Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42 results about "Exception rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Exceptions to the Rule. In personnel or disciplinary proceedings as long as you are unpaid. You can represent your immediate family members or any other person if you are serving as their guardian, executor, administrator, trustee or other personal fiduciary, provided: Your appointing authority approves.
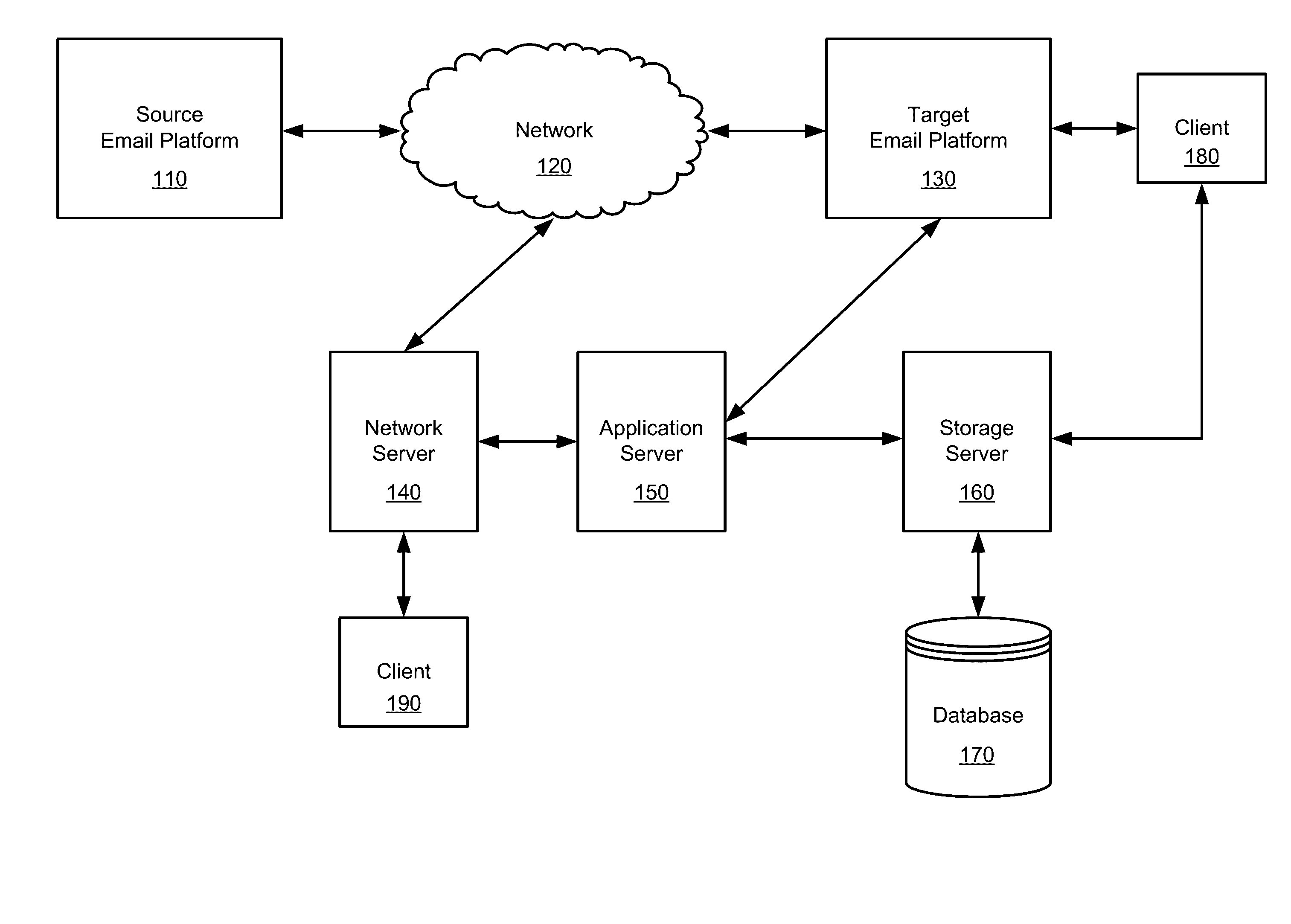
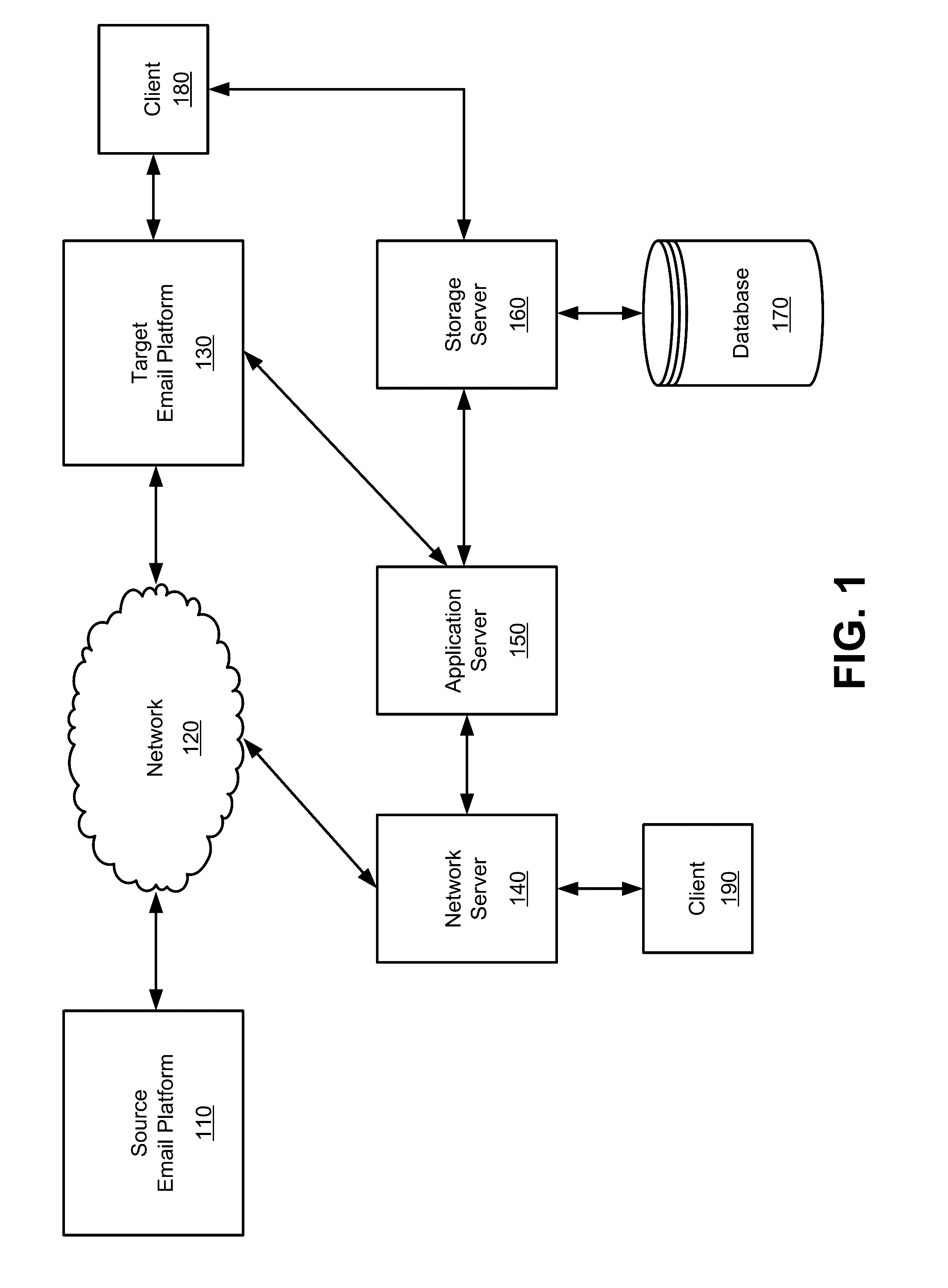
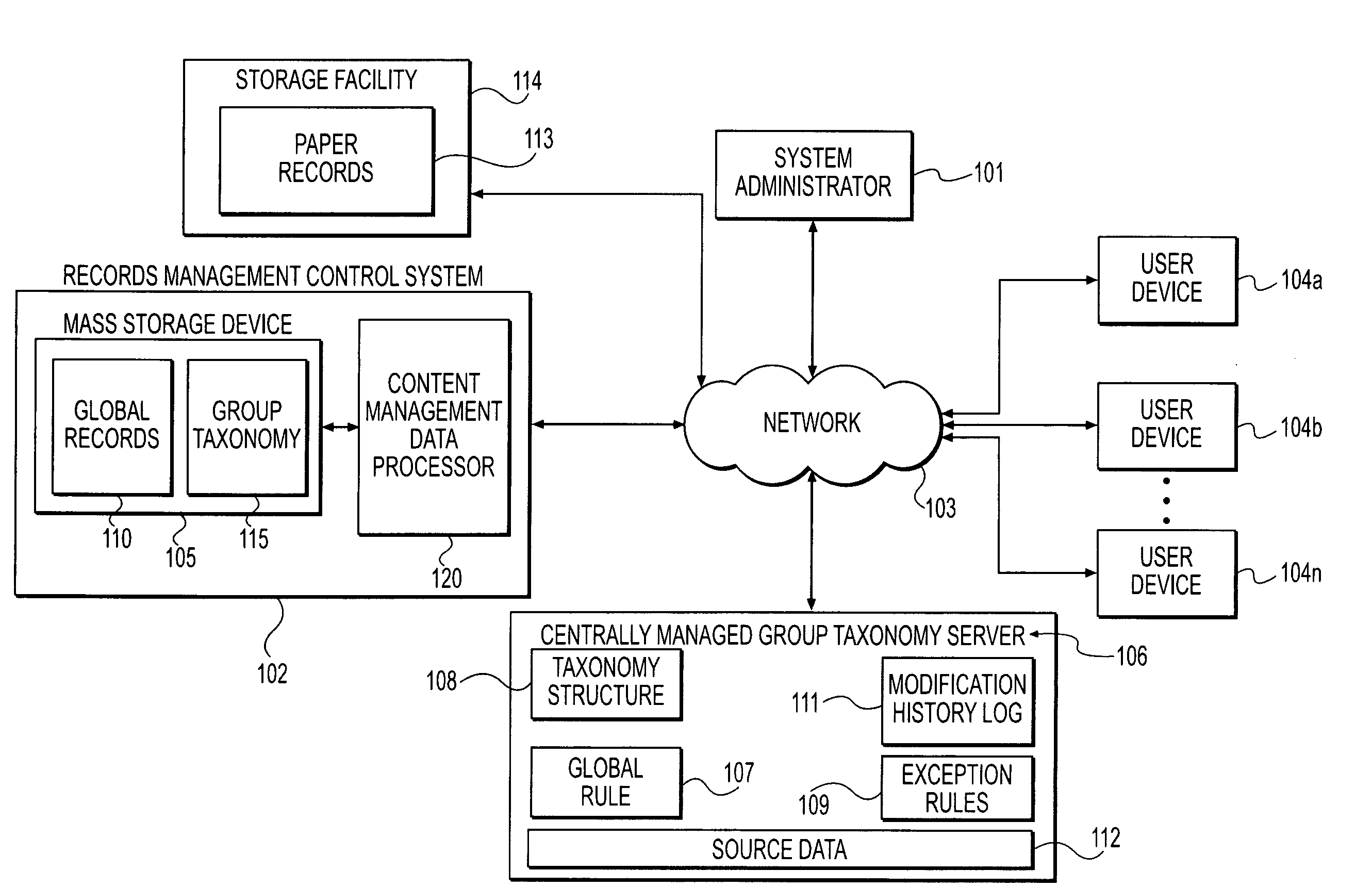
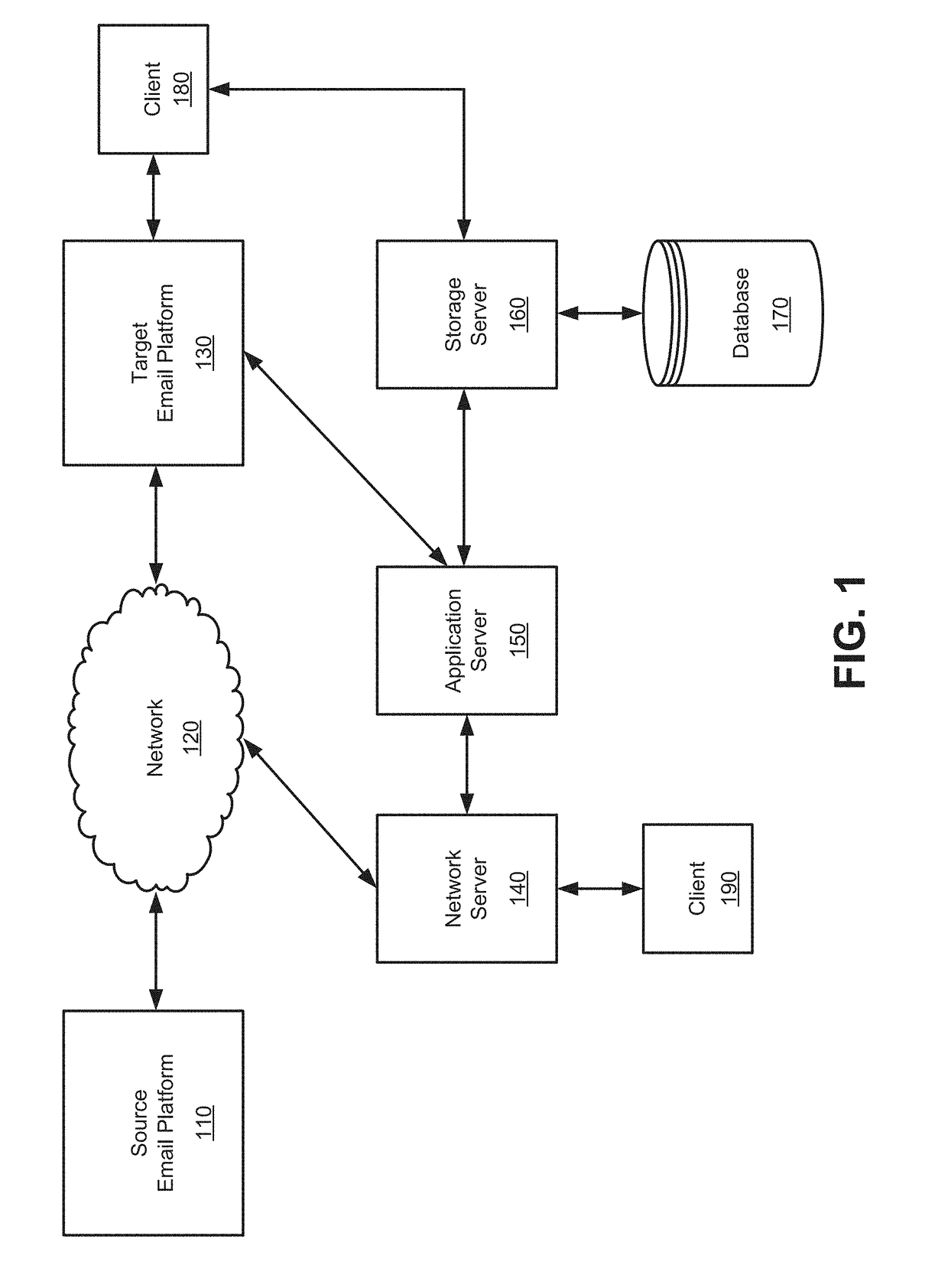
Enhanced management of migration and archiving operations
Owner:QUEST SOFTWARE INC
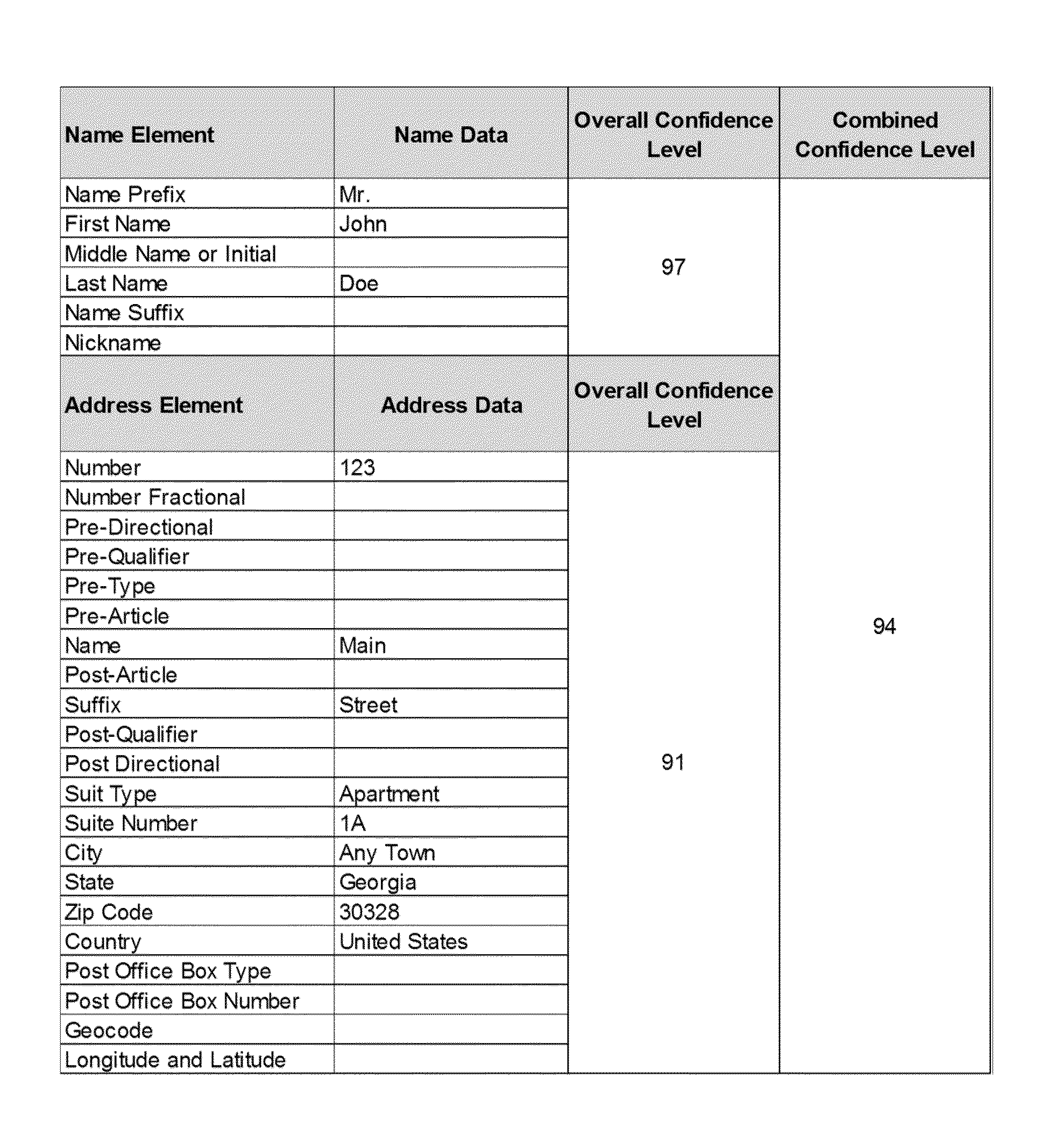
Concepts for address prediction or correction
Computer program products, methods, systems, apparatus, and computing entities are provided for predicting and correcting addresses. In one embodiment, this includes applying exception rules to determine whether to generate an exception for an address. If an exception exists, there are various approaches for predicting or correcting the addresses.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
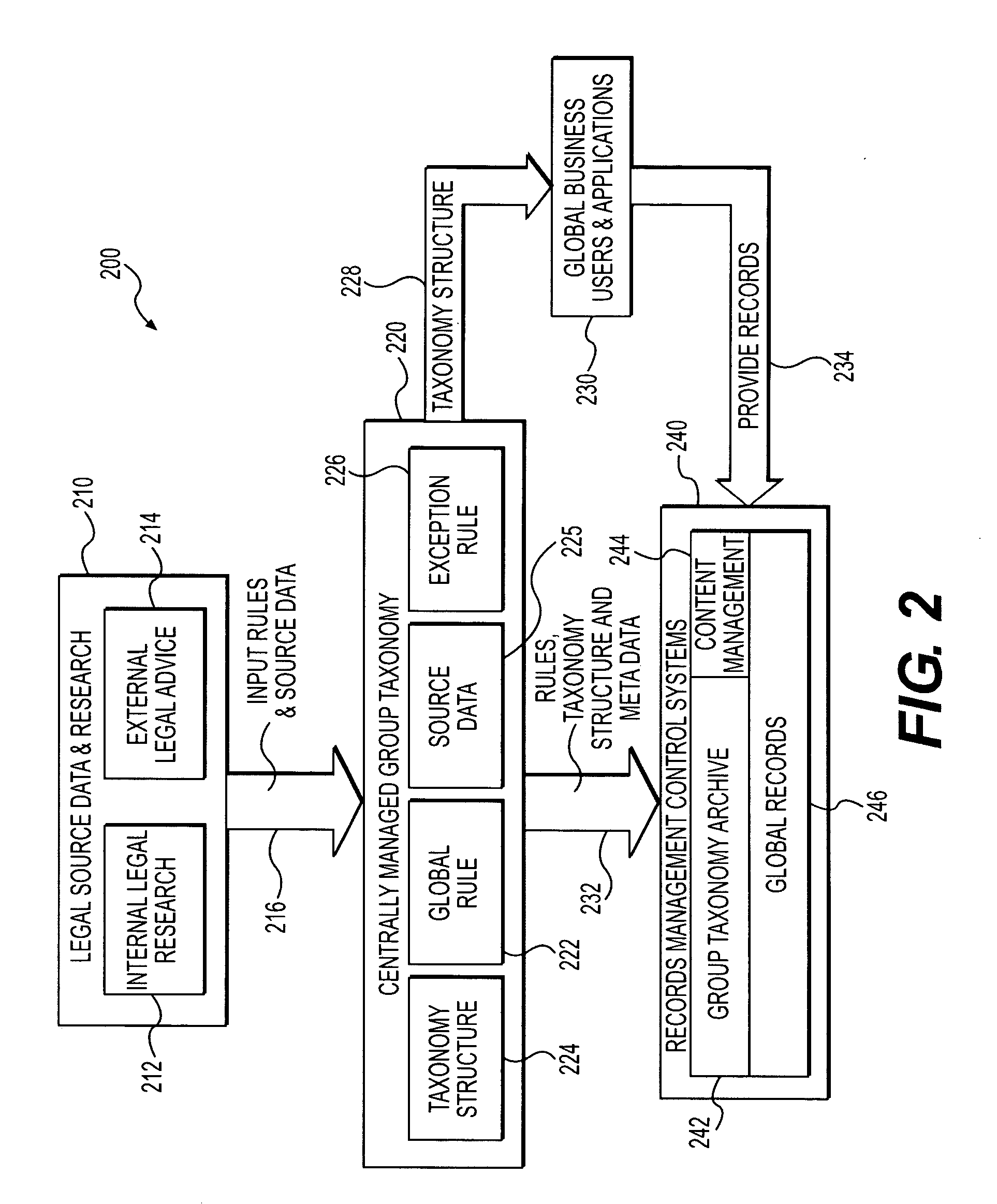
Methods and systems for group data management and classification
Methods and systems are provided for retaining and managing global records of an organization. In one implementation, a method is provided for retaining global records of an organization. The method may include storing, in a memory device, at least one arrangement of data items classified according to a hierarchical classification structure providing a normalization scheme for classifying the data items, the data items comprising global data of an organization and a retention schedule corresponding to the global data. Additionally, the method may include retaining the data items according to the retention schedule, wherein the retention schedule comprises a plurality of retention rules including a global retention rule defining a first duration for retaining the data items consistent with a set of predetermined requirements, and at least one exception rule for retaining at least one data item for a second duration.
Owner:IRON MOUNTAIN INCORPORATED
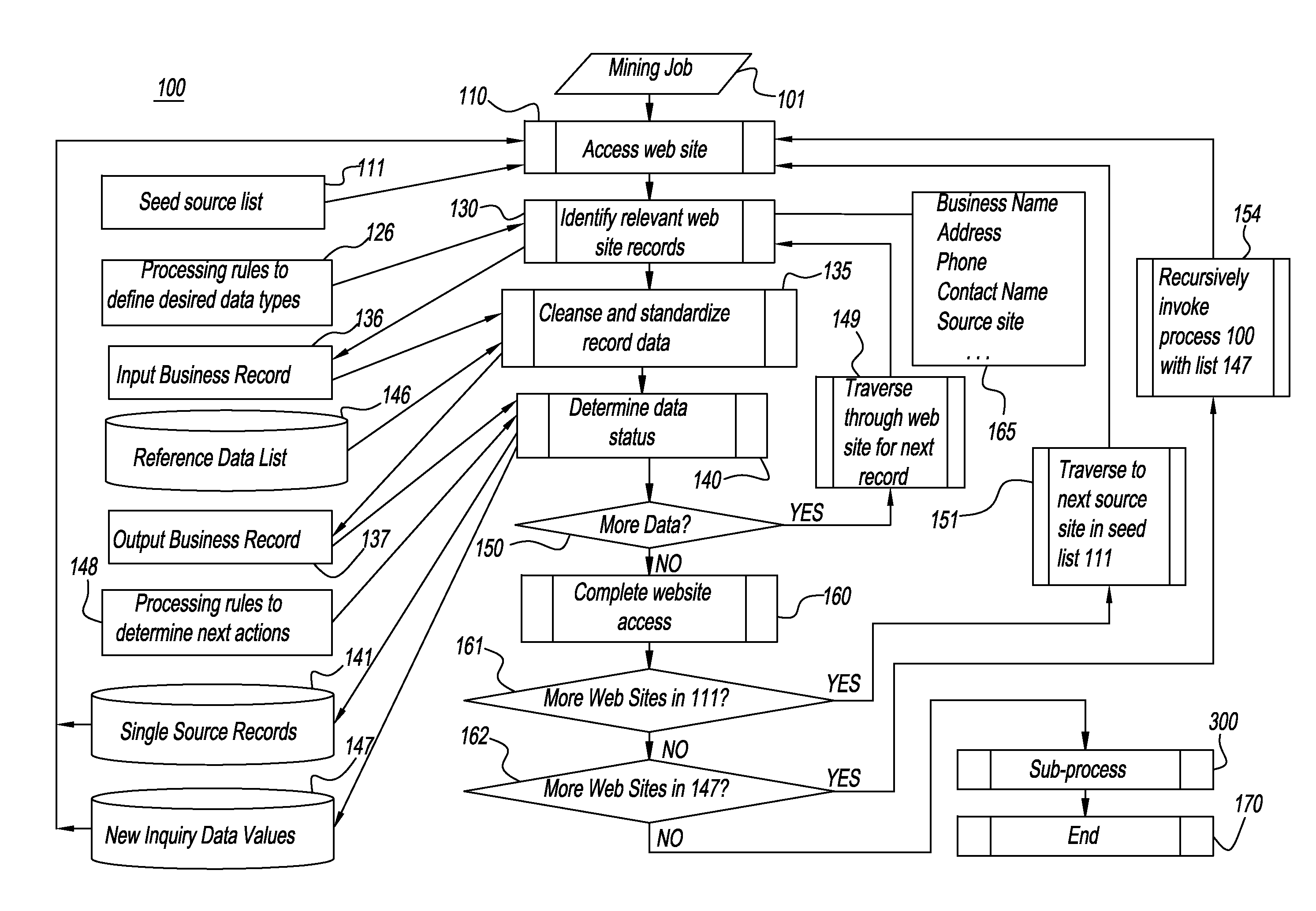
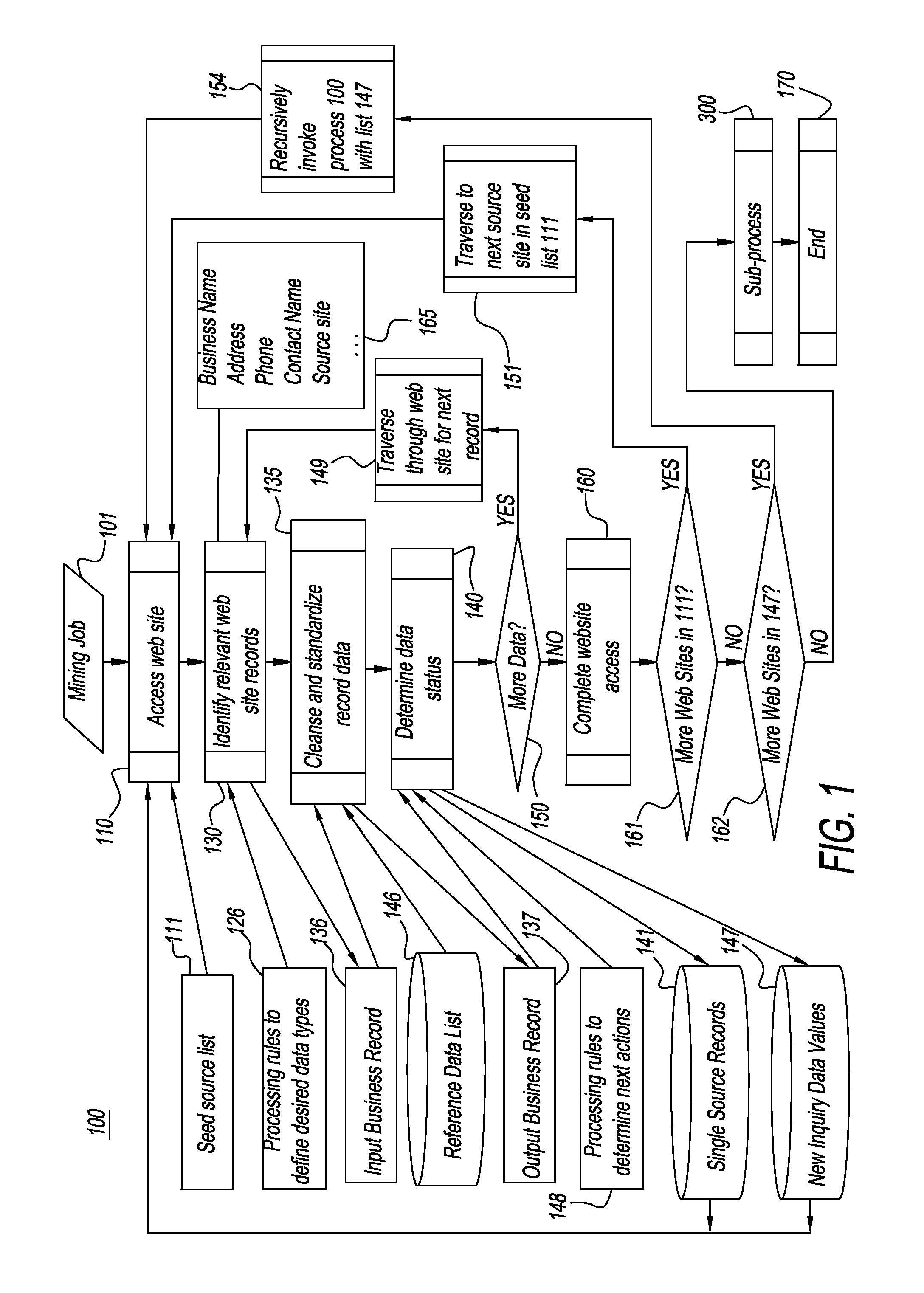
System and method for recursively traversing the internet and other sources to identify, gather, curate, adjudicate, and qualify business identity and related data
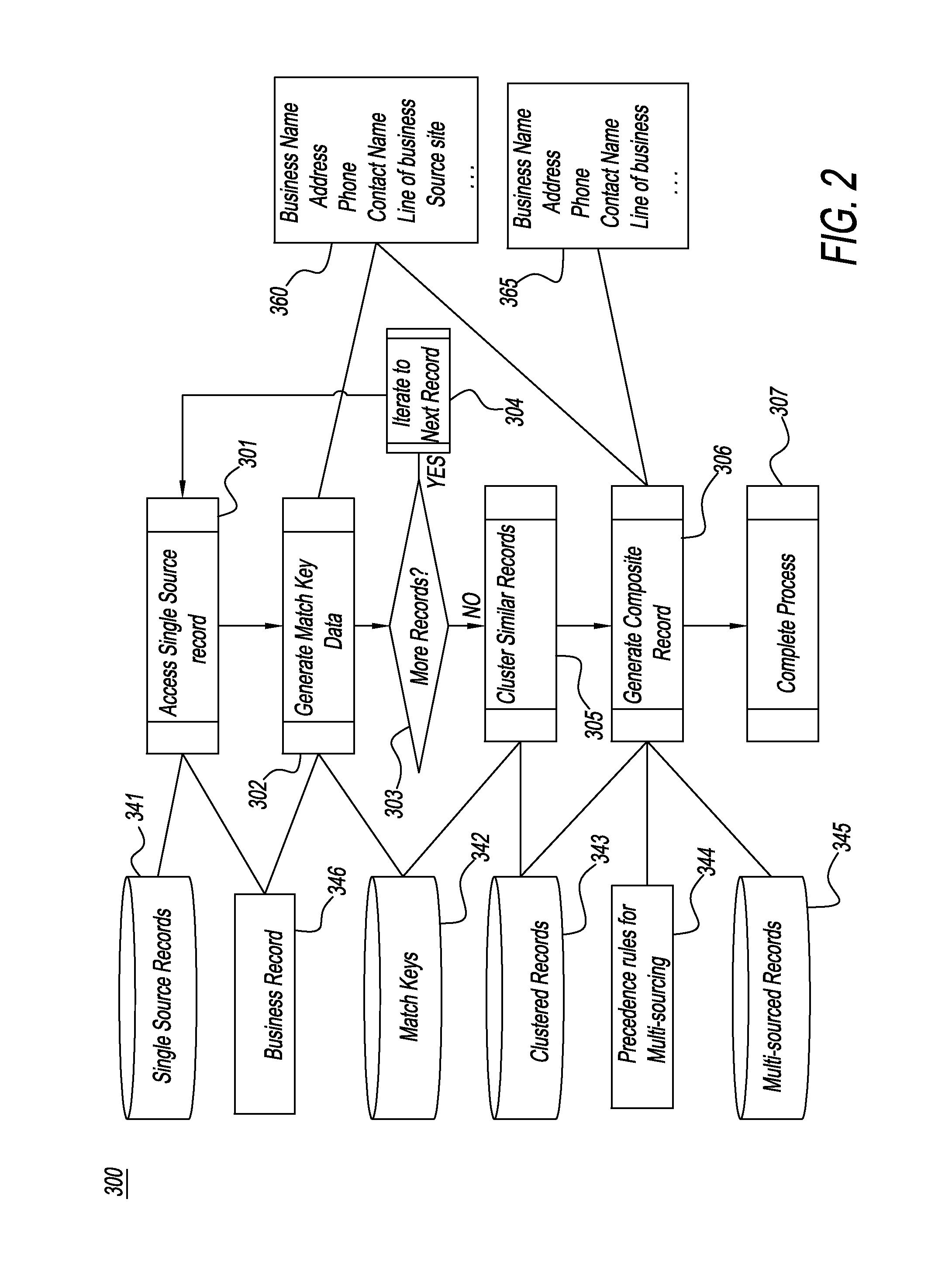
A system and a method used for data discovery in accordance with an inquiry in which multiple sources, which may be web sites or other data sources, are examined for data relevant to the inquiry. The process and method is performed recursively an indeterminate number of iterations, using data and metadata from multiple sources to corroborate discovered data and metadata from other sources, until no further relevant data or sources are found, or adjudication or exception rules have been met. Discovered data and metadata are curated, adjudicated to assess reliability, synthesized, and clustered into composite records using precedence rules and provenance to determine the most reliable data sources as well as terms of use for each source. Data, metadata, and information about each search are retained and can be used for subsequent purposes, such as subsequent searches or other downstream activities.
Owner:THE DUN & BRADSTREET CORPORATION
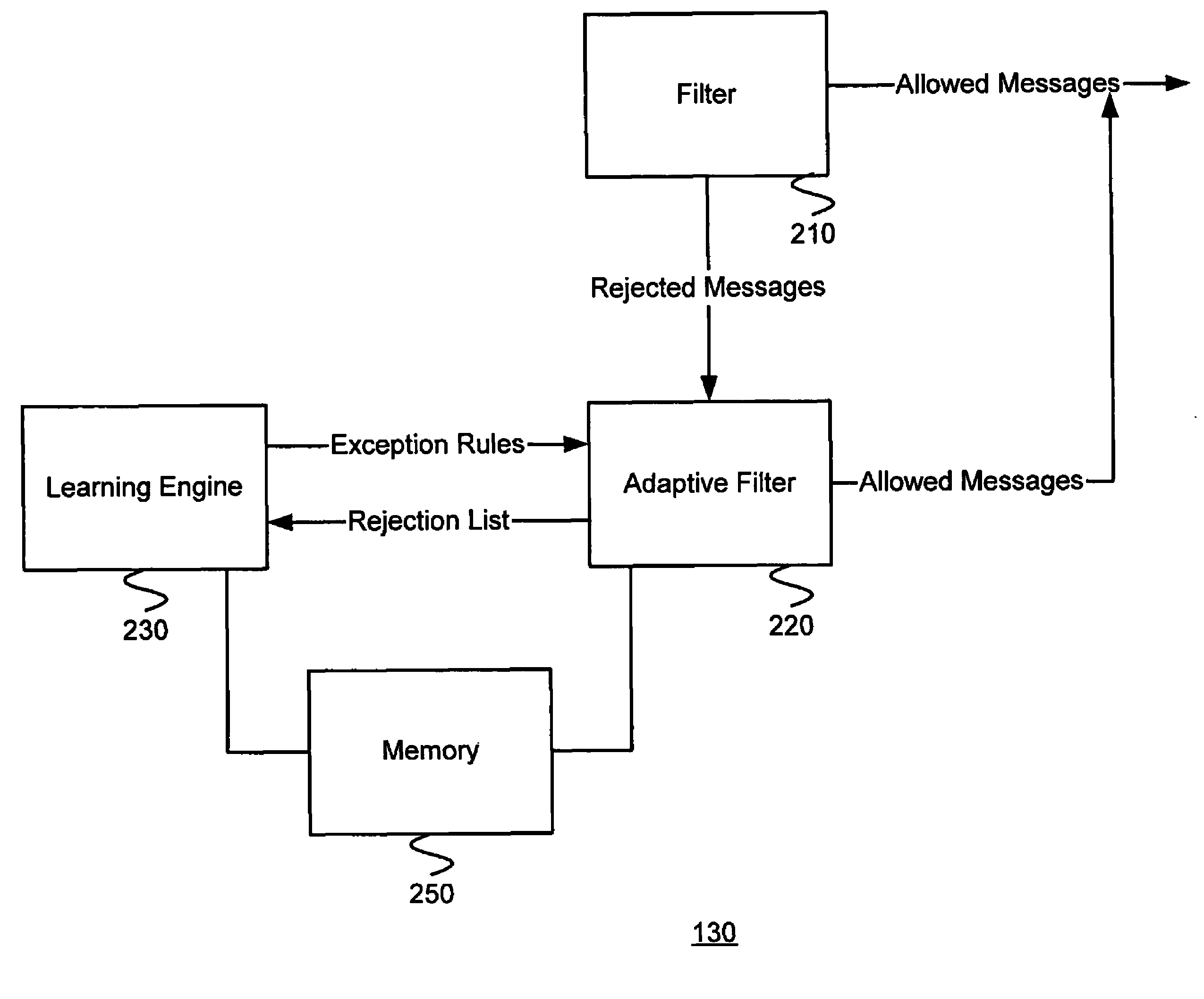
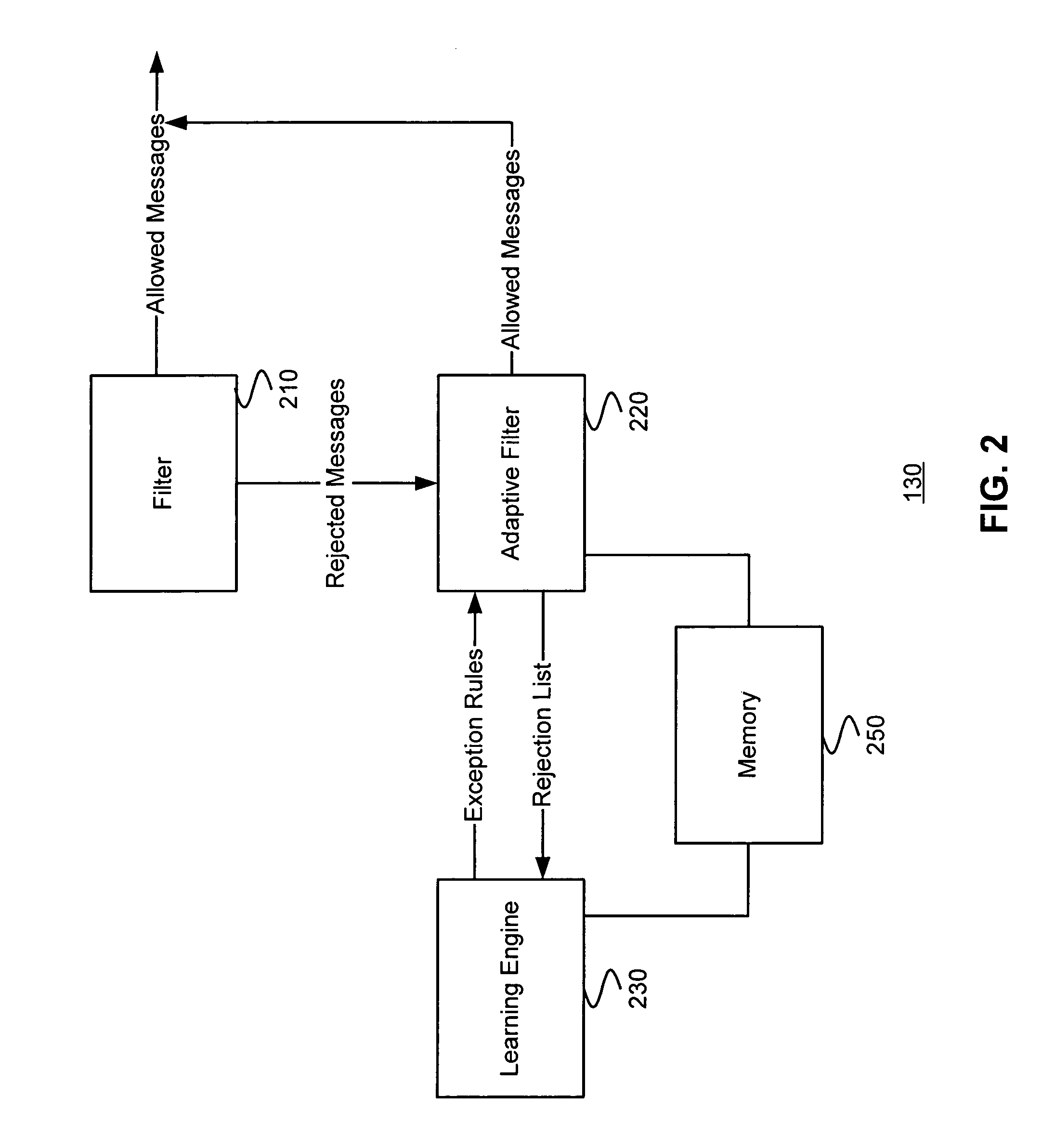
Using statistical analysis to generate exception rules that allow legitimate messages to pass through application proxies and gateways
ActiveUS7890996B1Multiple digital computer combinationsProgram controlStatistical analysisApplication software
A security gateway receives messages rejected by a message filter based on a set of rules. The security gateway also receives attributes of the rejected messages that triggered the rules. The security gateway maintains frequencies with which the messages with a particular attribute were rejected by the rules. The security gateway finds rejected messages or attributes having a high frequency of occurrence. Since messages or attributes having a high frequency of occurrences are more likely to represent legitimate requests rather than malicious attacks, the security gateway generates exception rules, which would allow messages that have similar attributes to pass through the gateway.
Owner:CITRIX SYST INC
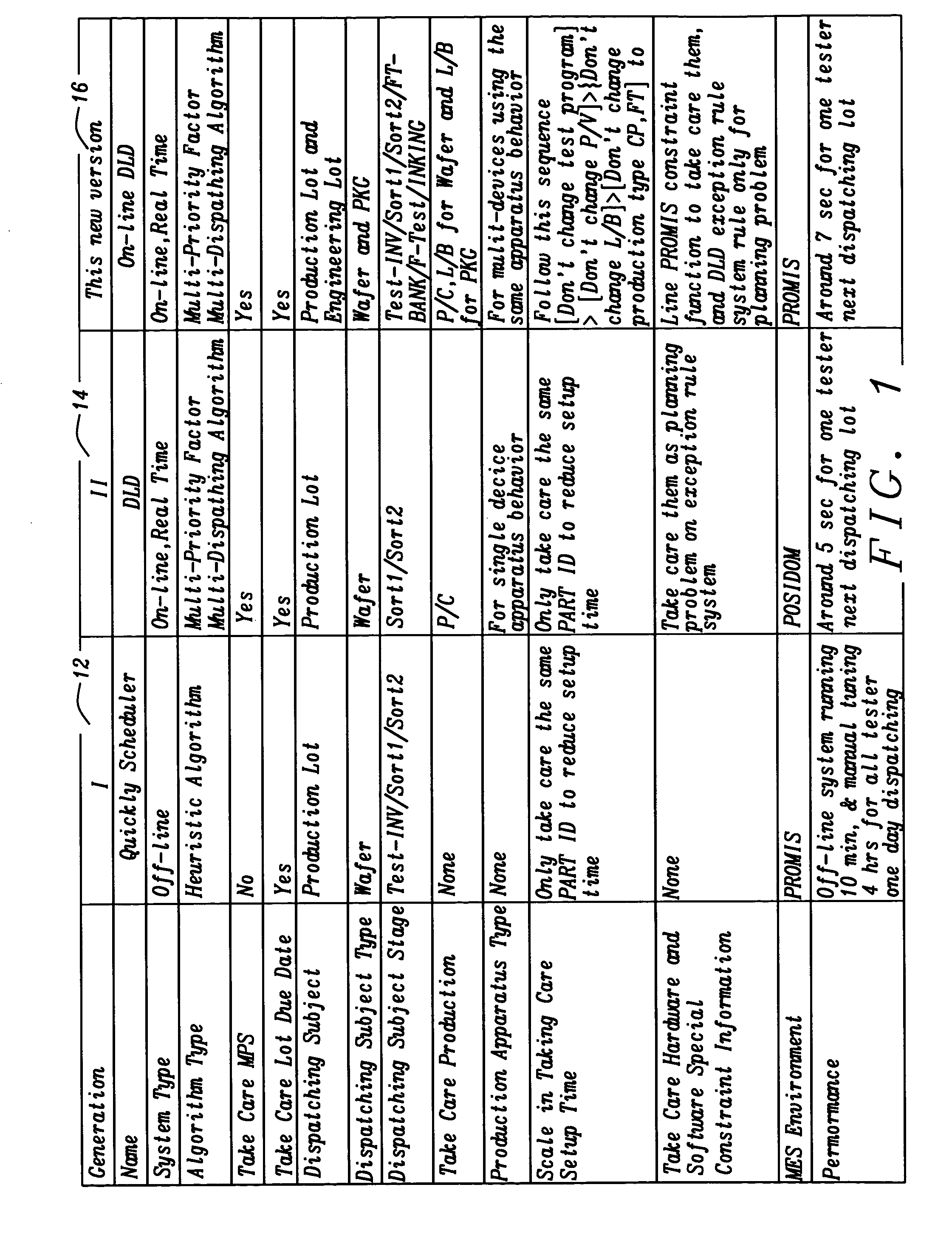
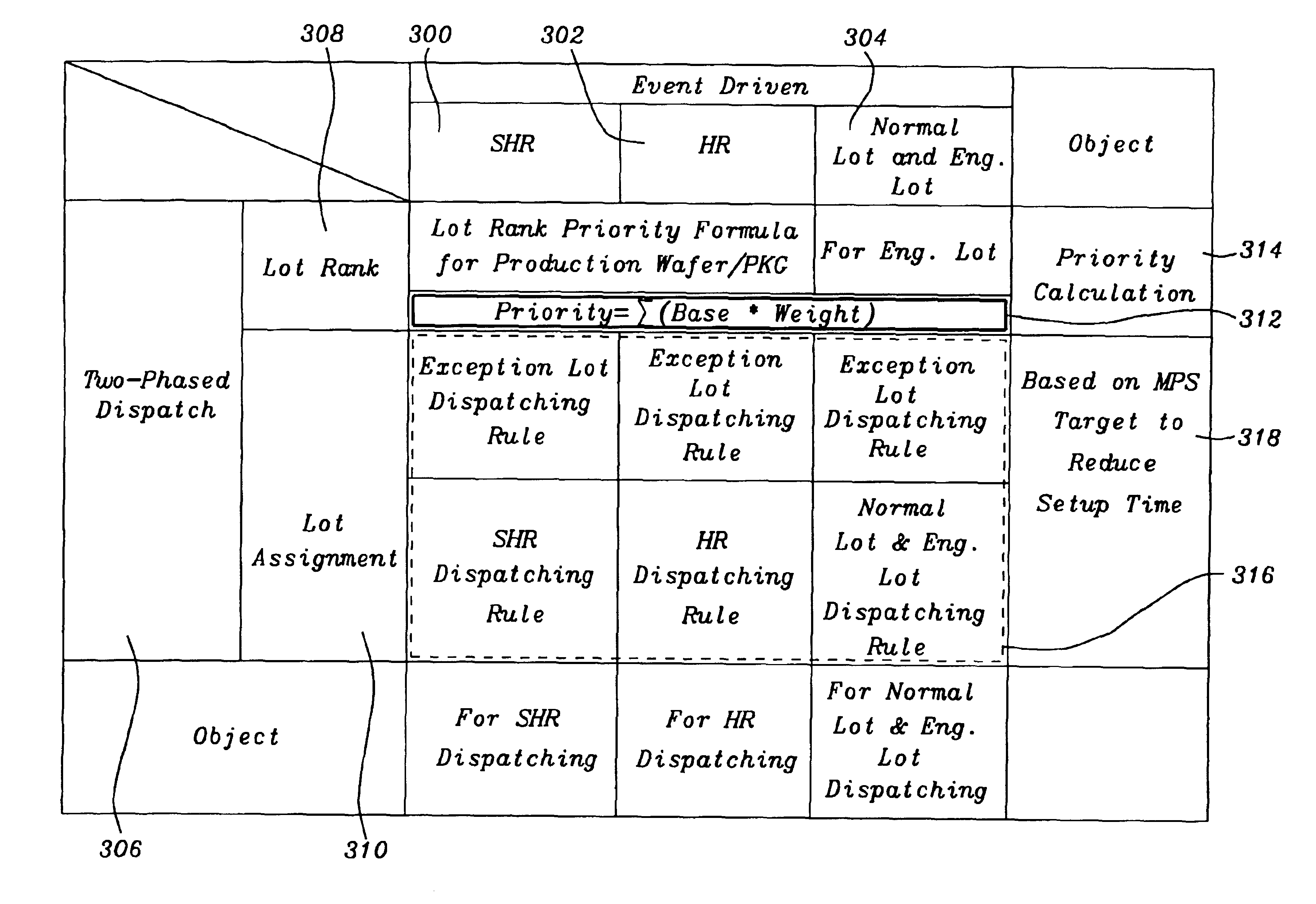
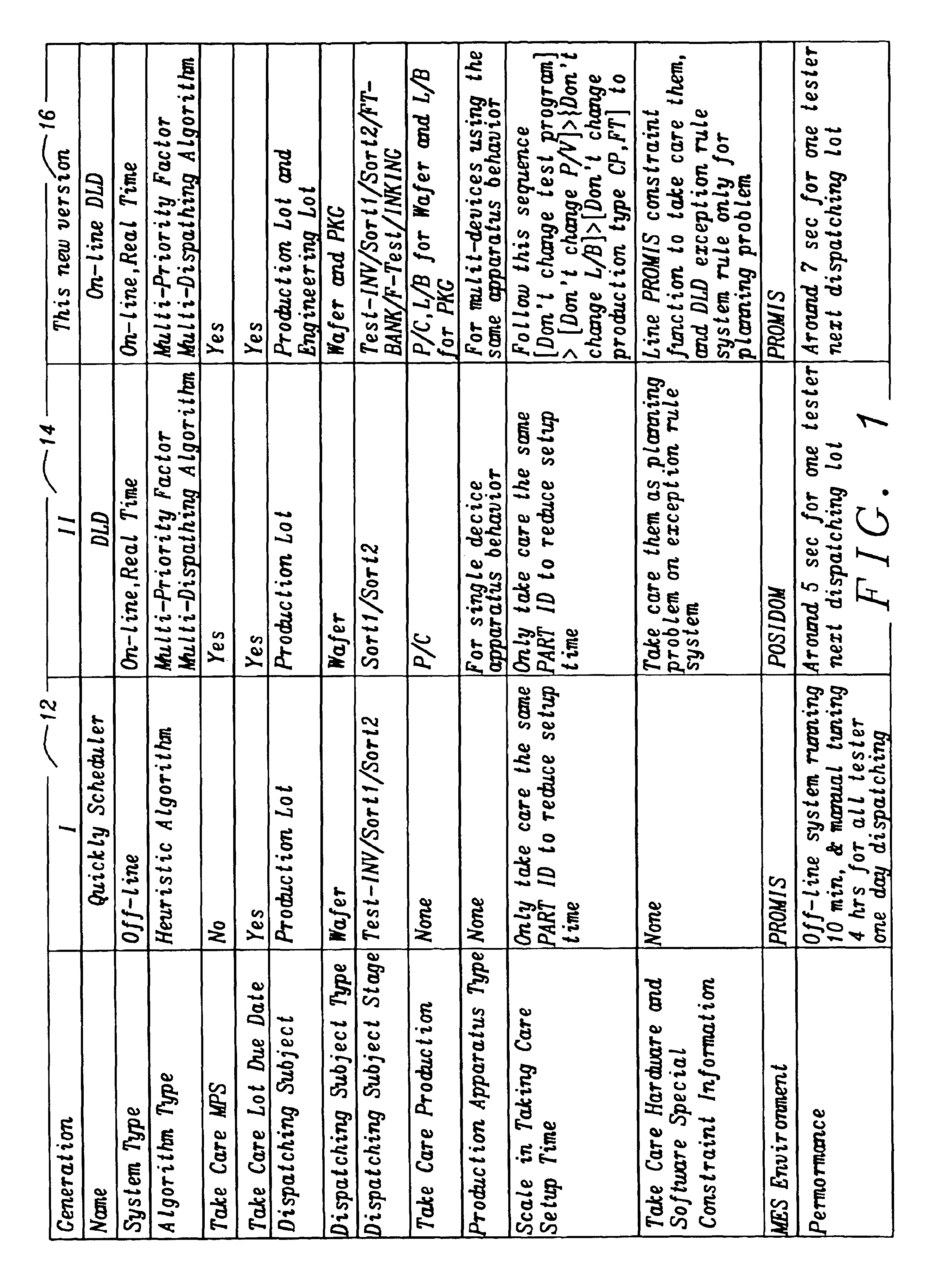
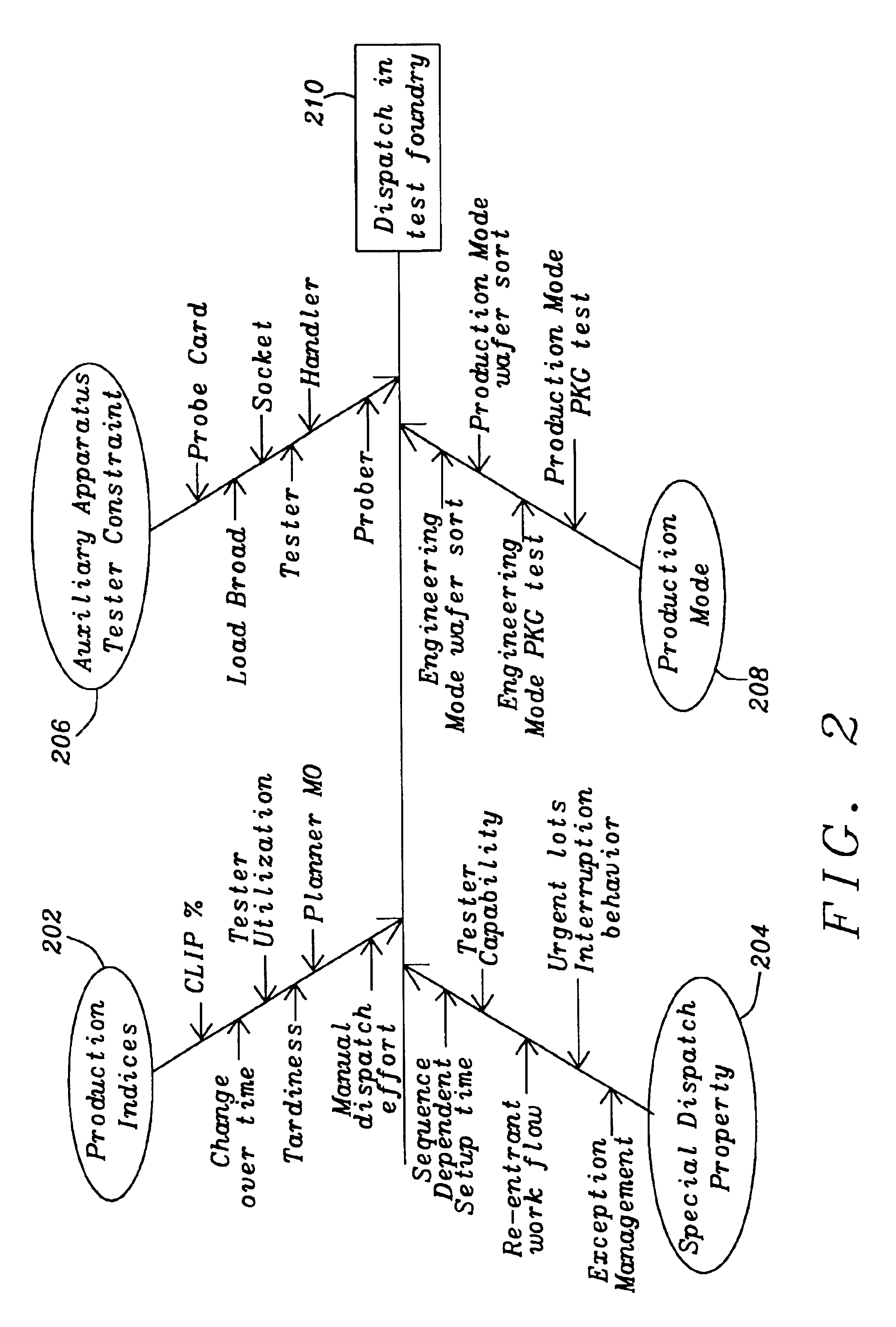
Algorithms tunning for dynamic lot dispatching in wafer and chip probing
InactiveUS20050071031A1Efficiently to chooseExceeding amountResistance/reactance/impedenceComputer controlSpecial eventsSystem structure
A method and system for flexible, comprehensive, on-line, real-time dynamic lot dispatching in a semiconductor test foundry based on a two-phased, event-driven dispatching system structure. An adjustable priority formula and tuned algorithms integrated with PROMIS' constraint function give a nearly optimum dispatching list on any tester at any time with reduced mistake operations. Exception rules take care of special events to improve daily dispatching manual effort. This invention can automatically dispatch engineering lots according to engineering lots' capacity of Testing, solve conflict between wafer and package lots, efficiently reduce tester setup times, replace daily manual-dispatching sheet and keep a high CLIP rate while fully following MPS.
Owner:TAIWAN SEMICON MFG CO LTD
Rule generalization for web application entry point modeling
A security gateway receives messages, such as URL requests, rejected by a message filter based on a set of rules. The security gateway maintains frequencies with which the messages were rejected by the rules. The security gateway finds rejected messages having a high frequency of occurrence. Since messages having a high frequency of occurrences are more likely to represent legitimate requests rather than malicious attacks, the security gateway generates exception rules, which would allow similar messages to pass through the gateway.
Owner:CITRIX SYST INC
Algorithms tunning for dynamic lot dispatching in wafer and chip probing
InactiveUS6931296B2Efficiently to chooseExceeding amountResistance/reactance/impedenceTotal factory controlSpecial eventsSystem structure
A method and system for flexible, comprehensive, on-line, real-time dynamic lot dispatching in a semiconductor test foundry based on a two-phased, event-driven dispatching system structure. An adjustable priority formula and tuned algorithms integrated with PROMIS' constraint function give a nearly optimum dispatching list on any tester at any time with reduced mistake operations. Exception rules take care of special events to improve daily dispatching manual effort. This invention can automatically dispatch engineering lots according to engineering lots' capacity of Testing, solve conflict between wafer and package lots, efficiently reduce tester setup times, replace daily manual-dispatching sheet and keep a high CLIP rate while fully following MPS.
Owner:TAIWAN SEMICON MFG CO LTD
Concepts for address prediction or correction
Computer program products, methods, systems, apparatus, and computing entities are provided for predicting and correcting addresses. In one embodiment, this includes applying exception rules to determine whether to generate an exception for an address. If an exception exists, there are various approaches for predicting or correcting the addresses.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
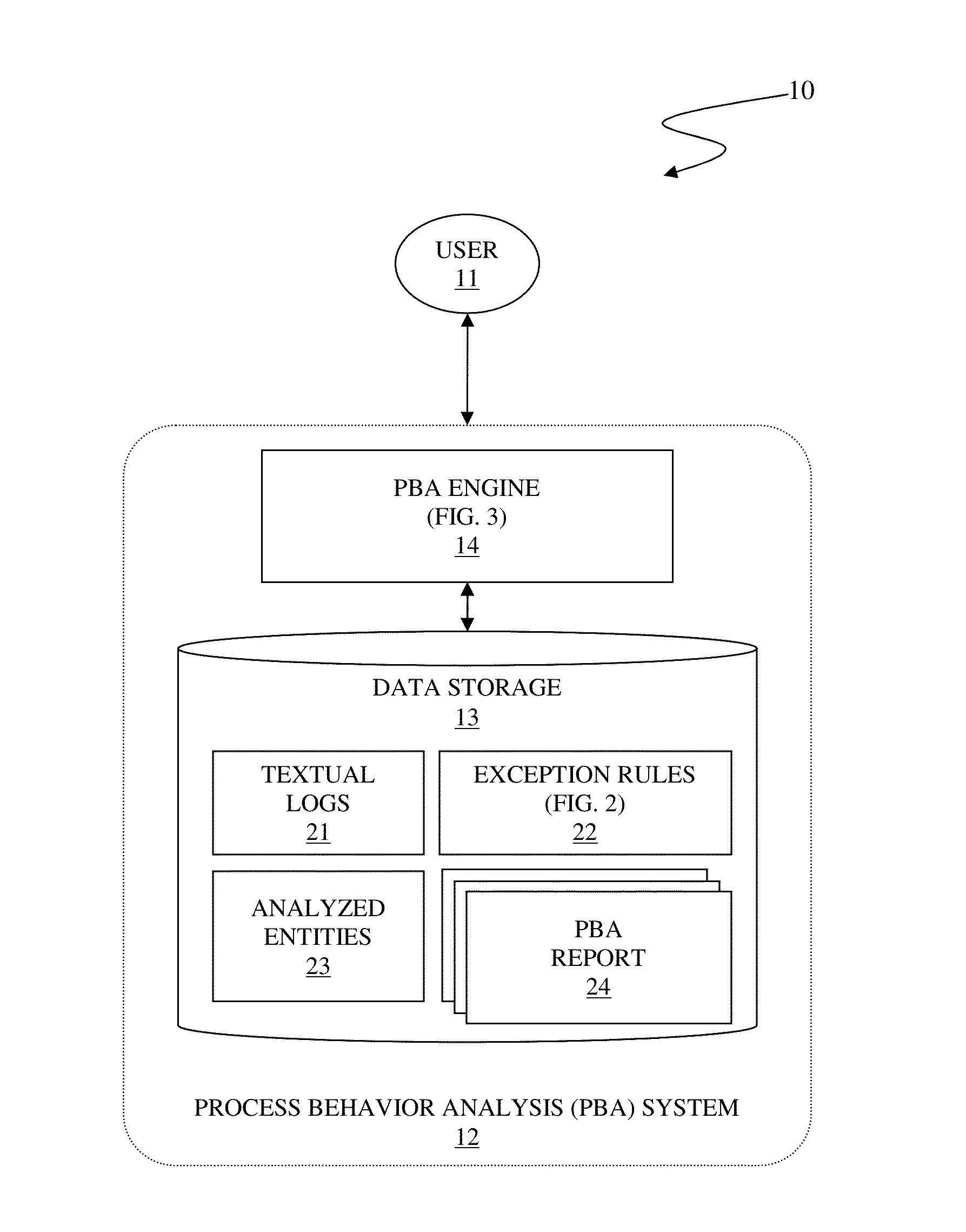
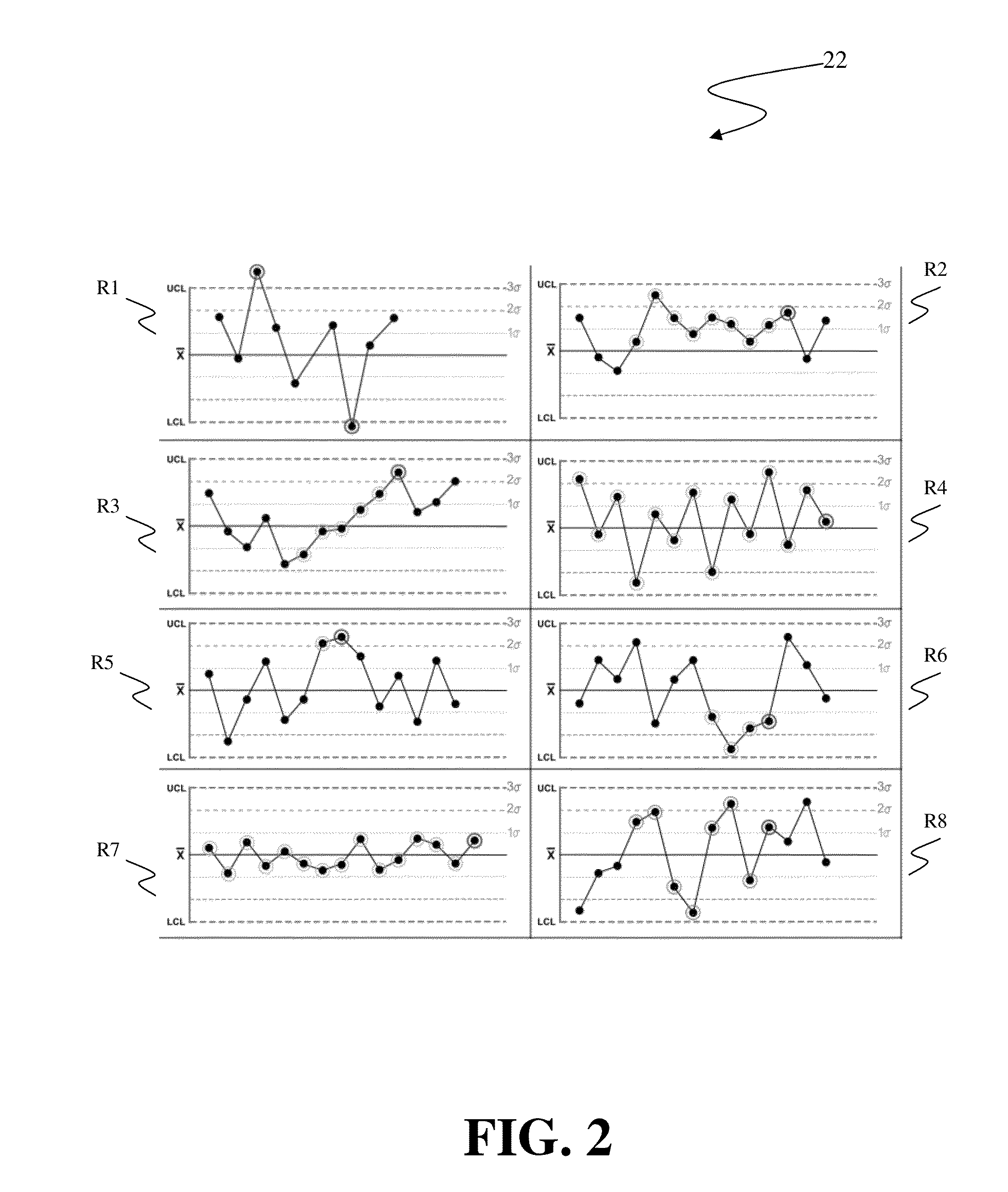
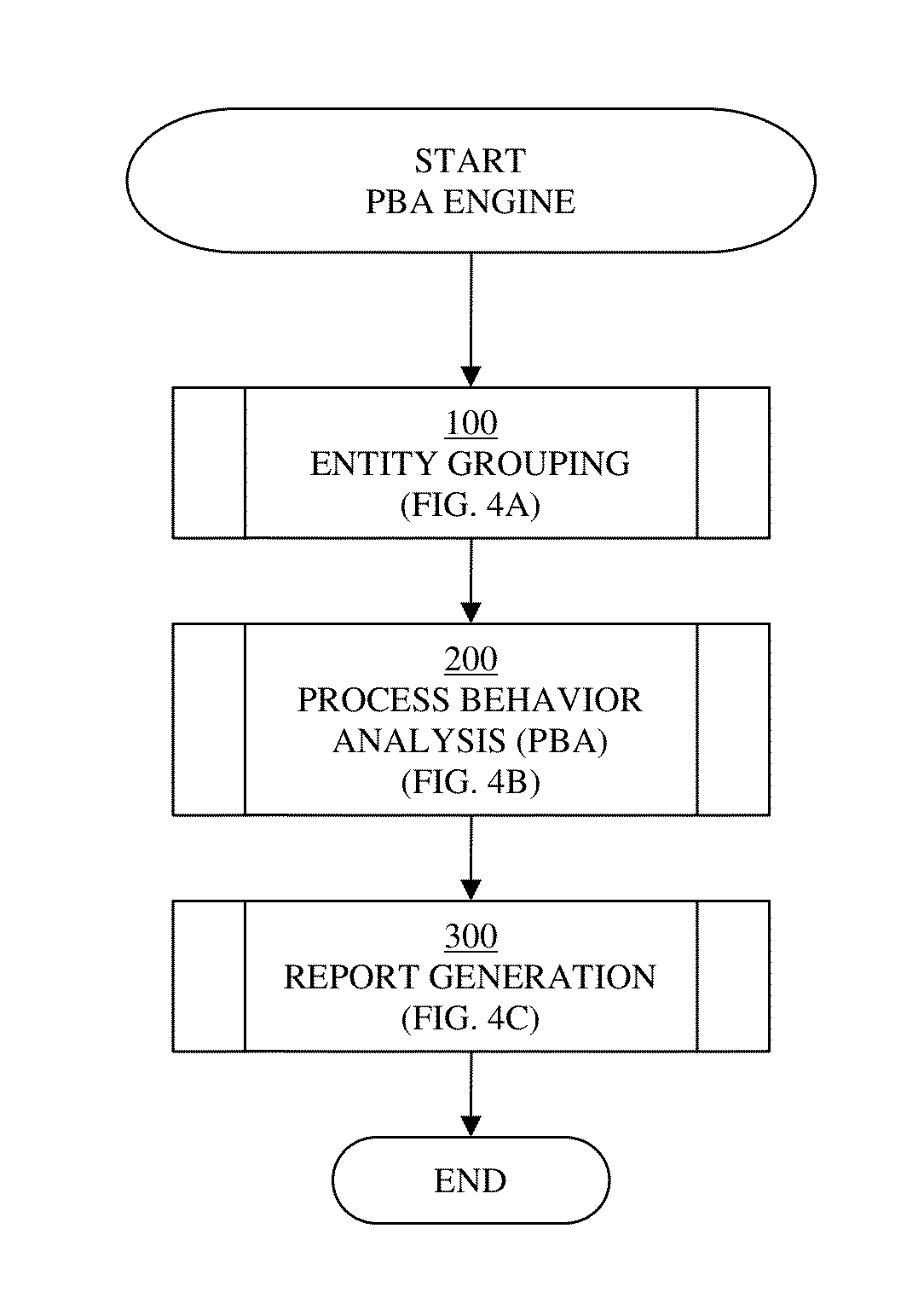
Detecting statistical variation from unclassified process log
InactiveUS20130198147A1Digital data processing detailsRegistering/indicating quality control systemsProcess behaviorException rule
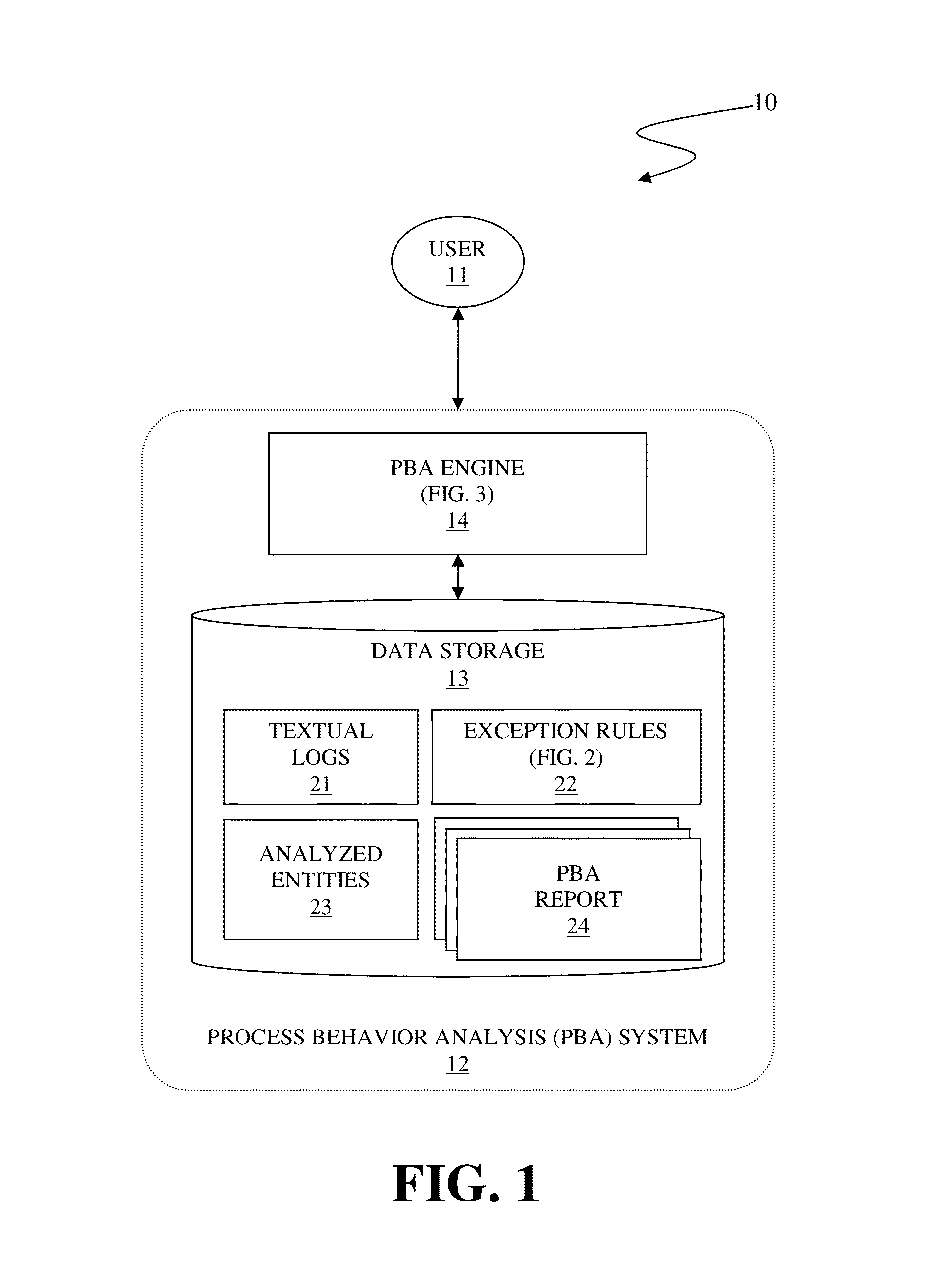
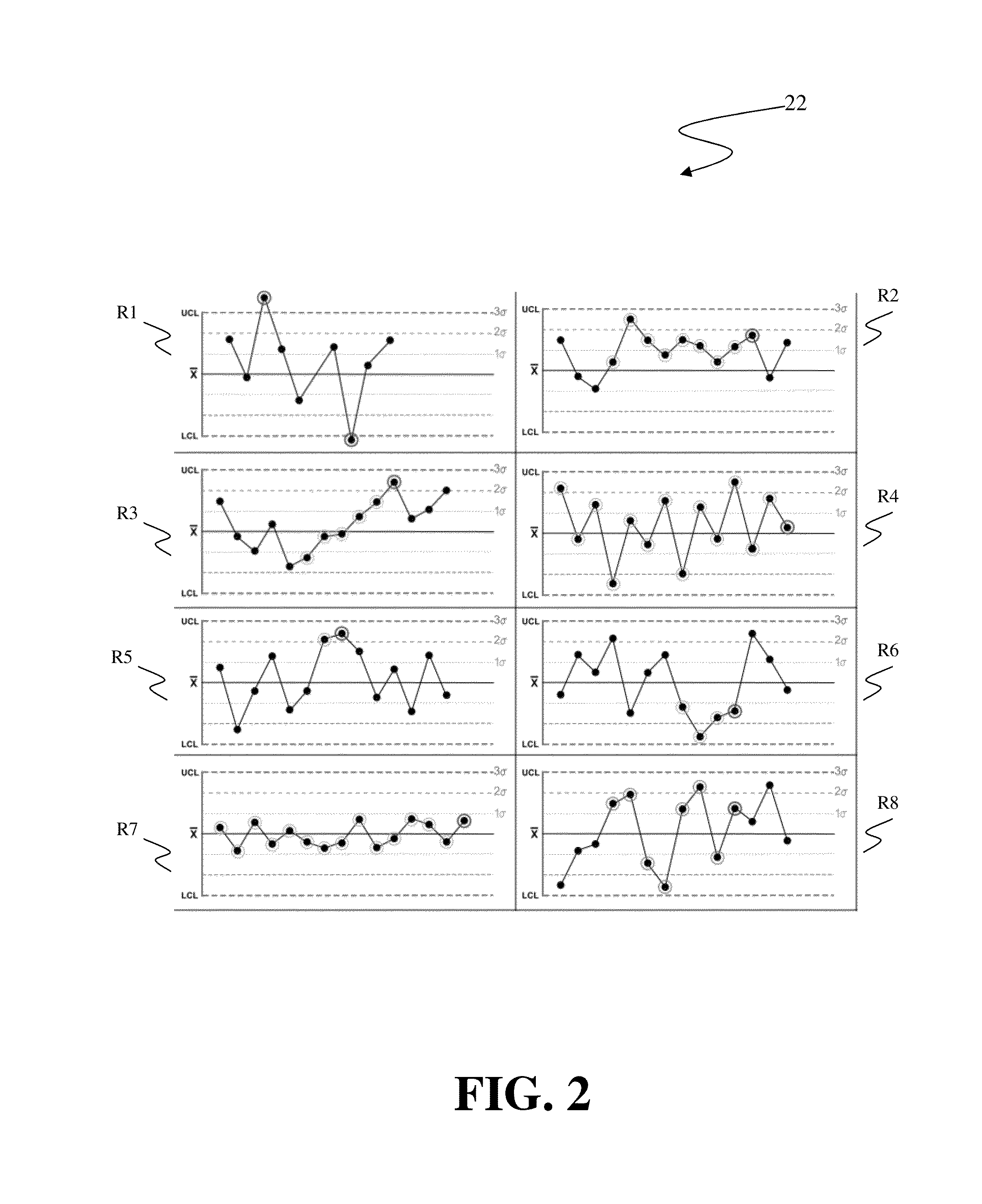
A system and associated method for detecting a statistical variation of a process from a textual log of the process as performed by a process behavior analysis (PBA) system for monitoring the process operating in an Information Technology (IT) delivery system. The PBA system includes a PBA engine and a data storage storing exception rules used by the PBA engine. The PBA engine merges entities appearing in the textual log into one or more groups based on similarities of respective time series of the entities. Control charts are generated for merged entities and the PBA engine subsequently analyzes process behavior of the process by use of the control charts for exceptions defined in the stored exception rules. The PBA engine generates a PBA report for the process pursuant to the analysis result of the textual log with detailed information including to what type of exceptions had or had not occurred.
Owner:IBM CORP
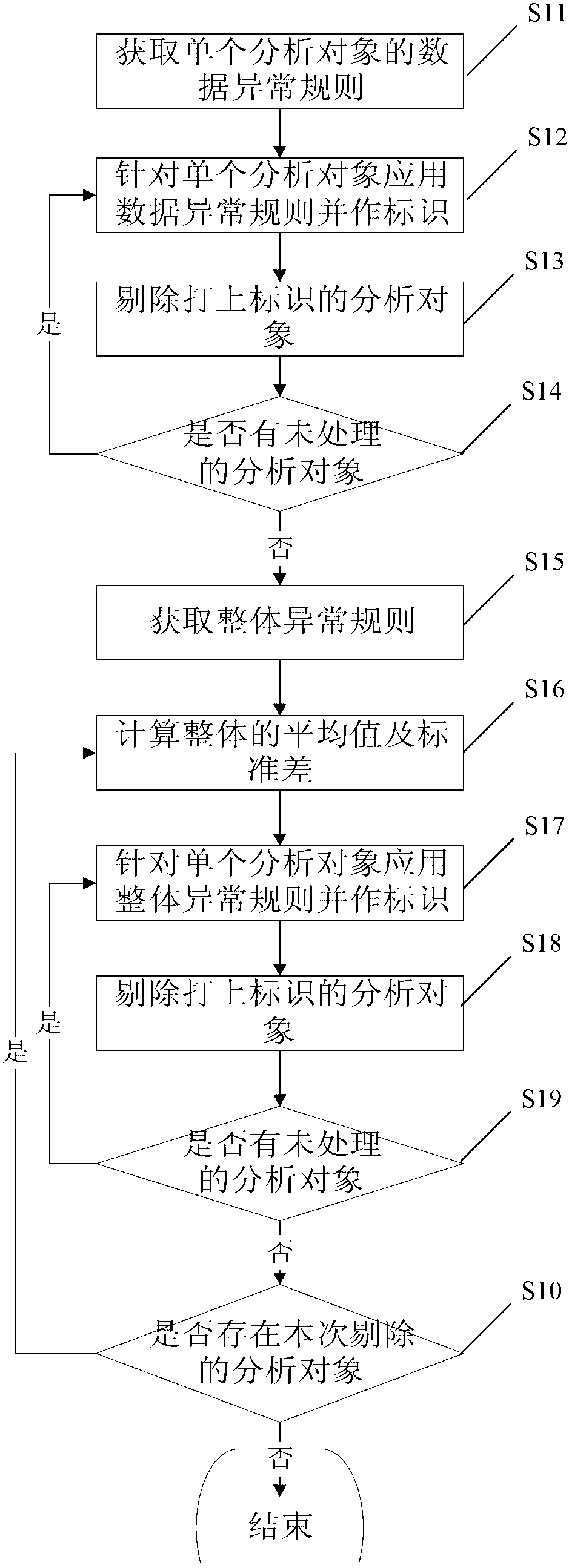
Method for removing exceptional data
ActiveCN103294768AGuaranteed accuracySpecial data processing applicationsProgramming languageData profiling
The invention discloses a method for removing exceptional data, which comprises the steps of acquiring a date exception rule of a single analysis object, applying the data exception rule for the single analysis object and making a mark, and removing the analysis object with the mark. According the method, the exceptional data are processed by the data exception rule and an entire exception rule, a user is allowed to customize a data exception rule, and the entire exception rule is recycled to remove the exceptional data. The exceptional data exists in a data analysis application generally, and the method can remove all the exceptional data, so that the precision of an analysis result is ensured.
Owner:SERVYOU SOFTWARE GRP
Concepts for address prediction or correction
Computer program products, methods, systems, apparatus, and computing entities are provided for predicting and correcting addresses. In one embodiment, this includes applying exception rules to determine whether to generate an exception for an address. If an exception exists, there are various approaches for predicting or correcting the addresses.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Concepts for address prediction or correction
Computer program products, methods, systems, apparatus, and computing entities are provided for predicting and correcting addresses. In one embodiment, this includes applying exception rules to determine whether to generate an exception for an address. If an exception exists, there are various approaches for predicting or correcting the addresses.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Monitoring method, device and system as well as monitoring equipment
InactiveCN110599721AImprove recognition accuracyRich in detailsBurglar alarmMonitoring systemMonitor equipment
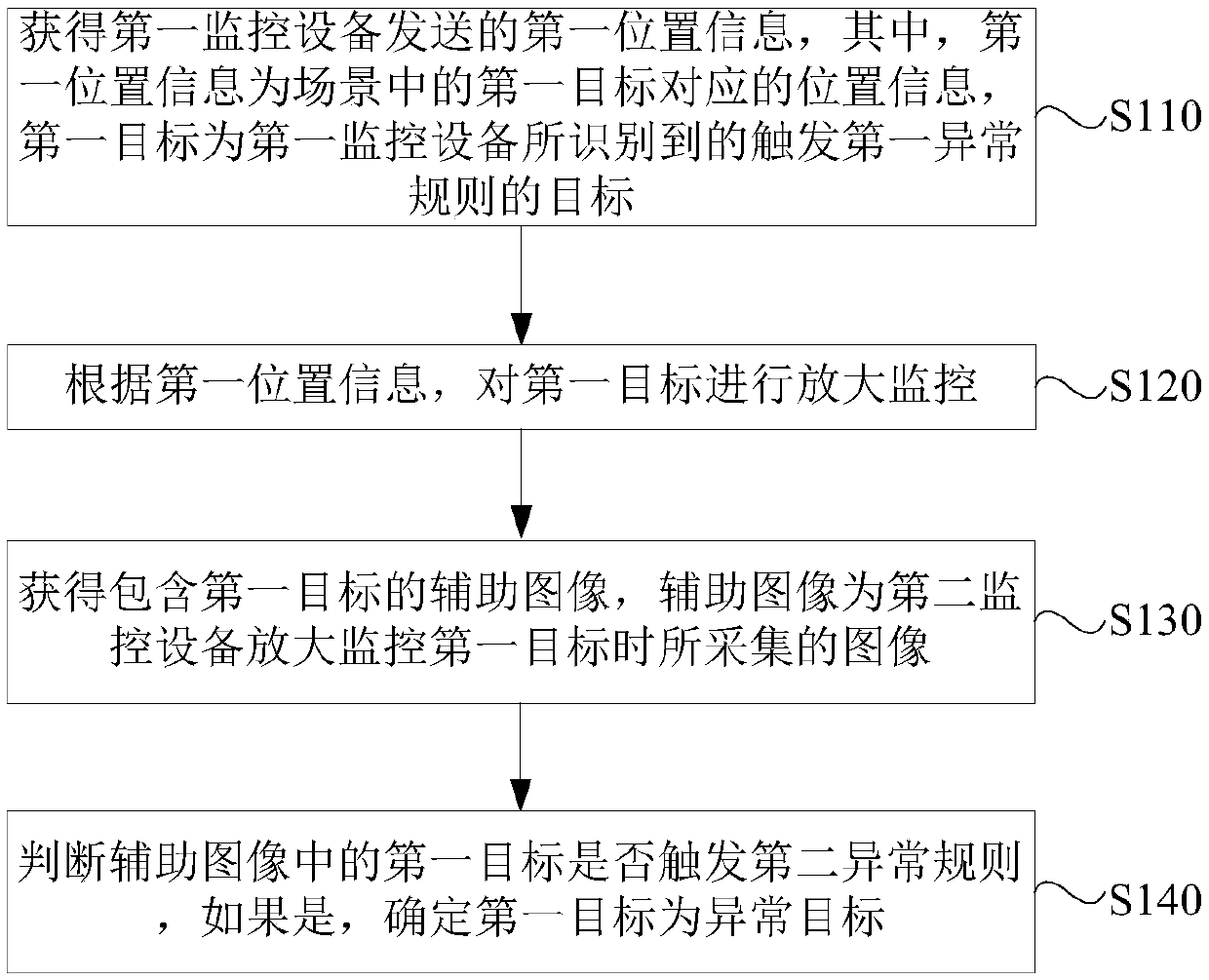
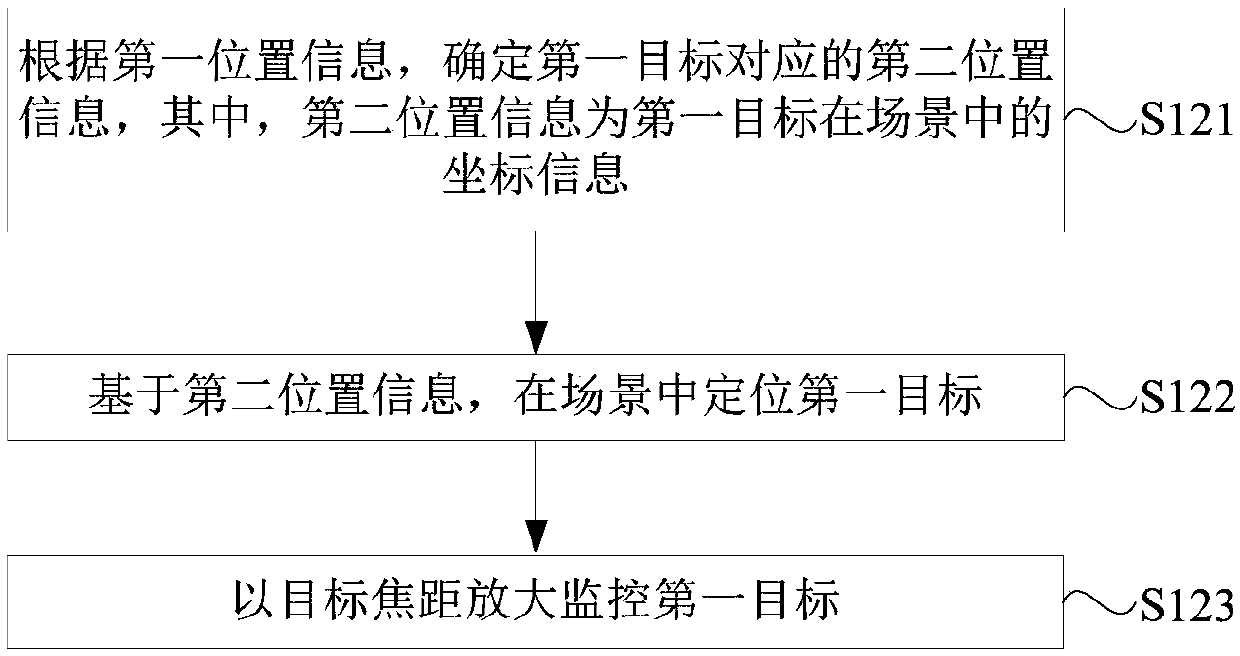
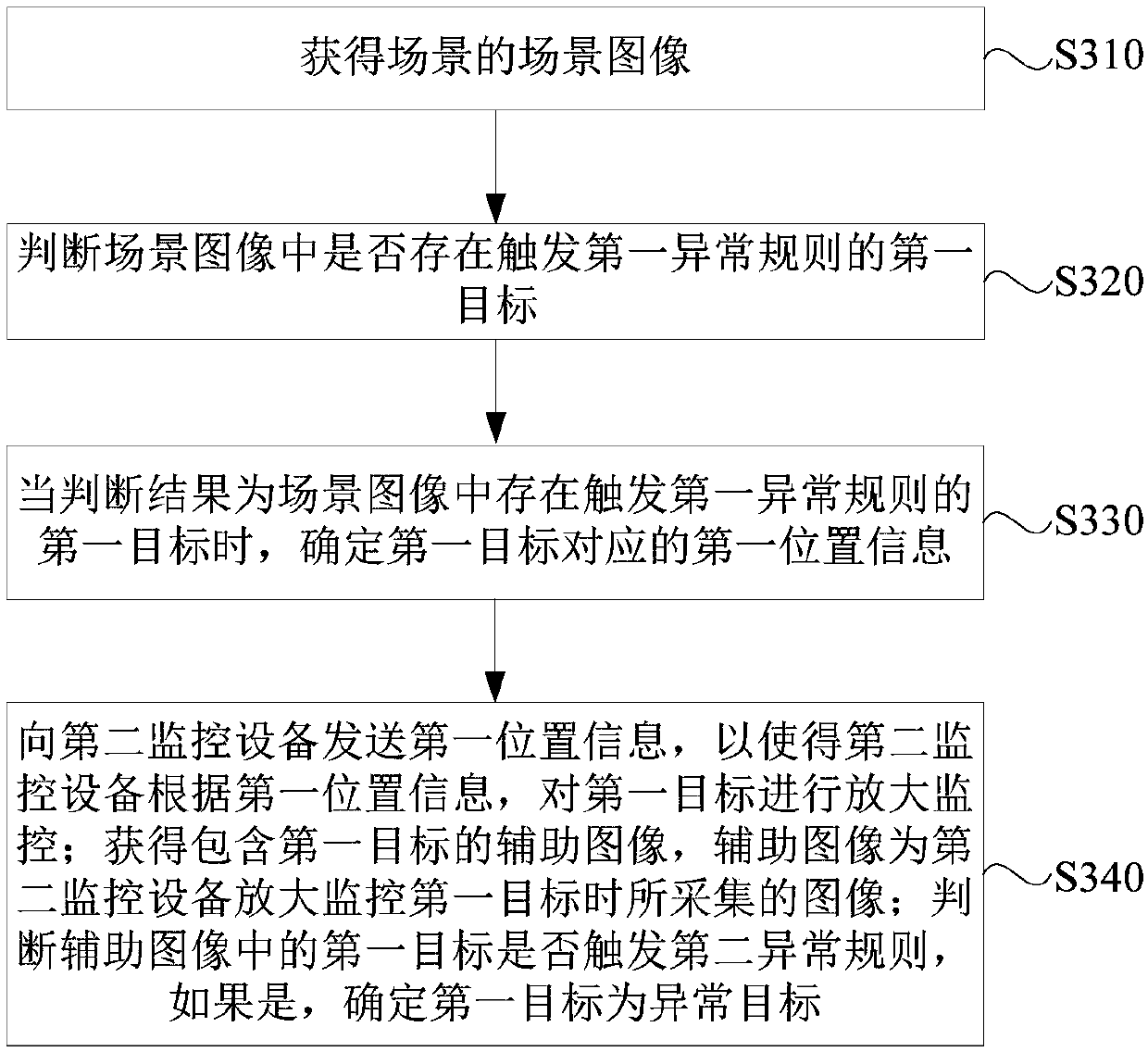
The embodiment of the invention discloses a monitoring method, device and system as well as monitoring equipment. The method is applied to second monitoring equipment in the monitoring system. The monitoring system further comprises first monitoring equipment. The method comprises the following steps: acquiring first position information transmitted by the first monitoring equipment, wherein the first position information is position information corresponding to a first target in a scene, and the first target is a target which is recognized by the first monitoring equipment and triggers a first exception rule; performing zoom-in monitoring on the first target according to the first position information; acquiring an auxiliary image including the first target, wherein the auxiliary image isan image acquired when the second monitoring equipment performs zoom-in monitoring on the first target; and judging whether the first target in the auxiliary image triggers a second exception rule ornot, and if so, determining the first target as an exceptional target. Through the technical scheme provided by the embodiment of the invention, the target included in the auxiliary image acquired bythe second monitoring equipment has relatively abundant detailed information, so that the recognition accuracy of the exceptional target can be improved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Quality review system with plug-ins
PendingUS20210019686A1Easy to useConvenient reviewOffice automationKnowledge representationBatch processingData source
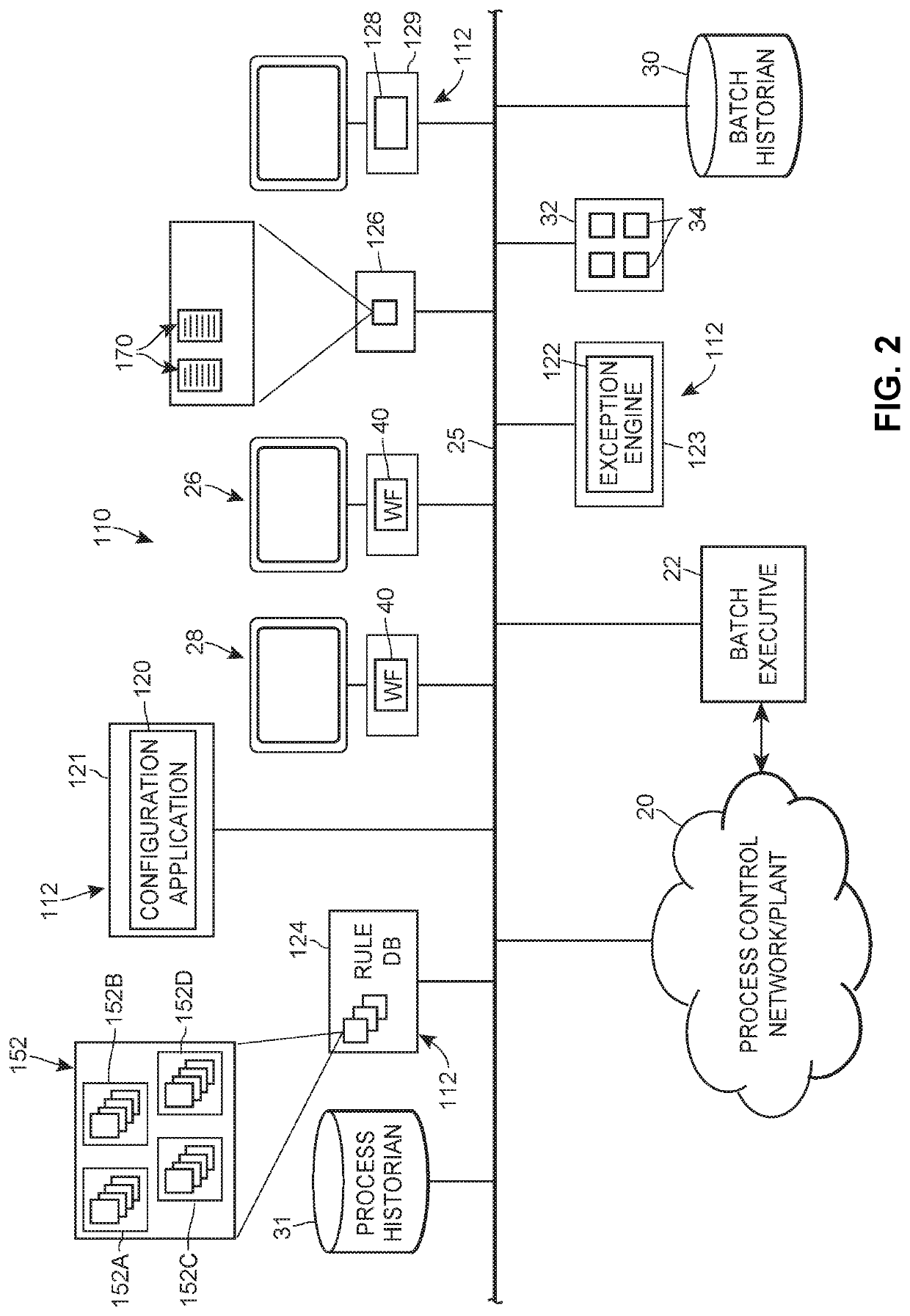
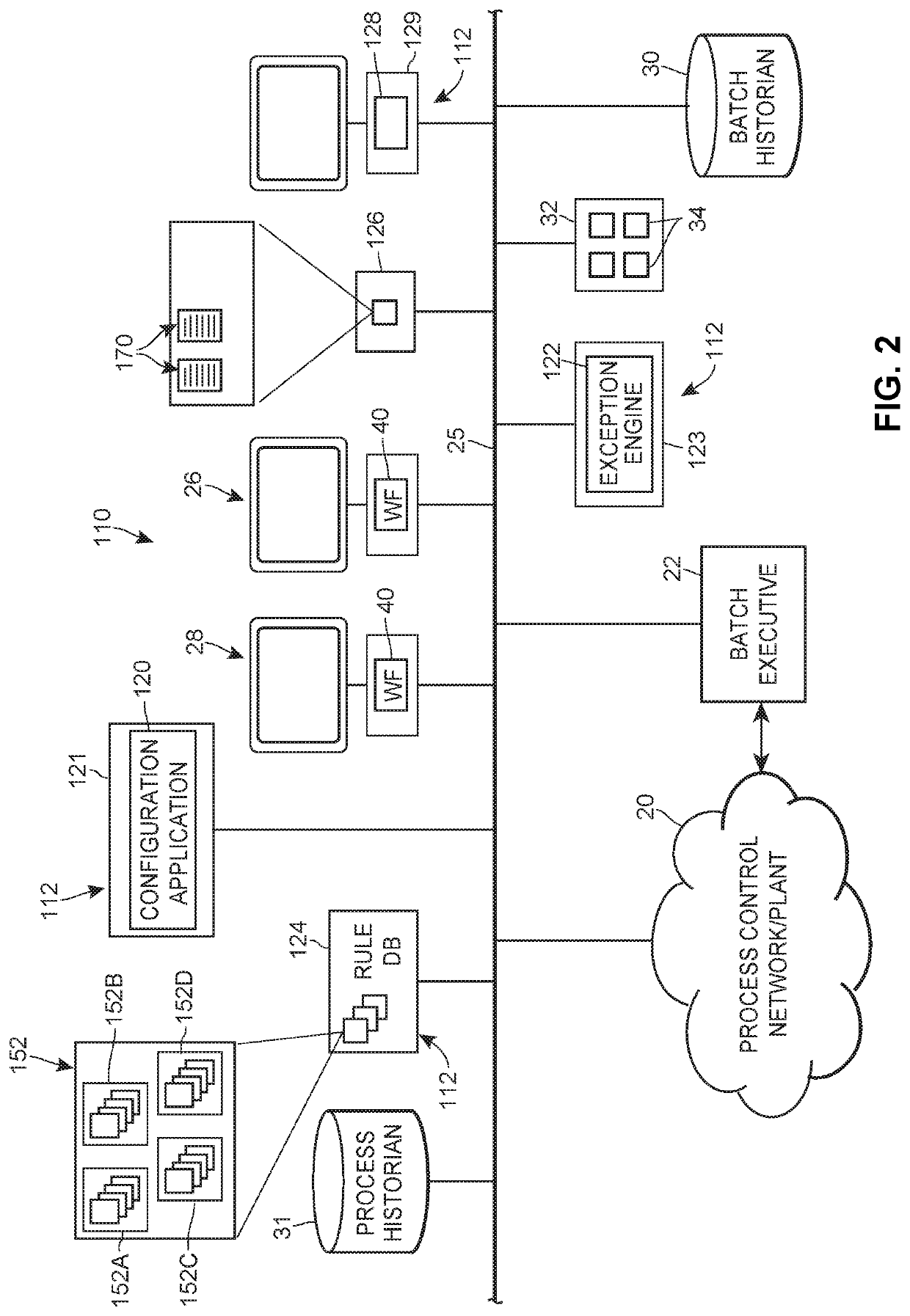
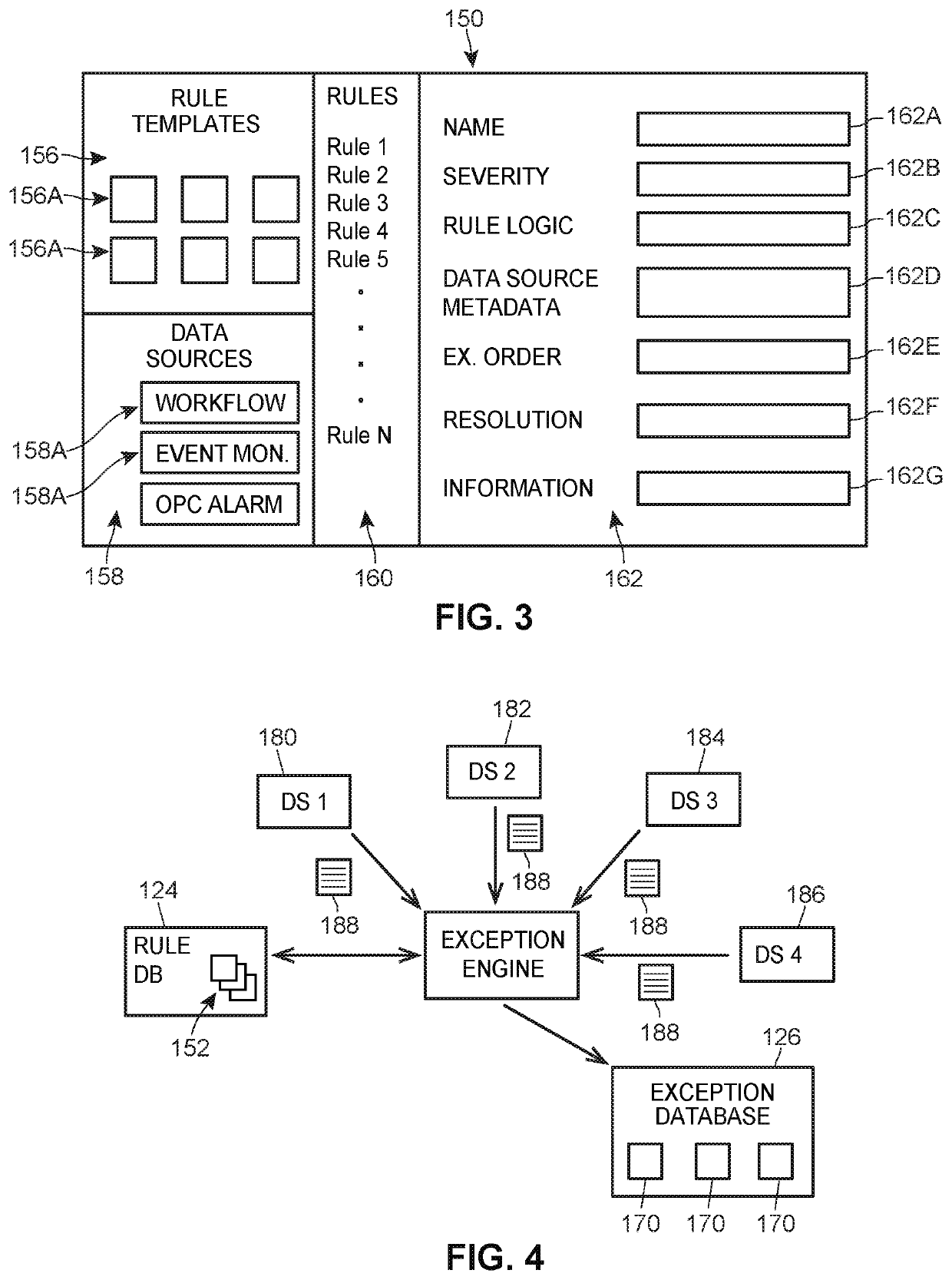
A quality review management system may be used to analyze the operation of manufacturing processes within a plant based on data collected by various data sources in the plant, such as batch executive applications, to automatically detect, store, and display exceptions within those processes for use by a quality review engineer to determine if the process operation meets certain quality standards. The quality review management system includes a configuration application that enables a user to create one or more exception rules, an exception engine that uses plug-ins in various devices to collect process data and to analyze the process data using the rules to detect one or more exceptions within the process, and a review application that enables quality review personnel to review each determined exception for resolution purposes.
Owner:FISHER-ROSEMOUNT SYST INC
Heuristic script detection method and system based on structured exception
InactiveCN104978525AEfficient detectionEfficient discoveryPlatform integrity maintainanceProgramming languageException rule
The invention provides a heuristic script detection method and system based on structured exception. The method comprises the following steps: reading a script code to be detected; carrying out structured scanning on the script code, and determining a code structure of the script code; according to a structured exception rule, matching the code structure of the script code, confirming that the code structure of the script code to be detected is exceptional if the code structure is successfully matched, and giving an alarm; and otherwise, confirming that the code structure of the script code to be detected is normal. The invention also provides a corresponding detection system. Through the method and the system provided by the invention, the scripts subjected to the structured exception can be quickly and effectively found, and a user can be given an alarm. The scheme can effectively make up deficiencies in a traditional detection method, and detects the scripts subjected to malicious deformation or the codes subjected to the structured exception.
Owner:HARBIN ANTIY TECH
Methods and systems for group data management and classification
ActiveUS8131683B2Digital data processing detailsOffice automationClassification methodsStructure of Management Information
Owner:IRON MOUNTAIN INCORPORATED
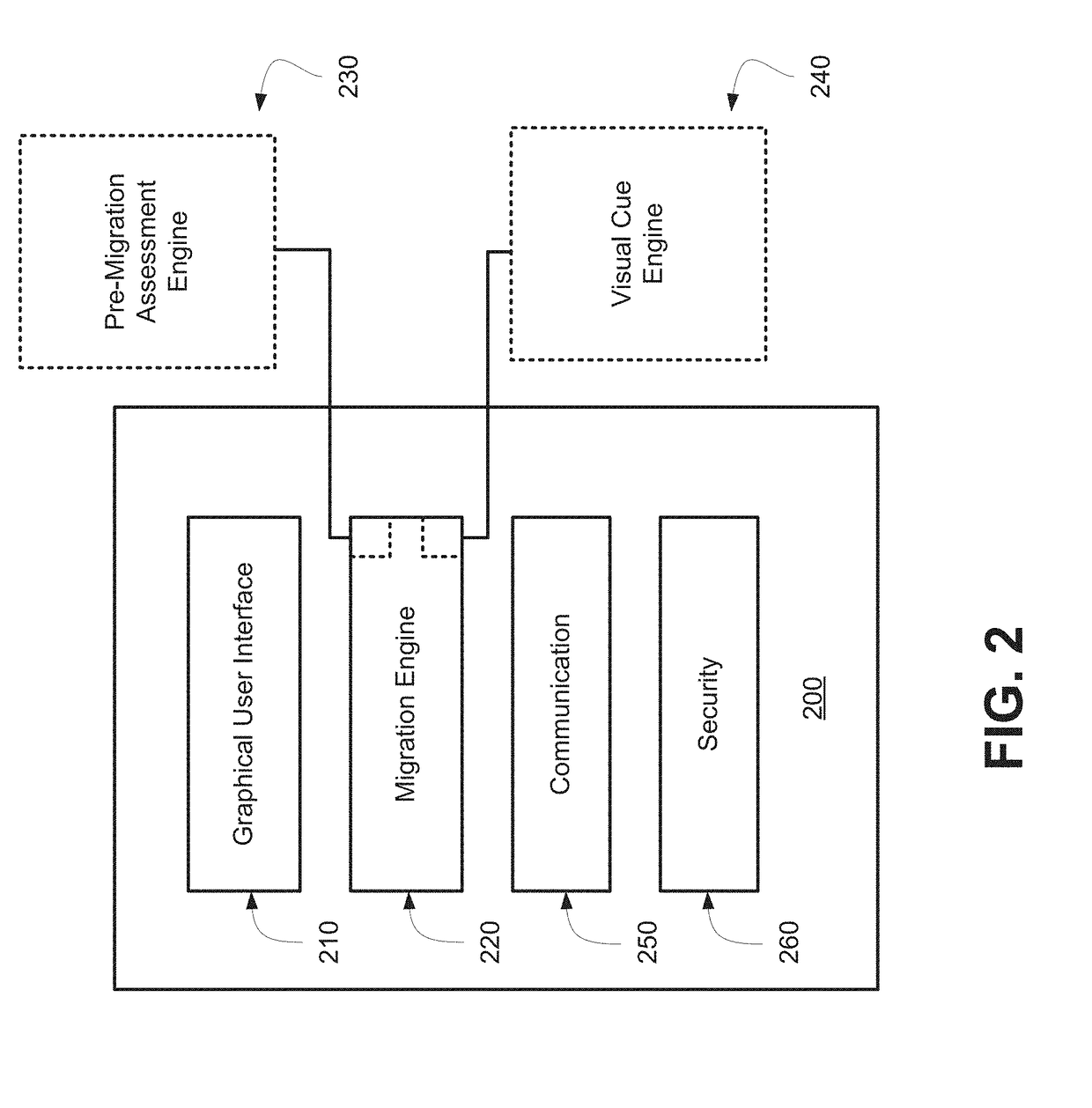
Enhanced management of migration and archiving operations
ActiveUS9819630B2Multiple digital computer combinationsData switching networksException ruleOperating system
Owner:QUEST SOFTWARE INC
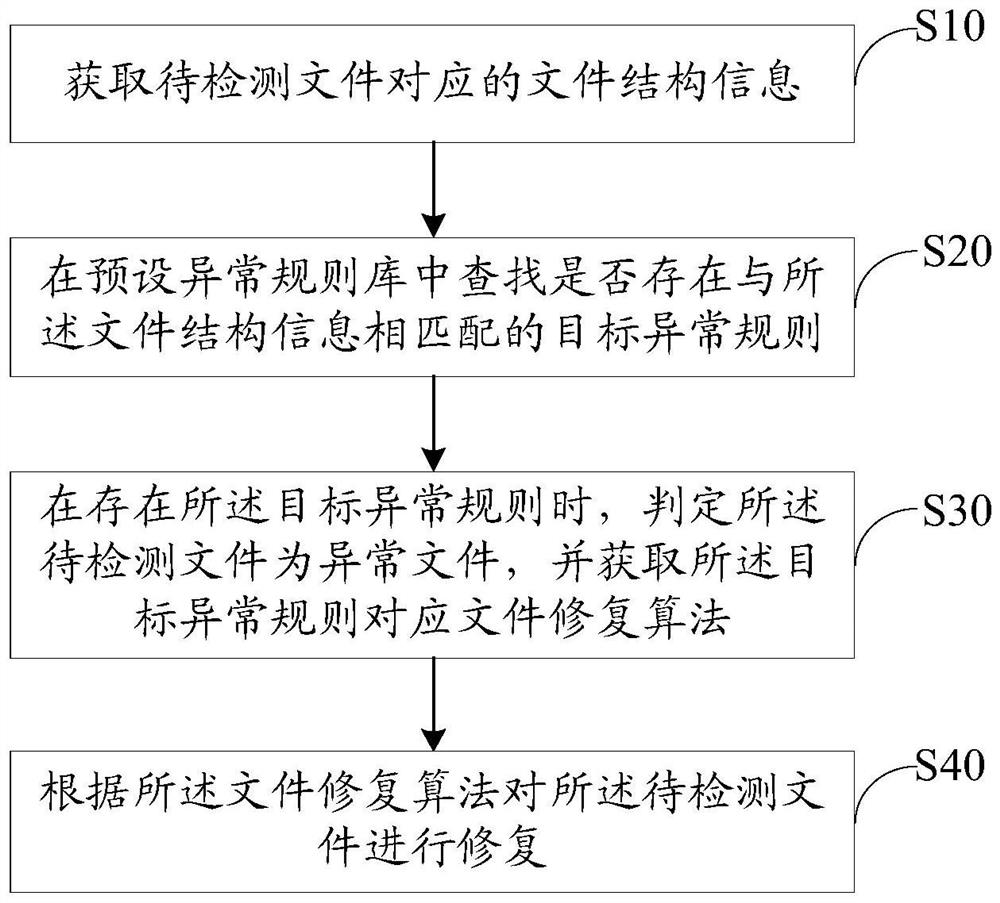
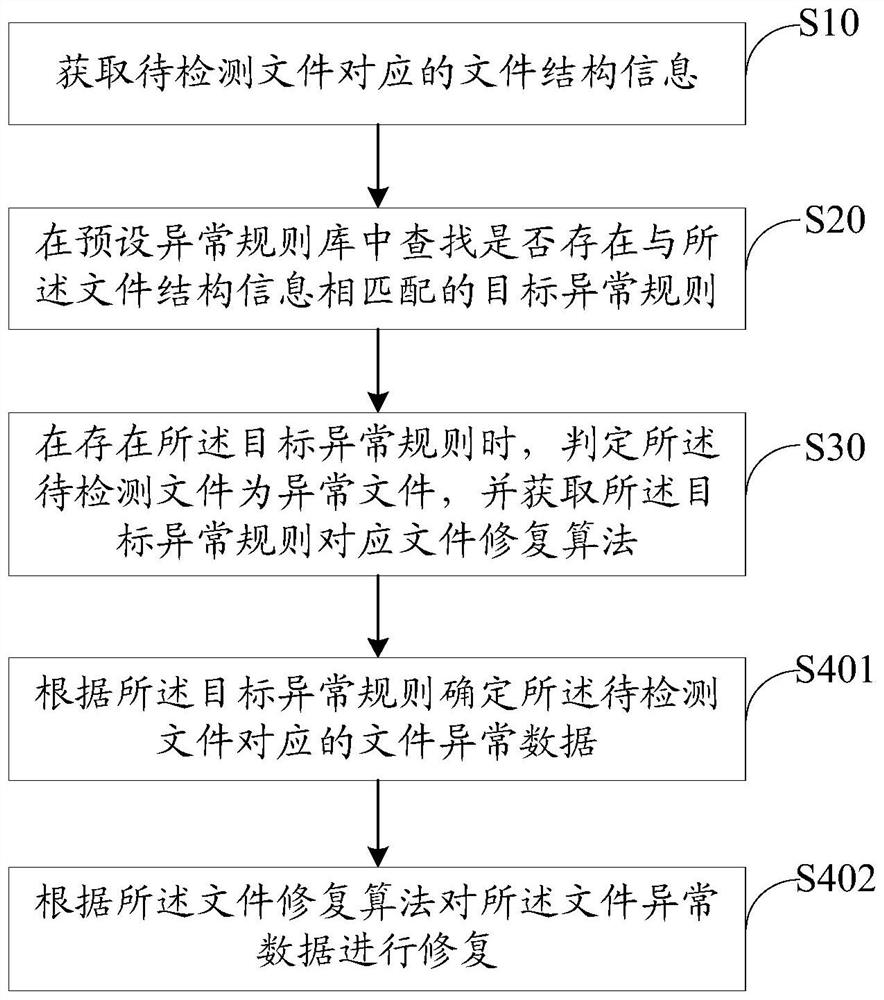
Abnormal file restoration method, device and equipment, and storage medium
PendingCN112612756AImprove repair rateGuaranteed accuracyFile metadata searchingFile/folder operationsRestoration methodFile Fixity
The invention discloses an abnormal file restoration method, device and equipment and a storage medium, and the method comprises the steps: obtaining the file structure information corresponding to a to-be-detected file, and searching a preset abnormal rule library for whether there is a target abnormal rule matched with the file structure information or not; and when the target exception rule exists, judging that the to-be-detected file is an exception file, obtaining a file repair algorithm corresponding to the target exception rule, and repairing the to-be-detected file according to the file repair algorithm. Compared with the existing mode of identifying or detecting the abnormal file through the feature code and repairing the file by searching the corresponding health file or the address information of the health file in the file database, the method, device and equipment have the advantages that whether the to-be-detected file triggers the abnormal rule or not is judged through the file structure information, and if yes, the to-be-detected file is judged to be abnormal; and the corresponding file repair algorithm is obtained according to the triggered exception rule to repair the file, so that the accuracy of exception identification is ensured, and the file repair rate is also improved.
Owner:三六零数字安全科技集团有限公司
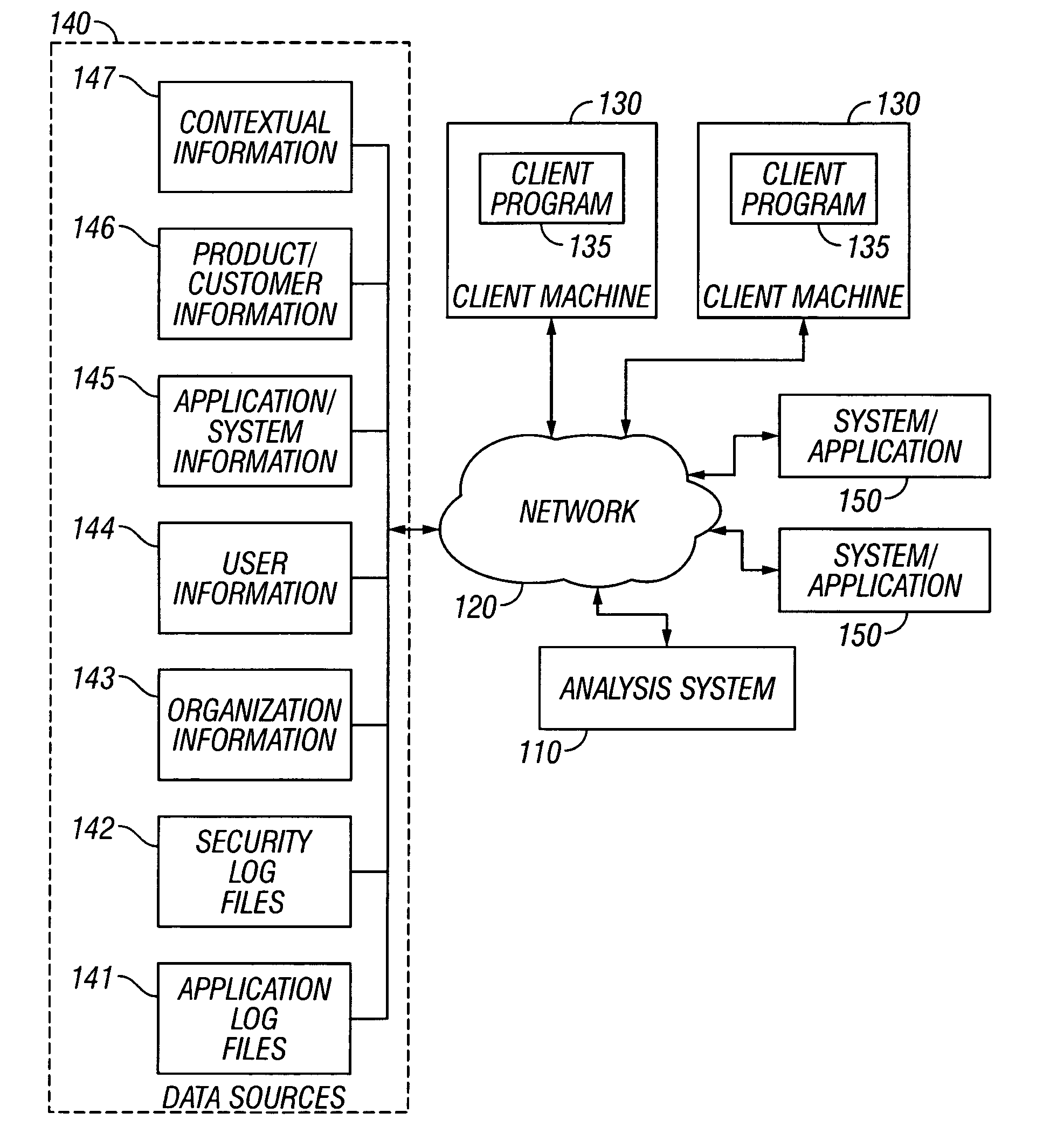
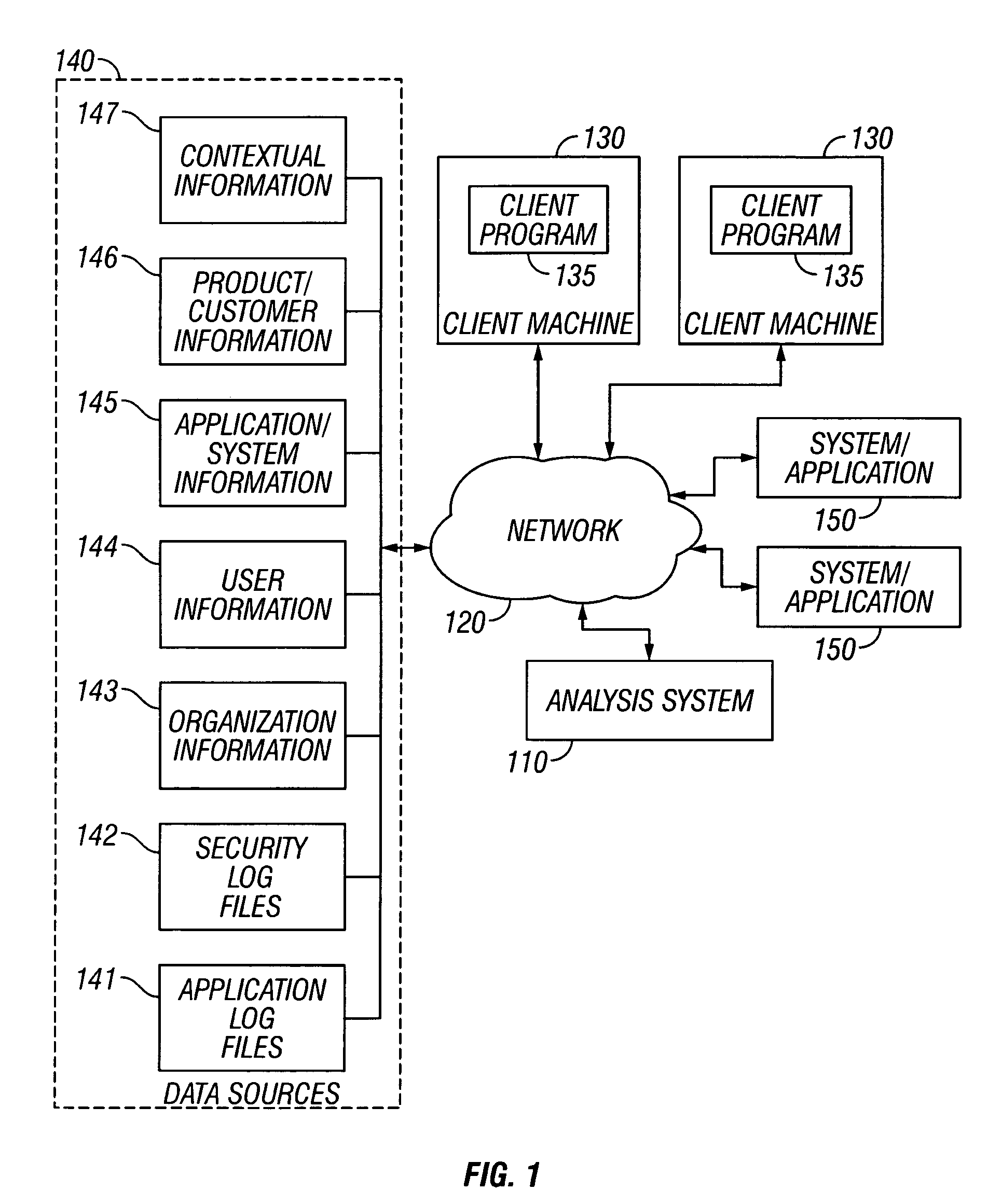
System and method for contextually understanding and analyzing system use and misuse
InactiveUS20060117004A1Computer security arrangementsSpecial data processing applicationsException ruleContextual information
A system and method for contextually understanding and analyzing system use and misuse are described. In one preferred embodiment, one or more trigger events are detected and information related to the events is received. One or more exception rules are retrieved from exception rules tables within a database and the exception rules are applied to the received information. If a valid exception is identified, an exception notification is created and stored in oversight record tables within the database for further processing. Appropriate recipient users to receive the exception notification are identified from the actions, transactions, and contextual information tables within the database and the exception notification is further transmitted to the identified recipient users.
Owner:WELLS FARGO BANK NA
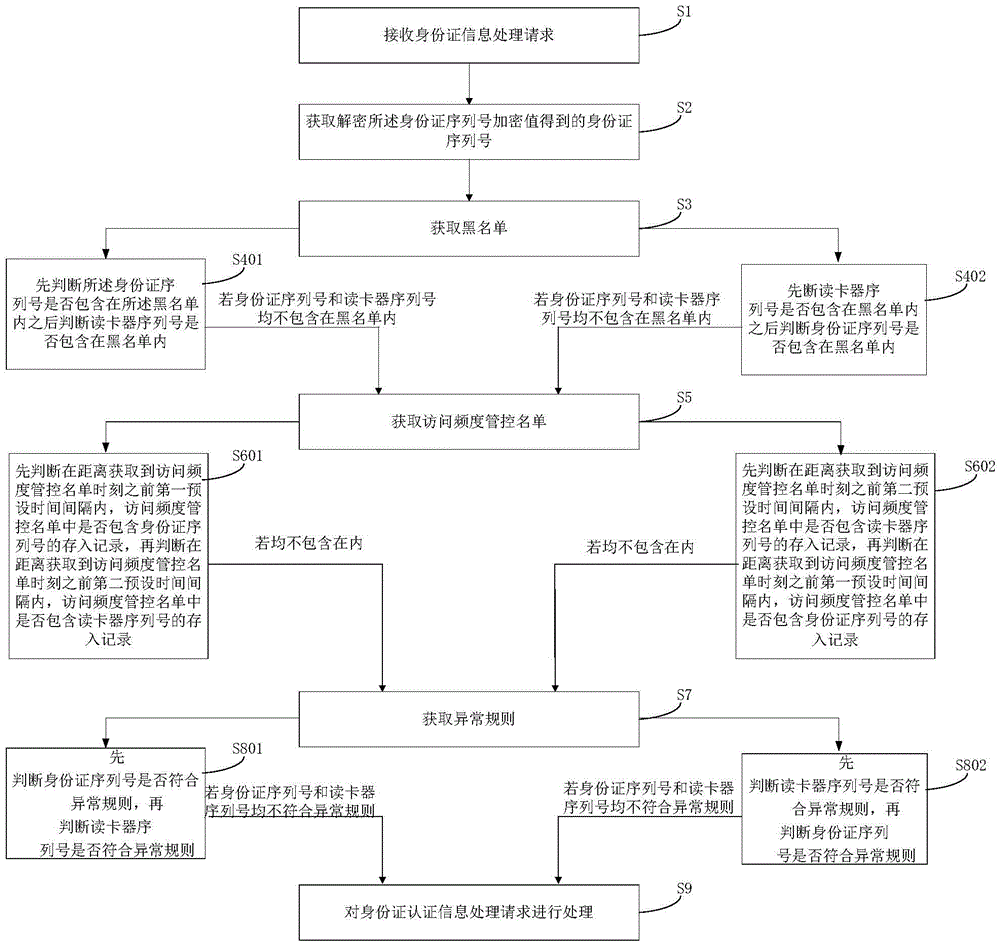
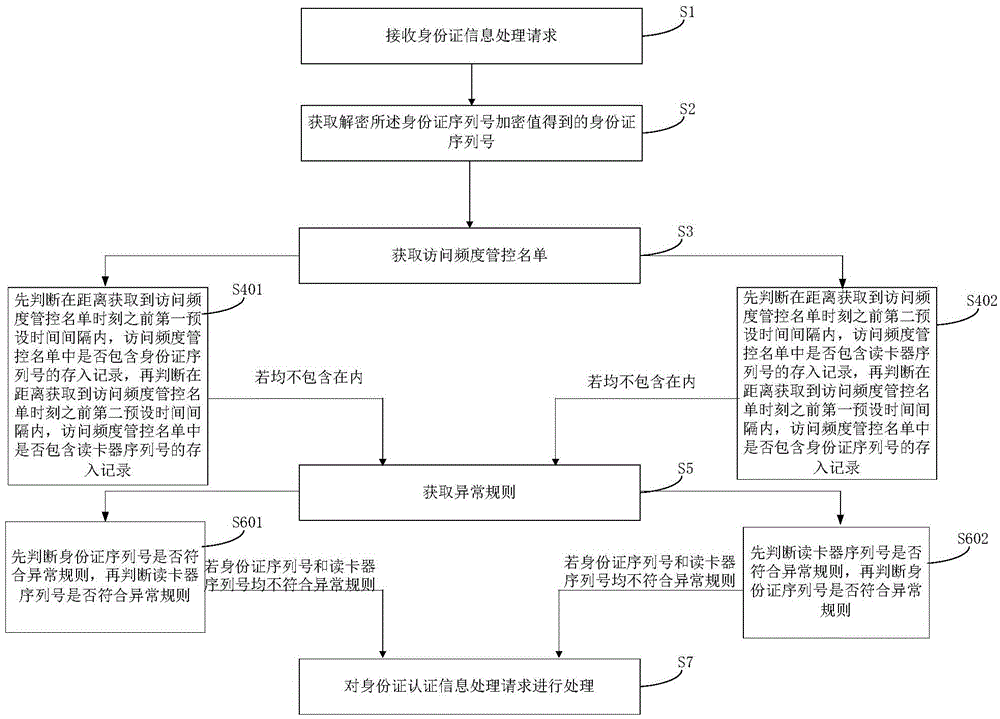
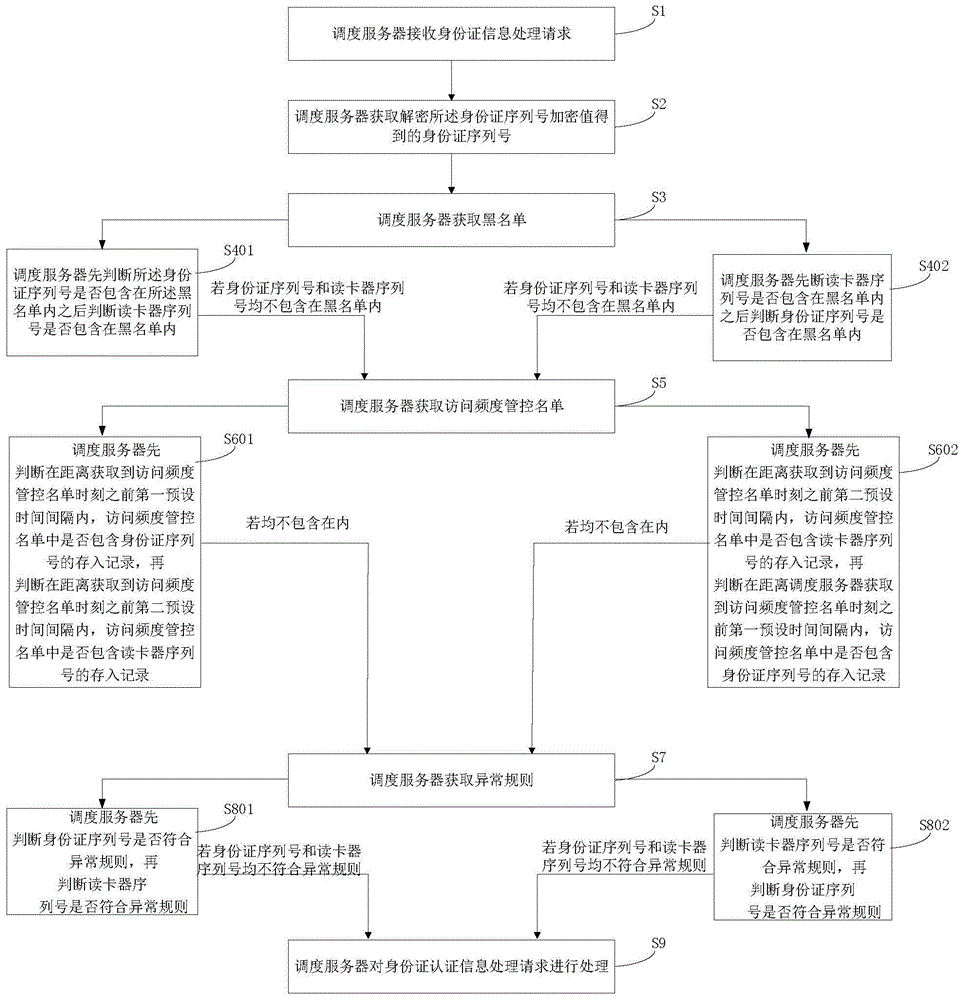
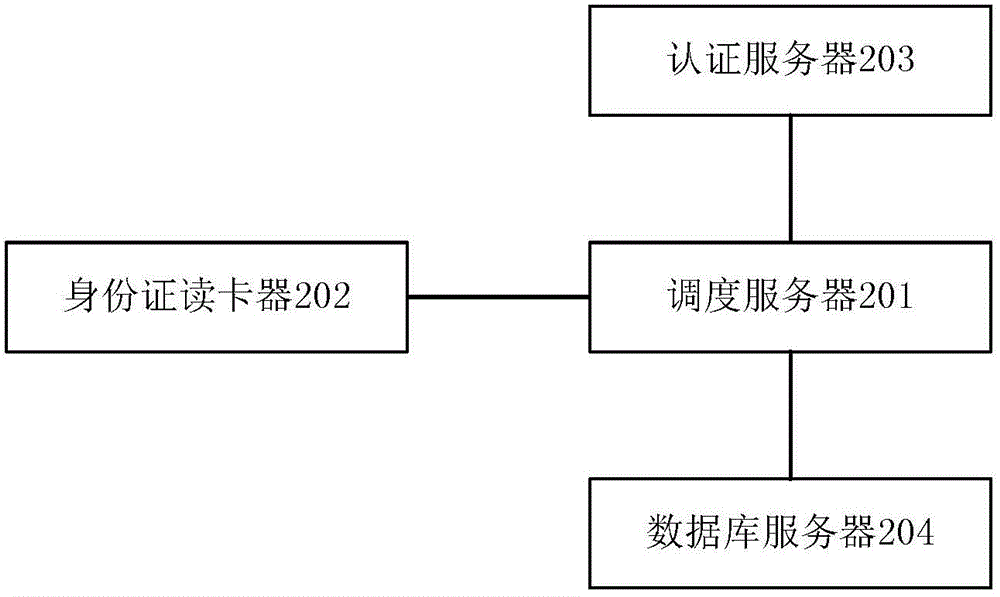
Method for processing identity card authentication information processing request
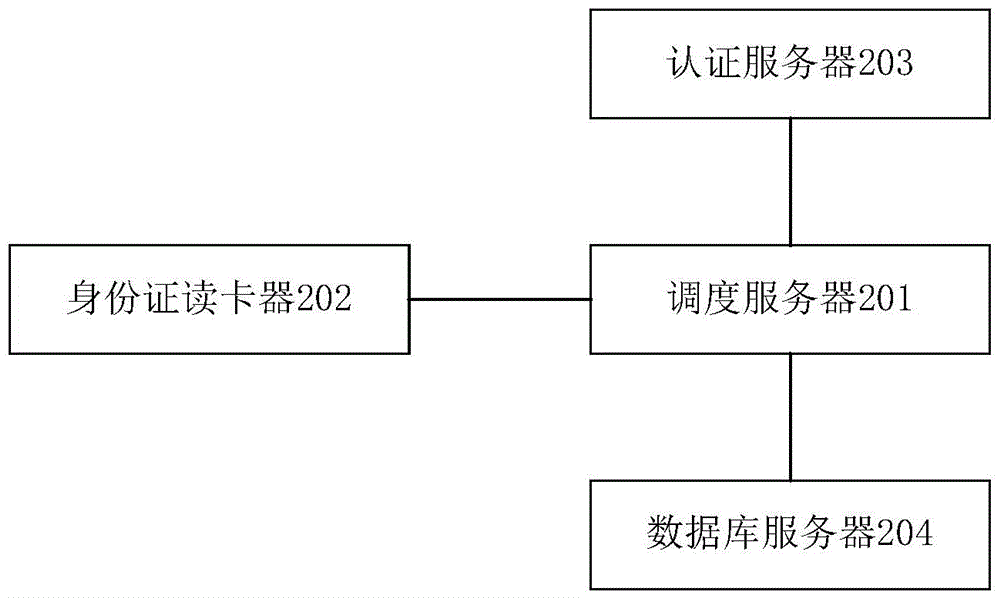
ActiveCN106027465ARealize dynamic updateAvoid Dynamic UpdatesTransmissionAccess frequencyCard reader
The invention provides a method for processing an identity card authentication information processing request, and the method comprises the steps: receiving the identity card authentication information processing request, obtaining a blacklist, and obtaining an access frequency management and control list if a serial number of an identity card and a serial number of a card reader are not in the blacklist; obtaining an exception rule if the access frequency management and control list does not contain storage record of the serial number of the identity card in a first preset time interval before the moment when the access frequency management and control list is obtained and the access frequency management and control list does not contain the storage record of the serial number of the card reader in a second preset time interval before the moment when the access frequency management and control list is obtained; carrying out the processing of the identity card authentication information processing request if the serial number of the identity card and the serial number of the card reader do not accord with the exception rule, thereby achieving the triple dynamic verification of the identity card and the identity card reader, and improving the processing safety and reliability of the identity card authentication information processing request.
Owner:TENDYRON CORP
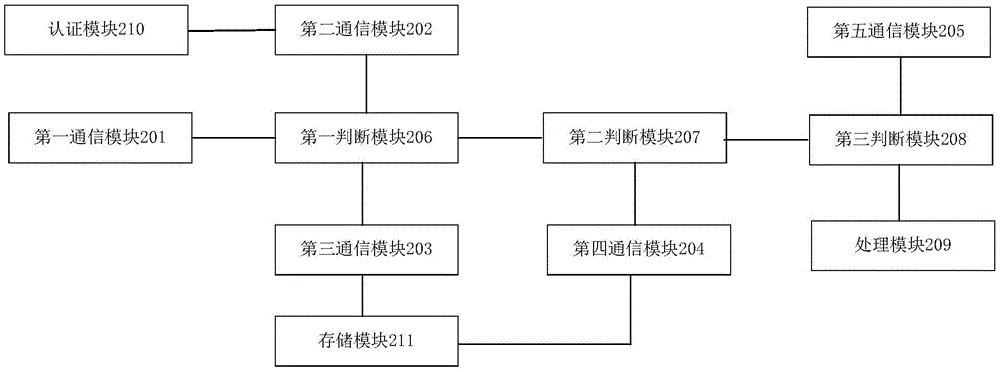
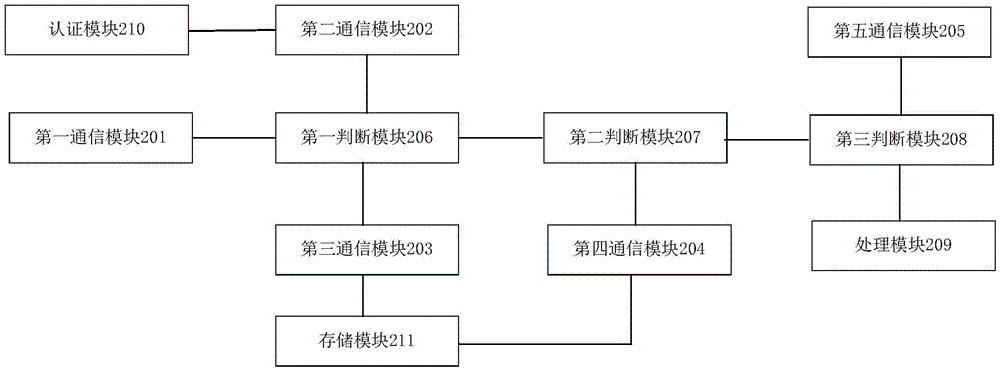
Access frequency management and control device for identity card authentication information
ActiveCN106027253AFreeze for a short timeImprove securityUser identity/authority verificationComputer moduleAccess frequency
The invention provides an access frequency management and control device for identity card authentication information, and the device comprises a fourth communication module which is used for obtaining an access frequency management and control list; a second judgment module which is used for judging whether the access frequency management and control list contains the storage record of the serial number of an identity card in a first preset time interval before the moment when the access frequency management and control list is obtained or not, or judging whether the access frequency management and control list contains the storage record of the serial number of a card reader in a second preset time interval before the moment when the access frequency management and control list is obtained or not; a fifth communication module which is used for obtaining an except rule; a third judgment module which is used for judging whether the serial number of the identity card or the serial number of the card reader accords with the exception rule or not; and a processing module which is used for processing an identity card authentication information processing request, thereby achieving the dual dynamic verification of the identity card and the identity card reader, and improving the processing safety and reliability of the identity card authentication information processing request.
Owner:TENDYRON CORP
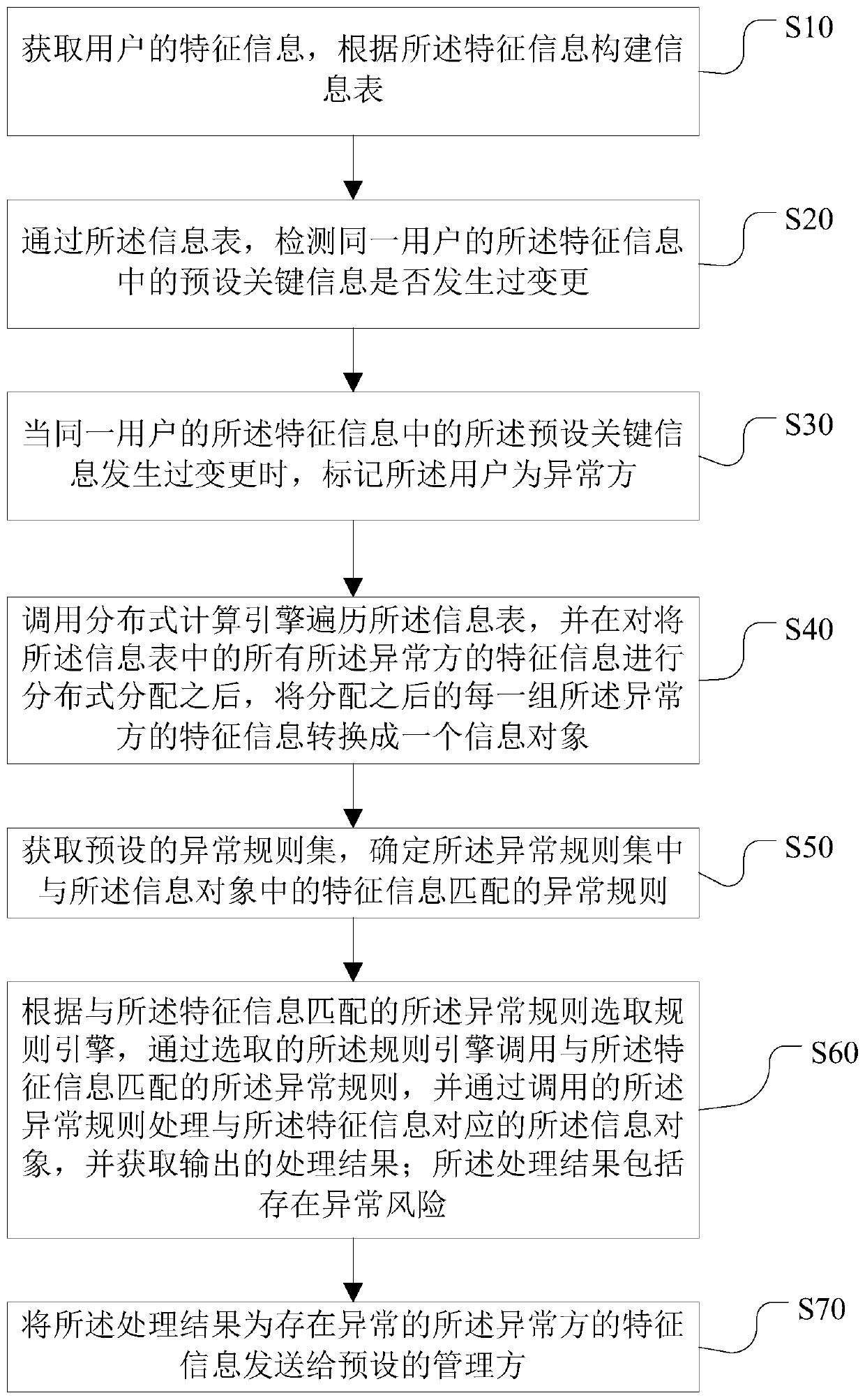
Abnormal information identification method and device, computer device and storage medium
The invention discloses an abnormal information identification method and device, a computer device and a storage medium, and the method comprises the steps: obtaining the feature information of a user, and constructing an information table; when the preset key information in the feature information of the same user is changed, marking the user as an abnormal party; calling a distributed computingengine to traverse the information table, and after carrying out distributed allocation on the feature information of all the abnormal parties in the information table, converting the allocated feature information of each group of abnormal parties into an information object; determining an exception rule matched with the feature information in the information object in the exception rule set; selecting a rule engine, and obtaining an output processing result by utilizing the rule engine; and sending the feature information of the abnormal party with the abnormal processing result to a presetmanagement party. According to the method, the accuracy and the efficiency of monitoring the abnormity of the user are improved, and the efficiency and the speed of judging the abnormity are also improved, so that the user is prevented from being damaged in time.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Exception handling system for identity card authentication information processing request
ActiveCN106027468AFreeze for a short timeImprove securityTransmissionAccess frequencyHandling system
The invention provides an exception handling system for an identity card authentication information processing request. A dispatch server receives the identity card authentication information processing request, obtains a blacklist, and obtains an access frequency management and control list if a serial number of an identity card and a serial number of a card reader are not in the blacklist. An exception rule is obtained if the access frequency management and control list does not contain storage record of the serial number of the identity card in a first preset time interval before the moment when the access frequency management and control list is obtained and the access frequency management and control list does not contain the storage record of the serial number of the card reader in a second preset time interval before the moment when the access frequency management and control list is obtained. The identity card authentication information processing request is processed if the serial number of the identity card and the serial number of the card reader do not accord with the exception rule, thereby achieving the triple dynamic verification of the identity card and the identity card reader, and improving the processing safety and reliability of the identity card authentication information processing request.
Owner:TENDYRON CORP
Detecting statistical variation from unclassified process log
InactiveUS8543552B2Digital data processing detailsRegistering/indicating quality control systemsProcess behaviorException rule
A system and associated method for detecting a statistical variation of a process from a textual log of the process as performed by a process behavior analysis (PBA) system for monitoring the process operating in an Information Technology (IT) delivery system. The PBA system includes a PBA engine and a data storage storing exception rules used by the PBA engine. The PBA engine merges entities appearing in the textual log into one or more groups based on similarities of respective time series of the entities. Control charts are generated for merged entities and the PBA engine subsequently analyzes process behavior of the process by use of the control charts for exceptions defined in the stored exception rules. The PBA engine generates a PBA report for the process pursuant to the analysis result of the textual log with detailed information including to what type of exceptions had or had not occurred.
Owner:IBM CORP
Quality review management system with configurable exception rules
ActiveUS20210019685A1Easy to useConvenient reviewOffice automationProgram controlBatch processingSoftware engineering
A quality review management system may be used to analyze the operation of manufacturing processes within a plant based on data collected by various data sources in the plant, such as batch executive applications, to automatically detect, store, and display exceptions within those processes for use by a quality review engineer to determine if the process operation meets certain quality standards. The quality review management system includes a configuration application that enables a user to create one or more exception rules, an exception engine that analyses process data using the rules to detect one or more exceptions within the process, and a review application that enables quality review personnel to review each determined exception for resolution purposes.
Owner:FISHER-ROSEMOUNT SYST INC
Dynamic processing method and system for identity card authentication information processing request
The invention provides a dynamic processing method and system for an identity card authentication information processing request. The method comprises the steps: enabling a dispatch server to receive the identity card authentication information processing request and to obtain a blacklist; obtaining an access frequency management and control list if a serial number of an identity card and a serial number of a card reader are not in the blacklist; judging whether the number of times that the serial number of the identity card and / or the serial number of the card reader appear or appears in the access frequency management and control list in a preset time interval before the obtaining of the access frequency management and control list is greater than a preset value or not; adding the serial number of the identity card and / or the serial number of the card reader to the blacklist if the number of times is greater than the preset value; obtaining an exception rule if the number of times is zero; judging whether the serial number of the identity card and / or the serial number of the card reader accord or accords with the exception rule; and adding the serial number of the identity card and / or the serial number of the card reader to the access frequency management and control list if the serial number of the identity card and / or the serial number of the card reader accord or accords with the exception rule. Therefore, the method achieves the triple dynamic verification of the identity card and the card reader, and improves the processing safety and reliability of the identity card authentication information processing request.
Owner:TENDYRON CORP
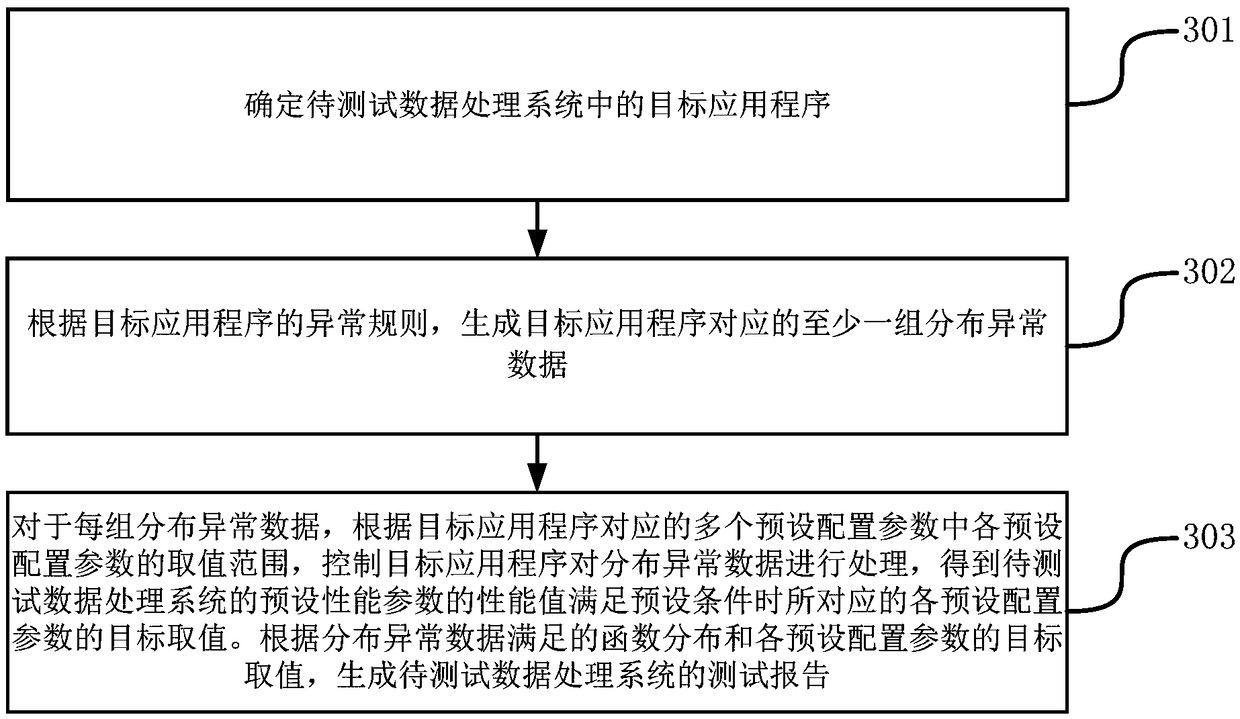
Method and apparatus for testing data processing system
ActiveCN109344049AGuaranteed uptimeImprove reliabilitySoftware testing/debuggingData processing systemException rule
The present application provides a method and apparatus for testing a data processing system, belonging to the field of big data processing. The method comprises when the data processing system to betested is tested, determining a target application in the data processing system to be tested, then obtaining the exception rules for the target application, in accordance with that exception rule, generating at least one set of distribute exception data, then for each set of distributed exception data, according to the value range of each configuration parameter in a plurality of preset configuration parameters corresponding to the target application, controlling the target application program to process the distribution abnormal data to obtain the target values of the preset configuration parameters corresponding to the preset performance parameters when the performance values of the preset performance parameters of the data processing system to be tested meet the preset conditions, andthen generating a test report based on the distribution of the distribution abnormal data and the target values of the preset configuration parameters. With this application, the method of testing thedata processing system is provided.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Concepts for address prediction or correction
Computer program products, methods, systems, apparatus, and computing entities are provided for predicting and correcting addresses. In one embodiment, this includes applying exception rules to determine whether to generate an exception for an address. If an exception exists, there are various approaches for predicting or correcting the addresses.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
An information security detection method, device, electronic equipment and storage medium
ActiveCN112700252BImprove detection efficiencyImprove detection accuracyEnsemble learningKernel methodsStatistical analysisException rule
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com