Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Effective and efficient and scalable and convenient solution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
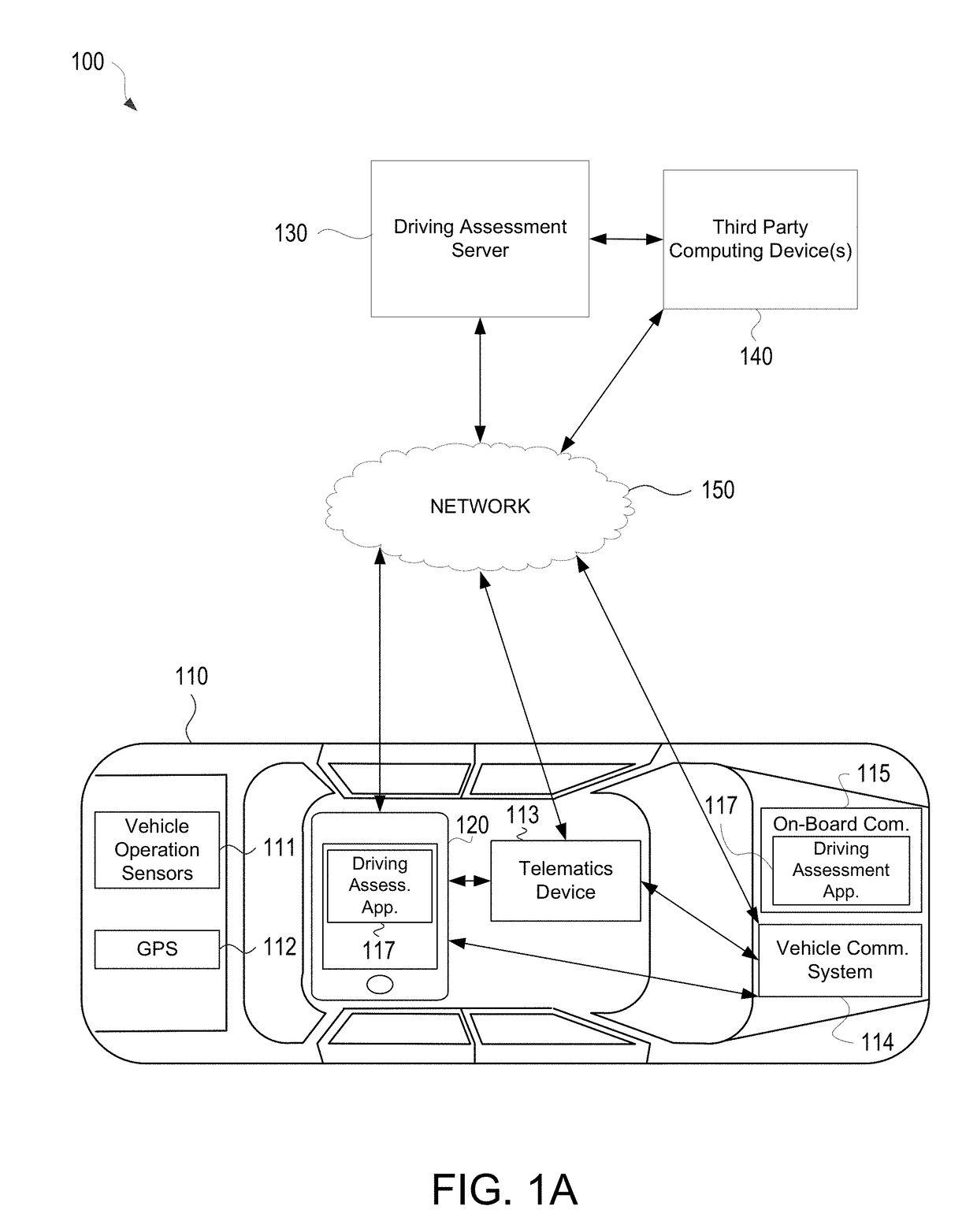
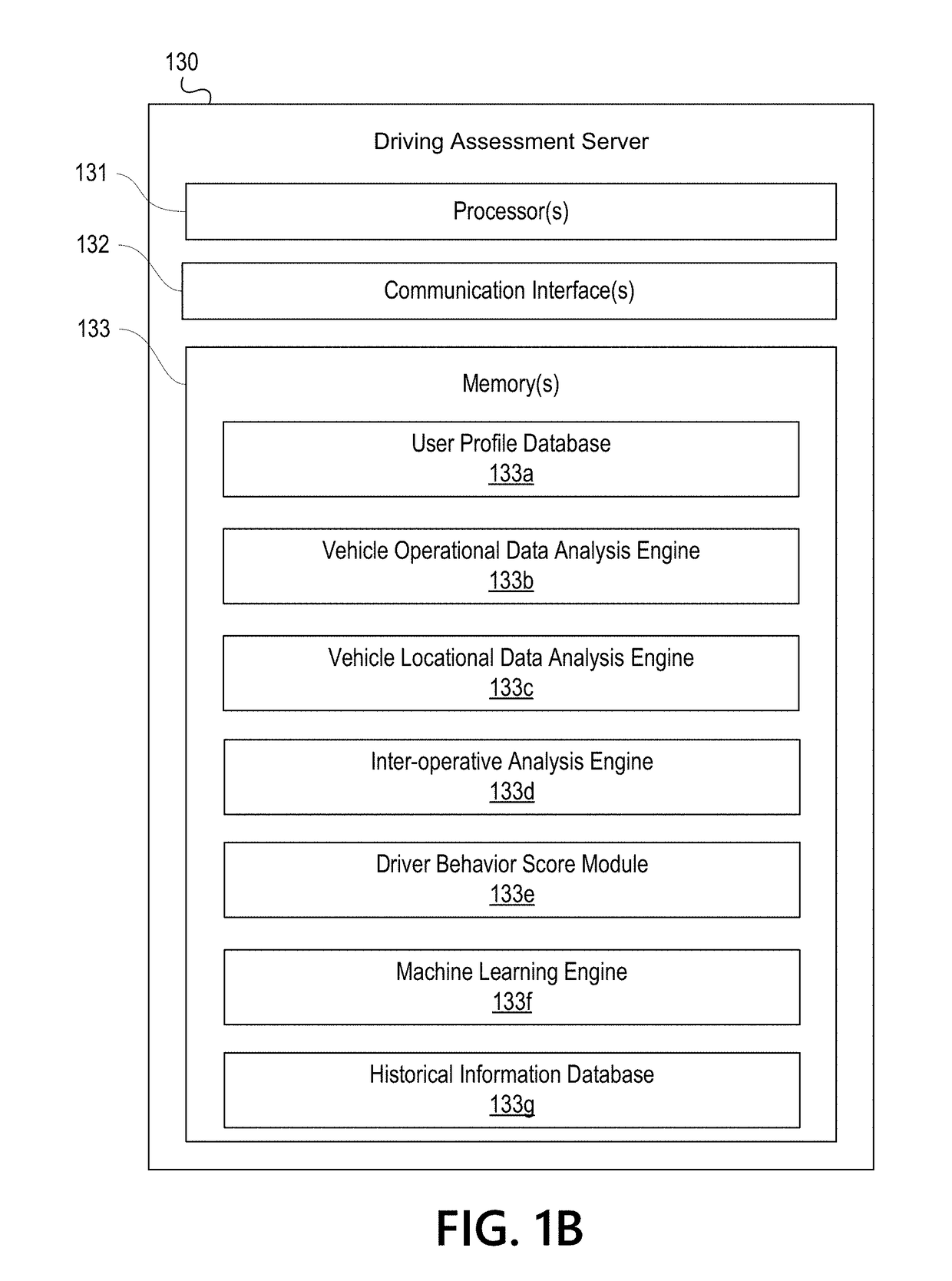
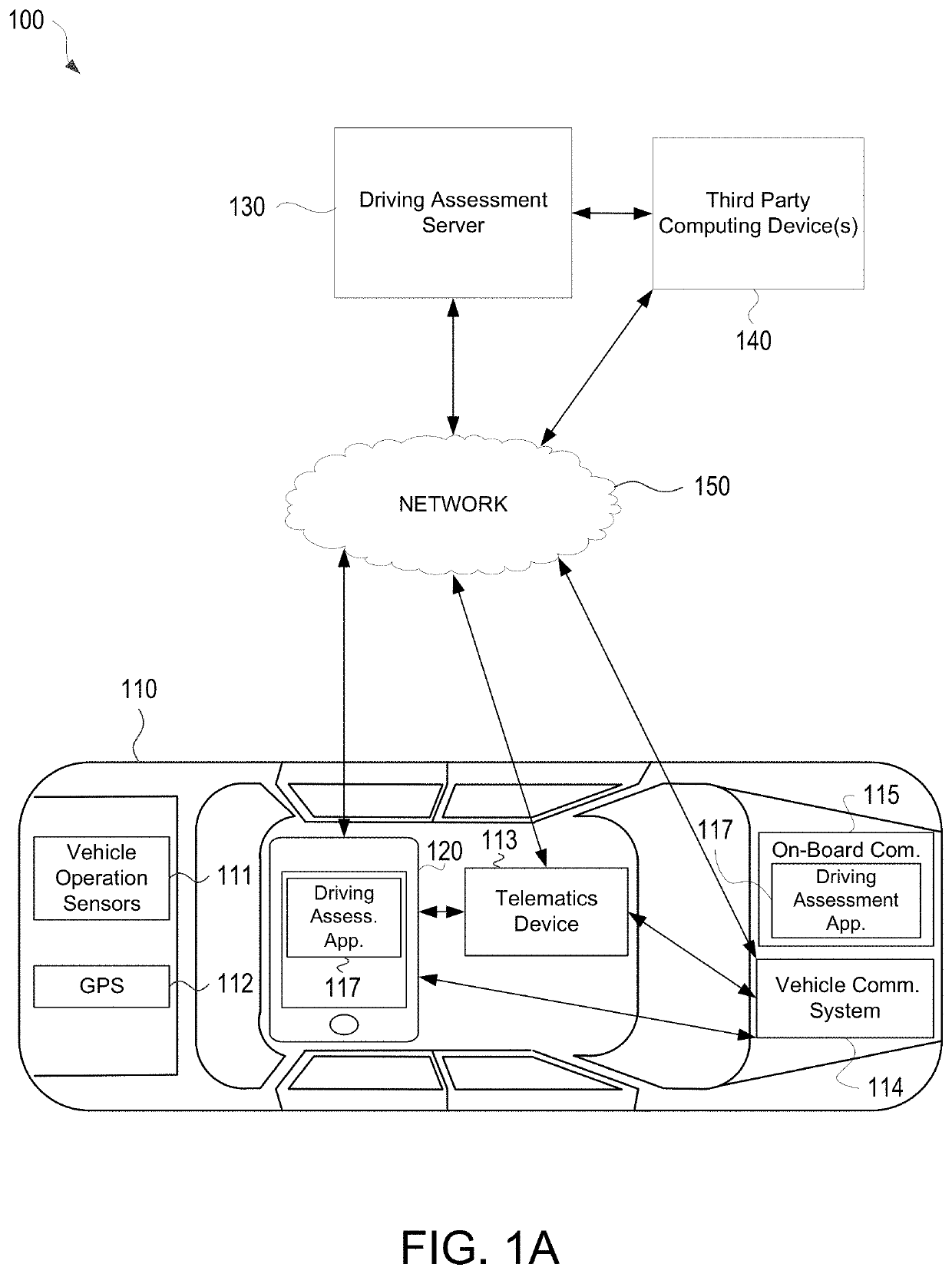
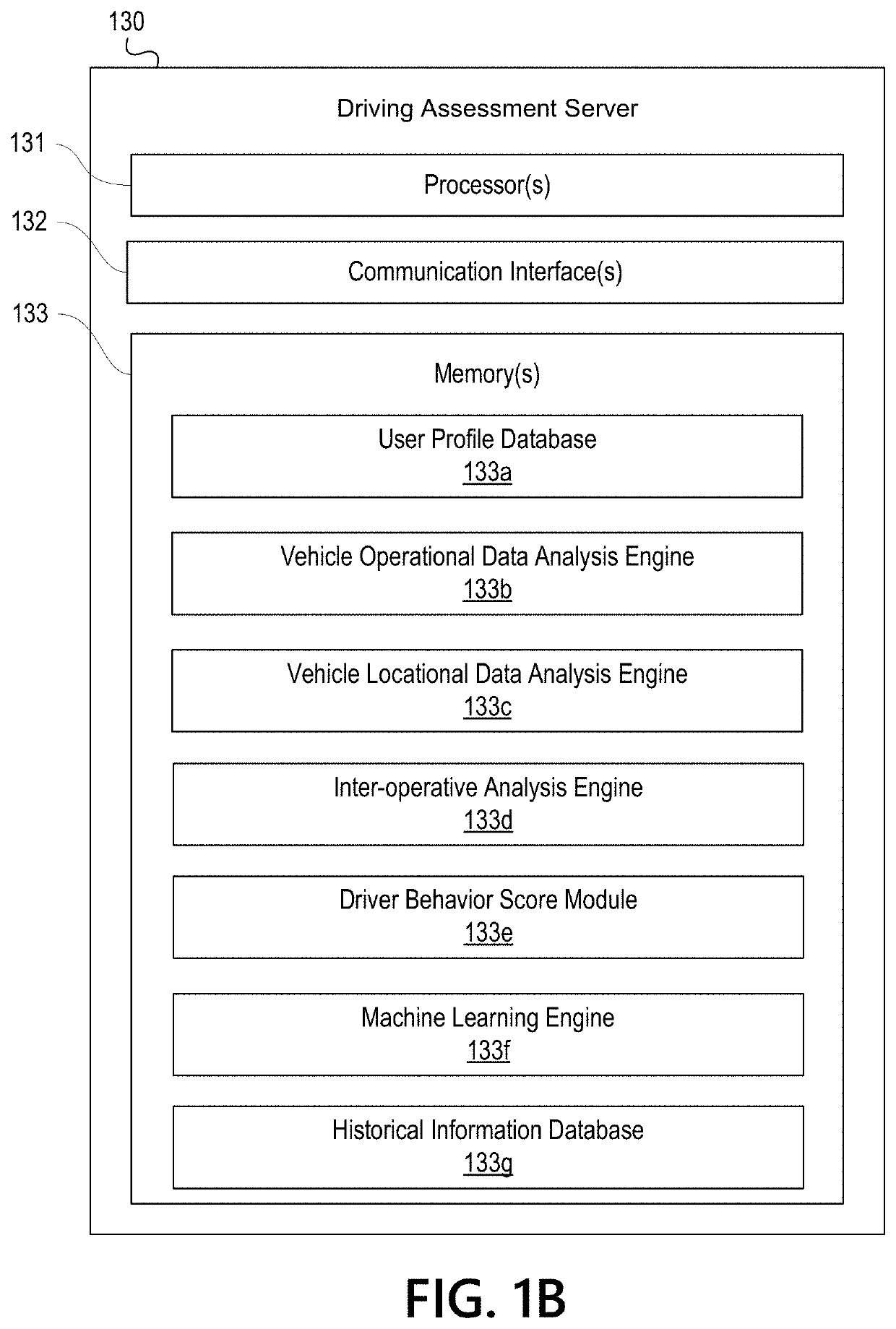
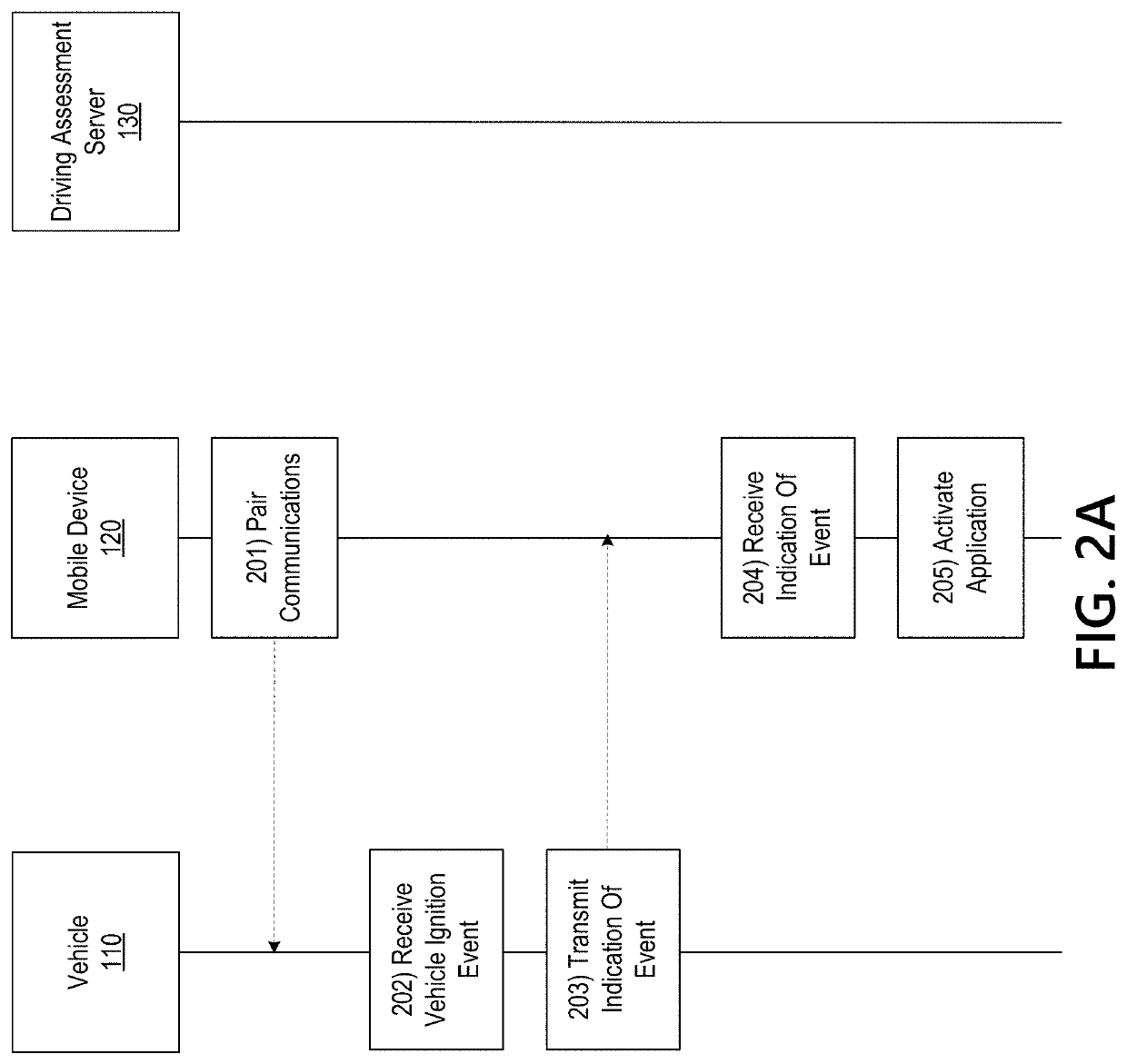
Vehicle Telematics Based Driving Assessment
ActiveUS20180345981A1Effective and efficient and scalable and convenient technical solutionEffective and efficient and scalable and convenient solutionFinanceRegistering/indicating working of vehiclesAccelerometerGlobal Positioning System
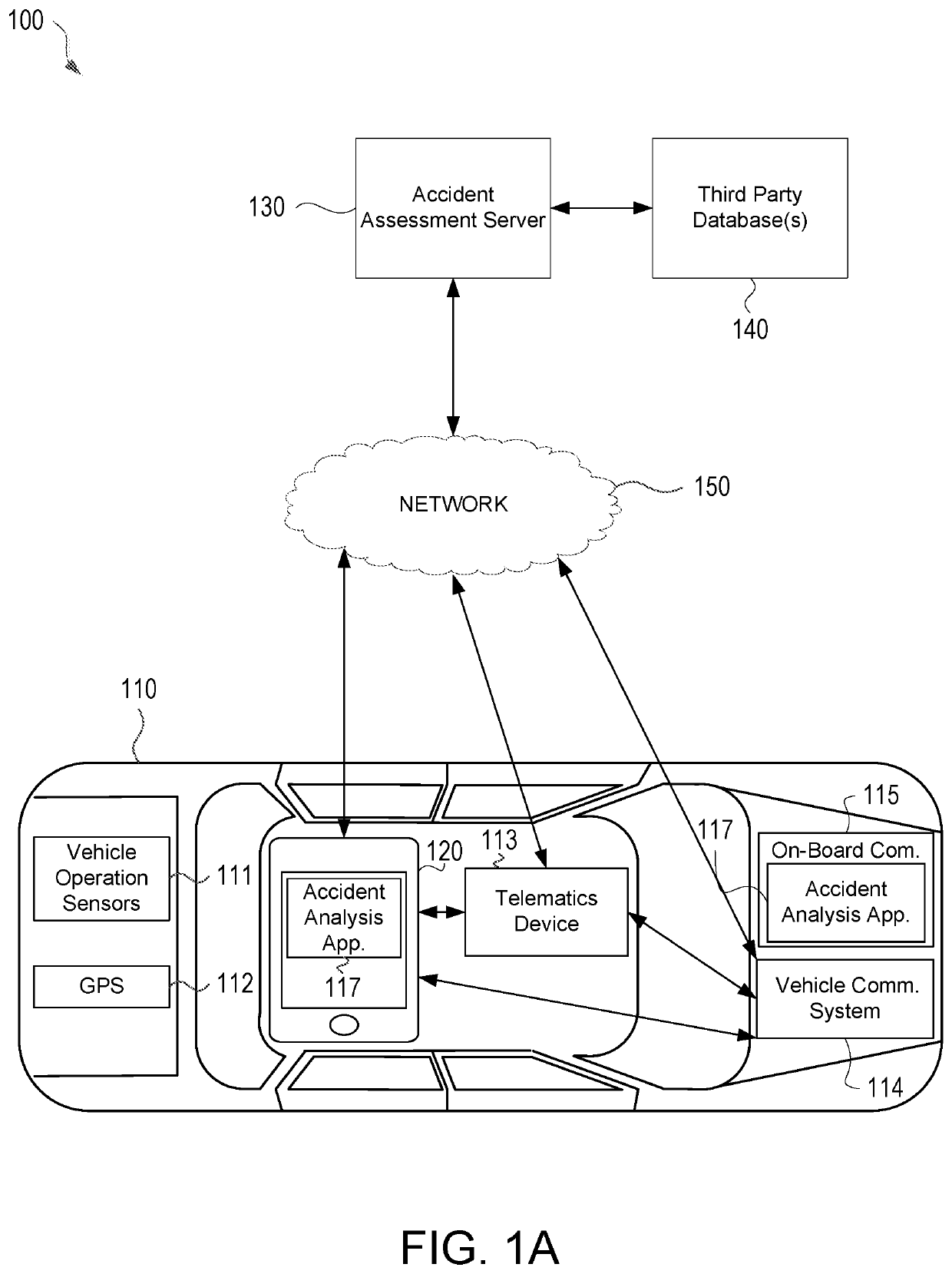
Aspects of the disclosure relate to using vehicle telematics data to assess parameters associated with vehicle operation. In some instances, a driving assessment system may include a first computing device associated with a user in a vehicle and a second computing located remotely from the first computing device. The first computing device may collect, by way of one or more of an accelerometer and global positioning system (GPS), vehicle operational data and vehicle locational information associated with the vehicle and corresponding to a trip of the vehicle and may transmit such information to the second computing device. The second computing device may identify actionable and second order actionable trip data from the vehicle operational data and vehicle locational information and may calculate a behavior score for the trip.
Owner:ALLSTATE INSURANCE
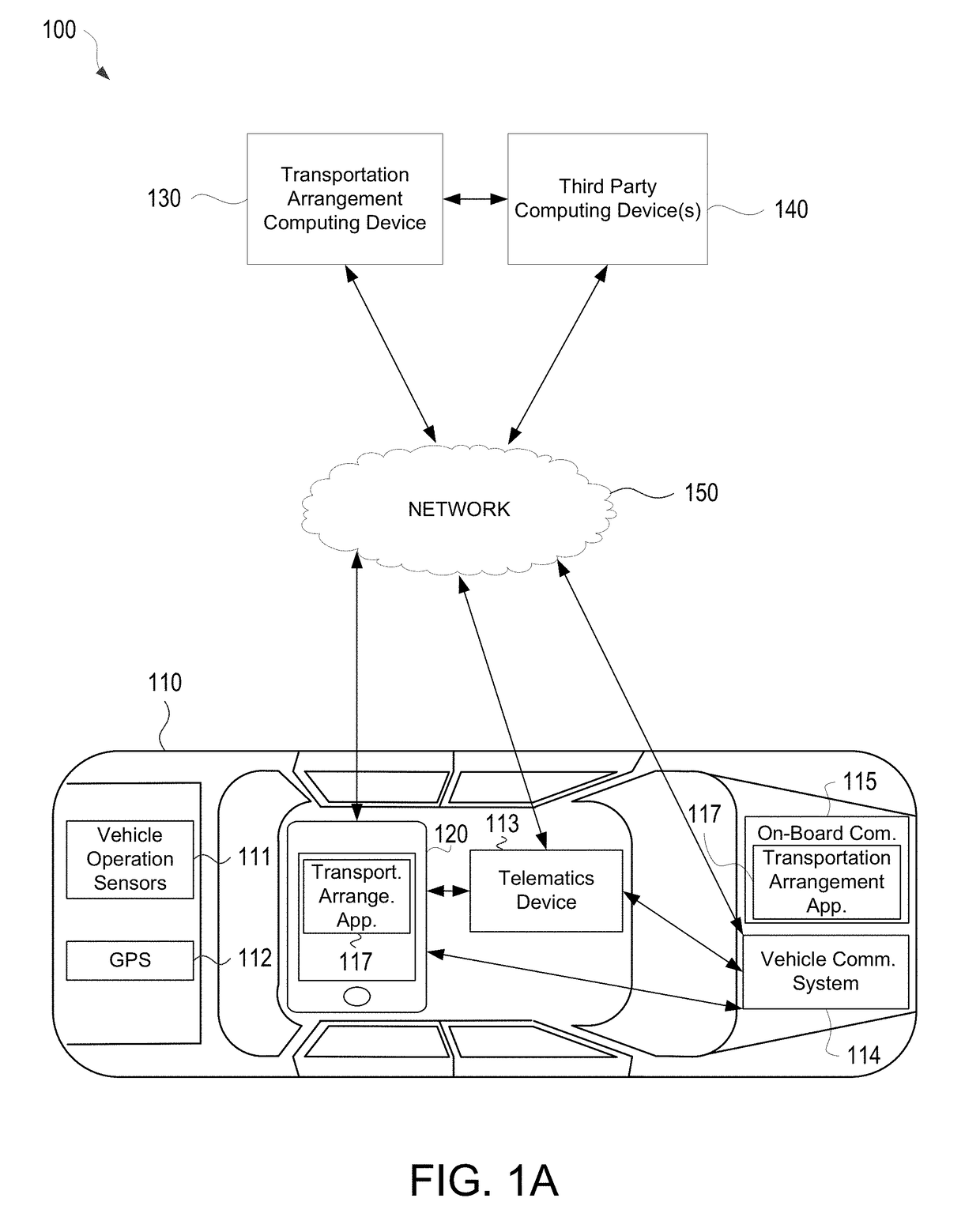
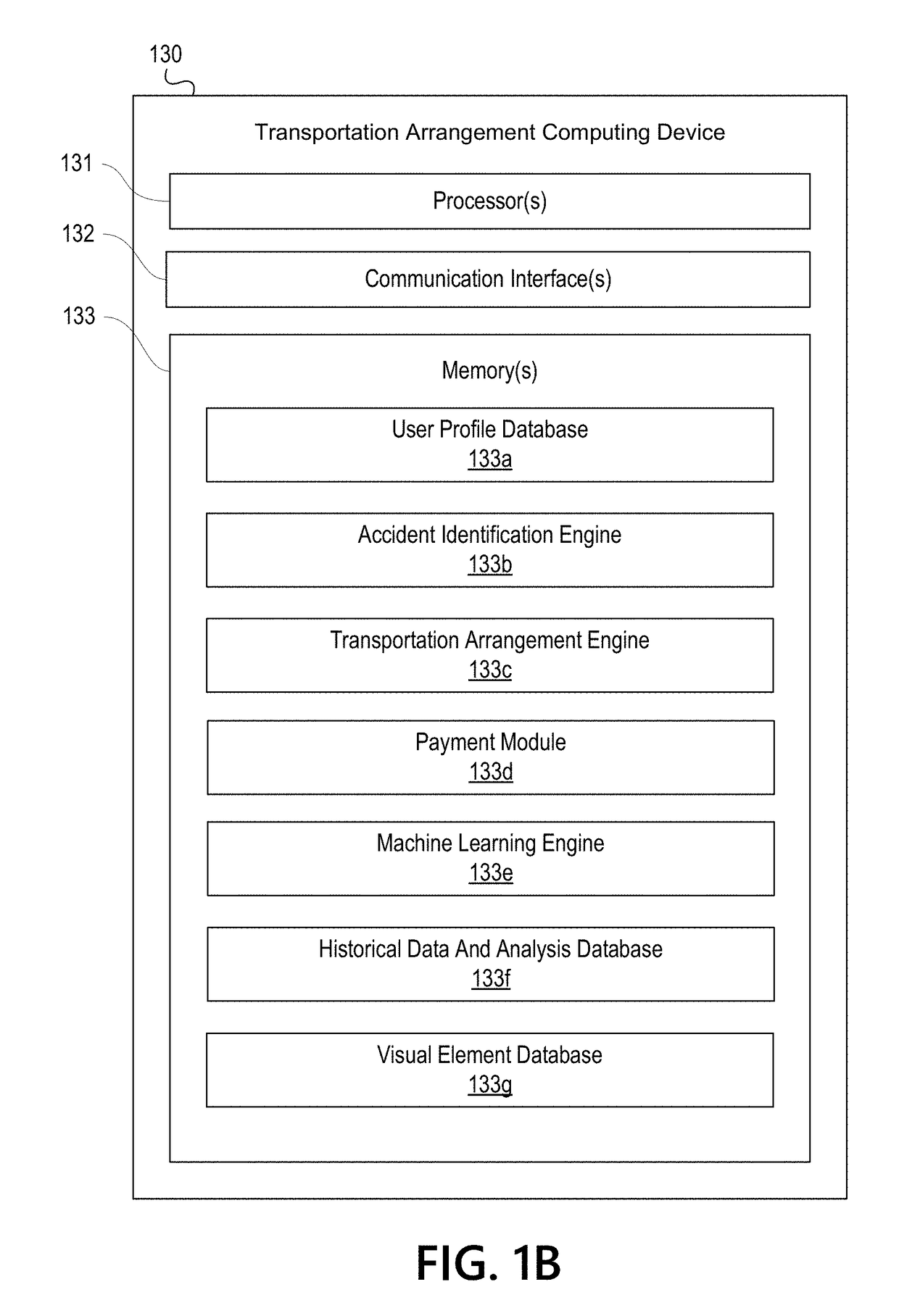
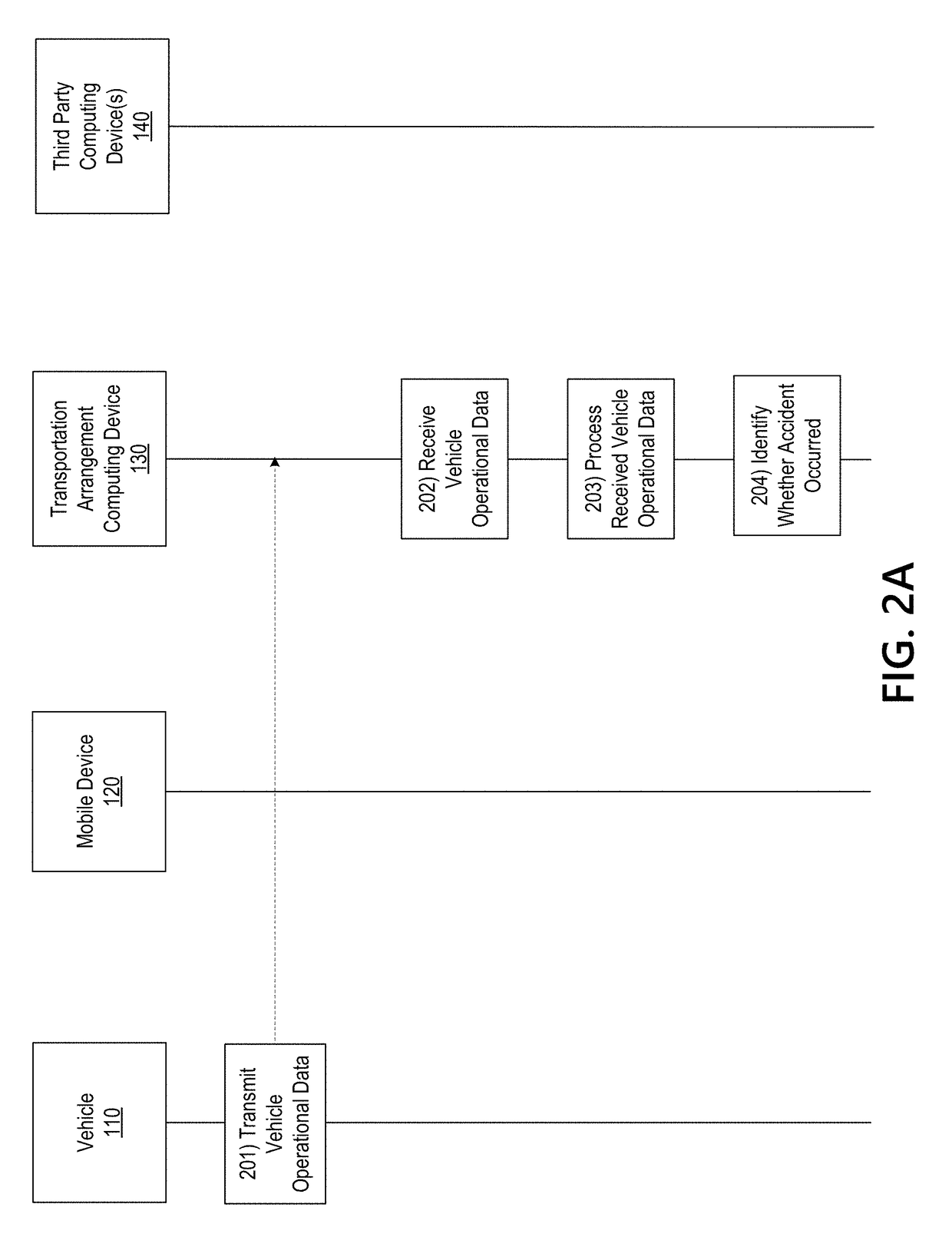
Facilitating Cross-Platform Transportation Arrangements with Third Party Providers
PendingUS20190073737A1Effective and efficient and scalable and convenient technical solutionEffective and efficient and scalable and convenient solutionPayment architectureCommerceThird partyComputer science
Aspects of the disclosure relate to facilitating cross-platform transportation arrangements with third party providers. In some instances, a first computing transportation may scrape information from one or more third party computing devices. The first computing device may populate a transportation arrangement resource shell with the scraped information from the one or more third party computing devices. In response to populating the transportation arrangement resource shell, the first computing device may retrieve stored data corresponding to visual elements of the first computing device. Using the retrieved data, the first computing device may generate a composite rendering that provides information associated with the one or more third party computing devices with visually perceptible elements of the retrieved data corresponding to the first computing device.
Owner:ALLSTATE INSURANCE
Preventing unauthorized access to secured information using identification techniques
ActiveUS20180137263A1Effective and efficient and scalable and convenientEffective and efficient and scalable and convenient solutionVehicle seatsSpeech analysisEngineeringSecurity information
Owner:BANK OF AMERICA CORP
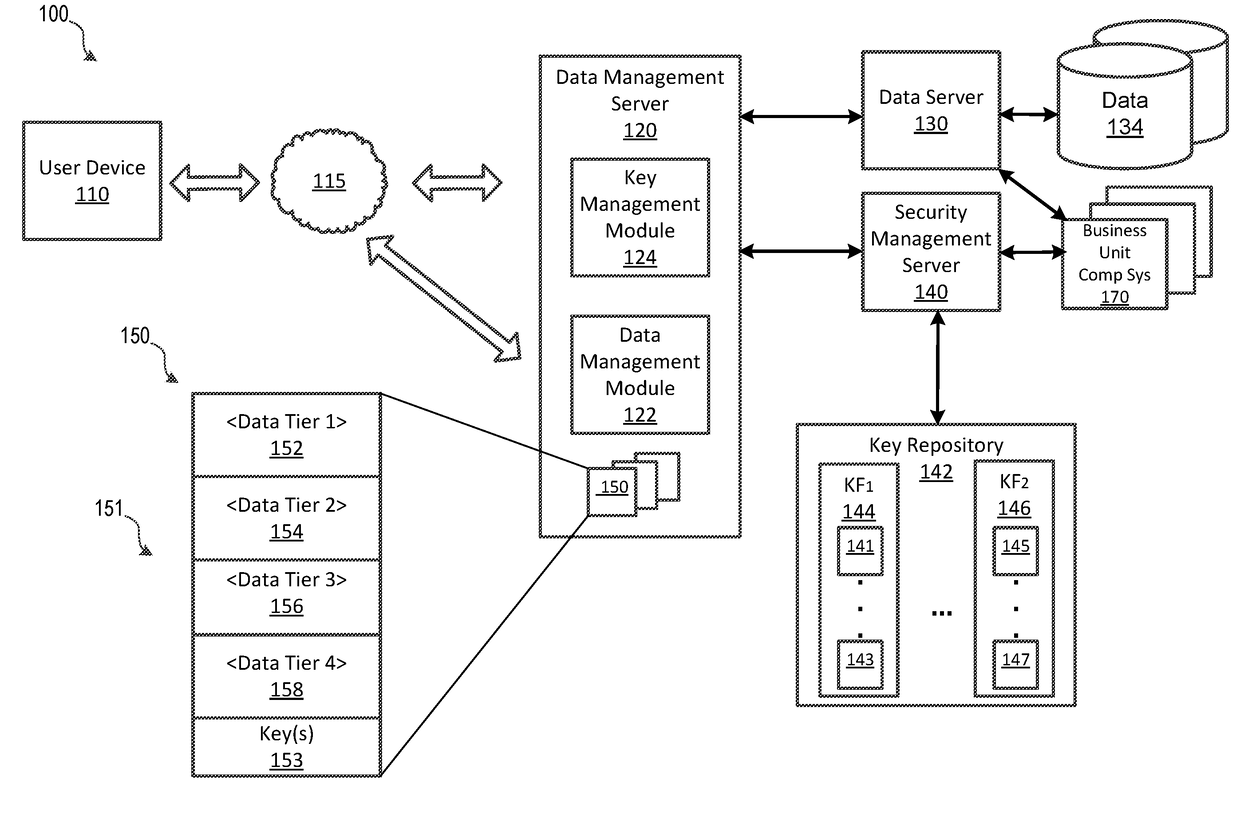
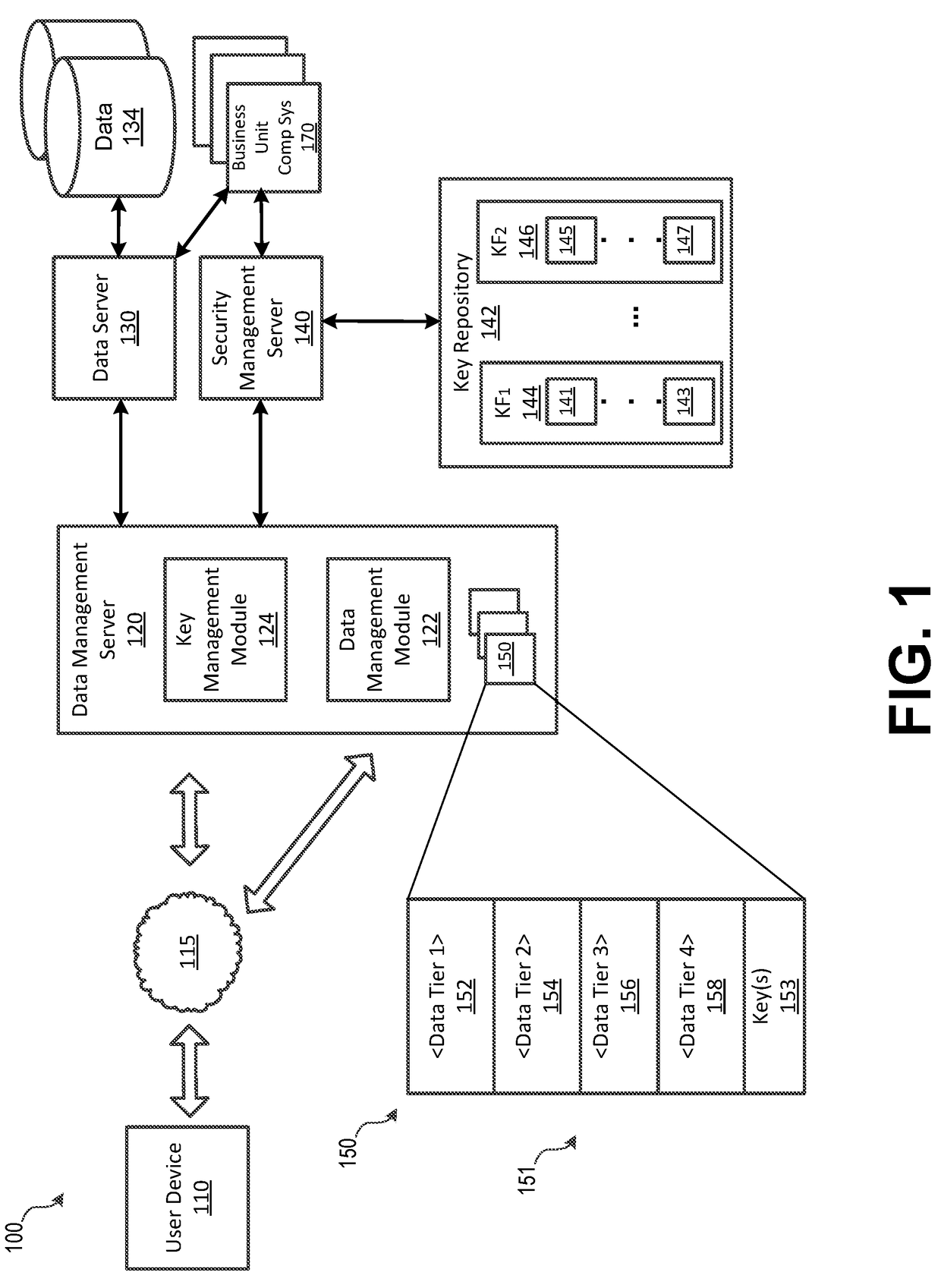
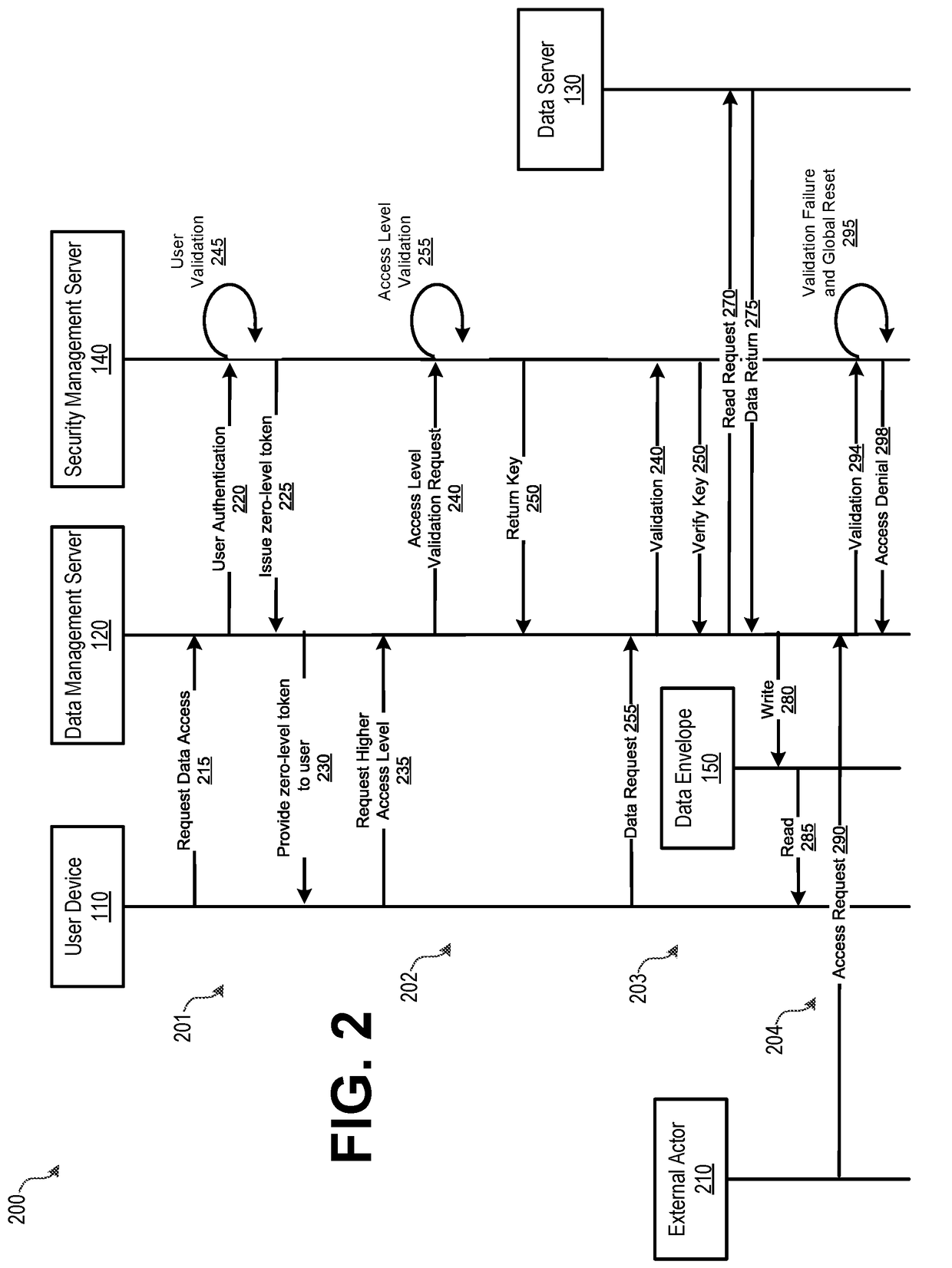
Dynamic Data Protection System
InactiveUS20180176206A1Effective and efficient and scalable and convenientEffective and efficient and scalable and convenient solutionComputer security arrangementsTransmissionUser deviceNetwork connection
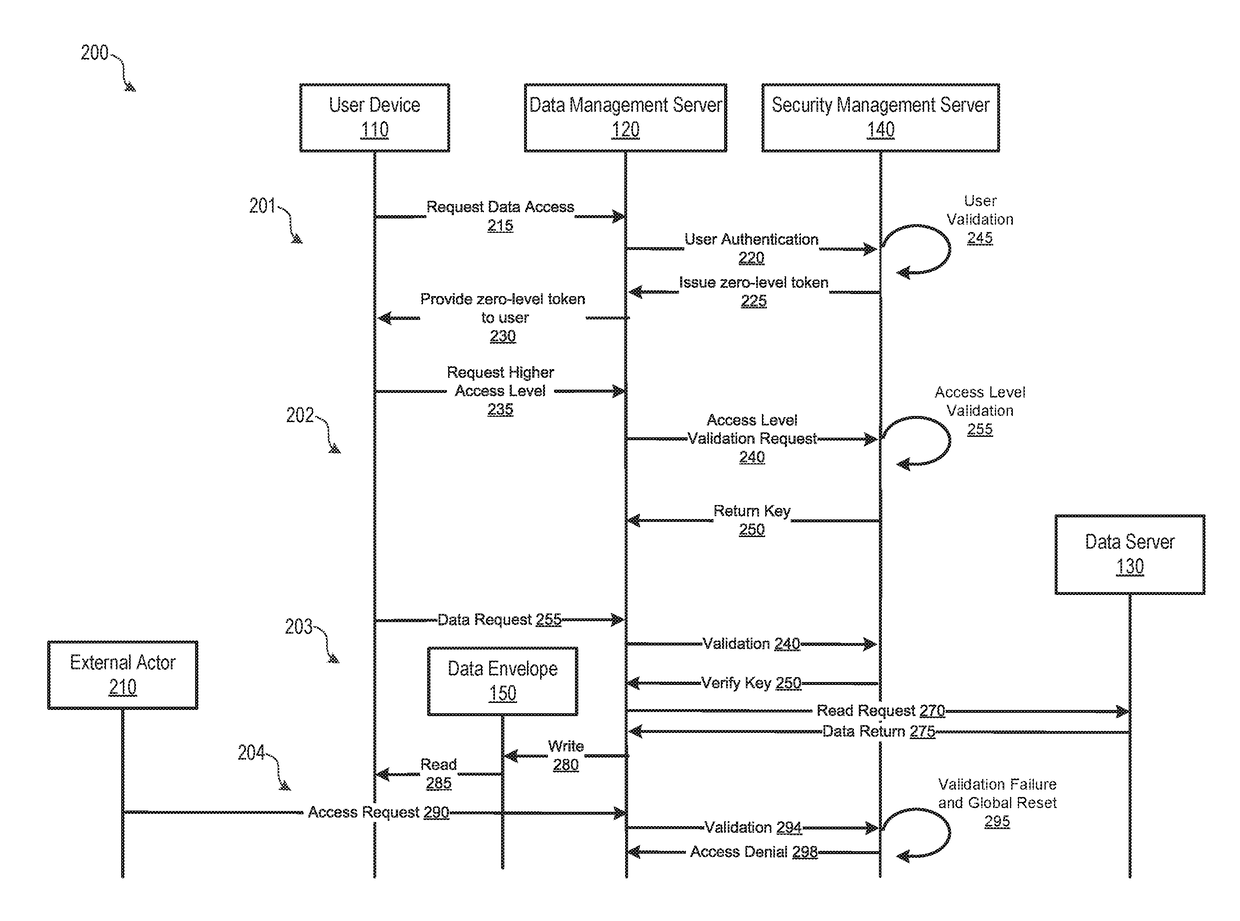
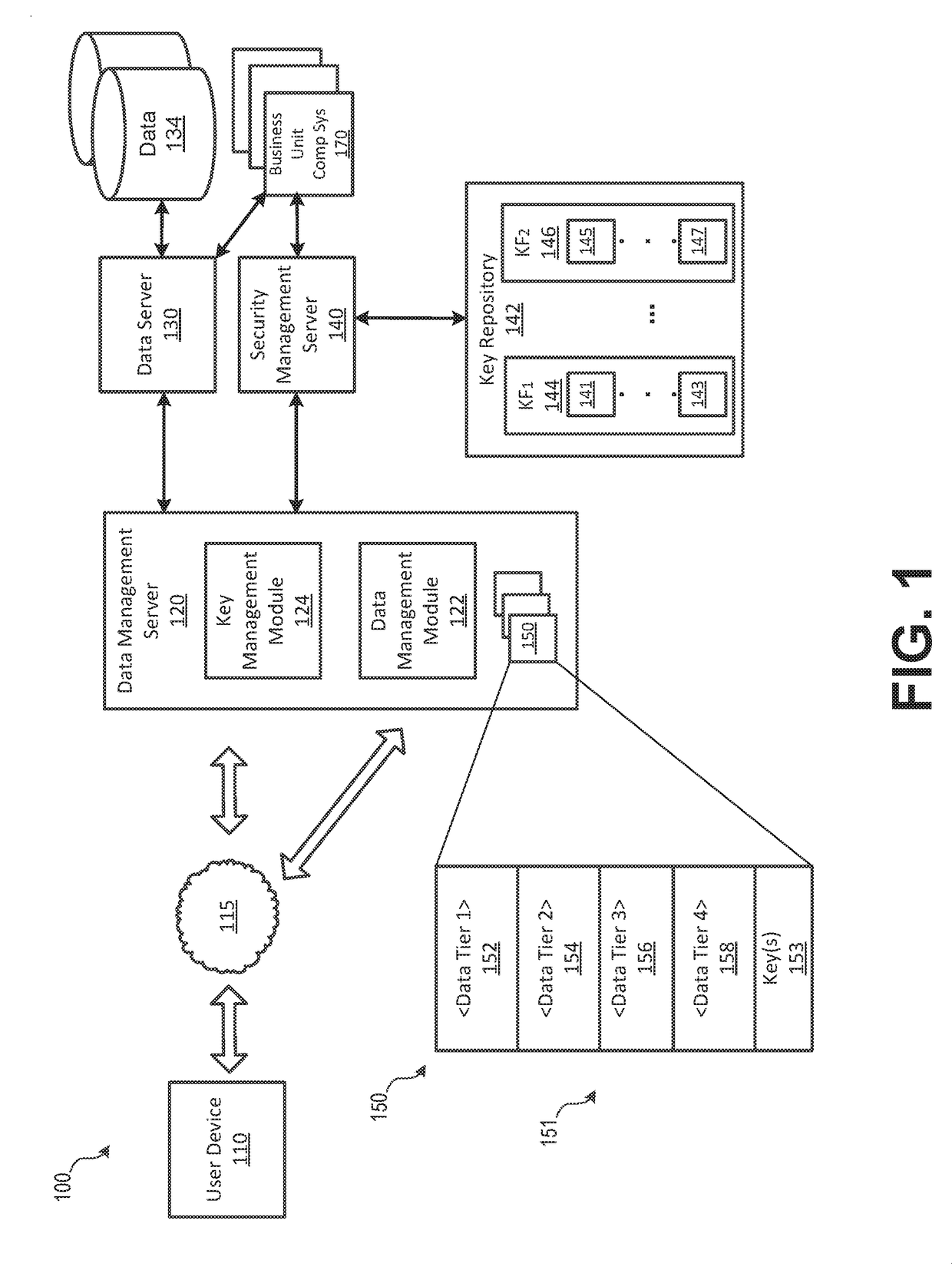
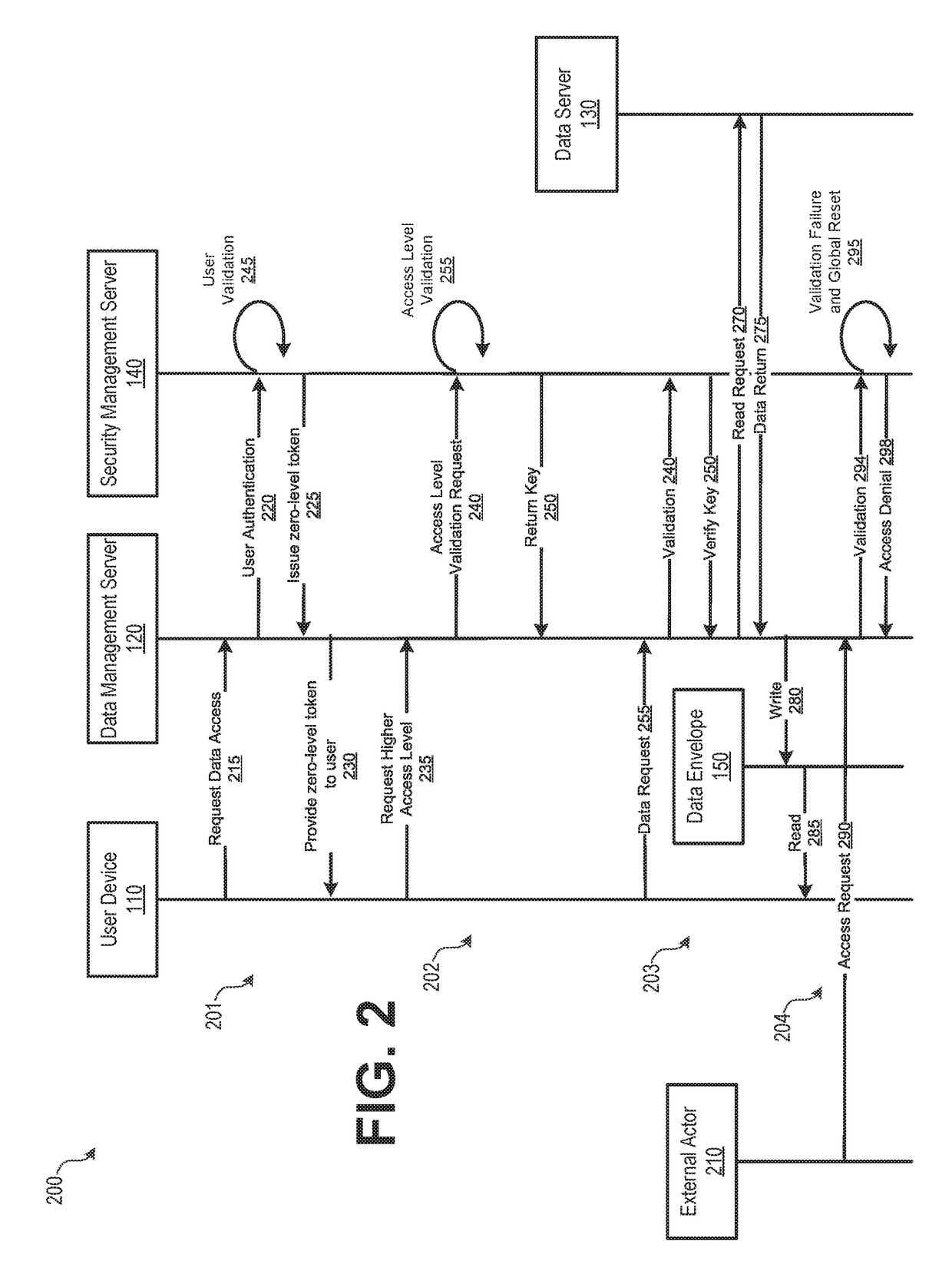
A dynamic data protection system may include a data management server includes a processor and a non-transitory memory device storing instructions that cause the data management server to receive, via a network connection from a user device, a request for access to data stored on an organization's network. The data management server may then communicate user authentication information associated with the received request. The security management server may process user authentication information to determine whether an authentication code associated with the user is valid and associated with the requested data. Upon validation of the user authentication information by the security management server, provide access to data via a secured data container of a data envelope corresponding to the data, wherein the data container corresponds to the validated user authentication information. When a data compromise event occurs, the secure data envelope may prevent unauthorized access to the data.
Owner:BANK OF AMERICA CORP
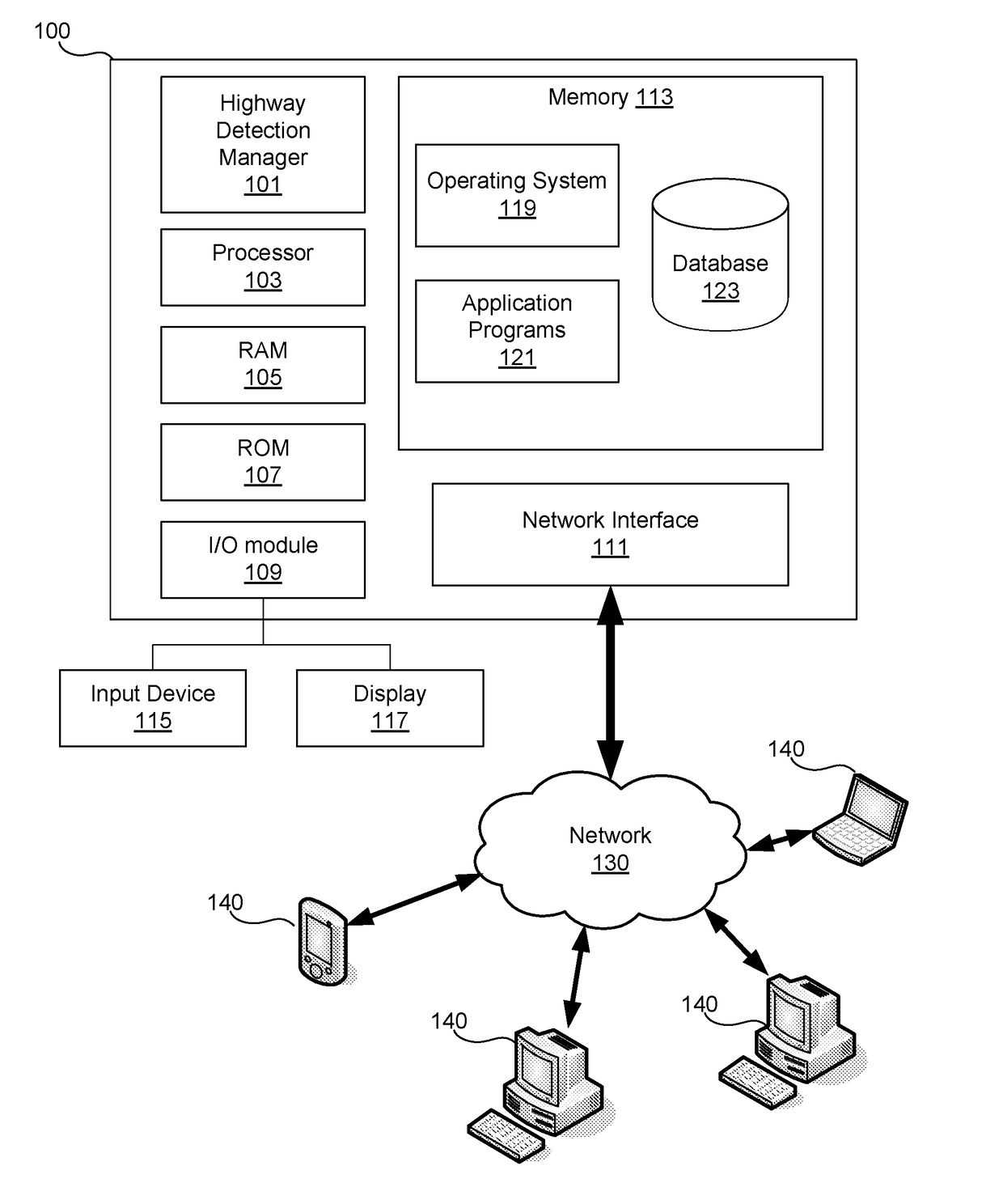
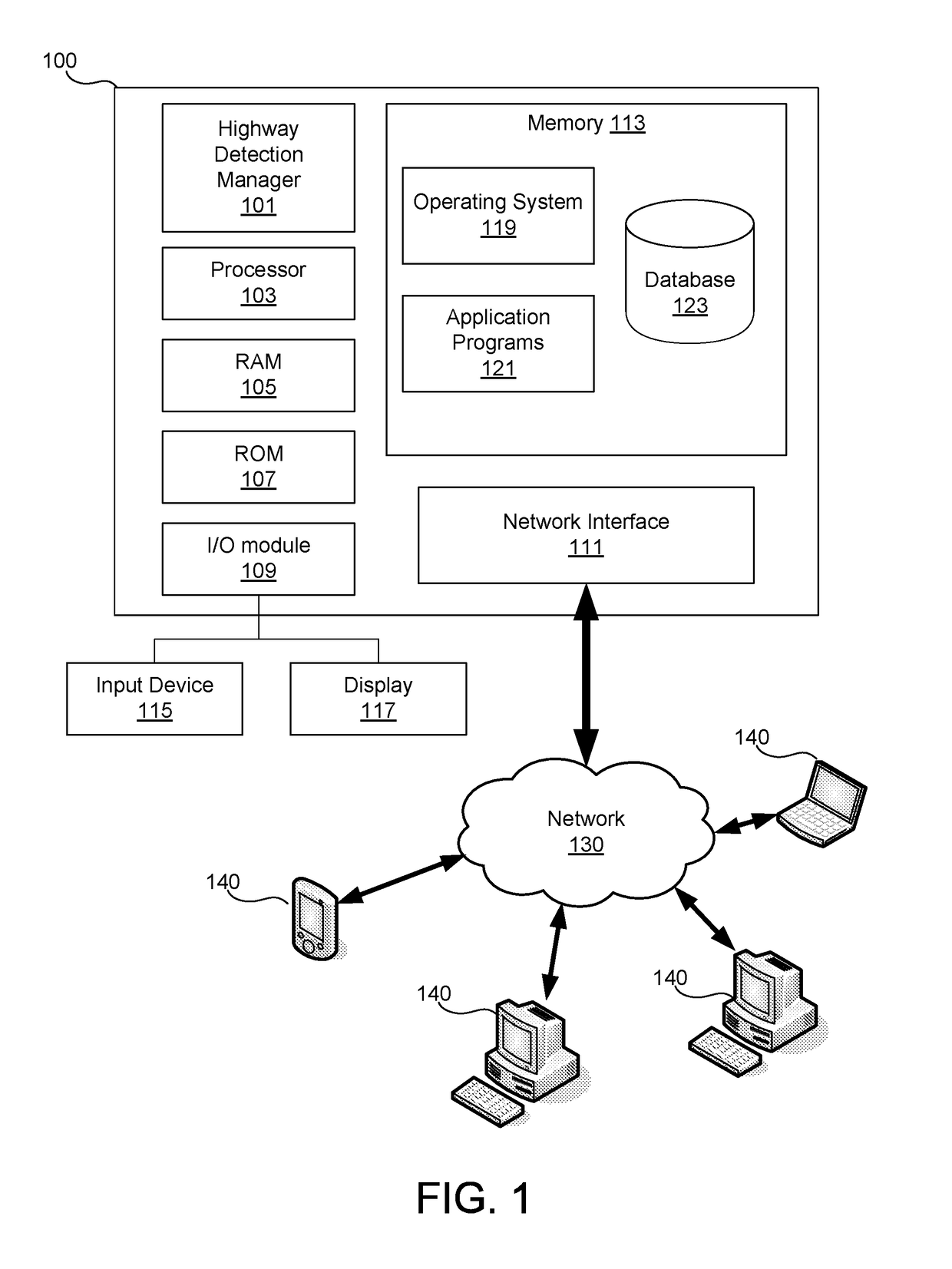
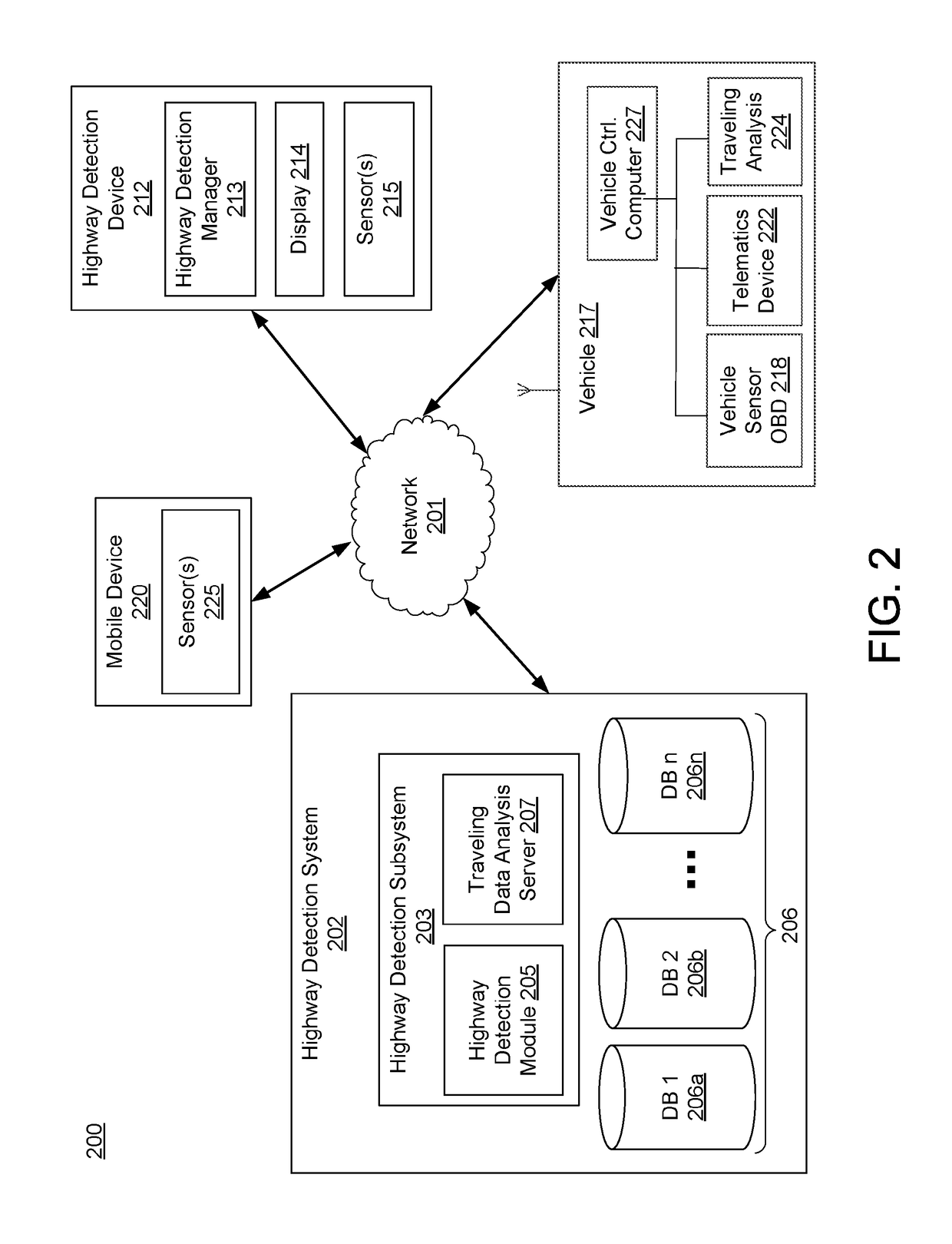
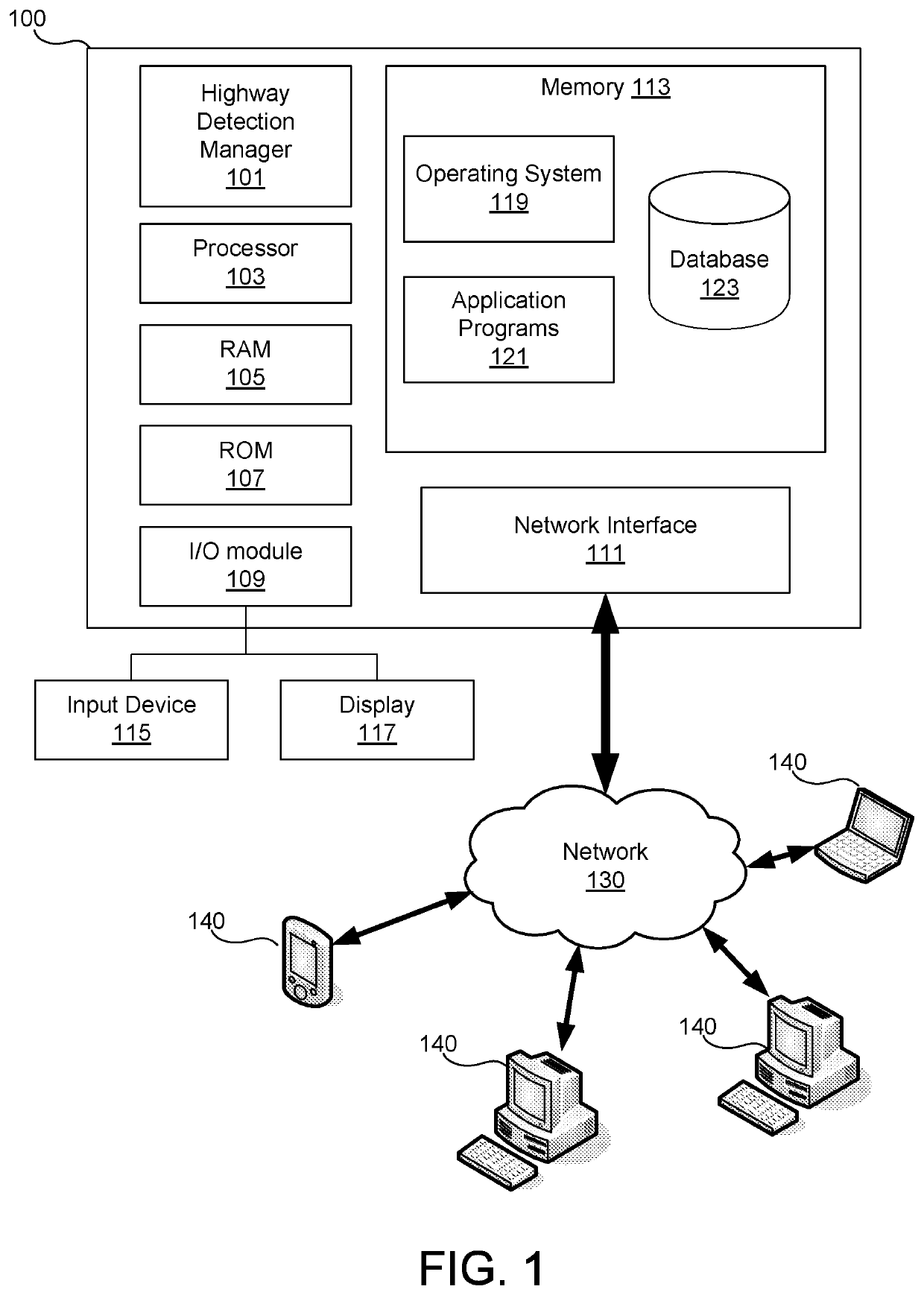
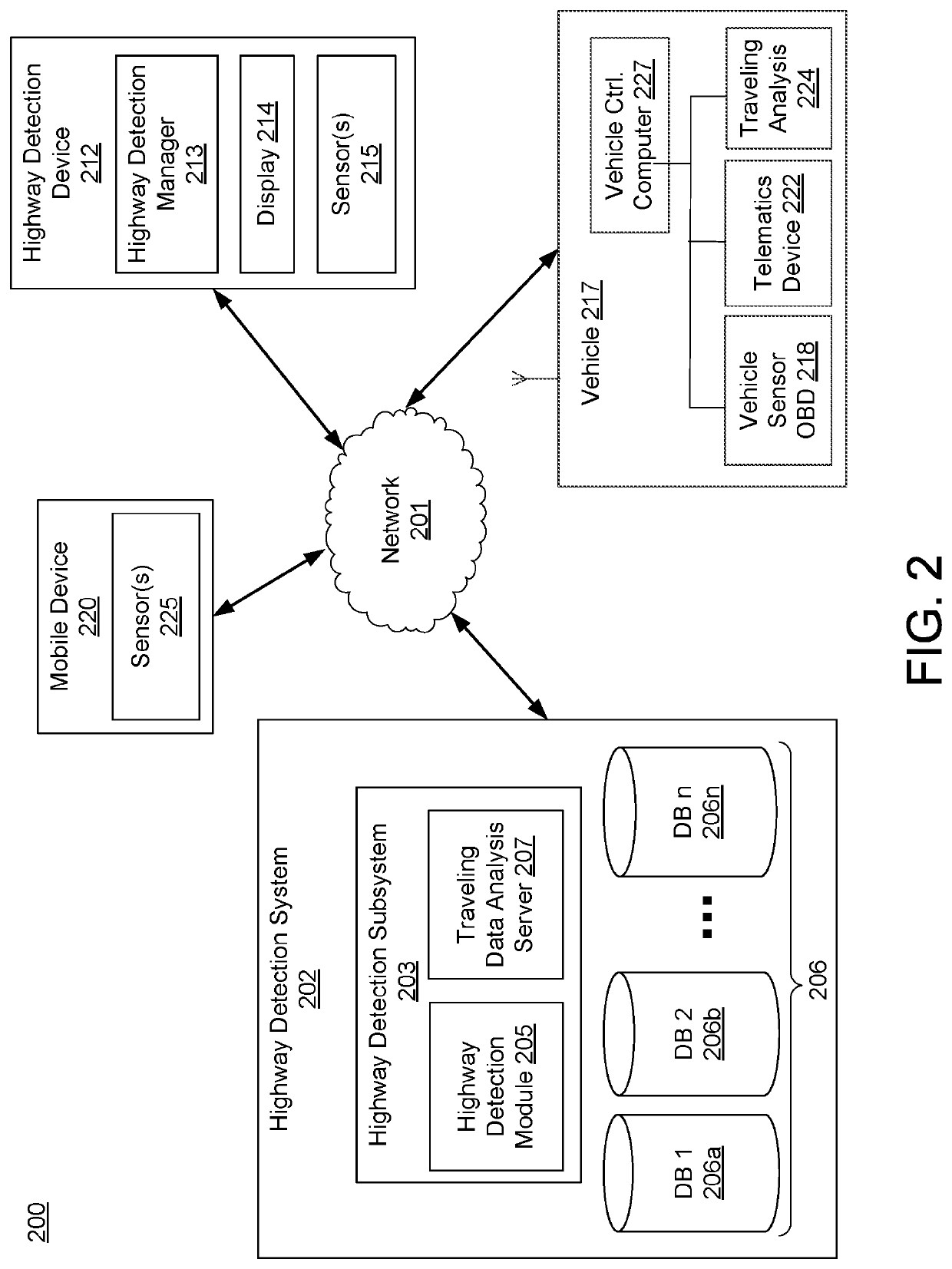
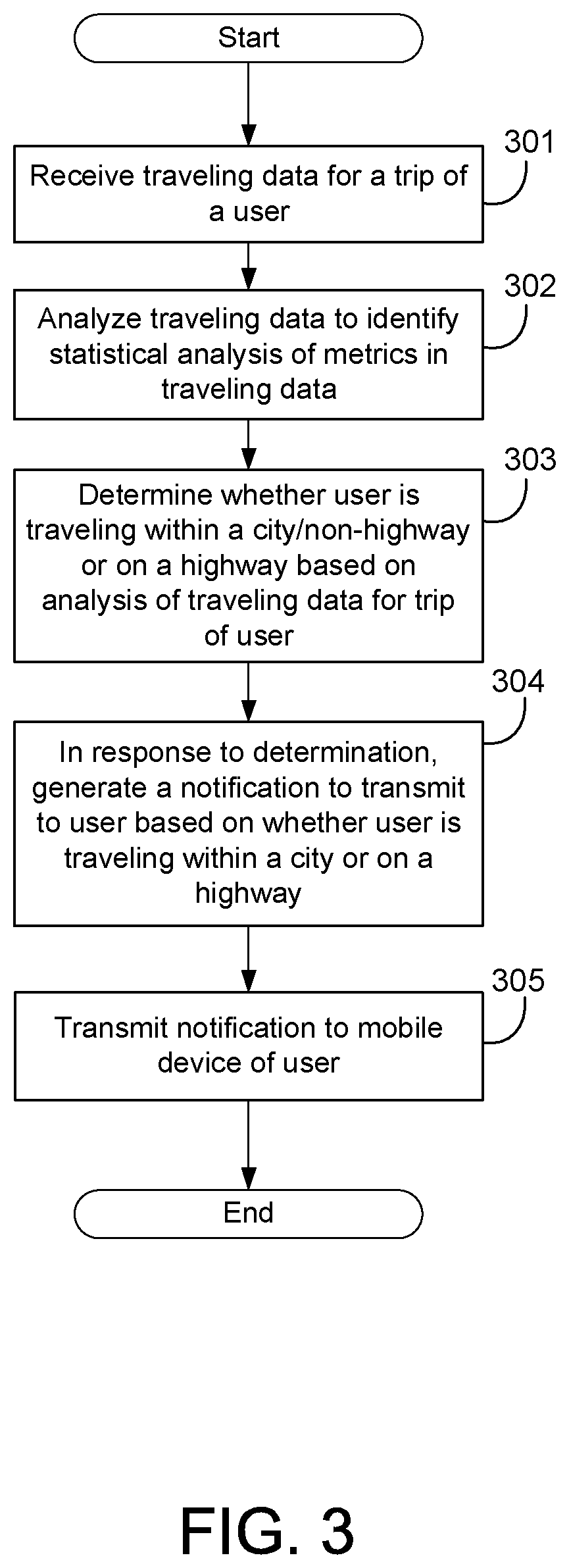
Highway Detection System for Generating Customized Notifications
ActiveUS20180302484A1Effective and efficient and scalable and convenientOperate efficiently and effectivelyVehicle testingInstruments for road network navigationStatistical analysisMobile device
A highway detection system may include a telematics device associated with a vehicle having one or more sensors arranged therein, a mobile device associated with a user traveling in the vehicle, and a server computer. The server computer may receive traveling data for a trip of the user from the one or more sensors and via the telematics device. The server computer may then determine whether the user is traveling within a city or on a highway based on analysis of the traveling data for the trip of the user, which may include a statistical analysis to calculate standard deviations of metrics in the traveling data. In response to the determination, the server computer may generate a notification to transmit to the user based on whether the user is traveling within a city or on a highway and transmit the notification to the mobile device associated with the user.
Owner:ALLSTATE SOLUTIONS PTE LTD
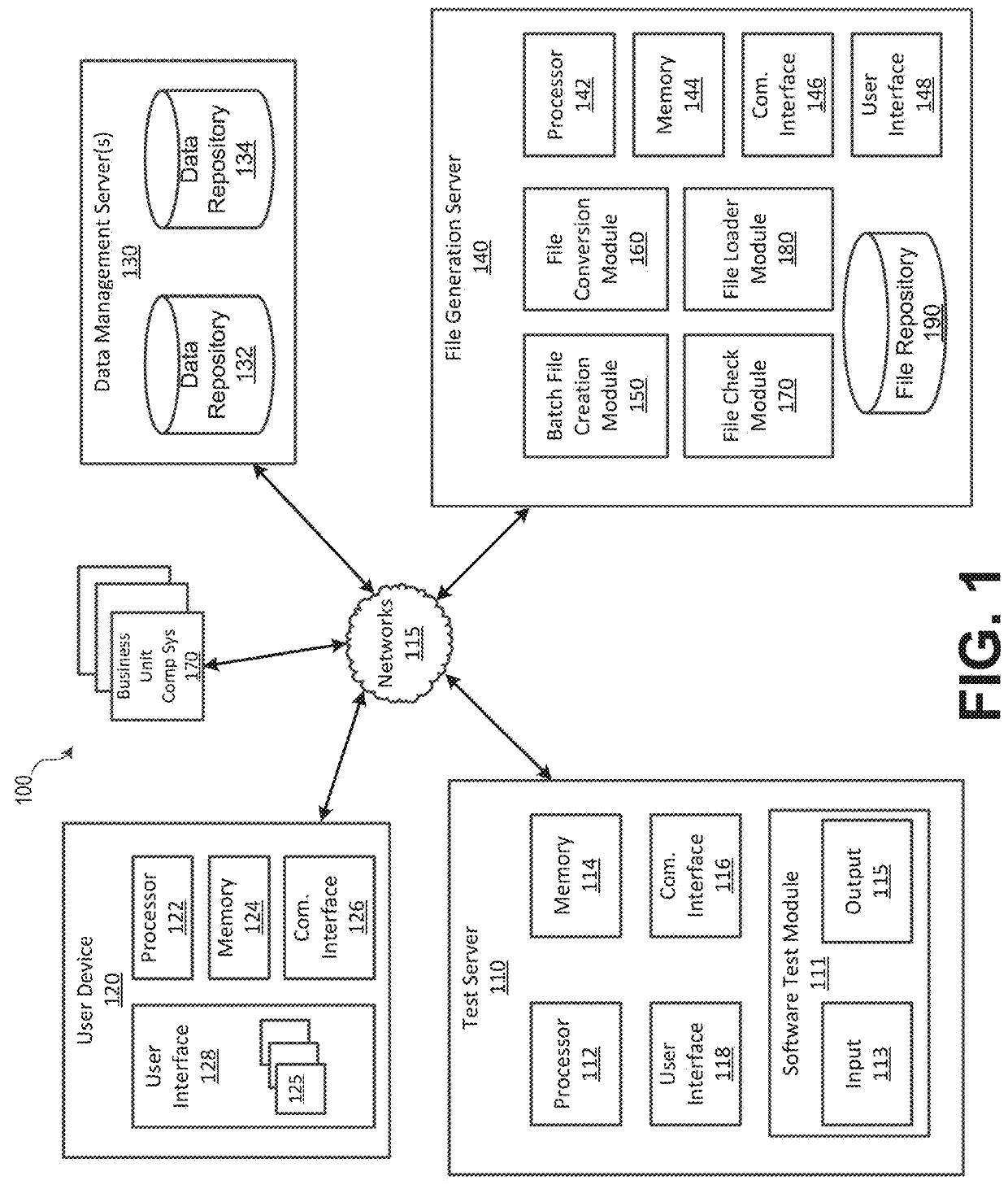
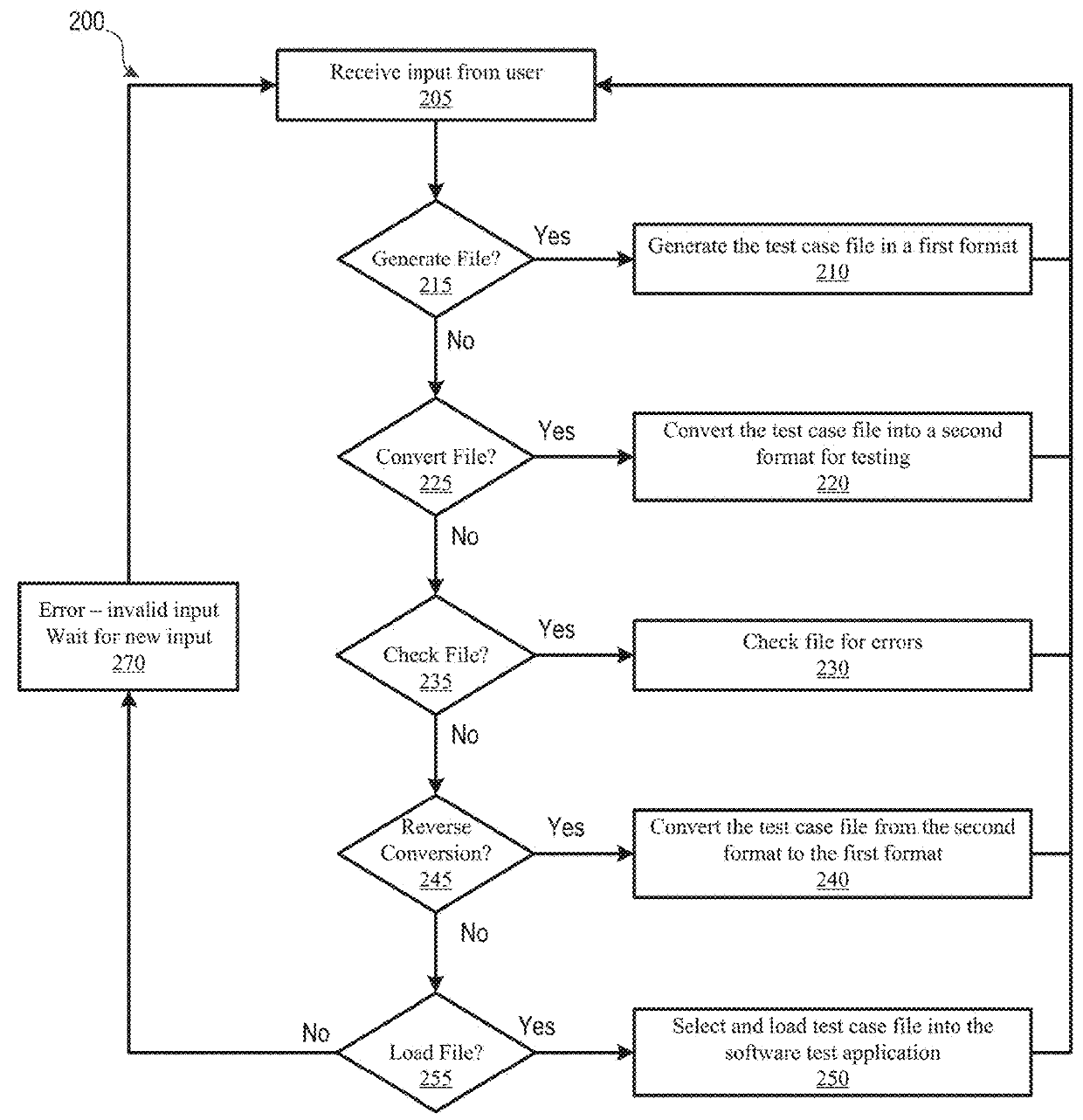
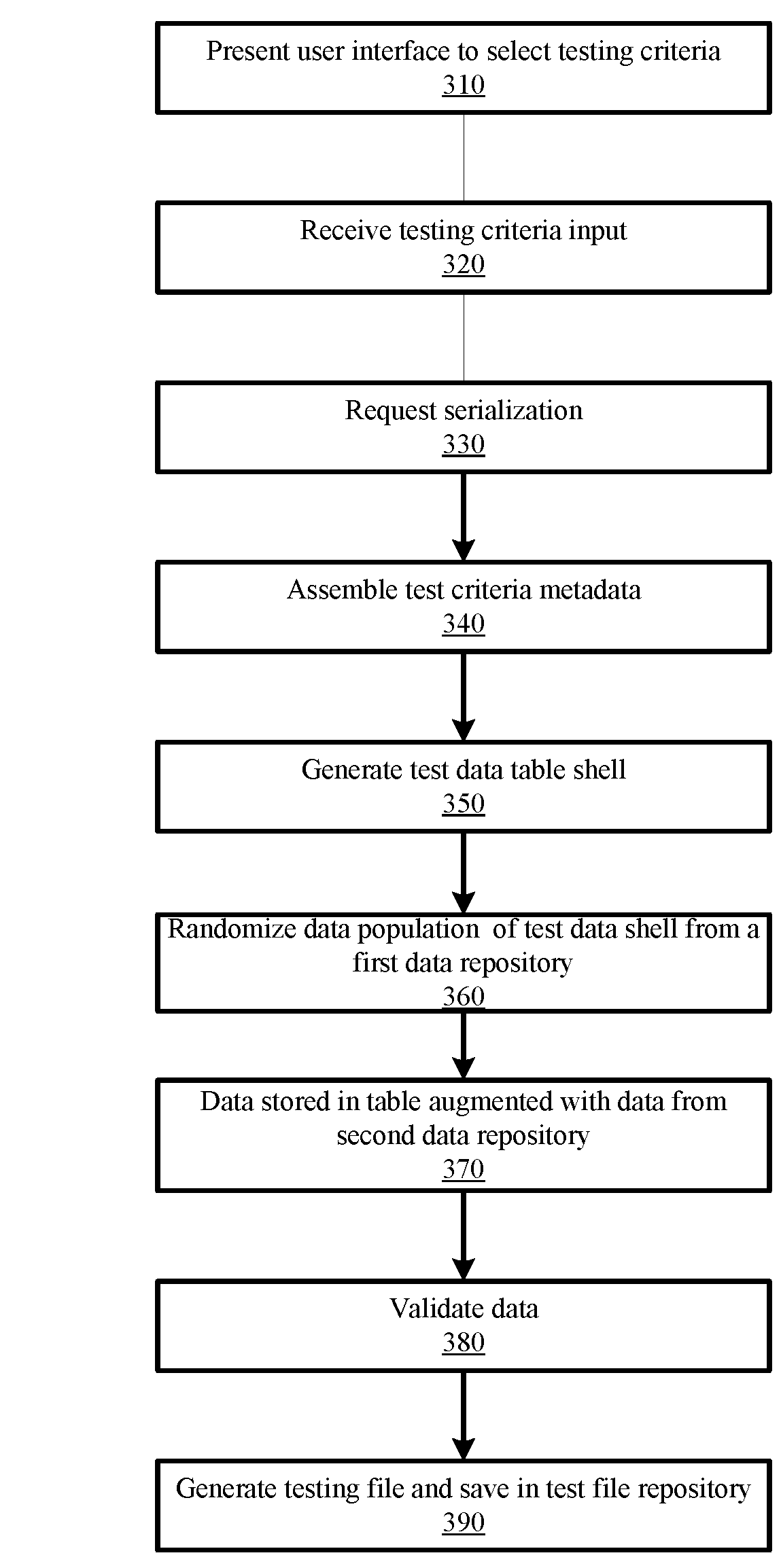
Batch File Creation Service
InactiveUS20180165180A1Effective and efficient and scalable and convenientEffective and efficient and scalable and convenient solutionSoftware testing/debuggingFile access structuresSearch data structureData set
A software testing computing system may include a batch file creation computing device, a user interface device communicatively coupled to the file creation computing device and a software testing computing system communicatively coupled to the batch file creation computing device to receive a batch file including a test case for use in testing a software application or service. The batch file creation computing device may receive criteria for testing a software application, generate a data structure formatted corresponding to a software test case associated with the criteria, retrieve and store in the data structure a first data set from a first data repository, merge, a second data set retrieved from a second data repository with the first data set stored in the data structure, and generate a batch test file using the data structure storing a merged data set including the first data set merged with the second data set.
Owner:BANK OF AMERICA CORP
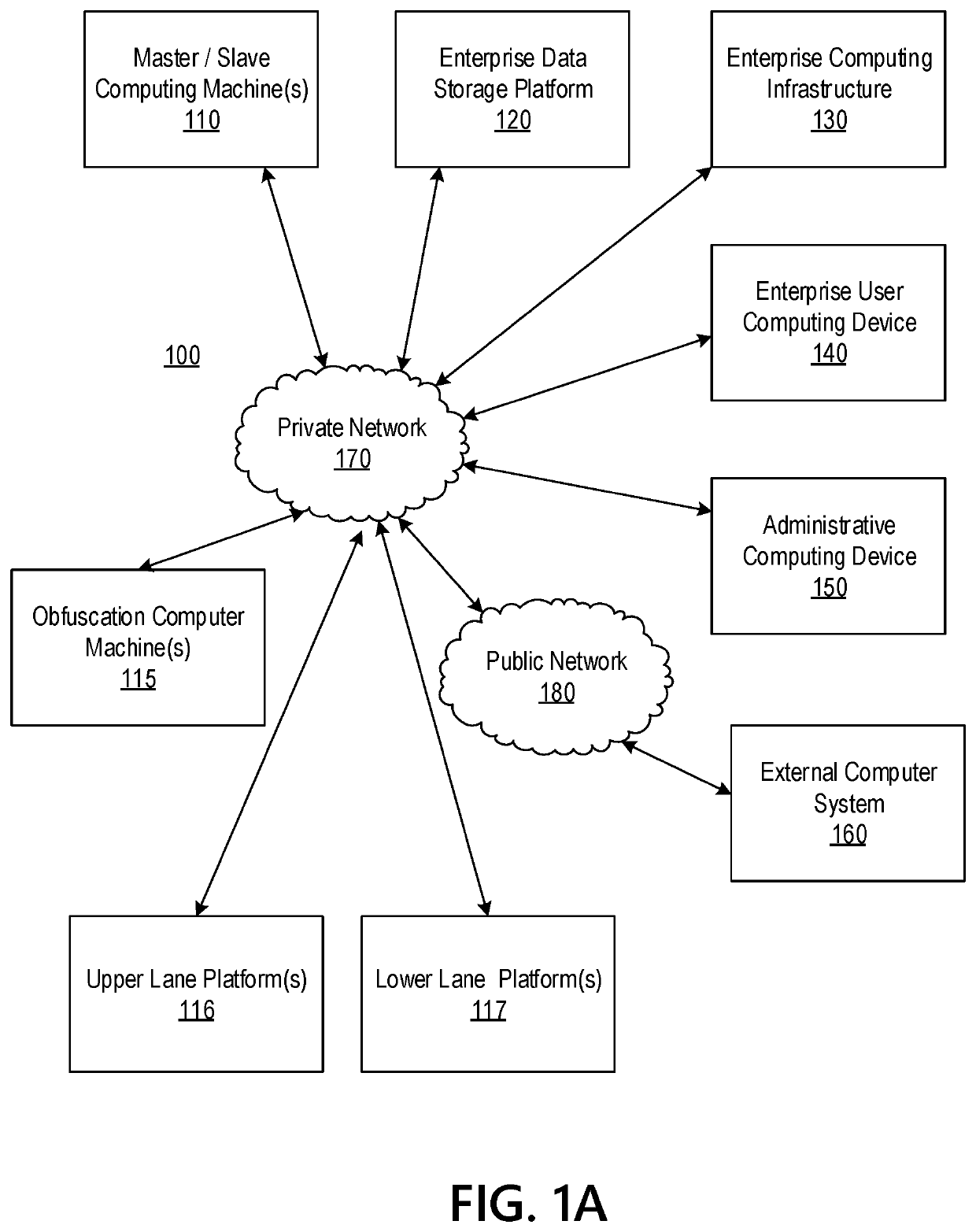
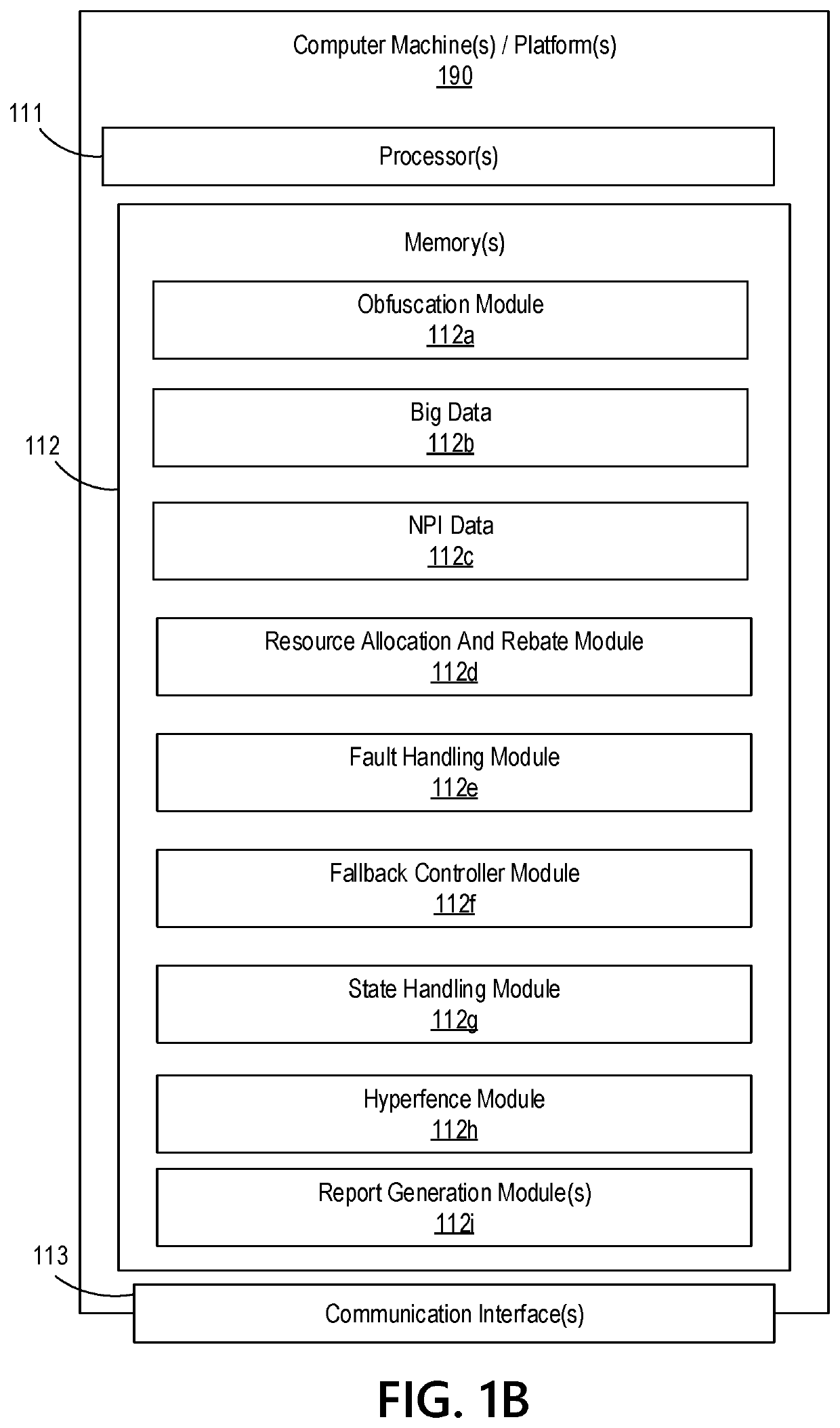
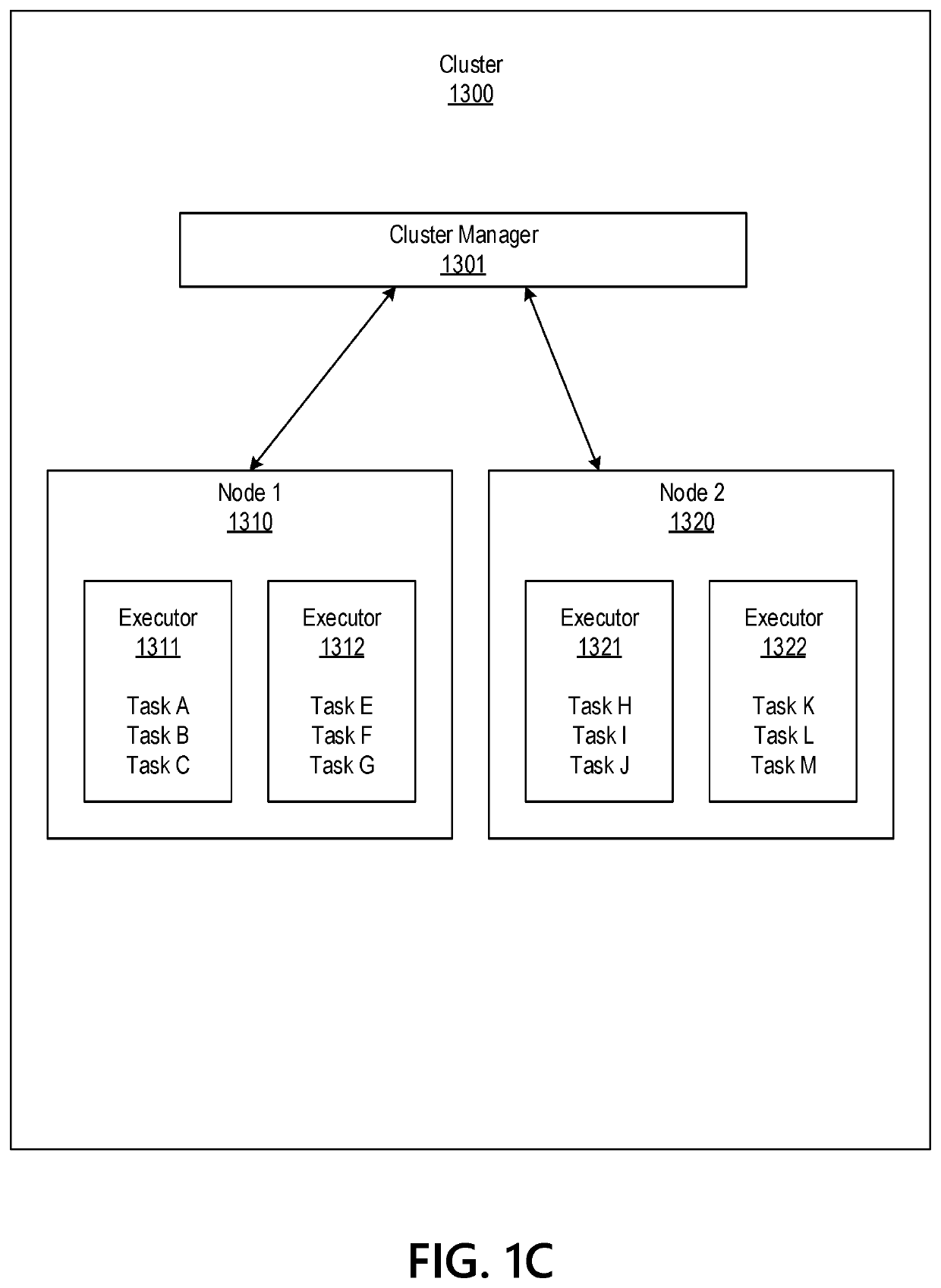
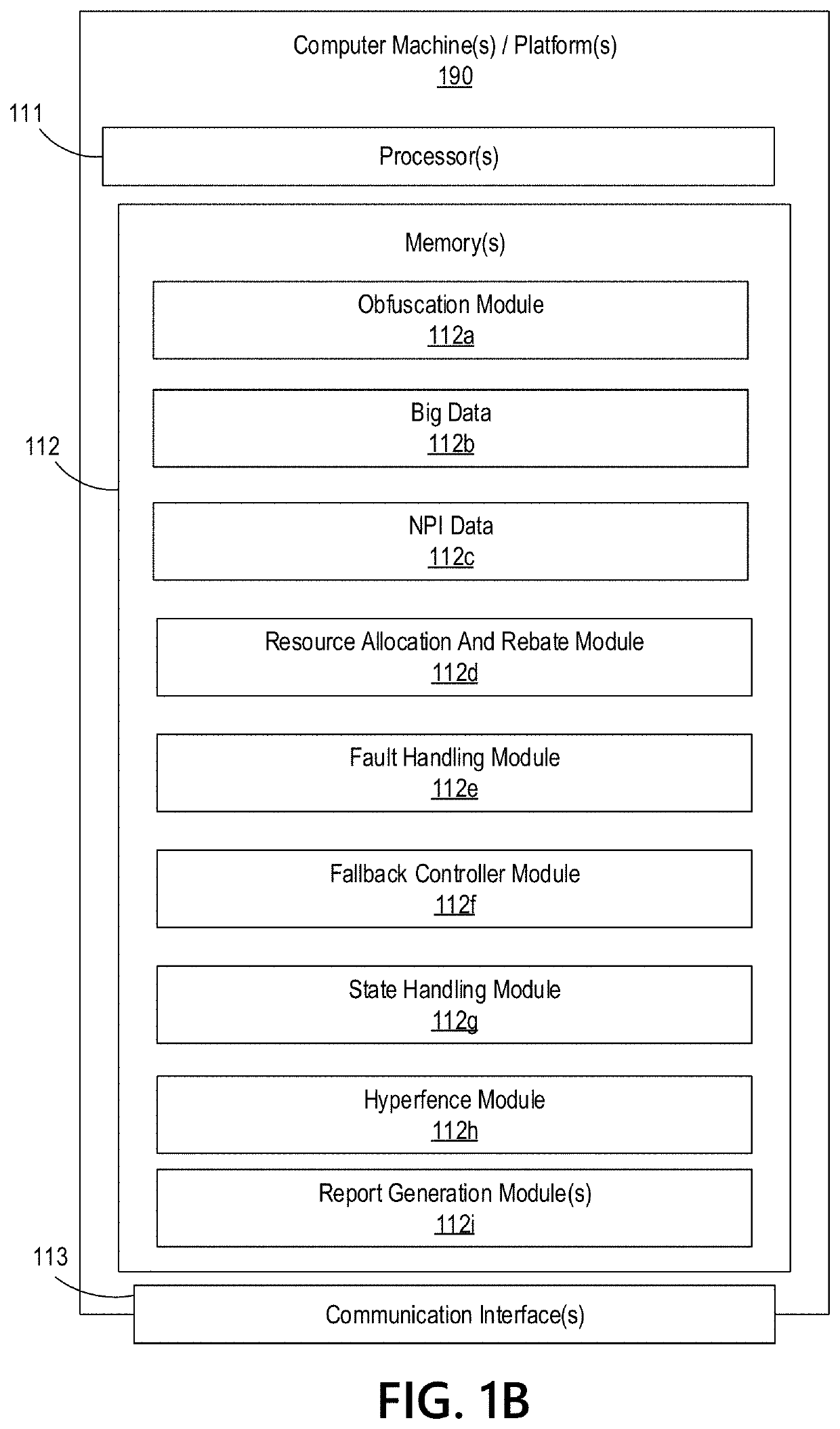
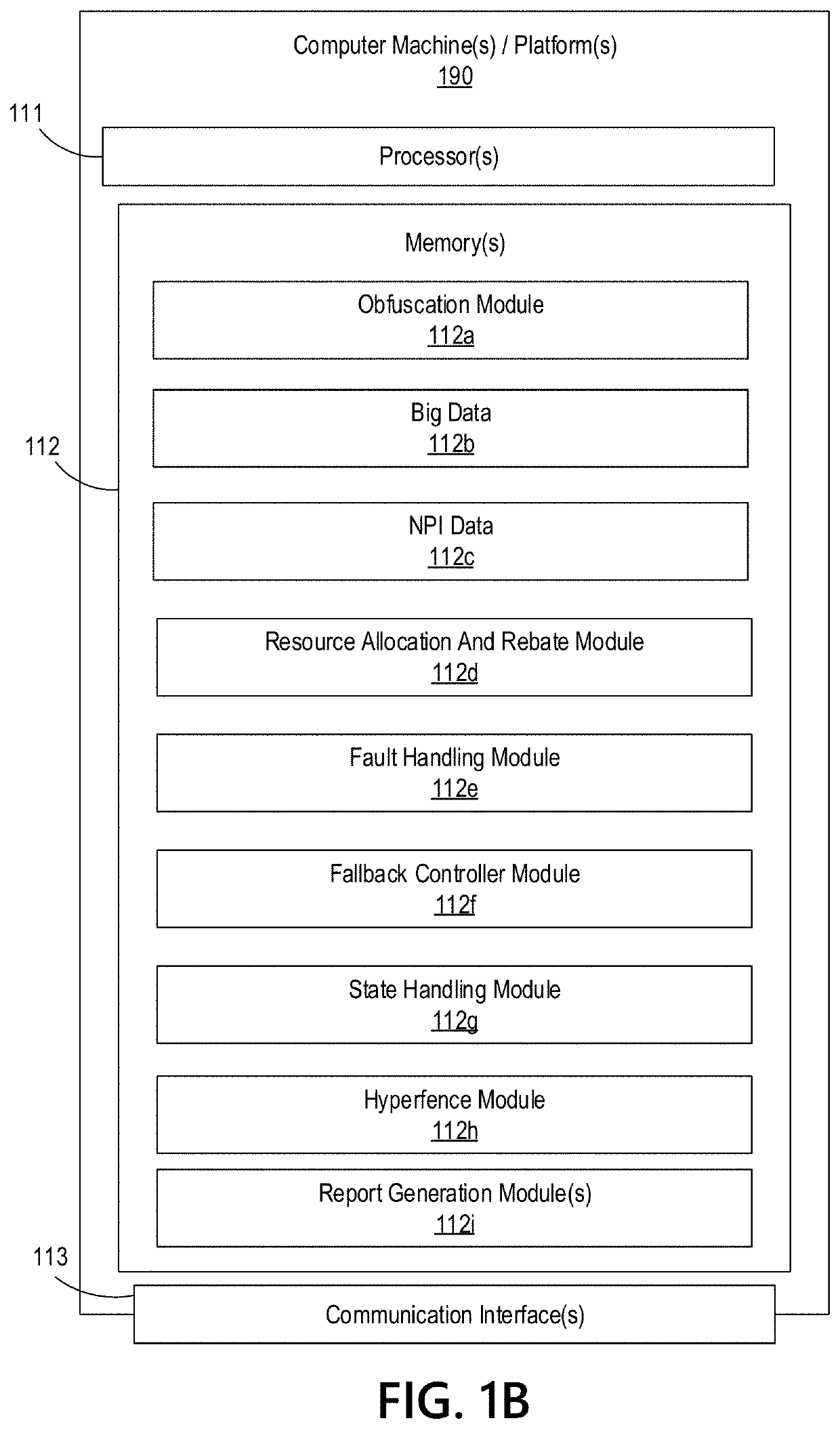
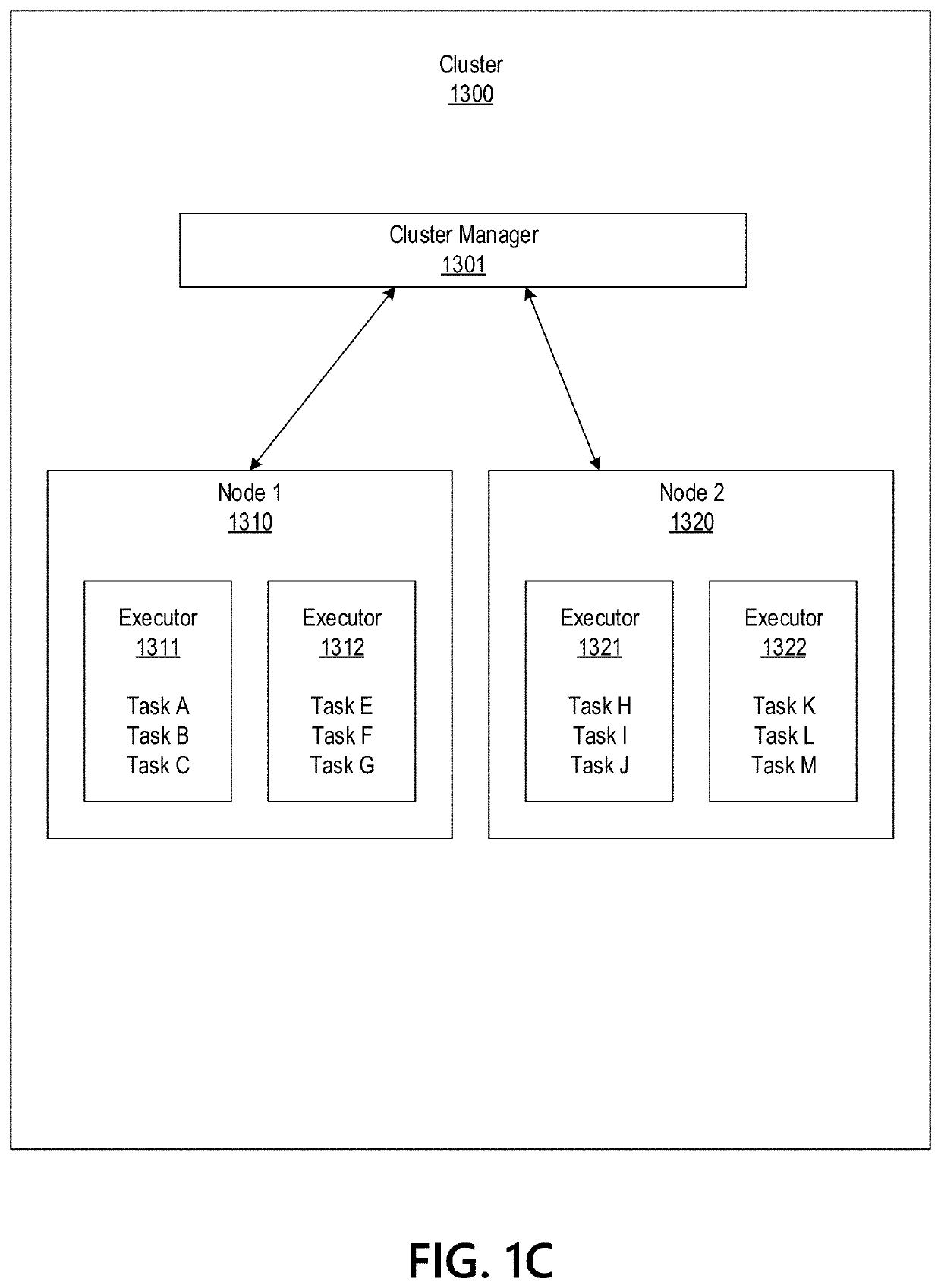
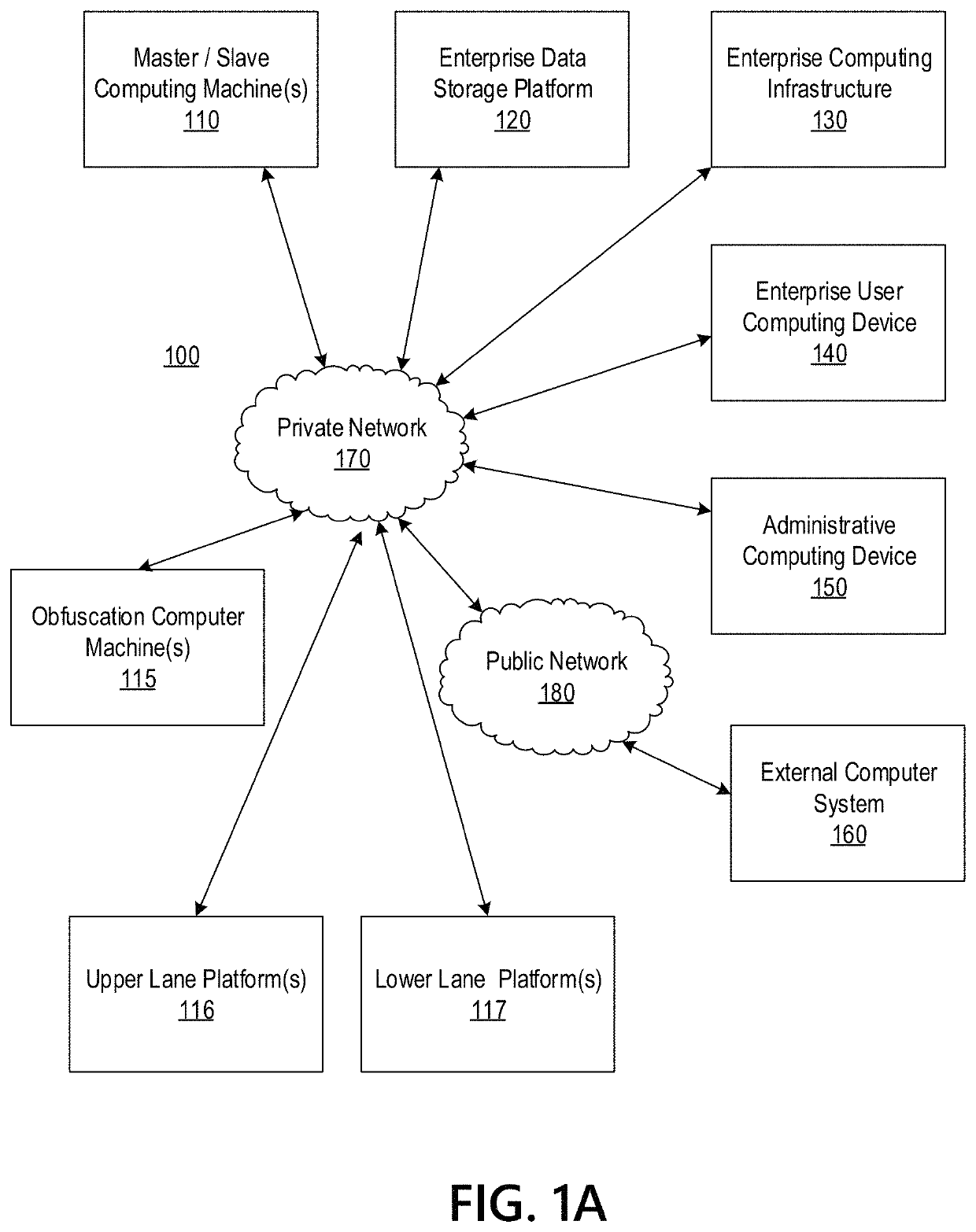
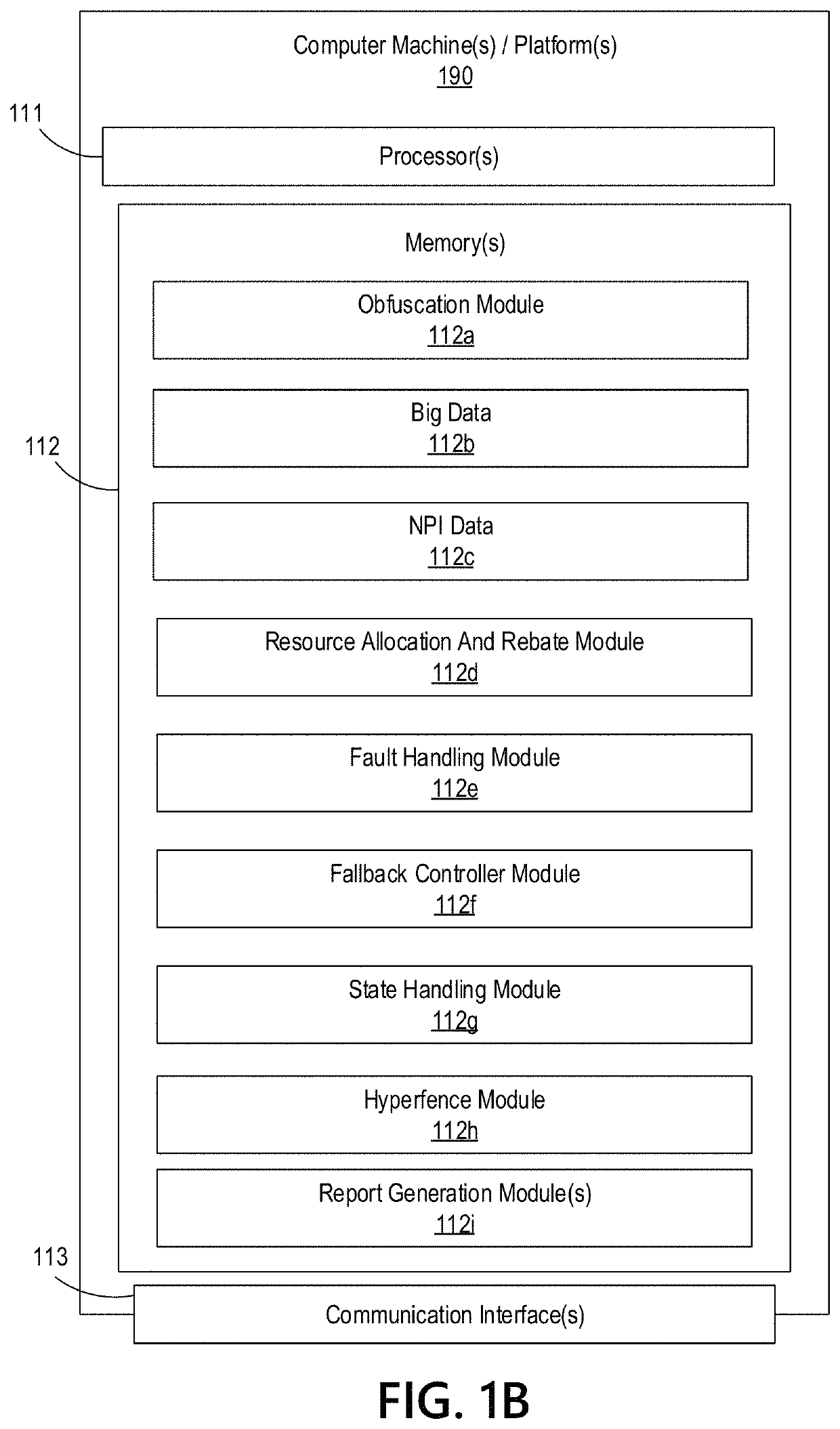
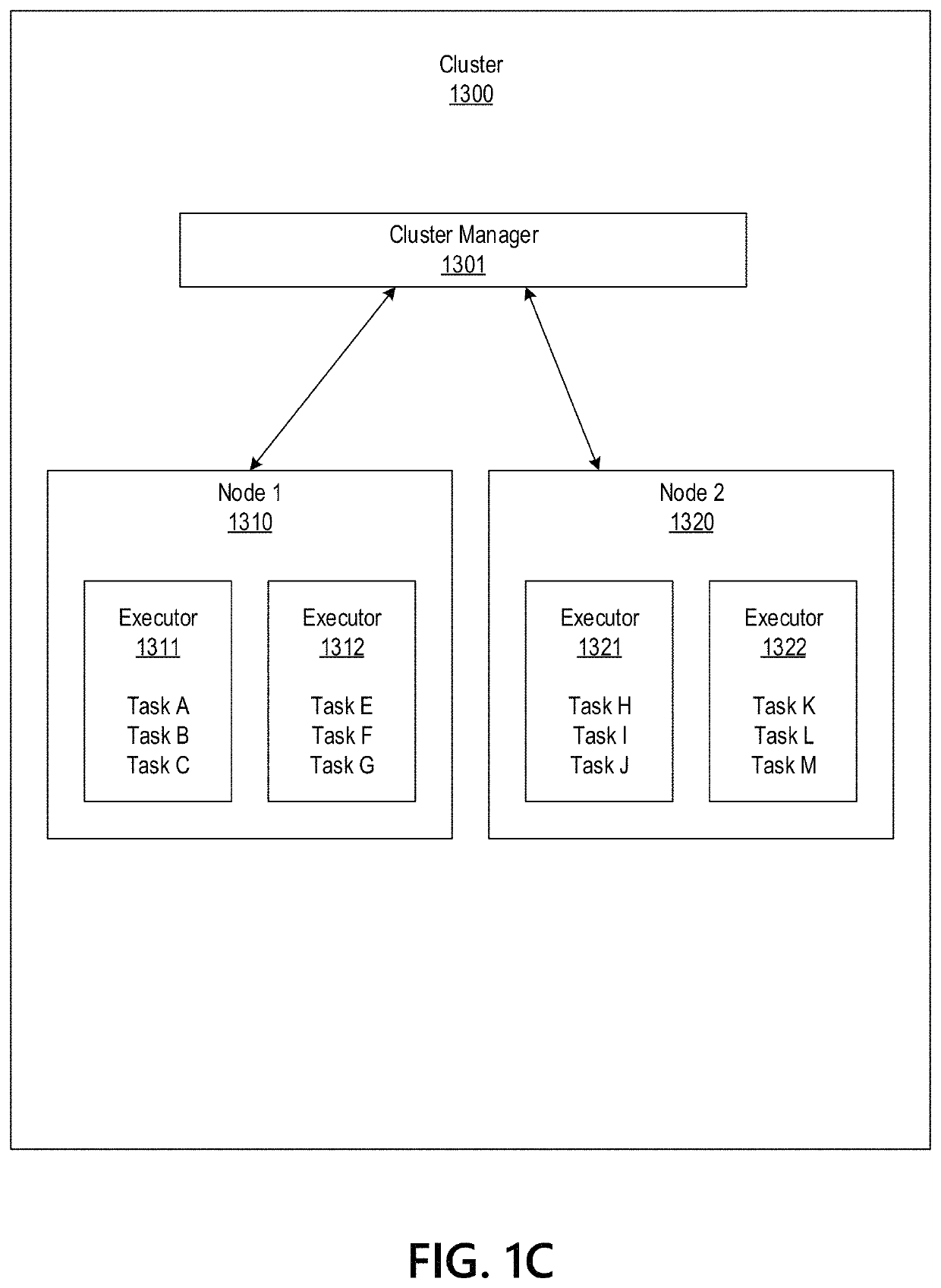
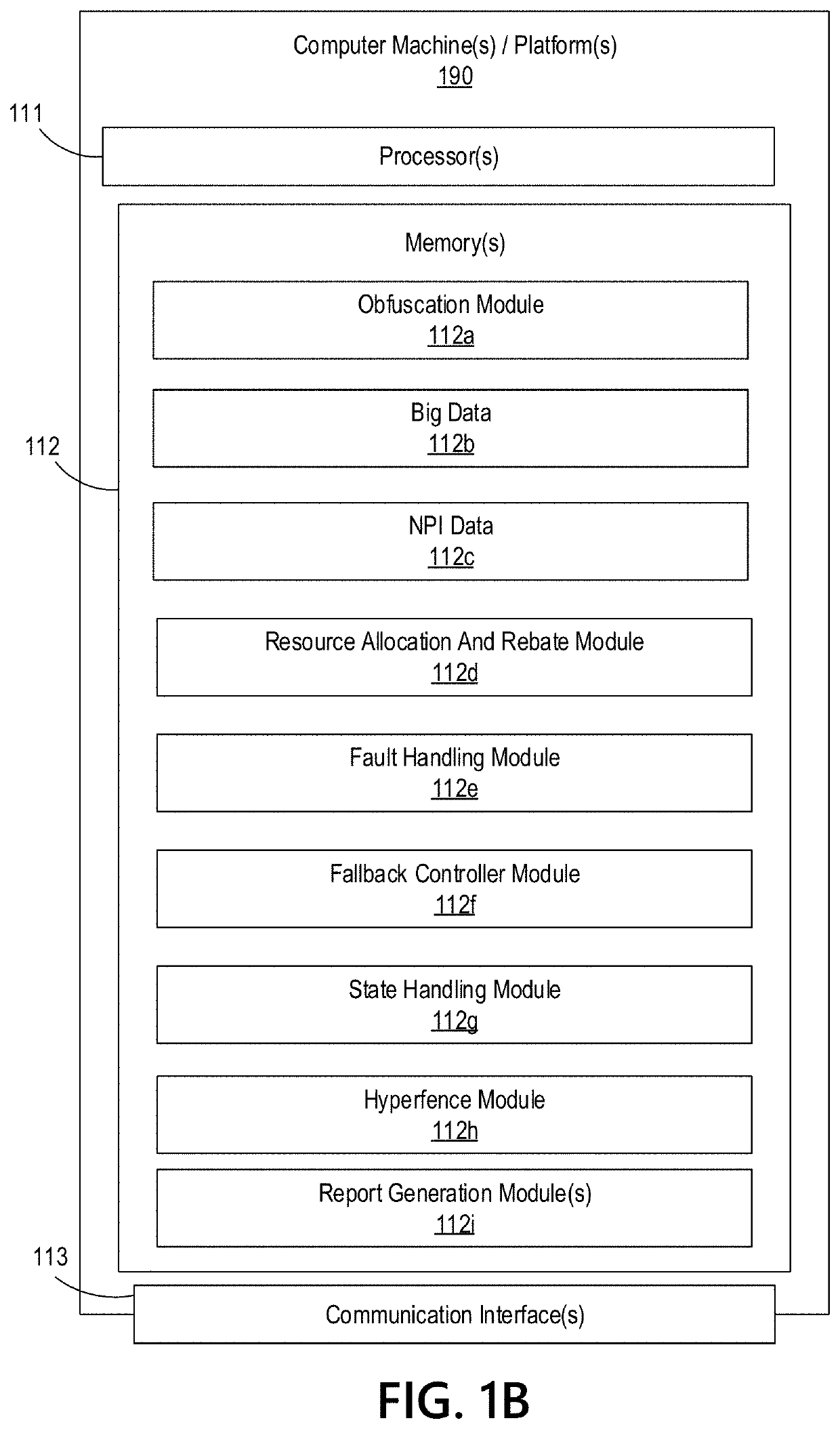
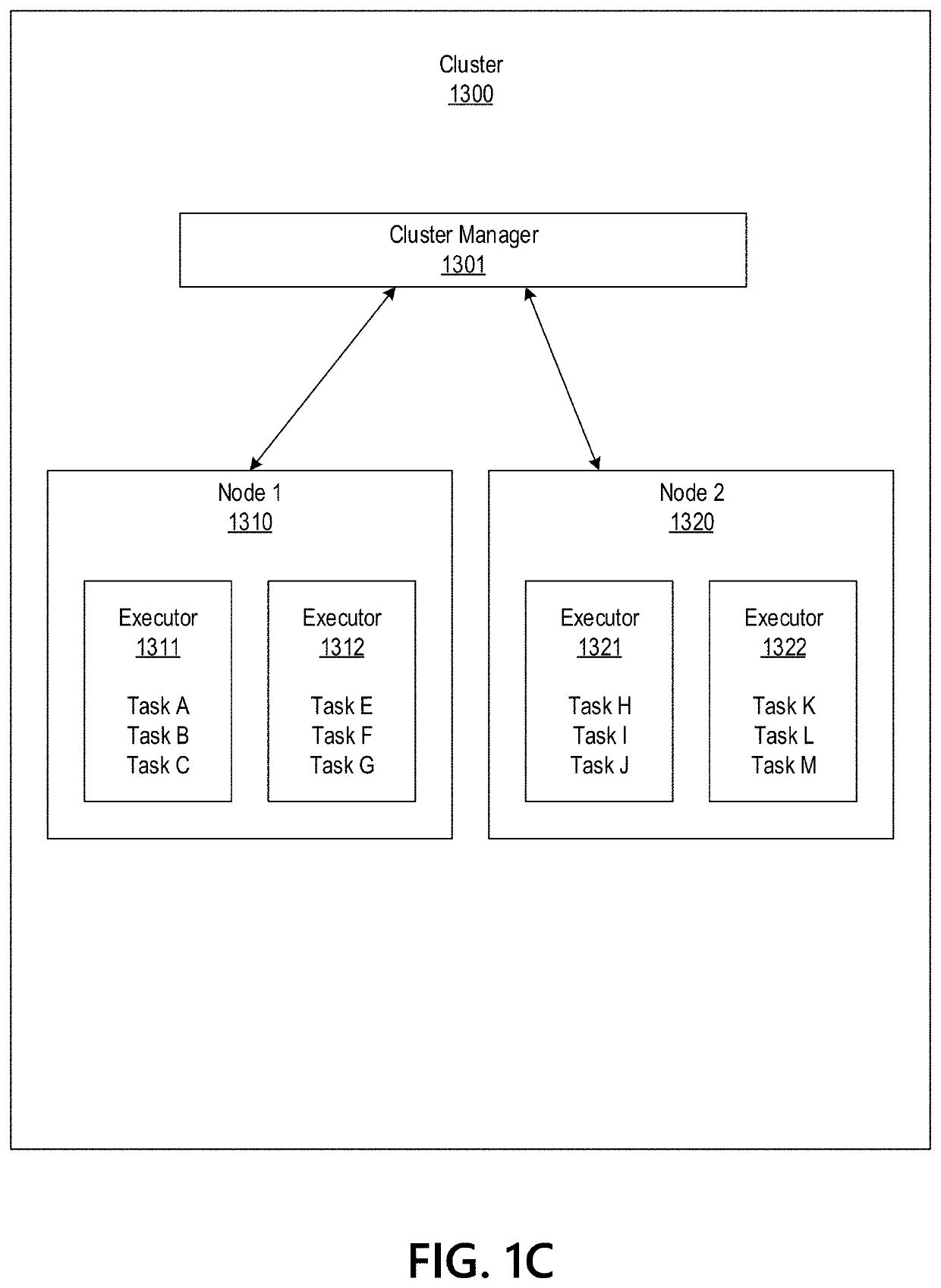
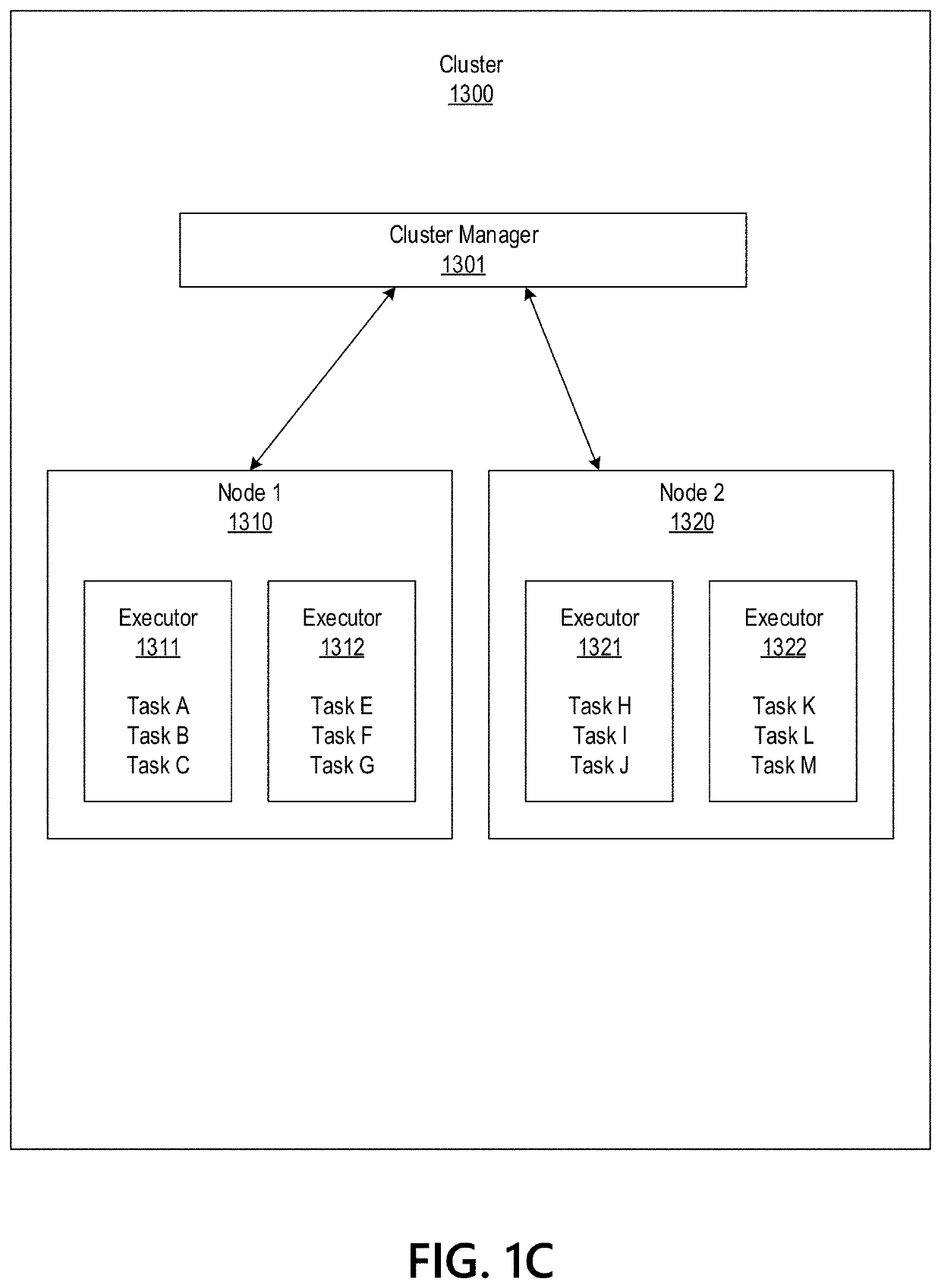
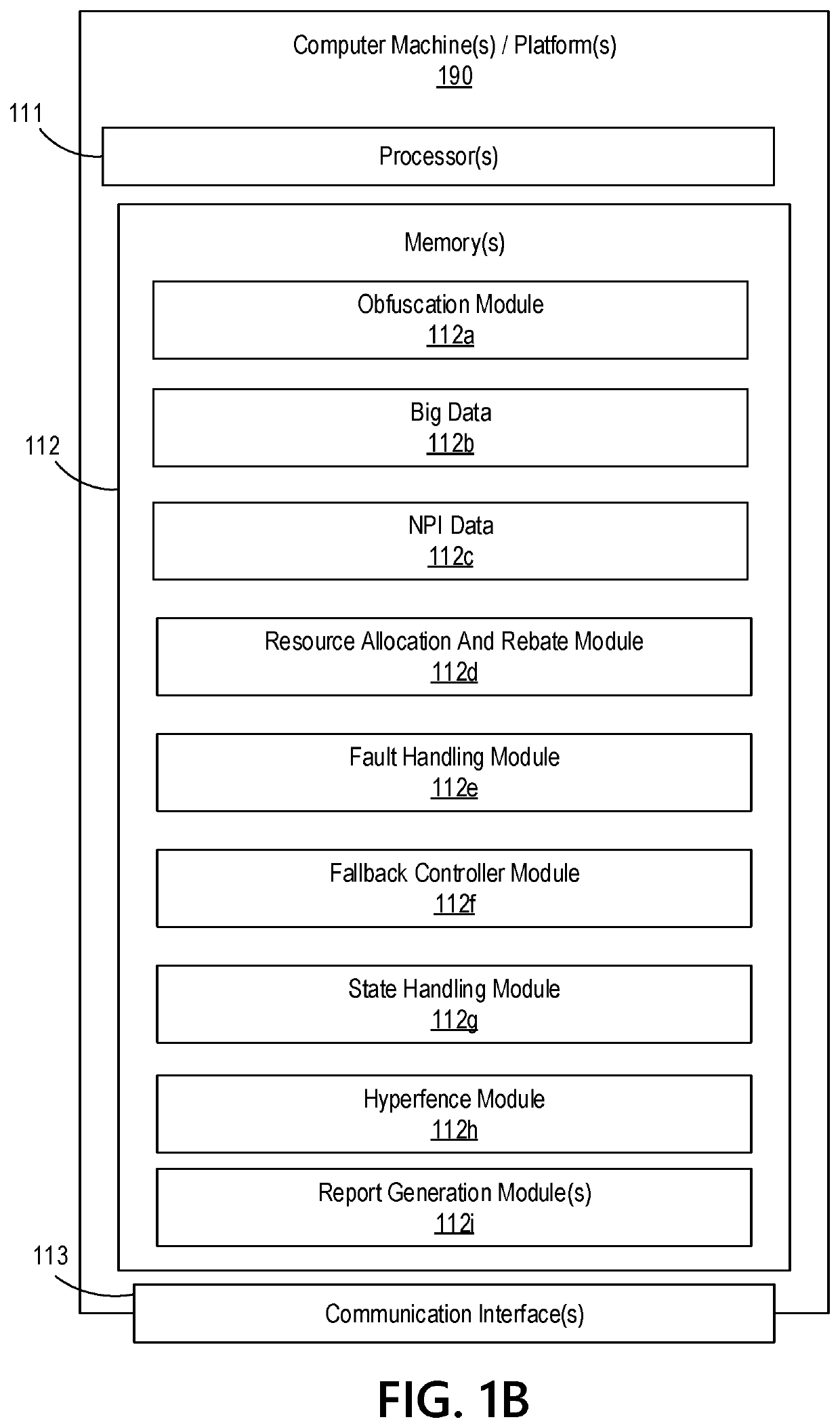
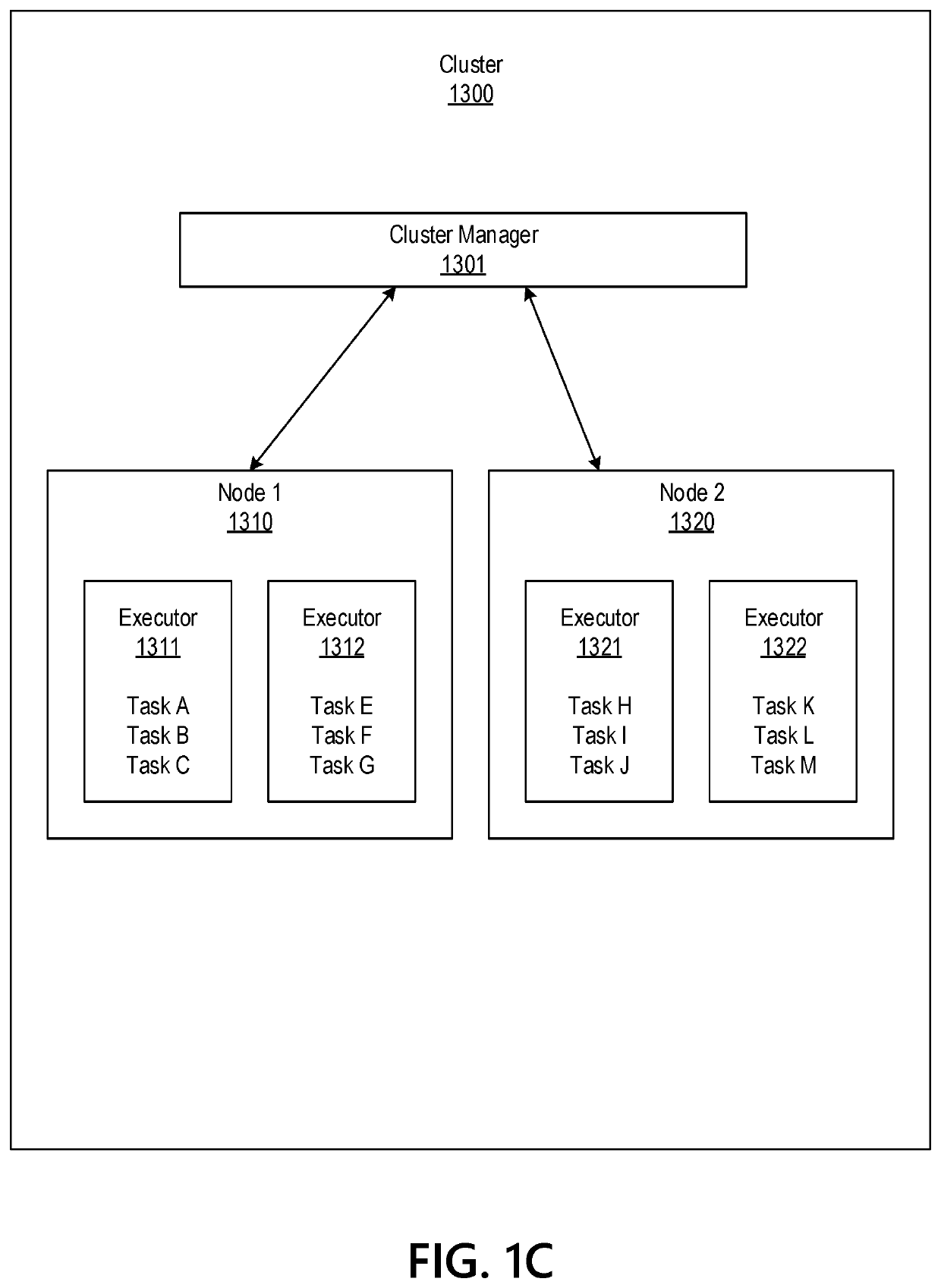
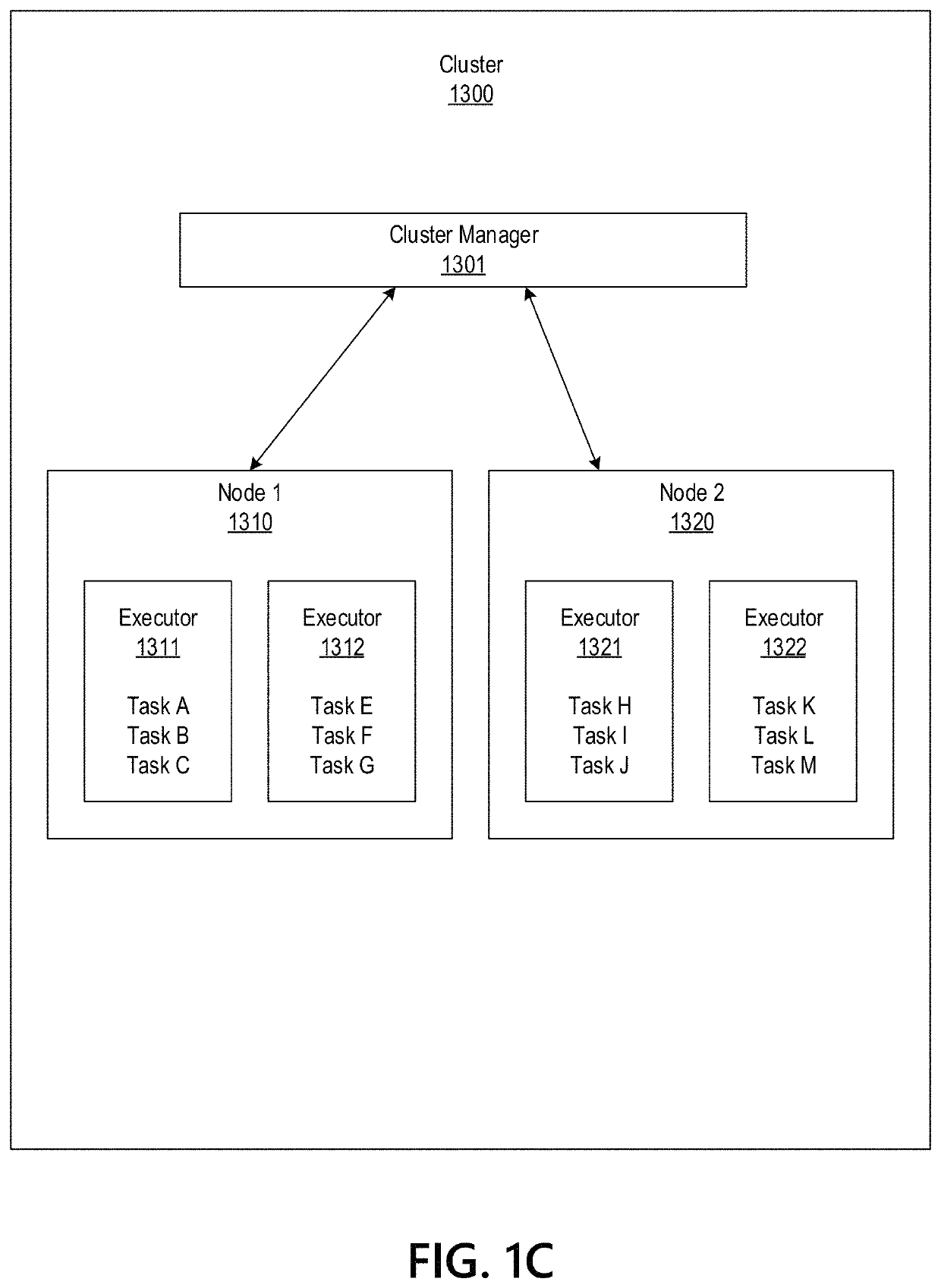
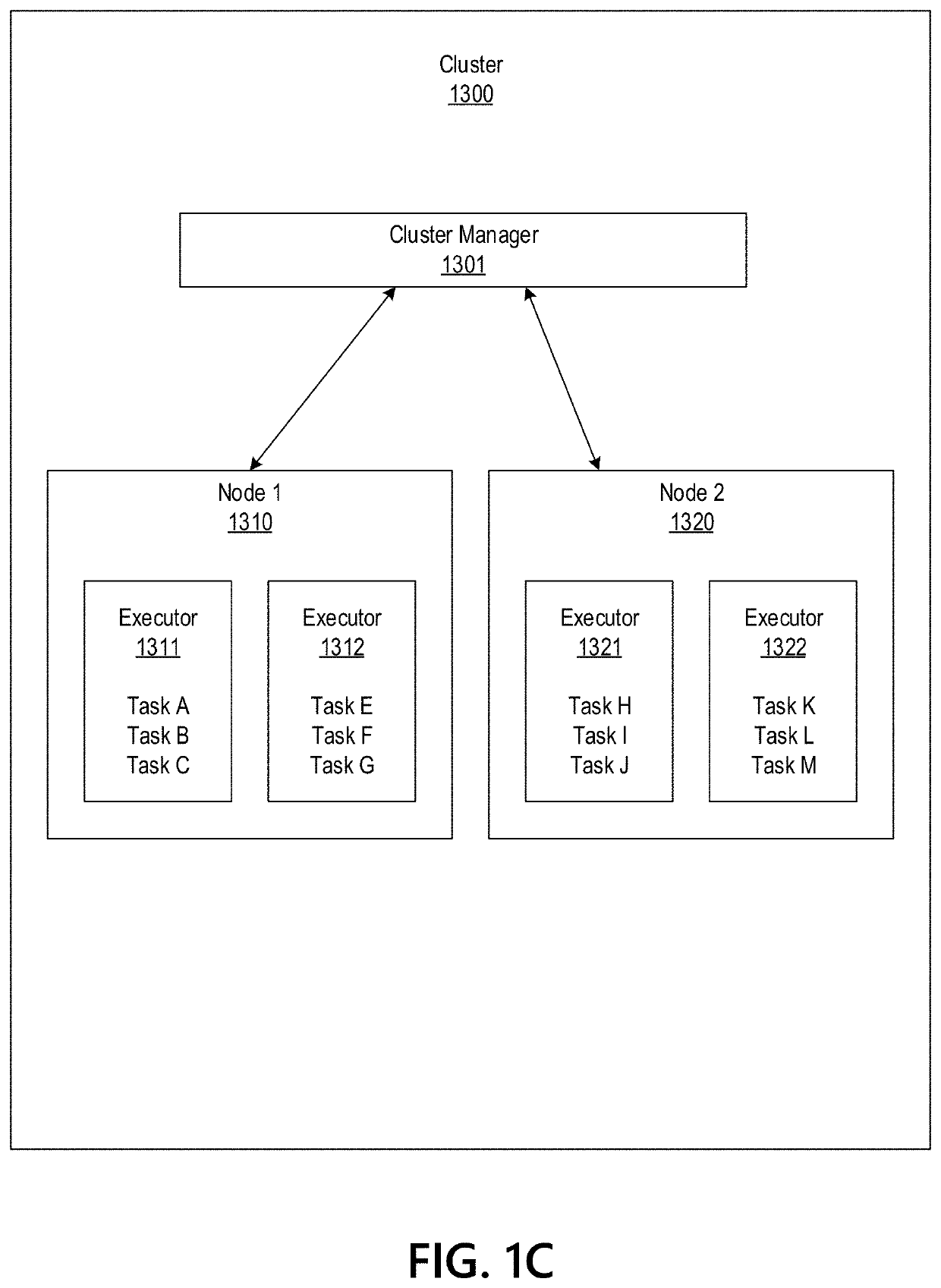
Big Data Distributed Processing and Secure Data Transferring with Fault Handling
ActiveUS20210208960A1Effective and efficient and scalable and convenient technicalResource efficientMultiple keys/algorithms usageDigital data protectionComputer clusterFlight data
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. Crashed executor(s) can be detected and caged to prevent further use. Uncompleted task(s) for crashed executor(s) can be reassigned. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
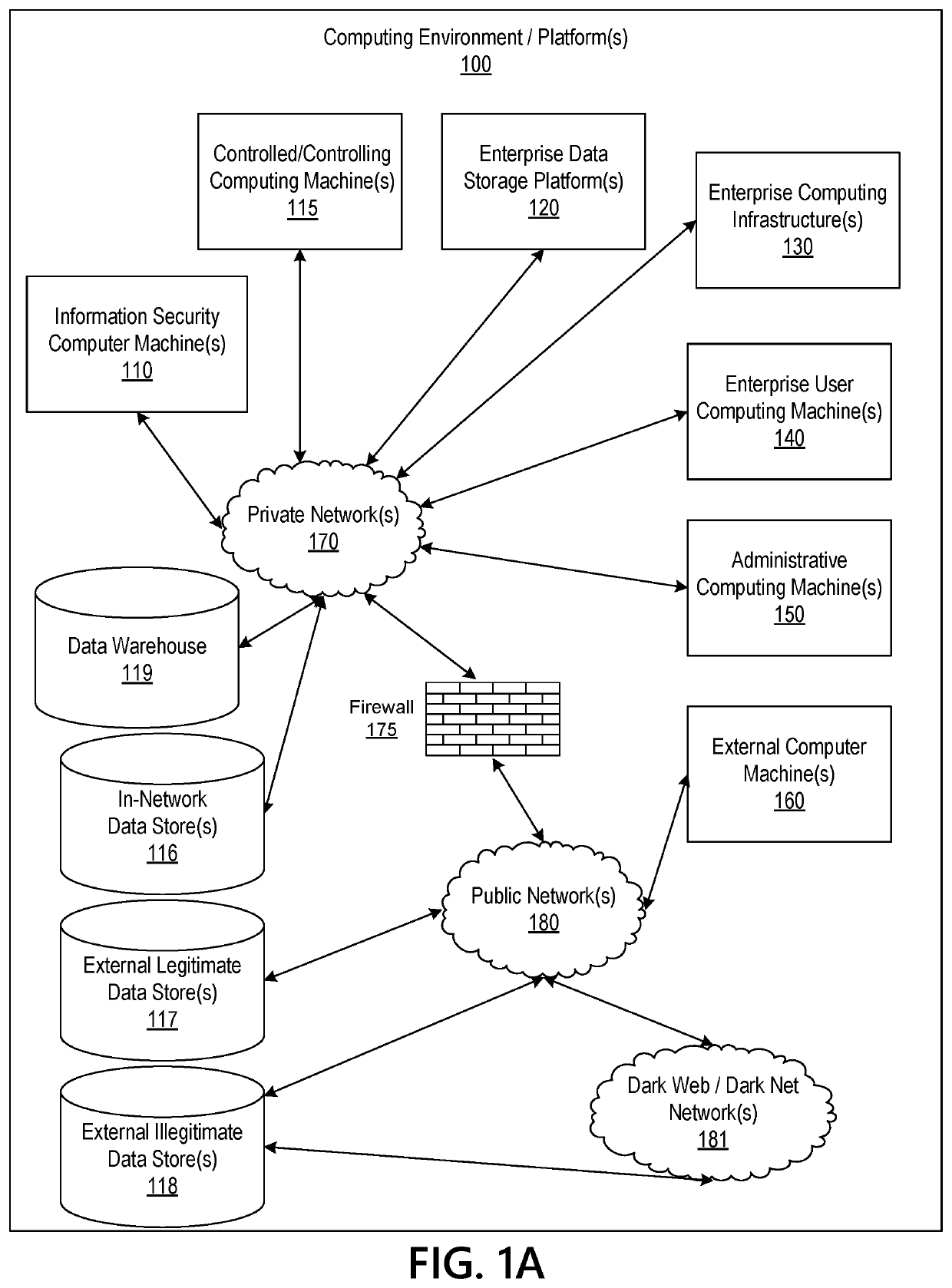
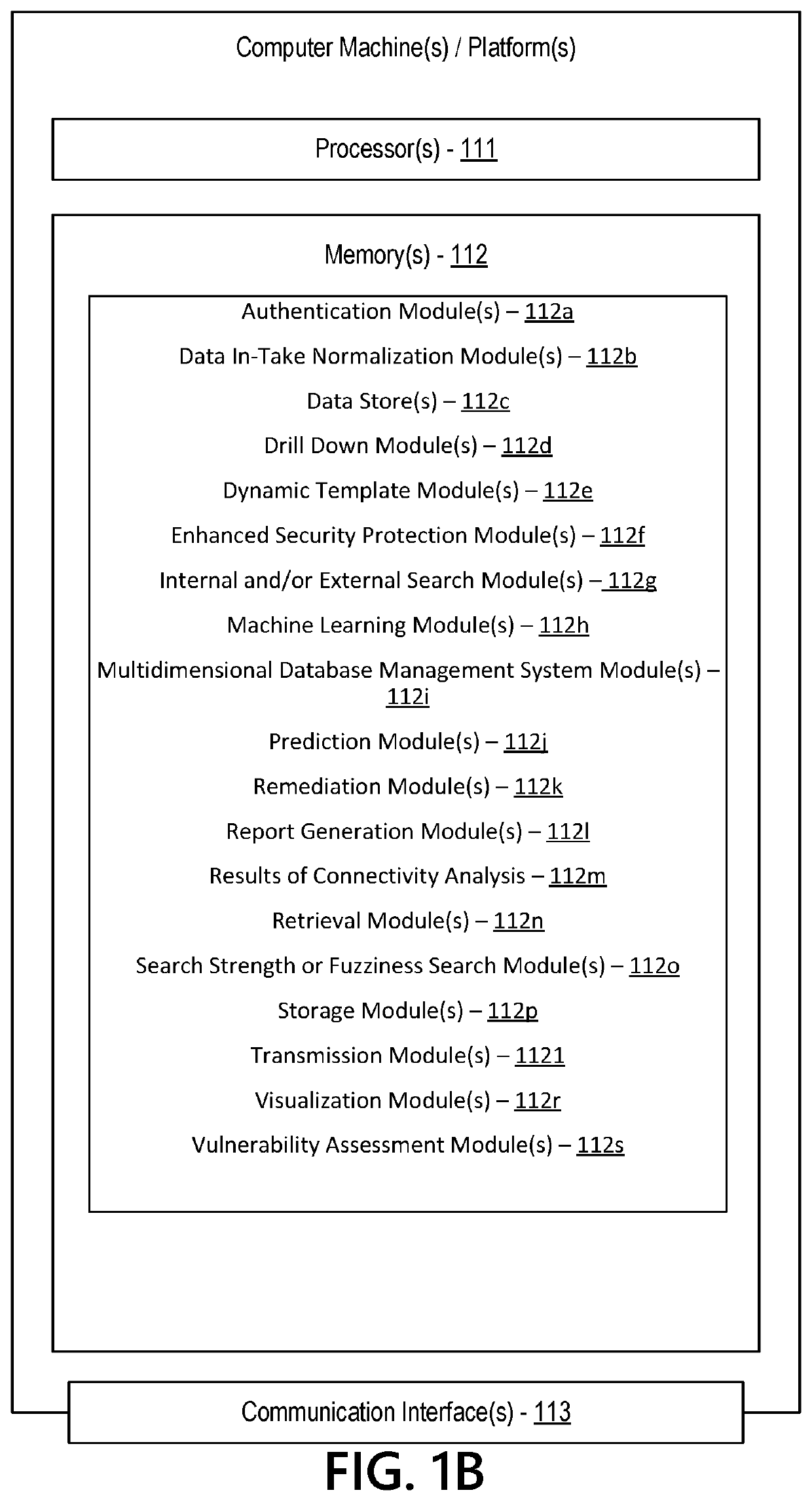
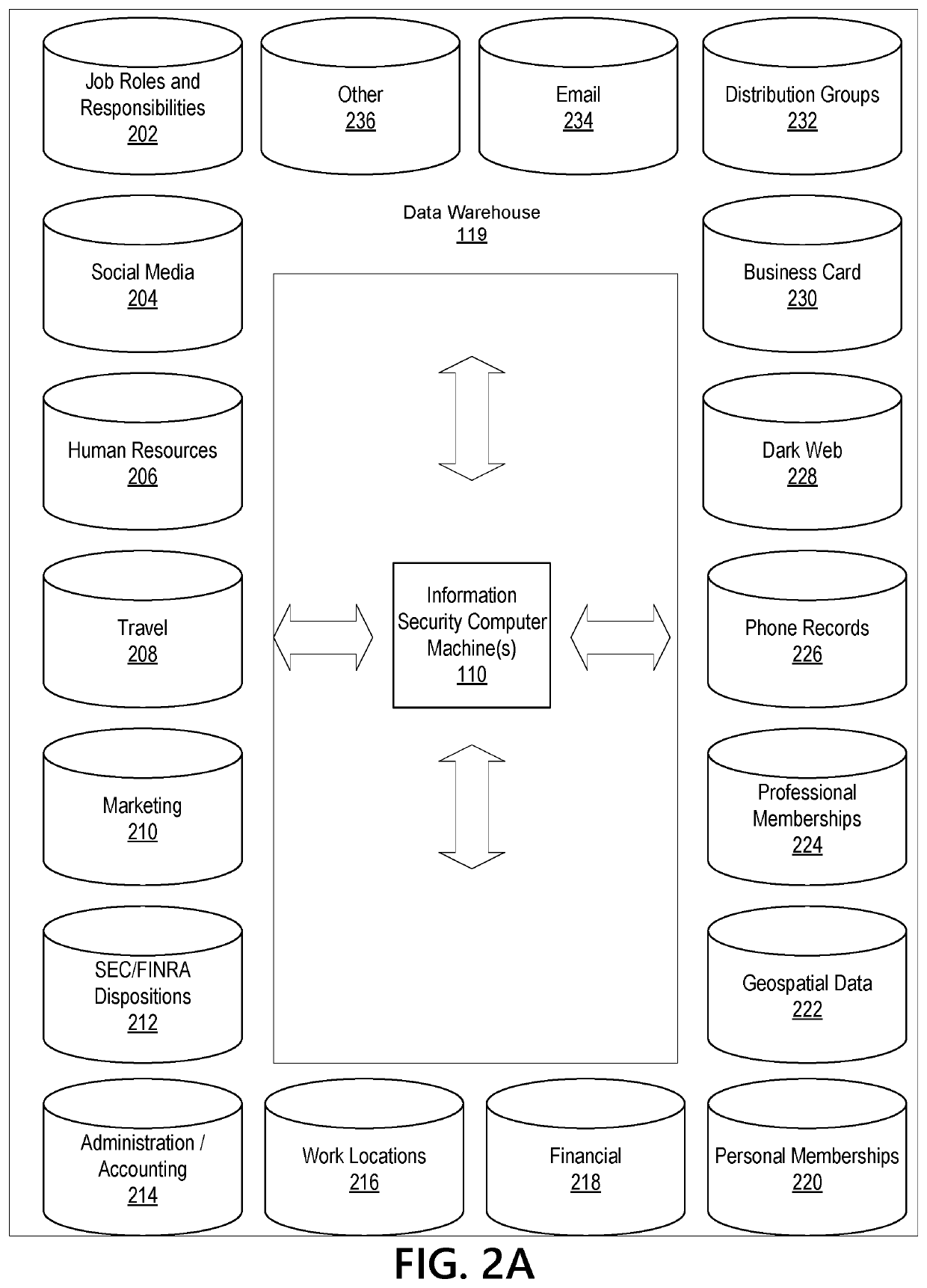
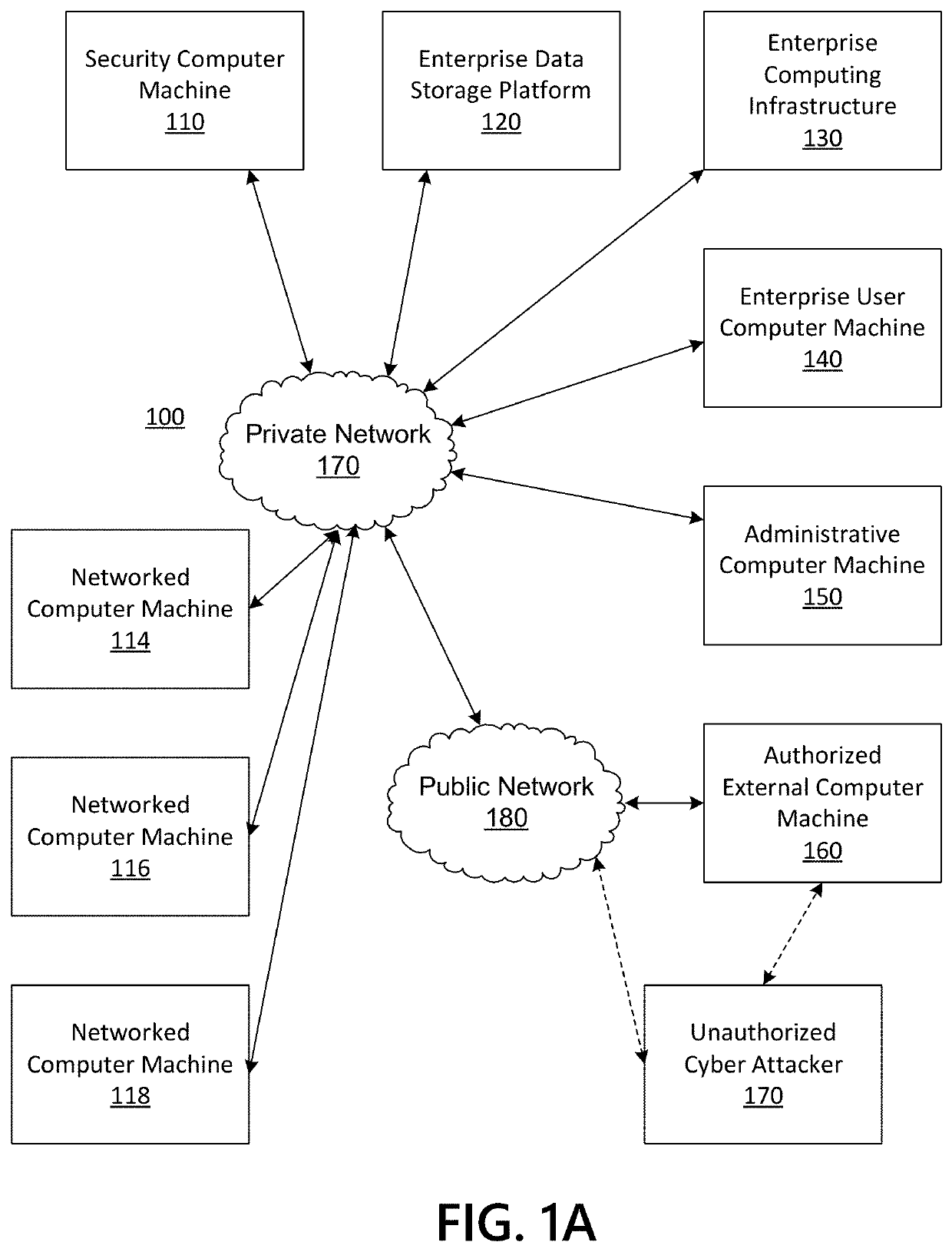
Information Security System Based on Multidimensional Disparate User Data
ActiveUS20210234884A1Efficient and effectiveEffective and efficient and scalable and convenient solutionMulti-dimensional databasesData switching networksData scienceInformation storage
Aspects of the disclosure relate to information security by identifying unique or related factors in common between individuals subject to a common threat vector. Data mining and data acquisition of public and non-public user information is performed to prevent, disrupt, and / or address criminal, cyber, and fraudulent threats. The information can be normalized into template(s) to align information across disparate datasets and enable efficient storage of the big data into appropriate fields to be tracked. The information can be stored in data warehouse(s) or in multidimensional data structure(s) for investigation if a threat vector against a group of individuals is detected. The multidimensional data can be analyzed to identify direct connections, common connecting entities, and / or connectivity clusters between individuals who were attacked or who may be attacked in the future. Remediation, machine learning, enhanced security, and / or vulnerability assessments may be implemented based on the results of the analysis.
Owner:BANK OF AMERICA CORP
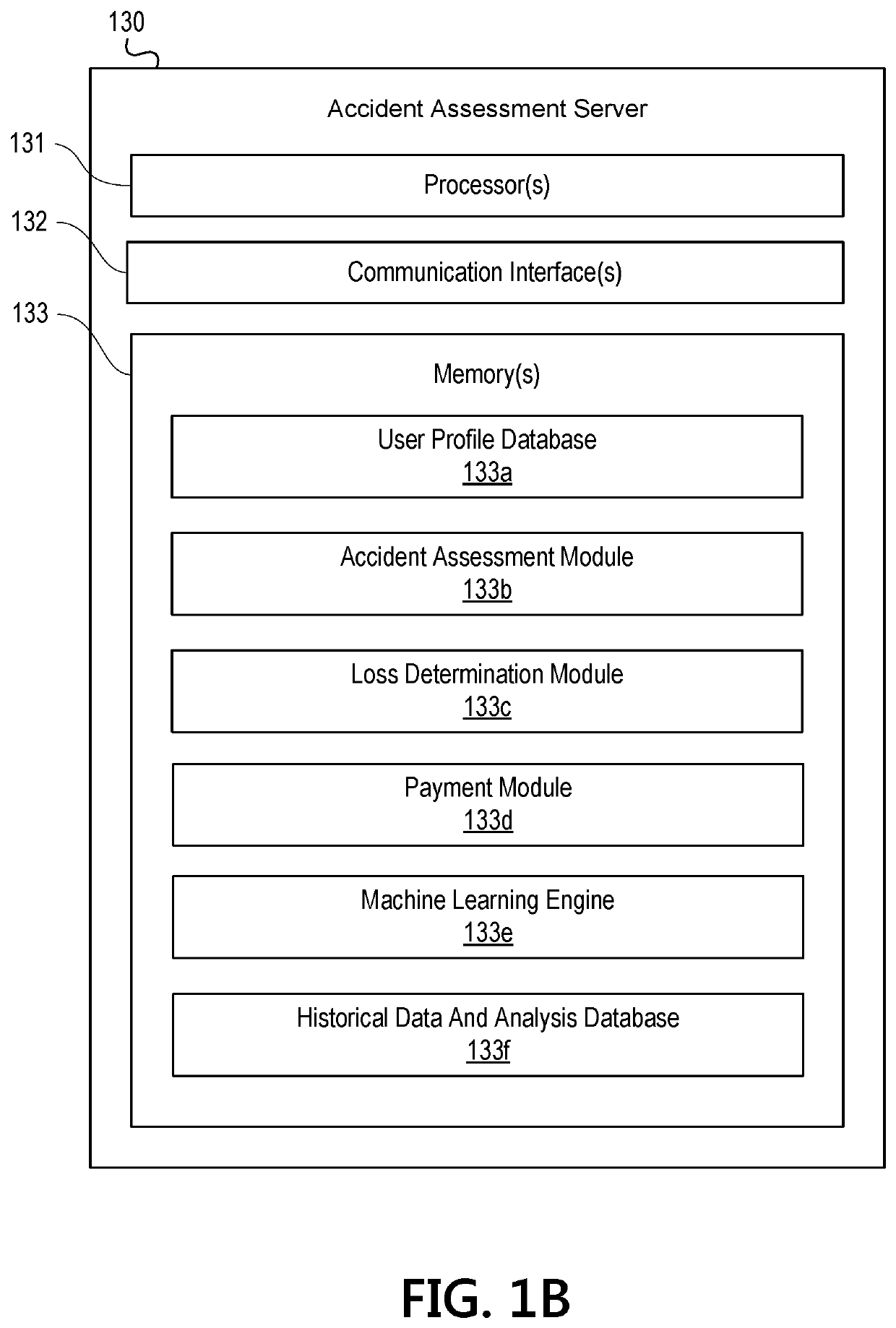
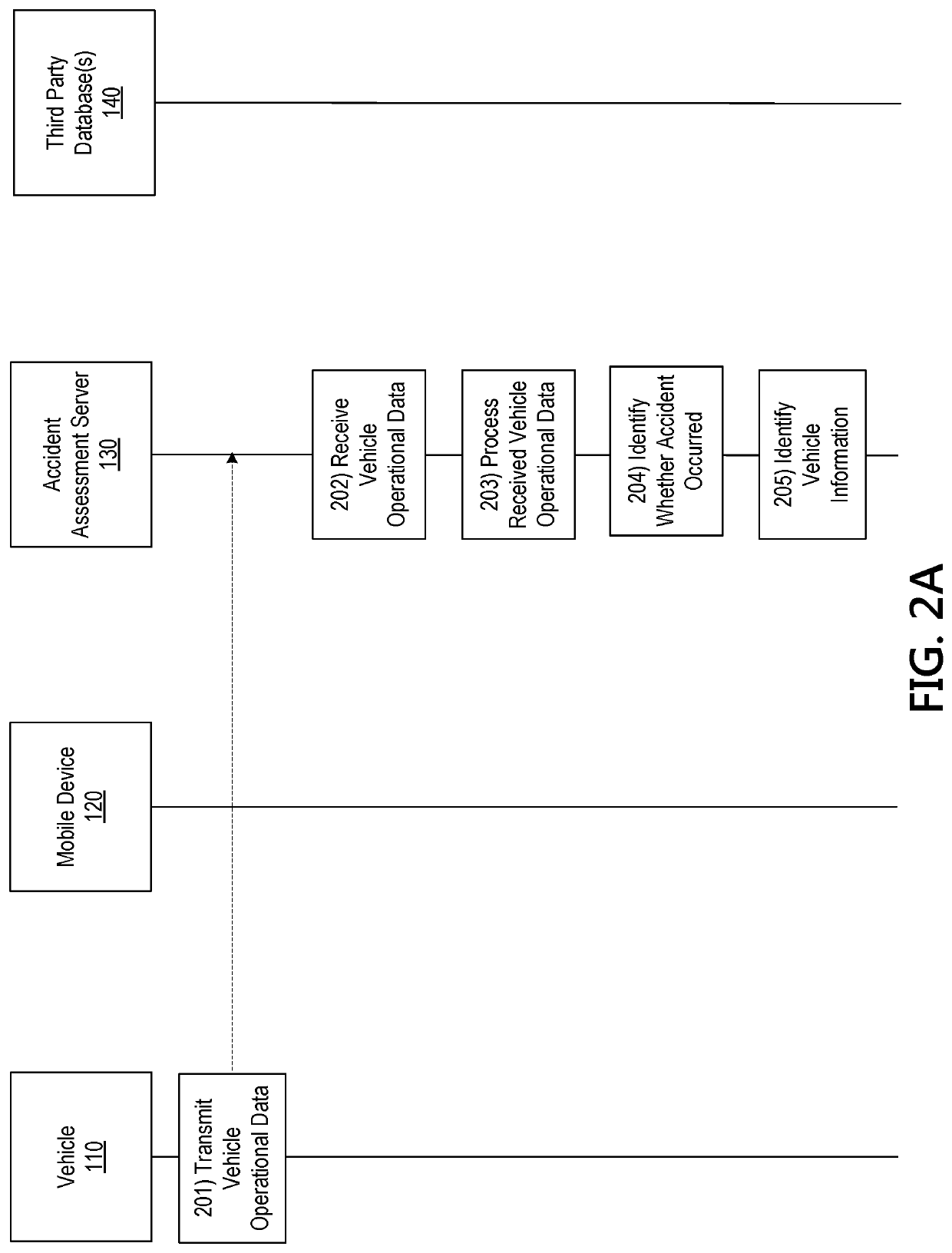
Machine learning based accident assessment
ActiveUS10937103B1Effective and efficient and scalable and convenient solutionFinanceMachine learningEngineeringArtificial intelligence
Aspects of the disclosure relate to using machine learning algorithms to analyze vehicle operational data associated with a vehicle accident. In some instances, an accident assessment server may receive data indicating that a vehicle was involved in an accident. The accident assessment server may compare the data with other known data, based on machine learning algorithms, to identify whether the accident resulted in a total loss. Responsive to determining that the accident resulted in the total loss, the accident assessment server may request further information regarding the vehicle and may identify a baseline value range for the vehicle. The accident assessment server may request updated information from the owner of the vehicle, identify, based on the updated information, a final value of the vehicle, and may pay the owner of the vehicle an amount corresponding to the final value if the final value is within the baseline value range.
Owner:ALLSTATE INSURANCE
Dynamic Data Protection System
InactiveUS20180176197A1Effective and efficient and scalable and convenientEffective and efficient and scalable and convenient solutionTransmissionUser deviceNetwork connection
A dynamic data protection system may include a data management server includes a processor and a non-transitory memory device storing instructions that cause the data management server to receive, via a network connection from a user device, a request for access to data stored on an organization's network. The data management server may then communicate user authentication information associated with the received request. The security management server may process user authentication information to determine whether an authentication code associated with the user is valid and associated with the requested data. Upon validation of the user authentication information by the security management server, provide access to data via a secured data container of a data envelope corresponding to the data, wherein the data container corresponds to the validated user authentication information. When a data compromise event occurs, the secure data envelope may prevent unauthorized access to the data.
Owner:BANK OF AMERICA CORP
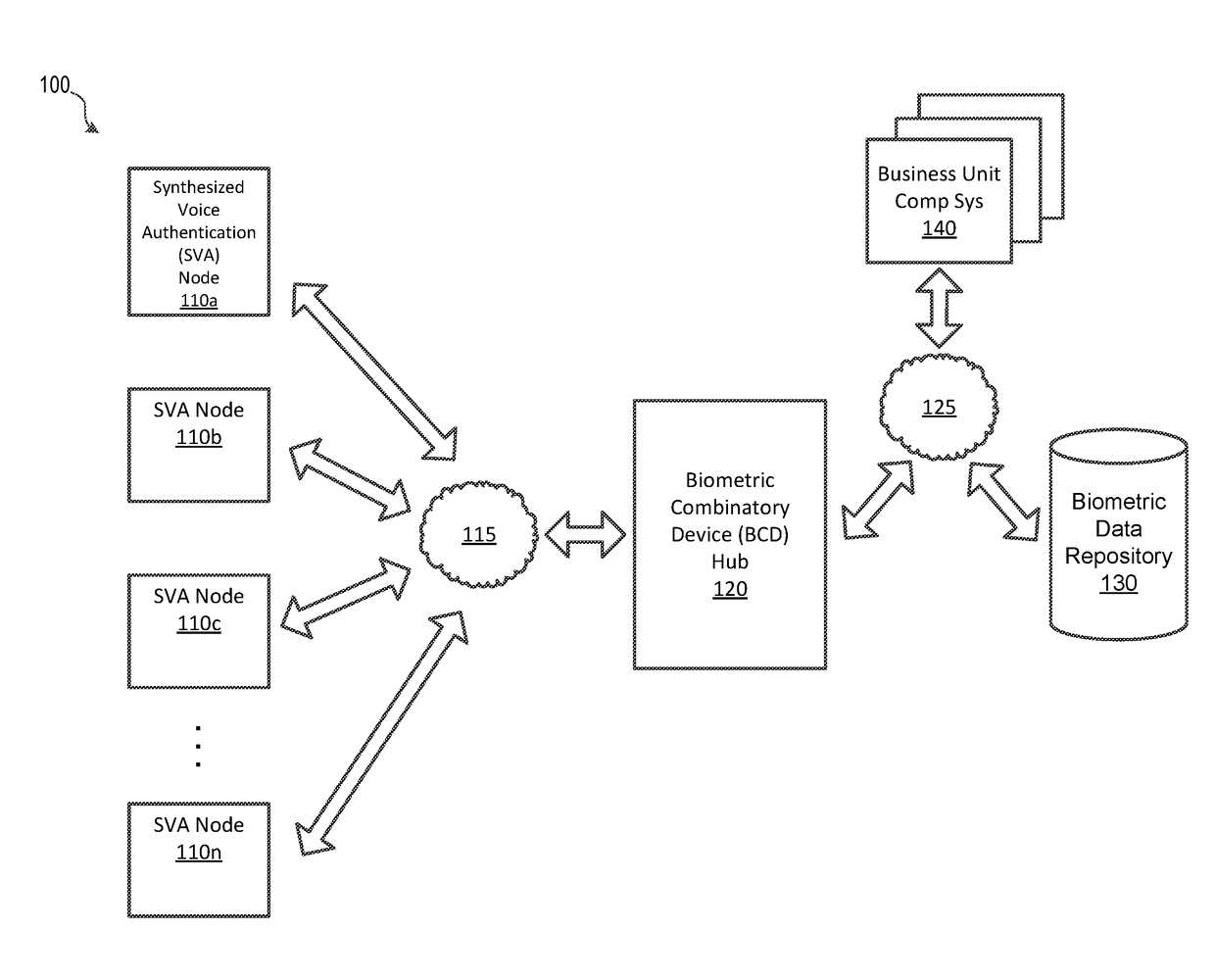
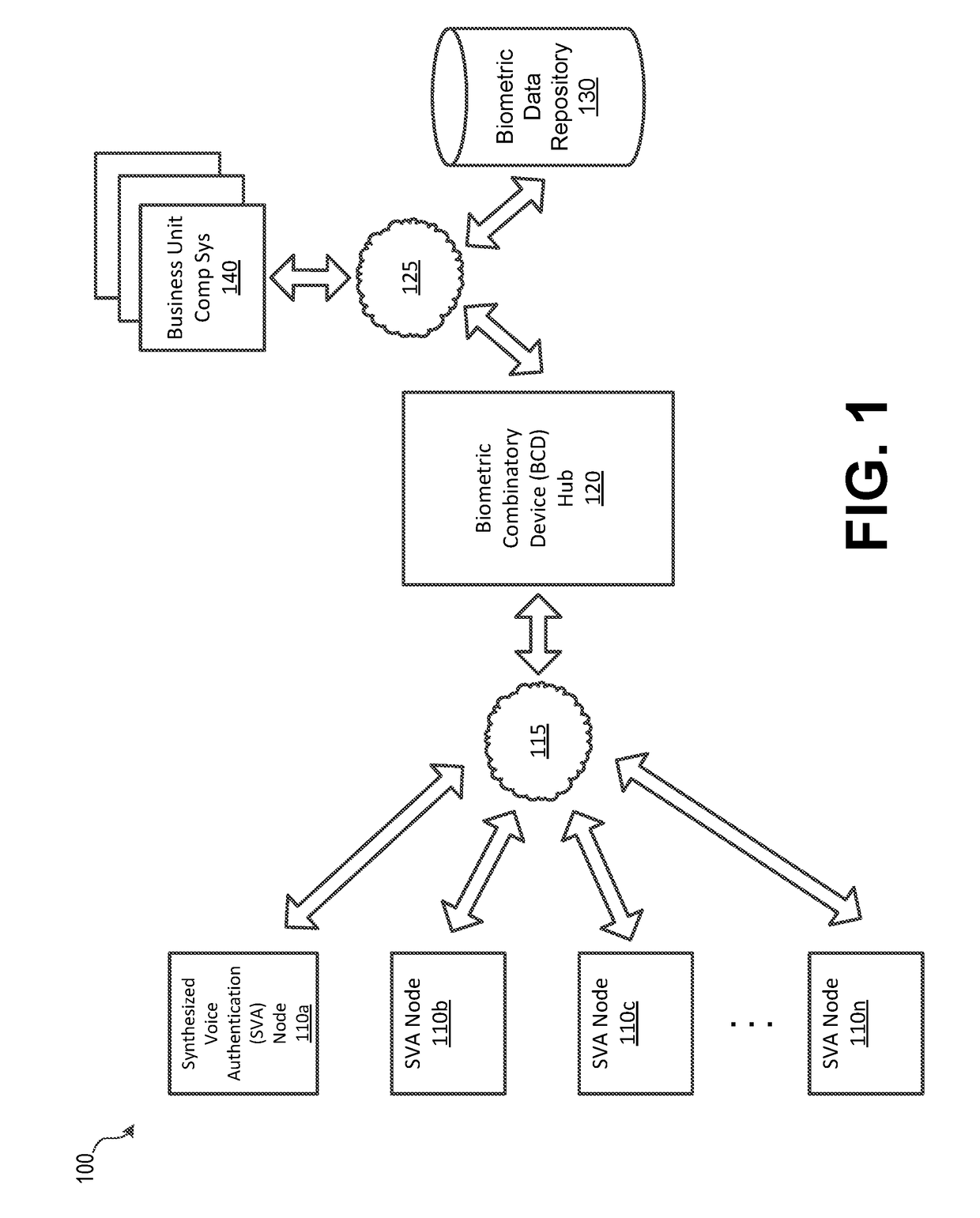
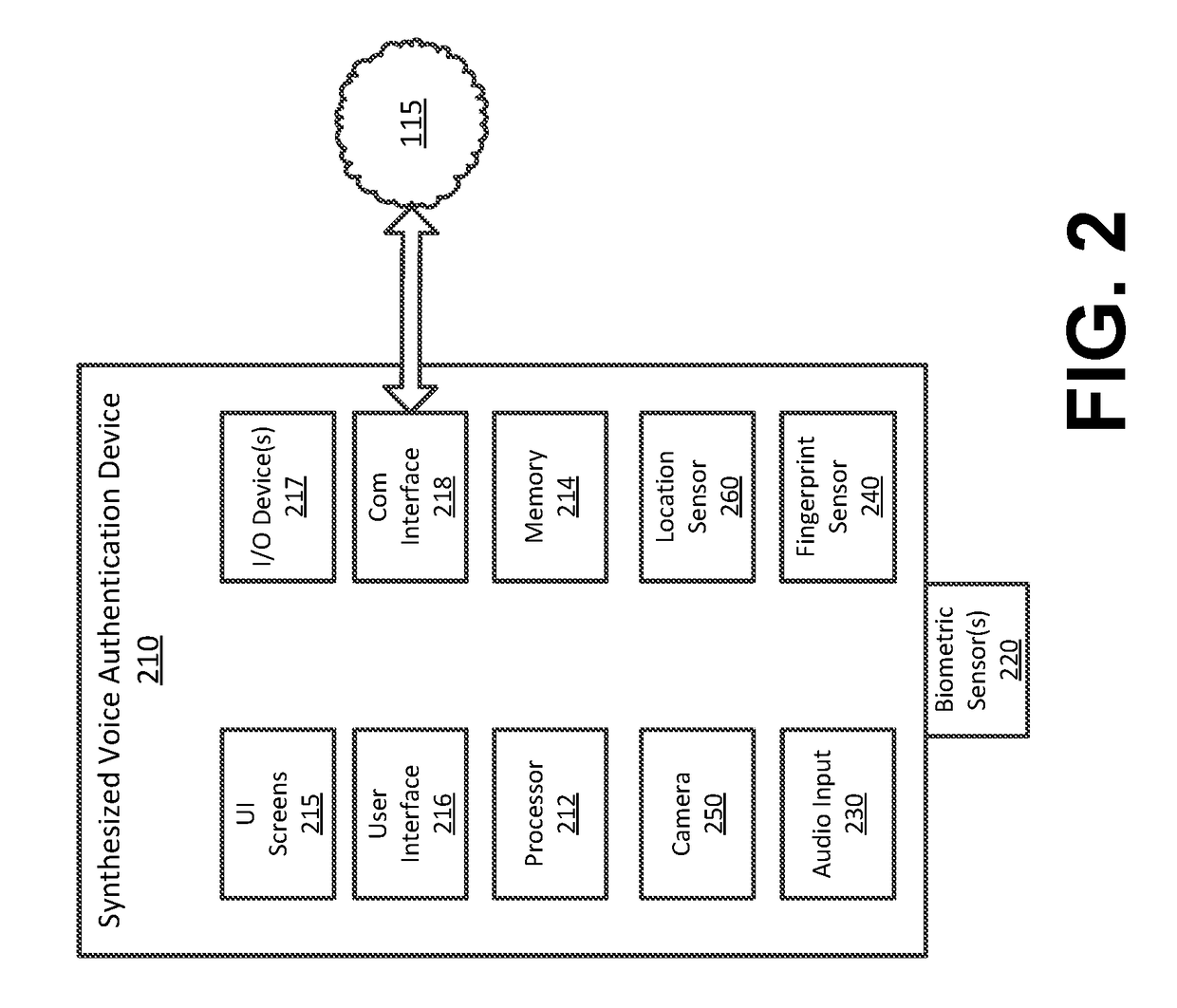
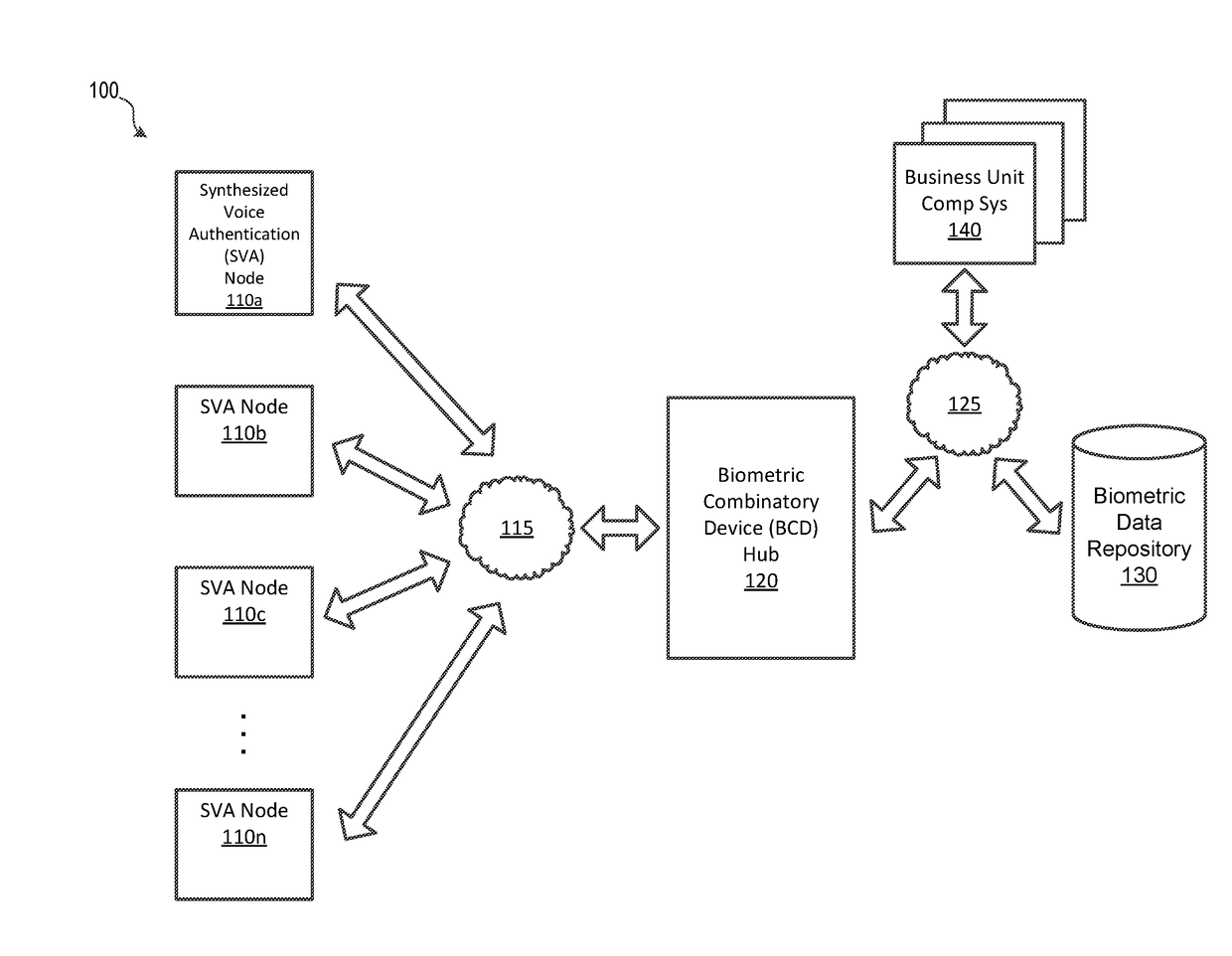
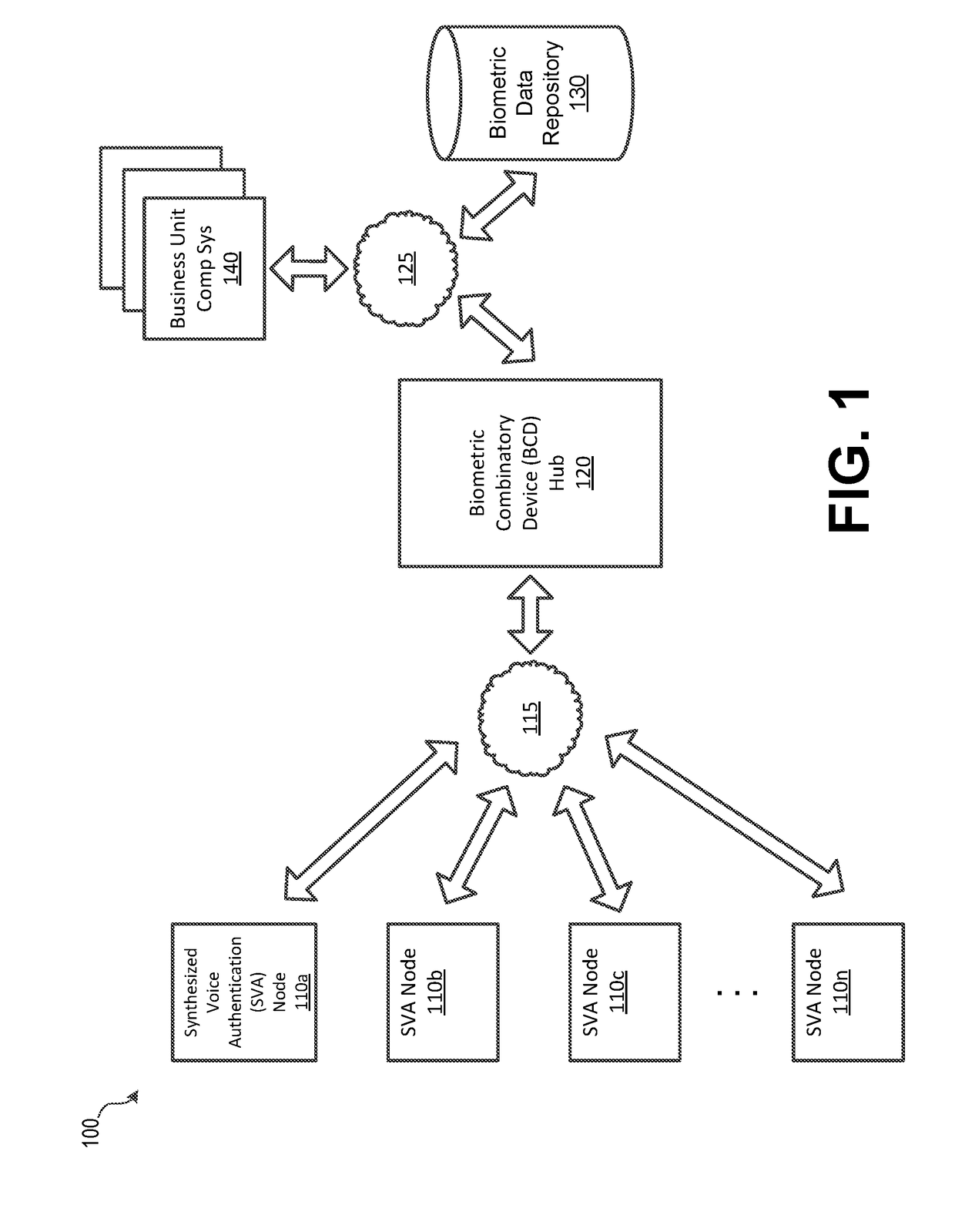
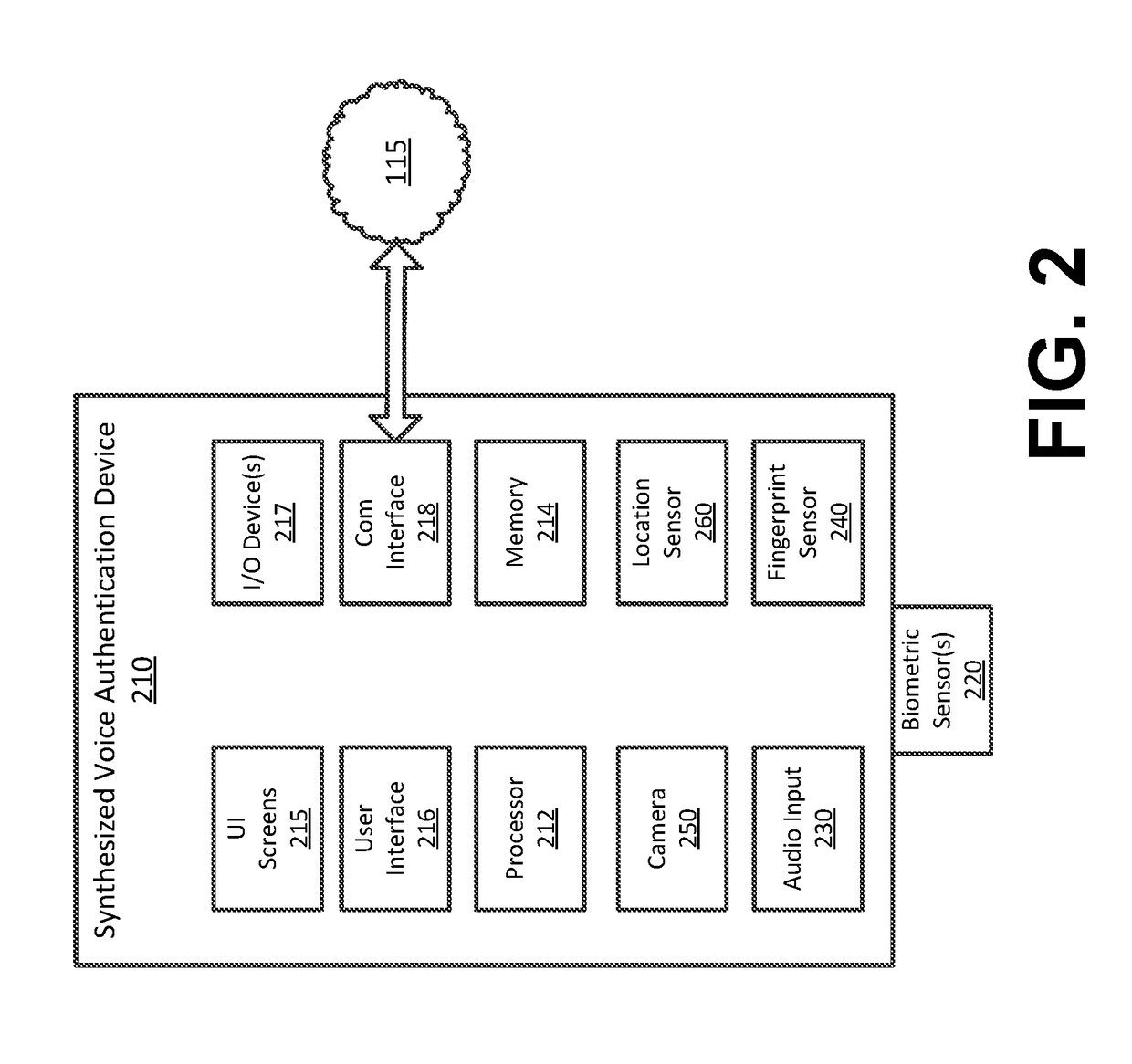
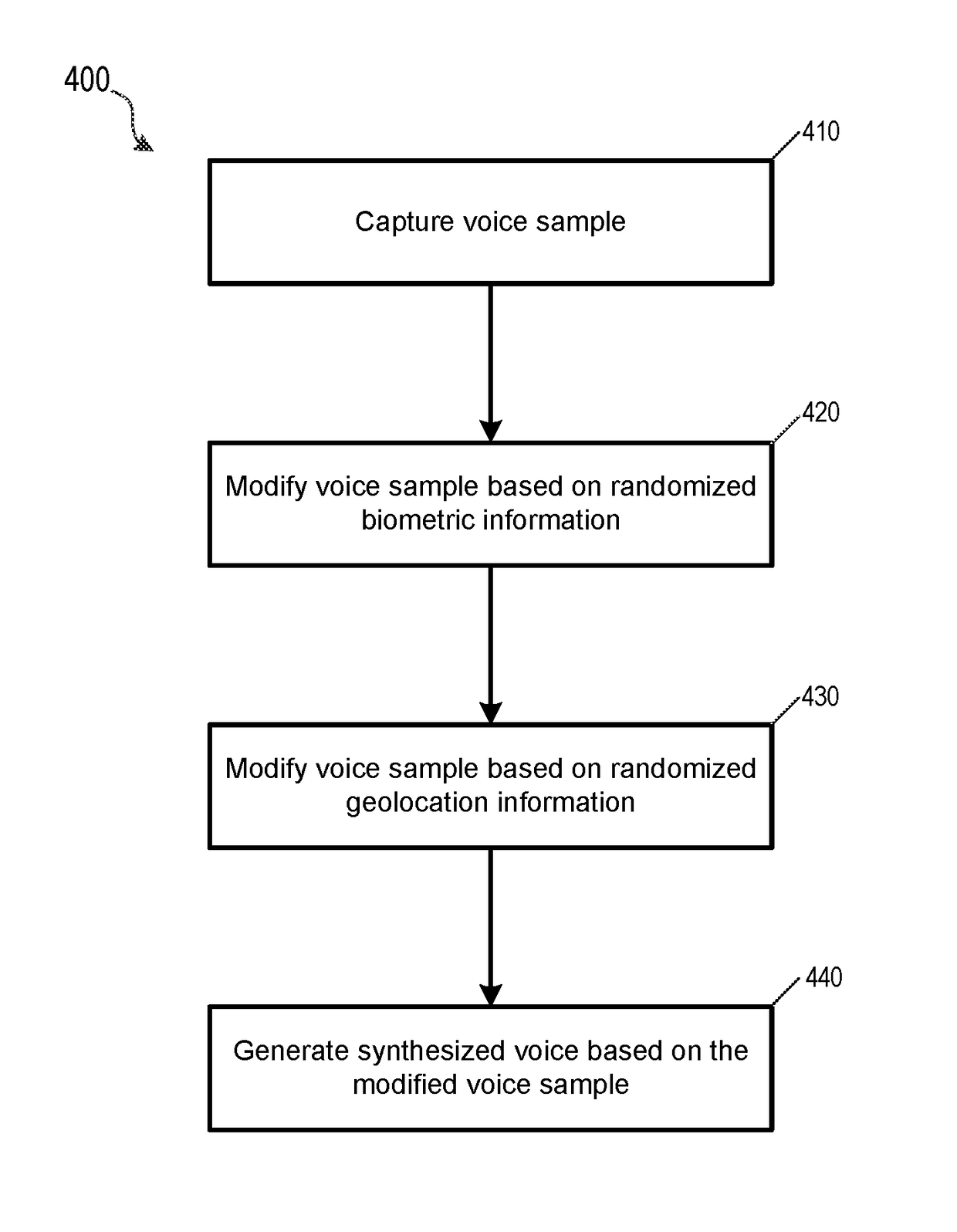
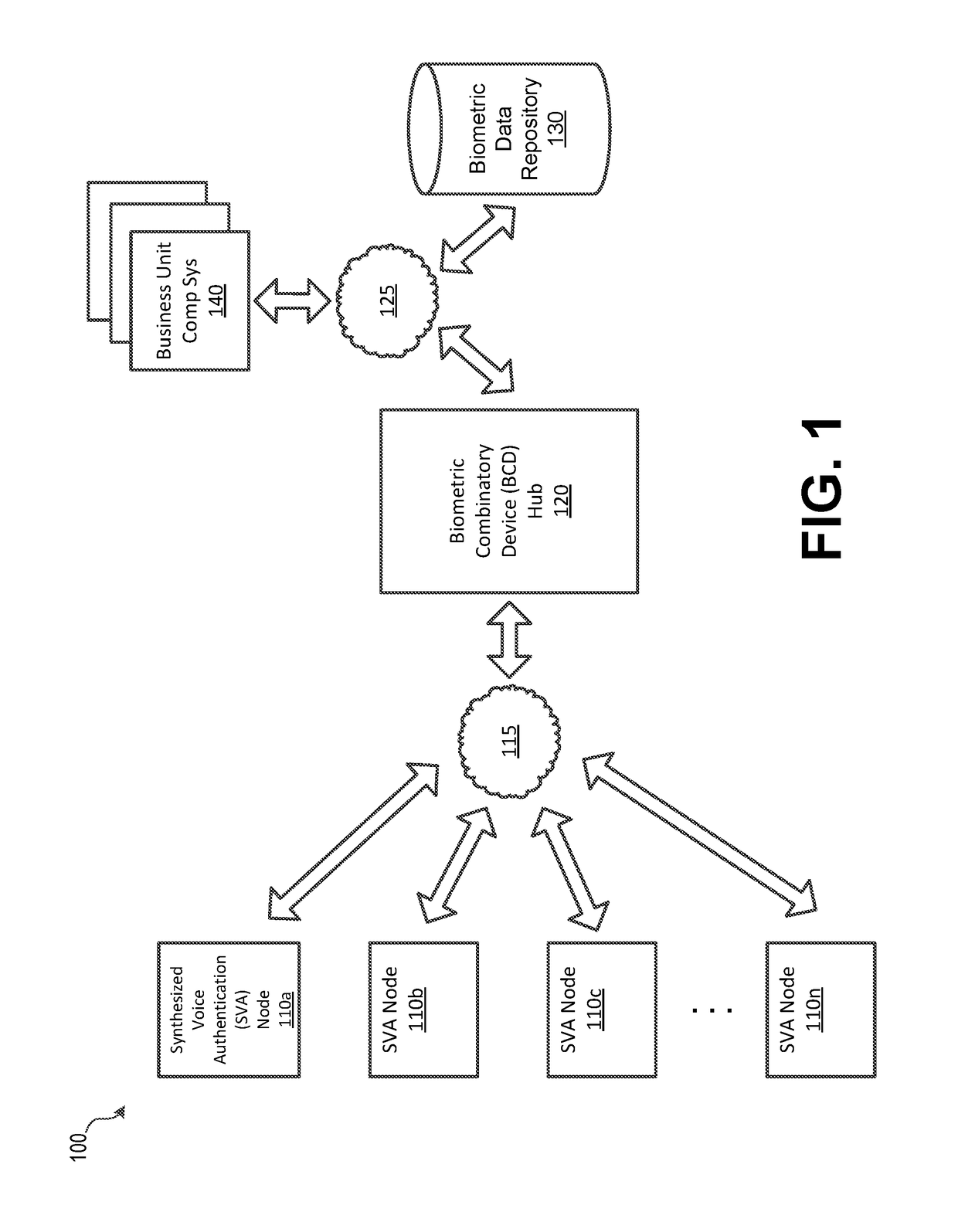
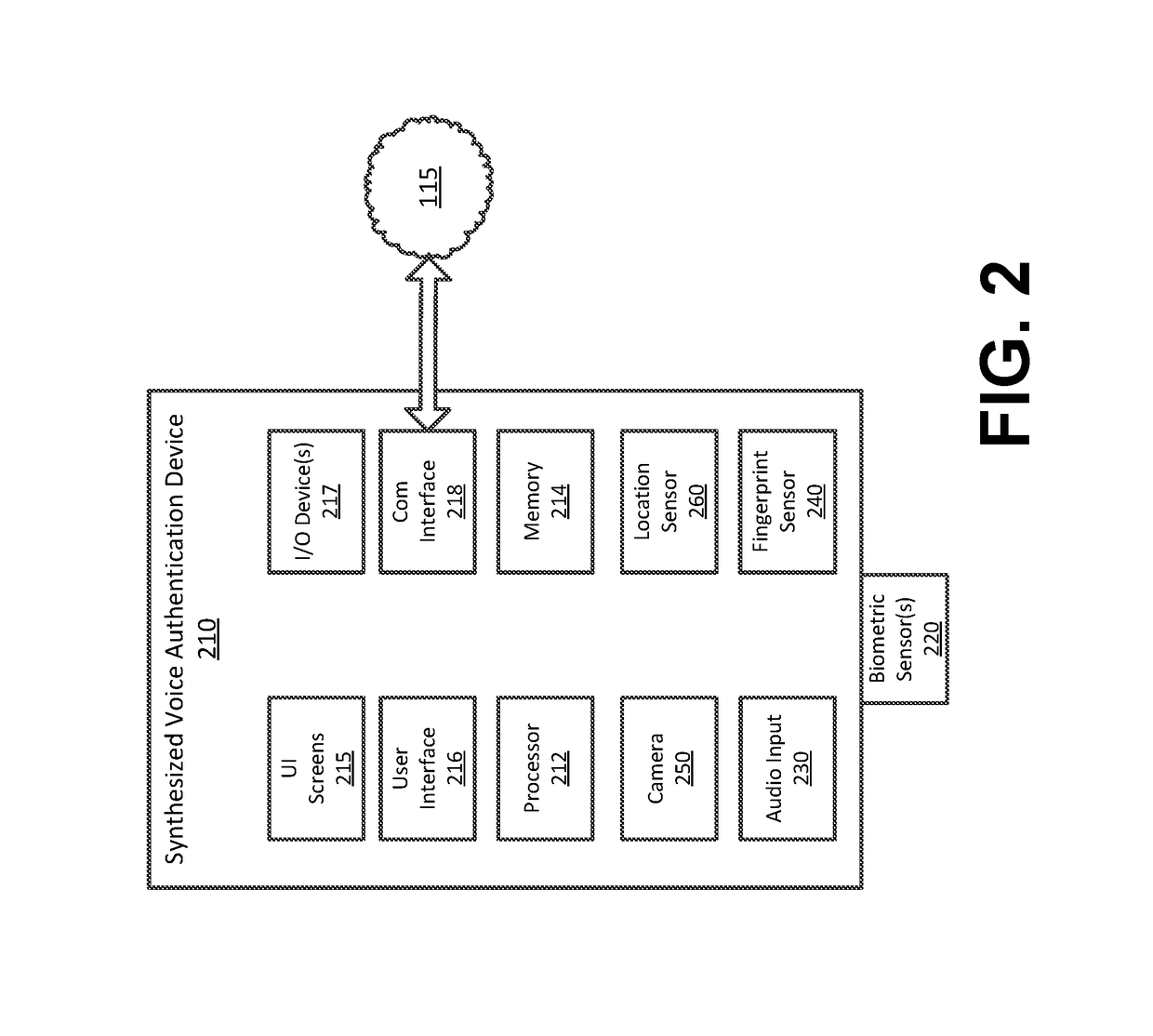
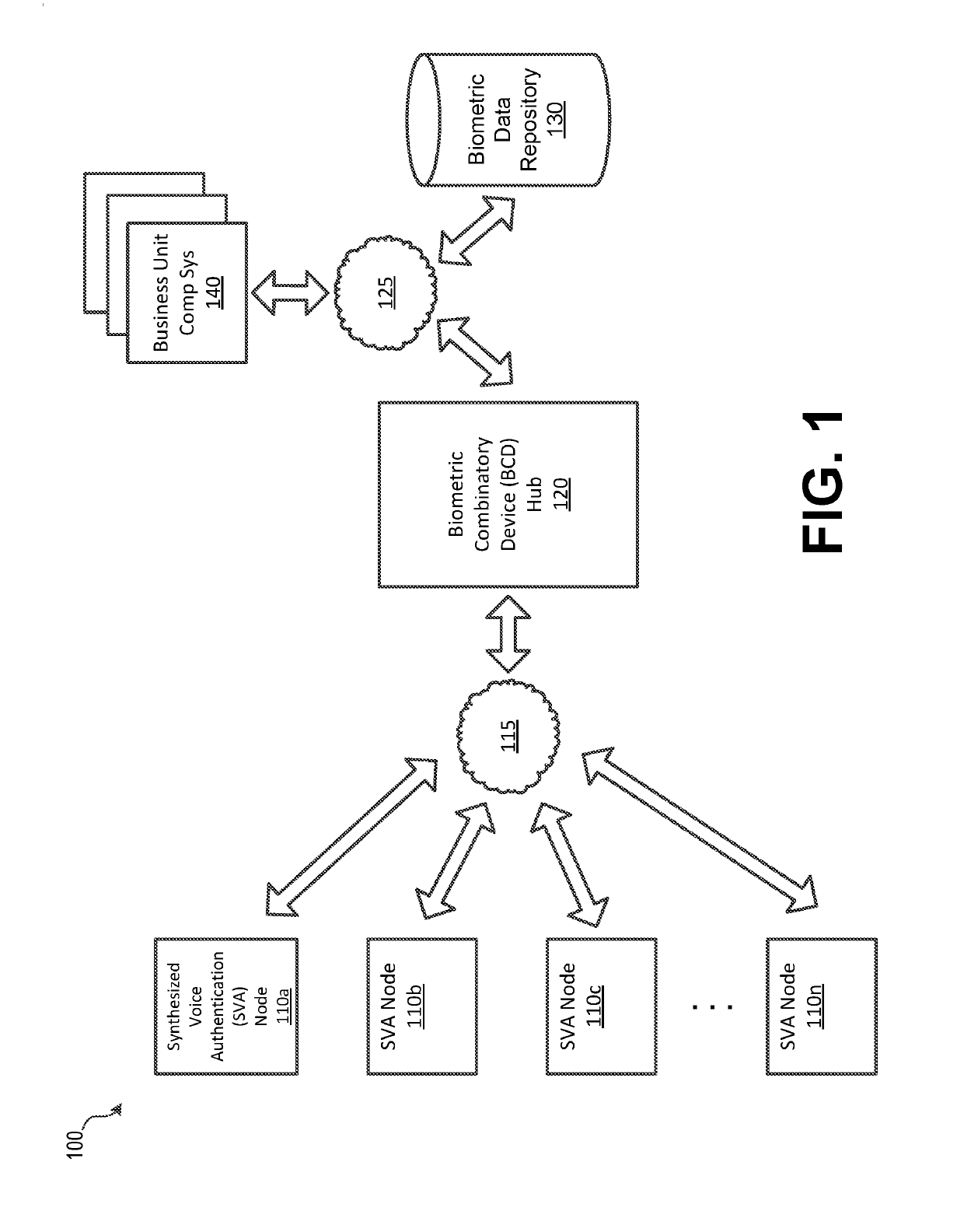
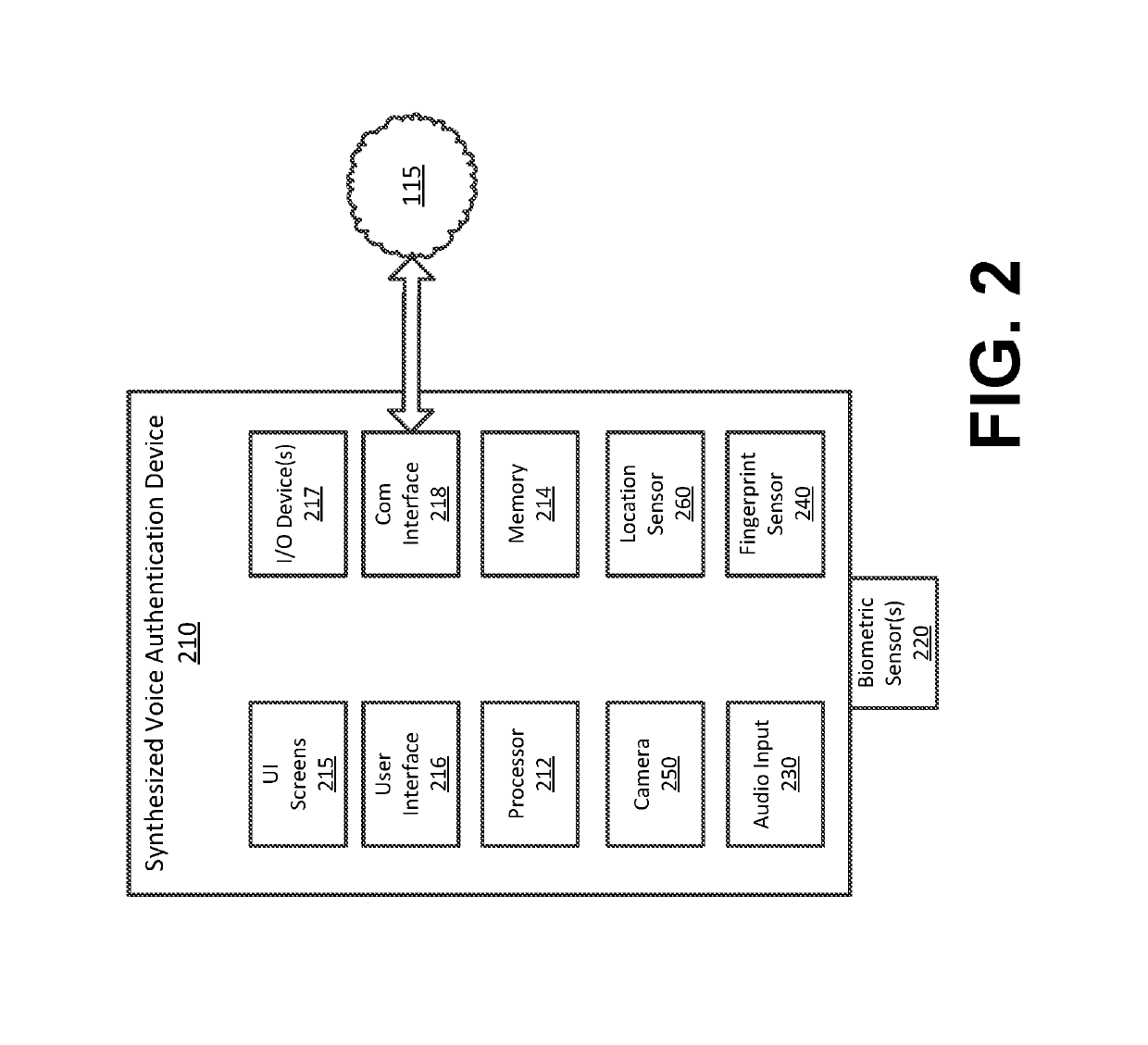
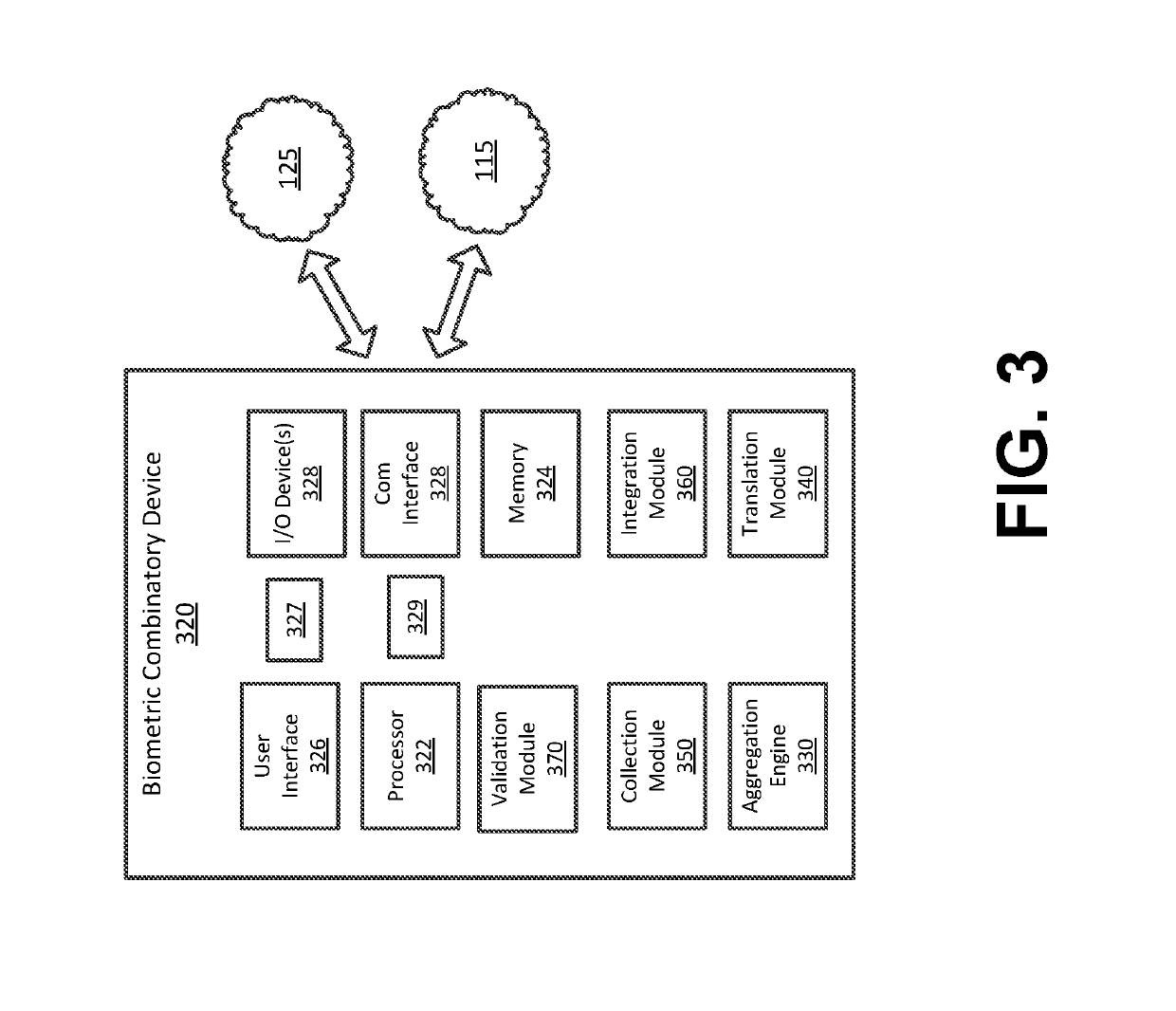
Synthesized Voice Authentication Engine
ActiveUS20180174590A1Effective and efficient and scalable and convenient solutionMultiple biometrics useSpeech synthesisAudio signal flowAudio frequency
A system for creating a synthetic voice identifier may include a plurality of synthesized voice authorization (SVA) devices and a biometric combinatory device (BCD). The SVAs may be communicatively coupled to the BCD via a network and may communicate utilizing a markup language. The SVA devices may capture an audio signal of a voice of a user, modify the audio signal with a randomized audio frequency signal to generate a modified audio signal, and communicate, the modified audio signal as a synthesized voice signal associated with the user. The BCD may receive biometric information corresponding to a user, the biometric information comprising at least audio information associated with a voice of the user, receive, at an integration module, location information corresponding to a location of the user, combine, the location information and audio signal information associated with the user to generate a synthesized voice identifier associated with the user, and communicate the synthesized voice identifier to a remote device for use in an authentication process of the user.
Owner:BANK OF AMERICA CORP
Synthesized Voice Authentication Engine
ActiveUS20180174591A1Effective and efficient and scalable and convenient solutionTransmissionSpeech synthesisAudio signal flowAudio frequency
A system for creating a synthetic voice identifier may include a plurality of synthesized voice authorization (SVA) devices and a biometric combinatory device (BCD). The SVAs may be communicatively coupled to the BCD via a network and may communicate utilizing a markup language. The SVA devices may capture an audio signal of a voice of a user, modify the audio signal with a randomized audio frequency signal to generate a modified audio signal, and communicate, the modified audio signal as a synthesized voice signal associated with the user. The BCD may receive biometric information corresponding to a user, the biometric information comprising at least audio information associated with a voice of the user, receive, at an integration module, location information corresponding to a location of the user, combine, the location information and audio signal information associated with the user to generate a synthesized voice identifier associated with the user, and communicate the synthesized voice identifier to a remote device for use in an authentication process of the user.
Owner:BANK OF AMERICA CORP
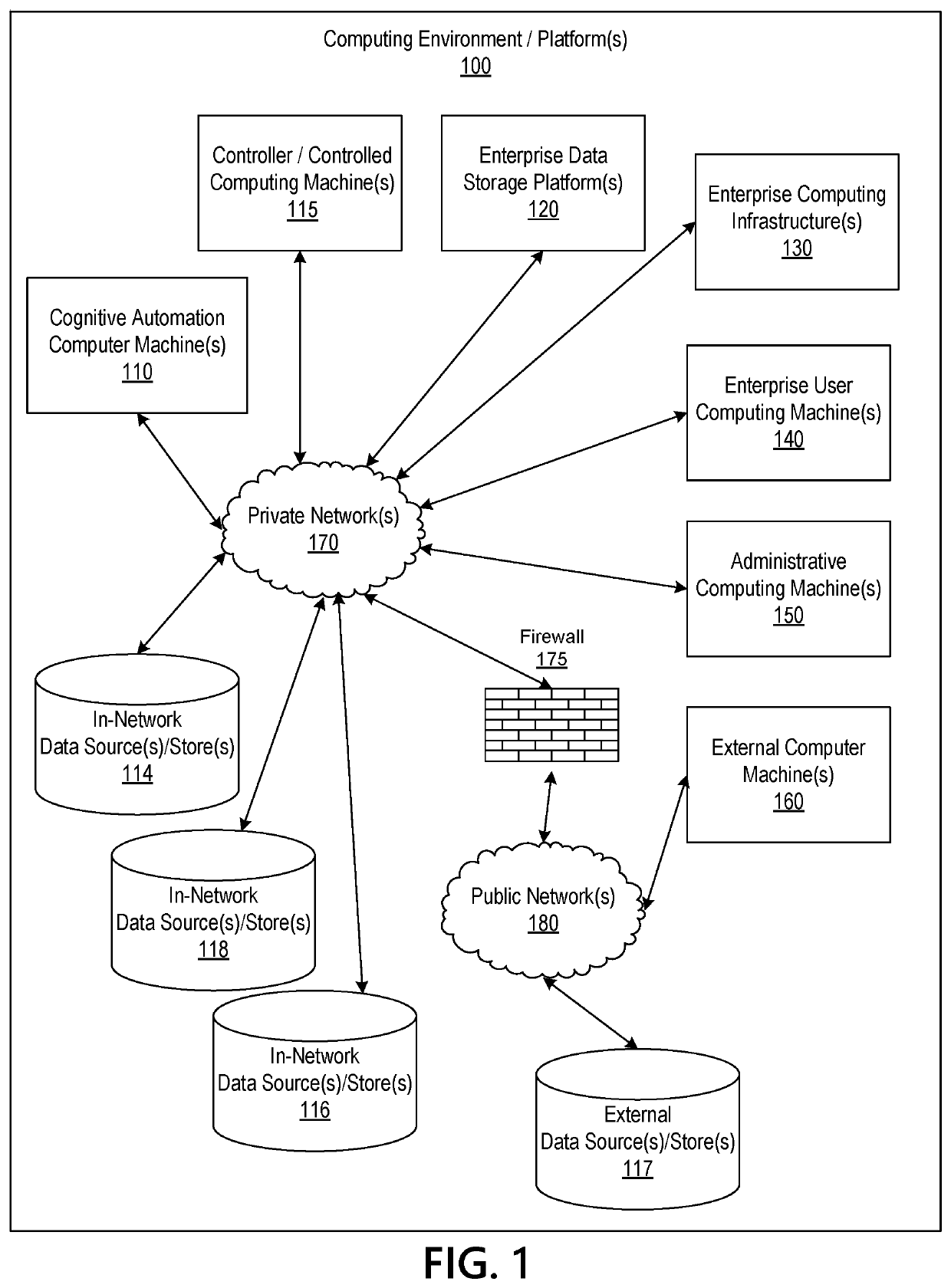
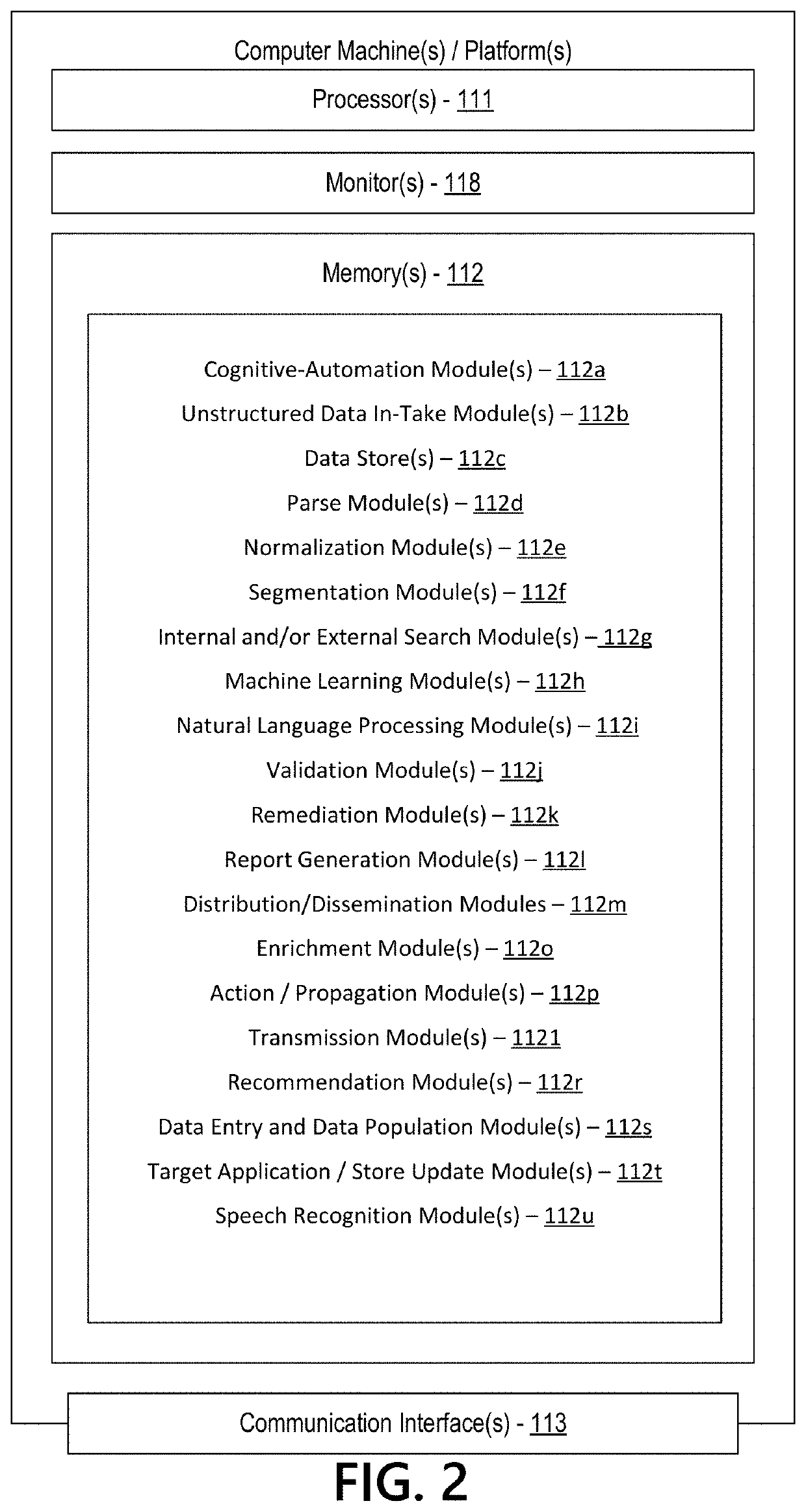
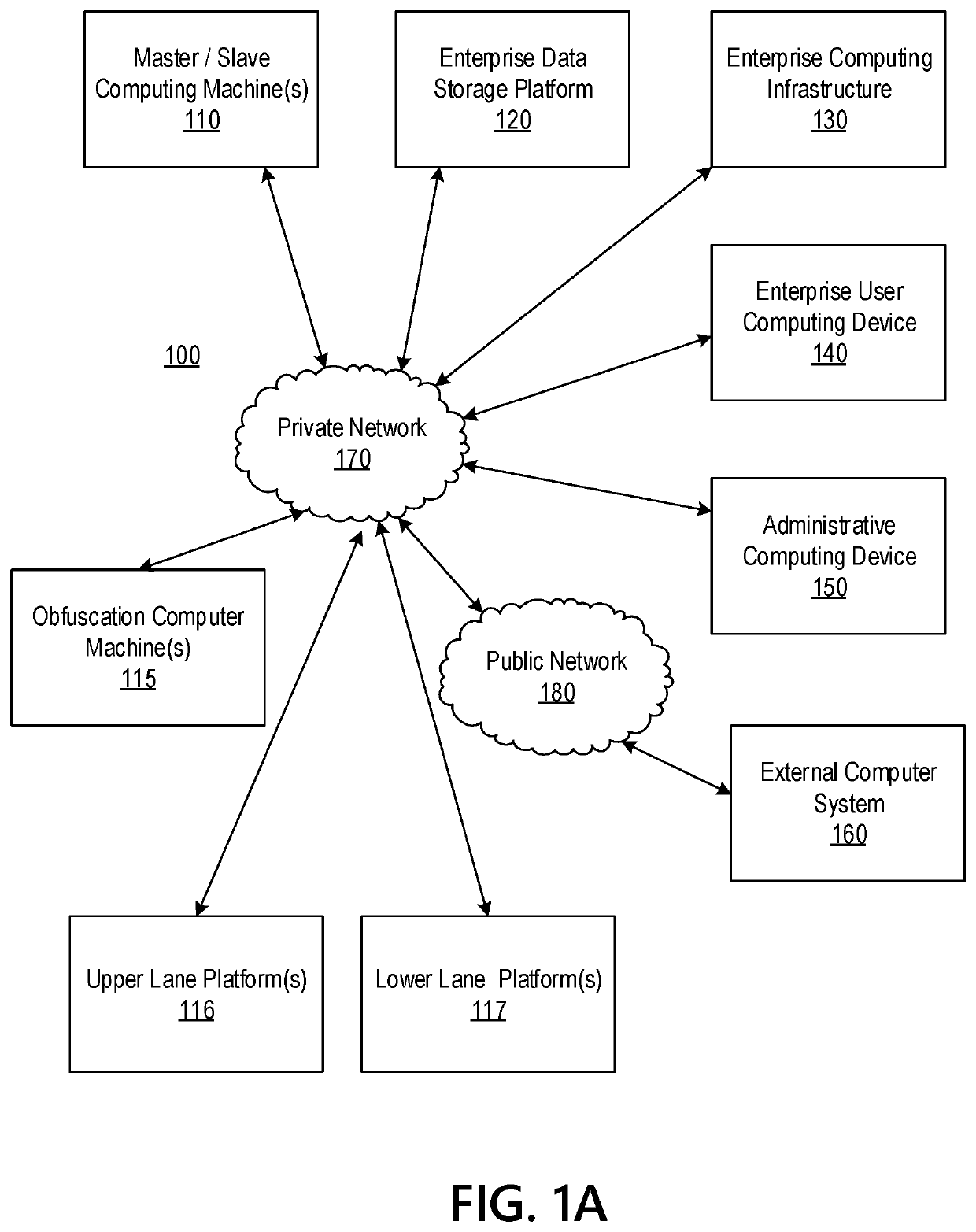
Cognitive automation-based engine to propagate data across systems
ActiveUS10917491B1Effective and efficient and scalable and convenientEffective and efficient and scalable and convenient solutionMachine learningInference methodsData packPrivate network
Aspects of the disclosure relate to cognitive automation-based engine processing to propagate data across multiple systems via a private network to overcome technical system, resource consumption, and architecture limitations. Data to be propagated can be manually input or extracted from a digital file. The data can be parsed by analyzing for correct syntax, normalized into first through sixth normal forms, segmented into packets for efficient data transmission, validated to ensure that the data satisfies defined formats and input criteria, and distributed into a plurality of data stores coupled to the private network, thereby propagating data without repetitive manual entry. The data may also be enriched by, for example, correcting for any errors or linking with other potentially related data. Based on data enrichment, recommendations of additional target(s) for propagation of data can be identified. Reports may also be generated. The cognitive automation may be performed in real-time to expedite processing.
Owner:BANK OF AMERICA CORP
Big Data Distributed Processing and Secure Data Transferring with Hyper Fencing
ActiveUS20210211430A1Effective and efficient and scalable and convenient technicalEffective resourcesConcurrent instruction executionTransmissionData connectionComputer cluster
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. The big data dataset can be uncompressed based on a codec and uncompressed data blocks can be distributed for processing. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
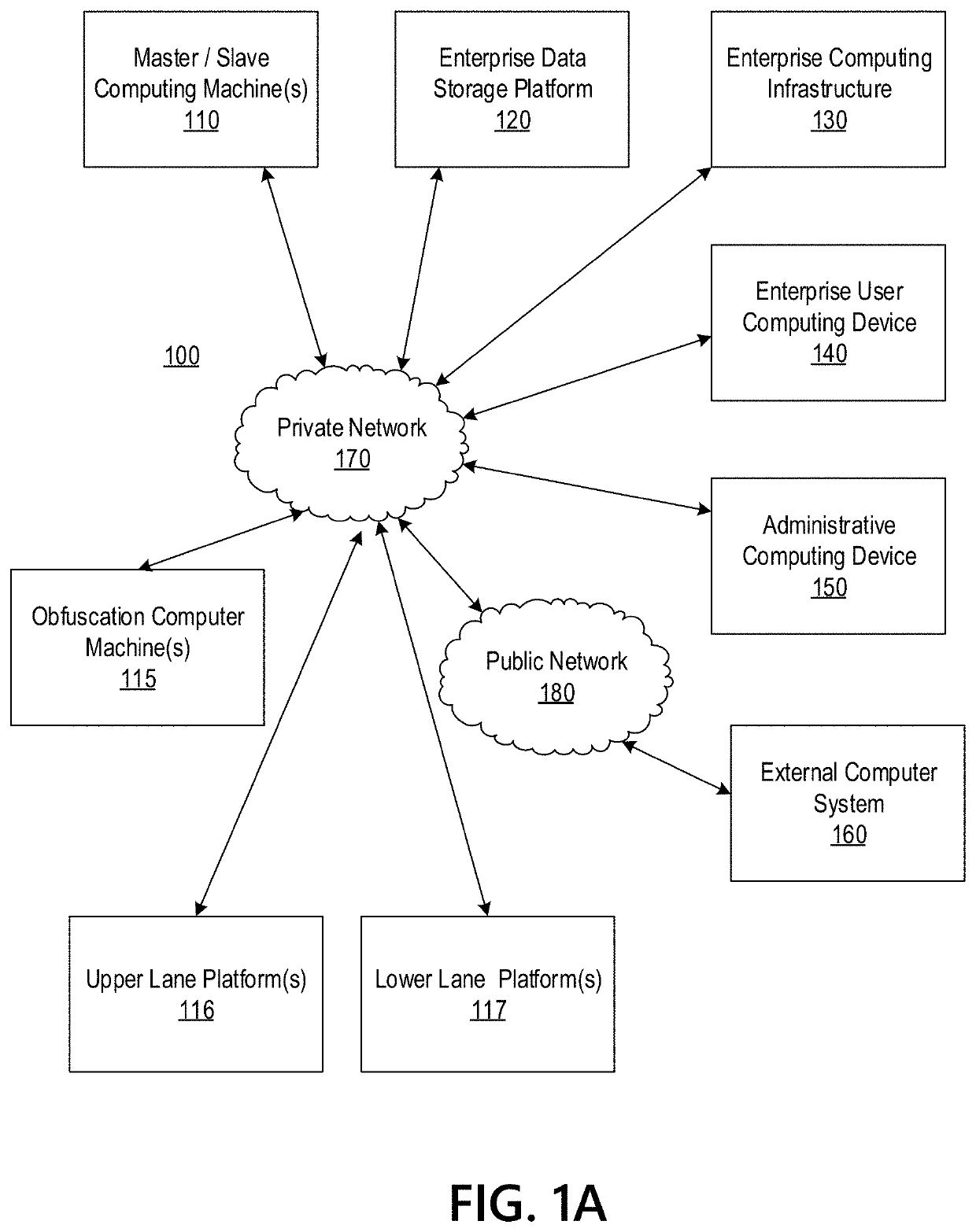
Big Data Distributed Processing and Secure Data Transferring with Obfuscation
ActiveUS20210209202A1Effective and efficient and scalable and convenient technicalEffective resourcesMultiple keys/algorithms usageDigital data protectionData connectionData set
Aspects of the disclosure relate to in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data, in a data store based on credentials received from a source. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. A secure connection to the data store can be established. The sensitive information in the big data dataset can be redacted into a sanitized dataset based on one or more data obfuscation types. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Synthesized voice authentication engine
ActiveUS10049673B2Effective and efficient and scalable and convenient solutionMultiple biometrics useSpeech synthesisAudio signal flowSpeech sound
Owner:BANK OF AMERICA CORP
Cognitve Automation-based engine to propagate data across systems
ActiveUS20210281655A1Effective and efficient and scalable and convenient solutionMachine learningInference methodsData packPrivate network
Aspects of the disclosure relate to cognitive automation-based engine processing to propagate data across multiple systems via a private network to overcome technical system, resource consumption, and architecture limitations. Data to be propagated can be manually input or extracted from a digital file. The data can be parsed by analyzing for correct syntax, normalized into first through sixth normal forms, segmented into packets for efficient data transmission, validated to ensure that the data satisfies defined formats and input criteria, and distributed into a plurality of data stores coupled to the private network, thereby propagating data without repetitive manual entry. The data may also be enriched by, for example, correcting for any errors or linking with other potentially related data. Based on data enrichment, recommendations of additional target(s) for propagation of data can be identified. Reports may also be generated. The cognitive automation may be performed in real-time to expedite processing.
Owner:BANK OF AMERICA CORP
Vehicle telematics based driving assessment
ActiveUS10633001B2Effective and efficient and scalable and convenient solutionFinanceRegistering/indicating working of vehiclesInformation processingData mining
Aspects of the disclosure relate to using vehicle telematics data to assess parameters associated with vehicle operation. In some instances, a driving assessment system may include a first computing device associated with a user in a vehicle and a second computing located remotely from the first computing device. The first computing device may collect, by way of one or more of an accelerometer and global positioning system (GPS), vehicle operational data and vehicle locational information associated with the vehicle and corresponding to a trip of the vehicle and may transmit such information to the second computing device. The second computing device may identify actionable and second order actionable trip data from the vehicle operational data and vehicle locational information and may calculate a behavior score for the trip.
Owner:ALLSTATE INSURANCE
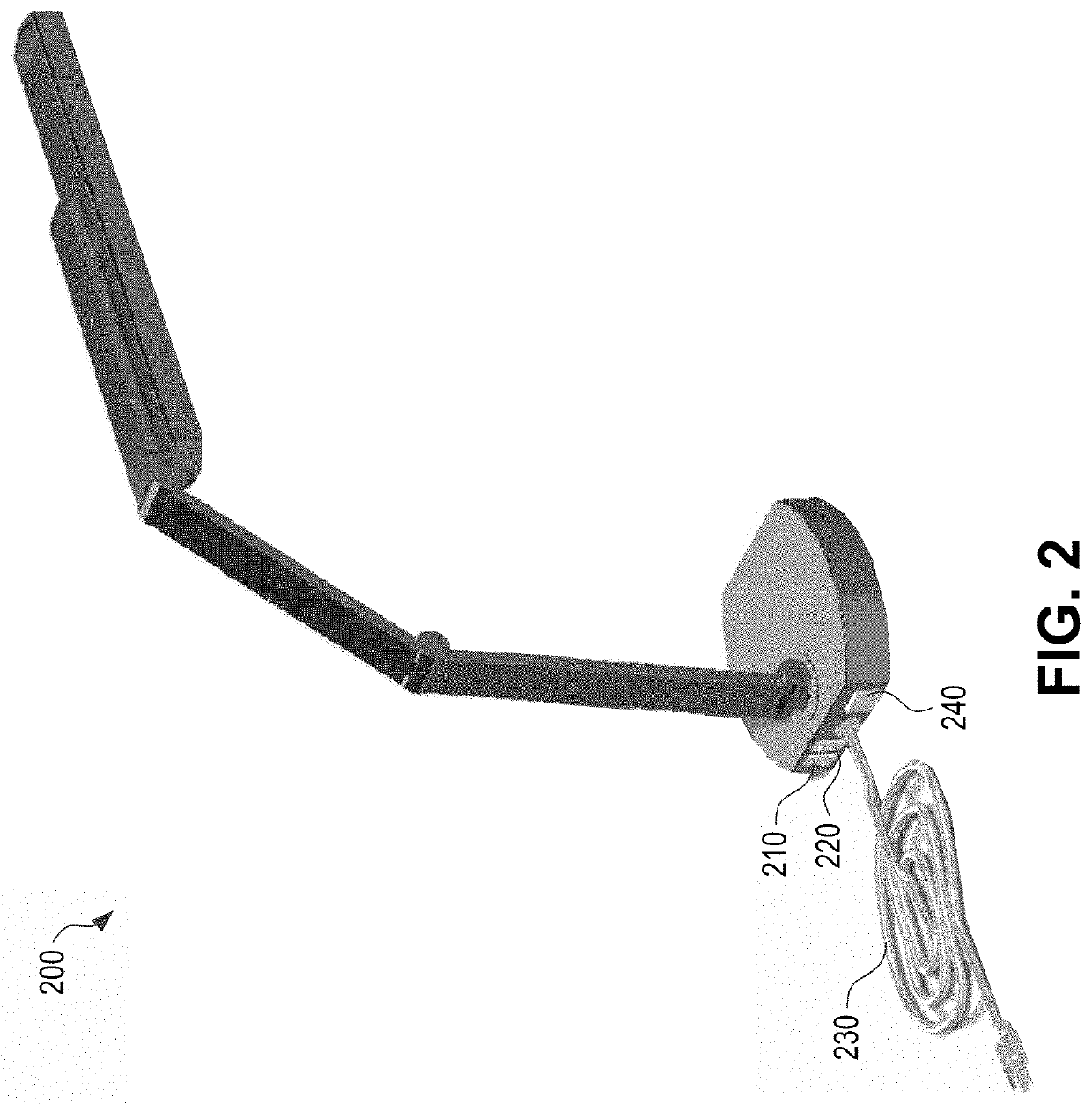
Heat Lamp
ActiveUS20200205609A1Effective and efficient and scalable and convenient solutionMinimizes visual obstructionMicrobiological testing/measurementLaboratory glasswaresEngineeringLight head
A heat lamp is provided that minimizes visual obstructions between an individual and a food service line, while more evenly distributing heat across food. The heat energy penetrates into the food and does not merely heat the surface. Different heating capabilities can be provided by locating the lamp head at different positions over a large adjustable height range. Additional lighting elements provide illumination to heated surfaces to improve visual appeal. Each heat lamp on a service line may be connected to an adjacent heat lamp through built-in power receptacles. The surfaces of the heat lamp are sealed and / or made of easily cleaned substances and have features compliant to one or more industry standards. The heat lamp may be easily transportable and may be resistant to damage.
Owner:SPRING US CORP
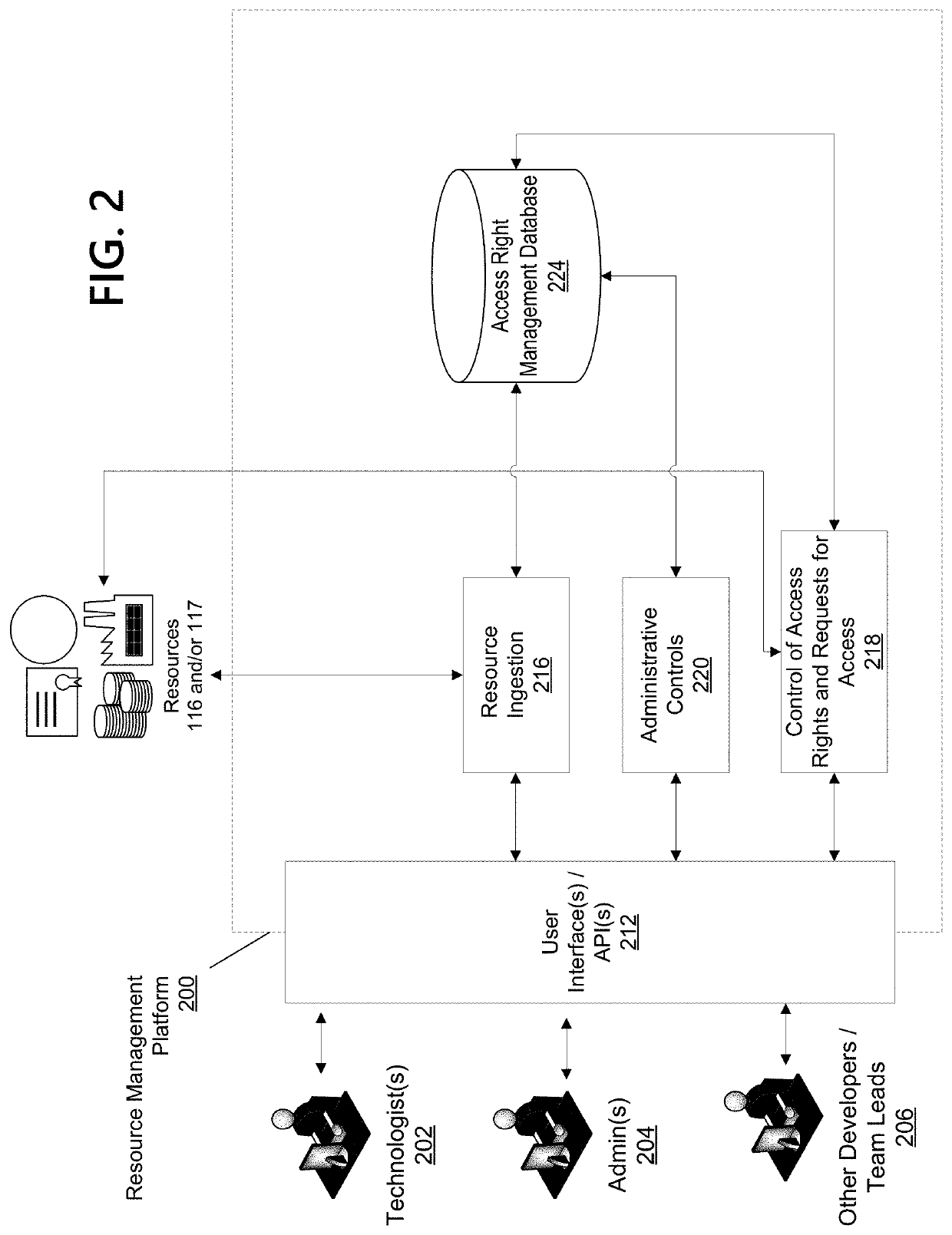
Expedited Authorization and Access Management
ActiveUS20220060470A1Effective and efficient and scalable and convenientStreamlined and provisioningTransmissionAccess networkGraphical user interface
Aspects of the disclosure relate to simplified and expedited processing of access requests to network resources. Authorized individuals can set rules for accessing network resources. The rules can be implemented as a series of macro steps assigned to various access rights and can be consolidated in a single button or widget for a particular user group. In response to a user's one-click selection of the button or widget, all applicable access rights can be requested sequentially from appropriate services or individuals without requiring complex instructions or myriad user actions. User interfaces and API(s) are provided to enable users to request access and managers to setup access requirements and button configurations. Novel logical systems, architectures, platforms, graphical user interfaces, and methods are disclosed.
Owner:BANK OF AMERICA CORP
Big data distributed processing and secure data transferring with hyper fencing
ActiveUS11363029B2Efficient transferEffective and efficient and scalable and convenient solutionConcurrent instruction executionSecuring communicationData connectionComputer cluster
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. The big data dataset can be uncompressed based on a codec and uncompressed data blocks can be distributed for processing. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Synthesized voice authentication engine
ActiveUS10446157B2Effective and efficient and scalable and convenient solutionTransmissionSpeech synthesisAudio signal flowAuthorization
A system for creating a synthetic voice identifier may include a plurality of synthesized voice authorization (SVA) devices and a biometric combinatory device (BCD). The SVAs may be communicatively coupled to the BCD via a network and may communicate utilizing a markup language. The SVA devices may capture an audio signal of a voice of a user, modify the audio signal with a randomized audio frequency signal to generate a modified audio signal, and communicate, the modified audio signal as a synthesized voice signal associated with the user. The BCD may receive biometric information corresponding to a user, the biometric information comprising at least audio information associated with a voice of the user, receive, at an integration module, location information corresponding to a location of the user, combine, the location information and audio signal information associated with the user to generate a synthesized voice identifier associated with the user, and communicate the synthesized voice identifier to a remote device for use in an authentication process of the user.
Owner:BANK OF AMERICA CORP
Big data distributed processing and secure data transferring with fallback control
ActiveUS11379603B2Efficient transferEffective and efficient and scalable and convenient solutionResource allocationDigital data protectionData connectionComputer cluster
Owner:BANK OF AMERICA CORP
Big Data Distributed Processing and Secure Data Transferring with Fallback Control
ActiveUS20210209244A1Effective and efficient and scalable and convenient technicalEffective resourcesResource allocationDigital data protectionData connectionComputer cluster
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. State point information for previously reached safe points can be stored and progressively released such that only the incomplete portion(s) of task(s) need to be resubmitted. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Big data distributed processing and secure data transferring with fault handling
ActiveUS11334408B2Efficient transferEffective and efficient and scalable and convenient solutionMultiple keys/algorithms usageDigital data protectionData connectionComputer cluster
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. Crashed executor(s) can be detected and caged to prevent further use. Uncompleted task(s) for crashed executor(s) can be reassigned. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Highway detection system for generating customized notifications
ActiveUS11082511B2Effective and efficient and scalable and convenient solutionOperate efficiently and effectivelyVehicle testingInstruments for road network navigationStatistical analysisMobile device
A highway detection system may include a telematics device associated with a vehicle having one or more sensors arranged therein, a mobile device associated with a user traveling in the vehicle, and a server computer. The server computer may receive traveling data for a trip of the user from the one or more sensors and via the telematics device. The server computer may then determine whether the user is traveling within a city or on a highway based on analysis of the traveling data for the trip of the user, which may include a statistical analysis to calculate standard deviations of metrics in the traveling data. In response to the determination, the server computer may generate a notification to transmit to the user based on whether the user is traveling within a city or on a highway and transmit the notification to the mobile device associated with the user.
Owner:ALLSTATE SOLUTIONS PTE LTD
Big data distributed processing and secure data transferring with resource allocation and rebate
ActiveUS11314874B2Efficient transferEffective and efficient and scalable and convenient solutionResource allocationDigital data protectionData connectionComputer cluster
Aspects of the disclosure relate to resource allocation and rebating during in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. Secure connection(s) to the data store can be established. Sensitive information can be redacted into a sanitized dataset based on one or more data obfuscation types. RAM requirements and current RAM allocation can be diagnosed. Portion(s) of the current RAM allocation exceeding the RAM requirements can be rebated. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Big data distributed processing and secure data transferring with obfuscation
ActiveUS11321430B2Efficient transferEffective and efficient and scalable and convenient solutionMultiple keys/algorithms usageDigital data protectionData connectionData set
Aspects of the disclosure relate to in-flight data masking and on-demand encryption of big data on a network. Computer machine(s), cluster managers, nodes, and / or multilevel platforms can request, receive, and / or authenticate requests for a big data dataset, containing sensitive and non-sensitive data, in a data store based on credentials received from a source. Profiles can be auto provisioned, and access rights can be assigned. Server configuration and data connection properties can be defined. A secure connection to the data store can be established. The sensitive information in the big data dataset can be redacted into a sanitized dataset based on one or more data obfuscation types. The encrypted data can be transmitted, in response to the request, to a source, a target, and / or another computer machine and can be decrypted back into the sanitized dataset.
Owner:BANK OF AMERICA CORP
Information security system based on multidimensional disparate user data
ActiveUS11381591B2Effective and efficient and scalable and convenient solutionEfficient storageMemory loss protectionError detection/correctionData warehouseData set
Owner:BANK OF AMERICA CORP
Lateral movement visualization for intrusion detection and remediation
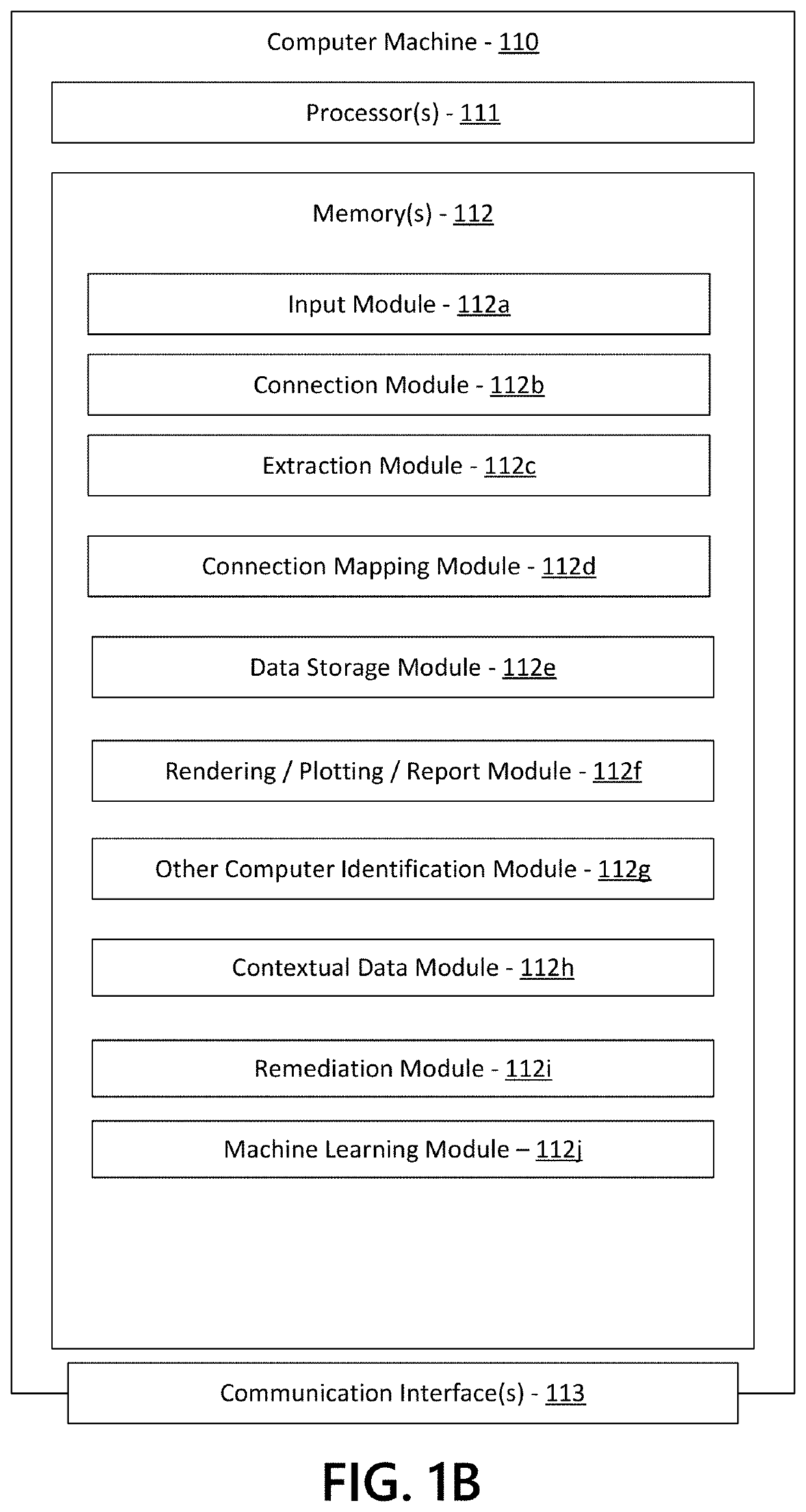
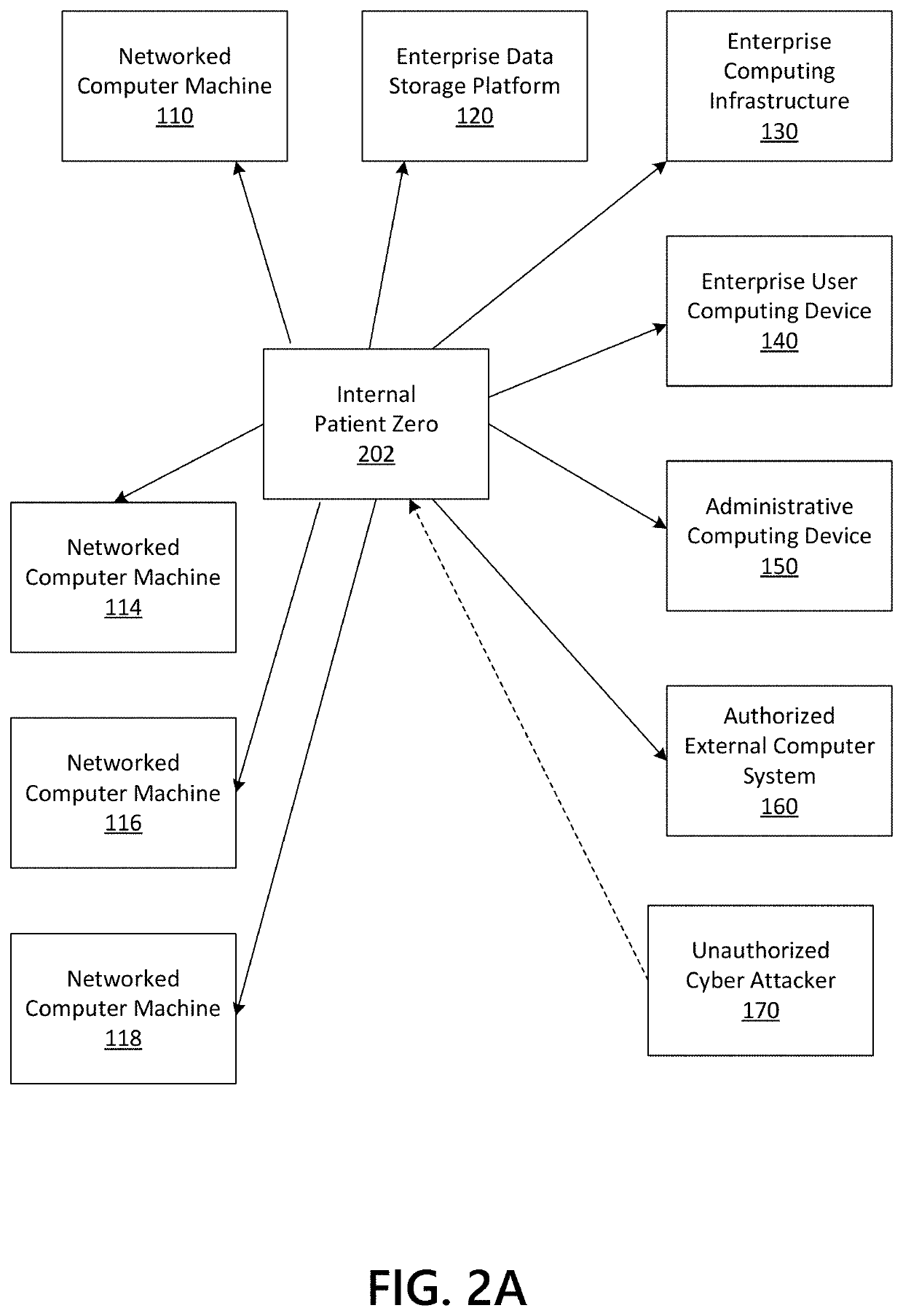
ActiveUS11425150B1Effective and efficient and scalable and convenient solutionRapid visualizationPlatform integrity maintainanceMachine learningDrill downComputer graphics (images)
Aspects of the disclosure relate to visualization of lateral movements of an intruder on a network by connecting to computers and / or resources under investigation. A first computer is identified for investigation. Logs regarding incoming and outgoing connections to the computer are extracted and can be prefiltered based on specific IDs or other criteria. Maps of incoming and outgoing connections are stored in memory along with event information. Each subsequent computer to which the computer connected or resource accessed is identified. The map is updated based on logs from that computer or resource. A graphical image showing each applicable host, its connections, the chronology, and / or contextual information is generated and displayed. Individual hosts and other displayed data can be user-selectable to drill down and / or provide additional information. The process can repeat until all hosts, from patient zero to all endpoints, have been identified and rendered.
Owner:BANK OF AMERICA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com