Digital certificate generation method, identity authentication method, quantum CA authentication center and quantum CA authentication system
A CA authentication, quantum technology, applied in identity authentication method, quantum CA authentication center and system, and digital certificate generation field, can solve problems such as system management burden, poor practical performance, complex encryption technology upgrade, etc., and achieve the effect of convenient certificate management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
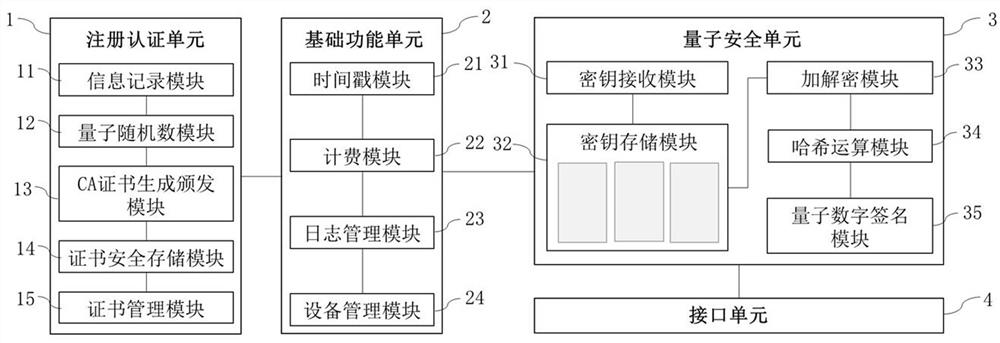
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. It should be understood, however, that the invention may be embodied in various forms, and some exemplary and non-limiting embodiments are shown in the drawings and described below, and are not intended to limit the invention to the specific embodiments described. .
[0038] A quantum-safe CA certification center, the CA certification center is set up in different levels of administrative areas, and the specific number of CA certification centers set up in each level of administrative area is determined by the user scale and business volume of the administrative area. With reference to the actual administrative divisions of our country and the actual situation of the establishment of the existing CA certification center, the present invention constructs a quantum-safe asymmetric key according to the national-provincial two-level model or the nation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com