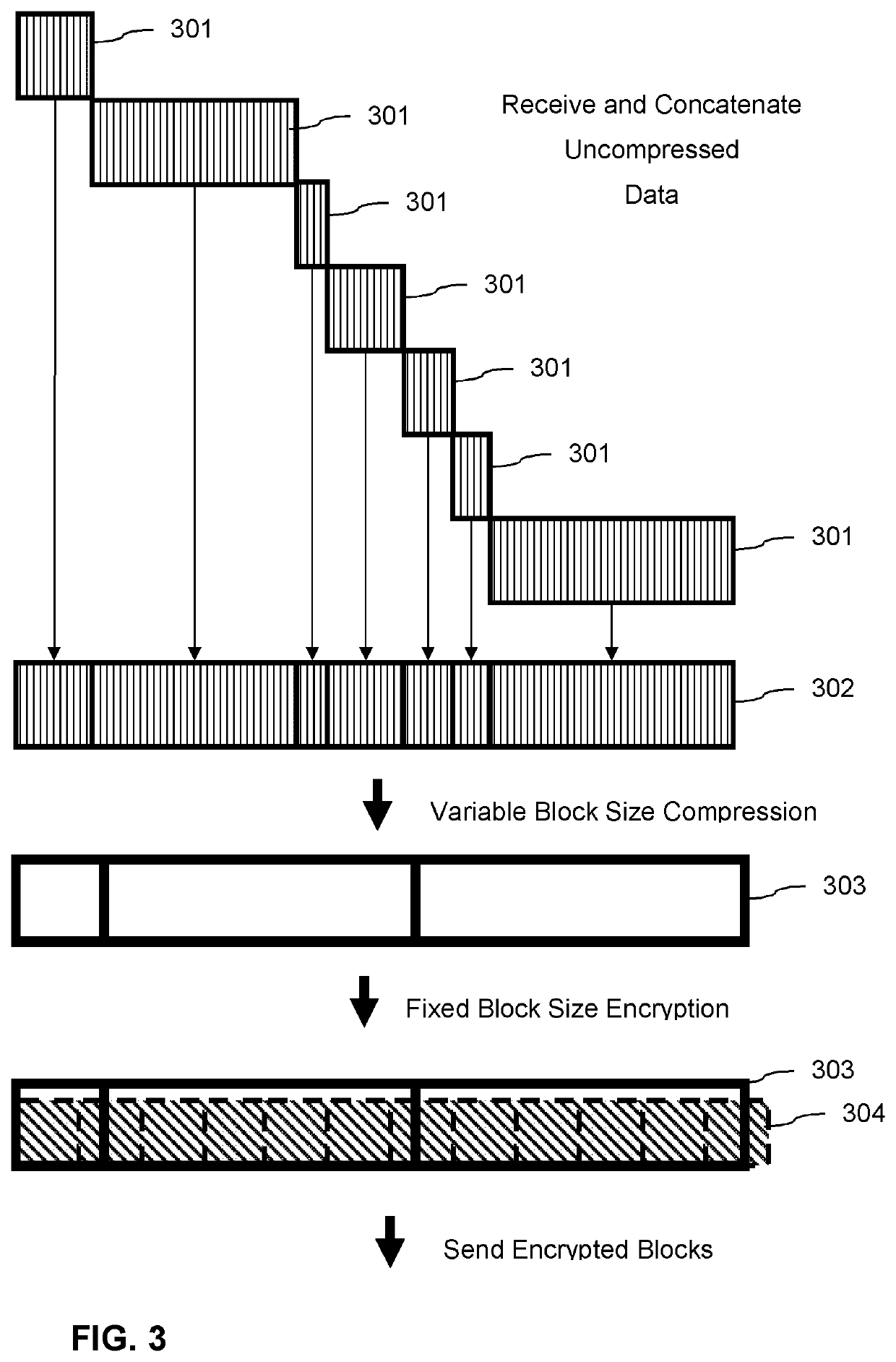
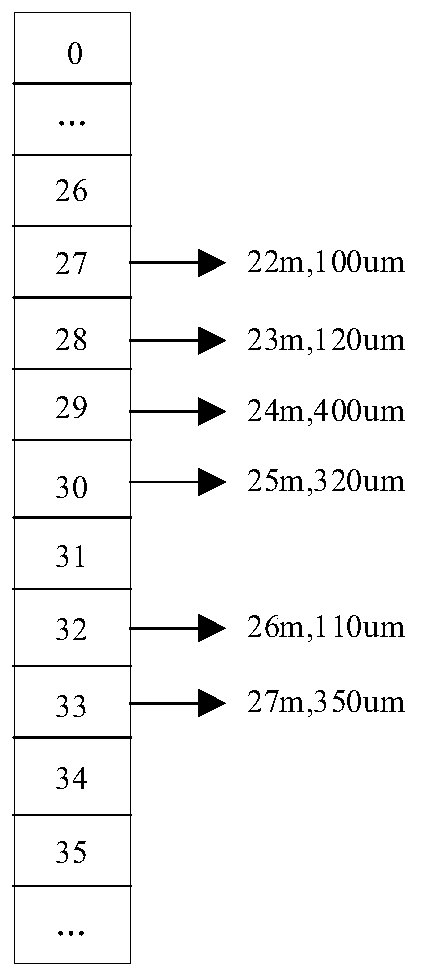
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Splaysort" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, splaysort is an adaptive comparison sorting algorithm based on the splay tree data structure.
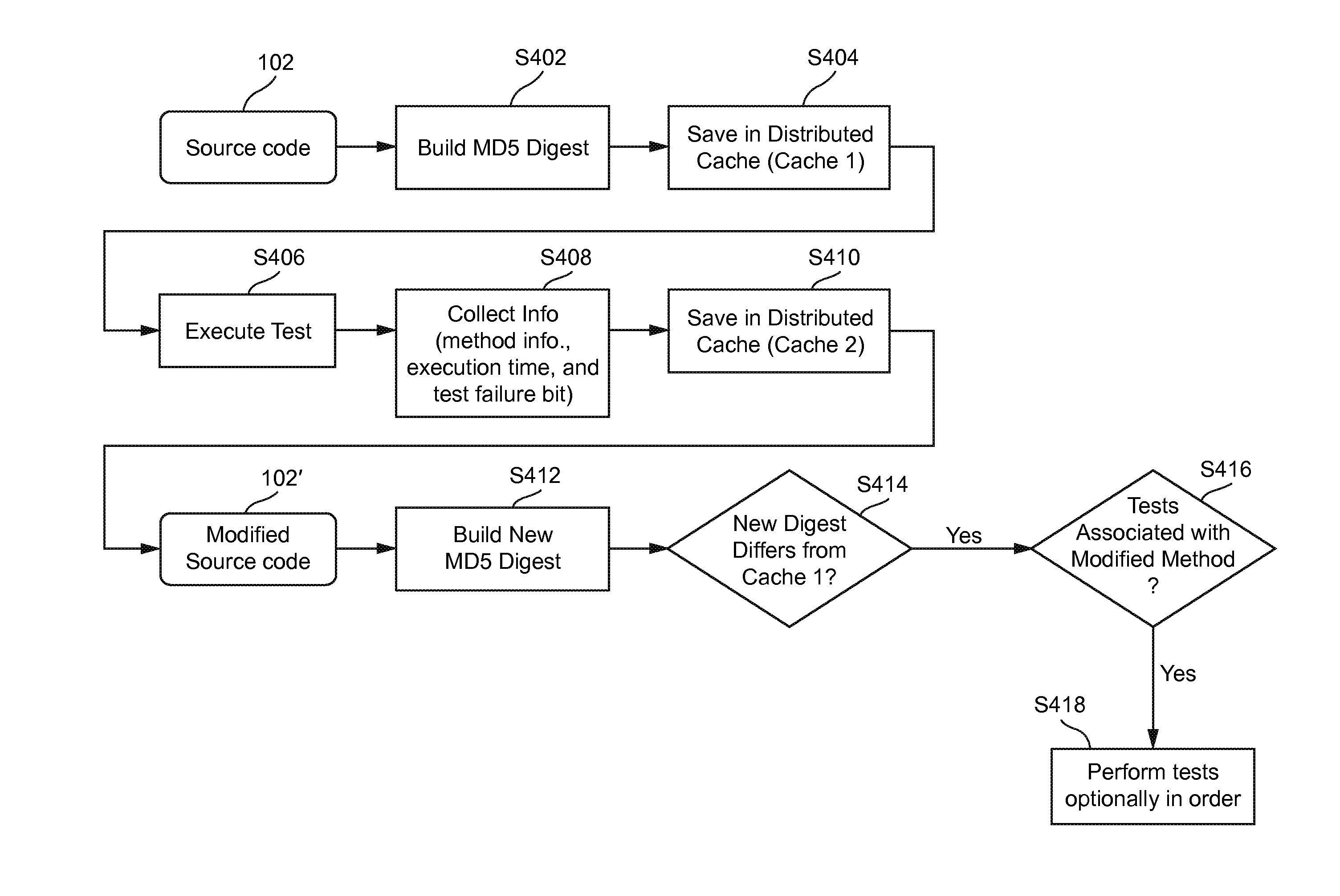
Systems and/or methods for executing appropriate tests based on code modifications using live, distributed, real-time cache and feedback loop
ActiveUS20130254746A1Error detection/correctionSpecific program execution arrangementsTheoretical computer scienceStructuring element
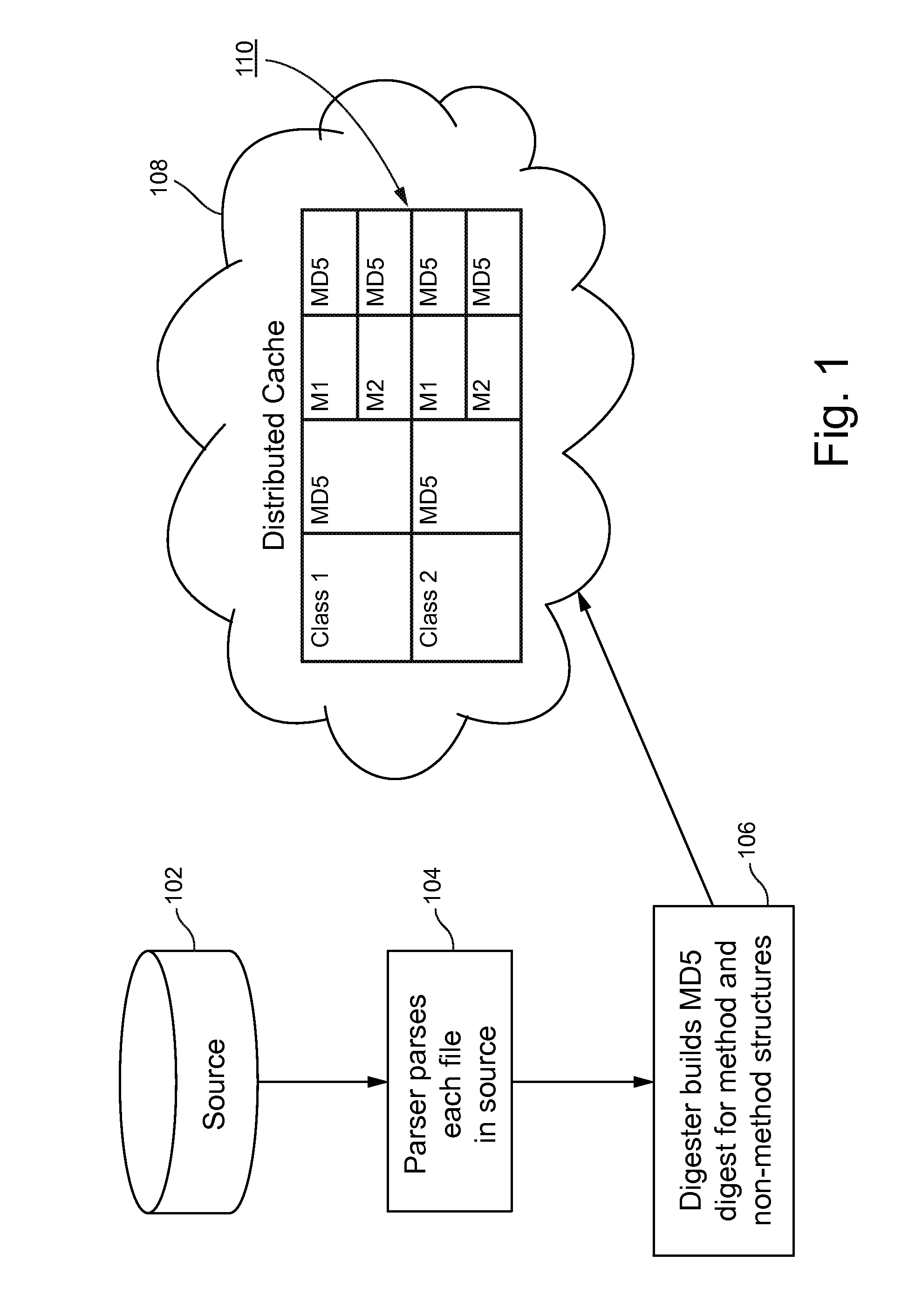
Certain example embodiments relate to systems and / or methods for determining and / or executing an appropriate subset of tests in response to a code change. In certain example embodiments, hash digests or other unique values for code structures (such as, for example, classes, methods, and / or other structural elements) may be created. Tests associated those associated code structures may be identified. New hash digests or other unique values may be generated for the code structures after the source code has been modified. In response to a mismatch as between the existing and new hash digests or other unique values, a list of associated tests for possible subsequent execution may be retrieved. Certain example embodiments additionally or alternatively provide an incremental but consistent way of analyzing performance issues, e.g., in connection with a profiler.
Owner:SOFTWARE AG
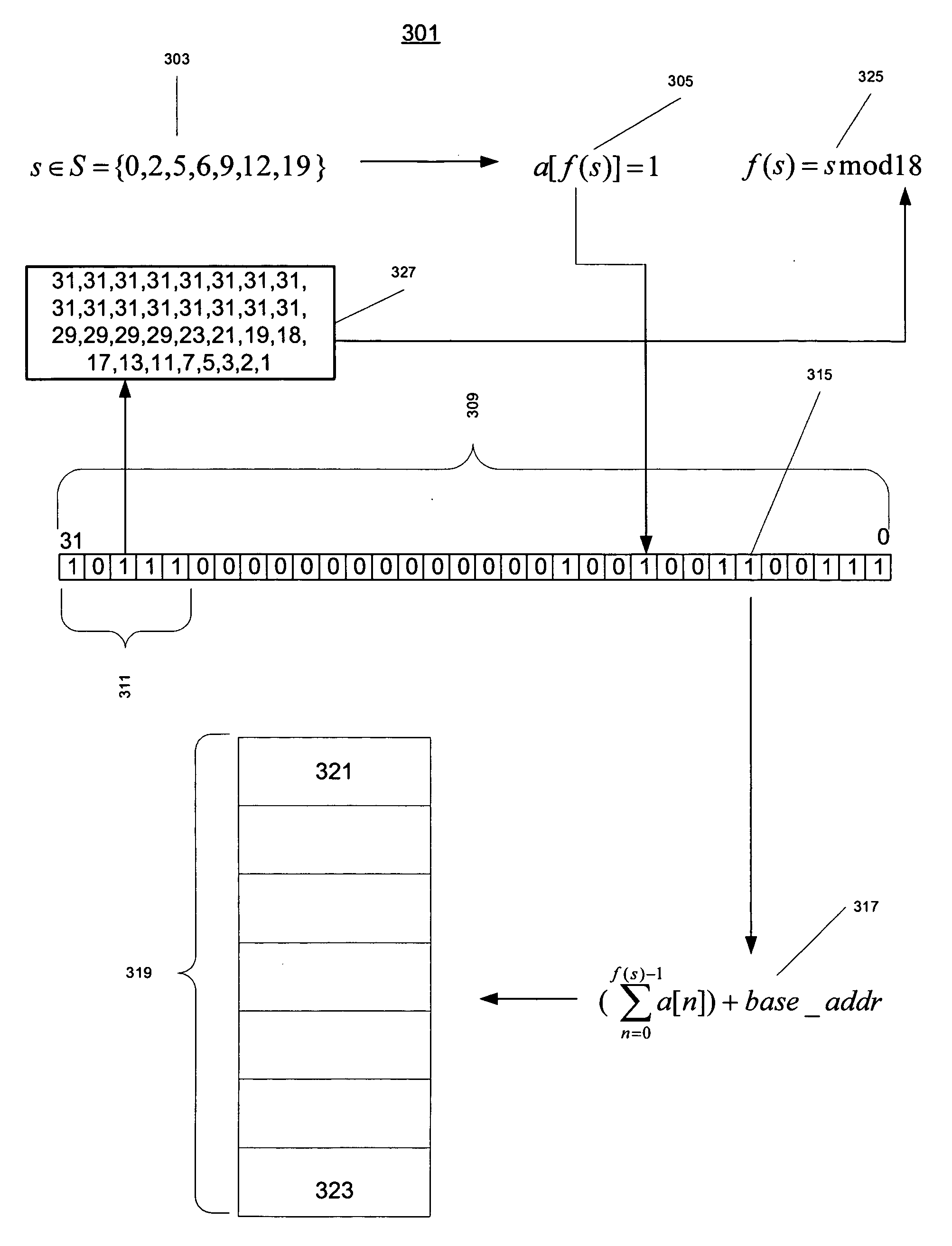
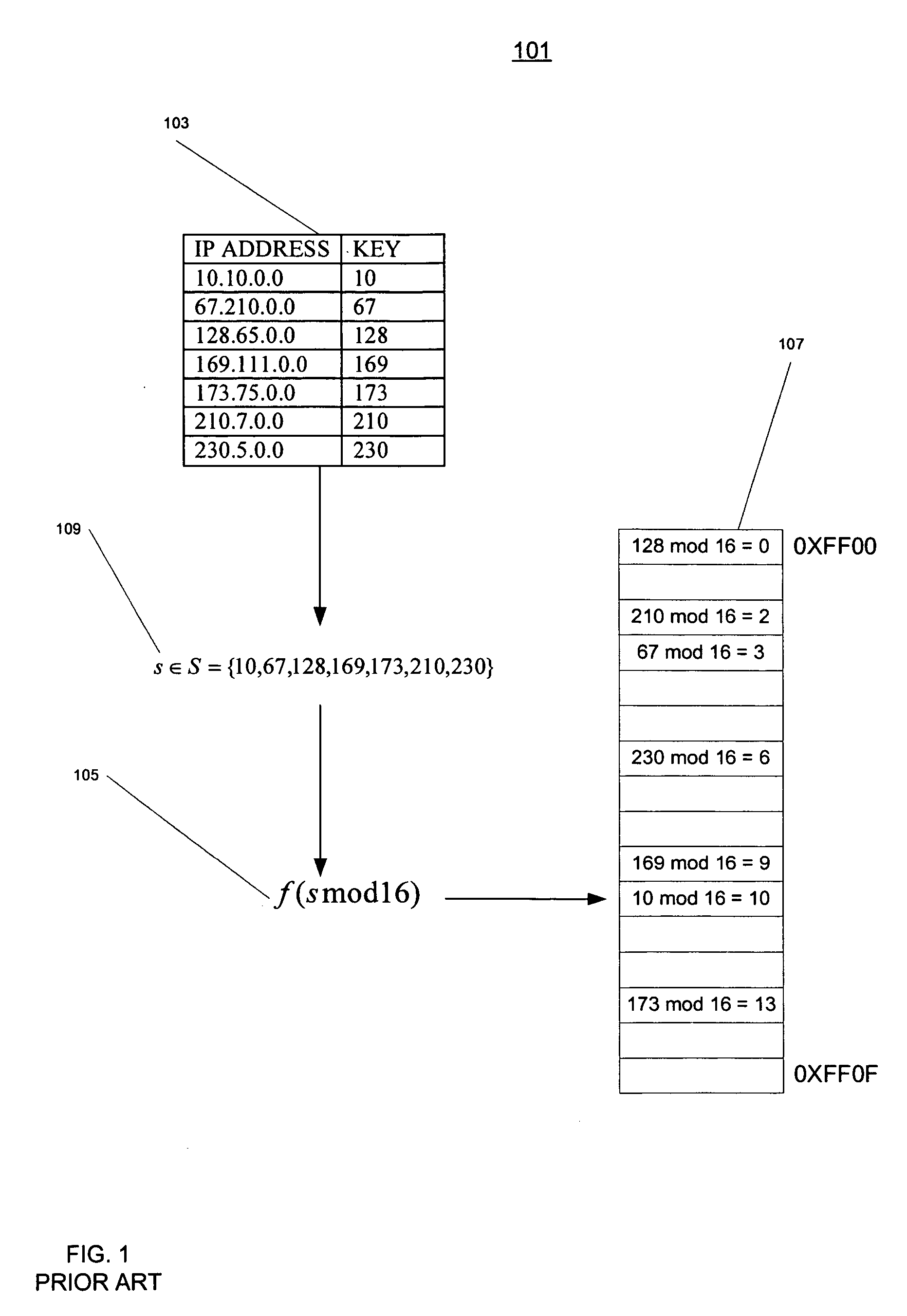
Method and apparatus for finding a perfect hash function and making minimal hash table for a given set of keys
InactiveUS20060248079A1Digital data information retrievalDigital data processing detailsTheoretical computer sciencePerfect hash function
A representation used in a computer system to represent a set of data items that correspond to and are accessible by means of a set of keys. The representation includes an array of the data items and a bit string associated with the array. Each key is mapped onto a bit of the bit string by means of a hash function that is perfect for the set of keys. The mapped bit is set. The data item corresponding to the key has a position in the array that corresponds to the position of the bit for the key in the bit string. Methods for reading and writing the representation are disclosed as well as a technique based on the mod operation and a set of co-prime numbers for finding a perfect hash function for a given set of keys.
Owner:FREESCALE SEMICON INC
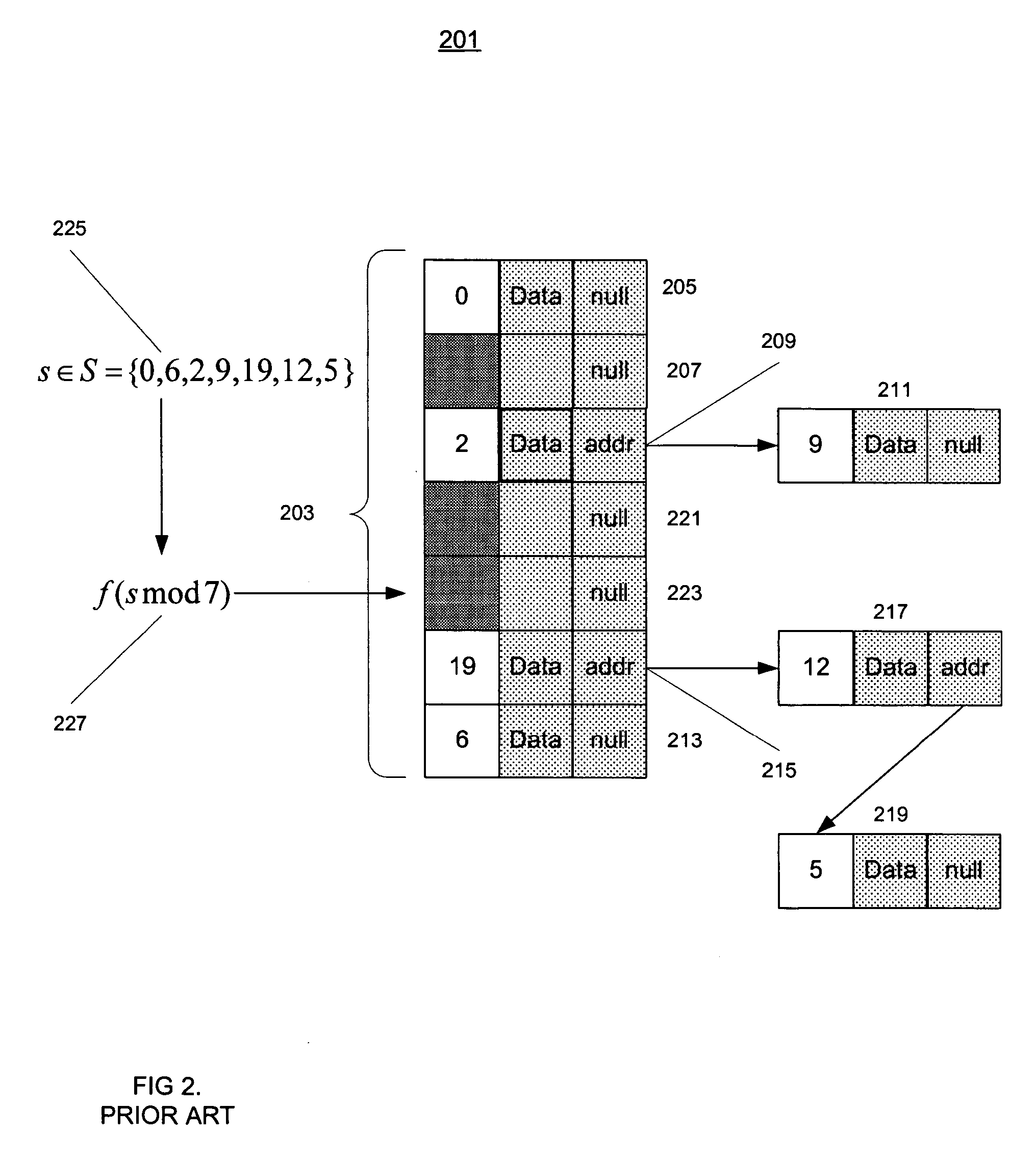
Binding by hash
InactiveCN1535417ADigital data processing detailsDigital data protectionTheoretical computer scienceSplaysort
A system and method is provided for providing security to components or assemblies employed by application programs during runtime. Assemblies carry version information that can be used to enforce the versioning rules described by the application program. At runtime, version numbers requested by the application programs are compared with those version numbers of the assemblies that are actually found. In addition to comparing version numbers, the present invention offers a stricter form of version checking based on cryptographic hashes. An assembly is provided with module information that contains a list of the files that make up the assembly. Part of the information recorded about each module is a hash of the module's contents at the time the manifest was built. An assembly referencing another assembly computes the hash of the manifest of the referenced assembly. An assembly manifest may include dependency information, which is information about other assemblies that the assembly depends on or references. Part of the information stored as part of an assembly reference or manifest is a hash of the dependent assembly's manifest.
Owner:MICROSOFT TECH LICENSING LLC
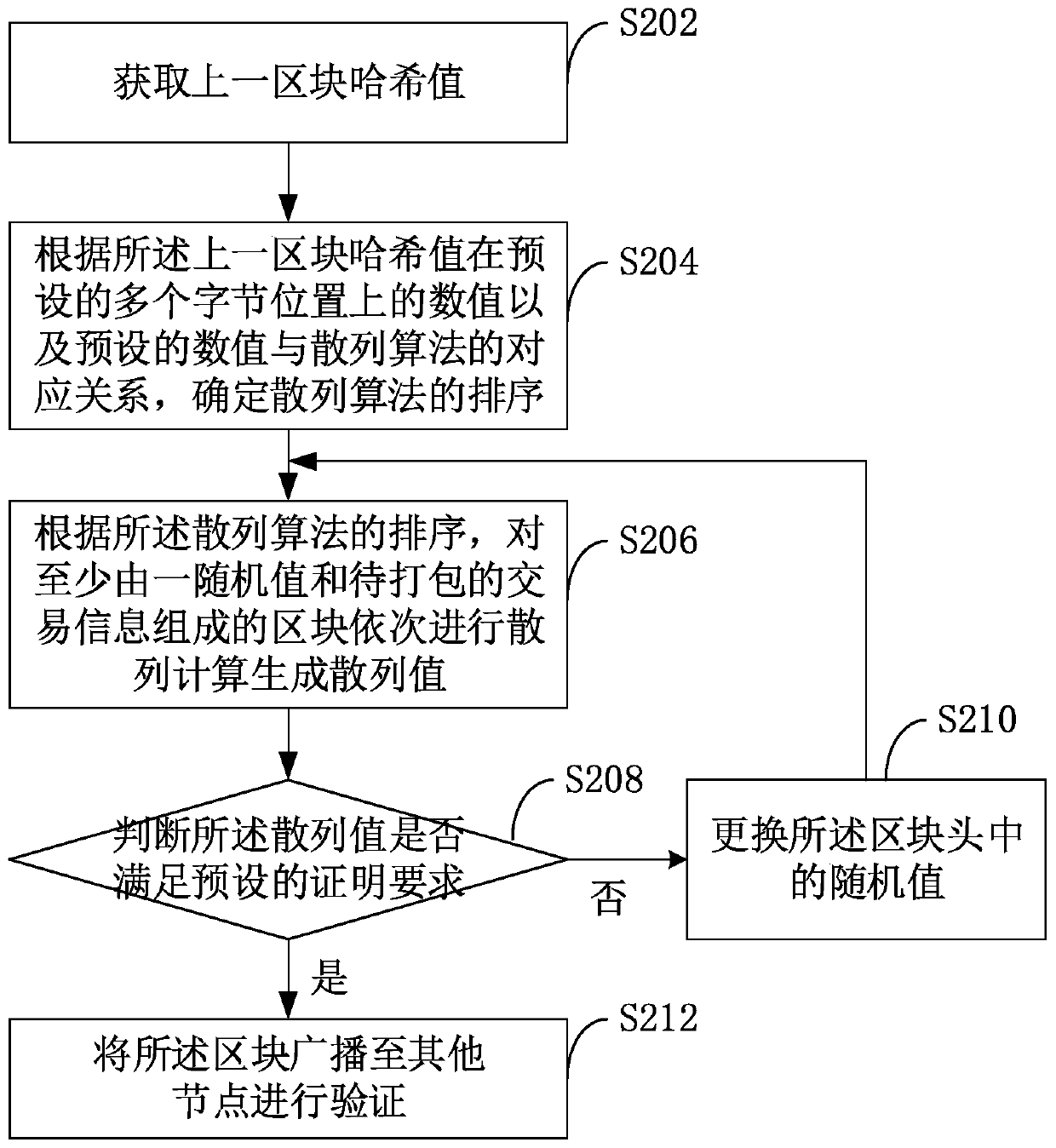
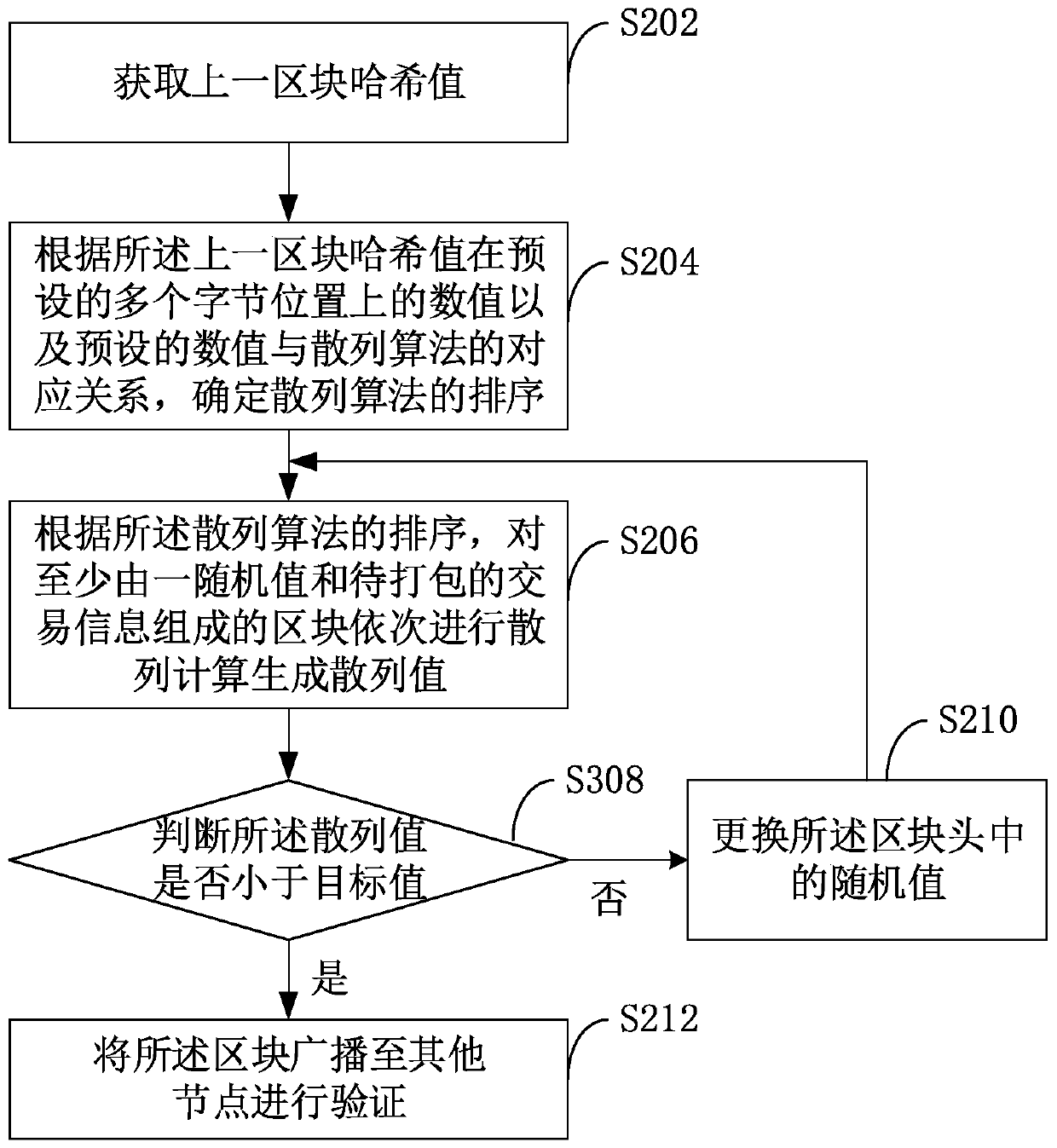
Proof of work (PoW) certification method in blockchain network and blockchain
PendingCN111563277AMaintain decentralized distributed thinkingMaintain Distributed ThoughtsDigital data protectionTheoretical computer scienceRandom order
The invention is applicable to the technical field of computers, and provides a PoW certification method in a blockchain network and a blockchain, the PoW certification method comprises the followingsteps: acquiring a hash value of a previous block; according to the numerical value of the hash value of the previous block and a corresponding relationship between the numerical value and a hash algorithm, determining the sequence of the hash algorithm; sequentially carrying out hash calculation on blocks consisting of a random value and the transaction information to be packaged according to thethe sequence of a hash algorithm to generate hash values; and replacing the random value, repeating the previous steps until the hash value meets the PoW certification requirement, and broadcasting the block to other nodes for verification. According to the PoW method provided by the invention, the sequence of the hash algorithm is linked with the numerical value of the previous block, so that ahash algorithm used by the blockchain decentralization method each time is a random sequence, and a CPU and a GPU can better adapt to the random sequence, so that the advantages of ASIC in computing power are offset, and the distributed idea of blockchain decentralization is maintained.
Owner:上海坤振集成电路有限公司
Adaptive Rate Compression Hash Processor
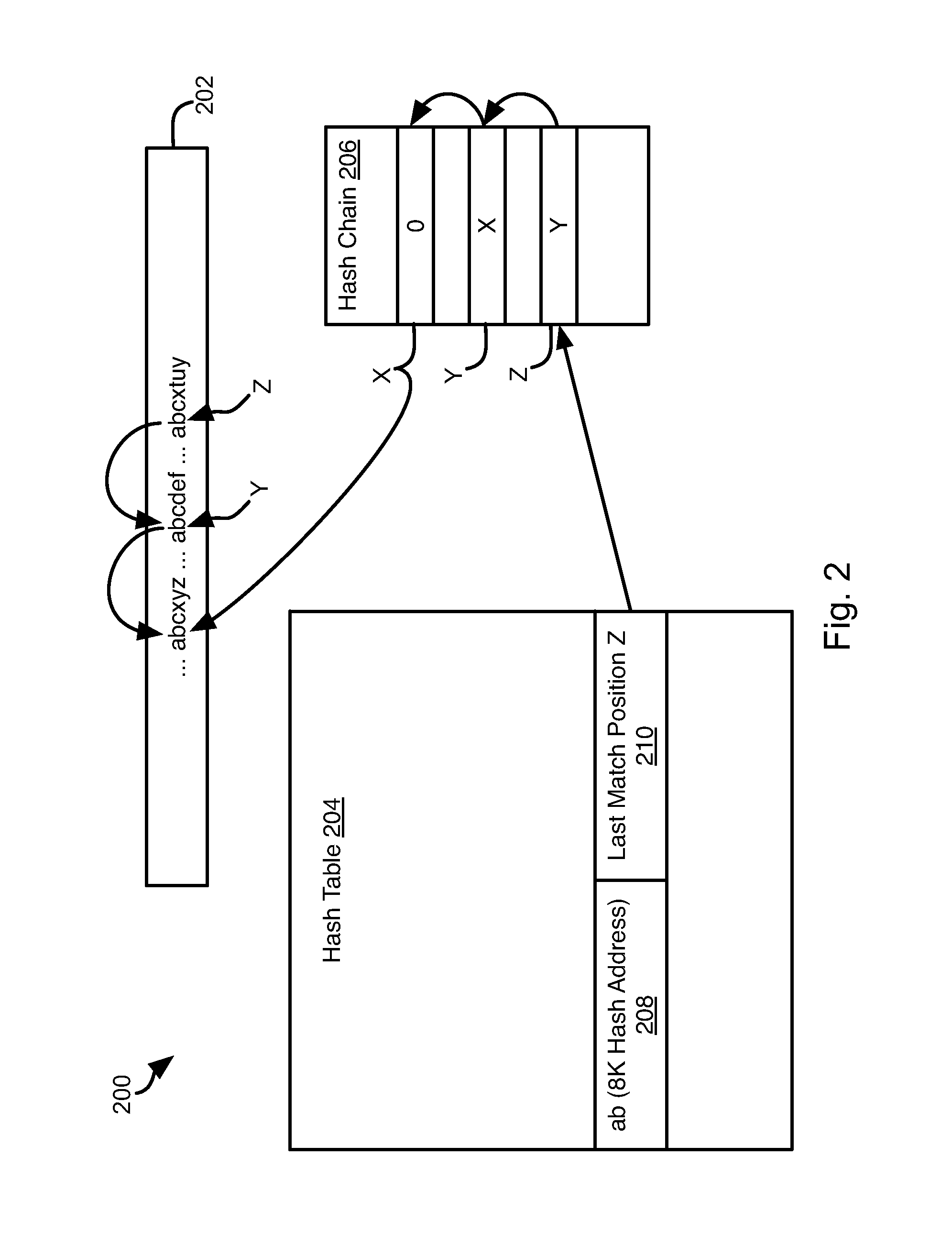
ActiveUS20160048531A1Digital data information retrievalDigital data processing detailsSelf adaptiveHash chain
An input file is processed according to hash algorithm that references sets of literals to preceding sets of literals to facilitate copy-offset command generation. Preceding instances are identified by generating a hash of the literal set and looking up a corresponding entry in a hash table. The hash table may be accessed by placing look-up requests in a FIFO buffer. When the FIFO buffer is full, generation of the hash chain is suspended until it is no longer full. When repeated literals are found, generation of the hash chain is likewise suspended. The hash chain is used to generate a command file, such as according to the LZ algorithm. Runs of consecutive literals are replaced by a run-length command. The command file may then be encoded using Huffman encoding.
Owner:TIDAL SYST
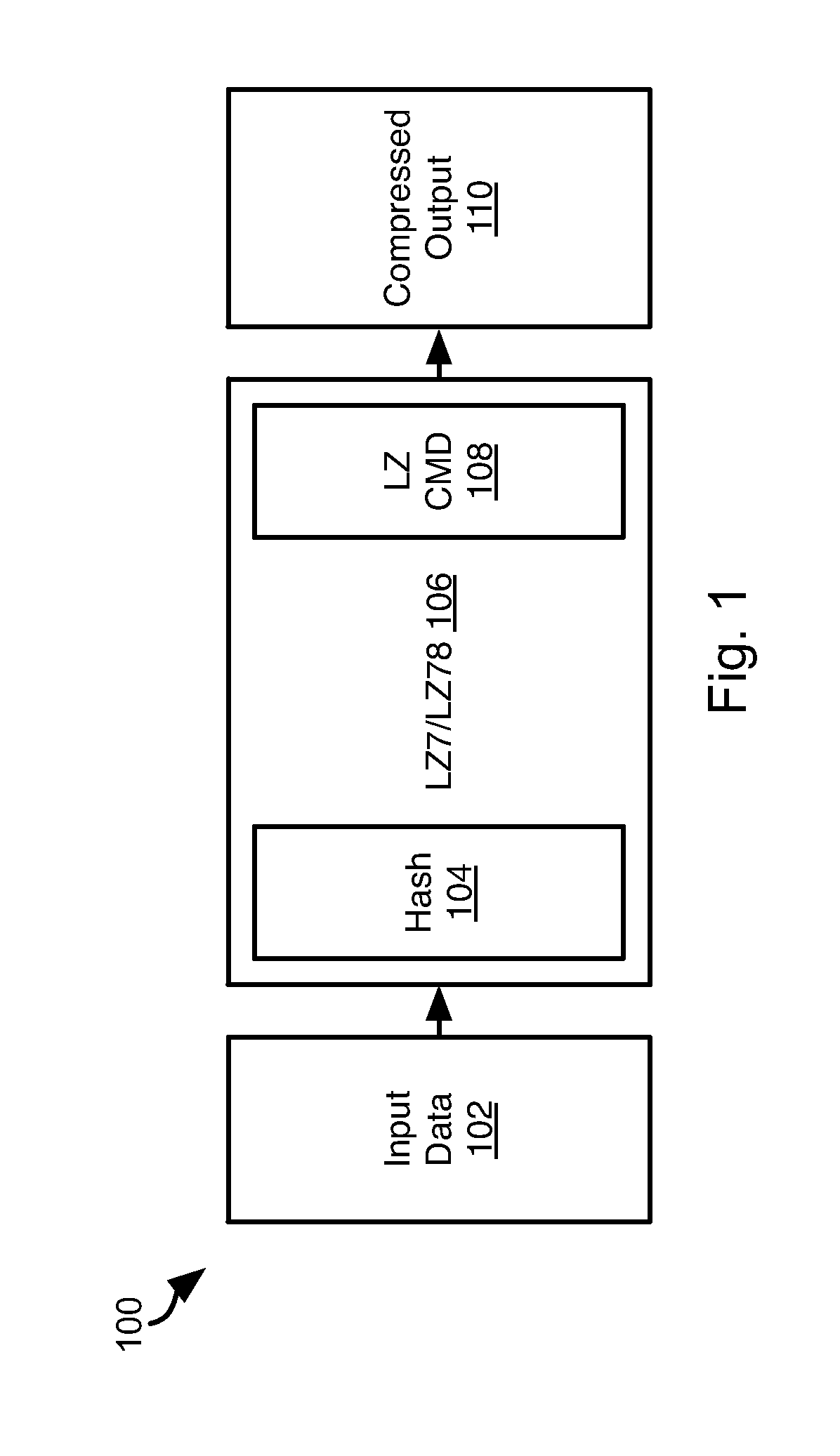
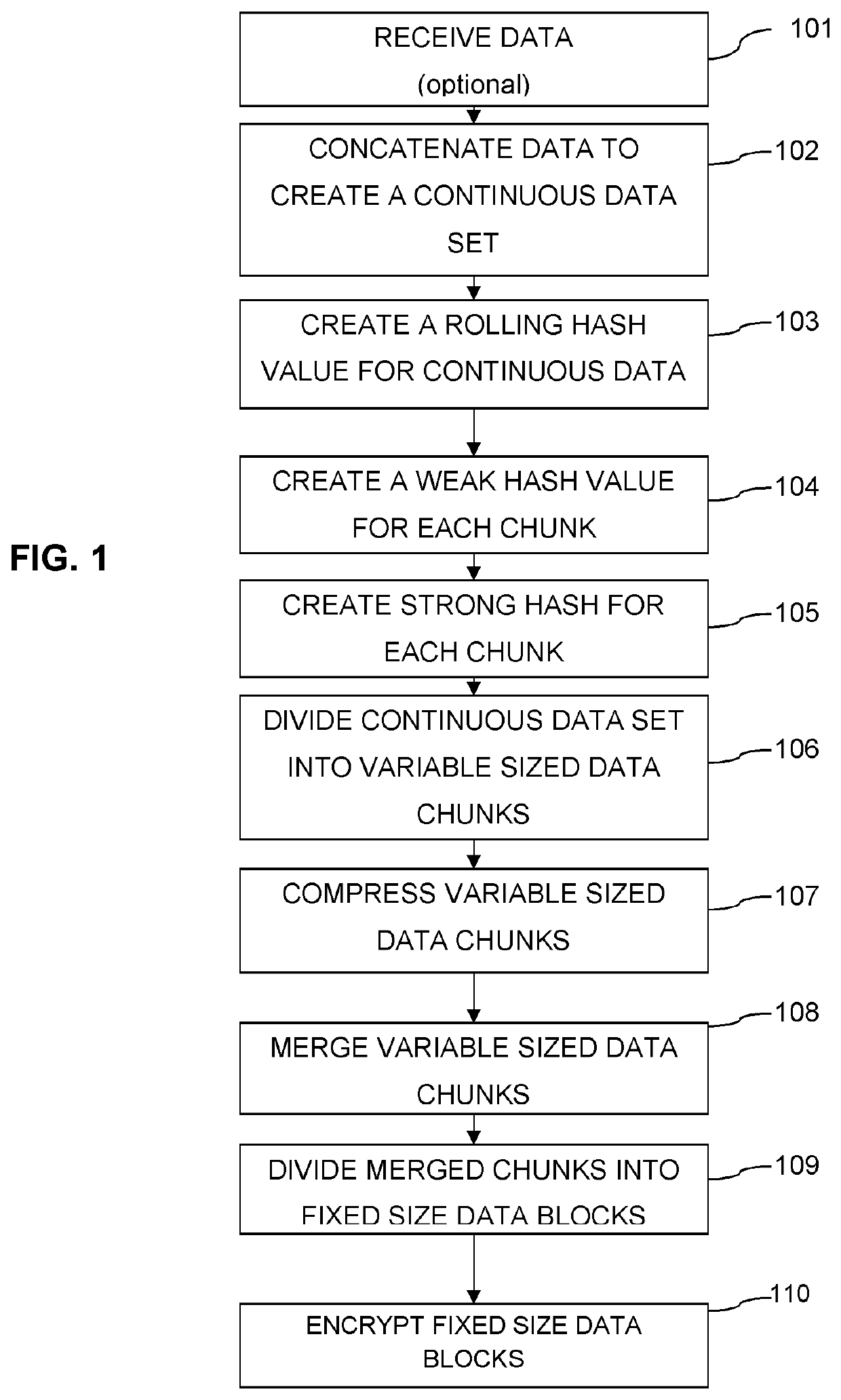
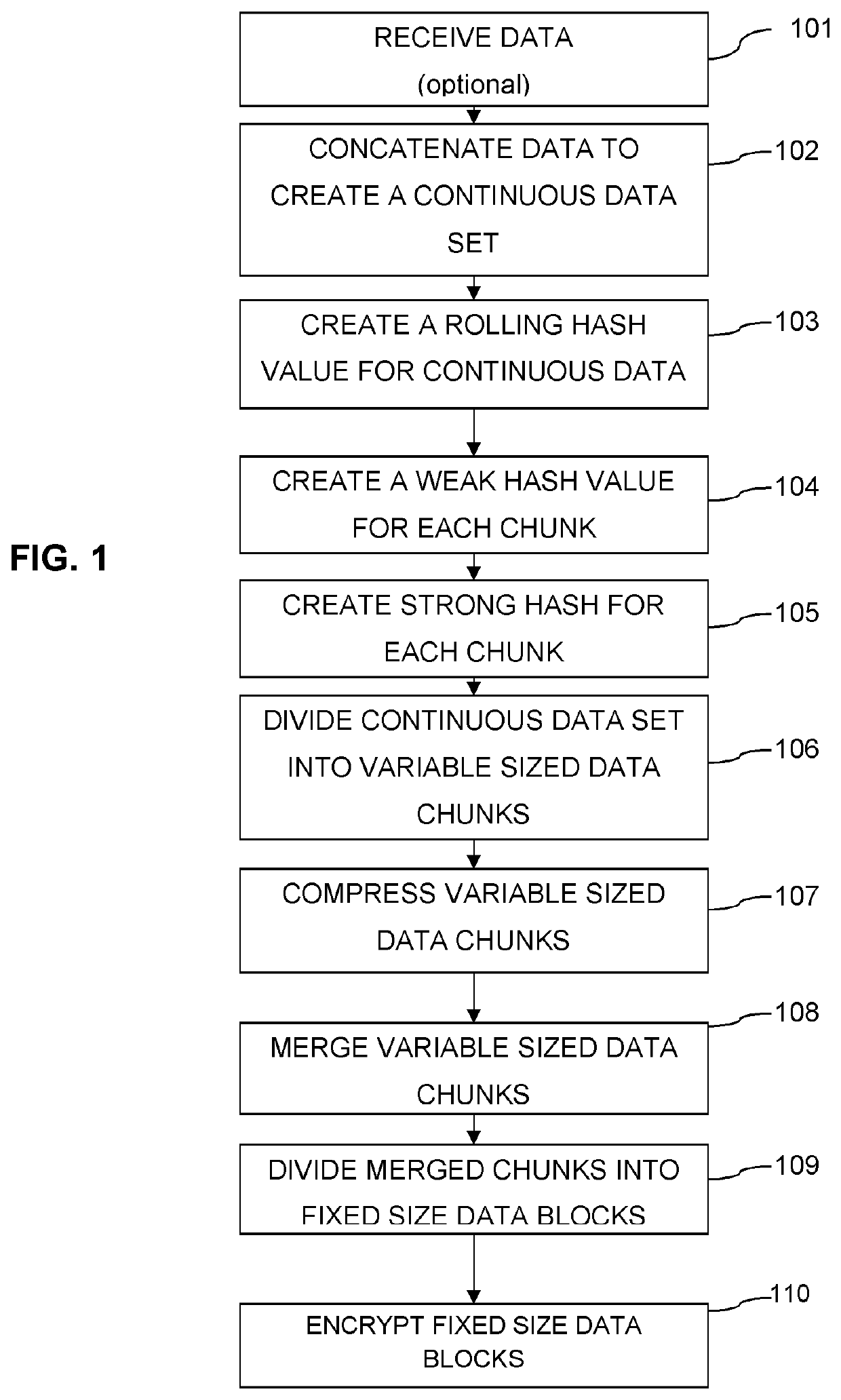
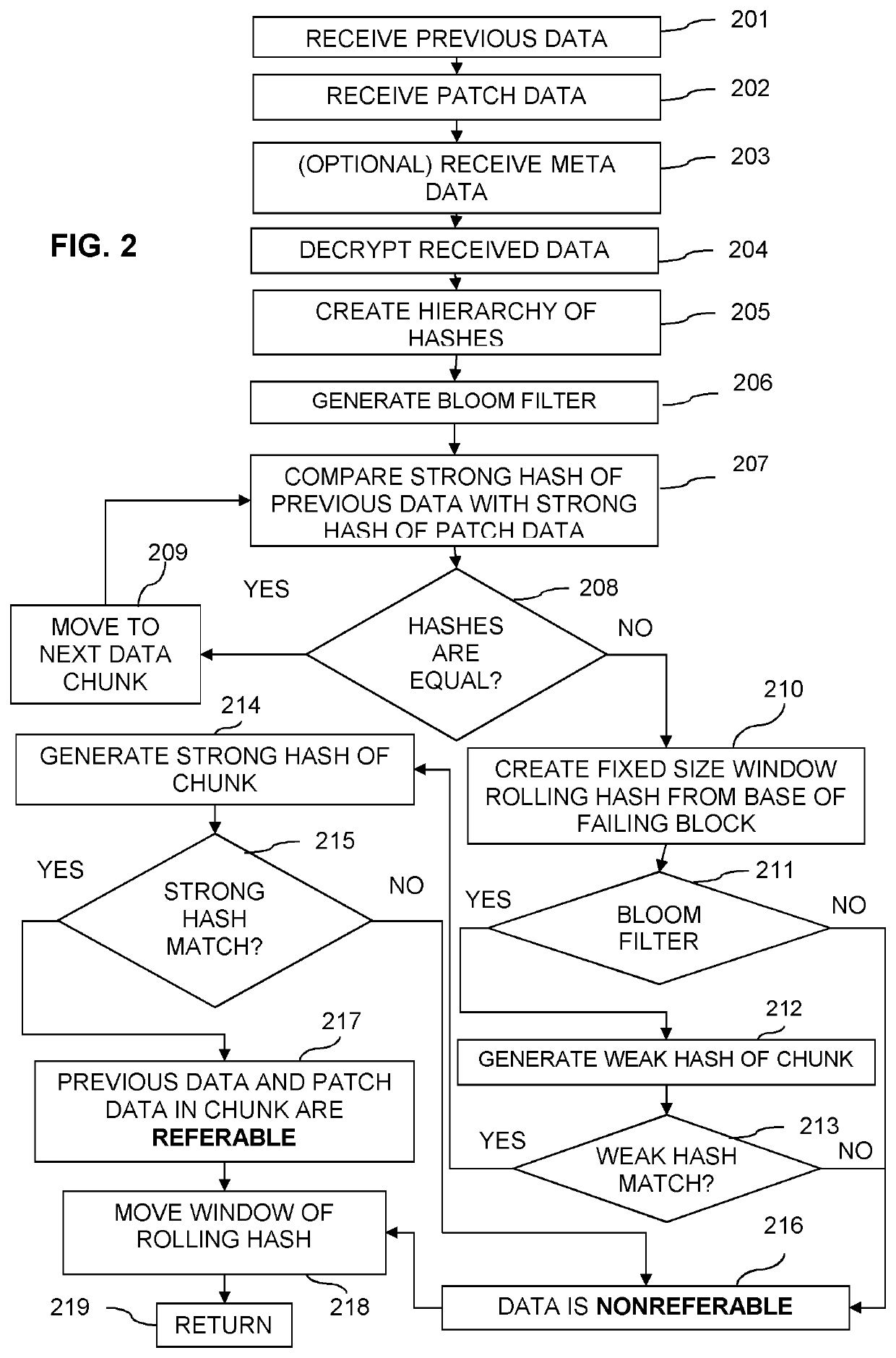
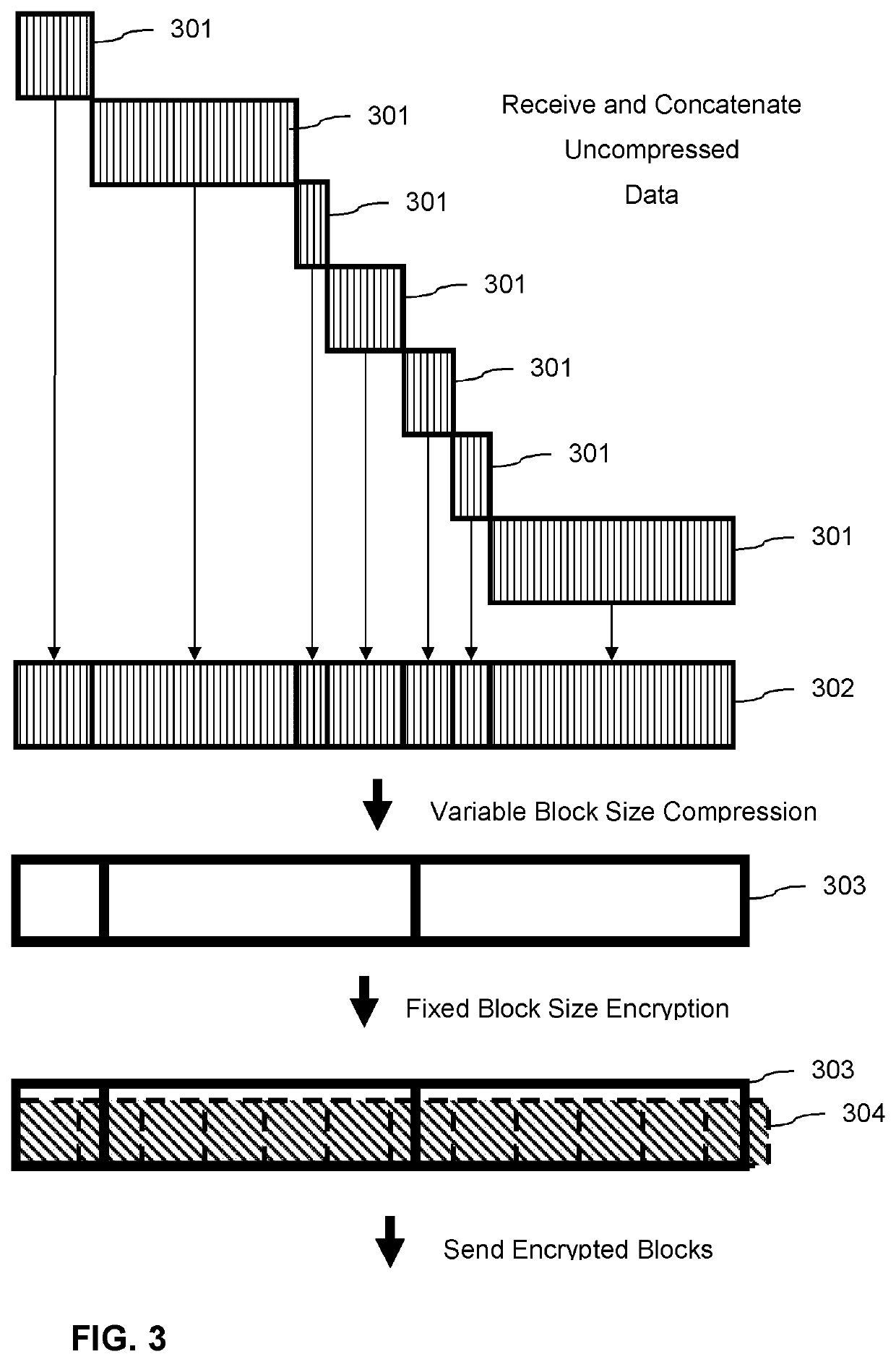
Data change detection using variable-sized data chunks
ActiveUS20210034349A1Encryption apparatus with shift registers/memoriesDigital data protectionData compressionRolling hash
A method, system and non-transitory computer readable instructions for data change detection includes decrypting encrypted patch data that includes compressed variable sized patch data chunks. The compressed variable sized patch data chunks are decompressed and a strong hash value is generated. The strong hash values are compared with strong hash values of corresponding variable sized application data chunks to determine a potentially non-referable patch data chunk. A bloom filter is generated for the variable sized application data chunks. A rolling hash value for a window of the potentially non-referable patch data chunk is used to determine a potentially referable area from the potentially non-referable patch data chunk. The potentially referable area is designated as referable when a weak hash and a strong hash of an application data chunk matches the weak hash and the strong hash of the potentially referable area.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
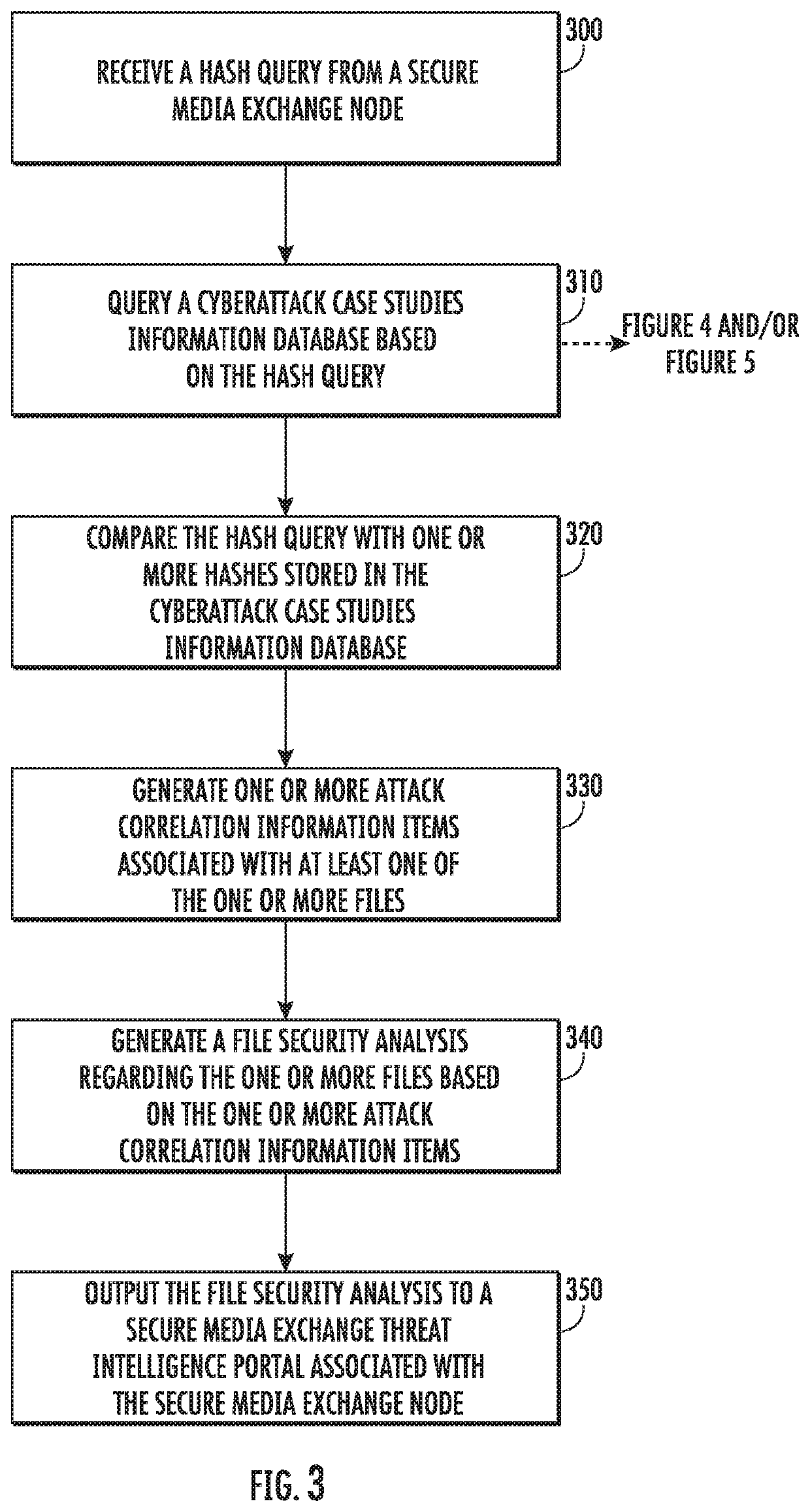
Mapping an attack tree and attack prediction in industrial control and iiot environment using hash data analytics
A method, apparatus and computer program product for detecting malicious content and predicting cyberattacks are described herein. In the context of a method, the method receives a hash query comprising a file hash based on one or more files. The method queries a cyberattack case studies information database based on the hash query to generate one or more attack correlation information items associated with at least one of the one or more files. The method also generates and outputs a file security analysis based on the attack correlation information items for authorization of the one or more files.
Owner:HONEYWELL INT INC
Cryptographic method for verifying data
PendingUS20200351100A1Improve the security of hashing techniquesReduce error rateUser identity/authority verificationDigital data protectionData setHash function
Cryptographic method for verifying data method, implemented by at least one apparatus, for comparing a first dataset and a second dataset, in particular with a view to determining whether these two datasets are identical, this method not requiring the presence of these two datasets in the apparatus, and comprising the following steps: a) mixing a number, called the mixer number, with the first dataset, using a mixing function in order to obtain mixed data, b) hashing the mixed data using a hash function, and c) comparing the hash thus obtained in step b) with a third dataset assumed to be the hash of the second dataset mixed with the same mixer number as that used in step a) and with the same mixing function.
Owner:SANGLE FERRIERE BRUNO
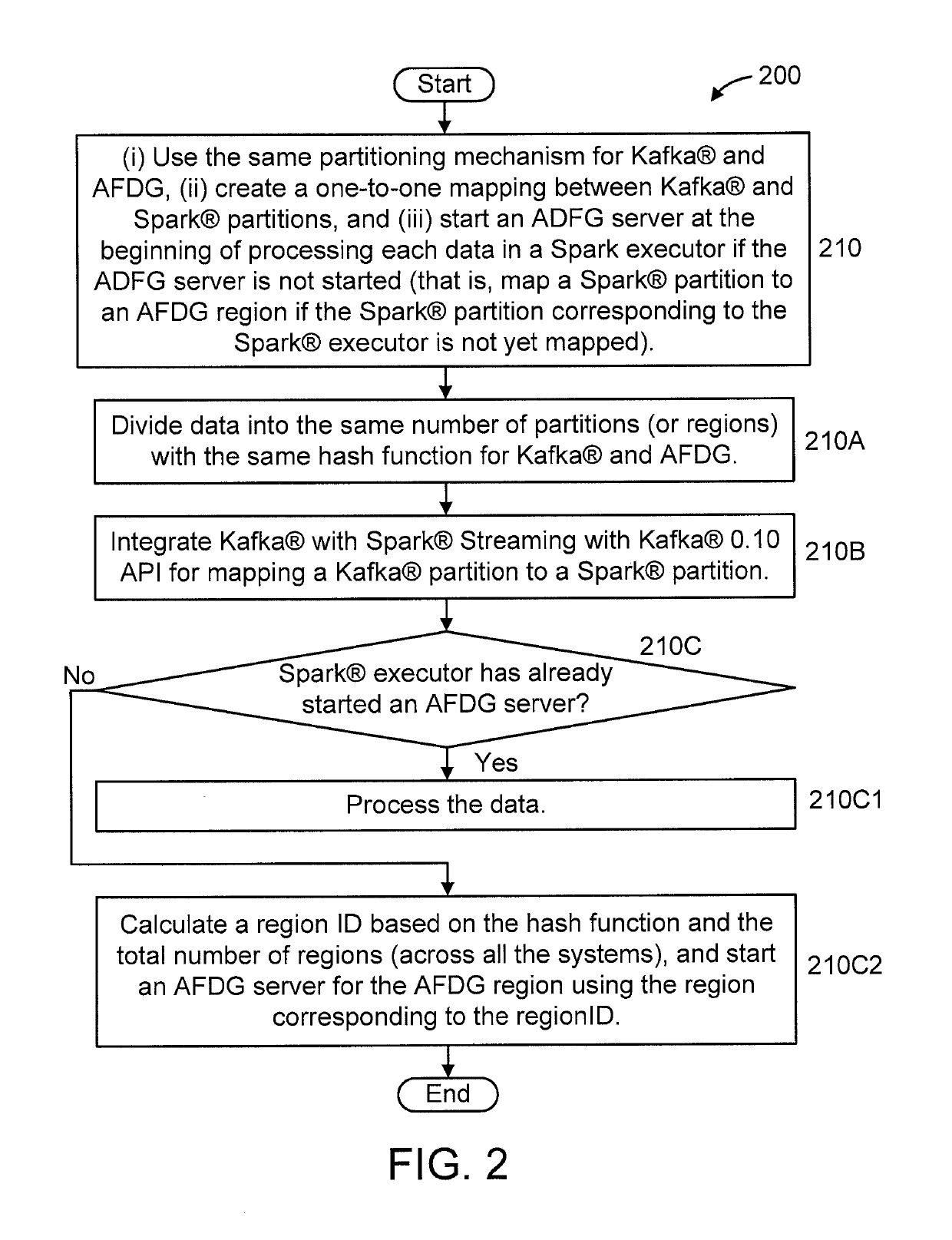
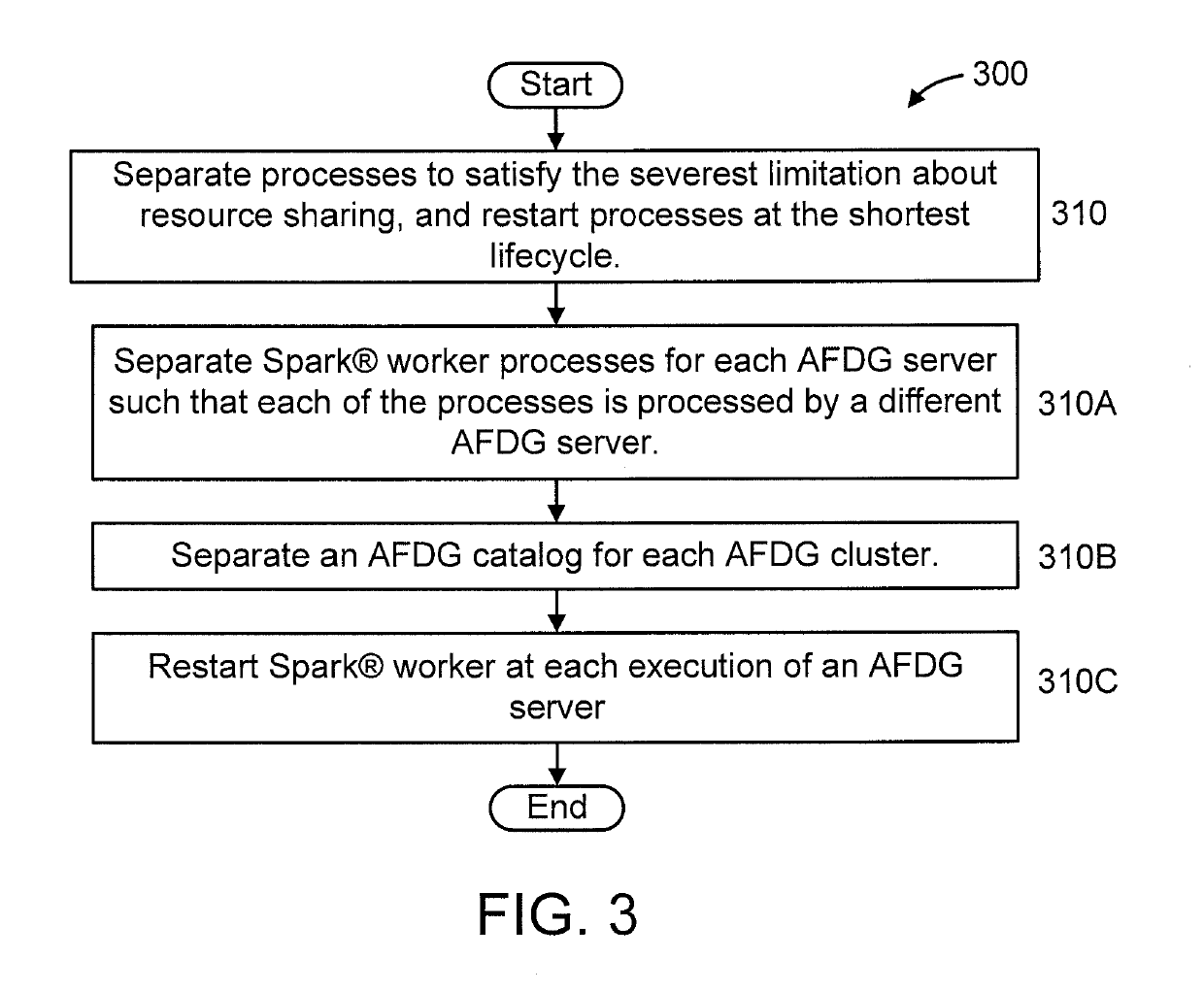
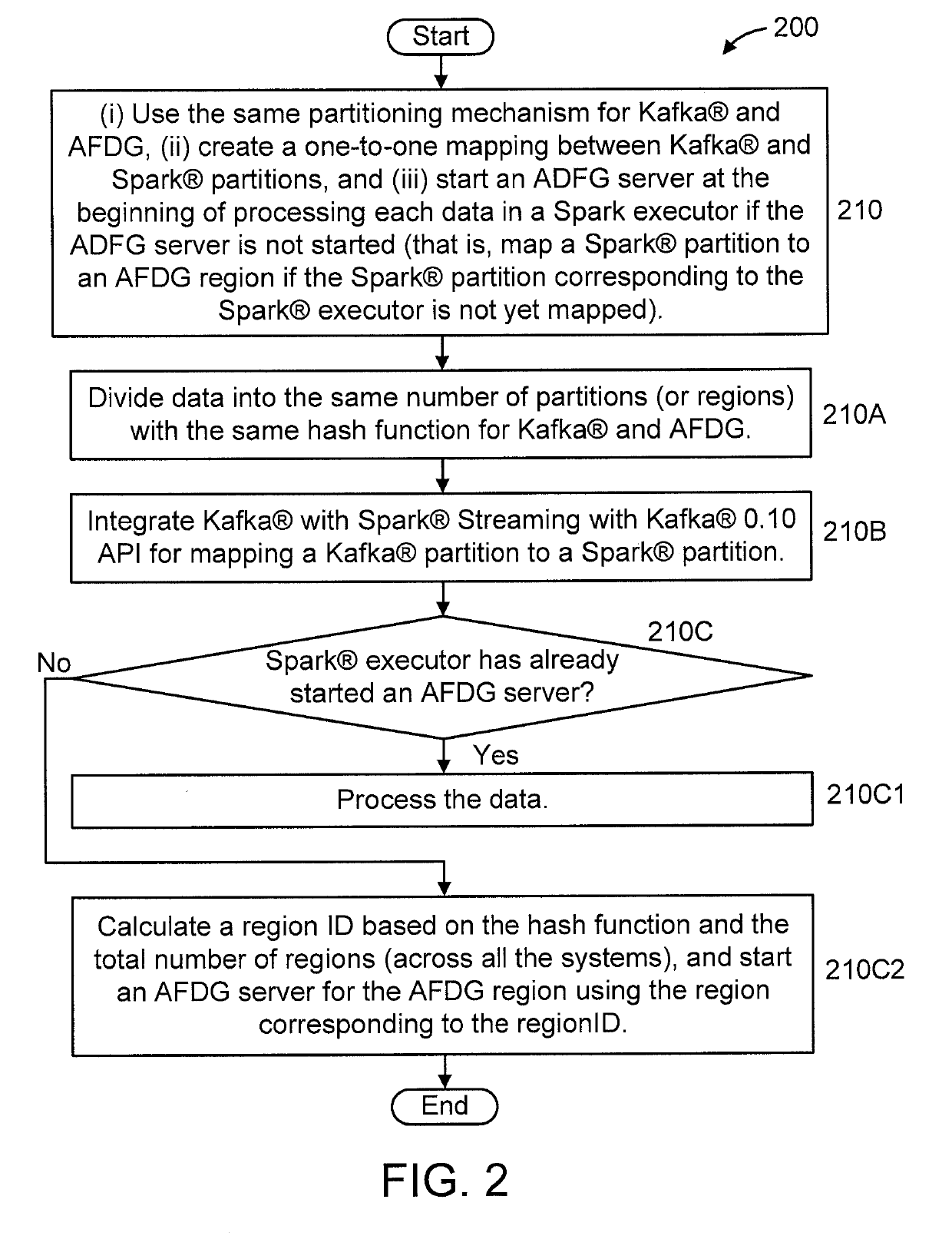
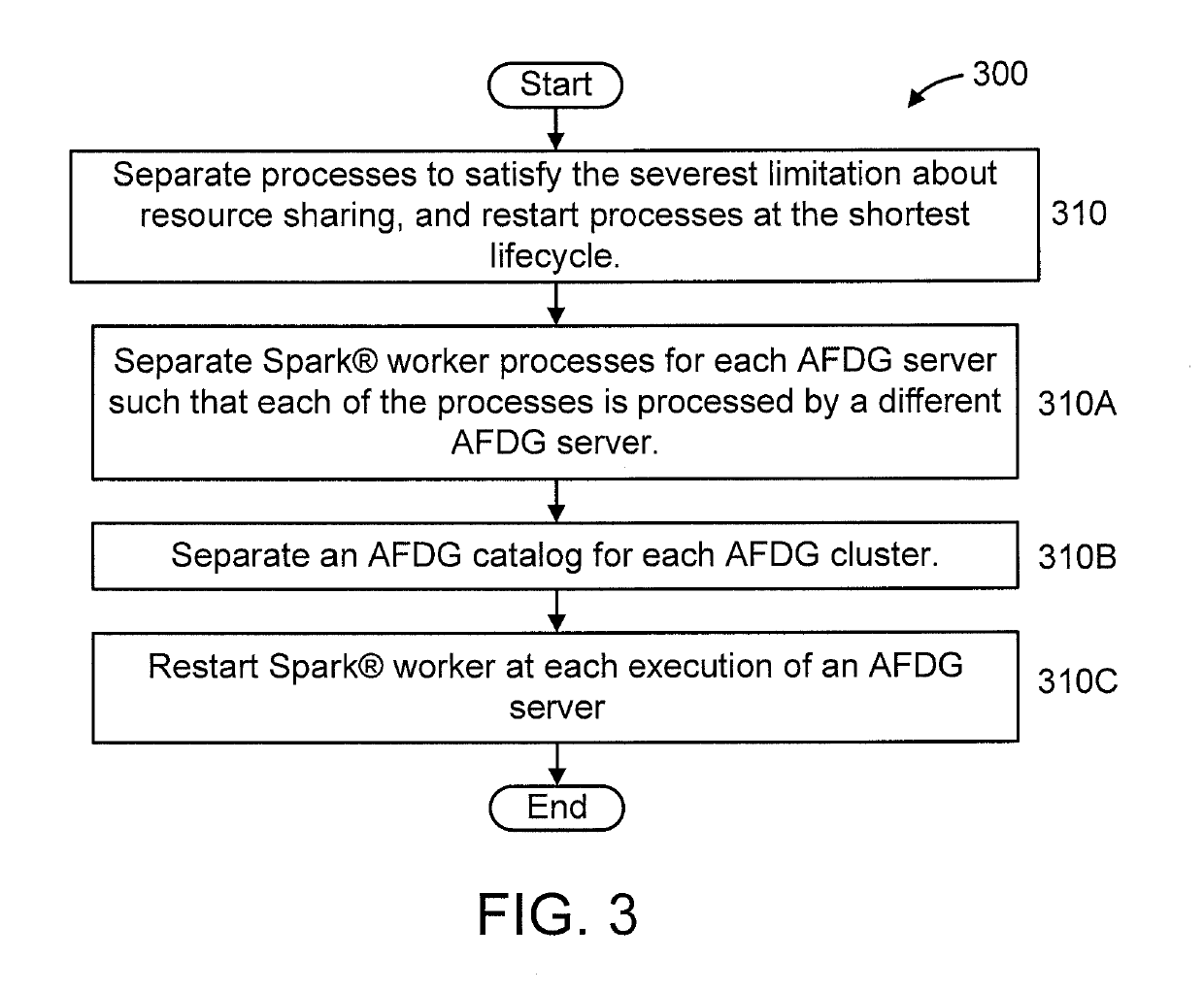
Integrating multiple distributed data processing servers with different data partitioning and routing mechanisms, resource sharing policies and lifecycles into a single process
A method is provided for consistent data processing by first and second distributed processing systems having different data partitioning and routing mechanisms such that the first system is without states and the second system is with states. The method includes dividing data in each system into a same number of partitions based on a same key and a same hash function. The method includes mapping partitions between the systems in a one-to-one mapping. The mapping step includes (i) checking if a partition in the first system is mapped to a partition in the second system; and (ii) calculating a partition ID based on the hash function and a total number of partitions, and dynamically mapping the partition in the first system to the partition in the second system, responsive to the partition in the first system being unmapped to the partition in the second system.
Owner:INT BUSINESS MASCH CORP
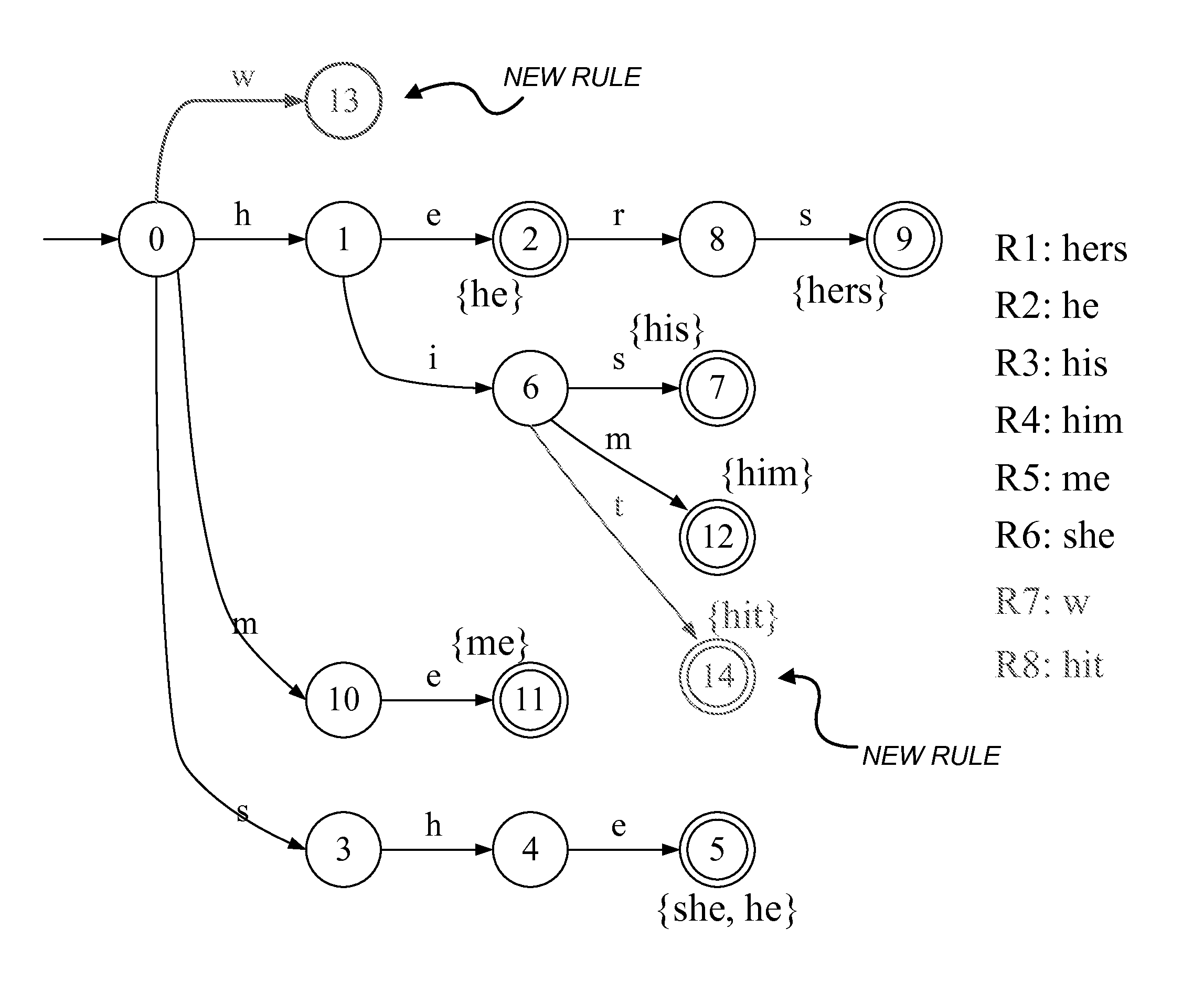
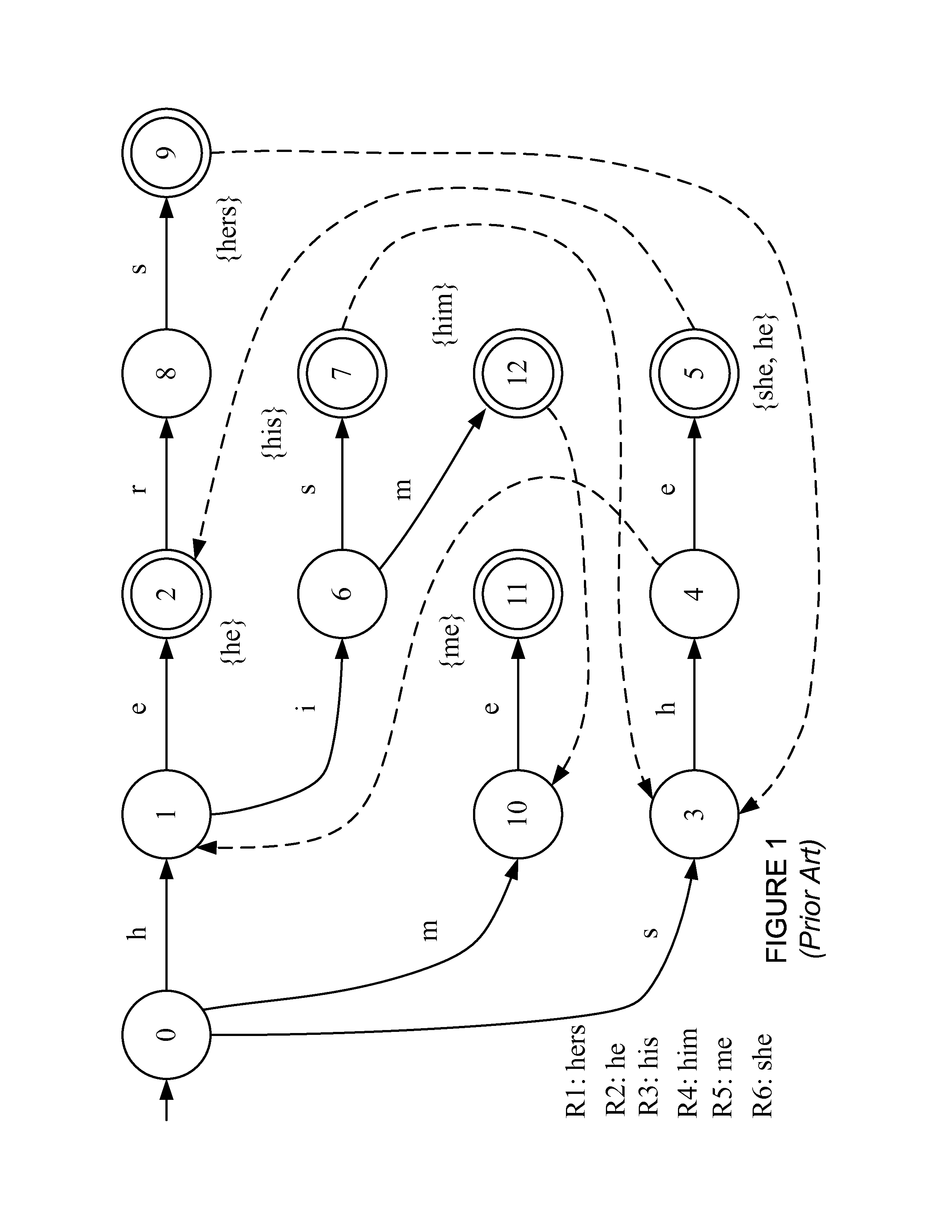
Updating a perfect hash data structure, such as a multi-dimensional perfect hash data structure, used for high-speed string matching
ActiveUS8775393B2Digital data processing detailsOther databases indexingTheoretical computer sciencePerfect hash function
A representation of a new rule, defined as a set of a new transition(s), is inserted into a perfect hash table which includes previously placed transitions to generate an updated perfect hash table. This may be done by, for each new transition: (a) hashing the new transition; and (b) if there is no conflict, inserting the hashed new transition into the table. If, however, the hashed new transition conflicts with any of the previously placed transitions, either (A) any transitions of the state associated with the conflicting transition are removed from the table, the hashed new transition is placed into the table, and the removed transitions are re-placed into the table, or (B) any previously placed transitions of the state associated with the new transition are removed, and the transitions of the state associated with the new transition are re-placed into the table.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
Method and system for data handling
A control module transferring data between a shard and destination shards within a database comprising a plurality of shards, the control module: generating a first hash wheel distribution of shard allocations by applying a defined hashing function to a first integer value per shard allocation; generating a further hash wheel distribution of shard allocations by applying the defined hashing function to a further integer value per shard allocation; determining a range of hash values associated with data to be transferred between the shard and a destination shard, wherein the range of hash values, the shard and the destination shard are defined based on determining a difference between the first hash wheel distribution of shard allocations and the further hash wheel distribution of shard allocations; selecting and controlling the transfer of data associated with the determined range of hash values between the shard and the destination shard.
Owner:KING COM
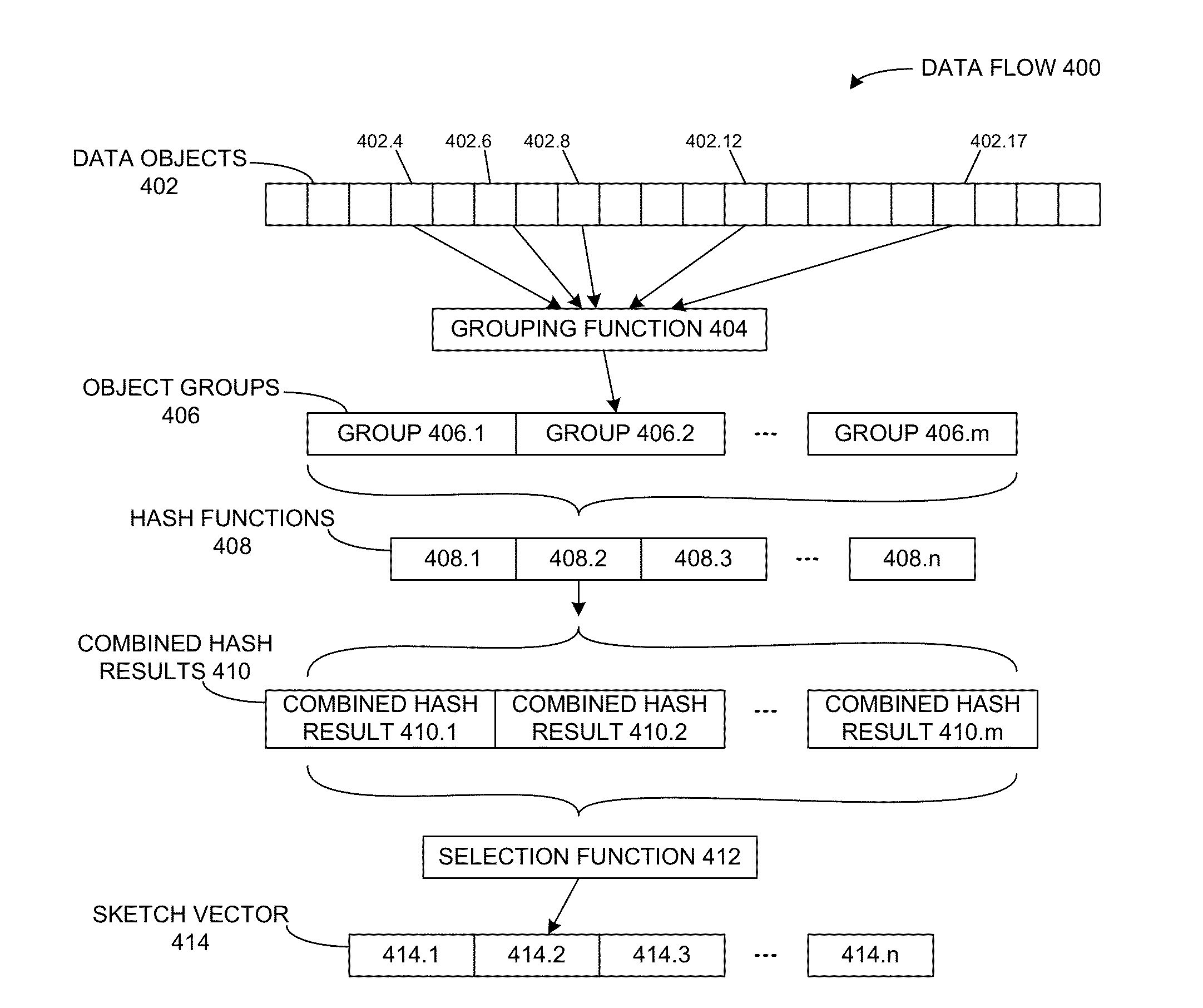
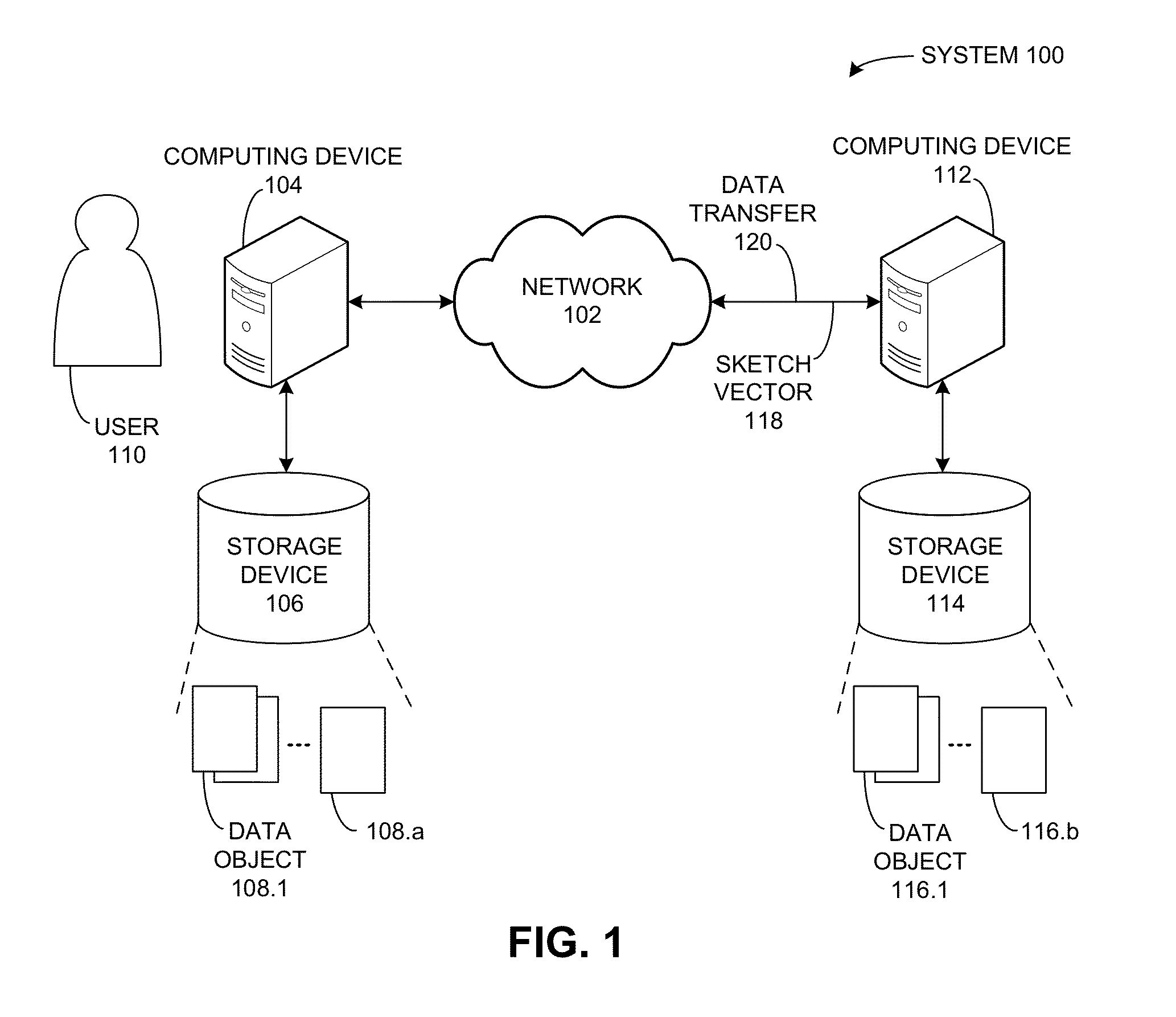
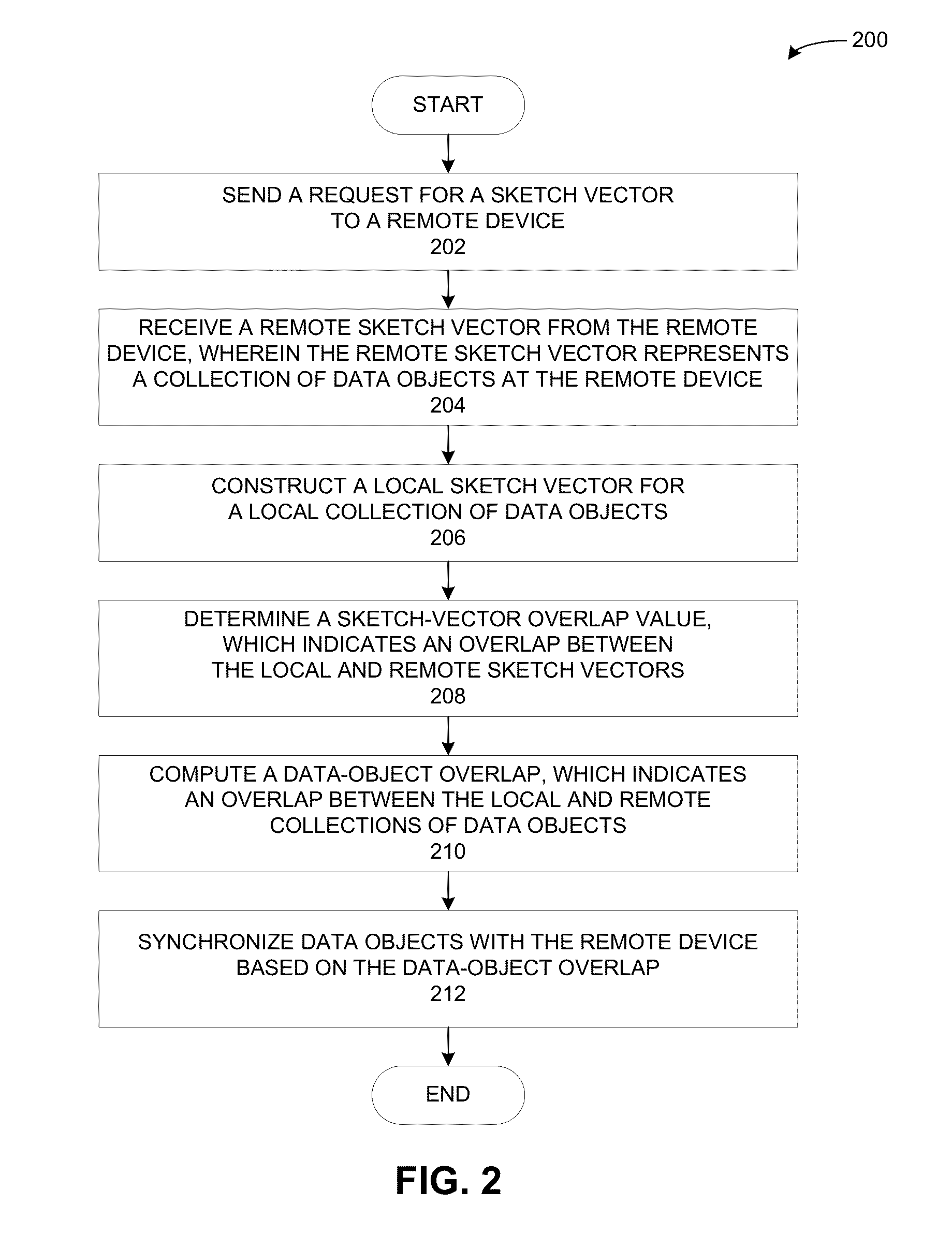
Generating sketches sensitive to high-overlap estimation
ActiveUS8572092B2Digital data information retrievalDigital data processing detailsHash functionObject based
A versioning system determines an amount by which a first collection and a second collection of data objects overlap. The system divides the first collection of data objects into m possibly overlapping groups of average size s and computes one combined hash result for each group. The system then constructs a first sketch vector with n elements based on the combined hash results. A respective element of the first sketch vector is selected, using a selection function, from the combined hash results that are computed with the hash function corresponding to the element's index. Next, the system receives a second sketch vector for the second collection of data objects, and determines a sketch-vector overlap between the first and second sketch vectors. The system then computes a data-object overlap between the first and second collections of data objects based on the sketch-vector overlap.
Owner:CISCO TECH INC +1
Integrating multiple distributed data processing servers with different data partitioning and routing mechanisms, resource sharing policies and lifecycles into a single process
A method is provided for consistent data processing by first and second distributed processing systems having different data partitioning and routing mechanisms such that the first system is without states and the second system is with states. The method includes dividing data in each system into a same number of partitions based on a same key and a same hash function. The method includes mapping partitions between the systems in a one-to-one mapping. The mapping step includes (i) checking if a partition in the first system is mapped to a partition in the second system; and (ii) calculating a partition ID based on the hash function and a total number of partitions, and dynamically mapping the partition in the first system to the partition in the second system, responsive to the partition in the first system being unmapped to the partition in the second system.
Owner:IBM CORP
System and method for hash-based entropy calculation
ActiveUS10733158B1The result is validCode conversionSpecial data processing applicationsTheoretical computer scienceSplaysort
A method, computer program product, and computing system for receiving a candidate data portion; calculating a distance-preserving hash for the candidate data portion; and performing an entropy analysis on the distance-preserving hash to generate a hash entropy for the candidate data portion.
Owner:EMC IP HLDG CO LLC
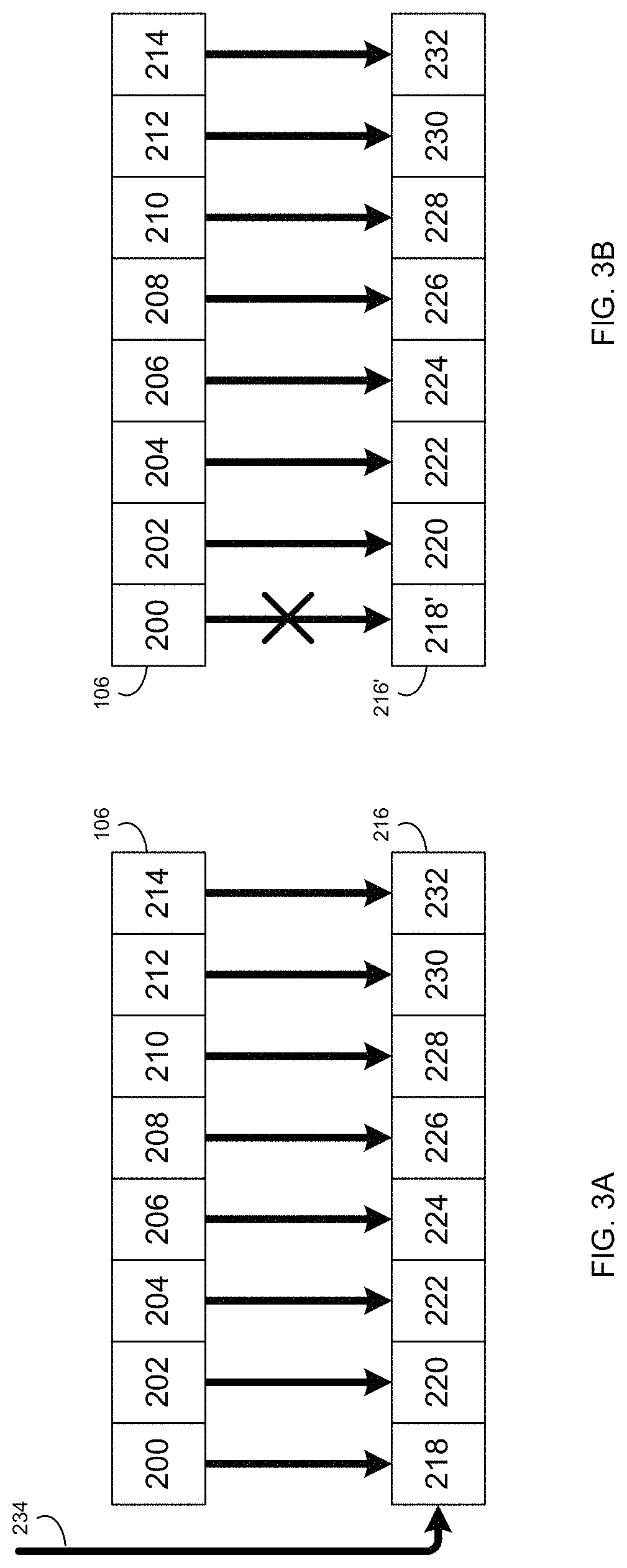
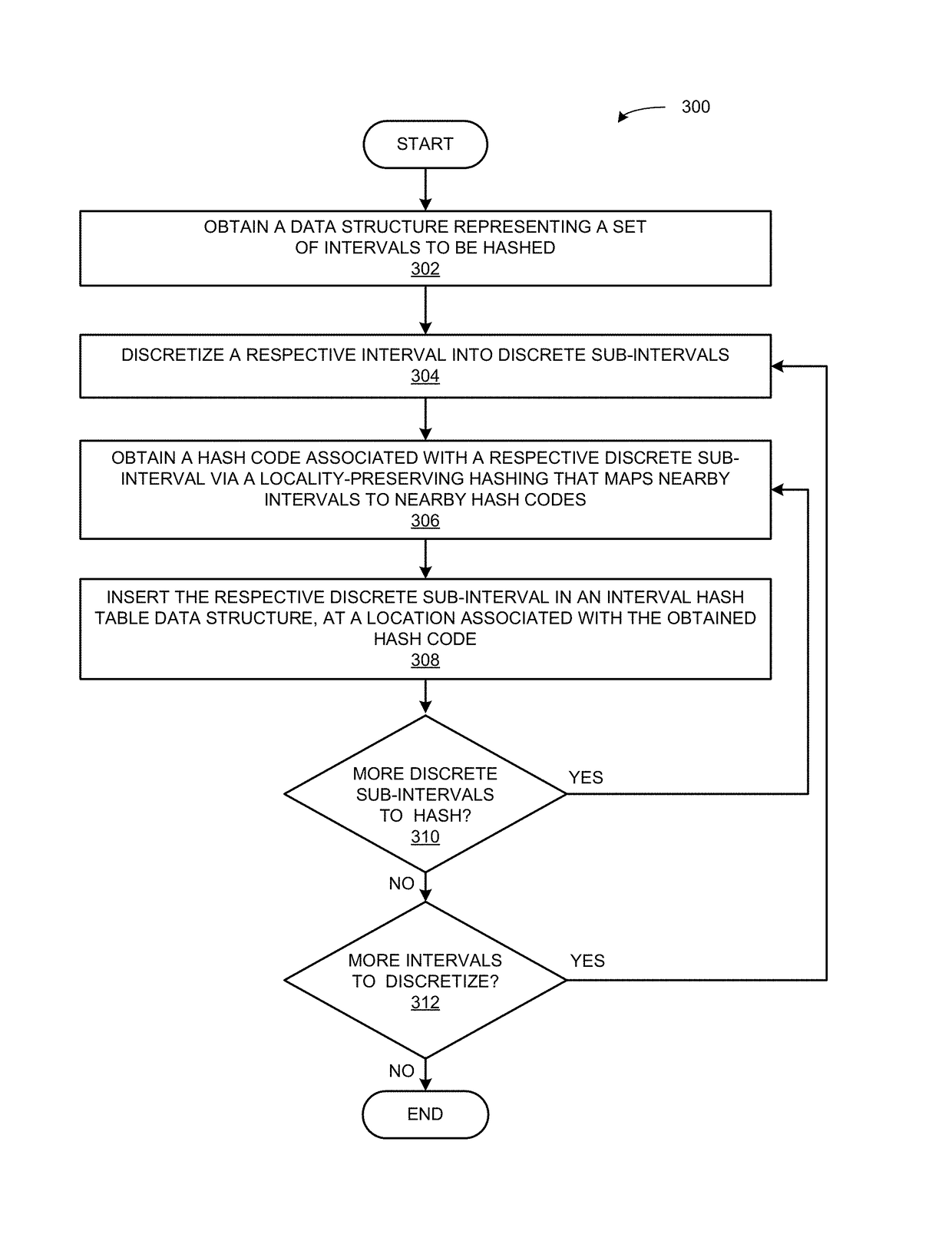
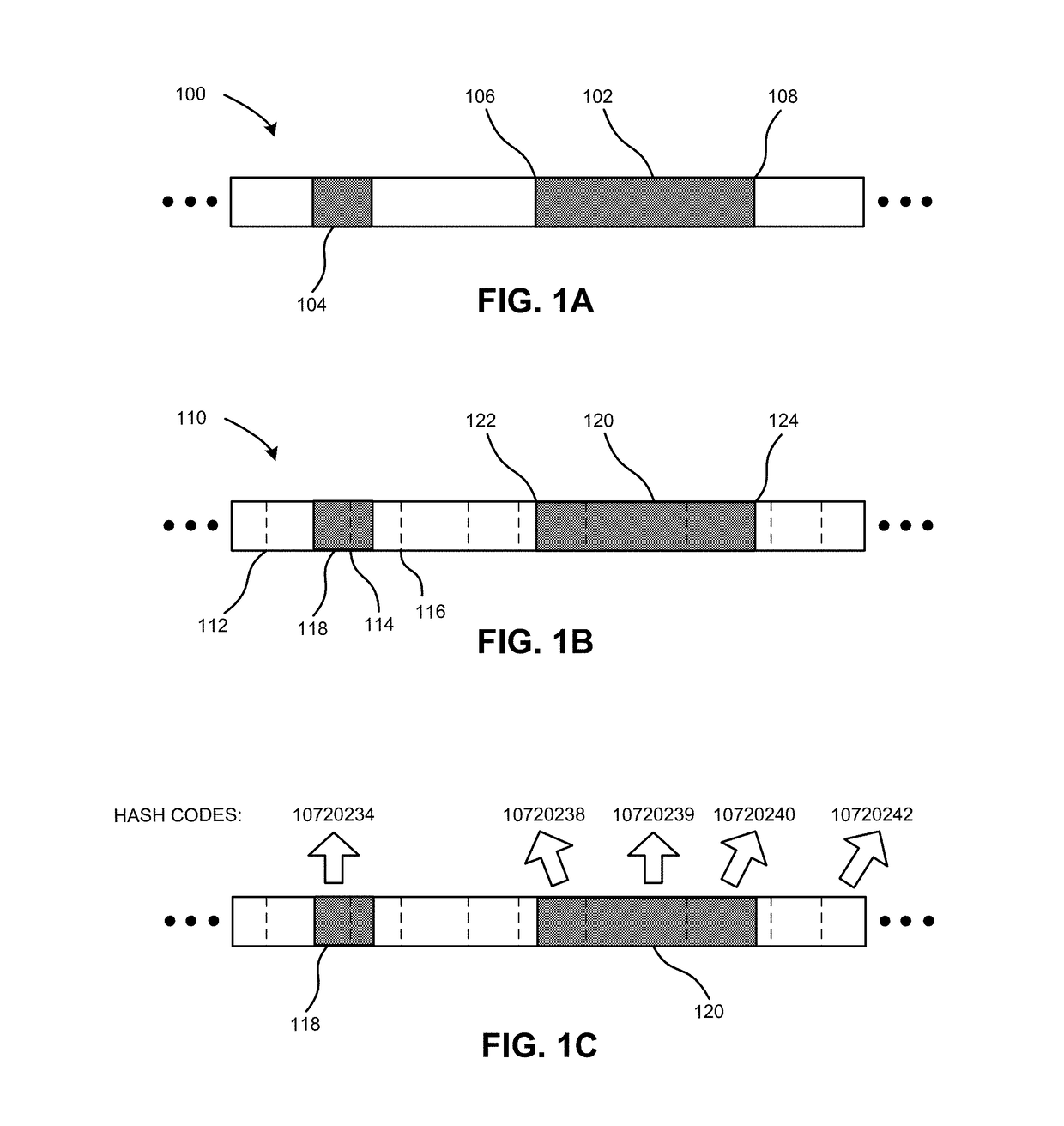
System and method for efficient interval search using locality-preserving hashing
ActiveUS20170357732A1Other databases indexingSpecial data processing applicationsAlgorithmHash table
Embodiments of the present invention provide a time- and space-efficient system for representing and searching a set of intervals to find all the intervals that overlap with a given query interval or point. A new structure called an interval hash table is introduced to significantly reduce the average search time, thereby improving computing and search technology. During operation, the system obtains data indicating a set of intervals to be hashed. The system divides a respective interval into a set of sub-intervals based on a locality-preserving hashing. The system then obtains a hash code associated with a respective sub-interval, and inserts the respective sub-interval into an interval hash table at a location corresponding to the hash code. The system may further search the interval hash table.
Owner:PALO ALTO RES CENT INC
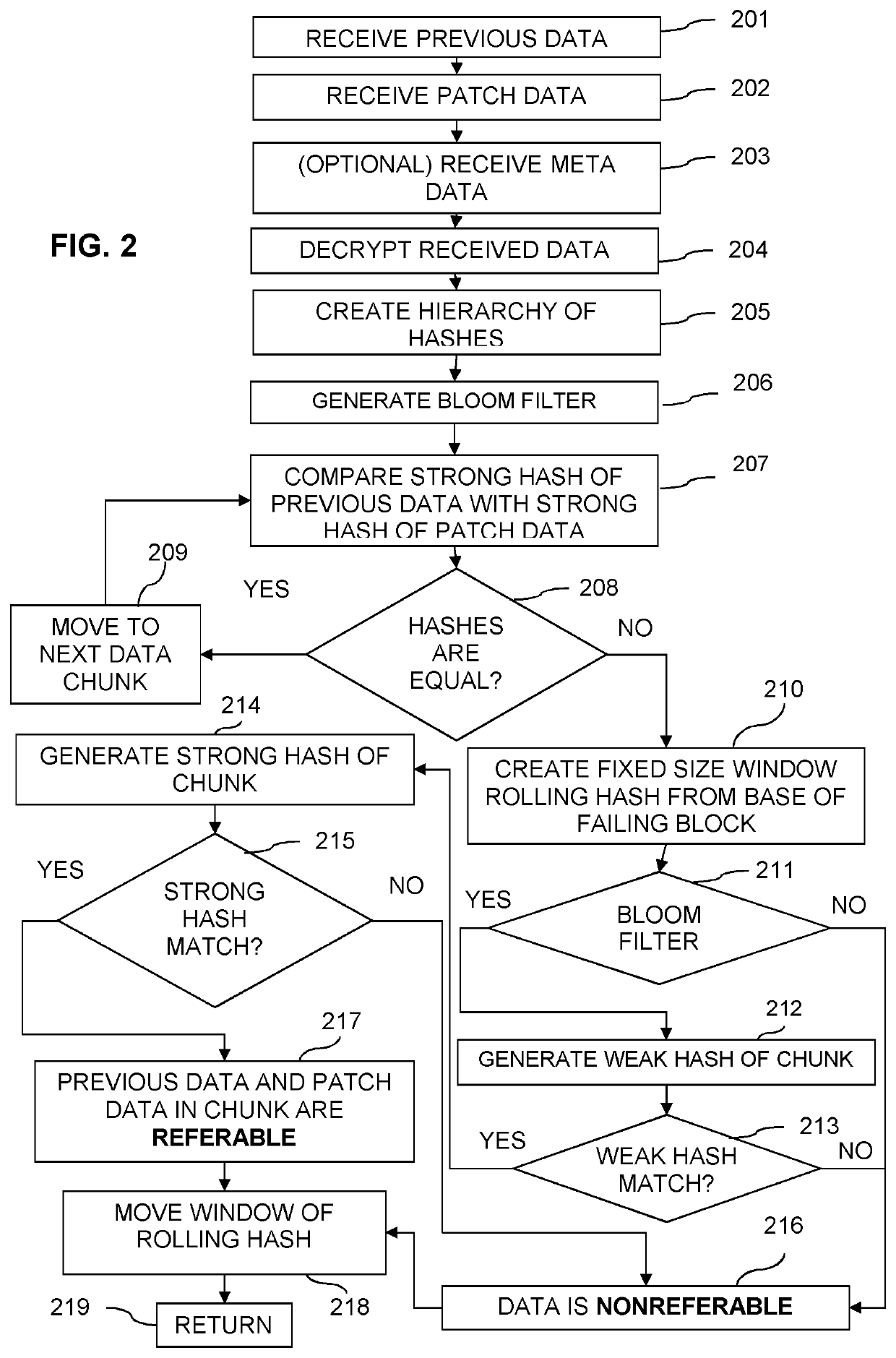
Data change detection using variable-sized data chunks
ActiveUS11449325B2Encryption apparatus with shift registers/memoriesDigital data protectionData compressionRolling hash
A method, system and non-transitory computer readable instructions for data change detection includes decrypting encrypted patch data that includes compressed variable sized patch data chunks. The compressed variable sized patch data chunks are decompressed and a strong hash value is generated. The strong hash values are compared with strong hash values of corresponding variable sized application data chunks to determine a potentially non-referable patch data chunk. A bloom filter is generated for the variable sized application data chunks. A rolling hash value for a window of the potentially non-referable patch data chunk is used to determine a potentially referable area from the potentially non-referable patch data chunk. The potentially referable area is designated as referable when a weak hash and a strong hash of an application data chunk matches the weak hash and the strong hash of the potentially referable area.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Distributed platform for computation and trusted validation
PendingCN112703499AUser identity/authority verificationDigital data protectionTheoretical computer scienceSequential data
An example operation may include one or more of obtaining data of a simulation, identifying checkpoints within the simulation data, generating a plurality of sequential data structures based on the identified checkpoints, where each data structure identifies an evolving state of the simulation with respect to a previous data structure among the sequential data structures, and transmitting the generated sequential data structures to nodes of a blockchain network for inclusion in one or more data blocks within a hash-linked chain of data blocks.
Owner:IBM CORP
Multi-window leakage processing method and device and computer readable storage medium
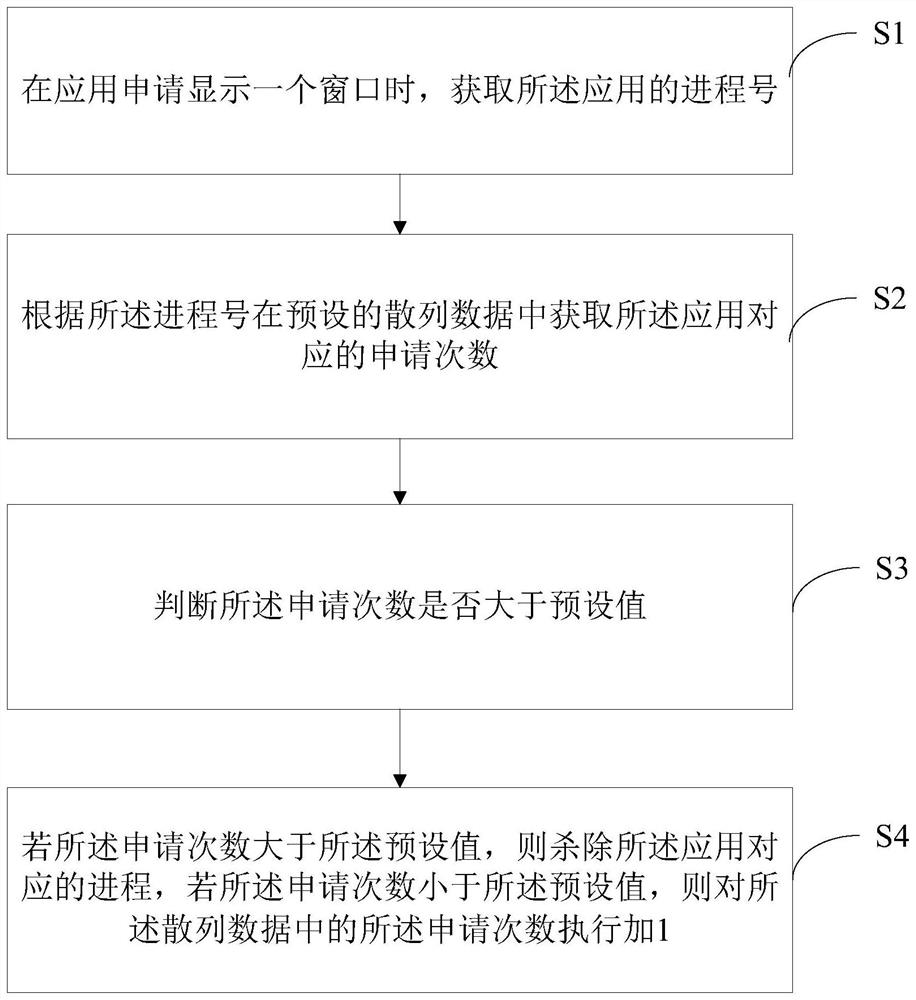
PendingCN114253687AImprove user experienceCreate effective controlsProgram initiation/switchingResource allocationComputer hardwareTerm memory
The invention discloses a multi-window leakage processing method and device and a computer readable storage medium, and the method comprises the steps: obtaining a process number of an application when the application applies to display a window; obtaining application times corresponding to the application in preset hash data according to the process number; judging whether the application frequency is greater than a preset value or not; if the number of times of application is larger than the preset value, a process corresponding to the application is killed, and if the number of times of application is smaller than the preset value, 1 is added to the number of times of application in the hash data. According to the technical scheme, an efficient memory leak processing scheme applying multiple windows is achieved, window creation is effectively controlled through clear and simple logic condition judgment, the jamming phenomenon is avoided, the fluency of a system is improved, and the use experience of a user is enhanced.
Owner:深圳市中兴移动软件有限公司
Creating a secure searchable path by hashing each component of the path
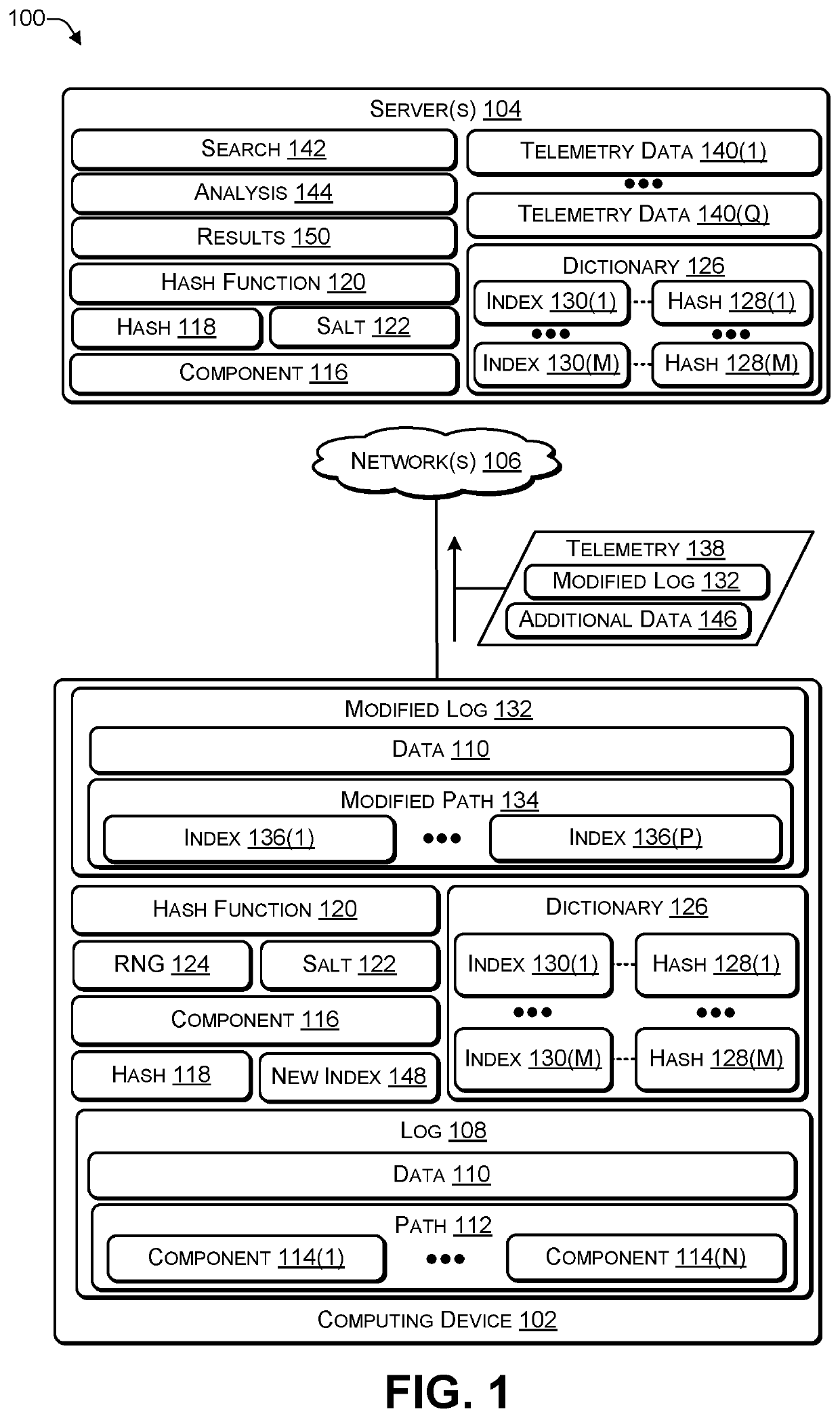
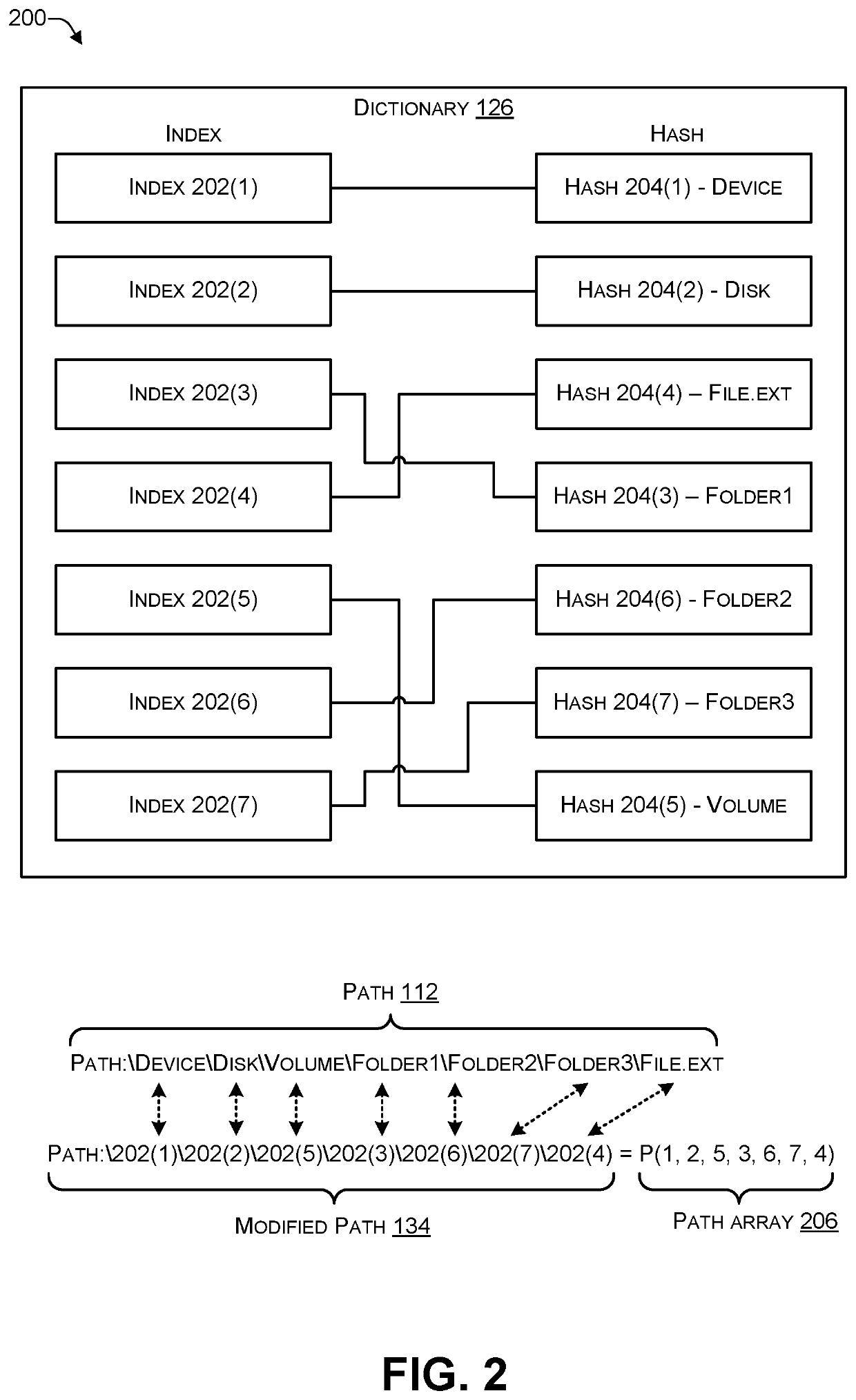
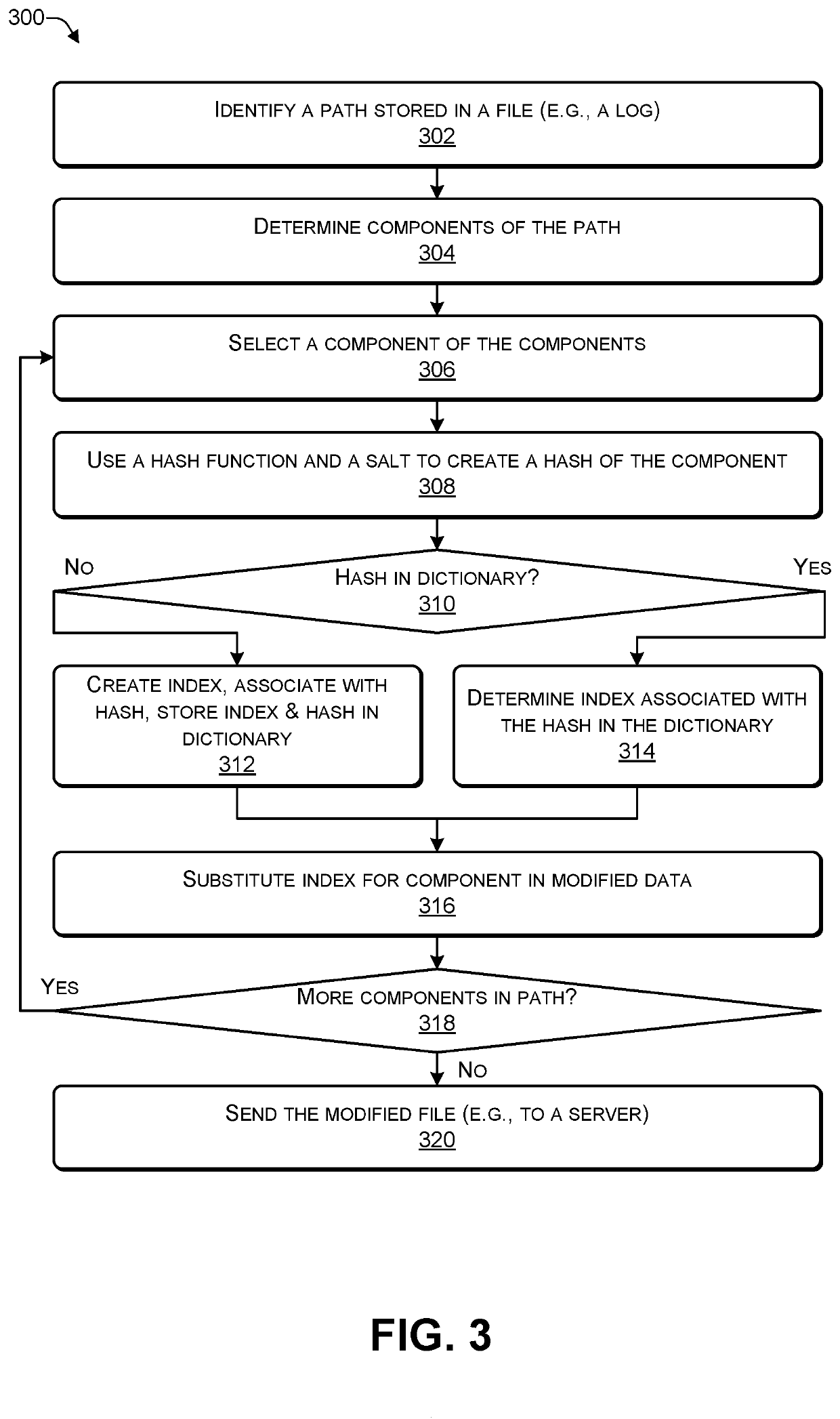
PendingUS20200302065A1Well formedInput/output to record carriersEncryption apparatus with shift registers/memoriesSearch wordsPathPing
In some examples, a computing device creates an event log when an event occurs. If the event log includes a path comprising one or more components, the computing device may determine a hash, using a hash function and a salt, for each of the components and substitute each component in the path with an index to the hash stored in a dictionary. In this way, the computing device replaces each component of the path with an index to a hash in the dictionary to create a modified path. The resulting modified path can be traversed and searched. For example, a search term may be hashed using the hash function and salt, and the dictionary associated with the logs searched for a match. In this way, a particular file name or a particular folder name can be identified in the modified path.
Owner:DELL PROD LP
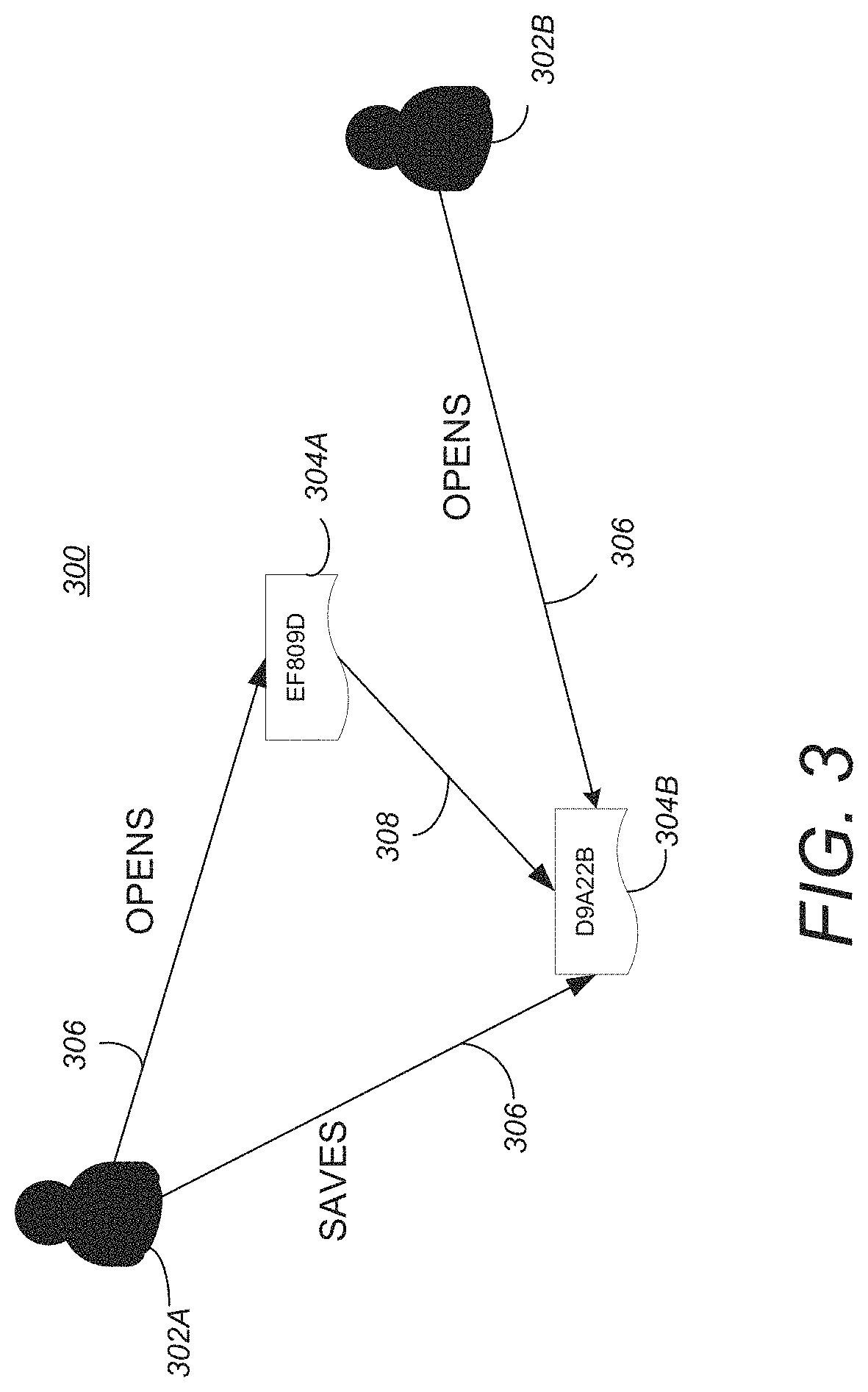
Document tracking through version hash linked graphs
ActiveUS11507741B2Natural language data processingFile access structuresTheoretical computer scienceTracking Document
Owner:AUTODESK INC
Structured document indexing and searching
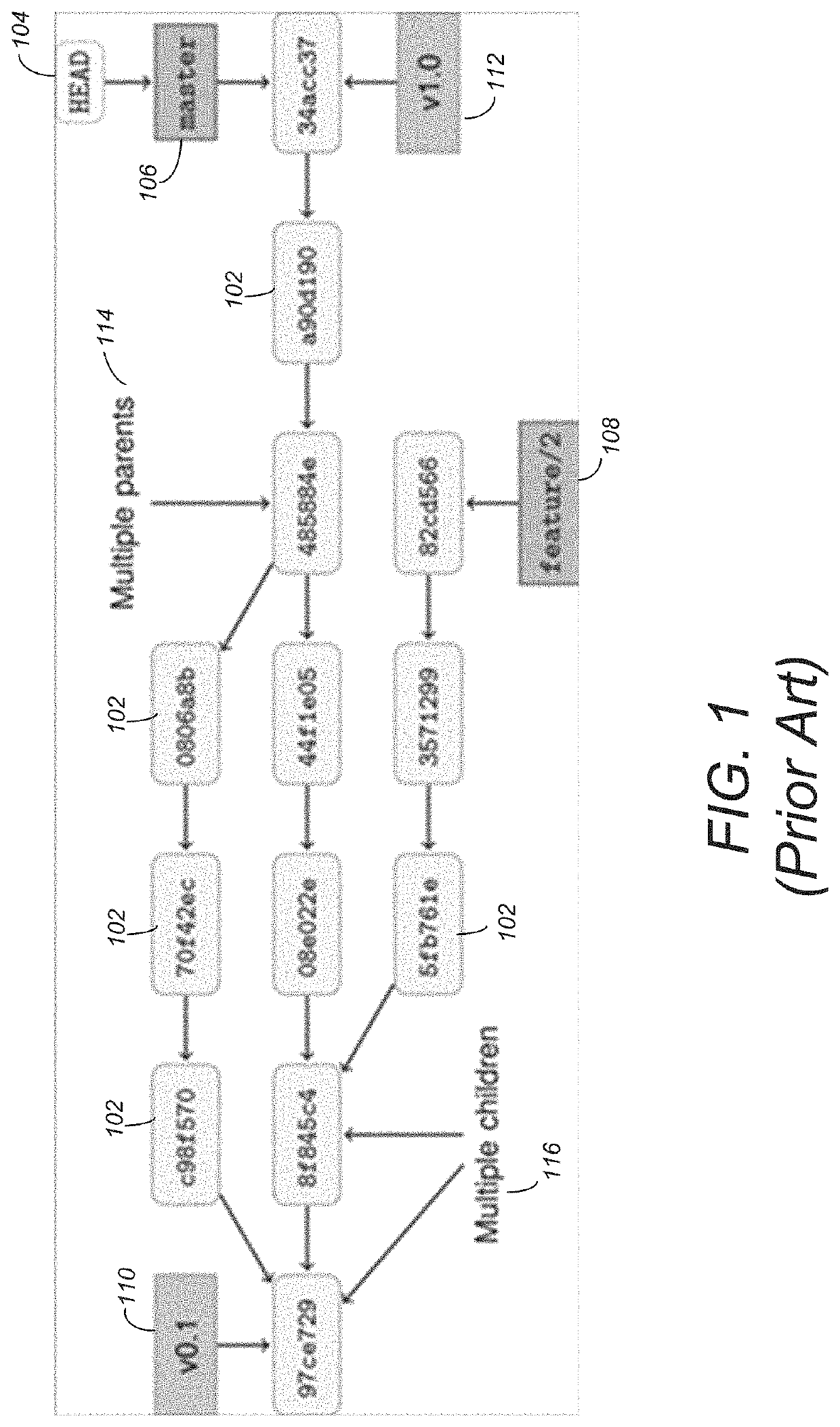
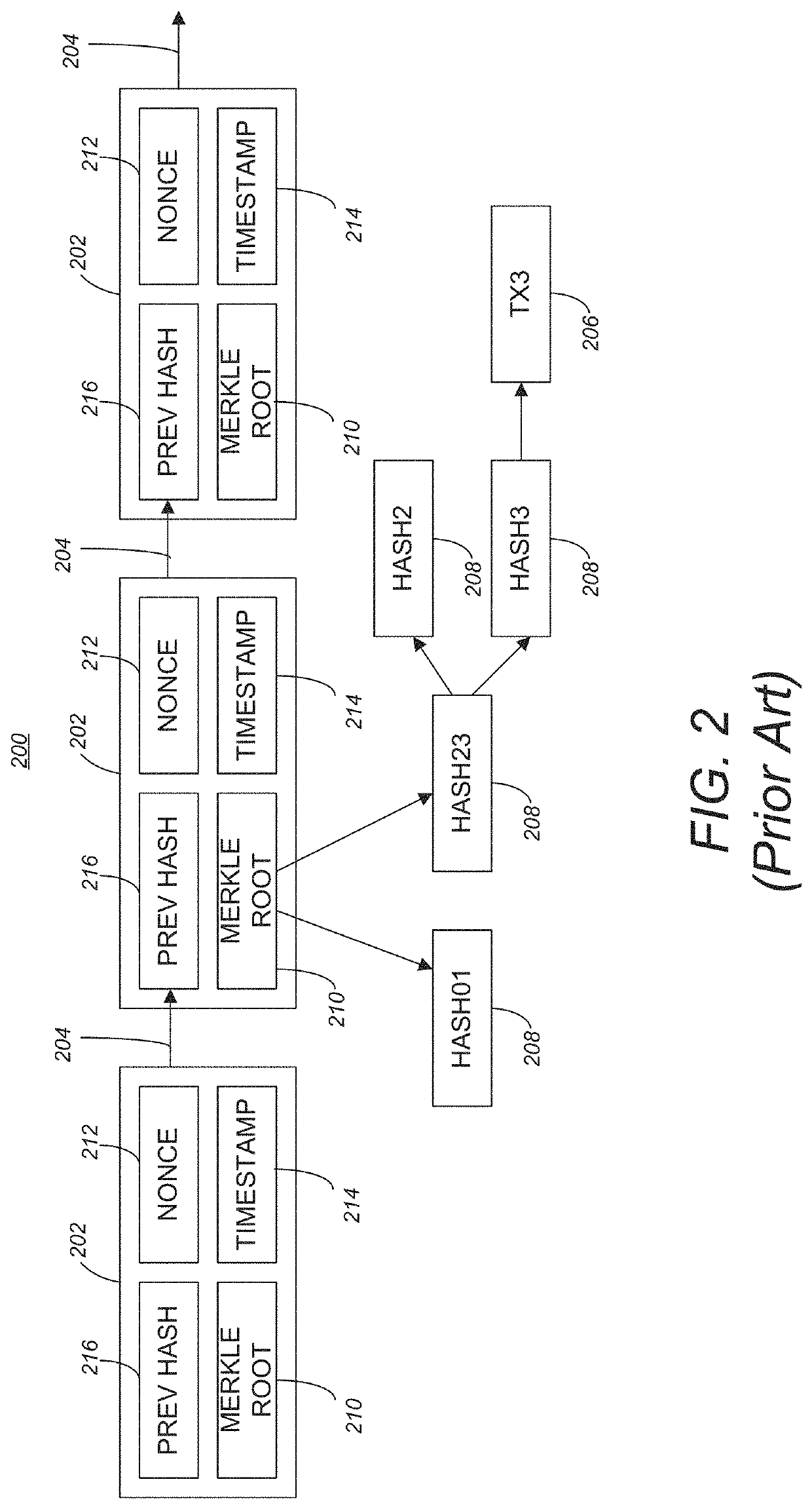
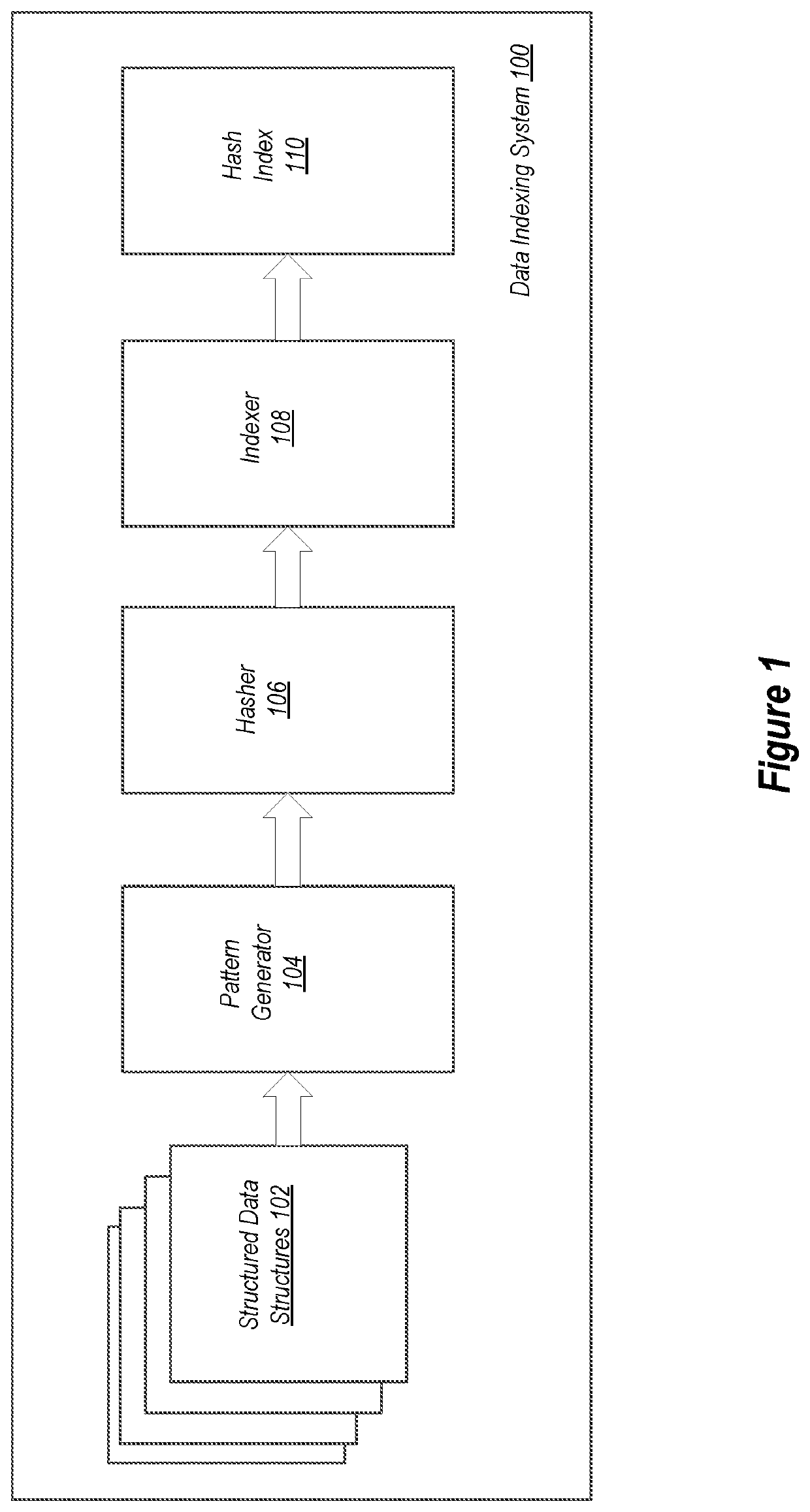
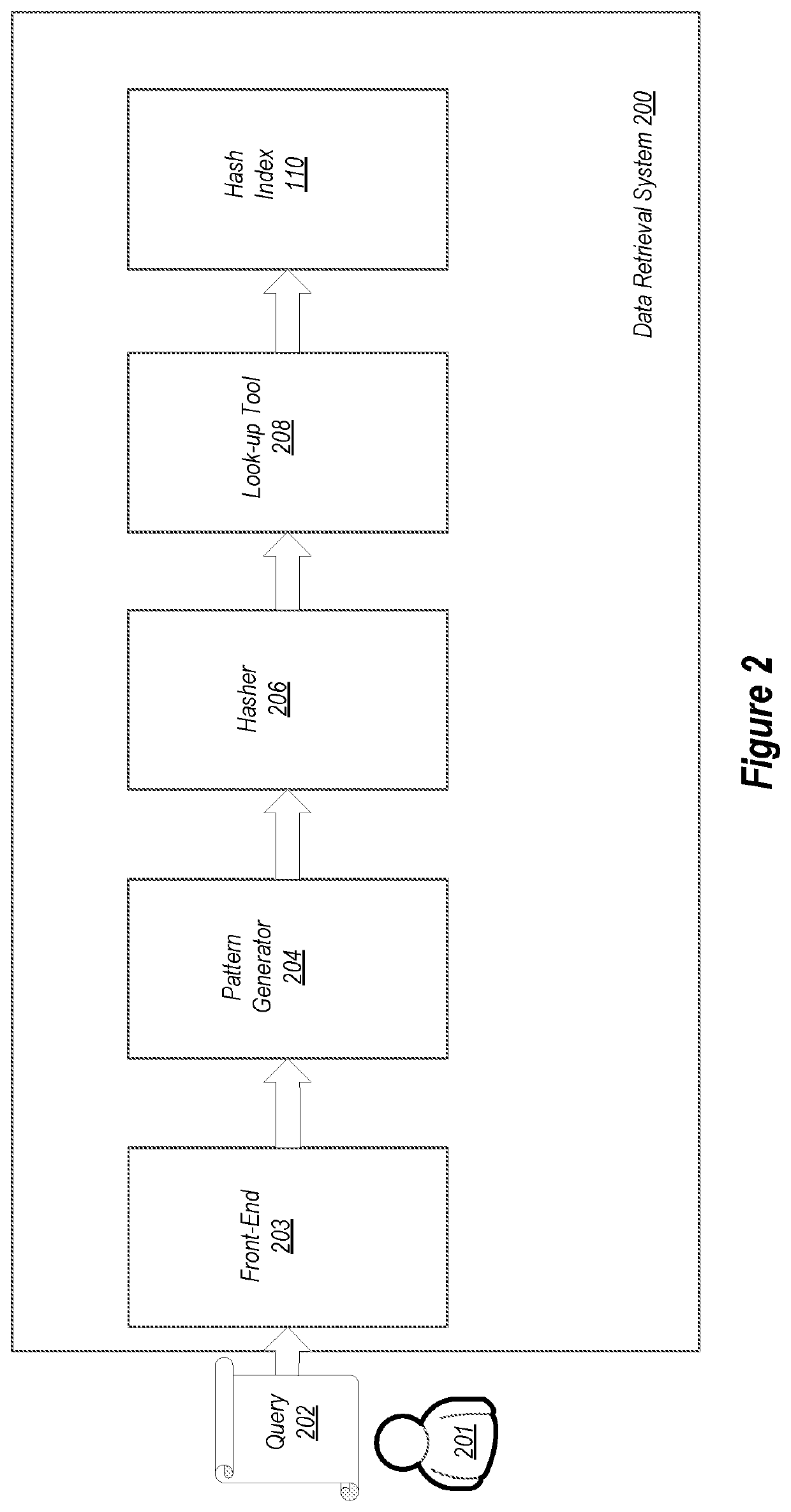
ActiveUS11200217B2Multiple digital computer combinationsSpecial data processing applicationsTheoretical computer scienceSplaysort
A method includes searching for data contained in a structured data structure. The method includes receiving a query. The query includes a structured data structure path and a first element related to the structured data structure path. One or more patterns are created comprising at least a portion of the structured data structure path and one or more elements related to the first element. For each of the one or more patterns, a hash is created. The created hashes are looked-up in a hash index to identify one or more structured data structures correlated to the hashes. The one or more structured data structures are identified to a user.
Owner:PERFECT SEARCH CORP
Data processing method, device, computer equipment and storage medium for stream computing
ActiveCN112069162BSolve the problem of unreliable calculation resultsSpecial data processing applicationsDatabase indexingBit arraySplaysort
The present application relates to a data processing method, device, computer equipment and storage medium. The method collects the data to be processed, extracts the key value from the data to be processed, uses the set hash rule to hash the key value, obtains the corresponding target hash value, and maps the target hash value to the pre-set hash value. The corresponding bit in the created bit array, if there is no data in the corresponding bit in the bit array, it means that the data to be processed is new data, so the data to be processed is processed according to the data processing request of the business system, and the processing is returned to the business system The target data obtained after processing the data is processed, because only the new data is processed, thus solving the problem of unreliable calculation results of stream processing due to data duplication.
Owner:太平金融科技服务(上海)有限公司
Method, electronic device and computer program for providing a hash value for a piece of data
ActiveCN107210910BUser identity/authority verificationDigital data protectionHash functionTheoretical computer science
A method of providing a hash value for a piece of data is disclosed, wherein the hash value specifies a time stamp for the piece of data when verified, for limiting the risk of collisions between the hash values. The method includes collecting one or more root timestamps for the root of a hash tree structure defining a hash function, where the root timestamp is a root timestamp from the past, determining whether a nonce value can be received from the server, and when the nonce value cannot be received from the server When a nonce is received, a hash value is provided by a hash function of the piece of data and the root timestamp, or when a nonce is successfully received from the server, by the nonce, the piece of data and the root timestamp A hash function of the root timestamp described above is used to provide the hash value. An electronic device and a computer program are also disclosed.
Owner:TELEFON AB LM ERICSSON (PUBL)
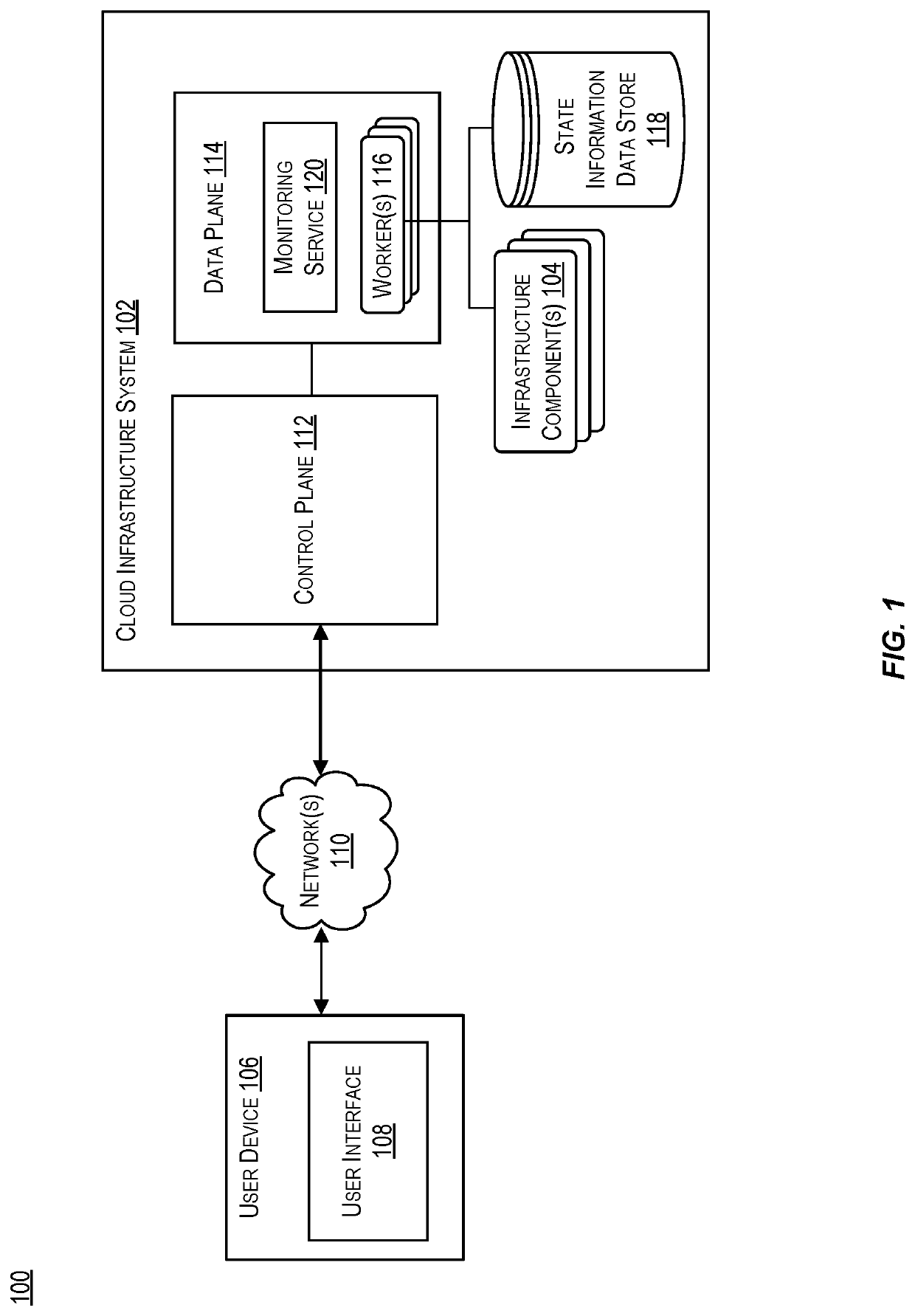
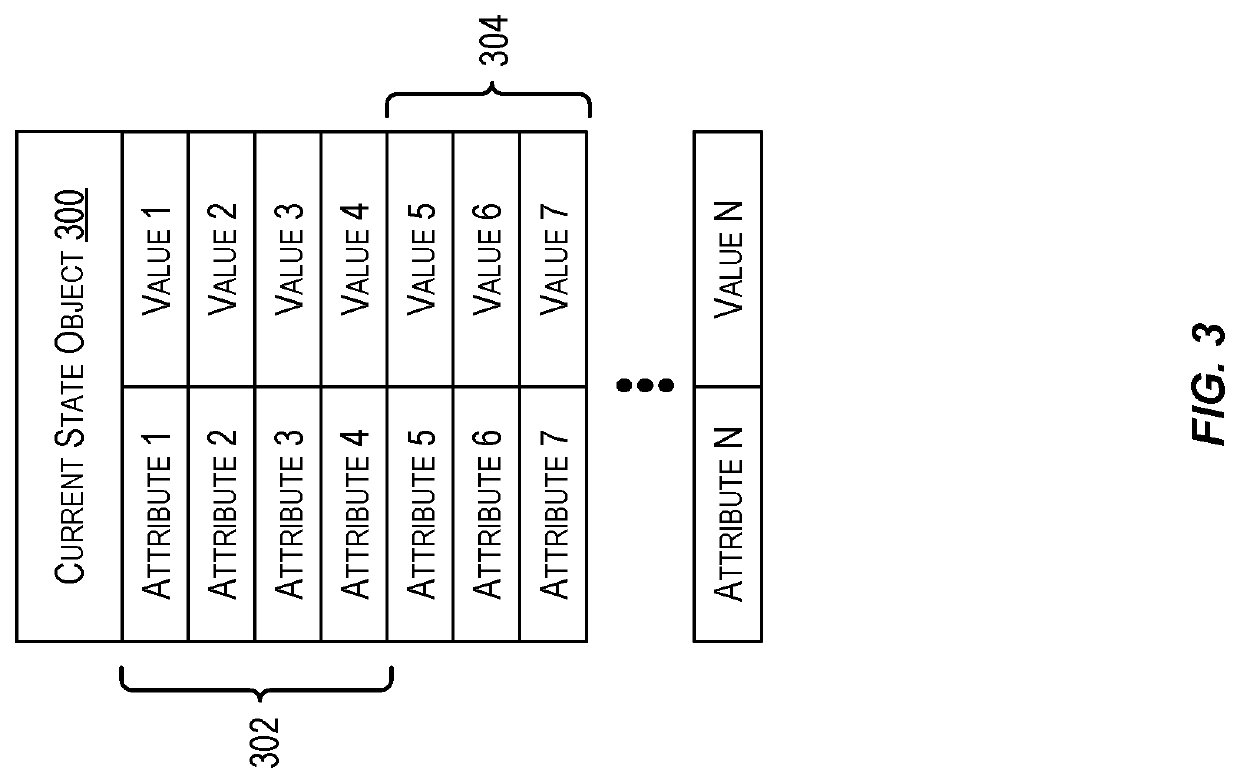
Techniques for modifying a compute instance
ActiveUS11481230B2Program loading/initiatingSpecial data processing applicationsTheoretical computer scienceEngineering
Systems, devices, and methods discussed herein are directed to modifying aspects of a compute instance. A user may request a change to the compute instance. The system may derive a state object indicating a future state of the compute instance were the change to be applied. A hash of a subset of the state object's attributes may be computed and provided to the requesting computing component. The system may subsequently proceed with applying the change. A current state object indicating a current state of the compute instance may be derived based on applying the change. An additional hash of the subset of the current state object's attributes may be computed and provided to the requesting computing component. The two hashes may be configured to enable the requesting computing component to verify the change to the compute instance has been implemented.
Owner:ORACLE INT CORP
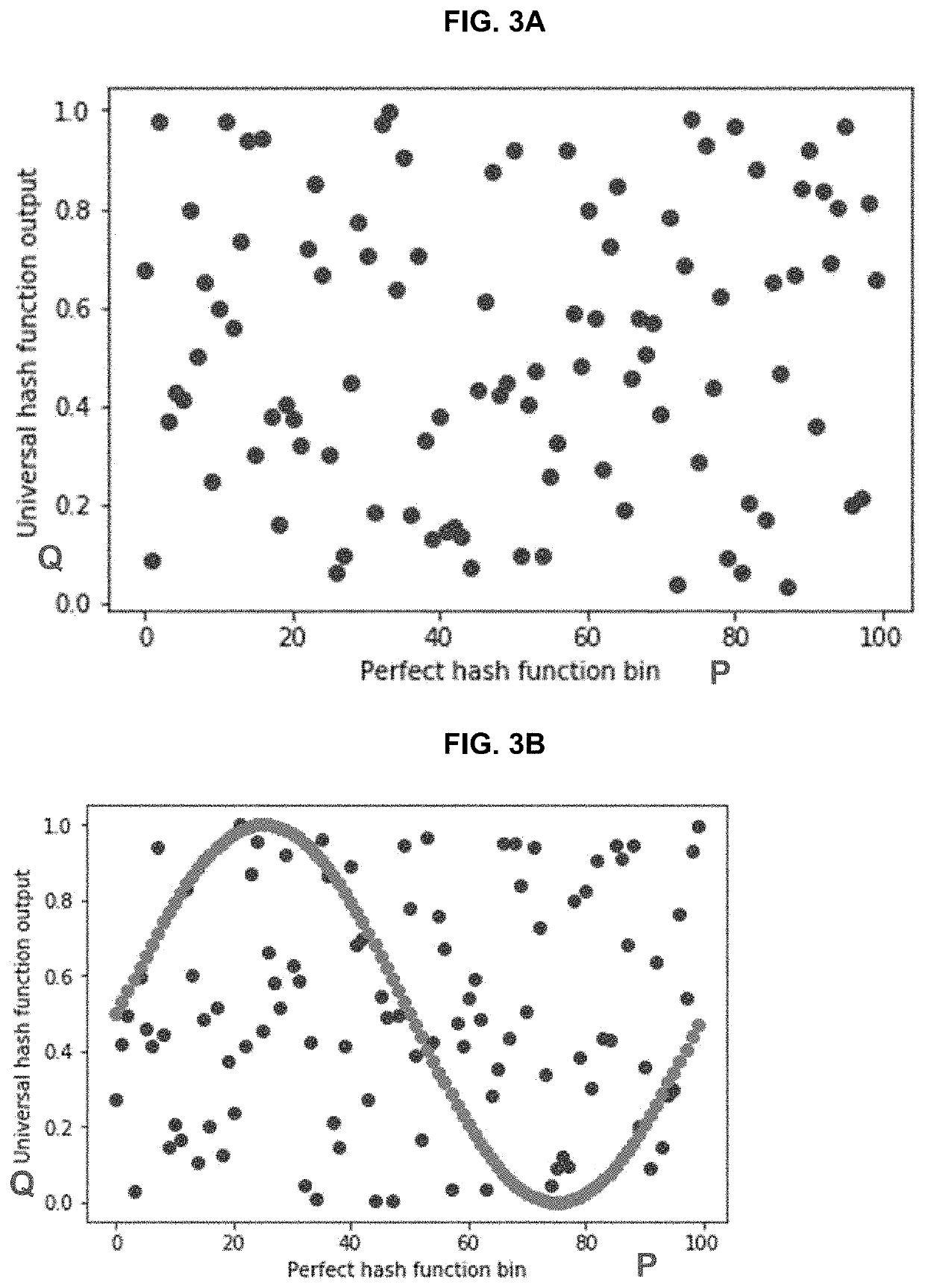
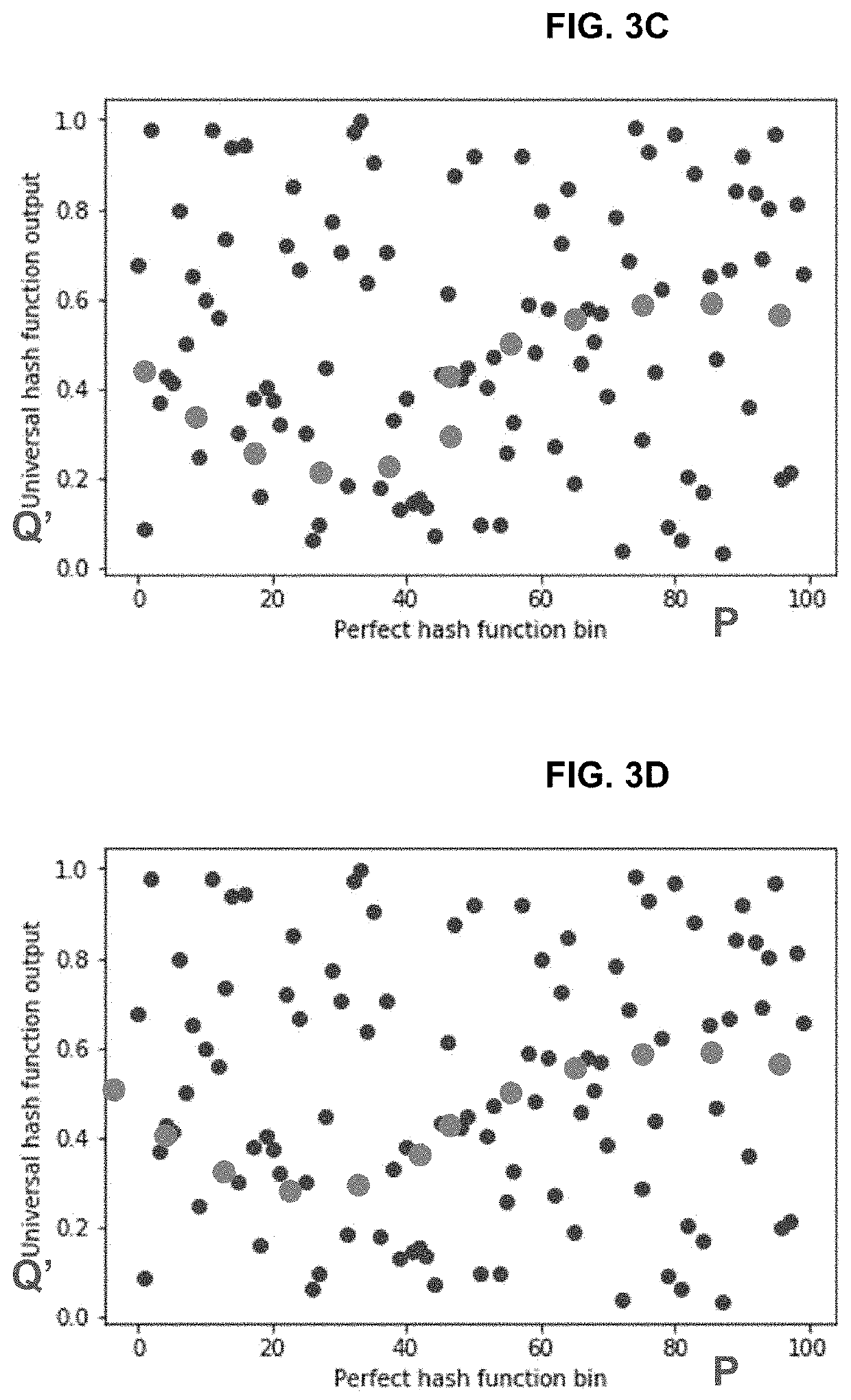
Parametric filter using hash functions with improved time and memory
PendingUS20220291925A1Minimize energy functionSpecial data processing applicationsMachine execution arrangementsData streamTheoretical computer science
Method for searching an item using a parametric hash filter includes forming an input vector from input data stream; forming a hash matrix having a first portion and a second portion; multiplying the hash matrix with the input vector to generate a second input vector including a hash values of the first input vector; generating a perfect hash vector and a universal hash vector, by applying a smooth periodic function to the second input vector; mapping onto a Markov random field the coordinates of locations of hash values in a search domain for which there is no possibility of collisions in the perfect hash vector to form an energy function; minimizing the energy function to generate a compressed hash table; fitting a band of acceptable locations in the compressed hash table, based on a predetermined false positive rate; and searching for a new item in the band of acceptable locations.
Owner:RAYTHEON BBN TECH CORP
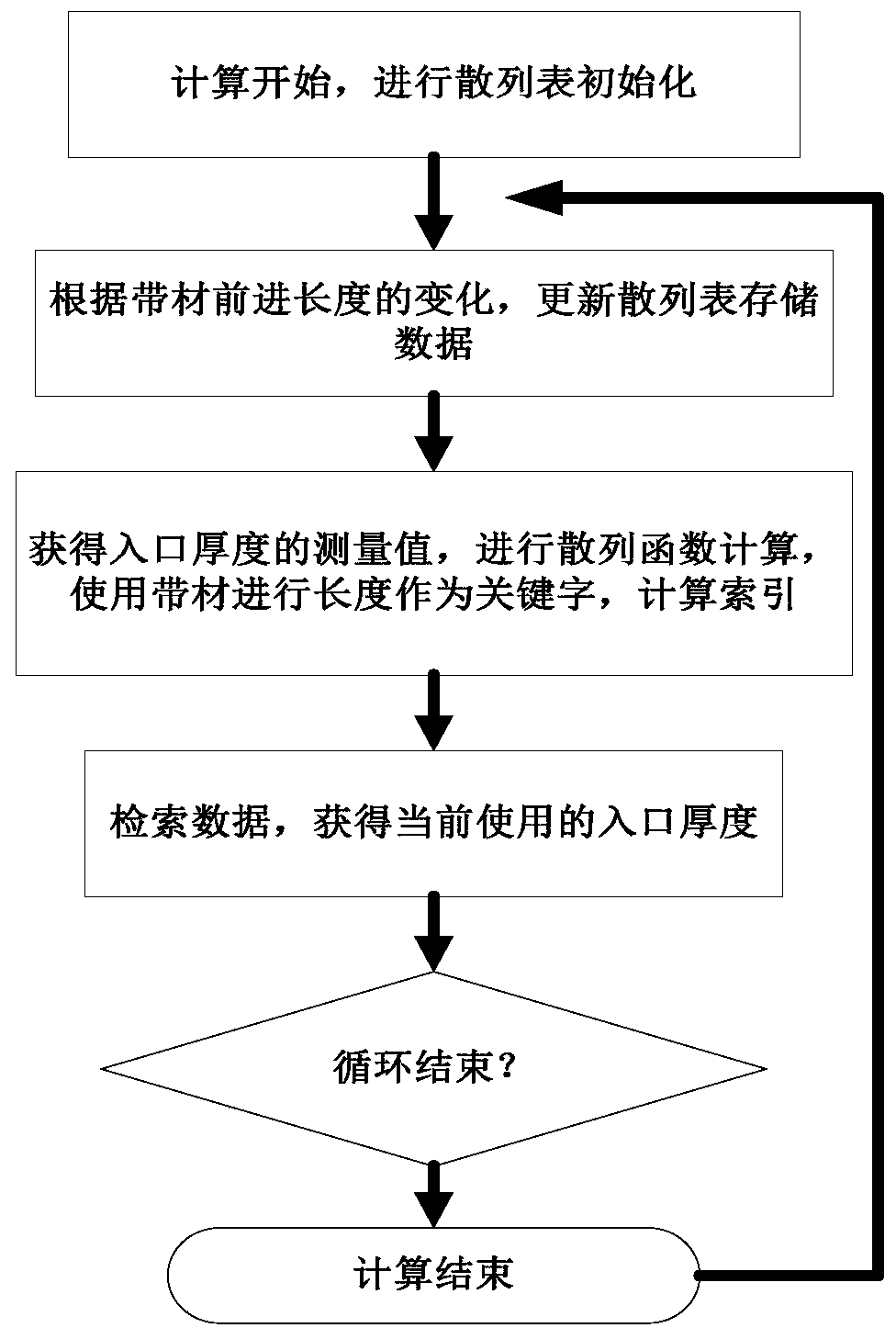
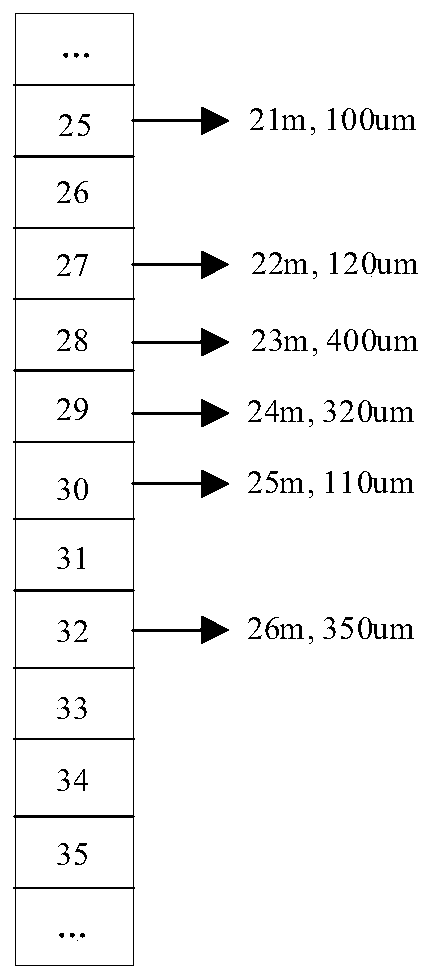
Hash mapping storage method and system for second flow thickness
ActiveCN110807029AImprove Data Retrieval EfficiencyAvoid successive shift operationsDatabase updatingRoll mill control devicesSplaysortData mining
The invention provides a hash mapping storage method for second flow thickness control. According to the method, second flow thickness control calculation is realized, a data structure of a hash tableis used, inlet thickness measurement values needed in the second flow calculation process are stored in the hash table with the fixed length, the advancing length of a strip serves as a keyword, a hash function is used for calculating a storage index, the thickness value of an inlet entering a roll gap at present is retrieved, and the method participates in calculation of a second flow controller. According to the method, a traditional first-in first-out queue data structure is replaced by a hash table data structure, when the currently used entrance thickness value is retrieved, only one-time calculation is needed, the shifting operation needed in the first-in first-out queue is omitted, the retrieval efficiency is high, the calculation time is short, and the method can be used for entrance thickness calculation in second flow thickness control.
Owner:RUYUAN DONGYANG UACJ PRECISION FOIL CO LTD
Data table processing method and device and storage medium
PendingCN112182120AImprove computing efficiencyImprove verification efficiencyEncryption apparatus with shift registers/memoriesRelational databasesDatasheetTheoretical computer science
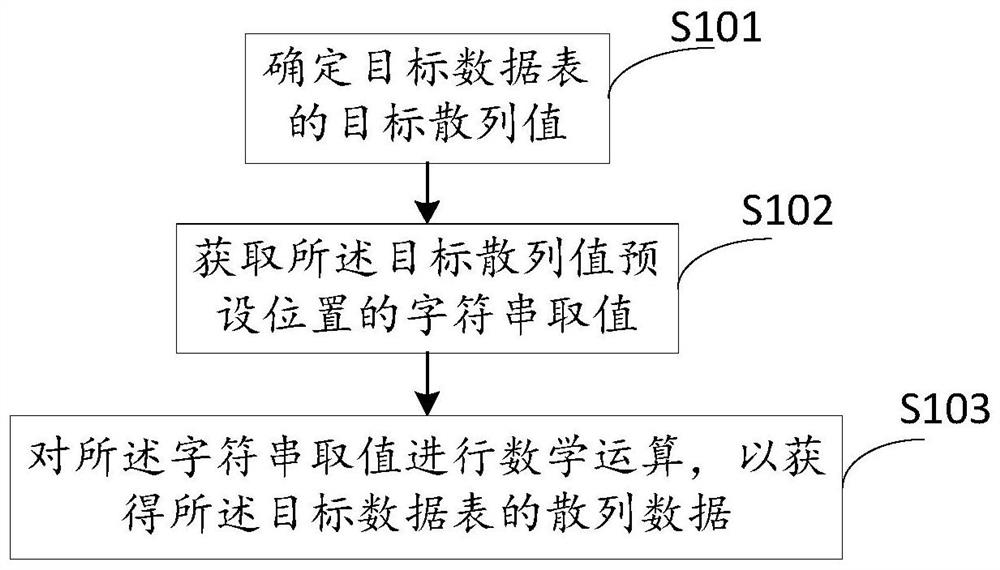
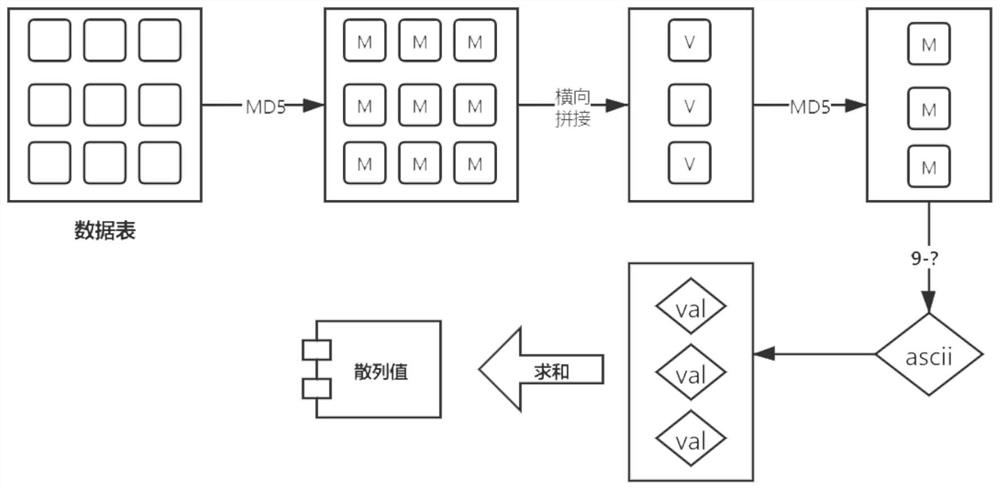
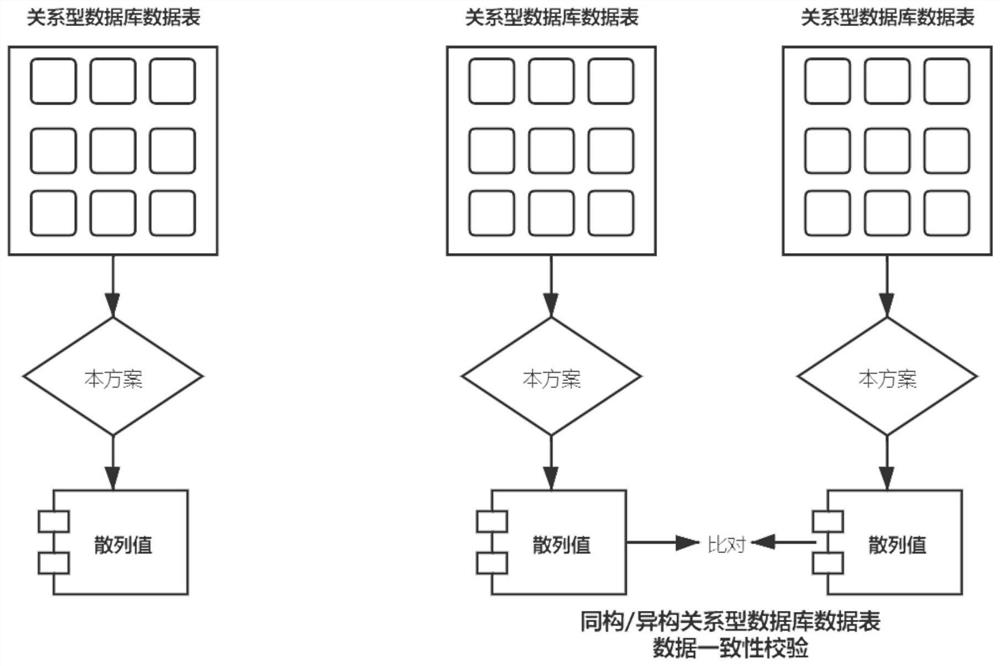
The invention discloses a data table processing method and device and a storage medium, and the method comprises the steps: determining a target hash value of a target data table; obtaining a character string value of a preset position of the target hash value; and performing mathematical operation on the character string value to obtain hash data of the target data table. According to the method,the target hash value of the target data table is determined, then the character string value of the preset position of the target hash value is obtained, and then the character string value is subjected to mathematical operation, so that the hash data of the whole data table can be determined, and the operation and verification efficiency of the data table is effectively improved.
Owner:HIGHGO SOFTWARE
Method and system for hybrid sort and hash-based query execution
ActiveUS11194778B2Special data processing applicationsDatabase indexingTheoretical computer scienceEngineering
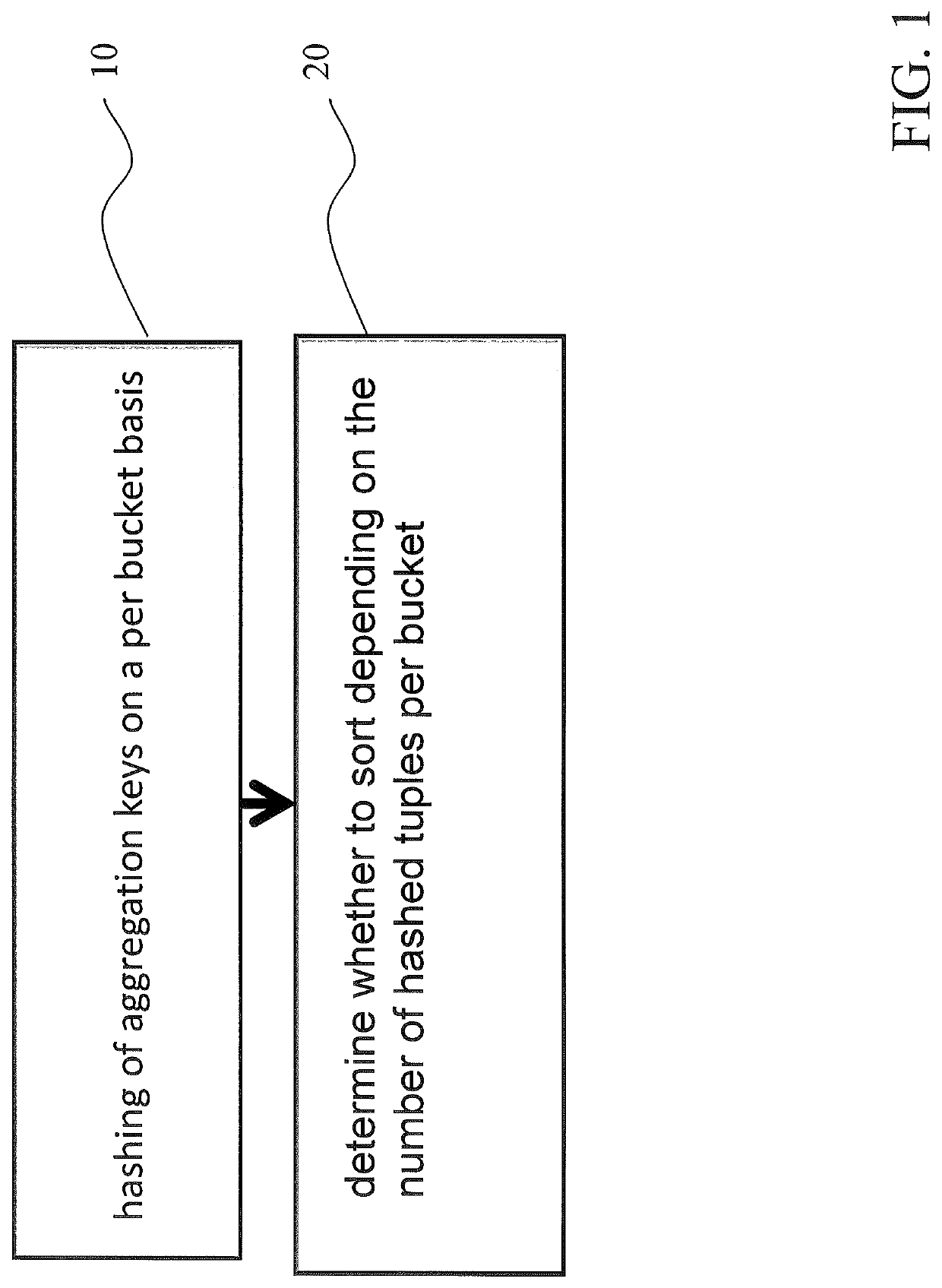
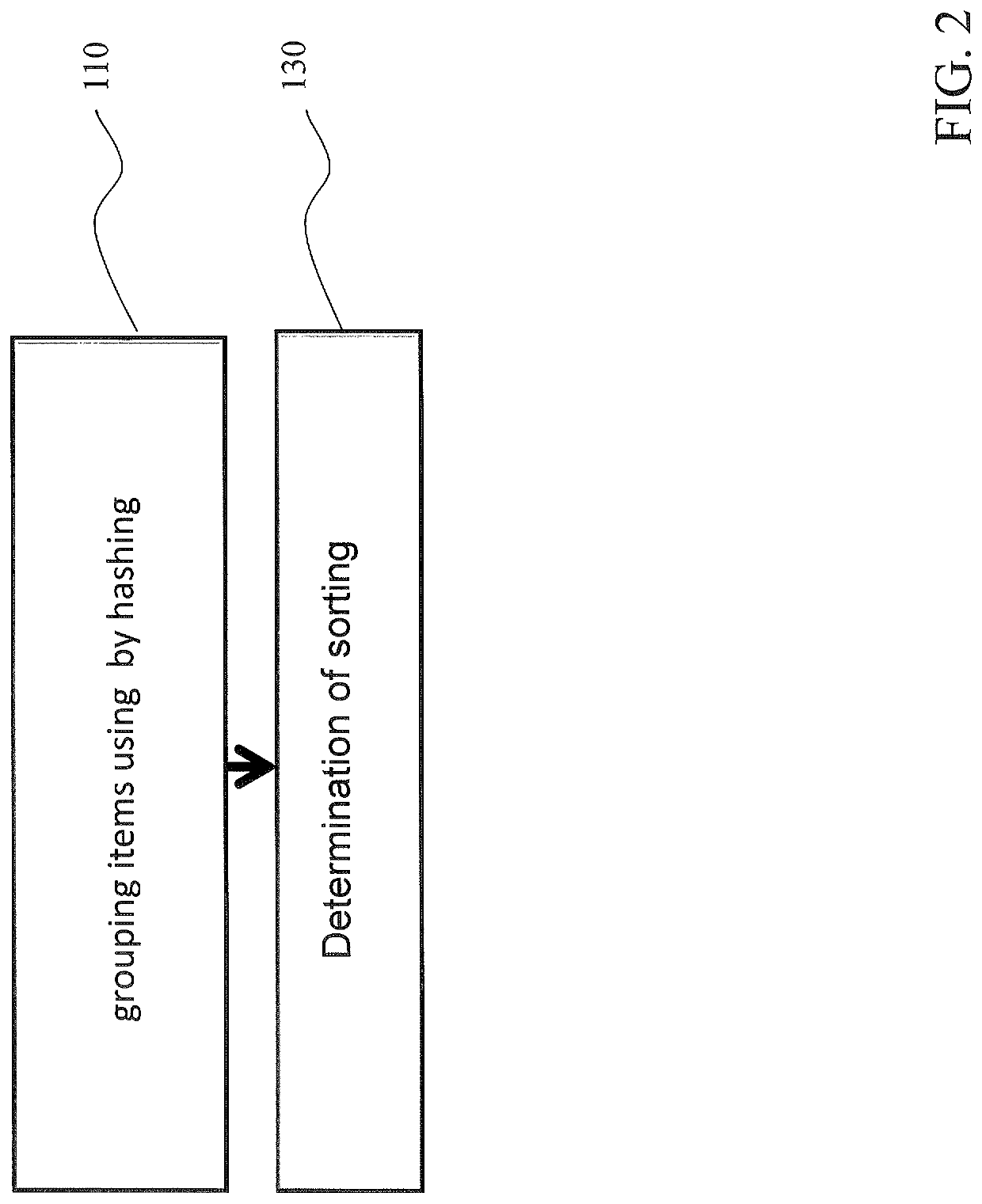
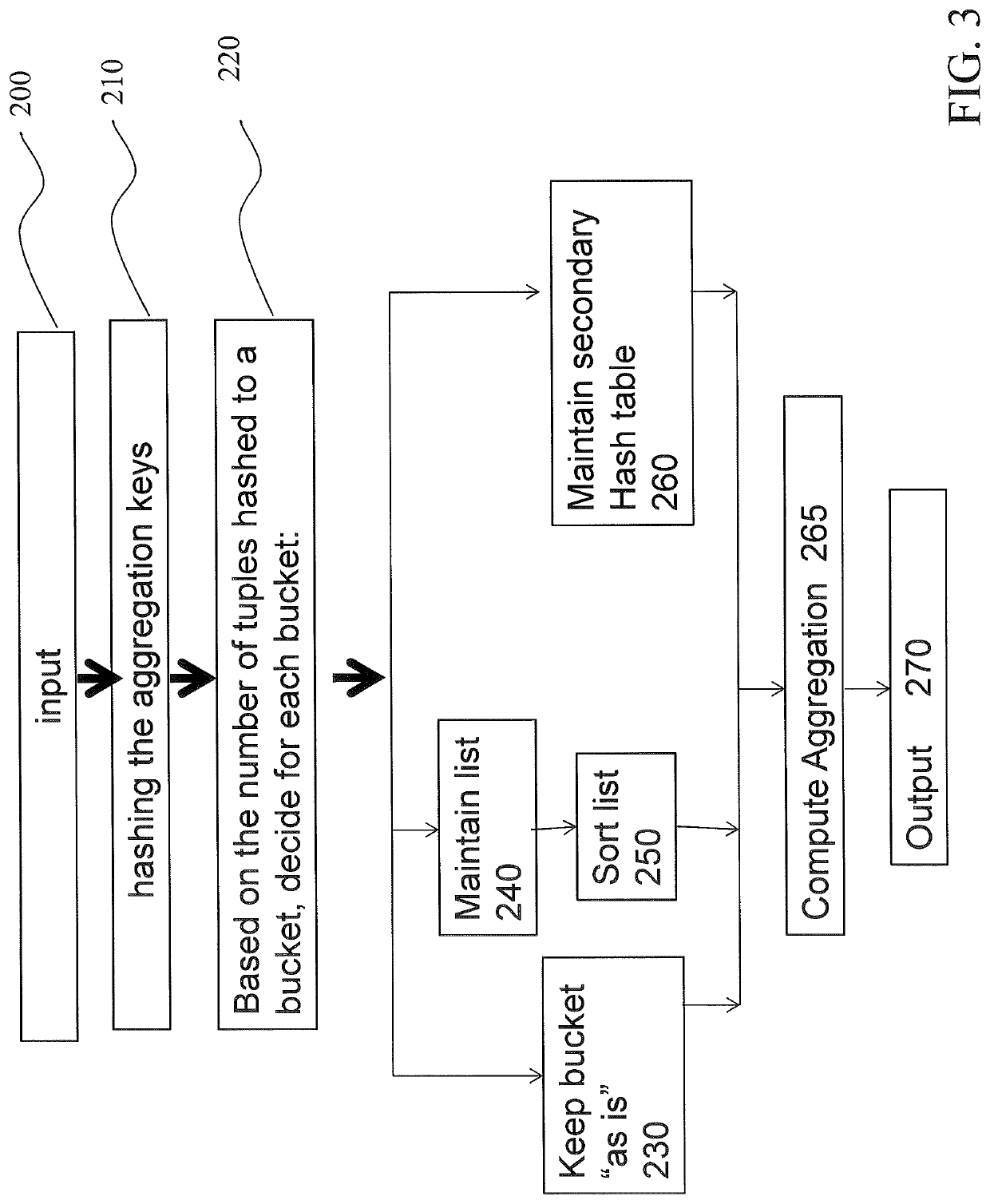
A database system, computer program product, and a method for evaluating aggregates in database systems includes hashing of aggregation keys on a per bucket basis, and depending on a number of hashed tuples per bucket, sorting said tuples. Additionally, depending on the number of hashed tuples per bucket, the bucket is kept without change. Moreover, depending on the number of hashed tuples per bucket, maintaining a secondary hash table for a particular bucket, map tuples to it, aggregate as you map.
Owner:INT BUSINESS MASCH CORP
Cryptographic data verification method
PendingCN113811874AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData setHash function
The invention relates to a comparison method implemented by at least one apparatus (A; B), between a first and a second dataset, in particular with a view to determining whether these two datasets are identical, this method not requiring the presence of these two datasets on the apparatus, and comprising the following steps: a) mixing a number, referred to as the mixing number, with the first dataset, using a mixing function (105; 405), in order to obtain mixed data, b) hashing the mixed data using a hash function (106); 406), and c) comparing the hash thus obtained in step b) with a third dataset assumed to be the hash of the second dataset mixed with the same mixing number as that used in step a) and with the same mixing function (105; 405).
Owner:布鲁诺桑格勒费列雷
A Filtering Method for Real-time Intrusion Detection System
ActiveCN112532598BSmall footprintSpeed up intrusion detectionTransmissionHash tablePerformance guarantee
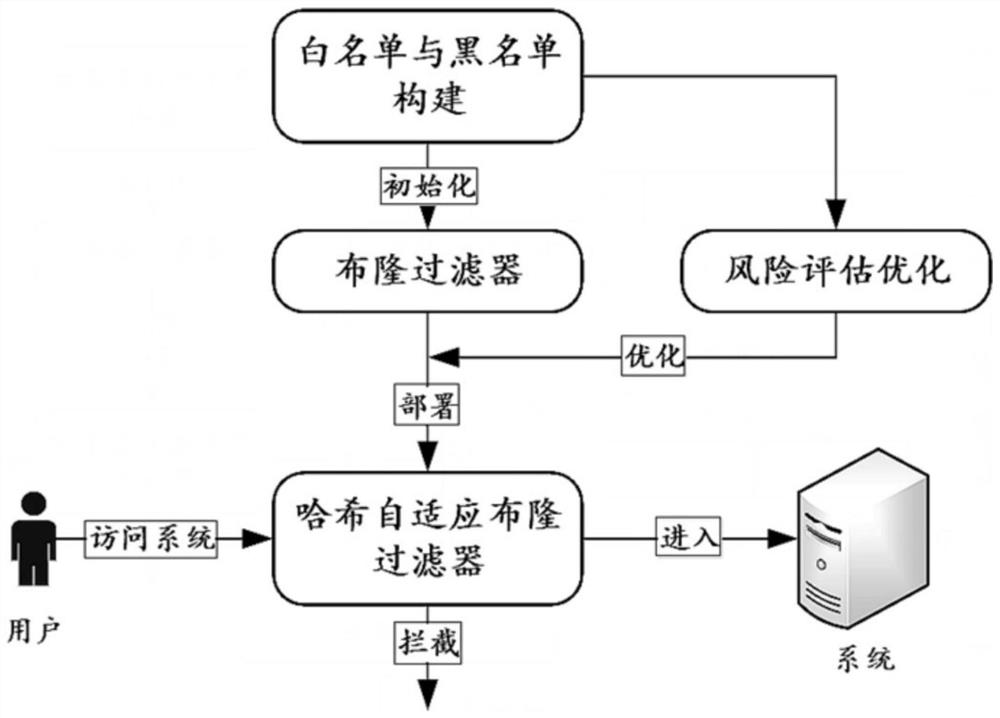
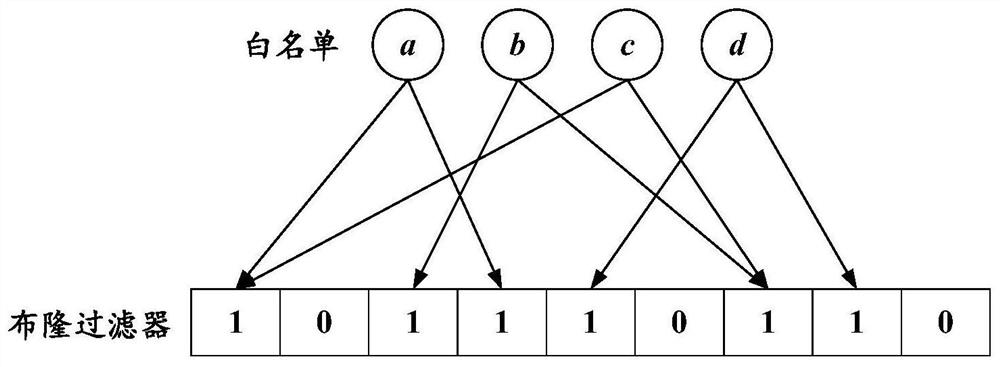
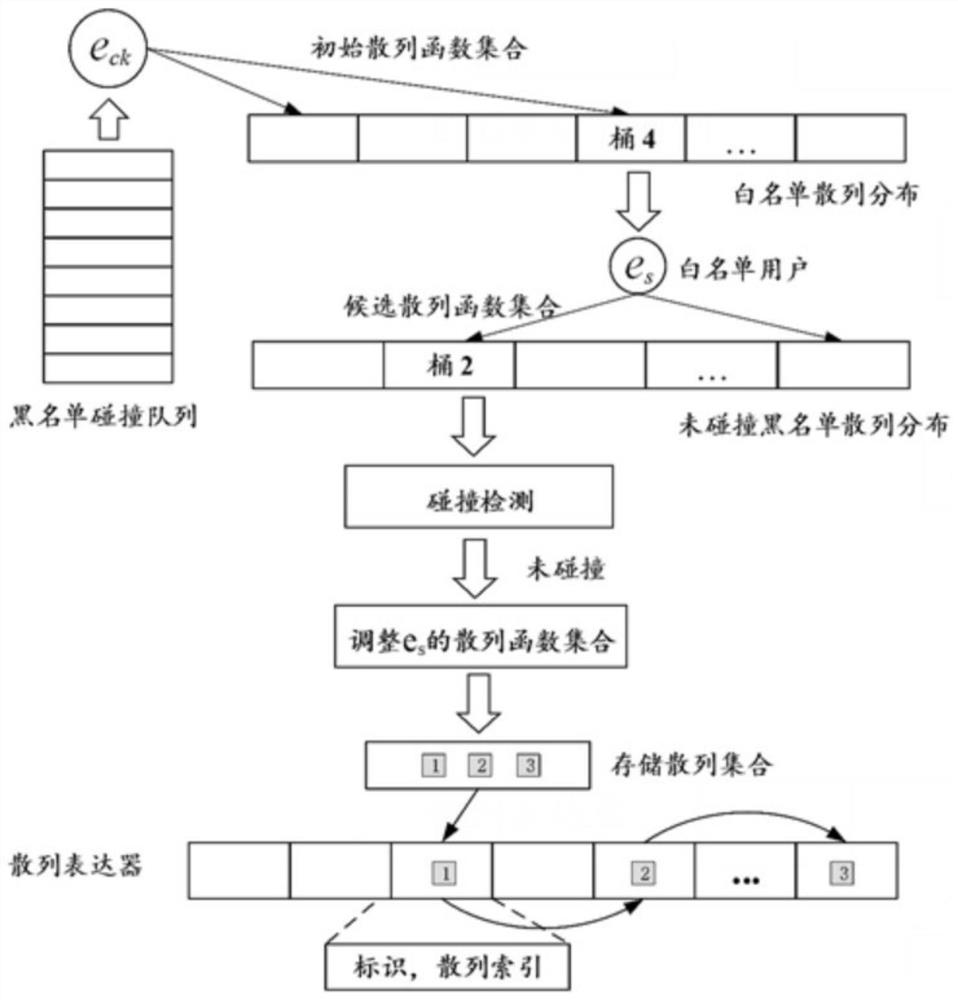
The invention discloses a filtering method for a real-time intrusion detection system, including: white list and black list construction; risk loss assessment; filter construction and deployment; white list users are assigned an initial hash for inserting a Bloom filter; Column function set; combined with blacklist users and their corresponding degree of harm, adaptively adjust the hash function set of whitelist users, so that blacklist users with high degree of harm have a higher probability of being blocked; the adjusted hash The function set is stored in the preset hash expressor; the whitelist user uses its hash function set to be inserted into the Bloom filter, combined with the hash expressor to obtain a hash adaptive Bloom filter, and then the hash Chi adaptive Bloom filters deployed to detection systems. The invention has the characteristics of high space efficiency and fast detection, can effectively reduce system losses caused by blacklisted users, provides effective theoretical performance guarantee, and can be applied to applications involving real-time intrusion detection.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com