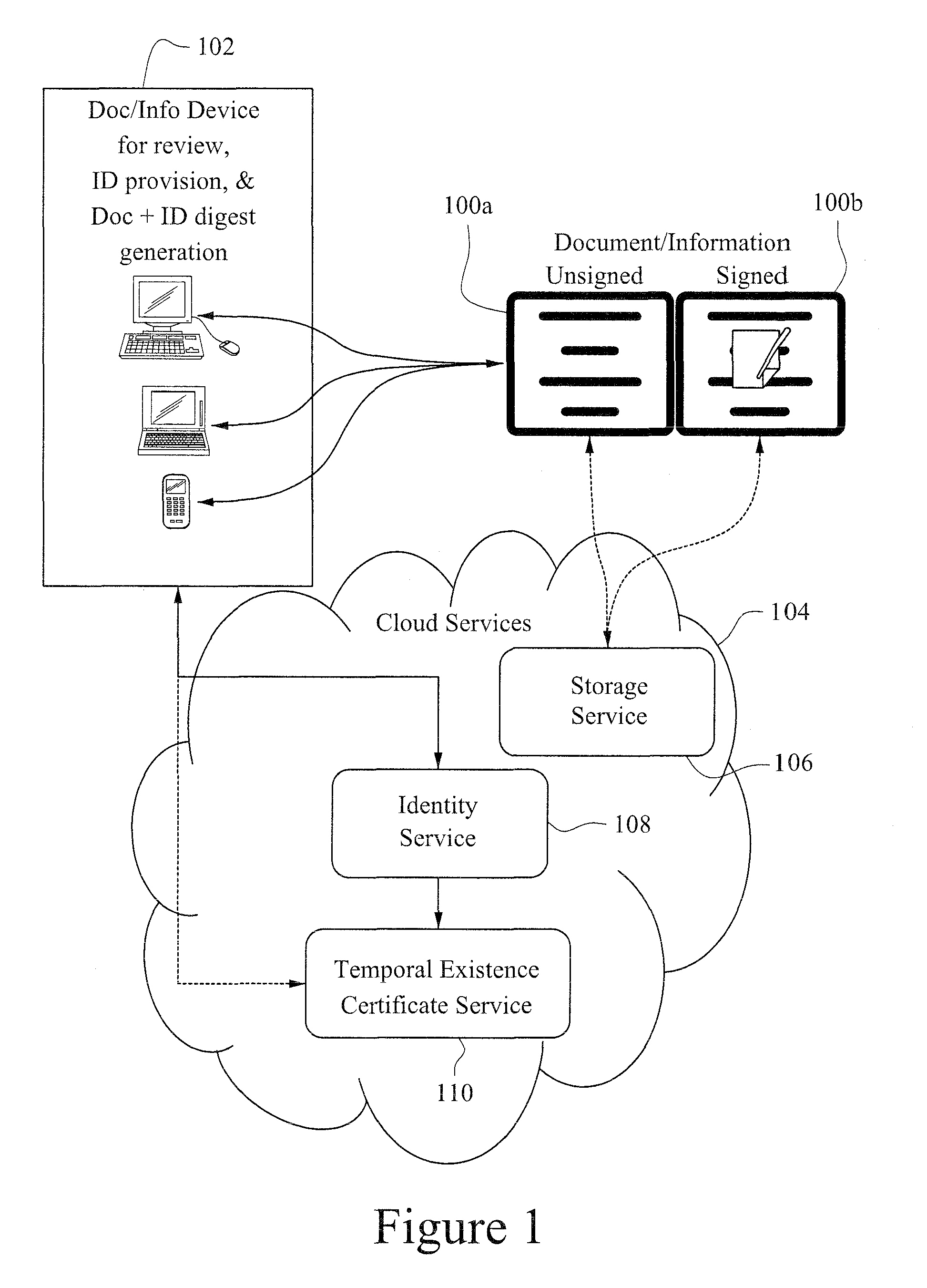
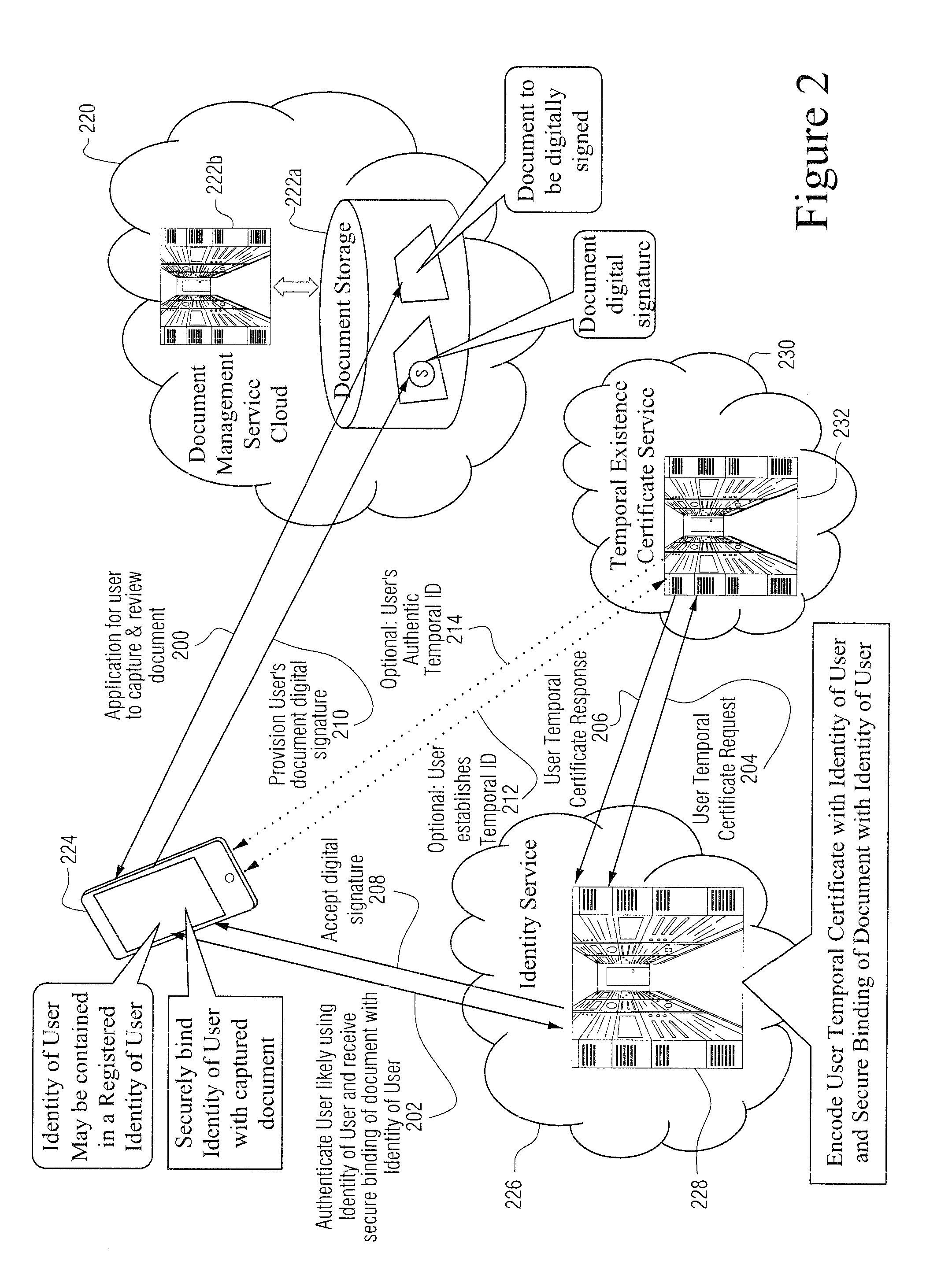
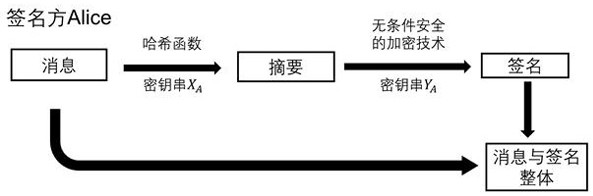
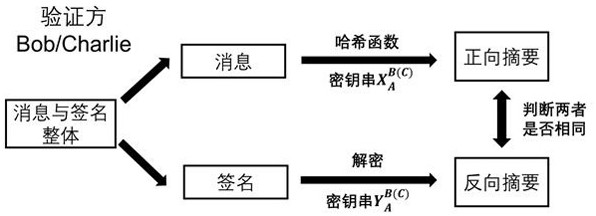
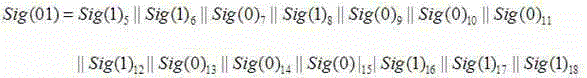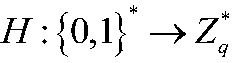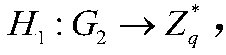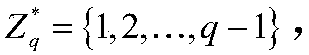Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48 results about "Quantum digital signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
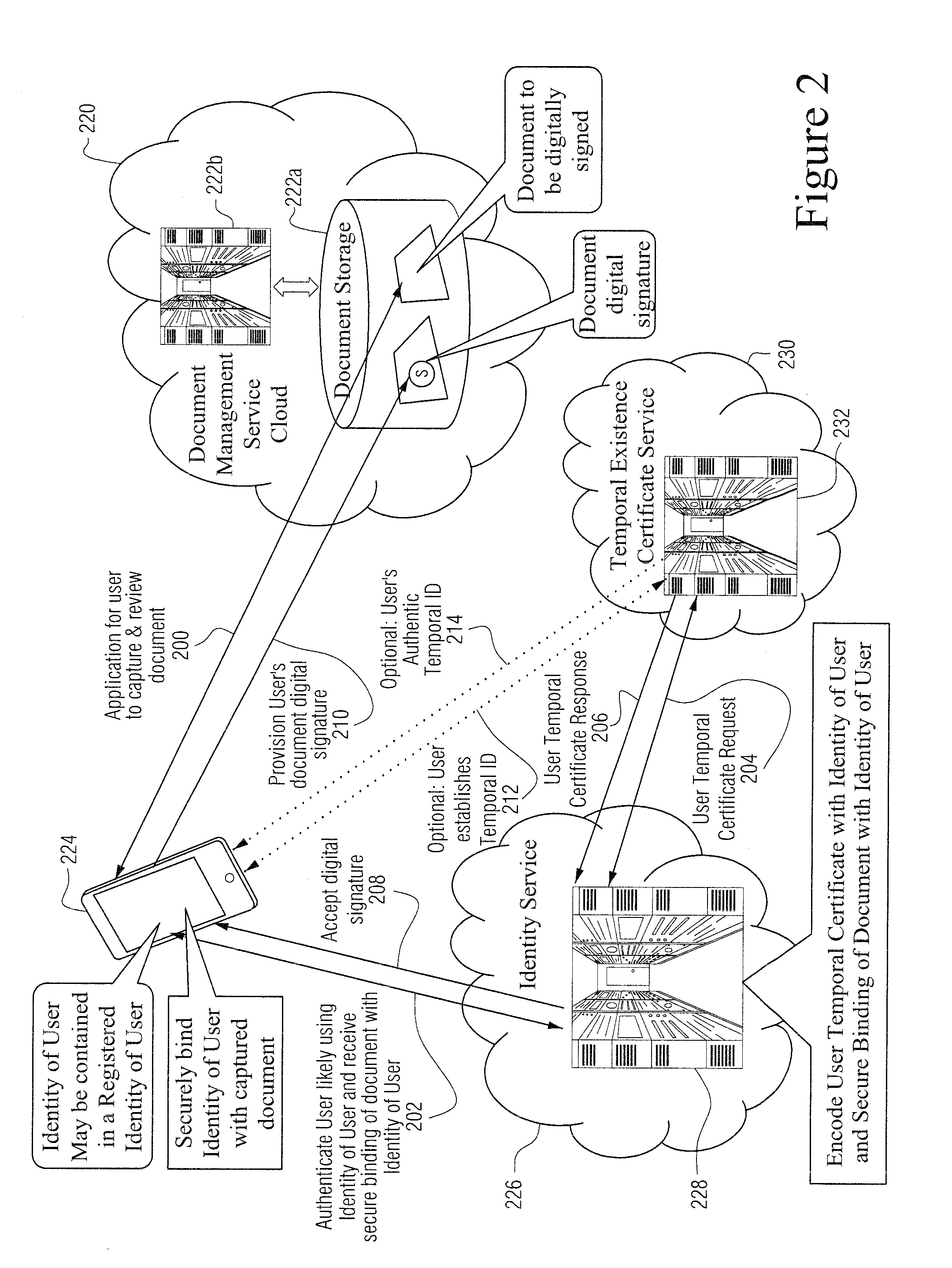
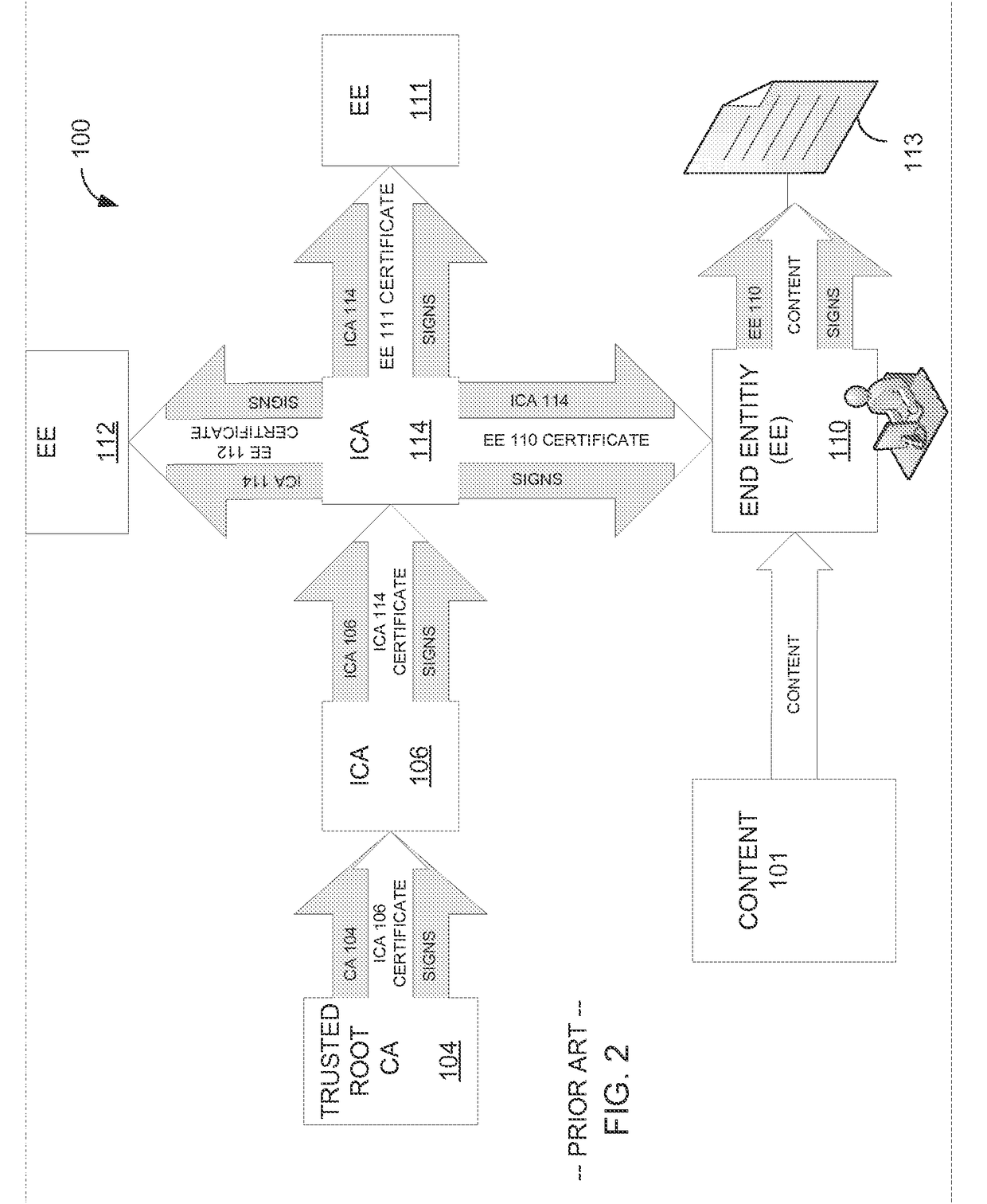
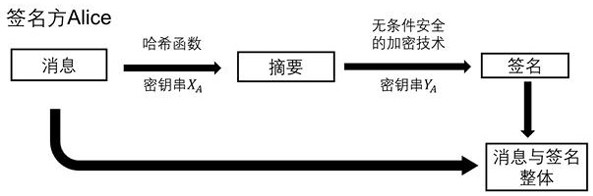
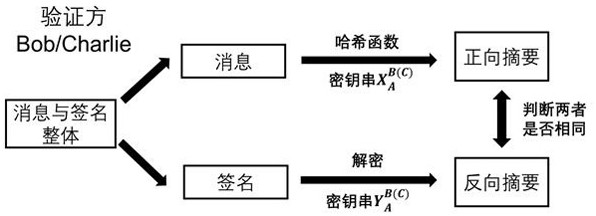
A Quantum Digital Signature (QDS) refers to the quantum mechanical equivalent of either a classical digital signature or, more generally, a handwritten signature on a paper document. Like a handwritten signature, a digital signature is used to protect a document, such as a digital contract, against forgery by another party or by one of the participating parties.
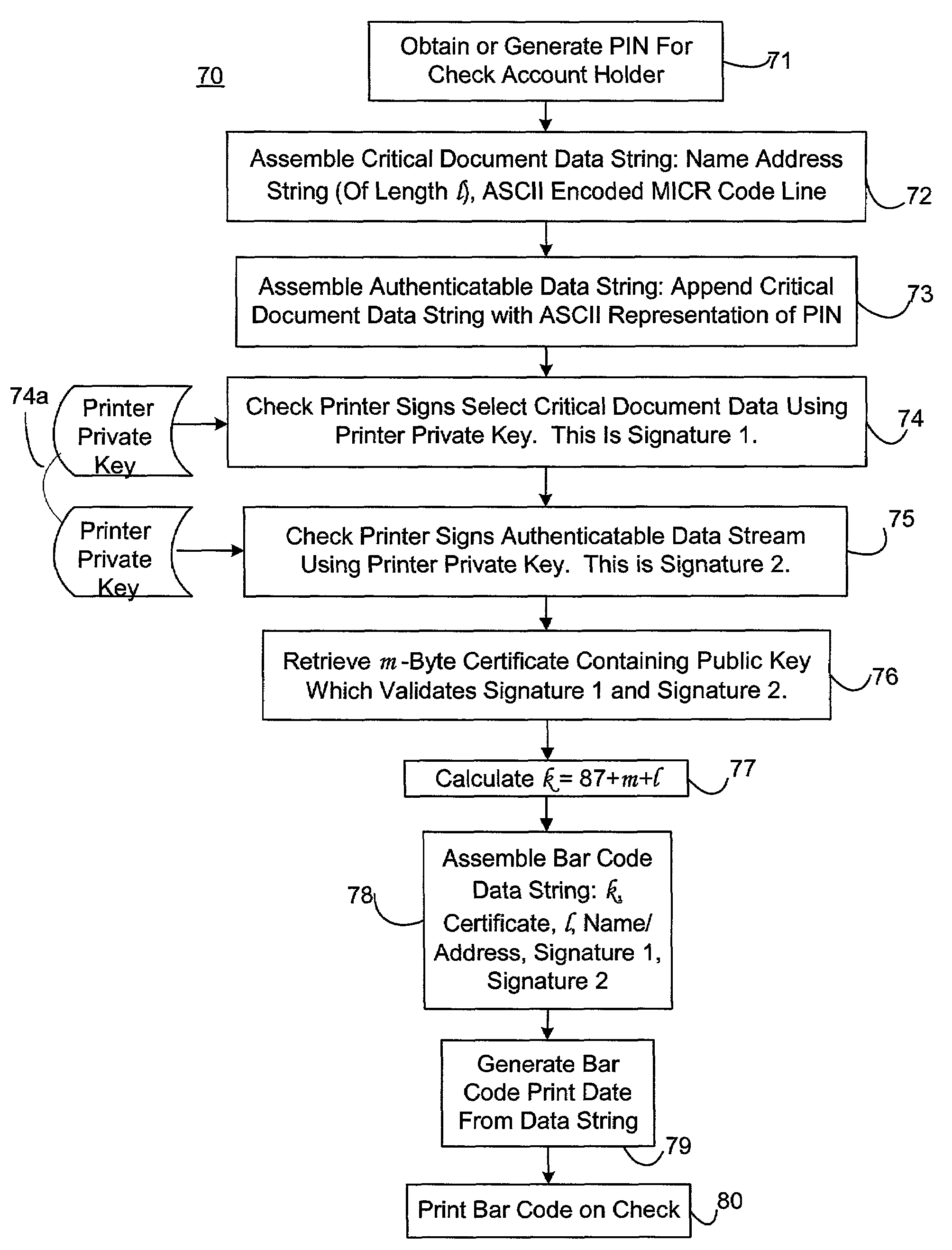
Self-authentication of value documents using digital signatures
ActiveUS7051206B1Low costImprove reliabilityKey distribution for secure communicationPaper-money testing devicesCredit cardPublic key certificate
An encryption-free technique for enabling the self-authentication of value documents (including personal and commercial checks) presented at a point of purchase or financial institution. Certain data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate issued from a trusted certificate authority. The signed data and public key certificate are stored on the value document, preferably in a two-dimensional bar code data format. In the case of certain personal value documents (such as checks, credit cards, passports, birth certificates, Social Security cards, etc.), a unique personal identification number (PIN) also may be included in the document data that is signed by a second digital signature. At a point of purchase, a merchant or teller can scan and read the data stored in the two-dimensional bar code and other magnetically recorded information, and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, if the personal value document contains the second digital signature, the document may be verified using a PIN-generating algorithm or other method that generates all permutations of PINs. The first digital signature alone may be used to authenticate selected data within the personal value document even when the PIN is not available. Similarly, in the case of a commercial value documents, authentication of pre-printed data may be based entirely upon only the first digital signature.
Owner:UNISYS CORP
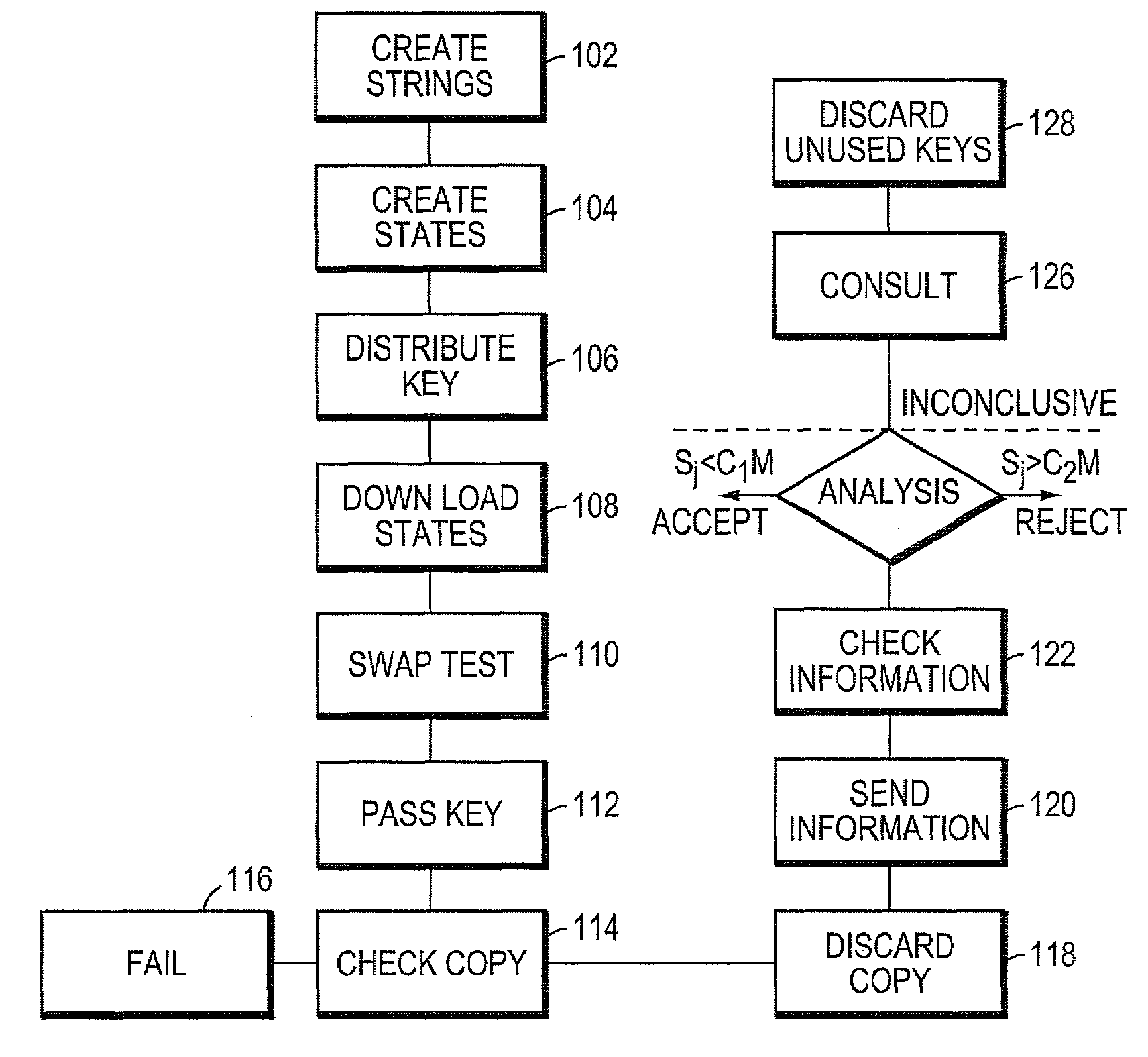
Quantum digital signatures
ActiveUS7246240B2User identity/authority verificationSecret communicationDigital signatureDigital signature forgery
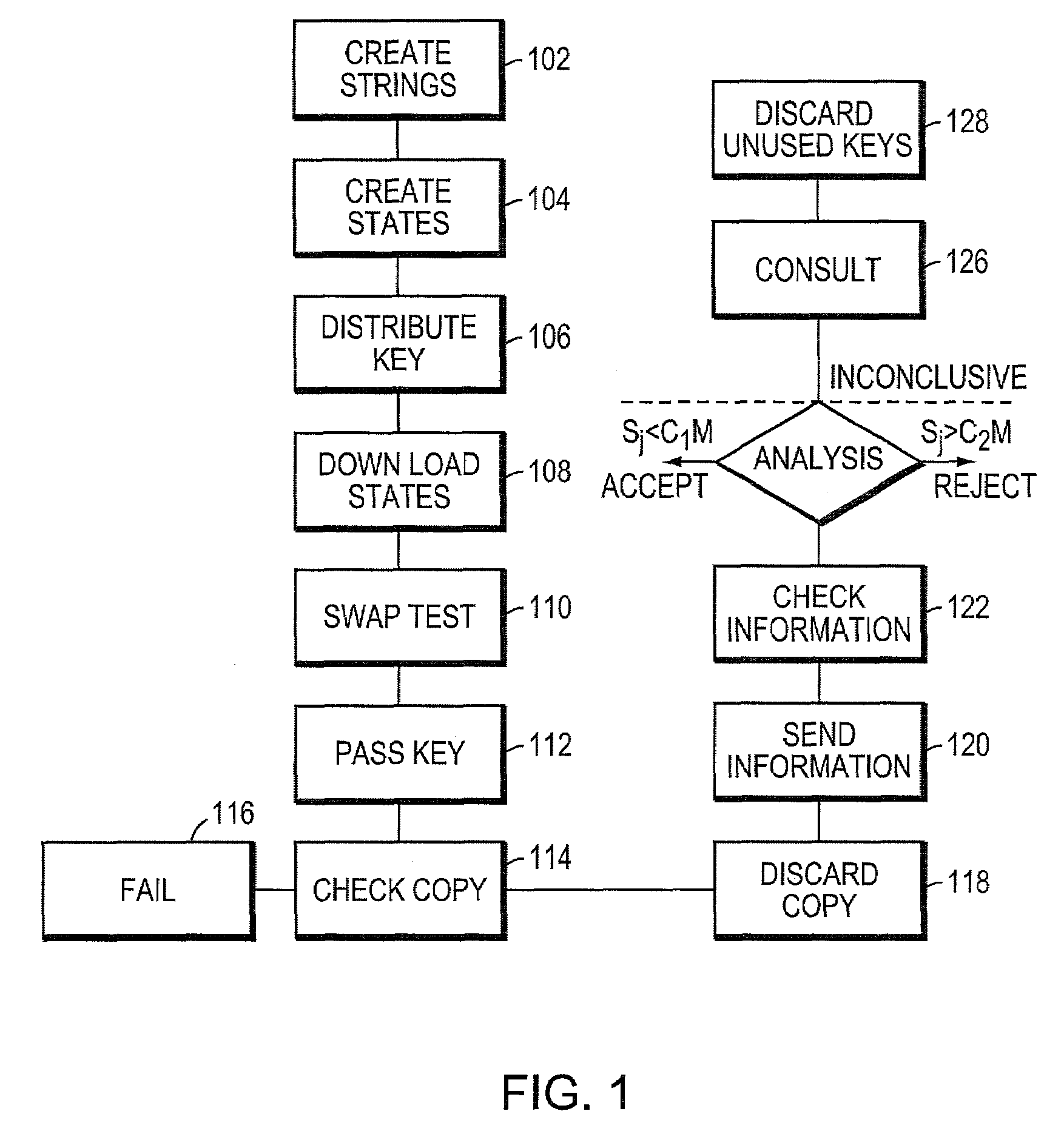
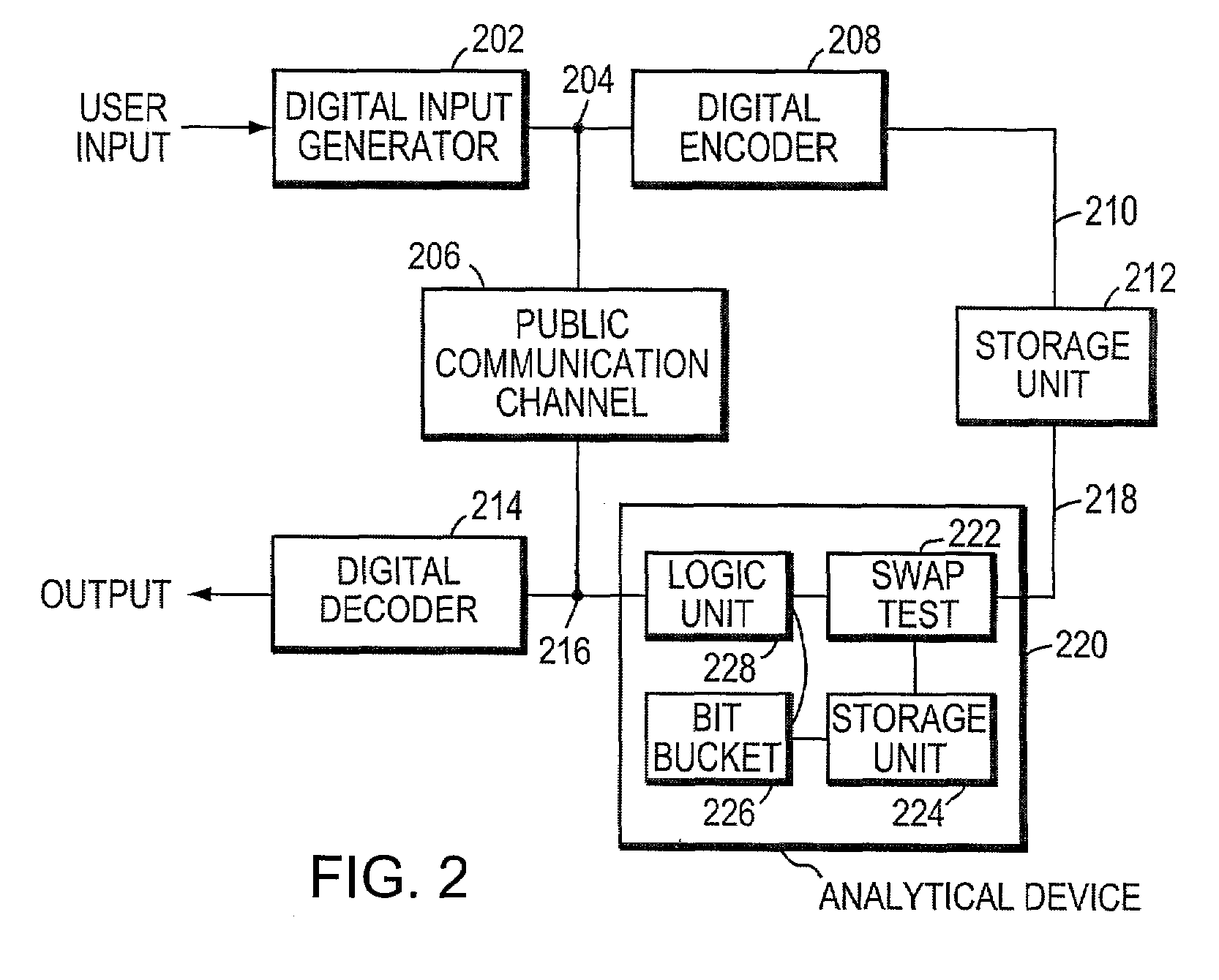
Systems and methods for providing secure quantum digital signatures. In one embodiment, a digital signature user creates a plurality of identical “public” keys having one or more bits and a corresponding quantum mechanical one-way function. Quantum digital signature recipients use a “swap test” to check the validity of a copy of the key, and compare the test results with others. The quantum digital signature user sends a signed message over any channel, including an insecure channel. The recipients evaluate the signed message, and quantify the number of incorrect keys. The message is deemed valid and original, or forged and / or tampered with, when the number of incorrect keys is less than a lower threshold, or exceeds an upper threshold, respectively. For an intermediate number of incorrect keys, the recipients determine message authenticity by comparing observations. Hardware useful for application of the method is disclosed.
Owner:MASSACHUSETTS INST OF TECH
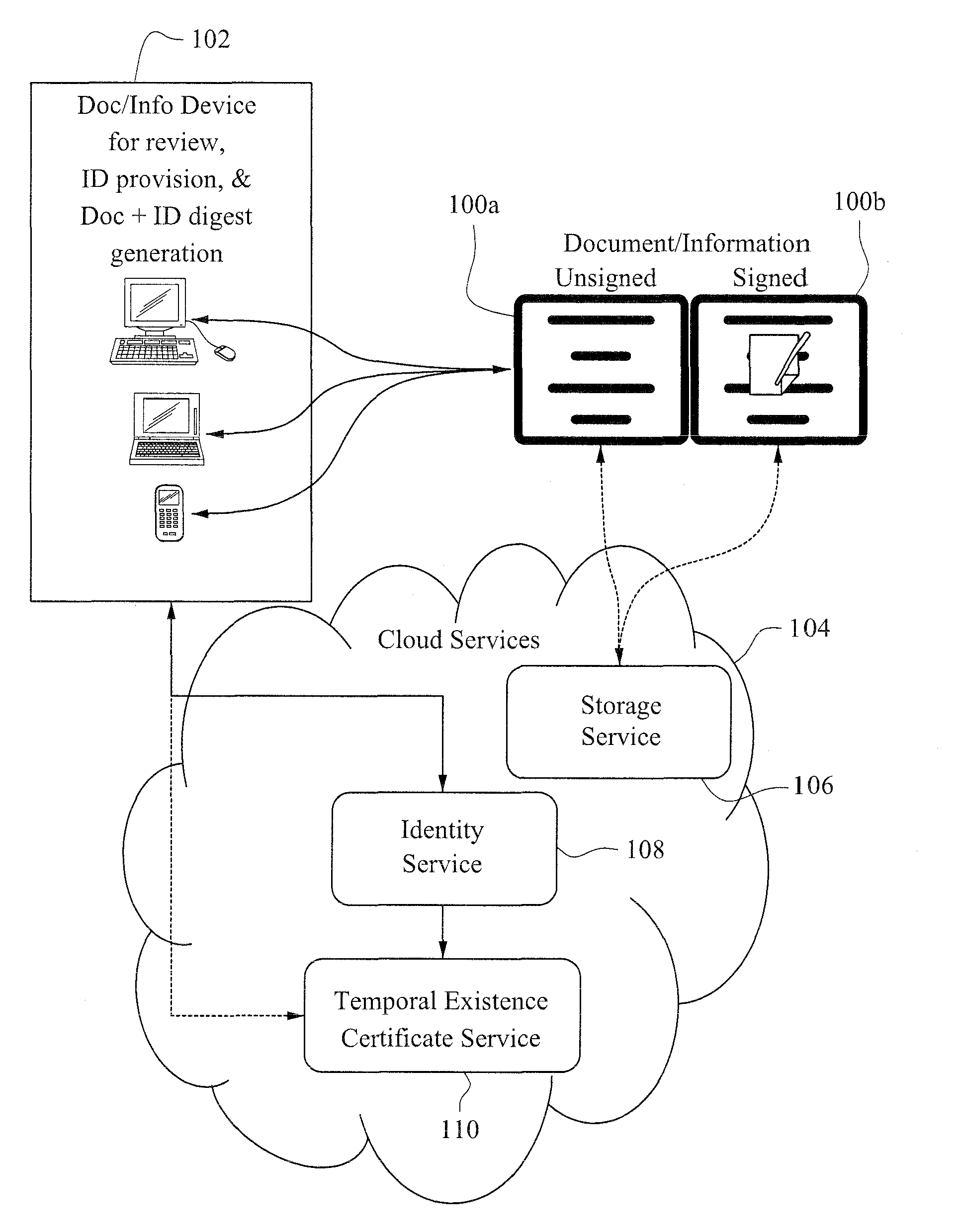
Non-PKI digital signatures and information notary public in the cloud
InactiveUS20130311772A1High user acceptanceMinimizes user information coordinationUser identity/authority verificationDocumentation procedureDigital signature
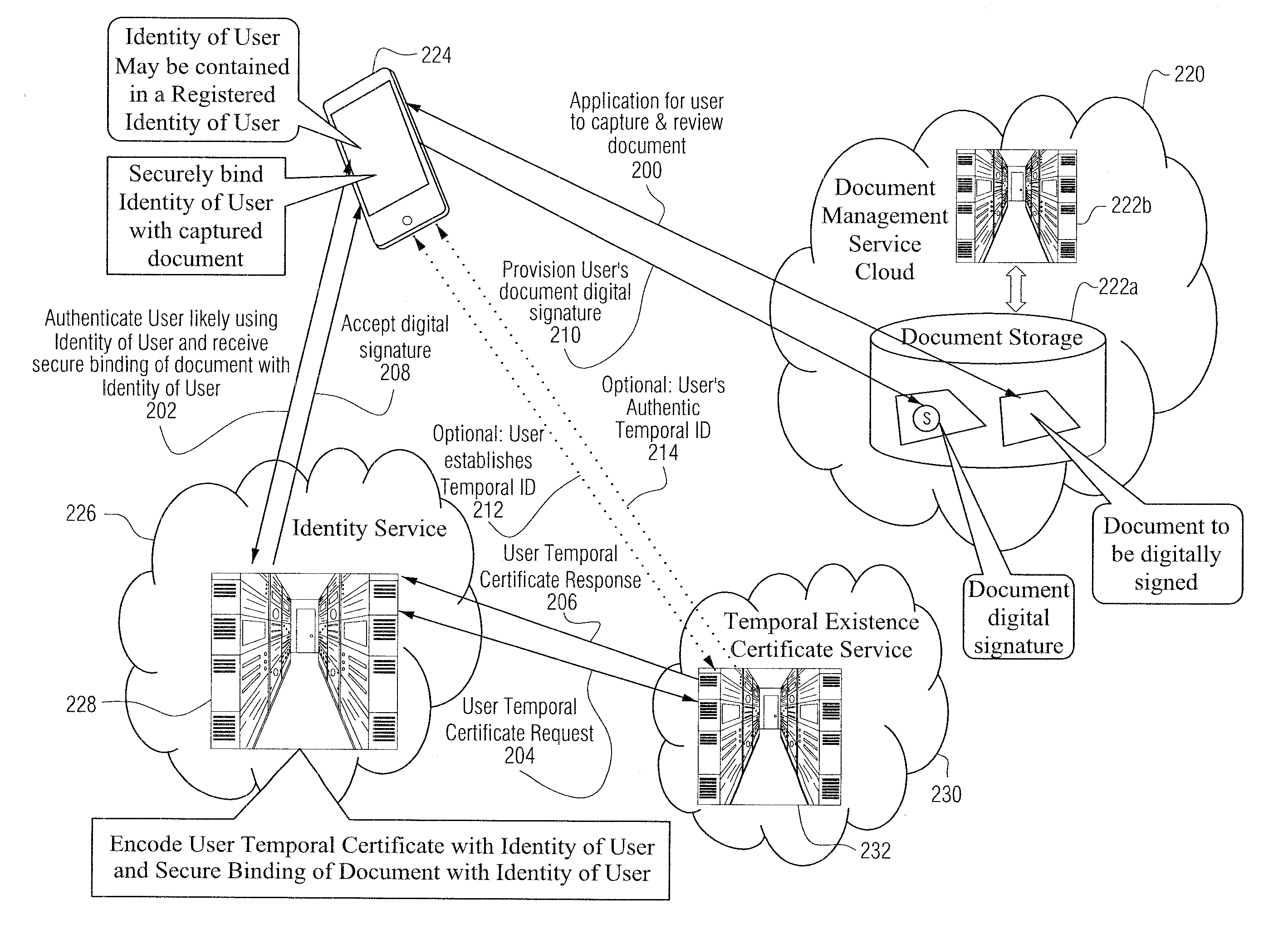
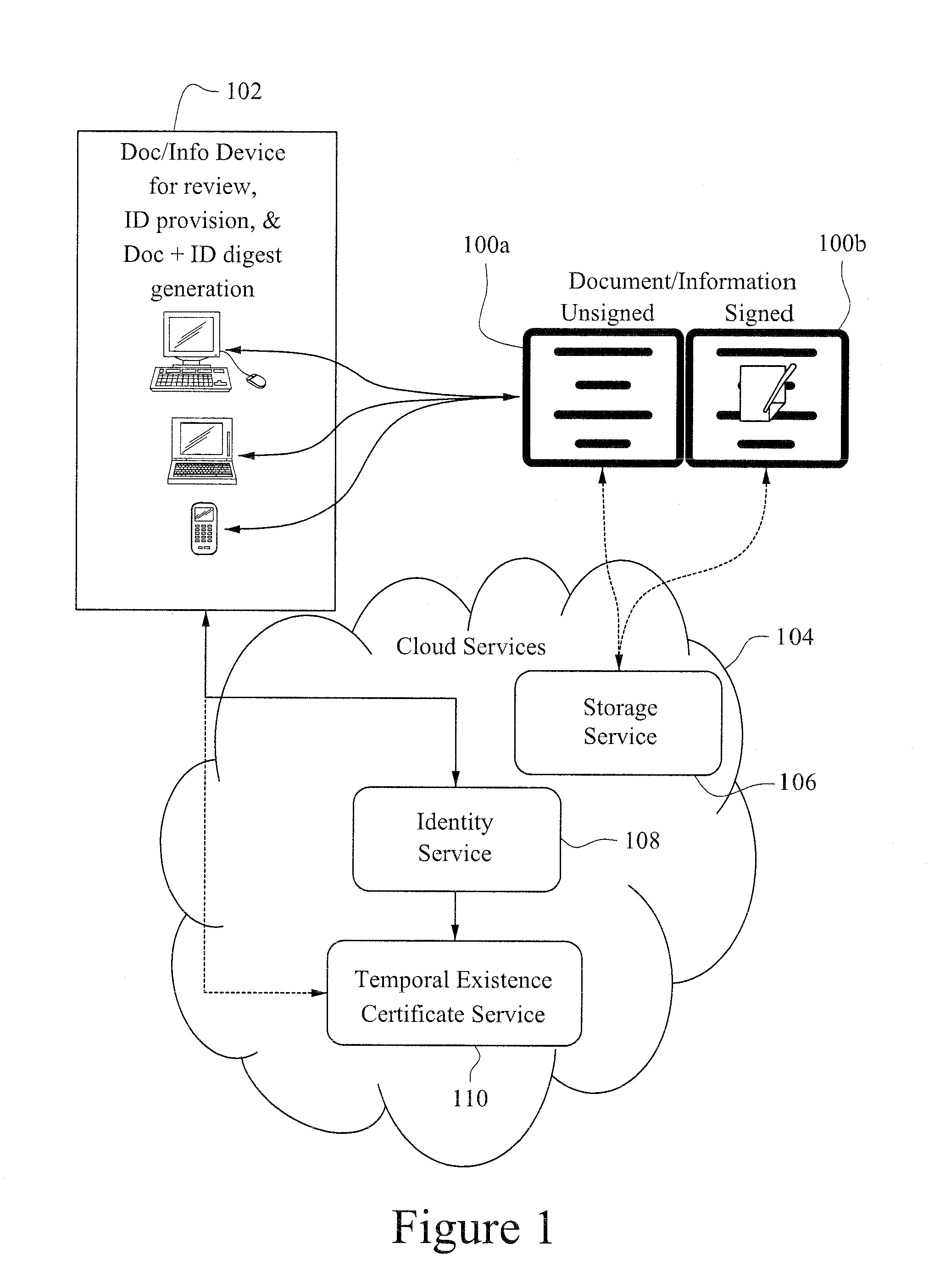
A digital signature is applied to digital documents / information. In certain instances, juridically strong digital signatures are achieved. Cloud computing technologies may be used to aid in the production of the cryptographically secure, authenticated digital signatures. Digital signatures may be produced with a digital notarization. The techniques of generating a digital signature may not require the use of traditional public key infrastructure (PKI).
Owner:ZENERJI
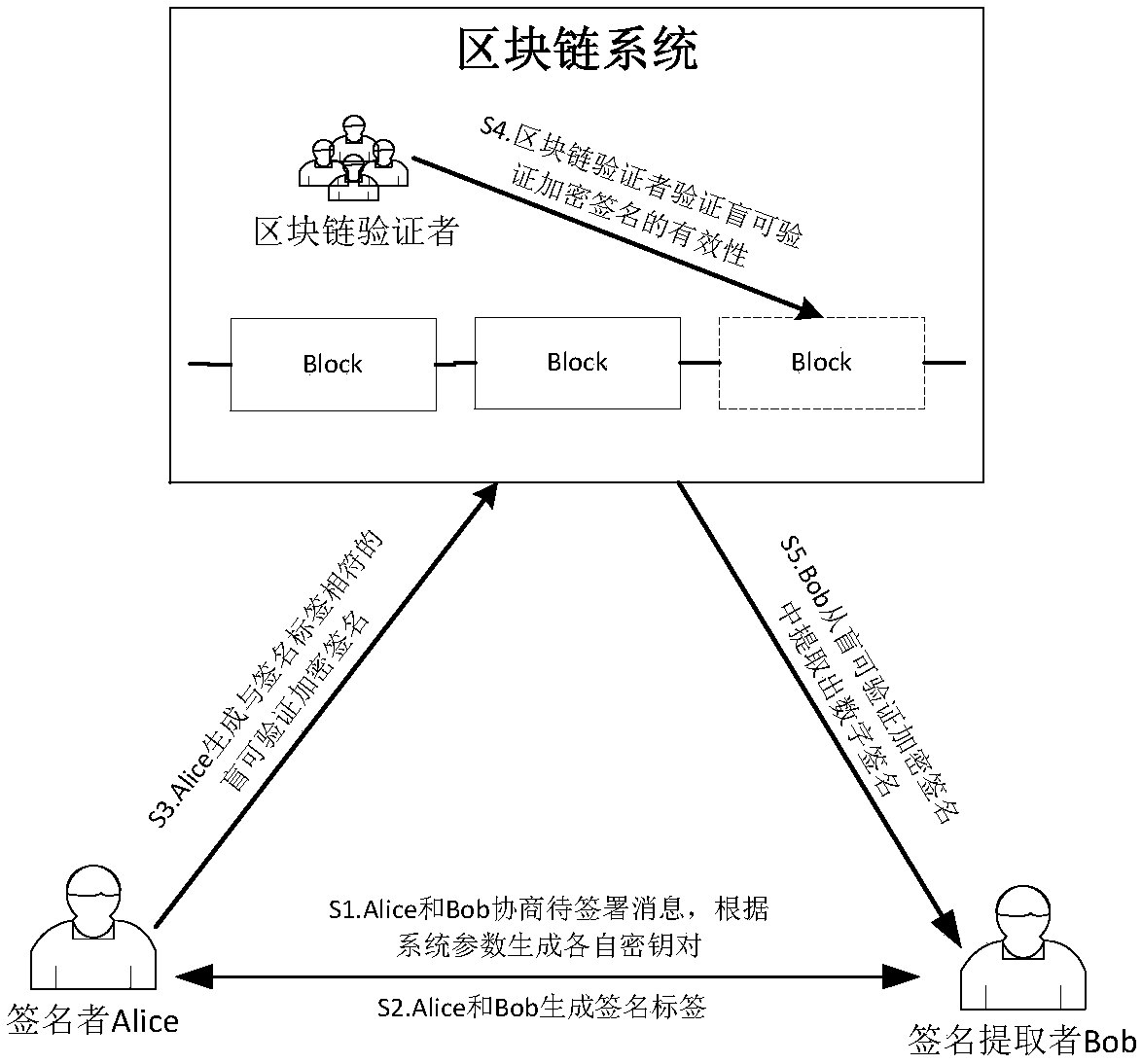
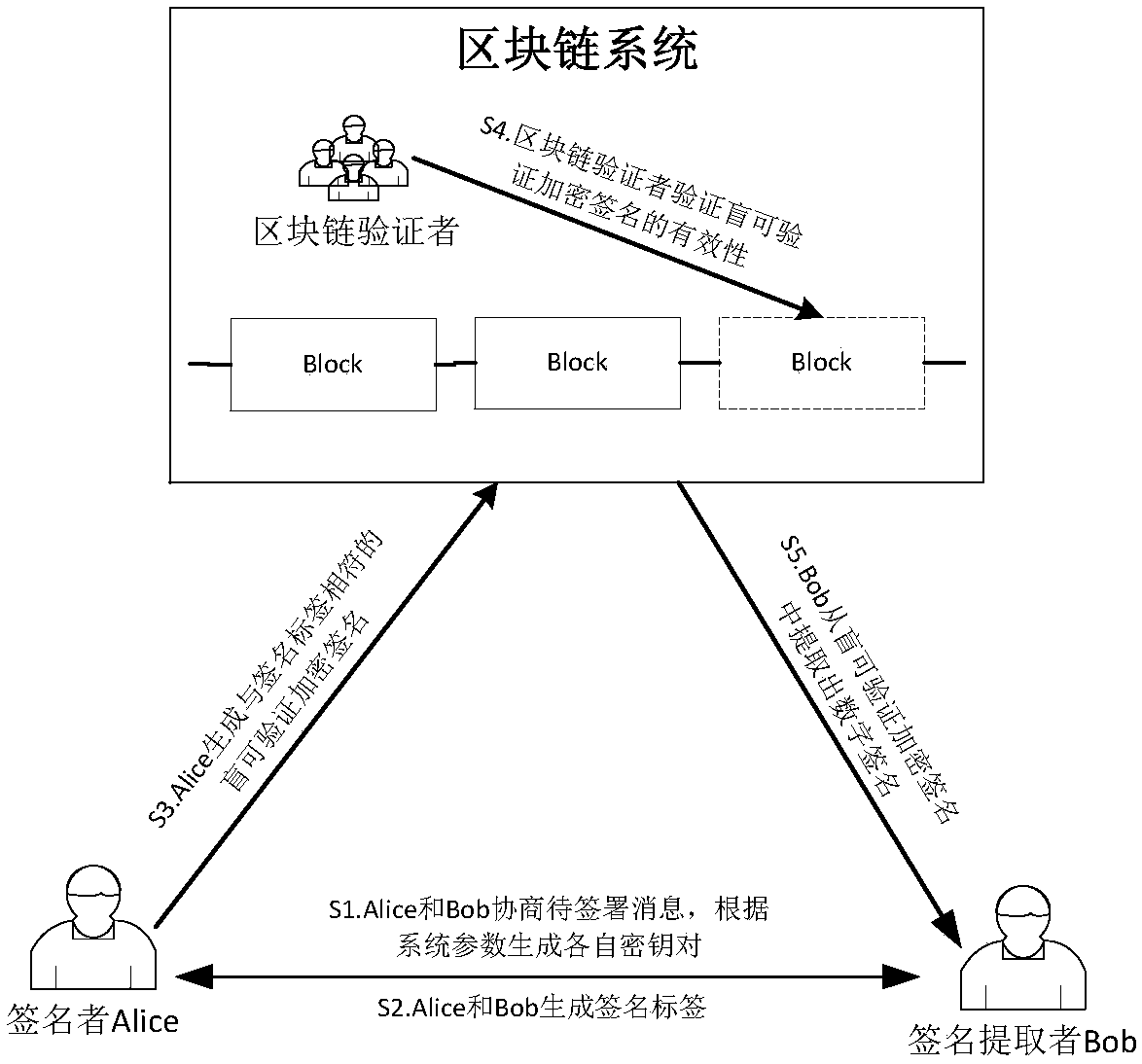
Blind verifiable cryptographic signature method based on block chain
InactiveCN107040383APrivacy protectionPublic key for secure communicationUser identity/authority verificationAlice and BobDigital signature
The invention relates to a blind verifiable cryptographic signature method based on a block chain. The method includes three parties: a signer Alice, a signature extractor Bob, and a block chain verifier. The method is implemented in the following steps: Alice and Bob negotiate a message to be signed and generate their own key pairs respectively according to system parameters; Alice and Bob generate signature tags; Alice generates a blind verifiable cryptographic signature that matches the signature tag; the block chain verifier verifies the validity of the cryptographic verifiable cryptographic signature; and Bob extracts a digital signature from the blind verifiable cryptographic signature. The method can be used to construct a fair digital signature exchange protocol that protects privacy in a public block chain environment. The method blindens the public key information of the signer so that a node on a block chain cannot obtain the real digital signature and the public key of the signer aside from verifying the validity of the signature, and the privacy protection for the signer is achieved.
Owner:深圳市数峰科技有限公司
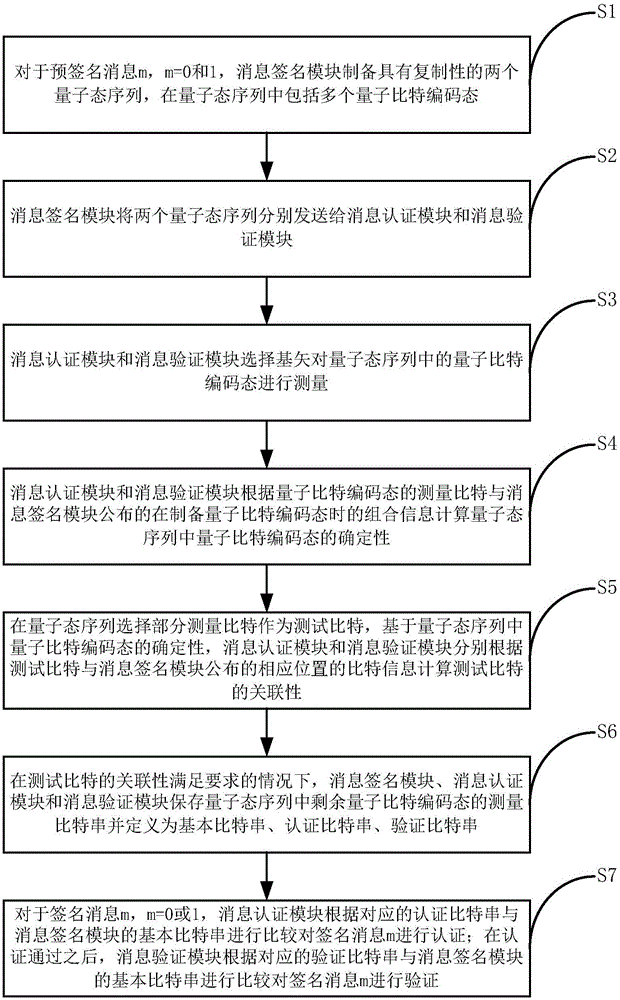
Quantum digital signing method and system
ActiveCN105007158AKey distribution for secure communicationUser identity/authority verificationComputer hardwareMessage authentication code
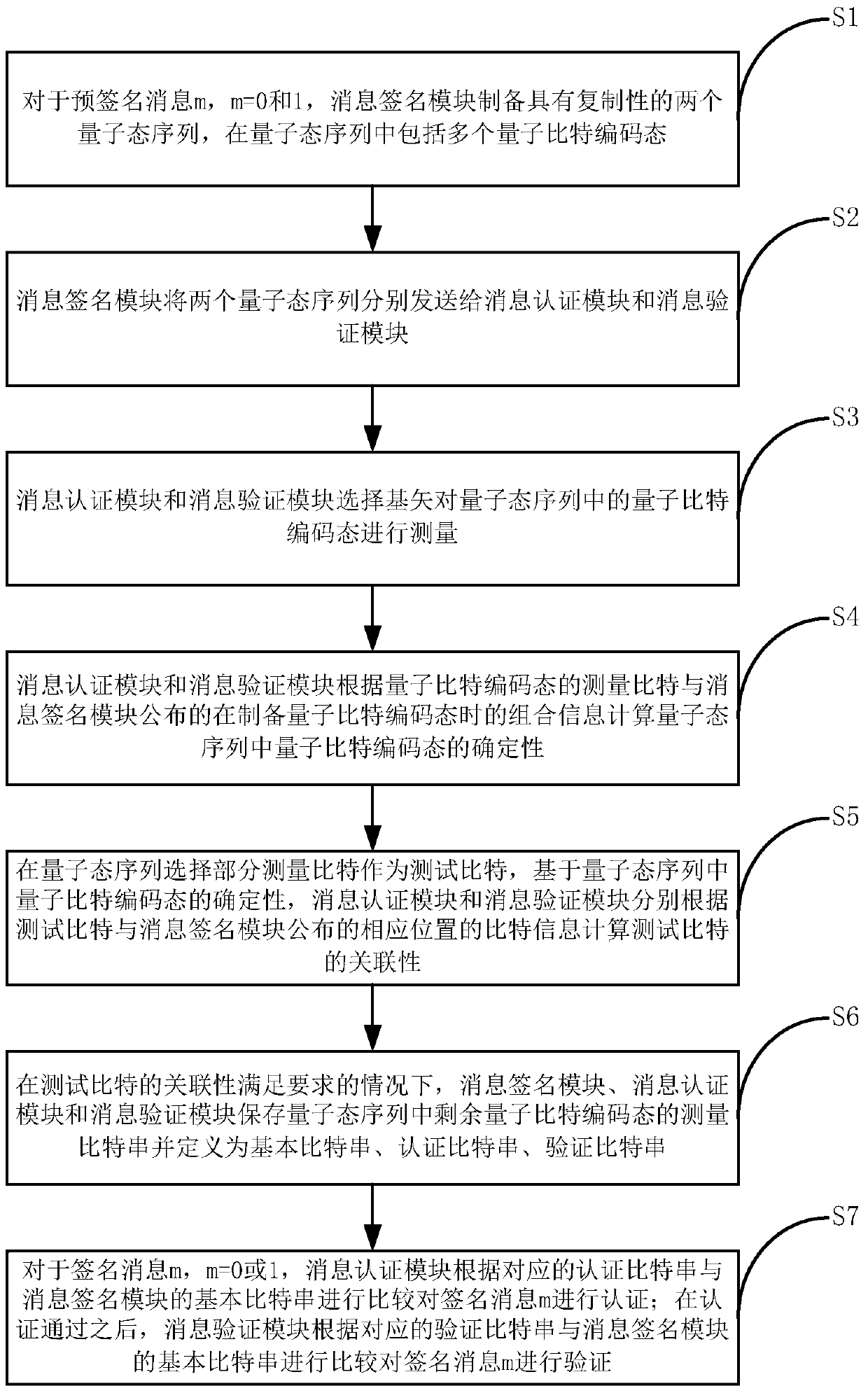
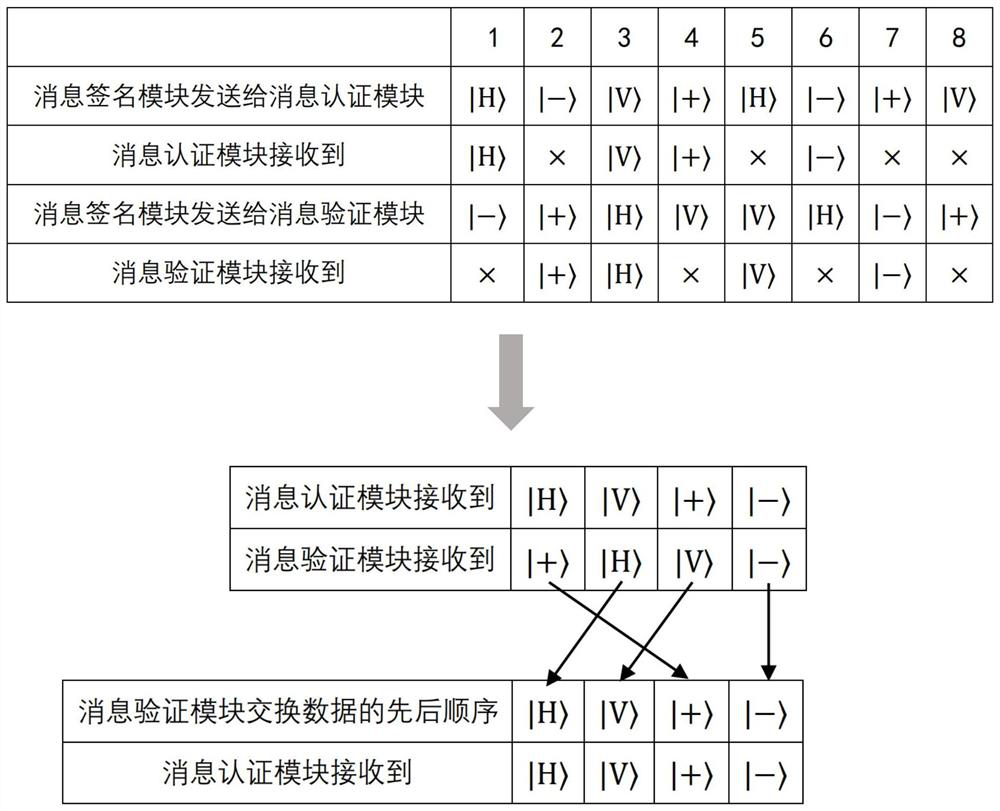
The invention provides a quantum digital signing method and system. For a pre-signing message m, m is equal to 0 and 1, a message signing module prepares two quantum state sequences with replicability and sends to a message authentication module and a message verifying module respectively; the message authentication module and the message verifying module measure quantum bit coding states and calculate the determinacy of the quantum bit coding states according to measured bits, and the message authentication module and the message verifying module respectively calculate the relevance of the measured bits based on the determinacy of the quantum bit coding states; when the relevance meets requirements, for a signing message m, m is equal to 0 or 1, the message authentication module authenticates the signing message m according to comparison between a corresponding authentication bit string and the basic bit string of the message signing module; after the authentication is successful, the message verifying module verifies the signing message m according to comparison between a corresponding verifying bit string and the basic bit string of the message signing module. The quantum digital signing method and system overcomes all technical challenges of the existing quantum digital signing schemes.
Owner:INST OF ADVANCED TECH UNIV OF SCI & TECH OF CHINA
Methods and equipment for generating and authenticating digital signatures and digital signature system
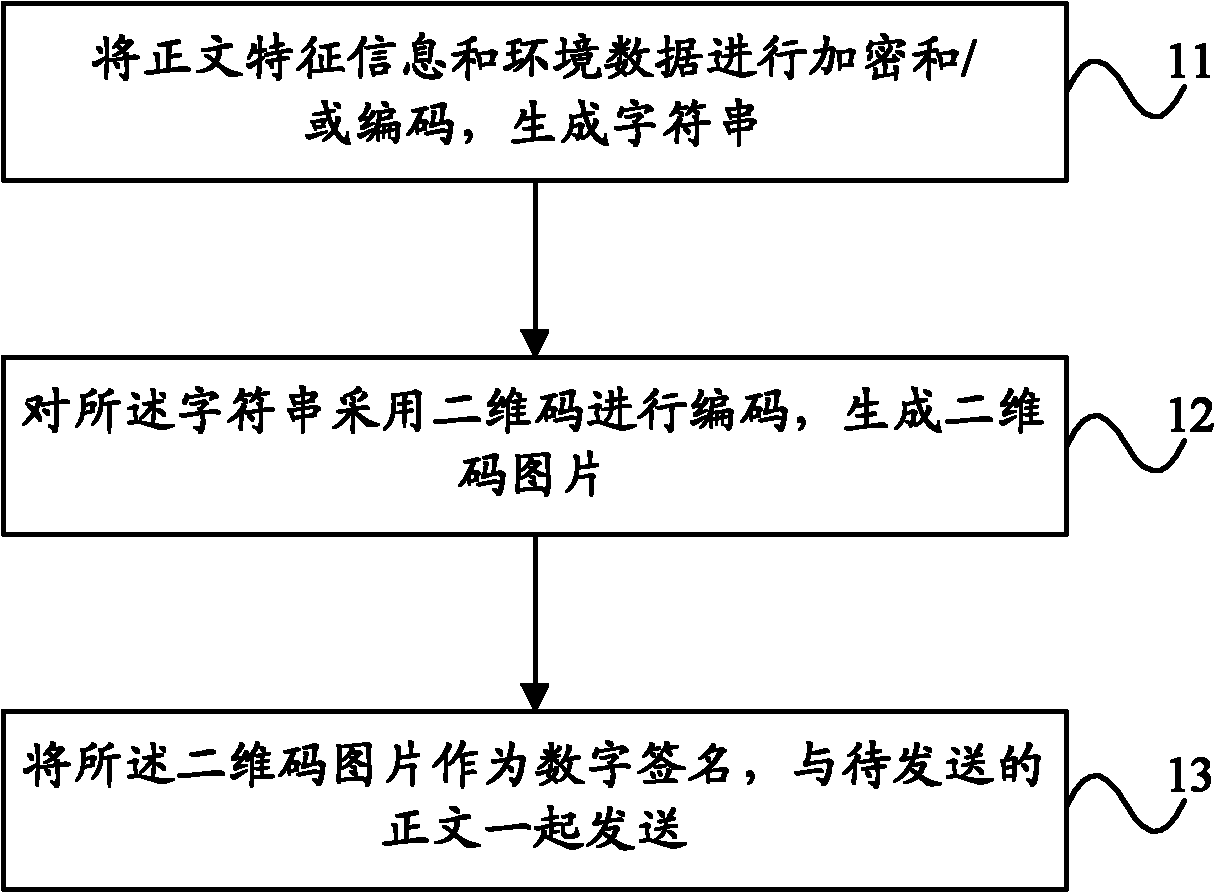
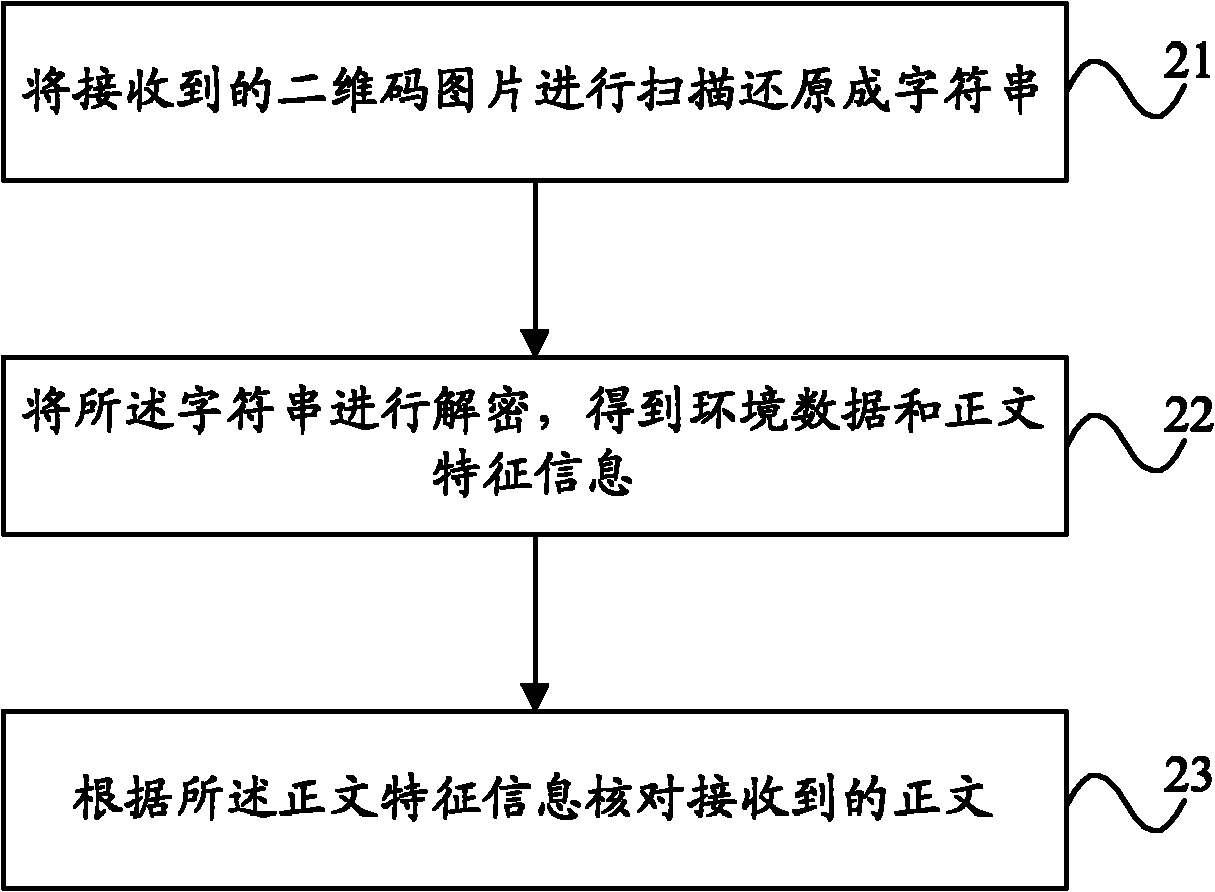
InactiveCN102073977AHighlight the effect of personal signatureImage data processing detailsTransmissionDigital signatureValidation methods
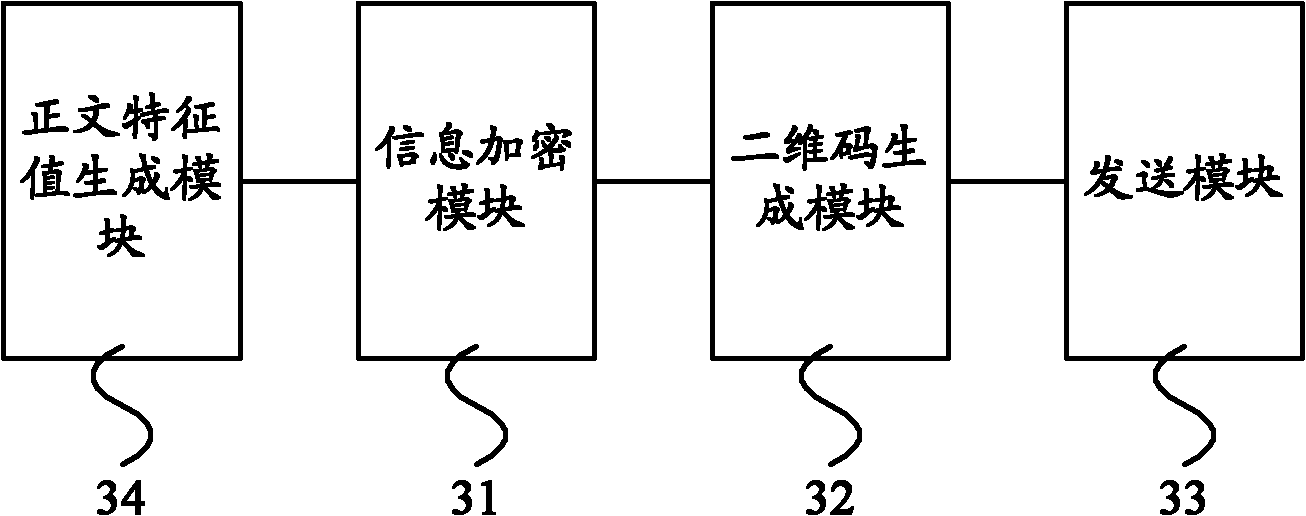
The invention provides methods and equipment for generating and authenticating digital signatures and a digital signature system. The method for generating digital signatures comprises the following steps: encrypting and / or coding text characteristic information and environmental data to generate character strings; coding the character strings with two-dimension codes to generate two-dimension code pictures; and using the two-dimension code pictures as digital signatures and sending the two-dimension code pictures together with the text to be sent. The method for authenticating digital signatures comprises the following steps: reducing the received two-dimension code pictures into the character strings through scanning; decrypting the character strings to obtain the environmental data and the text characteristic information; and checking the received text according to the text characteristic information. Compared with the prior art using the character strings as the digital signatures, the invention can realize more effective signature effect by using the two-dimension codes as the digital signatures.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
A method for passive decoy state quantum digital signature
ActiveCN109039604APrevent leakageEliminate Intensity Modulation ErrorsKey distribution for secure communicationUser identity/authority verificationBeam splitterSignal light
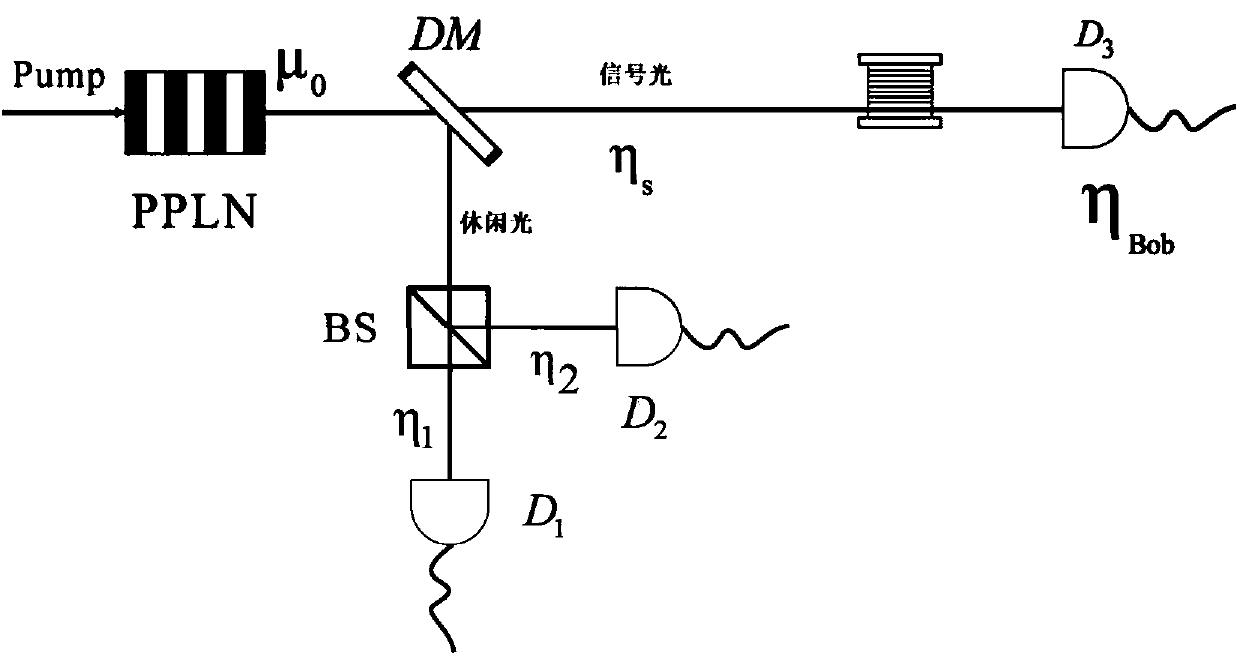
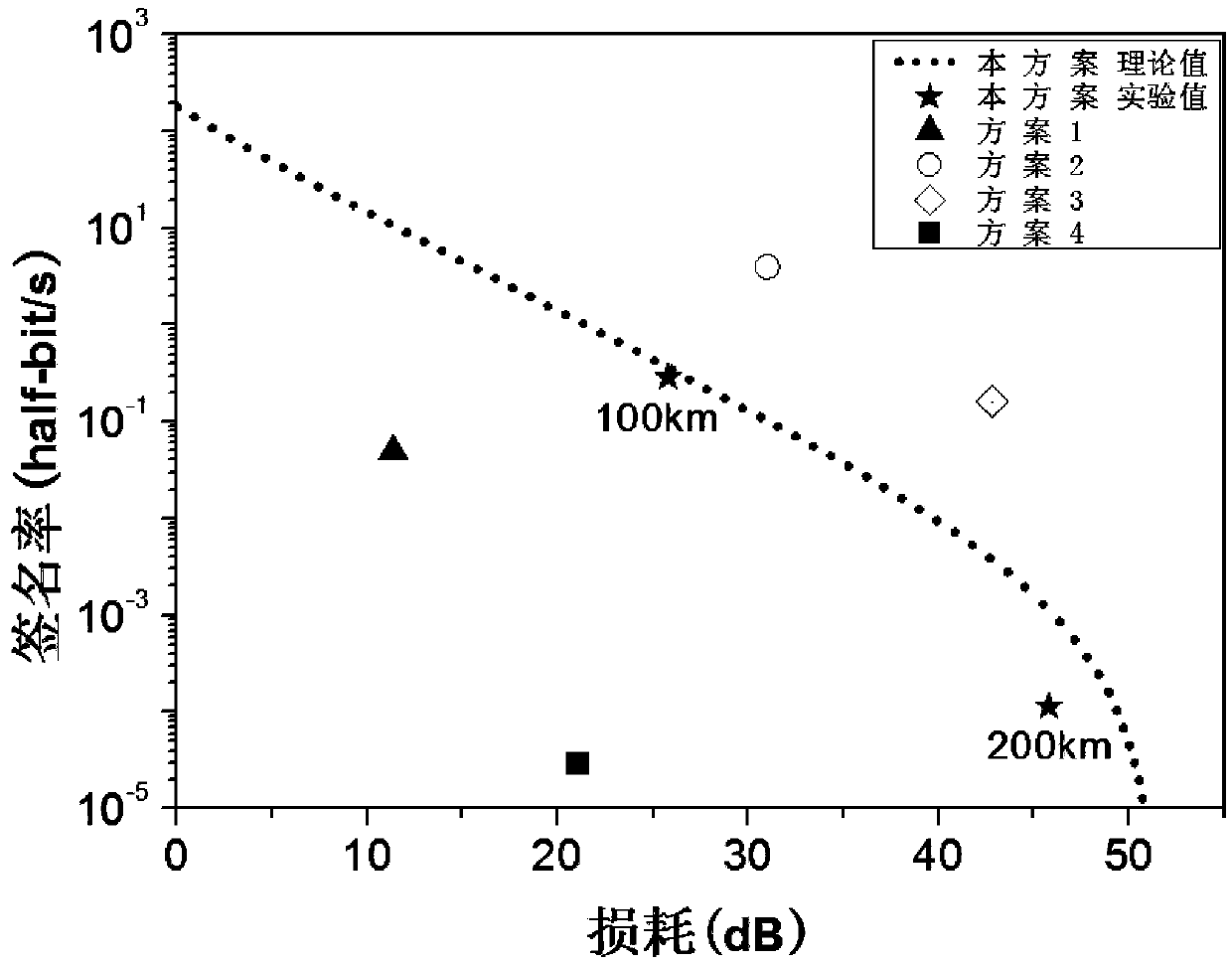
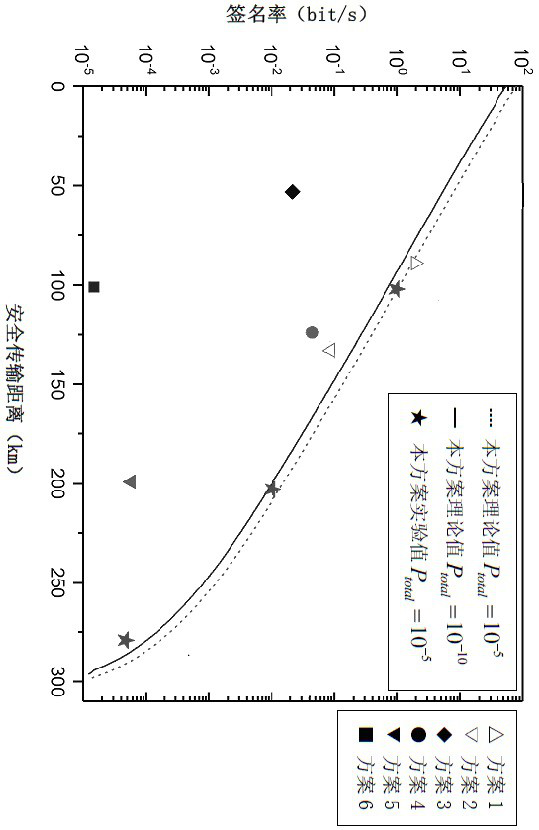
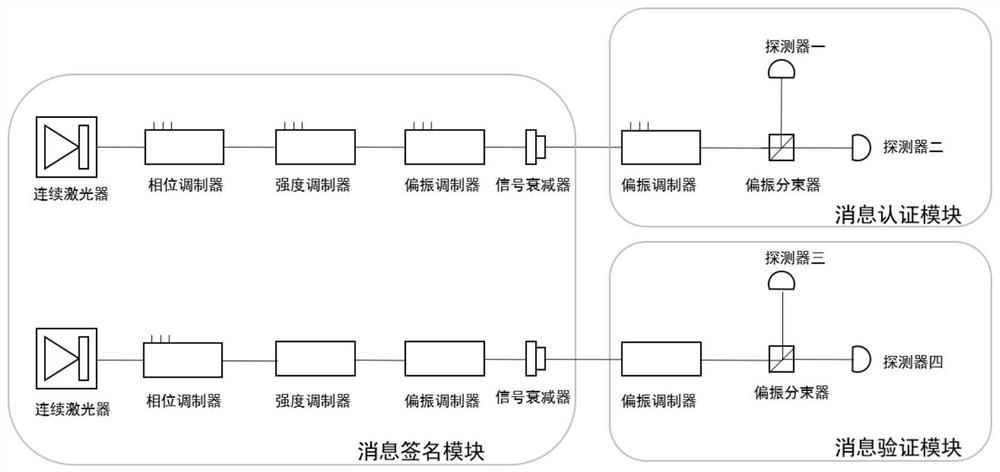
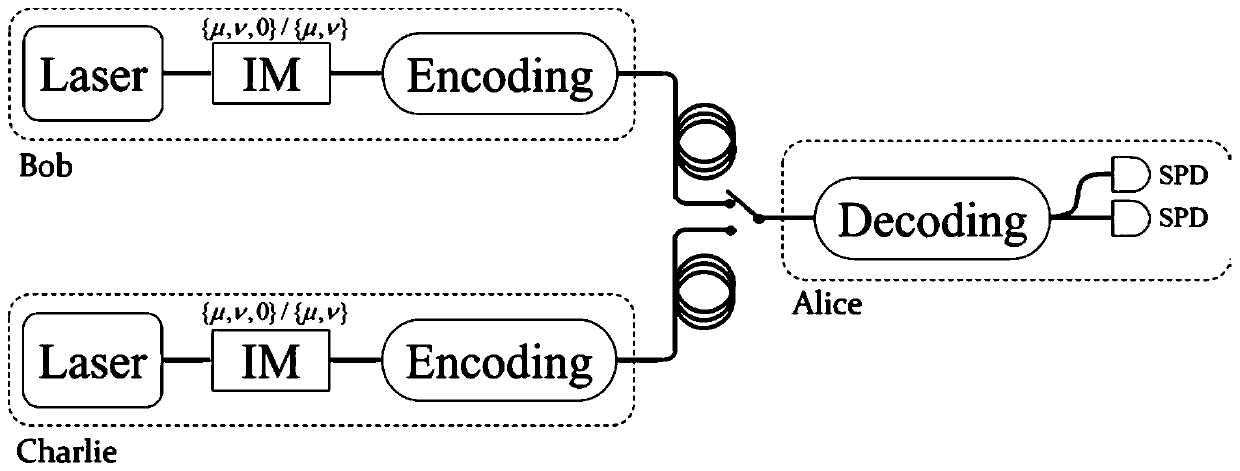
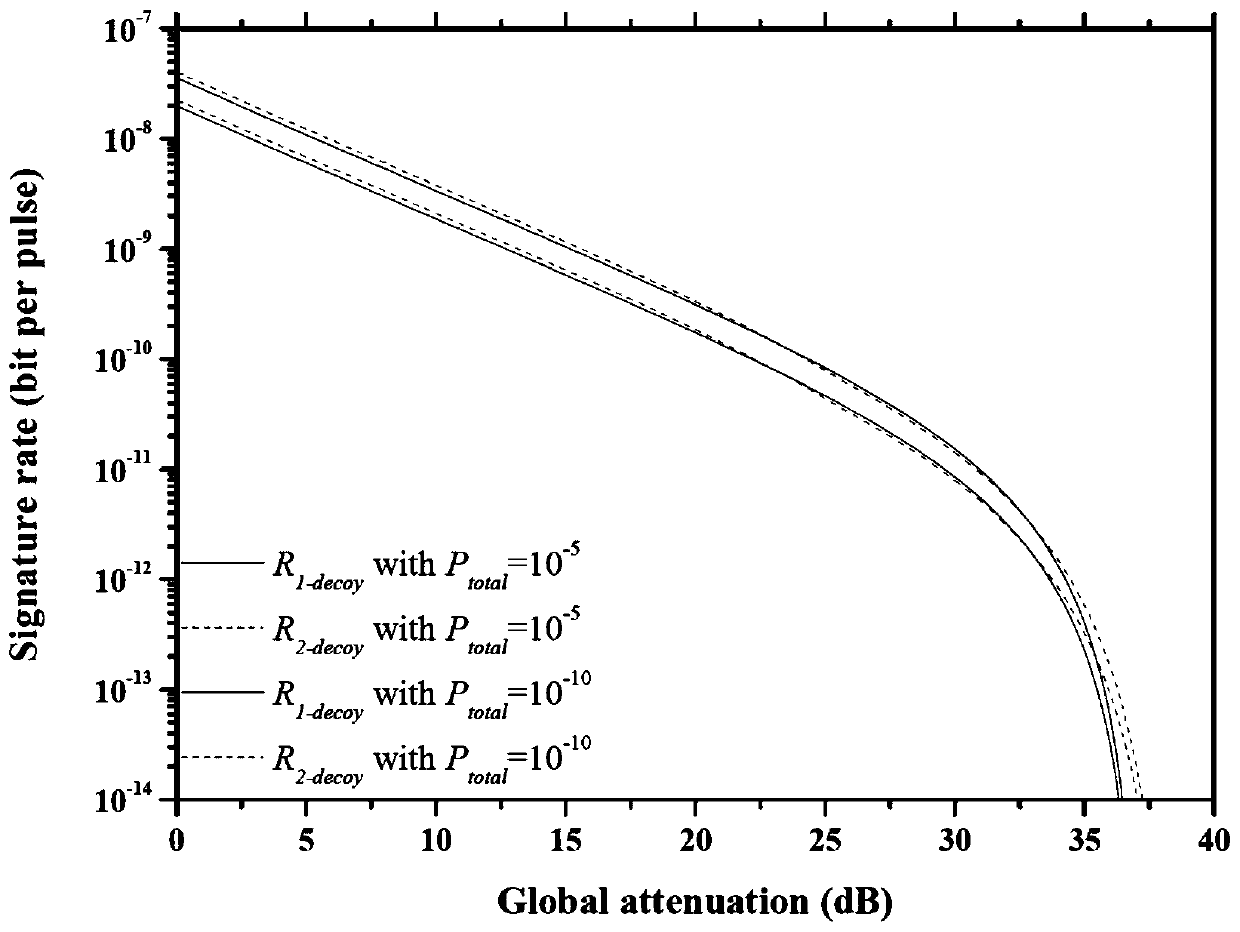
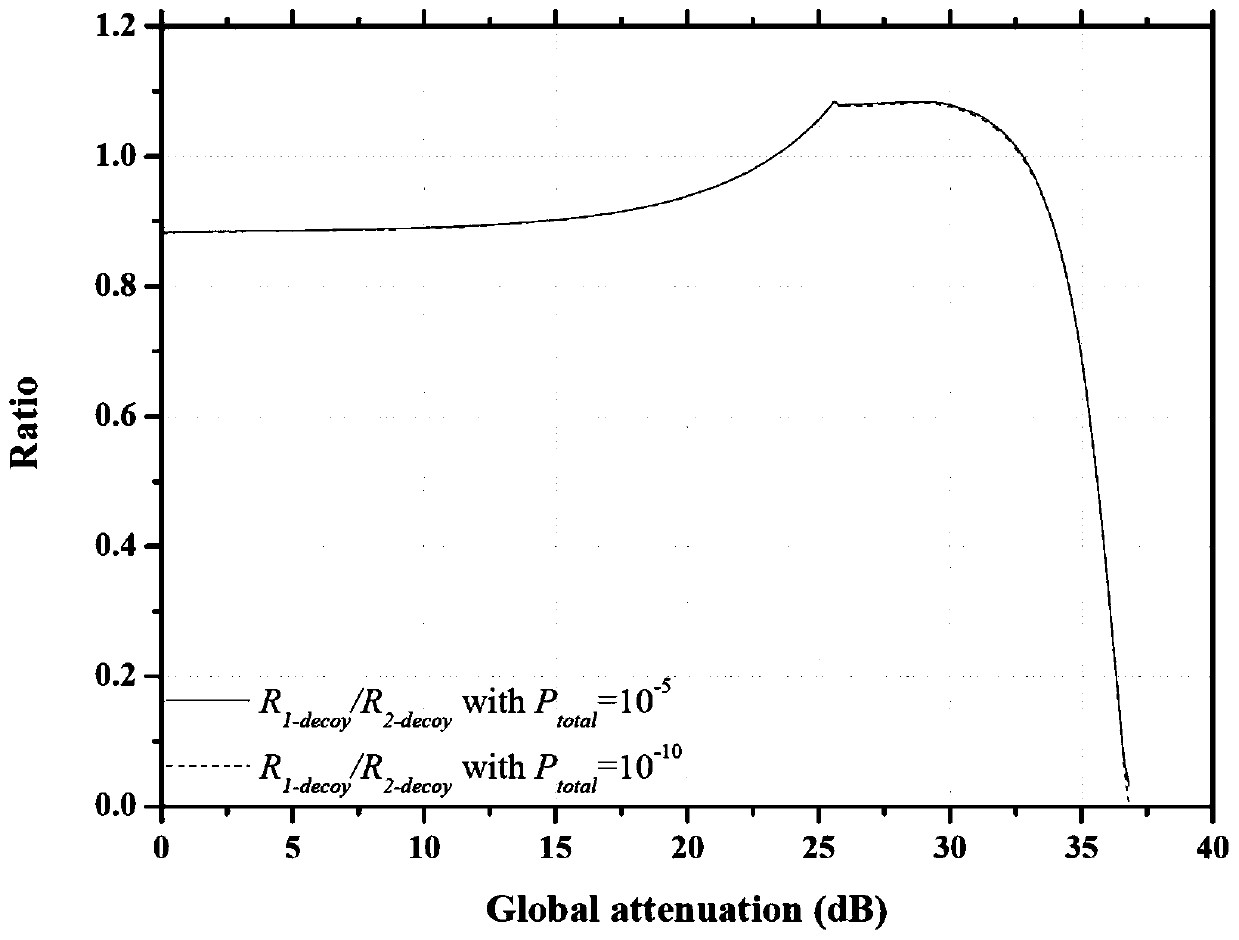
The invention provides a passive decoy state quantum digital signature method, which is applied in a quantum digital signature system. In the key distribution phase of the quantum digital signature, the invention utilizes the parametric down conversion process to generate signal light and casual light, the signal light is sent to the receiving end, and the casual light is used for local detection.The local detection at the transmitting end comprises a beam splitter (BS) and two detectors (D1, D2), After passing through the beam splitter, the casual light triggers two detectors to generate four different response events. The four response events are recorded and utilized to construct a new passive decoy state method, which greatly increases the number of keys that can be used for signatureunder the given security conditions. The method realizes over 200 km passive decoy state quantum digital signatures using a single mode standard commercial optical fiber, and the final signature rateis higher than that of some previous QDS systems. The scheme of the invention applies the passive decoy state technology to a quantum digital signature system for the first time.
Owner:NANJING UNIV OF POSTS & TELECOMM
Mail system based on quantum digital signature and transceiving method
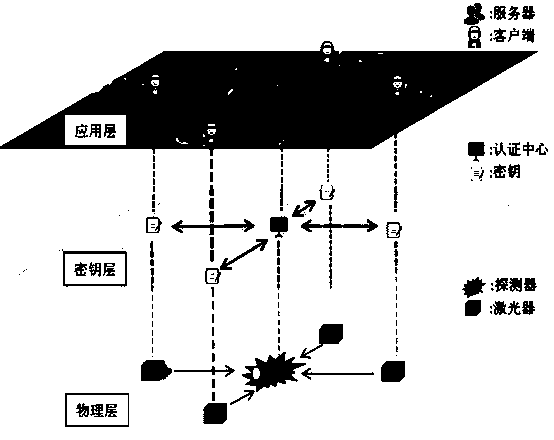
ActiveCN110493010AEnsure safetyKey distribution for secure communicationMultiple keys/algorithms usageDigital signaturePhysical layer
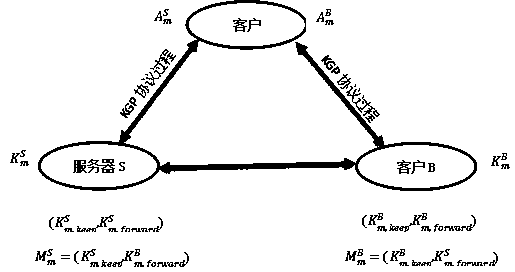
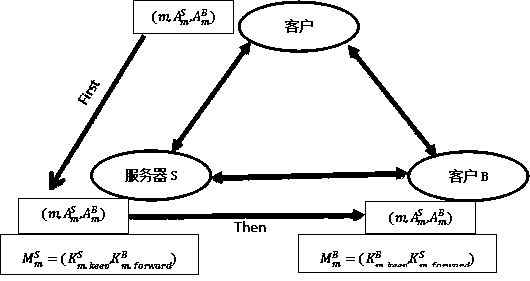
The invention discloses a mail system based on a quantum digital signature and a transceiving method. The system adopts a three-layer structure, namely a physical layer, a key layer and an applicationlayer. The physical layer is a key generation terminal and is responsible for generating a key string for signature in real time. The secret key layer is used for storing a secret key string generated by the physical layer and providing a needed secret key for the upper application layer when needed. The application layer is a software part for receiving and sending of the mail system, and encrypting the information required to be sent by extracting a key generated by the physical layer from the key layer. The mail receiving and sending method comprises a quantum key distribution stage, a mail signature stage and a signature verification stage. Compared with the algorithm signature, the safety of the mail encrypted by the quantum digital signature is more powerfully guaranteed.
Owner:NANJING UNIV OF POSTS & TELECOMM
Message integrity protection method in quantum digital signature
The invention relates to a message integrity protection method in a quantum digital signature. Through initialization, special signature and verification, a start character and an end character are 11, and no illegal codons 10 and 11 are therebetween. The conventional quantum digital signature technical scheme has the problem that the signed message integrity cannot be guaranteed. The message integrity protection method solves the above important problem of safety, provides a technical support for further research and development of the quantum digital signature technology, and has important and extensive application prospect.
Owner:LUOYANG NORMAL UNIV
Quantum digital signature method for untrusted center
ActiveCN106452791AOvercoming the Weakness of Computational ComplexitySafety proofKey distribution for secure communicationUser identity/authority verificationQuantumBit numbering
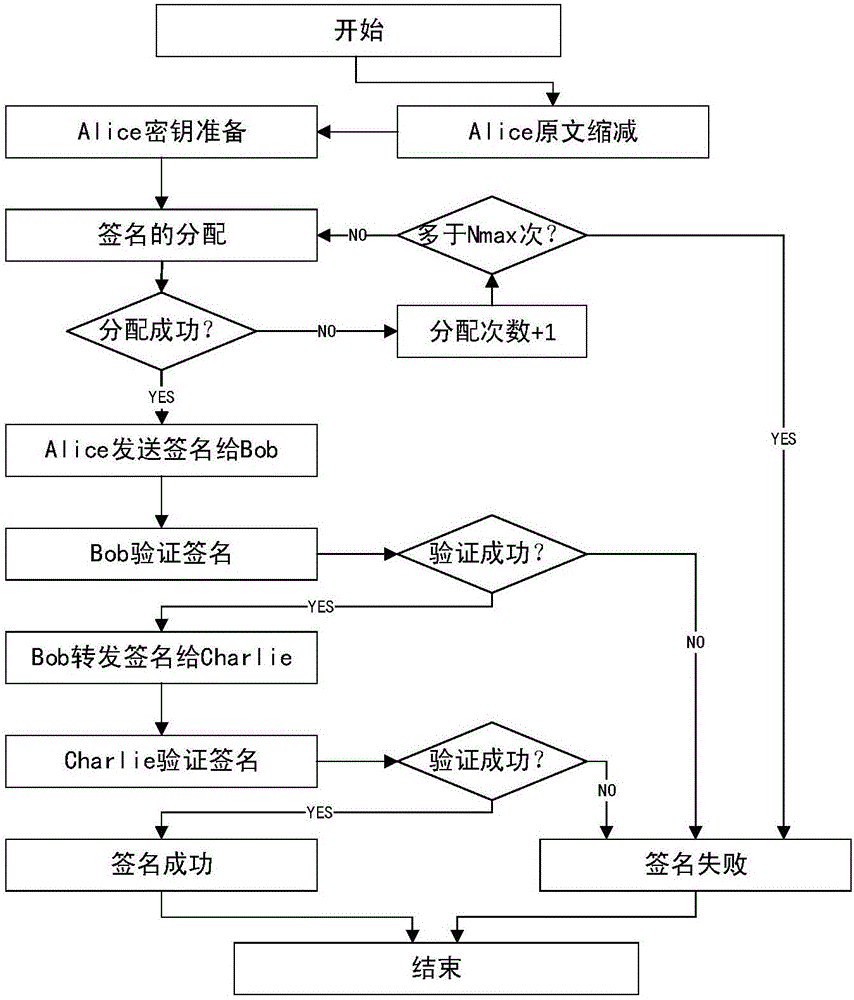
The invention discloses a quantum digital signature method for an untrusted center. The method comprises a distribution phase comprising the following steps: a, a sender operates on an original text to acquire a reduced original text; b, the sender generates signatures and respectively sends the signatures to a receiver and a verifier, wherein the quantity of the signatures is worked out according to a bit number of the reduced original text; and c, the receiver and the verifier mutually exchange a part of the owned signatures; and a verification phase comprising the following steps: d, the sender sends the original text and the signatures generated in the step b to the receiver; e, the receiver operates on the original text to acquire the reduced original text, compares the signatures received in the step d with the owned signatures after exchange in the step c for verification aiming at each bit of the reduced original text; and f, after the verification is passed, the receiver sends the original text and the signatures received in the step d to the verifier for verification. According to the method provided by the invention, consumption of quantum keys and pressure of quantum communication equipment are greatly reduced by reducing the length of the original text.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Quantum digital signature method based on double-field protocol
ActiveCN111541544AImprove transmission distanceImprove securityKey distribution for secure communicationUser identity/authority verificationDigital signatureSecure transmission
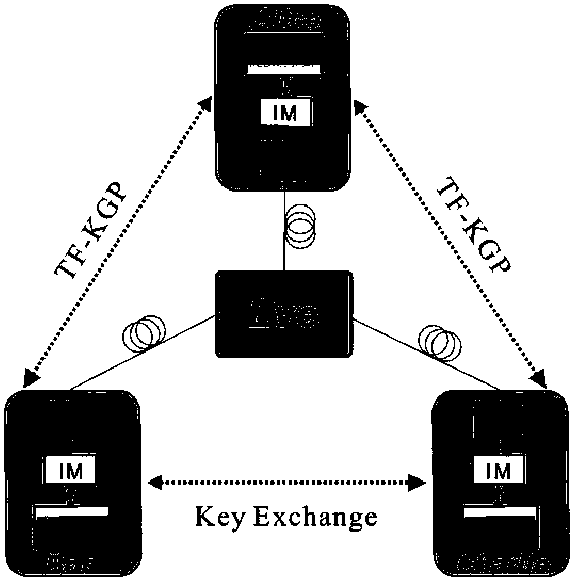
The invention aims to provide a quantum digital signature method based on a double-field protocol. In the secret key distribution stage of a quantum digital signature, a double-field secret key generation protocol (TF-KGP, Twin-Field KGP) is used for completing generation and distribution of secret keys, a user sends a quantum state to a special measuring party for measurement, and the credibilityof the measuring party does not need to be required. From the perspective of security, the TF-KGP is used, so the quantum digital signature system has the property irrelevant to measurement equipment, can resist side channel attacks aiming at the measurement equipment, and improves the security of the quantum digital signature system; from the perspective of practicability, under the same parameter condition, the number of secret keys which can be used for signature is greatly increased, so the secure transmission distance of signature and the signature rate at a long distance are improved, and the practical performance of the quantum digital signature system is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Multi-party quantum digital signature method without trusted center
ActiveCN106452790AOvercoming the Weakness of Computational ComplexitySafety proofKey distribution for secure communicationUser identity/authority verificationQuantumQuantum digital signature
The invention discloses a multi-party quantum digital signature method without a trusted center. The method comprises the following steps: step a, a sender performs operation on an original text to obtain a reduced original text; step b, the sender generates a signature and sends the signature to verification parties separately; step c, each two verification parties exchange the partially owned signature; step d, the sender sends the original text and the signature generated in step b to one verification party; step e, the current verification party performs operation on the received original text to obtain the reduced original text, and performs comparison verification on the signature received from the sender or the previous verification party and the owned signature after the exchange in step c according to each bit of the reduced original text; and after the verification is passed, the other verification parties perform verification in sequence until a preset number of verification parties pass the verification. By adoption of the multi-party quantum digital signature method disclosed by the invention, the problem that a large number of keys are needed in single bit signature is overcome, the multi-party signature demands can be satisfied, and the application scenes are greatly expanded.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Quantum digital signature and quantum digital signcryption method
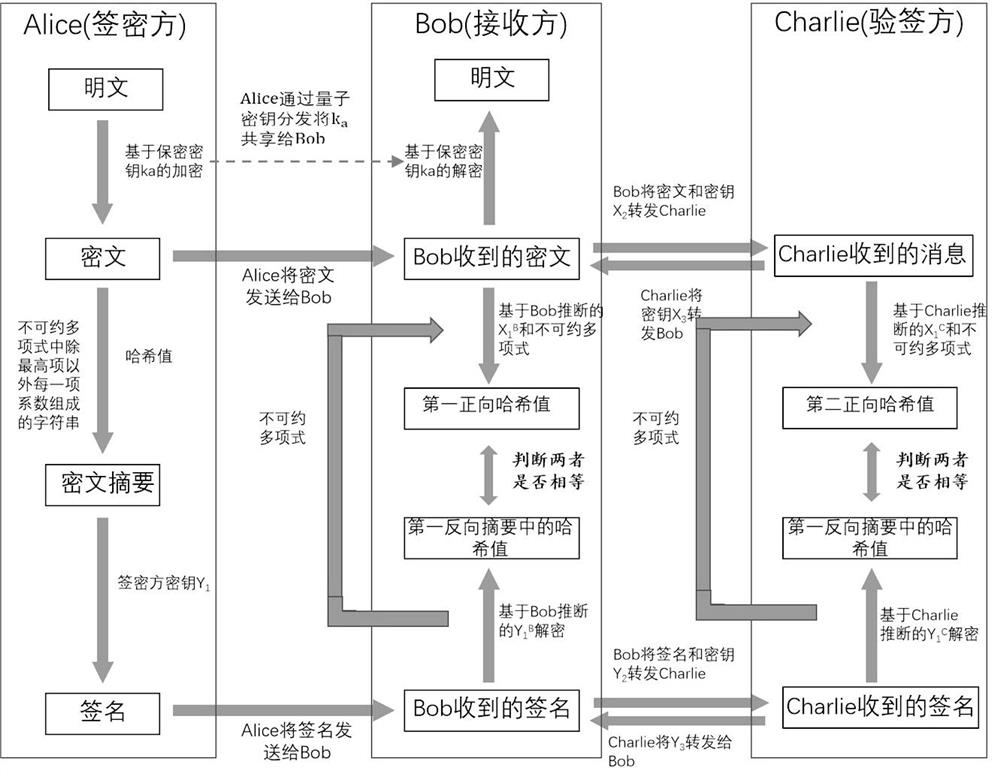
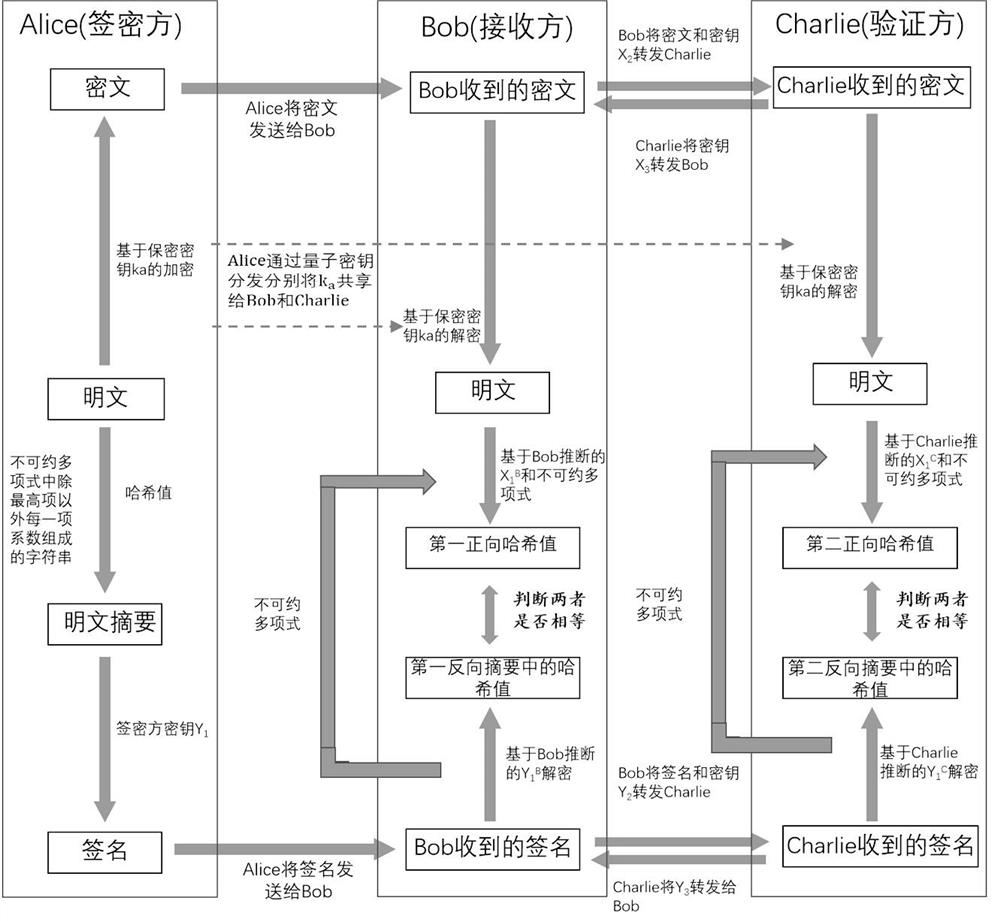
ActiveCN113779645AUnconditionally Secure SigncryptionSecure signcryptionQuantum computersDigital data protectionHash functionAlgorithm
The invention discloses a quantum digital signature and a quantum digital signcryption method. The quantum digital signature comprises the following steps: generating a secret key; generating a digital signature; and verifying the digital signature. The security of the hash function used in the signcryption or signature process is ensured by the irreducible polynomial and the hash function key serving as the input random number, and the irreducible polynomial depends on the local random number and cannot be known by a receiver and a signature verification party in advance before the signcryption or signature process; in other words, the unconditionally secure hash function is used so that the security of the whole signcryption or signature process is ensured, and the security risk caused by leakage of a fixed irreducible polynomial in other signatures is directly avoided; and moreover, the length of the message is not limited when the hash value is generated, the message with any length can be signed or signcrypted in each round of signature or signcryption, and the signature or signcryption efficiency is very high.
Owner:NANJING UNIV +1
Quantum digital signature system resistant to polarization disturbance
PendingCN113347005AThe structure is simple and identicalEasy to prepare in large batchesKey distribution for secure communicationUser identity/authority verificationTelecommunicationsDigital signature
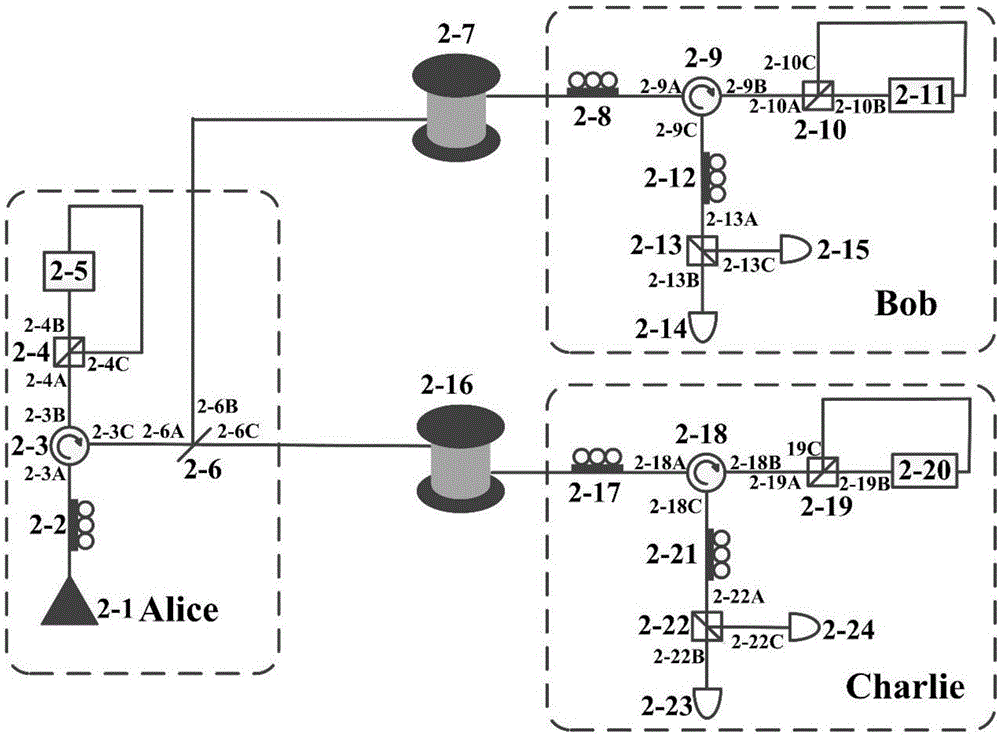
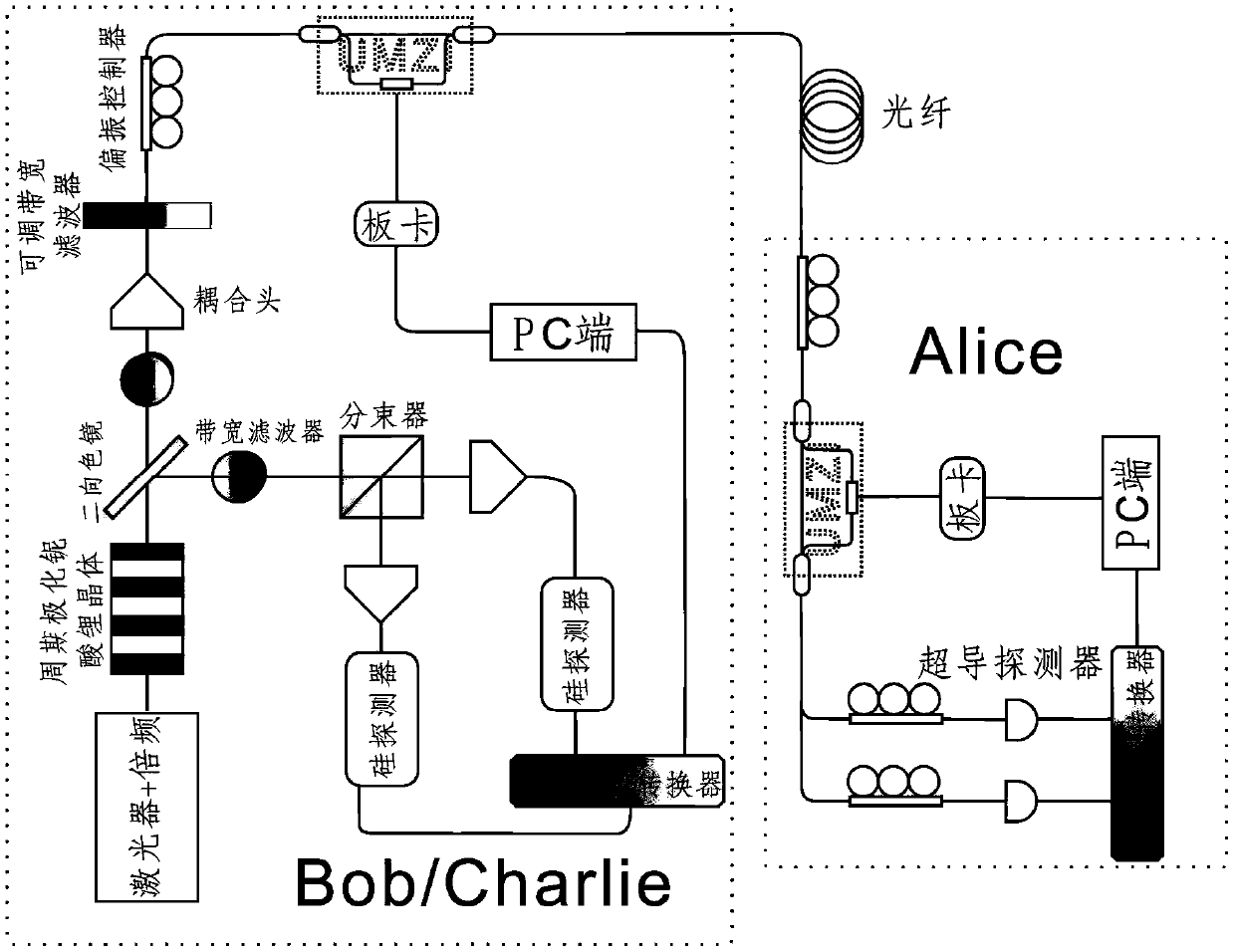
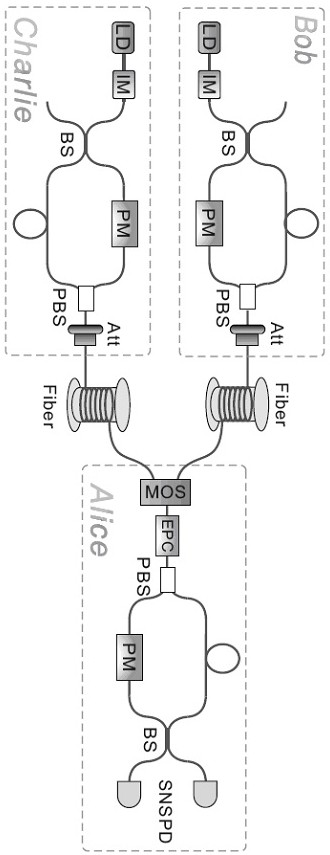
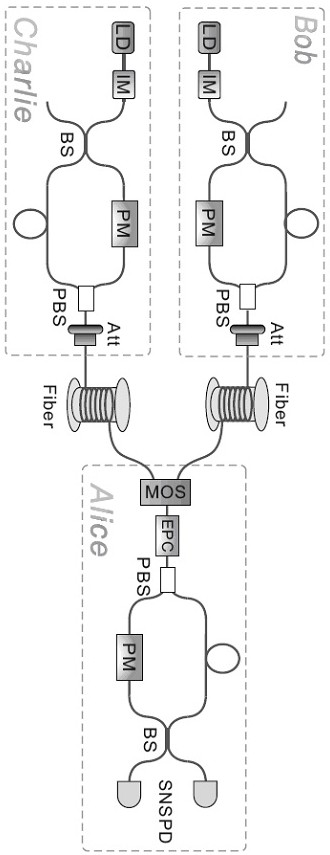
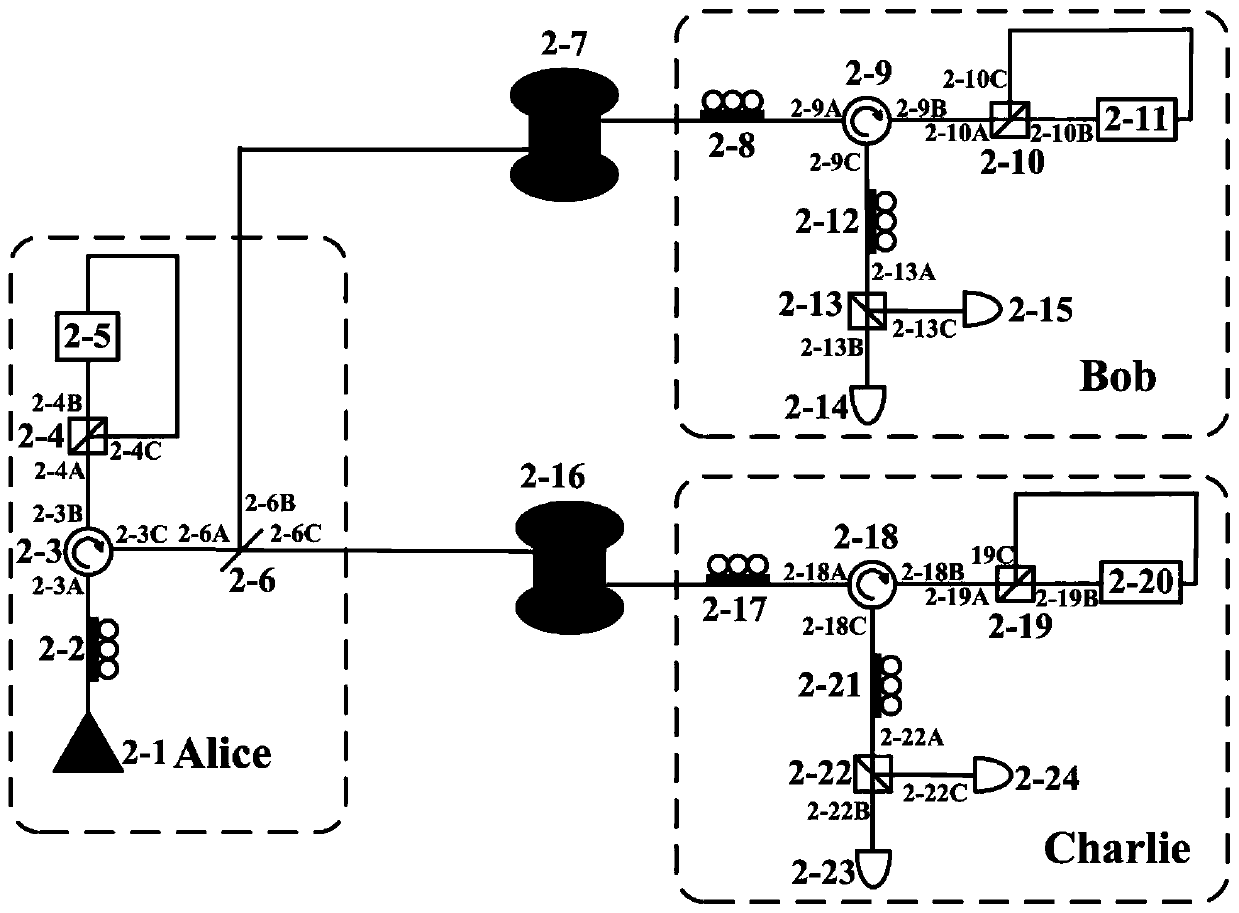
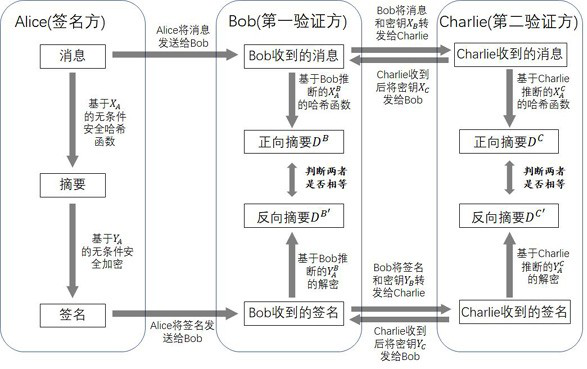
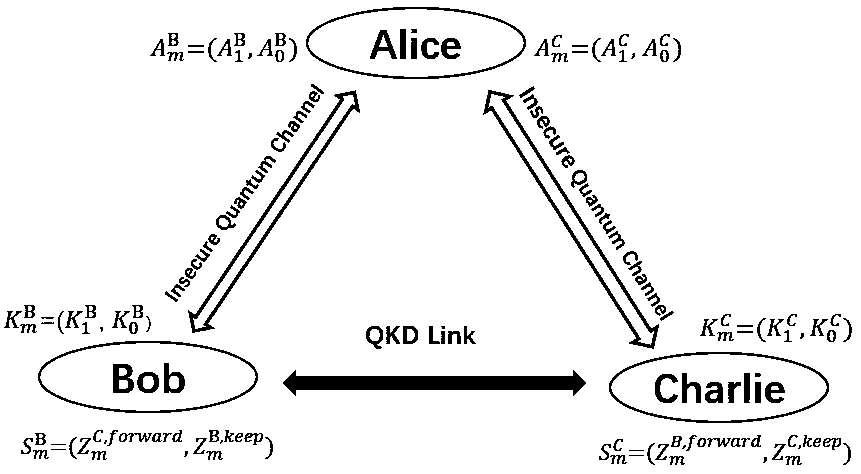
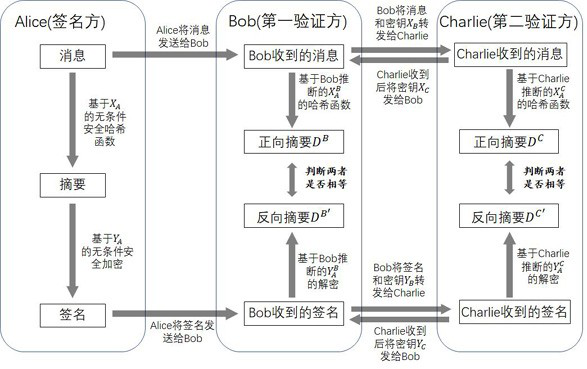
A quantum digital signature system resistant to polarization disturbance comprises a message sender Alice, two message receivers Bob and a receiver Charlie, the sender Alice sends a message to the receiver Bob and the receiver Charlie in combination with a digital signature, the receiver Bob serves as a message authenticator and forwards information sent by the sender Alice to the receiver Charlie, and the composition of the receiver Charlie is completely the same as that of the receiver Bob. Compared with the prior art, the quantum digital signature scheme based on the phase coding BB84 quantum key distribution system can resist channel polarization disturbance. The photon polarization state change caused by channel disturbance does not influence the final interference result of the system, namely, the stability of the system can be ensured.
Owner:神盾迅波(北京)量子科技发展有限公司
Single decoy state quantum digital signature method
ActiveCN111865599AExperiment operation is simpleRandom number reductionKey distribution for secure communicationUser identity/authority verificationDigital signatureEngineering
The present invention provides a single decoy state quantum digital signature method provided. In a key distribution stage, efficient parameter estimation and quantum digital signature can be carriedout only by modulating the light source intensity into two intensities, namely a signal state and a decoy state. According to the method, the requirement for preparing the vacuum state in a traditional multi-intensity decoy state quantum digital signature scheme is avoided, the difficulty of experiment implementation is lowered, and meanwhile consumption of random numbers is reduced. According tothe invention, a low-loss unequal-arm Mach-Zehnder interferometer and a real-time polarization compensation method are used to realize efficient key transmission and signature. The system provided bythe invention is simple to implement and stable in operation, and successfully realizes higher signature rate and farther transmission distance on the premise of meeting the safety requirements of non-repudiation, unforgeability and transferability of a quantum digital signature protocol compared with the previous work.
Owner:NANJING UNIV OF POSTS & TELECOMM
A quantum digital signature method and system
ActiveCN105007158BKey distribution for secure communicationUser identity/authority verificationComputer hardwareMessage authentication code
The invention provides a quantum digital signing method and system. For a pre-signing message m, m is equal to 0 and 1, a message signing module prepares two quantum state sequences with replicability and sends to a message authentication module and a message verifying module respectively; the message authentication module and the message verifying module measure quantum bit coding states and calculate the determinacy of the quantum bit coding states according to measured bits, and the message authentication module and the message verifying module respectively calculate the relevance of the measured bits based on the determinacy of the quantum bit coding states; when the relevance meets requirements, for a signing message m, m is equal to 0 or 1, the message authentication module authenticates the signing message m according to comparison between a corresponding authentication bit string and the basic bit string of the message signing module; after the authentication is successful, the message verifying module verifies the signing message m according to comparison between a corresponding verifying bit string and the basic bit string of the message signing module. The quantum digital signing method and system overcomes all technical challenges of the existing quantum digital signing schemes.
Owner:INST OF ADVANCED TECH UNIV OF SCI & TECH OF CHINA
Methods and apparatus for validating a digital signature
ActiveUS9768965B2User identity/authority verificationDigital data protectionDigital signatureDocumentation
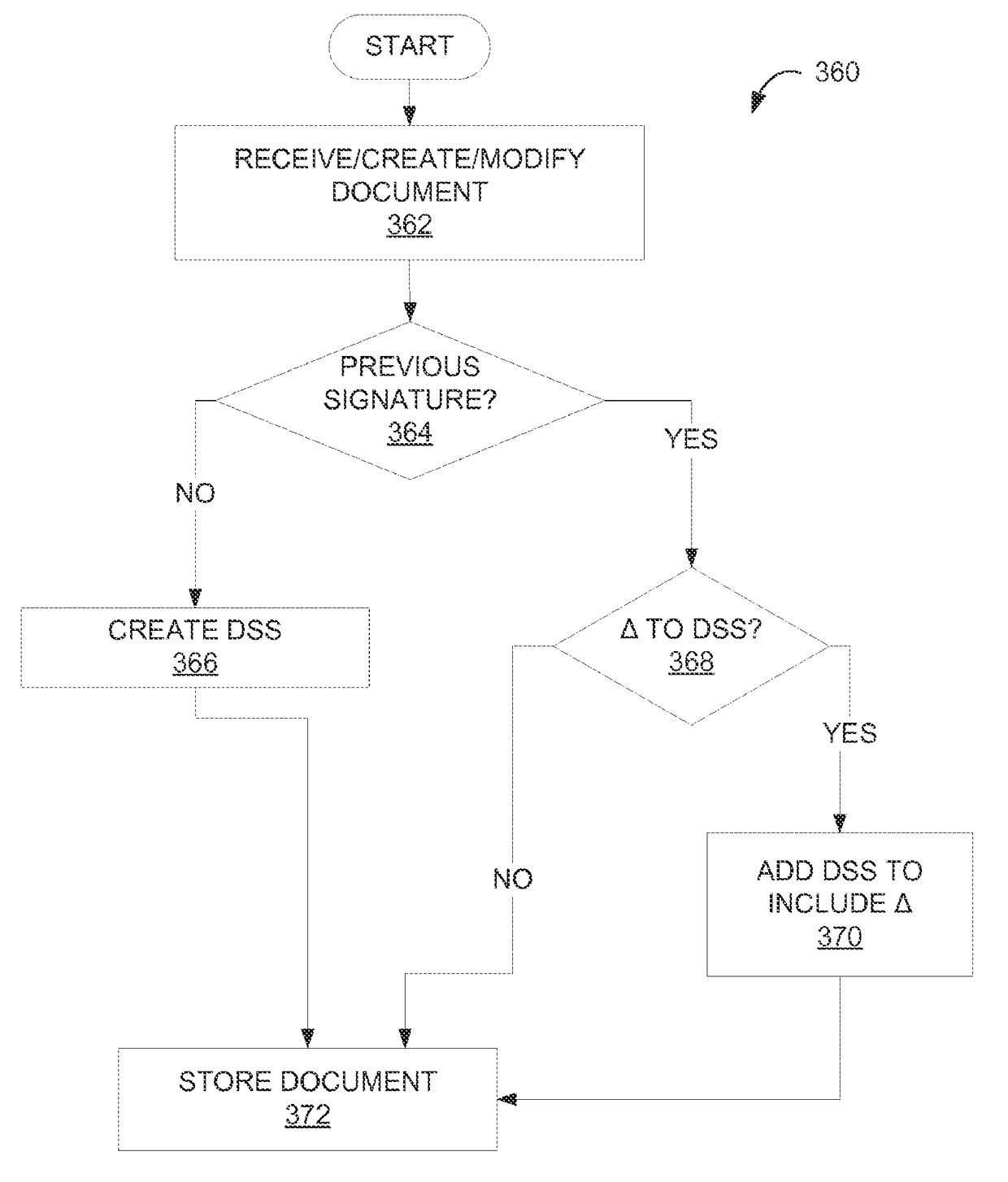
Various embodiments include one or more of systems, methods, software, and data structures for validating a digital signature, wherein common information in a certification chain is maintained in one entry of a Document Secure Store (DSS). The DSS separates the Long Term Validation (LTV) information from the digital signature, allowing amendment of and addition to the LTV information in the DSS after a digital signature is applied to a document.
Owner:ADOBE SYST INC
A public key arbitration quantum signature protocol based on quantum block encryption
ActiveCN109787770ASave resourcesEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey distributionProtocol for Carrying Authentication for Network Access
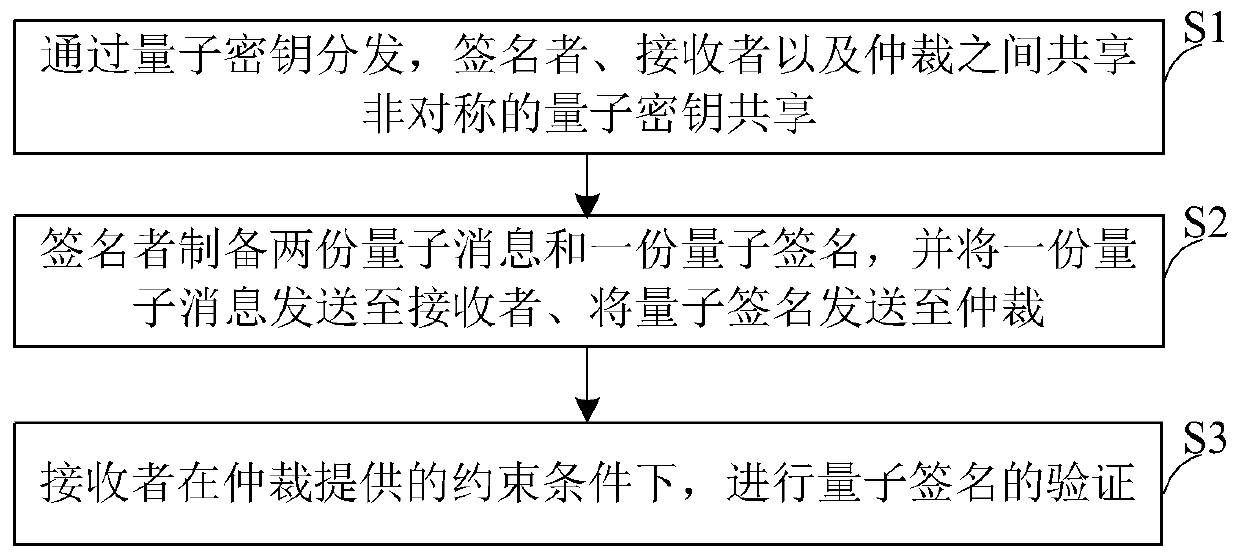
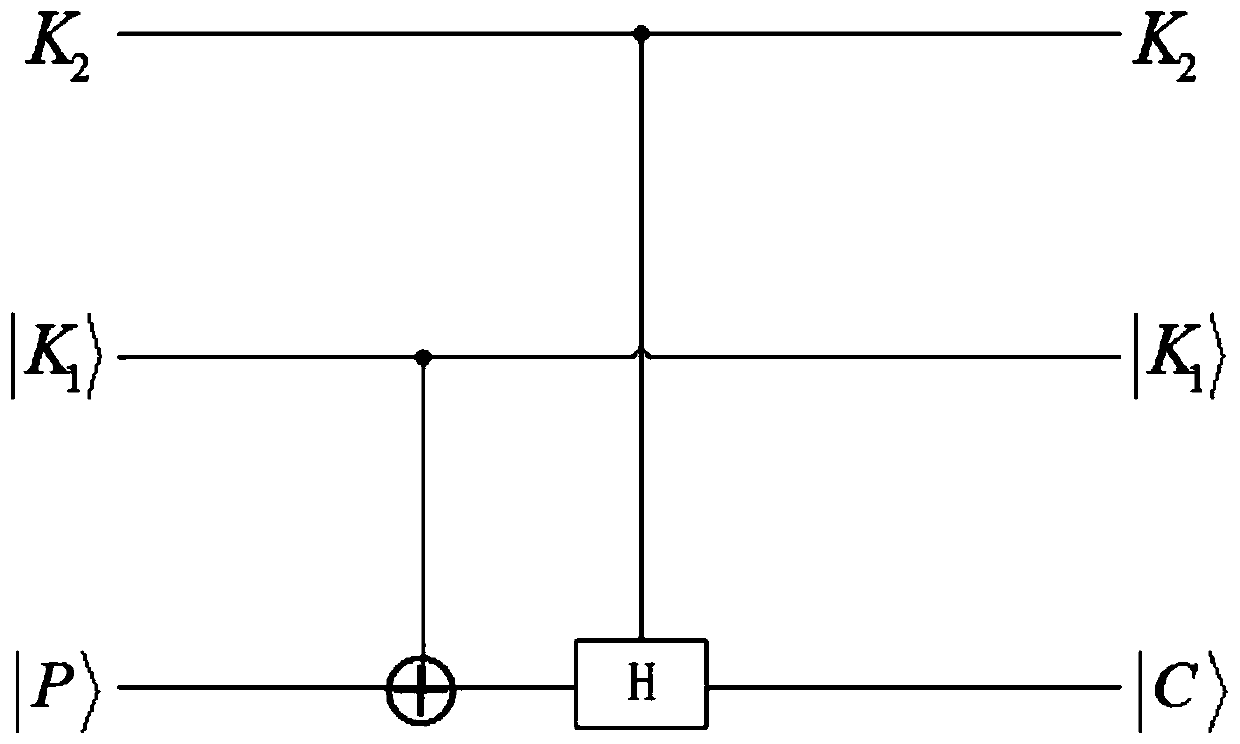
The invention discloses a public key arbitration quantum signature protocol based on quantum block encryption, which belongs to the technical field of quantum secret communication and comprises quantum key sharing among a signer, a receiver and arbitration through quantum key distribution. The signer prepares two parts of sub-messages and one part of sub-signature, sends one part of sub-message tothe receiver and sends the quantum signature to arbitration; And the receiver verifies the quantum signature under the constraint condition provided by arbitration. The protocol provided by the invention not only can ensure the security, but also has a better practical application value.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +6
Quantum digital signature method
ActiveCN113297633AUnconditional Security GuaranteedImprove signature efficiencyQuantum computersDigital data protectionComputer hardwareDigital signature
The invention discloses a quantum digital signature method, and belongs to the technical field of quantum security. In order to solve the problem that in the prior art, the security of a digital signature protocol and the efficiency of signing a message are generally not high, the invention provides a quantum digital signature method which comprises the following three steps: preparing a secret key, generating a signature and verifying the signature. The technical scheme provided by the invention is a real unconditional security scheme, solves the problem of low efficiency of the existing unconditional security digital signature protocol, has strong compatibility, can be realized by using various systems, can be realized in the current system, can be harmonious and free in the future quantum internet system, and has very strong application range and prospect in the present stage and in the future.
Owner:NANJING UNIV +1
High-efficiency quantum digital signature method and system
ActiveCN112468292AReduce lossReduce wasteKey distribution for secure communicationUser identity/authority verificationComputer hardwareDigital signature
The invention provides a high-efficiency quantum digital signature method and system, and the method comprises the steps that a message signature module prepares two different quantum state sequenceswith the same length, and transmits the two different quantum state sequences to a message authentication module and a message verification module; and then a data post-matching method is adopted to associate the quantum state sequences received by the message authentication module and the message verification module, and the condition that the message authentication module and the message verification module need to respond to a single pulse sent by the message signature module at the same time is removed. By adopting the scheme provided by the invention, the quantum states received by the message authentication module and the message verification module can be completely used for code forming after being matched, so that the key loss is reduced; in addition, the message signature modulecan separately select the pulse parameters sent to the other two modules and the length of the sent quantum state sequence, and can be implemented in a scene with asymmetric channels.
Owner:NANJING UNIV
Quantum digital signature method using marked single photon source
ActiveCN110086614AIncrease in signature rateIncreased safe transmission distanceKey distribution for secure communicationUser identity/authority verificationSpontaneous parametric down-conversionKey distribution
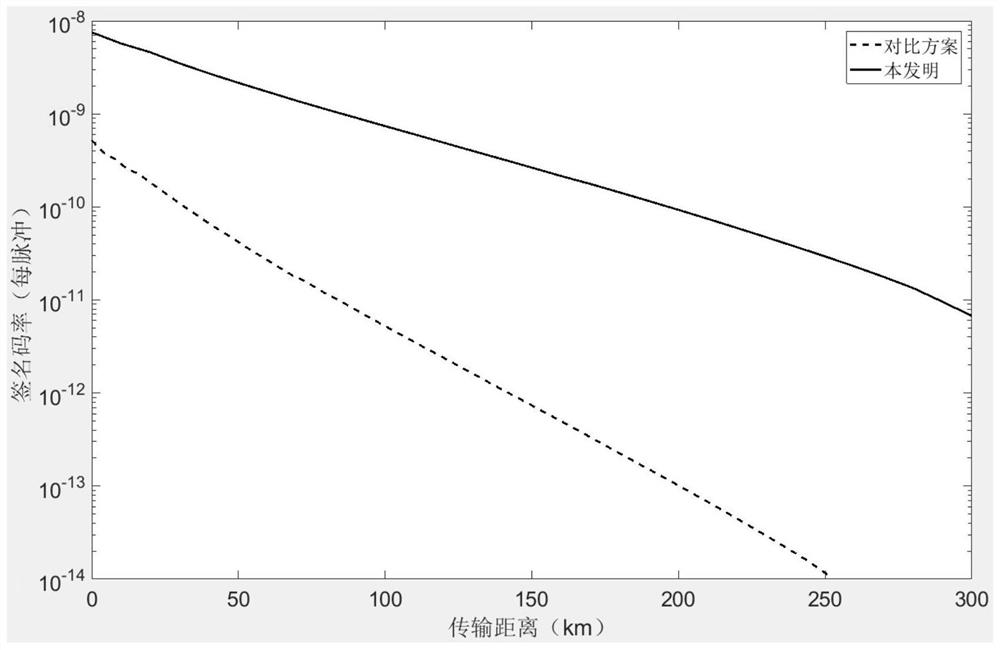
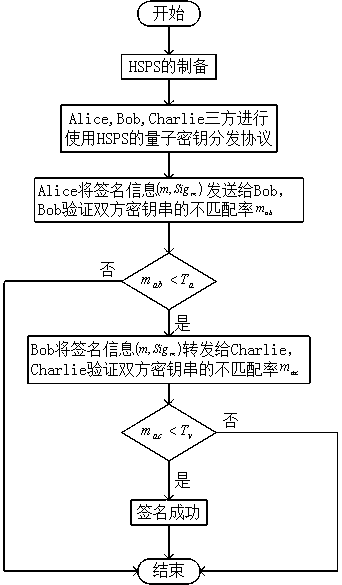
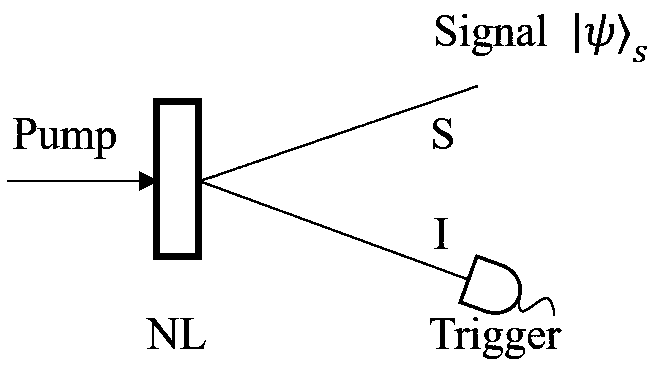
A quantum digital signature (QDS) method using a labeled single photon source (HSPS) is divided into a preparation phase of the HSPS, a key distribution phase using a QDS scheme of the HSPS, and a signed message phase. Firstly, HSPS is obtained through down-conversion of spontaneous parameters, and after the marking effect is achieved, most of vacuum pulses are effectively eliminated. A key distribution protocol (KGP) is then performed on this basis such that participants in the signature protocol all obtain signed key strings. Finally, the transmission, verification and receiving (refusal) process of the signature information is carried out, and on the premise that the security of non-repudiation, unforgeability and transferability of the QDS protocol is met, whether the signature is valid or not is judged by comparing the mismatching rate between the key strings of the two parties. Compared with an existing QDS scheme using a weak coherent light source (WCS), the scheme has the advantages that the vacuum state proportion is reduced to a greater extent, the safe transmission distance is greatly increased, the method is efficient, feasible, simple and easy to operate, and a certainreference value is provided for the practicability of quantum cryptology.
Owner:NANJING UNIV OF POSTS & TELECOMM
Decoy state configurable quantum digital signature method
ActiveCN111447056AExperiment operation is simpleEasy to operateKey distribution for secure communicationUser identity/authority verificationComputer hardwareDigital signature
The invention discloses a decoy state configurable quantum digital signature method. The method comprises a distribution stage and an information stage. The distribution stage comprises the followingsteps that: a sender prepares information to be signed into a quantum state and sends the quantum state to a receiver; the sender and a receiver perform basis matching through a channel to obtain a key; the sender and the receiver process the key to obtain an estimated bit error rate; and the key is updated through the estimated bit error rate. The information stage comprises the following steps that a verifier verifies signature information sent by a signer through a secret key; if the verification succeeds, the verifier receives the signature message and sends the signature message to a receiver; and the receiver verifies the signature message according to the key, and receives the signature message if the verification succeeds. In the quantum state preparation stage of the quantum digital signature, the purposes of improving the signature rate and simplifying system operation are achieved by configuring different numbers of decoy states.
Owner:NANJING UNIV OF POSTS & TELECOMM
Quantum key negotiation method, quantum key negotiation system, quantum digital signature method and quantum digital signature system
ActiveCN114244500ALong transmission distanceFacilitate the realization of long-distance quantum digital signature protocolKey distribution for secure communicationThird partyDigital signature
The invention provides a quantum key negotiation method, a quantum key negotiation system, a quantum digital signature method and a quantum digital signature system. According to the key negotiation method, an untrusted relay is introduced to serve as a third party, interference measurement is carried out on a coherent state and reference light sent by a sending end and a receiving end, and a phase plate difference value PR of a sending party and a receiving party is determined; constructing a calculation model based on the PR, and determining a flip processing mode of the receiver on the held bit string according to the measurement result of the untrusted relay and the calculation result of the calculation model; and finally, the sender and the receiver perform parameter estimation, error correction and privacy amplification based on the held bits to obtain keys of the sender and the receiver. The security of the key negotiation method is irrelevant to the measurement equipment, and the security of the generated key can also be ensured in the presence of an untrusted third party. In the signature method, a Toeplitz matrix is generated by using the key obtained by the key negotiation method, a digital signature can be generated for a message with the longest 264 bits, and the method has very high efficiency and practicability.
Owner:NANJING UNIV +1
Non-PKI digital signatures and information notary public in the cloud
InactiveUS9049027B2High user acceptanceMinimizes user information coordination and managementUser identity/authority verificationDocumentation procedureDigital signature
A digital signature is applied to digital documents / information. In certain instances, juridically strong digital signatures are achieved. Cloud computing technologies may be used to aid in the production of the cryptographically secure, authenticated digital signatures. Digital signatures may be produced with a digital notarization. The techniques of generating a digital signature may not require the use of traditional public key infrastructure (PKI).
Owner:ZENERJI
A new quantum electronic contract signing method
InactiveCN105591756BImprove securityKey distribution for secure communicationUser identity/authority verificationElectronic contractsDigital signature
A novel quantum electric contact signing method improves the scheme security through an initialization phase, a commitment phase, and an arbitration phase no longer based on mathematics problems of integer factorization or discrete logarithm. The novel method no longer needs both sides to exchange digital signatures on the information such as the contact beforehand, thus the technology of the invention no longer depends on the present quantum digital signature technology, and the scheme efficiency is improved.
Owner:LUOYANG NORMAL UNIV
A Quantum Digital Signature Method
ActiveCN113297633BUnconditional Security GuaranteedImprove signature efficiencyQuantum computersDigital data protectionDigital signatureTheoretical computer science
The invention discloses a quantum digital signature method, which belongs to the technical field of quantum security. Aiming at the problem that the security of the digital signature protocol and the efficiency of signing messages are generally not high in the prior art, the present invention provides a quantum digital signature method, which includes the following three steps: preparing a key, generating a signature, Verify the signature. The technical solution of the present invention is a real unconditional security solution, which solves the problem of low efficiency of the existing unconditional security digital signature protocol. This solution also has strong compatibility and can be realized by using various systems. It can be realized in the system, and it can also be harmonious and comfortable in the future quantum Internet system. It has a strong application scope and prospect at this stage and in the future.
Owner:NANJING UNIV +1
Quantum digital signature system and method based on Gaussian modulation and homodyne detection
PendingCN113572606ANo loss of securityImprove signature efficiencyKey distribution for secure communicationUser identity/authority verificationHash functionTelecommunications
The invention discloses a quantum digital signature system and method based on Gaussian modulation and homodyne detection, wherein the technology adopted by the digital signature system is different from the existing quantum digital signature technology, and the digital signature system generates a new hash function every time an abstract is generated; then, the generated abstract is combined with the secret key to perform the XOR encryption operation to obtain the signature, the length of the message is not limited when the abstract is generated, the message with any length can be signed in each round of signature, and the signature efficiency is very high; meanwhile, compared with the existing digital signature technology based on the asymmetric cryptosystem, the method provided by the invention adopts a Gaussian modulation mode to generate a security key, and unconditional security can be ensured while multi-bit messages are signed in one round of signature; furthermore, the digital signature system is based on the homodyne detection technology, so that the digital signature system can be realized by adopting the traditional optical communication technology, no extra instrument is needed, and large-scale deployment on the current optical communication network is facilitated.
Owner:MATRICTIME DIGITAL TECH CO LTD
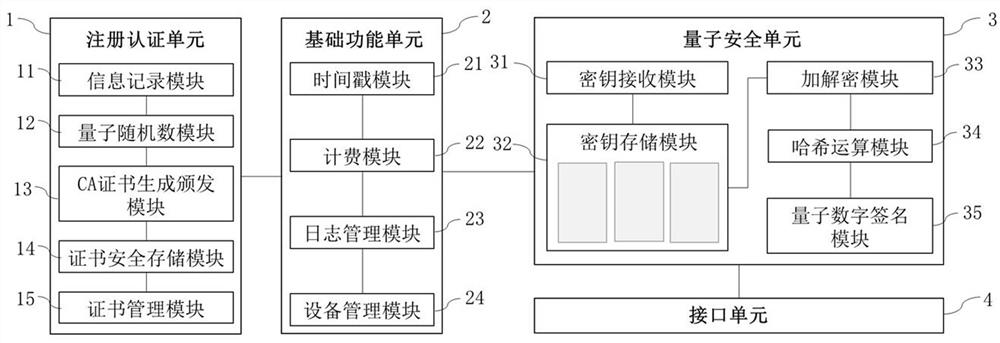
Digital certificate generation method, identity authentication method, quantum CA authentication center and quantum CA authentication system
ActiveCN114254284AImprove securityConvenient certificate managementQuantum computersDigital data protectionInternet privacyDigital signature
The invention provides a digital certificate generation method, an identity authentication method, a quantum CA authentication center and a quantum CA authentication system, and each CA authentication center is used for providing a message authenticity authentication function, namely a quantum digital signature service based on trusted identity authentication. The CA authentication center comprises a registration authentication unit, a basic function unit, a quantum security unit and an interface unit which are connected in sequence. When a signature is initiated between two users, a CA authentication center and two communication parties jointly form a message authenticity verification system, firstly, a signer requests one identity authentication from the CA authentication center, and then quantum security verification is completed on the authenticity of a sent message through the processes of secret key preparation, signature generation and signature verification. And completing the quantum digital signature. According to the invention, the CA needs to issue a trusted identity certificate to each user, but the certificate does not need to be bound with a secret key for verifying the signature, so that the certificate management of the CA with quantum security is more convenient.
Owner:NANJING UNIV +1
Fault-tolerant quantum digital signature method capable of resisting collective noise
ActiveCN113300849AEasy to implementImprove practicalityKey distribution for secure communicationUser identity/authority verificationTelecommunicationsDigital signature
The invention discloses a fault-tolerant quantum digital signature method capable of resisting collective noise. The fault-tolerant quantum digital signature method specifically comprises the following steps: step 1, a sender Alice generating a quantum signature and sending the quantum signature to a receiver Bob and a receiver Charlie; step 11, Alice generating two same copy sequences; step 12, the sender Alice sending the quantum signature to the receiver Bob and the receiver Charlie respectively; step 13, the receiver Bob and the receiver Charlie randomly selecting half of the received quantum signatures and sending the quantum signatures to the receiver Bob and the receiver Charlie; step 14, for all signature elements in the hand at present, the receiver Bob and the receiver Charlie being measured; step 2, the sender Alice sending an information private key pair (k, PKk) to the receiver Bob, and when the Bob meets the receiving condition, forwarding the information private key pair (k, PKk) to the receiver Charlie. According to the method disclosed by the invention, the decoherence-free subspace is introduced, and the physical quantum states with the same noise factor are utilized to form the logic quantum state, so that the quantum information is not influenced by collective noise in the transmission process, and the fidelity of the communication process is improved.
Owner:NORTHWEST UNIV
A Blindly Verifiable Encrypted Signature Method Based on Blockchain
InactiveCN107040383BPrivacy protectionPublic key for secure communicationUser identity/authority verificationAlice and BobDigital signature
The invention relates to a blind verifiable cryptographic signature method based on a block chain. The method includes three parties: a signer Alice, a signature extractor Bob, and a block chain verifier. The method is implemented in the following steps: Alice and Bob negotiate a message to be signed and generate their own key pairs respectively according to system parameters; Alice and Bob generate signature tags; Alice generates a blind verifiable cryptographic signature that matches the signature tag; the block chain verifier verifies the validity of the cryptographic verifiable cryptographic signature; and Bob extracts a digital signature from the blind verifiable cryptographic signature. The method can be used to construct a fair digital signature exchange protocol that protects privacy in a public block chain environment. The method blindens the public key information of the signer so that a node on a block chain cannot obtain the real digital signature and the public key of the signer aside from verifying the validity of the signature, and the privacy protection for the signer is achieved.
Owner:深圳市数峰科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com