Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
75results about "In Zigbee networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
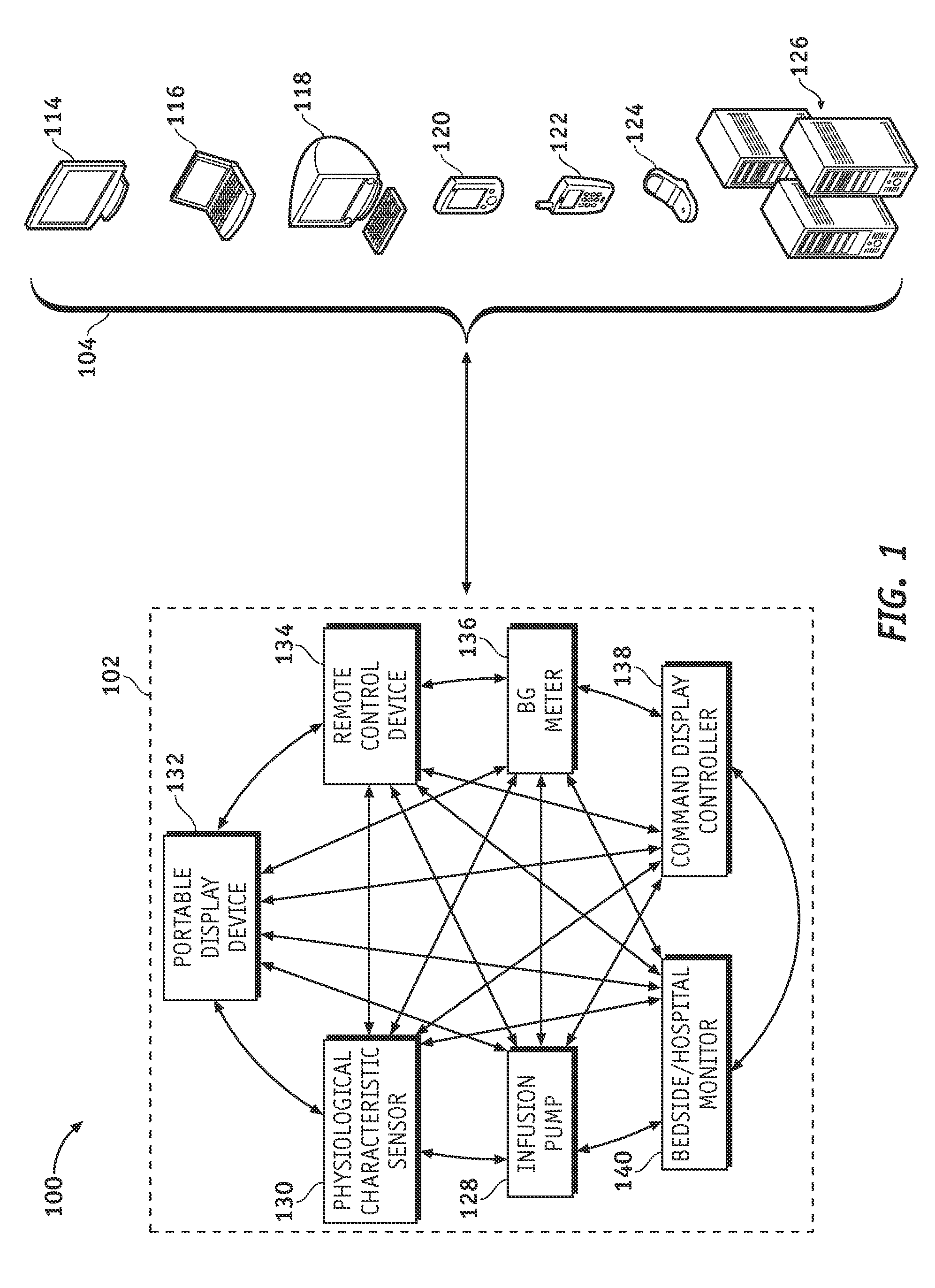
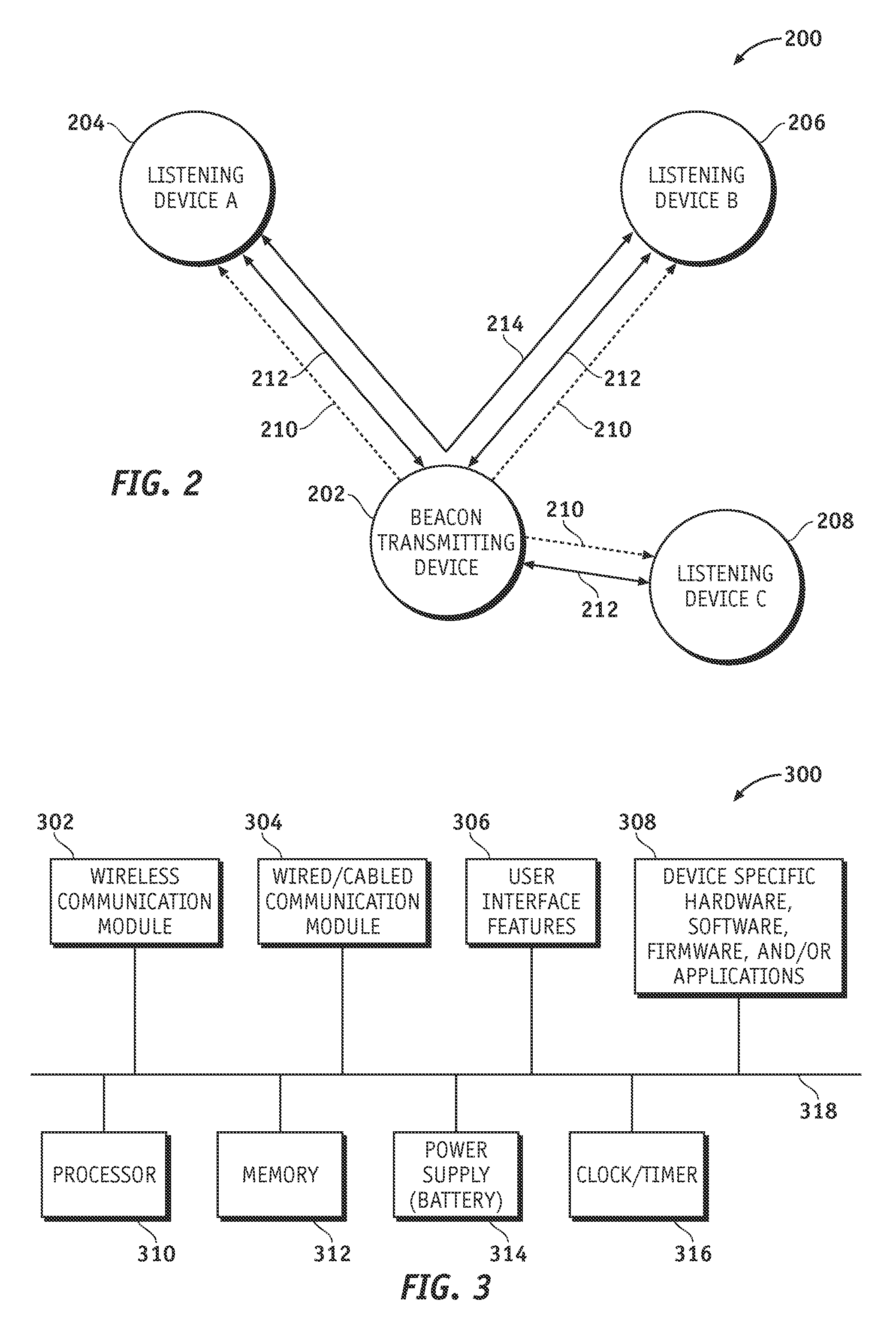
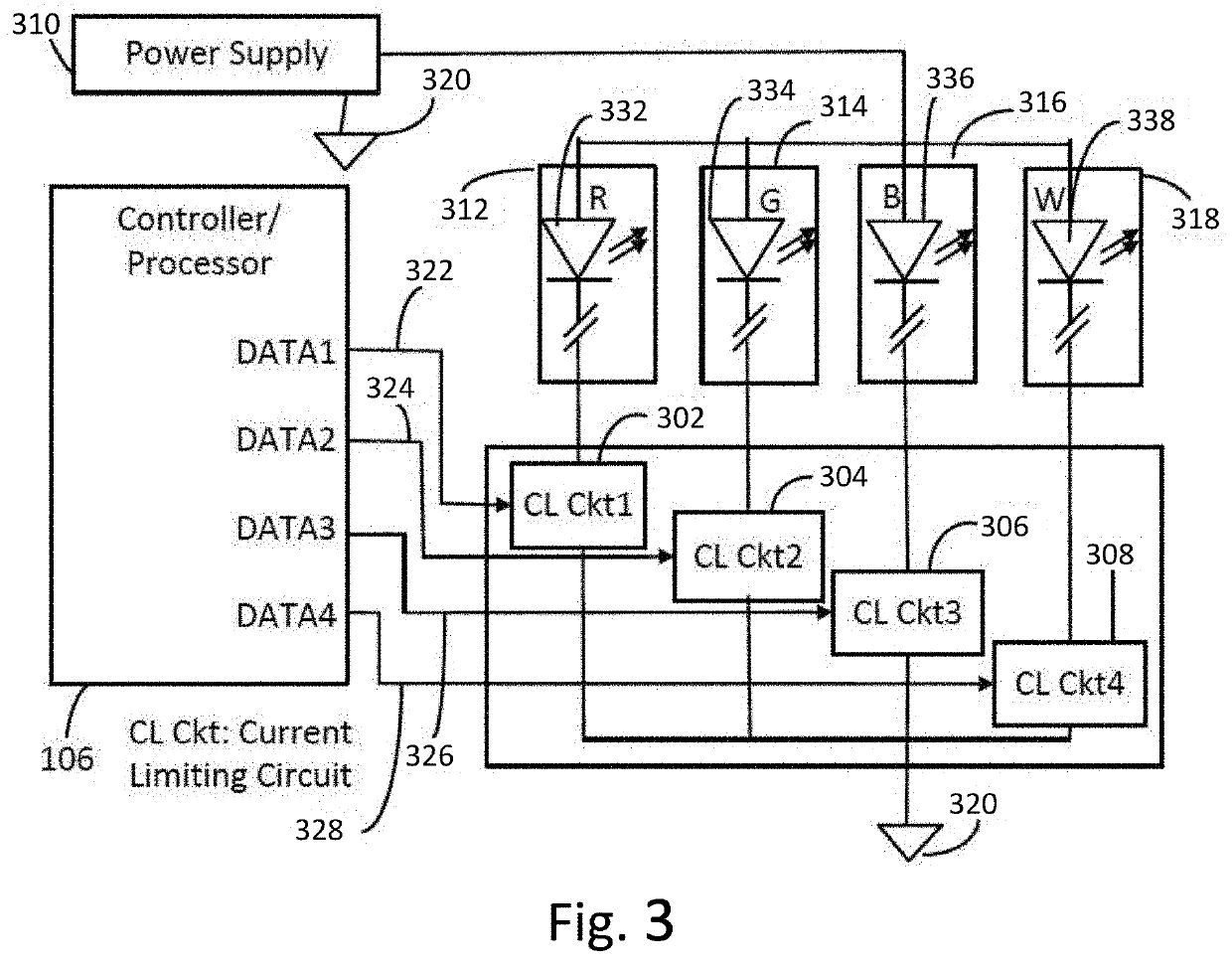
System and method for variable beacon timing with wireless devices
ActiveUS20100111066A1Well formedFrequency-division multiplex detailsIn ad hoc networksEngineeringOperation mode
Systems and methods for supporting variable beacon timing for a first wireless device and a second wireless device are provided. An exemplary system may include a number of wireless devices configured to wirelessly communicate with one another. The system includes a beacon-transmitting wireless device and a listening wireless device. The beacon-transmitting wireless device is configured to transmit, during a first operating mode, wireless beacons separated in time by relatively long time intervals. The beacon-transmitting device is also configured to transmit, during a second operating mode, wireless beacons separated in time by relatively short time intervals. The listening wireless device is configured to listen, during the first operating mode, for wireless beacons transmitted by the beacon-transmitting wireless device, and is configured to listen, during the second operating mode, for wireless beacons transmitted by the beacon-transmitting wireless device. The system may have more than two different operating modes, which may be desirable if the number of wireless devices in the system exceeds two.
Owner:MEDTRONIC MIMIMED INC
Wake-up radio system
Systems and methods may include a master device. The master device may include a wake-up transmitter to send a wake-up message to a slave device to wake-up the slave device. The master device may also include a short-range transmitter to communicate with the slave device once the slave device has been woken up. The master device may be a mobile phone that communicates with the slave device (e.g., Bluetooth accessory devices) over a Bluetooth network.
Owner:SONY CORP
Techniques to support multiple radio-access technologies
Techniques to permit scheduling of mixed radio access technologies. In some cases, a first radio access technology mode of a base station is scheduled during a first time region and a second radio access technology mode of a base station is scheduled during a sleep mode of the first radio access technology mode. In some cases, a first radio access technology mode of a base station is scheduled during a first time region and a second radio access technology mode of a base station is scheduled during an unused portion of the first time region. In some cases, a femto-base station is scheduled to snoop for local mobile stations during a sleep mode. Inactive regions of mobile stations are scheduled during a portion of sleep modes of the radio access technology modes.
Owner:APPLE INC
System and Method for an Energy Efficient Network Adaptor with Security Provisions
In accordance with an embodiment, a network device includes a network controller and at least one network interface coupled to the network controller that includes at least one media access control (MAC) device configured to be coupled to at least one physical layer interface (PHY). The network controller may be configured to determine a network path comprising the at least one network interface that has a lowest power consumption and minimum security attributes of available media types coupled to the at least one PHY.
Owner:STMICROELECTRONICS SRL
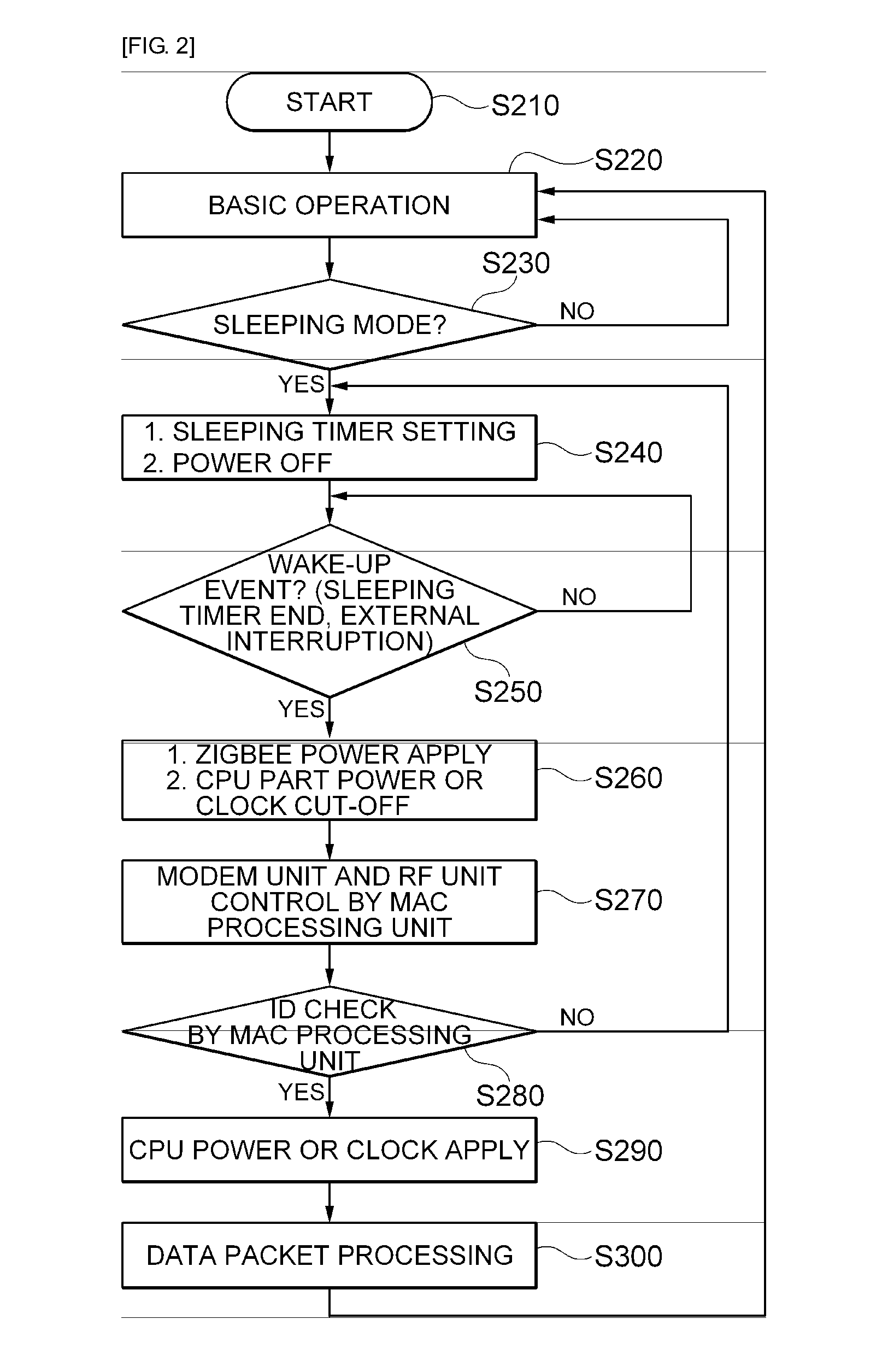
Low power zigbee device and low power wake-up method
InactiveUS20100115302A1Reduce unnecessary power consumptionPower managementVolume/mass flow measurementModem deviceMedia access control
Provided is a low-power ZigBee device provided with a sleeping mode and an active mode including a power supplying unit for supplying a power; a Medium Access Control (MAC) processing unit for receiving a wake-up packet and for controlling a modem unit and an Radio Frequency (RF) unit; and a Central Processing Unit (CPU) for receiving and processing a data packet, wherein the MAC processing unit makes the power supplying unit apply a power to the CPU based on a result of checking an identification (ID) of the wake-up packet.
Owner:SOLUM CO LTD
Mobile terminal and method of controlling external device using the same
InactiveUS20150381798A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordTouchscreen
A mobile terminal including a short-range communication module configured to provide short-range wireless communication; a touch screen; and a controller configured to deactivate the touch screen and enter the mobile terminal into a lock state, detect the mobile terminal is tilted more than a predetermined slope, receive a first touch input on the deactivated touch screen, and control the short-range communication module to transmit a first IR signal to an external device for controlling the external device when the first touch input matches a predetermined password for unlocking the mobile terminal into an unlocked state.
Owner:LG ELECTRONICS INC
Intelligent network sensor system
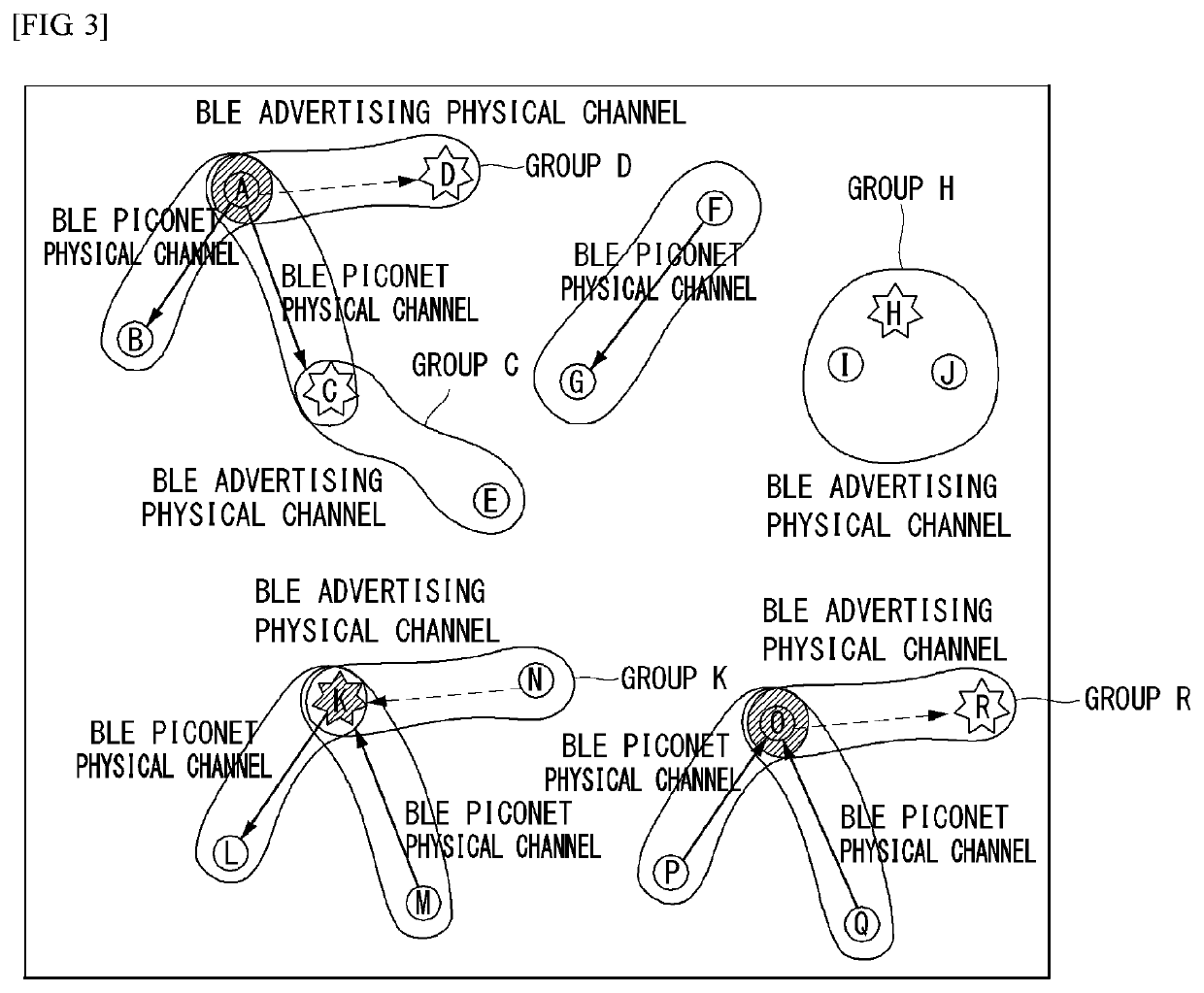
A network sensor system and method for using the same are disclosed herein. In one embodiment, the network sensor system comprises: a radio-frequency (RF) emitter; a first sensor tag including a transmitter, an energy harvesting unit operable to convert incident RF energy to direct current (DC) including RF energy from the RF emitter and RF energy from one or more ambient sources, a storage unit operable to store recovered DC power, one or more sensors for sensing and logging data, a controller coupled to the energy harvesting and storage units, the one or more sensors and the transmitter, to communicate data in the form of a Bluetooth Low Energy (BLE) advertising packet using energy previously harvested and stored by the energy harvesting and storage unit; and a first device to receive the BLE advertising packet.
Owner:RICOH KK
Devices and systems for consumer-installed hub-based intermediate-range packetized wireless networks utilizing assignable operational channels
Owner:SURE FI INC
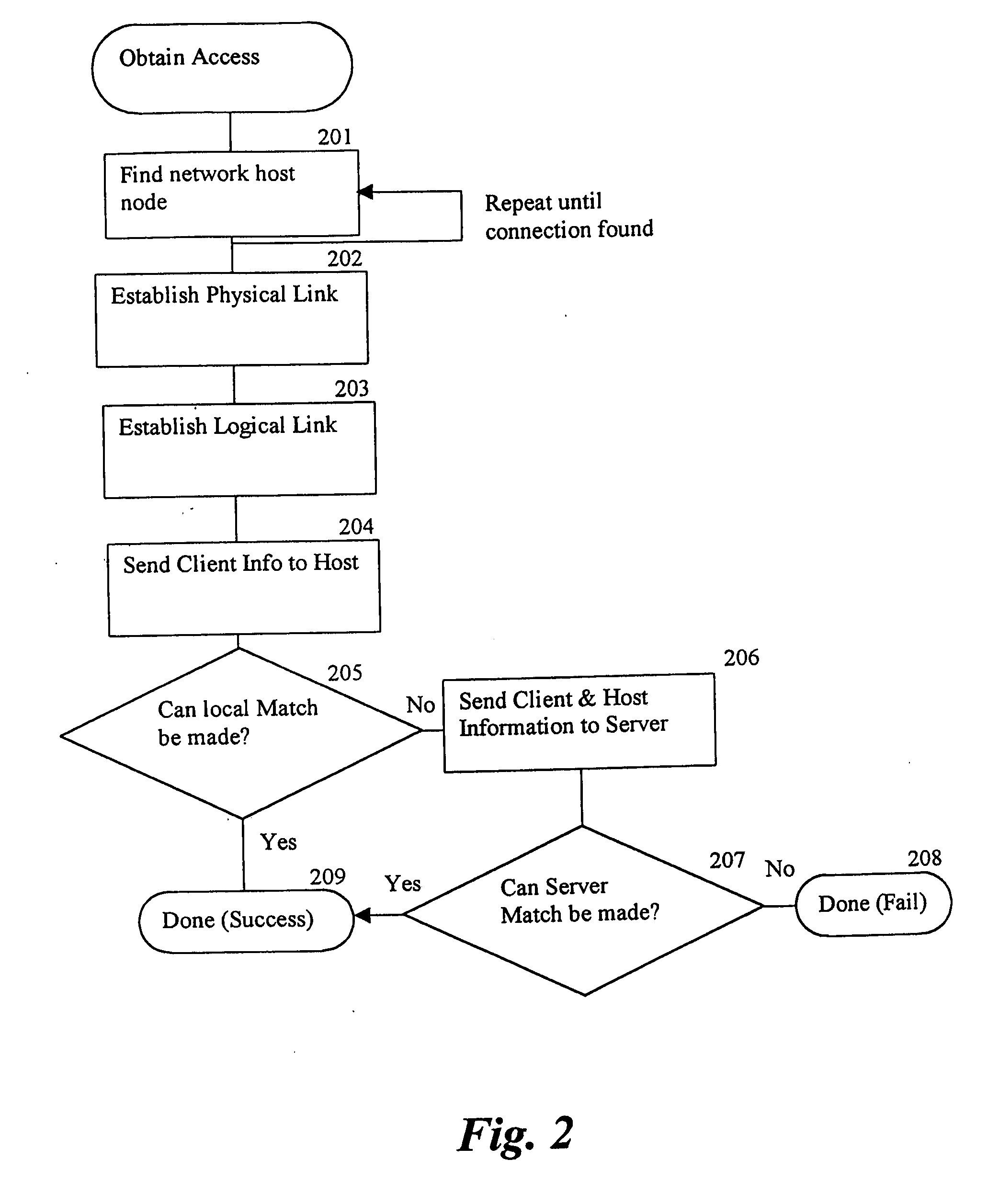
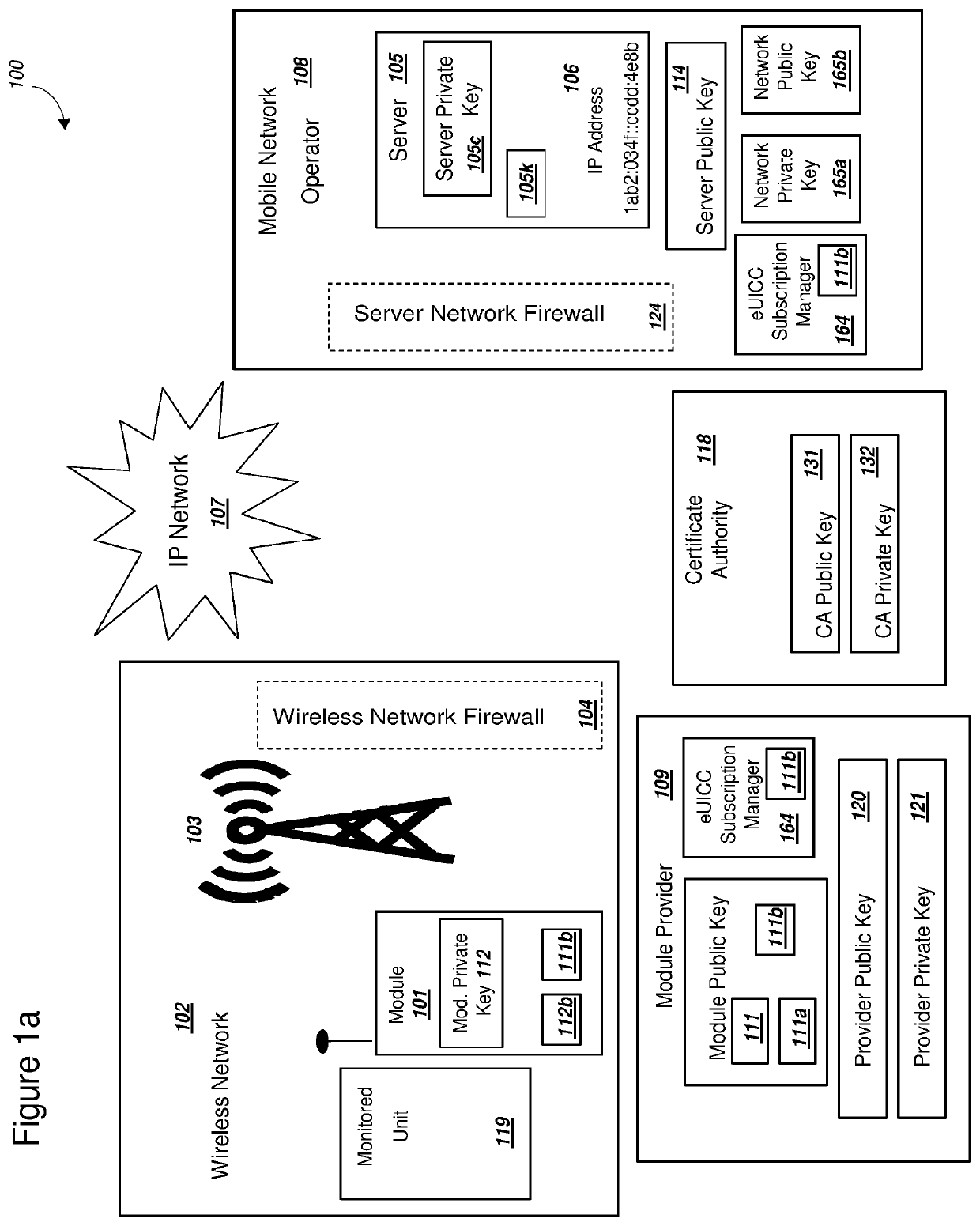
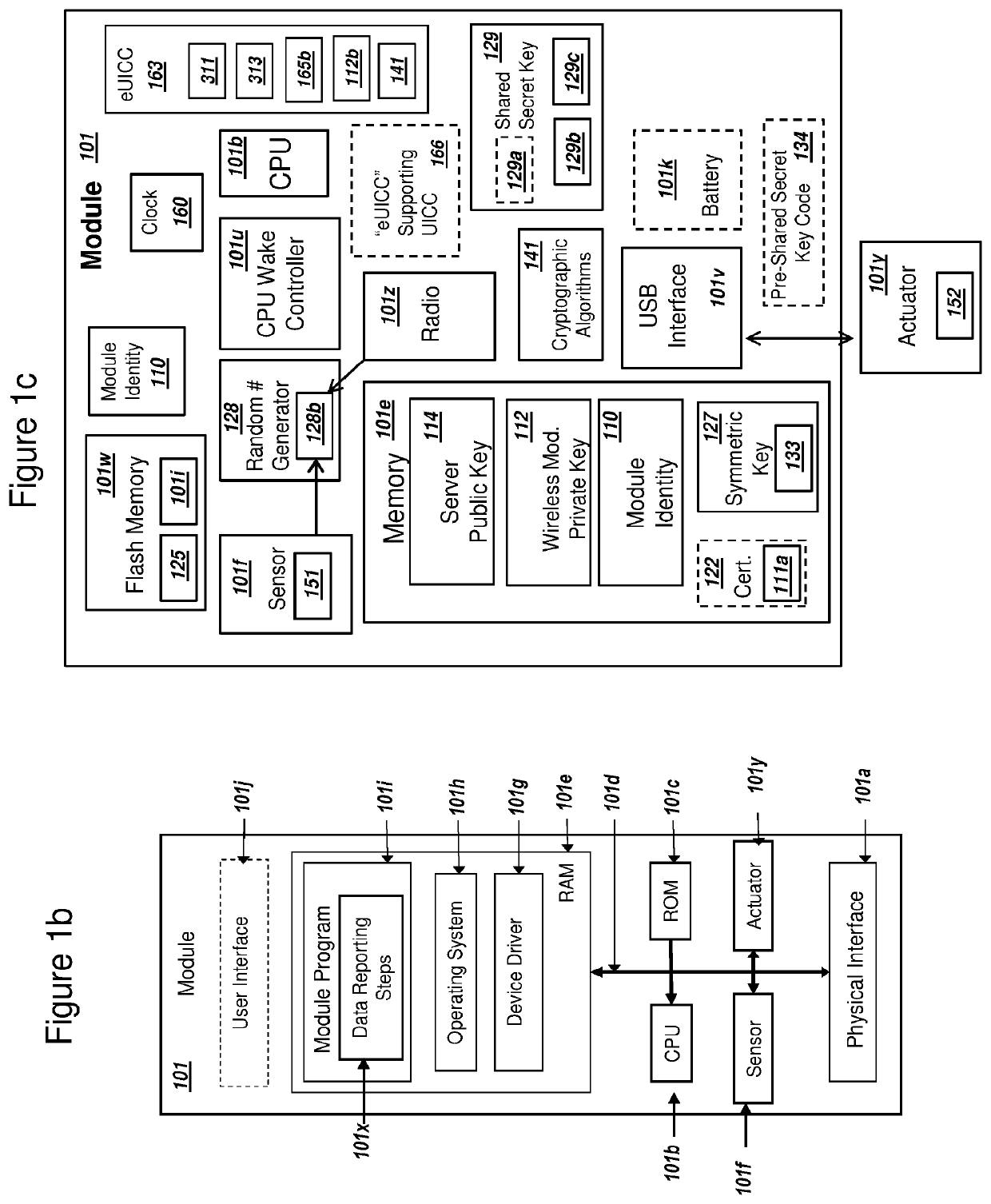
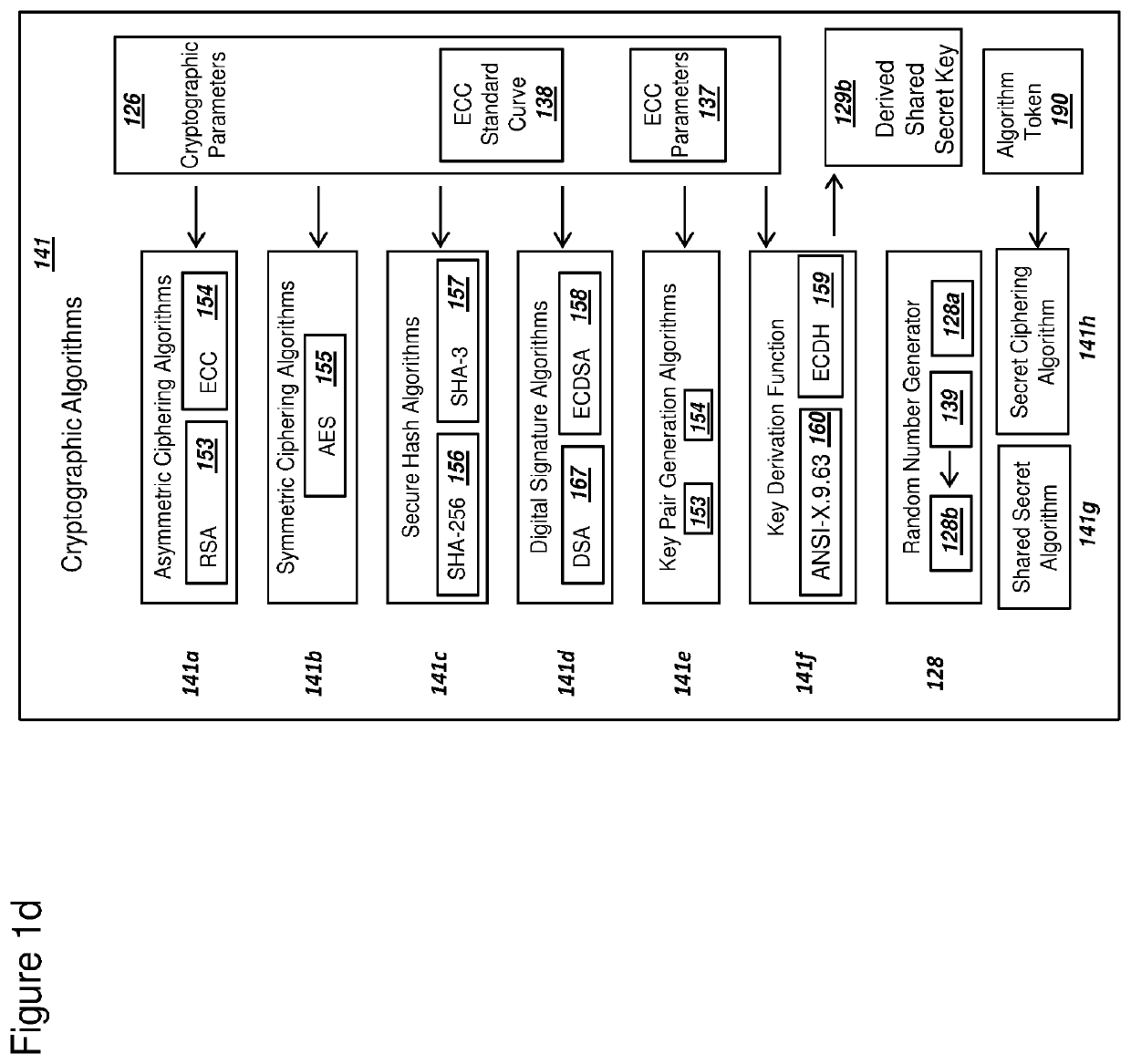
Secure pki communications for "machine-to-machine" modules, including key derivation by modules and authenticating public keys
ActiveUS20190097793A1Communication is efficient and secureReduce power consumptionKey distribution for secure communicationIn DRX networksDigital signatureComputer module
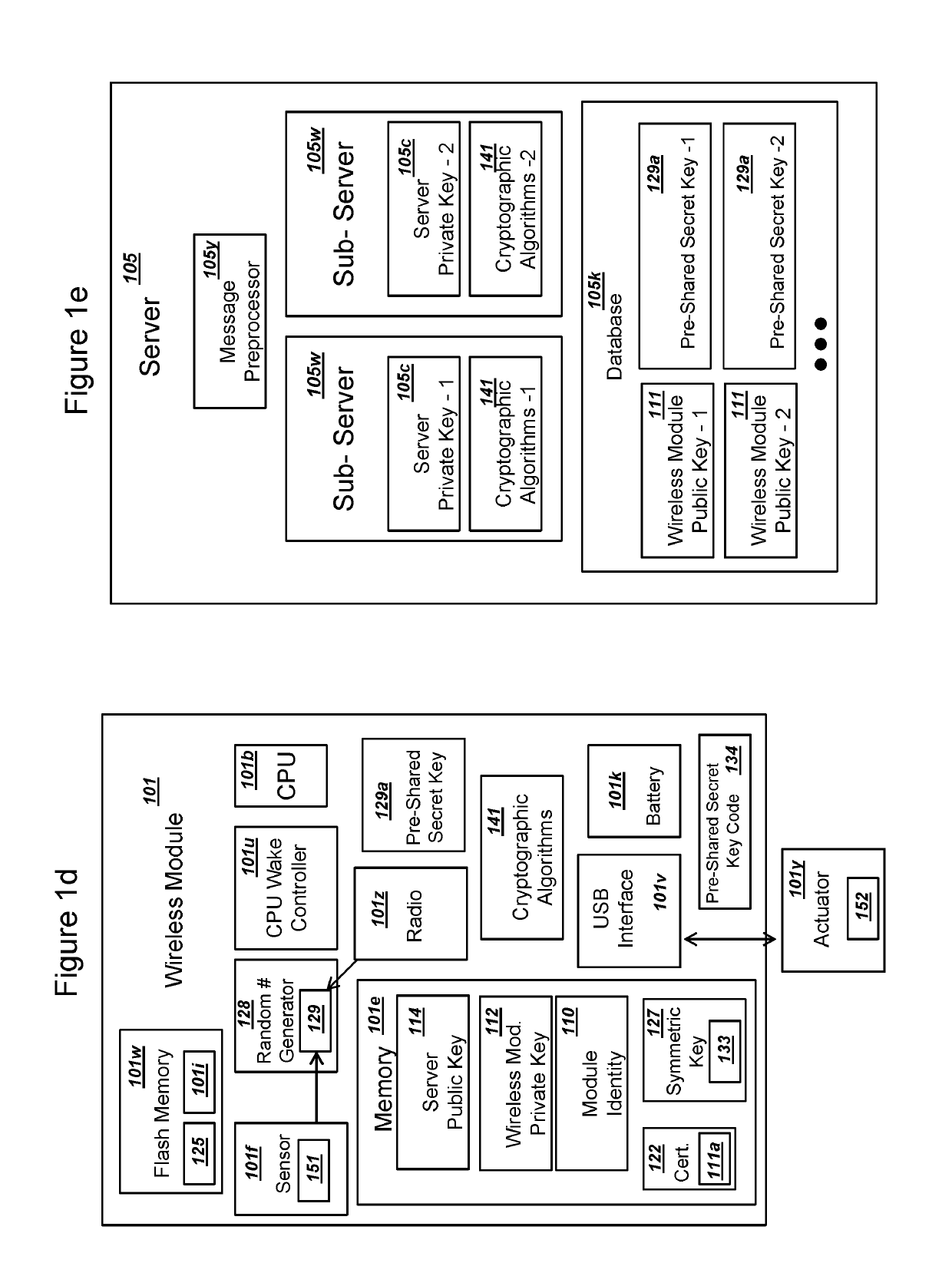
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
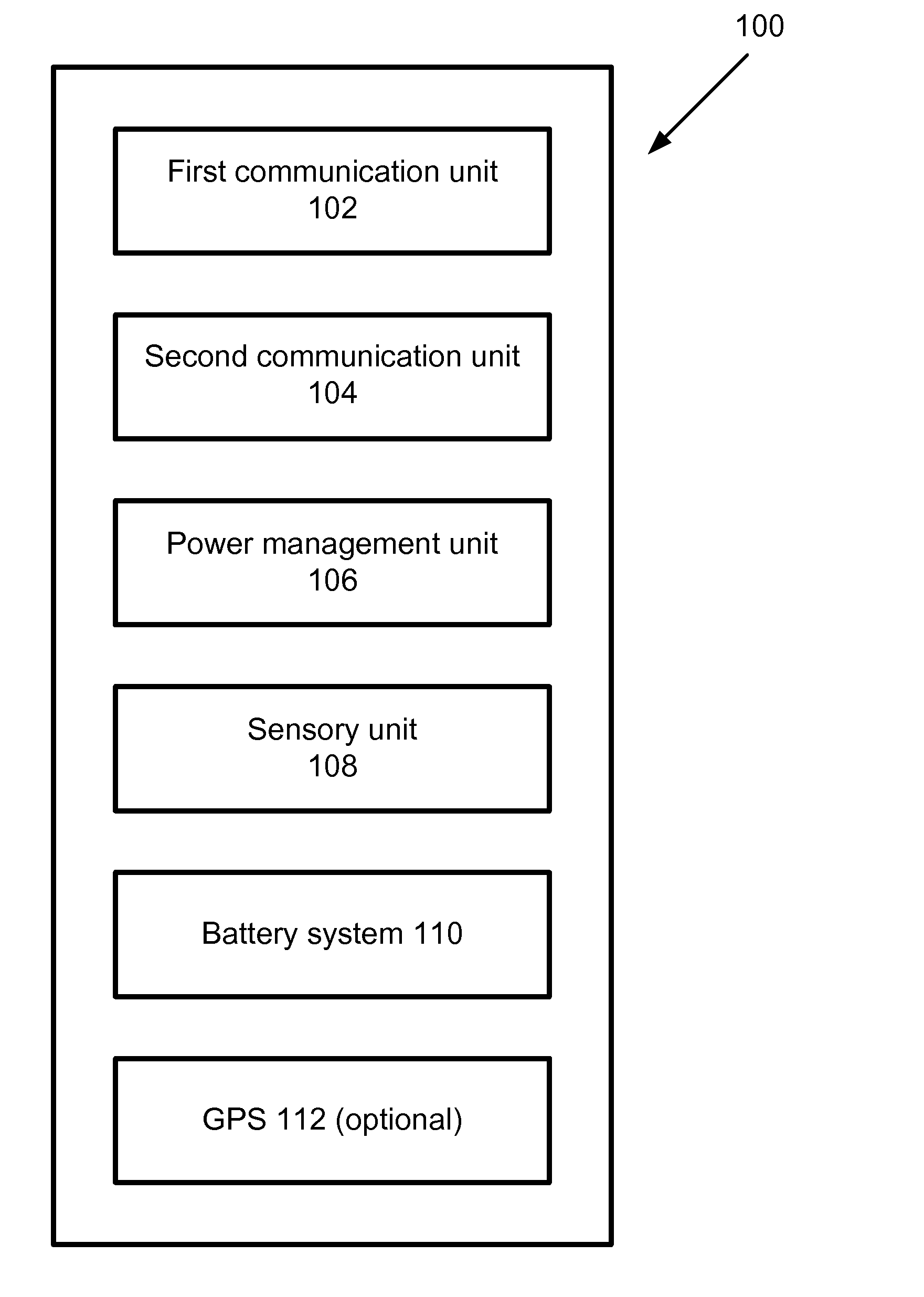
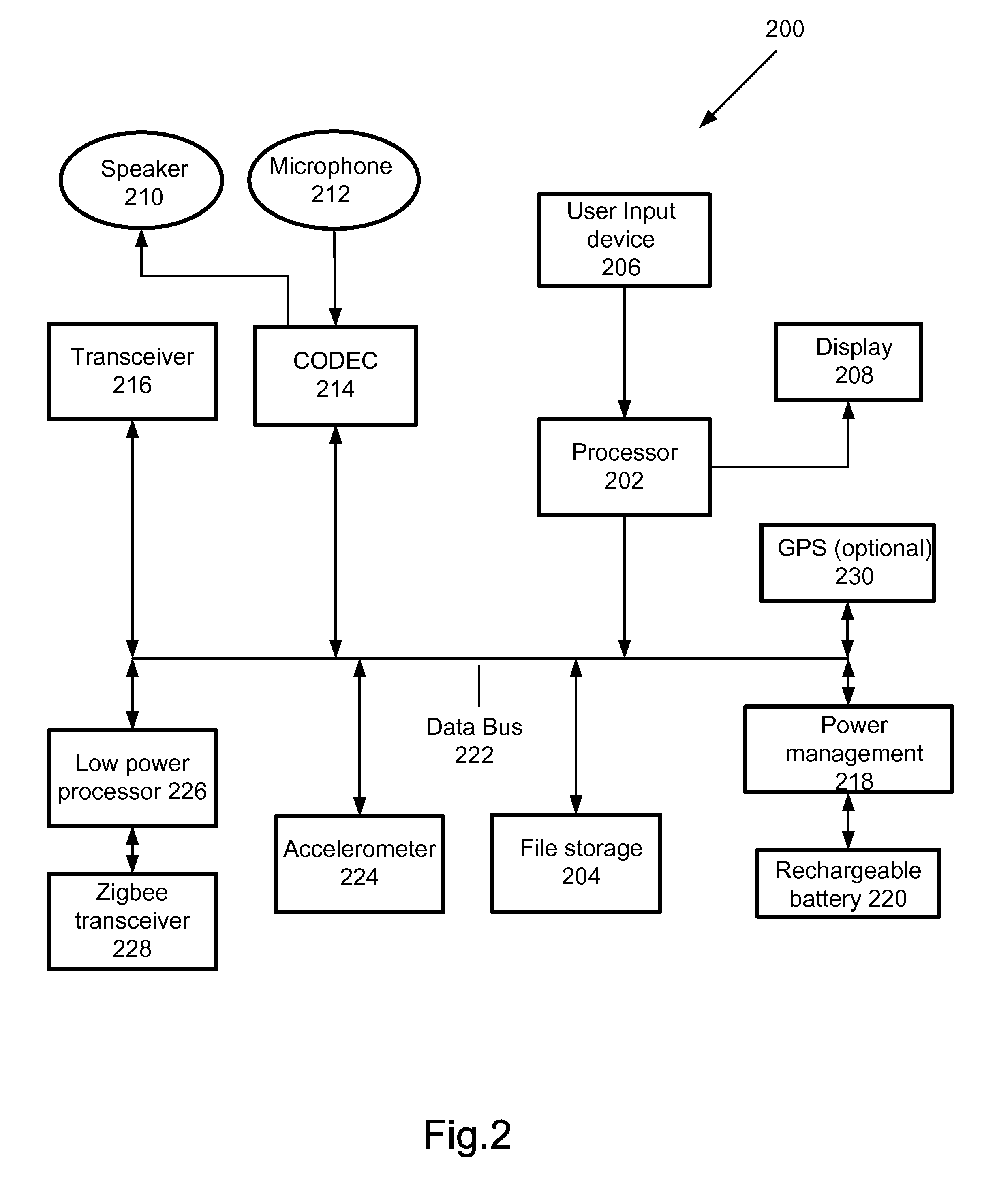
Method of power management for a handheld mobile computing and communiation device
A power management method for a handheld mobile computing and communication device for a normal and an emergency occasion is disclosed. The device, for example, is useful for a trapped person under a mound of debris created by a fallen building during an earthquake or a terrorist attack. The invention is based upon a conventional mobile communication device with a second communication unit and a sensory unit. The second communication unit is based upon a short-range and ad hoc communication network. The invention is characterized by that a power management unit is used to monitor the remaining power of a battery system for the mobile device. If the power is below a preset threshold, the main function of the mobile device as a mobile phone is switched off and the reserved power is used to supply power for the second communication unit, which consumes much less power, in particularly, in a mode as a receiver only. An authorized signal, delivered by a nearby mobile rescue station and received by the second communication unit, will trigger the power management unit to provide additional power to activate the sensory unit. The sensory unit such as an accelerometer and / or a gyroscope may detect a signal if the person touches and / or moves the device after receiving a triggering signal. Yet additional power is further supplied to send collected data through the second communication unit to the rescue station.
Owner:PAN YANG
Wireless communication methods, systems, and computer program products
A method, wireless device and computer program product for expanding the coverage of a cellular network. A wireless device (e.g., cellular telephone) is able to communicate with a base station in a cell of the cellular network over a non-cellular interface via another wireless device in a cell through the use of multi-hopping. A wireless device may request permission to communicate with the base station over a non-cellular interface via hopping off another wireless device when its signal strength is below a threshold. Alternatively, a wireless device may receive a request to communicate with the base station over a non-cellular interface via hopping off the wireless device that sent the request when that wireless device has excess capacity in its bandwidth with the base station. By enabling wireless devices to communicate with a base station in such a manner, the effective capacity of the cellular network is expanded and the effective capacity of the cellular network is improved.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
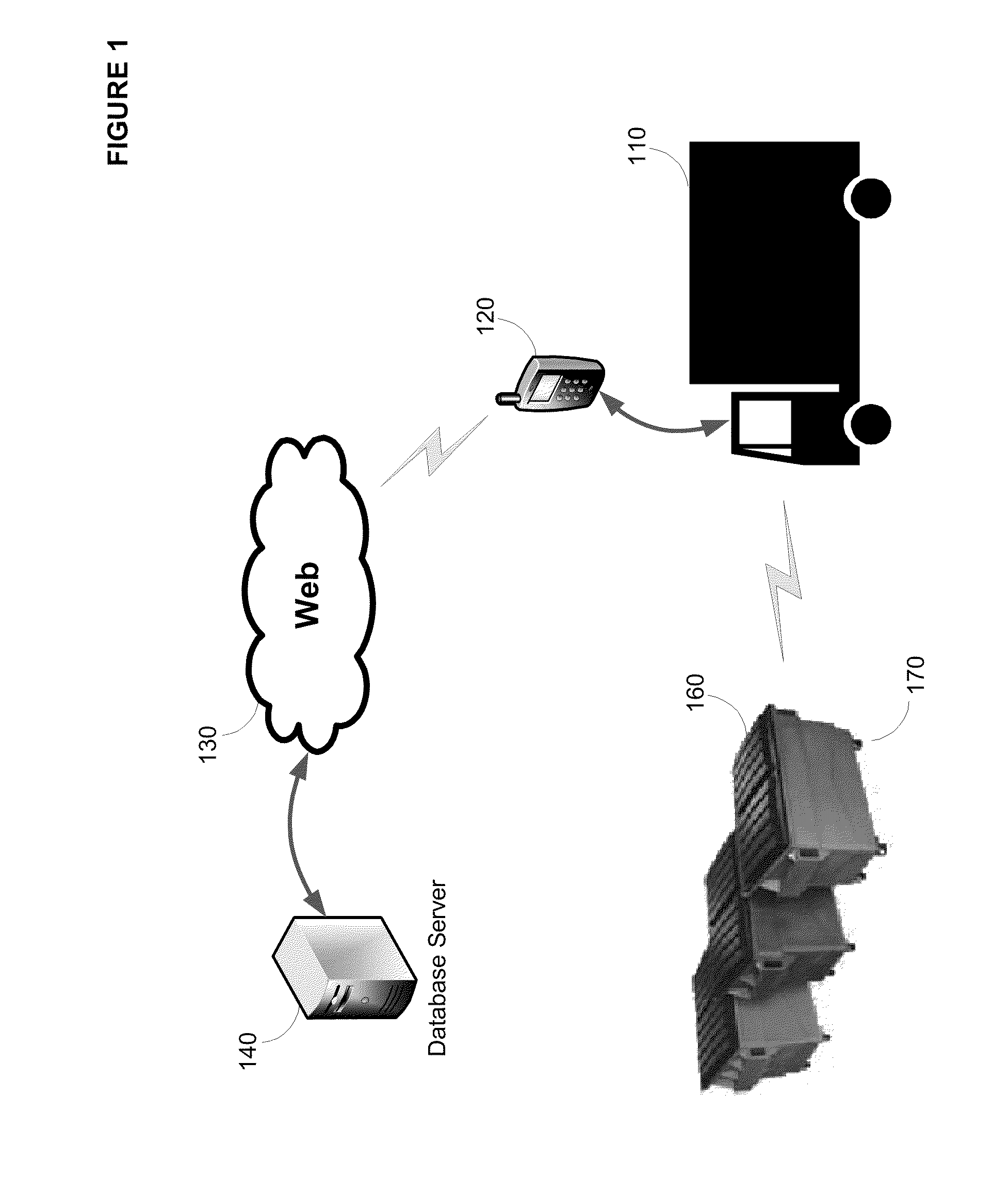
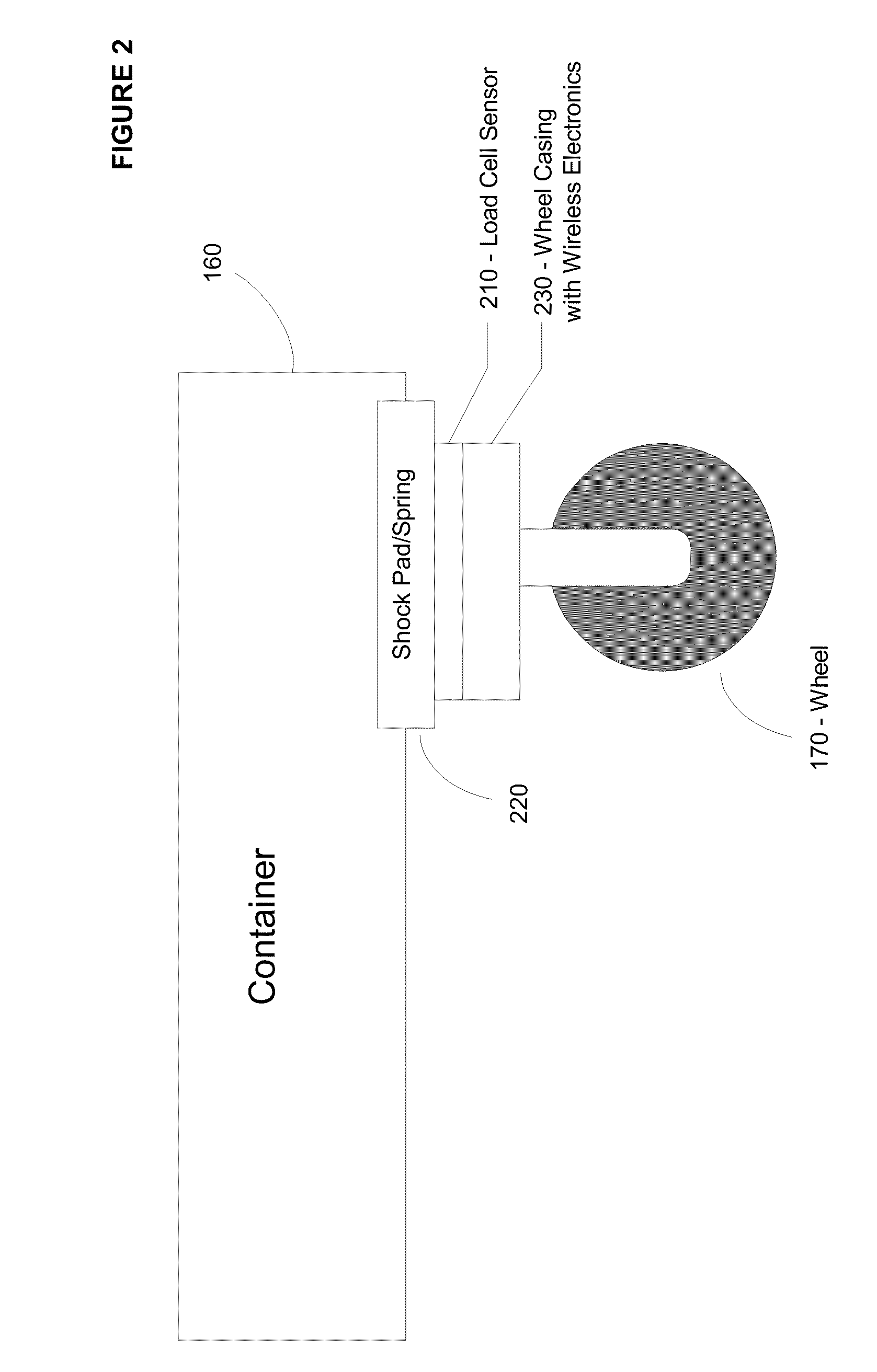
Wireless active monitor system for containers and carts
ActiveUS20100304672A1Rapid wireless data collectionPower managementWeighing apparatus testing/calibrationTransceiverActive monitoring
Wireless active monitor system for containers / carts that hold item(s). Includes a container mount, and sensor for example to weigh the item(s), and a wireless transmitter / transceiver to transmit sensor data from the sensor to a database for remote access. The sensor may be protected via shock pads to prevent damage to the sensor if the container is dropped. The system may be implemented with a printed circuit board having a central processing unit and memory that holds program code to execute on the central processing unit, for example to transmit sensor data via the wireless transmitter. May utilize a unique identifier associated with each container, and / or vehicle utilized to interface with the container. Enables rapid determination of the physical characteristics associated with items in the container without requiring physical contact with the container. For example, allows the weight of garbage containers to be determined remotely.
Owner:LERNER IAN
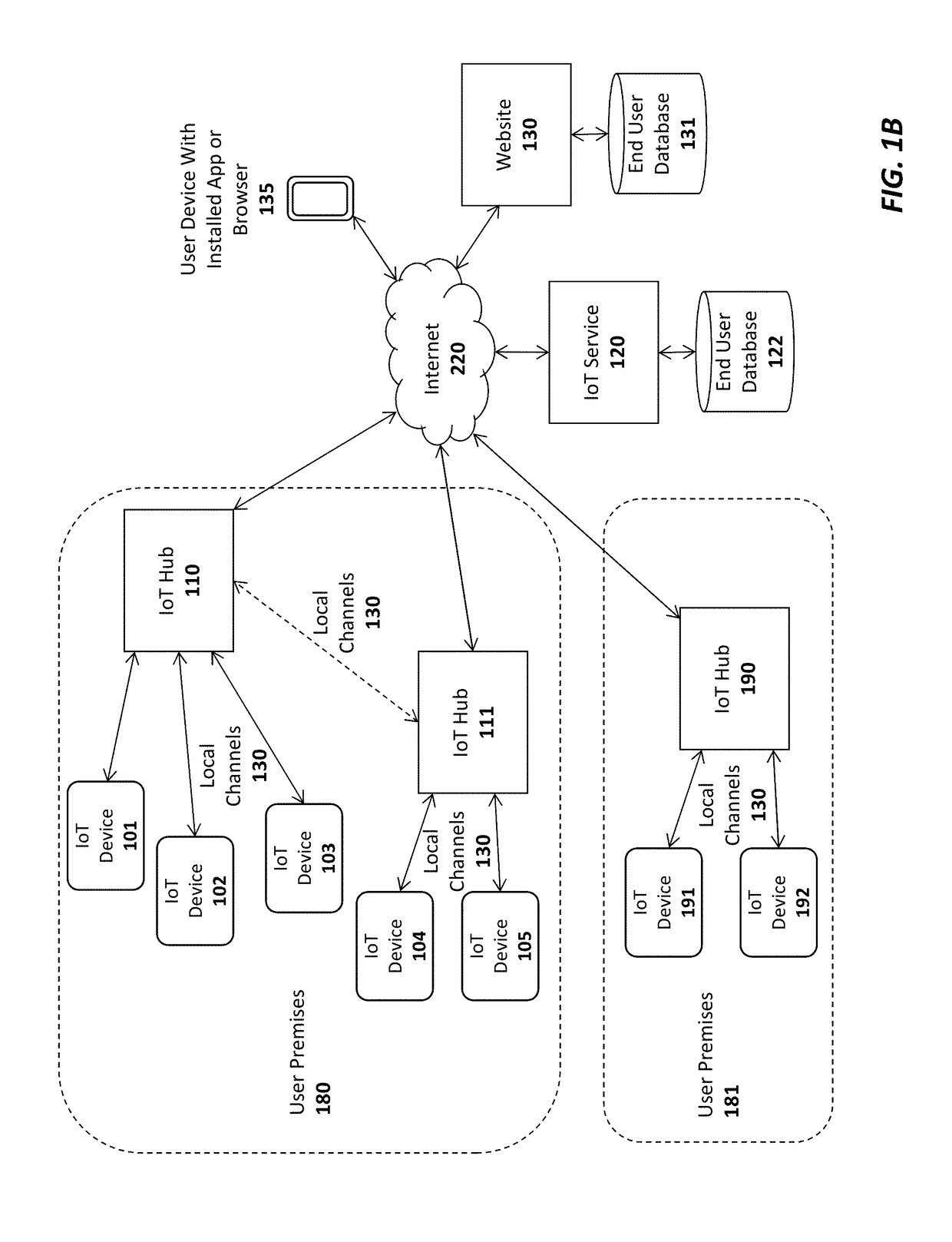
Communication system and IoT system
ActiveUS20180152889A1Reduce power consumptionPower managementNetwork topologiesCommunications systemNormal mode
A communication system and an IoT system are provided. The IoT system is applicable to a wireless network system including an access point. The IoT system includes a WiFi module and a GPIO device. The WiFi module is configured to connect to the access point. The GPIO device is configured to provide a plurality of wake-up signals to the WiFi module through a GPIO pin. A predetermined time period between any two of wake-up signals is greater than an interval between two delivery traffic indication messages from the access point. The WiFi module includes a timer and a power management unit, the power management unit drains power to transfer the WiFi module from a sleep mode to a normal mode after the timer receives the wake-up signal.
Owner:DIALOG SEMICON KOREA INC
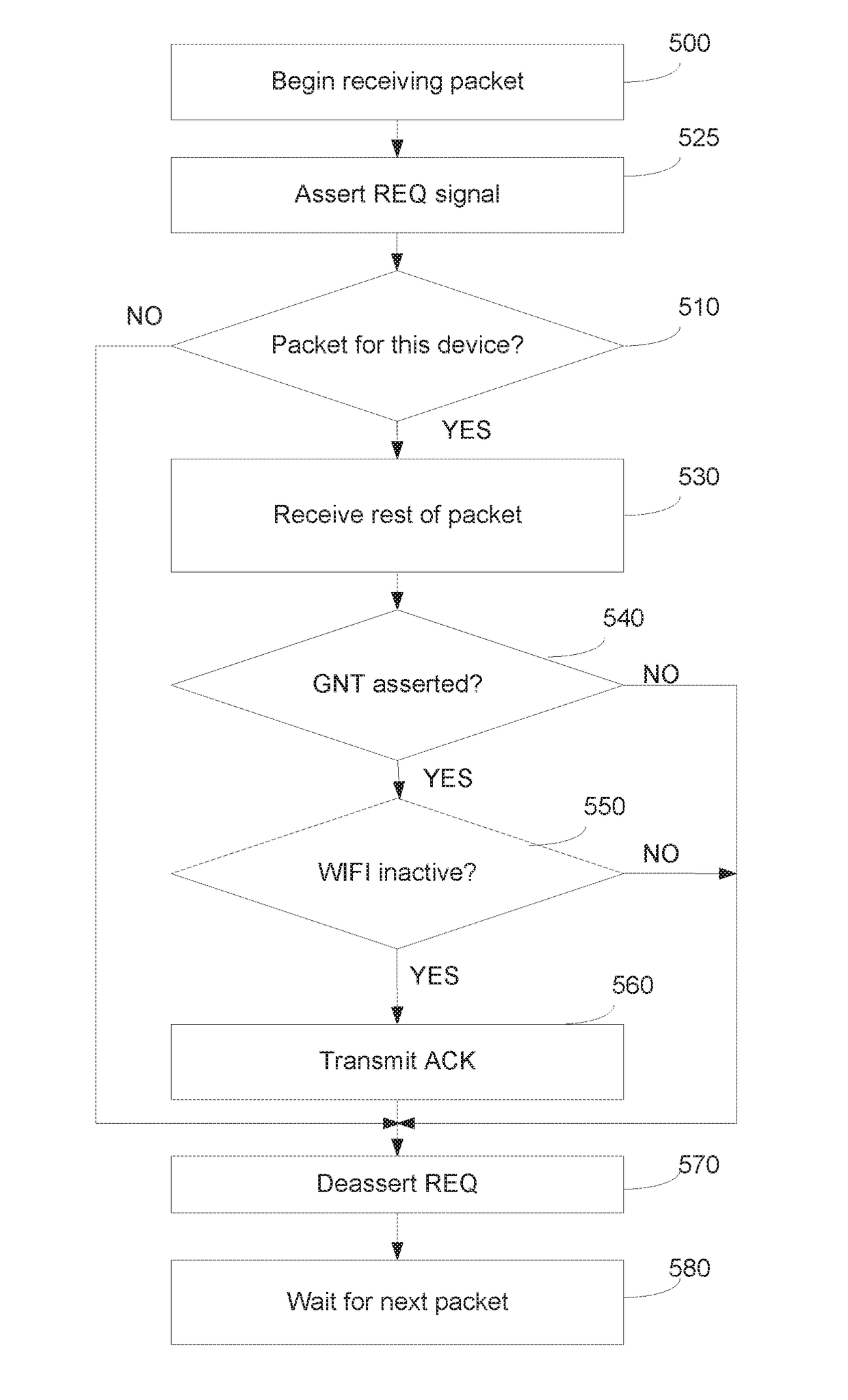
ZigBee, Thread And BLE Co-Existence With 2.4 GHz WIFI
ActiveUS20180242341A1Maximize likelihoodError prevention/detection by using return channelHigh level techniquesTraffic capacityFrequency spectrum
A system and method of minimizing interference and retries in an environment where two or more network protocols utilize the same frequency spectrum is disclosed. A lower-power network controller is co-located with a WIFI controller. The lower-power network controller parses incoming packets as they are received and generates a request signal once it is determined that the incoming packet is destined for this device. This maximizes the likelihood that no WIFI traffic will occur while the incoming packet is being received.
Owner:SILICON LAB INC
Method for automatically connecting a short-range communication between two devices and apparatus for the same
A method for automatically connecting two devices with each other through short-range communication an apparatus for the same are disclosed. The apparatus comprises a short-range communication module configured to enable short-range communication with an external device; an interrupt detector configured to sense an interrupt signal for short-range communication connection, which is received from the external device through the short-range communication module in a sleep mode where a standby power is supplied; and a controller, the interrupt detector wakes up the controller if the interrupt signal is sensed in the sleep mode, and the woken-up controller releases the sleep mode and controls the short-range communication module to perform short-range communication connection with the external device.
Owner:LG ELECTRONICS INC
Cooperative network for mobile internet access
InactiveUS20100115104A1The process is simple and fastEasy to set upIn ad hoc networksIn P2P networksCable Internet accessInterconnection
A method and system for connecting mobile users to the Internet using cooperative interconnection. A node consists of a network element that has two connections methodologies—typically a node will have a radio link and a wired link to the Internet. To obtain a connection, a member of the service located themselves in proximity to a network node which is commonly provided by another member and the cooperative tunneling agent requests a secure link. All members of the service agree to give connection to the Internet upon request from another member.
Owner:TRUPHONE
Key derivation for a module using an embedded universal integrated circuit card
ActiveUS10700856B2Improve the usefulnessIncrease valueKey distribution for secure communicationIn DRX networksSecret shareNetwork key
A module with an embedded universal integrated circuit card (eUICC) can include a received eUICC profile and a set of cryptographic algorithms. The received eUICC profile can include an initial shared secret key for authentication with a wireless network. The module can receive a key K network token and send a key K module token to the wireless network. The module can use the key K network token, a derived module private key, and a key derivation function to derive a secret shared network key K that supports communication with the wireless network. The wireless network can use the received key K module token, a network private key, and the key derivation function in order to derive the same secret shared network key K derived by the module. The module and the wireless network can subsequently use the mutually derived key K to communicate using traditional wireless network standards.
Owner:JOHN A NIX +1
Wireless monitoring system
A wireless monitoring system for monitoring at least one person in a building. The wireless monitoring system comprises a data collection device and a plurality of wireless signalling devices working in a star network topology, the data collection device being adapted to wirelessly receive data transmitted from each of the plurality of wireless signalling devices. The signalling devices and the data collection device being adapted to send and receive FSK modulated signals in a predetermined single channel and the signalling devices being adapted to send data packets such as a heartbeat message to the data collection device.
Owner:SENSO2ME NV
User terminal, rsu, method and program
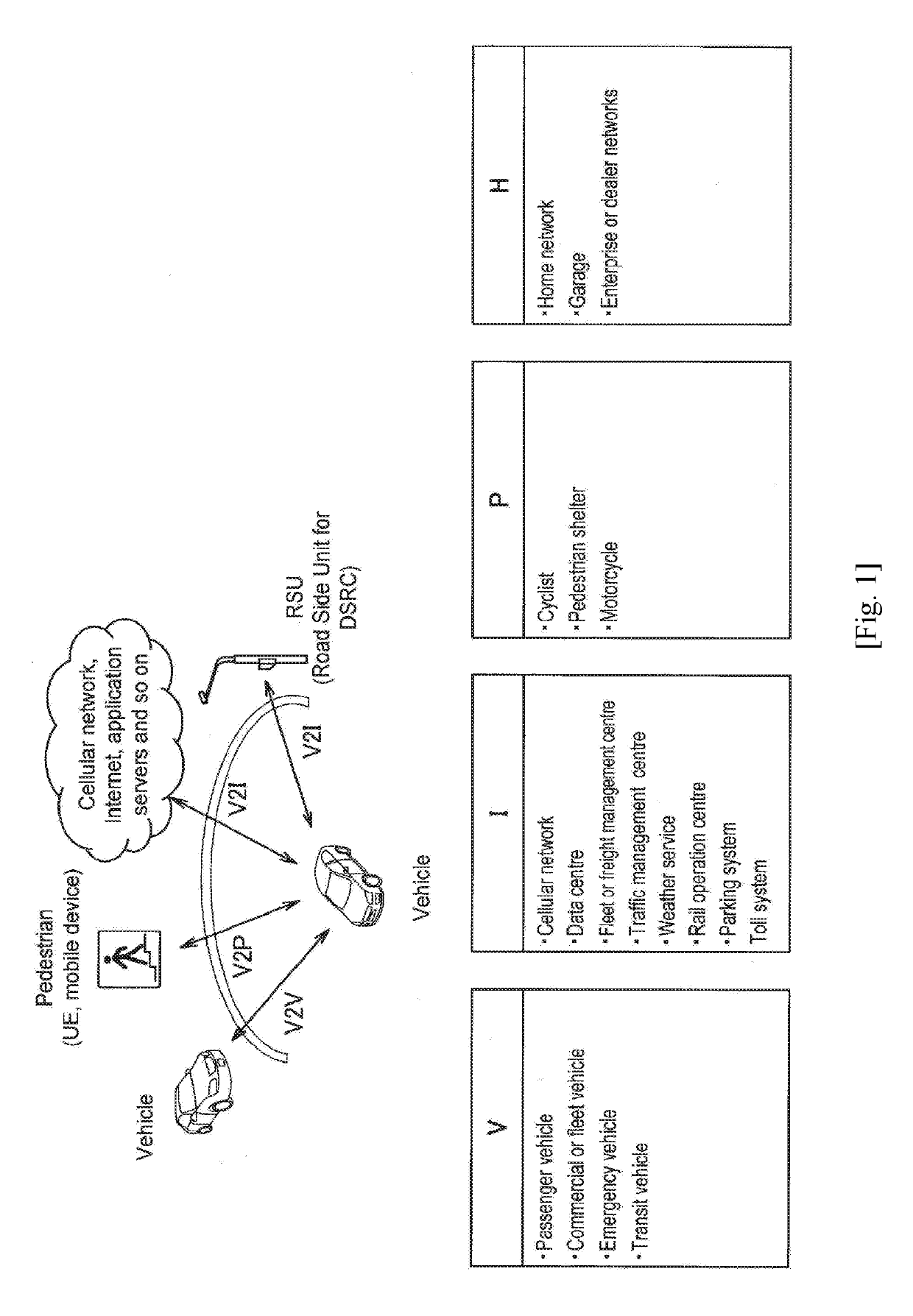
ActiveUS20190246250A1Reduce power consumptionIn DTX networksIn DRX networksComputer sciencePedestrian
An electronic device configured to perform wireless communication in accordance with vehicle-to-X (V2X) communication, the V2X communication including at least vehicle-to-vehicle (V2V) communication, vehicle-to-infrastructure (V2I) communication, and vehicle-to-pedestrian (V2P) communication, each of the V2V, V2I and V2P communications having an intermittent communication function; receive a signal associated with a location of the electronic device; determine whether to activate or deactivate a communication parameter corresponding to the V2P communication based on the signal associated with the location of the electronic device; activate or deactivate the communication parameter corresponding to the V2P communication based on the determining; and activate the intermittent communication function for the V2P communication in a case that that the parameter corresponding to the V2P communication is activated.
Owner:SONY CORP
Method and apparatus for controlling electronic device in wireless communication system supporting Bluetooth communication
ActiveUS10681591B2Improve user convenienceSimplify connection procedureIn ad hoc networksIn P2P networksCommunications systemControl electronics
Owner:LG ELECTRONICS INC
Mobile terminal and method for controlling the same
ActiveUS10504481B2Low powerUnauthorised/fraudulent call preventionIn wearable devicesComputer hardware
Disclosed are a mobile terminal and method for controlling the same. The present invention provides a mobile terminal including a sensing unit, a display unit, a processor, wherein the processor is configured to execute an Always on Display (AOD) mode for enabling the display unit to be always turned on at low power while executing at least one application in a background state, display the at least one application or at least one controller corresponding to the at least one application on the display unit in the AOD mode after executing the AOD mode, and perform a quick-operation after sensing an input signal for controlling the application or the controller.
Owner:LG ELECTRONICS INC
Cooperative network for mobile internet access
InactiveUS20100115103A1The process is simple and fastEasy to set upIn ad hoc networksIn P2P networksCable Internet accessInterconnection
Owner:TRUPHONE
Electronic device and method for transmitting information
An electronic device and a method of transmitting information in an electronic device a provided. The electronic device includes a communication unit that includes a first communication module and a second communication module, wherein the second communication module supports a low-power and short-range communication method; and a processor controls collection of information through the first communication module, and to transmit information related to the collected information through the second communication module.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and device for performing device-to-device synchronization in wireless communication system
ActiveUS10638435B2Valid choiceGood signalIn DTX networksError prevention/detection by using return channelCommunications systemDirect communication
The present invention relates to a method and a device for reselecting a synchronization signal in a wireless communication system supporting device-to-device direct communication and the method includes: receiving a first synchronization signal from a second UE and receiving a second synchronization signal from a third UE; comparing a first reception power level indicating reception power of the first synchronization signal and a second reception power level indicating the reception power of a second synchronization signal with a first threshold value indicating minimum reception power; and selecting the first synchronization signal or the second synchronization signal according to the comparison result, and the synchronization signal is a synchronization signal selected in the previously synchronization procedure.
Owner:LG ELECTRONICS INC
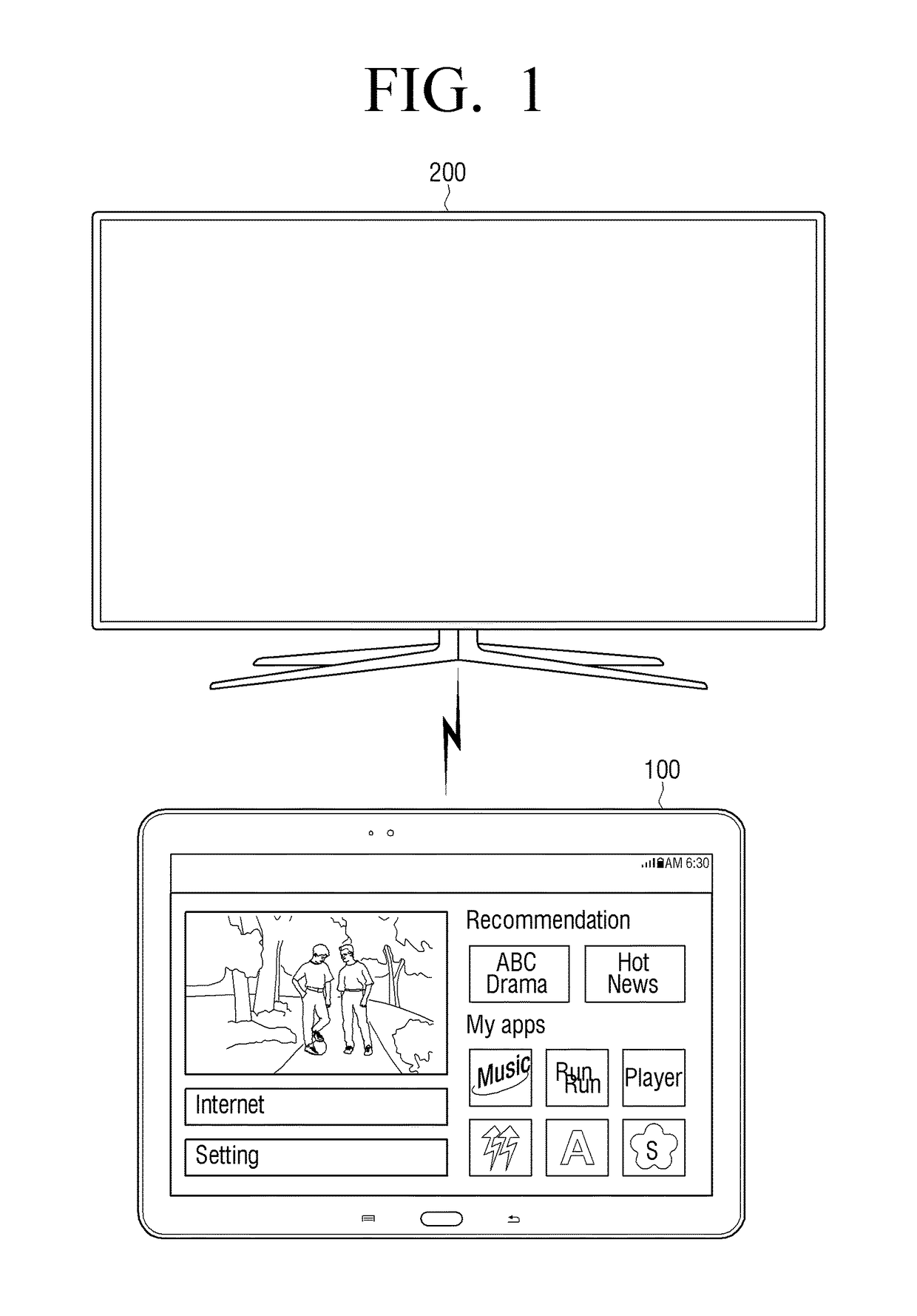
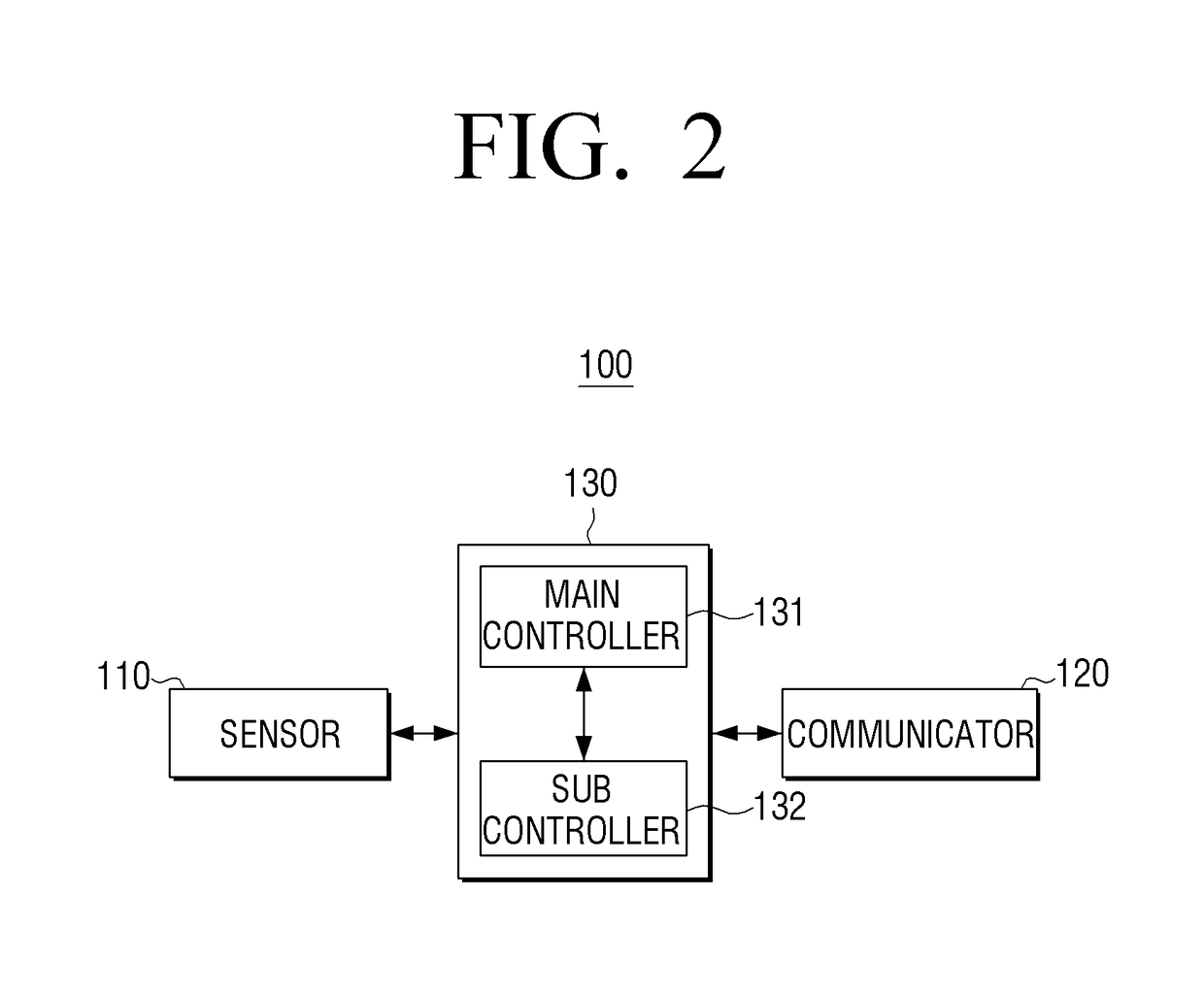
User terminal for controlling display device and control method thereof
ActiveUS10015739B2Efficient managementPower managementPower supply for data processingDisplay deviceComputer terminal
A user terminal for controlling a display device and a control method thereof are provided. The user terminal includes a communicator configured to communicate with the display device, a main controller configured to control the user terminal, and a sub-controller configured to control the user terminal while the user terminal is in a sleep mode, wherein the sub-controller is configured to change a mode of the user terminal from the sleep mode to a standby mode in response to the communicator receiving environmental change detection information or user detection information from the display device while the user terminal is in the sleep mode.
Owner:SAMSUNG ELECTRONICS CO LTD
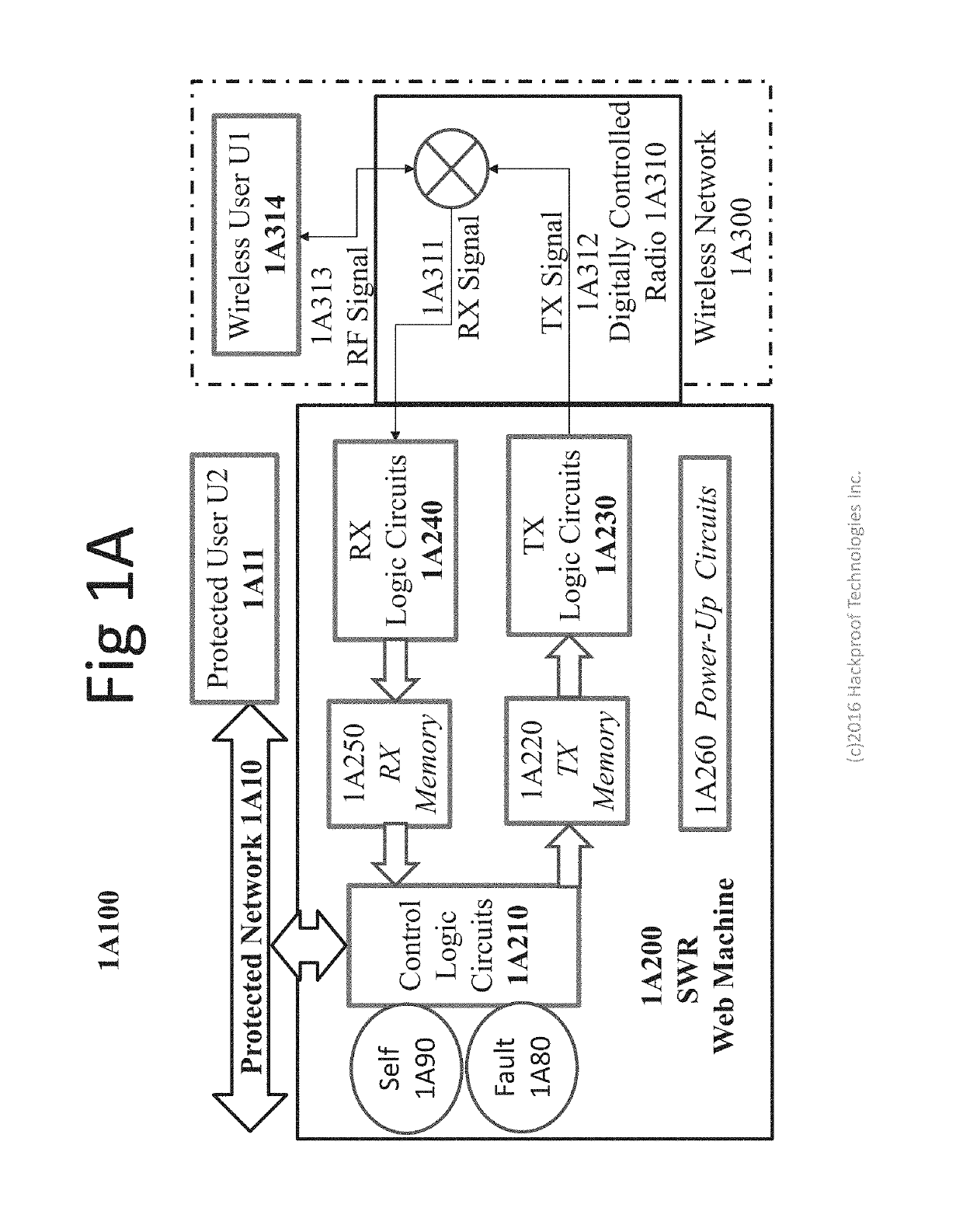
Soft-wired radio (SWR) web machine
ActiveUS10303881B2Improve securityReduce impactTransmission technology based selectionInternal/peripheral component protectionAnti virusOperational system
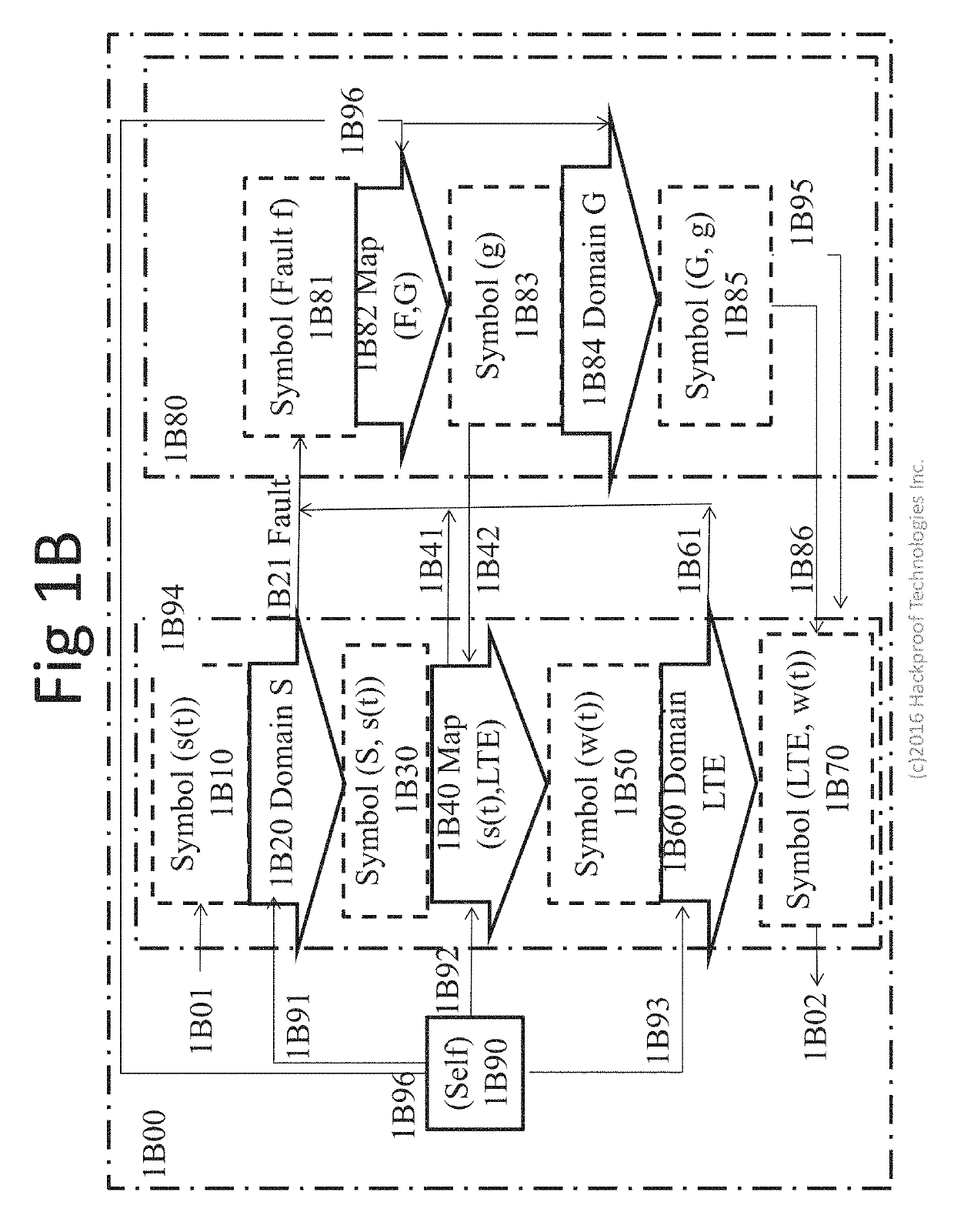
A domain-specific hardwired symbolic communications machine is described that processes information via the hardwired mapping of symbols from one or more domains onto other such domains, computing and communicating with improved security and reduced power consumption because it has no CPU, no Random Access Memory (RAM), no instruction registers, no Instruction Set Architecture (ISA), no operating system (OS) and no applications programming. The machine provides web services by recognizing valid requests based on the processing of symbols and the validating of those symbols according to various domains. In some embodiments the requests may conform or be related to, for example, Long Term Evolution (LTE), Hypertext Transfer Protocol (HTTP), or fourth generation (4G) wireless technology. Further, in some embodiments, the machine has no unconstrained RAM into which malware may insert itself and needs no anti-virus software.
Owner:HACKPROOF TECH
Communications device, communications apparatus operating as a relay node, infrastructure equipment and methods
A communications device includes a transmitter to transmit signals representing data to an infrastructure equipment of a mobile communications network via a first wireless access interface and to transmit signals via a second wireless access interface to one or more communications apparatus which can act as relay nodes, a receiver to receive signals from the infrastructure equipment via the first wireless access interface and to receive signals via the second wireless access interface from the one or more communications apparatus which can act as relay nodes, and a controller. The controller can form a relay assist request message and with the transmitter and receiver to transmit the relay assist request message on the second wireless access interface for reception by the one or more communications apparatus which can act as relay nodes to assist in communicating signals representing data to the infrastructure equipment via the first wireless access interface.
Owner:INTERDIGITAL PATENT HLDG INC
Wireless communication methods
ActiveUS10630820B2Reduce signal interferenceReduce total powerReceivers monitoringIn ad hoc networksEngineeringWireless
Various wireless communication methods are provided for controlling two or more wireless devices. In one embodiment, various processes optimize the wireless communication, especially when multiple devices are present in a system or a network. In another embodiment, various controlling devices are accommodated in a network of devices at different points in time. The speed at which the new controlling device comes into a range of the networked devices is improved with existing signatures of different wireless protocols or devices present in the network. In another embodiment, a change in the signal strength of a wireless device can be used to detect an object or person, such as an intruder.
Owner:ILUMI SOLUTIONS
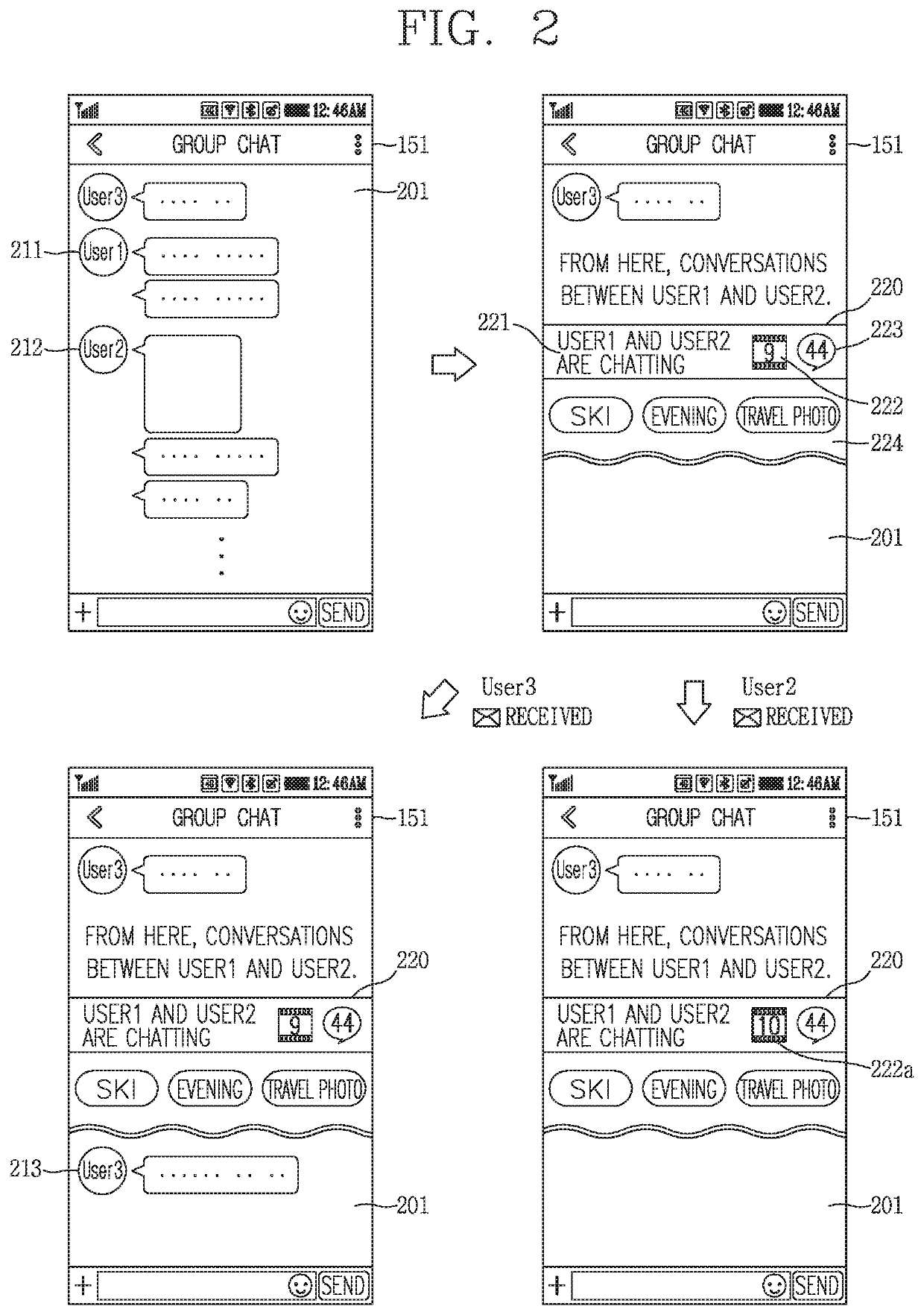
Mobile terminal and method for controlling the same
The present invention relates to a mobile terminal and a method for controlling the same. A mobile terminal displays a group chat screen corresponding to a group chat, determines whether exclusive conversations between several participants in the group chat are continued over a reference range, groups the exclusive conversations between those participants in the group chat when it is determined that the exclusive conversations between those participants are continued over a reference range, and displays a skip area for selectively confirming the grouped exclusive conversations within the group chat screen, wherein the mobile terminal restricts download and output of received information belonging to the skip area and updates an indication related to the exclusive conversations corresponding to the skip area, when the information is received.
Owner:LG ELECTRONICS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com