Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
93 results about "Shared environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
SHARED ENVIRONMENT: "A shared environment occurs when people living in a household all interact with the same environment.".
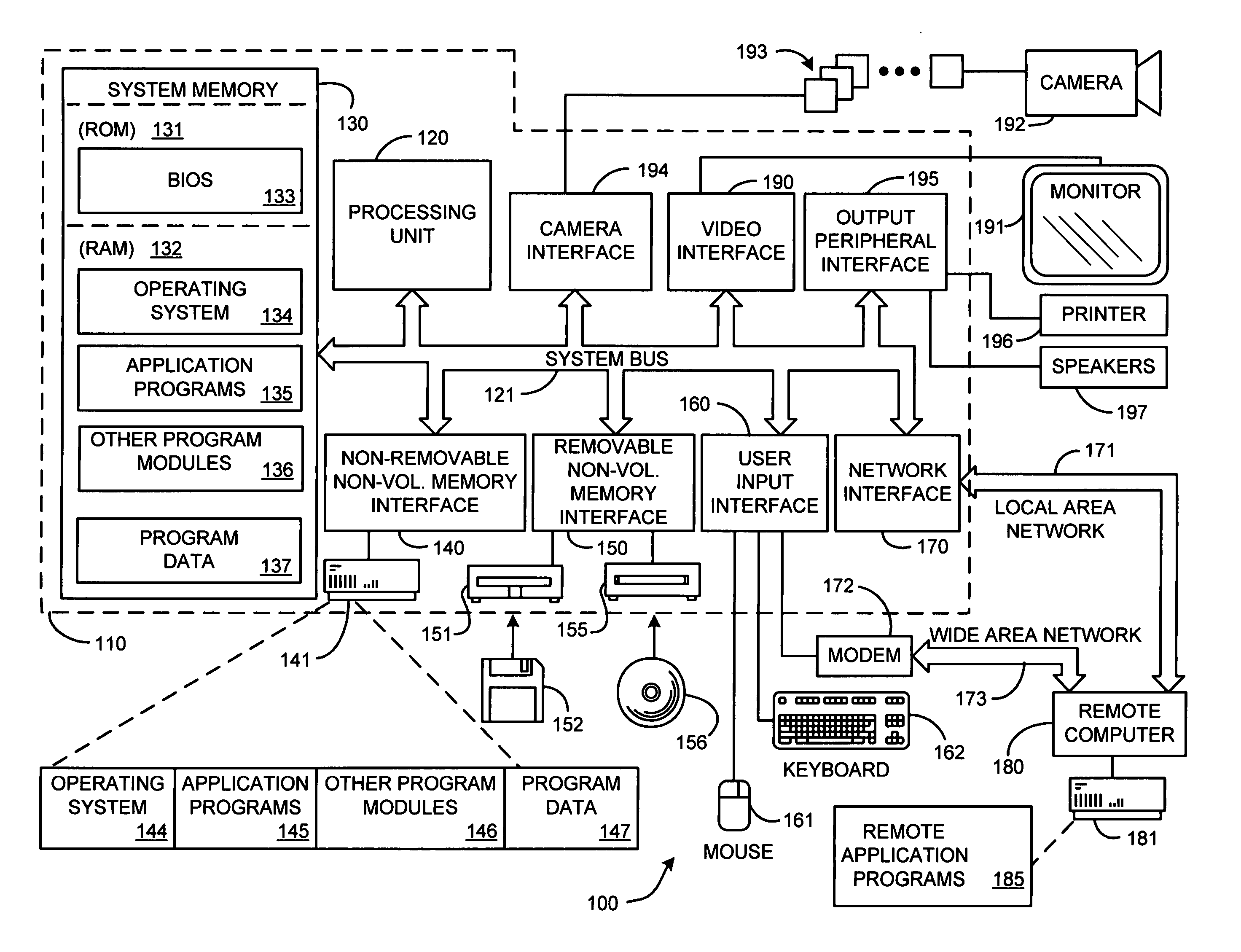
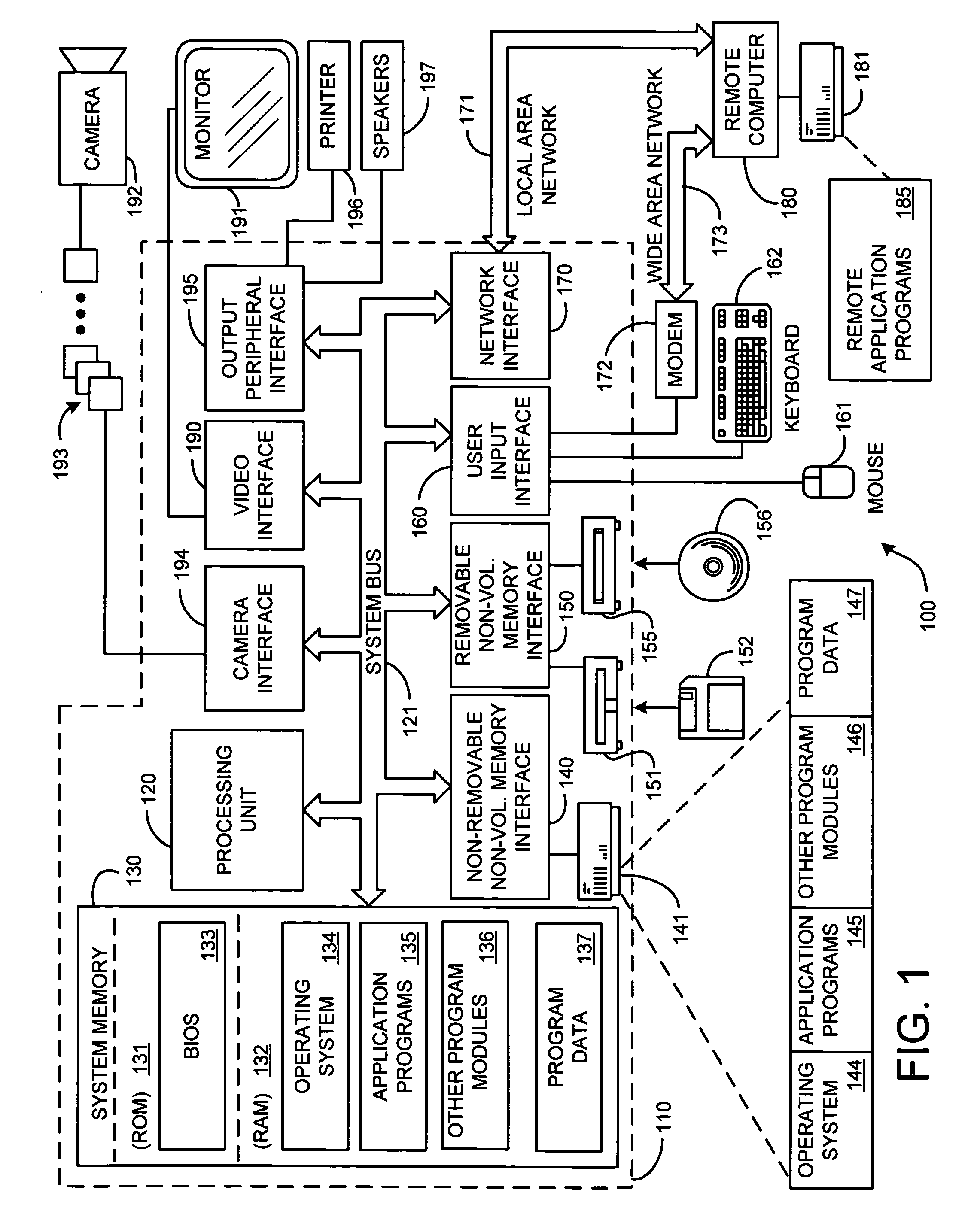
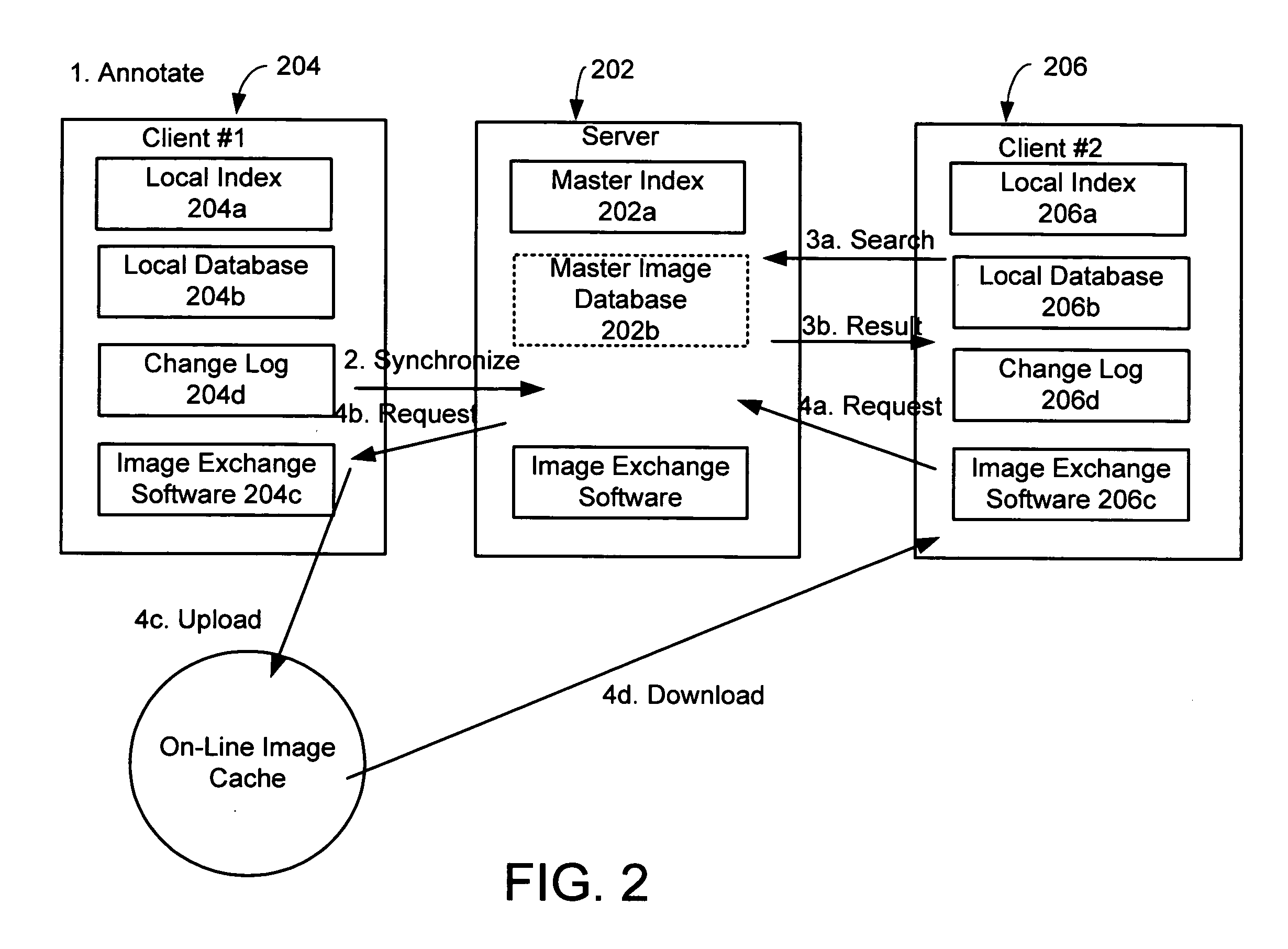
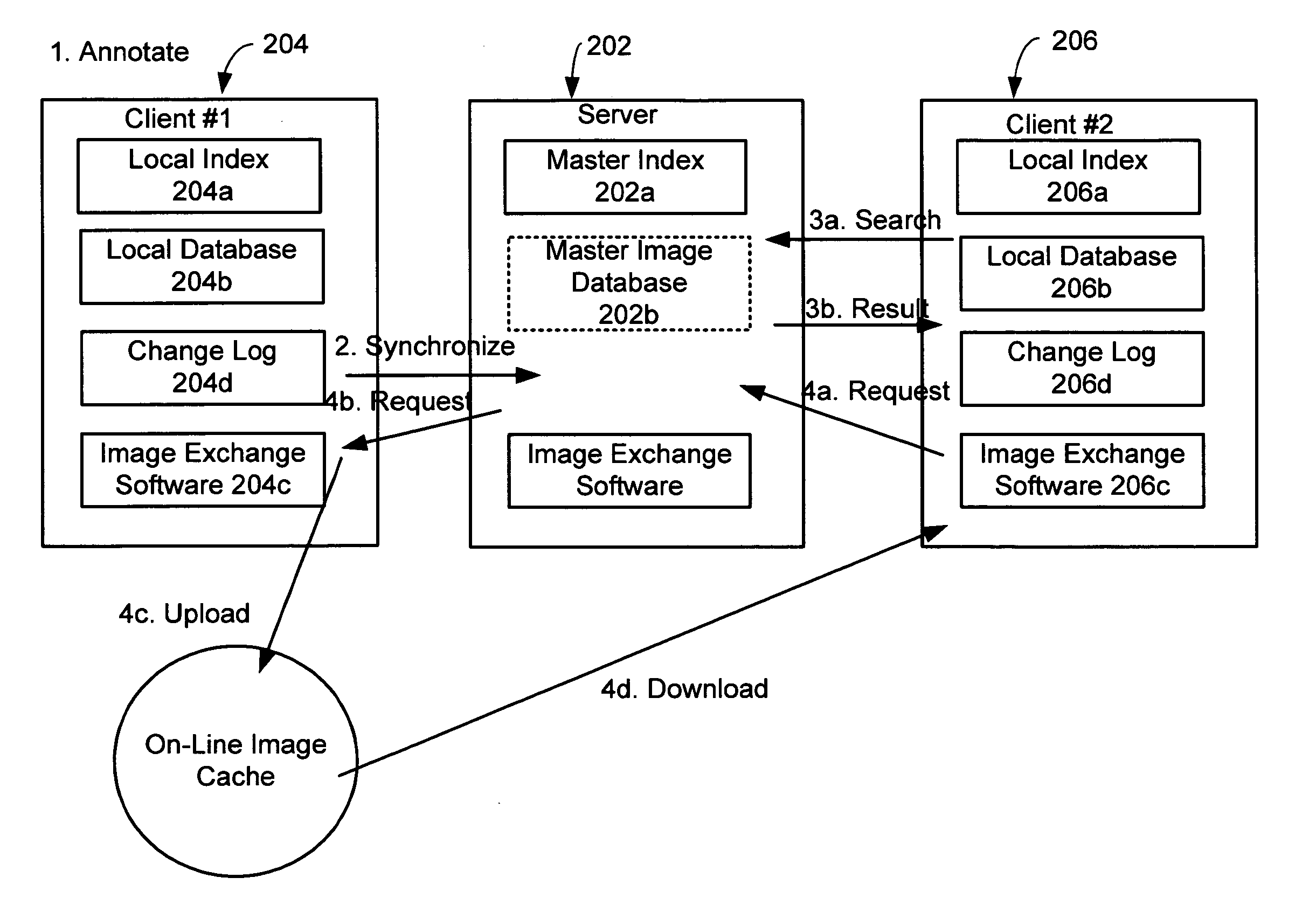
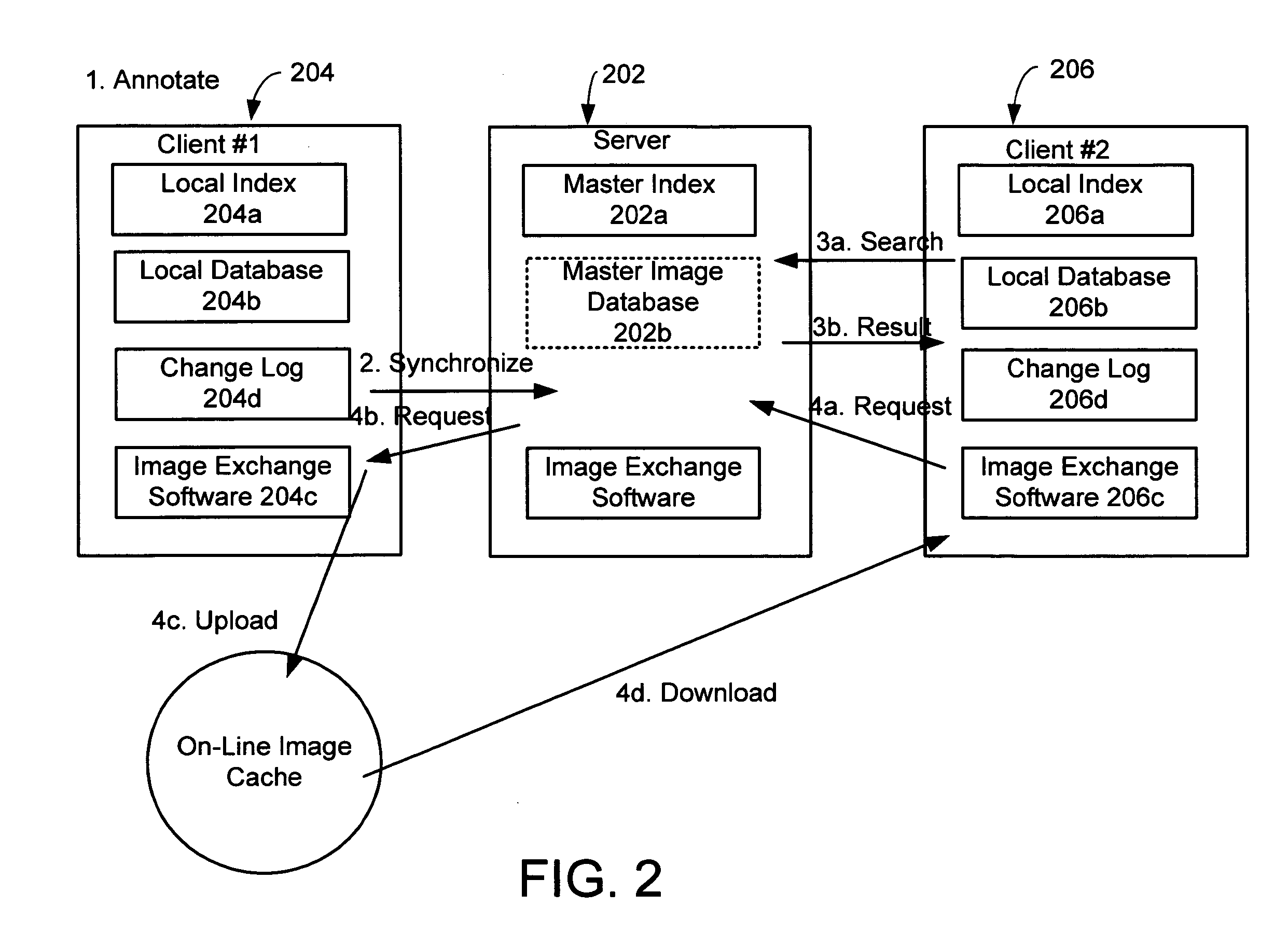
System and method for exchanging images
InactiveUS20060107297A1Easy to shareReduce labor intensityTelevision system detailsData processing applicationsShared environmentImage sharing
A system and method for providing a peer-to-peer photo-sharing environment. The system includes: manual and automatic photo annotation at the client; periodic client-server synchronization; an index of client photos on a central server or a photo database that is resident on the central server, which is updated by the client-server synchronization function; end-user search functionality to search the centralized index or photo database; and transmission of the relevant photos to the client via an on-line image cache. In one embodiment, one client's new photos are automatically displayed on another client's computer (e.g., via screen saver or another mechanism).
Owner:MICROSOFT TECH LICENSING LLC
Generation and Sharing Coordinate System Between Users on Mobile
InactiveUS20140267234A1Cathode-ray tube indicatorsLocation information based serviceMultiple deviceShared environment
A multi-device system for mobile devices to acquire and share 3D maps of an environment. The mobile devices determine features of the environment and construct a local map and coordinate system for the features identified by the mobile device. The mobile devices may create a joint map by joining the local map of another mobile device or by merging the local maps created by the mobile devices. To merge maps, the coordinate system of each system may be constrained in degrees of freedom using information from sensors on the devices to determine the global position and orientation of each device. When the devices operate on a joint map, the device share information about new features to extend the range of features on the map and share information about augmented reality objects manipulated by users of each device.
Owner:DEKKO
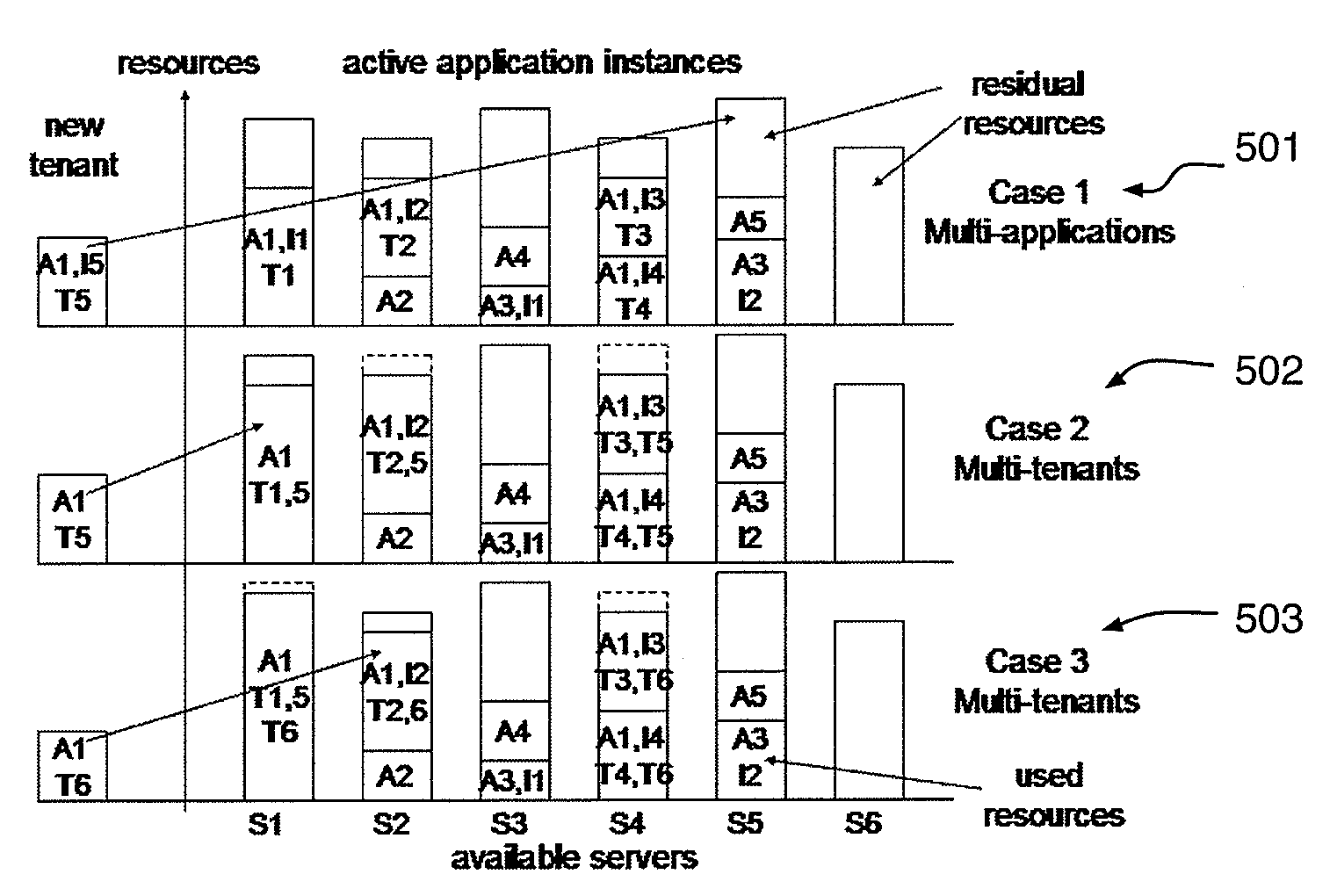
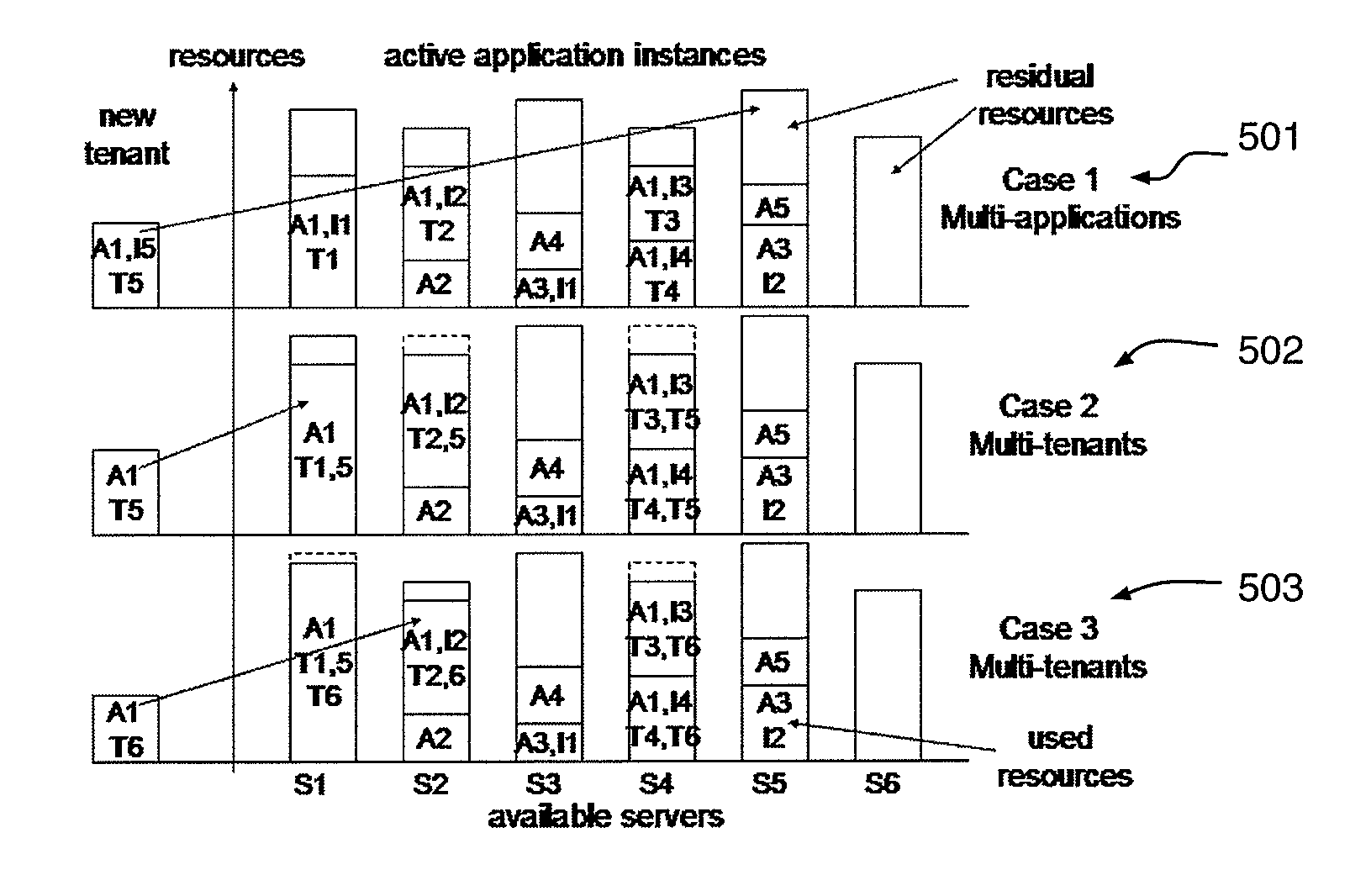
Calculating multi-tenancy resource requirements and automated tenant dynamic placement in a multi-tenant shared environment
ActiveUS20100077449A1Increase residual resourceDigital data processing detailsMultiprogramming arrangementsShared environmentMiddleware
A method for assigning tenants of users to offering instances of an application or middleware includes representing a set of offerings as respective offering instances of the application or middleware available from a server, determining server resource capacity of the server, representing constraints associated with the tenants and the offering instances, generating a mapping of the tenants to the offering instances based on the server resource capacity and constraints, and assigning a tenant to an offering instance according to the mapping, wherein the offering instance is made accessible to the users of the assigned tenant.
Owner:IBM CORP
System and method for exchanging images
InactiveUS20050190273A1Easy to shareReduce labor intensityTelevision system detailsData processing applicationsShared environmentImage sharing
A system and method for providing a peer-to-peer photo-sharing environment. The system includes: manual and automatic photo annotation at the client; periodic client-server synchronization; an index of client photos on a central server or a photo database that is resident on the central server, which is updated by the client-server synchronization function; end-user search functionality to search the centralized index or photo database; and transmission of the relevant photos to the client via an on-line image cache. In one embodiment, one client's new photos are automatically displayed on another client's computer (e.g., via screen saver or another mechanism).
Owner:MICROSOFT TECH LICENSING LLC
Application sharing single document sharing
InactiveUS7418664B2Multiple digital computer combinationsOffice automationDocumentation procedureShared environment
An improved application sharing system and method allow sharing of documents on a per document basis rather than on a per application basis, in order to simplify the user experience and to provide a more secure sharing environment. A window marking method is used to construct a window list describing the shared and unshared status of various windows. In an embodiment of the invention, a viewer machine displays only a most recently active shared document window even when other windows are also marked as shared. In this way, a viewer's attention can be automatically focused on a current document of interest.
Owner:MICROSOFT TECH LICENSING LLC
Sso in volatile session or shared environment
InactiveUS20090217367A1Improve securityDigital data processing detailsUser identity/authority verificationShared environmentApplication software
Apparatus and methods utilize a single-sign-on (SSO) framework on one or more physical or virtual computing devices. During use, it is determined whether SSO credentials are for use in a volatile session and / or for use amongst an application suite or a plurality of applications. In the former, the SSO credentials are either made temporarily available in a memory of the computing devices, if relatively high security is desired, or a credential store and its contents are made available to a disk, if relatively low security is acceptable. In the latter, the SSO credentials are shared during authentication of a single user as individual applications of the application suite or the plurality of applications are used or started independently. Other features contemplate credential lifetime, the destruction of credentials, timing of application usage relative to credentials as well as retrofitting existing SSO services. Computer program products and computing interaction are also disclosed.
Owner:EMC CORP
Migrating a web hosting service between a virtualized environment and a shared environment for multiple clients
InactiveUS20110179112A1Easy to storeEnhanced interactionMultiple digital computer combinationsResourcesVirtualizationShared environment
An automated tool for migrating a website hosting service from a first website hosting architecture to a second website hosting architecture, the first architecture comprising a virtualized server architecture that serves the services necessary for a client's websites from a specific virtual machine and the second web hosting architecture comprising a server architecture that serves a plurality of unrelated clients from a plurality of shared servers.
Owner:ENDURANCE INTERNATIONAL GROUP
System and method for monitoring the security of participants in a rideshare environment
ActiveUS8086400B2Instruments for road network navigationDiscounts/incentivesShared environmentSecurity check
A system and method for monitoring the security of participants in a rideshare environment is provided. A rideshare transaction is monitored between two or more rideshare participants. At least one of the rideshare participants is associated with a rideshare participant device. A predetermined route for the rideshare transaction is identified. A location of the rideshare participant device is monitored. A security check is triggered when the rideshare participant device location is inconsistent with the predetermined route.
Owner:UBER TECH INC
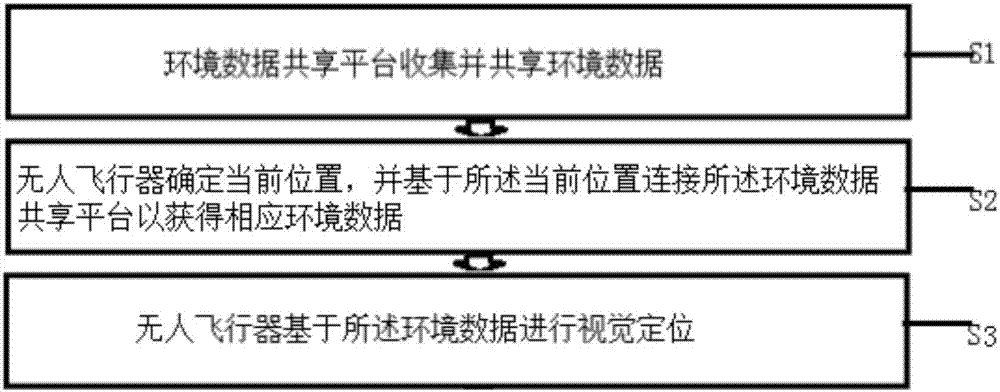
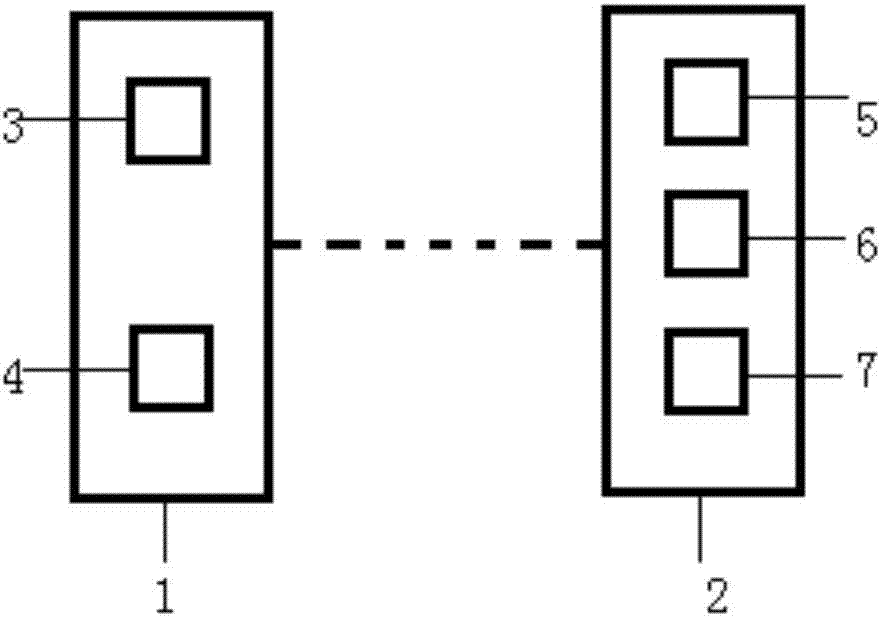
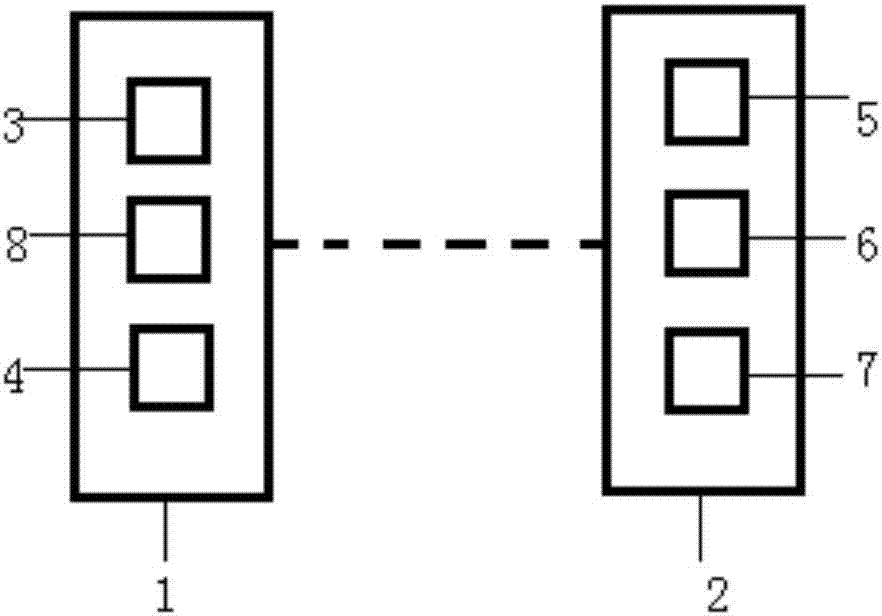
Environment data sharing platform, unmanned aerial vehicle and positioning method and system
PendingCN106931963AImprove accuracyImprove reliabilityNavigational calculation instrumentsSatellite radio beaconingAmbient dataRadar
The invention discloses a positioning method and system of an unmanned aerial vehicle capable of sharing environment data, an environment data sharing platform and the unmanned aerial vehicle. The positioning method includes the following steps that the environment data sharing platform (1) collects and shares environment data; the unmanned aerial vehicle (2) conducts visual positioning on the basis of the environment data. The positioning system comprises the environment data sharing platform (1) capable of collecting and sharing the environment data, and the unmanned aerial vehicle (2); the environment data sharing platform (1) comprises a storage device (3) and a communication port (4), the storage device (3) saves a database of the environment data, and the communication port (4) is used for having access to the database and is in wireless communication connection with the unmanned aerial vehicle (2). The unmanned aerial vehicle (2) comprises a communication device (5) for receiving the environment data, a processor (6) for processing the environment data and a camera and / or a laser radar (7) used for visual positioning, and the unmanned aerial vehicle (2) conducts visual positioning through the camera and / or the laser radar (7) on the basis of the environment data.
Owner:高域(北京)智能科技研究院有限公司
Migrating a web hosting service between a dedicated environment for each client and a shared environment for multiple clients
ActiveUS20110179142A1Easy to storeEnhanced interactionMultiple digital computer combinationsResourcesWeb siteShared environment
An automated tool for migrating a website hosting service from a first website hosting architecture to a second website hosting architecture, the first architecture comprising a server architecture that serves the services necessary for a client's web sites from a dedicated machine and the second web hosting architecture comprising a server architecture that serves a plurality of unrelated clients from a plurality of shared servers.
Owner:NEWFOLD DIGITAL INC
Migrating a web hosting service from a shared environment for multiple clients to a shared environment for multiple clients
InactiveUS20110179156A1Easy to storeEnhanced interactionDigital computer detailsResourcesShared environmentSchema for Object-Oriented XML
An automated tool for migrating a website hosting service from a first website hosting architecture to a second website hosting architecture, each website hosting architecture comprising a server architecture that serves a plurality of common services from a plurality of machines to a plurality of unrelated websites.
Owner:ENDURANCE INTERNATIONAL GROUP
Exclusion of selected data from access by collaborators
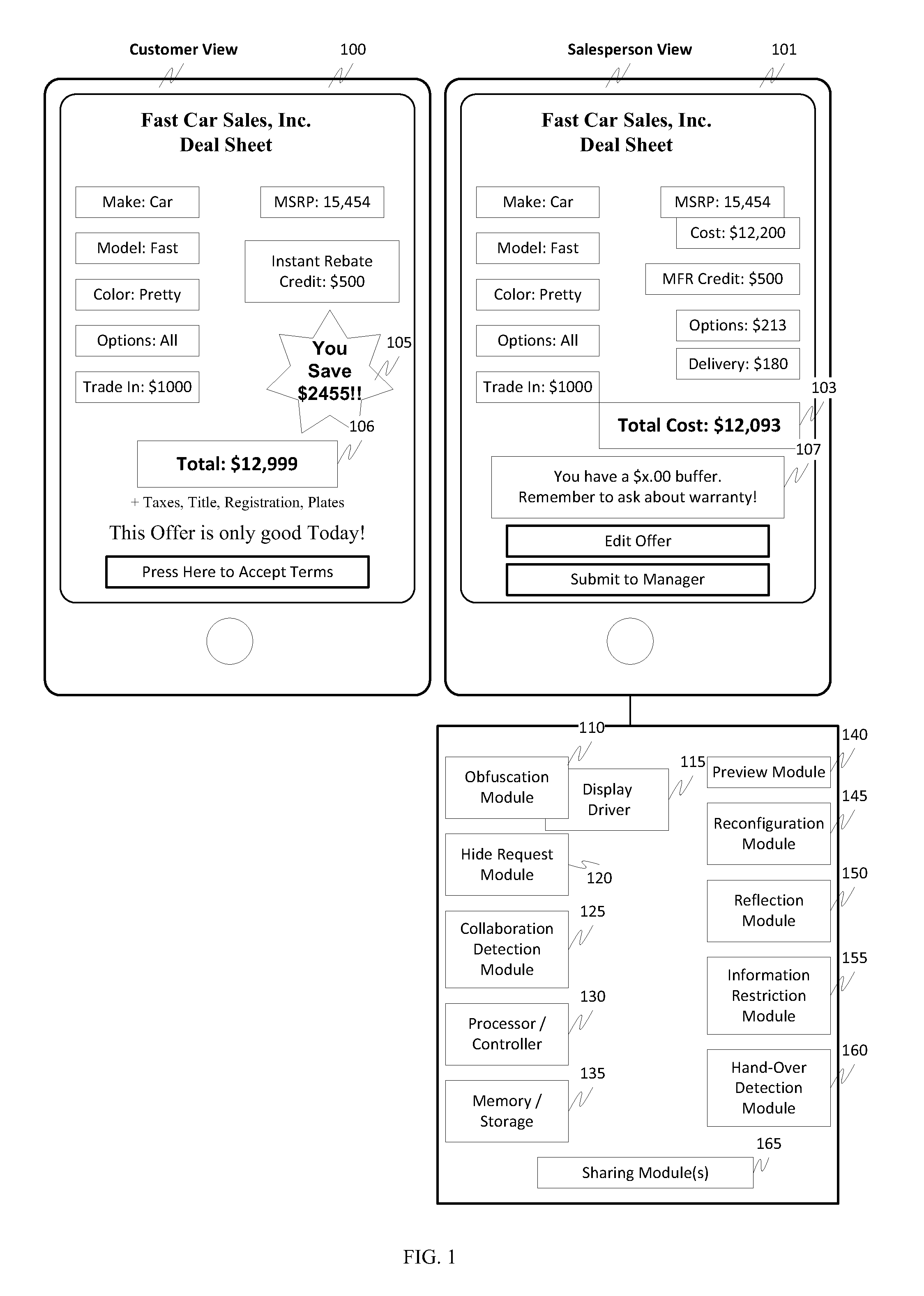
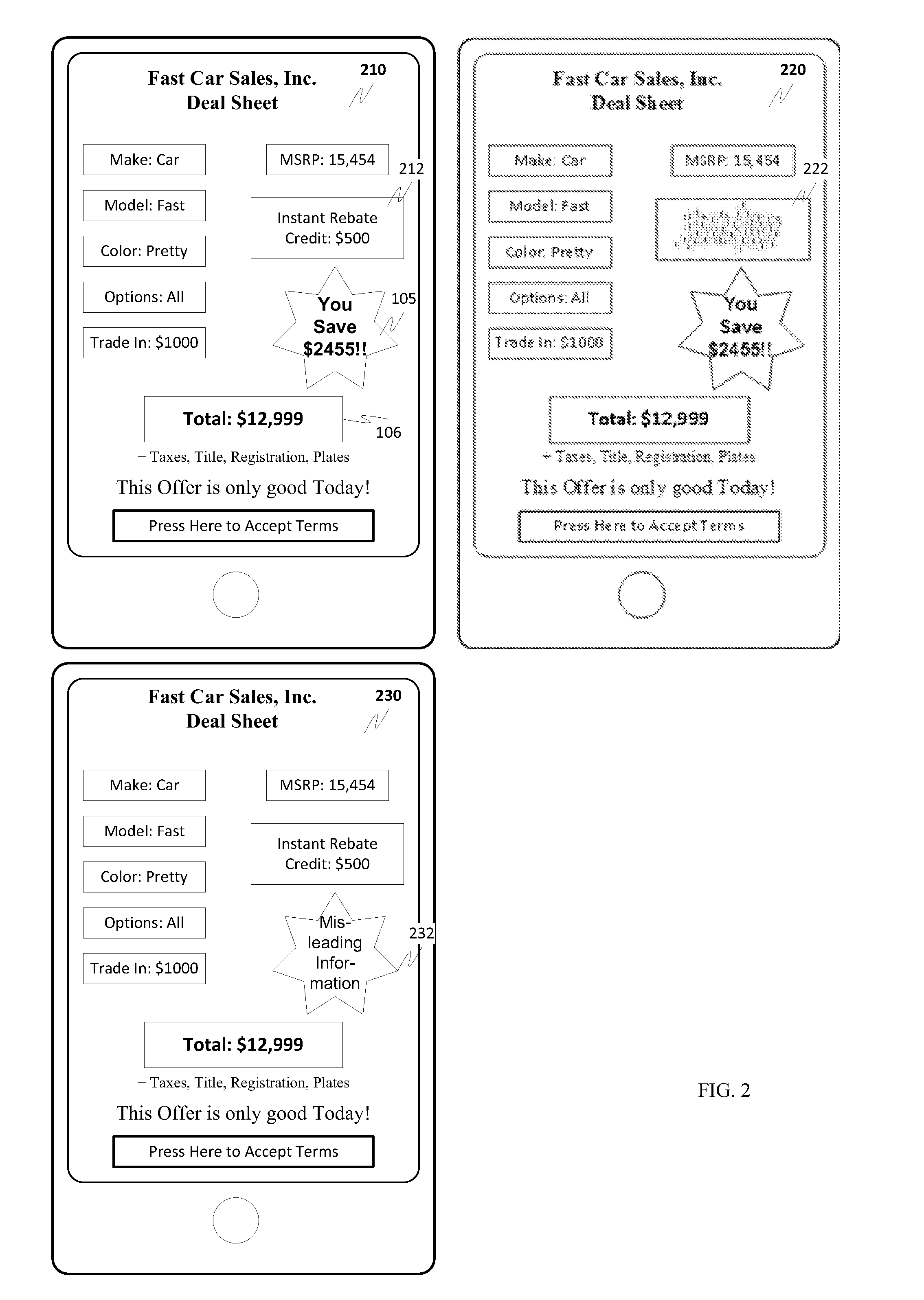
ActiveUS20130036370A1Simple interfaceSimple processDigital data authenticationTransmissionData setShared environment
One exemplary aspect is a blackout feature that can be used in connection with touchscreen devices to hide selected data in a shared display environment. An exemplary embodiment may be provided as a service running in the background or on a touchscreen device. A service may pop-up in response to the initiation of a collaboration session or entry of the device into a data transfer or sharing environment to prompt the user as to handle they would like to handle the shared information, e.g., “hide” sensitive information. Another exemplary aspect can display data in a constellation fashion. For example, data included in a file or data set to be shared is displayed by the touchscreen device. The user can then run their finger over the data that the user does not wish to share. The selected data / information can then be prevented from delivery to and / or display on the collaborating device(s).
Owner:AVAYA INC
Network selection in a shared network environment
ActiveUS20130265954A1Delay minimizationAssess restrictionWireless commuication servicesPublic land mobile networkShared environment
A method for performing a selection of a public land mobile network identity in a shared network environment, in which environment at least two public land mobile network identities are available for providing circuit switched based service to user equipment. The method includes at least a step of determining a capability of the user equipment (201) and a step of selecting the public land mobile network identity (202) at least partly on the basis of the capability of the user equipment among the at least two public land mobile network identities. Information on the capability of the user equipment is either received from the user equipment or from a database including capability information on the user equipment. Furthermore, a network element and a system for implementing at least partly the method are described.
Owner:TELIASONERA
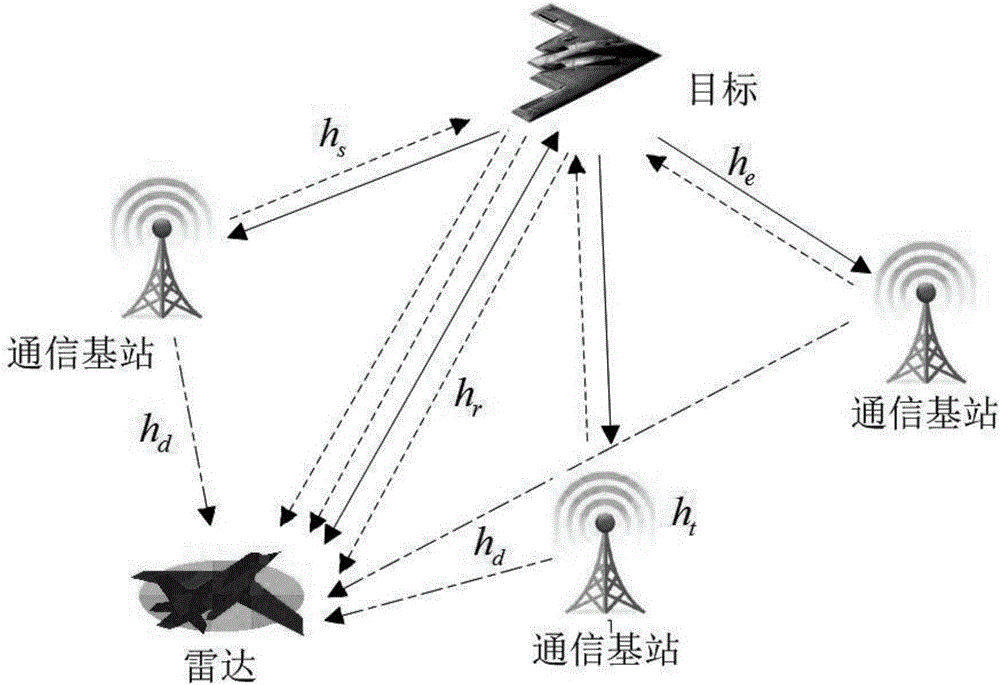
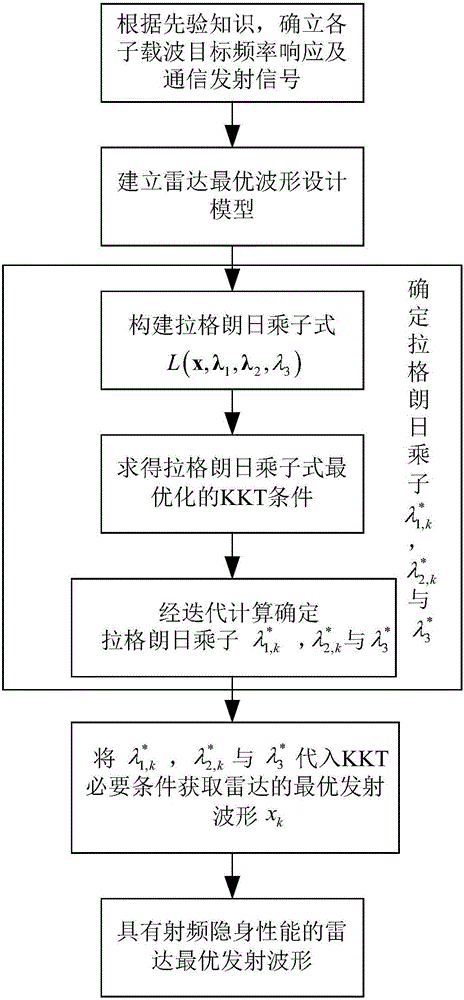
Radar optimal waveform design method based on radio frequency stealth in frequency spectrum shared environment
ActiveCN106680780AGuaranteed channel capacityGuaranteed communication qualityRadio wave reradiation/reflectionRadar systemsFrequency spectrum
The present invention discloses a radar optimal waveform design method based on radio frequency stealth in a frequency spectrum shared environment, belonging to the radar design and manufacturing field. The method comprises: obtaining priori knowledge of detection area target frequency response of a radar and communication system and signals of a communication system, and assuming that the echo of the communication signals reflected through the target to the radar can be received and processed by the radar; and establishing an optimal waveform design mathematic model; and employing the Lagrange multiplier method to solve the optimal waveform design mathematic model and performing iterative computation to determine the optimal emission waveform of the radar system. The minimization of the total emission power of the radar is taken as a target, the emission waveform of the radar system is subjected to adaptive optimization design in the conditions of satisfying a certain target parameter estimation performance and the communication system channel capacity so as to ensure the channel capacity and the communication quality of the communication system and allow the radar system to ensure the optimal radio frequency stealth performance in the condition of satisfying a certain target parameter estimation performance.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Information sharing method and apparatus using object oriented technology
ActiveUS7099919B2Multiprogramming arrangementsMultiple digital computer combinationsInformation processingInformation sharing
An information sharing method and apparatus using an object oriented technology are provided for mutually sharing any manipulation events in a shared environment which operates in a plurality of computers on a network. The method provides a plurality of objects to be used by users for information processing on their information processing apparatuses, and an environment in which the objects operate. Each of the objects transmits an event made thereto by an operator as a message. A shared field object is shared by a plurality of users, and one or more objects operate on the shared field object. These objects are distributed to the plurality of users to share the same environment among the users. A message of the event is distributed to each of the users through the shared field object to recall the event in the respective environments to share the operation of the object.
Owner:K PLEX
Contents simultaneous playback terminal, the same system and method thereof
InactiveUS20120303705A1Simple procedureServices signallingMultiple digital computer combinationsShared environmentComputer terminal
The present invention relates to a contents simultaneous playback terminal, the same system and method thereof. The contents simultaneous playback terminal, system and method is capable of allowing both terminals to share and simultaneously replay contents in a one-to-one correspondence by identifying terminals through terminal information broadcast in a single wireless access point network environment and setting a sharing environment for simultaneous playback of the contents of both terminals, without requiring a complicated separate sharing procedure. In addition, the contents simultaneous playback terminal, system and method is capable of, when both terminals connected in a one-to-one correspondence share contents, streaming the contents from one terminal to the other terminal and receiving in the other terminal the streamed contents for simultaneous playback of the contents, thereby extinguishing the contents after the playback.
Owner:M SERVICE
Shared environment for vehicle occupant and remote user
ActiveUS20190355178A1Provide experienceTelevision conference systemsParticular environment based servicesComputer graphics (images)Shared environment
A method, system, computer-readable media, and apparatuses for providing a shared vehicle experience. The method includes capturing an exterior video stream that depicts an exterior environment of a vehicle, and receiving remote user information indicating a bodily movement of a remote user. The method further includes generating and displaying an augmented video stream comprising a dynamic avatar representing the remote user as a virtual passenger, the dynamic avatar being updated based on the remote user information while the augmented video stream is being displayed in the vehicle. At least a portion of the exterior video stream and occupant information are sent to a computer device that causes, based on the at least a portion of the exterior video stream and the occupant information, a display device of the remote user to output an additional augmented video stream that provides the remote user with an experience of being in the vehicle.
Owner:VALEO COMFORT & DRIVING ASSISTANCE
Constructing method of self-organized cloud resource sharing distributed peer-to-peer network model
InactiveCN105743980ATake advantage of computing powerConvenient saleTransmissionExtensibilityRouting table
The invention relates to a self-organized model constructing method of a cloud resource sharing peer-to-peer network, a distributed peer-to-peer network for short. The topology structure of the distributed peer-to-peer network is constructed through adoption of a space division concept. Physically closed cloud noses are self-organized. A reachable routing table is extended. The cloud peer-to-peer network which takes data as a core and is equipped with performances such as low delay and extensibility is realized. According to the method, in a large scale cloud resource distributed sharing environment, cloud node information is managed in real time, rapid resource positioning is carried out to the computing resource demand of each user, and an inquiring result is returned. Compared with the prior art, the method has the advantages that the method has clear average cloud resource inquiring delay advantage, the computing capabilities of the nodes are utilized fully, the actual performance of the cloud computing application is satisfied, and the method has wide application prospects in cloud resource sharing aspects.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
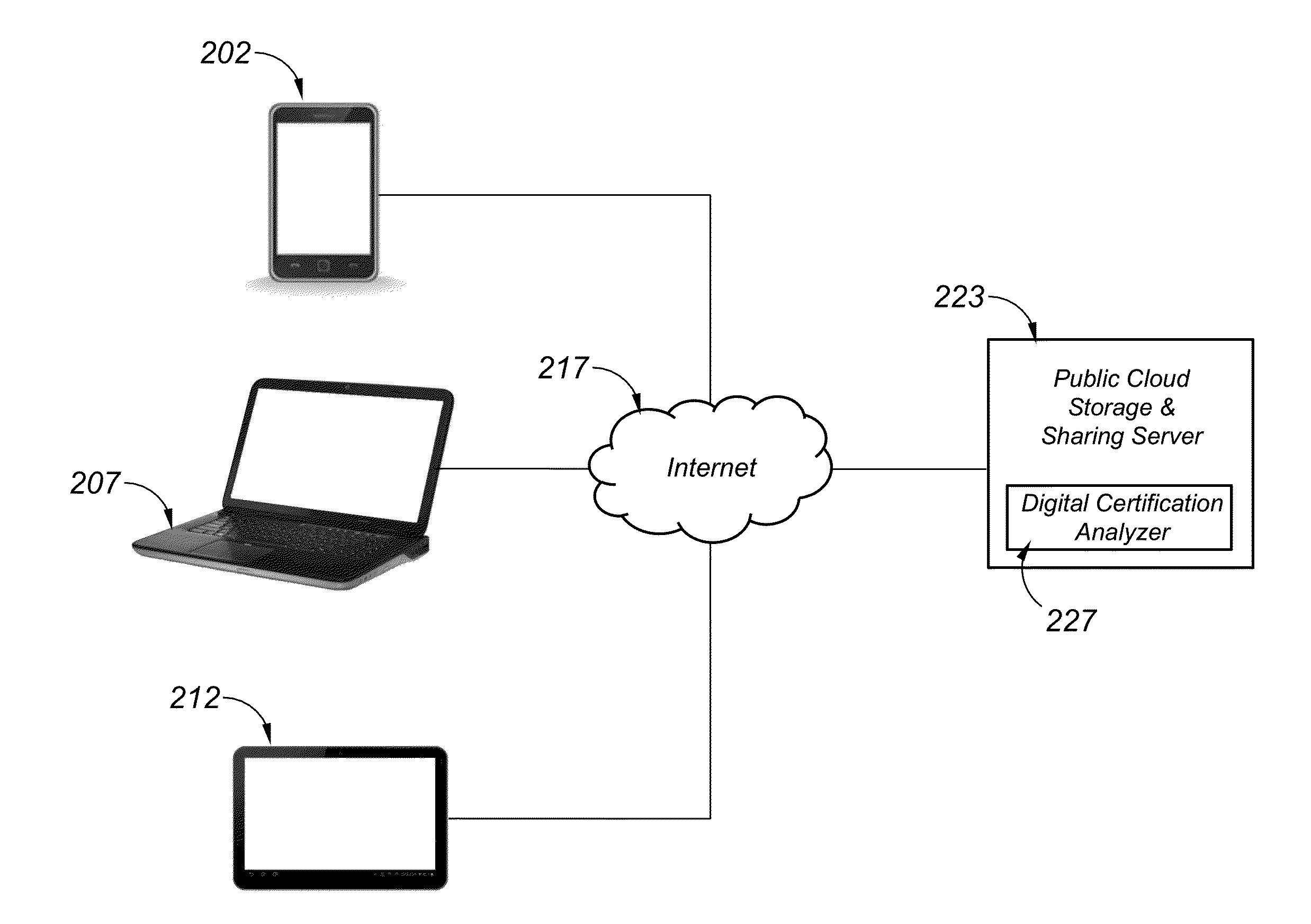
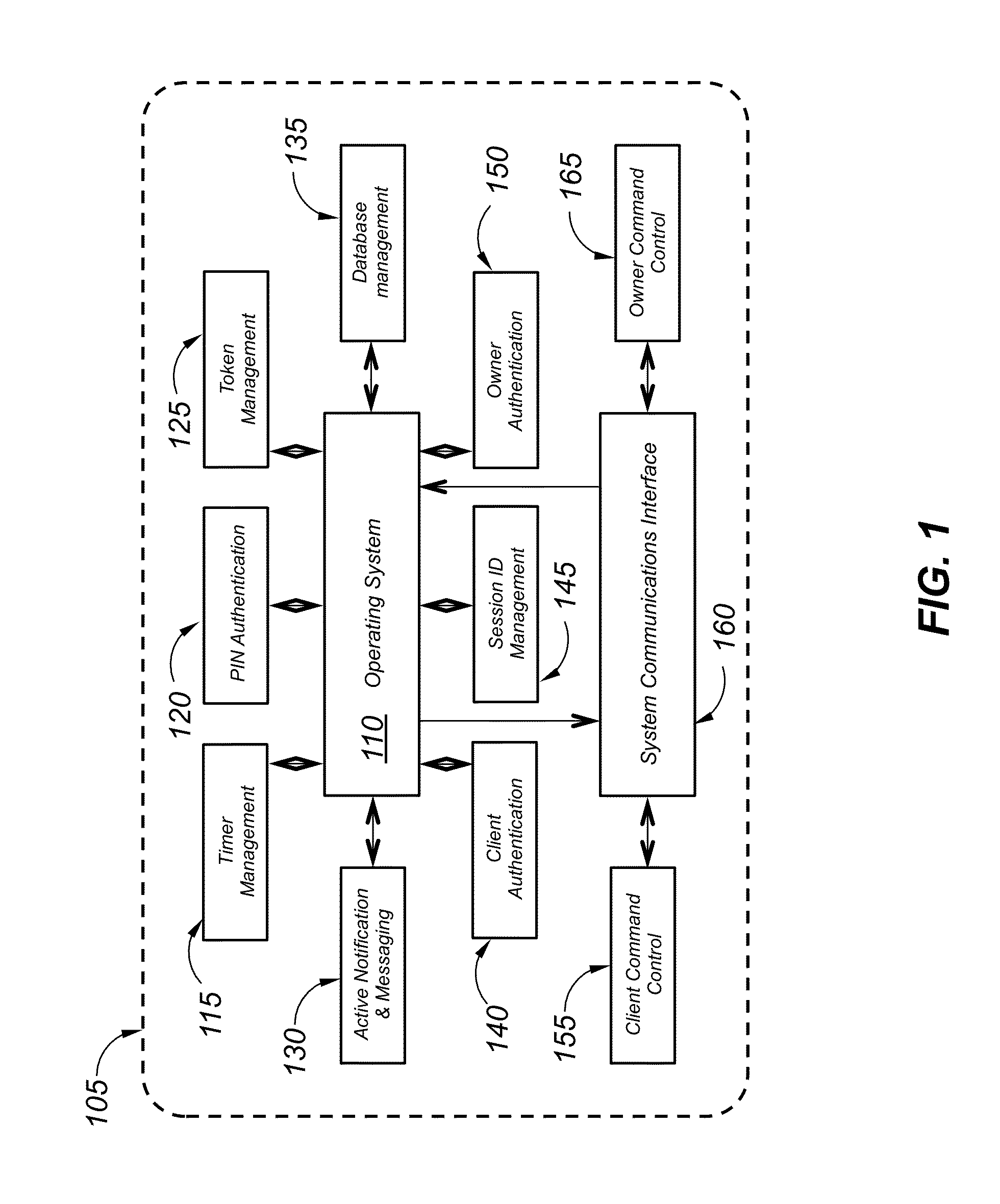
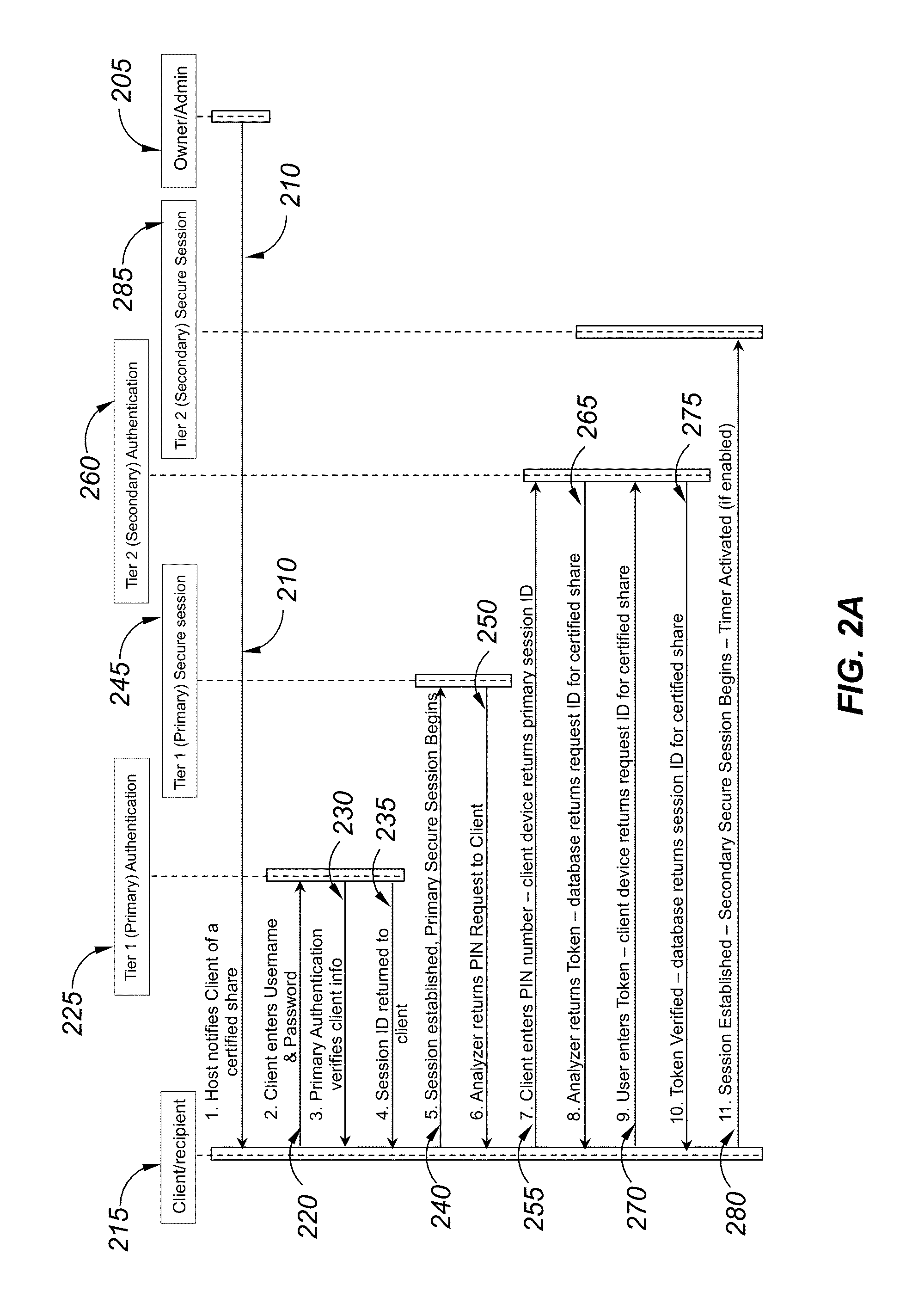
Digital certification analyzer
ActiveUS20160094541A1Improve securityImprove privacyProgram/content distribution protectionSecuring communicationHard disc driveDigital content
A digital certification analyzer (or “analyzer”) provides protection for digital content stored on servers, file sharing systems, hard drives and USB enabled external drives or other digital repositories. The analyzer prevents unauthorized access from both owners / administrators and recipients of digital content being shared through a web based or file sharing type service. The analyzer protects the owner of the shared digital content from unauthorized access, while allowing multiple protection instances to be applied to multiple digital content shares within a digital file hosting and sharing environment. Timers are provided to limit access to digital content at the discretion of the owner of the digital content.
Owner:TAN ANTHONY
Driver-specific context for kernel-mode shimming
ActiveUS20050149947A1Improve developmentEasy to deployProgram control using stored programsProgram loading/initiatingShared environmentClient-side
A kernel-mode shimming system and method are disclosed herein. The kernel is a shared environment. Accordingly, many different kernel-mode drivers utilize services provided by the kernel. Furthermore, when shimming of drivers is necessary, it is desirable to support shim reuse amongst drivers with similar problems or issues, rather than generating a customized shim for each driver. To facilitate kernel-mode shimming and shim reuse, context information needs to be retrieved and maintained so that shims can identify particular driver calls and preserve driver specific linkage information. The present invention accomplishes the forgoing by employing an intermediate structure, a content component, between a client or driver call and a common shared shim to provide the shim with contextual information. A system is also provided herein to implement and support kernel-mode shimming with driver specific context information.
Owner:ZHIGU HLDG
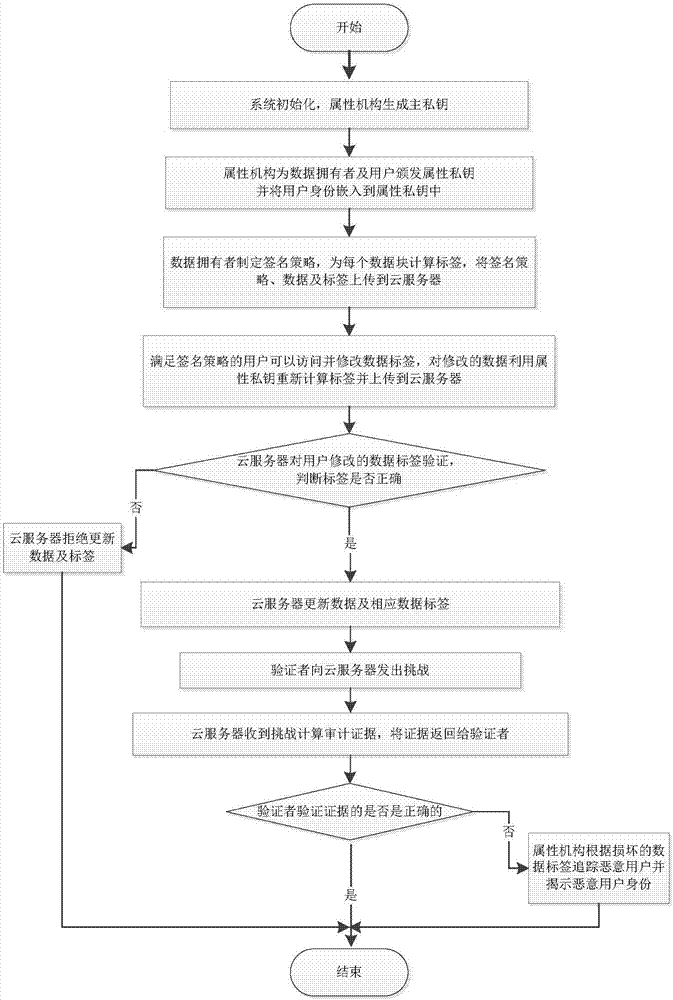
Traceable effective open auditing method and system in cloud storage data sharing
ActiveCN107147720AProtect identity privacyEnable traceabilityKey distribution for secure communicationShared environmentData sharing
The invention discloses a traceable effective open auditing method in cloud storage data sharing, and a cloud computing application system. The method comprises the following steps: initializing the system, generating a main private key and open parameters by using an attribute mechanism, allocating an attribute private key to each user, and embedding the user identity in the attribute private key; formulating a signature strategy by a data owner, generating a label for a data block, and uploading the label to a cloud server; modifying the data by a user satisfying the signature strategy; verifying the label of the modified data by the cloud server; sending challenge to the cloud server by a verifier; calculating auditing evidence by the cloud server, and returning the auditing evidence to the verifier; verifying the correctness of the evidence by the verifier; and tracing the malicious user. According to the traceable effective open auditing method disclosed by the invention, the privacy of the user identity is protected in a multi-user data sharing environment, the traceability of the malicious user is realized at the same time, and the storage overhead for tracing is a constant.
Owner:ANHUI UNIVERSITY
Systems and methods of providing collaborative consumer-controlled advertising environments
Targeted or other advertising may comprise one or more advertisements presented to multiple users in a virtual world environment such that participating users can interact with one another and / or with executed advertisements. Groups of users may be invited to participate in collaborative virtual world environments based on consumer contact lists or profiles establishing matching preferences for such groups. Synchronized data may be narrowcasted or broadcasted to invited users. Such data may define one or more virtual world environments as well as traditional and / or virtual world advertisements for execution in the shared environment(s). Advertisements may be selected based on one or more consumer preferences associated with one or more of the users participating in the shared virtual world environment.
Owner:ZAMA INNOVATIONS LLC
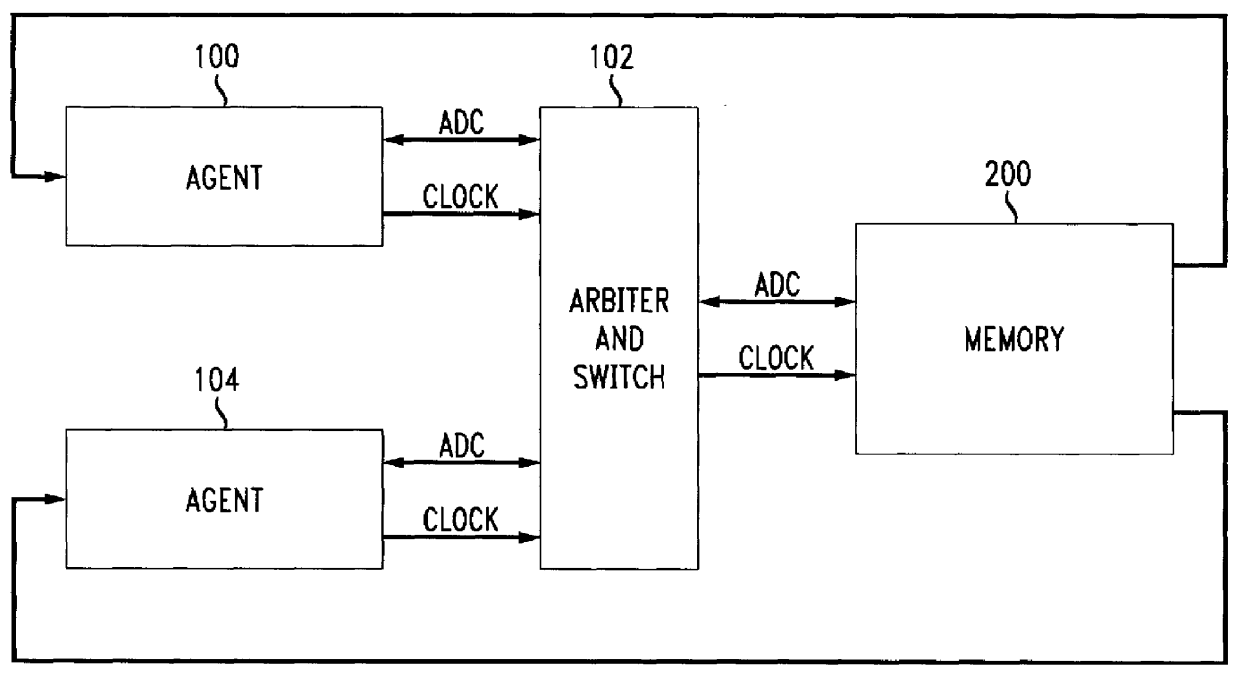
Minimum refractory period in a multiple agent resource sharing environment
A multiple agent system providing each of a plurality of agents, i.e., processors, access to a shared synchronous memory. A super agent may be an agent from among a plurality of agents which accesses a shared synchronous memory most frequently. The super agent has direct access to the shared synchronous memory, without negotiation and / or arbitration, while the non-super agents access the shared synchronous memory under the control of an arbiter-and-switch. Open windows are generated when the super agent is not accessing the shared synchronous memory. The non-super agents can be allowed interim access to the shared synchronous memory even before the super agent terminates ownership of the shared synchronous memory. In another aspect of the present invention, subsequent memory access request signals from an agent to the shared synchronous memory are suppressed for a minimum refractory period until a previously received acknowledge signal is cleared to prevent erroneous detection of memory access granted acknowledge signals. In yet another aspect, a pre-arbiter intercepts memory access request signals from each of the agents and outputs a respective conditioned pre-arbitrated memory access request signal to provide the ability for one or more agents to lock ownership of the shared synchronous memory.
Owner:LUCENT TECH INC
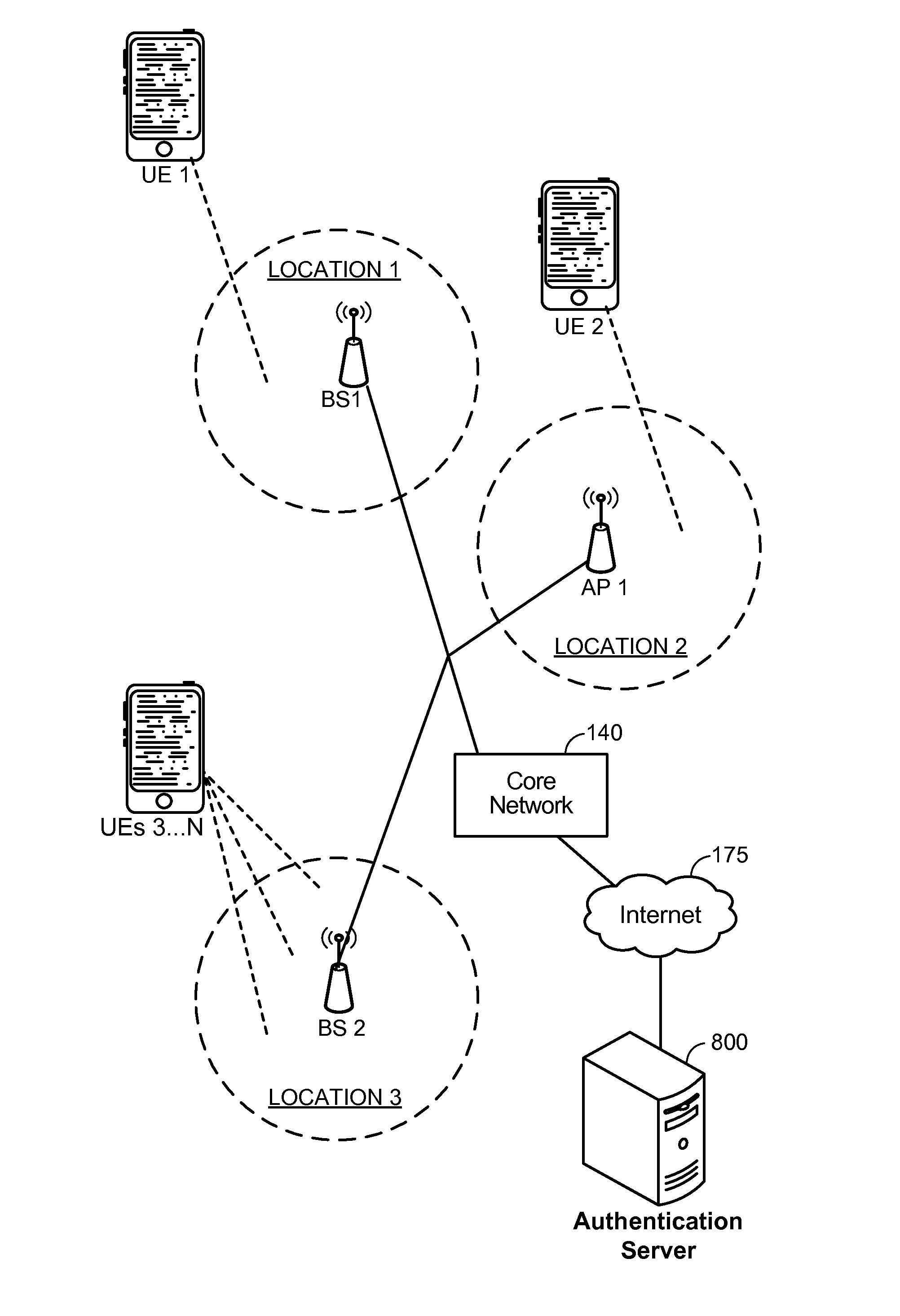
Selectively authenticating a group of devices as being in a shared environment based on locally captured ambient sound
InactiveUS20140324591A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsShared environmentComputer science
In an embodiment, two or more local wireless peer-to-peer connected user equipments (UEs) capture local ambient sound, and report information associated with the captured local ambient sound to an authentication device. The authentication device compares the reported information to determine a degree of environmental similarity for the UEs, and selectively authenticates the UEs as being in a shared environment based on the determined degree of environmental similarity. A given UE among the two or more UEs selects a target UE for performing a given action based on whether the authentication device authenticates the UEs as being in the shared environment.
Owner:QUALCOMM INC
Efficient sequence number generation in a multi-system data-sharing environment
InactiveUS6952707B1Data processing applicationsDigital data information retrievalShared environmentComputerized system
Owner:INT BUSINESS MASCH CORP
Securing decrypted files in a shared environment
ActiveUS7167982B2Data processing applicationsUnauthorized memory use protectionShared environmentDocumentation
A method, system and computer program product for securing decrypted files in a shared environment. A filter driver in a kernel space may be configured to control service requests to encrypted files stored in a shared area, e.g., a shared directory on a disk unit, accessible by multiple users. The filter driver may receive a service request to open an encrypted document in the shared area issued from an authorized user. Upon receiving the encrypted data, the filter driver may decrypt the encrypted data. The filter driver may subsequently store the decrypted data in a file in a non-shared area, e.g., a non-shared directory. The non-shared area may be accessible only by the authorized user that requested access to the encrypted file. By storing the decrypted data in a file in the non-shared area, a file once decrypted may be protected in a file sharing environment.
Owner:LENOVO PC INT
Monitoring client information in a shared environment
A method for monitoring client information within a shared environment. The method includes identifying a first physical location of a server computer, the server computer providing computing resources to a client within a shared environment, and collecting information associated with the client, the information including computing resources of the server computer provided to the client. The method includes creating a map showing the first physical location of the server computer and the collected information associated with the client. The method includes identifying a current physical location of the server computer and determining whether the current location is different than the first location. The method then, in response to determining the current location is different than the first location, includes updating the map with the identified current physical location of the server computer.
Owner:IBM CORP
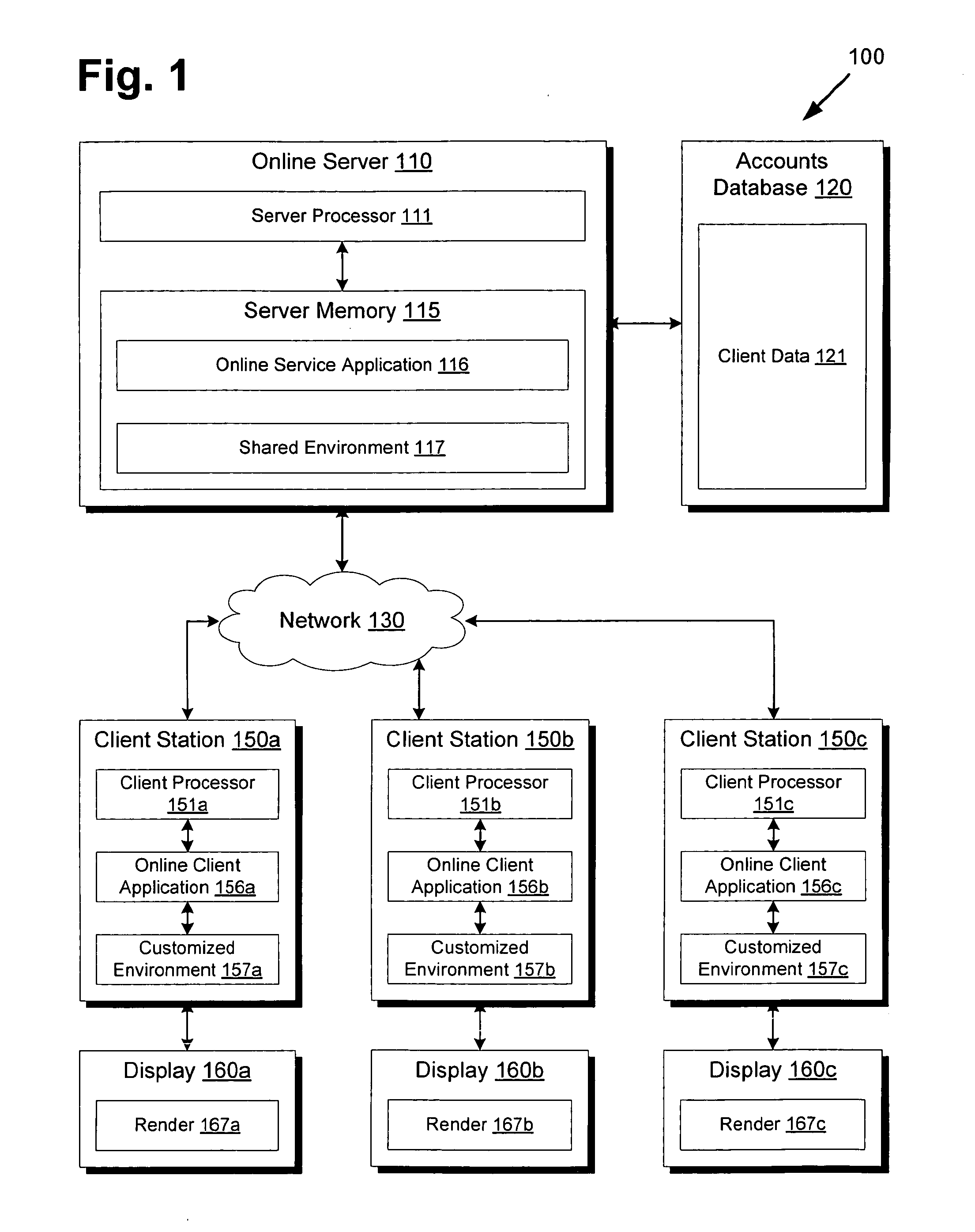
System and Method for Customized Experiences in a Shared Online Environment
ActiveUS20100185721A1Relational databasesMultiple digital computer combinationsDisplay deviceShared environment
There is provided a system and method for providing customized experiences to a plurality of client stations in a shared environment. There is provided an accounts database having data relating to a plurality of clients, an online server having a server processor and hosting the shared environment for access by the plurality of client stations, and an online client application for execution by a client processor of a client station. The server processor is configured to retrieve client data from the accounts database relating to a client, determine client preferences of the client based on the client data, create a customized environment from the shared environment according to the client preferences, and send the customized environment to the online client application of a client station associated with the client for rendering the customized environment on a client display. User interactions may be filtered to maintain a shared environment perception.
Owner:DISNEY ENTERPRISES INC
Driver-specific context for kernel-mode shimming
ActiveUS7392527B2Facilitate development and deployment and managementProgram control using stored programsMultiprogramming arrangementsShared environmentClient-side
The kernel is a shared environment. Accordingly, many different kernel-mode drivers utilize services provided by the kernel. Furthermore, when shimming of drivers is necessary, it is desirable to support shim reuse amongst drivers with similar problems or issues, rather than generating a customized shim for each driver. To facilitate kernel-mode shimming and shim reuse, context information needs to be retrieved and maintained so that shims can identify particular driver calls and preserve driver specific linkage information. The present invention accomplishes the forgoing by employing an intermediate structure, a content component, between a client or driver call and a common shared shim to provide the shim with contextual information.
Owner:ZHIGU HLDG
Calculating multi-tenancy resource requirements and automated tenant dynamic placement in a multi-tenant shared environment
ActiveUS8424059B2Digital data processing detailsMultiprogramming arrangementsShared environmentMiddleware
A method for assigning tenants of users to offering instances of an application or middleware includes representing a set of offerings as respective offering instances of the application or middleware available from a server, determining server resource capacity of the server, representing constraints associated with the tenants and the offering instances, generating a mapping of the tenants to the offering instances based on the server resource capacity and constraints, and assigning a tenant to an offering instance according to the mapping, wherein the offering instance is made accessible to the users of the assigned tenant.
Owner:INT BUSINESS MASCH CORP
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com