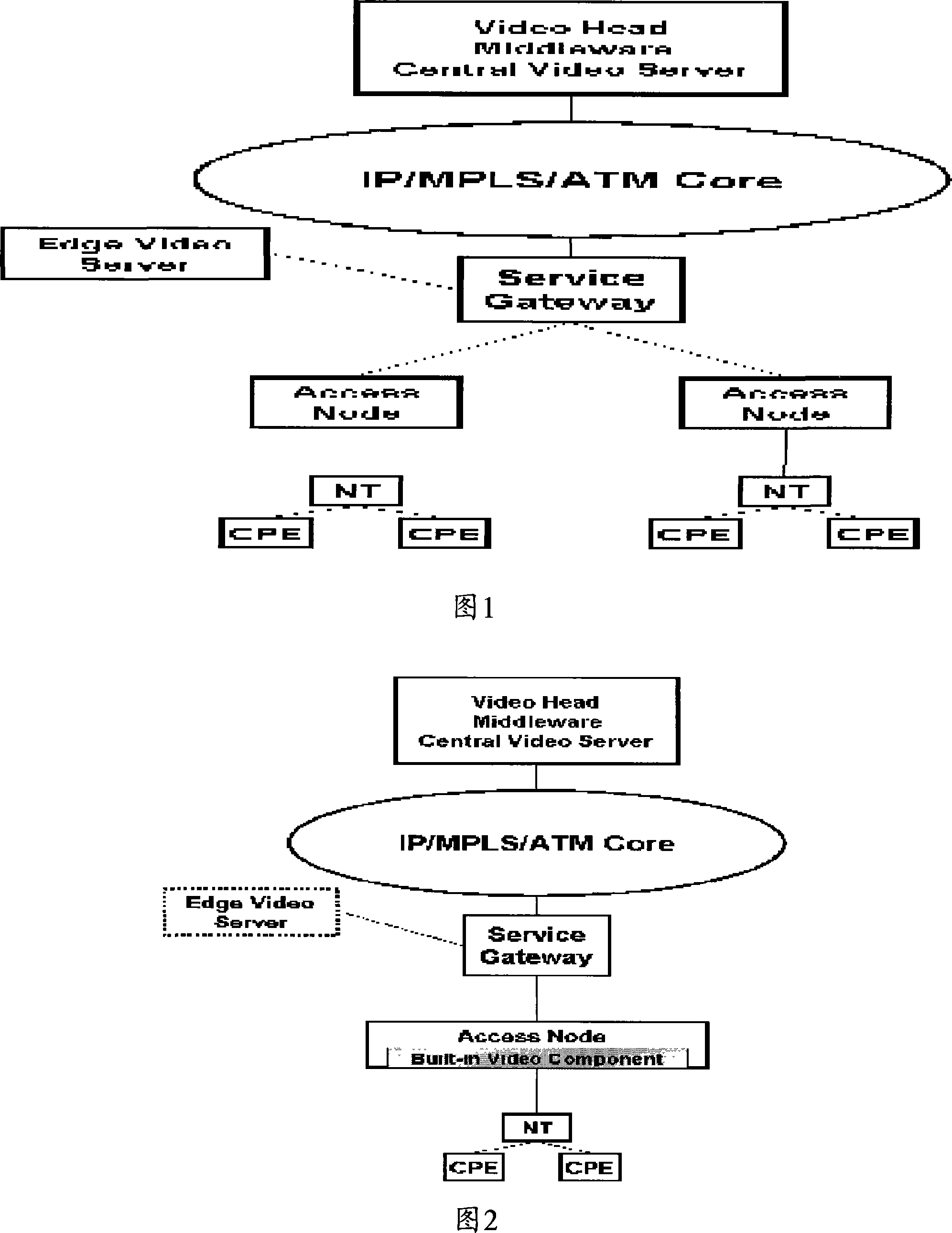
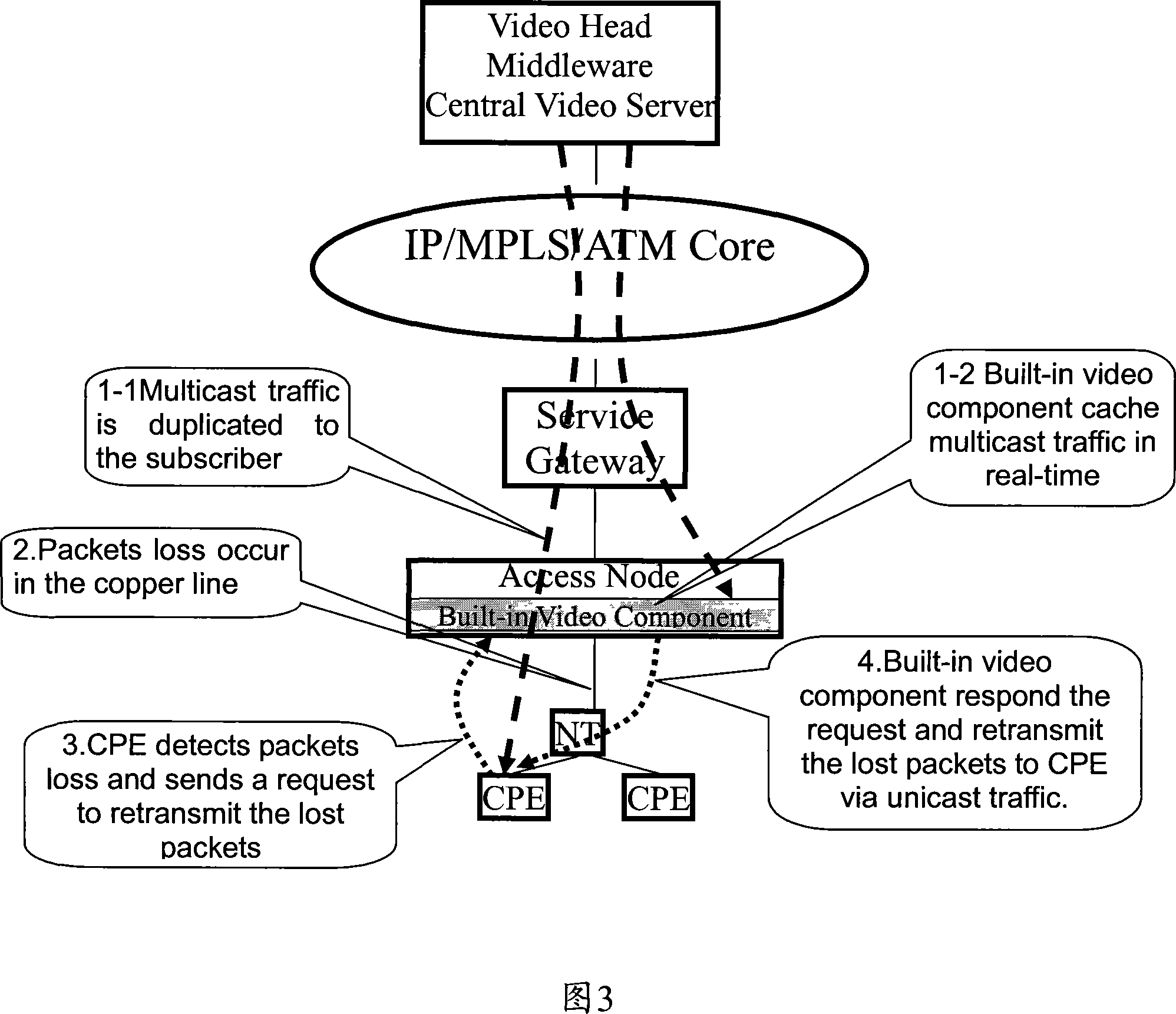
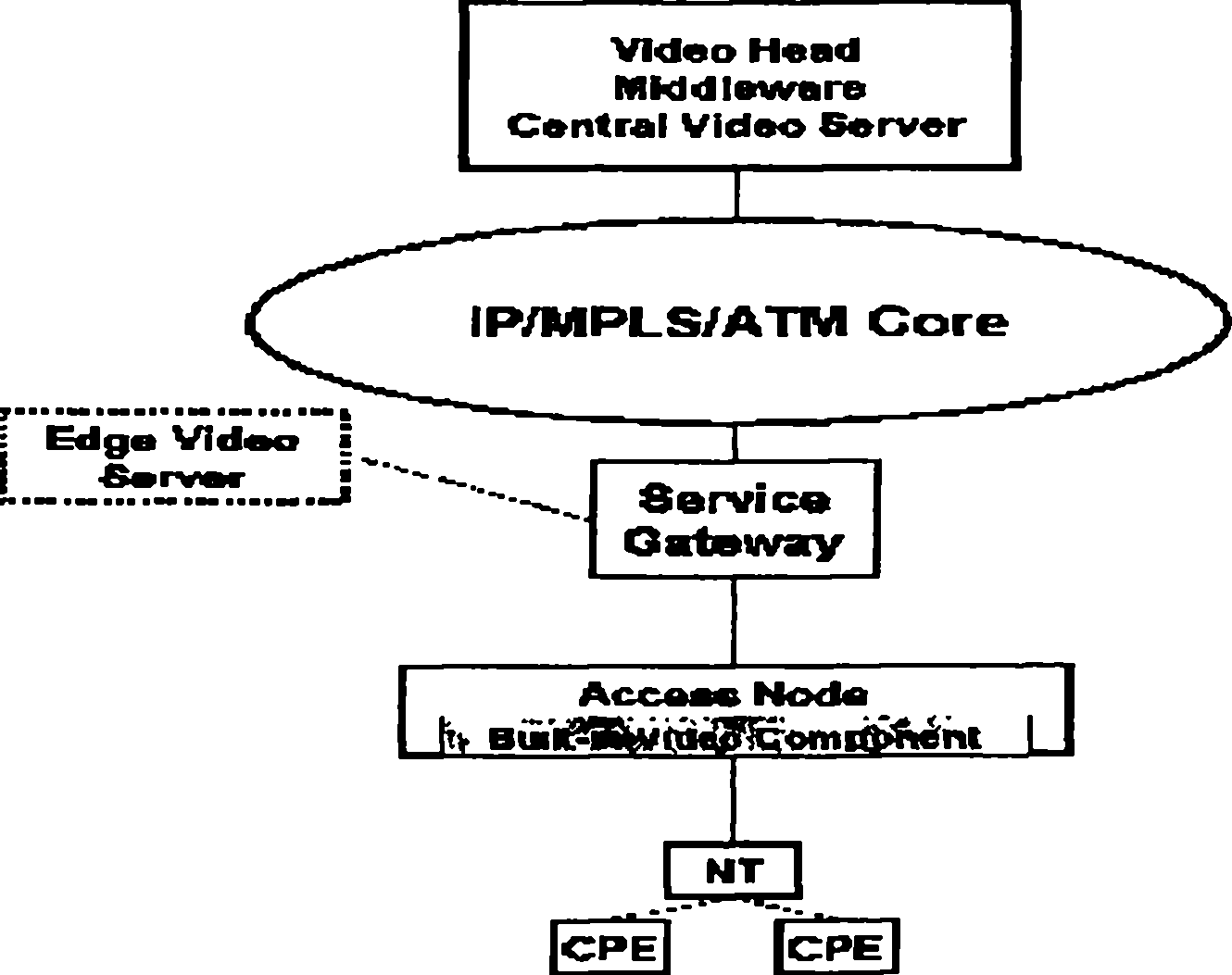
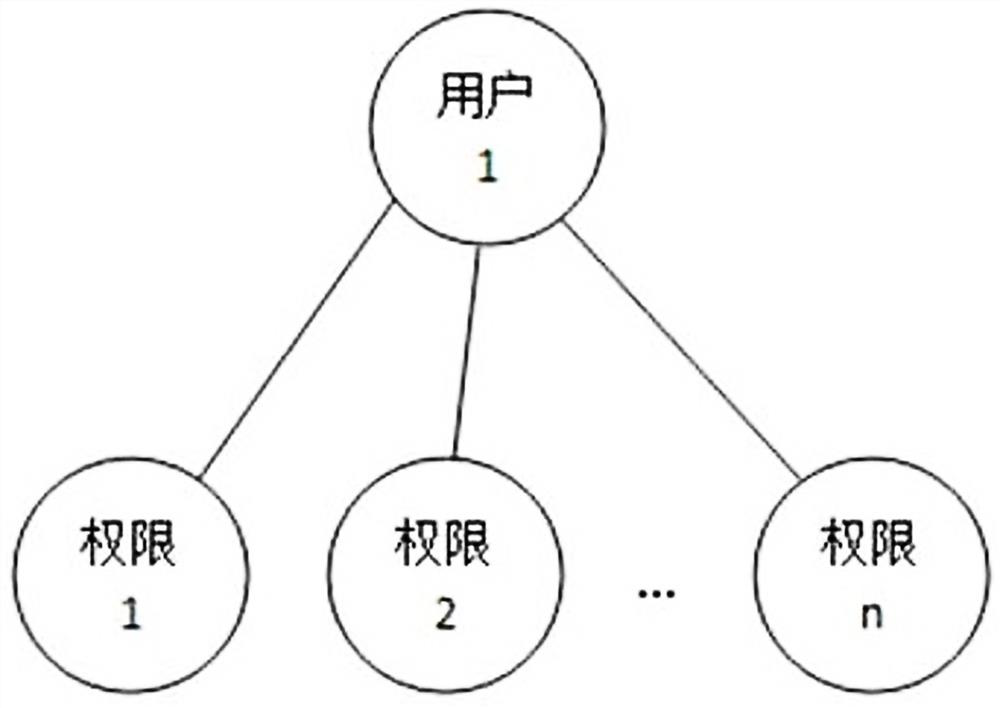
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38results about How to "Simplify permissions management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
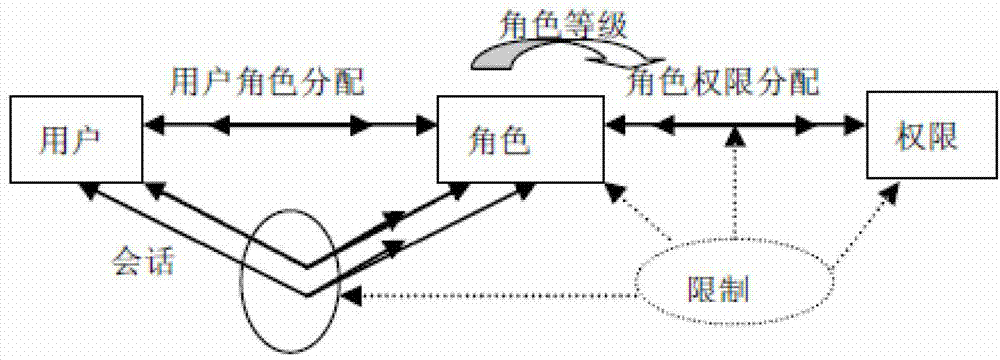
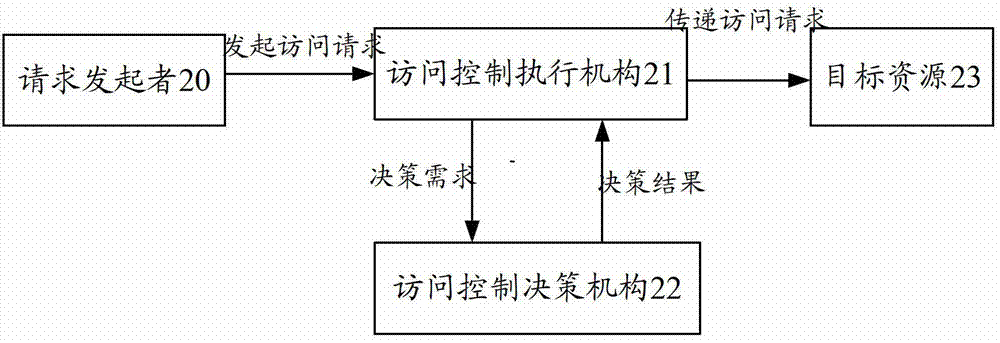
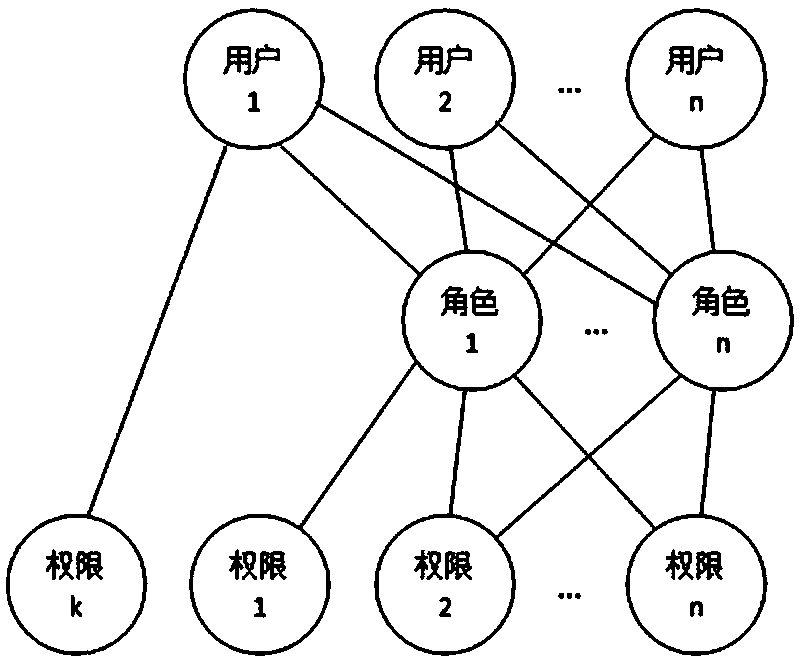
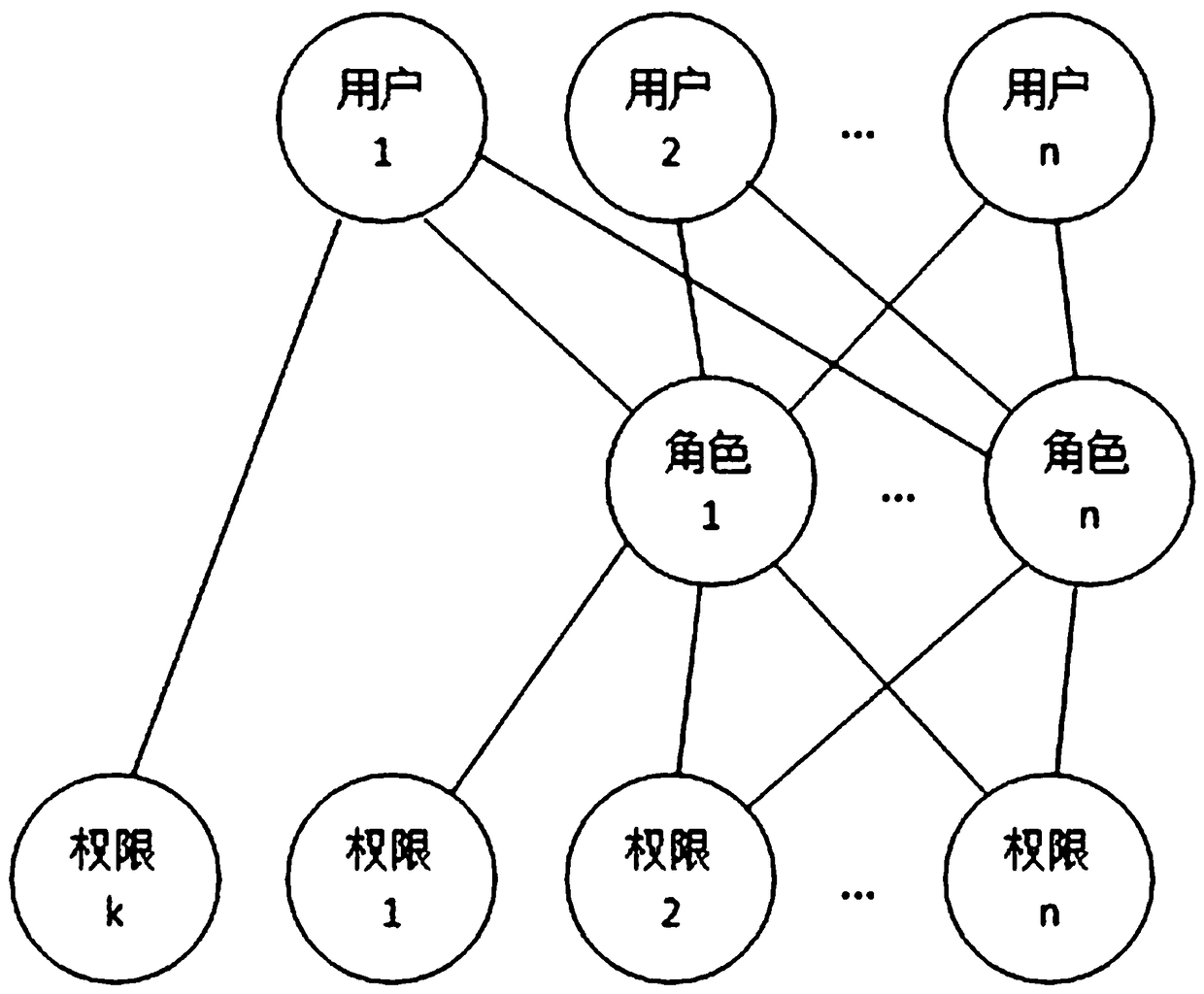
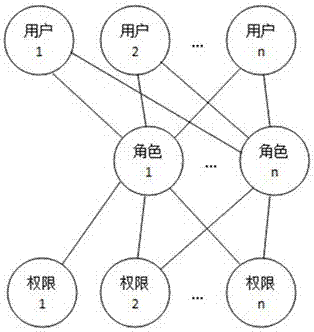
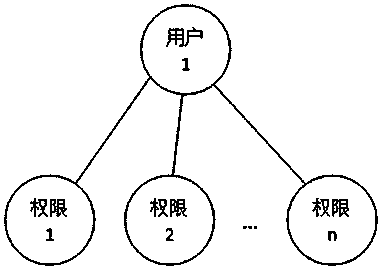
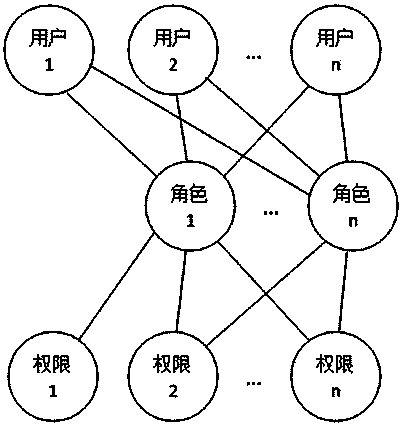
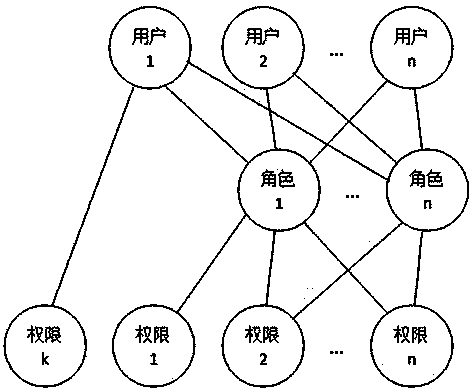
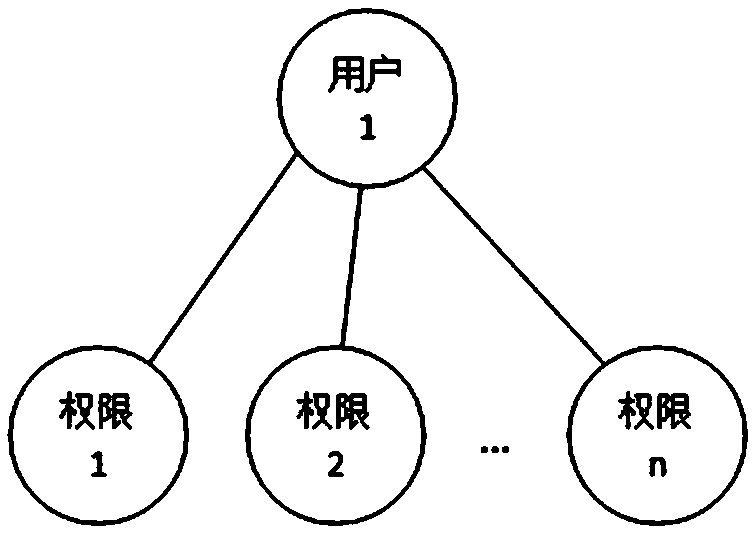
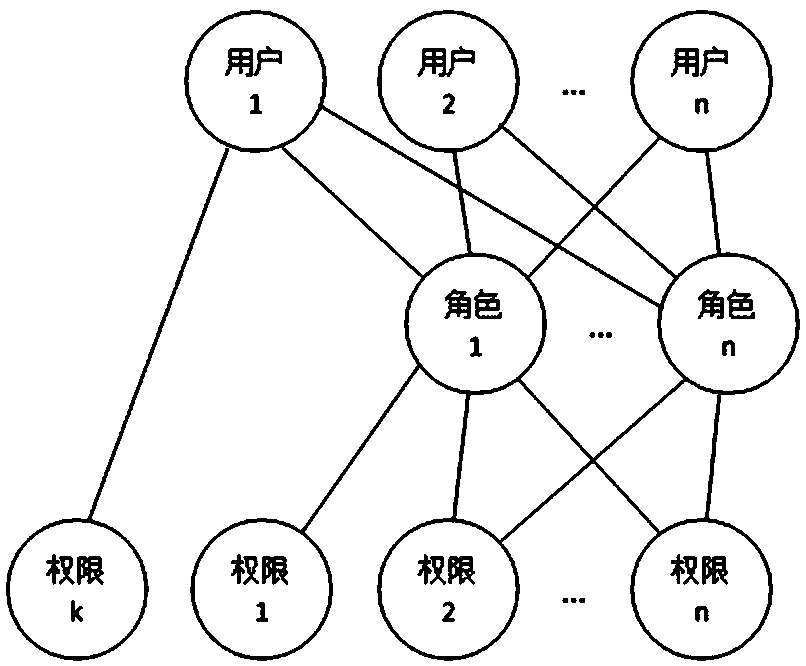
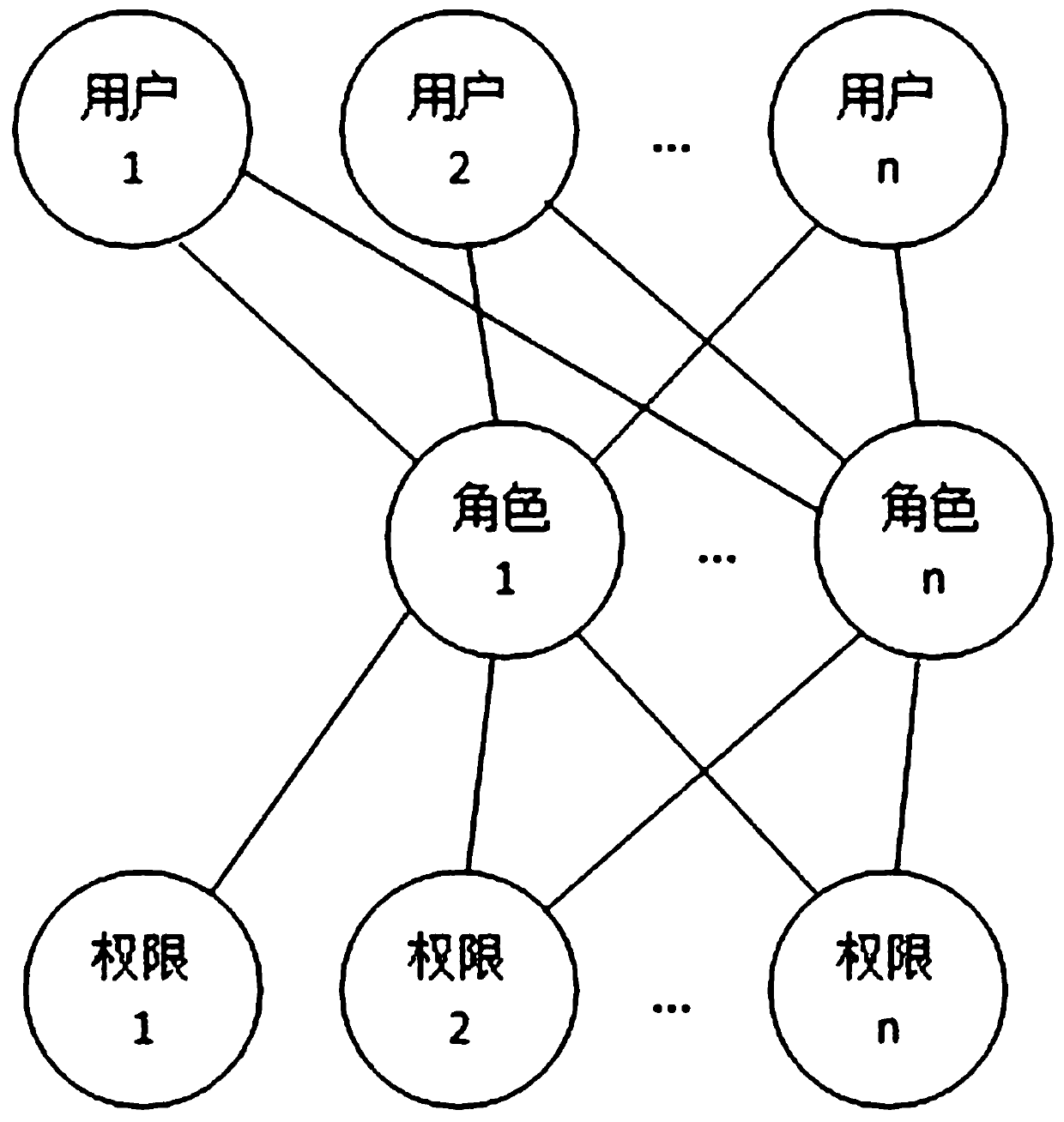
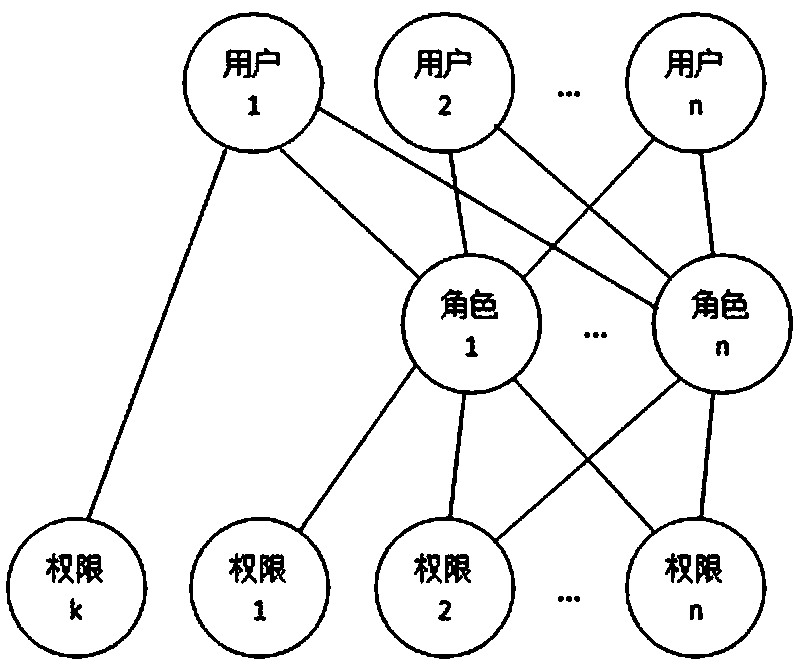
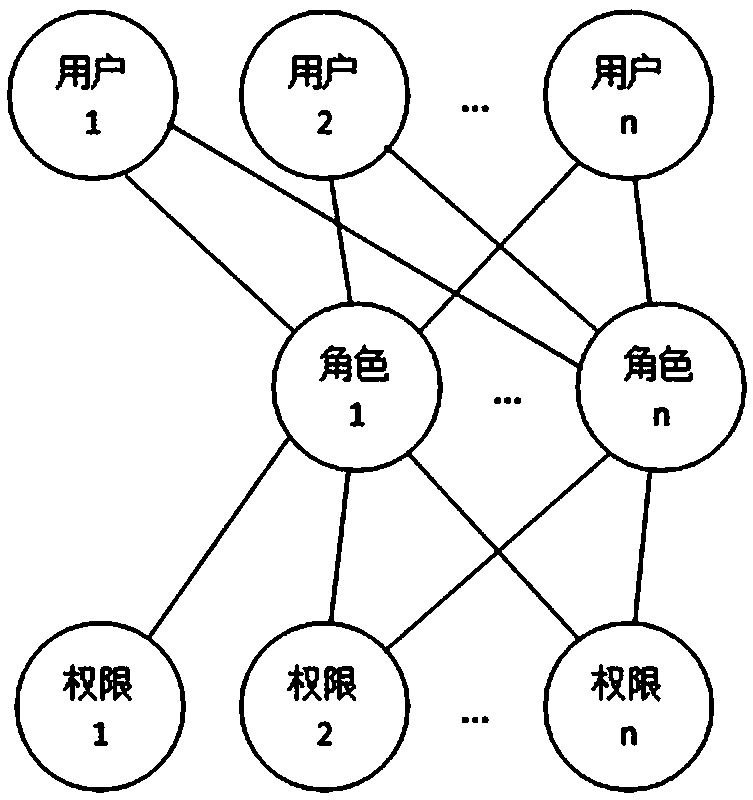
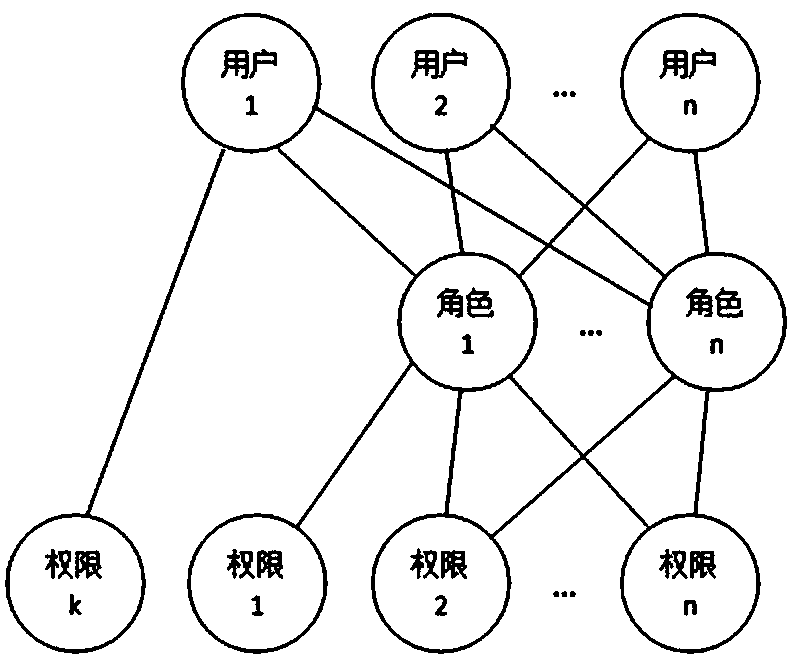
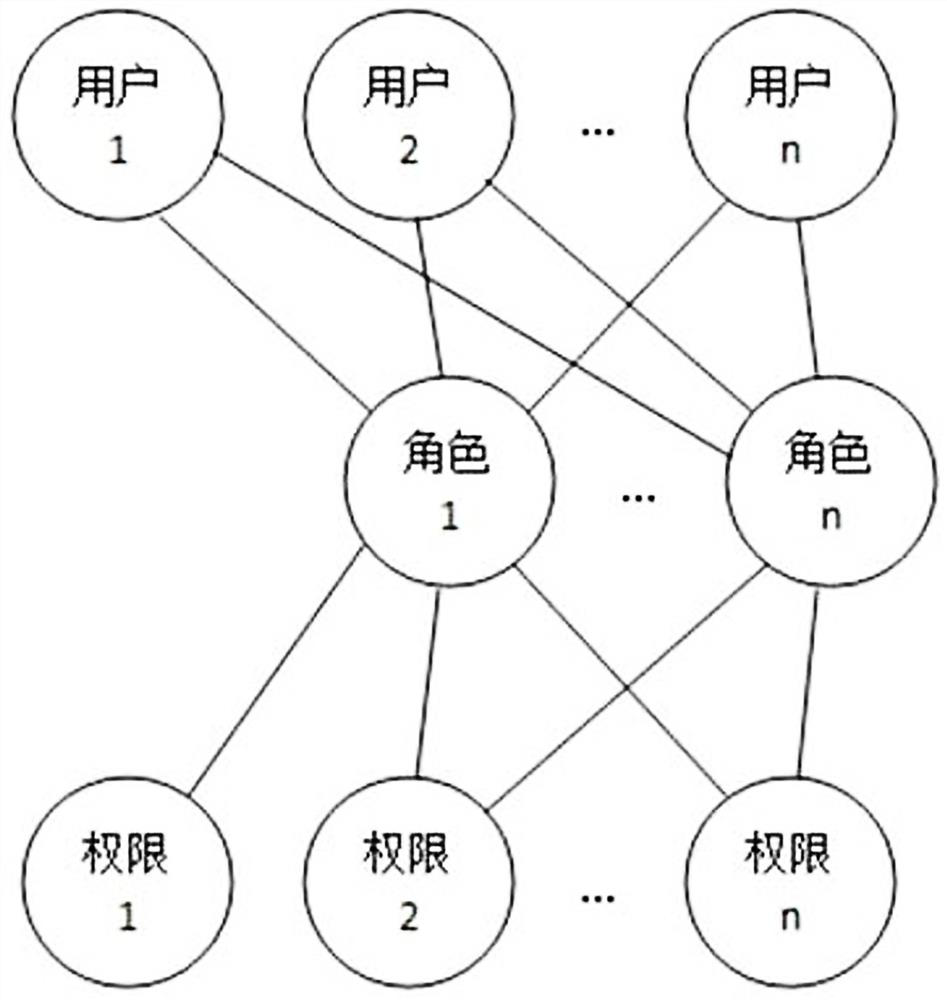
System and method for role-based access control
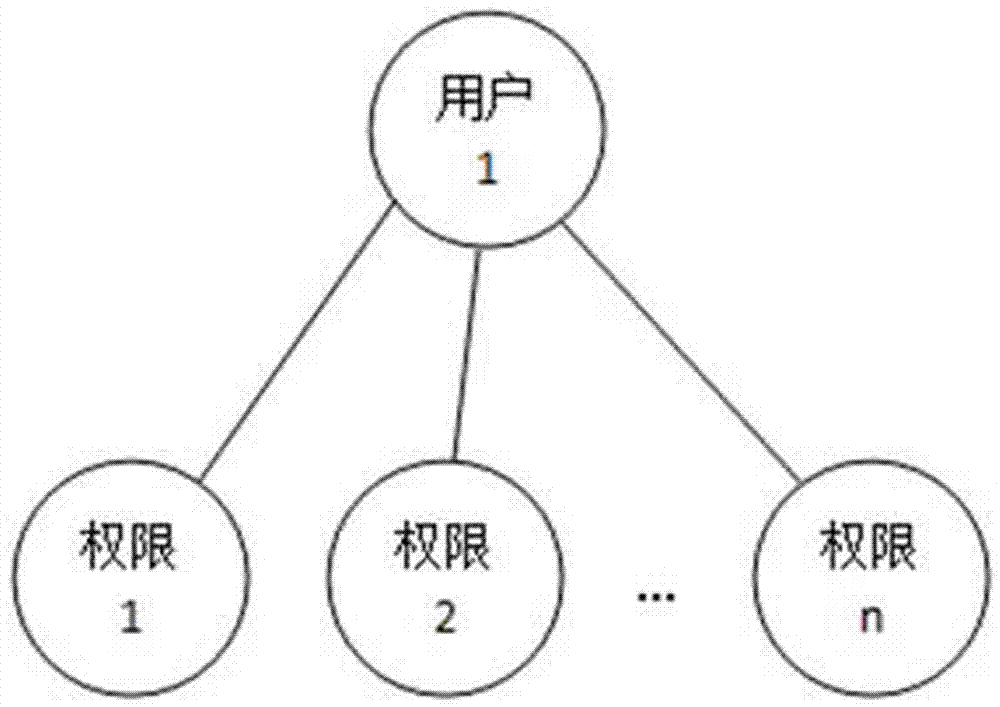
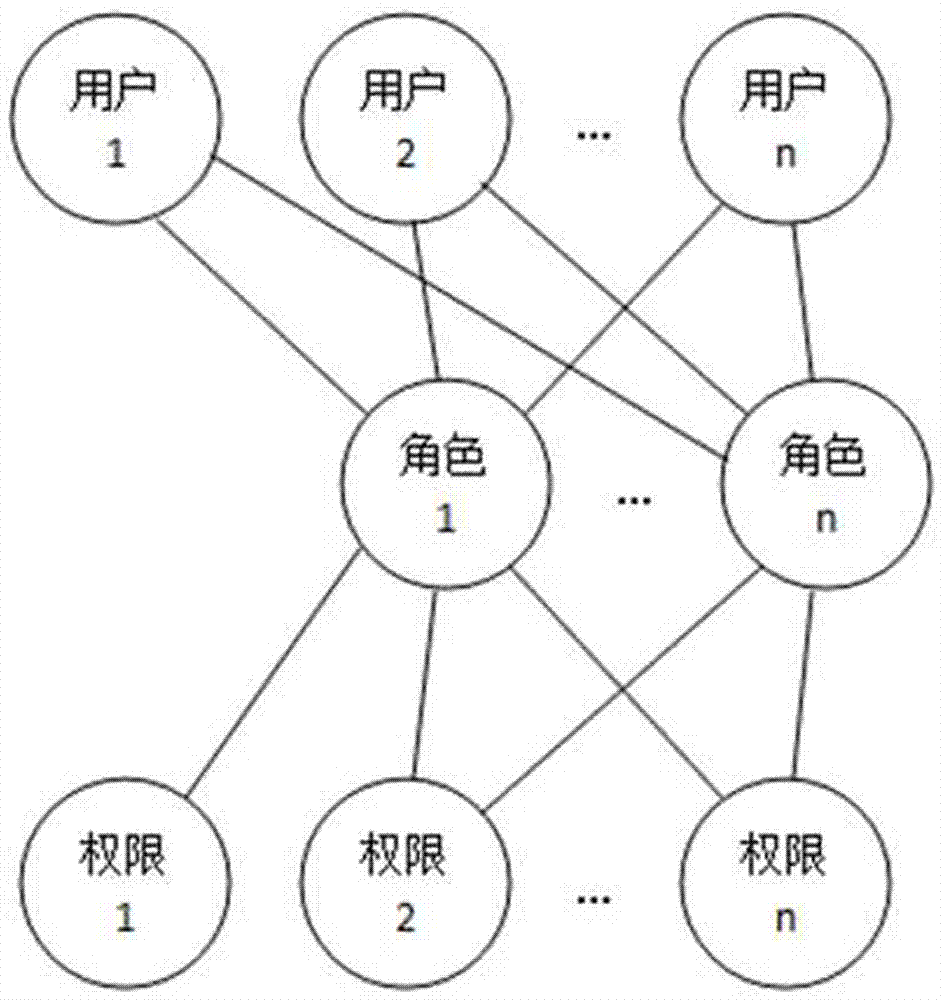
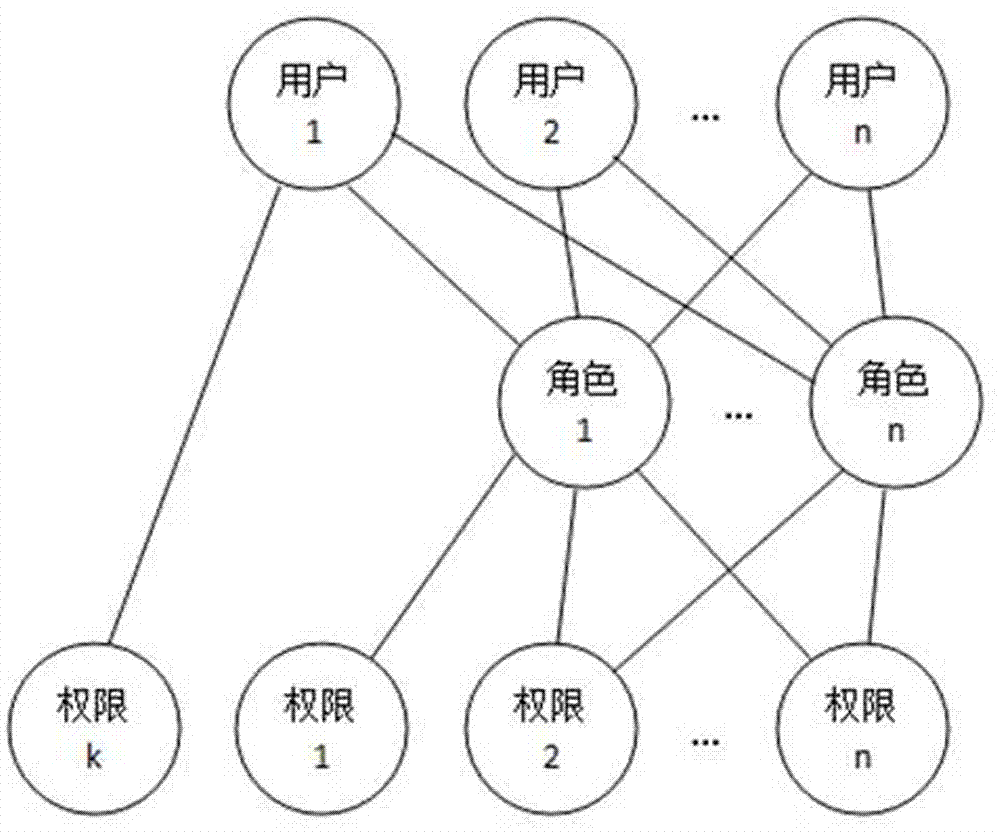
InactiveCN102932340AReduce workloadAvoid the confusion of authority divisionTransmissionControl systemSoftware system
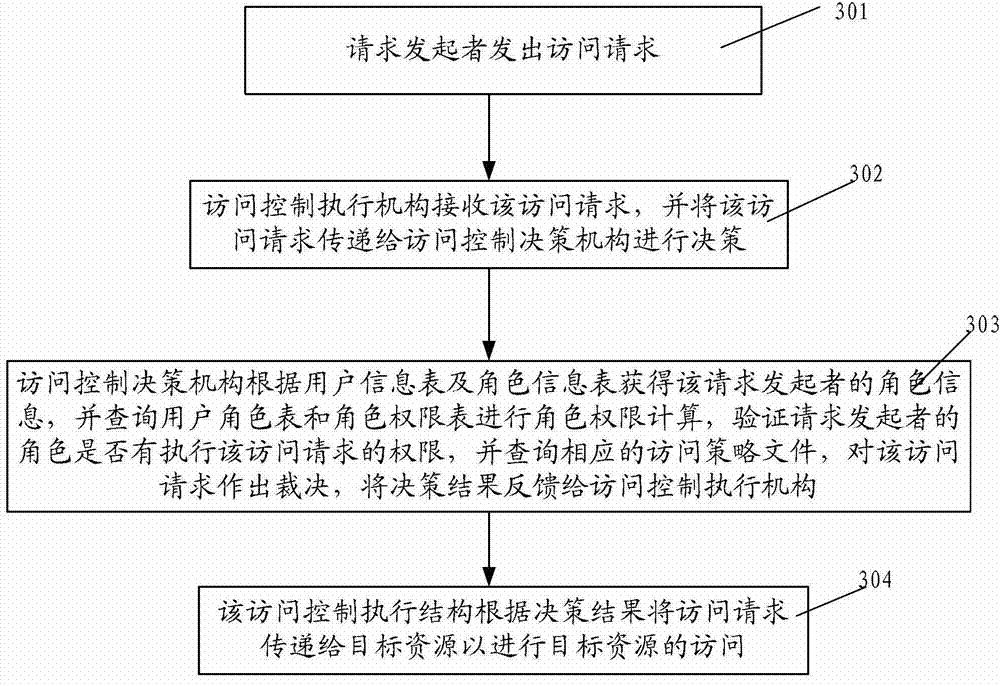
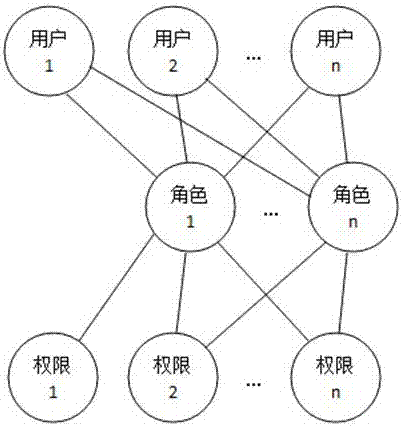
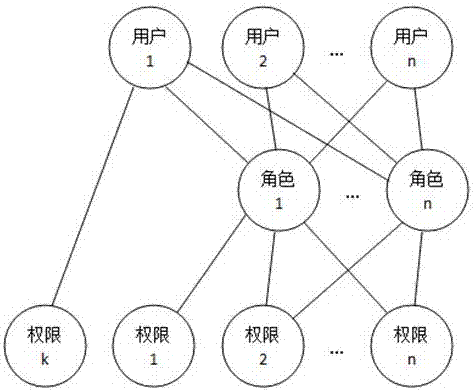
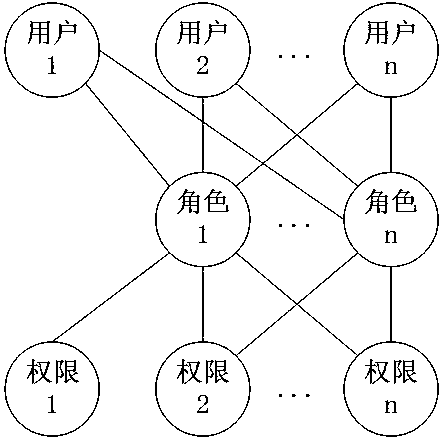
The invention discloses a system and a method for role-based access control. The system comprises a request initiator, an access control executing mechanism, an access control decision mechanism and a target resource, wherein the request initiator sends an access request to the access control executing mechanism, the access control executing mechanism transmits the request to the access control decision mechanism, the access request is transferred to the target resource according to the decision result of the access control decision mechanism, the access control decision mechanism obtains the role information of the request initiator according to a user information table and a role information table after receiving the decision requirement, the role of the request initiator is verified to have the right to execute the access request or not through checking the user role table and a role right table, the access request is judged, and the decision result is fed back to the access control executing mechanism. With the adoption of the system and the method, the right management and distribution work are simplified, so that a role-based access control mechanism in a software system is close to the practical conditions of an organization.
Owner:SHANGHAI DIANJI UNIV
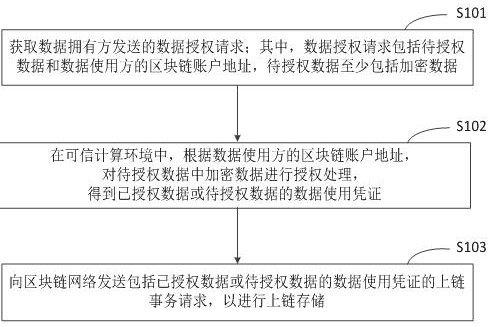
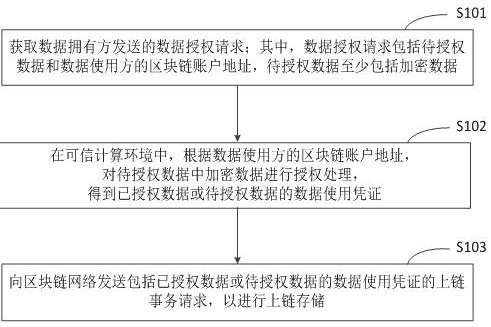
Private data processing method, device and equipment of block chain and storage medium
ActiveCN111737366ASolve the problem of high management complexitySimplify permissions managementDatabase distribution/replicationDigital data protectionTrusted ComputingEngineering
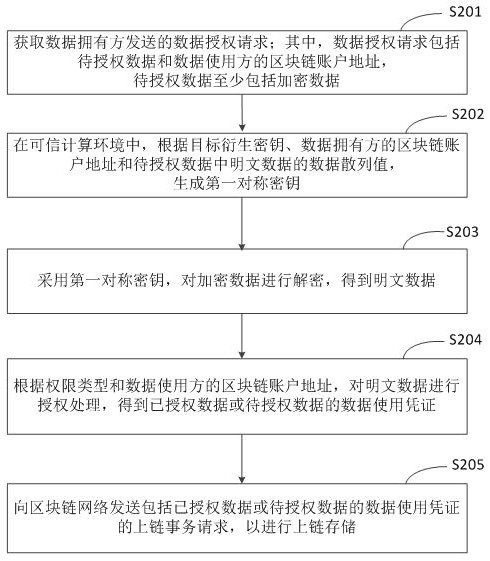
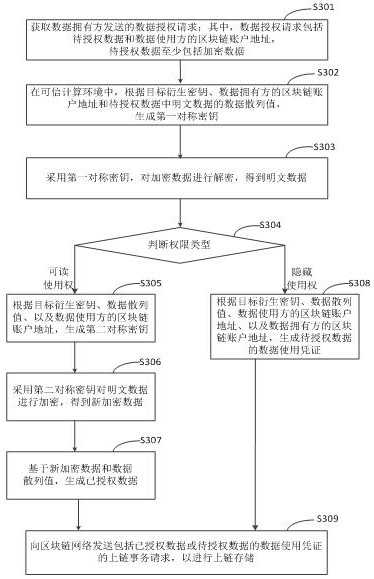
The invention discloses a private data processing method, device and equipment of a block chain and a storage medium, relates to the technical field of block chains, and can be used for cloud computing and cloud service. According to the specific implementation scheme, acquiring a data authorization request sent by a data owner, wherein the data authorization request comprises to-be-authorized data and a block chain account address of a data user, and the to-be-authorized data at least comprises encrypted data; in the trusted computing environment, according to the block chain account addressof the data user, performing authorization processing on the encrypted data in the to-be-authorized data to obtain authorized data or a data use certificate of the to-be-authorized data; and sending an uplink transaction request comprising a data use certificate of the authorized data or the to-be-authorized data to a block chain network for uplink storage. Therefore, the complexity of privacy data authority management is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Authority management method and device based on micro-service calling and storage medium
PendingCN111786998AConvenient rights managementImprove efficiencyTransmissionSpecial data processing applicationsIp addressComputer security
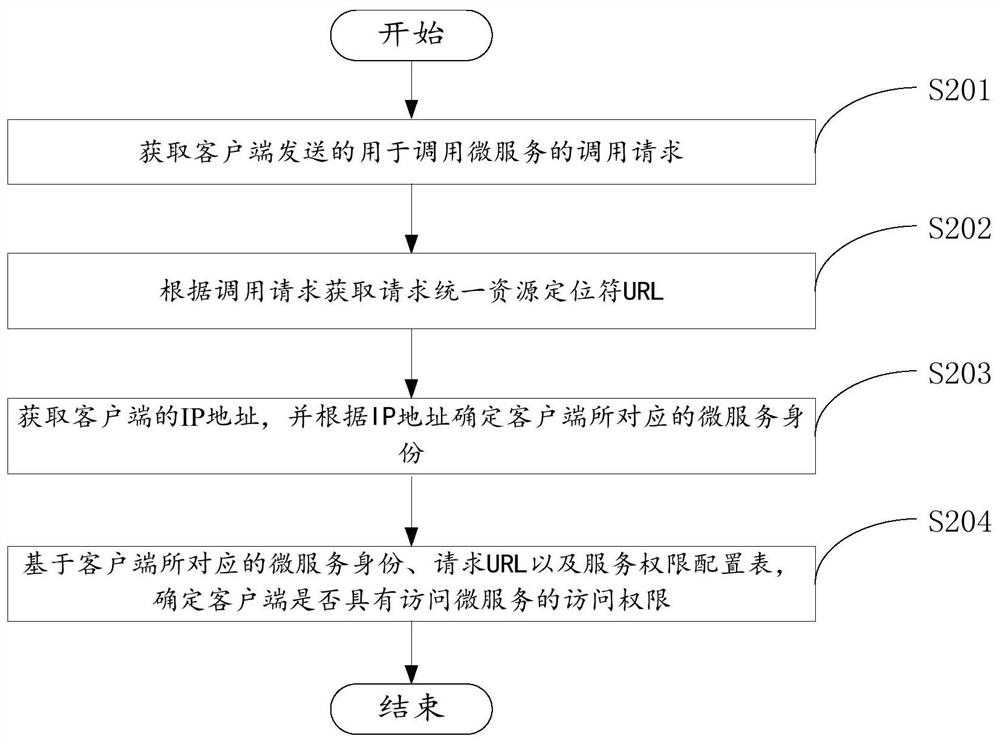
The invention relates to the technical field of micro-service calling, and discloses an authority management method and device based on micro-service calling and a storage medium. The method comprisesthe following steps: obtaining a calling request sent by a client for calling a micro-service; acquiring a request uniform resource locator (URL) according to the calling request; obtaining an IP address of the client, and determining a micro-service identity corresponding to the client according to the IP address; based on the micro-service identity, the request URL and the service authority configuration table corresponding to the client, determining whether the client has the access authority of accessing the micro-service or not, wherein at least one group corresponding to the micro-service identity and an interface address corresponding to each group in the at least one group are configured in the service authority configuration table. According to the method and device, authority management of micro-service calling can be simply, conveniently and quickly completed under the condition of no user information.
Owner:CHENGDU XINCHAO MEDIA GRP CO LTD
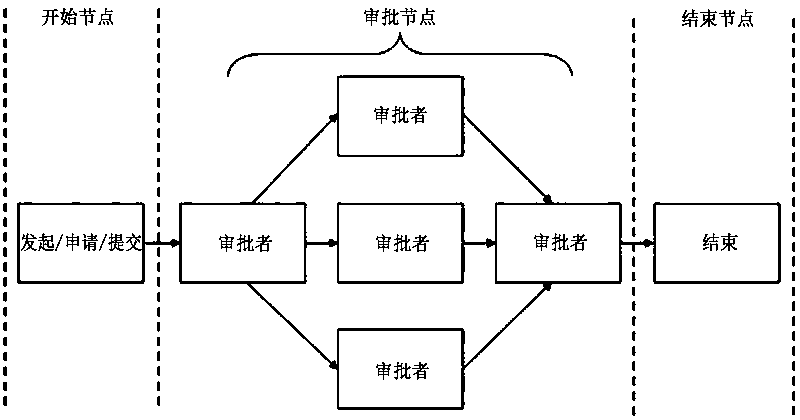
Workflow and method for setting form field operation authority of approval nodes thereof
InactiveCN107169365AReduce workloadShorten the approval cycleDigital data protectionDigital data authenticationWorkloadInformation security
The invention discloses a workflow and a method for setting form field operation authority of approval nodes thereof. The workflow comprises a start node and an approval node; the setting modes of form field operation authority of the start node and the approval node are different. In addition, a method for setting form field operation authority of approval nodes is also disclosed; the approval node comprises one or more approvers; the form field operation authority of each approver in the approval node is customized. The method comprises following steps: selecting approvers from the approval node; obtaining default settings of the form field operation authority; modifying the default settings of the form field operation authority according to the approval items of the selected approvers in the workflow. By means of the method of the invention, the approval cycle is shortened, the approval workload is reduced and information security is enhanced.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
System dispatching method
InactiveCN107368968AReduce workloadRealize seamless dockingOffice automationResourcesComputer scienceUnique user
The invention discloses a system dispatching method. The method includes: determining dispatched tasks, wherein the tasks which need to be dispatched are determined, determining dispatched objects, wherein the dispatched objects are determined, the objects are roles, the roles are independent individuals rather than groups / classes, one role can only be associated with a unique user in the same time period, and one user is associated with one or more roles; and carrying out dispatching, wherein the tasks which need to be dispatched are distributed to the dispatched roles. According to the method, the tasks are distributed to the roles, the user obtains the tasks through associations with the role, the association of an employee and the role is canceled when a turnover of the employee occurs, a newly recruited employee is directly enabled to be associated with the role without the need for re-dispatching for the newly recruited employee, and operations are convenient and quick; the association of an employee and the original role is canceled when position transferring of the employee occurs, the tasks dispatched for the new role can be automatically obtained by associating with the new role; and for a dispatcher, no operation needs to be carried out when the turnover or position transferring occurs.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Setting method of form field operation authority of workflow and setting method of form field operation authority of approval node
ActiveCN108694557AReduce workloadShorten the approval cycleDigital data authenticationOffice automationWorkloadInformation security
The invention discloses a setting method of a form field operation authority of a workflow. The workflow includes a start node and an approval node, and the form field operation authority of the startnode and the form field operation authority of the approval node are set differently. In addition, a setting method of a form field operation authority of the approval node is disclosed. The approvalnode includes one or more approvers, the form field operation authority of each approver in the approval node is customized, specifically including: selecting an approver from the approval node; obtaining the default setting of the form field operation authority; modifying the default setting of the form field operation authority according to an approval item of the selected approver in the workflow. According to the invention, the approval period is shortened, the workload of examination and approval is reduced, and the information security is enhanced.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
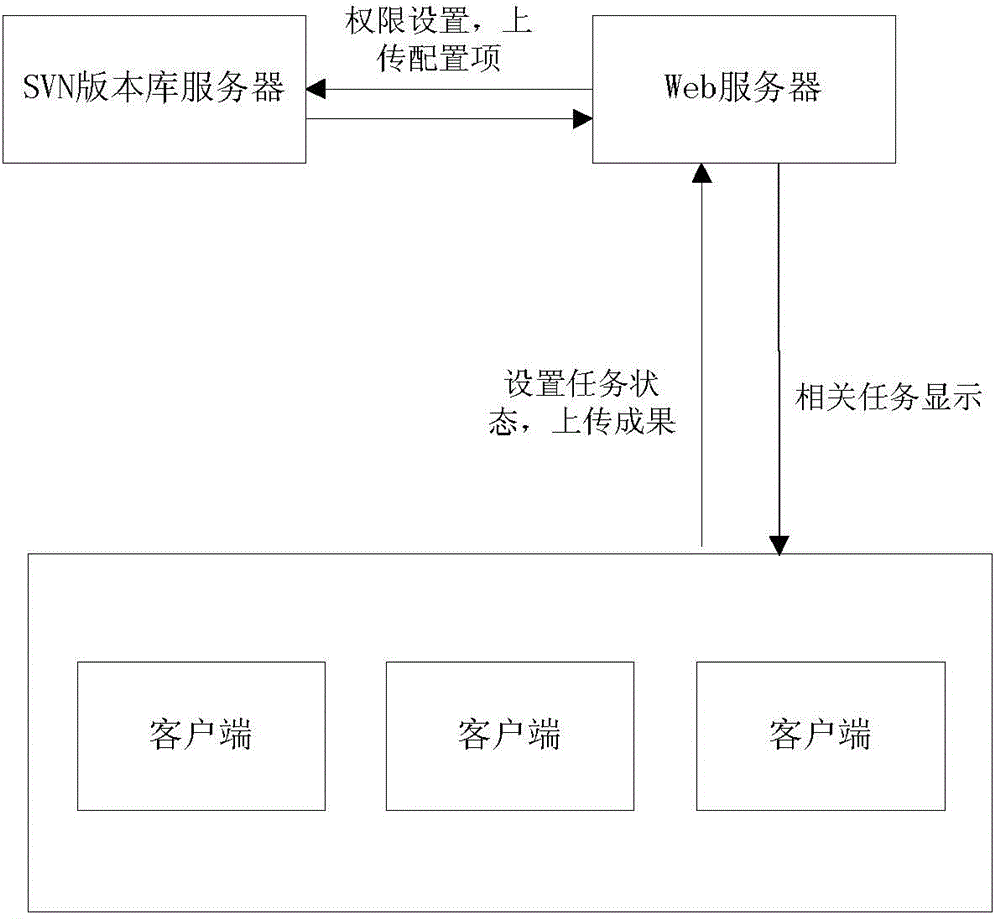
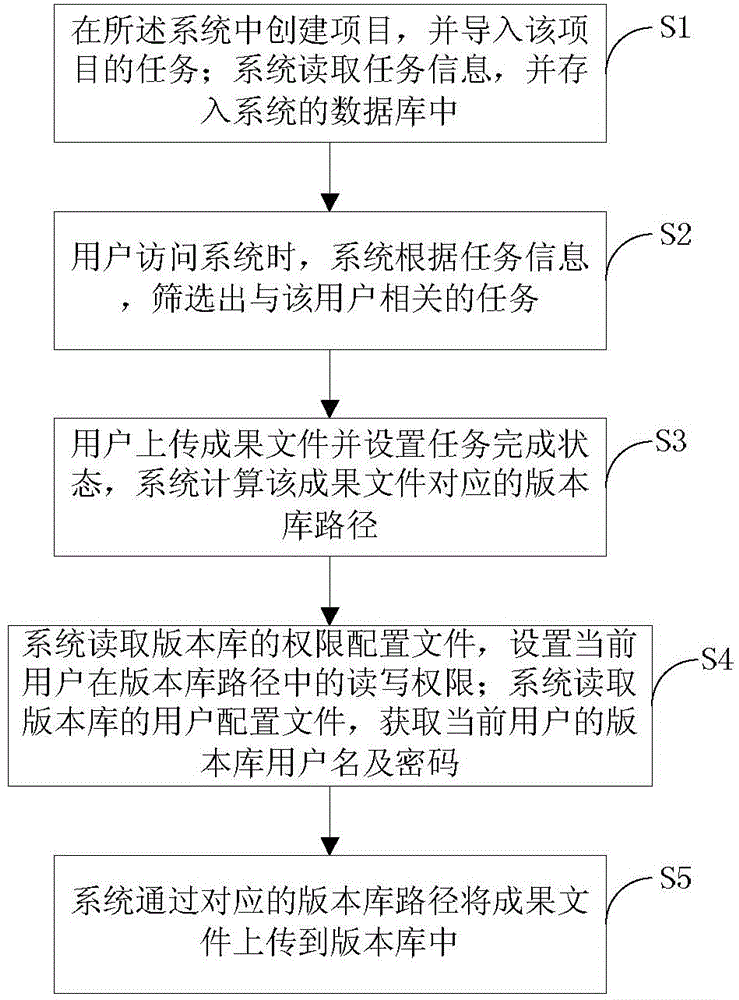
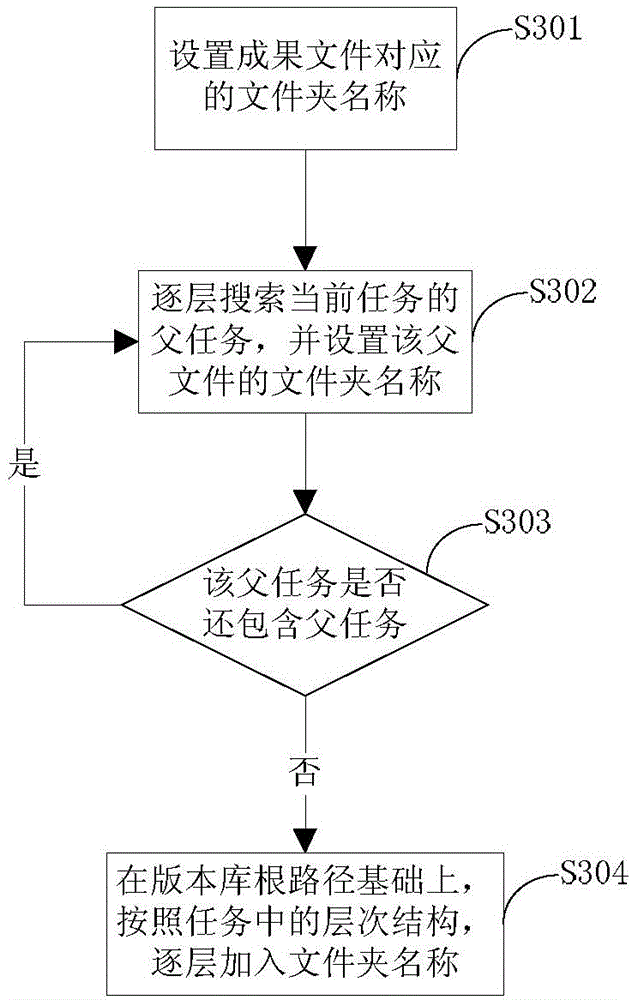
Task management system and method for automatically submitting files into version library
InactiveCN104008441AReduce operating steps and chances of operating errorsSimplify operation stepsResourcesLibrary scienceProject management
The invention discloses a task management system and method for automatically submitting files into a version library. The system comprises a user management module, an item management module, a task management module and an achievement management module. The method comprises the following steps that 1, items are created in the system, tasks of the items are guided in, and the system reads the task information and stores the task information into a system database; 2, when a user has access to the system, the system screens out tasks related to the user according to the task information; 3, the user uploads an achievement file and sets the task finishing state, and the system calculates a version library route corresponding to the achievement file; 4, the system reads a permission configuration file of the version library and sets the read-write permission of the current user in the version library route, and the system reads a user configuration file of the version library and obtains the version library user name and the password of the current user; 5, the system uploads the achievement file to the version library through the corresponding version library route.
Owner:FENGHUO COMM SCI & TECH CO LTD
Method for setting approval node an approval process based on countersignature
ActiveCN108764691ALess authoritySimplify permissions managementOffice automationResourcesDependabilityComputer science
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Role and user one-to-one correspondence-based workflow control method and system
PendingCN108717620AImprove reliabilityWill not affect normal operationDigital data protectionOffice automationComputer scienceWorkflow
The invention discloses a role and user one-to-one correspondence-based workflow control method and system. The method comprises the following steps of: constructing a three-layer structure model of users, roles and authorities, wherein each role is an independent individual, and at a same time period, one role only can be associated with a unique user but one user can be associated with one or more roles; controlling a workflow by utilizing the three-layer structure model, selecting an approval role and authorizing the approval role; and determining to-be-processed approval tasks by the usersaccording to the associated roles, and carrying out approval operations according to the authorities of the associated roles. According to the method and system, subjects of the approval operations in workflows are roles, and even employee / user change (such as position transfer, demission and the like) or employee approval authority change occurs, employees are re-associated with the roles or role approval authorities are adjusted without resetting / adjusting the process, so that the setting is convenient, errors or omissions are not easy to occur, normal operation of enterprises is not influenced, and the reliability of the workflows is greatly improved.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Method for setting approval role of approval node of workflow according to roles
InactiveCN108734400AEasy to operateNot easy to make mistakesOffice automationResourcesWorkflowSystem organization
The invention discloses a method for setting an approval role of an approval node of a workflow according to roles. The method comprises the following steps of creating roles included in a system organization structure; displaying candidate roles when the approval node of the workflow is set; and selecting one or more roles from the candidate roles as the approval role / roles of the node. When thesystem workflow setting personnel set the approval role, the system workflow setting personnel only need to select the corresponding role instead of paying attention to a specific user, and even if the user associated with the role is changed, the approval role does not need to be reset, so that the method is easy to operate and less error-prone. A main body of approval operation in the workflow is the role, and the role is an independent individual, even if an employee / user change occurs, a new employee is associated to the role in the approval process again; or when the approval authority ofthe employee is changed, the approval authority of the role is adjusted in a targeted way instead of resetting / adjusting the process; and the setting is convenient, and the reliability of the workflow is improved greatly.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Approval method for form data operations
ActiveCN109086627ATimely feedbackFlexible review methodDigital data protectionOffice automationData operationsDatabase
The invention discloses an auditing method for form data operation, which comprises the following steps: a role in a system is created, the role is an independent individual, one role can only be associated with a unique user at the same time period, and one user is associated with one or more roles; one or more roles in the system are selected as approvers, and each approver is authorized to haveaudit privileges for the operation of the form data; an audit request for an operation for which the requestor submits data for a form is audited; the approval request is audited by an approver who has the approval authority for the operation on the form data. As the audit of the invention has only one audit step, once the audit is agreed / passed or disagreed / not passed, the audit task ends without creating a process, and the audit cycle of the form data operation is shortened. The auditor adopts the role of an independent individual, and can realize the seamless transfer of audit authority when the employee leaves office or changes his post, which will not affect the normal operation of the enterprise, and also avoid the risk of confidential information leakage.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Examination and approval task transfer method based on improved RBAC authority control mechanism
The invention discloses an examination and approval task transfer method based on an improved RBAC authority control mechanism. The method includes the steps that a role is created in a system, the role is an independent individual nature role, one independent individual nature role can only be associated with a unique user in the same time period, and one user is associated with one or more independent individual nature roles; a transferring person obtains an examination and approval task in the examination and approval process; the transferring person transfers the examination and approval task to a transferred person, and the transferred person is one independent individual nature role. According to the examination and approval task transfer method based on the improved RBAC authority control mechanism, the transferred person adopts the independent individual nature role, when an employee corresponding to the user associated with the role of the transferred person leaves or is transferred, the original association is simply released, and the user corresponding to the new employee is associated with a role to automatically obtain all the currently transferred examination and approval tasks of the role, and the handover of the examination and approval task is achieved through the association of the role in the meantime. The workload is small, and seamless docking can be achieved, lag or omission of transferring the examination and approval tasks cannot appear, and it is ensured that urgent tasks are dealt with in a timely manner.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Management method of instant messaging account in management system
ActiveCN109167755AEasy to superviseEasy to manageDigital data protectionData switching networksWork contentHandover
The invention discloses a management method of an instant messaging account in a management system, which comprises the following steps: creating a system role, and the role is an independent individual; according to the work content of the role in the management system is role-related role instant messaging account, at the same time, a role-related instant messaging account can only be associatedwith one role, and a role can only be associated with one role-related instant messaging account; establishing the association relationship between users and roles, and taking the role-based instantmessaging accounts associated with all roles associated with users as the role-based instant messaging accounts of the users and / or the employees corresponding to the users. The employee of the invention obtains the instant messaging account number of the role nature through the role associated with the corresponding user, and when the employee leaves office, the association between the user corresponding to the employee and the role is canceled, so that the employee who leaves office automatically loses the authority, thereby avoiding the risk of revealing the confidential information of theenterprise. Employee transfer, can achieve seamless docking, there will be no communication account handover delay or omission.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
System task dispatching method
The invention discloses a system task dispatching method. The method comprises determining tasks to be dispatched, namely, determining the tasks requiring dispatching; determining dispatching objects,namely, determining the objects to which the tasks are to be dispatched, wherein the objects are roles which are independent individuals but not groups / classes and one role can only be associated with a unique user in the same time period, and one user can be associated with one or more roles; dispatching, namely, dispatching tasks that require dispatching to the dispatching roles. According to the invention, the tasks are dispatched to the roles, and the user obtains the tasks through the association with the roles. When an employee leaves his / her post, the association between the employee and his / her role is canceled, and a new employee can be directly associated with the role. Re-dispatching for the new employee is not needed, and the operation is convenient and quick. When the employee is transferred to another position, the association with the original role is cancelled, and the tasks dispatched to a new role can be automatically obtained by associating with the new role. The dispatching object needs no action in the event of job termination or post transfer.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Form operation permission authorization method based on role
InactiveCN107301335AImprove form authorization efficiencyConvenient authorizationDigital data authenticationOffice automationAuthorizationDatabase
The invention discloses a form operation permission authorization method based on a role. The method comprises the following steps that: selecting an authorized role: selecting one or a plurality of roles as authorized roles, wherein each role is an independent individual but is not groups / categories, one role in the same time period only can be associated with a unique user, and one user is associated with one or a plurality or roles; selecting a form: when the number of the selected authorized role is one and the number of the selected form is one, displaying the existing permission state of the authorized role for the selected form; when the number of the selected forms is at least two, displaying blank form operation permission; carrying out form operation permission authorization on the authorized form; and after above steps are finished, storing the permission of the authorized role. By use of the method, the authorization efficiency of the form operation permission is improved, the method is simple in operation, the safety performance of a system is improved, and a risk that losses are caused for enterprises due to the leakage of information can be reduced.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
A role-based method of authorizing permissions for form operations
ActiveCN109214150ASave time at workImprove work efficiencyDigital data authenticationOffice automationComputer scienceAuthorization
The invention discloses a method for authorizing form operation authority based on role, which comprises the following steps of: selecting one or more roles as authorized roles; each role is an independent individual, not a group / class; one role can only be associated with unique users at the same time period, and one user can be associated with one or more roles; the authorization method comprises the following steps of: selecting one or more roles as authorized roles; slecting form: when the selected authorized role is one and the selected form is one, the existing operation permission status of the authorized role on the selected form is displayed; displaying blank form operation permissions when the selected form is two or more; performing form operation permission authorization on authorized roles; after the above steps are complete, saving the permissions for the authorized role. The invention improves the authorization efficiency of the form operation authority, is simple to operate, improves the safety performance of the system, and reduces the risk of loss caused by the information leakage of the enterprise.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
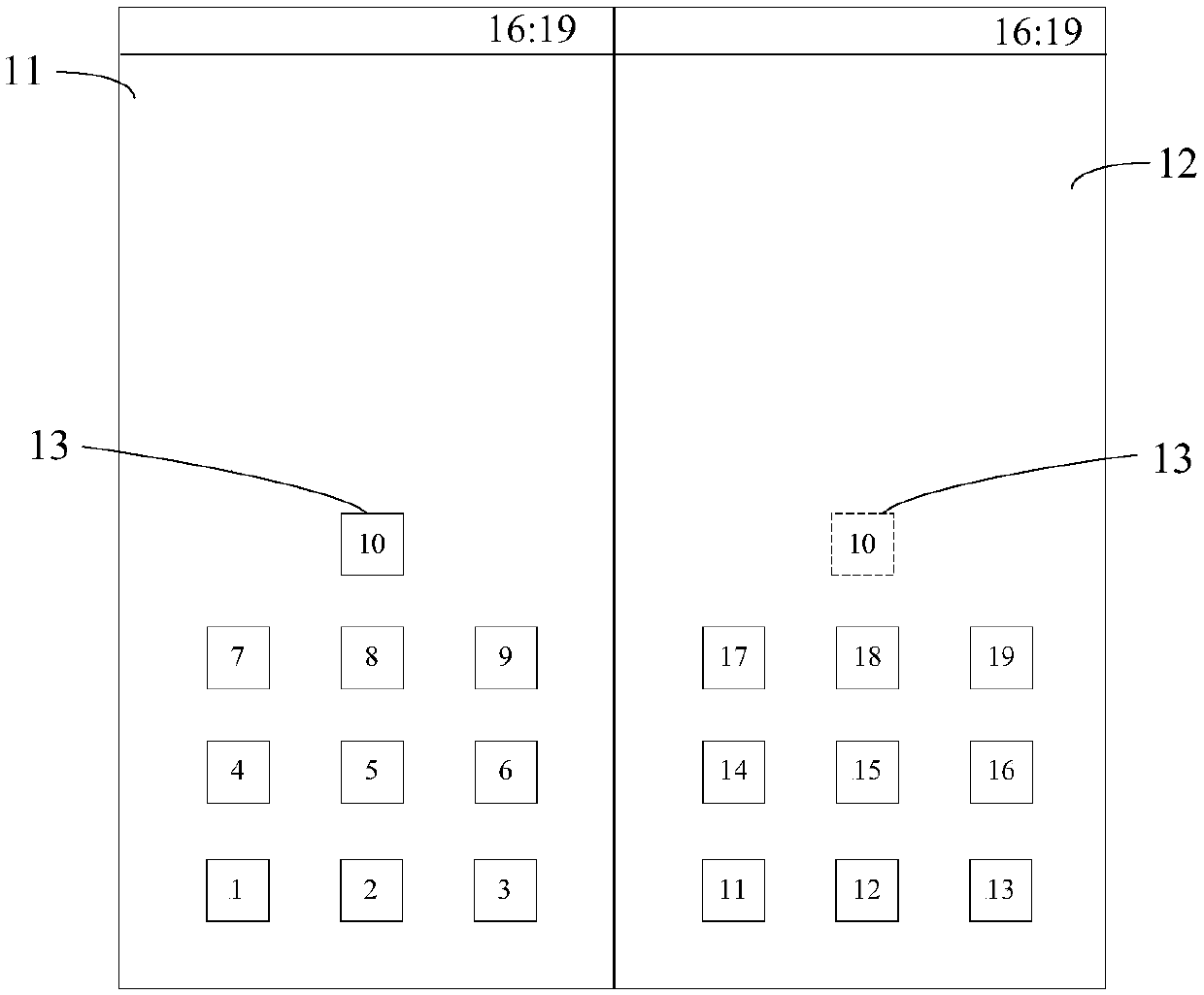
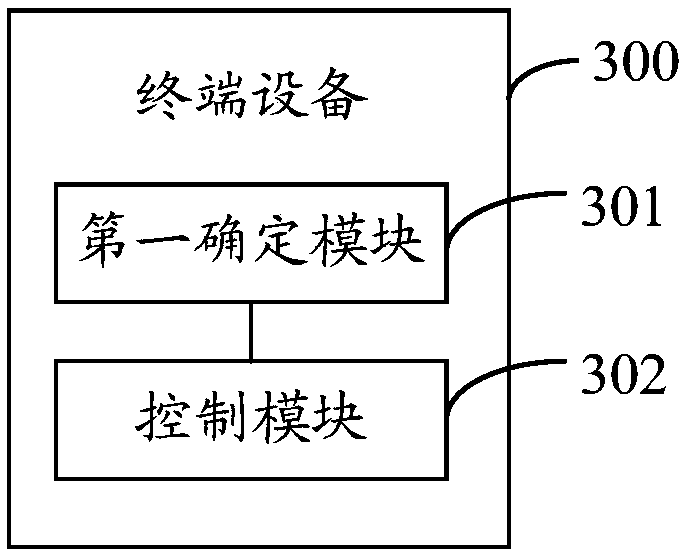
A permission management method and terminal equipment
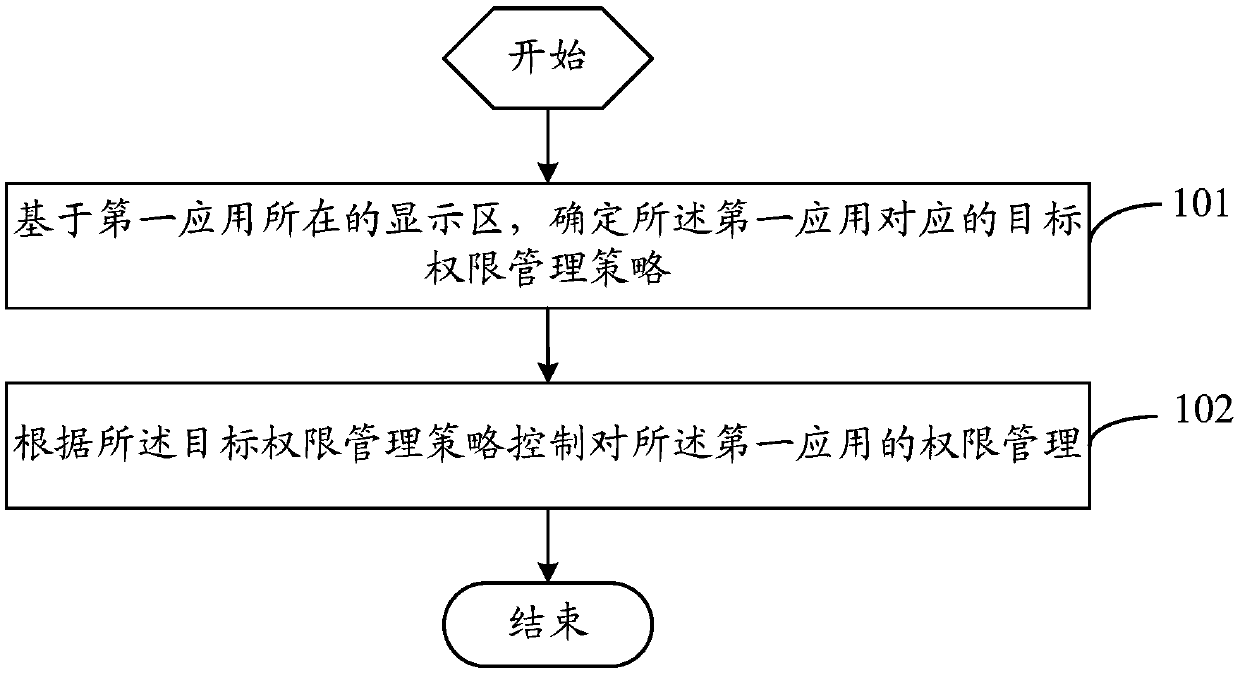
ActiveCN109684825ASimplify permissions managementImprove processing efficiencyDigital data authenticationPlatform integrity maintainanceTerminal equipmentComputer terminal
The invention provides an authority management method and terminal equipment, the authority management method is applied to the terminal equipment comprising a first display area and a second displayarea, and the authority management method comprises the following steps: determining a target authority management strategy corresponding to a first application based on the display area where the first application is located; Controlling authority management of the first application according to the target authority management strategy; Wherein the target authority management strategy comprises afirst authority management strategy corresponding to the first display area and / or a second authority management strategy corresponding to the second display area. According to the technical scheme provided by the invention, the problem that the operation of permission control of an application by the existing terminal equipment is relatively tedious is solved.
Owner:VIVO MOBILE COMM CO LTD
Method for supervising approval operation, authorization operation and form operation
InactiveCN107392494AMeet the needs of actual operationAchieve seamless handoverDigital data protectionOffice automationWork contentData mining
The invention discloses a method for supervising approval operation, authorization operation and form operation. The method comprises the following steps: creating roles in a system, wherein the roles are independent individuals, and in the same period, one role can only associate with only one user, and one user can associate with one or more roles; when the role executes approval / authorization / form operation, recording the role executing the operation; setting one or more roles as a monitoring role / monitored role, and setting a monitored role / monitoring role for each monitoring role / monitored role; and through the monitoring role, monitoring the approval / authorization / form operation recordings executed by the monitored role. The monitoring and monitored subjects are independent individual roles respectively; work content of users / staffs is distinguished according to post number / station number, and each post number / station number is corresponding to one independent individual role; setting of supervision authority is realized for each role; monitoring and monitored authorities are subjected to refined authorization; and the method meets actual operation and use requirements of enterprises.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Shortcut function setting method
InactiveCN107292198AImprove new management efficiencyReduce workloadDigital data protectionOffice automationManagement efficiencyTime duration
The invention discloses a shortcut function setting method. The method includes the steps of setting shortcut menus and newly-added shortcut forms, wherein the step of setting the shortcut menus includes the substeps of setting a shortcut menu inlet, setting the shortcut menus, displaying the shortcut menus through the shortcut menu inlet and displaying the shortcut menu selected in the second step through the shortcut menu inlet; selecting any shortcut menu in the first step according to needs, and displaying a function interface corresponding to the shortcut menu. The checking and operating of the frequently-used menus and the newly adding of the forms can be conveniently and rapidly completed, and the office efficiency is improved; a role can only be related to a unique user at the same time duration, the user only needs to be related to a new role when the user gets a new job or is transferred to a new position, then the frequently-used shortcut menu corresponding to the role can be obtained through the shortcut menu inlet, the form with newly-added authority corresponding to the role can also be obtained through a newly-added shortcut form inlet, and the authority management efficiency in the use of a system is greatly improved.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Efficient examination and approval method for workflow examination and approval node
ActiveCN108805532ALess authoritySimplify permissions managementOffice automationComputer scienceData science
The invention discloses an efficient examination and approval method for a workflow examination and approval node. The method comprises the steps of setting the examination and approval role of the examination and approval node and carrying out efficient examination and approval of the examination and approval role. The step of setting the examination and approval role of the examination and approval node comprises three ways of appointing a role, appointing a department (department manager role) and setting the examination and approval role according to a level. The process of carrying out efficient examination and approval of the examination and approval role comprises the following steps that: the examination and approval opinions of the first examination and approval role who submits the examination and approval opinion are taken as the examination and approval result of the examination and approval node; and if any one examination and approval role submits the examination and approval opinions, the examination and approval node finishes examination and approval. For the examination and approval node, when any one examination and approval role submits the examination and approval opinion, the examination and approval result of the examination and approval node is determined, the examination and approval node finishes examination and approval, and the examination and approval tasks of other examination and approval roles are automatically removed so as to realize efficient and quick examination and approval. The method is especially suitable for a situation that any person can give the examination and approval opinions since multiple people have the same examination and approval permission for the same examination and approval task.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
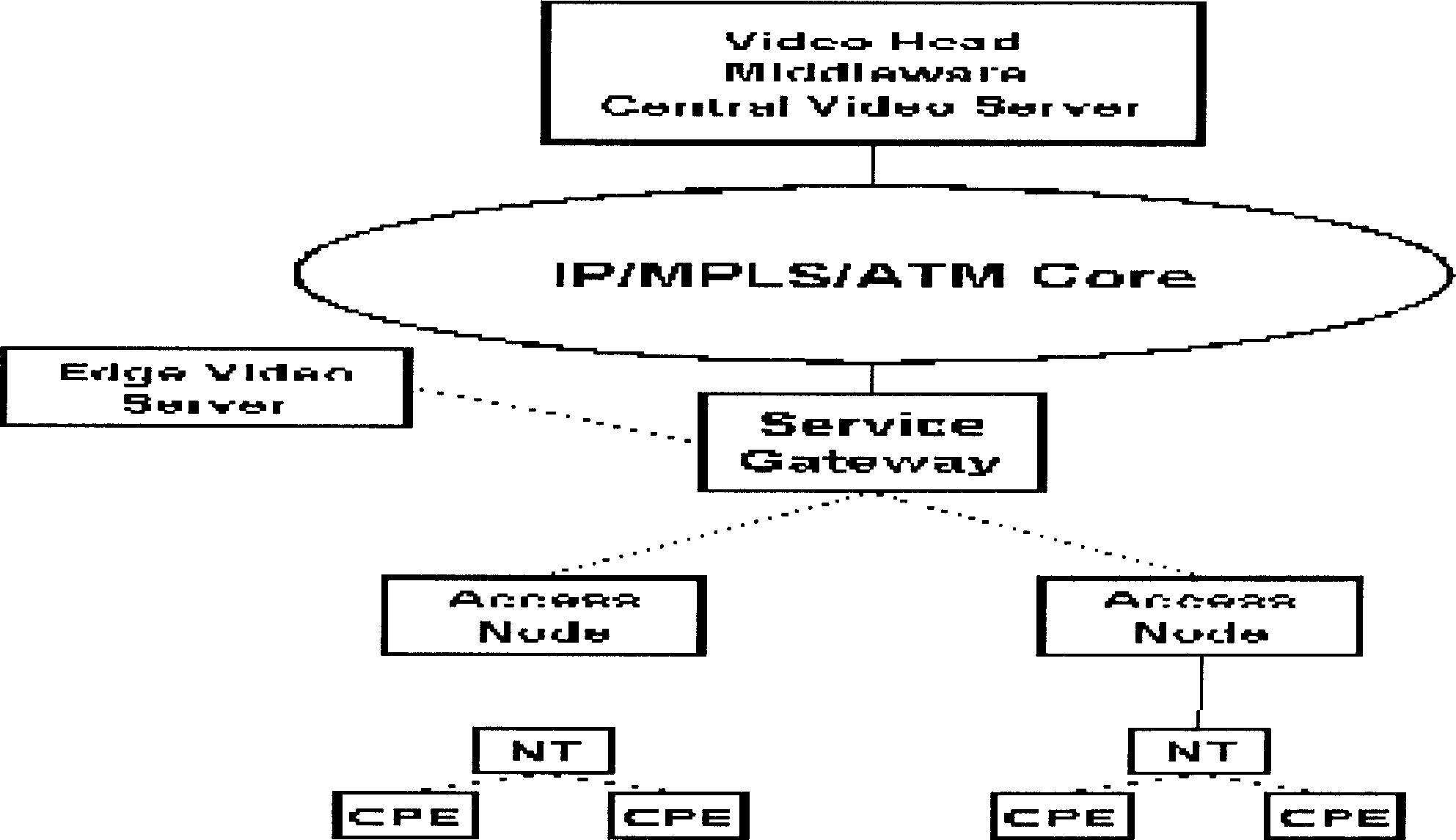
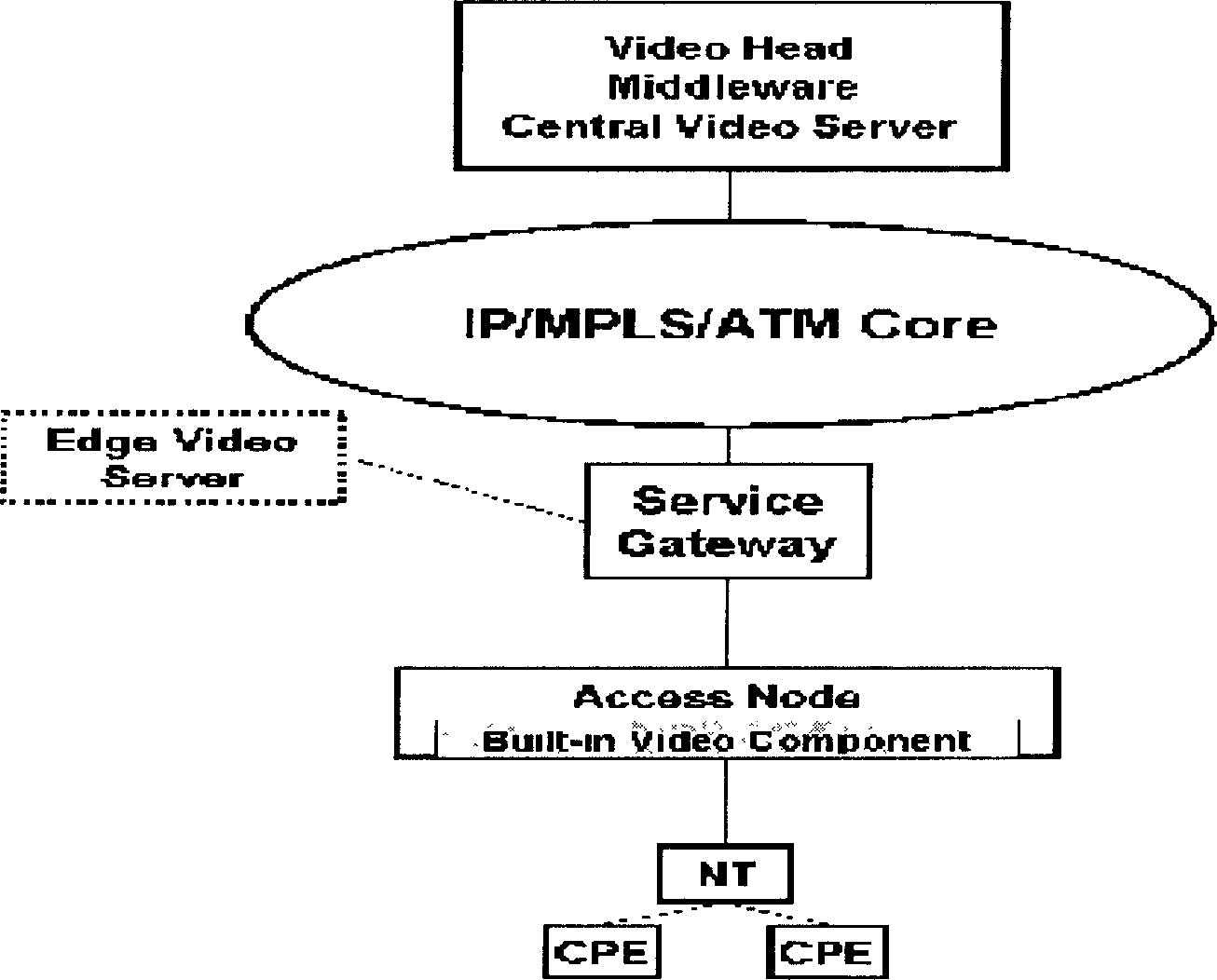
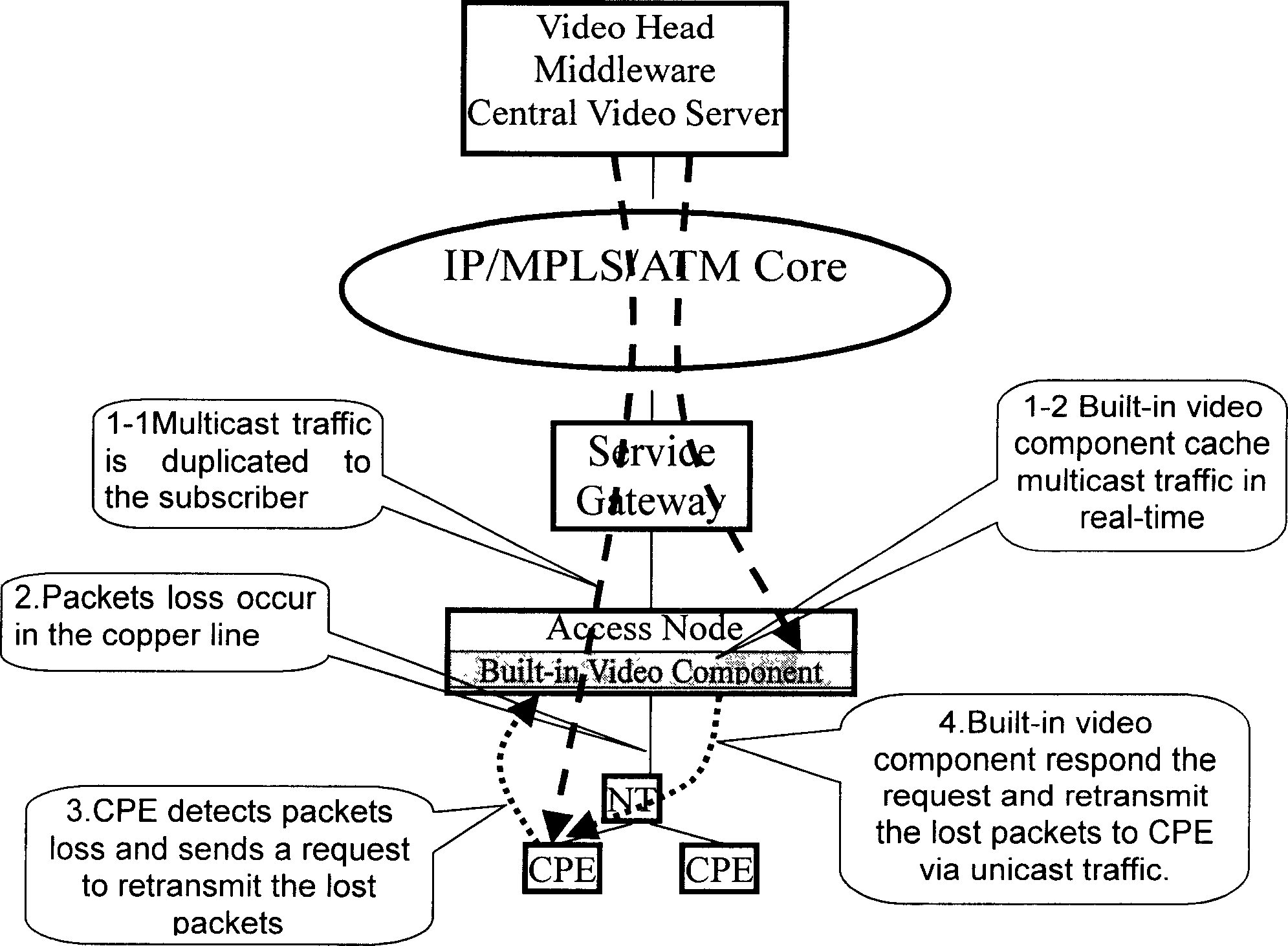
Broadband access device and its application
InactiveCN1866831AImprove experienceReduce bandwidth requirementsTwo-way working systemsSelective content distributionNetwork resource managementBroadband
Owner:HUAWEI TECH CO LTD
Method for setting voting-based approval node in approval process
ActiveCN108694560ALess authoritySimplify permissions managementVoting apparatusOffice automationDatabaseDecision-making
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Method for seeking reference for approval tasks by approvers
ActiveCN109102253ASimplify permissions managementLittle change in the number of rolesComputer security arrangementsOffice automationButt jointConfusion
The invention discloses a method for seeking reference for approval tasks by approvers, which comprises the following steps: the examining and approving persons obtain examining and approving tasks inthe examining and approving process; the approver initiates a request for reference to one or more of the persons consulted for the approval task. The interviewee is an independent individual character role, and only one user can be associated with an independent individual character role at the same time, and one user can be associated with one or more independent individual character roles. Theapprover of the invention initiates a reference opinion inquiry request through the management system, and the reference opinion can assist the approver to make a more scientific and correct examination and approval result, and can form an effective inquiry record in the system. The consultant adopts the independent individual character role, and the employee can realize seamless butt joint whenhe leaves his post or transfers his post, and there will be no delay or omission in the handover of the consulted task, so as to ensure that the consultant gives reference opinions in time, and avoidthe leakage of company secrets and the confusion of management.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
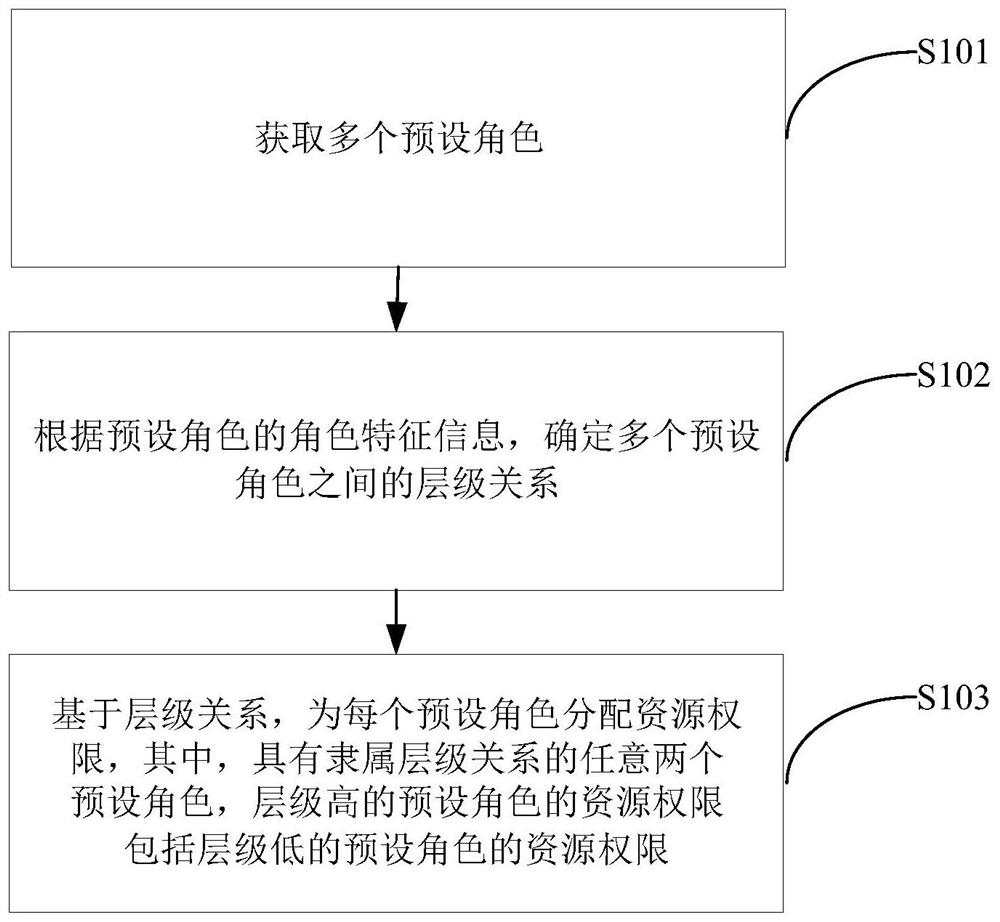
Resource allocation method and device, computer equipment and storage medium
PendingCN112733162ASatisfy fine-grained controlSimplify permissions managementDigital data protectionOffice automationResource assignmentDistribution method
The invention provides a resource allocation method and device, computer equipment and a storage medium, and the method comprises the steps of obtaining a plurality of preset roles; determining a hierarchical relationship among a plurality of preset roles according to the role feature information of the preset roles; and based on the hierarchical relationship, allocating resource permissions to each preset role, the resource permissions of any two preset roles having the membership hierarchical relationship being included in the resource permissions of the preset roles having the high hierarchy, and the resource permissions of the preset roles having the low hierarchy. According to the embodiment of the invention, the authority management of the user is simplified and the system overhead is reduced by presetting a plurality of roles; when the user role is changed, other roles having a membership hierarchical relationship with the role do not need to be modified, so that the replicability of the operation is reduced; besides, when the resources corresponding to the roles are changed, only the resources of the preset roles with low hierarchies need to be adjusted, and the resources of the preset roles with high hierarchies do not need to be modified, so that the operation replicability is reduced, the resource management and control efficiency is improved, and the refined management and control of the resource permission is met.
Owner:北京乐学帮网络技术有限公司
Method for setting an approval process based on a field
ActiveCN108984715AMeet the needs of actual operation managementEasy to operateComputer security arrangementsSpecial data processing applicationsDatabase
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Shortcut function setting method
ActiveCN108958870AEasy to viewEasy to operateComputer security arrangementsExecution for user interfacesManagement efficiencyHuman–computer interaction
The invention discloses a shortcut function setting method, which comprises the steps of setting a shortcut menu and a shortcut new list, wherein setting the shortcut menu includes setting a quick menu entry, setting a shortcut menu, displaying the shortcut menu through the shortcut menu entry, and displaying the shortcut menu selected in the step S2 through the shortcut menu entry; according to any shortcut menu in step K1 needed to be selected, displaying a function interface correspond to that shortcut menu. The method is convenient for quickly completing the viewing and operation of a common menu, quickly completing the addition of a form, and improves the office efficiency. Only unique users can be associated with a role at the same time. When a user enters a new job or transfers a new post, he / she only needs to associate the user with a new role, the common shortcut menu corresponding to the role can be obtained through the shortcut menu entry, and the form corresponding to the role with the new permission can also be obtained through the shortcut new form entry, which greatly improves the permission management efficiency of the system in use.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Broadband access equipment and uses thereof
InactiveCN101282263BImprove experienceReduce bandwidth requirementsError prevention/detection by using return channelData switching by path configurationNetwork resource managementRadio access network
The invention provides a digital subscriber line access multiplexer and application thereof. The core of the digital subscriber line access multiplexer comprises: arranging a video service unit in the digital subscriber line access multiplexer, and the inner-arranged video service unit transmitting the stored video service to a subscriber terminal through the digital subscriber line access multiplexer where the video service unit is according to the request of the subscriber terminal. The invention reduces the bandwidth requirement of the video service to the access network and convergence network, and solves efficiently the bottleneck problem of bandwidth of a backbone network and the convergence network; the invention does not have influence on design principles that the current bandwidth access network and the convergence network do not realize exchange for video services, simplifies resource management mechanism for entire access network and the convergence network and complexity for managing the resources of the access network, thereby enhancing utilization rate of the network bandwidth, reducing complexity for managing the network resources and eliminating bottleneck of the video server.
Owner:HUAWEI TECH CO LTD
Approval task transfer method based on improved rbac authority control mechanism
ActiveCN109165524BTimely processingAvoid affecting normal operationsDigital data protectionDigital data authenticationSoftware engineeringWorkload
The invention discloses an approval task transfer method based on an improved RBAC authority control mechanism, including: creating a role in the system, the role is an independent individual role, and an independent individual role can only be associated with a unique user at the same time period. Associate one or more independent individual roles; the transferer obtains the approval tasks in the approval process; the transferer transfers the approval tasks to the transferee, and the transferee is an independent individual role. In the present invention, the transferee adopts an independent individual character role. When the employee corresponding to the user associated with the transferee's role leaves or transfers, he only needs to cancel the original association and associate the user corresponding to the new employee with the role to automatically obtain the current status of the role. All transferred approval tasks are handed over through role association, with a small workload and seamless connection, without delay or omission in the transfer of approval tasks, ensuring that urgent tasks are processed in a timely manner.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Dynamic access control method based on business body
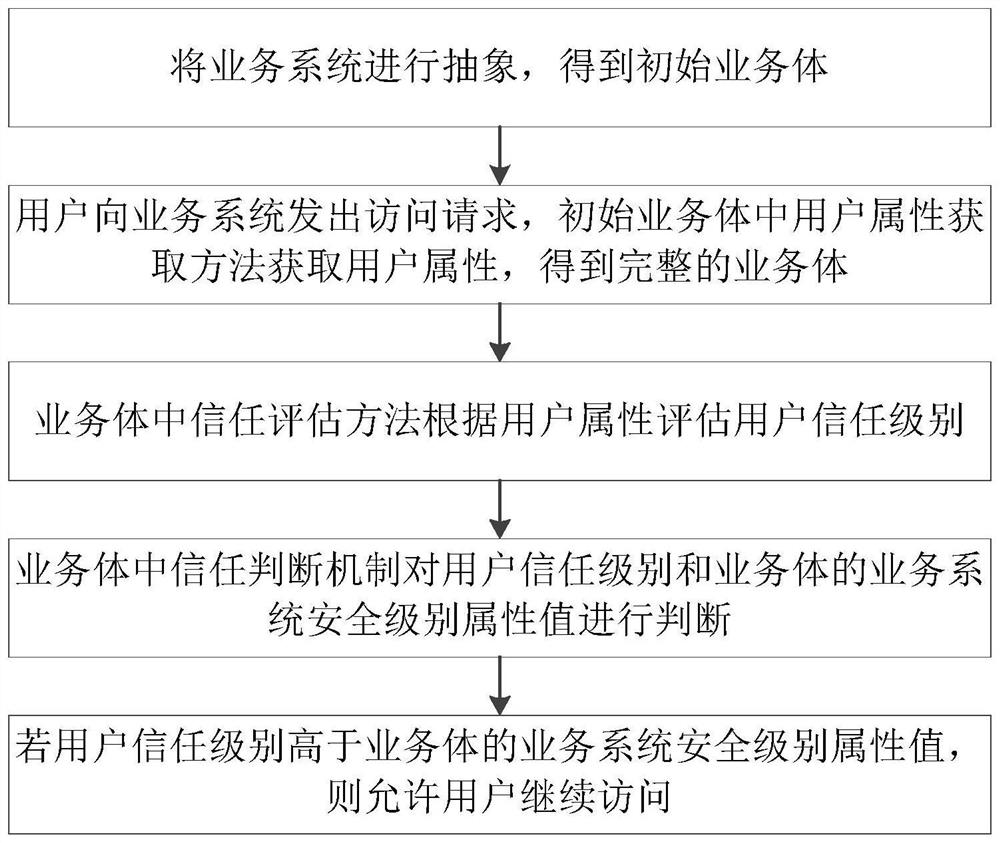
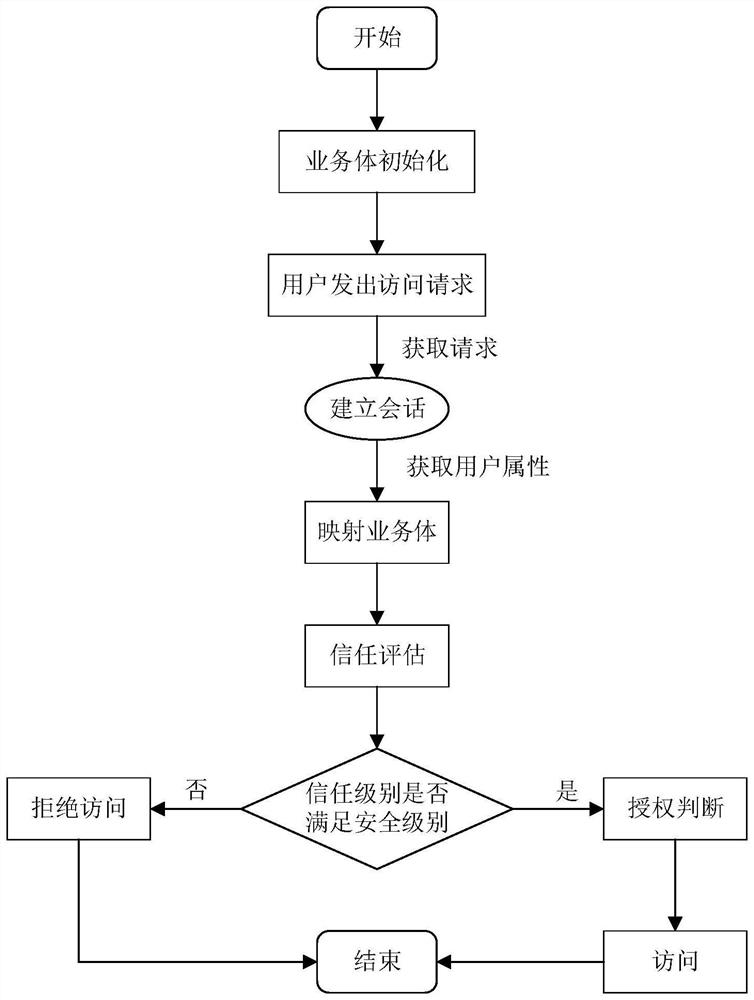
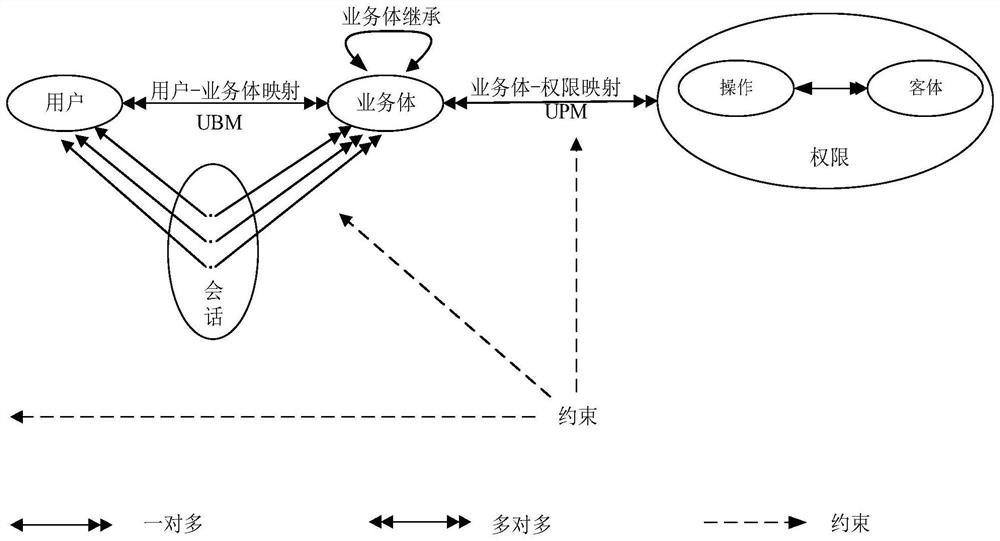
PendingCN114567489AEnsure safetyQuick access controlSecuring communicationService systemAuthorization
The invention provides a dynamic access control method based on a business body, which relates to the technical field of system access control, and comprises the following steps: abstracting a business system to obtain an initial business body BEInit; a user sends an access request to a service system, a user attribute acquisition method in an initial service body BEInit acquires user attributes, a complete service body is obtained, and a trust evaluation method in the service body evaluates a user trust level according to the user attributes; a trust judgment mechanism in the service body judges a user trust level and a service system security level attribute value of the service body; and if the user trust level is higher than the service system security level attribute value of the service body, allowing the user to continue to access. According to the method, access control is carried out based on the business body by introducing a business body concept, and flexible, rapid and safe access control authorization is realized in an open and complex super application system environment.
Owner:LINYI UNIVERSITY
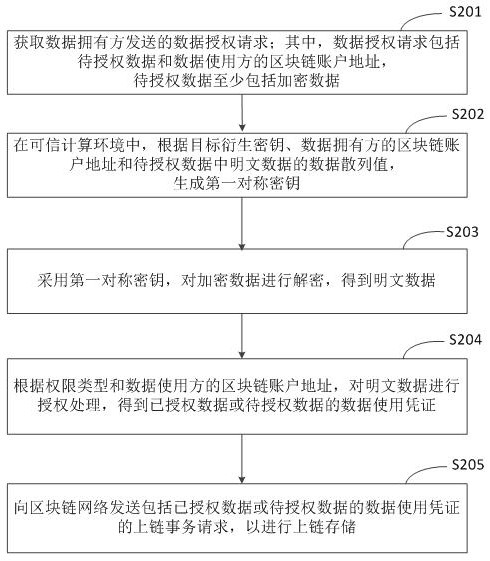
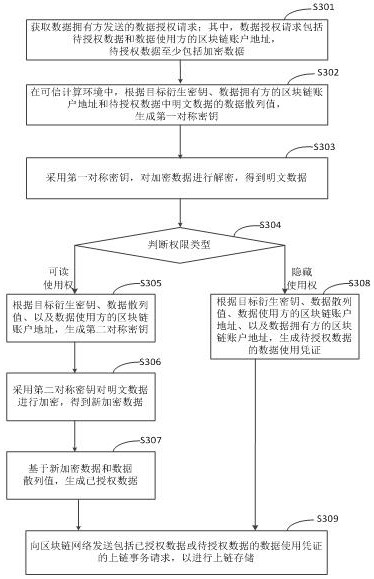
Block chain privacy data processing method, device, equipment and storage medium
ActiveCN111737366BSolve the problem of high management complexitySimplify permissions managementDatabase distribution/replicationDigital data protectionTrusted ComputingEngineering
The invention discloses a private data processing method, device and equipment of a block chain and a storage medium, relates to the technical field of block chains, and can be used for cloud computing and cloud service. According to the specific implementation scheme, acquiring a data authorization request sent by a data owner, wherein the data authorization request comprises to-be-authorized data and a block chain account address of a data user, and the to-be-authorized data at least comprises encrypted data; in the trusted computing environment, according to the block chain account addressof the data user, performing authorization processing on the encrypted data in the to-be-authorized data to obtain authorized data or a data use certificate of the to-be-authorized data; and sending an uplink transaction request comprising a data use certificate of the authorized data or the to-be-authorized data to a block chain network for uplink storage. Therefore, the complexity of privacy data authority management is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com