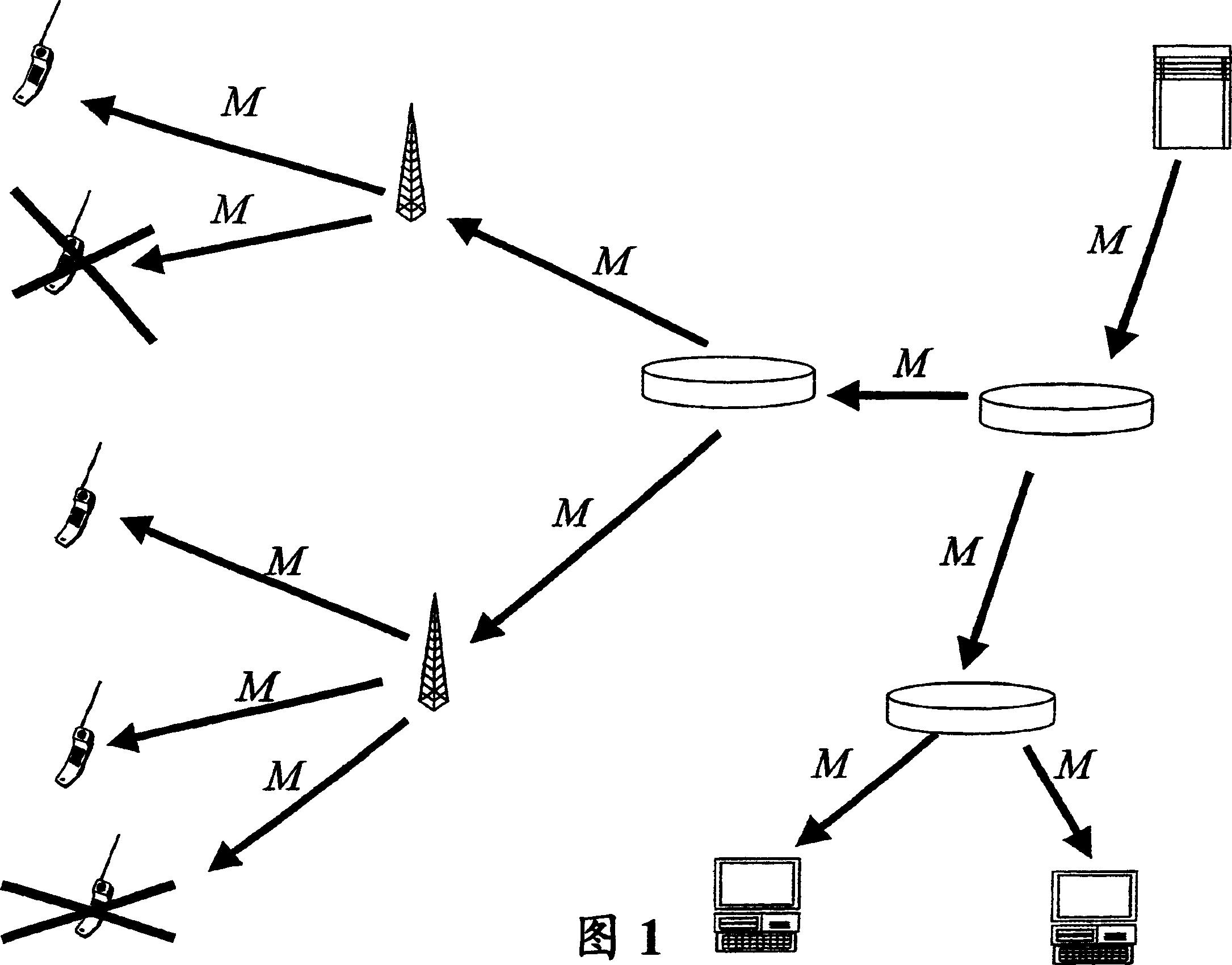
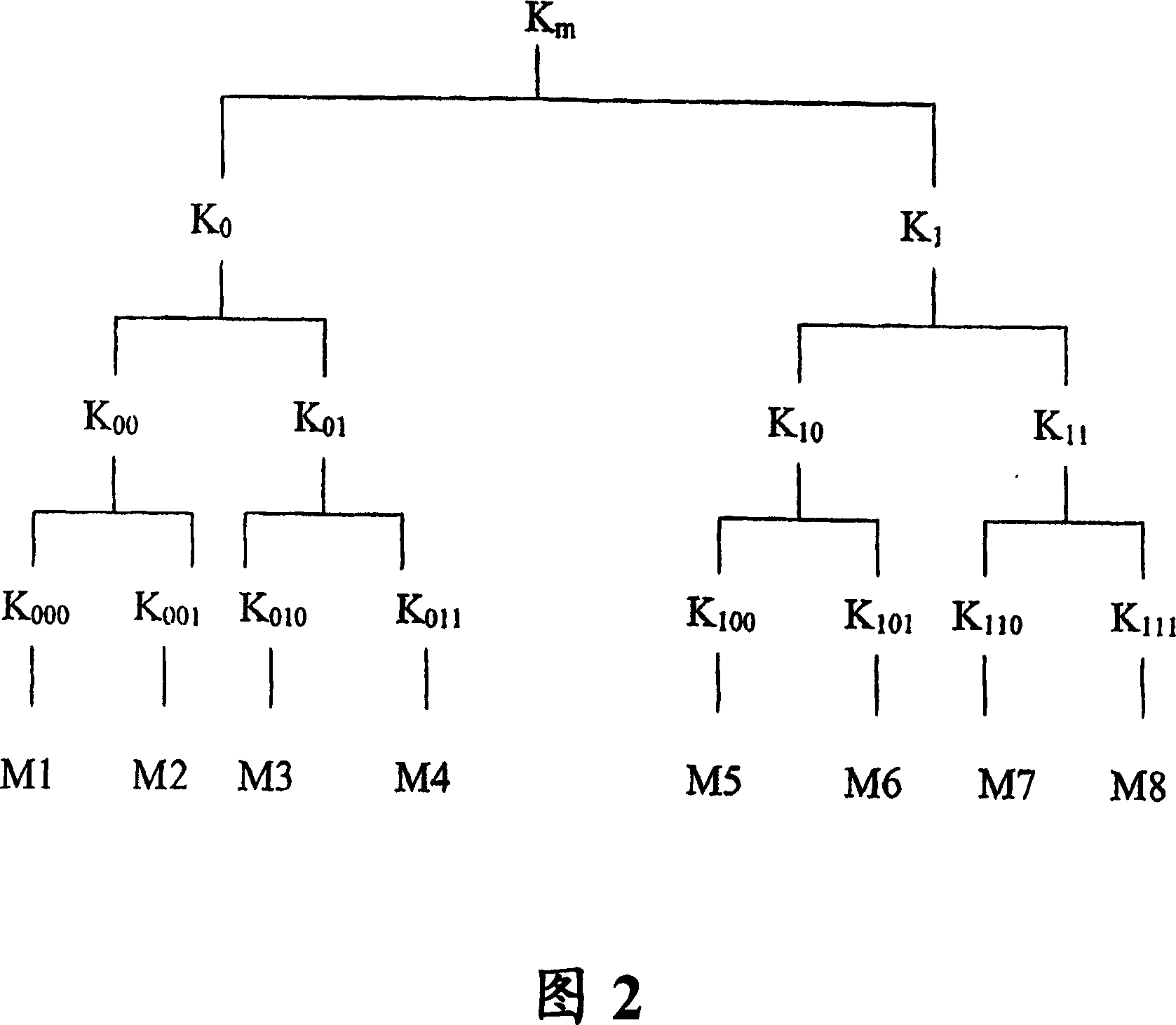
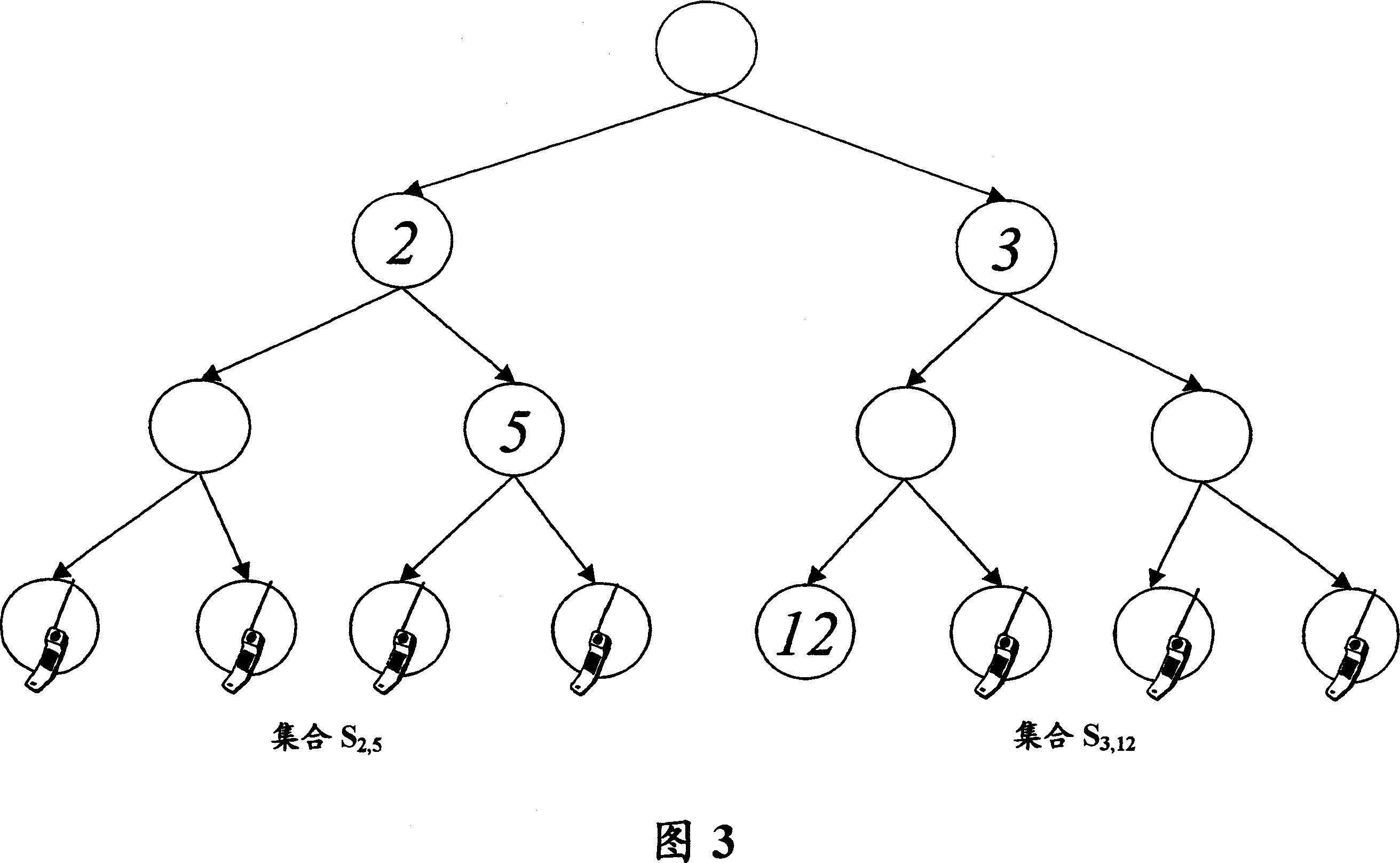
Key management messages for secure broadcast
By introducing top-level key encryption and authentication signatures into the group key distribution protocol, the group key management message is optimized, the problem of excessive message size and computational consumption in group key distribution is solved, and high fault tolerance and security are achieved, which is applicable for broadcast and multicast systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Throughout the drawings, the same reference numerals will be used for corresponding or similar elements.
[0055] As schematically shown in Figure 4, a first aspect of the invention involves the introduction of a new abstraction layer containing top-level keys that are commonly used as MDP keys. The new abstraction layers are represented on top of the exemplary base protocols LKH and SD, respectively.
[0056] Figure 5 is a schematic flow diagram of a preferred basic embodiment of this aspect of the invention. In step S1 a new top-level key is established (eg for media protection) and in step S2 the top-level key is preferably encrypted according to the output key of the particular group key distribution protocol used. Then, at step S3, the authentication signature is applied to at least the encrypted top-level key. In step S4, the group key management message is modified by eg adding the encrypted top-level key and the authentication signature in the same message ele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com