Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Determine authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
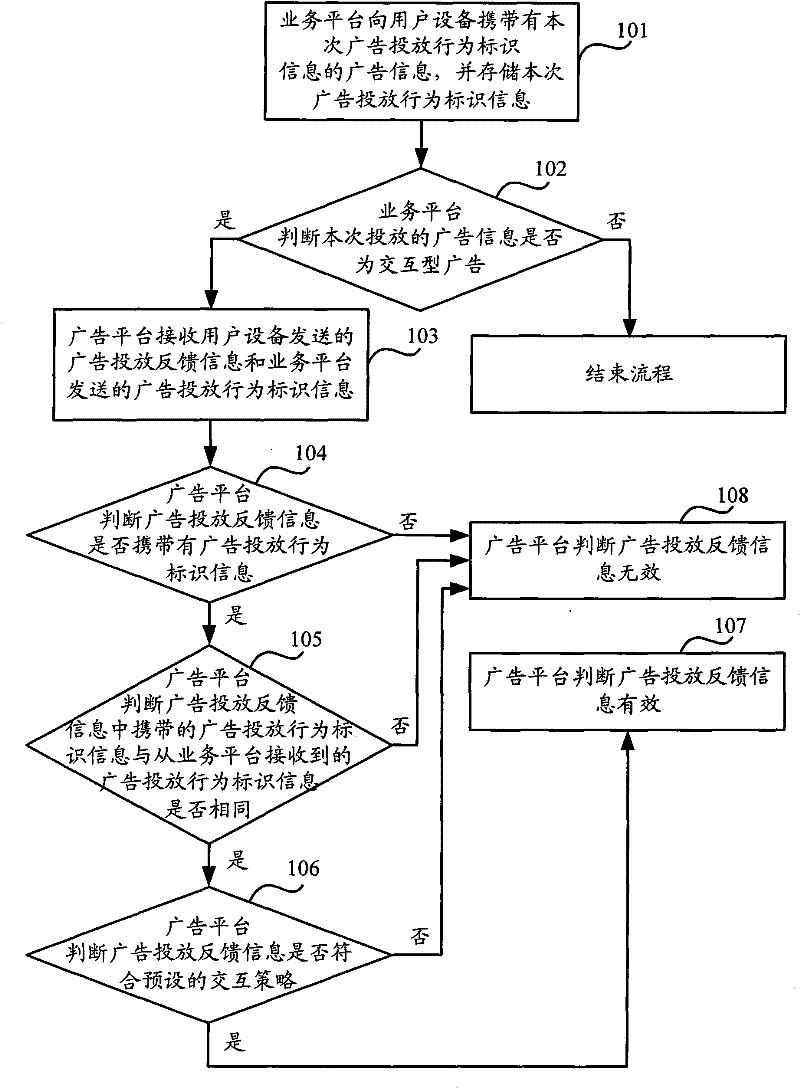
Effectiveness verification method, equipment and system for advertisement feedback information
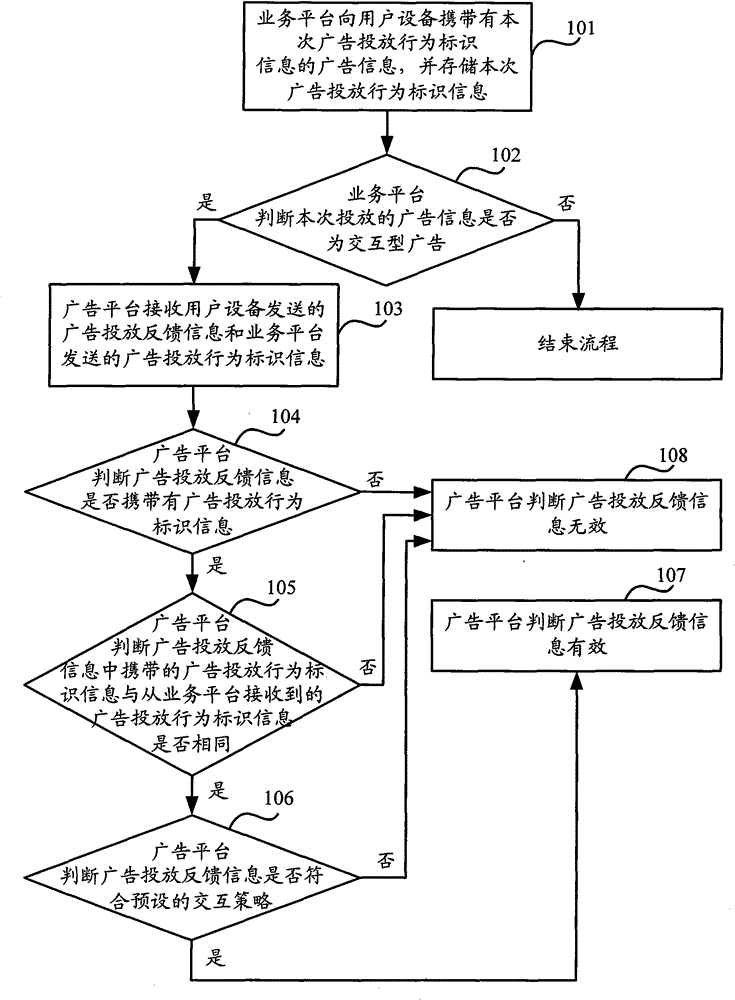
ActiveCN102546972ADetermine authenticitySolve the problem of interactive validity verificationSpecial service for subscribersMessaging/mailboxes/announcementsValidation methodsUser equipment
The invention discloses an effectiveness verification method for advertisement feedback information, equipment and a system. The method comprises the following steps that: a network side publishes advertisement information carrying advertisement behavior identification information to user equipment, and stores the advertisement behavior identification information; and the network side receives the advertisement feedback information from the user equipment, and performs effectiveness verification on the advertisement feedback information according to the advertisement behavior identification information in the advertisement feedback information and the advertisement behavior identification information stored by the network side. By the method, the equipment and the system, the authenticity of the advertisement feedback information can be accurately determined.
Owner:CHINA MOBILE COMM GRP CO LTD
Verification technique for biological statistical identifying system
InactiveCN1410938ADetermine authenticityLow costPerson identificationSensorsComputer scienceRecognition system
Owner:BMF GMBH
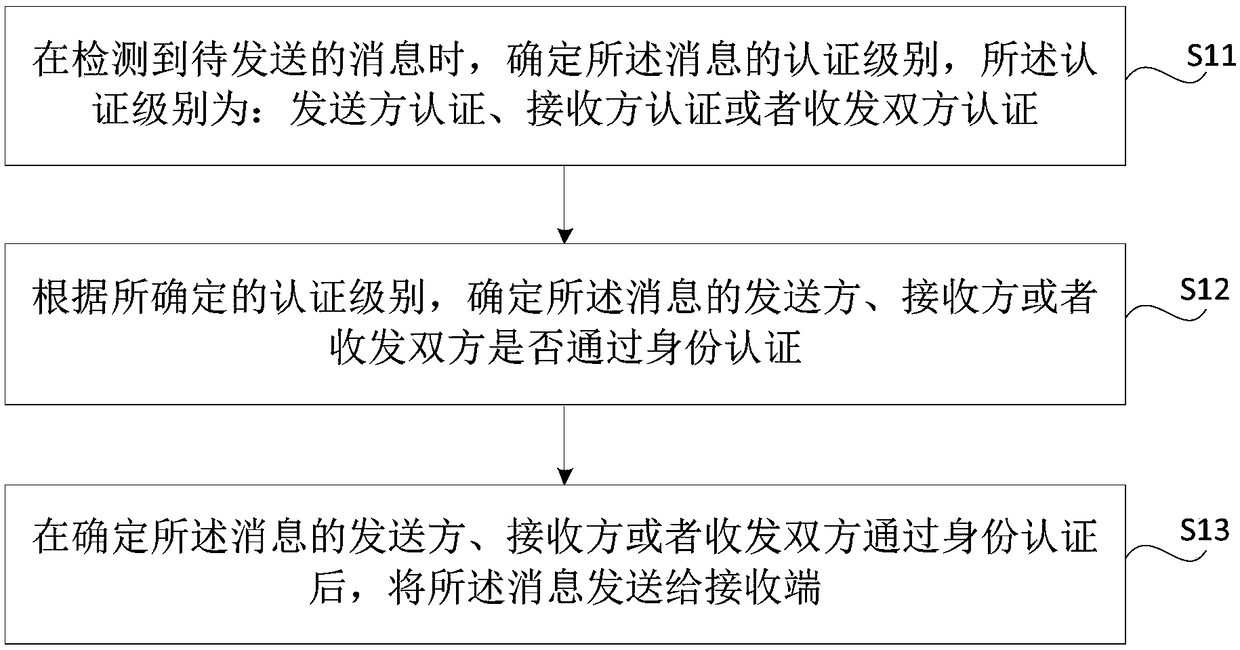
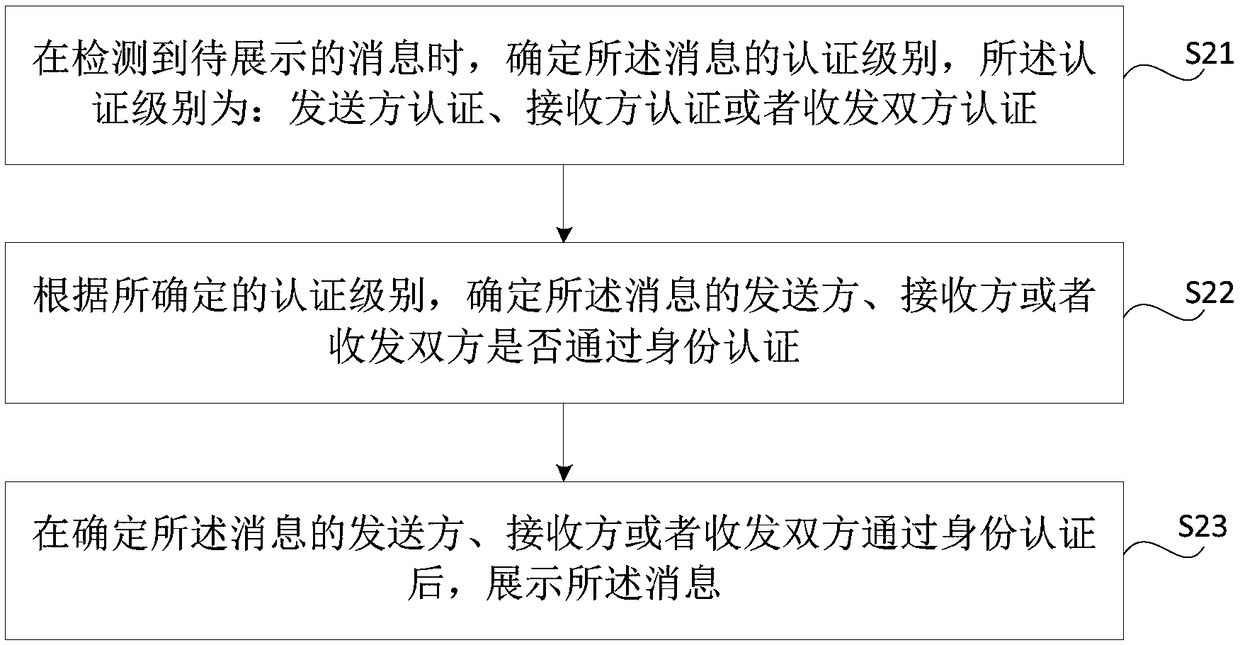
Method and apparatus for sending and presenting message, an identity authentication method and apparatus
ActiveCN109039860ADetermine authenticityAchieve protectionData switching networksInternet privacyAuthentication
The present disclosure relates to a method and apparatus for sending and presenting messages, an identity authentication method and apparatus. By the method provided by the present disclosure, the sender can ensure that only the receiver sees the sent message, thereby ensuring the privacy and security of the sender; In addition, the recipient can determine the authenticity of the received messageand avoid being harmed by the false message.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
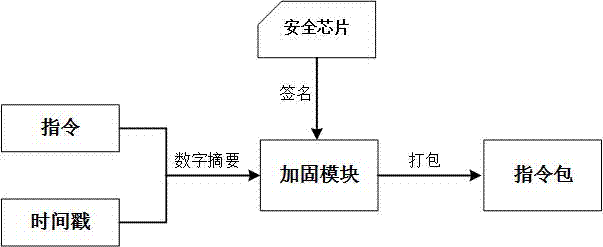
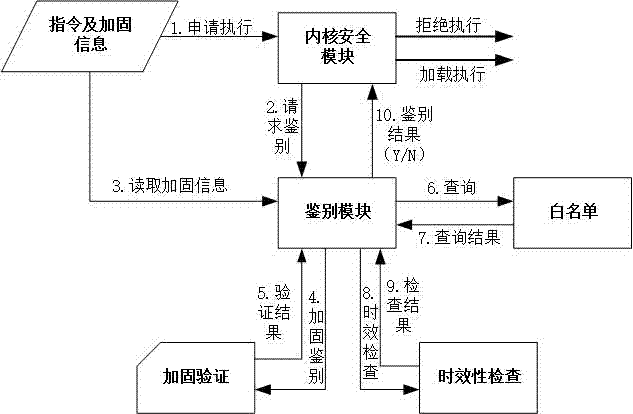
Instruction reinforcing and discriminating method and system for unmanned plane
InactiveCN107154854AEnsure intelligenceDetermine authenticityPublic key for secure communicationUser identity/authority verificationTime rangeTimestamp
The invention discloses an instruction reinforcing and discriminating method and system for an unmanned plane. During the implementation of instruction reinforcing, the method comprises a step of instruction reinforcing: reinforcing the instruction through the identification secret key of an instruction sender when the instruction sender sends an instruction to an opposite side, packaging the instruction and reinforcing data, and transmitting the package to the opposite side; a step of instruction discriminating which comprises the substeps: (1), enabling an instruction receiving side to receive the instruction and the reinforcing data, verifying the authenticity of the instruction reinforcing information, and switching to a substep (2) if the verification is passed; (2), obtaining the identification of the instruction sender and an instruction timestamp from the reinforcing data, and verifying whether the identification of the instruction sender is valid or not and whether the instruction is in an allowed time range or not: executing the instruction if the verification is passed, or else refusing the execution. The instruction reinforcing and discriminating is based on a combined public key system and a national commercial password algorithm SM9. The method achieves a purpose that the unmanned plane carries out the verification of the validity of a remote instruction, and can effectively prevents a hacker from attacking the unmanned plane.
Owner:李维刚 +1
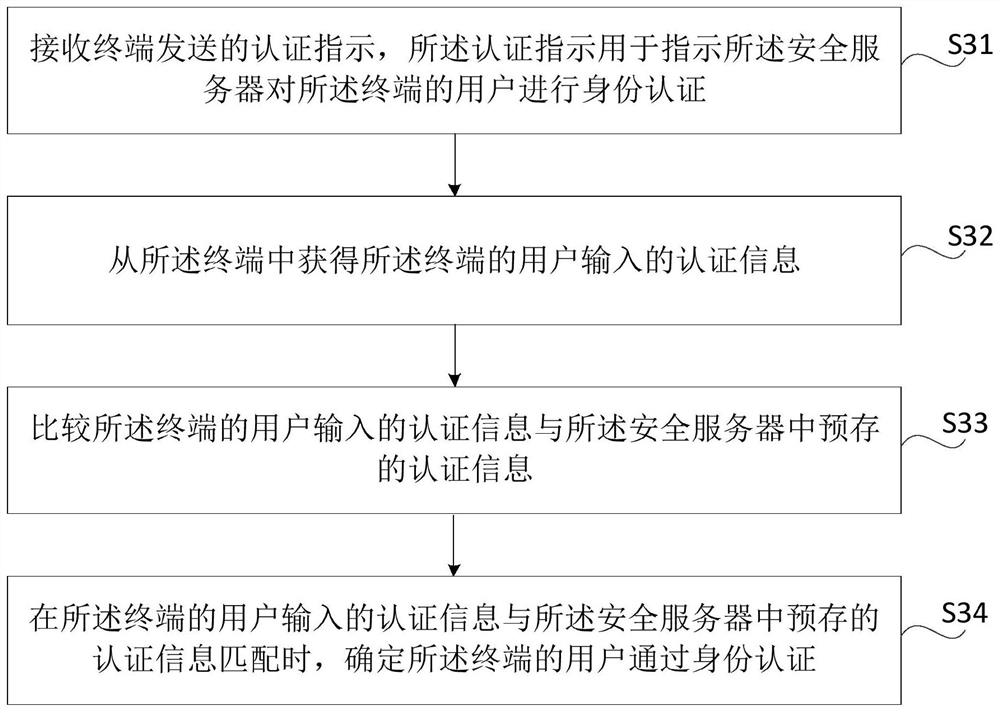
Face recognition payment information anti-counterfeiting method combined with spatial information
ActiveCN109285008ADetermine authenticityPrevent counterfeitingProtocol authorisationPaymentEntry Level
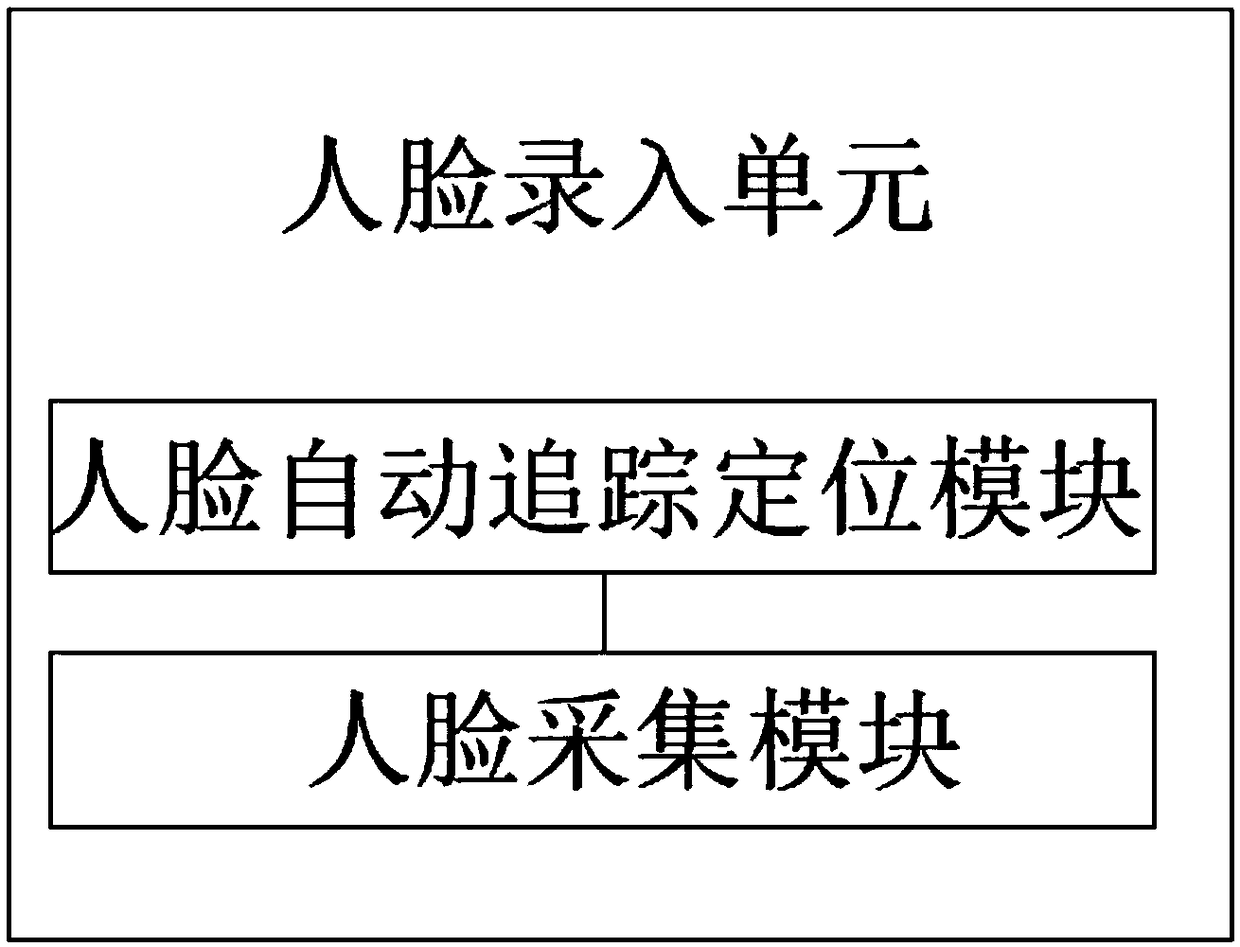
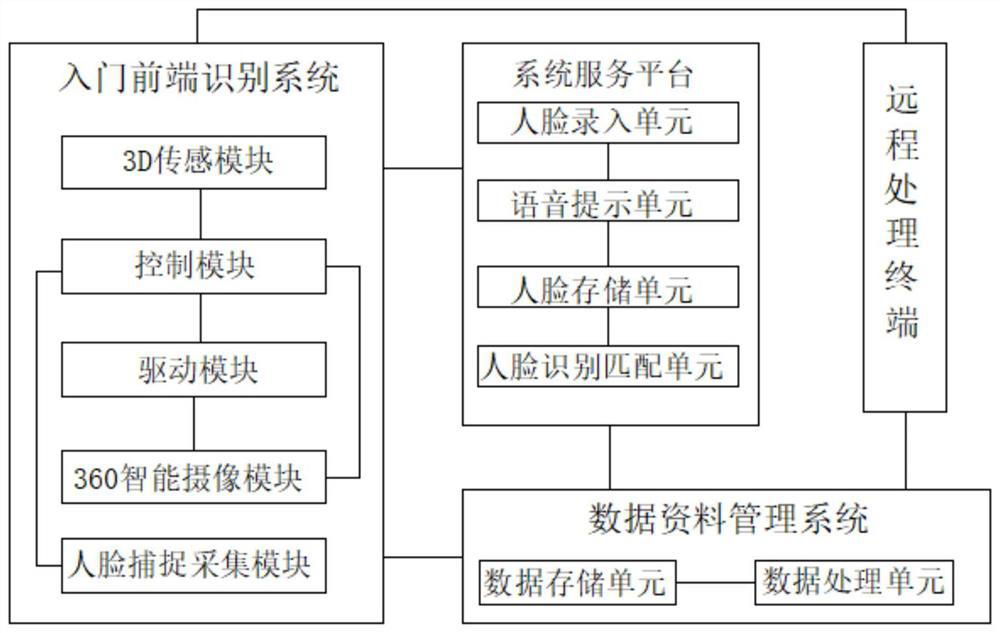
The invention discloses a face recognition payment information anti-counterfeiting method combined with spatial information, including an entry-level front-end identification, a system service platform, a remote processing terminal and a data management systems. The entry-level front-end recognition system comprises a 3D sensing module, a control module, a driving module, a 360 intelligent cameramodule and a face capture and collection module. The system service platform comprises a face input unit, a voice prompt unit, a face storage unit, a face recognition matching unit and a data feedbackunit. At that time of face recognition payment, the invention carry out multiple real face recognition confirmation. The invention not only prevents the payer from borrowing the false model face forpayment, but also combines the spatial information of the payer user entry front end with the current paid face for recognition, improves the anti-counterfeiting function of the face during payment, and ensures the security of the account, which is suitable for popularization and use.
Owner:珠海横琴井通容智科技信息有限公司
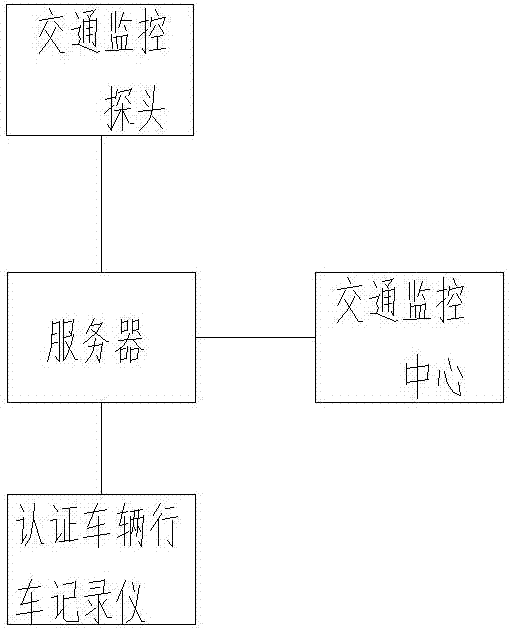
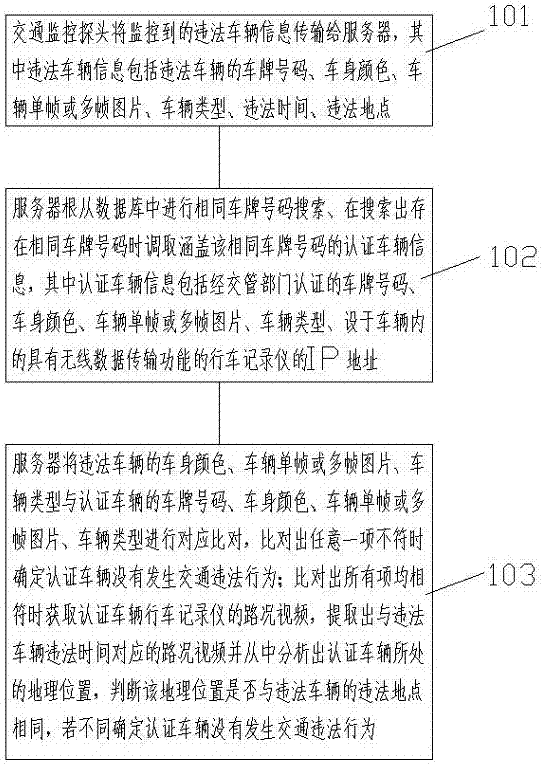
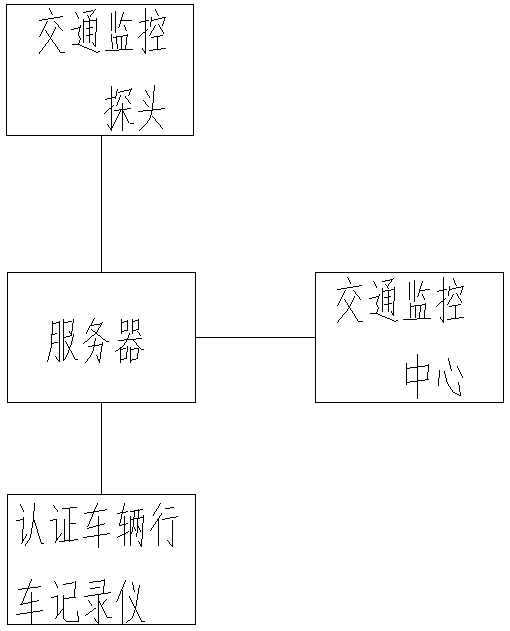
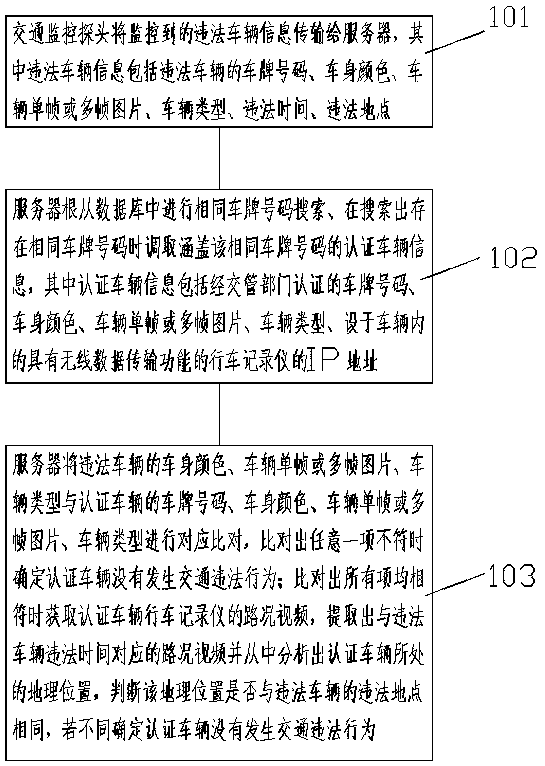
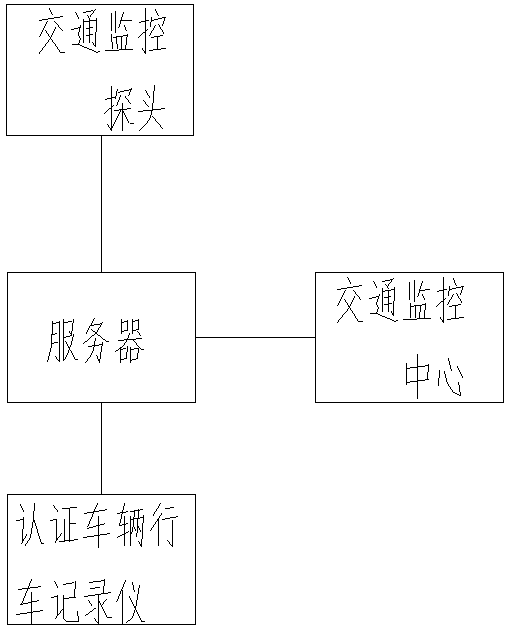
Vehicle traffic illegal behavior authenticity detection method
ActiveCN106960574AEfficient analysisDetermine authenticityRoad vehicles traffic controlMultiple frameGeolocation
A vehicle traffic illegal behavior authenticity detection method comprises the following steps: allowing a traffic monitor probe to transmit monitored illegal vehicle information to a server; allowing the server to search the same license plate number in a database, and invoking the authentication vehicle information containing the license plate number; allowing the server to compare the illegal vehicle color, vehicle single frame or multi-frame image, and vehicle type with the authentication vehicle license plate number, vehicle color, vehicle single frame or multi-frame image, and vehicle type, and considering the authentication vehicle to have no traffic illegal behavior if one of said compared items does not comply; obtaining the road condition video of an authentication vehicle data recorder when all said compared items comply, extracting the road condition video corresponding to the illegal vehicle illegal time, parsing the authentication vehicle located geography position from the video, determining whether the geography position is same with the illegal vehicle illegal position or not, and if not, determining the authentication vehicle to have no traffic illegal behavior.
Owner:上海工业控制安全创新科技有限公司
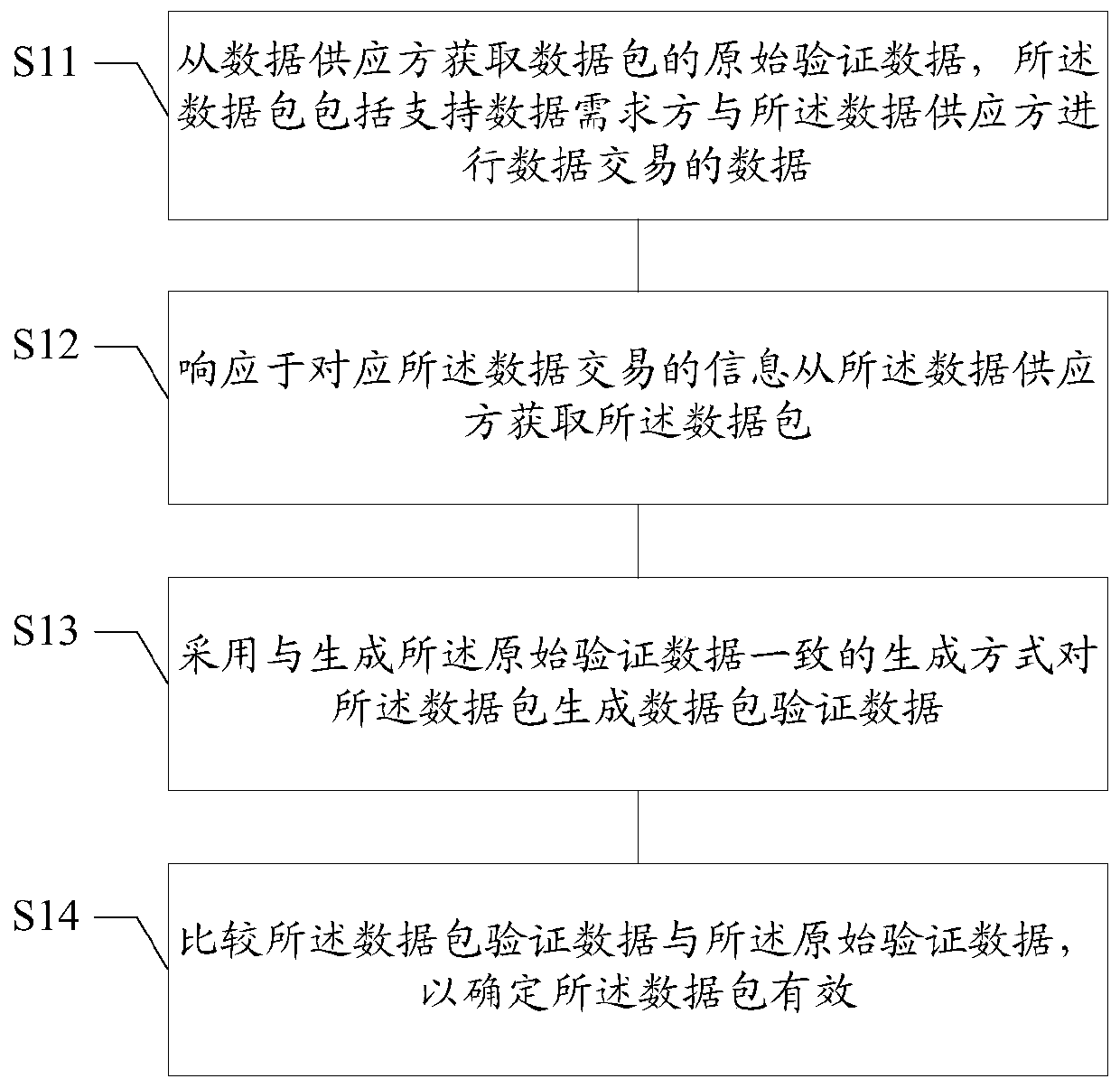
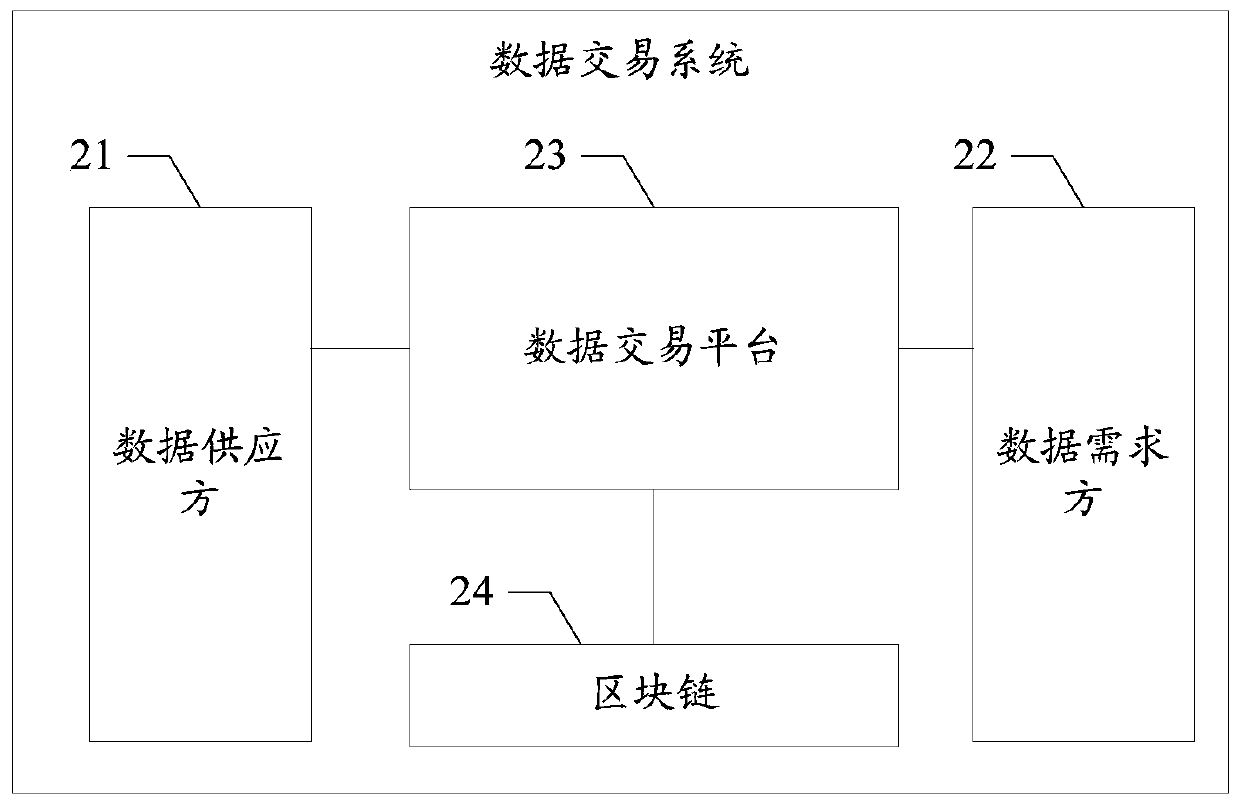
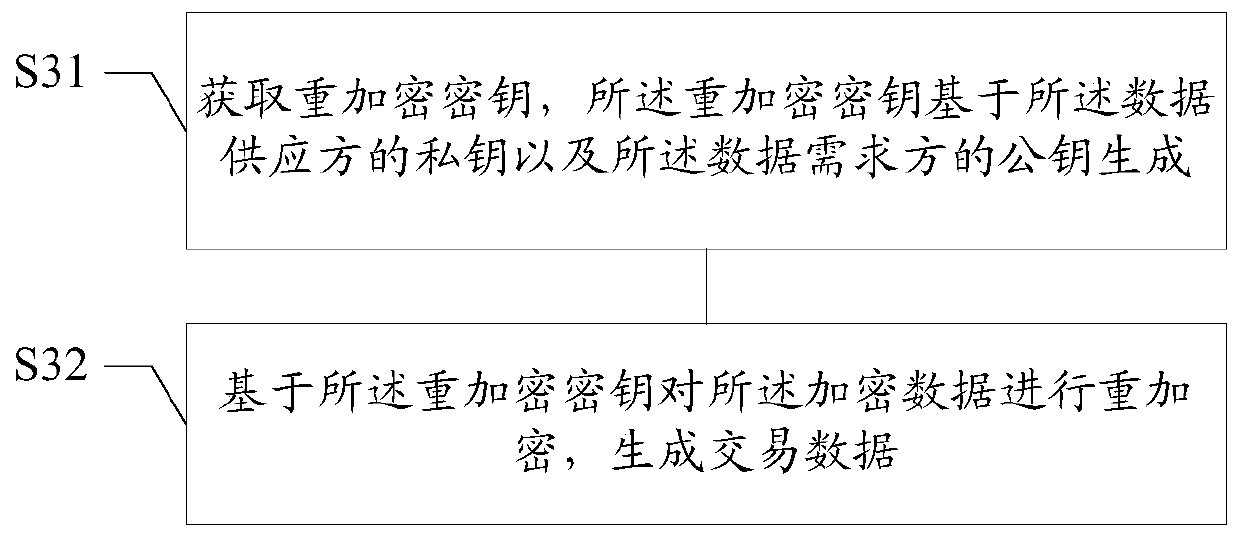
Data processing method and device, medium and terminal
InactiveCN109816525AMeet data requirementsImprove experienceFinancePayment protocolsNetwork packetData provider
The embodiment of the invention discloses a data processing method and device, a medium and a terminal, and the method comprises the steps: obtaining the original verification data of a data packet from a data supplier, and enabling the data packet to comprise the data supporting the data transaction between a data demander and the data supplier; obtaining the data packet from the data provider inresponse to information corresponding to the data transaction; generating data packet verification data for the data packet by adopting a generation mode consistent with that of the generated original verification data; And comparing the data packet verification data with the original verification data to determine that the data packet is valid. According to the technical scheme provided by the embodiment of the invention, the security of data transaction can be improved.
Owner:石更箭数据科技(上海)有限公司
Rotating printing unit for a machine of the tobacco processing industry
InactiveCN1575670AShorten speedUniform printingCigarette manufactureTypewritersEngineeringMechanical engineering
This invention relates to the process and the devices (23, 230) for applying print marks along the conveying direction by printing elements (70, 170) on the articles (21, 210.1, 210.2; 90) conveyed in a predetermined conveyor speed of the tobacco processing industry, in particular wrapping strips (21, 210.1, 210.2), preferably cigarette paper strips or a rod-shaped smoking article (90). The method is realized by reduction of a relative speed between the printing elements (70, 170) and the articles (21, 210.1, 210.2; 90) to be printed in the printing process along the conveying direction. The invention relates to a machine in the tobacco processing industry, in particular cigarette rod forming machine or a filter installing machine.
Owner:HAUNI MASCHINENBAU AG
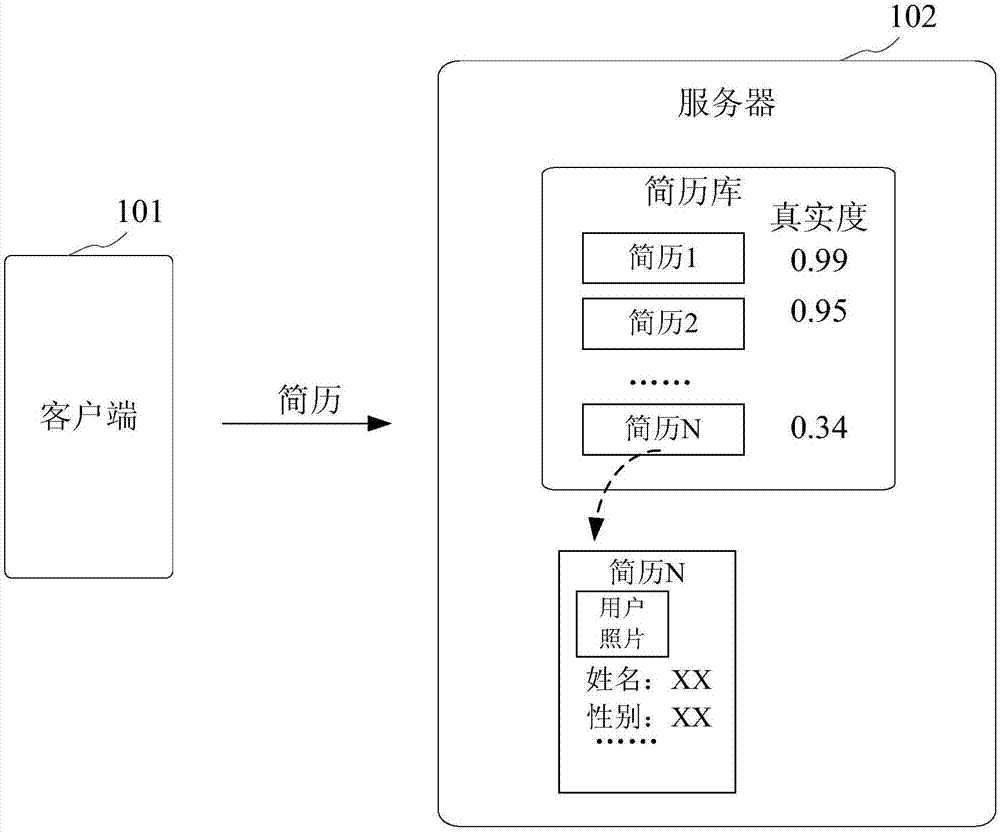
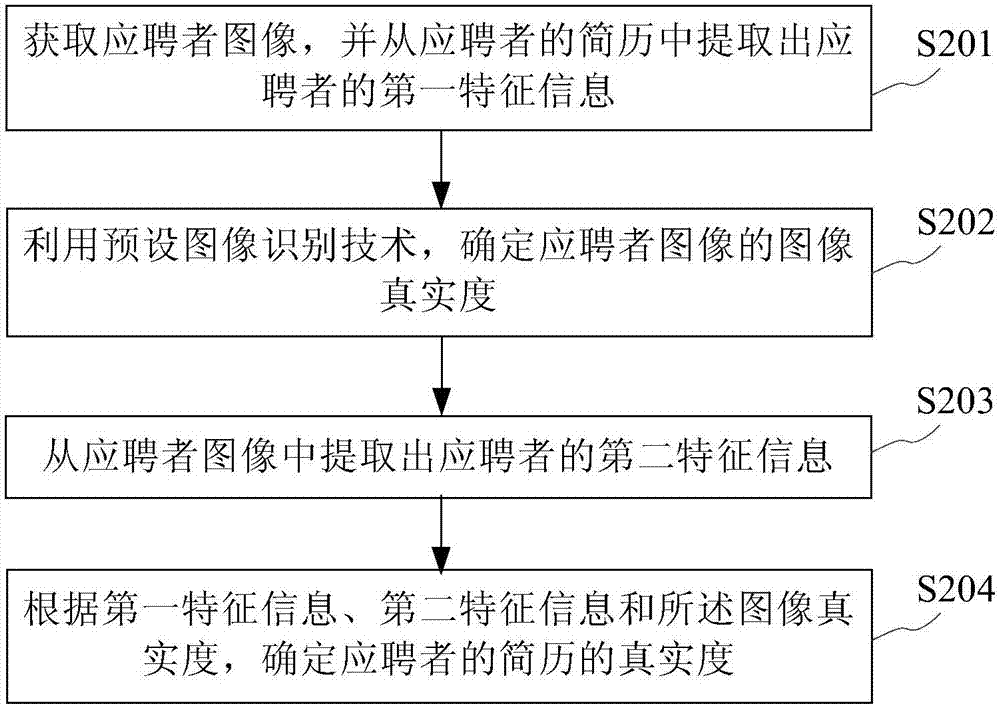
Resume validity detection method and device
InactiveCN107480582ADetermine authenticityImprove efficiencyCharacter and pattern recognitionSpecial data processing applicationsPattern recognitionImage identification
The embodiment of the invention provides a resume validity detection method and device; the method comprises the following steps: obtaining an applicant image and extracting applicant first characteristic information from the applicant resume; using a preset image identification technology to determine the applicant image validity, and extracting applicant second characteristic information from the applicant image; determining the applicant resume validity according to the first characteristic information, the second characteristic information and the image validity. The method and device can improve the resume validity detection efficiency and accuracy.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
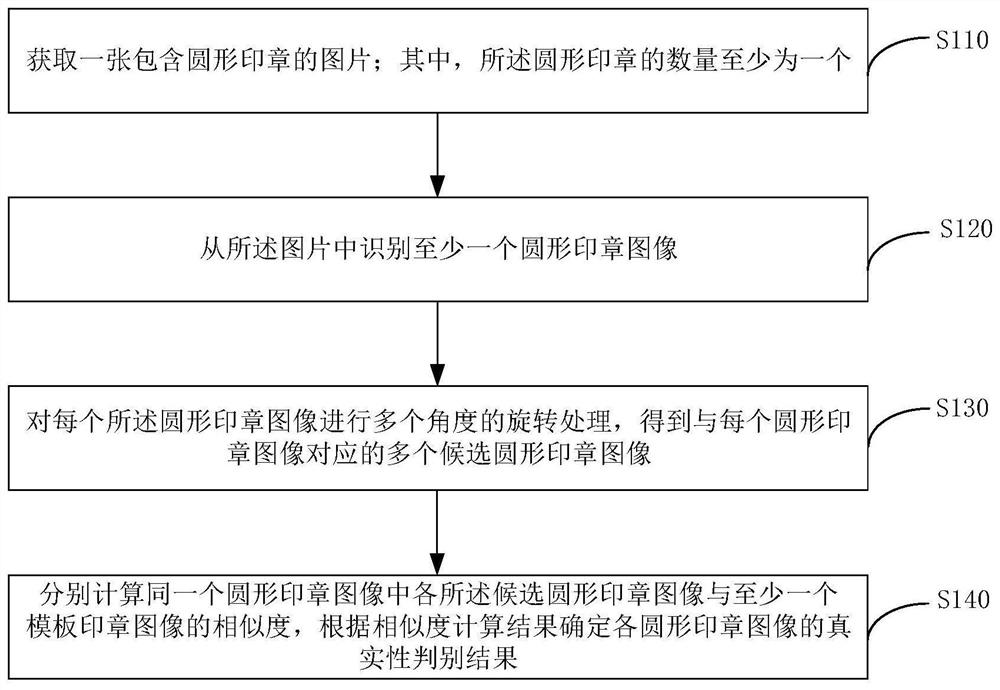
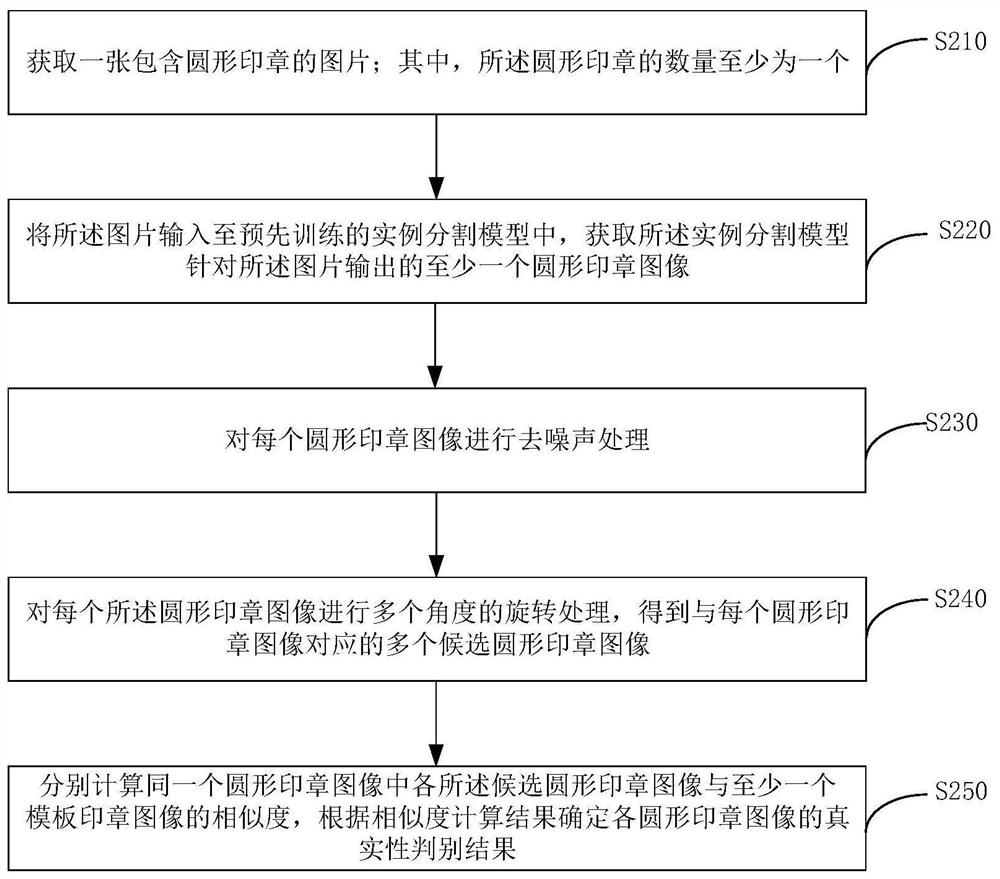
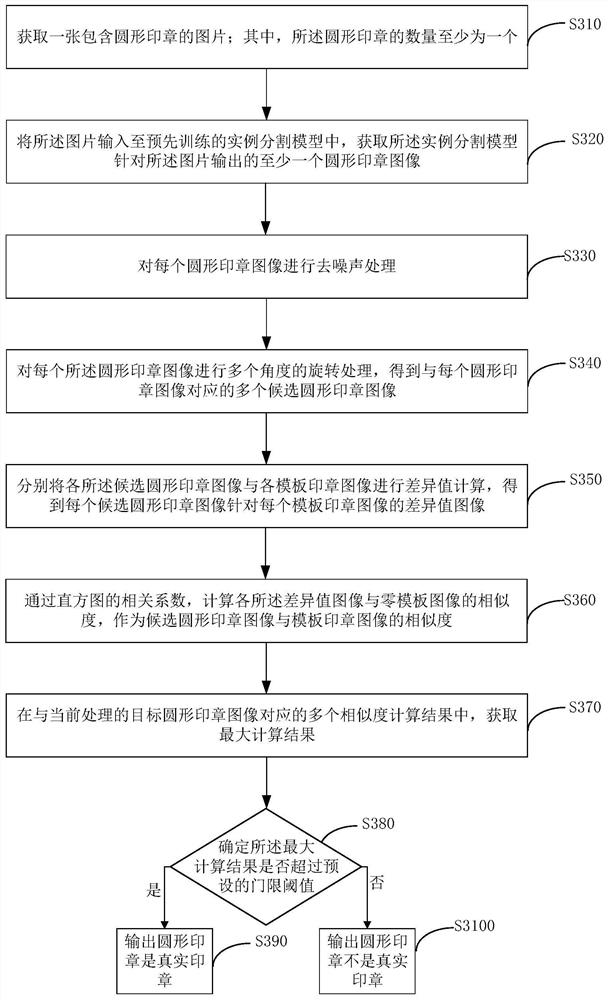
Round seal authenticity identification method and device, electronic equipment and storage medium
PendingCN112784835ADetermine authenticityImprove recognition accuracyCharacter and pattern recognitionNeural architecturesEngineeringImage pair
The embodiment of the invention discloses a round seal authenticity identification method and device, electronic equipment and a storage medium. The method comprises: acquiring a picture containing a circular seal, wherein the number of the circular seal is at least one; identifying at least one circular seal image from the picture; performing multi-angle rotation processing on each circular seal image to obtain a plurality of candidate circular seal images corresponding to each circular seal image; and respectively calculating the similarity between each candidate circular seal image in the same circular seal image and at least one template seal image, and determining the authenticity judgment result of each circular seal image according to the similarity calculation result, so that the authenticity of the circular seal can be determined, and the identification accuracy of the circular seal can be improved.
Owner:EVERSEC BEIJING TECH
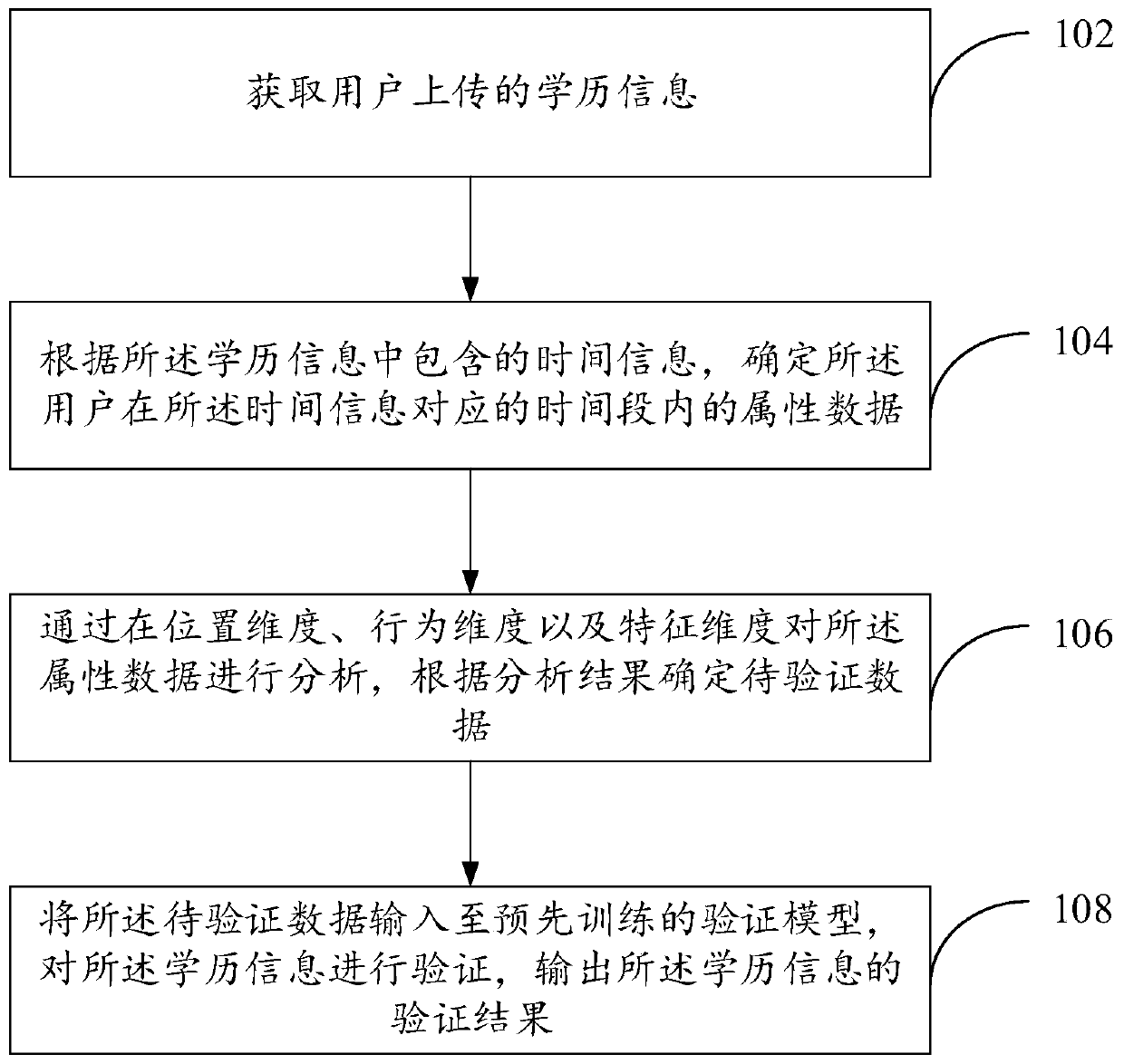
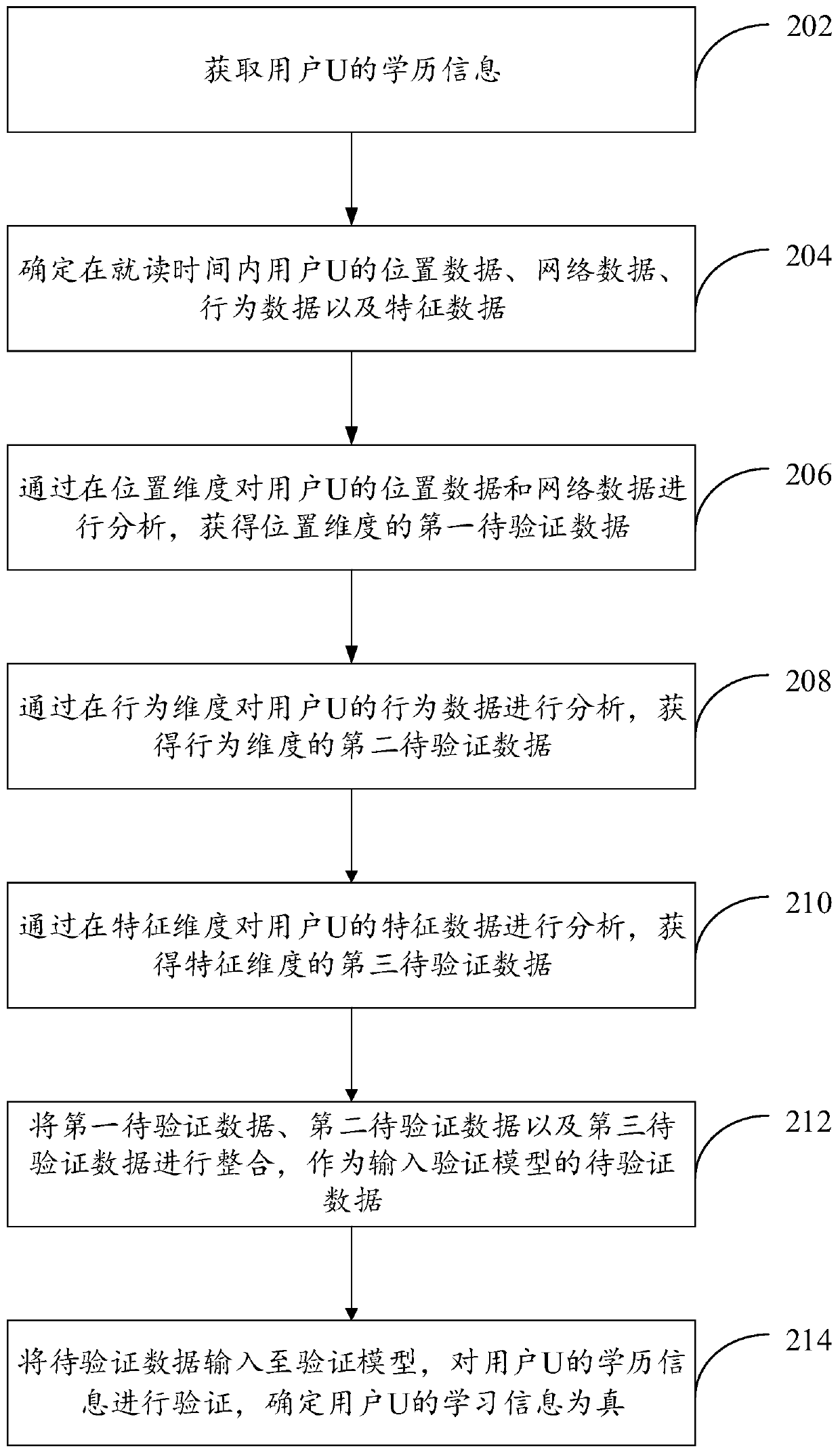
Education background information verification method and device
PendingCN110569418ADetermine authenticityImprove accuracyData processing applicationsCharacter and pattern recognitionTemporal informationFeature Dimension
The invention provides an education background information verification method and device. The education background information verification method comprises the steps of obtaining education background information uploaded by a user; determining attribute data of the user in a time period corresponding to time information according to the time information contained in the education background information; analyzing the attribute data in a position dimension, a behavior dimension and a feature dimension, and determining to-be-verified data according to an analysis result; and inputting the to-be-verified data into a pre-trained verification model, verifying the education background information, and outputting a verification result of the education background information. By means of the education information verification method, the to-be-audited data of the user is determined in different dimensions according to the education information uploaded by the user, and the education information uploaded by the user is verified in combination with the verification model, so that the education information uploaded by the user is verified in a short time, and the accuracy of a verificationresult for verifying the education information is guaranteed.
Owner:ADVANCED NEW TECH CO LTD
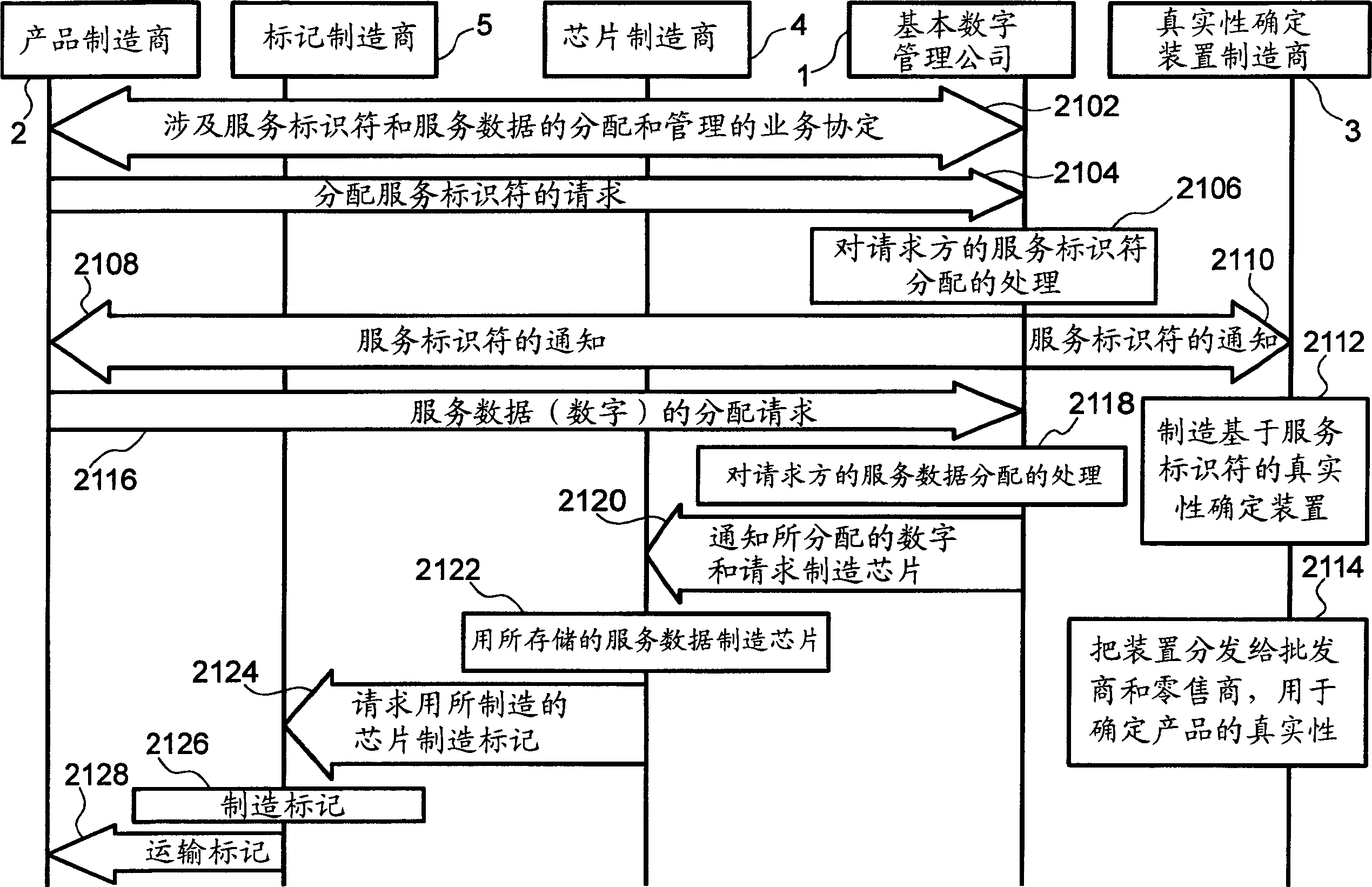
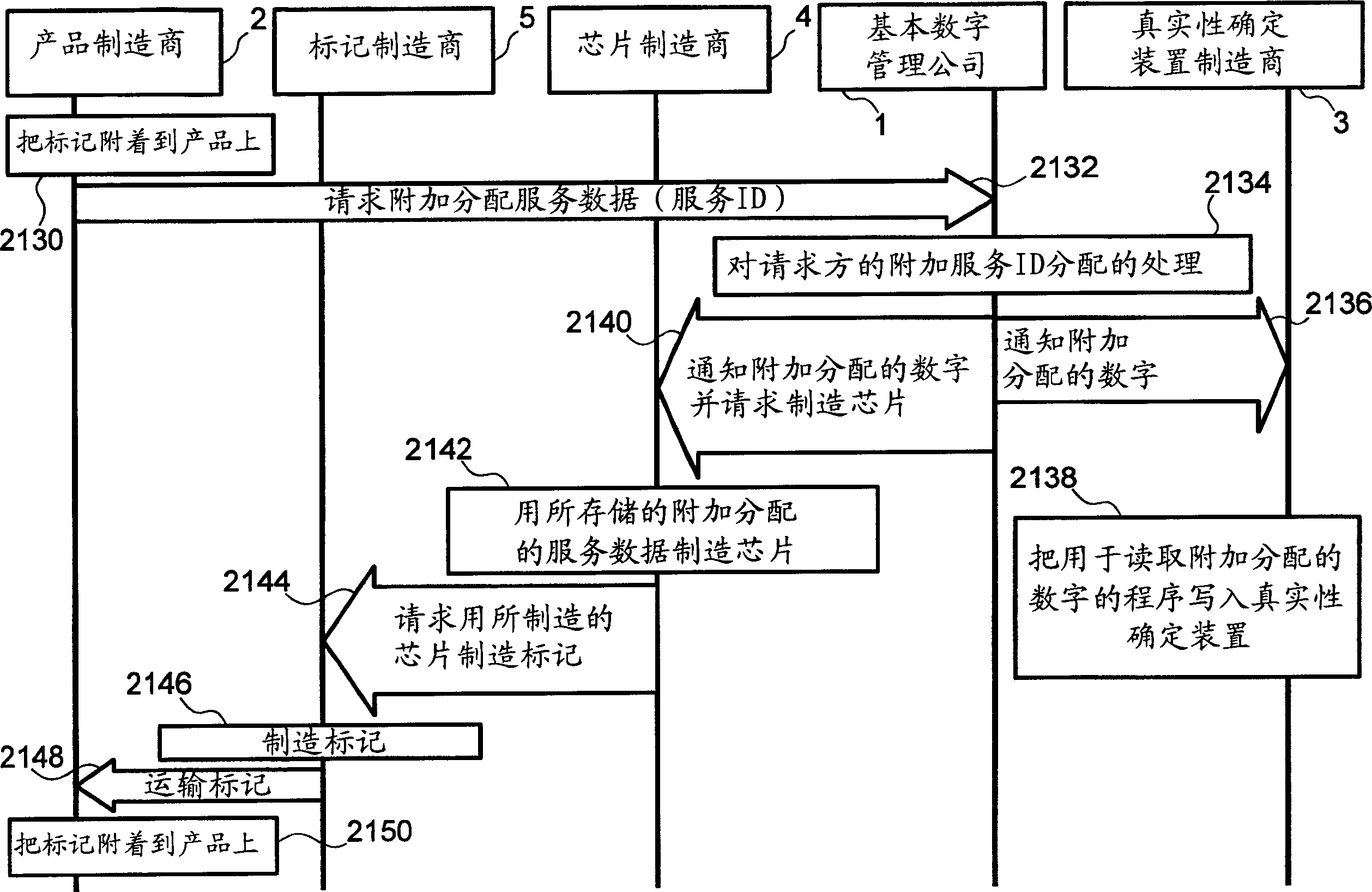
Radio-frequency identification mark and related deterministic device and method, and management system and method
InactiveCN1444177ASuitable for determining authenticityDetermine authenticityCo-operative working arrangementsCharacter and pattern recognitionInformation processingData set
The present invention provides an RFID (Radio Frequency Identification) tag structure suitable for determining the authenticity of goods or parts, and also provides an information processing system for reading RFID tags that can accurately perform read-only RFID tags Authenticity determination of goods or components. A plurality of RFID tags are designed to have a service identifier and service data as tag information, each RFID tag holds tag information in a ROM (Read Only Memory), and responds to tag information via radio waves upon receiving radio waves from a reader, The service identifier designates a common utilization target with the same value, and the service data sets different values for each RFID tag. Then, by dividing the data structure of an RFID tag with a read-only memory into a service identifier and serial data, it is possible to confirm that the commodity is genuine by simply confirming the service identifier, which is common to a certain commodity, and the serial Data is used to manage individual products.
Owner:HITACHI LTD
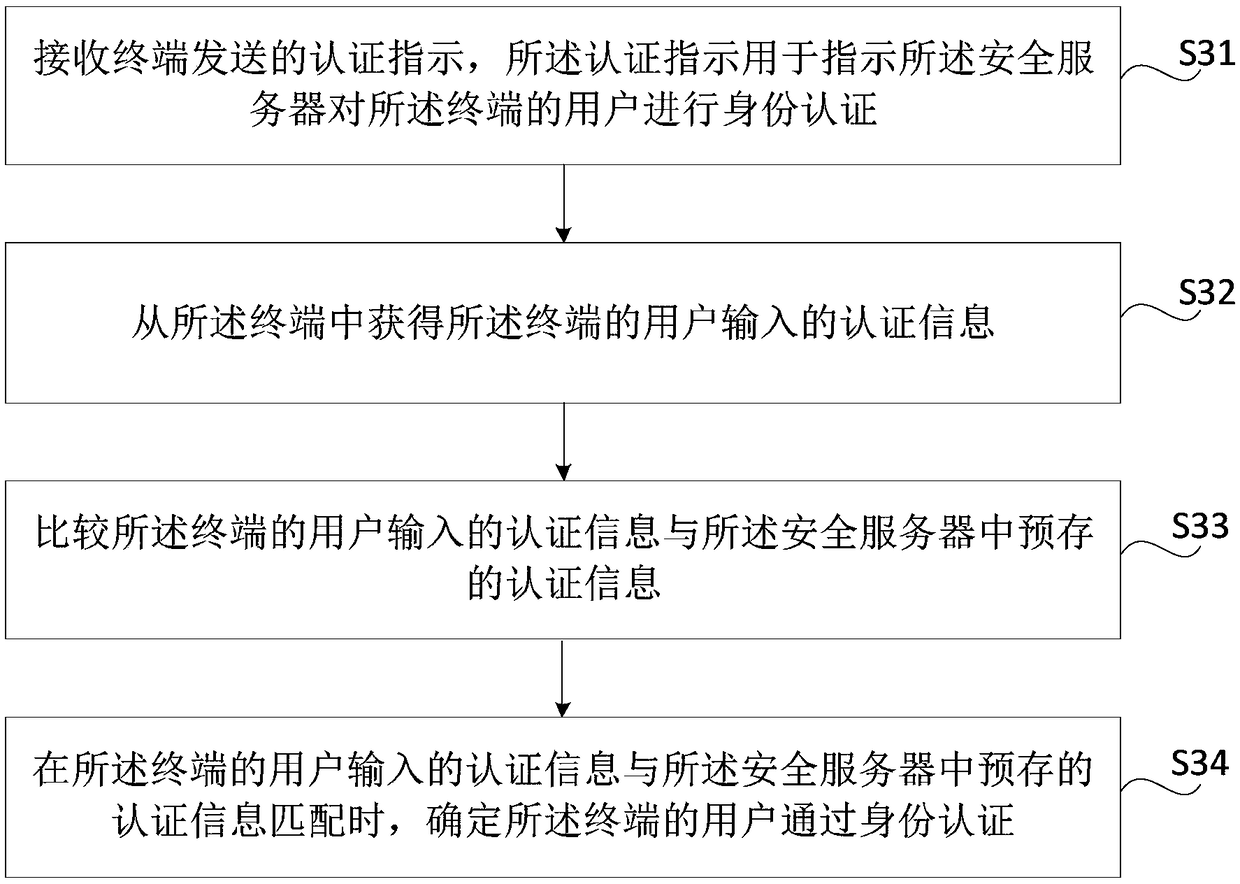
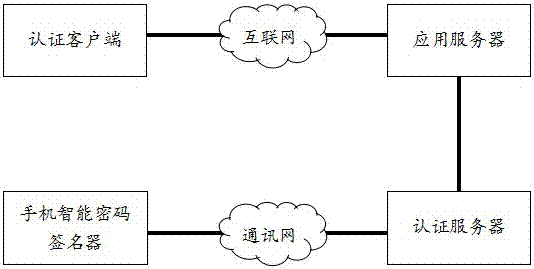
Intelligent password signature identity authentication method and system
ActiveCN106921501ADetermine authenticityDetermining non-repudiationMultiple keys/algorithms usageUser identity/authority verificationApplication serverPassword
The invention relates to an intelligent password signature identity authentication method and system, and is a method and system for preventing identity counterfeiting and identity denying. The method and system include a mobile phone intelligent password signature device, a communication network, an authentication server, an authentication client, an internet and an application server, and the operating steps of the method and system include a step of mobile phone intelligent password signature device operation, a step of rule key operation, a step of rule key signature calculation algorithm operation, and a step of performing identity authentication through the rule key and a calculation signature-converted intelligent password of a mobile phone intelligent password signature device. By adoption of the intelligent password signature identity authentication method and system, a signature is calculated through the rule key and a mobile phone intelligent password signature device dynamic password to perform identity authentication, thereby ensuring uniqueness and undeniability of user identity, and realizing true and reliable identity authentication security and system security.
Owner:BEIJING PASSWORD TECH
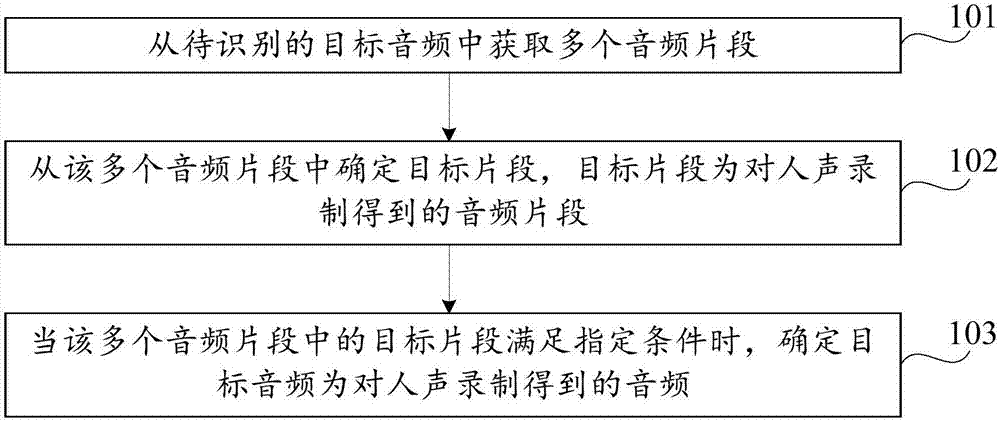
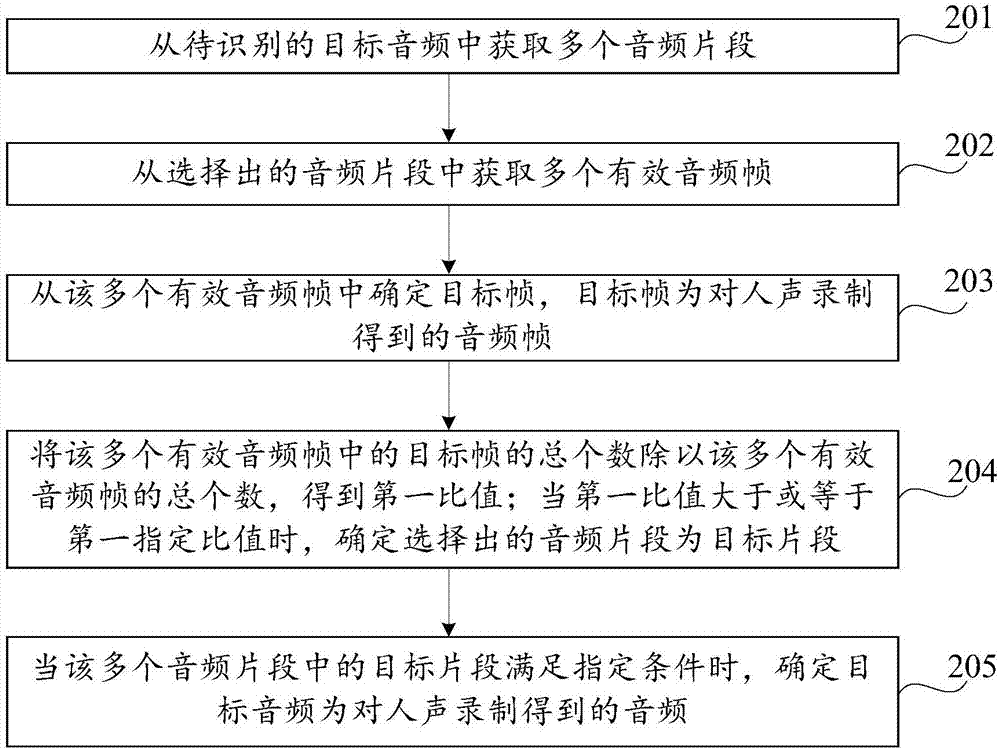
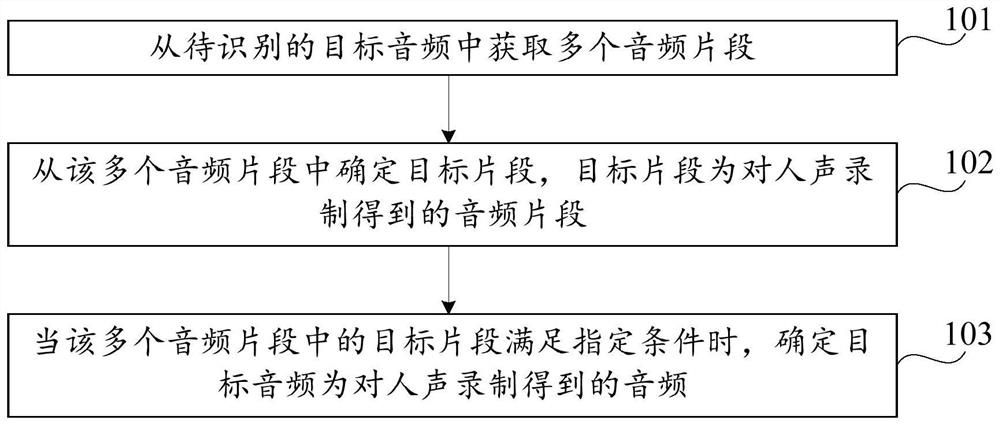
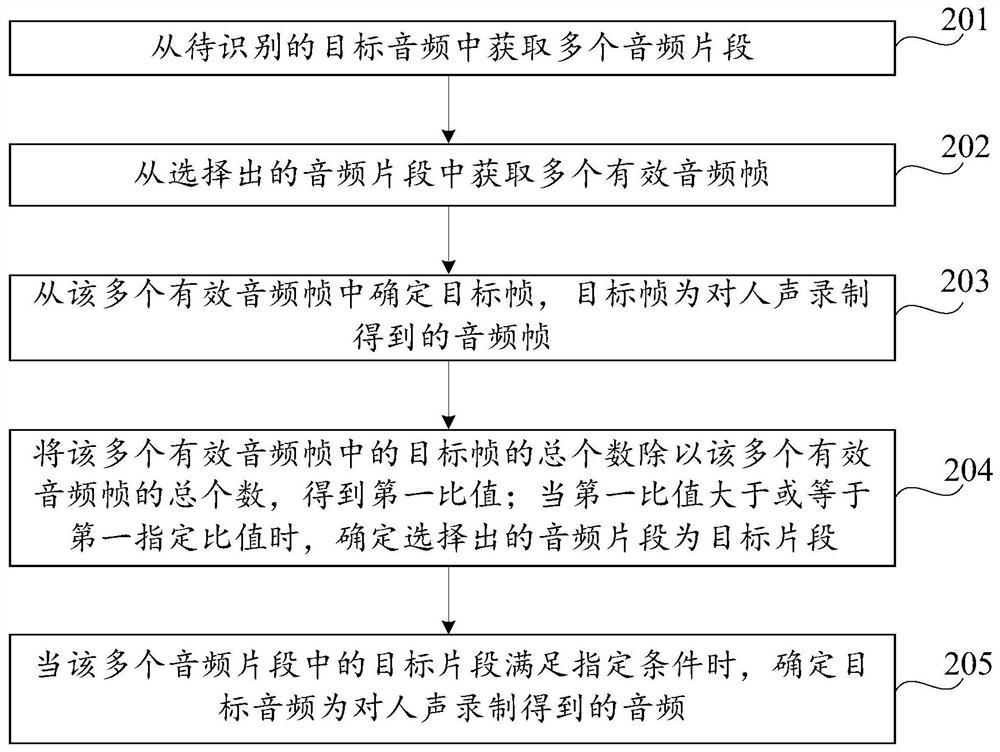
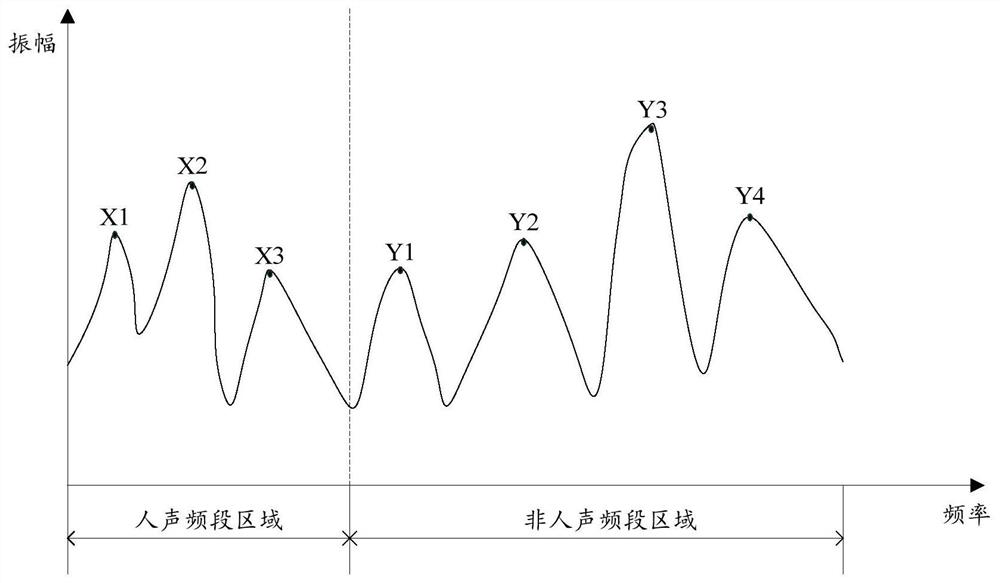
Audio recognition method and device and computer storage medium
ActiveCN107886956ADetermine authenticitySpeech analysisSpecial data processing applicationsAudio recognitionVocal sound
The invention discloses an audio recognition method and device and a computer storage medium, belonging to the technical field of electronics. The method includes the following steps: acquiring a plurality of audio segments from a target audio to be recognized; determining a target fragment from the audio segments, wherein the target fragment is an audio fragment obtained by recording human voice;and if the target fragment in the audio segments satisfies a specified condition, determining that the target audio is an audio obtained by recording human voice. Through analysis of the audio fragments in the target audio, whether the target audio is an audio obtained by recording human voice can be accurately recognized, and the authenticity of the target audio can be determined.
Owner:GUANGZHOU KUGOU COMP TECH CO LTD
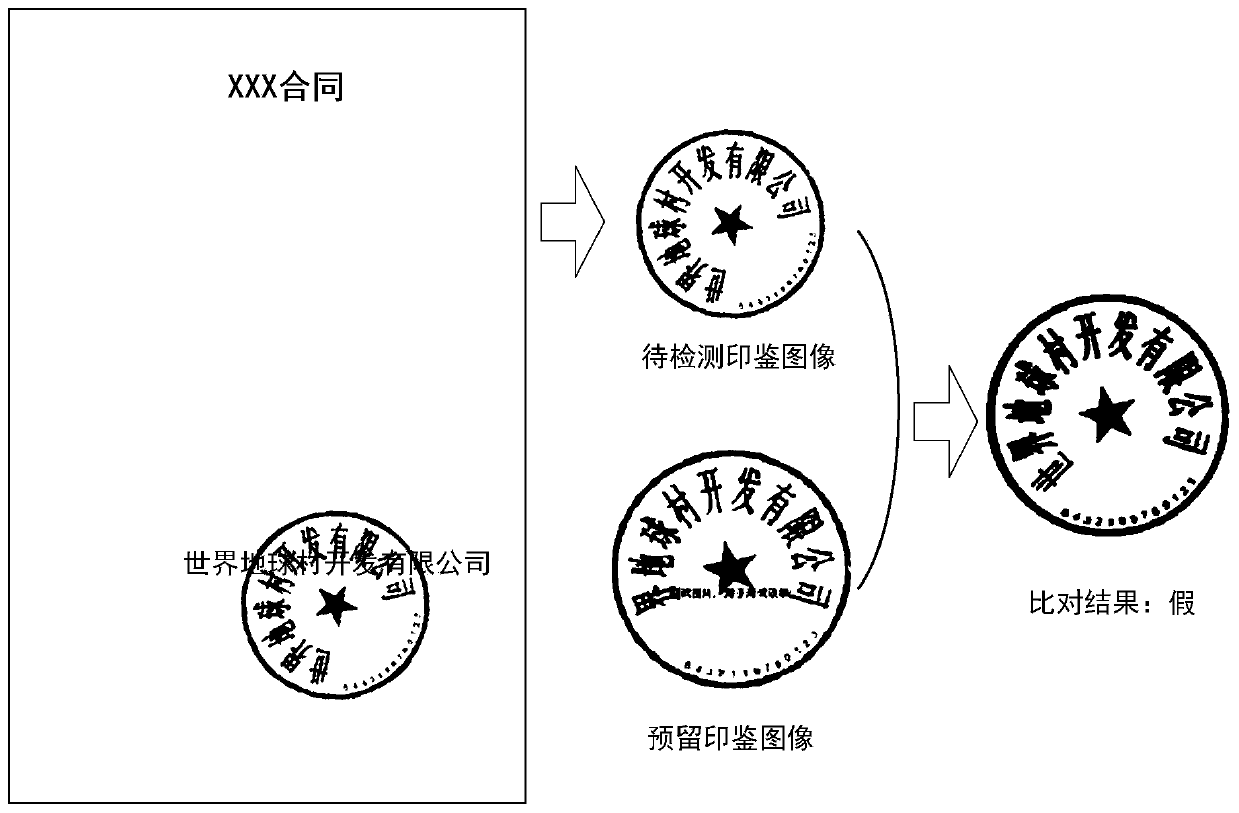
Image comparison method, image comparison device, electronic equipment and medium
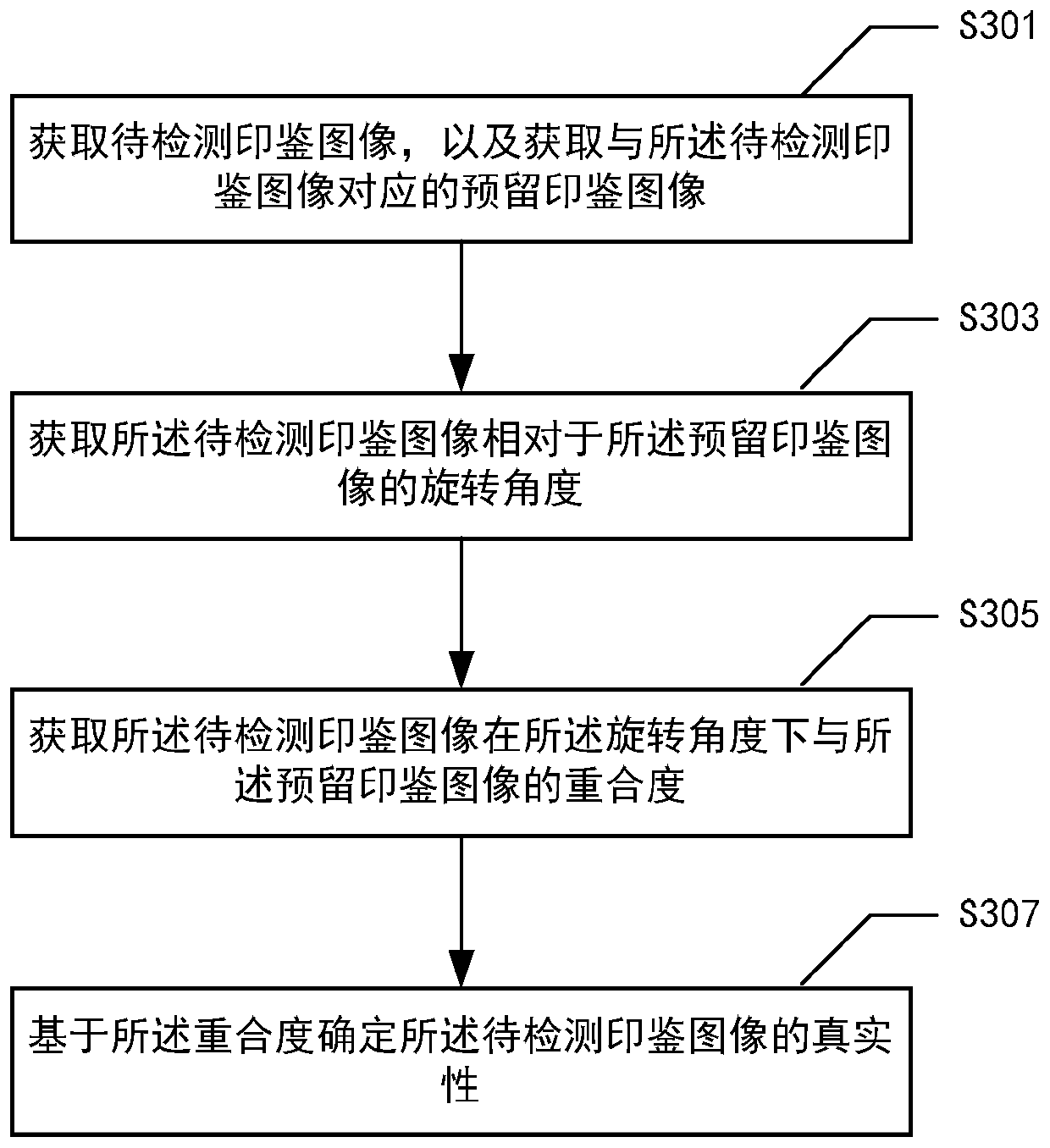
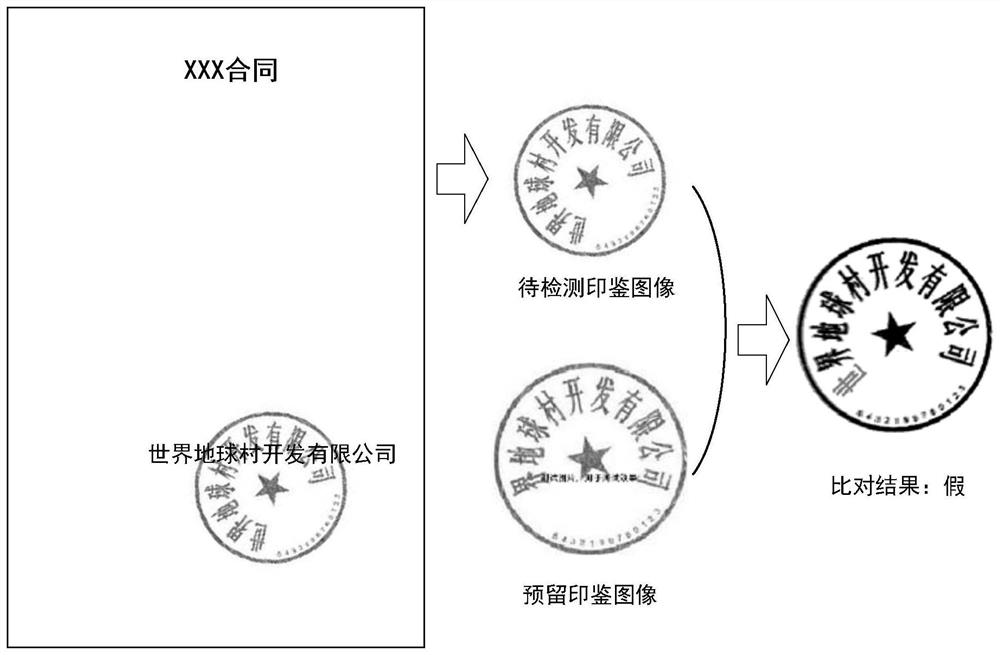
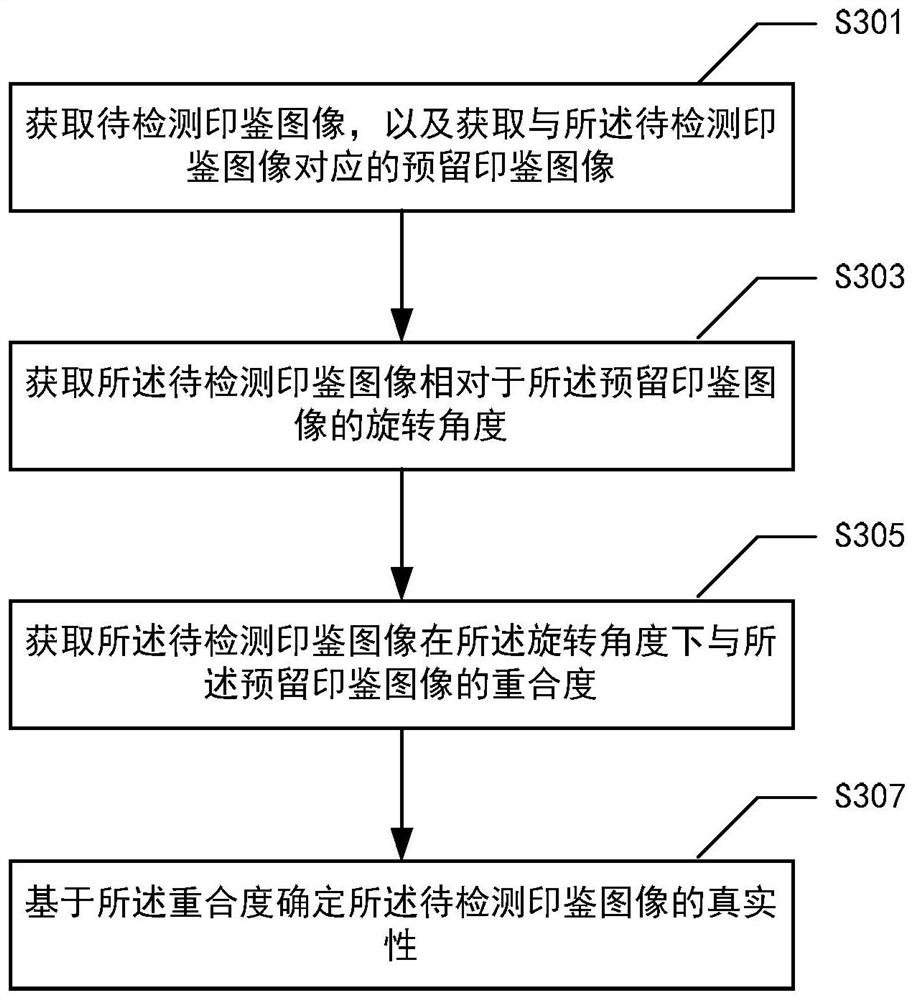
ActiveCN110378886ADetermine authenticityImage analysisCharacter and pattern recognitionOverlap ratioElectronic equipment
The invention provides an image comparison method, an image comparison device, electronic equipment and a medium. The image comparison method comprises the steps of acquiring a to-be-detected seal image, and acquiring a reserved seal image corresponding to the to-be-detected seal image; obtaining a rotation angle of the to-be-detected seal image relative to the reserved seal image; obtaining the overlap ratio of the to-be-detected seal image and the reserved seal image under the rotation angle; and determining the authenticity of the to-be-detected seal image based on the overlap ratio.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
A method, device and system for verifying the validity of advertising feedback information
ActiveCN102546972BDetermine authenticitySolve the problem of interactive validity verificationSpecial service for subscribersMessaging/mailboxes/announcementsValidation methodsUser equipment
The invention discloses an effectiveness verification method for advertisement feedback information, equipment and a system. The method comprises the following steps that: a network side publishes advertisement information carrying advertisement behavior identification information to user equipment, and stores the advertisement behavior identification information; and the network side receives the advertisement feedback information from the user equipment, and performs effectiveness verification on the advertisement feedback information according to the advertisement behavior identification information in the advertisement feedback information and the advertisement behavior identification information stored by the network side. By the method, the equipment and the system, the authenticity of the advertisement feedback information can be accurately determined.
Owner:CHINA MOBILE COMM GRP CO LTD
An anti-counterfeiting method for metering seals based on cryptographic technology
ActiveCN102890786BDetermine authenticityImplement injectionStampsCo-operative working arrangementsPasswordConfidentiality
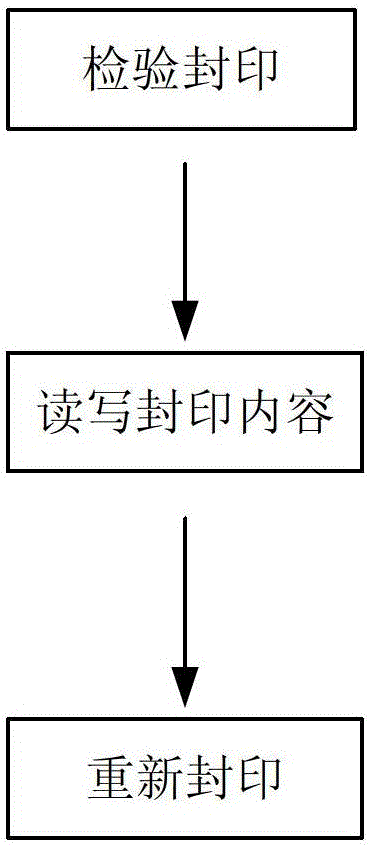
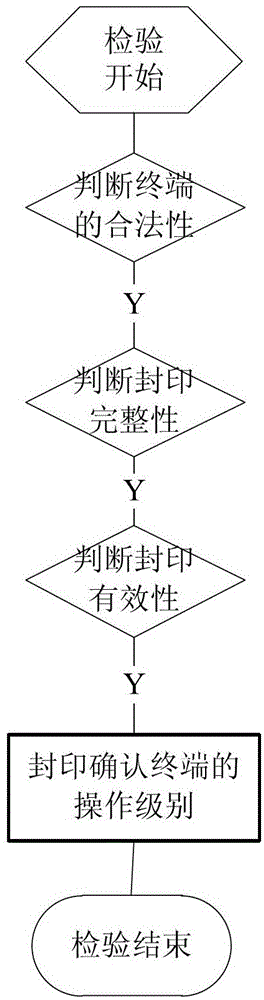
The invention relates to a password technology-based metering seal anti-counterfeiting method. The method comprises the following steps of: checking a seal, reading and writing a seal content and resealing. The steps are sequentially performed, and the next step cannot be performed when the current step is not finished. By the method, various requirements of the metering seal can be well met, and a high safety class is reached; and compared with the traditional electronic seal anti-counterfeiting method, the password technology-based metering seal anti-counterfeiting method has the advantages of confidentiality, integrity, non-repudiation, identity authentication, access control, password configuration and the like.
Owner:CHINA ELECTRIC POWER RES INST +1
Image comparison method, image comparison device, electronic equipment and medium
ActiveCN110378886BDetermine authenticityImage analysisCharacter and pattern recognitionComputer graphics (images)Engineering
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Face recognition payment information anti-counterfeiting method combined with spatial information
ActiveCN109285008BDetermine authenticityPrevent counterfeitingProtocol authorisationPayment3d sensing
The invention discloses a face recognition payment information anti-counterfeiting method combined with spatial information, including an entry-level front-end identification, a system service platform, a remote processing terminal and a data management systems. The entry-level front-end recognition system comprises a 3D sensing module, a control module, a driving module, a 360 intelligent cameramodule and a face capture and collection module. The system service platform comprises a face input unit, a voice prompt unit, a face storage unit, a face recognition matching unit and a data feedbackunit. At that time of face recognition payment, the invention carry out multiple real face recognition confirmation. The invention not only prevents the payer from borrowing the false model face forpayment, but also combines the spatial information of the payer user entry front end with the current paid face for recognition, improves the anti-counterfeiting function of the face during payment, and ensures the security of the account, which is suitable for popularization and use.
Owner:珠海横琴井通容智科技信息有限公司
Nonlinear time lag remote monitoring system for industrial production
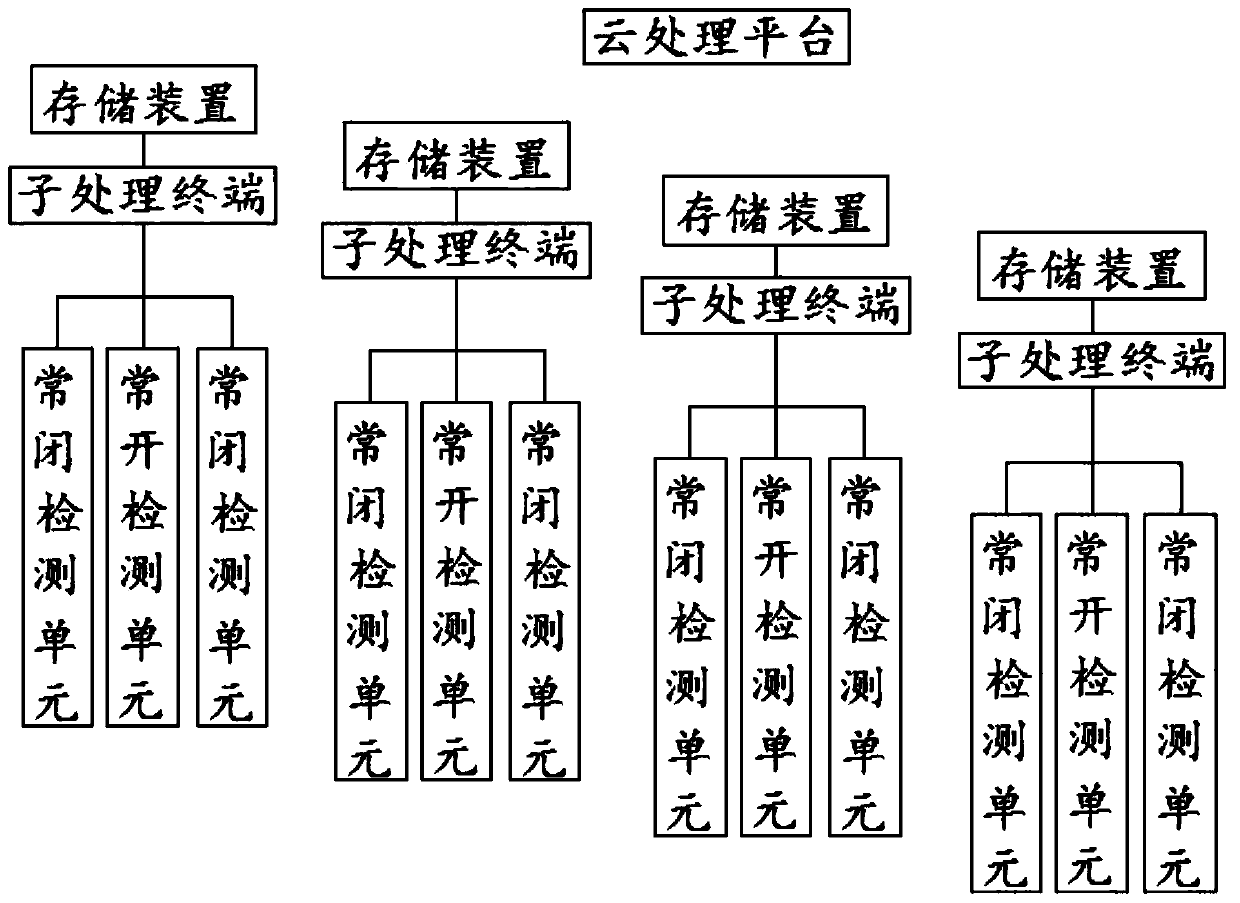
PendingCN111413903AGuaranteed stabilityAvoid interferenceProgramme controlComputer controlCloud processingTime lag
The invention discloses a nonlinear time lag remote monitoring system used for industrial production, which comprises a cloud processing platform and a plurality of sub-processing terminals arranged in sequence. Each sub-processing terminal comprises a microprocessor, a normally open detection unit, a normally closed detection unit and an actuator; the microprocessor is connected with the cloud processing platform through a wireless transmission protocol; the normally open detection unit comprises a temperature and humidity sensor and a pH value sensor; each sub-processing terminal is connected with an independent storage device. The cloud processing platform is used to comprehensively analyze all the sub-processing terminals which are connected in sequence, carry out delay processing on information fed back by the first sub-processing terminal, and carry out advanced processing on information fed back by the last sub-processing terminal, so that the stability of overall industrial production is guaranteed, and interference of sudden change signals on the whole detection system is prevented.
Owner:镇江颀珑工程技术服务有限公司
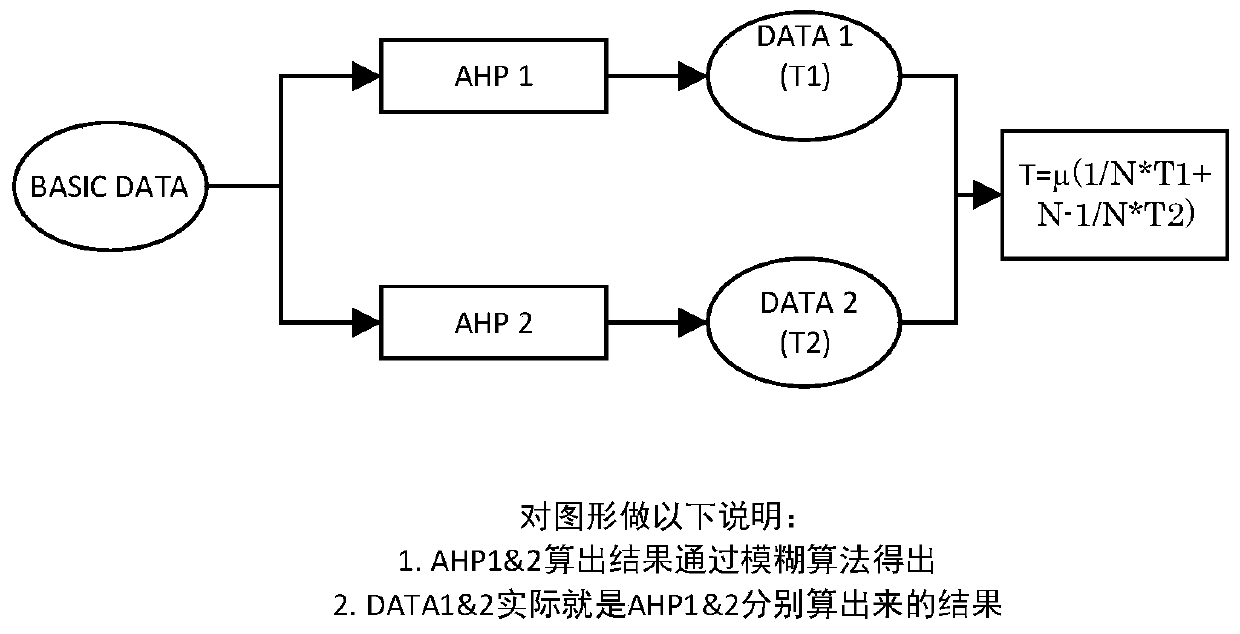
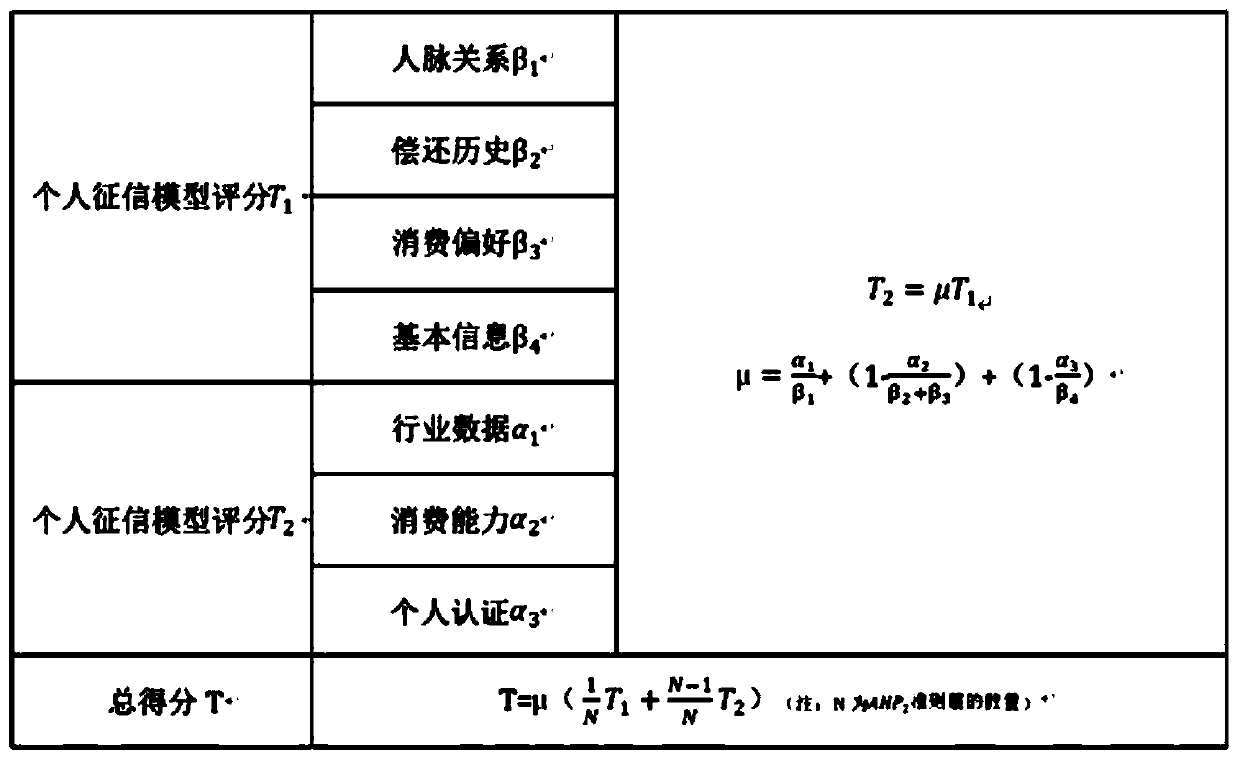
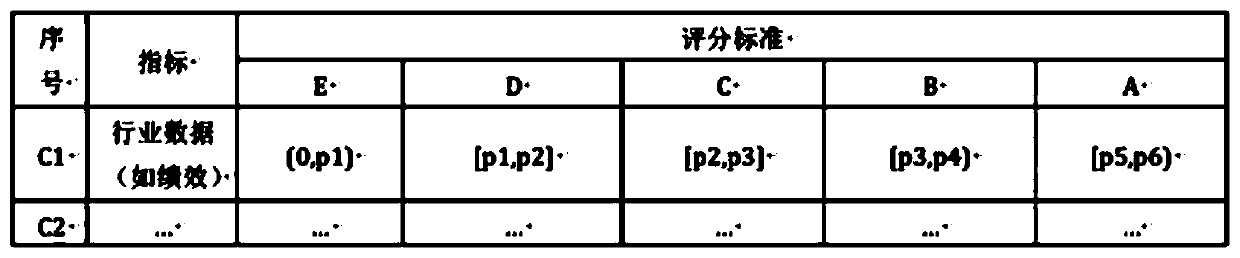
Credit investigation method based on Internet behaviors
The invention discloses a credit investigation method based on Internet behaviors. The credit investigation method comprises the following steps: 1, acquiring actor data information; 2, importing twoAHP models T1 and T2, endowing corresponding weights, and performing fuzzy evaluation to perform score interval grading; and 3, outputting the credit investigation interval level of the actor. The credit investigation method has the advantages that the influence of various indexes on the evaluated object is brought into consideration; uncertainty occurring in the evaluation process is effectivelyprocessed; a qualitative evaluation method and a quantitative evaluation method are combined; and a good scientific theoretical basis is provided. Compared with a traditional 5C model, the credit investigation model is more accurately positioned on the user network behavior, and the association between the internet surfing behavior of the network user and the personal credit investigation system is pointed out.
Owner:无锡优级先科信息技术有限公司
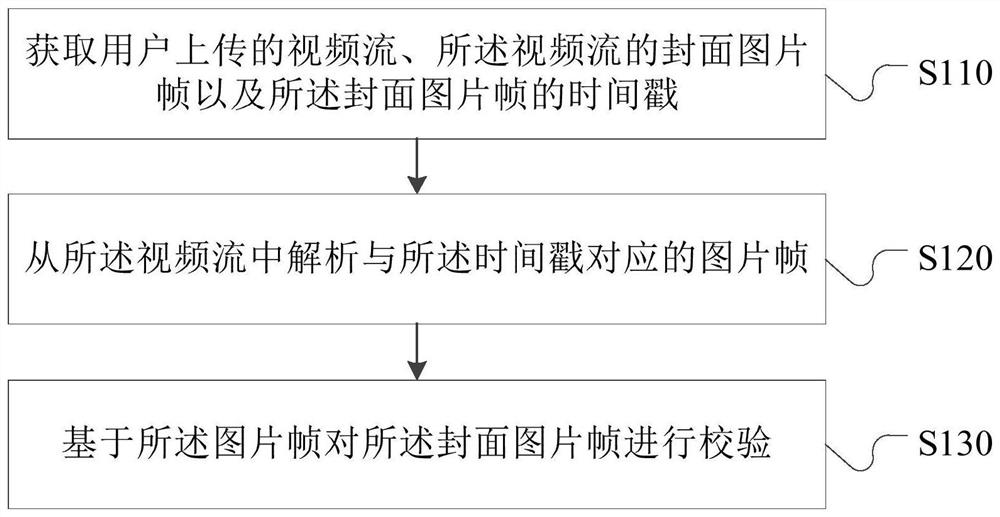
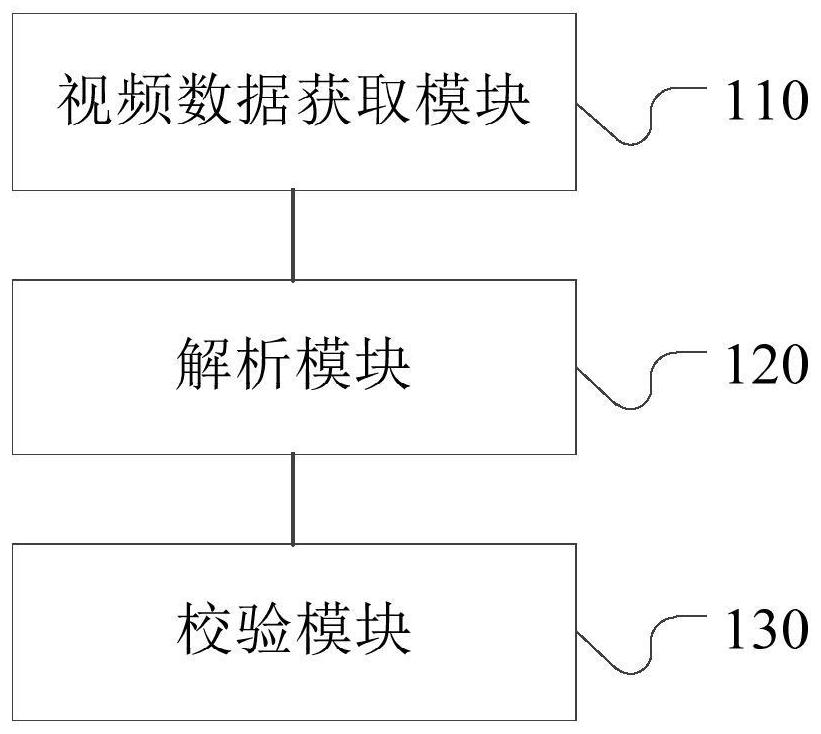
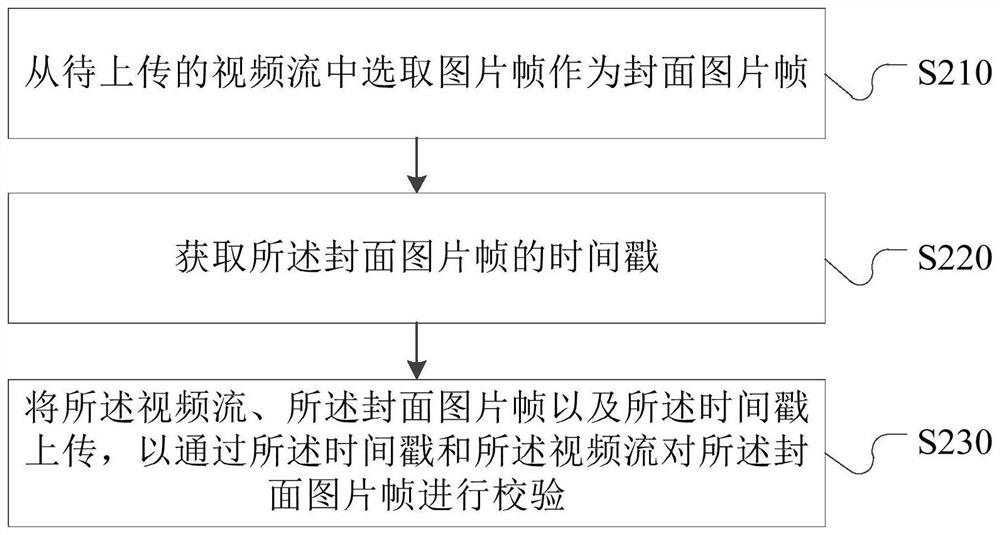
Video cover verification method, device, server and terminal
ActiveCN108419144BDetermine authenticityImprove verification speedSelective content distributionTimestampComputer graphics (images)
The invention provides a video cover verification method, a video cover verification device, a server, and a terminal, which are used to solve a technical problem of conventional video cover verification methods of low efficiency. The video cover verification method comprises steps that a video flow uploaded by a user, the cover image frame of the video flow, and the time stamp of the cover imageframe are acquired; the image frame corresponding to the time stamp is analyzed from the video flow; the verification of the cover image frame is carried out based on the image frame. The efficiencyof the video cover verification can be improved.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
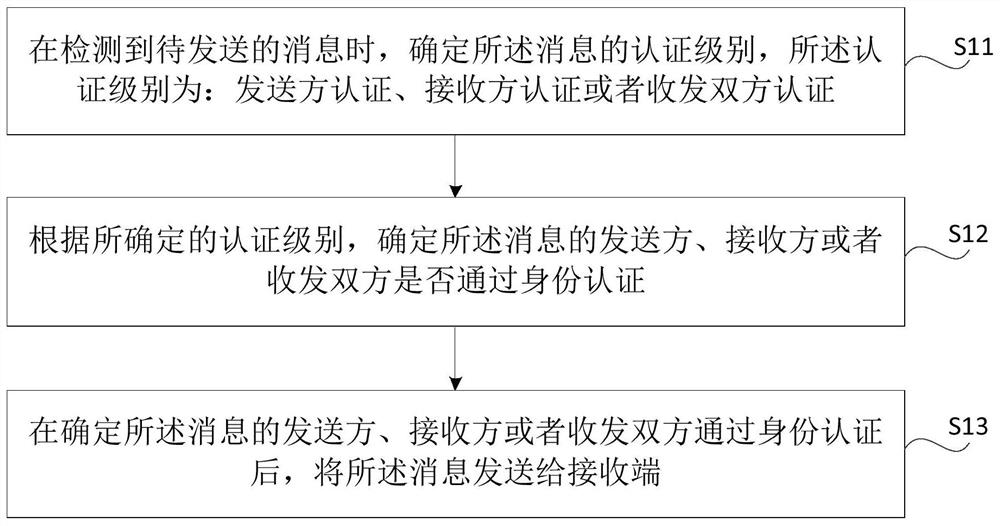
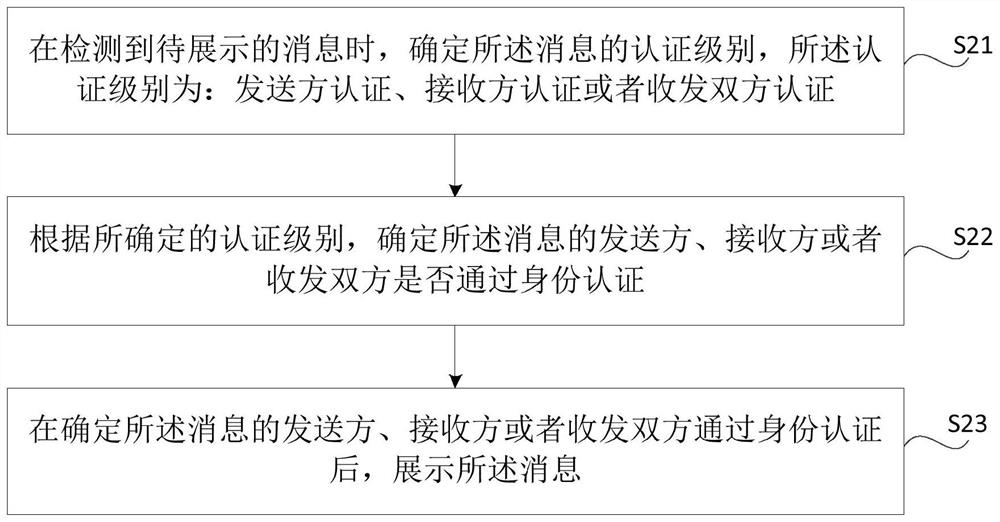
Method and device for sending and displaying messages, method and device for identity authentication
ActiveCN109039860BDetermine authenticityAchieve protectionData switching networksInternet privacyRecipient side
The present disclosure relates to methods and apparatuses for sending and presenting messages, and methods and apparatuses for identity authentication. Through the method provided by the present disclosure, the sender can ensure that the sent message can only be seen by the receiver, thereby ensuring the privacy and security of the sender; in addition, the receiver can determine the authenticity of the received message and avoid false news harm caused.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Warehouse monitoring method and device as well as server
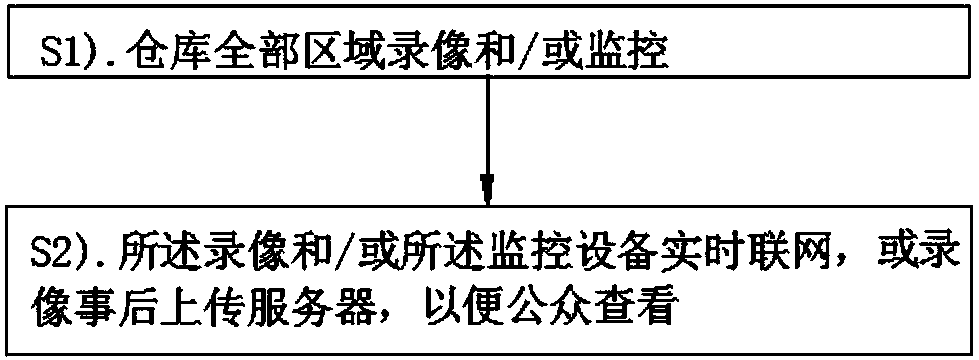
InactiveCN109547739AIncrease credibilityDetermine authenticityCharacter and pattern recognitionClosed circuit television systemsVideo recordingMonitor equipment
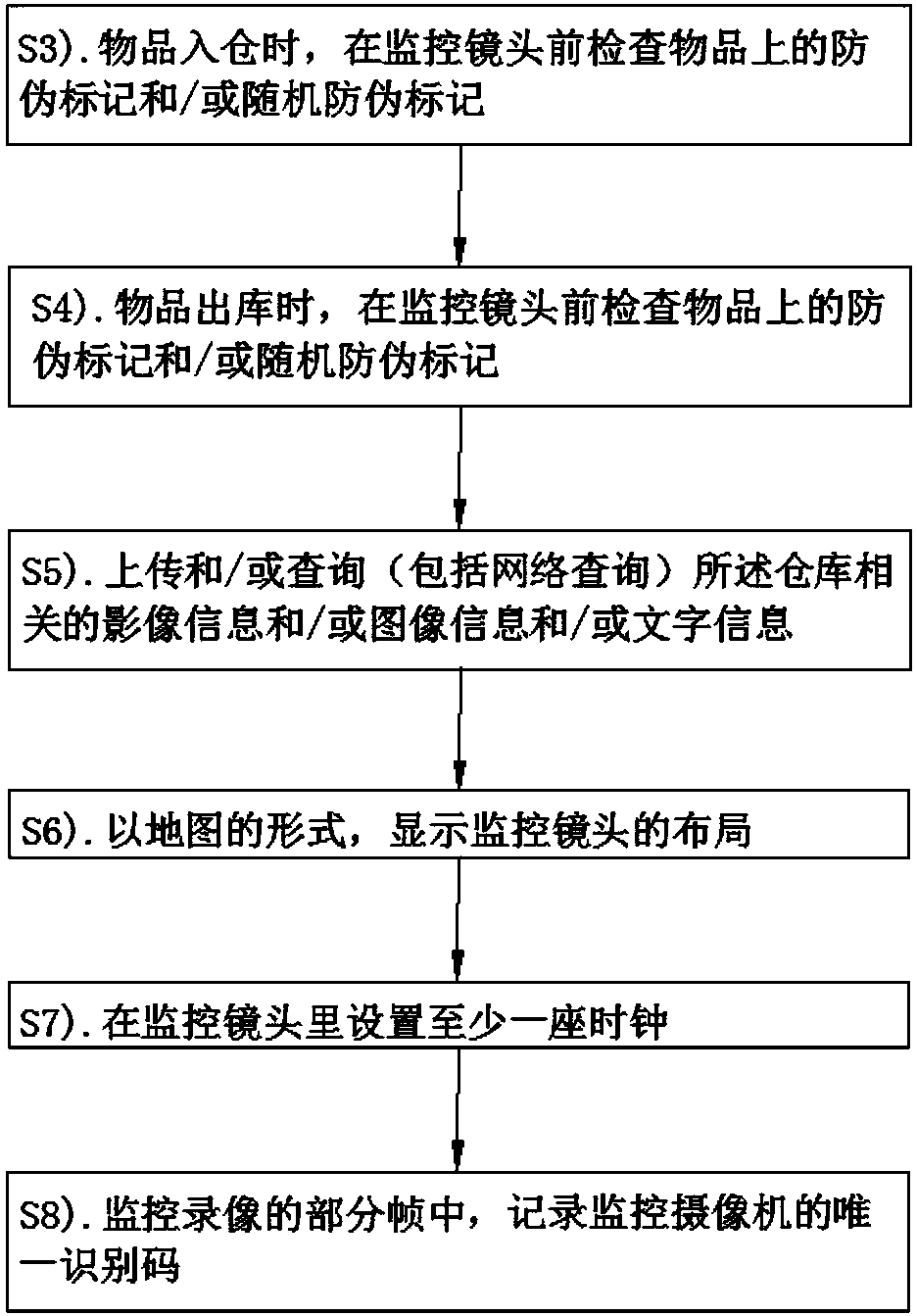
A warehouse monitoring method comprises the following processing steps: S1), performing video recording and / or monitoring on all the regions of a warehouse; and S2), networking video recording and / ormonitoring equipment in real time, or uploading a monitoring video to a server after the video recording, so that the public can view the monitoring video conveniently. A warehouse monitoring device and a server are respectively a computer device supporting the method. The warehouse monitoring method provided by the invention continuously monitors and records related information of the warehouse,and the public can inquire the monitoring video, photographs and related information by virtue of the network; by identifying true or false of a false-proof mark and / or a random false-proof mark, trueor false of an article can be identified; and the public not only can see the situation of the article at any moment in the warehouse but also can determine truth of the article, so that credibilityof the warehouse is improved.
Owner:郑州玄一机器人有限公司
Relay Performance Tester
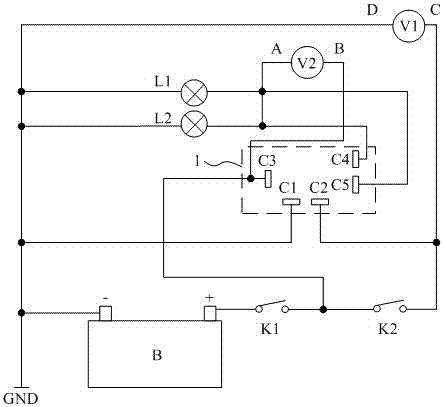
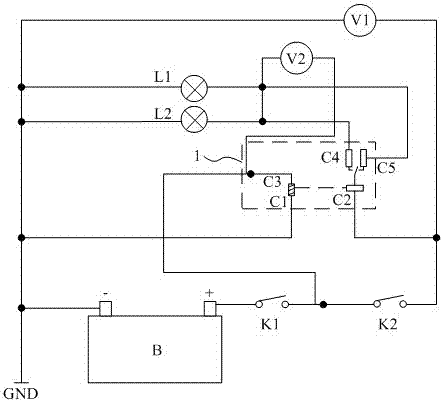
InactiveCN104330731BDetermine authenticityCircuit interrupters testingMicrocontrollerLiquid-crystal display
The invention discloses a relay performance detector, which comprises a battery, two switches, two indicating devices, two voltmeters, a relay socket, a single-chip microcomputer and a liquid crystal display; the negative pole of the battery is connected with the first contact piece of the relay socket, and the positive pole passes through two switches Afterwards, it is connected with the second contact piece, and the node between the two switches is connected with the third contact piece; the second contact piece is also directly connected with one end of a voltmeter, and the negative pole is connected with the other end of the voltmeter and the first contact piece, The fourth contact piece is connected to the negative pole through an indicating device, and the fourth contact piece is also connected to the first end of another voltmeter, and the second end is connected to the third contact piece; the fifth contact piece is connected to the battery through another indicating device. The node between the fifth contact piece and the other indicating device is also connected to the first end of the voltmeter, and the single-chip microcomputer is used to receive the voltage value measured by the two voltmeters and display it on the liquid crystal display superior. The above-mentioned relay performance detection device can truly measure the performance and quality of the relay.
Owner:CHONGQING TELECOMM POLYTECHNIC COLLEGE
Intelligent fire judgment system
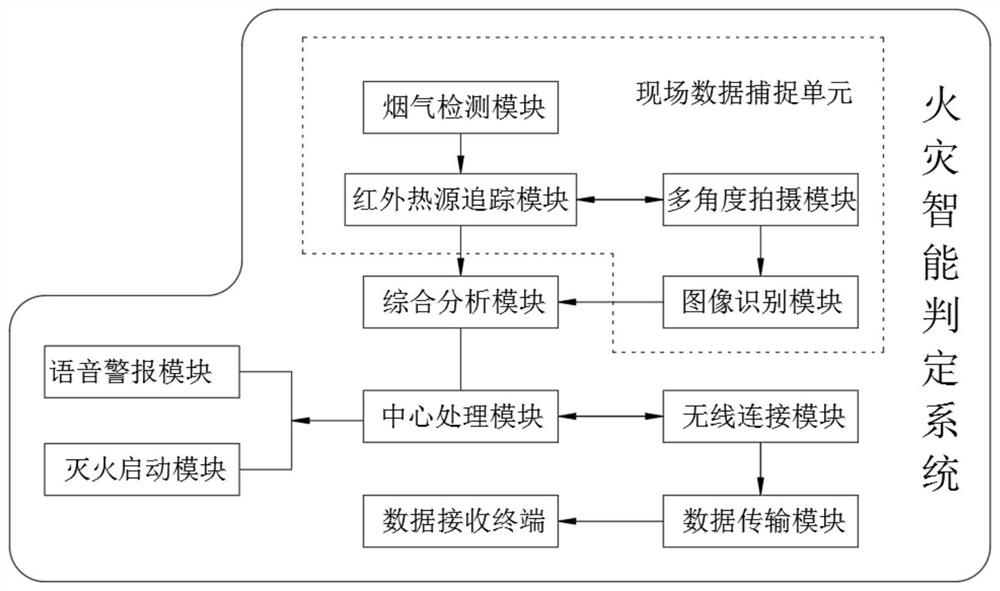
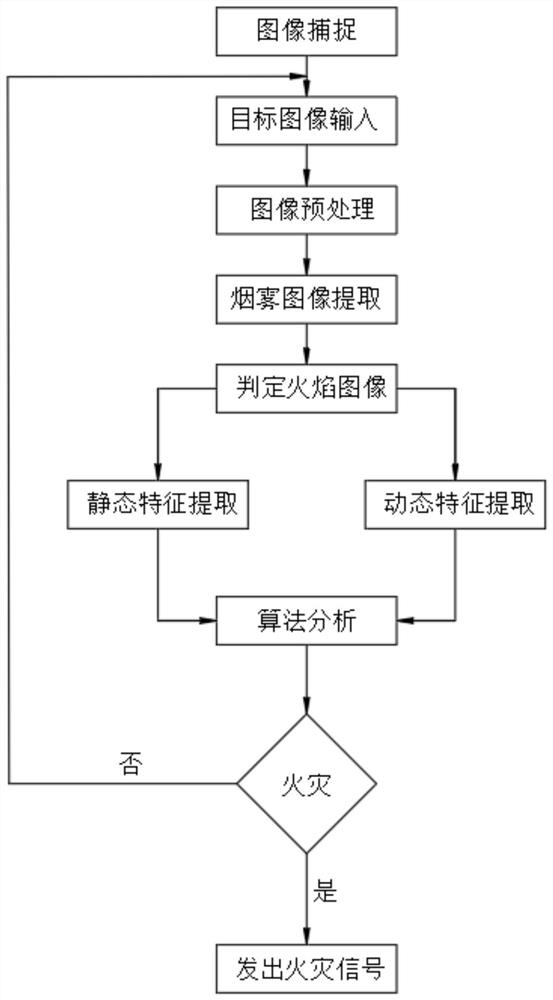
InactiveCN112509272ADetermine authenticityGuarantee authenticityCharacter and pattern recognitionNeural architecturesEngineeringFire detection
The invention relates to the technical field of fire detection and judgment, and discloses an intelligent fire judgment system, which comprises a field data capture unit, a comprehensive analysis module, a central processing module, a wireless connection module, a data transmission module and a data receiving terminal; and the field data capture unit comprises a flue gas detection module, an infrared heat source tracking module, a multi-angle shooting module and an image recognition module. The intelligent fire judgment system is designed, during actual operation, the system carries out tripledetermination through comparison and analysis of smoke conditions in the field environment, smoke image pixel thresholds extracted through image shooting and existing fire image data as well as the field flame conditions, so that the authenticity of a fire is further determined, and false alarm is prevented. Intelligent monitoring and judgment can bring great convenience to fire extinguishment ofworkers and crowd evacuation work.
Owner:天津天雾智能科技有限公司
A detection method for the authenticity of vehicle traffic violations
ActiveCN106960574BEfficient analysisDetermine authenticityRoad vehicles traffic controlMultiple frameGeolocation
A vehicle traffic illegal behavior authenticity detection method comprises the following steps: allowing a traffic monitor probe to transmit monitored illegal vehicle information to a server; allowing the server to search the same license plate number in a database, and invoking the authentication vehicle information containing the license plate number; allowing the server to compare the illegal vehicle color, vehicle single frame or multi-frame image, and vehicle type with the authentication vehicle license plate number, vehicle color, vehicle single frame or multi-frame image, and vehicle type, and considering the authentication vehicle to have no traffic illegal behavior if one of said compared items does not comply; obtaining the road condition video of an authentication vehicle data recorder when all said compared items comply, extracting the road condition video corresponding to the illegal vehicle illegal time, parsing the authentication vehicle located geography position from the video, determining whether the geography position is same with the illegal vehicle illegal position or not, and if not, determining the authentication vehicle to have no traffic illegal behavior.
Owner:上海工业控制安全创新科技有限公司
In-trench sawtooth anti-counterfeiting method
InactiveCN112455121AImprove recognition accuracyImprove query accuracyStampsPattern printingComputer graphics (images)Engineering
The invention provides an in-trench sawtooth anti-counterfeiting method which comprises the following steps: forming trenches in a printing stock; printing ink codes / images and texts on a printing stock in a jet printing mode, wherein some ink falls into the trenches and diffuses and extends along the trenches, and sawtooth in the trenches are formed. and storing the sawtooth feature information in a cloud database, so that the public can check authenticity by using a photographing mobile phone. The product using the in-trench sawtooth anti-counterfeiting method cannot be copied, and is easy to identify and high in query accuracy rate.
Owner:HAINAN PAIPAIKAN INFORMATION TECH CO LTD
Audio recognition method, device and computer storage medium
ActiveCN107886956BDetermine authenticitySpeech analysisSpecial data processing applicationsAudio frequencyAudio recognition
The invention discloses an audio recognition method and device and a computer storage medium, belonging to the technical field of electronics. The method includes the following steps: acquiring a plurality of audio segments from a target audio to be recognized; determining a target fragment from the audio segments, wherein the target fragment is an audio fragment obtained by recording human voice;and if the target fragment in the audio segments satisfies a specified condition, determining that the target audio is an audio obtained by recording human voice. Through analysis of the audio fragments in the target audio, whether the target audio is an audio obtained by recording human voice can be accurately recognized, and the authenticity of the target audio can be determined.
Owner:GUANGZHOU KUGOU COMP TECH CO LTD
Apparatus and method
InactiveCN106164986ADetermine authenticityPaper-money testing devicesComputer scienceSpontaneous emission
The present invention provides apparatus for indicating if a security document comprises one or more specified characteristics, said apparatus comprising: an effect sensing device operative to sense at least one of: a stimulated effect arising due to: an interaction of a plurality of energy carrying particles and / or waves with a passive taggant material in said at least one reference layer; and an interaction of a plurality of energy carrying particles and / or waves with an interface between said at least one reference layer and at least one adjacent layer; and a spontaneous effect arising due to spontaneous emission of a plurality of energy carrying particles and / or waves from an active taggant material in said at least one reference layer; and output, to a processor of said apparatus, a sensed effect profile representative of said spontaneous and / or stimulated effect as sensed; wherein said processor is arranged to: derive a first data profile from said sensed effect profile; compare said first data profile with a second data profile representative of a specified effect profile; and produce an authentication signal representative of a match or otherwise between said first data profile and said second data profile. The invention also provides a method of indicating if a security document comprises one or more specified characteristics, and a banknote counting apparatus comprising the apparatus.
Owner:INNOVIA FILMS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com