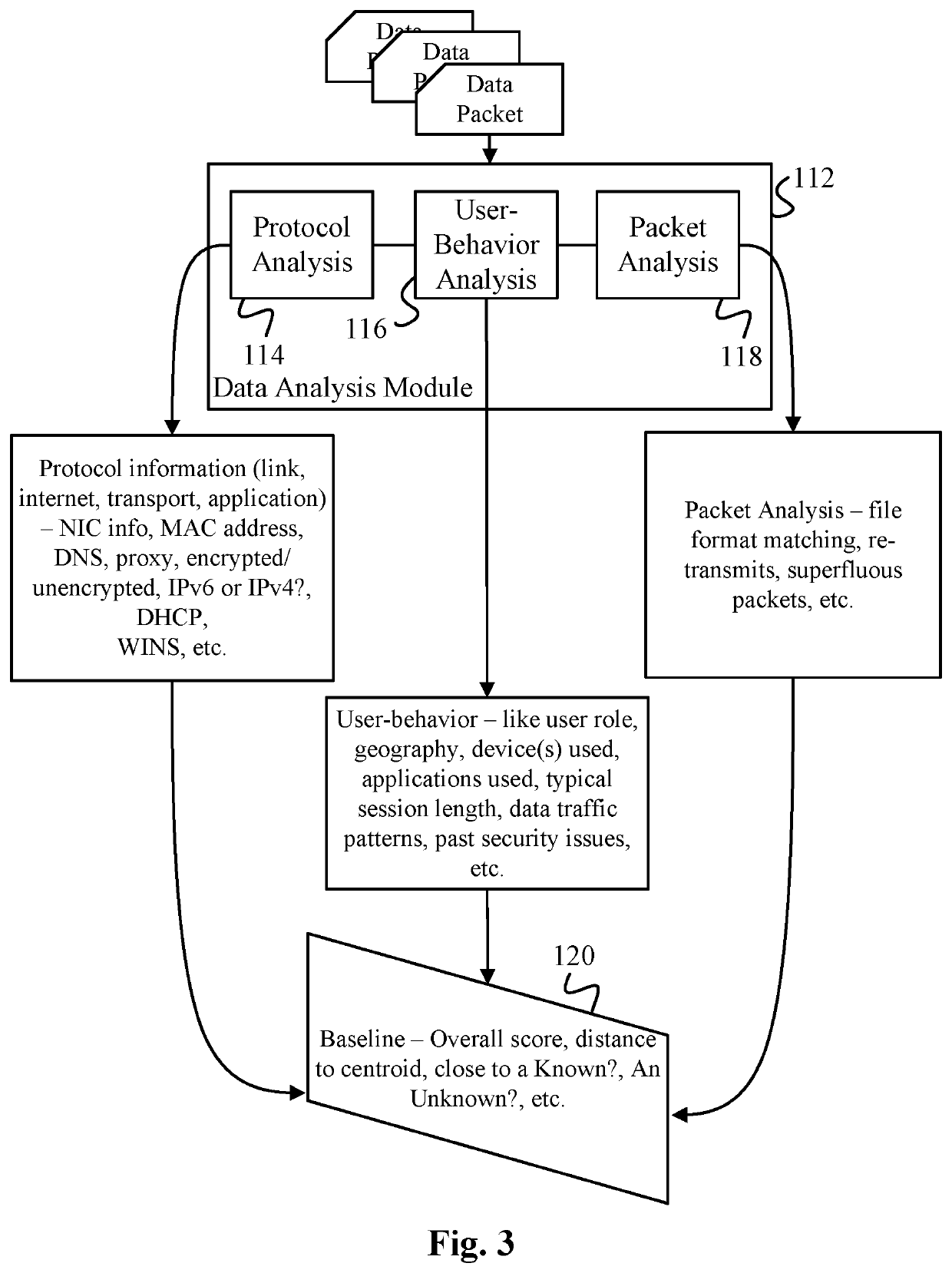
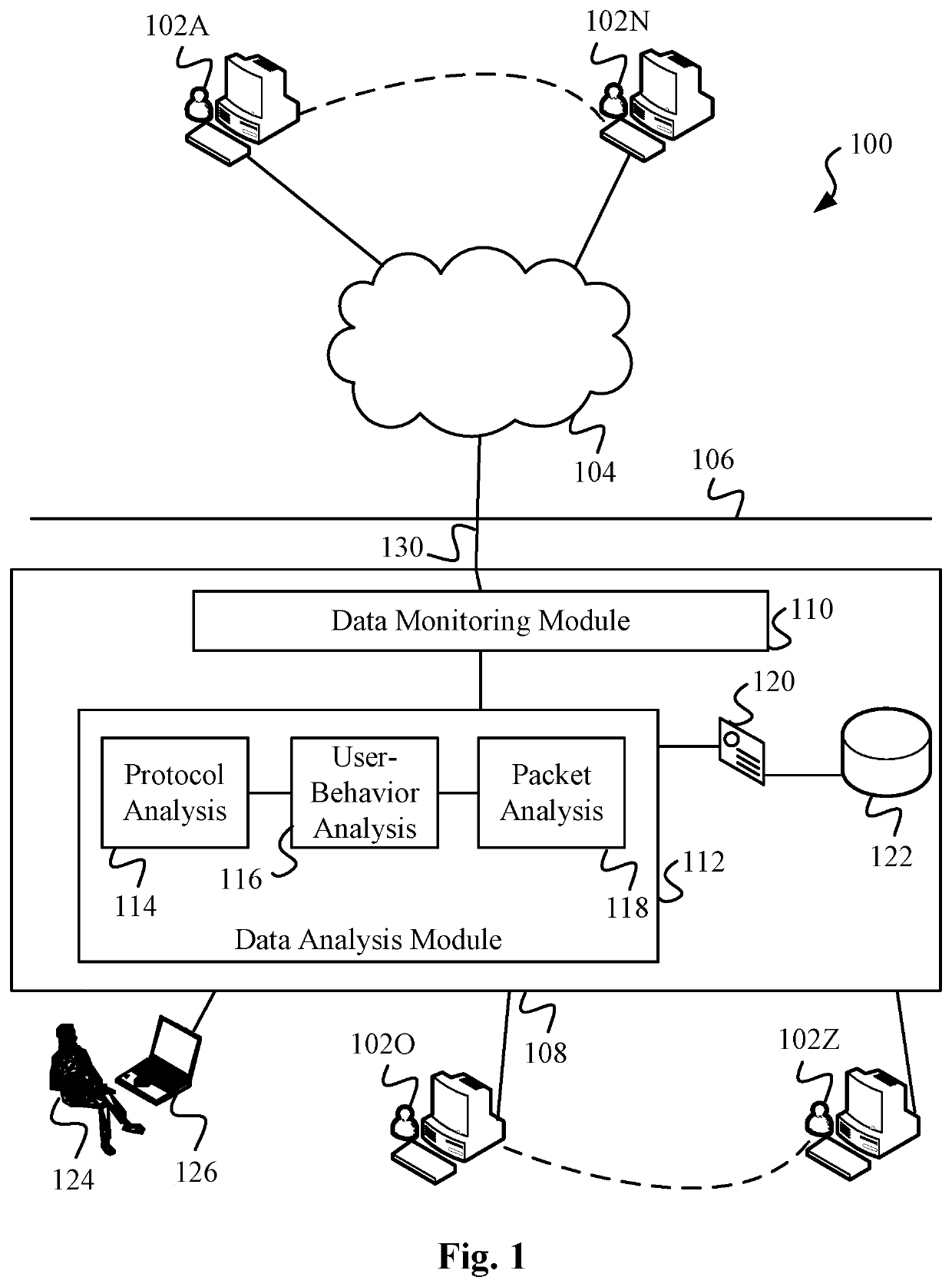
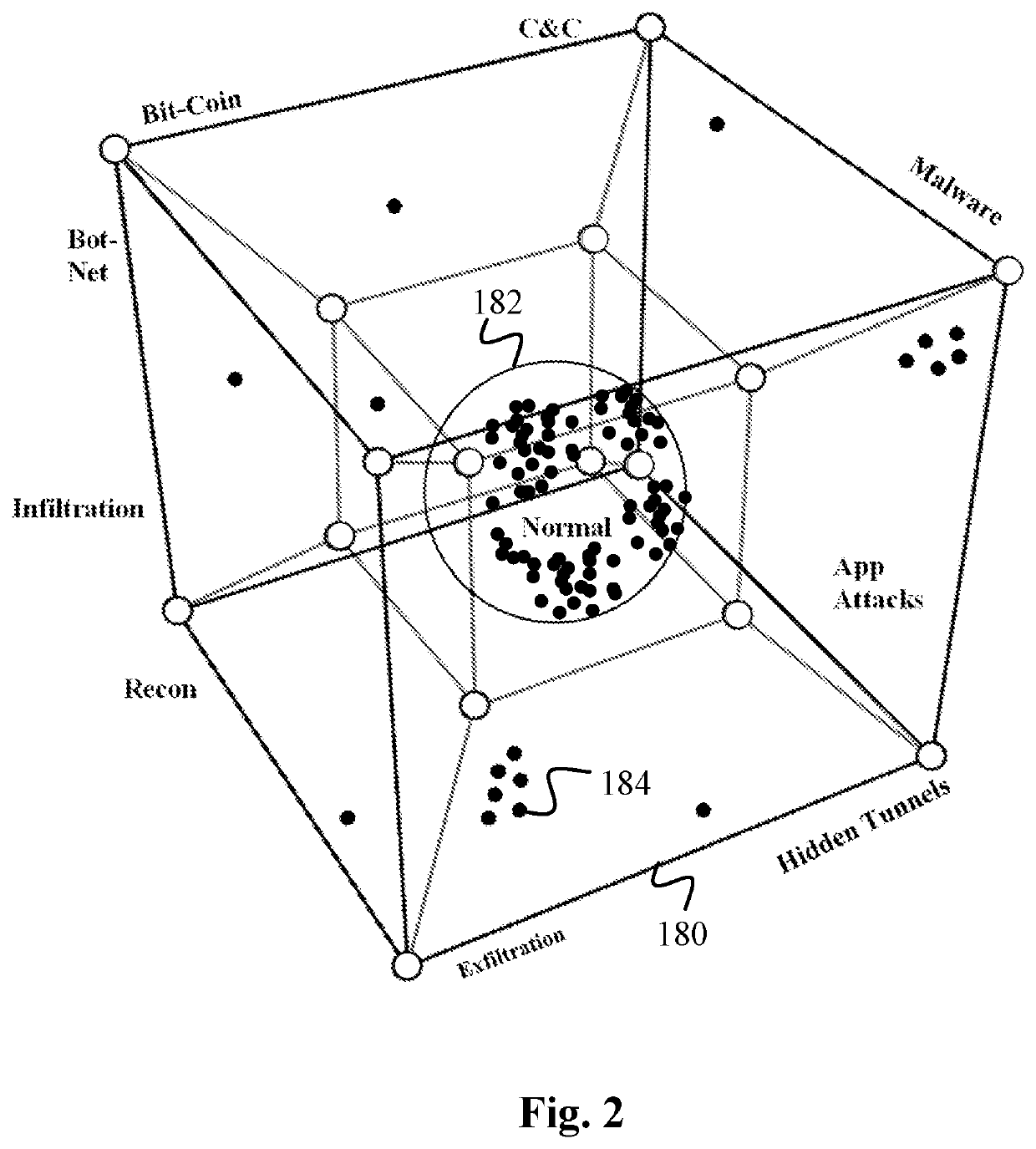
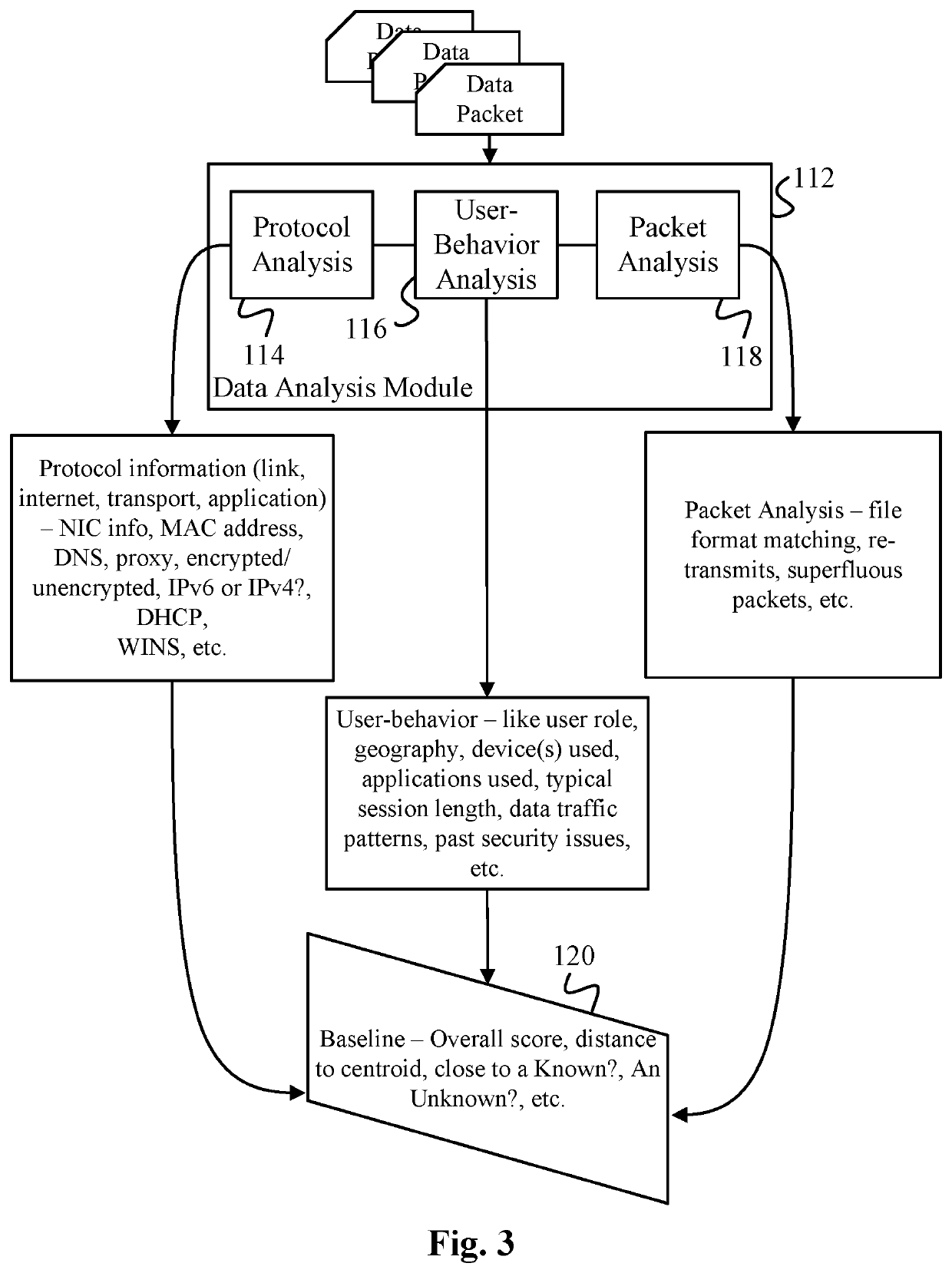
Data Surveillance for Privileged Assets based on Threat Streams
ActiveUS20200204574A1Quick fixMinimal user interactionEncryption apparatus with shift registers/memoriesCharacter and pattern recognitionStreaming dataData pack
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization. Such detection may be performed based on analyzing threat stream data from threat intelligence providers.
Owner:FLYING CLOUD TECH INC
System and method for lesion segmentation in whole body magnetic resonance images
InactiveUS8155405B2The result is accurateMinimal user interactionImage enhancementImage analysisWhole body mriVoxel
A method for lesion segmentation in 3-dimensional (3D) digital images, includes selecting a 2D region of interest (ROI) from a 3D image, the ROI containing a suspected lesion, extending borders of the ROI to 3D forming a volume of interest (VOI), where voxels on the borders of the VOI are initialized as background voxels and voxels in an interior of the VOI are initialized as foreground voxels, propagating a foreground and background voxel competition where for each voxel in the VOI, having each neighbor voxel in a neighborhood of the voxel attack the voxel, and, if the attack is successful, updating a label and strength of the voxel with that of the successful attacking voxel, and evolving a surface between the foreground and background voxels in 3D until an energy functional associated with the surface converges in value, where the surface segments the suspected lesion from the image.
Owner:SIEMENS HEALTHCARE GMBH
Wireless device authentication at mutual reduced transmit power
InactiveUS20050265552A1Minimal user interactionEase in selection of networkPower managementEnergy efficient ICTPower modeTransmitted power
Owner:AVAGO TECH INT SALES PTE LTD
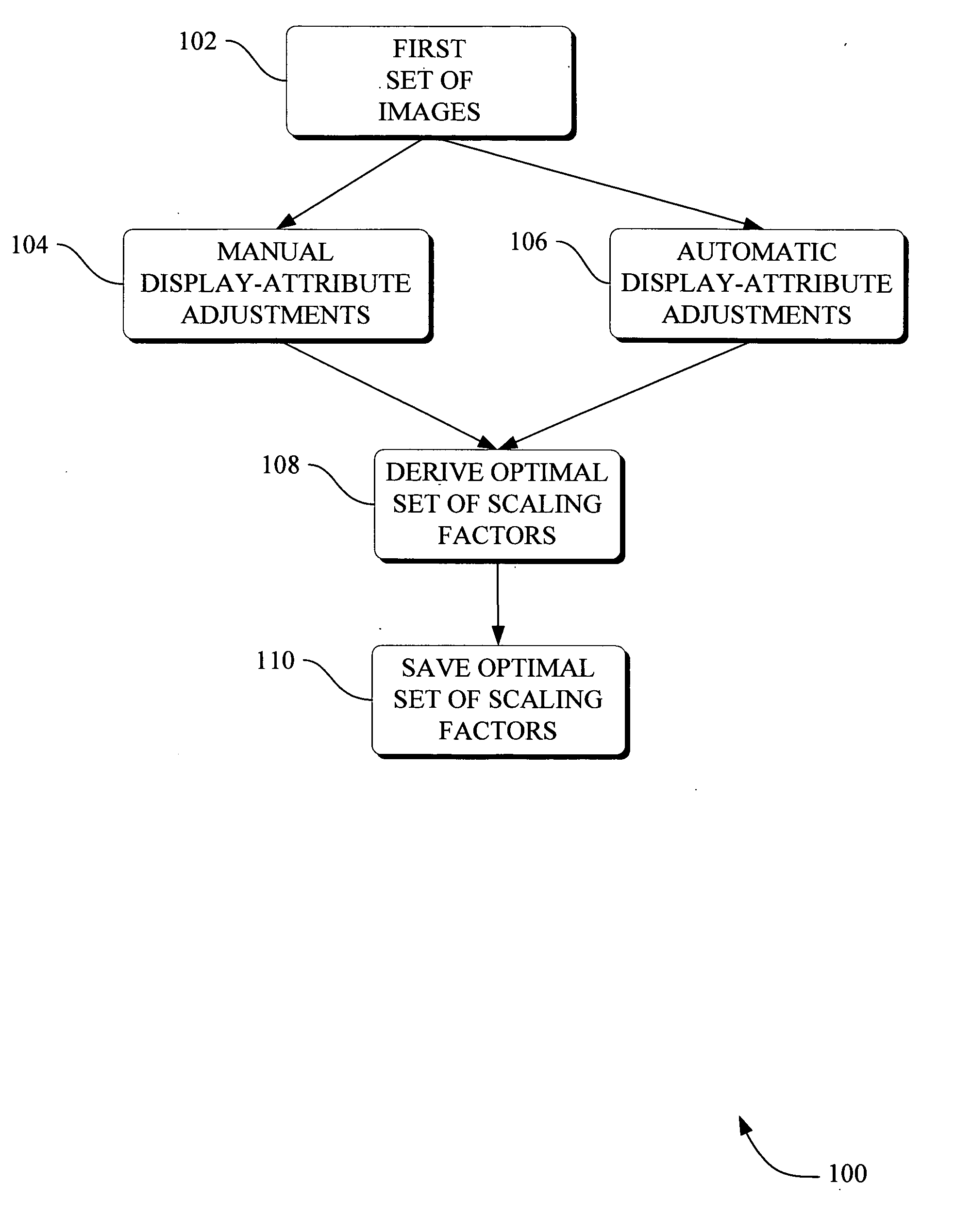
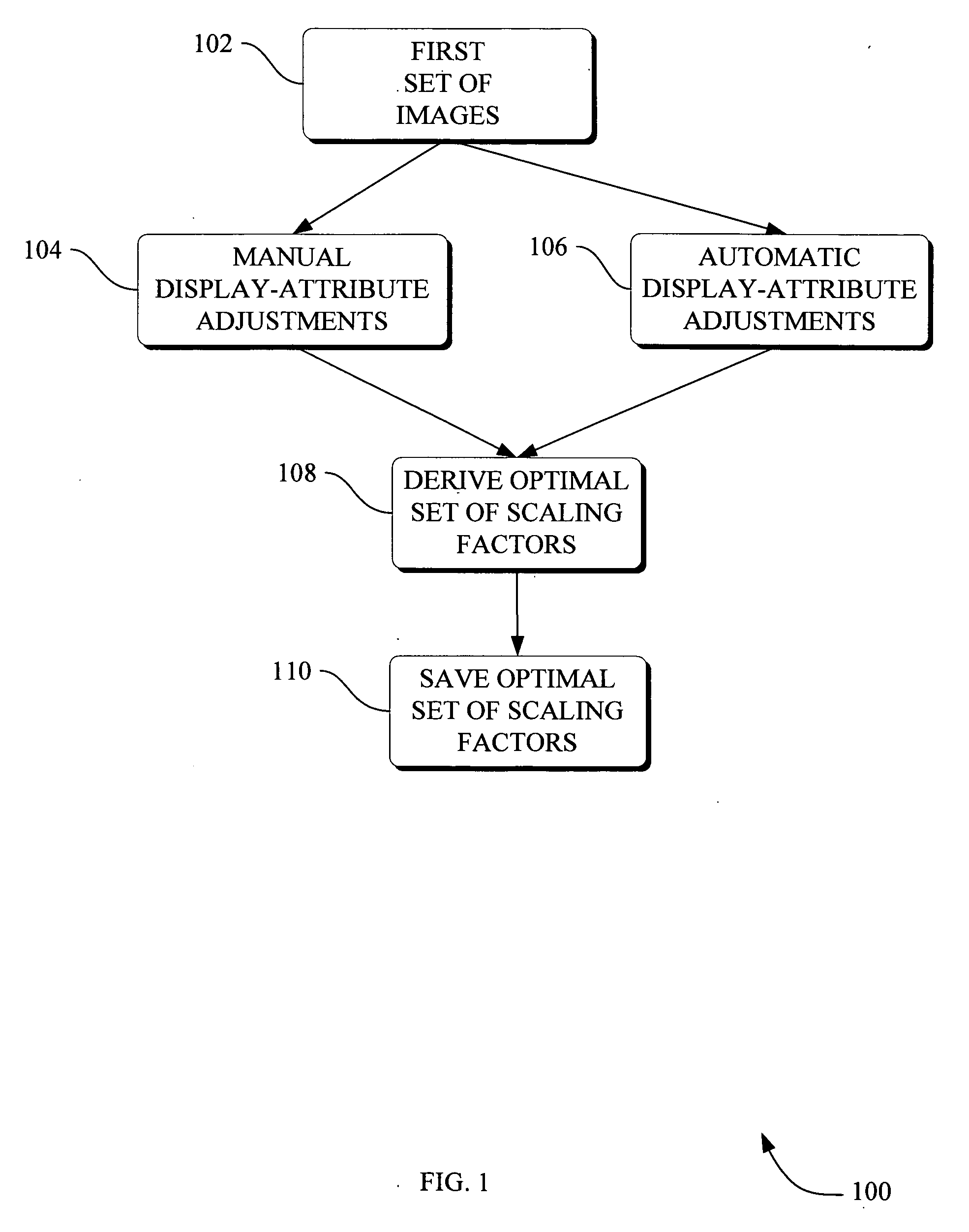
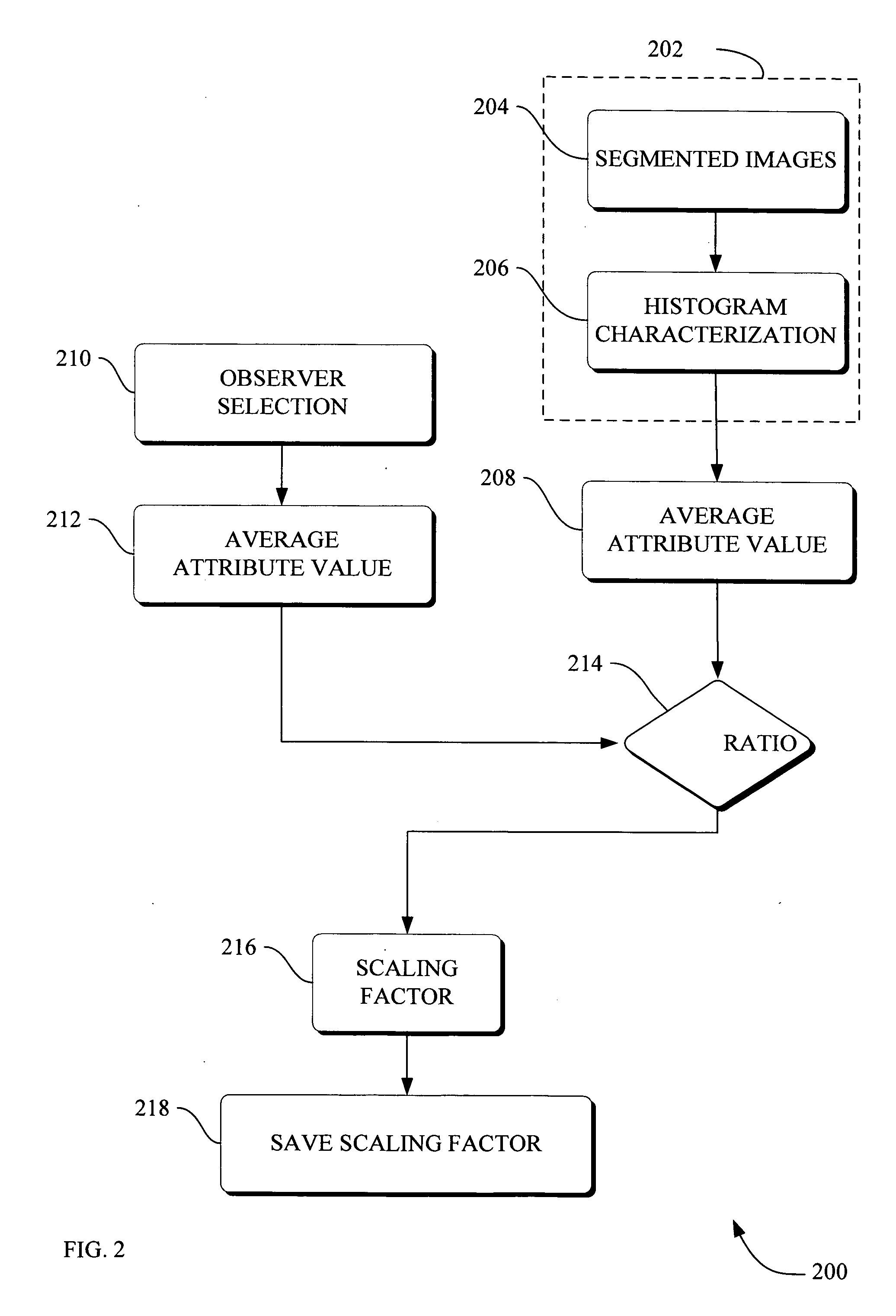
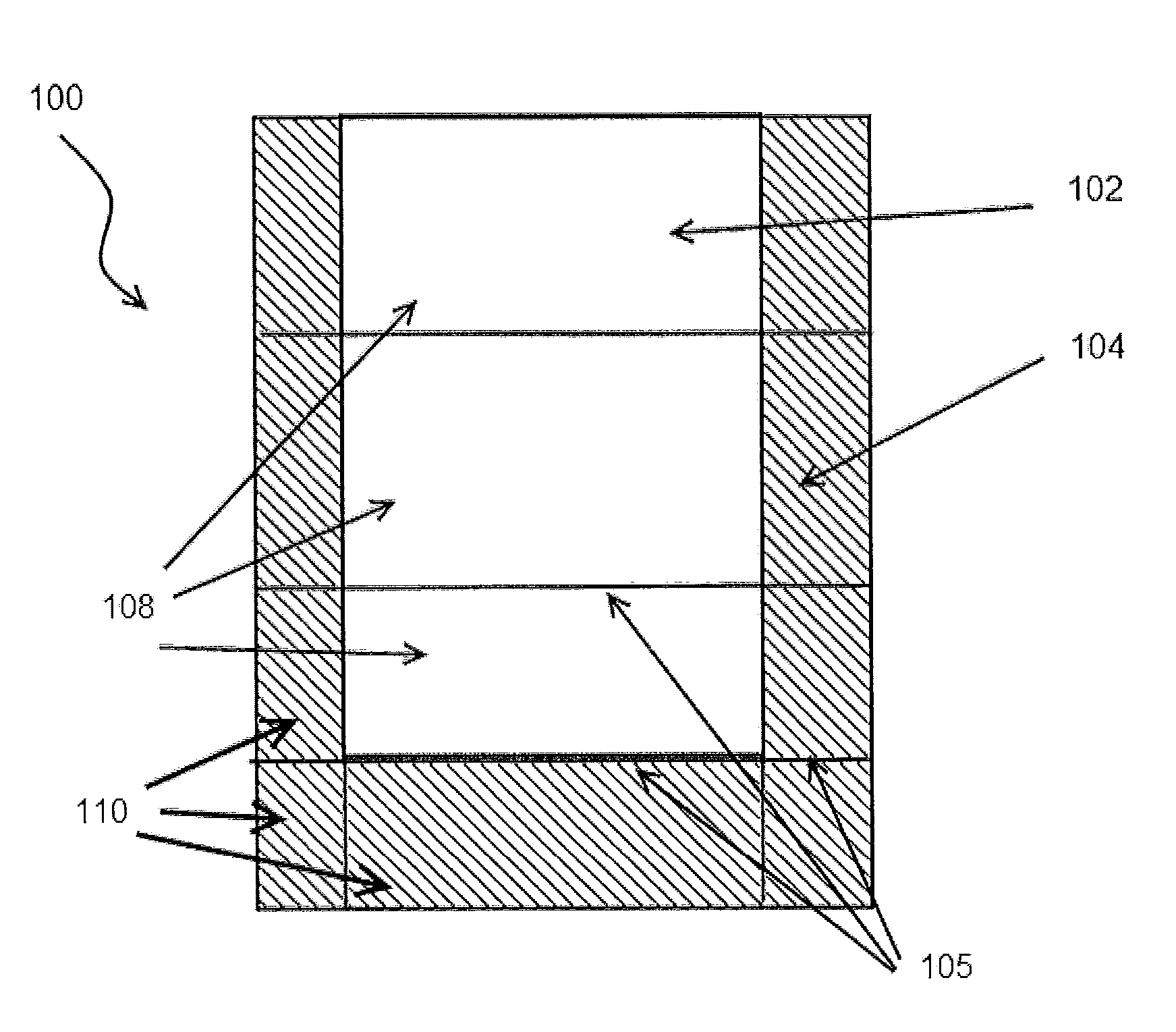
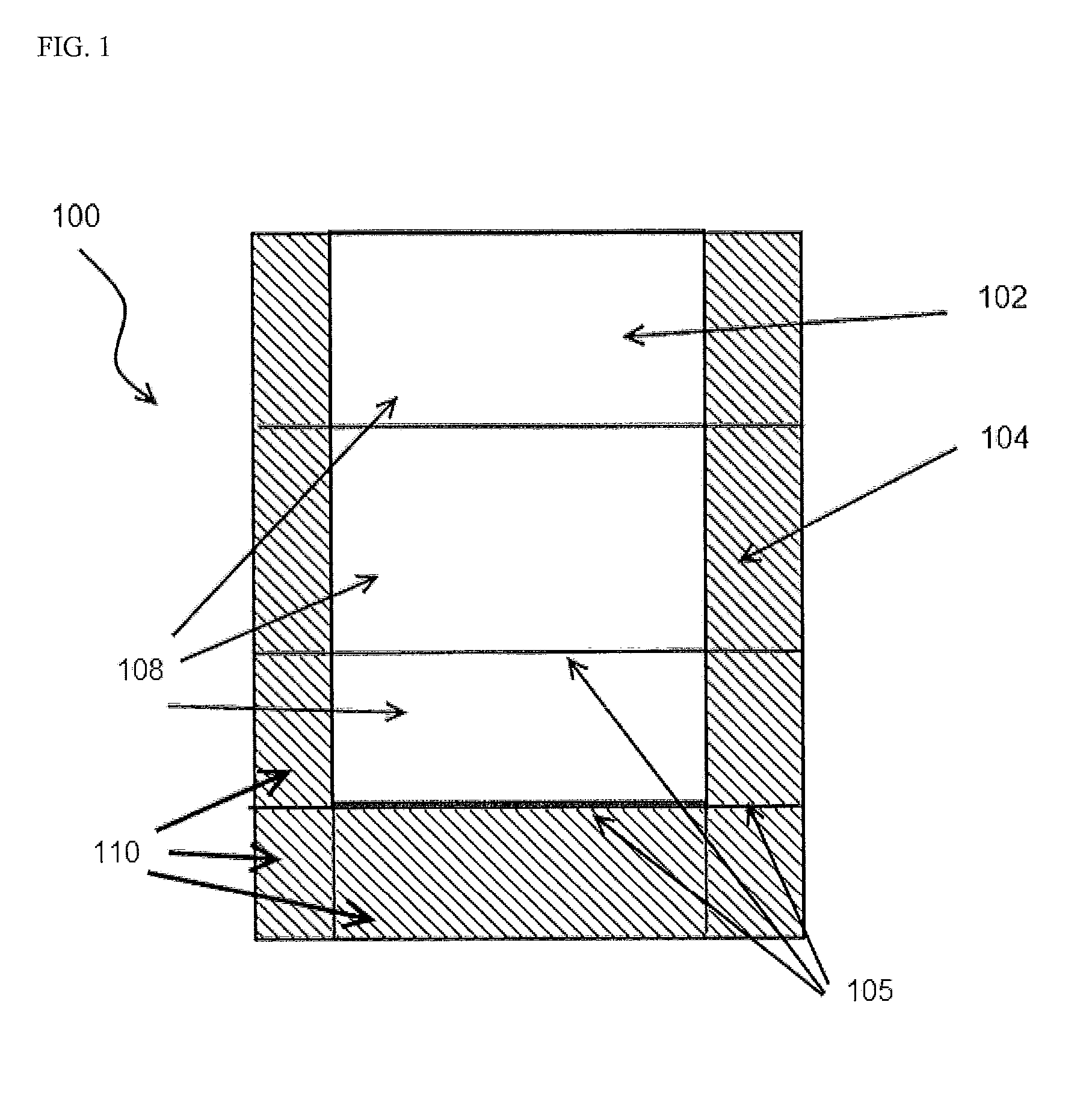
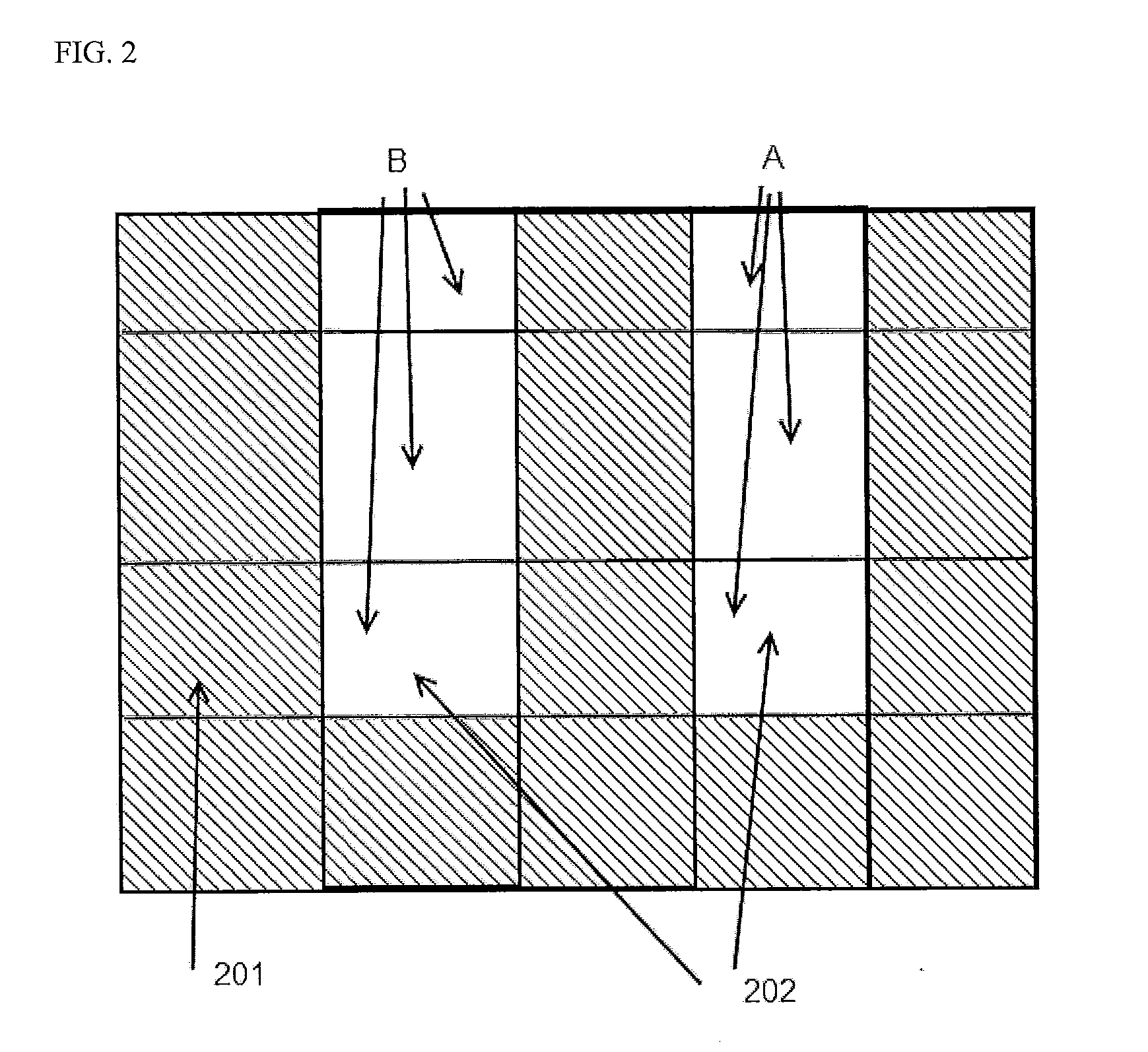
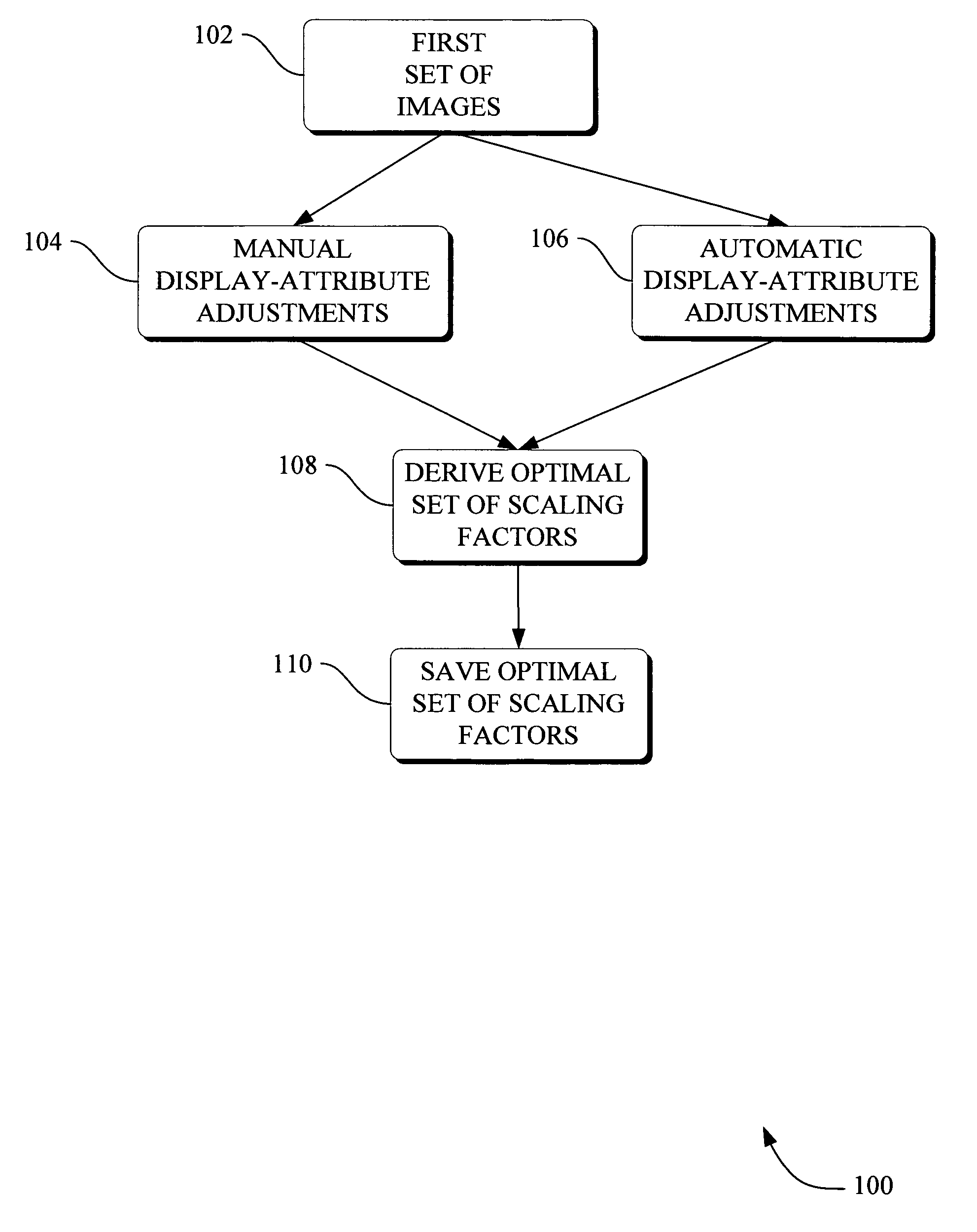
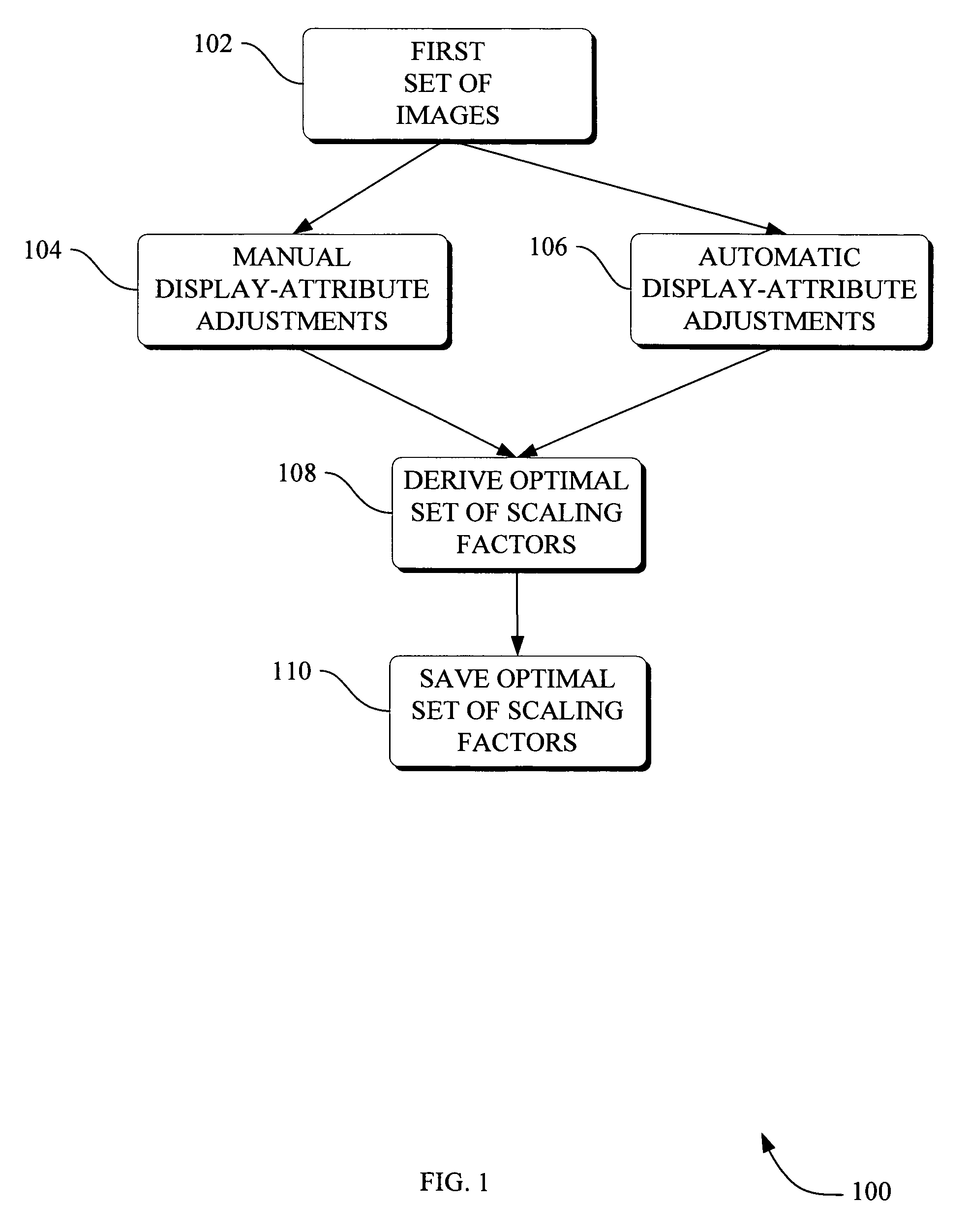
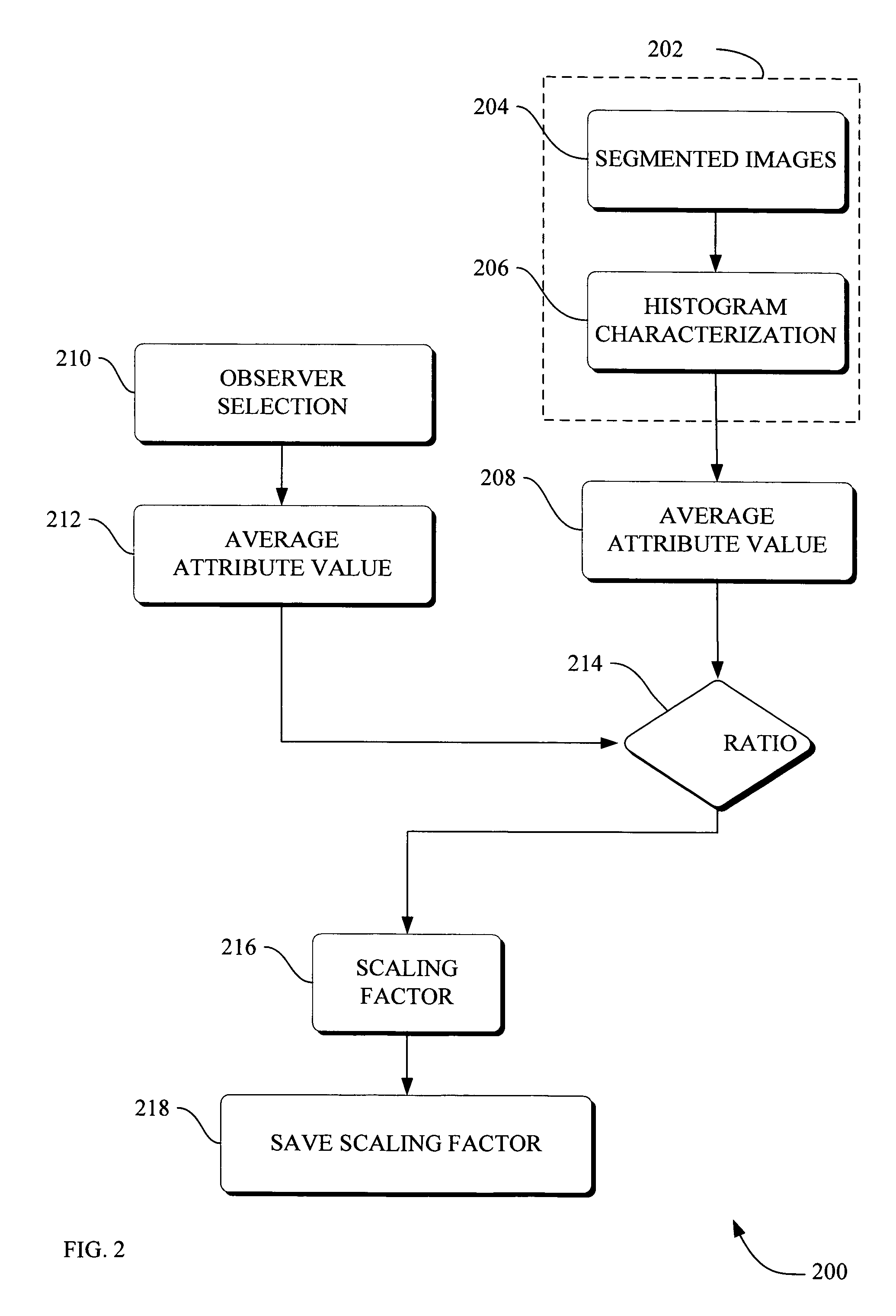
Methods and apparatus for method to optimize visual consistency of images using human observer feedback
InactiveUS20070052716A1Minimal user interactionImage enhancementTelevision system detailsData setDisplay device
Systems and methods are provided for optimizing visual consistency for a dataset of images by using observed and formulated display attributes. The formulated display attributes are derived from an analysis of a first set of images from the image repository. The formulated display attributes from the first set are combined with observer's display attributes to determine scaling factors. The optimized display attributes are then derived from the calculated scaling factors for a second set of images. In another aspect, a system and method is described where a digital image is processed in order to enhance viewing of the image on a display device in accordance to the optimized attributes associated with the observer.
Owner:GENERAL ELECTRIC CO
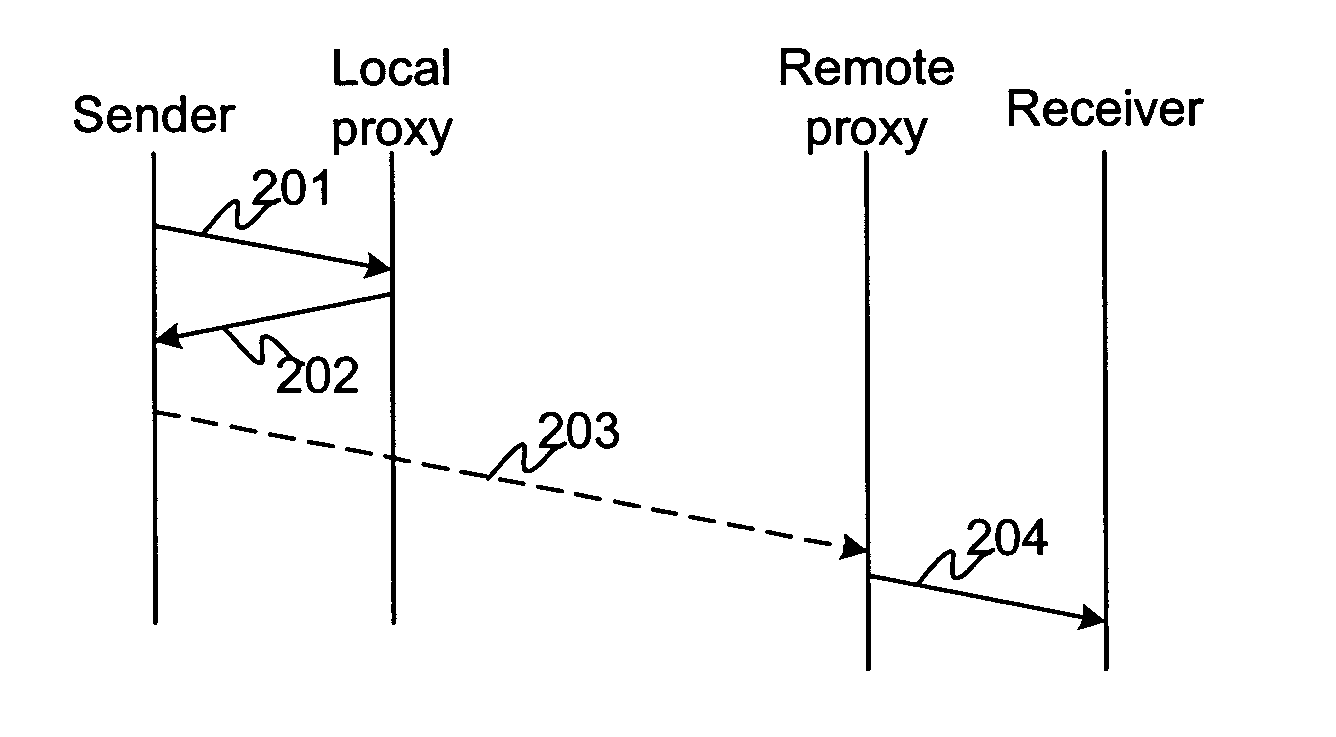
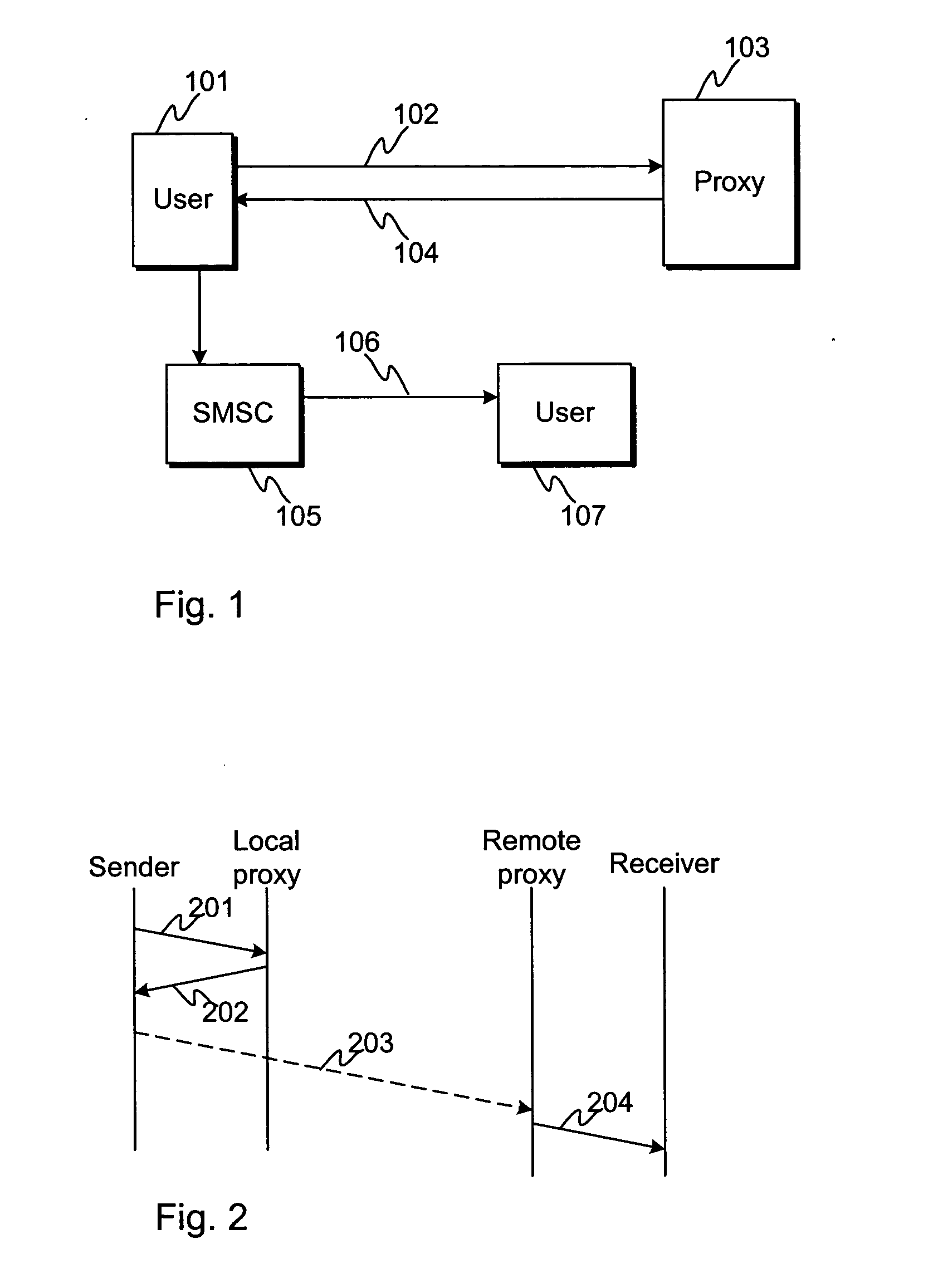
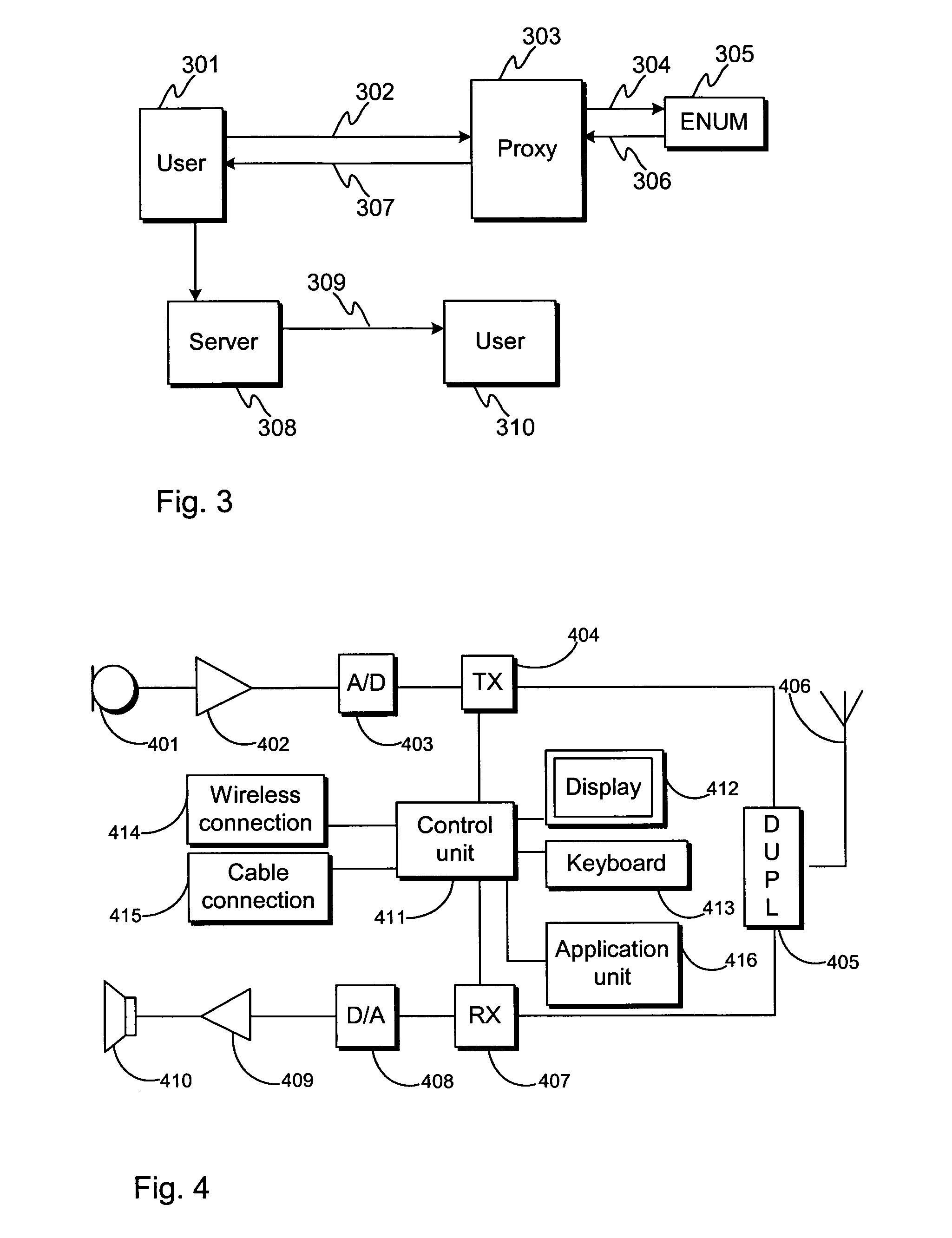
Method and an apparatus for enhancing messaging
InactiveUS20050021840A1Easily accessMinimal user interactionMultiple digital computer combinationsData switching networksMessage passingInformation delivery
The invention concerns a method and an apparatus for enhancing delivery of information and accessibility of a receiver. In particular the invention concerns a method for establishing a communication comprising a step of transmitting a request for establishing a communication by a communication terminal, which request is handled by a server. As a response to inability to establish the requested communications, the server returns a failure response including rerouting details to the communication terminal. The communication terminal receives the failure response including rerouting details, and forwards data according to the received rerouting details.
Owner:NOKIA CORP
Data Surveillance System
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The techniques are also applicable for detecting performance issues indicative of a system malfunction or deterioration.
Owner:FLYING CLOUD TECH INC
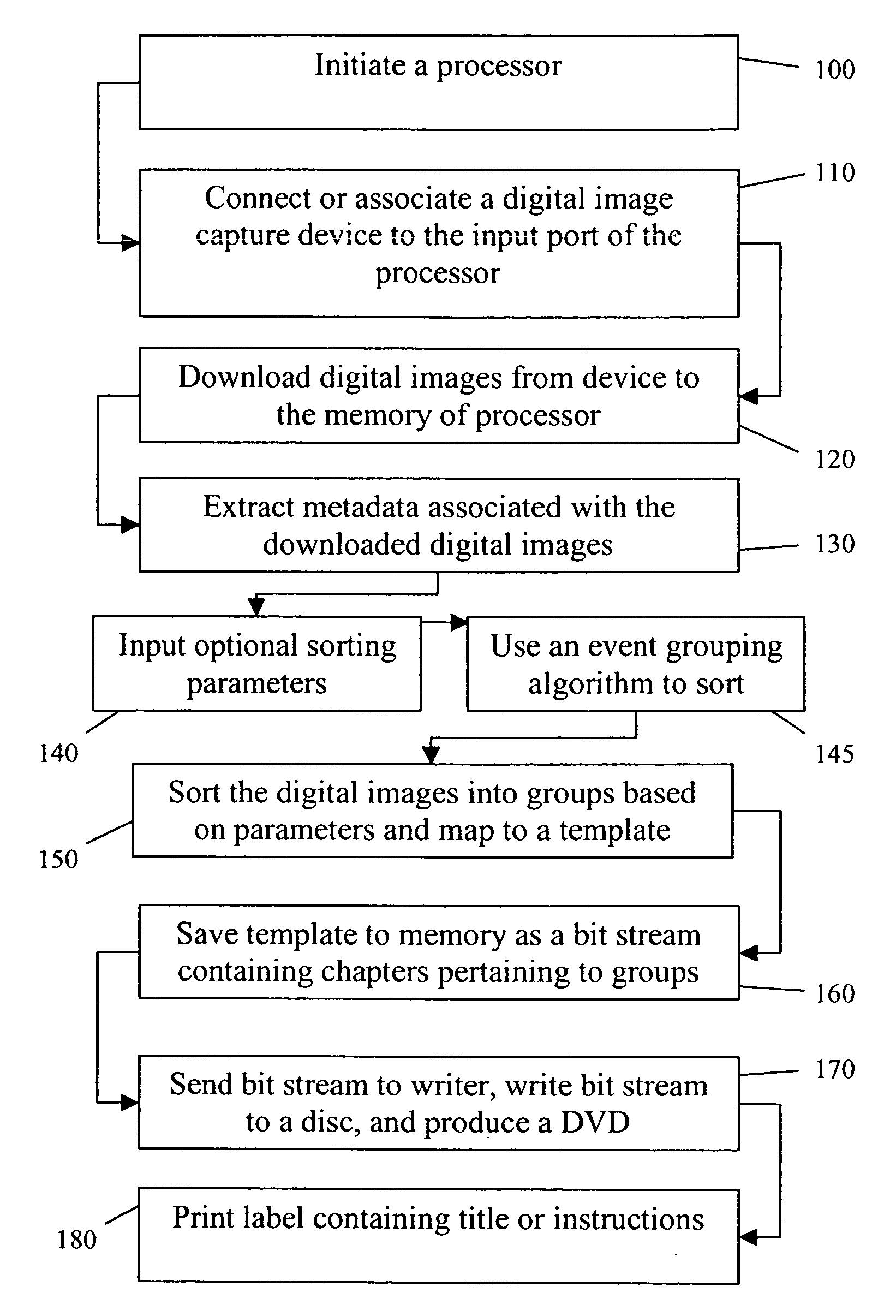
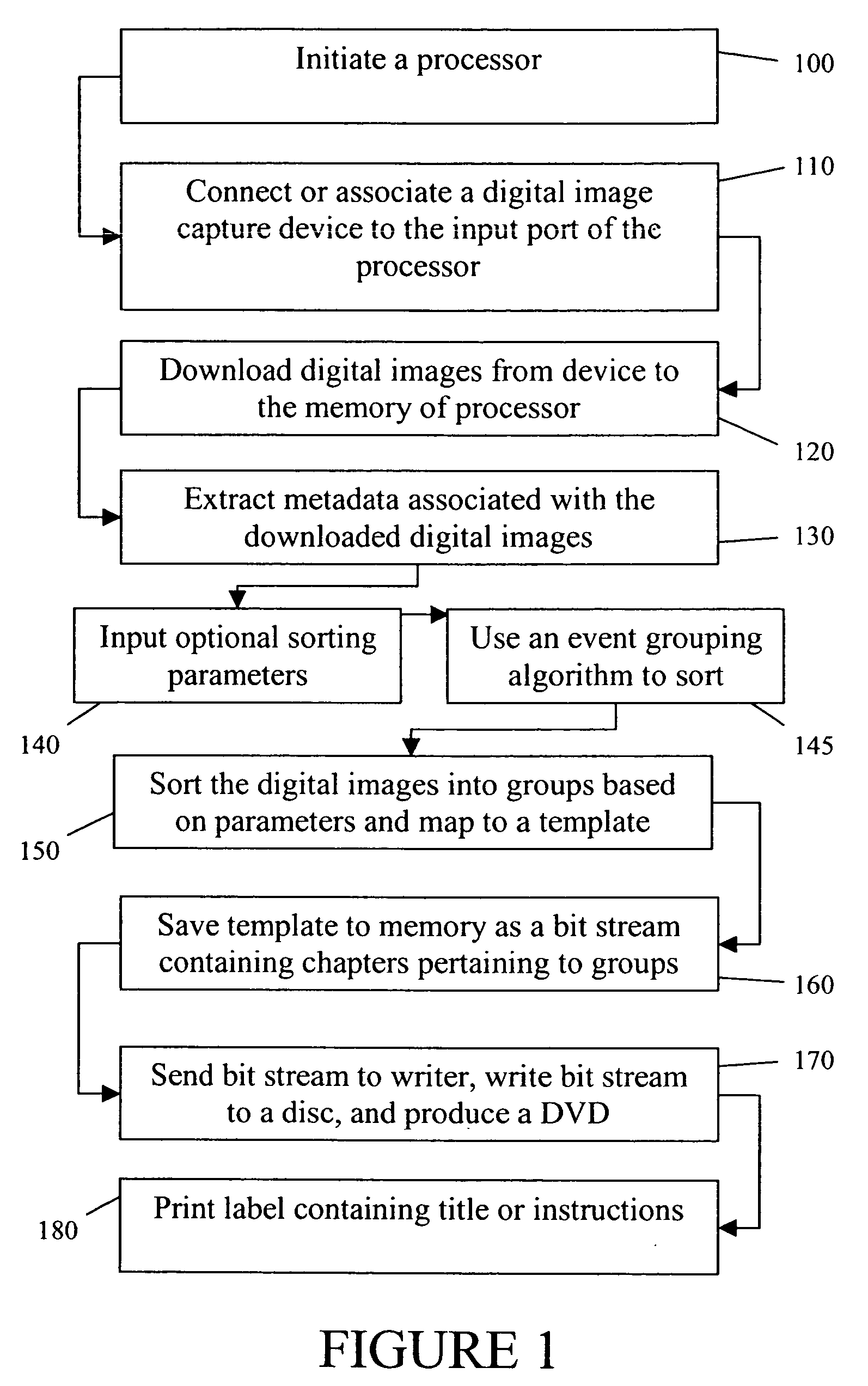
Automated method and system for creating an image storage device for playback on a playback mechanism
InactiveUS20060092771A1Improve efficiencyMinimal user interactionRecord information storageUsing detectable carrier informationComputer graphics (images)CD-ROM
An automated method for creating an image storage device such as a disk, and more particularly a DVD, CD, or CD-ROM for playback on a playback mechanism entails initiating a device with a processor. A user is instructed to connect a digital image capture device to the device, wherein digital records with image content and metadata are downloaded from the digital device into the processor's memory. Metadata extracted from the image metadata is sorted into groups based upon set parameters. The groups are mapped into a digital file template forming a digital file with chapters, wherein each group corresponds to a chapter. A bit stream representing the chapters is a sequential order is created from the digital file. The bit stream is saved to memory, sent to a writer, and written to a DVD, CD or CD-ROM. The written DVD, CD or CD-ROM is provided to the user.
Owner:EASTMAN KODAK CO
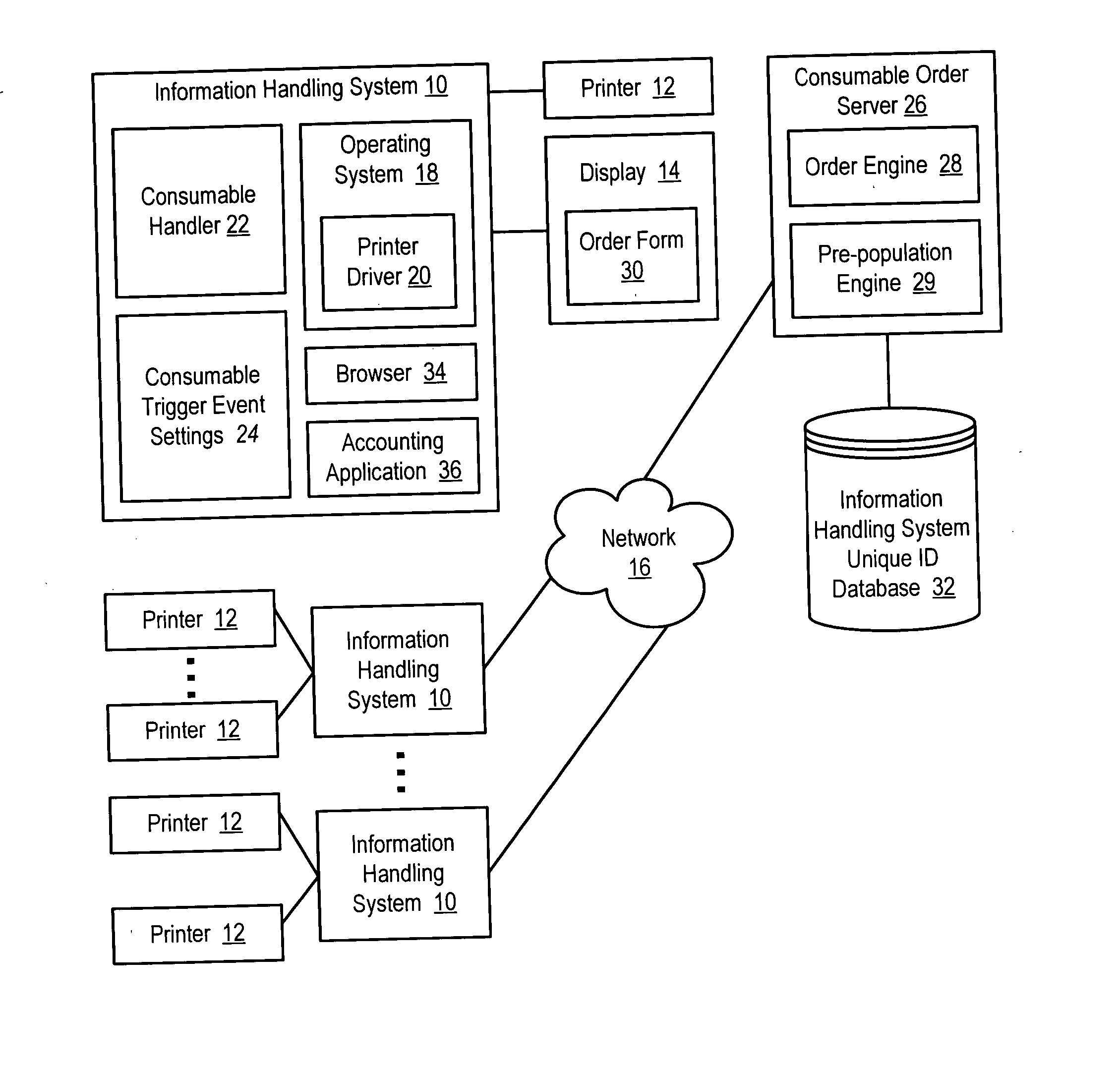
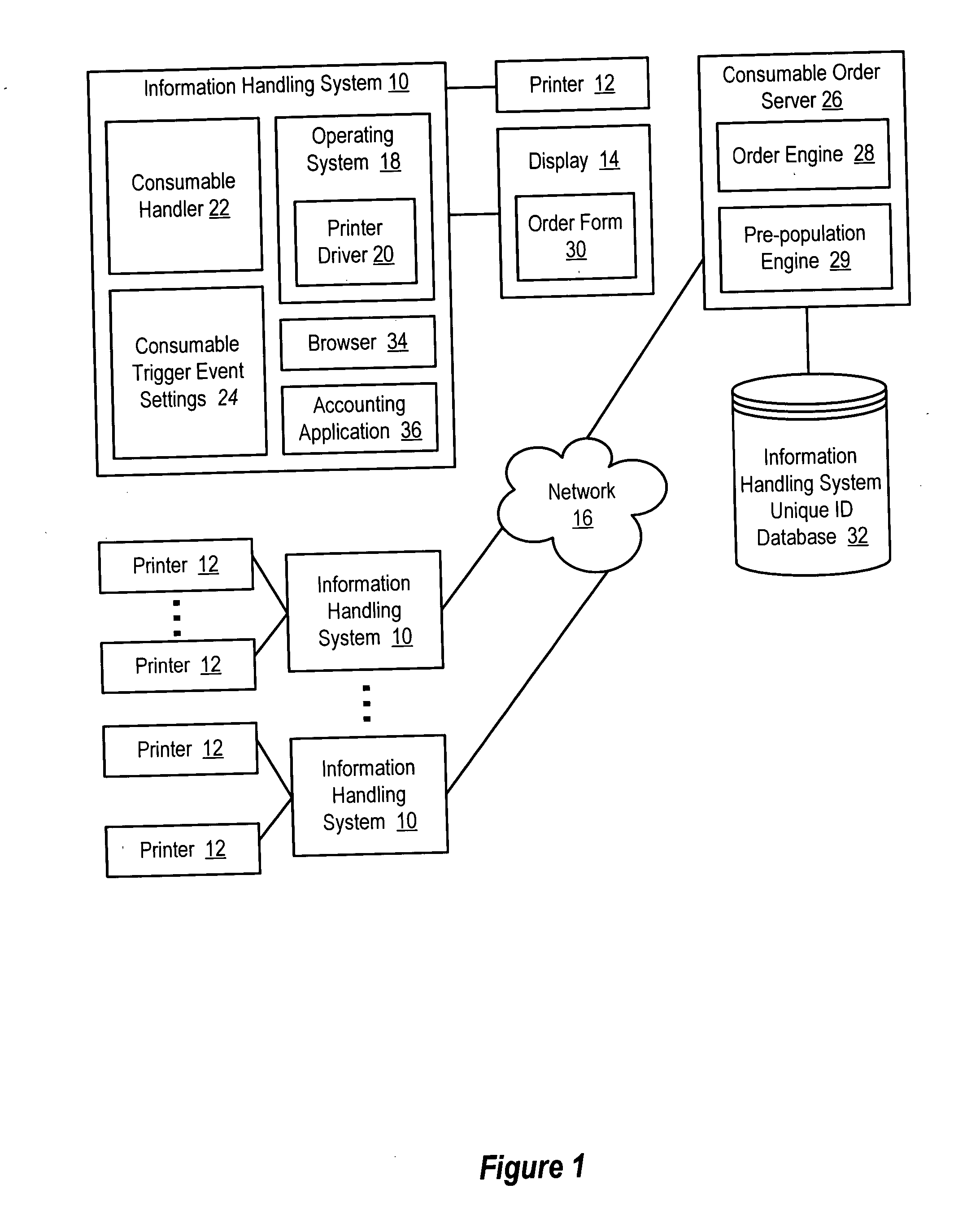
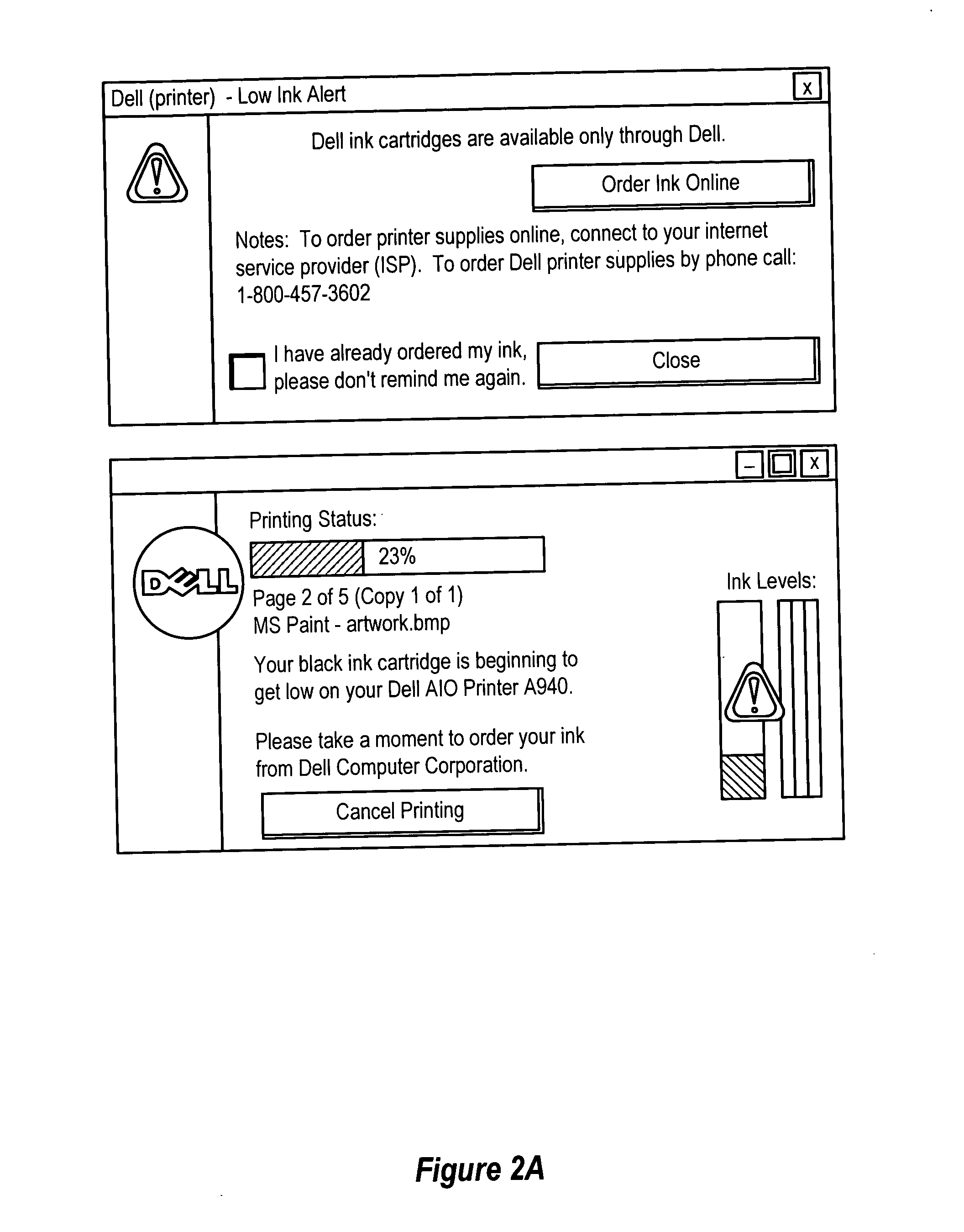
System and method for information handling system consumable automatic ordering
InactiveUS20050192817A1Reduce riskMinimal interactionHand manipulated computer devicesPayment architecturePaymentUser needs
Information handling system consumable orders, such as orders for printer supplies, are placed through a network, such as the Internet, by automatically monitoring consumable quantity to detect a consumable order trigger event for presentation at the information handling system. User initiated selection of a consumable order communicates order information to a consumable order server, which pre-populates a completed order form for display at the information handling system, such as an order form with consumable information, payment information and delivery information. For instance, the consumable order server is associated with the manufacturer of the information handling system and applies the payment and delivery information from the purchase of the information handling system to complete the order form so that a user need only confirm the accuracy of the completed order form to place the consumable order.
Owner:DELL PROD LP
Data Surveillance for Privileged Assets on a Computer Network
ActiveUS20200106797A1Minimal user interactionQuick fixMachine learningTransmissionData packNetwork on
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization.
Owner:FLYING CLOUD TECH INC
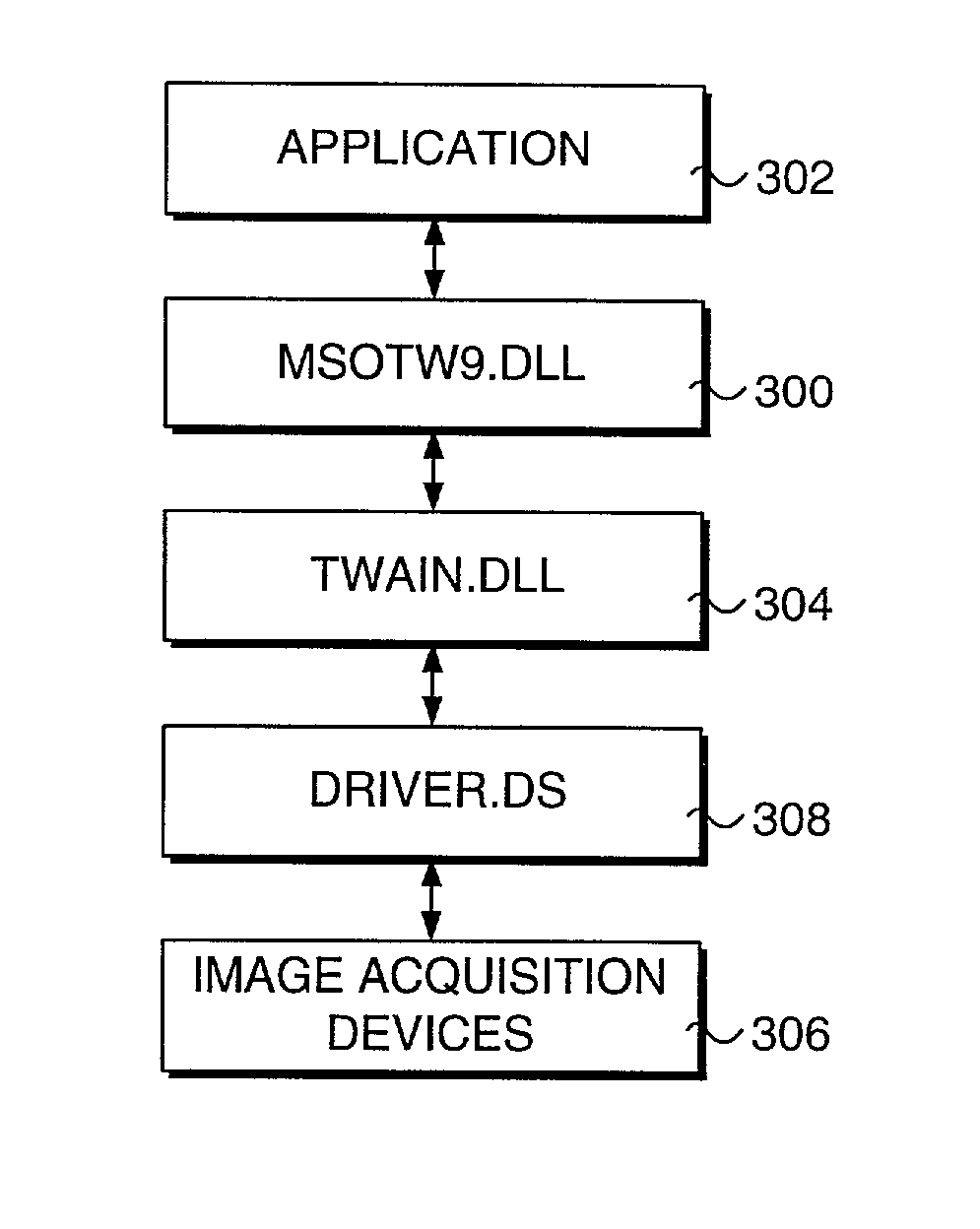
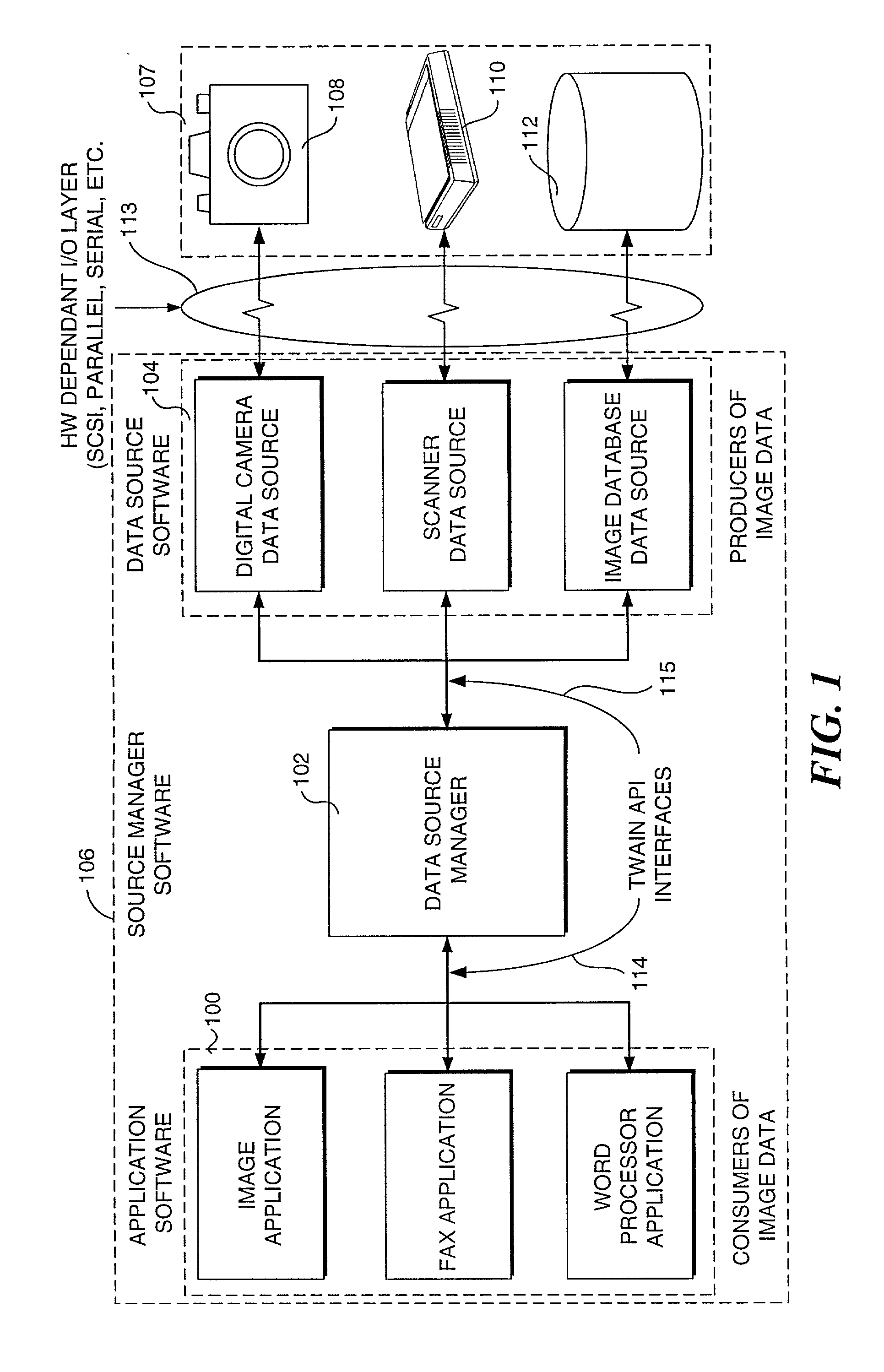
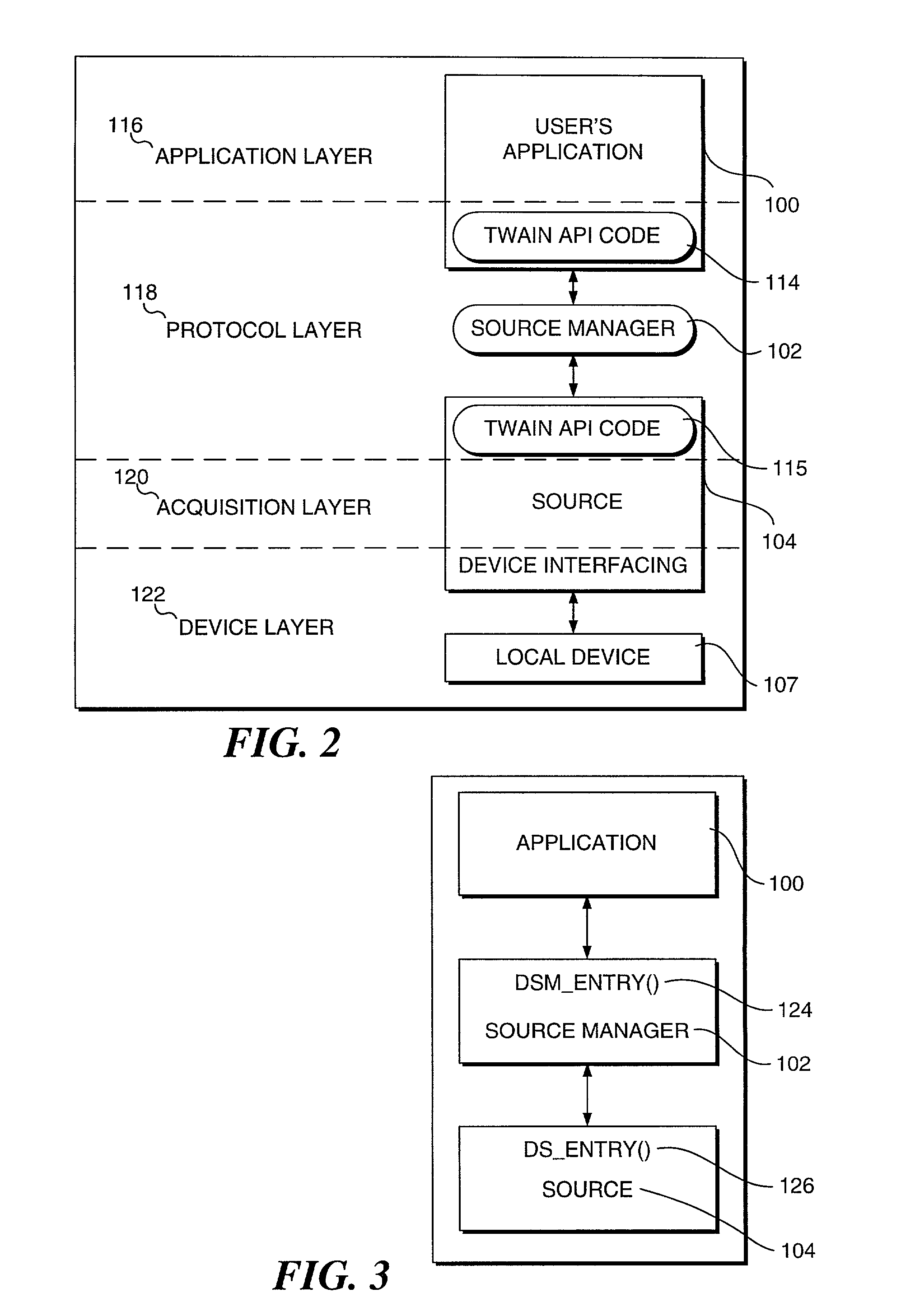
Special API interface for interfacing an application with a TWAIN module, negotiating and presenting a user interface for inserting an image into a document
InactiveUS7266761B2Easy to getMinimal user interactionDigital computer detailsCharacter and pattern recognitionApplication programming interfaceApplication software
Inserting images into documents. An image source device is made active with an application used to create text in a document. An application programming interface (API) module is accessed from within the application. The API interfaces the application with a TWAIN module used for acquiring an image with the image source device. The API module is separate from the TWAIN module and isolates users from directly interacting with the TWAIN module. The application uses the API module for negotiating with the image source device to determine a set of image capture parameters that control the image source device when acquiring the image. Data representing the image is communicated from the image source device into the memory of a computer hosting the application used to create text so that the data representing the image is a portion of a document stored in the memory.
Owner:MICROSOFT TECH LICENSING LLC
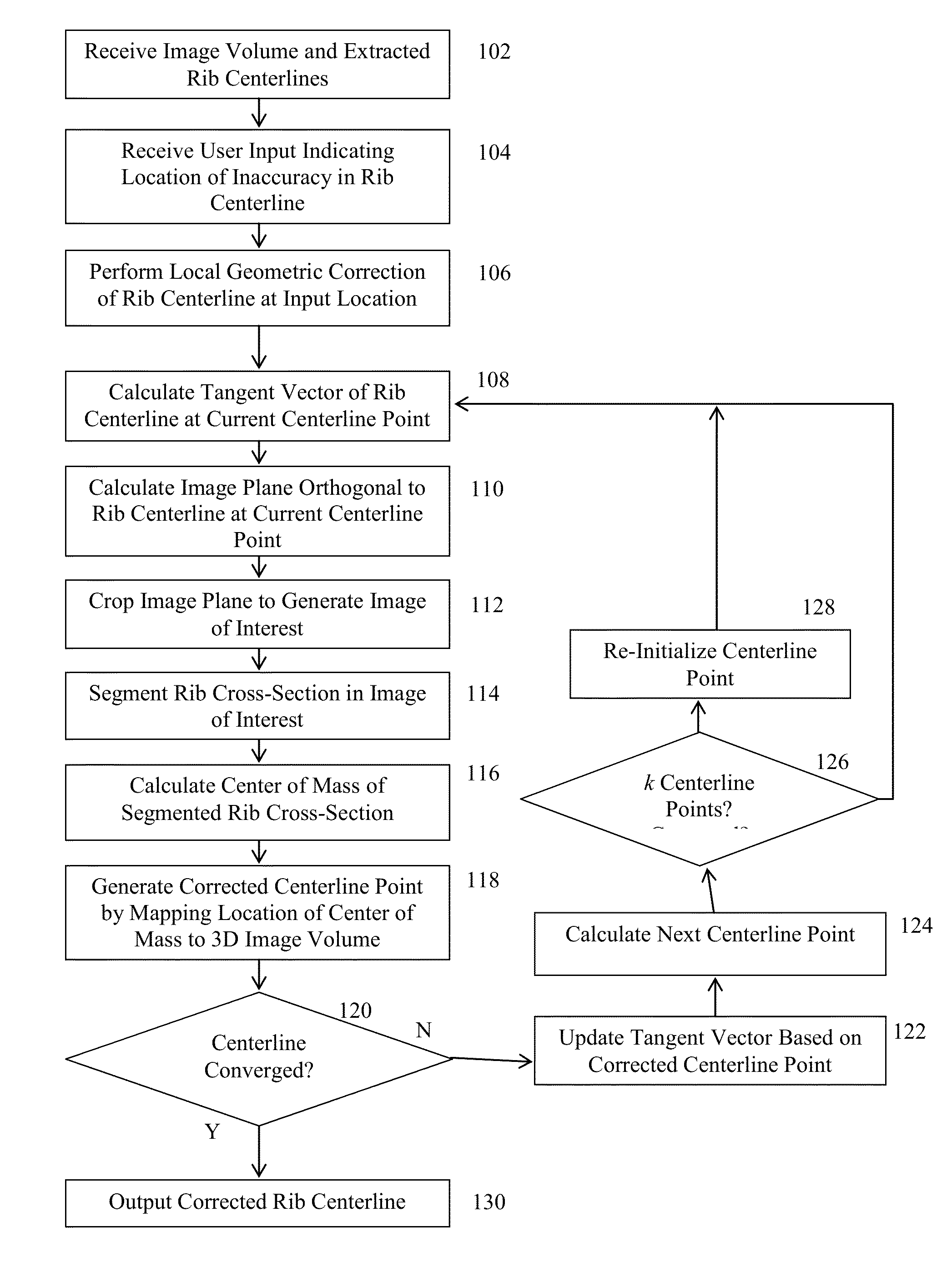
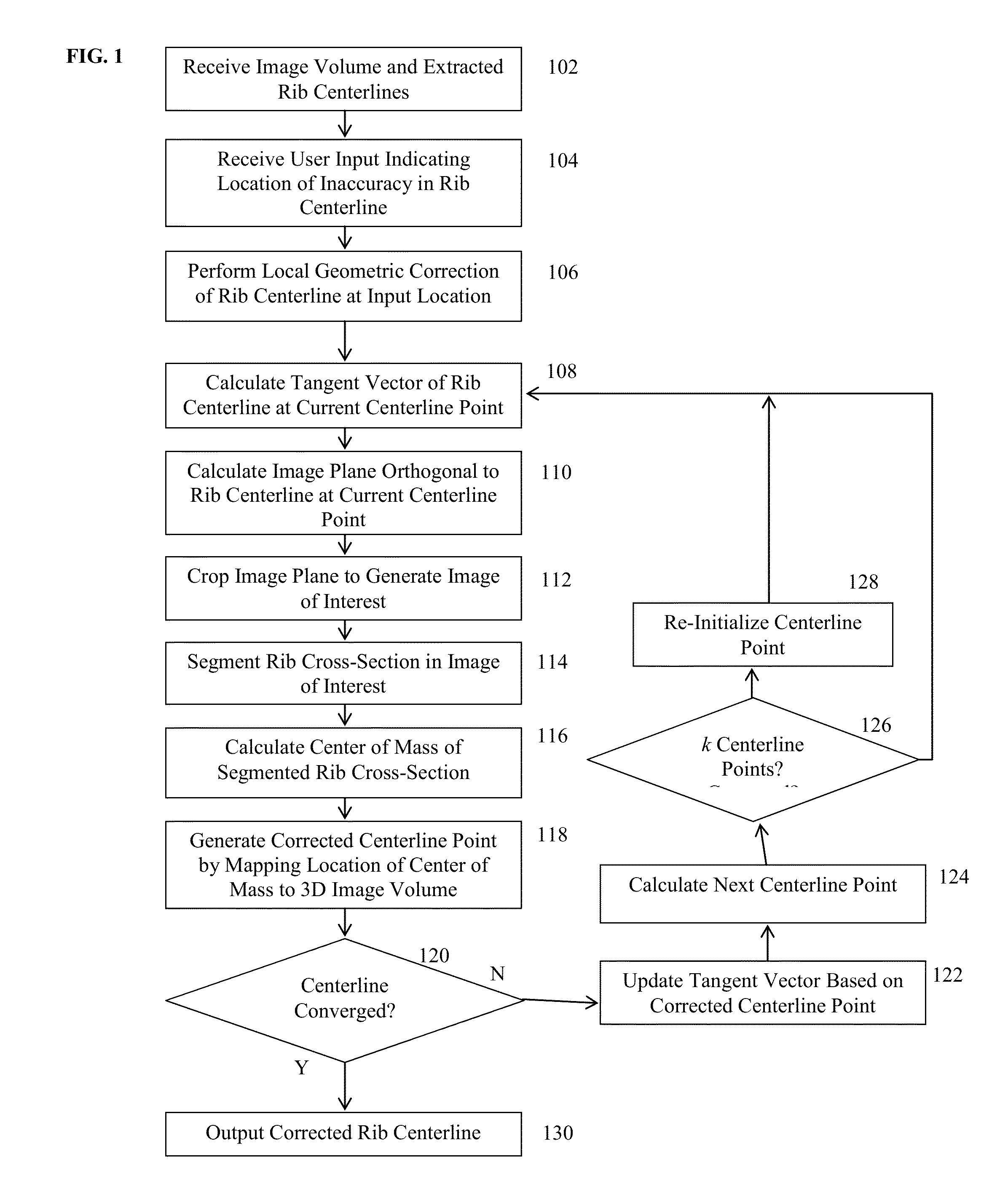
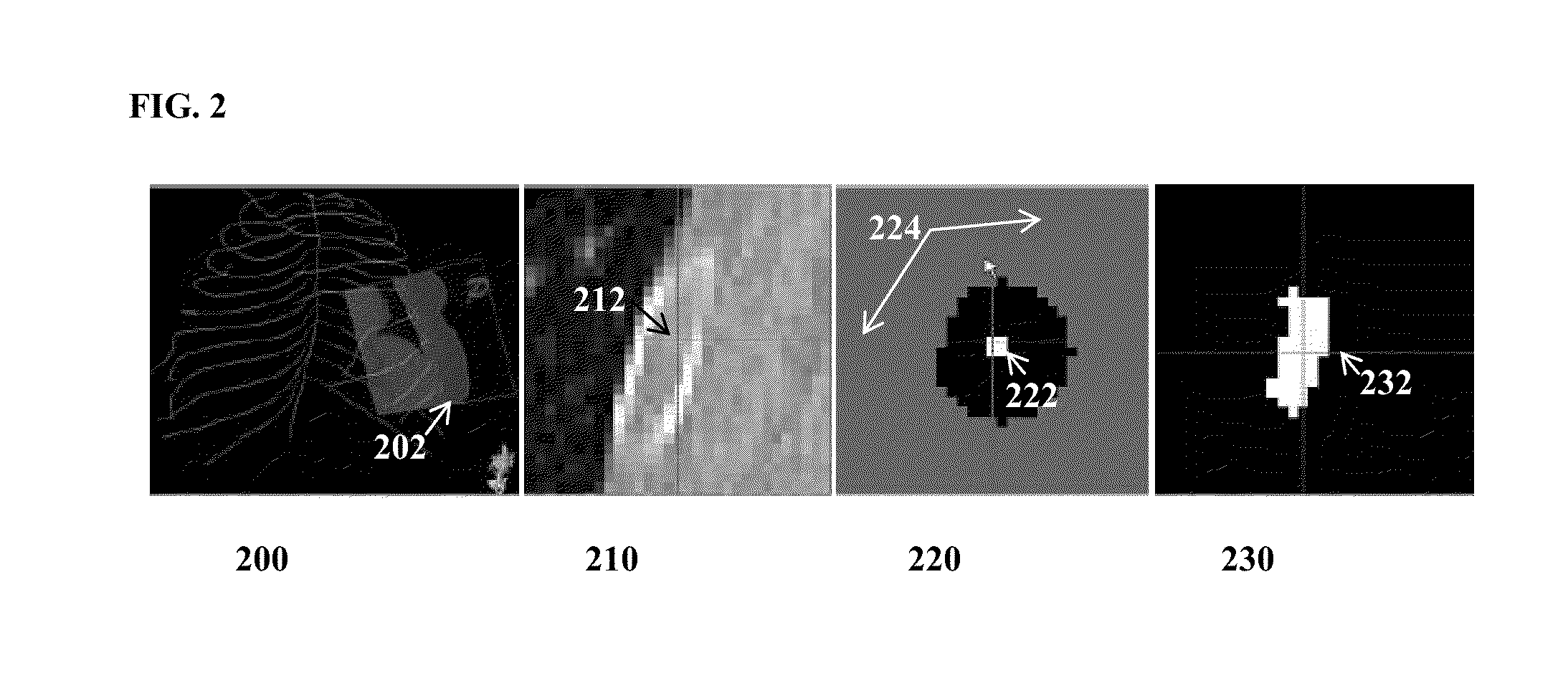
System and Method for Data Driven Editing of Rib Unfolding
ActiveUS20150078645A1Inaccuracy can be correctedMinimal user interactionImage enhancementImage analysisUser inputData-driven
A method and apparatus for data driven editing of rib centerlines is disclosed. A user input location indicating an inaccuracy in a rib centerline extracted from a medical image volume is received. A local correction of the rib centerline is performed. A portion of the rib surrounding a current centerline point to be corrected is segmented based on image data of the medical image volume. A corrected centerline point for the current centerline point is generated based on the segmented portion of the rib. The centerline correction is then extended to subsequent points along the rib centerline.
Owner:SIEMENS HEALTHCARE GMBH
Configurable electronic communication element
ActiveUS10140001B2Facilitate communicationEasy to configureData switching networksInput/output processes for data processingElectronic communicationAnimation
One or more embodiments of the disclosure include an electronic communication system that allows a user to select, configure, and send an electronic communication element to another user. For example, an electronic communication element can include a symbol, icon, animation, sound, and / or other elements that can be sent via an electronic communication. In particular, one or more embodiments of the electronic communication system allow a user to configure the electronic communication element to send a customized message to another user with the configured communication element.
Owner:META PLATFORMS INC
Building Long Search Queries
ActiveUS20140172814A1Quick buildQuickly lengthyWeb data indexingDigital data processing detailsSystems approachesInformation retrieval
Owner:MICROSOFT TECH LICENSING LLC
Data surveillance for privileged assets based on threat streams
ActiveUS10887330B2Minimal user interactionQuick fixEncryption apparatus with shift registers/memoriesDigital computer detailsStreaming dataData pack
Owner:FLYING CLOUD TECH INC
Method and apparatus for automatically sending a captured image to a phone call participant
InactiveUS20080200174A1Minimal user interactionSubstation equipmentRadio/inductive link selection arrangementsCommunication deviceTelephony
Owner:SCENERA TECH
Filled bedding articles consisting of more than one filler
ActiveUS20140373277A1Improve performanceMaximum effectivenessBlanketBed linenFilling materialsEngineering
The present invention is directed to a bedding article which provides a structured construction for filling with filler material. Specifically, the present invention is directed to a bedding article that incorporates a number of pattern arrangements. The pattern arrangements allow for the sequestration of high performance filler material to areas of maximum effectiveness. Likewise, the pattern arrangement allows for standard performance material to be used in areas where user interaction is likely to be minimal, in order to minimize the amount of material needed in manufacture.
Owner:PAC FUNG FEATHER
Methods and apparatus for method to optimize visual consistency of images using human observer feedback
InactiveUS7719543B2Minimal user interactionTelevision system detailsImage enhancementData setComputer graphics (images)
Systems and methods are provided for optimizing visual consistency for a dataset of images by using observed and formulated display attributes. The formulated display attributes are derived from an analysis of a first set of images from the image repository. The formulated display attributes from the first set are combined with observer's display attributes to determine scaling factors. The optimized display attributes are then derived from the calculated scaling factors for a second set of images. In another aspect, a system and method is described where a digital image is processed in order to enhance viewing of the image on a display device in accordance to the optimized attributes associated with the observer.
Owner:GENERAL ELECTRIC CO
Data surveillance for privileged assets on a computer network
ActiveUS10848514B2Minimal user interactionQuick fixDigital computer detailsMachine learningData packNetwork on
Data surveillance techniques are presented for the detection of security issues, especially of the kind where privileged data may be stolen by steganographic, data manipulation or any form of exfiltration attempts. Such attempts may be made by rogue users or admins from the inside of a network, or from outside hackers who are able to intrude into the network and impersonate themselves as legitimate users. The system and methods use a triangulation process whereby analytical results pertaining to data protocol, user-behavior and packet content are combined to establish a baseline for the data. Subsequent incoming data is then scored and compared against the baseline to detect any security anomalies. The above data surveillance techniques are also applied for detecting intentional or unintentional exfiltration / leak of privileged data / assets between unauthorized users / groups of the organization.
Owner:FLYING CLOUD TECH INC
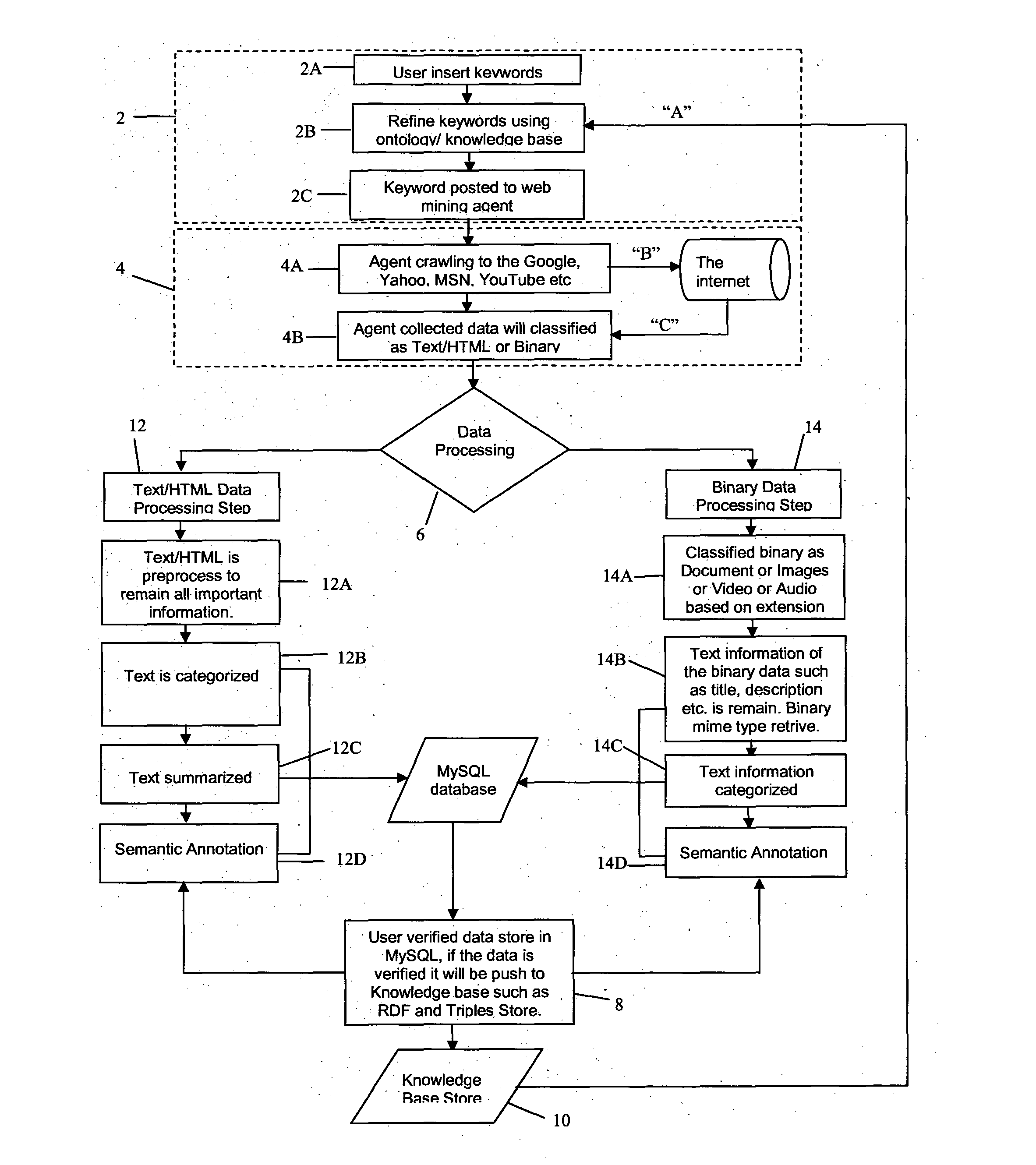
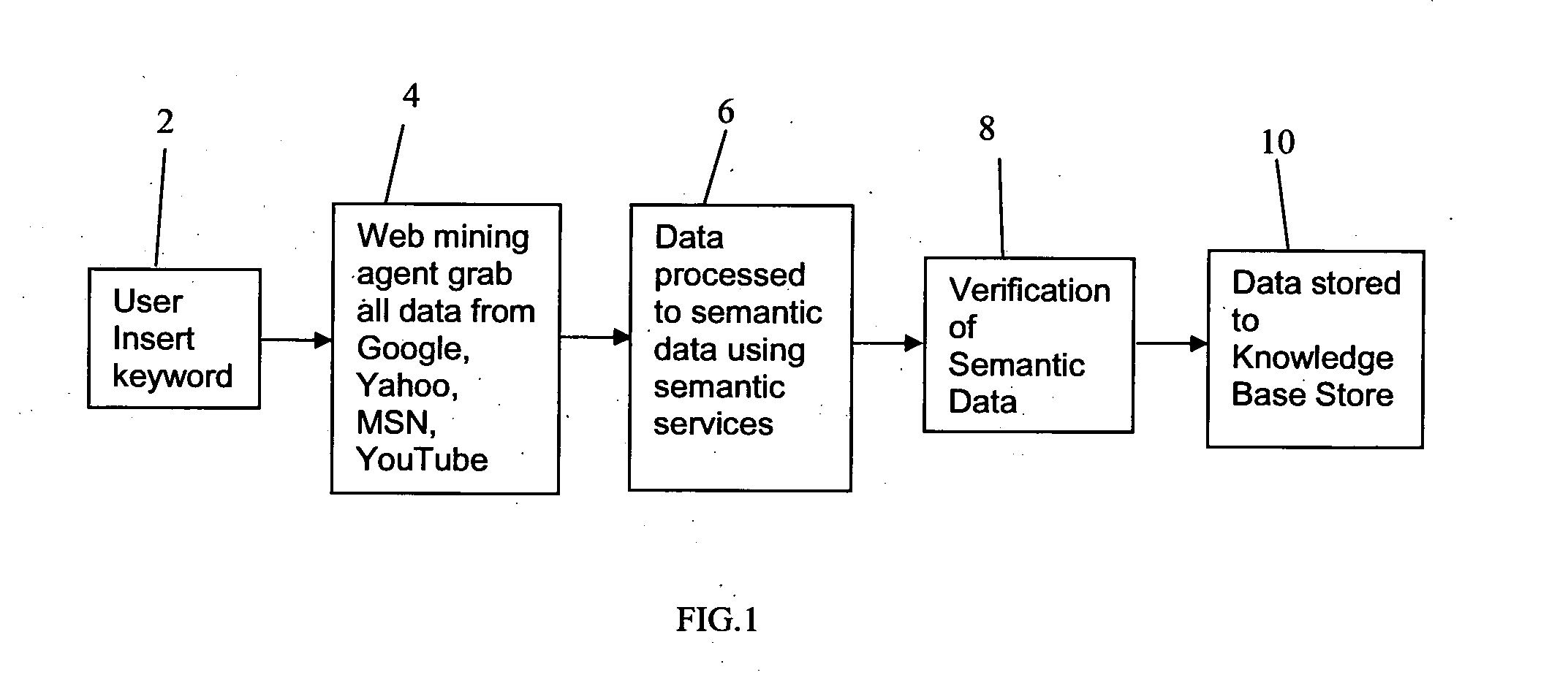
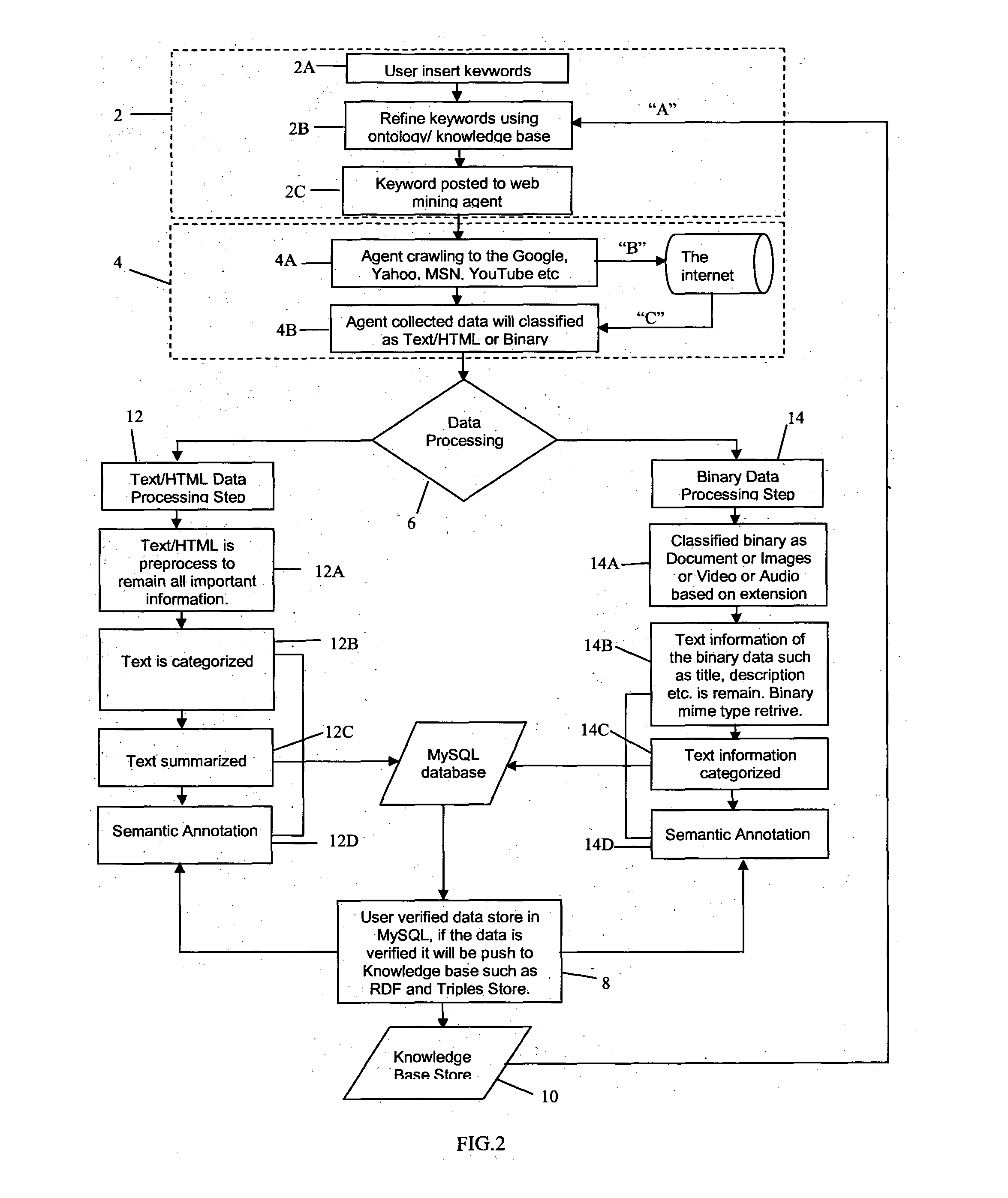
System for automatic semantic-based mining
InactiveUS20120109965A1Minimal user interactionQuick and speedy discovery and extractionWeb data indexingDigital data processing detailsData miningWeb mining
Owner:MIMOS BERHAD
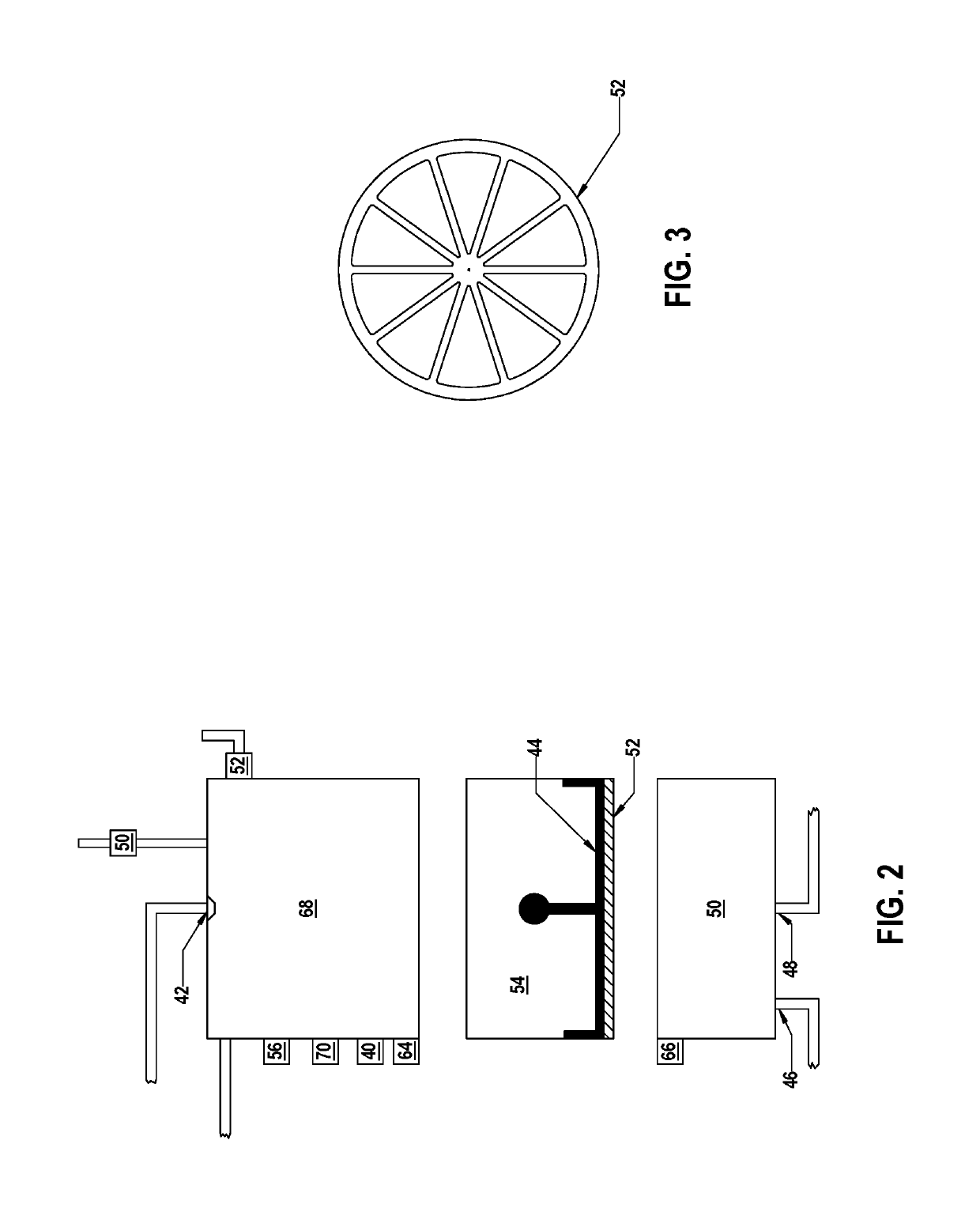
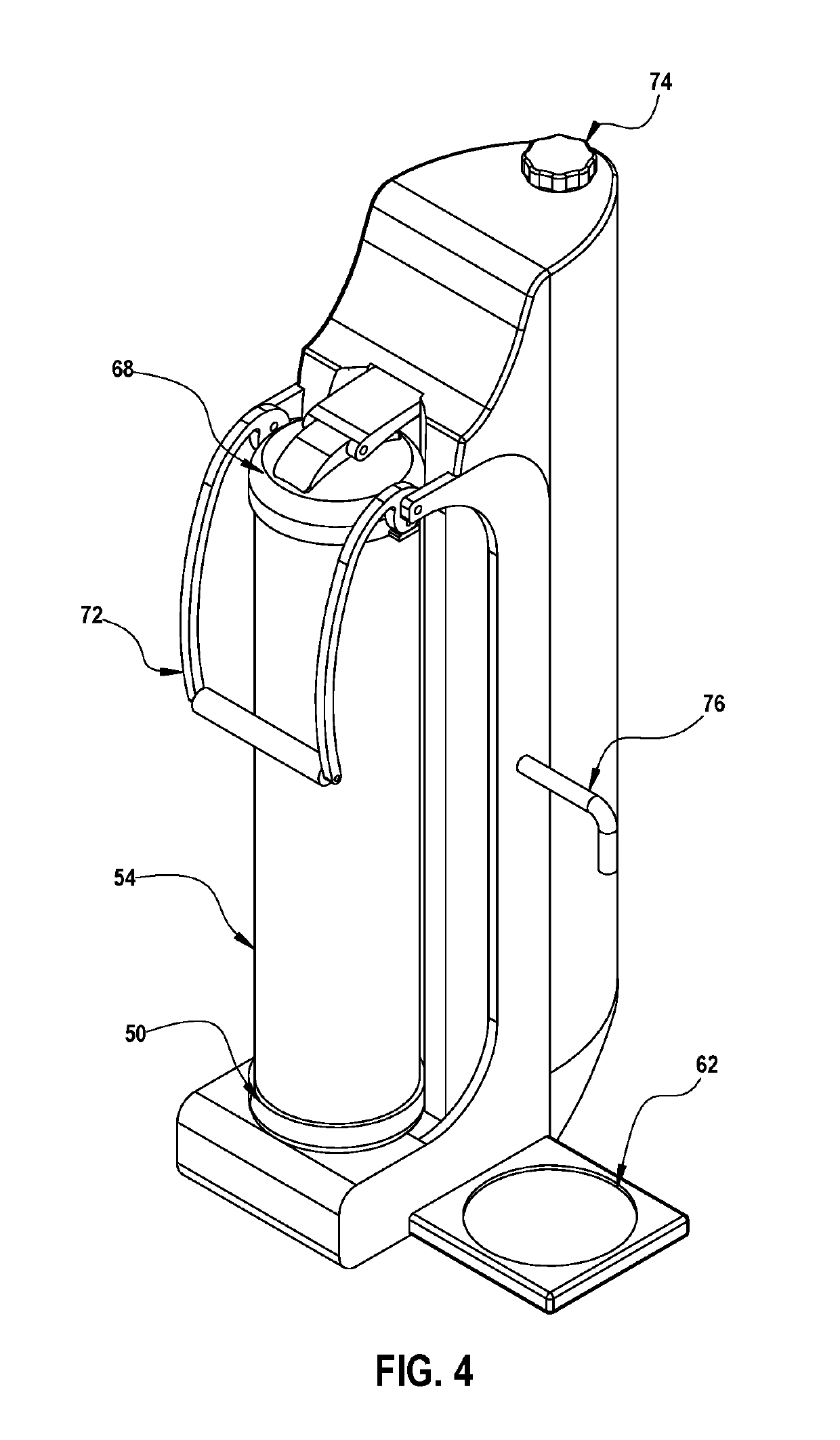
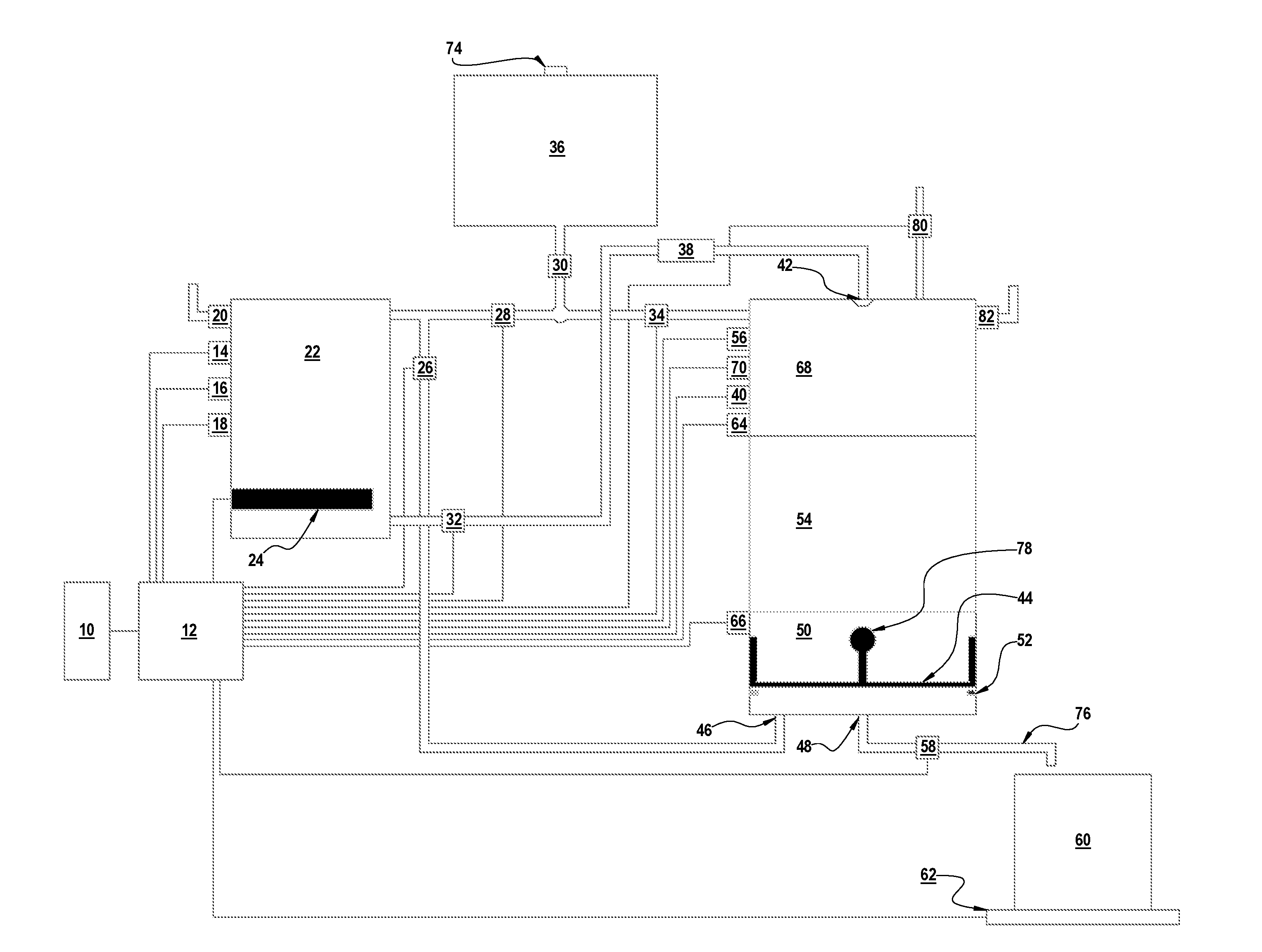
Beverage brewing apparatus and related method
ActiveUS10376088B2Minimal user interactionOptimal and uniform extractionBeverage vesselsCoffee extractionEngineeringTimer
The present inventive concept consists of a logic controlled submersion brewing device that operates reliably with minimal user interaction. The brewer employs a submersion brewing technique to ensure a uniform extraction of beverage from solid extraction media. The device may be programmable to start on a timer. Parameters of the brew program may be customizable including serving size and extraction settings. The device will use vapor pressure to forcibly move beverage liquid across a sieve thereby separating the liquid from spent extraction media. Reliability and repeatability of the separation procedure is enhanced using a novel method of pressure control.
Owner:MARVELL WORLD TRADE LTD
Beverage Brewing Apparatus and Related Method
ActiveUS20170027370A1Minimal user interactionOptimal and uniform extractionBeverage vesselsCoffee extractionEngineeringTimer
The present inventive concept consists of a logic controlled submersion brewing device that operates reliably with minimal user interaction. The brewer employs a submersion brewing technique to ensure a uniform extraction of beverage from solid extraction media. The device may be programmable to start on a timer. Parameters of the brew program may be customizable including serving size and extraction settings. The device will use vapor pressure to forcibly move beverage liquid across a sieve thereby separating the liquid from spent extraction media. Reliability and repeatability of the separation procedure is enhanced using a novel method of pressure control.
Owner:MARVELL WORLD TRADE LTD
Filled bedding articles consisting of more than one filler
ActiveUS9186002B2Improve performanceMaximum effectivenessBlanketBed linenFilling materialsEngineering
Owner:PAC FUNG FEATHER
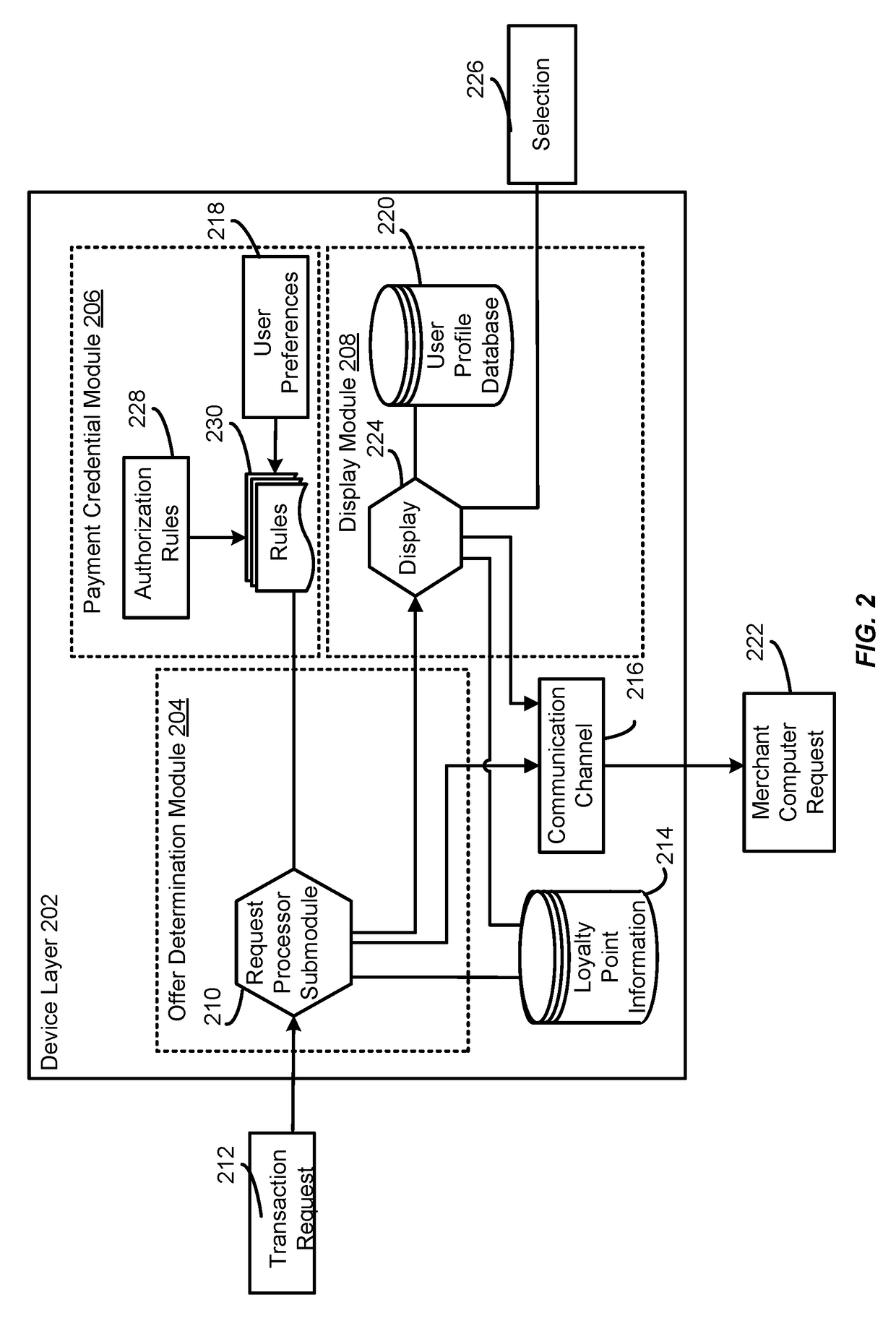
Platform for offer determination and presentation via internet of things
ActiveUS20170344982A1Minimal user interactionEasily shop and inquire and purchase itemLogisticsData switching networksPaymentInternet of Things
Techniques described herein include a platform and process enabling an electronic appliance to locally store payment credentials, loyalty point information, receive price comparison information for an item, redeem rewards or loyalty points to determine a best offer for the item, and enable delivery of said item to a user with minimal user interaction. In some embodiments, an electronic appliance can receive a query for offers for an item, receive order information from a plurality of merchants about the item, and apply loyalty points to determine an offer for the item. Upon receiving confirmation the electronic appliance may transmit access credentials for ordering the item for delivery and updating the loyalty point information for the account utilized to purchase the item from the determined offer.
Owner:VISA INT SERVICE ASSOC
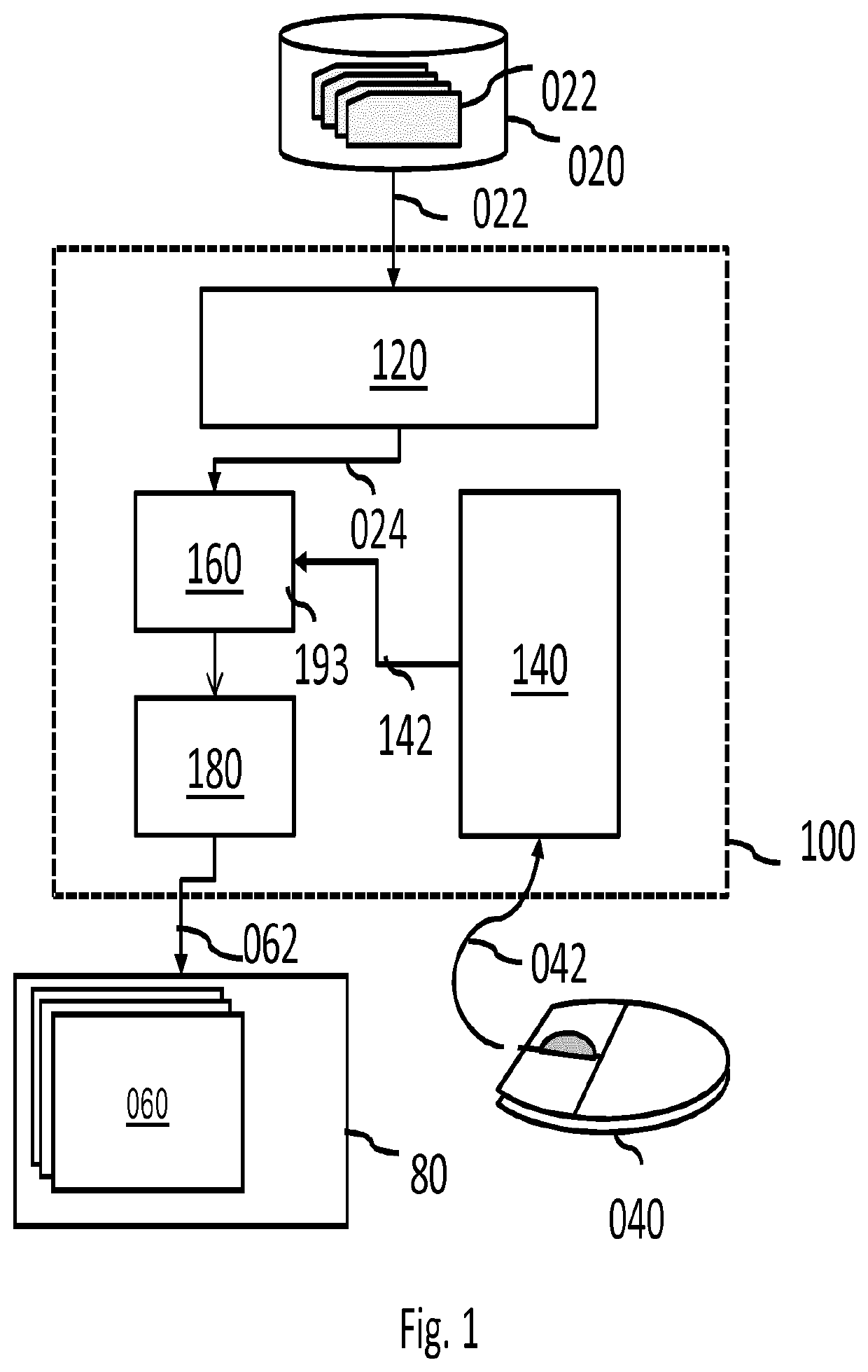
System and method for viewing medical image
ActiveUS20200321098A1Optimize workflowMinimal user interactionImage enhancementImage analysisImage ViewNuclear medicine
A system for enabling an automatic image viewing workflow, comprising a patient medical data interface 120 for obtaining medical data of a patient; one or more image viewing subsystems 180; a processing subsystem 160 configured to extracting context specific data from the patient medical data, and initiating at least one medical image viewing subsystems 180 based on the extracted context specific data.
Owner:KONINKLJIJKE PHILIPS NV
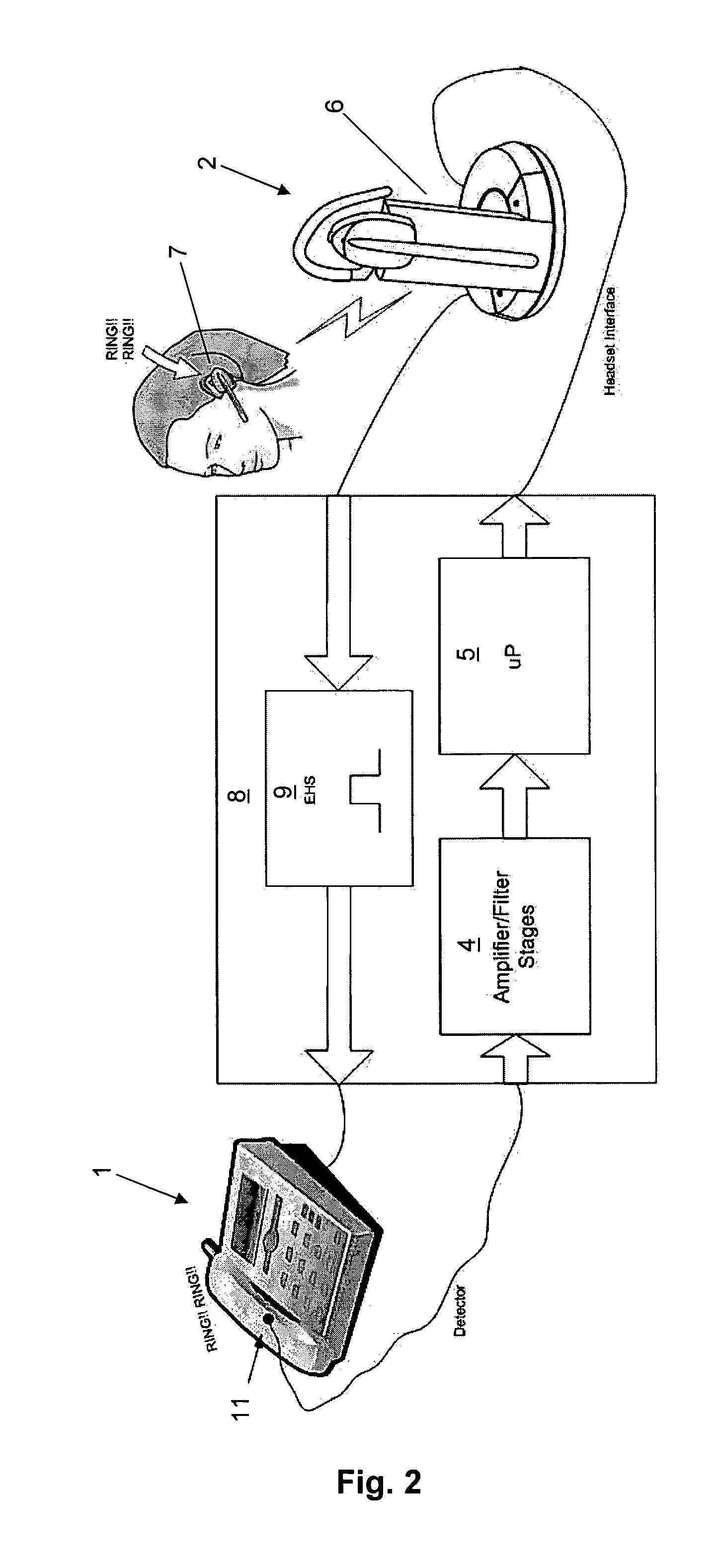
Adaptive Ringtone Detector
ActiveUS20110312304A1Reduce the amount requiredEliminate the calibration processSpecial service for subscribersTelephone set constructionsCommunications systemAudio power amplifier
A communications system and a method of detecting and learning new ringtones in an automatic manner, comprising a desk phone (1), a hook switch, a ringtone detector (3), and a communications device (2). In a first embodiment a mechanical hook switch device is connected to the desk phone (1), and in a second embodiment an electronic hook switch unit (9) is connected to the desk phone (1). The ringtone detector (3) adaptively sets the filter and amplifier parameters according to the sensor position and pick-up sensitivity. The ringtone detector (3) automatically detects and learns the characteristics of new ringtones. The communications device (2) may comprise a base station (6) and a headset (7).
Owner:GN NETCOM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com