Quantum digital signature method
A quantum digital signature and digital signature technology, applied in the field of quantum security, can solve the problems of long key length, poor system compatibility, and inability to meet the security of the digital signature scheme, and achieve the improvement of signature efficiency, high efficiency and security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] The preferred technologies in this embodiment include: quantum secret sharing, LFSR-Toeplitz hash function for each signature update, and one-time pad unconditionally secure XOR encryption.
[0040] The present embodiment adopts the digital signature method based on 128 bit LFSR-Toeplitz matrix, and described method comprises the following steps:
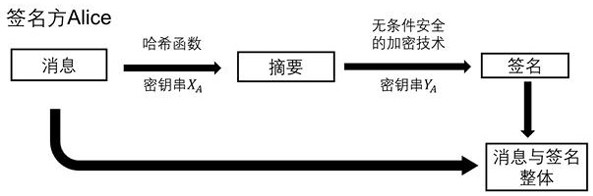
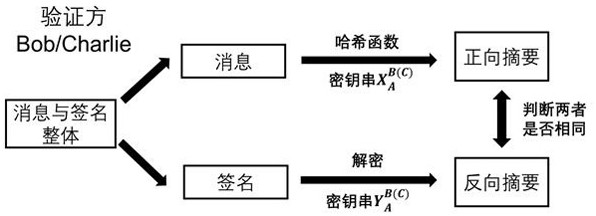
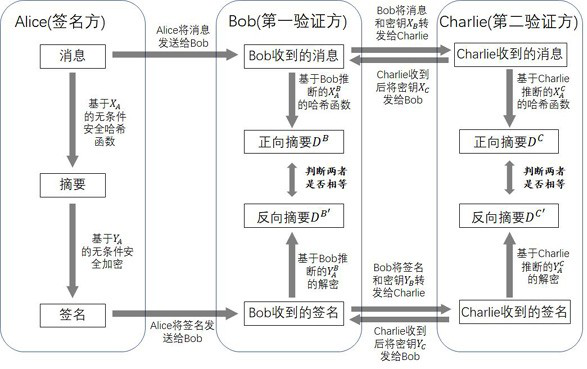
[0041] Step 1, prepare the key. Alice, Bob, and Charlie each hold two 128-bit key strings. These 6 strings of keys are divided into two groups, denoted as X group and Y Group. The two strings of keys held by Alice are denoted as X A , Y A . Similarly, Bob holds X B and Y B , Charlie holds X C and Y C . The satisfying relationship between these keys is: only hold X B and X C to infer X A , while holding Y B and Y C to infer Y A . Preferably, quantum secret sharing technology is selected in the key preparation stage, and the schematic diagram of secret sharing is shown in the attached Figure 4 ; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com