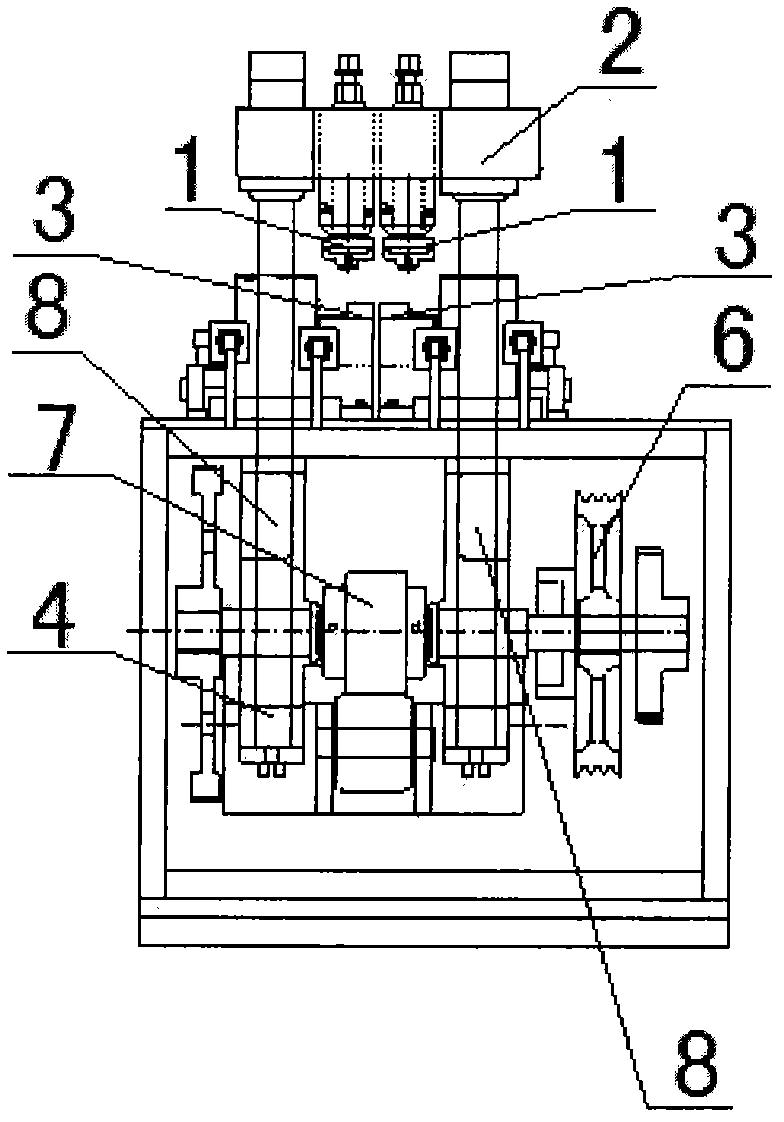
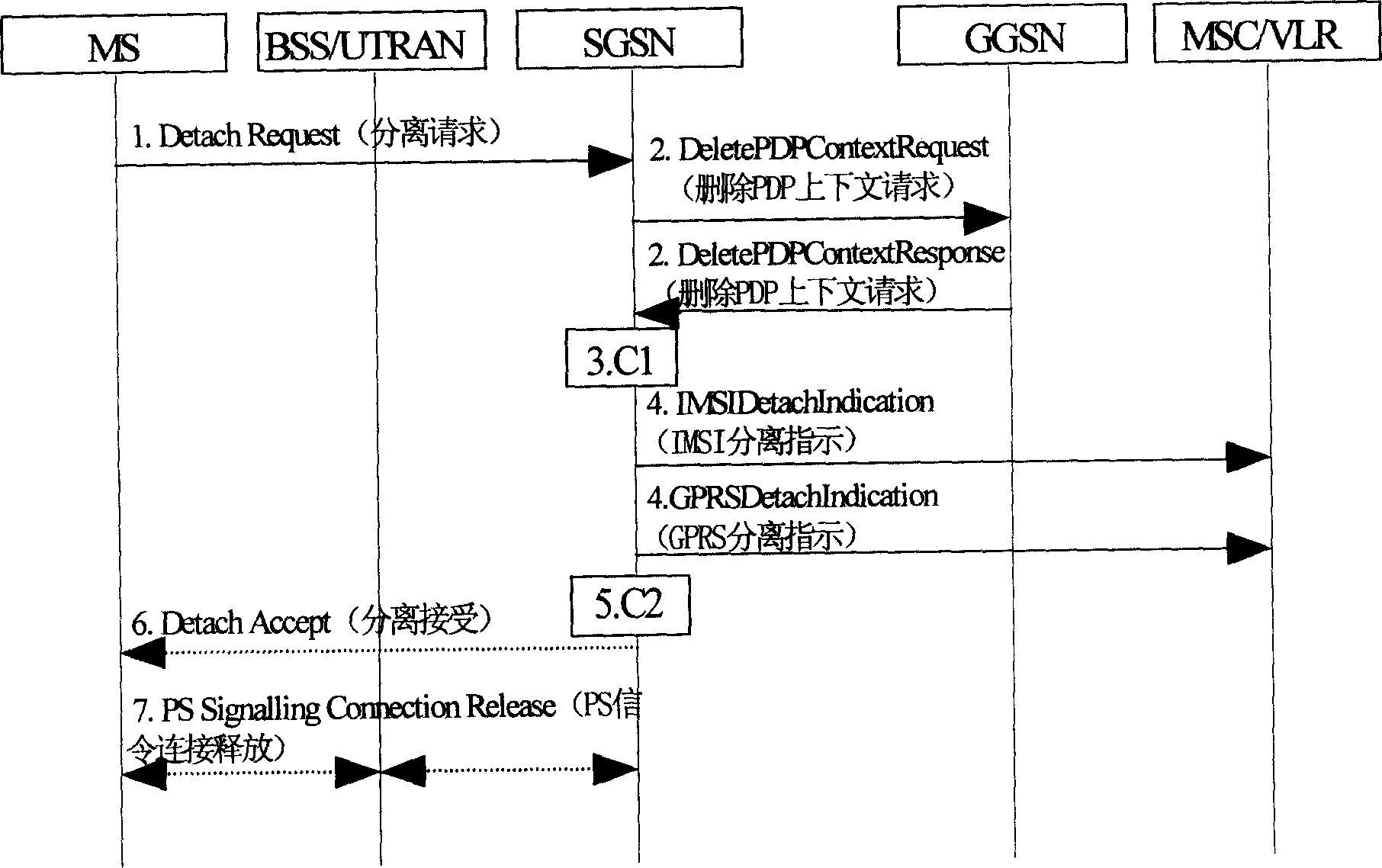
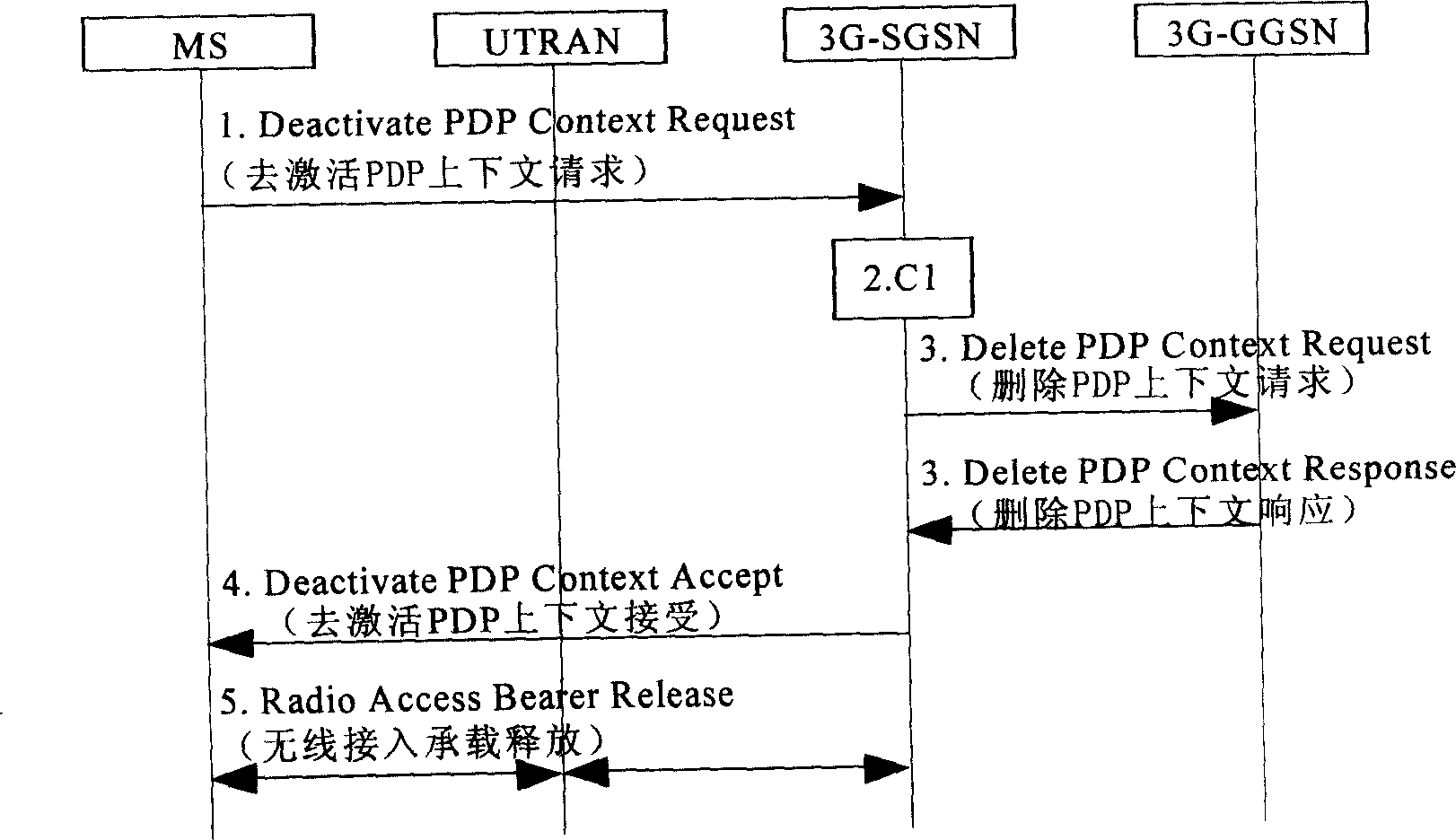
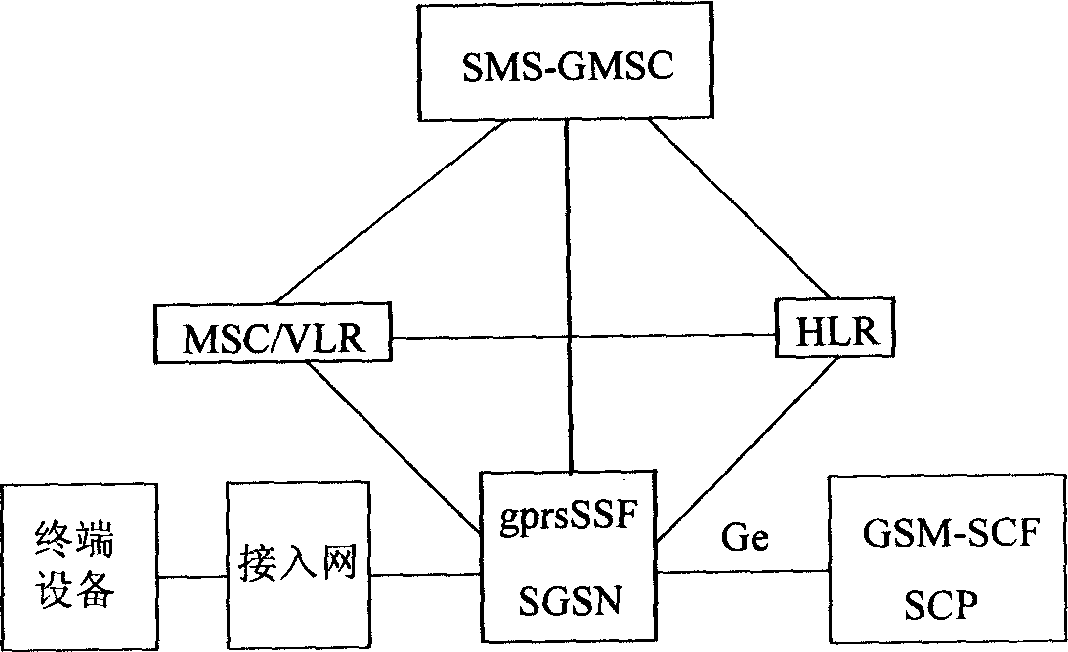
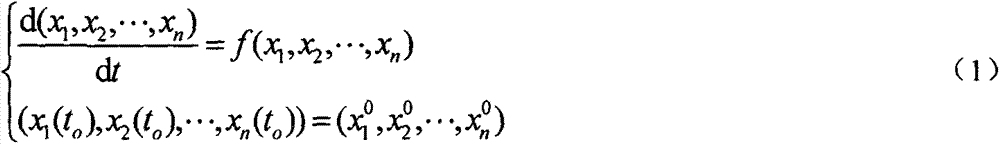Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Safeguard the interests of" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
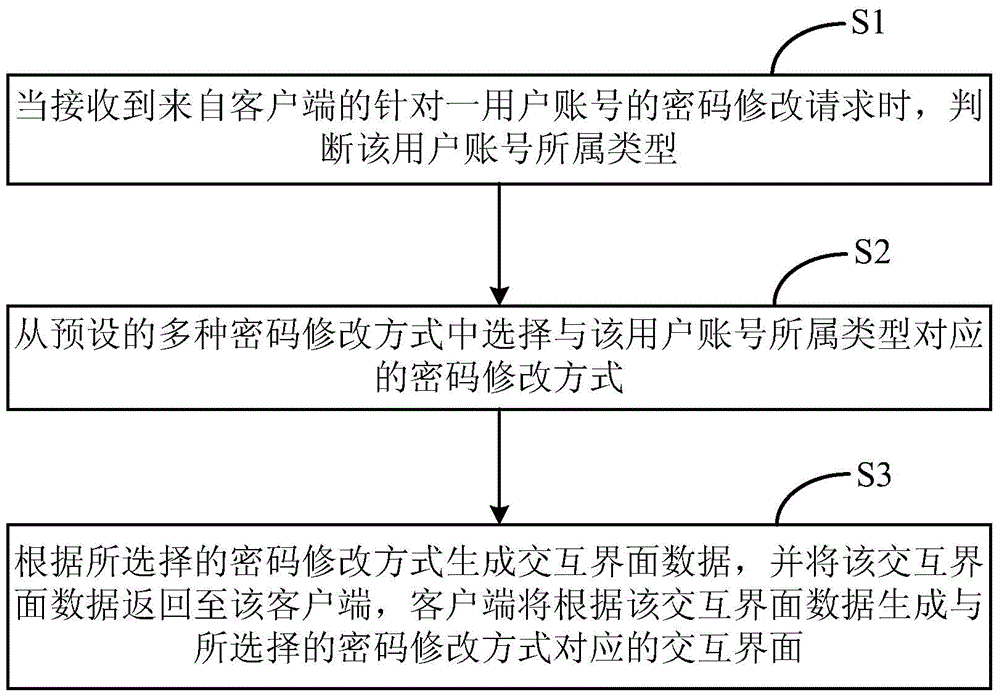
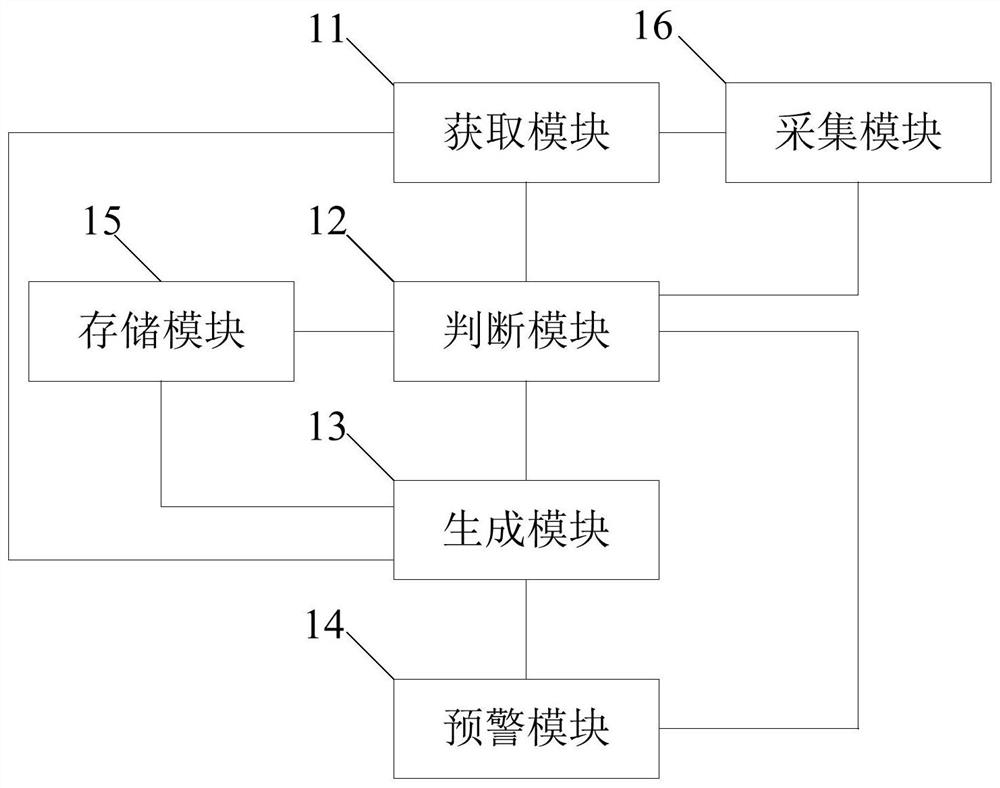
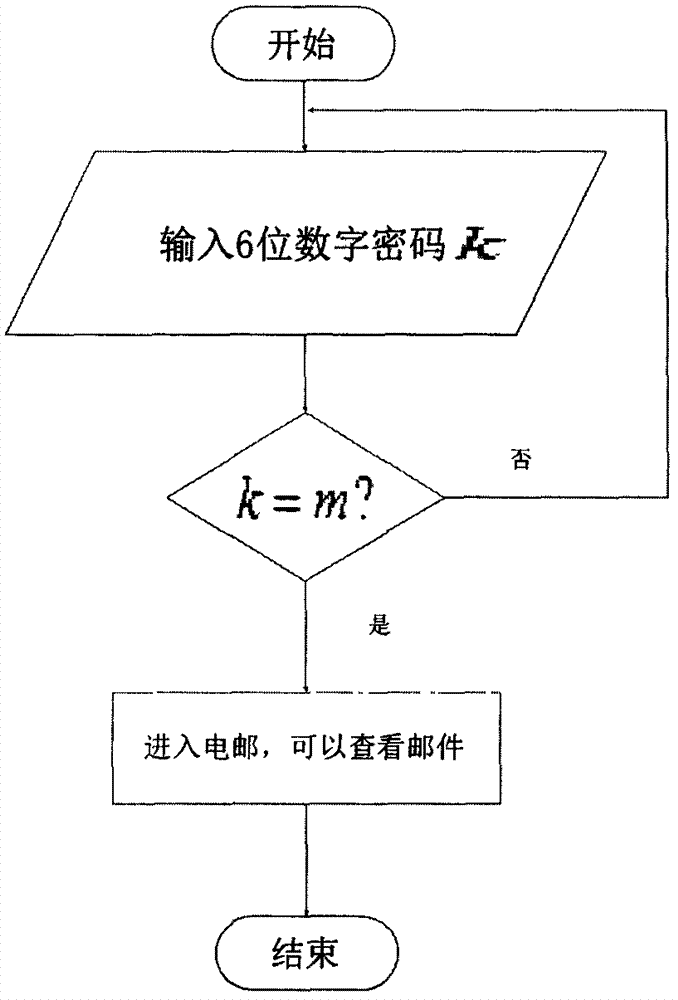
Method and device for recommending password change mode
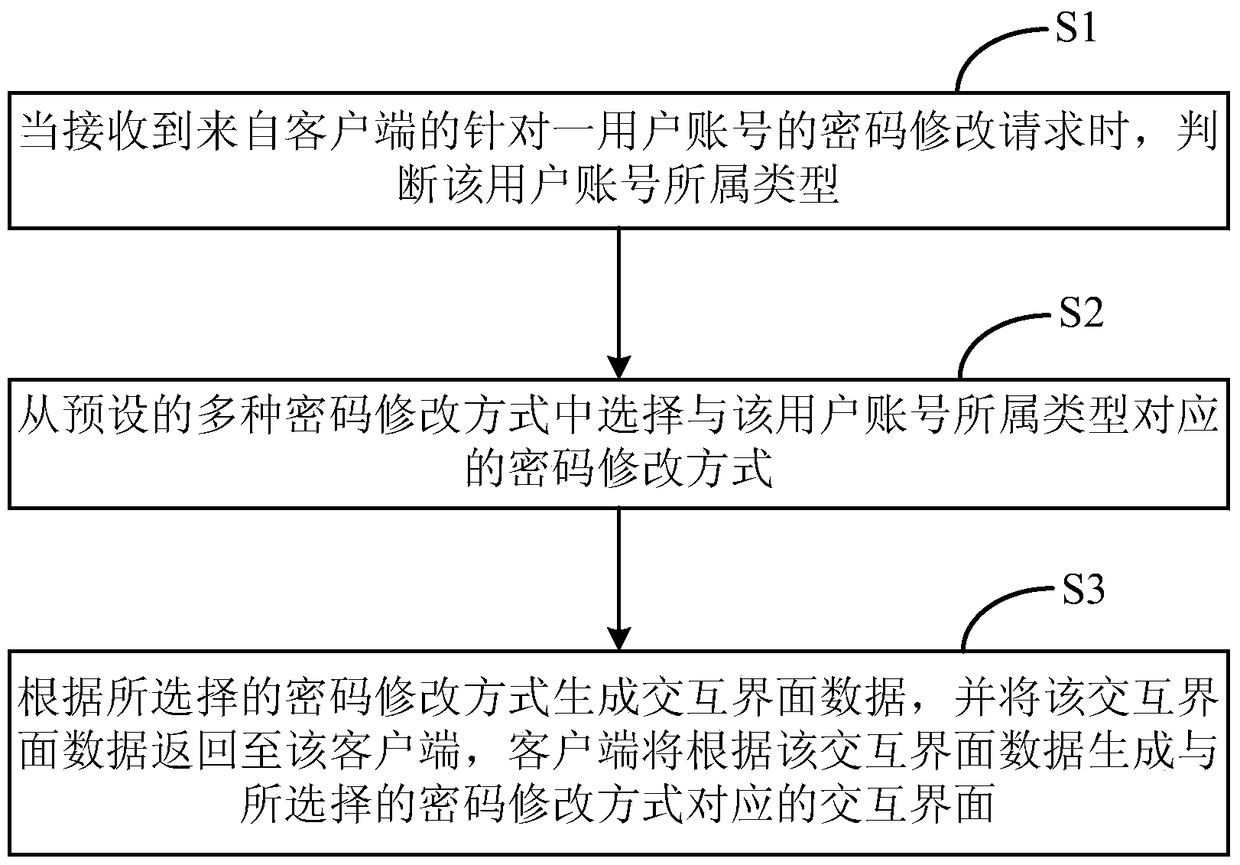
The invention relates to a method for recommending a password change mode. The method comprises the following steps: (1) judgment: when a request for changing the password of a user account is received from a client, judging the type of the user account; (2) selection: selecting a password change mode corresponding to the type of the user account from a plurality of preset password change modes; (3) recommendation: generating interactive interface data according to the selected password change mode, and feeding back the interactive interface data to the client, wherein an interactive interface corresponding to the selected password change mode is created on the client according to the interactive interface data. The invention further provides a device for recommending the password change mode. Through the adoption of the method and the device, the password change security can be improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
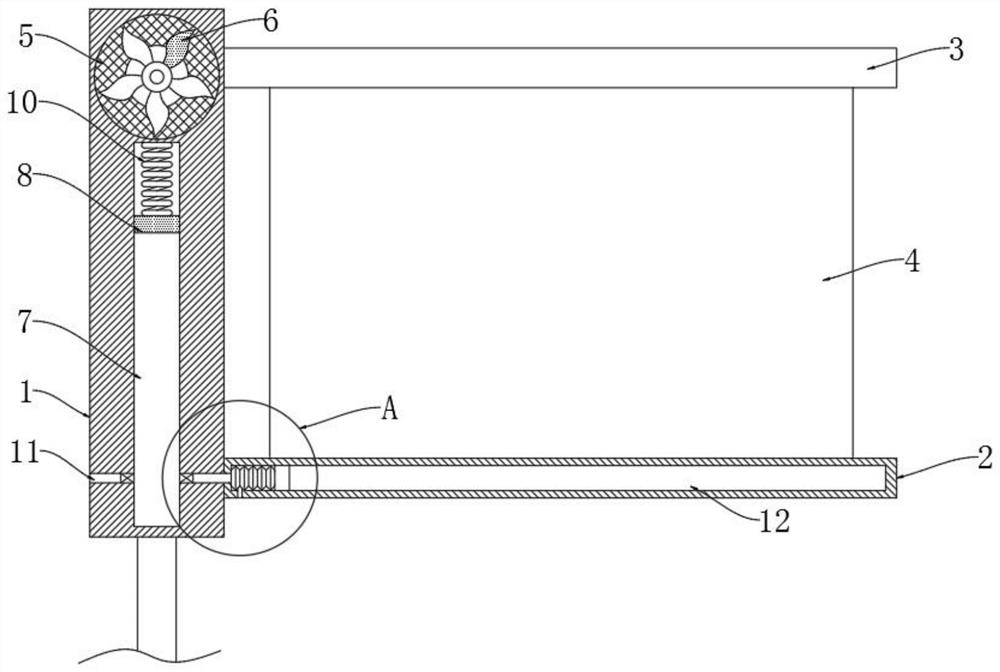
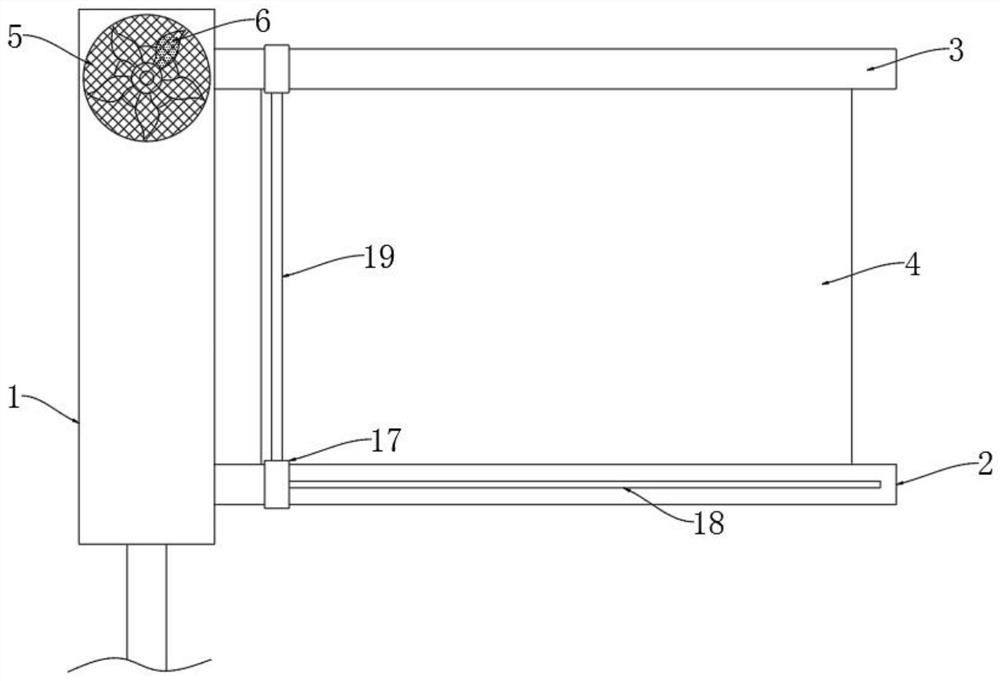
Self-cleaning outdoor advertising board
InactiveCN111627358AGuaranteed aestheticsMaintain imageCleaning using toolsIlluminated signsEngineeringMechanical engineering
The invention discloses a self-cleaning outdoor advertising board. The self-cleaning outdoor advertising board comprises a main rod, a lower fixing plate and an upper fixing plate, the lower fixing plate and the upper fixing plate are fixedly connected to the side wall of the main rod, an advertising board body is fixedly connected between the lower fixing plate and the upper fixing plate, a through hole is formed in the upper end of the main rod, and net plates are arranged at two openings of the through hole. An impeller, a magnetic sliding plug, a wiping mechanism, a spiral coil and a magnetic rod are arranged, when the wind power is large, the wind power drives the impeller to rotate, the magnetic sliding plug is pushed to slide up and down by magnetic force, and an elastic balloon isinflated and expanded, so a sliding ring is driven by a sliding block to slide along a fixed plate, a cleaning brush wipes the surface of the advertising board without manual cleaning, the danger thatthe advertising board is prone to falling off during manual cleaning is avoided, and the labor intensity of cleaning personnel is reduced; and meanwhile, colored lamps can emit light when the magnetic sliding plug slides, the attraction of the advertising board is enhanced, and the better advertising effect is achieved.
Owner:田园园
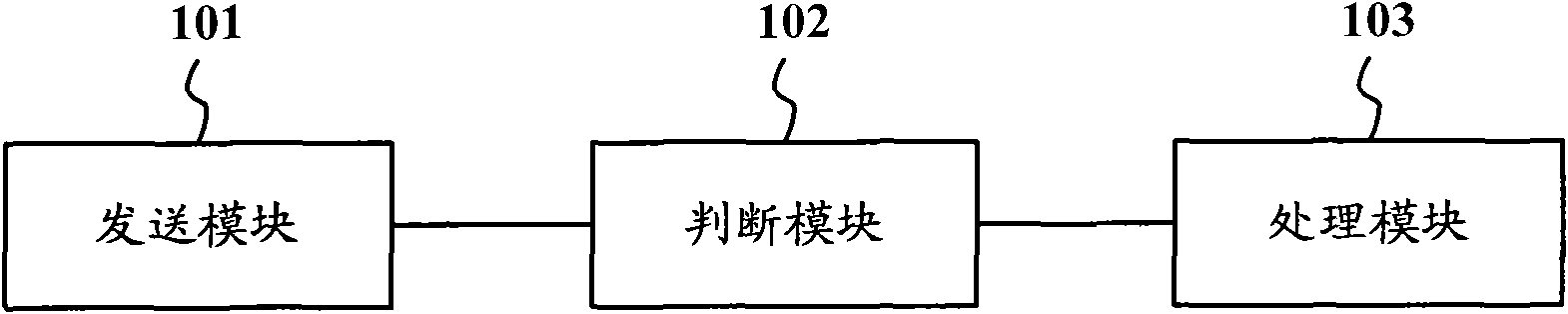
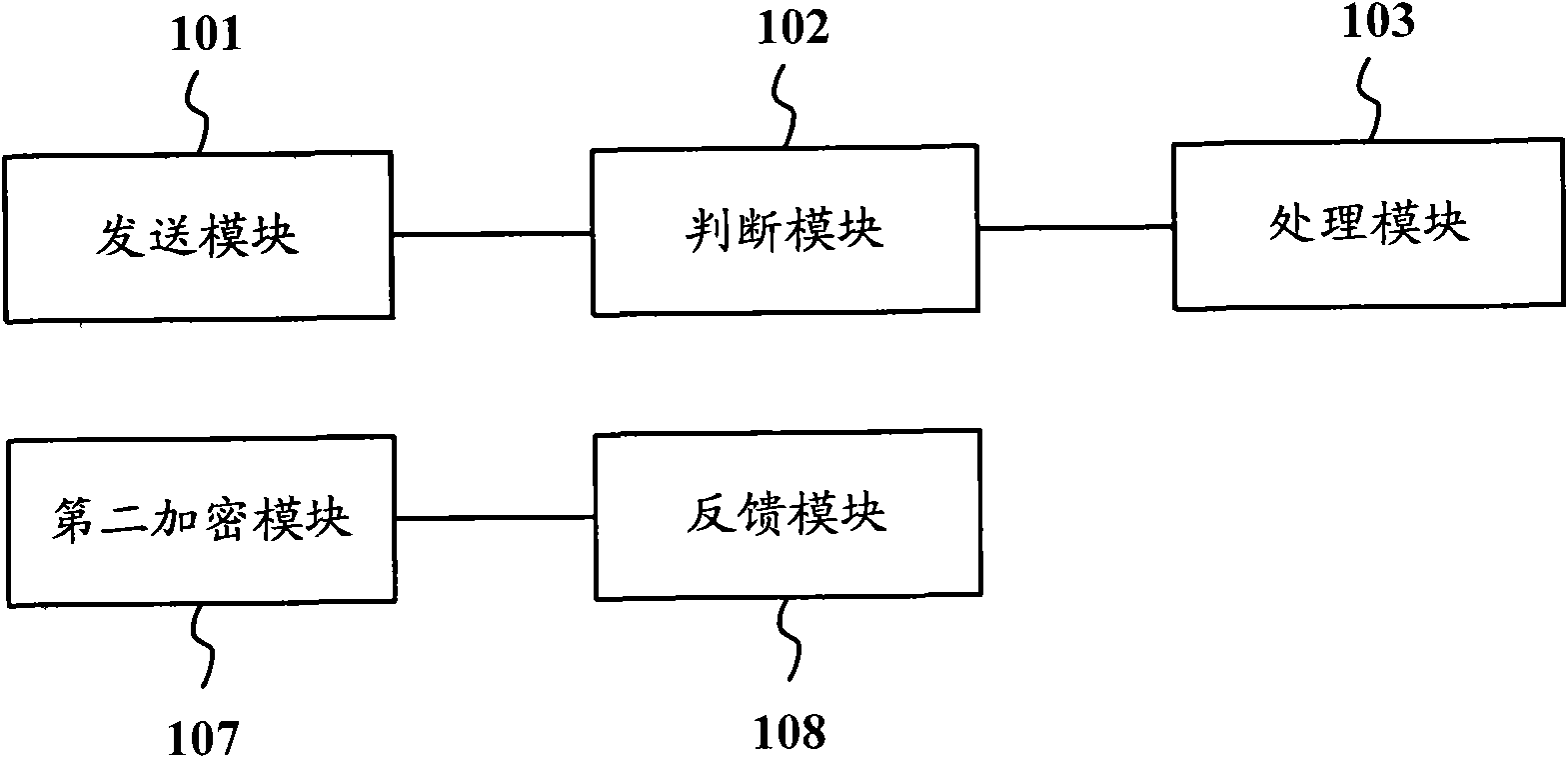
Service providing client terminal, wireless terminal and binding realizing method
ActiveCN101635920ASafeguard the interests ofAvoid chaosComputer security arrangementsSecurity arrangementClient-sideTelecommunications
The invention provides a service providing client terminal, a wireless terminal and a binding realizing method. The service providing client terminal comprises a sending module, a judging module and a processing module, wherein the sending module is used for sending authentication information to the wireless terminal; the judging module is used for judging if the wireless terminal is a legal binding object or not according to the response of the wireless terminal to the authentication information; and the processing module is used for providing service to the wireless terminal when the wireless terminal is the legal binding object, otherwise, the service provided for the wireless terminal is limited. The invention can determine the binding between the service providing client terminal and the wireless terminal.
Owner:ZTE CORP
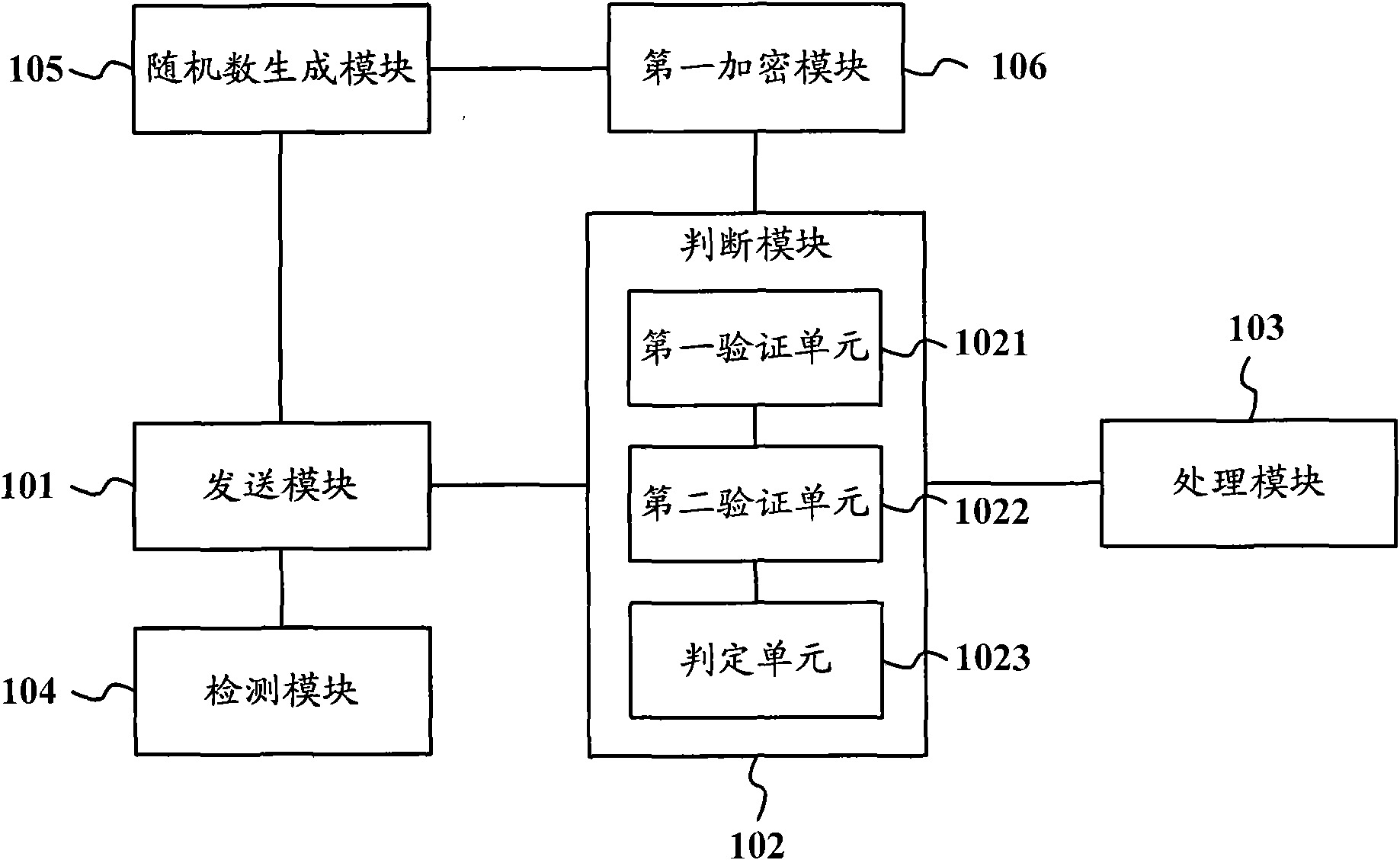
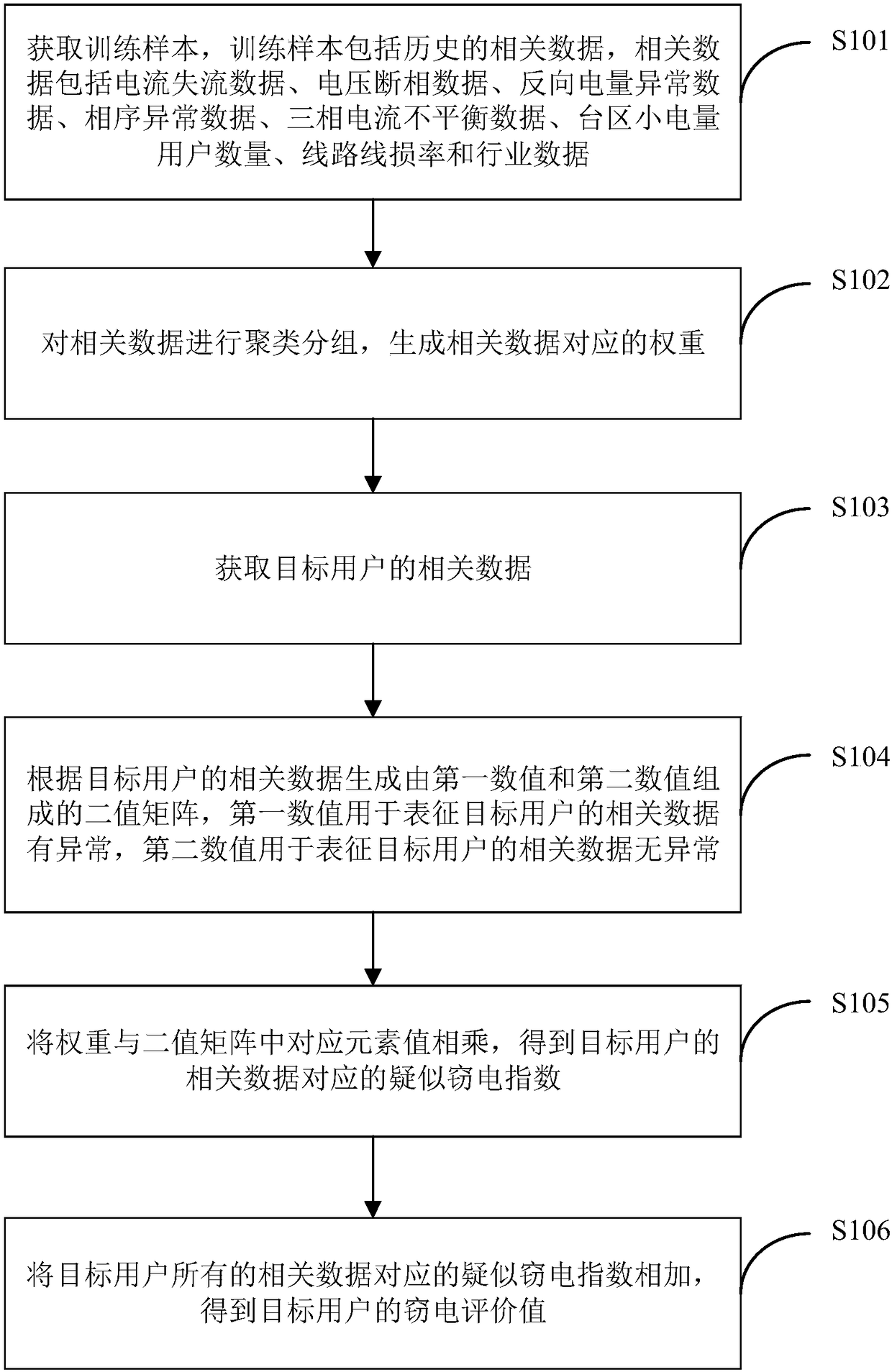
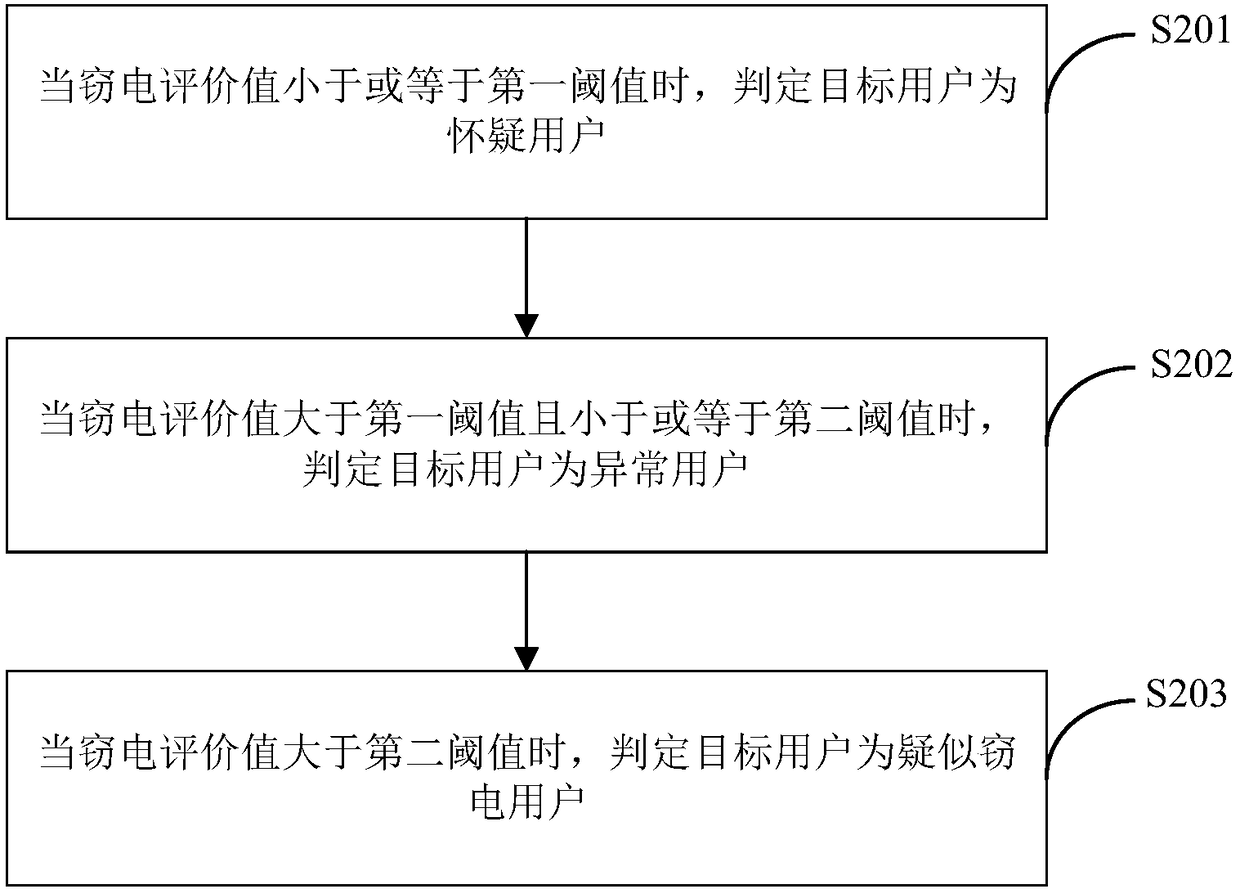
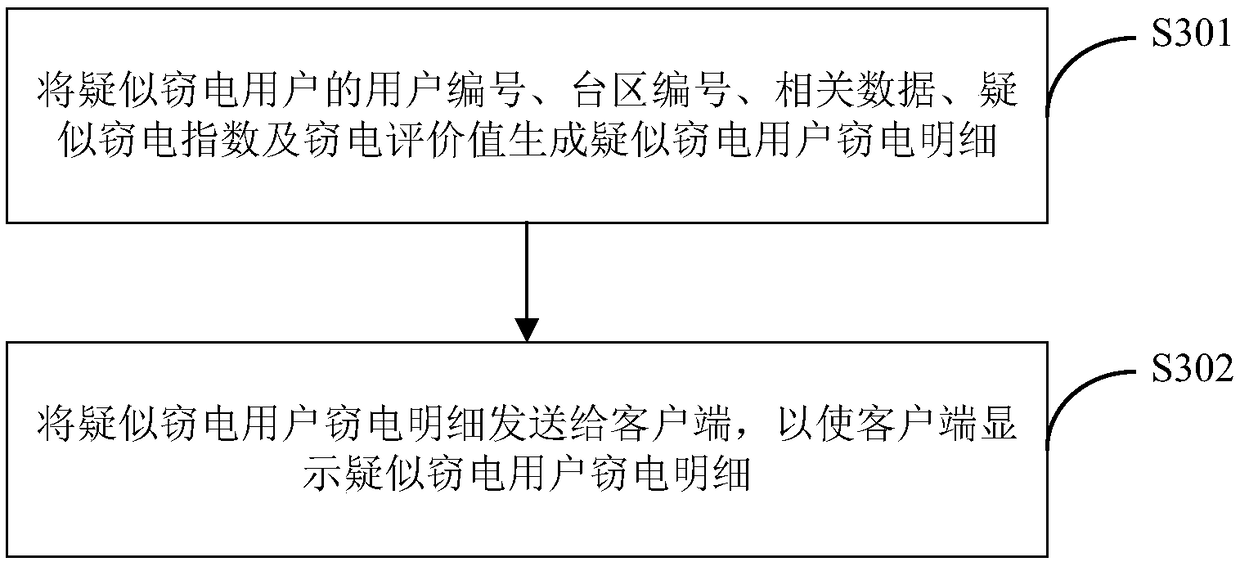
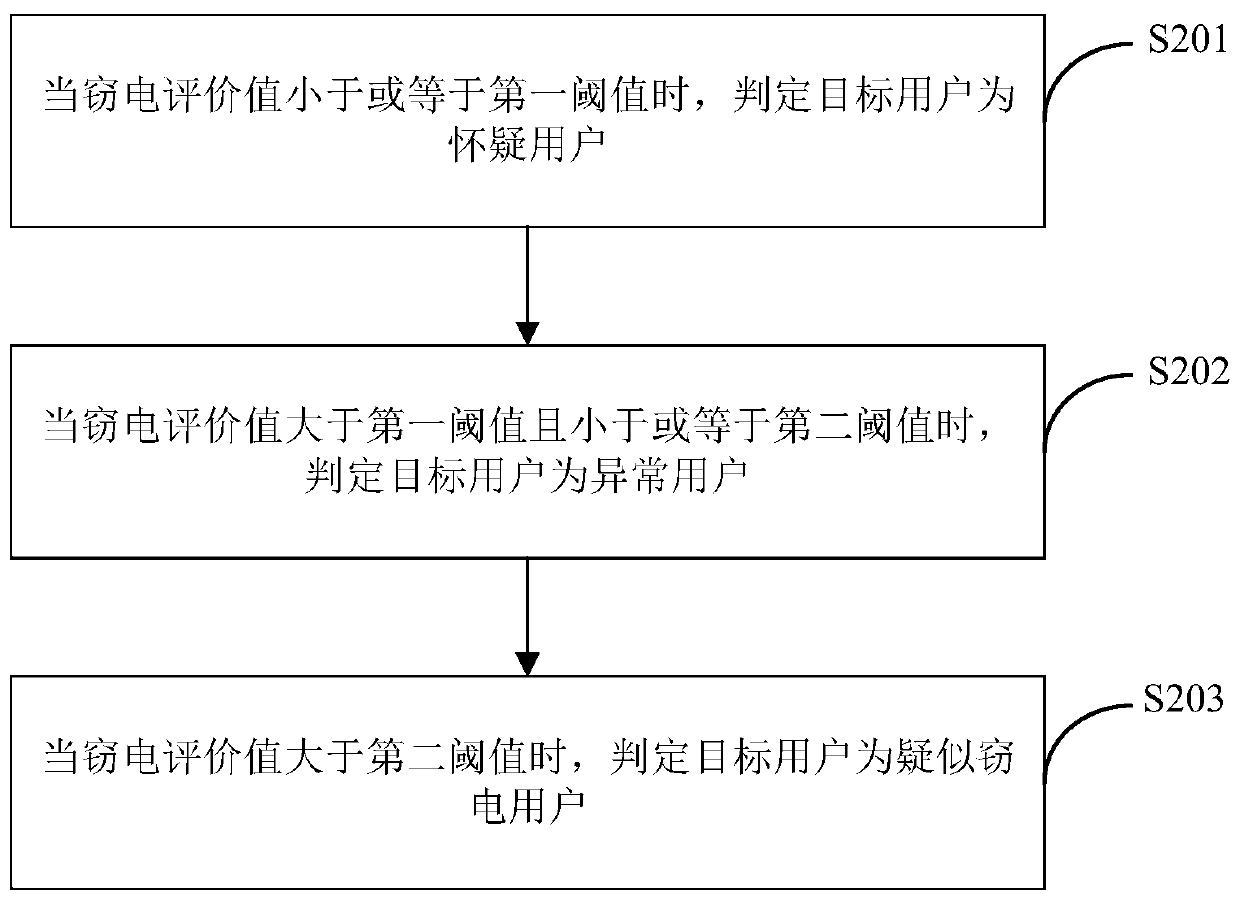
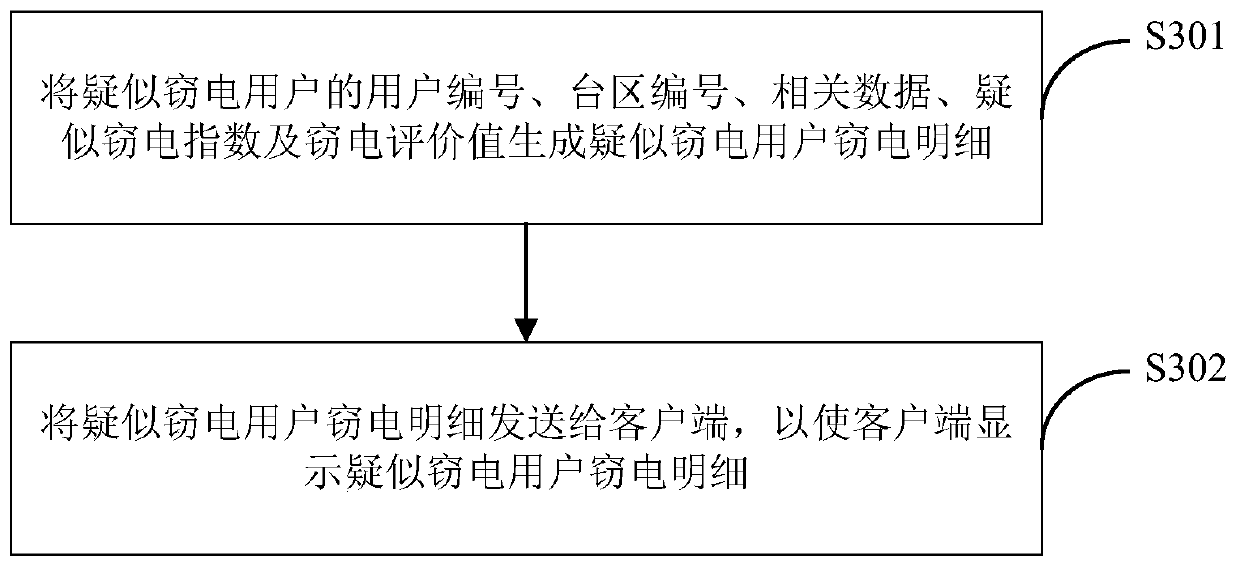
Self-adaptive electricity-stealing-preventing monitoring method and system based on electricity consumption information acquisition system
ActiveCN108198408AAccurately determineEliminate potential safety hazardsElectric signal transmission systemsCharacter and pattern recognitionElectricityMonitoring system
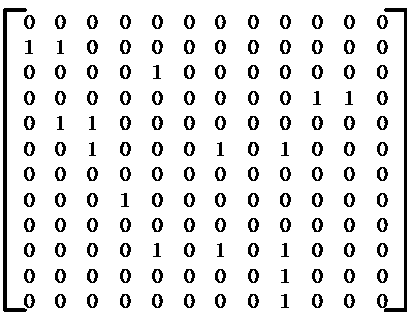
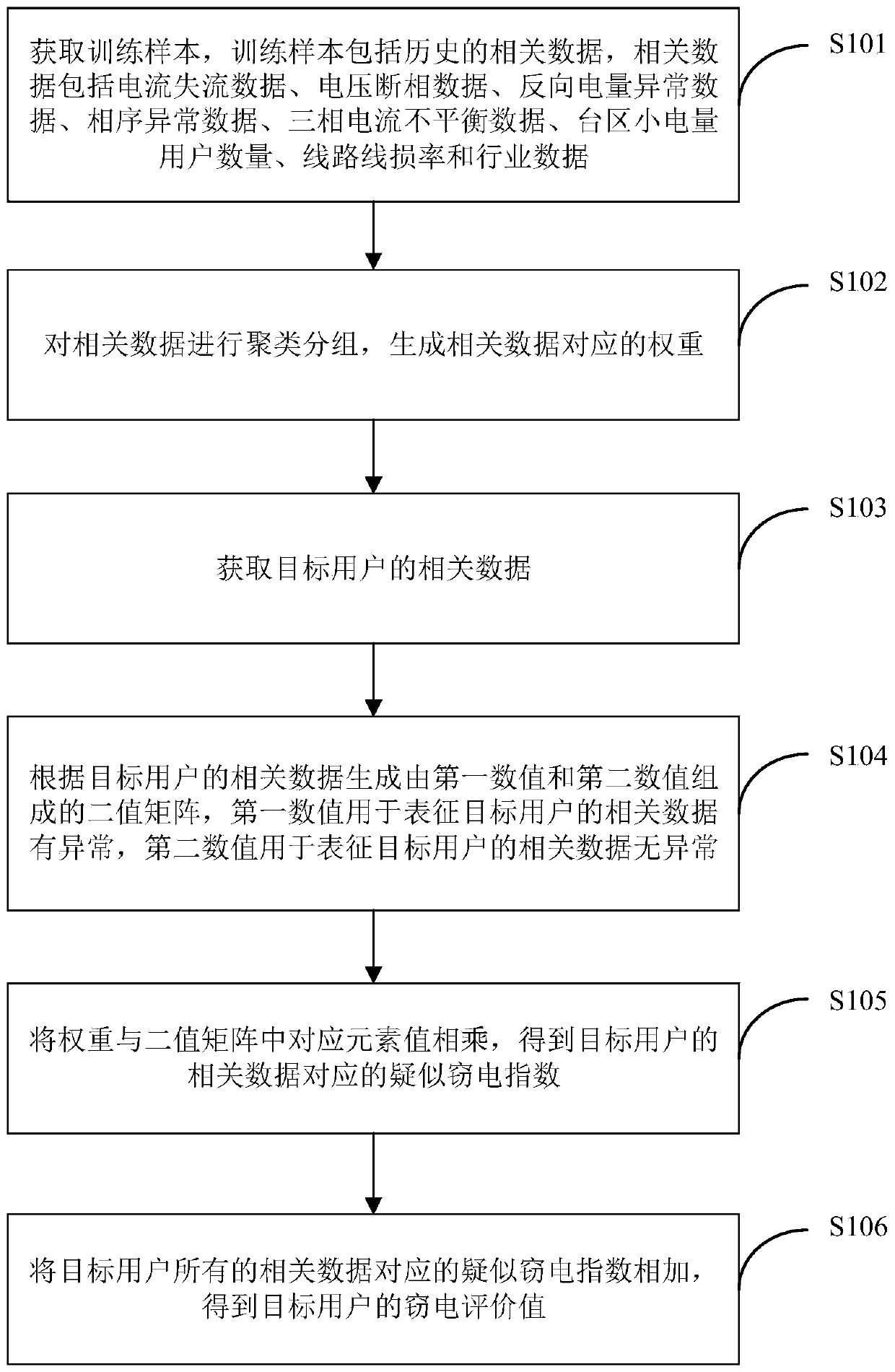
The invention is applicable in the technical field of electric quantity monitoring, and provides a self-adaptive electricity-stealing-preventing monitoring method and a self-adaptive electricity-stealing-preventing monitoring system based on an electricity consumption information acquisition system. The method comprises the following steps: obtaining a training sample, clustering and group the related data and generating weight corresponding to the related data, wherein the training sample comprises historical related data; generating a binary matrix consisting of a first numerical value and asecond numerical value according to the related data of a target user, multiplying the weight and the corresponding element value in the binary matrix to obtain suspected electricity-stealing indexescorresponding to the related data of the target user; and adding all the suspected electricity-stealing indexes of the target user to obtain an electricity-stealing evaluation value of the target user. By the method and the system, data interaction with the electricity consumption information acquisition system is realized, the electricity-stealing user can be determined accurately, the labor force is saved, the potential safety hazard of the on-site electricity-stealing inspection work is eliminated, the accuracy and the working efficiency of electricity-stealing inspection are improved, andthe national interest and the company's right are further maintained.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +3
Biserial chain quadrangular riveting machine
InactiveCN102615242ASmooth runningImprove operating conditionsMetal chainsEngineeringMechanical engineering
The invention discloses a biserial chain quadrangular riveting machine which comprises a power device, a support device, a stamping die and a safety protection device; a chain to be riveted is arranged in the stamping die; the power device is arranged below a working platform of the riveting machine and is matched with the stamping die through being connected with the support device; and the safety protection device is arranged on the support device for protection. According to the riveting machine, riveting heads are arranged side by side and in pairs so as to enable the number of the riveting heads to be increased by two times, so that the original yield can be achieved at half of the original rotation speed, the machine can rotate more stably, the breakdown rate is greatly reduced, and the quantity and quality of products can be improved favorably; and the additionally arranged safety protection device can prevent fracture of an upper cross beam to safeguard the interests and safety of a user in the case of misoperation by the user.
Owner:QINGDAO JIAFU MACHINERY
Method of charging communication flow
ActiveCN1863055AReduce Billing ErrorsSafeguard the interests ofMetering/charging/biilling arrangementsTraffic volumeEngineering
The invention relates to a method to take charging to communicating flow that includes the following steps: deducting the negative flow from the monitored communication flow to gain the actual communication flow, taking charging to the actual flow through SCP. The invention could reduce charging error and maintain the benefit for user.
Owner:HUAWEI TECH CO LTD
Charging method, equipment and system for e-wallet
ActiveCN101488251AMaintain consistencySafeguard the interests ofAccounting/billing servicesPayment architectureElectronic purseTreatment system
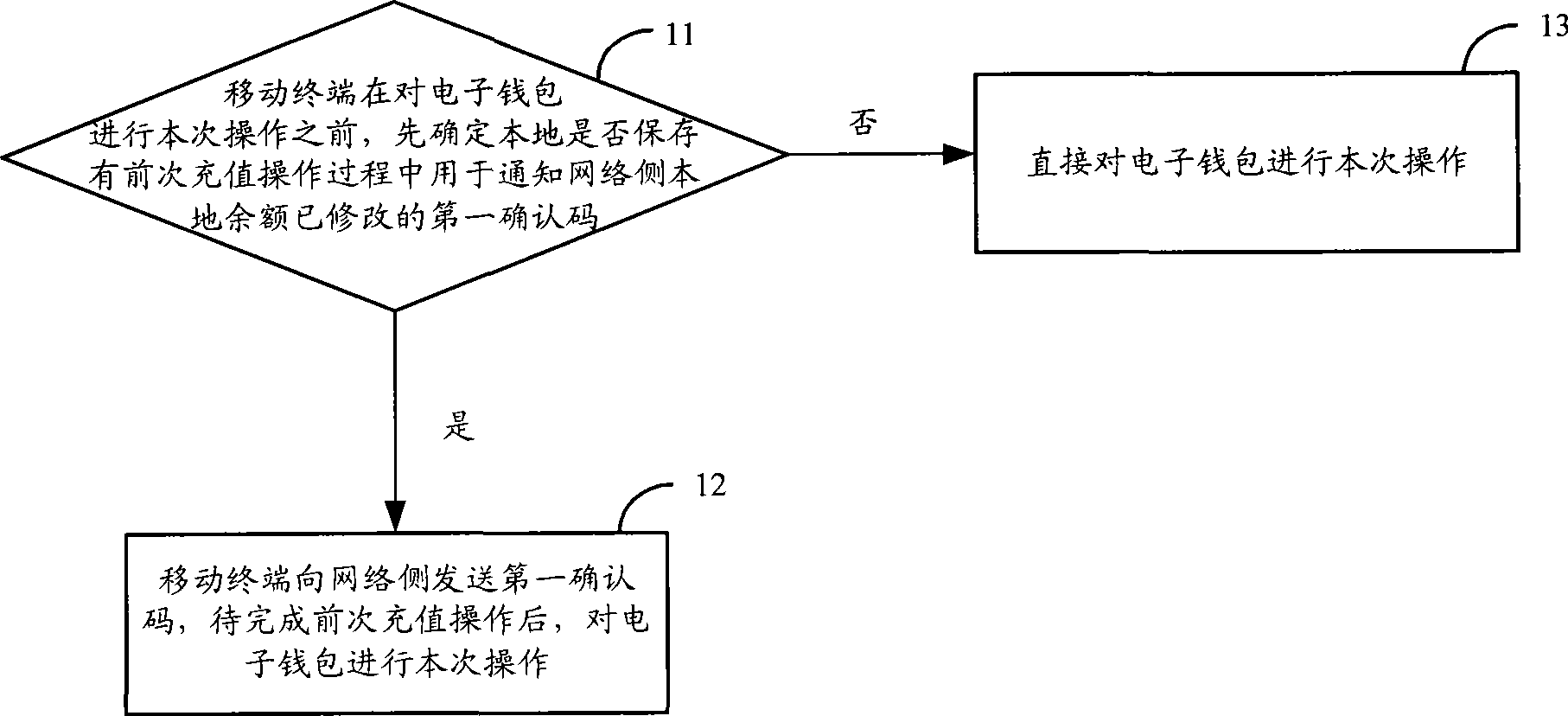
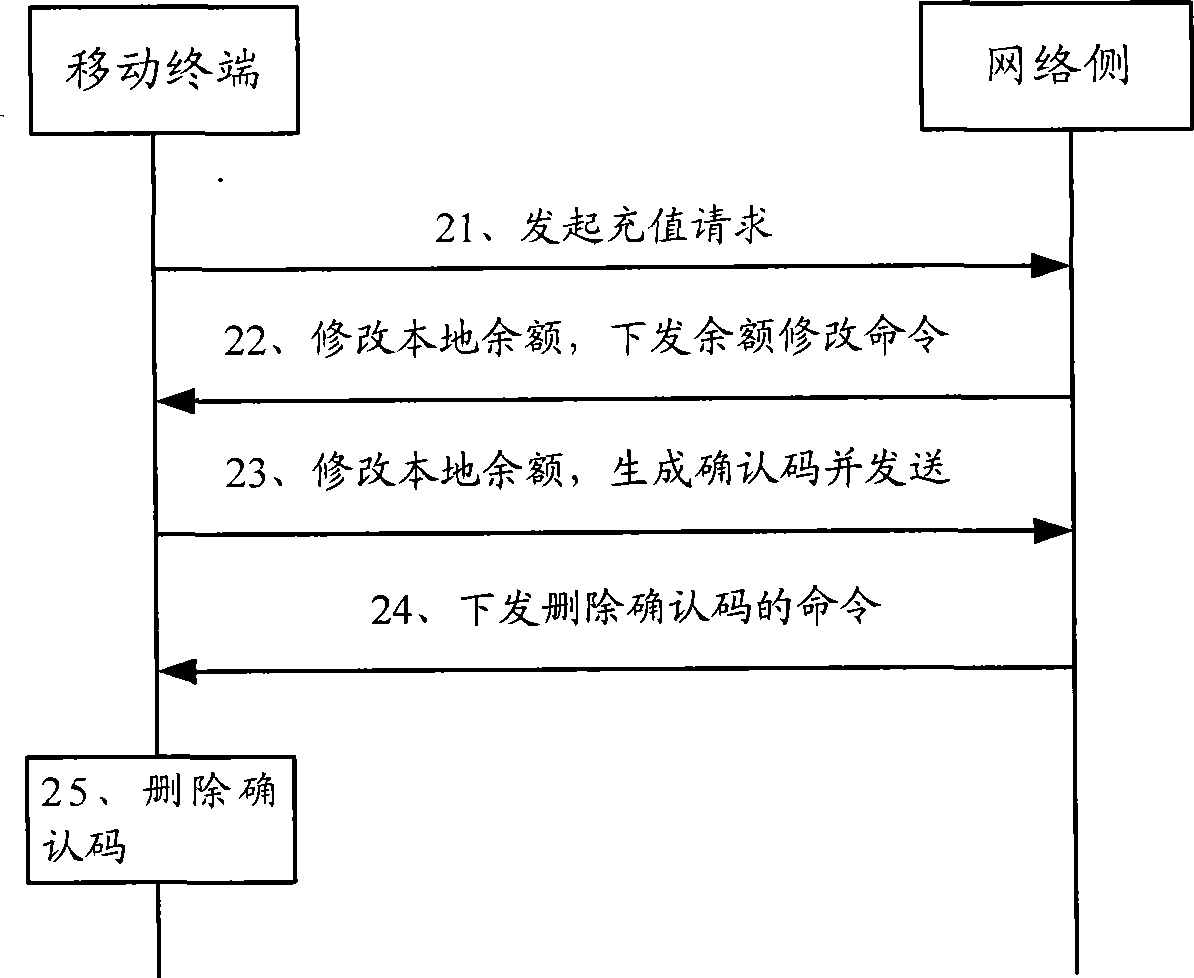
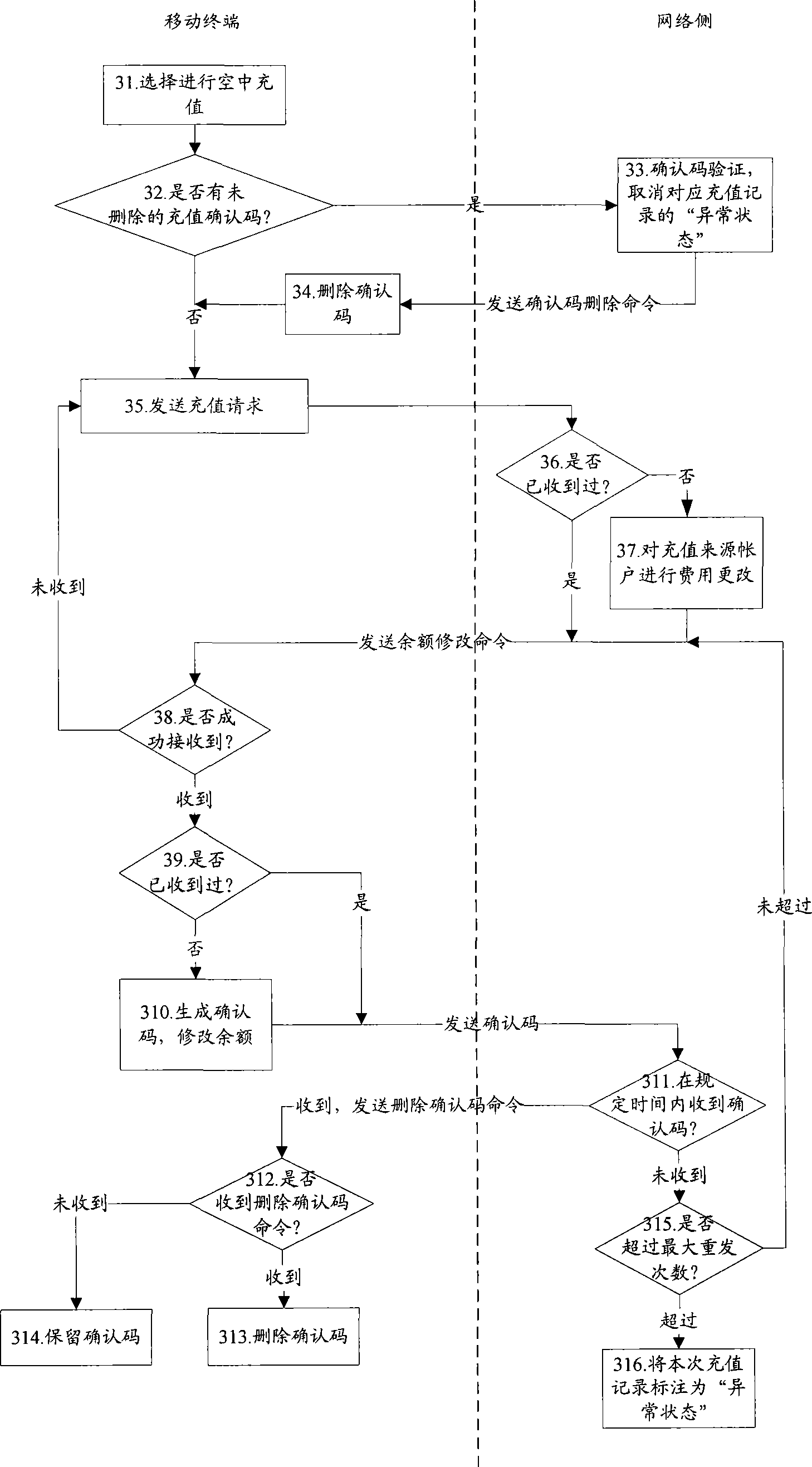
The invention discloses an operation method for an E-wallet which comprises the following steps: before carrying out the operation on the E-wallet, a movable termination confirms whether a first confirming code used for informing a network side that the local balance is corrected during the front supplement process is stored locally or not; if yes, then the movable terminal transmits the first confirming code to the network side and carries out the operation on the E-wallet after accomplishing the previous supplement operation, and if not, the movable terminal directly carries out the operation on the E-wallet. The invention simultaneously discloses a movable termination, network side equipment and a processing system for the E-wallet. The invention can be employed to maintain the consistency in the amount of consumption between the movable terminal and the network side, and maintain the benefits of both parties of a business supplier and a consumer.
Owner:CHINA MOBILE COMM GRP CO LTD
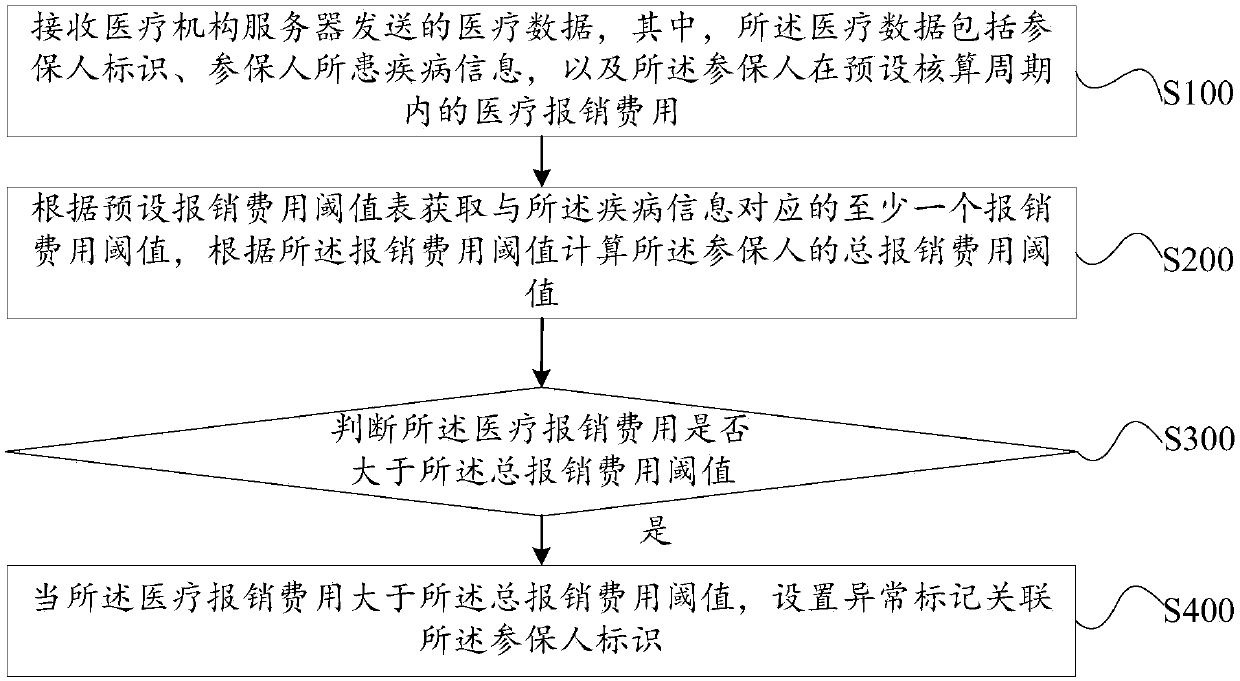
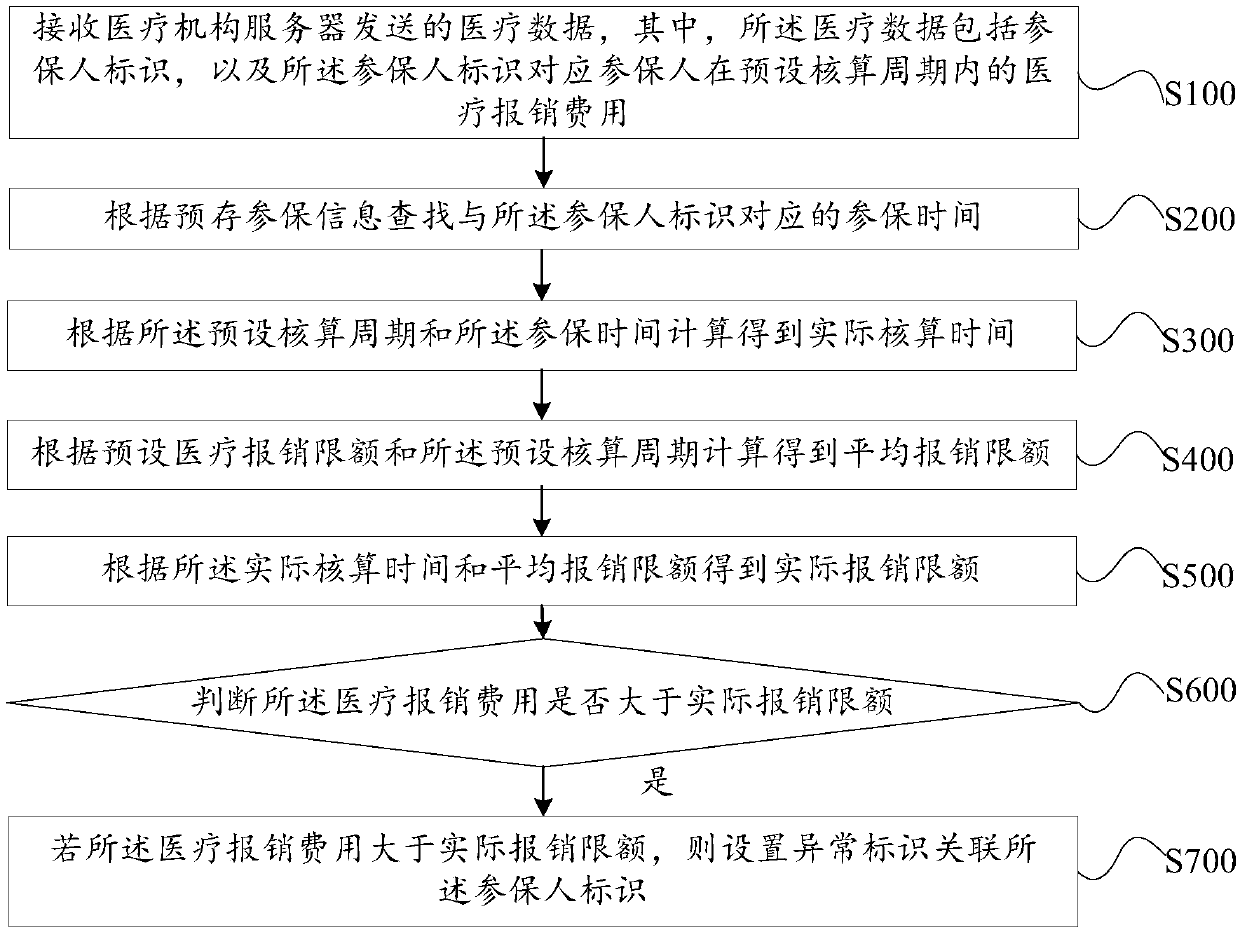
Medical expense abnormity monitoring method, monitoring server and storage medium
The invention discloses a medical expense abnormity monitoring method, a server and a storage medium, and the method comprises the steps: receiving medical data sent by a medical institution server, the medical data comprising an insurer identifier, disease information of an insurer, and a medical reimbursement expense of the insurer in a preset accounting period; Obtaining at least one reimbursement expense threshold value corresponding to the disease information according to a preset reimbursement expense threshold value table, and calculating a total reimbursement expense threshold value ofthe insurer according to the reimbursement expense threshold value; Judging whether the medical reimbursement cost is greater than the total reimbursement cost threshold; And when the medical reimbursement cost is greater than the total reimbursement cost threshold, setting an abnormal mark to be associated with the insurer identifier. According to the invention, medical cost abnormal behaviors can be conveniently and rapidly identified based on the neural network, and medical cost is monitored.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD
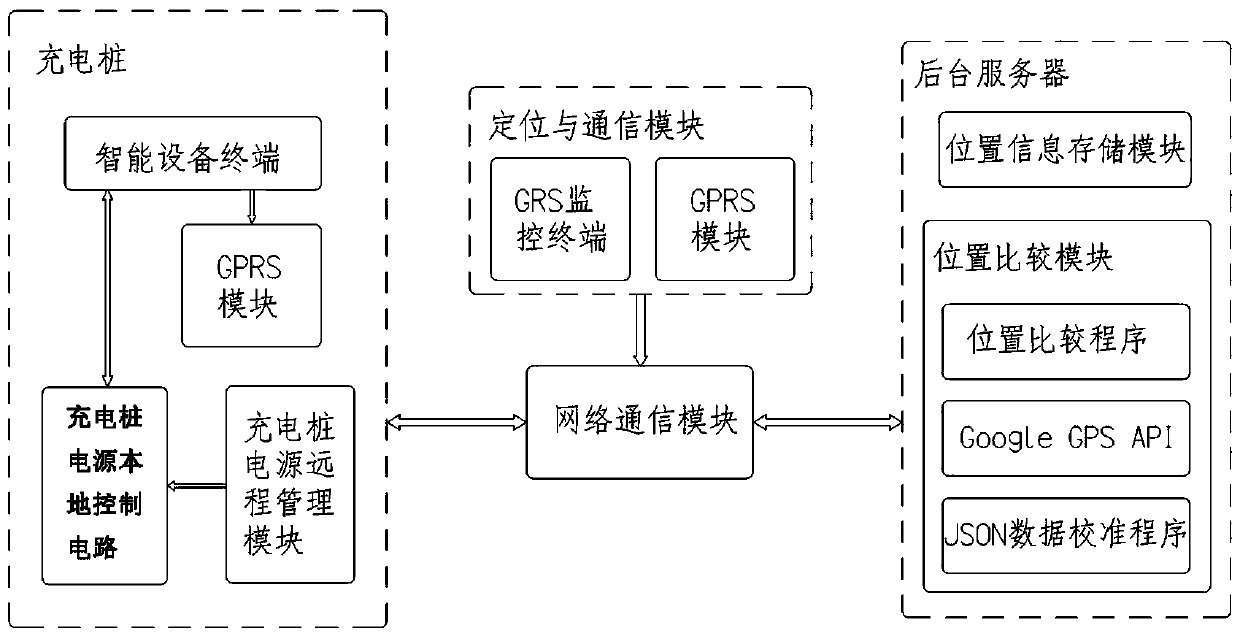
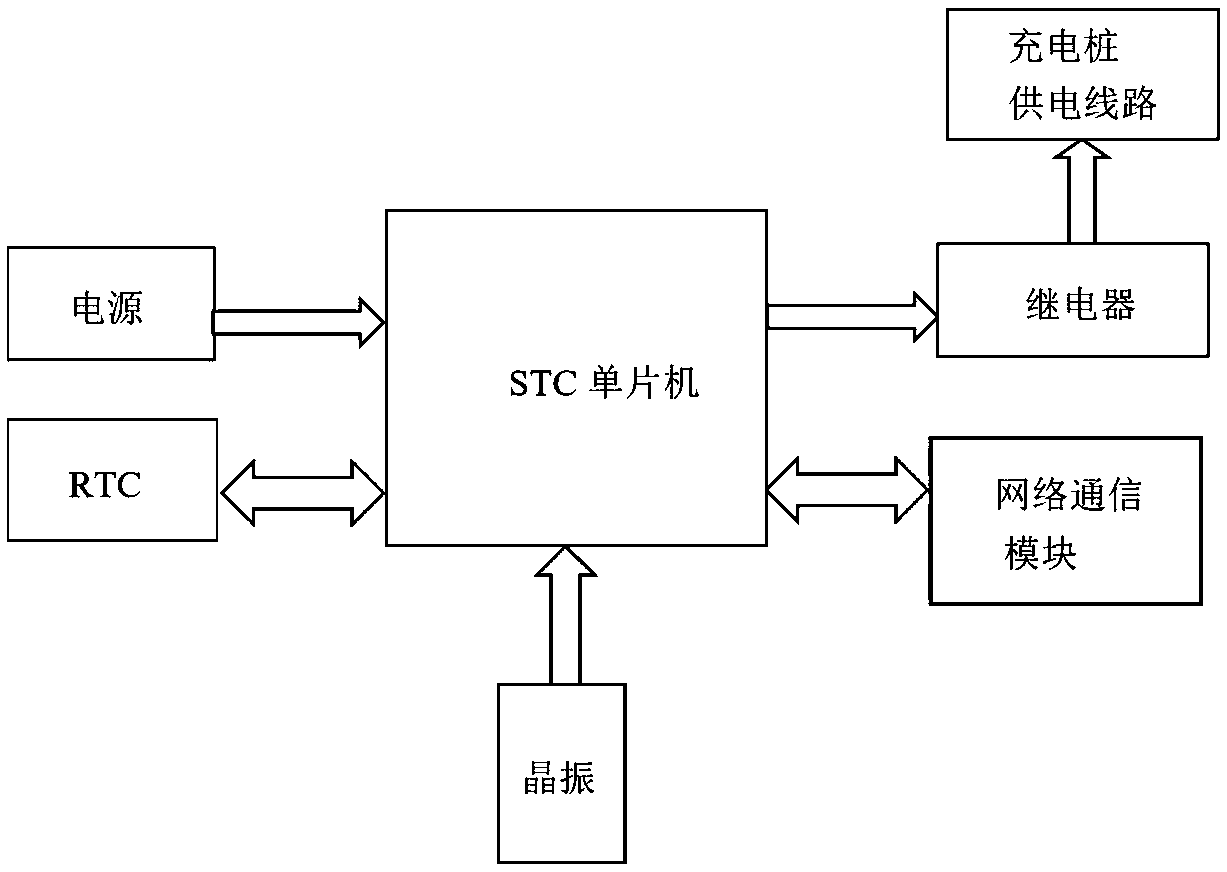
Shared automobile charging pile intelligent electricity stealing preventing method and system
InactiveCN108909513AImprove securitySafeguard the interests ofElectric vehicle charging technologyInformation technology support systemElectricityOrder form
The invention relates to a shared automobile charging pile intelligent electricity stealing preventing method and system. The shared automobile charging pile intelligent electricity stealing preventing method includes the steps that a license number of a rented automobile is input in a user interface of a charging pile, and an intelligent device terminal of the charging pile sends license number information to a background server through an internally-arranged GPRS module; and the background server obtains position information of the corresponding automobile and position information of the charging pile sending the information according to the order license number input by a user into the user interface, the position information is compared, if the position information of the user automobile is the same as the position information of the charging pile sending the information, a relay in a module is controlled through a remote power management module to be turned on, and the shared electric automobile enters a charging pile power local control circuit to be charged. According to the shared automobile charging pile intelligent electricity stealing preventing system, the intelligent device terminal and the GPRS module are installed in the charging pile, and the charging pile remote power management module is installed and is in control connection with a charging pile power local management module.
Owner:河南小明知行新能源有限公司
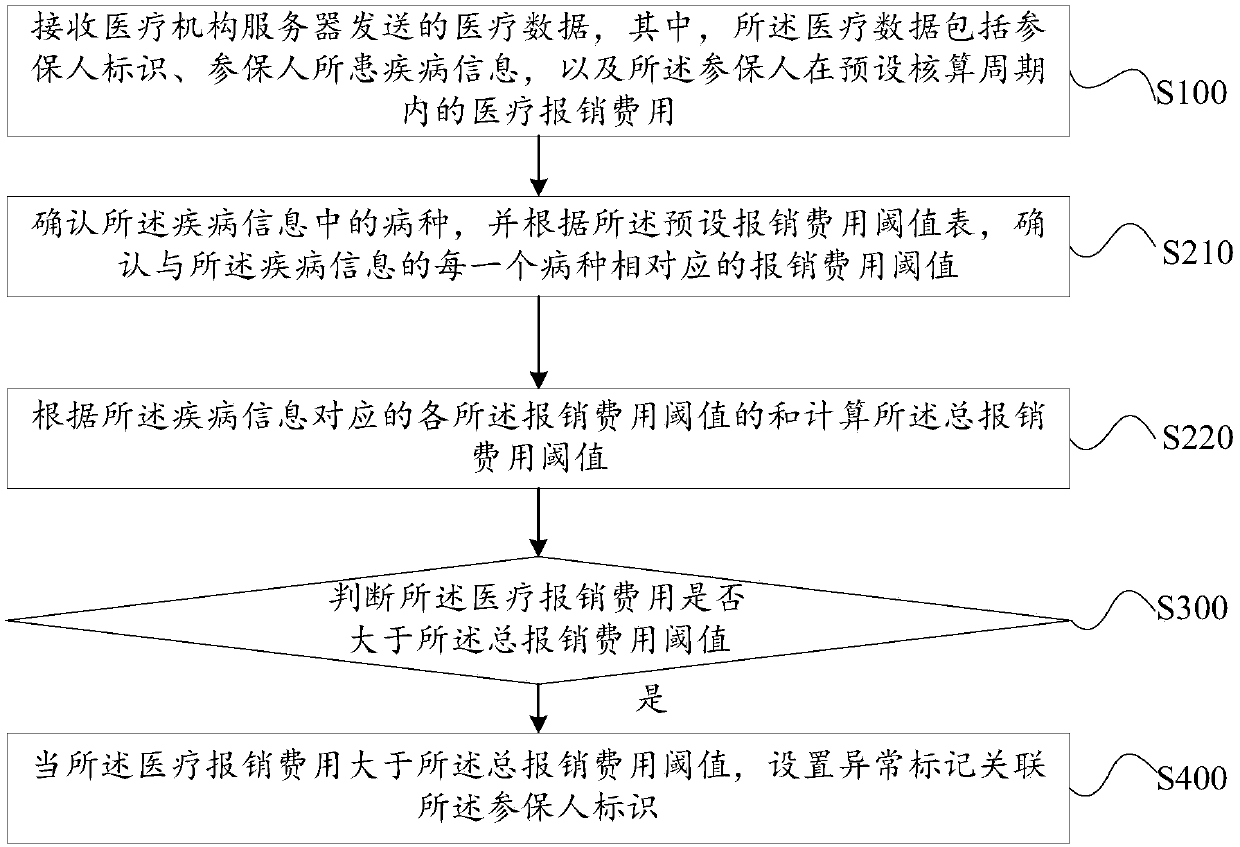
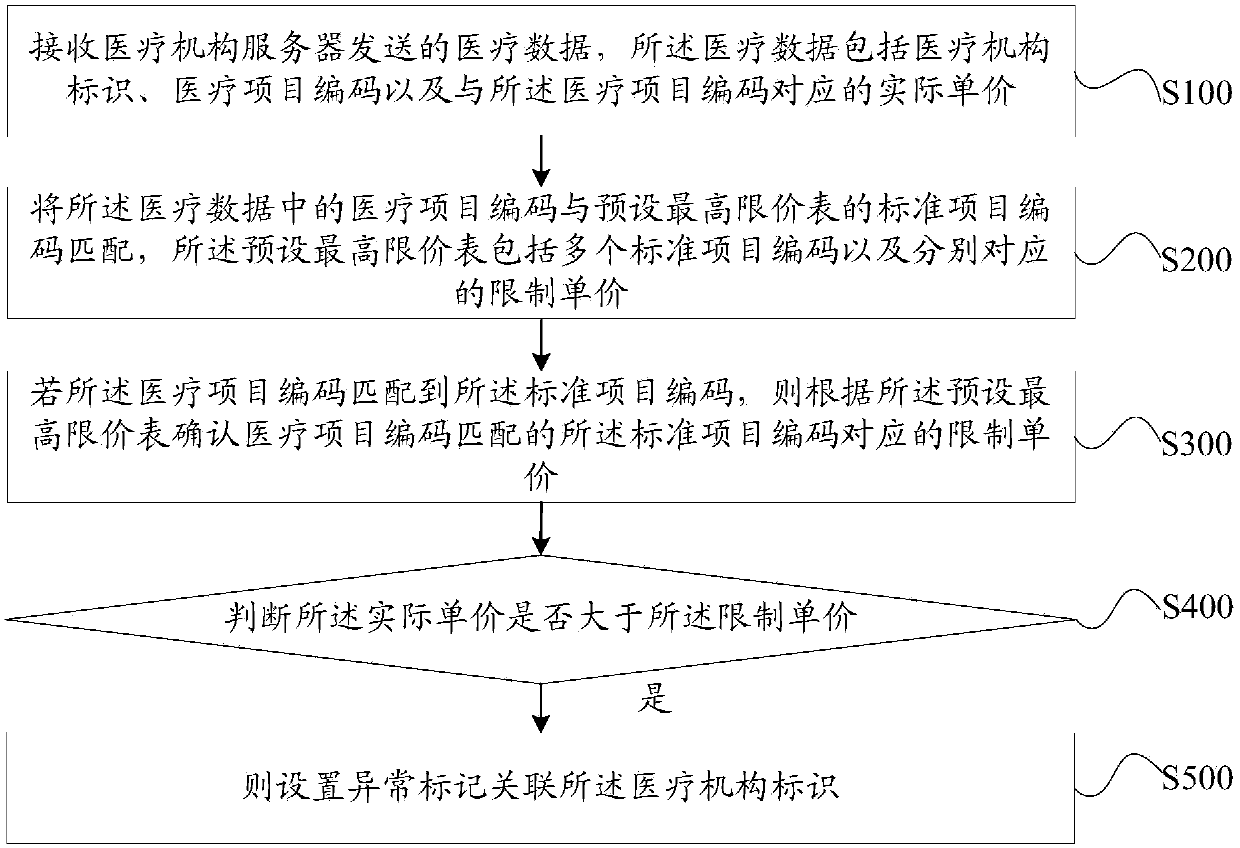
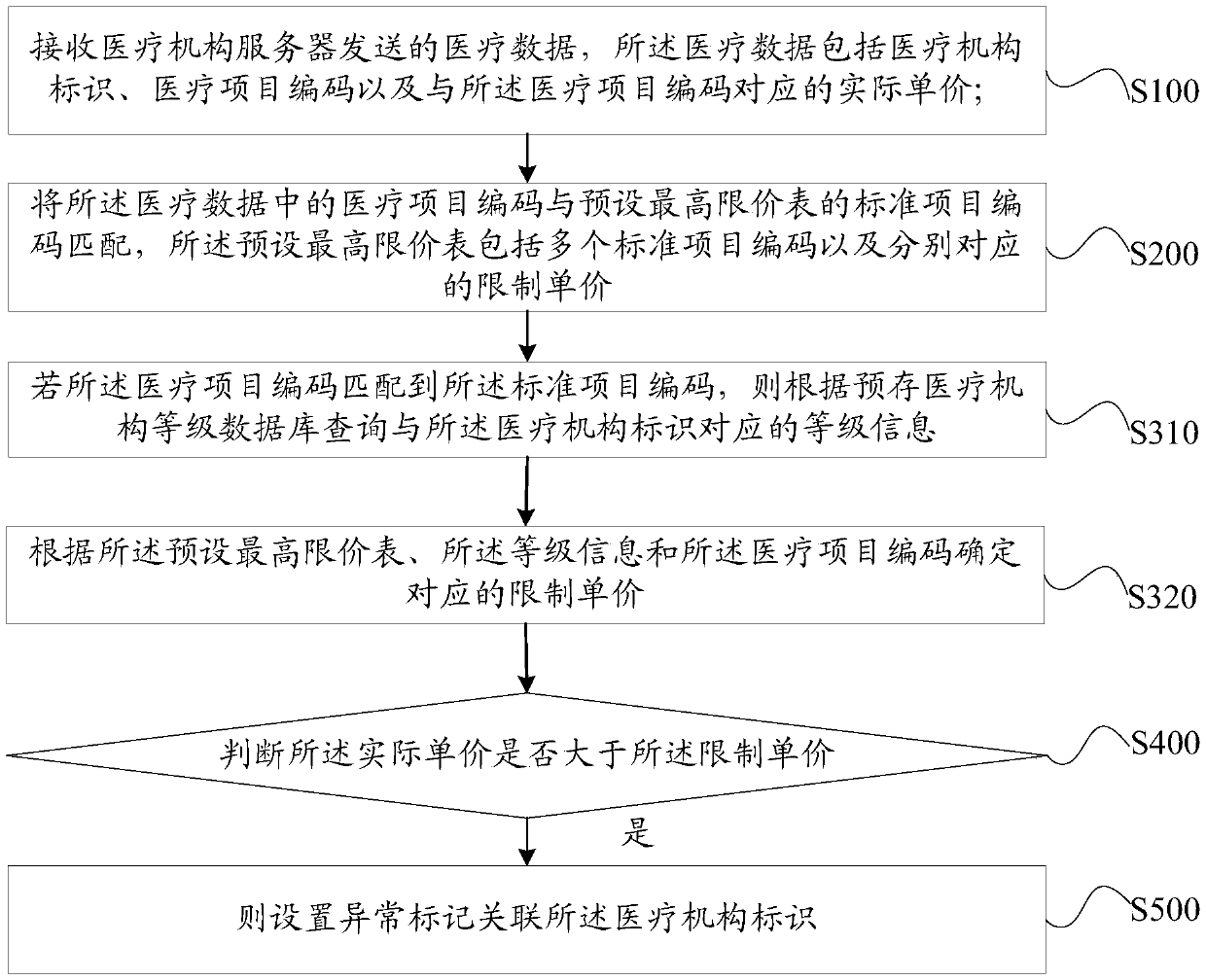
Medical expense abnormity monitoring method, monitoring server and storage medium
PendingCN109616188ASafeguard the interests ofImprove the accuracy of comparisonDigital data information retrievalHealthcare resources and facilitiesMedical expensesMedical treatment
The invention discloses a medical expense abnormity monitoring method, a monitoring server and a storage medium, the method comprises the following steps: receiving medical data sent by a medical institution server, the medical data comprising a medical institution identifier, a medical project code and an actual unit price corresponding to the medical project code; Matching the medical project code with a standard project code of a preset highest price limit table, wherein the preset highest price limit table comprises a plurality of standard project codes and limiting unit prices corresponding to the standard project codes respectively; if the medical project code is matched with the standard project code, determining a limit unit price corresponding to the standard project code matchedwith the medical project code according to the preset highest limit price table; Judging whether the actual unit price is greater than the limited unit price; and if the actual unit price is greater than the limited unit price, setting an abnormal mark and associating the abnormal mark with the medical institution identifier. Based on the neural network, the ultra-highest limit price charging behavior of the medical institution can be conveniently and quickly identified.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD
Works copyright protection method
InactiveCN101533389ASafeguard the interests ofEasy to distinguishProgram/content distribution protectionSpecial data processing applicationsString lengthTypeface
The invention discloses a works copyright protection method, comprising the following steps: 1) constructing font libraries and numbering each font library; 2) coding the copyright to form a group of numeral strings with length as L; 3) typesetting a (K*L+i)th character in the works according to the font corresponding to an ith number in the numeral strings; wherein, K>=0 and i<=L; the numbers in the numeral strings correspond to the numerical symbols in the font libraries. In the method, by coding the copyright and presenting the codes in the typeset works in the form of fonts, the unauthorized persons are hard to crack the copyright and only can ruin the copyright for pirating, therefore, consumers and departments to crack down on fake goods can easily distinguish whether the works are pirated and the benefits of the consumers and copyright owners are safeguarded.
Owner:王琳
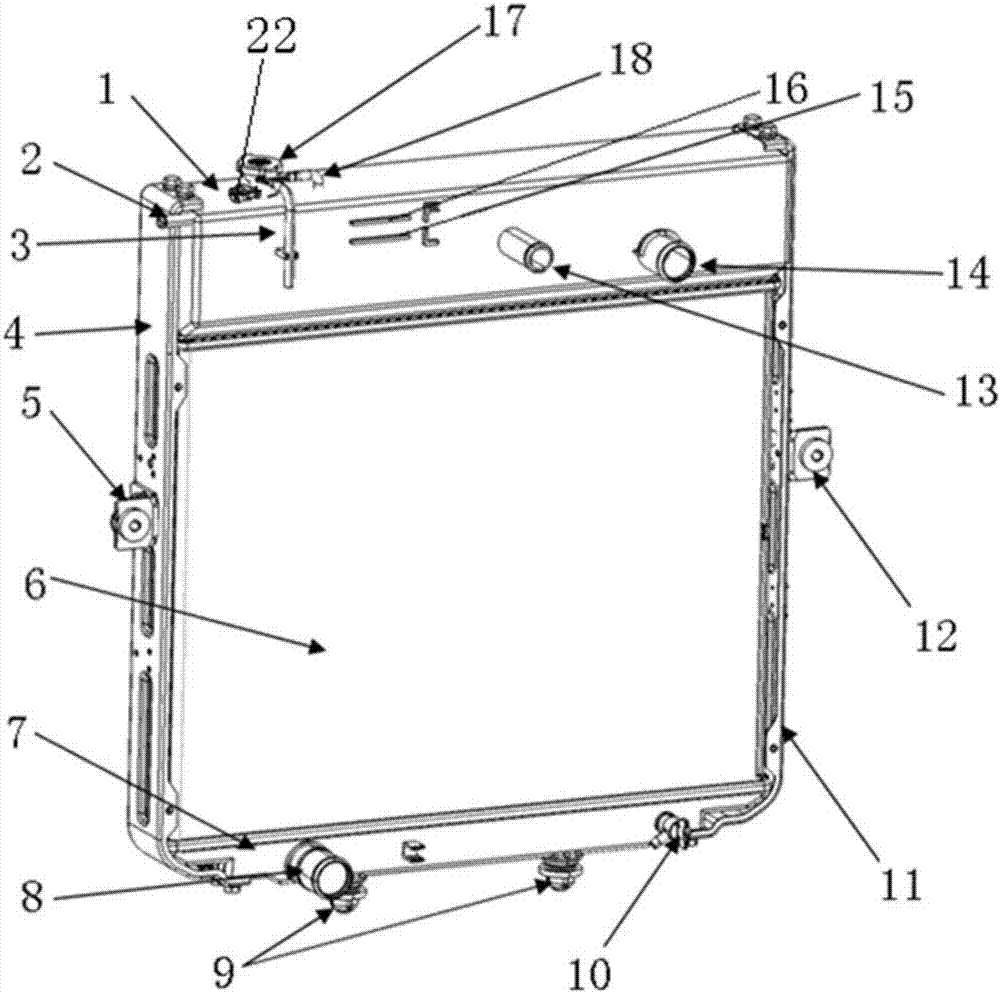
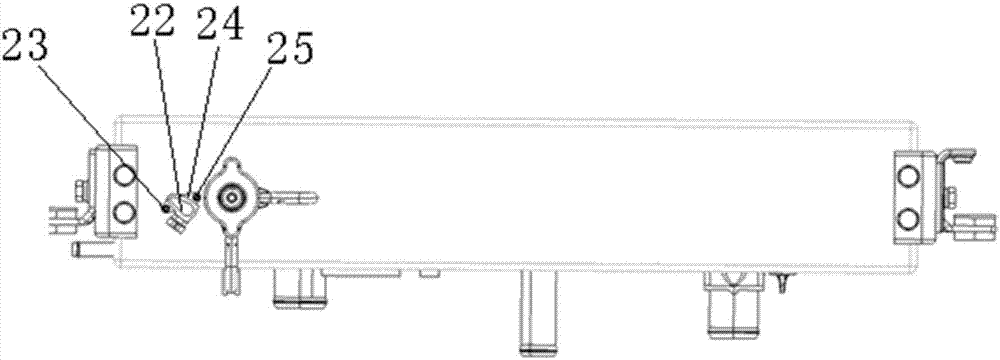
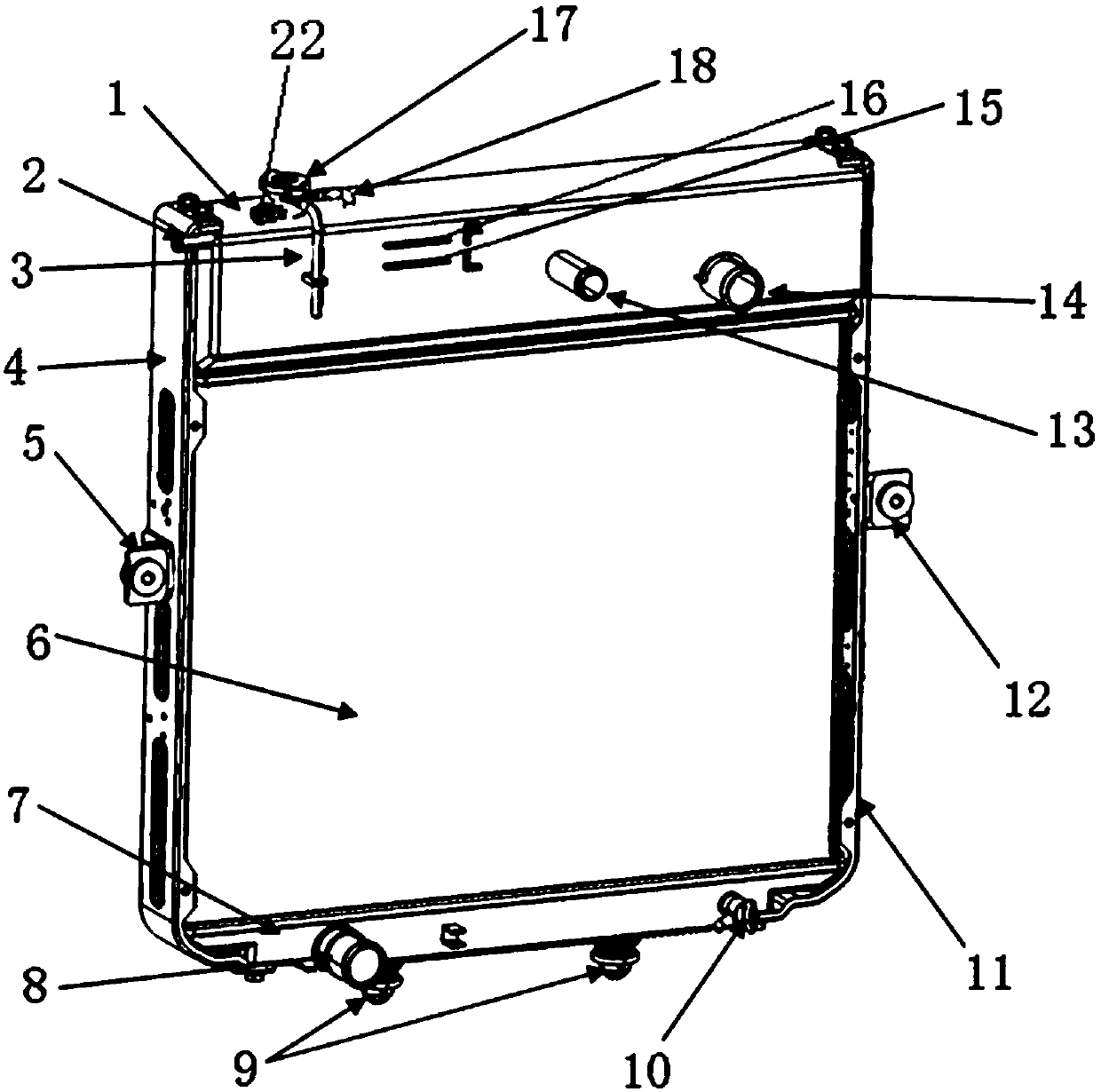
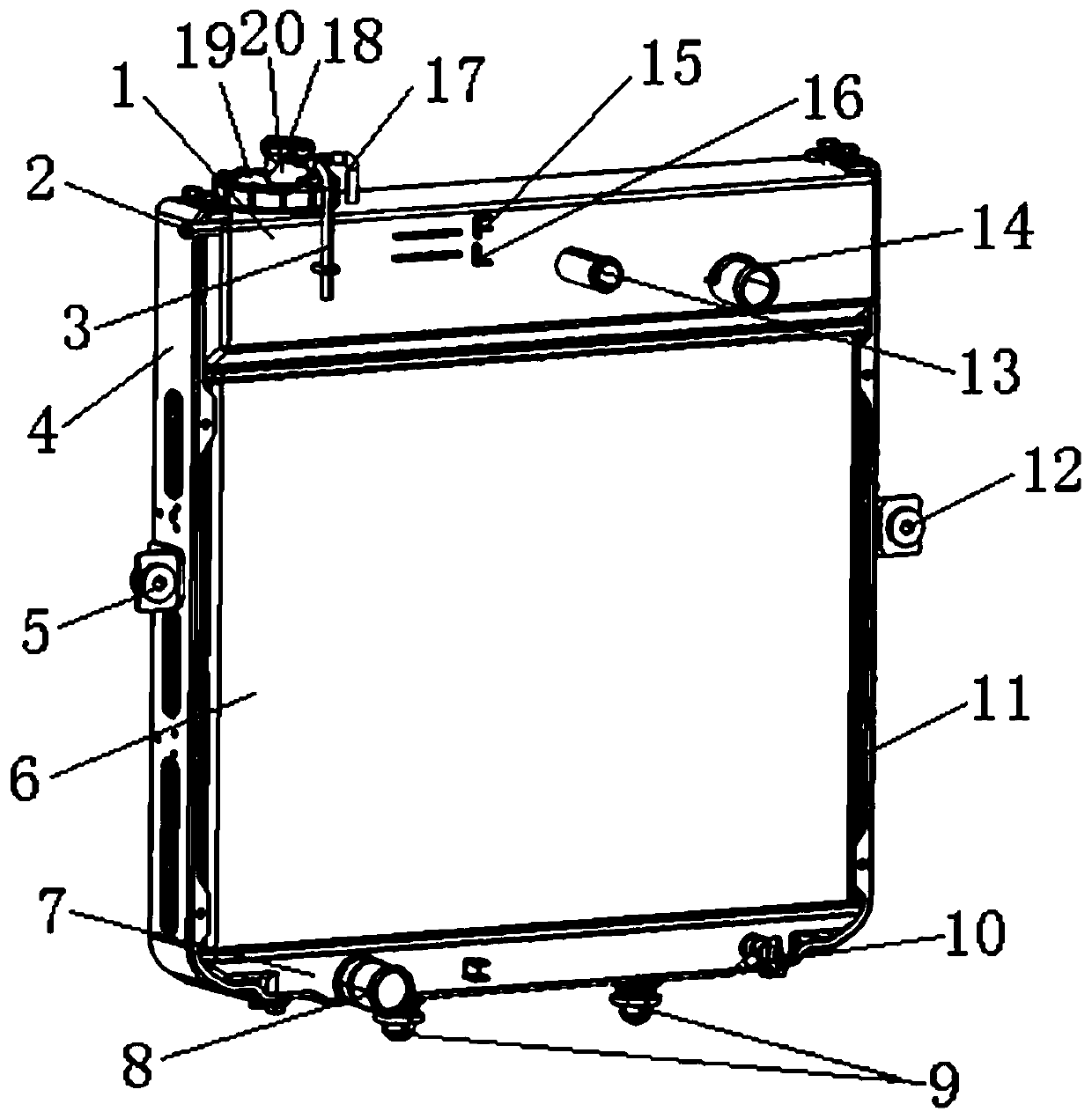
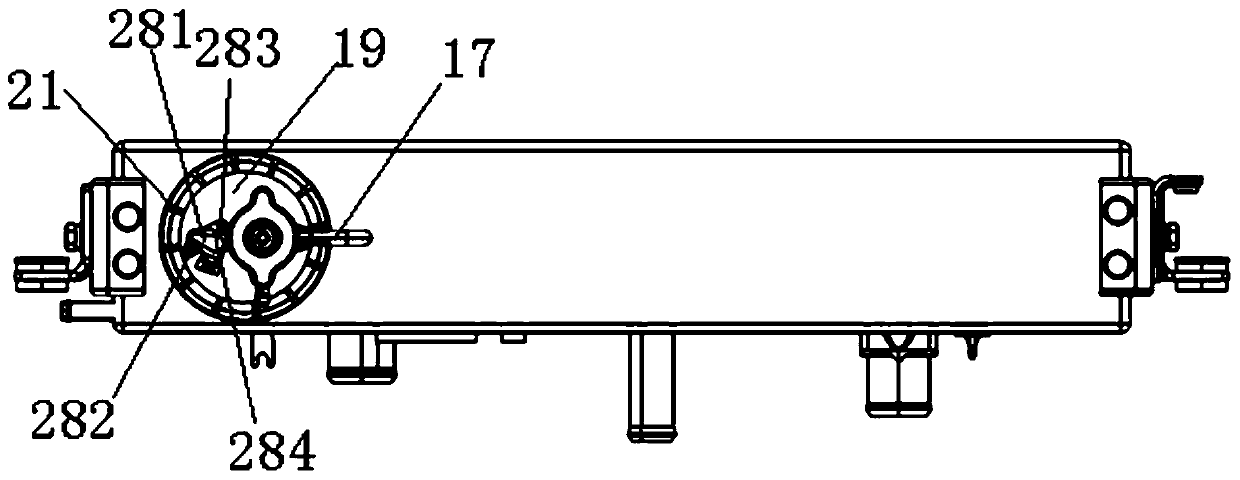
Radiator
ActiveCN106894884ASafe, durable and efficient operationGuaranteed uptimeMachines/enginesEngine cooling apparatusFailure rateFiltration
The invention relates to a radiator. The radiator comprises a life indicating alarm device, an upper water chamber, a radiating core body and a lower water chamber. The upper water chamber is arranged on the upper portion of the radiating core body and communicates with the radiating core body. The lower water chamber is arranged on the lower portion of the radiating core body and communicates with the radiating core body. The upper water chamber comprises three cavities which are the first cavity, the second cavity and the third cavity. According to the radiator, on the one hand, through chemical action during first-stage physical absorption and isolation, second-stage filtration and third-stage filtration, rust, incrustation and bubbles generated in work of a cooling system are absorbed, potential threats of calcium and magnesium ions, iron ions, acid irons and the like are processed through reaction, the PH value of a cooling liquid is kept constant, clean and safe cooling liquid is output for the system, and thus safe, lasting and efficient operation of the cooling system is ensured. The radiator is provided with an excellent engine water jacket, radiator degassing is achieved, a space expansion function is provided for water replenishing of the engine water jacket and for the cooling system, an expansion kettle is canceled for the whole vehicle, complex water ways are reduced, and the whole vehicle failure rate and user vehicle usage cost are reduced.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
Radiator
ActiveCN106870110ASafe, durable and efficient operationGuaranteed uptimeMachines/enginesEngine cooling apparatusFailure rateFiltration
The invention relates to a radiator which comprises a service life indication alarm device, an upper water chamber, a radiator core and a lower water chamber. The upper water chamber is arranged on the upper portion of the radiator core and communicates with the radiator core. The lower water chamber is arranged on the lower portion of the radiator core and communicates with the radiator core. The upper water chamber comprises three cavities, namely, the first cavity, the second cavity and the third cavity. On one hand, through first-stage physical absorption and isolation and the chemical action of second-stage filtration and third-stage filtration, iron rust, water scale and bubbles generated during operation of a cooling system are absorbed, a reaction is carried out, potential threats including calcium and magnesium ions, iron ions and acid ions are handled, constancy of the PH value of a cooling solution is maintained, the clean and safe cooling solution is output to the system, and accordingly the effect that the cooling system operates safely, durably and efficiently is ensured; and on the other hand, the excellent functions of carrying out degassing on an engine water jacket and the radiator, carrying out water replenishing on the engine water jacket, and providing an expansion space for the cooling system are achieved, an expansion kettle is omitted for a finished vehicle, complex water paths are reduced, the failure rate of the finished vehicle is decreased, and the vehicle usage cost is reduced for users.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
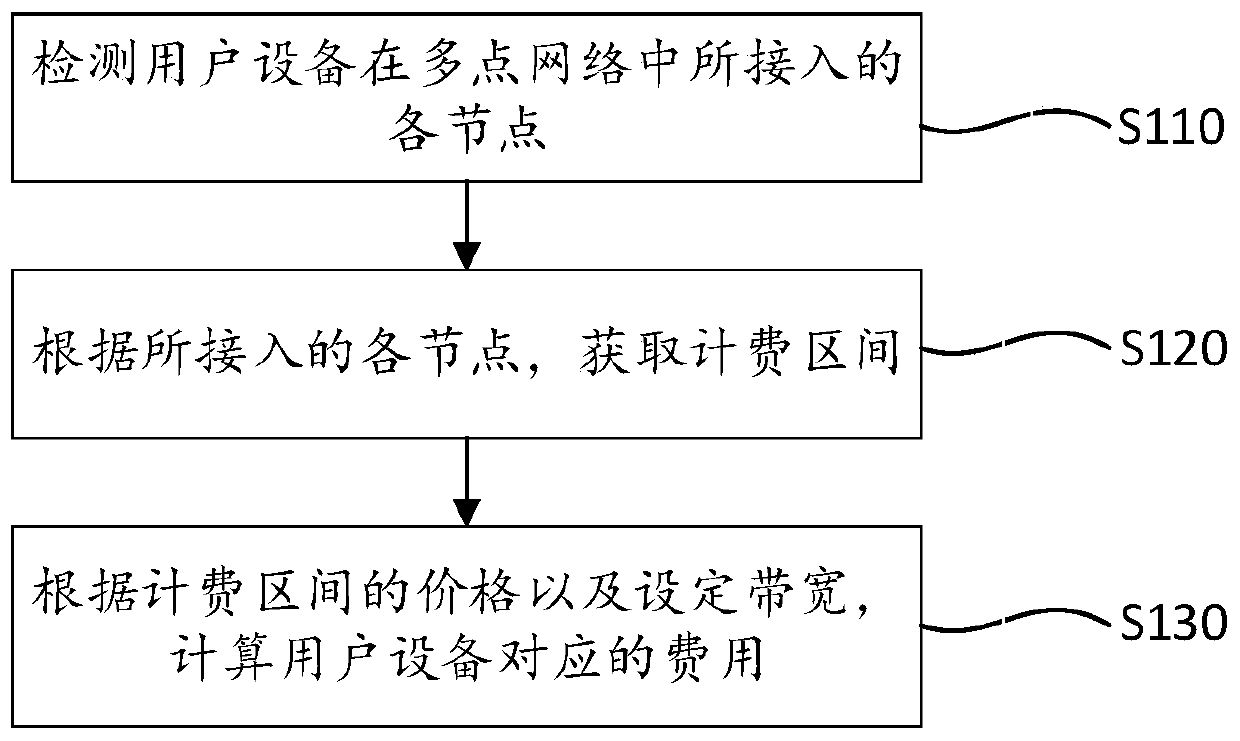
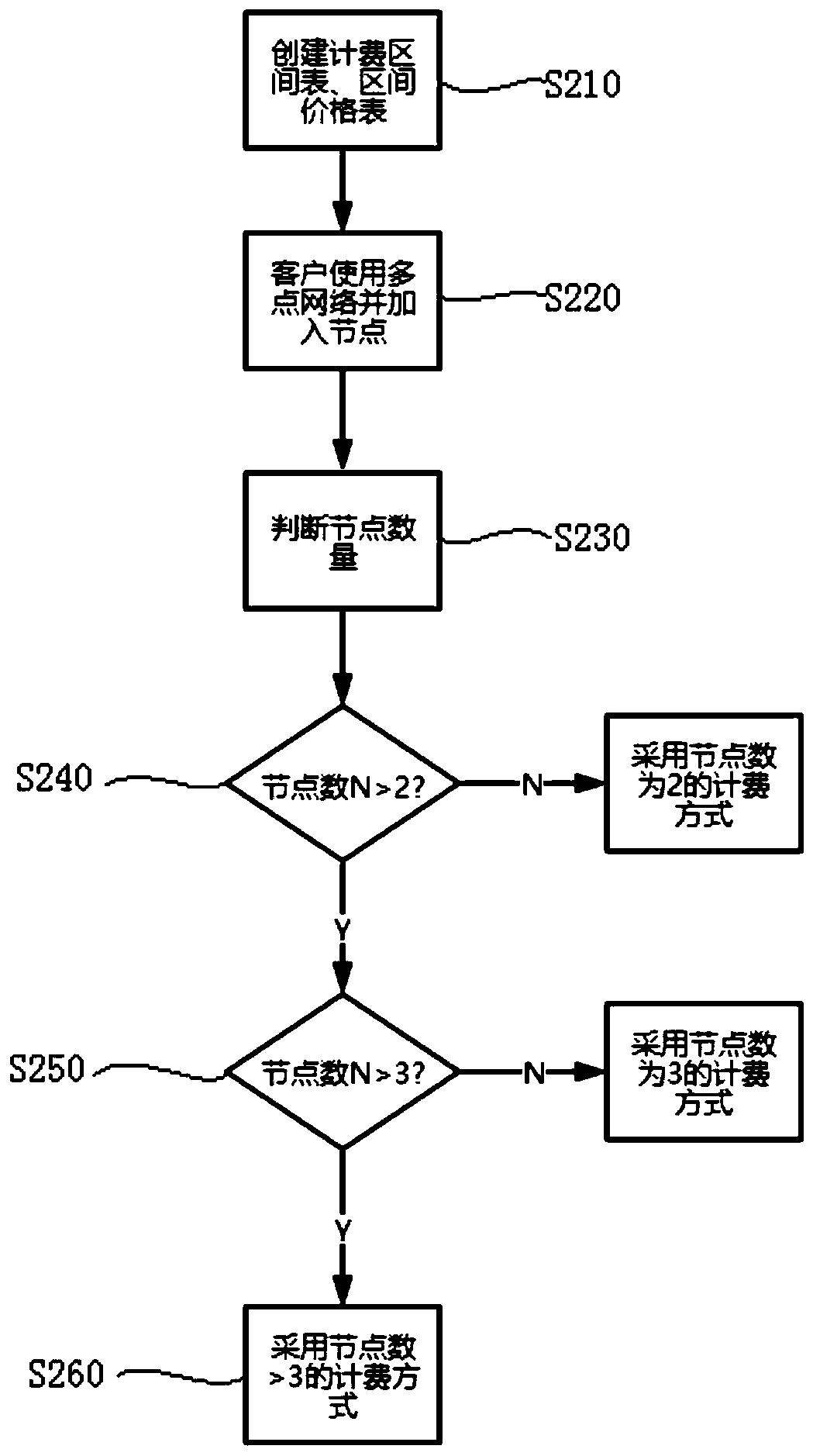
Multipoint network charging method and system
ActiveCN110166260AGuaranteed business incomeSafeguard the interests ofMetering/charging/biilling arrangementsComputer networkMulti point
The invention provides a multipoint network charging method and system. The method comprises the following steps: detecting each node accessed by user equipment in a multi-point network; acquiring a charging interval according to each accessed node; and calculating the cost corresponding to the user equipment according to the price of the charging interval and the set bandwidth. According to the method, when multi-point network charging is carried out, the charging of each node accessed by the user equipment in the multi-point network is detected, the enterprise income can be ensured, and thebenefits of the user can be maintained.
Owner:北京首都在线科技股份有限公司
Annotation-based business process value declaration, monitoring and regulation method in cross-border service
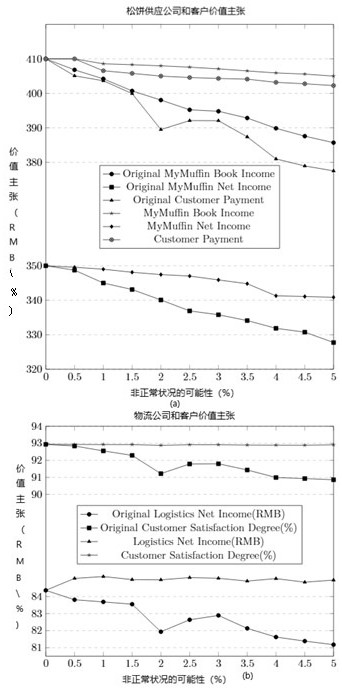
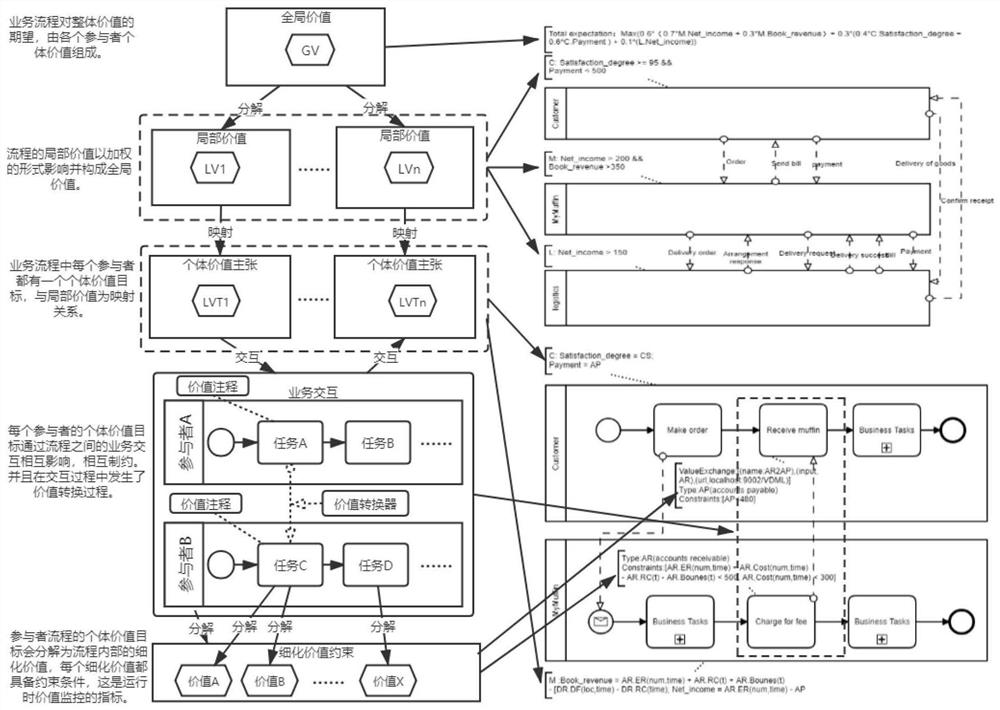
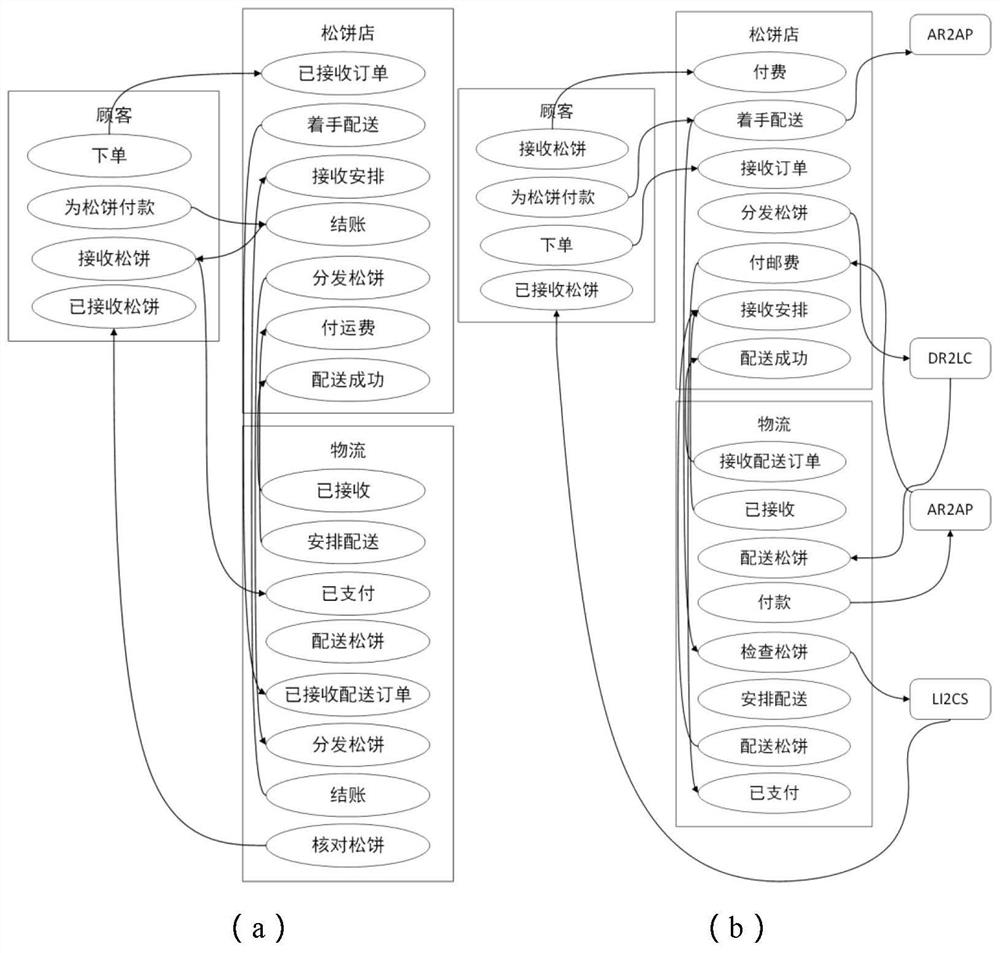
InactiveCN113379180AEasy to graspSafeguard the interests ofResourcesLogisticsElement modelPerformance index
The invention relates to an annotation-based business process value declaration, monitoring and regulation method in a cross-border service. In a cross-border service fused by breaking management or industry boundaries, value orientations of all parties are different and change at any time and space, and value monitoring in the scene cannot be completed by existing business process management. The method comprises the following steps: (1) defining a global value target by taking an annotation mechanism of the BPMN as a process, and defining value orientation for each collaboration party; (2) establishing a time-space-boundary three-element model to represent the spatial-temporal change of the value; (3) perceiving and explaining the annotation through a script or an extended business process execution engine; and (4) in the process of perceiving, explaining and calculating the value, paying attention to key performance index constraints, events and value exchange rules on the cooperative relationship according to the service monitor designed in the step (2). Therefore, value monitoring, evaluation, balancing and optimizing capabilities are provided for developing the BPMN business process model or transforming the existing BPMN business process model in a non-intrusive manner, and the goal of trans-boundary service value innovation is achieved.
Owner:FUDAN UNIV
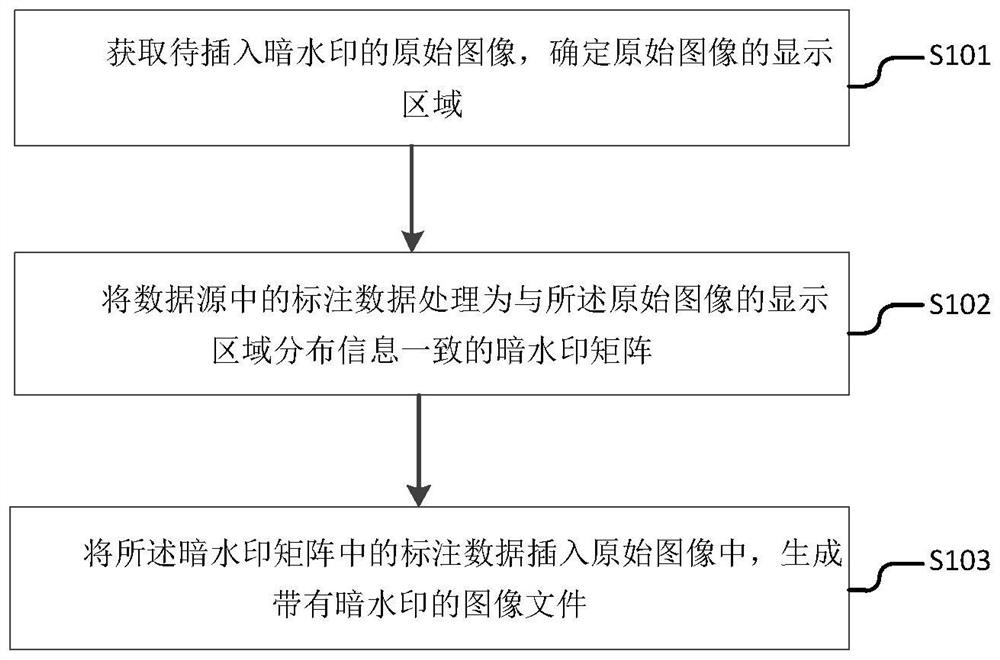
Label processing method and system based on dark watermark
PendingCN114693497APrevent pirated appsSafeguard the interests ofImage data processing detailsProgram/content distribution protectionComputer visionData processing
The invention discloses an annotation processing method and system based on a dark watermark, and the method comprises the steps: obtaining an original image to be inserted with the dark watermark, and determining a display region of the original image; processing annotation data in a data source into a dark watermark matrix consistent with display area distribution information of the original image; and inserting the annotation data in the dark watermark matrix into an original image to generate an image file with a dark watermark. According to the scheme, while the concealment of the dark watermark is ensured, the problem of picture embezzlement caused by removing the dark watermark in the local region of the picture is effectively avoided.
Owner:天津象小素科技有限公司
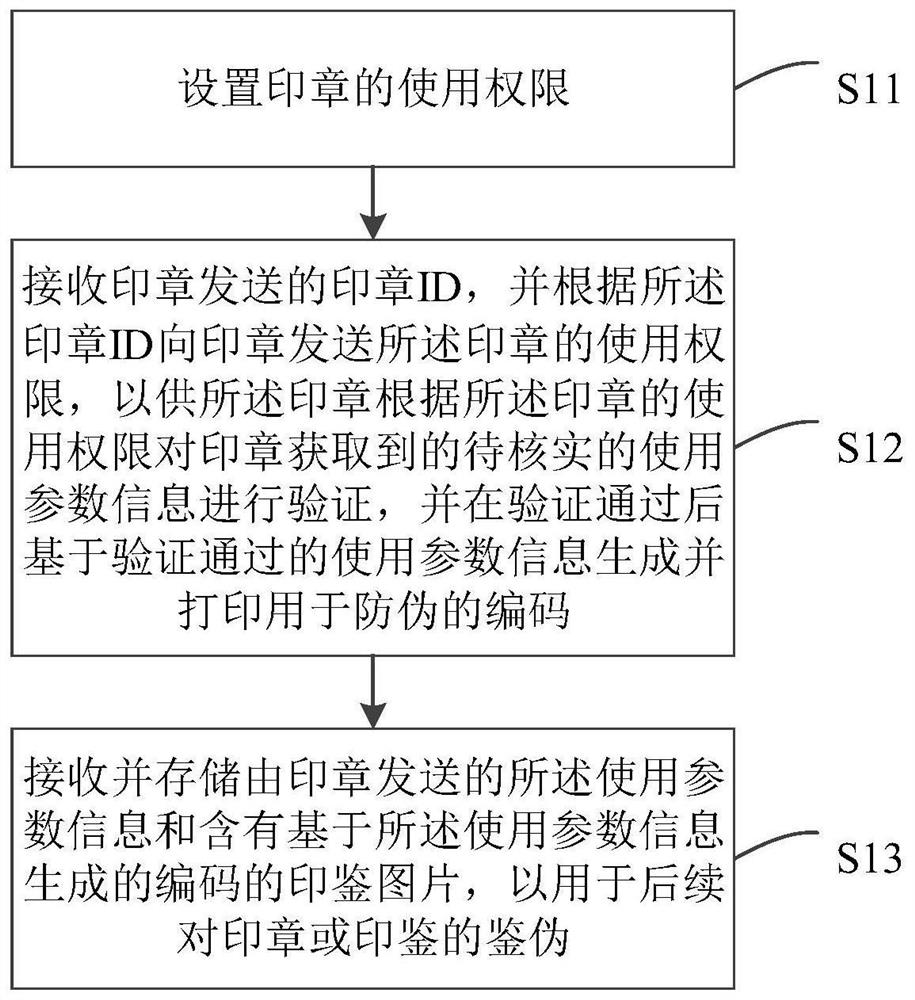
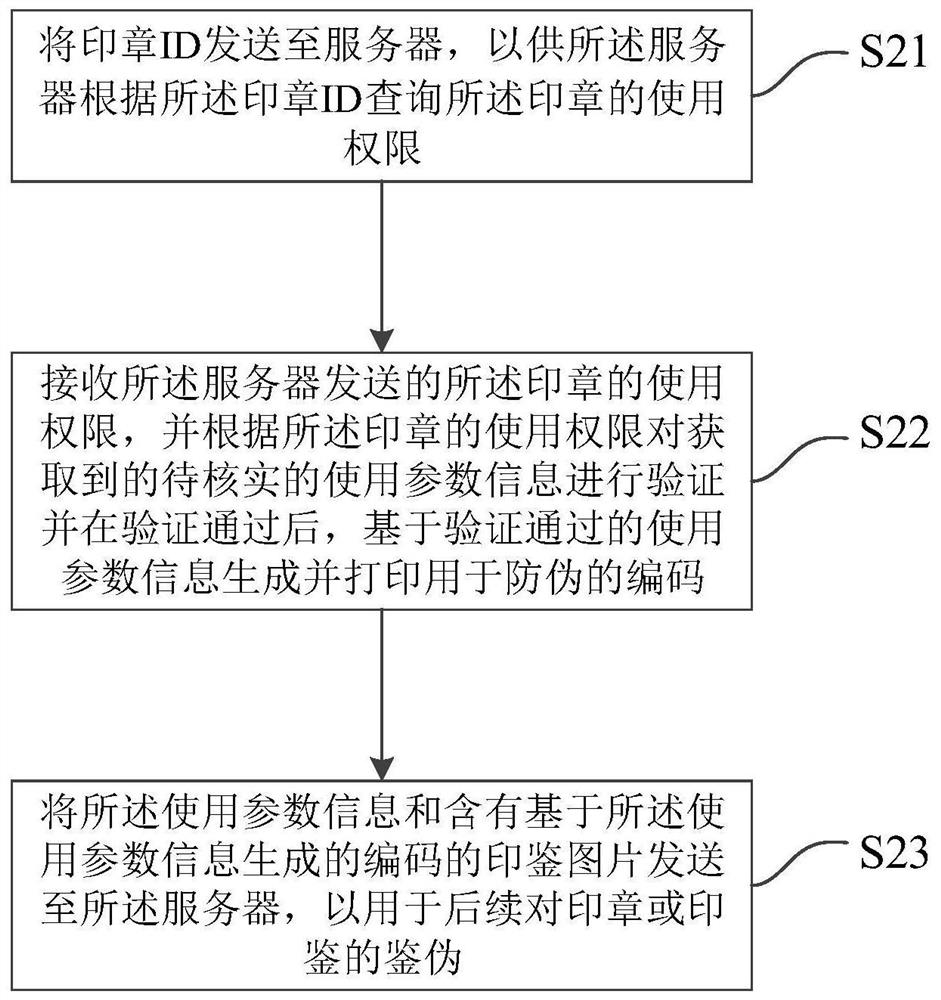
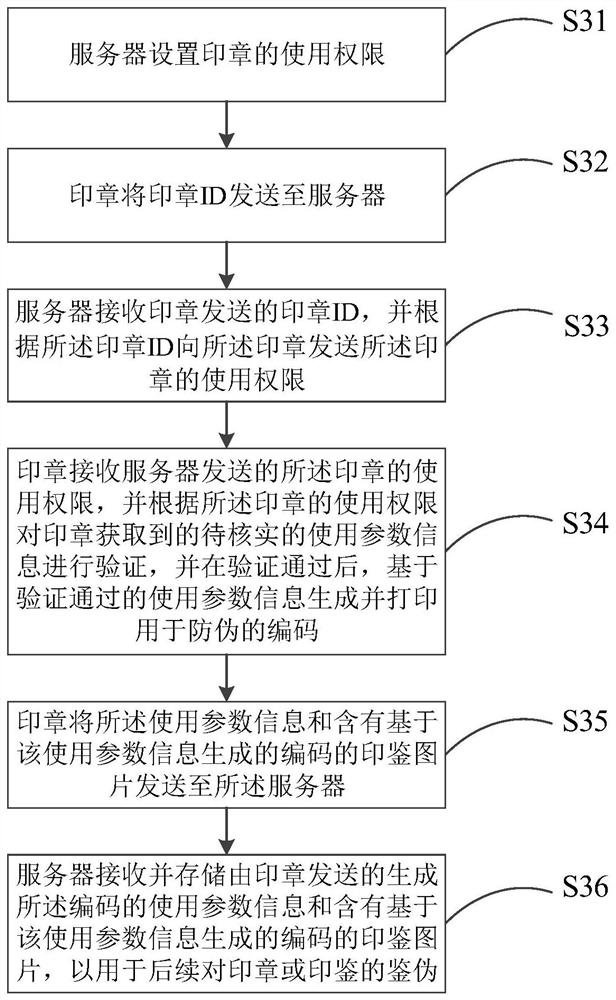
Stamp safety management method, server and stamp
PendingCN112464273ASafeguard the interests ofPut an end to injusticeDigital data protectionDigital data authenticationServerComputer engineering
The invention relates to a seal safety management method, a server and a stamp, the method is applied to the server, and the method comprises the following steps: setting the use permission of the stamp; receiving a seal ID sent by the stamp, sending the use permission of the stamp to the stamp according to the stamp ID so that the stamp can verify the use parameter information to be verified obtained by the seal according to the use permission of the stamp and sending the use parameter information to be verified to the server after verification is passed; generating and printing an anti-counterfeiting code based on the use parameter information passing verification; and receiving and storing the use parameter information sent by the stamp and a stamp image containing a code generated based on the use parameter information for subsequent authentic identification of the stamp or a seal.
Owner:褚海威
Two-dimensional code anti-counterfeiting method for metal part
ActiveCN107844820ASafeguard the interests ofNot easy to wear and tearCo-operative working arrangementsCommerceProduct identificationMetal
The invention belongs to the field of anti-counterfeiting labels, and in particular relates to a two-dimensional code anti-counterfeiting method for a metal part. The method is used for authenticity identification by randomly marking different depths on a metal part, and includes a first step of generating a product two-dimensional code from a product identification code; a second step of selecting a random point in the two-dimensional code, and storing the random point information in a database; a third step of marking the product two-dimensional code on the surface of the metal part, and enabling a depth difference between the marking depth of the random point in the two-dimensional code and the reference marking depth of the rest points of the two-dimensional code; and a fourth step ofobtaining the product identification code by scanning the product two-dimensional code on the metal part with a client, connecting to the database, inquiring whether the product identification code and the corresponding random position location match the information in the database, and finally obtaining authenticity information of the metal part. The invention discloses the two-dimensional code anti-counterfeiting method for the metal part, the two-dimensional code is allowed to have an anti-counterfeiting function and, combined with the characteristics of the metal part, a counterfeiter cannot perform batch copying.
Owner:中国东方电气集团有限公司
A recommended method and device for modifying a password
The invention relates to a method for recommending a password change mode. The method comprises the following steps: (1) judgment: when a request for changing the password of a user account is received from a client, judging the type of the user account; (2) selection: selecting a password change mode corresponding to the type of the user account from a plurality of preset password change modes; (3) recommendation: generating interactive interface data according to the selected password change mode, and feeding back the interactive interface data to the client, wherein an interactive interface corresponding to the selected password change mode is created on the client according to the interactive interface data. The invention further provides a device for recommending the password change mode. Through the adoption of the method and the device, the password change security can be improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
A self-adaptive anti-stealing electricity monitoring method and system based on an electricity consumption information collection system
ActiveCN108198408BAccurately determineEliminate potential safety hazardsElectric signal transmission systemsCharacter and pattern recognitionCollection systemMonitoring system
The present invention is applicable to the technical field of electricity monitoring, and provides an adaptive anti-stealing electricity monitoring method and system based on an electricity consumption information collection system, including: obtaining training samples, the training samples include historical related data, and clustering related data Grouping, generating weights corresponding to the relevant data; obtaining relevant data of the target user; generating a binary matrix consisting of the first value and the second value according to the relevant data of the target user, multiplying the weight by the corresponding element value in the binary matrix, Obtain the suspected electricity theft index corresponding to the relevant data of the target user; add all the suspected electricity theft indexes of the target user to obtain the electricity theft evaluation value of the target user. The invention realizes the data interaction with the electricity information collection system, can accurately determine the electricity stealing users, saves labor, eliminates the potential safety hazards of the on-site electricity stealing inspection work, improves the accuracy and work efficiency of the electricity stealing inspection, and further Safeguarded national interests and company rights and interests.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +3
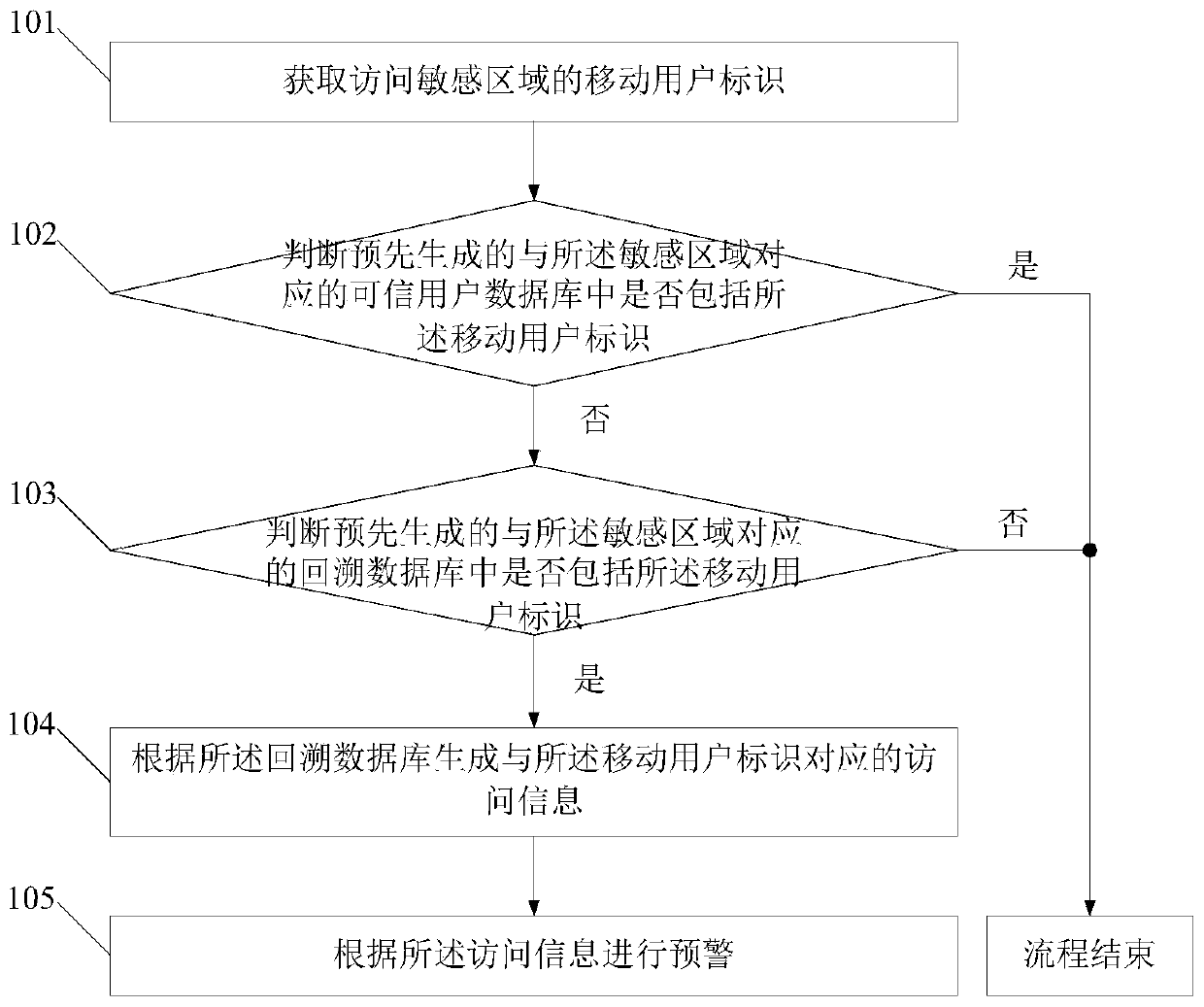
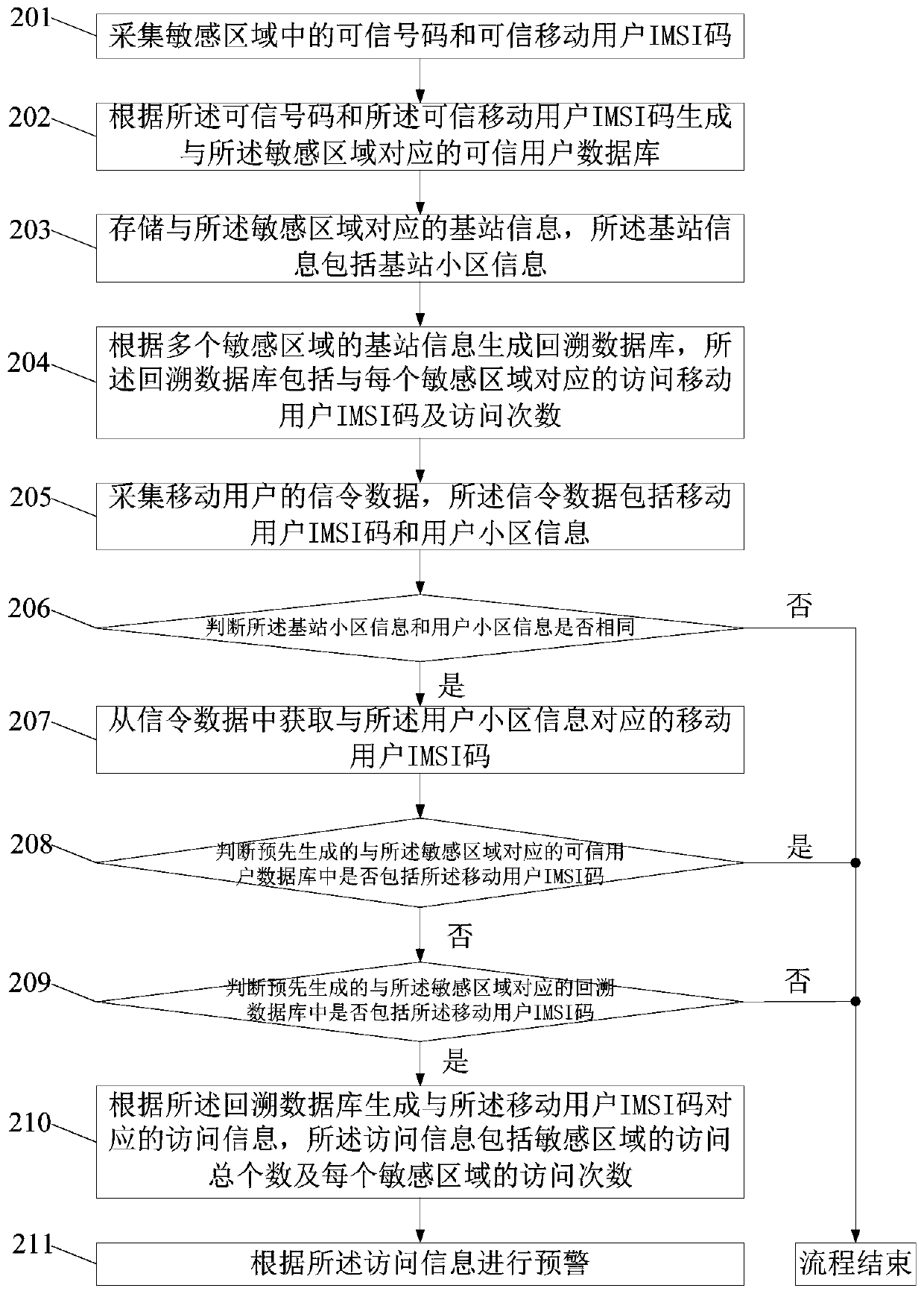
A security method and platform for sensitive areas
ActiveCN108718440BMaintain securitySafeguard the interests ofAssess restrictionMessaging/mailboxes/announcementsInternet privacyEngineering
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Anti-counterfeiting sign pen
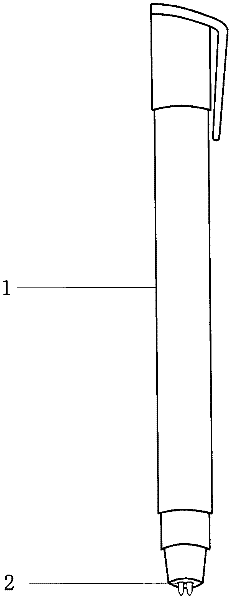
InactiveCN102398450ASafeguard the interests ofUniqueMultiple-point writing implementsHandwritingEngineering
The invention relates to an anti-counterfeiting sign pen and breaks through the mode that currently, characters signed by one pen have one line of handwriting and one color, are easy to counterfeit to cause loss of a party and is lack of artistry and ornamental property. Two or a plurality of pen refills are assembled in a pen tube of the anti-counterfeiting sign pen; hard penpoint pen refills and / or soft penpoint pen refills are to be assembled in the pen tube; a thick-handwriting main pen refill and a thin-handwriting auxiliary pen refill are to be assembled in the pen tube; and a main black pen refill and an auxiliary gray pen refill are to be assembled in the pen tube. The anti-counterfeiting sign pen have the obvious and remarkable advantages and beneficial effects that when the anti-counterfeiting sign pen is used to sign, the mode that the existing pen has one line of handwriting in the signing process is broken through, two or a plurality of lines of handwriting are shown and the main pen refill and the auxiliary pen refill have different handwriting and colors; additionally, different people have differences on the way of writing characters, the angle of holding the pen and the strength of writing; the anti-counterfeiting sign pen has uniqueness, artistic quality and ornamental property; the anti-counterfeiting sign pen is a powerful remedy of sign counterfeiting personnel; the benefits of the party and the normal social order are reliably maintained; political and law resources are reduced and saved; and the benefits are created for all people who can write around the world.
Owner:王顺桥
a radiator
ActiveCN106870110BSafe, durable and efficient operationGuaranteed uptimeMachines/enginesEngine cooling apparatusFailure rateFiltration
The invention relates to a radiator which comprises a service life indication alarm device, an upper water chamber, a radiator core and a lower water chamber. The upper water chamber is arranged on the upper portion of the radiator core and communicates with the radiator core. The lower water chamber is arranged on the lower portion of the radiator core and communicates with the radiator core. The upper water chamber comprises three cavities, namely, the first cavity, the second cavity and the third cavity. On one hand, through first-stage physical absorption and isolation and the chemical action of second-stage filtration and third-stage filtration, iron rust, water scale and bubbles generated during operation of a cooling system are absorbed, a reaction is carried out, potential threats including calcium and magnesium ions, iron ions and acid ions are handled, constancy of the PH value of a cooling solution is maintained, the clean and safe cooling solution is output to the system, and accordingly the effect that the cooling system operates safely, durably and efficiently is ensured; and on the other hand, the excellent functions of carrying out degassing on an engine water jacket and the radiator, carrying out water replenishing on the engine water jacket, and providing an expansion space for the cooling system are achieved, an expansion kettle is omitted for a finished vehicle, complex water paths are reduced, the failure rate of the finished vehicle is decreased, and the vehicle usage cost is reduced for users.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
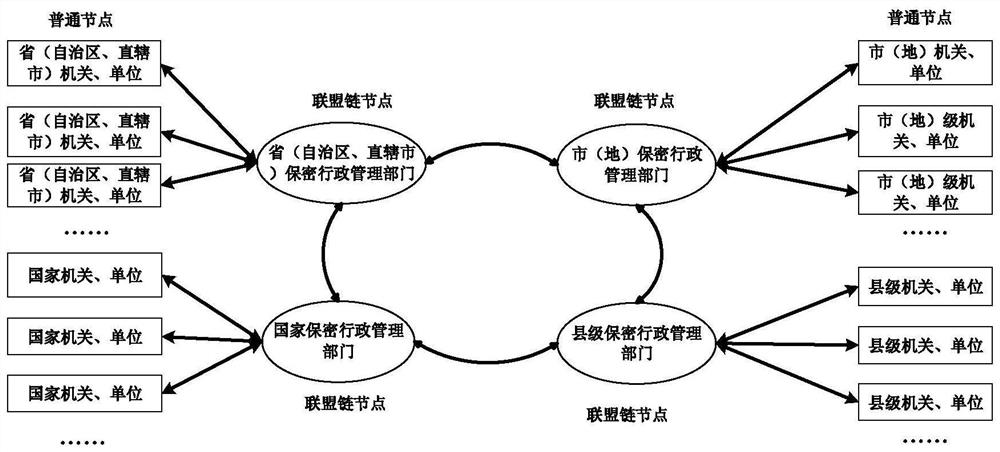
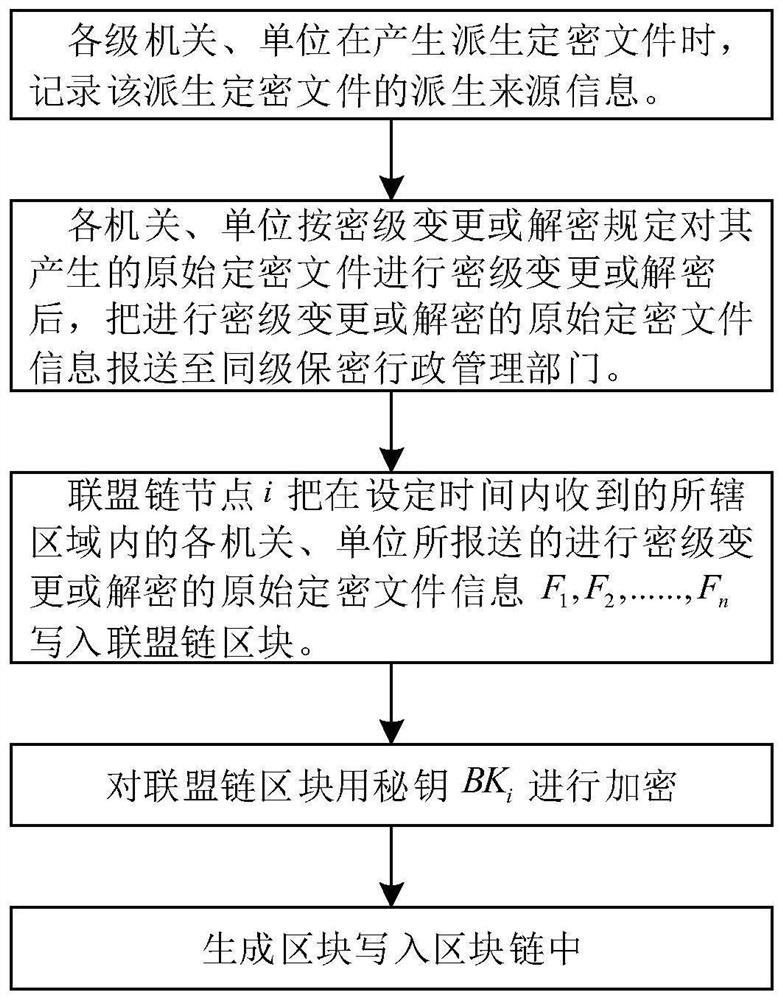
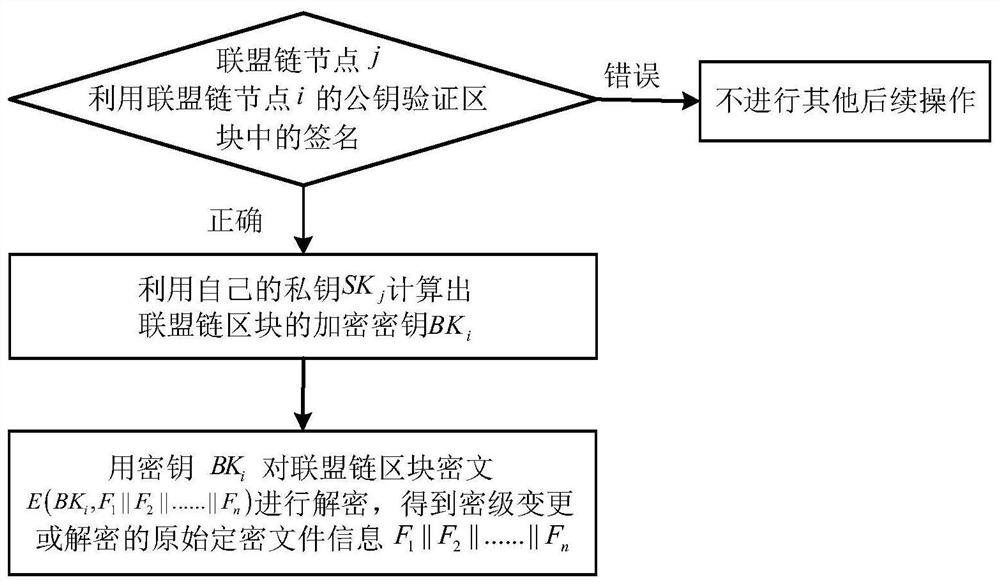
Block chain-based method for notification of secret level changes and decryption reminders for deriving encrypted files
ActiveCN110516451BConservativeMaintain securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityServer
The invention discloses a block chain-based derivation and encryption file encryption level change, decryption reminder notification method. At present, the unit that generates the derived classified file cannot be effectively notified of the original classified file after the classification level has been changed or decrypted. When the method of the present invention generates a derived encrypted file, it records the derived source information of the derived encrypted file, and after changing or decrypting the original encrypted file, the information of the original encrypted file that has been changed or decrypted is reported. Send it to the confidential administrative department at the same level, the server writes it into the alliance chain block, encrypts the alliance chain block, generates the block and writes it into the blockchain, and other alliance chain nodes or ordinary nodes obtain the content through signature verification , to change or decrypt the derived secret-related files. The method of the invention realizes prompting and notification of the change of secret level and decipherment in time for the derived secret file, can better realize secrecy, reduces the number of secret-related files, and is beneficial to the effective utilization of information.
Owner:HANGZHOU DIANZI UNIV
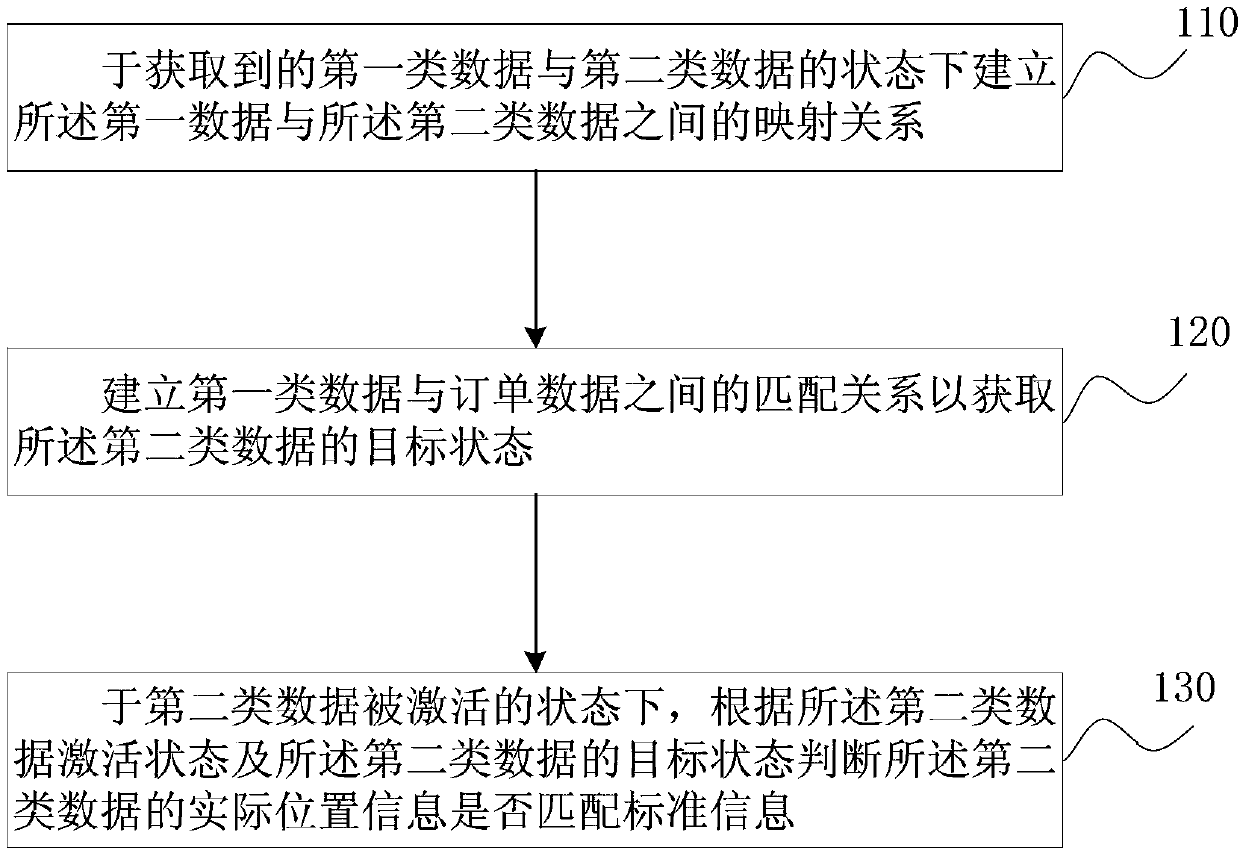
Transportation management method and system
InactiveCN108038703AGood interestSafeguard the interests ofCo-operative working arrangementsCommerceTransshipmentData type
The embodiment of the invention discloses a transportation management method and system. The method comprises the following steps: establishing a mapping relation between first data and second data inacquired states of a first data type and a second data type; establishing a matching relation between the first data type and order data so as to acquire a target state of the second data type; and judging whether actual position information of the second data type is matched with standard information in a state that the second data type is activated according to the activated state of the seconddata type and the target state of the second data type. According to the method in the embodiment of the invention, products are identified according to the first data type and the second data type,and whether the products are in inventory transshipment in the transportation process is intelligently monitored according to state comparison of the second data type, so that benefits of manufacturers and consumers can be well protected.
Owner:SHANGHAI MXCHIP INFORMATION TECHN
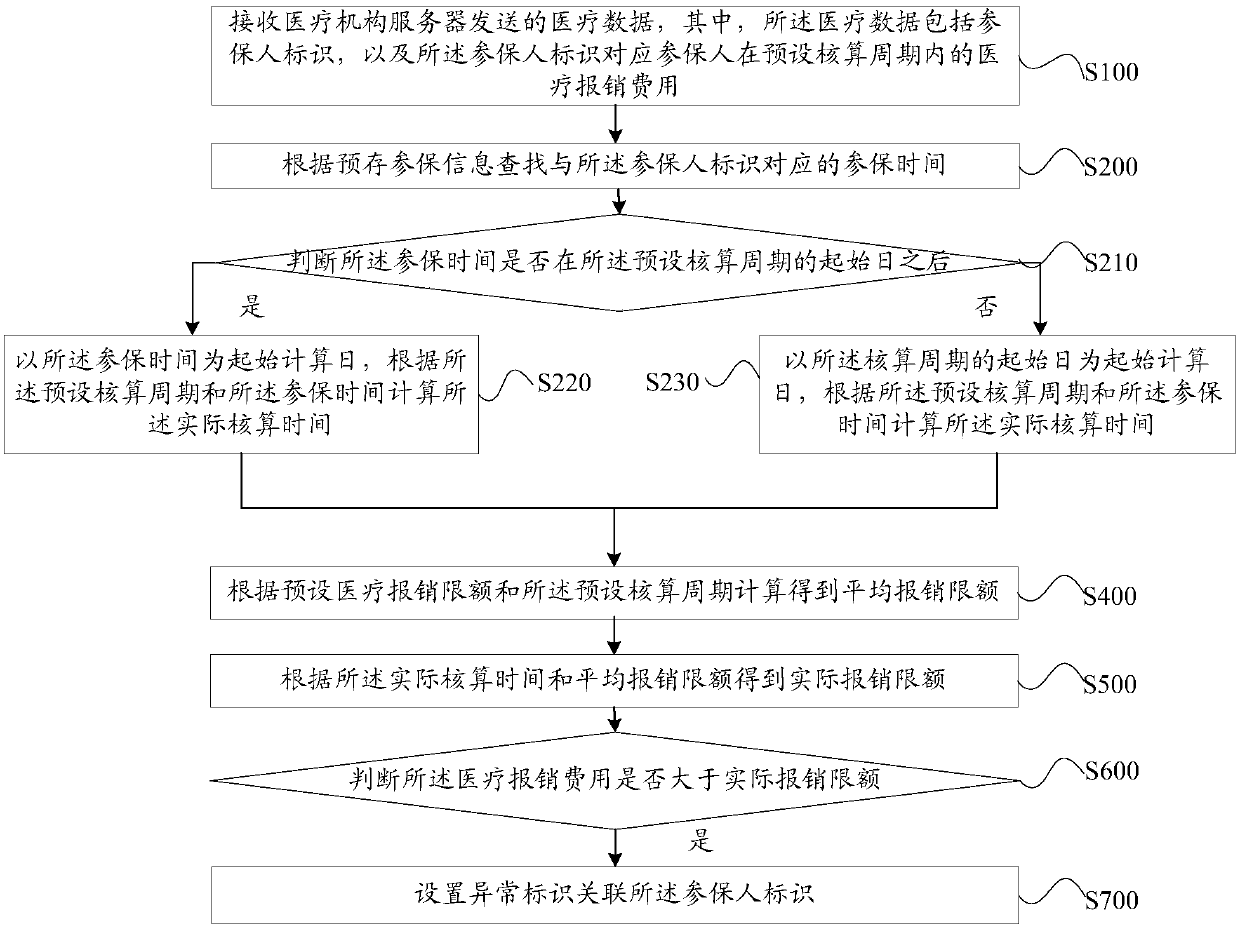
Medical expense abnormity monitoring method, monitoring server and storage medium
PendingCN109636649ASafeguard the interests ofProtect interestsMedical data miningFinanceMedical expensesMedical treatment
The invention discloses a medical expense abnormity monitoring method, a server and a storage medium, and the method comprises the steps: receiving medical data sent by a medical institution server, the medical data comprising insurer identifications and medical reimbursement fees of insurers corresponding to the insurer identifications in a preset accounting period; Searching the insured time corresponding to the insured person identifier according to pre-stored insured information; performing Calculating to obtain actual accounting time according to the preset accounting period and the insured time; performing Calculating to obtain an average reimbursement limit according to a preset medical reimbursement limit and the preset accounting period; Obtaining an actual reimbursement limit according to the actual accounting time and the average reimbursement limit; Judging whether the medical reimbursement cost is greater than an actual reimbursement limit or not; And if the medical reimbursement cost is greater than the actual reimbursement limit, setting an abnormal identifier and associating the abnormal identifier with the insurer identifier. According to the invention, medical cost abnormal behaviors can be conveniently and rapidly identified based on the neural network, and medical cost is monitored.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD
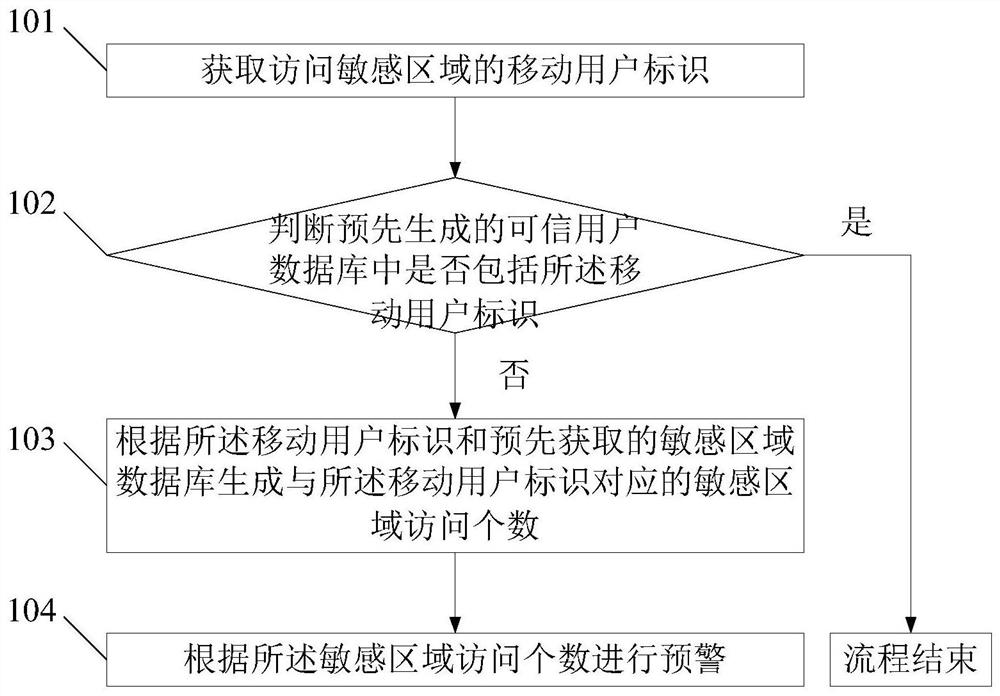
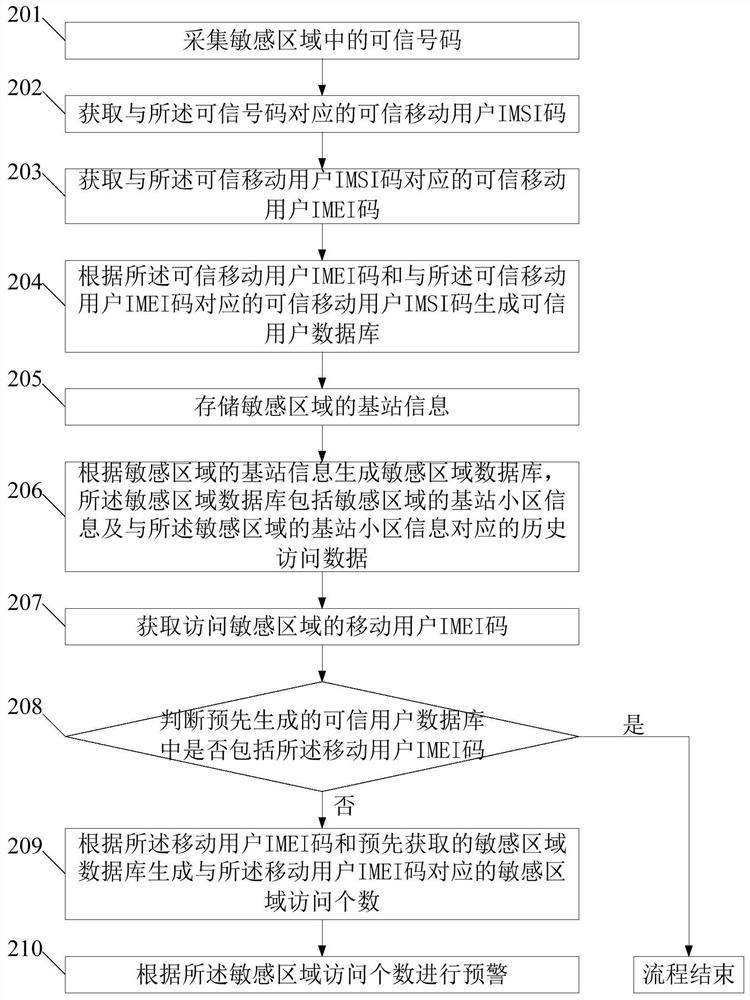
A security method and platform for sensitive areas
ActiveCN108495268BMaintain securitySafeguard the interests ofData miningLocation information based serviceInternet privacyEngineering
The invention discloses a security method and platform for a sensitive area. The method comprises the following steps: acquiring a mobile subscriber identity for accessing the sensitive area; judgingwhether a pre-generated trusted user database corresponding to the sensitive area includes the mobile subscriber identity or not; if not, judging whether a pre-generated backtracking database corresponding to the sensitive area includes the mobile subscriber identity or not; and if so, generating access information corresponding to the mobile subscriber identity according to the backtracking database, and making an early warning according to the access information. The tracks of mobile subscribers are mined on the basis of core network data of an operator, so that mobile subscribers frequentlyapproaching the sensitive area can be found in time, and the national security and interests are maintained effectively.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
a radiator
ActiveCN106894884BSafe, durable and efficient operationGuaranteed uptimeMachines/enginesEngine cooling apparatusFailure rateFiltration
The invention relates to a radiator. The radiator comprises a life indicating alarm device, an upper water chamber, a radiating core body and a lower water chamber. The upper water chamber is arranged on the upper portion of the radiating core body and communicates with the radiating core body. The lower water chamber is arranged on the lower portion of the radiating core body and communicates with the radiating core body. The upper water chamber comprises three cavities which are the first cavity, the second cavity and the third cavity. According to the radiator, on the one hand, through chemical action during first-stage physical absorption and isolation, second-stage filtration and third-stage filtration, rust, incrustation and bubbles generated in work of a cooling system are absorbed, potential threats of calcium and magnesium ions, iron ions, acid irons and the like are processed through reaction, the PH value of a cooling liquid is kept constant, clean and safe cooling liquid is output for the system, and thus safe, lasting and efficient operation of the cooling system is ensured. The radiator is provided with an excellent engine water jacket, radiator degassing is achieved, a space expansion function is provided for water replenishing of the engine water jacket and for the cooling system, an expansion kettle is canceled for the whole vehicle, complex water ways are reduced, and the whole vehicle failure rate and user vehicle usage cost are reduced.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
Private key identity authentication taking equation as tool
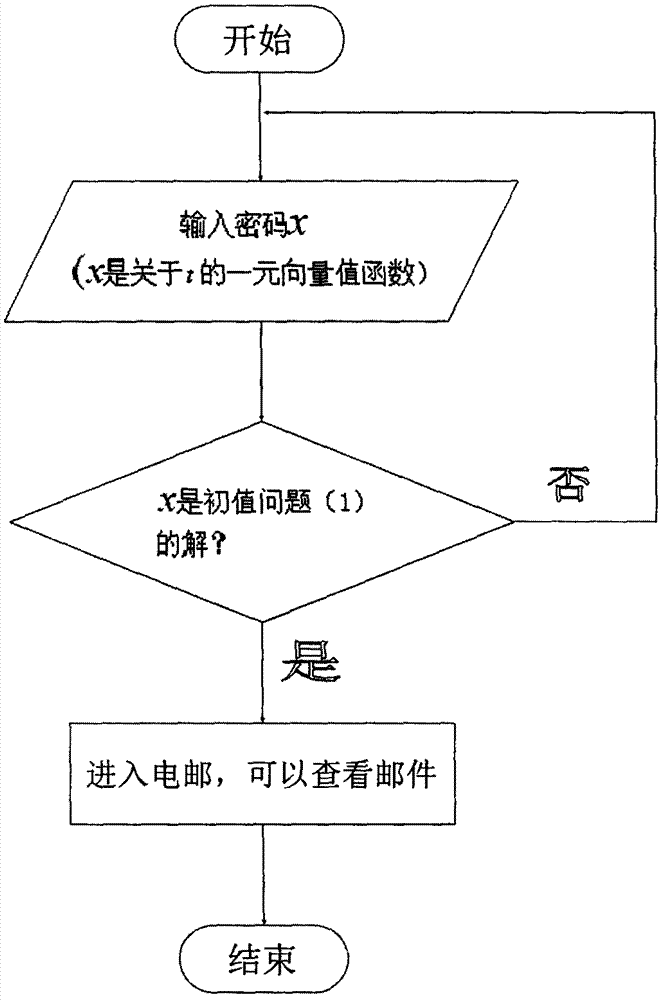
InactiveCN107359995AMaintain securitySafeguard the interests ofUser identity/authority verificationCryptographic attack countermeasuresValidation methodsPassword
In order to prevent criminals from destroying the new international political and economic order after World War II by using network and system attack technologies such as monitoring and injection attacks, to keep state secrets, to safeguard national security and interests, and to ensure the smooth progress of reform, opening up, and socialist construction, the present invention Trying to improve the existing means of identity verification, by constructing various forms of equations and equations such as differential equation well-posed problems, a class of identity verification methods based on private keys using equations as tools is proposed, which effectively reduces the need for password cracking techniques. and the risk of leaking secrets caused by the verification party's self-stealing and stealing of the verified party's information. Its name is private key authentication using equations as a tool. It belongs to the technical field of identity verification. The application field of the present invention includes not only communication, artificial intelligence, The second nuclear strike also includes access control to computer systems and non-computer systems, access control mechanisms, and identification of friend and foe.
Owner:刘旭 +1
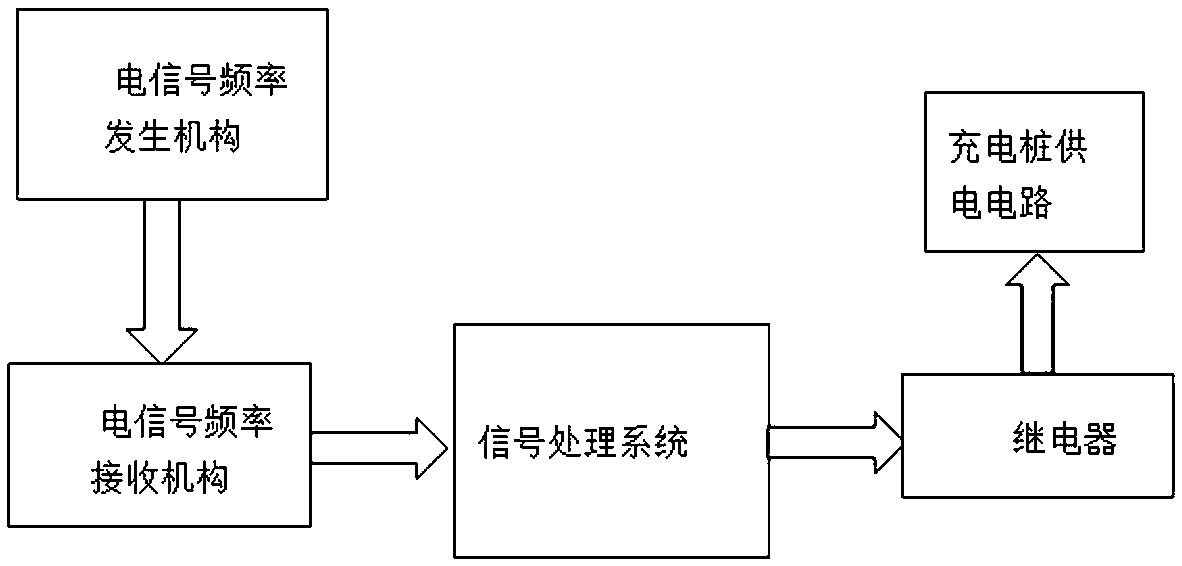
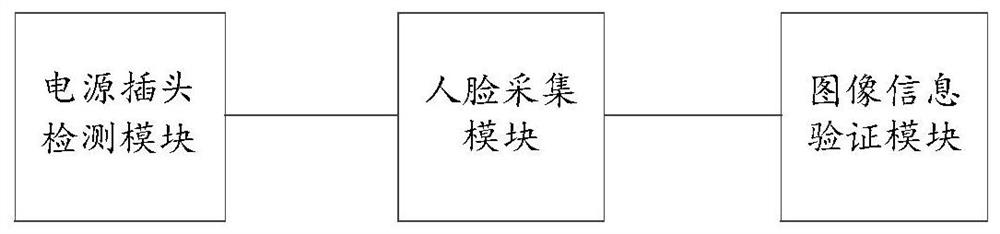
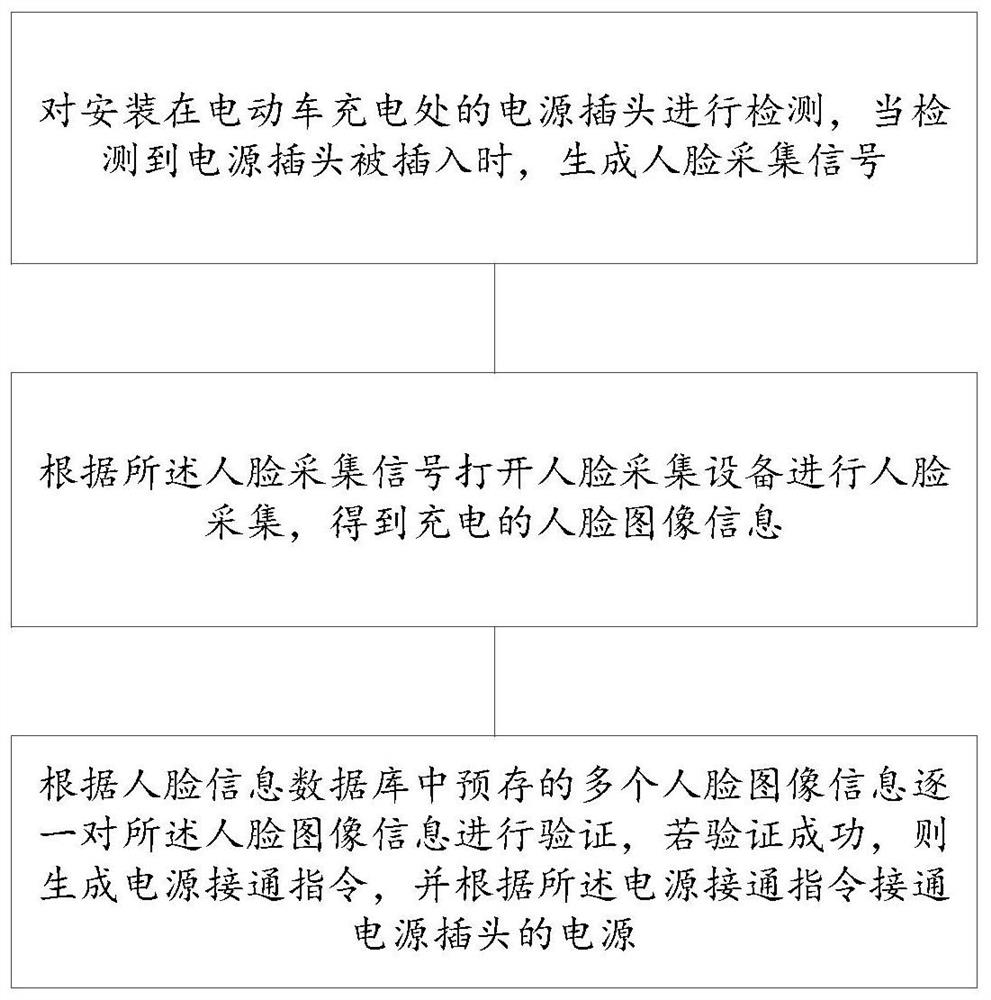
Electric vehicle charging management device and method and storage medium
InactiveCN112440776ASafeguard the interests ofMaintain orderCharging stationsCharacter and pattern recognitionAutomotive engineeringAcquisition apparatus
The invention provides an electric vehicle charging management device and method and a storage medium. The device comprises a power plug detection module, a face acquisition module and an image information verification module, wherein the power plug detection module is used for detecting a power plug installed at a charging position of an electric vehicle, and generating a face acquisition signalwhen the power plug is detected to be inserted; the face acquisition module is used for turning on face acquisition equipment to perform face acquisition according to the face acquisition signal to obtain charged face image information; and the image information verification module is used for verifying the face image information one by one according to a plurality of pieces of face image information pre-stored in a face information database, generating a power-on instruction if the verification succeeds, and switching on a power supply of the power plug according to the power-on instruction.According to the invention, the problem that rented electric vehicle charging positions are occupied is solved, the benefits of tenants are maintained, the order of communities is also maintained, meanwhile, the contradiction between owners in the communities is avoided, and the community aggregation is facilitated.
Owner:覃建华
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com