Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
579 results about "Software feature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In software, a feature has several definitions. The Institute of Electrical and Electronics Engineers defines the term feature in IEEE 829 as "A distinguishing characteristic of a software item (e.g., performance, portability, or functionality)."
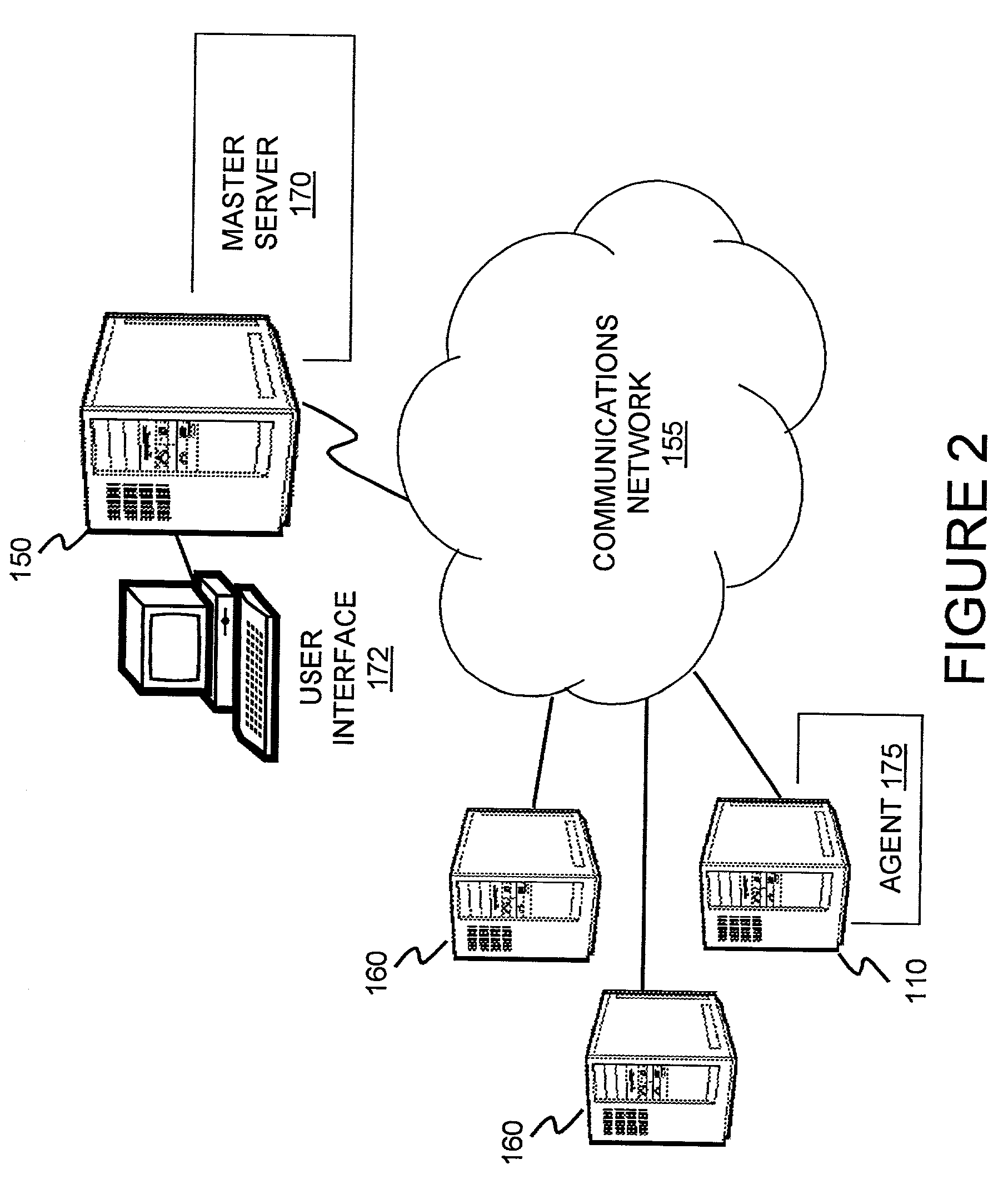
Location-based feature enablement for mobile terminals
ActiveUS8583924B2Digital data processing detailsUser identity/authority verificationComputer terminalComputer science
Owner:HAND HELD PRODS
Method and system for binding enhanced software features to a persona
InactiveUS6891953B1Preventing unchecked proliferationKey distribution for secure communicationDigital data processing detailsBiological activationUniform resource locator
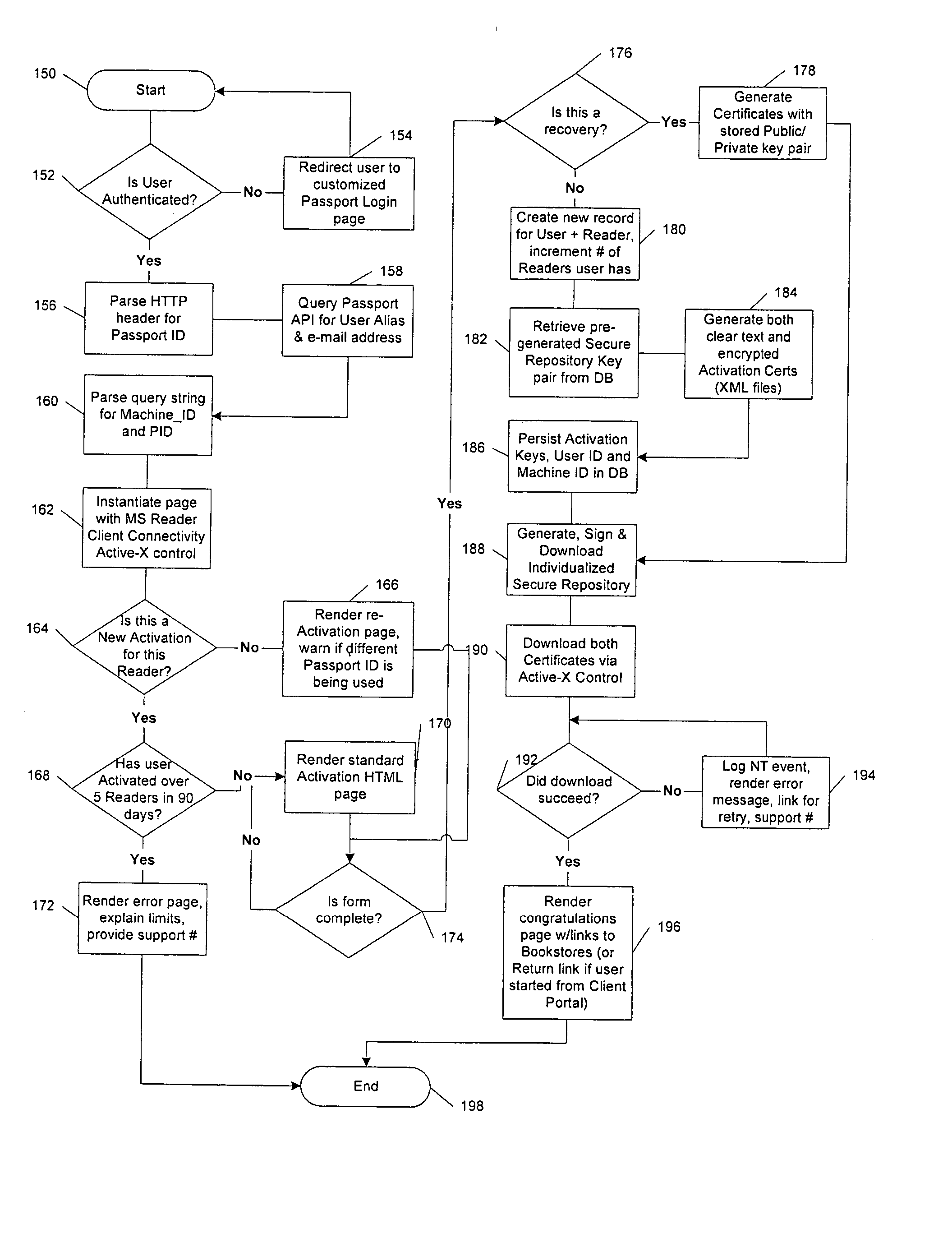
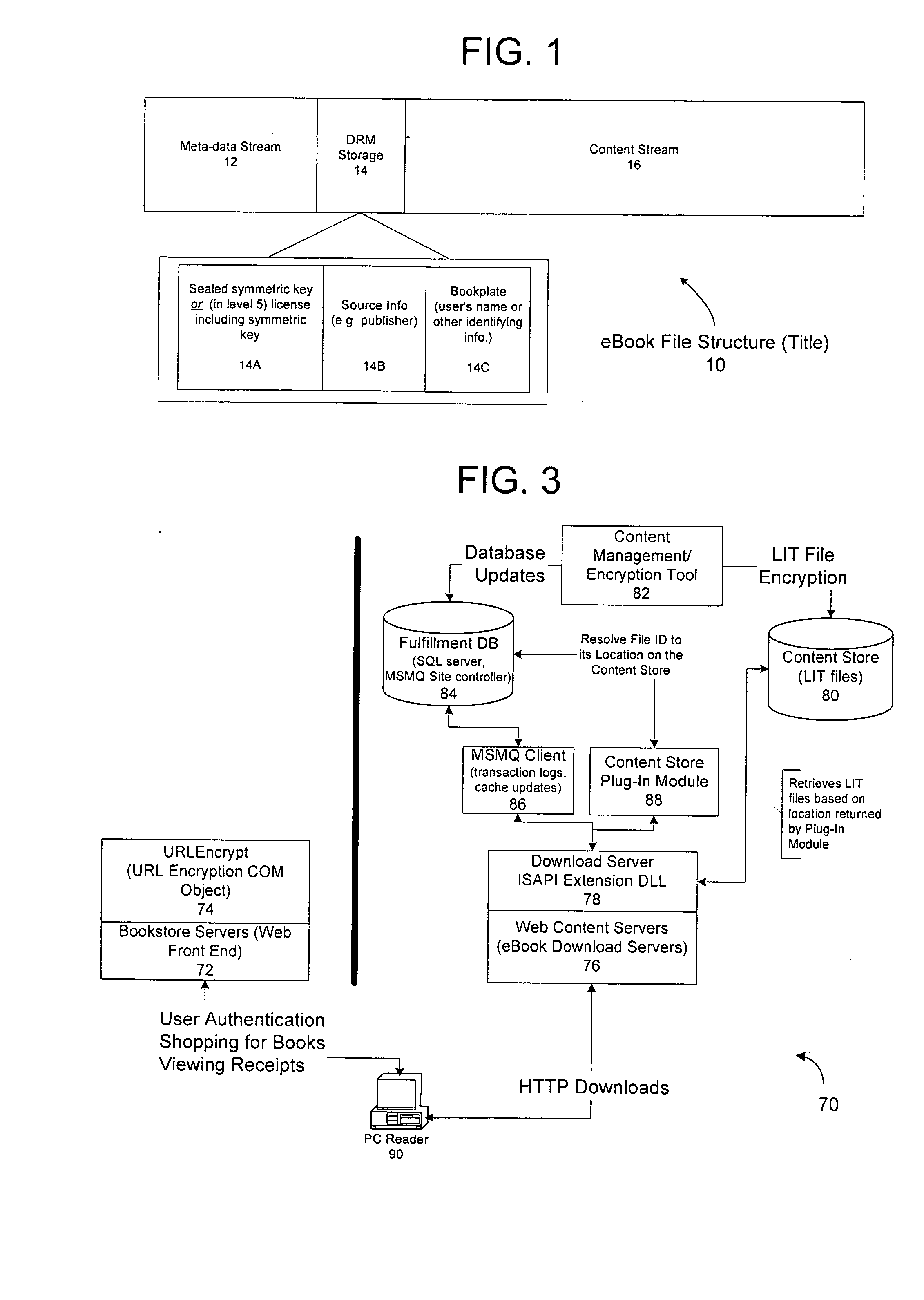
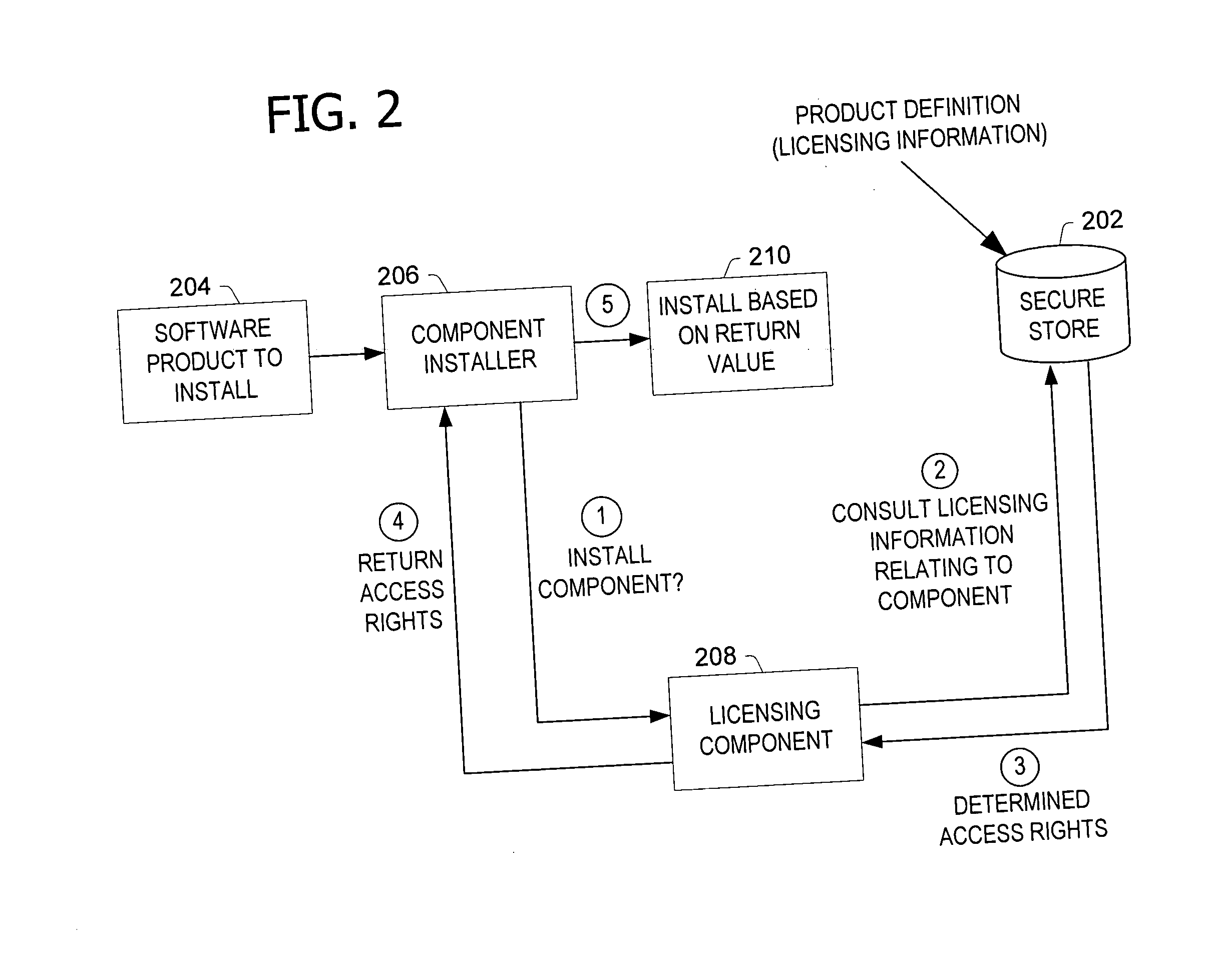
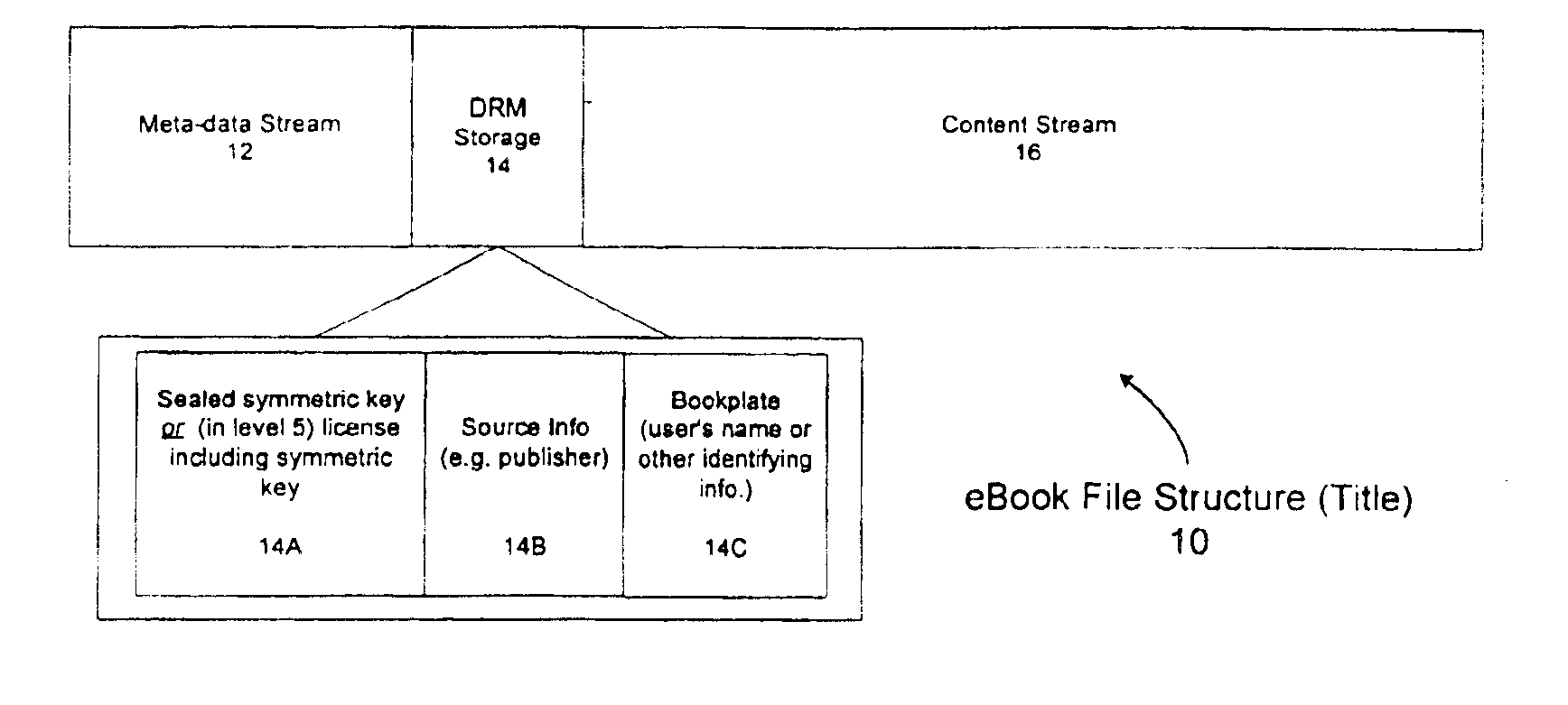
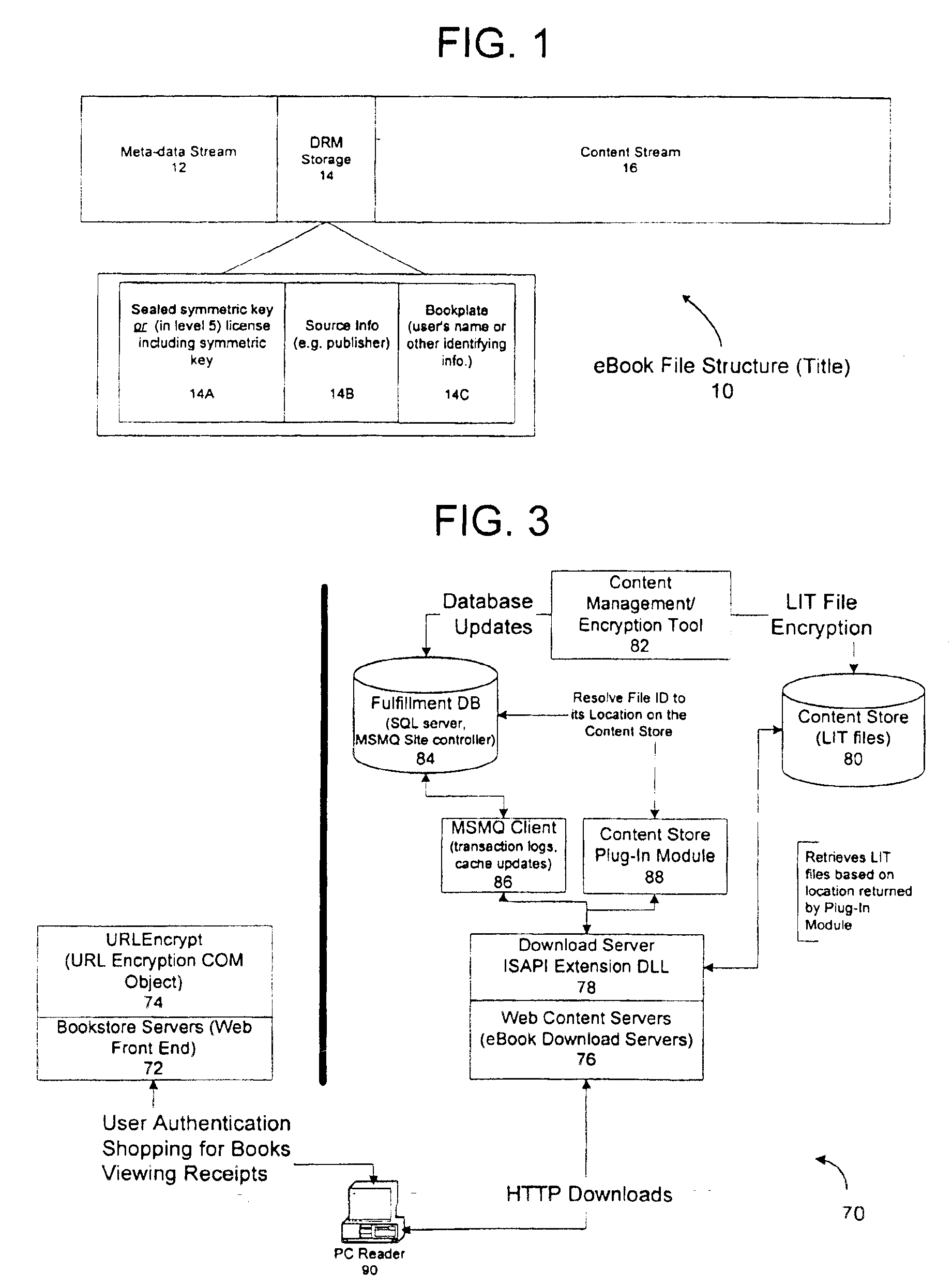
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
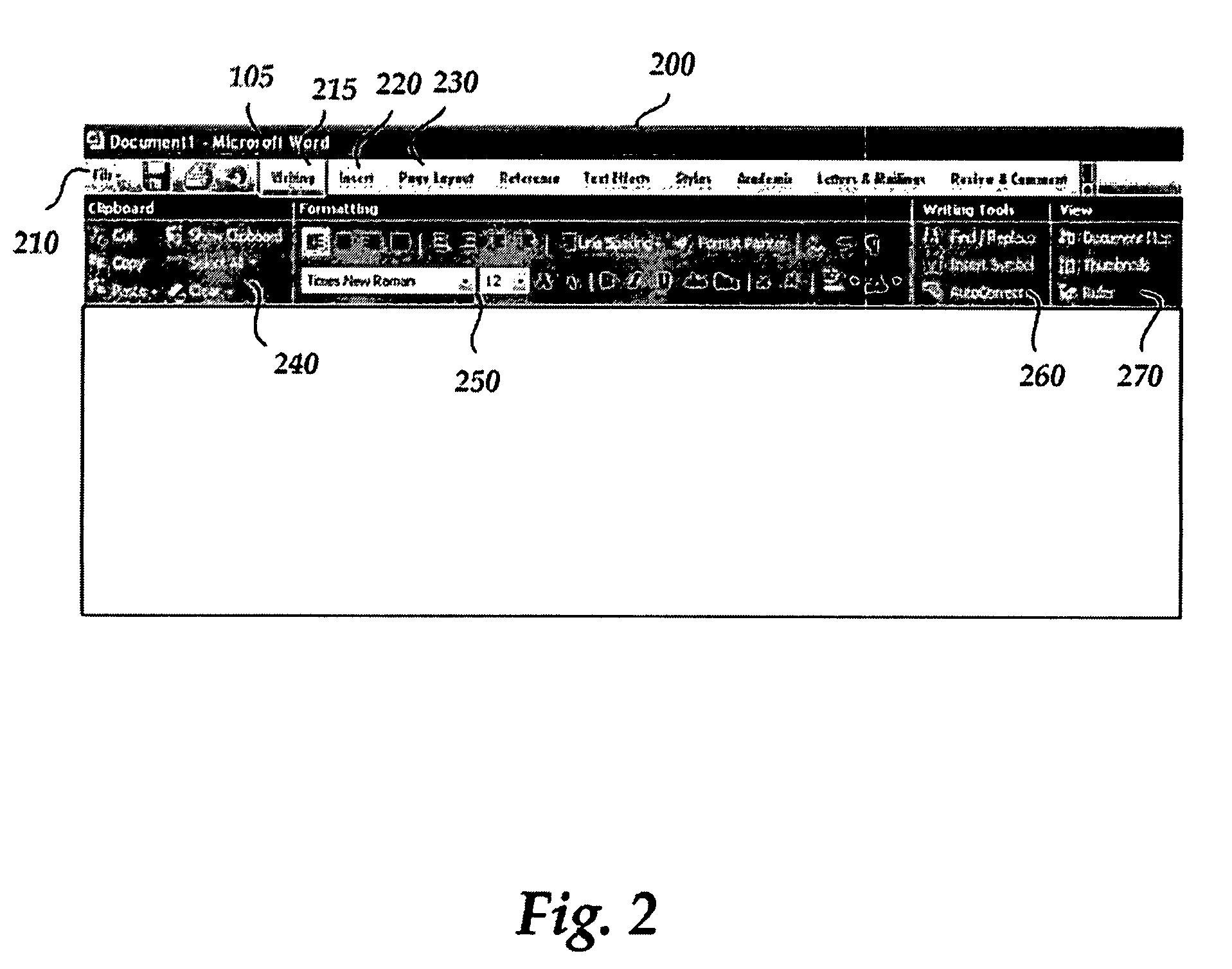
User interface for displaying selectable software functionality controls that are contextually relevant to a selected object
ActiveUS8117542B2Efficient switchingExecution for user interfacesDigital output to display deviceAssociated functionObject context
An improved user interface is provided for displaying selectable functionality controls that identifies the context of the object to which the user interface is relevant, which contains rich functionality controls for applying contextually relevant functionality to a selected object, and which may be efficiently switched to a different context for applying a different set of functionalities to a different or neighboring editable object. A context menu of functionalities is displayed adjacent to a selected object where the menu of functionalities includes functionalities associated with editing the selected object. The context menu includes an identification of the object context and a control for selectively changing the context and associated functionalities of the menu to a different object context for displaying a different set of functionalities associated with the different context.
Owner:MICROSOFT CORP
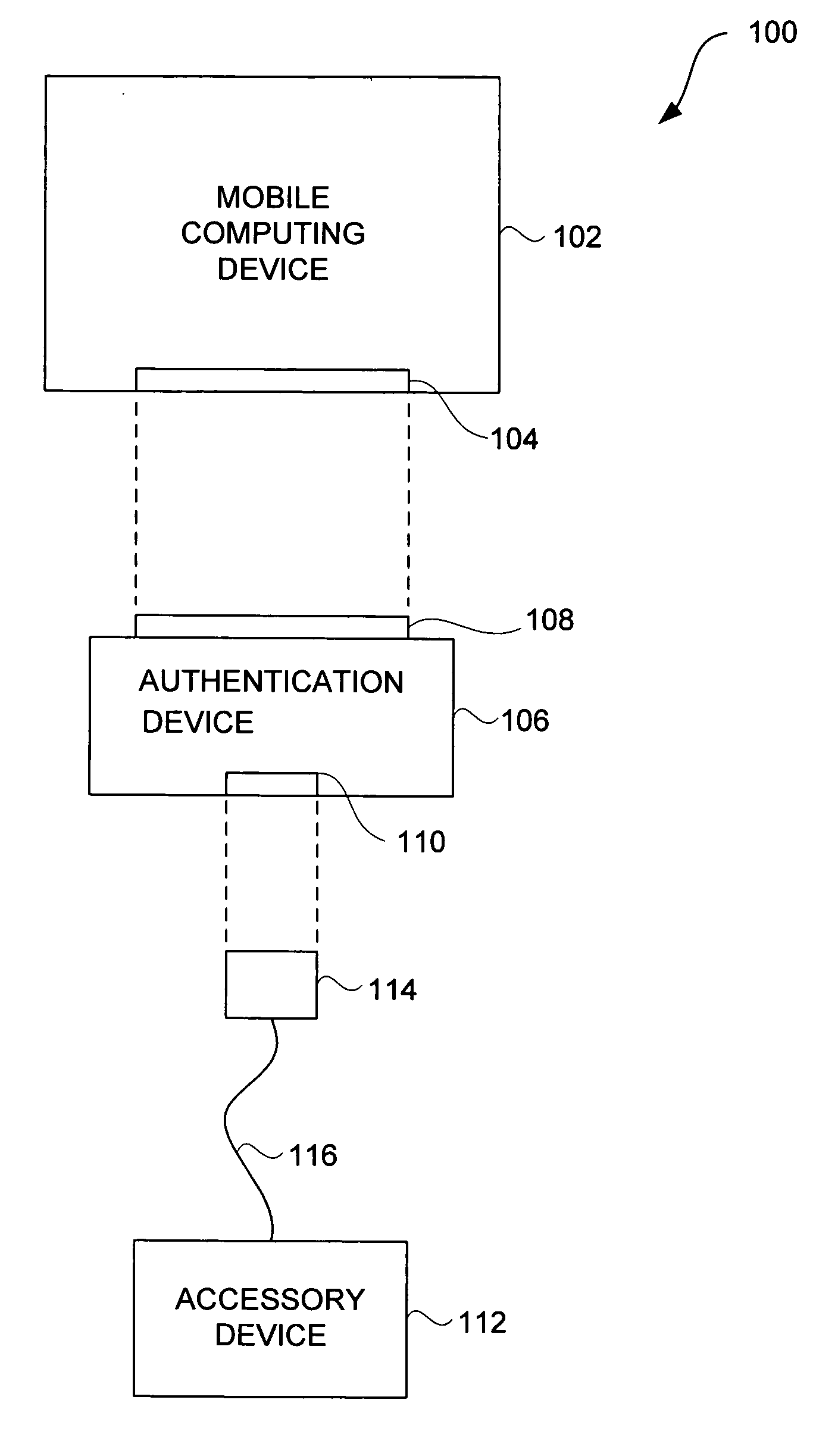
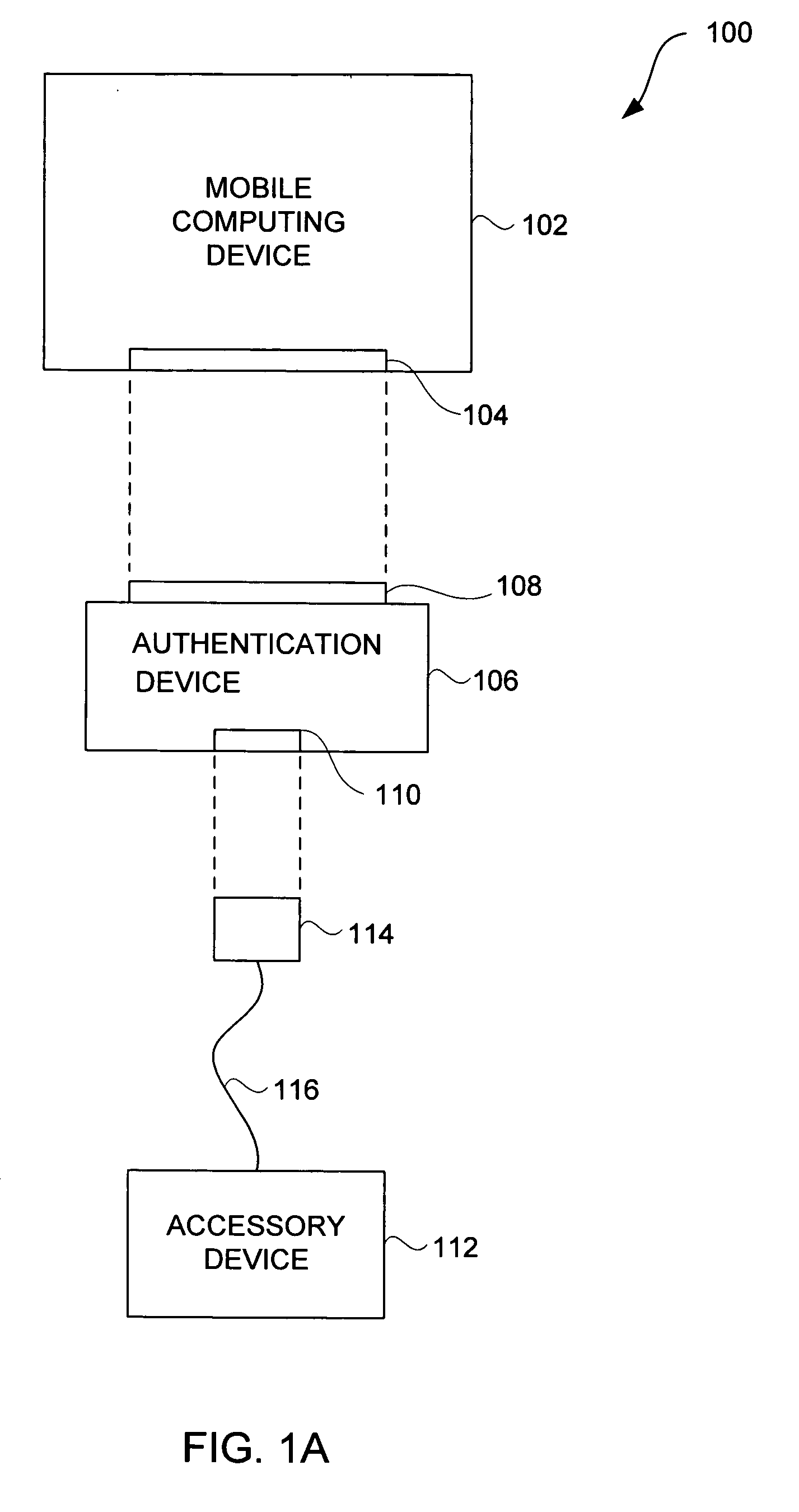
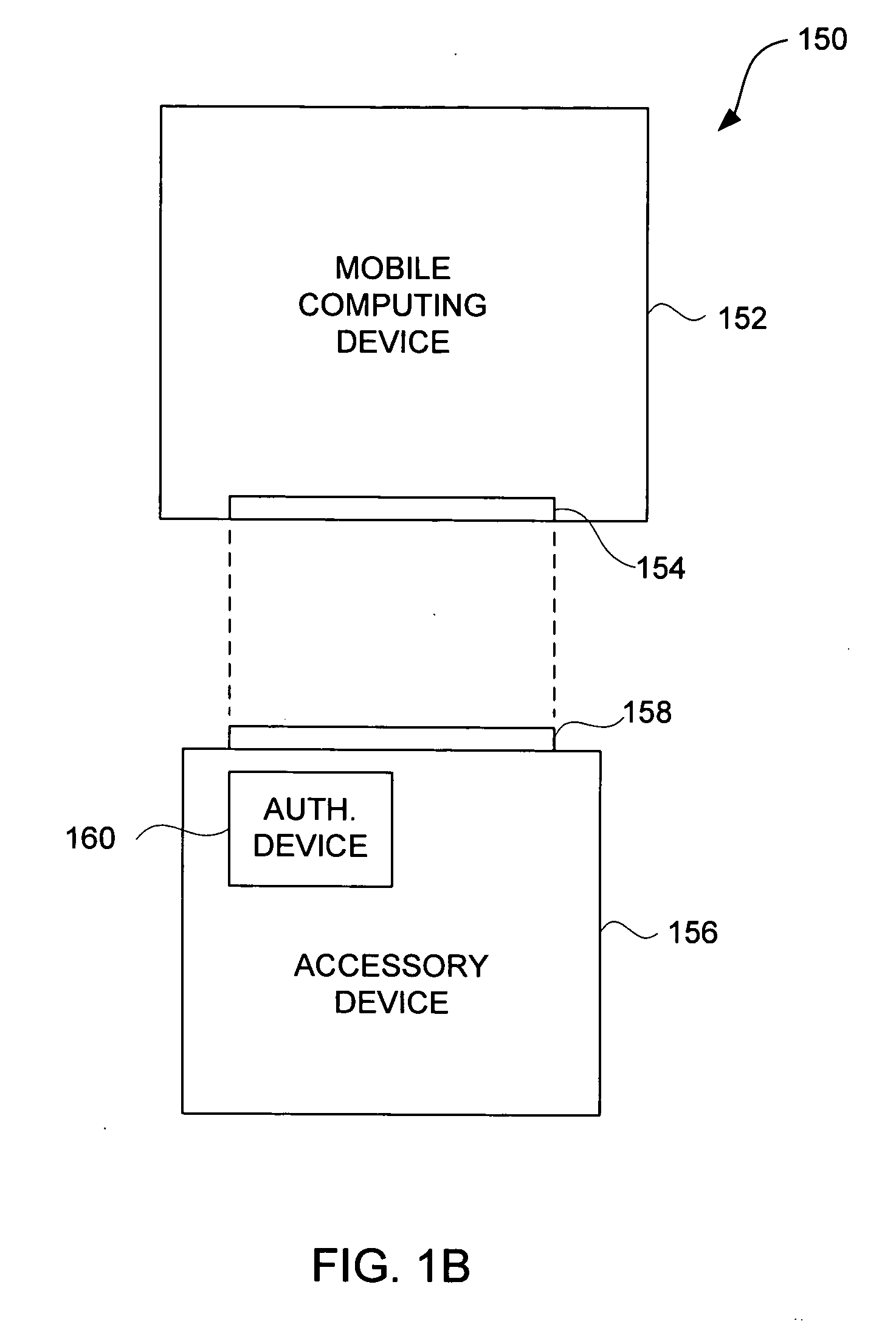
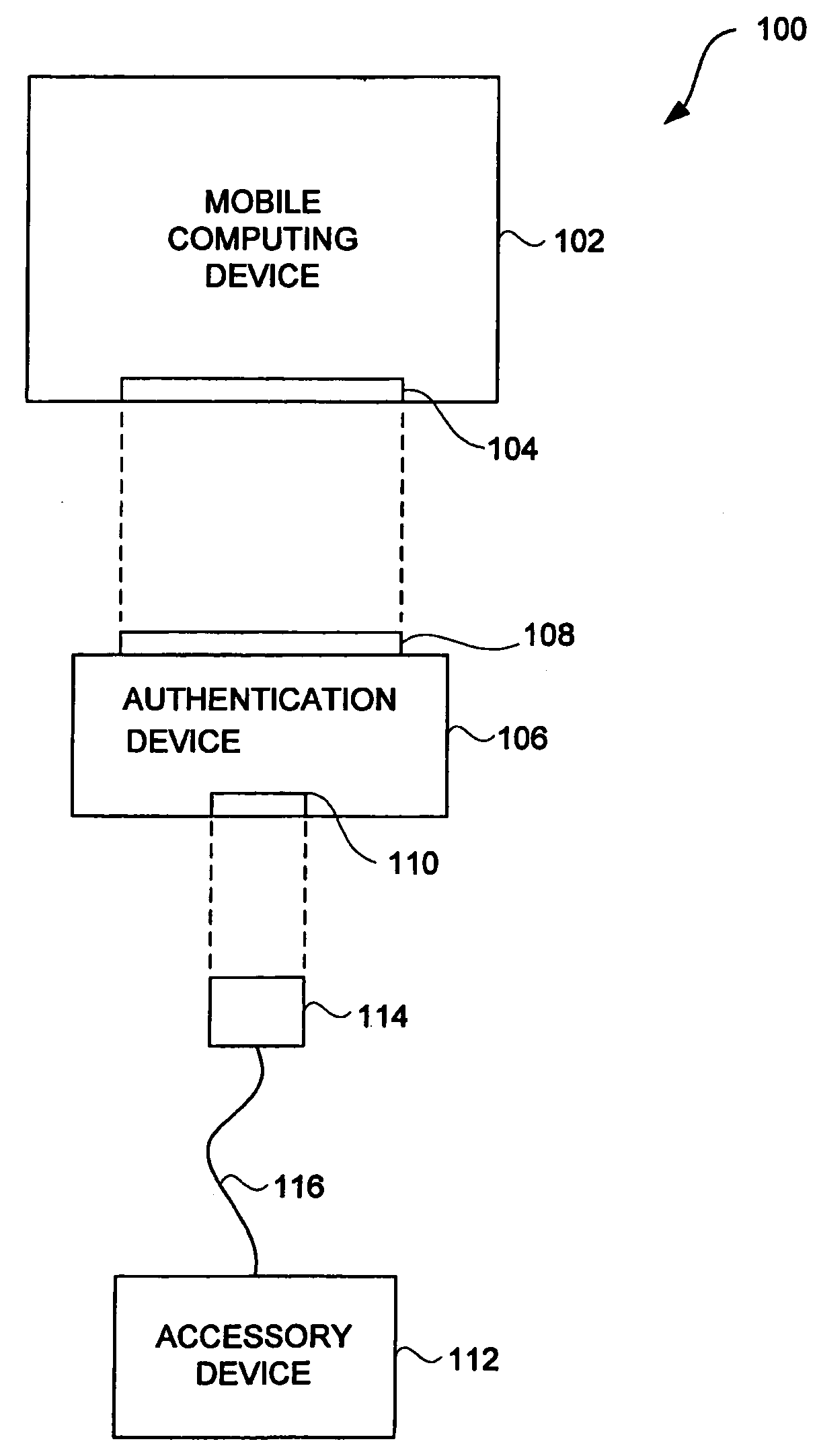
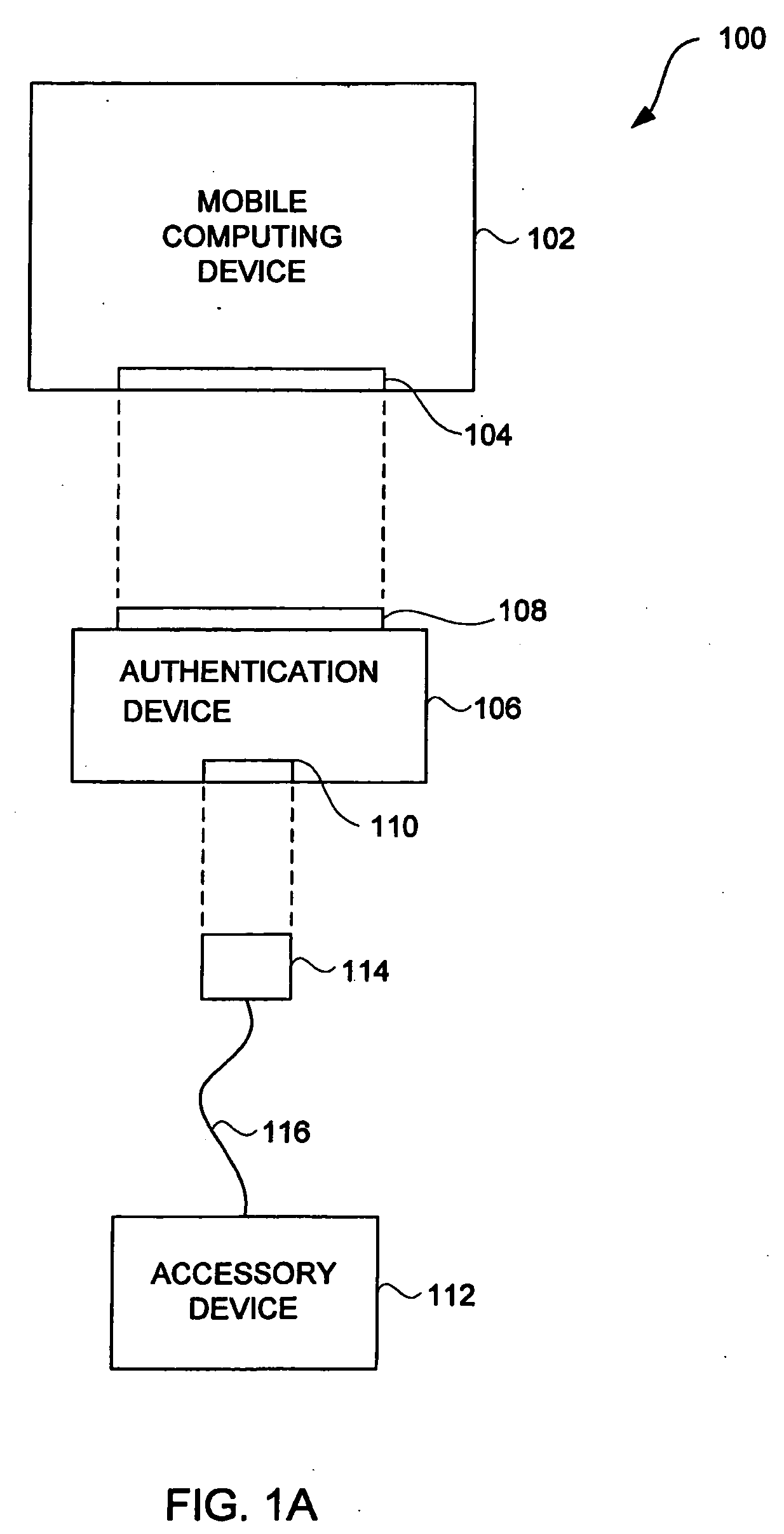
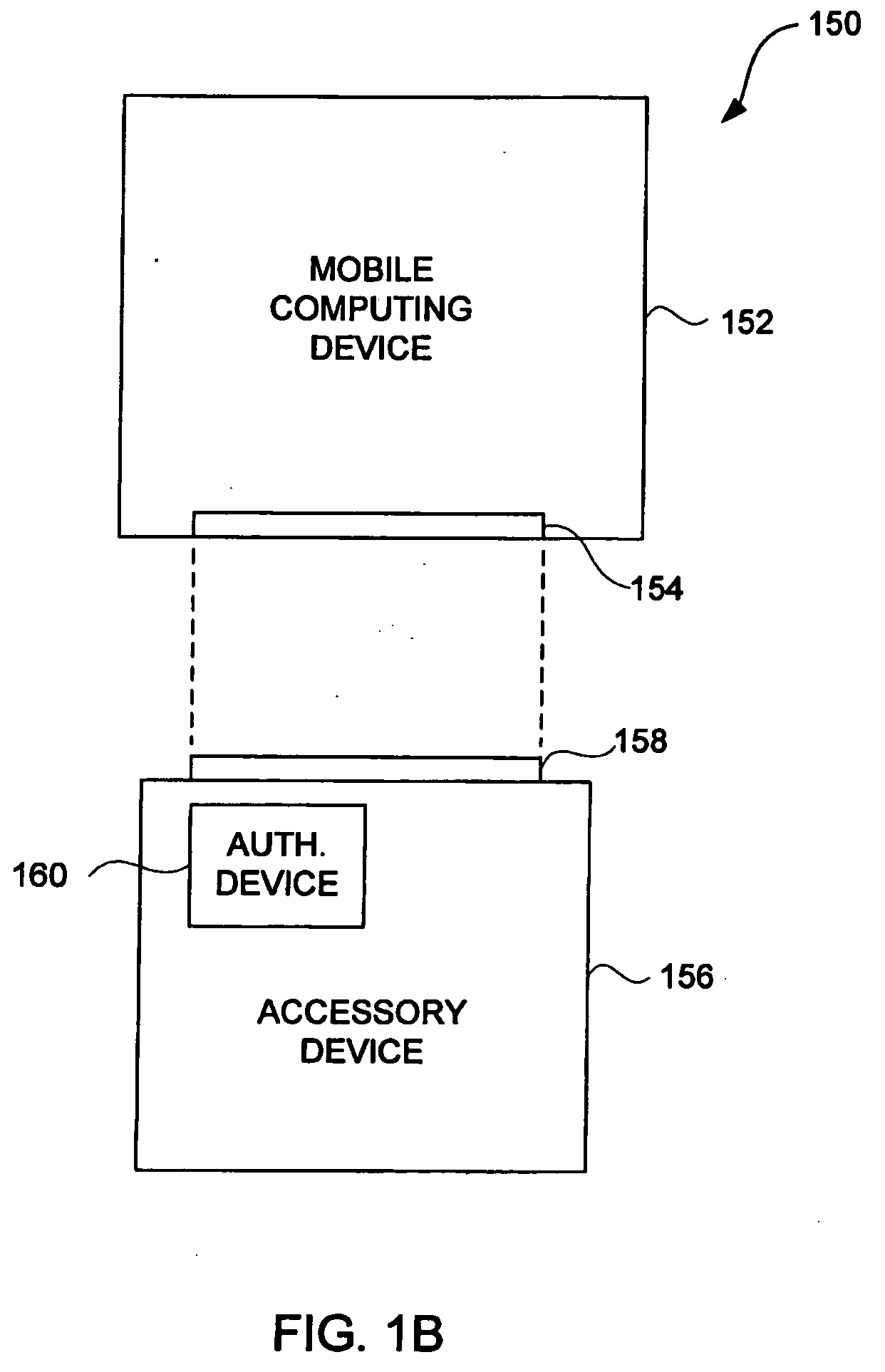
Accessory authentication for electronic devices
ActiveUS20060156415A1Simple technologyDigital data processing detailsUser identity/authority verificationHand heldMusic player
Improved techniques to control utilization of accessory devices with electronic devices are disclosed. The improved techniques can use cryptographic approaches to authenticate electronic devices, namely, electronic devices that interconnect and communicate with one another. One aspect pertains to techniques for authenticating an electronic device, such as an accessory device. Another aspect pertains to provisioning software features (e.g., functions) by or for an electronic device (e.g., a host device). Different electronic devices can, for example, be provisioned differently depending on different degrees or levels of authentication, or depending on manufacturer or product basis. Still another aspect pertains to using an accessory (or adapter) to convert a peripheral device (e.g., USB device) into a host device (e.g., USB host). The improved techniques are particularly well suited for electronic devices, such as media devices, that can receive accessory devices. One example of a media device is a media player, such as a hand-held media player (e.g., music player), that can present (e.g., play) media items (or media assets).
Owner:APPLE INC
Method and system for limiting the use of user-specific software features
InactiveUS20050060266A1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationSchema for Object-Oriented XMLUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
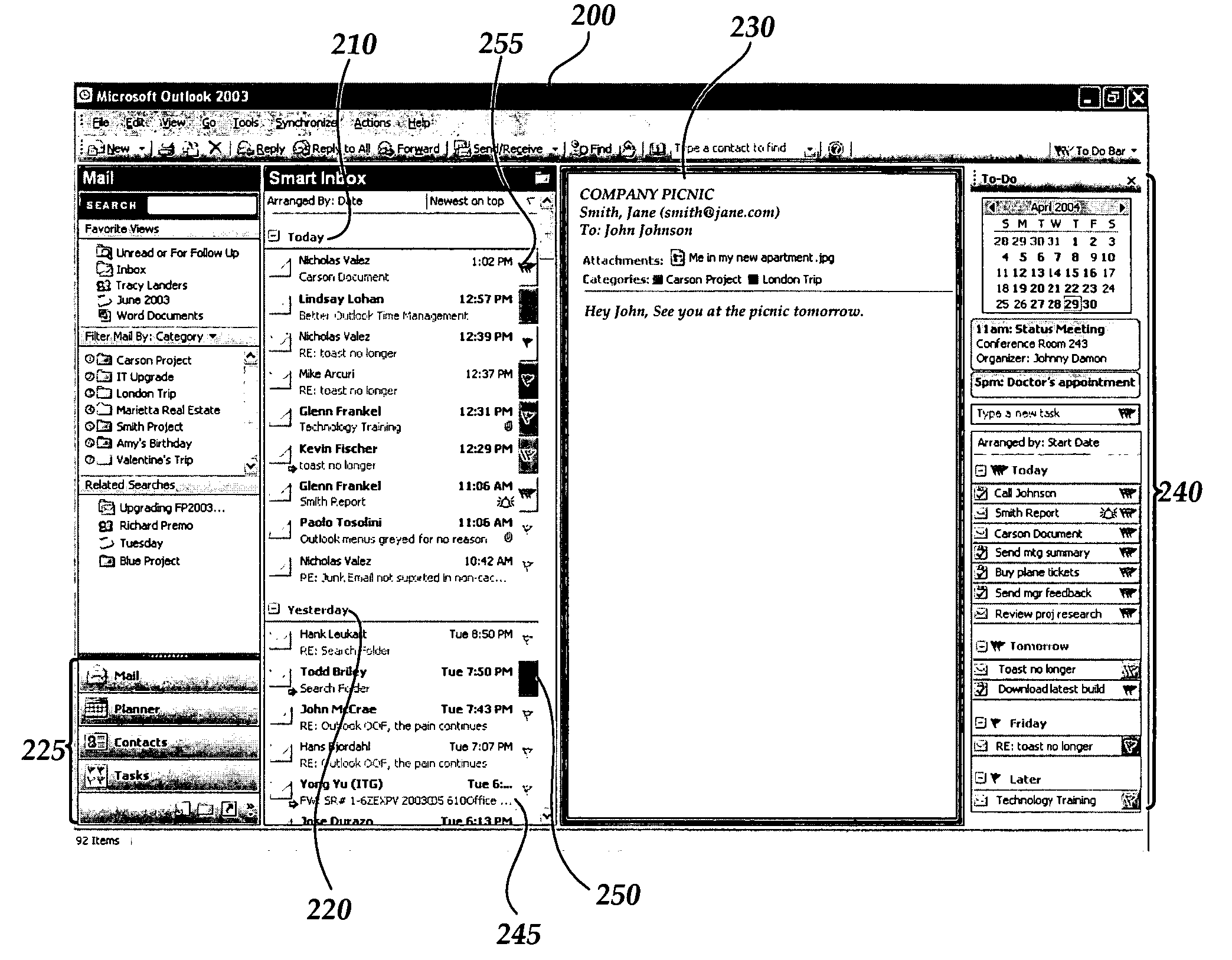
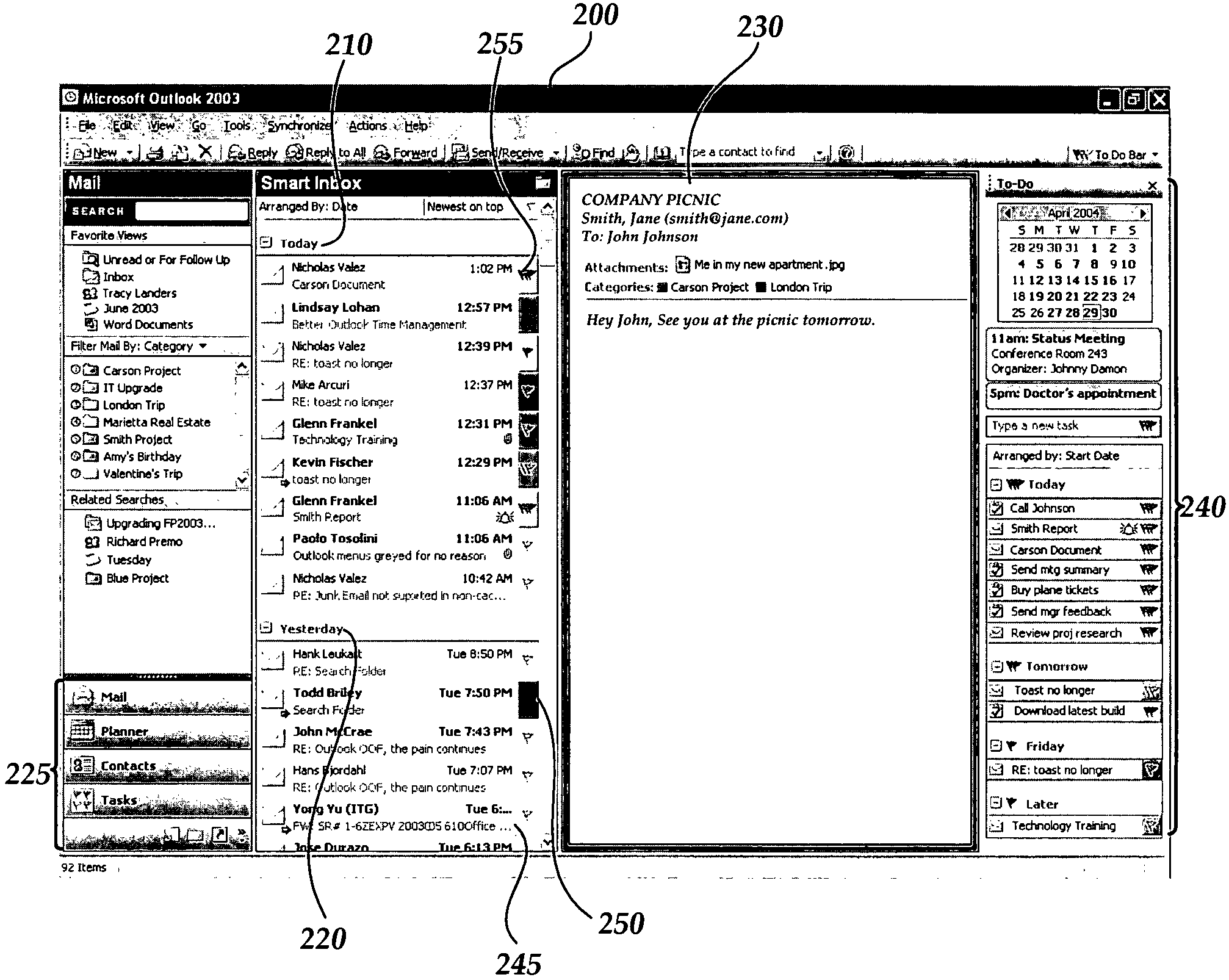
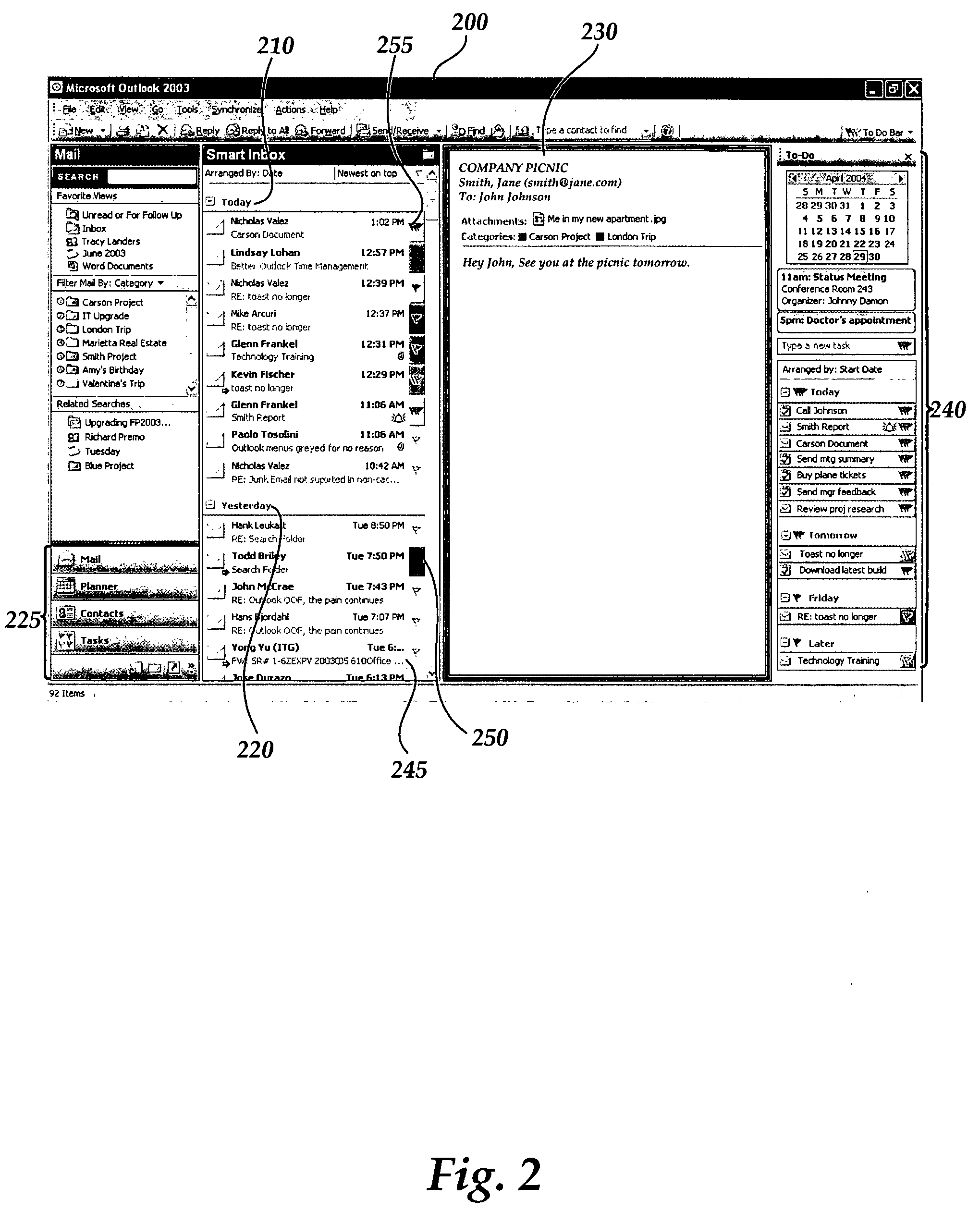
User interface for providing task management and calendar information
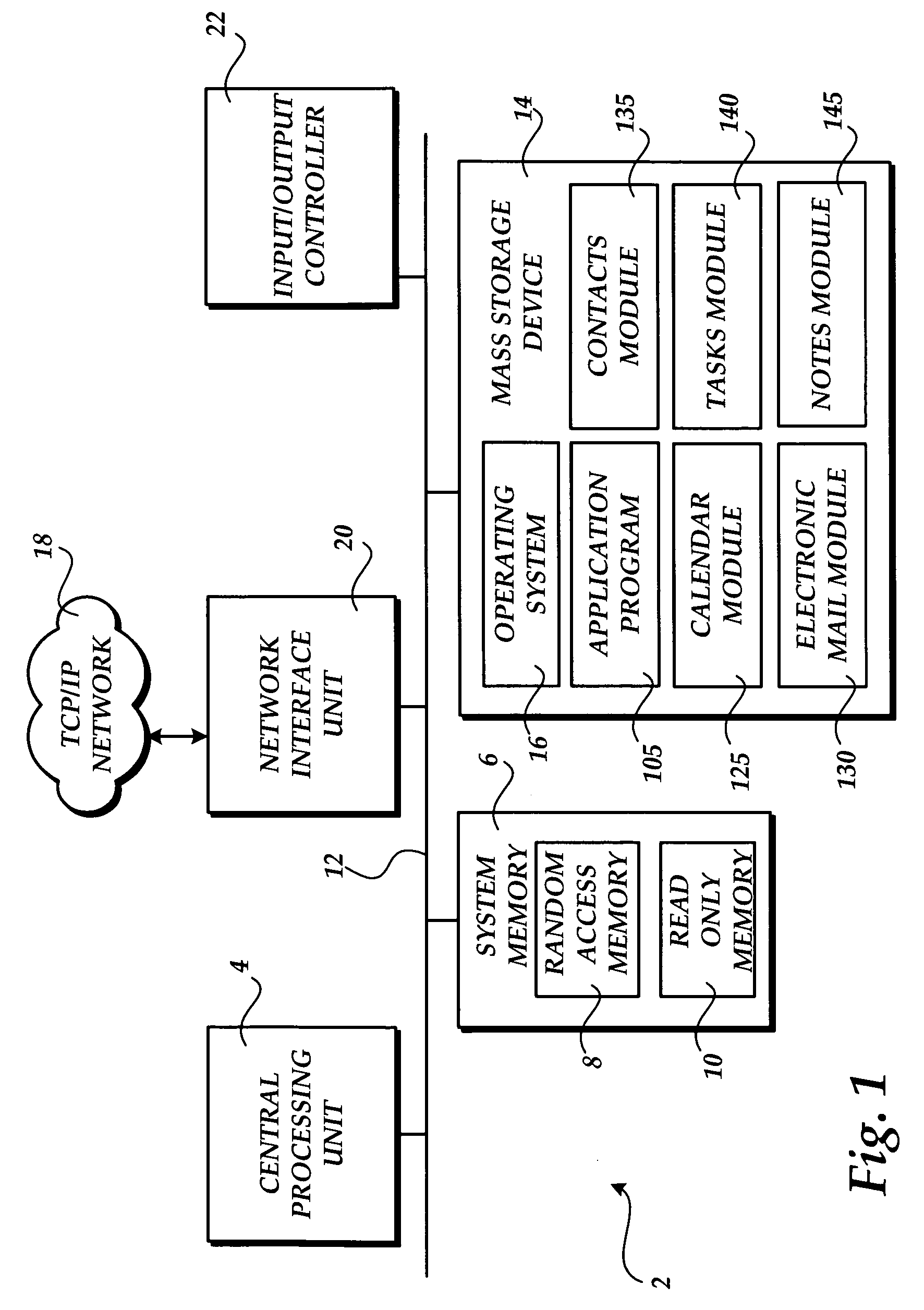
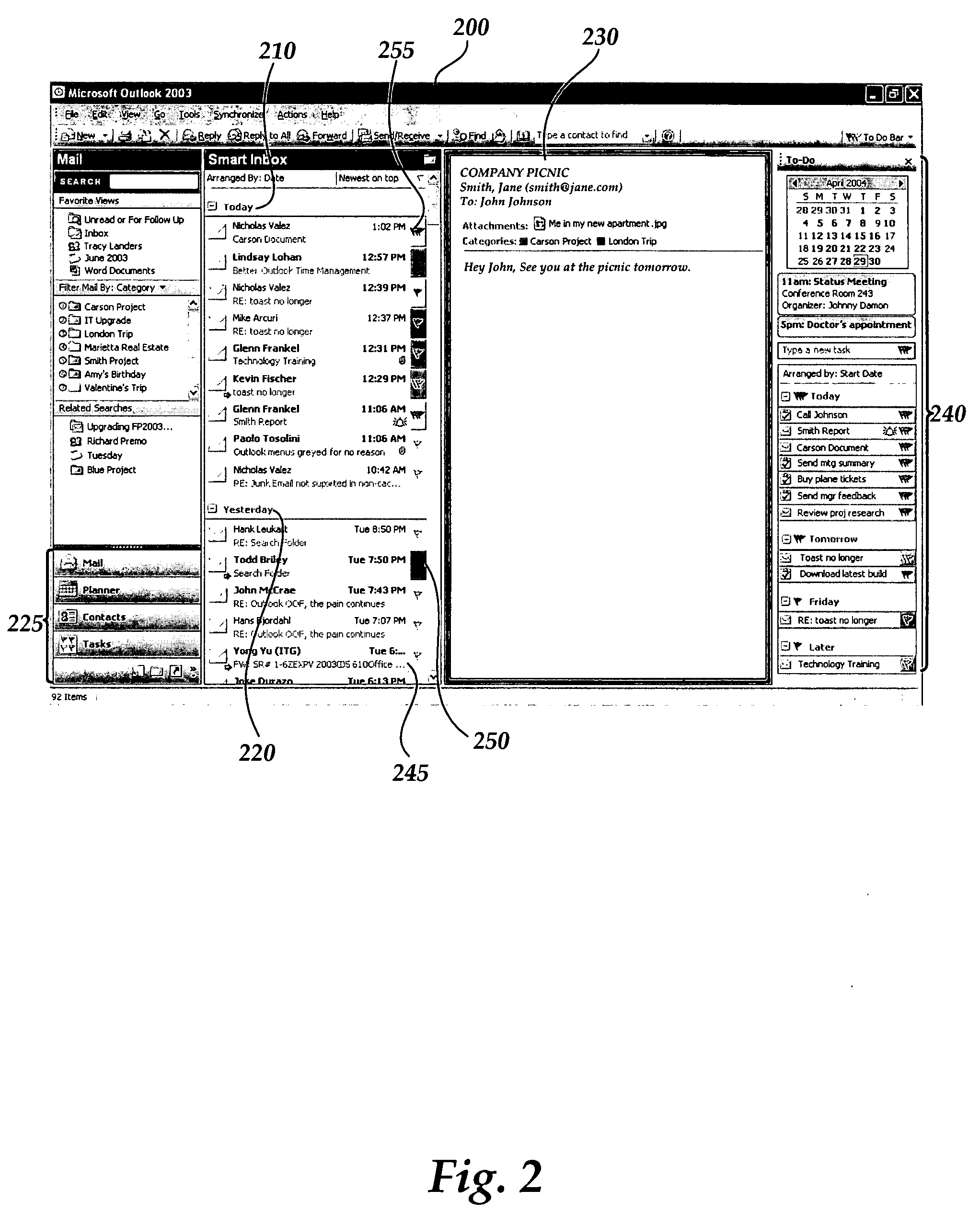
ActiveUS20060069604A1Multiprogramming arrangementsOffice automationApplication softwareTask management
An electronic “To-Do” bar is provided in which displayed upcoming tasks, meetings, appointments and the like. The electronic To-Do bar is displayed in a lightweight menu of tasks, meetings and appointments and is displayed persistently in addition to other software functionality or user interfaces displayed on a user's computer display screen according to other software applications or other software functionality in use. A user is presented with an always-visible list of upcoming tasks, meetings and appointments without the need to launch a separate tasks application or calendar application to view upcoming tasks, meetings or appointments.
Owner:MICROSOFT TECH LICENSING LLC
User interface for displaying selectable software functionality controls that are contextually relevant to a selected object
ActiveUS20060036945A1Efficient switchingExecution for user interfacesDigital output to display deviceSoftware featureObject context
An improved user interface is provided for displaying selectable functionality controls that identifies the context of the object to which the user interface is relevant, which contains rich functionality controls for applying contextually relevant functionality to a selected object, and which may be efficiently switched to a different context for applying a different set of functionalities to a different or neighboring editable object. A context menu of functionalities is displayed adjacent to a selected object where the menu of functionalities includes functionalities associated with editing the selected object. The context menu includes an identification of the object context and a control for selectively changing the context and associated functionalities of the menu to a different object context for displaying a different set of functionalities associated with the different context.
Owner:MICROSOFT CORP
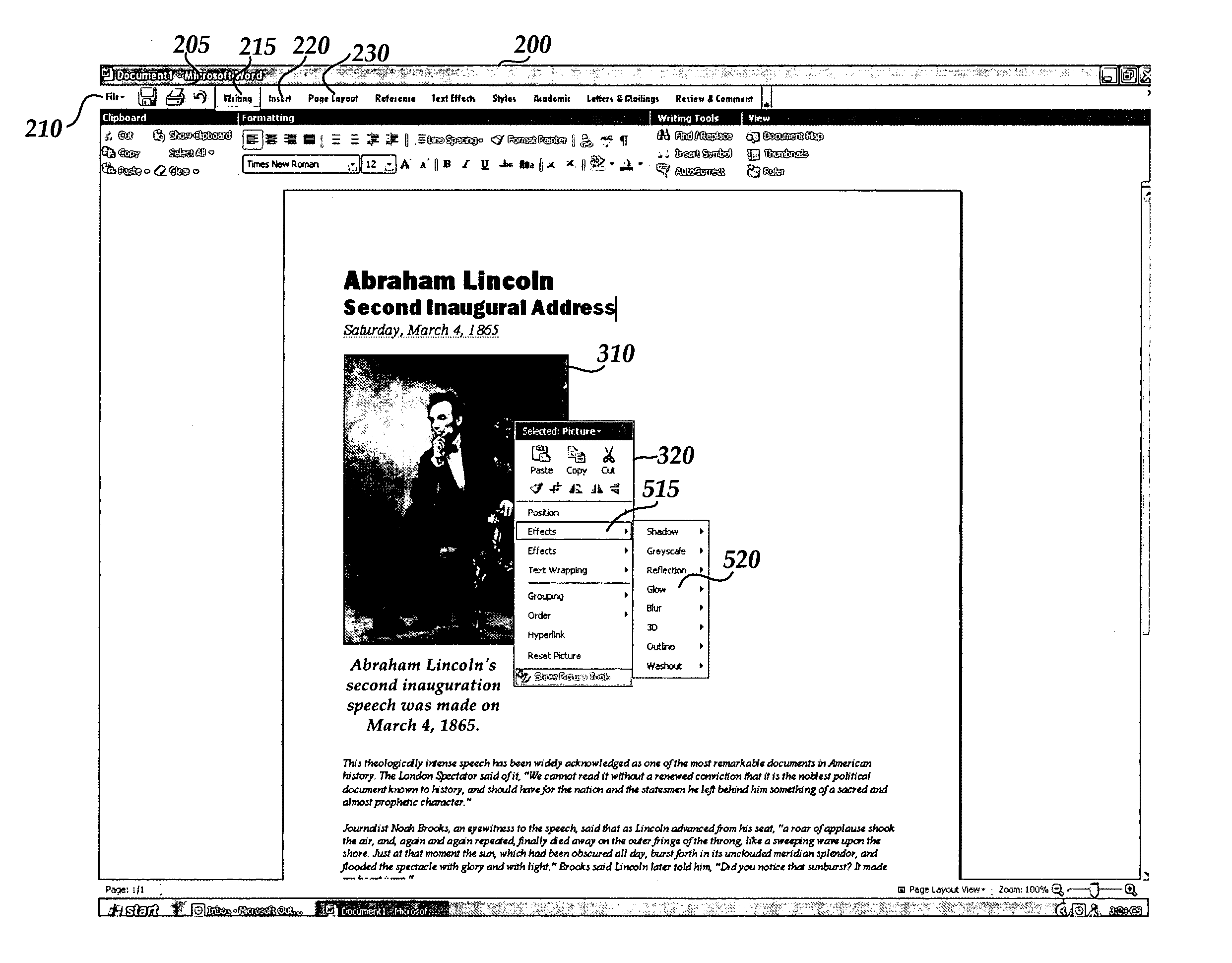
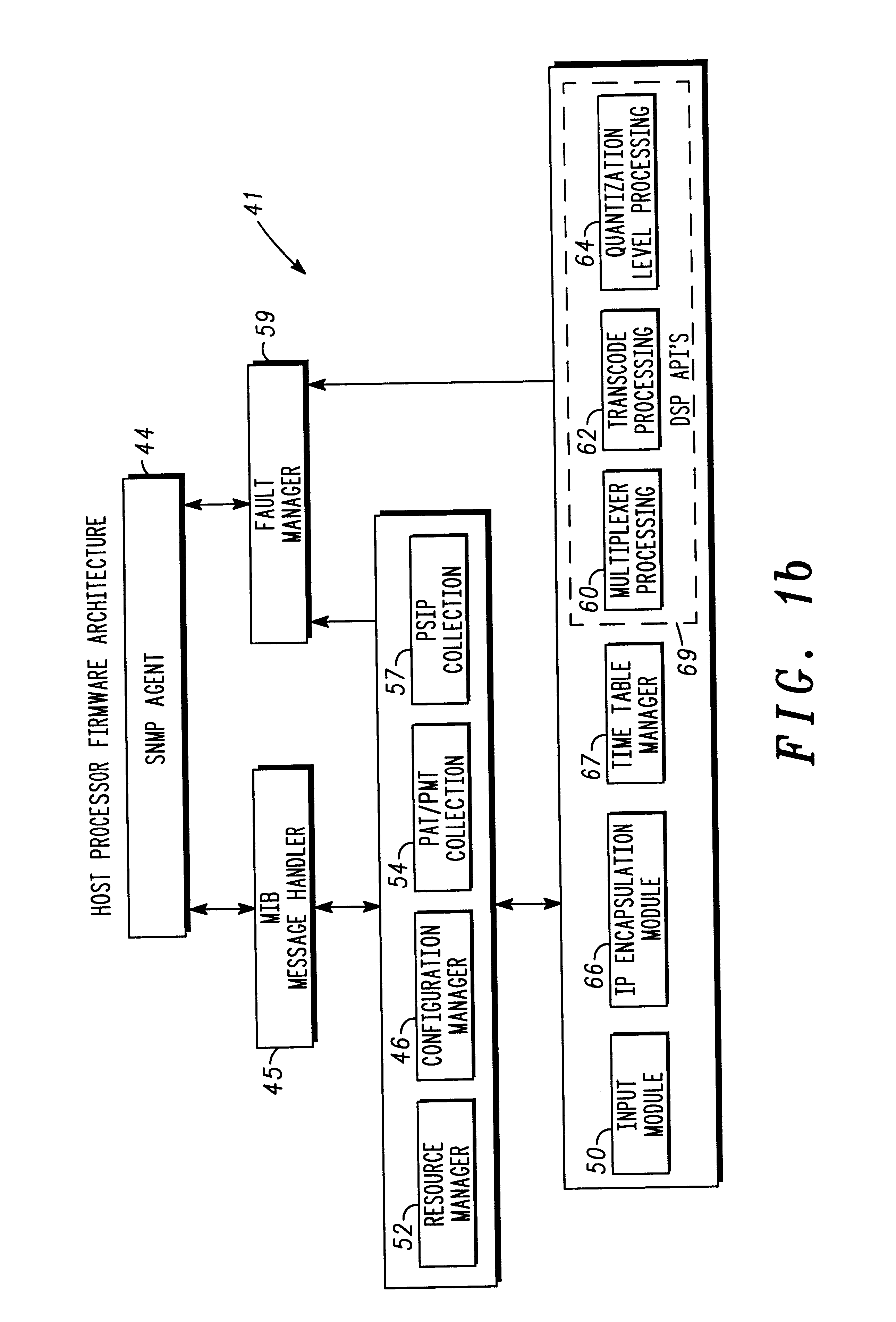
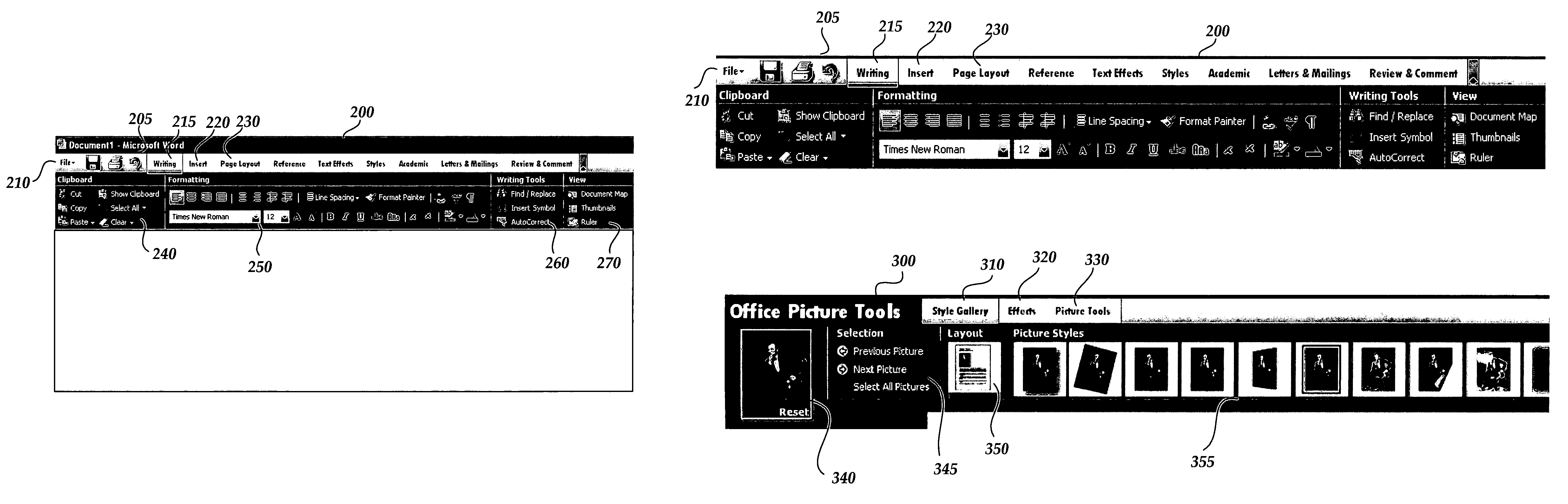
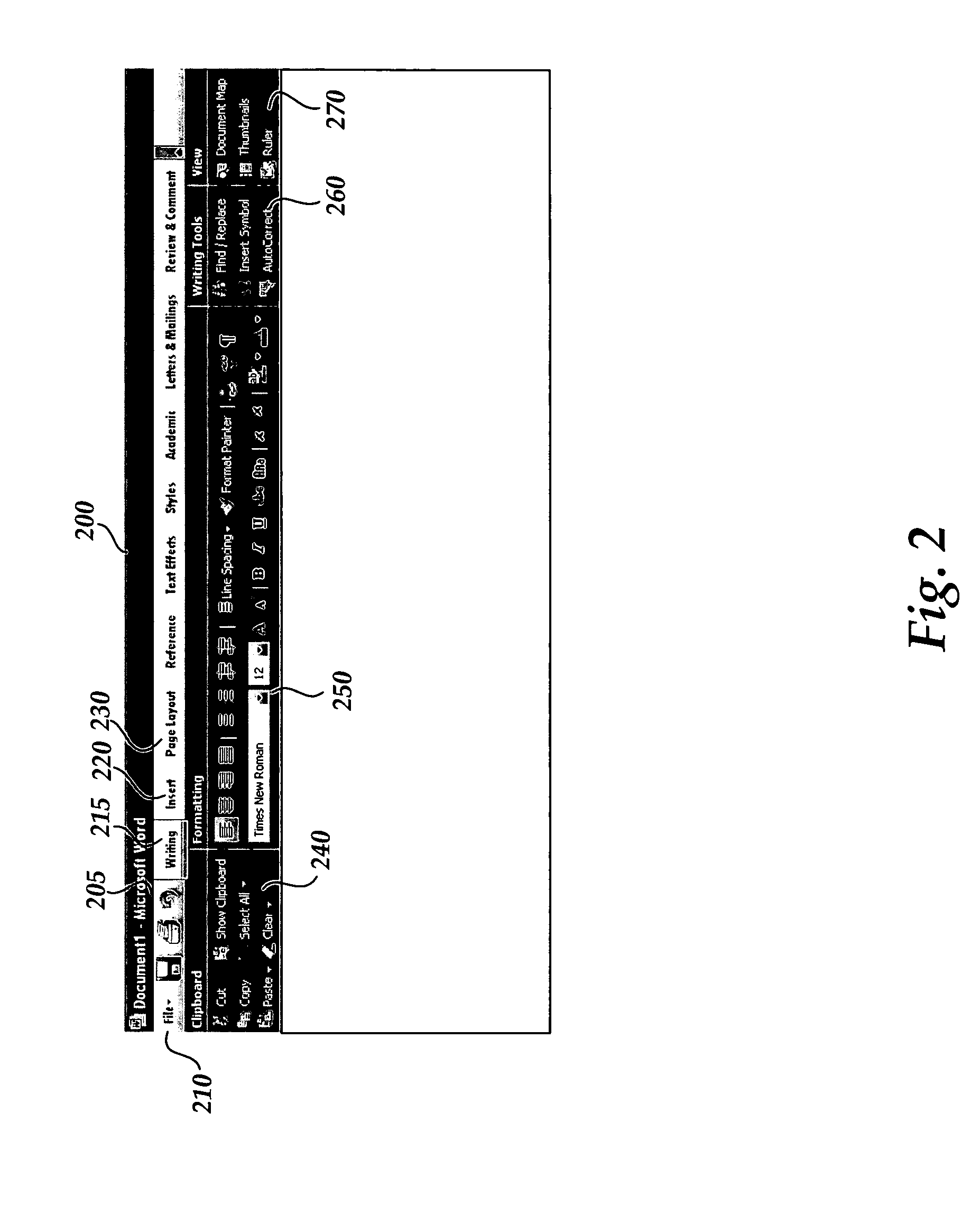
User interface for displaying selectable software functionality controls that are relevant to a selected object
ActiveUS20060036964A1Execution for user interfacesSpecial data processing applicationsBand shapeWorkspace
An improved user interface is provided for displaying selectable software functionality controls that are relevant to a selected object and that remain visibly available for use while the selected object is being edited. Upon selection of a particular object for editing, functionality available for editing the object is presented in a ribbon-shaped user interface above the software application workspace to allow the user ready and efficient access to functionality needed for editing the selected object. The display of relevant functionality controls is persisted until the user dismisses the display, selects another top-level functionality control or selects another object for editing.
Owner:MICROSOFT CORP
Command user interface for displaying selectable software functionality controls
ActiveUS20060036965A1Good user interfaceSelective content distributionExecution for user interfacesHuman–computer interactionUser interface
An improved user interface is provided for displaying selectable software functionality controls and for presenting logical groupings of particular functionality controls associated with a selected top-level functionality. Underneath a row of top-level functionality tabs, functionalities controls associated with a given top-level functionality tab are presented in logical groupings. Selection of a particular tab switches modes of the user interface to present controls for functionalities associated with the selected tab.
Owner:MICROSOFT CORP
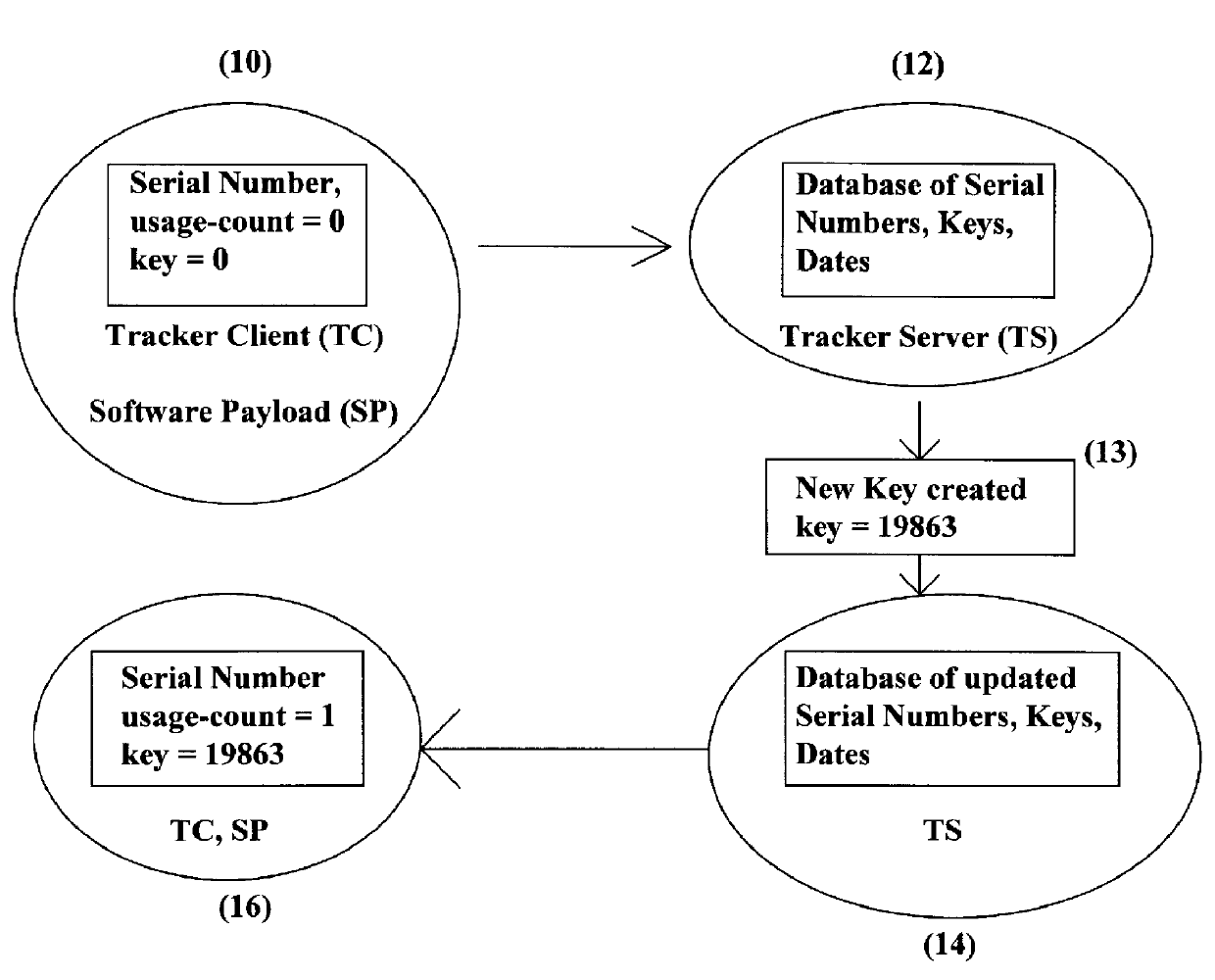
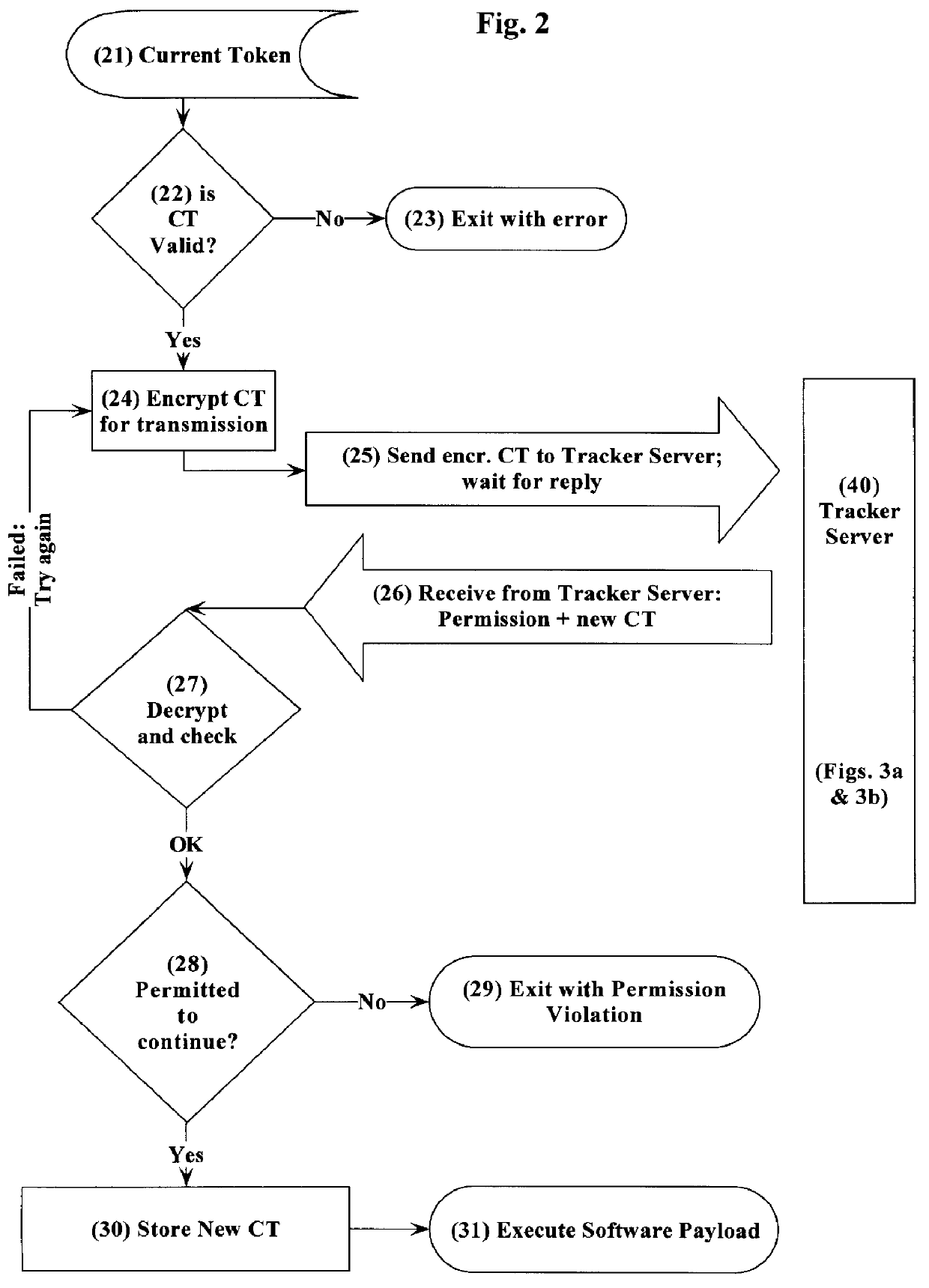
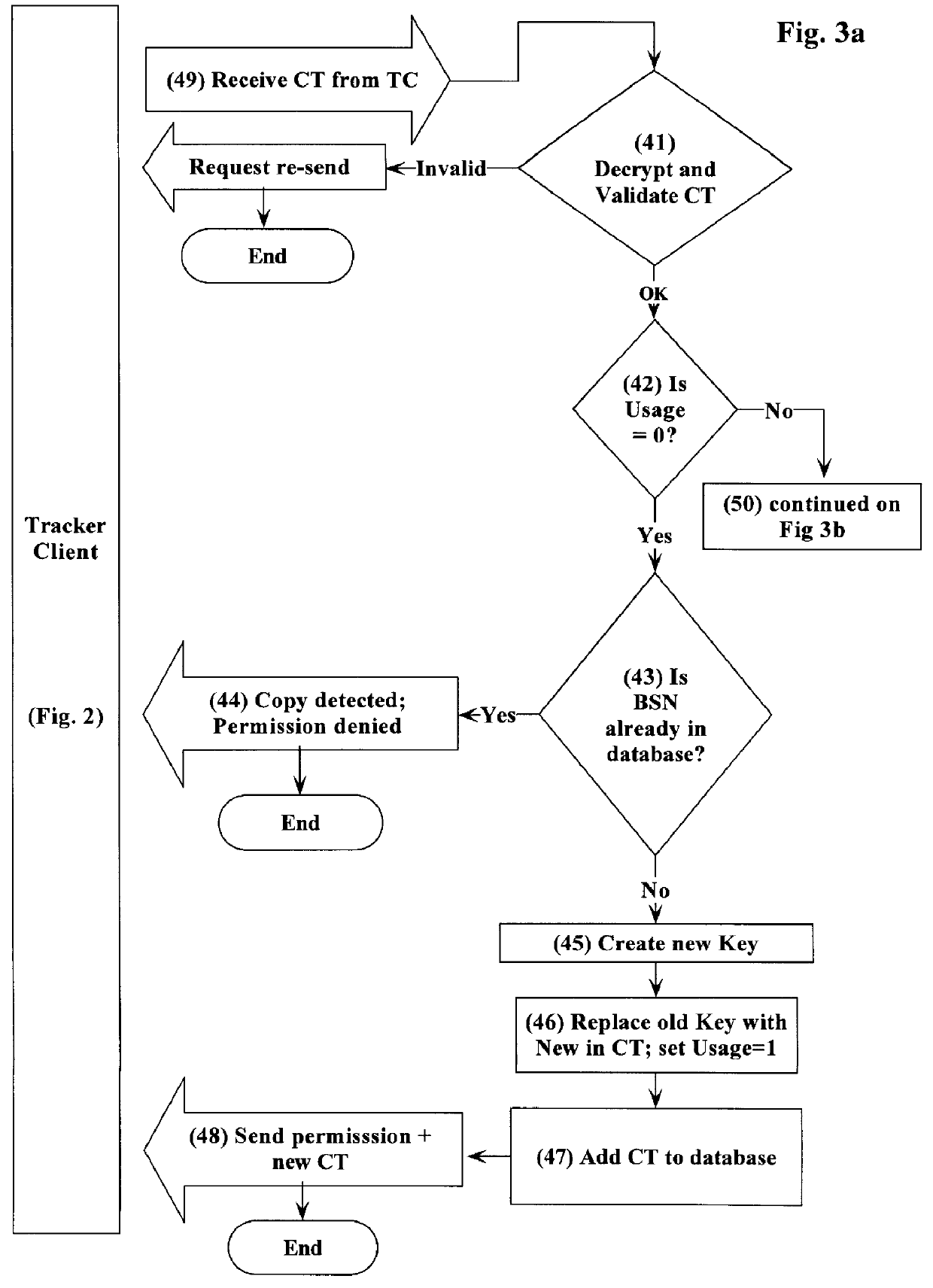
Method and system for copy-tracking distributed software featuring tokens containing a key field and a usage field
InactiveUS6070171AData processing applicationsDigital data processing detailsThe InternetFinancial transaction
The present invention provides a central computer site on a computer network for detecting authorized or unauthorized duplication of software on computers connected to such a network. The computers on the network may be continually connected, like computers on a Local Area Network, or intermittently connected, like computers on the Internet. Every time a user of the distributed software attempts to execute that software, a connection to the central computer site on the network is made, and a previously-created information token is presented by the user's software to the central site. The central site evaluates that token, and possibly issues a new token to be kept by the user for the next transaction. These transactions need no human intervention, and may take place without the software user's knowledge. At the same time, the central site may provide or withhold permission for the user to execute the distributed software. Using this information token, the central site can detect when a user uses a copy not made at the factory and track the execution of any such software copies. The central site need not know the identity of those using the software, nor the identities of the computers on which the software is executed.
Owner:PALANTIR SOFTWARE +1
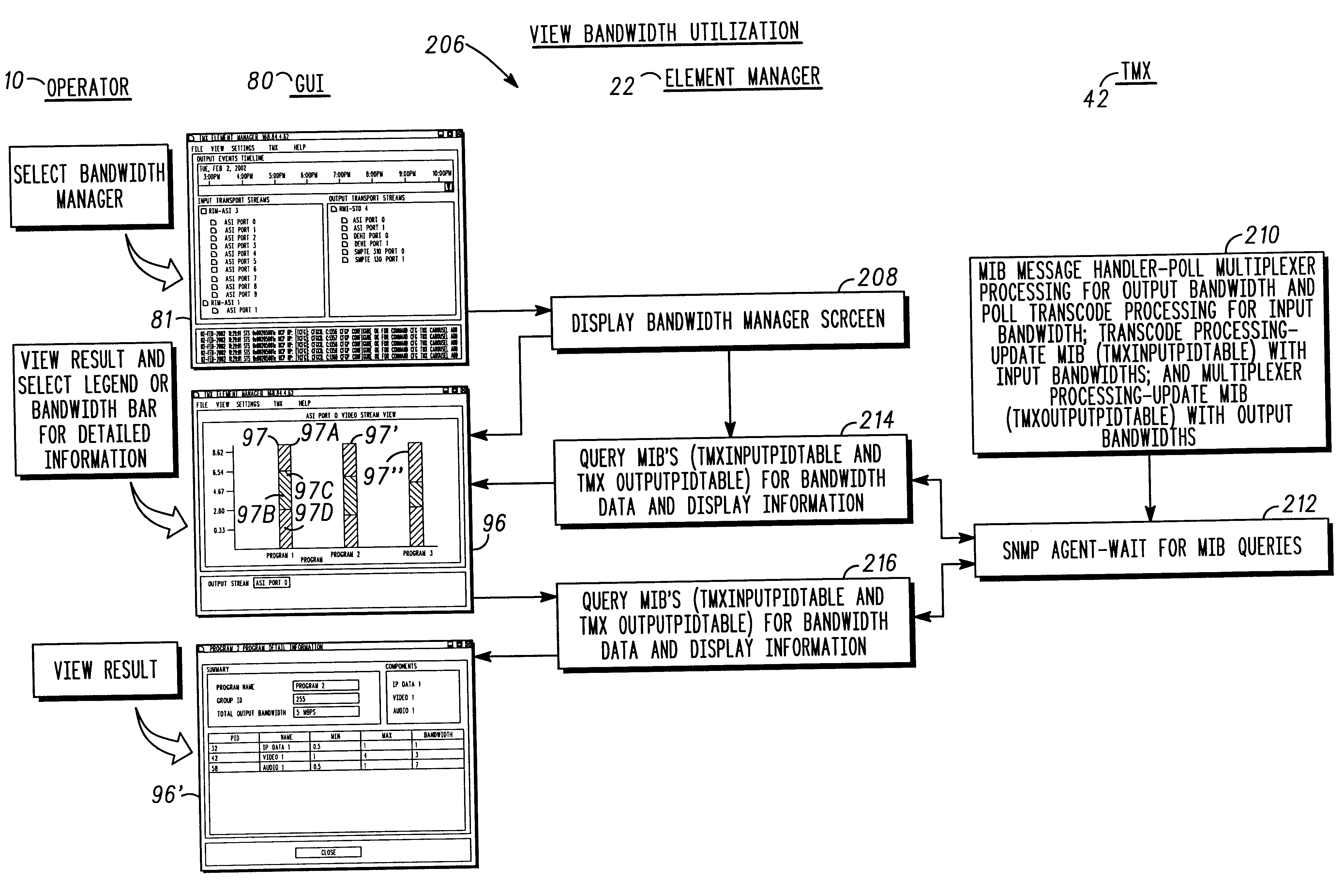
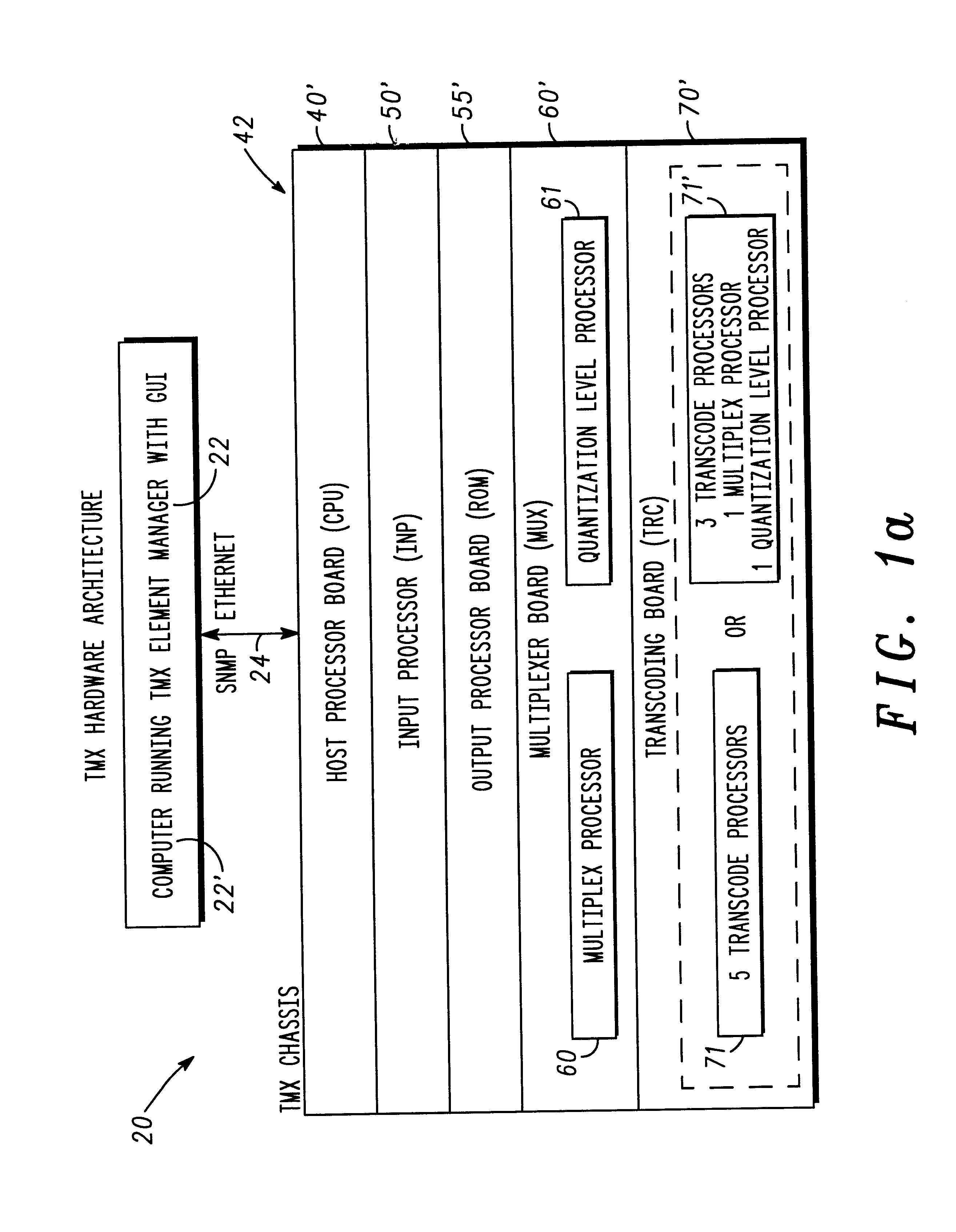
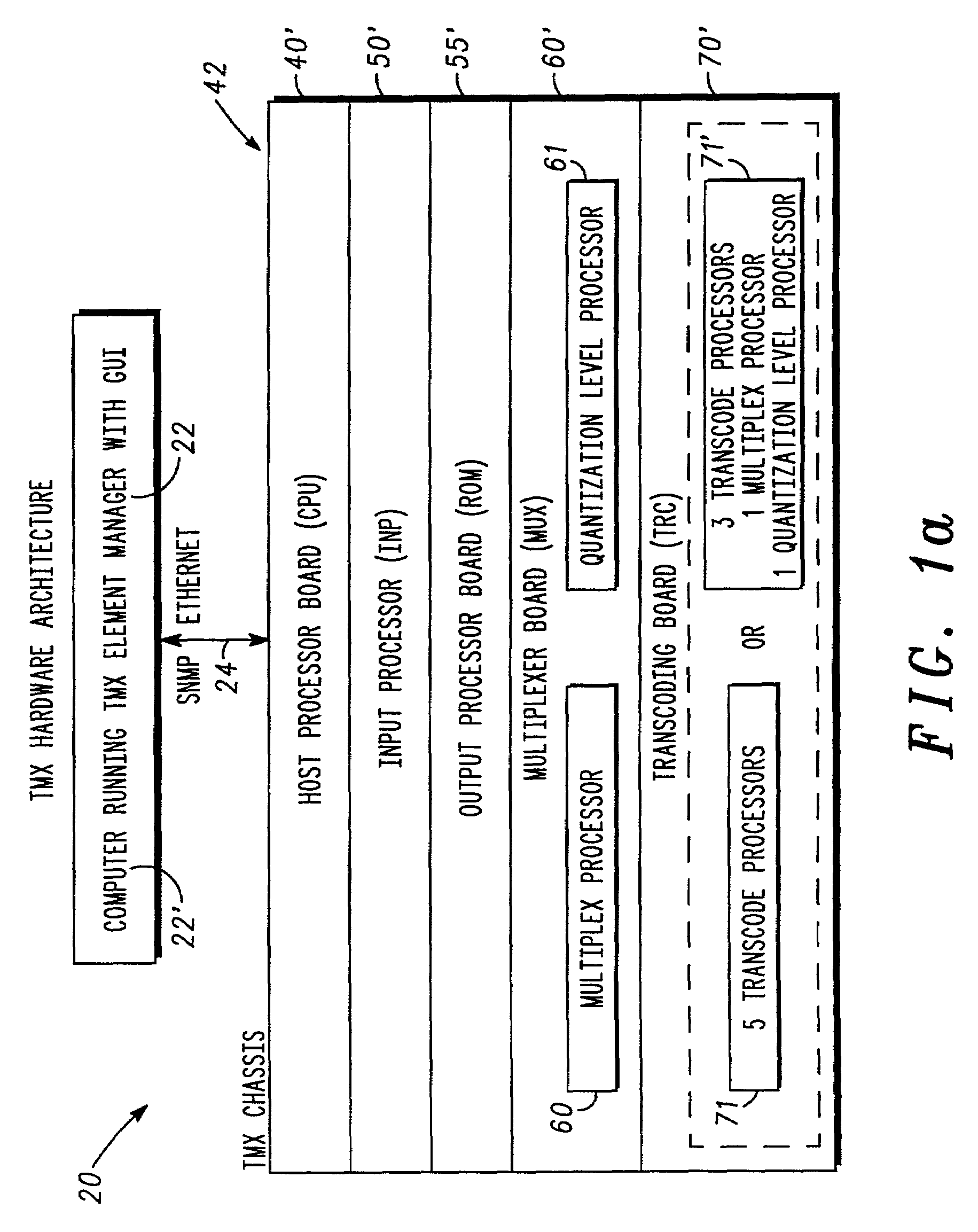
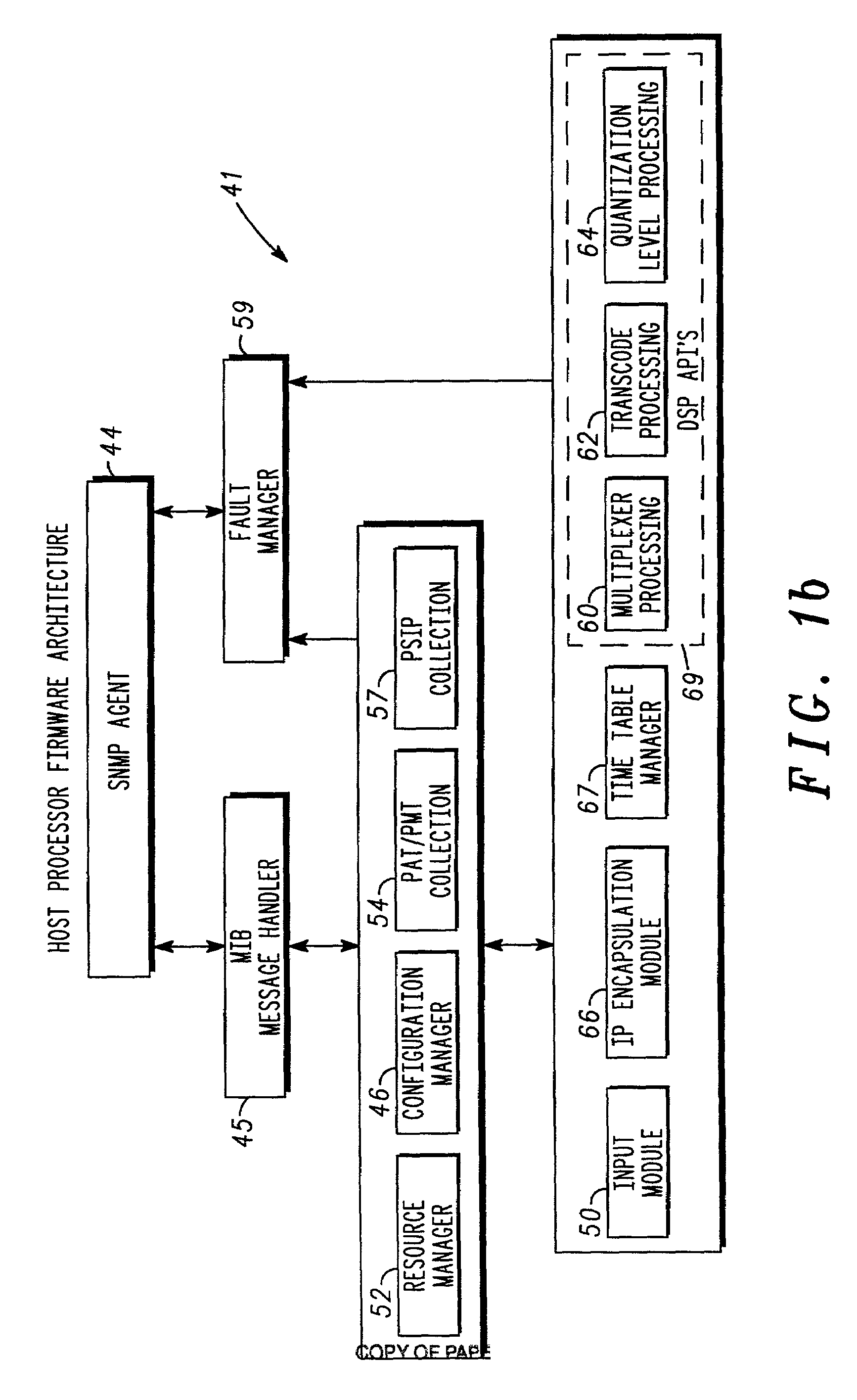
Real-time display of bandwidth utilization in a transport multiplexer
InactiveUS6839070B2Improve effectivenessEasy to displaySpecial service provision for substationDrawing from basic elementsDrag and dropData stream
A feature-rich transport multiplexer and a number of associated methods, systems, subsystems, software features, graphical user interfaces and control systems are disclosed. The disclosure includes GUI's that enable operators to easily monitor and manipulate content streams flowing through a transport multiplexer in real-time. The disclosed interfaces include screens that supply operators with identity, structure, configuration, bandwidth utilization and / or status information for system hardware and software. The disclosed features also provide computer assisted routing configuration for present and future routing events through simple manipulation, such as drag and drop operations, of graphical objects. Routing control is further simplified by permitting operators to configure routing control of individual content stream components as well as groups of such components simultaneously. Further flexibility is permitted by predetermination of future routing events, thereby enabling the automatic execution of configuration changes at a future time. Various types of content, such as video, audio, IP data can be manipulated to achieve various results such as one or more multiplexed MPEG data streams.
Owner:GOOGLE TECH HLDG LLC
User interface for displaying selectable software functionality controls that are relevant to a selected object
ActiveUS7703036B2Execution for user interfacesSpecial data processing applicationsWorkspaceUser interface
An improved user interface is provided for displaying selectable software functionality controls that are relevant to a selected object and that remain visibly available for use while the selected object is being edited. Upon selection of a particular object for editing, functionality available for editing the object is presented in a ribbon-shaped user interface above the software application workspace to allow the user ready and efficient access to functionality needed for editing the selected object. The display of relevant functionality controls is persisted until the user dismisses the display, selects another top-level functionality control or selects another object for editing.
Owner:MICROSOFT CORP
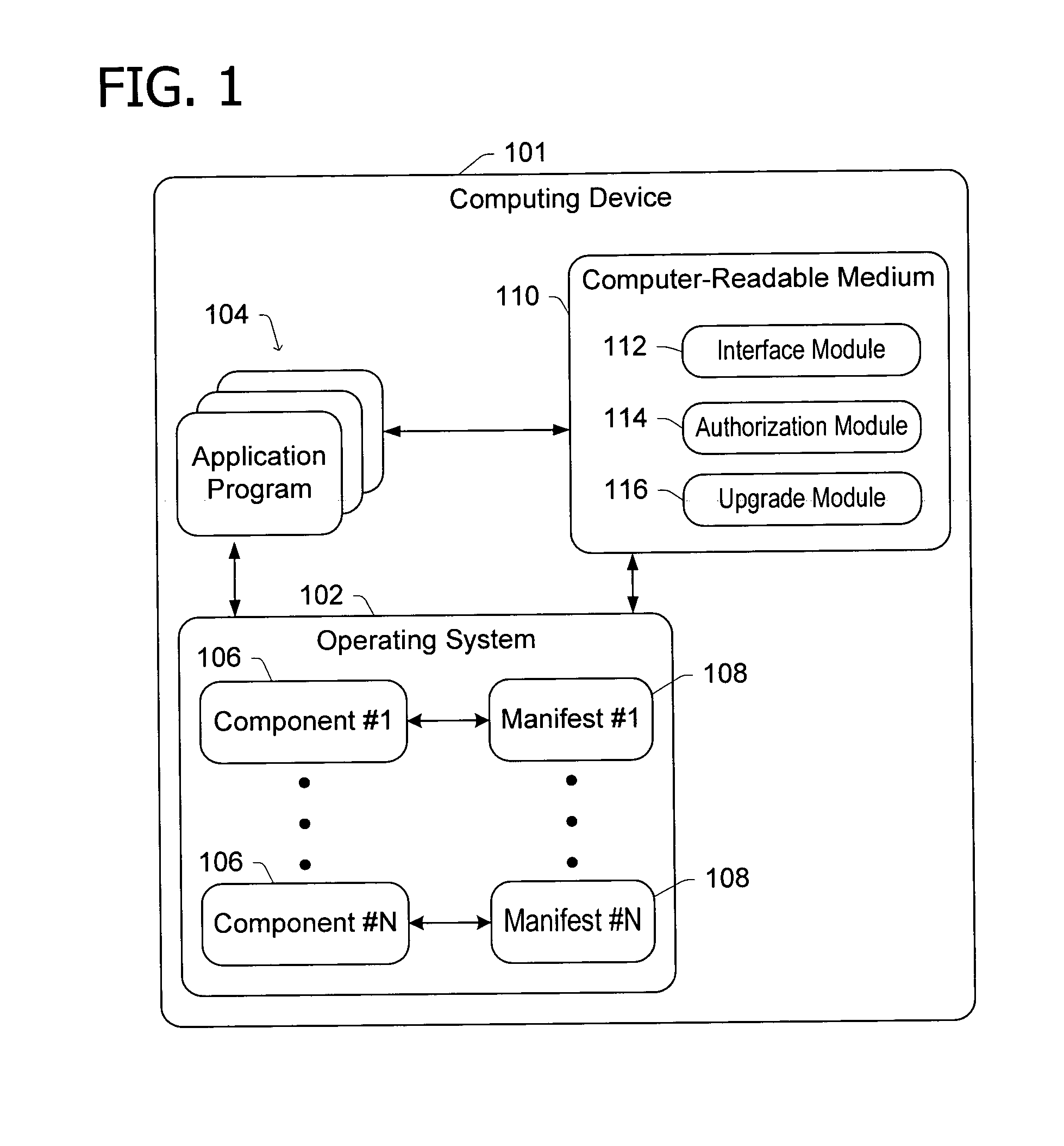
Licensing the use of a particular feature of software
InactiveUS20060048132A1Not easy to changeDigital data processing detailsUnauthorized memory use protectionWeb siteUnique identifier
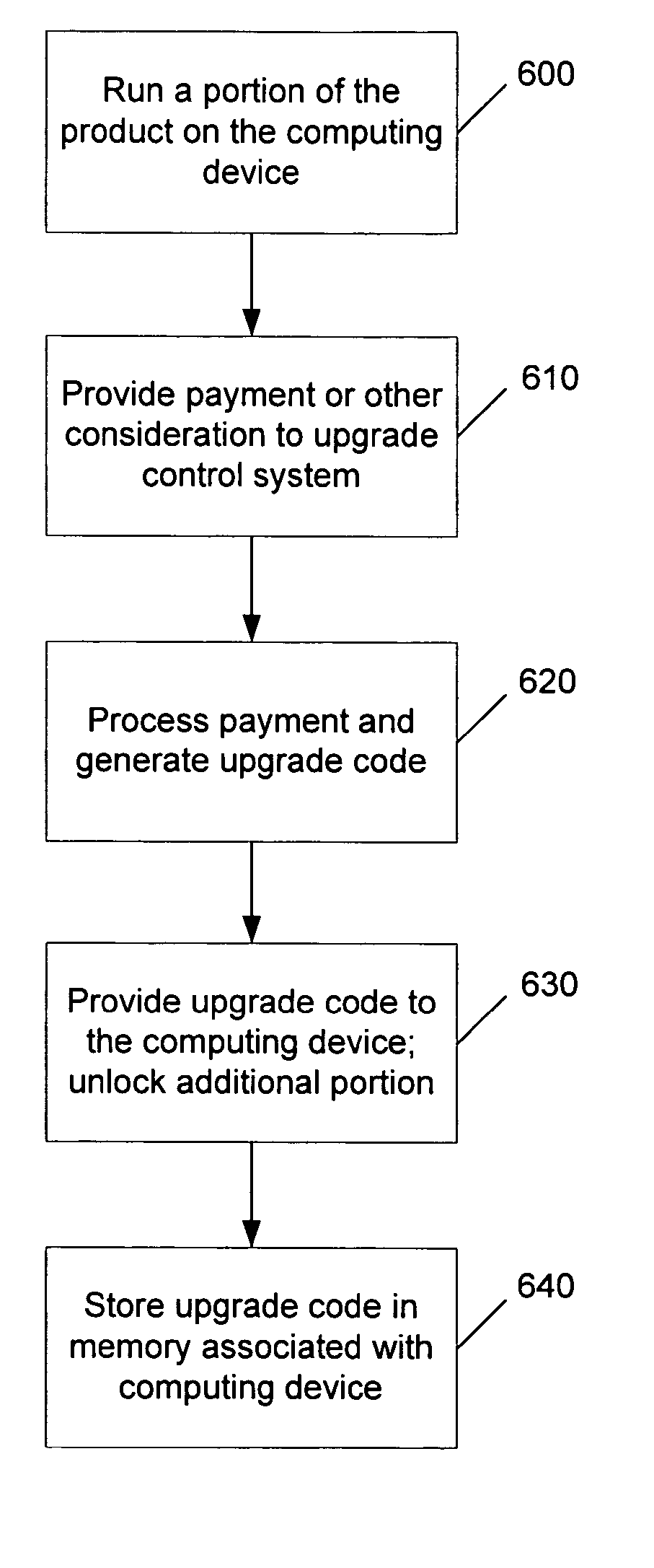
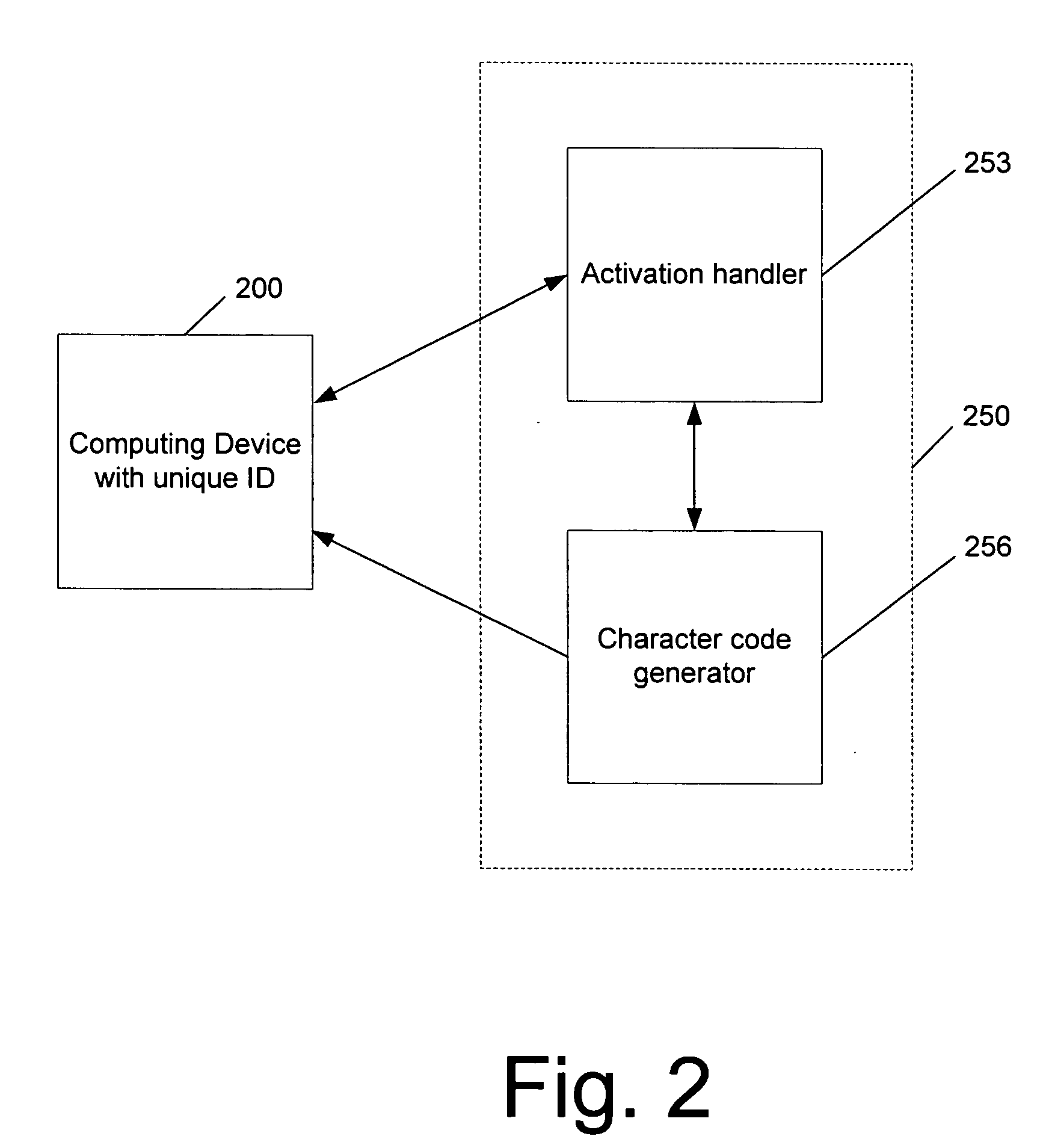
Software is licensed for use on a particular computing device, such as a gaming console or a multimedia console. An unlocking code is provided from a distribution service to the computing device (either directly or via a user), which in turn, unlocks the appropriate software or portion of software for use with the associated computing device. The software may reside on a computer-readable medium, such as a CD-ROM or DVD disk, that is being used in conjunction with the computing device. The unlocking code may be provided directly to the user in private (e.g., via email or a mobile phone) or in public (e.g., published on a website). Portions of the software that may be unlocked include a particular level of a game or other features (such as additional characters or weapons), or a working or more advanced version of an application that was otherwise provided as a demo or older version. The unlocking code may be based on a unique identifier of the computing device and an identifier associated with the software seeking to be accessed. Thus, the code may only be used by the computing device having that unique identifier. This prevents unauthorized or unlicensed computing devices from using the software.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for debugging, verifying and validating computer software
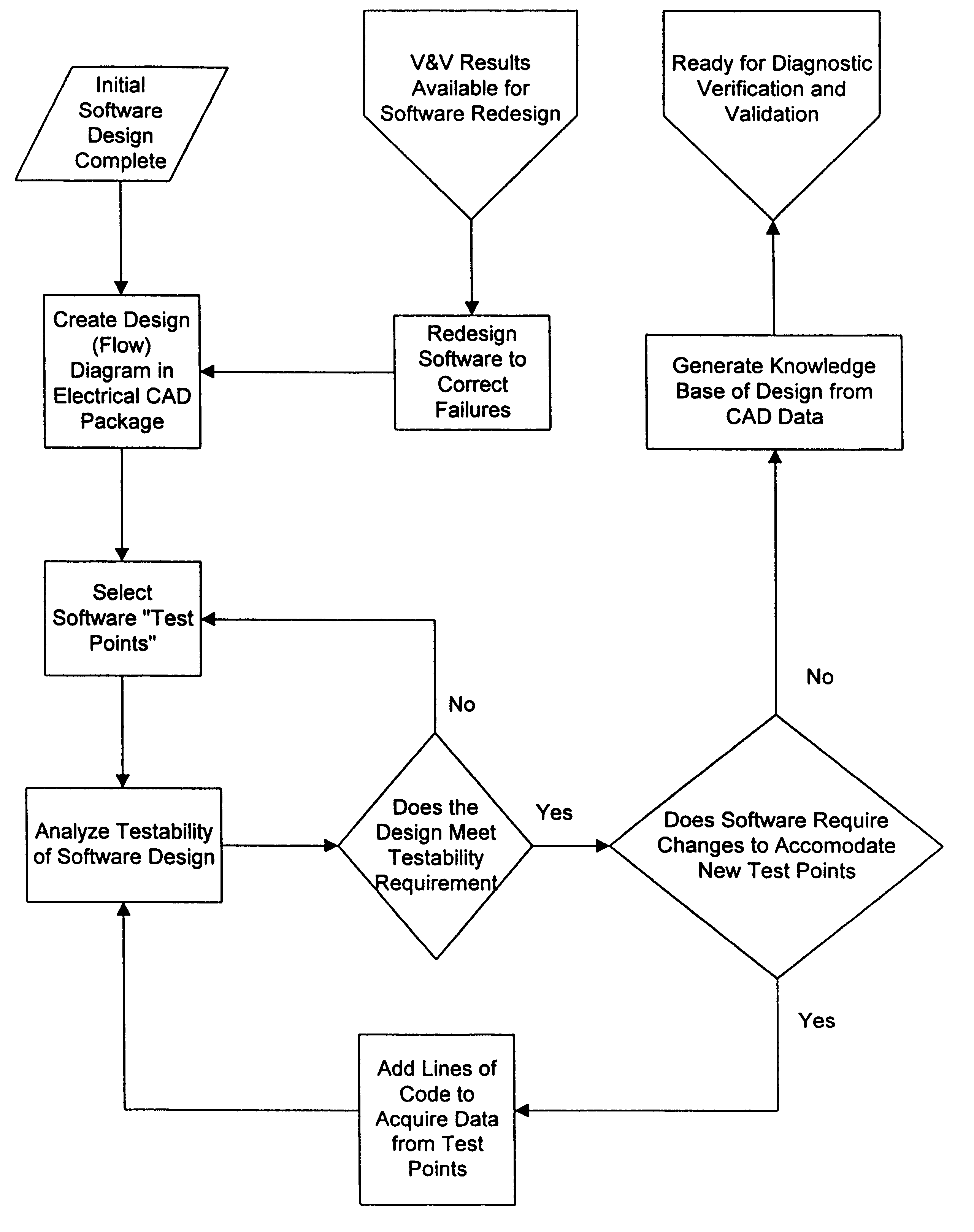
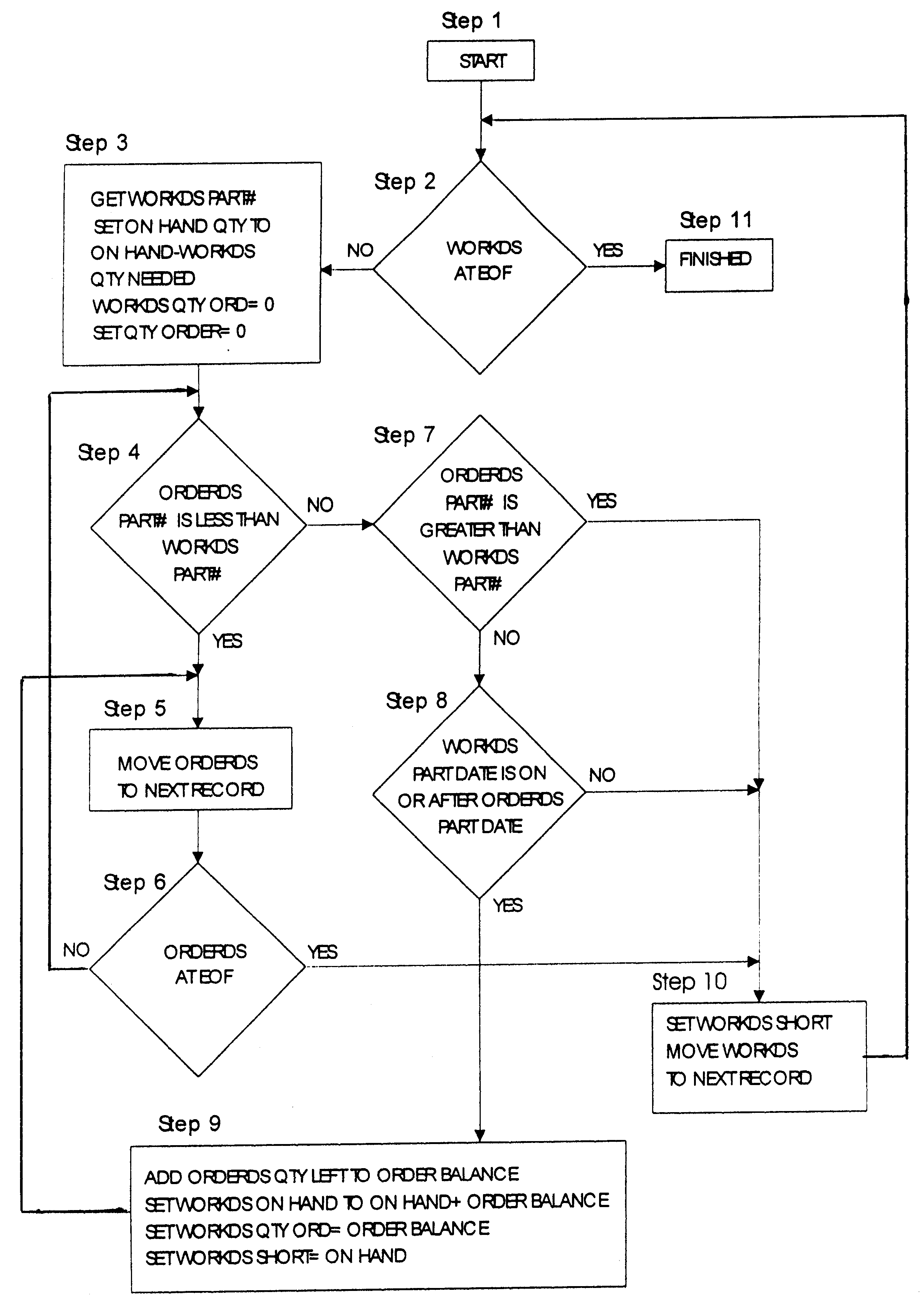
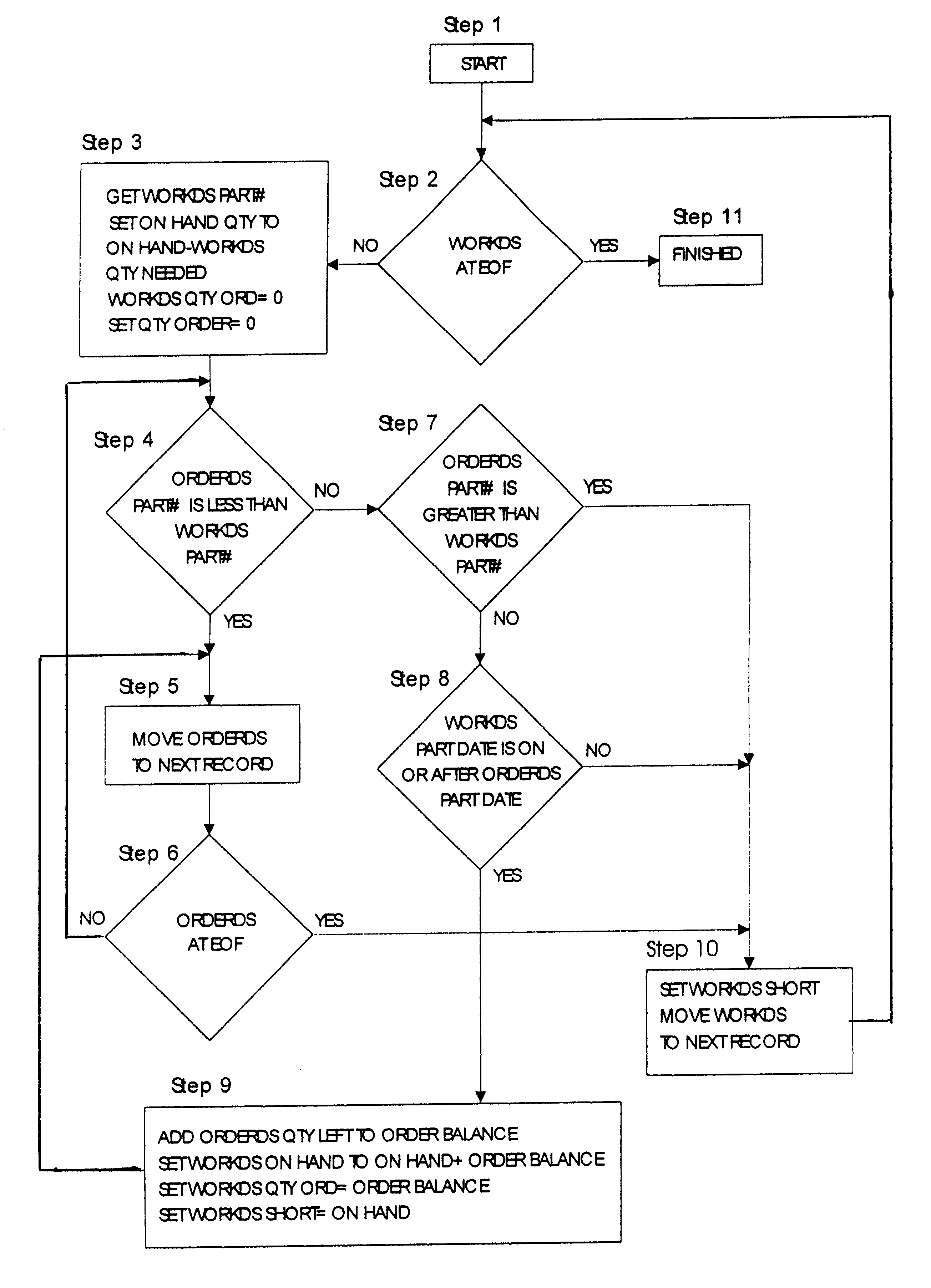
InactiveUS6173440B1Software testing/debuggingProgram loading/initiatingSoftware designVerification procedure
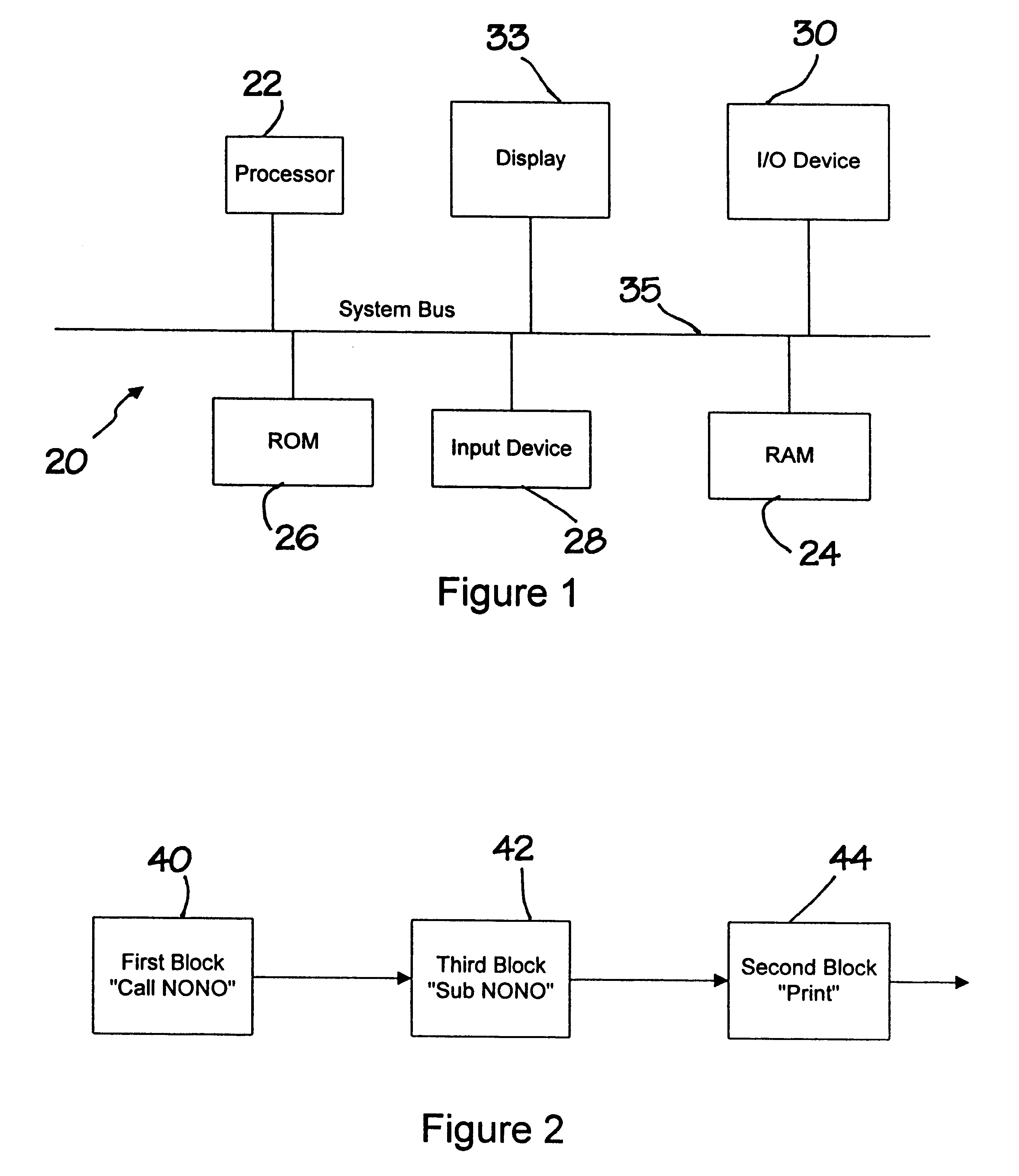
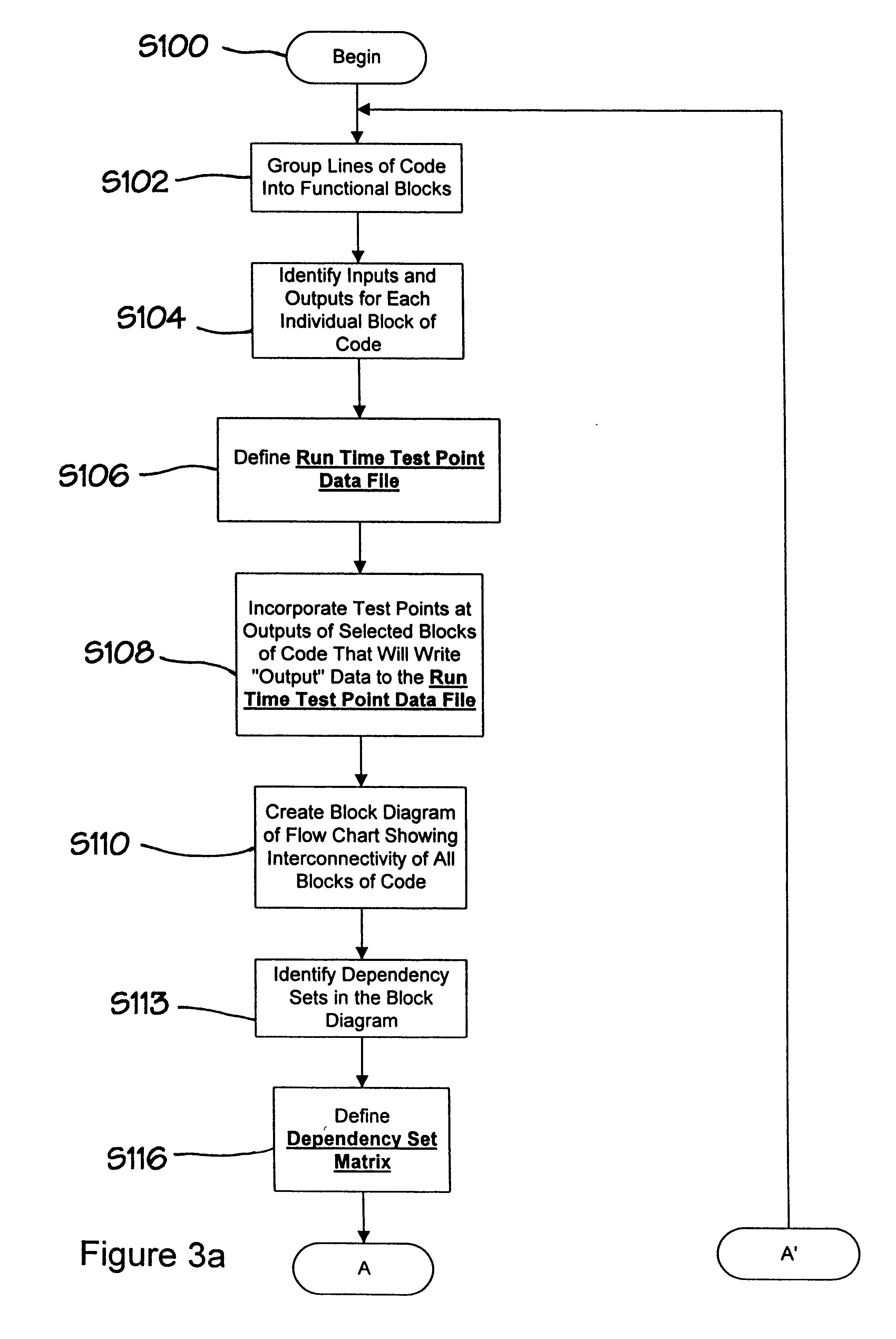
A new approach for software debugging, verification and validation is disclosed. The present invention utilizes a knowledge-based reasoning approach to build a functional model of the software code for identifying and isolating failures in the software code. The knowledge-based reasoning approach of the present invention uses the software design, which is preferably based upon a flow chart or block diagram representation of the software functionality, to build the functional model. The software block diagram contributes to the functional model by defining the inputs and outputs of the various blocks of code, as well as defining data interconnections between the various blocks of code. In accordance with a method of the present invention, test points are strategically inserted throughout the code, and each test point is associated with a corresponding block of code. Expected values of the test points for an expected proper-operation execution of the computer program are generated. The computer program is then executed on a computer, and the actual values of the test points from the program execution are compared with the expected values of the test points. Failed test points which do not agree with corresponding expected values are determined. The functional model, which includes information functionally relating the various test points to one another, is then used to isolate the failed test points to one or more sources of failure in the code.
Owner:MCDONNELL DOUGLAS
System and method for configurable software provisioning
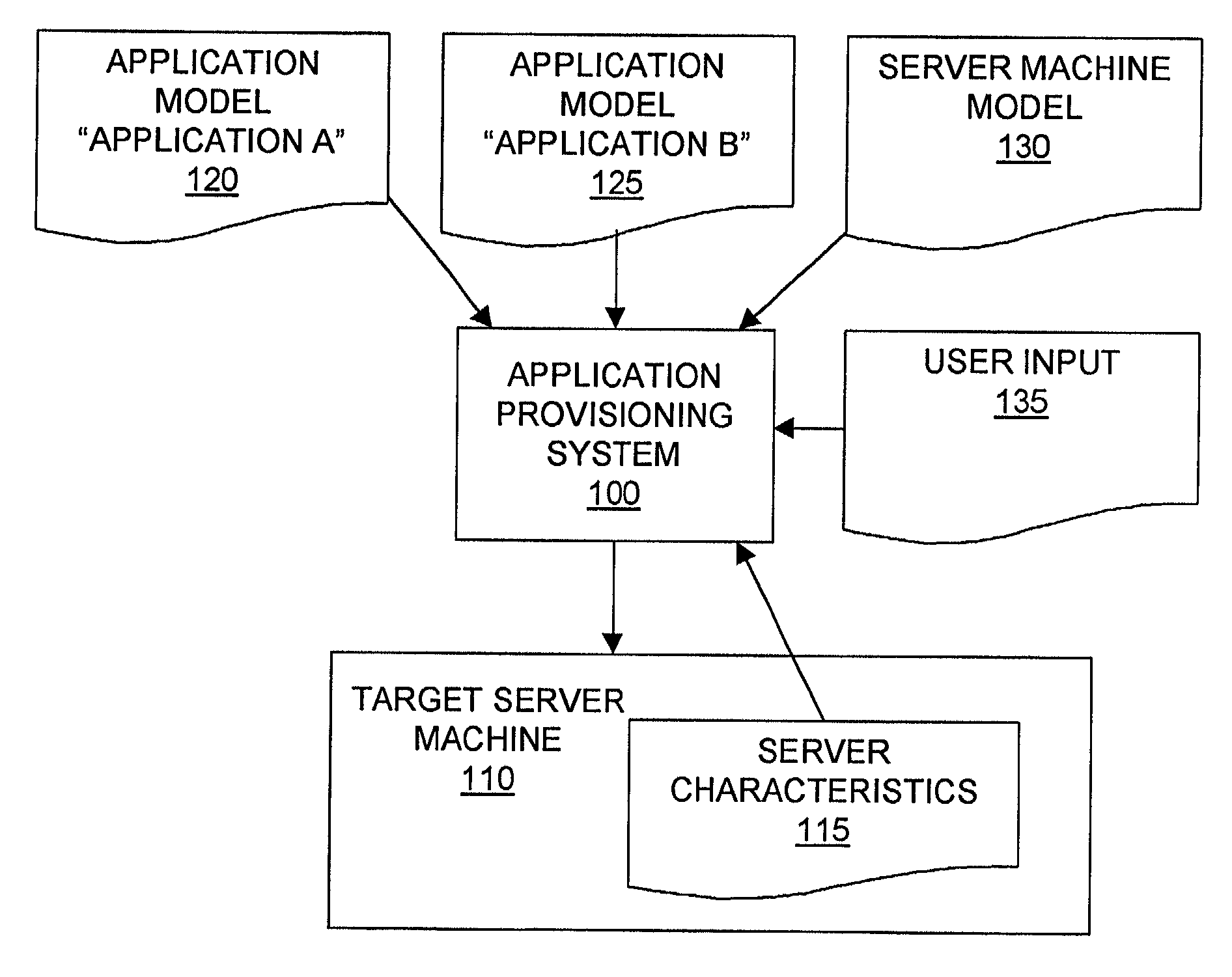
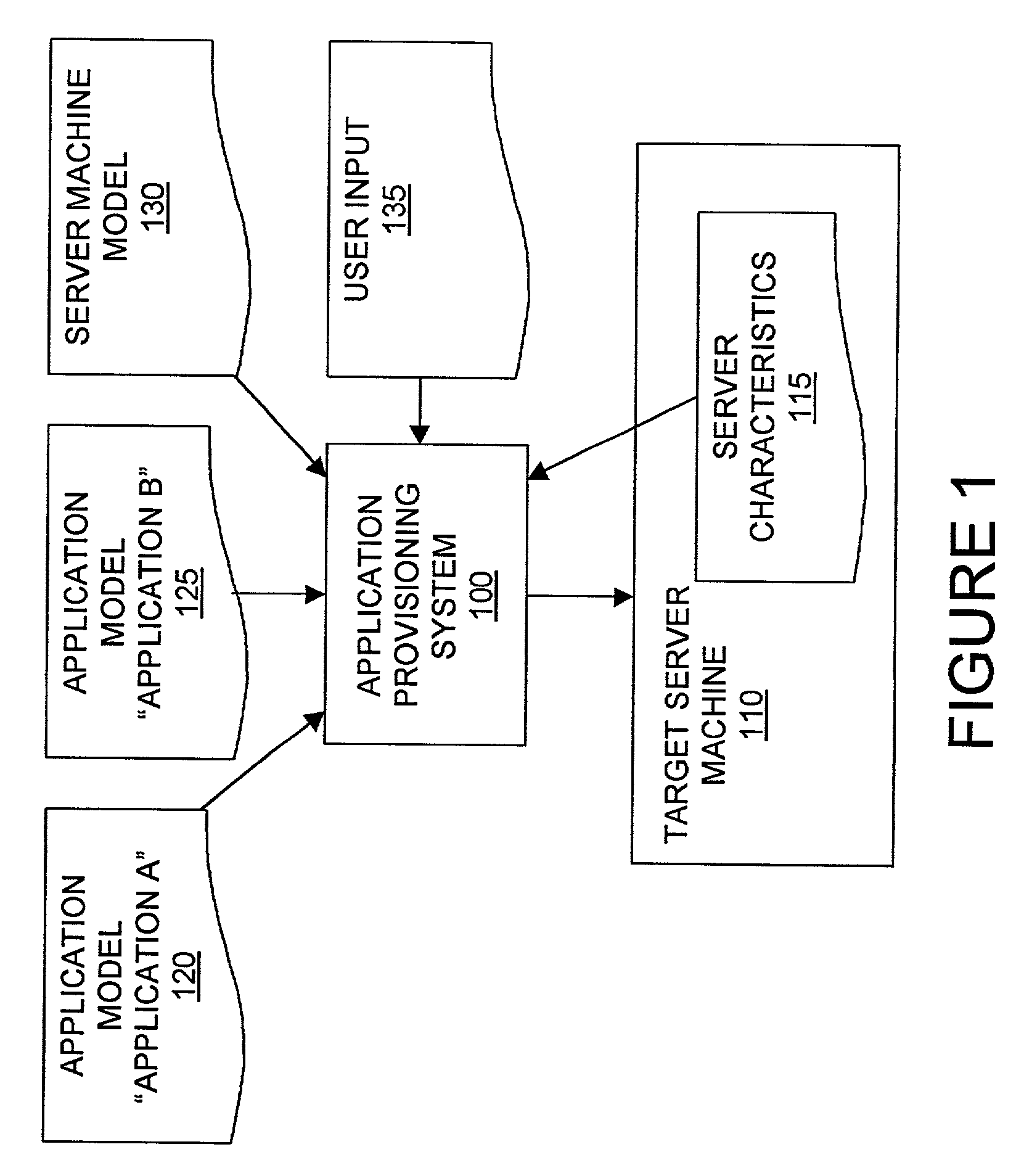
ActiveUS7171659B2Multiple digital computer combinationsSpecific program execution arrangementsComputer hardwareApplication software
A system and method for the automated provisioning of software applications onto one or more computers. The provisioning system uses a model of the application, which describes the application in terms of its software features and the actions to manipulate the application. The model preferably describes this information in a general way, such that it is independent of any environmental characteristics associated with the computers. The provisioning system also receives as input a set of references to selected ones of the computers onto which the application is to be provisioned.
Owner:ORACLE INT CORP
User interface for providing task management and calendar information
An electronic “To-Do” bar is provided in which displayed upcoming tasks, meetings, appointments and the like. The electronic To-Do bar is displayed in a lightweight menu of tasks, meetings and appointments and is displayed persistently in addition to other software functionality or user interfaces displayed on a user's computer display screen according to other software applications or other software functionality in use. A user is presented with an always-visible list of upcoming tasks, meetings and appointments without the need to launch a separate tasks application or calendar application to view upcoming tasks, meetings or appointments.
Owner:MICROSOFT TECH LICENSING LLC
System and method for distributed and parallel video editing, tagging, and indexing
InactiveUS20090097815A1Efficient editingTelevision system detailsElectronic editing digitised analogue information signalsClient-sideWorkflow engine
A system and method for having a media engine, client, workflow engine and server. The media engine takes digital or analog real-time video or video-on-demand as an input. Clients connect to the media engine, workflow engine and server. Depending on the client's capabilities, including software features, training and location, the workflow engine will drive required units of work to the client asking them to be fulfilled. This system enables efficient offline, real-time or faster than real-time editing, tagging and indexing of media by one or more clients at the same time. Unlimited numbers of users, tags and indexing functions to take place in parallel on a single video feed at the same time and managed through a rule based workflow engine.
Owner:SYNERGY SPORTS TECH
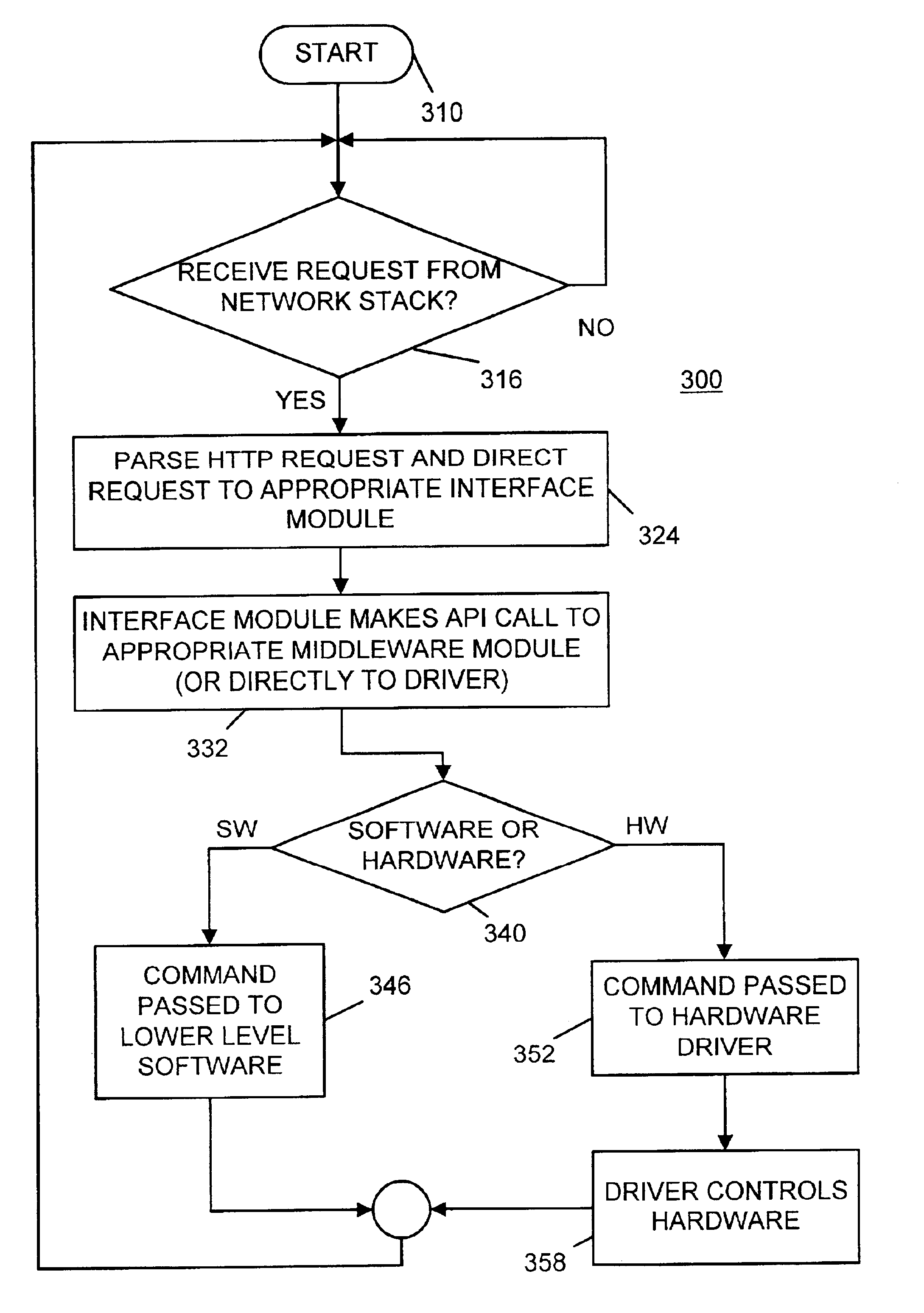
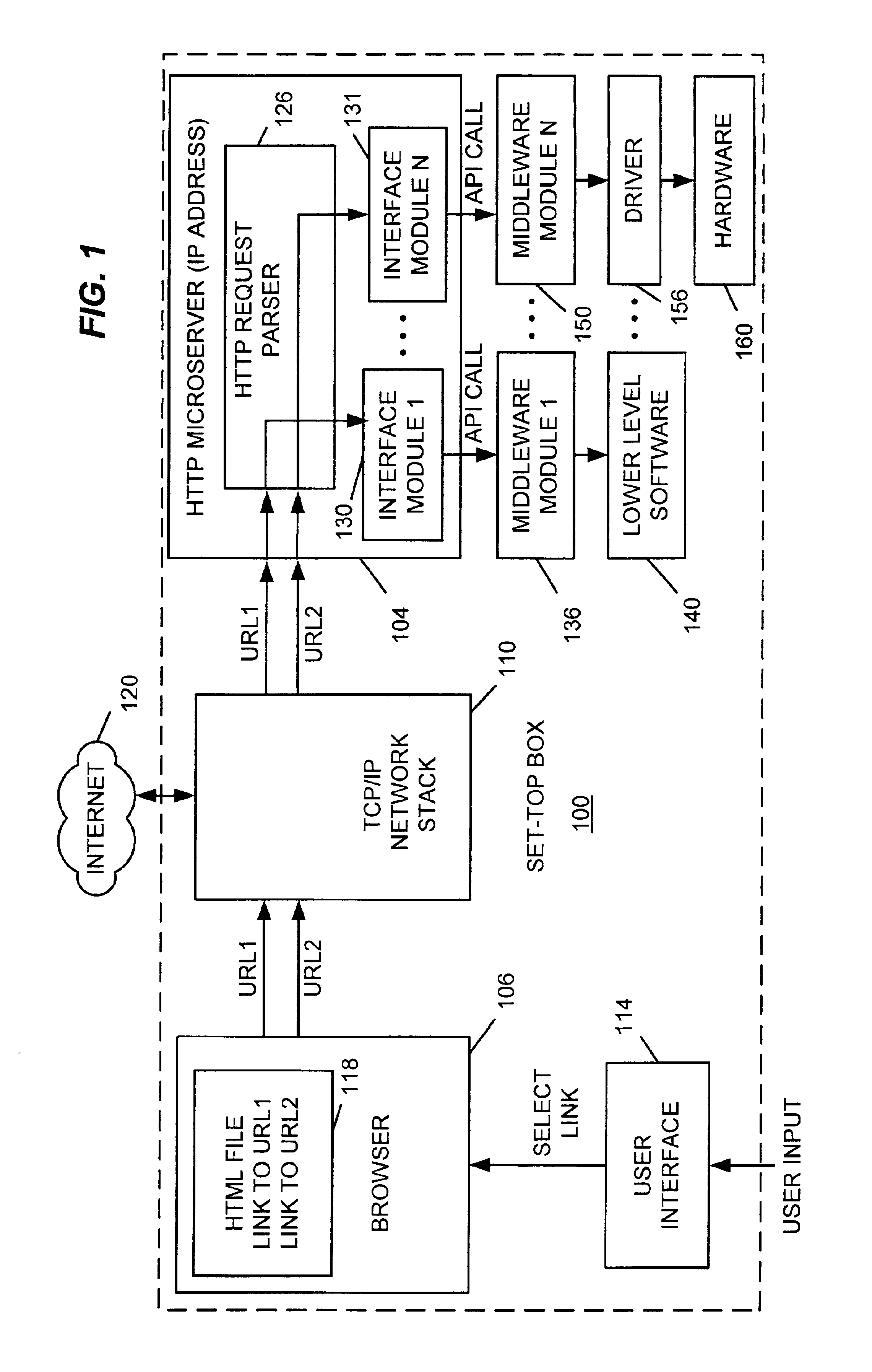
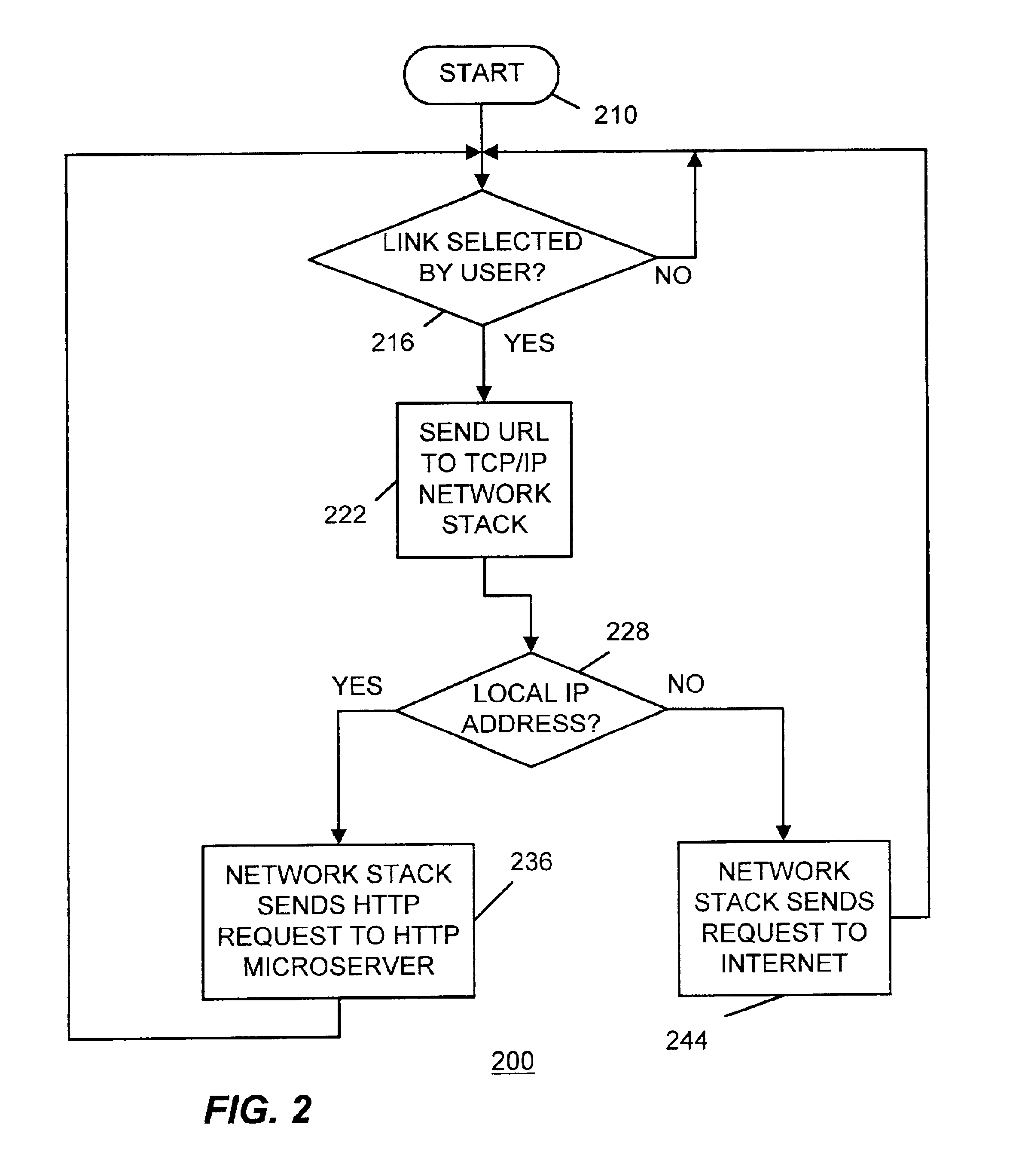
Method and apparatus for controlling set-top box hardware and software functions
ActiveUS6915525B2Television system detailsPulse modulation television signal transmissionControl setUniform resource locator
A method and apparatus for controlling set-top box hardware and software functions. An HTTP microserver is used to intercept HTTP requests for access to local devices and software. When the HTTP microserver receives a URL from the TCP / IP network stack, it directs instructions to an appropriate interface module that in turn generates an API call for an appropriate middleware module. The middleware module may then appropriately control a lower level software module to effect a software function or to drive hardware.
Owner:SONY CORP +1
Drag-and drop dynamic distributed object model
ActiveUS7178129B2Easy to manageLow costMultiprogramming arrangementsVisual/graphical programmingDrag and dropDistributed object
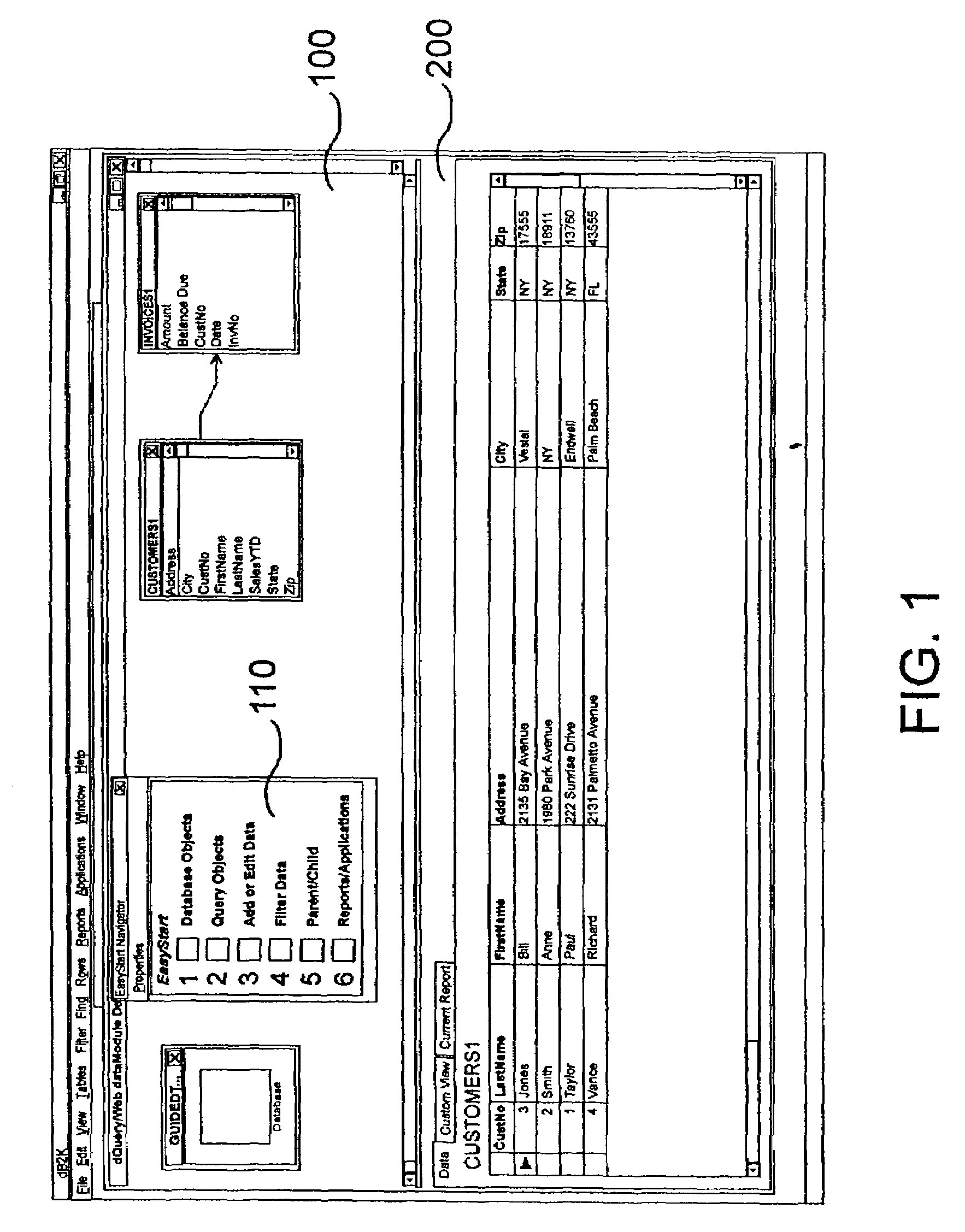
An external object model is built into a comprehensive, drag-and-drop, dynamic, distributed object model, to offer its users lower total cost of ownership than do conventional user interface applications and application builders. A Windows® workstation user computer is provided with a quick, simple, easily-managed path to combinations of available applications on a network of systems, in such a way that the user can establish and exploit complex data relationships and software capabilities on the workstation without application installation, significant access effort, or specialized knowledge. Runtime binding prepares and links user forms and reports to application programs as desired, without preparatory steps. The definition and use of query objects to view concurrently multiple database tables offers the unique ability to combine fields from dissimilar database engines into a single view.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
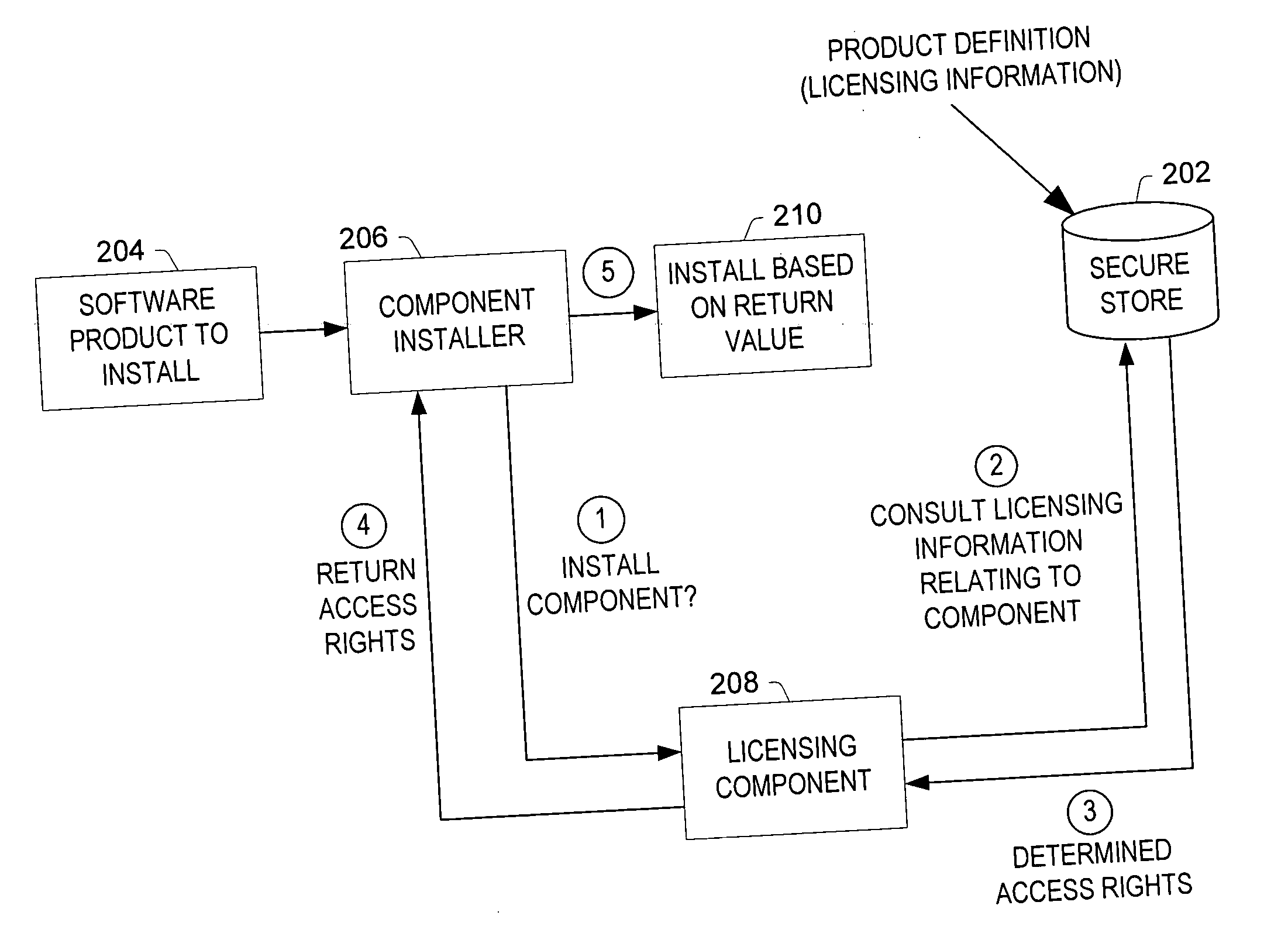
Selectively authorizing software functionality after installation of the software
ActiveUS20050050315A1Prevent unauthorized accessDigital data processing detailsUnauthorized memory use protectionAuthorizationSoftware feature
Controlling access to functionality within an installed software product. The invention includes an authorization module that dynamically references authorization information when specific functionality is requested by a requesting entity such as a user or an application program to determine if the requested functionality is authorized to be executed. Further, the invention dynamically provides an opportunity to the requesting entity to purchase unauthorized functionality. In this manner, functionality within the software product may be enabled or disabled at any time (e.g., during installation, post-installation, and re-installation).
Owner:MICROSOFT TECH LICENSING LLC
Method and system for limiting the use of user-specific software features
InactiveUS7158953B1Preventing unchecked proliferationDigital data processing detailsUnauthorized memory use protectionDigital rights management systemClient-side
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
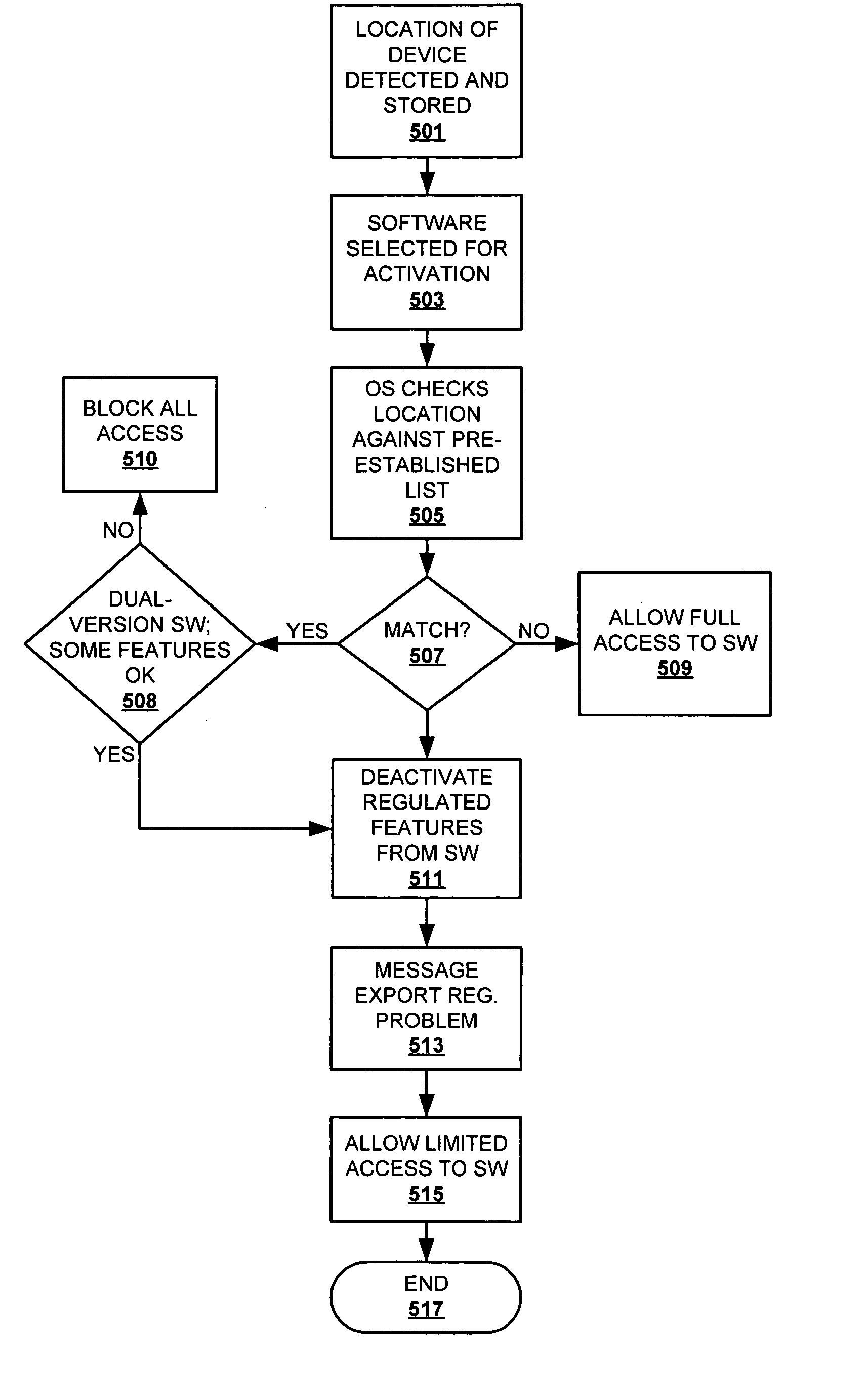
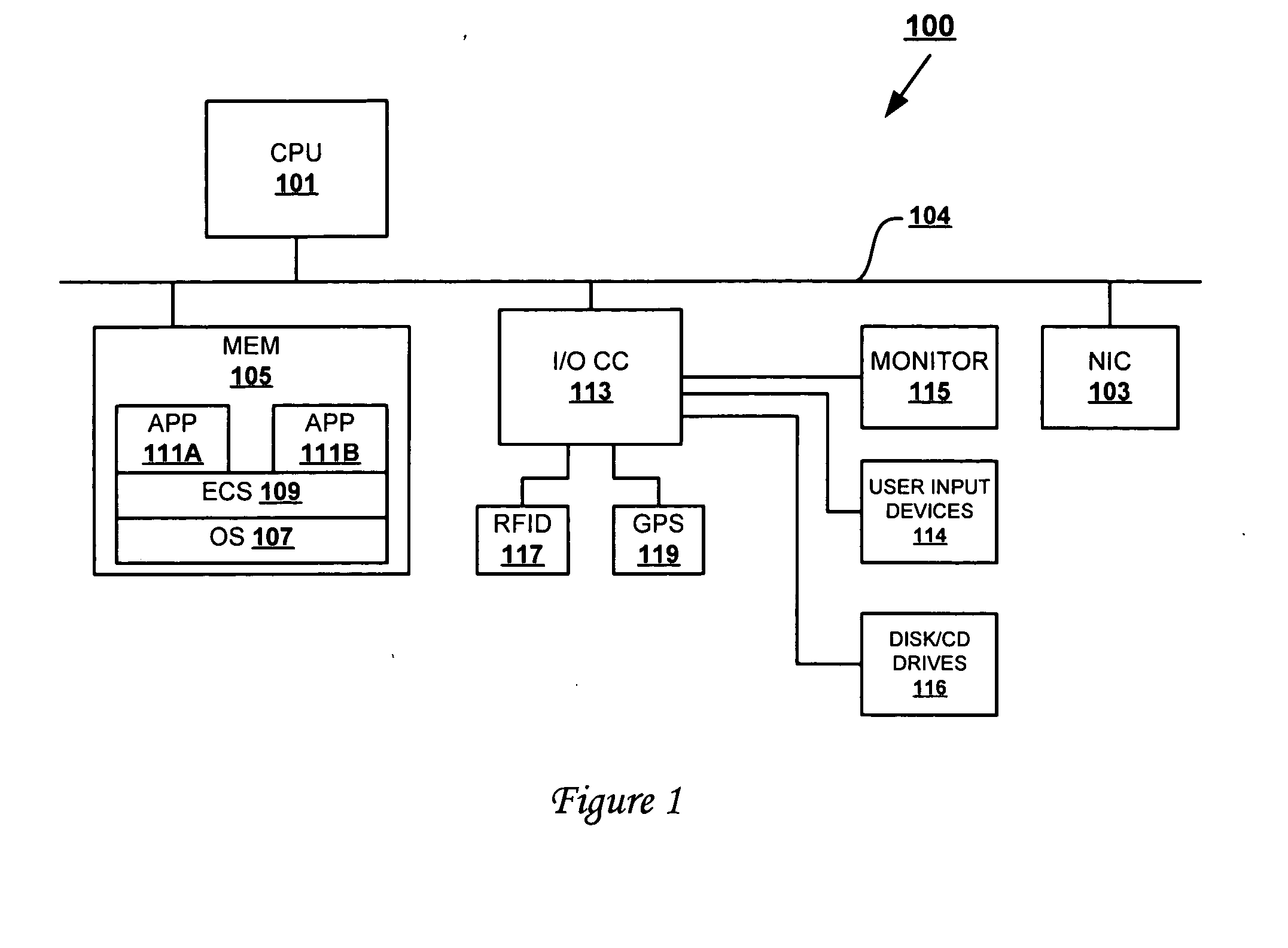
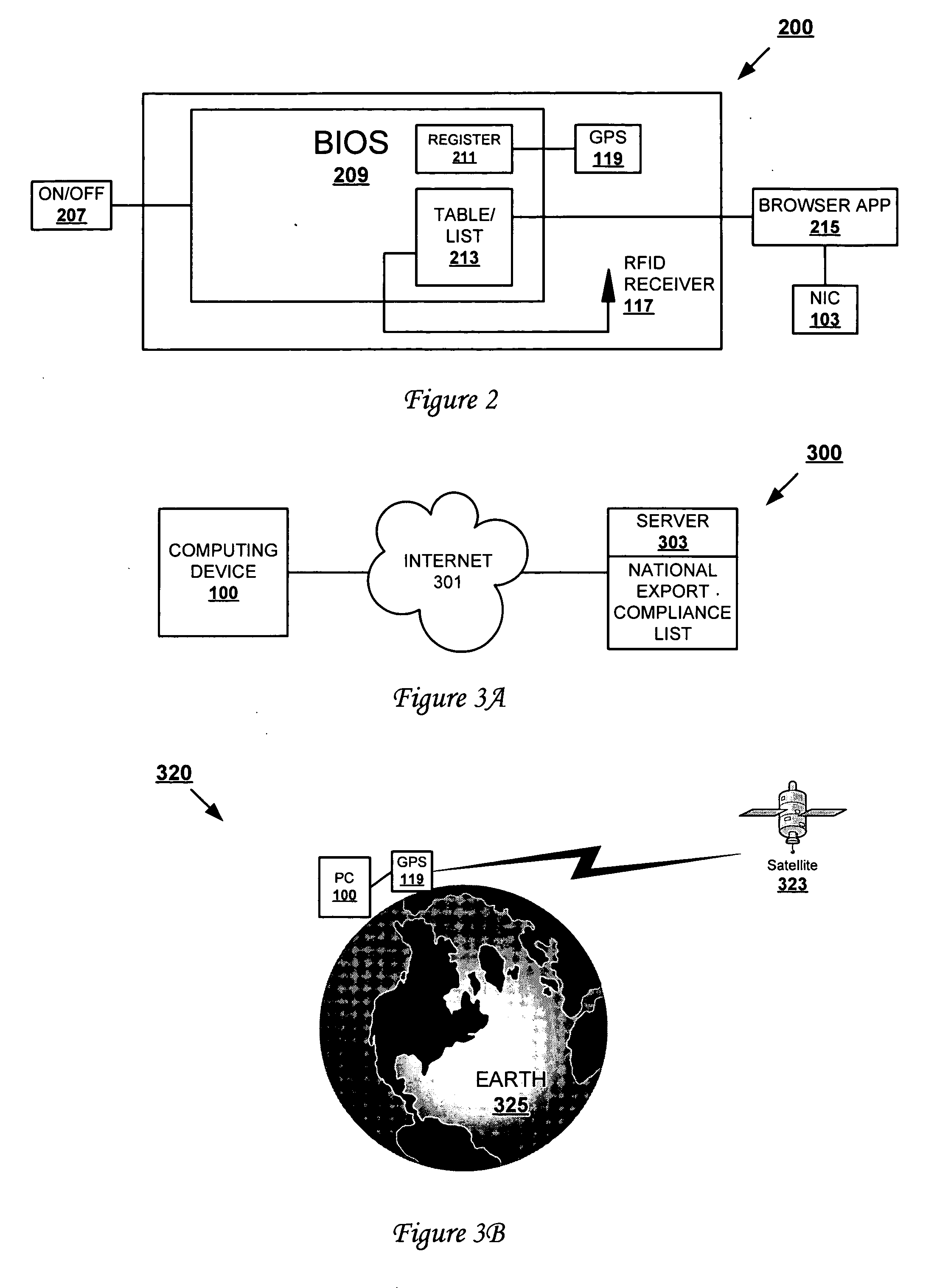
Method and apparatus for an intelligent, export/import restriction-compliant portable computer device
InactiveUS20050154904A1Digital data processing detailsPublic key for secure communicationSoftware engineeringComputers technology
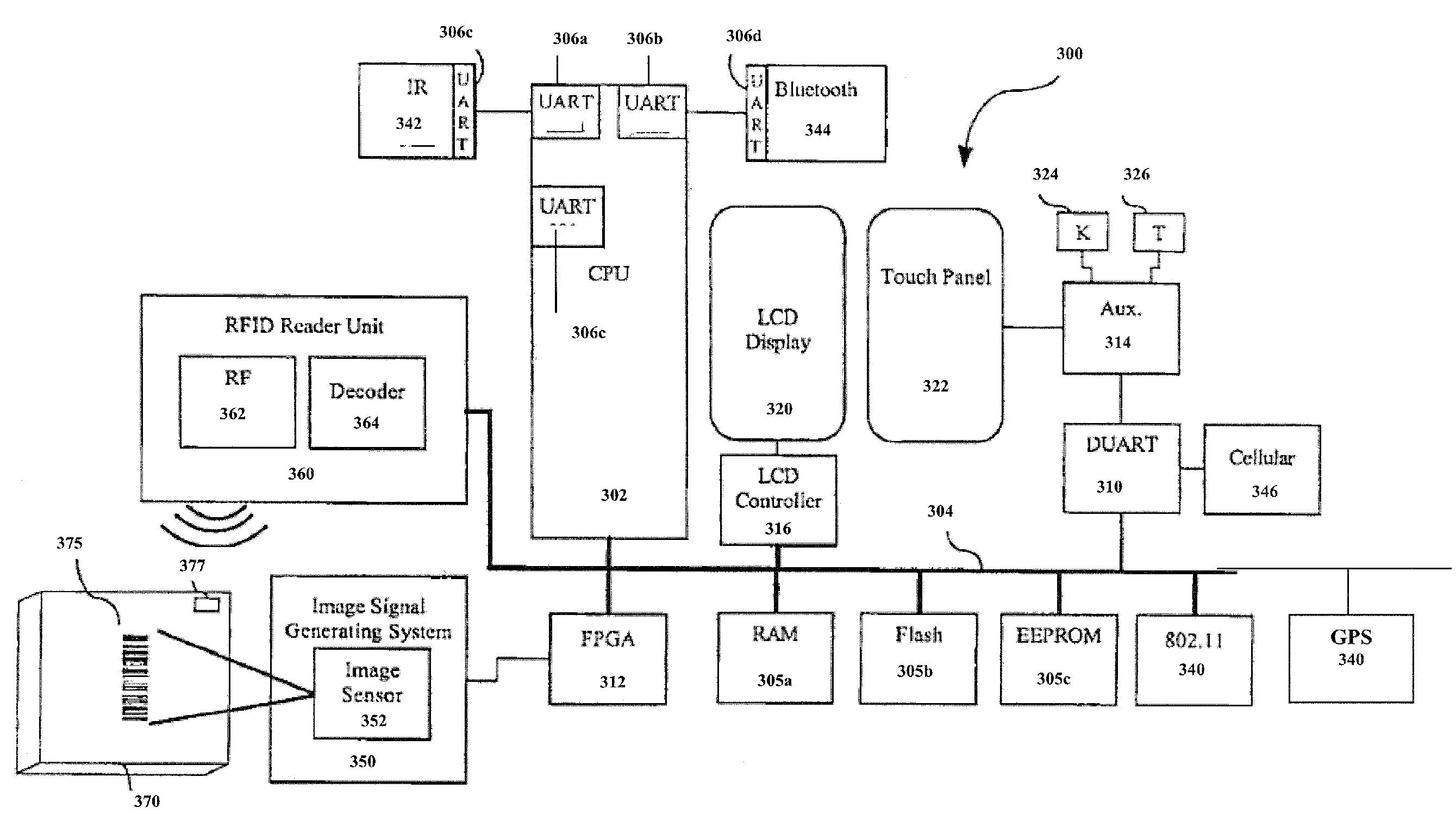
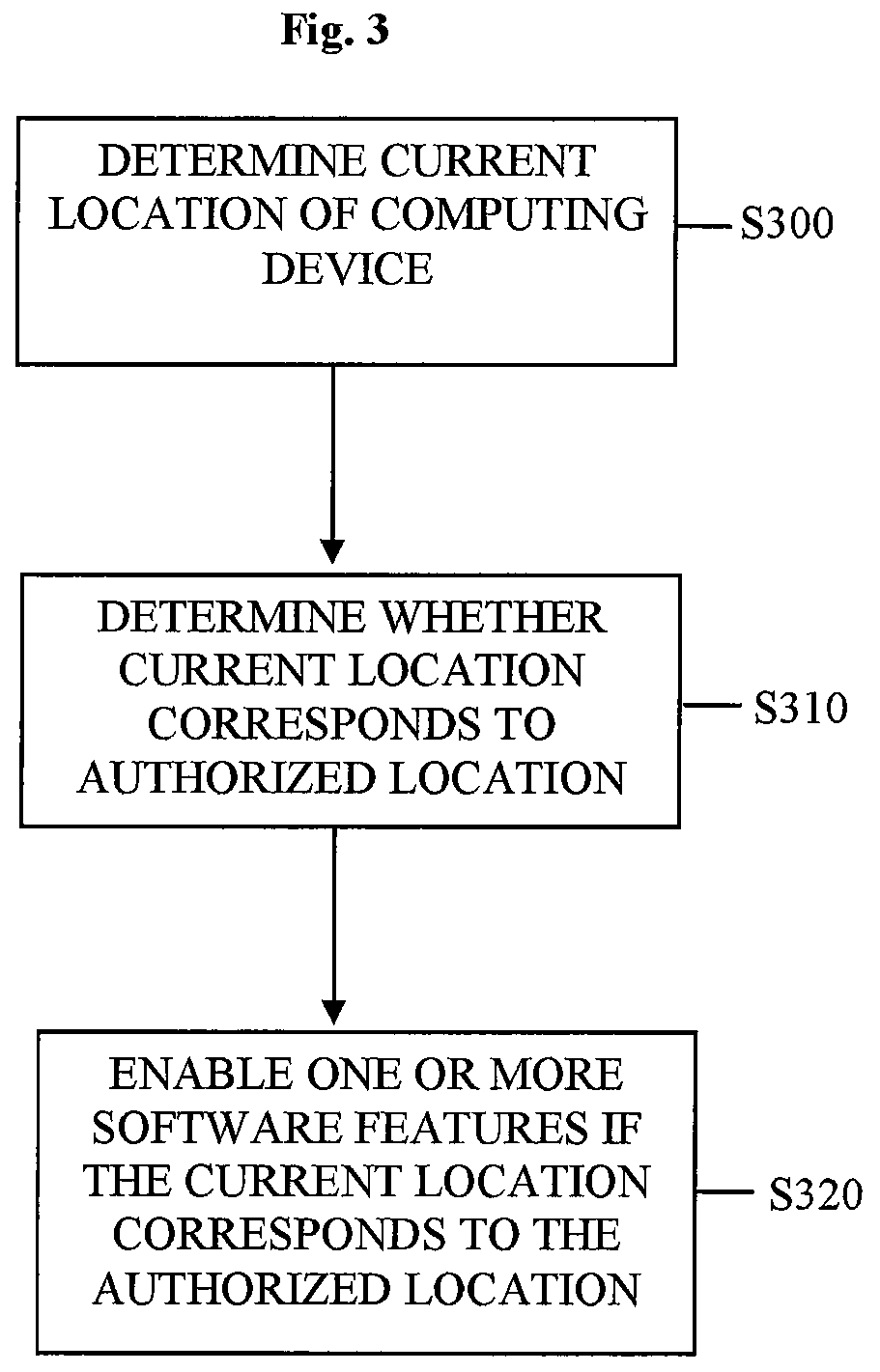
A method and system that enables cross-border compliance with export restrictions of particular computer technology, including software loaded on a computing device. The computing device is loaded with software, and has a country location device, such as a low-end GPS device. The country location device (country locator) stores the present geographic location of the device in a location register. When the computing device is turned on or the software is activated for operation on the computing device, a security utility of the software compares the value in the register against a list of pre-established locations that are export-restricted. When the value matches (or falls within a range) of one of pre-established locations, the features of the software that are export restricted are automatically disabled.
Owner:IBM CORP
Graphical user interface for a transport multiplexer
InactiveUS6996779B2Easy to operateEasy to controlSpecial service provision for substationPulse modulation television signal transmissionDrag and dropData stream
A feature-rich transport multiplexer and a number of associated methods, systems, subsystems, software features, graphical user interfaces and control systems are disclosed. The disclosure includes GUI's that enable operators to easily monitor and manipulate content streams flowing through a transport multiplexer in real-time. The disclosed interfaces include screens that supply operators with identity, structure, configuration, bandwidth utilization and / or status information for system hardware and software. The disclosed features also provide computer assisted routing configuration for present and future routing events through simple manipulation, such as drag and drop operations, of graphical objects. Routing control is further simplified by permitting operators to configure routing control of individual content stream components as well as groups of such components simultaneously. Further flexibility is permitted by predetermination of future routing events, thereby enabling the automatic execution of configuration changes at a future time. Various types of content, such as video, audio, IP data can be manipulated to achieve various results such as one or more multiplexed MPEG data streams.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
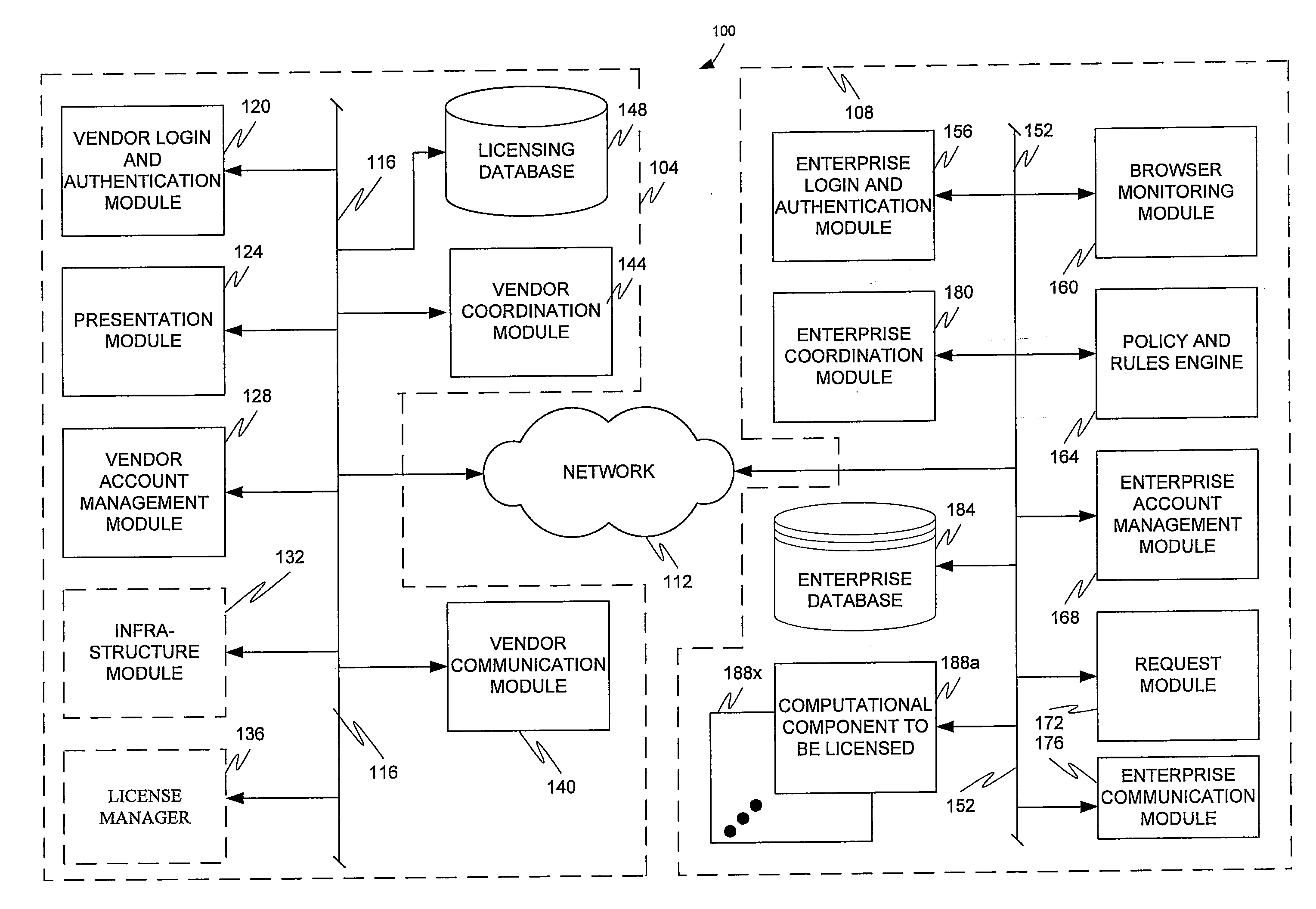
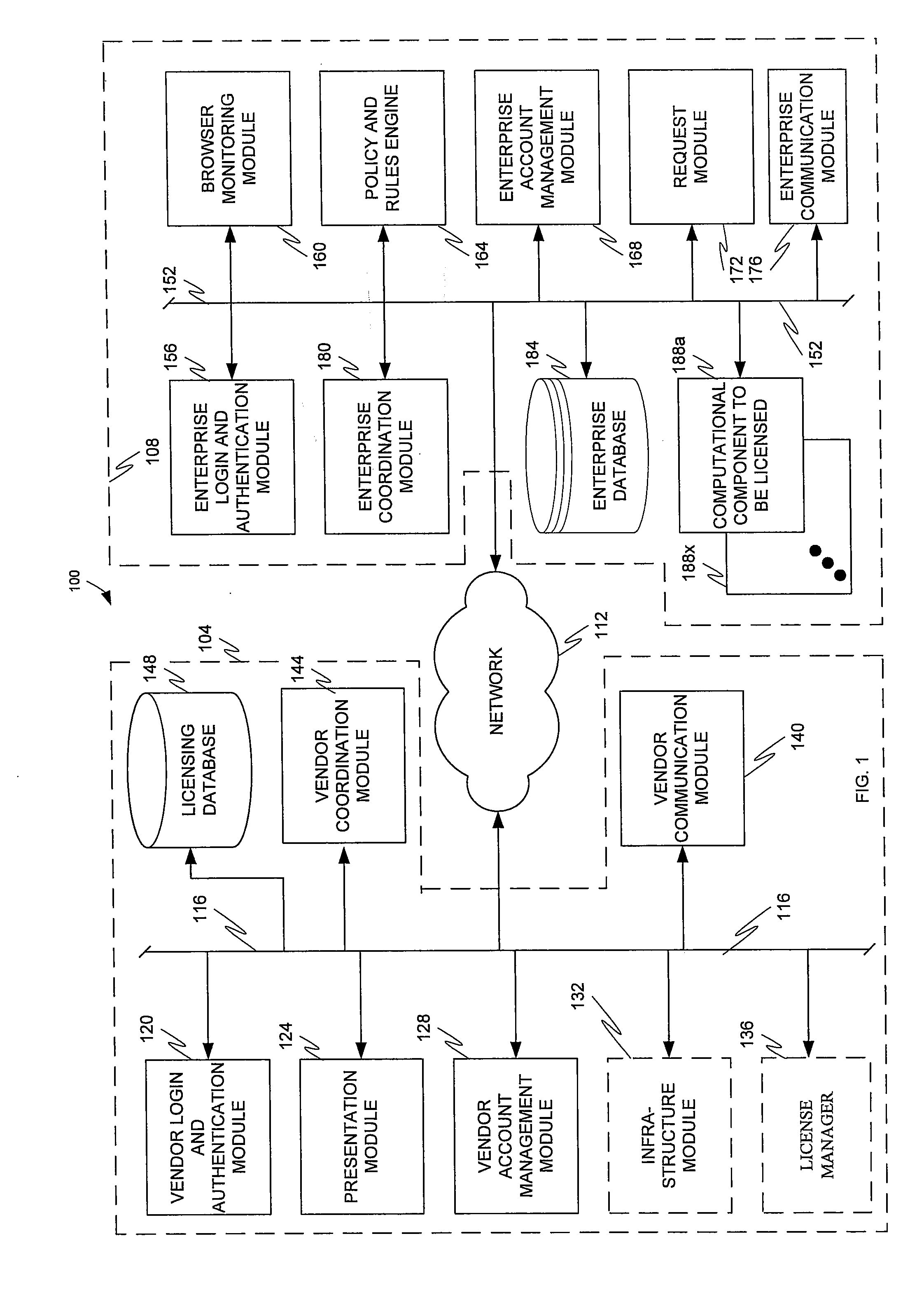
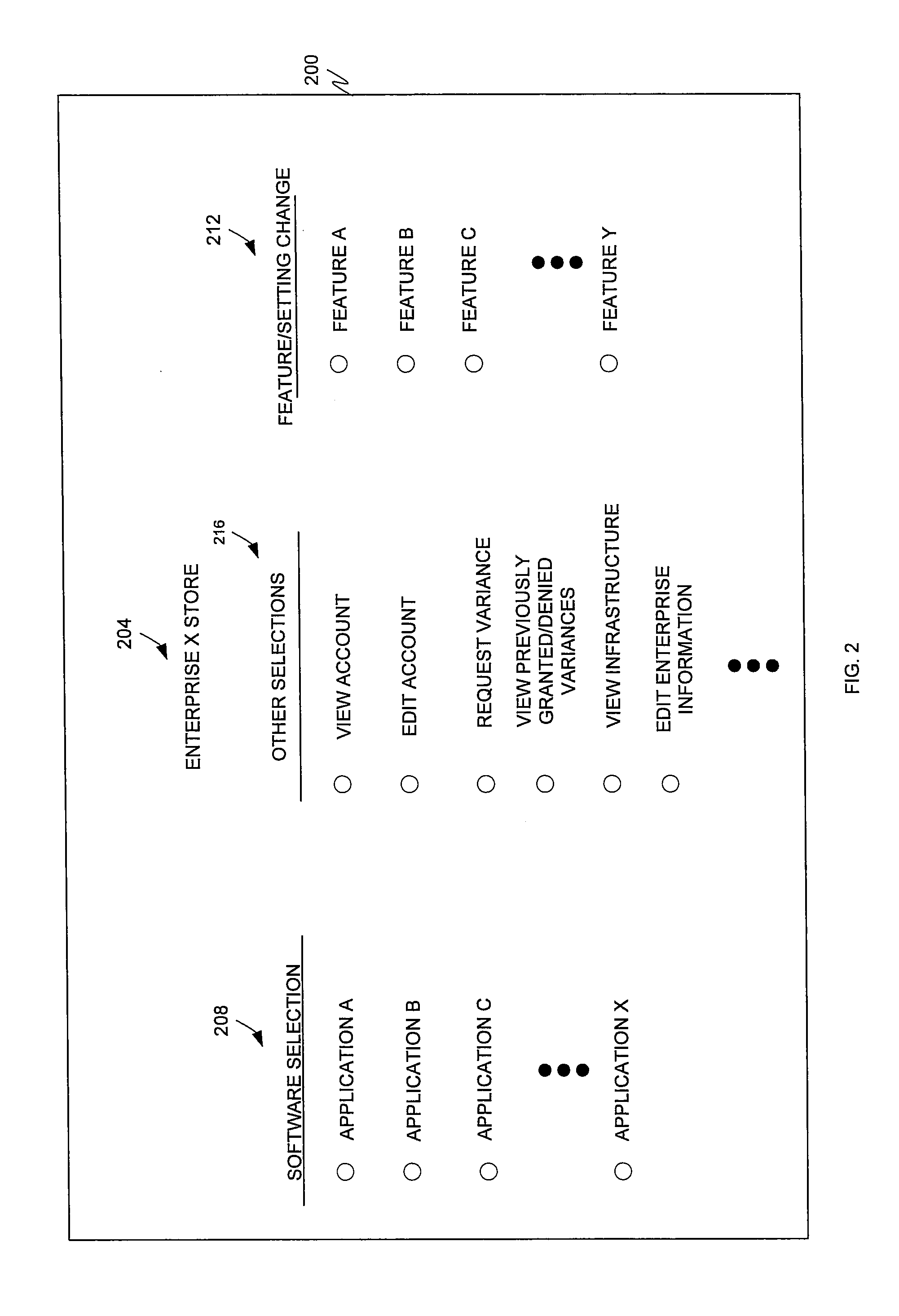
Application and open source information technology policy filter
ActiveUS20110302623A1The process is simple and convenientQuickly and efficiently locating and purchasingComputer security arrangementsTransmissionSoftware distributionOpen source
The present invention is directed to a software distribution architecture in which an enterprise has a filter that screens user requested software, software upgrade(s), software feature(s), and / or software setting option(s) against enterprise rules or policies. Disapproved software, software upgrade(s), software feature(s), and / or software setting option(s) are blocked for download.
Owner:AVAYA INC
Method and apparatus for material requirements planning
InactiveUS6625616B1Fast data processingAvoid necessary capital expenditureHand manipulated computer devicesDigital data processing detailsNetwork connectionData access
A method and apparatus for materials requirements planning that implements a client / server computer network with an algorithm which enables receiving and preserving input data from the client in a stateless protocol in the server, the input data from a client is preprocessed to determine the MPR state, and stored for each client in the server in a separate side container using stateless protocols. A side container containing a client's data is accessed by distinct SQL and VB code routines to perform specific reports, modification of a required materials order and / or adjustment of material availability for use dates. The preprocessing arranges the input data into record sets of all scheduled material requirements, all currently available and required materials and all unfulfilled ordered materials. The preprocessing is executed via SQL, and the processing is executed via executable code into a temporary record set that is placed into a storage container. The apparatus consists of a server side processor having a network connection and provided with software to supply network server functions, server side general purpose programming functions, and database functions using SQL code. A client side processor connected to the network and provided with software to enable login to the server side processor via the network, and to supply software functions including data access reports and / or modification in order to be able to control server access.
Owner:MRPONLINE COM
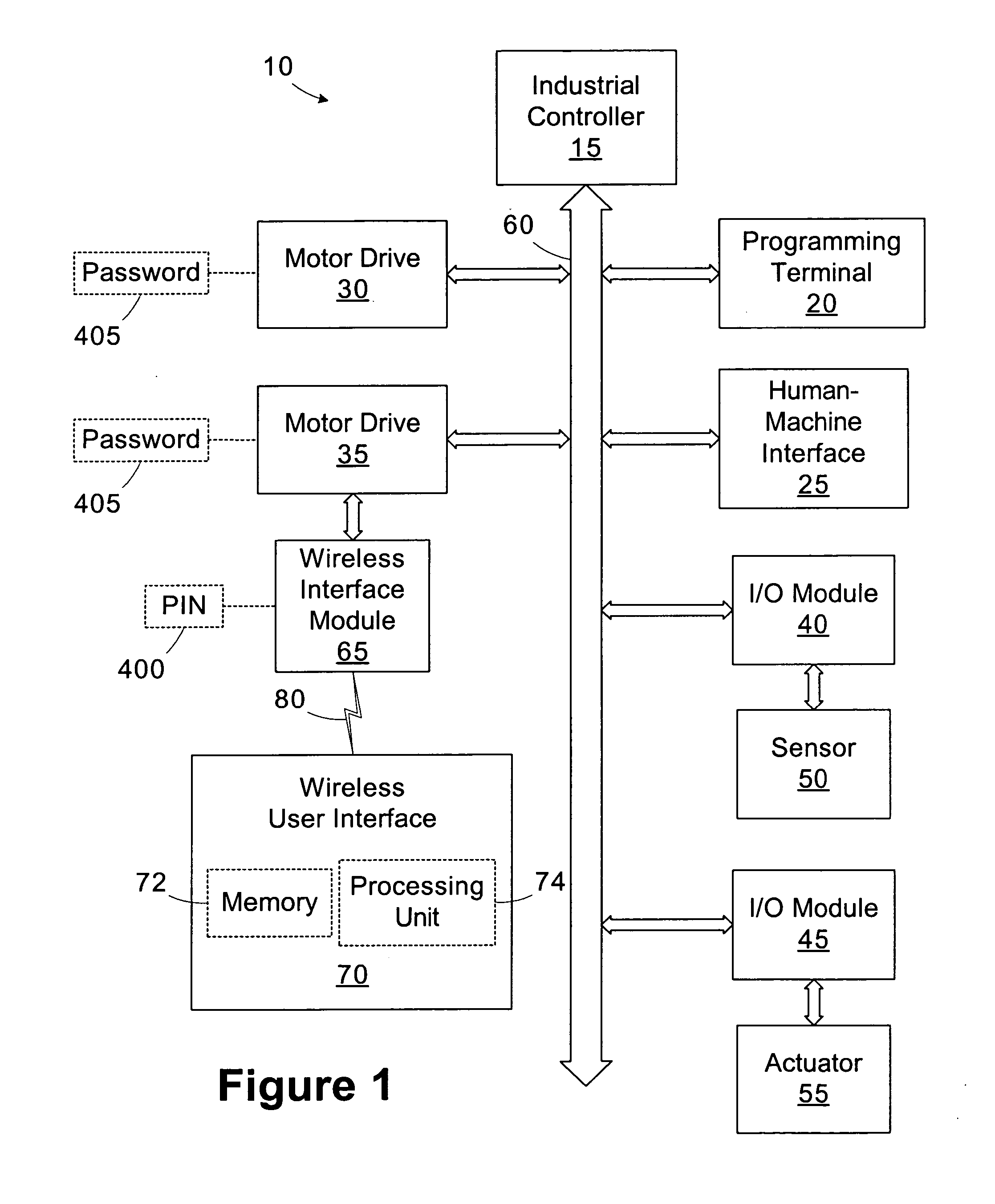
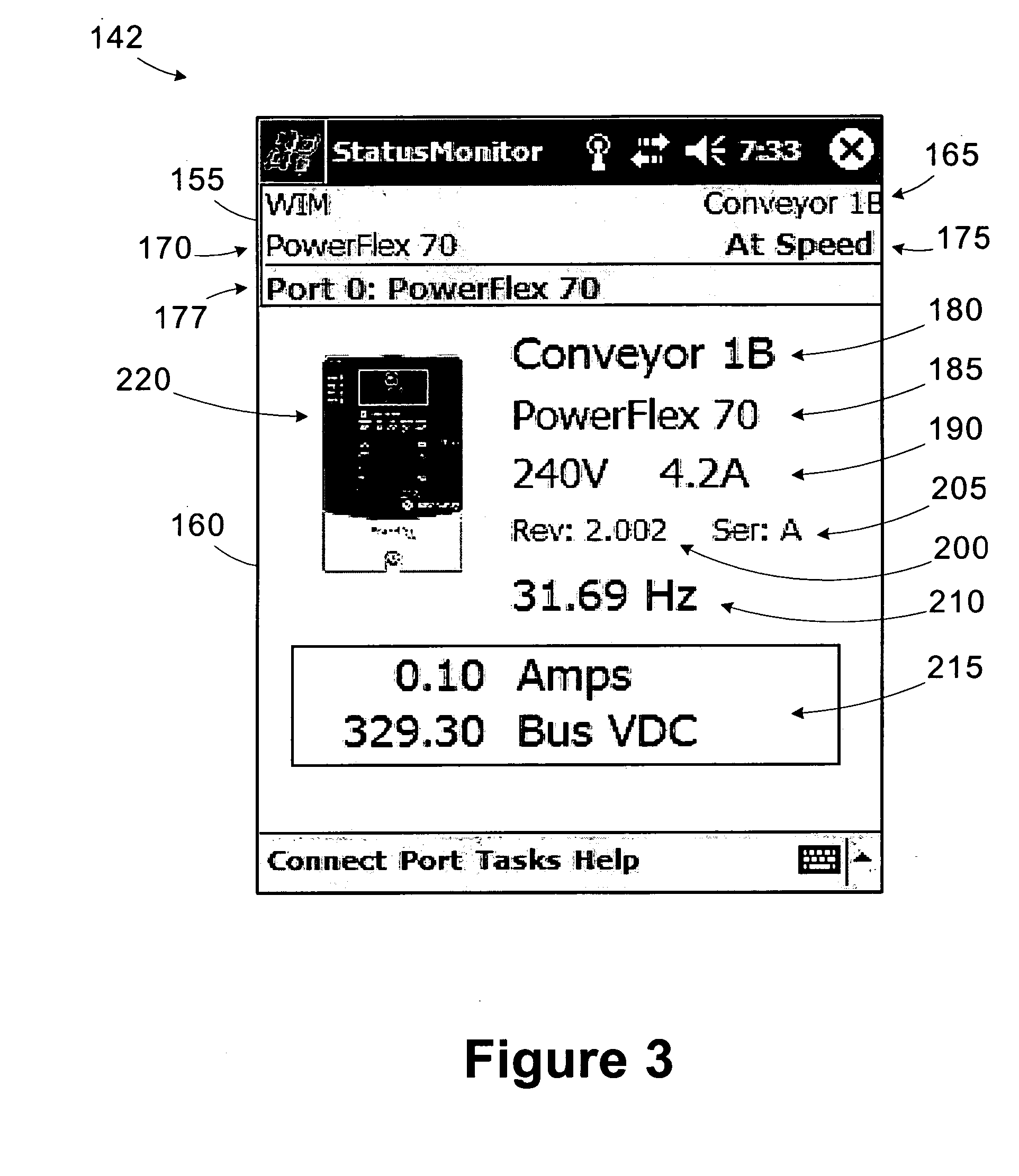
Wireless industrial control user interface with configurable software capabilities
A user interface operable to connect to a device within an industrial control system includes a memory and a processing unit. The memory is operable to store a plurality of software applications for interfacing with the device and a configuration mask including access rights for at least a subset of the software applications. The processing unit is operable to establish a first connection with the device and disable selected software applications based on the configuration mask.
Owner:ROCKWELL AUTOMATION TECH
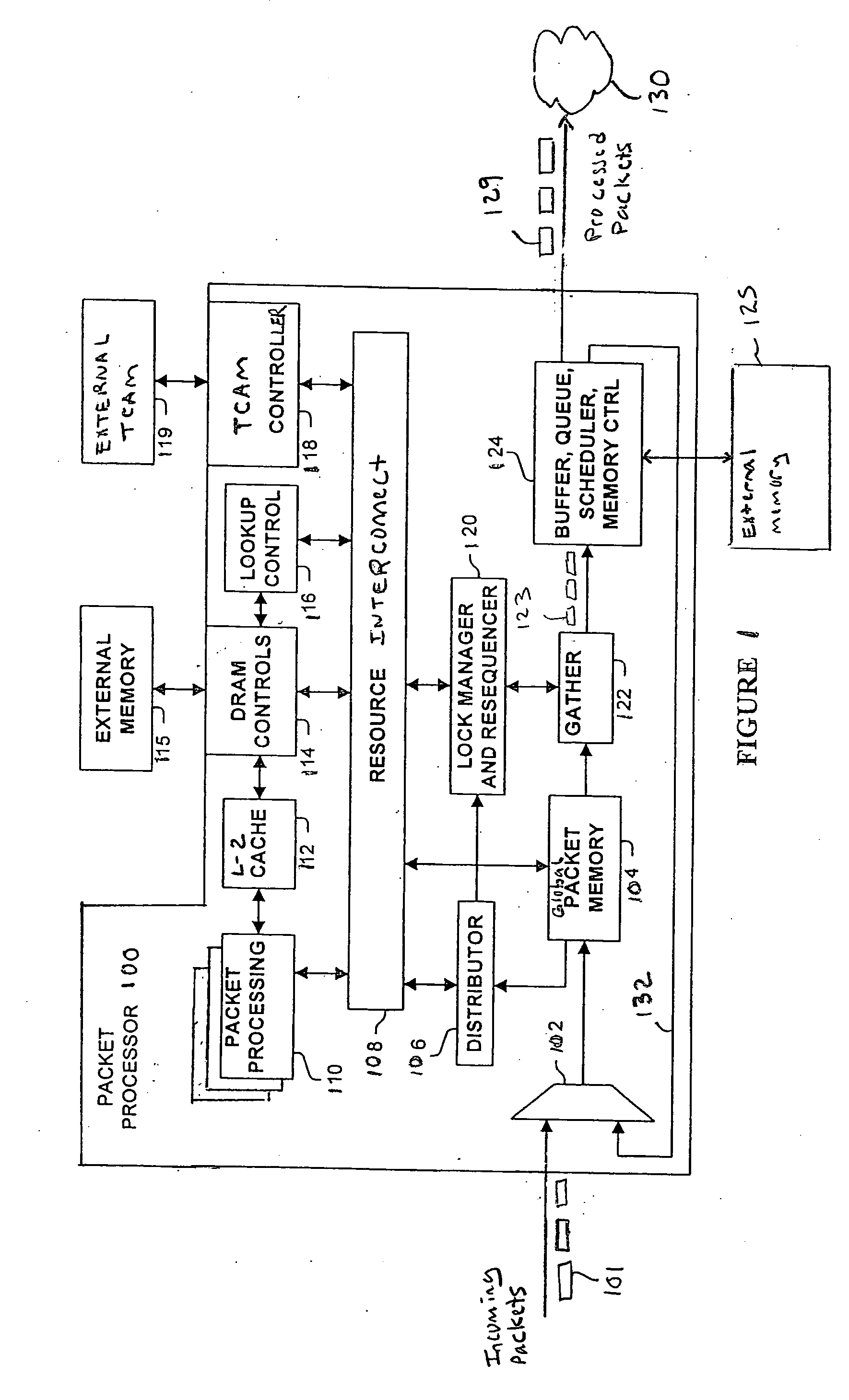
Multi-threaded packeting processing architecture
InactiveUS20060179156A1Quicker and high quality portingIncrease data rateDigital computer detailsData switching by path configurationData packHardware architecture
A network processor has numerous novel features including a multi-threaded processor array, a multi-pass processing model, and Global Packet Memory (GPM) with hardware managed packet storage. These unique features allow the network processor to perform high-touch packet processing at high data rates. The packet processor can also be coded using a stack-based high-level programming language, such as C or C++. This allows quicker and higher quality porting of software features into the network processor. Processor performance also does not severely drop off when additional processing features are added. For example, packets can be more intelligently processed by assigning processing elements to different bounded duration arrival processing tasks and variable duration main processing tasks. A recirculation path moves packets between the different arrival and main processing tasks. Other novel hardware features include a hardware architecture that efficiently intermixes co-processor operations with multi-threaded processing operations and improved cache affinity.
Owner:CISCO TECH INC
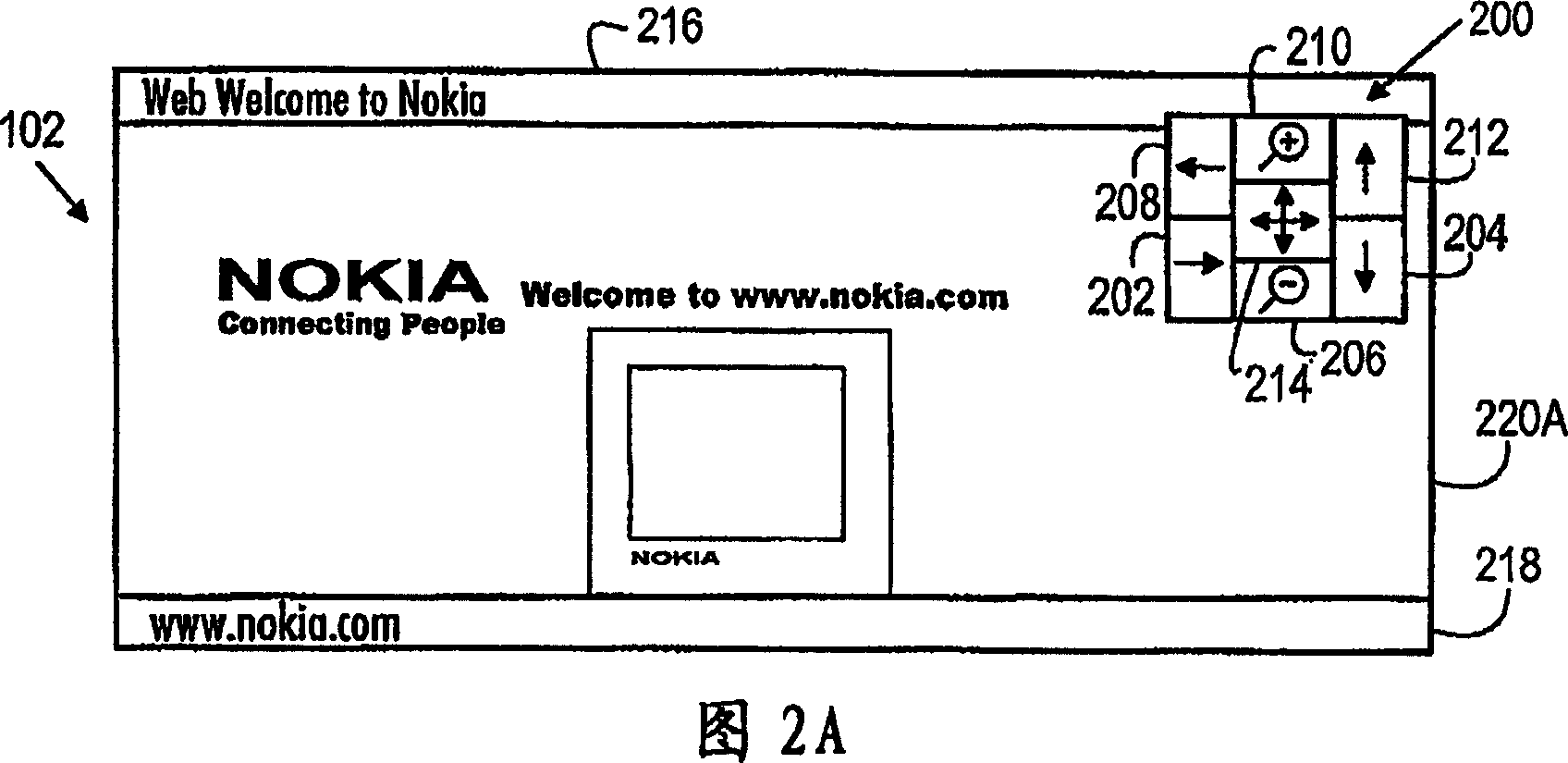
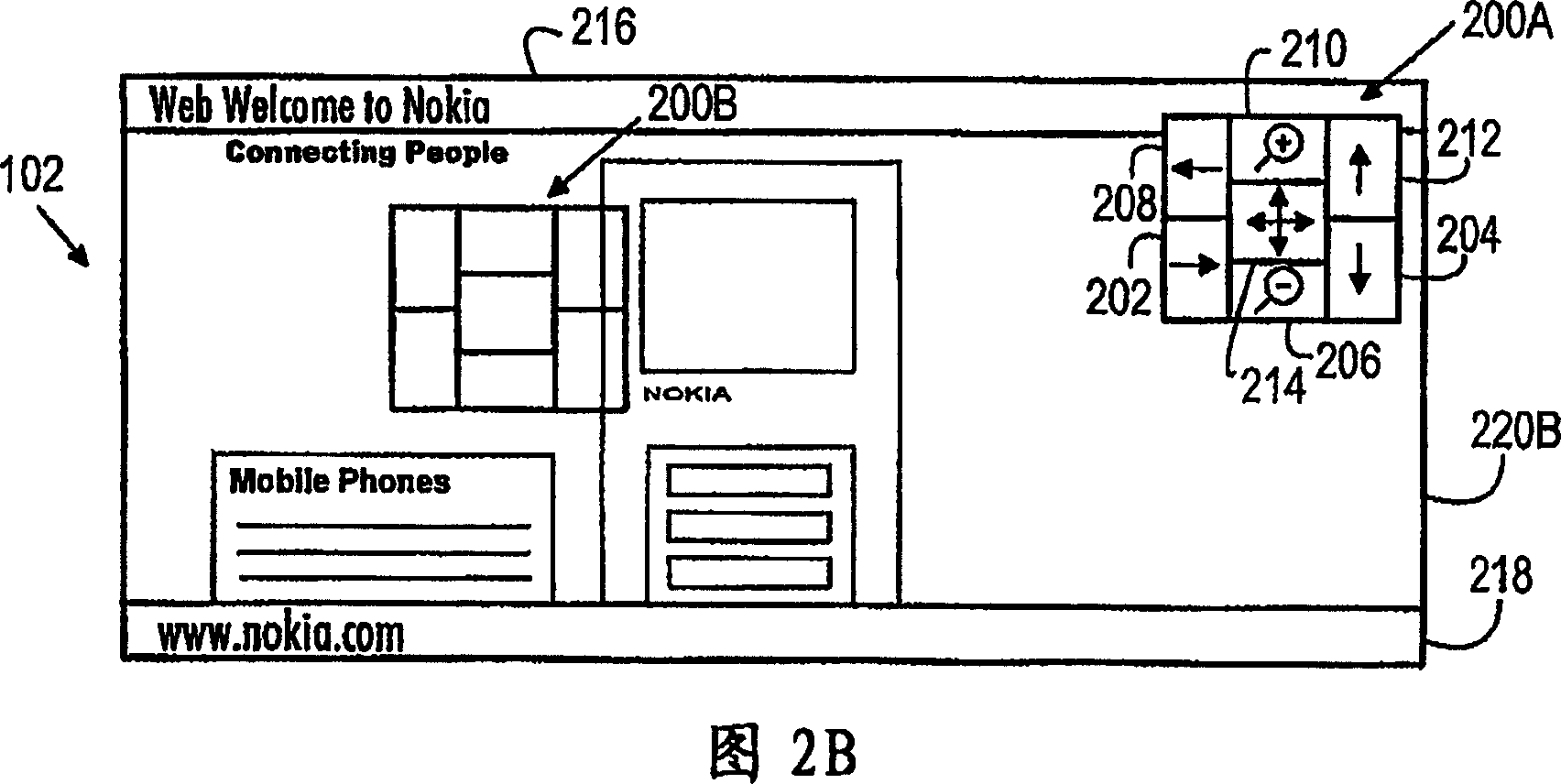
Navigating method, electronic device, user interface and computer program product
InactiveCN1957320ASave spaceImprove understandingCathode-ray tube indicatorsInput/output processes for data processingGraphicsGraphical user interface
The invention relates to a method of navigating in application views of an electronic device, to an electronic device, to a graphical user interface, and to a computer program product. The electronic device is configured to: display an initial application view on the display, provide a floatable navigation area displayed at least partly over the application views on the display, the floatable navigation area comprising navigation blocks for controlling given software functions, detect a selection of a given navigation block indicated by the input device, perform software functions associated with the selected navigation block once the selection of said navigation block is detected, and to display a current application view on the basis of the performed software functions.
Owner:NOKIA CORP
Accessory authentication for electronic devices
ActiveUS20090083834A1Digital data processing detailsUser identity/authority verificationHand heldMusic player
Improved techniques to control utilization of accessory devices with electronic devices are disclosed. The improved techniques can use cryptographic approaches to authenticate electronic devices, namely, electronic devices that interconnect and communicate with one another. One aspect pertains to techniques for authenticating an electronic device, such as an accessory device. Another aspect pertains to provisioning software features (e.g., functions) by or for an electronic device (e.g., a host device). Different electronic devices can, for example, be provisioned differently depending on different degrees or levels of authentication, or depending on manufacturer or product basis. Still another aspect pertains to using an accessory (or adapter) to convert a peripheral device (e.g., USB device) into a host device (e.g., USB host). The improved techniques are particularly well suited for electronic devices, such as media devices, that can receive accessory devices. One example of a media device is a media player, such as a hand-held media player (e.g., music player), that can present (e.g., play) media items (or media assets).
Owner:APPLE INC
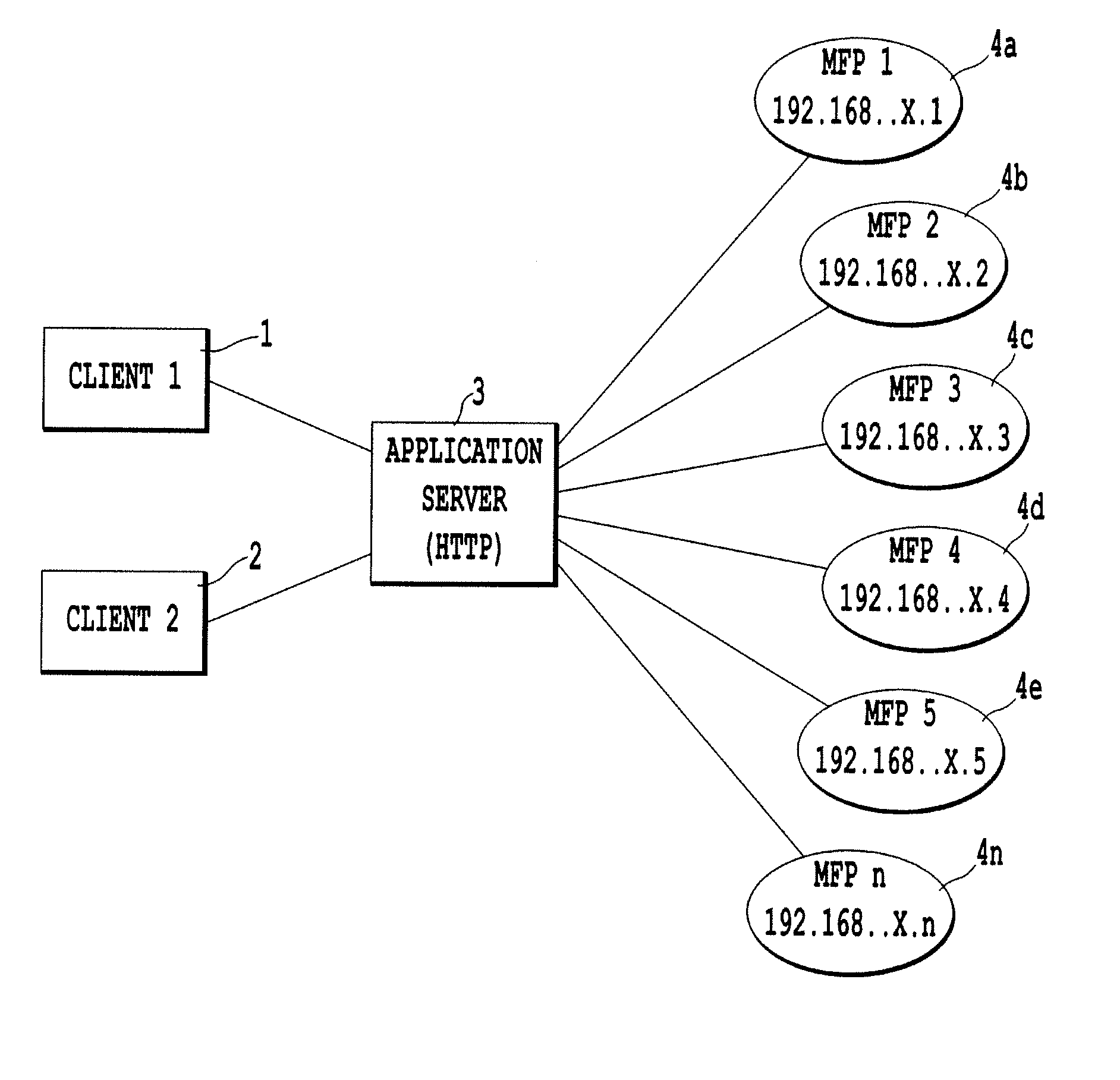
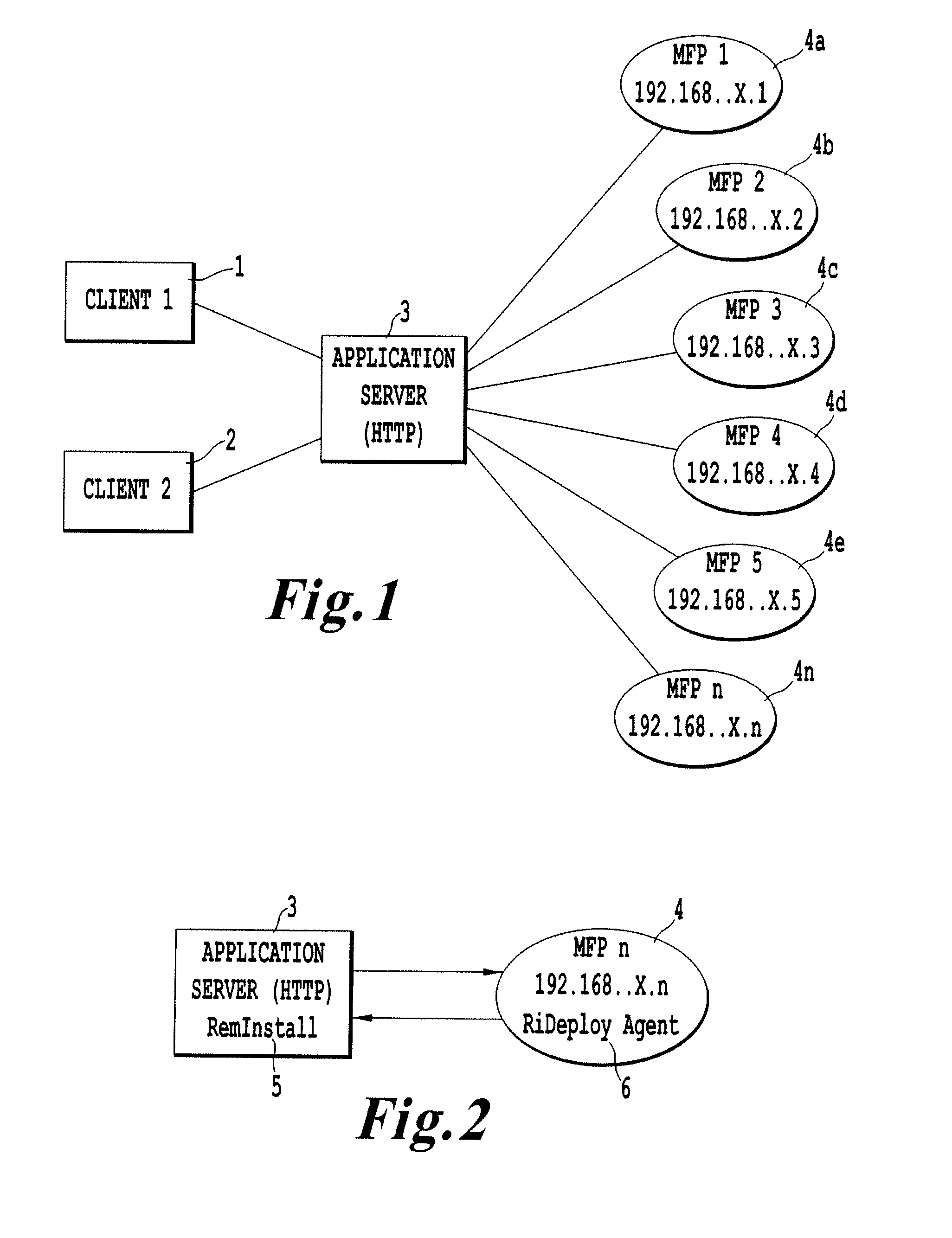
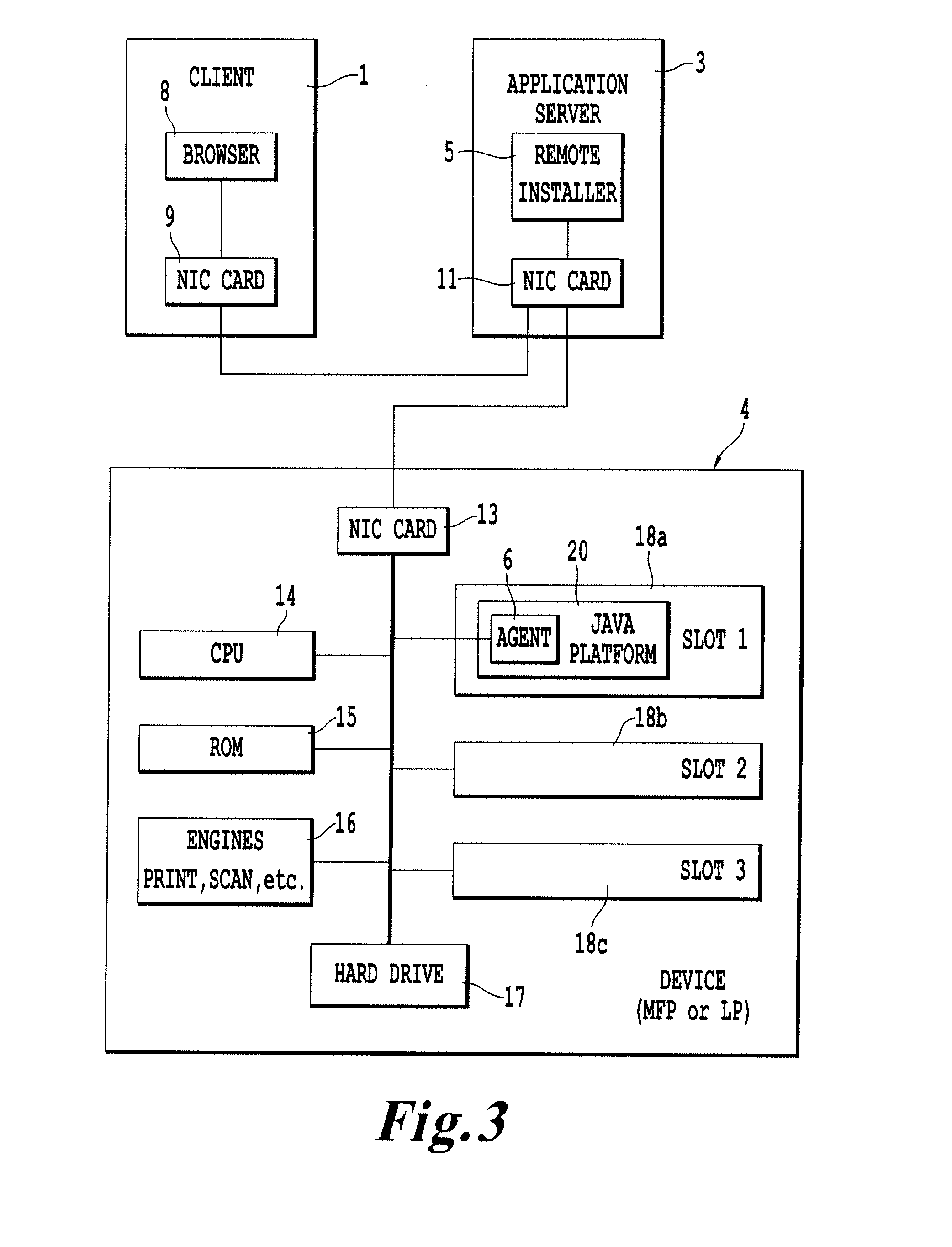
Remote distribution/installation utility & associated method of deploying executable code
InactiveUS20080114860A1Multiple digital computer combinationsSoftware deploymentDynamic managementGeneral purpose computing
A method of dynamically managing software functionality of a plurality of non-general purpose computing devices via a network including receiving a management request, storing an identification file and a modification package, accessing the identification file with a management agent in response to the reception of the management request, establishing communication between the management agent and a corresponding deployment agent of the selected ones of the plurality of non-general purpose computing devices via the interface and receiving a status designation from each of the selected ones of the plurality of non-general purpose computing devices via a corresponding deployment agent, delaying the transfer of the modification package with deployment agents currently indicating a status of processing a previously initiated management request and initiating transfer of the modification package with deployment agents currently indicating an available status.
Owner:RICOH AMERICAS CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
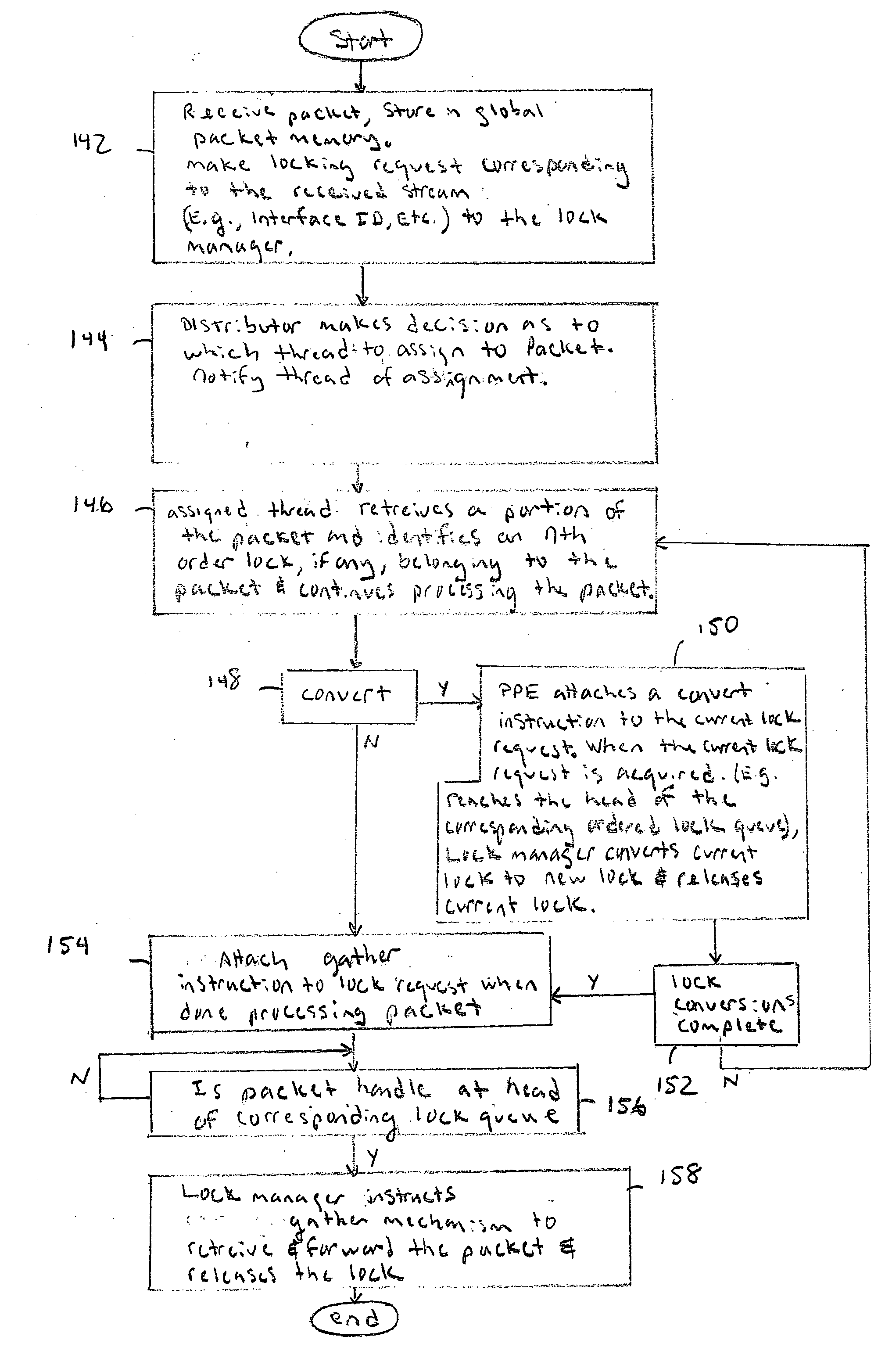
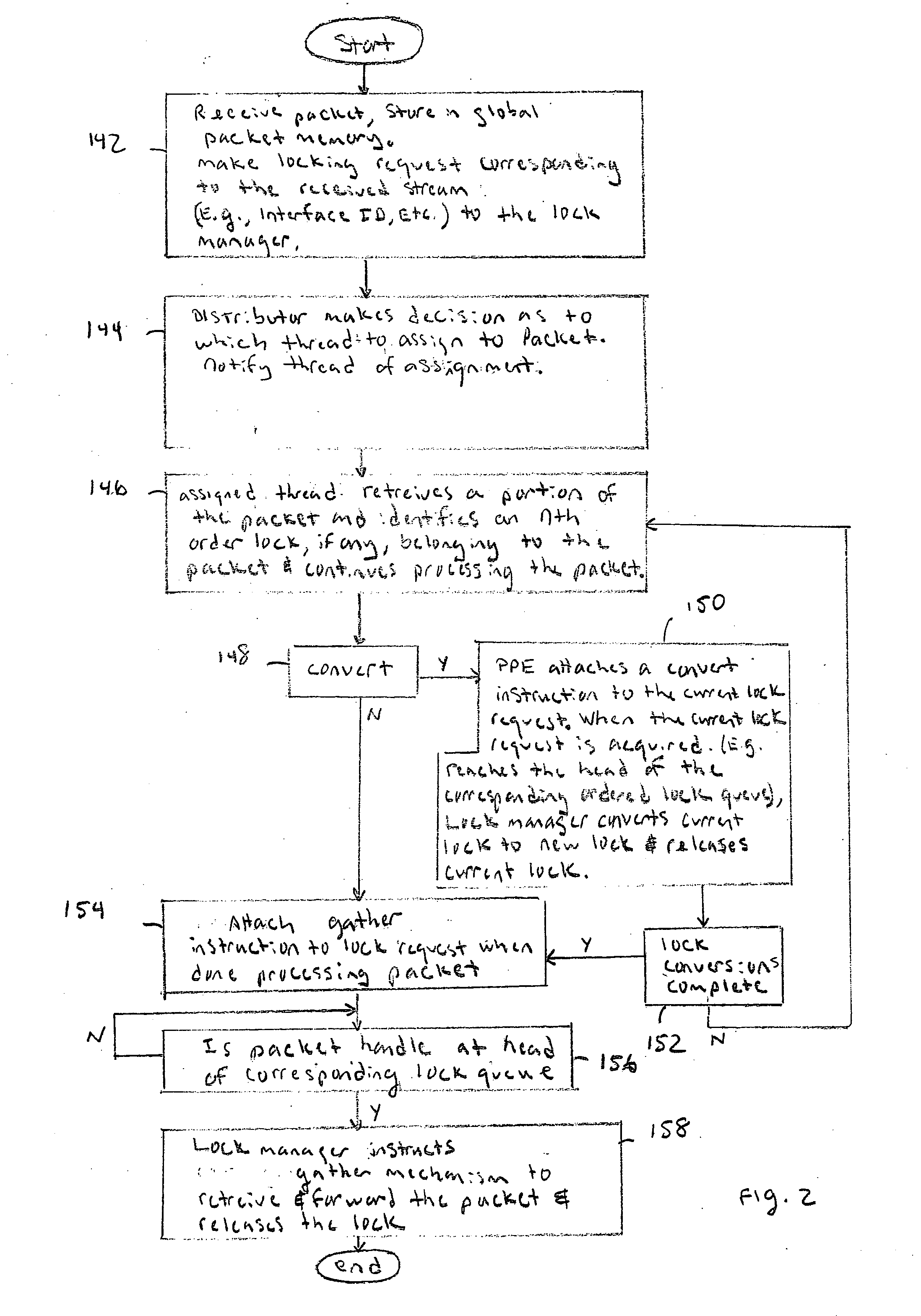
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com