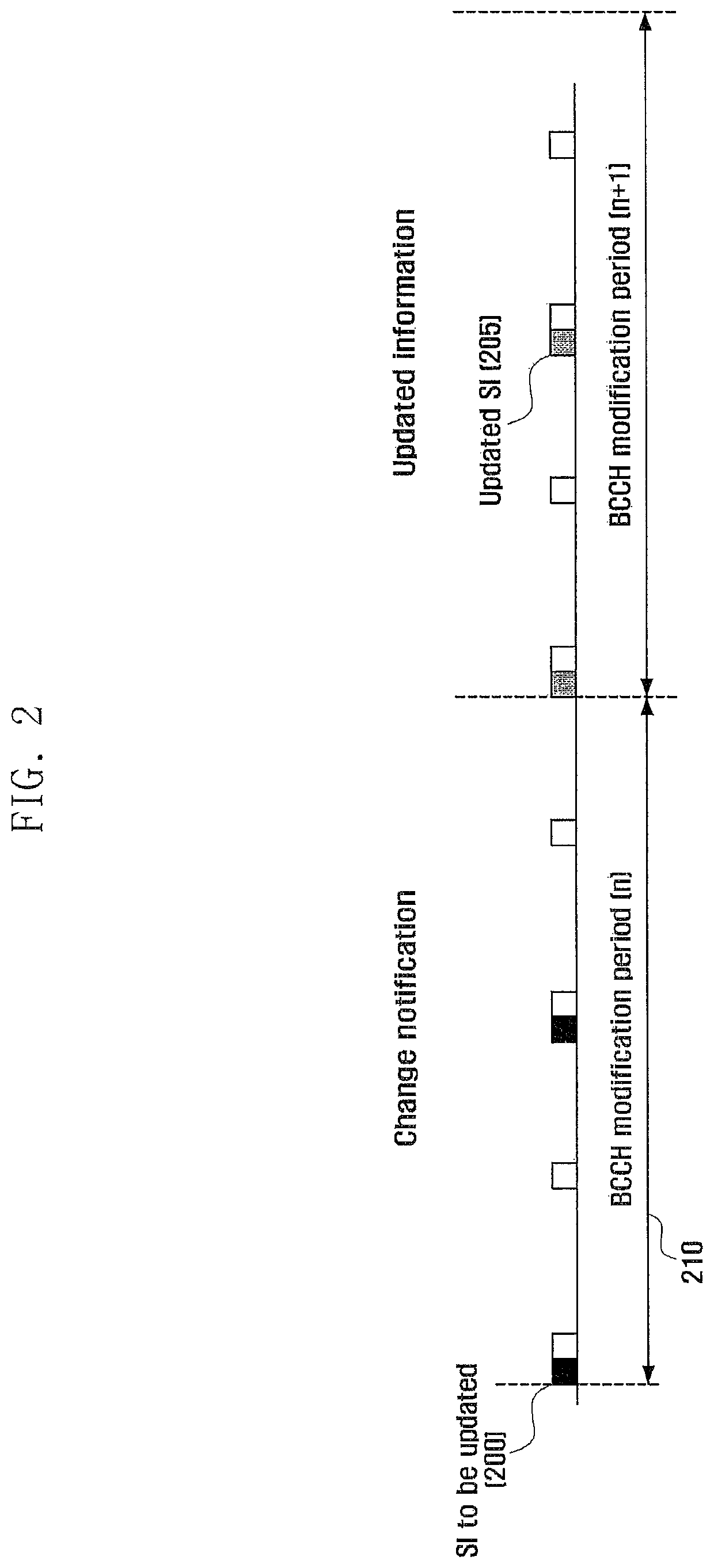
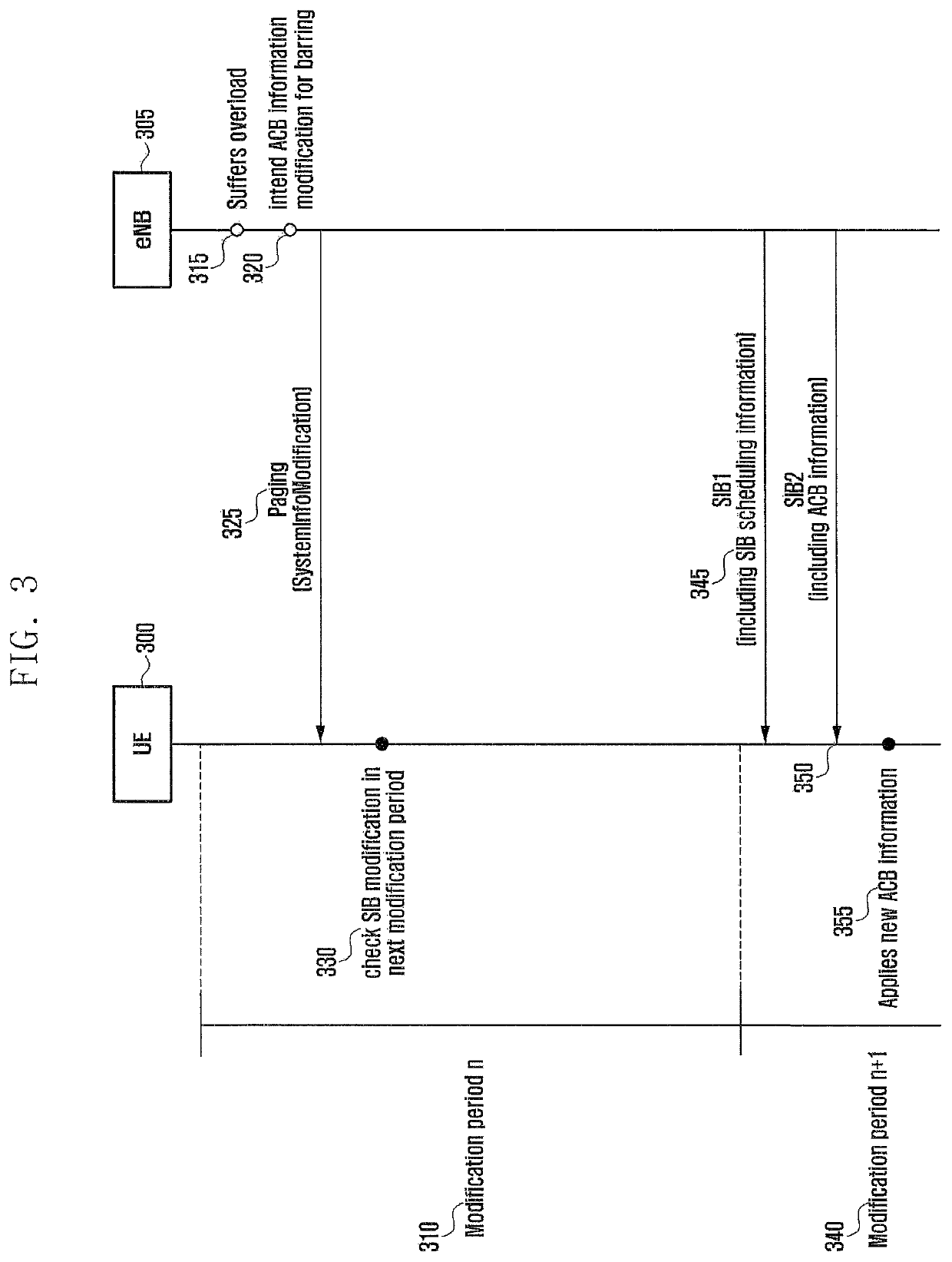
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40results about How to "Reduce message size" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
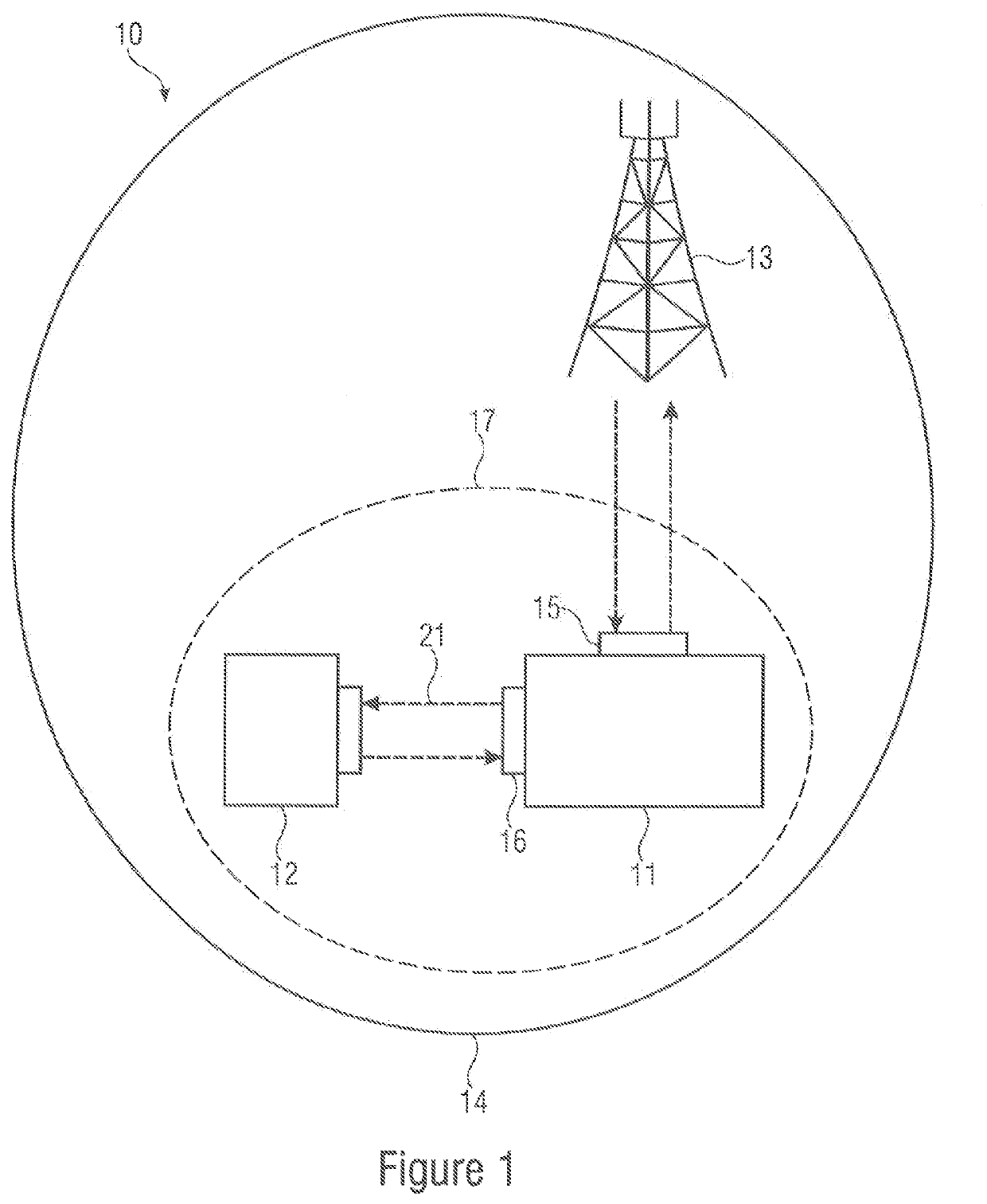
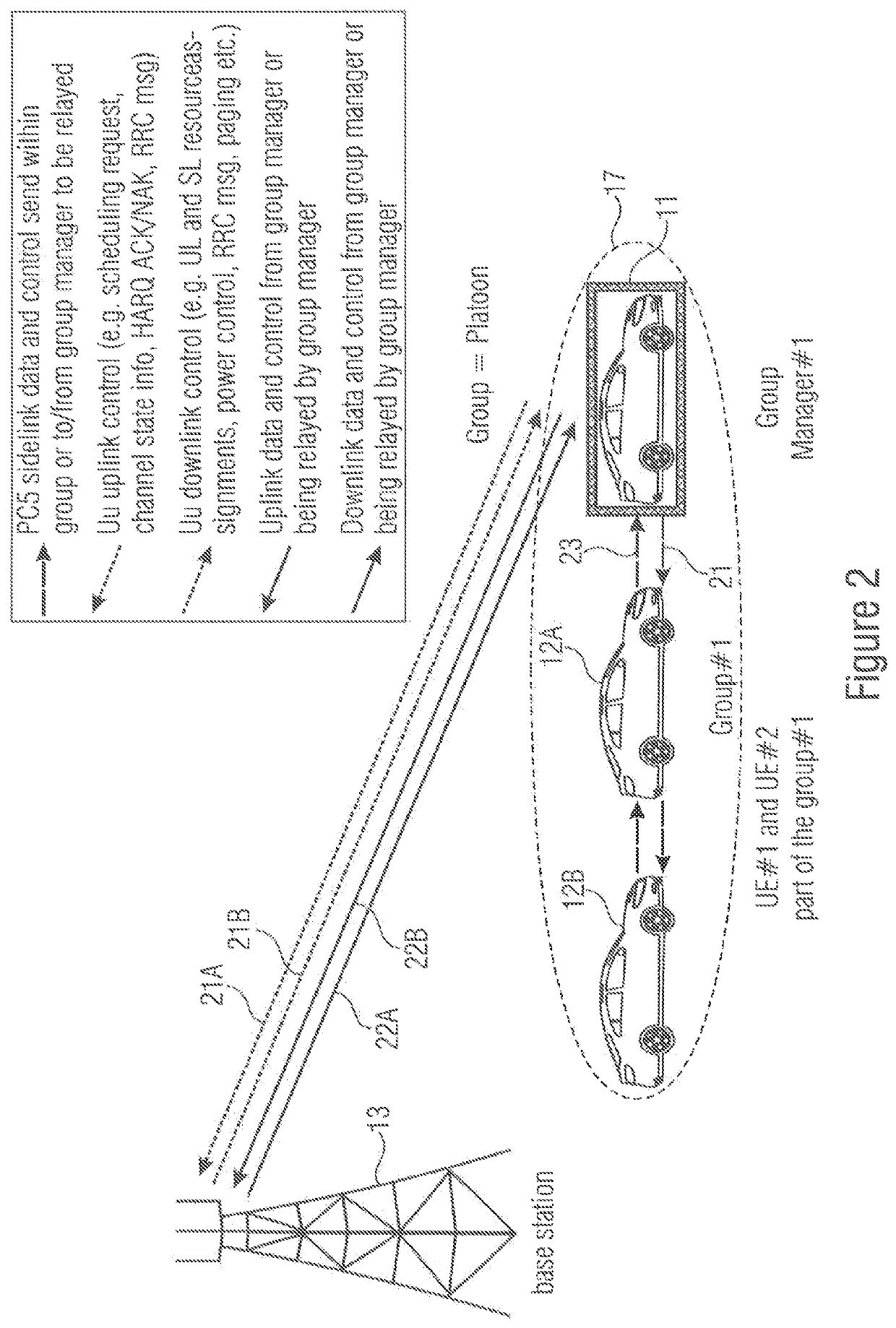
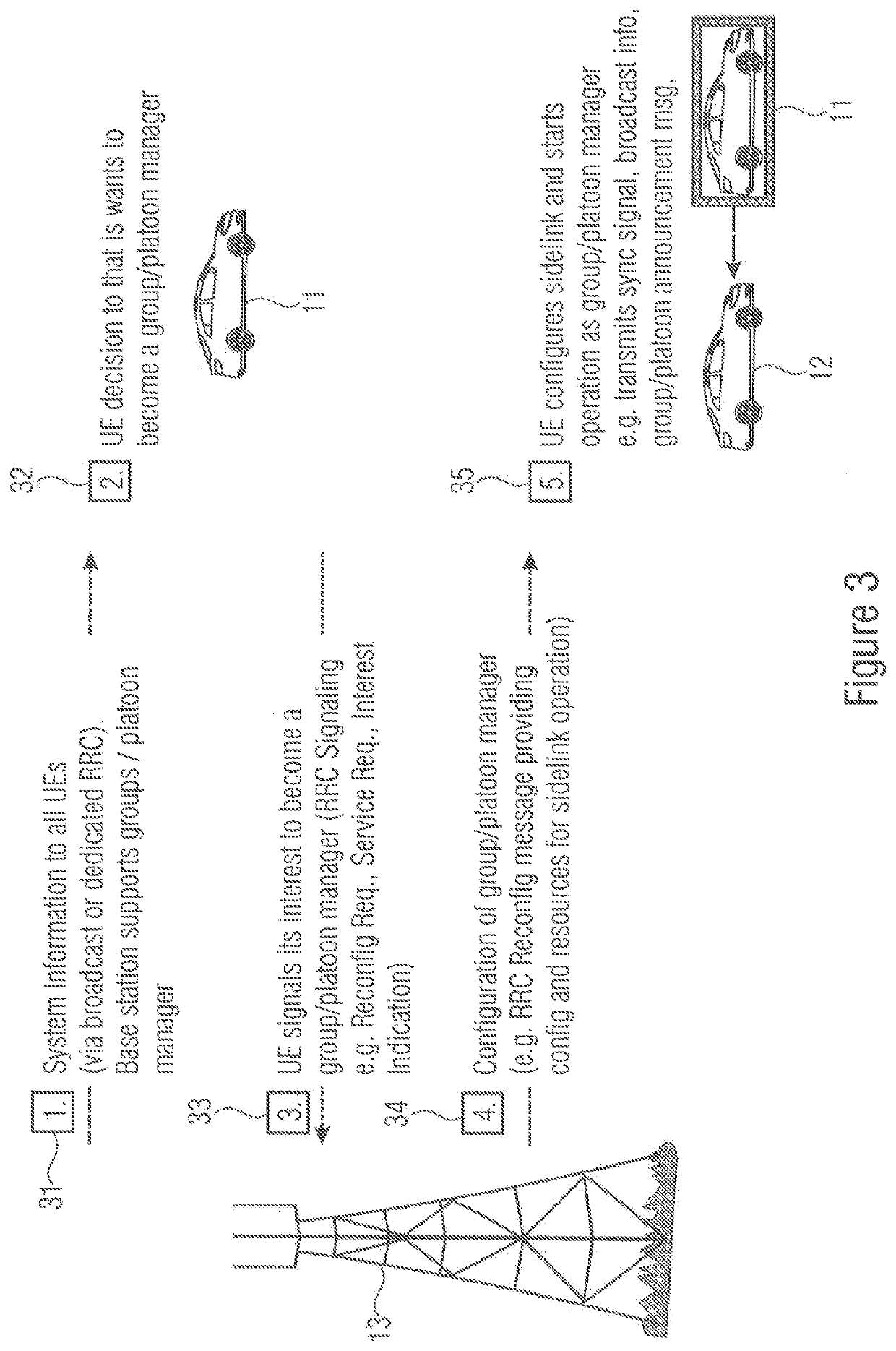
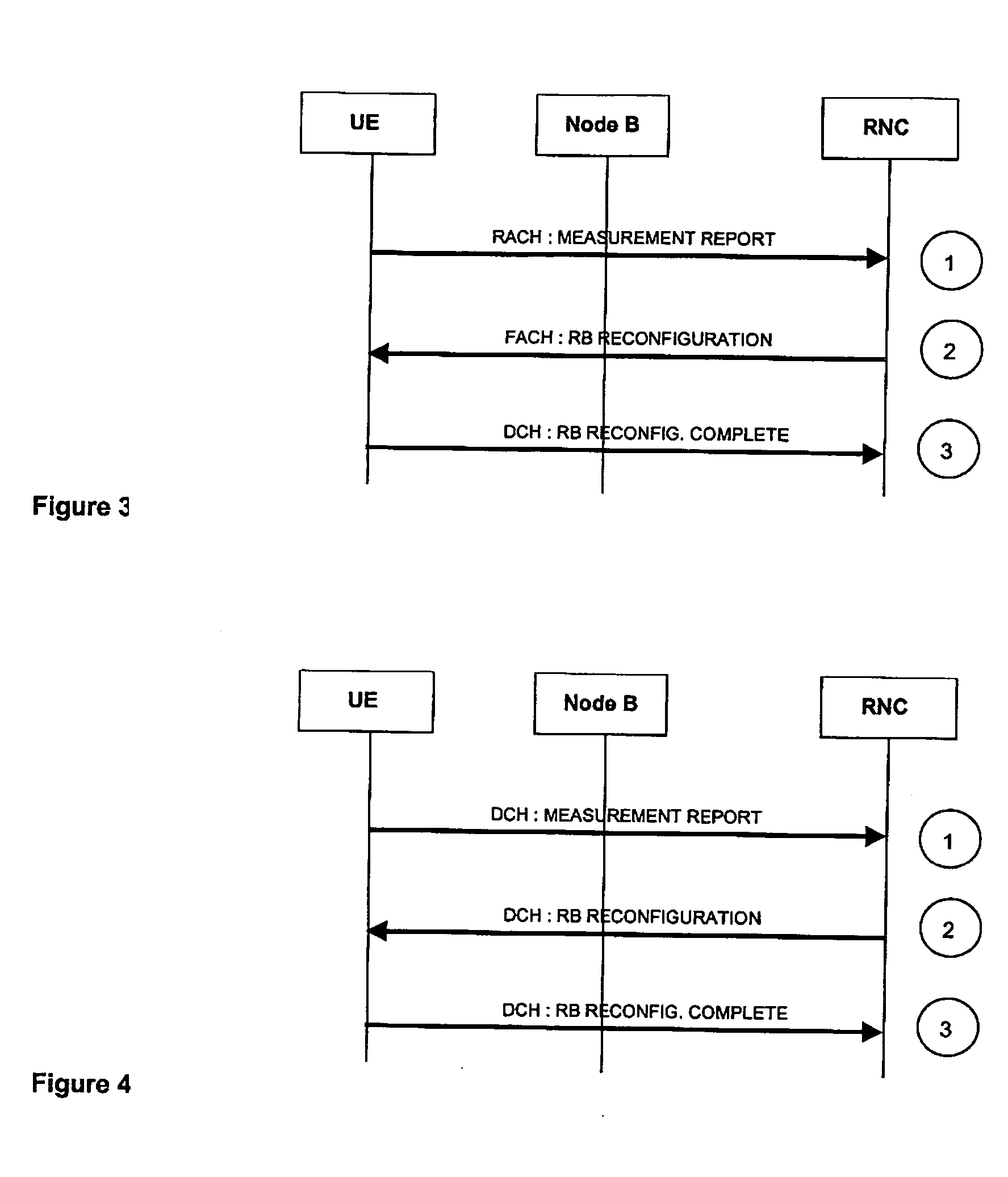
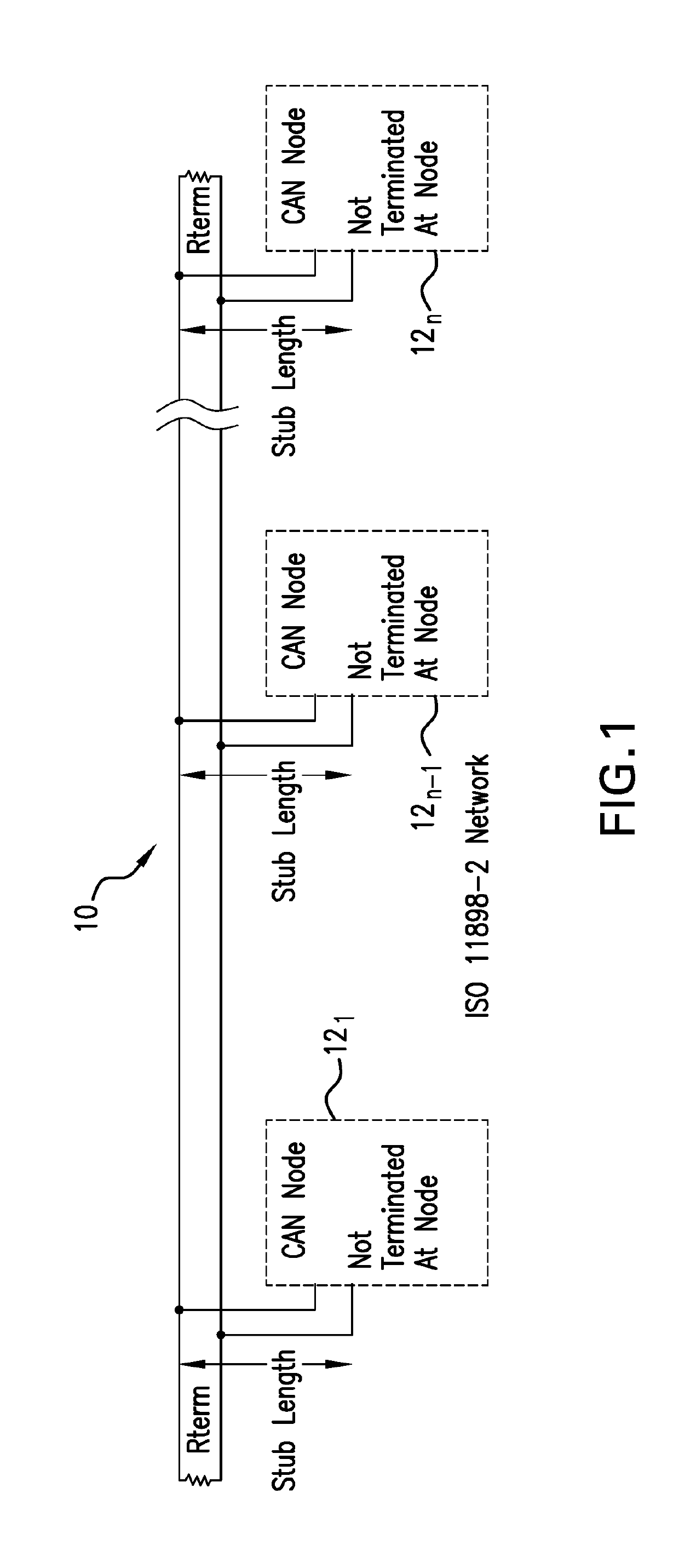
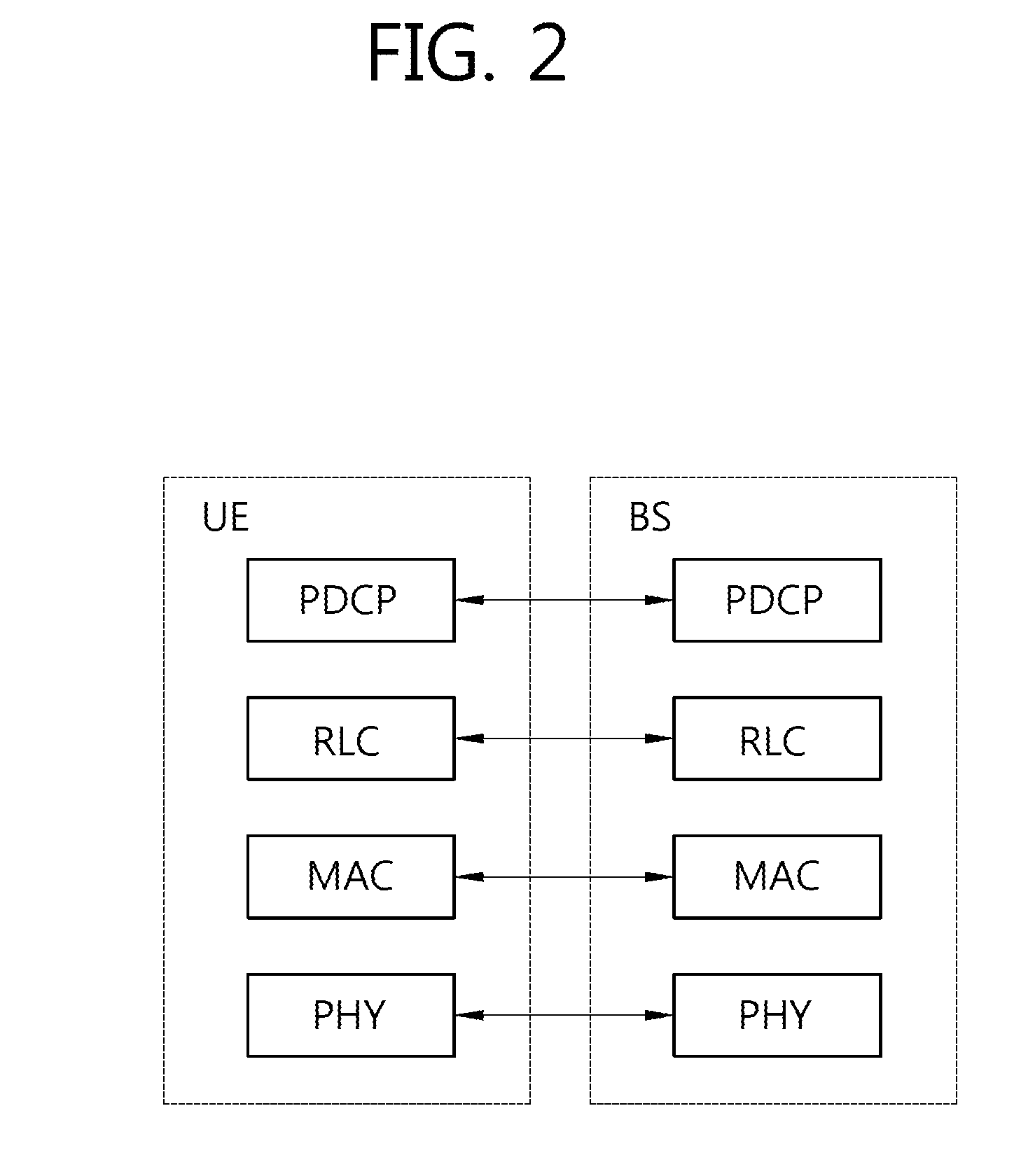
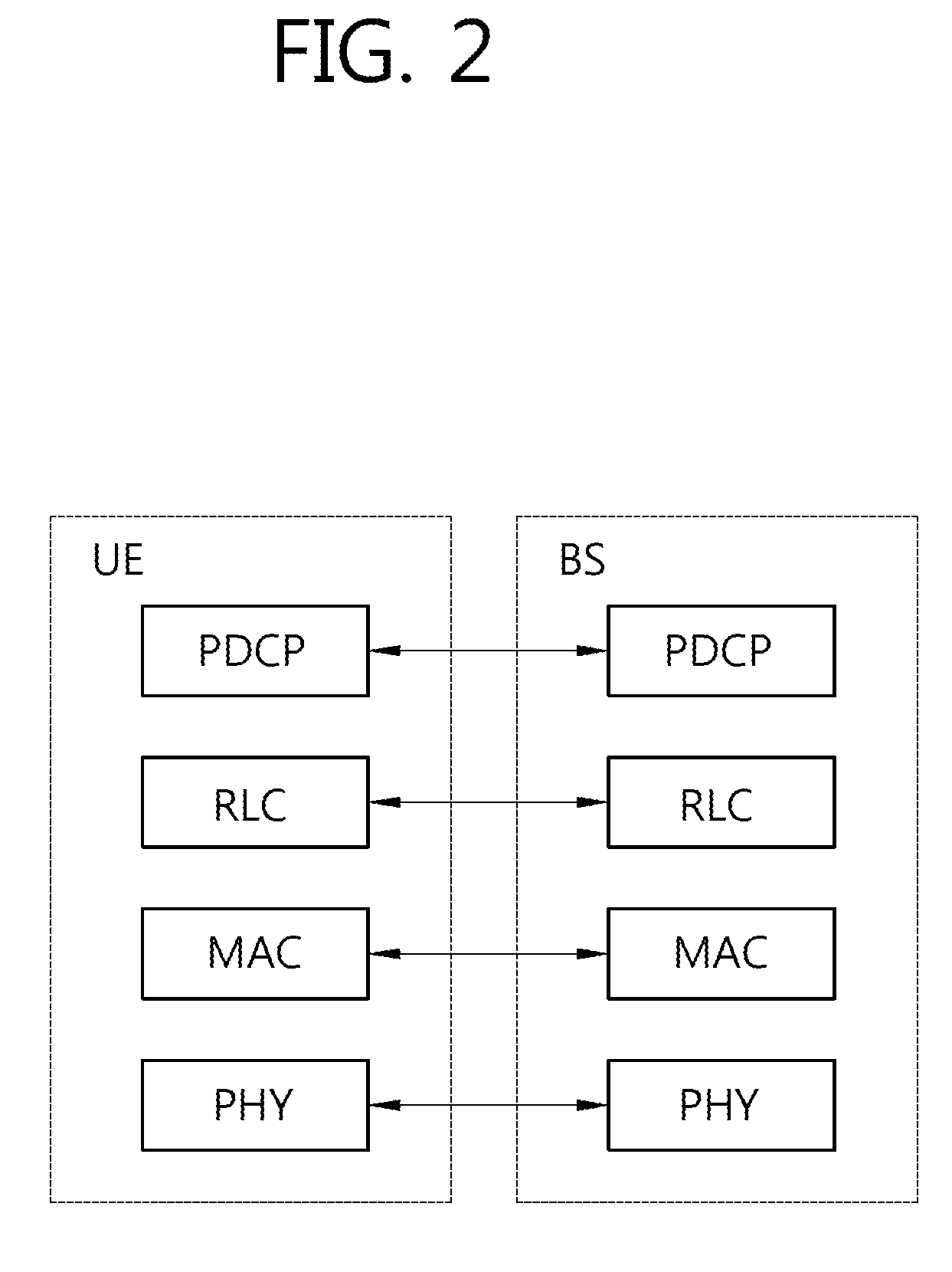
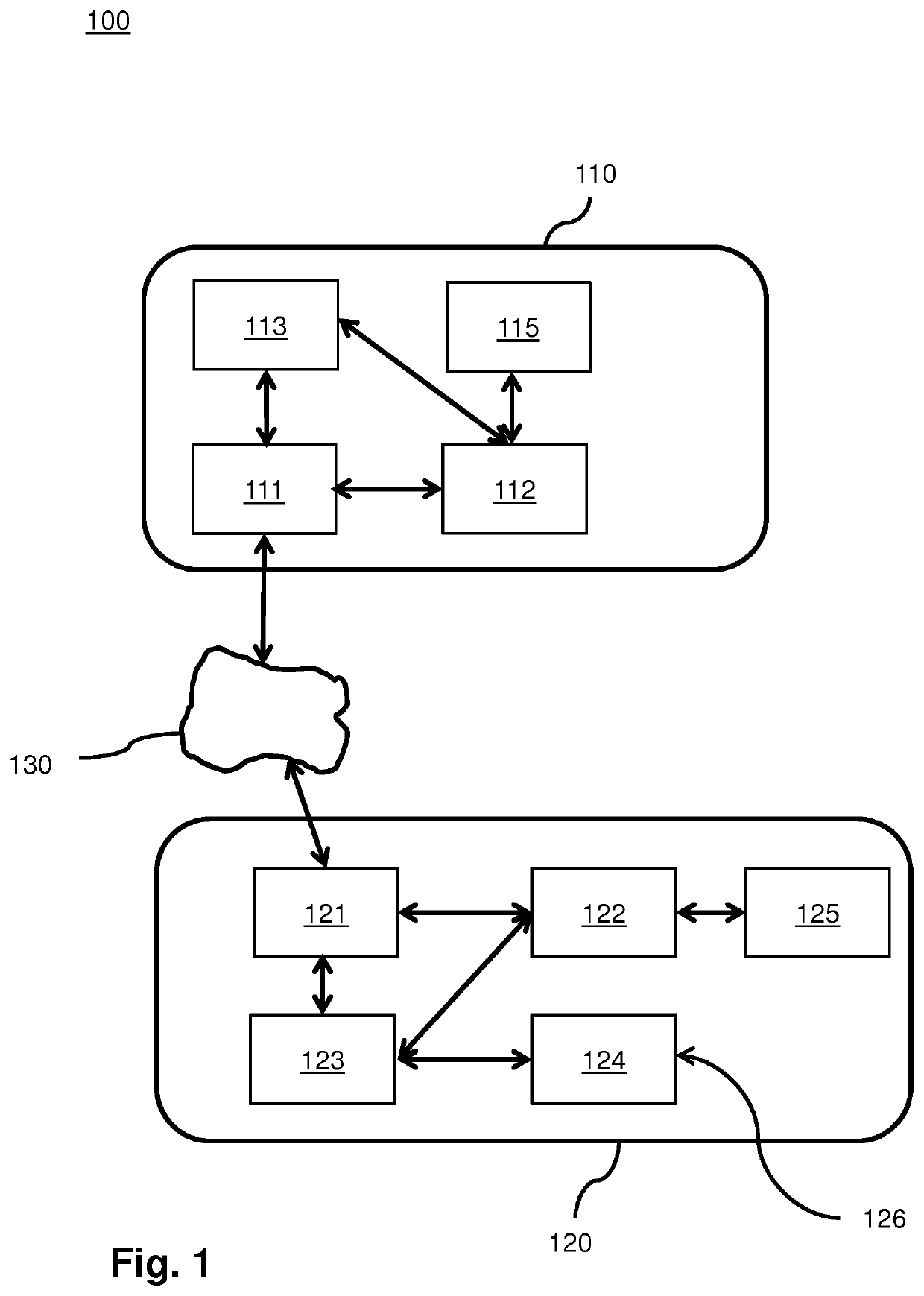
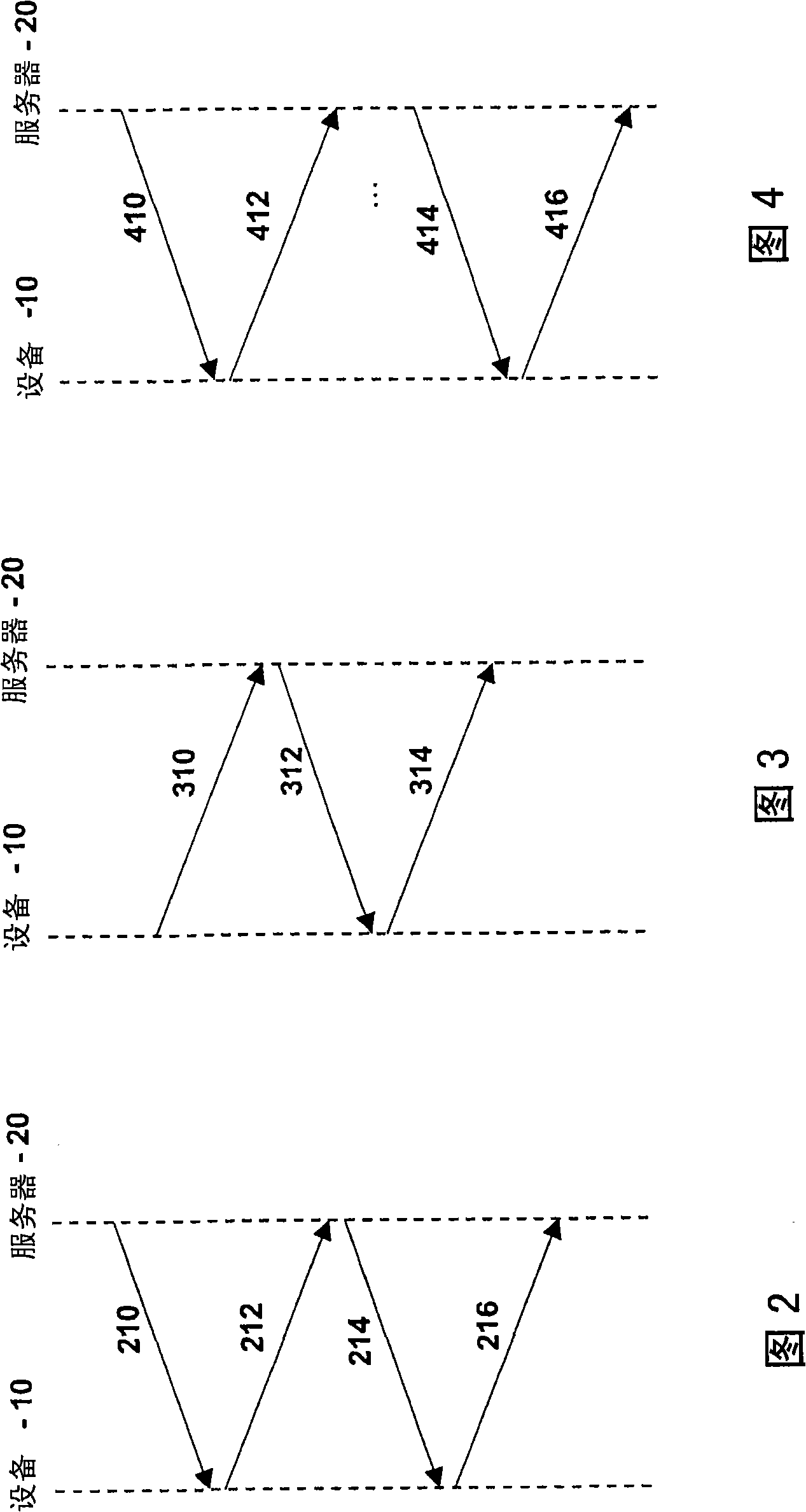
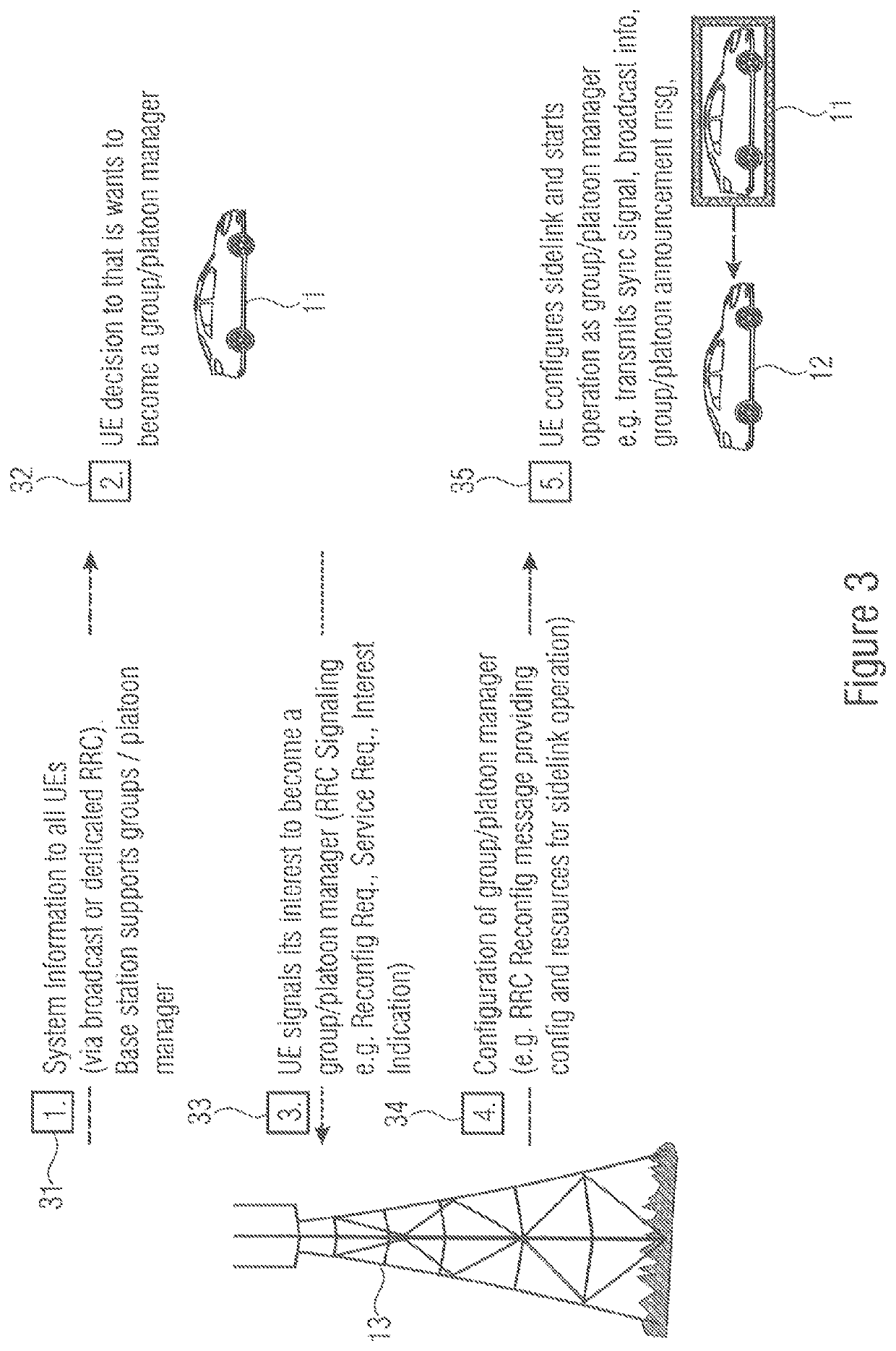
UE GROUPS, UE GROUP MANAGER UEs AND UE GROUP MEMBER UEs
ActiveUS20200092685A1Positive impact on accuracyImprove accuracyParticular environment based servicesNetwork topologiesUser equipmentElectrical and Electronics engineering
The present invention concerns a novel form of communication within a cellular wireless communication network. One aspect of the invention concerns a User Equipment for a cellular network, wherein the UE inter alia includes a first interface for UE-to-Basestation communication configured to communicate with a base station of the cellular network and a second interface for UE-to-UE communication configured to communicate with one or more other UEs of a UE-Group to which the UE belongs. According to the invention the UE is configured to receive via its first interface configuration data for configuring its second interface, and to coordinate, via the second interface, a communication within the UE Group.
Owner:KONINKLJIJKE PHILIPS NV
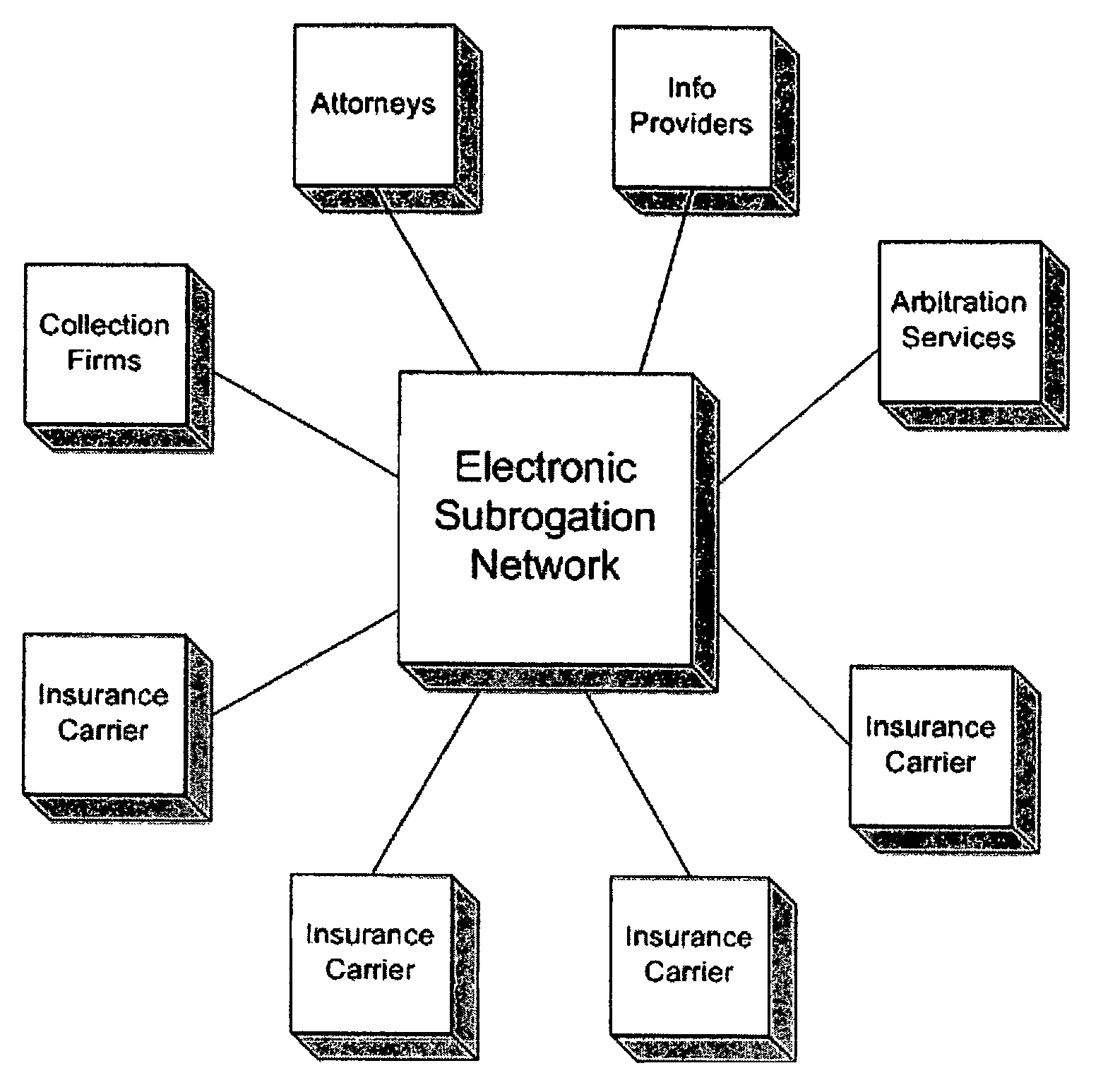
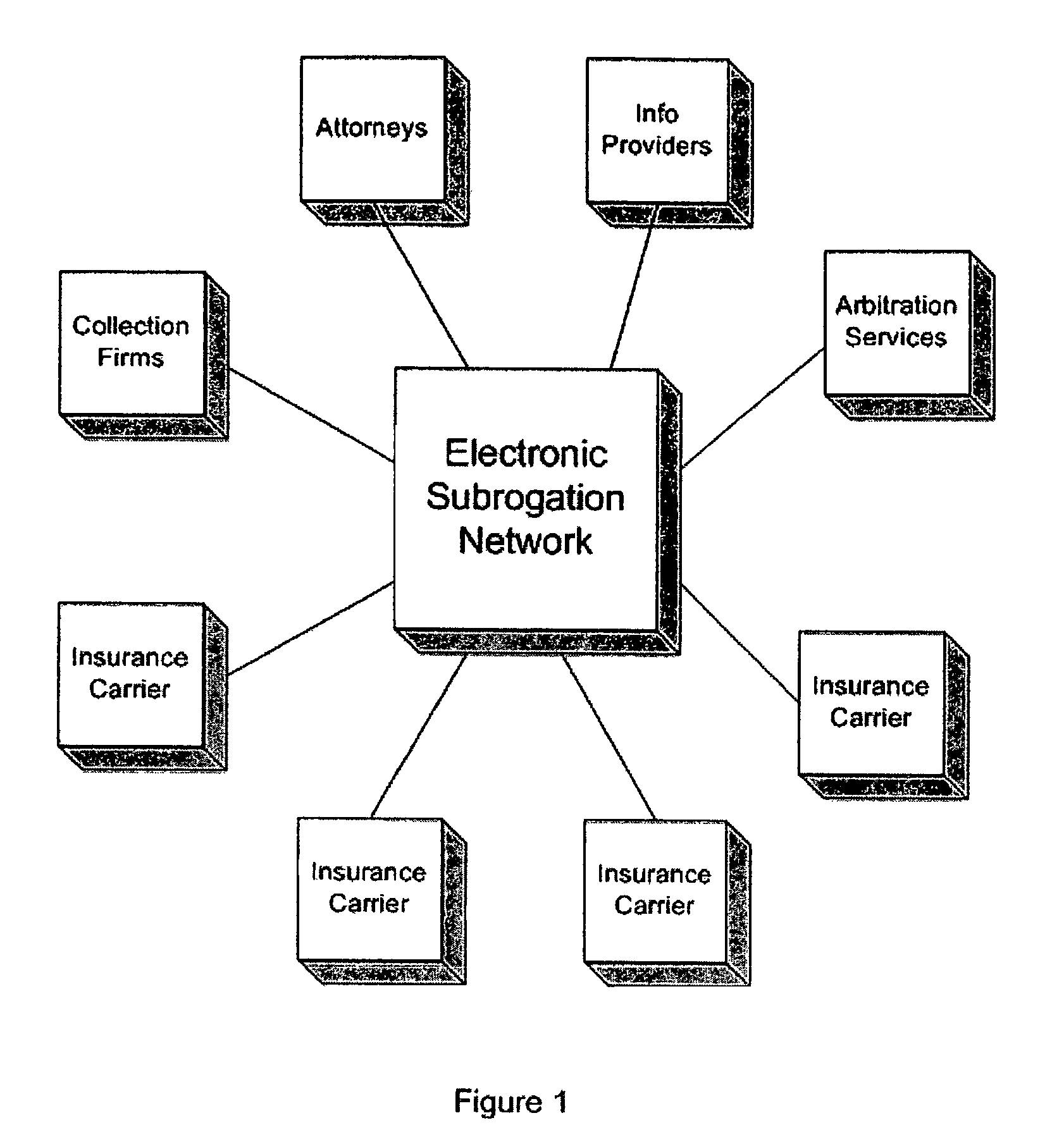
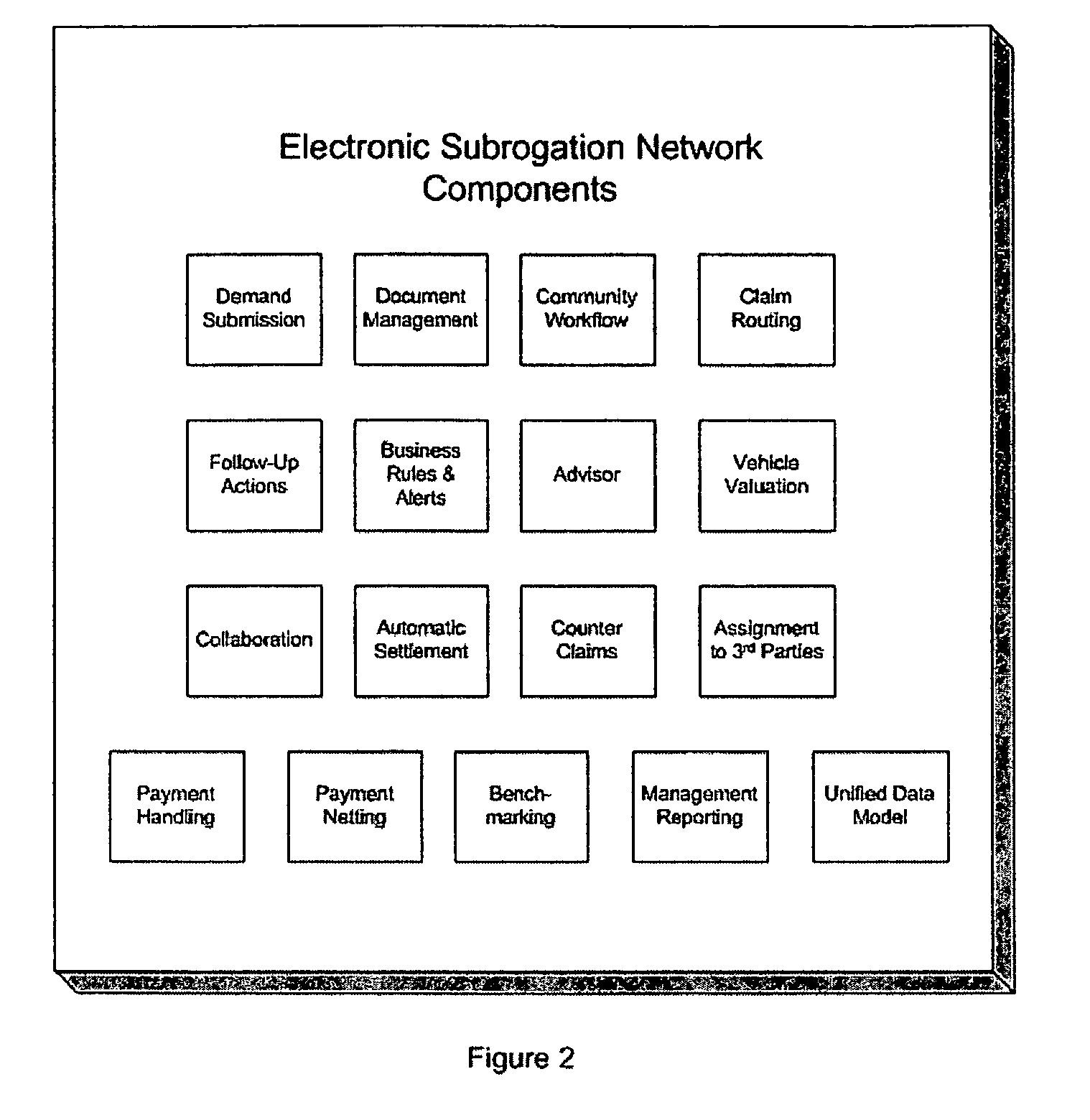
System and process for electronic subrogation, inter-organization workflow management, inter-organization transaction processing and optimized web-based user interaction
ActiveUS7962385B2Reduced processing power requirementsReduce message sizeFinanceOffice automationInter organizationalTransaction processing system
An intelligent electronic subrogation network (“ESN”) automates intra-organization workflow, inter-organization workflow and collaboration for insurance subrogation. This ESN is facilitated by a novel system architecture and process that includes an inter-organizational workflow management system, an inter-organizational transaction processing system, and a unique mechanism for optimizing and enriching web-based user interaction within any such system.
Owner:ARBITRATION FORUMS
Channel setup in a wireless communication network
InactiveUS20050250504A1Shorten the timeImprove reliabilityRadio/inductive link selection arrangementsNetwork data managementComputer hardwareTransmission channel
A method, user terminal and network entity sets up channels in a wireless communications network by receiving a broadcast message including at least one predefined radio configuration at a user terminal. The method also includes receiving a configuration message from a network controller at the user terminal. The configuration message includes an indication to configure the user terminal to adopt the predefined radio configuration for a new transmission channel. The method also includes indicating that the user terminal is configured to transmit data to the network controller according to the predefined radio configuration.
Owner:NOKIA CORP
Managing user profile information in a mobile telecommunications network
InactiveUS20070280177A1Reduce message sizeConnection managementRadio/inductive link selection arrangementsSeparated stateTelecommunications network
A method of managing user profile information in a mobile telecommunications network comprising a plurality of control nodes which can send signals to, and receive signals from, mobile user equipment, the method comprising the step of transferring user profile information from an old control node to a new control node when a mobile user equipment moves from a detached state to an active state.
Owner:NOKIA CORP
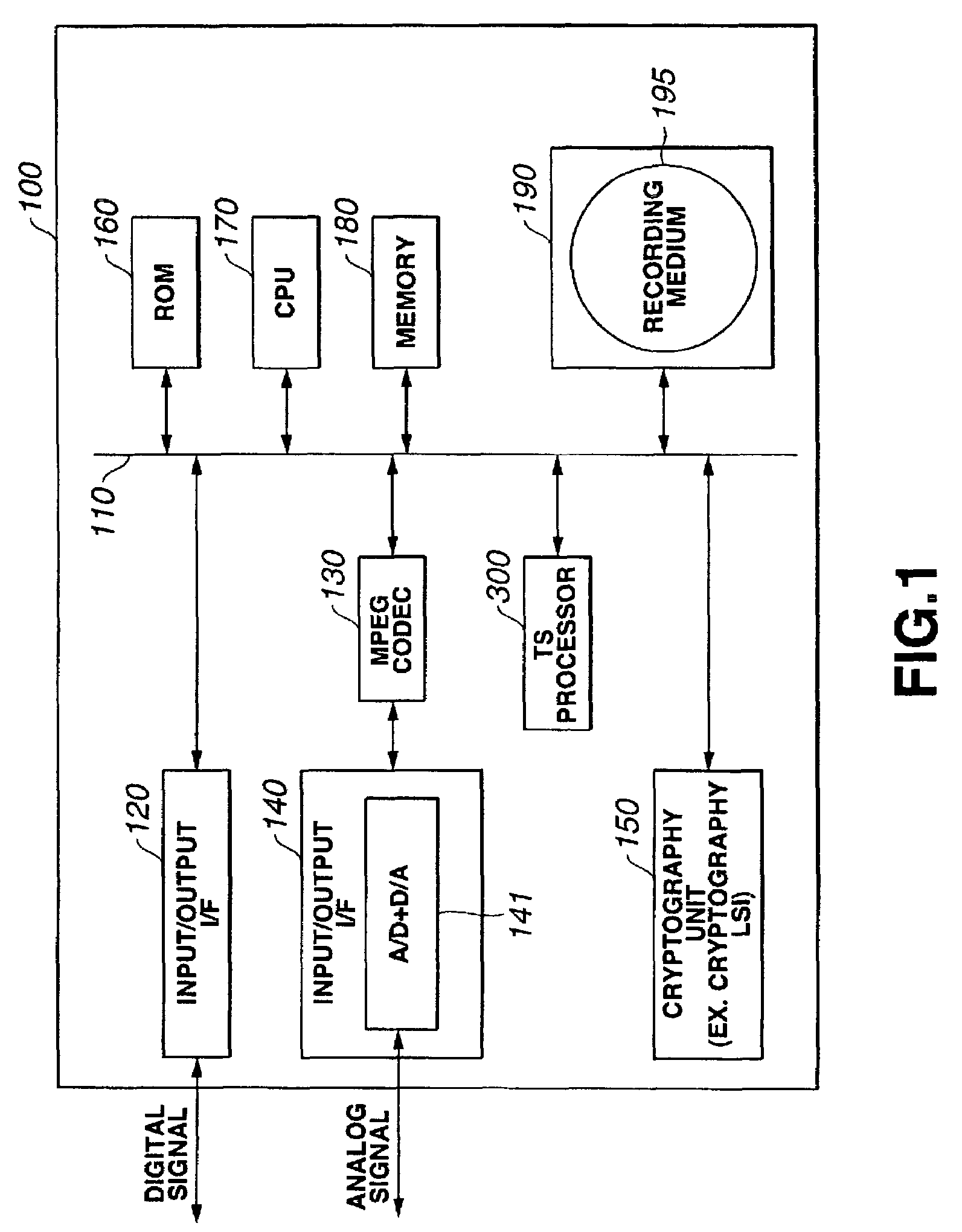
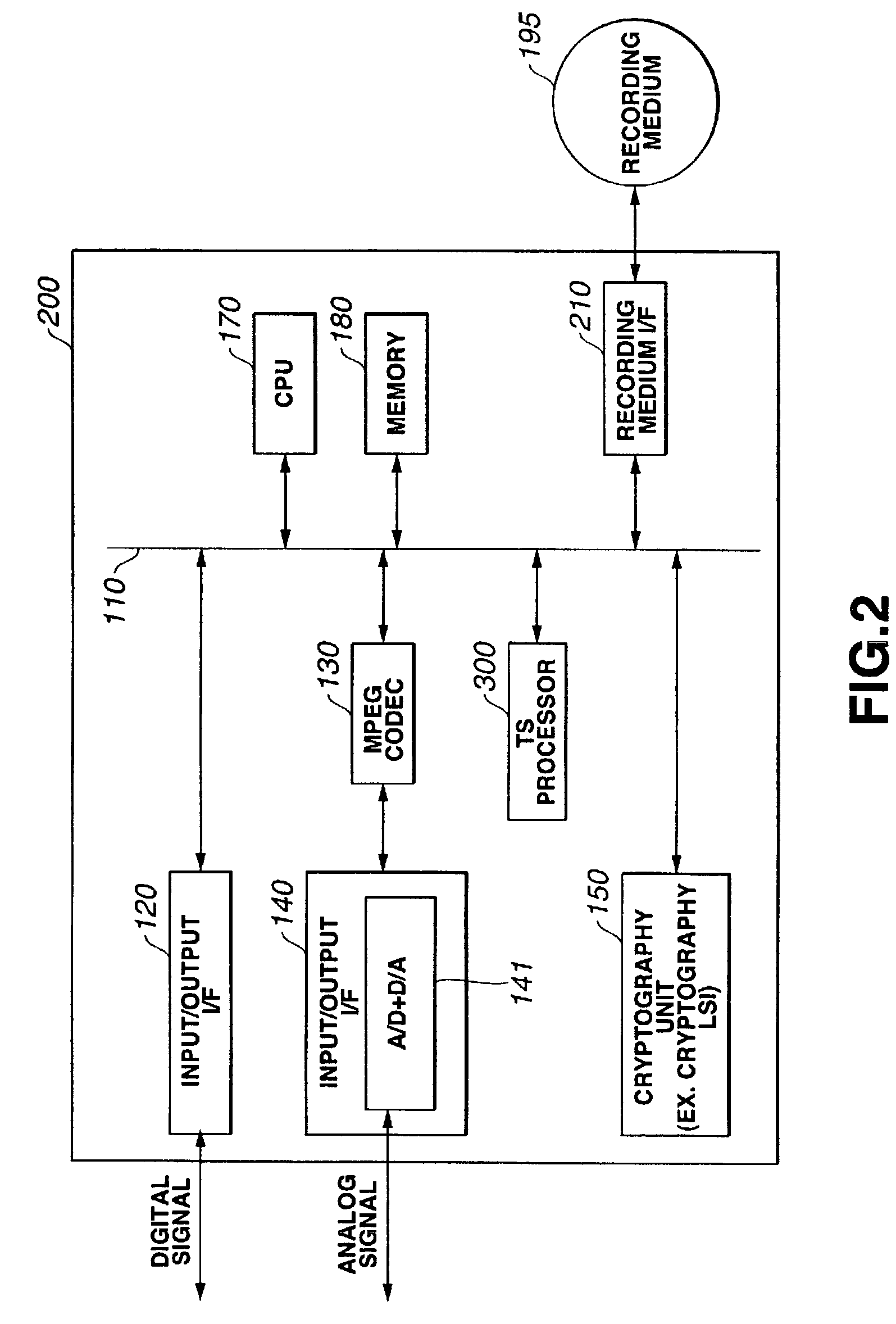
Information recording/playback apparatus and method
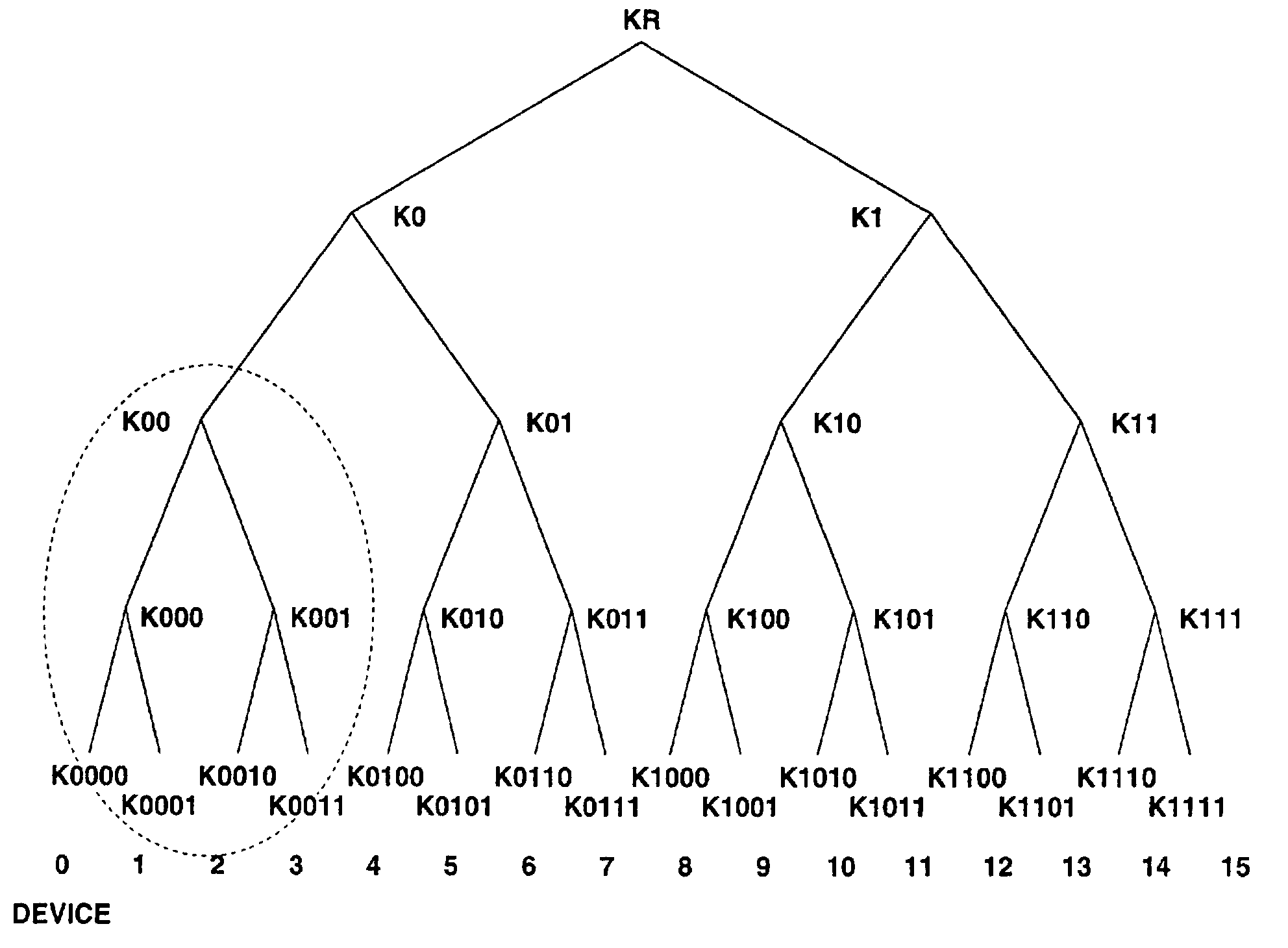
ActiveUS7225339B2Minimize loadReduce message sizeTelevision system detailsKey distribution for secure communicationKey distributionTree structure
In a tree-structural key distribution system, renewed data of a master key and medium key are sent along with a key renewal block (KRB). KRB is such that each of devices included as leaves of a tree structure has a leaf key and restricted node key. A specific KRB can be generated for a group identified by a specific node and distributed to the group to restrict a device for which the key can be renewed. Any device not belonging to the group cannot decrypt the key, whereby the security of key distribution can be assured. Especially in a system using a generation-managed master key, a master key renewed with KRB can be distributed.
Owner:SONY CORP
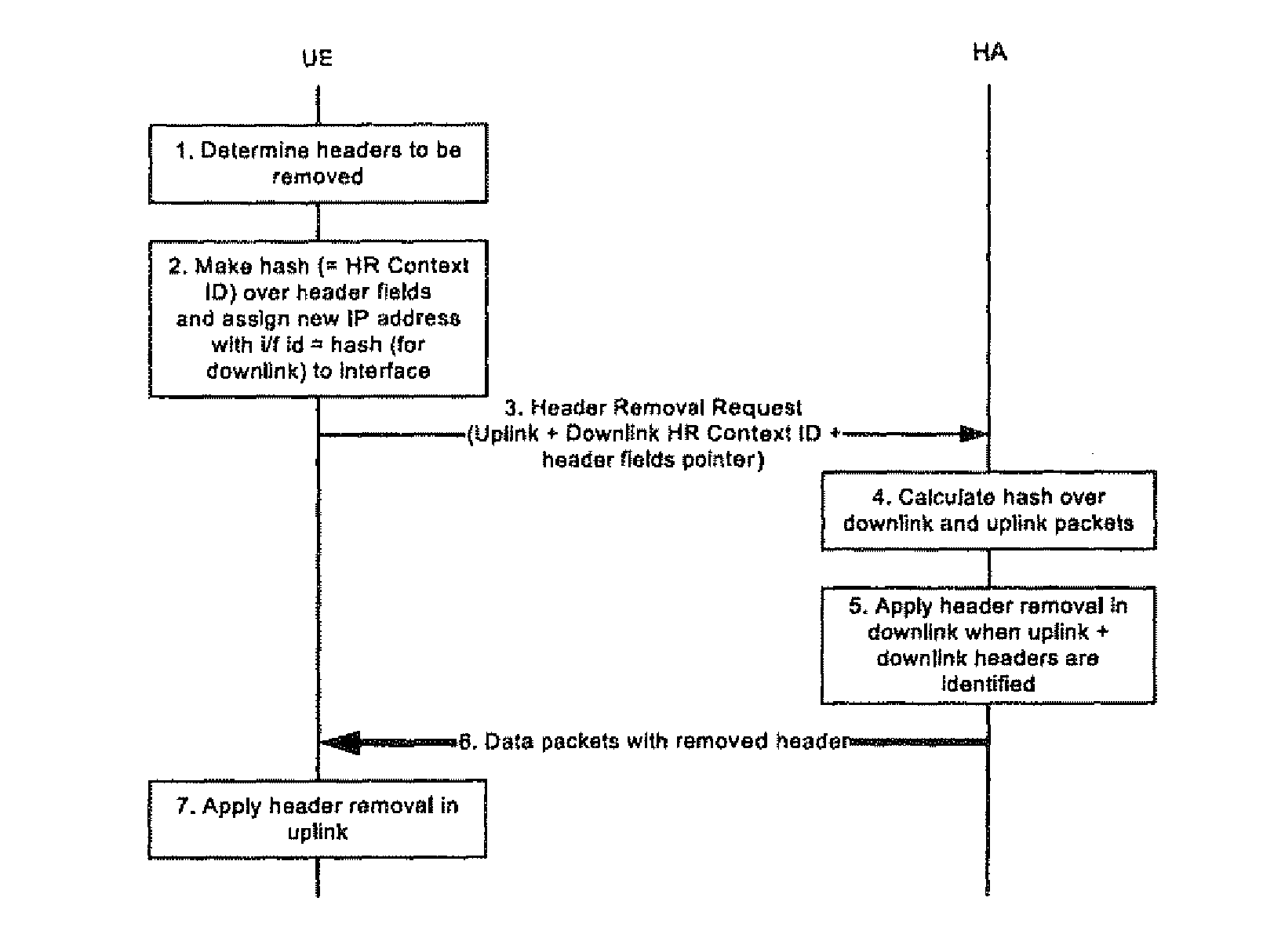
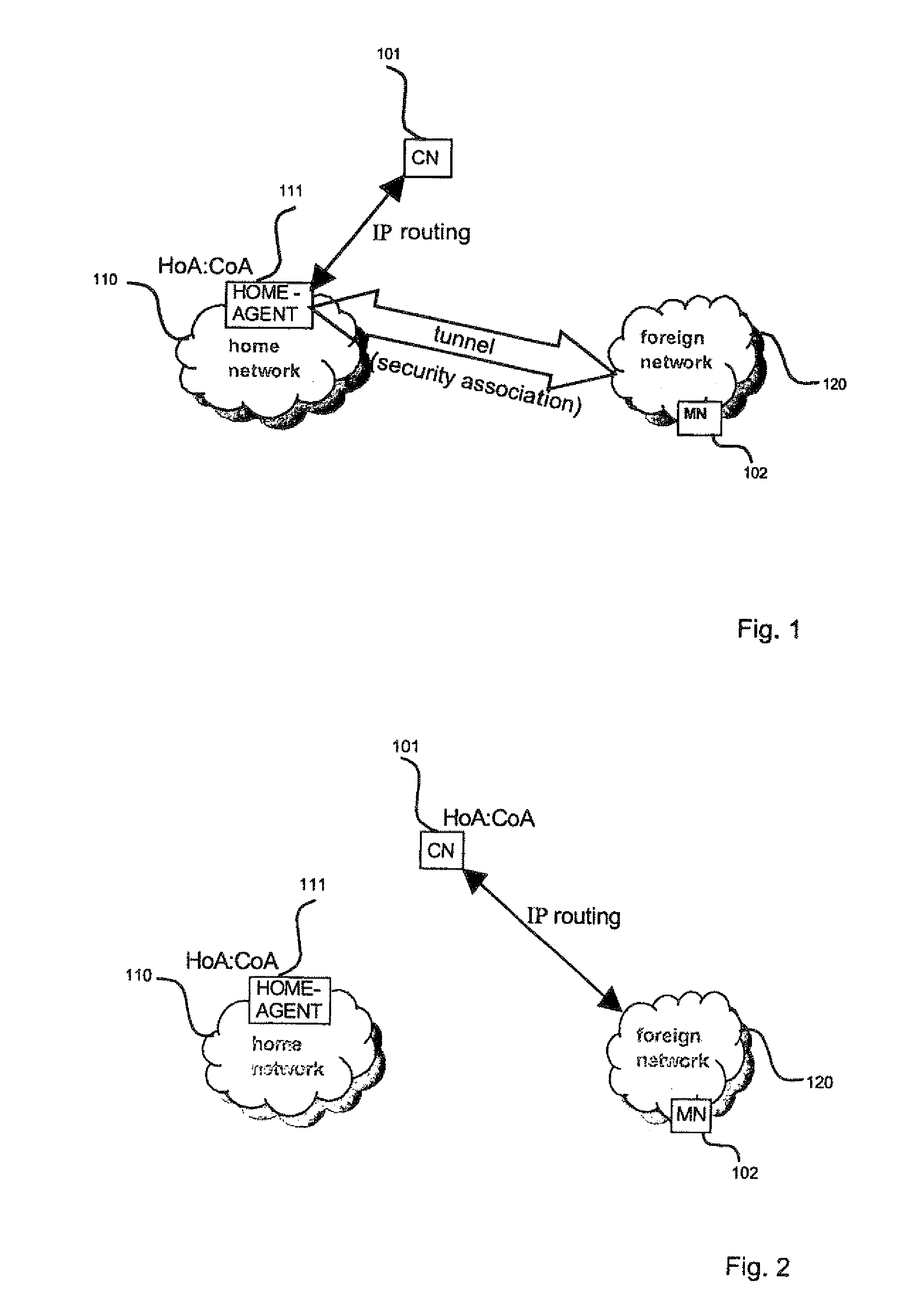
Header Size Reduction of Data Packets
InactiveUS20100189103A1Reduce message sizeAdditional exchangeNetwork traffic/resource managementTime-division multiplexNetwork packetInternet privacy
The invention relates to a method for reducing the header size of data packets by removing inner headers from the data packets, wherein at least an outer header remains for routing purposes. When removing the inner headers from a data packet, a newly configured address of the receiving and / or the transmitting entity is inserted in the remaining outer header of the data packet. Context information is provided in the receiving entities for reconstructing the removed inner headers, wherein the context information is referred to by the newly configured address that is in the source and / or destination address of the outer header. The reduced data packet is transmitted with only one header, thereby significantly reducing the size of each data packet. The original packet is completely reconstructed at the receiving entity thereby allowing to proceed with the usual processing of each data packet.
Owner:SOVEREIGN PEAK VENTURES LLC
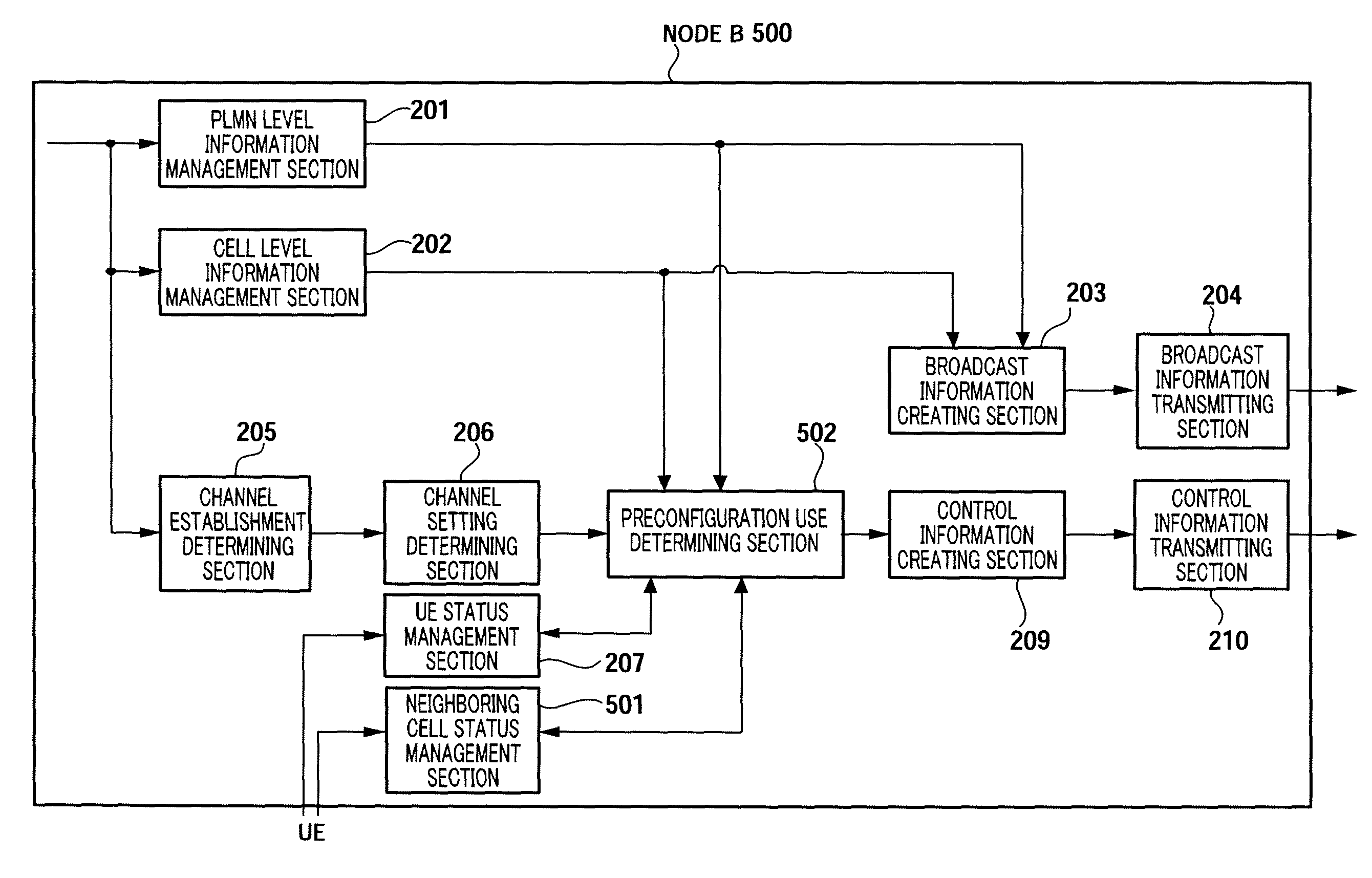
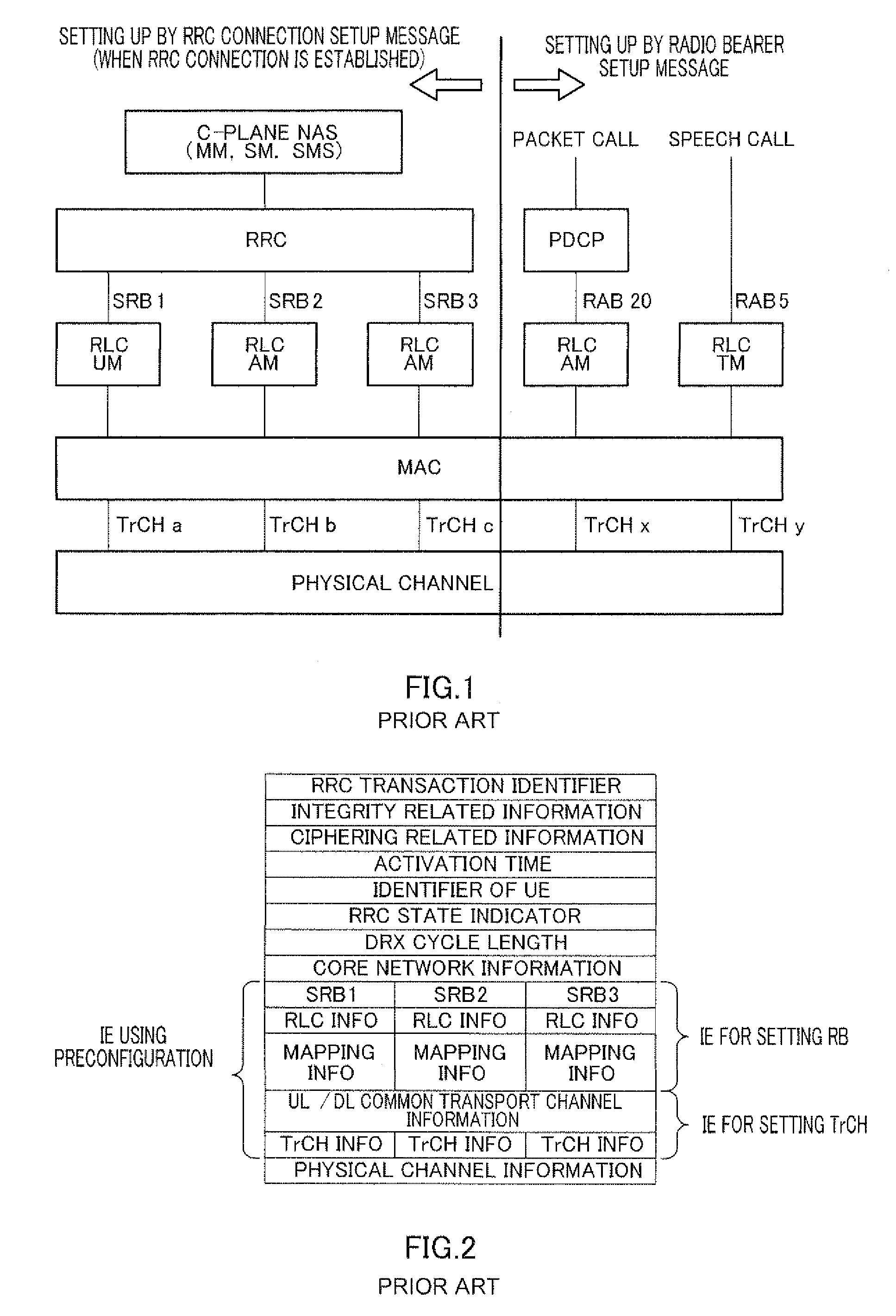
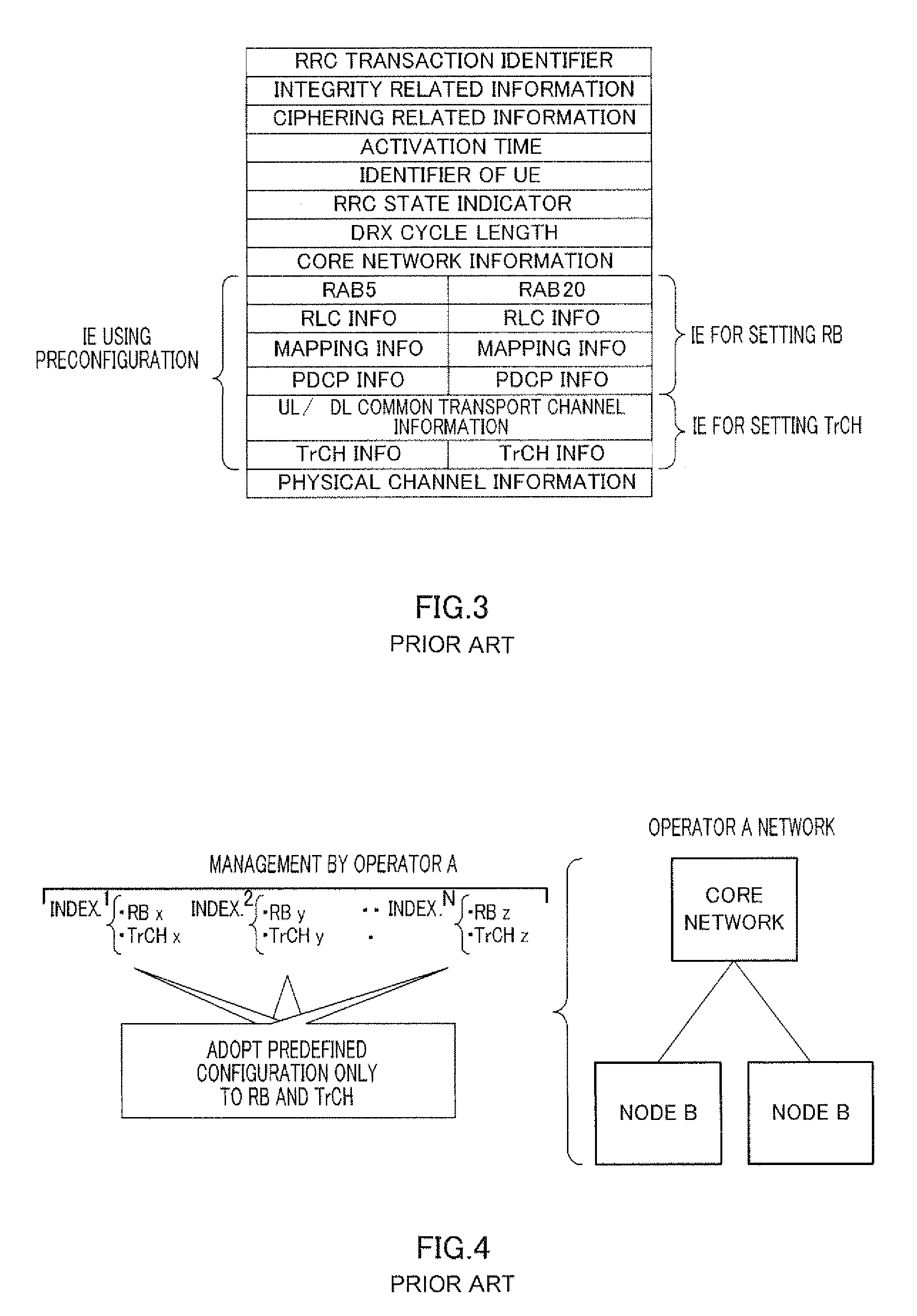
Radio communication base station device
InactiveUS20090247163A1Reduce message sizeAssess restrictionSubstation equipmentInformation transmissionMessage size
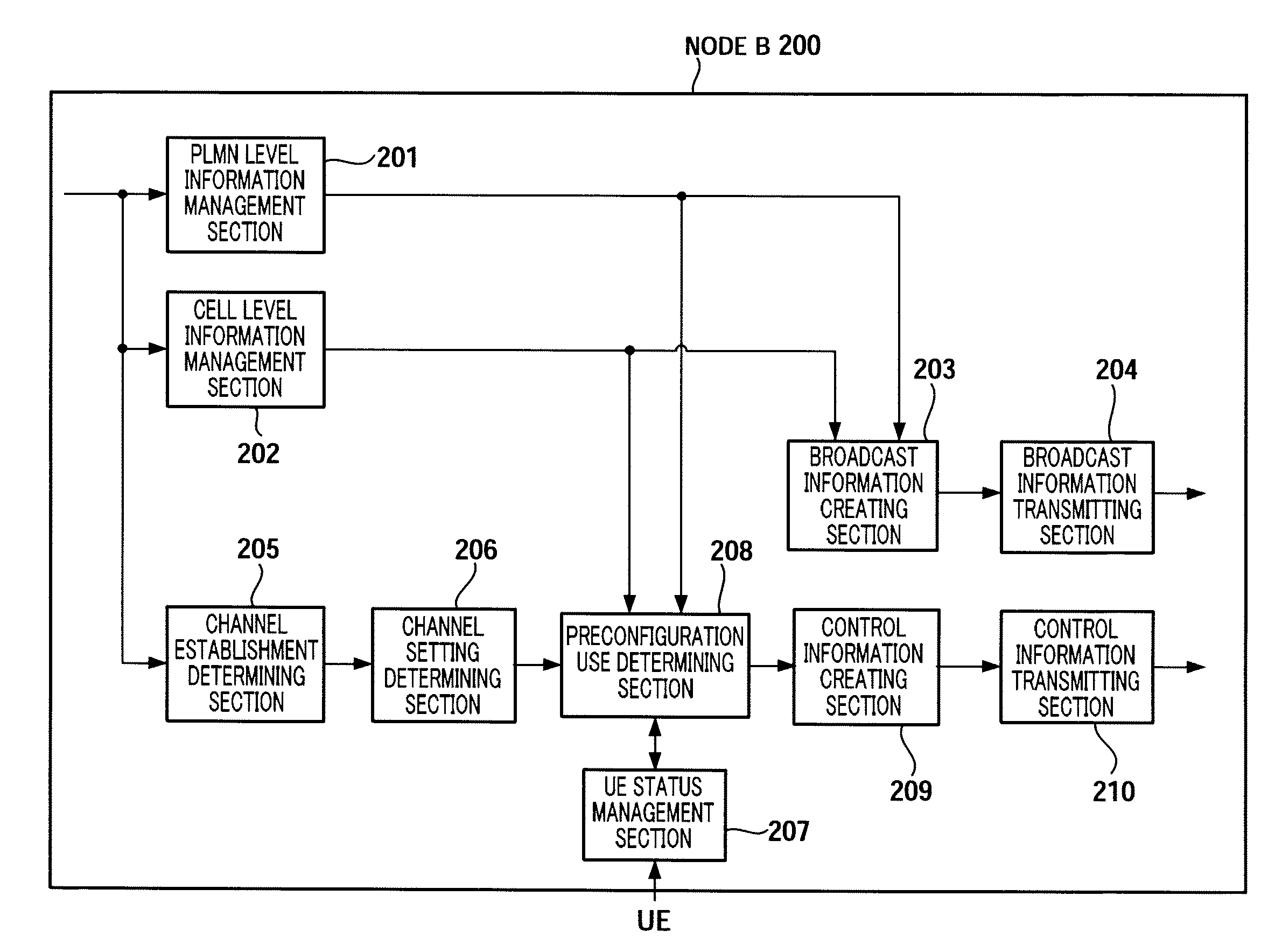
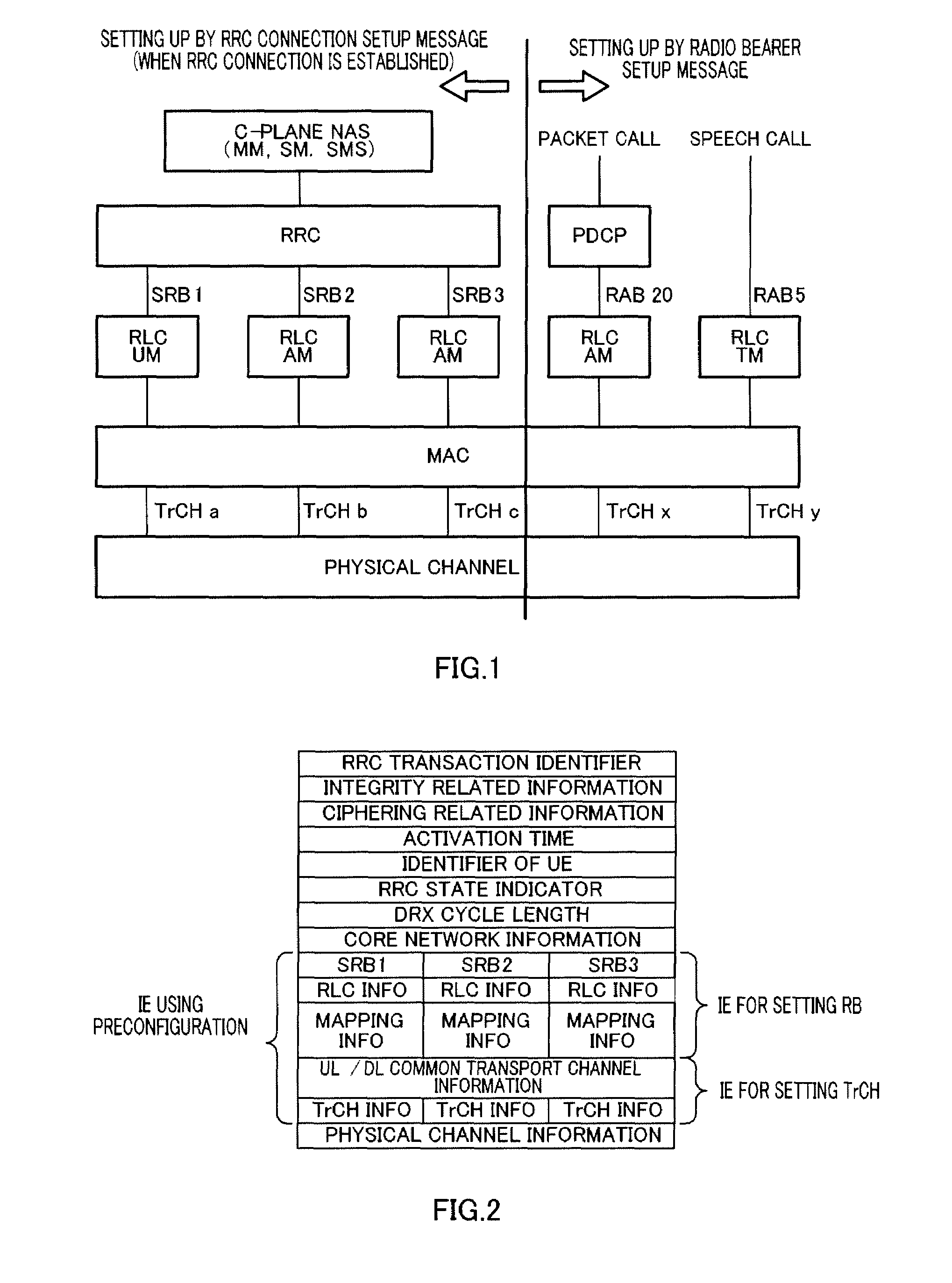
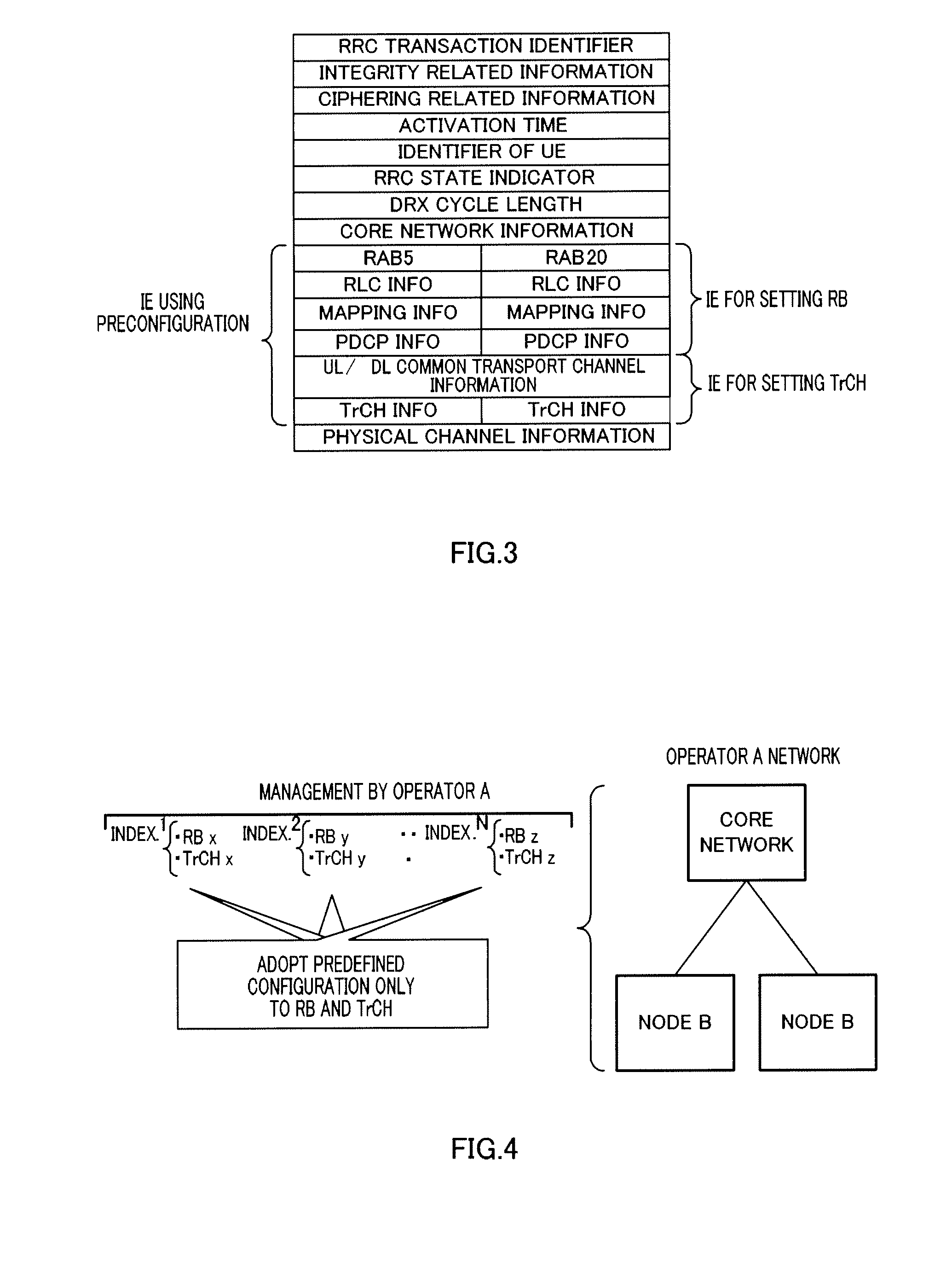
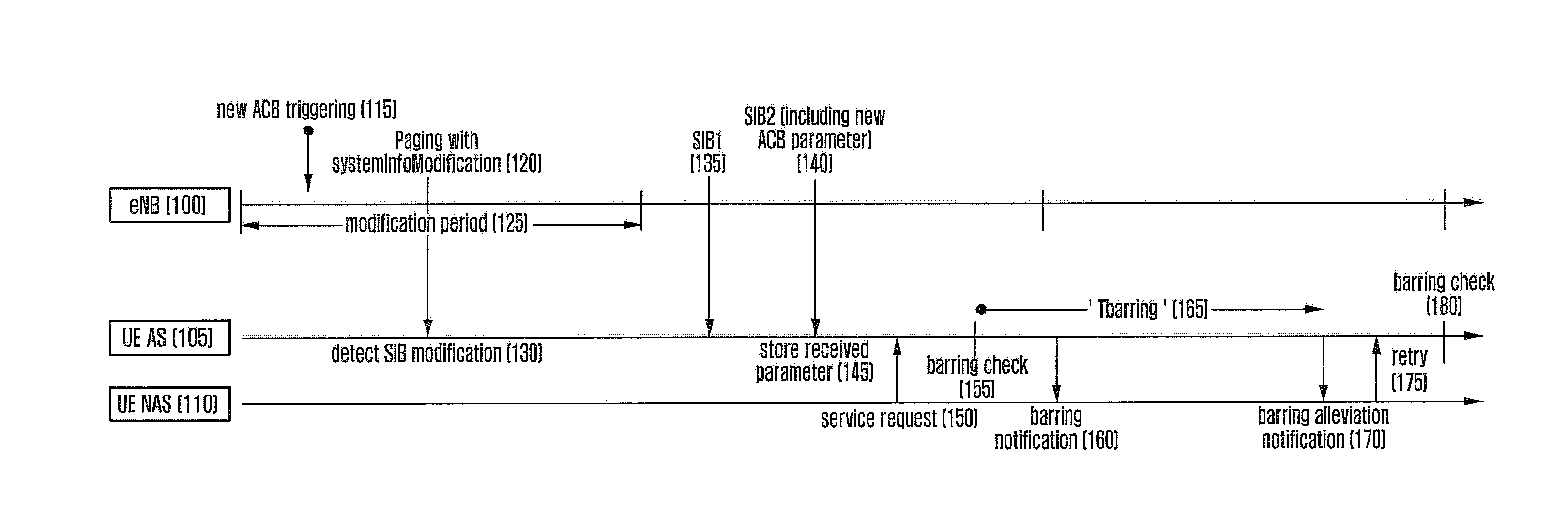
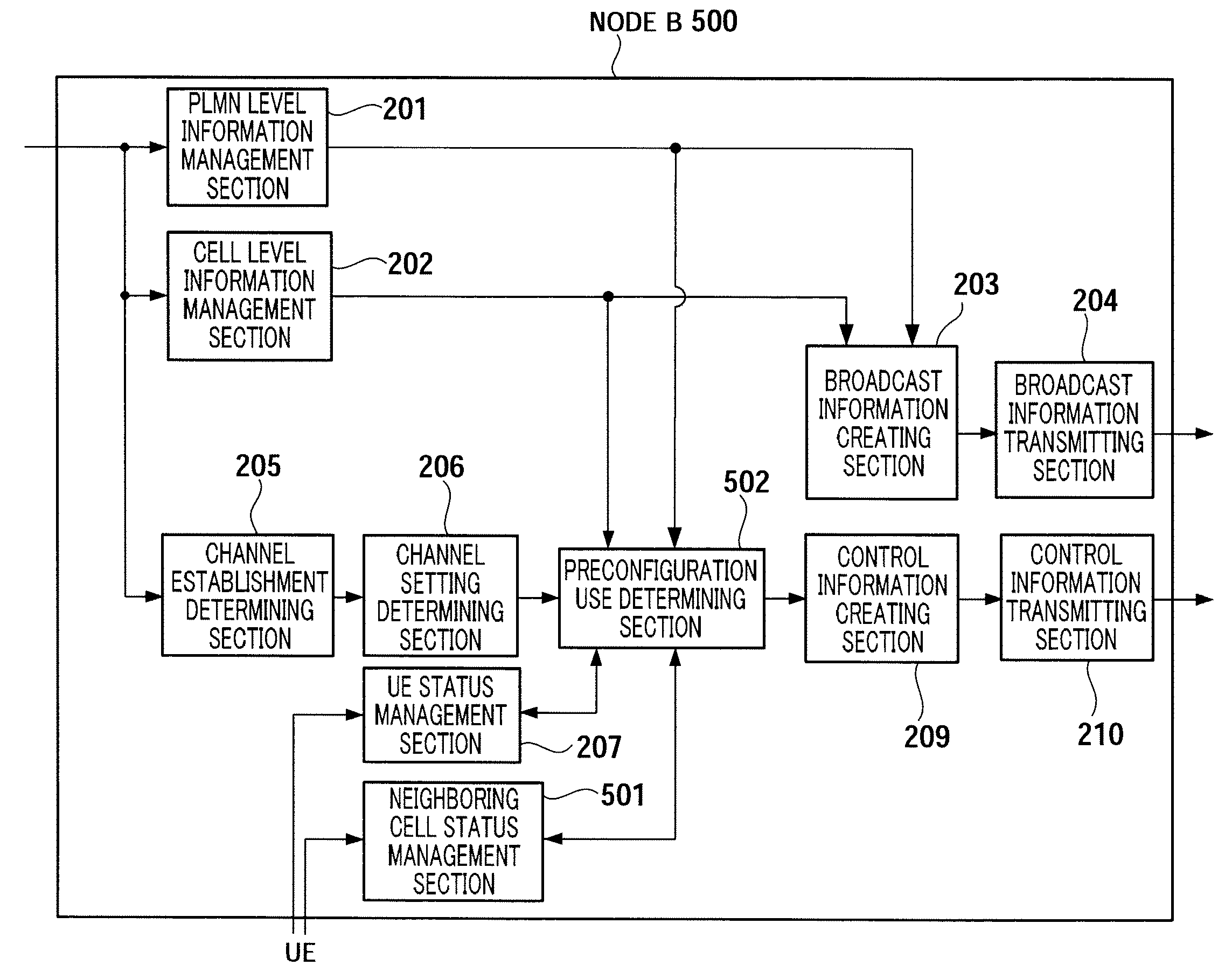
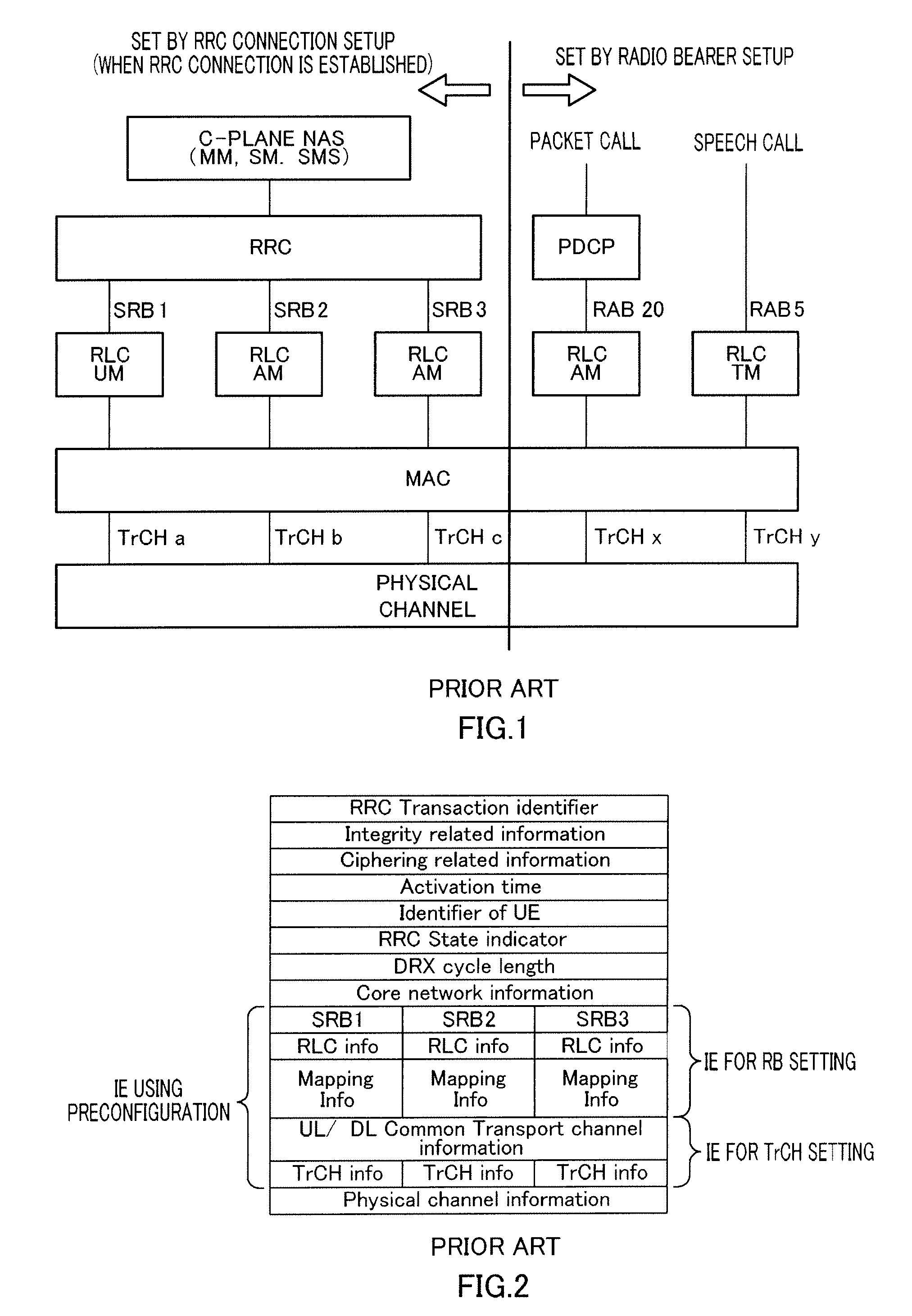
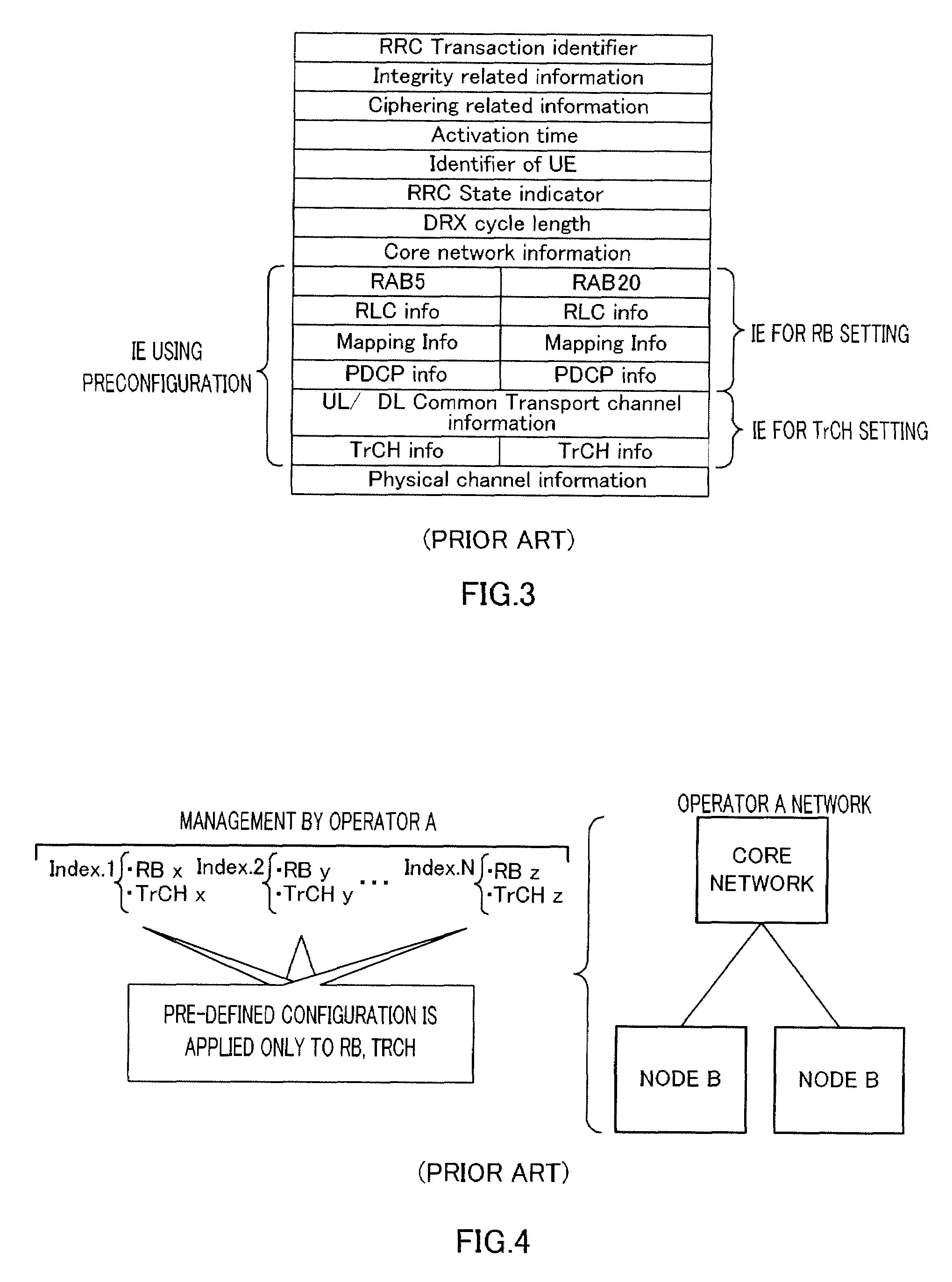
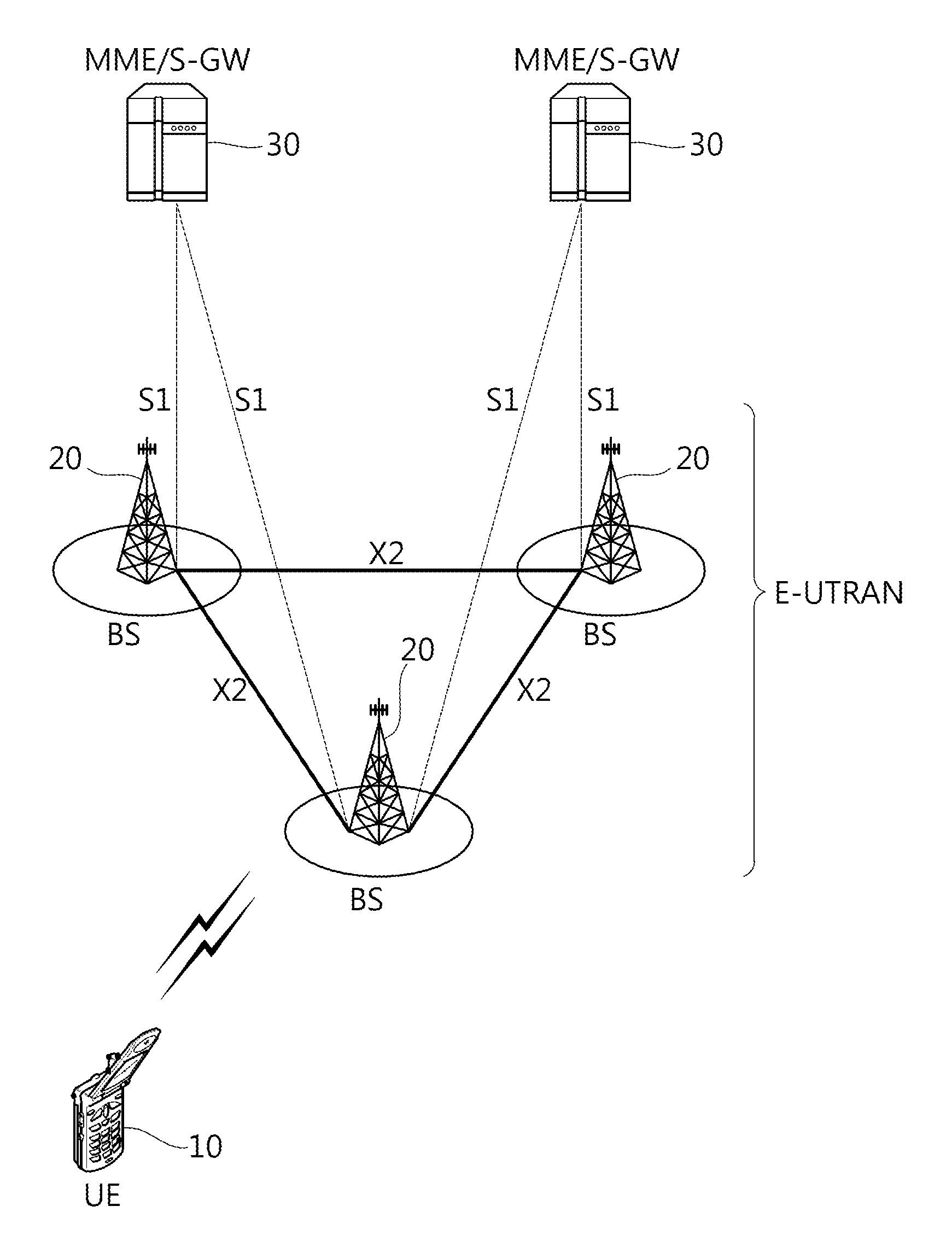
Provided is a radio communication base station device capable of reducing a message size in a call connection. In the device, a report information creation unit (203) creates report information by allocating cell level information as Preconfiguration information managed at a cell level and PLMN level information as Preconfiguration information managed at a PLMN level to different transmission units and the created report information is reported from a report information transmission unit (204) to UE. A Preconfiguration use decision unit (208) judges whether the UE which sets a channel can use Preconfiguration. If yes, a control information creation unit (209) includes the corresponding Index in control information and the control information is transmitted from a control information transmission unit (210) to the UE.
Owner:SOVEREIGN PEAK VENTURES LLC
Hardware module-based authentication in intra-vehicle networks
ActiveUS20190104149A1Minimal latencyImprove securityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesElectronic control unitVehicle networks
A secure hardware-based module or Security Electronic Control Unit (SECU) for a Controller Area Network (CAN) prevents an attacker from sending malicious messages through the CAN bus to take over control of a vehicle. The SECU shares a unique key and counter with each ECU on the CAN bus. When a legitimate ECU sends a message, it first compresses the message and then generates a MAC of the counter and a secret key. The counter is increased by one for each transmitted message. The ECU then fits the compressed message and the MAC into one CAN frame and sends it onto the CAN bus. The SECU performs the message verification on behalf of the intended receiver(s) of the message. If the verification passes, the receiver(s) simply decompress the message and use it as a normal CAN message. If the verification fails, the SECU will corrupt the CAN frame before it is fully received by the intended receiver(s). The corrupted CAN frame will be ignored by the intended receiver(s) as if it was never received. Therefore, a malicious message generated by an attacker will inflict no damage on the system.
Owner:GEORGE MASON UNIVERSITY
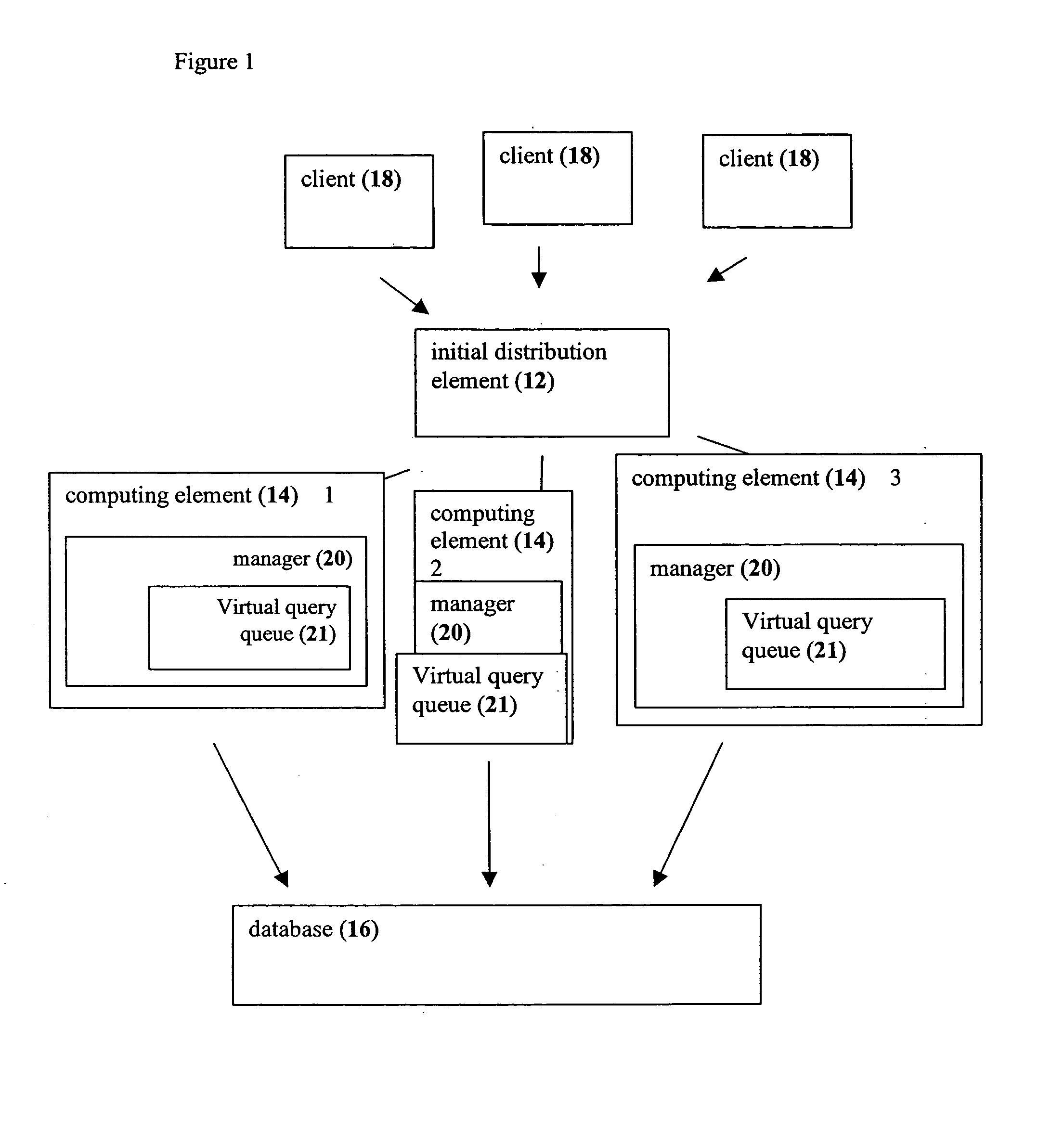
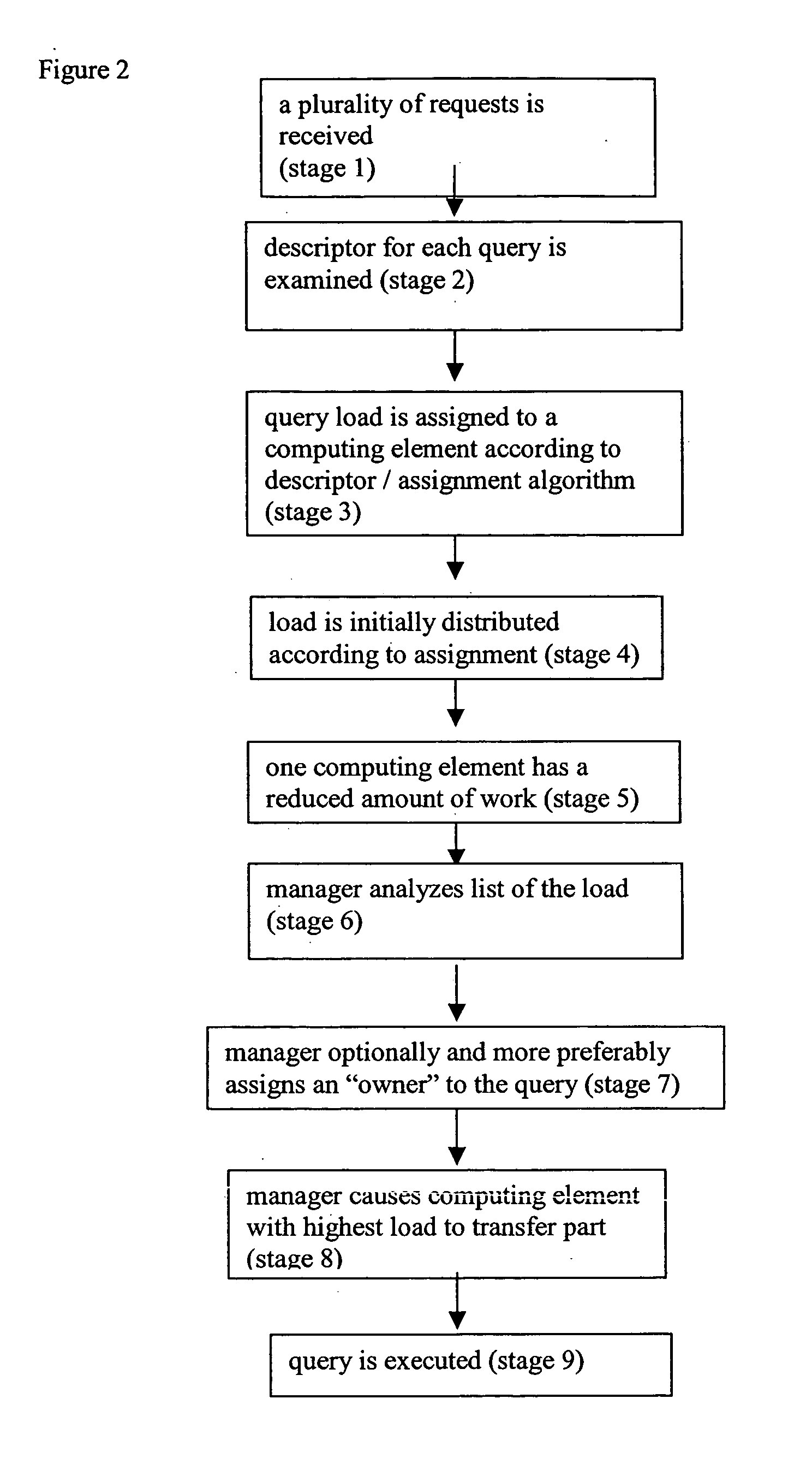
System and method for load balancing in database queries
InactiveUS20050021511A1Reduce in quantityReduce the numberDigital data information retrievalDigital data processing detailsDatabase queryLoad Shedding
A system and method in which query load balancing process is performed in a cluster of middle-tier computing elements according to the load on at least one, but more preferably a plurality, of the computing elements of the group, this by passing pointers to queries between machines with information or processes pertinent to the query. Optionally the balancing may be carried out in two stages. The first stage performed rapidly, preferably implemented as a hardware device such as a switch for example in which a plurality of queries is distributed to a plurality of computing elements according to at least one descriptor attached to each query or a simple algorithm is used. The second stage preferably performed as above by at least one computing element of the group, but may optionally be performed by a plurality of such elements. Alternatively, the second stage may be performed by a separate computer.
Owner:KCI LICENSING INC +1
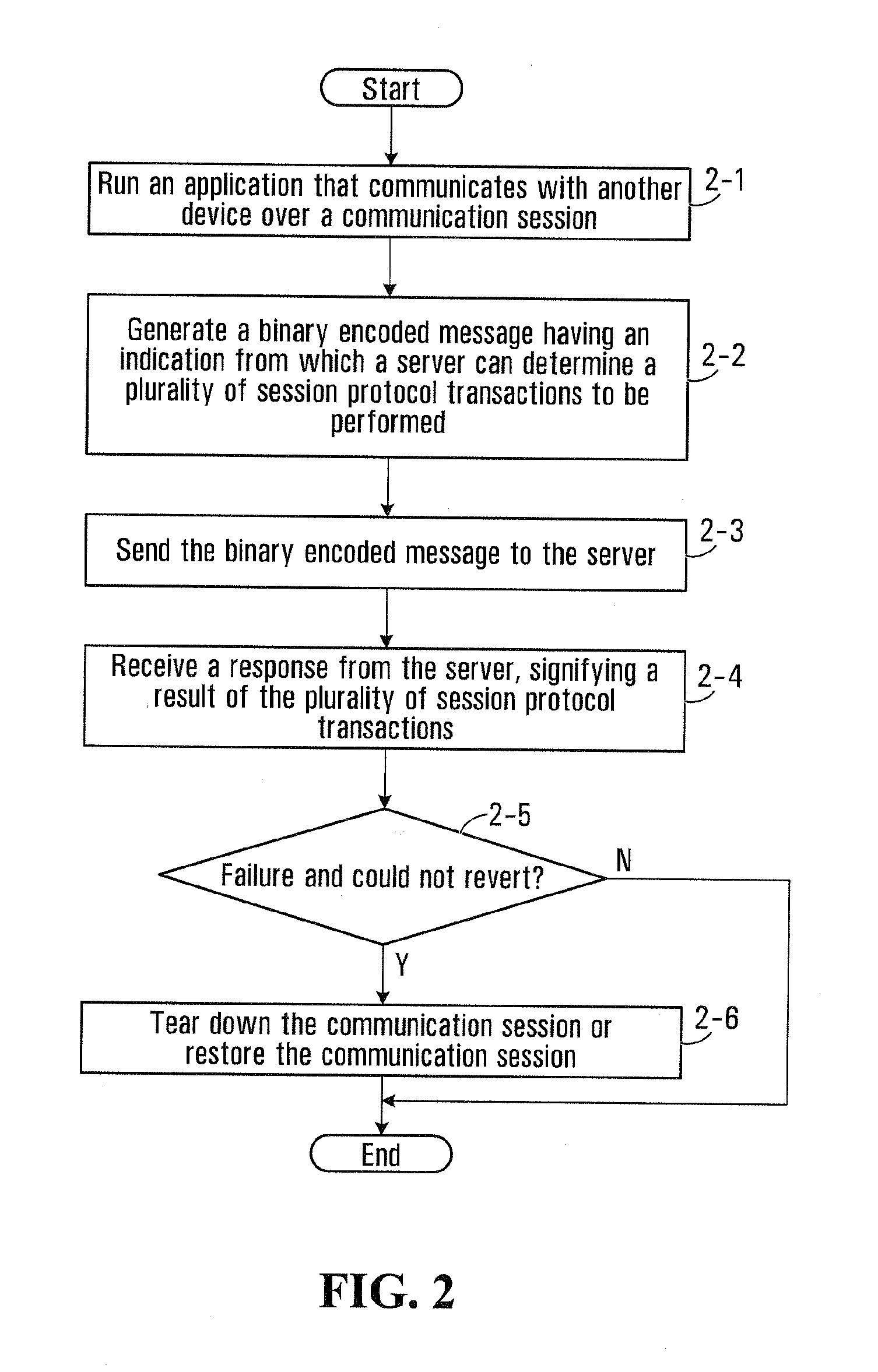
Apparatus and method for reducing responses when executing a session initiation protocol operation
InactiveUS20110225307A1Reduce message sizeSimple processMultiple digital computer combinationsTransmissionComputer hardwareComputer science
An apparatus and method for reducing responses when executing a session protocol operation is disclosed. In accordance with an embodiment of the disclosure, a mobile device generates a binary encoded message having an indication from which a server can determine a session protocol operation to be performed without communicating all responses for the SIP transaction. The binary encoded message is sent from the mobile device and received by the server. In accordance with an embodiment of the disclosure, the server determines, based on the indication in the binary encoded message, the SIP transaction to be performed without communicating all SIP responses relating to the SIP transaction. The server then attempts the SIP transaction. By reducing the number of SIP responses, communication resources for the mobile device can be conserved. Also battery power for the mobile device can be conserved apparatus and method for reducing responses when executing a session initiation protocol operation
Owner:BLACKBERRY LTD
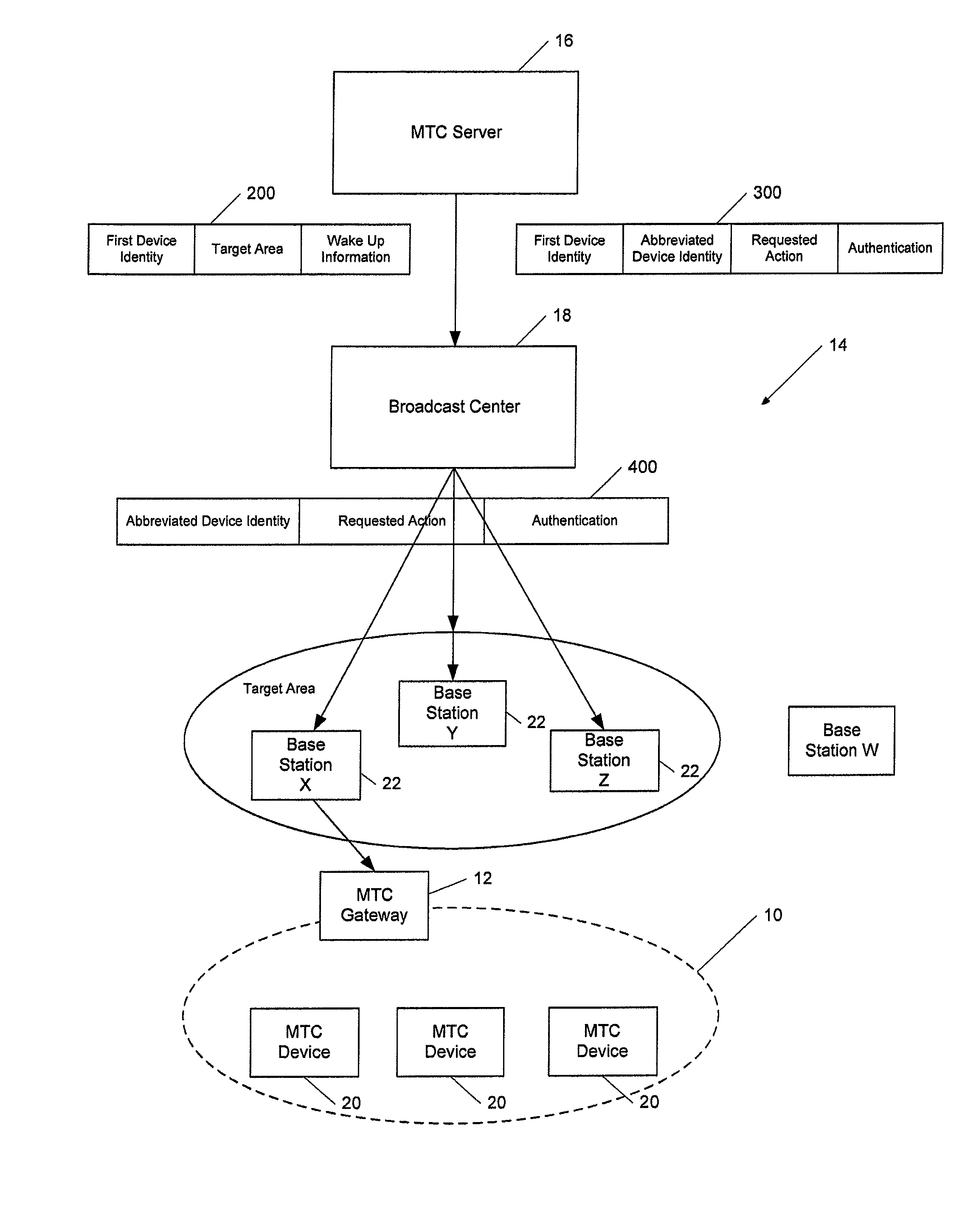
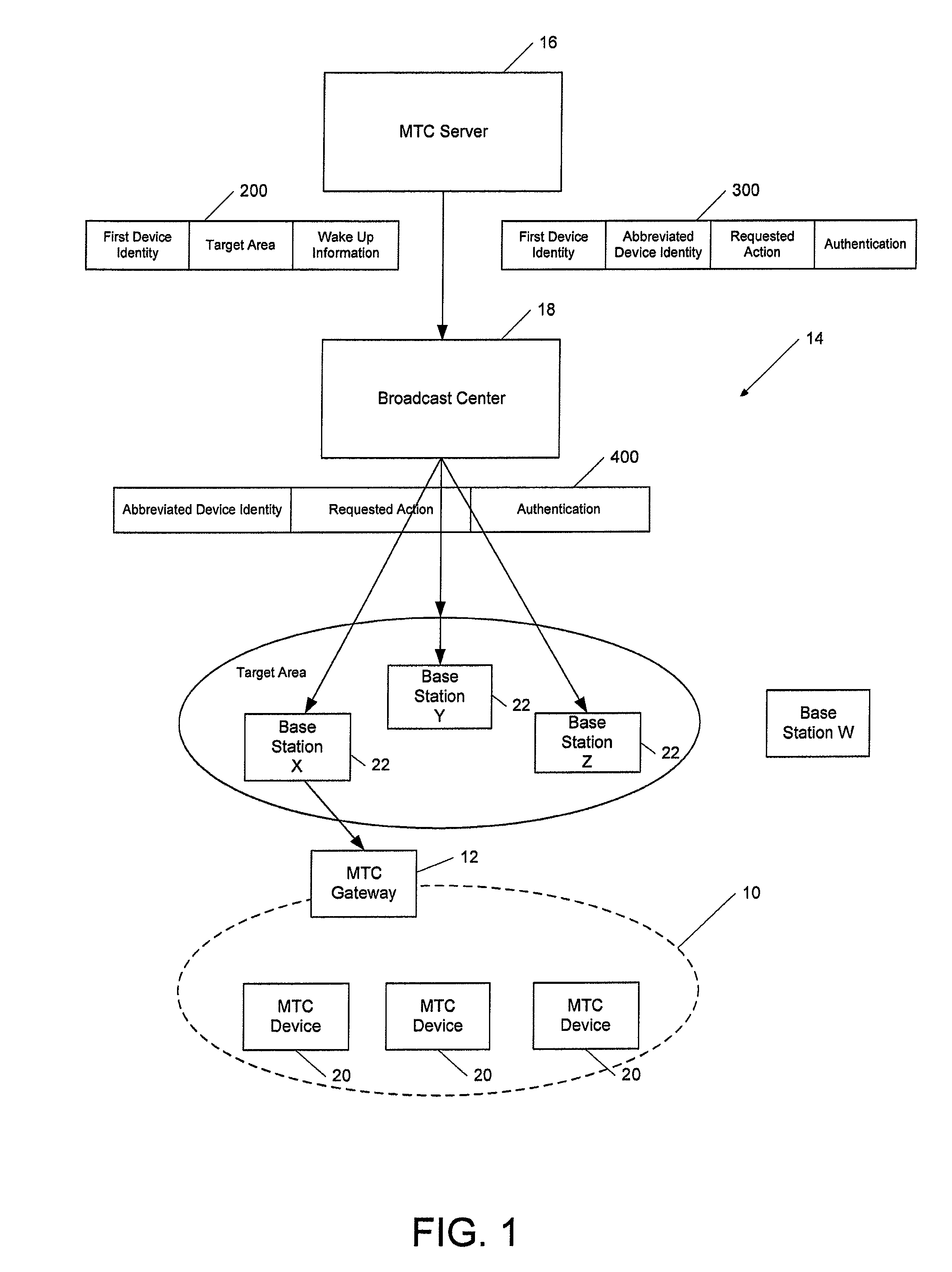
Method and apparatus for facilitating machine-type communication
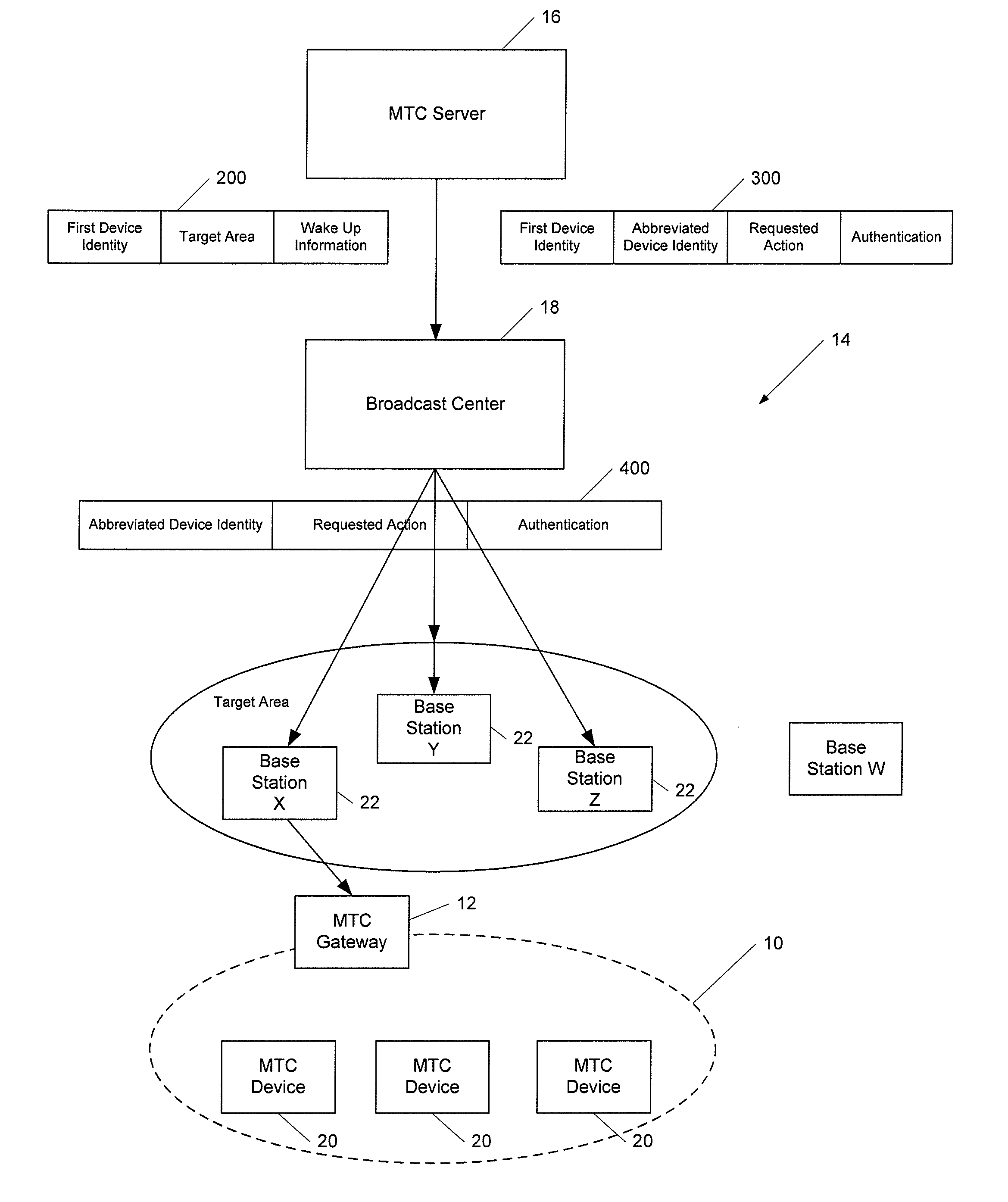
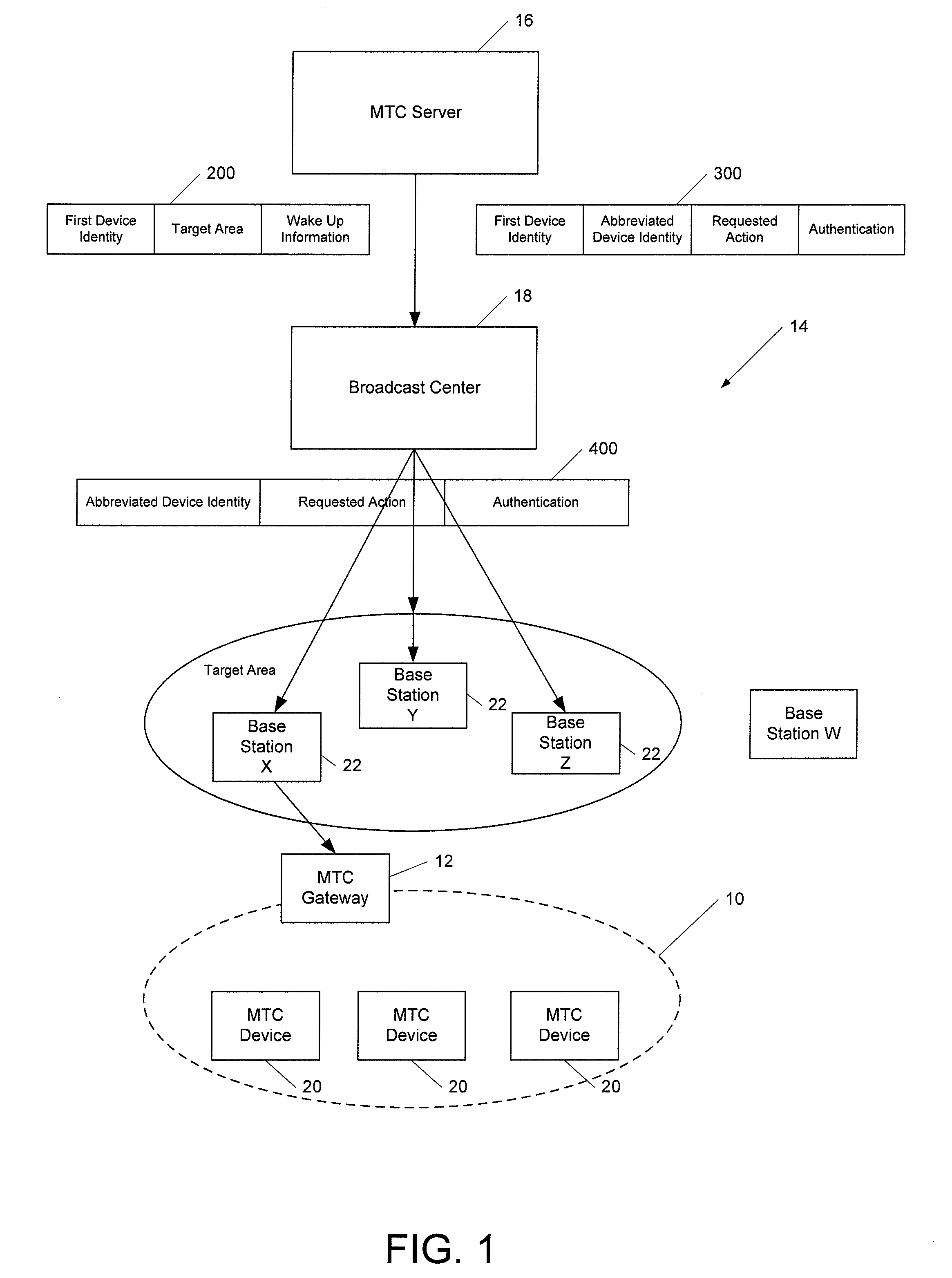
ActiveUS8125892B1Facilitate communicationConserve network signalingError preventionFrequency-division multiplex detailsCapillary networkComputer hardware
A method and apparatus are provided to facilitate communications with MTC devices. An apparatus may include processing circuitry configured at least to receive a broadcasted triggering message and to determine whether the triggering message identifies a machine-type communication (MTC) gateway or another device within a capillary network supported by the MTC gateway. The processing circuitry may cause at least a portion of the triggering message to be provided to a device within the capillary network in an instance in which the triggering message identifies the device within the capillary network. The processing circuitry may also be configured to determine an action requested by the triggering message in an instance in which the triggering message identifies the MTC gateway.
Owner:BROADCOM INT +1
Method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems
ActiveUS20150004924A1Facilitating congestion controlPossible changeEmergency connection handlingNetwork traffic/resource managementCommunications systemMobile communication systems
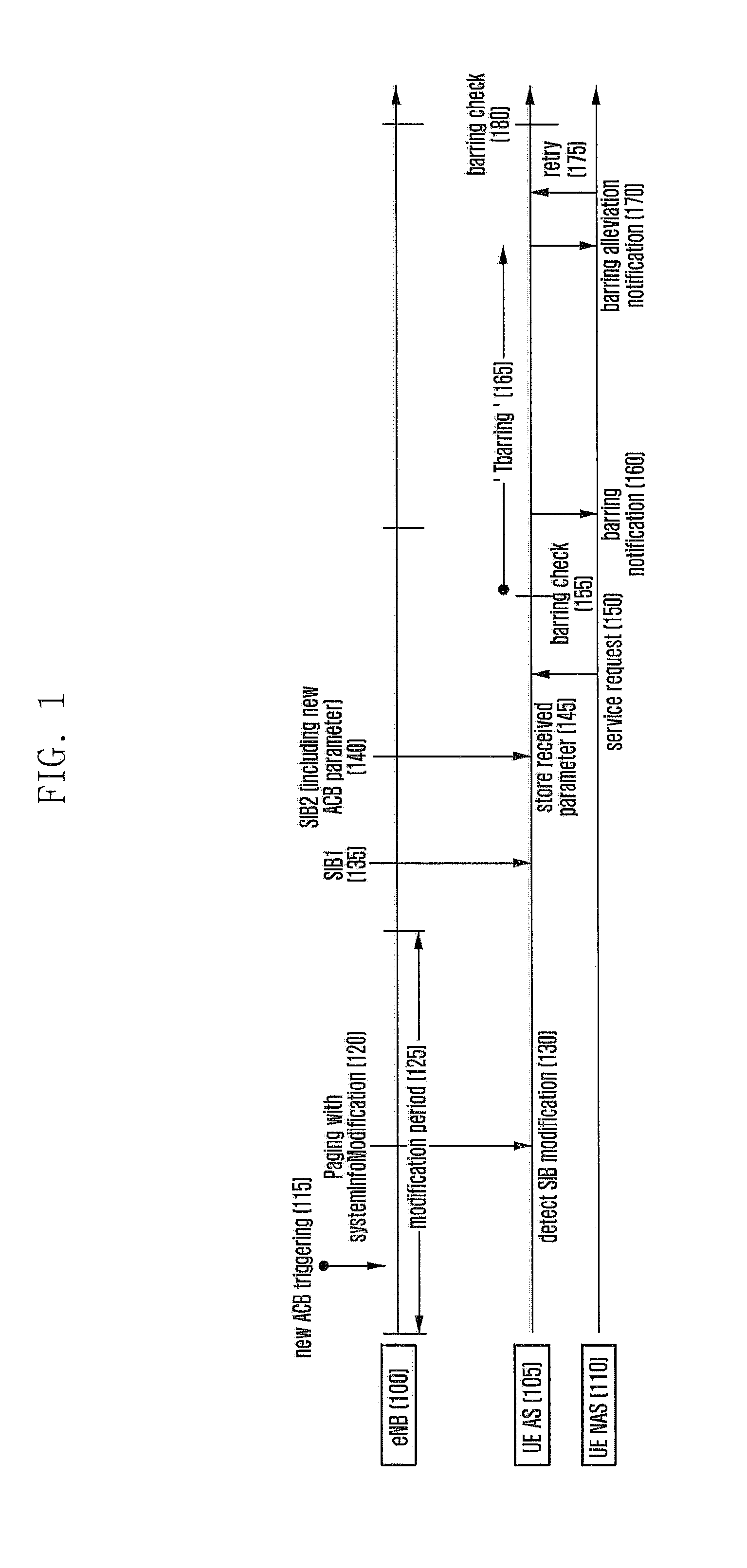
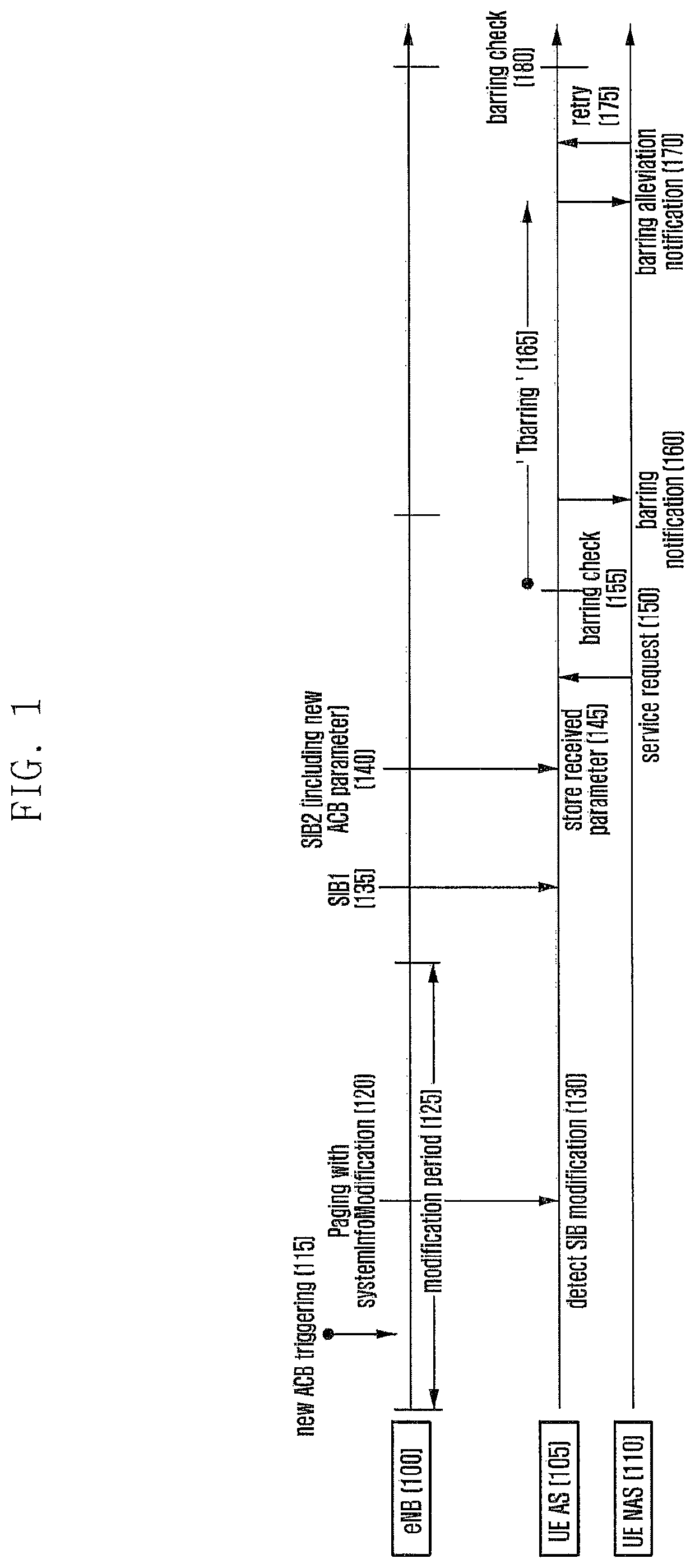
The present invention relates to a method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems. In a wireless communication system according to one embodiment, the method for transmitting and receiving data by a terminal including a user equipment (UE) non access stratum (NAS) and a UE access stratum (AS) includes the steps of: receiving by the UE AE, information including emergency call-related information which includes barring information by type for the emergency call, from a base station; transmitting, by the UE NAS, a service request for the emergency call to the UE AS; and determining, by the UE AS, whether to bar the service request on the basis of emergency call-related information. According to one embodiment, during the emergency call transmission, network congestion can be easily controlled by enabling various types of emergency calls to be transmitted, and enabling access to be barred information according to the situation of a communication network and types of emergency calls. Also, even when a specific type of emergency call is barred from access, the terminal can change to another type of emergency call and try for access. Therefore, it is effective in that an emergency call can be transmitted in various schemes even in a state where the network is congested.
Owner:SAMSUNG ELECTRONICS CO LTD
Wireless communication terminal apparatus, wireless communication base station apparatus, wireless communication system and telephone call connecting method
InactiveUS20090275319A1Reduce message sizeAssess restrictionConnection managementCommunications systemTerminal equipment
A wireless communication terminal apparatus, a wireless communication base station apparatus, a wireless communication system and a telephone call connecting method wherein the message size in a telephone call connection can be reduced. A broadcast information producing part (203) assigns cell level information, which is preconfiguration information managed by the cell level, and PLMN level information, which is preconfiguration information managed by the PLMN level, to different transmission units to produce broadcast information, which is then broadcasted from a broadcast information transmitting part (204) to UEs. A preconfiguration usage deciding part (208) determines whether a UE, which sets a channel, can use a preconfiguration. If the UE can use a preconfiguration, a control information producing part (209) causes control information to include the corresponding index, and then the control information is transmitted from a control information transmitting part (210) to the UE.
Owner:PANASONIC CORP
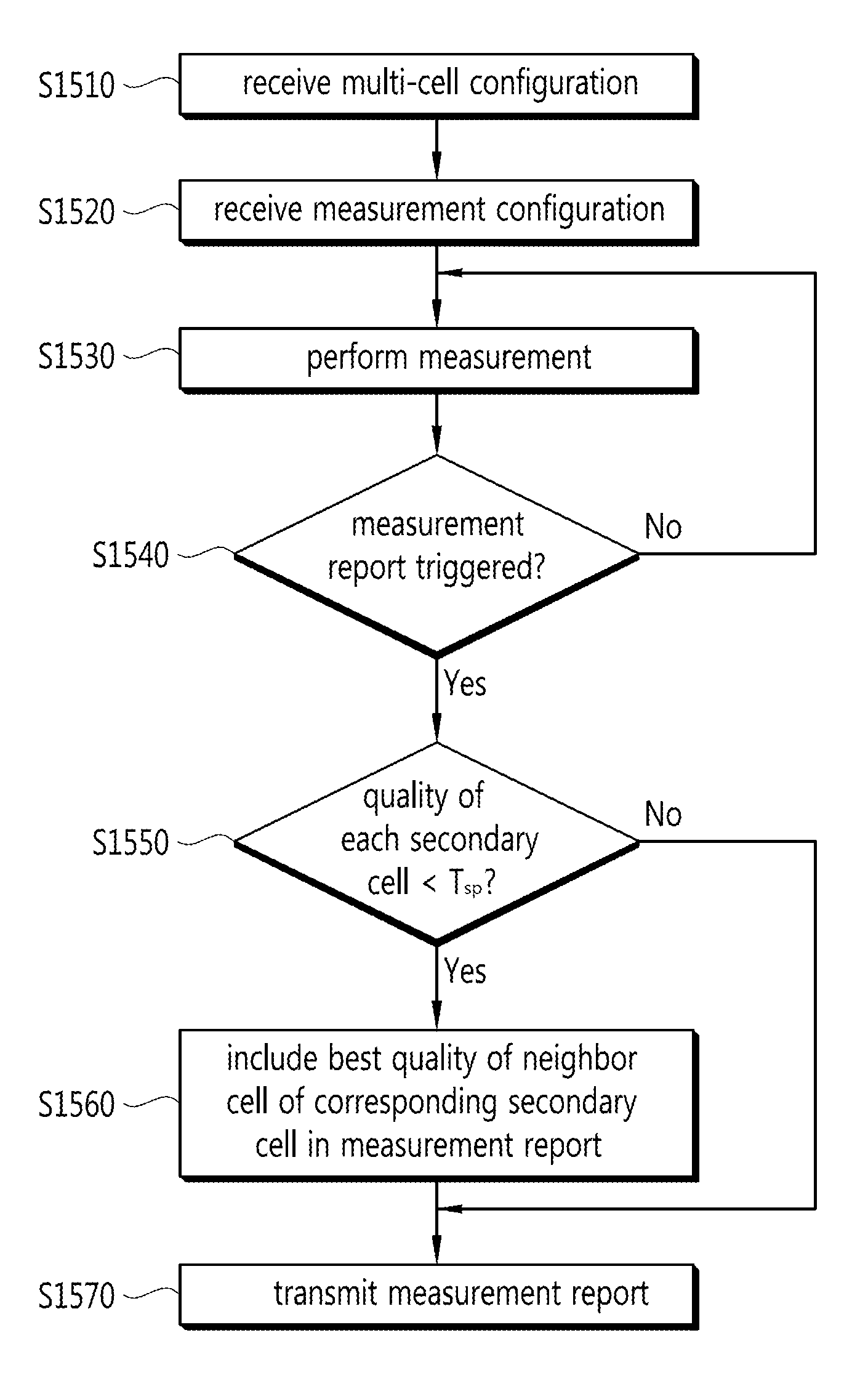
Method and Apparatus for Reporting a Measurement Result in a Wireless Communication System
ActiveUS20130148534A1Inhibition of informationReduce message sizeError preventionTransmission systemsCommunications systemComputer terminal
The present invention relates to a method and apparatus for reporting a measurement result in a wireless communication system. A terminal configures a plurality of serving cells, and performs measurement on the plurality' of serving cells. When a measurement report is triggered, the terminal determines whether or not a quality of at least one serving cell from among the plurality of serving cells is lower than an auxiliary' threshold value. The measurement report includes the quality of a best neighboring cell at a serving frequency of the serving cell the quality of which is lower than the auxiliary threshold value.
Owner:QUALCOMM INC
Method and apparatus for facilitating machine-type communication
ActiveUS8565100B2Facilitate communicationConserve network signalingPower managementError preventionComputer hardwareCapillary network
A method and apparatus are provided to facilitate communications with MTC devices. An apparatus may include processing circuitry configured at least to receive a broadcasted triggering message and to determine whether the triggering message identifies a machine-type communication (MTC) gateway or another device within a capillary network supported by the MTC gateway. The processing circuitry may cause at least a portion of the triggering message to be provided to a device within the capillary network in an instance in which the triggering message identifies the device within the capillary network. The processing circuitry may also be configured to determine an action requested by the triggering message in an instance in which the triggering message identifies the MTC gateway.
Owner:AVAGO TECH INT SALES PTE LTD +1
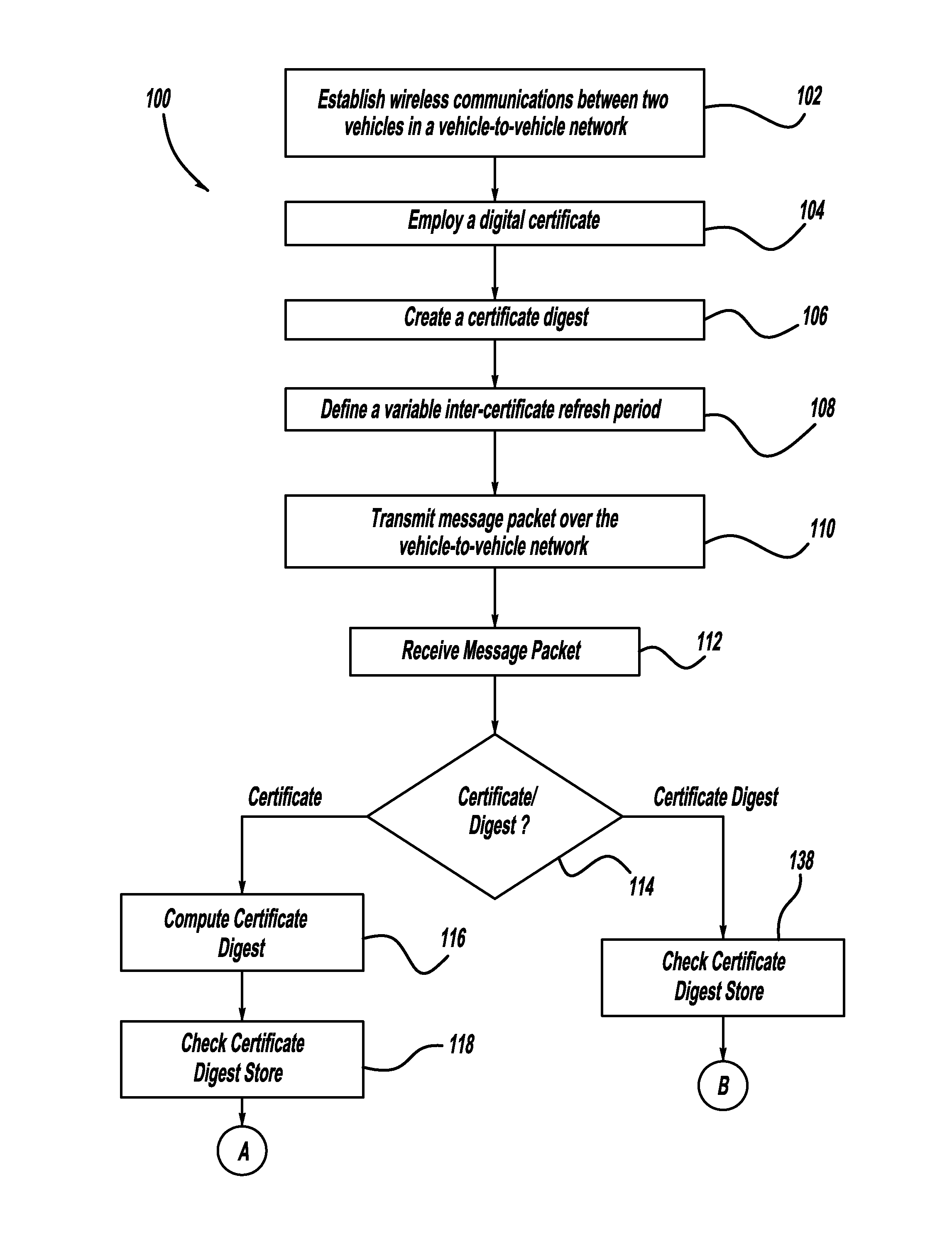
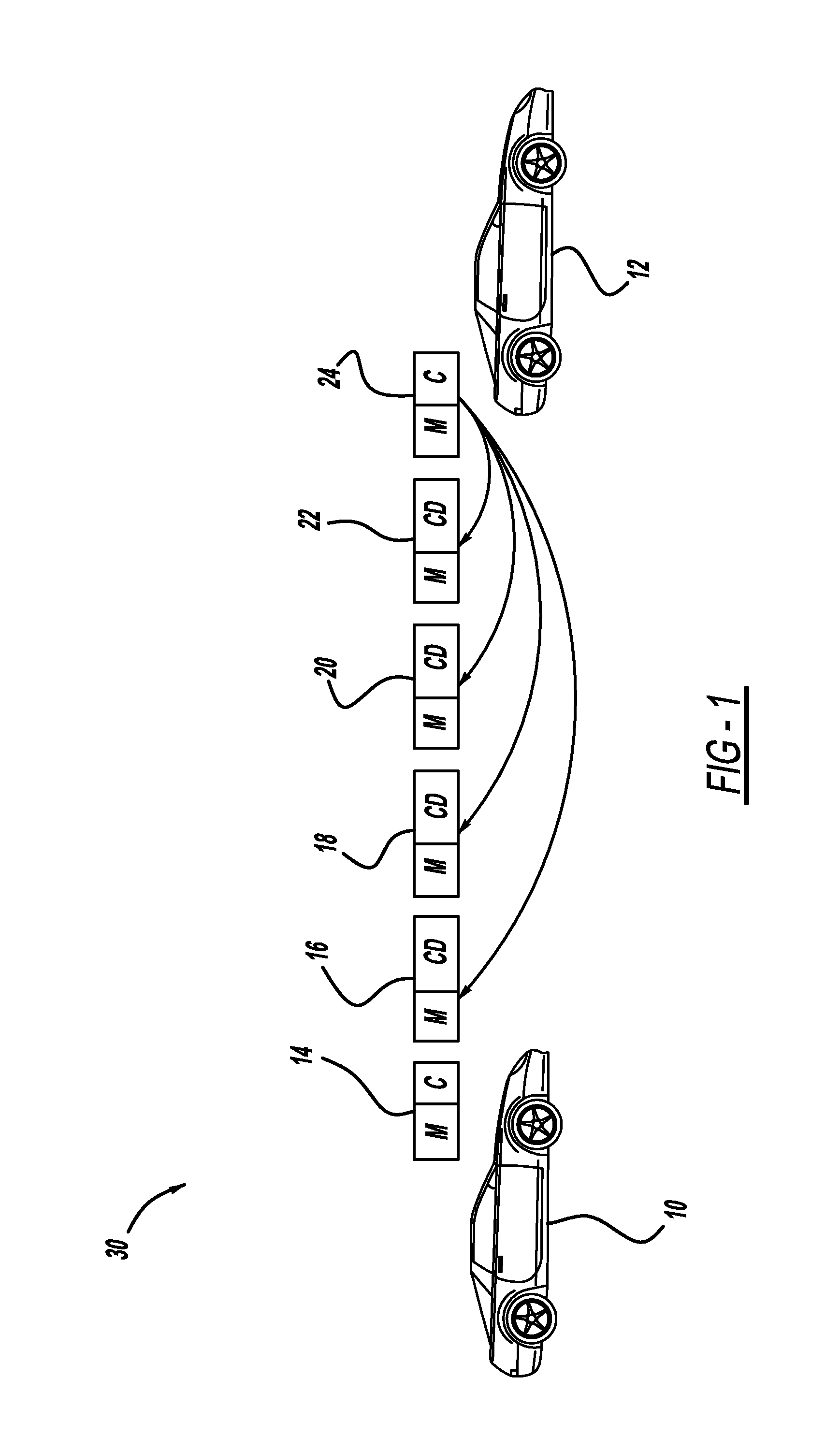
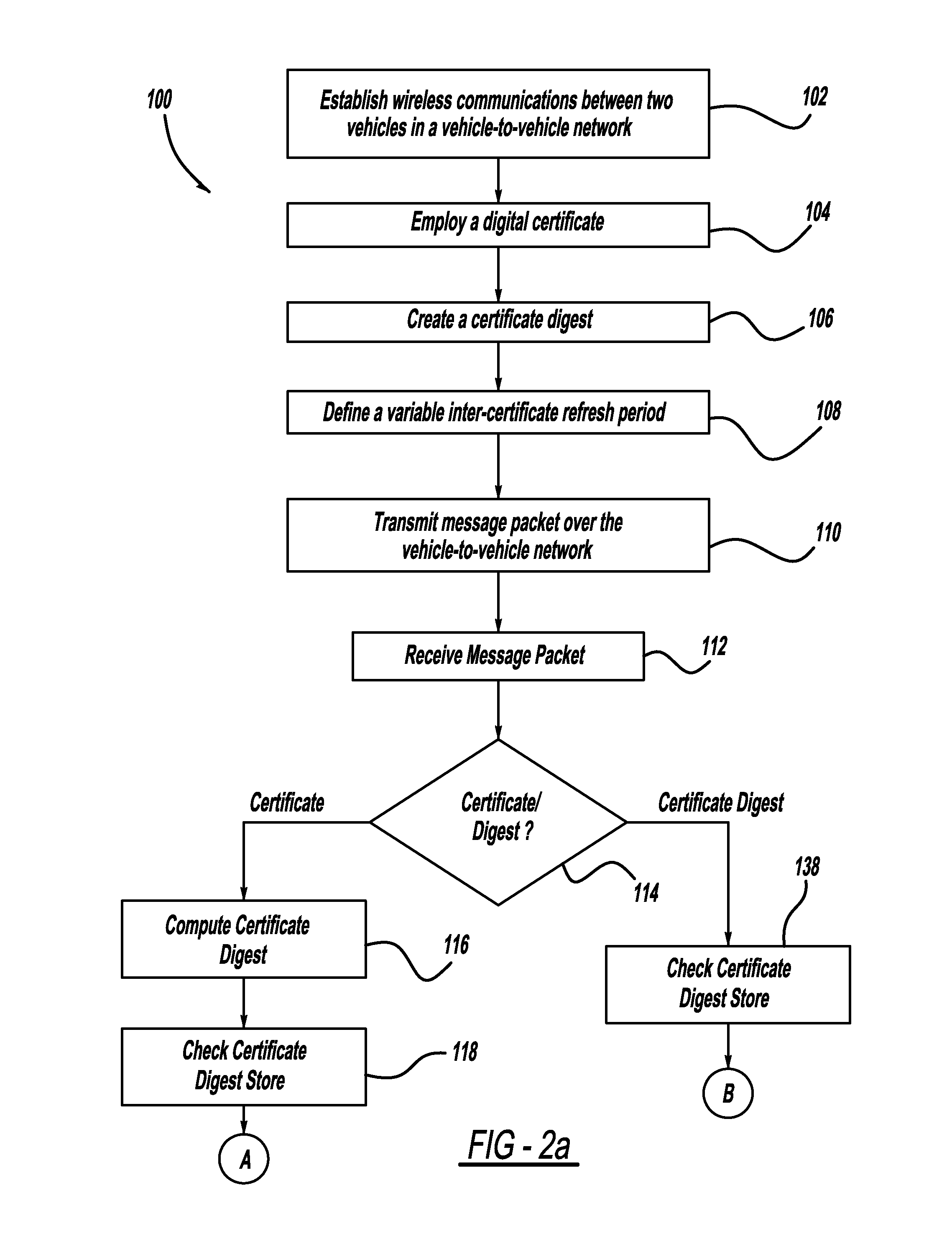
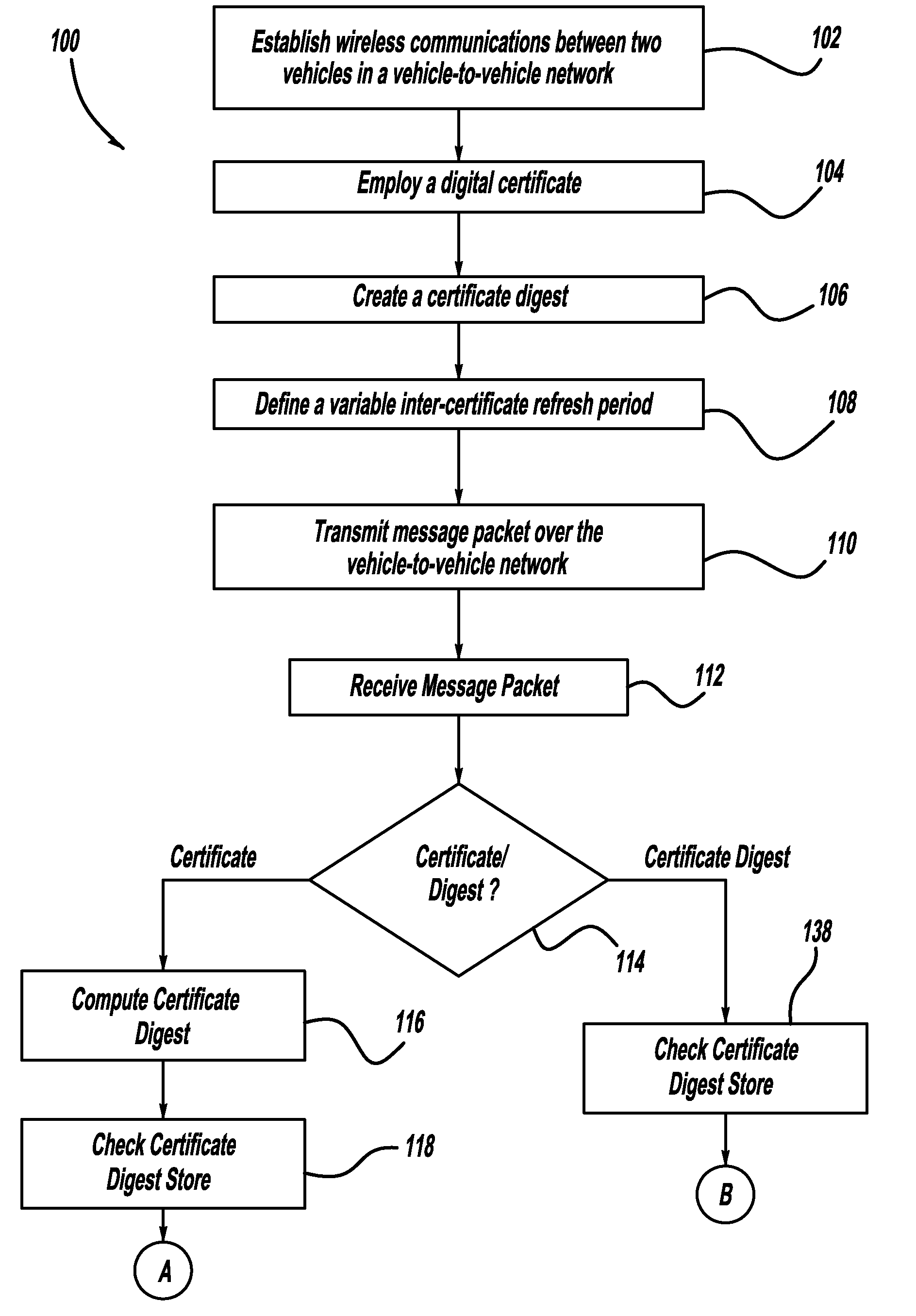
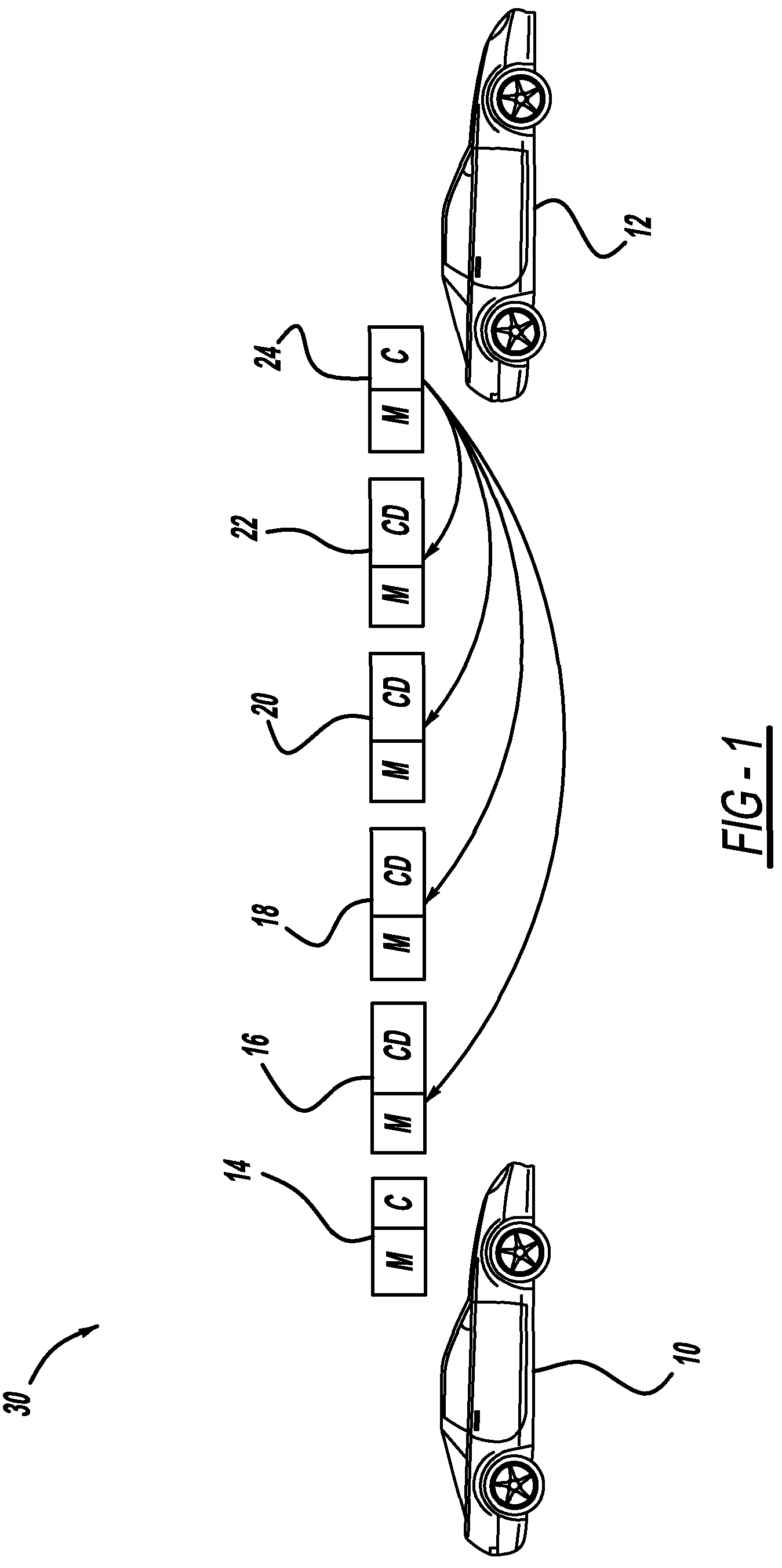
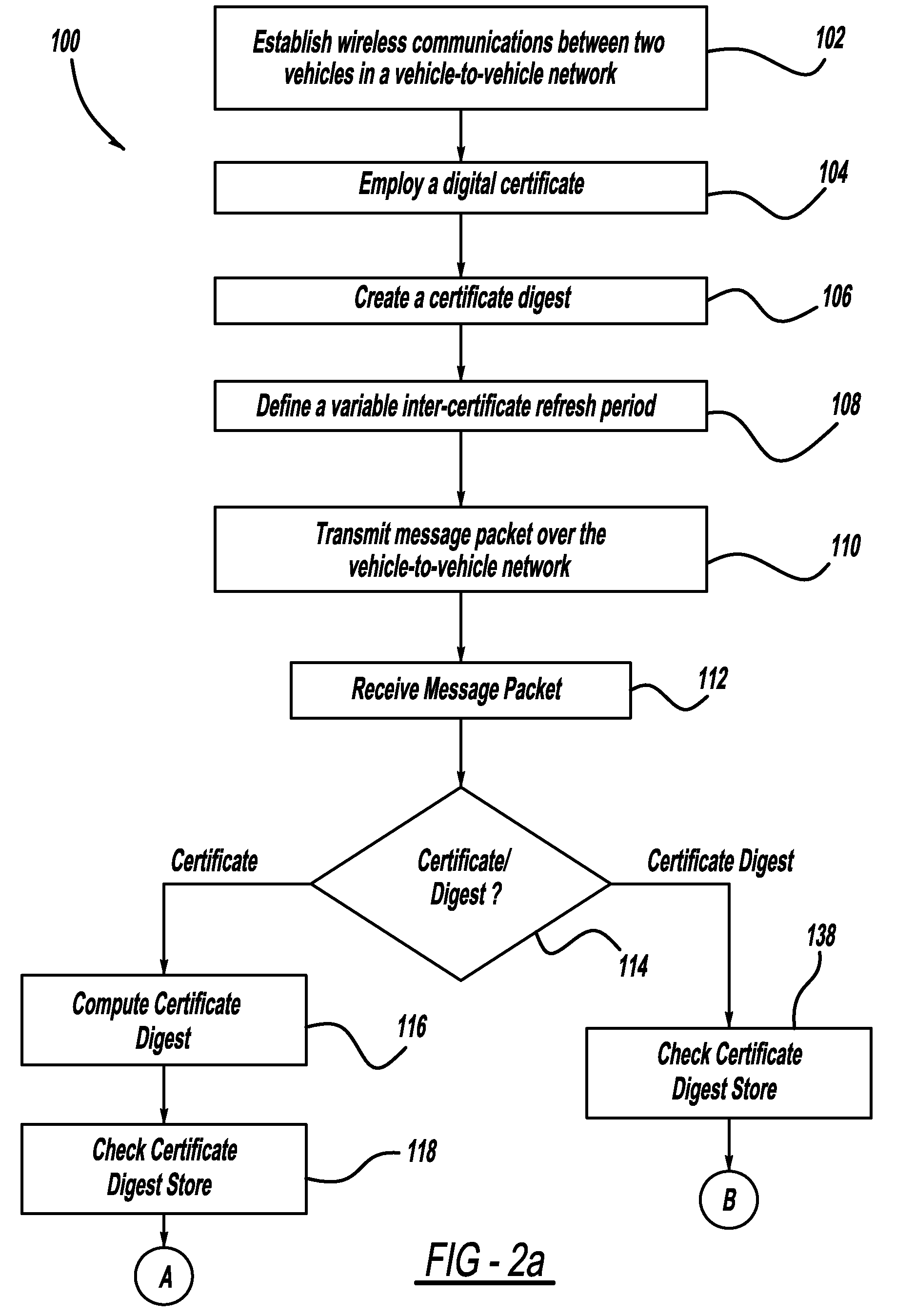
Adaptive certificate distribution mechanism in vehicular networks using variable inter-certificate refresh period
ActiveUS20110238986A1Improve performanceImprove reliabilityError preventionDigital data processing detailsRefresh cycleNetwork conditions
A method for improving the reliability and performance of Vehicle-to-Vehicle (V2V) networks where digital certificates are necessary for message authentication and some messages may be lost in transmission. The method uses a variable inter-certificate refresh period to optimize communications throughput based on network conditions such as node density and bandwidth saturation. In some network conditions, the inter-certificate refresh period may be increased, such that more certificate digests are sent between full digital certificates, to decrease average message size. In other network conditions, the inter-certificate refresh period may be decreased, to allow for more frequent message authentication by receiving nodes. Empirical data and an adaptive controller are used to select the refresh period which will provide the best performance based on network conditions.
Owner:GM GLOBAL TECH OPERATIONS LLC
Radio communication base station device
InactiveUS8126464B2Reduce message sizeAssess restrictionSubstation equipmentInformation transmissionMessage size
Provided is a radio communication base station device capable of reducing a message size in a call connection. In the device, a report information creation unit (203) creates report information by allocating cell level information as Preconfiguration information managed at a cell level and PLMN level information as Preconfiguration information managed at a PLMN level to different transmission units and the created report information is reported from a report information transmission unit (204) to UE. A Preconfiguration use decision unit (208) judges whether the UE which sets a channel can use Preconfiguration. If yes, a control information creation unit (209) includes the corresponding Index in control information and the control information is transmitted from a control information transmission unit (210) to the UE.
Owner:SOVEREIGN PEAK VENTURES LLC
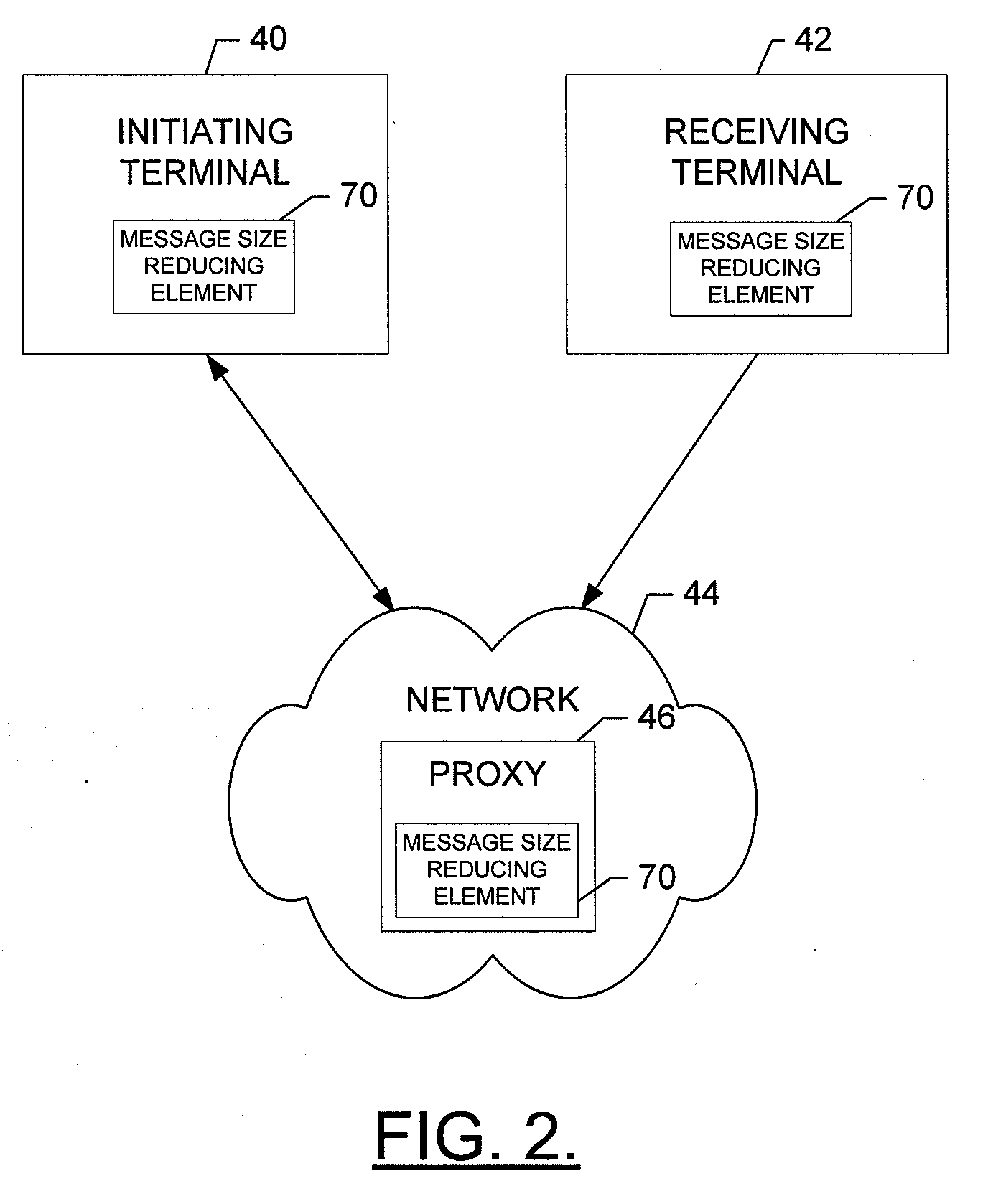
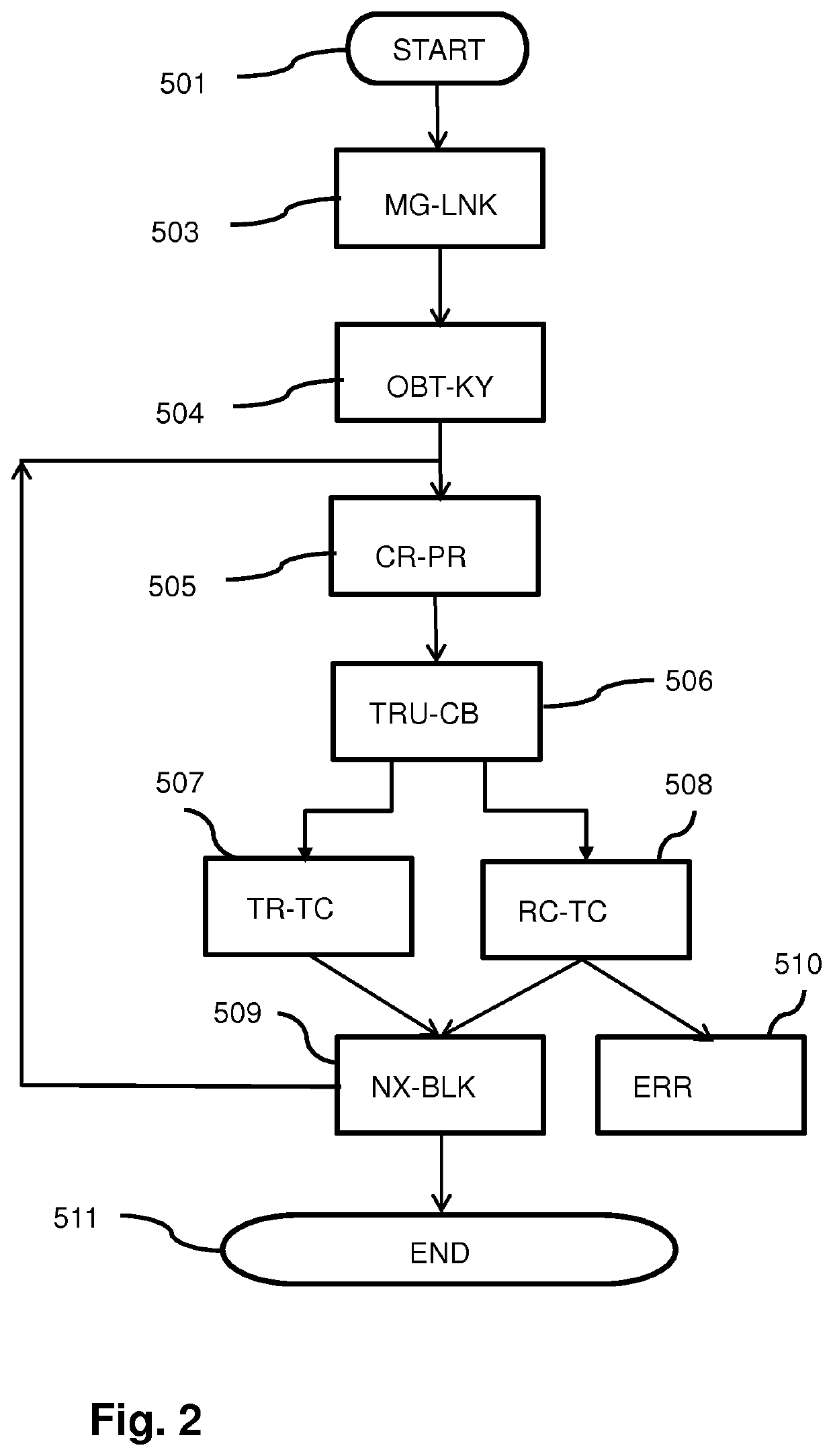
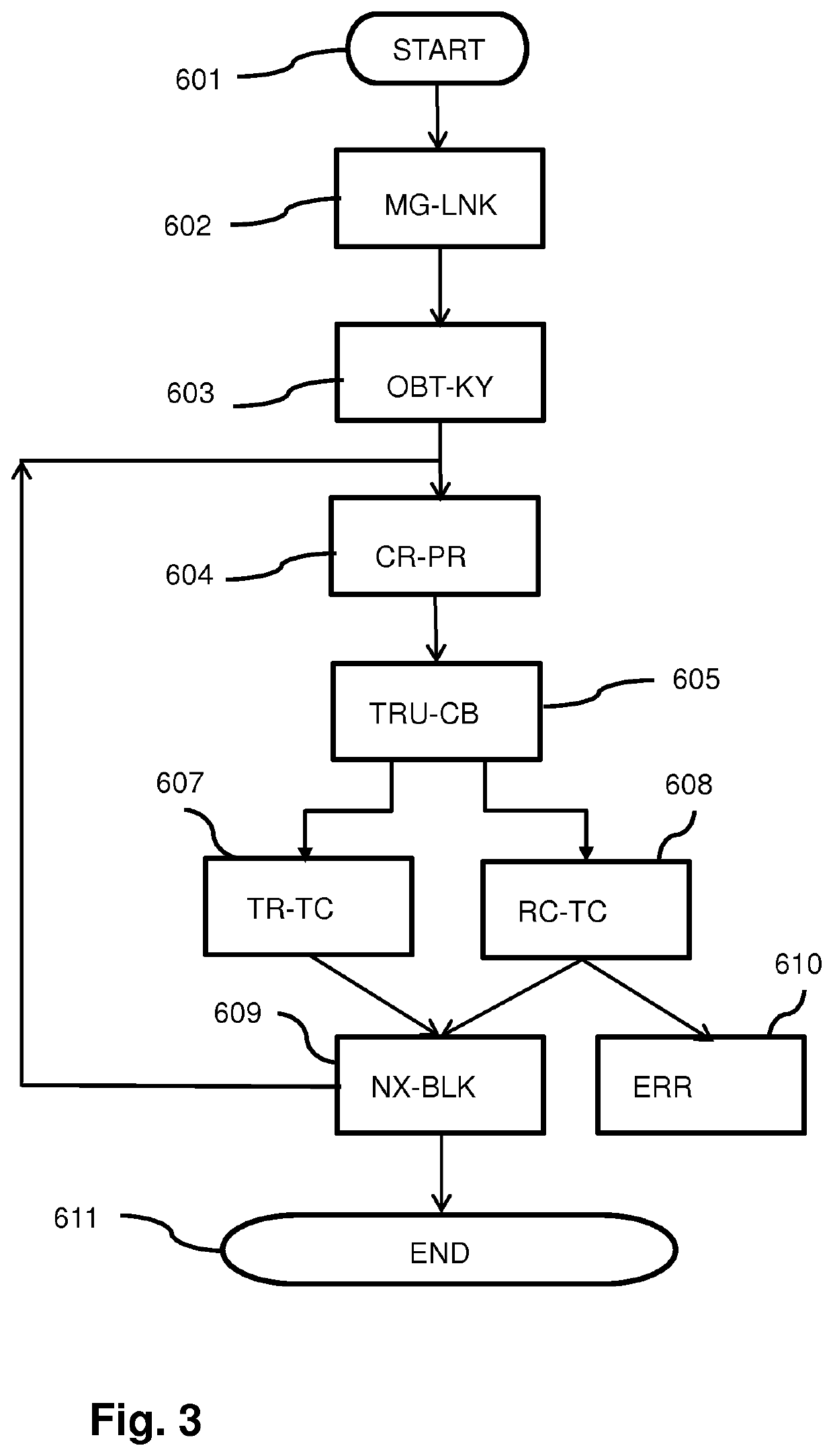
Method, Apparatus, and Computer Program Product for Reducing Session Related Message Size
InactiveUS20080270542A1Reduce message sizeSmall sizeError preventionTransmission systemsInternet privacyUnique identifier
An apparatus for reducing session related message size includes a processing element. The processing element may be configured to determine a domain-wide unique identifier and generate a message including a first field for identifying a message sequence associated with the message and a second field including a tag. The second field including the tag may be associated with an identifier of a source or recipient of the message. At least one of the first and second fields may be without data. The processing element may be further configured to include, in the message, a third field comprising at least the domain-wide unique identifier. The third field may be associated with data otherwise intended for the first and second fields.
Owner:CELLCO PARTNERSHIP INC
Enhanced refresh in SIP network
ActiveUS20070294345A1Reduce the amount of processingReduce message sizeMultiple digital computer combinationsNetwork connectionsComputer hardware
Embodiments of the present invention provide techniques for refreshing a session. A session is refreshed using a refresh message that is enhanced for a refresh. For example, the refresh message does not include an SDP or any other message body. The message includes only a reduced header. This reduces time spent building and parsing the refresh message. Also, less bandwidth is used in sending the refresh messages.
Owner:CISCO TECH INC
Adaptive certificate distribution mechanism in vehicular networks using variable inter-certificate refresh period
ActiveUS8499155B2Improve performanceImprove reliabilityError preventionDigital data processing detailsComputer hardwareRefresh cycle
A method for improving the reliability and performance of Vehicle-to-Vehicle (V2V) networks where digital certificates are necessary for message authentication and some messages may be lost in transmission. The method uses a variable inter-certificate refresh period to optimize communications throughput based on network conditions such as node density and bandwidth saturation. In some network conditions, the inter-certificate refresh period may be increased, such that more certificate digests are sent between full digital certificates, to decrease average message size. In other network conditions, the inter-certificate refresh period may be decreased, to allow for more frequent message authentication by receiving nodes. Empirical data and an adaptive controller are used to select the refresh period which will provide the best performance based on network conditions.
Owner:GM GLOBAL TECH OPERATIONS LLC
Optimizing size of protocol communication in a vehicle internal networks
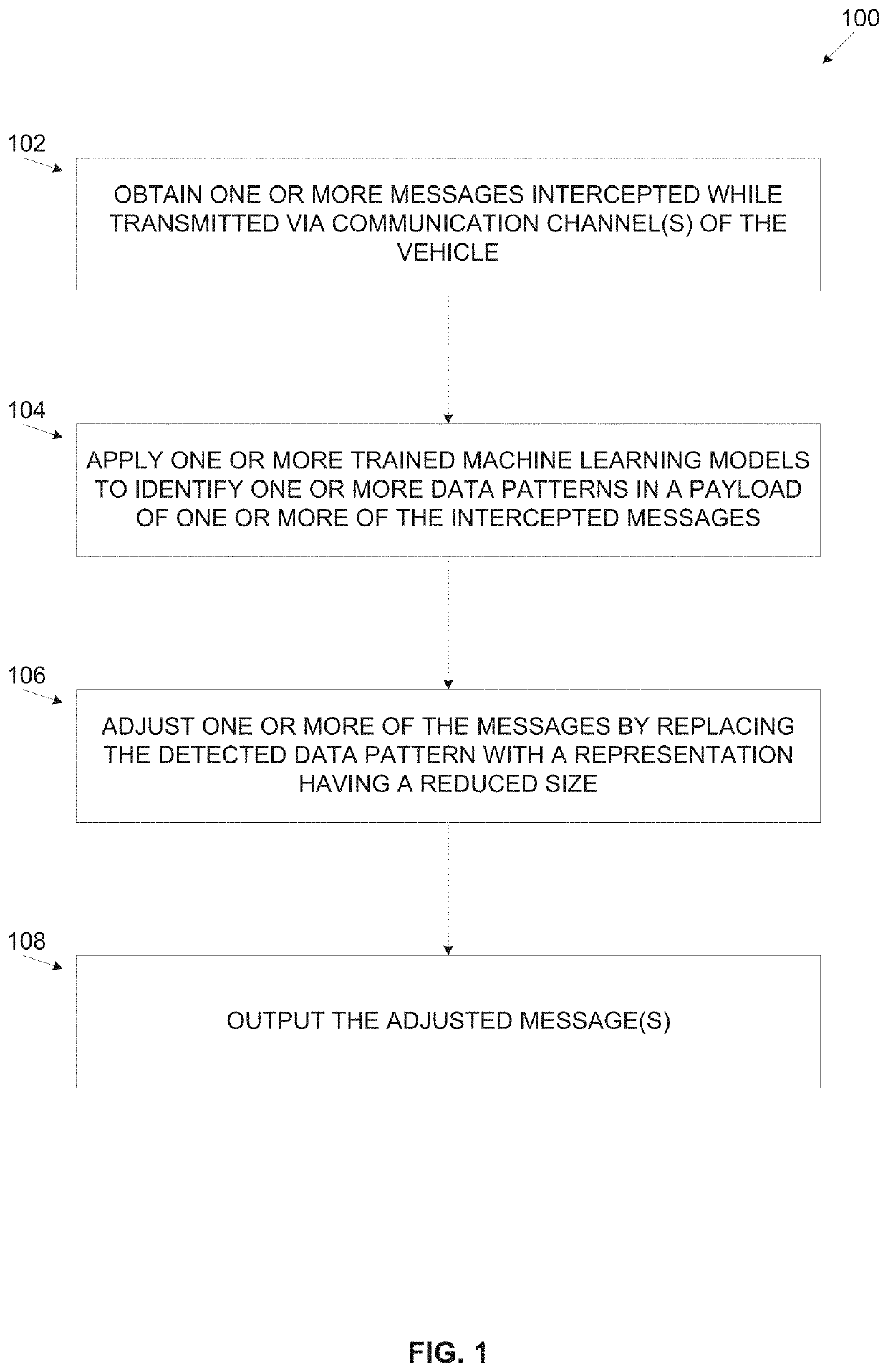
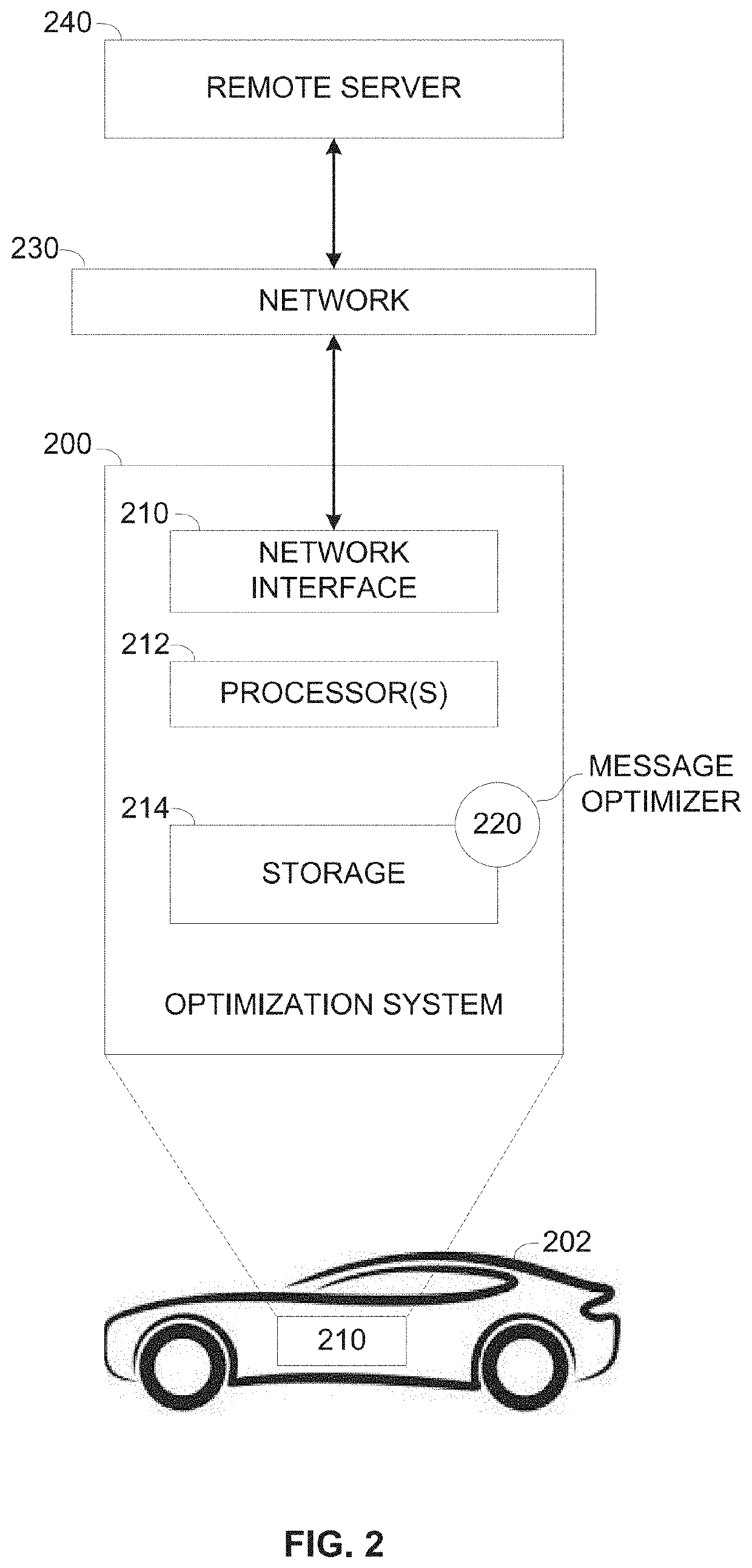
ActiveUS20210274010A1Small valueSmall sizeNetwork traffic/resource managementParticular environment based servicesComputer networkRemote system
A computer implemented method of reducing a size of a message intercepted on a communication channel of a vehicle, comprising using one or more processors of a vehicular device. The processor(s) is adapted for receiving one or more of a plurality of messages intercepted by one or more devices adapted to monitor messages transmitted via one or more segments of one or more communication channels of a vehicle, applying one or more trained machine learning models to identify one or more of a plurality of data patterns in one or more of the messages, adjusting one or more of the messages by replacing each of the identified data pattern(s) with a respective predefined lossless representation having a reduced size compared to the identified data pattern and transmitting the adjusted message(s) to a remote system via one or more upload communication channels.
Owner:SAFERIDE TECH LTD
Hardware module-based authentication in intra-vehicle networks
ActiveUS10701102B2Improve securityReduce overheadKey distribution for secure communicationSynchronising transmission/receiving encryption devicesArea networkHardware modules
A secure hardware-based module or Security Electronic Control Unit (SECU) for a Controller Area Network (CAN) prevents an attacker from sending malicious messages through the CAN bus to take over control of a vehicle. The SECU shares a unique key and counter with each ECU on the CAN bus. When a legitimate ECU sends a message, it first compresses the message and then generates a MAC of the counter and a secret key. The counter is increased by one for each transmitted message. The ECU then fits the compressed message and the MAC into one CAN frame and sends it onto the CAN bus. The SECU performs the message verification on behalf of the intended receiver(s) of the message. If the verification passes, the receiver(s) simply decompress the message and use it as a normal CAN message. If the verification fails, the SECU will corrupt the CAN frame before it is fully received by the intended receiver(s). The corrupted CAN frame will be ignored by the intended receiver(s) as if it was never received. Therefore, a malicious message generated by an attacker will inflict no damage on the system.
Owner:GEORGE MASON UNIVERSITY
Key management messages for secure broadcast
InactiveCN1954538AReduce message sizeWithout compromising securityKey distribution for secure communicationPublic key infrastructure trust modelsContext dataUser profile
The present invention involves establishing a top-level key and optionally also a verification tag. The top-level key is used as the MDP key for encrypting a broadcast medium. Only the part of the key message that contains the encrypted top-level key is authenticated, e.g. using a signature or a Message Access Code (MAC). Any known group-key distribution protocol can be used that is based on the creation of a hierarchy of keys. Examples of such methods are the LKH and SD methods. The group-key distribution protocol output key H, traditionally used as the MDP key, or a derivative thereof is used to encrypt the top-level MDP-key. The invention, further, includes optimization of a group-key message by eliminating unnecessary message components relative a specified group or sub-group of users. The optimization can be made in dependence of contextual data such as user profile, network status, or operator policies.
Owner:TELEFON AB LM ERICSSON (PUBL)
Enhanced Messaging Transaction Performance With Auto-Selected Dual-Tag Fields
InactiveUS20130232108A1Reduce message sizeDigital data processing detailsNatural language data processingData processing systemData synchronization
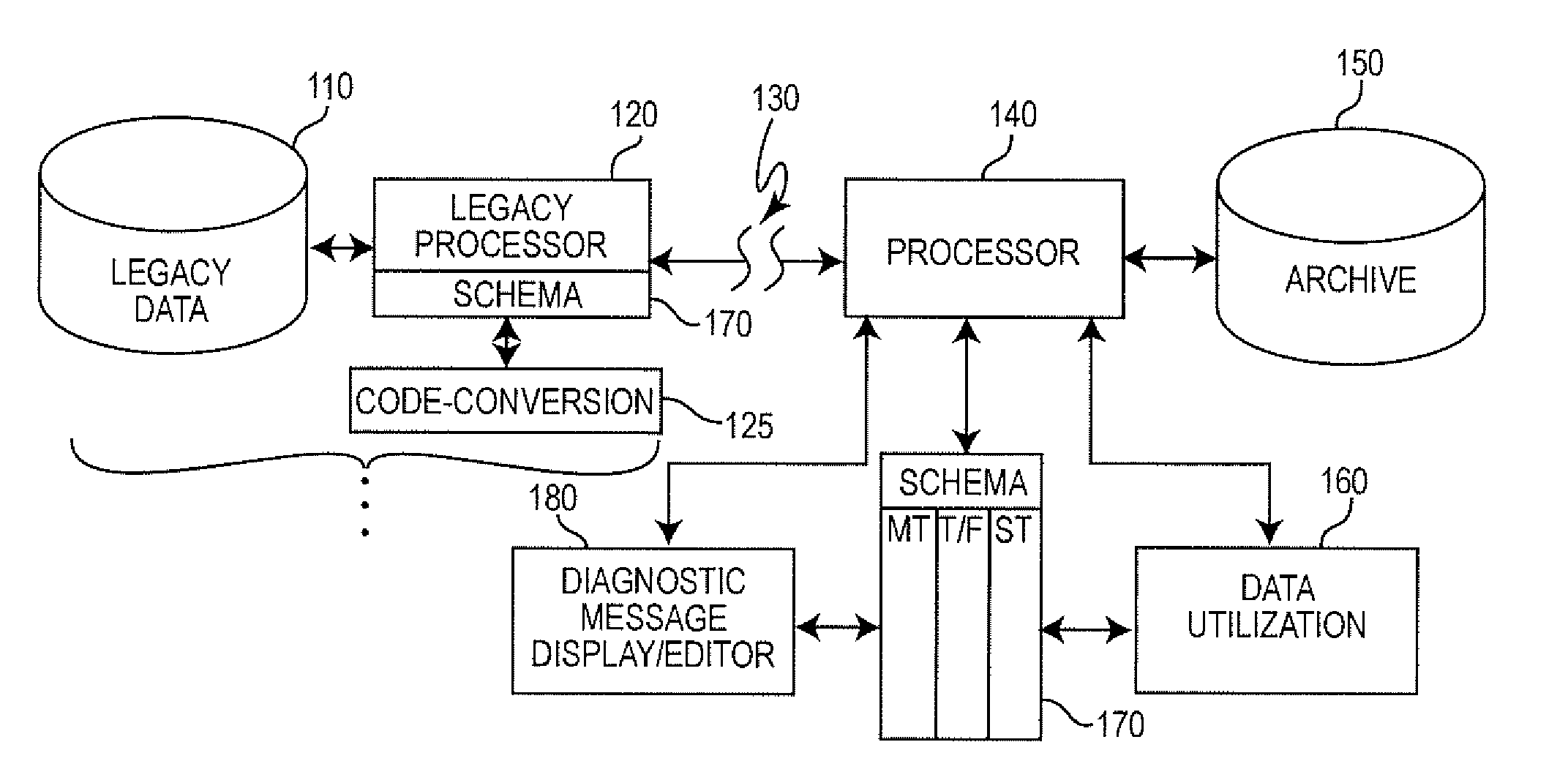
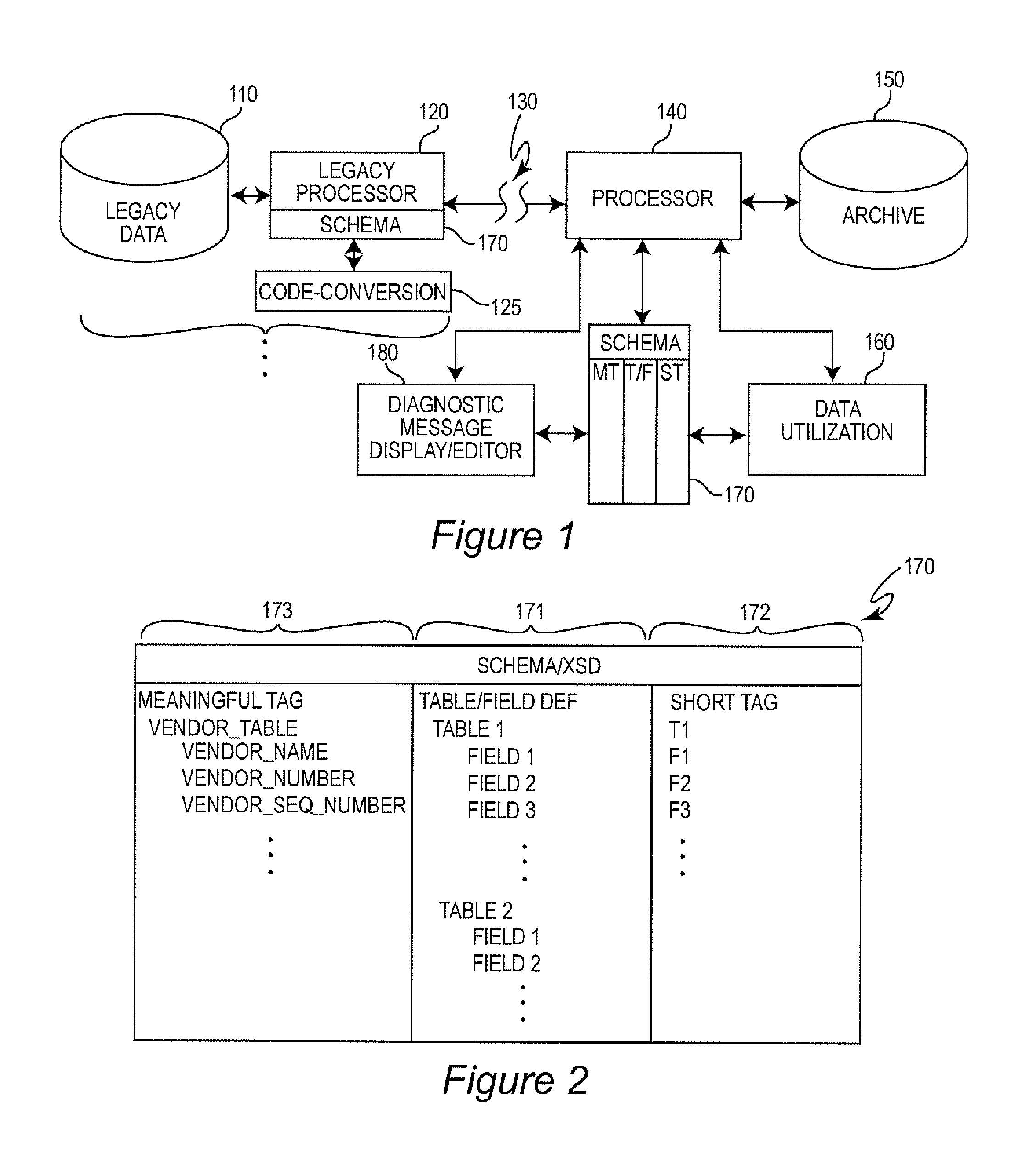
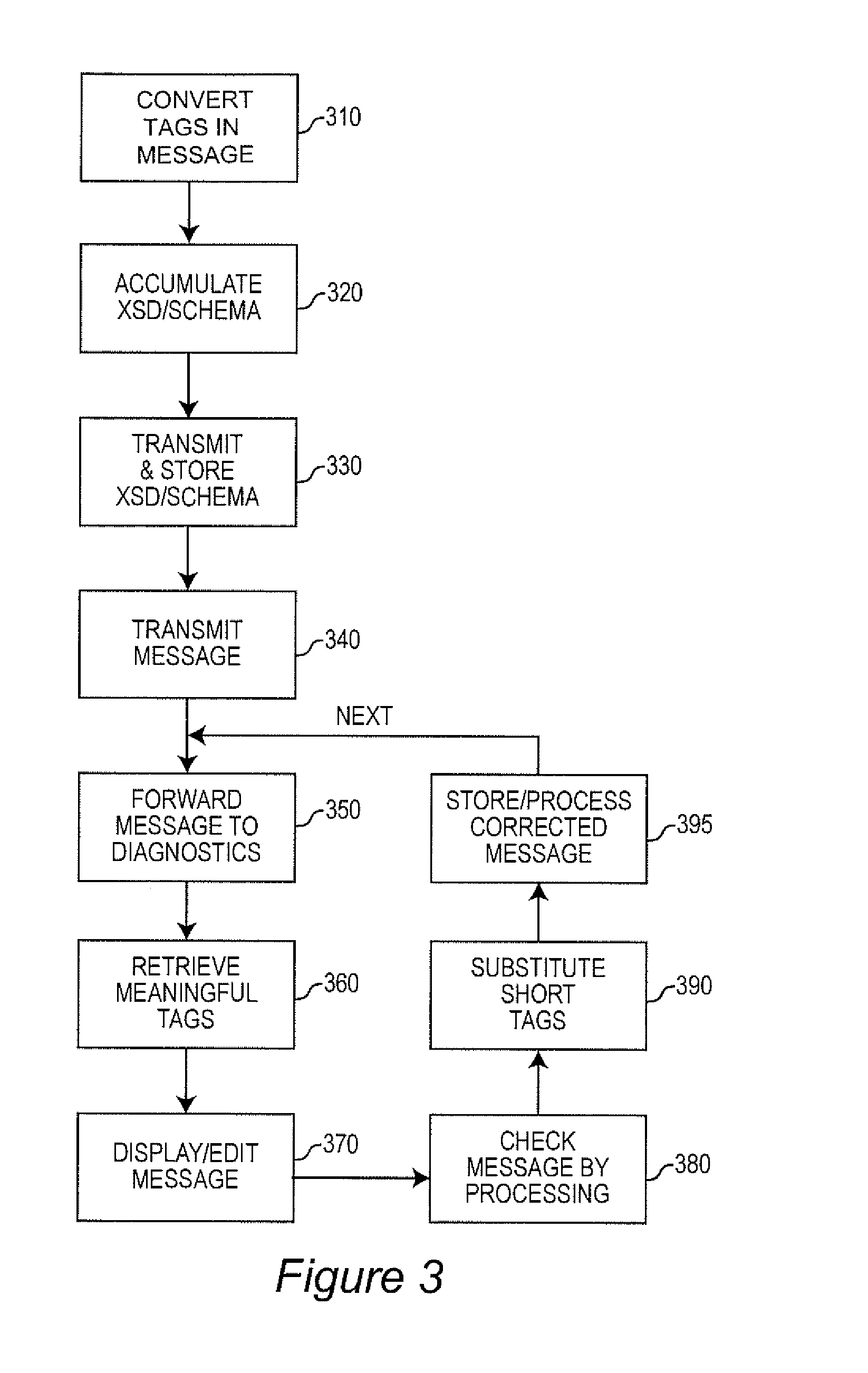
A schema for a mark-up language provides a meaningful name and a short name, both of which are valid, for each of a plurality of data fields in messages coded in a mark-up language such as extensible mark-up language (XML). Code conversion of legacy data to use the short names reduces data volume for transmission, storage and processing while allowing the message to be automatically displayed for inspection, diagnostics and data synchronization during a transformation project such as an upgrade of a data processing system for verification of system operation. The ability to display meaningful names only for such purposes allows text editor arrangements to be used for data synchronization while use of short names improves virtually all aspects of system performance.
Owner:AIRBNB
Method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems
ActiveUS10531264B2Facilitating congestion controlPossible changeNetwork traffic/resource managementAssess restrictionCommunications systemMobile communication systems
The present invention relates to a method and apparatus for efficiently controlling access for system load adjustment in mobile communication systems. In a wireless communication system according to one embodiment, the method for transmitting and receiving data by a terminal including a user equipment (UE) non access stratum (NAS) and a UE access stratum (AS) includes the steps of: receiving by the UE AE, information including emergency call-related information which includes barring information by type for the emergency call, from a base station; transmitting, by the UE NAS, a service request for the emergency call to the UE AS; and determining, by the UE AS, whether to bar the service request on the basis of emergency call-related information. According to one embodiment, during the emergency call transmission, network congestion can be easily controlled by enabling various types of emergency calls to be transmitted, and enabling access to be barred information according to the situation of a communication network and types of emergency calls. Also, even when a specific type of emergency call is barred from access, the terminal can change to another type of emergency call and try for access. Therefore, it is effective in that an emergency call can be transmitted in various schemes even in a state where the network is congested.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for reporting a measurement result in a wireless communication system
ActiveUS9161240B2Inhibition of informationReduce message sizeError preventionTransmission systemsCommunications systemComputer terminal
Owner:QUALCOMM INC
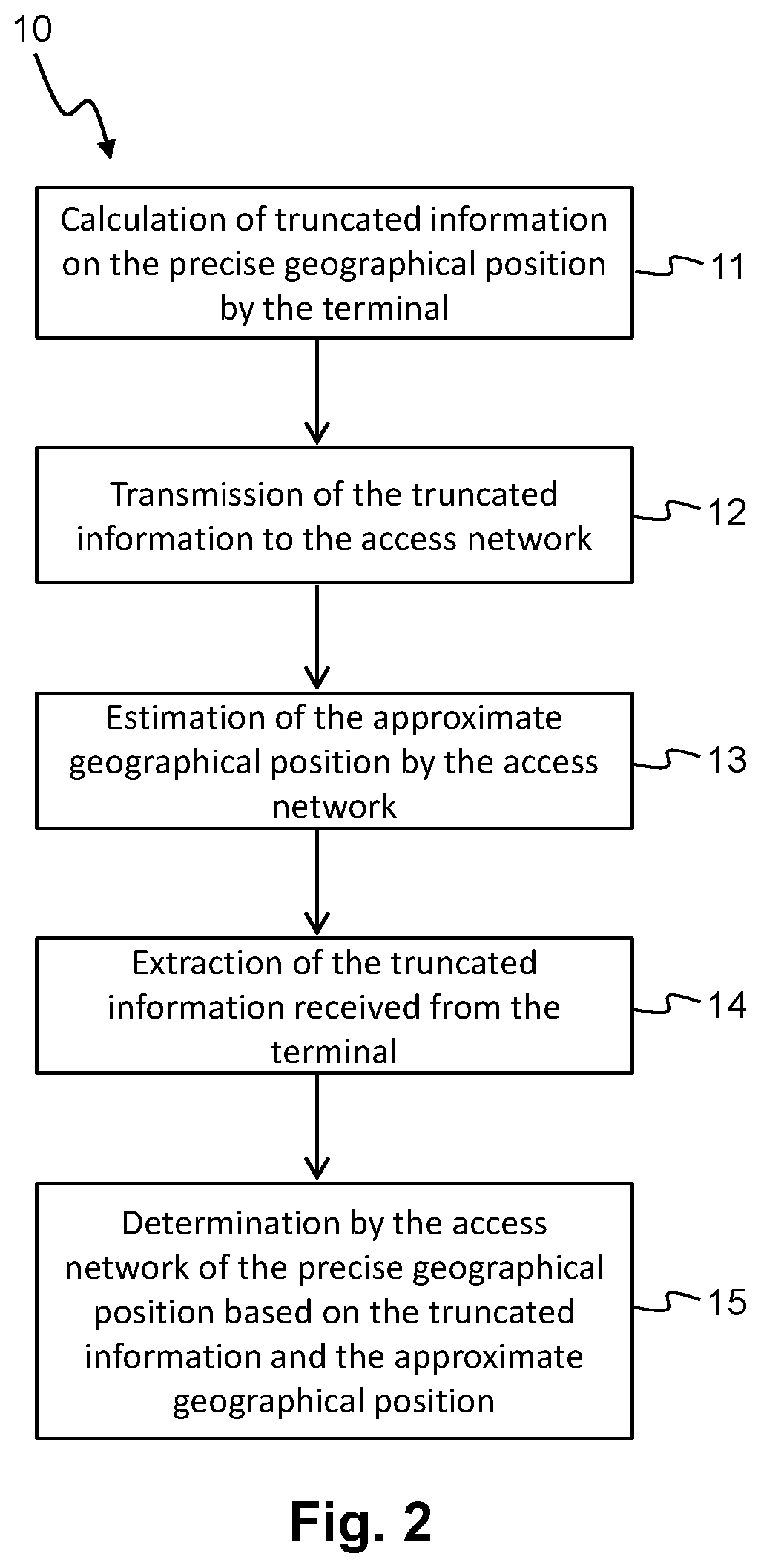
Method and system for geolocating a terminal of a wireless communication system
PendingUS20210263127A1Limit in quantityControl quantityPosition fixationSatellite radio beaconingReal-time computingGeolocation
A method for geolocating a terminal of a wireless communication system. The terminal includes a positioning device for obtaining a precise geographical position of the terminal. An access network of the communication system estimates an approximate geographical position of the terminal. In order to limit the size of the messages exchanged between the terminal and the access network, only a truncated part of the information about the precise geographical position of the terminal is transmitted by the terminal to the access network. The access network determines the precise geographical position of the terminal by combining the truncated information received from the terminal with the approximate geographical position estimated by the access network.
Owner:SIGFOX
Methods and devices for providing message authentication code suitable for short messages
PendingUS20220006644A1Reduce message sizeReduce overheadUser identity/authority verificationDigital data authenticationEngineeringMessage authentication code
This application relates to devices and methods of authenticating messages exchanged over a network between a transmitter and a receiver, the method comprising: at a transmitter side, for transmitting a message, generating a truncated MAC code by selecting or generating predetermined bits from a message authentication code (MAC) computed over a concatenation of a predetermined part of the message with at least one predetermined part of a previously transmitted message; wherein a bitlength of truncated MAC code is smaller than a bitlength of the message authentication code (MAC) appending the truncated MAC code to the message for transmission; at a receiver side, for authenticating a message, receiving a previously transmitted message, the message and the truncated MAC code, generating an expected truncated MAC code by selecting or generating predetermined bits from a message authentication code (MAC) computed over a concatenation of a predetermined part of the message with at least one predetermined part of a previously transmitted message; authenticating the message and the previously transmitted message if the truncated MAC code as received is identical to the expected truncated MAC code.
Owner:KONINKLJIJKE PHILIPS NV
System and method for correlating messages within a wireless transaction
ActiveCN101309453AReduce message sizeSave network capacityNetwork traffic/resource managementRadio/inductive link selection arrangementsWorld Wide Web
A method and system for correlating messages within a wireless transaction, each of the messages requiring a unique message identifier, the method having the steps of: creating a transaction identifier, the transaction identifier being the same for related messages; and adding to the transaction identifier a message index, the message index corresponding to a number of a message within a transaction, whereby the transaction identifier and message index form the unique message identifier for each of the messages.
Owner:RES IN MOTION LTD
UE groups, UE group manager UEs and UE group member UEs
ActiveUS11438736B2Improve accuracyLower performance requirementsParticular environment based servicesNetwork topologiesUser equipmentCellular network
Owner:KONINKLJIJKE PHILIPS NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com