A method for passive decoy state quantum digital signature
A decoy state quantum, digital signature technology, applied in photon quantum communication, digital transmission system, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
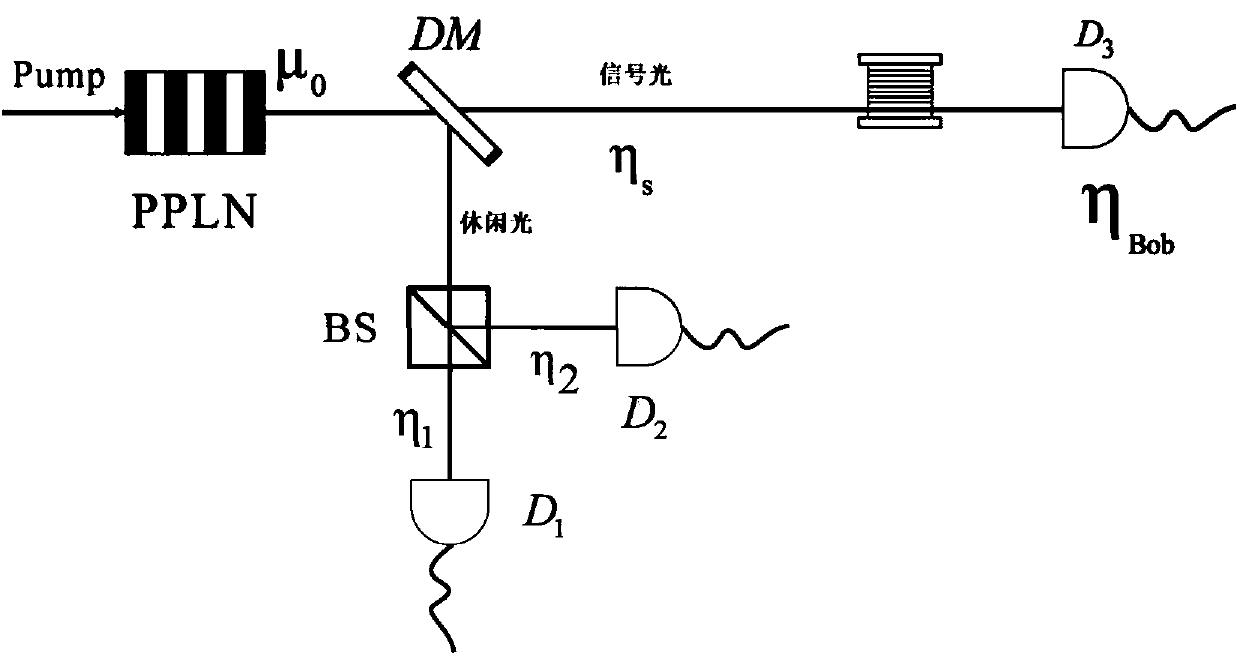
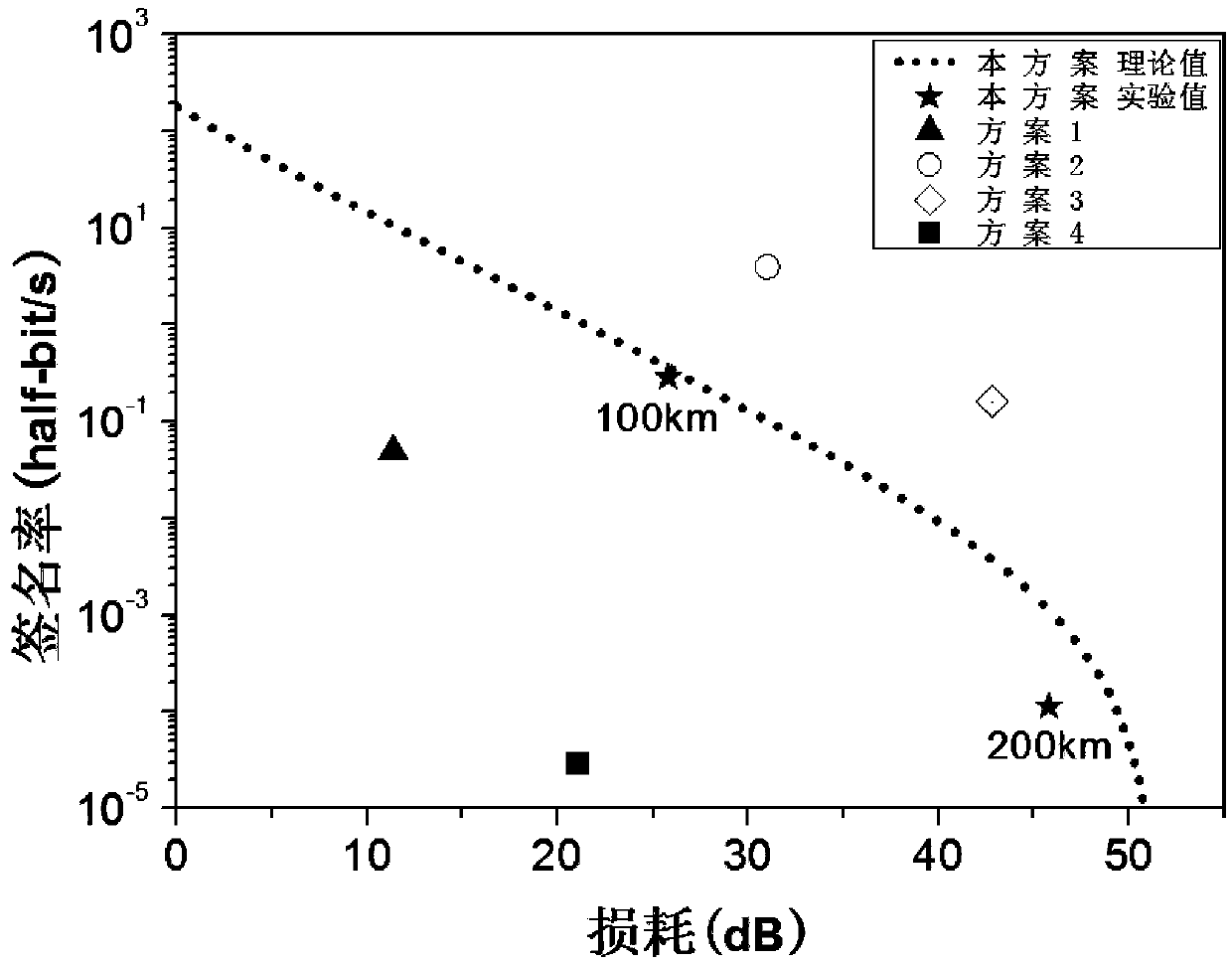
[0042] In the scheme of the present invention, a decoy state method and a novel low-loss unequal-arm MZ (AMZI, asymmetricMach-Zehnde interferometer) interferometer are used.
[0043] The following will introduce the implementation process of passive decoy QDS in detail:
[0044] distribution stage
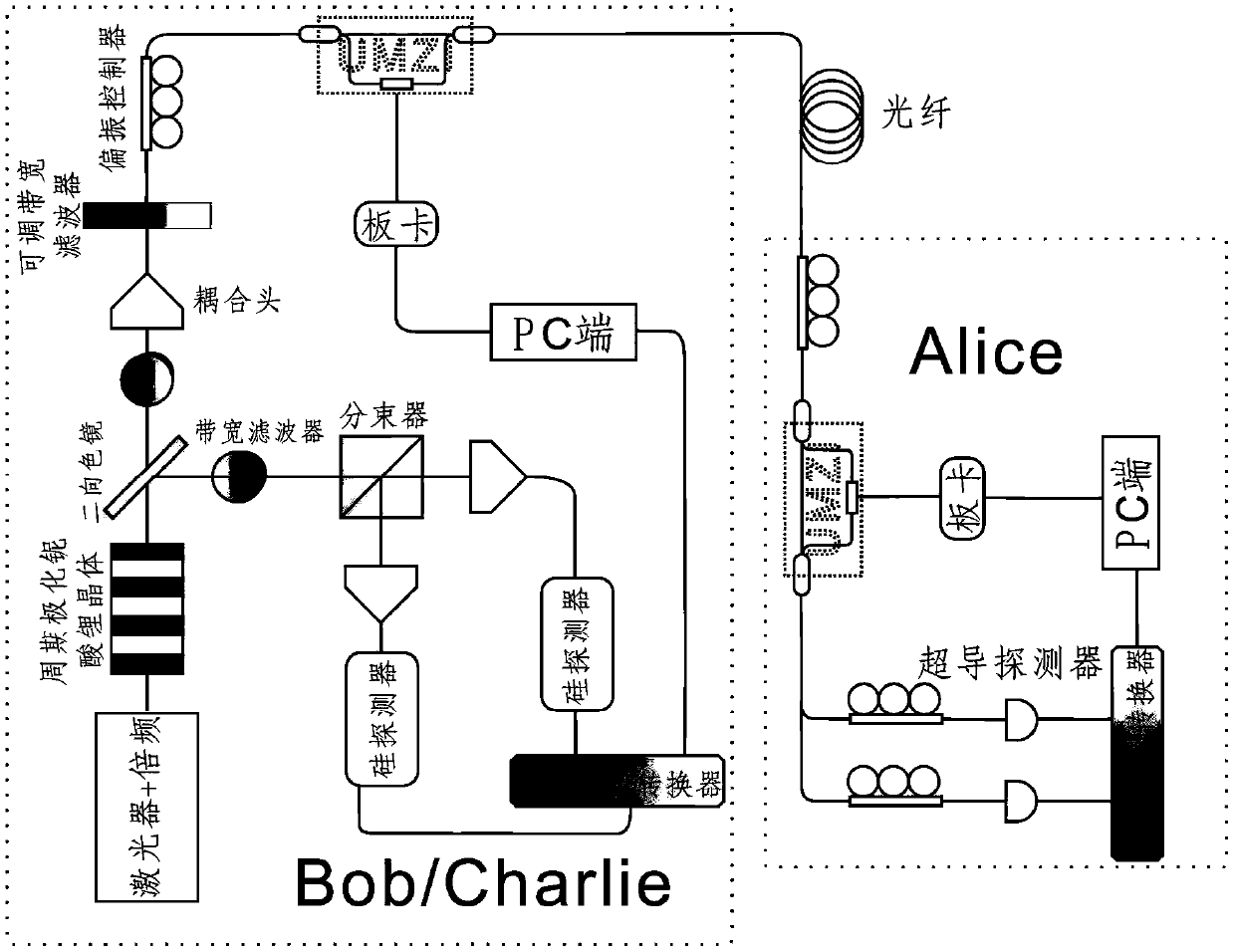
[0045] In the distribution phase, the client Bob and Charlie act as the sender, and Alice acts as the receiver. The distribution phase includes the following steps:
[0046] (1) Bob / Charlie at the sending end uses the PDC process to generate N pulse pairs, and disassembles each pulse pair to form two beams containing N pulses, one of which is leisure light and the other is signal light ;
[0047] (2) Divide leisure light into two beams, and these two beams of leisure light are respectively set on two local detectors D 1 、D 2 Collect; 4 response events are generated according to the triggering results of the detector, which are recorded as X 1 ~X 4 :
[0048] x 1 :D 1 、D 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com