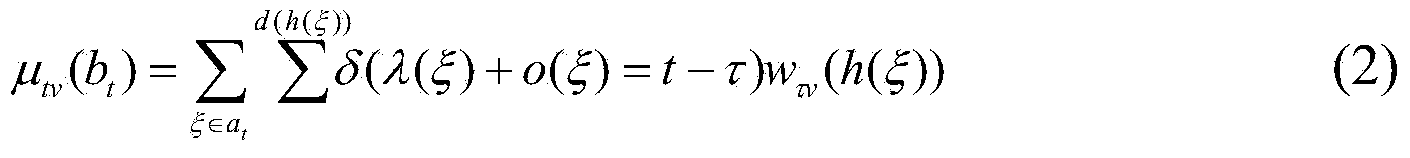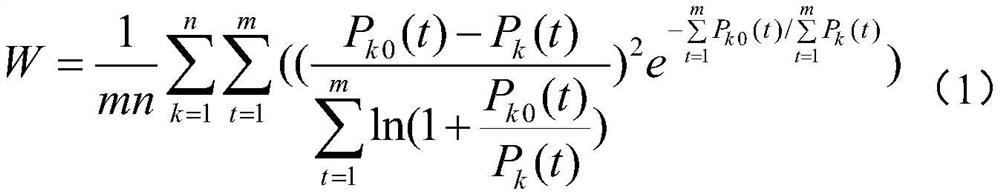Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63 results about "Cognitive analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
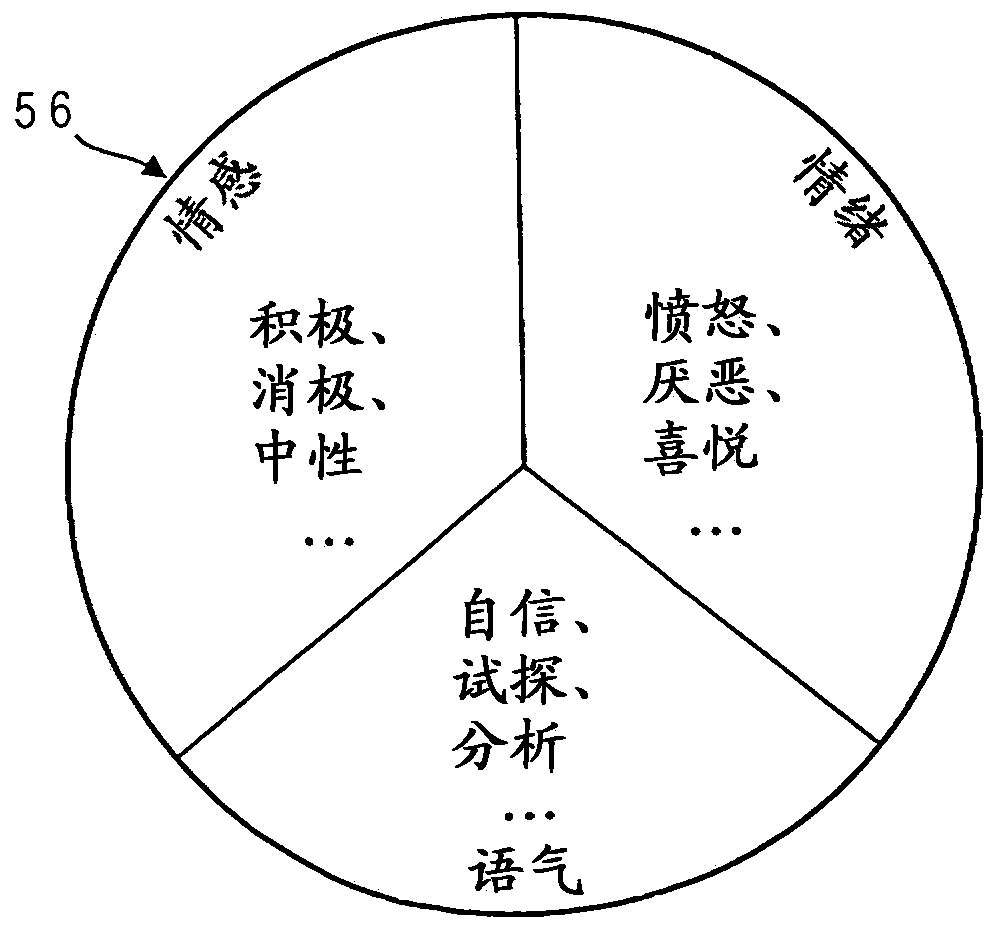
Cognitive Task Analysis. Cognitive task analysis (CTA) is a type of Task analysis aimed at understanding tasks that require a lot of cognitive activity from the user, such as decision-making, problem-solving, memory, attention and judgement.
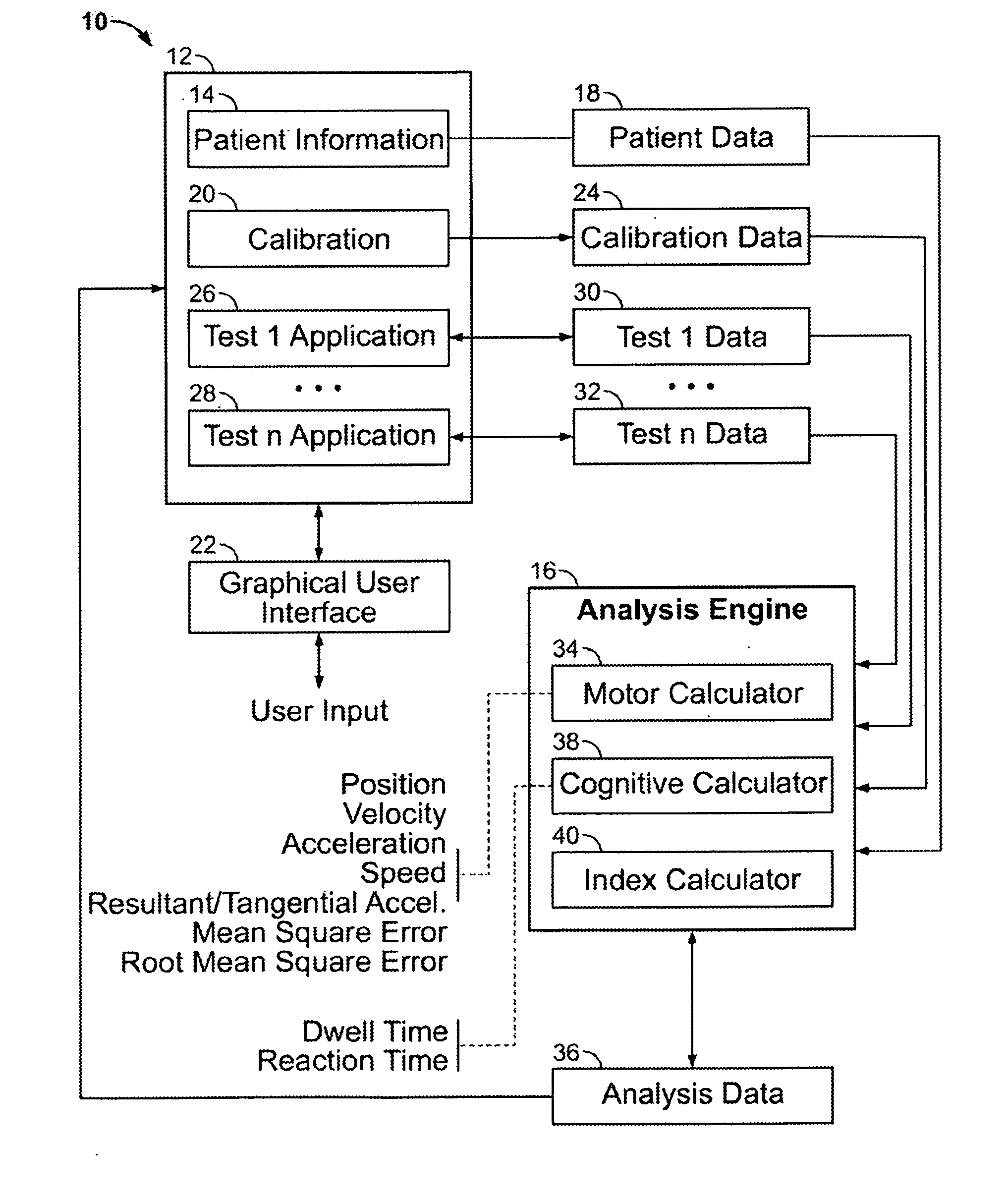
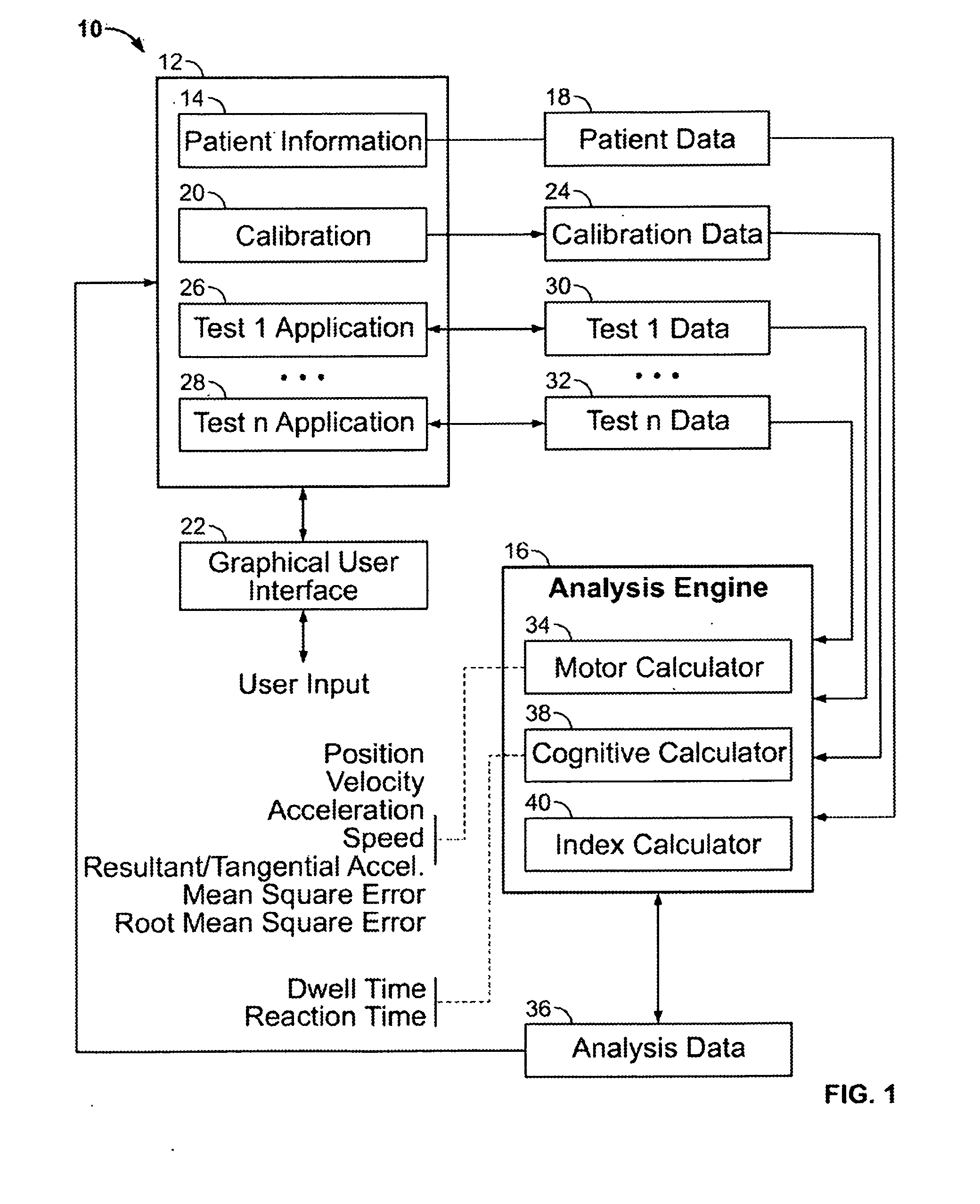
System and method for motor and cognitive analysis
A cognitive and / or motor skill testing system and method may include a processor that records respective time information for each of multiple positions of a display device that are traced during administration of a test, that determines speed and / or velocity values based on the recorded time information, and that outputs test result information based on the determined values. The test result information may be based on a comparison between a graphed curve of such values to an ideal curve. The positions may correspond to a path between displayed targets whose size and / or distance therebetween depend on past test performance. The system and / or method may output a change expected with a change to therapy parameters for a patient, where the expected change is determined based on changes which occurred in other patients having similar test results and therapy parameters as those of the patient.
Owner:THE CLEVELAND CLINIC FOUND
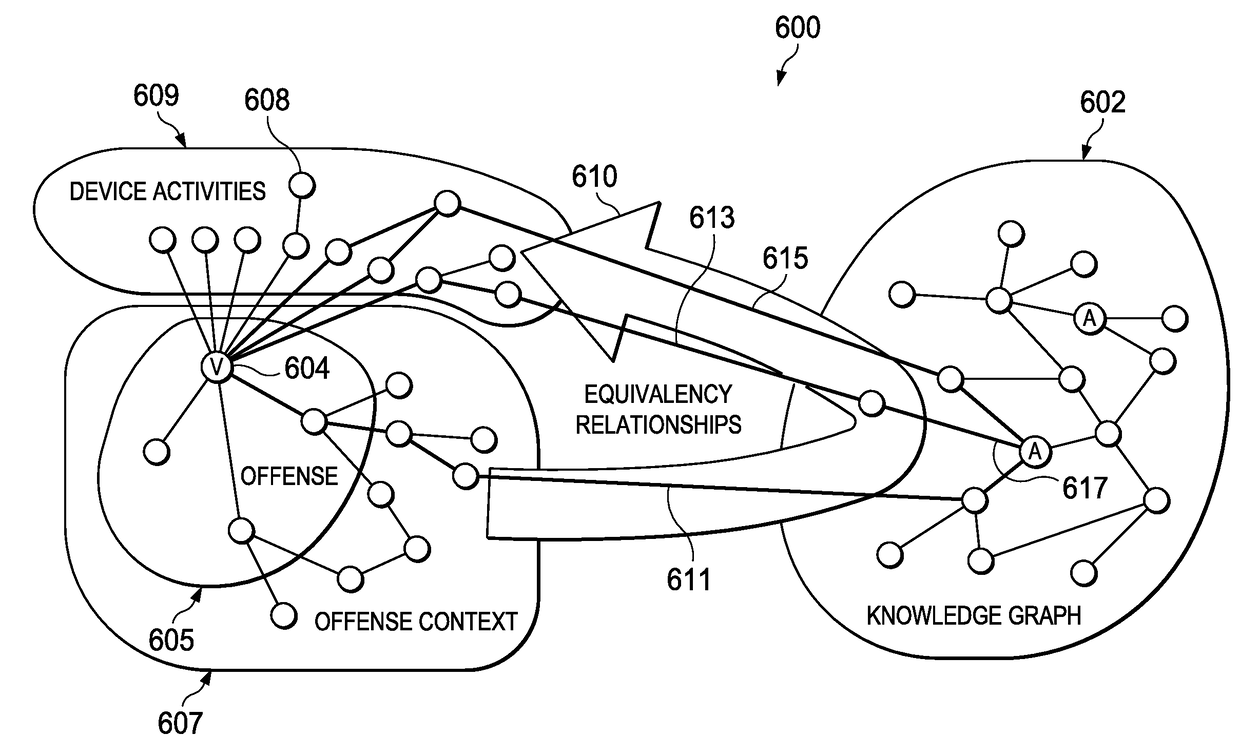
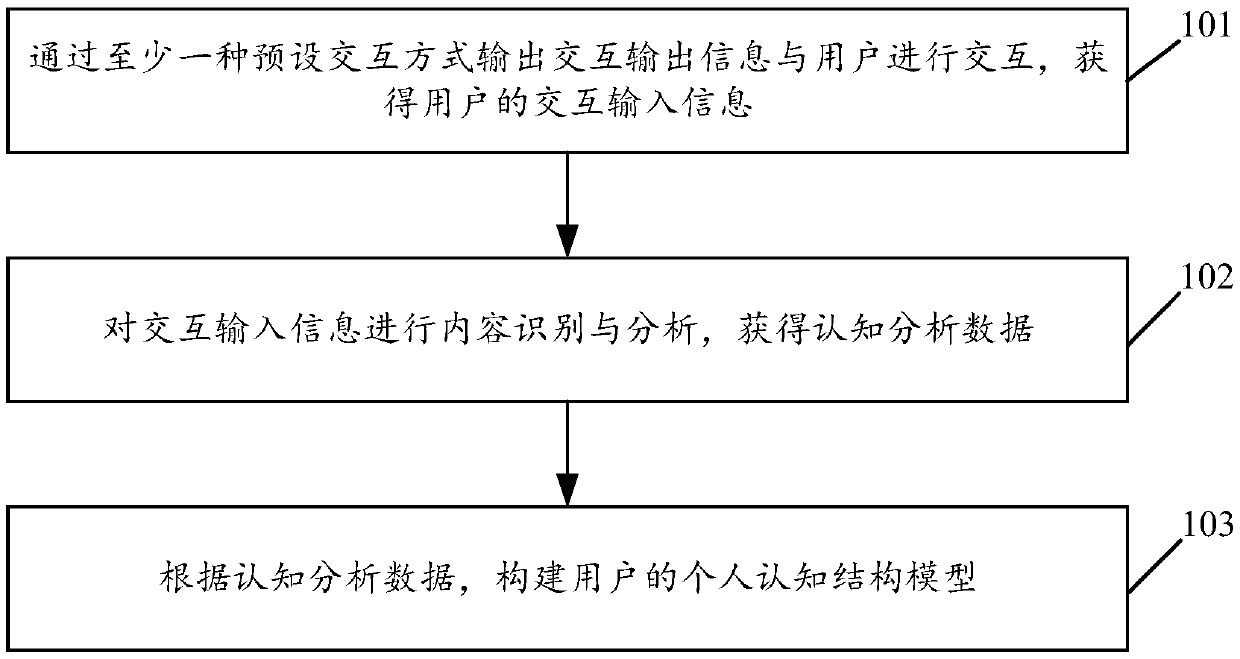
Feedback-based prioritized cognitive analysis
ActiveUS20180367549A1Easy to analyzeDigital data information retrievalMachine learningEvent dataGraph Node
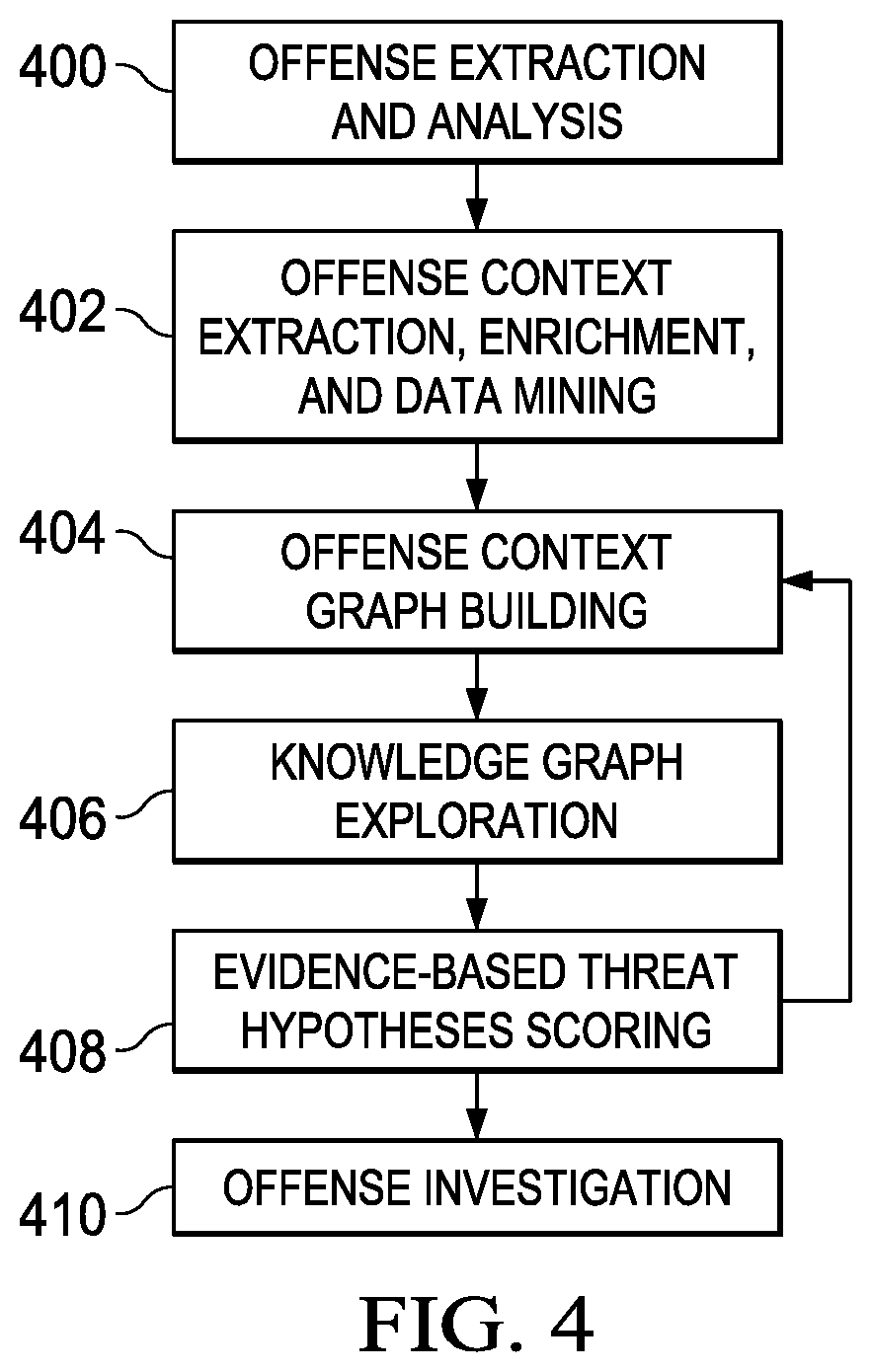
An automated method for processing security event data in association with a cybersecurity knowledge graph having nodes and edges. It begins by receiving from a security system (e.g., a SIEM) information representing an offense. An offense context graph is built. Thereafter, and to enhance the offense context graph, given nodes and edges of the knowledge graph are prioritized for traversal based on an encoding captured from a security analyst workflow. This prioritization is defined in a set of weights associated to the graph nodes and edges, and these weights may be derived using machine learning. The offense context graph is then refined by traversing the nodes and edges of the knowledge graph according to a prioritization tailored at least in part by the encoding. In addition to using security analyst workflow to augment generation of weights, preferably the machine learning system provides recommendations back to the security analysts to thereby influence their workflow.
Owner:IBM CORP
Cognitive analysis of security data with signal flow-based graph exploration
This disclosure provides for a signal flow analysis-based exploration of security knowledge represented in a graph structure comprising nodes and edges. “Conductance” values are associated to each of a set of edges. Each node has an associated “toxicity” value representing a degree of maliciousness associated with the node. The conductance value associated with an edge is a function of at least the toxicity values of the nodes to which the edge is incident. A signal flow analysis is conducted with respect to an input node representing an observable associated with an offense. The flow analysis seeks to identify a subset of the nodes that, based on their conductance values, are reached by flow of a signal representing a threat, wherein signal flow over a path in the graph continues until a signal threshold is met. Based on the analysis, nodes within the subset are designated as hypothesis nodes for further examination.
Owner:IBM CORP
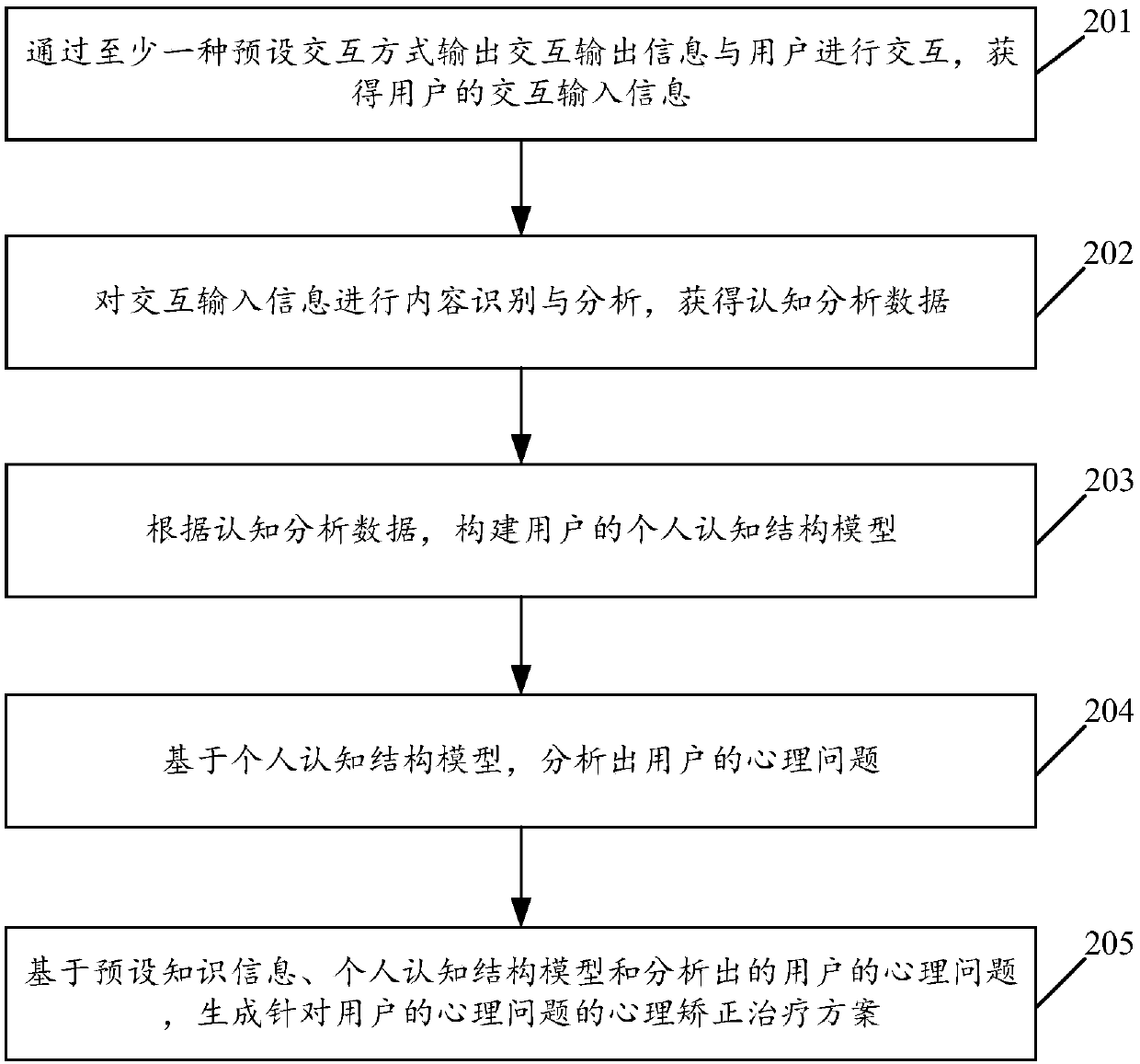
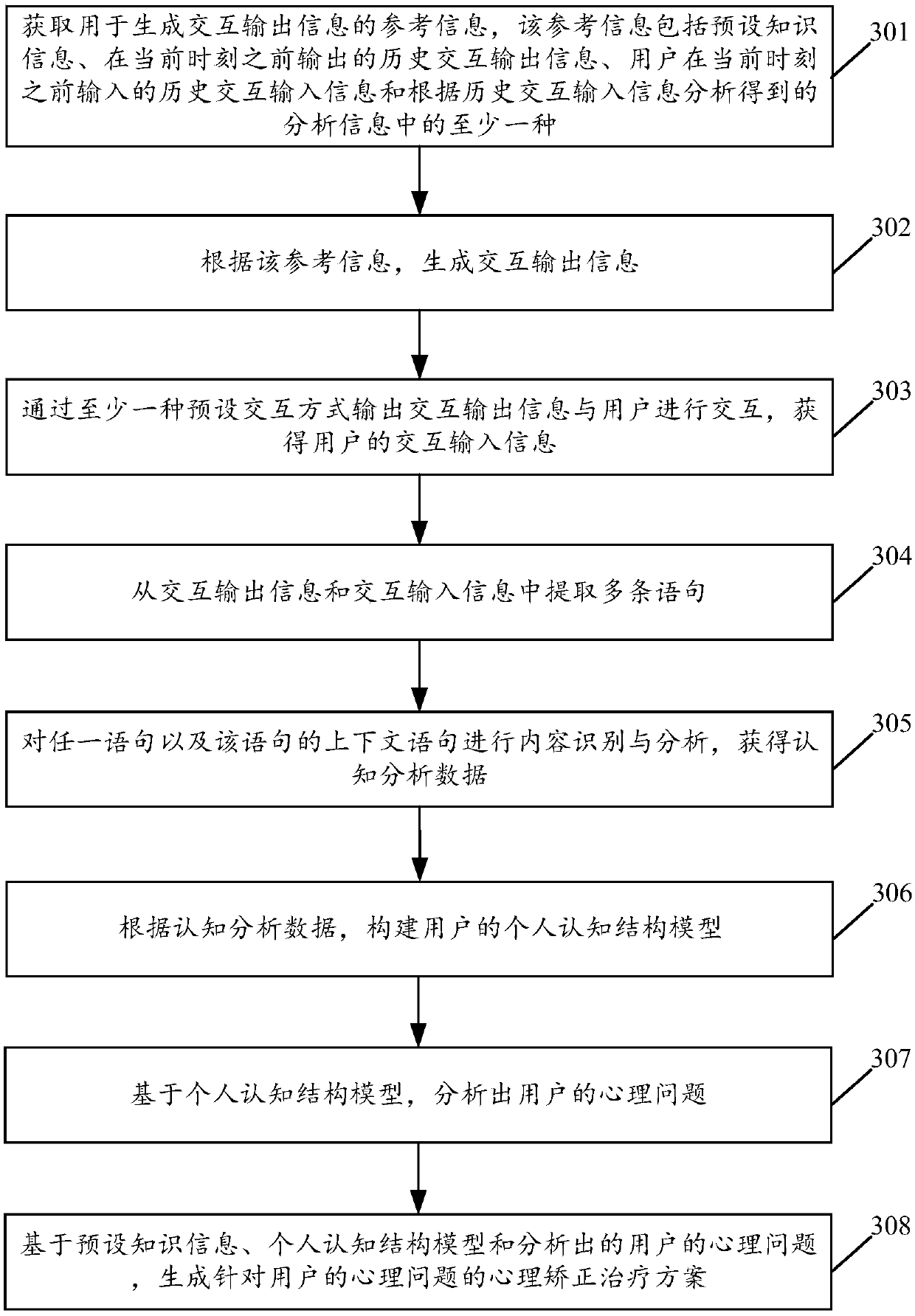
Cognitive analysis method and system based on interaction
InactiveCN109524085ASolve psychological problemsStrong helpMedical automated diagnosisNatural language data processingCognitive structureHuman–computer interaction
The embodiment of the invention relates to the field of data analysis and processing, and discloses a cognitive analysis method and system based on interaction. The method includes the steps: outputting interactive output information to interact with a user in at least one preset interaction manner, and obtaining the interactive input information of the user; performing the content recognition andanalysis of interactive input information to obtain cognitive analysis data; constructing a user's personal cognitive structure model based on cognitive analysis data. By implementing the embodimentsof the present invention, the user's personal cognitive information can be analyzed, thereby providing more powerful help for the user's mental health service.
Owner:GUANGZHOU HESONG INFORMATION TECH CO LTD
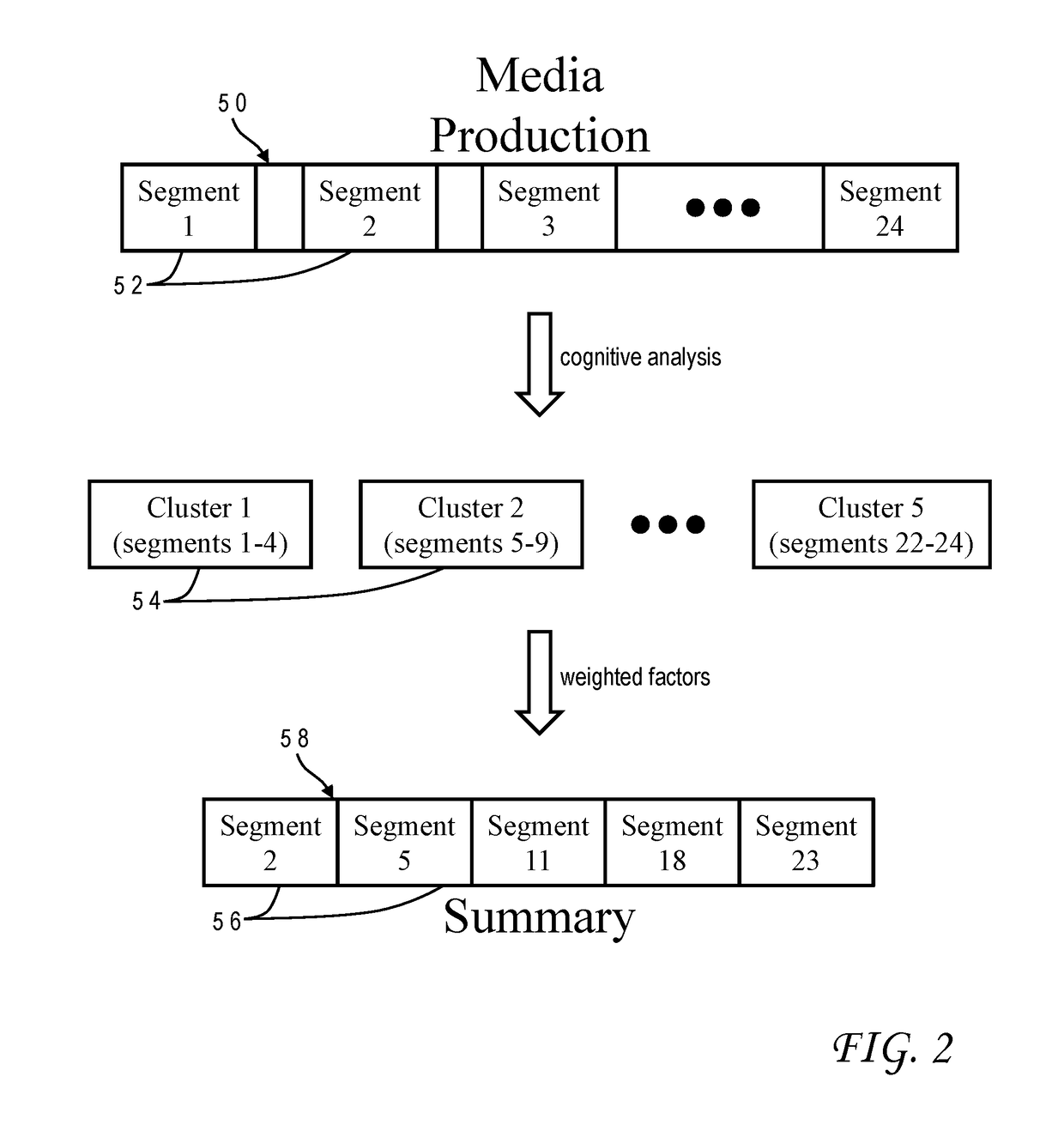
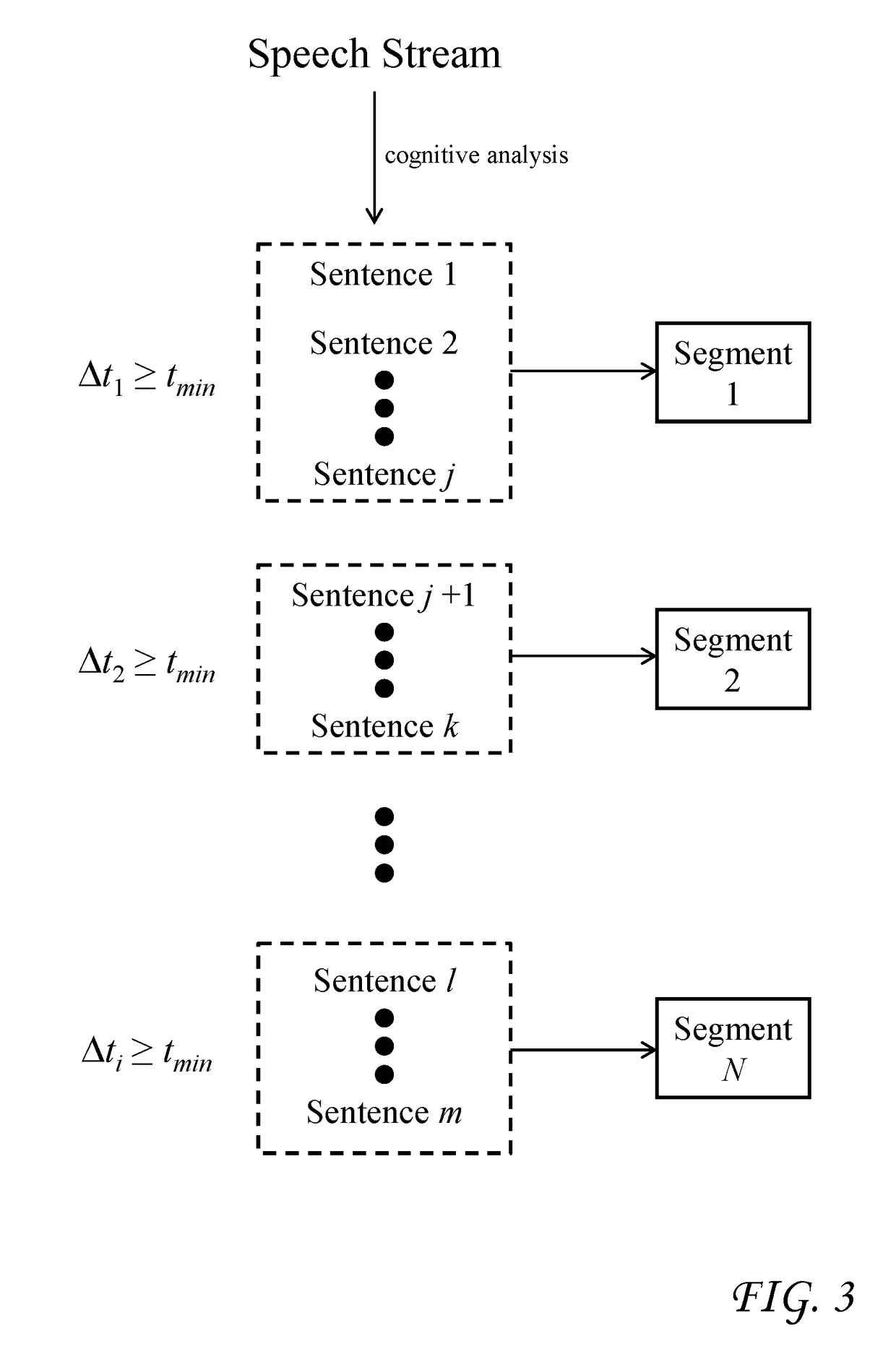
Cognitive dynamic video summarization using cognitive analysis enriched feature set
InactiveUS20190027188A1Natural language analysisElectronic editing digitised analogue information signalsPattern recognitionFeature set
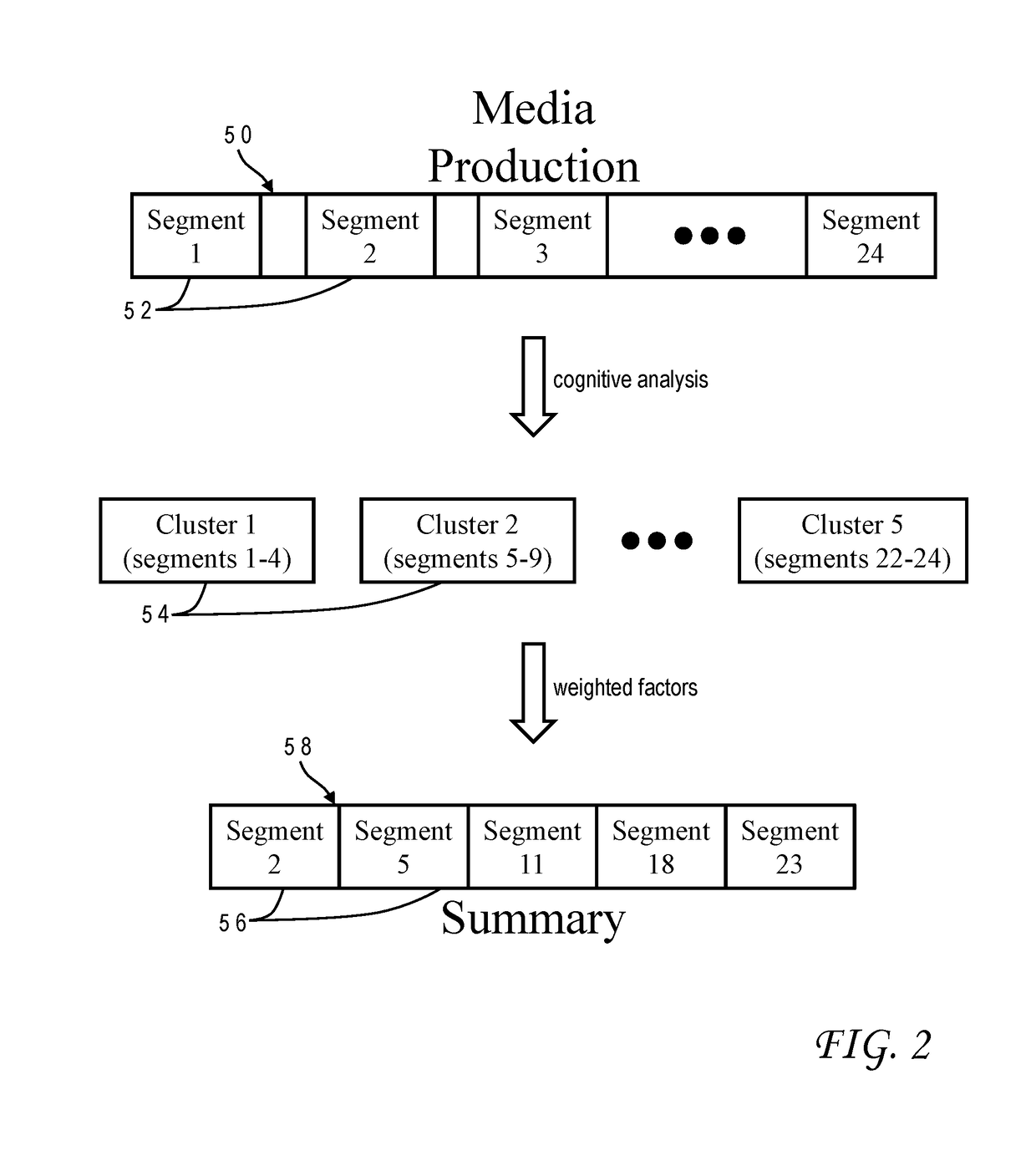
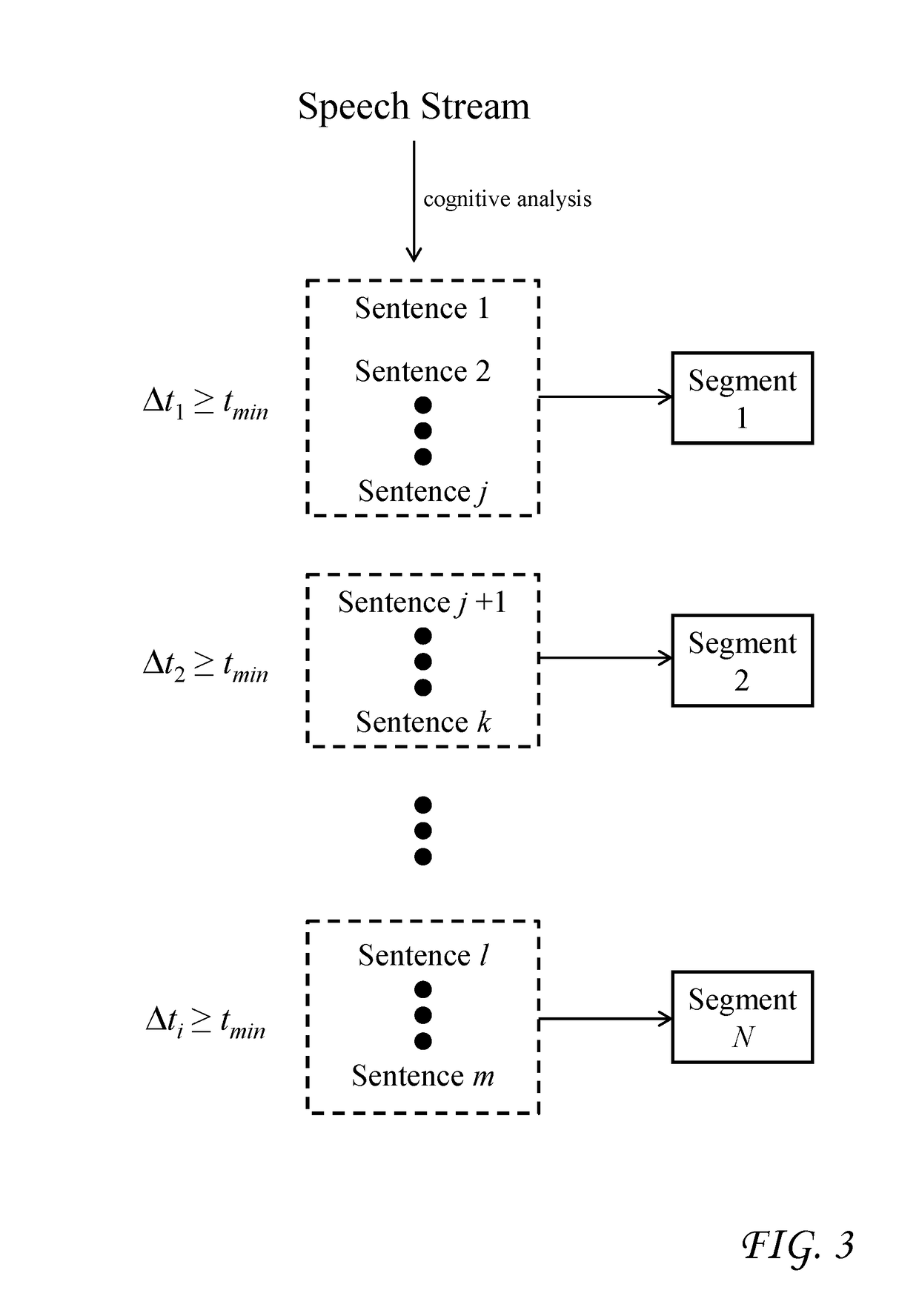
Accurate and concise summarization of a media production is achieved using cognitive analysis which groups segments of the production into clusters based on extracted features, selects a representative segment for each cluster, and combines the representative segments to form a summary. The production is separated into a video stream, a speech stream and an audio stream, from which the cognitive analysis extracts visual features, textual features, and aural features. The clustering groups segments together whose visual and textual features most closely match. Selection of the representative segments derives a score for each segment based on factors including a distance to a centroid of the cluster, an emotion level, an audio uniqueness, and a video uniqueness. Each of these factors can be weighted, and the weights can be adjusted in accordance with user input. The factors can have initial weights which are based on statistical attributes of historical media productions.
Owner:IBM CORP
Smart contact lens system with cognitive analysis and aid
ActiveUS20190332168A1Input/output for user-computer interactionNon-optical adjunctsCommunication interfacePhysiological movement
A smart lens system may include a hardware processor coupled to a smart contact lens, which may include a microprocessor, an image capturing sensor, and a wireless communication interface. The smart lens system may determine reading factors associated with a user with respect to the user reading content item, based on data related to the user's physiological movements captured by the smart contact lens. The reading factors may include a user's cognitive state determined at least from analyzing data representing the user's physiological movements. Responsive to determining that the user's cognitive state is above a threshold value, the smart lens system may generate an assistive action associated with the content item and transmit a signal to at least one assistive device to perform the assistive action. The assistive device performs the assistive action responsive to receiving the signal.
Owner:IBM CORP
Natural Language Processing Correction Based on Treatment Plan
InactiveUS20160110501A1Data processing applicationsPatient personal data managementMedicinePaper document
An approach is provided in which an information handling system extracts treatment segments from documents corresponding to a patient and uses cognitive analysis to identify common treatment properties of a subset of the treatment segments. The information handling system combines the subset of treatment segments into a treatment aggregation that corresponds to a treatment history of the patient. In turn, the information handling system ingests the treatment aggregation into a domain for subsequent processing.
Owner:IBM CORP
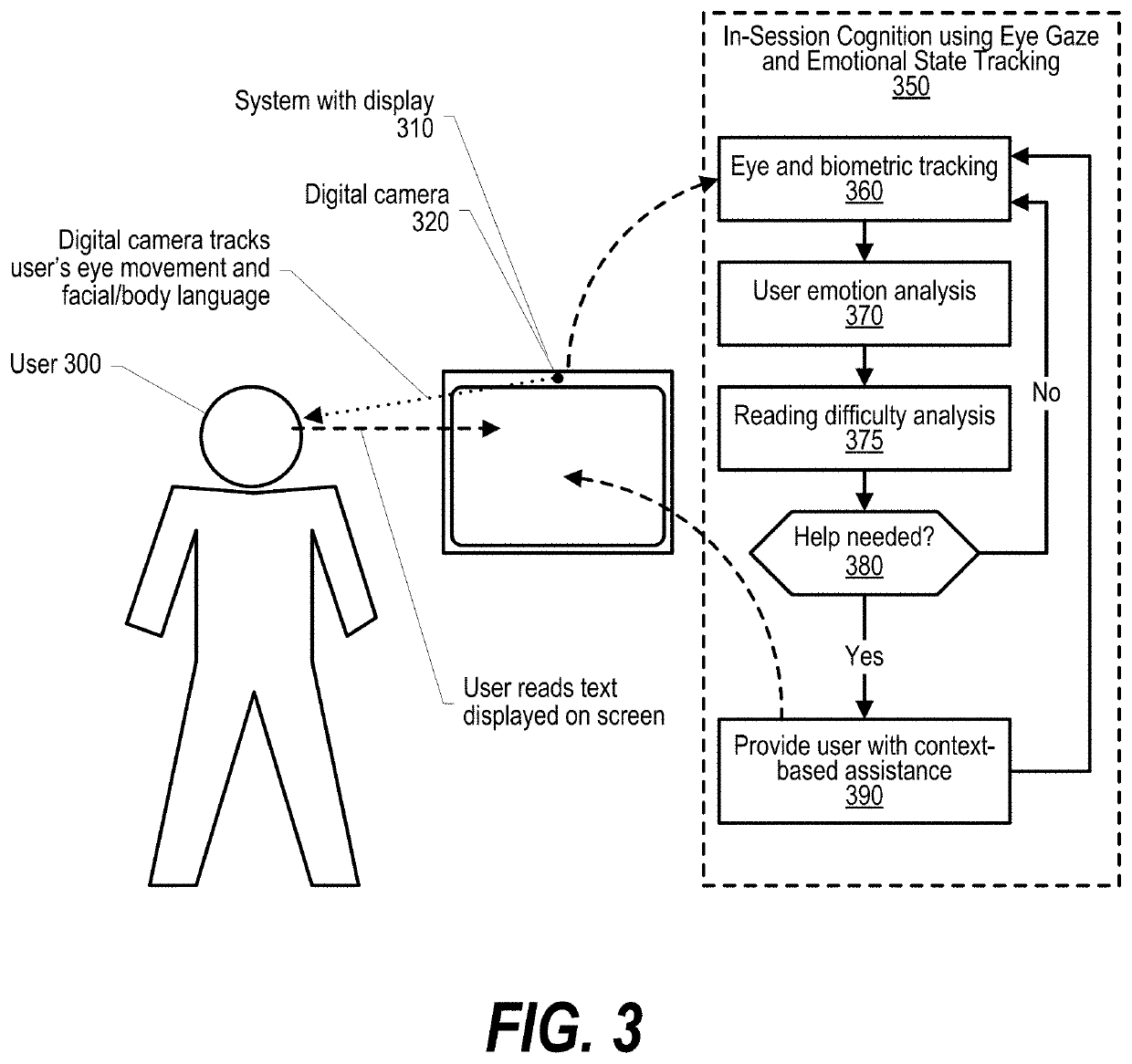
Assisting Learners Based on Analytics of In-Session Cognition
ActiveUS20200098283A1Input/output for user-computer interactionSemantic analysisDisplay deviceKnowledge management
An approach is provided that detect a section of a document that is currently being read by a user on a display device as well as the user's current emotional state. In response to determining, based on the detected current emotional state, that reading assistance would be helpful to the user, the approach identifies terminology within the section of the document that is currently being read by the user, retrieves assistive texts related to the identified terminology, and provides the assistive texts to the user at the display screen.
Owner:IBM CORP
Human brain language cognition modeling method
InactiveCN103530505ASolving Cognitive Modeling ProblemsGuaranteed correctnessSpecial data processing applicationsSmall sampleComplex cognition
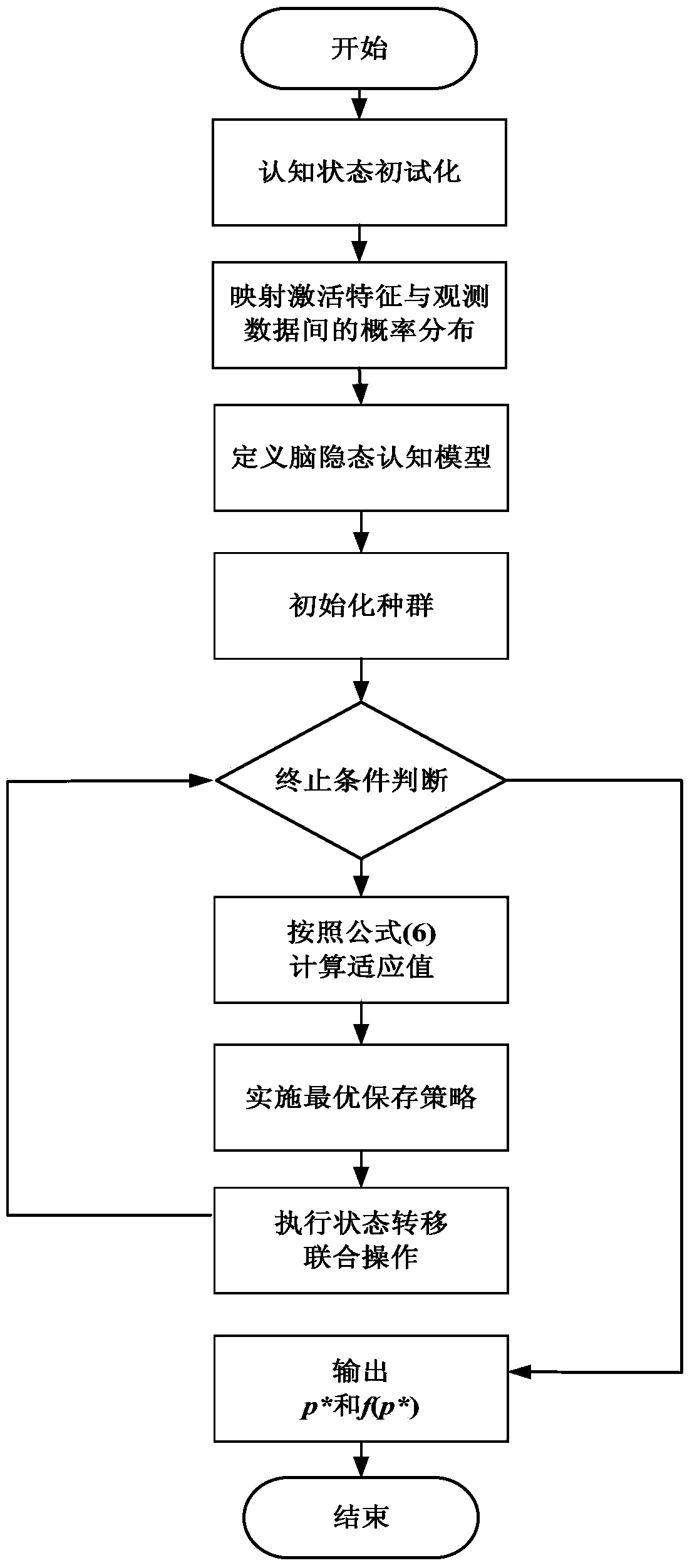
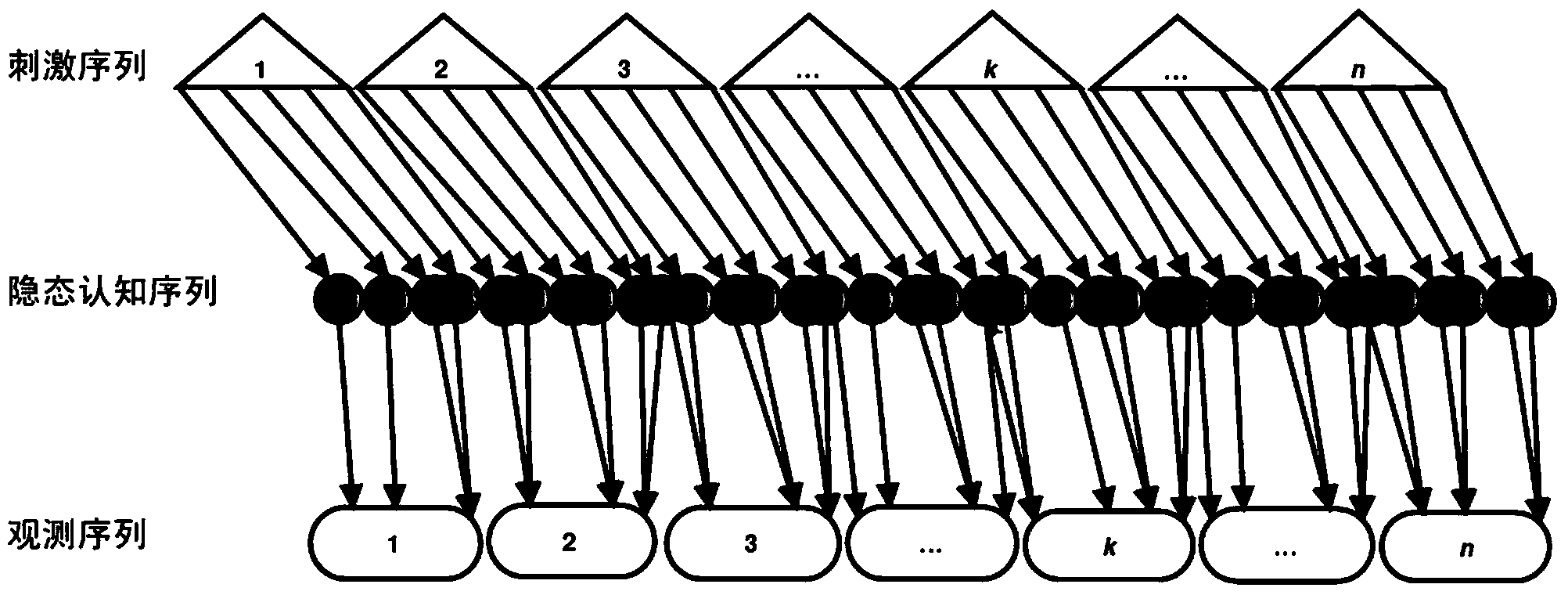
The invention discloses a human brain language cognition modeling method. The human brain language cognition modeling method comprises the following steps of initialization of a cognitive state example, mapping of probability distribution between activation characteristics and observation data, definition of a brain tacit cognition model and parameter analysis of the tacit cognition model. In the cognition modeling process, input stimulation, the observation result and the tacit cognition state are defined as triple time sequences related to a dynamic event, namely a cognition stimulation task time sequence, an observation characteristic time sequence and a tacit cognition state time sequence, the triple time sequences are related to one another through a set of probability distribution, and not all collected brain data are treated as static information for statistics. Therefore, the human brain language cognition modeling method does not need to meet the basic assumption based on statistics, is established under a small sample data condition, and guarantees the correctness of the cognition analysis result, thereby achieving cognition modeling under the small sample data condition. The human brain language cognition modeling method improves the accuracy of cognition modeling, and provides an effective approach for complex cognition analysis.
Owner:DALIAN MARITIME UNIVERSITY
Cognitive analysis and classification of apparel images
ActiveCN110363213ACharacter and pattern recognitionBuying/selling/leasing transactionsCognitive analysisNeuron
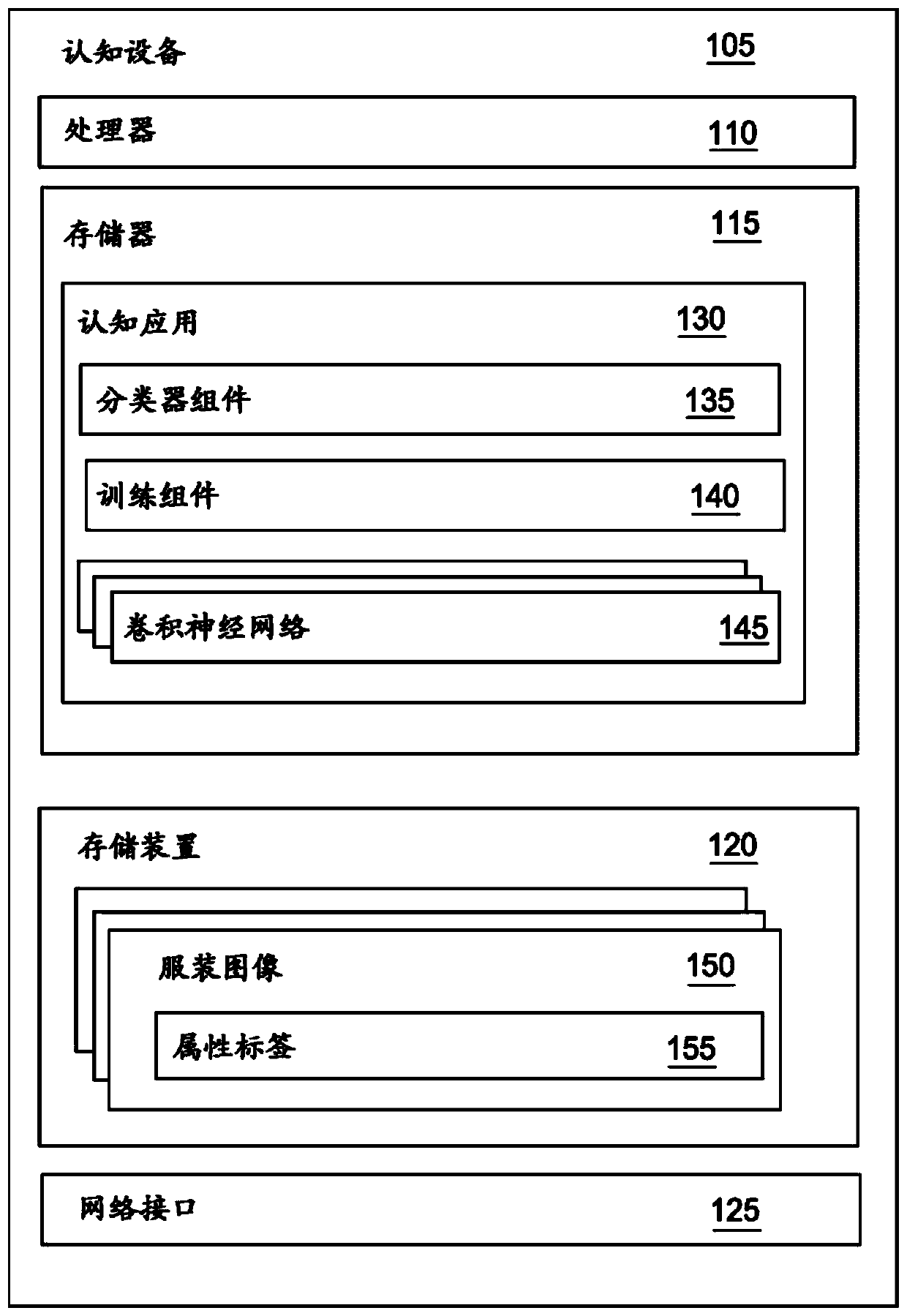
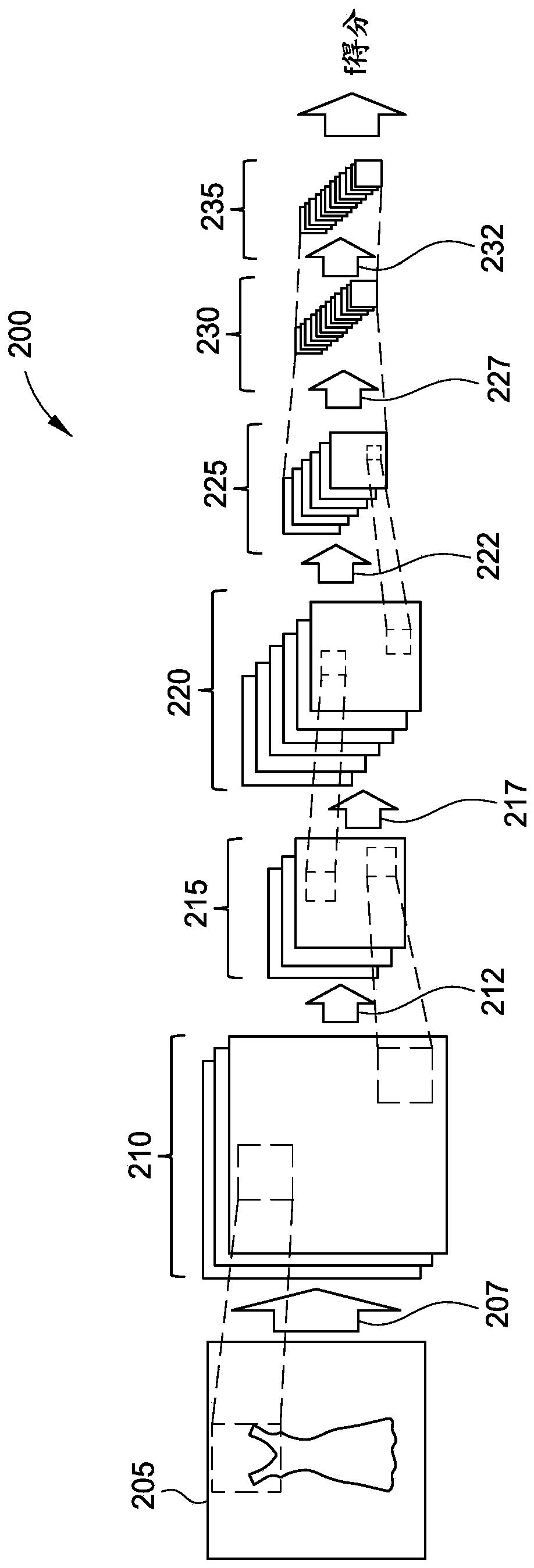
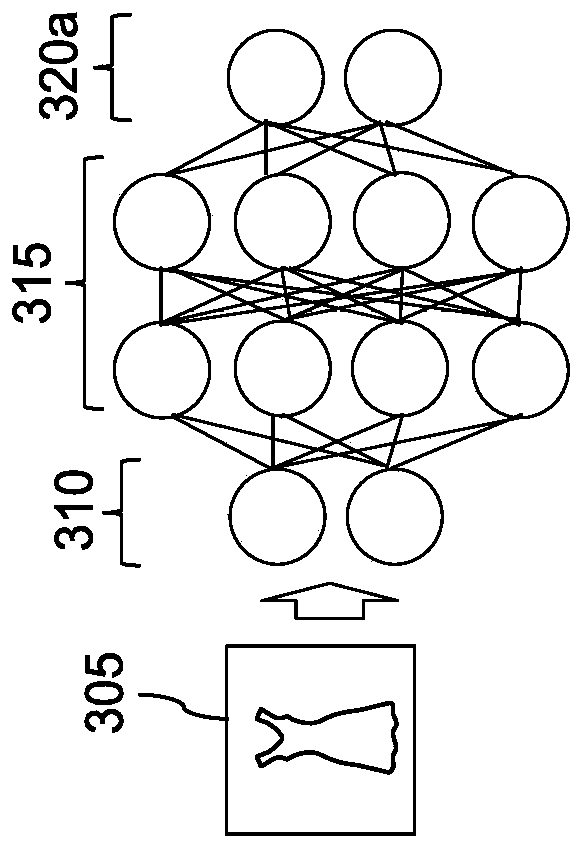
The present invention relates to cognitive analysis and classification of apparel images. The present disclosure relates to convolutional neural networks, and more particularly, to performing cognitive analysis of images of apparel items using a customized convolutional neural network. As disclosed, f-scores can be generated for apparel items. Training images are identified, where each training image is associated with a corresponding set of tags including information about a plurality of attributes. A first convolutional neural network (CNN) is trained based on the plurality of training images and a first attribute. The first CNN is iteratively refined by, for each respective attribute, removing a set of neurons from the first CNN and retraining the first CNN based on the training imagesand the respective attribute. Upon determining that the first CNN has been trained based on each of the attributes, one or more CNNs are generated based on the first CNN. An image is received, where the image depicts an apparel item. The image is processed using the one or more CNNs, and an f-score for the apparel item is determined based on the output.
Owner:IBM CORP
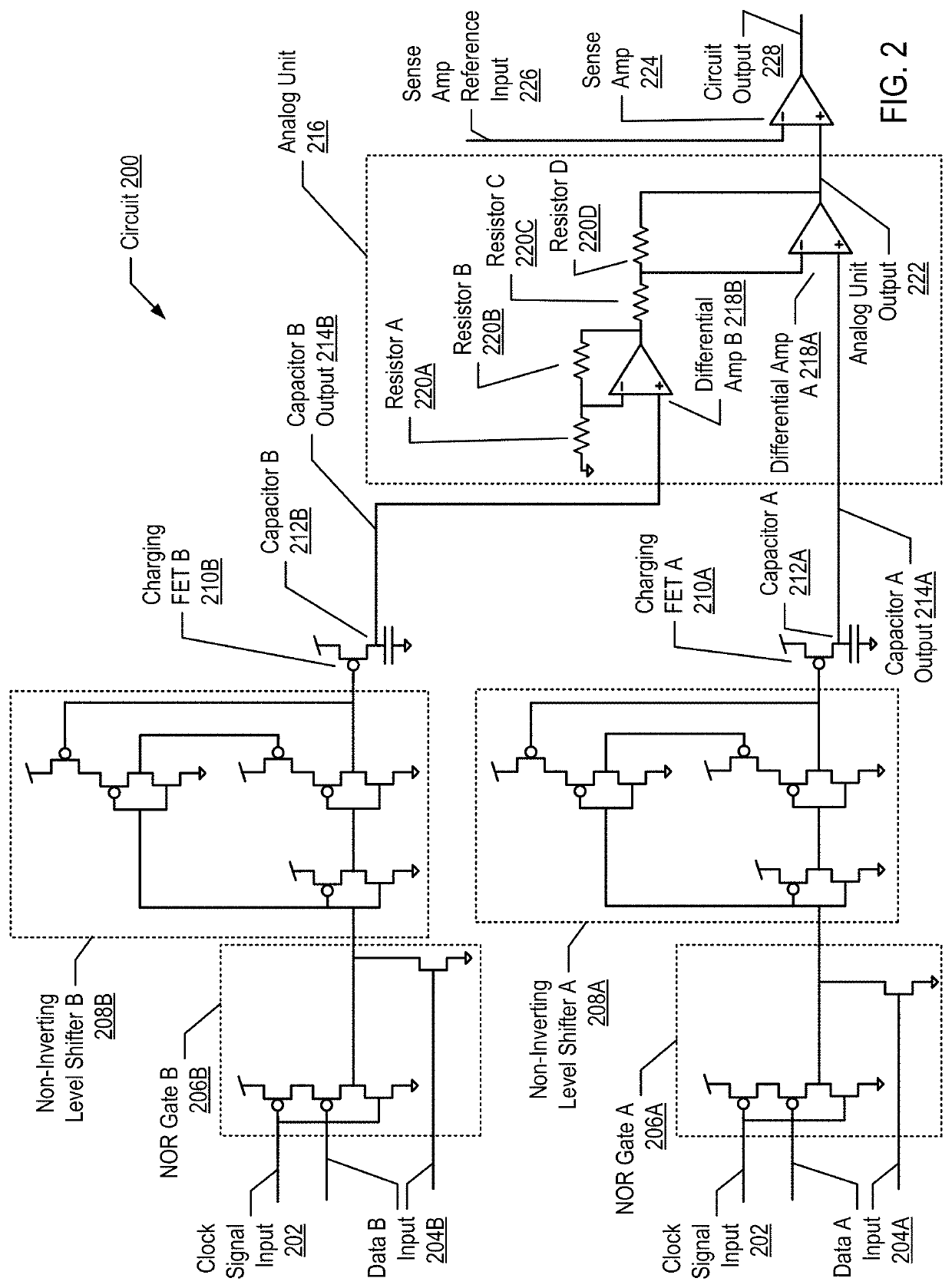
Cognitive analysis using applied analog circuits
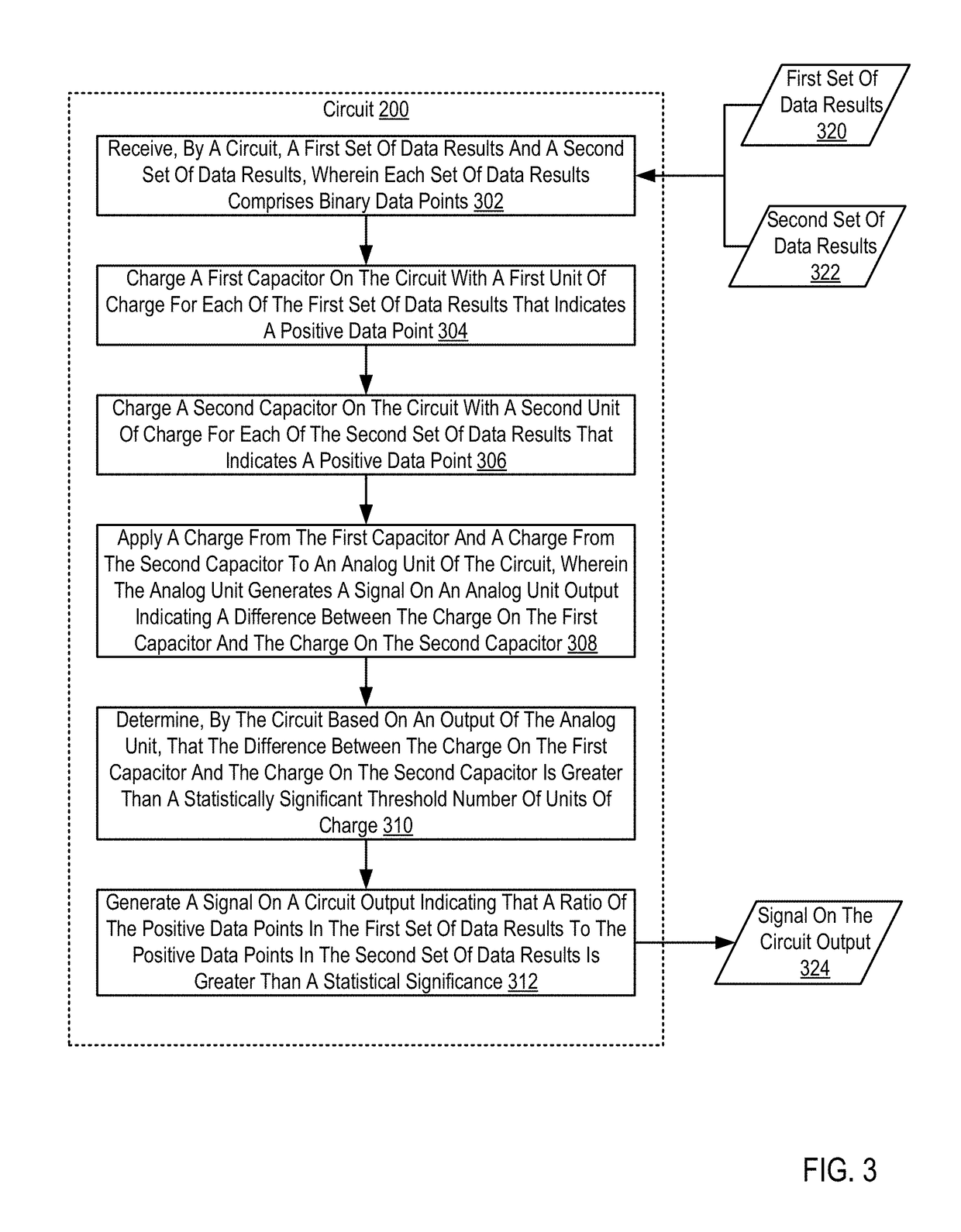
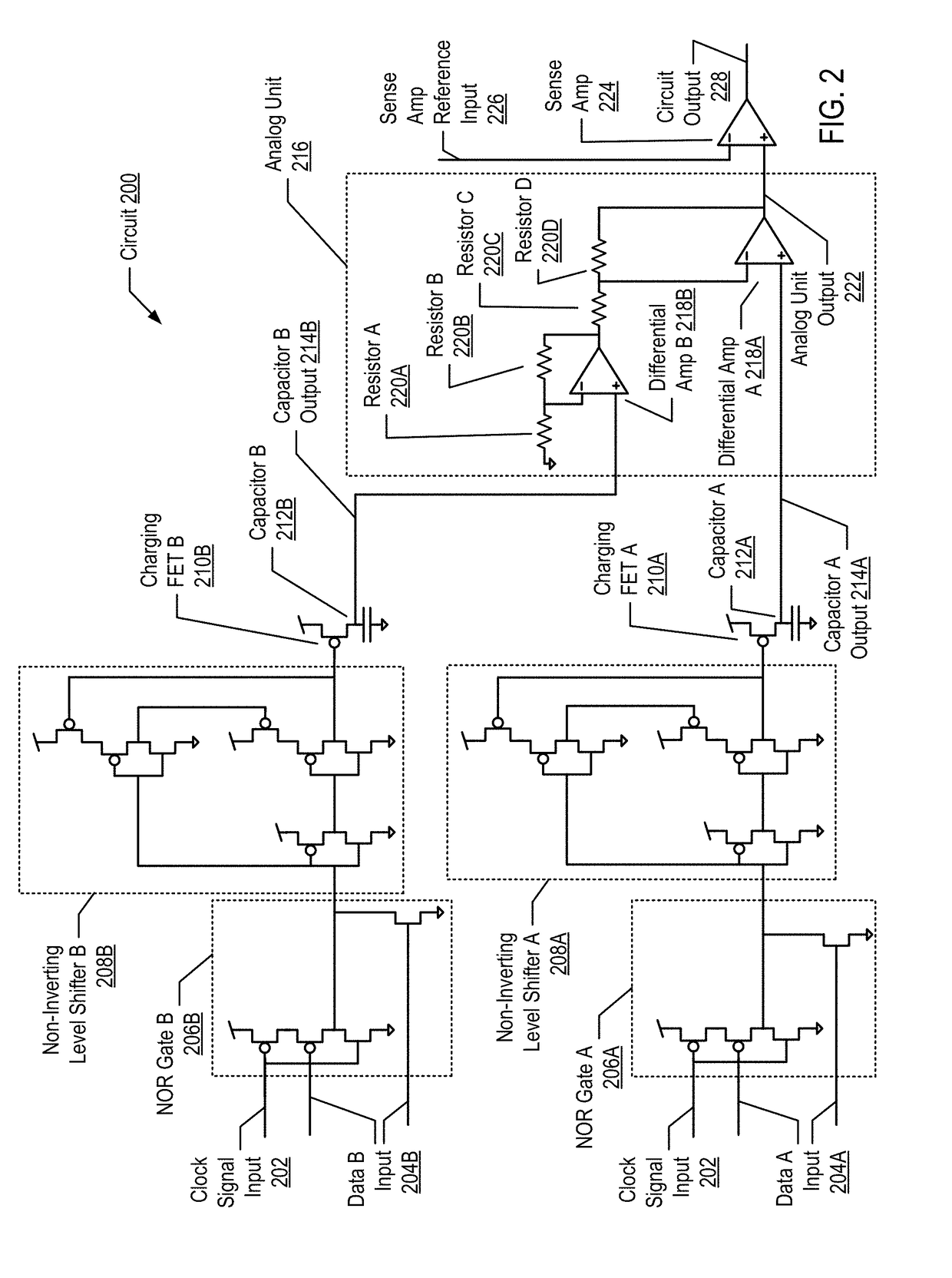
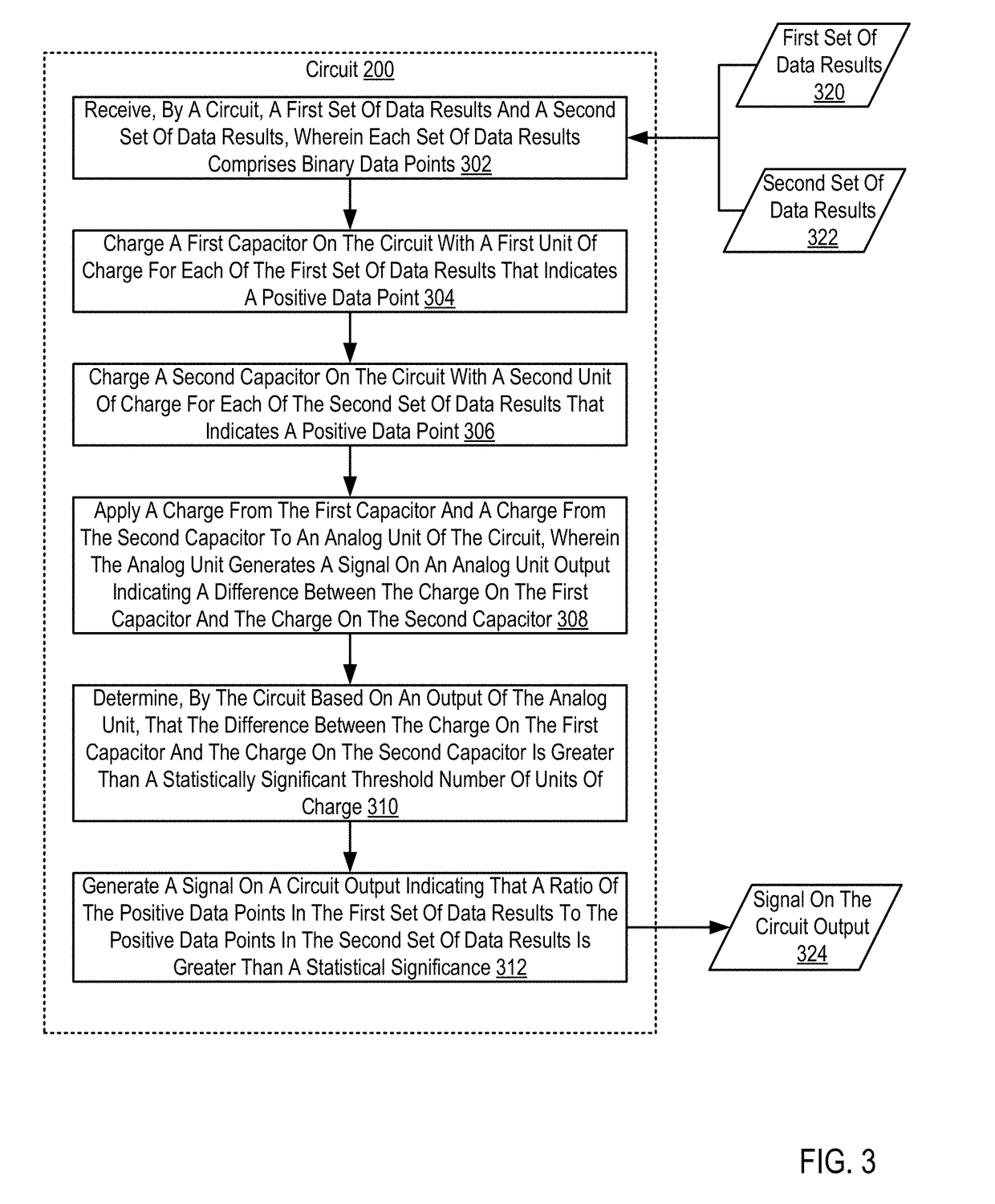
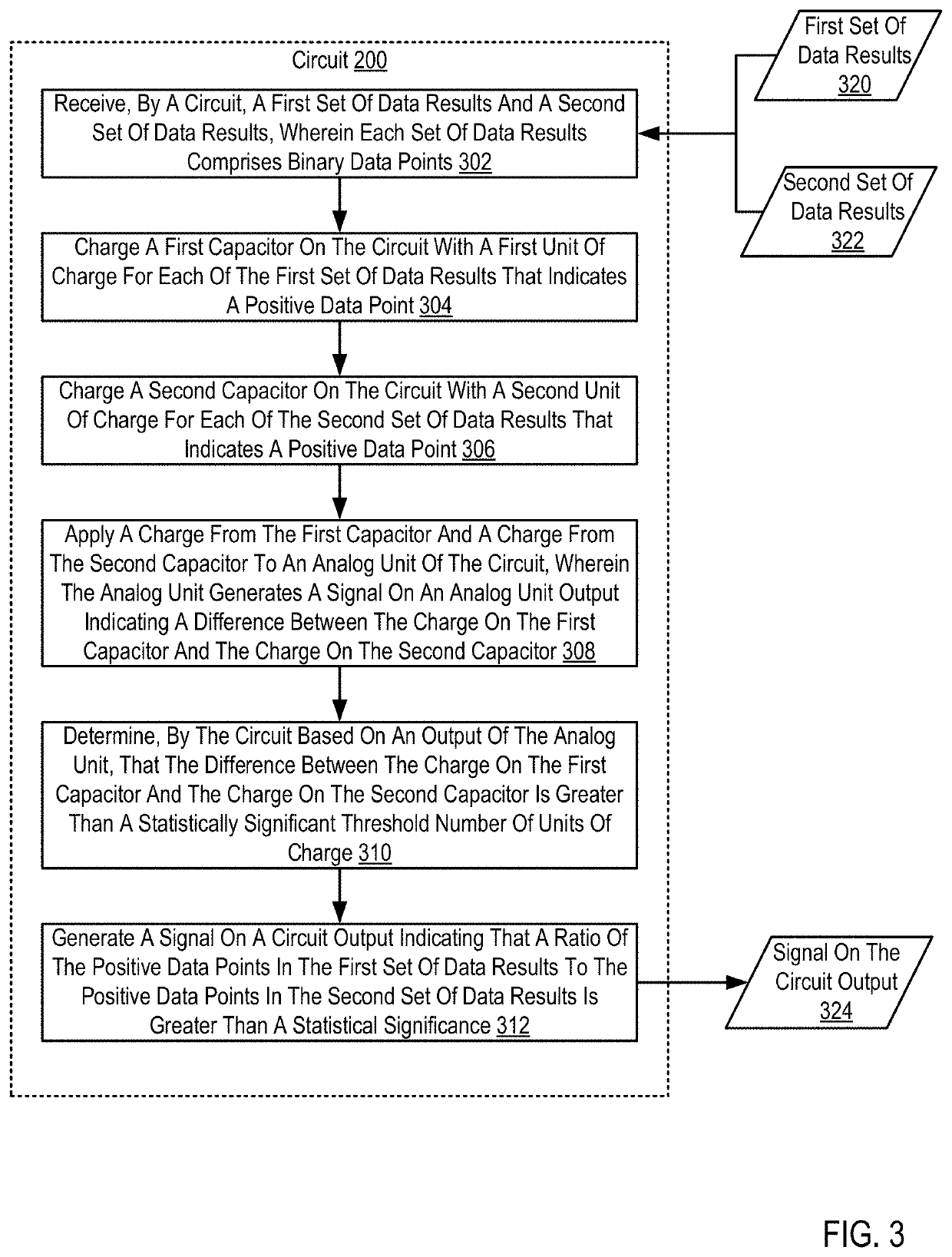
ActiveUS20180348273A1Capacitance measurementsComputing operations for addition/subtractionCapacitanceSignal on
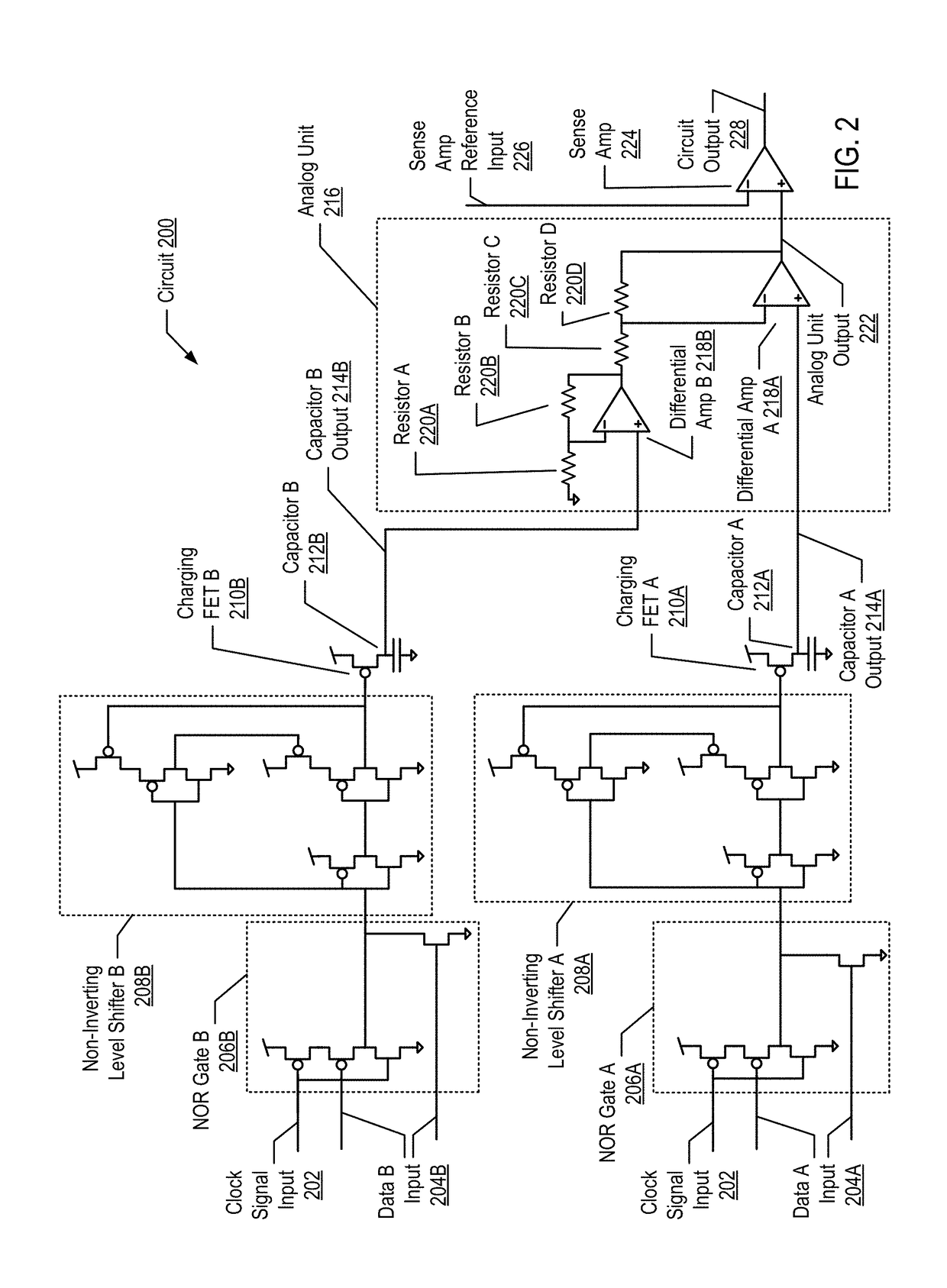
Cognitive analysis using applied analog circuits including receiving, by a circuit, a first set of data results and a second set of data results; charging a first capacitor on the circuit with a first unit of charge for each of the first set of data results that indicates a positive data point; charging a second capacitor on the circuit with a second unit of charge for each of the second set of data results that indicates a positive data point; applying a charge from the first capacitor and a charge from the second capacitor to an analog unit of the circuit; and generating a signal on a circuit output indicating that a ratio of the positive data points in the first set of data results to the positive data points in the second set of data results is greater than a statistical significance.
Owner:IBM CORP
Cognitive analysis using applied analog circuits
ActiveUS20180348271A1Capacitance measurementsComputing operations for addition/subtractionCapacitanceSignal on
Cognitive analysis using applied analog circuits including receiving, by a circuit, a first set of data results and a second set of data results; charging a first capacitor on the circuit with a first unit of charge for each of the first set of data results that indicates a positive data point; charging a second capacitor on the circuit with a second unit of charge for each of the second set of data results that indicates a positive data point; applying a charge from the first capacitor and a charge from the second capacitor to an analog unit of the circuit; and generating a signal on a circuit output indicating that a ratio of the positive data points in the first set of data results to the positive data points in the second set of data results is greater than a statistical significance.
Owner:IBM CORP
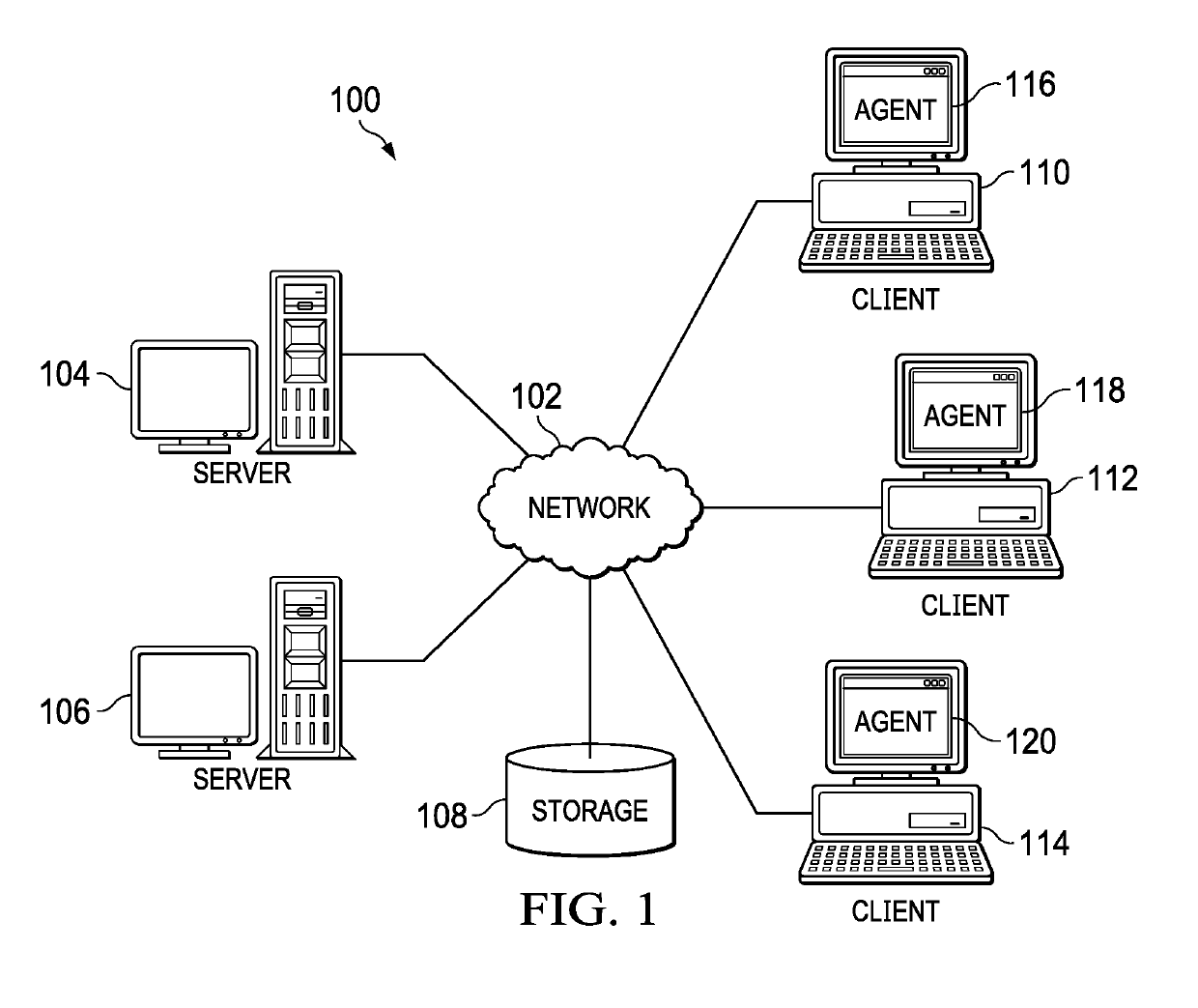
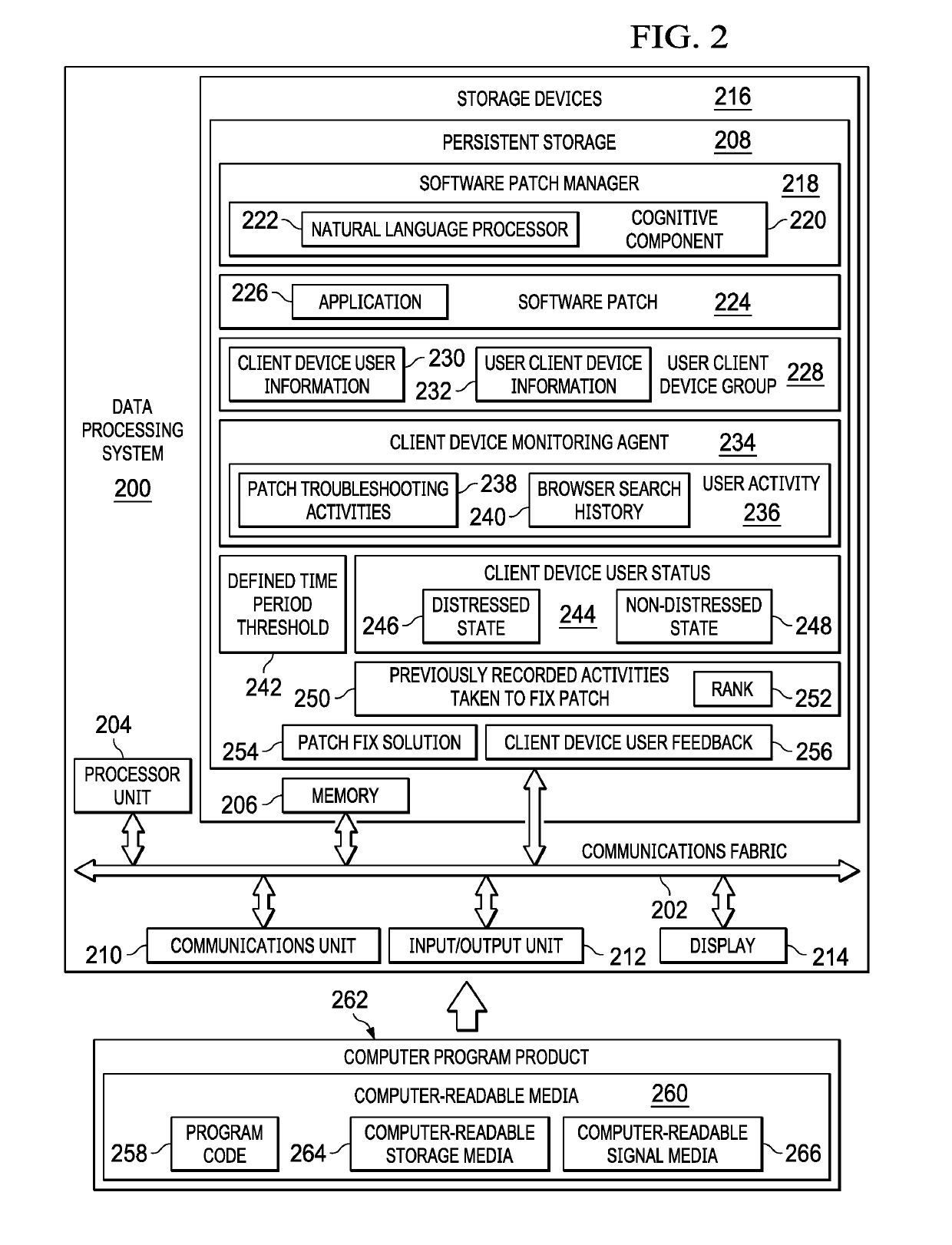
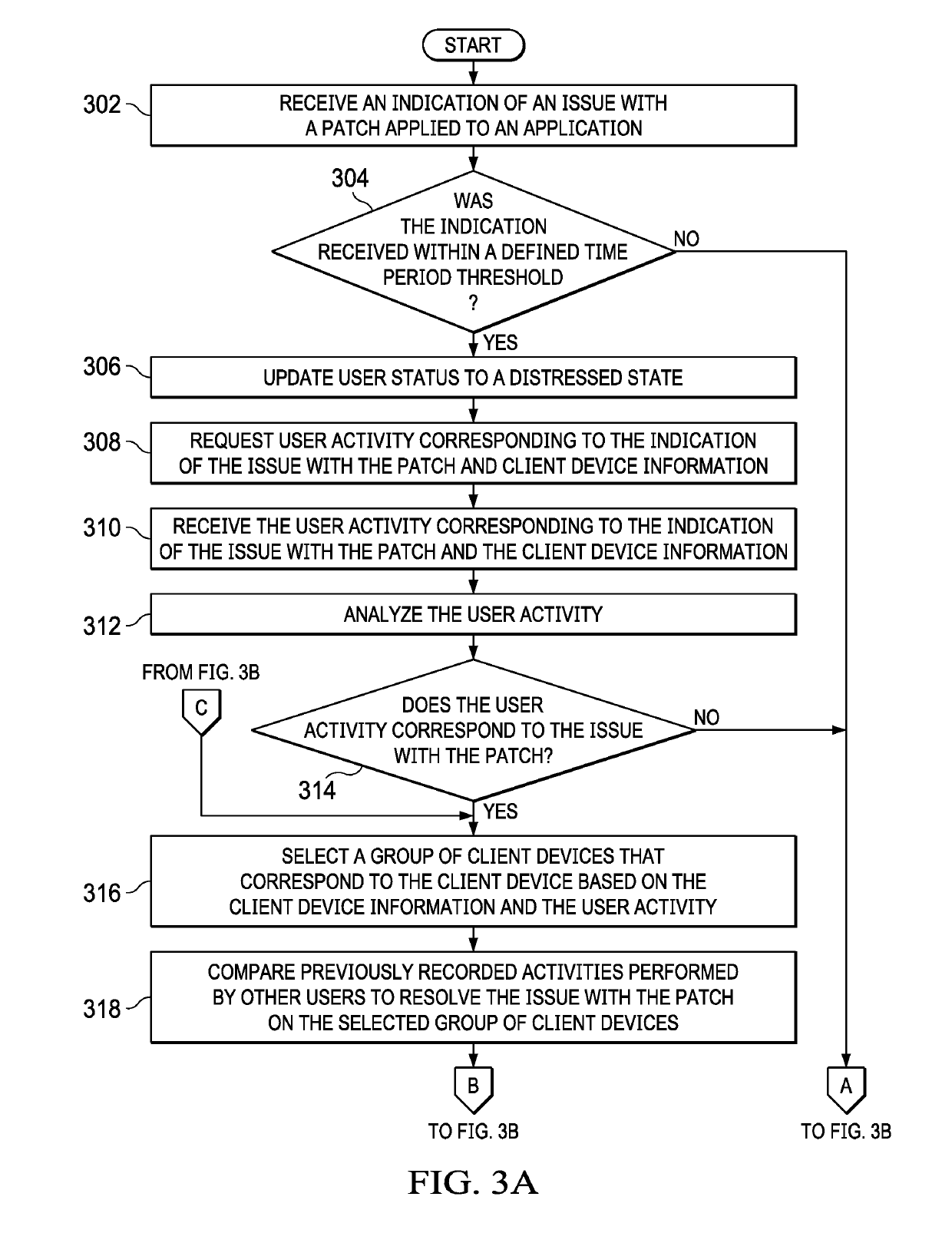
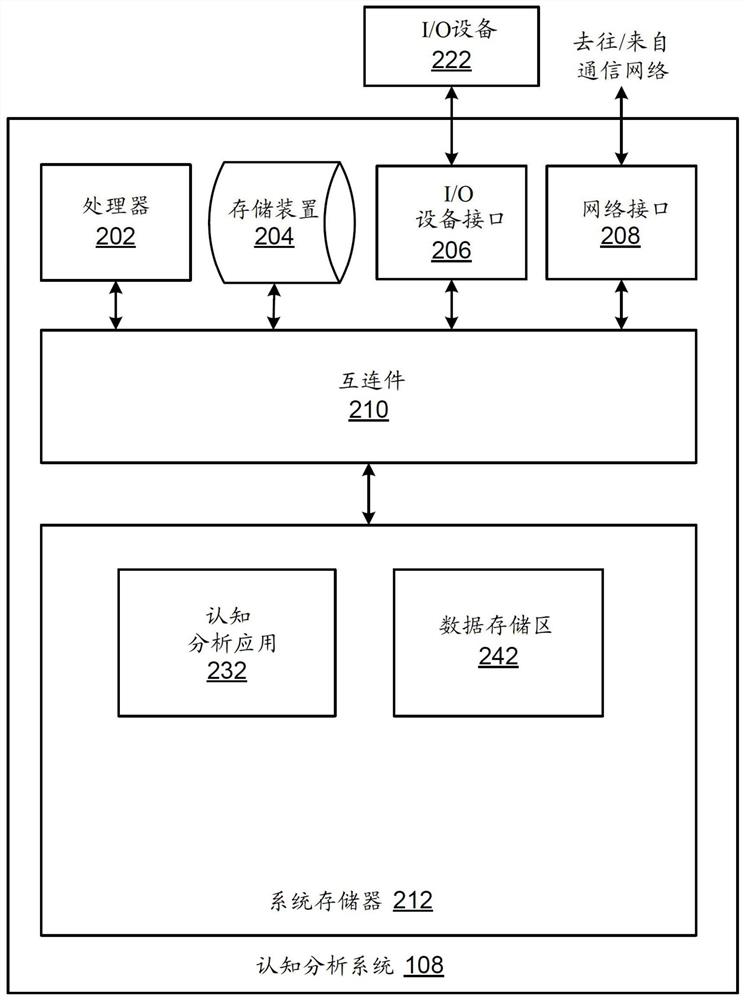
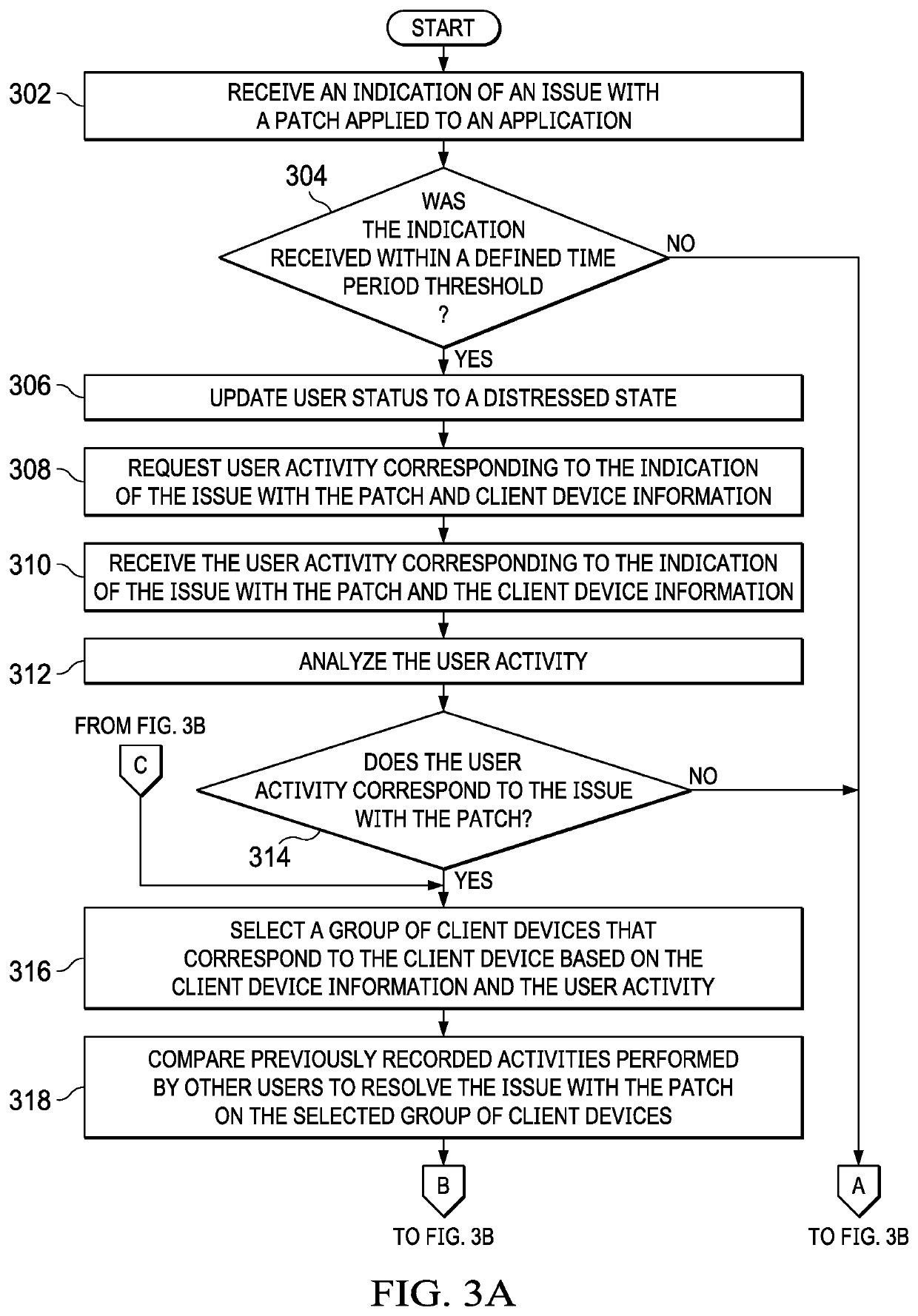
Cognitive Analysis and Resolution of Erroneous Software Patches
ActiveUS20190102255A1Non-redundant fault processingProgram loading/initiatingClient-sideKnowledge management
Resolving software patch issues is provided. Recorded activities performed by users to resolve an issue with a patch applied to an application on a group of client devices are compared. A set of common user activities are identified within the recorded activities performed by the users. A subset of highest ranking common user activities is selected from the set of common user activities. A fix for the issue with the patch is generated based on the subset of highest ranking common user activities. Corrective action based on the fix is taken to resolve the issue with the patch on a client device, the client device experiencing the issue resolved by users on the group of client devices.
Owner:IBM CORP
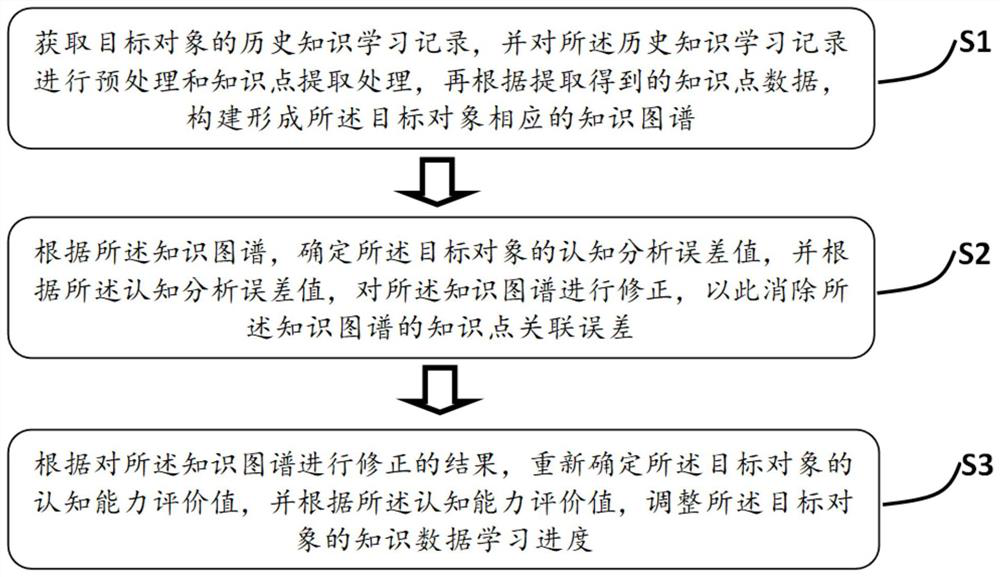
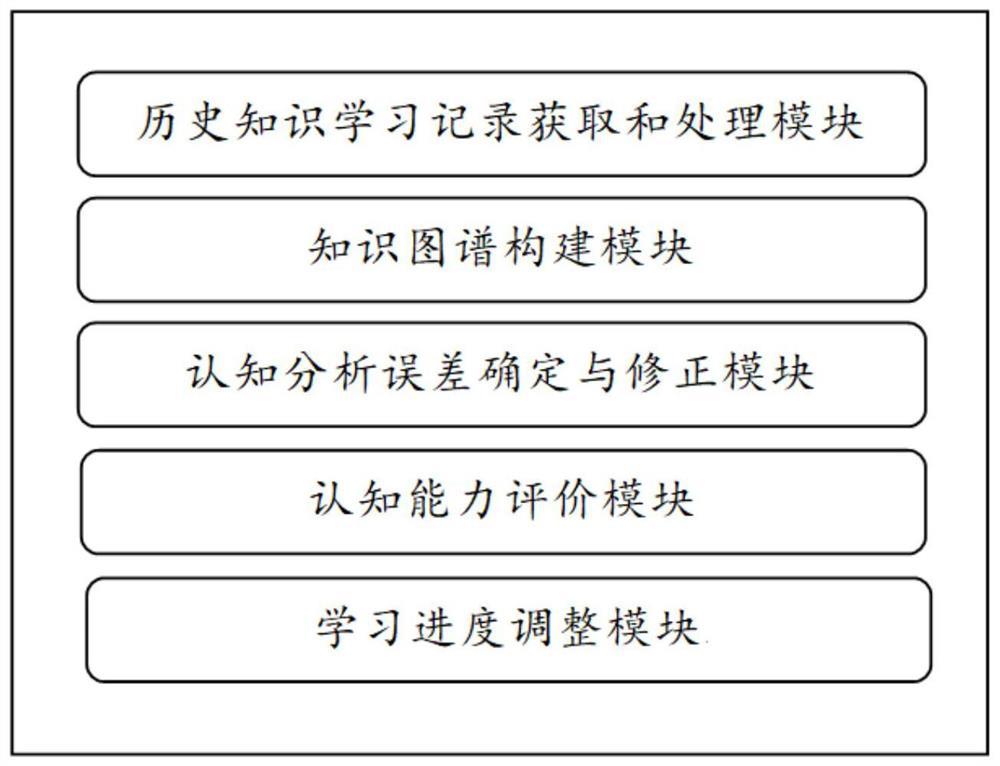
Cognitive competence analysis method and system based on knowledge graph
PendingCN112131408AAvoid build biasImprove learning efficiencyData processing applicationsSemantic analysisKnowledge graphArtificial intelligence
The invention provides a cognitive competence analysis method and system based on a knowledge graph, a corresponding knowledge graph is constructed and formed according to historical knowledge learning records of different target objects, cognitive analysis error conditions of the target objects are determined according to the knowledge graph, and the knowledge graph is corrected according to thecognitive analysis error conditions. Therefore, knowledge graph construction deviation caused by data defects of historical knowledge learning records can be effectively avoided, and finally, the cognitive competence evaluation value of the target object is re-determined according to the corrected knowledge graph, so that the target object is accurately and reliably evaluated. The knowledge data learning progress of the target object is adjusted according to the cognitive ability evaluation value, so that the learning efficiency and the learning quality of the target object are improved to thegreatest extent.
Owner:SHANGHAI SQUIRREL CLASSROOM ARTIFICIAL INTELLIGENCE TECH CO LTD
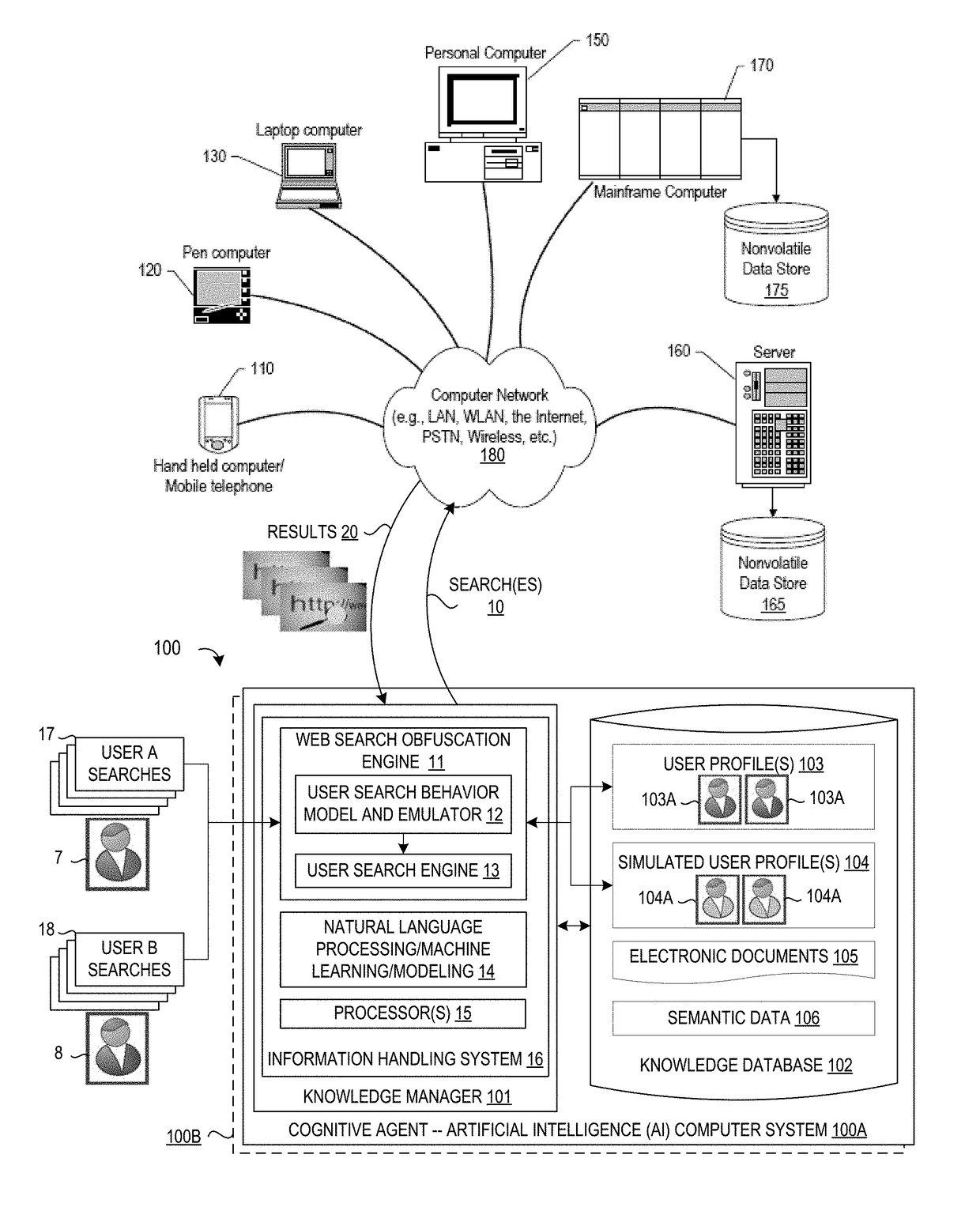
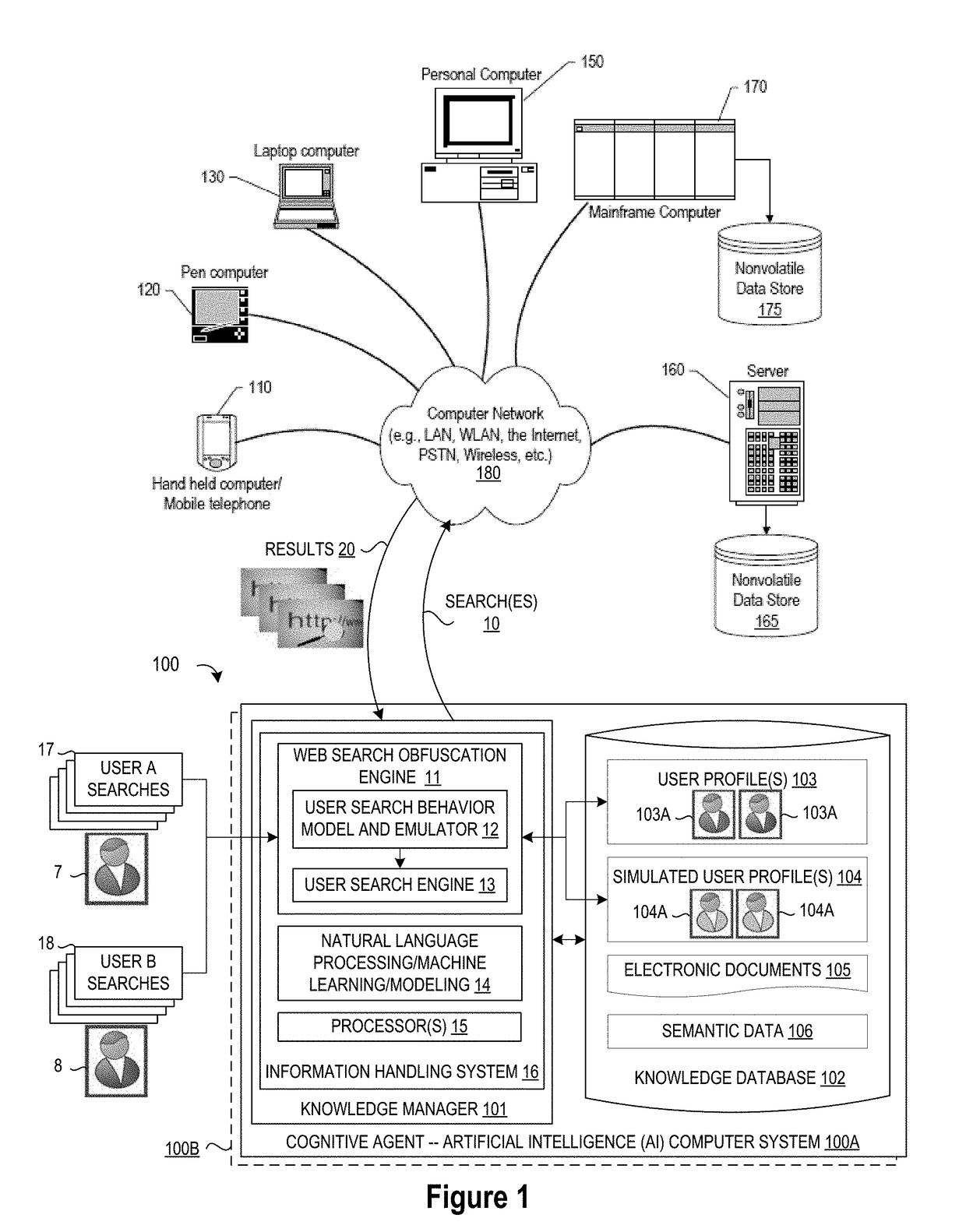
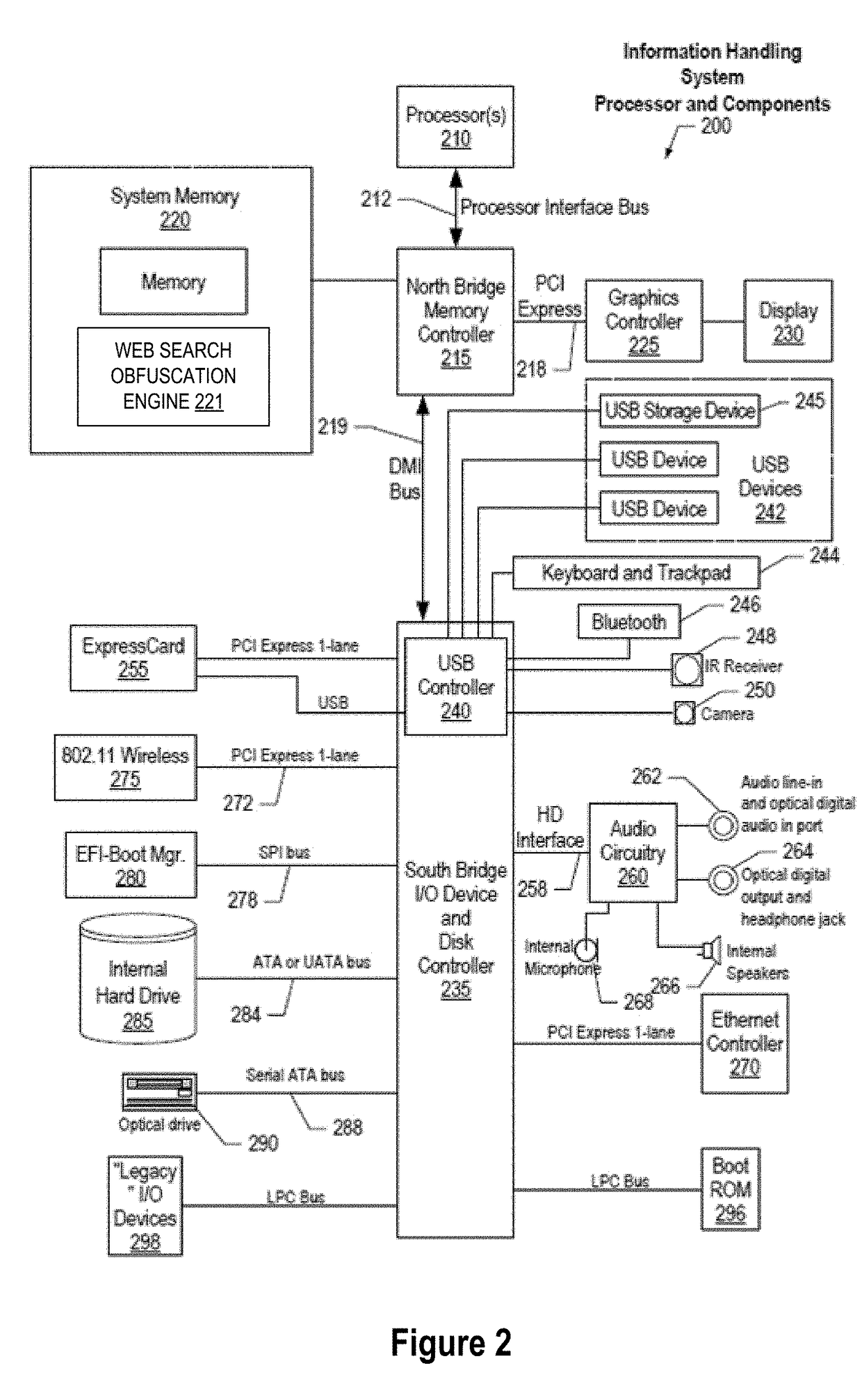
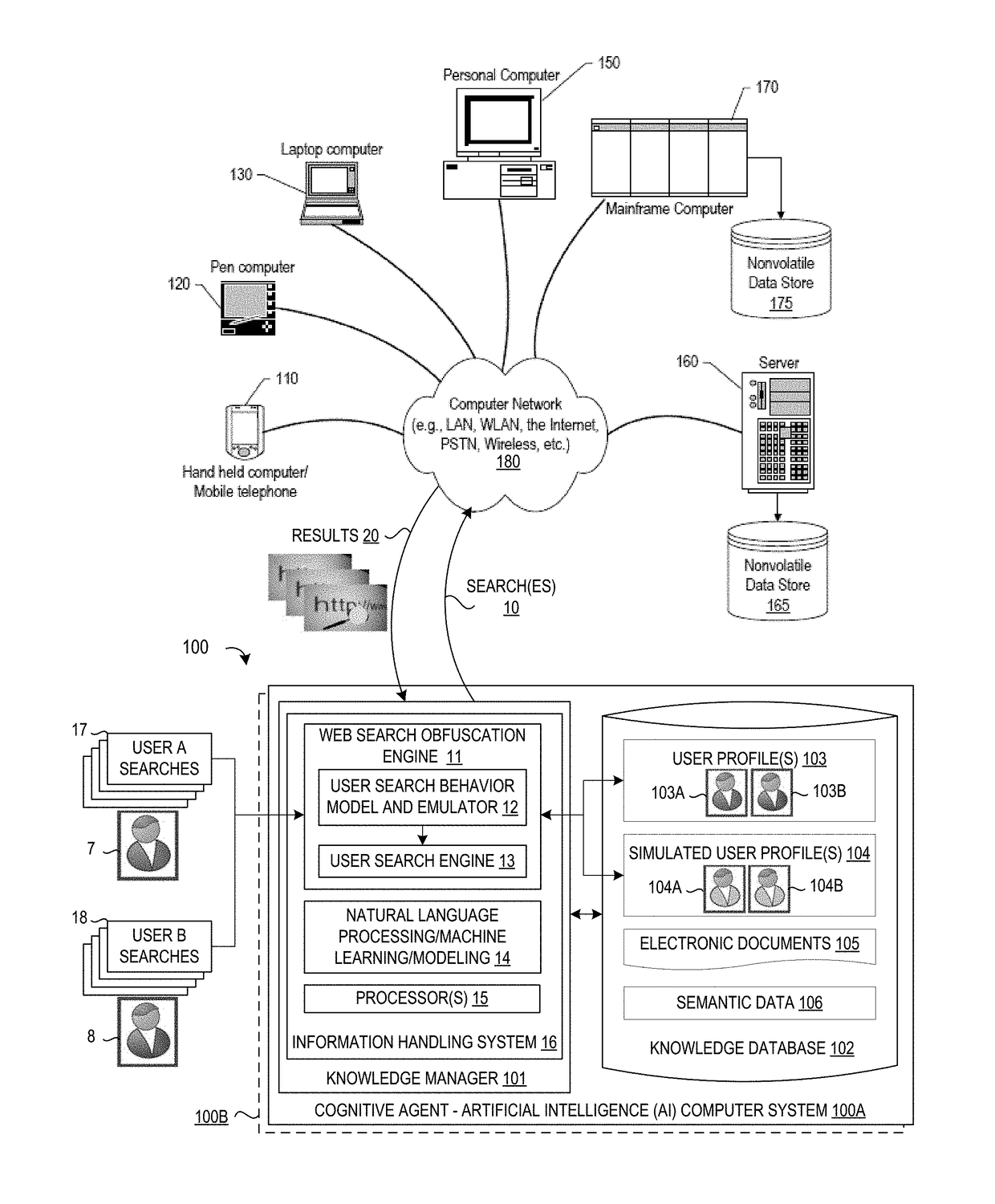
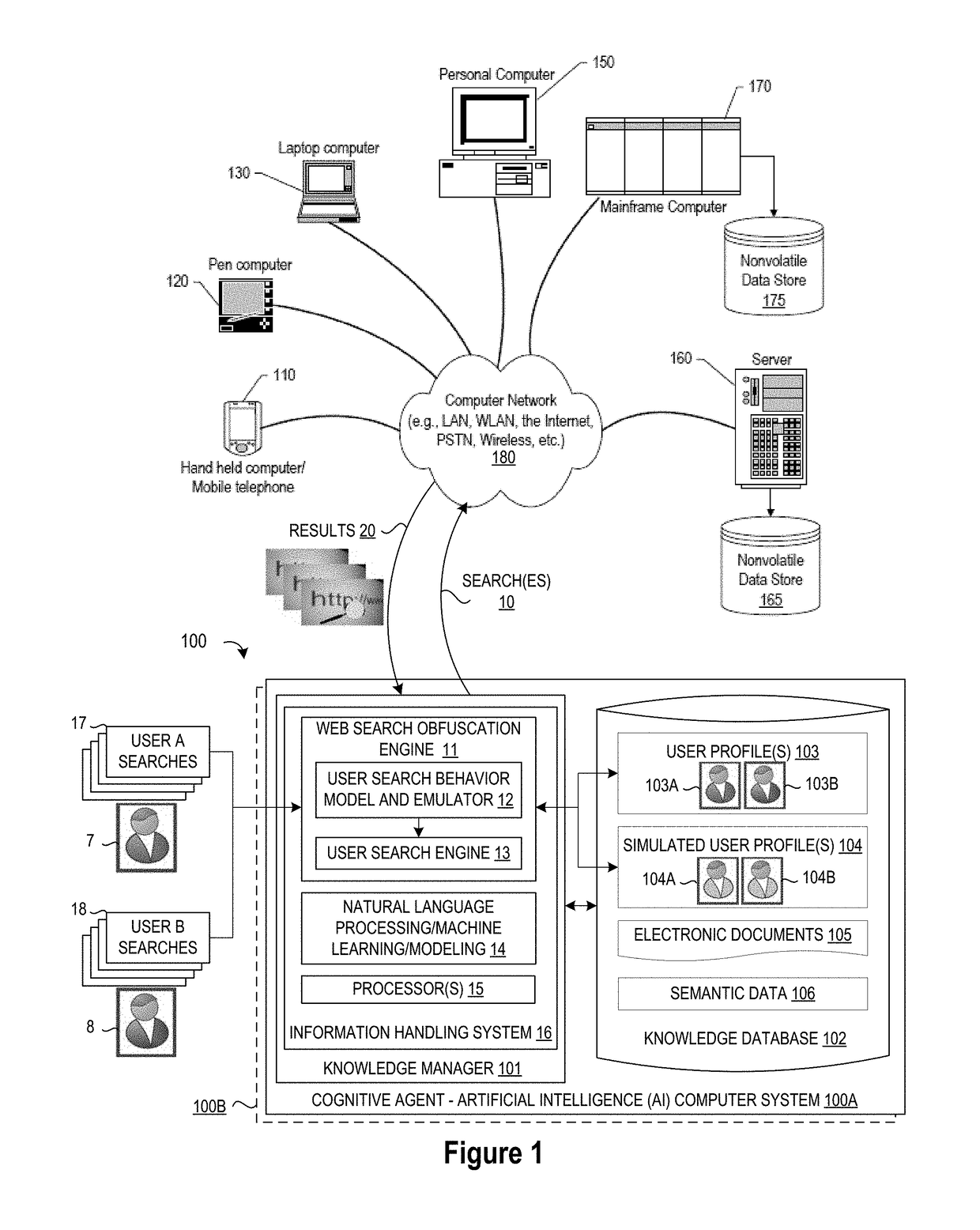
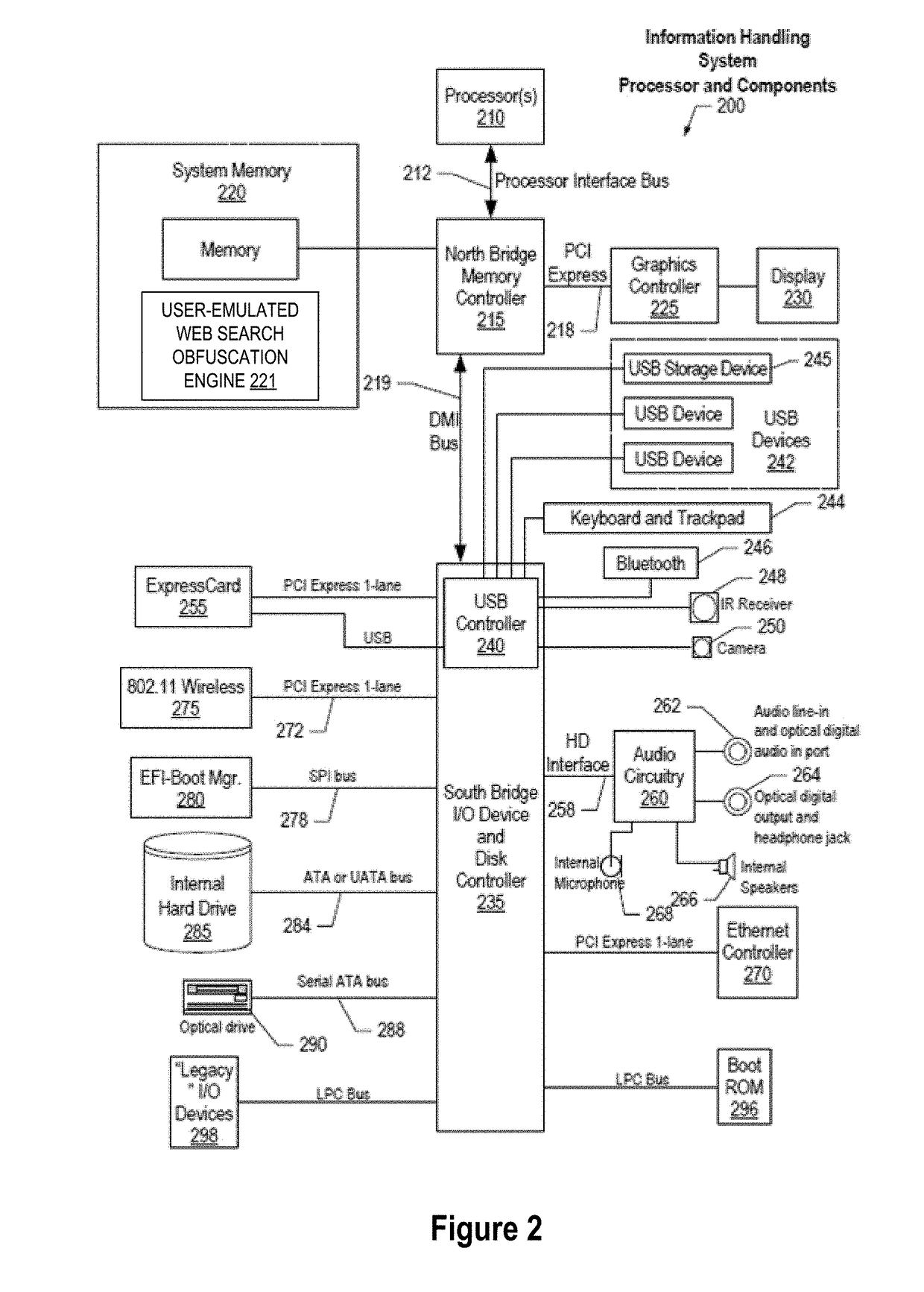
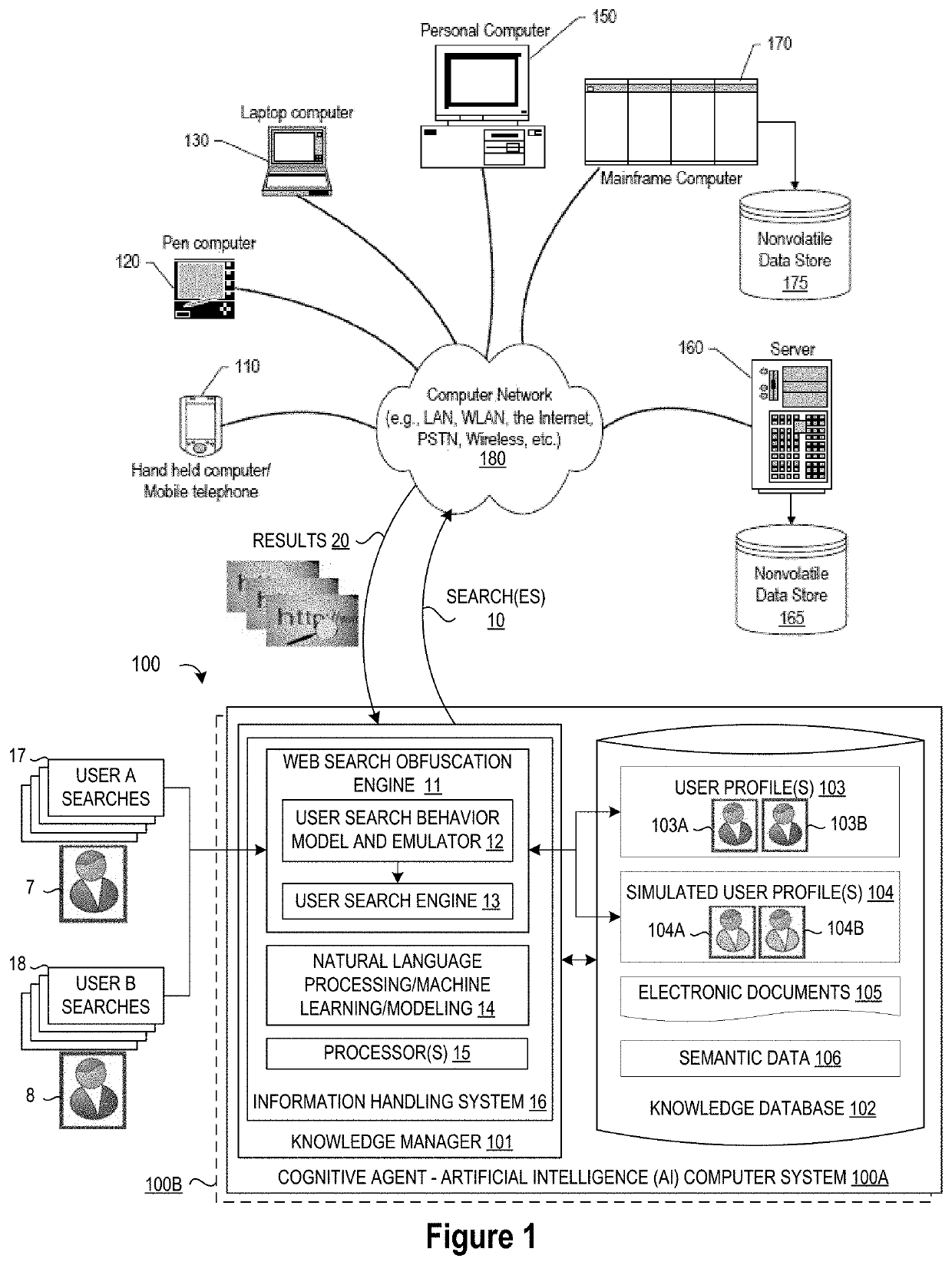
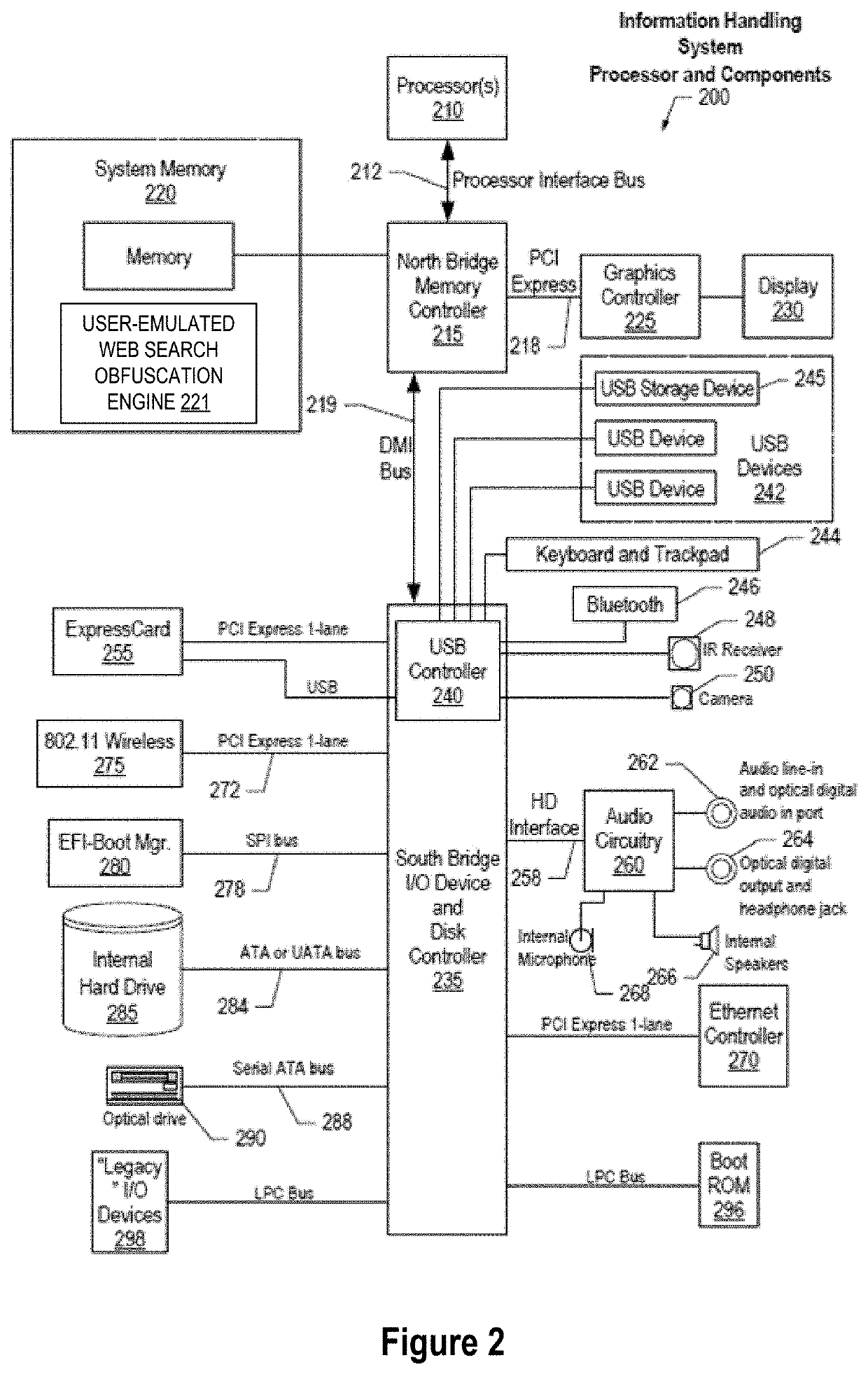
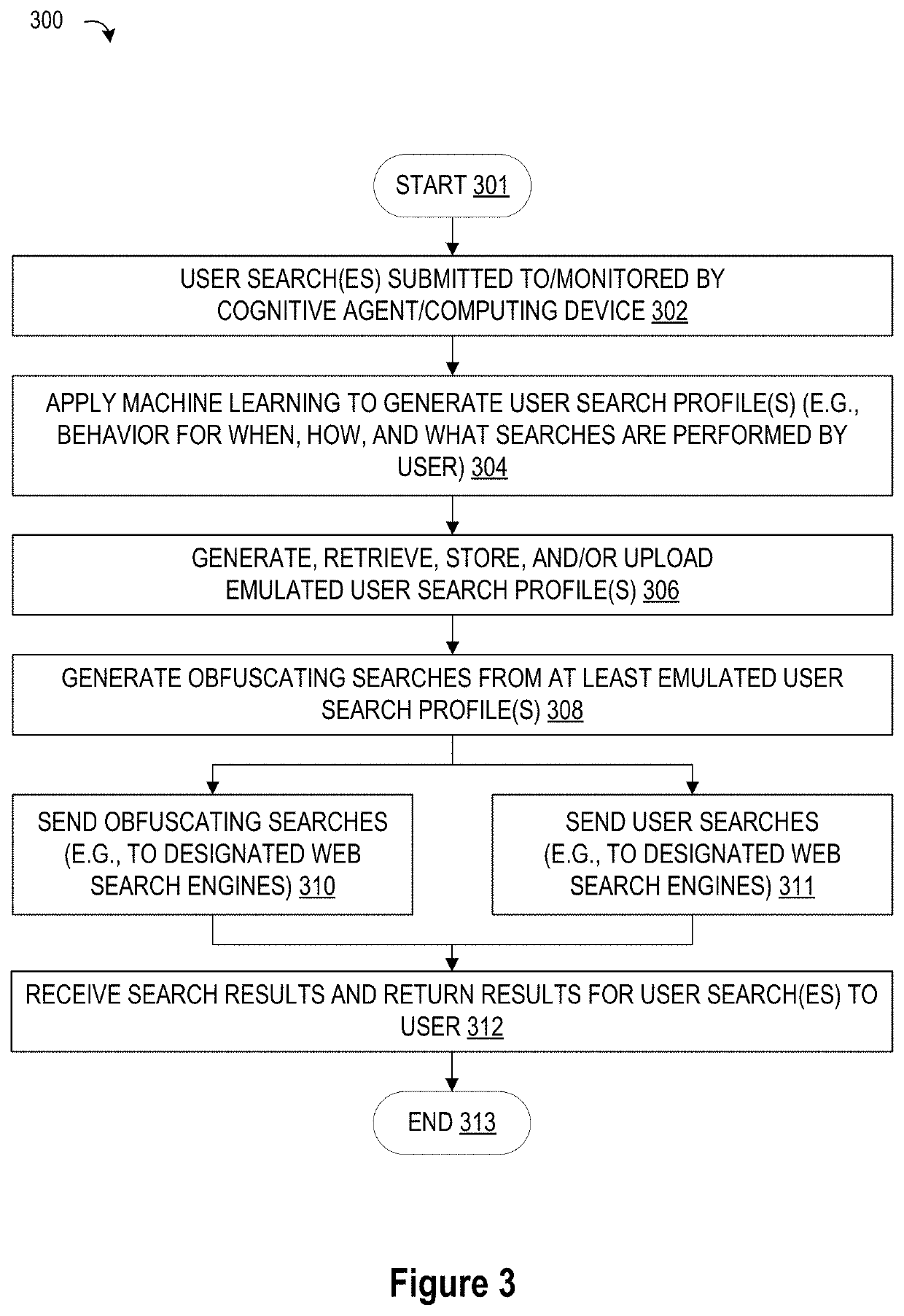
System and Method for Cognitive Agent-Based Web Search Obfuscation
ActiveUS20180121677A1Easy to understandAccurately reflectWeb data indexingDigital data protectionObfuscationCognitive analysis
A method, system and a computer program product are provided for obscuring web searches by performing cognitive analysis on one or more user search inquiries from a first user to identify a user search behavior profile for the first user, and then generating one or more obfuscating search inquiries consistent with the user behavior search profile for the first user for issuance with the user search inquiries to impair the search engine from accurately characterizing search information related to the first user.
Owner:IBM CORP
Cognitive analysis-oriented Chinese event representation method
InactiveCN106484673AImplement extractionRealize judgmentSemantic analysisSpecial data processing applicationsEvent typeEvent data
The invention discloses a cognitive analysis-oriented Chinese event representation method, provides a structured event representation model and provides a Chinese text analytic processing-based assignment method of key attributes of the event type and the like. The cognitive analysis-oriented Chinese event representation method supports attribute extraction and presentation of social events in the fields of politics, military, diplomacy and the like; and the realistic feasibility is provided for representation, organization, storage management and cognitive analysis application of massive event data.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
System and Method for Monitoring User Searches to Obfuscate Web Searches By Using Emulated User Profiles
ActiveUS20180121553A1Easy to understandAccurately reflectDigital data information retrievalMachine learningCognitive analysisData mining
A method, system and a computer program product are provided for obscuring web searches by performing cognitive analysis on the one or more user search inquiries to identify a user search behavior profile and user characterization information for the first user and generating or retrieving one or more simulated user search behavior profiles for one or more simulated users, and then generating one or more obfuscating search inquiries consistent with the one or more simulated user search behavior profiles for issuance with the user search inquiries to impair the search engine from accurately determining the user characterization information for the first user.
Owner:IBM CORP
Cognitive analysis using applied analog circuits
ActiveUS10598710B2Capacitance measurementsComputing operations for addition/subtractionSignal onHemt circuits
Owner:IBM CORP
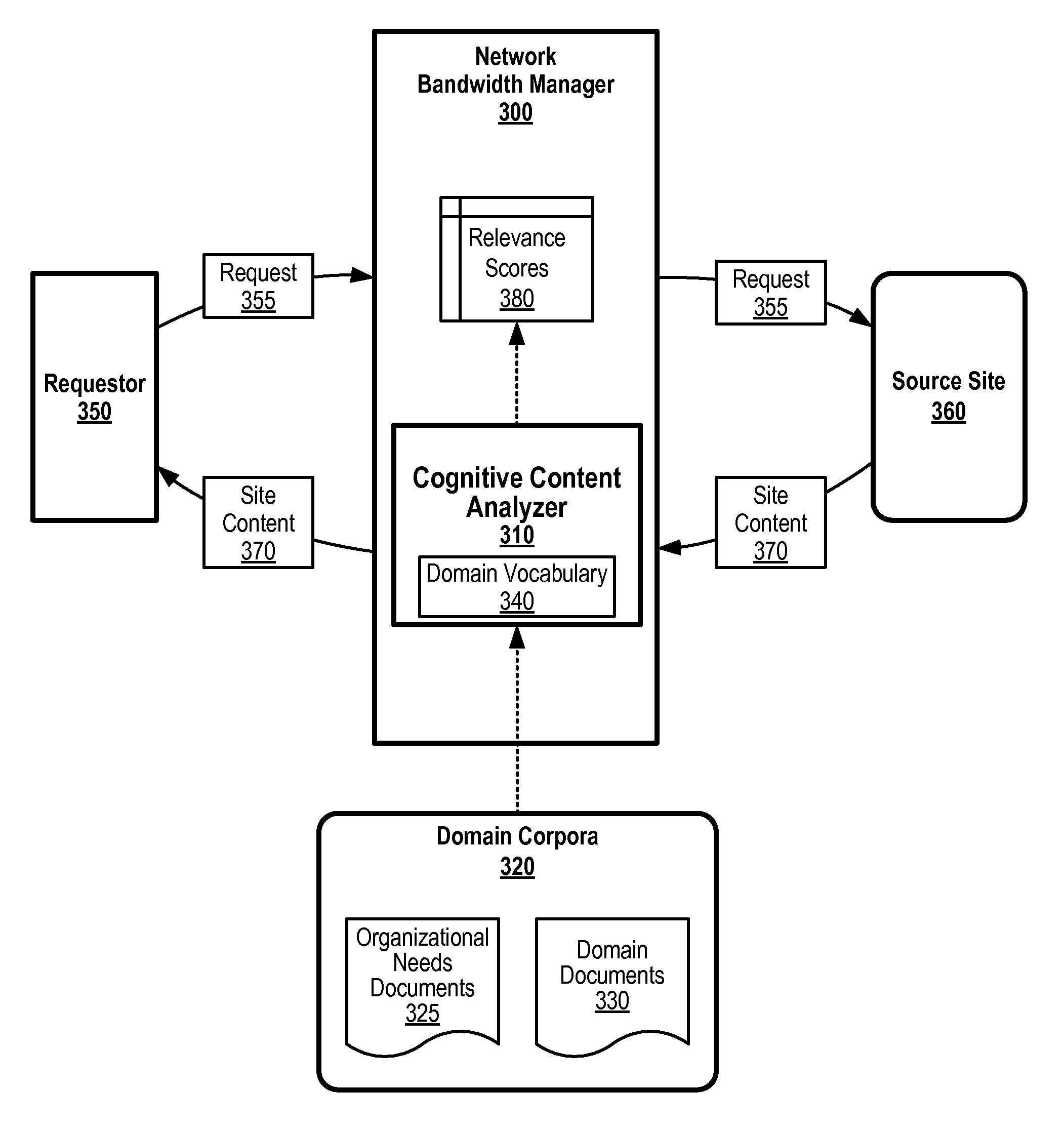
Managing Network Bandwidth Based on Cognitive Analysis of Site Content Against Organizational Needs
InactiveUS20160099846A1Digital computer detailsData switching networksQuality of serviceRequirements management
An approach is provided in which a network bandwidth manager receives a first request to access site content from a source site over a computer network. The network bandwidth manager analyzes the site content against a domain corpora that corresponds to one or more organizational needs of an organization. When the network bandwidth manager receives a second request corresponding to the source site, the network bandwidth manager modifies a quality of service of the computer network to access the source site based upon the previous analysis. In turn, the network bandwidth manager provides access to the source site over the computer network utilizing the modified quality of service.
Owner:IBM CORP
Predicting paths of underground utilities
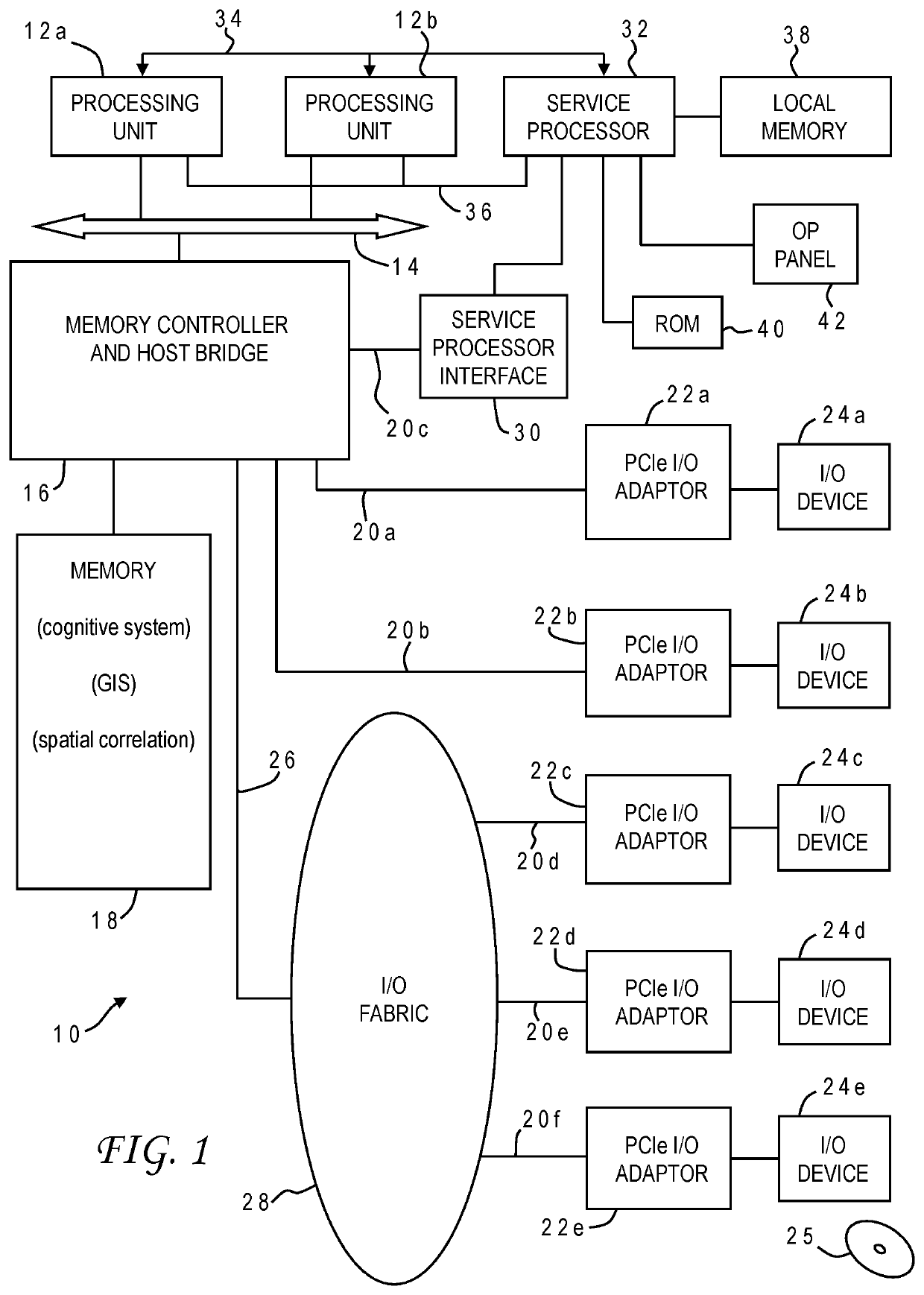
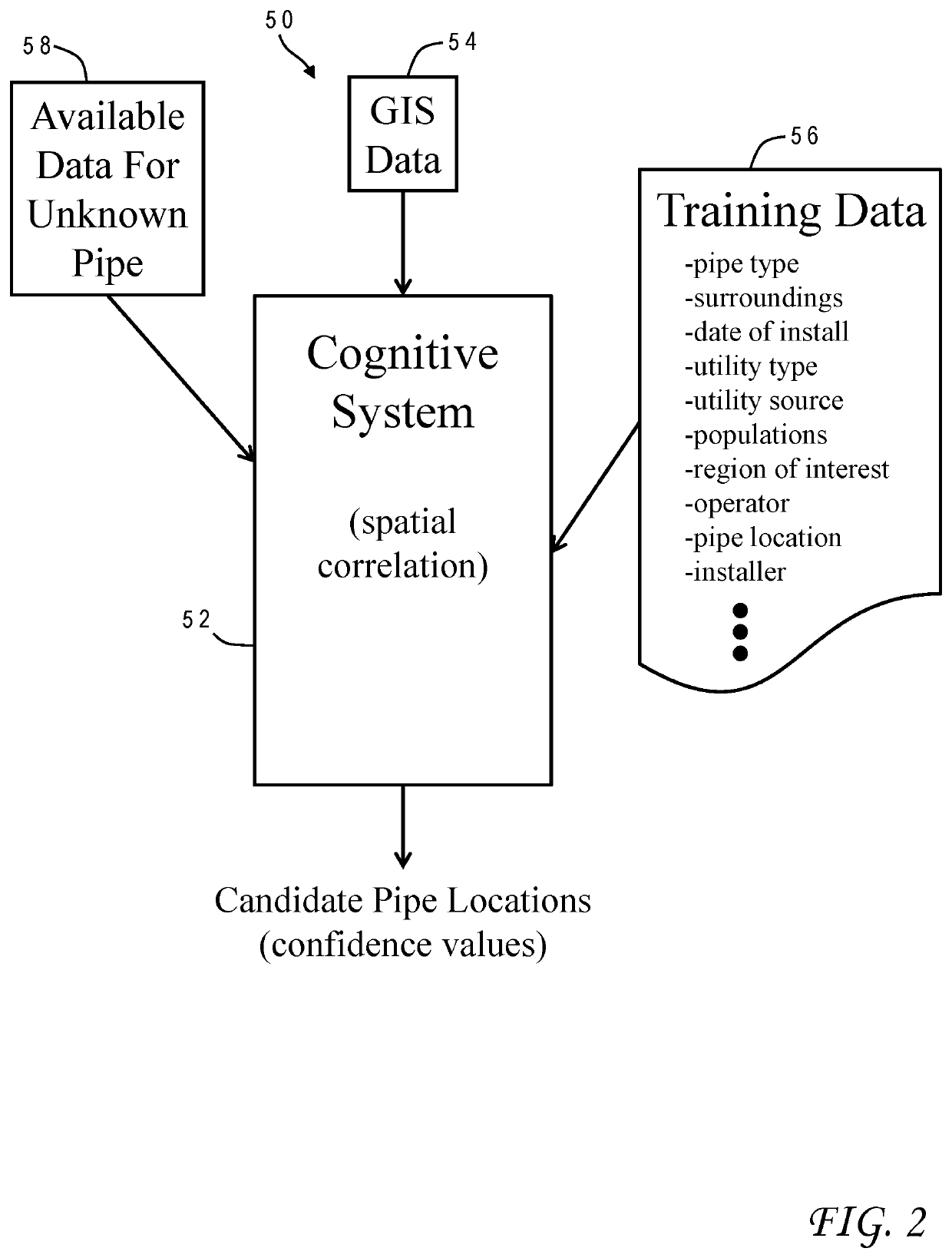
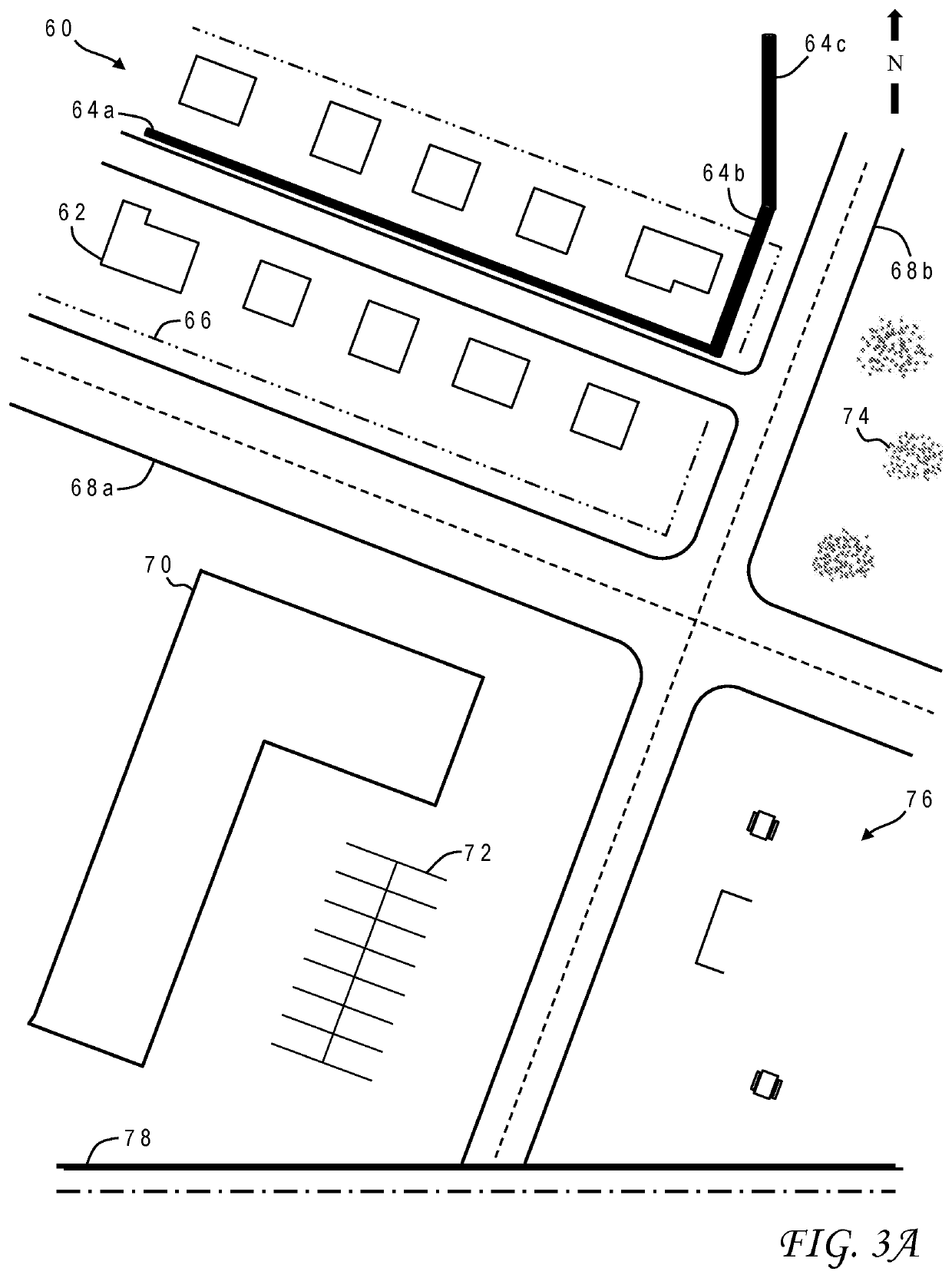
The most likely path for an underground utility having an unknown location is predicted using artificial intelligence. A cognitive system is trained with details associated with historical utility installations whose underground paths are known. The system is applied to whatever installation details are available for the unknown underground utility such as geographic features which are subjected to spatial correlation to derive geographic locations relative to a region of interest for the underground utility. Cognitive analysis is performed on the locations in association with the features to generate candidate paths for the utility. The candidate paths are presented to the user along with computed confidence scores. The installation details may further include nongeographic features used in the cognitive analysis such as a date of installation of the utility or an entity associated with the utility.
Owner:MINAROVIC JOE T
Graphical user interface using continuous authentication and encryption for selective display of data
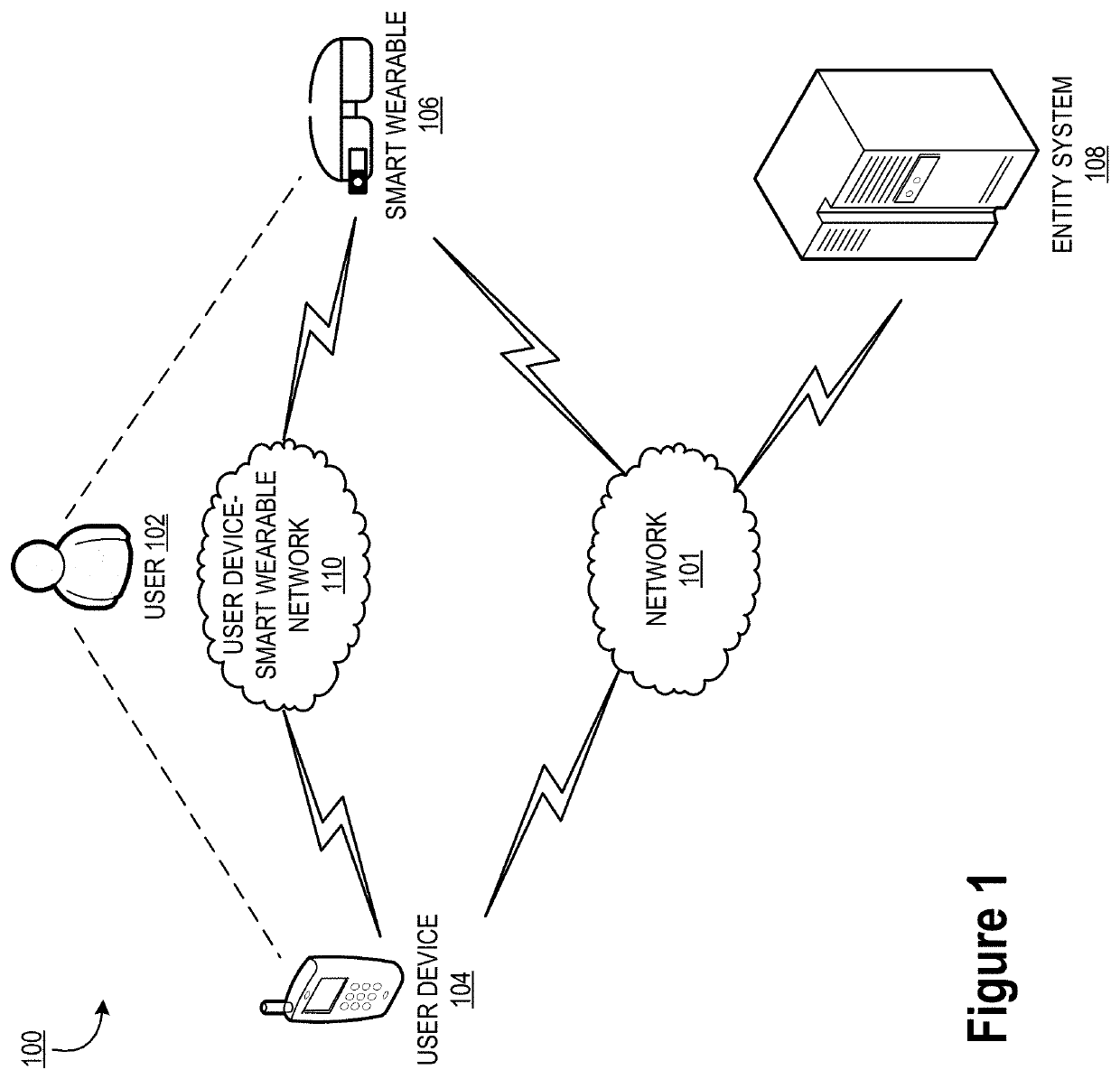
ActiveUS20210385067A1Well formedInput/output for user-computer interactionEncryption apparatus with shift registers/memoriesSmartglassesGraphical user interface
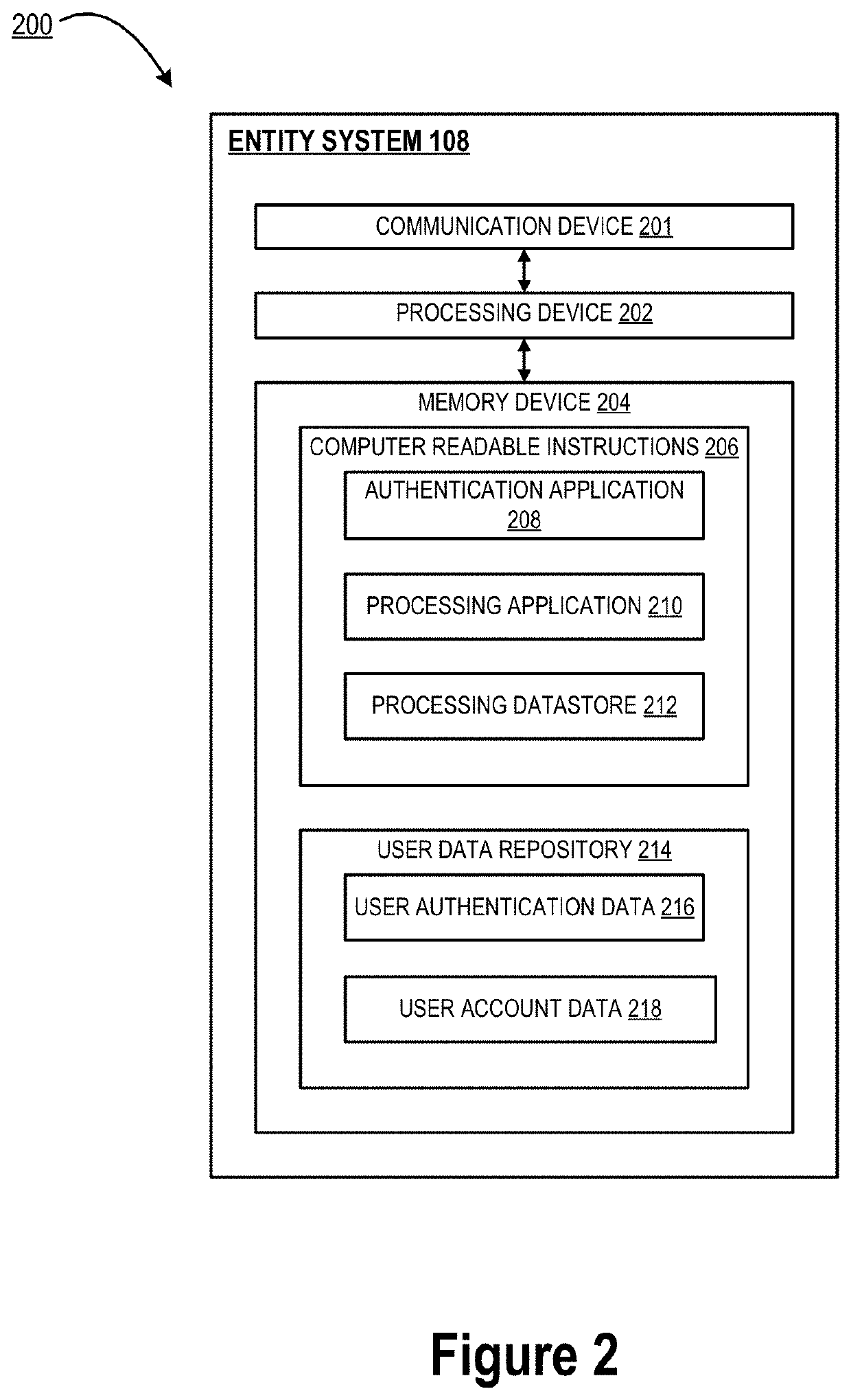
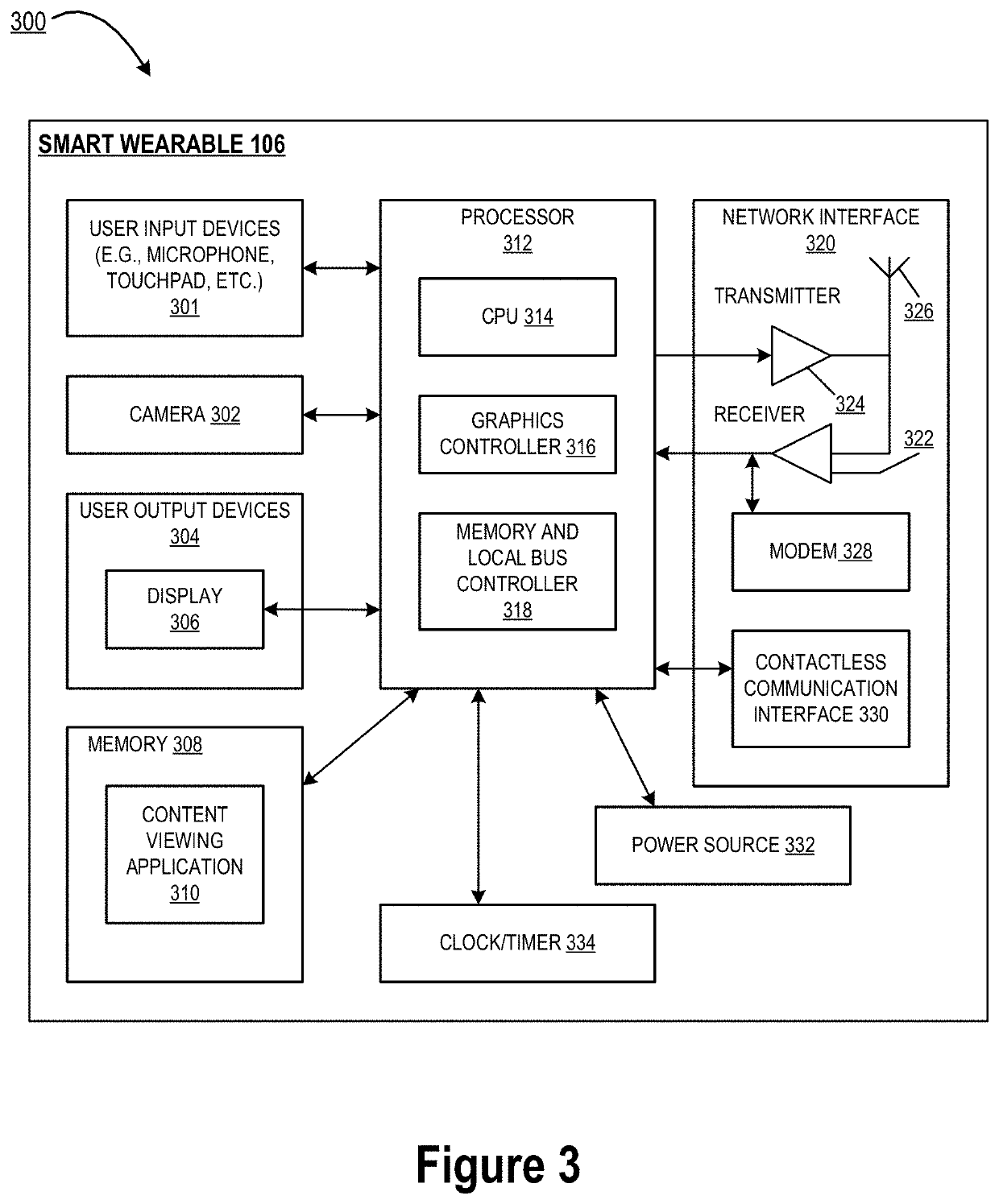
Embodiments of the invention are directed to a system, method, or computer program product structured for continuous authentication and encryption. In some embodiments, the system is structured for receiving content from an entity system, displaying the content as masked content, and determining, using cognitive analysis, that a user wearing smart glasses is viewing a first portion of the masked content through the smart glasses, where the first portion of the masked content is associated with a first content hash. The system is also structured for identifying a first decryption key associated with the first content hash and determining a first cognitive hash. The system is also structured for receiving a first wearable hash from the smart glasses, comparing the first cognitive hash to the first wearable hash, and in response to the first cognitive hash matching the first wearable hash, transmitting the first decryption key to the smart glasses.
Owner:BANK OF AMERICA CORP
In-set access control improved by fully utilizing natural language processing
ActiveCN110232281AObvious purposeDigital data protectionText database queryingMedia access controlDocument preparation
The invention relates to in-set access control improved by fully utilizing natural language processing. Natural language processing is enhanced by linguistically extracting intelligence about a user.A history of user queries is analyzed by a natural language classifier to determine various user intents, and these intents are combined to form a user intent profile. The profile includes elements ofsentiment, emotion and tone. The profile can be used in various ways including restricting access to documents in a collection, or refining a cognitive analysis of a query. For access restriction, adetermination is made that the user intent is inconsistent with a document, and the user is denied access to the document. This determination involves a user intent score which is compared to a scoreof the document. For cognitive analysis, searching of reference documents is filtered by excluding documents based on the user intent. The searching includes a comparison of meta-data tags of the documents to the user intent.
Owner:HYUNDAI MOTOR CO LTD +1
System and method for computing critical data of an entity using cognitive analysis of emergent data
System and method for computing critical data of multiple entities is provided. Elements, from a set of predetermined elements, are assigned to sentences of a first dataset associated with an entity of an industry type. Predetermined elements characterize reputation of entities of various industries. Features determined from sentences of first dataset are categorized into groups. Features of a new dataset of a different entity of said industry type are matched with grouped features and same groups are allotted thereto. Classification rules are applied on matched features. Elements are assigned to sentences of new dataset based on allotted groups, which elements are same as those assigned to first dataset. Reputation scores are generated for said entities by determining positive and negative sentiments from the first and new dataset. Steps of assigning elements and grouping are repeated for datasets associated with entities of different industry types for creating a taxonomy for them.
Owner:MPHASIS
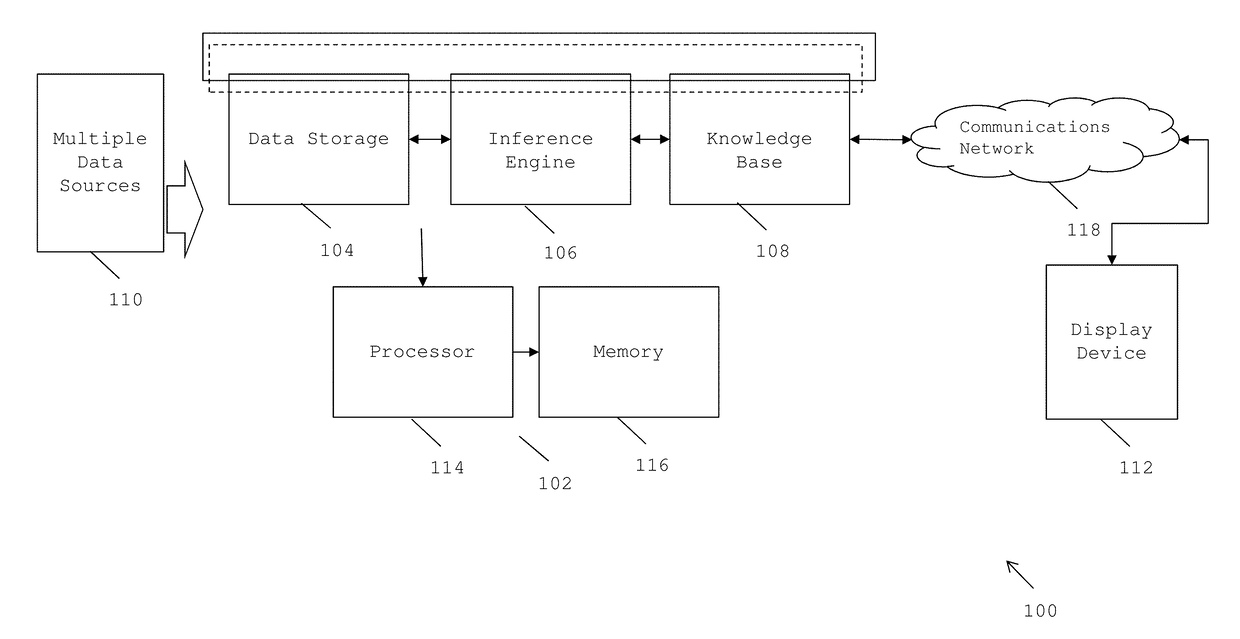
Feedback-based prioritized cognitive analysis
ActiveUS10681061B2Easy to analyzeOther databases indexingKnowledge representationTheoretical computer scienceEngineering
An automated method for processing security event data in association with a cybersecurity knowledge graph having nodes and edges. It begins by receiving from a security system (e.g., a SIEM) information representing an offense. An offense context graph is built. Thereafter, and to enhance the offense context graph, given nodes and edges of the knowledge graph are prioritized for traversal based on an encoding captured from a security analyst workflow. This prioritization is defined in a set of weights associated to the graph nodes and edges, and these weights may be derived using machine learning. The offense context graph is then refined by traversing the nodes and edges of the knowledge graph according to a prioritization tailored at least in part by the encoding. In addition to using security analyst workflow to augment generation of weights, preferably the machine learning system provides recommendations back to the security analysts to thereby influence their workflow.
Owner:INT BUSINESS MASCH CORP
Assessing cognitive reaction to over-the-air updates
PendingCN111858696ALess biased impactError detection/correctionSpeech analysisCognitive responseArtificial intelligence
One or more embodiments include a cognition analysis system for determining a cognitive reaction to a software application update. The cognition analysis system determines that a software applicationexecuting on a computing device has been modified into an updated software application. The cognition analysis system acquires, via at least one sensor, sensor data associated with a user of the updated software application. The cognition analysis system determines, based on the sensor data, at least one of a cognitive workload and an emotional state associated with a user interaction with a feature of the updated software application.
Owner:HARMAN INT IND INC
Cognitive analysis and resolution of erroneous software patches
ActiveUS10592343B2Non-redundant fault processingRedundant operation error correctionEngineeringData mining
Resolving software patch issues is provided. Recorded activities performed by users to resolve an issue with a patch applied to an application on a group of client devices are compared. A set of common user activities are identified within the recorded activities performed by the users. A subset of highest ranking common user activities is selected from the set of common user activities. A fix for the issue with the patch is generated based on the subset of highest ranking common user activities. Corrective action based on the fix is taken to resolve the issue with the patch on a client device, the client device experiencing the issue resolved by users on the group of client devices.
Owner:INT BUSINESS MASCH CORP
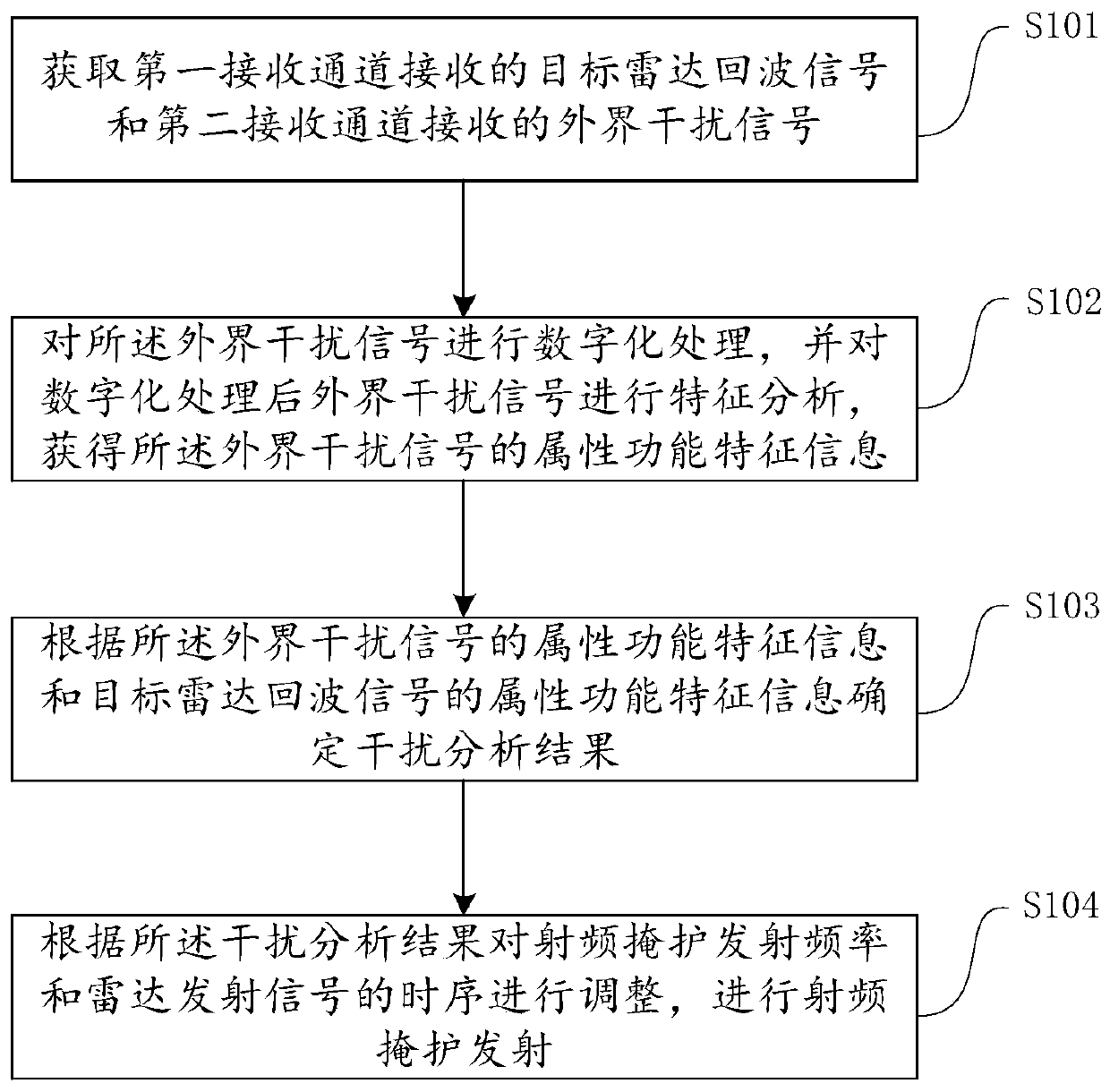
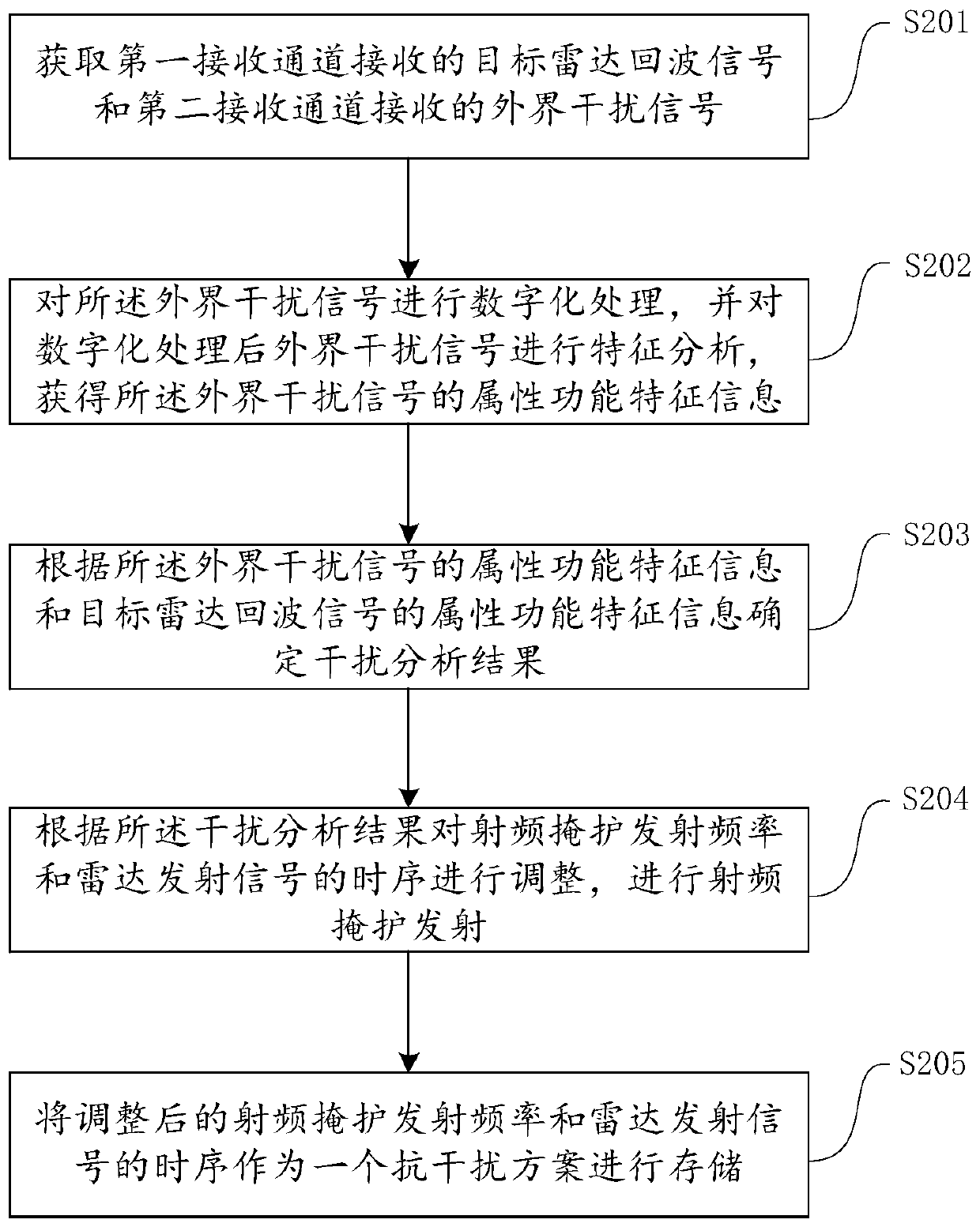
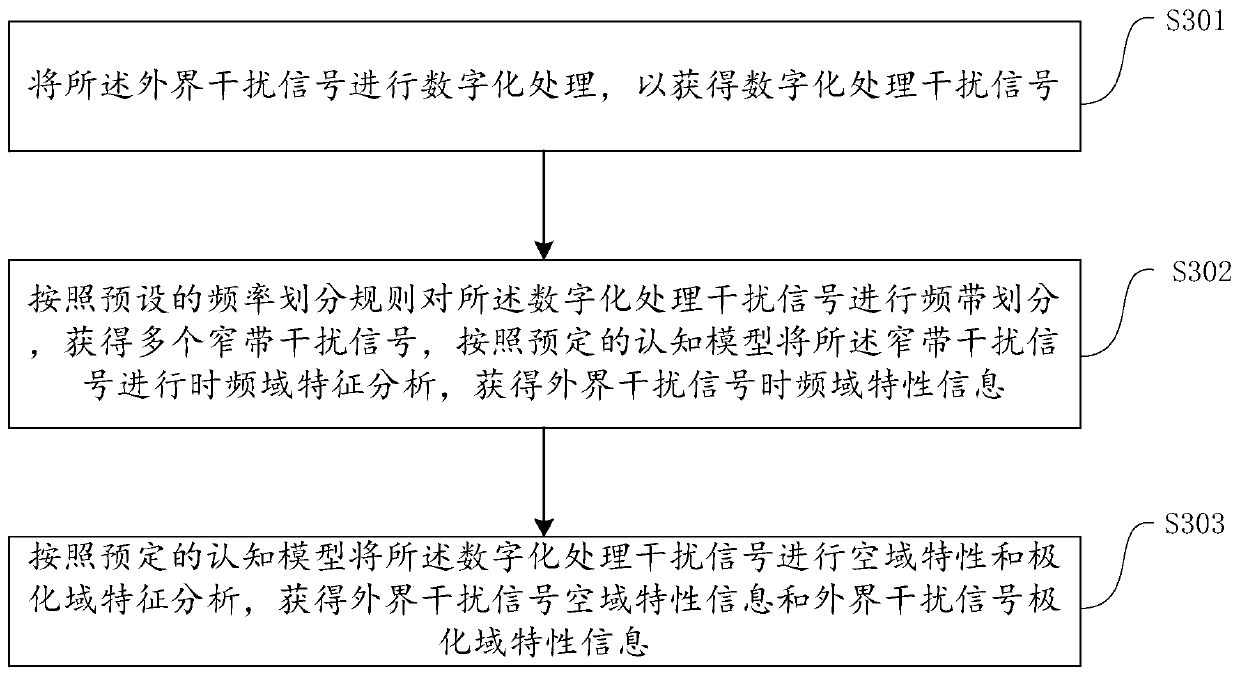
Radio frequency shielding method and device, and computer equipment
PendingCN109884598ARealize intelligent anti-jammingImprove anti-interference abilityWave based measurement systemsInterference resistanceRadar
The invention is applicable to the technical field of computers, and particularly relates to a radio frequency shielding method and device, and computer equipment. The radio frequency shielding methodspecifically comprises the steps of acquiring a target radar echo signal received by a first receiving channel and an external interference signal received by a second receiving channel; carrying outdigital processing on the external interference signal, and carrying out characteristic analysis on the digitalized external interference signal to obtain attribute function characteristic information of the external interference signal; determining an interference analysis result according to the attribute function characteristic information of the external interference signal and attribute function characteristic information of the target radar echo signal; and adjusting a radio frequency shielding emission frequency and a time sequence of radar emitted signals according to the interferenceanalysis result, and carrying out radio frequency shielding emission. According to the method, the external interference signal is acquired in real time and is subjected to cognitive analysis, and ananti-interference strategy is adjusted, so that intelligent interference resistance of a radar radio frequency shielding system is realized.
Owner:XIDIAN UNIV
Cognitive analytics using group data
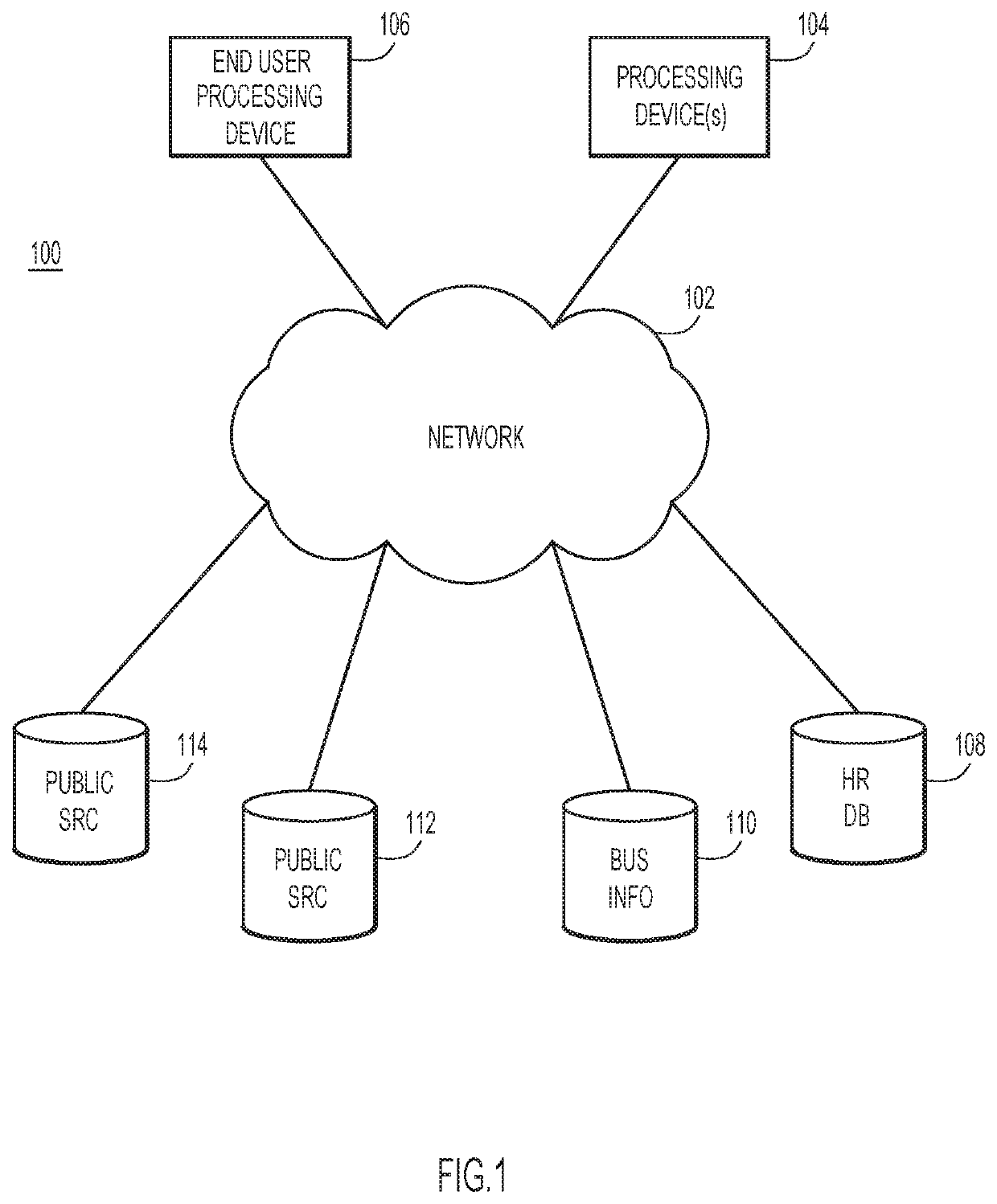
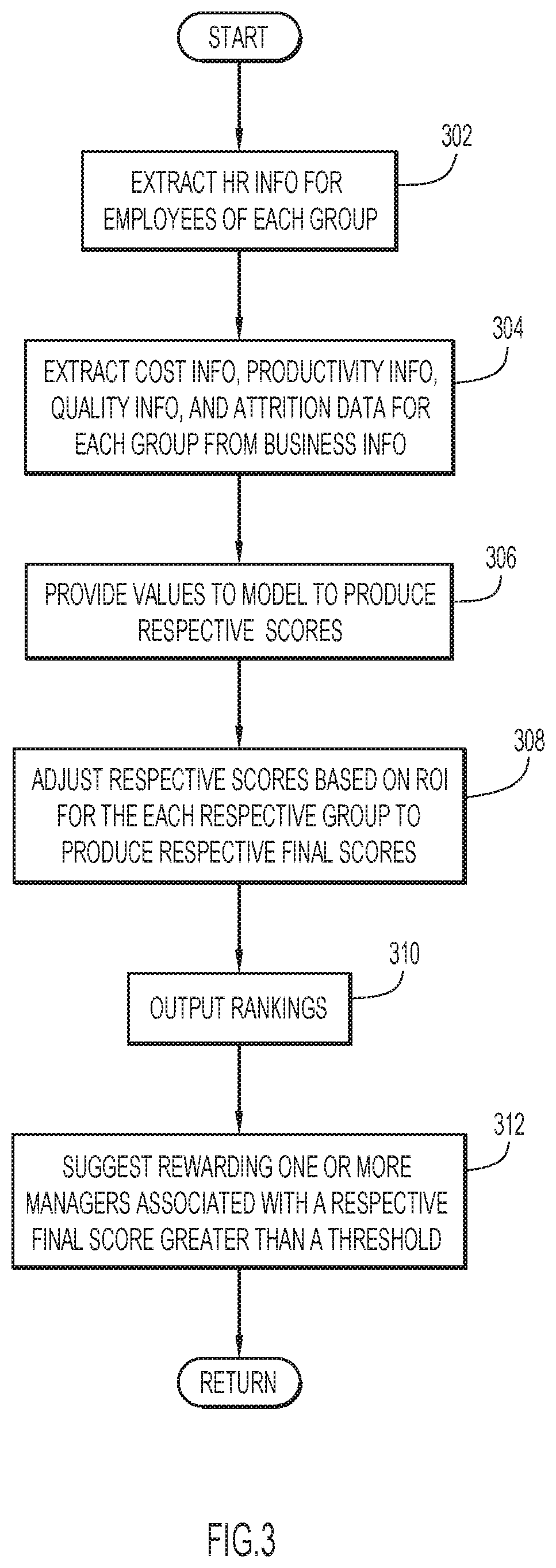
A method, a system, and a computer program product are provided for performing cognitive analytics. Human resource information for respective groups of a business unit of an organization may be extracted from stored business information. The human resource information may include, for employees of the respective groups, salary information and employee experience information. For the respective groups, cost information, productivity information, quality information, and attrition data may be extracted from the business information. At least the human resource information, the cost information, the productivity information, the quality information, and the attrition data may be provided, for the respective groups, to a model trained via machine learning. The model may produce respective scores for the groups. The groups may be ranked based at least partly on the respective scores and the ranking of the groups may be output.
Owner:IBM CORP
System and method for monitoring user searches to obfuscate web searches by using emulated user profiles
ActiveUS10740418B2Easy to understandAccurately reflectDigital data information retrievalMachine learningEngineeringData mining
Owner:INT BUSINESS MASCH CORP
Cognitive dynamic video summarization using cognitive analysis enriched feature set
InactiveUS10192584B1Natural language analysisElectronic editing digitised analogue information signalsPattern recognitionFeature set
Accurate and concise summarization of a media production is achieved using cognitive analysis which groups segments of the production into clusters based on extracted features, selects a representative segment for each cluster, and combines the representative segments to form a summary. The production is separated into a video stream, a speech stream and an audio stream, from which the cognitive analysis extracts visual features, textual features, and aural features. The clustering groups segments together whose visual and textual features most closely match. Selection of the representative segments derives a score for each segment based on factors including a distance to a centroid of the cluster, an emotion level, an audio uniqueness, and a video uniqueness. Each of these factors can be weighted, and the weights can be adjusted in accordance with user input. The factors can have initial weights which are based on statistical attributes of historical media productions.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com