Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48results about How to "Solve problems with high computational complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Neural network black box aggressive defense method based on knowledge distillation
ActiveCN111027060AGuaranteed successful attackReduce the pitfalls of losing variance between classesPlatform integrity maintainanceNeural architecturesData setSample sequence
The invention discloses a neural network black box aggressive defense method based on knowledge distillation, and the method comprises the steps: selecting a plurality of sub-networks to construct a teacher network, softening the input vectors of softmax layers of all sub-networks, and then reloading the model parameters of the sub-networks for training to obtain a new sub-network; obtaining a prediction label of each sub-network, and taking all prediction labels as soft labels after averaging or weighted averaging; inputting the Image Net data set into a student network, and guiding student network training by adopting a soft label, a data set hard label and a black box model special label to obtain a substitution model; adopting a white box attack algorithm to attack the substitution model to generate an adversarial sample sequence, adopting the adversarial sample sequence to attack the black box model, and selecting an adversarial sample successfully attacked in the adversarial sample sequence; and adding the successfully attacked countermeasure sample into a training set of the black box model, and performing countermeasure training by adopting the updated training set to generate the black box model with attack defense.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Log likelihood estimation based novel passive locating and tracking method
ActiveCN106446422ASolve problems with high computational complexityRealize target location trackingDesign optimisation/simulationSpecial data processing applicationsLog likelihoodComputer science
The invention relates to a log likelihood estimation based novel passive locating and tracking method. A multistation angle-measurement passive-location non-linear measurement equation is subjected to pseudo-linearization processing by the aid of log likelihood estimation, target position is obtained by means of maximum likelihood estimation, a closed-form solution of a target locating algorithm is given, then a 'current' statistical maneuver model and Kalman filtering are utilized to calculate target position, velocity and acceleration online in real time, and real-time accurate positioning and tracking on the target is realized.
Owner:XIJING UNIV
Infrared moving small target detection method of a complex scene
ActiveCN109345472AReduce complexitySolve problems with high computational complexityImage enhancementImage analysisMotion vectorRadiology
The invention discloses an infrared moving small target detection method of a complex scene, which mainly comprises the following steps: 1) extracting a moving target area. 2) The image is divided into two parts: foreground and background according to the gray characteristics of the image. 3) Optical flow estimation is performed on the extracted moving target region by optical flow method, and thetarget motion vector information is extracted. 4) The extracted moving target region is morphologically filtered, the connected regions of the filtered moving target region are analyzed, and different moving target regions are identified. 5) the detection probability of the connected region is set, and the number of sample characteristic quantities to be detected in the connected region is determined. All connected domains are randomly sampled. The invention reduces the complexity of the algorithm, improves the detection accuracy rate, and effectively solves the problems of target misdetection, missed detection and mismatch caused by the large difference between the background and the target and the partial occlusion of the target.
Owner:CHONGQING UNIV +1
Method and device for timing shift estimation
ActiveCN102104951ASolve problems with high computational complexityReduce complexitySynchronisation arrangementRadio transmission for post communicationPeak valueRandom-access channel
The invention discloses a method and device for timing shift estimation. The method comprises a step of filling zero at two ends of a sequence p, so as to acquire a sequence s(k), wherein the sequence p is a result of conjugate multiplication between a frequency domain mark received on a preset channel by user equipment (UE) and a Zadoff-Chu sequence; k is equal to 0,...,M-1; M is the number of sub-carriers occupied by signals in the preset channel; and the preset channel comprises a PRACH (physical random access channel) or a PUSCH (physical uplink shared channel). The method further comprises the following steps: converting s(k) into a power sequence b(k); calculating the center of the power sequence b(k); and calculating the timing shift according to the expected peak position of UE and the center. By using the method and device provided by the invention, the complex rate of calculation is reduced.
Owner:ZTE CORP
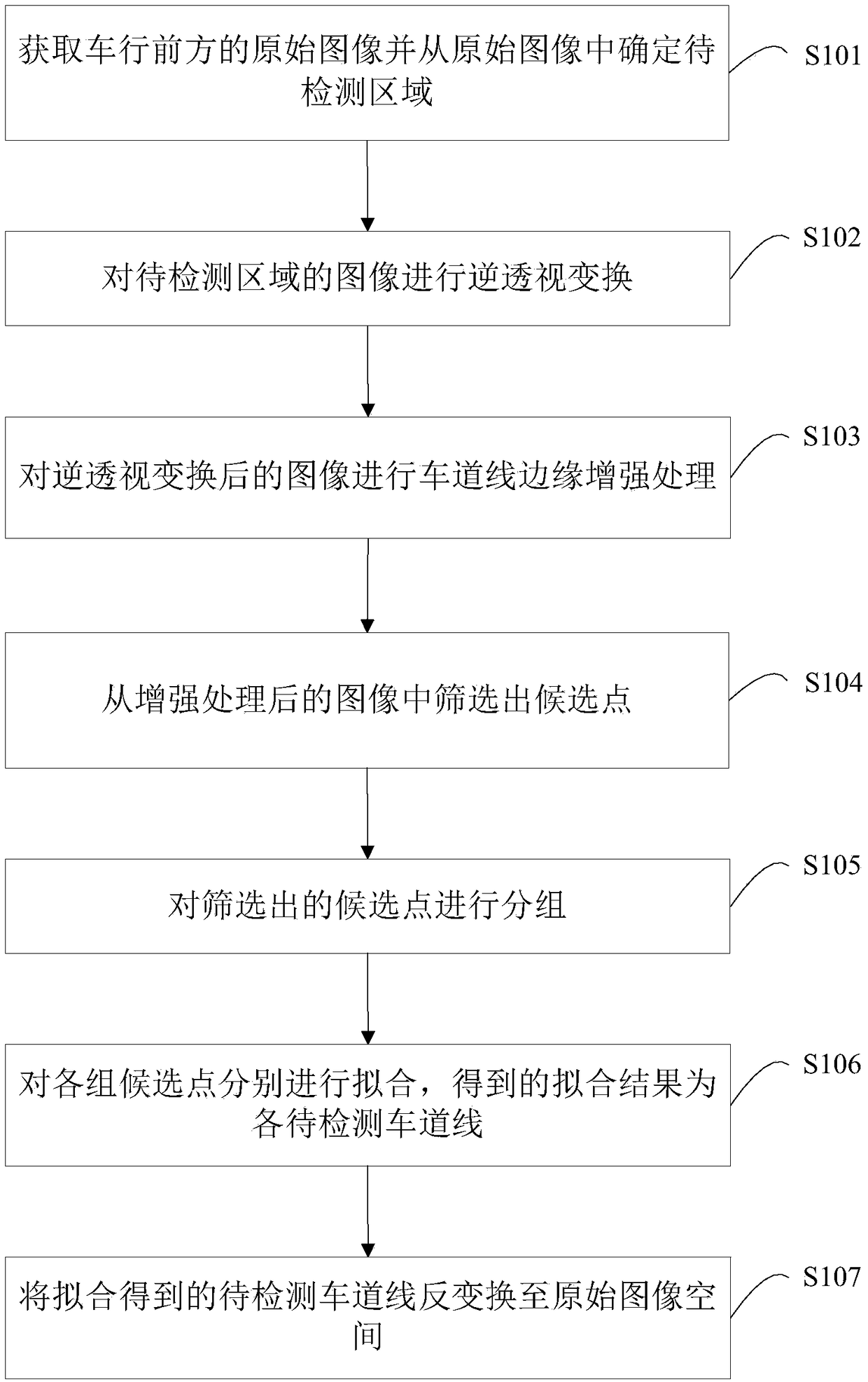
Lane line detection method and system
ActiveCN108256445AImprove robustnessImprove real-time performanceImage enhancementImage analysisPerspective transformationHistogram
The invention relates to a lane line detection method and system. The method comprises: acquiring an original image in front of a driving vehicle and determining a to-be-detected area from the original image; carrying out inverse perspective transformation on the image of the to-be-detected area; carrying out lane line enhancement processing on the image after the inverse perspective transformation; screening out candidate points from the image after enhancement; the screened candidate points are grouped; fitting is carried out on all candidate point groups to obtain fitting results being allto-be-detected lane lines; and carrying out inverse transformation on all to-be-detected lane lines obtained by fitting to original image space. According to the invention, after inverse transformation on the a to-be-detected area, lane line enhancement processing is carried out by using an image filter and rotary transformation is carried out on the image by combining principal direction estimation, so that the fluencies caused by lane changing and the like are eliminated and the robustness of the subsequent lane detection is improved. The image after enhancement processing is divided into aplurality of histograms, so that the computing load is reduced substantially by block division processing and the real-time performance of the system detection is enhanced.
Owner:BEIJING HUAHANG RADIO MEASUREMENT & RES INST
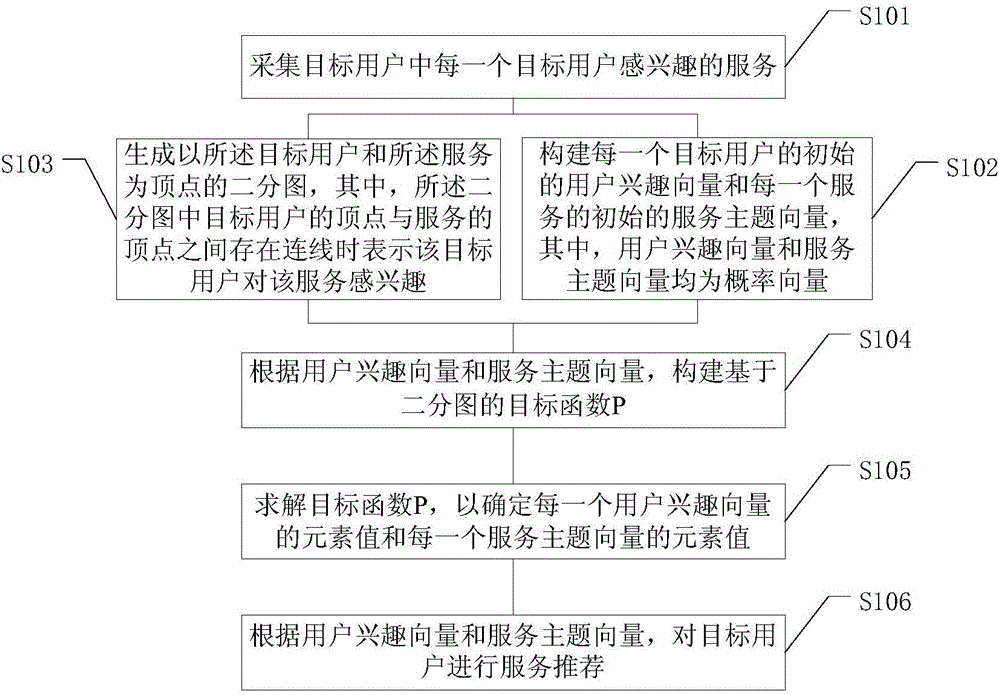
Bipartite graph-based service recommendation method and apparatus
ActiveCN106708978ASolve problems with high computational complexityEasy to buildSpecial data processing applicationsComputation complexityProbability vector
Embodiments of the invention provide a bipartite graph-based service recommendation method and apparatus. The method comprises the steps of acquiring a service which each target user is interested in; constructing an initial user interest vector of each target user and an initial service topic vector of each service, wherein the user interest vector and the service topic vector are both probability vectors; generating a bipartite graph by taking the target users and the services as vertexes, and constructing a bipartite graph-based target function P according to the user interest vectors and the service topic vectors; solving the target function P to determine an element value of each user interest vector and an element value of each service topic vector; and performing service recommendation on the target users according to the user interest vectors and the service topic vectors. By applying the method and the apparatus, the calculation complexity of bipartite graph-based service recommendation is lowered, and the user interest vectors and the service topic vectors output by a model are all the probability vectors, so that more probability-based actual applications can be constructed conveniently.
Owner:BEIJING UNIV OF POSTS & TELECOMM
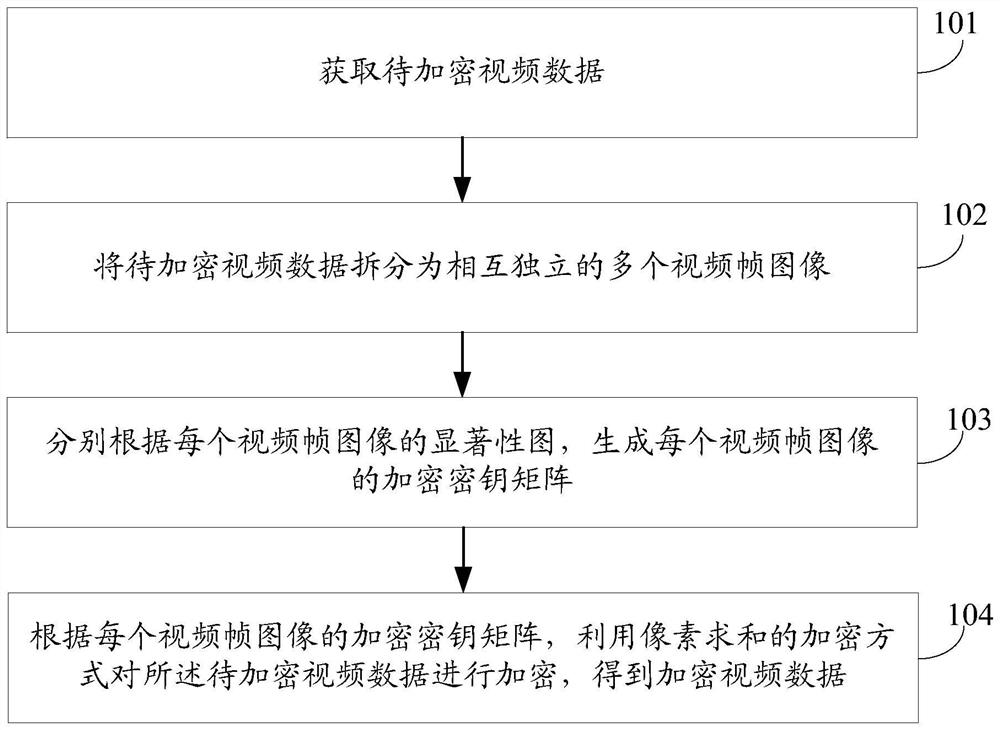
Video encryption method, device and equipment
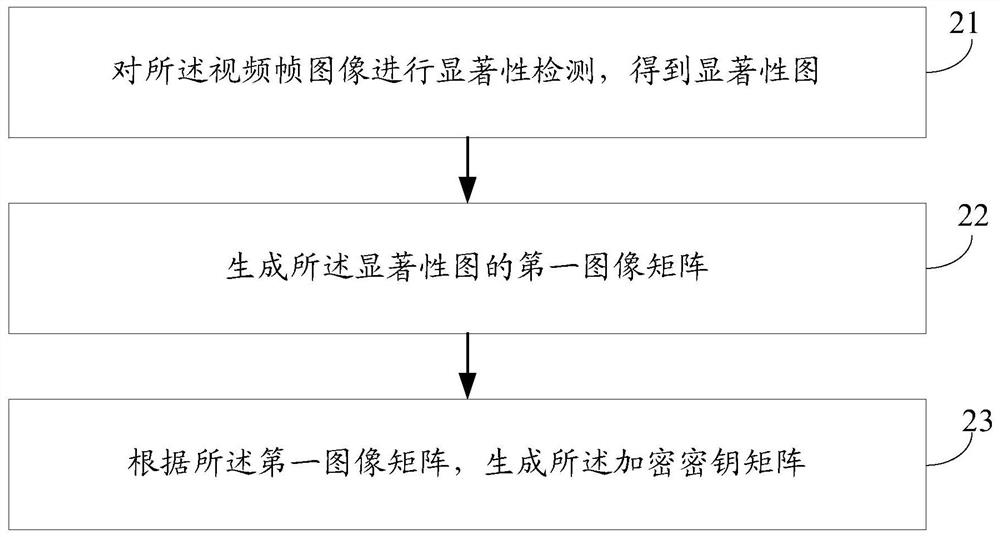
ActiveCN112218161AImprove accuracyImplement encryptionSelective content distributionImaging processingSaliency map
The invention provides a video encryption method, apparatus and device. The video encryption method comprises the steps of obtaining to-be-encrypted video data; splitting the to-be-encrypted video data into a plurality of mutually independent video frame images; generating an encryption key matrix of each video frame image according to the saliency map of each video frame image; and encrypting theto-be-encrypted video data in a pixel summation encryption mode according to the encryption key matrix of each video frame image to obtain encrypted video data. According to the embodiment of the invention, the method can achieve the encryption of the salient region of the to-be-encrypted video data, achieves the encryption process in an encryption mode of pixel summation which is easy to achieve, at least solves a problem that the calculation complexity is high when the video data is completely encrypted at present. And on the basis of reducing the calculation complexity and reducing the workload, the image processing accuracy is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
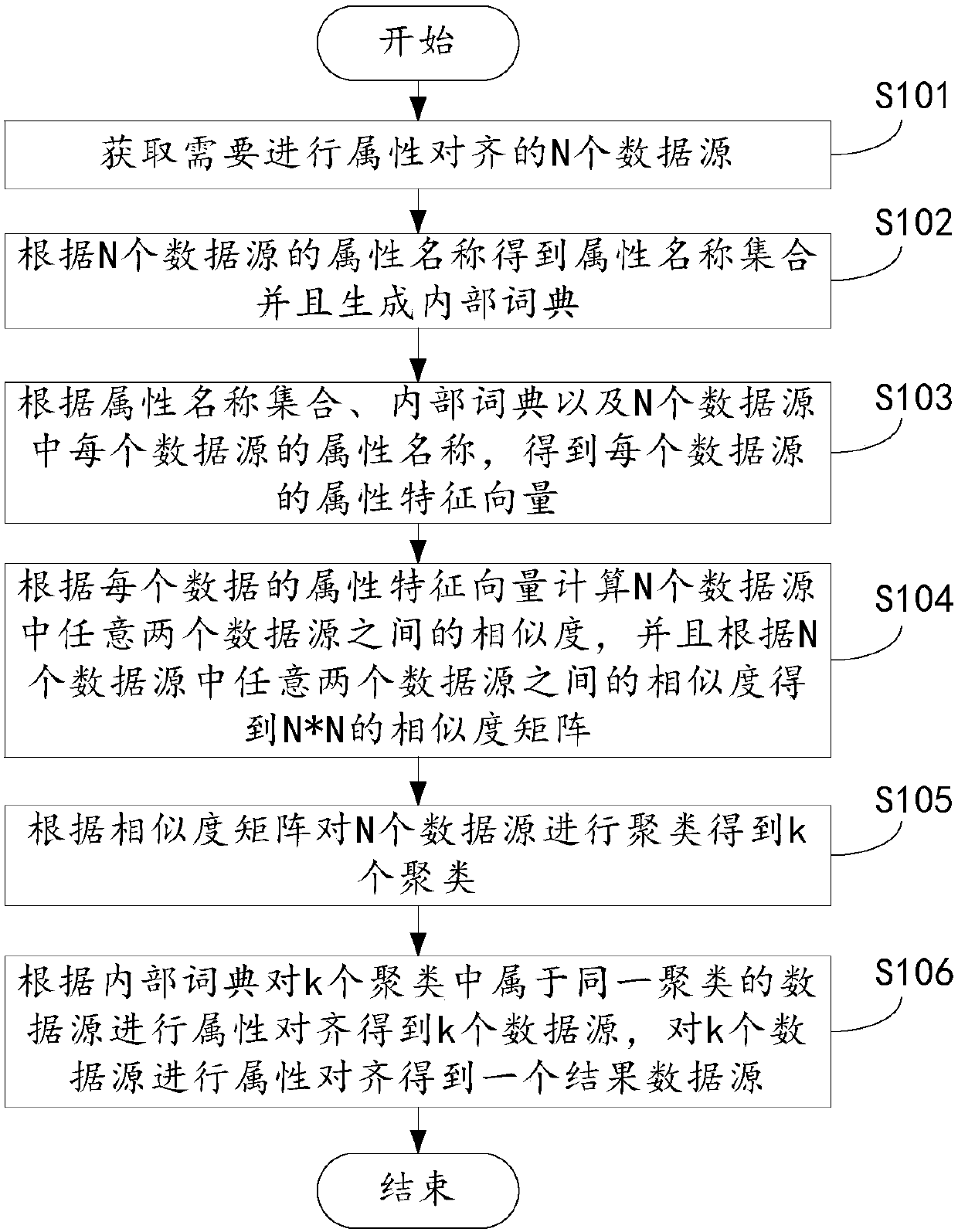
Attribute alignment method and apparatus
ActiveCN107704474ASmall difference in attribute namesSolve problems with high computational complexitySpecial data processing applicationsComputation complexityMultiple attribute
The invention discloses an attribute alignment method and apparatus, relates to the field of data analysis, and aims to solve the problem of high calculation complexity caused by matching between an attribute of a data source and multiple attributes of another data source. The attribute alignment method comprises the steps of obtaining N data sources; according to the N data sources, obtaining anattribute name set and generating an internal dictionary; according to the attribute name set, the internal dictionary and an attribute name of each data source in the N data sources, obtaining an attribute eigenvector of each data source; according to the attribute eigenvector of each data source, calculating the similarity between any two data sources in the N data sources and a similarity matrix; according to the similarity matrix, clustering the N data sources to obtain k clusters; and according to the internal dictionary, performing attribute alignment on the data sources of the same cluster in the k clusters to obtain k data sources, and performing attribute alignment on the k data sources to obtain a result data resource. The attribute alignment method and apparatus is applied to the data analysis.
Owner:HUAWEI TECH CO LTD
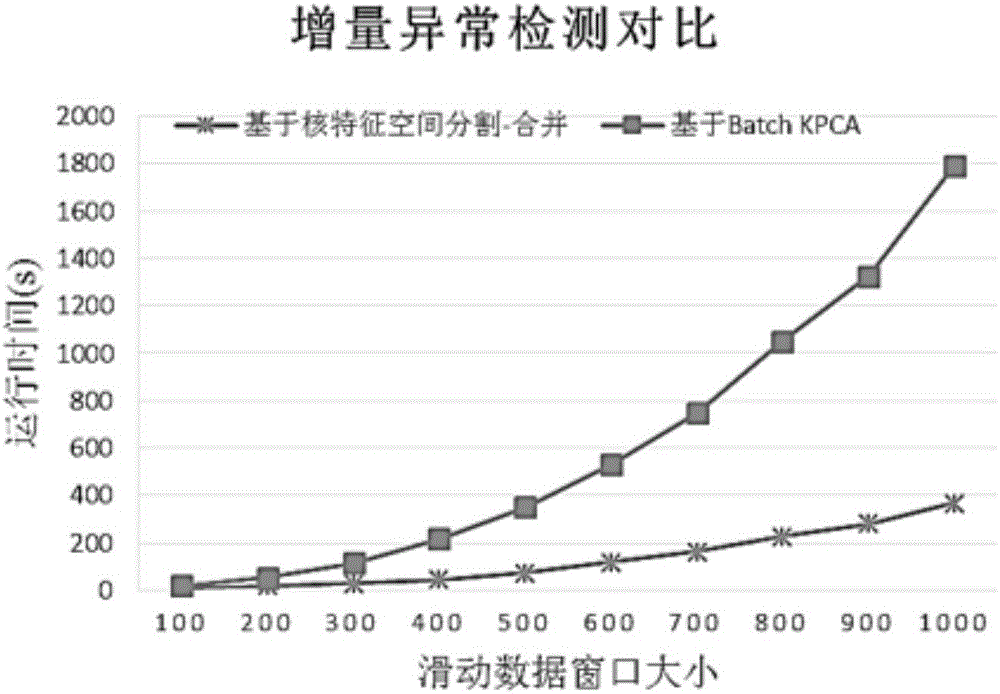
Incremental track anomaly detection method based on incremental kernel principle component analysis
ActiveCN106022368AReduce computational complexityImprove efficiencyCharacter and pattern recognitionKernel principal component analysisCharacteristic space
The invention provides an incremental track anomaly detection method based on incremental kernel principle component analysis, and belongs to the field of an incremental track anomaly detection method. The method comprises the following steps: to begin with, carrying out model initialization calculation, carrying out initial kernel feature space calculation through conventional Batch KPCA, and when M newly-increased track data comes, carrying out standardization on the M track data first; then, calculating kernel feature space of the newly-increased data through Batch KPCA; calculating average reconstruction error of the newly-increased data and training data, and if the error of the two is larger than a preset threshold value, using a follow-up kernel feature space division-merging method to update kernel feature space; then, carrying out projection on the updated kernel feature space and extracting a principal component; and finally, carrying out unsupervised learning and anomaly detection by utilizing a support vector machine. The advantages are that the method is superior to a conventional kernel principle component analysis method; computing complexity is reduced; and track anomaly detection efficiency is improved.
Owner:CHINA UNIV OF MINING & TECH
Gesture identification method and apparatus, and electronic device
ActiveCN107678551AReduce operational complexityComputational Complexity ResolutionInput/output for user-computer interactionImage enhancementImaging processingTerminal equipment
The invention provides a gesture identification method and apparatus, and an electronic device. The method comprises the steps of collecting a first image comprising a gesture; according to the firstimage, obtaining central coordinates of the gesture; according to the central coordinates, determining a control range of the gesture on a terminal device; and obtaining a control object from the control range, and according to a control instruction corresponding to the gesture, performing operation on the control object. In an image processing mode, the central coordinates of the gesture are obtained, so that the terminal device can be accurately controlled, the calculation complexity is lowered, and the problem of high calculation complexity of an existing gesture identification method for calculating a motion track of the gesture by adopting a spatial algorithm to control the terminal device is solved.
Owner:BOE TECH GRP CO LTD
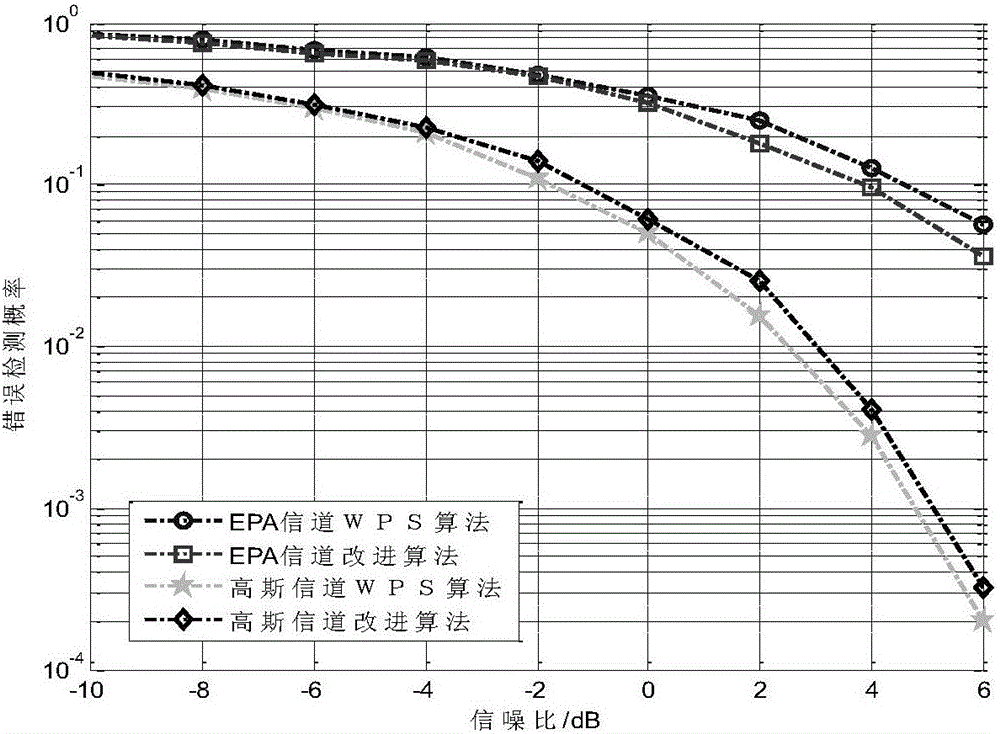
Timing synchronization method based on CAZAC sequence under distributed MIMO-OFDM system
InactiveCN106357583AReduce complexitySolve problems with high computational complexitySpatial transmit diversityMulti-frequency code systemsComputation complexityTime delays
The invention discloses a timing synchronization method based on a CAZAC sequence under a distributed MIMO-OFDM system, relates to a timing synchronization algorithm based on the CAZAC sequence under the distributed MIMO-OFDM system in the field of radio communication, and aims at solving the problems that local synchronization sequences of a WPS algorithm are excessive under the distributed MIMO-OFDM system and computation complexity is high. In a distributed cellular system, ID information in a cell physical group is born on one transmitting main antenna by virtue of three groups of CAZAC sequences of different root values, and fixed CAZAC sequences of other root values are transmitted on other antennae to distinguish time delays among different transmitting antennae, so that timing synchronization of the distributed antenna cellular system is realized. The method disclosed by the invention can be applied to the distributed MIMO-OFDM system in a cellular network environment.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
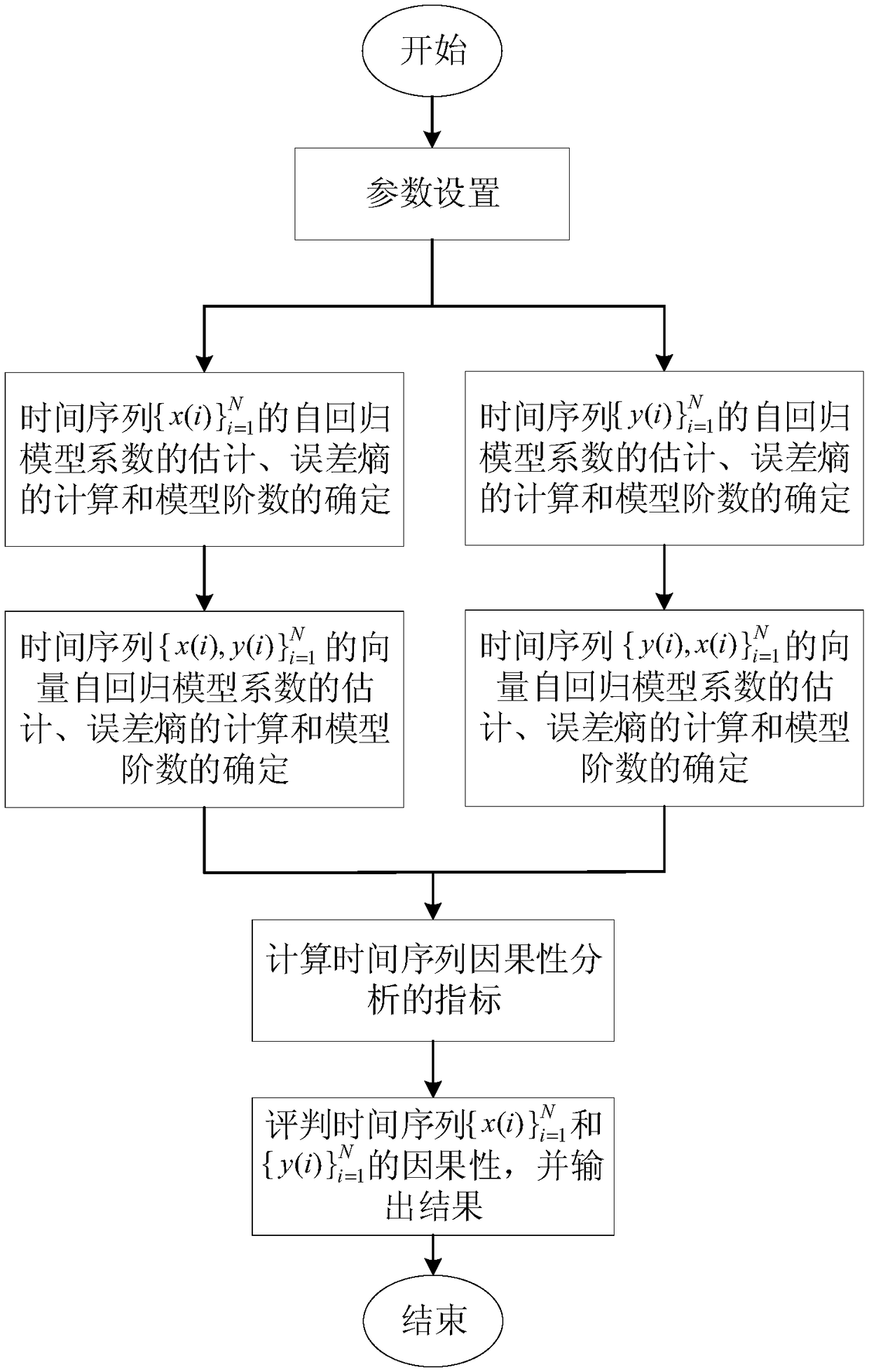
Granger causality discrimination method based on quantitative minimum error entropy criterion
InactiveCN108959188AResolve accuracySolve the errorComplex mathematical operationsComputation complexityCalculation error
The invention provides a Granger causality discrimination method based on a quantitative minimum error entropy criterion. According to the method, the coefficient and the order of a regression model are determined by adopting the quantitative minimum error entropy criterion and a Bayesian information criterion, a causality discrimination index is obtained by calculating the error entropy and coefficient, and the causality between two time sequences is determined according to a causality judgment standard. Compared with a traditional Granger causality discrimination method based on a minimum mean square error criterion, the method is more accurate in estimating coefficients of the regression model, the obtained error entropy is smaller, and the causality discrimination index can be more accurately calculated. Due to the adoption of a quantization method, the calculation complexity of the method is remarkably reduced. The method integrates the error entropy and the coefficient when calculating the causality discrimination index, which makes the calculation of the causality discrimination index more accurate and robust. Therefore, the Granger causality discrimination method based on the quantitative minimum error entropy criterion provided by the invention is more easily promoted and used in practical applications.
Owner:XI AN JIAOTONG UNIV
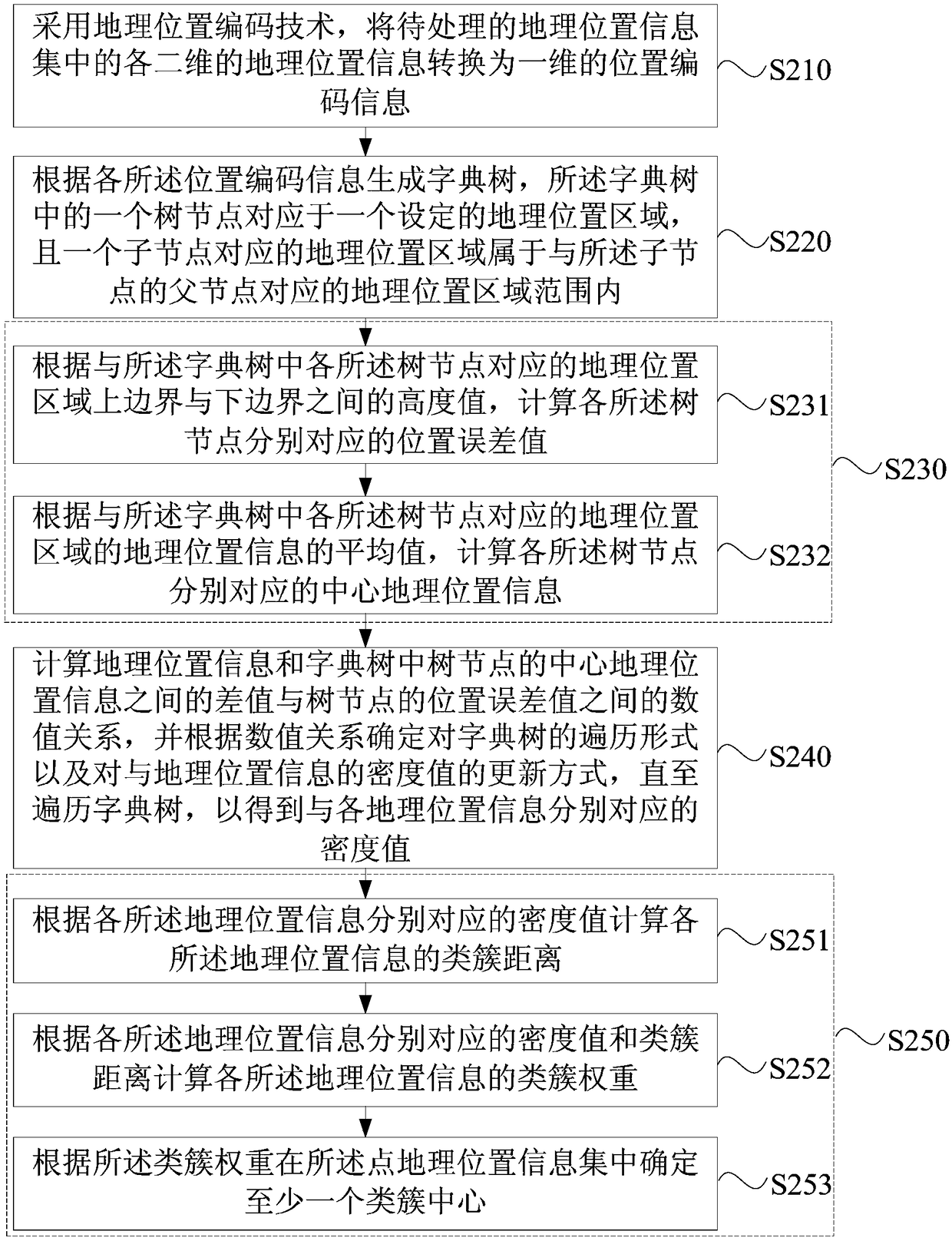
Cluster-like center determination method, device, computer device and storage medium
ActiveCN109299747ASolve problems with high computational complexityReduce computational complexityCharacter and pattern recognitionGeographical information databasesGeographic siteCluster algorithm
The disclosed embodiment discloses a method, a device, a computer device and a storage medium for determining a cluster-like center. The method comprises the following steps: adopting a geographic position coding technique, converting each two-dimensional geographic position information in a geographic position information set to be processed into one-dimensional geographic position coding information; A dictionary tree is generated according to the location coding information. A tree node in the dictionary tree corresponds to a set geographic location area, and a geographic location area corresponding to a child node belongs to a geographic location area range corresponding to a parent node of the child node. Calculating a density value corresponding to each geographic position information according to a positional relationship between each tree node and each geographic position information in the dictionary tree and a quantity value of geographic position information associated witheach tree node; At least one cluster center is determine in that geographic location information set based on the density value. The technical proposal of the disclosed embodiment can reduce the computational complexity of the cluster center in the clustering algorithm.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Target tracking method and device
InactiveCN106295548ASolve problems with high computational complexityCharacter and pattern recognitionPositive sampleObject tracking algorithm
The invention provides a target tracking method and device, belonging to the field of computer vision and mode identification. The method and the device are used for solving the problem of high complexity of an existing target tracking algorithm. The method comprises the steps of selecting a first target position in an Ith frame, determining the tracking result of a first target as a first positive sample, determining the characteristic set of a first sample set from multiple first positive sample packets and first negative sample packets through a formula (1), determining a first MIL1-norm SVM through the characteristic matrix formula (2) of first training data, constructing a first minimum support sample set through a formula (3), determining the weight of the first minimum support sample set through a formula (4), determining the classification score of the first support sample set corresponding to the MIL1-norm SVM based on weight distribution through a formula (5), and classifying candidates through the first MIL1-norm SVM in an (I+1)th frame and determining the second target position in a (I+1)th frame image according to the weight of a second minimum support sample set and a formula (6).
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Black box aggressive defense system and method based on neural network interlayer regularization
ActiveCN112464230ASolve problems with high computational complexityImprove migration abilityInternal combustion piston enginesPlatform integrity maintainanceSample sequenceEngineering
The invention relates to the field of artificial intelligence security, in particular to a black box aggressive defense system based on neural network interlayer regularization, which comprises a first source model, a second source model and a third source model, a black box aggressive defense method based on neural network interlayer regularization comprises the steps of S1, inputting a picture into a first source model for white box attack and outputting a first adversarial sample sequence, S2, inputting the first adversarial sample sequence into a second source model, outputting a second adversarial sample sequence, and S3, outputting a second adversarial sample sequence. and S3, inputting the second adversarial sample sequence into a third source model for black box attack, and outputting a third identification sample sequence, S4, inputting the third identification sample sequence into the third source model for adversarial training, and updating the third source model. An adversarial sample generated by using the algorithm has the characteristic of high mobility to a target model, and the target model can also be effectively defended from being attacked through adversarial training.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Self-adaptive image segmentation method based on Otsu method and K-means method
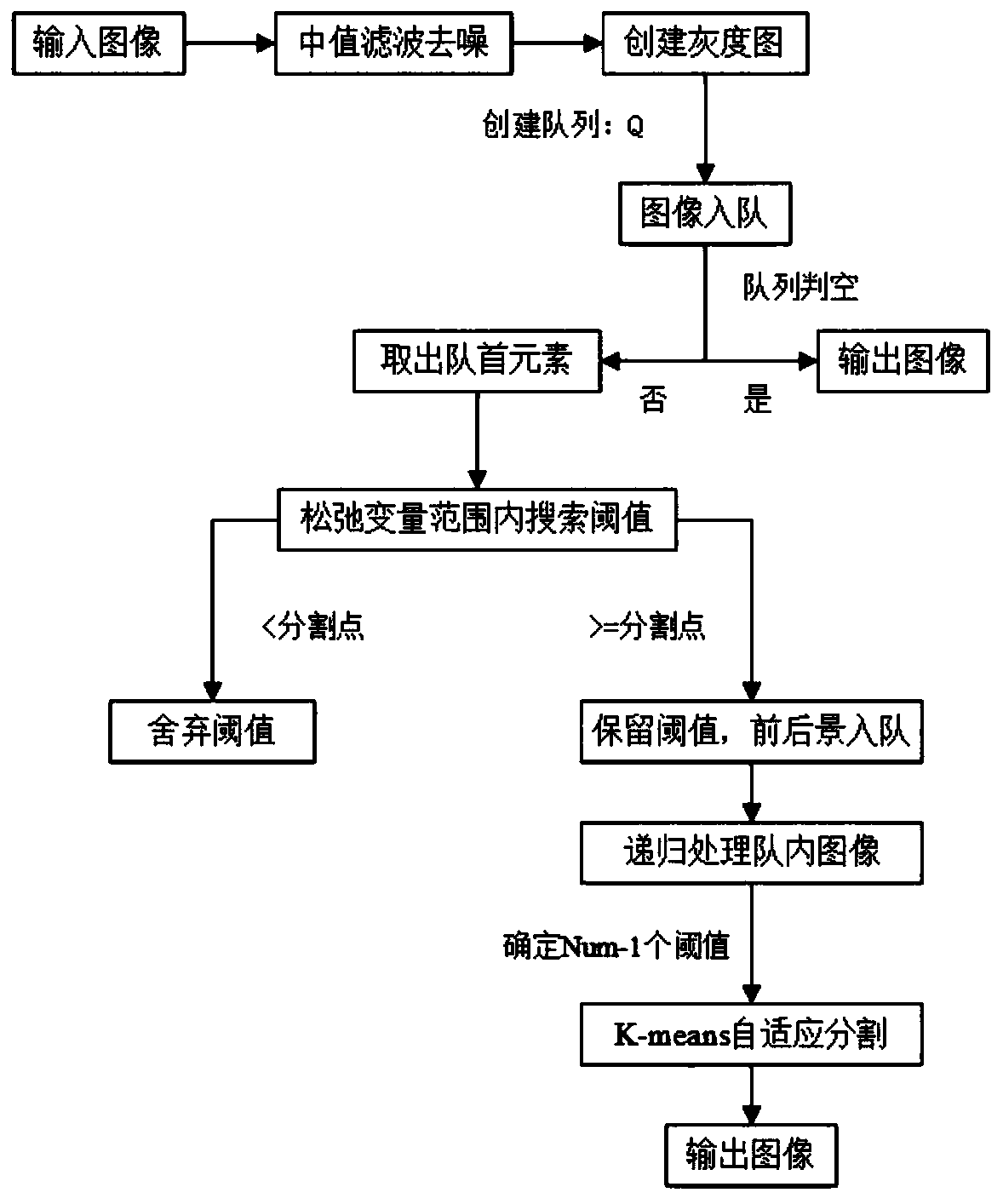
ActiveCN111340815ASolve problems with high computational complexityAccurate segmentationImage enhancementImage analysisImage segmentationThresholding
The invention relates to the field of image segmentation, in particular to a self-adaptive image segmentation method based on an Otsu method and a K-means method. According to the method, the slack variable is introduced, the threshold value in the variable range is used as the local threshold value, the new threshold value search method is cyclically called by using the queue, and the plurality of local optimal threshold values are quickly and adaptively obtained, so that the problem of high calculation complexity of a multi-threshold Otsu method in an existing adaptive K-means image segmentation method is solved; the plurality of obtained thresholds are taken as the initial centroid of the K-means method, and the number of iterations of the K-means method is reduced; and the threshold obtained by clustering through the K-means method is used as the global optimal threshold, so that the image can be segmented accurately. According to the method, image illumination preprocessing servesas the purpose, the image can be segmented rapidly, accurately and adaptively, then the segmented area is corrected, and therefore information, lost due to illumination influence, of the image is recovered.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Feature-based factory manufacturing process difference detection method
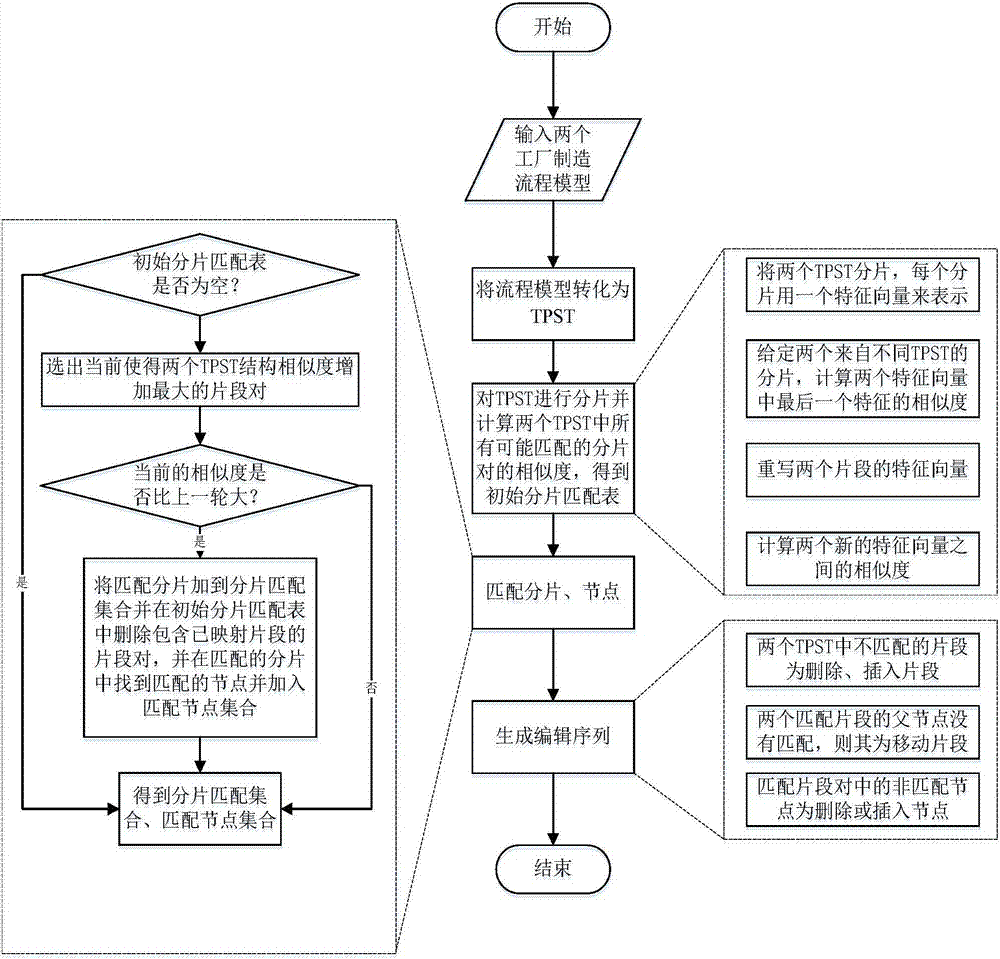
InactiveCN107045670AImprove efficiencySolve problems with high computational complexityResourcesManufacturing computing systemsComputation complexityTheoretical computer science
The invention discloses a feature-based factory manufacturing process difference detection method, which comprises the steps of: converting two factory manufacturing process models into corresponding task-based process structure trees (TPST) based on task nodes; fragmenting the two TPST separately, and calculating similarities between all fragment pairs which are possibly matched; finding out the matched fragment pairs and nodes in the two TPST; and generating editing sequences of the two TPST as the difference based on the matched fragment pairs and nodes. The feature-based factory manufacturing process difference detection method has the advantages of representing the process models by adopting reasonable tree structures, the method of representing the tree structure fragments by means of features is more flexible, the efficiency is significantly improved since a divide-and-conquer strategy is adopted for conducting difference detection, and the problem of high computational complexity is solved.
Owner:ZHEJIANG UNIV OF TECH
Multi-input multi-output visible light communication system based on coefficient separation
ActiveCN107040313ASolve problems with high computational complexityReduce computational complexityClose-range type systemsChannel estimationMulti inputComputation complexity
The invention discloses a multi-input multi-output visible light communication system based on coefficient separation. At a transmitting end, LEDs are divided into two groups. The first group of LEDs transmits the positive integer part of a bipolar pulse amplitude modulation signal, and the second group of LEDs transmits the absolute value of the negative integer part of the bipolar pulse amplitude modulation signal. At a receiving end, a novel receiver with low computing complexity is utilized; the receivers utilizes the characteristic of a transmitted signal; the absolute value of the bipolar pulse amplitude modulation signal is estimated; and then the polarity of the bipolar pulse amplitude modulation signal is estimated; and finally estimation of the bipolar pulse amplitude modulation signal is finished. The multi-input multi-output visible light communication system with separated positive coefficient and negative coefficient according to the invention has advantages of low computing complexity, high performance, etc.
Owner:SOUTHEAST UNIV
Plug-and-play large-scale efficient robust phase recovery method and system
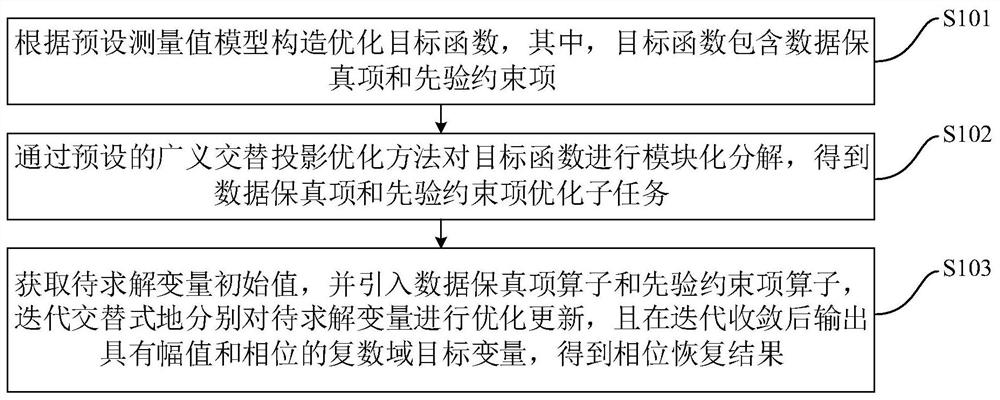
ActiveCN112163186AImprove efficiencyNoise robustnessImage enhancementImage analysisAlgorithmModularity
The invention discloses a plug-and-play large-scale efficient robust phase recovery method and system, and the method comprises the following steps: constructing an optimization target function according to a preset measurement value model, wherein the target function comprises a data fidelity term and a priori constraint term; performing modular decomposition on the target function through a preset generalized alternate projection optimization method to obtain data fidelity term and prior constraint term optimization subtasks; and obtaining an initial value of a variable to be solved, introducing a data fidelity term operator and a priori constraint term operator, iteratively, alternately and respectively optimizing and updating the variable to be solved, and outputting a complex domain target variable with an amplitude and a phase after iterative convergence to obtain a phase recovery result. According to the method, iterative updating is simple and rapid, a flexible and variable priori constraint item operator is introduced, and the problem of large-scale phase recovery can be efficiently solved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
An uncertain data classification method based on direct discriminant sequence mining
InactiveCN109447138ASolve problems with high computational complexityImprove efficiencyCharacter and pattern recognitionData miningProbitSupport vector machine
The invention discloses an uncertain data classification method based on direct distinguishing sequence mining. For the uncertain data set UTD, firstly, a class label is initialized and a class labelset is given. Under the class label set, the minimum support threshold is derived based on the given information gain threshold. The pattern growth strategy is used to enumerate the sub-sequences, generate the pattern candidate x, mine the discrimination sequence, and adopt the reduction strategy to generate the final discrimination sequence result set Rs. Then, the result set Rs is checked, and the closed sequence detection algorithm is used to determine whether each candidate sequence in Rs is a probabilistic frequent closed sequence or not. If the sequence is probabilistic frequent closed sequence, the discriminant sequence satisfying the condition is added to the result set RsTmp. Finally, by combining with the rule-based classification method or support vector machine existing maturedata classification methods, the data classification is completed. As that complement of the discriminate pattern mining on the uncertain data set, the method of the invention remarkably improves theefficiency, and the result set is more concise.
Owner:NORTHEASTERN UNIV
Real-time target detection method combining convolutional neural network and Transform network
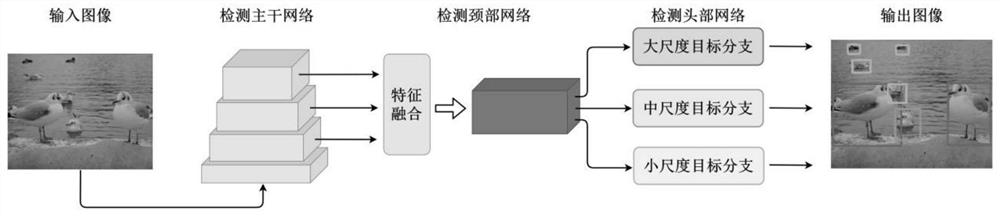
PendingCN114842316ASolve problems with high computational complexitySolving High Computational Complexity ProblemsCharacter and pattern recognitionNeural architecturesData setData graph
The invention provides a real-time target detection method combining a convolutional neural network and a Transform network, and belongs to the field of image processing. Comprising the following steps: S1, inputting image data; s2, the image passes through a convolutional neural backbone network, so that the extracted features have inductive bias characteristics; and S3, designing a neck detection network, performing transition between the detection backbone network and the head network, and providing high-resolution and high-semantic features for the detection head network. S4, designing a detection head network, introducing Transform into the head network, constructing a plurality of remote dependency relationships among the generated local features, and representing target categories and coordinates existing in the image; s5, designing a nonlinear combination method for reducing false negative samples and improving the capturing capability of the detection model on the target; and S6, carrying out detection on the natural data set. Based on the method, better performance is realized on challenging PASCAL VOC 2007, 2012 and MS COCO 2017 data sets, and the method is superior to many more advanced real-time detection methods.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Online distributed multi-task graph filter construction method based on recursive least squares
ActiveCN112865748BEstimated speedCooperate wellDigital technique networkDesign optimisation/simulationGraphicsComputation complexity
Owner:SOUTHWEST UNIV
Gesture recognition method and device, electronic device
ActiveCN107678551BReduce operational complexityComputational Complexity ResolutionInput/output for user-computer interactionImage enhancementImaging processingComputer graphics (images)
The present invention proposes a gesture recognition method and device, and electronic equipment, wherein the method includes: collecting a first image including a gesture; acquiring the center of the gesture according to the first image; and determining the control of the gesture on the terminal device according to the center coordinates Range: Get the control object from the control range, and operate the control object according to the control instruction corresponding to the gesture. Through image processing, the center coordinates of gestures can be obtained, and the terminal equipment can be precisely controlled, and the computational complexity is reduced, which solves the existing gesture recognition method that uses spatial algorithms to calculate the motion trajectory of gestures, and then controls terminal equipment. , a problem with high computational complexity.
Owner:BOE TECH GRP CO LTD
An Incremental Trajectory Anomaly Detection Method Based on Incremental Kernel Principal Component Analysis
ActiveCN106022368BSolve problems with high computational complexityImprove Anomaly Detection EfficiencyCharacter and pattern recognitionKernel principal component analysisSupport vector machine
The invention relates to an incremental trajectory anomaly detection method based on incremental kernel principal component analysis, which belongs to the incremental trajectory anomaly detection method. This method: first perform the initial calculation of the model, and use the traditional Batch KPCA to calculate the initial kernel feature space. Whenever there are M new trajectory data coming, first standardize the M trajectory data; then use Batch KPCA to calculate the new Increase the kernel feature space of the data; calculate the average reconstruction error of the new data and the training data respectively, if the error of the two is greater than the given threshold, execute the subsequent kernel feature space segmentation-merging method to update the kernel feature space; then update The final kernel feature space is projected to extract the principal components; finally, a class of support vector machines is used for unsupervised learning and anomaly detection. Advantages: This method is superior to the traditional kernel principal component analysis method, reduces computational complexity, and improves the efficiency of trajectory anomaly detection.
Owner:CHINA UNIV OF MINING & TECH
A New Method of Passive Location Tracking Based on Logarithmic Likelihood Estimation
ActiveCN106446422BSolve problems with high computational complexityRealize target location trackingDesign optimisation/simulationSpecial data processing applicationsLocation trackingLog likelihood
The invention relates to a log likelihood estimation based novel passive locating and tracking method. A multistation angle-measurement passive-location non-linear measurement equation is subjected to pseudo-linearization processing by the aid of log likelihood estimation, target position is obtained by means of maximum likelihood estimation, a closed-form solution of a target locating algorithm is given, then a 'current' statistical maneuver model and Kalman filtering are utilized to calculate target position, velocity and acceleration online in real time, and real-time accurate positioning and tracking on the target is realized.
Owner:XIJING UNIV
A method and system for oil and gas pipeline routing planning
InactiveCN113158384BSolve problems with high computational complexityHigh quality designGeometric CADForecastingRoute planningIndustrial engineering
Owner:NORTHEAST GASOLINEEUM UNIV
A multi-input multi-output visible light communication system based on coefficient separation
ActiveCN107040313BSolve problems with high computational complexityReduce computational complexityClose-range type systemsChannel estimationMulti inputComputation complexity
Owner:SOUTHEAST UNIV
Black-box attack defense system and method based on neural network middle layer regularization
ActiveCN112464230BSolve problems with high computational complexityImprove migration abilityInternal combustion piston enginesPlatform integrity maintainancePattern recognitionSample sequence
The invention relates to the field of artificial intelligence security, in particular to a black-box attack defense system based on the regularization of the middle layer of the neural network, including a first source model, a second source model and a third source model; The box attack defense method includes S1, inputting pictures into the first source model for white-box attack, outputting the first adversarial sample sequence, S2, inputting the first adversarial sample sequence into the second source model, and outputting the second adversarial sample sequence , S3, inputting the second adversarial sample sequence into the third source model for black-box attack, outputting the third recognition sample sequence, S4, inputting the third recognition sample sequence into the third source model for adversarial training, updating the third source model ; The adversarial samples generated by this algorithm have the characteristics of high transferability to the target model, and can also effectively defend the target model from being attacked through confrontation training.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Infinitesimal normalized cut method for image segmentation
ActiveCN1841408ASolve problems with high computational complexityWide applicabilityCharacter and pattern recognitionImage segmentationComputer vision
The related minimal normalization image segmentation method comprises: 1) reducing dimension to the target image; 2) taking minimal normalization segmentation to obtain the low-dimension segmentation boundary; 3) taking additional sampling, reconstructing an image with same dimension as the target; 4) connecting the discontinuous segmentation boundary to obtain the required segmentation boundary. This invention has acceptable time and space complexity and wide application.
Owner:XIAMEN PRIMA TECH
Method, device, computer equipment and storage medium for determining cluster centers
ActiveCN109299747BSolve problems with high computational complexityReduce computational complexityCharacter and pattern recognitionGeographical information databasesCluster algorithmGeographic site
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com