Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Manufacturer identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
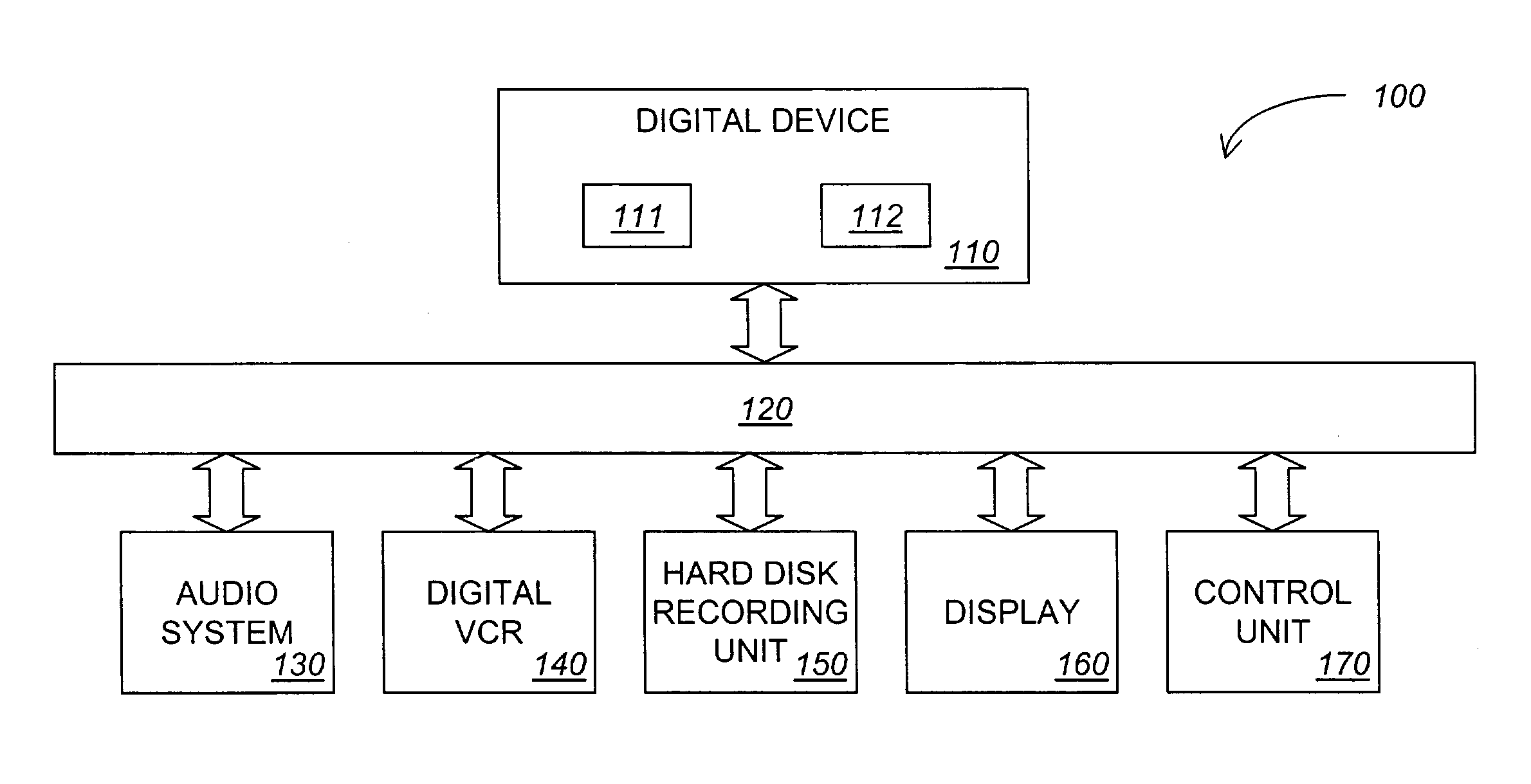
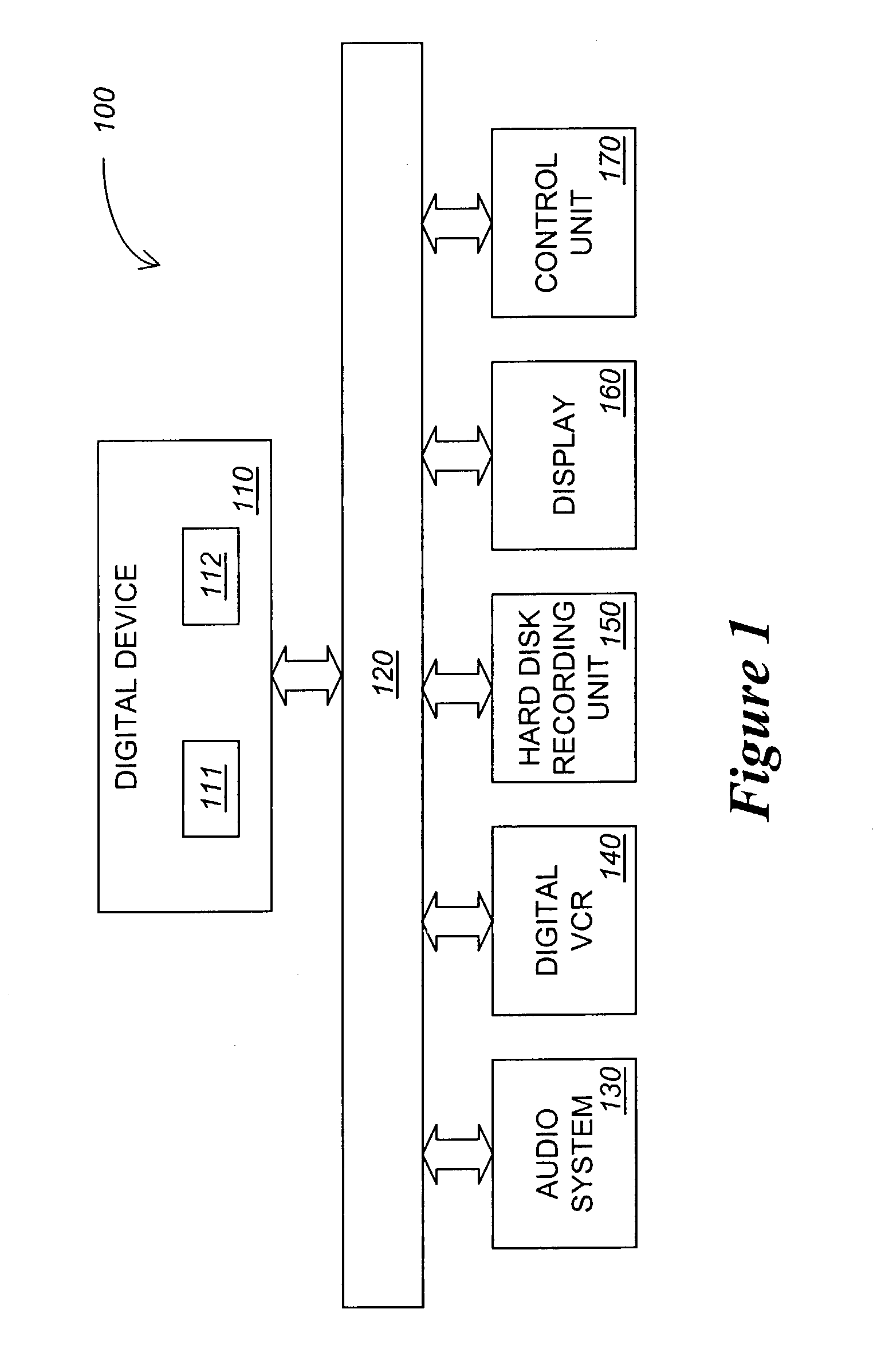
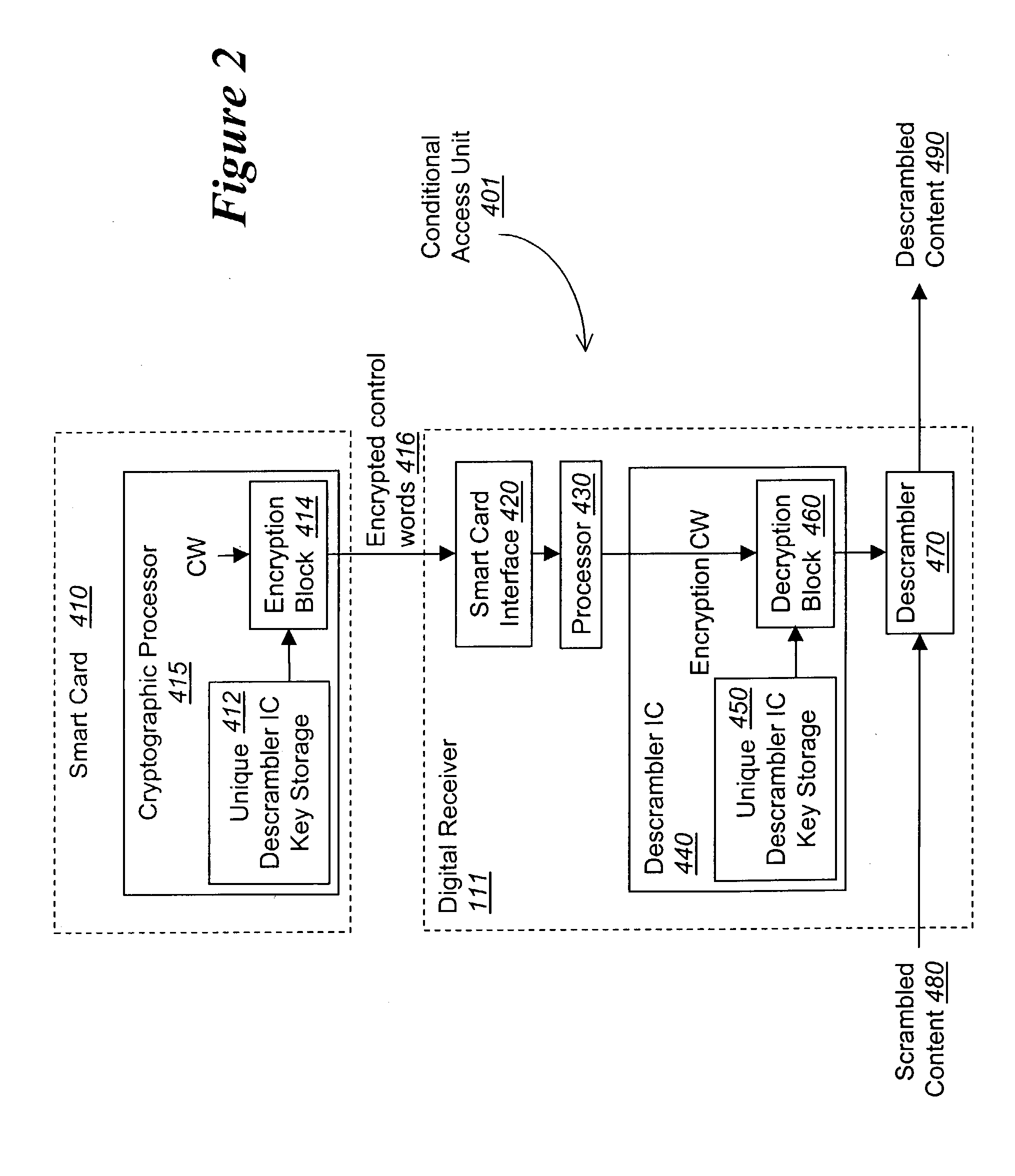
Method and apparatus for protecting the transfer of data
ActiveUS7730300B2Digital variable displayKey distribution for secure communicationComputer hardwareKey generator
According to one embodiment, a method for scrambling and descrambling program data comprises the receipt of a mating key generator message including a manufacturer identifier. The mating key generator message is transmitted to a first remote source identified by the manufacturer identifier. In response, a mating key is received from the first remote source. Then, the mating key is supplied to a second remote source, the mating key being subsequently used to encrypt a service key used for scrambling program data.
Owner:SONY CORP +1
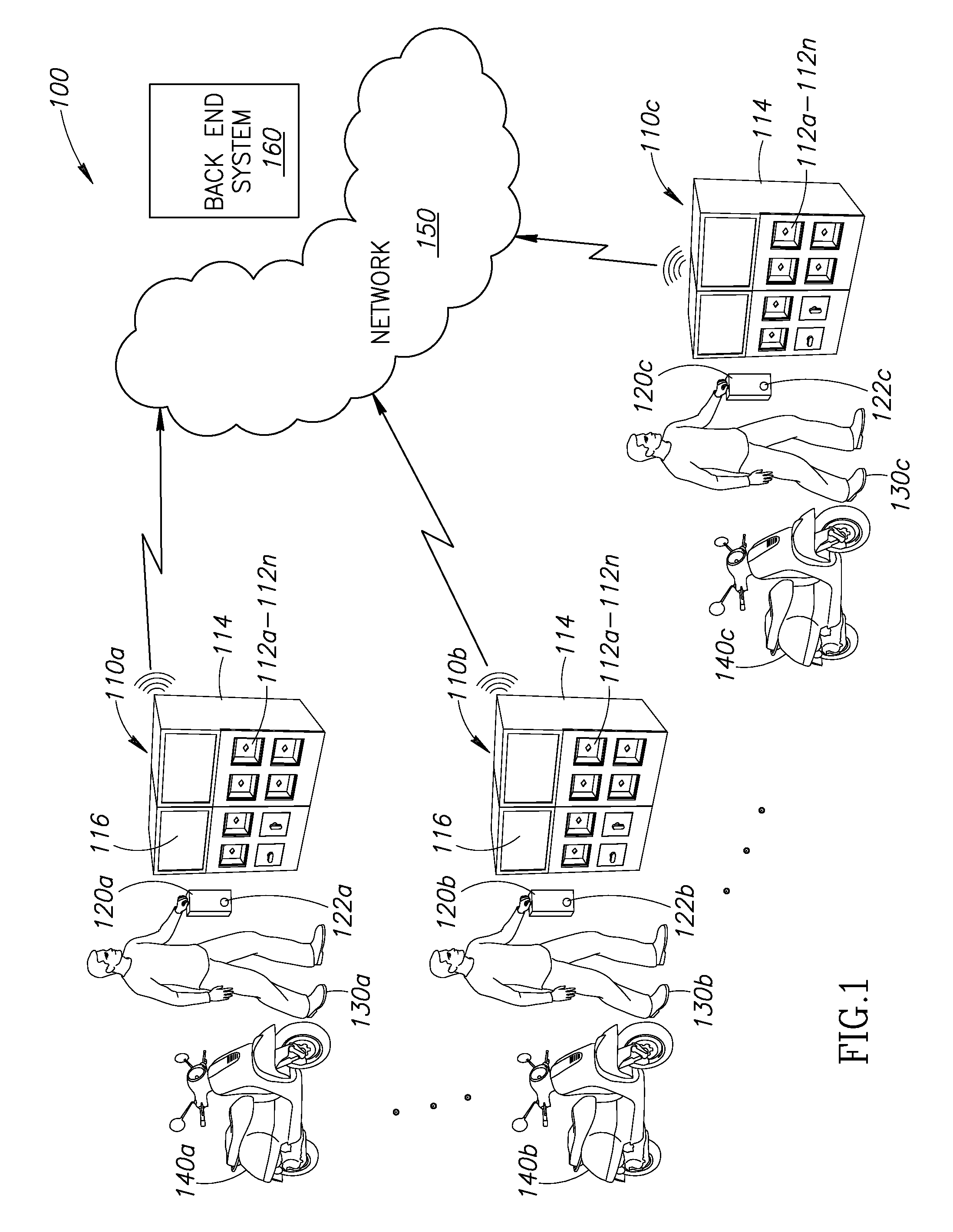
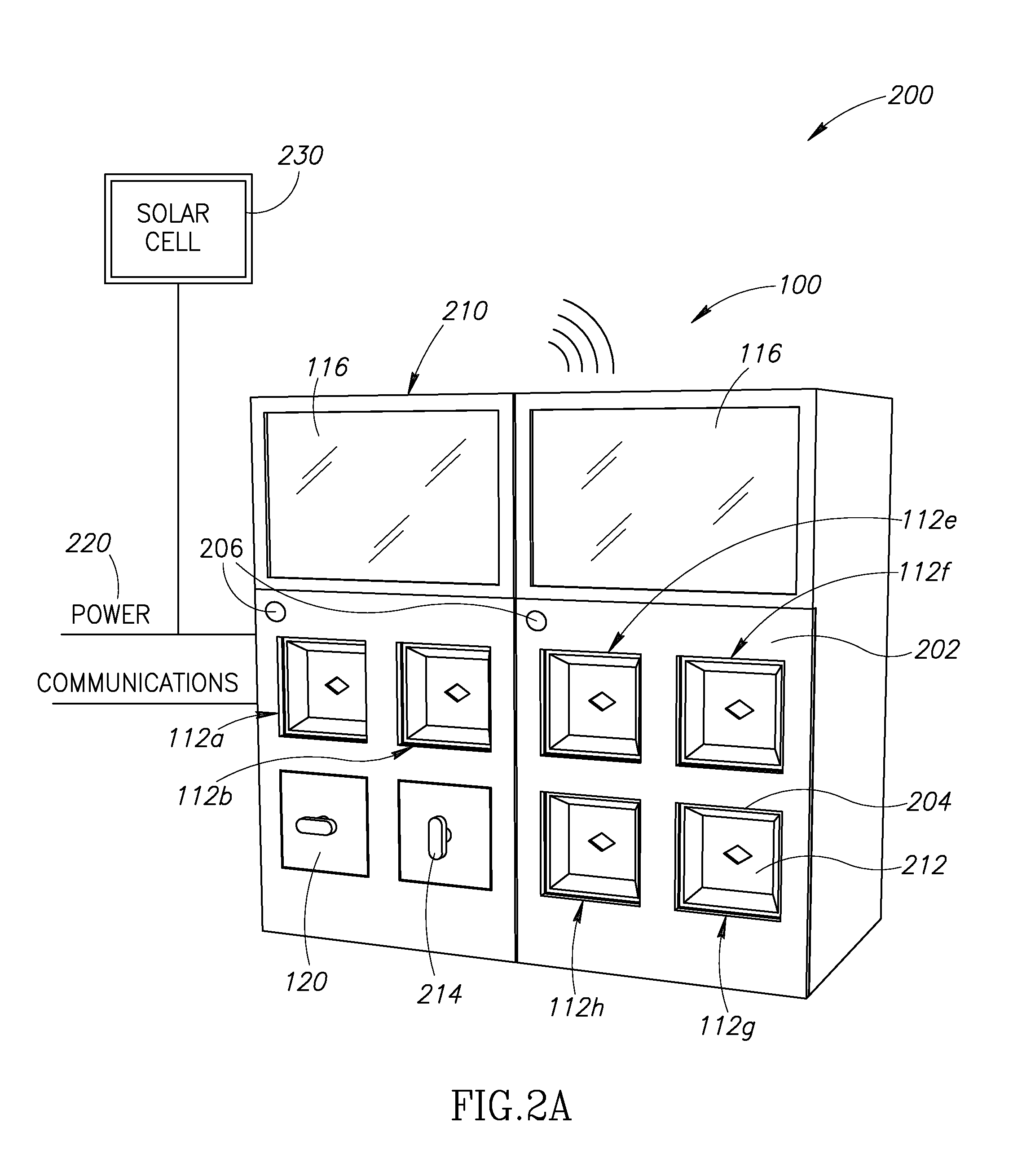
Apparatus, system, and method for vending, charging, and two-way distribution of electrical energy storage devices
ActiveUS20160068075A1Limited accessEliminate needCircuit authenticationVehicular energy storageComputer hardwareConverters
A two-way distribution, charging, and vending system permits a subscriber to exchange one or more partially or completely discharged portable electric energy storage devices for a comparable number of charged portable electric energy storage devices. The two-way distribution, charging, and vending system includes a number of charging modules, each with a dedicated power converter, communicably coupled to at least one two-way distribution system controller and to a power distribution grid. Upon receipt of a discharged portable electric energy storage device, the at least one two-way distribution system controller validates a manufacturer identifier and a subscriber identifier stored in a nontransitory storage media carried by the discharged portable electric energy storage device. Responsive to a successful authentication and validation, the at least one two-way distribution system controller dispenses a charged portable electric energy storage device to the subscriber.
Owner:GOGORO
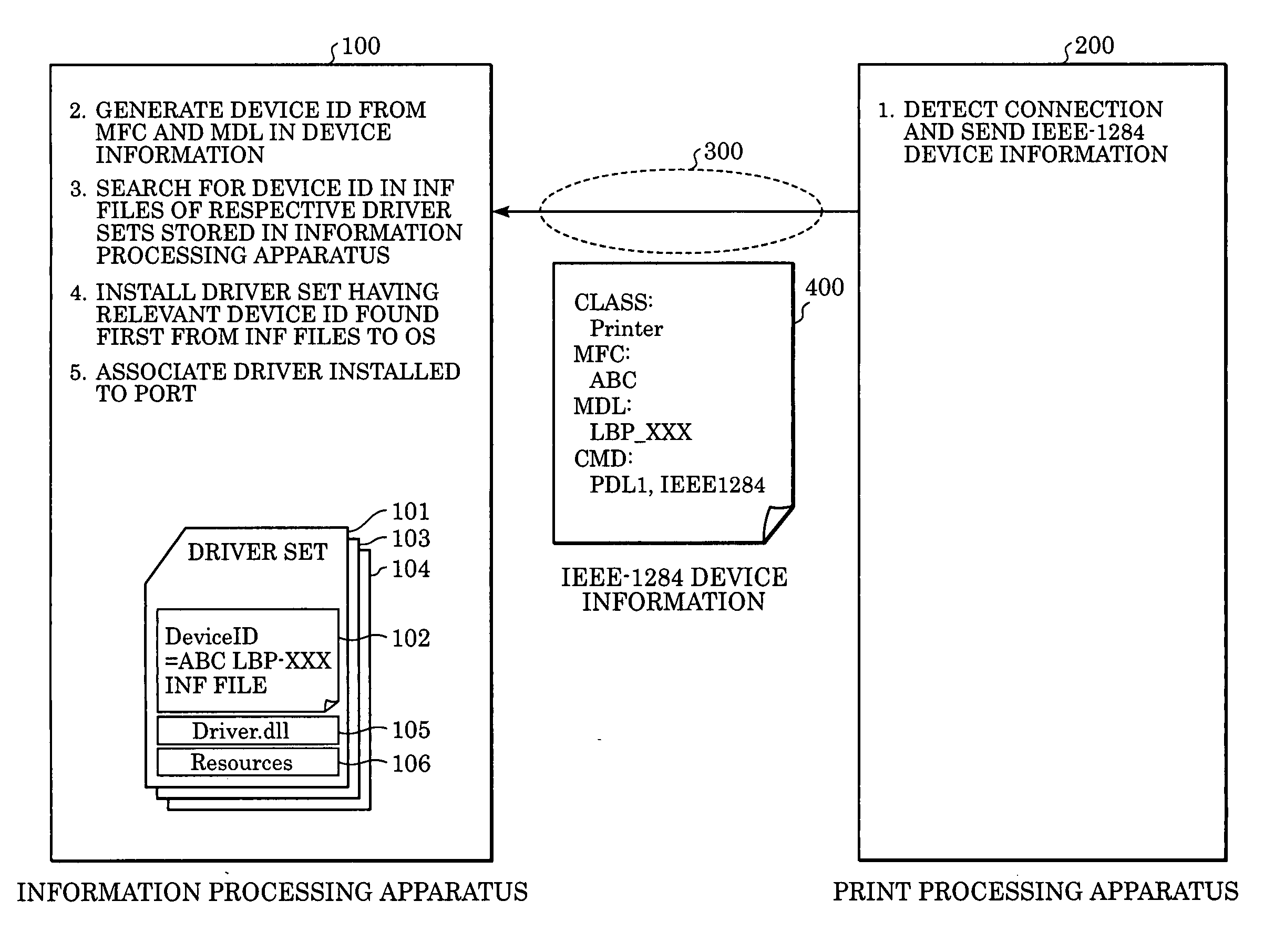
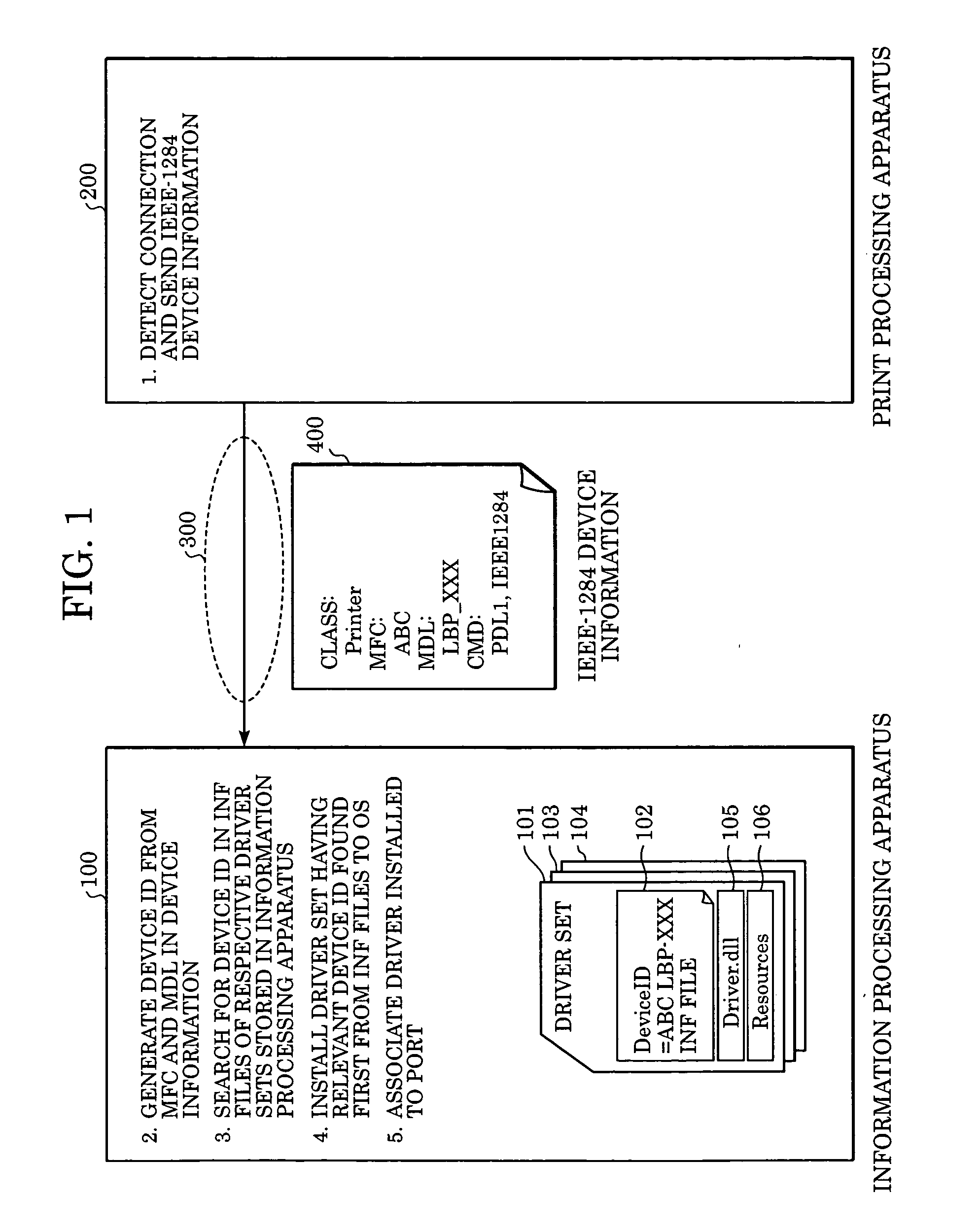
Information processing apparatus, image forming apparatus, method therefor, and system
InactiveUS20050200889A1Digitally marking record carriersBrush bodiesInformation processingImage formation
An image forming method that is capable of interpreting a plurality of image forming processes includes a setting step of setting an image forming process that is activated by the image forming method, and an issuing step of issuing a manufacturer identifier and machine-type identifier and process identification information representing the image forming process set in the setting step.
Owner:CANON KK
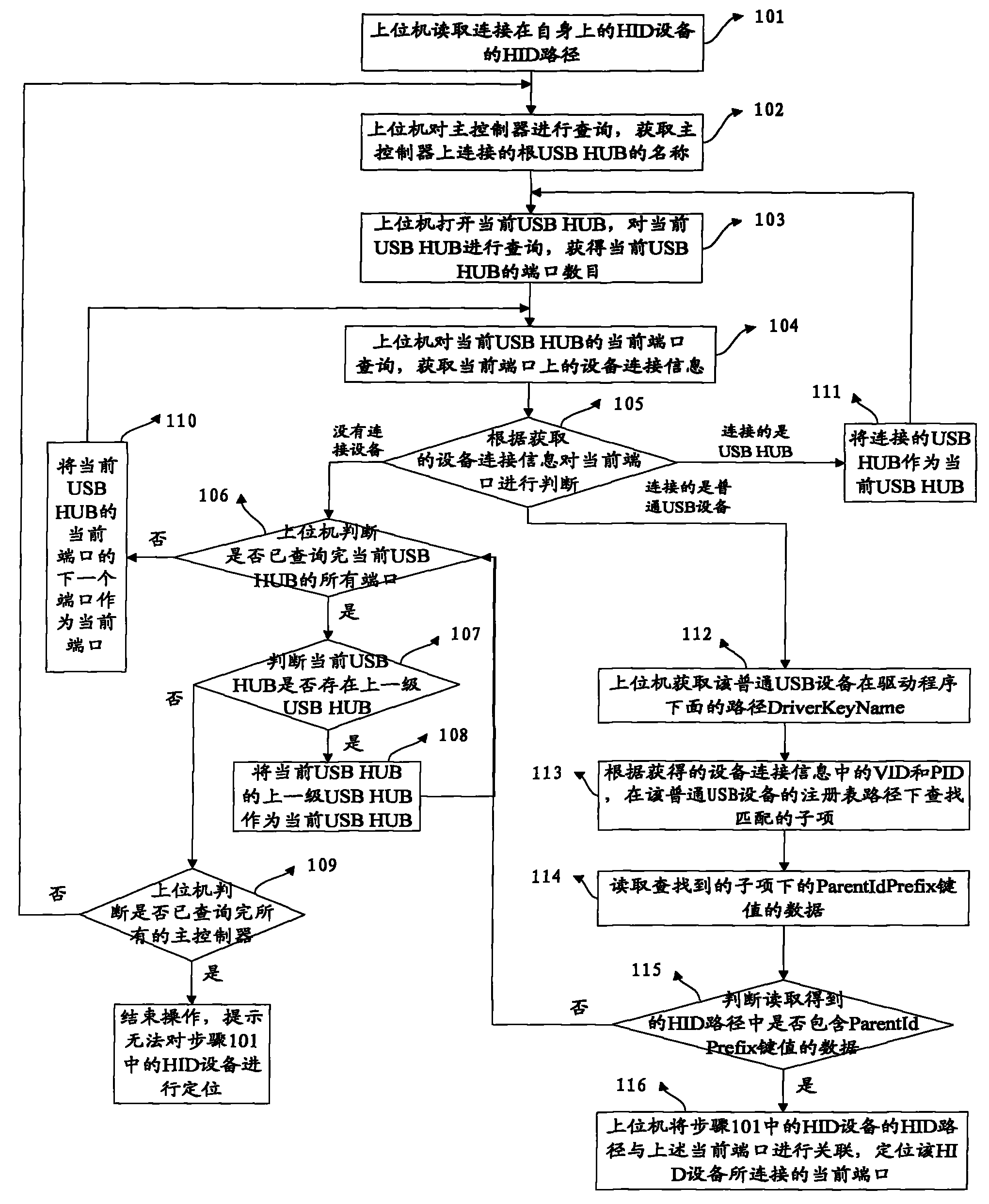
Method for positioning USB port in connection of device
The invention discloses a method for positioning a USB port in connection of a device, relates to the field of computer communication and can solve the problem that an upper computer can not position the USB port in connection of the ordinary USB device. The method comprises the following steps: using the upper computer to read a path of a first device connected on the upper computer, obtaining device connection information on the current port of a current USB HUB, judging the current port according to the device connection information, obtaining the path of the ordinary USB device under a driving program when the ordinary USB device is connected on the current port, looking up first information under the paths of a registration form of the ordinary USB device according to manufacturer identifier information and device identifier information in the device connection information, using the upper computer to associate the path of the first device with the current port and positioning the USB port in connection of the first device, wherein when the path of the first device contains the first information, the situation represents that the first device and the ordinary USB device are the same device.
Owner:FEITIAN TECHNOLOGIES
Apparatus, system, and method for vending, charging, and two-way distribution of electrical energy storage devices
ActiveUS10040359B2Limited accessEliminate needCircuit authenticationVehicular energy storageDistribution systemComputer module
A two-way distribution, charging, and vending system permits a subscriber to exchange one or more partially or completely discharged portable electric energy storage devices for a comparable number of charged portable electric energy storage devices. The two-way distribution, charging, and vending system includes a number of charging modules, each with a dedicated power converter, communicably coupled to at least one two-way distribution system controller and to a power distribution grid. Upon receipt of a discharged portable electric energy storage device, the at least one two-way distribution system controller validates a manufacturer identifier and a subscriber identifier stored in a nontransitory storage media carried by the discharged portable electric energy storage device. Responsive to a successful authentication and validation, the at least one two-way distribution system controller dispenses a charged portable electric energy storage device to the subscriber.
Owner:GOGORO
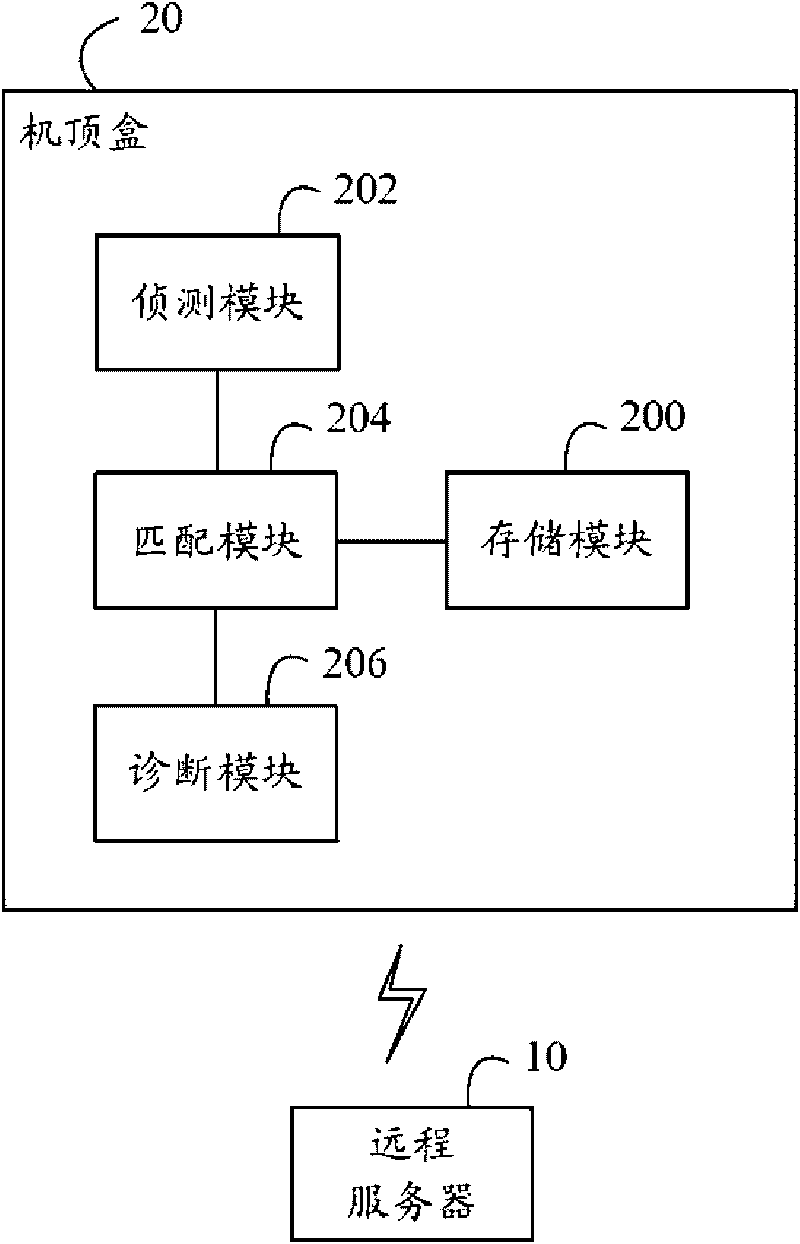
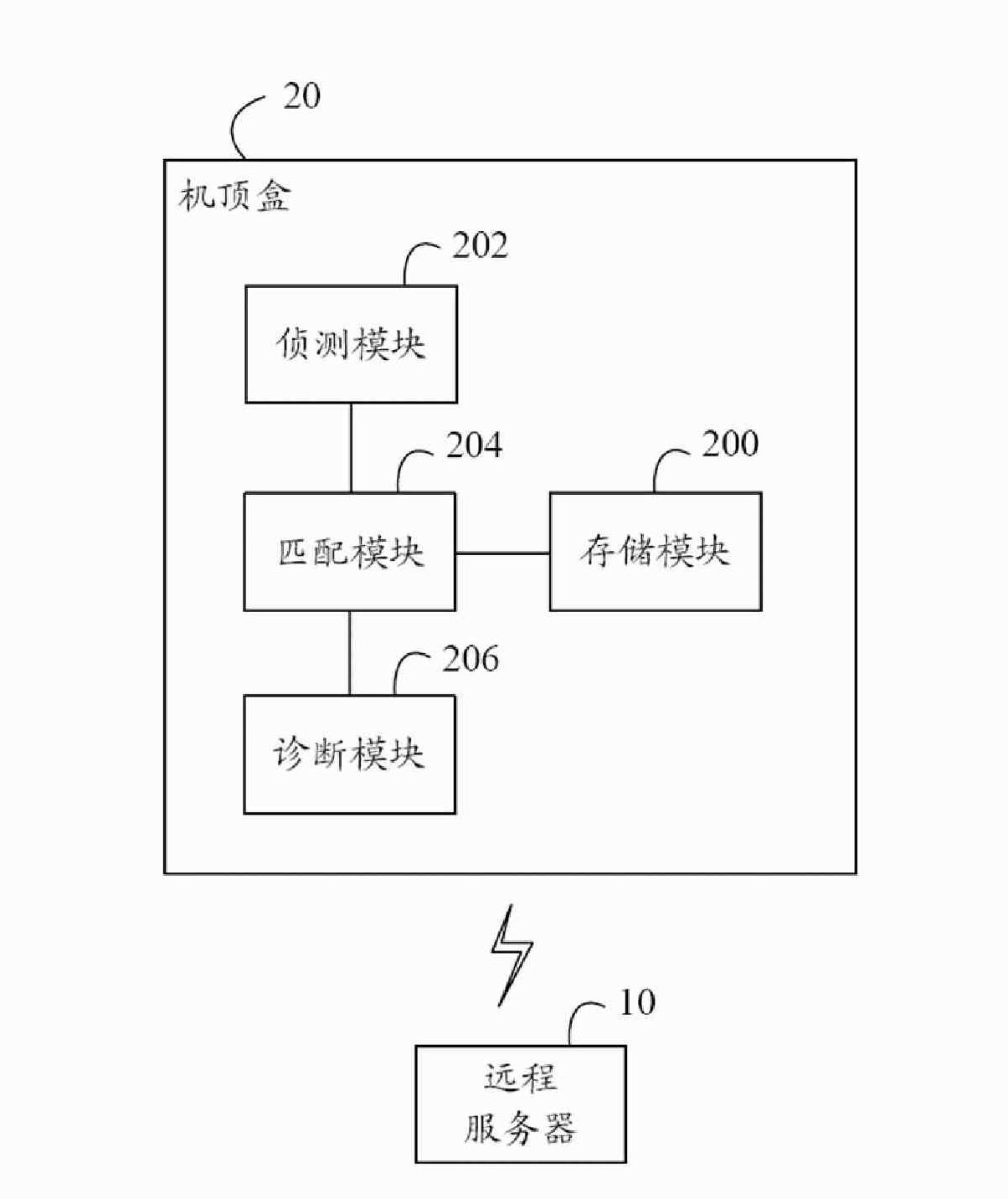
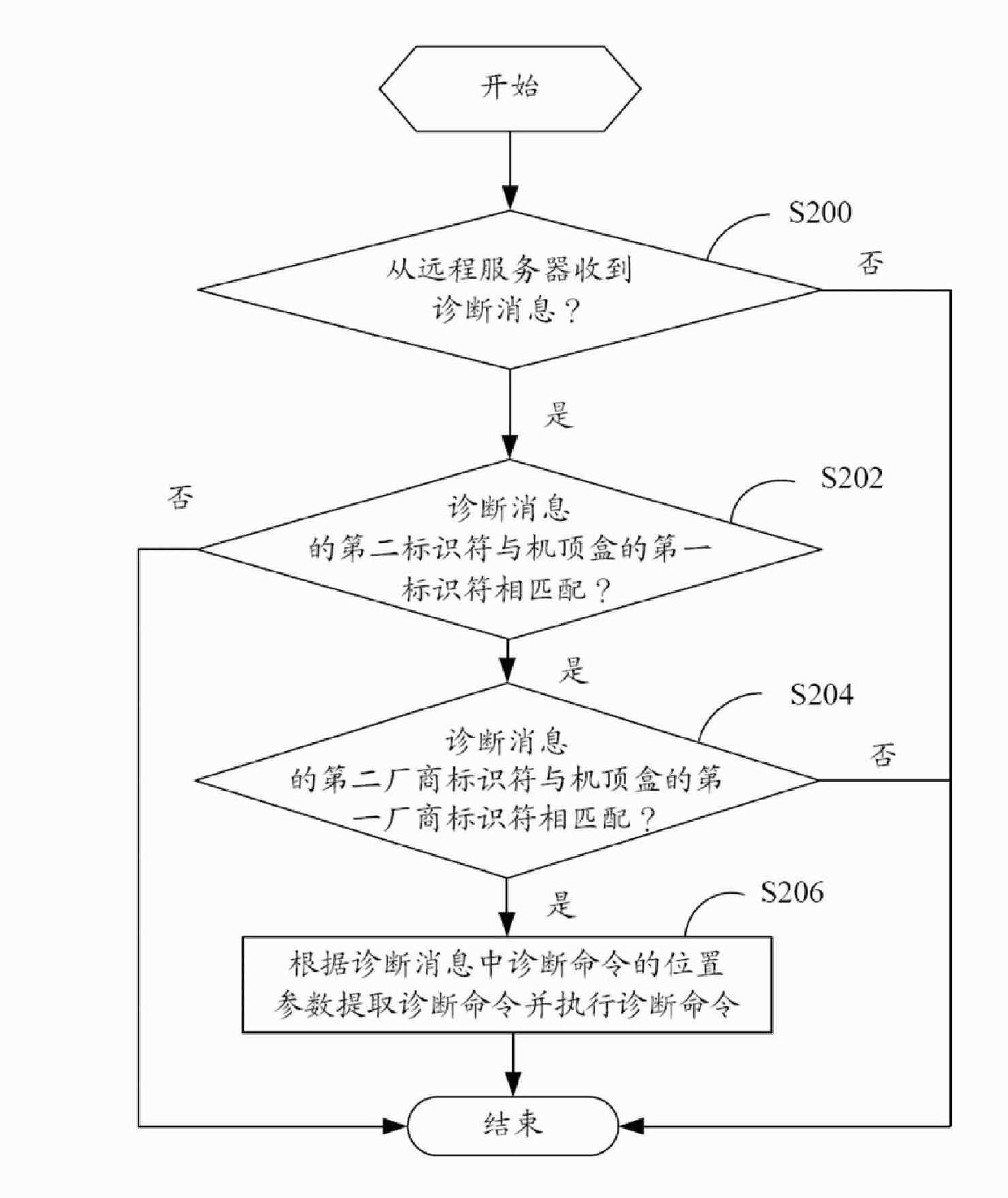
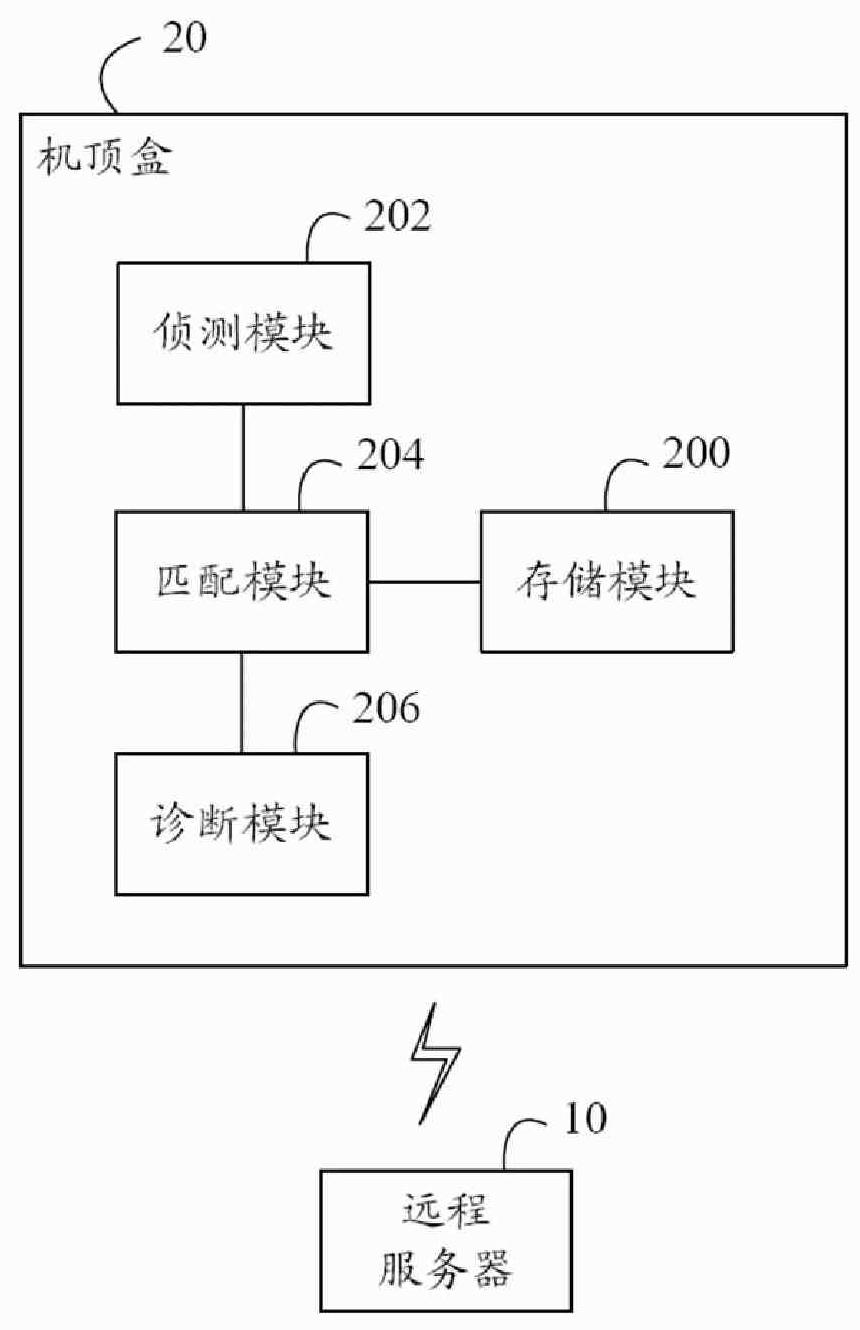
Set top box and remote diagnostic method thereof
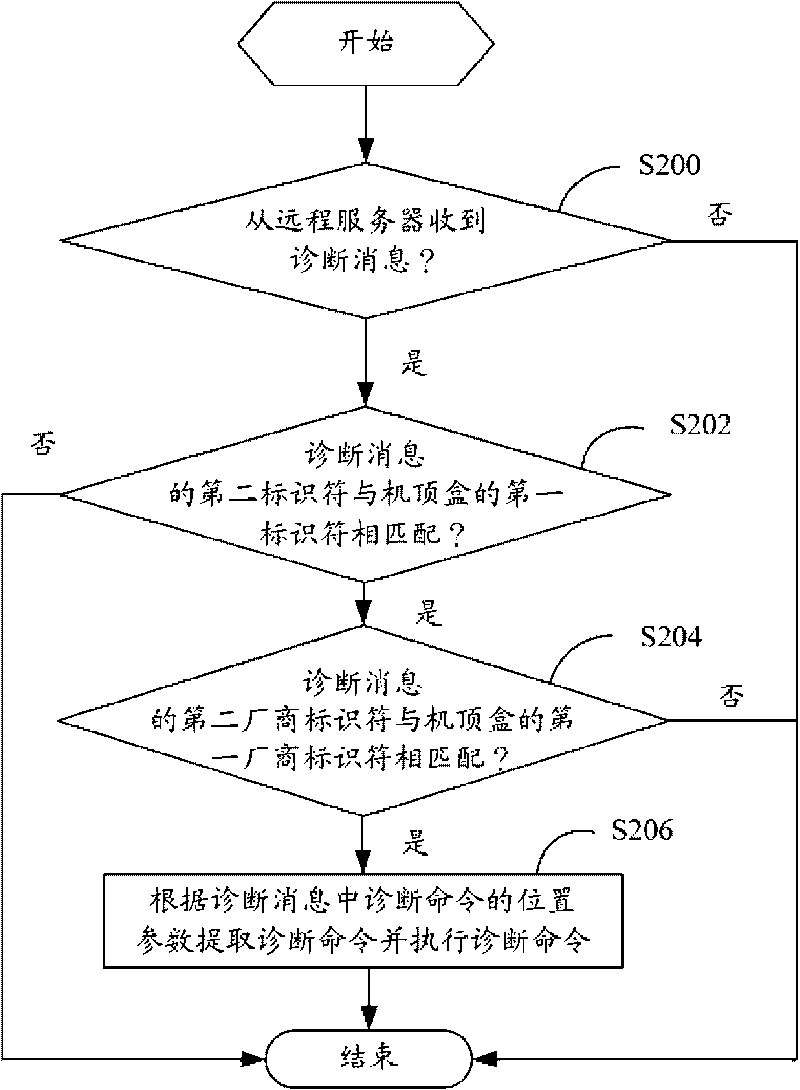
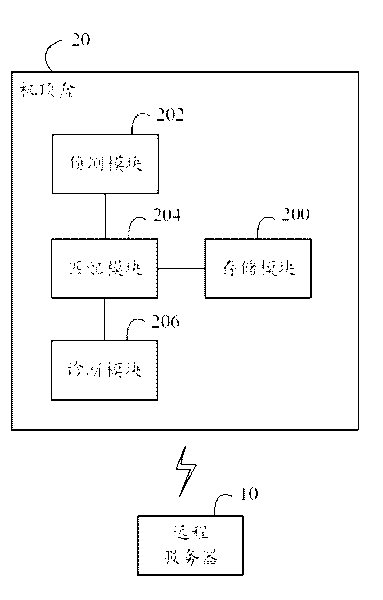
InactiveCN101729922ARealize remote diagnosisTelevision systemsDiagnostic informationRemote diagnostics
The invention discloses a set top box, comprising a memory module, a detection module, a matching module and a diagnostic module, wherein, the memory module stores a first identifier and a first manufacturer identifier; the detection module detects whether diagnostic information is received or not from a remote server; the diagnostic information comprises a second identifier, a second manufacturer identifier and a position parameter of a diagnostic order; the matching module judges whether the second identifier and the second manufacturer identifier of the diagnostic information are respectively matched with the first identifier and the first manufacturer identifier or not; if so, the diagnostic module extracts the diagnostic order and executes the diagnostic order according to the position parameter of the diagnostic order. The invention also provides the remote diagnostic method of the set top box; the set top box provided by the implementation mode of the invention and the remote diagnostic method position the fault set top box singly through the identifier and the manufacturer identifier of the set top box, and can realize remote fault diagnosis.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Hybrid cloud charging method and system
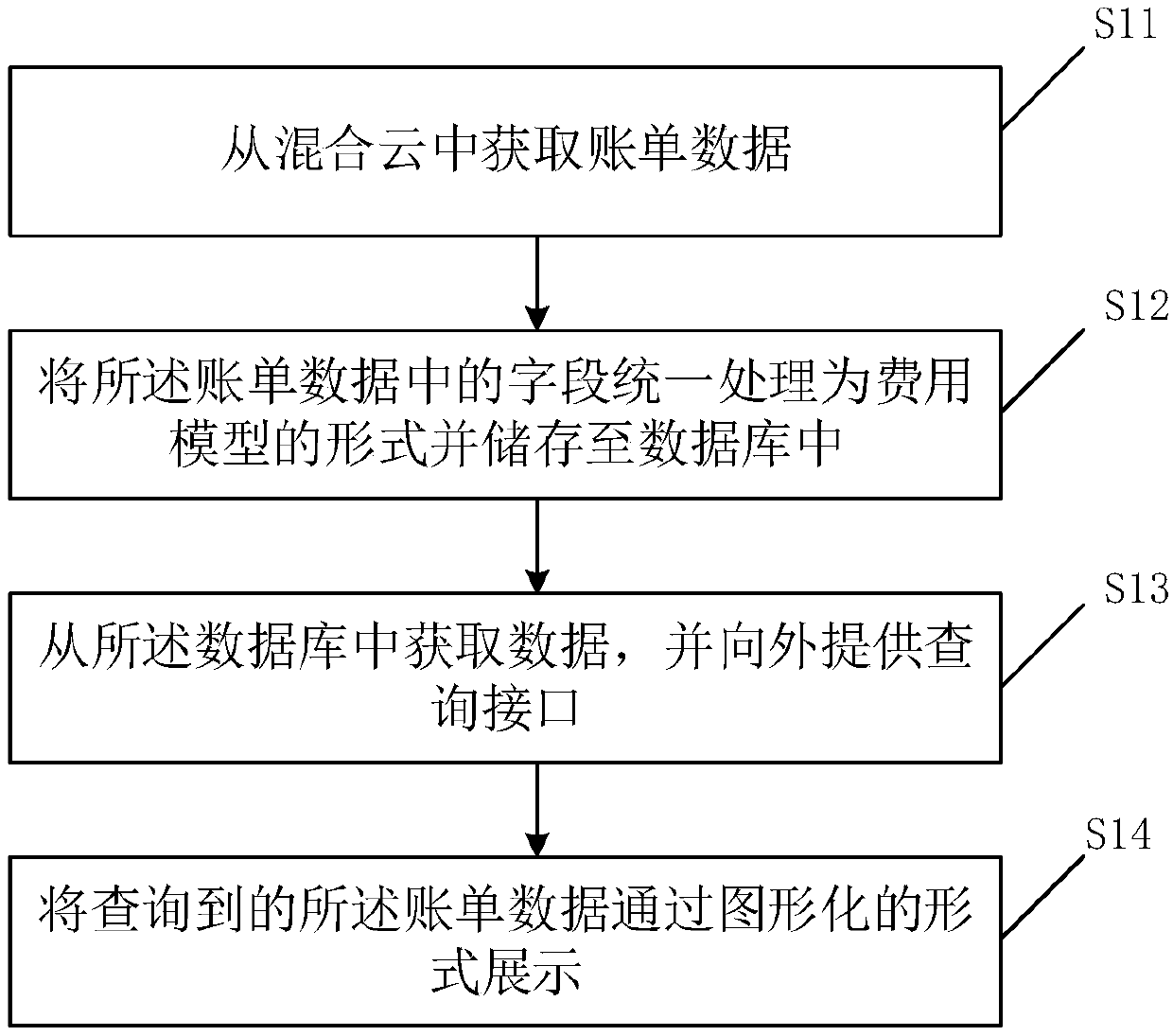
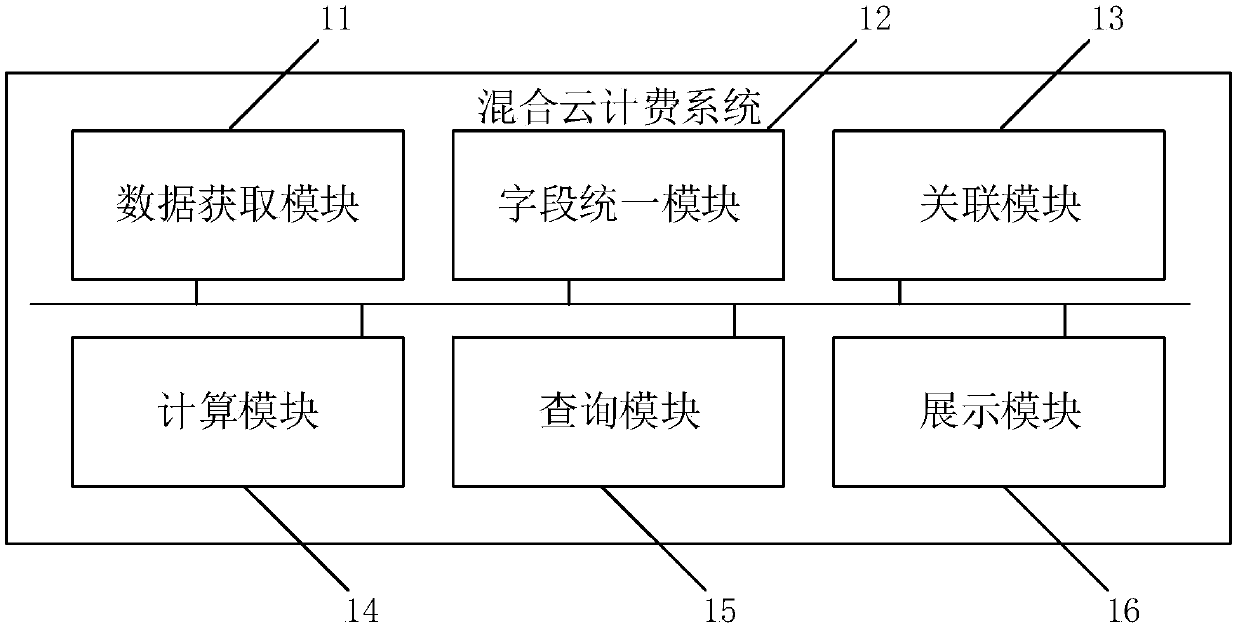
ActiveCN109660366AImprove interactive experienceEfficient queryMetering/charging/biilling arrangementsTimestampUnique identifier
The invention discloses a hybrid cloud charging method and system. The method comprises the following steps: acquiring bill data from hybrid cloud, wherein the hybrid cloud comprises public cloud and / or private cloud, and different clouds comprise the bill data in different forms; processing fields in the bill data as a way of cost model in a unified way, and storing in a database; wherein the cost model comprises an unique identifier, a manufacturer identifier, a region identifier, a resource type, a charge mode, a resource identifier, the cost, a charging timestamp, a resource usage department and the resource subordinated application identifier. The query efficiency is improved by unifying the bill data of different cloud manufacturers, the bill data of different cloud manufacturers areassociated with an internal system, so that the different query demands of different users are satisfied, the queried data is displayed in a pattern manner, a user interaction interface is friendlier, and the user experience is better.
Owner:携程旅游信息技术(上海)有限公司
Terminal safety starting method and device and storage medium
ActiveCN110688660AAvoid Modified SituationsImprove securityDigital data protectionBootstrappingSoftware engineeringOperating system
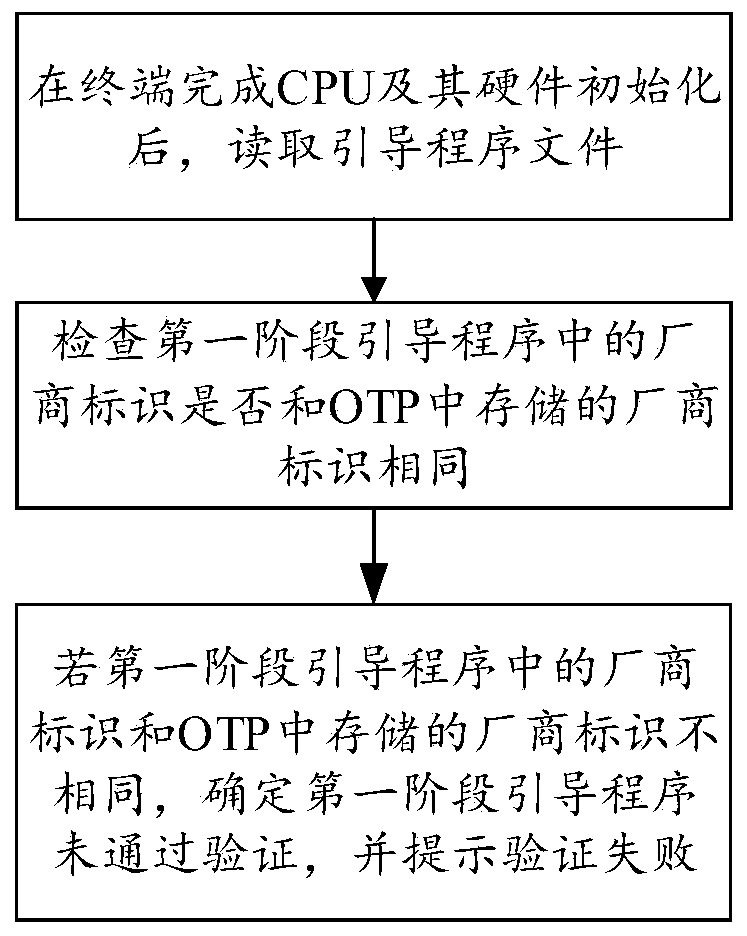
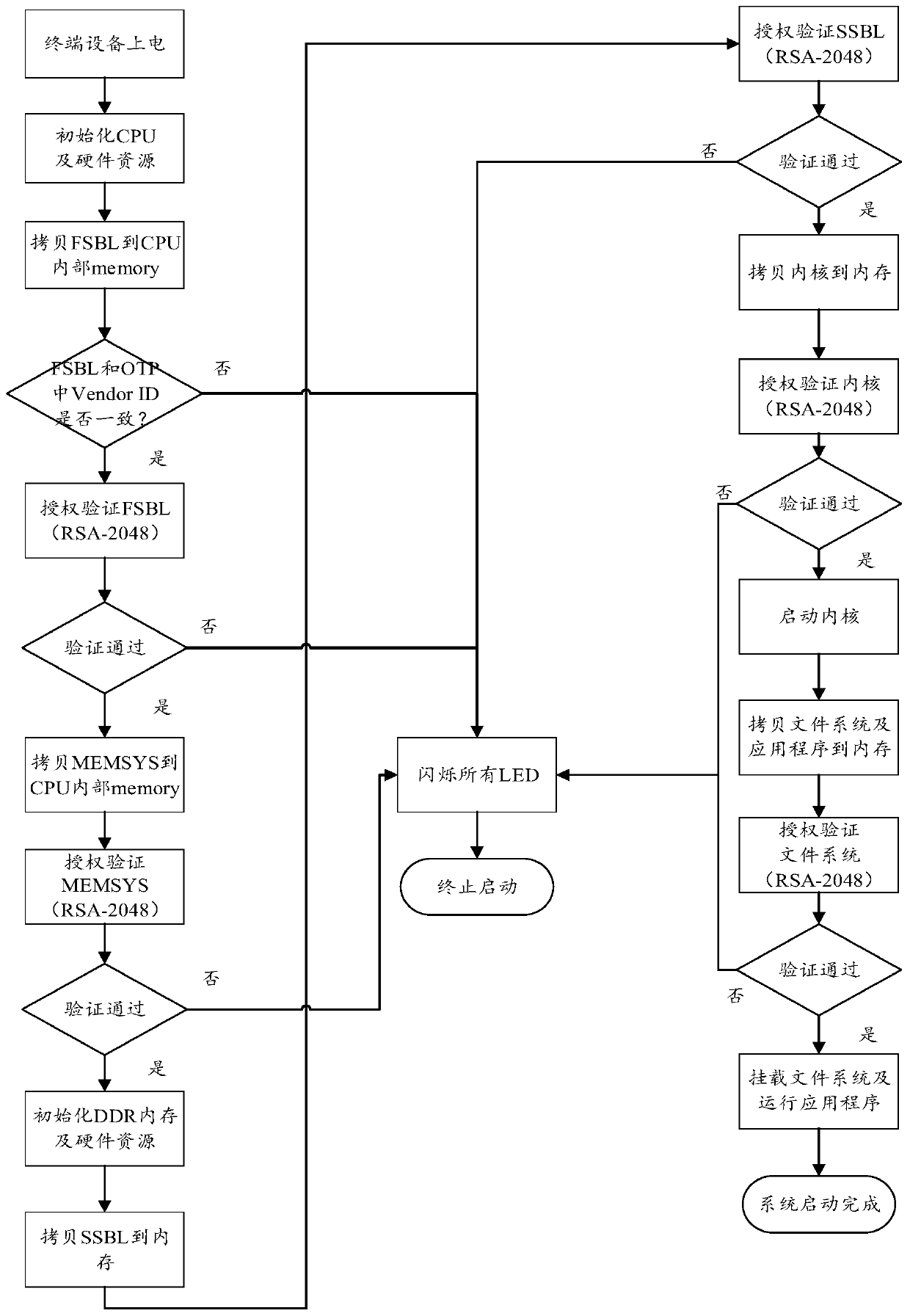
The invention provides a terminal safety starting method and device and a storage medium. The method for safely starting the terminal comprises the steps that after the terminal completes initialization of a CPU and hardware of the CPU, a bootstrap program file is read, and the bootstrap program file comprises a first-stage bootstrap program; checking whether the manufacturer identifier in the first-stage bootstrap program is the same as the manufacturer identifier stored in the OTP or not; and if the manufacturer identifier in the first-stage bootstrap program is different from the manufacturer identifier stored in the OTP, determining that the first-stage bootstrap program does not pass the verification, and prompting that the verification fails. The method for safely starting the terminal ensures the safety of the terminal system.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Windows Virtual machine remote detecting method
InactiveCN103220298AChange the situation of lack of effective management meansDetect relevanceTransmissionIp addressMedia access control
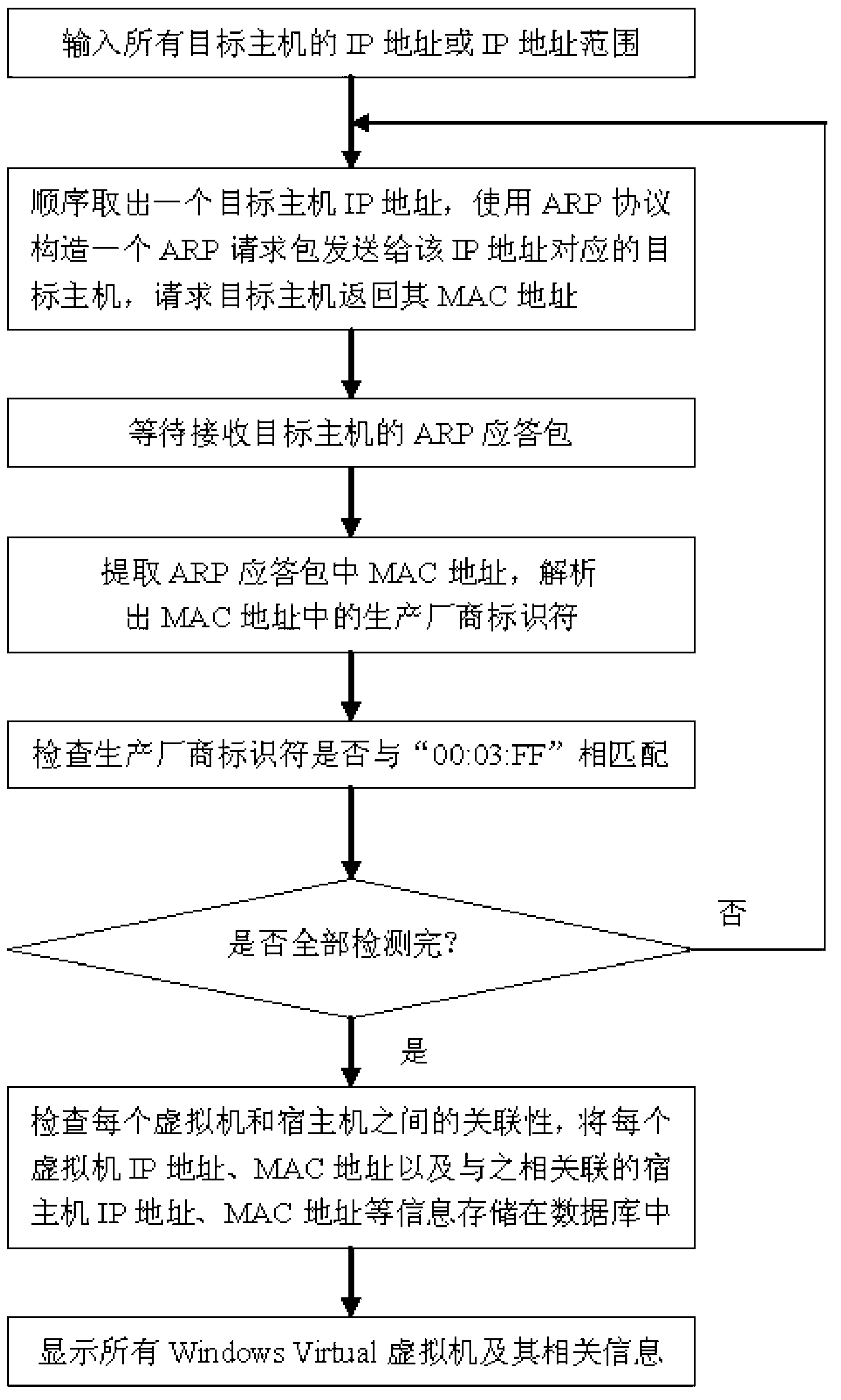
The invention discloses a Windows Virtual machine remote detecting method which is used for solving the technical problem that an existing Windows Virtual machine has security holes. According to the technical scheme, firstly, an internet protocol (IP) address of a known target host machine of a main machine is detected to acquire a media access control (MAC) address of the target host machine, and the MAC address is sent to the detection main machine; then, manufacturer identifiers in the MAC address are extracted after the detection main machine receives the MAC address of the target host machine, and then whether the manufacturer identifiers are matched with 00:03:FF is checked; all target host machines in a local area network are processed in an ergodic mode to detect all opened Windows Virtual machines and a host machine; and afterwards, the relevance between each virtual machine and the host machine is analyzed according to the 32nd bit to the 47th bit in the MAC address to detect the relevance between the virtual machines and the host machine. The Windows Virtual machine remote detecting method can detect the relevance between the Windows Virtual machines and the host machine according to the manufacturer identifiers in the MAC address. Furthermore, the detection accuracy can reach to 100%.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
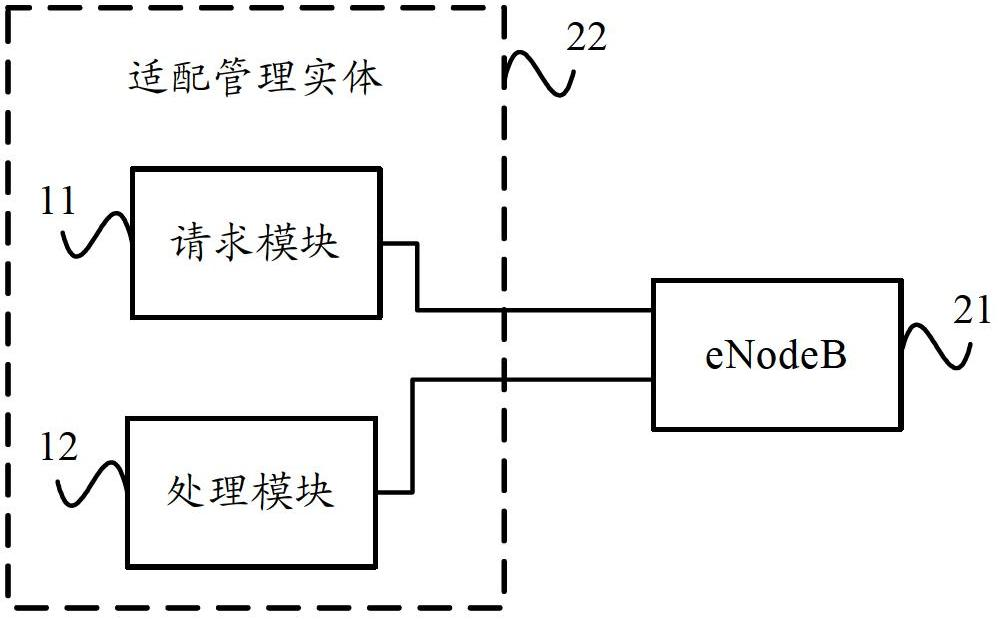
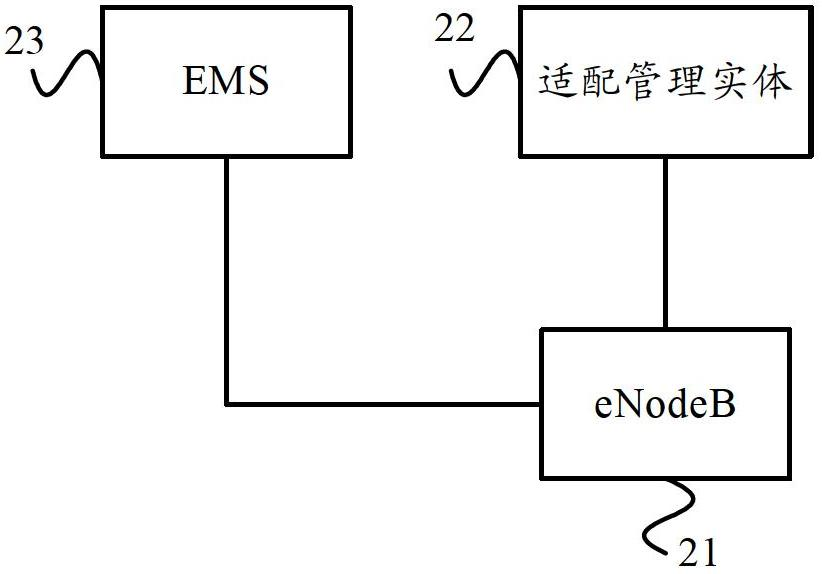
Adaptive management entity, base station self-configuring method and base station self-configuring system
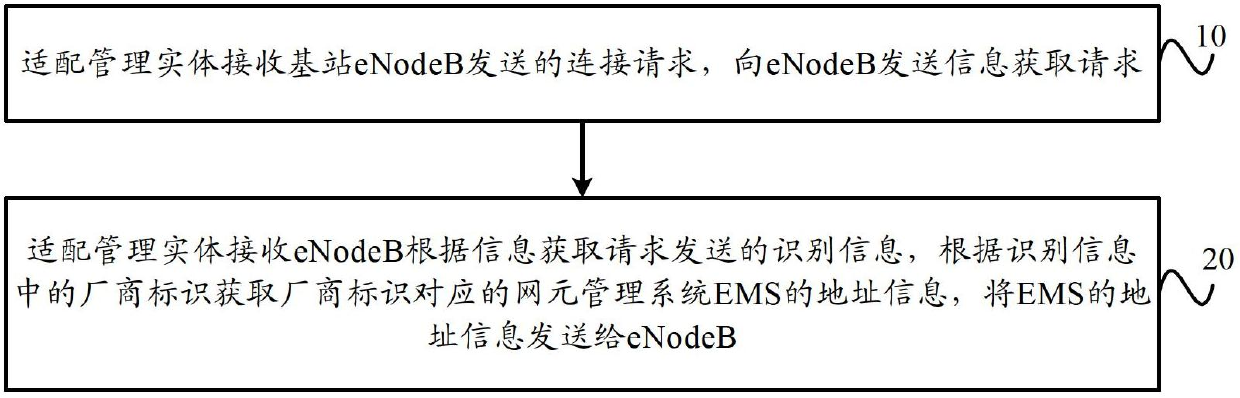
ActiveCN102685726AImplement the self-configuration processNetwork data managementAdaptive managementElement management system
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
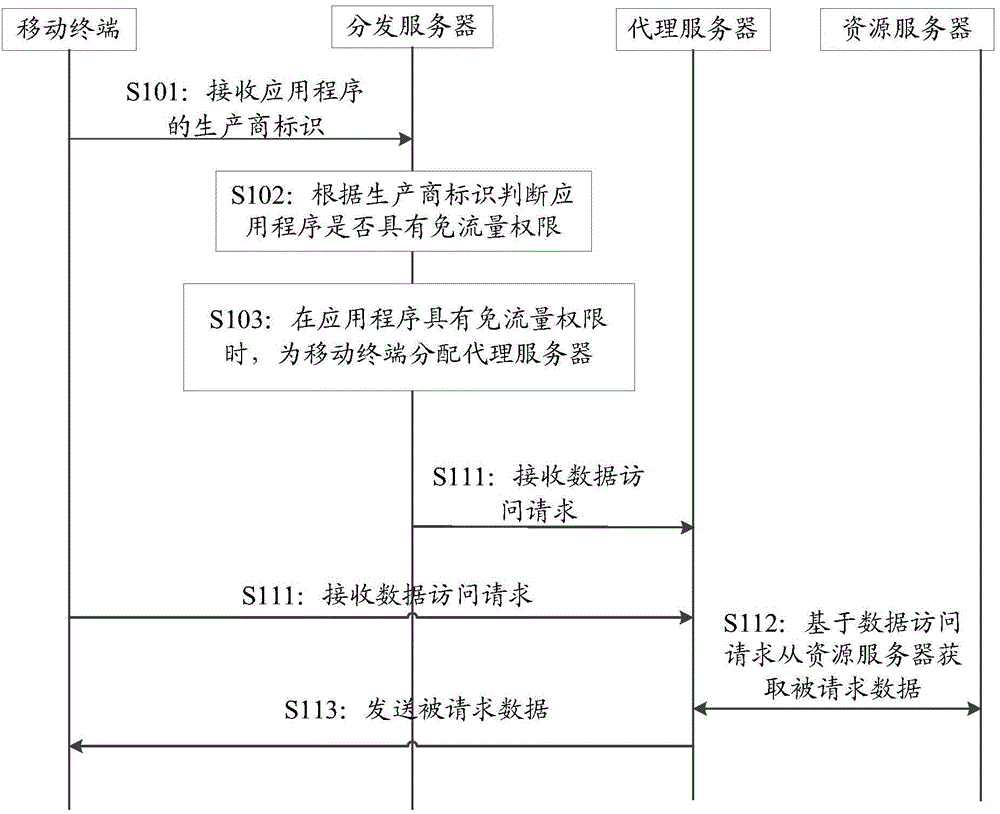
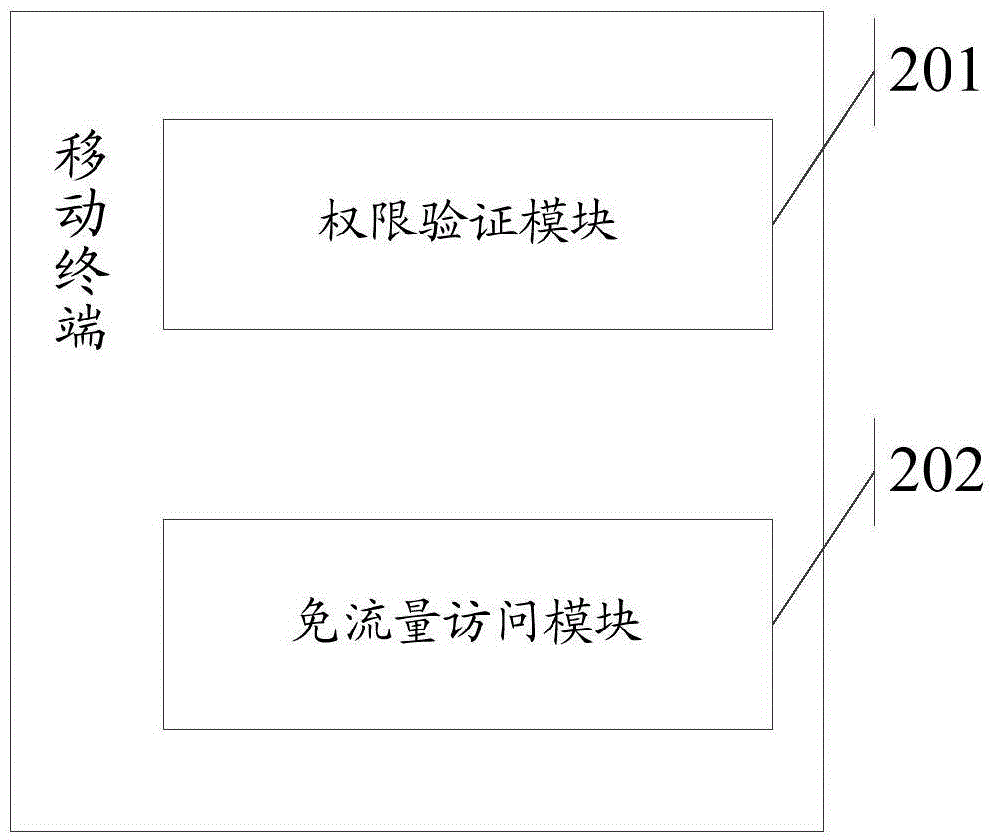
Method for accessing network by application program in mobile terminal, distribution server and system
The invention relates to the field of communication and discloses a method for accessing a network by an application program in a mobile terminal, a distribution server and a system and aims at solving the technical problem in the prior art that the mobile terminal accesses the network by consuming a large amount of data traffic of the mobile terminal. The method comprises the following steps that the mobile terminal transmits a manufacturer identifier of the application program in the mobile terminal to the distributor server through a mobile communication network; if the distribution server determines that the application program has the traffic-free permission according to the manufacturer identifier, when the application program initiates a data access request, the mobile terminal accesses the network by a proxy server distributed by the distribution server; data generated by accessing the network by the mobile terminal through the proxy server are marked with a traffic-free identifier; all or partial data traffic generated by accessing the network by the mobile terminal through the proxy server is counted into a designated service provider by a mobile communication operator based on the traffic-free identifier. The method achieves the technical effect of accessing the network by the mobile terminal in a traffic-free mode.
Owner:360 TECH GRP CO LTD
Apparatus, system, and method for vending, charging, and two-way distribution of electrical energy storage devices
ActiveUS20190168627A1Limited accessEliminate needCircuit authenticationVehicular energy storageComputer hardwareConverters
A two-way distribution, charging, and vending system permits a subscriber to exchange one or more partially or completely discharged portable electric energy storage devices for a comparable number of charged portable electric energy storage devices. The two-way distribution, charging, and vending system includes a number of charging modules, each with a dedicated power converter, communicably coupled to at least one two-way distribution system controller and to a power distribution grid. Upon receipt of a discharged portable electric energy storage device, the at least one two-way distribution system controller validates a manufacturer identifier and a subscriber identifier stored in a nontransitory storage media carried by the discharged portable electric energy storage device. Responsive to a successful authentication and validation, the at least one two-way distribution system controller dispenses a charged portable electric energy storage device to the subscriber.
Owner:GOGORO
Information processing apparatus, image forming apparatus, method therefor, and system
InactiveUS7551304B2Digitally marking record carriersBrush bodiesInformation processingImage formation
An image forming method that is capable of interpreting a plurality of image forming processes includes a setting step of setting an image forming process that is activated by the image forming method, and an issuing step of issuing a manufacturer identifier and machine-type identifier and process identification information representing the image forming process set in the setting step.
Owner:CANON KK
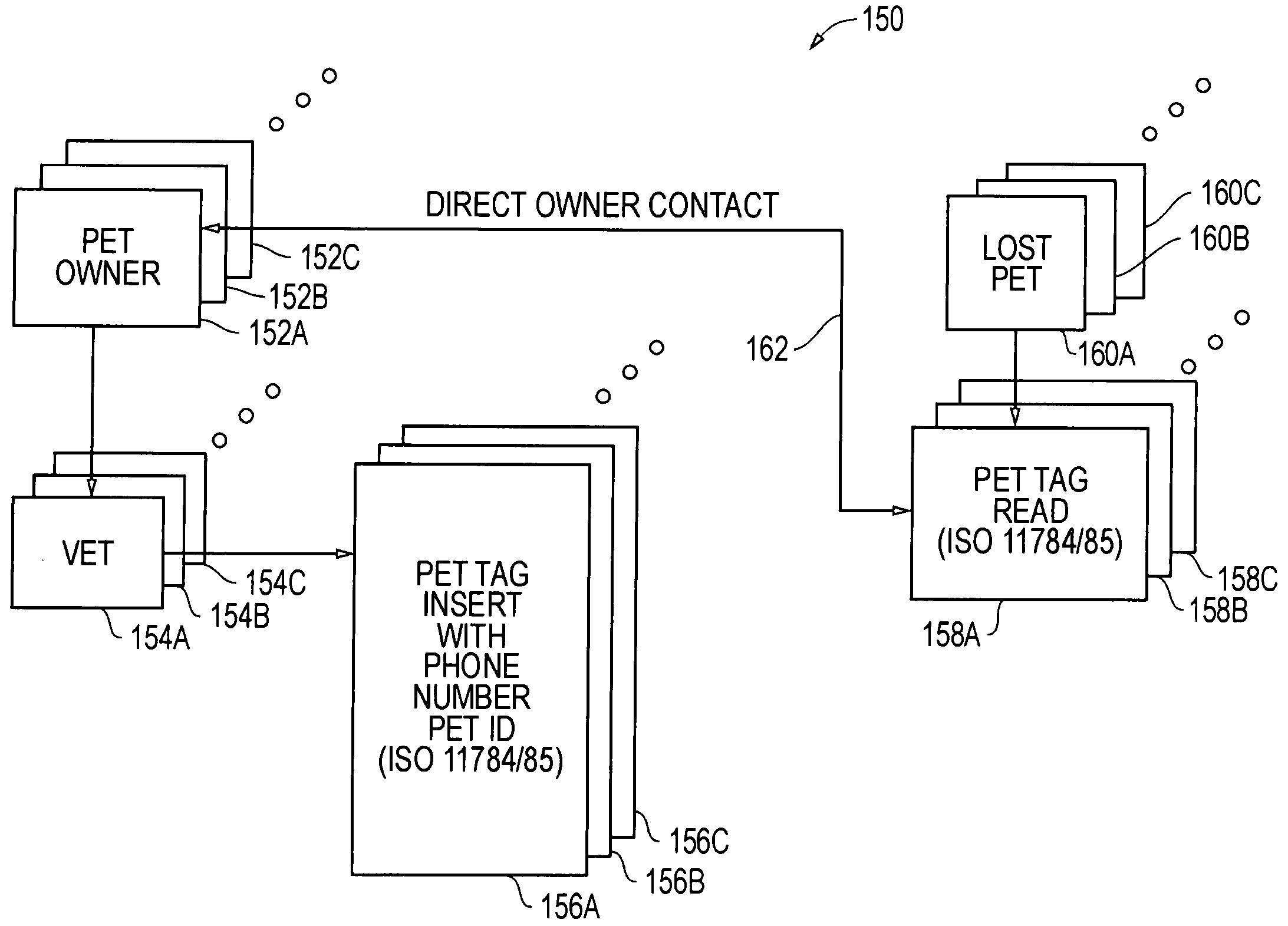
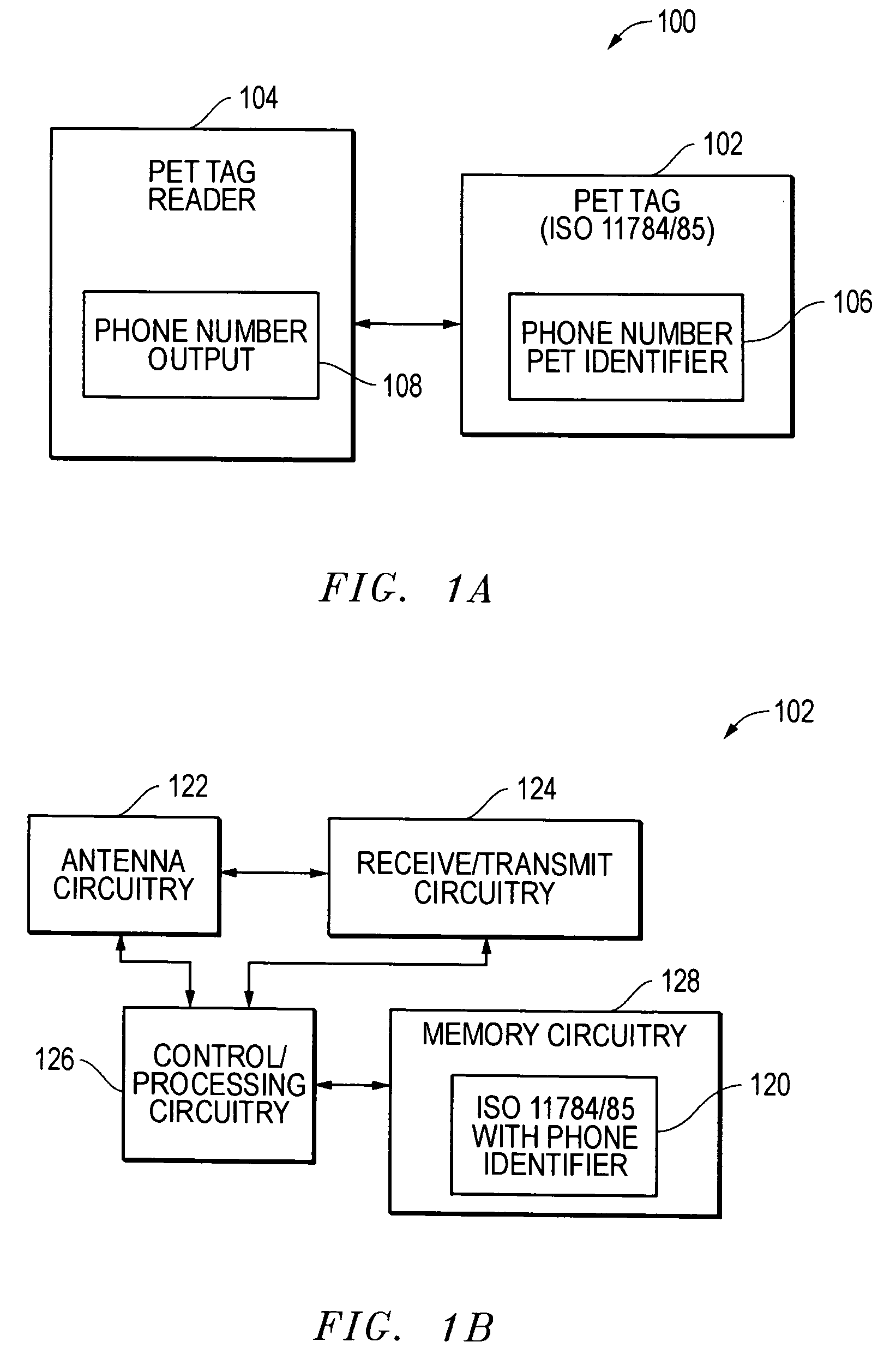
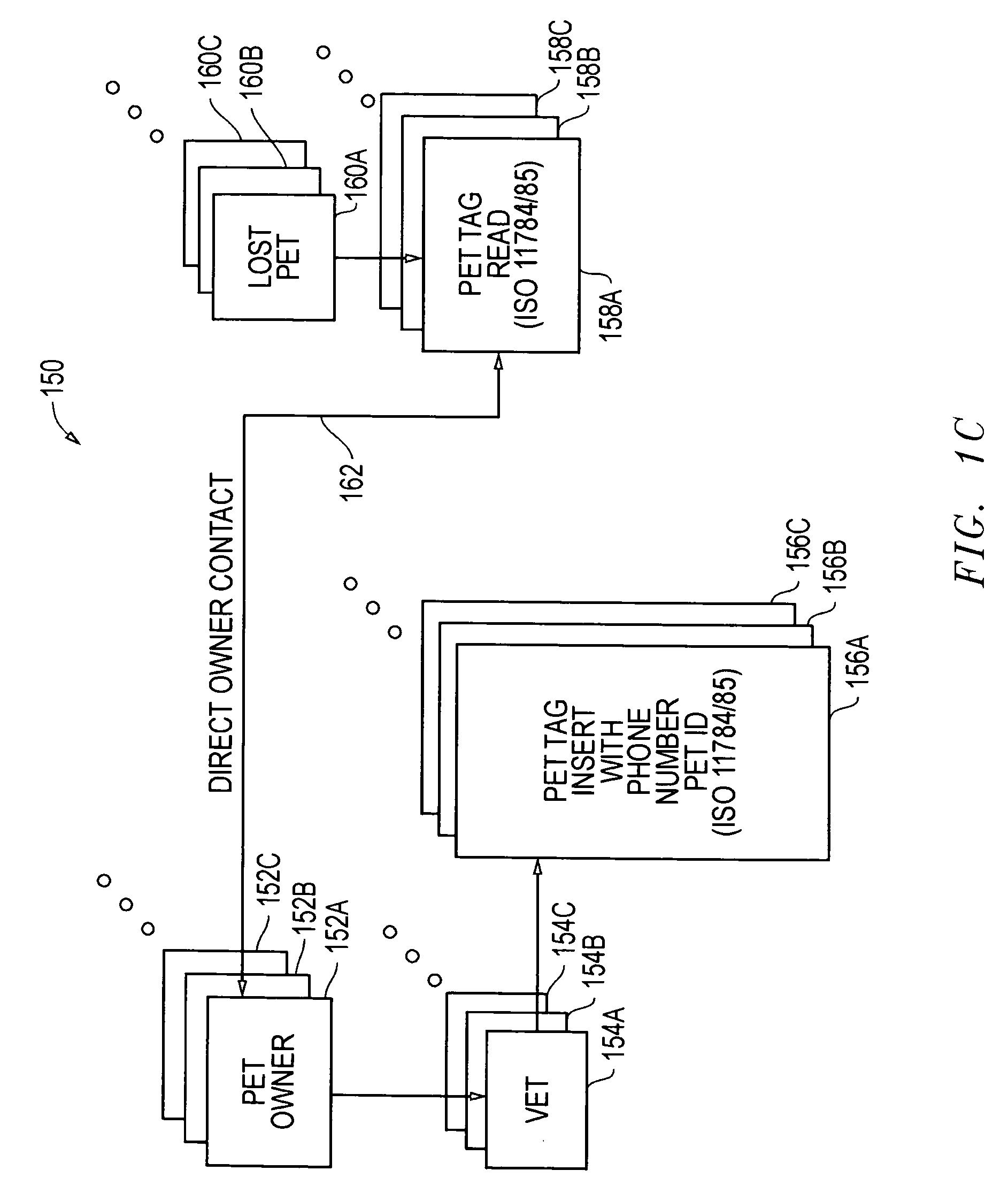
Phone number and manufacturer identifiers for ISO 11784/85 compatible transponders and associated systems and methods
InactiveUS20090207001A1Multiplex system selection arrangementsSubscribers indirect connectionManufacturer codeCompanion animal
Systems and methods are disclosed for identifying animals with radio frequency identification transponders using phone number identifiers and manufacturer codes stored within ISO 11784 code structures in ISO 11784 / 85 compatible implantable transponders. These phone identification (ID) transponders feature unique telephone numbers, allowing pets to be returned to their owners through direct phone contact, for which ISO 11784 standard does not provide. The phone number information can be stored prior to implantation or after implantation depending upon the type of transponders being utilized. More particularly, within the ISO 11784 code structure, phone number related country codes are stored in bits 17-26, and phone numbers and manufacturer codes are stored in bits 27-64.
Owner:TROVAN
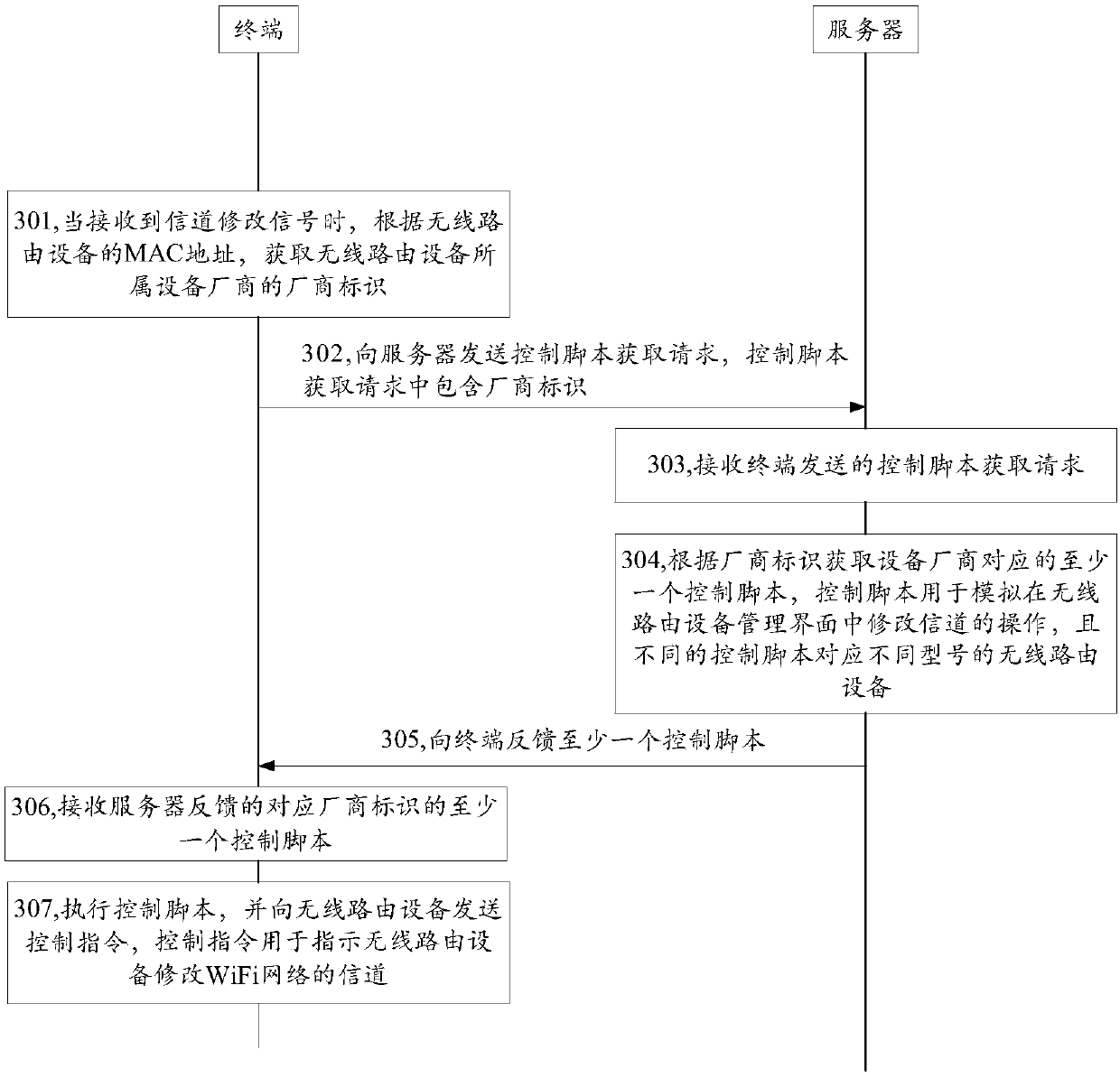
WiFi network channel modification method, terminal, server and storage medium
ActiveCN110392375ASimple processImprove channel modification efficiencyData switching networksWireless communicationWifi networkExecution control
The invention discloses a WiFi network channel modification method, a terminal, a server and a storage medium, and belongs to the field of wireless networks. The method comprises the following steps:when a channel modification signal is received, acquiring a manufacturer identifier of an equipment manufacturer to which wireless routing equipment belongs according to an MAC address of the currently accessed wireless routing equipment; sending a control script acquisition request to a server, wherein the control script acquisition request comprises a manufacturer identifier; receiving at leastone control script which is fed back by the server and corresponds to the manufacturer identifier; and executing the control script, and sending a control instruction to the wireless routing device, the control instruction being used for instructing the wireless routing device to modify the channel of the WiFi network. According to the embodiment of the invention, the process of modifying the channel is simplified, and the efficiency of modifying the channel is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
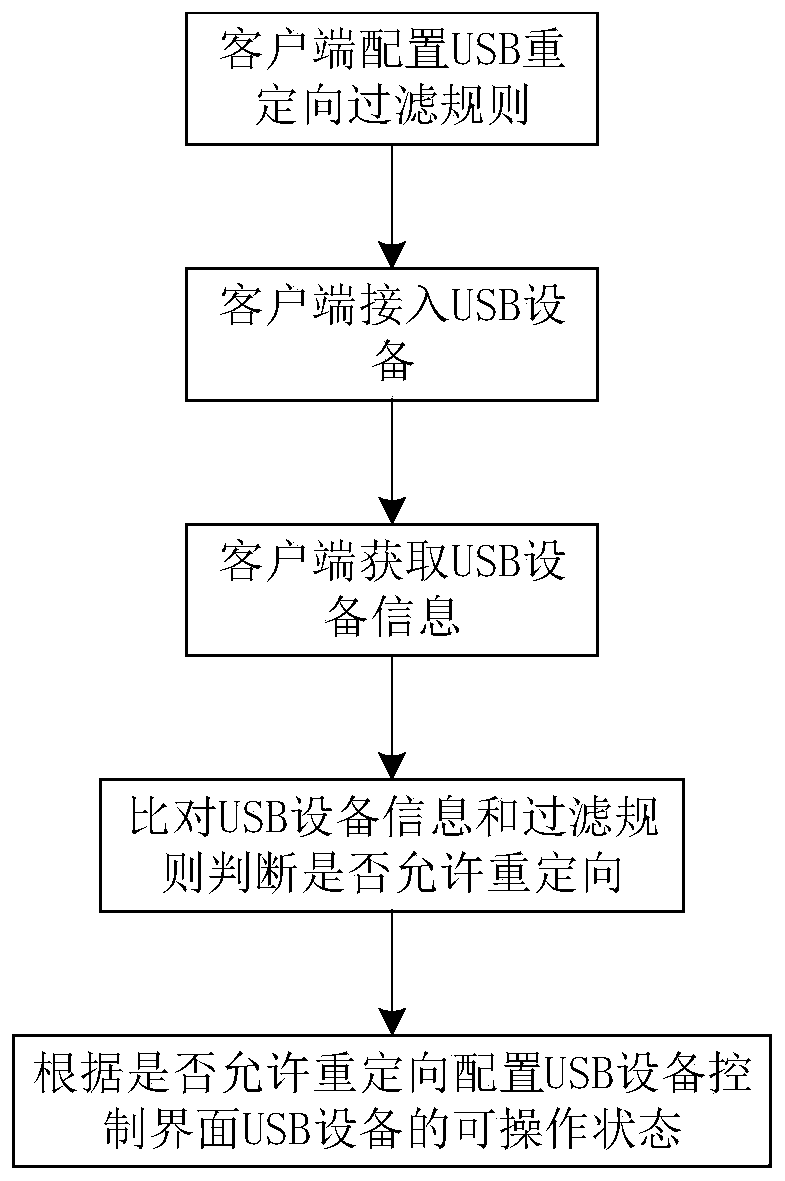
USB redirection filtering method based on cloud desktop
The invention discloses a USB redirection filtering method based on a cloud desktop. The method comprises the following steps: 1) configuring a USB redirection filtering rule at a client; 2) the client identifying the accessed USB equipment and acquiring USB equipment information; wherein the USB equipment information comprises a USB equipment type, a manufacturer identifier, a product identifierand a product description; 3) the client program performing rule comparison according to the configured USB filtering rule and the accessed USB equipment information; 4) if the USB equipment meets thepermission rule, allowing the USB equipment to be redirected to the cloud desktop, and 5) for the USB equipment allowed to be redirected, the client supporting the user to select redirection to the cloud desktop or uninstalling the local equipment serving as the client from the cloud desktop after selection is canceled according to the selection of the user. According to the method, the USB equipment redirected to the cloud desktop can be accurately controlled, and a redirection filtering function is provided for all the USB equipment.
Owner:YANGTZE OPTICAL FIBRE & CABLE CO LTD
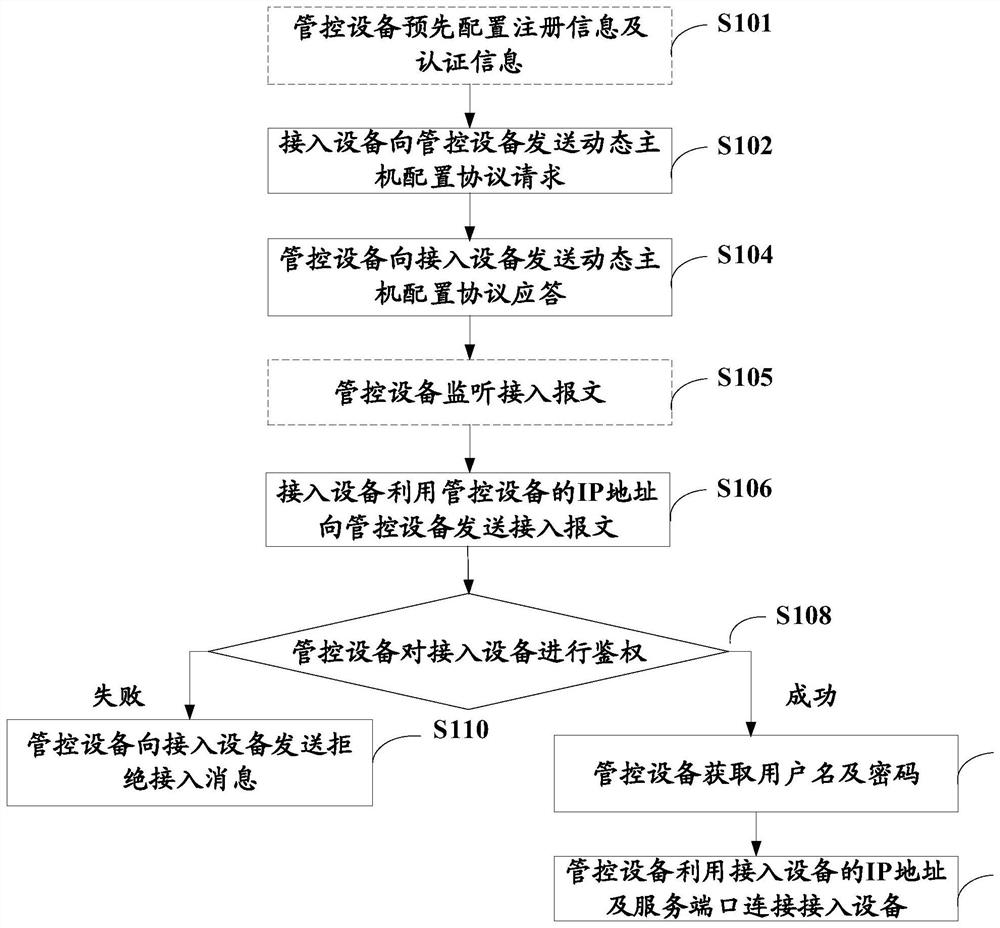
Equipment connection method, system, equipment and computer readable storage medium
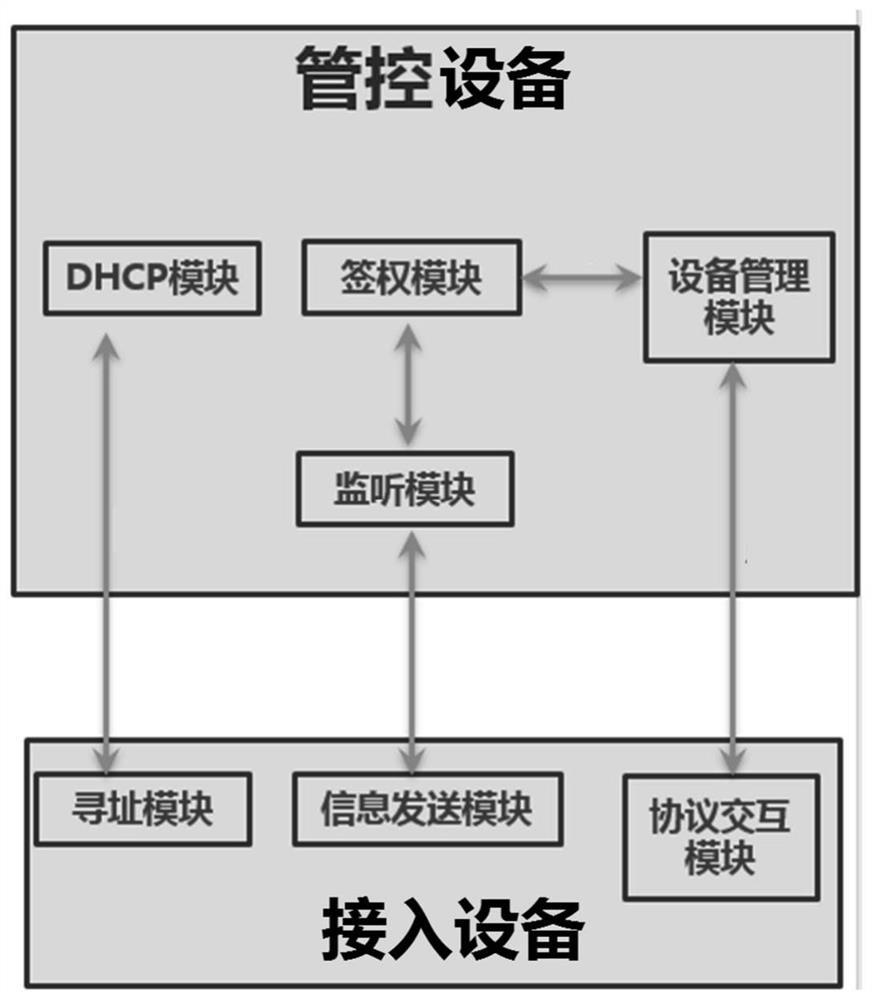
ActiveCN112929188AImplement auto-discoveryRealize automatic authenticationData switching networksIp addressPassword
The invention provides an equipment connection method, a system, a equipment and a computer readable storage medium, and relates to the technical field of equipment management. The equipment connection method comprises the following steps: an access equipment sends a dynamic host configuration protocol request to a management and control equipment; the management and control equipment sends a dynamic host configuration protocol response to the access equipment; the access equipment sends an access message to the management and control equipment by using the IP address of the management and control equipment; the management and control equipment authenticates the access equipment according to the manufacturer identifier, the equipment model and the unique equipment identifier which are configured in advance; under the condition that the authentication is successful, the management and control equipment queries pre-configured authentication information by utilizing the authentication identifier and the manufacturer identifier, and obtains a user name and a password; and the management and control equipment is connected with the access equipment by using the IP address and the service port of the access equipment. According to the invention, the automatic discovery, automatic authentication and automatic authentication of the access equipment are realized, the access equipment can be configured quickly and automatically, and the access safety of the equipment can be improved.
Owner:CHINA TELECOM CORP LTD
Systems and methods using an origin pattern to verify the authenticity of a host object
InactiveCN105069623AReduce resource consumptionCharacter and pattern recognitionCoding/ciphering apparatusGraphicsData store
Systems and methods use an origin pattern to verify the authenticity of a host object. The origin pattern includes a text-based serial number and a computer-graphics based surface-texture component. The serial number includes a public manufacturer identifier and an object identifier sequence that is based on a hash of a private manufacturer identifier and a private object identifier. The surface-texture component includes a two dimensional texture mapped onto a three dimensional surface, the generation of the surface being based on the hash. In response to an authentication request for an origin pair, the system may verify the serial number component exists in a data store and generate a challenge surface-texture component based on data in the data store. If the challenge surface-texture component matches, the system may use a time-location stamp to determine an authenticity probability and provide an indication of authenticity in response to the verification request.
Owner:ENCELADUS IP HLDG
Security test method and device for voice service equipment
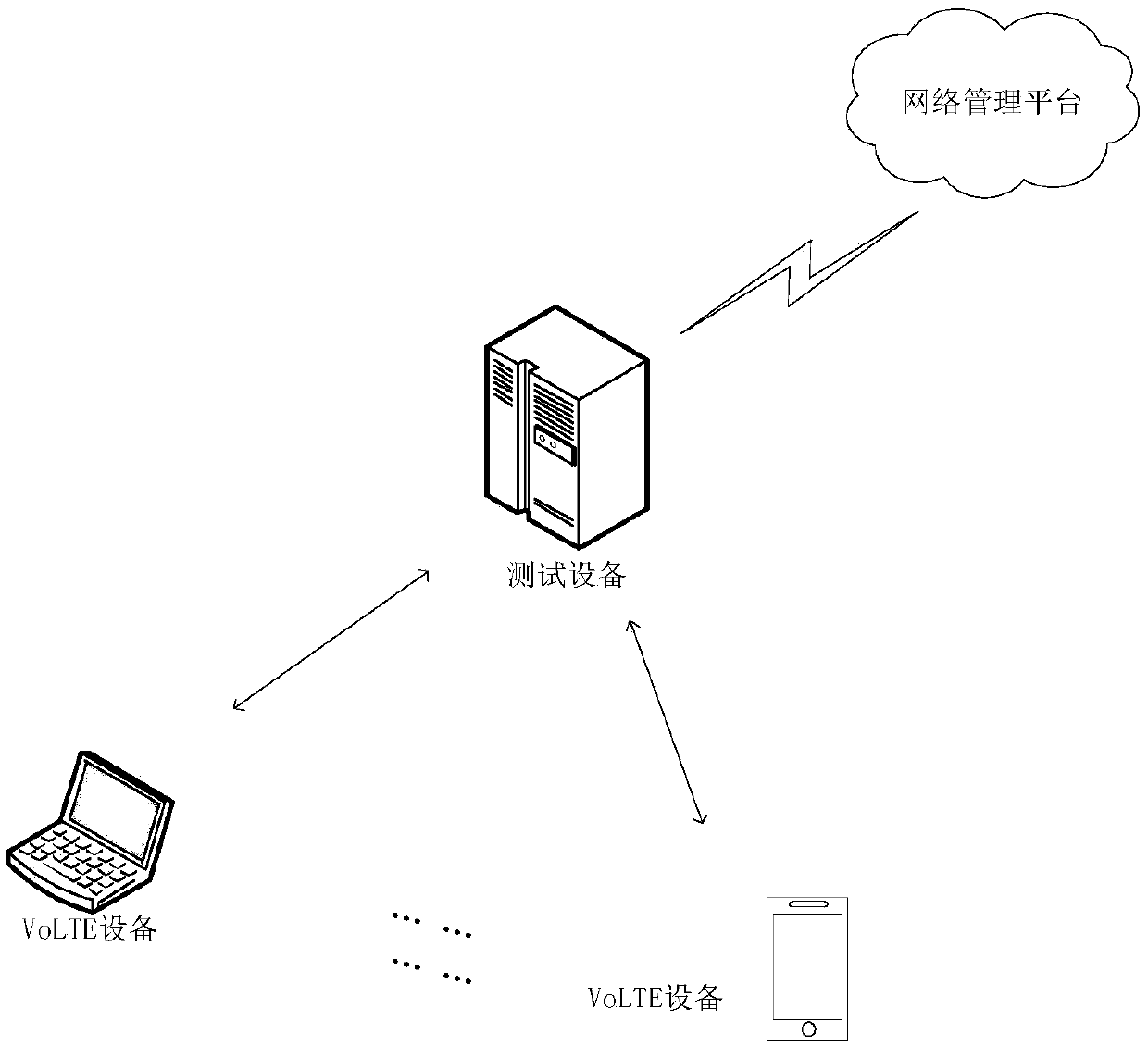
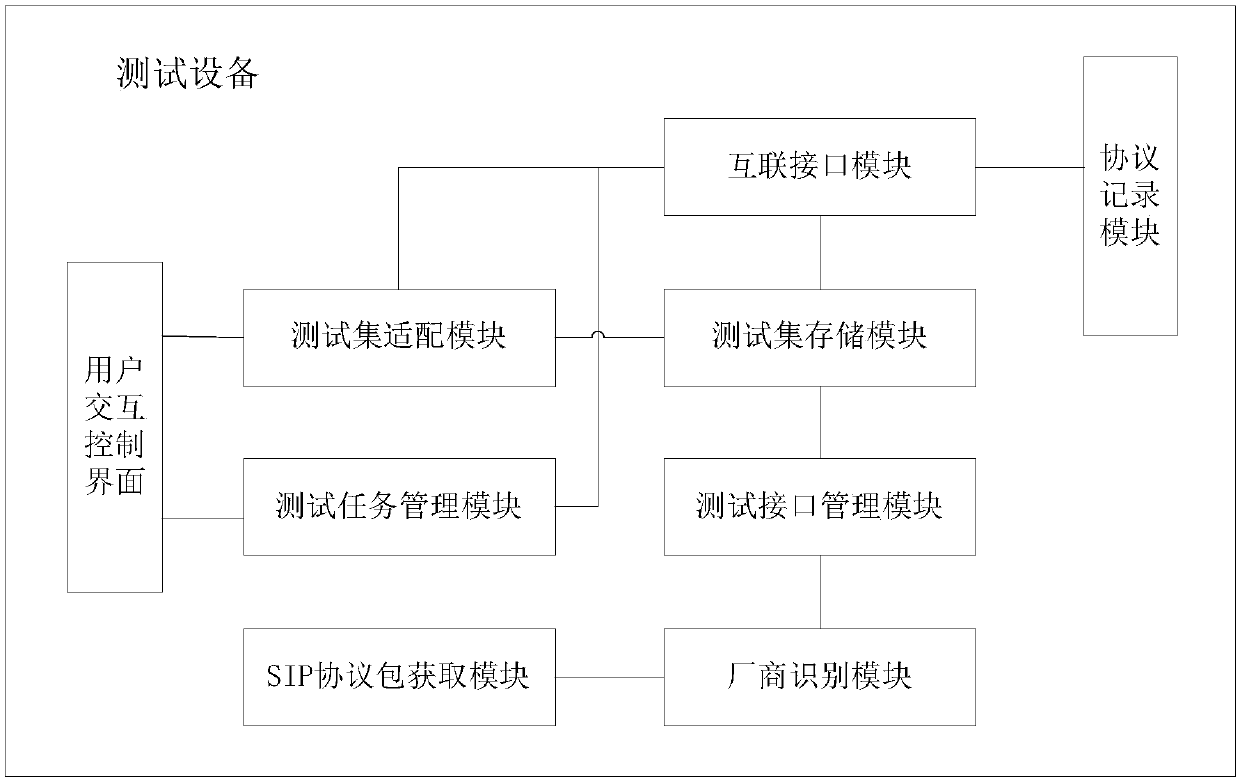
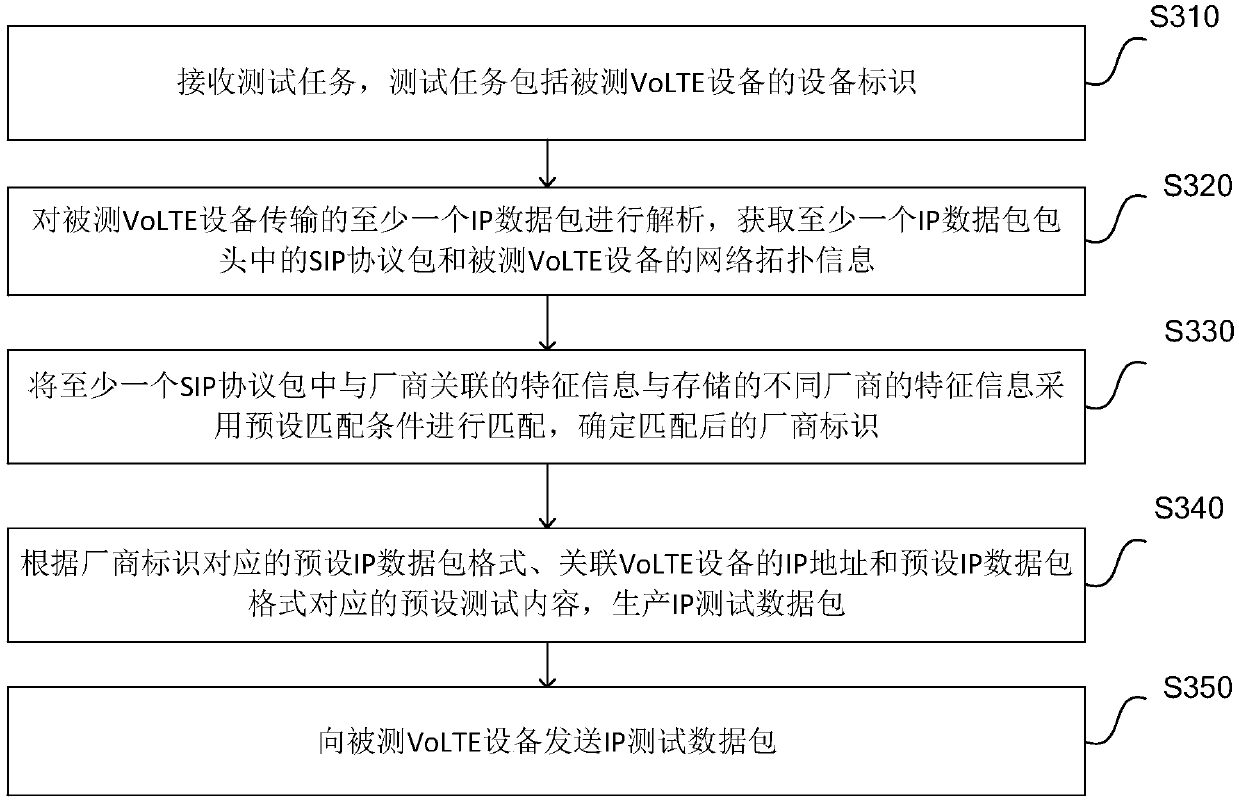
ActiveCN111277449AImprove test efficiencySolve the untestableData switching networksData packTelecommunications
The invention discloses a security test method and device for voice service equipment. The method comprises the following steps: analyzing at least one IP data packet transmitted by VoLTE equipment ofa tested voice service in a received test task; after obtaining an SIP protocol packet in the at least one IP data packet header and network topology information of the tested VoLTE equipment, matching the feature information associated with the manufacturer in the at least one SIP protocol packet with stored feature information of different manufacturers by adopting a preset matching condition,and determining a matched manufacturer identifier; and according to a preset IP data packet format corresponding to the manufacturer identifier, associating the IP address of the VoLTE equipment witha preset test content corresponding to the preset IP data packet format, generating an IP test data packet, and sending the IP test data packet to the tested VoLTE equipment. Therefore, the method canimprove the test efficiency.
Owner:中国移动通信集团广西有限公司 +1
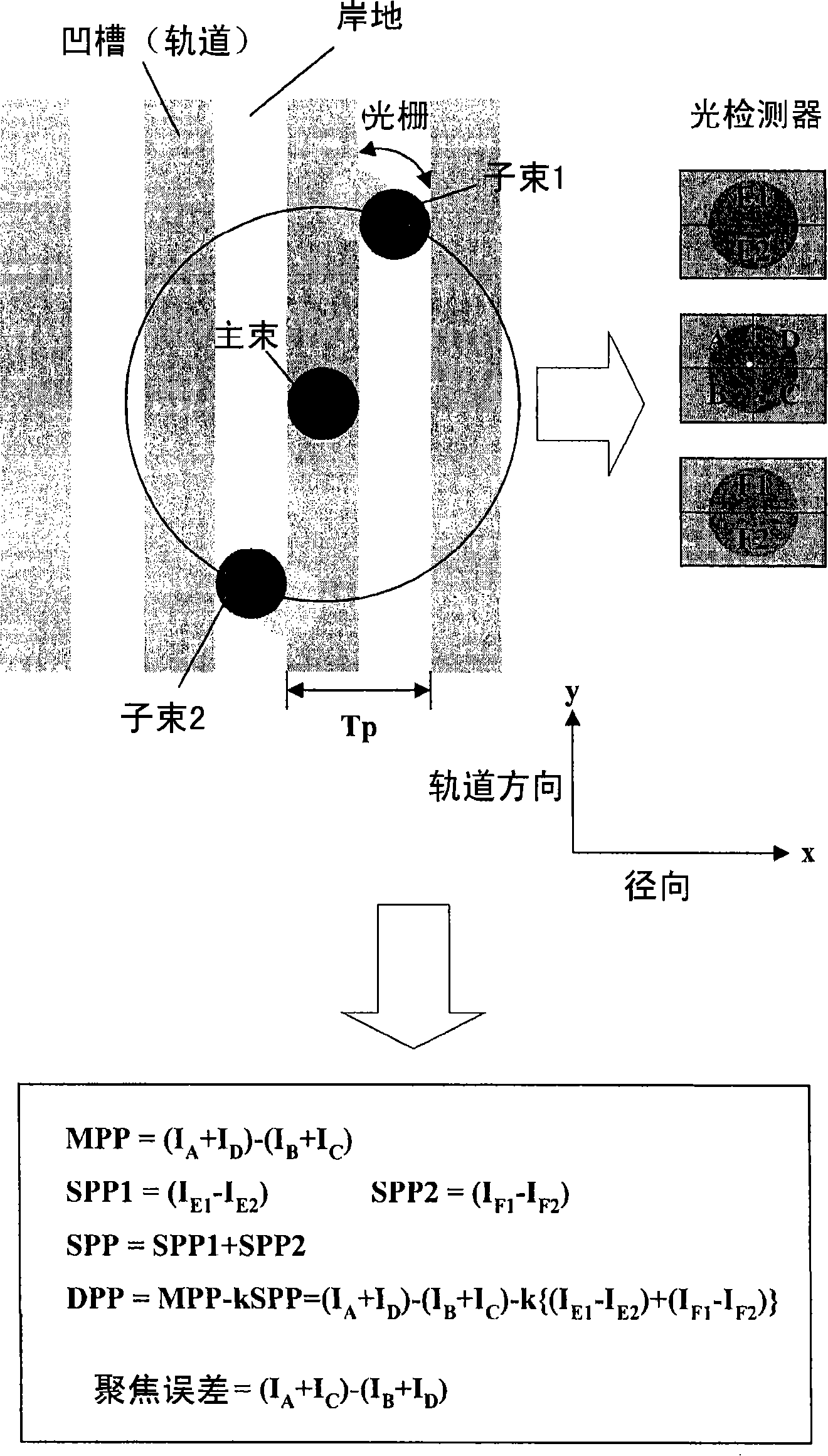
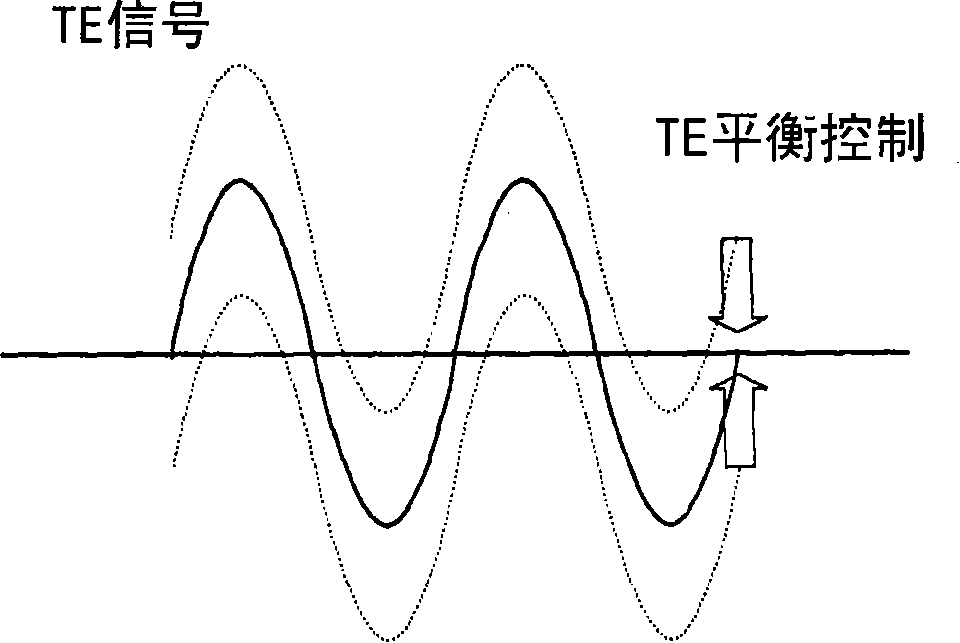
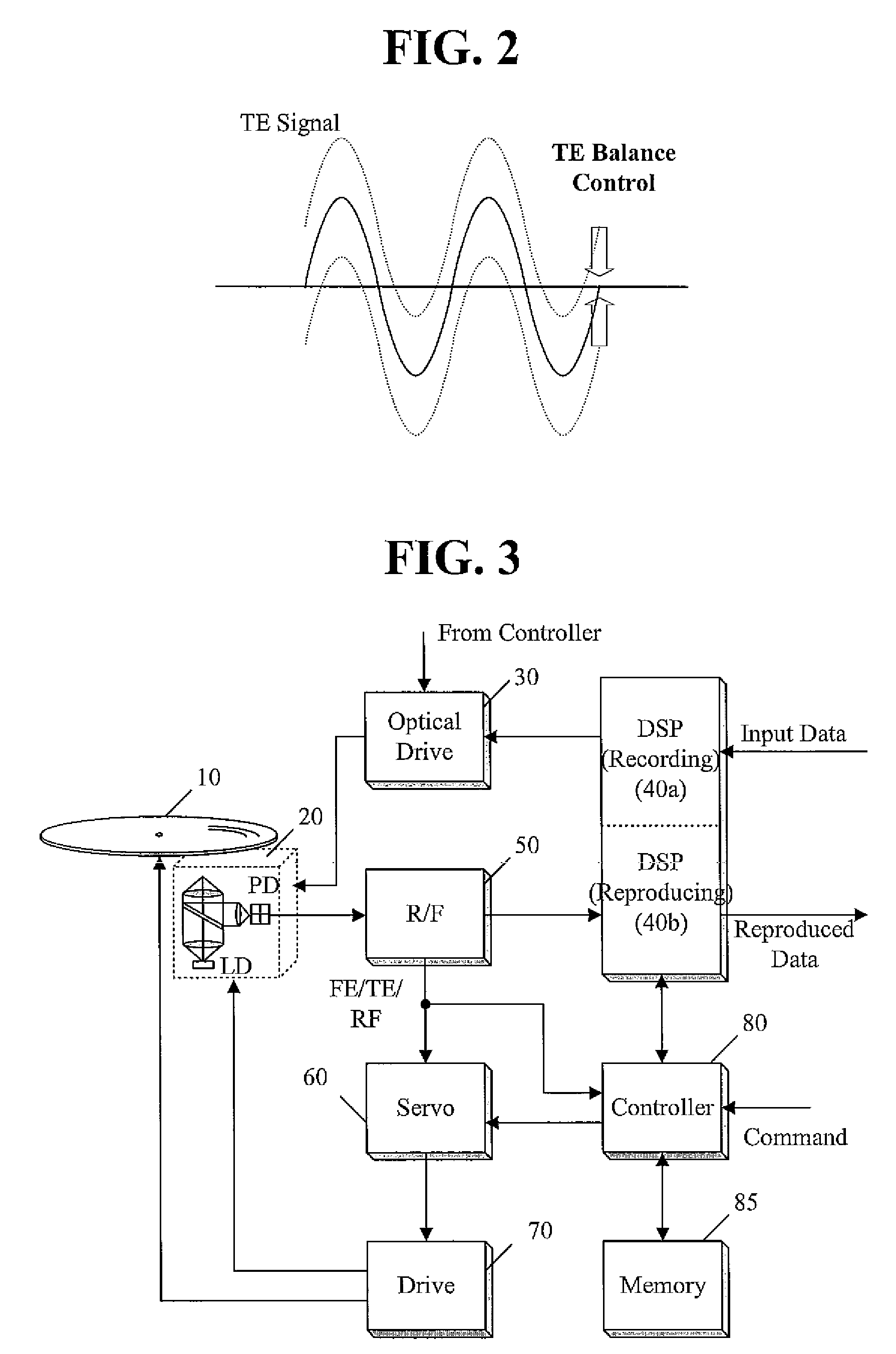
Apparatus and method for controlling tracking error balance in optical disc apparatus
A method of controlling a tracking error balance in an optical disc apparatus, and the optical disc apparatus are discussed. In an embodiment of the present invention, when a tracking error balance for writing is controlled, a beam power that is appropriate for the writing characteristics of an optical disc is applied. The beam power can be determined based on the Manufacturer Identifier (MID) of the optical disc and writing power information for different MIDs. The beam power can be determined to be a value of 20 to 50% of the prestored writing power for the MID of the optical disc.
Owner:LG ELECTRONICS INC
Apparatus and method for controlling tracking error balance in optical disc apparatus
ActiveUS20080123488A1Combination recordingDisposition/mounting of recording headsLight beamEngineering
A method of controlling a tracking error balance in an optical disc apparatus, and the optical disc apparatus are discussed. In an embodiment of the present invention, when a tracking error balance for writing is controlled, a beam power that is appropriate for the writing characteristics of an optical disc is applied. The beam power can be determined based on the Manufacturer Identifier (MID) of the optical disc and writing power information for different MIDs. The beam power can be determined to be a value of 20 to 50% of the prestored writing power for the MID of the optical disc.
Owner:LG ELECTRONICS INC
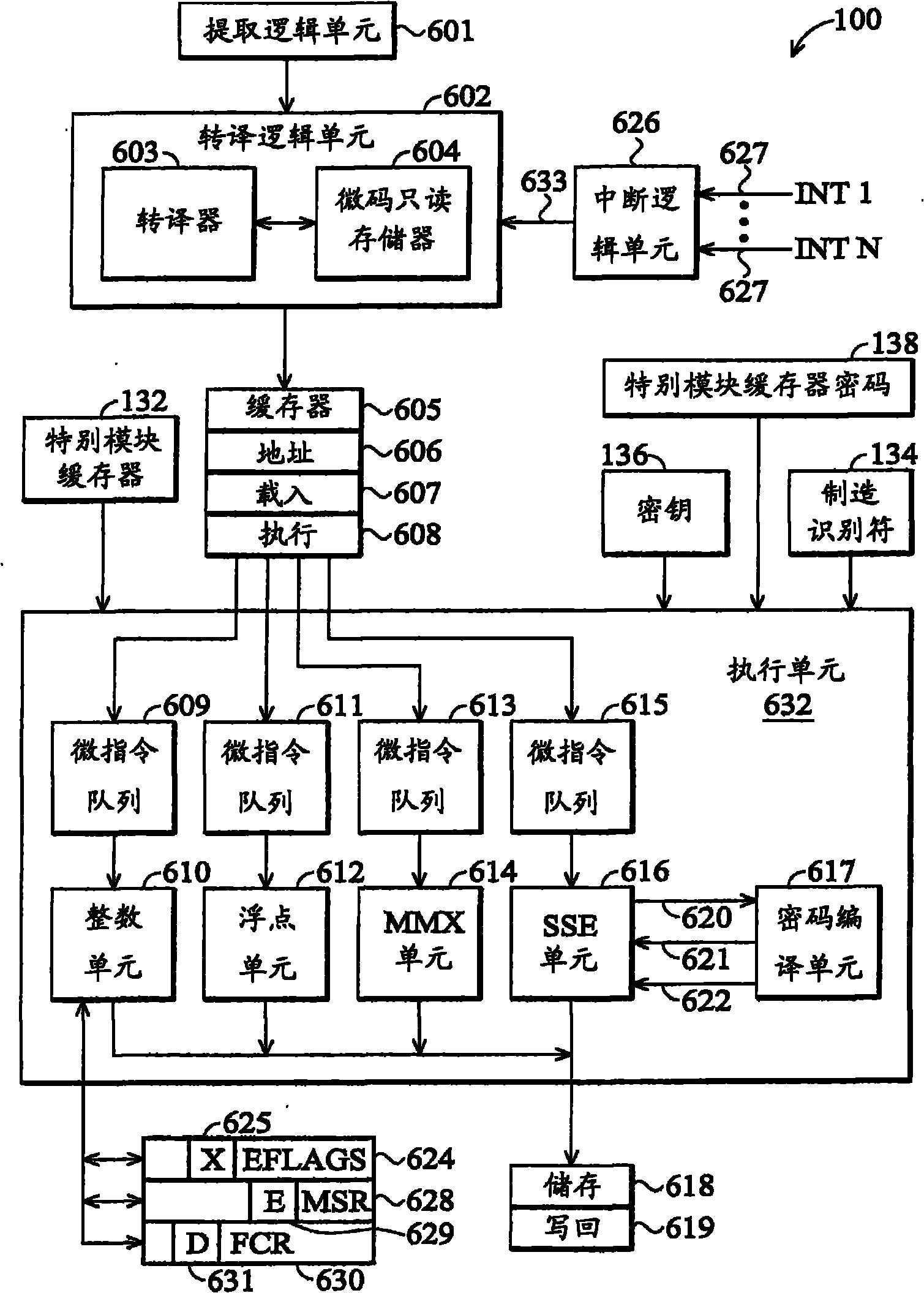
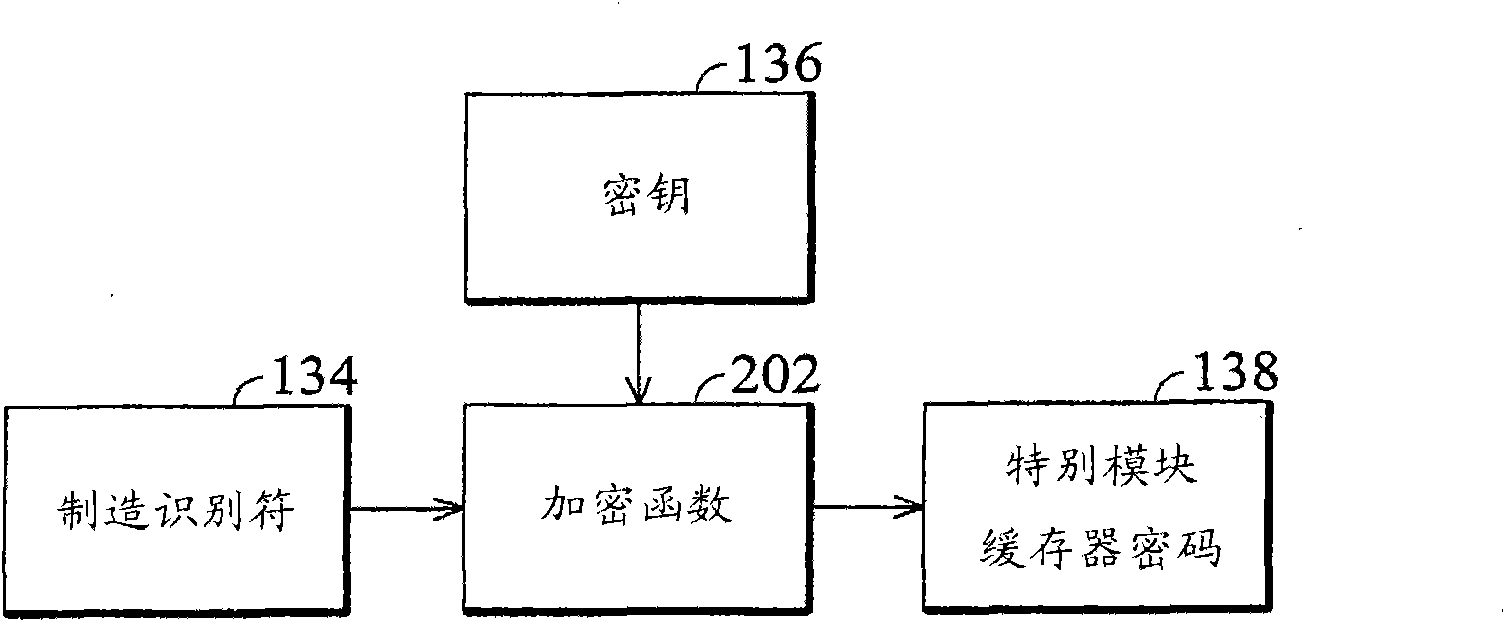
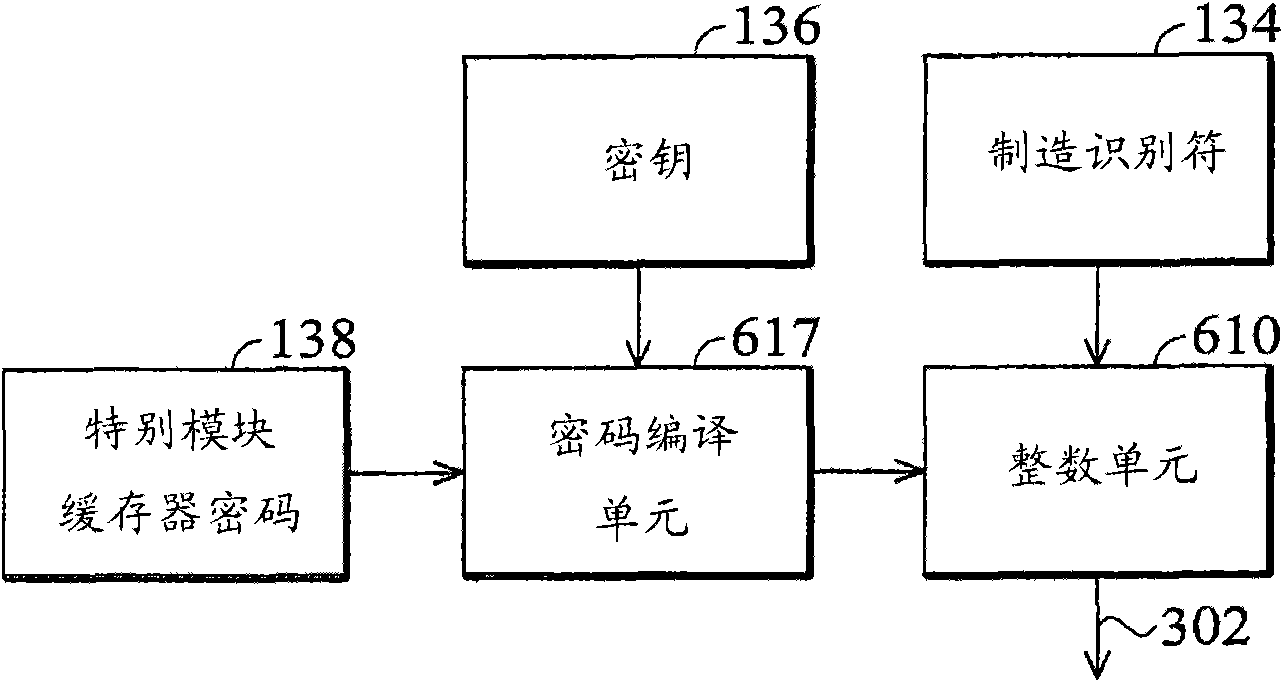
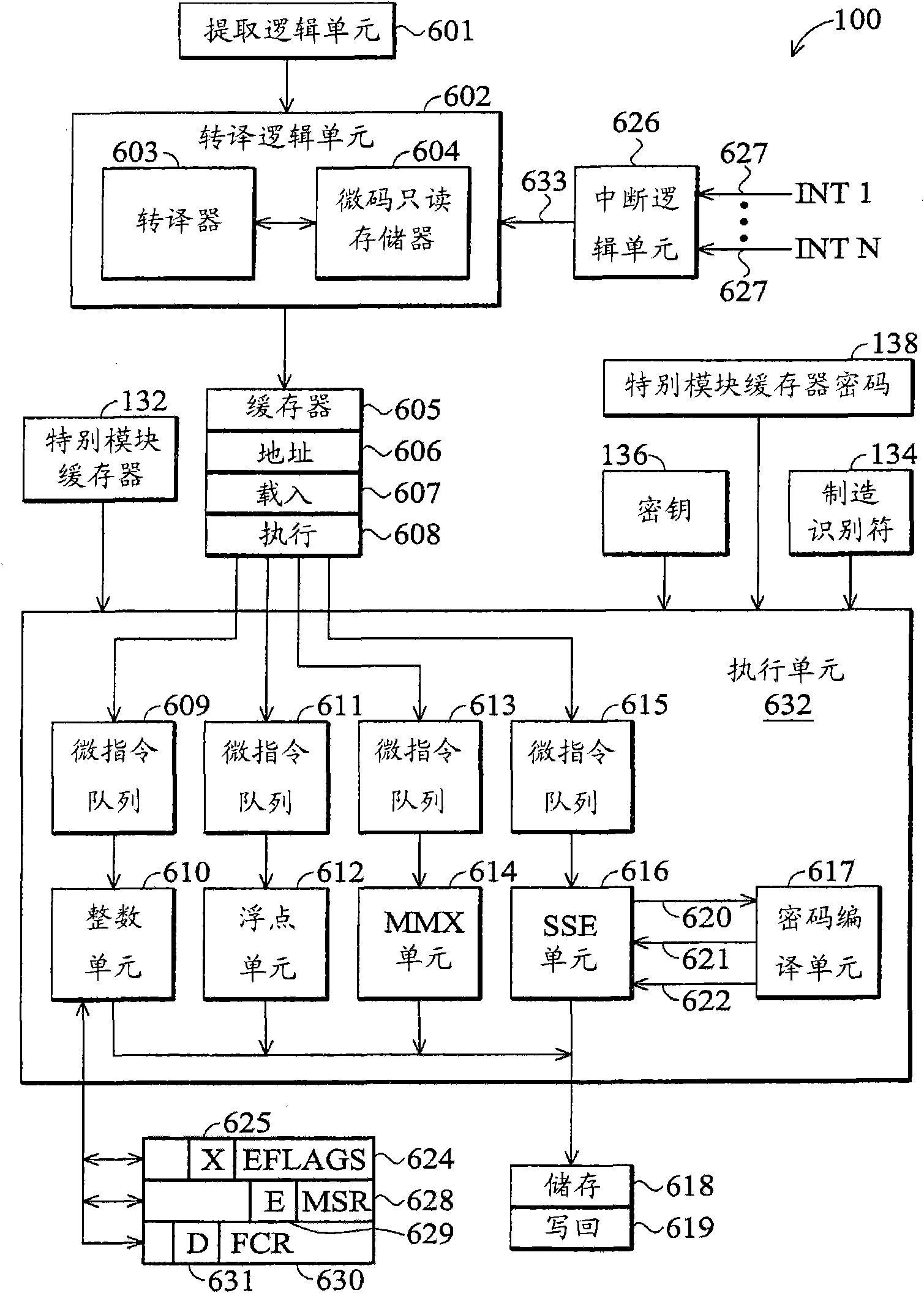
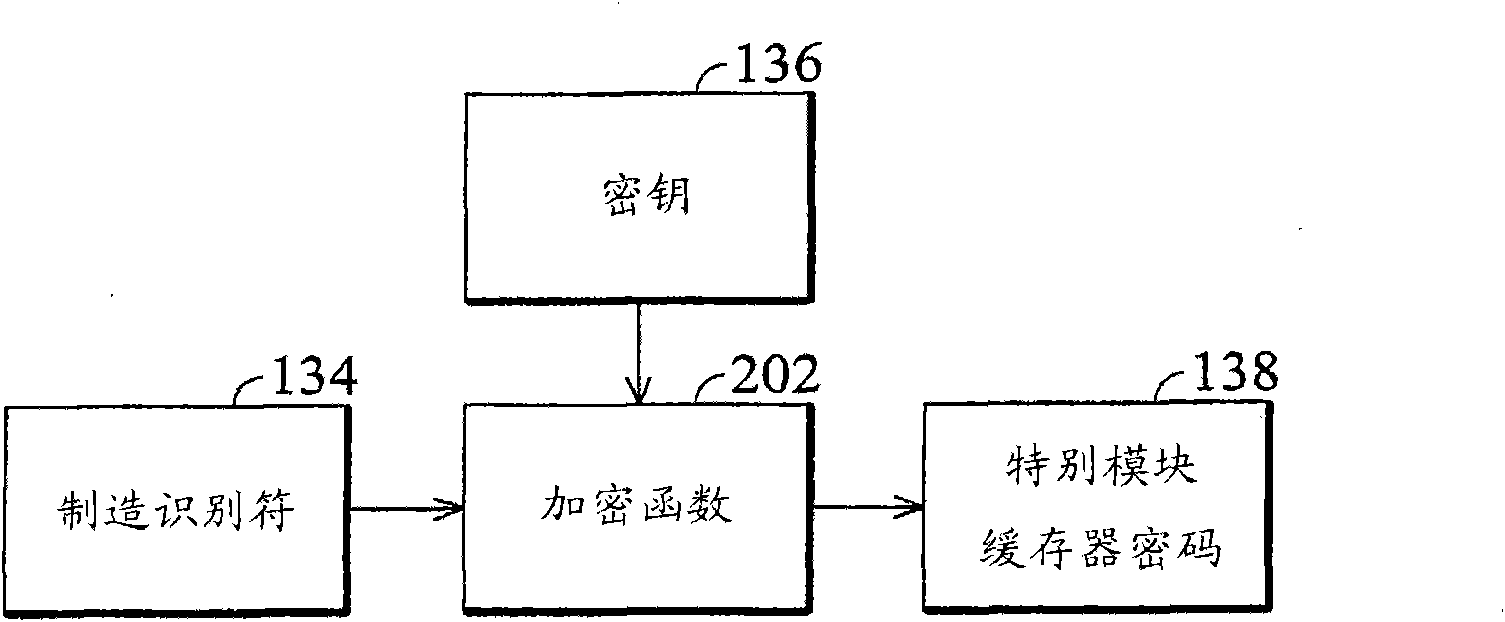
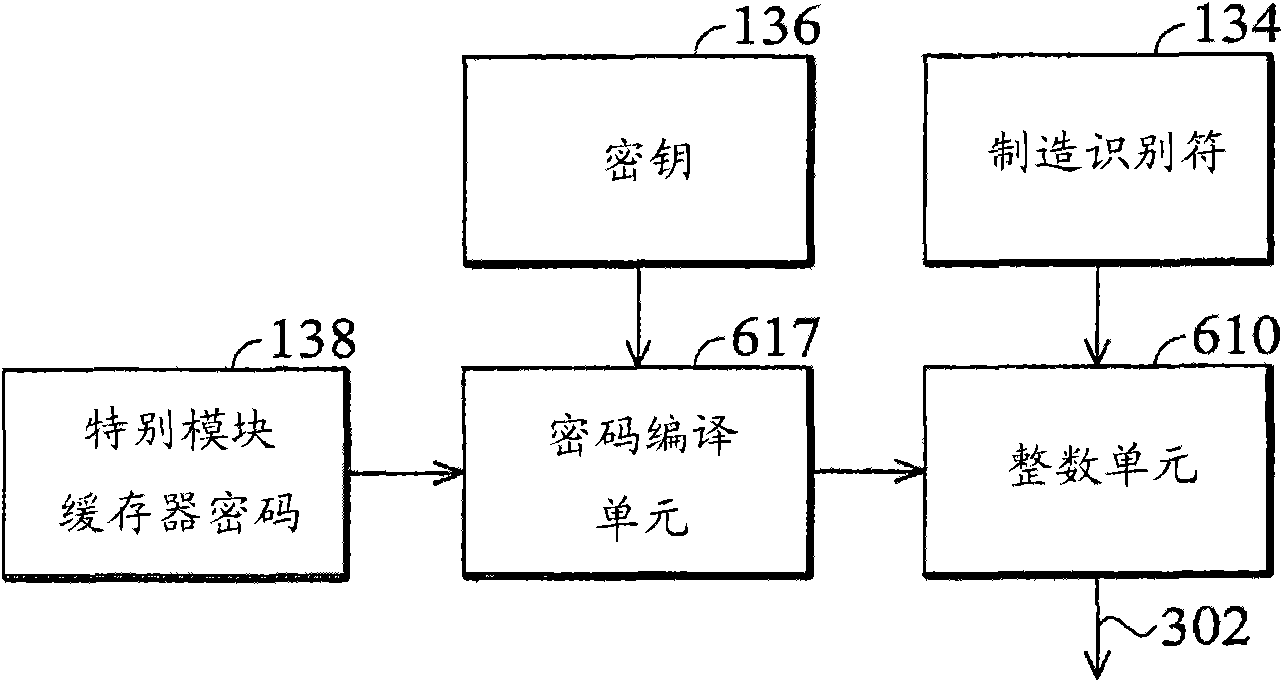
Microprocessor and method for limiting access
A microprocessor is provided with a control cache for a manufacturer to limit access. A manufacturer identifier is arranged for identifying the manufacturer. A user can read the manufacturer identifier from the exterior of the microprocessor. A key is arranged inside the microprocessor and can not be seen from outside. Corresponding to an order of the user, an encrypting engine is arranged for decoding a password provided by the user through the key, so as to generate a decoding result. The order of the user indicates the microprocessor to access the control cache and the password provided bythe user is specific to the microprocessor. When the decoding result contains the manufacturer identifier, an execution unit allows the order of the user to access the control cache, or refuses.
Owner:VIA TECH INC
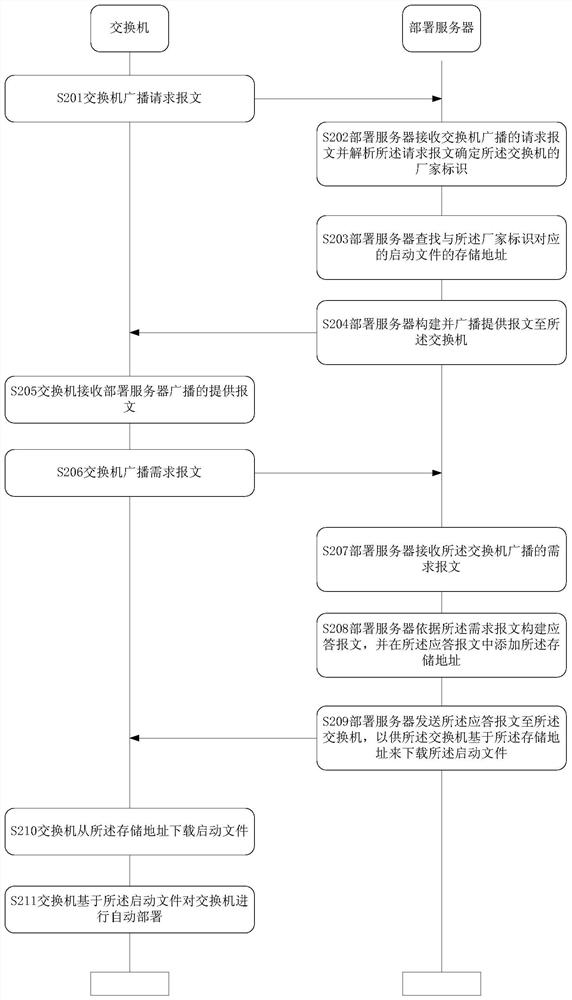
Switch automatic deployment method, device and system
The invention provides a switch automatic deployment method, device and system. The switch automatic deployment method comprises the following steps of: receiving a request message broadcasted by a switch and analyzing the request message to determine a manufacturer identifier of the switch; searching a storage address of a startup file corresponding to the manufacturer identifier; constructing and broadcasting a providing message to the switch; receiving a demand message broad-casted by the switch; constructing a response message according to the demand message, and adding a storage address into the response message; and sending the response message to the switch, so that the switch downloads the startup file based on the storage address. According to the switch automatic deployment method, a single deployment server can be adopted, and the purpose of automatically deploying the startup files of switches of different manufacturers is simply and conveniently achieved.
Owner:UCLOUD TECH CO LTD
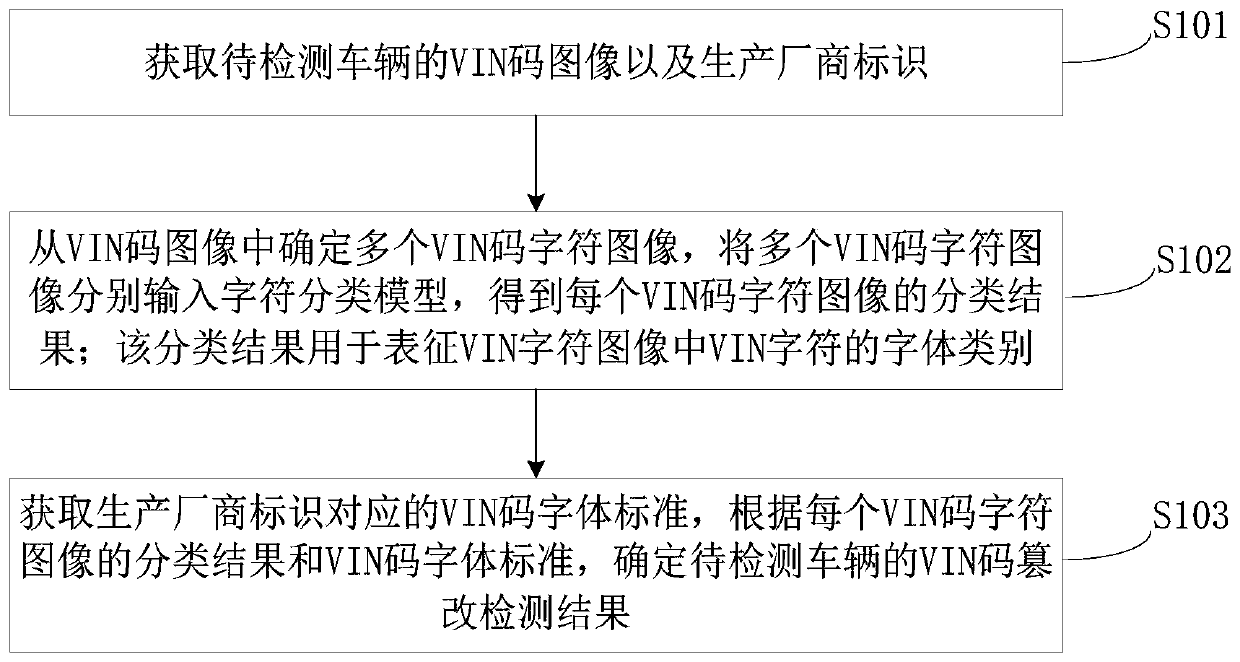
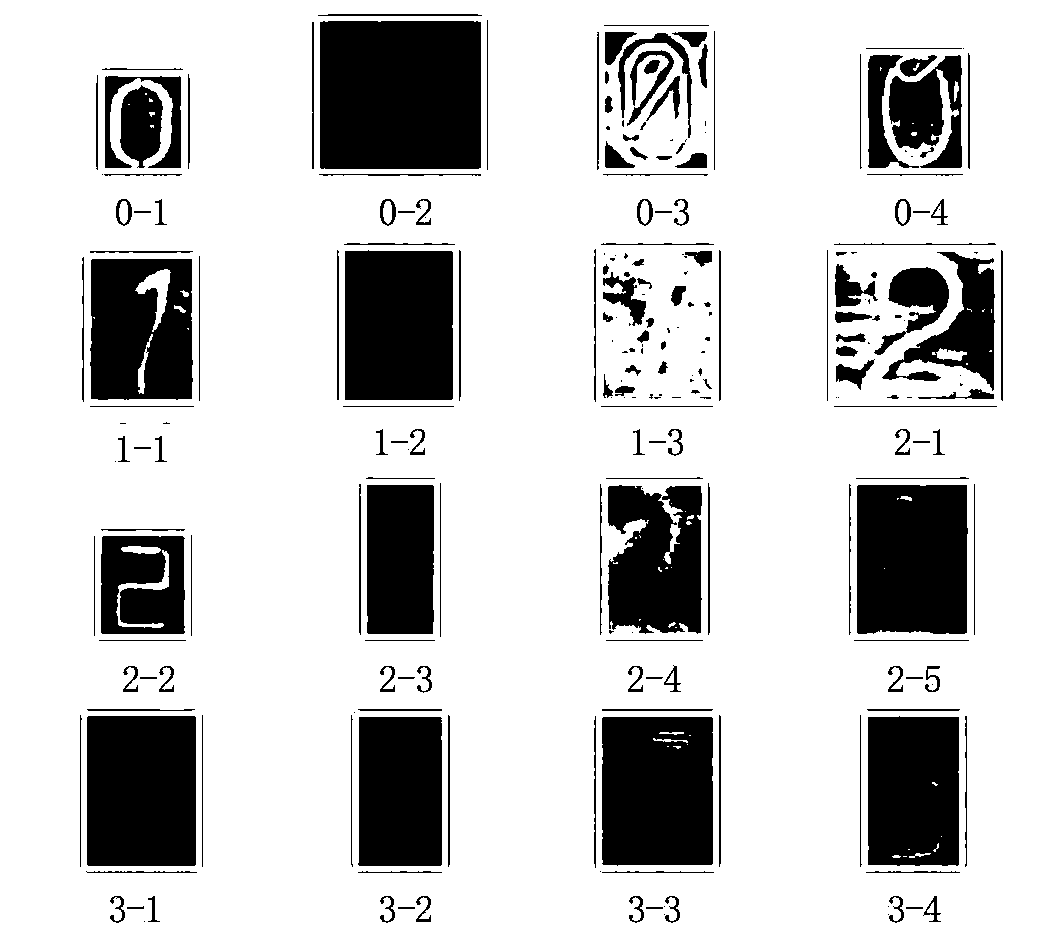
Vehicle VIN code tampering detection method and device, equipment and storage medium
PendingCN111401362AImprove accuracyImprove efficiencyCharacter recognitionAlgorithmReliability engineering
The invention relates to a vehicle VIN code tampering detection method and device, equipment and a storage medium. The method comprises the steps of obtaining a VIN code image and a manufacturer identifier of a to-be-detected vehicle; determining a plurality of VIN code character images from the VIN code images, and respectively inputting the plurality of VIN code character images into a characterclassification model to obtain a classification result of each VIN code character image, wherein the classification result is used for representing the font type of the VIN character in the VIN character image; and obtaining a VIN code font standard corresponding to the manufacturer identifier, and determining a VIN code tampering detection result of the to-be-detected vehicle according to the classification result of each VIN code character image and the VIN code font standard. According to the method, the VIN code tampering detection process can be completed only by acquiring the VIN code image of the to-be-detected vehicle and the manufacturer identifier, so that the method is wider in application range and higher in efficiency in an actual scene; and the VIN code character images areclassified by adopting the character classification model, so that the detection speed is greatly increased, and the accuracy of a detection result is also improved.
Owner:上海眼控科技股份有限公司
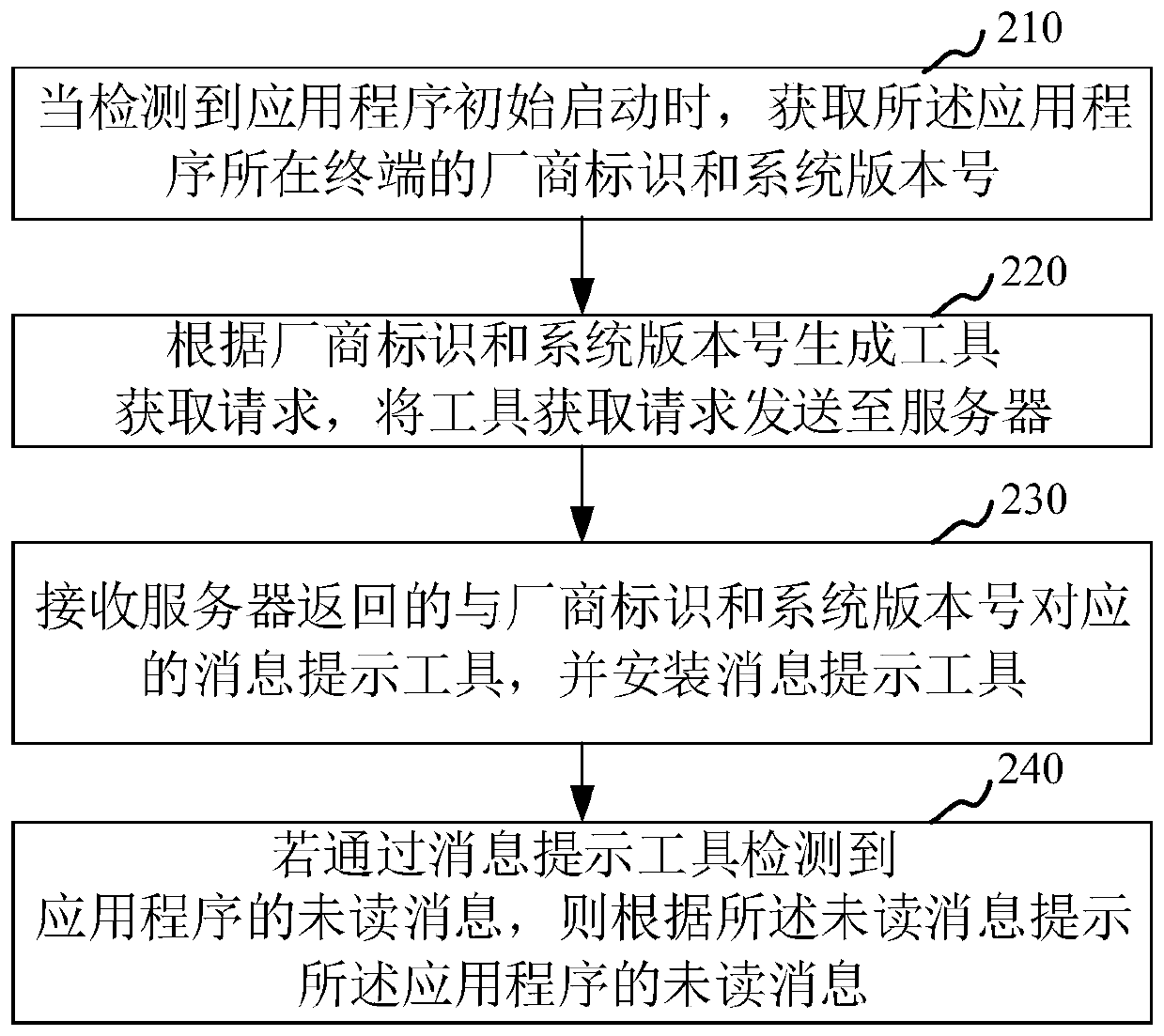
Unread message prompt implementation method and device, computer device and storage medium
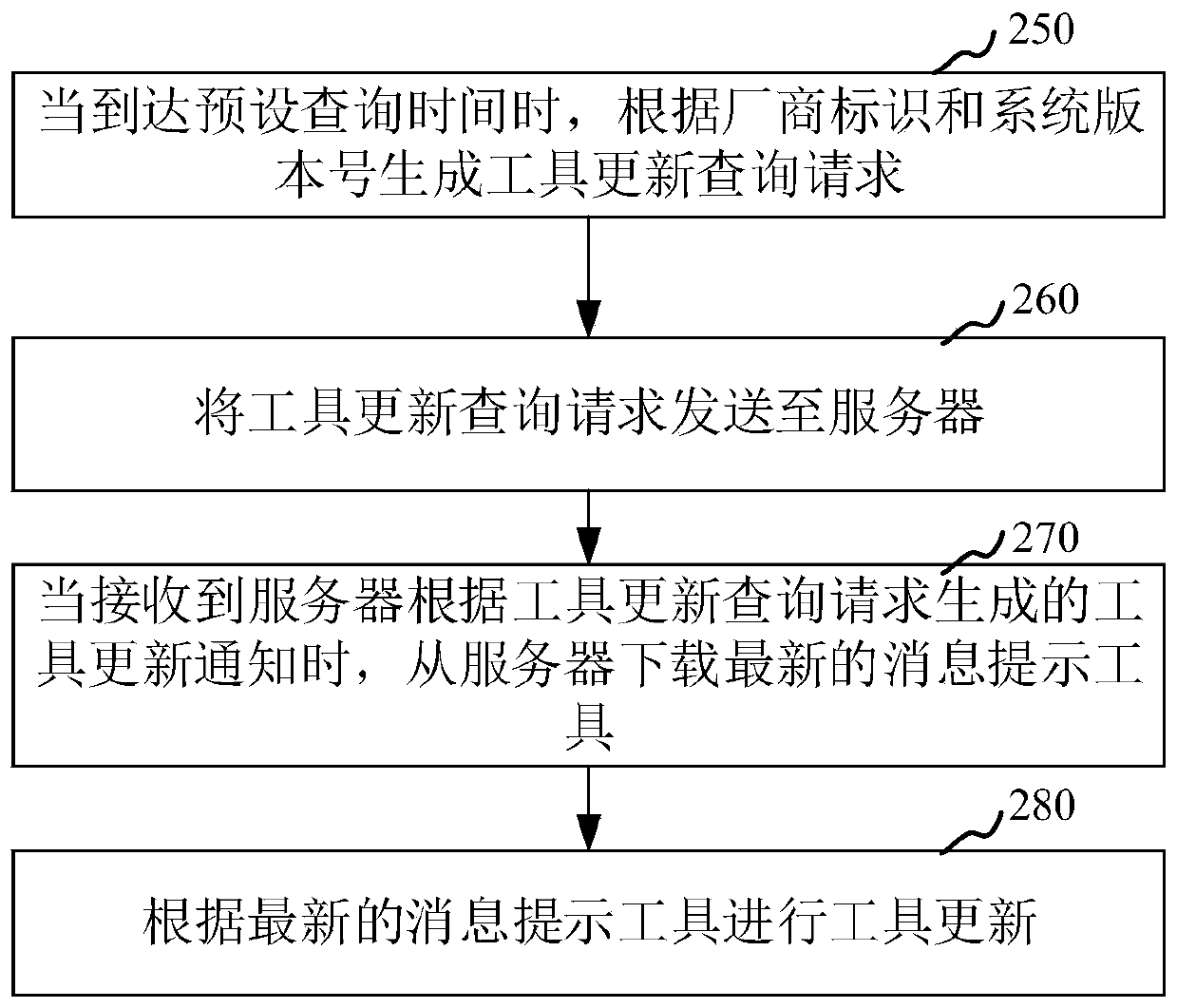
PendingCN110119276AMeet the needs of useReduce redundant codeData switching networksSoftware deploymentComputer terminalApplication software
The invention relates to the technical field of research and development optimization of mobile terminals, in particular to an unread message prompt implementation method and device, a computer deviceand a storage medium. The method comprises: when it is detected that an application program is started initially, obtaining a manufacturer identifier and a system version number of a terminal where the application program is located; generating a tool acquisition request according to the manufacturer identifier and the system version number, and sending the tool acquisition request to a server; receiving a message prompting tool which is returned by the server and corresponds to the manufacturer identifier and the system version number, and installing the message prompting tool; and if the unread message of the application program is detected through the message prompting tool, prompting the unread message of the application program according to the unread message. By adopting the method,the coverage rate of the unread message prompt function on the user terminal can be improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
An extensible IoT bottom device adapter and construction method
Owner:WUHAN HONGXIN TECH SERVICE CO LTD
Microprocessor and method for limiting access
ActiveCN101872297BUnauthorized memory use protectionInternal/peripheral component protectionPasswordExecution unit
A microprocessor is provided with a control cache for a manufacturer to limit access. A manufacturer identifier is arranged for identifying the manufacturer. A user can read the manufacturer identifier from the exterior of the microprocessor. A key is arranged inside the microprocessor and can not be seen from outside. Corresponding to an order of the user, an encrypting engine is arranged for decoding a password provided by the user through the key, so as to generate a decoding result. The order of the user indicates the microprocessor to access the control cache and the password provided bythe user is specific to the microprocessor. When the decoding result contains the manufacturer identifier, an execution unit allows the order of the user to access the control cache, or refuses.
Owner:VIA TECH INC
Set top box and remote diagnostic method thereof
The invention discloses a set top box, comprising a memory module, a detection module, a matching module and a diagnostic module, wherein, the memory module stores a first identifier and a first manufacturer identifier; the detection module detects whether diagnostic information is received or not from a remote server; the diagnostic information comprises a second identifier, a second manufacturer identifier and a position parameter of a diagnostic order; the matching module judges whether the second identifier and the second manufacturer identifier of the diagnostic information are respectively matched with the first identifier and the first manufacturer identifier or not; if so, the diagnostic module extracts the diagnostic order and executes the diagnostic order according to the position parameter of the diagnostic order. The invention also provides the remote diagnostic method of the set top box; the set top box provided by the implementation mode of the invention and the remote diagnostic method position the fault set top box singly through the identifier and the manufacturer identifier of the set top box, and can realize remote fault diagnosis.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
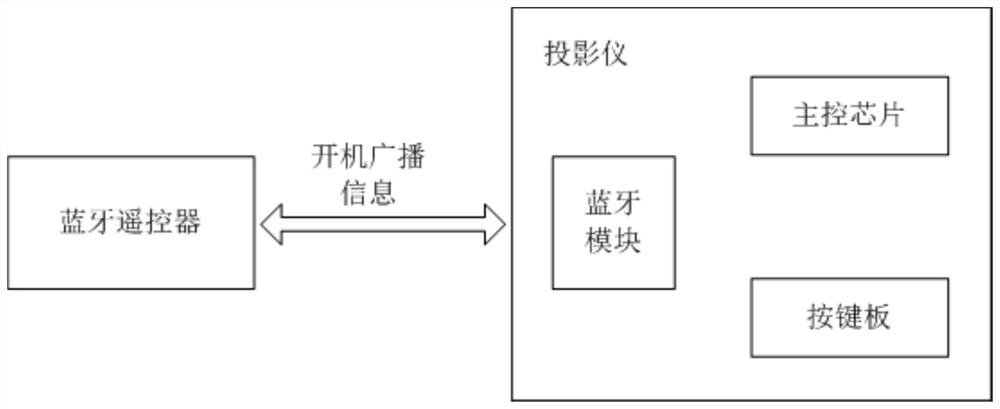
Projection interaction system
ActiveCN113284331AImproved cross-compatibilityError preventionTransmission systemsComputer hardwareEmbedded system
The invention discloses a projection interaction system. The interaction process of the projection interaction system comprises the steps that: a remote controller sends a Bluetooth pairing request to a projector, and a Bluetooth module of the projector completes the Bluetooth pairing connection with the remote controller based on the Bluetooth pairing request; the Bluetooth module of the projector transmits a pre-stored custom attribute to the remote controller in Bluetooth pairing connection through a GATT protocol; the remote controller receives the custom attribute and stores a chip manufacturer identifier in the custom attribute in a GATT transaction of the remote controller; the remote controller extracts the chip manufacturer identifier in the GATT transaction, synthesizes a power-on broadcast according to the chip manufacturer identifier, and broadcasts the power-on broadcast outwards as broadcast information; and when the Bluetooth module of the projector receives broadcast information and a main control chip successfully analyzes the broadcast information, a power button in the key board is triggered. The interactive compatibility of the remote controller relative to various projectors is improved.
Owner:杭州当贝网络科技有限公司
System and method for realizing authentication monitoring
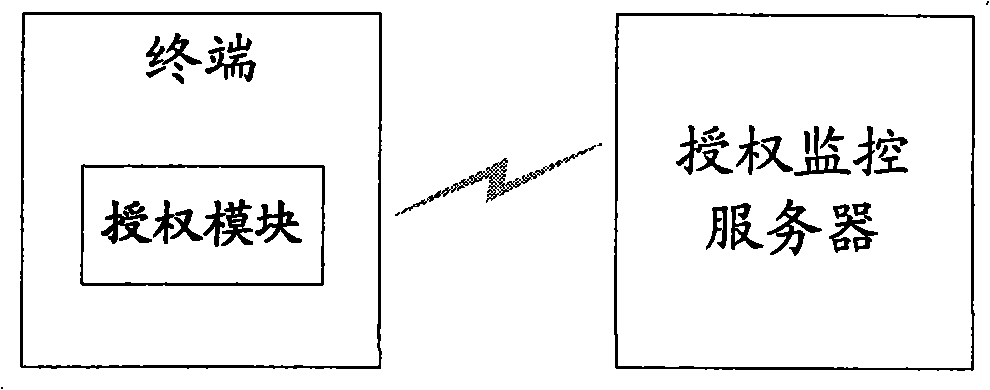
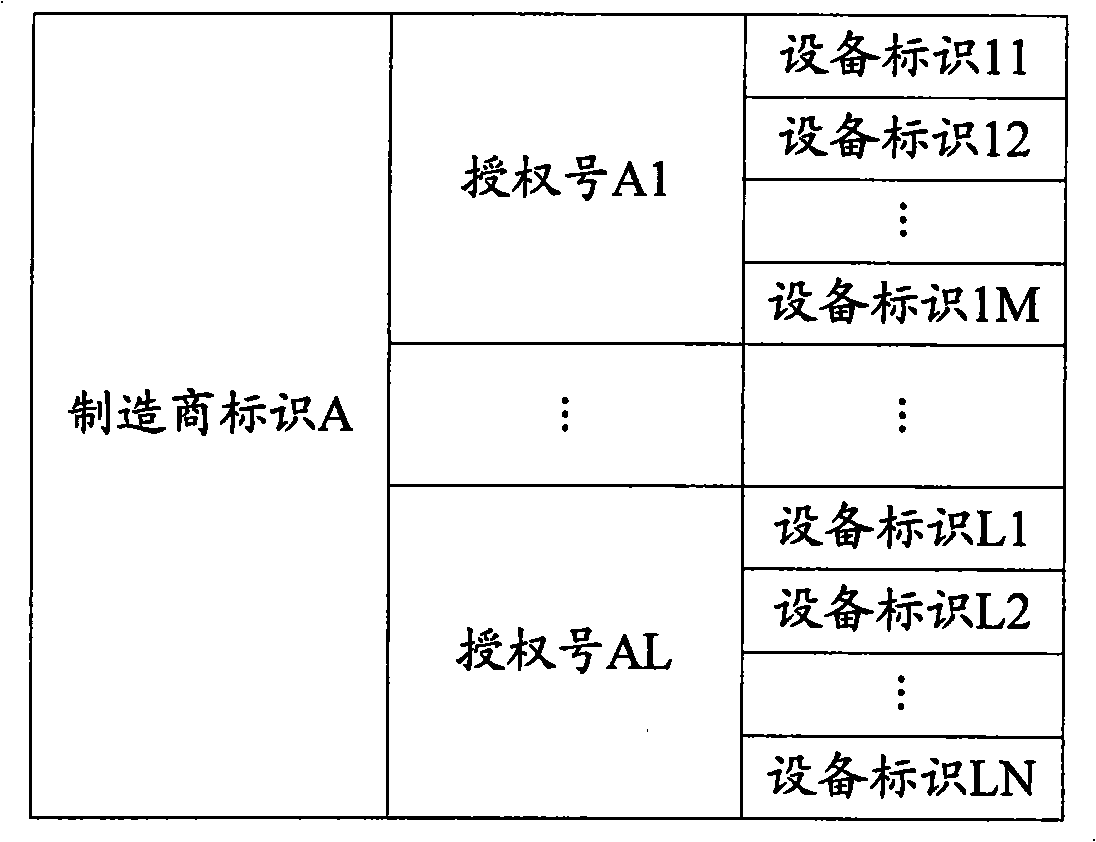
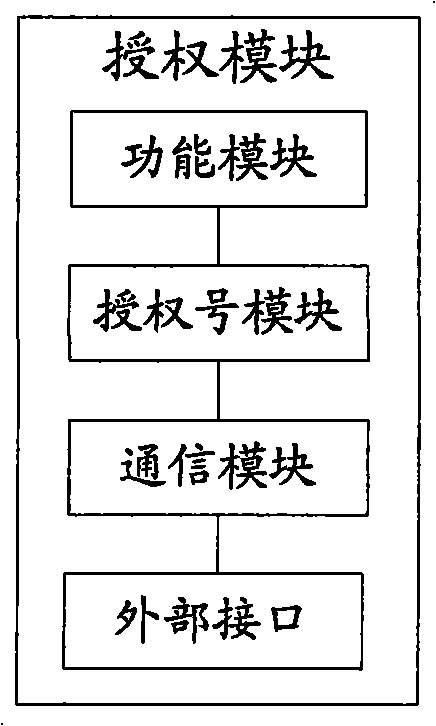
ActiveCN101938627BProtect intellectual propertyMonitor illegal infringementTransmissionSelective content distributionIntellectual propertyComputer terminal
The invention discloses a system and a method for realizing authentication monitoring. The method comprises the following steps that: a terminal transmits a manufacturer identifier, an authorization number and an equipment identifier of the terminal to an authentication monitoring server; the authentication monitoring server determines whether illegal infringement exists or not according to a comparison between the number of the equipment identifiers corresponding to the counted manufacturer identifiers and authentication numbers and an authentication range in a scheme for monitoring whether the authentication range is surpassed or not; and in a scheme for performing authentication monitoring on a specific terminal, the existence of the illegal infringement in a functional module corresponding to the equipment identifier is judged according to the manufacturer identifier and the authentication number and a limited use mark is transmitted to the terminal when limit on the use of the functional module is further determined according to a limit strategy if the illegal infringement exists. Therefore, the monitoring server can grasp the authentication situation of the functional module, effectively monitor an illegal infringement action, protect the intellectual property of the functional module owned by a terminal system manufacturer to the maximum extent, ensure healthy development of an industrial chain and promote the benign development of functional application.
Owner:北京中智润邦科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com