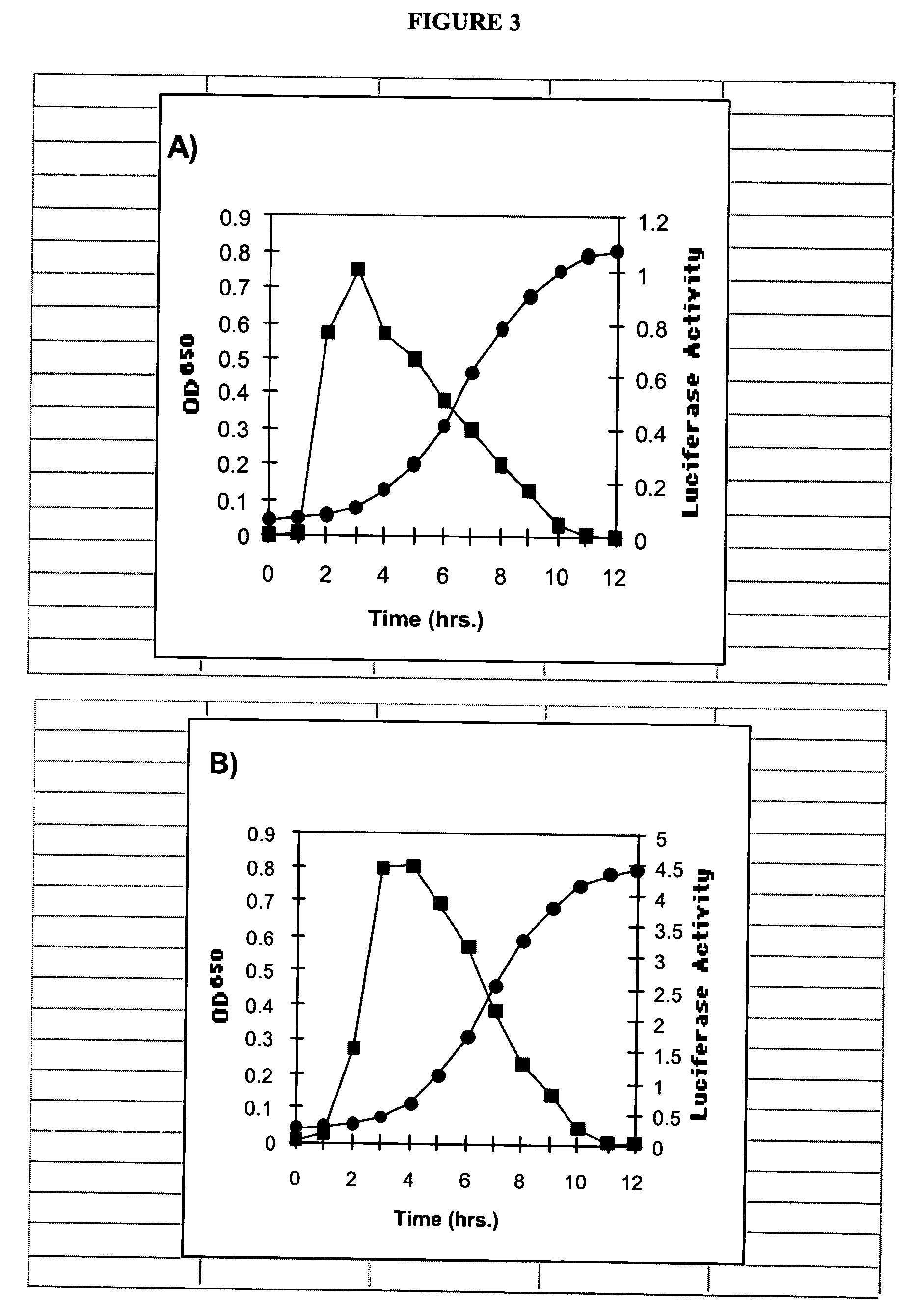
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
231results about How to "Minimize consequences" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
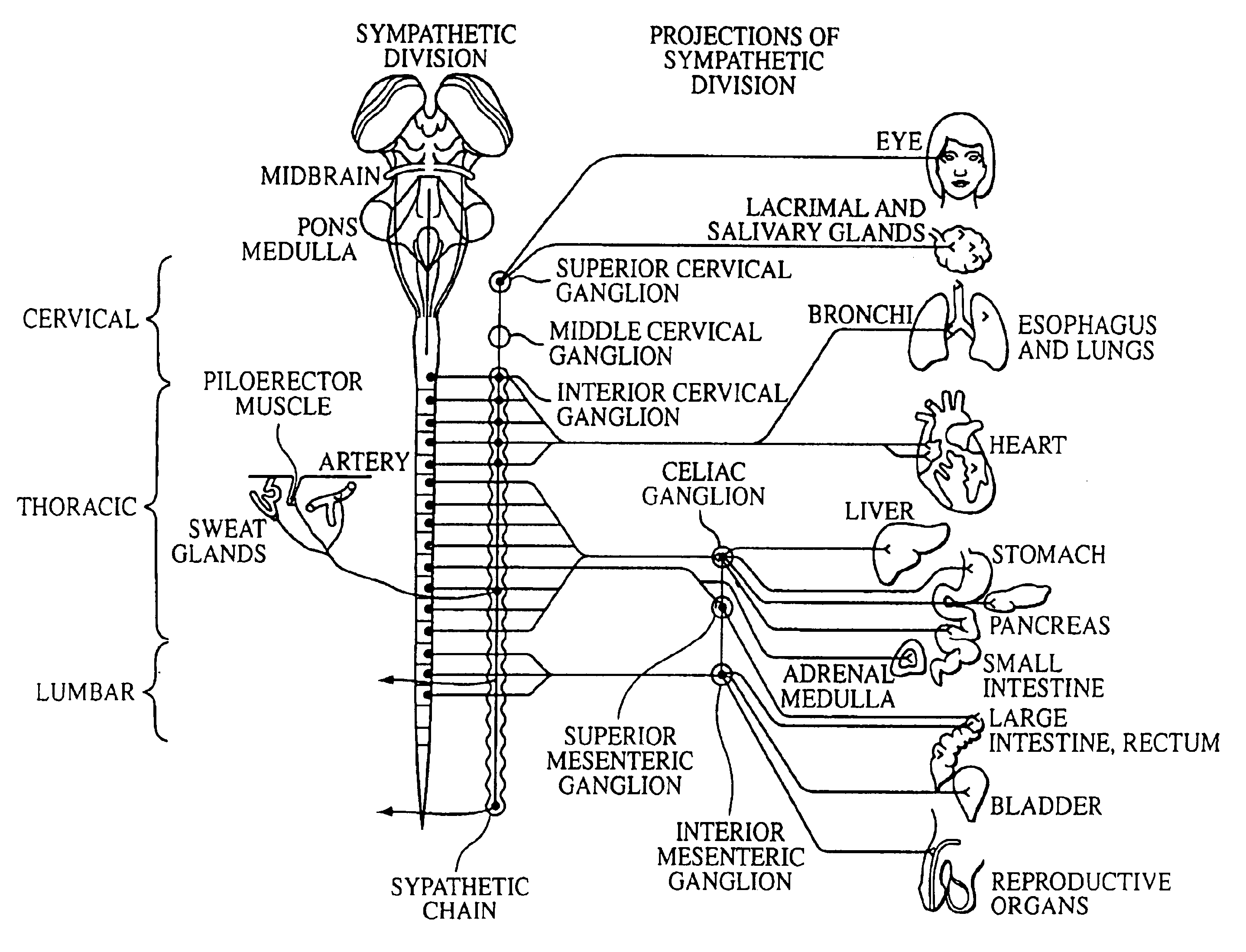
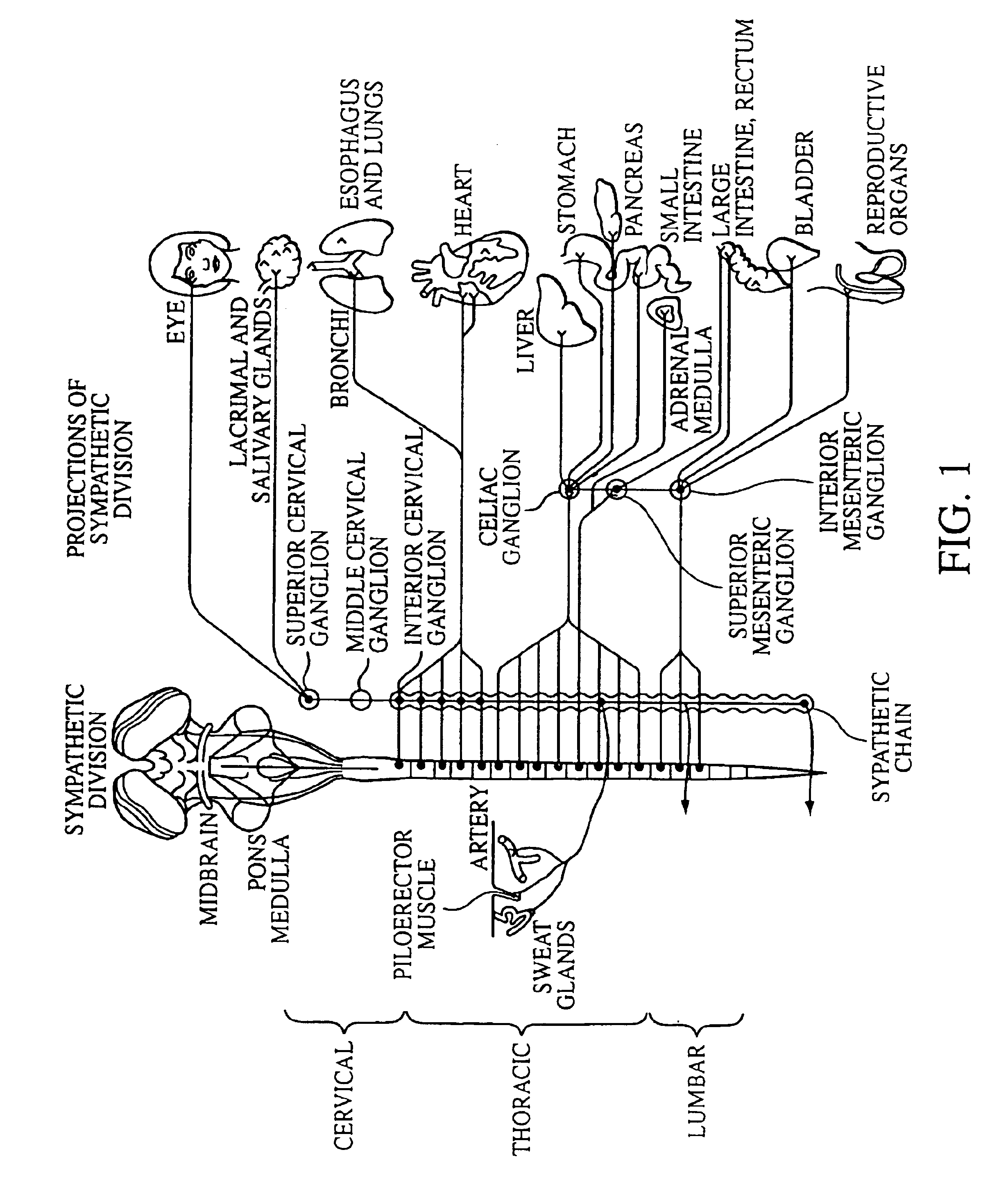
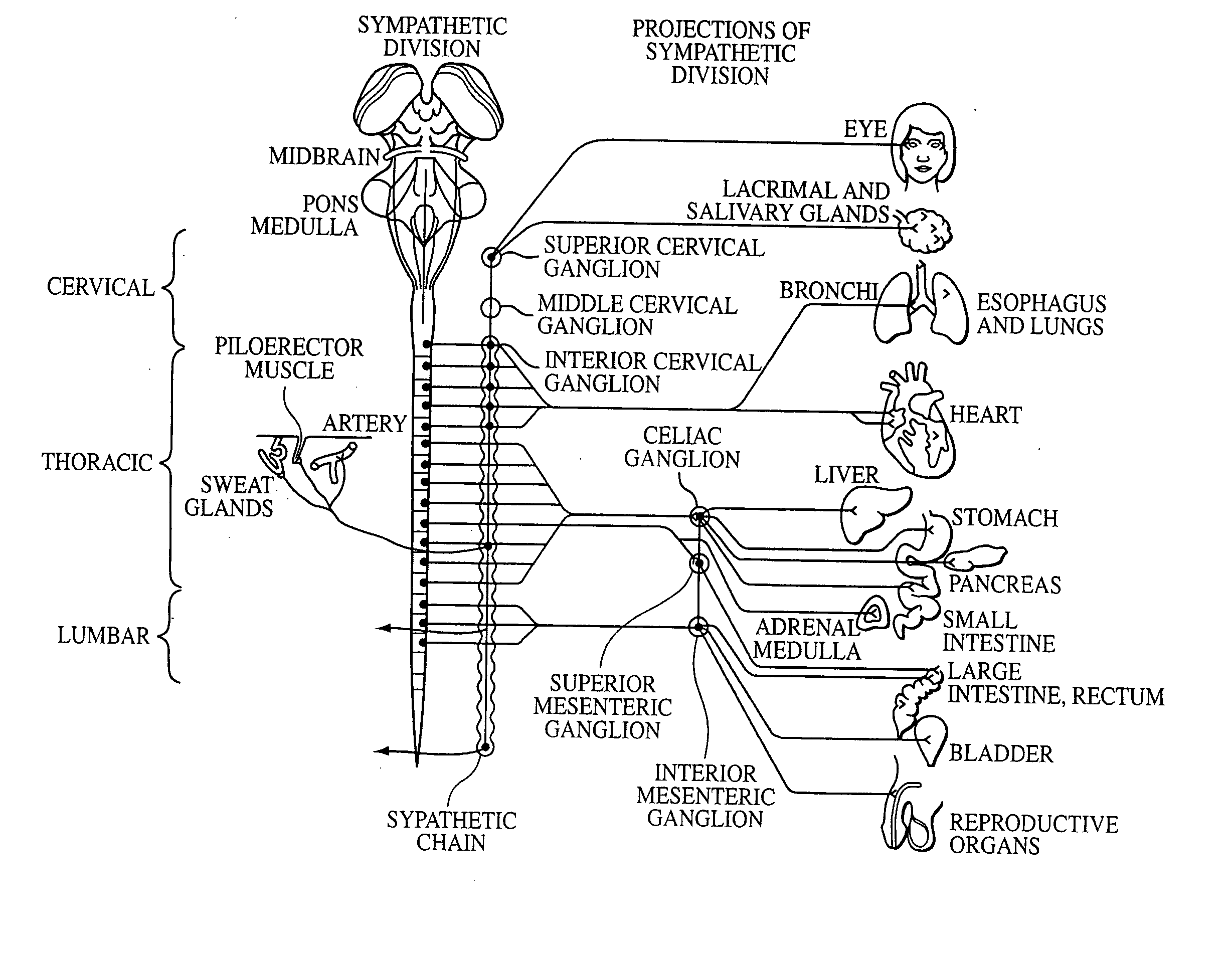
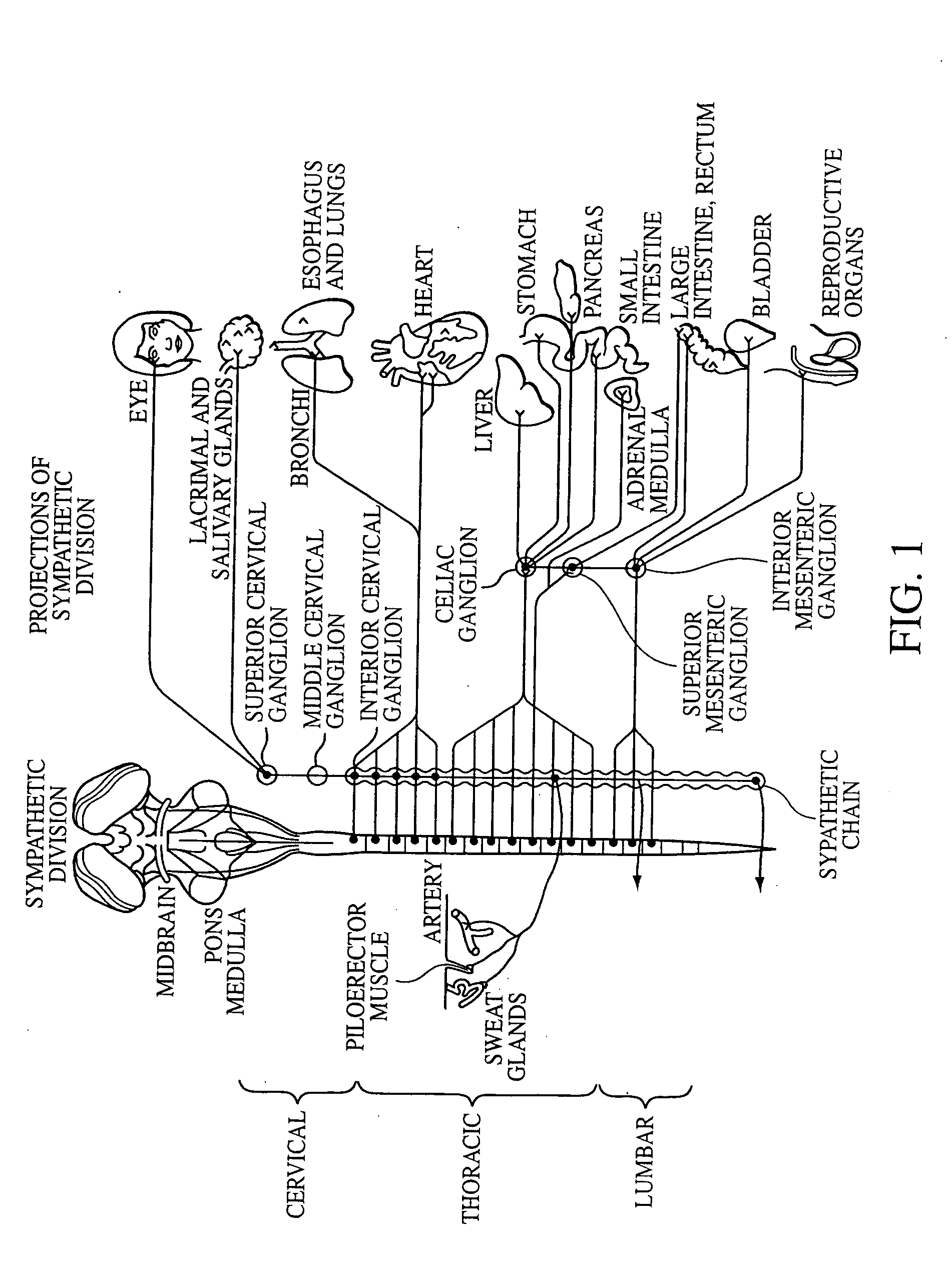
Electrical stimulation of the sympathetic nerve chain
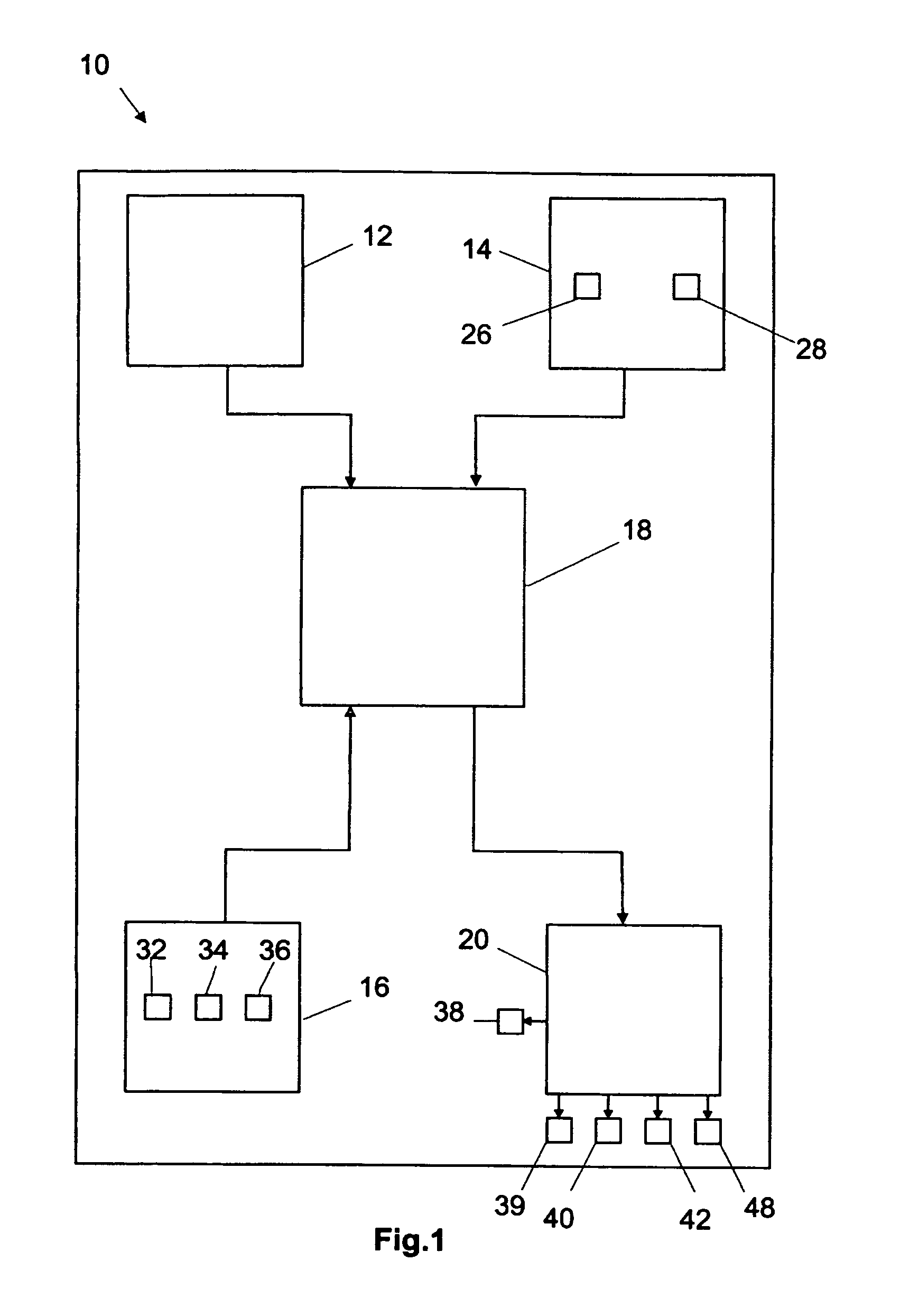
InactiveUS6885888B2Minimizing stimulationMinimize complicationsSpinal electrodesExternal electrodesSympathetic nerveSacral sympathetic chain
The present invention provides a method of affecting physiological disorders by stimulating a specific location along the sympathetic nerve chain. Preferably, the present invention provides a method of affecting a variety of physiological disorders or pathological conditions by placing an electrode adjacent to or in communication with at least one ganglion along the sympathetic nerve chain and stimulating the at least one ganglion until the physiological disorder or pathological condition has been affected.
Owner:THE CLEVELAND CLINIC FOUND
Electrical stimulation of the sympathetic nerve chain
InactiveUS20050065573A1Minimizing stimulationMinimize complicationsSpinal electrodesExternal electrodesSympathetic nerveSacral sympathetic chain
The present invention provides a method of affecting physiological disorders by stimulating a specific location along the sympathetic nerve chain. Preferably, the present invention provides a method of affecting a variety of physiological disorders or pathological conditions by placing an electrode adjacent to or in communication with at least one ganglion along the sympathetic nerve chain and stimulating the at least one ganglion until the physiological disorder or pathological condition has been affected.
Owner:THE CLEVELAND CLINIC FOUND
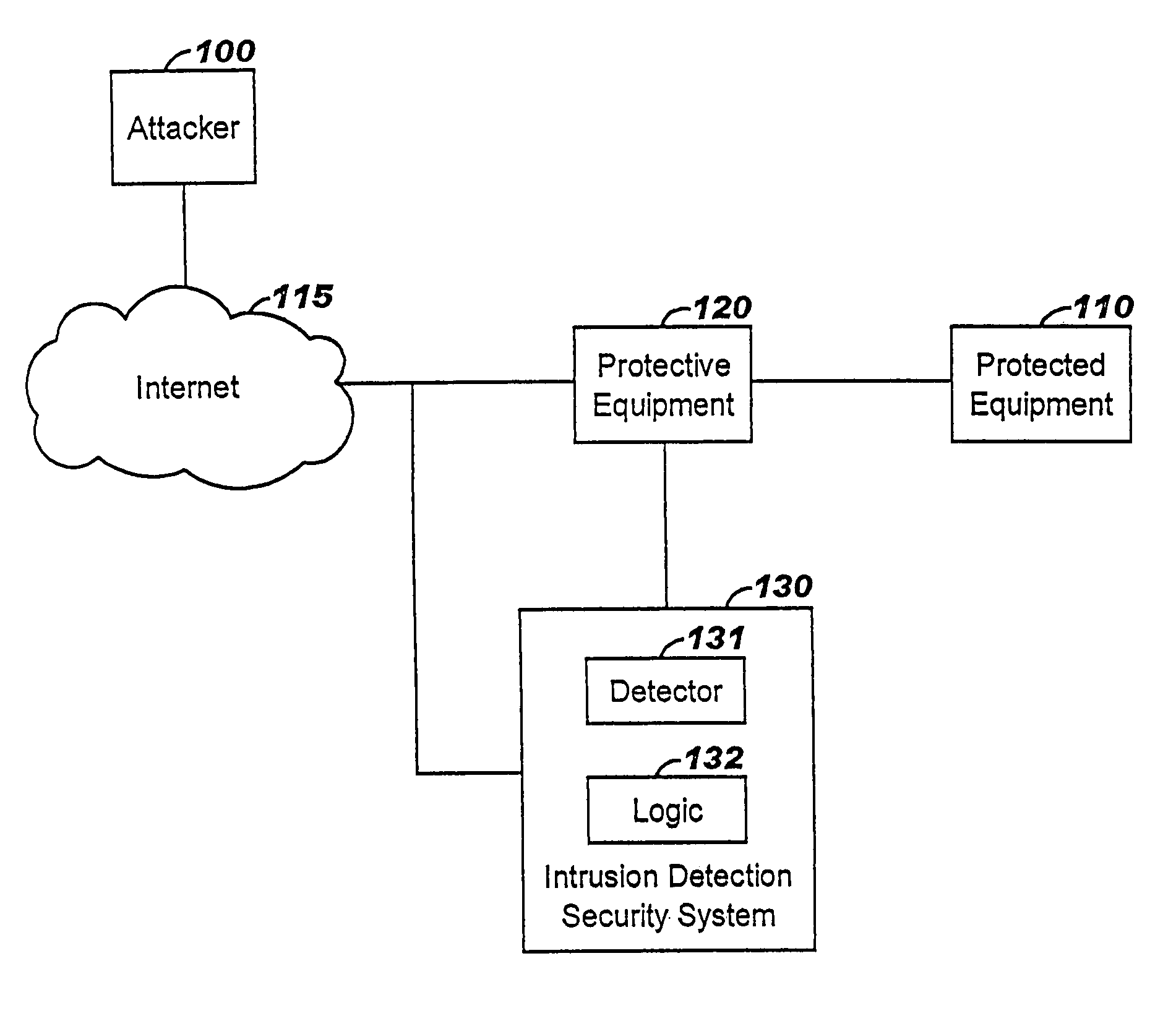
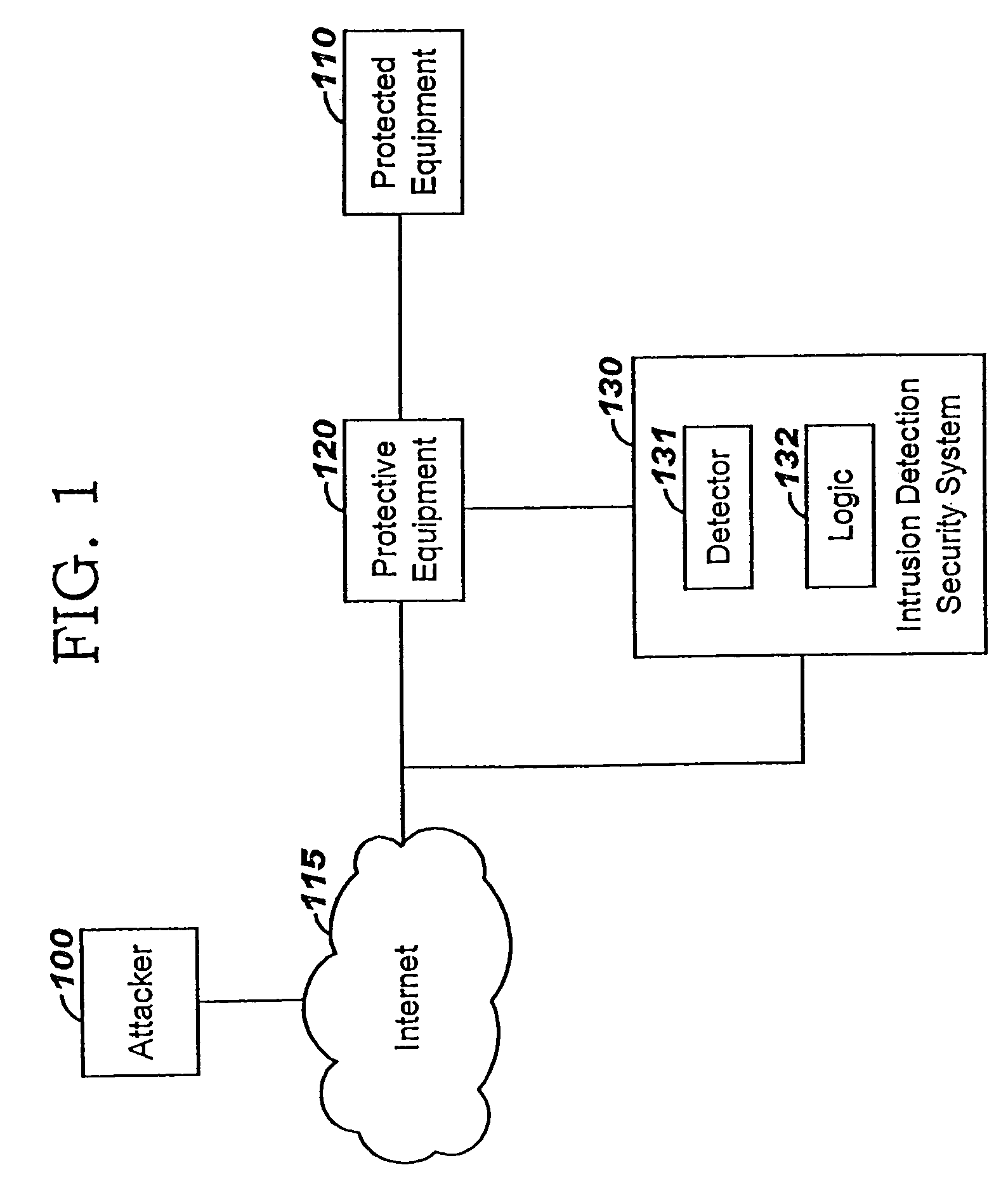
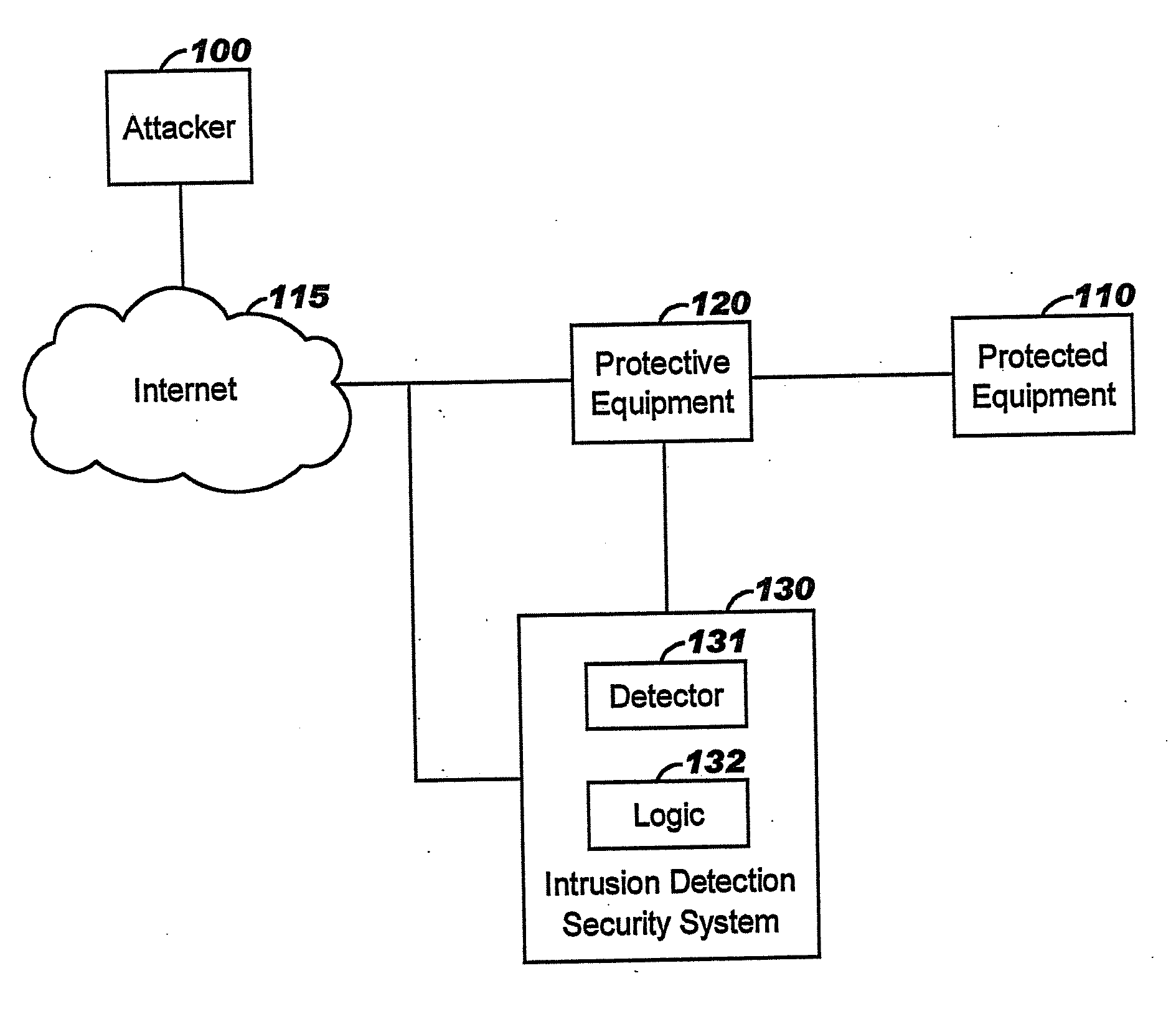
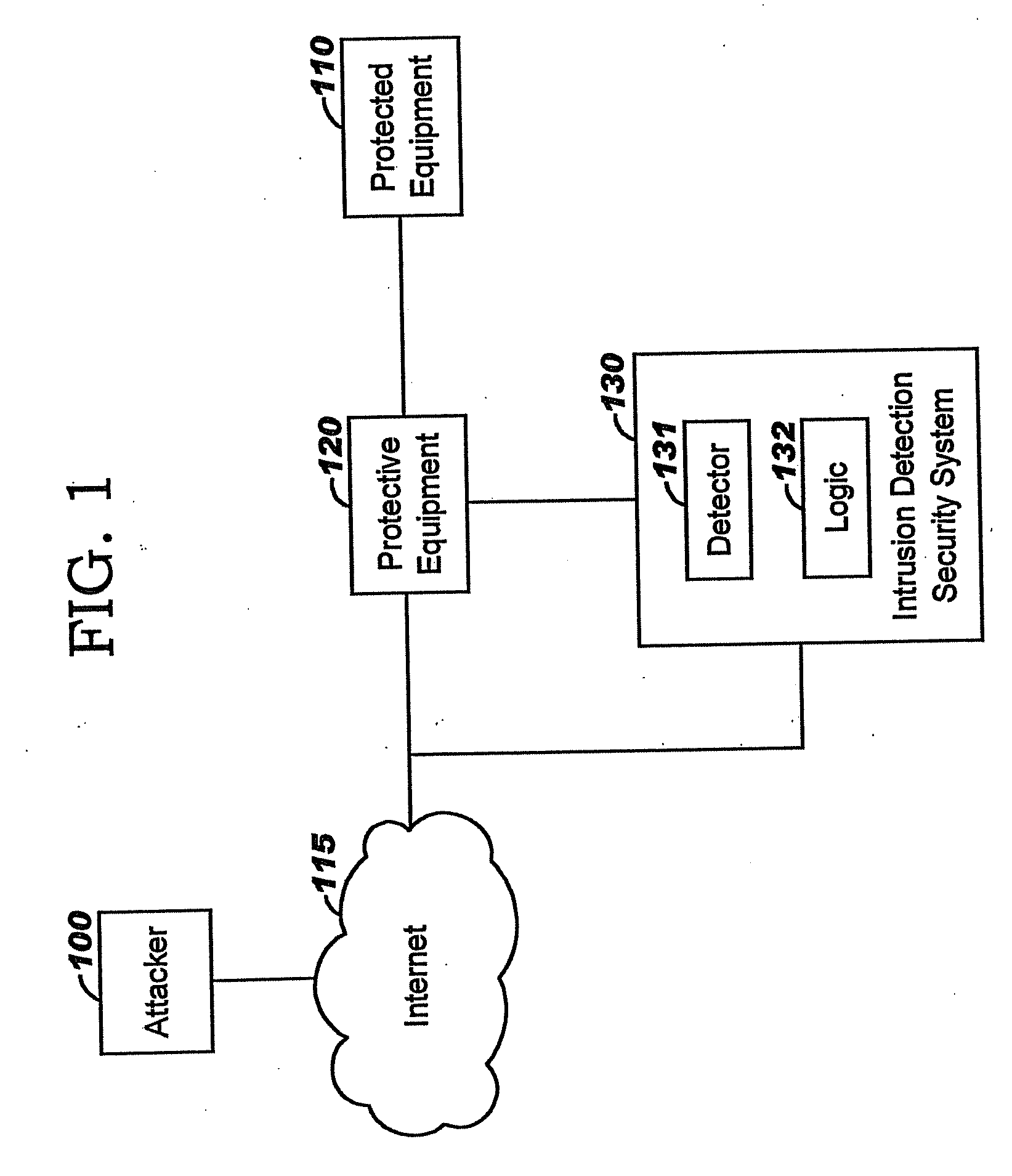
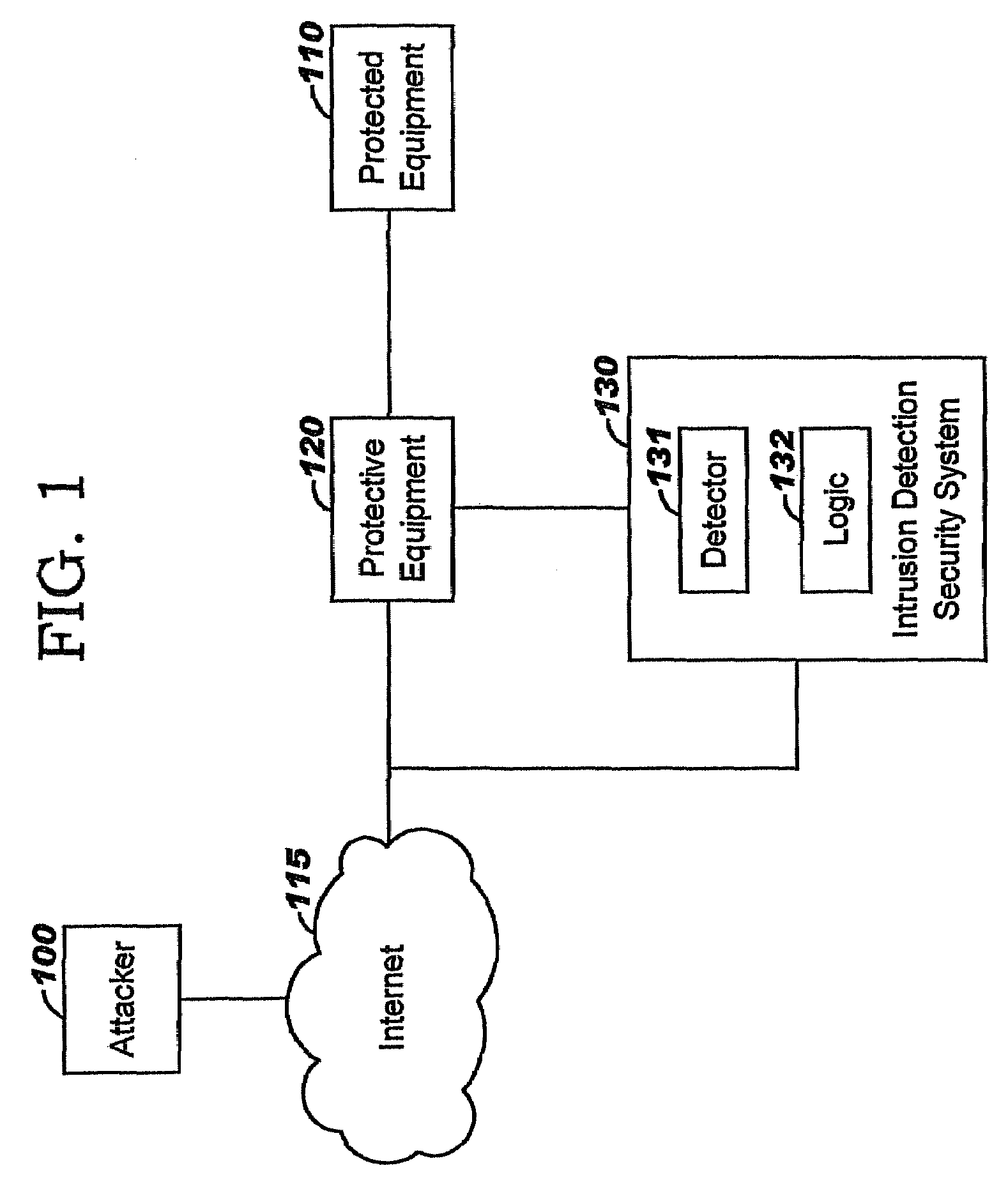
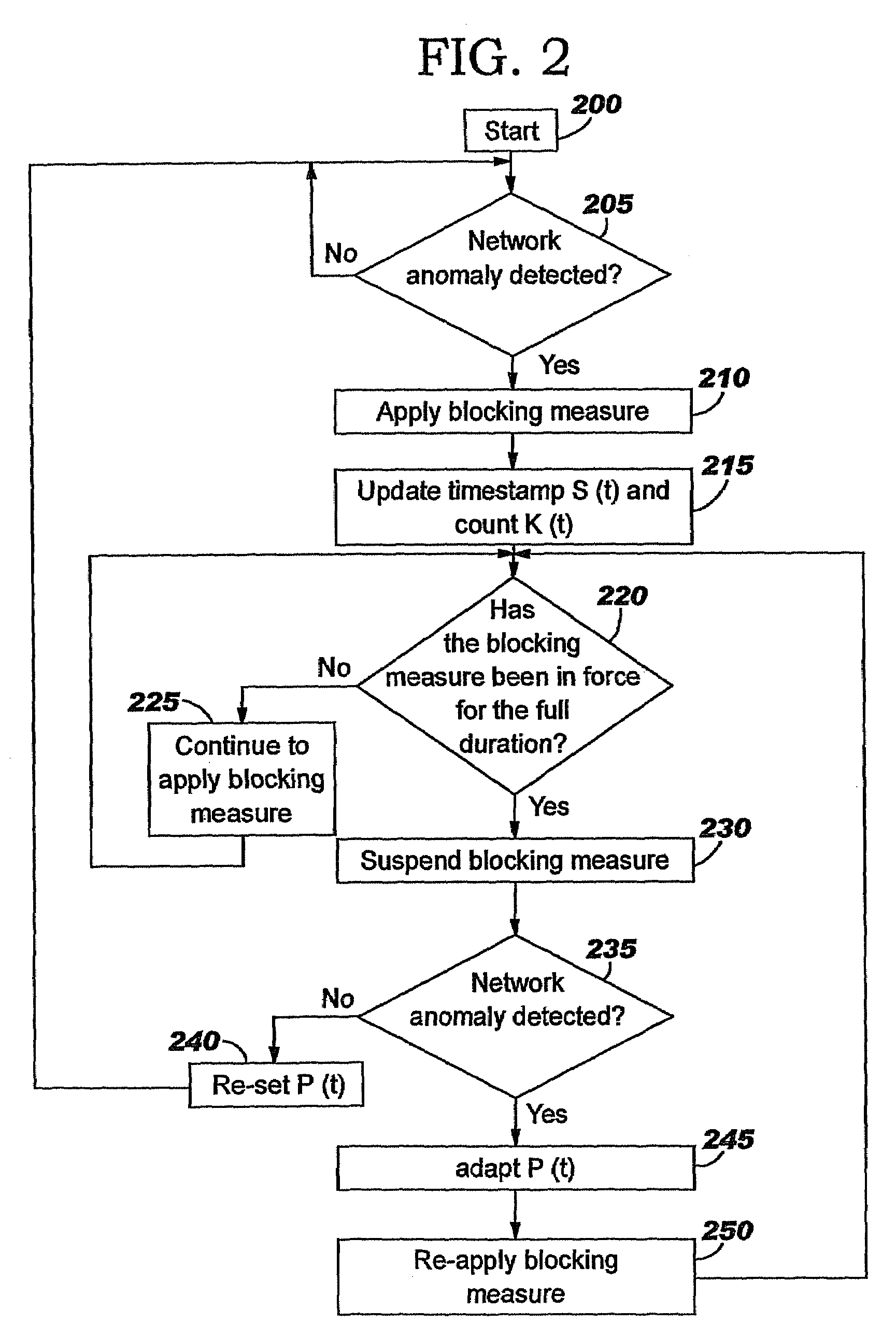
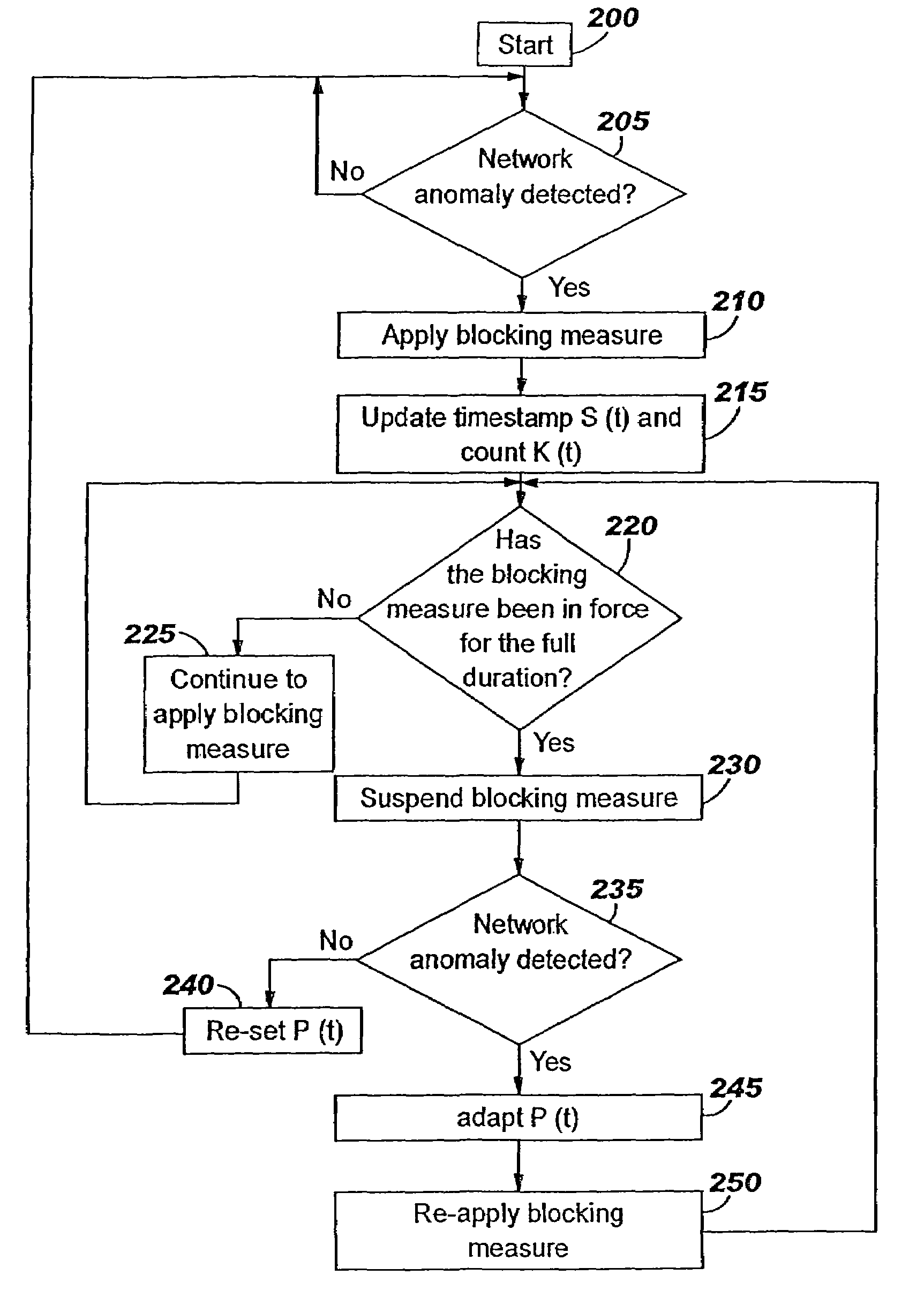
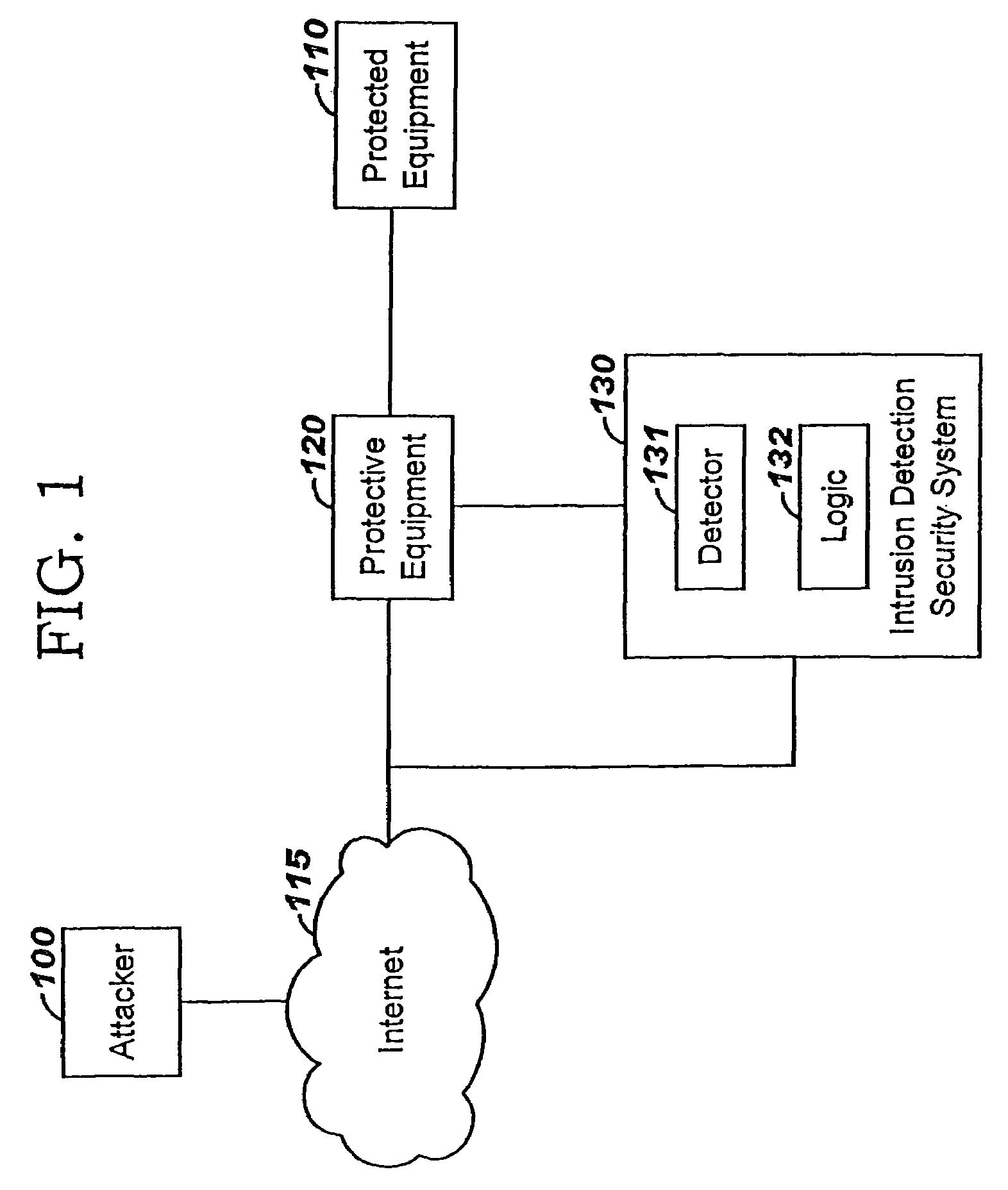
Applying blocking measures progressively to malicious network traffic
InactiveUS20060075496A1Minimizing adverse consequenceMinimize consequencesMemory loss protectionUnauthorized memory use protectionResponse methodFalse positives and false negatives
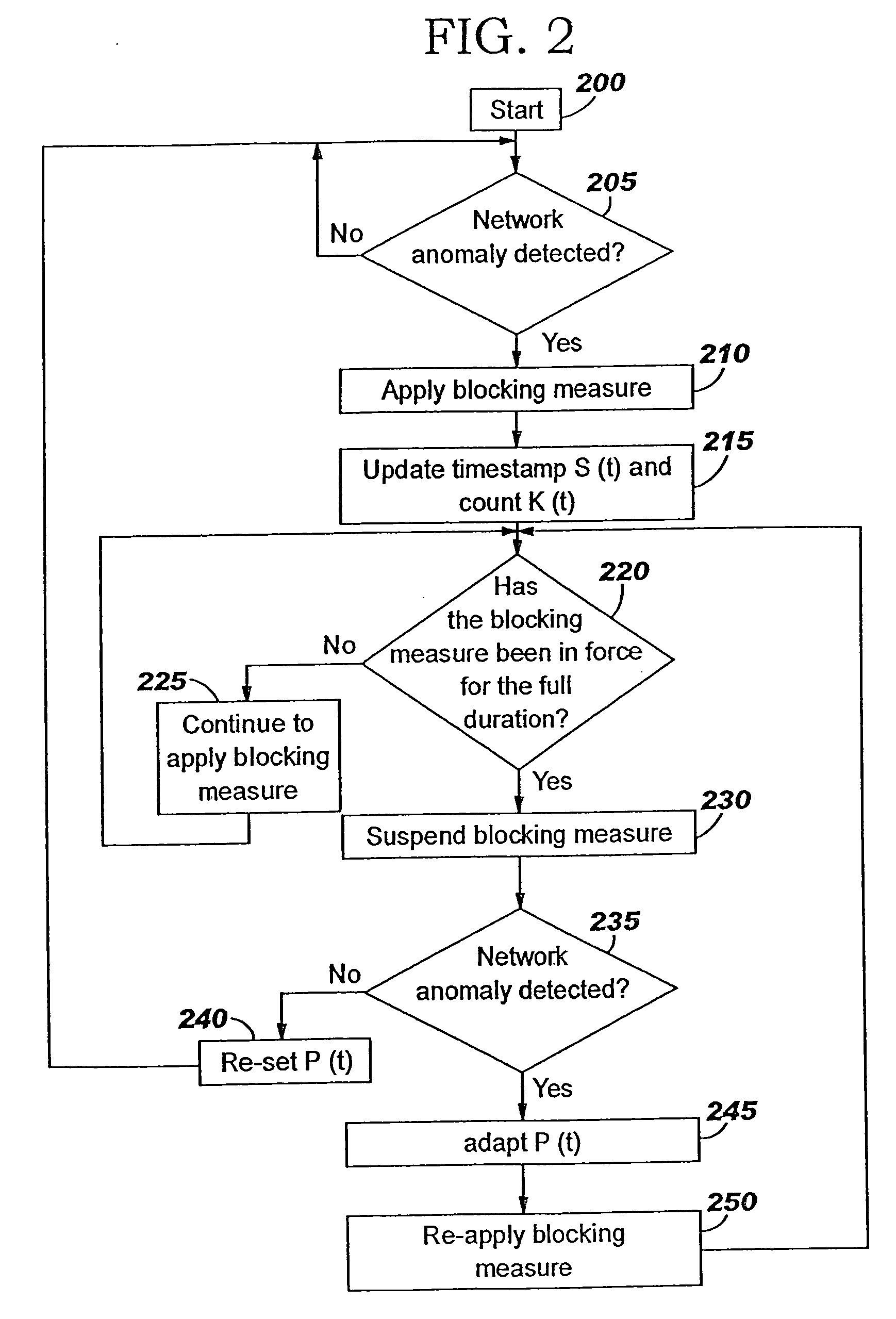
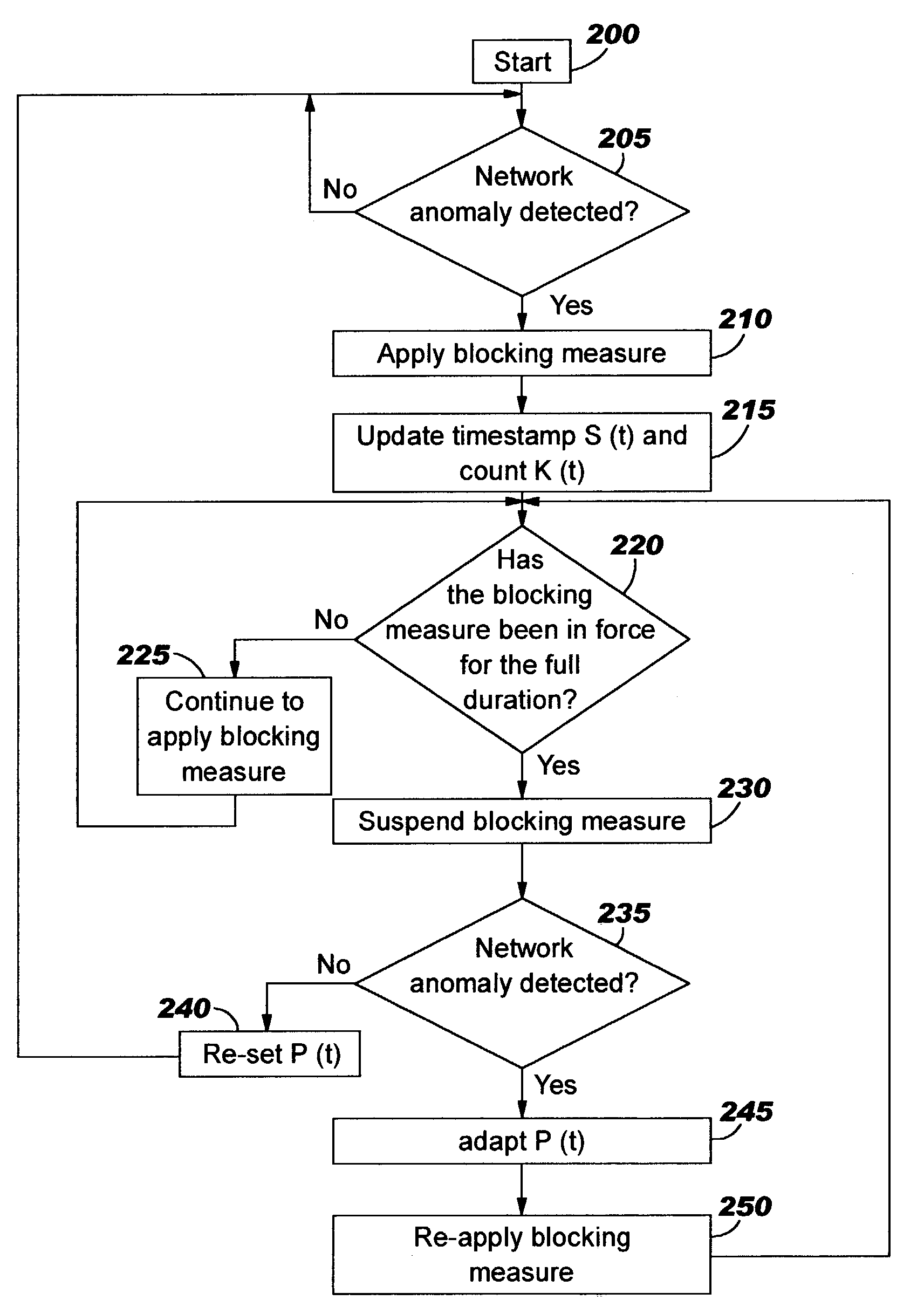
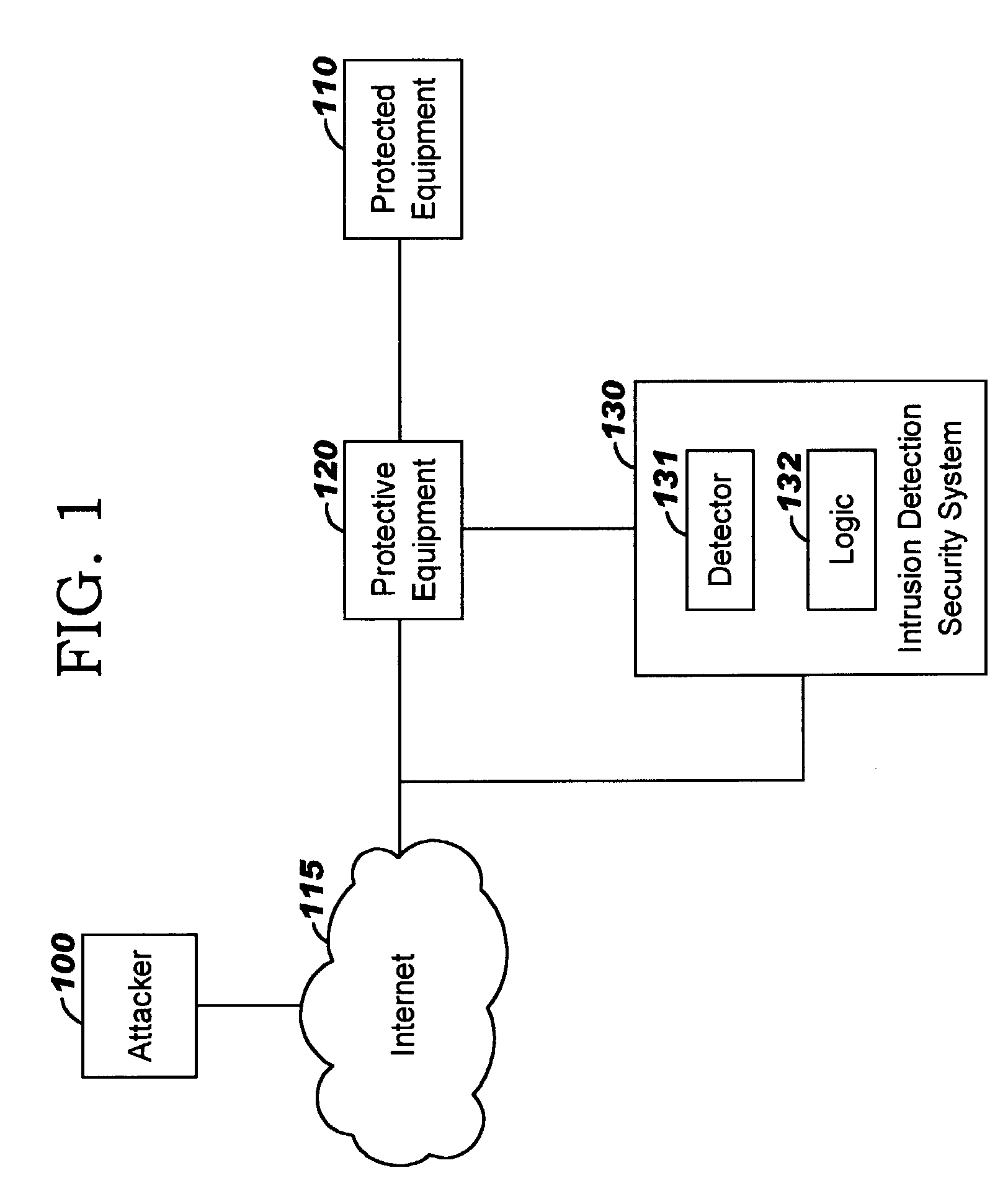
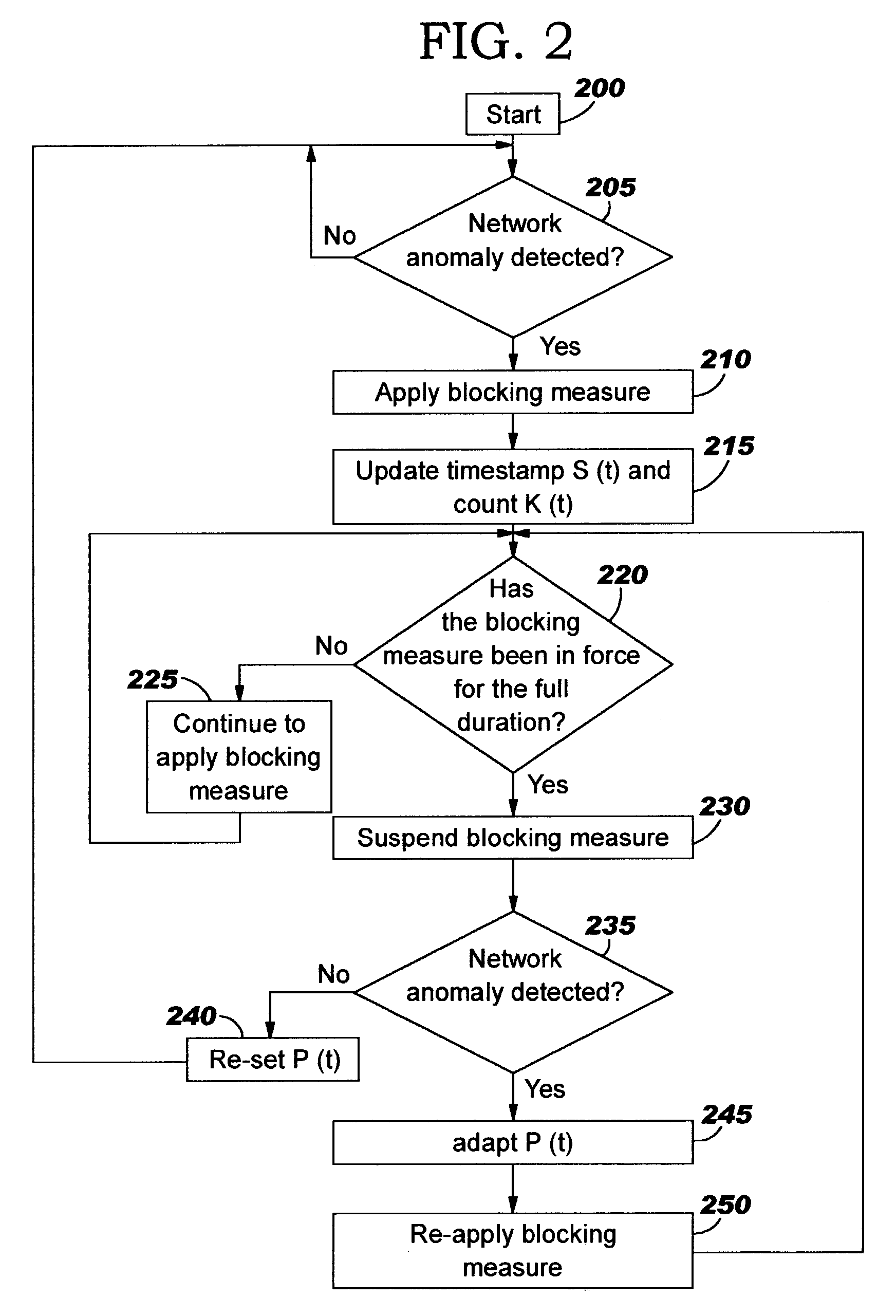
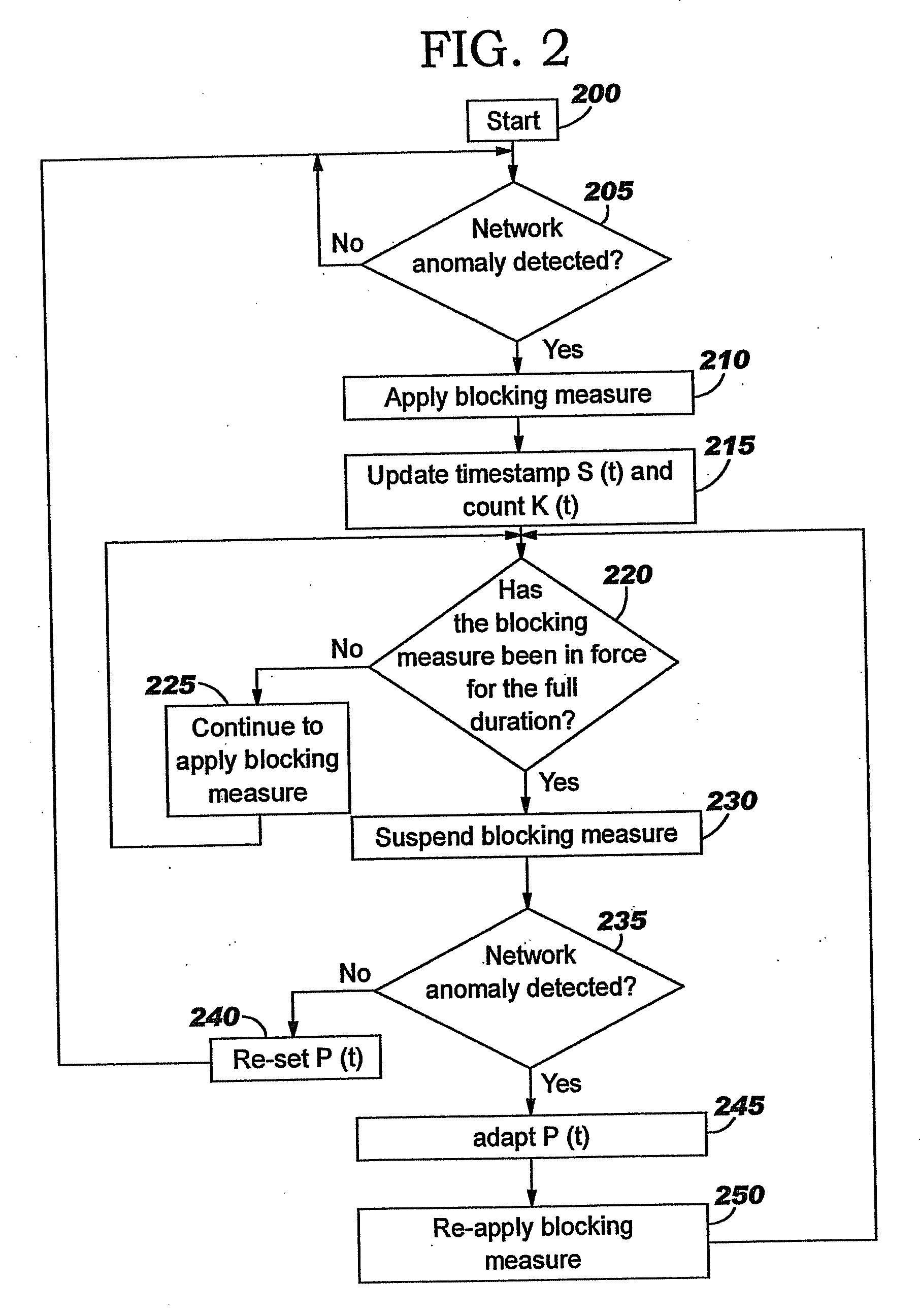
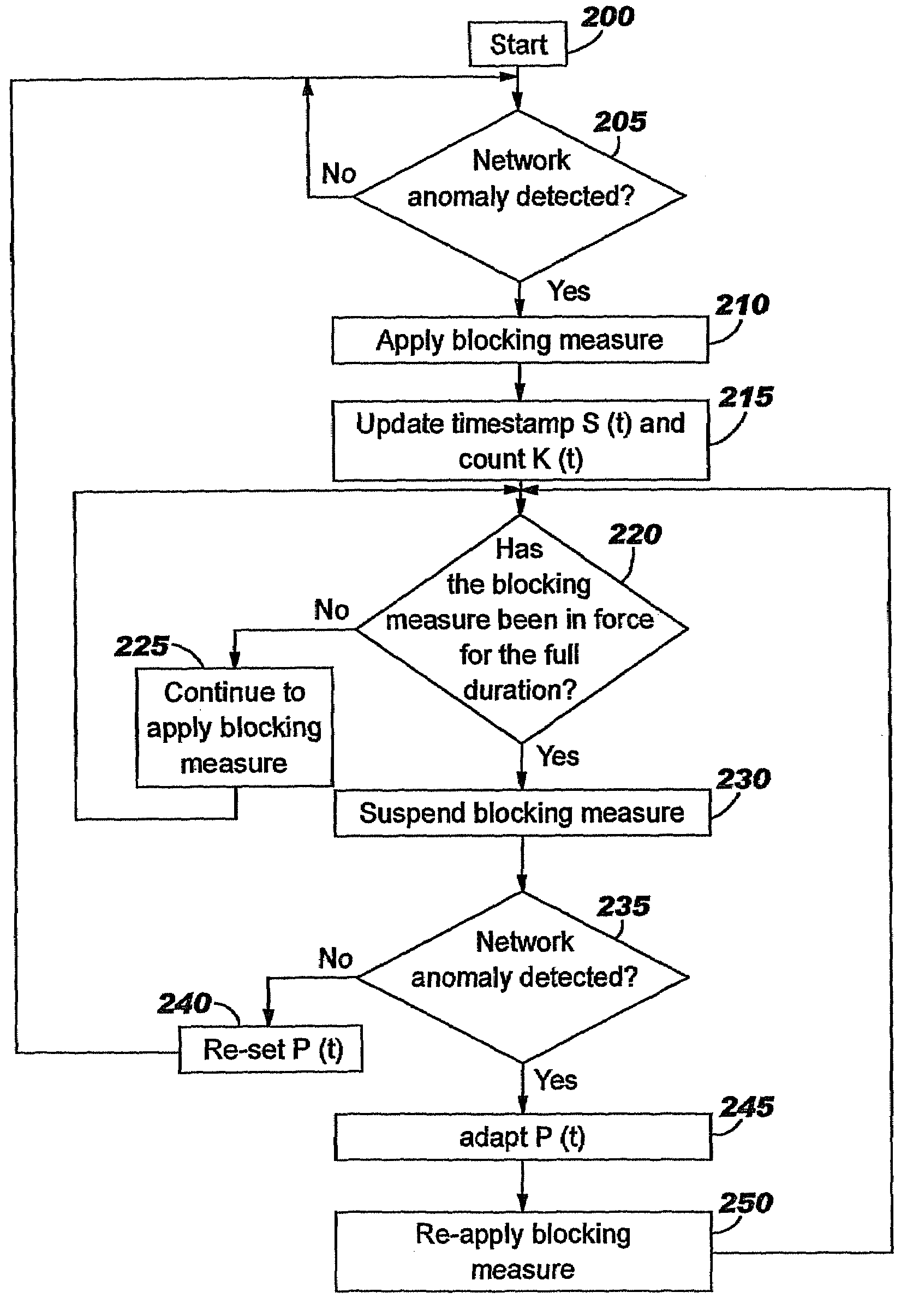
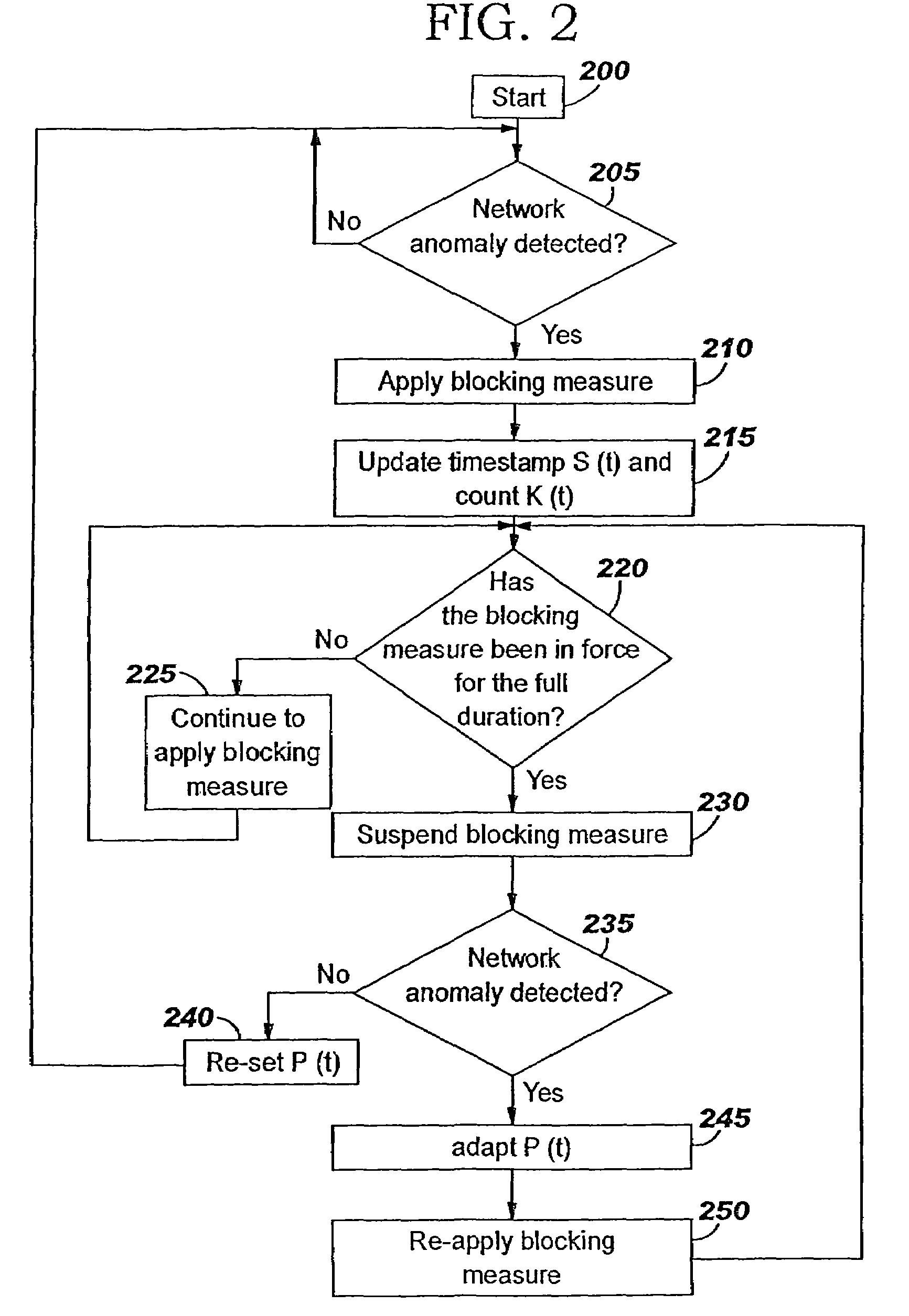
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When a truncated secure session attack is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the attack is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the attack. If the attack is detected, the blocking measure is re-applied, and its duration is adapted. If the attack is no longer detected, the method returns to the state of readiness.
Owner:TREND MICRO INC
Applying blocking measures progressively to malicious network traffic
ActiveUS7308716B2Minimizing adverse consequenceMinimize consequencesMemory loss protectionUnauthorized memory use protectionTraffic capacityFalse positives and false negatives
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When an anomaly is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the anomaly is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the anomaly. If the anomaly is detected, the blocking measure is re-applied, and its duration is adapted. If the anomaly is no longer detected, the method returns to the state of readiness.
Owner:TREND MICRO INC
Applying blocking measures progressively to malicious network traffic
InactiveUS20080072326A1Minimizing adverse consequenceMinimize consequencesMemory loss protectionDigital computer detailsResponse methodFalse positives and false negatives
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When an anomaly is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the anomaly is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the anomaly. If the anomaly is detected, the blocking measure is re-applied, and its duration is adapted. If the anomaly is no longer detected, the method returns to the state of readiness.
Owner:IBM CORP
Applying blocking measures progressively to malicious network traffic
InactiveUS7707633B2Minimizing adverse consequenceMinimize consequencesMemory loss protectionDigital computer detailsTraffic capacityFalse positives and false negatives
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When an anomaly is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the anomaly is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-apply the blocking measure for a specified duration, then suspend the blocking measure and test again for the anomaly. If the anomaly is detected, the blocking measure is re-applied, and its duration is adapted. If the anomaly is no longer detected, the method returns to the state of readiness.
Owner:INT BUSINESS MASCH CORP
Method of responding to a truncated secure session attack
InactiveUS7464404B2Minimizing adverse consequenceMinimize consequencesMemory loss protectionUnauthorized memory use protectionTraffic capacityFalse positives and false negatives
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When a truncated secure session attack is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the attack is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the attack. If the attack is detected, the blocking measure is re-applied, and its duration is adapted. If the attack is no longer detected, the method returns to the state of readiness.
Owner:TREND MICRO INC
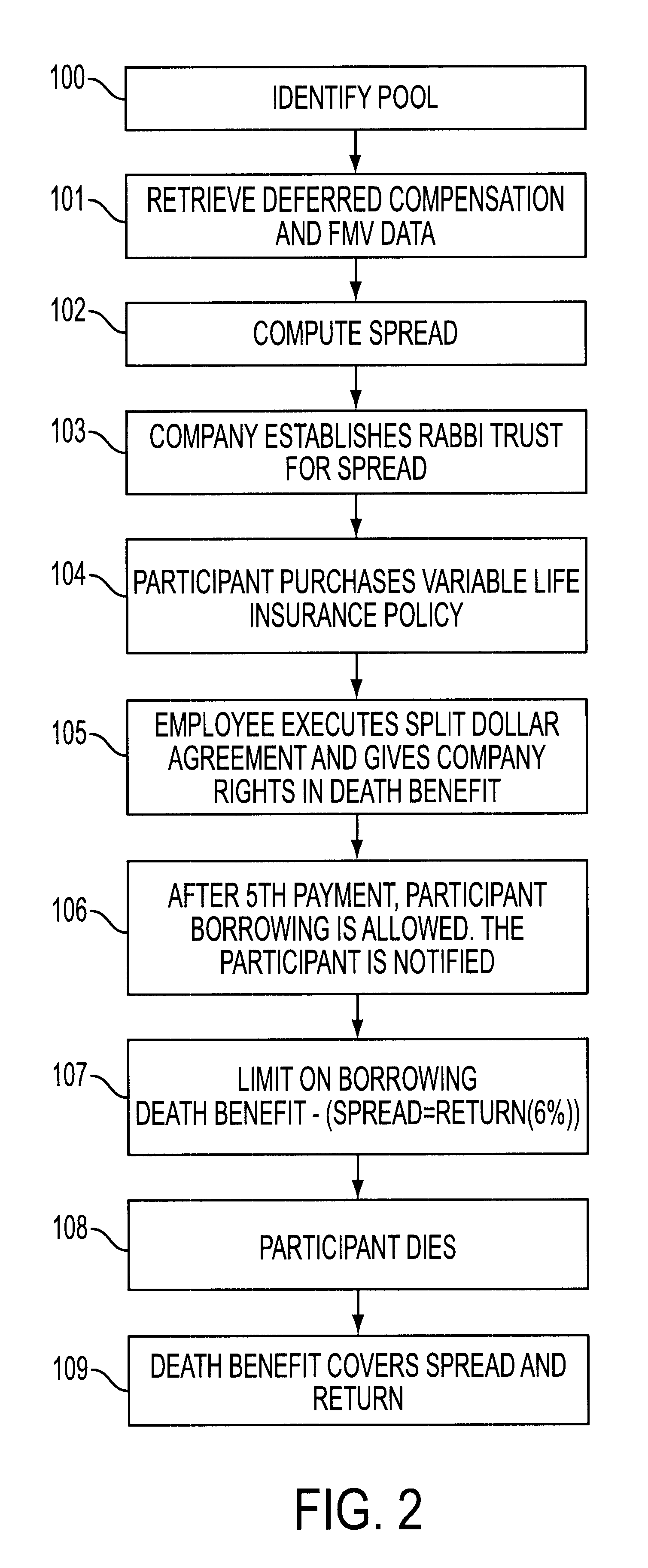
Method and apparatus for modeling and executing deferred award instrument plan
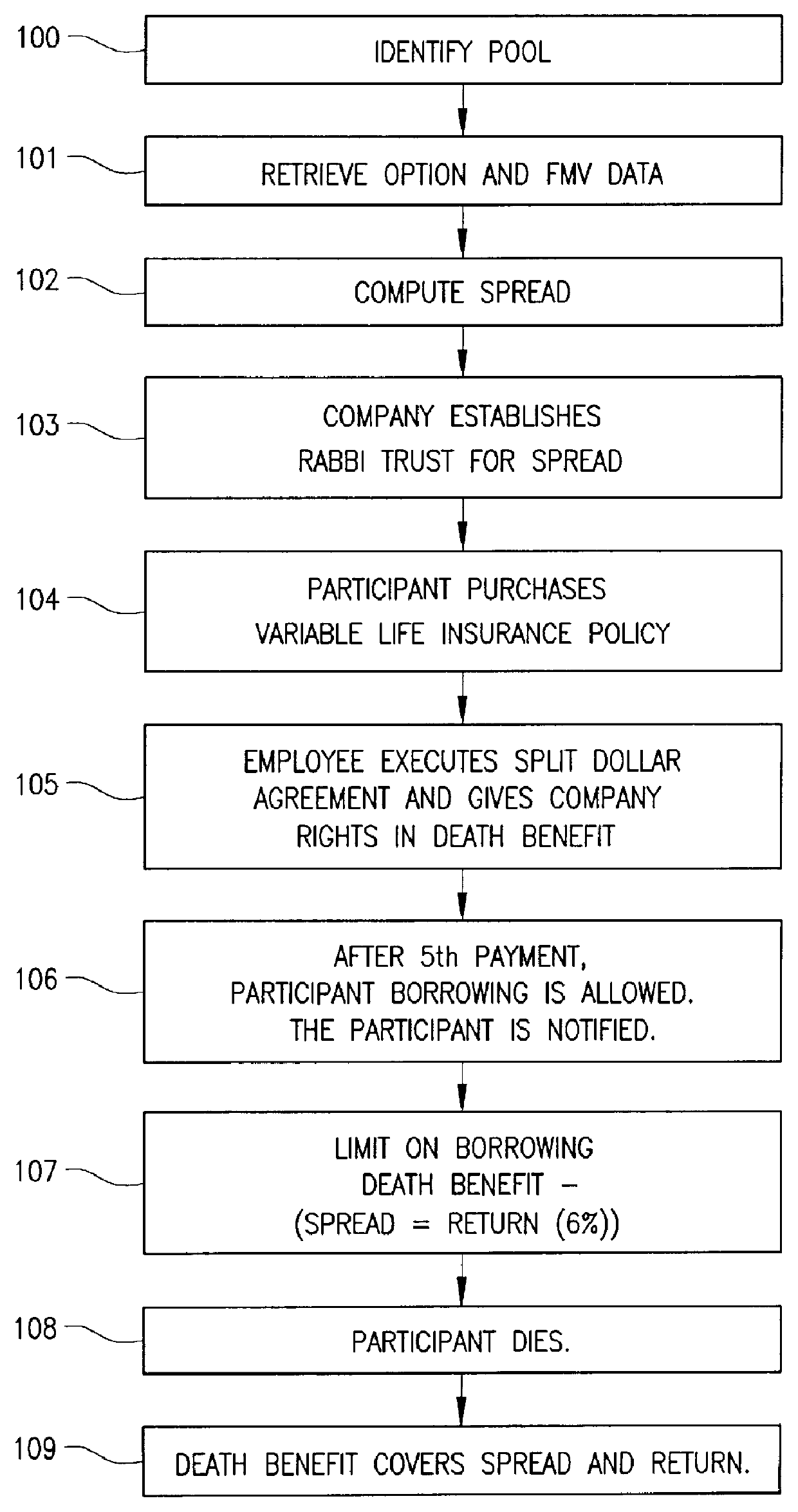
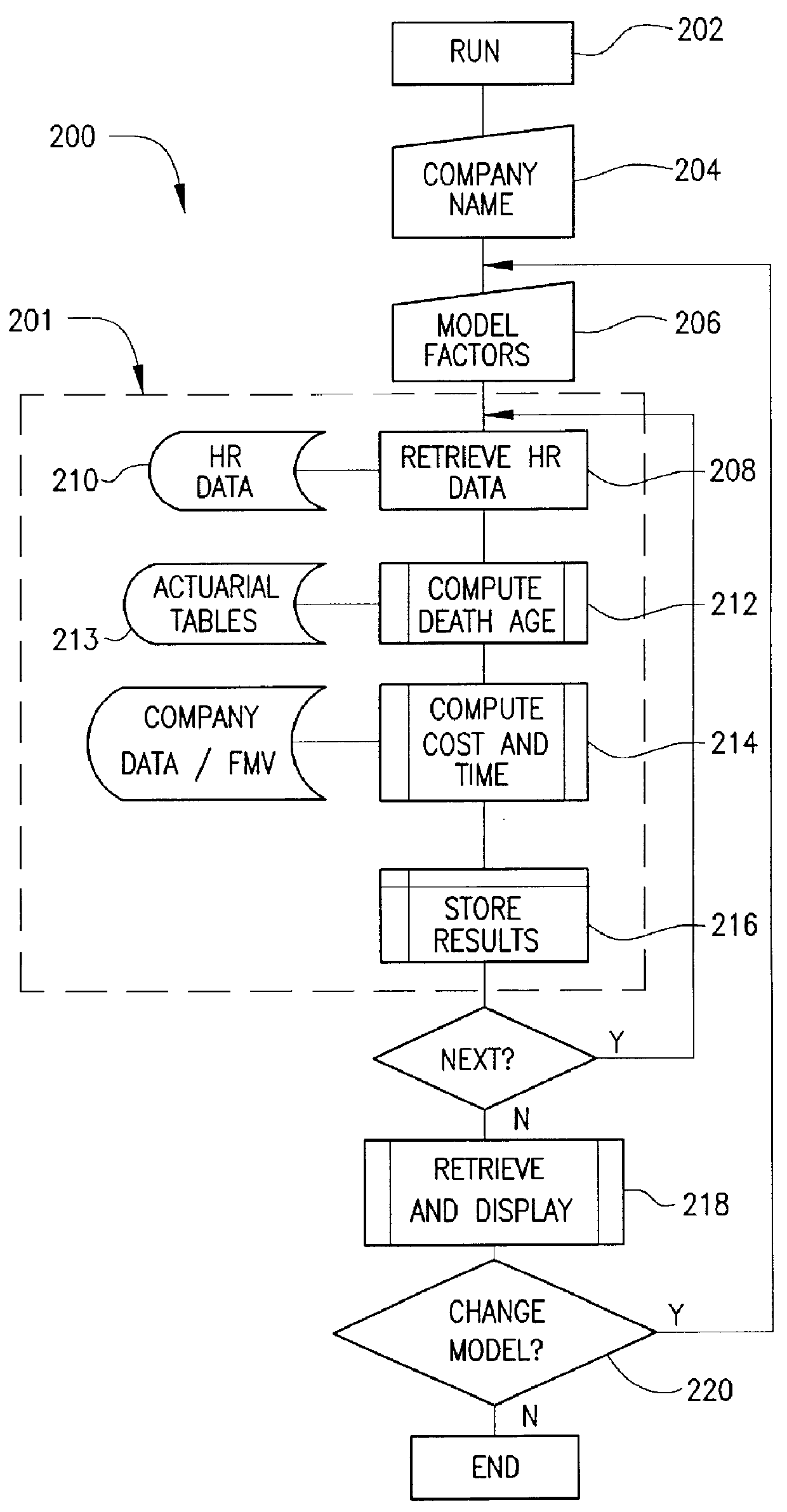
A method and apparatus for deferred award instrument plan by identifying at least one participant in the deferred award plan, retrieving financial data related to stock options corresponding to the identified participant, computing a spread associated with the retrieved stock options, establishing a rabbi trust with the spread, determining whether a life insurance policy has been purchased by the participant, determining whether a split dollar agreement has been executed, monitoring and paying at least one premium for the life insurance policy and notifying the participants that a payment associated with the life insurance policy has been paid.
Owner:ASCENSUS INSURANCE SERVICES
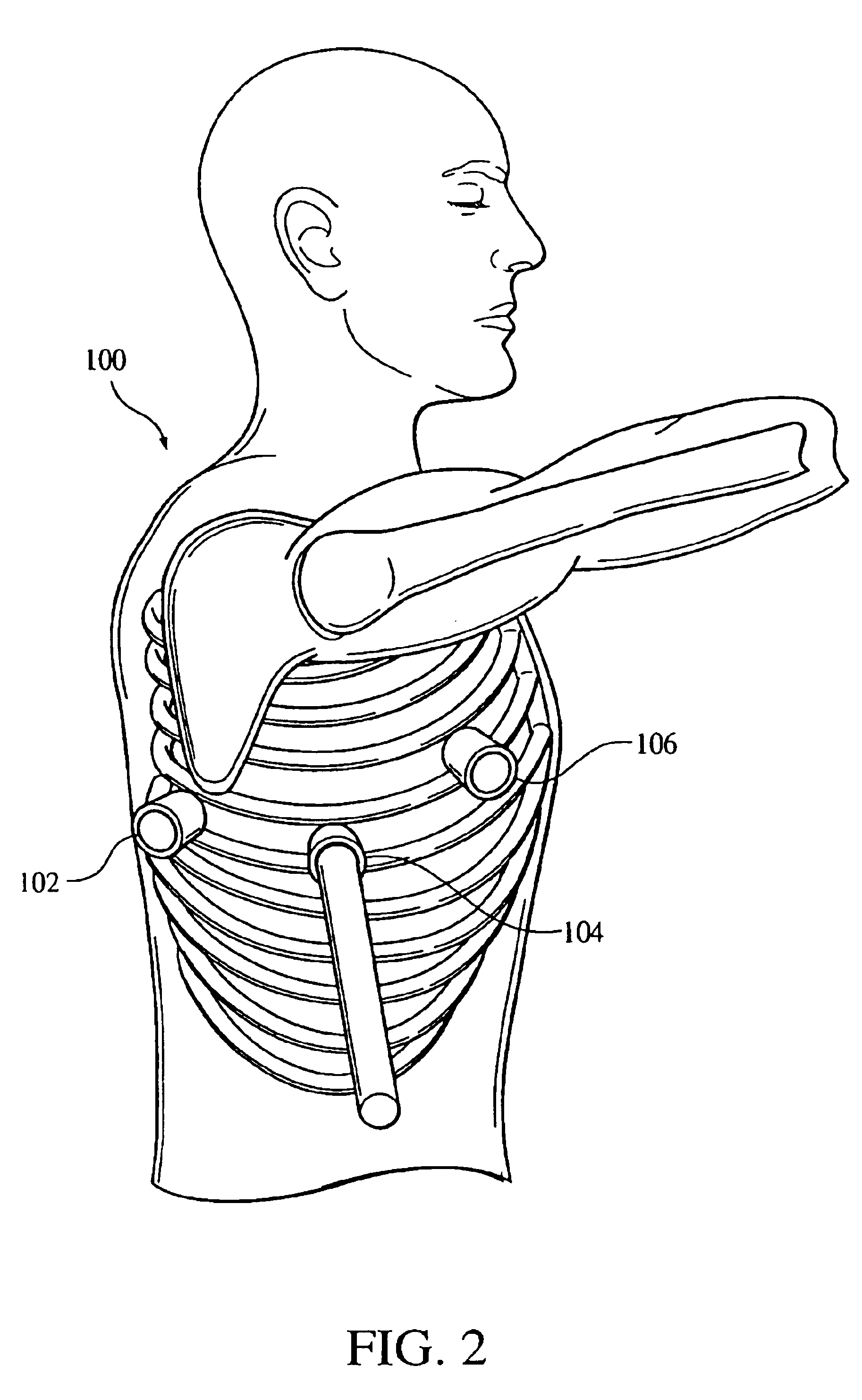
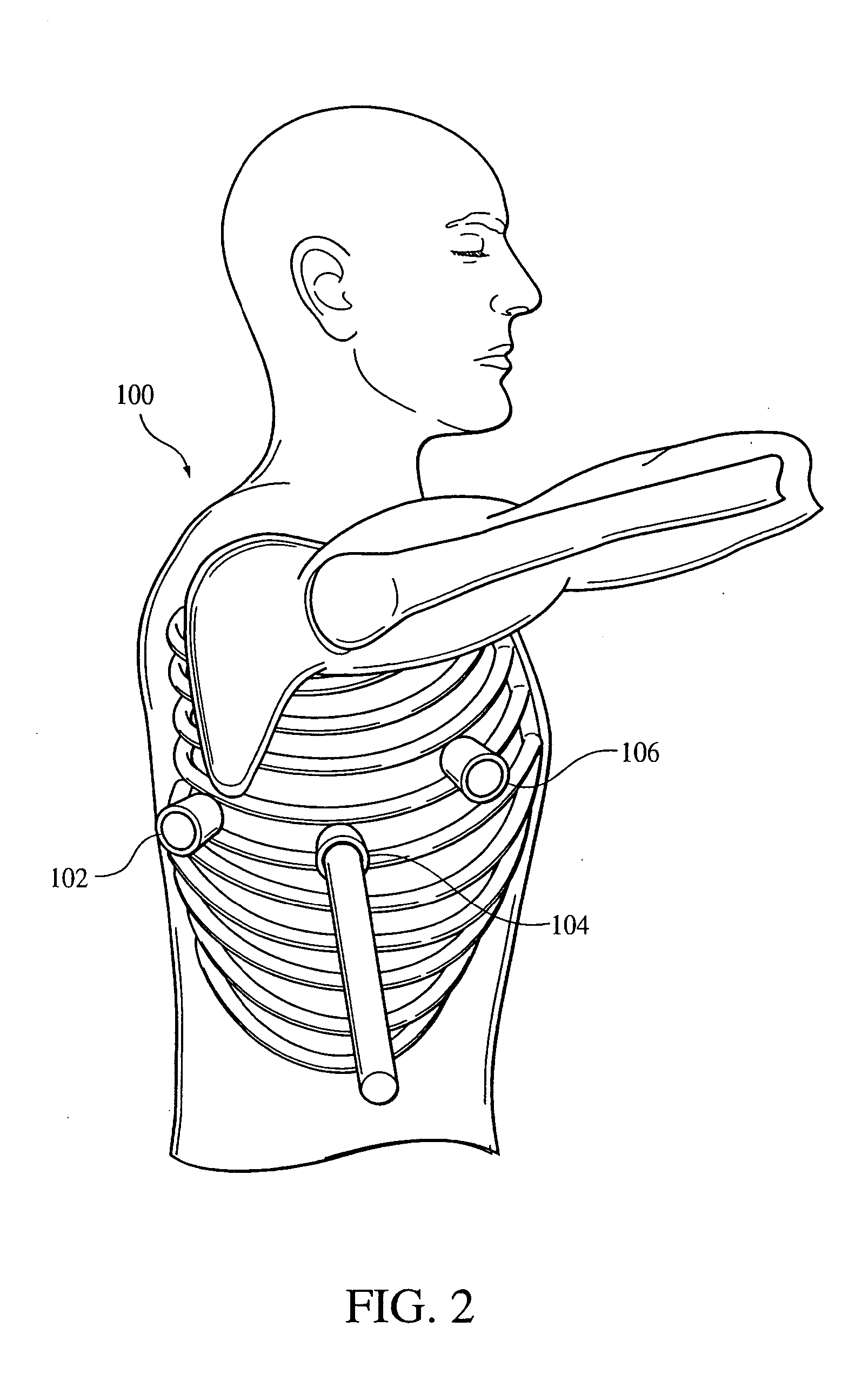
Systems and Methods for Providing Percutaneous Electrical Stimulation
ActiveUS20130096641A1Easy to implementReduce riskElectrotherapyArtificial respirationTreatment painPeripheral neuron
Systems and methods according to the present invention relate to a novel peripheral nerve stimulation system for the treatment of pain, such as pain that exists after amputation.
Owner:SPR THERAPEUTICS
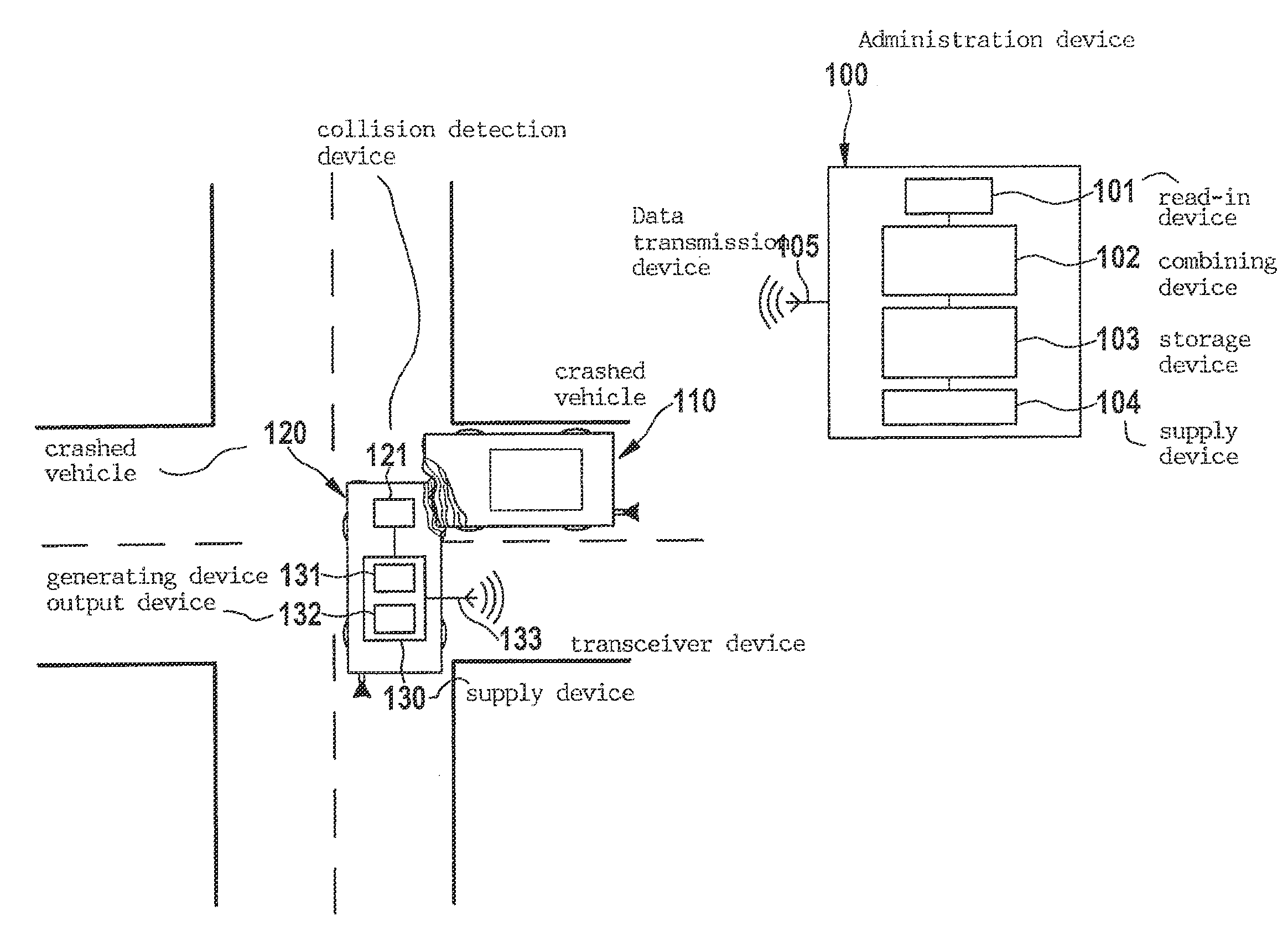
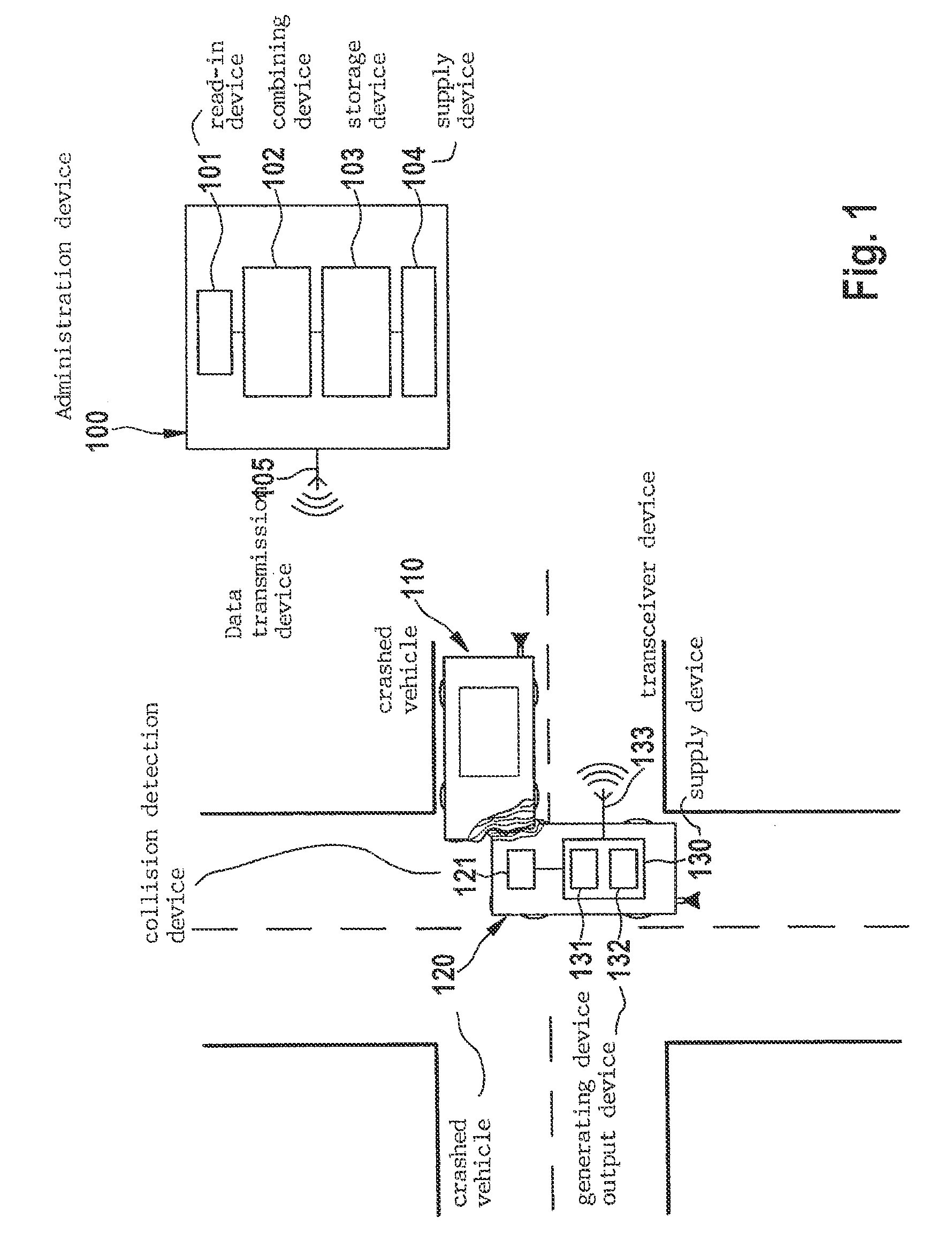
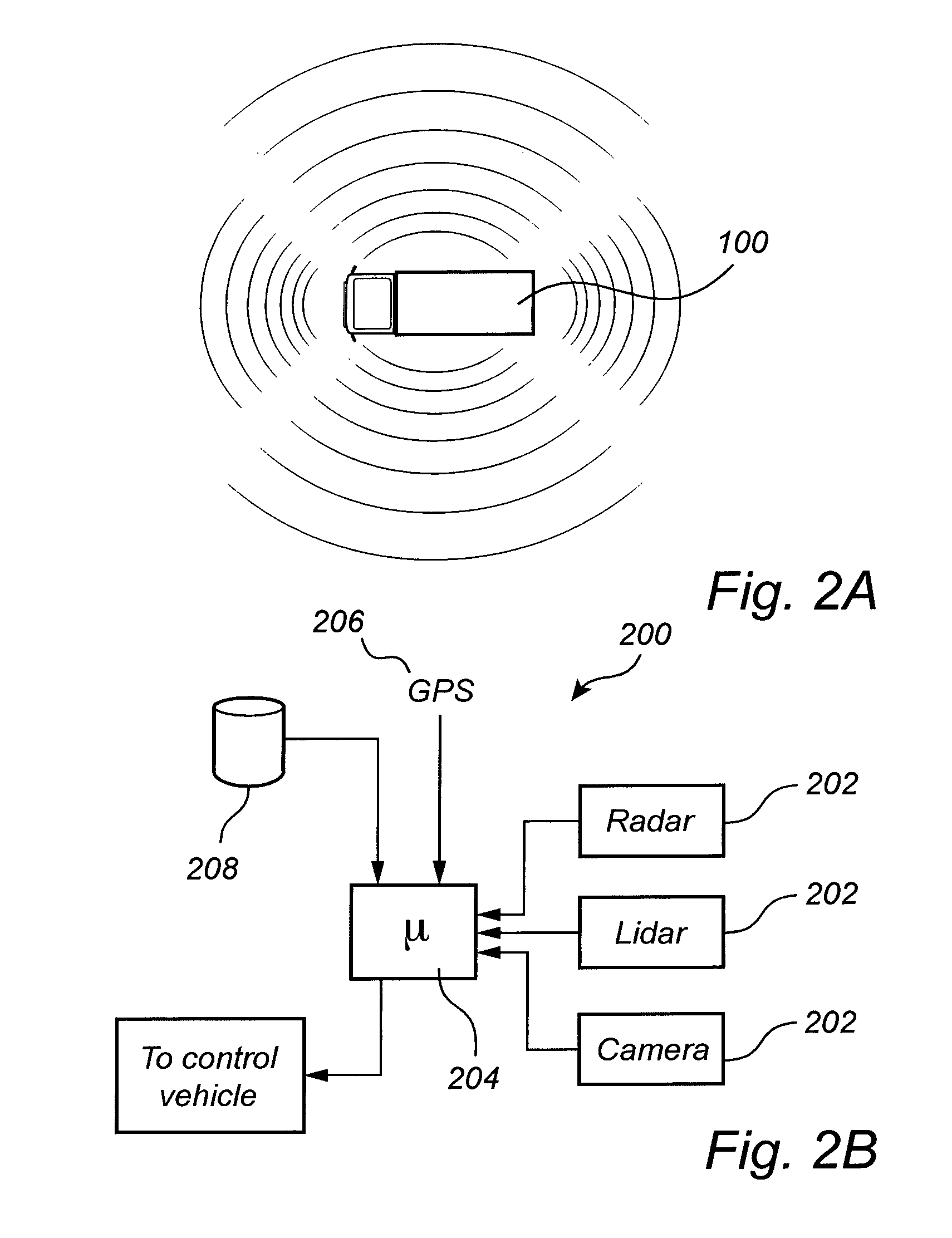
Method and device for supplying a collision signal pertaining to a vehicle collision, a method and device for administering collision data pertaining to vehicle collisions, as well as a method and device for controlling at least one collision protection device of a vehicle
ActiveUS9466214B2Minimize consequencesEasy to measureNavigational calculation instrumentsRegistering/indicating working of vehiclesSimulationData administration
A method for supplying a collision signal pertaining to a vehicle collision includes: generating a collision signal that represents at least one characteristic of a collision involving at least one crashed vehicle and position data of the collision, using collision-relevant sensor data of the crashed vehicle; and outputting the collision signal via an interface to a central collision data administration device.
Owner:ROBERT BOSCH GMBH
Method and apparatus for modeling and executing deferred award instrument plan
InactiveUS6609111B1Minimal impactMinimizes taxFinanceOffice automationProgram planningInsurance life
The present invention is directed to the administration of various deferred compensation programs that can effectively reduce an individual's income or estate tax by assisting a company in the identification of appropriate employees, and through the use of a novel modeling method and apparatus to implement a deferred compensation program through a novel Rabbi Trust maintenance plan that permits the employees to benefit from their deferred compensation (such as stock options or life insurance benefits), while having a minimal financial impact on the company.
Owner:BELL LAWRENCE L
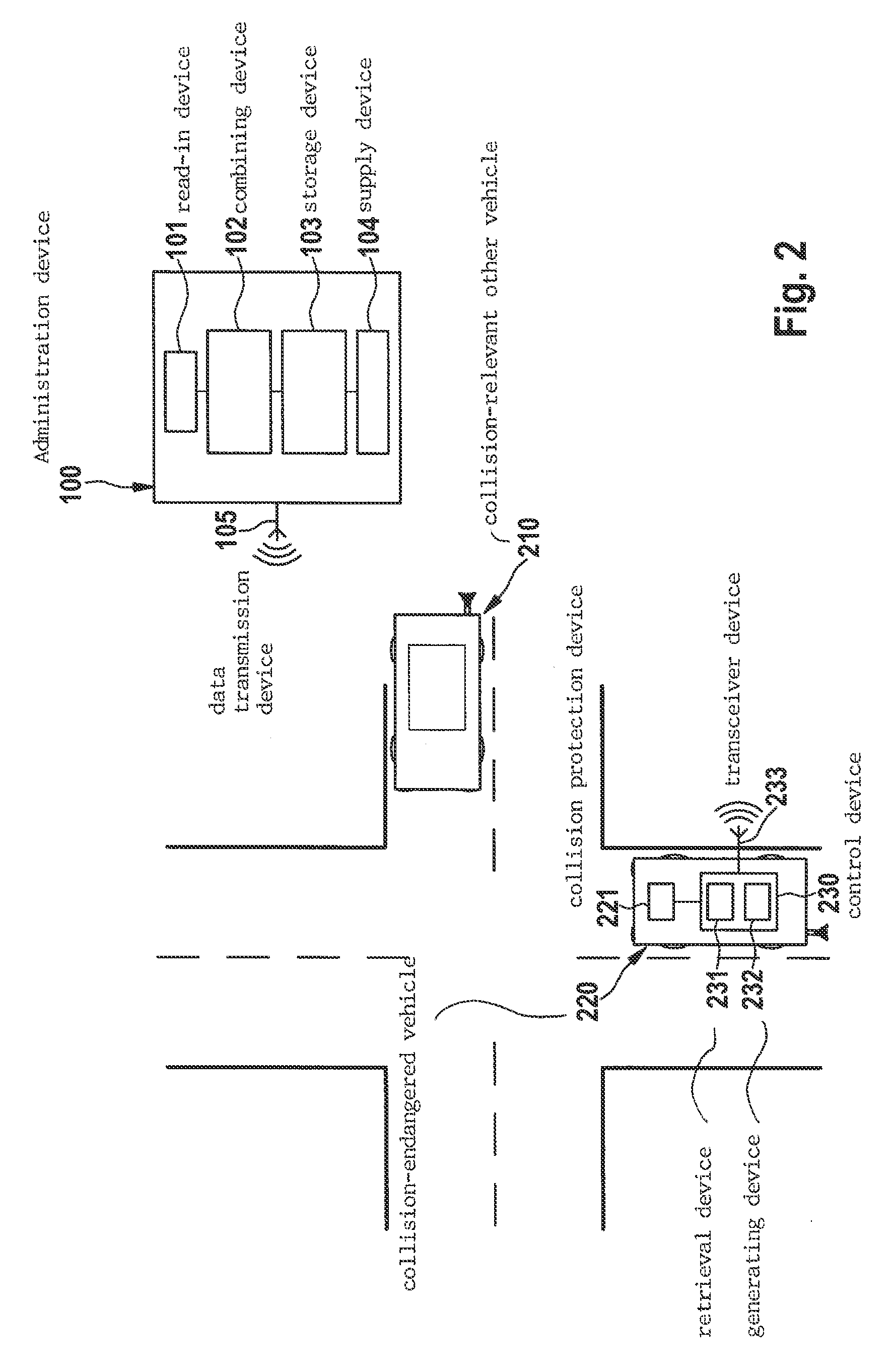
Method and Device for Avoiding and/or Reducing the Consequences of Collisions Upon Evasion with Respect to Obstacles
InactiveUS20080319610A1Minimize consequencesAvoidance and reduction of consequenceDigital data processing detailsAnti-collision systemsEngineeringEnvironmental sensor
Owner:ROBERT BOSCH GMBH
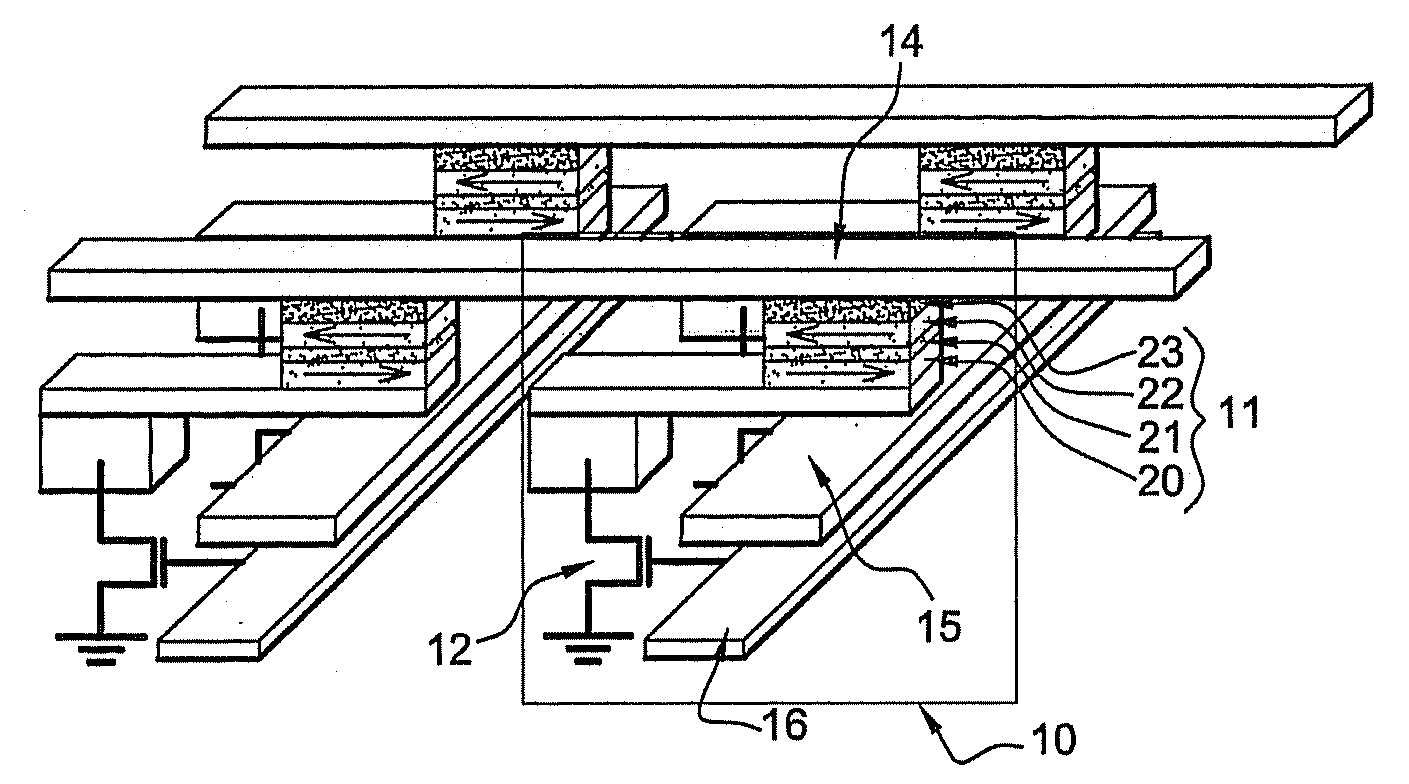
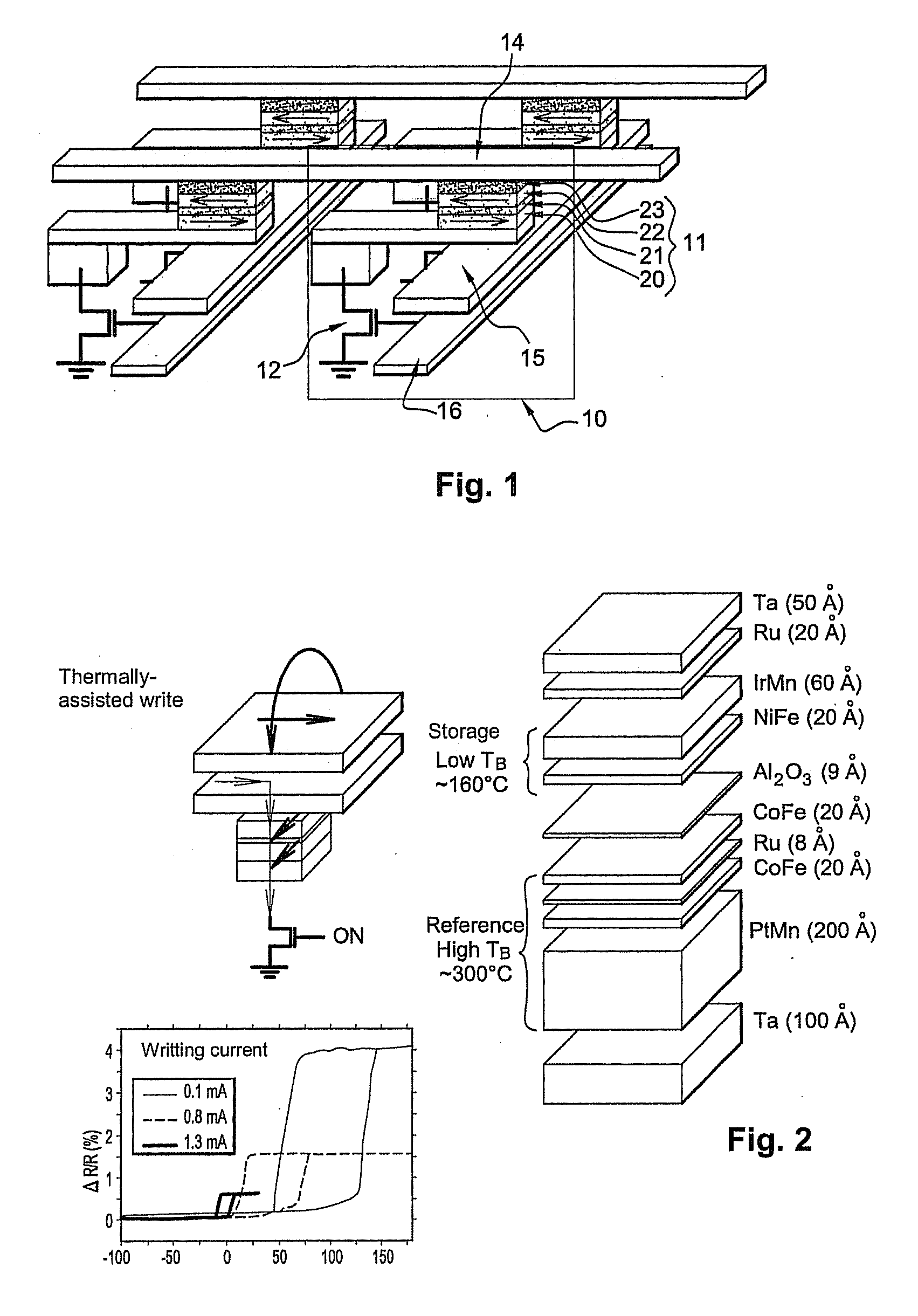
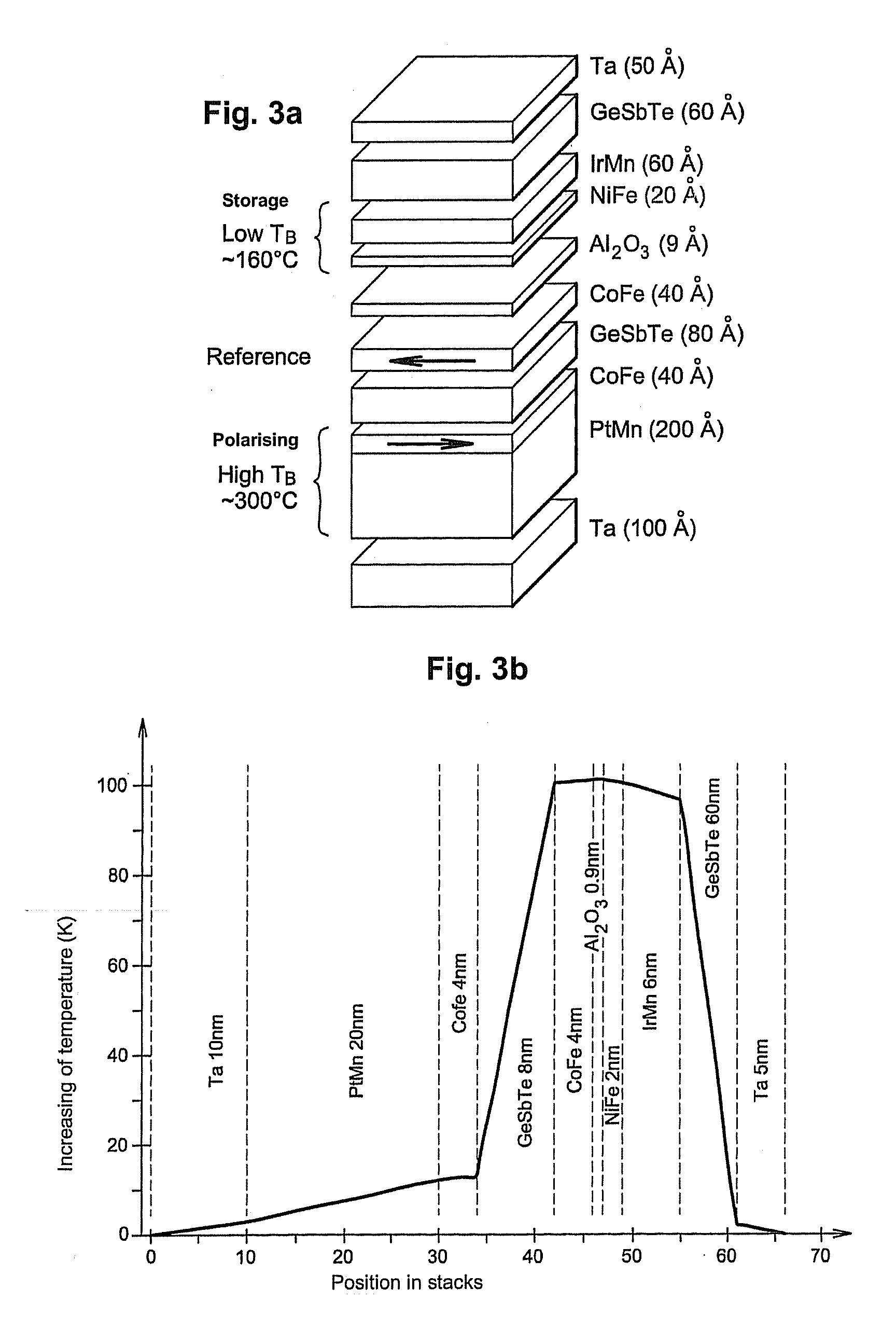
Magnetic tunnel junction magnetic memory
This magnetic memory with a thermally-assisted write, every storage cell of which consists of at least one magnetic tunnel junction, said tunnel junction comprising at least:one magnetic reference layer, the magnetization of which is always oriented in the same direction at the time of the read of the storage cell;one so-called “free” magnetic storage layer, the magnetization direction of which is variable;one insulating layer sandwiched between the reference layer and the storage layer.The magnetization direction of the reference layer is polarized in a direction that is substantially always the same at the time of a read due to magnetostatic interaction with another fixed-magnetization layer called the “polarizing layer”.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Systems and methods for providing percutaneous electrical stimulation
Systems and methods according to the present invention relate to a novel peripheral nerve stimulation system for the treatment of pain, such as pain that exists after amputation.
Owner:SPR THERAPEUTICS
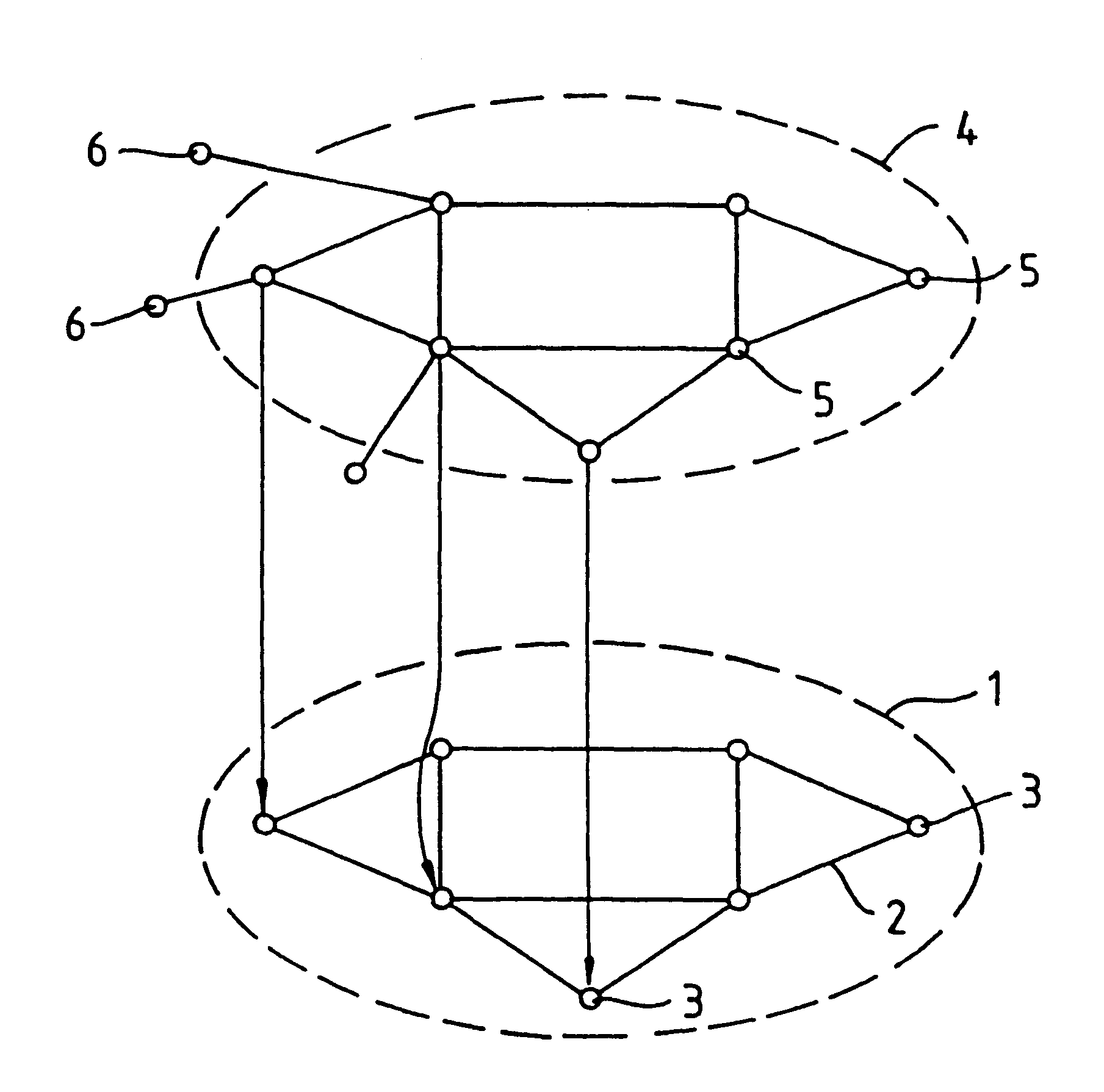
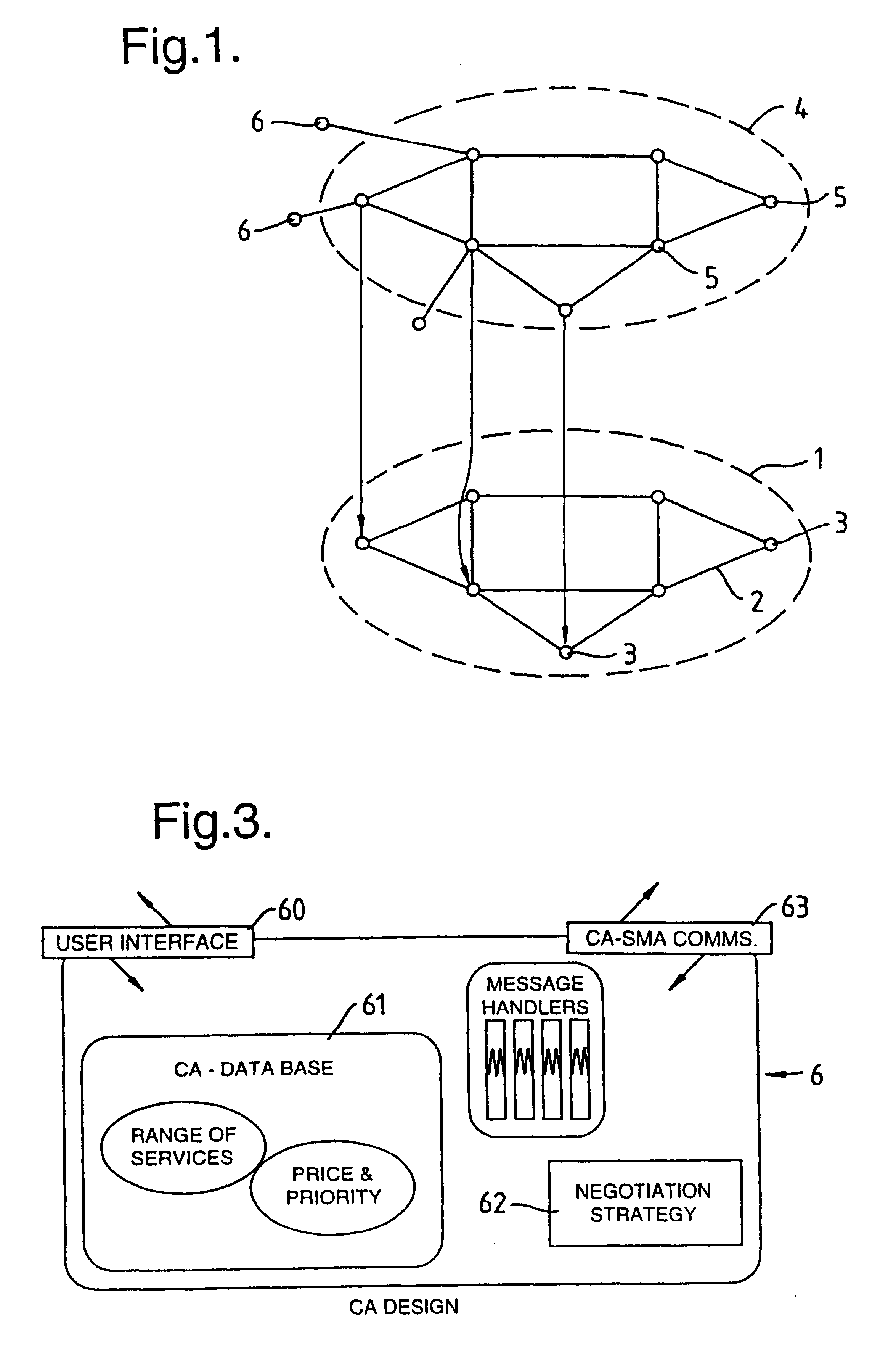
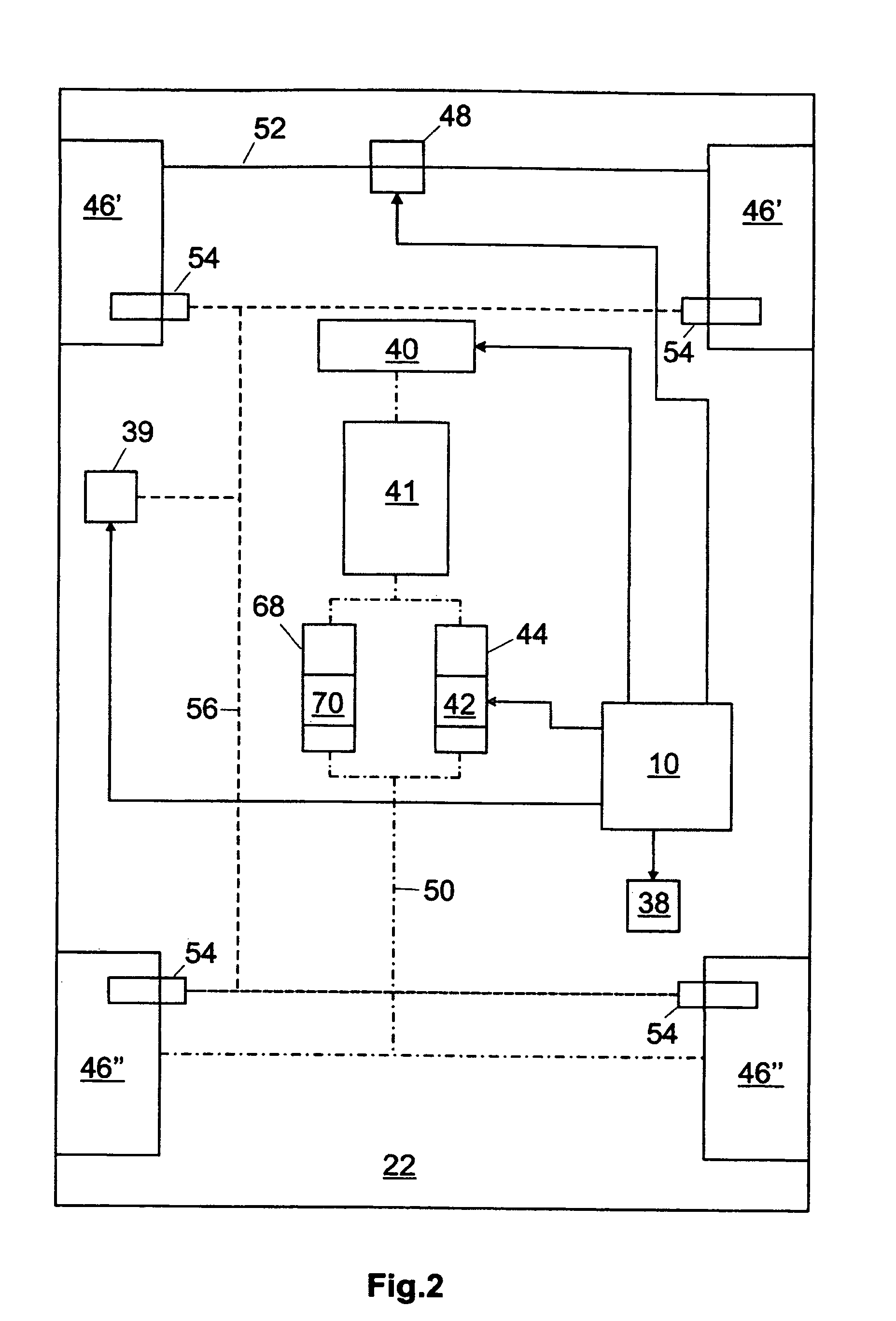
Communications network management
InactiveUS6226273B1Minimize consequencesCarry-out quicklyMultiplex system selection arrangementsSpecial service provision for substationNetwork managementService networks
A communications network such as a Global Multi Service Network is provided with a management system which includes a distributed control system. The distributed control system is an open community of co-operation intelligent software agents which individually have control, or responsibility for managing, one or more nodes of the communications network. There are software agents of more than one type and the service management agents which have control over nodes of the network enter a negotiation process with customer agents in the provision of new services, so as to meet the constraints of both customer requirements and the interest of the relevant service provider. In the event of agent failure, the service management agents initiate a bidding process to reallocate the responsibilities of a failed agent.
Owner:BRITISH TELECOMM PLC
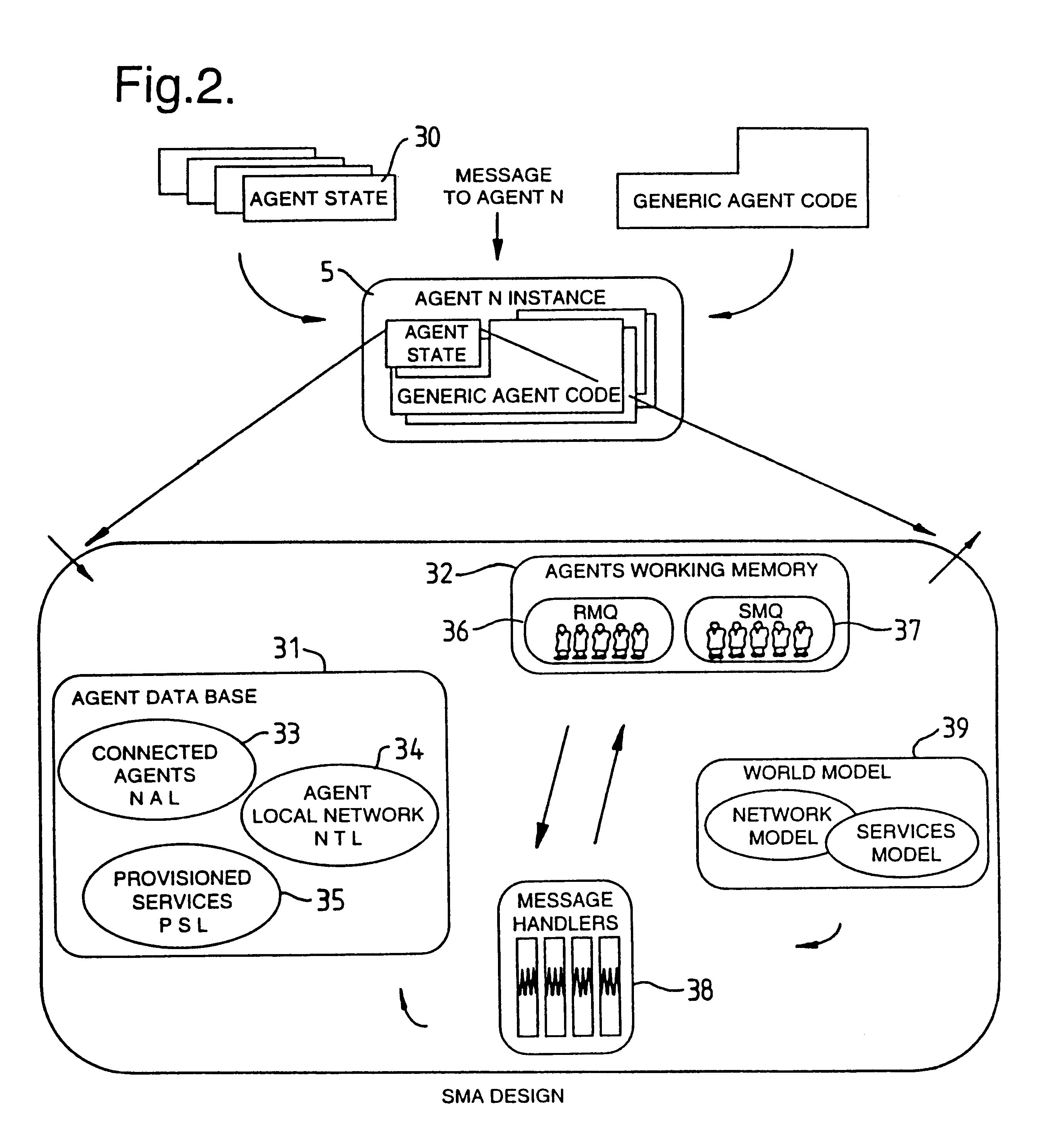
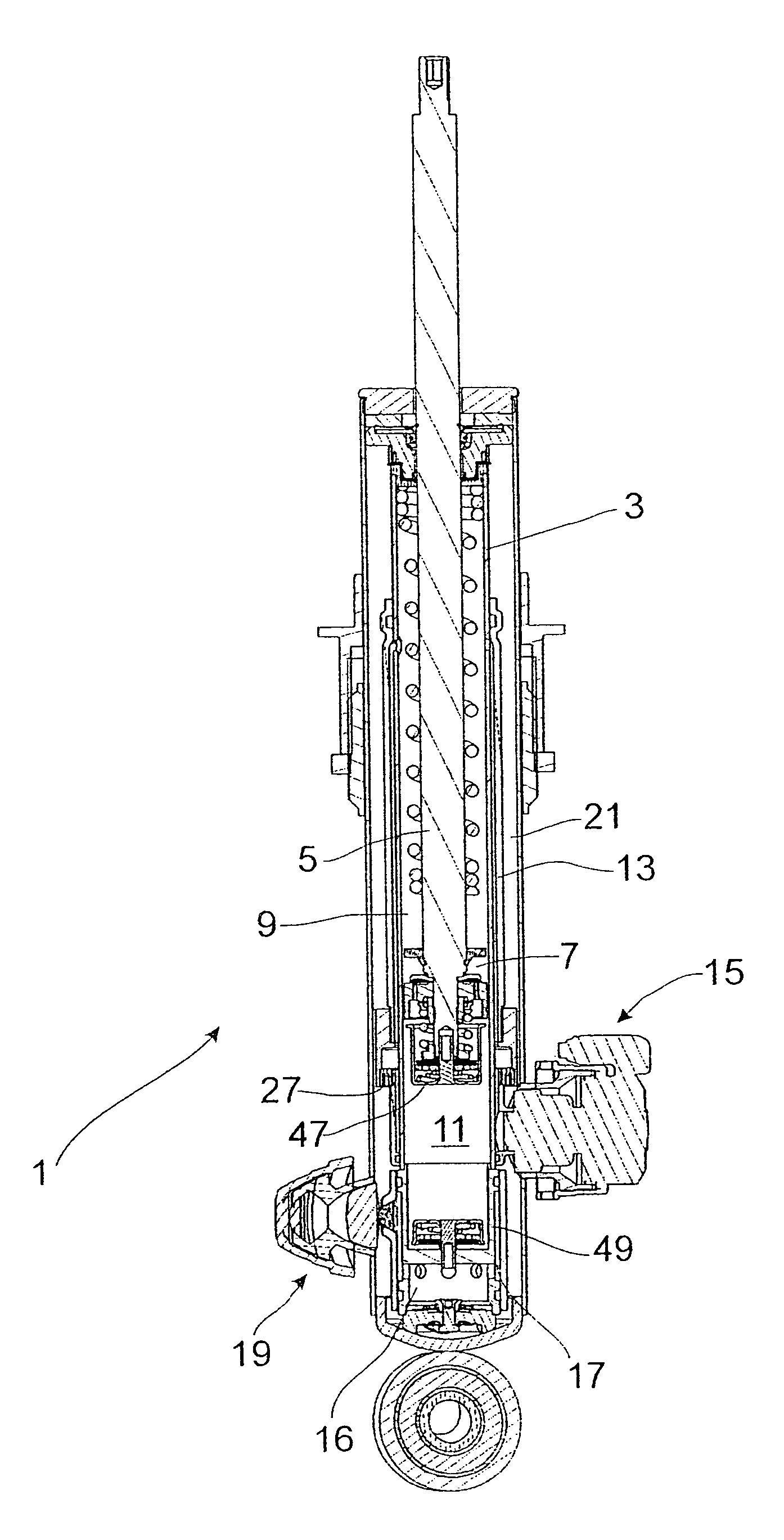
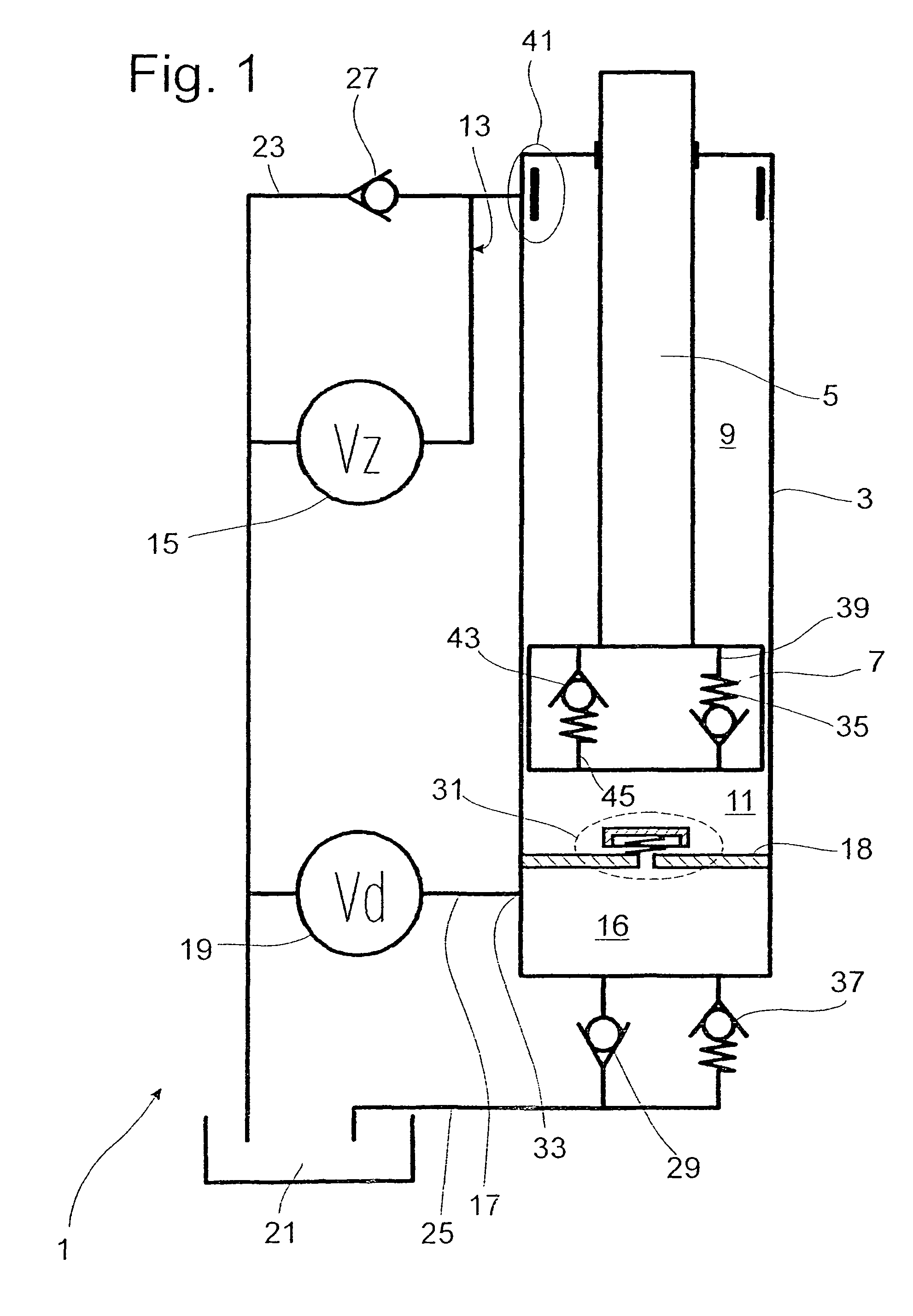
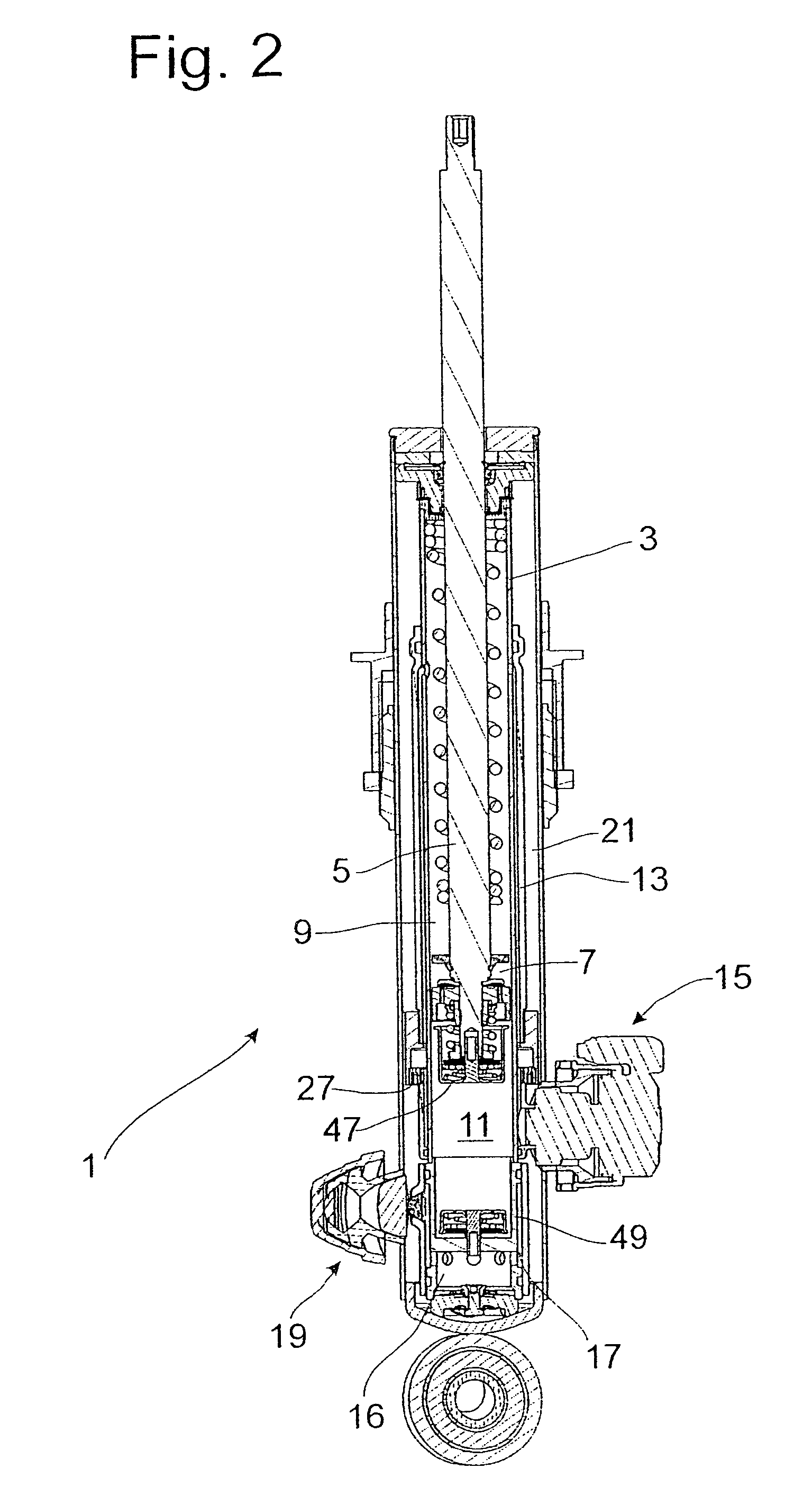
Vibration damper with adjustable damping force
InactiveUS8307965B2Efficient designMinimize consequencesSpringsLiquid based dampersControl theoryPiston rod
The vibration damper with an adjustable damping force includes a cylinder filled with a damping medium, a piston rod axially movable in the cylinder and carrying a piston which divides the cylinder into a first working space on the piston rod side and a second working space on the side away from the piston rod, a first adjustable damping valve which is connected to at least one of the two working spaces by means of a fluid connection, at least one second valve which is connected hydraulically in parallel to the first adjustable damping valve, and a third damping valve arranged in series to and upstream from both the first and second valves, the third damping valve moving in a closing direction as a function of a flow velocity of the damping medium through the third damping valve.
Owner:ZF FRIEDRICHSHAFEN AG
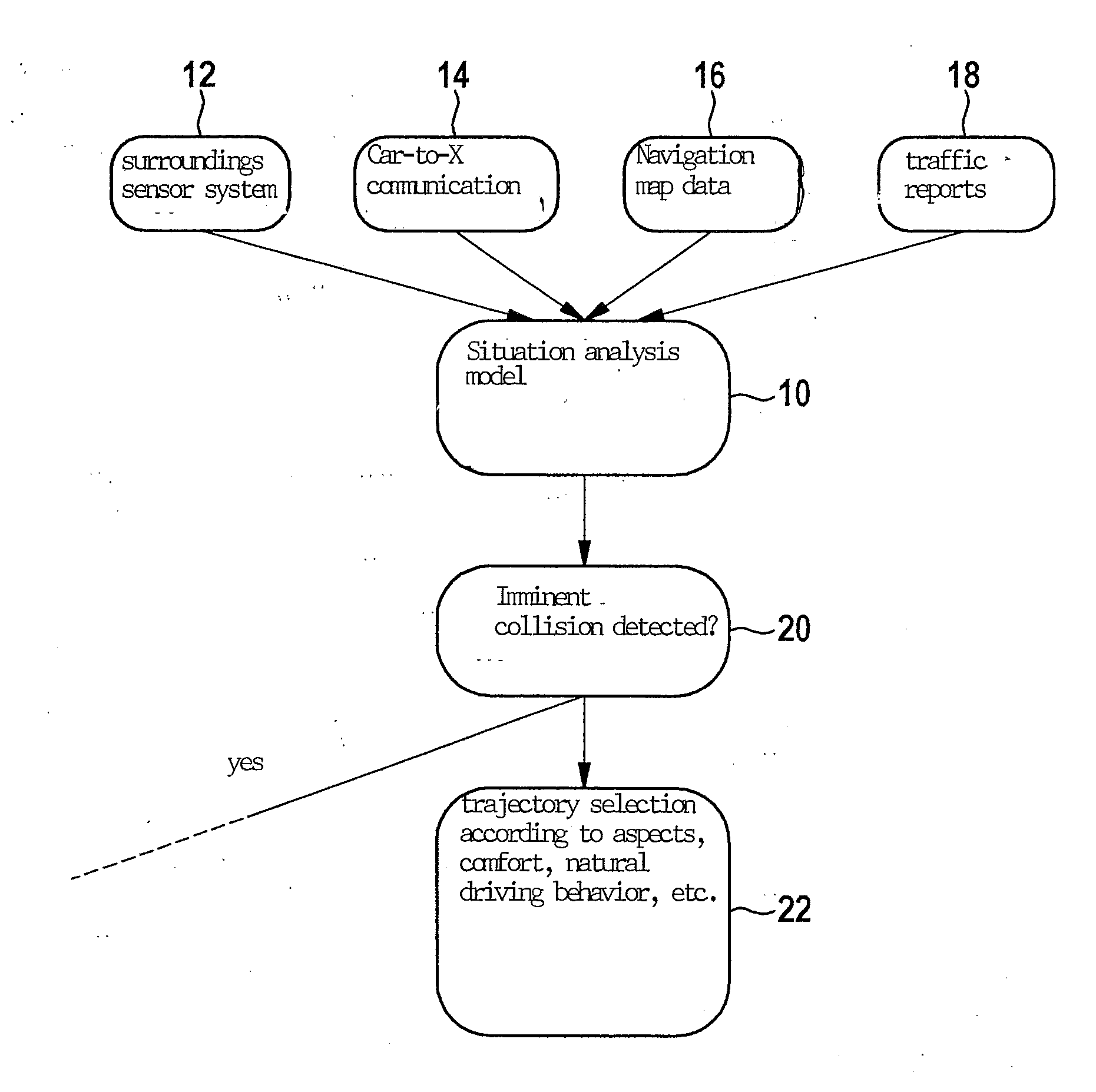
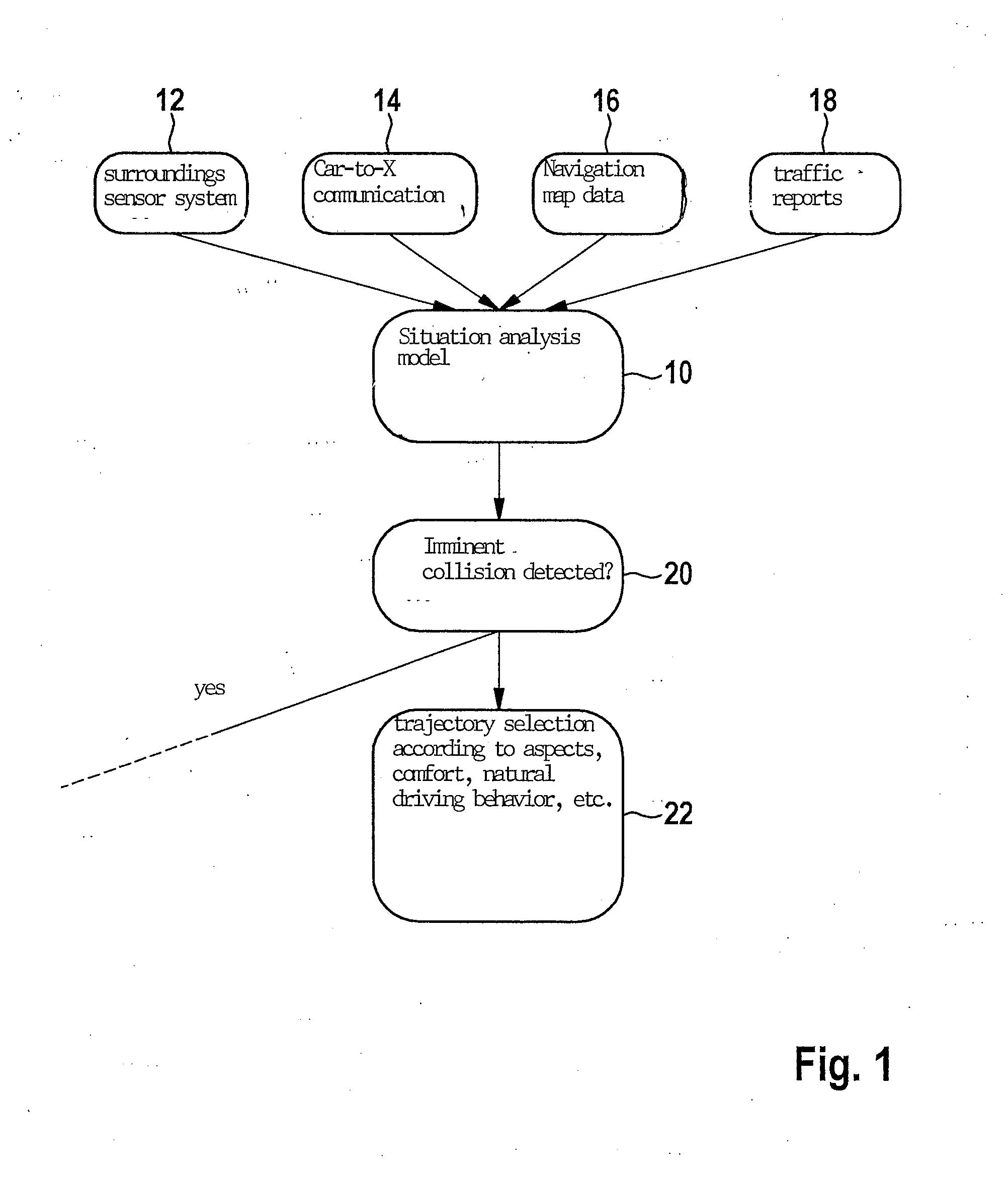
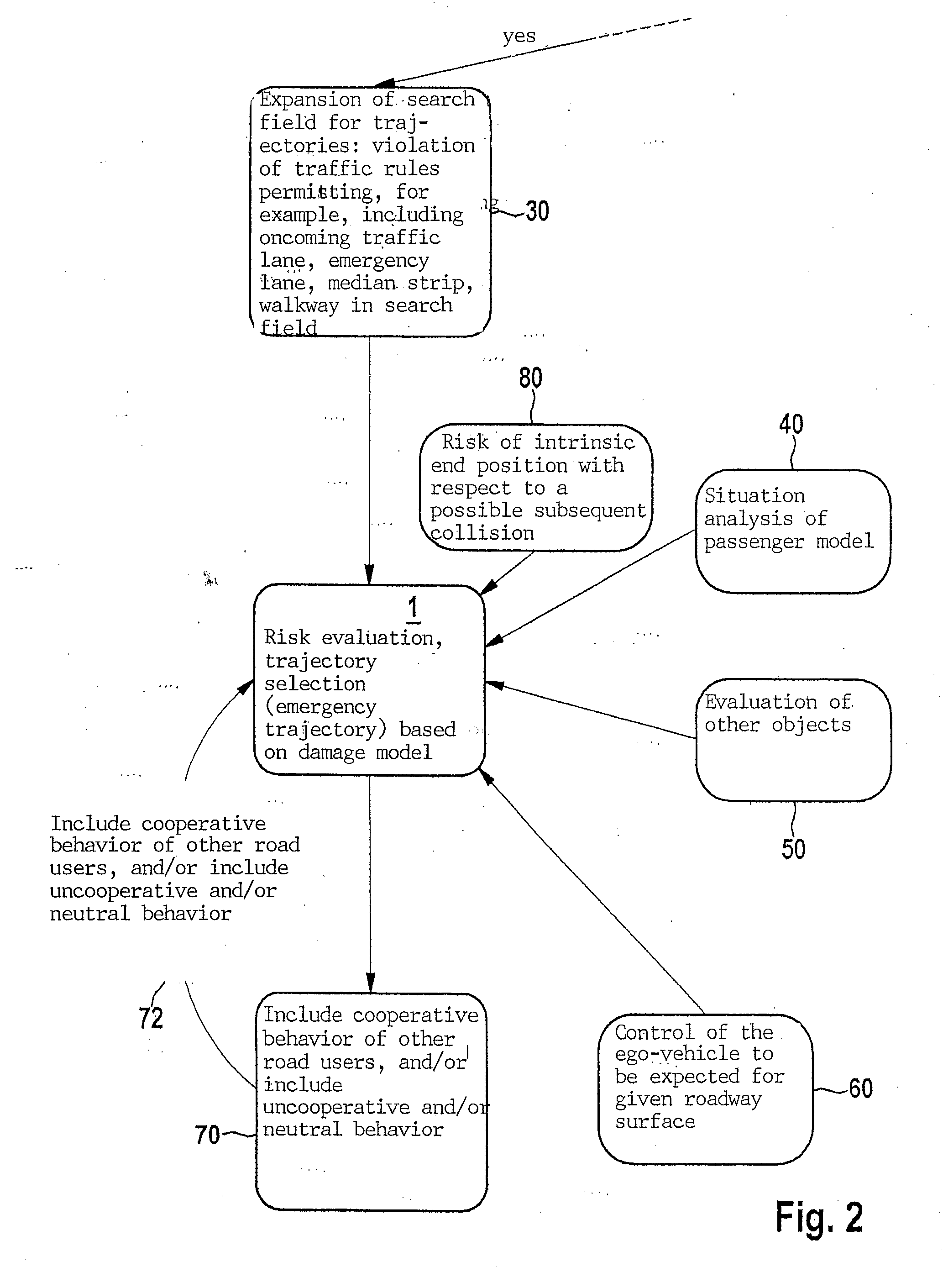
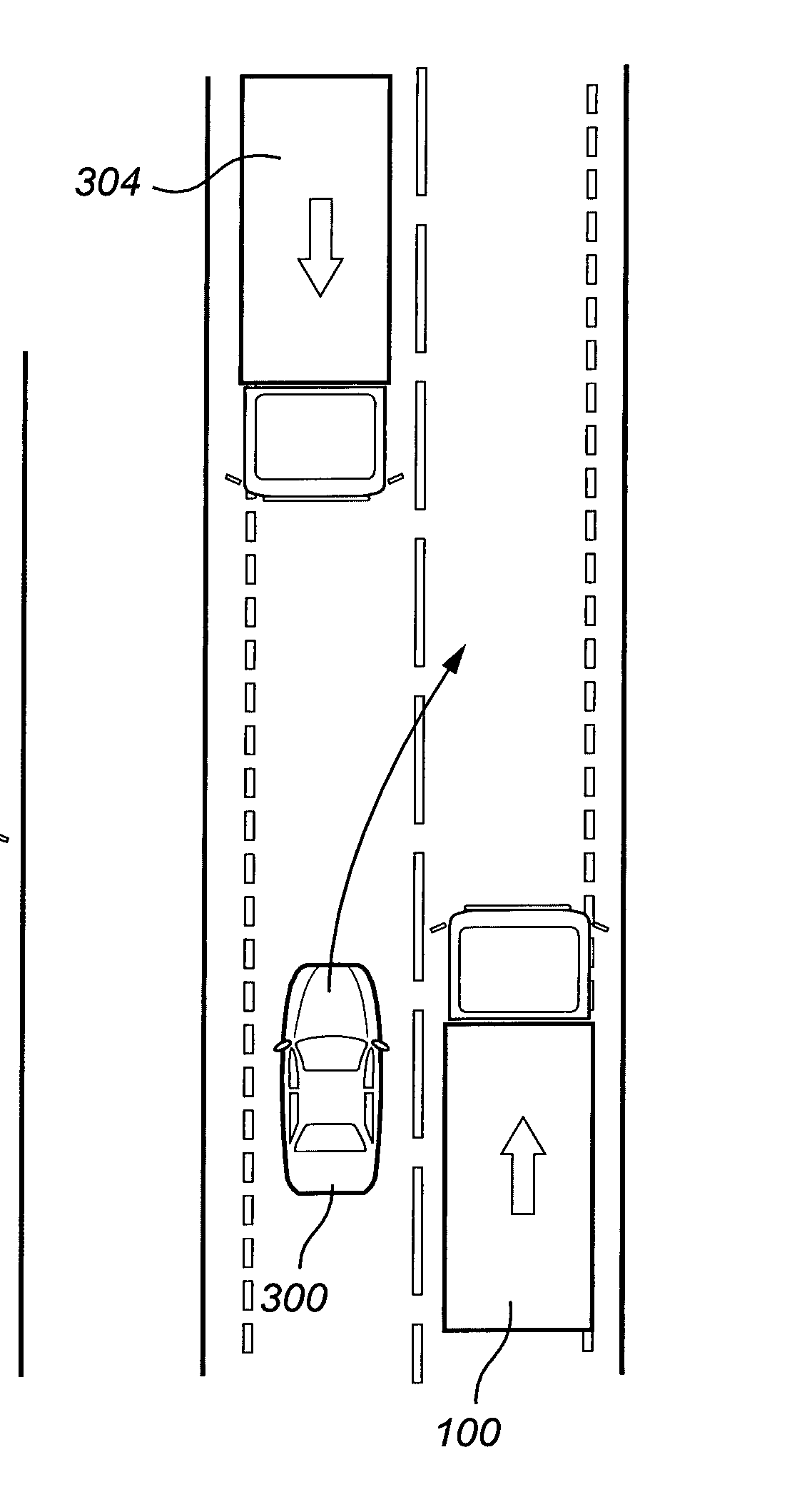
Method for ascertaining an emergency trajectory and method for partially automated or automated driving of an ego-vehicle
InactiveUS20160001775A1Improve protectionImprove securityExternal condition input parametersSignalling/lighting devicesDriver/operatorProcessing element
A method for ascertaining at least one emergency trajectory of an ego-vehicle using an assistance system, in particular a driver assistance system of the ego-vehicle, and / or an automatic driving function, upon detection of an imminent collision of the ego-vehicle, at least one emergency trajectory of the ego-vehicle being ascertained by the assistance system or the automatic driving function under consideration of at least one other trajectory of at least one other object which is different from the ego-vehicle. Also described is a computer program or a computer program product, a computer unit or a processing unit, and a safety device, in particular having an assistance system and / or an automatic driving function for a vehicle, including a motor vehicle.
Owner:ROBERT BOSCH GMBH
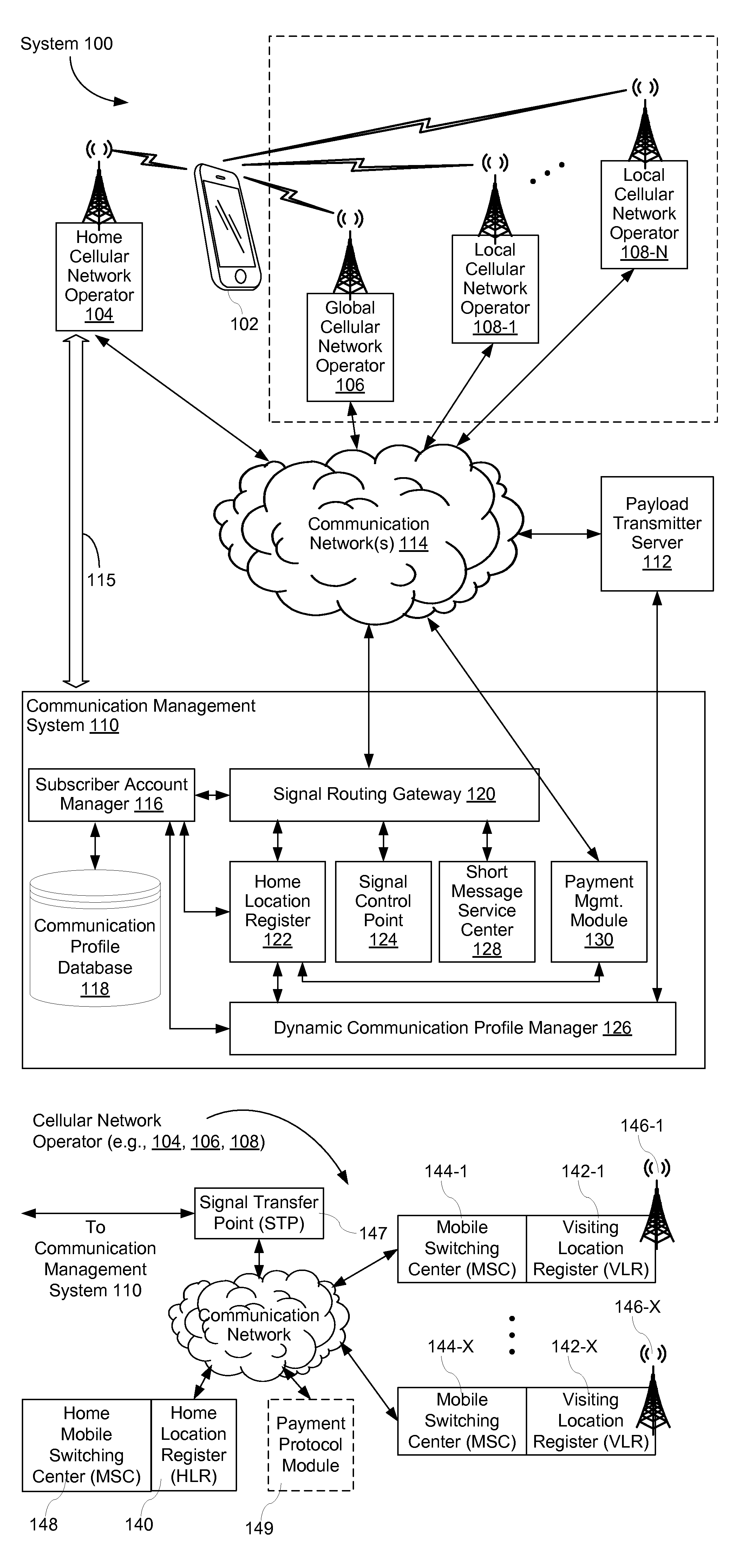
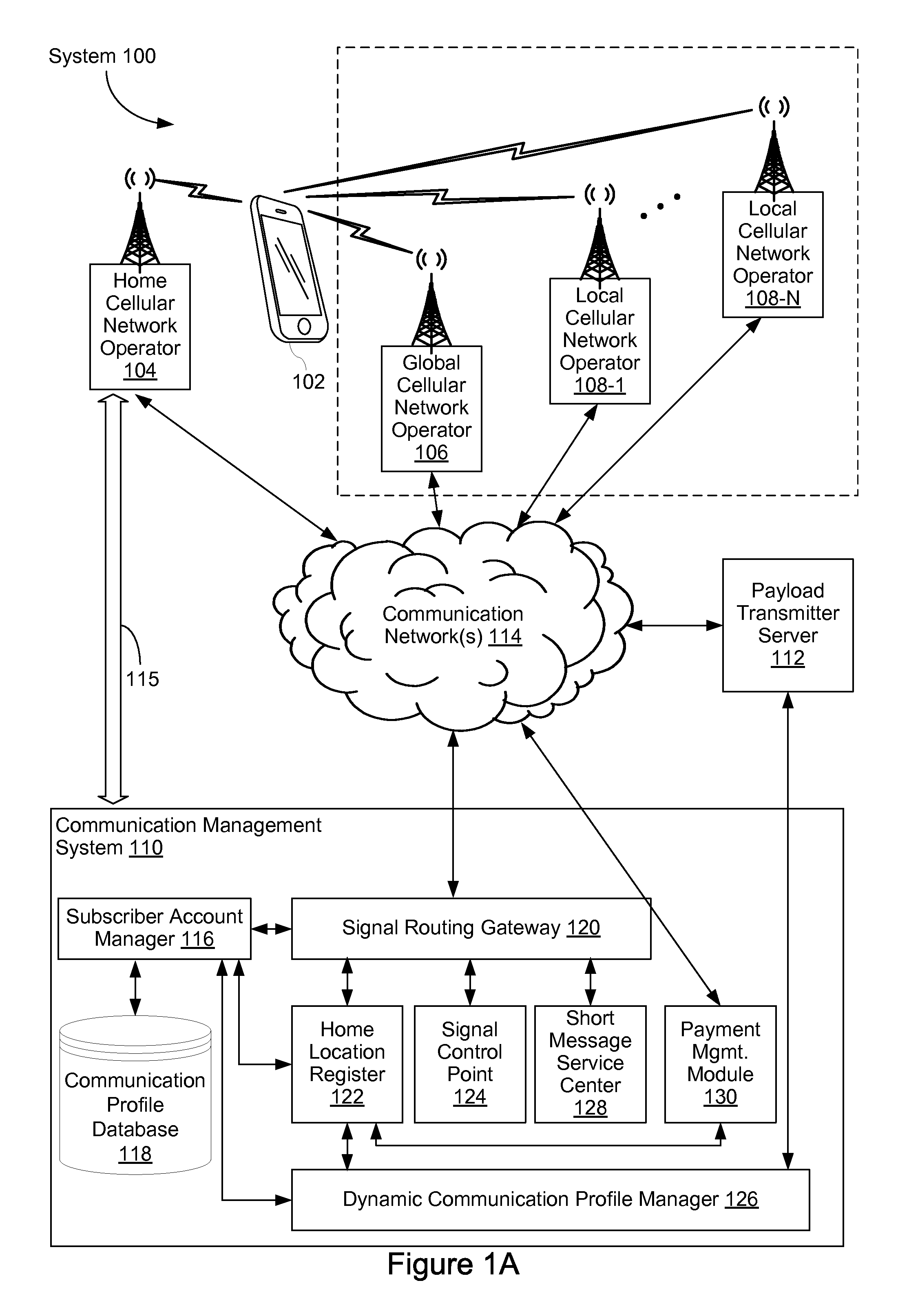
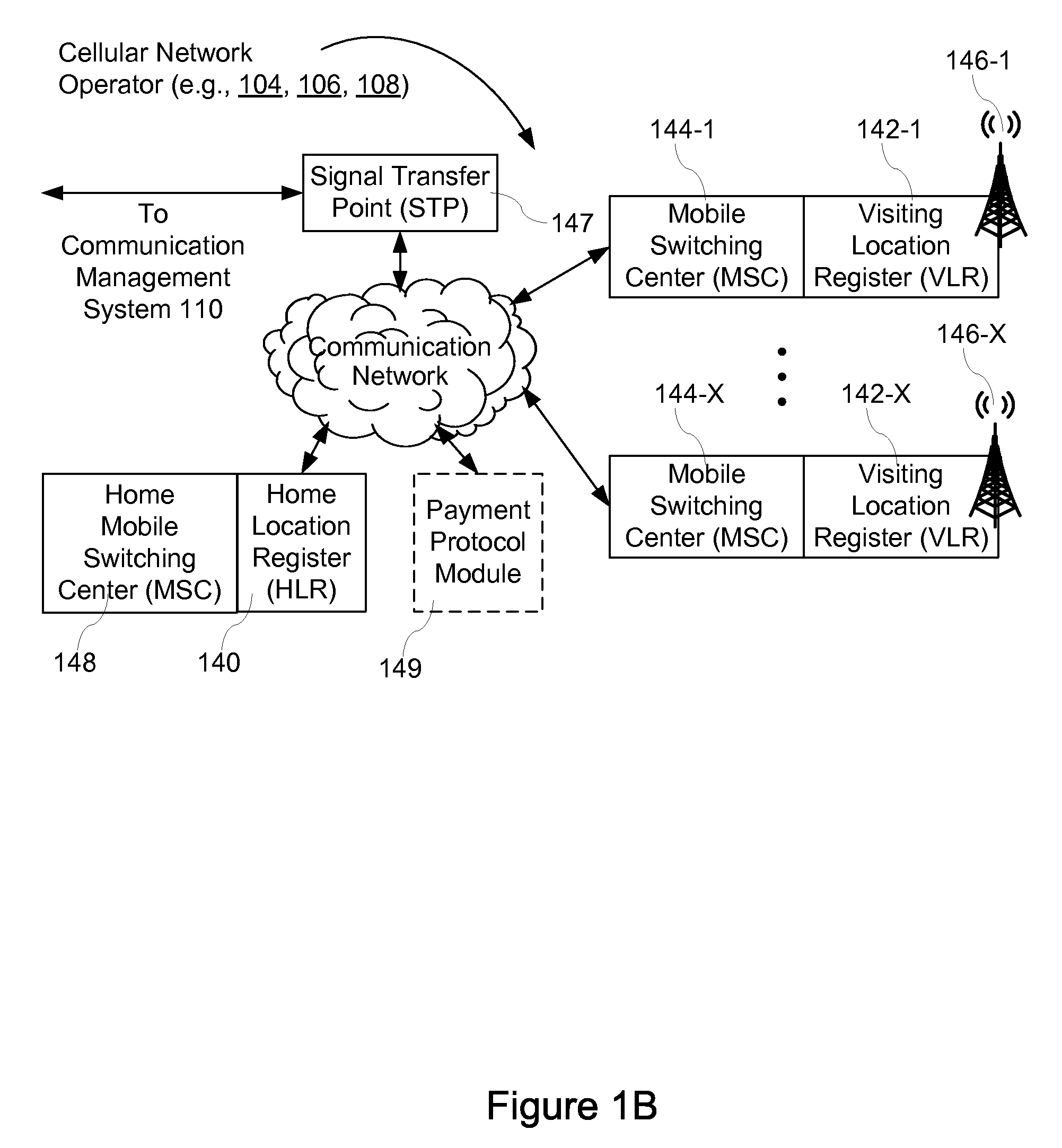
System and Method for Routing Signals Using Network-Specific Identifiers for a Common Server Module
InactiveUS20110268022A1Improve efficiencyImprove convenienceMessaging/mailboxes/announcementsWireless commuication servicesSignal routingManagement system
A communication management system has a server module and a signal routing gateway that is connected to a plurality of different cellular network operators. At the signal routing gateway a request is received. The request is addressed to a network-specific address assigned to the server module in accordance with an addressing scheme of a cellular network operator. In response to the request the network-specific address is replaced with an internal address assigned to the server module in accordance with an internal addressing scheme of the communication management system. A response to the request is obtained from the server module. The response is addressed from the internal address. The internal address is replaced with the network-specific address. The response is sent to the cellular network operator. In some embodiments, this process is repeated for multiple requests from the plurality of different cellular network operators.
Owner:7 TEL
Glazing element and laminate for use in the same
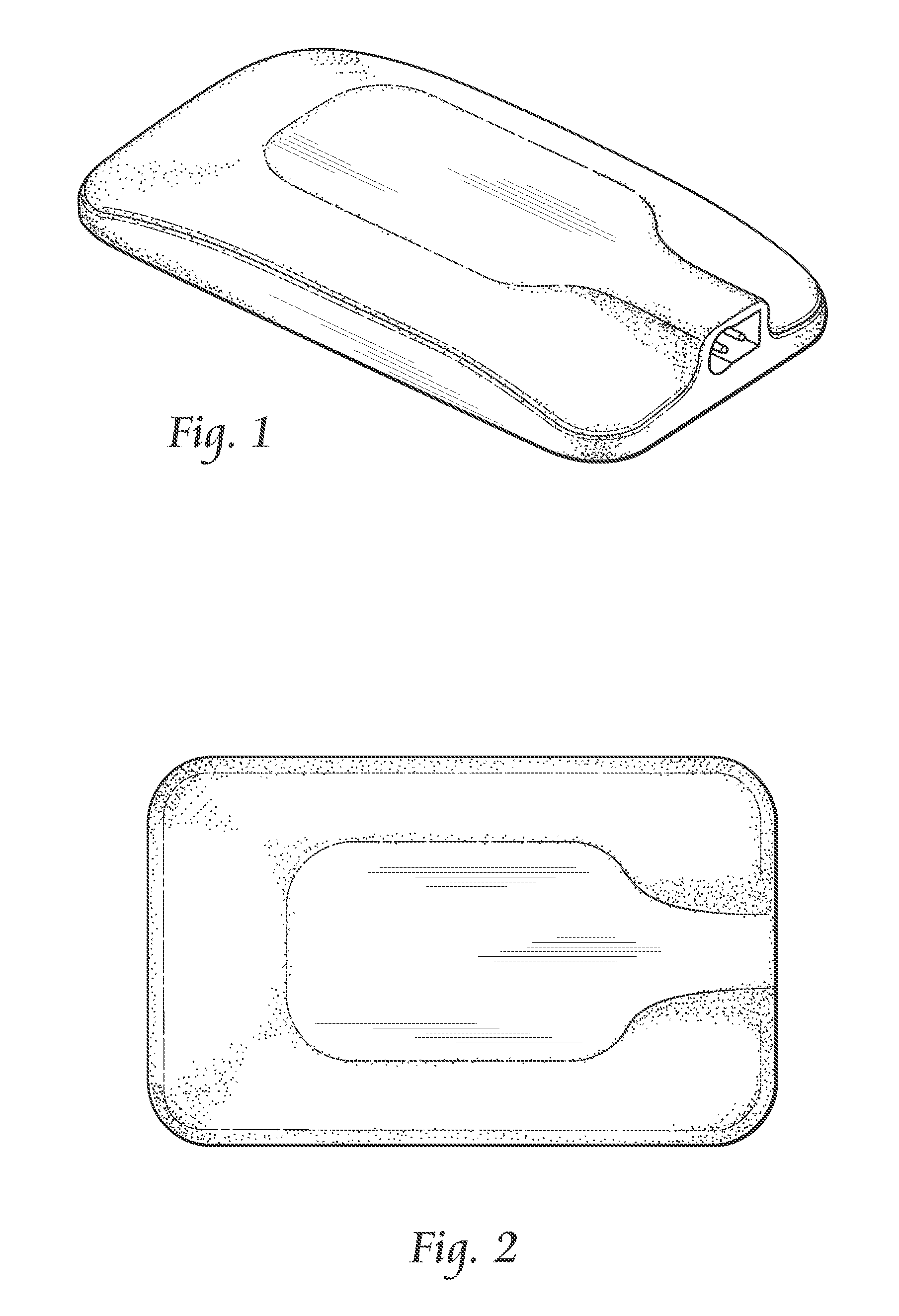
InactiveUS7238401B1Easily retain impact fractureEasy to installWindowsWindscreensEngineeringSurface cover
A multi-layer optically clear laminate suited for attachment to window glass to provide a glazing element which has reduced spall and lacerative consequences on fracture impact of the window glass is provided by the invention. The laminate is comprised of at least two films of nonadhesive polymeric material directly adhered together by pressure sensitive adhesive and includes an exposed surface covered with a hard coat composition and an opposite surface covered with an ambient temperature attachable pressure sensitive adhesive. A glazing element comprised of the laminate attached to glass is also provided.
Owner:3M INNOVATIVE PROPERTIES CO
Method and system for driver assistance for a vehicle
ActiveUS20160318511A1High trafficReduced risk of collisionRoad vehicles traffic controlExternal condition input parametersDriver/operatorEngineering
A method for driver assistance for a first vehicle includes monitoring, using a detection arrangement provided with the first vehicle, a predefined area surrounding the first vehicle, identifying a road condition ahead of the first vehicle and within the predefined area, the road condition fulfilling a predetermined risk criteria, identifying a second vehicle initiating a maneuver for overtaking the first vehicle, and determining a collision risk level for the first and / or second vehicle during the overtaking maneuver.
Owner:VOLVO LASTVAGNAR AB
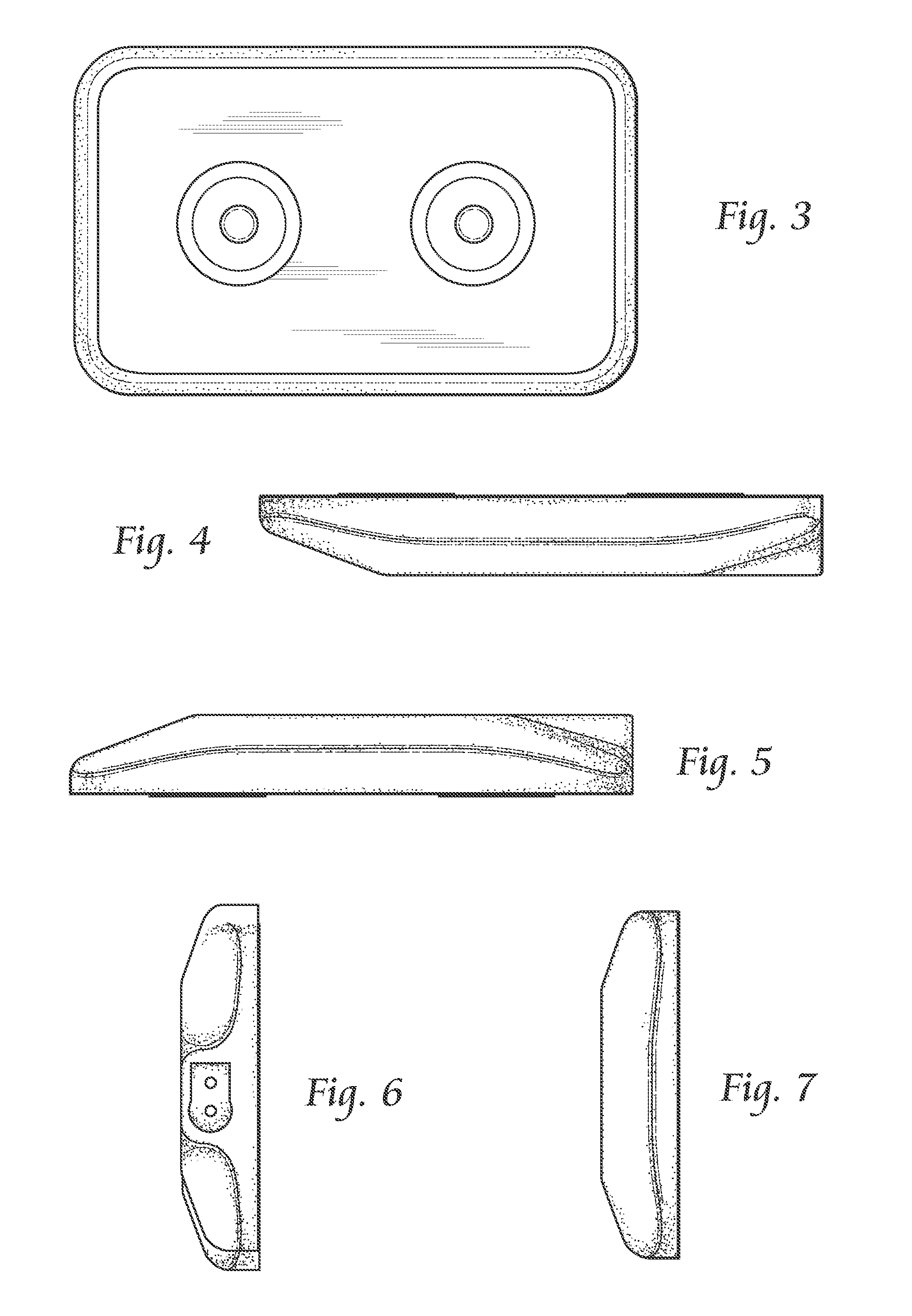
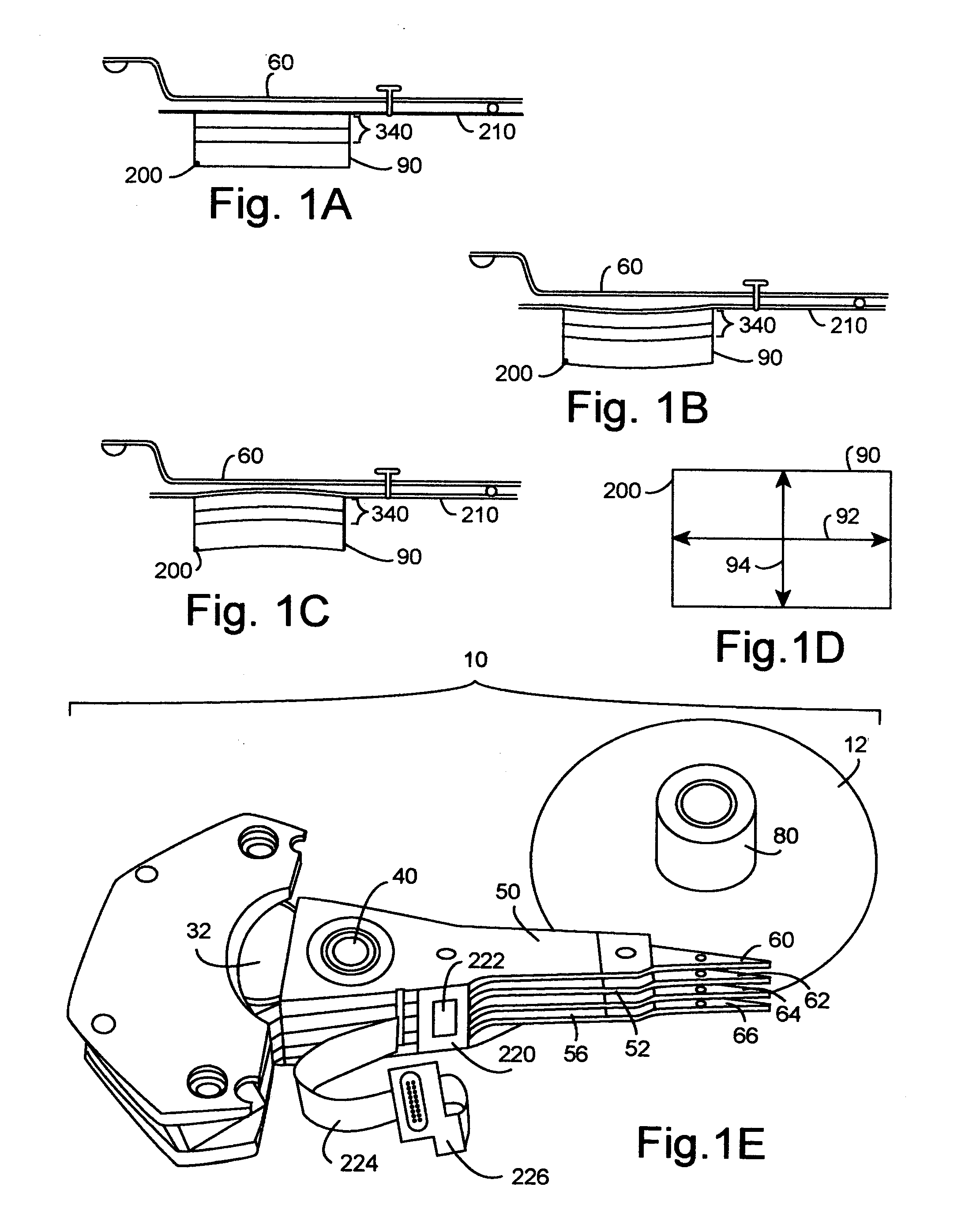
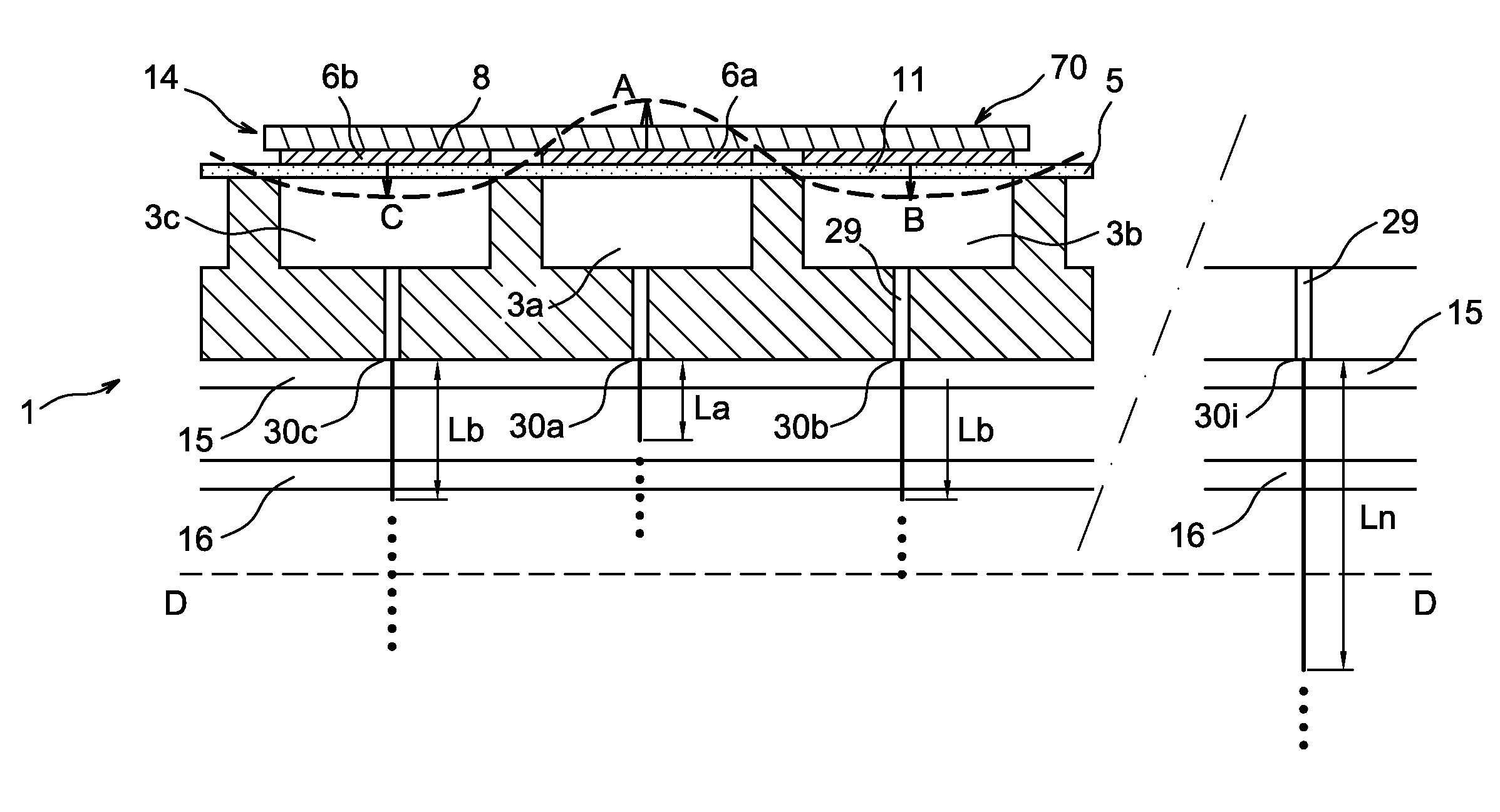
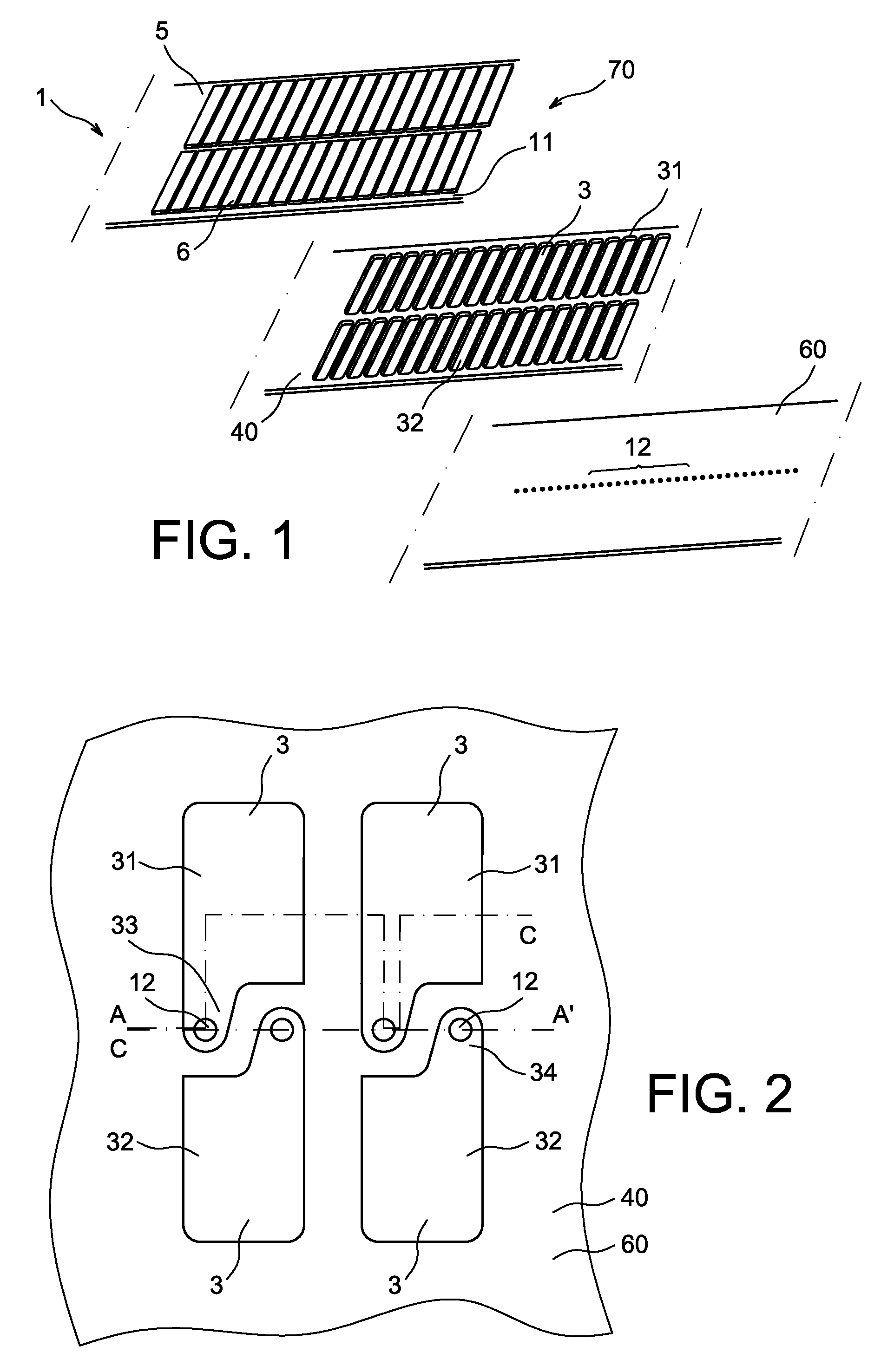
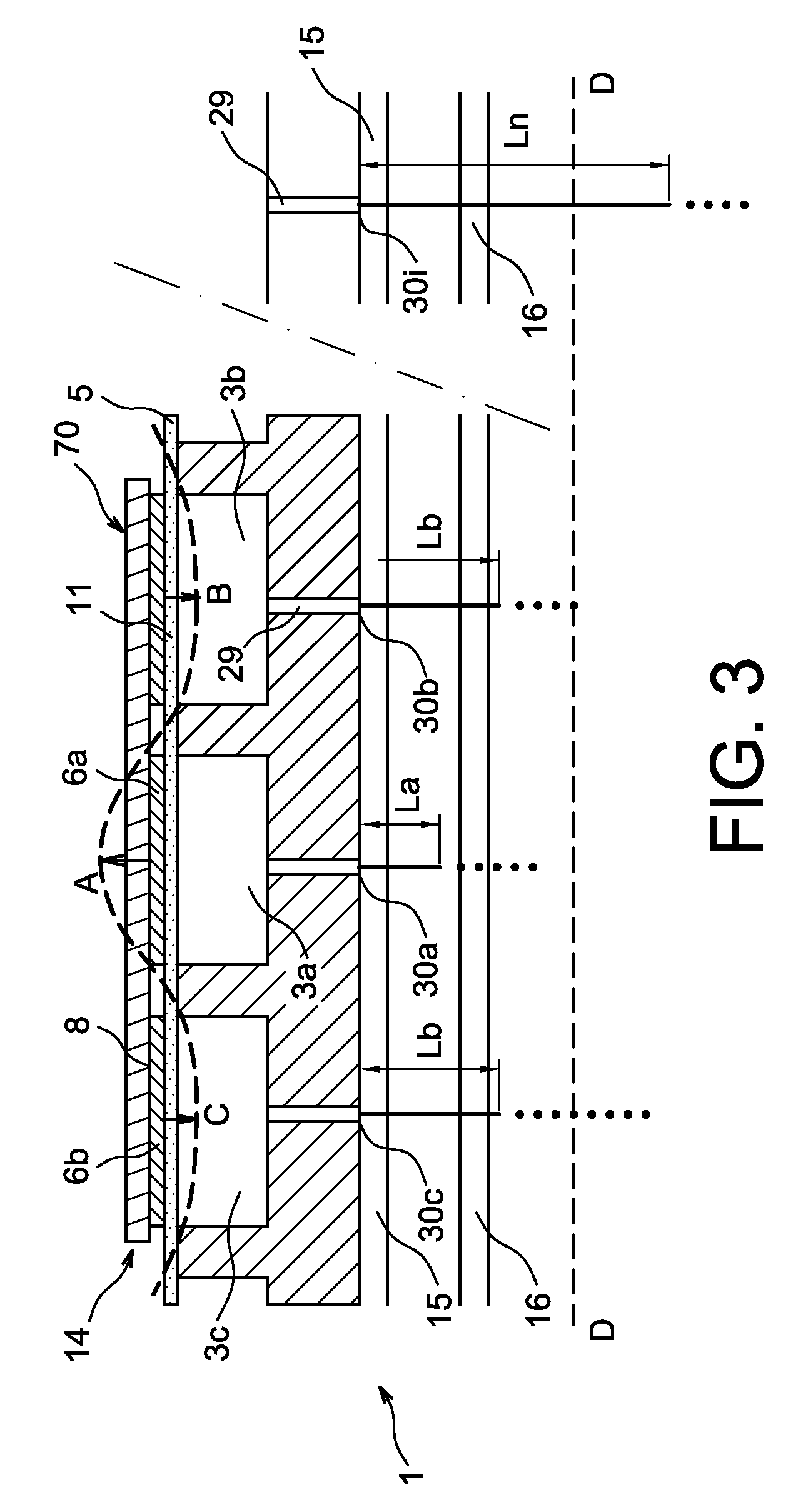
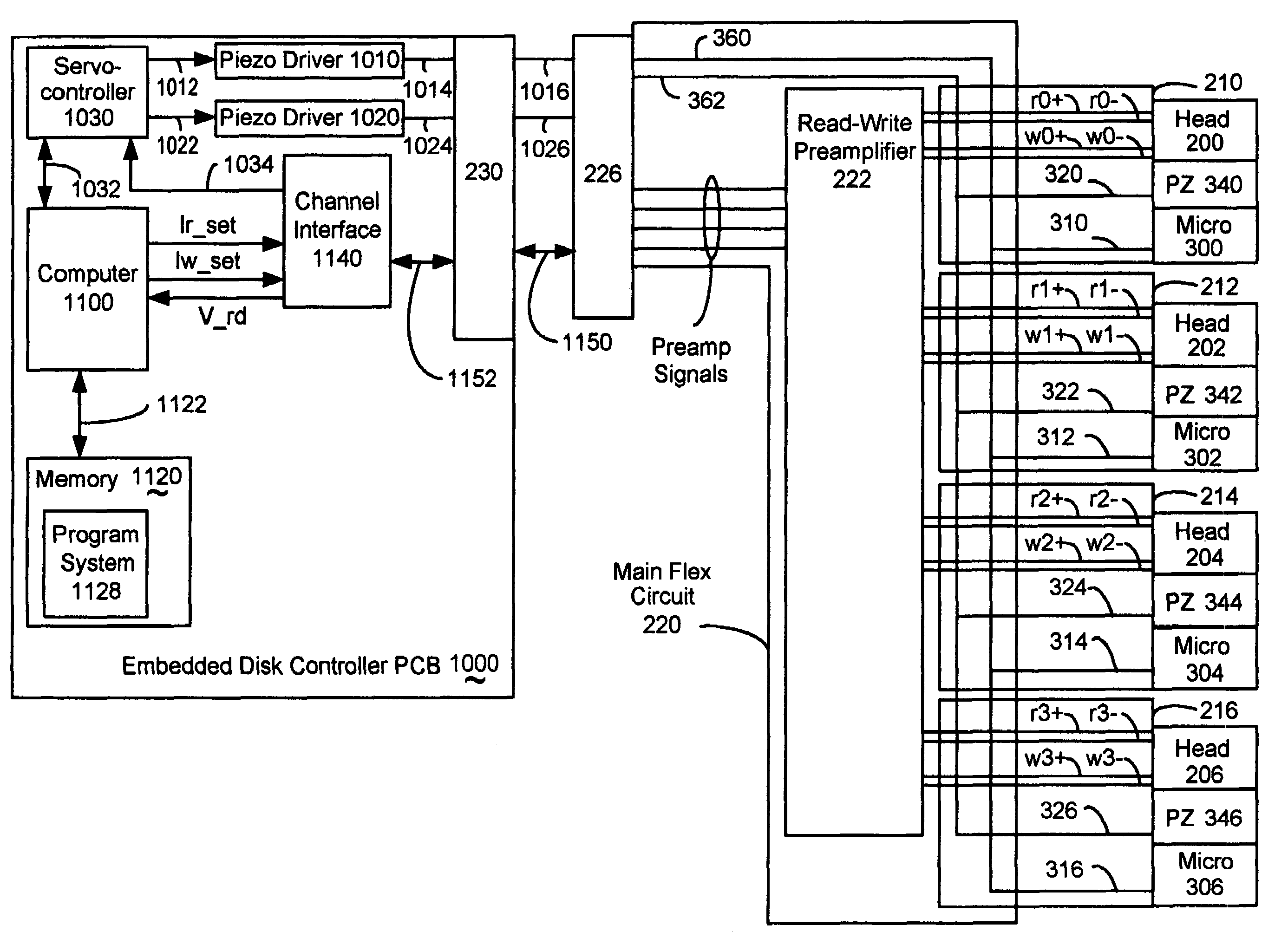
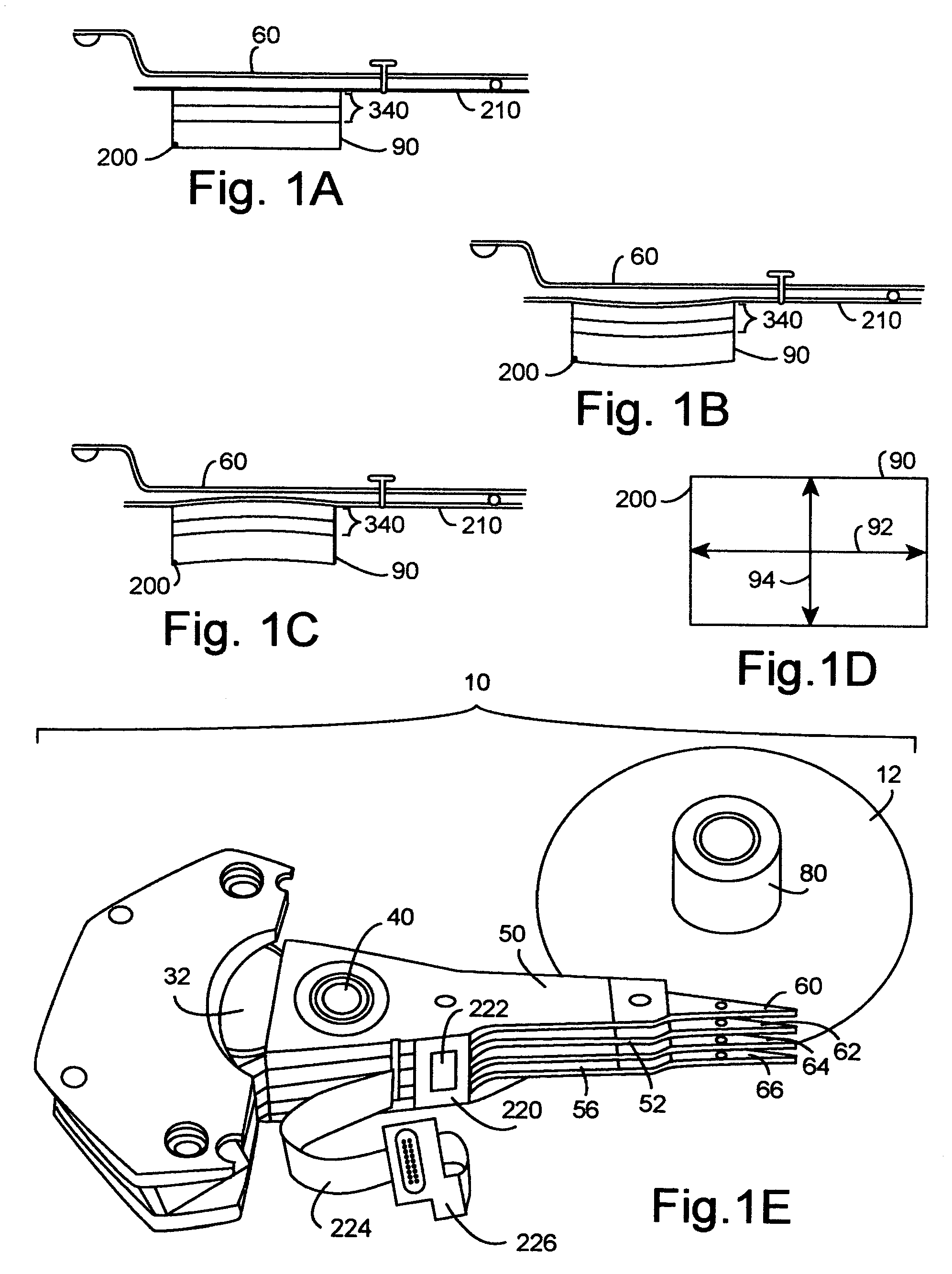
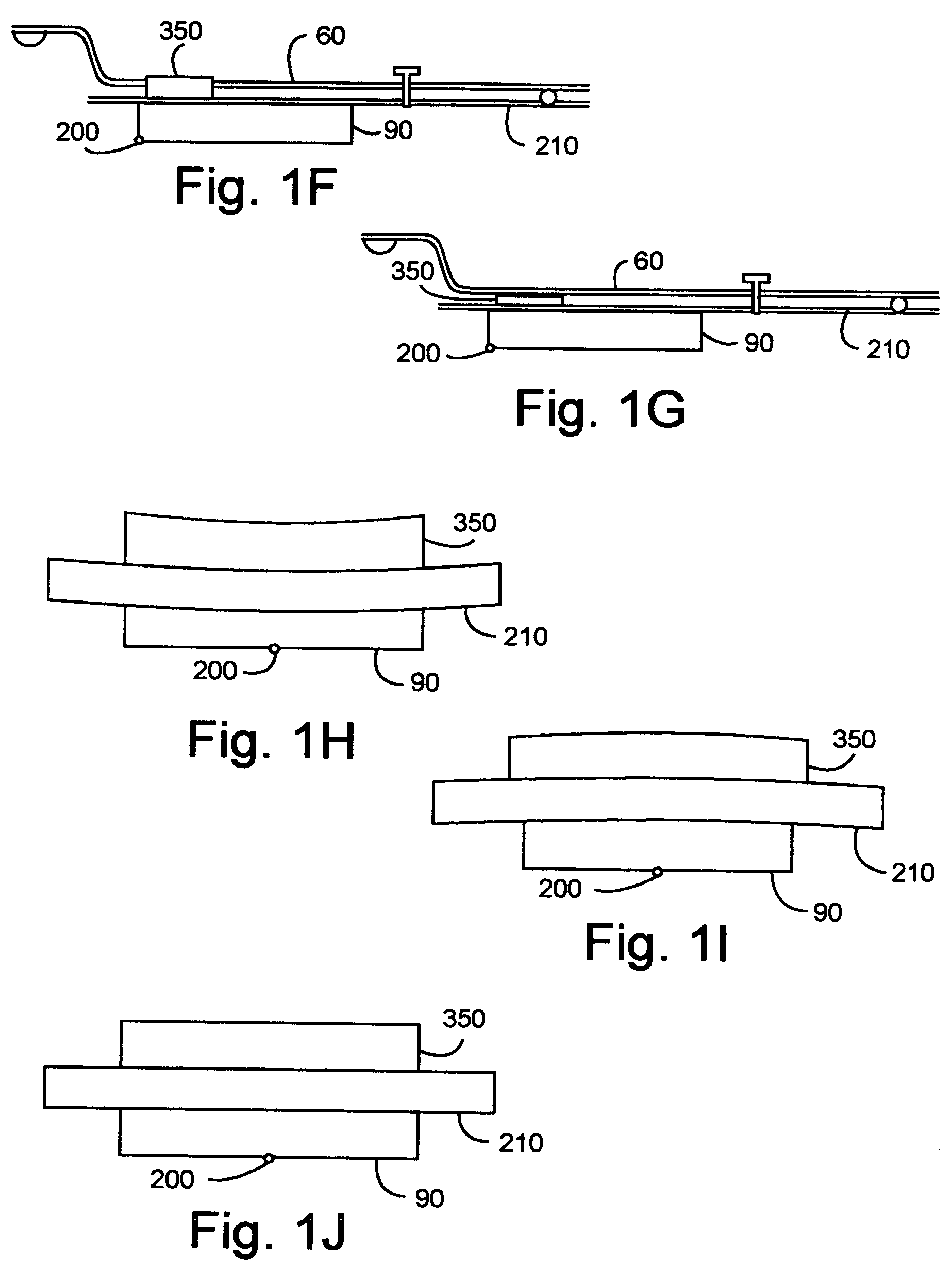
Head gimbal assemblies for very low flying height heads with optional micro-actuators in a hard disk drive
InactiveUS20060023338A1ContactHigh data reliabilityElectrical connection between head and armElectrical transducersGimbalMicro actuator
A head gimbal assembly may include a piezo layer mechanically coupled with the slider. Bending the piezo layer alters flying height. Alternatively, it may include a piezo element mechanically coupled by a flexure to the slider top near the read-write head, which when excited, bends the flexure to alter the flying height. A bridge flex circuit is included, providing a piezo-control bundle to at least one of the piezo layer leads. The flex circuit assembly may further provide a piezo control bundle, shared with the piezo control bundles for multiple read-write heads. The head gimbal assembly may include a micro-actuator to position the read-write head near a track on the accessed, rotating disk surface. The flex circuit assembly may provide a source control bundle, shared with micro-actuator control bundles for multiple read-write heads. When accessing, all micro-actuators perform the same positioning action, insuring proper positioning of the read-write head. This applies to co-located and non co-located micro-actuators. Wire bundles may include one or two active signal wires. Voice coil actuators and the hard disk drives, as well as making these, are included.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for redeeming keno tickets
InactiveUS7934986B2Less federal taxLower taxDiscounts/incentivesApparatus for meter-controlled dispensingThe InternetComputerized system
A method and apparatus is provide for playing keno-type games wherein a player can redeem a winning ticket remotely (e.g., over the Internet, by email or phone, etc.) instead of having to return to a point of purchase of the ticket to redeem the ticket. The keno-type game can be played using paper tickets or on a computer system, for example, coupled to the Internet.
Owner:SCI GAMES HLDG
Operating an engine with reformate
InactiveUS20110137537A1Improve combustion stabilityImprove knock resistanceAnalogue computers for vehiclesElectrical controlAutomotive engineering
Owner:FORD GLOBAL TECH LLC
Graphic display adapter device for mobile virtual stereoscopic vision
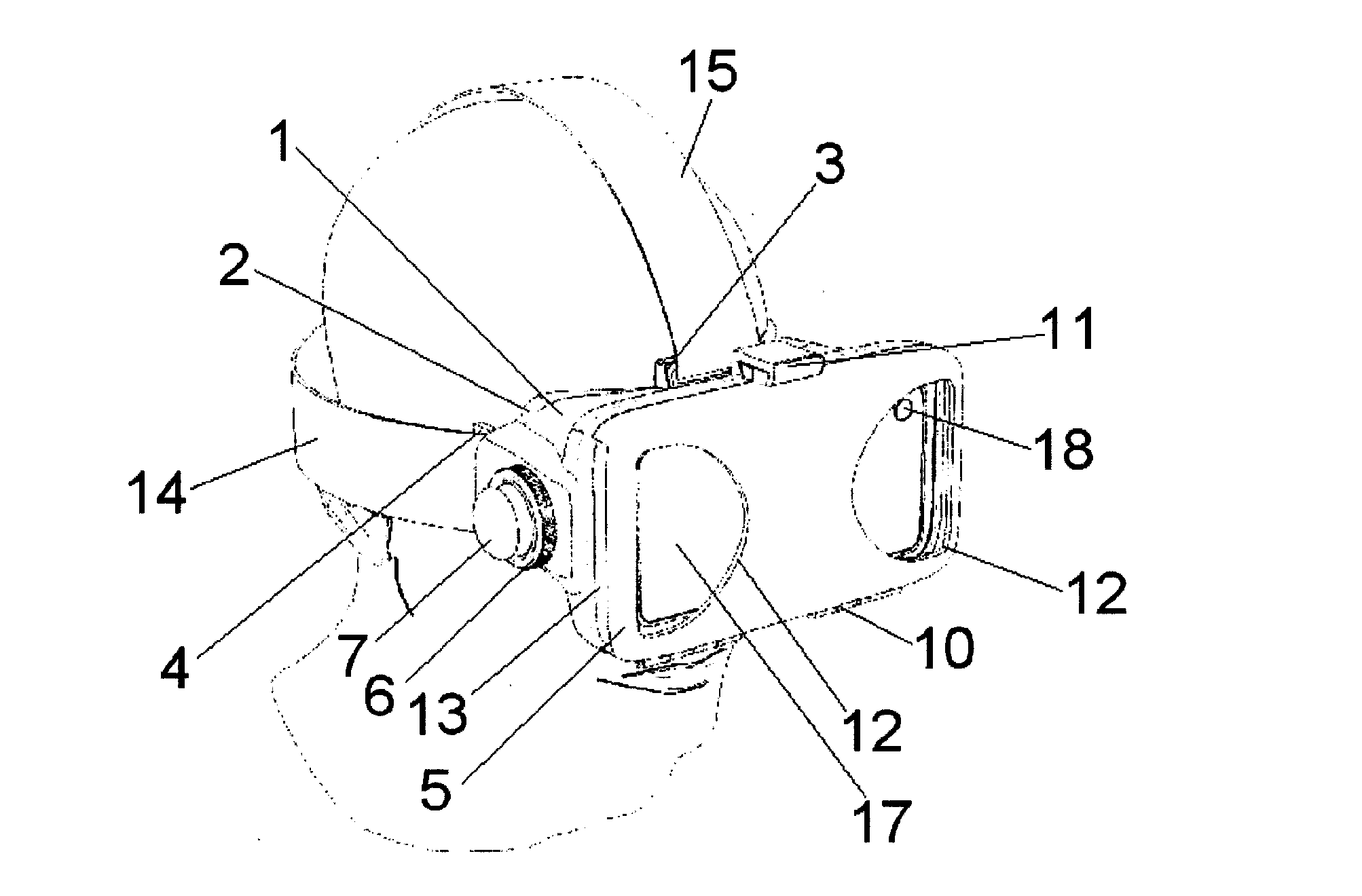
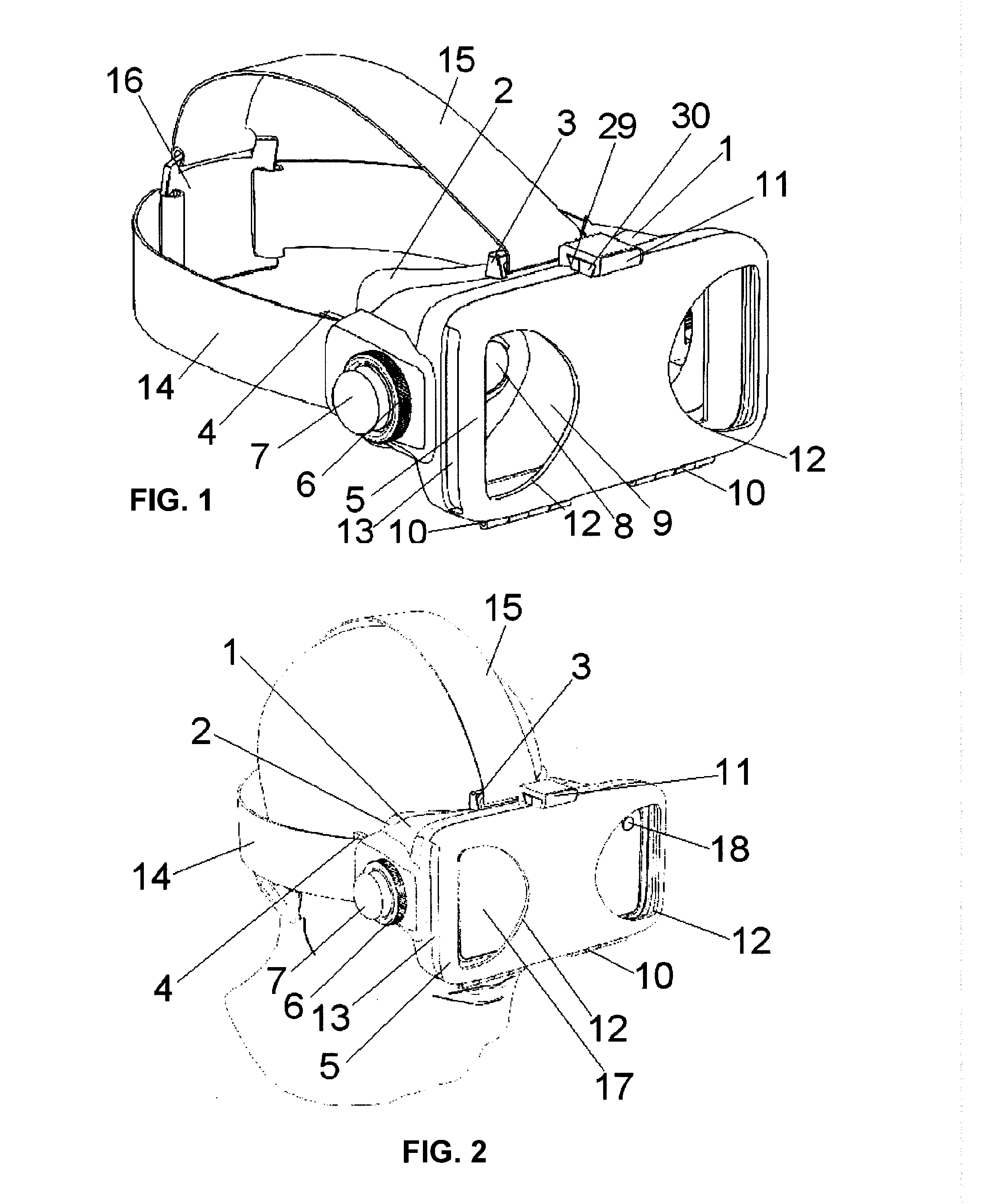
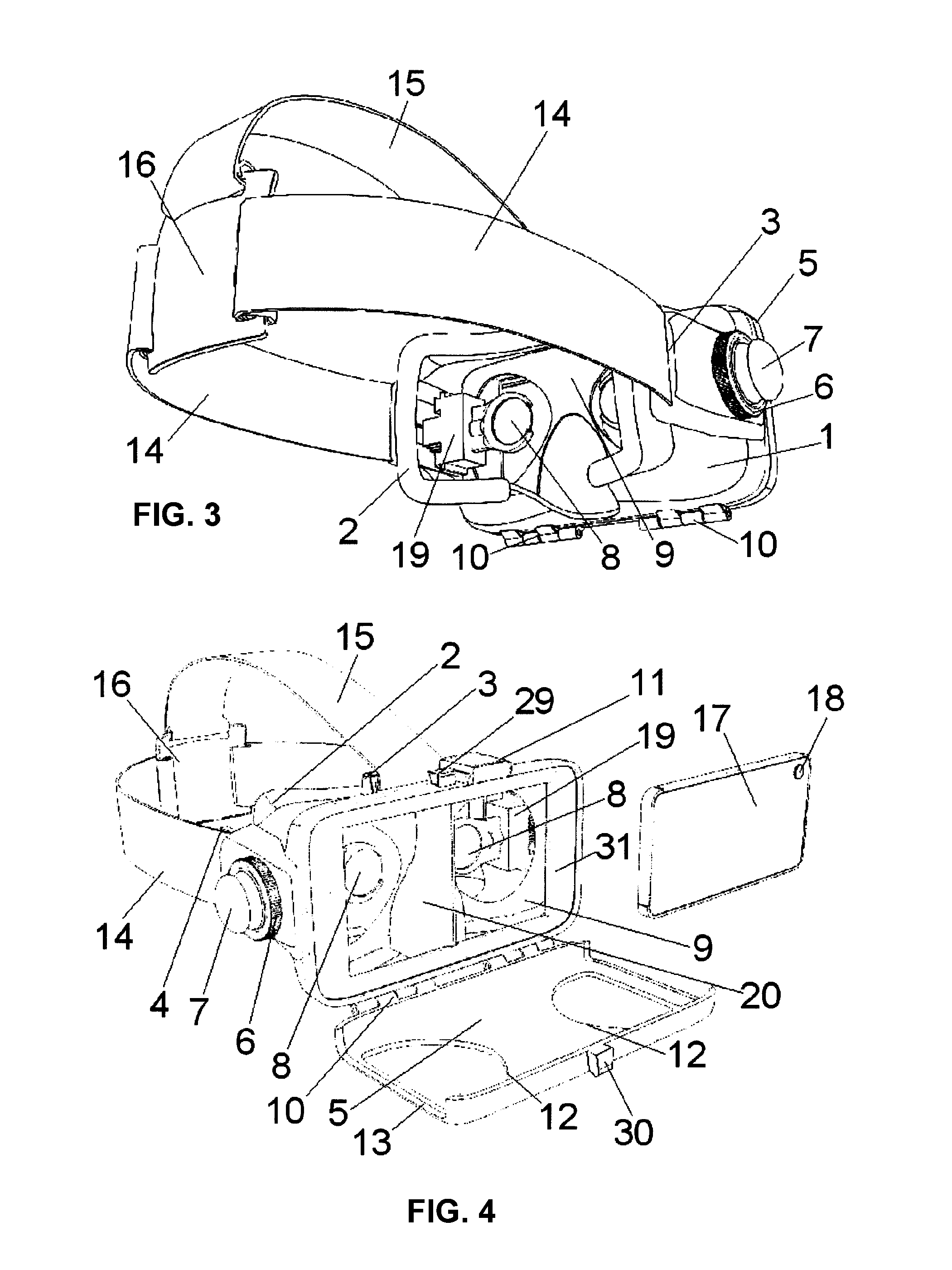
InactiveUS20170010471A1Loss of qualityPrecision of movementImage data processingSteroscopic systemsGraphicsMultiplexing
An adapter device is provided to be disposed on the wearer's head. A mobile phone or other mobile graphical device can be inserted in the front of the device so this is opposite the user's eyes at a short distance. The device also incorporates lenses and adjustment mechanisms of the lenses that allow proper display of the graphic display device that is inserted in the adapter. Thus the device is designed to achieve stereoscopic 3D vision, configuring the adapter assembly and the device graphic as a device that allows multiplexing (two or more information channels on a single means of transmission) for position (side-by-side) in a mobile phone or other device with graphic screen TV, merging both visual content and receiving a three-dimensional image.
Owner:IMMERSIONVRELIA INC
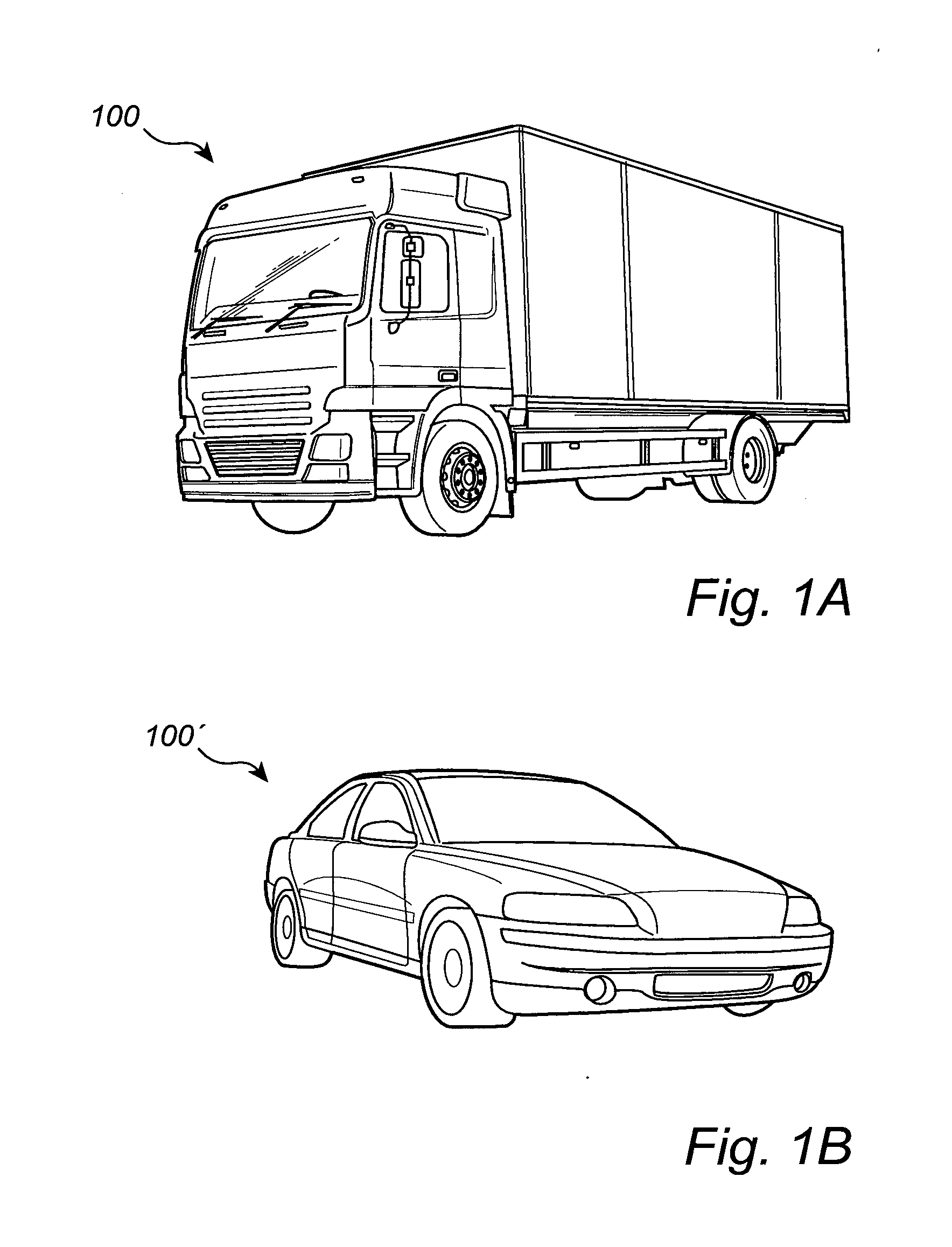
Vehicle collision avoidance apparatus and method
ActiveUS8538674B2Reduce severityReduce disadvantagesVehicle testingVehicle fittingsControl signalEngineering
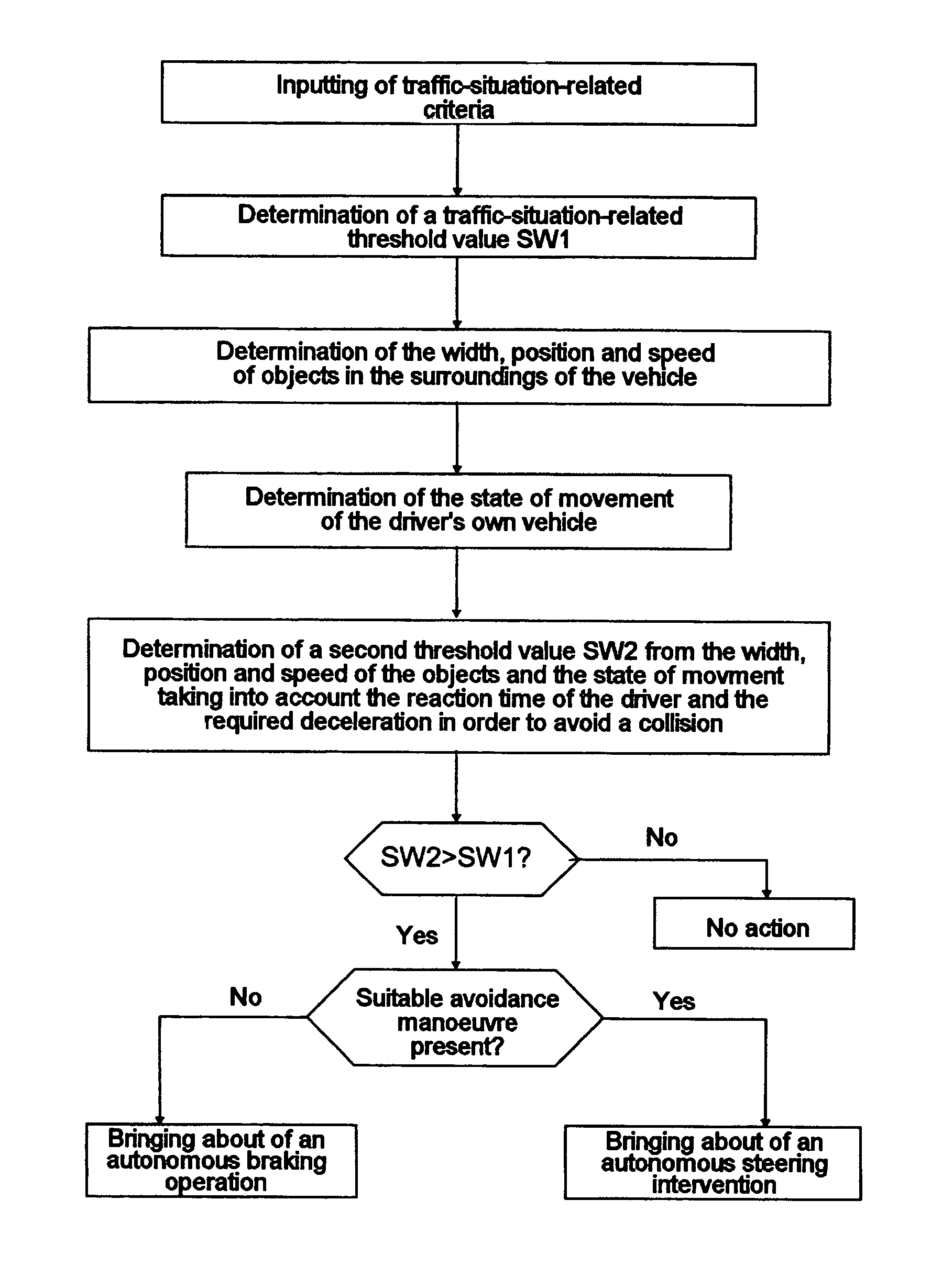
The present invention relates to a device for avoiding collision or for minimizing the collision severity in case of a collision, for vehicles, particularly for commercial vehicles, comprising an input unit for inputting criteria related to traffic conditions, and for determining threshold values related to traffic conditions, a detection unit for detecting objects in the environment of the vehicle, a measurement unit for determining the motion condition of the vehicle, a controller for processing the information obtained from the input unit, the detection unit, and the measuring unit, and for generating control signals for controlling the components related to the motion state of the vehicle, and an output unit for outputting the generated control signals. The invention further relates to a corresponding method and a computer program.
Owner:ZF CV SYST EURO BV
Preventing tooth decay and infective endocarditis using natural oligopeptides
InactiveUS7087228B2Minimize attachmentPrevention or prophylaxis of dental caries and endocarditisBiocideCosmetic preparationsBacteroidesCementum caries
The present invention provides compositions, medicaments, and methods for the treatment or prophylaxis of conditions associated with the binding of Streptococcus mutans to teeth. Specifically, the present invention provides a method for preventing dental caries and infective endocarditis in a subject by treating the subject's oral cavity with a composition or medicament comprising the competence stimulating peptide (CSP) of the causative bacterium, which inhibits the ability of the said bacteria to attach to the surface of teeth. Novel anti-caries compositions using the CSP are also disclosed.
Owner:UNIV OF SOUTHERN CALIFORNIA
Histamine H3 Receptor Agents, Preparation and Therapeutic Uses
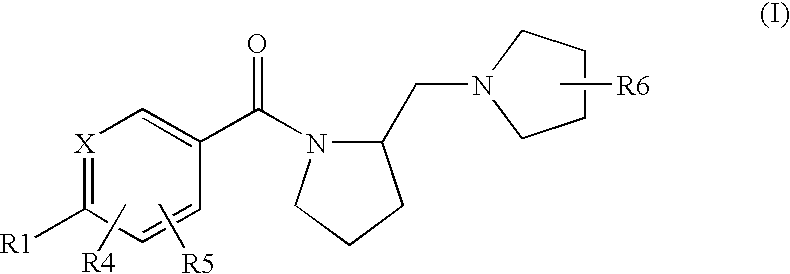
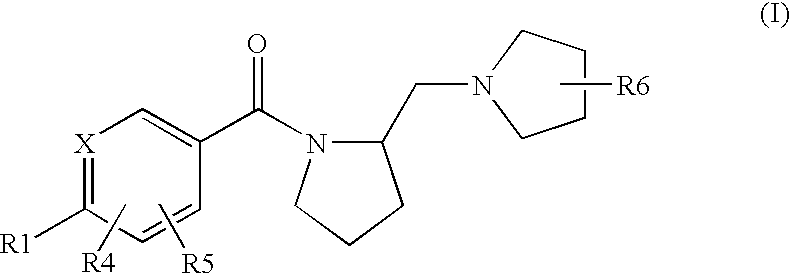
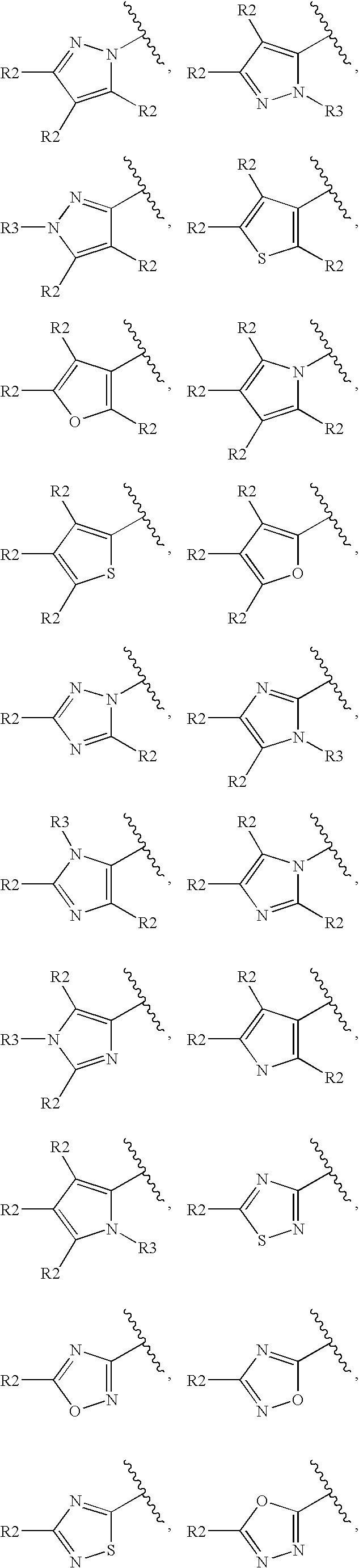
The present invention provides a novel compound of Formula (I) or a pharmaceutically acceptable salt thereof, having histamine-113 receptor antagonist or inverse agonist activity, as well as methods for preparing such compounds. In another, embodiment, the invention discloses pharmaceutical compositions comprising compounds of Formula (I) as well as methods of using them to treat obesity, cognitive deficiencies, narcolepsy, and other histamine H3 receptor-related diseases.
Owner:FINLEY DON RICHARD +5
Continuous ink-jet printing device, with improved print quality and autonomy
A continuous ink-jet printer or a print head of such a printer which includes electrical means for compensating for mechanical crosstalk between adjacent stimulation chambers, where these means simultaneously with the transmission, to a stimulated chamber, of a stimulation pulse on a stimulation line send a pulse for compensating for mechanical crosstalk on each of the lines supplying an actuator for the chamber adjacent to the stimulated chamber. Specific ratios between the peak amplitude of pulse for compensating for crosstalk and the peak voltage value of the stimulation pulse are provided as a function of the gaps between consecutive nozzles.
Owner:MARKEM IMAJE HLDG
Head gimbal assemblies for very low flying height heads with optional micro-actuators in a hard disk drive
InactiveUS7336436B2Change shapeContactElectrical connection between head and armDriving/moving recording headsHard disc driveFlexible circuits
Owner:SAMSUNG ELECTRONICS CO LTD
Compositions And Methods For Lipo Modeling
InactiveUS20090317376A1Conducive to survivalReduce adverse metabolic consequence of obesityBiocidePeptide/protein ingredientsFat graftingNK1 receptor antagonist
Methods for lipomodeling by peripherally administering a modulator of a Y receptor are provided. Methods may comprise reduction of a fat depot by administering a Y receptor antagonist proximally and / or directly to the site of the fat depot. Other methods comprise increasing or stabilizing a fat depot or fat graft by administering a Y receptor agonist proximally and / or directly to the site of the fat depot or fat graft. Also provided are methods for stimulating wound healing by administering a Y receptor agonist proximally to a wound site.
Owner:GEORGETOWN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com