Access frequency management and control device for identity card authentication information
A technology of access frequency and authentication information, applied in the electronic field, can solve problems such as theft, loss of ID card, and application value that is far from being tapped, so as to avoid security risks, improve security and reliability, and enhance dynamics and real-time effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
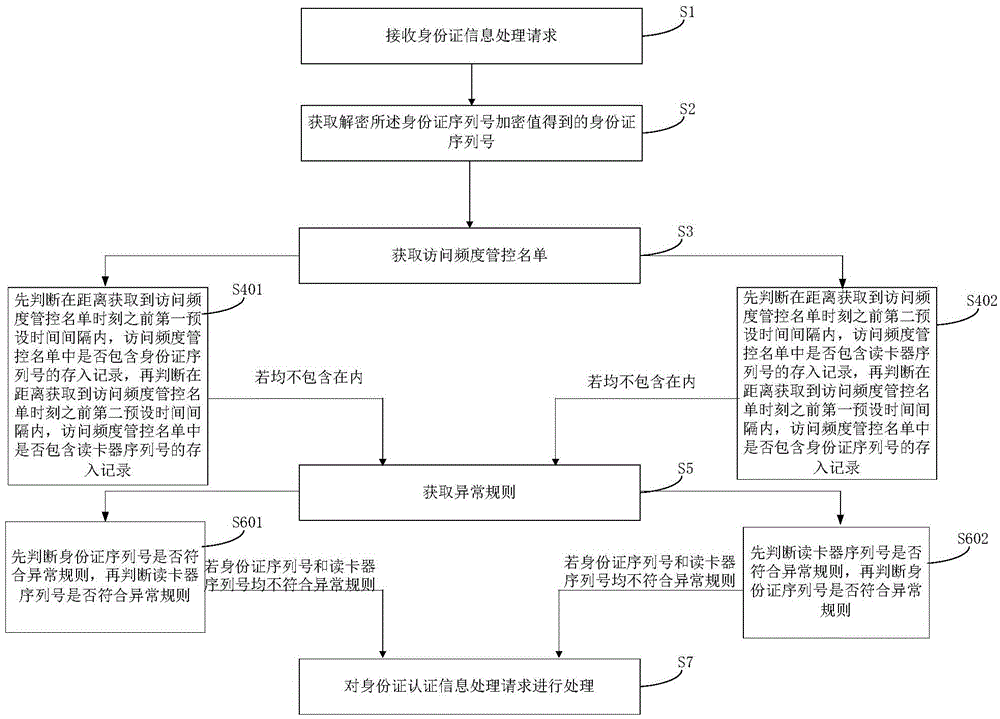
[0023] This embodiment provides a method for processing a request for processing ID card authentication information, such as figure 1 shown, including the following steps:
[0024] S1: Receive the ID card authentication information processing request, the ID card authentication information processing request includes: the encrypted value of the ID card serial number and the serial number of the card reader;
[0025] The ID card processing request is a processing request initiated by the ID card reader. After judging that the ID card processing request is a legal processing request, according to the preset rules, an idle security authentication module is allocated for the ID card processing request. The allocated security authentication module Perform data interaction with the originator of the ID card processing request, where the ID card serial number encryption value is obtained by encrypting the ID card serial number obtained from the ID card reader, and the card reader ser...
Embodiment 2
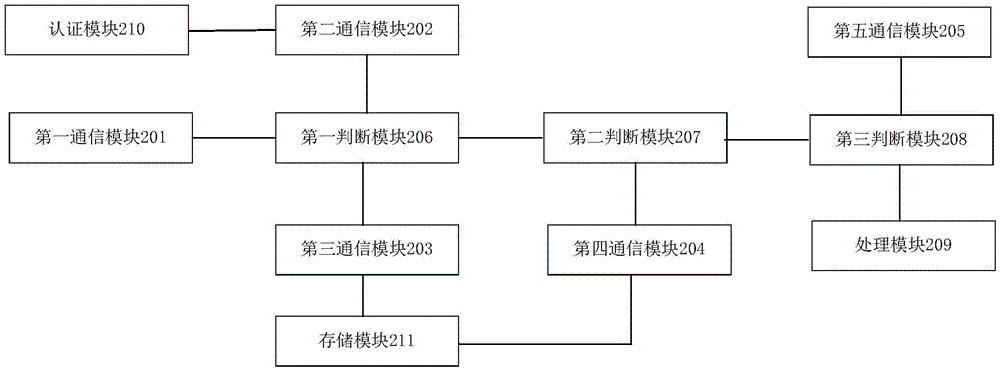
[0098] This embodiment provides an ID card cloud authentication device, such as figure 2 shown, including:
[0099] The first communication module 201 is configured to receive an ID card authentication information processing request, the ID card authentication information includes: an encrypted value of an ID card serial number and a card reader serial number, wherein the card reader serial number is ID card information Read the serial number of the terminal;
[0100] The ID card processing request is a processing request initiated by the ID card reader. After the ID card cloud authentication platform judges that the ID card processing request is a legal processing request, it allocates an idle security authentication module 210 for the ID card processing request according to preset rules, The assigned security authentication module 210 performs data interaction with the initiator of the ID card processing request, wherein the ID card serial number encryption value is obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com