Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38results about "Virtual private networks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
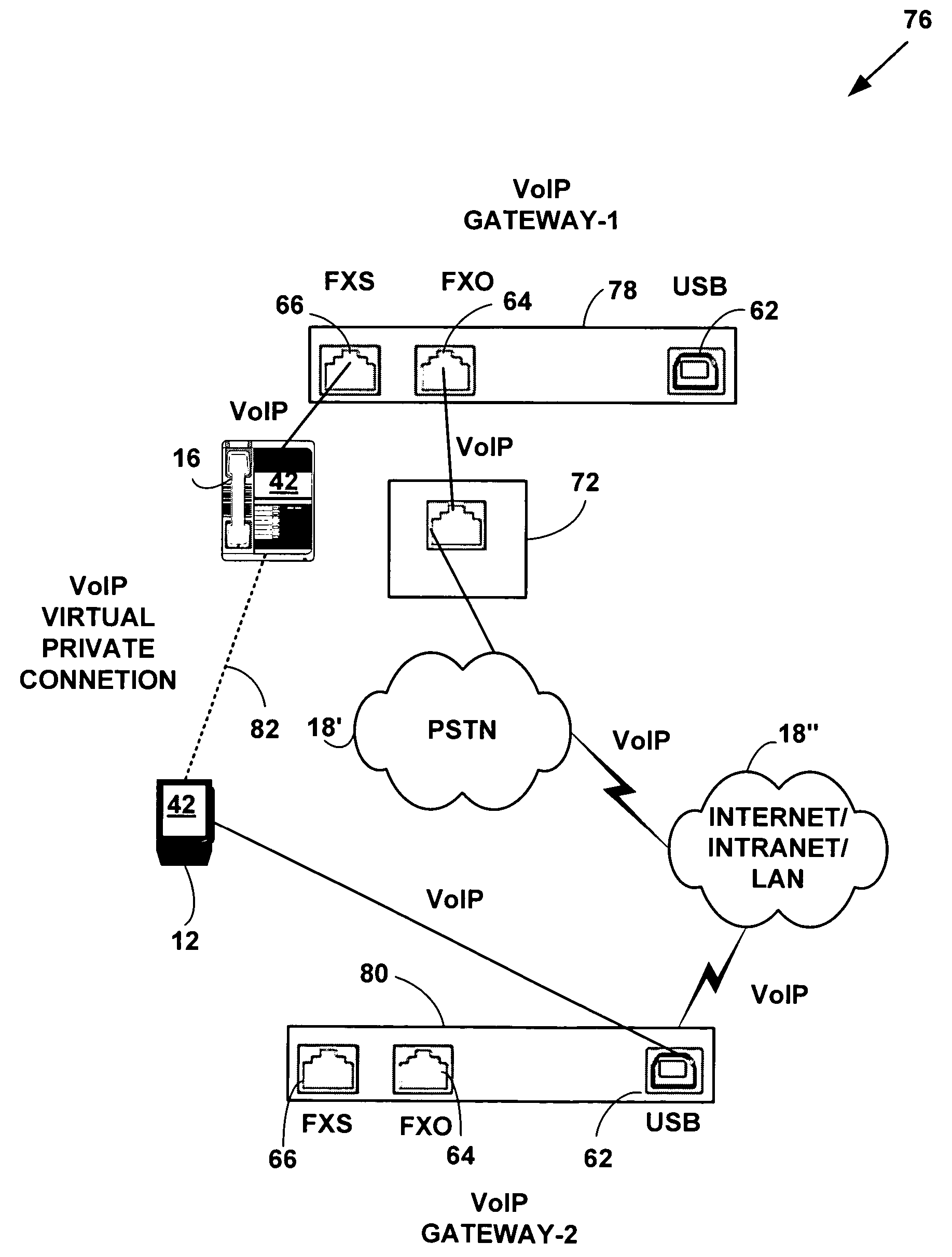
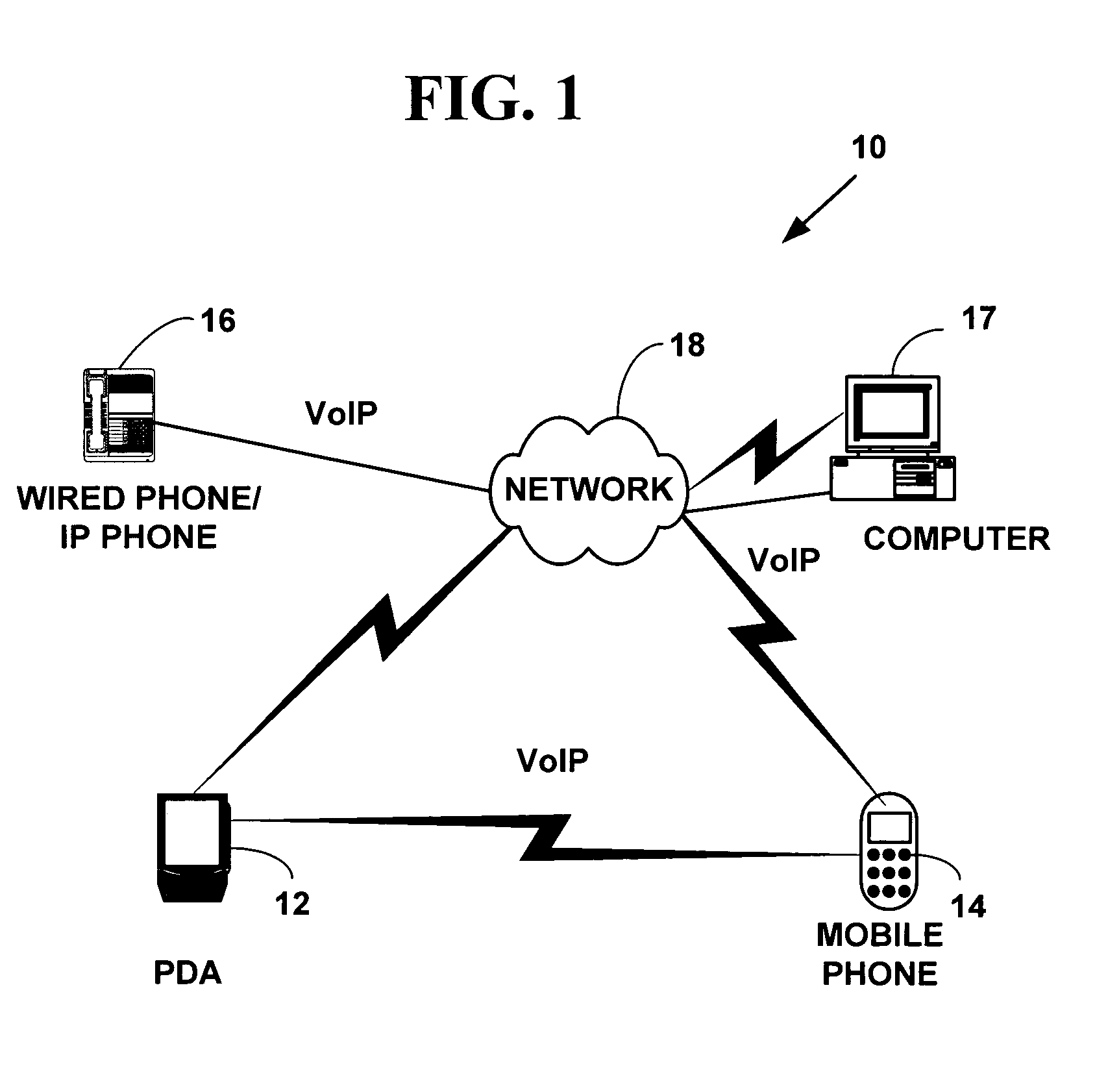
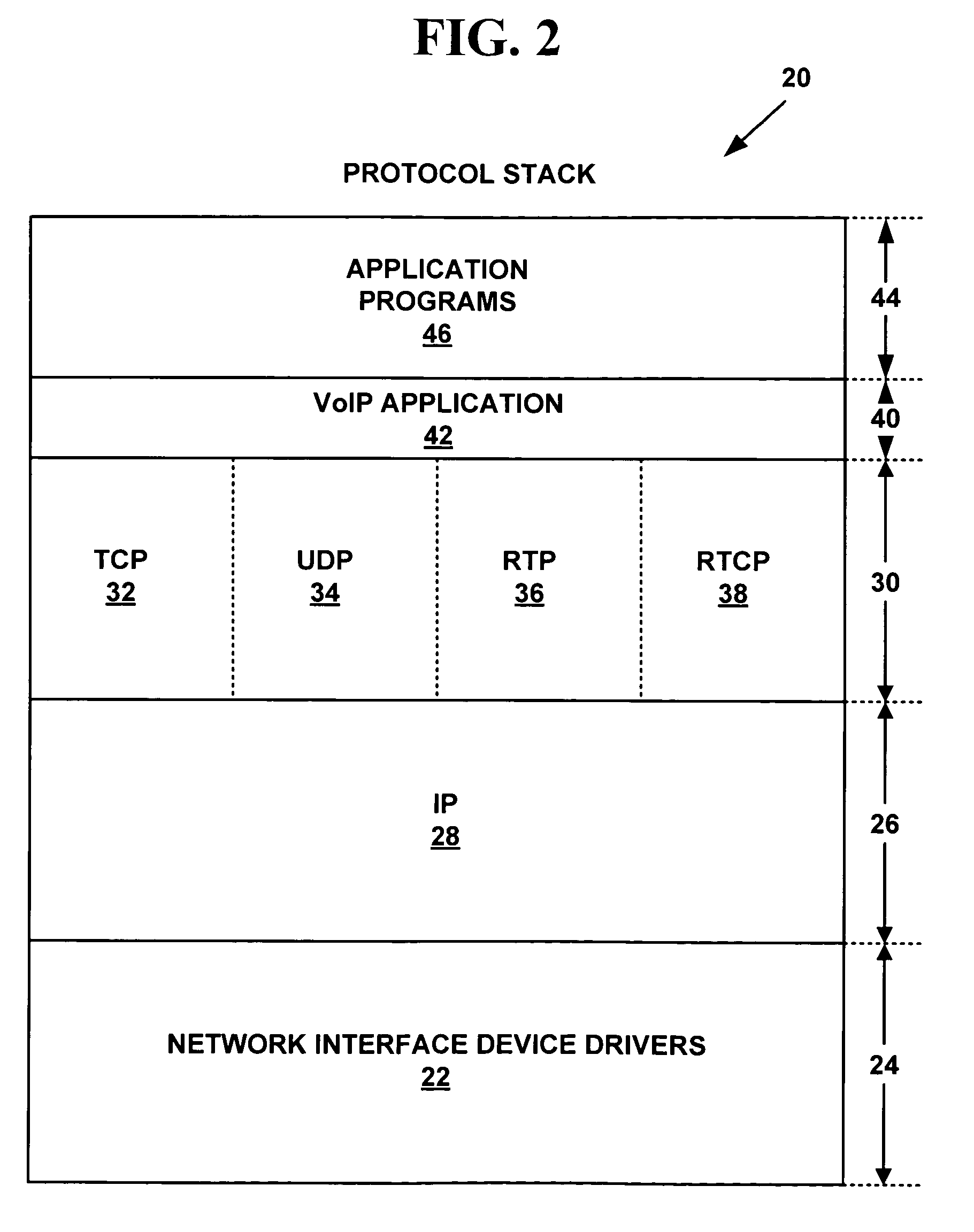
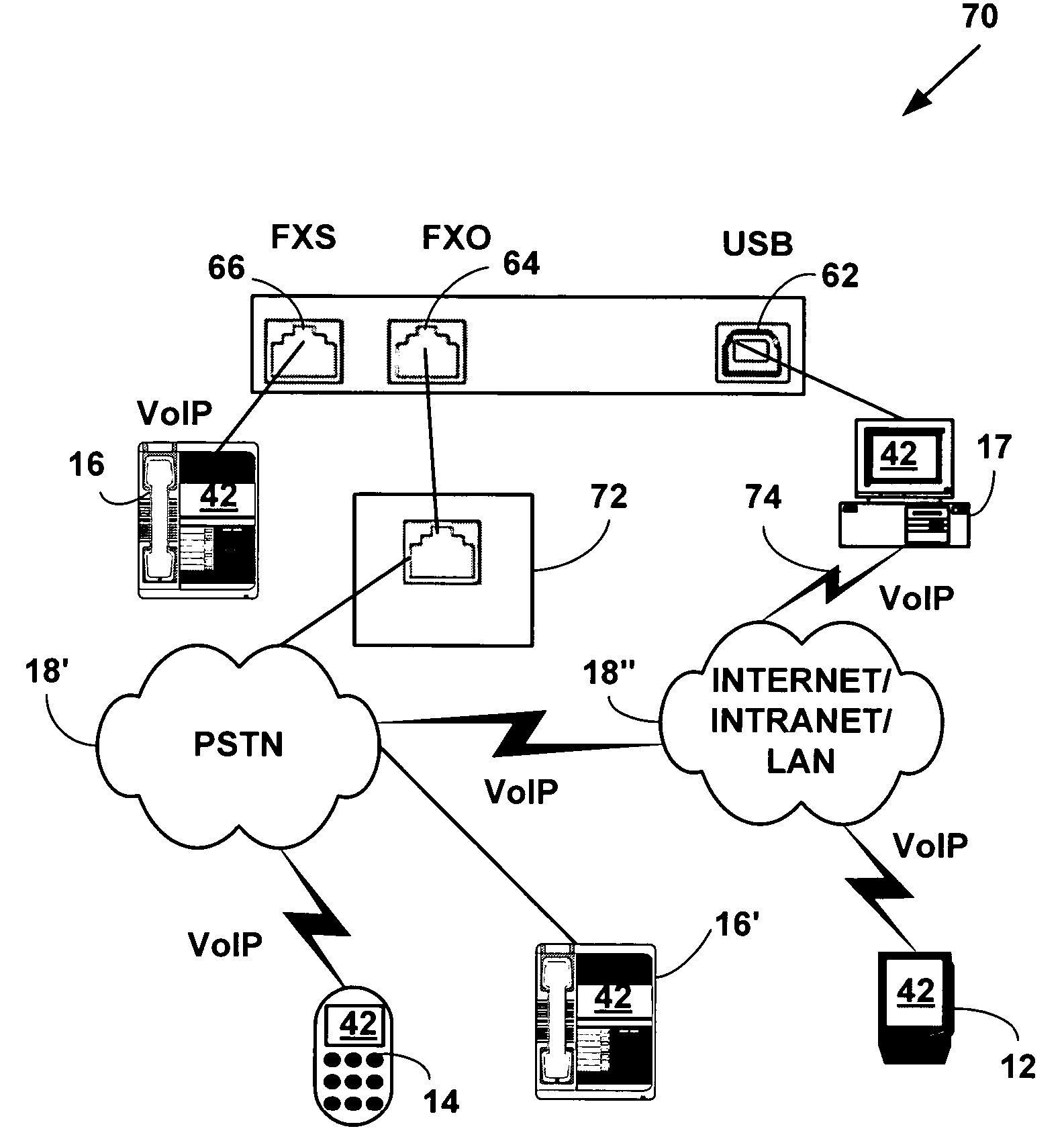
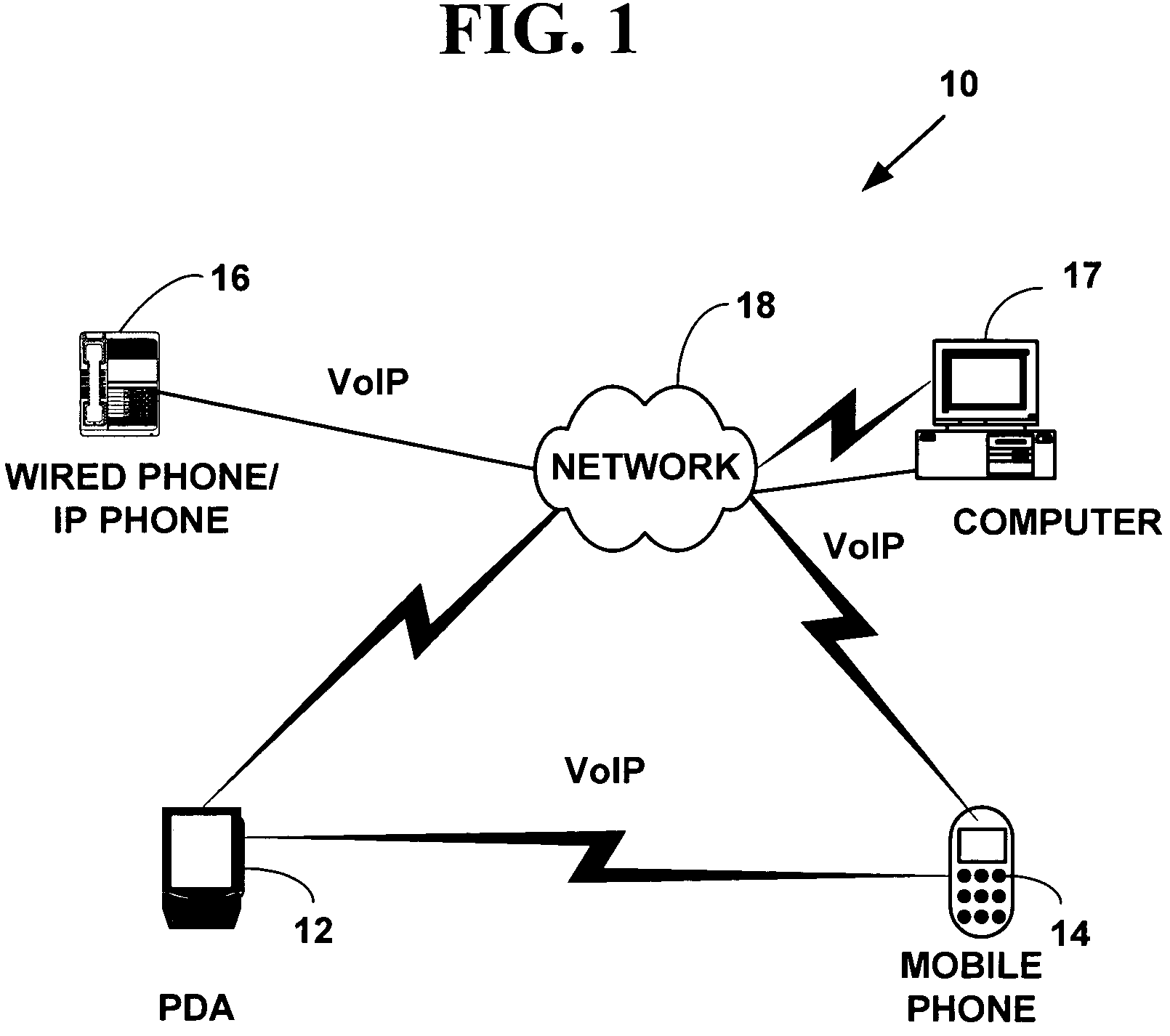
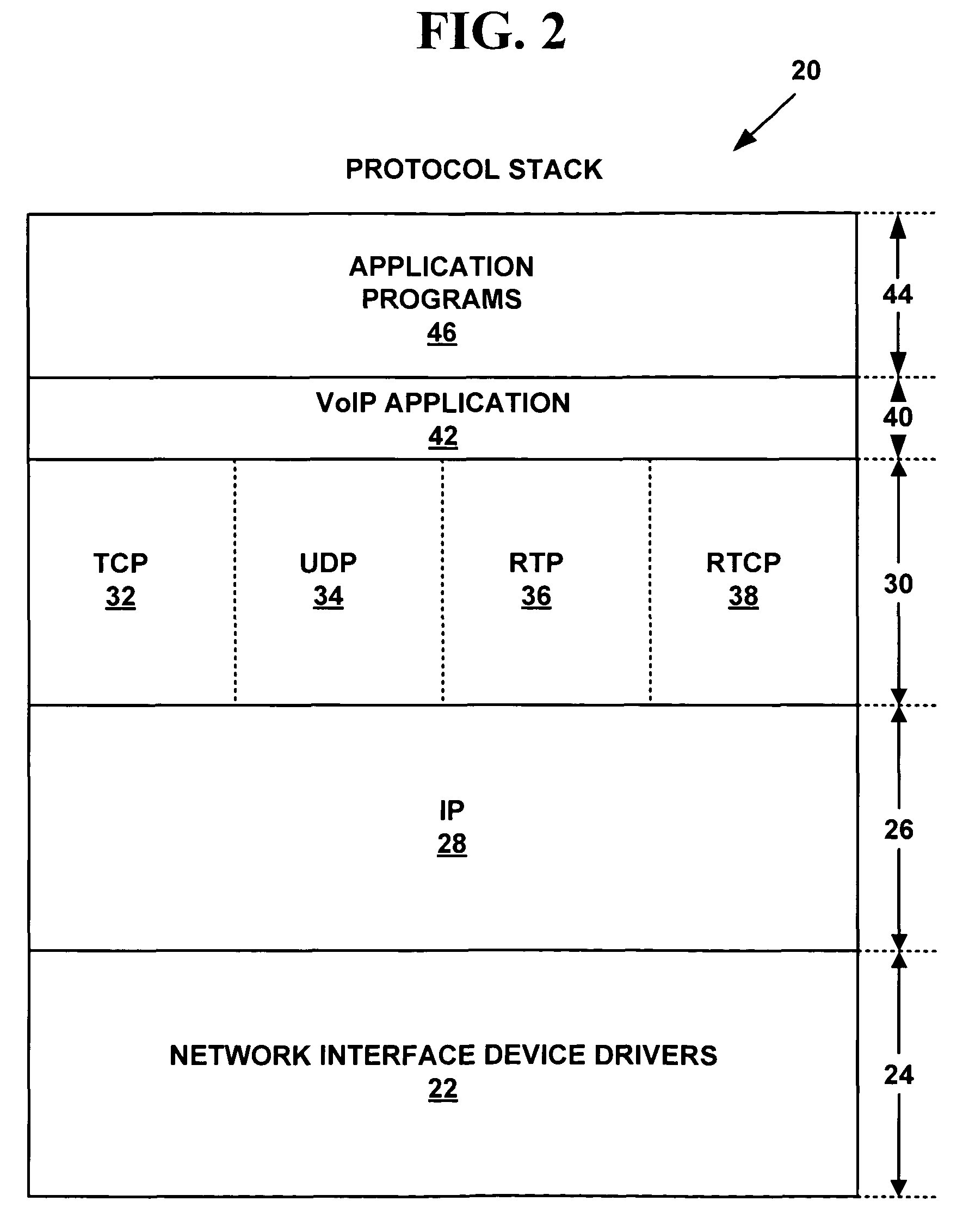
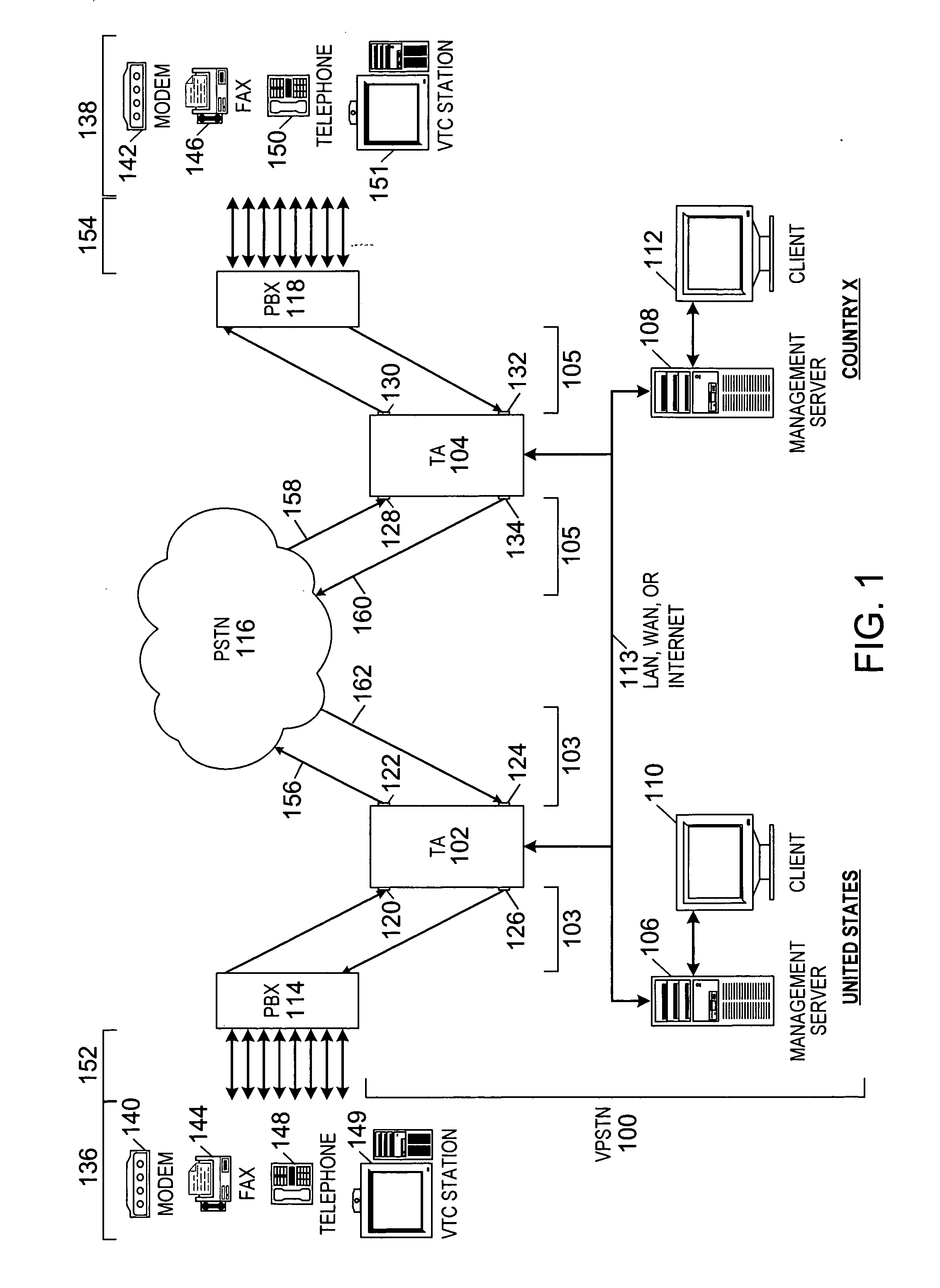
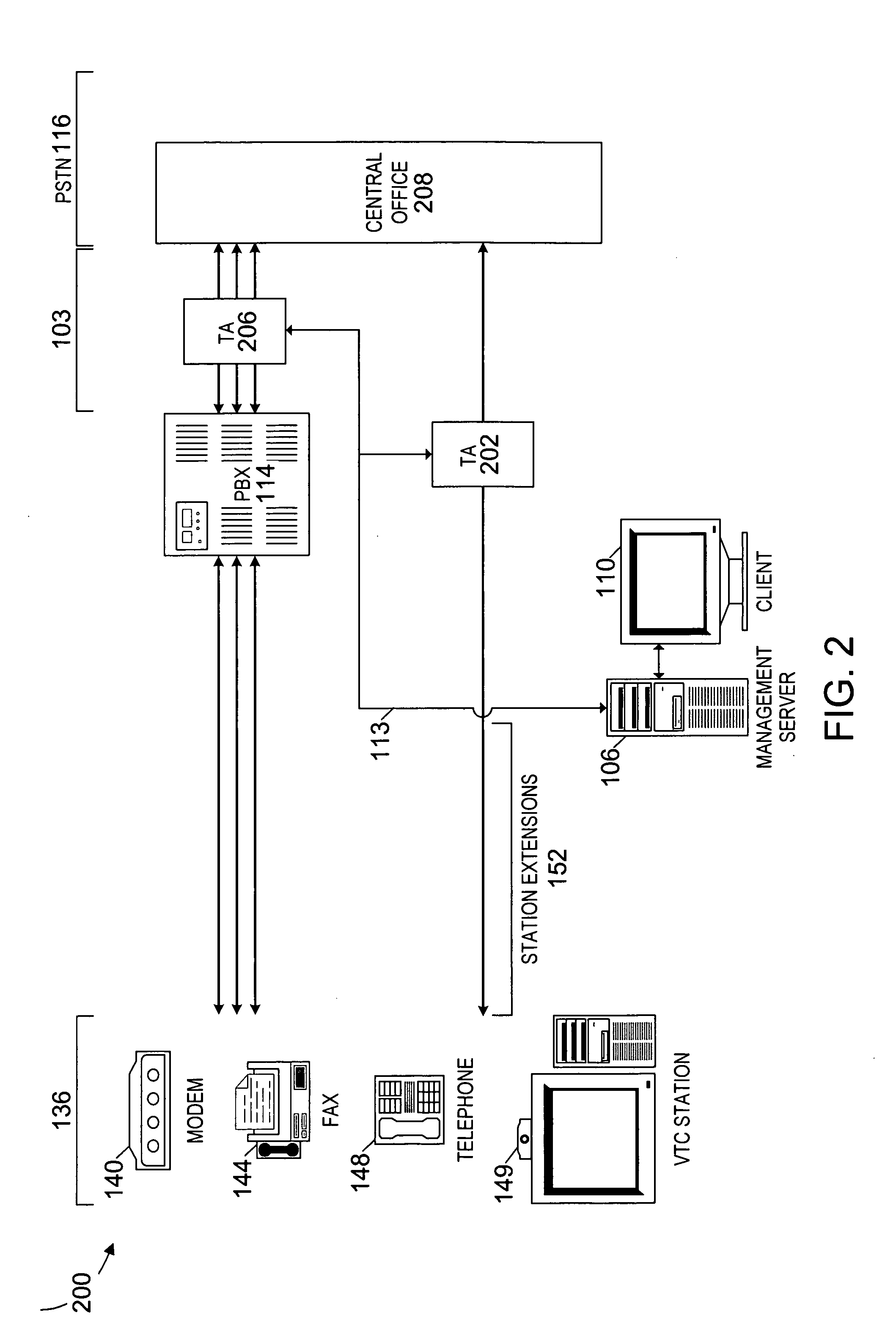
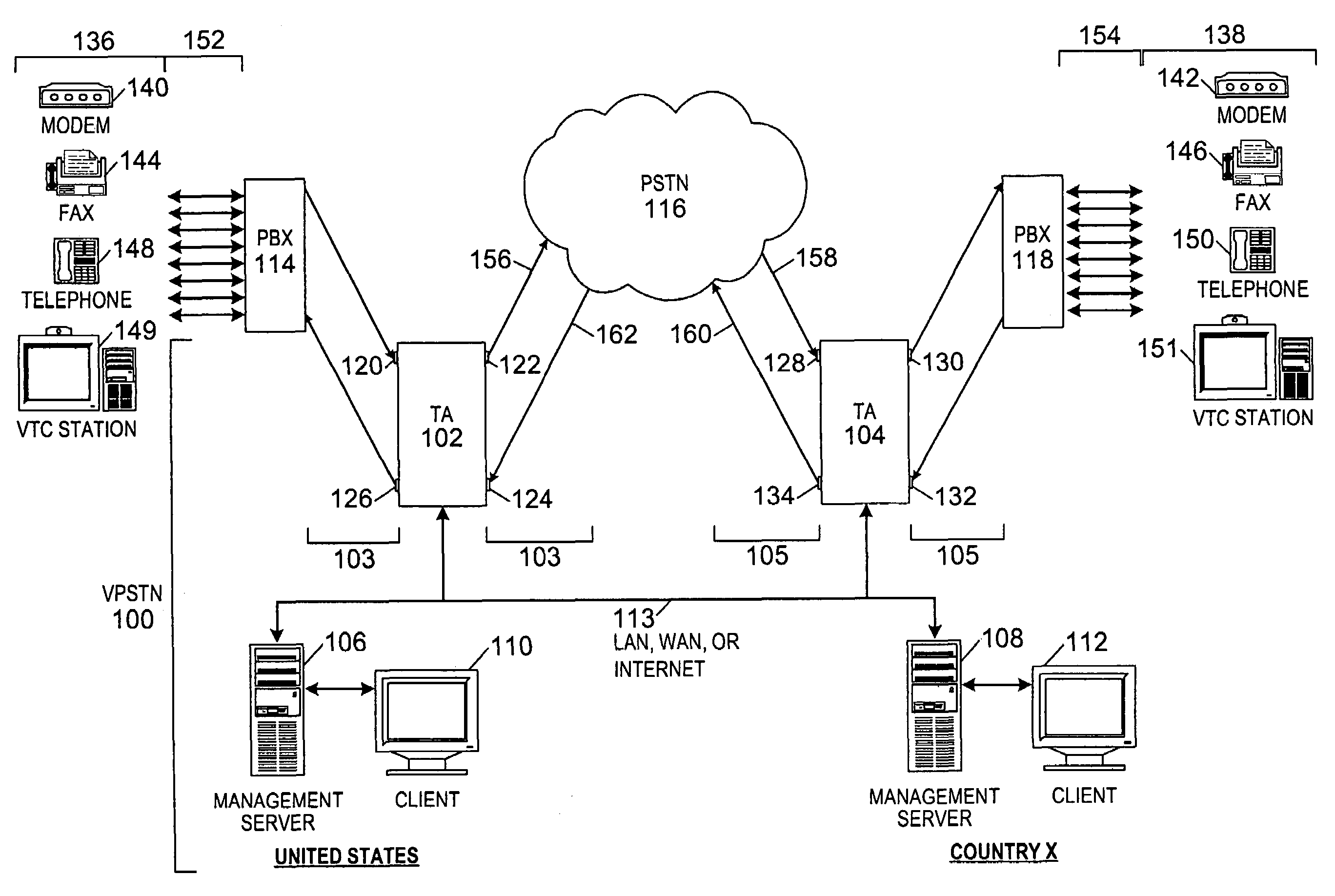
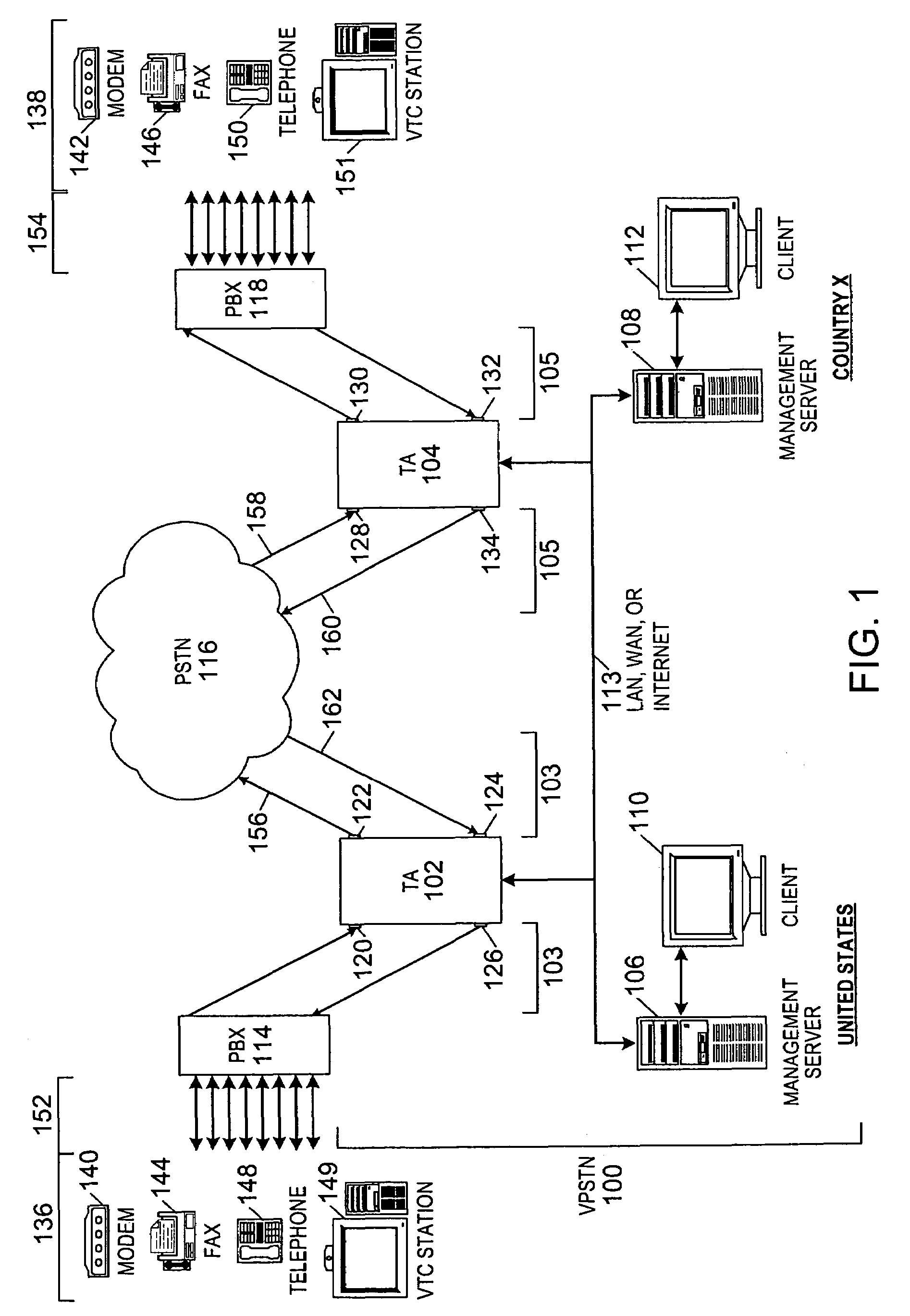
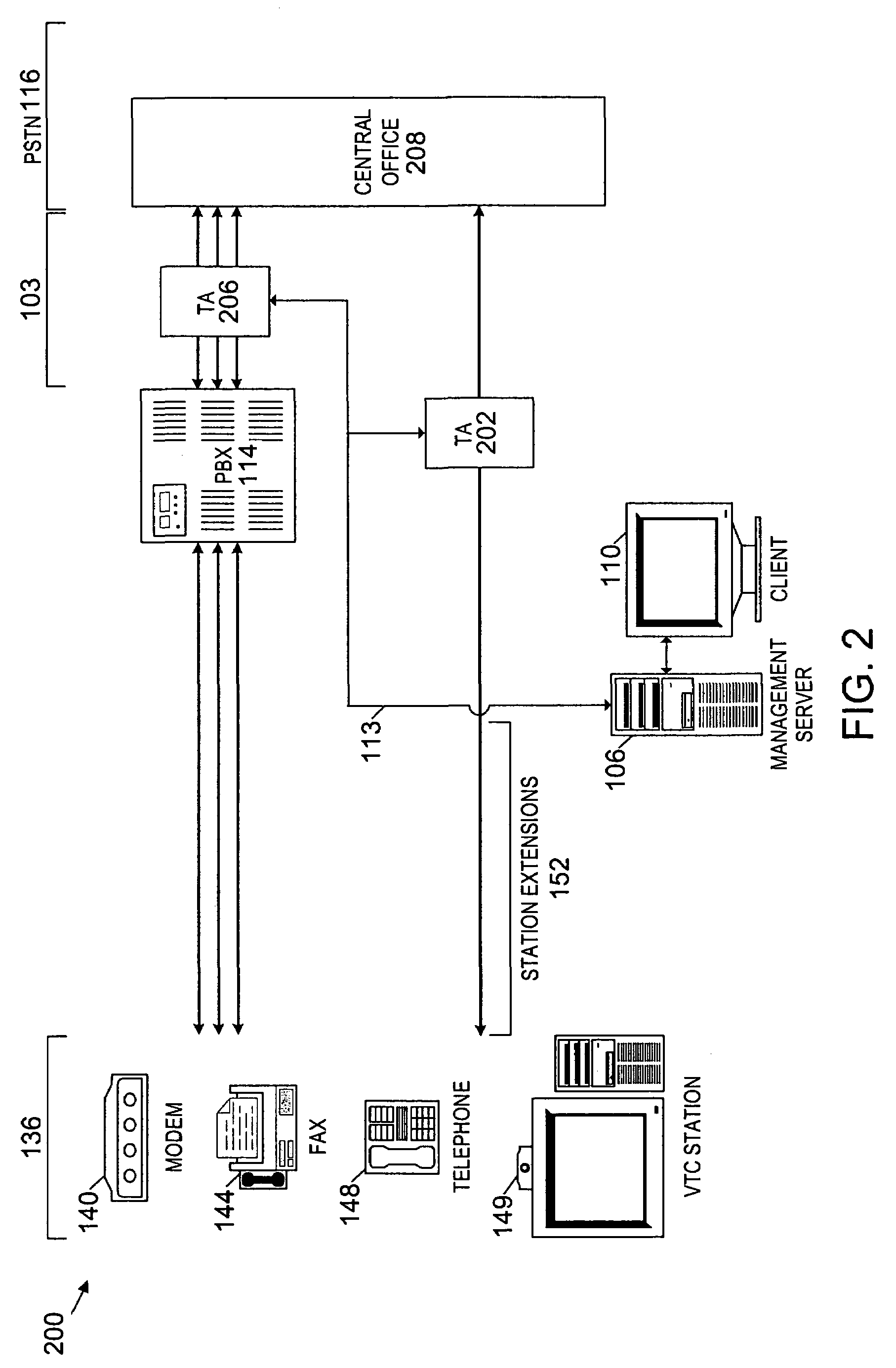
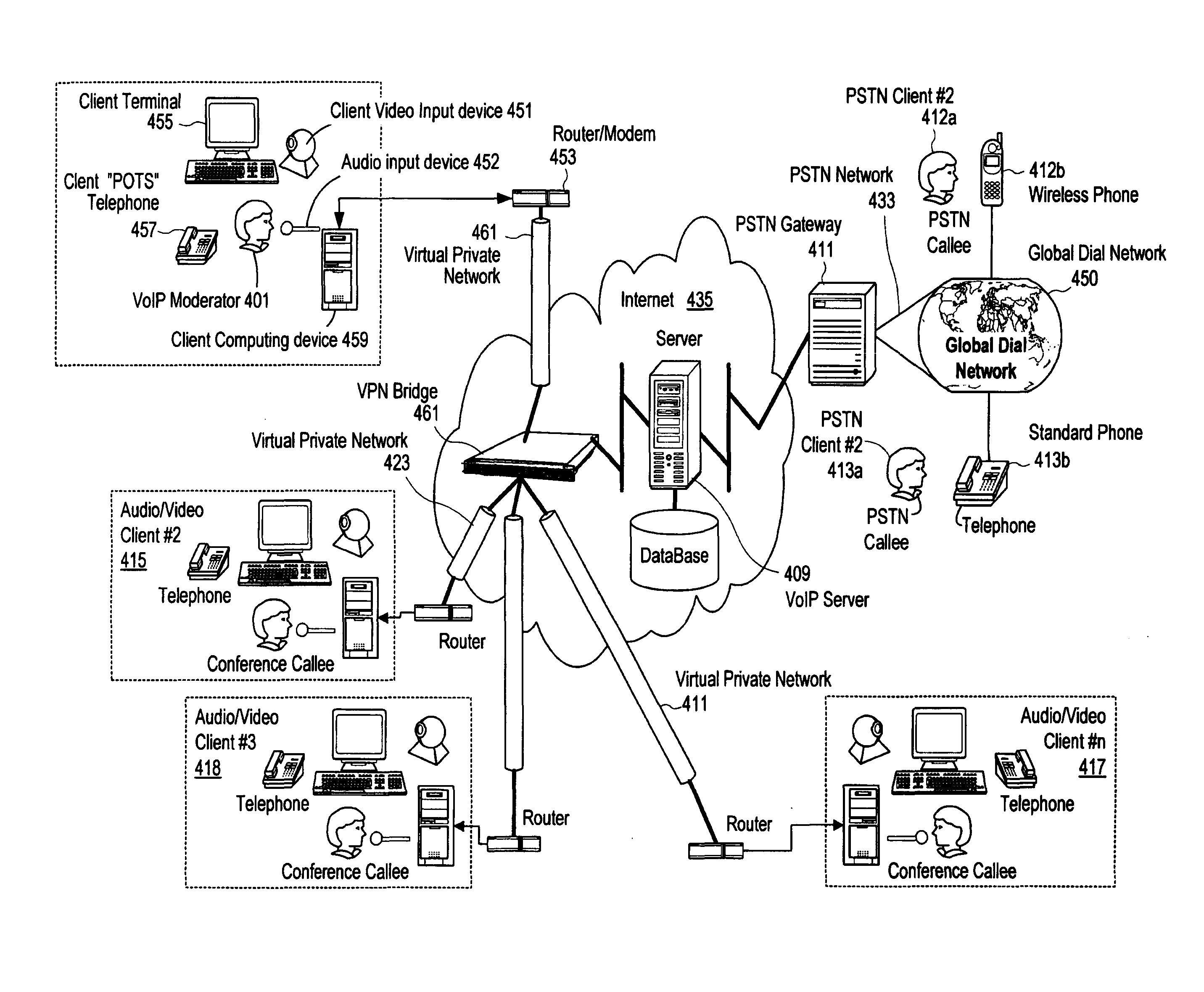
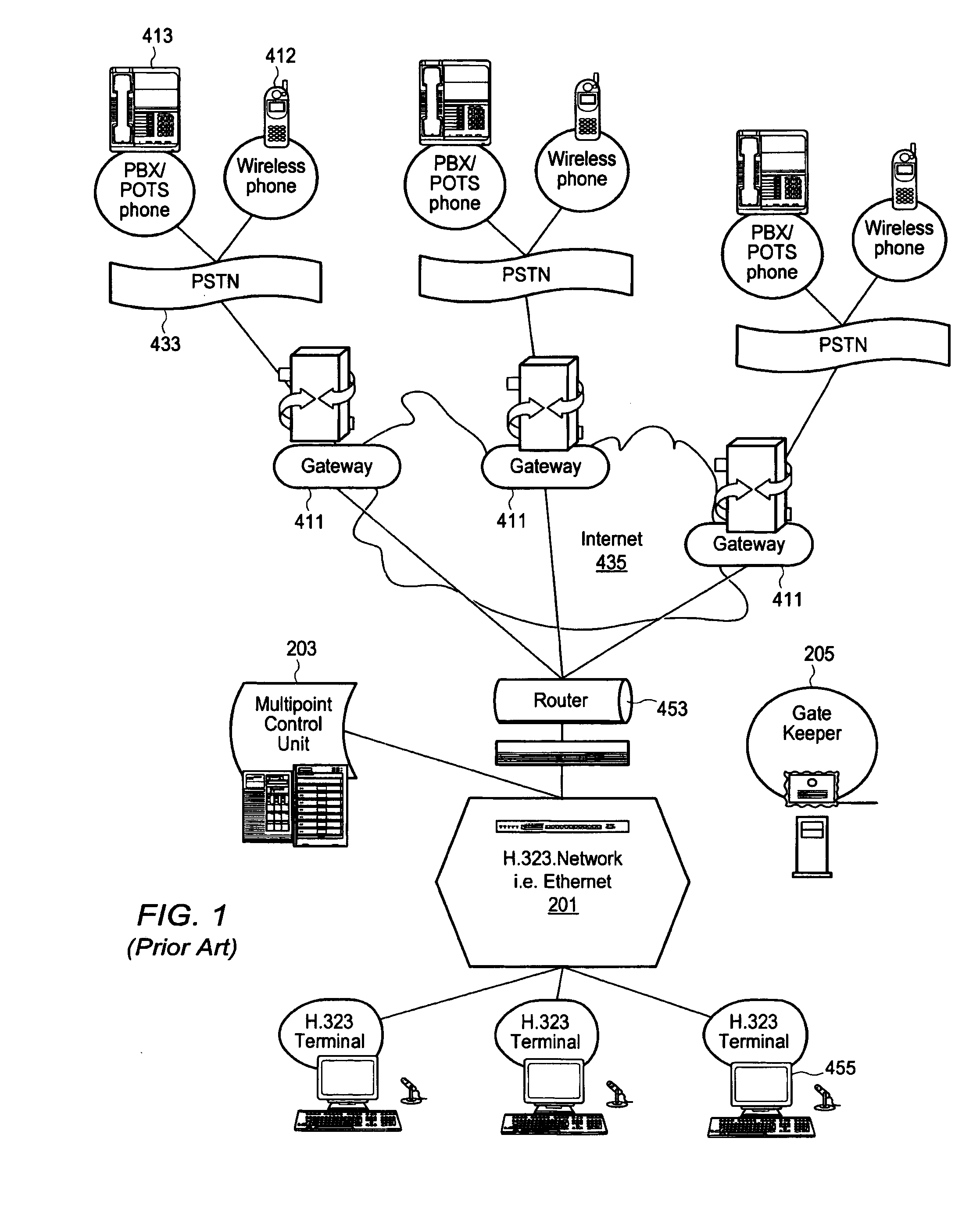
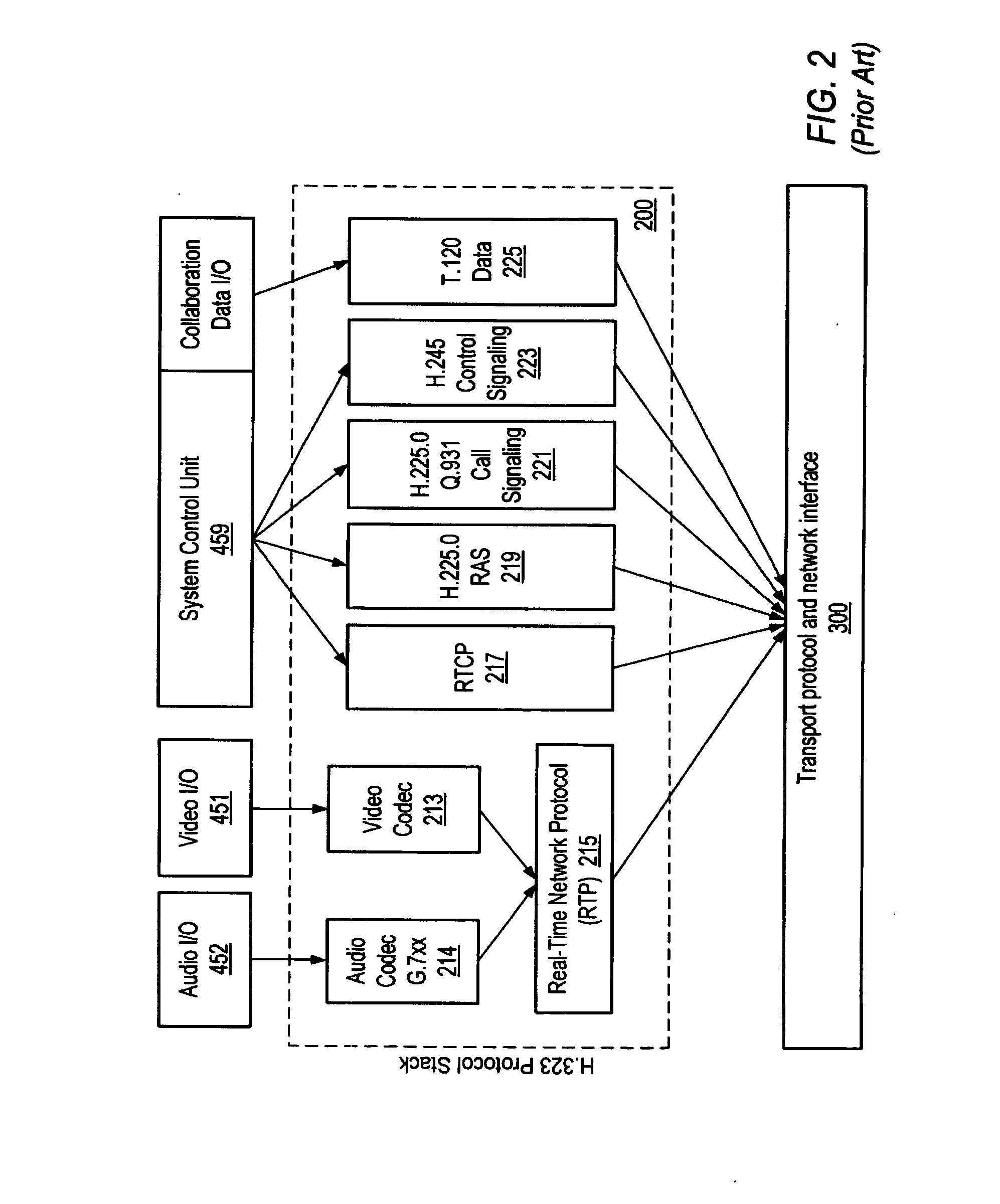
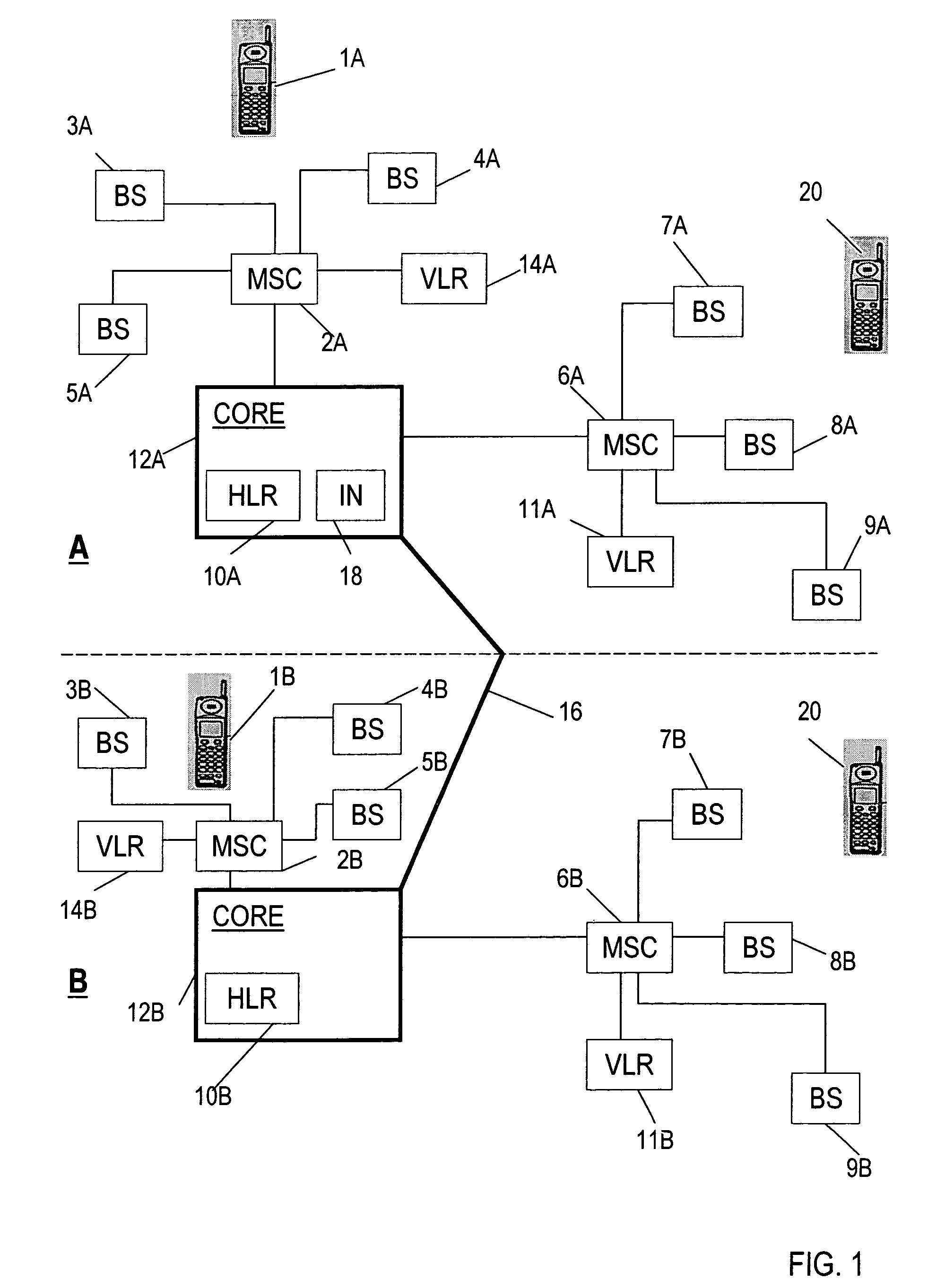
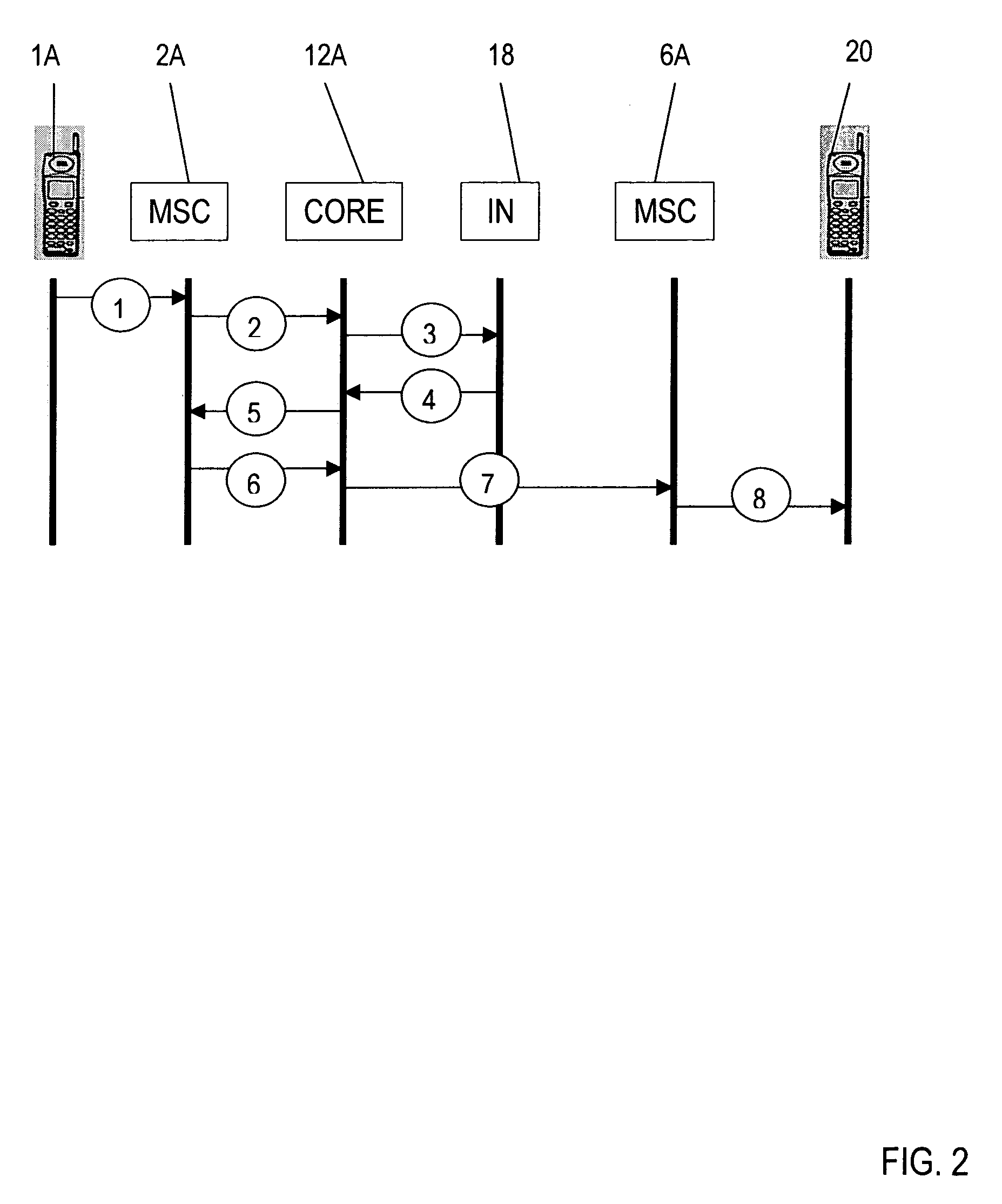
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
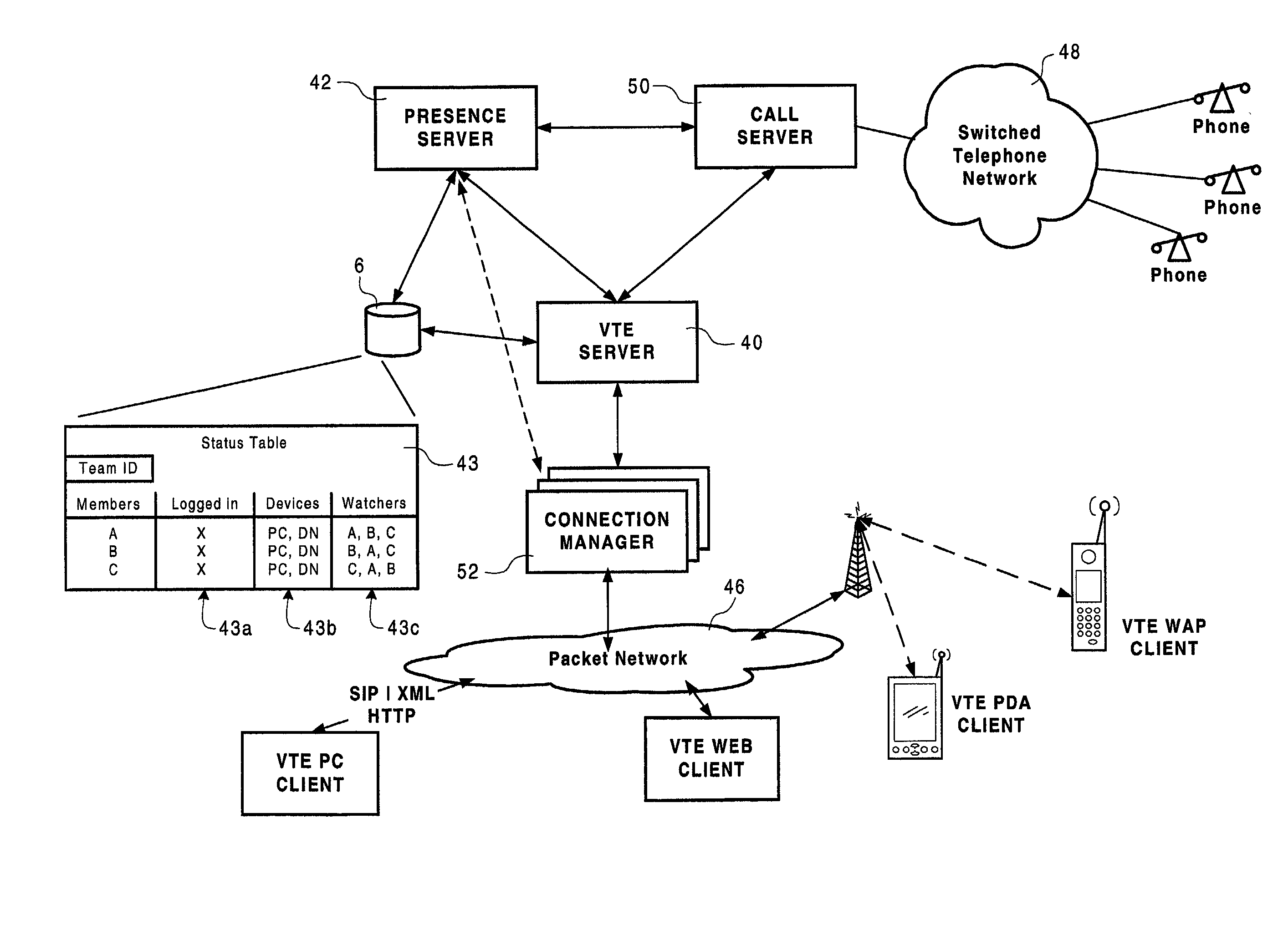
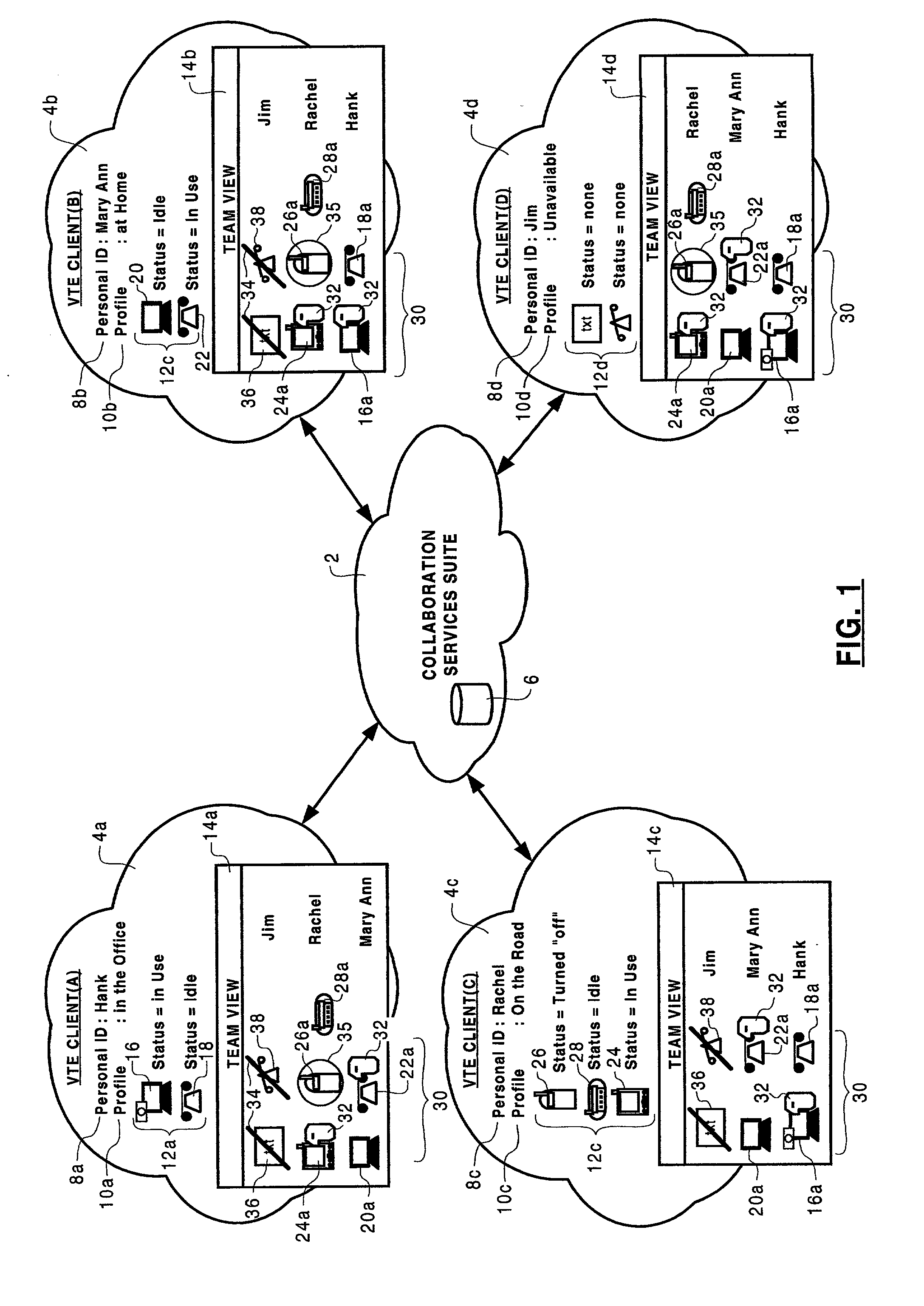
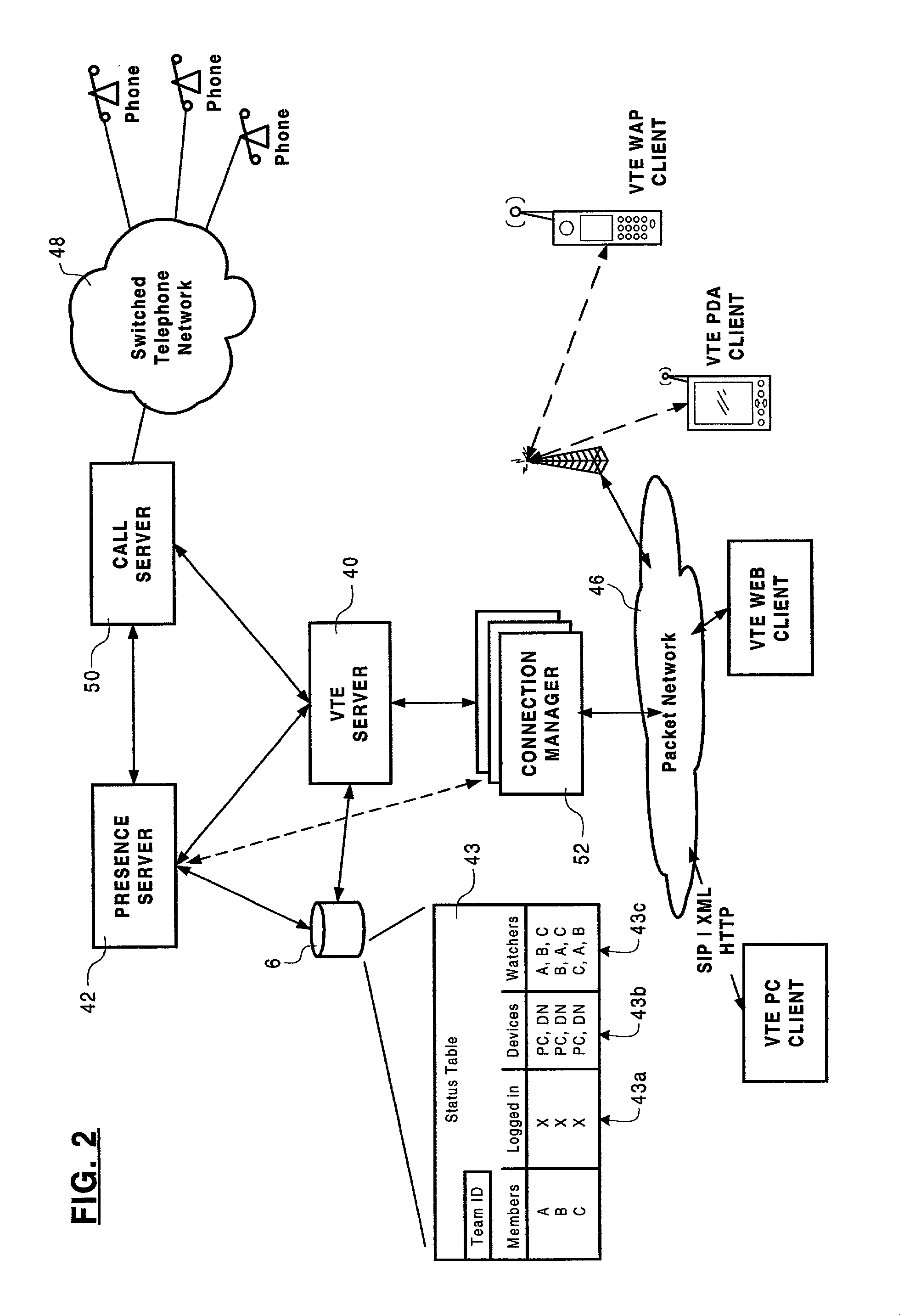
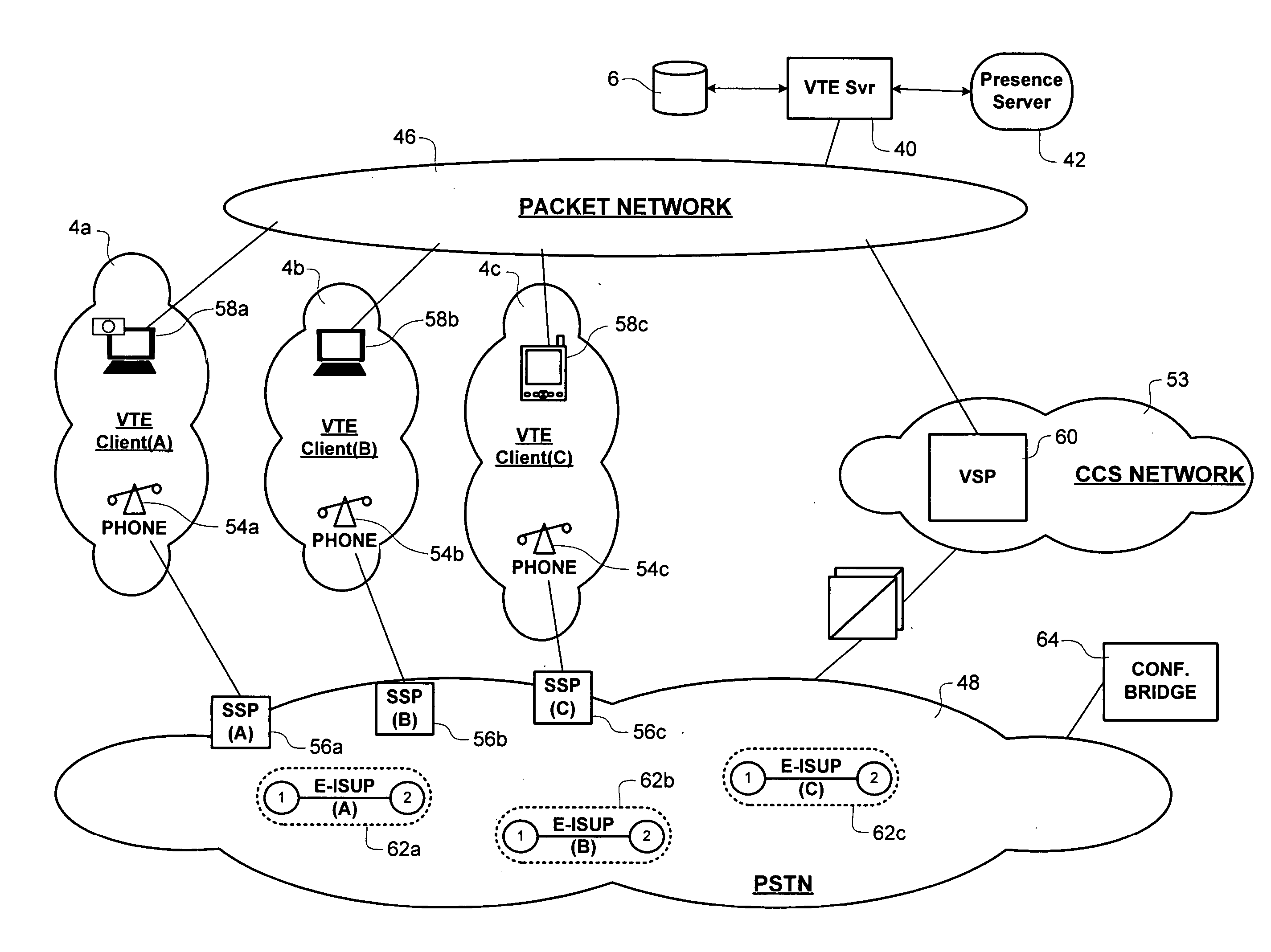
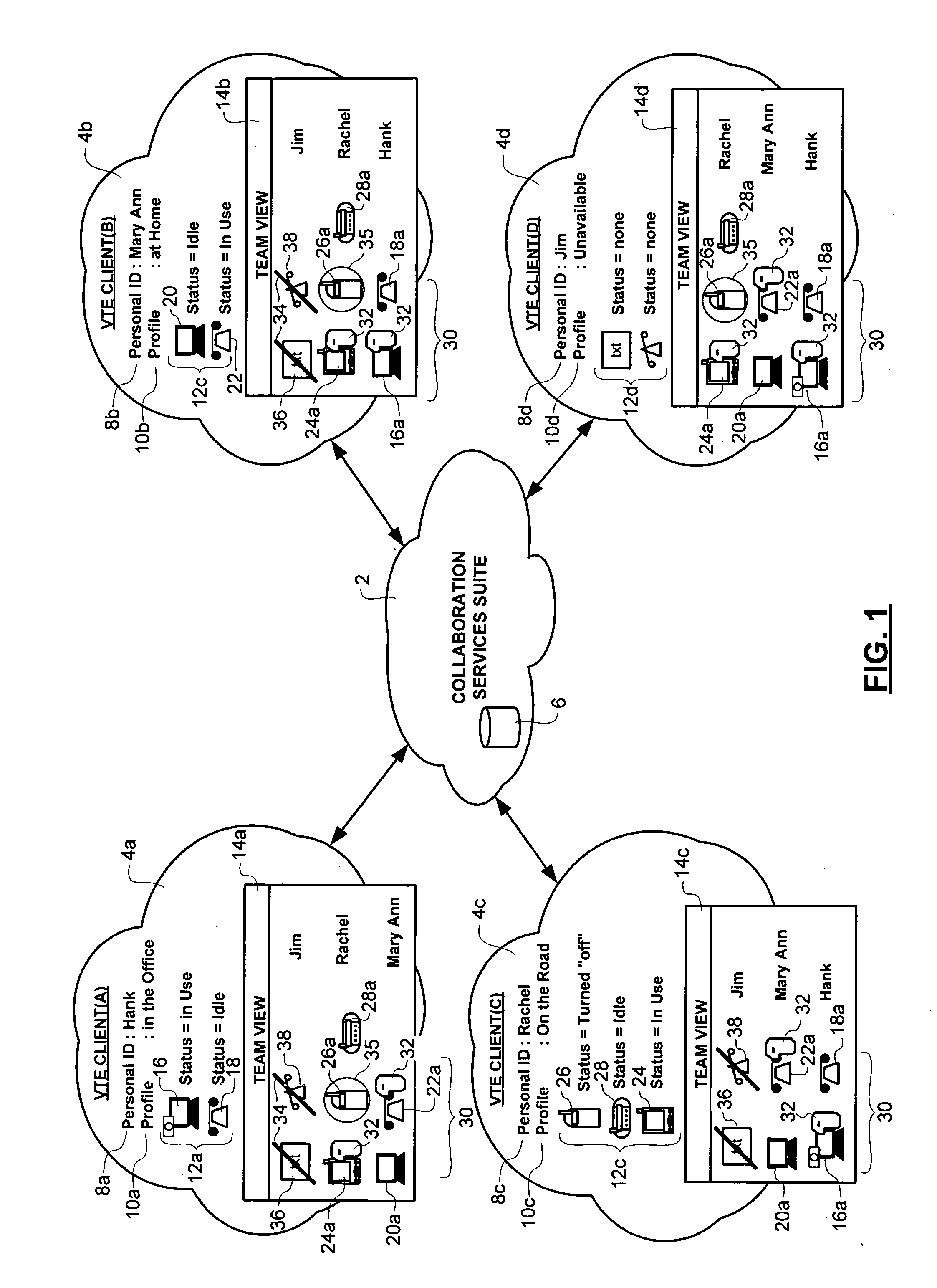
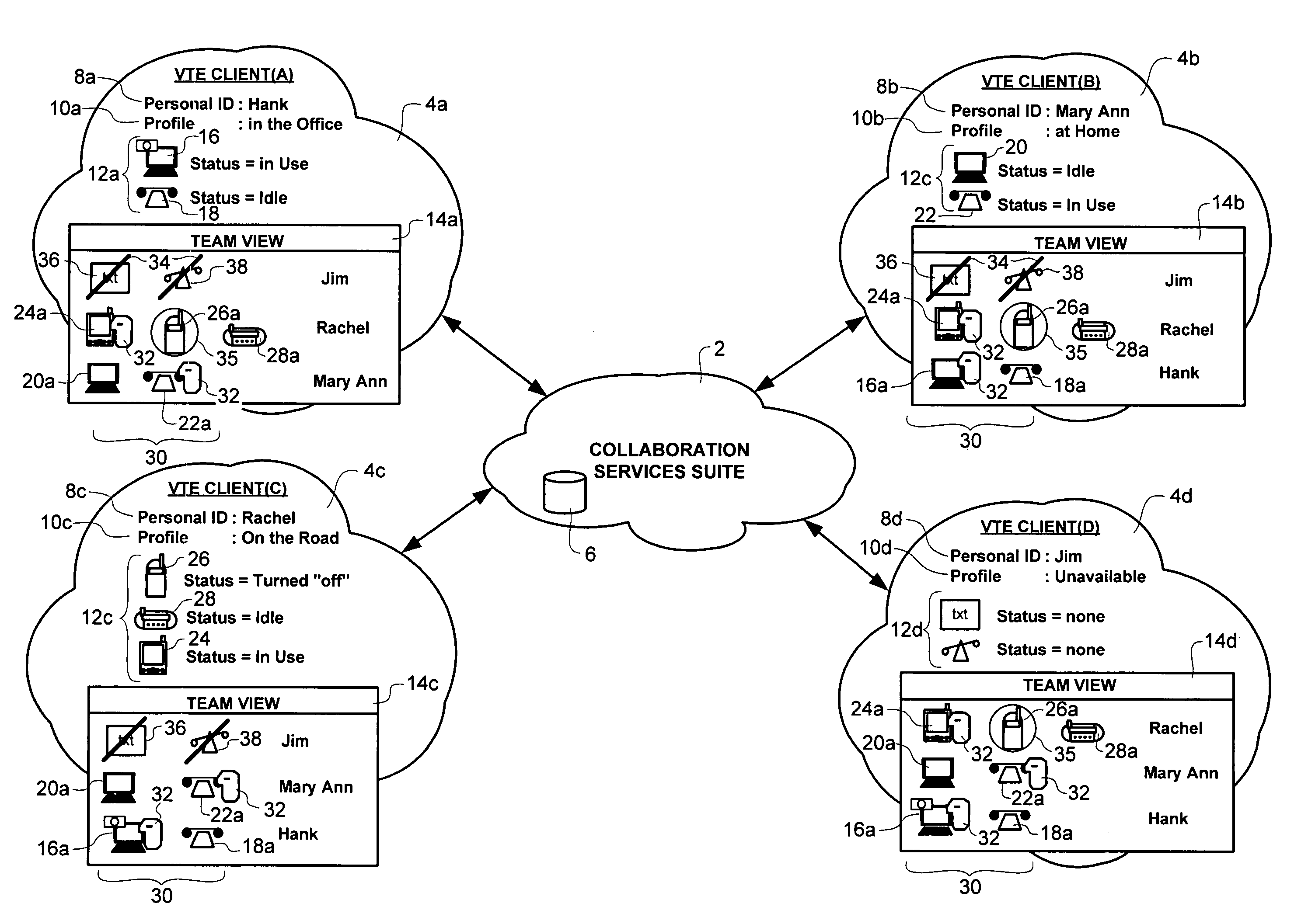
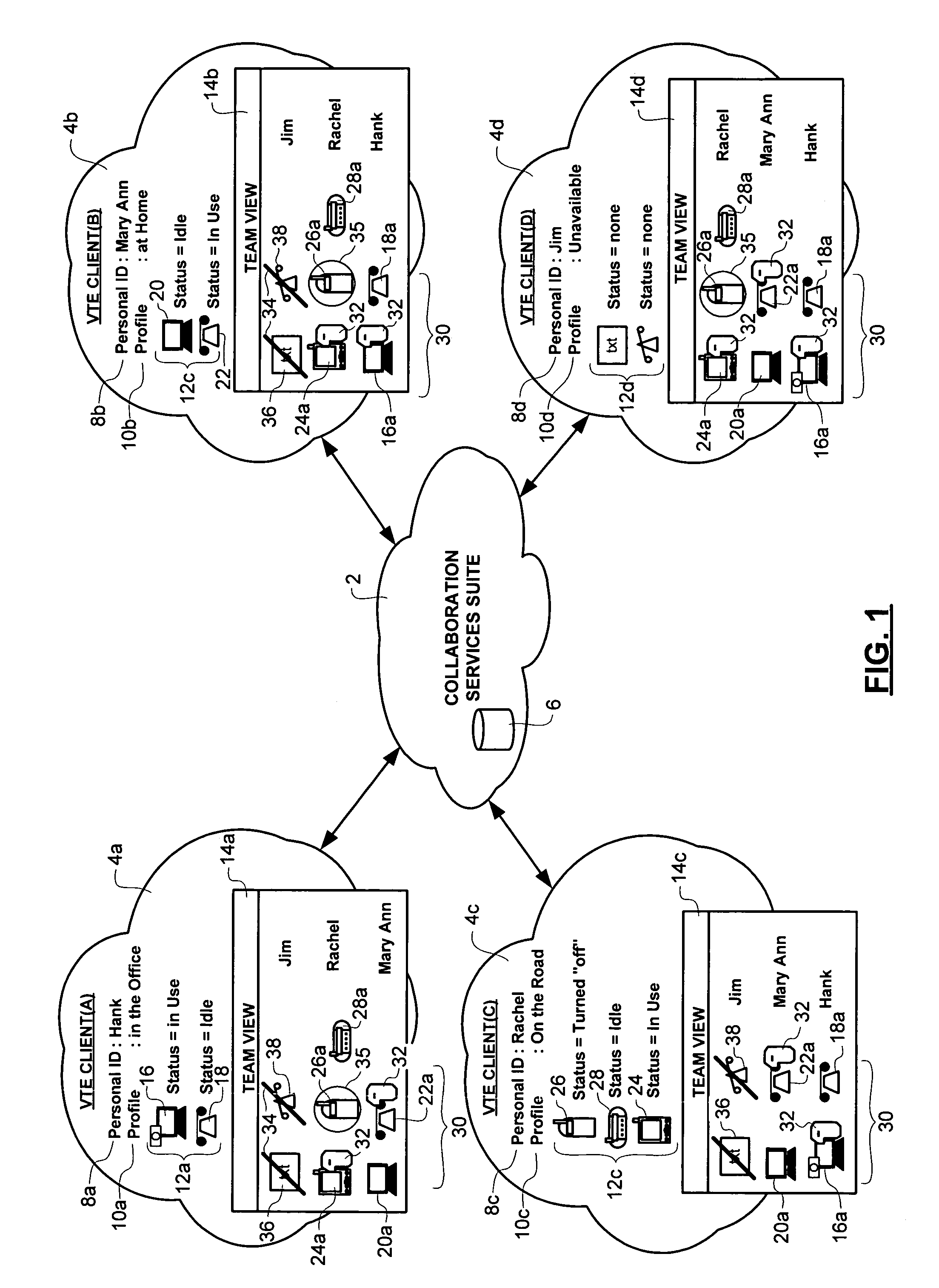
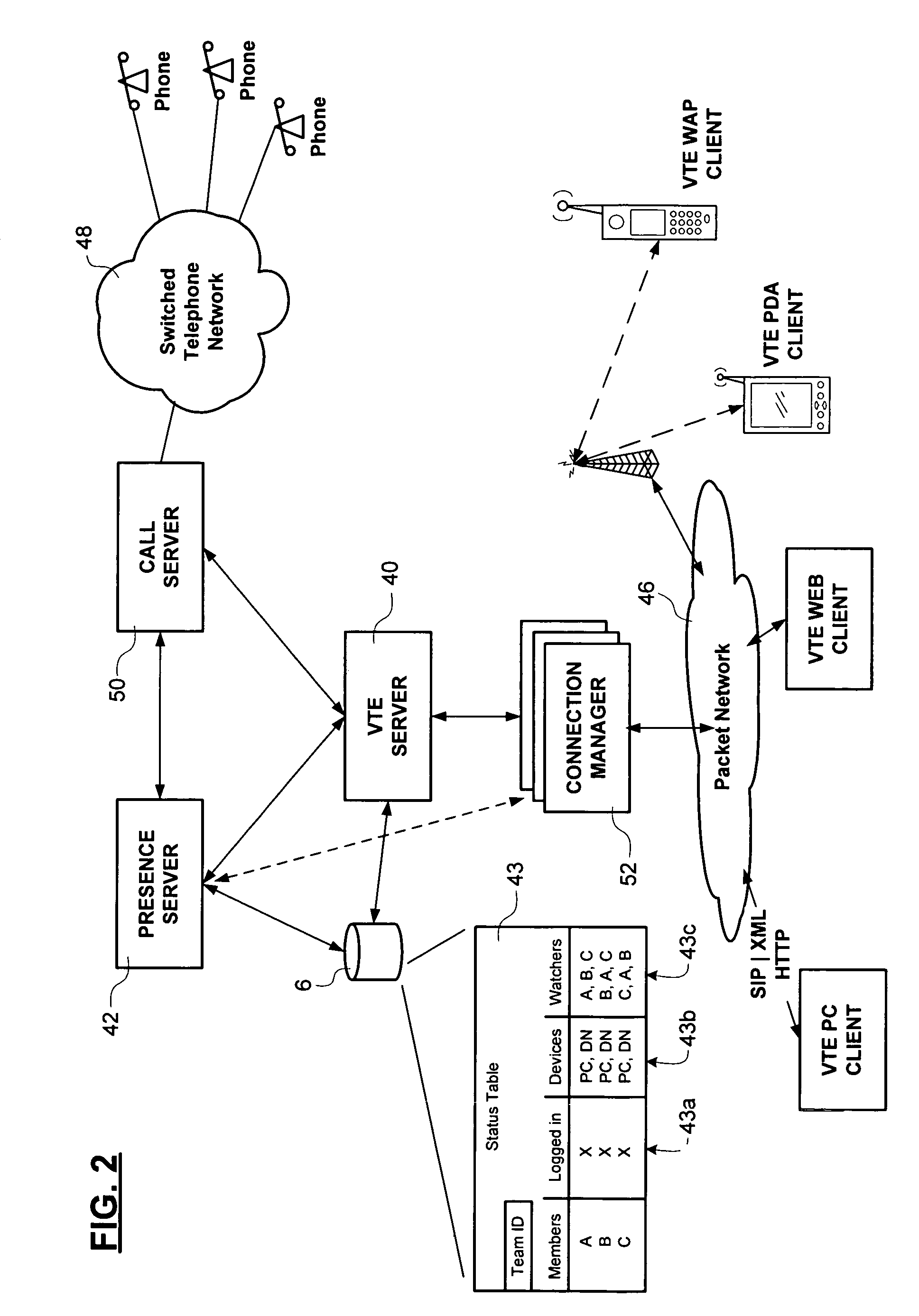
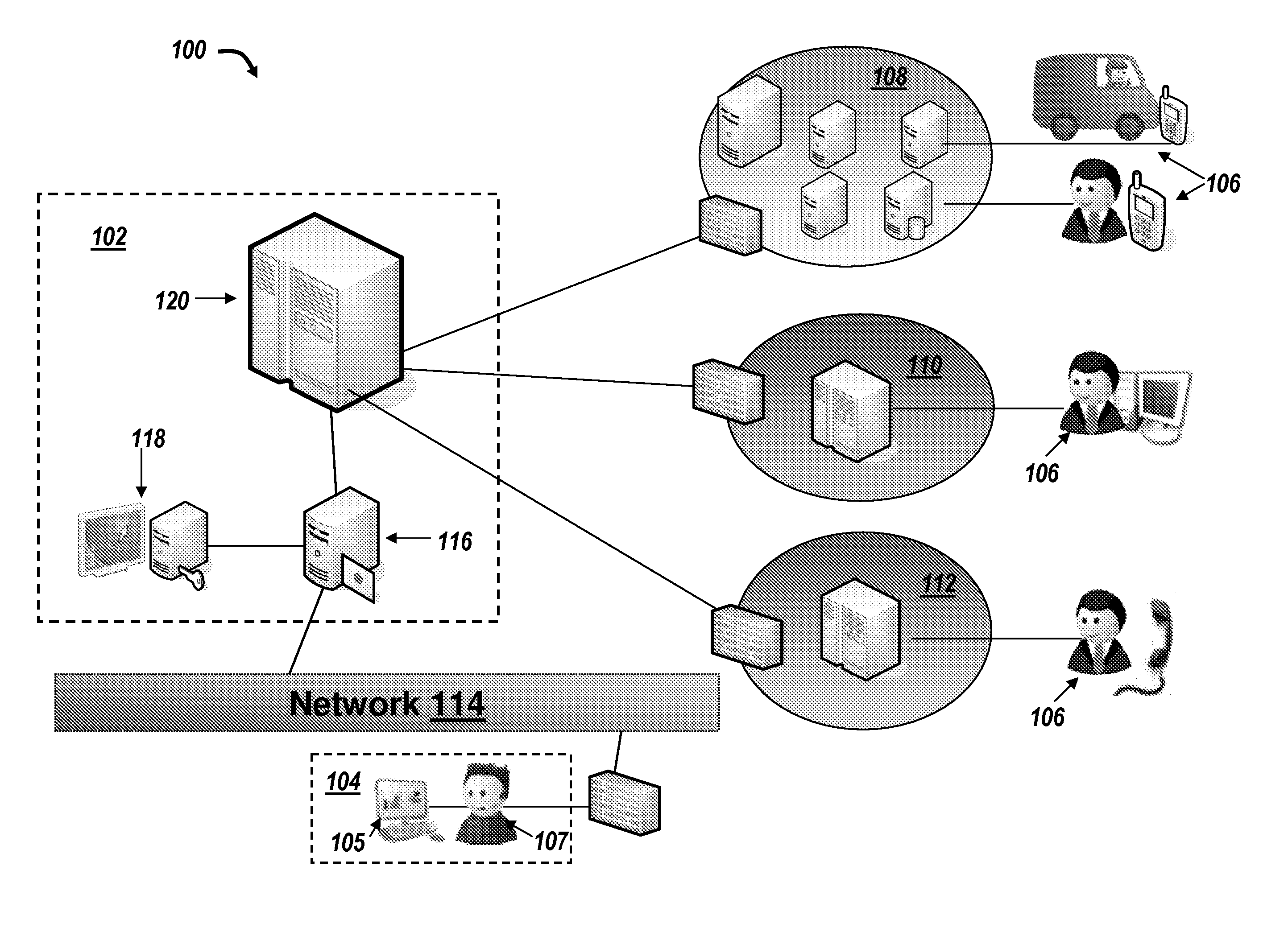
Method of team member profile selection within a virtual team environment
InactiveUS20020078150A1Special service provision for substationSpecial service for subscribersGraphicsGraphical user interface
A collaboration services suite is adapted to support a plurality of integrated telecommunications services accessed by geographically dispersed team members using a virtual team environment (VTE) client that generates a graphical user interface (GUI) for each of the respective team members. Communications sessions are automatically set up by the collaboration services suite in response to request messages generated by the VTE client when a team member initiates a communications session request using the GUI. Team members require no knowledge of another team member's communications device address in order to initiate a communications session. The collaboration services suite includes a VTE server that communicates with the VTE clients, a presence engine that collects and maintains a status of communications devices specified in a current profile of the team member; and, a call server for handling setup and control of a voice component of each communications session completed.
Owner:NORTEL NETWORKS LTD +1
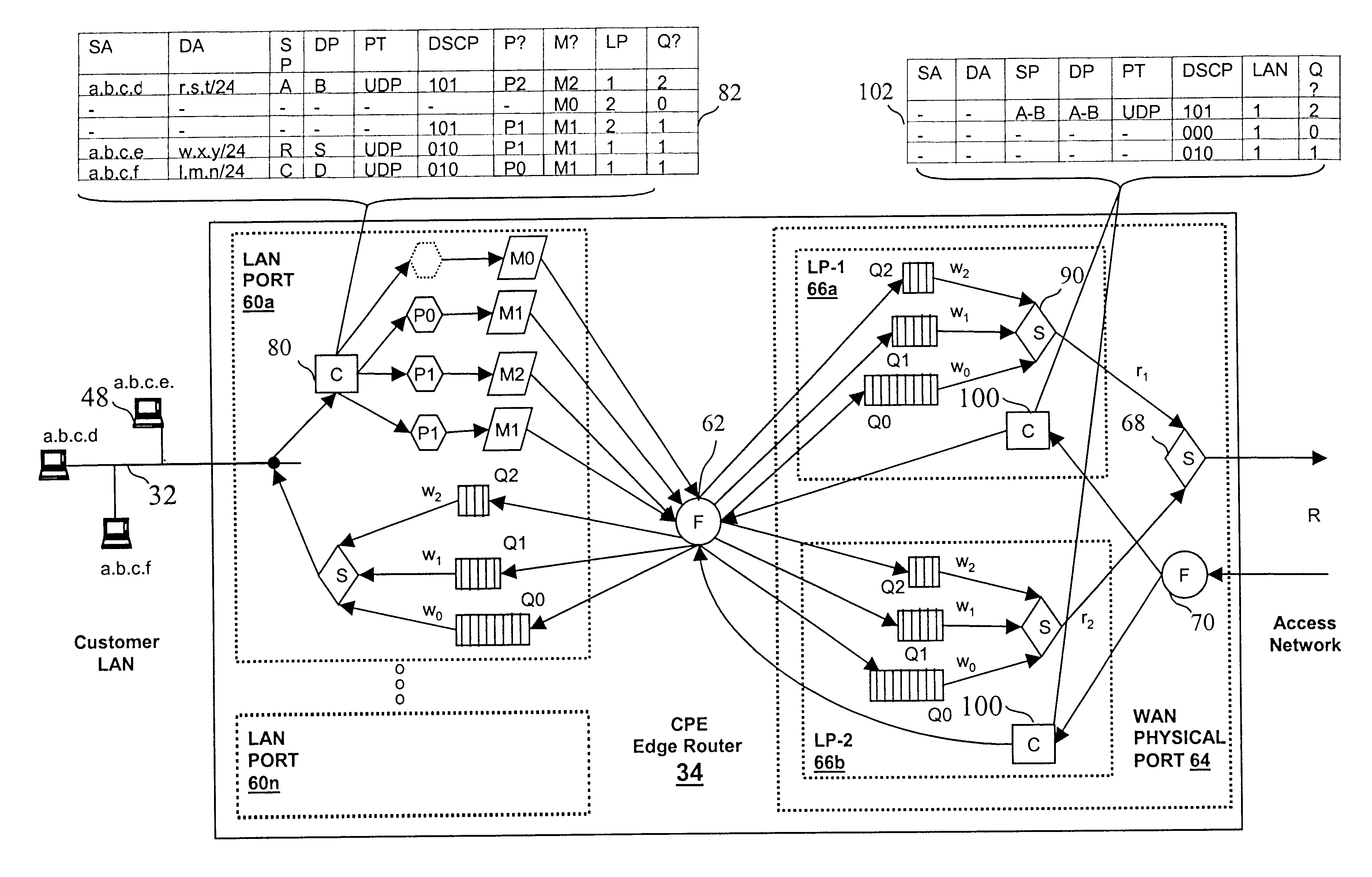
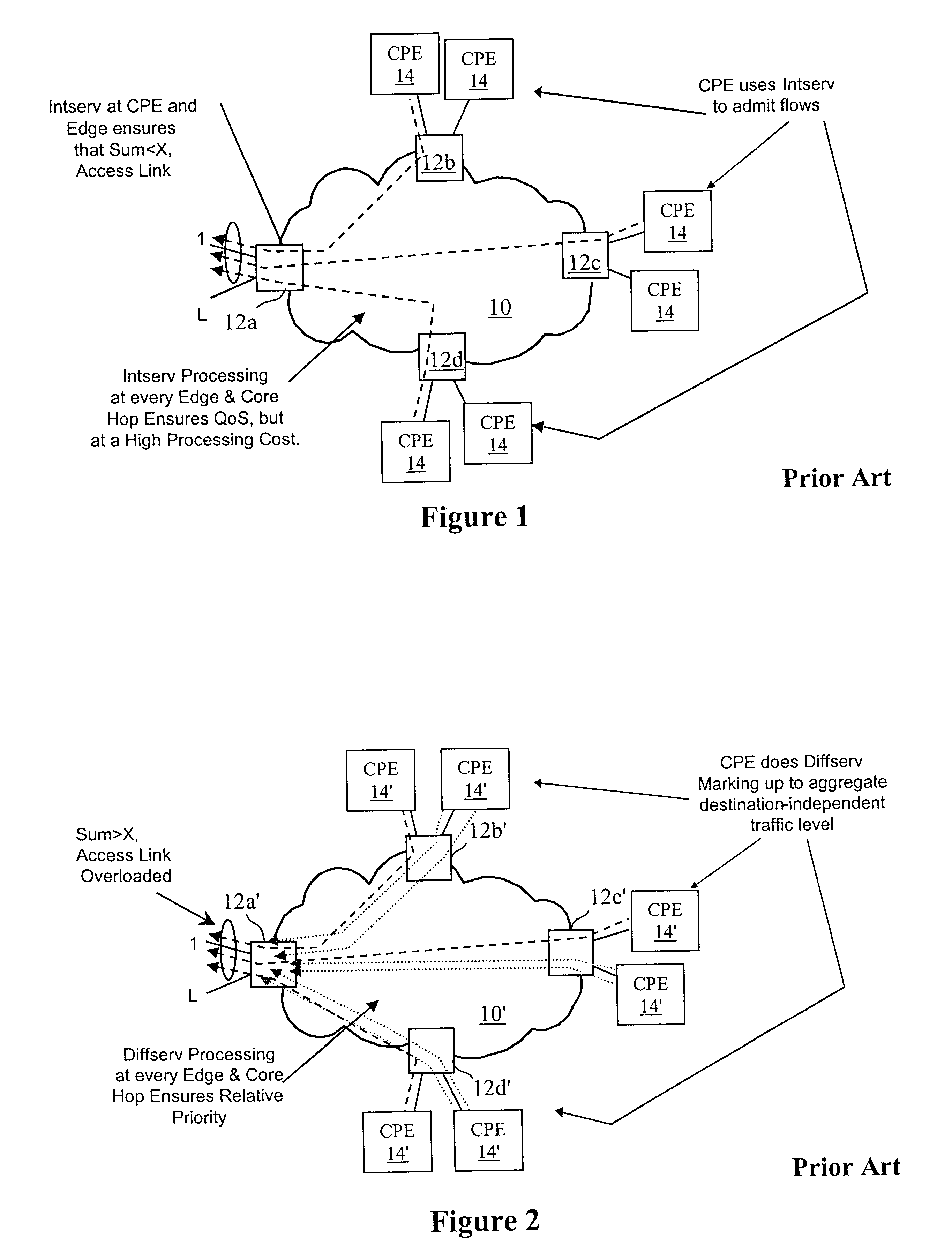
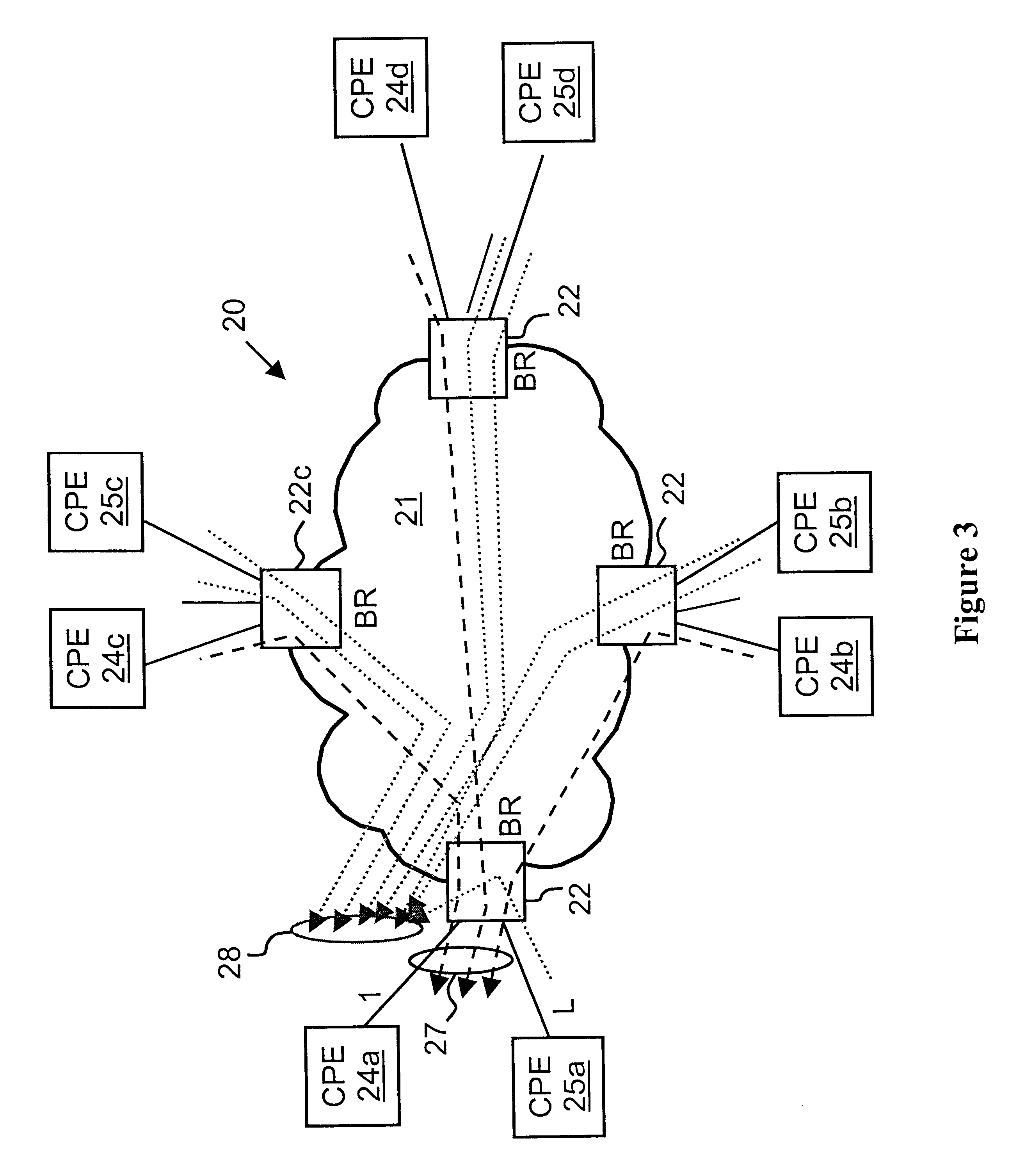
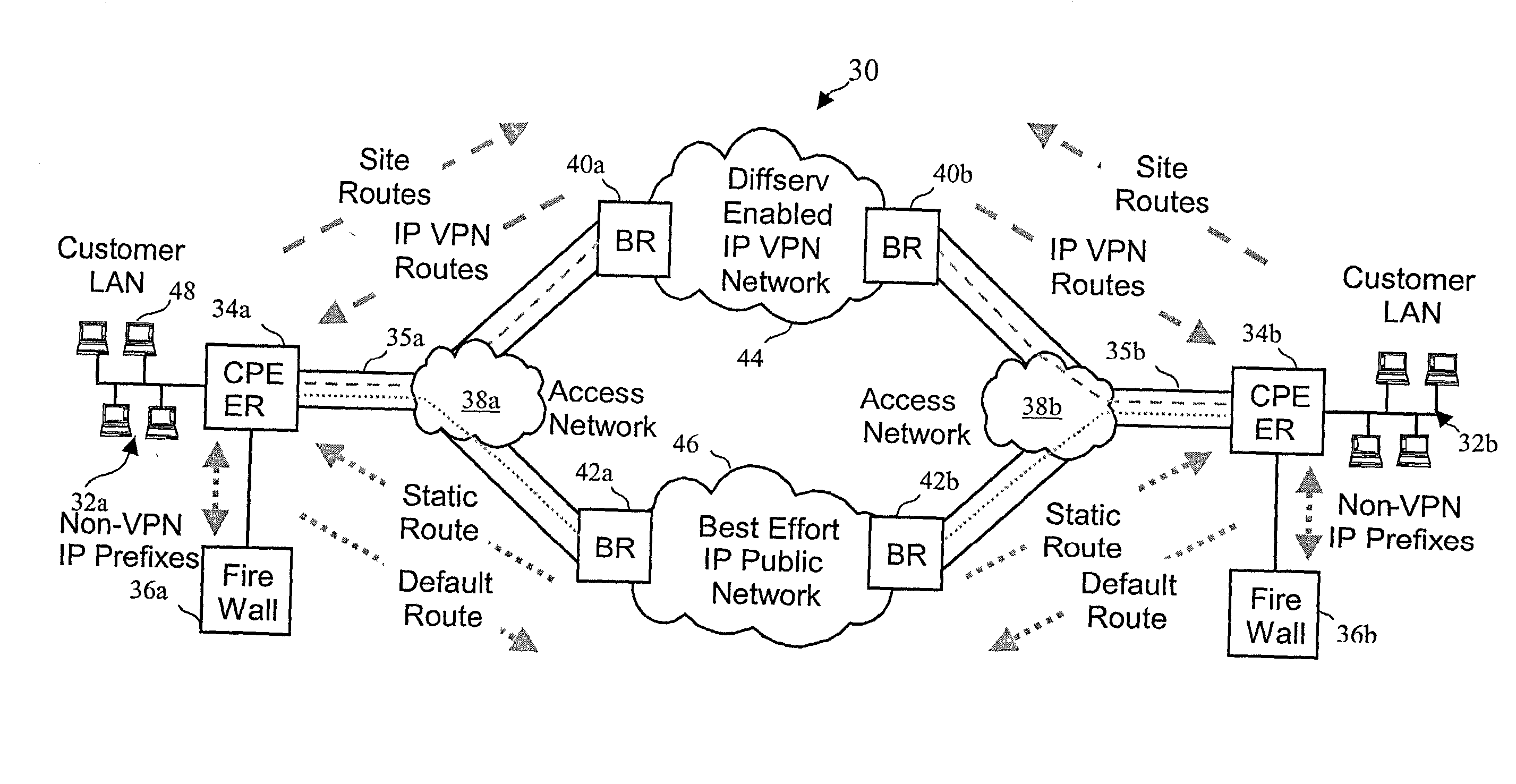
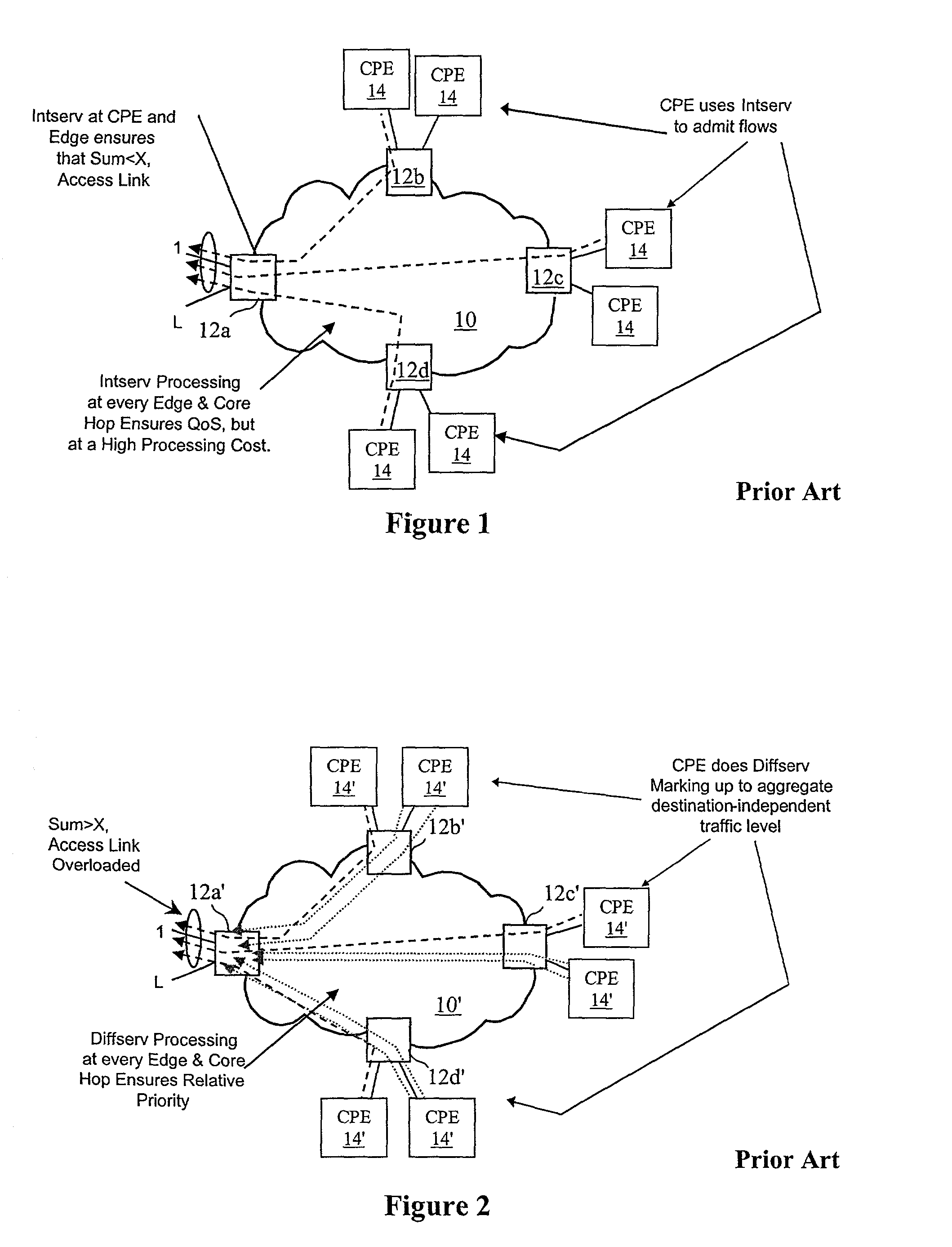
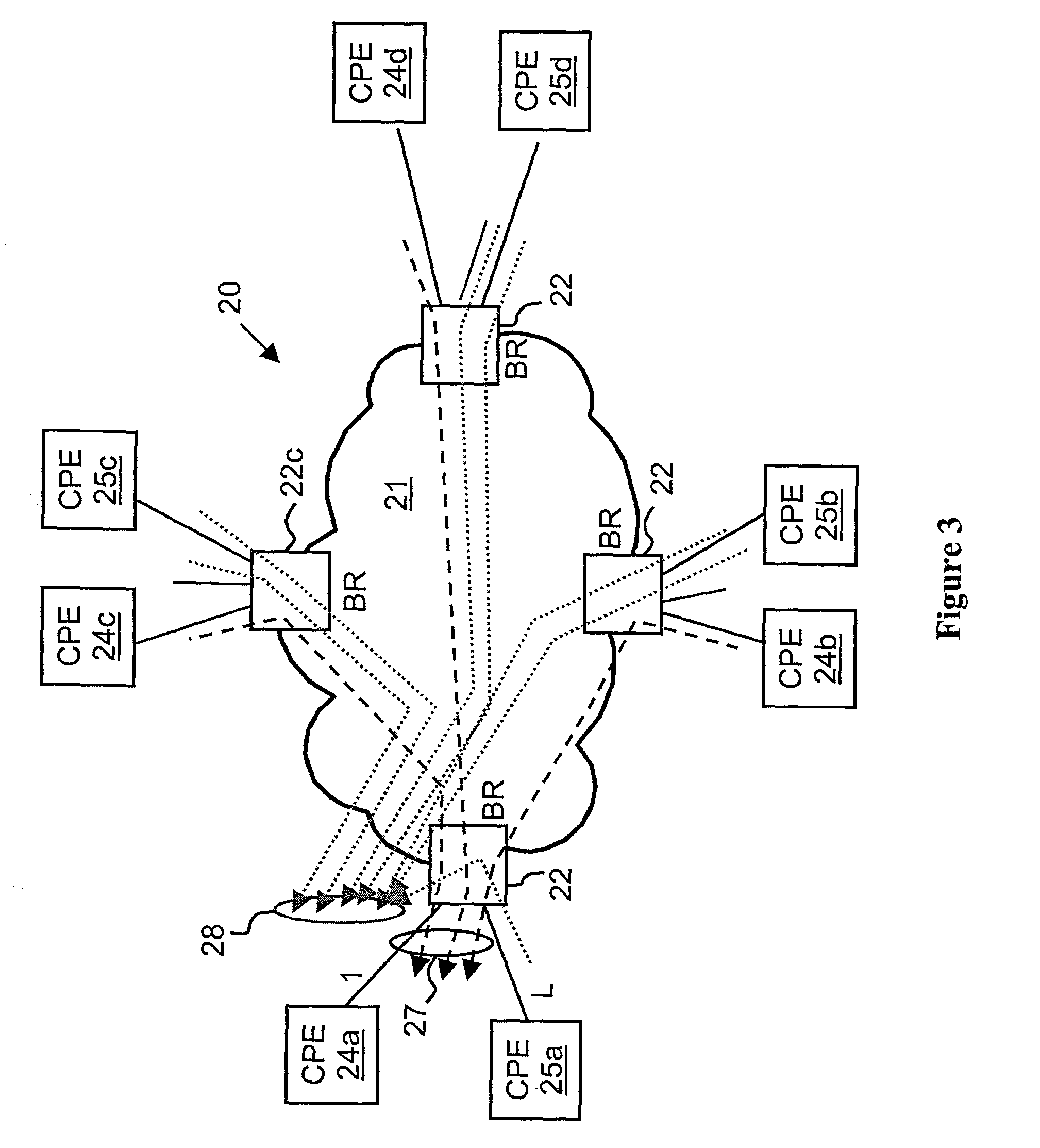
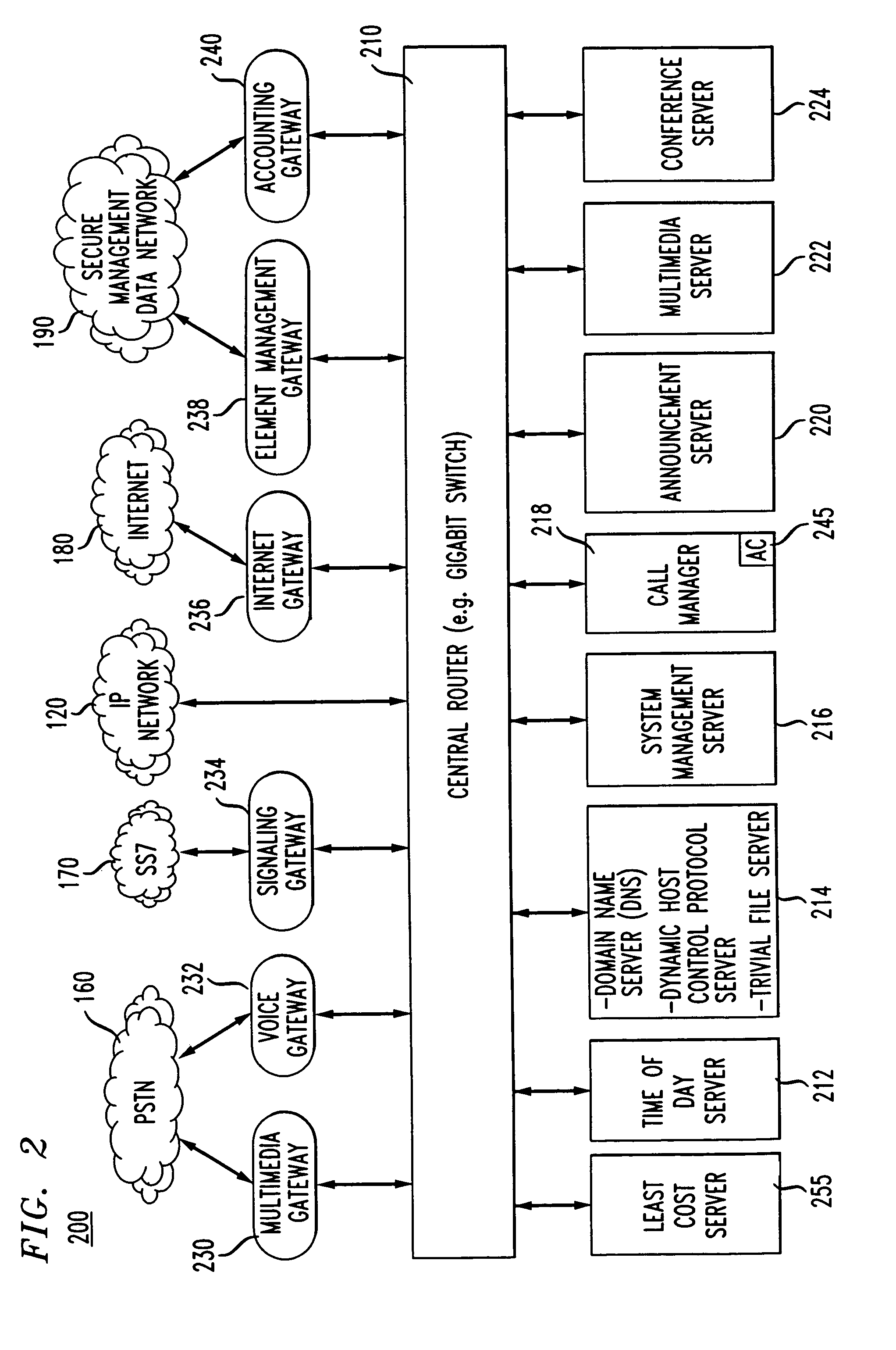
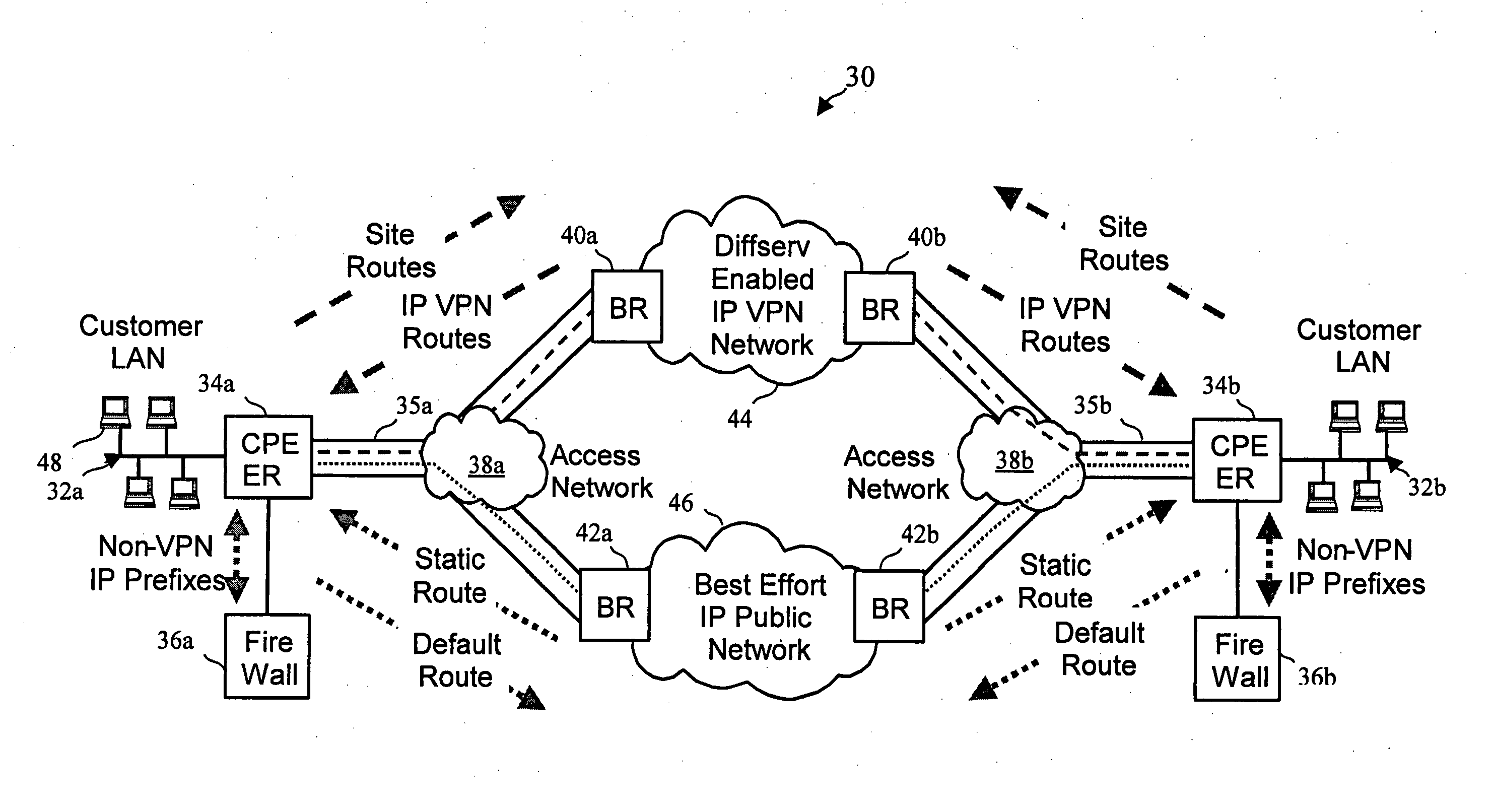
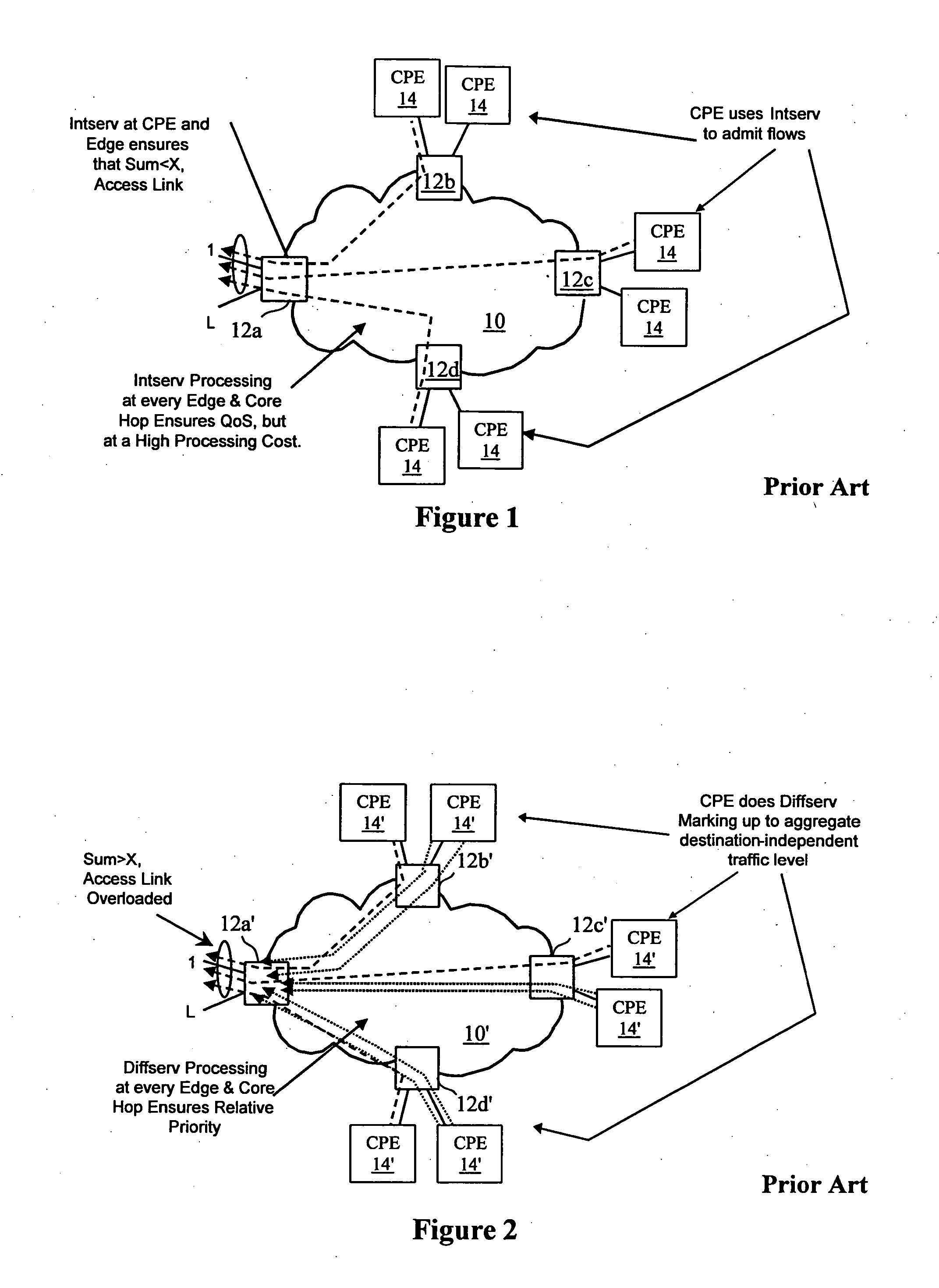
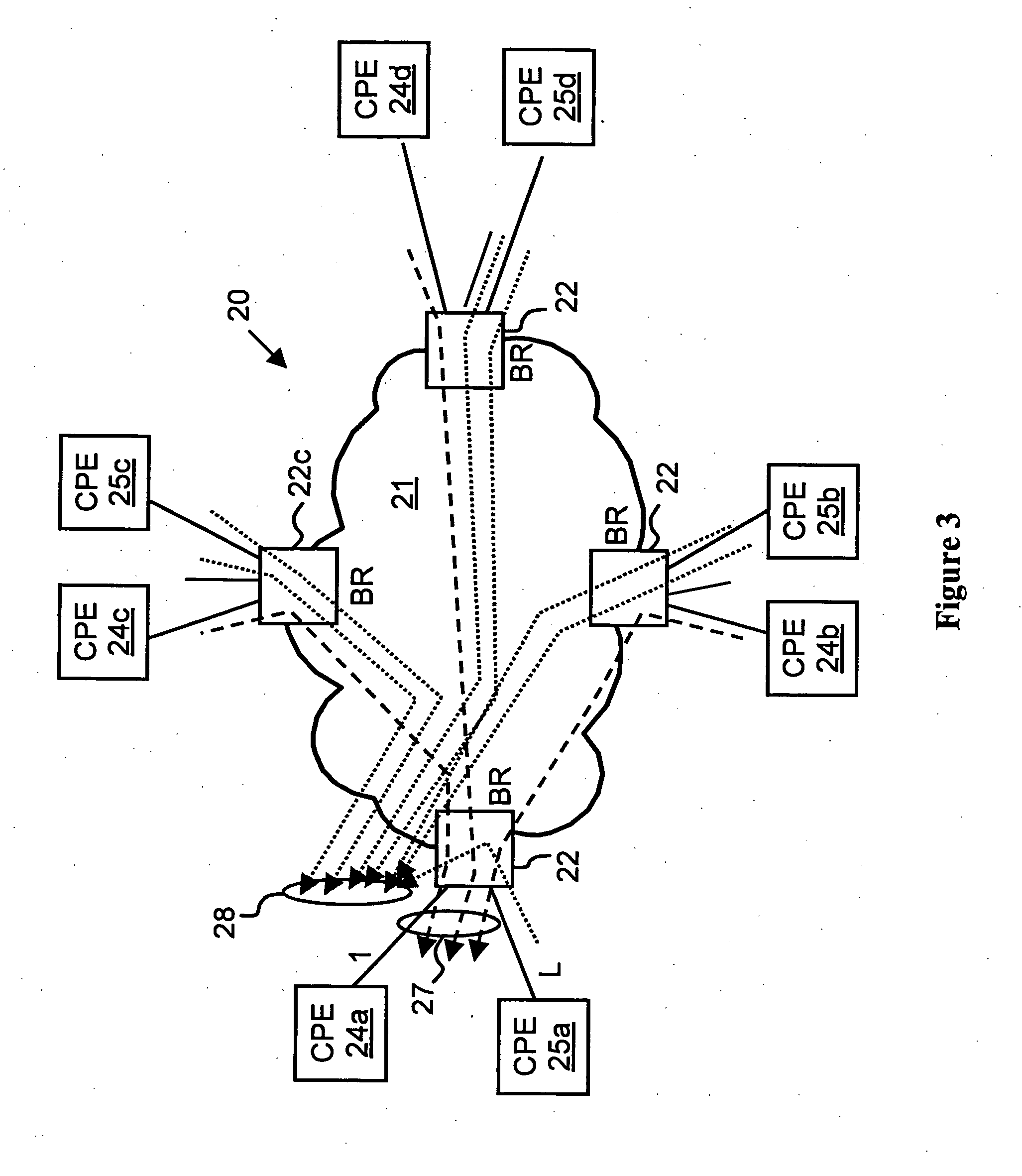
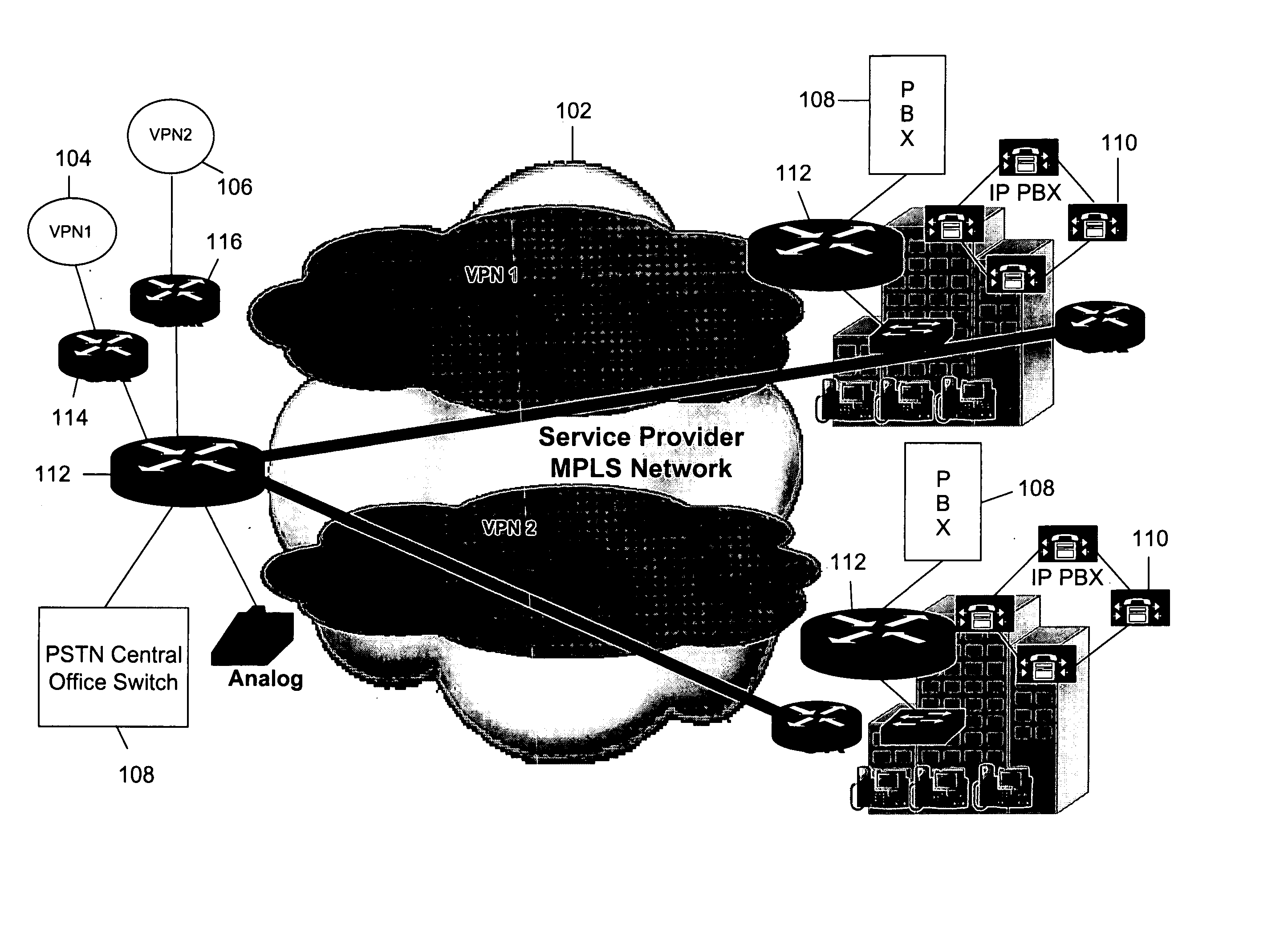
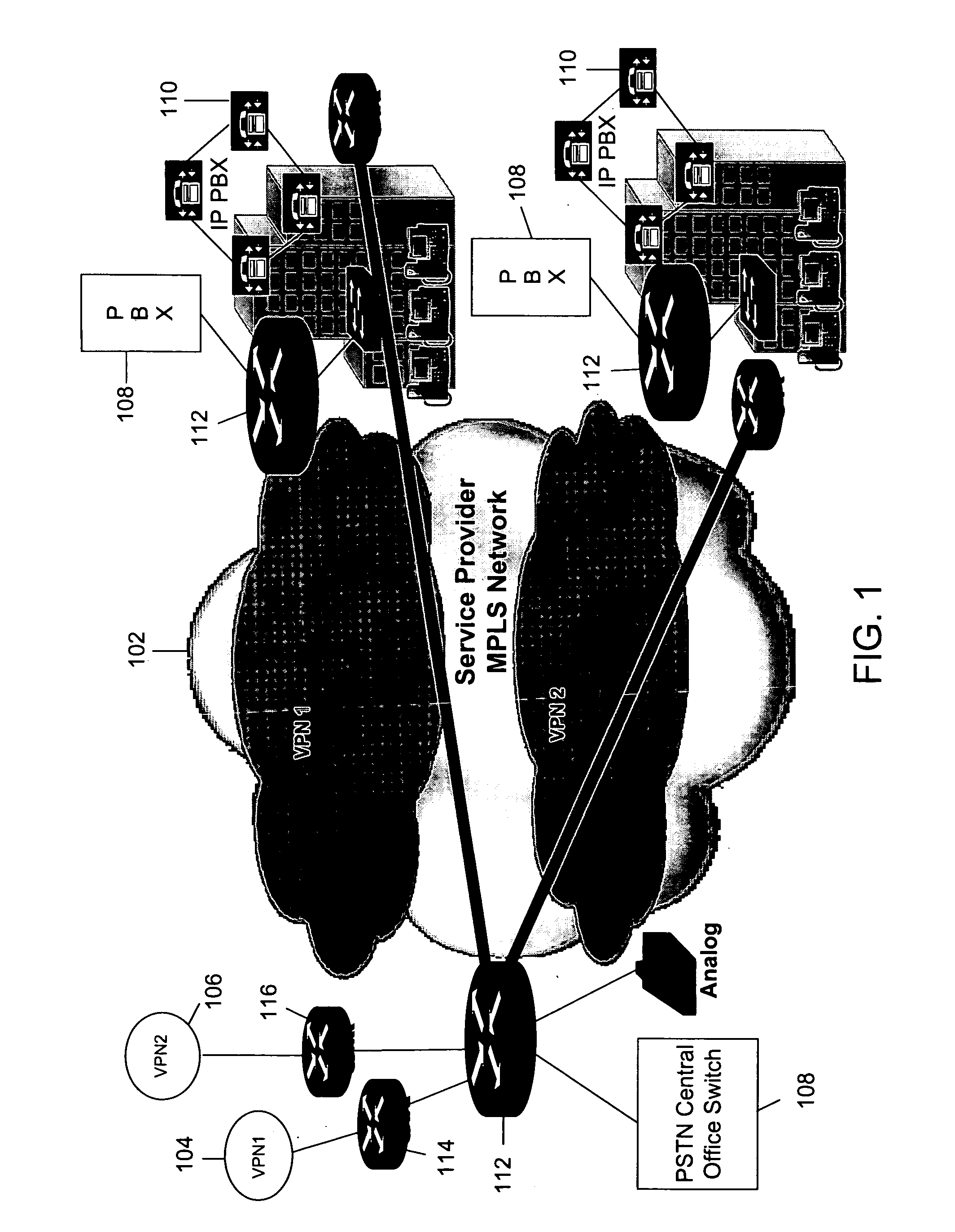
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS6778498B2Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS20030112755A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
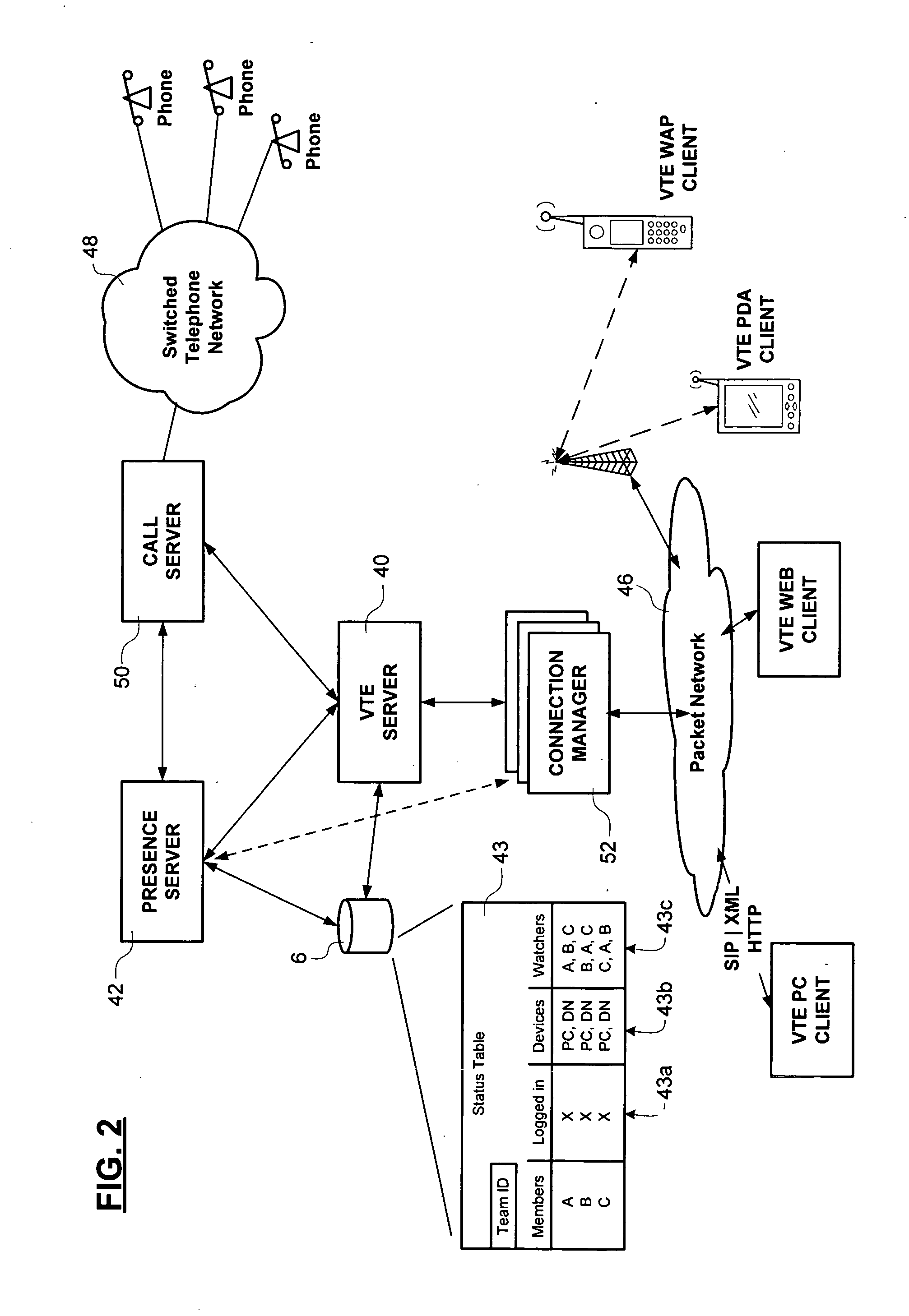
Method and system for automatic handling of invitations to join communications sessions in a virtual team environment
InactiveUS20070192410A1Special service provision for substationSpecial service for subscribersGraphicsGraphical user interface
A collaboration services suite is adapted to support a plurality of integrated telecommunications services accessed by geographically dispersed team members using a virtual team environment (VTE) client that generates a graphical user interface (GUI) for each of the respective team members. Communications sessions are automatically set up by the collaboration services suite in response to request messages generated by the VTE client when a team member initiates a communications session request using the GUI. Team members require no knowledge of another team member's communications device address in order to initiate a communications session. The collaboration services suite includes a VTE server that communicates with the VTE clients, a presence engine that collects and maintains a status of communications devices specified in a current profile of the team member; and, a call server for handling setup and control of a voice component of each communications session completed.
Owner:NORTEL NETWORKS LTD +1
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS7852831B2Interconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
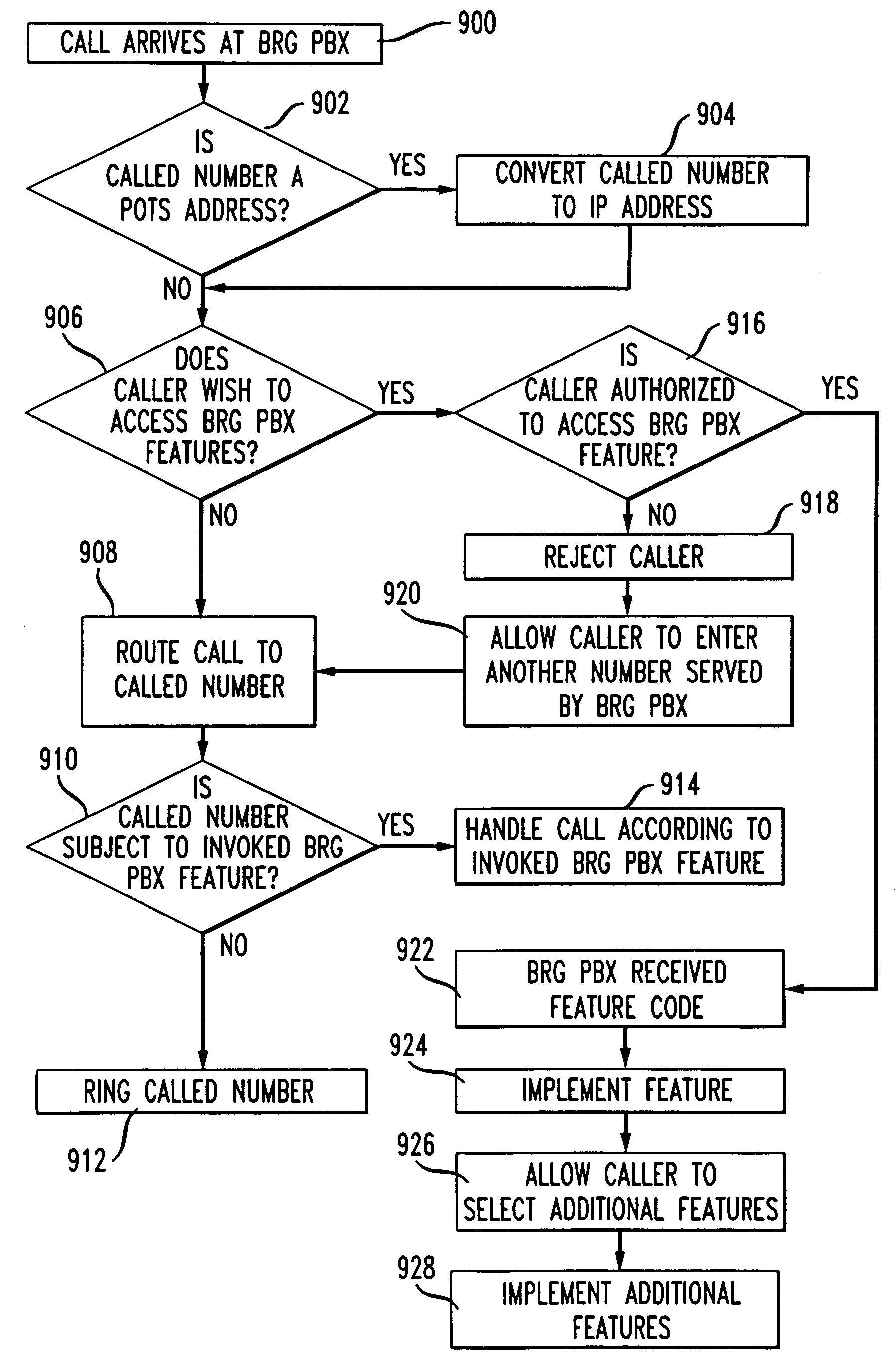
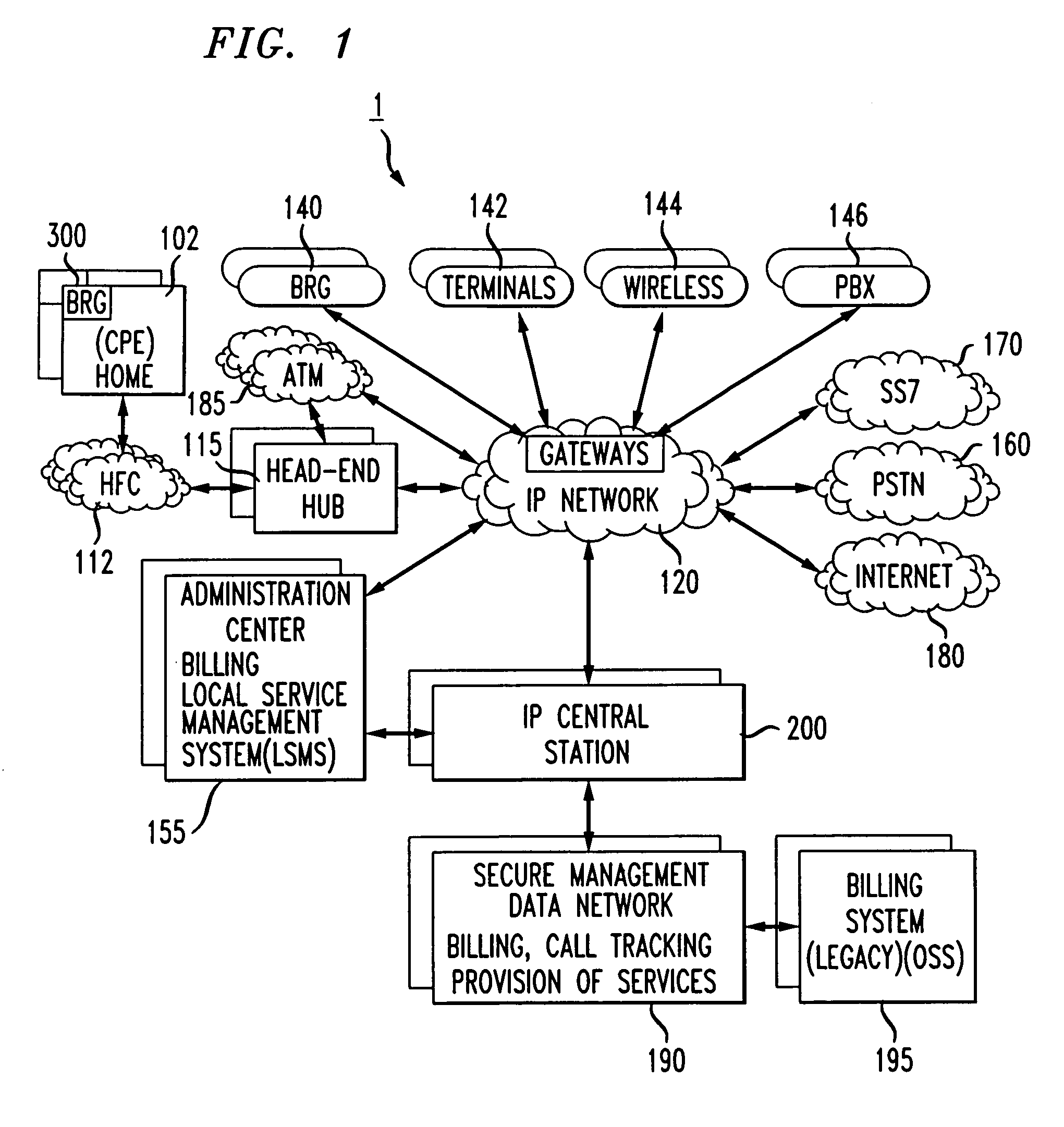
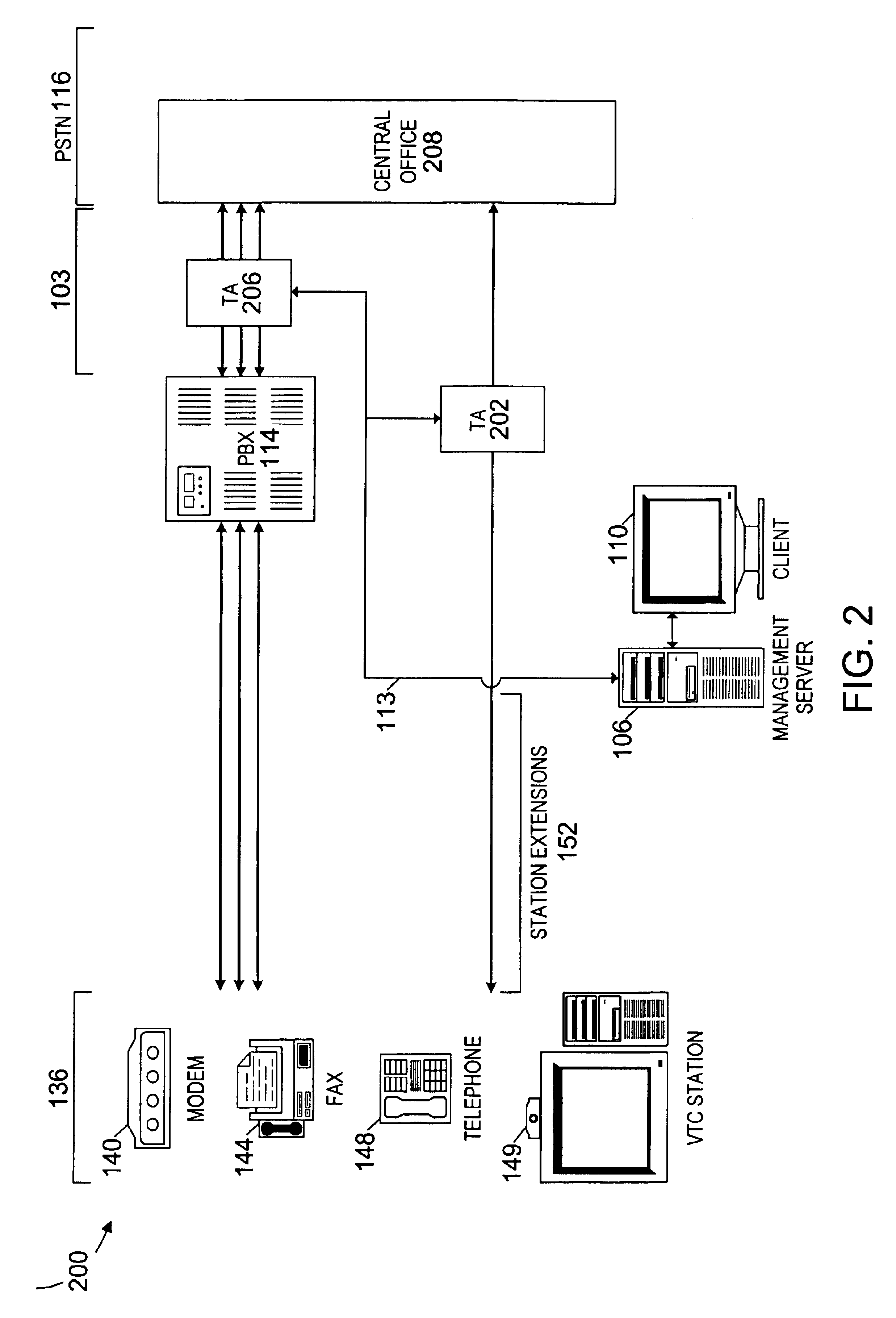
BRG with PBX capabilities
InactiveUS7075918B1Minimizing problems during installationMinimizes problemInterconnection arrangementsSpecial service for subscribersGeographic regionsResidence
A residential private branch exchange (PBX) allowing IP telephones, analog telephones and computers to connect to an IP communication network. A broadband residential gateway (BRG) PBX provides residences with multiple phone lines capability and the implementation of complex calling features traditionally associated with complex and expensive business PBX systems. The BRG PBX provides an open architecture interface minimizing problems during installation and operation, minimizes interoperability problems across multi-vendor equipment platforms and may provide customers with an option to bypass the local telephone company's high cost infrastructure. The BRG PBX may also provide a range of services from basic calling with few features to highly sophisticated calling features servicing multiple phone lines to the residence. The BRG PBX may be configured to connect multiple BRG PBX systems together in a Local Area Network (LAN) or Wide Area Network (WAN) configuration. These network configurations may be implemented to connect neighborhoods or families across multiple geographic regions. In addition to having the capability of connecting to each other, the BRG PBXs may be connected to IP Central Stations forming an IP communication network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
ActiveUS20040208122A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Method and system for automatic handling of invitations to join communications sessions in a virtual team environment
InactiveUS7472352B2Special service provision for substationSpecial service for subscribersGraphicsGraphical user interface
A collaboration services suite is adapted to support a plurality of integrated telecommunications services accessed by geographically dispersed team members using a virtual team environment (VTE) client that generates a graphical user interface (GUI) for each of the respective team members. Communications sessions are automatically set up by the collaboration services suite in response to request messages generated by the VTE client when a team member initiates a communications session request using the GUI. Team members require no knowledge of another team member's communications device address in order to initiate a communications session. The collaboration services suite includes a VTE server that communicates with the VTE clients, a presence engine that collects and maintains a status of communications devices specified in a current profile of the team member; and, a call server for handling setup and control of a voice component of each communications session completed.
Owner:NORTEL NETWORKS LTD +1
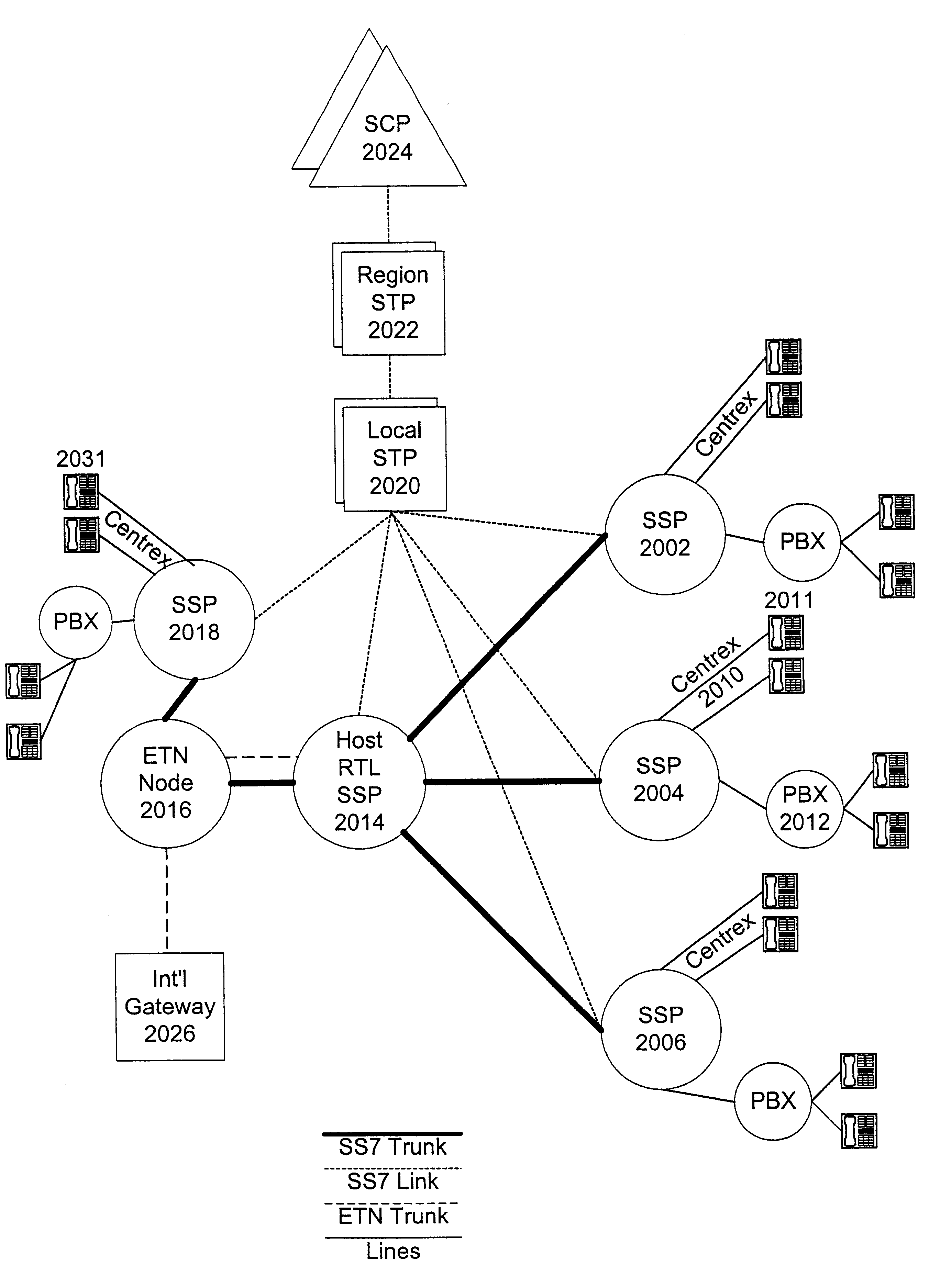
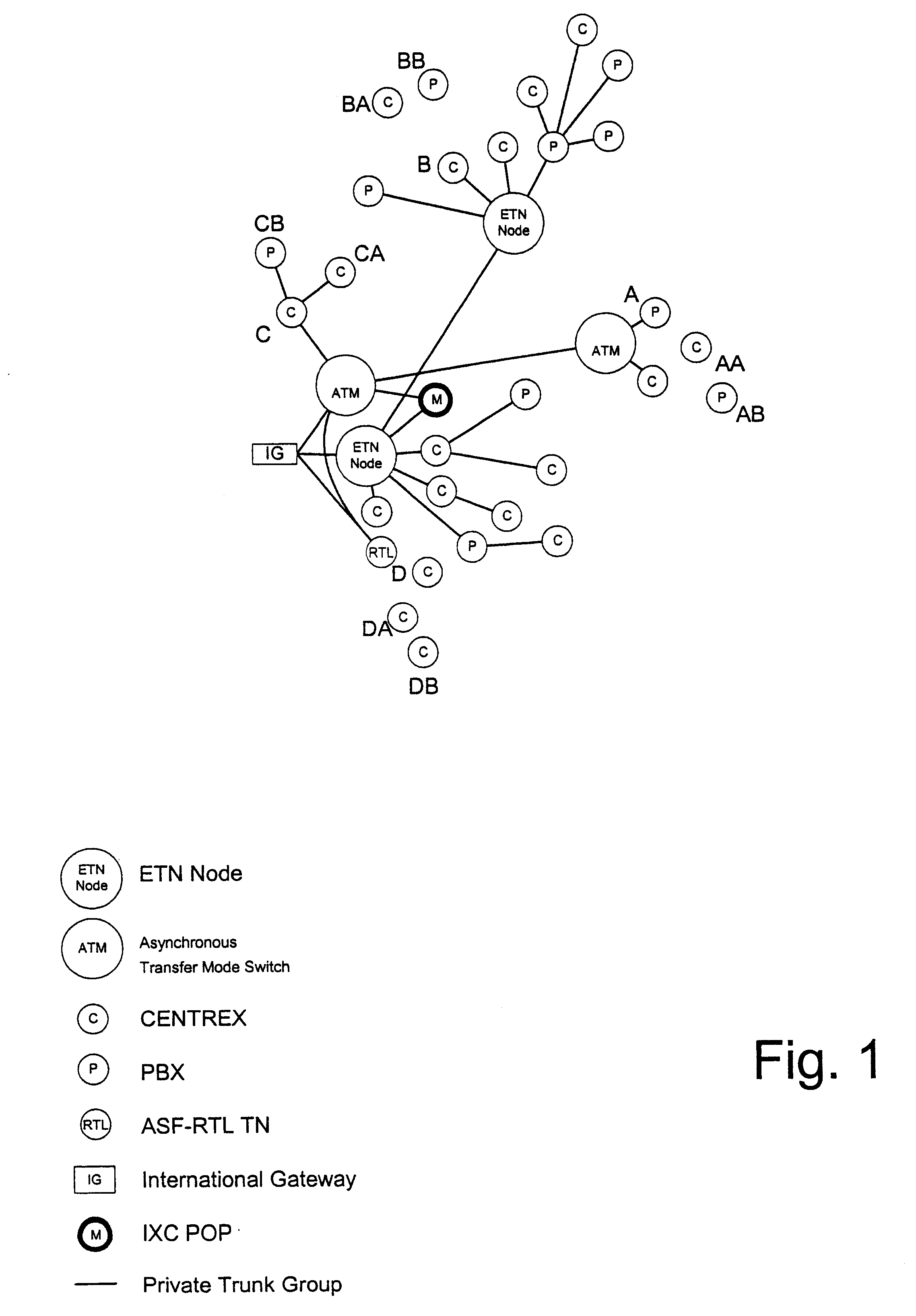
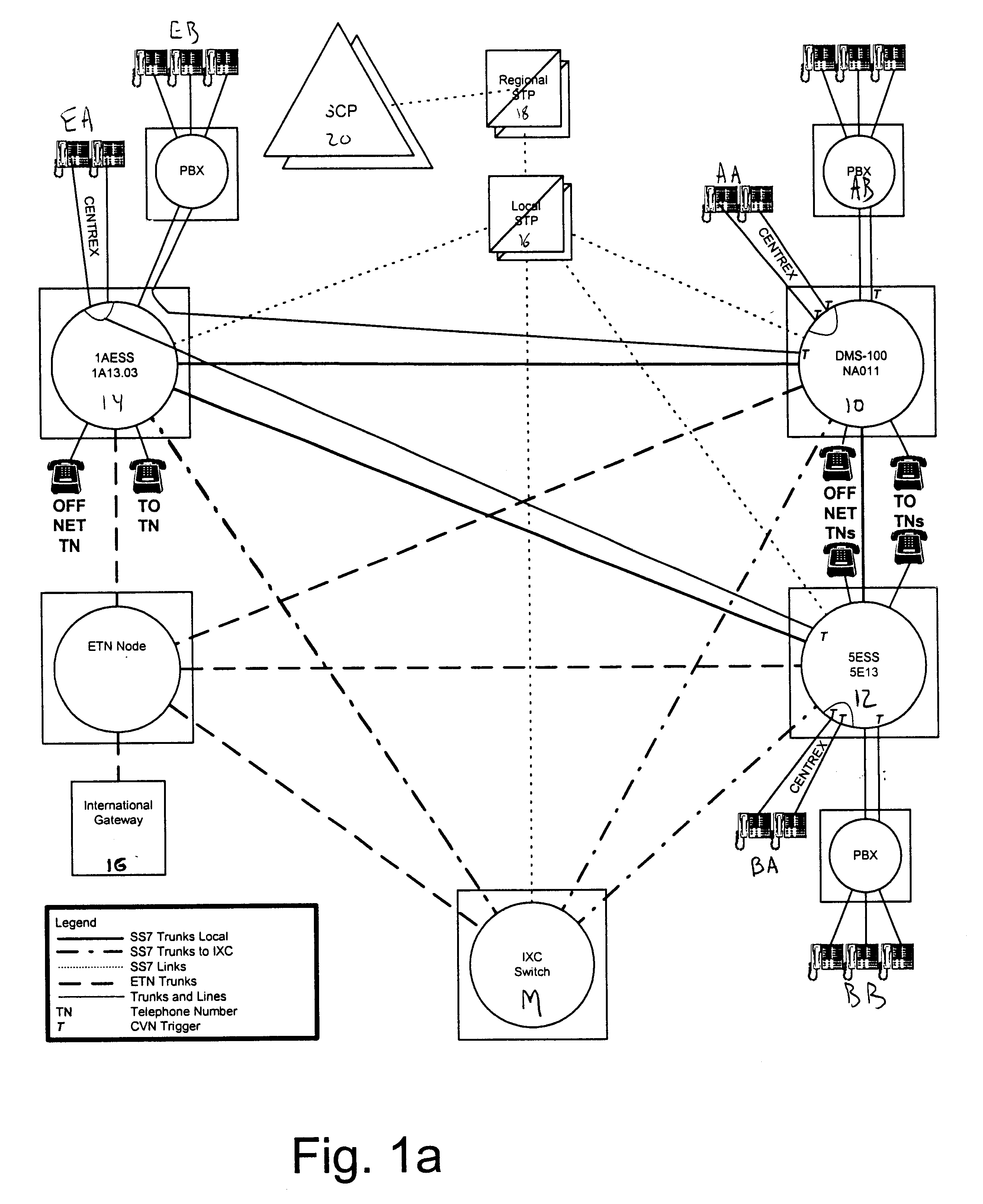
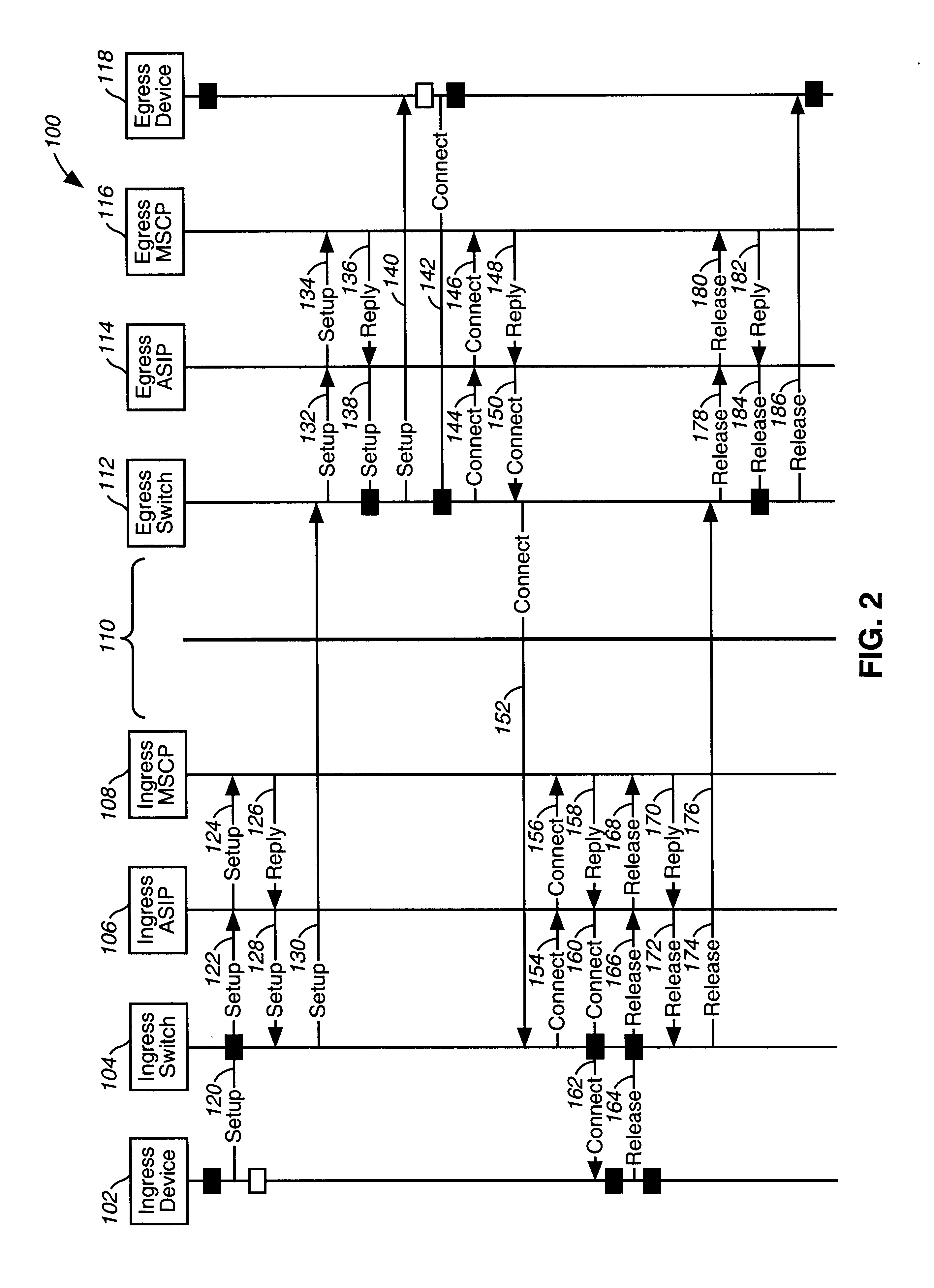
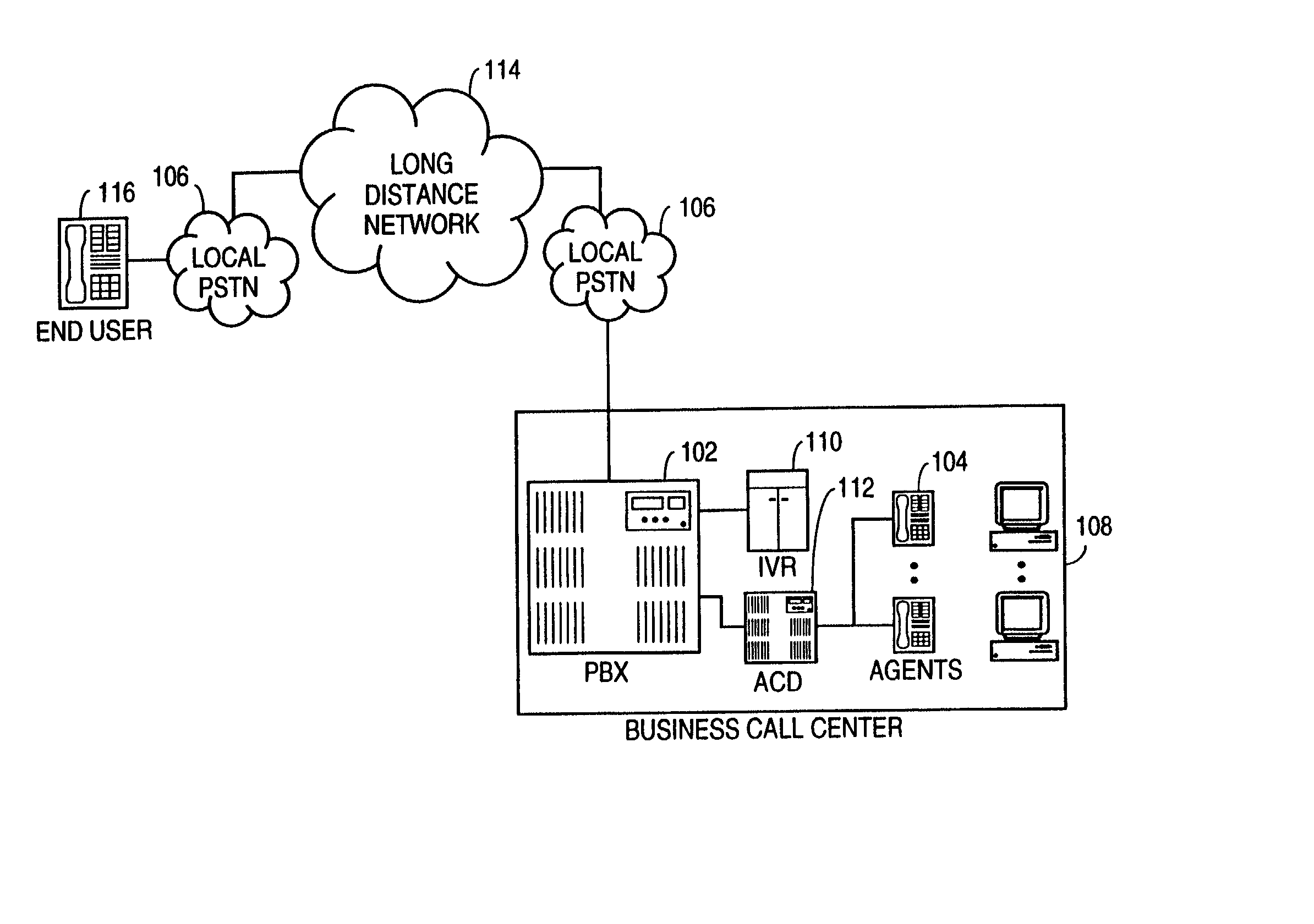
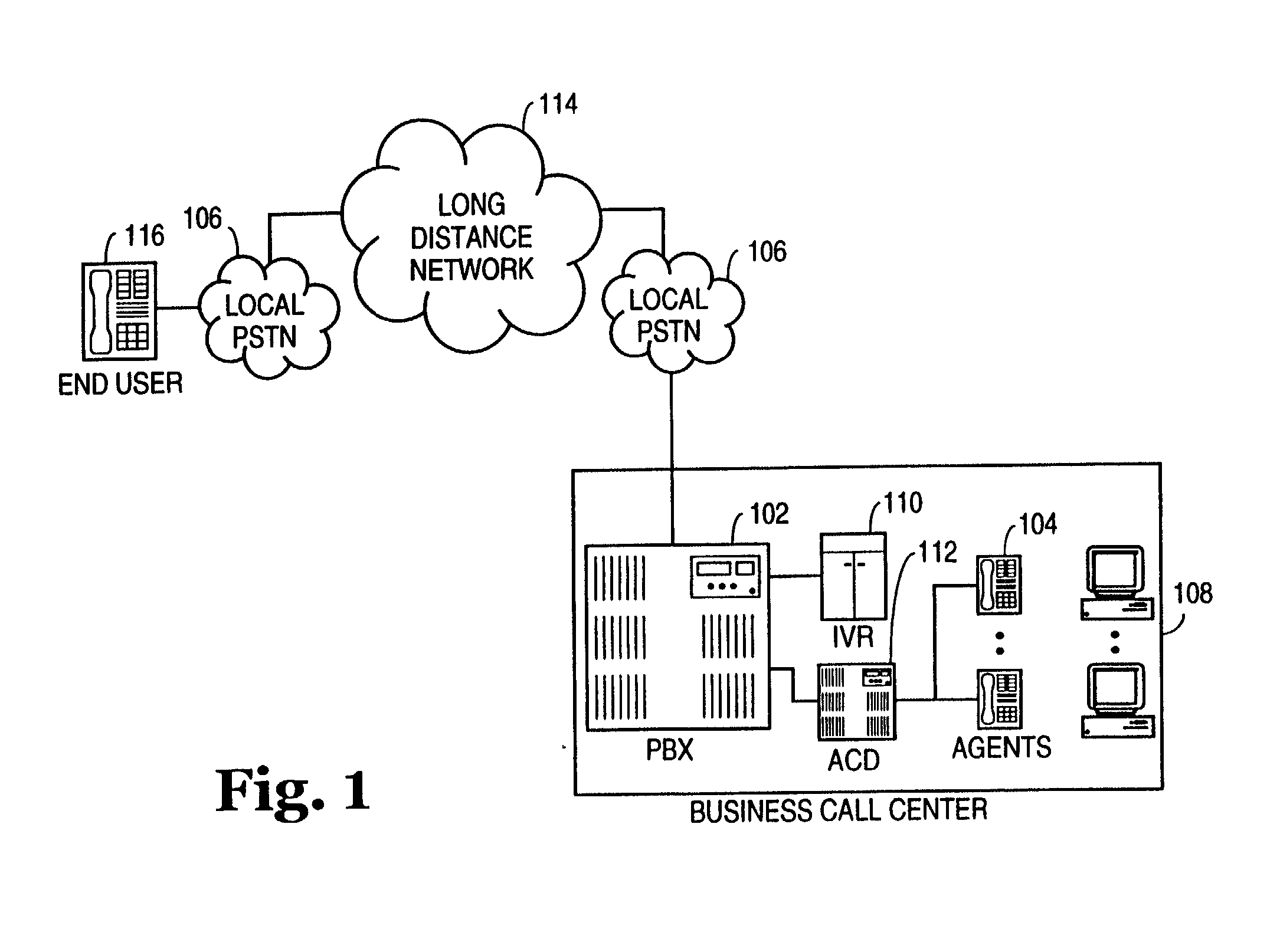
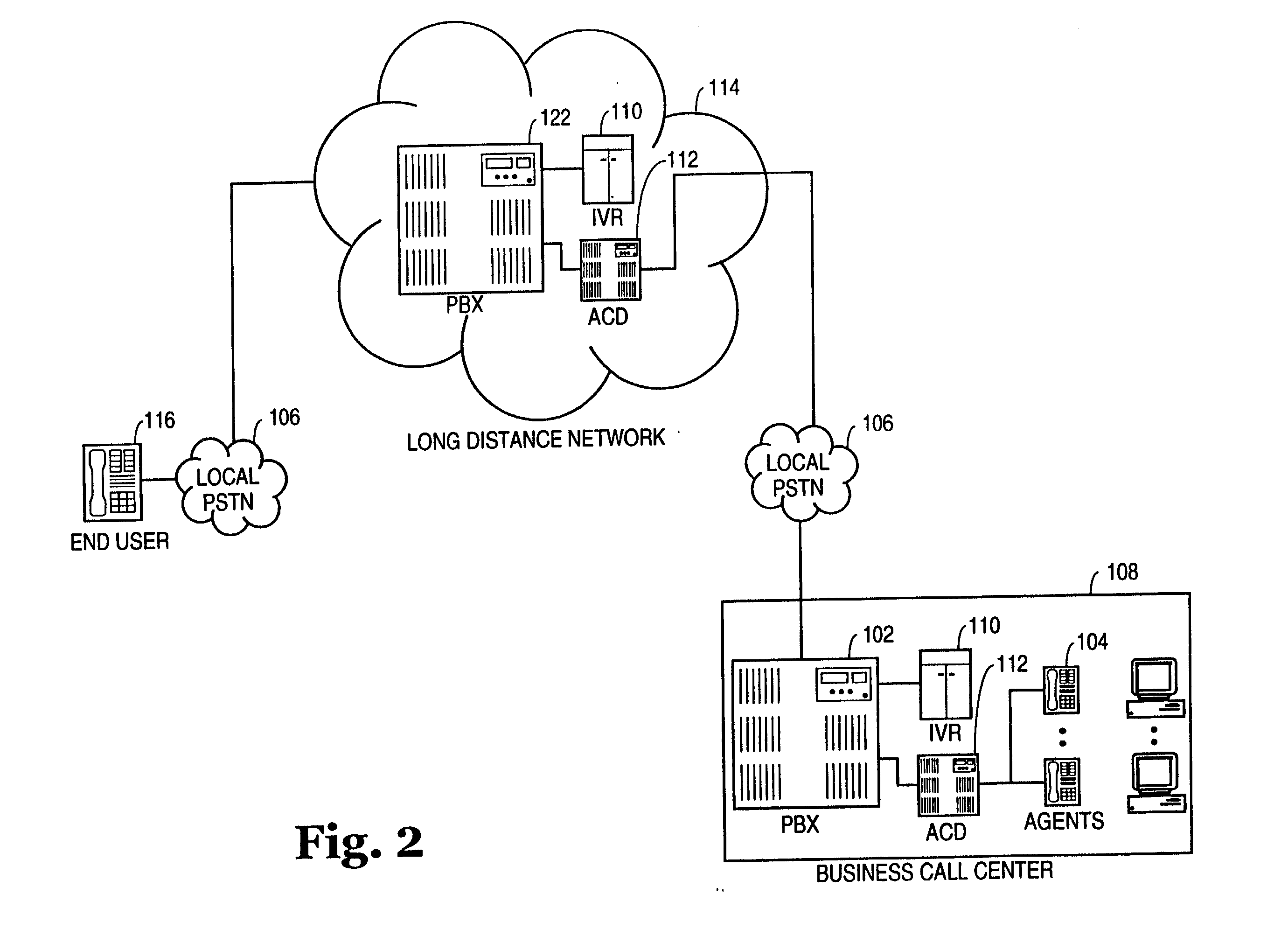
Method and system for processing telephone calls via a remote tie-line
A method and system include routing telephone calls from multiple private networks via public lines and trunks in a public switched telephone network (PSTN) to a host switch, at which the connections would begin to run parallel. The host switch routes the telephone calls via a private trunk group to a private facility, such as an electronic tandem network (ETN) node or an asynchronous transfer mode (ATM) switch. If the private trunk group is full or unavailable, the host switch routes the telephone calls over alternate private or public trunk groups and selected carriers.
Owner:AT&T LABS
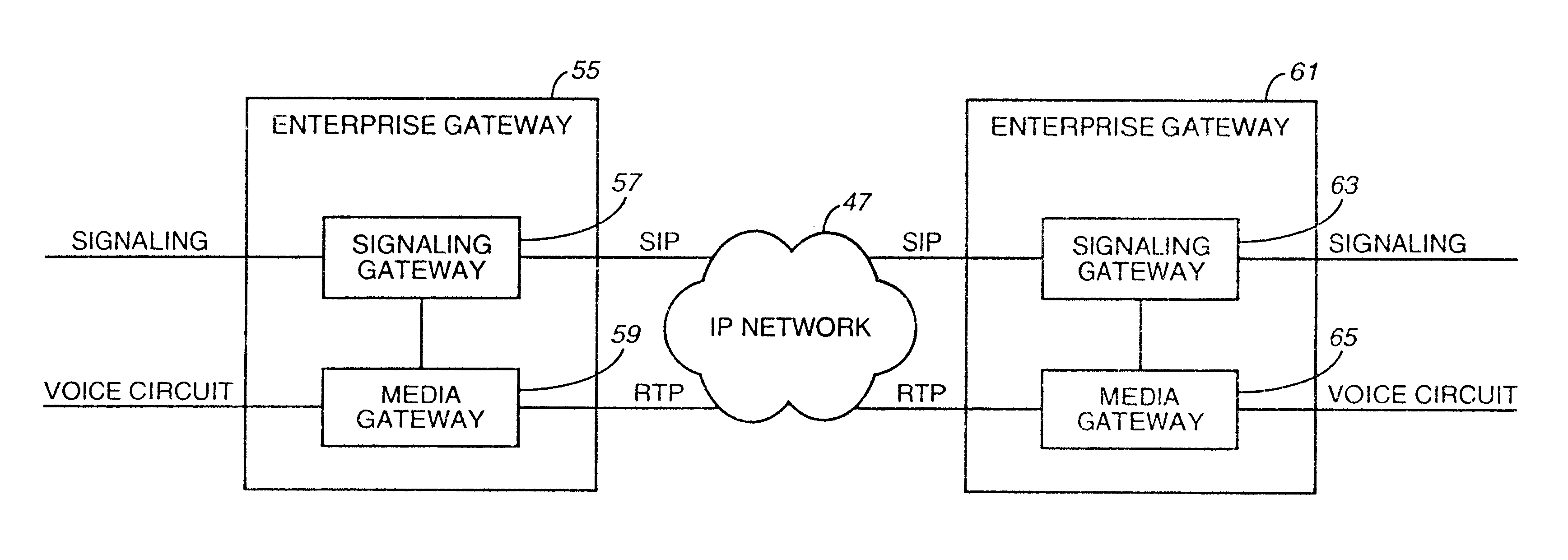
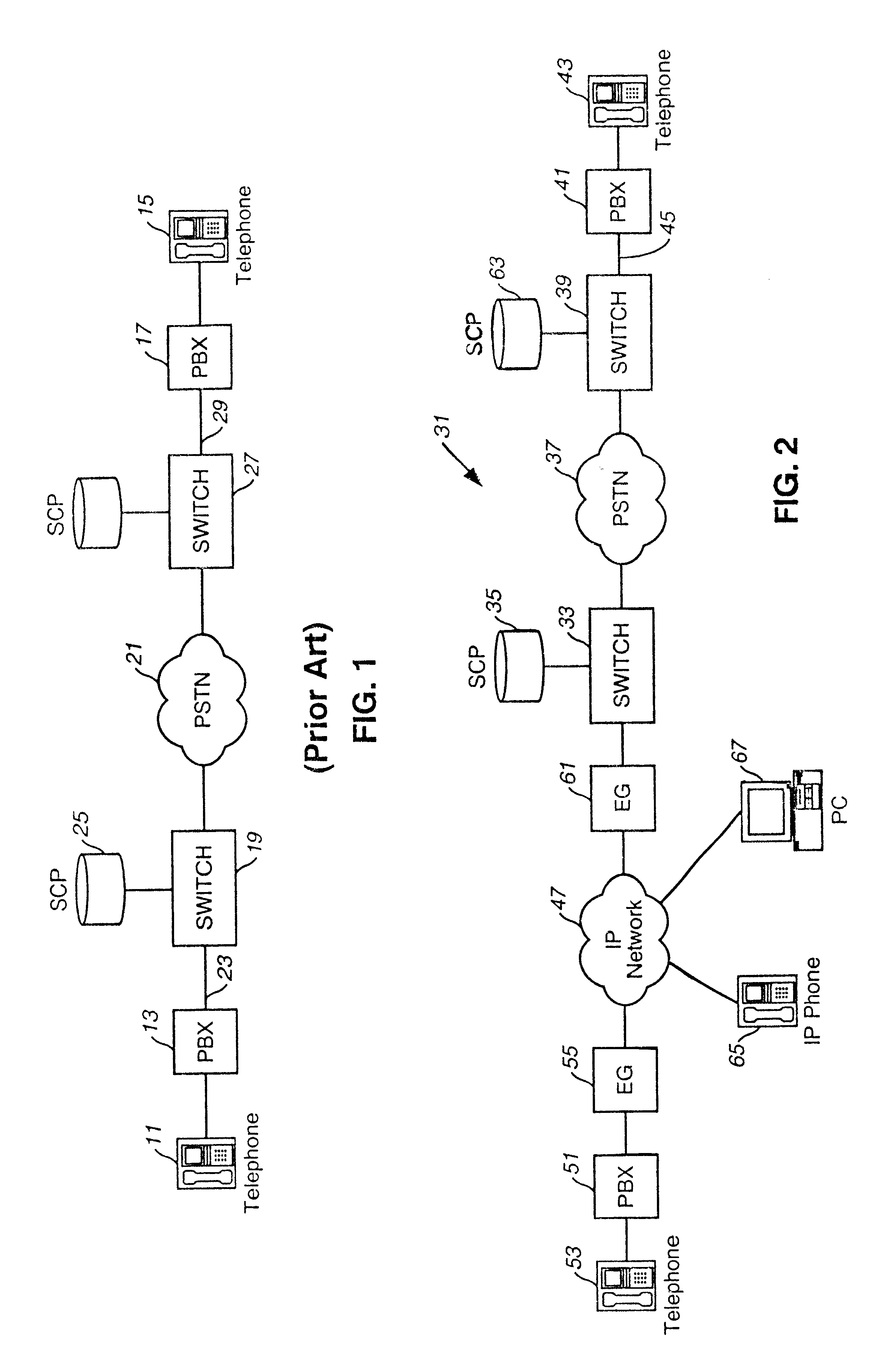
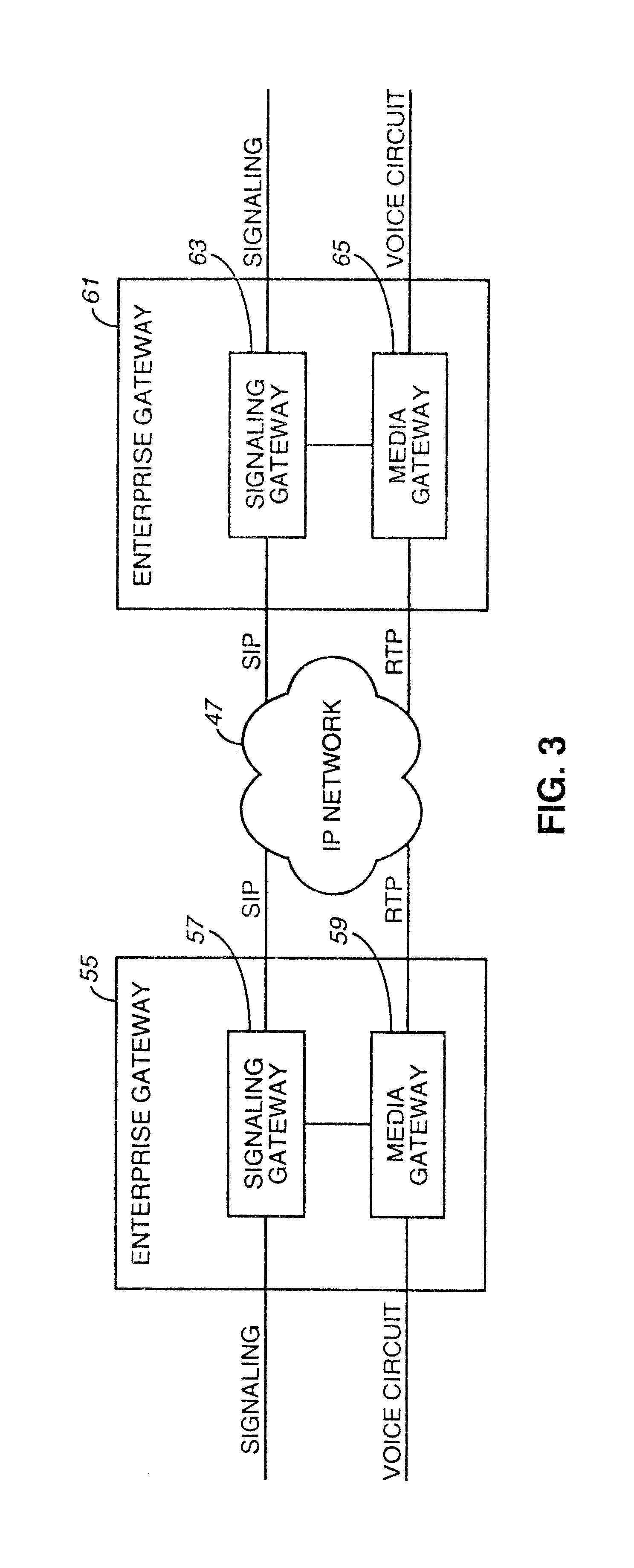
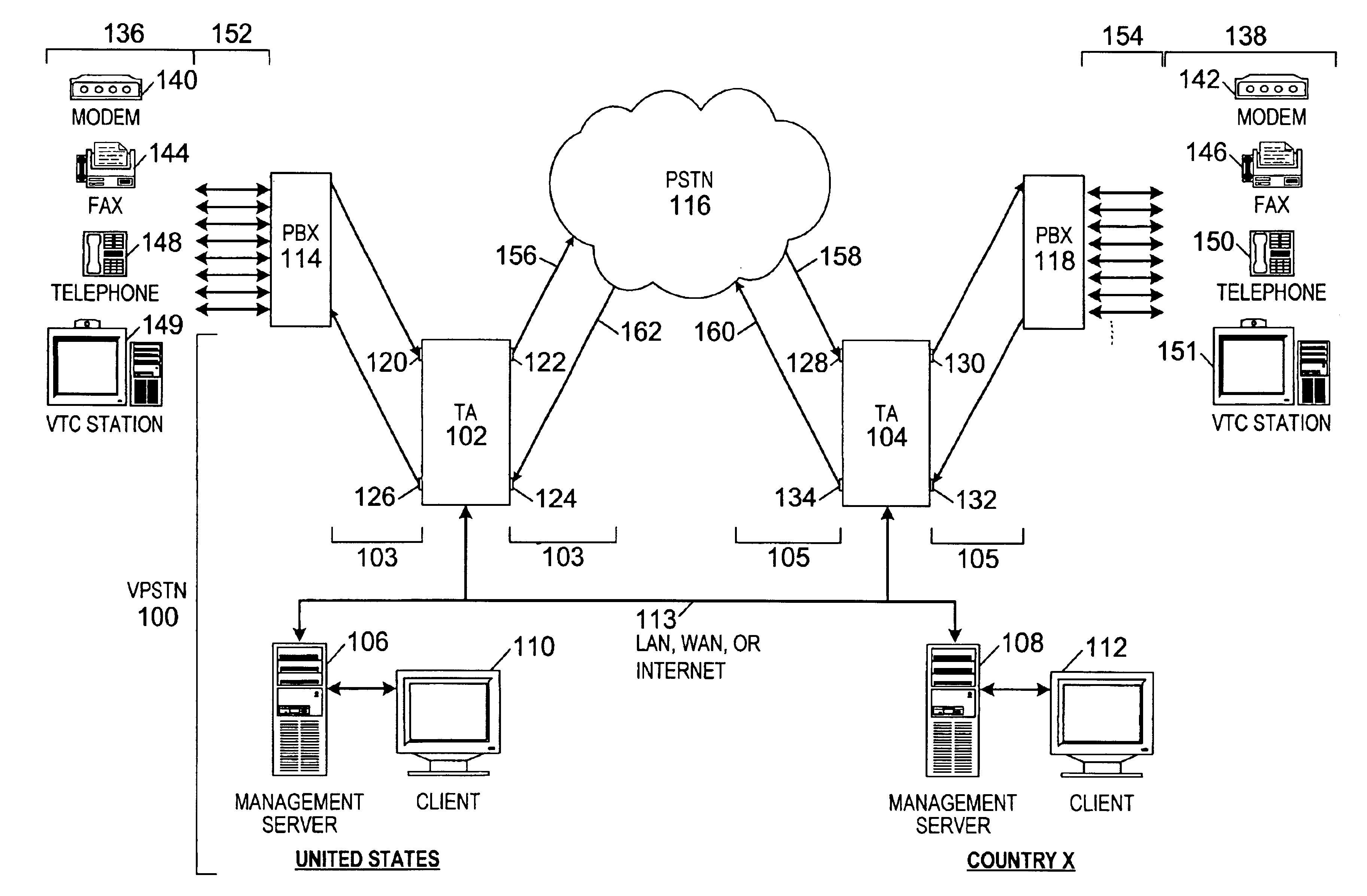
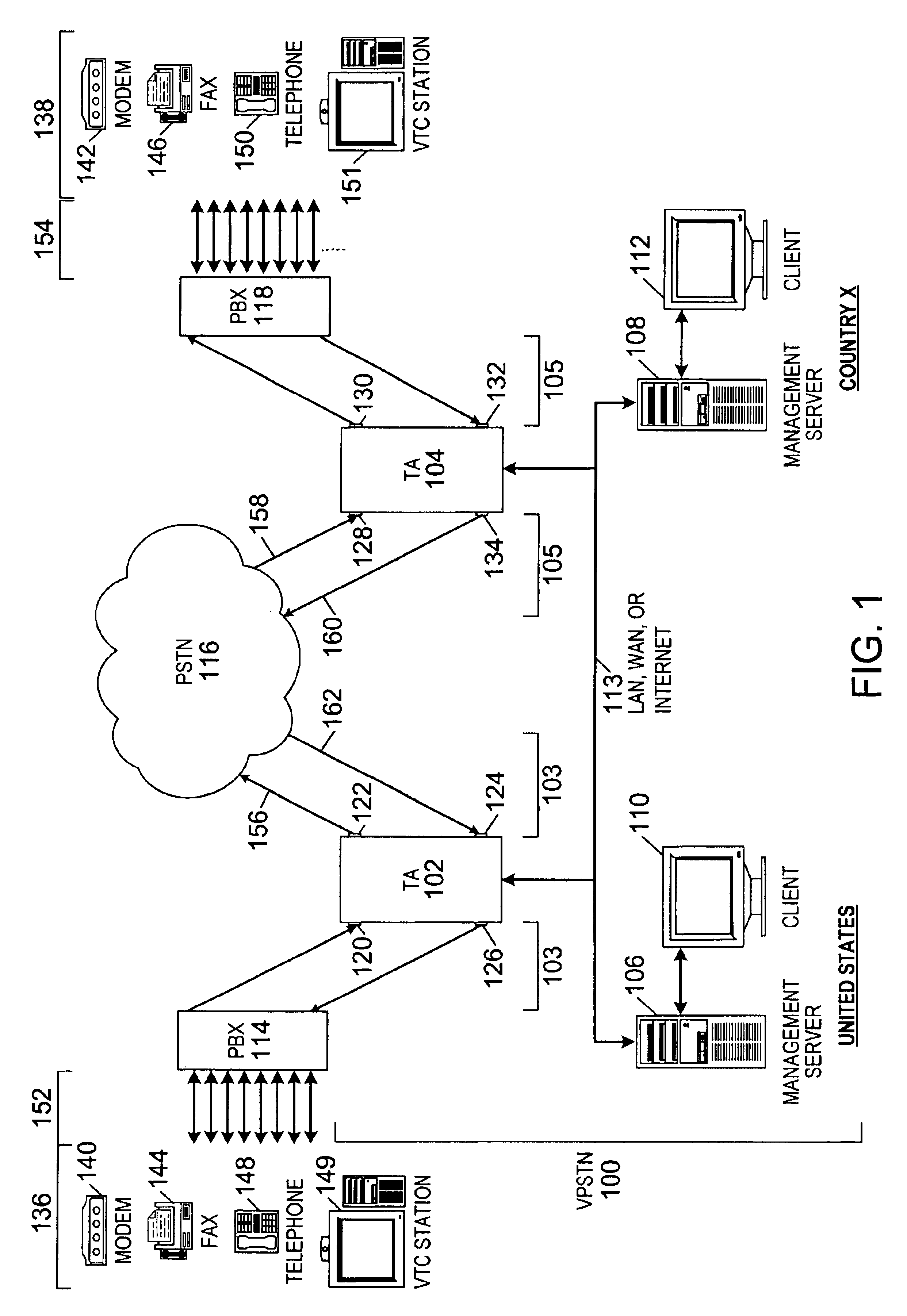
Method of and system for extending internet telephony over virtual private network direct access lines
InactiveUS6879680B2Interconnection arrangementsSpecial service for subscribersTTEthernetPrivate network
A virtual private network includes an internet protocol (IP) network and a public switched telephone network (PSTN). An enterprise gateway is operably connected to the IP network. The enterprise gateway is operably connected to a switch of the PSTN through a direct access line (DAL). The set-up signaling for virtual private network calls and the calls themselves are transported across the internet protocol network and the public switched telephone network through the direct access line.
Owner:VERIZON PATENT & LICENSING INC
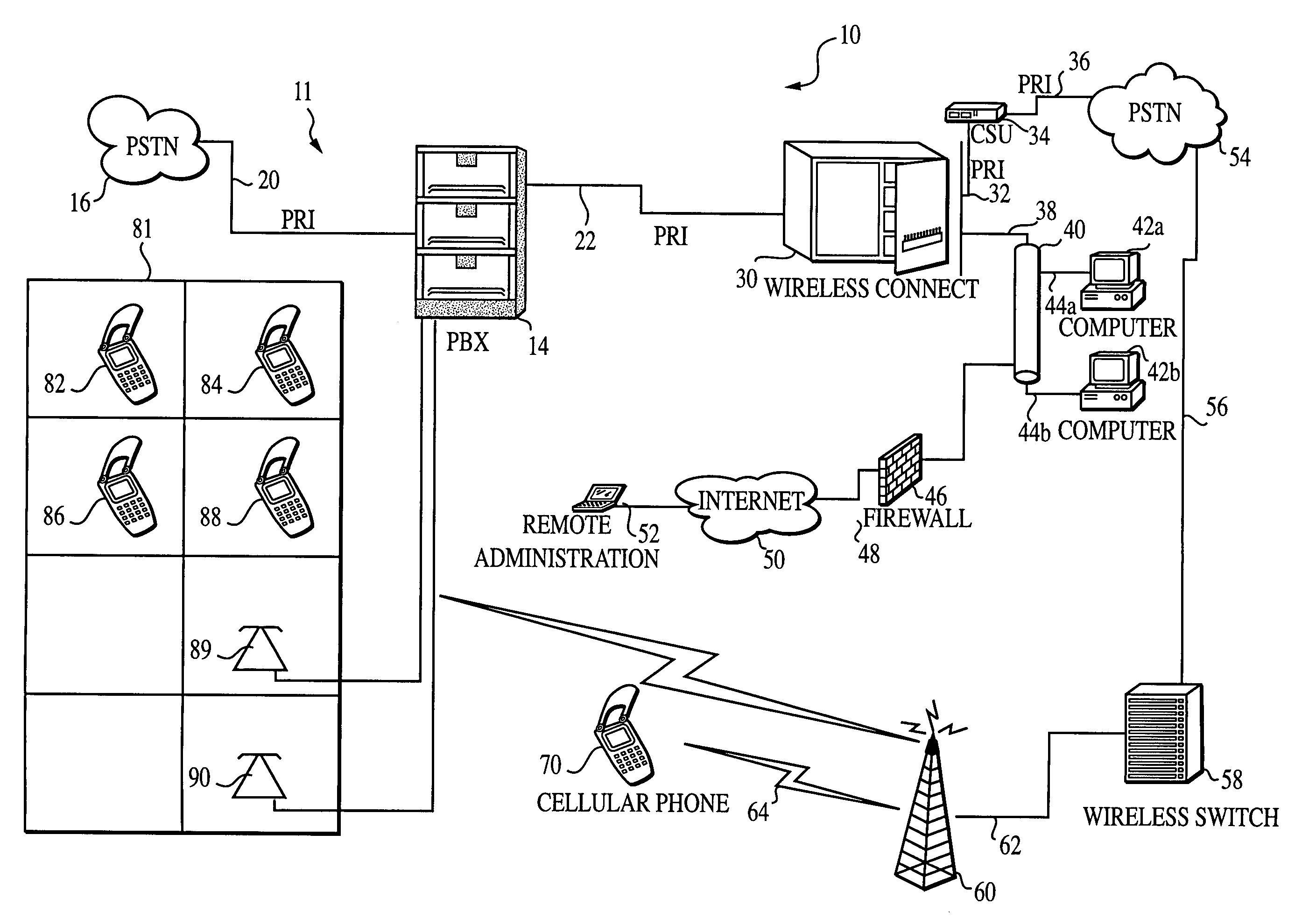
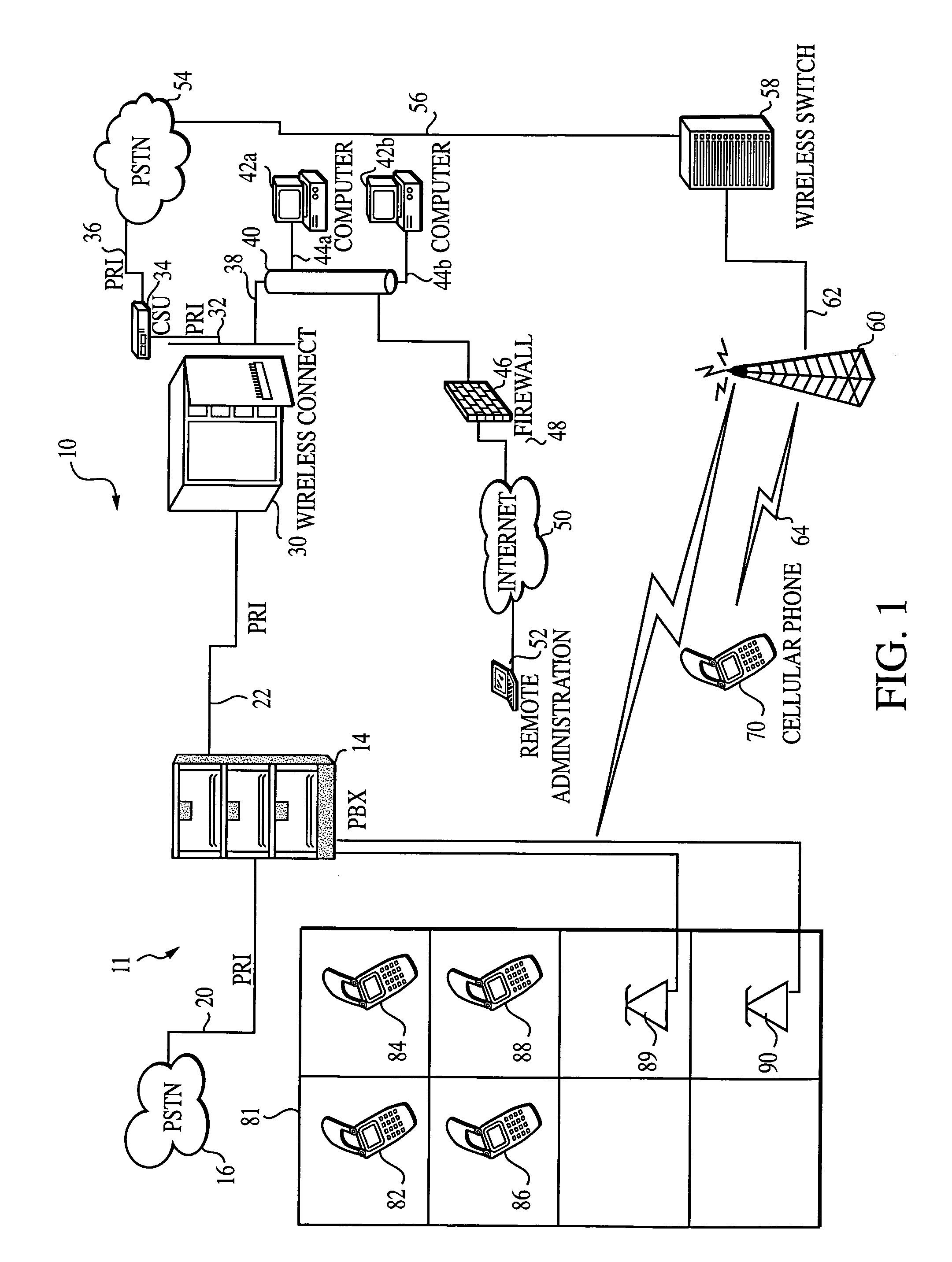
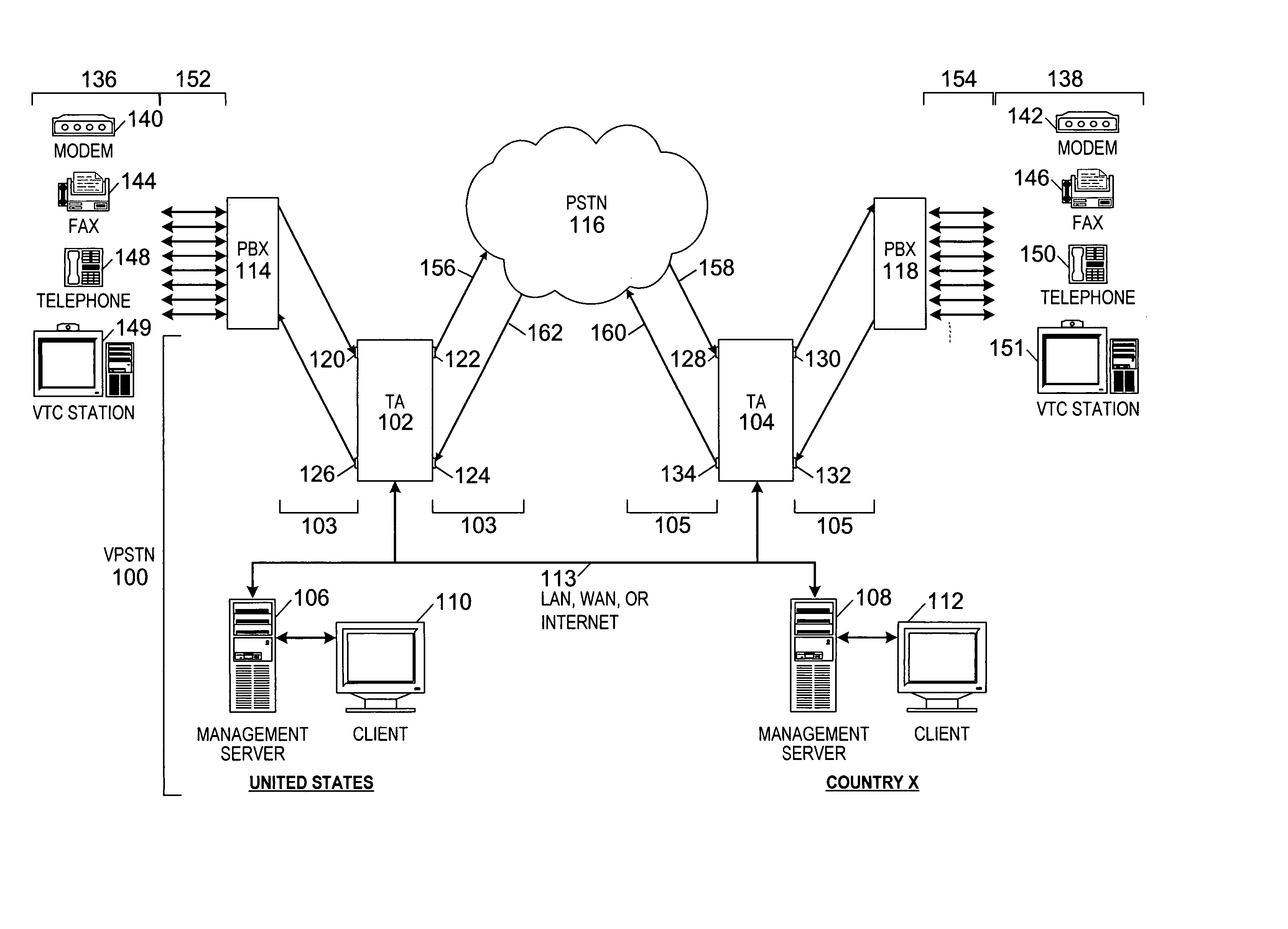
Method and apparatus for communicating via virtual office telephone extensions
A system for (and a method of) selectively establishing communication with at least one wireless device associated with a single telephone number serving as a virtual office extension is provided. In a preferred embodiment, the system includes a wireless connect unit in communication with an enterprise private branch exchange (PBX) network. The wireless connect unit preferably serves as a gateway between the PBX and one or more remote communication devices, including at least one wireless device, associated with a virtual extension telephone number. The remote wireless device can be used as a standard PBX office telephone for both inbound and outbound telephone calls. Thus, features of the PBX network (e.g., voice mail, direct extension dialing, corporate calling plan, etc.) are available to the remote wireless device even though it is not physically connected to the PBX. When the system receives an incoming call, it can route the call to a remote wireless device associated with a virtual extension, or to combination of devices simultaneously, or as desired by the user.
Owner:MALIKIE INNOVATIONS LTD
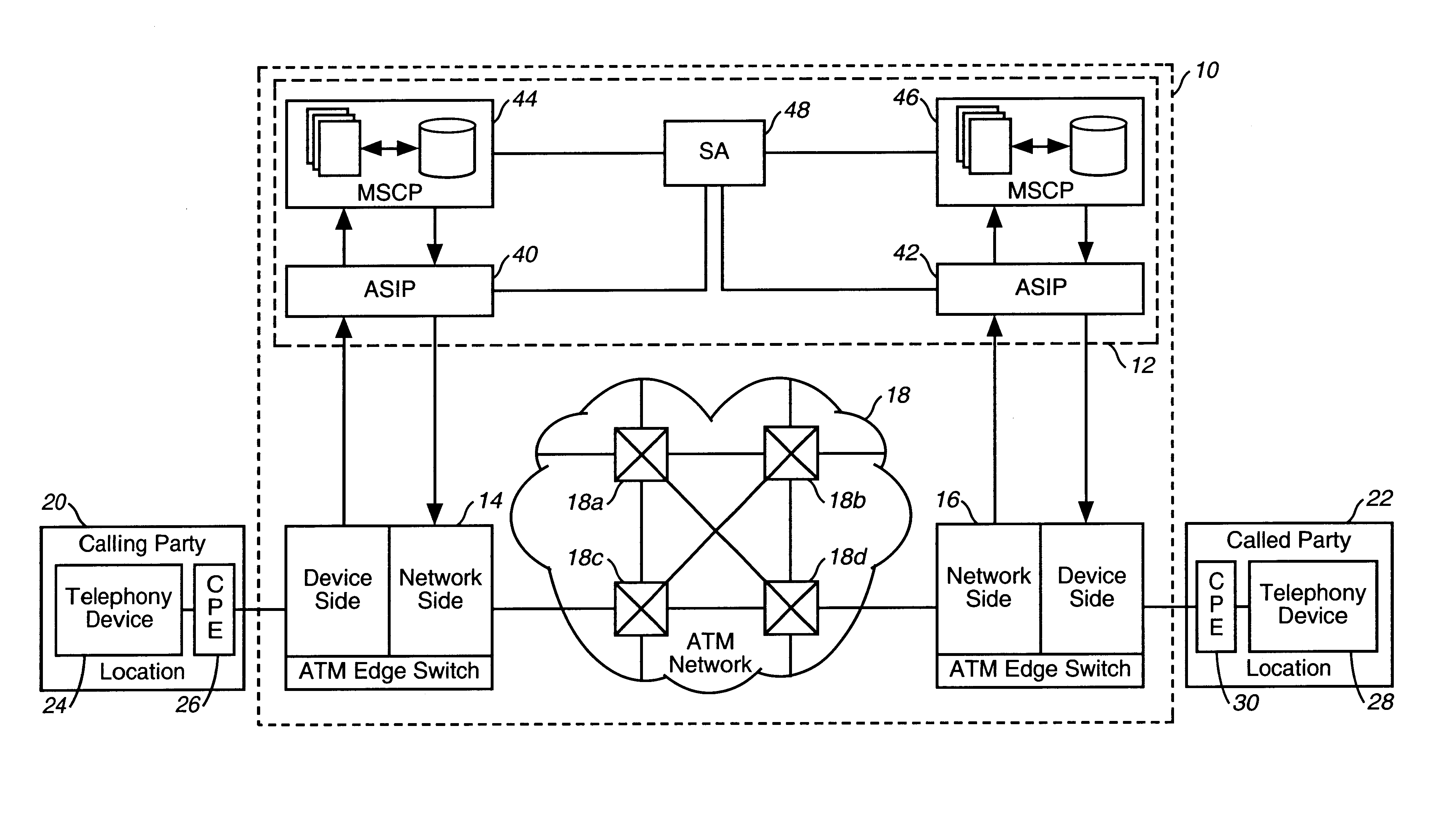
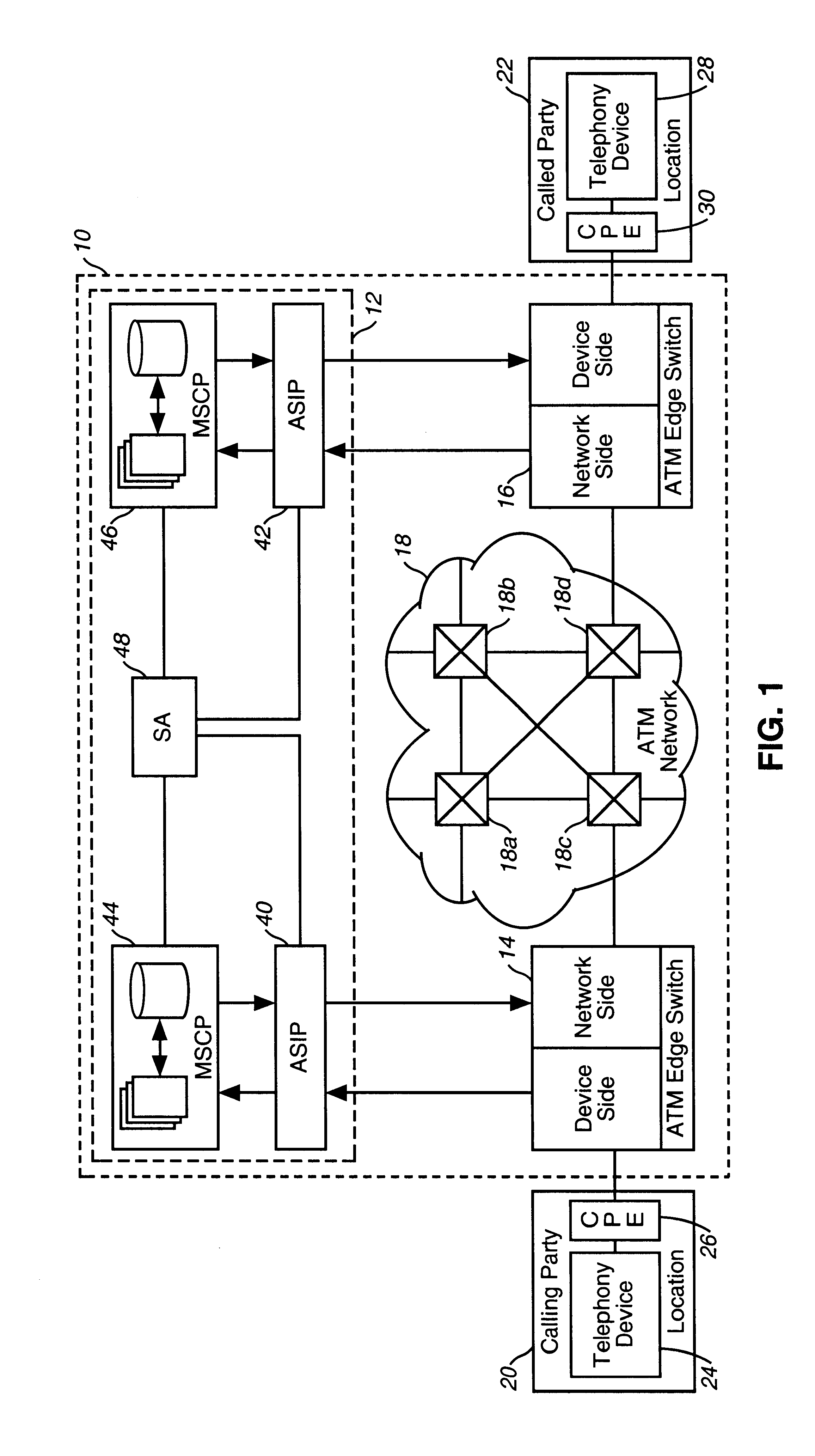
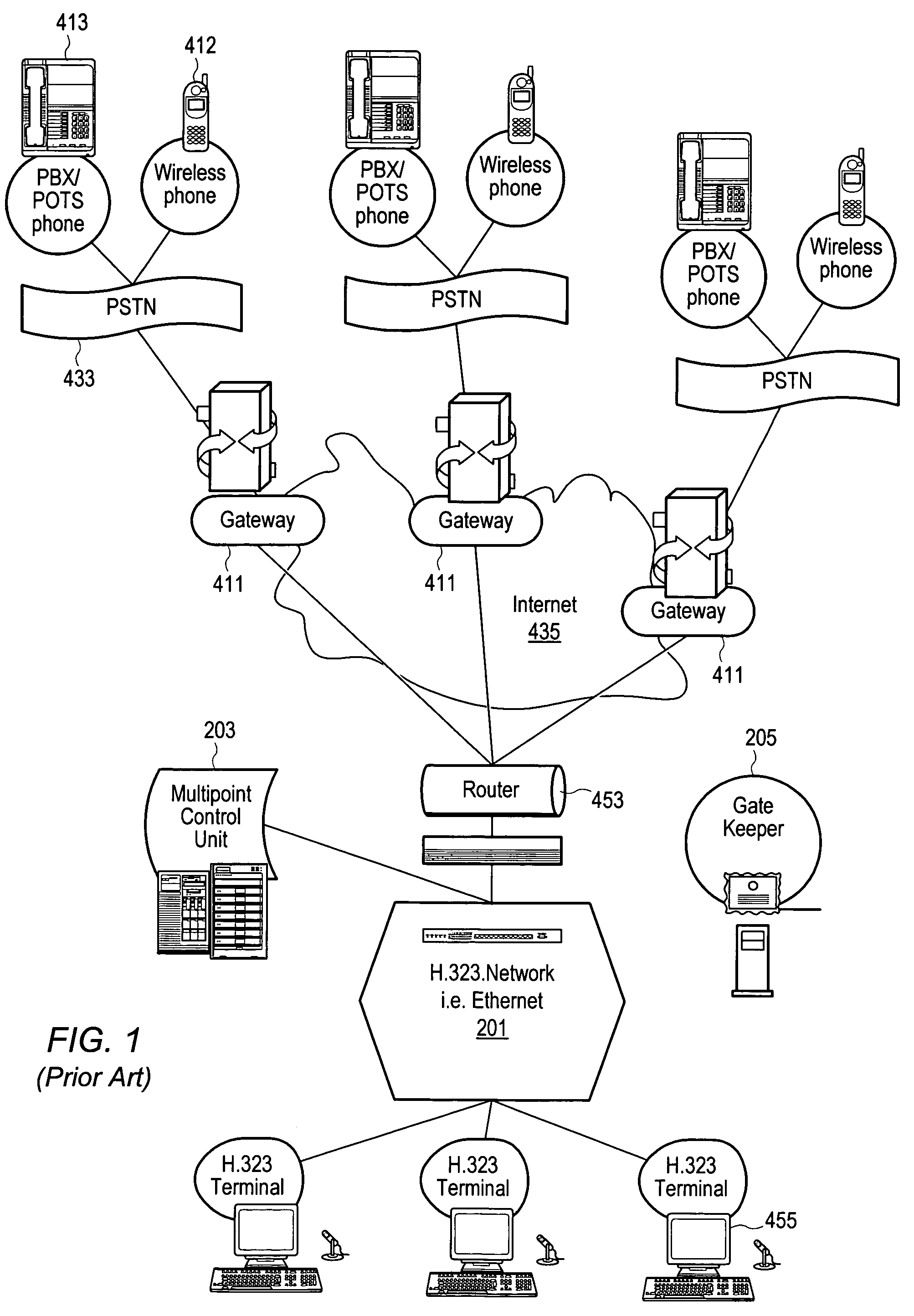
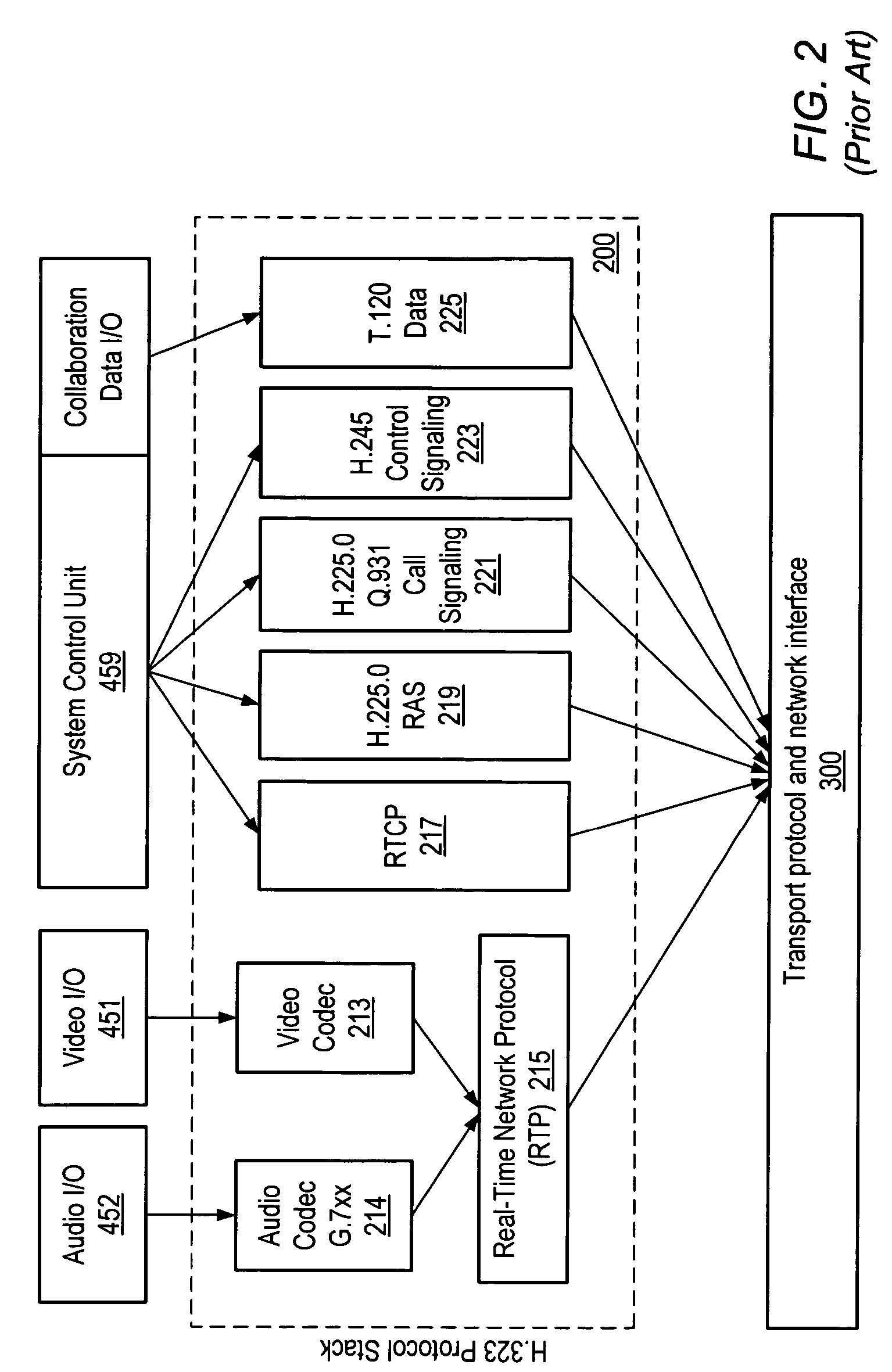
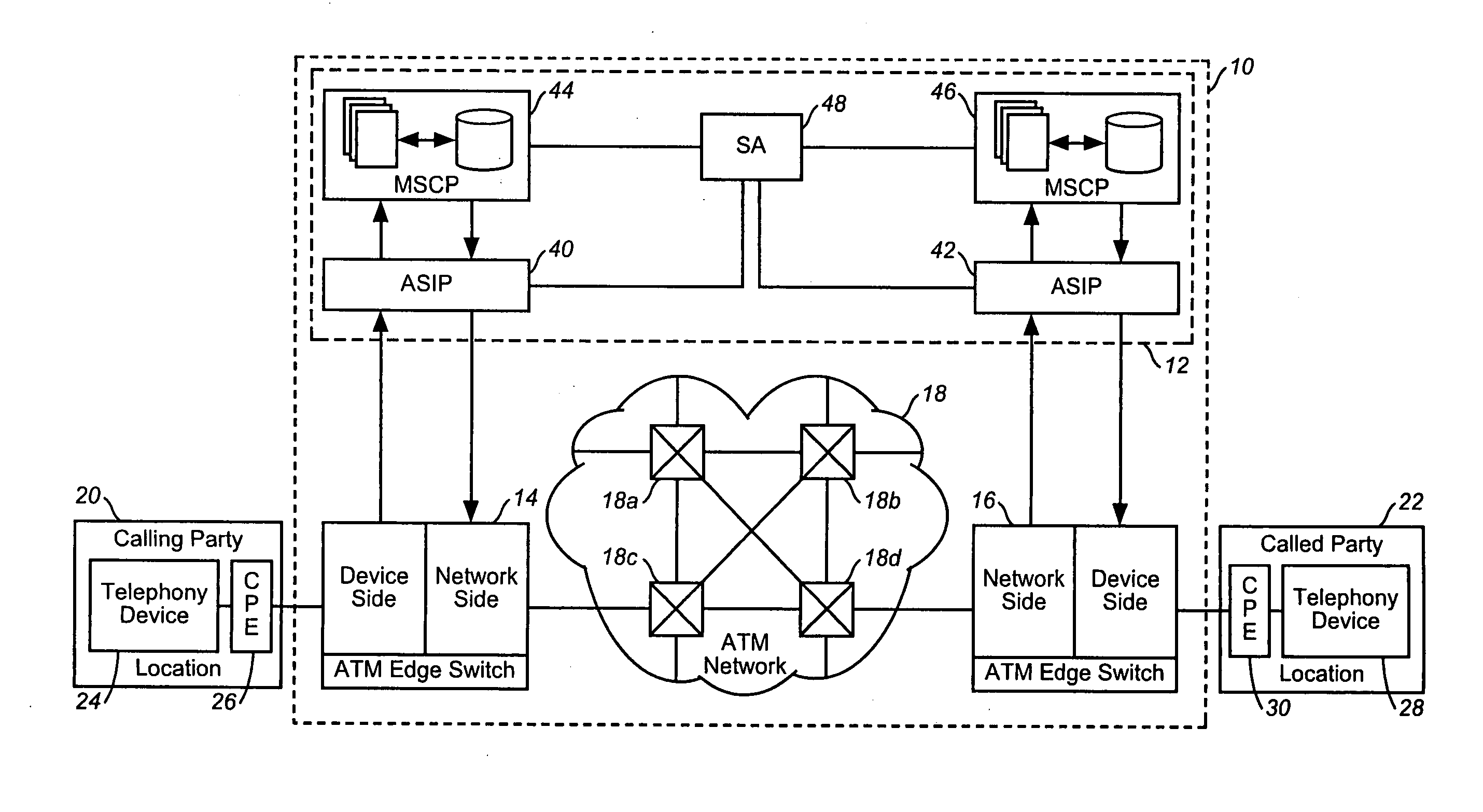
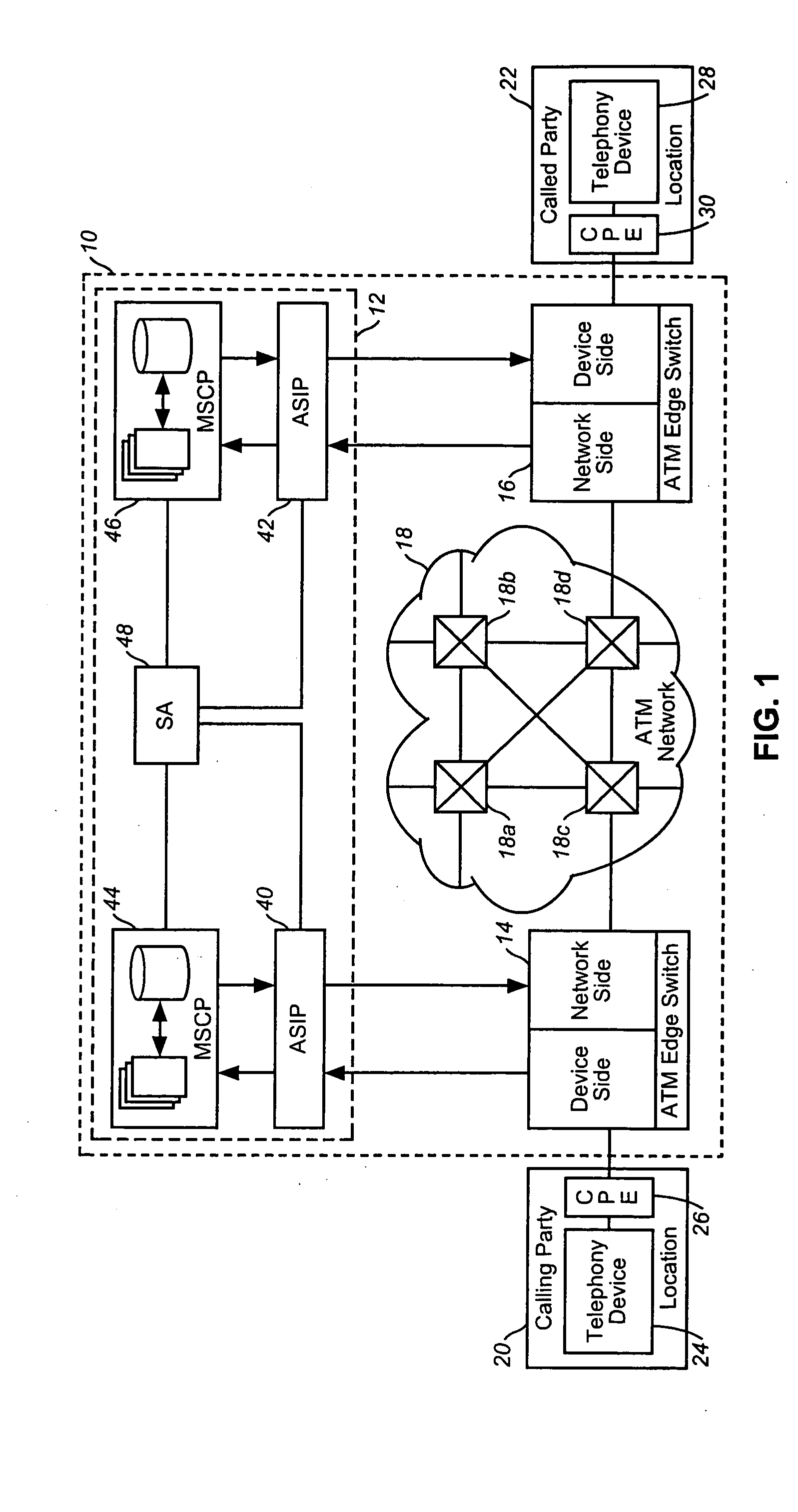
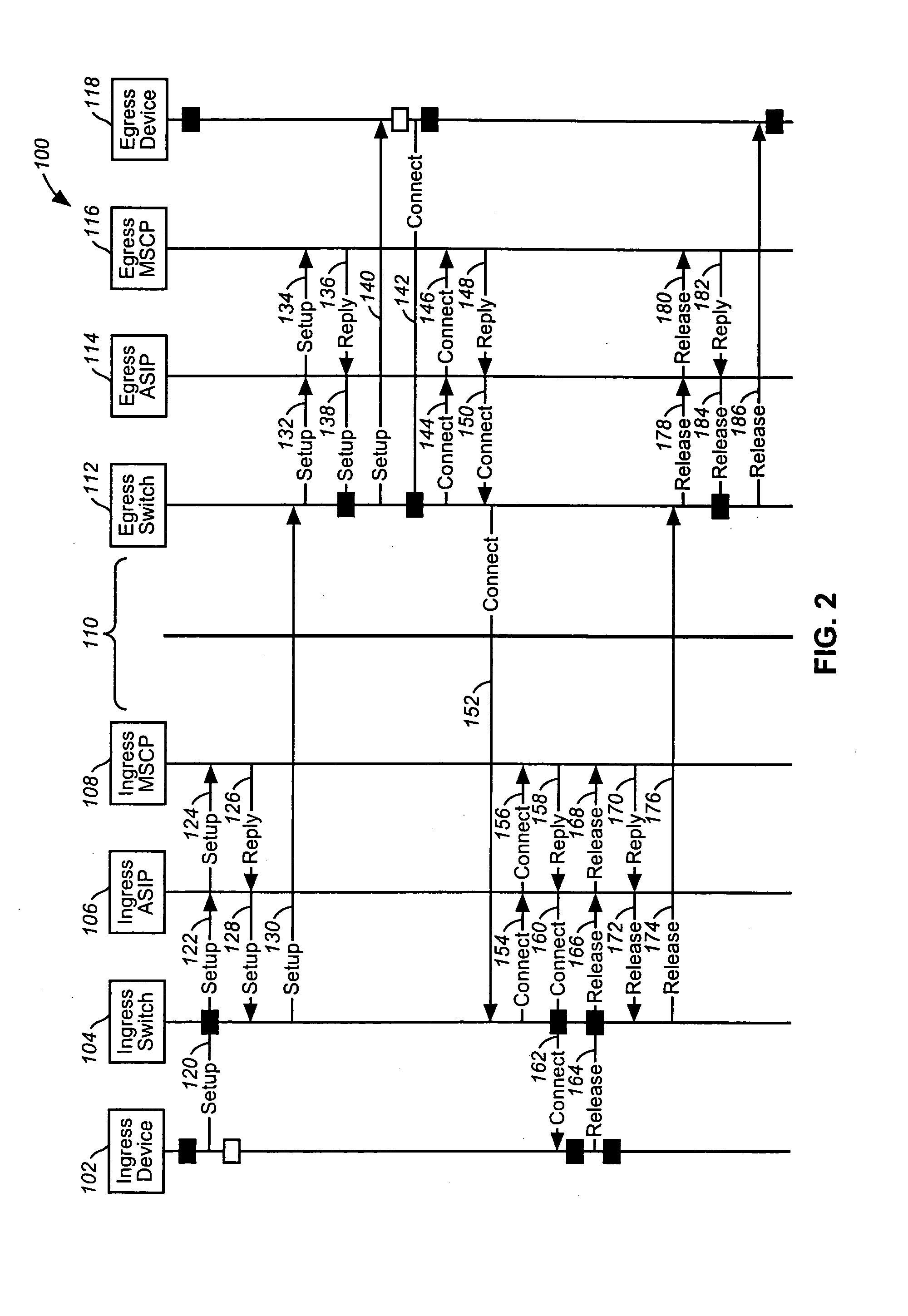
Intelligent network and method for providing voice telephony over ATM and private address translation
InactiveUS6931010B2Effective bandwidthUtilize bandwidthIntelligent networksHybrid switching systemsIntelligent NetworkPrivate address
An illustrative intelligent network and method for providing voice telephony over Asynchronous Transfer Mode (“ATM”) and private address translation are provided that can provide significant advantages. The method includes generating an input ATM setup message at the calling party CPE that includes a VToA designator and a called party phone number, extracting information from the input ATM setup message, analyzing the information, designating an ATM address of a called party CPE to be stored in the first parameter of an output ATM setup message, determining if private address translation is needed, designating the ATM address of the called party CPE to be stored in a first instance of the second parameter of the output ATM setup message, designating an ATM address of an egress ATM edge switch to be stored in the first parameter of the output ATM setup message, and generating an output ATM setup message.
Owner:VERIZON PATENT & LICENSING INC
Virtual private switched telecommunications network
InactiveUS20050047570A1Interconnection arrangementsUnauthorised/fraudulent call preventionSecure communicationTelecommunications network
A system and method to provide secure communication across the untrusted public switched telephone network includes a set of rules in a security policy which are implemented by a virtual private switched telecommunications network (VPSTN). The VPSTN provides for intercepting voice calls and modifying their set-up to include a request for bearer capability to support a data call.
Owner:SECURELOGIX CORP
Method and system for customer-managed call routing
InactiveUS20060274723A1Data switching by path configurationAutomatic exchangesPrivate networkTelephone network
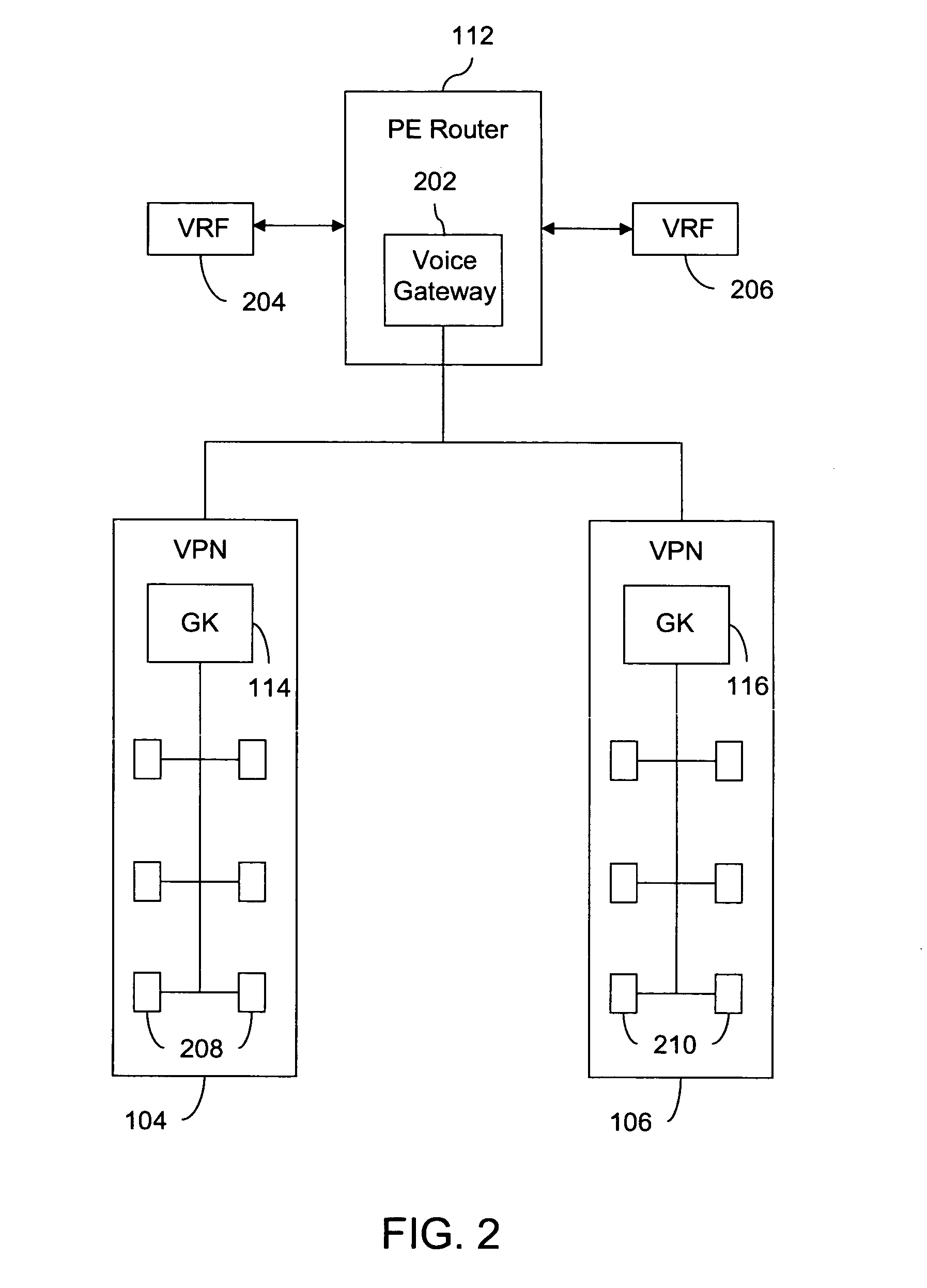
A method, system and apparatus are provided for call routing in a telephony network. The telephony network includes at least one voice gateway and is associated with a plurality of Virtual Private Networks (VPNs). The telephony network provider provides conventional telephony network access to all its VPN customers, while providing VPN customers with the freedom to manage call routing / processing in their networks. This is done by co-locating the voice gateway with the Provider Edge (PE) router of the provider network and registering the voice gateway with the routing entity in each VPN.
Owner:CISCO TECH INC
Point-of-presence call center management system
InactiveUS20020090076A1Telephone data network interconnectionsSpecial service for subscribersPrivate networkCall origination
A point-of-presence (POP) call center system capable of answering, servicing, queuing and routing of calls at local points of presence to reduce communications costs and enhance operational efficiency for toll-free inbound call centers. The POP call center system of the includes a set of point-of-presence call center gateways distributed at points of presence close to the point of call origination that are connected by a virtual private network to premises call center gateways at business locations where the call centers reside.
Owner:UPPALURU PREM +1
Communications systems
ActiveUS20060040664A1Facilitate communicationInterconnection arrangementsNetwork topologiesCommunications systemNetwork communication
This disclosure concerns systems and methods for network communications. In one example, the method includes: providing subscriber terminals of each network with a respective publicly-known telephone number for allowing communications to be addressed to each subscriber terminal; associating selected subscriber terminals of each network together in a group such that those subscriber terminals can address communications to one another using a respective code allocated to each of the selected subscriber terminals; and, maintaining a database of the codes and corresponding publicly-known telephone numbers of all of the networks and providing to one of the networks a publicly-known telephone number corresponding to a code of a subscriber terminal of another one of the networks to allow communication from a subscriber terminal of one of the networks to be addressed to a subscriber terminal of the other of the networks using the code of the latter subscriber terminal.
Owner:VODAFONE GRP PLC
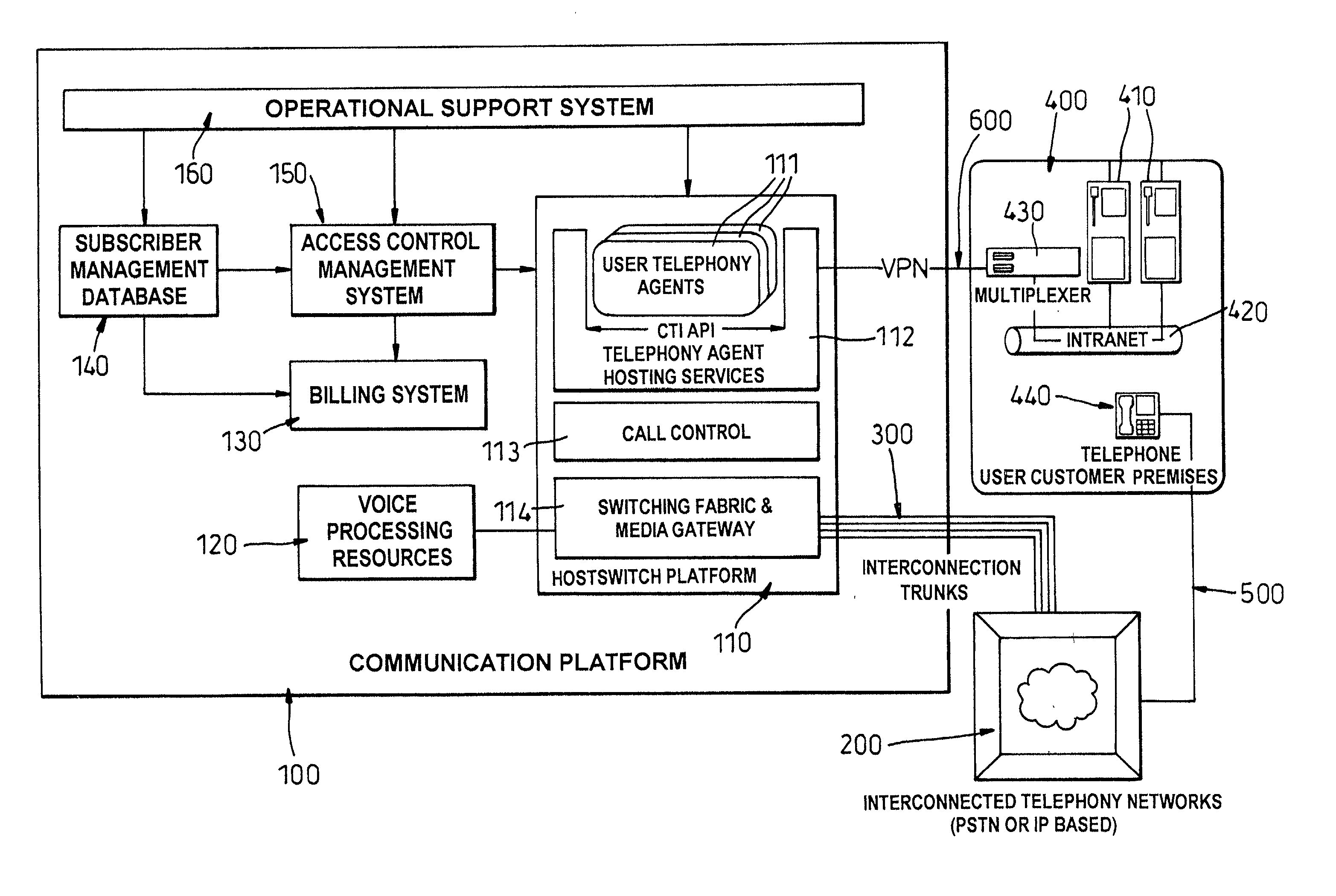
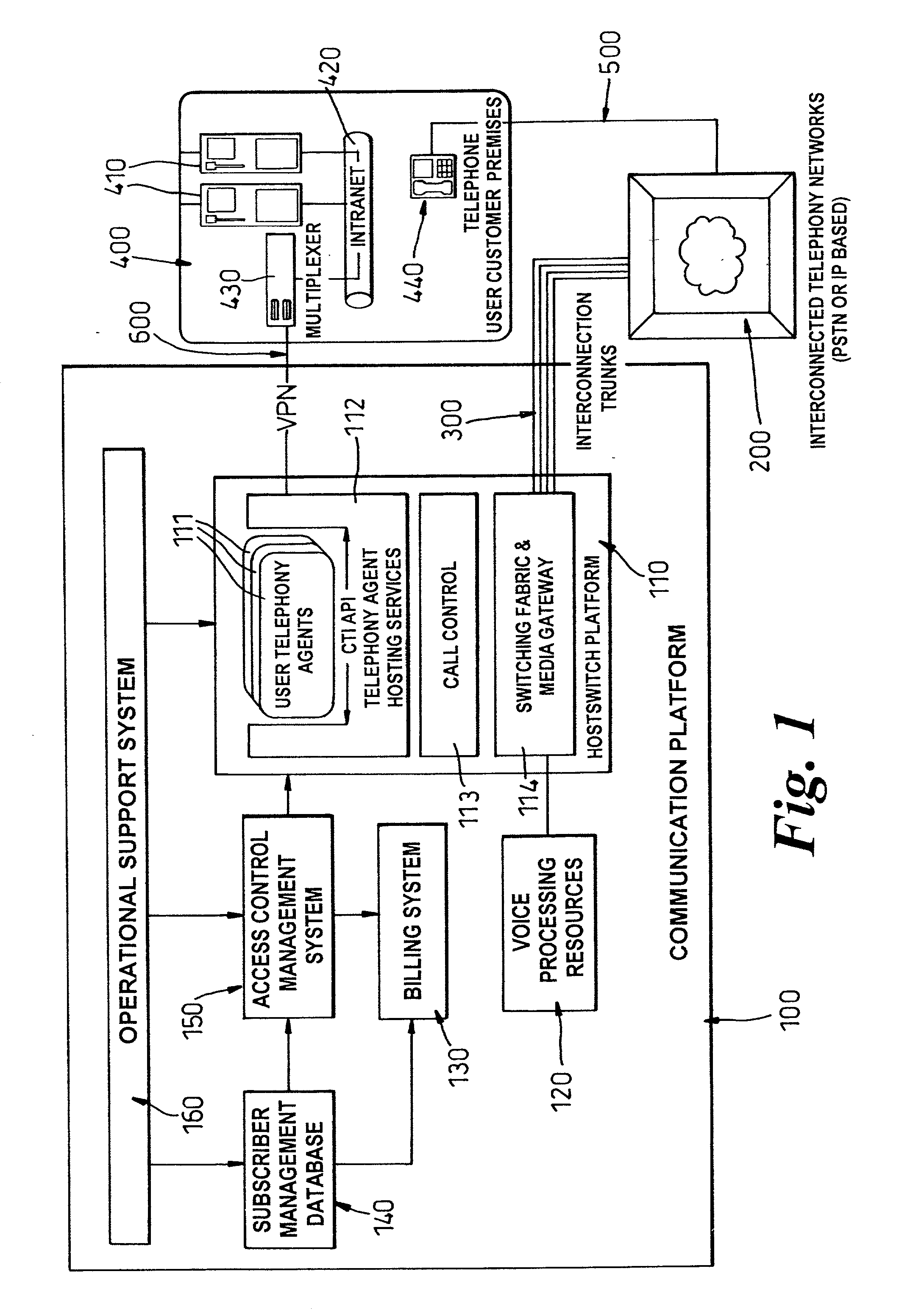
Communication platform for providing computer telephony intergration services to remote subscribers, and associated method
ActiveUS20020009188A1Eliminate needMinimizing costlyMultiplex system selection arrangementsSpecial service for subscribersData controlTelephone network
A communication platform for providing computer / telephony integration services to remote subscribers comprises: a hosted call switching unit in communication with an external telephone network or interconnected networks through a communications trunk; for each subscriber, a subscriber telephony component, such as an intelligent agent, executed by processing means belonging to the communication platform and connected to an external subscriber's information system through a permanent private secure data channel, whereby said subscriber telephony component can communicate in a private manner with other information system components of said subscriber so as to be logically part of said information system, each subscriber component being capable of controlling said switching unit according to subscriber data; resources available to each subscriber telephony component in association with call processing or routing; means for allocating resources to each telephone call handled by a subscriber telephony component in response to data communication with said component through a secure interface.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Virtual private switched telecommunications network
InactiveUS6879671B2Interconnection arrangementsUnauthorised/fraudulent call preventionSecure communicationTelecommunications link
A system and method to provide secure communication across the untrusted public switched telephone network includes a set of rules in a security policy which are implemented by a virtual private switched telecommunications network (VPSTN). The VPSTN provides for intercepting voice calls and modifying their set-up to include a request for bearer capability to support a data call.
Owner:SECURELOGIX CORP
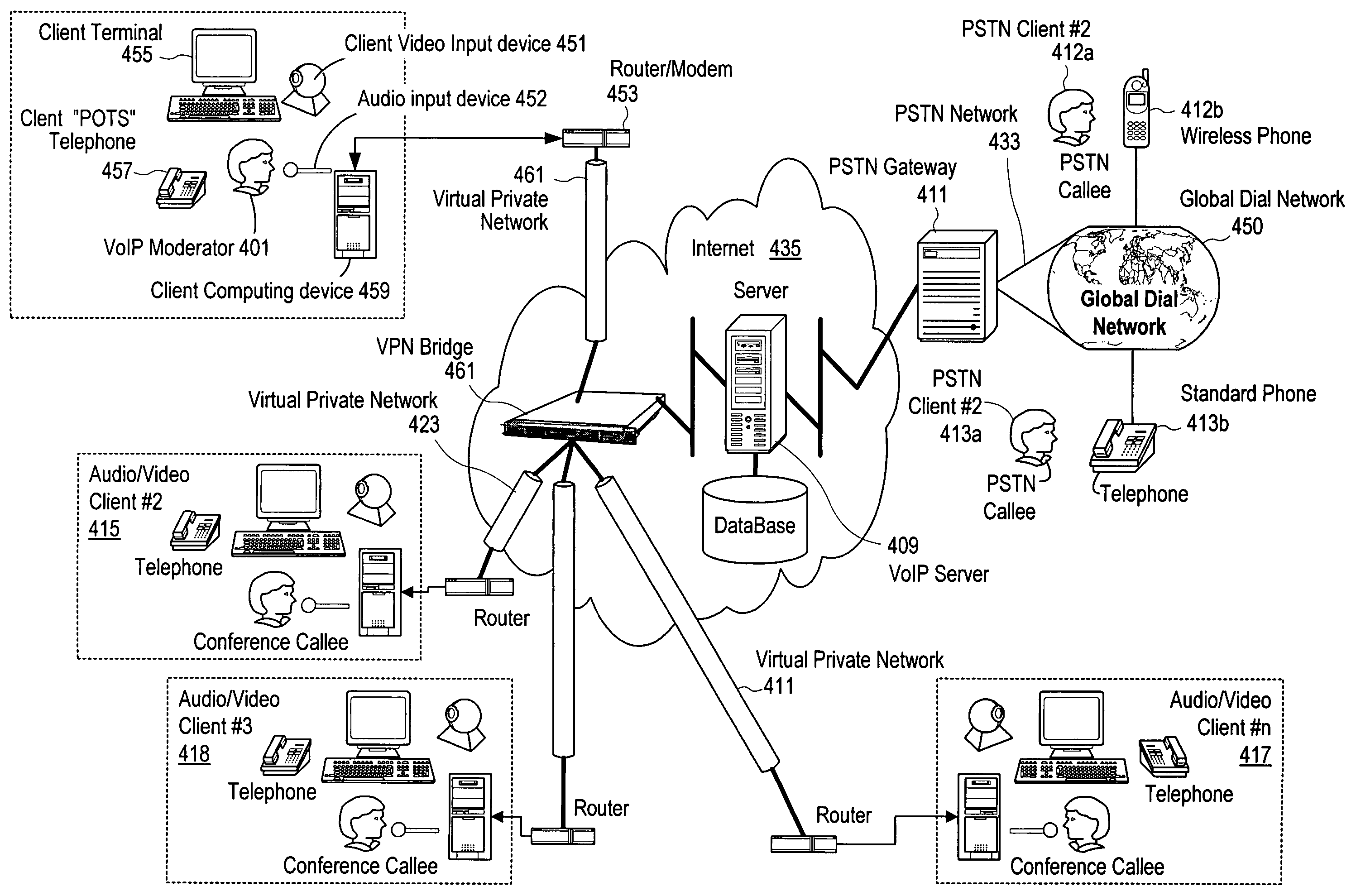
Media based collaboration using mixed-mode PSTN and internet networks
InactiveUS7664056B2Efficient transportMinimizes transport bandwidthMultiplex system selection arrangementsSpecial service provision for substationGeneral purposeInternet network
A method which allows standard telephone users to audio conference with video conferencing participants over IP networks in a private secure environment. A dial-out is performed from one or more conference client terminals bridging audio between the Internet and the PSTN networks. The process uses a mixed mode hybrid network architecture for call set-up, initialization and teardown including the method to mix audio at the desktop terminal instead of in a general purpose server as in the prior art. The method conferences video and audio between multiple clients and include audio from a standard telephone network within the conference. A virtual private network connects all of the IP clients together including the voice over IP server used to transcode the proprietary audio into the H.323 standard for transport into the telephony network.
Owner:MEETRIX IP LLC
Encapsulation, compression, and encryption of PCM data
InactiveUS7231027B2Minimum delayTelephone data network interconnectionsAutomatic exchangesSecurity policyEncryption
A system and method to provide secure access across the untrusted public switched telephone network is described. The system and method can be initiated by a security policy defining actions to be taken based upon at least one attribute of the call.
Owner:SECURELOGIX CORP
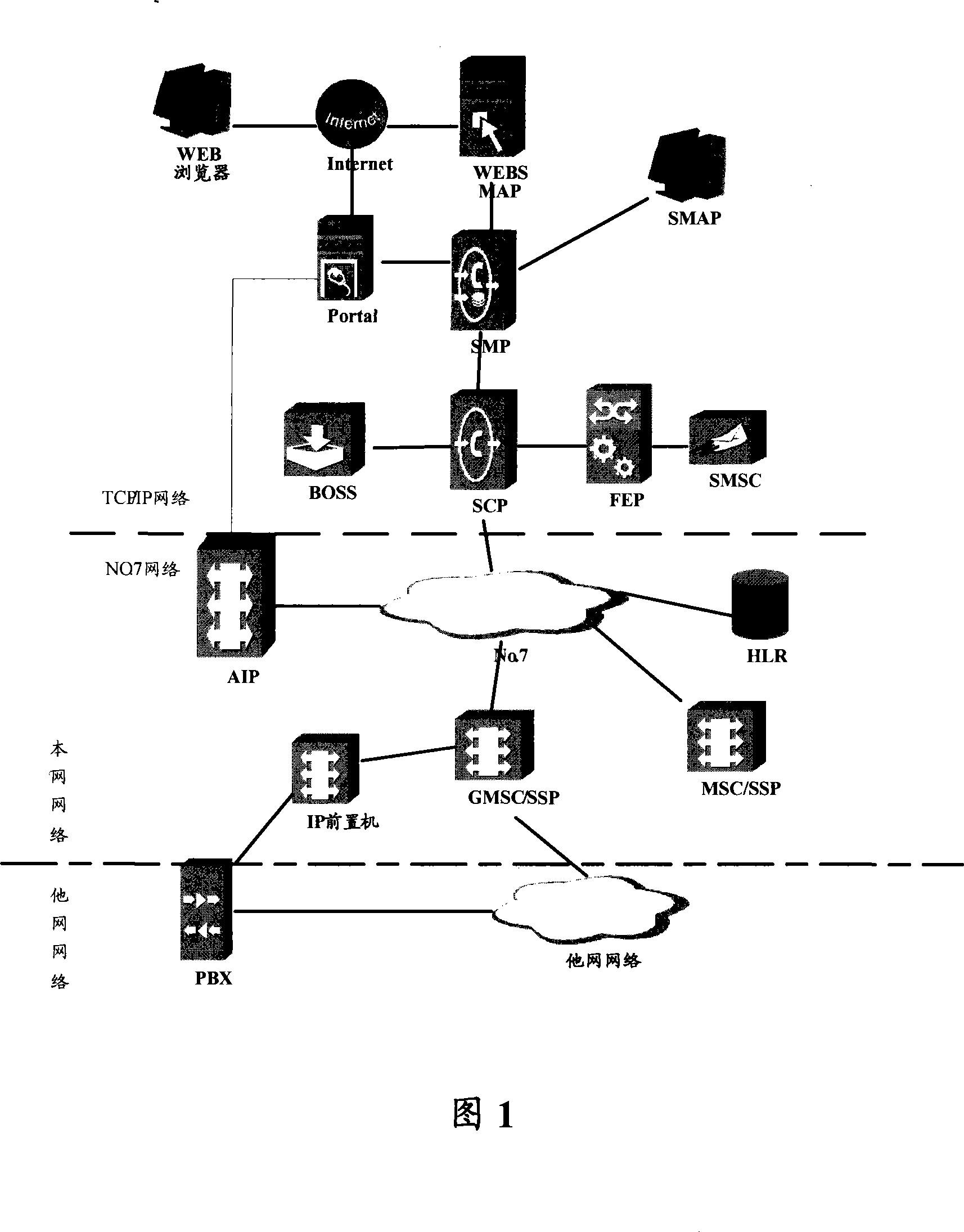
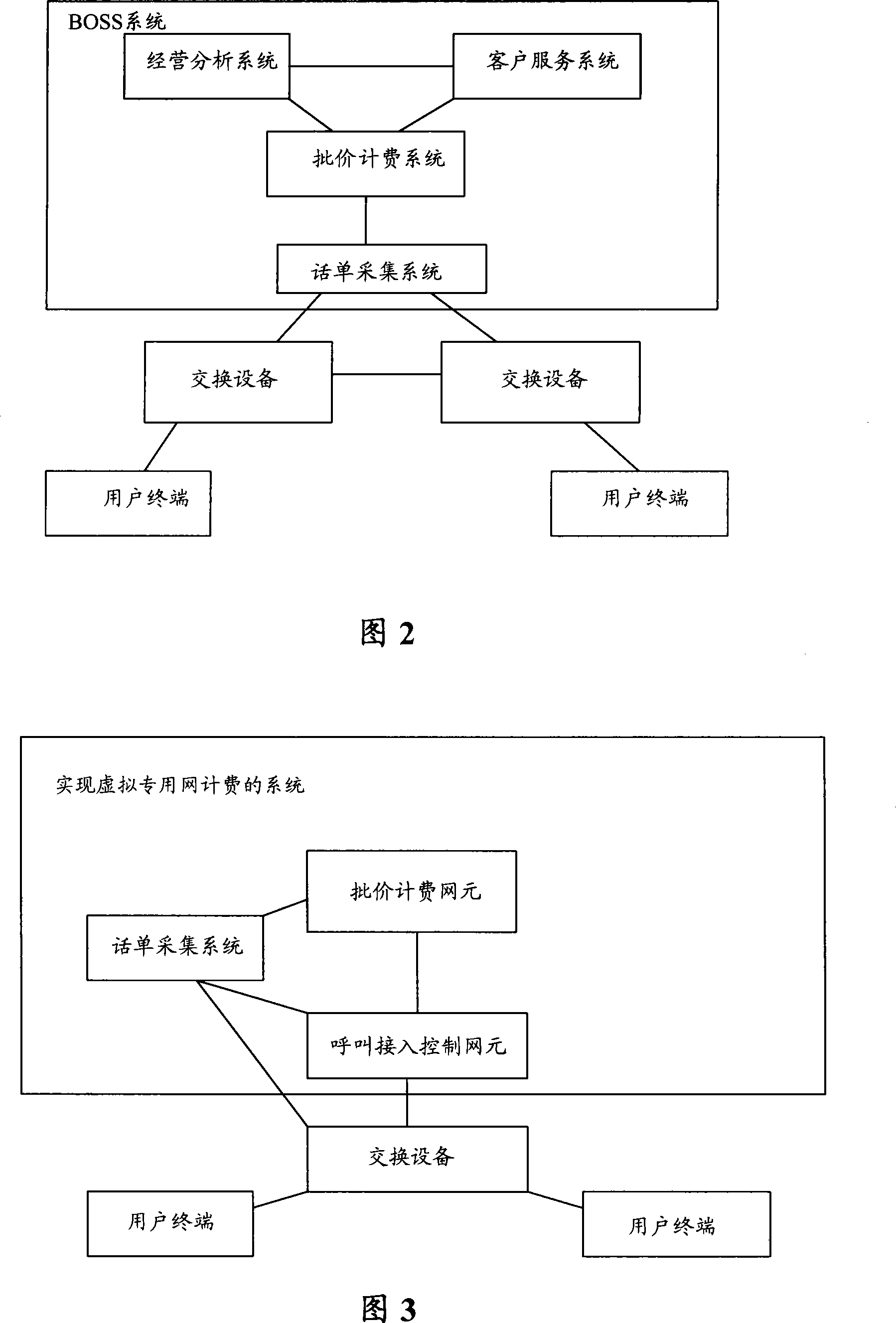
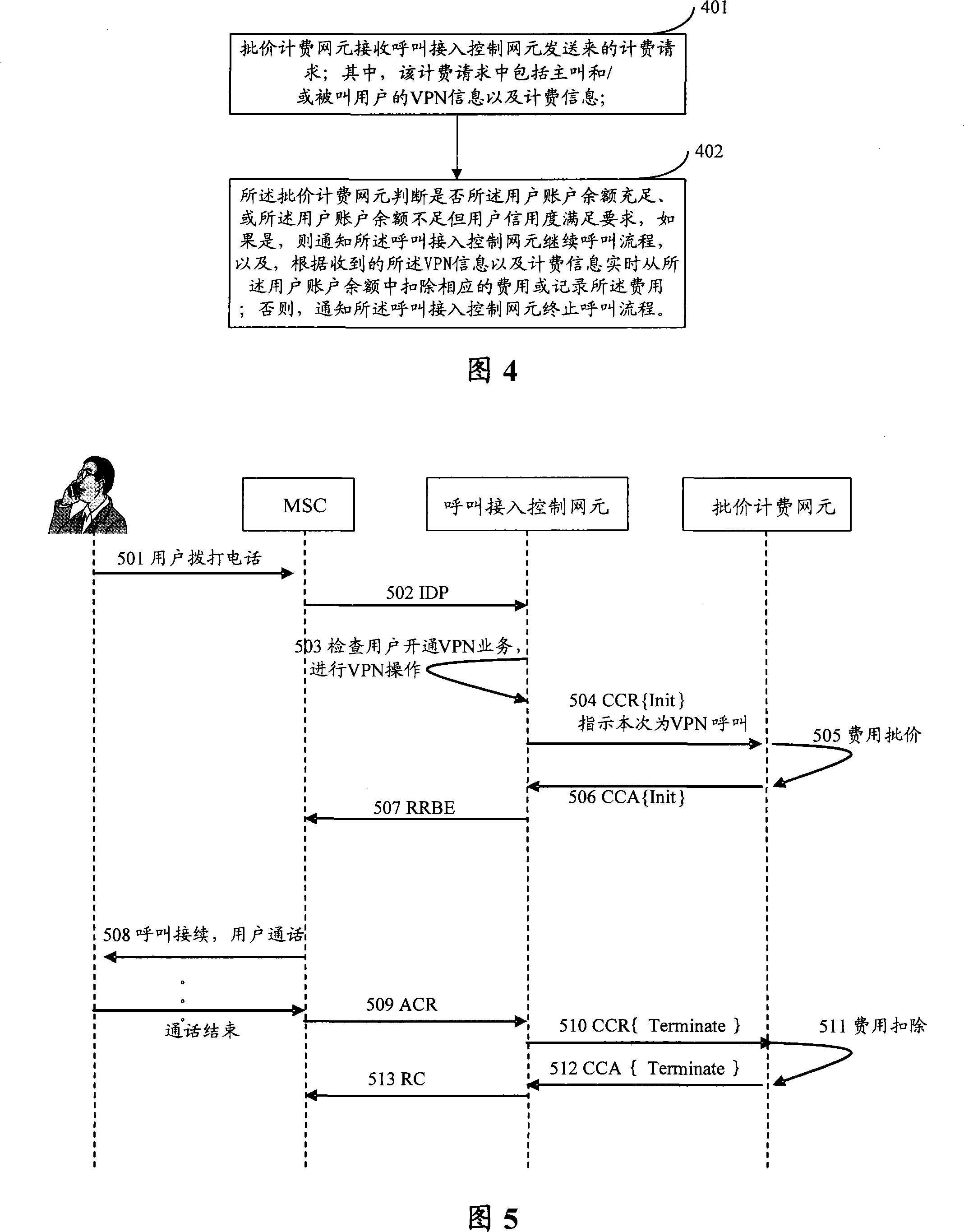
Method, device and system to realize virtual private network charging
InactiveCN101217384AFlexible switchingSame experienceMultiplex system selection arrangementsMetering/charging/biilling arrangementsPrivate networkComputer science
The embodiment of the invention discloses a method which realizes the accounting of virtual private networks and comprises the following steps that an accounting network element receives and calls the accounting requests sent by an access control network element; wherein, the accounting requests comprise the VPN information and accounting information of call subscribers and / or called subscribers; the accounting network element judges whether the user account balance is adequate, or whether the user account balance is insufficient but the credits of users meet the requirements, if yes, the access control network element is informed to go on with the call flow and deducts corresponding expenses from the user account balance or records the expenses real-timely according to the received VPN information and the accounting information, otherwise, the access control network element is informed to stop the call flow. The embodiment of the invention also discloses a device and a system which realize the accounting of virtual private networks. With the adoption of the embodiment of the invention, the mutual fusion of prepayment and postpaid accounting can be well realized, which ensures different users to get the same experience.
Owner:HUAWEI TECH CO LTD
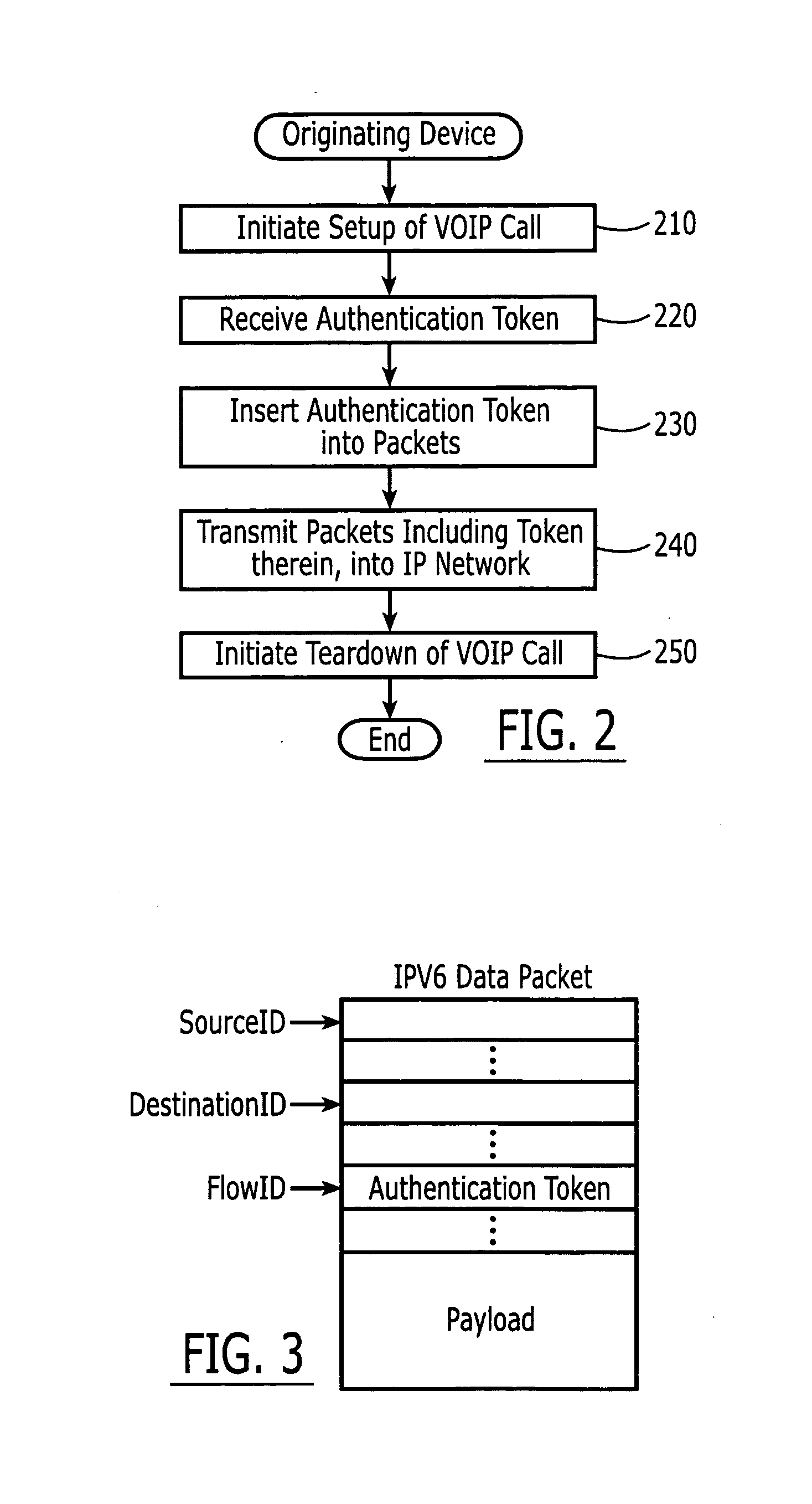
Authentication tokens for Voice over Internet Protocol (VOIP) calling, and VOIP devices, methods and computer program products using same
InactiveUS20070201447A1Easy to useDigital data processing detailsMultiple digital computer combinationsData packSpeech sound
Setup of a Voice over Internet Protocol (VoIP) call is initiated and an authentication token is received for the VoIP call that is set up, that indicates that the VoIP call is authorized. The authentication token is inserted into packets for the VoIP call. The packets, including the authentication token therein, are transmitted into an IP network. The authentication token may be placed in an IP version 6 (IPv6) flowID field.
Owner:BELLSOUTH INTPROP COR
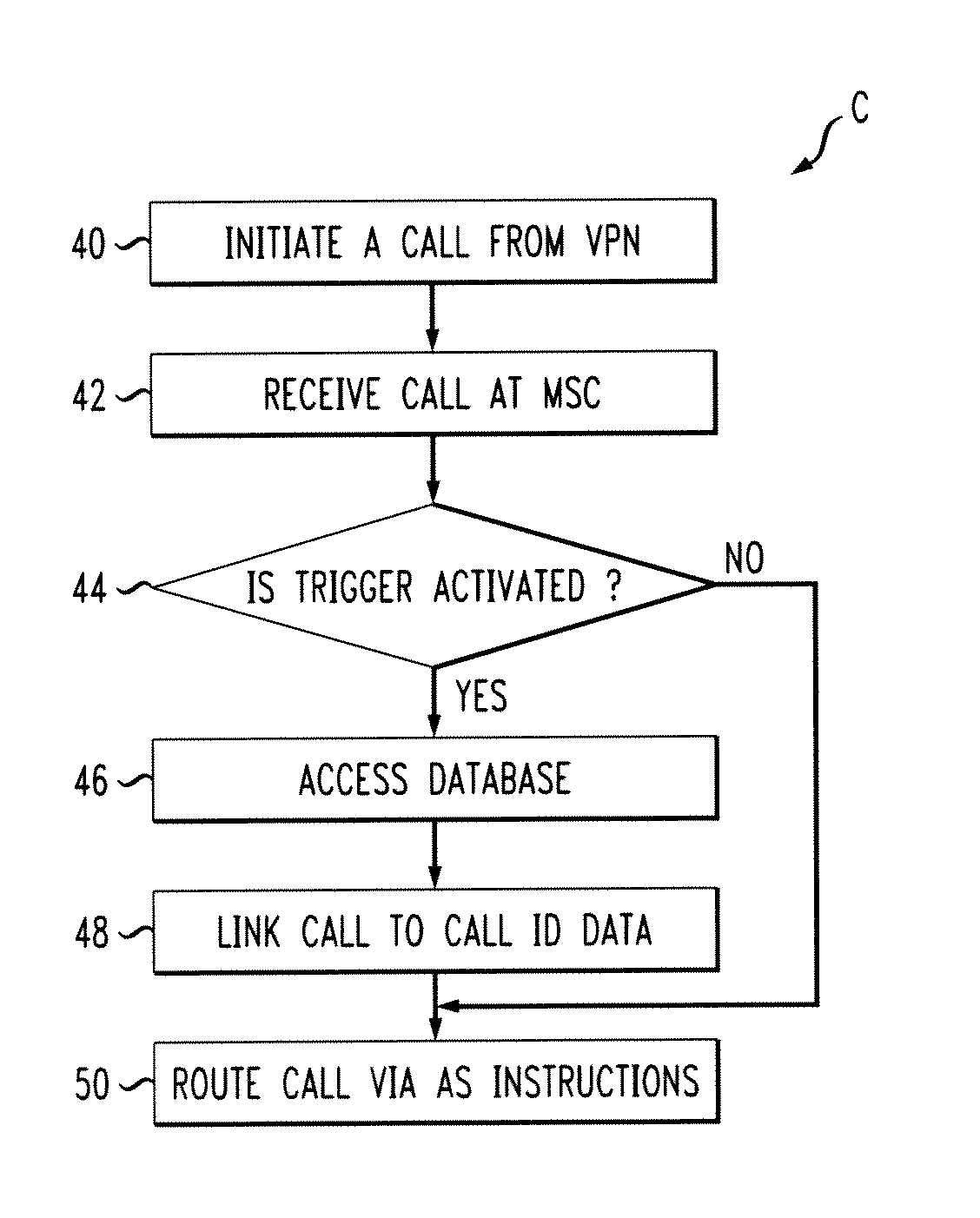
Method and apparatus for linking identification data to a call in a network
InactiveUS7929544B2Multiplex system selection arrangementsData switching by path configurationApplication serverPrivate network
A method and apparatus for linking caller identification data to a call that originates from a virtual private network is disclosed. Steps relating to the method receiving a call, including an identifier at a mobile switching center. The identifier would identify a termination point that initiated the call. The method also includes accessing a database with call identification information in response to a trigger and linking the call with caller identification data via the identifier. The method could also include that the call is received from a cellular VPN. The system implementing the method would include a database having stored within caller identification data corresponding to an identifier, a mobile switching center configured to receive the call from a VPN and an application server configured to access the database and link the call.
Owner:ALCATEL-LUCENT USA INC
Media Based Collaboration Using Mixed-Mode PSTN and Internet Networks
ActiveUS20110043601A1Minimizes transport bandwidthSpecial service provision for substationMultiplex system selection arrangementsGeneral purposeInternet network
A method which allows standard telephone users to audio conference with video conferencing participants over IP networks in a private secure environment. A dial-out is performed from one or more conference client terminals bridging audio between the Internet and the PSTN networks. The process uses a mixed mode hybrid network architecture for call set-up, initialization and teardown including the method to mix audio at the desktop terminal instead of in a general purpose server as in the prior art. The method conferences video and audio between multiple clients and include audio from a standard telephone network within the conference. A virtual private network connects all of the IP clients together including the voice over IP server used to transcode the proprietary audio into the H.323 standard for transport into the telephony network.
Owner:MEETRIX IP LLC
Systems and methods for call routing
InactiveUS20080123831A1Multiplex system selection arrangementsInterconnection arrangementsCall routingMobile phone
Systems and methods for call routing are shown and described. The method can include receiving, at a site external to a mobile telephone network, an incoming telephone call via a first fixed line telephone number, signaling a mobile telephone network to initiate a call to the site external to the mobile telephone network, receiving a second incoming call from a mobile telephone of the mobile telephone network via a second fixed line telephone number, and connecting the first incoming telephone call to the second incoming telephone call to establish a connected call.
Owner:GOHELLO
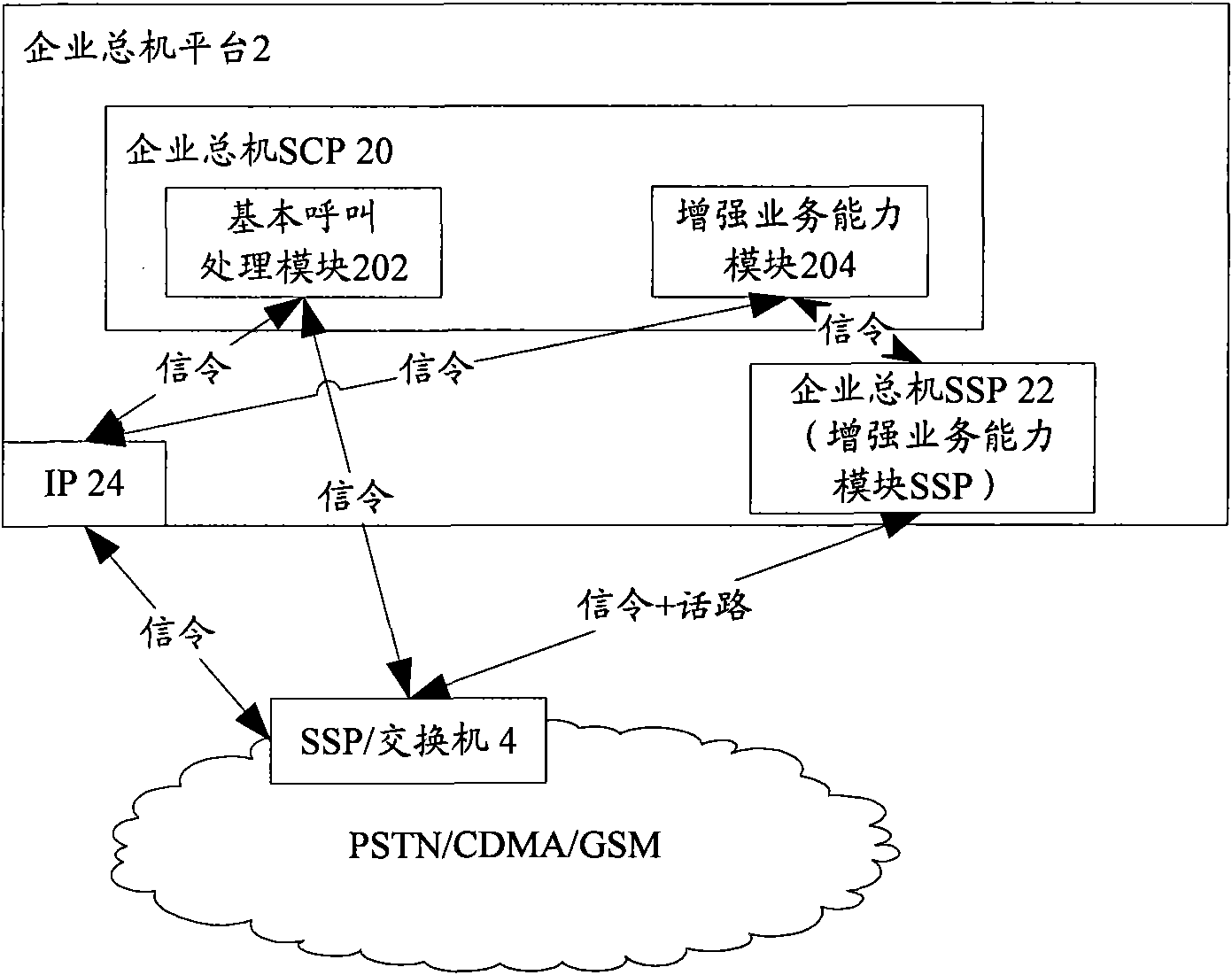
Enterprise telephone exchange platform and call processing method
InactiveCN101808168ARich business featuresReduce detour overheadSpecial service for subscribersVirtual private networksTelecommunicationsSystem capacity
The invention discloses an enterprise telephone exchange platform and a call processing method. The enterprise telephone exchange platform comprises an enterprise telephone exchange service control point, an enterprise telephone exchange service exchange point and an intelligent peripheral, wherein the enterprise telephone exchange service control point comprises a basic call processing module and a service capability enhancement module; the basic call processing module is used for judging whether current network exchange equipment can support a call triggered by an exchange network service exchange point or not and transmitting the call to the service capability enhancement module when judging that the current network exchange equipment cannot support the call triggered by the exchange network service exchange point; and the service capability enhancement module is used for controlling the intelligent peripheral and the enterprise telephone exchange service exchange point to perform the service associated with the call. Through the technical scheme, compared with an enterprise telephone exchange system based on an intelligent platform technique, the enterprise telephone exchange platform provides larger system capacity and reduces network weaving expenditure.
Owner:ZTE CORP
Intelligent network and method for providing voice telephony over ATM and private address translation
InactiveUS20050083914A1Efficiently using ATM bandwidthLower cost of capitalIntelligent networksHybrid switching systemsIntelligent NetworkPrivate address
An illustrative intelligent network and method for providing voice telephony over Asynchronous Transfer Mode (“ATM”) and private address translation are provided that can provide significant advantages. The method includes generating an input ATM setup message at the calling party CPE that includes a VToA designator and a called party phone number, extracting information from the input ATM setup message such as the VToA designator and the called party phone number, analyzing the information, designating an ATM address of a called party CPE to be stored in the first parameter of an output ATM setup message, determining if private address translation is needed, designating the ATM address of the called party CPE to be stored in a first instance of the second parameter of the output ATM setup message, designating an ATM address of an egress ATM edge switch to be stored in the first parameter of the output ATM setup message, and generating an output ATM setup message. The method also includes extracting information from the output ATM setup message such as the ATM address of the called party CPE, designating the ATM address of the called party CPE that was stored in the first instance of the second parameter of the output ATM setup message to be stored in the first parameter of a destination ATM setup message, and generating a destination ATM setup message that includes the ATM address of the called party CPE stored in the first parameter and the called party phone number value stored in the second parameter. An illustrative intelligent network for providing VToA and private address translation is also provided.
Owner:VERIZON PATENT & LICENSING INC
Telephone exchange apparatus
InactiveCN101083682AInterconnection arrangementsAutomatic exchangesTelephone terminalTelephone exchange
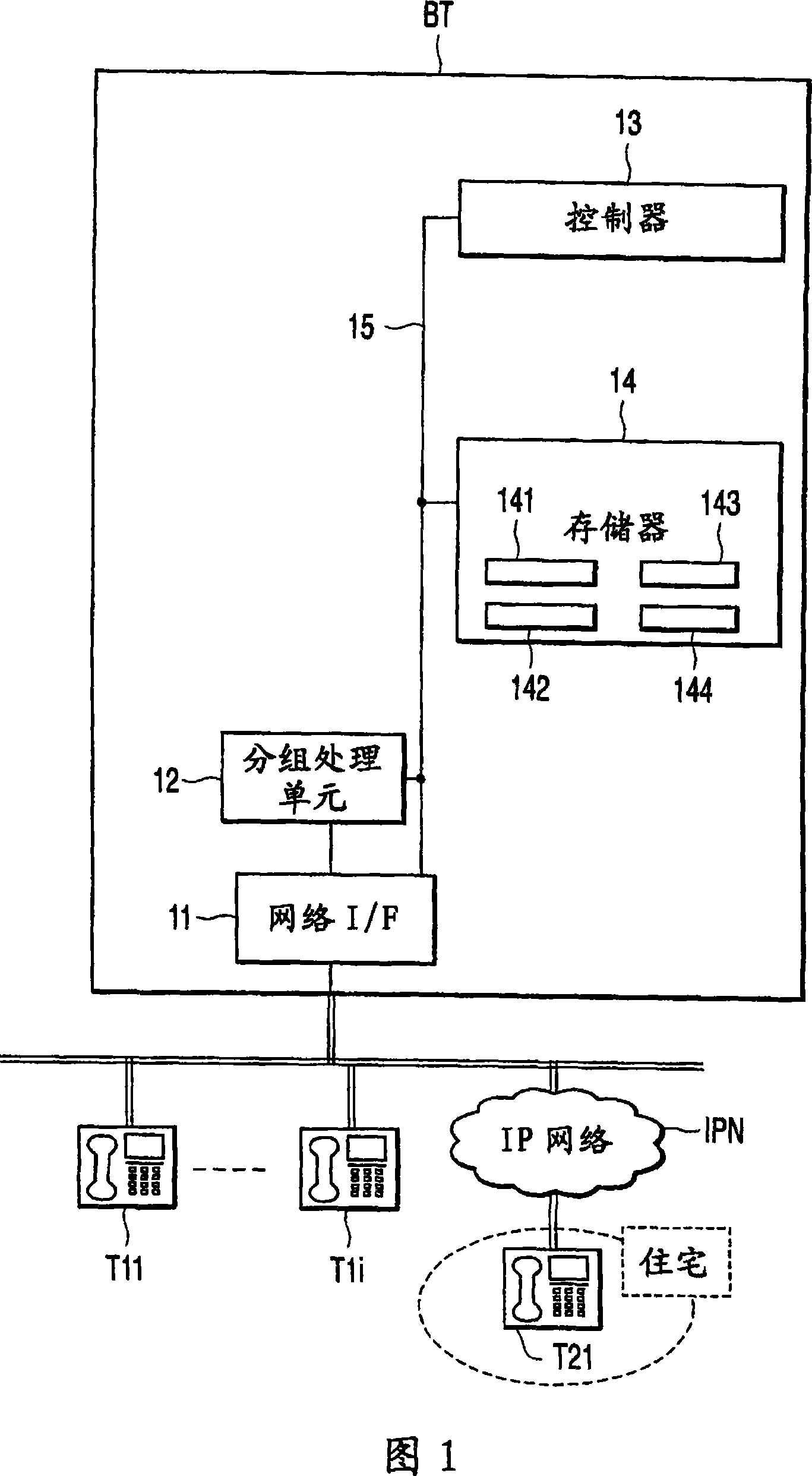
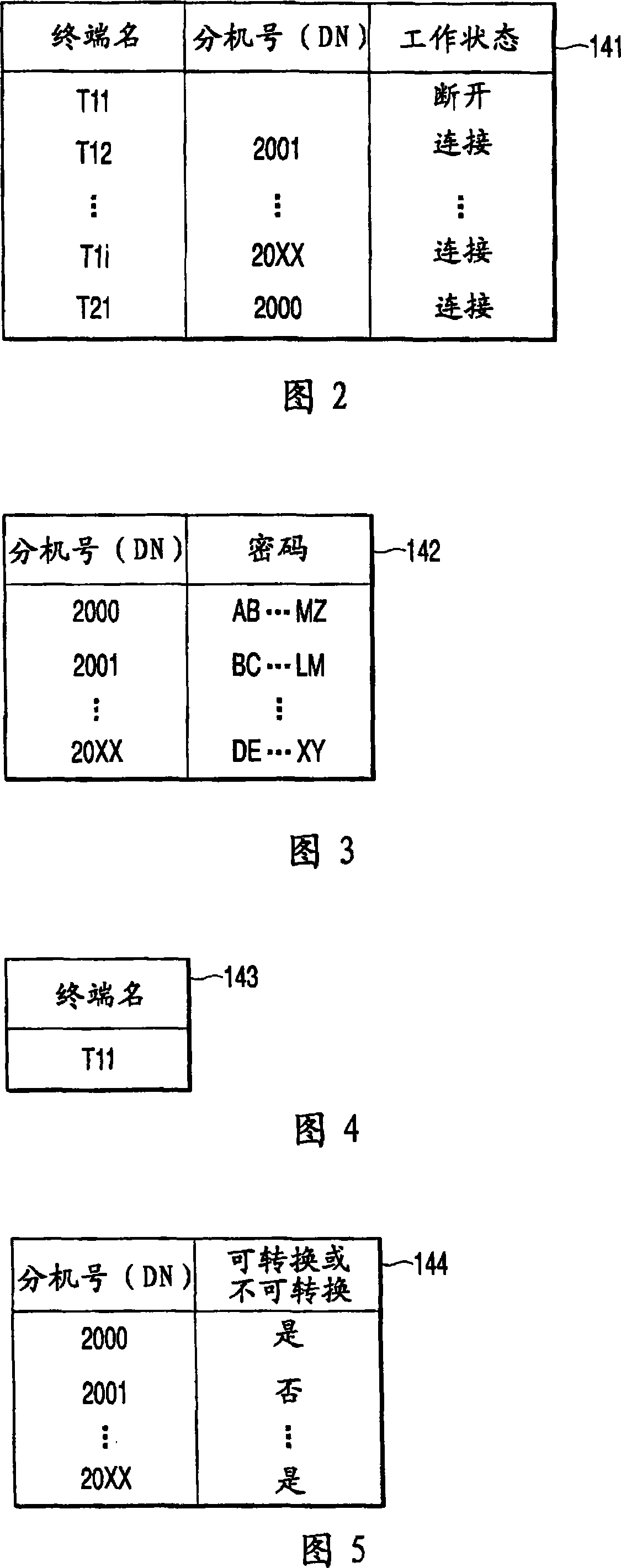
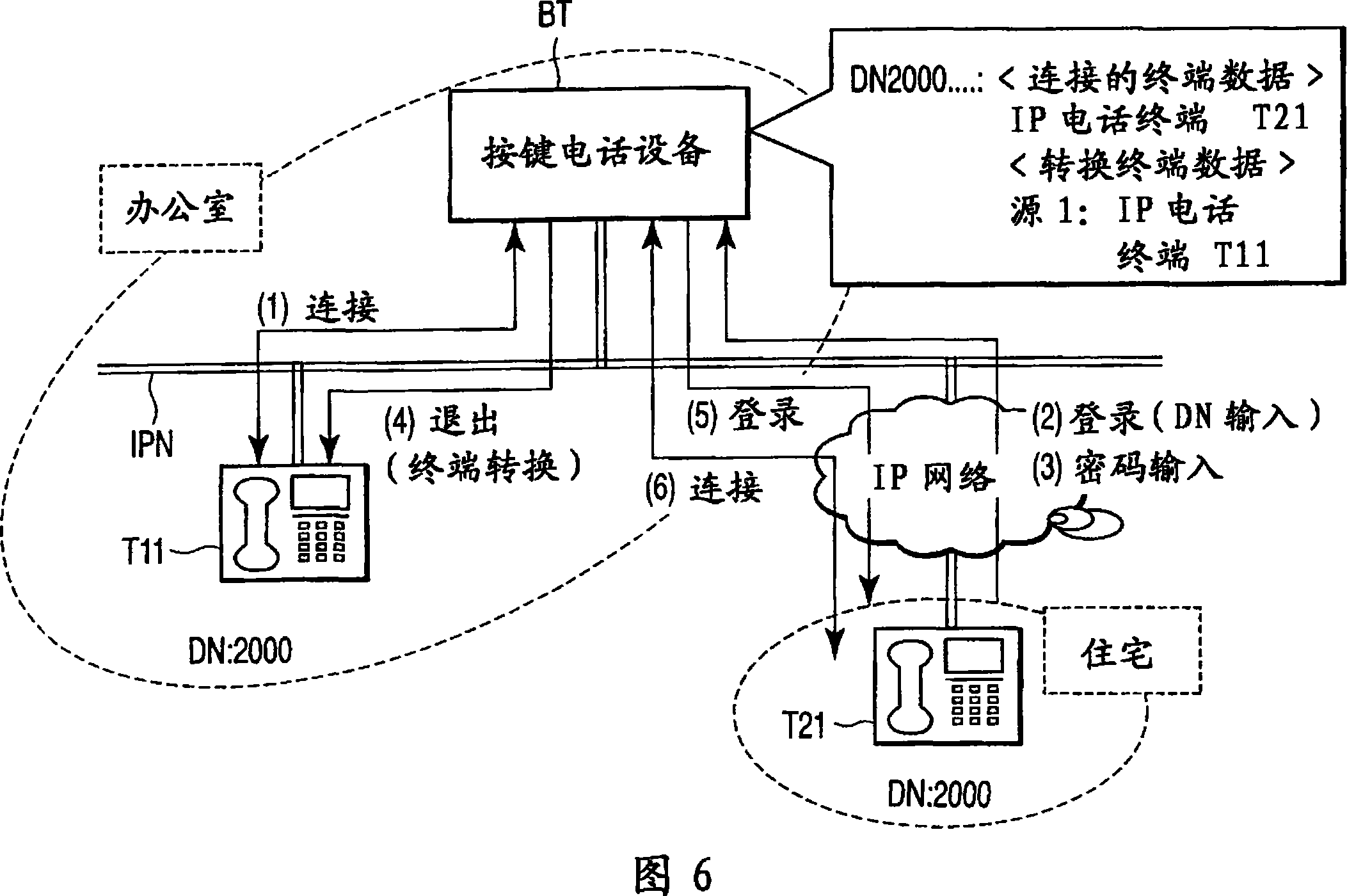
According to one embodiment, a telephone exchange apparatus which accommodates a plurality of telephone terminals includes a memory(14) to store a management table wherein a terminal identification data (terminal ID) and a connection identification data (connection ID) correspond to an operation data indicating a connected / disconnect status with respect to each of the plurality of telephone terminals, and a controller(13) to connect communication between the plurality of telephone terminals in operation based on the management table, and to update the operation data corresponding to the terminal ID of the relevant telephone terminal within the management table based on a predetermined condition.
Owner:KK TOSHIBA
Network communication system including a database of codes and corresponding telephone numbers
ActiveUS7426384B2Interconnection arrangementsNetwork topologiesCommunications systemNetwork communication
This disclosure concerns systems and methods for network communications. In one example, the method includes: providing subscriber terminals of each network with a respective publicly-known telephone number for allowing communications to be addressed to each subscriber terminal; associating selected subscriber terminals of each network together in a group such that those subscriber terminals can address communications to one another using a respective code allocated to each of the selected subscriber terminals; and, maintaining a database of the codes and corresponding publicly-known telephone numbers of all of the networks and providing to one of the networks a publicly-known telephone number corresponding to a code of a subscriber terminal of another one of the networks to allow communication from a subscriber terminal of one of the networks to be addressed to a subscriber terminal of the other of the networks using the code of the latter subscriber terminal.
Owner:VODAFONE GRP PLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com