Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
86 results about "SSH File Transfer Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
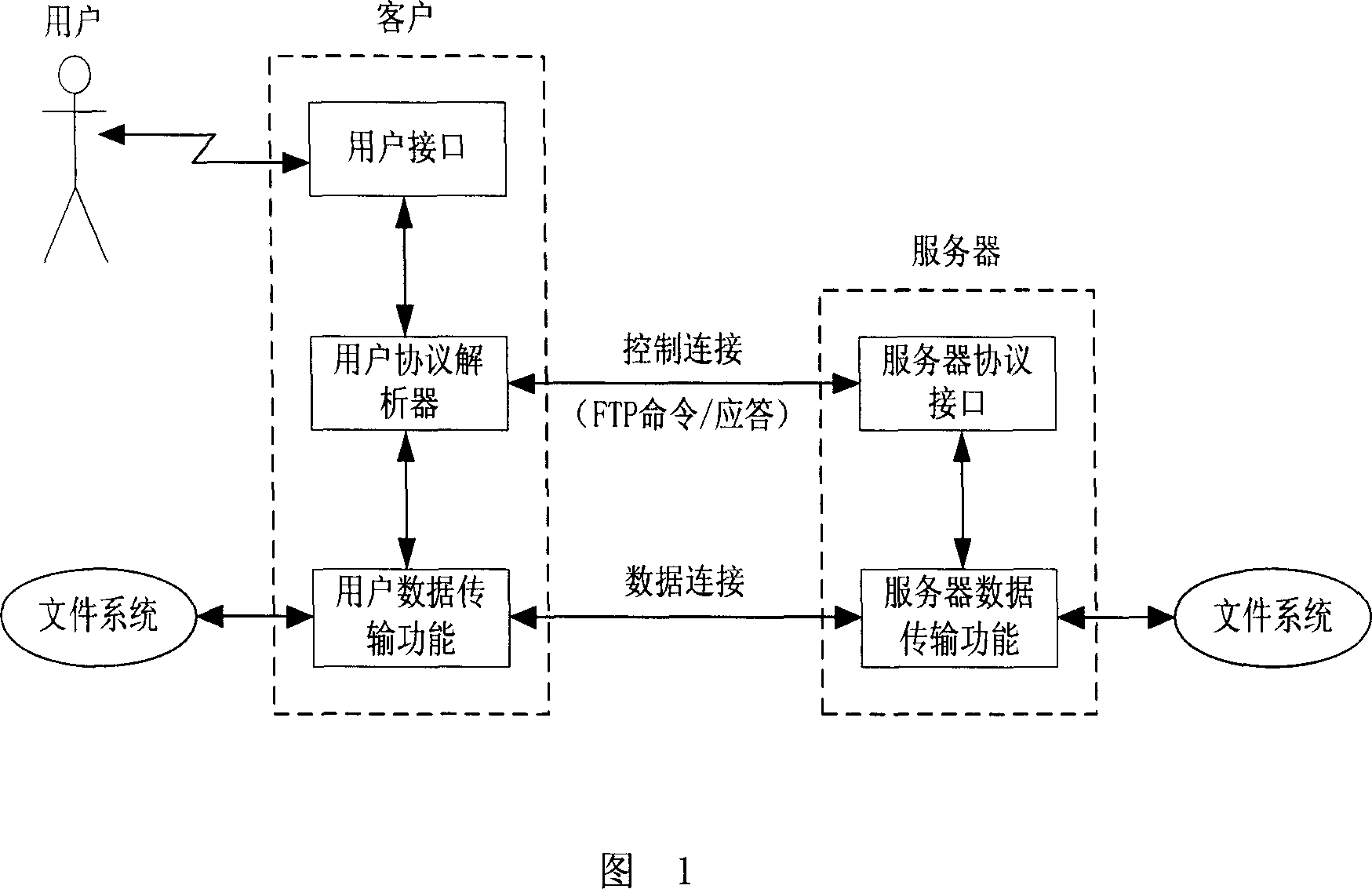
In computing, the SSH File Transfer Protocol (also Secure File Transfer Protocol, or SFTP) is a network protocol that provides file access, file transfer, and file management over any reliable data stream. It was designed by the Internet Engineering Task Force (IETF) as an extension of the Secure Shell protocol (SSH) version 2.0 to provide secure file transfer capabilities. The IETF Internet Draft states that, even though this protocol is described in the context of the SSH-2 protocol, it could be used in a number of different applications, such as secure file transfer over Transport Layer Security (TLS) and transfer of management information in VPN applications.
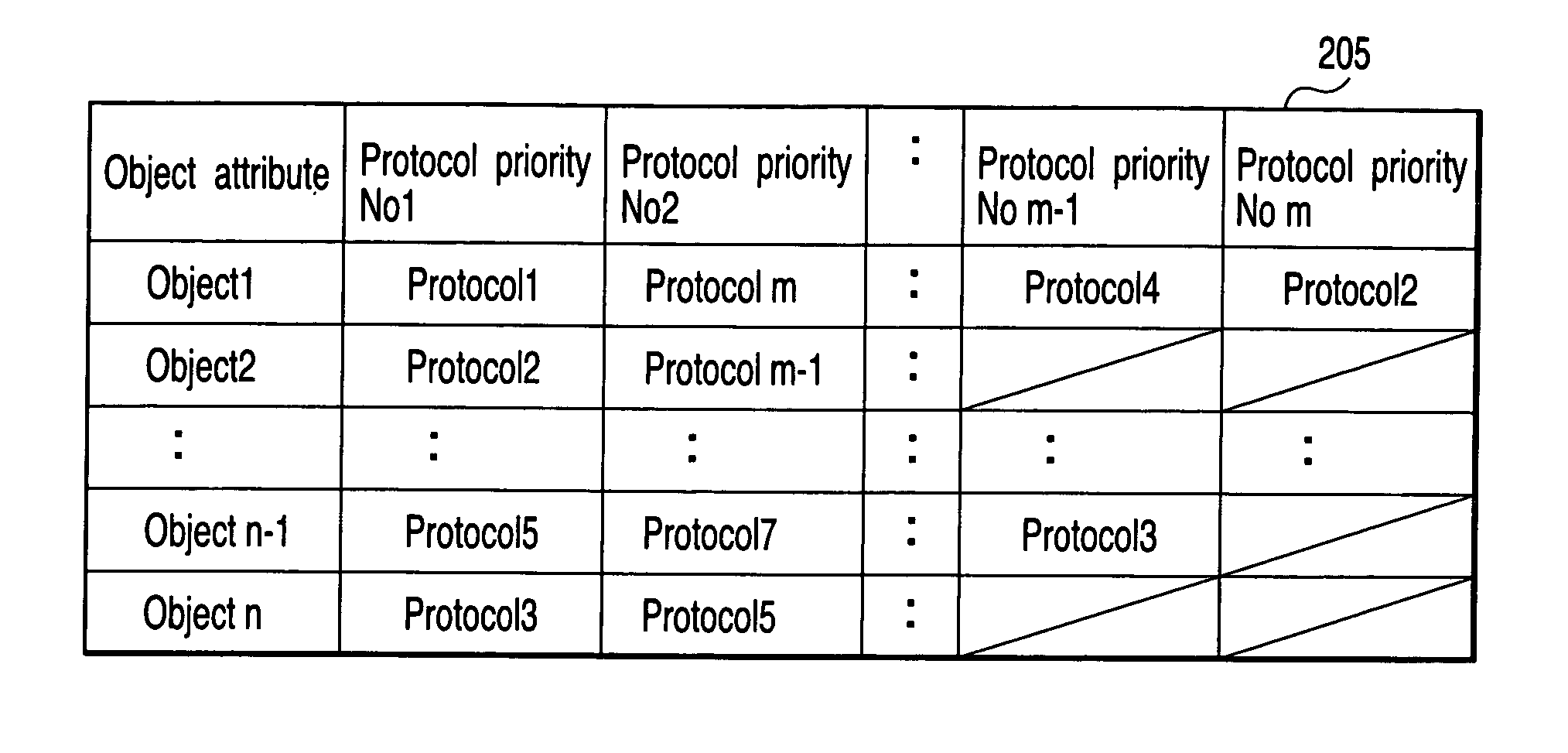
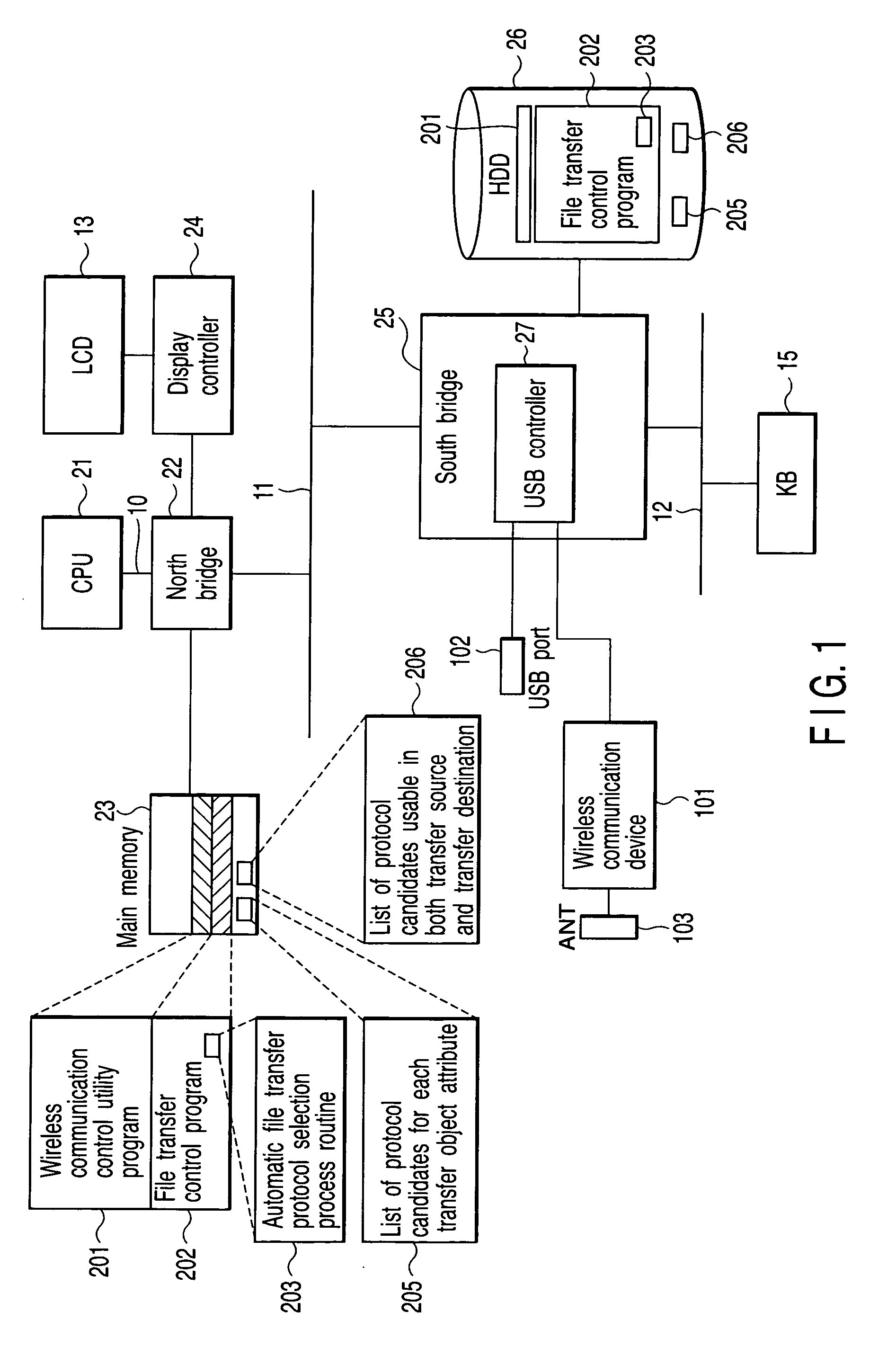
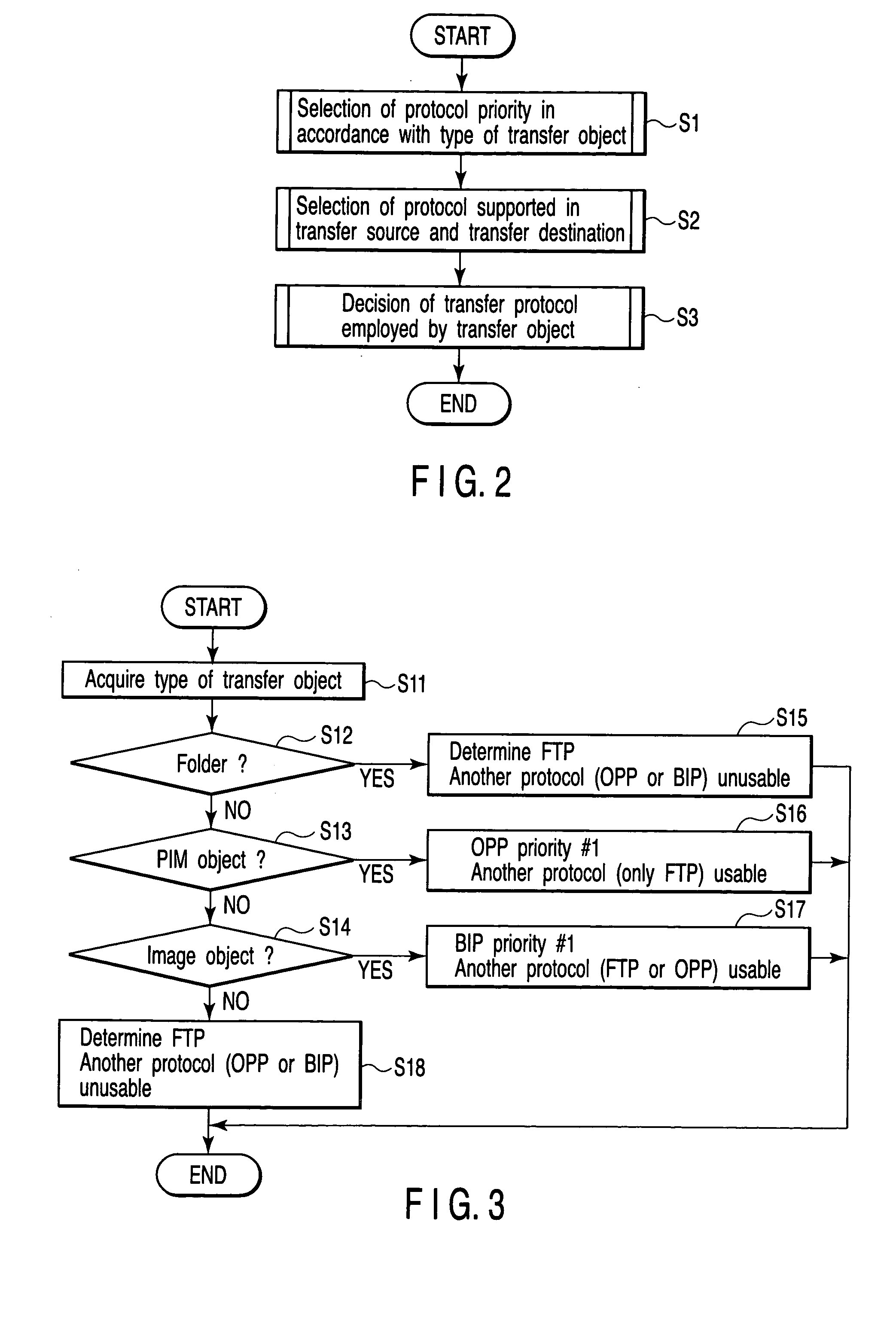
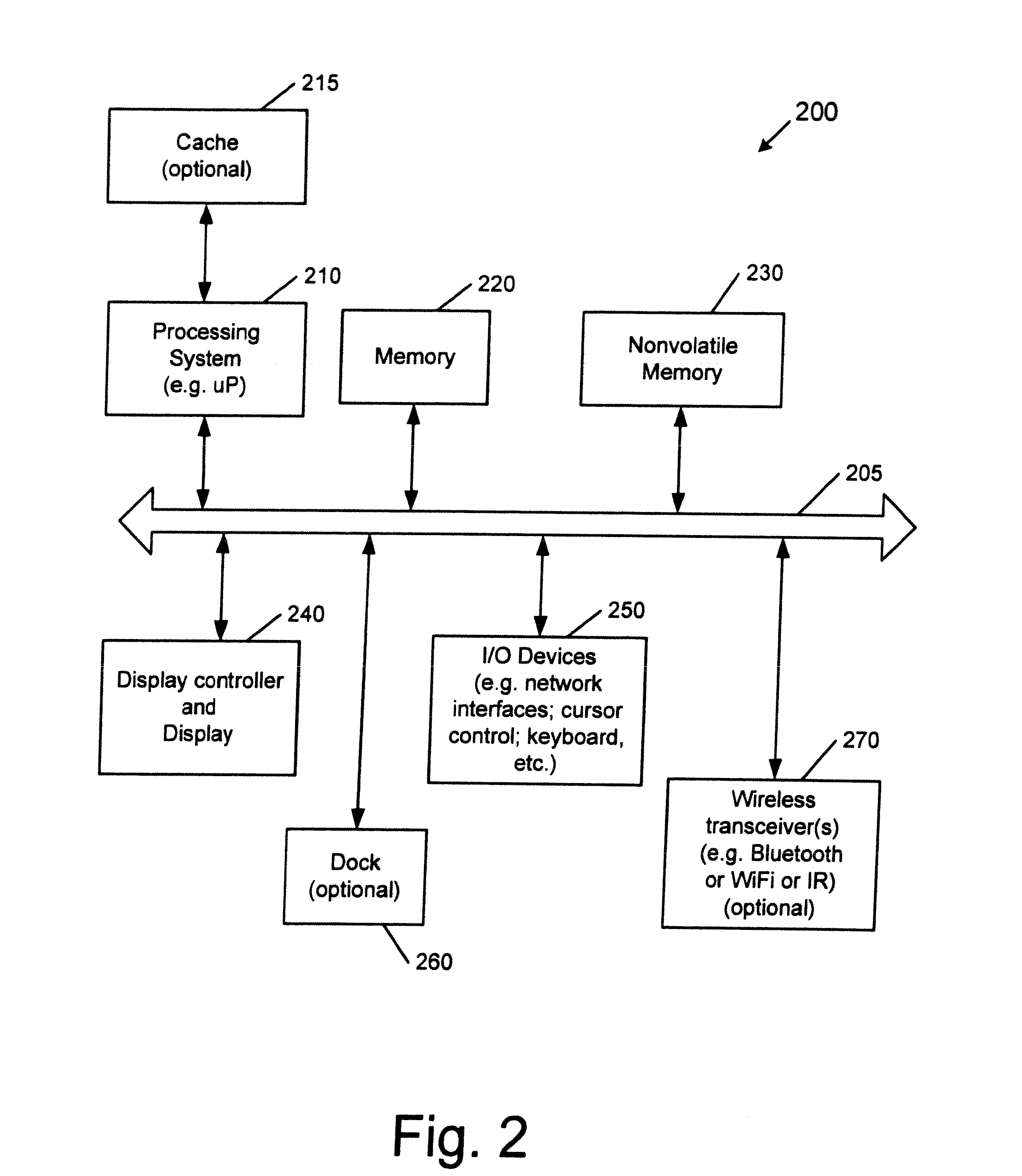
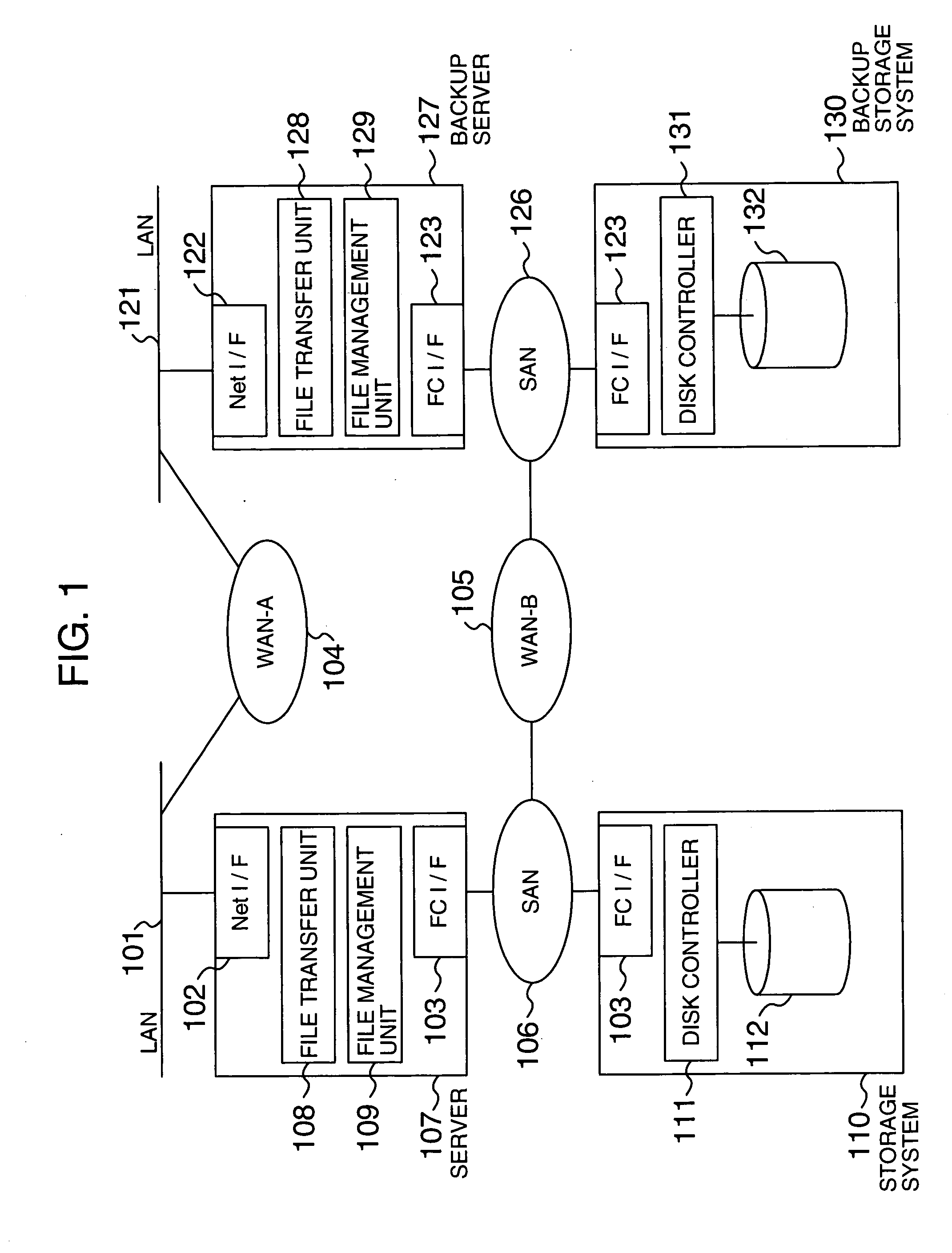
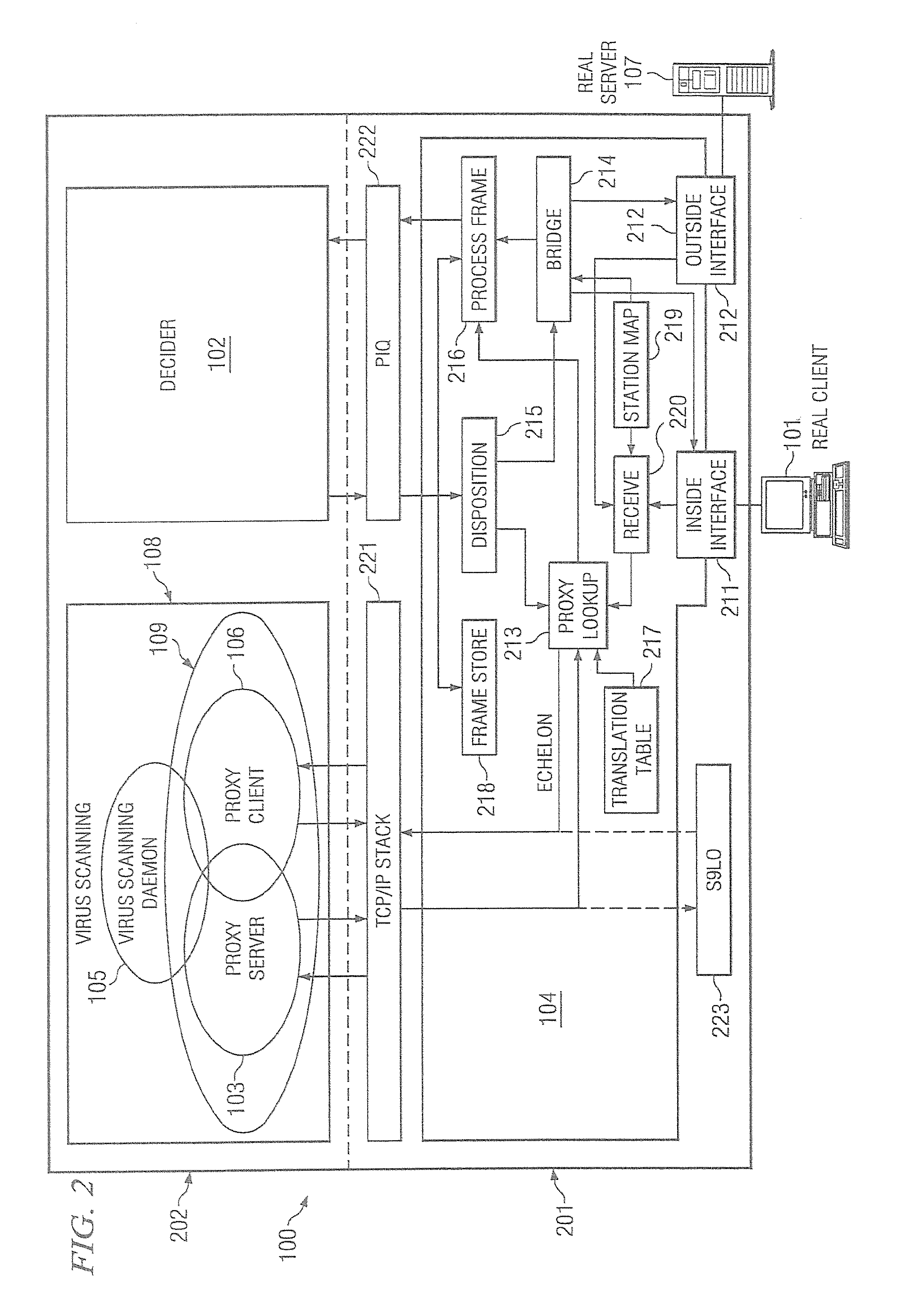
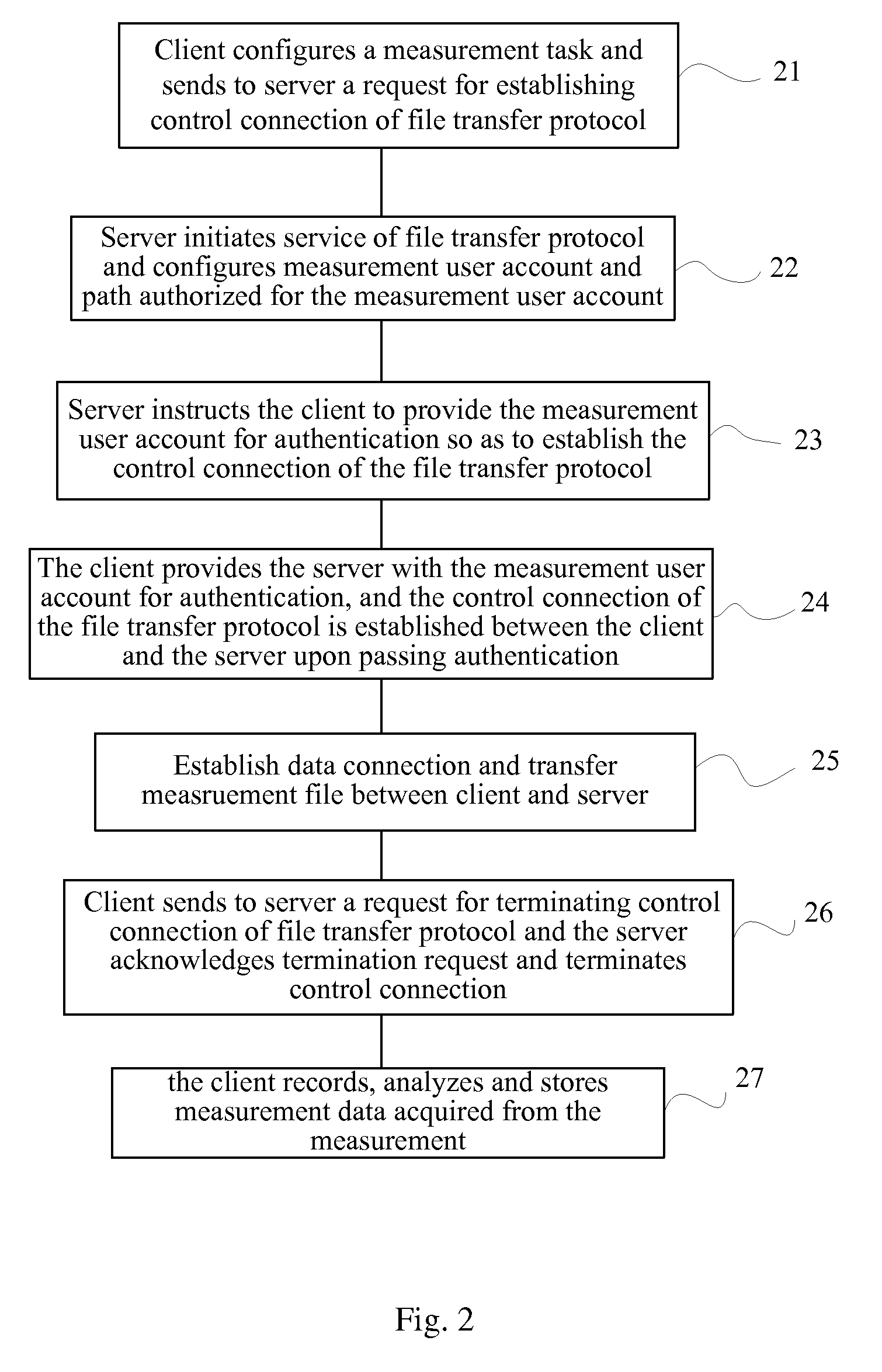
Data transfer apparatus and data transfer method
InactiveUS20050105530A1Data switching by path configurationMultiple digital computer combinationsData shippingData transmission
A data transfer apparatus according to this invention executes a protocol priority determination process of selecting usable transfer protocols in accordance with the type of transfer object and determining the priorities of the transfer protocols in accordance with the process of an automatic file transfer protocol selection process routine. The data transfer apparatus then executes a protocol selection process of selecting transfer protocols commonly usable in the transfer source apparatus and transfer destination apparatus of the transfer object. The data transfer apparatus executes a transfer protocol determination process of determining a transfer protocol for use on the basis of the transfer protocol and its priority which are determined in the protocol priority determination process, and the transfer protocols selected in the protocol selection process.
Owner:KK TOSHIBA
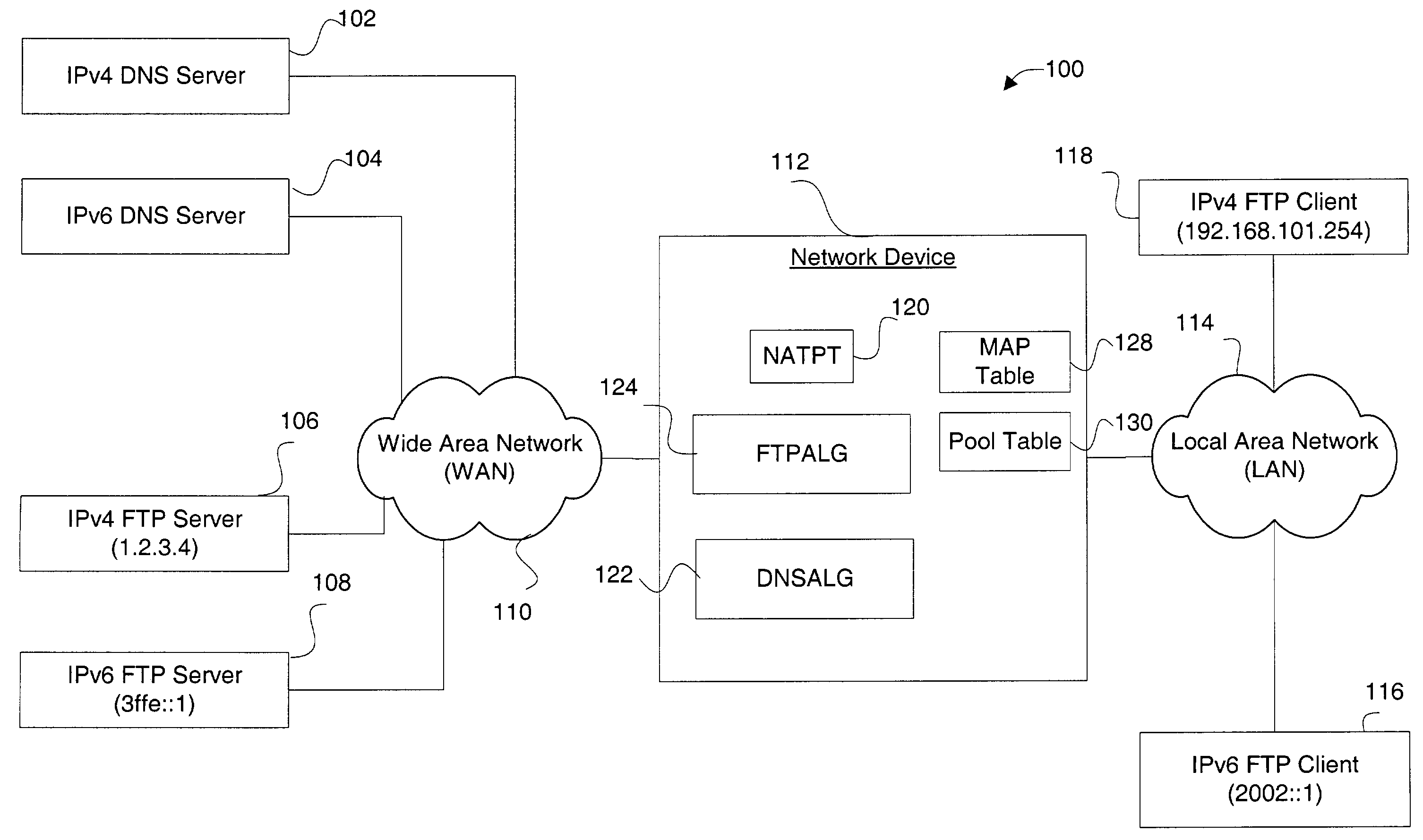
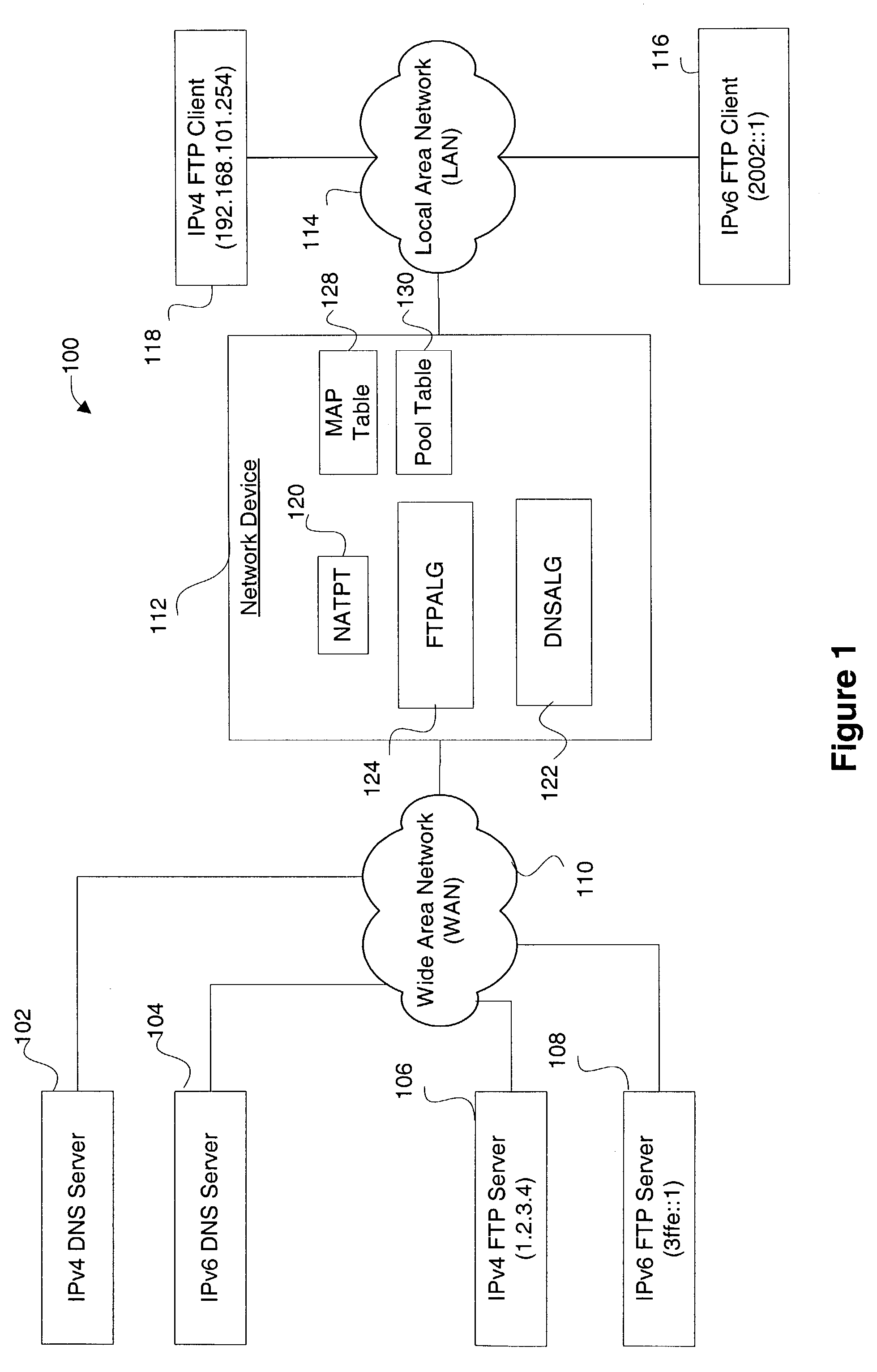
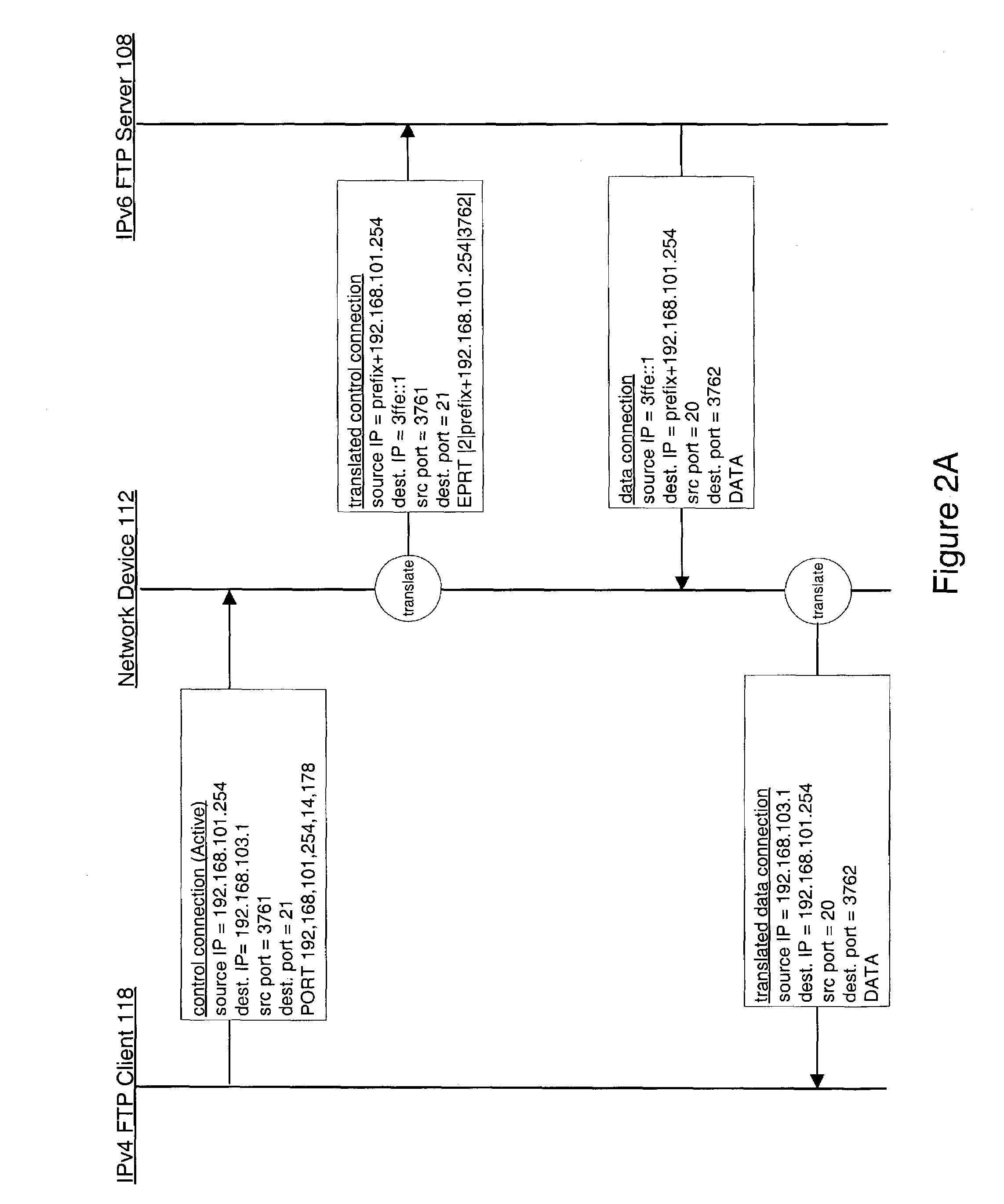
IPv4-IPv6 FTP application level gateway
ActiveUS7391768B1Data switching by path configurationMultiple digital computer combinationsClient-sideComputer science
Disclosed are methods and apparatus for handling FTP (file transfer protocol) control packets. In general terms, mechanisms are provided for facilitating FTP sessions between devices utilizing different protocols, such as IPv4 and IPv6. For example, FTP control packets from an IPv6 client to an IPv4 server are handled to facilitate such communication. Likewise, FTP control packets from an IPv4 client to an IPv6 server are handled to facilitate such communication. Communication is also facilitated when either or both of the client or server is in the form of a dual-stack device. To facilitate FTP session between devices having different protocols, FTP control packets between two different protocol devices are translated from one protocol to another protocol when required, e.g., from an IPv6 to an IPv4 format or visa versa.
Owner:CISCO TECH INC
Fault Localization and Fiber Security in Optical Transponders
ActiveUS20120224846A1Accurate locationTransmission monitoringElectromagnetic transmission optical aspectsDigital signal processingFiber
Designs, methods, and applications for fault localization and fiber security in optical transponders is described. In one embodiment a two-way time transfer protocol or other suitable method for synchronizing clocks between distant transponders is used. The clock synchronized transponders have digital signal processing to continually detect high precision time-histories of physical layer attributes in the transmission between the two transponders. Physical layer attributes can include: state-of-polarization changes, changes in polarization-mode-dispersion, change in propagation delay, changes or loss-of-light, changes in OSNR, changes in BER between the two nodes. By recording these physical layer changes and time-stamping them information on the magnitude and estimated location of the changes can be inferred by from the time records. In one aspect the method may be used in a distributed optical sensor for monitoring trespassing events that are a risk to fiber security of an optical transmission link.
Owner:ACACIA CHEM
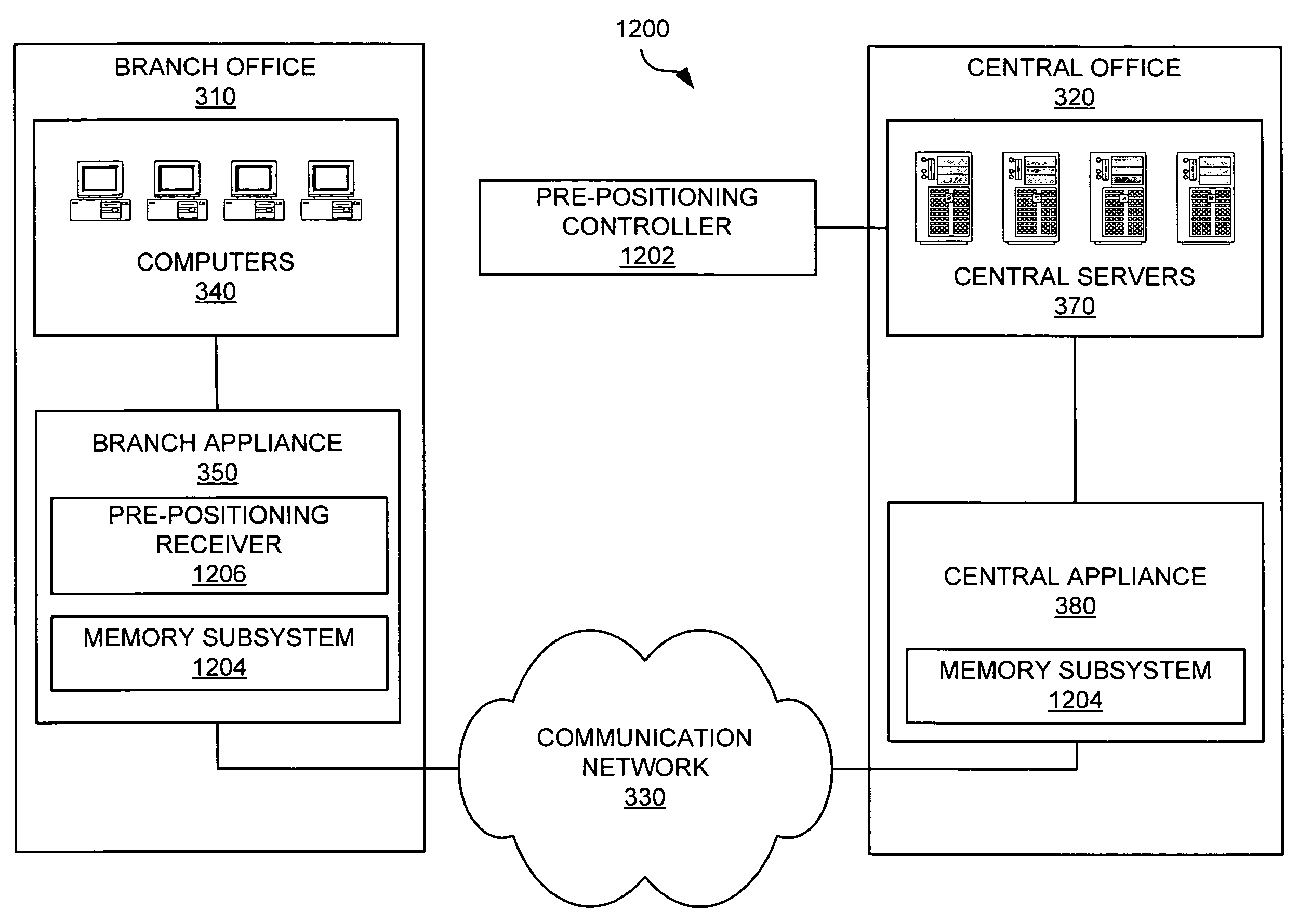
Pre-positioning data in a network memory appliance
InactiveUS7698431B1Quick searchWithout license feeDigital computer detailsNetwork connectionsFile systemSoftware update
Systems and methods for pre-positioning data in a network memory are described. A pre-positioning command may be executed to position specific data at one or more network memory appliances before the data is requested at a branch office. For example, the first download of a software update over the communication network at a branch office may require several minutes. To make the first download of the software update faster, the software update may be downloaded previously to the branch appliance. According to various embodiments, the pre-positioning command may comprise a time of transfer and / or a schedule. The data may be received by a pre-positioning receiver such as a file system server, a hypertext transfer protocol server, a file transfer protocol server, or a virtual client.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
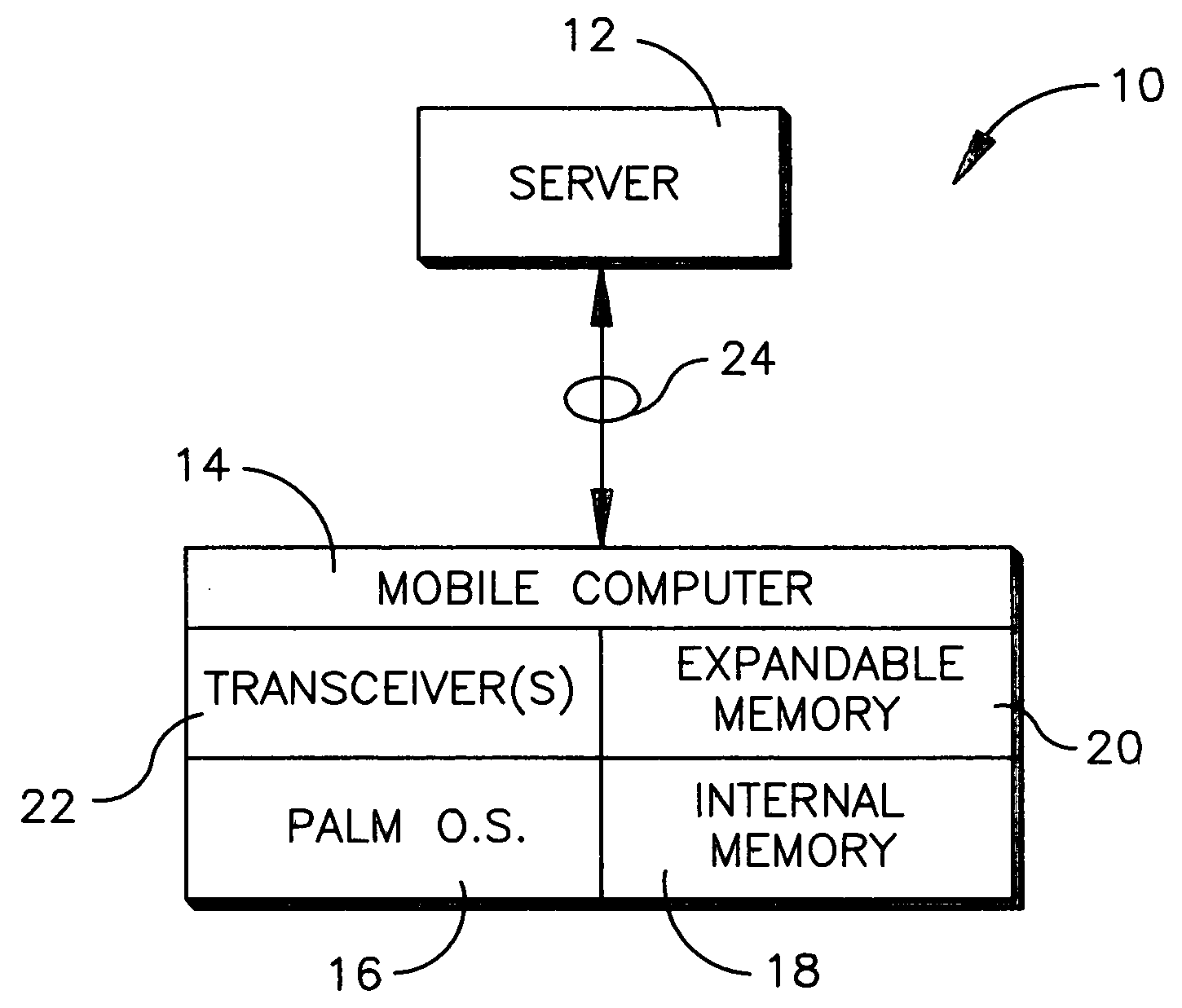
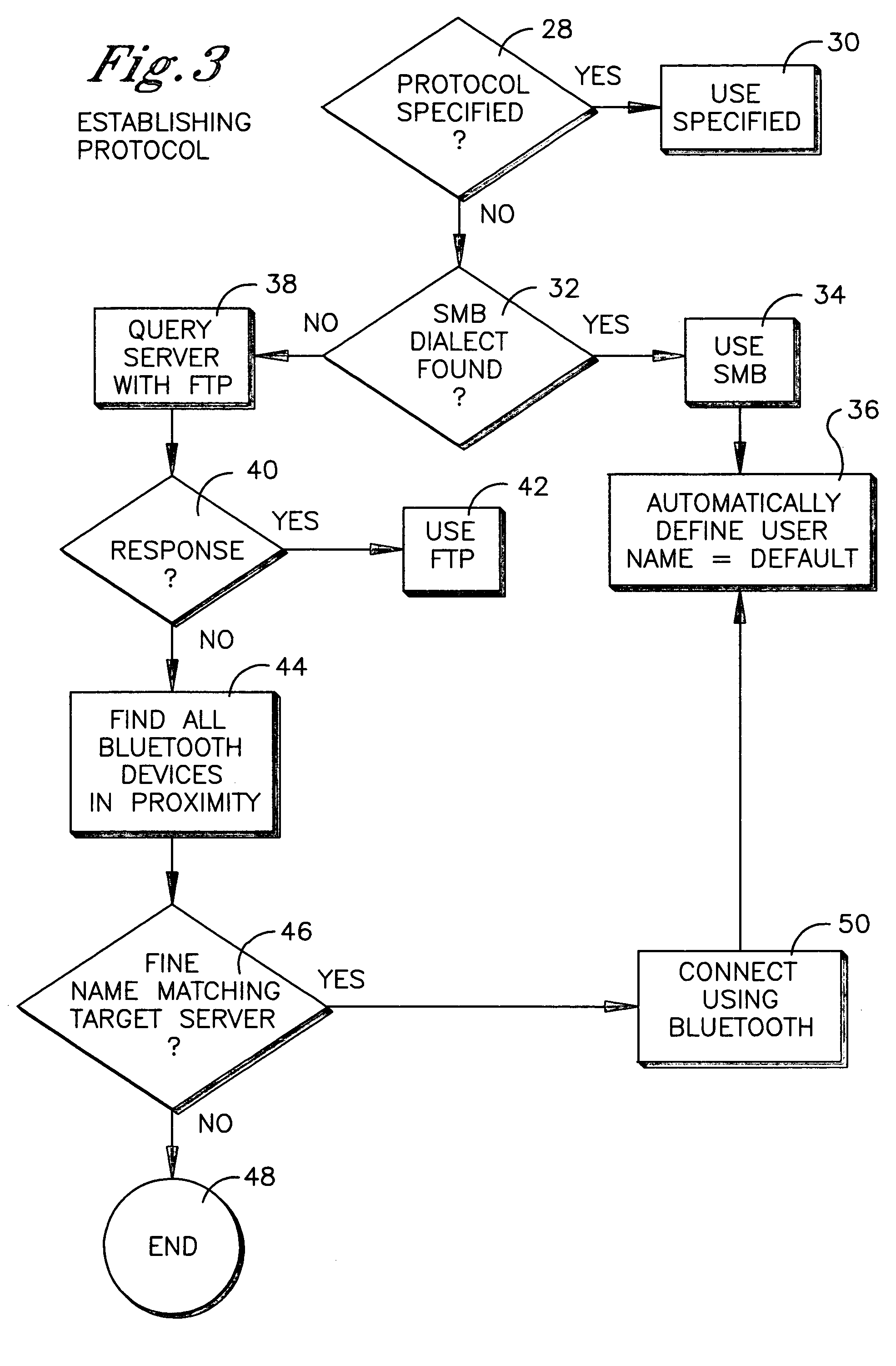
File transfer protocol for mobile computer
InactiveUS20050102537A1Digital data processing detailsPicture reproducers using cathode ray tubesInternal memoryBluetooth
A method is disclosed for communicating using a device having a Palm OS. SMB is preferentially used to communicate with a node, and if use of SMB is not possible, FTP is used, and if use of FTP is not possible, Bluetooth is used. If FTP or Bluetooth is selected as the protocol, file sharing between the device and node that entails a read or write is executed by temporarily copying a file to an internal Palm OS memory of the device, performing the read or write on the file, and then copying the file back to the node to overwrite a previous version of the file at the node. For non-Palm OS file transfer to the internal memory, the file is wrapped in a Palm OS stream in the internal memory for executing reads or writes. For file transfer to an expansion Palm OS memory card, byte-to-byte copying of the file is executed using the FAT of the expansion memory, with the file being transferred through an internal Palm OS memory of the device.
Owner:SONY CORP +1
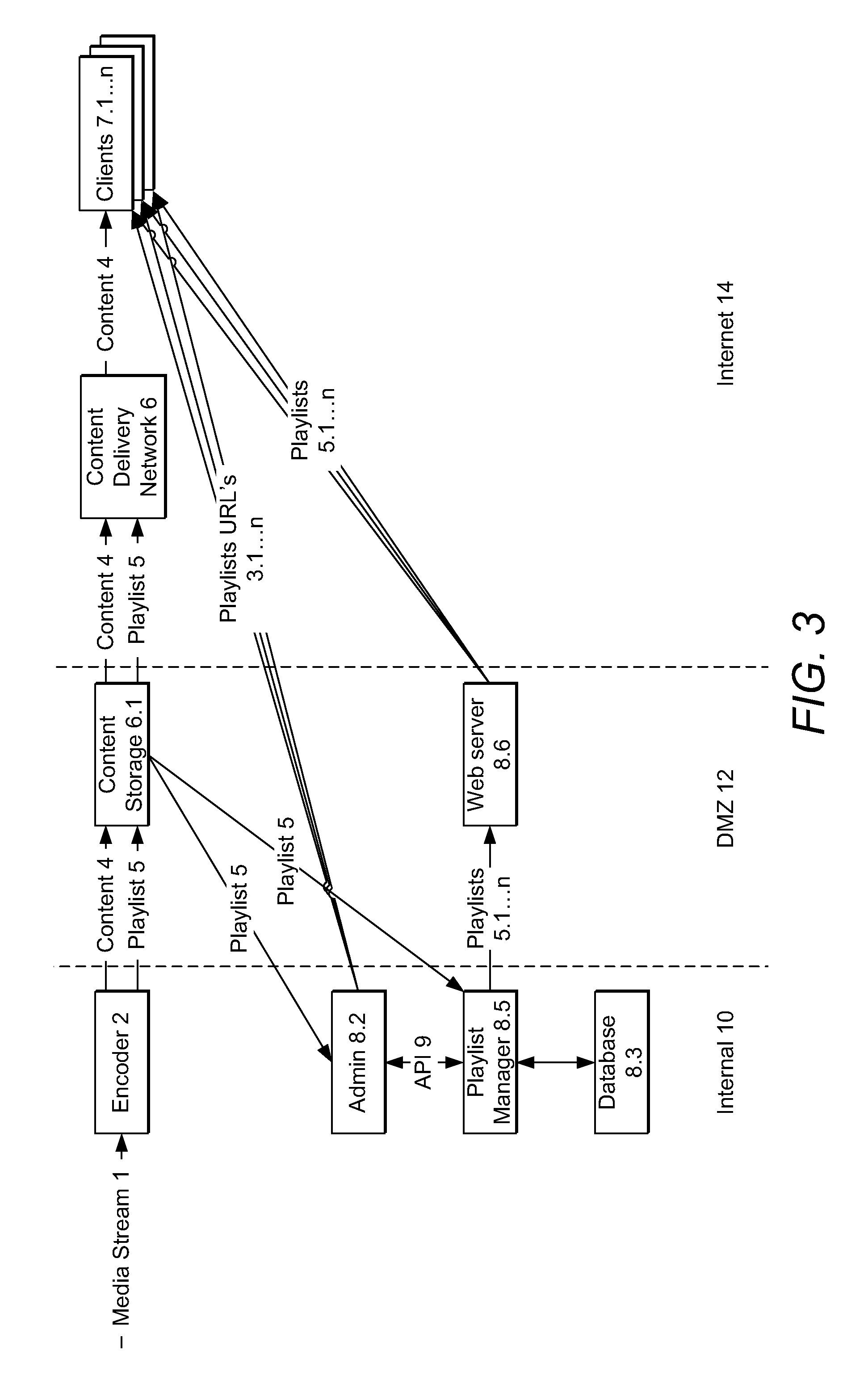
Media System
Streaming media is provided over a network using a non-streaming-specific transfer protocol, in which a media stream is stored on a server as multiple individual media files, and a playlist is provided indicating which media files are required for output of a specific part of the media stream; wherein multiple different playlists are provided to respective different media streaming clients, in response to requests relating to corresponding different parts of the media stream. A user interface is provided on the client device, in which an interactive media event is displayed including streaming media, and secondary media content.
Owner:SKY CP LTD
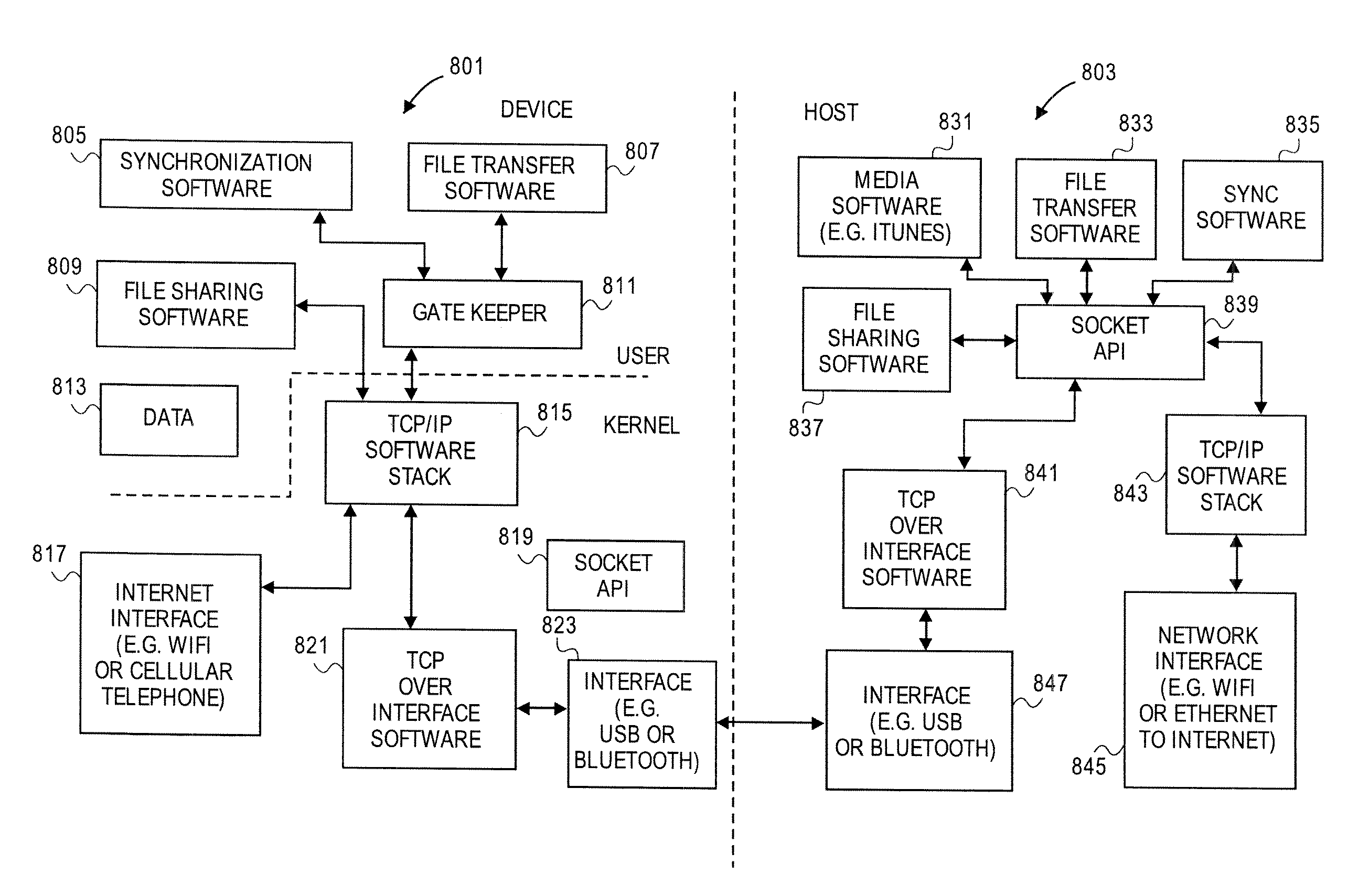
File protocol for transaction based communication
InactiveUS20080307109A1Multiple digital computer combinationsData switching networksSoftware architectureApplication software
File protocols for transaction based communication are described. In one embodiment, a method to provide a file transfer protocol includes receiving packets containing headers, the packets being received at a first network stack software through an interface, and extracting data from he packets and reconstructing a file from data in the packets. The extracting may be performed by a first network stack software, and the interface is not designed to use Internet Protocol (IP) addresses, and the headers contain data for flow control and sequencing and are associated with a port for a file transfer application, and the headers allow multiple applications to maintain multiple concurrent sessions through the interface, which may be a USB compliant or BLUETOOTH compliant interface. Systems, computer readable media, software architectures and other methods are also described.
Owner:APPLE INC
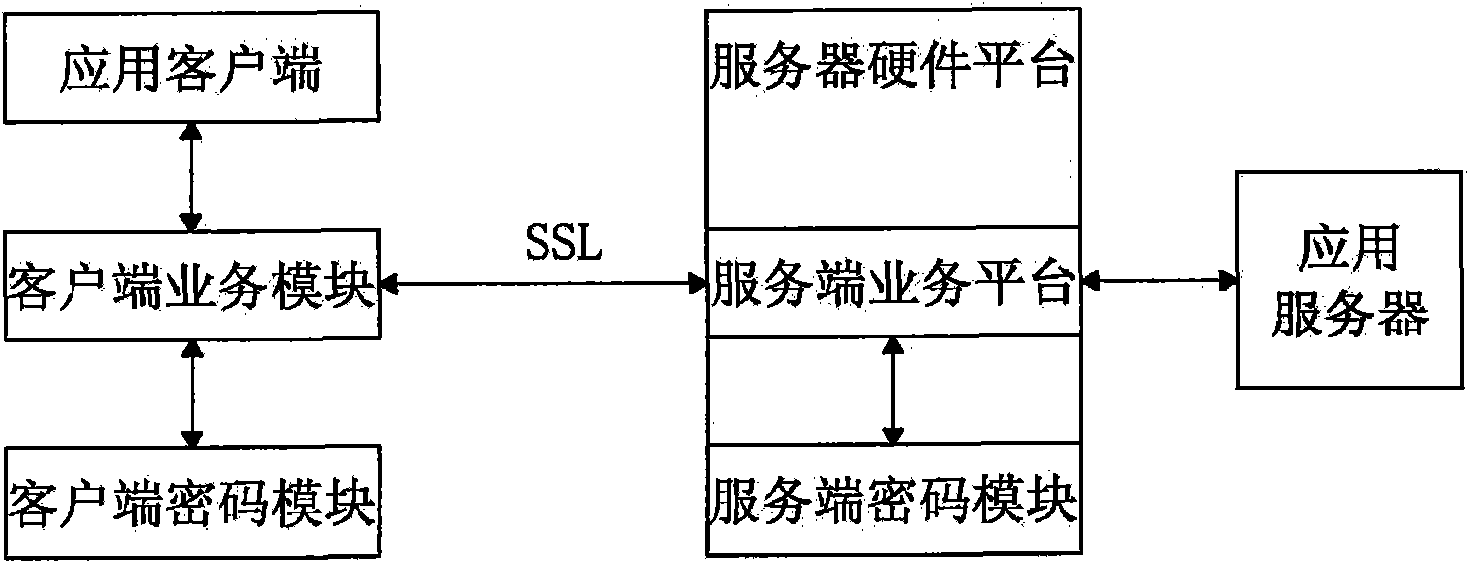
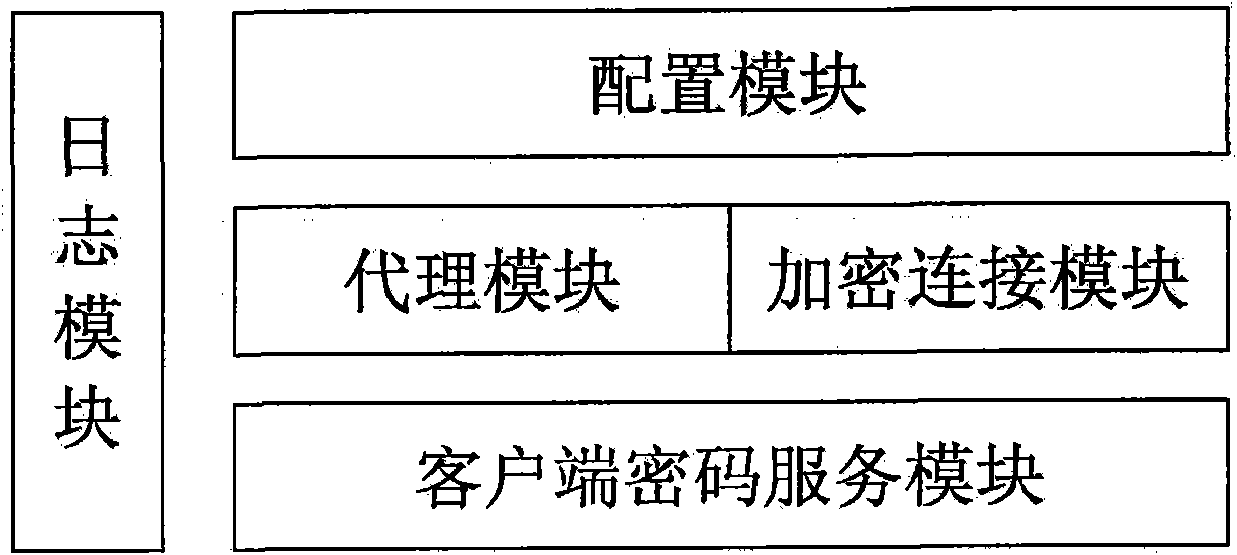
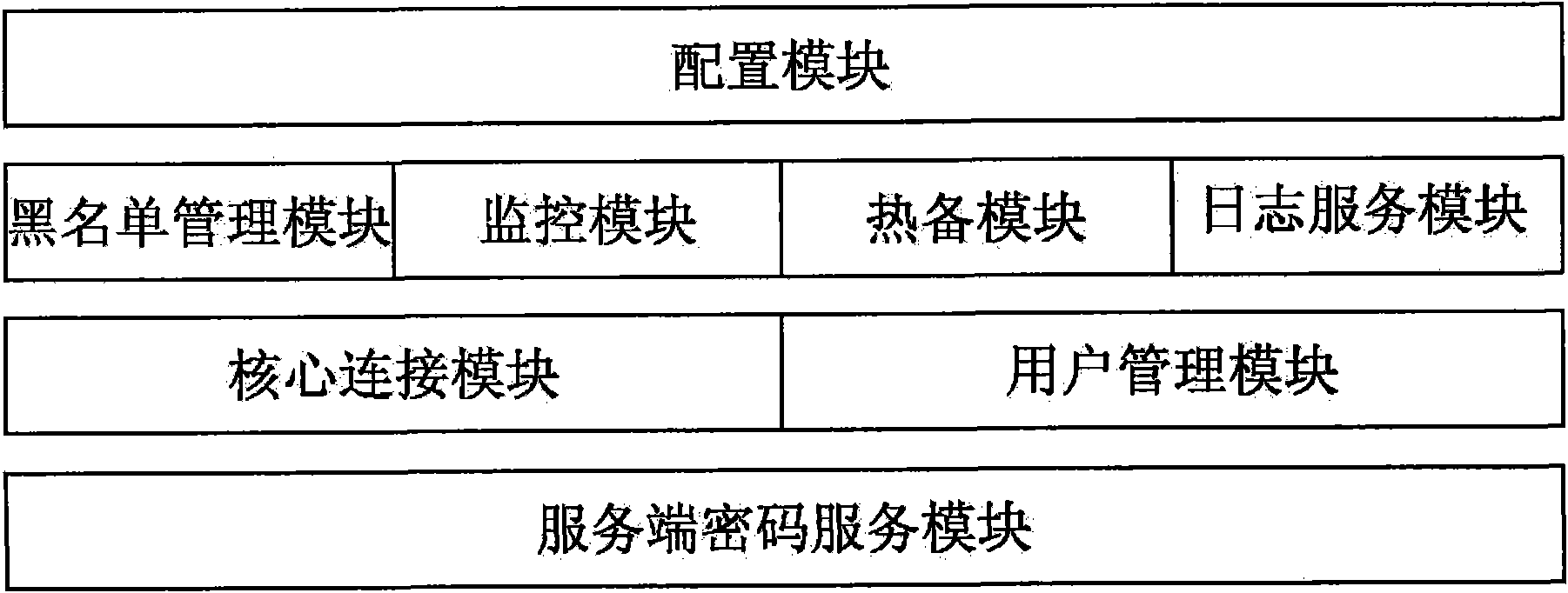
Security certificate gateway
InactiveCN102111349ARealize data transmission securityAchieving Valid AuthenticationNetwork connectionsInternet Authentication ServiceRemote desktop
The invention discloses a security certificate gateway, comprising a client crypto module, a client business module, a service business module and a service crypto module, wherein the client business module is used as an agent of an application client and used for calling the client crypto module and the service business module interactively to build an encrypted connection; and the service business module is used for calling the service crypto module and the service business module to build a secure encrypted channel. Based on the high-strength identity authentication service, the high-strength data link encryption service and the digital signature and authentication service of a digital certificate, the gateway provided by the invention effectively protects secure access of network resources, and supports B / S applications of a hypertext transport protocol (HTTP) and hypertext transfer protocol secure (HTTPS) as well as common C / S applications of a file transfer protocol (FTP), a remote desktop and the like.
Owner:KOAL SOFTWARE CO LTD
Authenticated exchange of public information using electronic mail
InactiveUS7721093B2Key distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessDigital object
Methods and systems are provided for using an existing email transfer protocol, such as SMTP, to exchange digital objects in an authenticated manner. The provided methods and systems solve the bootstrapping problem of computer identities for P2P communication by authenticating the exchange of public information. If the electronic mail protocols are strong, in that sending an email message to a given address results in the message reaching that address with a high degree of confidence, then the exchange of public information performed in accordance with embodiments of the invention is confidently authenticated.
Owner:MICROSOFT TECH LICENSING LLC
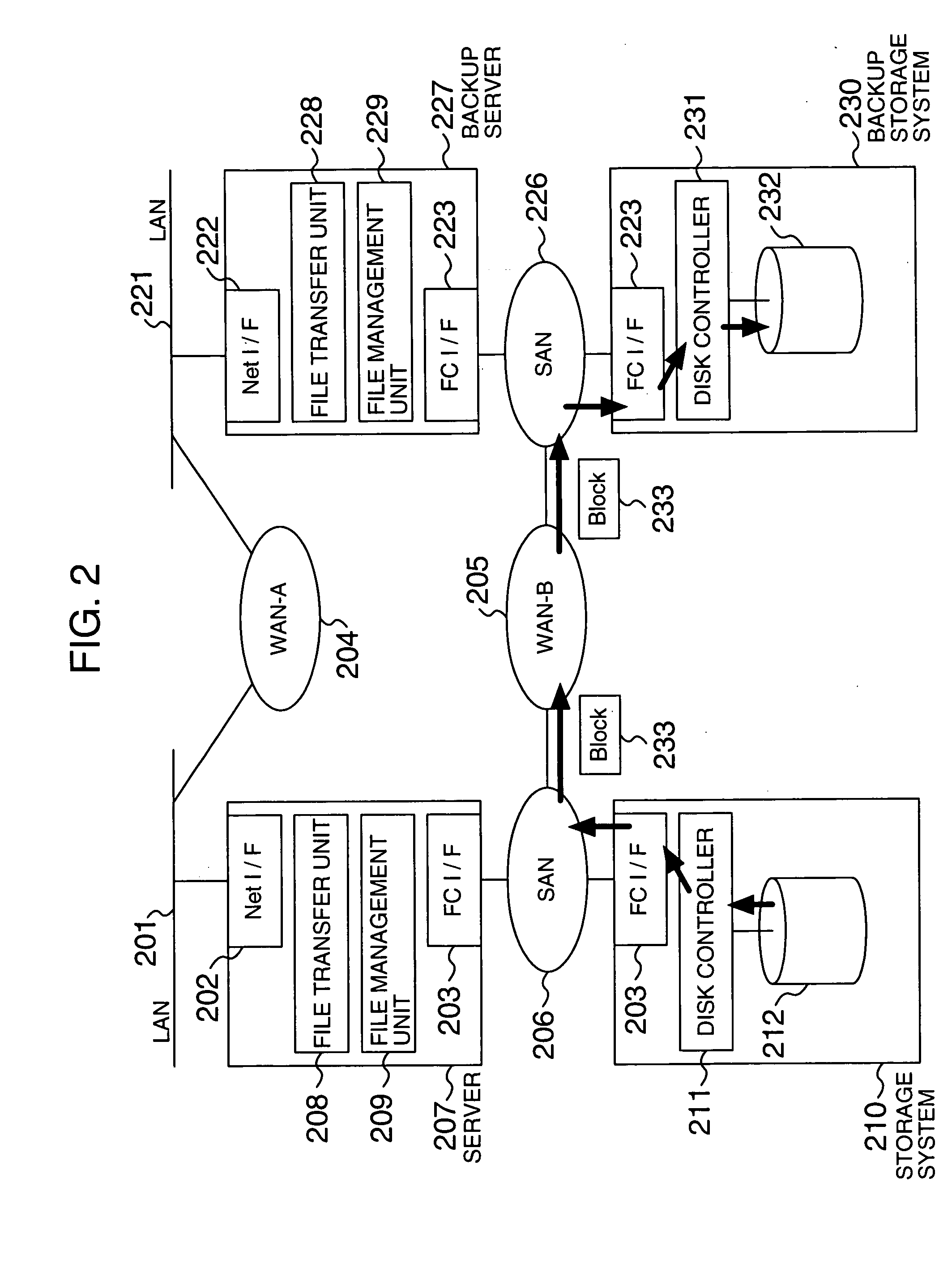
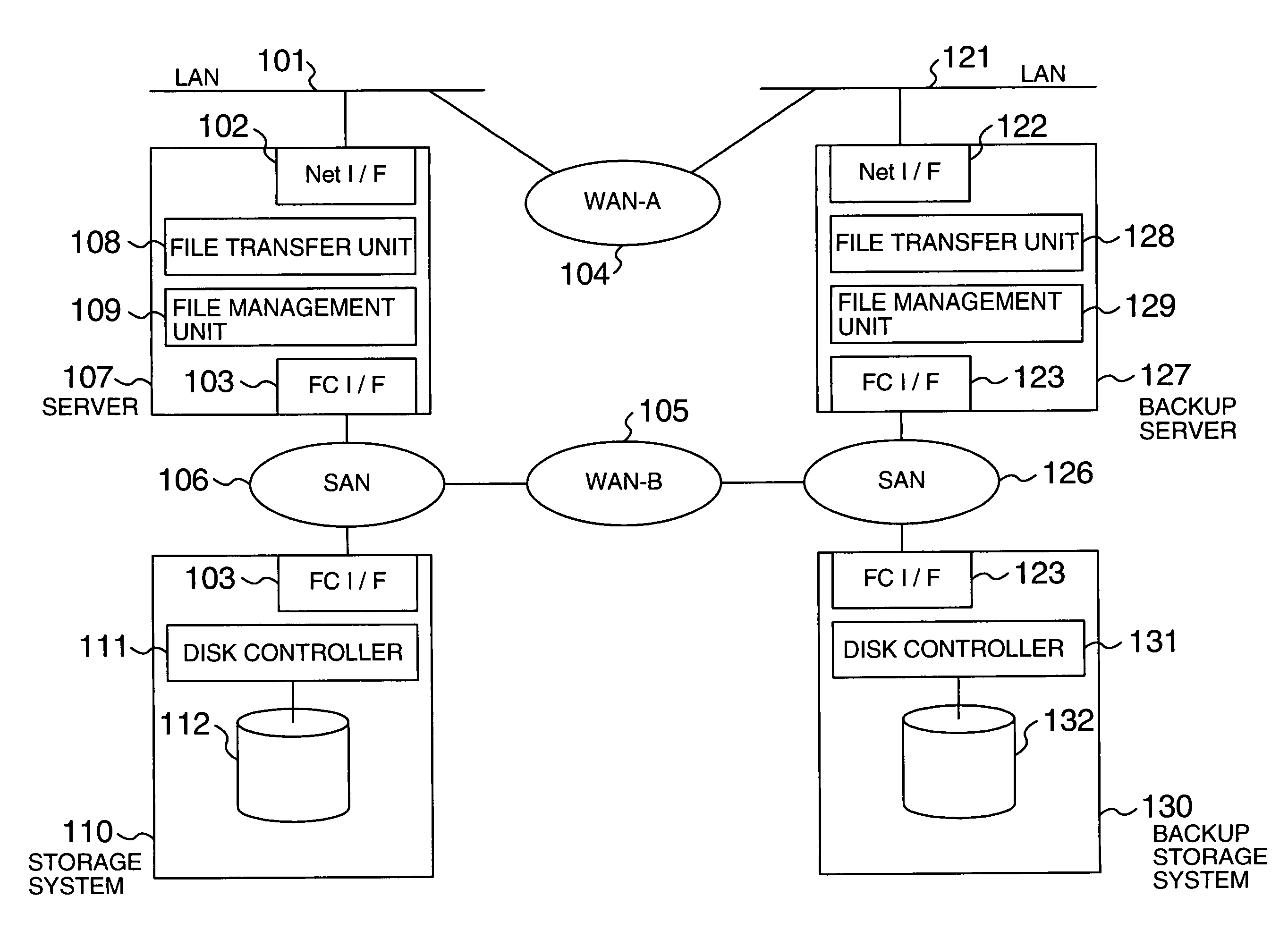
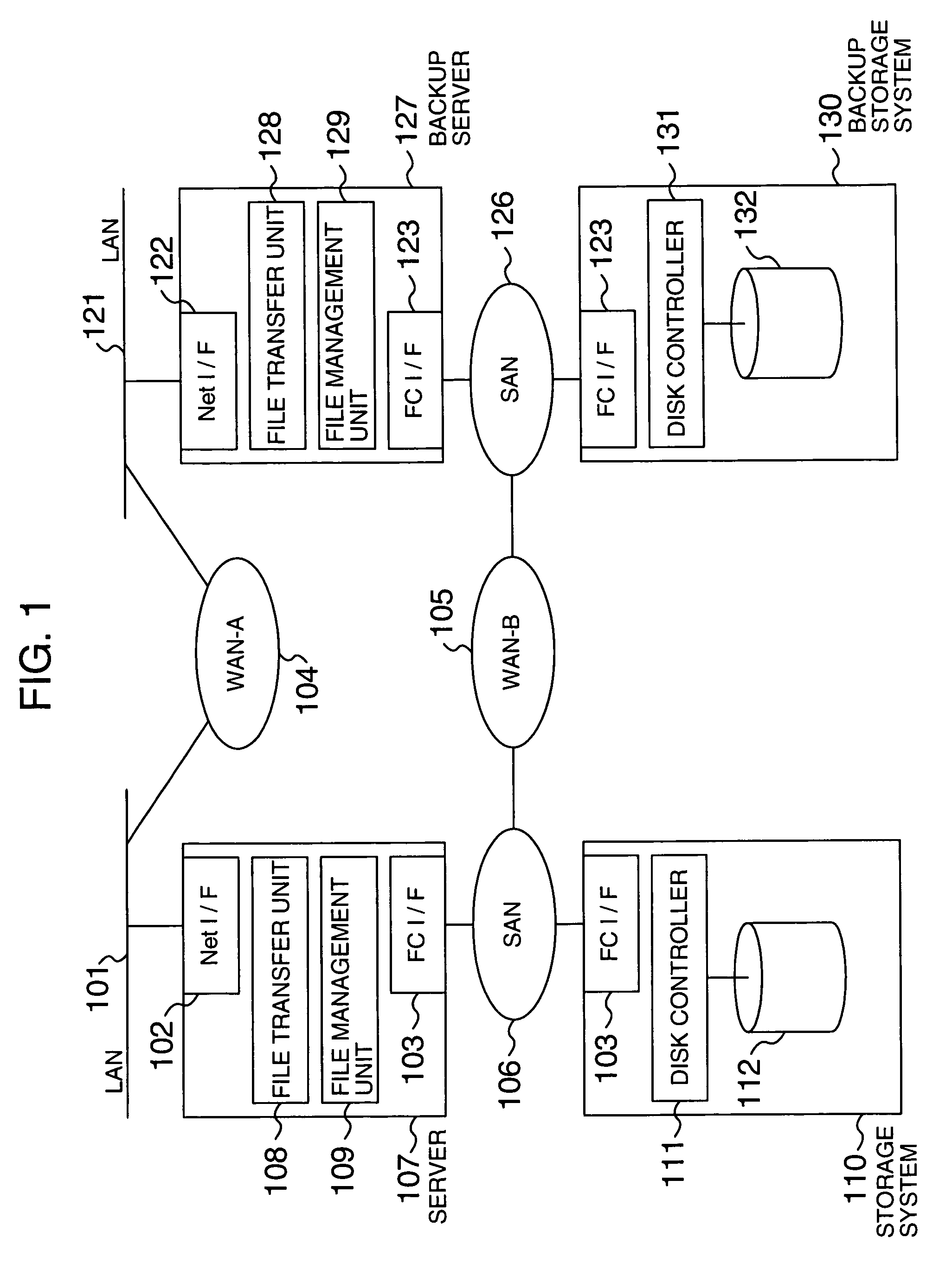
Data transfer method and system
InactiveUS20050144254A1Increase speedImprove reliabilityInput/output to record carriersMultiple digital computer combinationsTransmission protocolComputerized system
A computer system that transfers data from a first storage unit to a second storage unit via a network. The computer system includes a first controller that transfers data, stored in the first storage unit, to the second storage unit using a block transfer protocol; a table that associates a file composed of a plurality of blocks of data with blocks of data constituting the file; and a second controller that, in response to information that identifies a block from the first controller, identifies a file corresponding to the block using the table and transfers the identified file to the second storage unit using a file transfer protocol.
Owner:HITACHI LTD
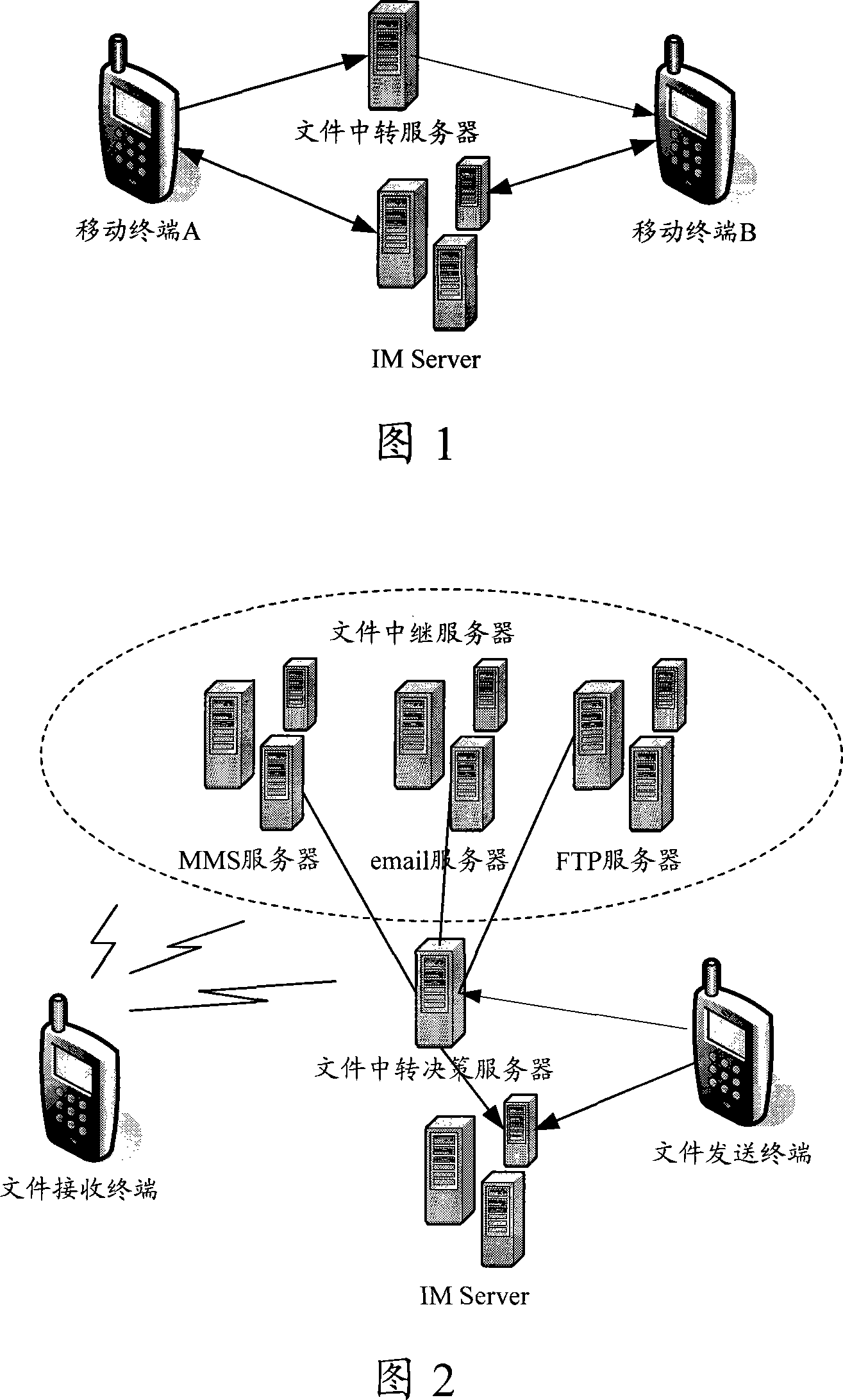
File transmission system, method and file forward decision server
ActiveCN101170523AImprove experienceEasy file transferData switching networksMobile communication systemsInstant messaging
A file transfer system including: a file sender, a file receiver, an Instant Messaging (IM) server, a file relay policy server and a file relay server. Also disclosed are the internal structures of the above file relay policy server and IM server and a file transfer method. If the file receiver has not logged in the IM system, it is possible that the file sender sends a file to the file relay policy server, the file relay policy server forwards the file to an appropriate file relay server, and the file relay server transfers the file to a mobile terminal as the file receiver according to a file transfer protocol of the file relay server itself, thereby facilitating the file transfer for the mobile subscriber and enhancing the mobile subscriber's experience in using the mobile IM service.
Owner:TENCENT TECH (SHENZHEN) CO LTD
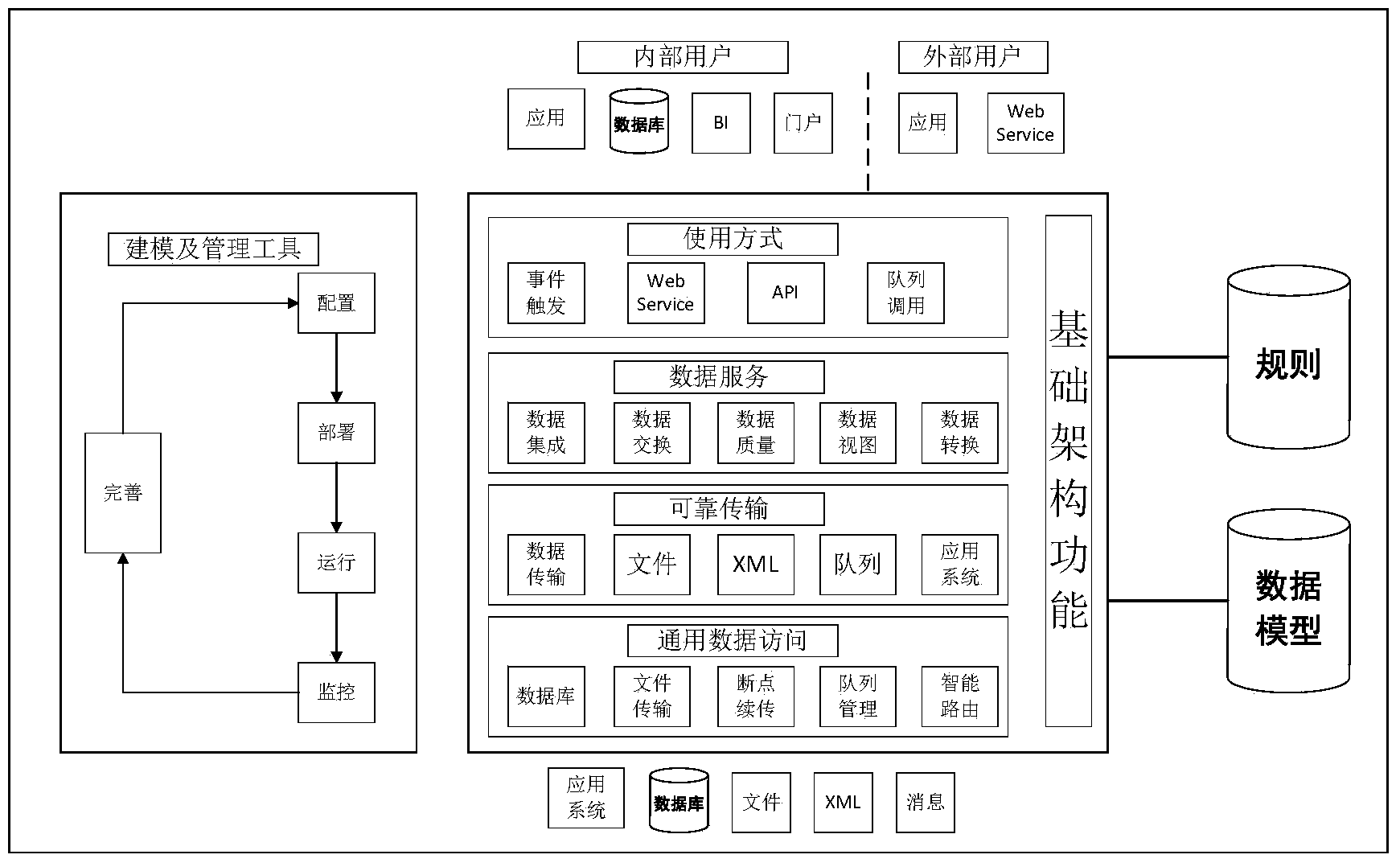
FTP-based (file transfer protocol-based) data exchange system
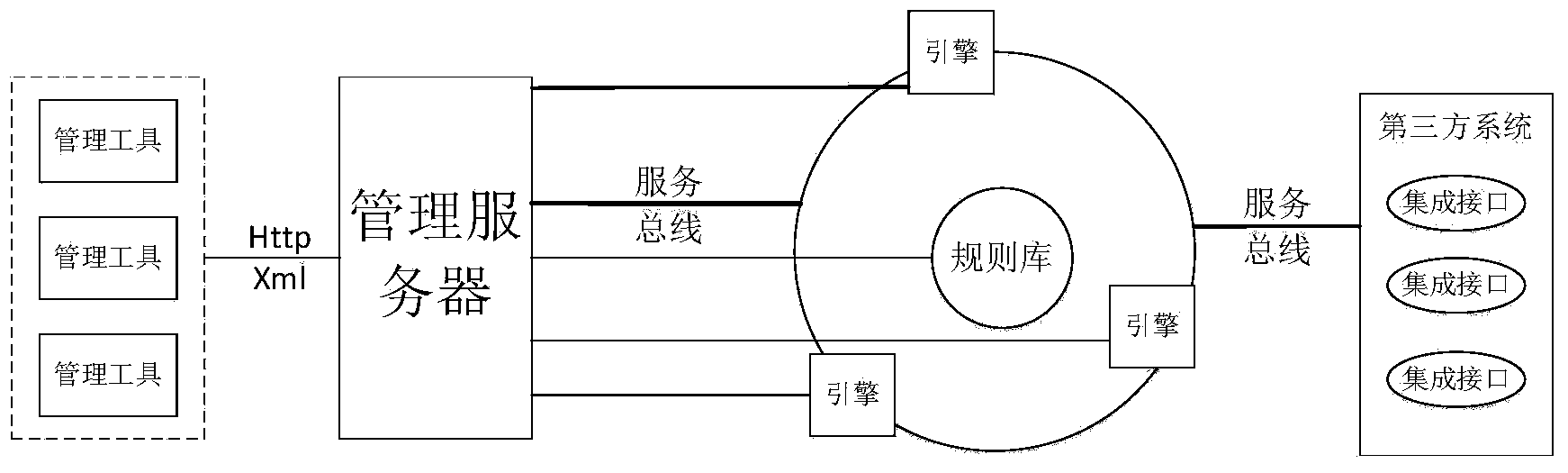
ActiveCN104104738AAccess to all functions of the operationAccurate transmissionTransmissionSpecial data processing applicationsManagement toolElectric power system
The invention discloses an FTP-based data exchange system for achieving unified exchange of data of a power system. The FTP-based data exchange system mainly comprises an engine (node), a rule base, a management server, a management tool and a development interface. The FTP-based data exchange system is based on standard data specifications and interface standards to configure data exchange services and to achieve data aggregation, integration and publication in different manners. The FTP-based data exchange system comprises the function modules including a data extraction module, a forward data processing module, a batch data transmission module, a reverse data processing module and a data storage module. The FTP-based data exchange system can achieve the sharing channels with crosswise integration and lengthwise communication of information systems of enterprises or organizations, obtains accurate transmission of mass data and ensures hierarchical data transferring, data sharing and application integration of the power system.
Owner:CHINA REALTIME DATABASE
Secure block read and write protocol for remotely stored files
ActiveUS20090216907A1Communications are efficient and secureDirect accessDigital data processing detailsMultiple digital computer combinationsReliable transmissionClient-side
A file transfer system including a client and a server capable of updating portions of the file stored on the server. The system is capable of uploading portions of a file before the file has been specified at the client side. The files are stored in raw at the client and the server, which preserves the block list mapping. The file transfer protocol is capable of compressing and encrypting transferred data. As a result, the partial file writes are possible while maintaining current bandwidth usage. The write request data structure is provided with additional features in the form of flags and fields to provide reliable transmission of partial file data.
Owner:SYNACOR
Wireless local area network upgrading method based on thin AP architecture
InactiveCN101801110ARelieve performance pressureNetwork topologiesWireless network protocolsWireless controlWireless access point
The invention discloses a wireless local area network upgrading method which is composed of a wireless controller and a wireless access point, the method comprises the following steps: firstly, download an upgrading file from an AC by utilizing a file transfer protocol (File Transfer Protocol, FTP) or a trivial file transfer protocol (Trivial File Transfer Protocol, TFTP) by a first batch of APs which is composed of a few APs of a large batch APs; download the upgrading file from the first batch of APs by other APs except the first batch of APs by utilizing the FTP or the TFTP.
Owner:北京傲天动联技术有限公司
File transfer protocol based network throughput testing approach
InactiveCN101136791AReflect actual throughputEliminate distractionsData switching networksUsabilityStart up
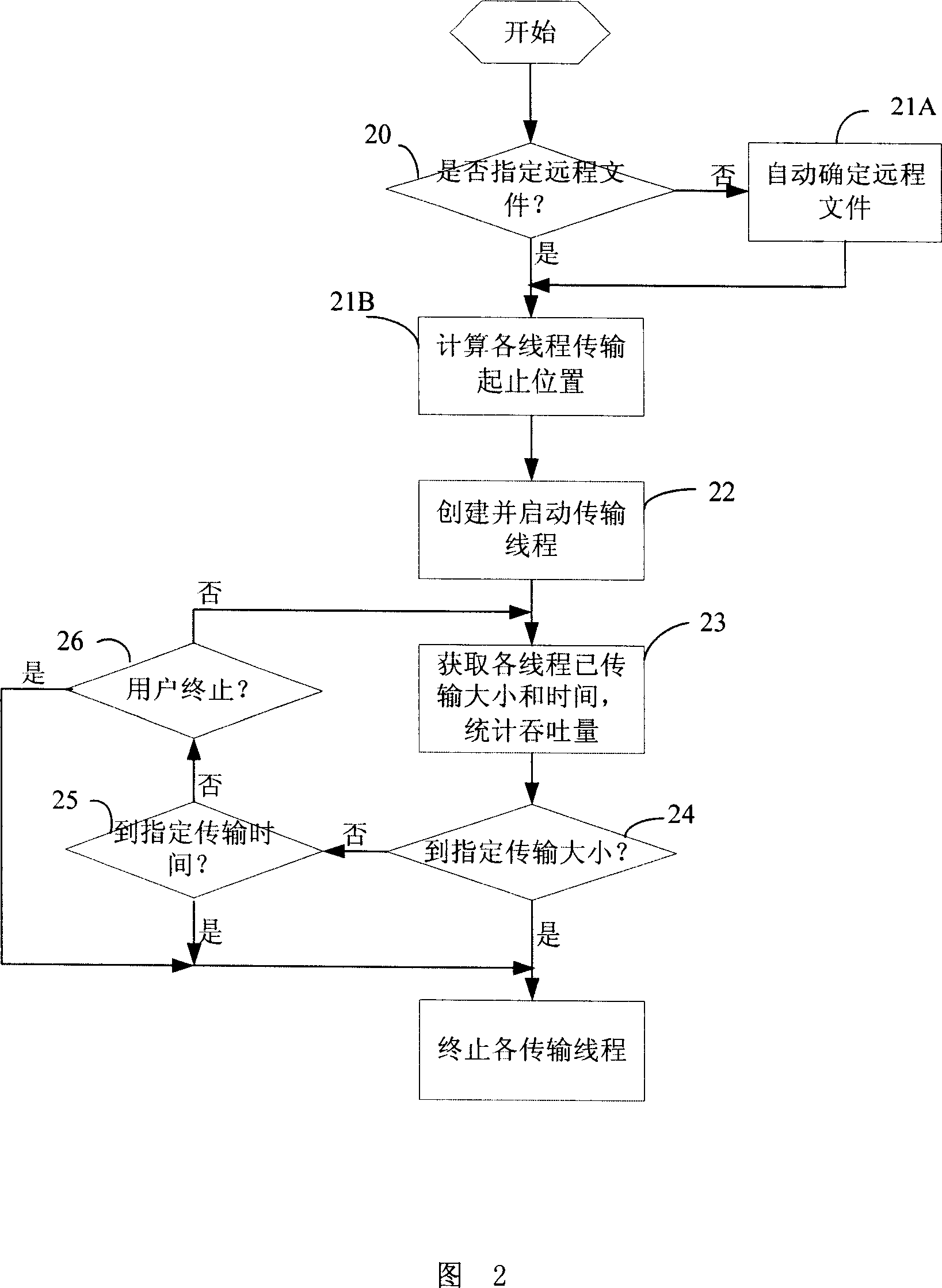
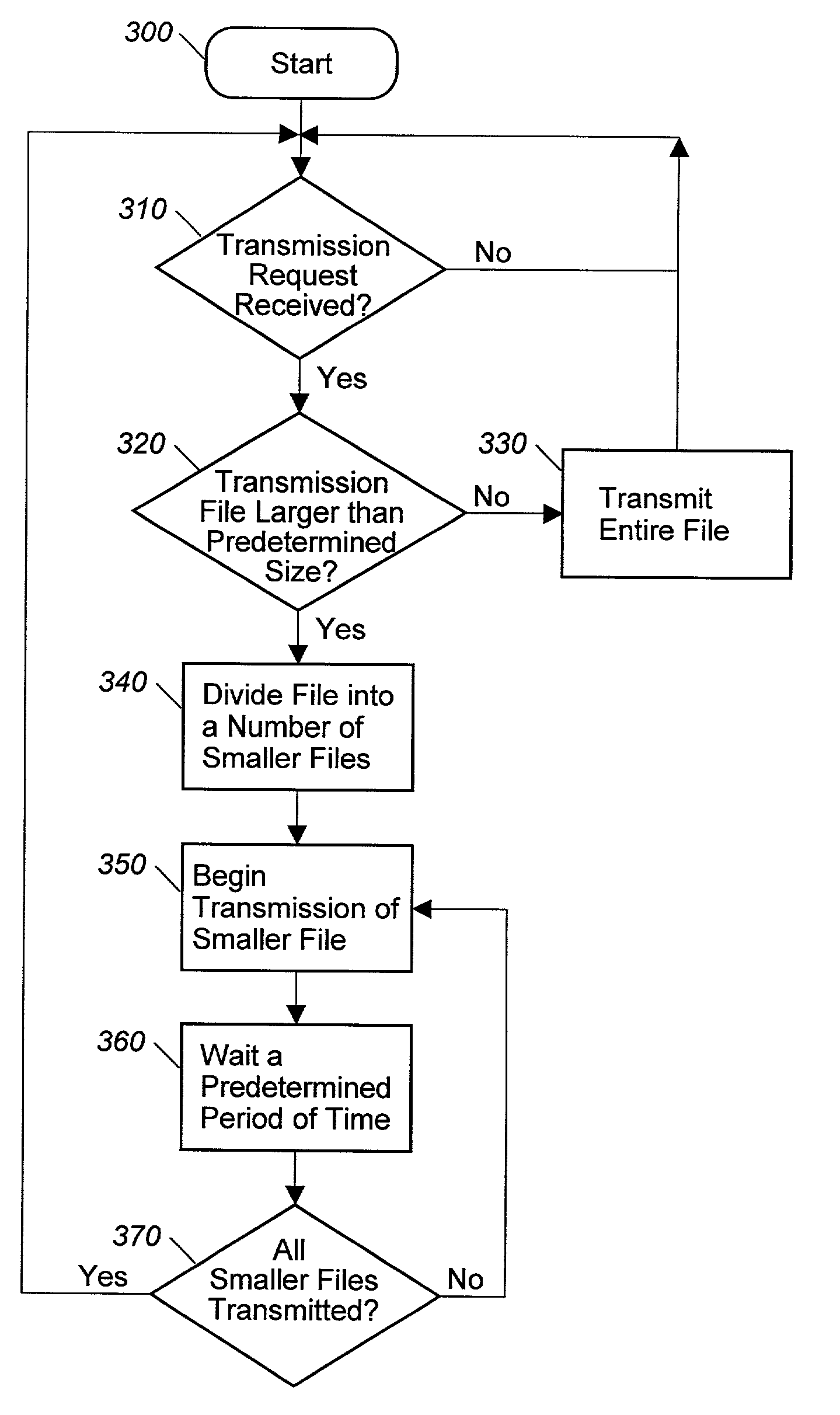
In the invention, the sending party sets up buffer area, and fills data as data source of simulation file; and the receiving party creates buffer area to receive data. After test is started, the method executes steps: specifying remote server file (RSF), or determining route, name and size of RSF; calculating transmission positions of starting and stopping each thread; creating prearranged number of transmission thread, and starting up execution of transmission; obtaining size of transmitted data (TD) and transmission time (TT) of each thread, making statistics for throughput; when TD reach specified size, or TT reaches specified time, or user stops testing, the method stops each transmission thread. Making the most of network capacity, the invention eliminates unnecessary interference from reading / writing files so as to reflect actual throughput of network precisely and raise reliability. Moreover, automation control increases easy to use the test device and efficiency of test.
Owner:ZTE CORP
System and method for network edge data protection
ActiveUS20090320135A1Quick implementationAvoid the needMemory loss protectionDigital data processing detailsDomain nameNetwork Communication Protocols
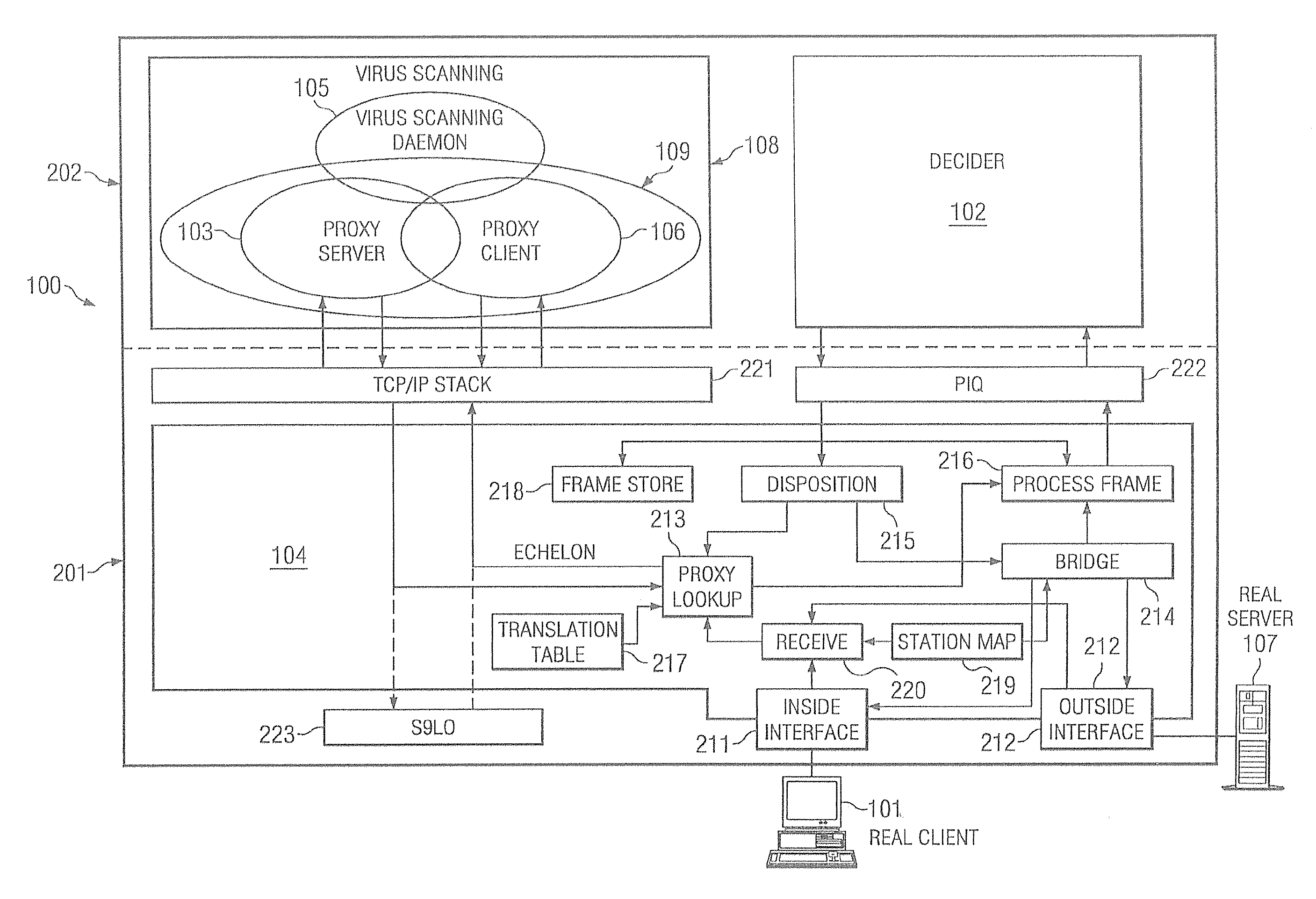
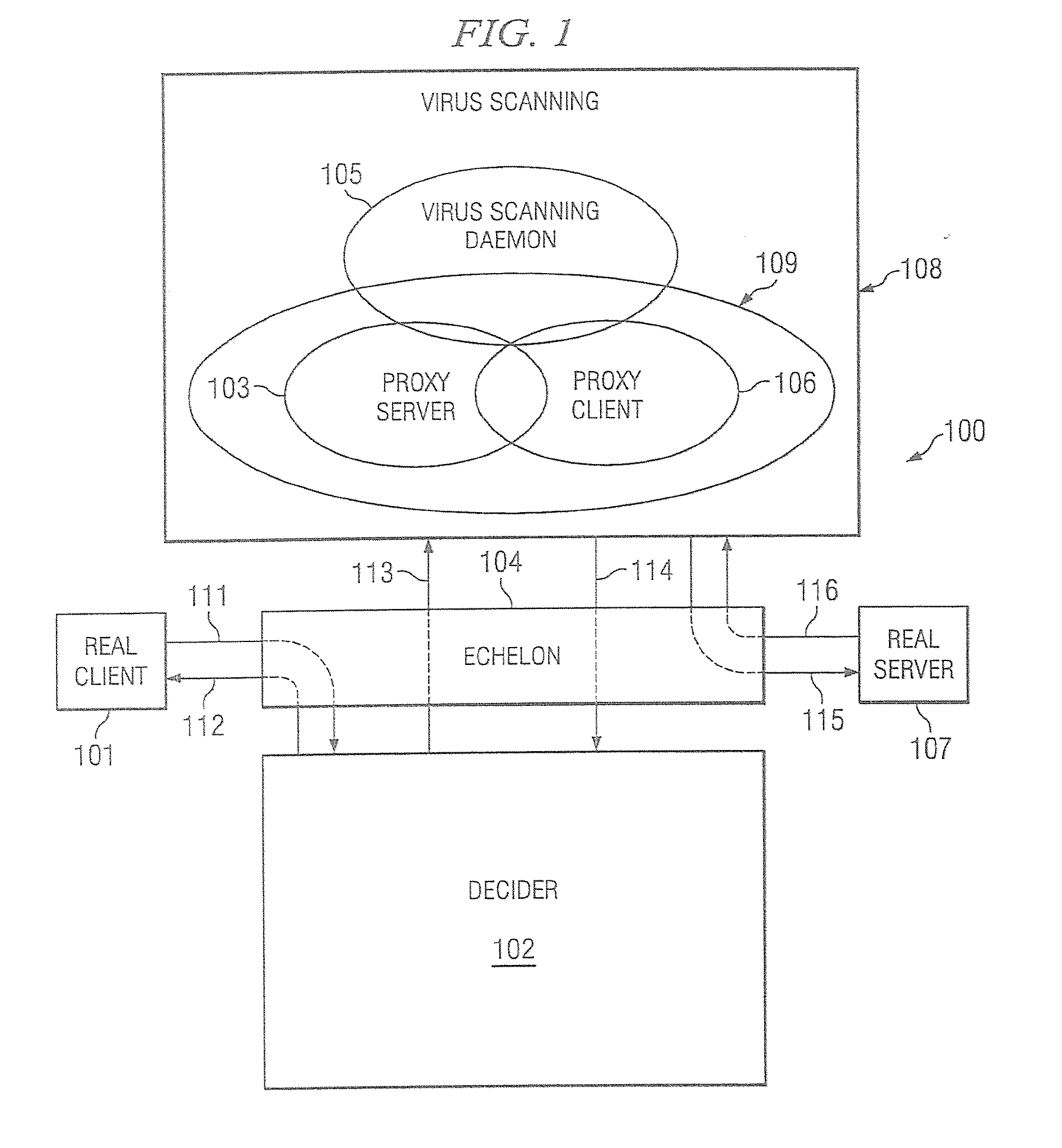
Disclosed are systems and methods which examine information communication streams to identify and / or eliminate malicious code, while allowing the good code to pass unaffected. Embodiments operate to provide spam filtering, e.g., filtering of unsolicited and / or unwanted communications. Embodiments provide network based or inline devices that scan and scrub information communication in its traffic pattern. Embodiments are adapted to accommodate various information communication protocols, such as simple mail transfer protocol (SMTP), post office protocol (POP), hypertext transfer protocol (HTTP), Internet message access protocol (IMAP), file transfer protocol (FTP), domain name service (DNS), and / or the like, and / or routing protocols, such as hot standby router protocol (HSRP), border gateway protocol (BGP), open shortest path first (OSPF), enhanced interior gateway routing protocol (EIGRP), and / or the like.
Owner:TREND MICRO INC
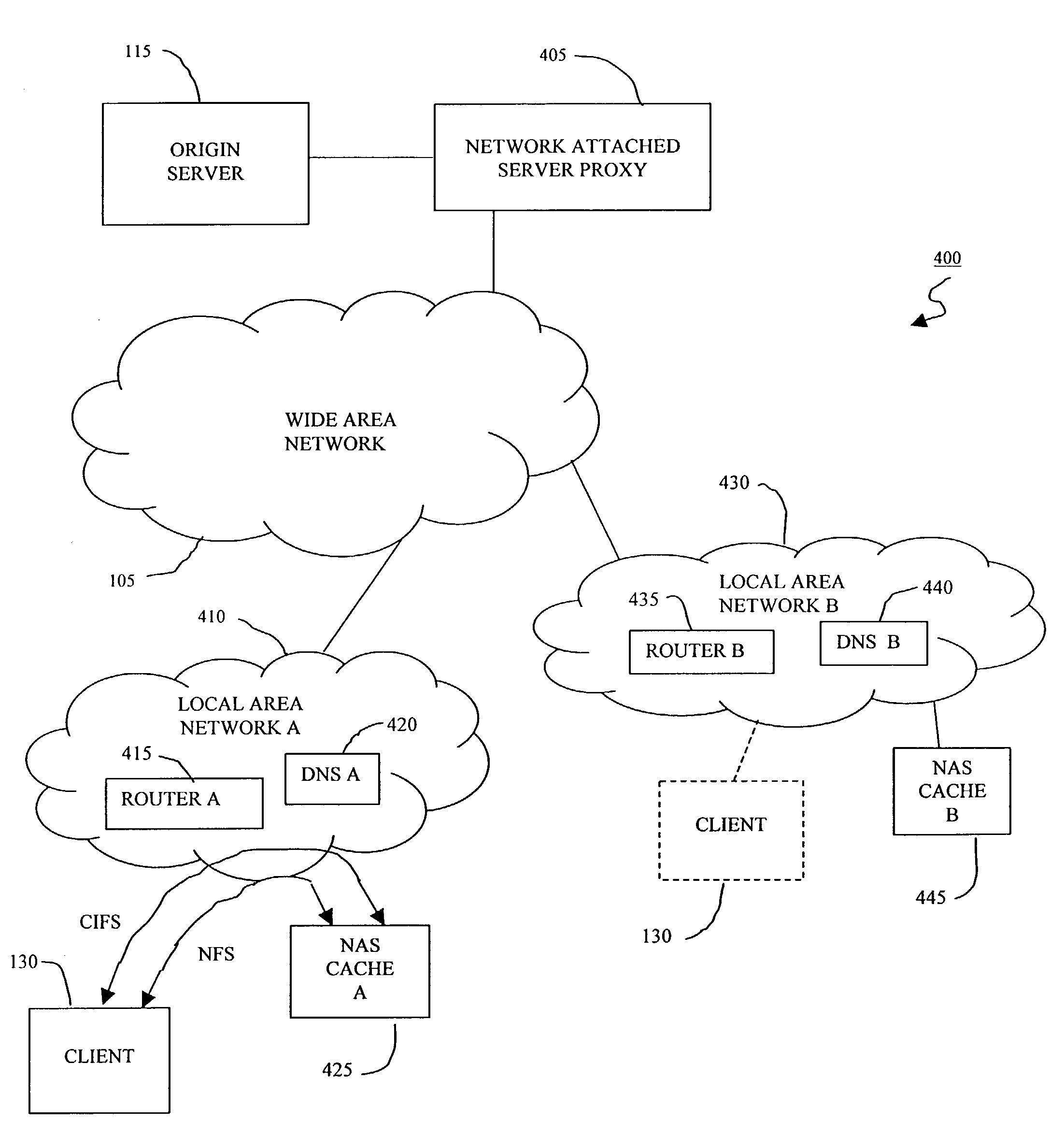
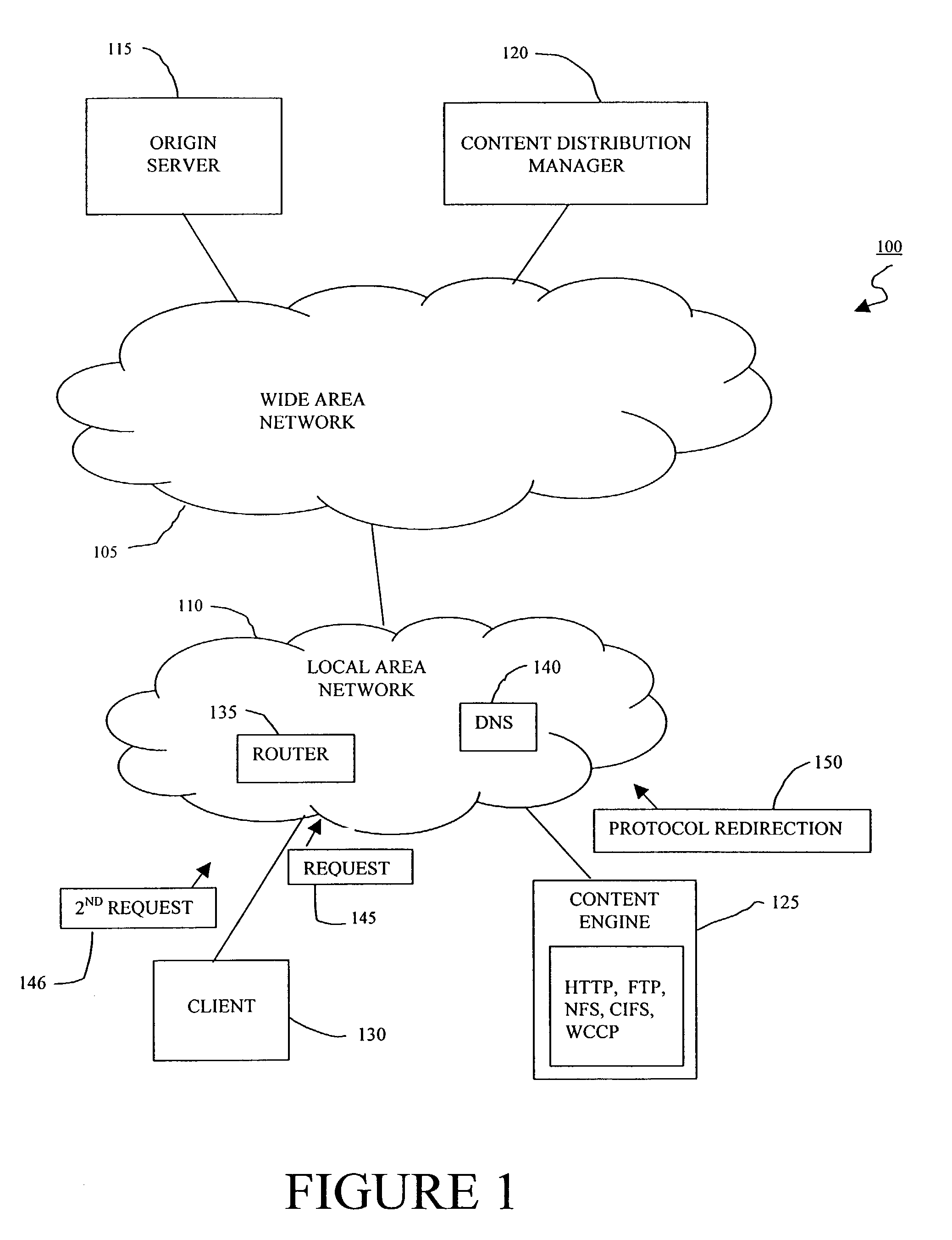
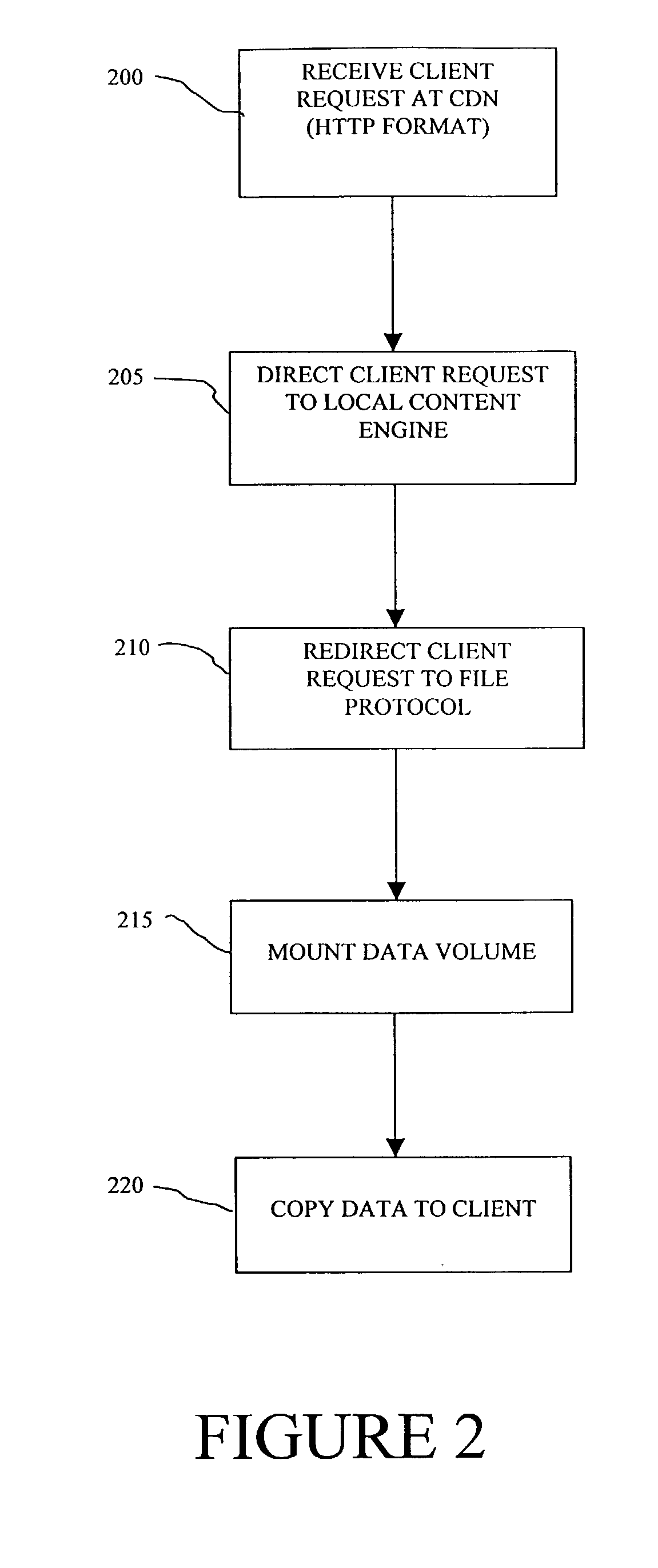
Content request redirection from a web protocol to a file protocol
A method and apparatus for routing a data request in a content delivery network receives a Hypertext Protocol (HTTP) format client data request and redirects the client data request to a file transfer protocol such that the data is transferred to the client in the file transfer protocol rather than HTTP. The redirection from HTTP, for example, to FTP or some other fileserver protocol outsources the load on the content engines while taking advantage of well-established methods of data handling and security. In addition, the network can dynamically be provisioned to handle a data load. In one embodiment, WCCP and HTTP redirection methods are used separately or in combination to provide a distributed file system in which client's requests benefit from content routing prior to interacting (via a file protocol) with a file server.
Owner:CISCO TECH INC
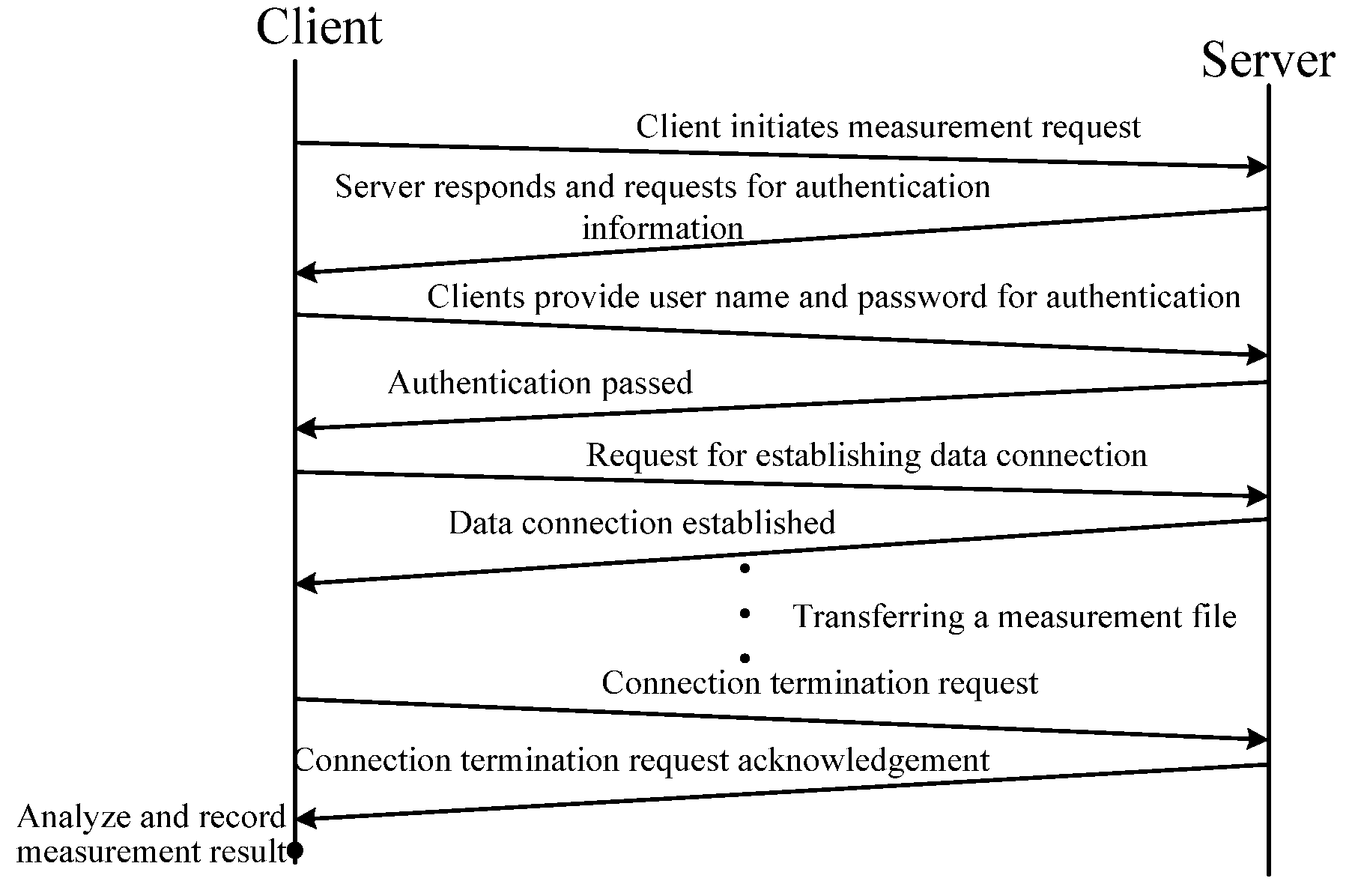
Method for testing the service performance of the file transfer protocol
InactiveUS20080172457A1Guaranteed reliabilityMultiple digital computer combinationsData switching networksClient-sideProtocol Application
A method for testing the service performance of the file transfer protocol in an IPv6 network, the network, including having a client and a server. The method includes the steps of (a) the client transmits a test connection request to the server to establish a connection controlled by the file transfer protocol, (b) after receiving the test connection request, the server establishes the connection controlled by the file transfer protocol, and (c) a connection is established by the server between the client and the server to transfer the test file and perform the performance test of the file transfer protocol. The server can transfer the detecting message for the file transfer protocol in the application layer between nodes in the file transfer protocol network, thereby realizing the detecting and the monitoring in the file transfer protocol. A service performance condition of the file transfer protocol of the network can be instantly detected. Once an abnormity occurs, it can be discovered instantly, and solved by the user, so that the network provides a guarantee of reliability.
Owner:HUAWEI TECH CO LTD
Online firmware batch upgrading method
InactiveCN104182261AShorten the timeReduce workloadProgram loading/initiatingData switching networksIntelligent Platform Management InterfaceSystems management
The invention provides an online firmware batch upgrading method. The online firmware batch upgrading method comprises creating a tftp (trivial file transfer protocol) server at a far-end, and placing firmware images to be upgraded into the tftp directory of the tftp server; transmitting an IPMI (intelligent platform management interface) instruction to inform the BMC (baseboard management controller) of the server, wherein the IPMI instructions contain the IP address and the tftp directory of the tftp server; after the BMC receives the IPMI instruction, mounting an ramfs (random-access memory file system) onto a system, receiving the firmware mirrors to be upgraded from the tftp server side to the ramfs; updating the firmware mirrors in the ramfs into an entire Flash. Compared with the prior art, the online firmware batch upgrading method can greatly reduce the time and workload for upgrading BMC firmware images in batches and bring great convenience to system maintaining personnel and system managing personnel, thereby reducing the system management and maintenance cost and meanwhile guaranteeing smooth service operations of users.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Application management system for on-line editing network file
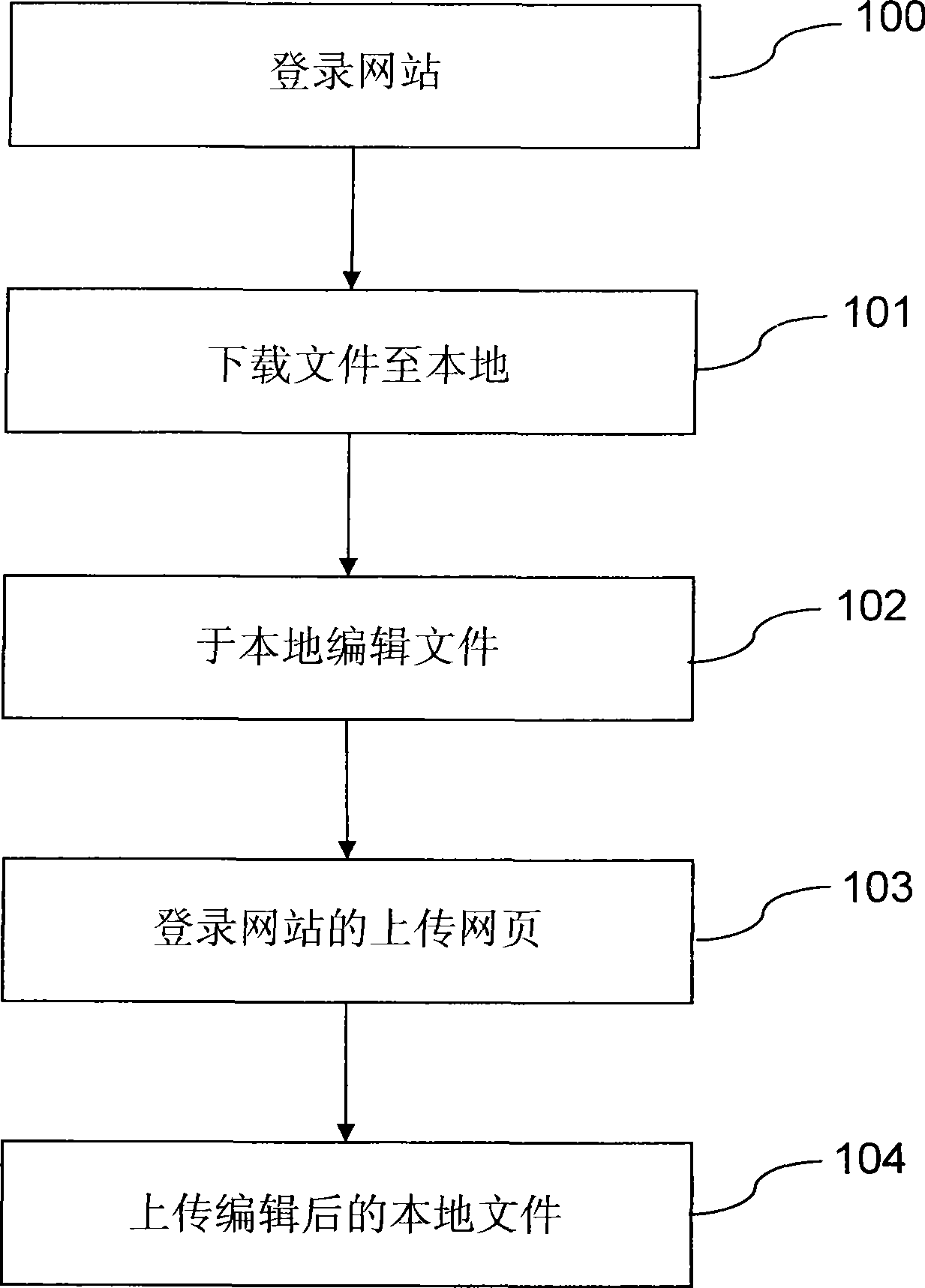
InactiveCN101398813ARealize editingReduce stepsTransmissionSpecial data processing applicationsWeb siteSystem usage
The invention discloses an application management system used for editing files, in particular an application management system which can online edit the network files; the application management system is provided with an application management interface; the user can complete the file editing operation on the website only by calling the network file starting program and the network file memorizing program of the application management interface without manually downloading and uploading files; the system uses the hyper-file transfer protocol type to automatically start the file and automatically updates the file to the website after completing the edition of the file.
Owner:INVENTEC CORP
System and method for network edge data protection
ActiveUS7607010B2Quick implementationAvoid the needMemory loss protectionUnauthorized memory use protectionDomain nameNetwork Communication Protocols
Disclosed are systems and methods which examine information communication streams to identify and / or eliminate malicious code, while allowing the good code to pass unaffected. Embodiments operate to provide spam filtering, e.g., filtering of unsolicited and / or unwanted communications. Embodiments provide network based or inline devices that scan and scrub information communication in its traffic pattern. Embodiments are adapted to accommodate various information communication protocols, such as simple mail transfer protocol (SMTP), post office protocol (POP), hypertext transfer protocol (HTTP), Internet message access protocol (IMAP), file transfer protocol (FTP), domain name service (DNS), and / or the like, and / or routing protocols, such as hot standby router protocol (HSRP), border gateway protocol (BGP), open shortest path first (OSPF), enhanced interior gateway routing protocol (EIGRP), and / or the like.
Owner:TREND MICRO INC
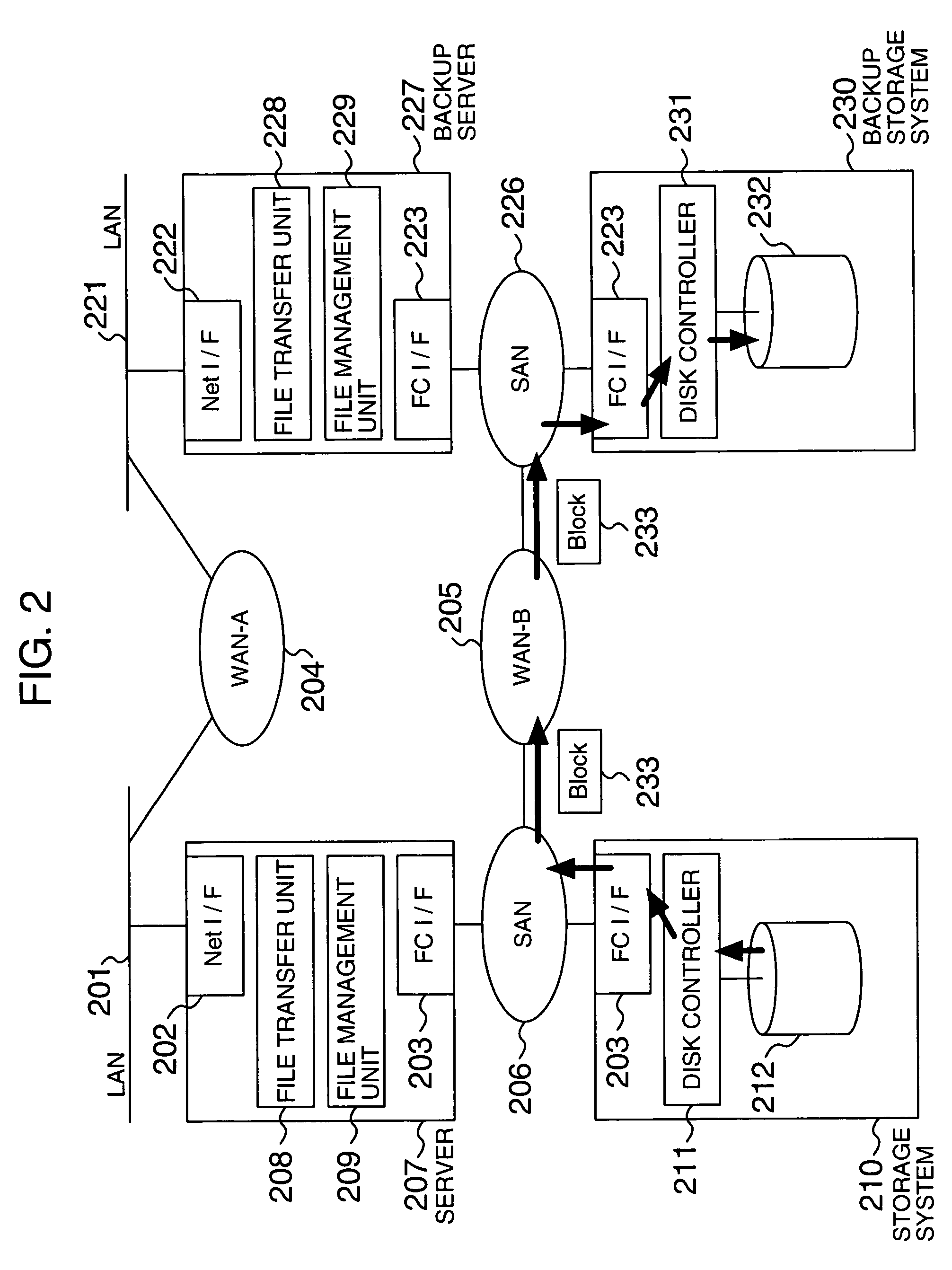
Data transfer method and system
InactiveUS7467235B2Increase speedImprove reliabilityInput/output to record carriersMultiple digital computer combinationsTransmission protocolComputerized system
Owner:HITACHI LTD
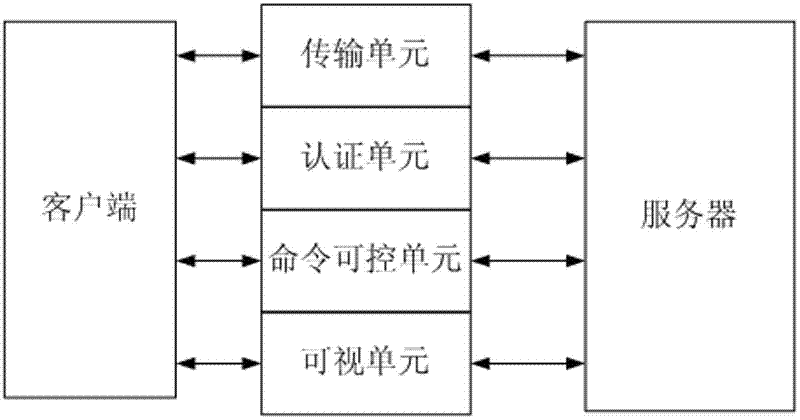
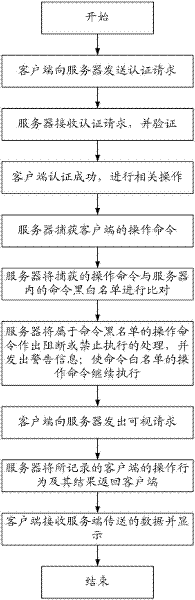
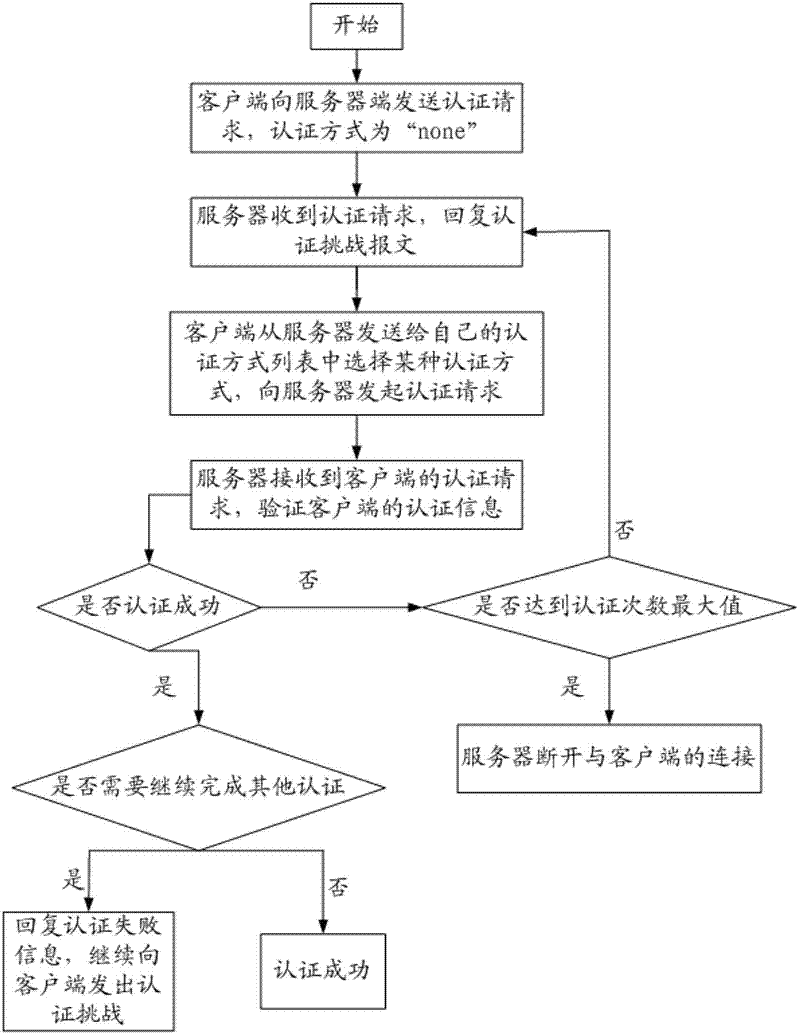
SSH and SFTP (Secure Shell and Ssh File Transfer Protocol)-based tunnel intelligent management and control system and method
ActiveCN102333068AUnderstand operabilityUnderstand the resultsTransmissionControl systemIntelligent management
The invention relates to an SSH and SFTP (Secure Shell and Ssh File Transfer Protocol)-based tunnel intelligent management and control system which comprises a transmission unit and an authentication unit, and also comprises a command controllable unit, wherein the command controllable unit is used for capturing an operation command used by a client end and judging and processing the feasibility of the operation command. The invention relates to an SSH and SFTP-based tunnel intelligent management and control method. The invention has the beneficial effects of enabling the tunnel management and operation to be visible, controllable and manageable, solving the safety problem and the safety threats of SSH and SFTP server system levels and providing reliable safety guarantee for normal order operation of the server in a company IT environment.
Owner:北京思特奇信息技术股份有限公司
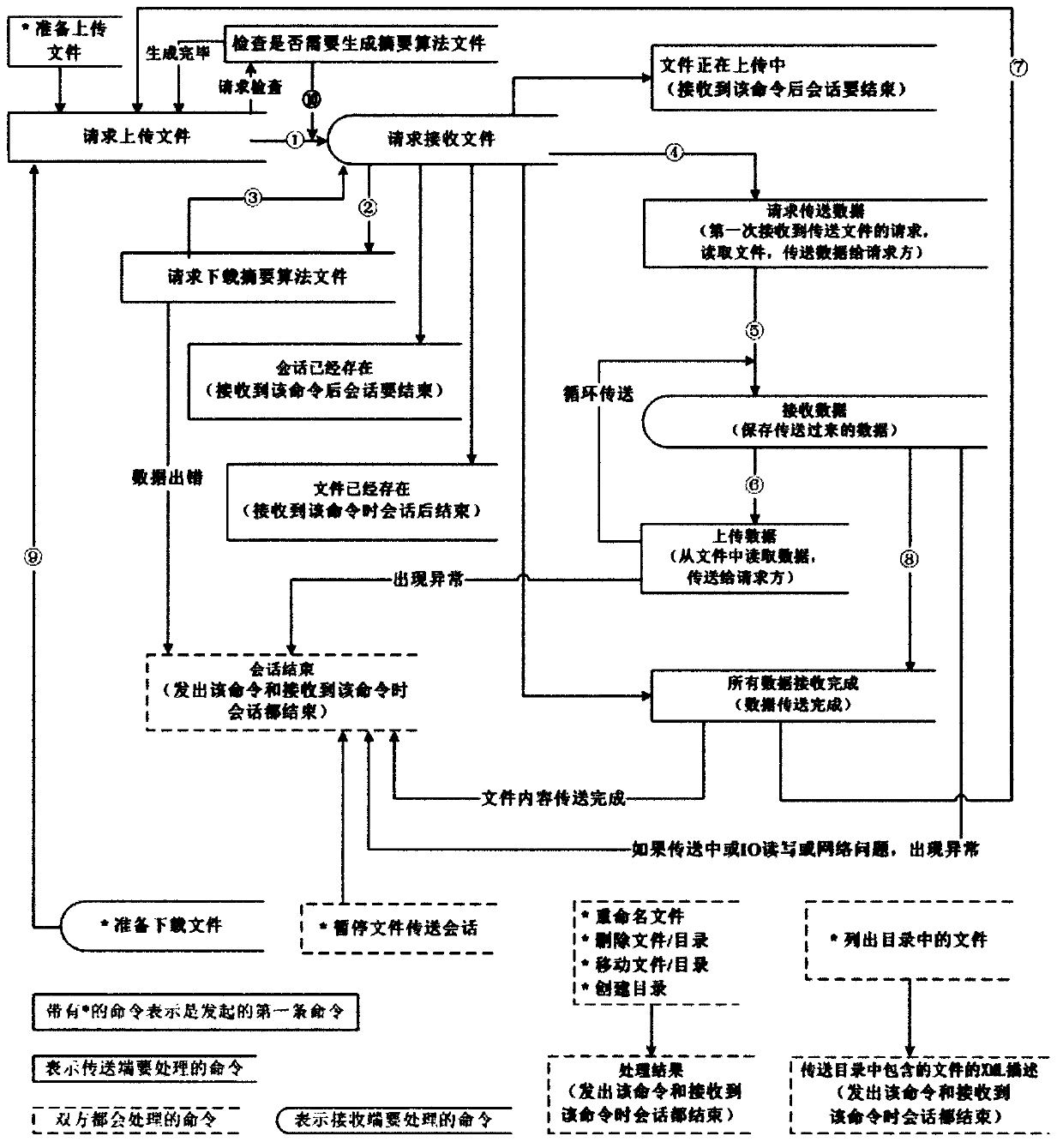
File transfer protocol
InactiveCN103281362ARealize uploadRealize downloadTransmissionTransmission protocolSSH File Transfer Protocol
The invention discloses a file transfer protocol. Under the condition of only establishing a connection, a plurality of files are simultaneously uploaded and downloaded, and other commands such as deletion, pause, shift, listing and directory creation can be synchronously executed. When the files are uploaded or downloaded, digest algorithm files are automatically generated, and the whole file transfer flow is completed by transmitting the digest algorithm files, checking the file integrity and transferring file main bodies. A user is required to transmit a file name comprising a path only, and a file can be uploaded and downloaded; and moreover, whether the content of the file existing in a terminal and the content of a file existing in a server are completely consistent can be immediately detected, and if difference is discovered, the file can be automatically uploaded again, the file transfer reliability is improved and the file transfer protocol can replace the conventional file transfer protocol (FTP).
Owner:周信兰
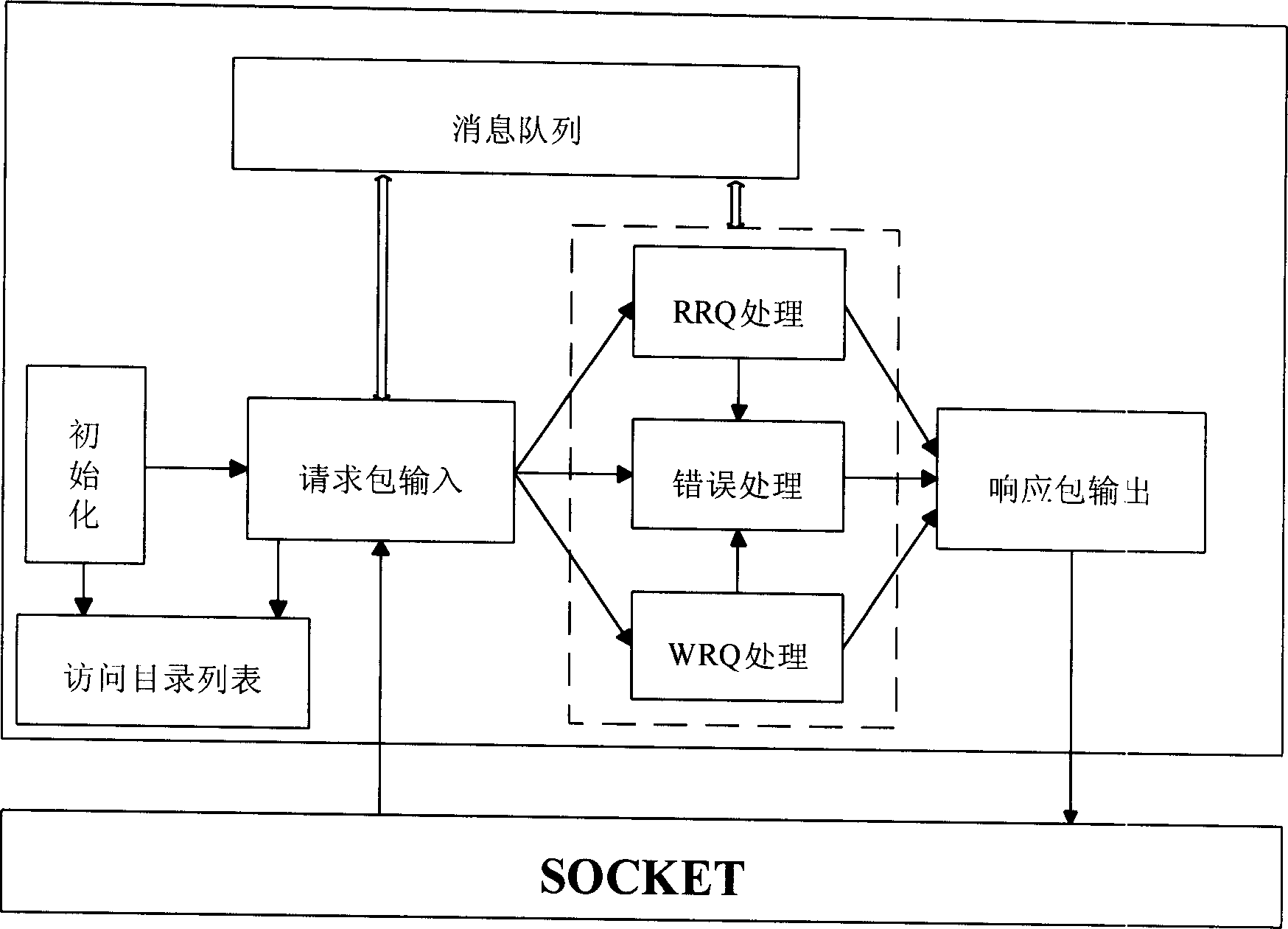
File transmission method, system, client and server based on trivial file transfer protocol (TFTP)
InactiveCN102355480AEnhanced Defense MechanismsImprove transmission success rateError prevention/detection by using return channelFile transmissionClient-side
The invention provides a file transmission method, a system, a client and a server based on a trivial file transfer protocol (TFTP). The file transmission method comprises the following steps that: a client sends a first authentication information to a server so that the server performs authentication to the client; when the authentication to the client from the server passes, file data transmission can be performed between the client and the server. By using the method, the system, the client and the server, security of a TFTP transmission system can be raised.
Owner:ZTE CORP
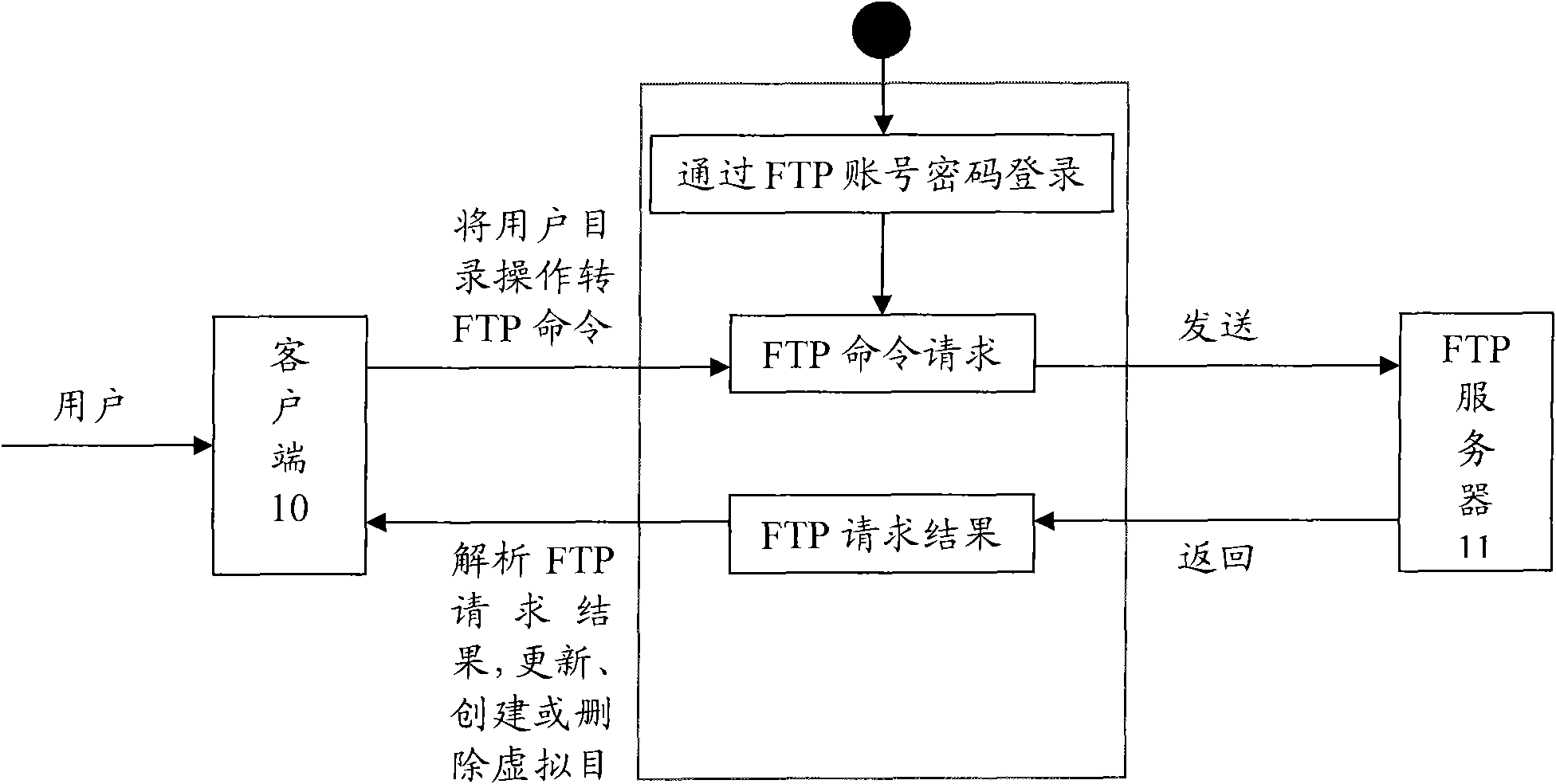
Method, device and system for managing FTP (file transfer protocol) server
ActiveCN102148839AReduce complexityImprove management efficiencyData switching networksManagement processNetworked system
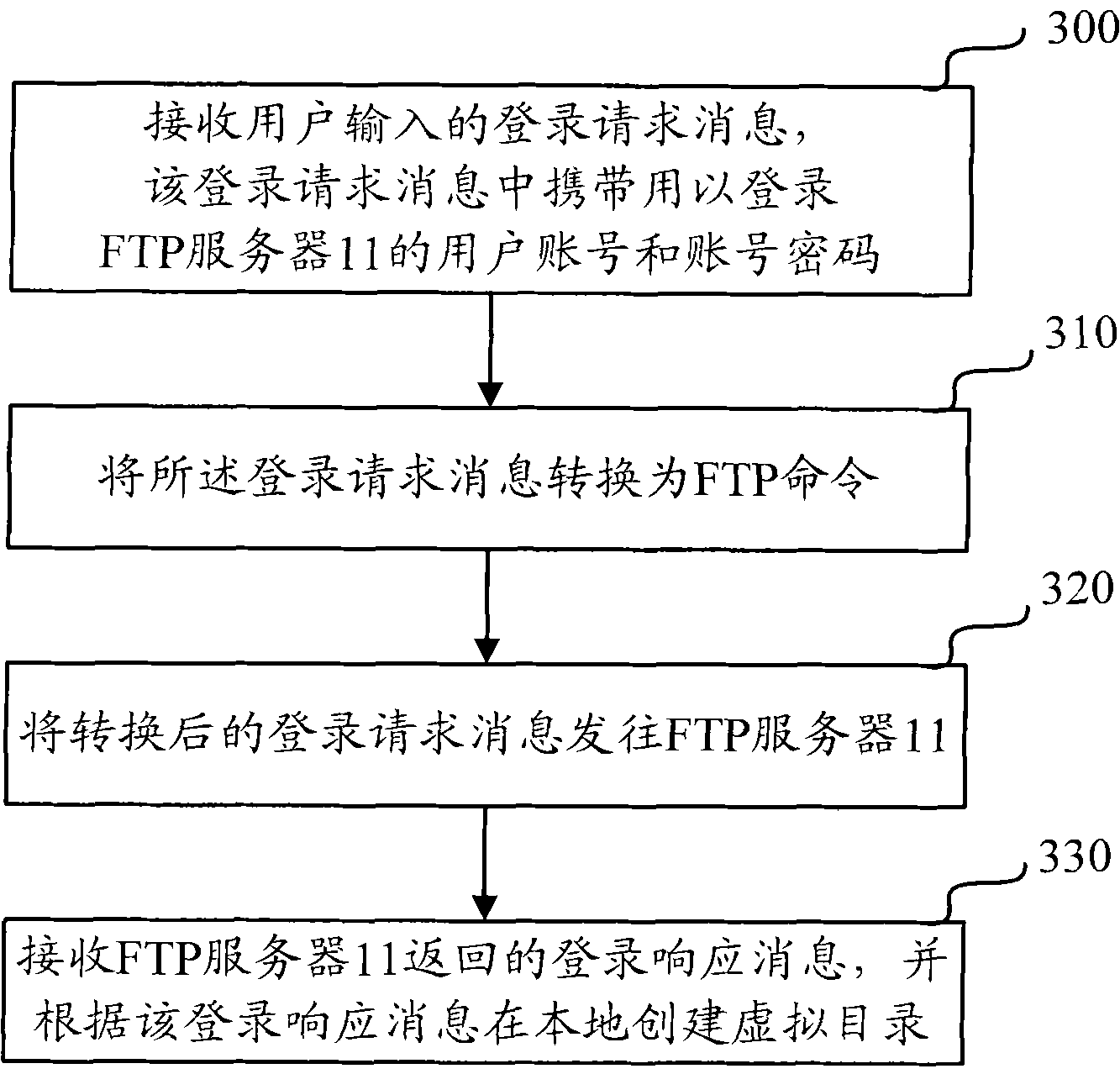
The invention relates to the communication technology and discloses a method, a device and a system for managing an FTP (file transfer protocol) server, which are used for reducing the complexity of the management flow of the FTP server. The method comprises the steps as follows: an FTP virtual directory is configured in a client; the FTP virtual directory is the virtual mapping of the data on the FTP server at a client; after a user logins the FTP server, non-FTP format data management command information inputted by the user through the virtual directory is received; then the non-FTP format data management command information is converted into FTP format data management command information, and sent to the FTP server to indicate the FTP server to execute corresponding data management operations. In this way, operations like downloading, modification, uploading are implemented on the data in the FTP server; therefore, the complexity of the management flow of the FTP server is effectively reduced; and the management efficiency of the management flow of the FTP server is improved. Meanwhile, the running load of a system is obviously reduced. The invention also discloses a client and a network system.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Methodology for fast file transfer protocol
ActiveUS7016967B2Multiple digital computer combinationsElectric digital data processingFile Transfer ProtocolDatabase
Owner:NORTHROP GRUMMAN SYST CORP
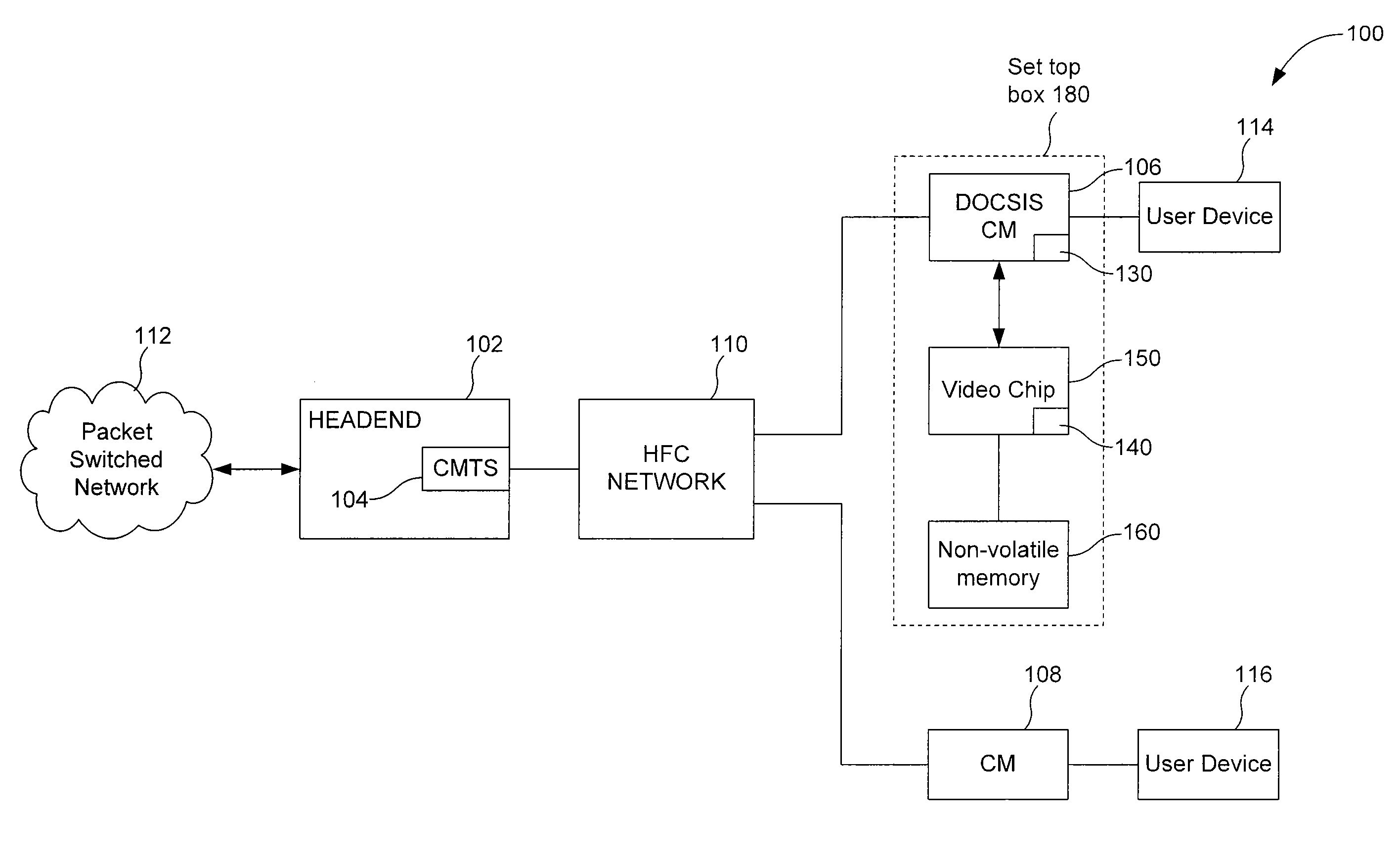
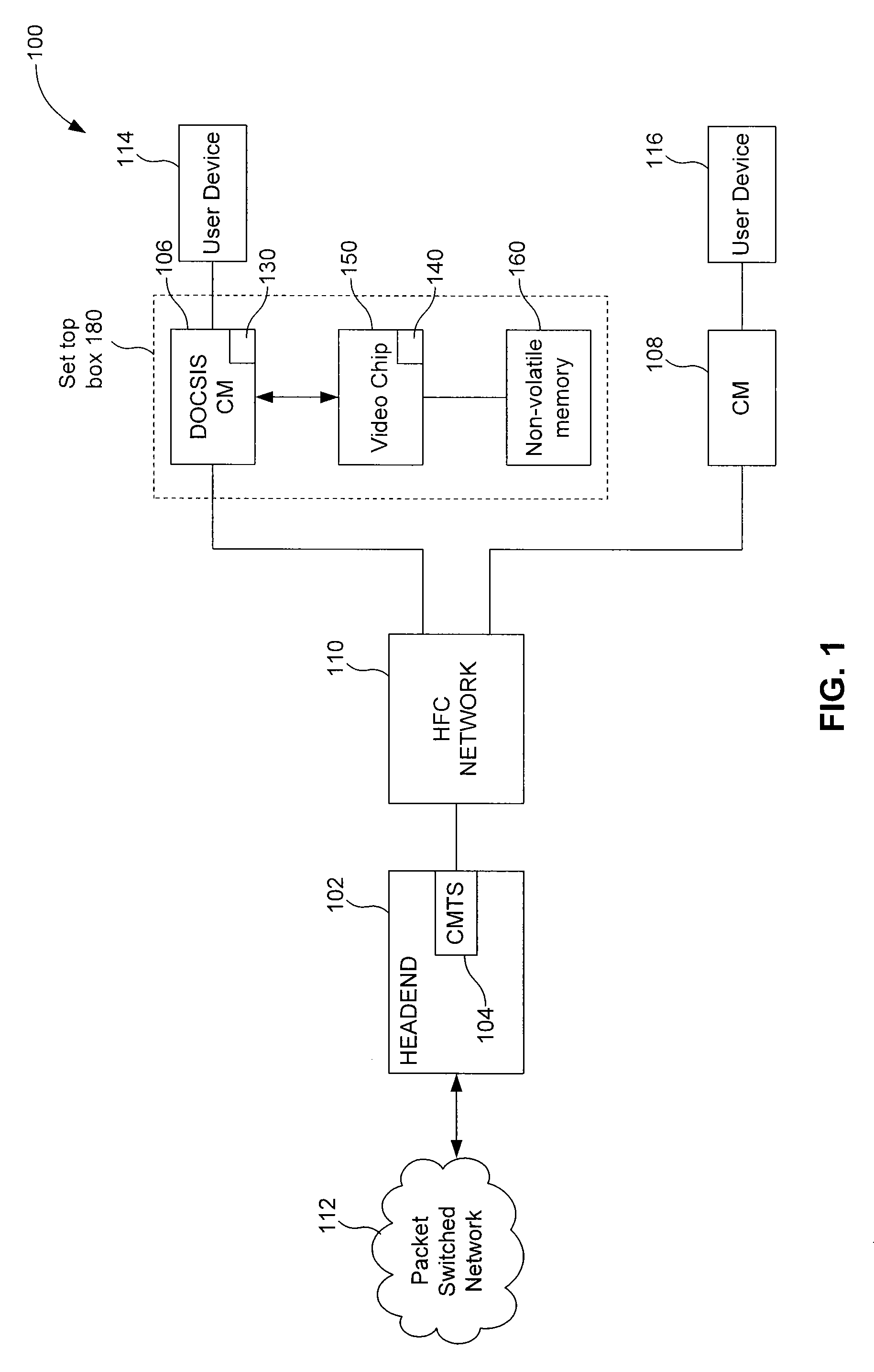
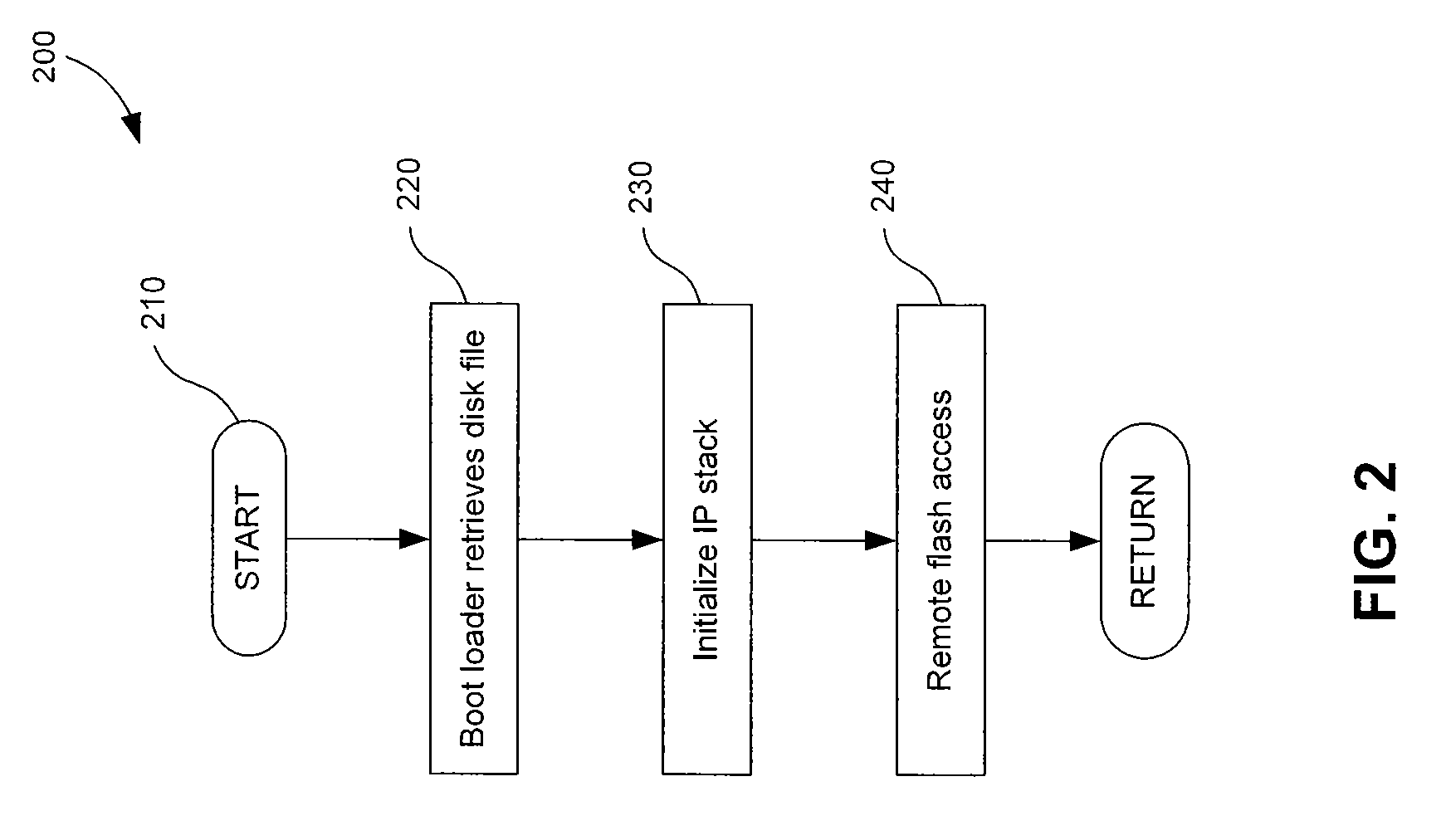
Remote Flash Access
InactiveUS20080043781A1Time-division multiplexInput/output processes for data processingByteComputer science
A system, method, and computer program product for allowing a first processor to access flash or other non-volatile memory that is associated with a second processor. The first processor obtains parameters that allow the initialization of an internet protocol (IP) stack. The parameters can be obtained using the trivial file transfer protocol (TFTP), for example. The first processor communicates with the second processor using a socket protocol, sending a command word that represents either a read or write command. The command word specifies where in the non-volatile memory the access is to occur, and for how many bytes. Information is then returned to the first processor, allowing the first processor to verify the success of the access.
Owner:AVAGO TECH INT SALES PTE LTD
Remote file transmission method
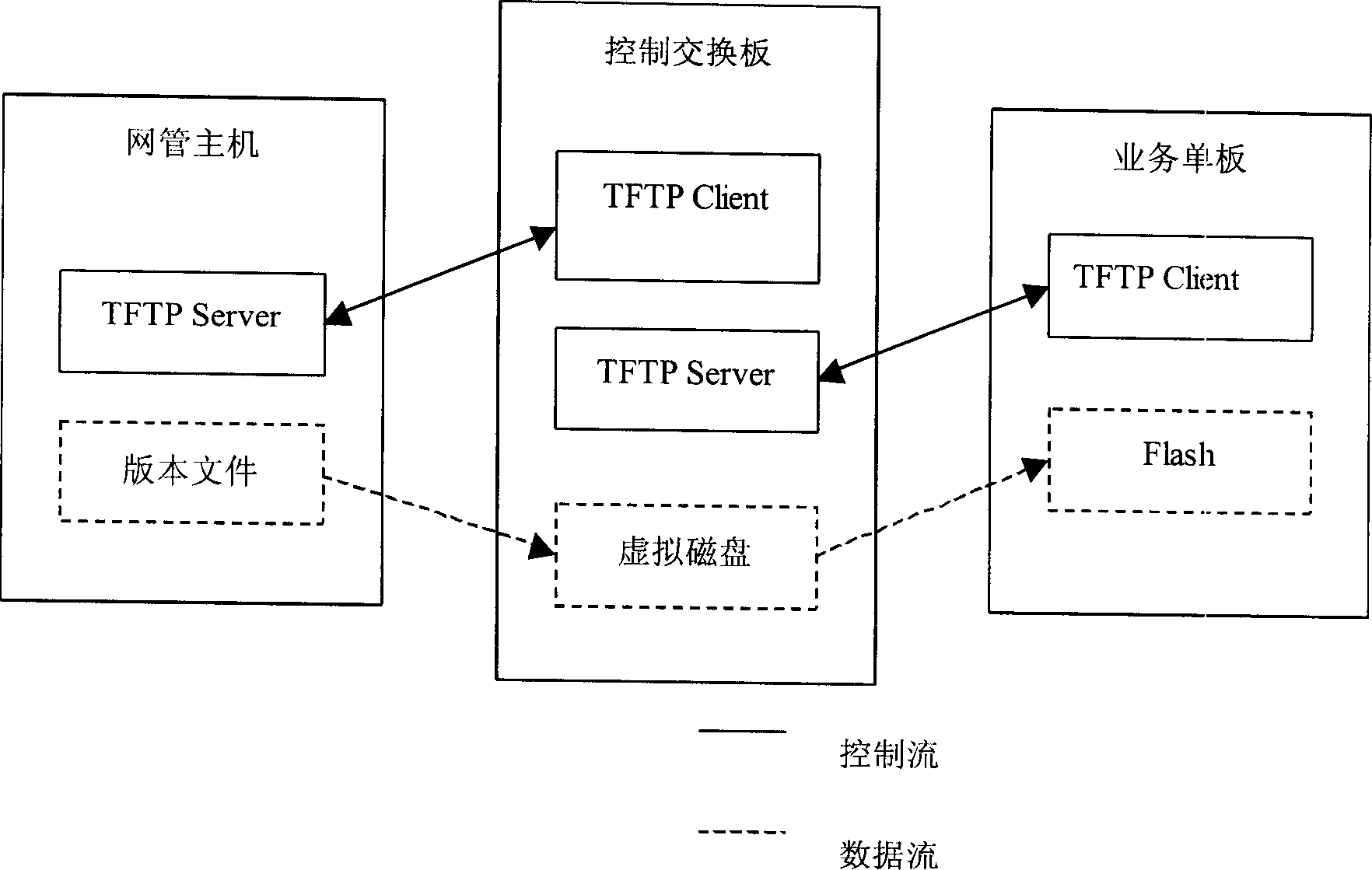
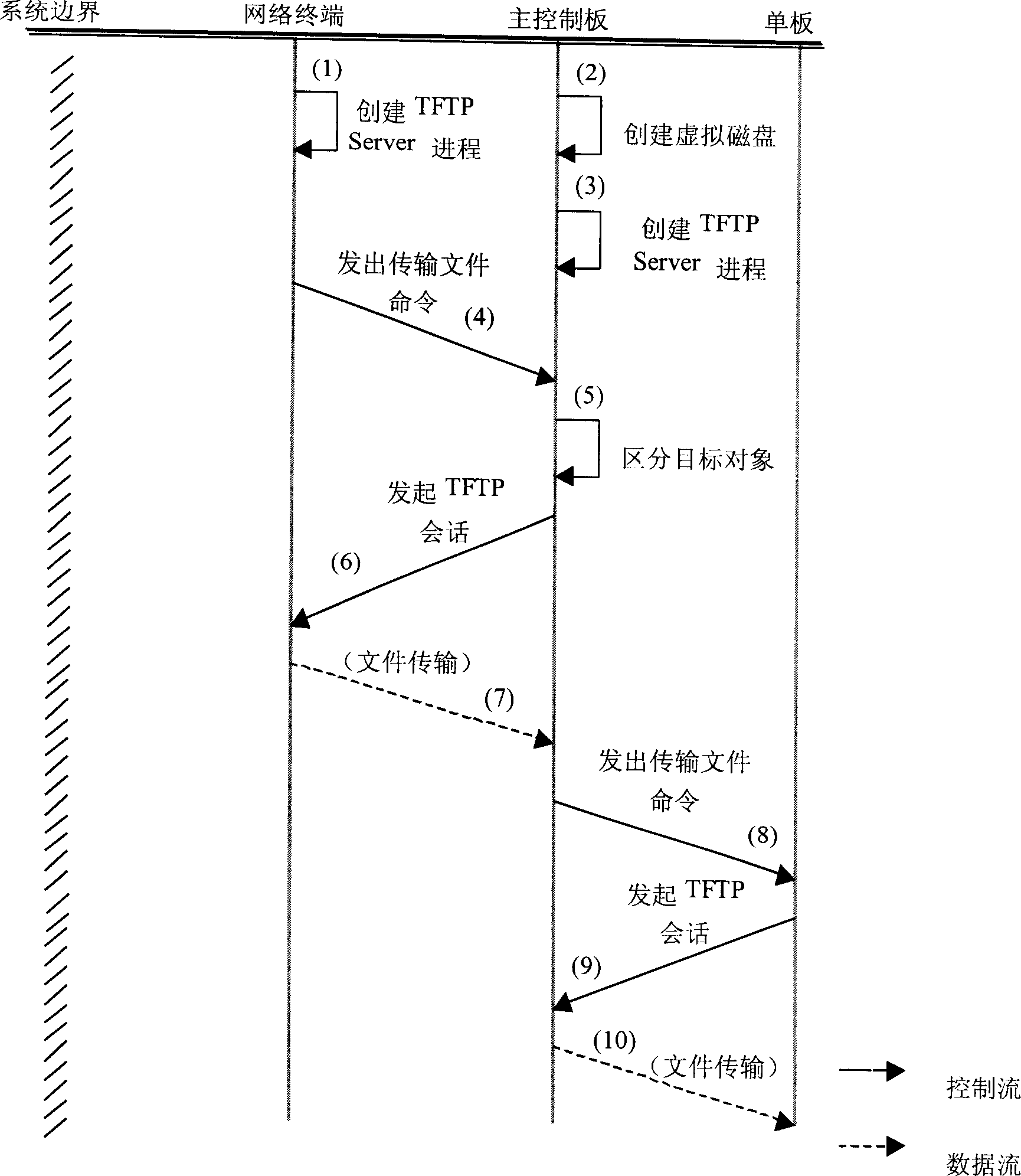
InactiveCN1426209ARealize transmissionImprove reading and writing efficiencyData switching by path configurationNetwork terminationClient-side
This invention provides a telecommunication level high efficiency, reliable remote file transfer method realizing file transfer function based on TFTP (trivial file transfer protocol). The basic idea is to start TFTP server on network terminal and start TFTP customer end on the main control panel to realize file transfer between them, and at the second level file transfer, TFTP server operates on the main control panel and TFTP customer program is started at service single panel, again to utilize TFTP protocol to transfer file to the service single panel, fully utilizing TFTP to realize file transfer without storing file in flash memory first with very high read, write efficiency. 0
Owner:ZTE CORP
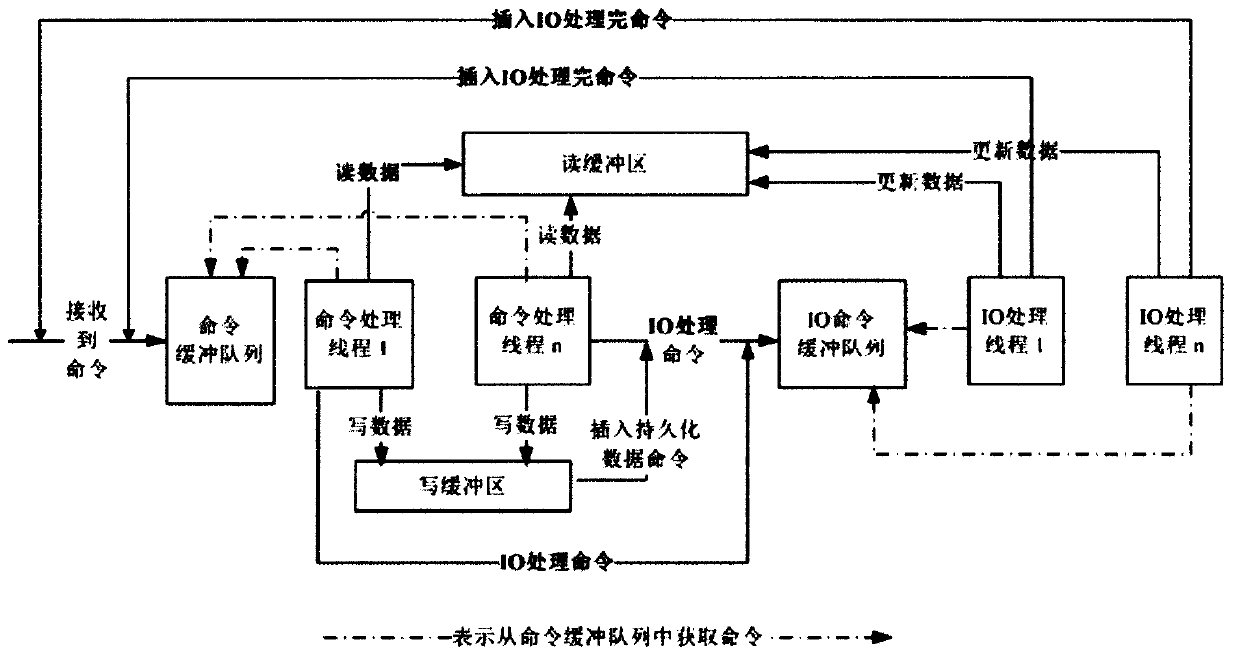
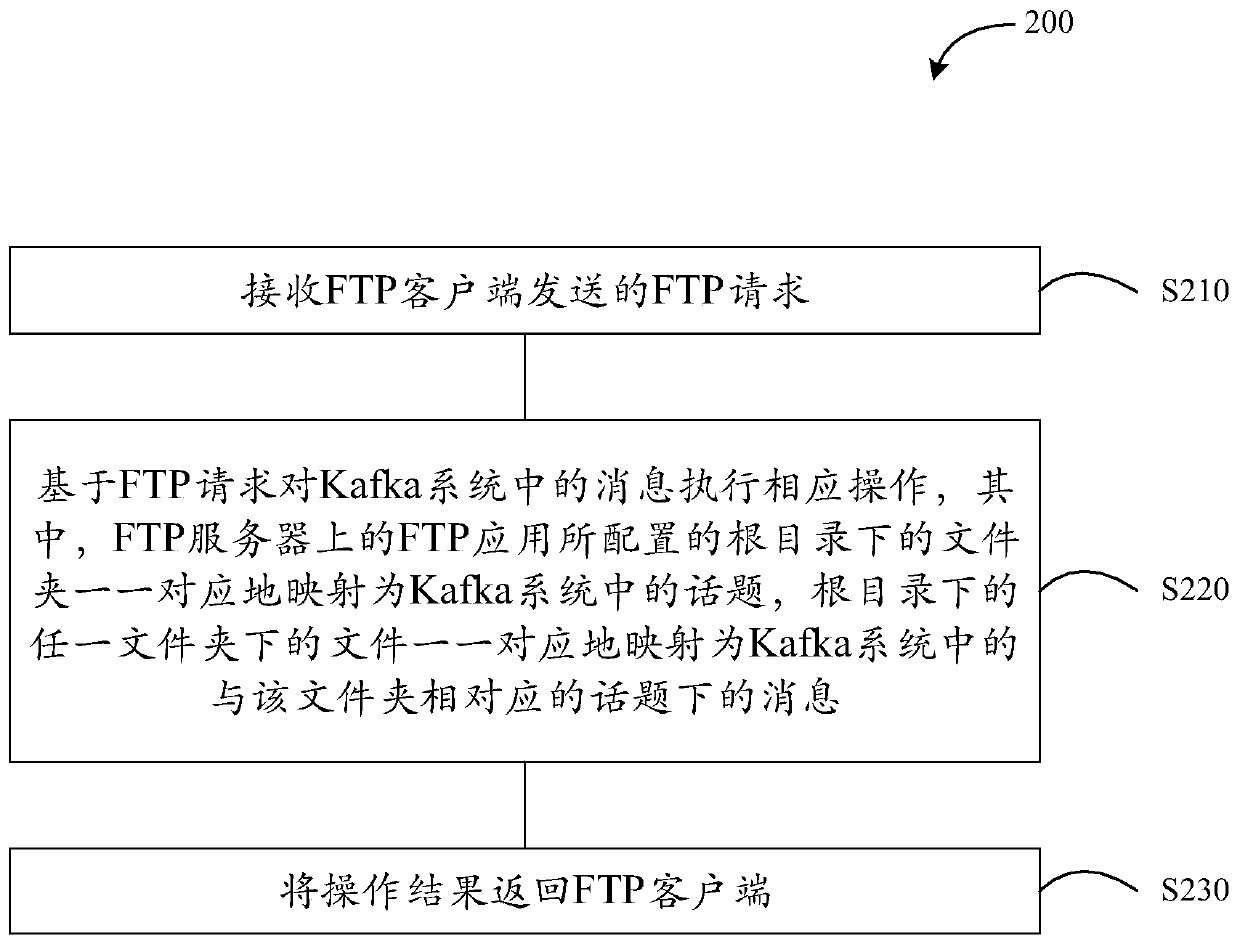
File management method, file transfer protocol server and storage medium
ActiveCN110401724AReduce the number of IOsReduce the transmission linkTransmissionClient-sideData transmission
The embodiment of the invention provides a file management method, an FTP server and a storage medium. The method comprises the following steps: receiving an FTP request sent by an FTP client; executing corresponding operation on the message in the kafka system based on the FTP request, wherein folders under a root directory configured by an FTP application on the FTP server are mapped into topicsin a kafka system in a one-to-one correspondence manner, and files under any folder under the root directory are mapped into messages under topics corresponding to the folders in the kafka system ina one-to-one correspondence manner; and returning the operation result to the FTP client. According to the method, the transmission link can be shortened, and the disk IO frequency can be reduced, sothat the fault probability can be reduced, and the data transmission efficiency of the FTP system can be effectively improved.
Owner:BEIJING KUANGSHI TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com