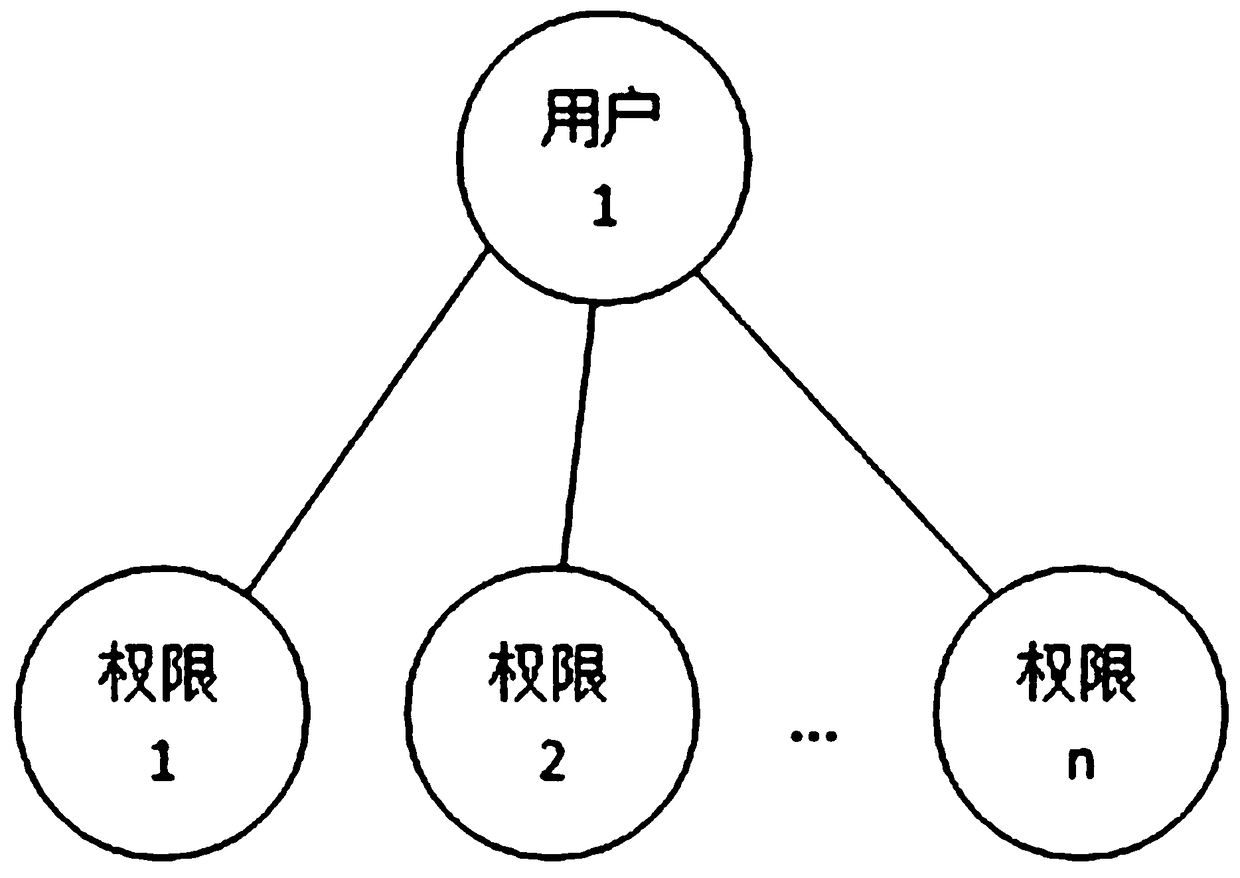
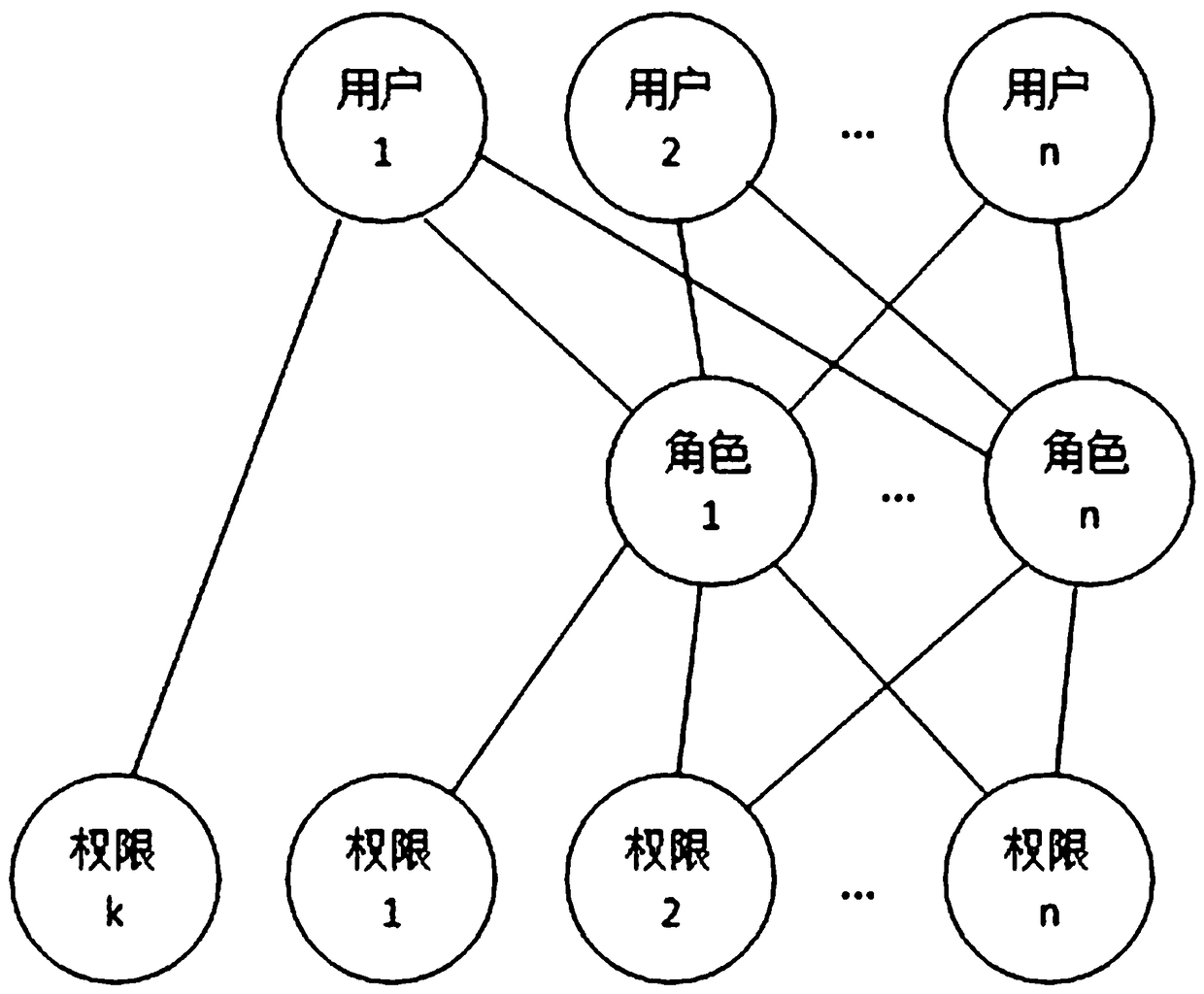
Approval method for form data operations
A form data and form technology, applied in digital data protection, data processing applications, structured data retrieval, etc., can solve the problems of confusing similar roles and permissions, indistinguishable submitters, disagreement, etc., to avoid leakage of confidential information, The effect of shortening the review cycle and small changes in quantity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
[0120] [Embodiment 3] When there are multiple reviewers for one review request, the review result is obtained according to the preset review rules.
[0121] Specifically, the review rule may be: take the review result of the first reviewer who gives the review opinion as the review result, and as long as any reviewer gives the review opinion, the review will end.
[0122] As long as any reviewer submits an review opinion, the review result is determined, and the review is over, and the review tasks of other reviewers are automatically removed, realizing efficient and fast review. It is especially applicable to situations where multiple people (multiple approval roles) have the same approval authority for the same review task, and any one person (role) can decide the review result.
[0123] It can be: among multiple reviewers, as long as any one of the reviewers gives "Agree / Pass", the review result is "Agree / Pass", as long as any one of the reviewers gives "Agree / Pass" " revi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com