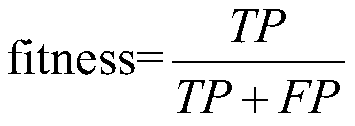Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
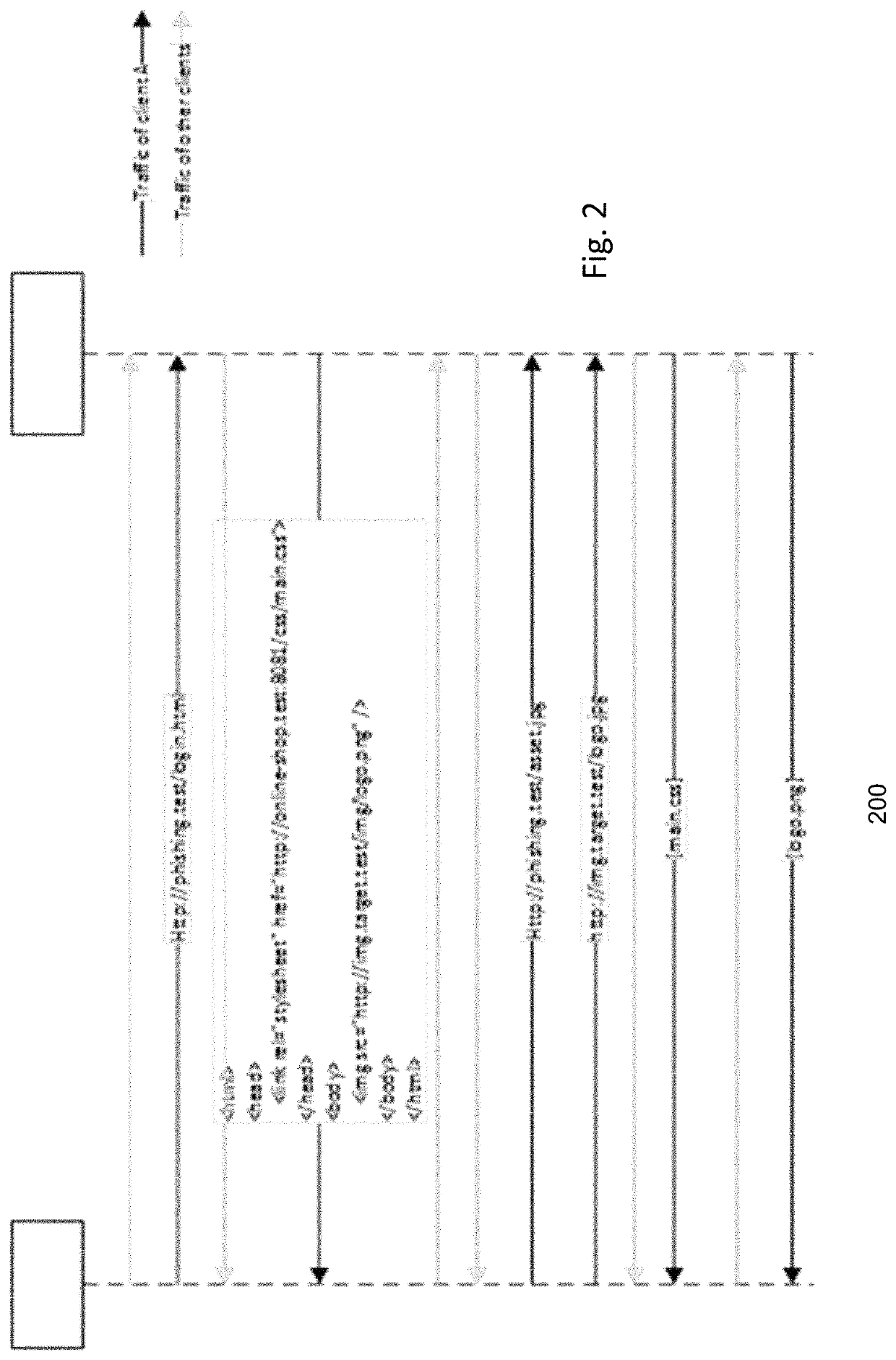
30 results about "Phishing detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
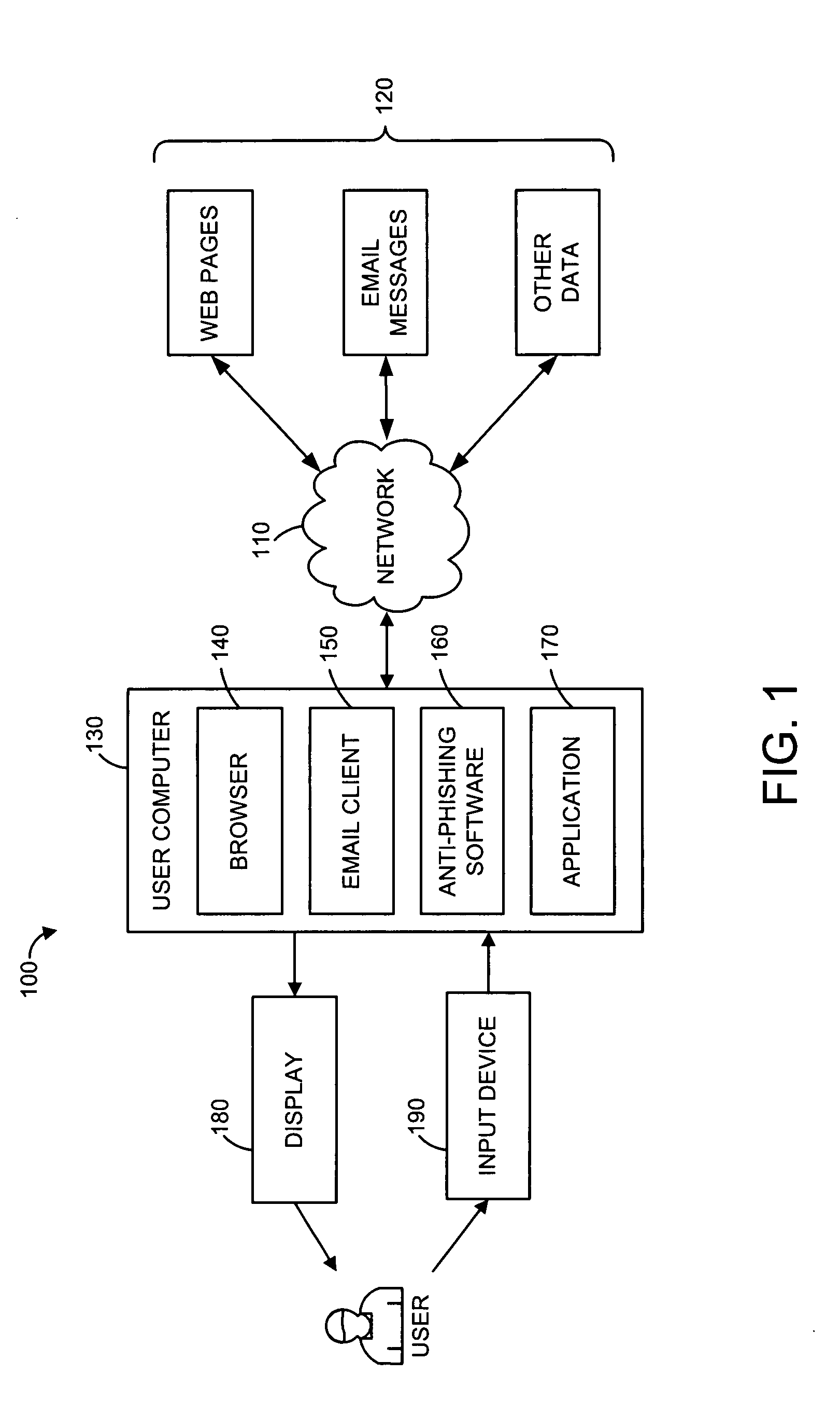
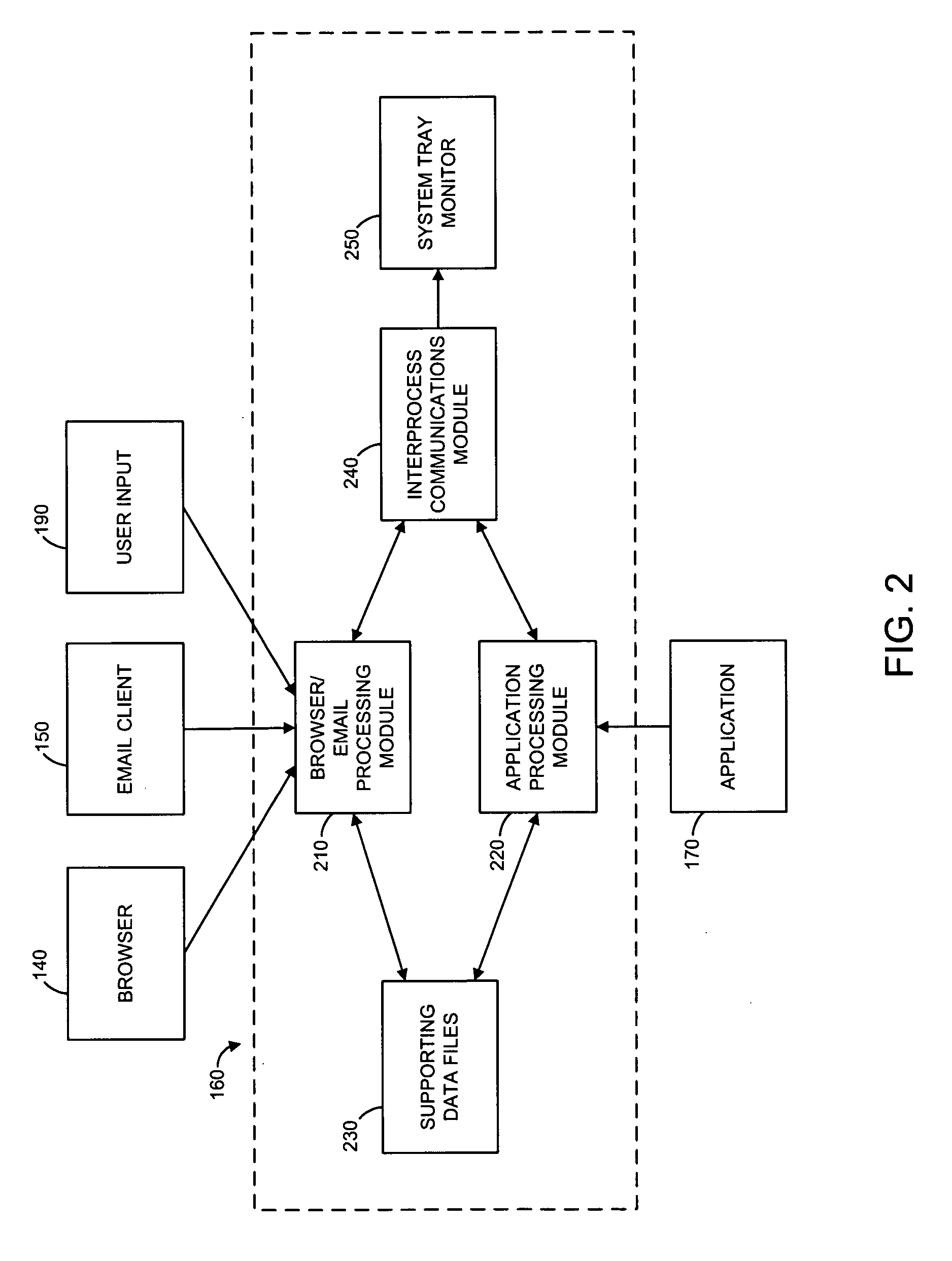
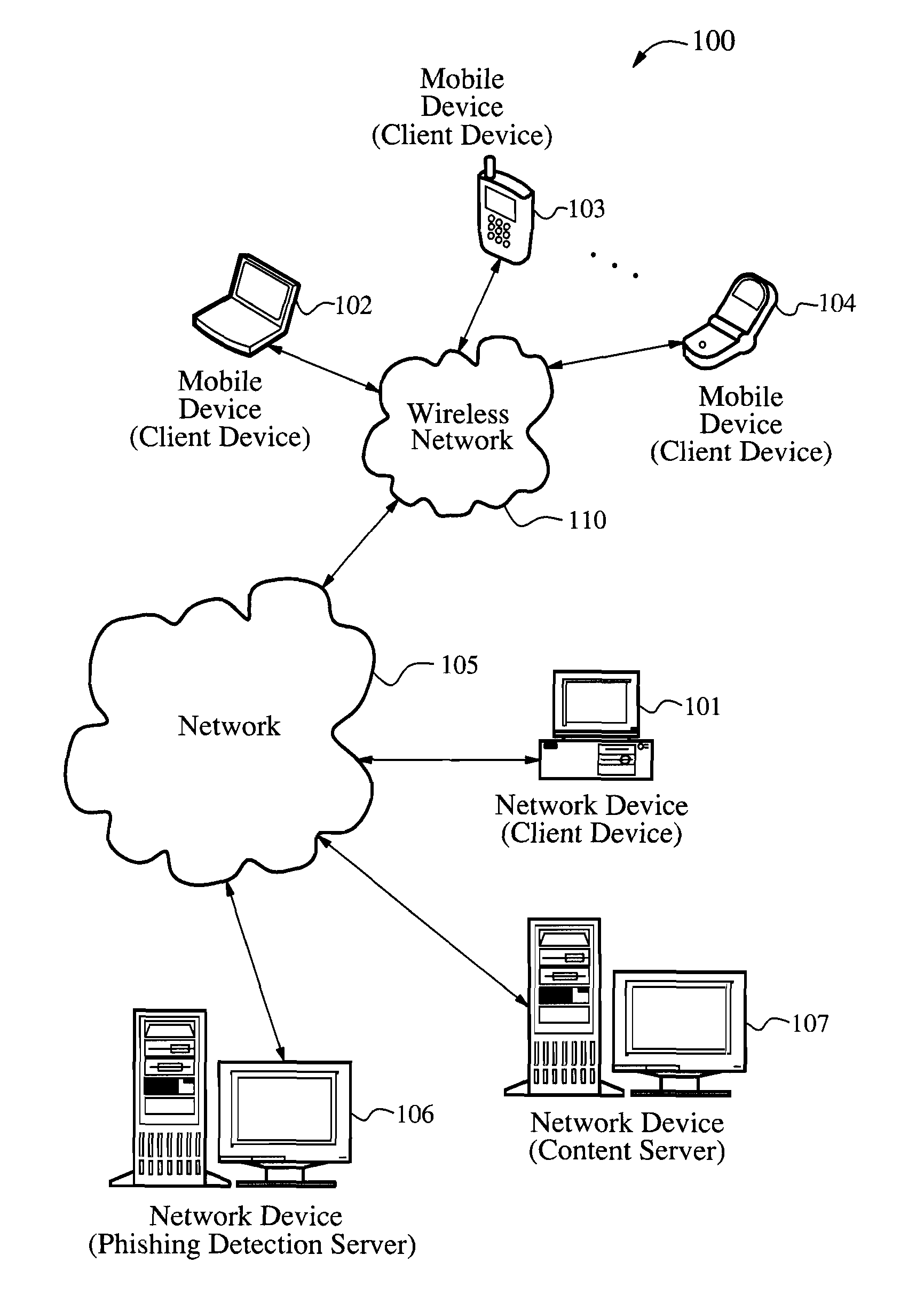
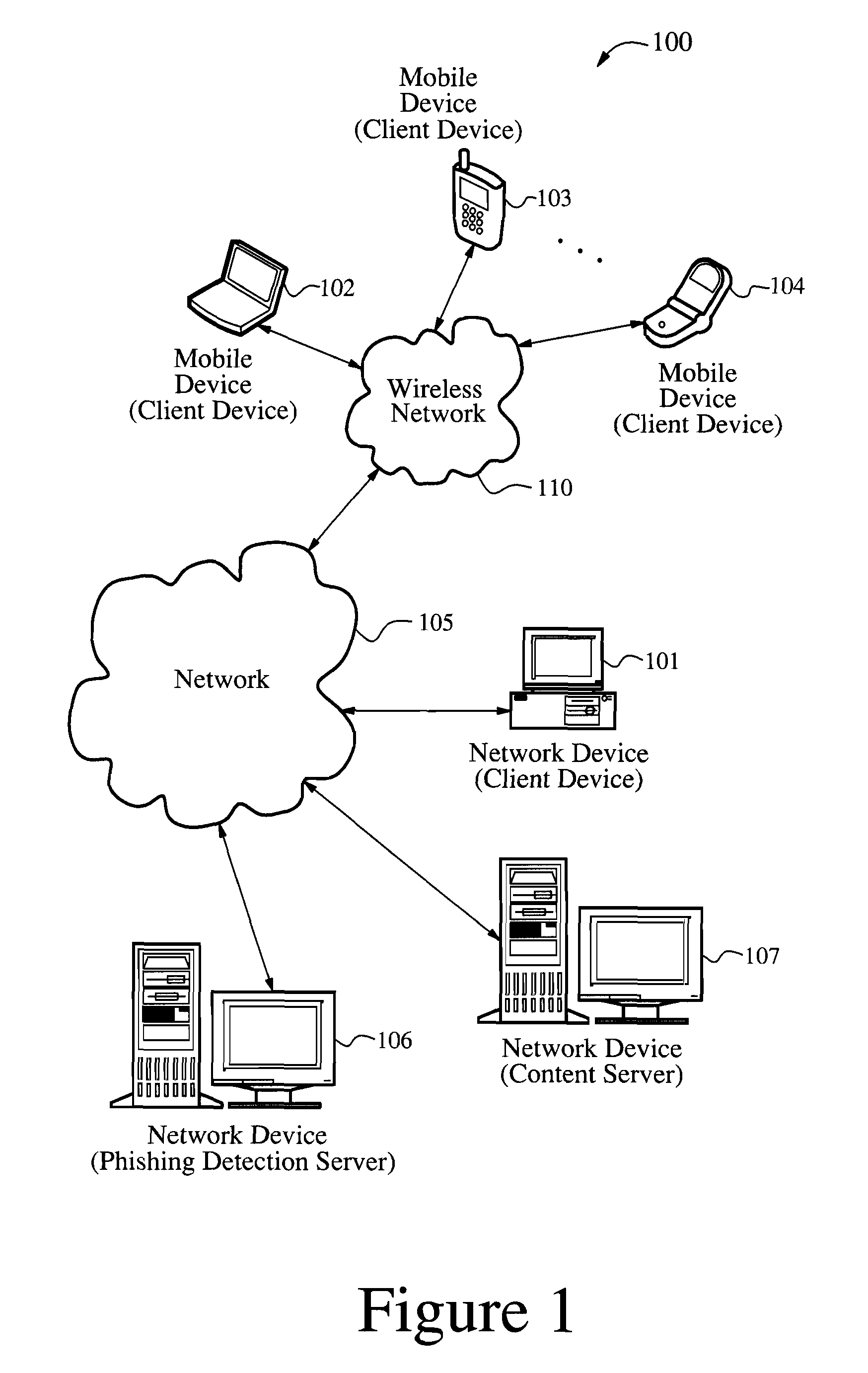
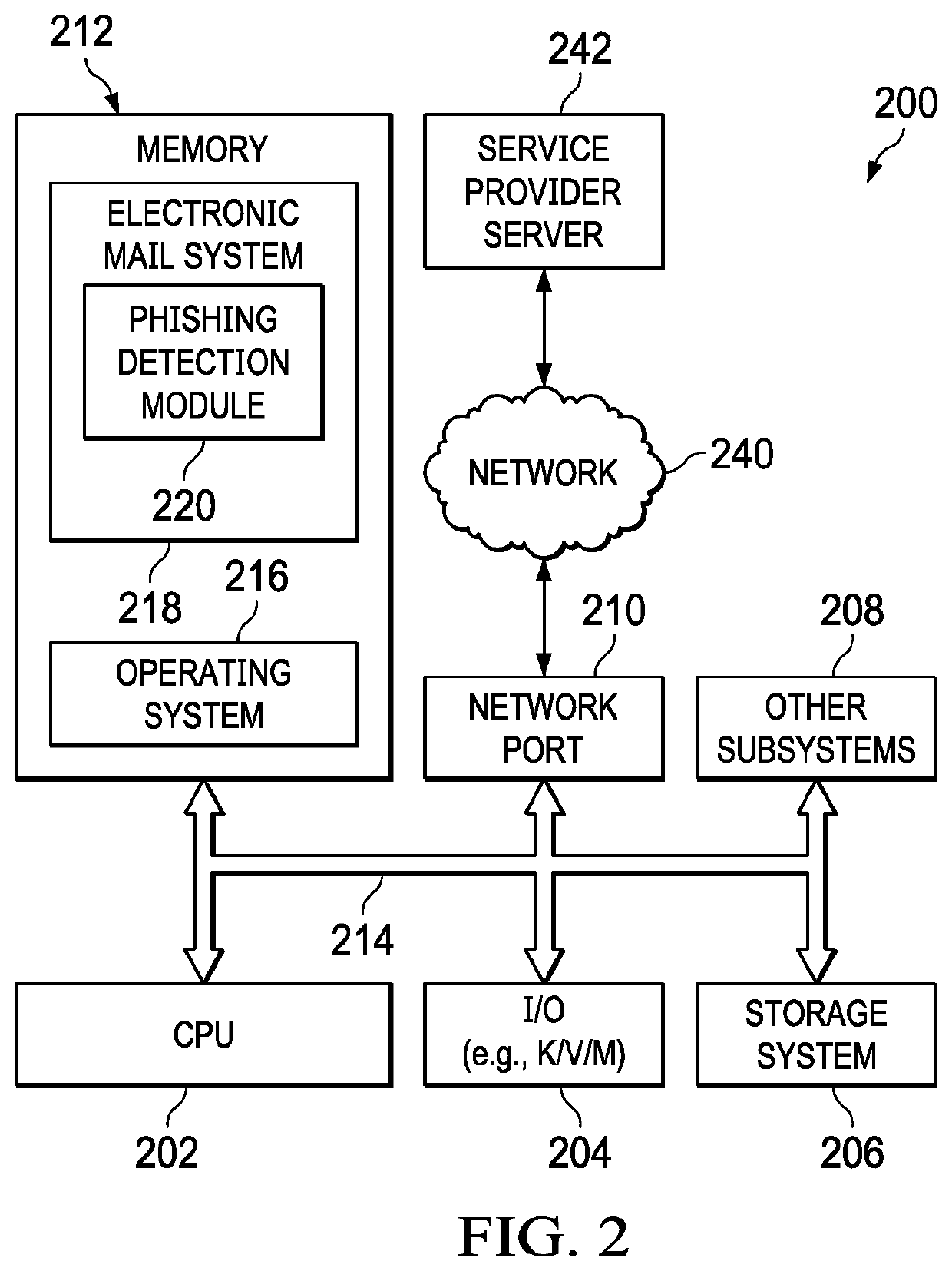
Systems and methods for electronic message analysis
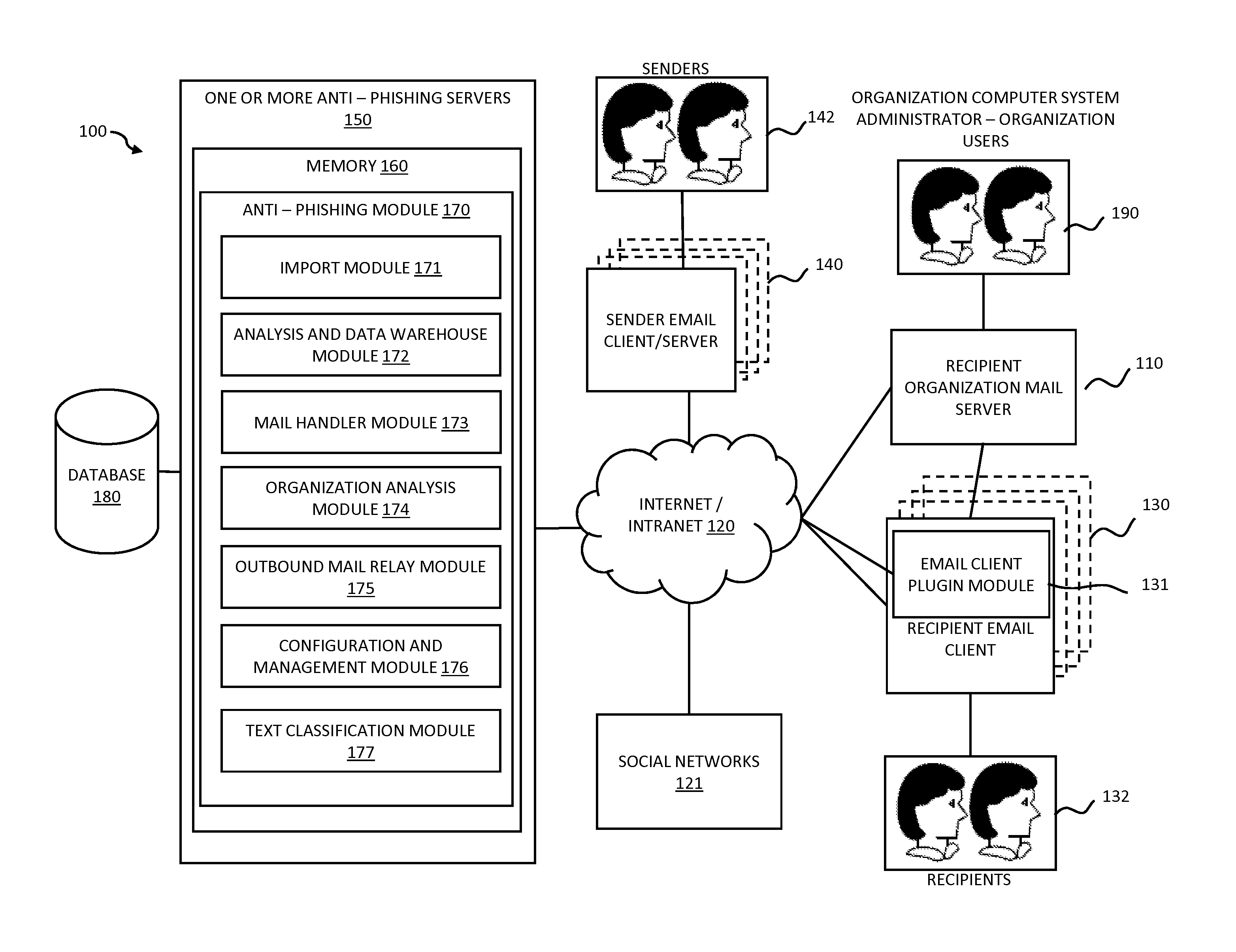
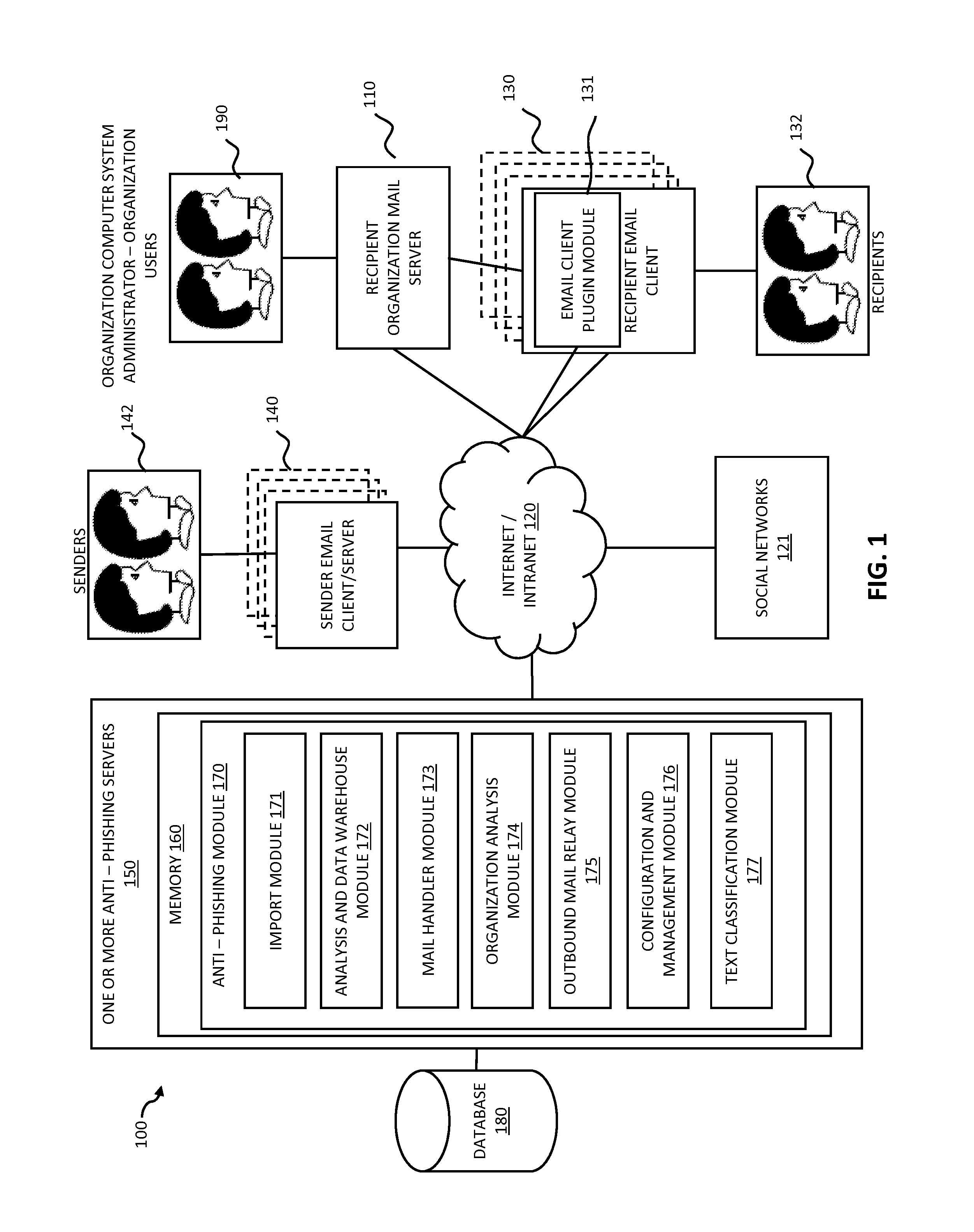
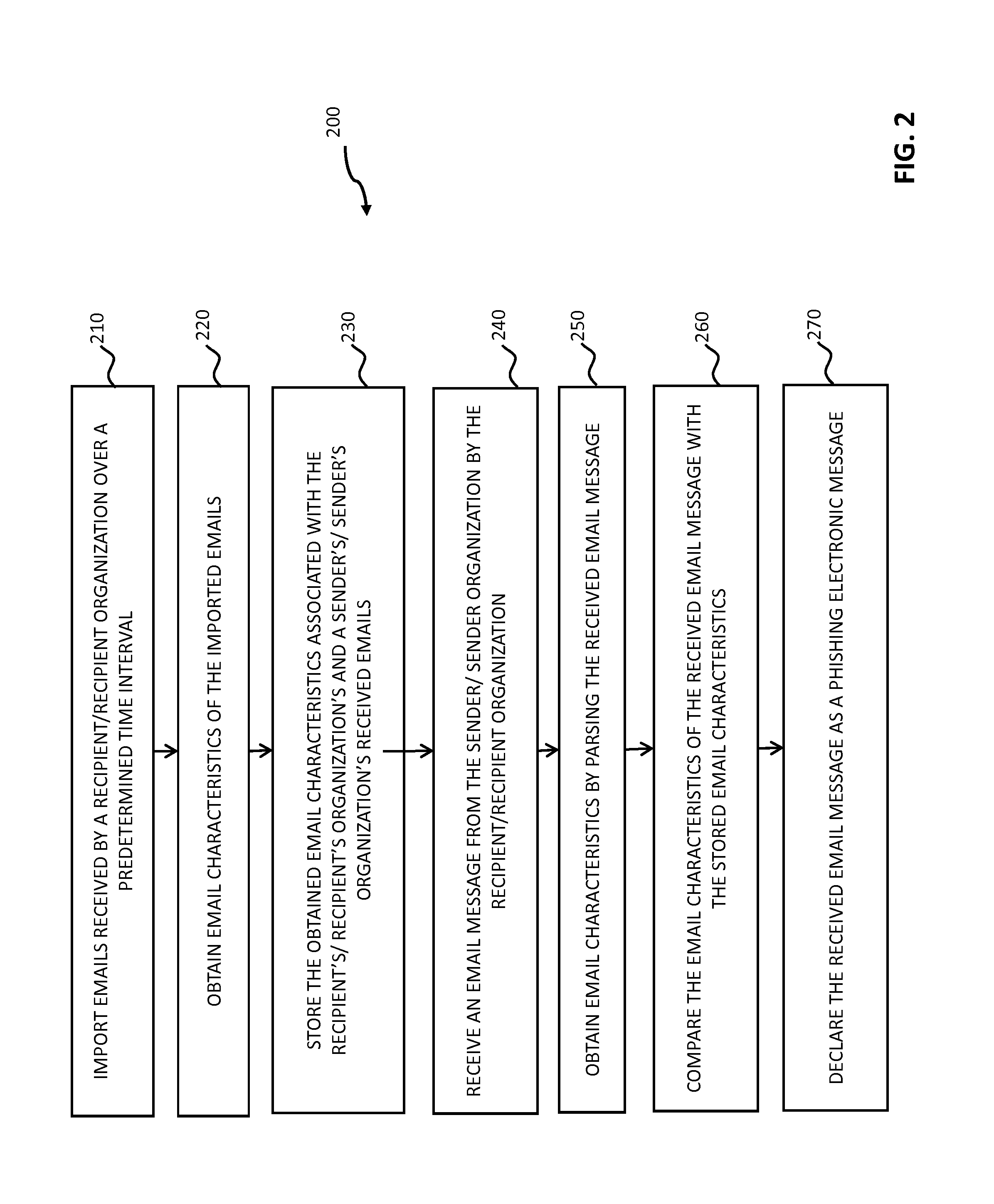
Systems and methods for analyzing electronic messages for phishing detection are disclosed. In one example embodiment, whether a received email message is a phishing message is determined based on the outcome of a comparison of a recipient background information to a email characteristic wherein the recipient background information is obtained from an online social network. In some embodiments, whether the received email message is a phishing message is determined by comparing a new received email message profile to an email characteristic profile to determine whether the new received email message profile is similar to the email characteristic profile. In some embodiments, whether the received email message is a phishing message is determined by comparing the email characteristics of the new received email message with pattern characteristics. In some embodiments, the determination is made by comparing a email characteristics of the received message with a historical email characteristic.
Owner:VADE SECURE SAS
Methods and systems for phishing detection and notification
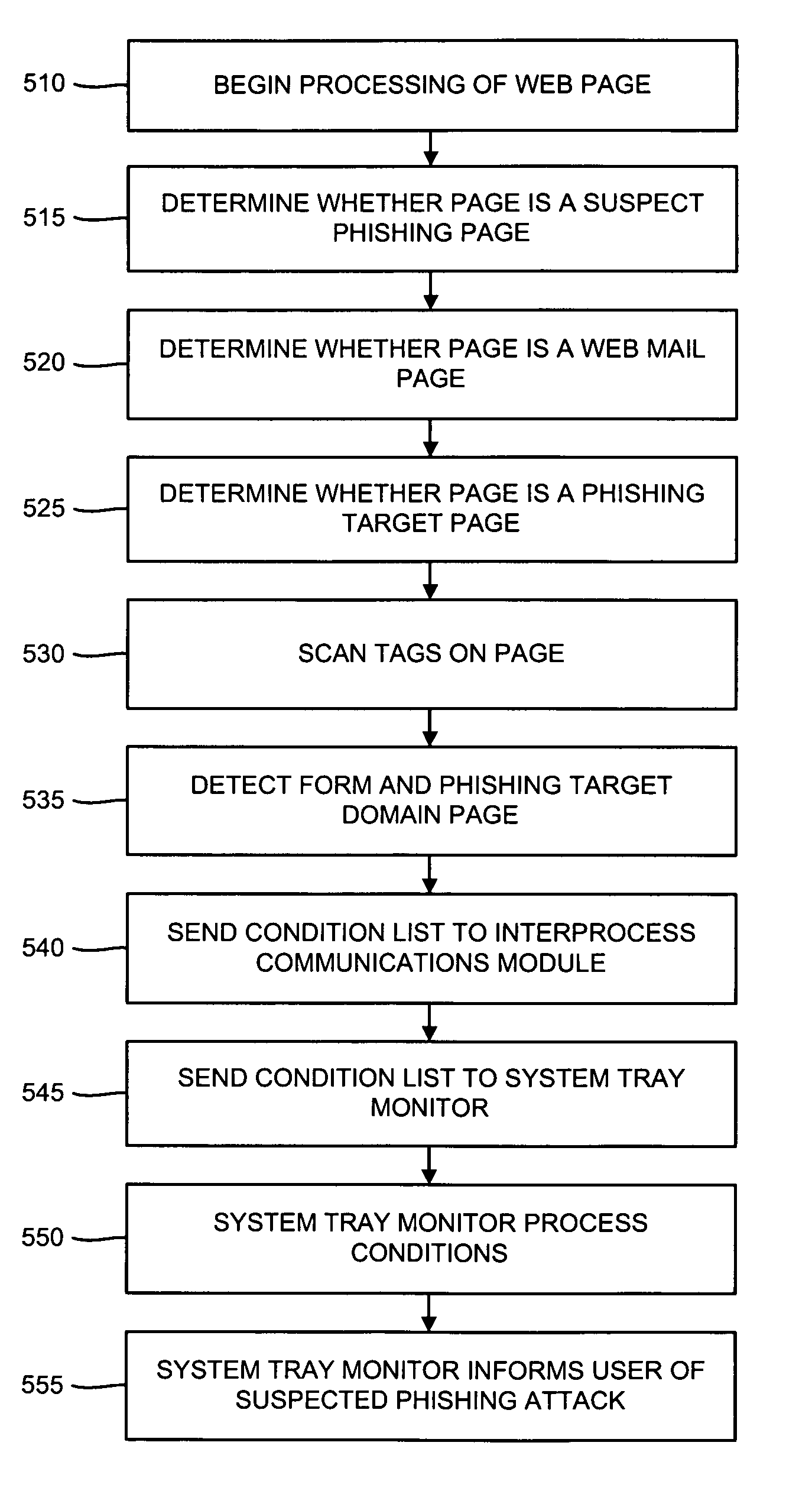
Various techniques are provided for detecting phishing attacks and notifying users of such attacks. In one example, a machine-implemented method can be provided for detecting a phishing attack over a computer network. A web page can be accessed and information associated with the web page can be processed. One or more conditions can be set in response to the processing. The conditions can be compared to a set of conditions indicative of a phishing attack. A user can then be informed of a potential phishing attack corresponding to the conditions through the display of an alert window and / or an icon. Such actions can also be performed in response to a user's selection of a link appearing in an email message. Appropriate systems and / or computer readable media incorporating these features can also be provided.
Owner:SEARCH INITIATIVES LLC
Anti-phishing agent
A phishing detection agent is provided. In one embodiment, a user's browser includes a plug-in application or agent that may capture a visual record of a webpage and, with a cached copy of known, authentic websites provided to it via periodic updates, perform a series of image comparison functions to determine if the suspected website is attempting to deceive the user. The phishing detection agent is capable of performing an image recognition algorithm, such as logo recognition algorithm, optical character recognition, an image similarity algorithm, or combination of two or more of the above. If the suspected webpage corresponds to one of the authentic web pages, but the domain name of the suspected web page does not match the domain name of one of the authentic web pages, the suspected web page is flagged as a phishing web site.
Owner:OATH INC
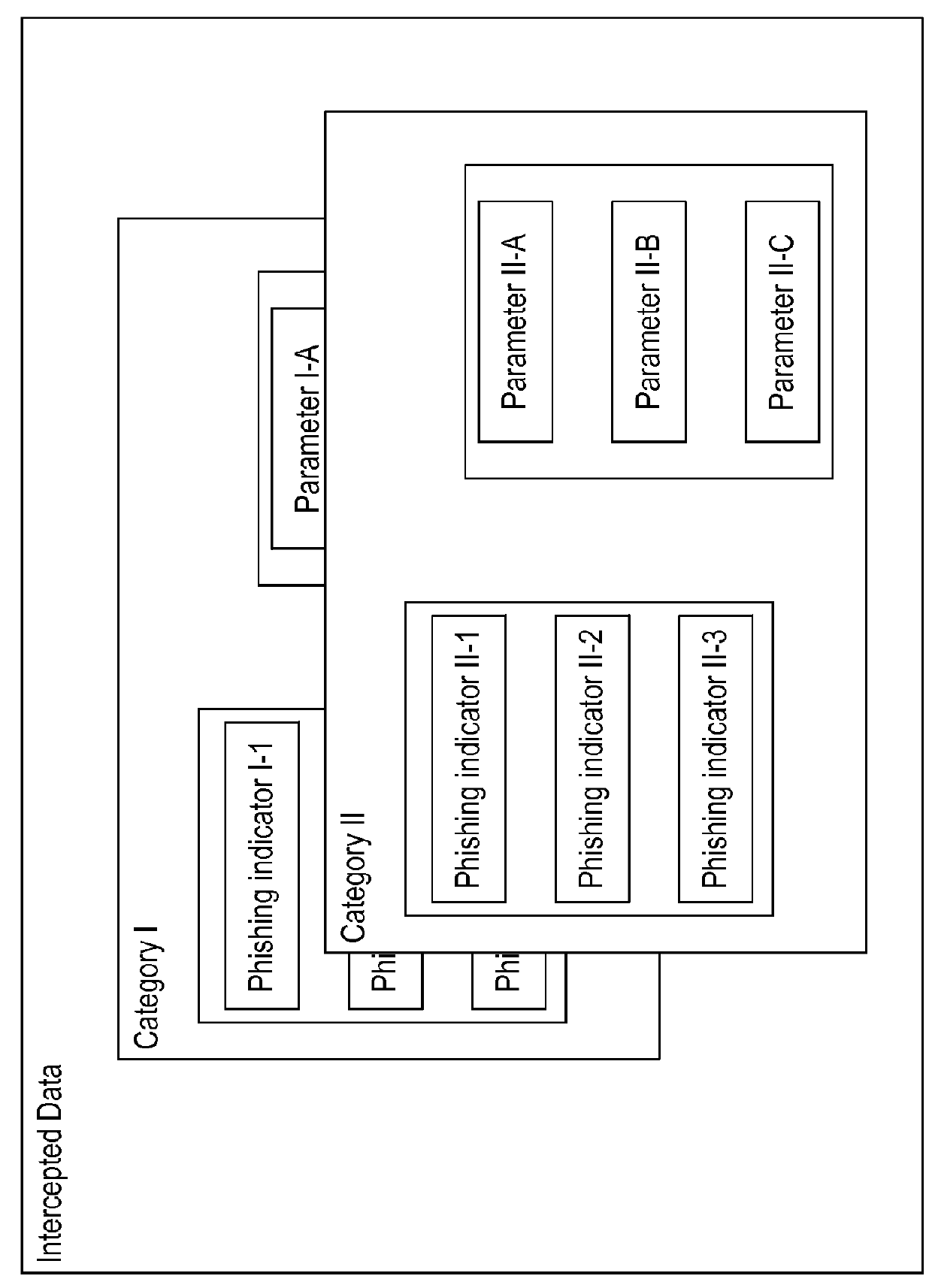
System and method for selectively evolving phishing detection rules
ActiveUS20160261618A1Reduce maliciousness of the phishing-related objectsRelational databasesPlatform integrity maintainanceRule systemData mining
System and method for automatically developing phishing detection rules. Based on detected phishing indicia, a quantitative score is computed for each of a plurality of predefined parameters, with each of the parameters relating to at least one of the phishing indicia. A requirement for evolving a phishing detection rule is assessed, and a new phishing detection rule is generated based on selected parameter scores meeting the rule evolution criteria and on corresponding content of the phishing indicia relating to those selected parameter scores. New phishing detection rules are applied recursively to detect phishing indicia, and more new rules can be further evolved in recursive fashion.
Owner:AO KASPERSKY LAB
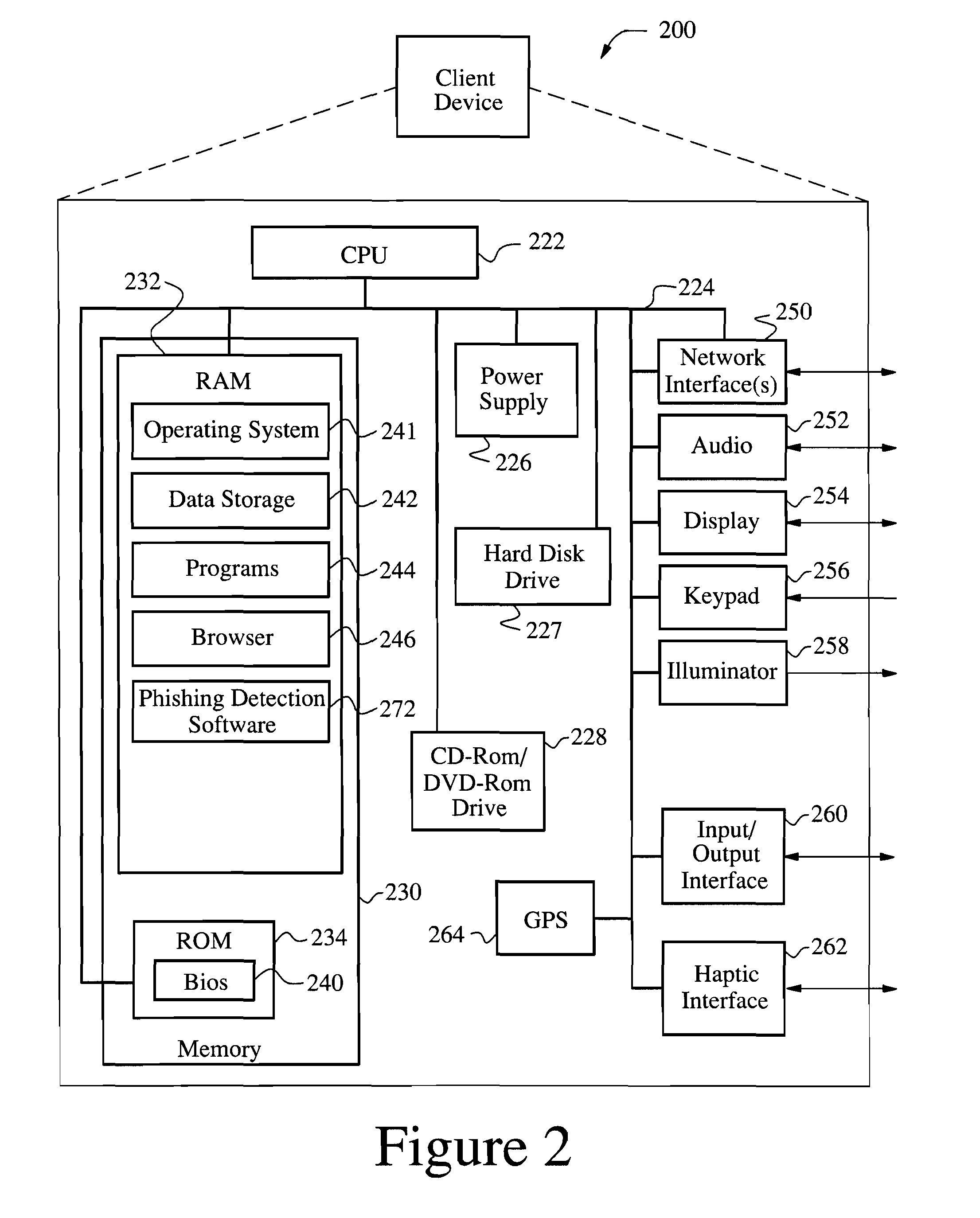
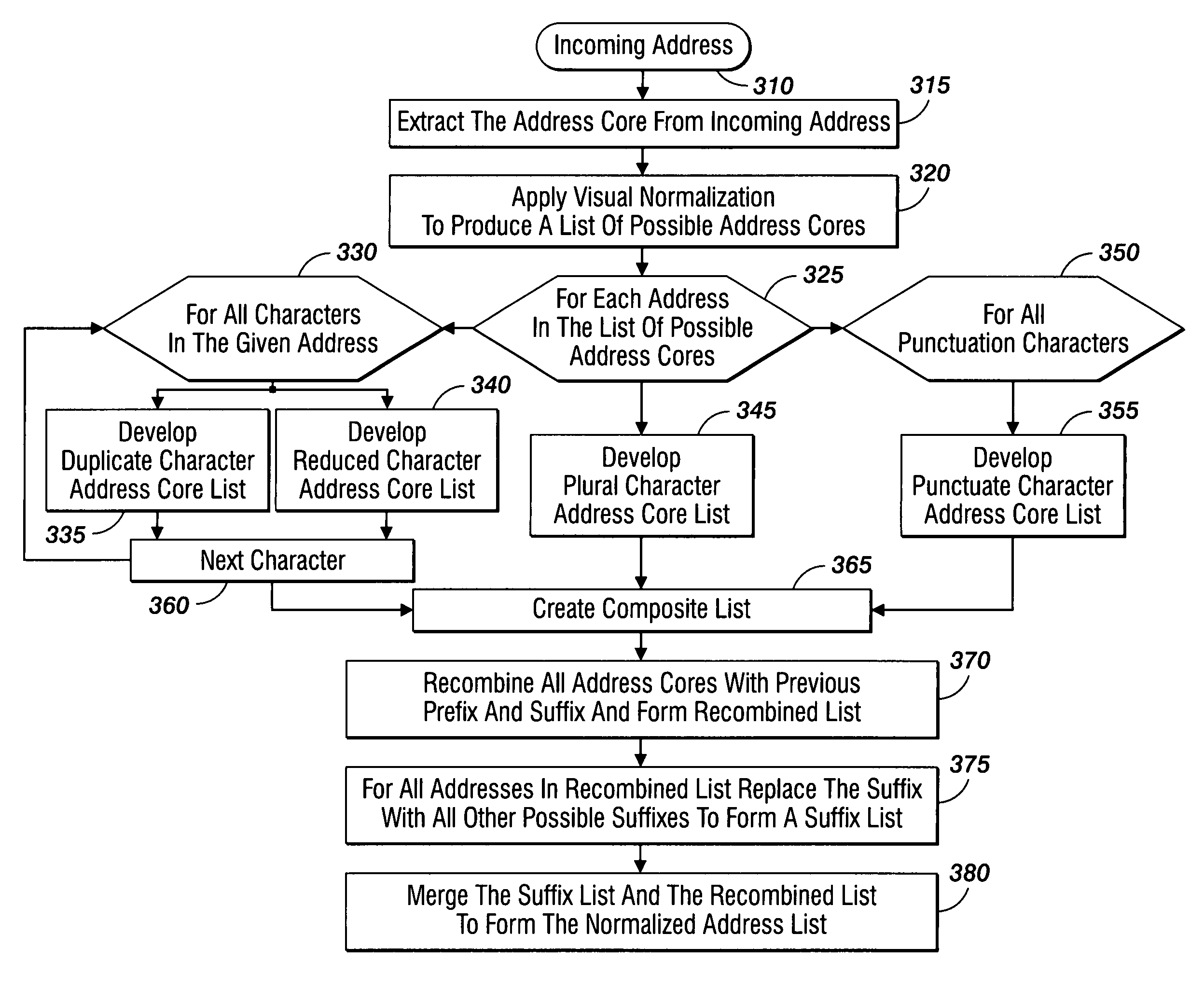
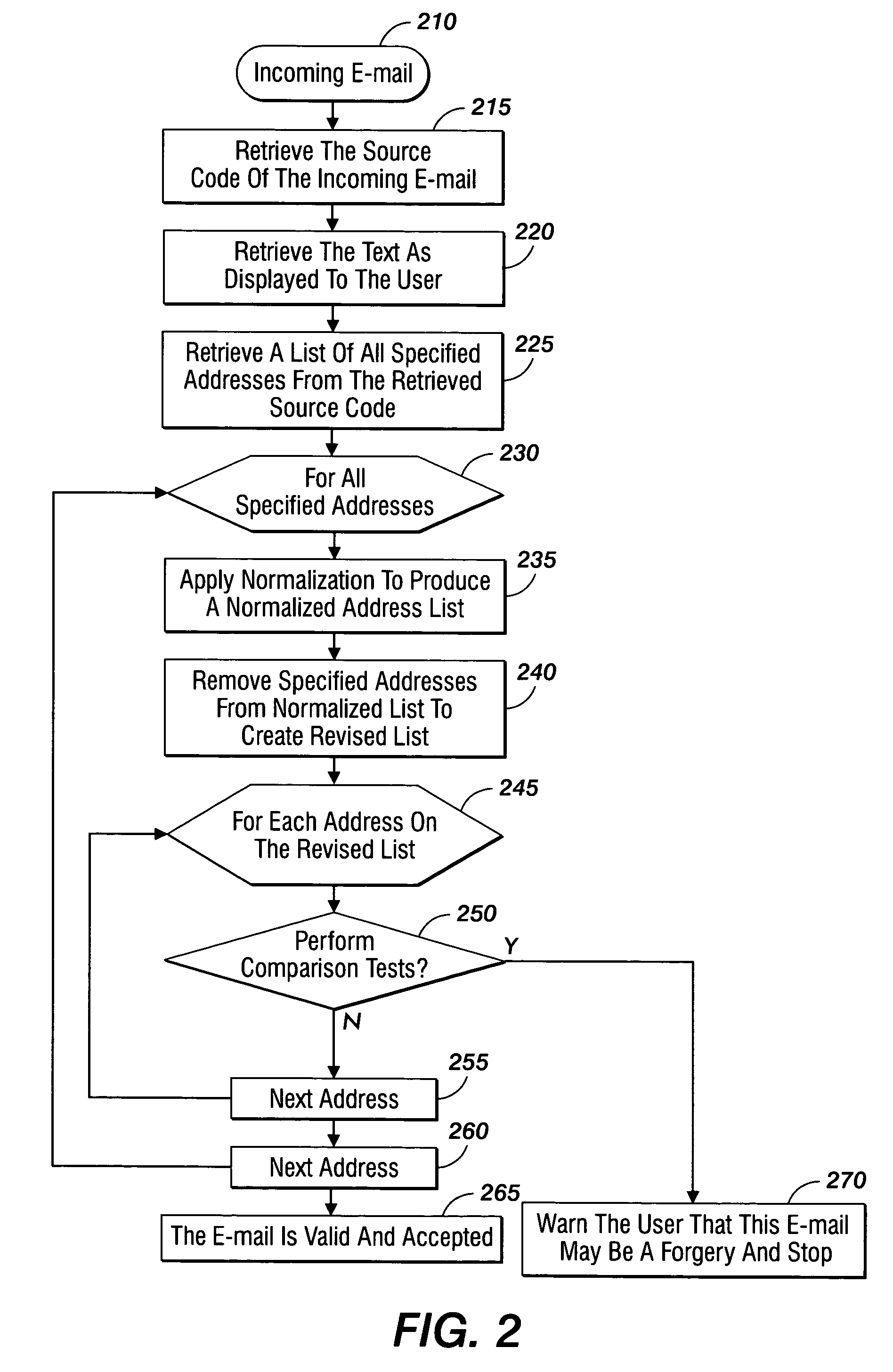
Method and system for phishing detection
InactiveUS7668921B2Multiple digital computer combinationsData switching networksSMS phishingSource code
A method for detection of phishing attempts in received electronic mail messages includes retrieving the source code, displayed text, and a list of all specified addresses contained within the source code of a received electronic message. Visual character normalization is applied to each specified address to develop all possible address combinations and to form a normalized address list. The specified addresses are removed from the normalized address list to create a revised address list, upon which comparison tests are performed to determine if each address in the revised address list is from a valid source. The recipient of the electronic message is informed of any message found to be from an invalid source.
Owner:XEROX CORP
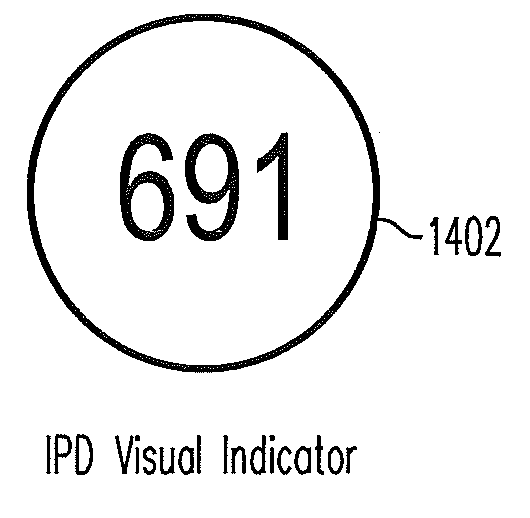
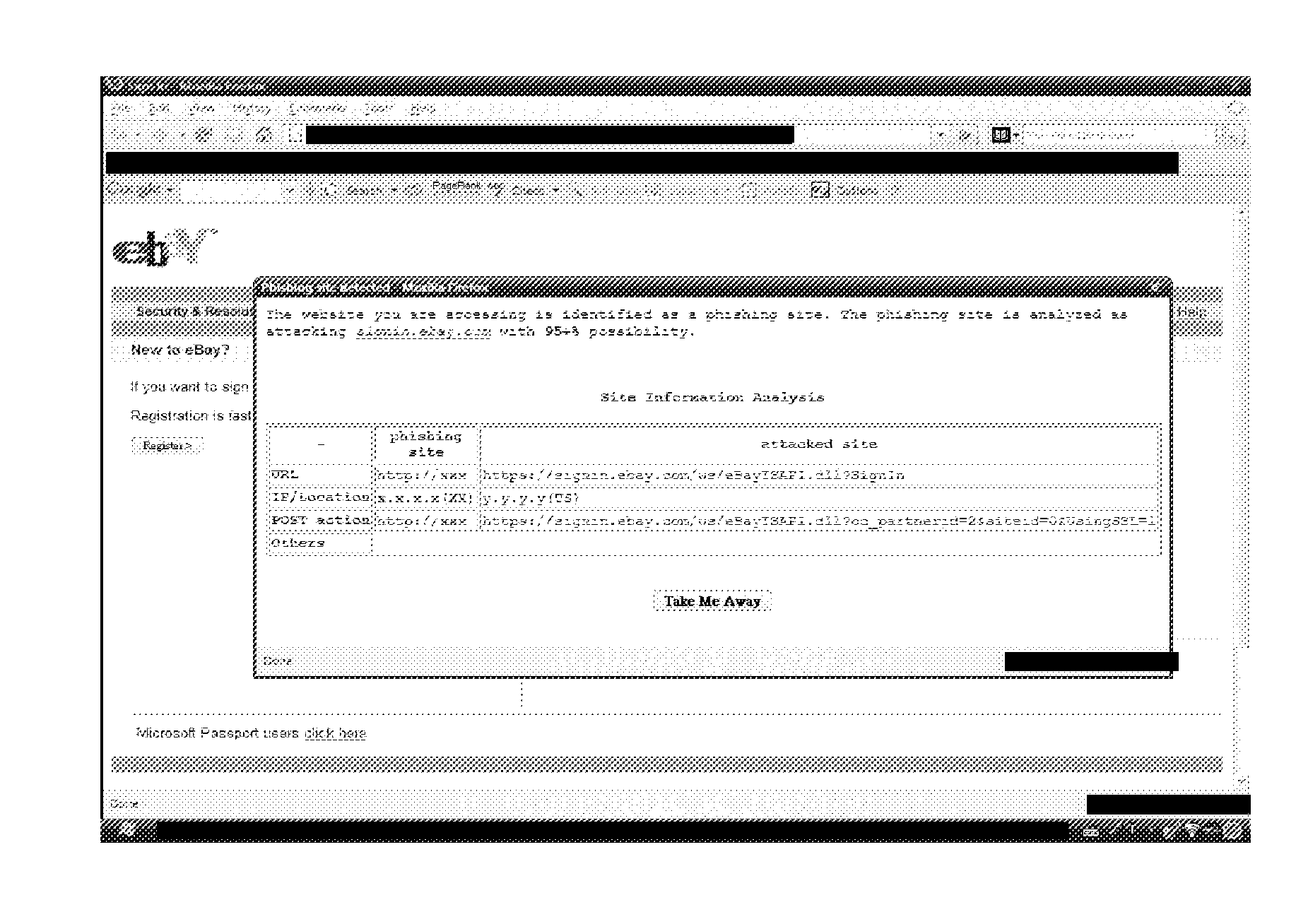
Interactive phishing detection (IPD)
ActiveUS20100306819A1Reduce riskDigital data processing detailsComputer security arrangementsUser verificationWeb site
Systems and methods for use with a client device and a server provide interactive phishing detection at the initiation of the user. Detection of phishing is based on the user's comparison of a visual indicator sent from the server to the client device with a another identical looking visual indicator displayed, for example, on a trusted website. Several security measures may be employed such as changing the visual indicator periodically, generating the visual indicator in a random manner, and authenticating the client device to the server before the server will transmit the visual indicator to the client device. User comparison of the website-displayed visual indicator with the user's client device user interface-displayed visual indicator may facilitate user verification of authenticity of a software application.
Owner:PAYPAL INC
System and method for automated phishing detection rule evolution
ActiveUS9253208B1Reduce maliciousness of the phishing-related objectsRelational databasesPlatform integrity maintainanceData miningPhishing detection
System and method for automatically developing phishing detection rules. Based on detected phishing indicia, a quantitative score is computed for each of a plurality of predefined parameters, with each of the parameters relating to at least one of the phishing indicia. A requirement for evolving a phishing detection rule is assessed, and a new phishing detection rule is generated based on selected parameter scores meeting the rule evolution criteria and on corresponding content of the phishing indicia relating to those selected parameter scores. New phishing detection rules are applied recursively to detect phishing indicia, and more new rules can be further evolved in recursive fashion.
Owner:AO KASPERSKY LAB
Dynamic phishing detection methods and apparatus
A computer-implemented method for detecting a phishing attempt by a given website is provided. The method includes receiving a webpage from the given website, which includes computer-readable code for the webpage. The method also includes ascertaining hyperlink references in the computer-readable code. Each hyperlink reference refers to at least a component of another webpage. The method further includes performing linking relationship analysis on at least a subset of websites identified to be referenced by the hyperlink references, which includes determining whether a first website is in a bi-directional / uni-directional linking relationship with the given website. The first website is one of the subset of websites. The method yet also includes, if the first website is in the bi-directional linking relationship, designating the given website a non-phishing website. The method yet further includes, if the first website is in the uni-directional linking relationship, performing anti-phishing measures with respect to the given website.
Owner:TREND MICRO INC
Systems and methods for identifying phishing websites
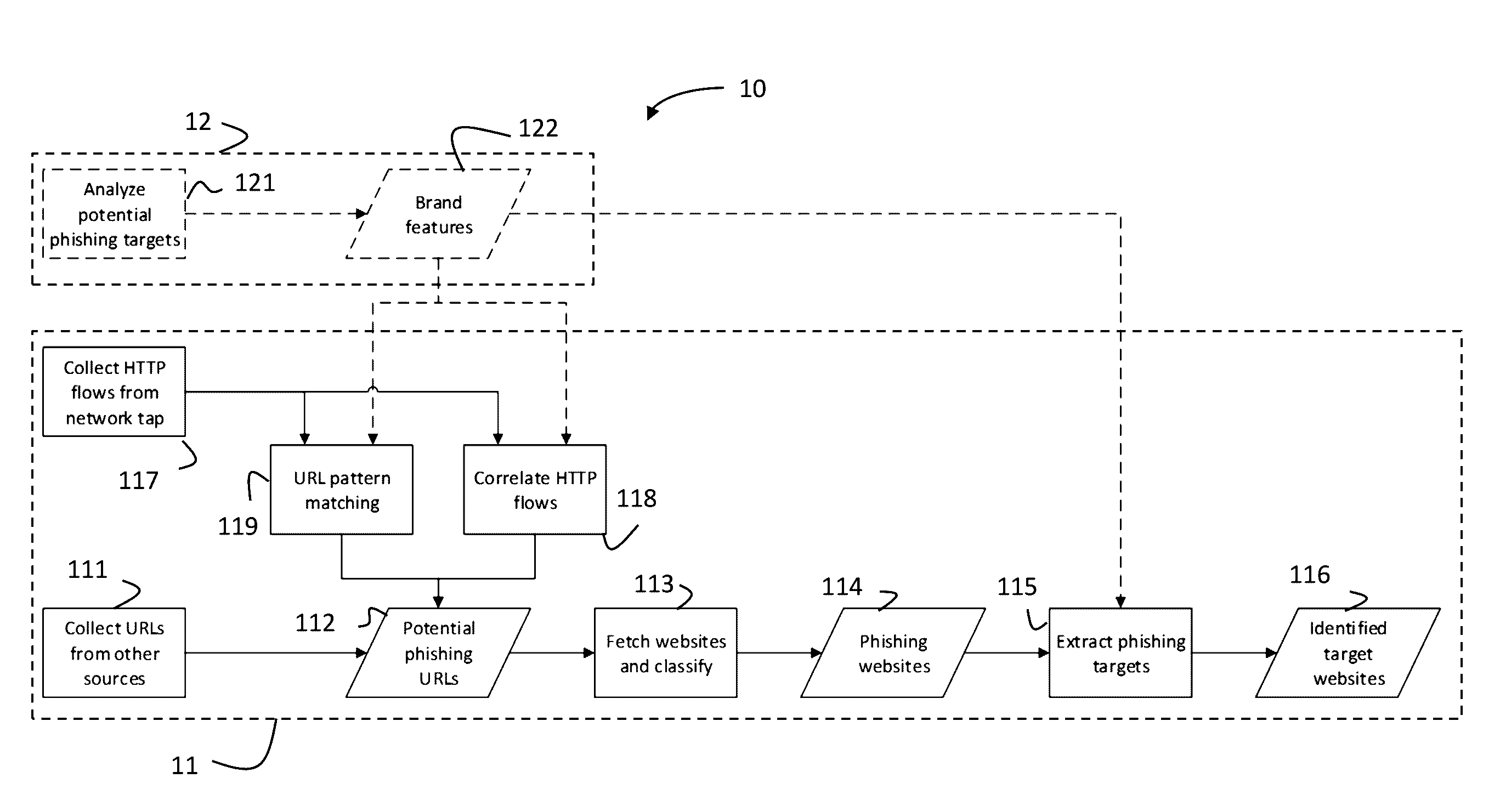
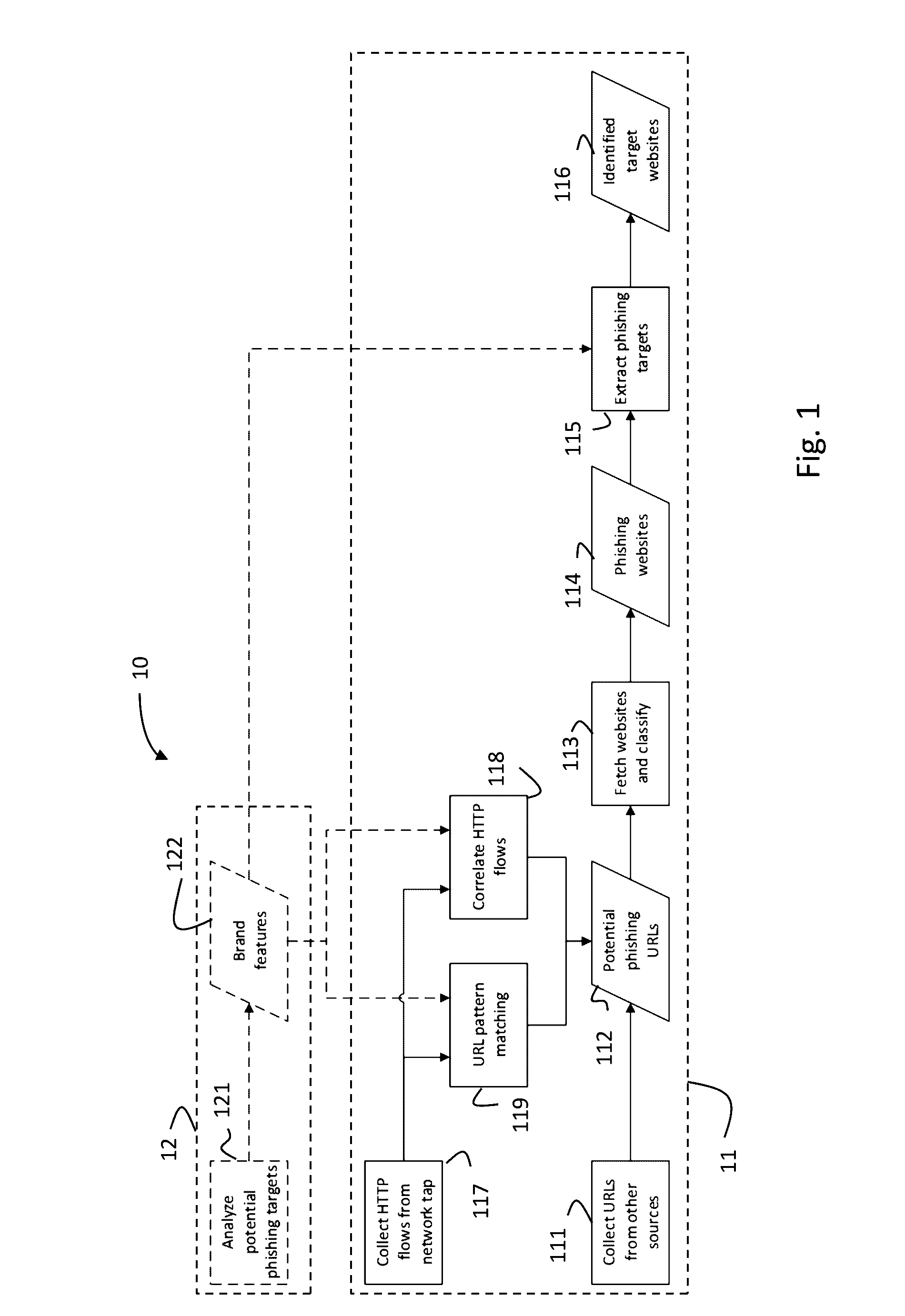
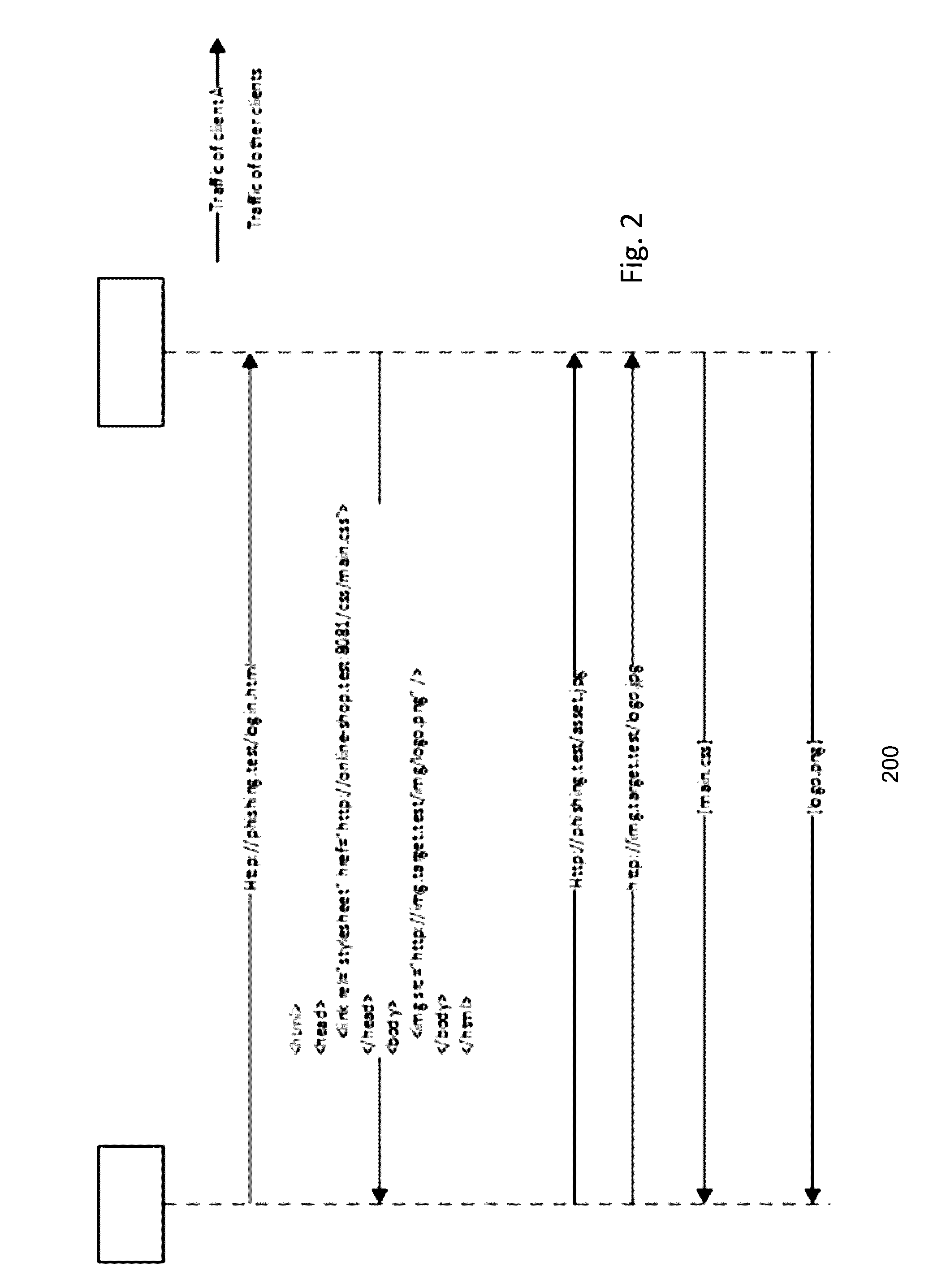
Systems and methods are provided for automatically detecting phishing attacks. Network traffic may be monitored to detected phishing attacks and / or identify phishing websites and / or target websites. The monitoring may comprise generating and analysing logs corresponding to the monitored network traffic, with the logs comprising network traffic events and / or information relating to requesting and responding addresses. The network traffic events used in detecting phishing attacks may comprise sequences each comprising one or more requests and responses. Requested websites may be identified as phishing websites based on event sequences meeting particular criteria. Components and / or functions utilized for monitoring the network traffic and / or automatic phishing detection based thereon may be implemented as parts of a browser and / or network routers utilized during typical and normal use operations.
Owner:SWISSCOM
Network fishing detection method and apparatus thereof
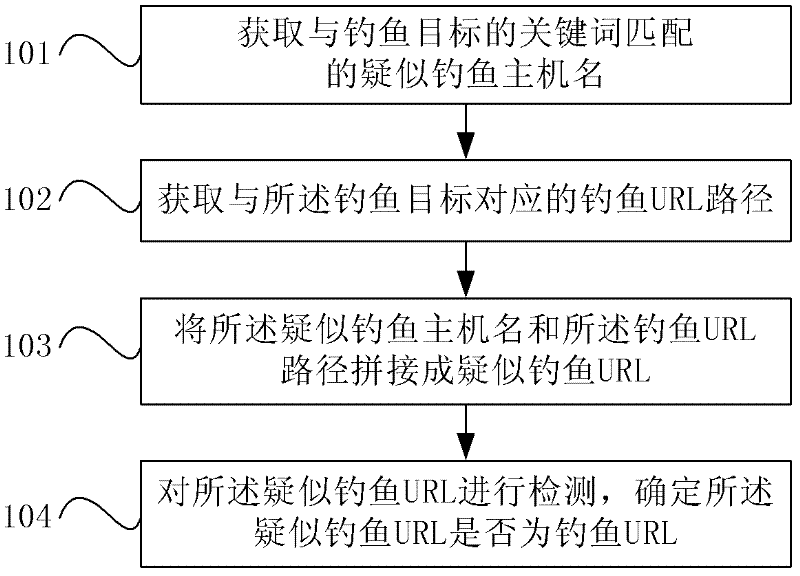
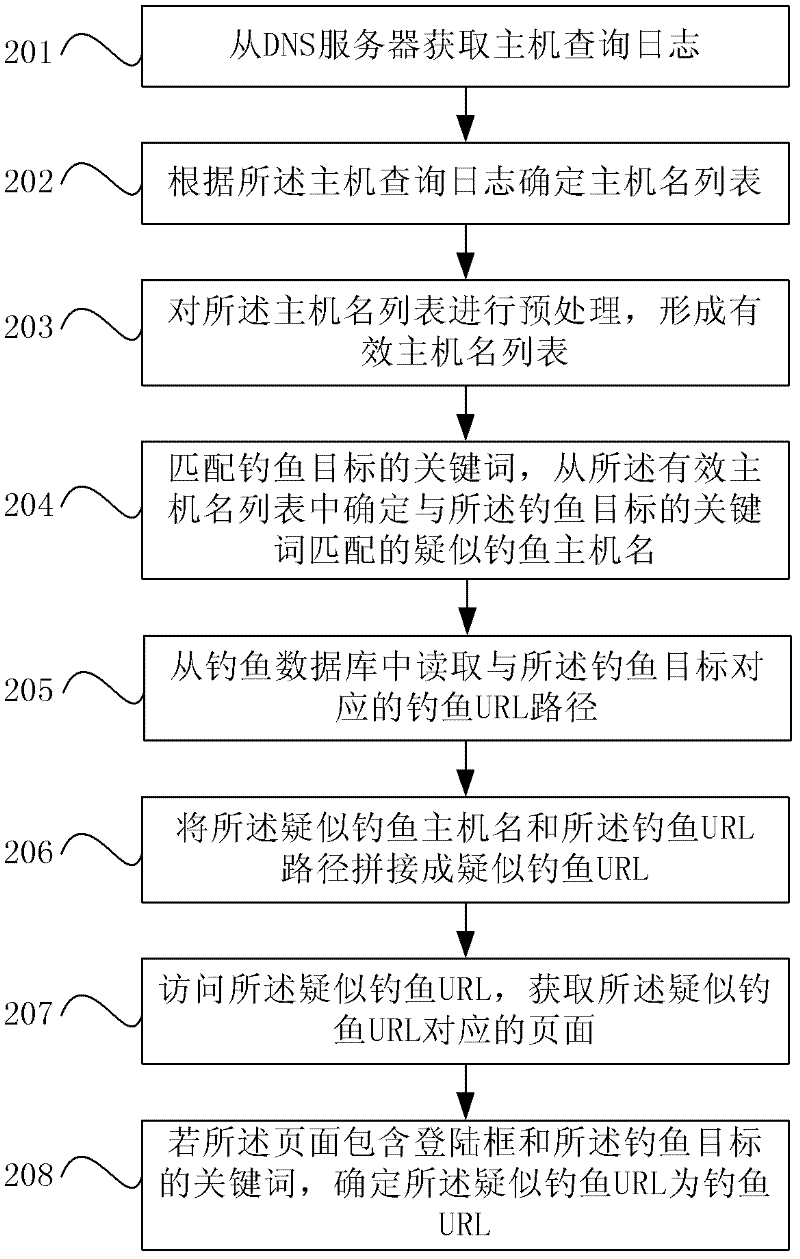
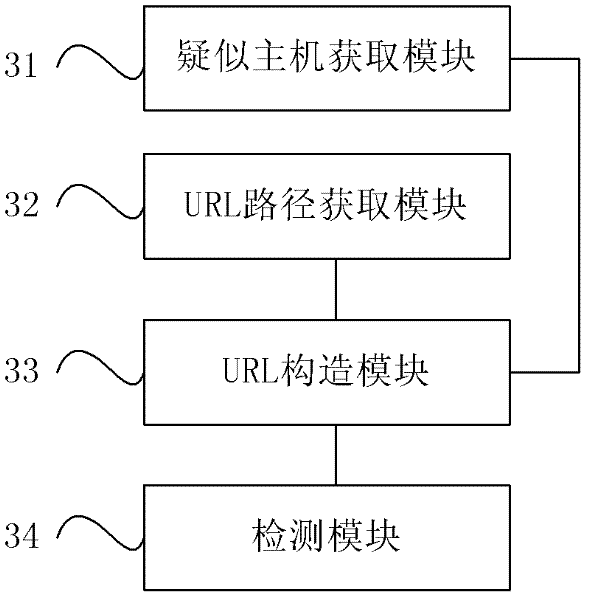
ActiveCN102316099AEarly detectionImprove detection efficiencyDigital data information retrievalTransmissionPassive detectionUniform resource locator
The invention provides a network fishing detection method and an apparatus thereof. The method comprises the following steps: acquiring a suspected fishing host name matching a fishing object keyword; acquiring a fishing Uniform Resource Locator (URL) path corresponding to a fishing object; jointing the suspected fishing host name and the fishing URL path to form a suspected fishing URL; detecting the suspected fishing URL, and determining whether the suspected fishing URL is a fishing URL or not. According to an embodiment of the invention, through a technique of actively acquiring the suspected fishing host name matching the fishing object keyword and the fishing URL path corresponding to the fishing object, jointing them to form the suspected fishing URL, detecting the suspected fishing URL, and determining whether the suspected fishing URL is a fishing URL or not, a problem that in the prior art passive detection triggered by a user can not deal with more and more rampant and general fishing attack is overcome, early discovery of a fishing website is realized, and fishing website detection efficiency is raised.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
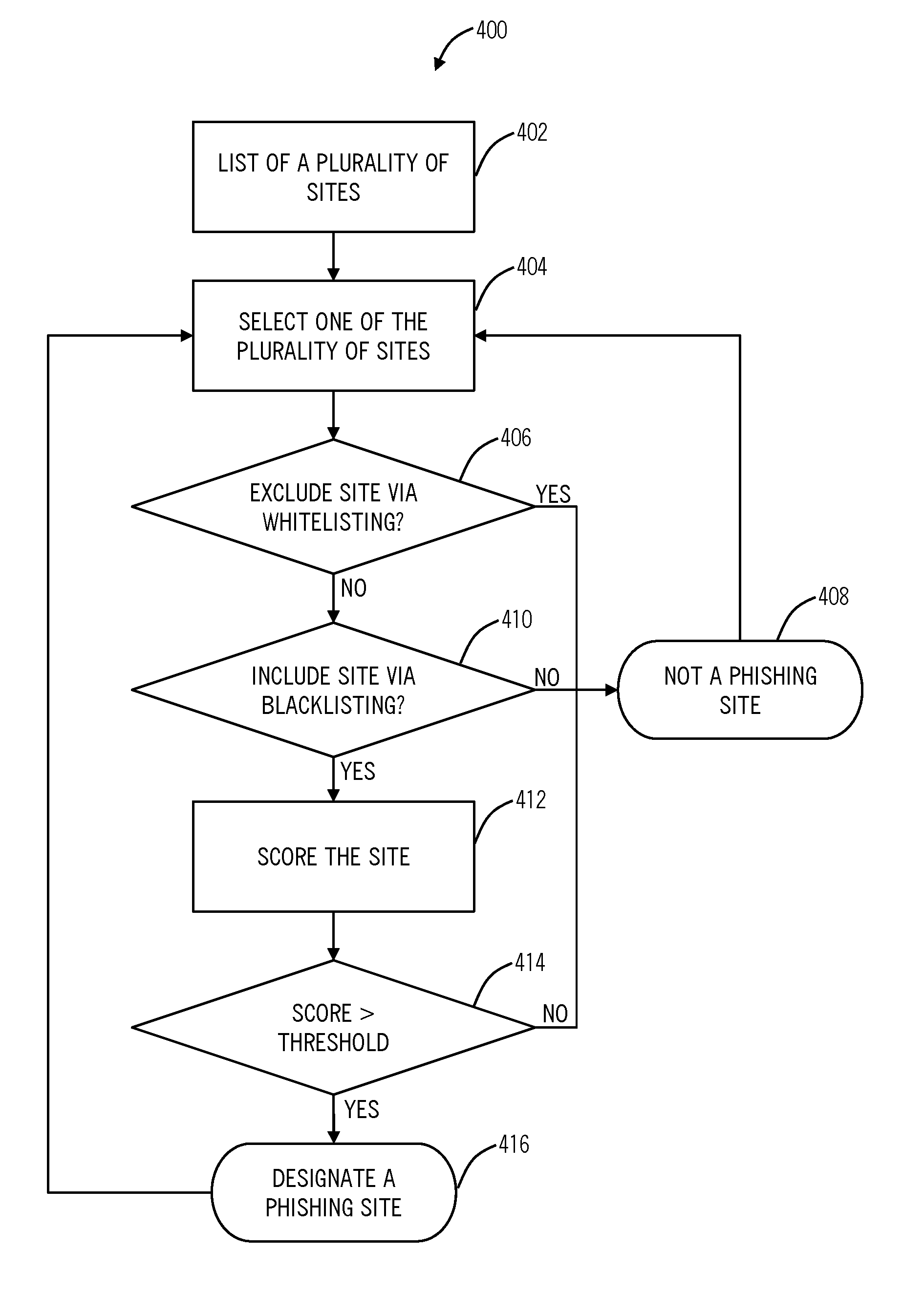
Phishing detection systems and methods
The present disclosure provides phishing heuristic systems and methods that detect phishing sites. The present invention may be implemented via a server connected to the Internet, via a distributed security system, and the like. Phishing sites may be detected in a single transaction, i.e. client request plus server reply, while knowing as little as possible about the site being masqueraded. In an exemplary embodiment, a phishing site detection system and method utilized three steps—whitelisting, blacklisting, and scoring. For example, if a particular page meets all requirements of blacklisting without any elements of whitelisting and has a score over a particular threshold, that particular site may be designated as a phishing page.
Owner:ZSCALER INC
Phishing detection and targeted remediation system and method
PendingUS20200028876A1Minimize information security damageComputer security arrangementsTransmissionAttackInformation security
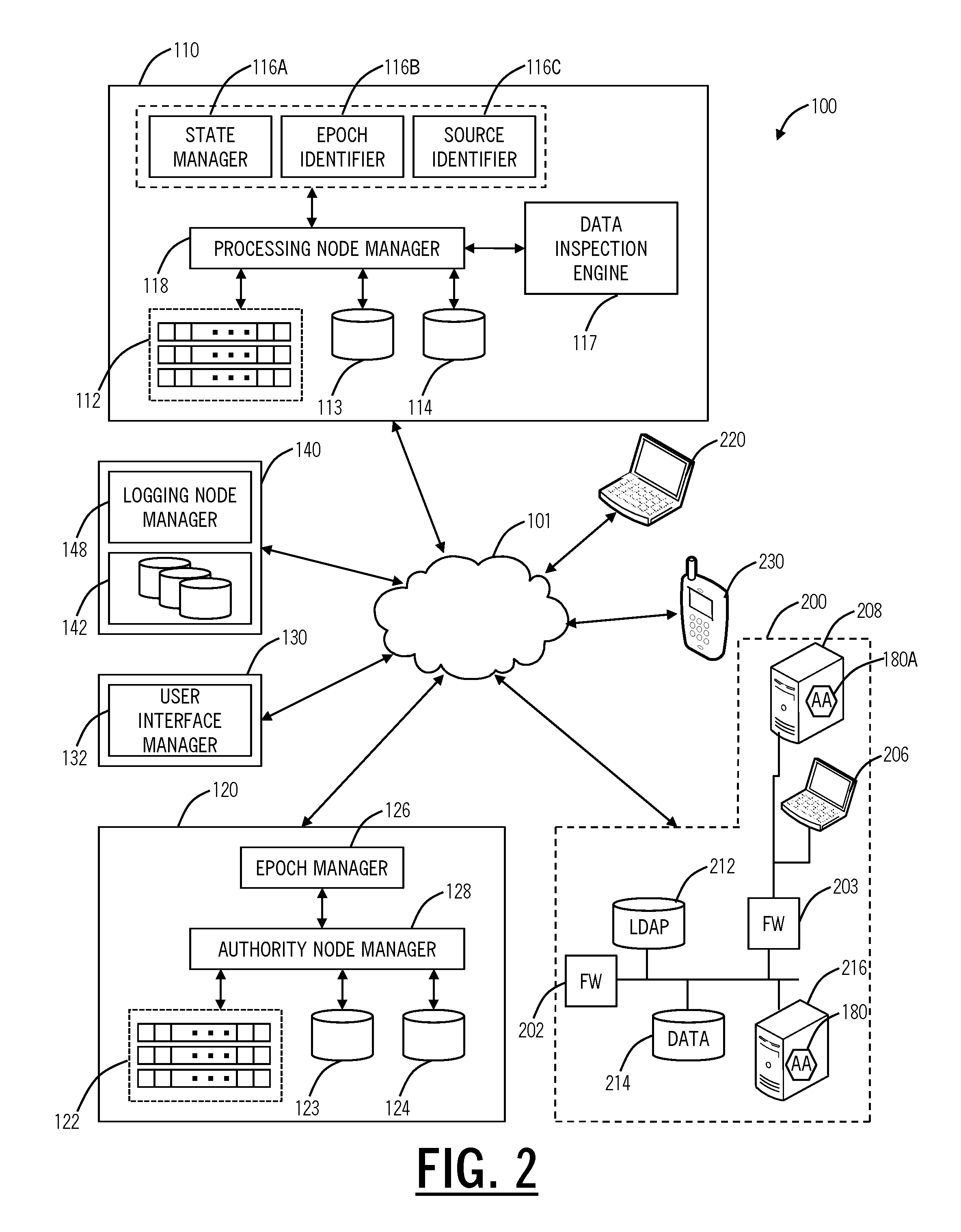
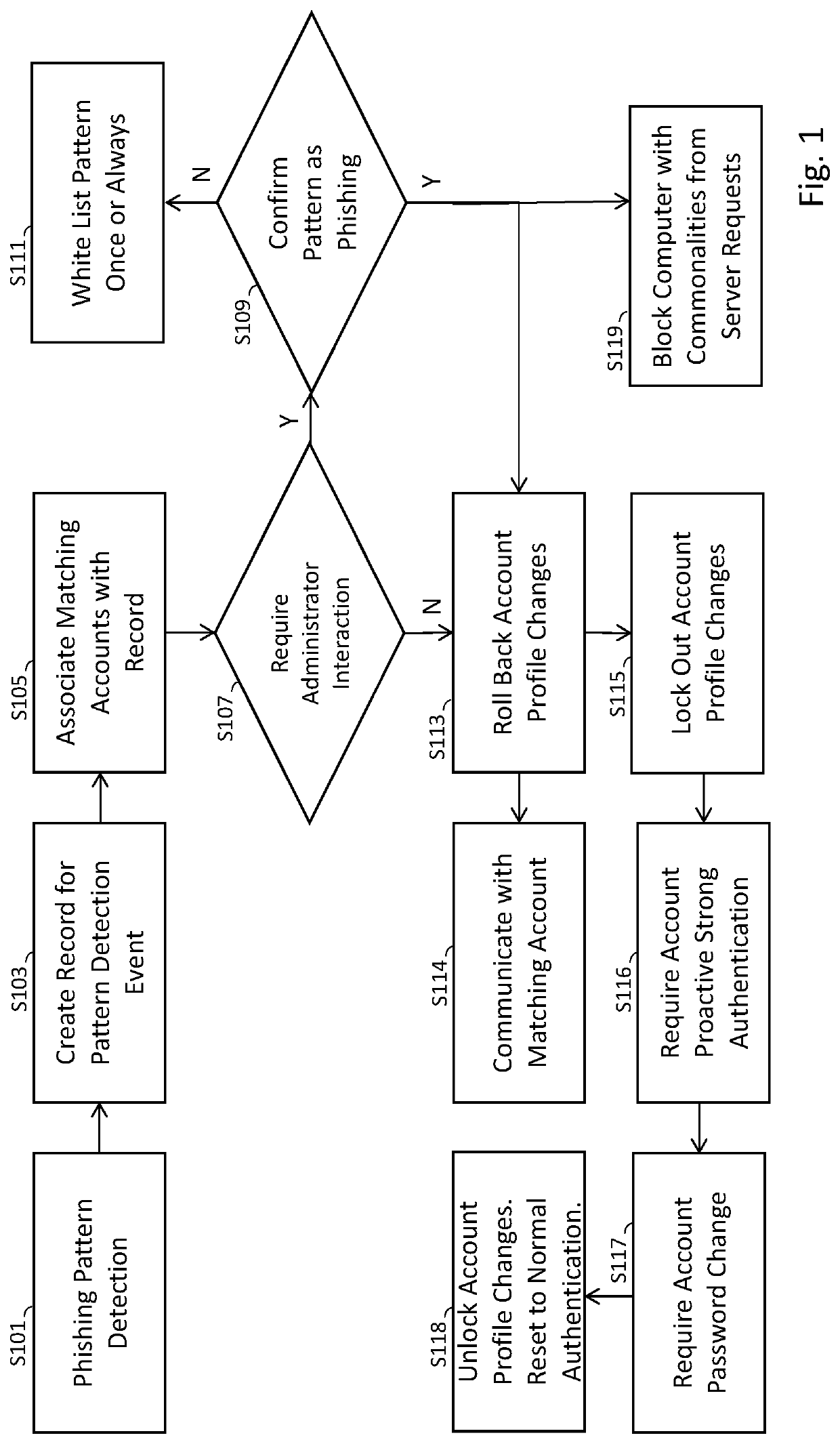
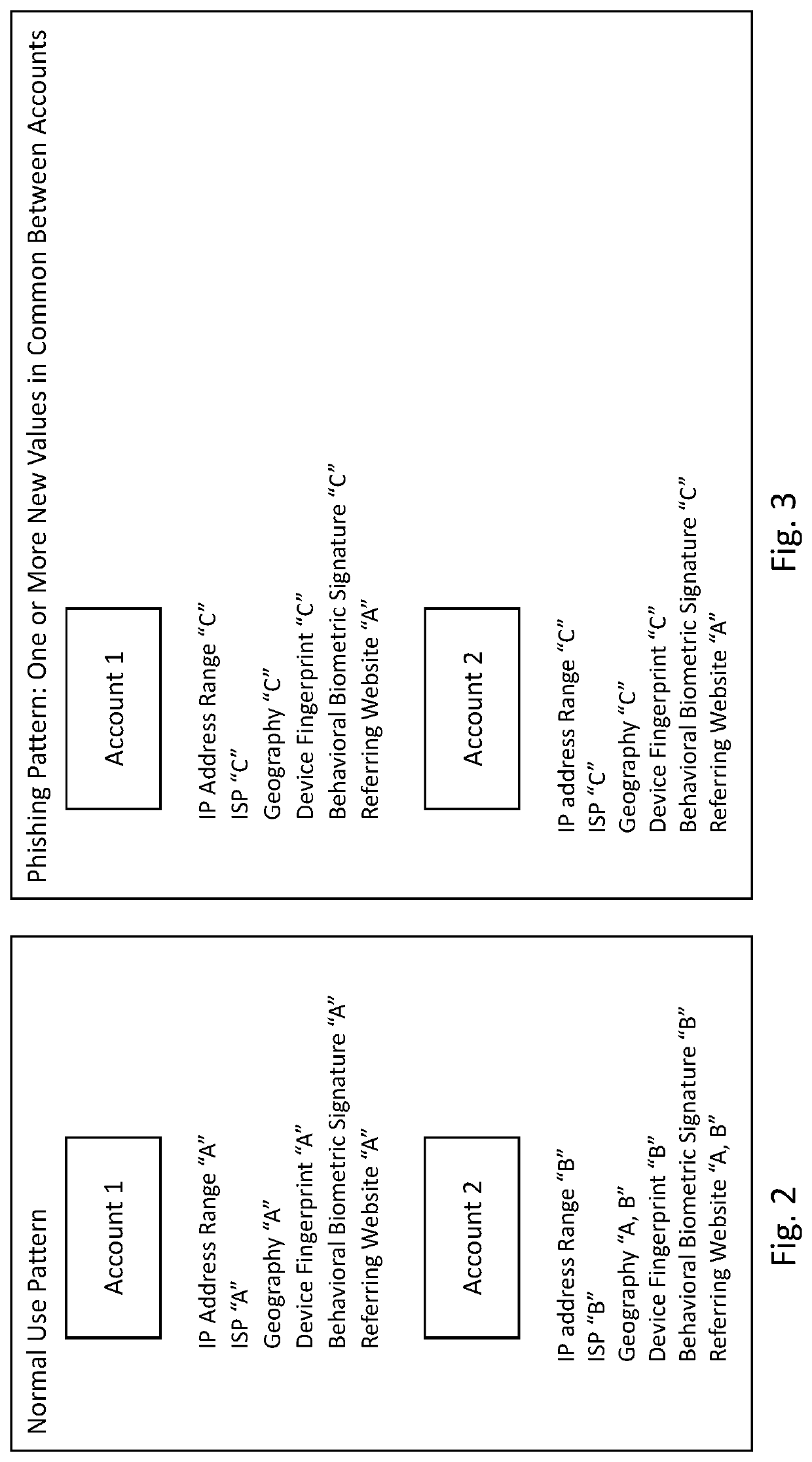
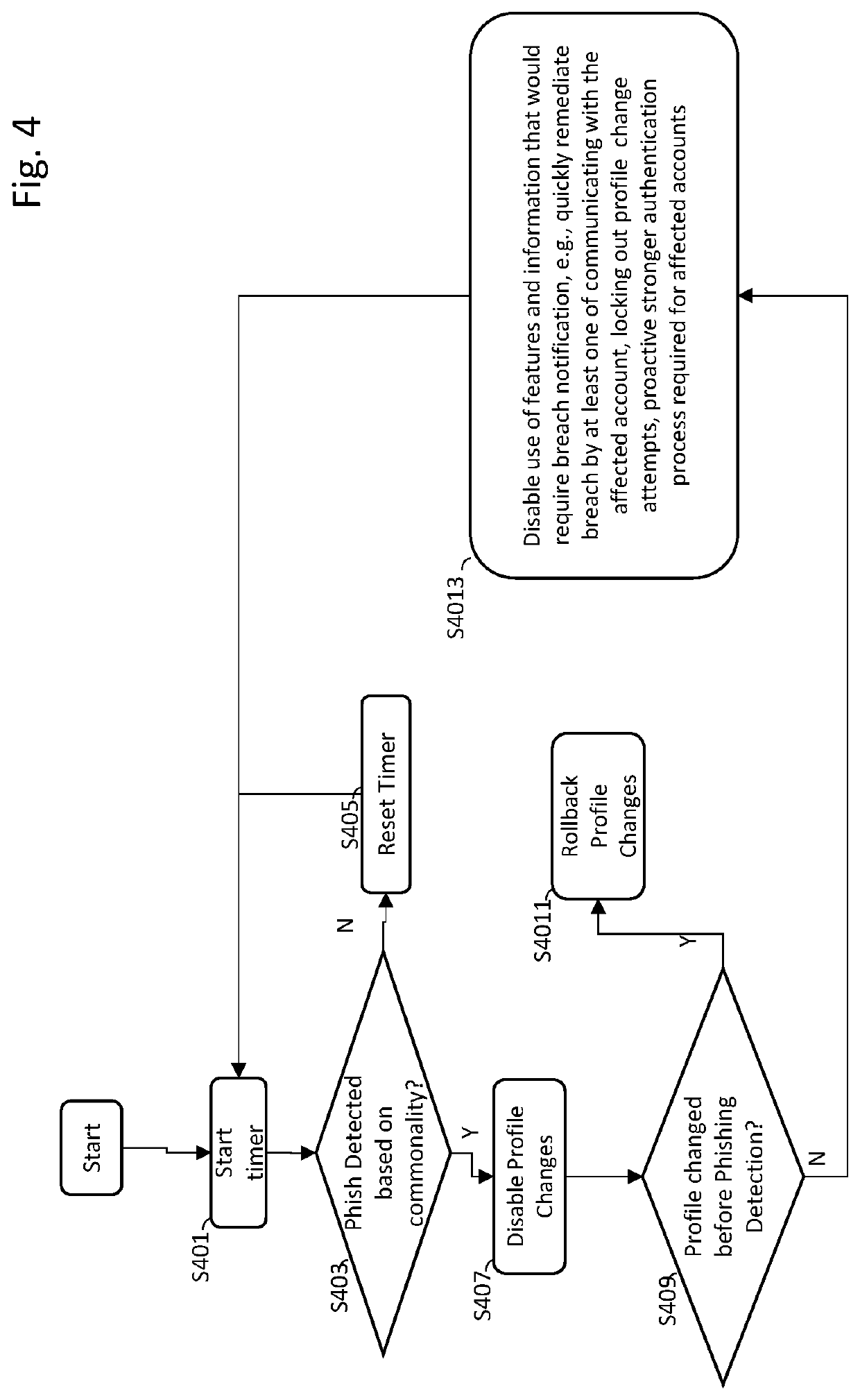
A system and method exploit information gained by observing abnormal commonality factors from multiple accounts over a predetermined time frame. The presence of an abnormal commonality factor serves as an indication that a group of accounts may have been compromised by a common actor via information gained by successful phishing of multiple users' information to improperly gain access to their respective accounts. Once this commonality associated with phishing is detected, the system provides a mechanism and process to rapidly respond to the phishing-originated attack to minimize information security damage to the affected accounts.
Owner:CORELOGIC SOLUTIONS
Phishing website detection method excavated based on network group
InactiveCN102999638AImprove the efficiency of phishing detectionSave resourcesSpecial data processing applicationsWeb siteEngineering
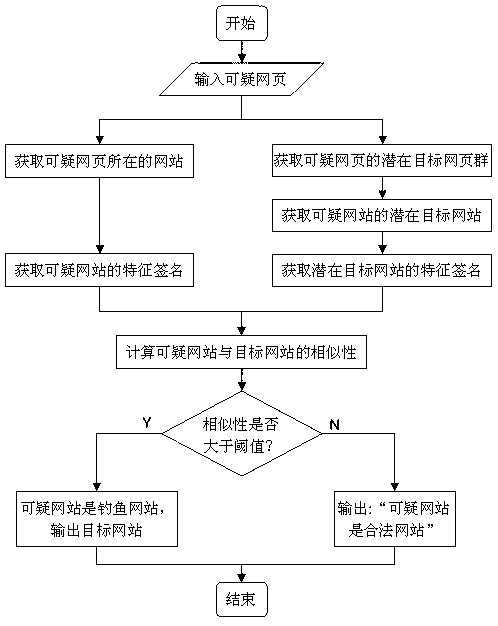
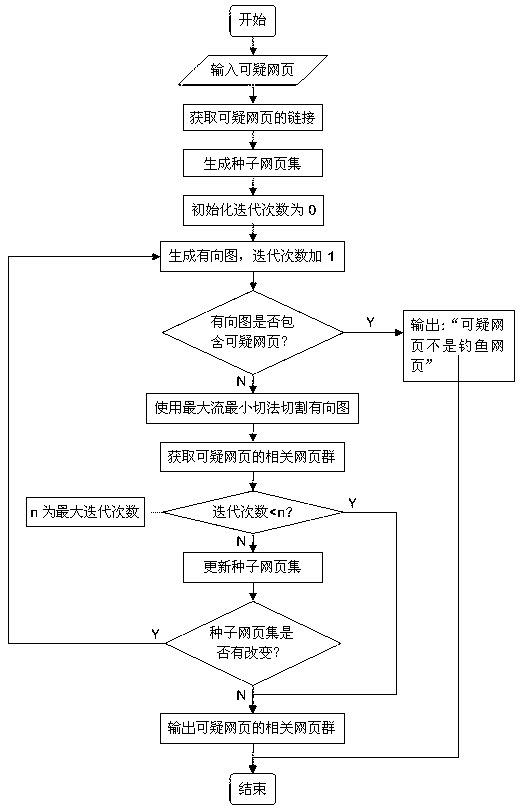
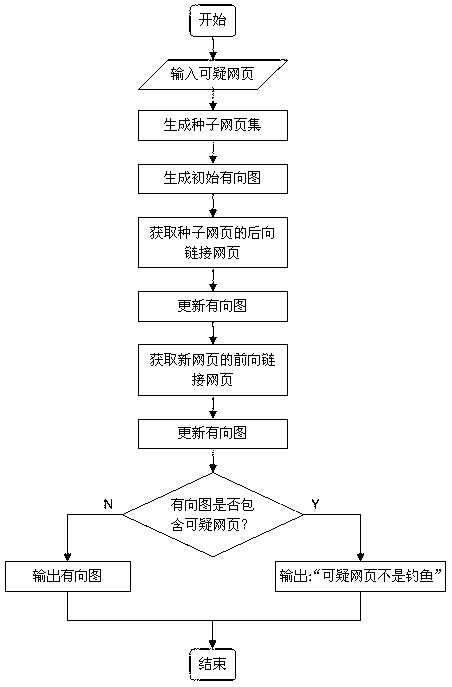
The invention provides a phishing website detection method excavated based on a network group. The phishing website detection method includes constructing a webpage set related to a given iffy webpage by using a crawler, then obtaining an iffy website and a potential target website thereof, furthermore calculating website feature signatures, and judging whether the iffy website is a phishing website or not through similarity calculations of the website feature signatures, if yes, returning to the target website thereof. The purpose of the phishing website detection method is detecting whether the website which the iffy webpage is located in is the phishing website so as to find the target website of the phishing website when detection is finished. The process of phishing detection is the process of finding the target website, and due to the fact that the iffy website is only calculated with the related potential target website for similarity, comparisons of the iffy website with irrelevant legal websites in internet are reduced, phishing detection efficiency is improved, resources are saved effectively, and work efficiency is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
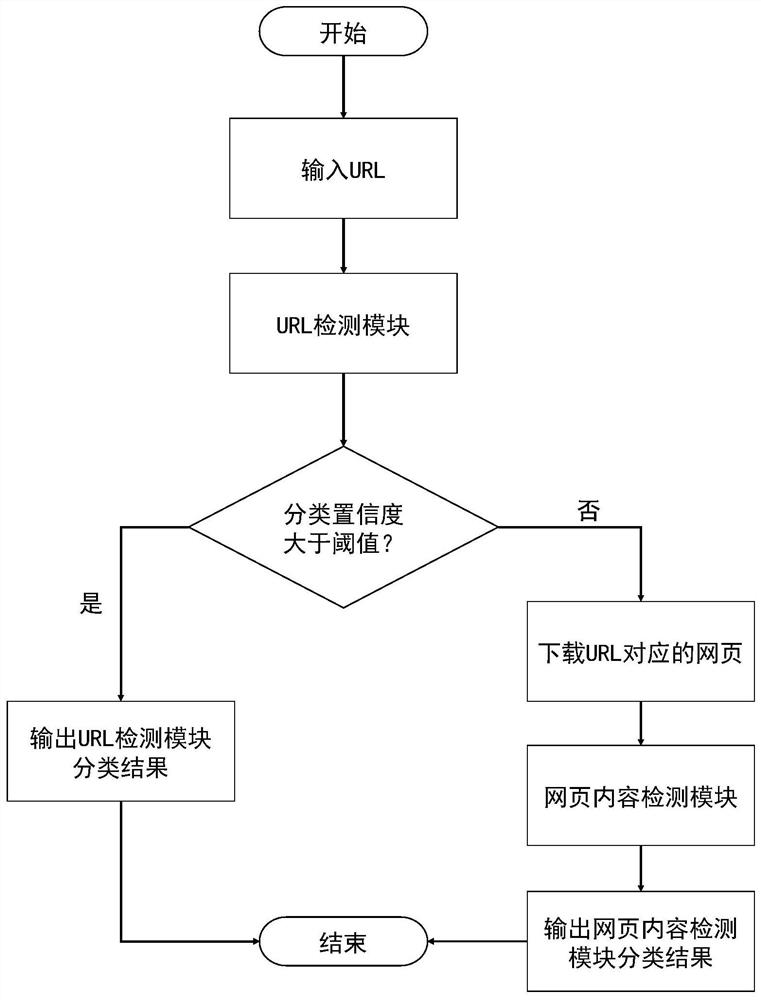
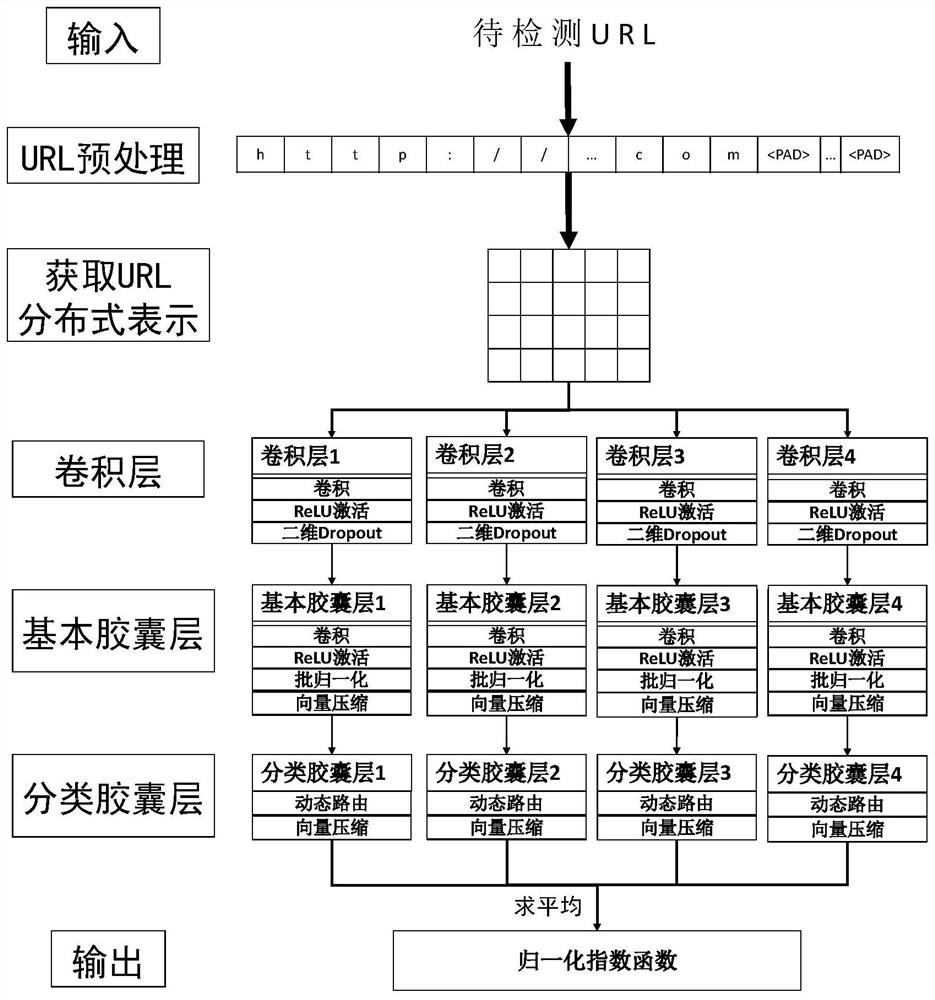
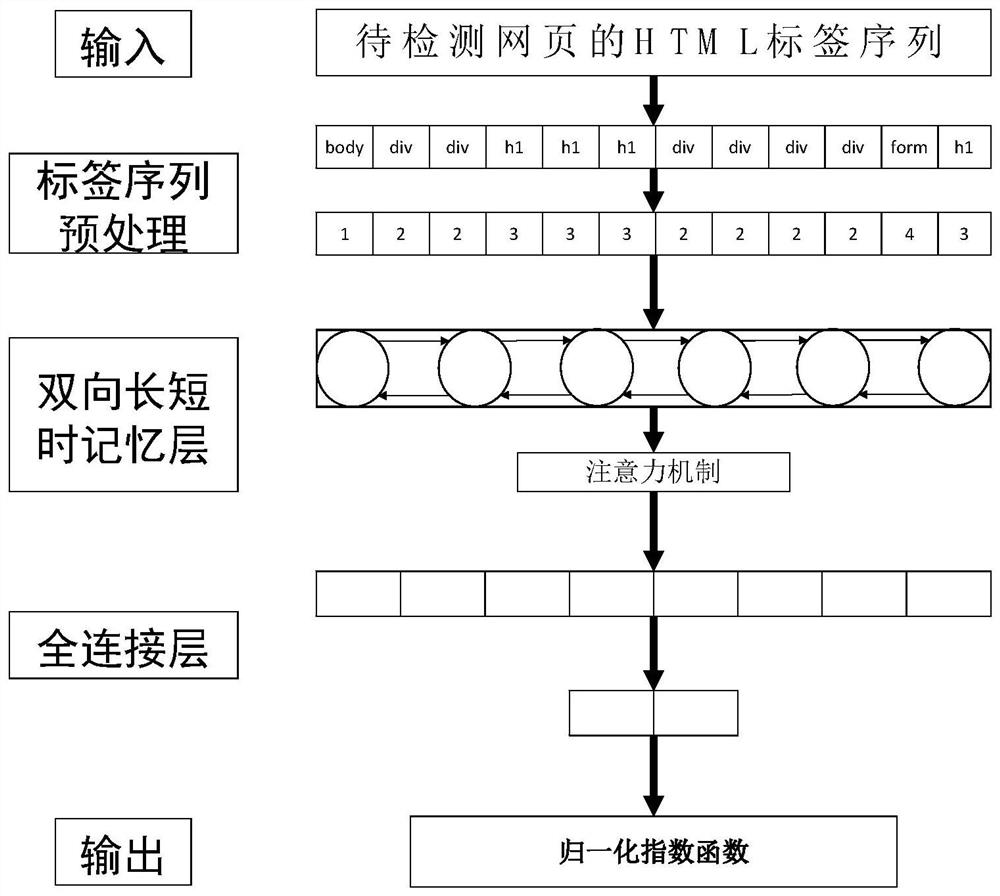
Hierarchical phishing website detection method based on deep learning
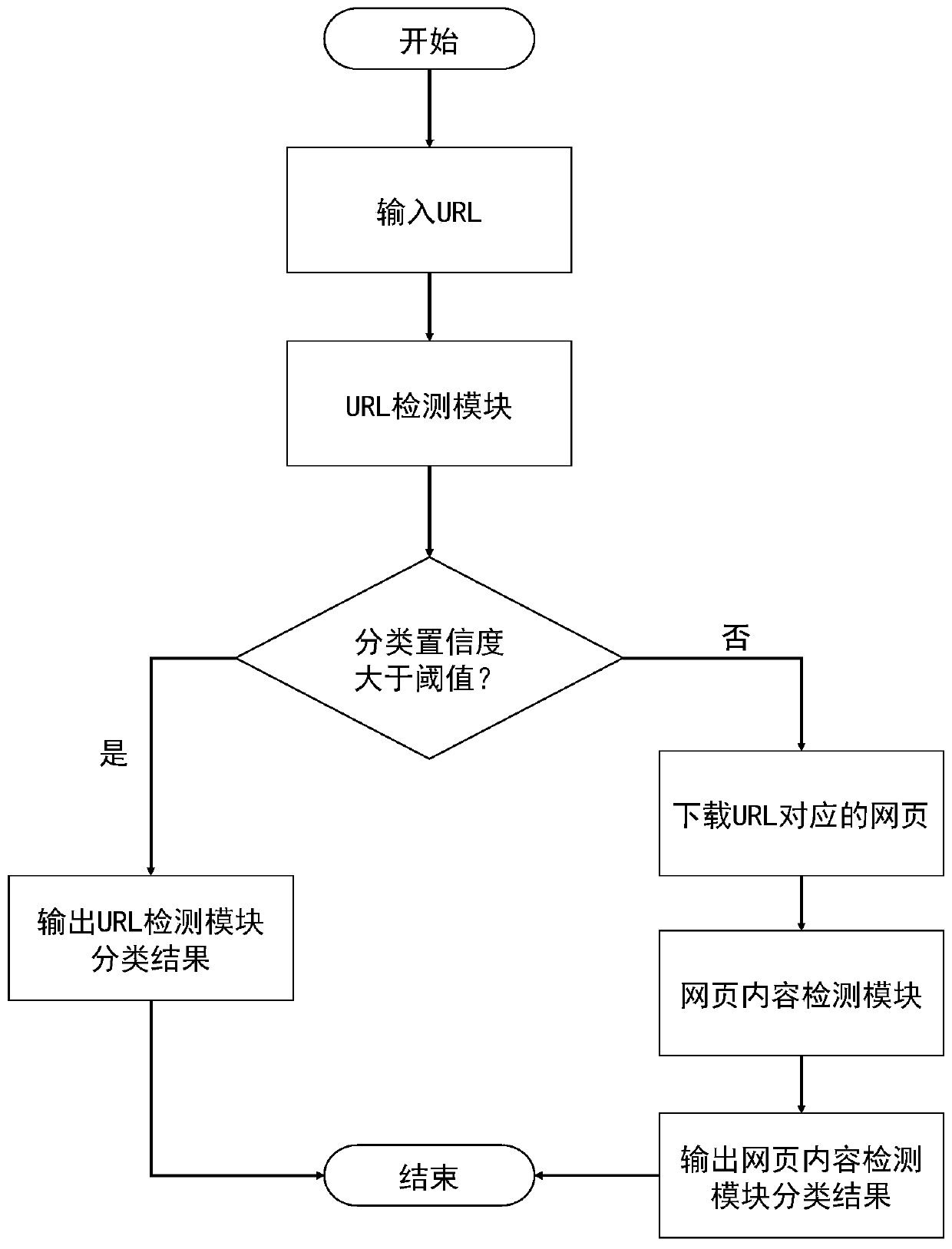
ActiveCN110602113AThe detection process is fastImprove accuracyCharacter and pattern recognitionNeural architecturesPattern recognitionUniform resource locator
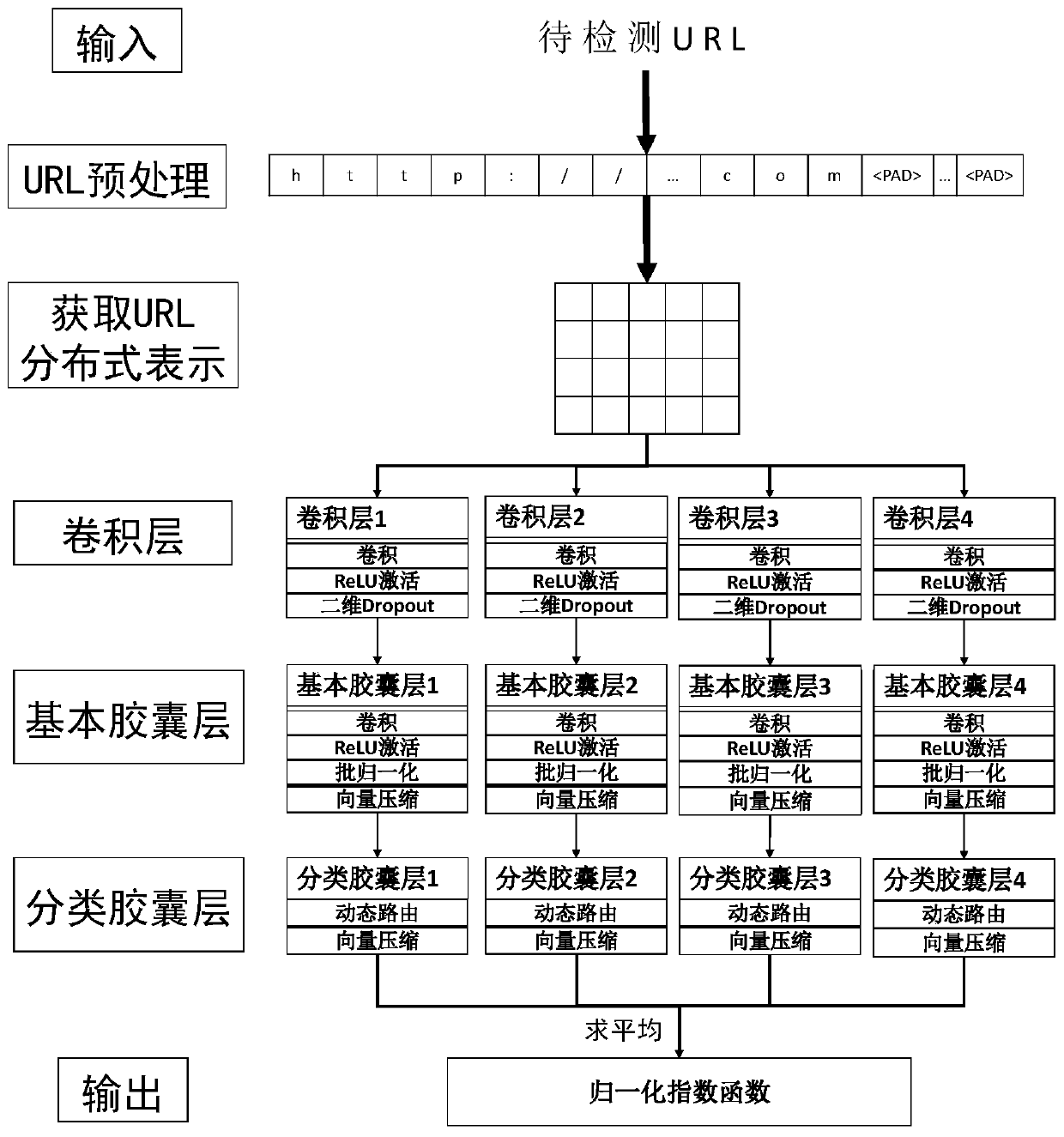
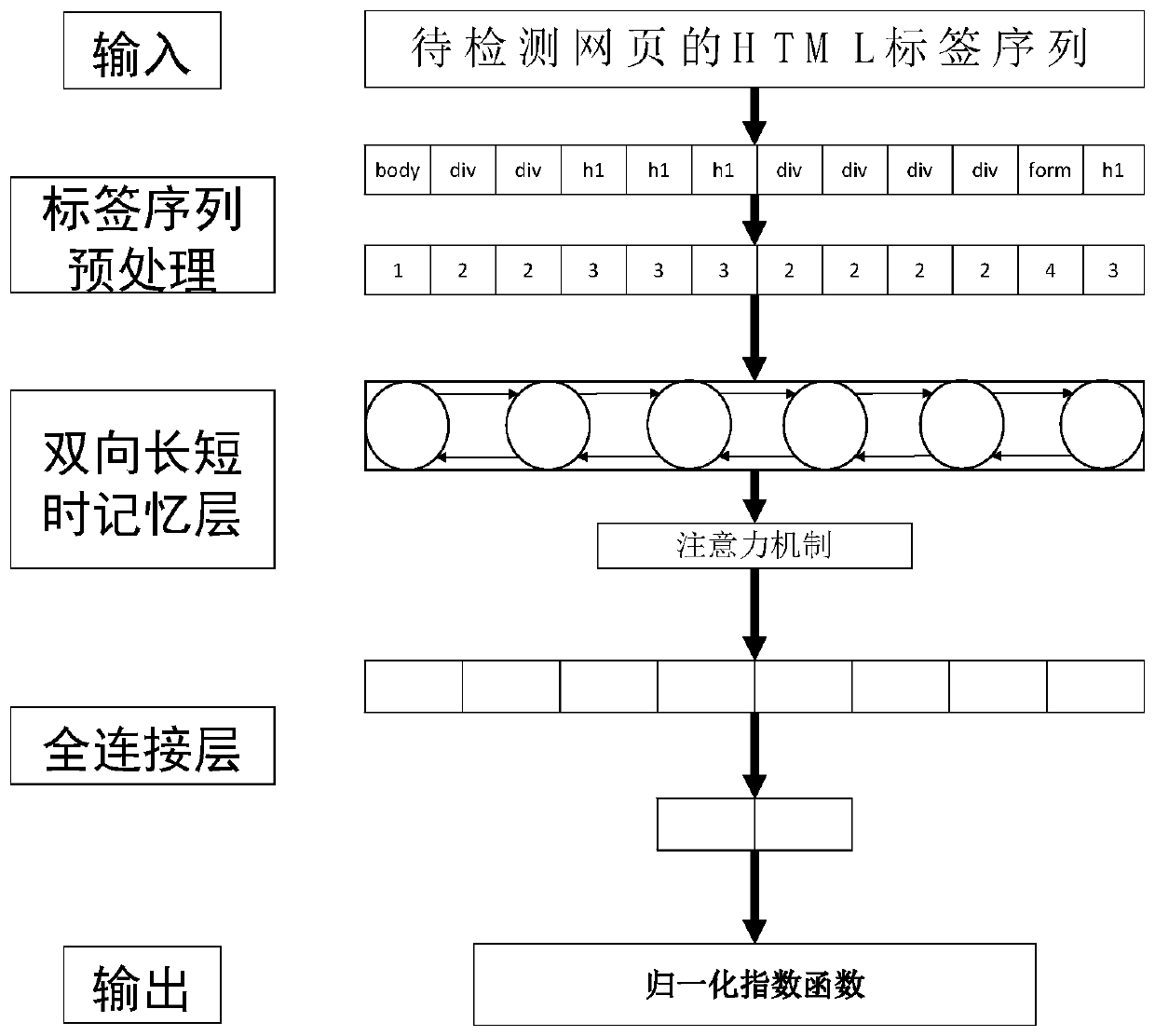
According to the hierarchical phishing website detection method based on deep learning, the URL and the webpage content are combined for phishing website detection, and phishing detection modules of different hierarchies can be selected and used in a self-adaptive mode for rapid and accurate phishing website detection. The method comprises the following steps: firstly, detecting an input URL; outputting the probability that the URL belongs to the phishing website; if the output probability is greater than a preset threshold value, judging that the to-be-detected website is a phishing website;otherwise, downloading a webpage corresponding to the URL to be detected; counting the number of HTML tags of the webpage, vectorizing a statistical result by utilizing an HTML tag list, extracting accurate webpage content feature representation according to a vectorized HTML tag sequence, and classifying through a full connection layer to obtain the probability that the URL belongs to a phishingwebsite.
Owner:SUN YAT SEN UNIV
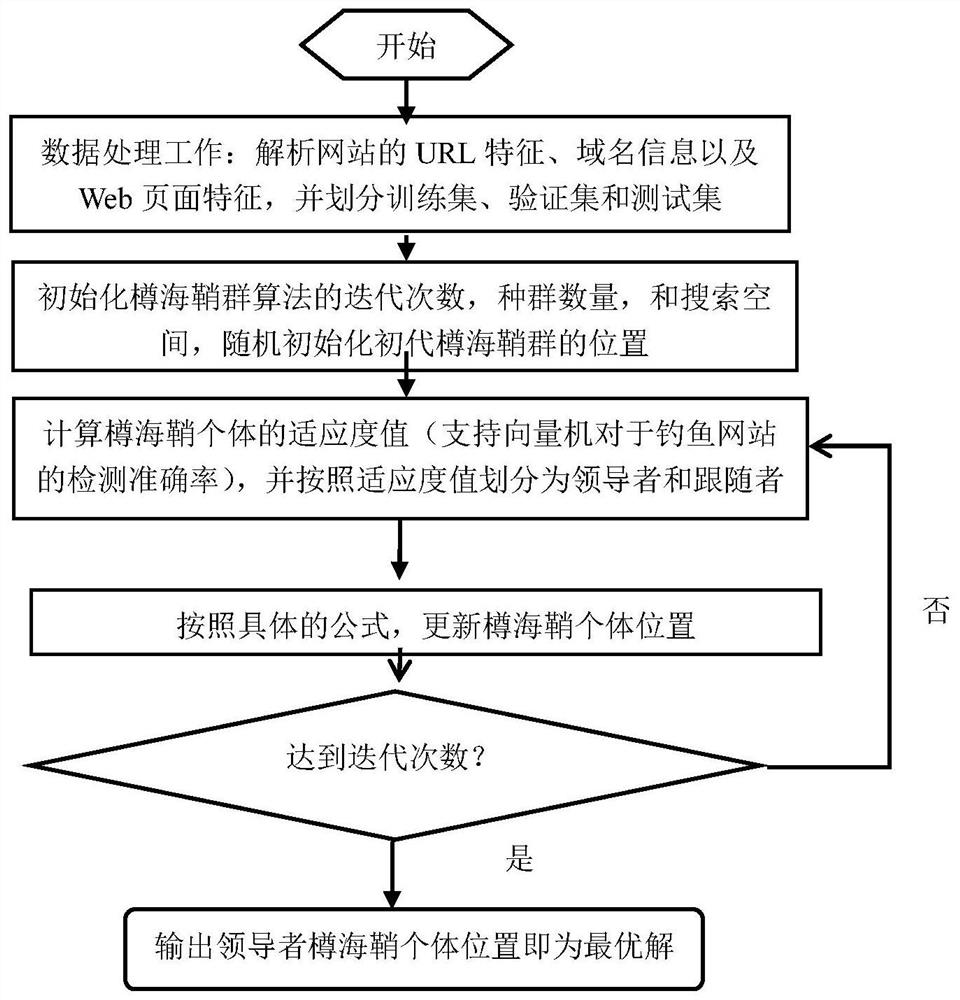
A network fishing detection method based on a Schizothorax group algorithm support vector machine
ActiveCN109873810AAvoid local optimaAvoid convergence speedCharacter and pattern recognitionBiological modelsSupport vector machineData set
The invention discloses a network fishing detection method based on a douche group algorithm support vector machine. The method comprises the following steps of firstly, initializing basic parametersof the douche group algorithm, including population number, iteration times, individual dimension and search space; randomly initializing the position and range of the individual; and then dividing into leader vessel sea sheaths and follower vessel sea sheaths according to the magnitude of the fitness value, and excavating the optimal parameters of the support vector machine by using the coordination and cooperation of the two vessel sea sheaths. In each iteration, the function for evaluating the fitness value of the individual is the detection accuracy of the parameter carried by the individual on the phishing website data set by the support vector machine. Compared with the common optimization algorithms such as a genetic algorithm, a gravitation search algorithm, a bat algorithm and a particle swarm algorithm, the optimal parameter parameters of the support vector machine can be mined as much as possible on the optimized support vector machine, and the fishing detection accuracy ofthe support vector machine is improved.
Owner:HUBEI UNIV OF TECH
Phishing detection methods and systems
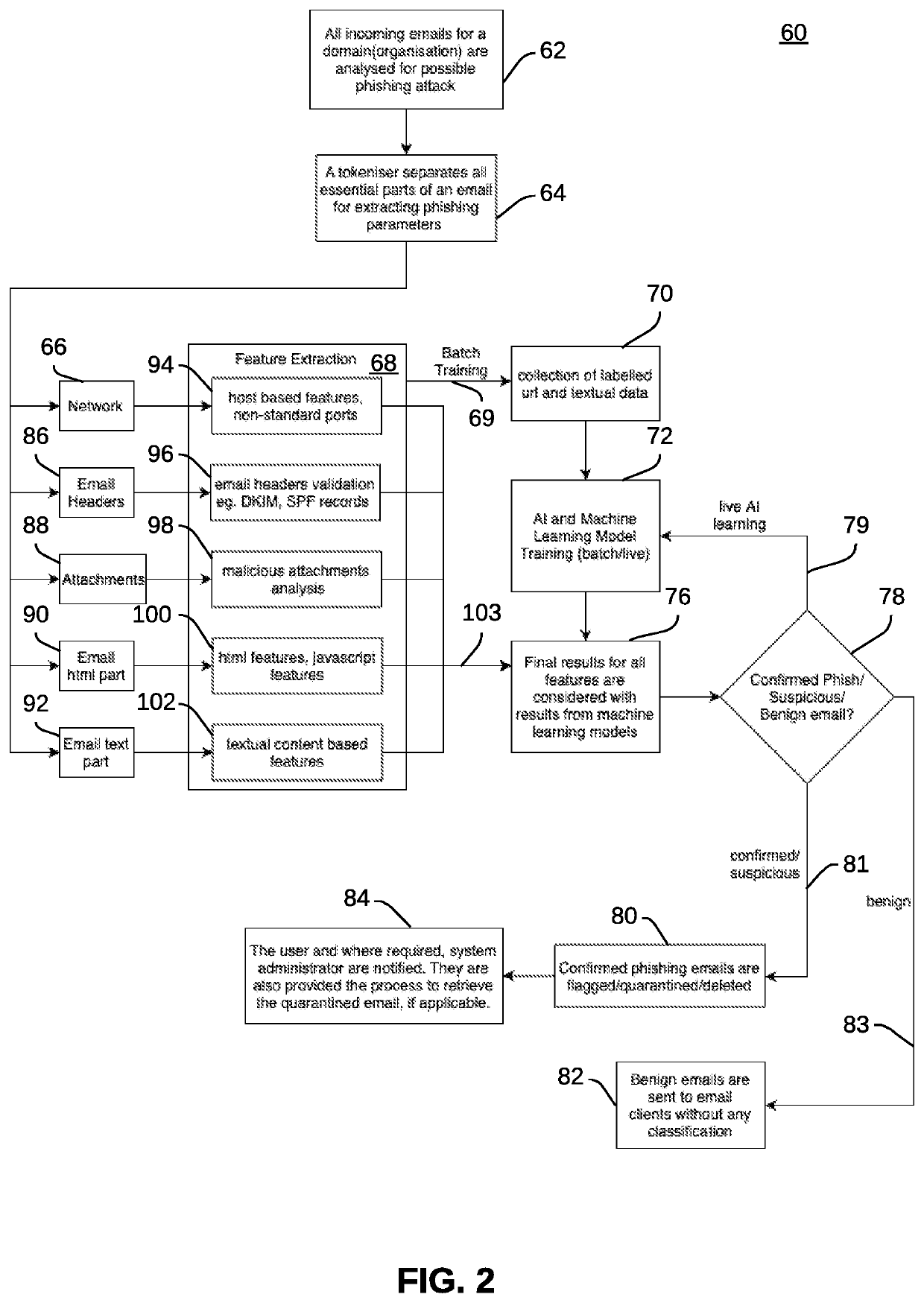
ActiveUS20210281606A1Easy to understandMathematical modelsOffice automationFeature extractionMedicine
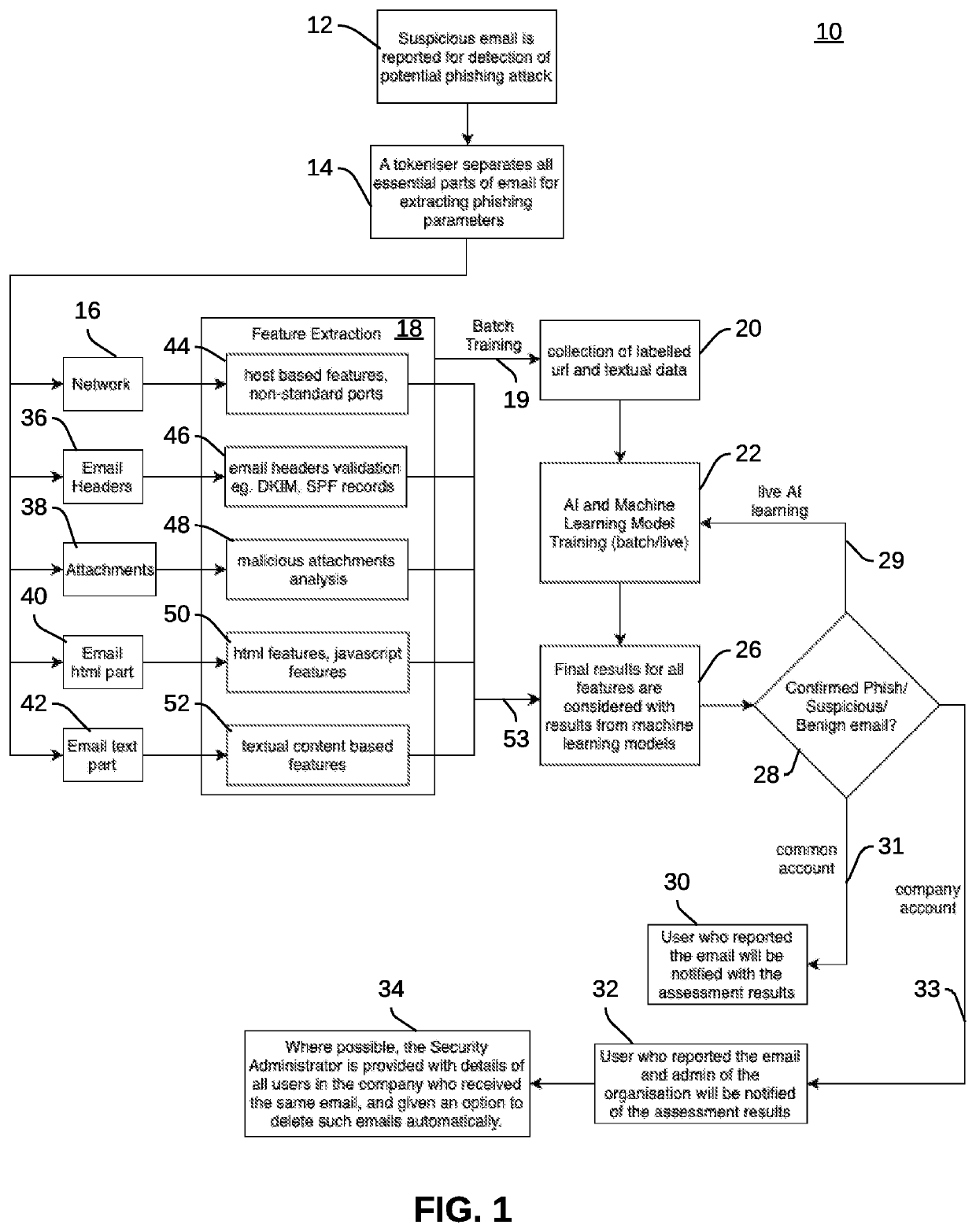
Methods and systems for detecting a phishing attack on a computer device can involve scanning one or more email messages, and separating email parts from the one or more email messages, in response to scanning the at least one email message. In addition, the email parts of the at least one email message can be subject to a feature extraction operation. The email features extracted from the email parts can be then analyzed to determine whether or not any of the email features contain suspected phishing content, confirmed phishing content and benign email content.
Owner:EC COUNCIL INT LTD
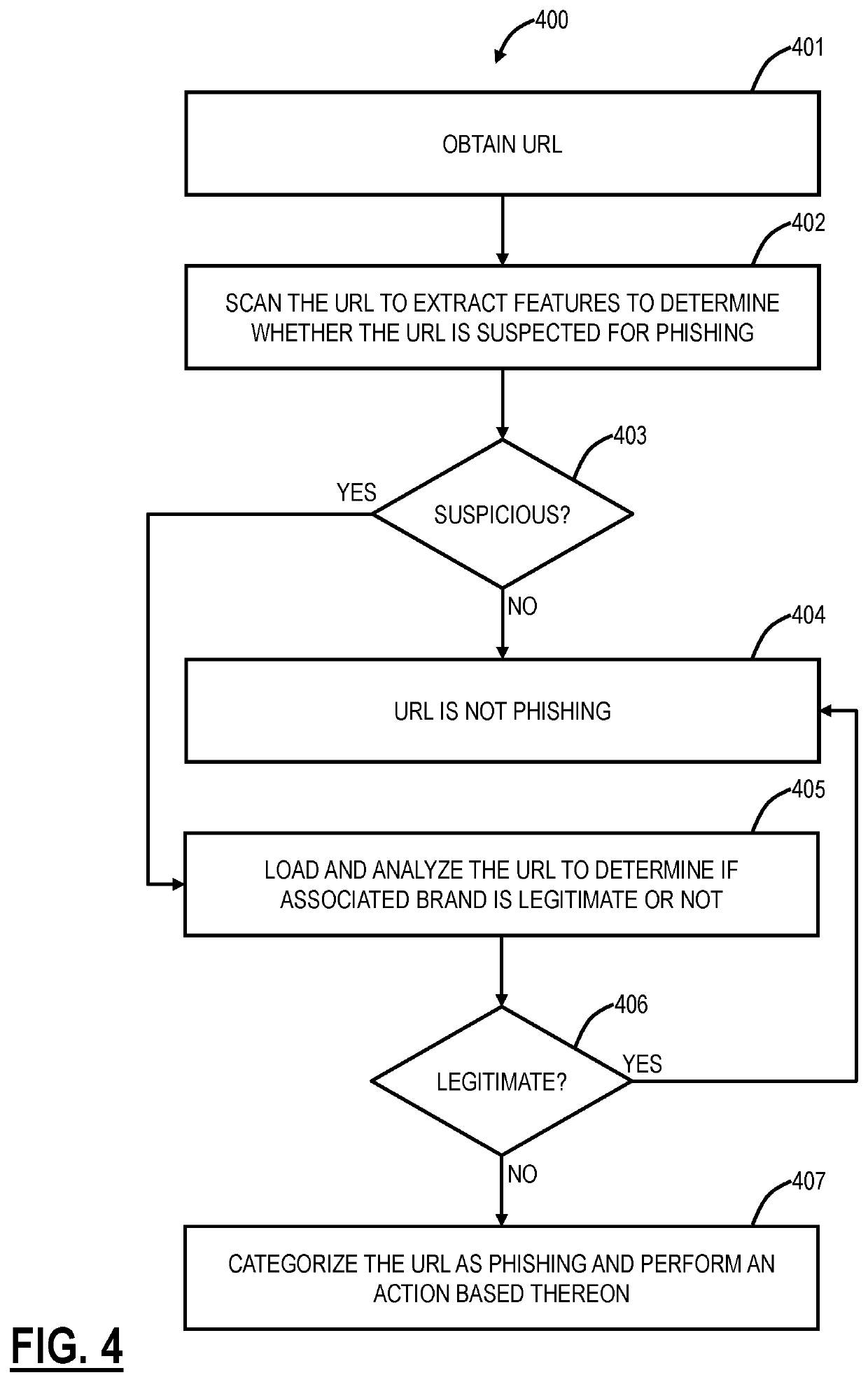
Phishing detection of uncategorized URLs using heuristics and scanning
PendingUS20210377301A1Quickly and correctly and efficiently categorizeNatural language data processingPlatform integrity maintainanceWeb siteHeuristic
Systems and methods include obtaining a Uniform Resource Locator (URL) for a site on the Internet; analyzing the URL with a Machine Learning (ML) model to determine whether or not the site is suspicious for phishing; responsive to the URL being suspicious for phishing, loading the site to determine whether or not an associated brand of the site is legitimate or not; and, responsive to the site being not legitimate for the brand, categorizing the URL for phishing and performing a first action based thereon. The systems and methods can further include, responsive to the URL being not suspicious for phishing or the site being legitimate for the brand, categorizing the URL as legitimate and performing a second action based thereon.
Owner:ZSCALER INC
Interactive phishing detection (IPD)
ActiveUS8650614B2Reduce riskDigital data processing detailsUser identity/authority verificationUser verificationSecurity Measure
Systems and methods for use with a client device and a server provide interactive phishing detection at the initiation of the user. Detection of phishing is based on the user's comparison of a visual indicator sent from the server to the client device with a another identical looking visual indicator displayed, for example, on a trusted website. Several security measures may be employed such as changing the visual indicator periodically, generating the visual indicator in a random manner, and authenticating the client device to the server before the server will transmit the visual indicator to the client device. User comparison of the website-displayed visual indicator with the user's client device user interface-displayed visual indicator may facilitate user verification of authenticity of a software application.
Owner:PAYPAL INC
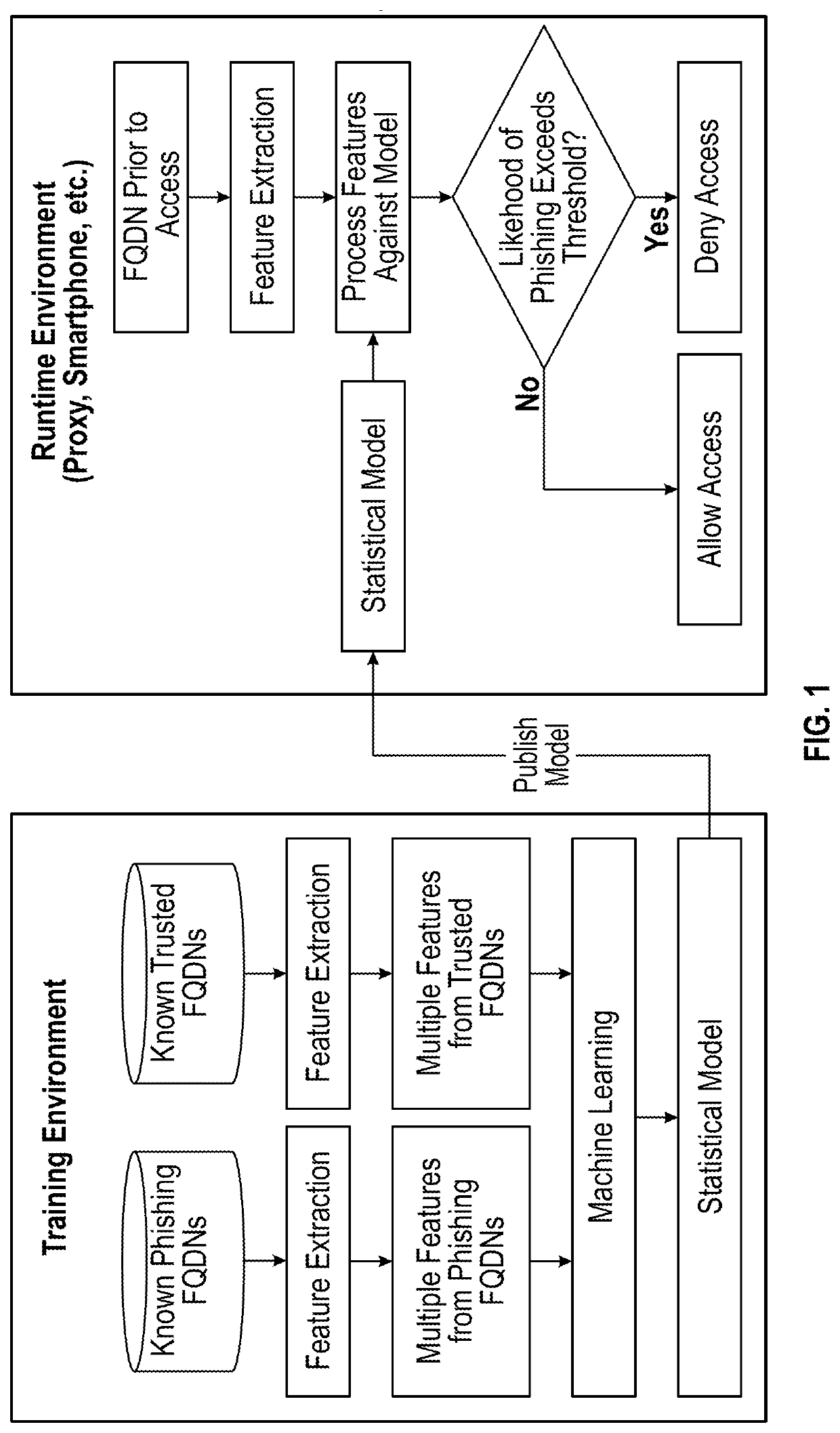
Dynamic phishing detection
ActiveUS20190394235A1Avoid the needAvoid accessCharacter and pattern recognitionTransmissionResource identifierStatistical model
A computer implemented method of detecting a phishing threat using a pre-defined statistical model to determine whether a network resource is a potential phishing threat based on features extracted from a network resource identifier for the network resource. The method includes: receiving a request to access a network resource; determining, from the request, a network resource identifier for the requested network resource; extracting one or more features from the network resource identifier; applying the pre-defined statistical model to the extracted features; and classifying the network resource as a phishing threat if the output of the statistical model, when applied to the extracted features, determines that the network resource is a potential phishing threat.
Owner:WANDERA
Dynamic phishing detection methods and apparatus
A computer-implemented method for detecting a phishing attempt by a given website is provided. The method includes receiving a webpage from the given website, which includes computer-readable code for the webpage. The method also includes ascertaining hyperlink references in the computer-readable code. Each hyperlink reference refers to at least a component of another webpage. The method further includes performing linking relationship analysis on at least a subset of websites identified to be referenced by the hyperlink references, which includes determining whether a first website is in a bi- directional / uni-directional linking relationship with the given website. The first website is one of the subset of websites. The method yet also includes, if the first website is in the bi-directional linking relationship, designating the given website a non-phishing website. The method yet further includes, if the first website is in the uni-directional linking relationship, performing anti-phishing measures with respect to the given website.
Owner:TREND MICRO INC
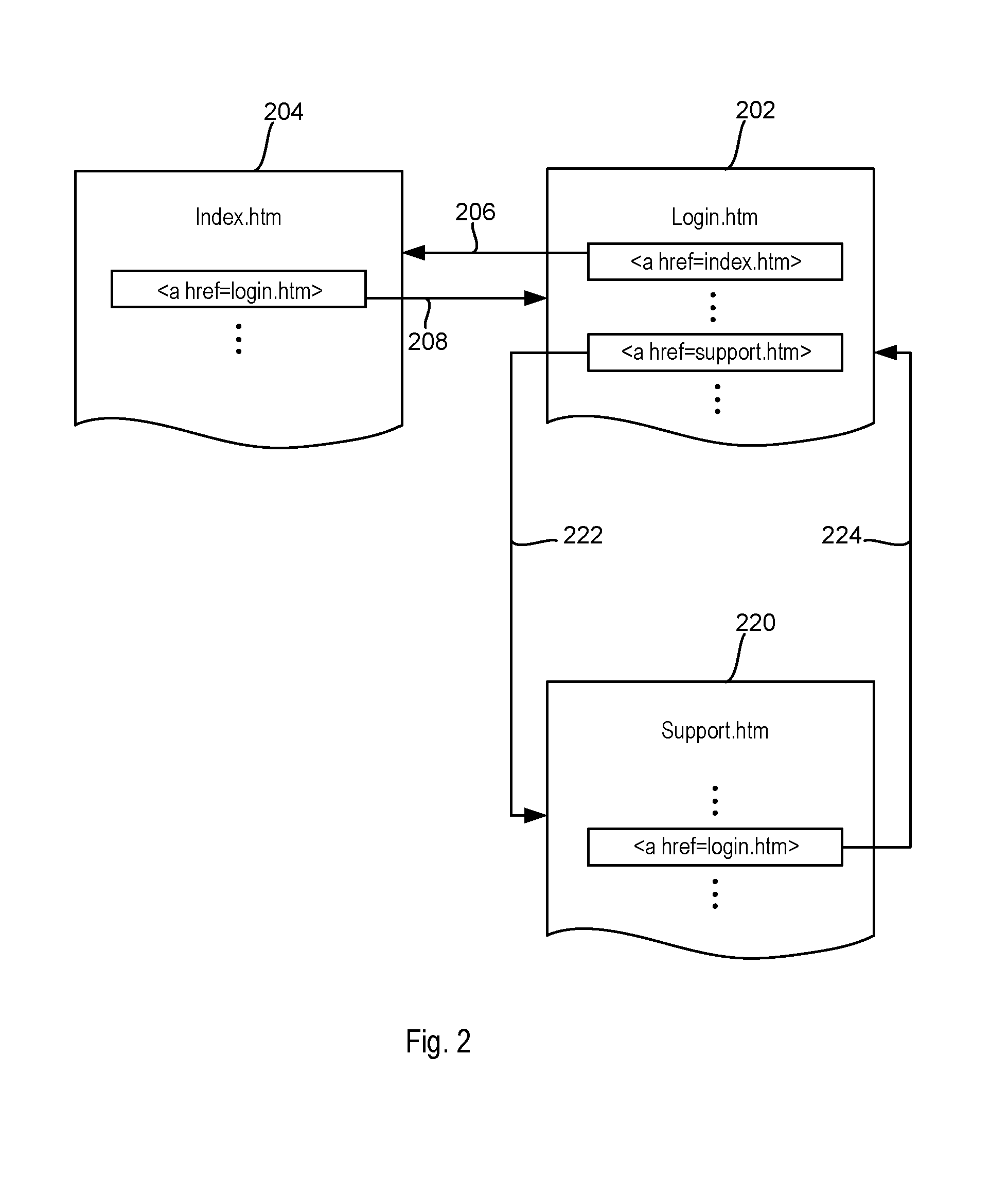
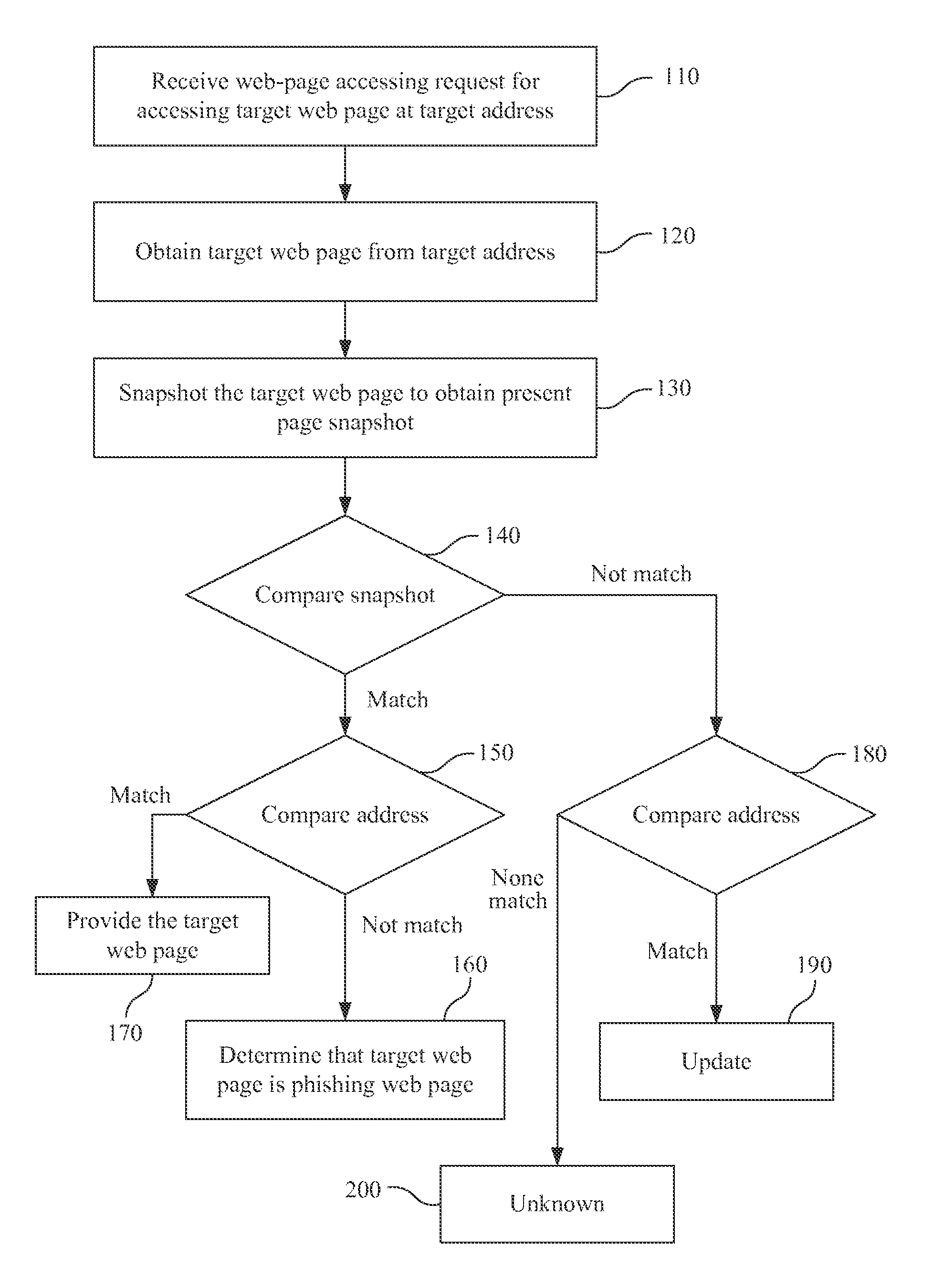
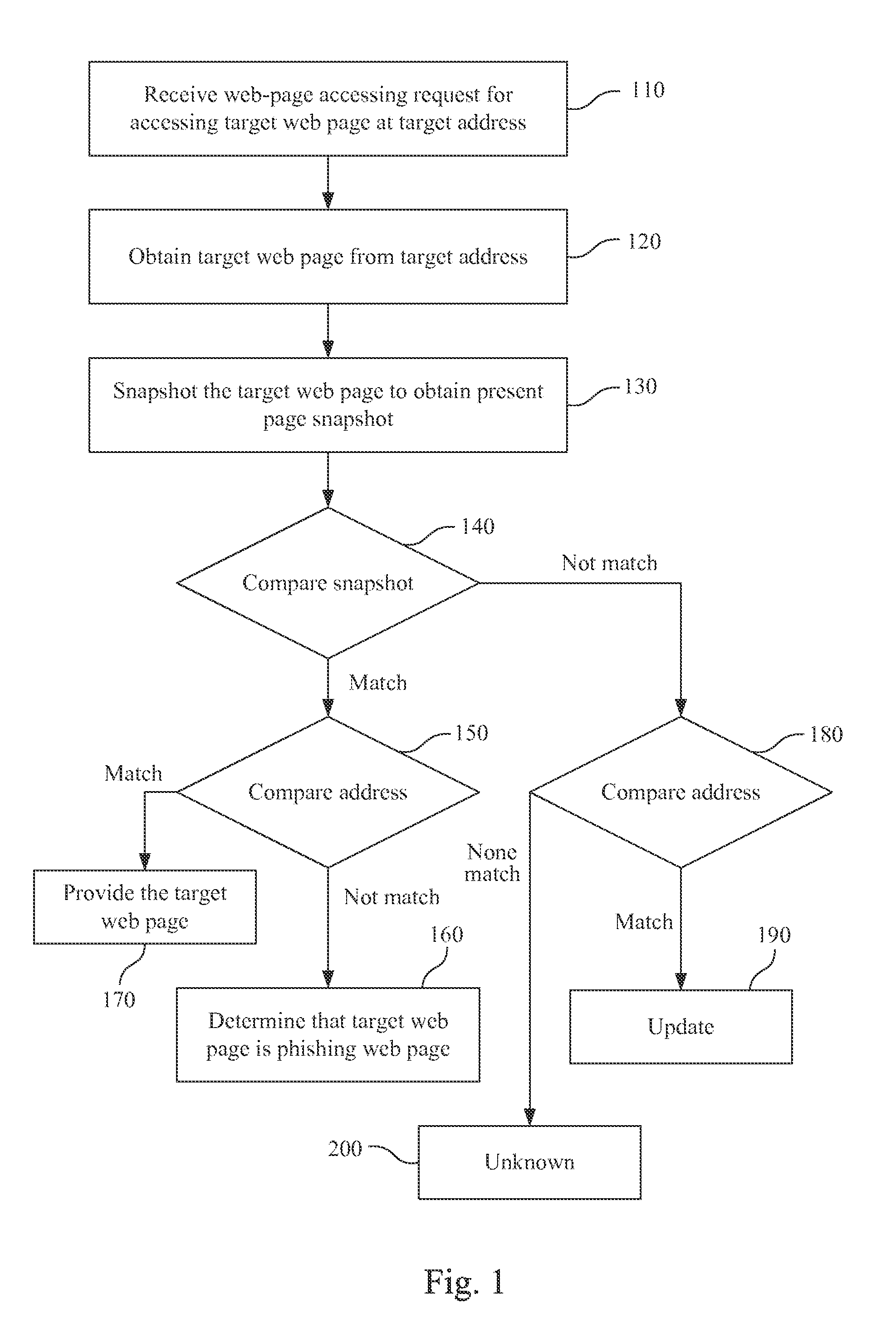
Phishing detecting system and method operative to compare web page images to a snapshot of a requested web page
A phishing detecting method includes: a web-page accessing request for accessing a target web page at a target address is received; the target web page from the target address is obtained; the target web page is snapshotted to obtain a present page snapshot; the present page snapshot is compared with several pre-stored page snapshots stored in a database, wherein each of the pre-stored page snapshots corresponds to a pre-stored address; if the present page snapshot matches one of the pre-stored page snapshots, the target address is compared with the pre-stored address, corresponding pre-stored page snapshot of which matches the present page snapshot; if the target address does not match the pre-stored address, the corresponding pre-stored page snapshot of which matches the present page snapshot, it is determined that the target web page is a phishing web page.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
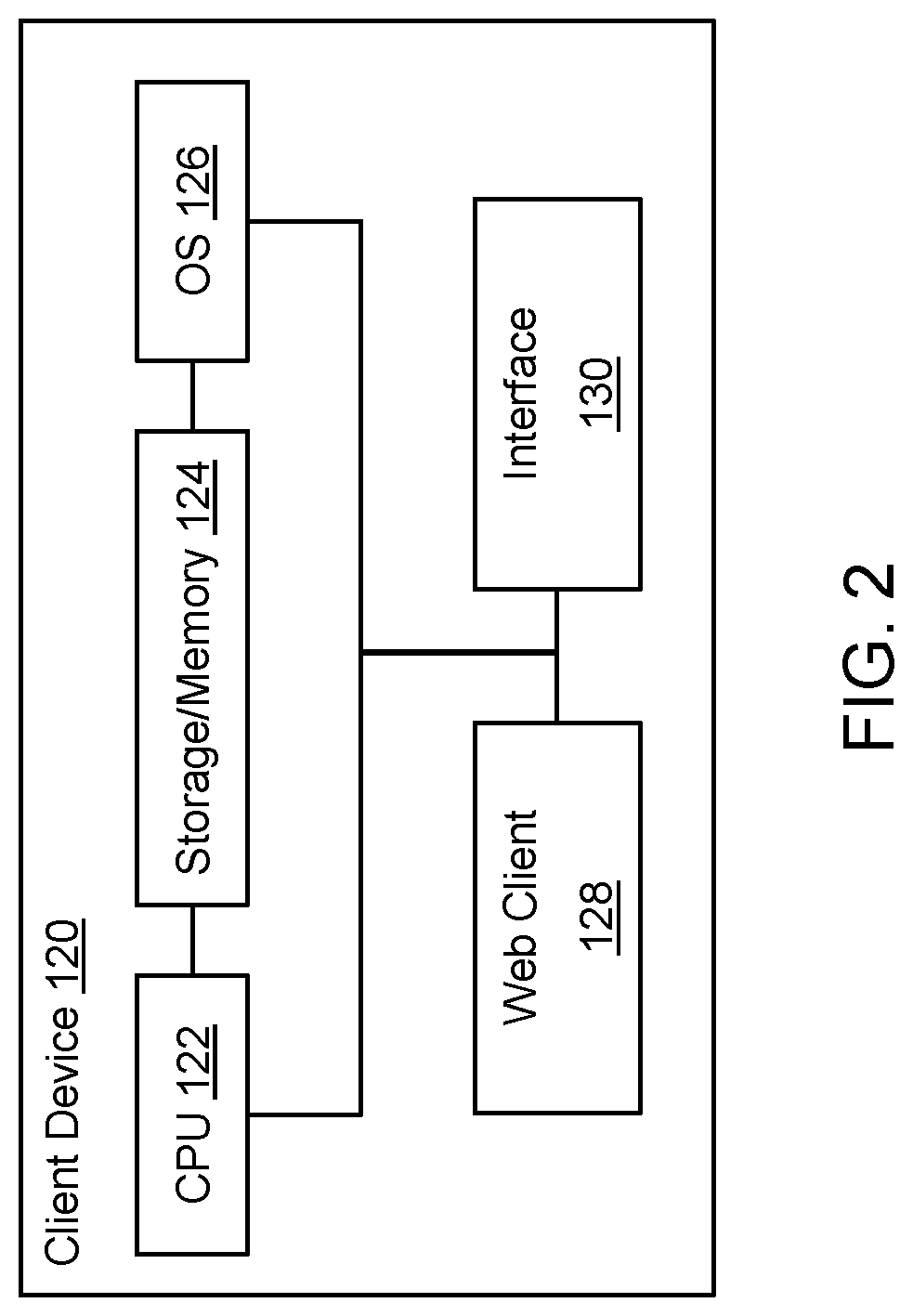
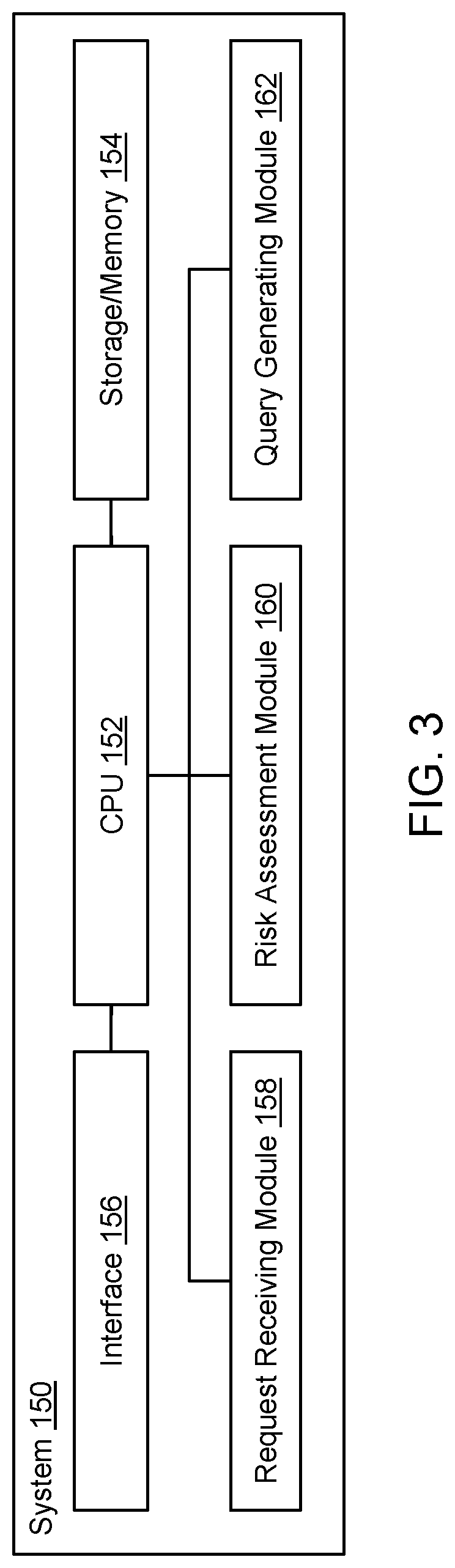
Phishing Detection based on Interaction with End User
Computerized methods and systems receive, from a web client of a client device, a request, addressed to a web server, to retrieve a requested web resource hosted by the web server. An initial reputation associated with the requested web resource is determined. A user of the client device is prompted to respond to at least one generated query corresponding to the requested web resource, in response to the determined initial reputation. At least one response to the at least one generated query is received from the user. The initial reputation associated with the requested web resource is updated, based in part on the at least one response to the at least one generated query received from the user.
Owner:ERICOM SOFTWARE
Message phishing detection using machine learning characterization
An email phishing detection mechanism is provided that utilizes machine learning algorithms. The machine learning algorithms are trained on phishing and non-phishing features extracted from a variety of data sets. Embodiments extract embedded URL-based and email body text-based feature sets for training and testing the machine learning algorithms. Embodiments determine the presence of a phishing message through a combination of examining an embedded URL and the body text of the message for the learned feature sets.
Owner:FORCEPOINT LLC
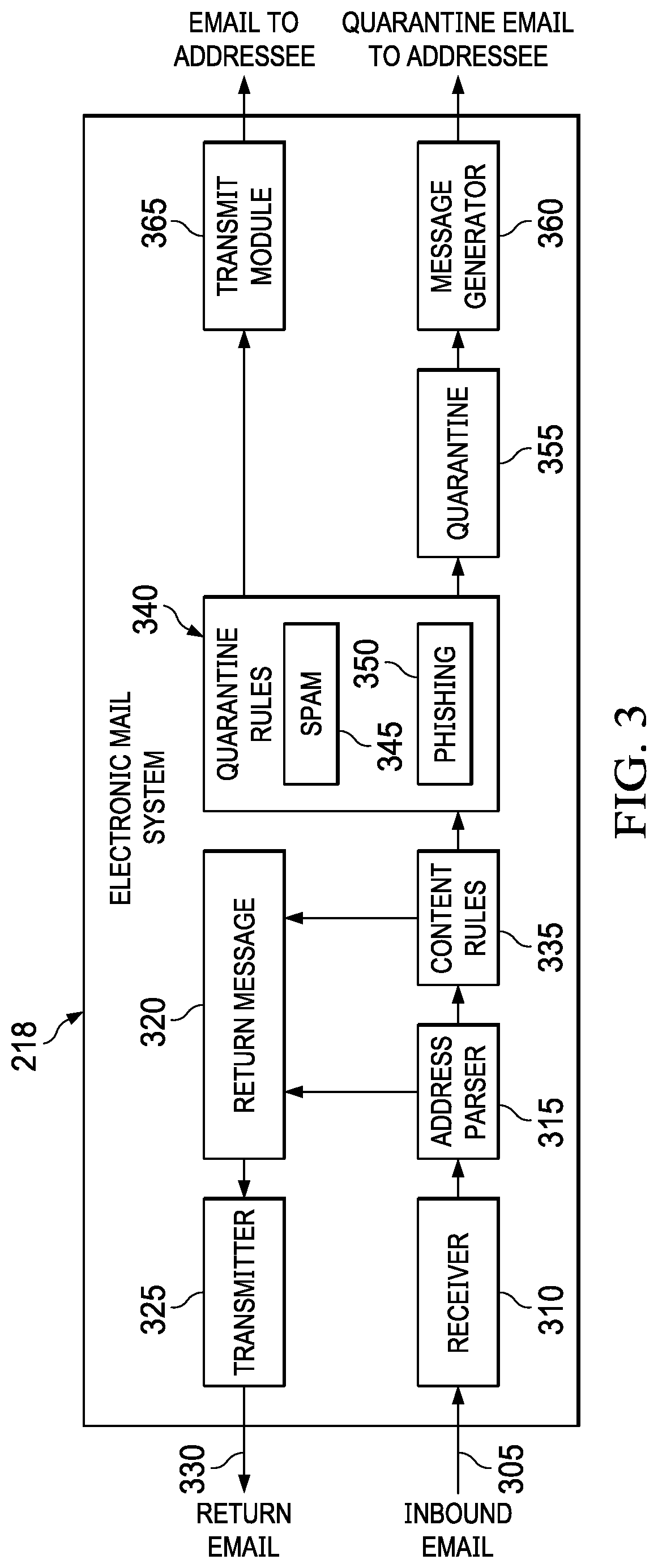
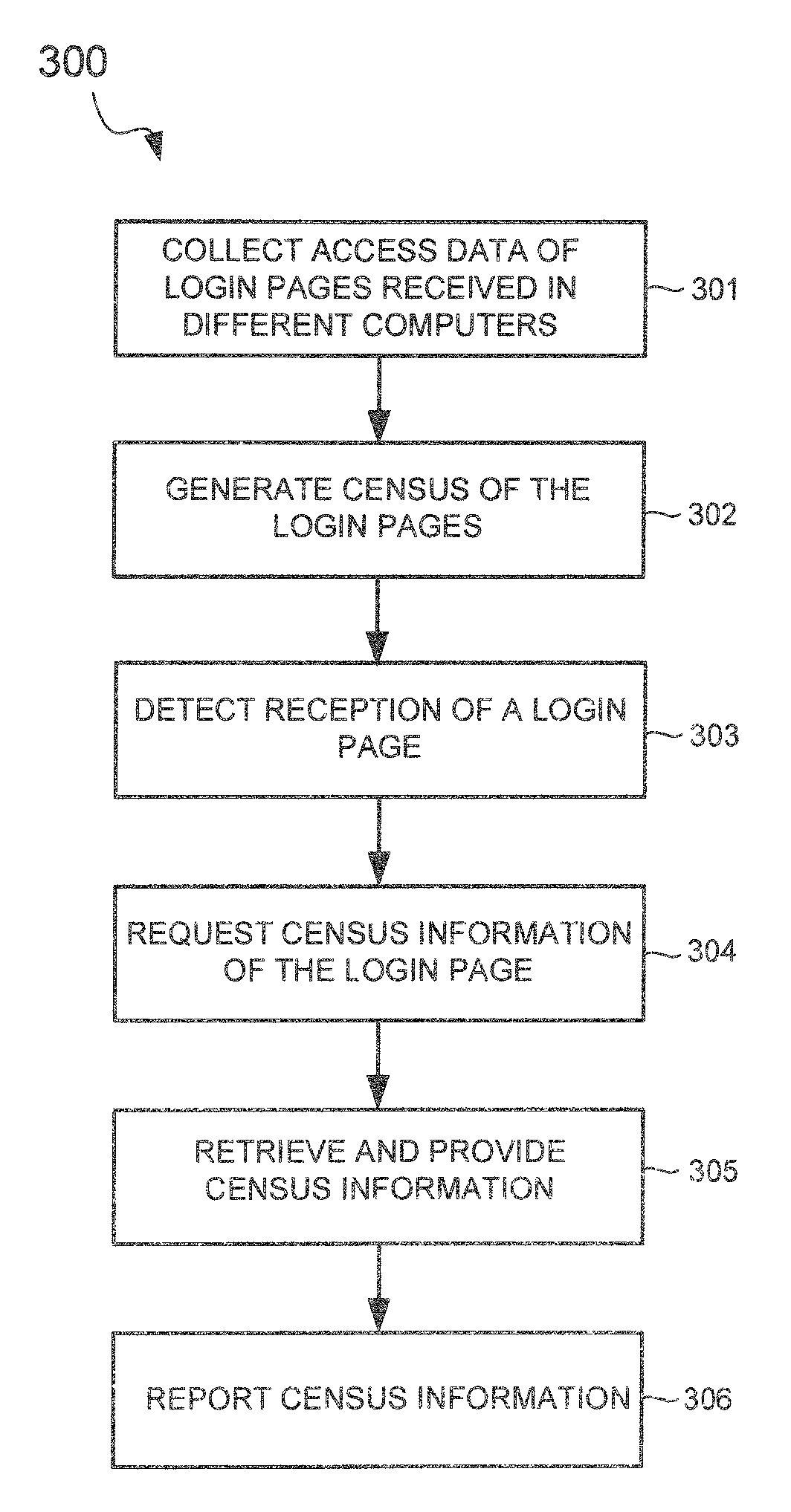
Phishing detection by login page census
A system for detecting phishing includes a phishing detection system that generates census of login pages received in different computers of different end users. An end user computer receives a login page and retrieves census information of the login page, such as from the phishing detection system. The census information indicates a number of different end users who employed the login page to log into their respective online accounts. The end user computer reports the census information to the end user of the end user computer. The end user computer reports the census information in numerical, graphical, or other format. The census information of the login page allows the end user to make an informed decision on whether or not to use the login page.
Owner:TREND MICRO INC
A hierarchical phishing website detection method based on deep learning
ActiveCN110602113BThe detection process is fastImprove accuracyCharacter and pattern recognitionNeural architecturesWeb siteEngineering
The present invention is a hierarchical phishing website detection method based on deep learning, which combines URL and webpage content to detect phishing websites, and can adaptively select and use phishing detection modules of different levels to detect phishing websites quickly and accurately. The present invention firstly detects the input URL, and outputs the probability that the URL belongs to a phishing website. If the output probability is greater than a preset threshold, the website to be detected is judged to be a phishing website, otherwise, the webpage corresponding to the URL to be detected is downloaded, and the statistics The number of HTML tags of the webpage is used to vectorize the statistical results by using the HTML tag list, and the precise feature representation of the webpage content is extracted according to the vectorized HTML tag sequence.
Owner:SUN YAT SEN UNIV
Systems and methods for identifying phishing web sites
Systems and methods are provided for automatically detecting phishing attacks. Network traffic may be monitored to detected phishing attacks and / or identify phishing websites and / or target websites. The monitoring may comprise generating and analysing logs corresponding to the monitored network traffic, with the logs comprising network traffic events and / or information relating to requesting and responding addresses. The network traffic events used in detecting phishing attacks may comprise sequences each comprising one or more requests and responses. Requested websites may be identified as phishing websites based on event sequences meeting particular criteria. Components and / or functions utilized for monitoring the network traffic and / or automatic phishing detection based thereon may be implemented as parts of a browser and / or network routers utilized during typical and normal use operations.
Owner:SWISSCOM AG
Dynamic phishing detection methods and apparatus
A computer-implemented method for detecting a phishing attempt by a given website is provided. The method includes receiving a webpage from the given website, which includes computer-readable code for the webpage. The method also includes ascertaining hyperlink references in the computer-readable code. Each hyperlink reference refers to at least a component of another webpage. The method further includes performing linking relationship analysis on at least a subset of websites identified to be referenced by the hyperlink references, which includes determining whether a first website is in a bi-directional / uni-directional linking relationship with the given website. The first website is one of the subset of websites. The method yet also includes, if the first website is in the bi-directional linking relationship, designating the given website a non-phishing website. The method yet further includes, if the first website is in the uni-directional linking relationship, performing anti-phishing measures with respect to the given website.
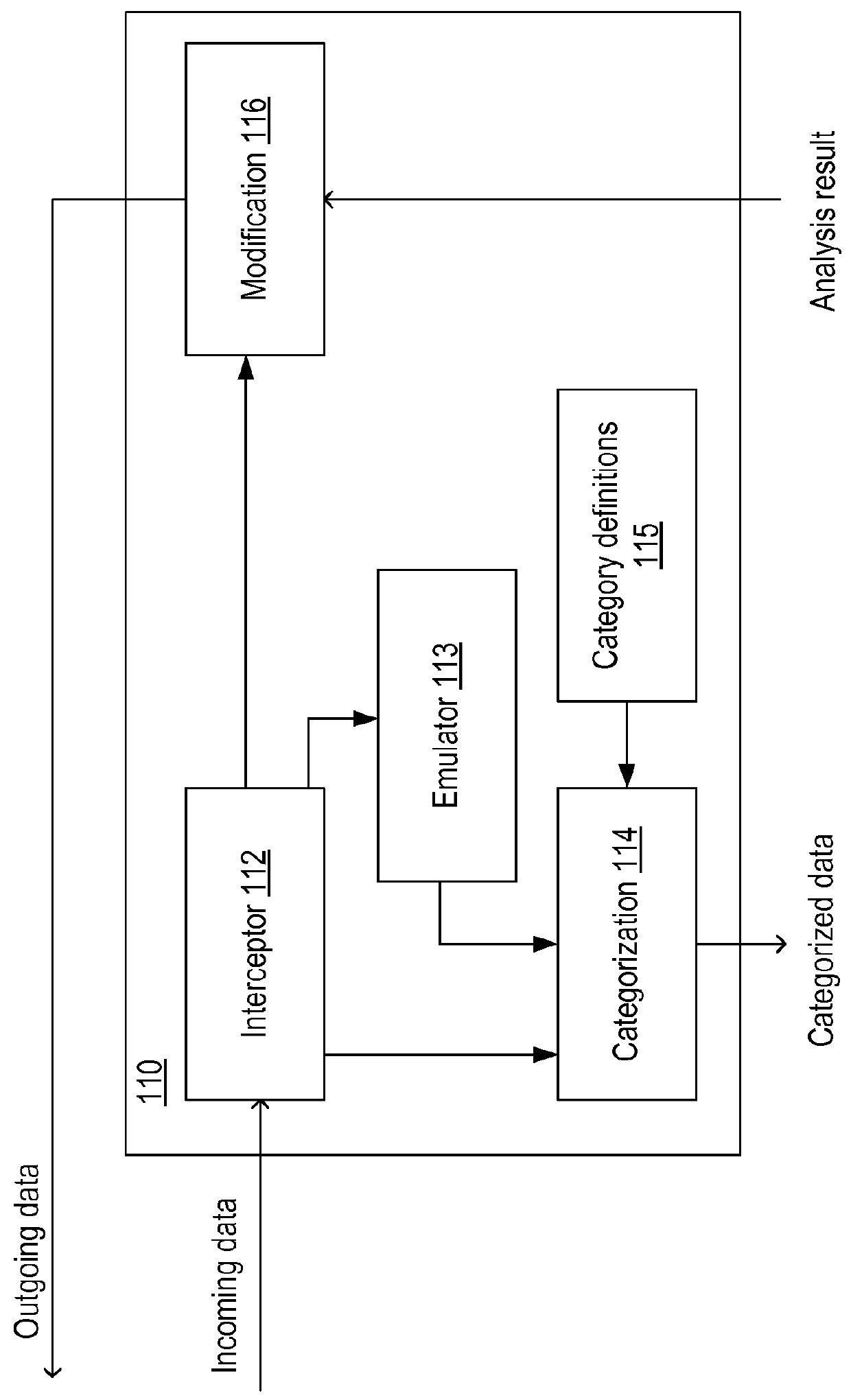
Owner:TREND MICRO INC
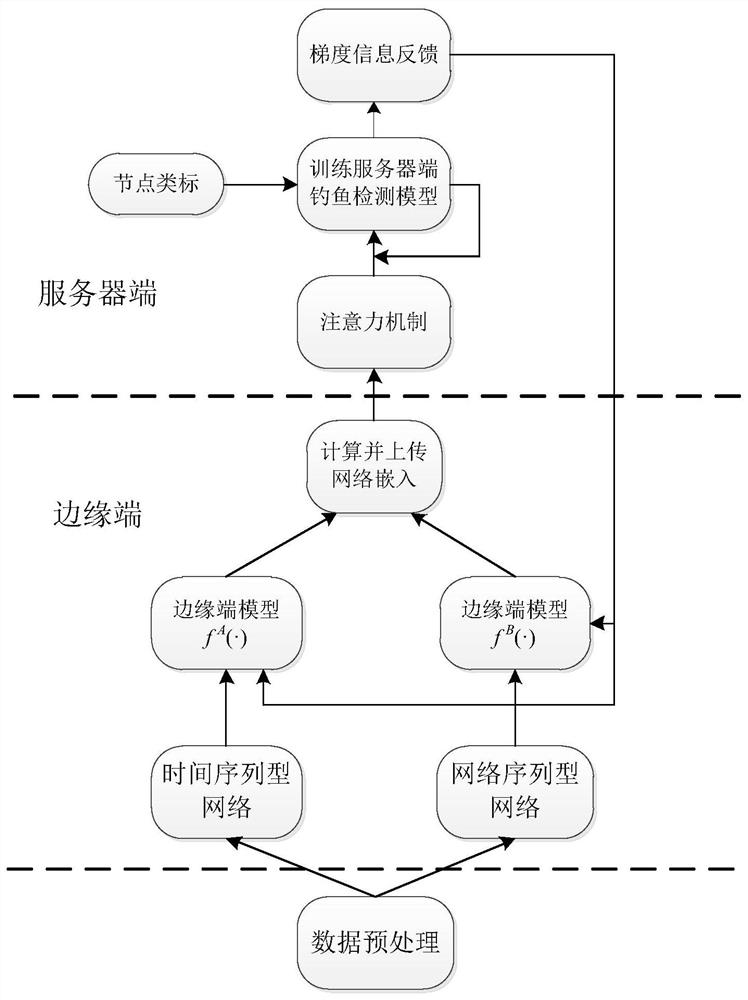
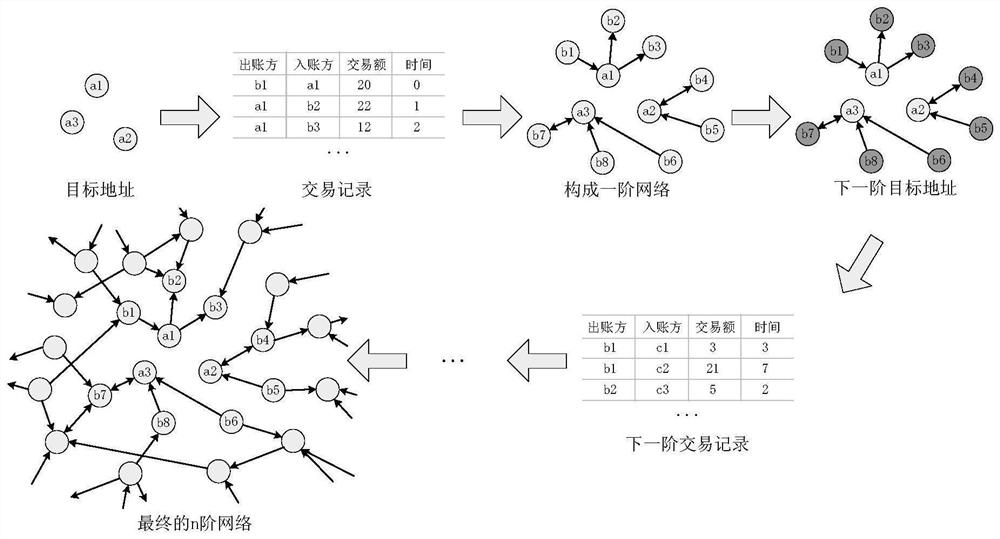
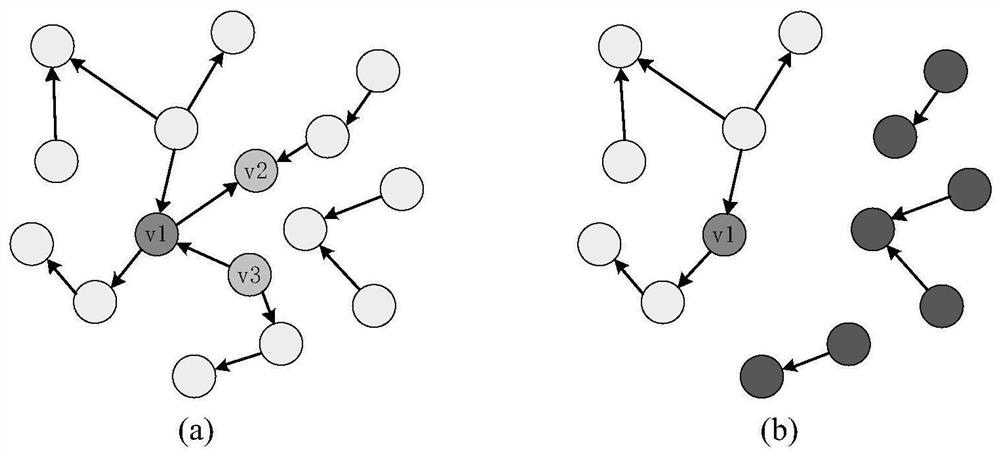
A blockchain phishing node detection method based on vertical federated learning
ActiveCN112738034BRealize detectionImprove effectivenessMachine learningSecuring communicationEngineeringData mining
The invention discloses a block chain phishing node detection method based on vertical federated learning, which is mainly applied to the detection of phishing nodes in a block chain transaction network. By querying the transaction records related to the target users, two small-scale sub-networks of time-series type and network-sequence type are constructed for training. Using the vertical federated learning strategy, the network embedding and original node class labels calculated by each edge-end phishing detection model are uploaded to the server, and the server-side combines the network embedding from the edge-end detection model through the attention mechanism. The server uses the combined network embedding to train its own detection model, and distributes the edge detection model to improve the performance of the blockchain phishing detection model at each edge.
Owner:HANGZHOU QULIAN TECH CO LTD
Malicious advertisement attack detection method
InactiveCN106202197ARealize unified detectionImprove detection efficiencySpecial data processing applicationsWeb siteOpen source
The invention discloses a malicious advertisement attack detection method. URL information in a to-be-detected website is extracted by utilizing an open-source crawler Nutch; compared with a commercial search engine, the Nutch can grab billions of web pages per month and provide high-quality retrieval results; only URL links related to advertisements are extracted in URL extraction; the detection efficiency can be improved; phishing detection is realized through a Google Safe Browser API; a to-be-detected URL is sent to the API for performing verification; whether the URL is secure or not can be judged according to response information; a library is realized by Google search and an international anti-phishing union, is very huge in scale and can detect a large amount of attack behaviors; for an attack URL confirmed by the API, the URL needs to be extracted from a to-be-detected set and information of the URL is recorded in a log file; the log record of the URL information is realized through Log4j; a flexible record way is provided; an output position, an output format and a log level of a log can be configured separately; malicious advertisement attack behaviors detected in log analysis are displayed in the form of a pie chart and a bar chart, so that a detection result can be vividly displayed; and the detection method is complete in rule, is based on a client, and not only realizes unified detection of malicious advertisement attacks but also has a good detection effect.
Owner:合肥酷睿网络科技有限公司
A phishing detection method based on salps swarm algorithm support vector machine
ActiveCN109873810BHigh discrimination accuracyBiological modelsCharacter and pattern recognitionWeb siteData set
The invention discloses a phishing detection method based on a salps swarm algorithm support vector machine. First, the basic parameters of the salps swarm algorithm are initialized: the population number, the number of iterations, the individual dimension, and the search space; the position and range of the individual are randomly initialized; Then it is divided into leader salps and follower salps according to the size of the fitness value, and the optimal parameters of the support vector machine are excavated by the coordination and cooperation of these two salps. In each iteration, the function used to evaluate the fitness value of the individual is the detection accuracy of the parameters carried by the individual on the phishing website dataset. The present invention and general optimization algorithms such as genetic algorithm, gravitational search algorithm, bat algorithm, particle swarm algorithm, etc., can dig out the optimal parameter parameters of the support vector machine as much as possible on the optimization support vector machine, and improve the performance of the support vector machine in fishing. detection accuracy.
Owner:HUBEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com