Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
45 results about "Protected health information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
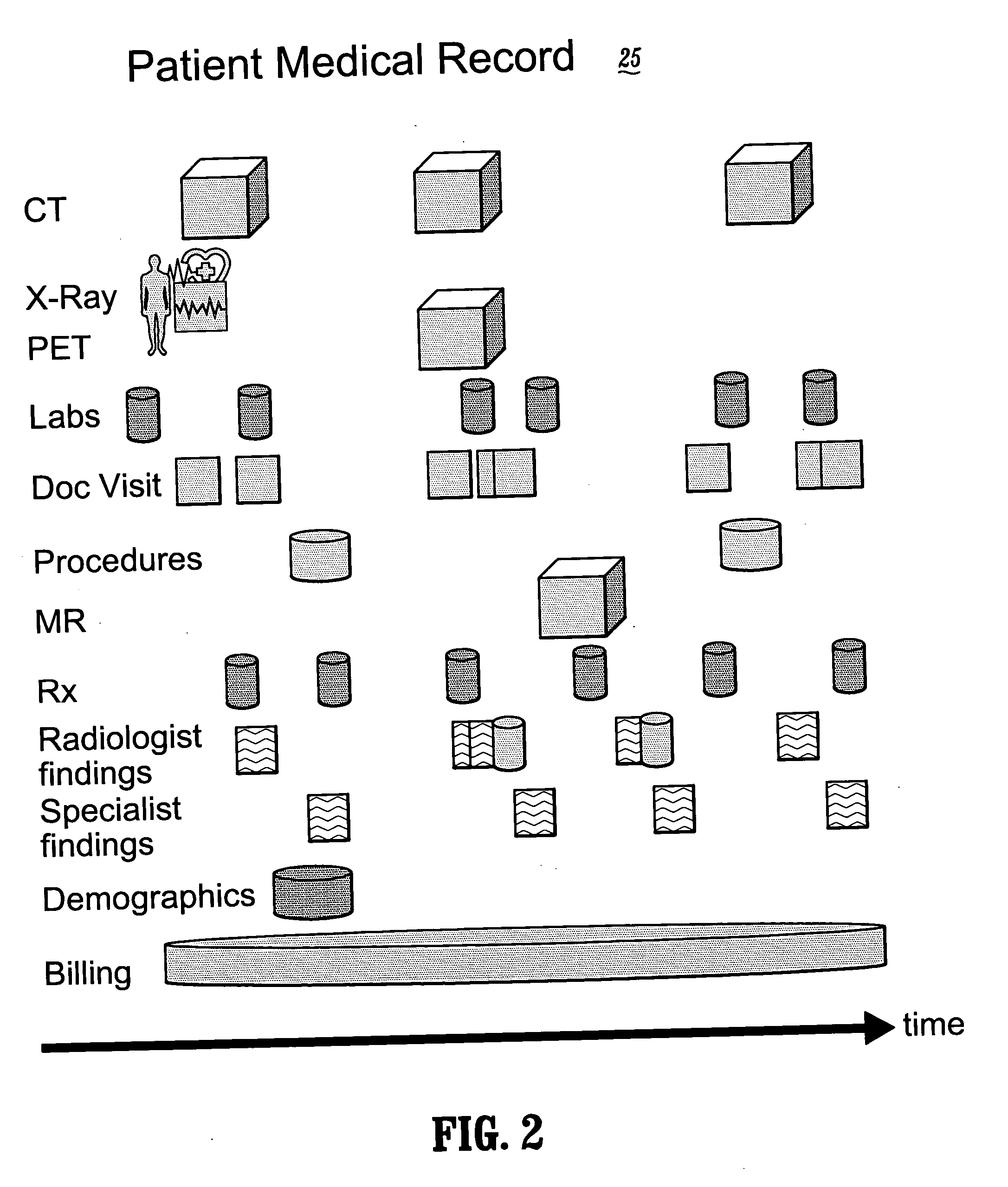
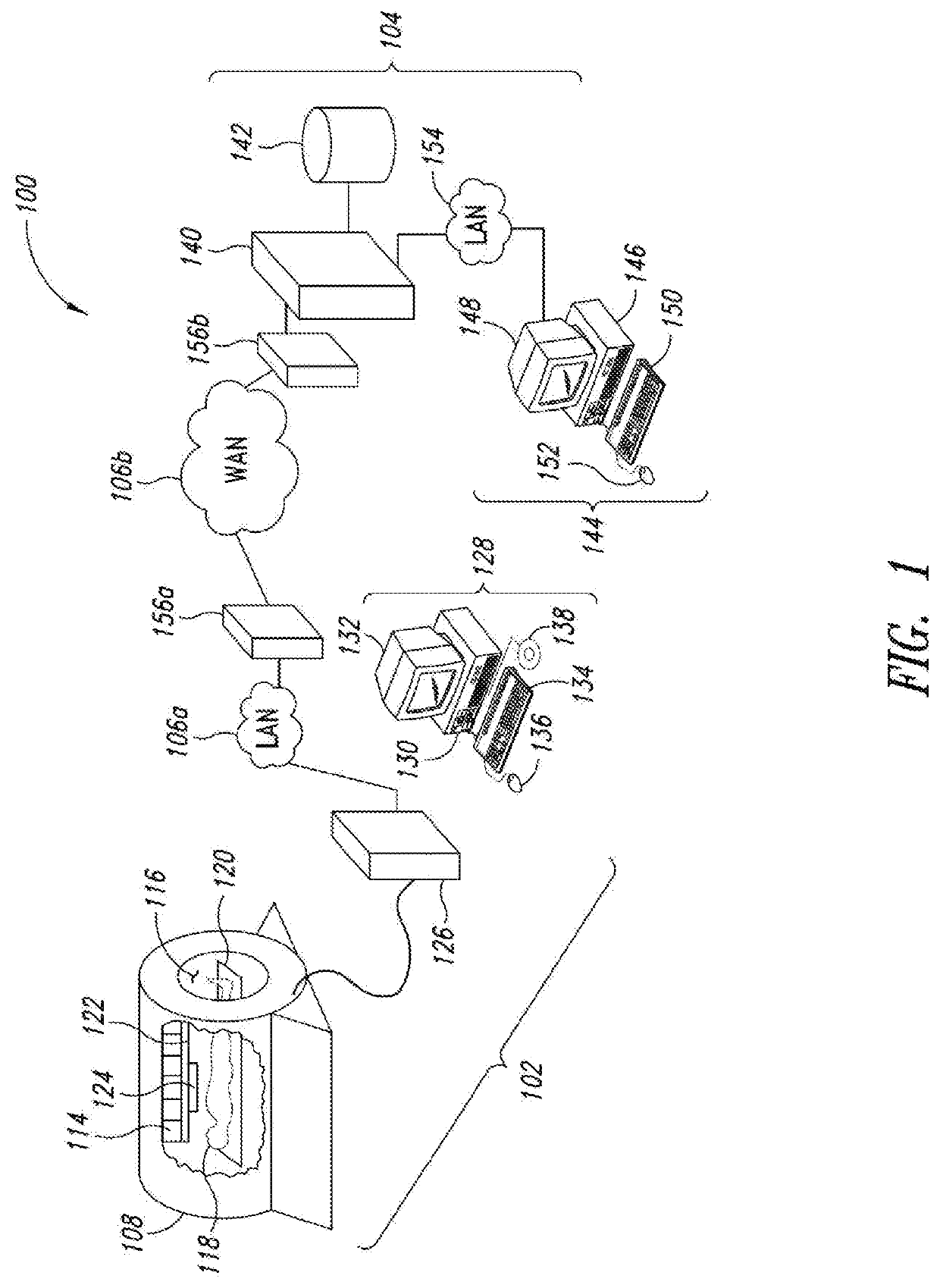
Protected health information (PHI) under the US law is any information about health status, provision of health care, or payment for health care that is created or collected by a Covered Entity (or a Business Associate of a Covered Entity), and can be linked to a specific individual. This is interpreted rather broadly and includes any part of a patient's medical record or payment history.
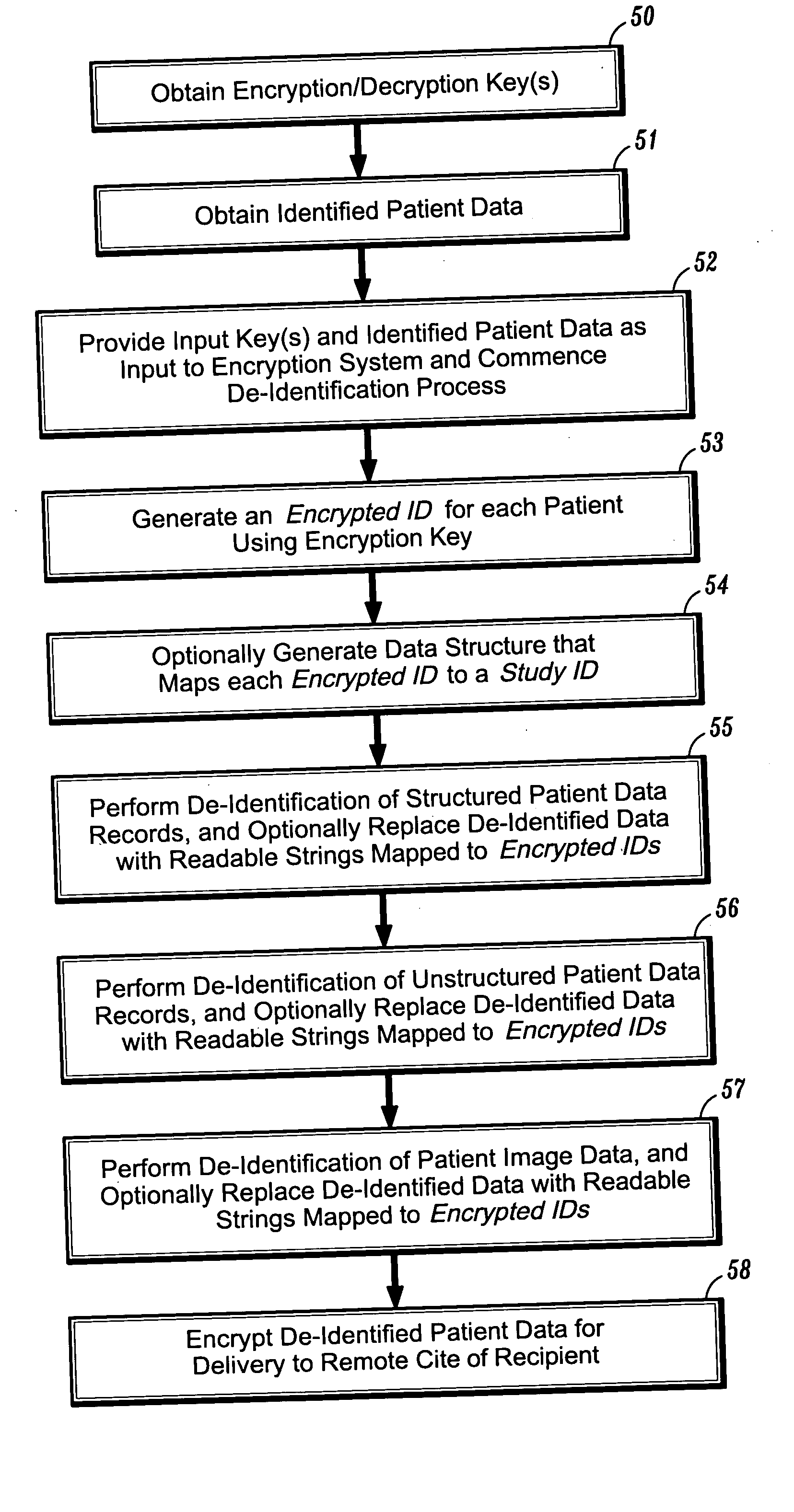
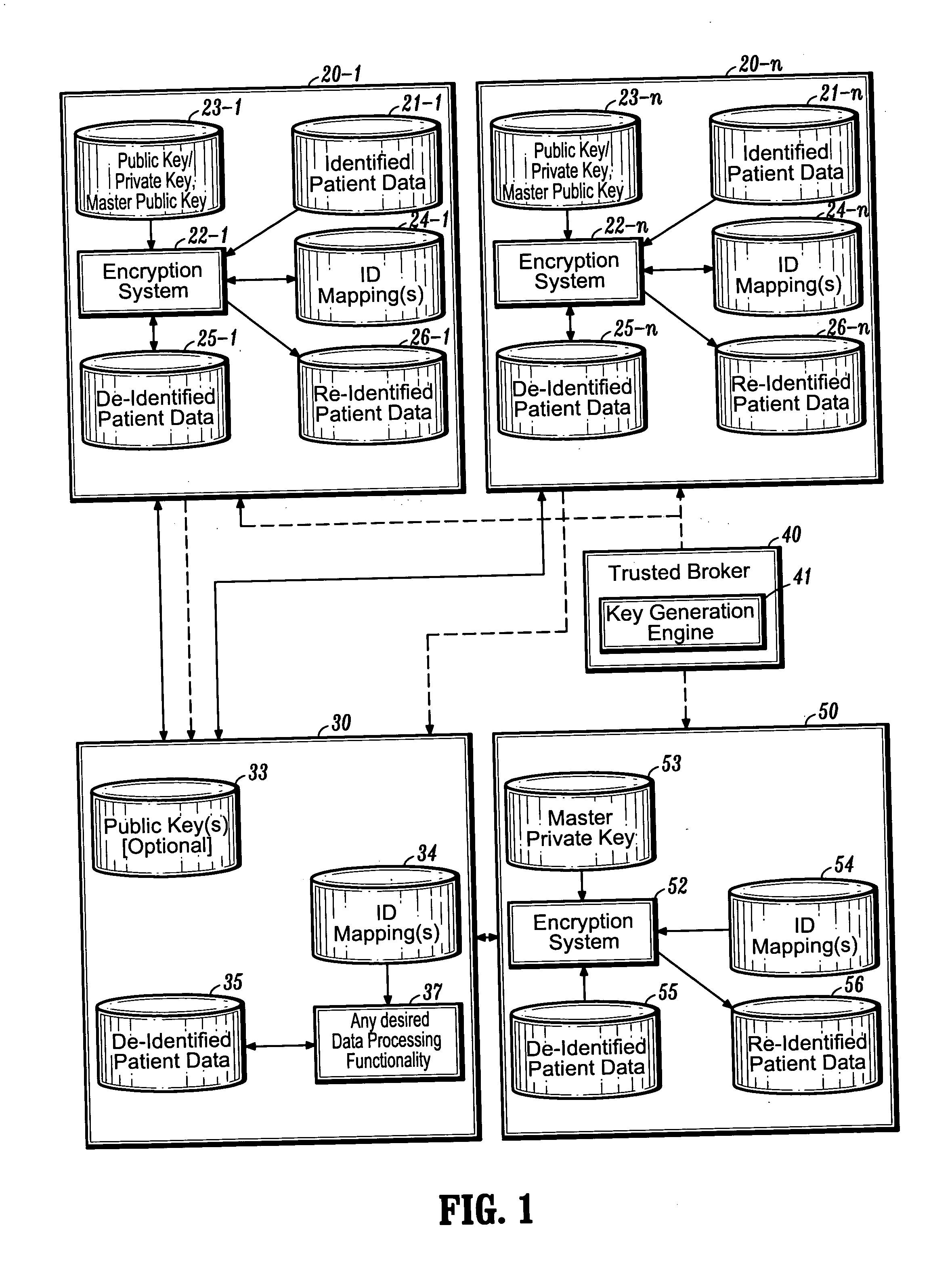
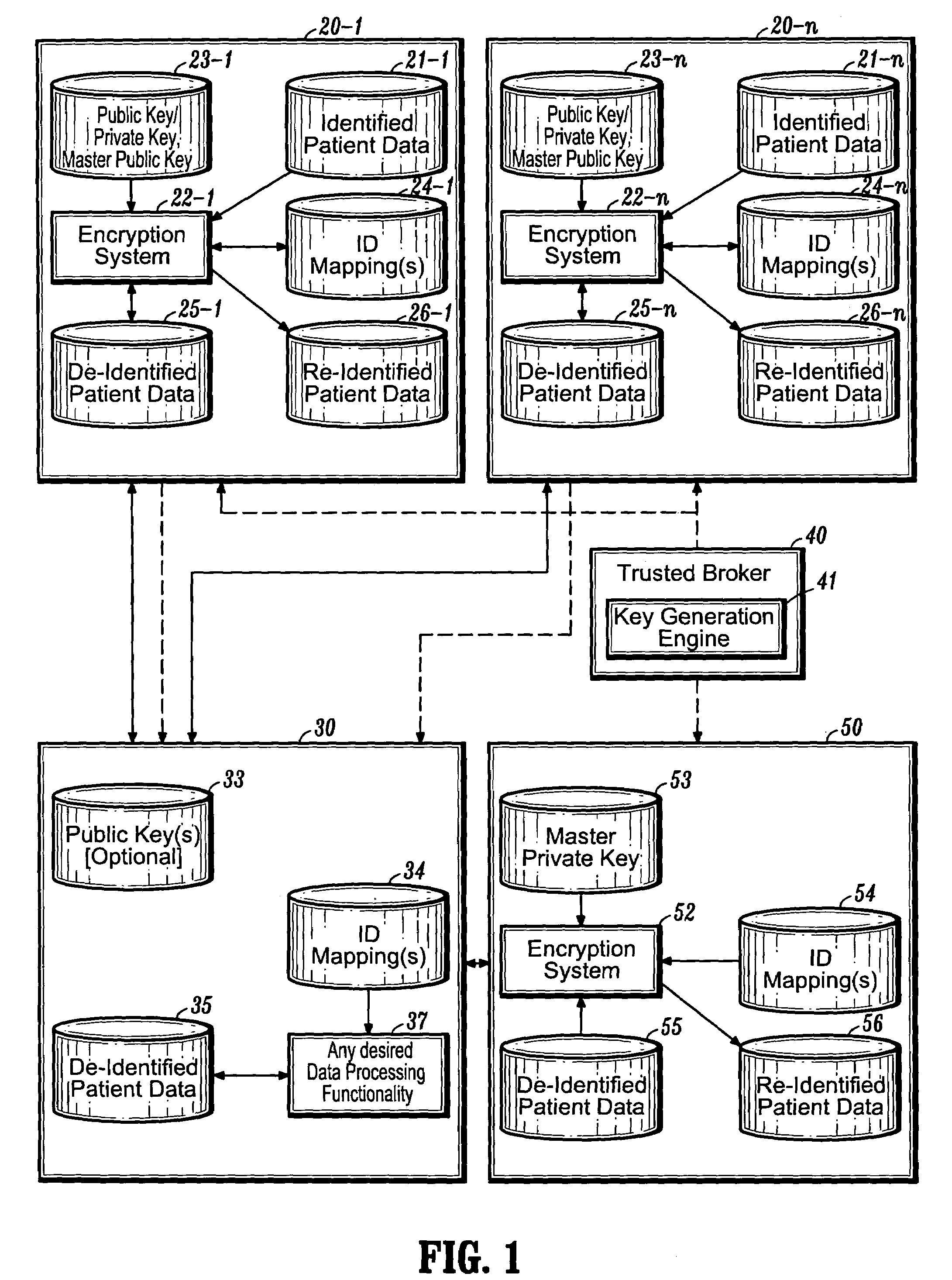
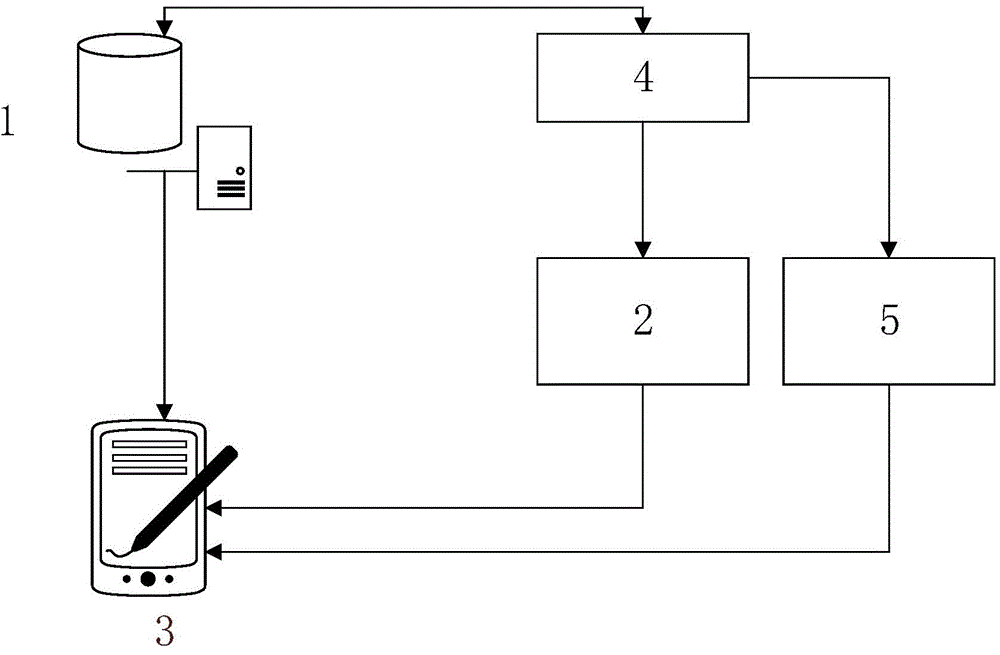
Systems and methods for encryption-based de-identification of protected health information
ActiveUS20050165623A1Ensuring privacyData processing applicationsMultiple keys/algorithms usagePatient dataProtected health information
Systems and methods are provided for protecting individual privacy (e.g., patient privacy) when individual data records (e.g., patient data records) are shared between various entities (e.g., healthcare entities). In one aspect, systems and methods are provided which implement secured key encryption for de-identifying patient data to ensure patient privacy, while allowing only the owners of the patient data and / or legally empowered entities to re-identify subject patients associated with de-identified patient data records, when needed.
Owner:CERNER INNOVATION
Systems and methods for encryption-based de-identification of protected health information
ActiveUS7519591B2Data processing applicationsMultiple keys/algorithms usageInternet privacyPatient data
Owner:CERNER INNOVATION
Computerized method and system for restricting access to patient protected health information
InactiveUS20100077487A1Prevents unauthorized disclosureImprove securityMechanical/radiation/invasive therapiesDigital data processing detailsLimited accessComputerized system
Owner:CERNER INNOVATION
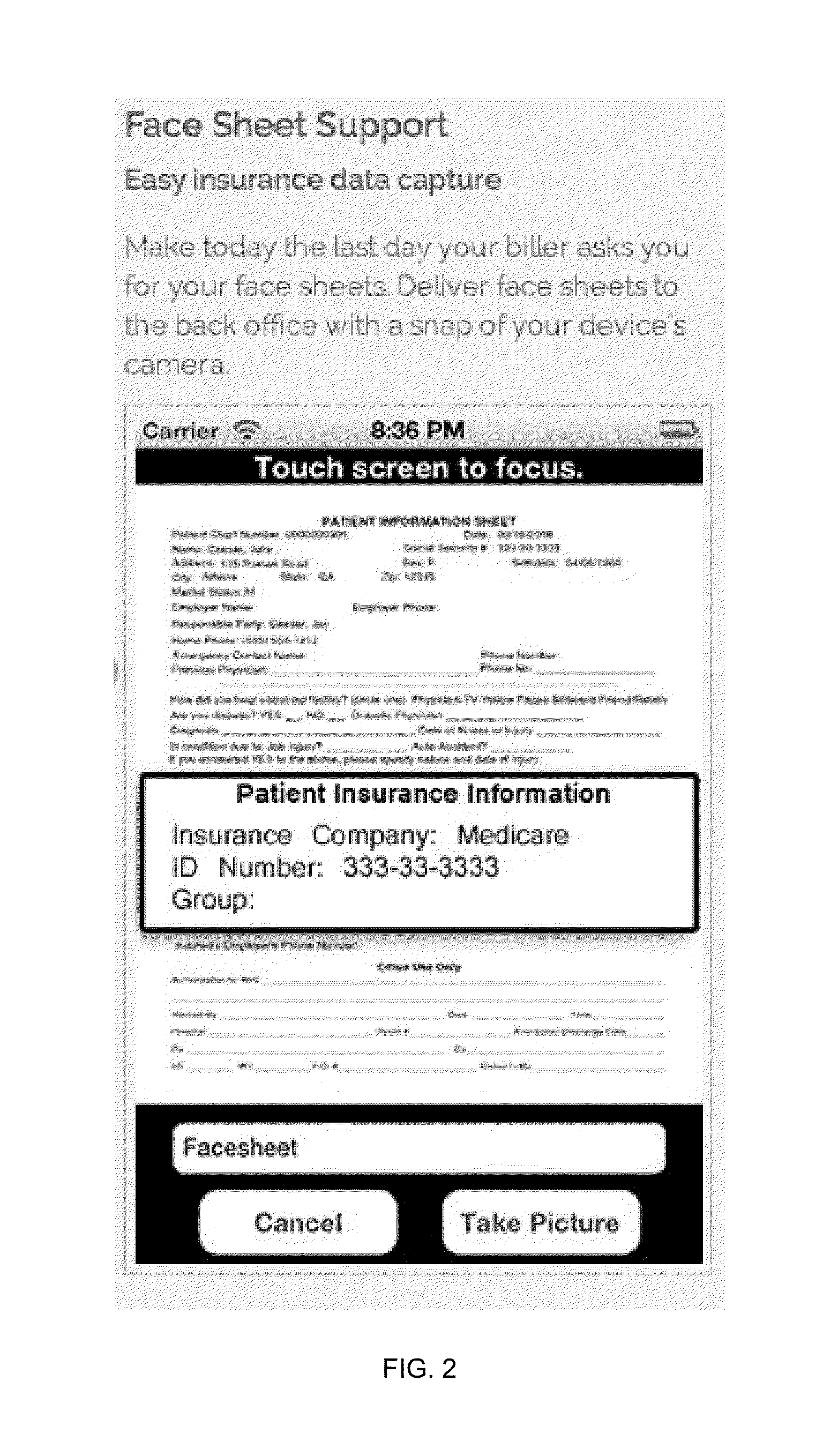
Physician documentation workflow management methods
InactiveUS20100094656A1Facilitate communicationComputer-assisted medical data acquisitionHospital data managementMedical recordPhysicians Assistants
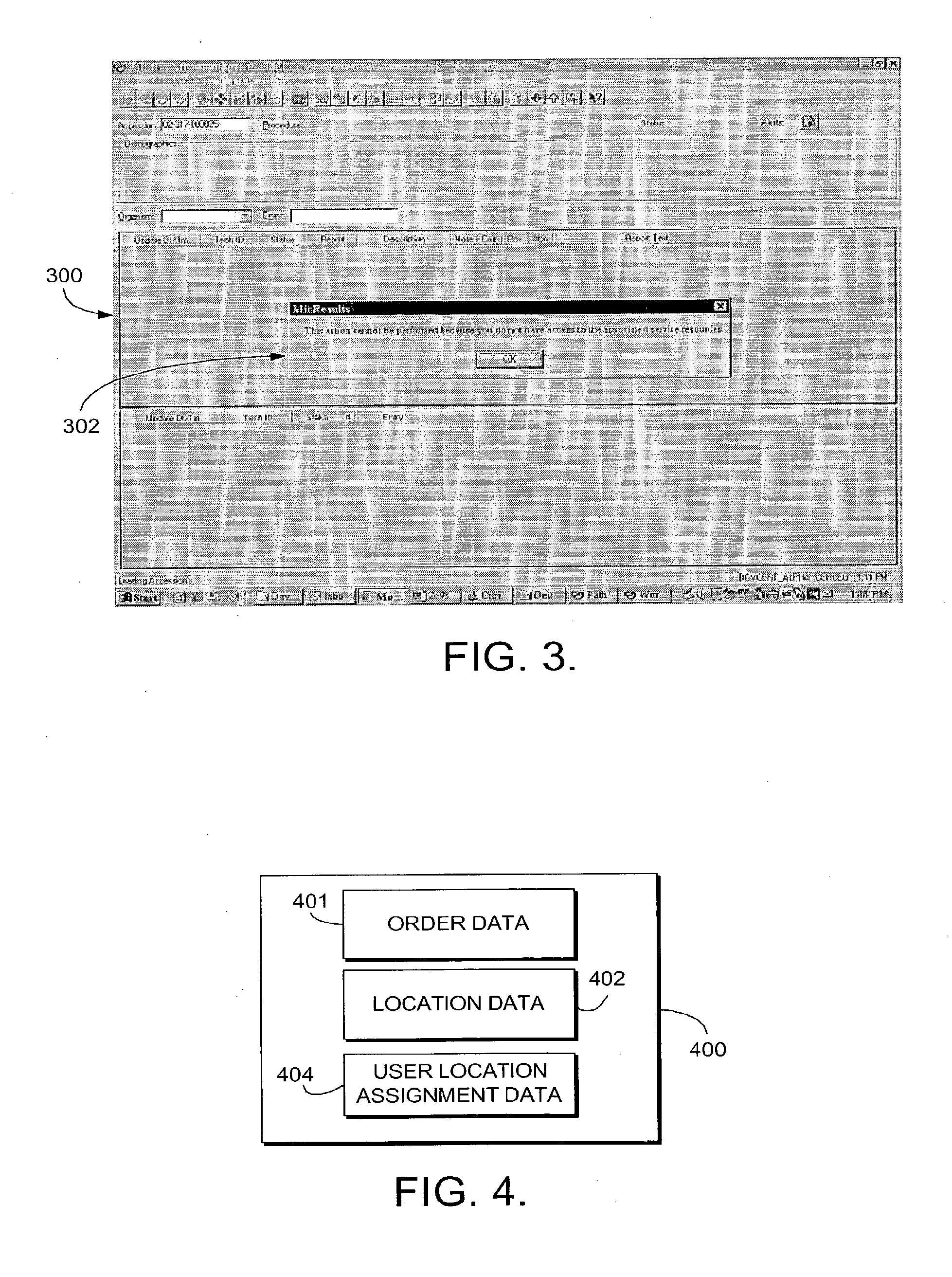
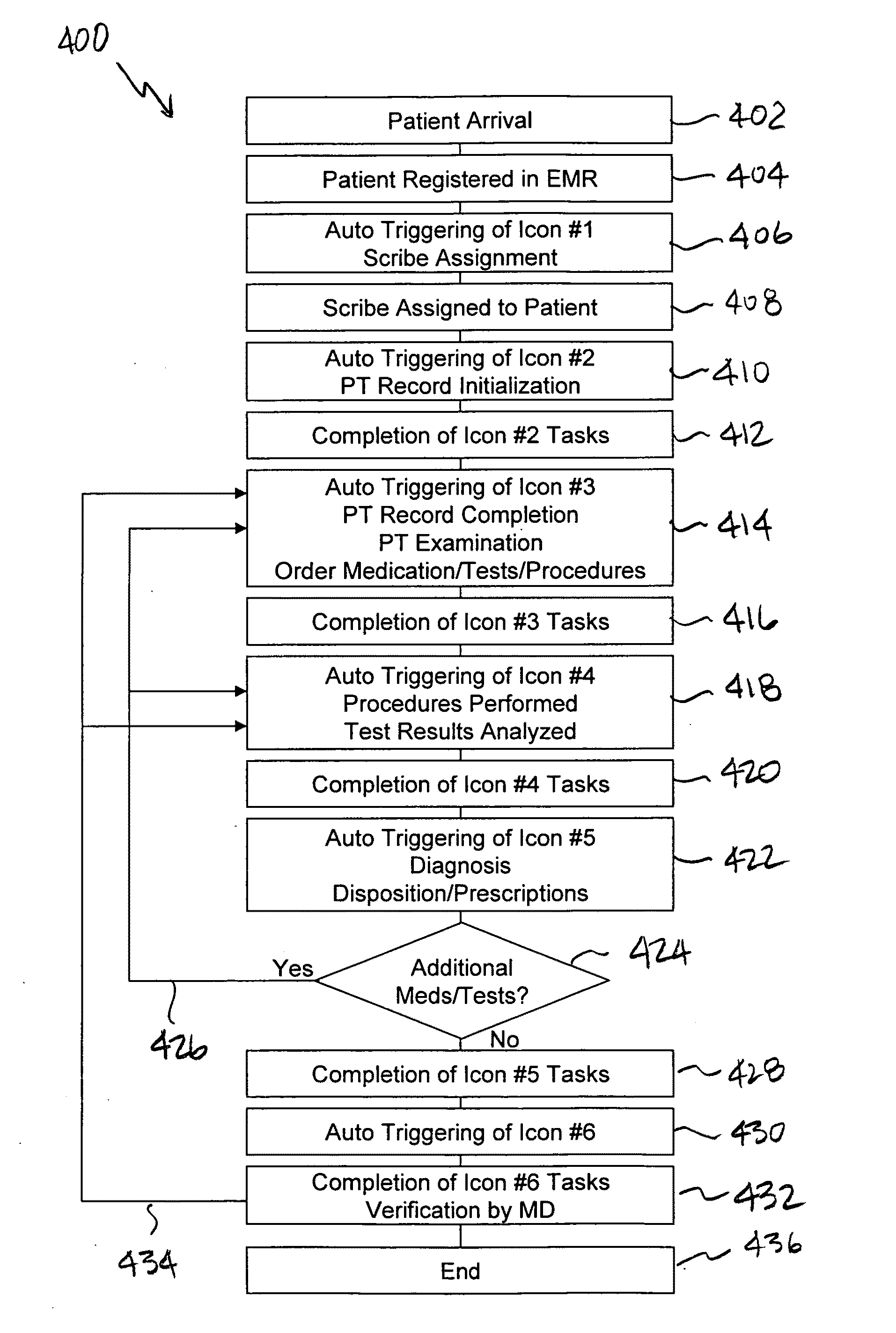
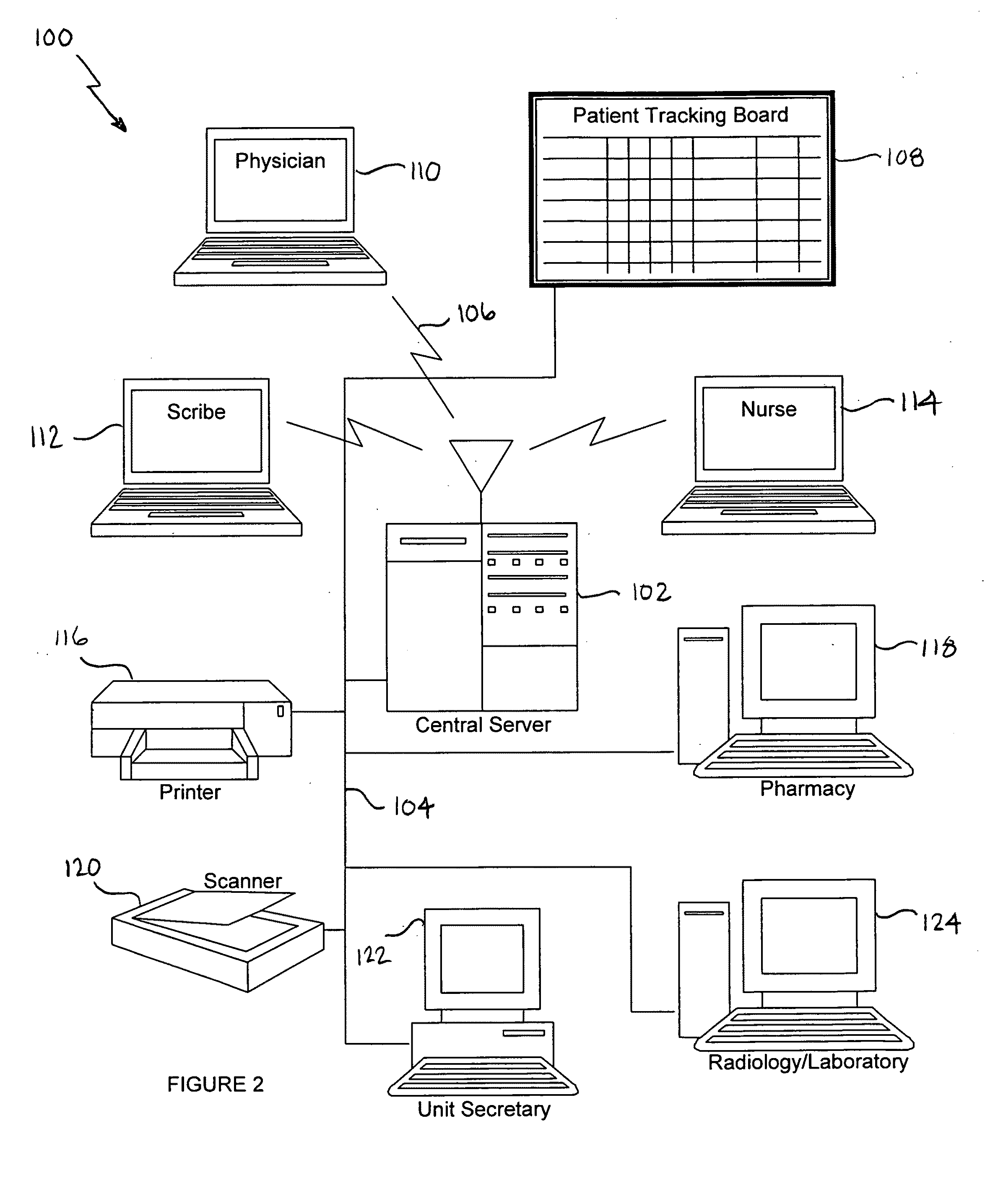
Improved systems and methods for collecting Protected Health Information (PHI) with or without the assistance of a physician scribe are described. Documenting a patient encounter utilizing a template-based charting system (either electronic or paper-based), and the tracking of this document status and patient clinical status throughout the encounter, for purposes of managing multiple patients and multiple patients' documents, as well as improved communication between providers and assistants. The systems and methods of this invention generally comprise an electronic records system for creating and maintaining information in electronic records; patient tracking system (either computerized or not) for managing tasks specific to provider documentation of specific clinical care actions and patient clinical status; complimentary utilization of medical history questionnaires which are designed to correlate with template-based charting tools; methods of communication between provider assistants (including physician assistants, nurses, secretaries, scribes, patients, or other assistants) to convey the status of the collection and management of the PHI, including patient history, patient examination, testing results, medical decision making, patient disposition plan, follow-up information and other elements of provider charting of PHI; sequence of patient tracking indicators that represent steps in the care of the patient, status of the document, and clinical or documentation-related tasks for completion by providers or provider assistants; improvements on a real-time compliance system for identifying the specific stage or status of each electronic record, and allowing providers and assistants to track this completion status, thereby streamlining documentation and compliance workflows.
Owner:CONANT & ASSOCS
Protected health information voice data and / or transcript of voice data capture, processing and submission
ActiveUS20150278449A1Streamlined and timely medical claim generationStreamlined and timely and submissionMedical automated diagnosisComputer security arrangementsProtected health informationMobile device
A system and method that permits a user to utilize a means of capturing and managing one or more voice files containing speech utterances (“Voice Utterances”) and / or the corresponding transcript (“Transcript”) containing protected health information (PHI) on a mobile device.
Owner:LABORDE DAVID
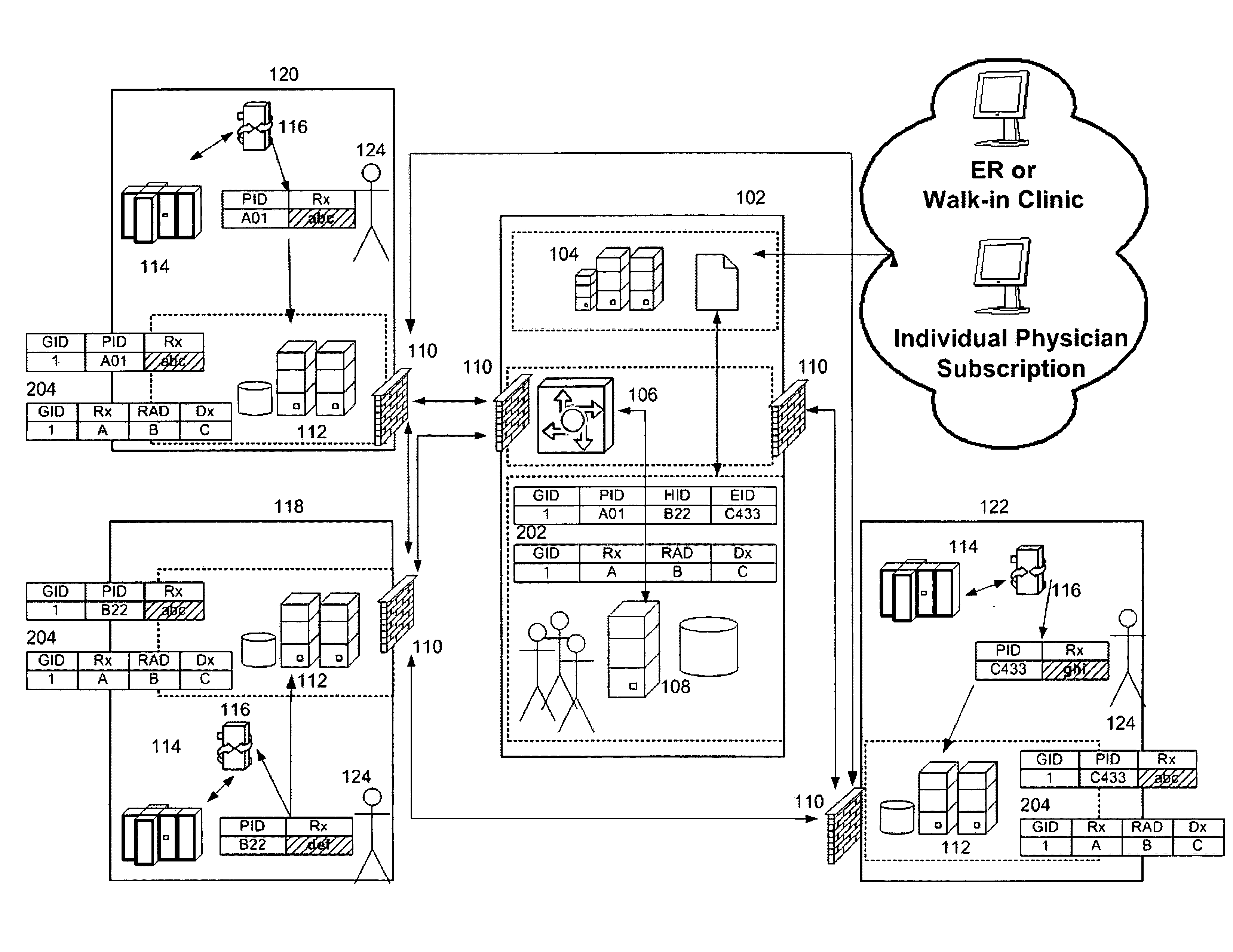
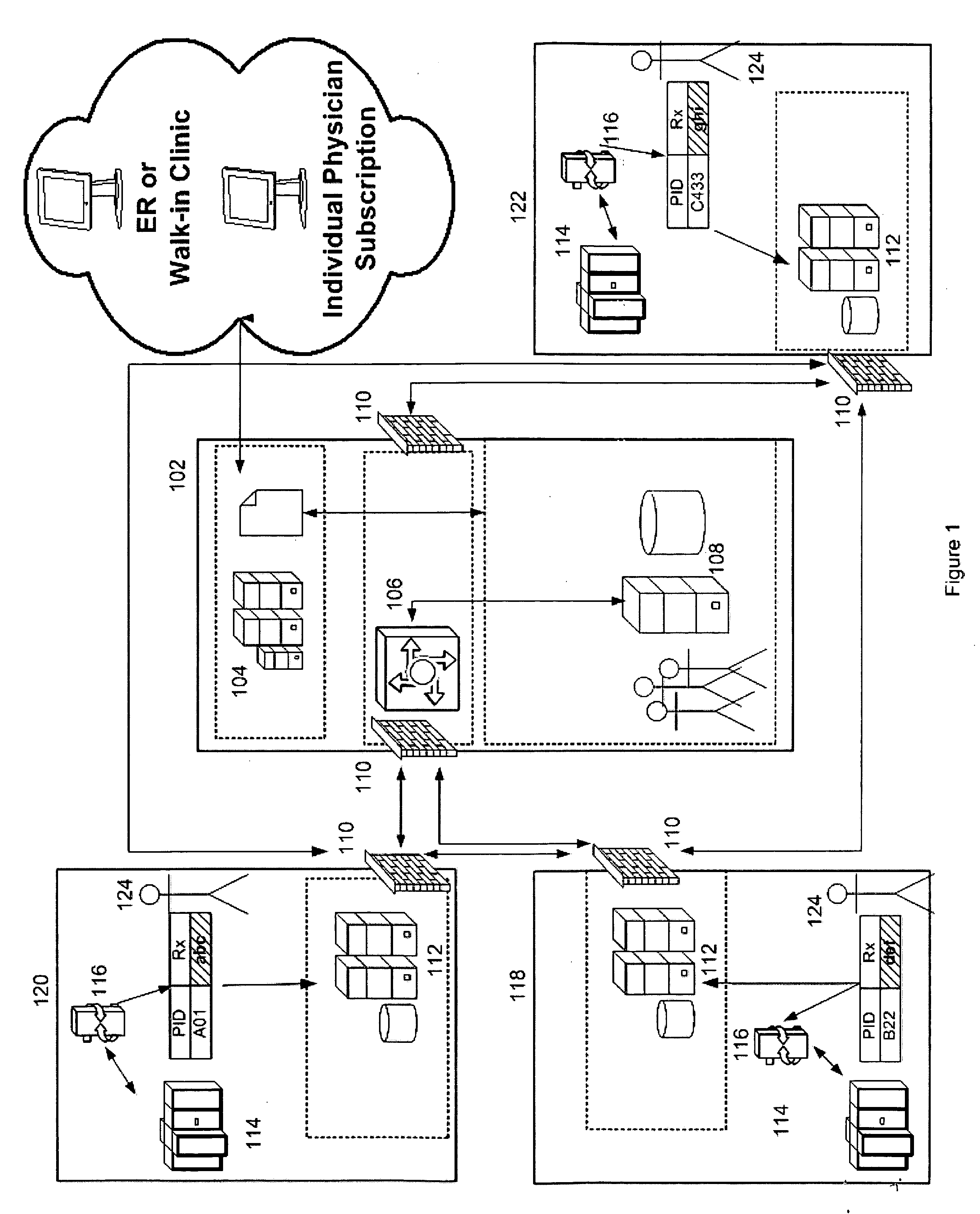
Data sharing infrastructure
InactiveUS20050246205A1Continuous operationData efficientData processing applicationsPatient personal data managementData streamData set
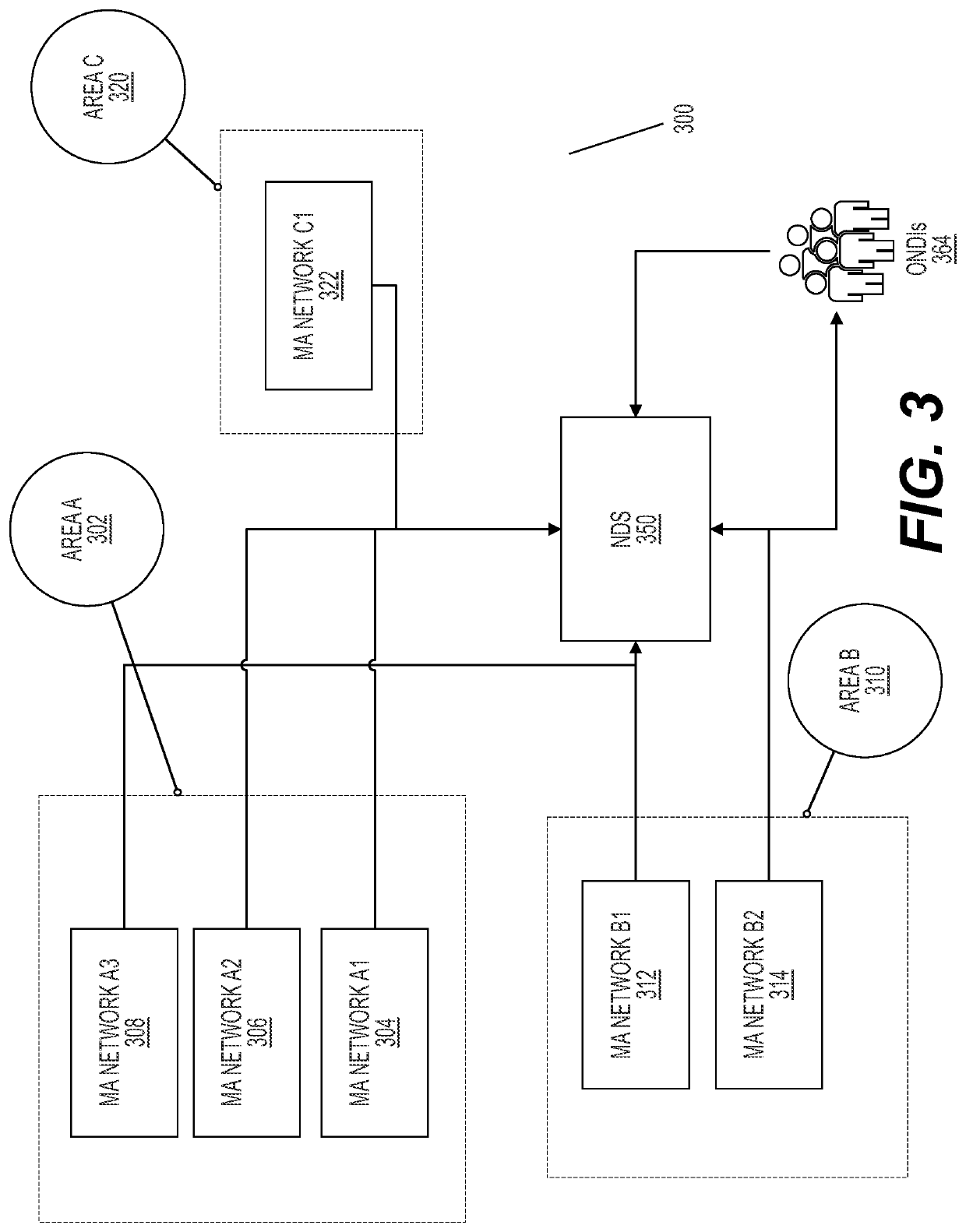
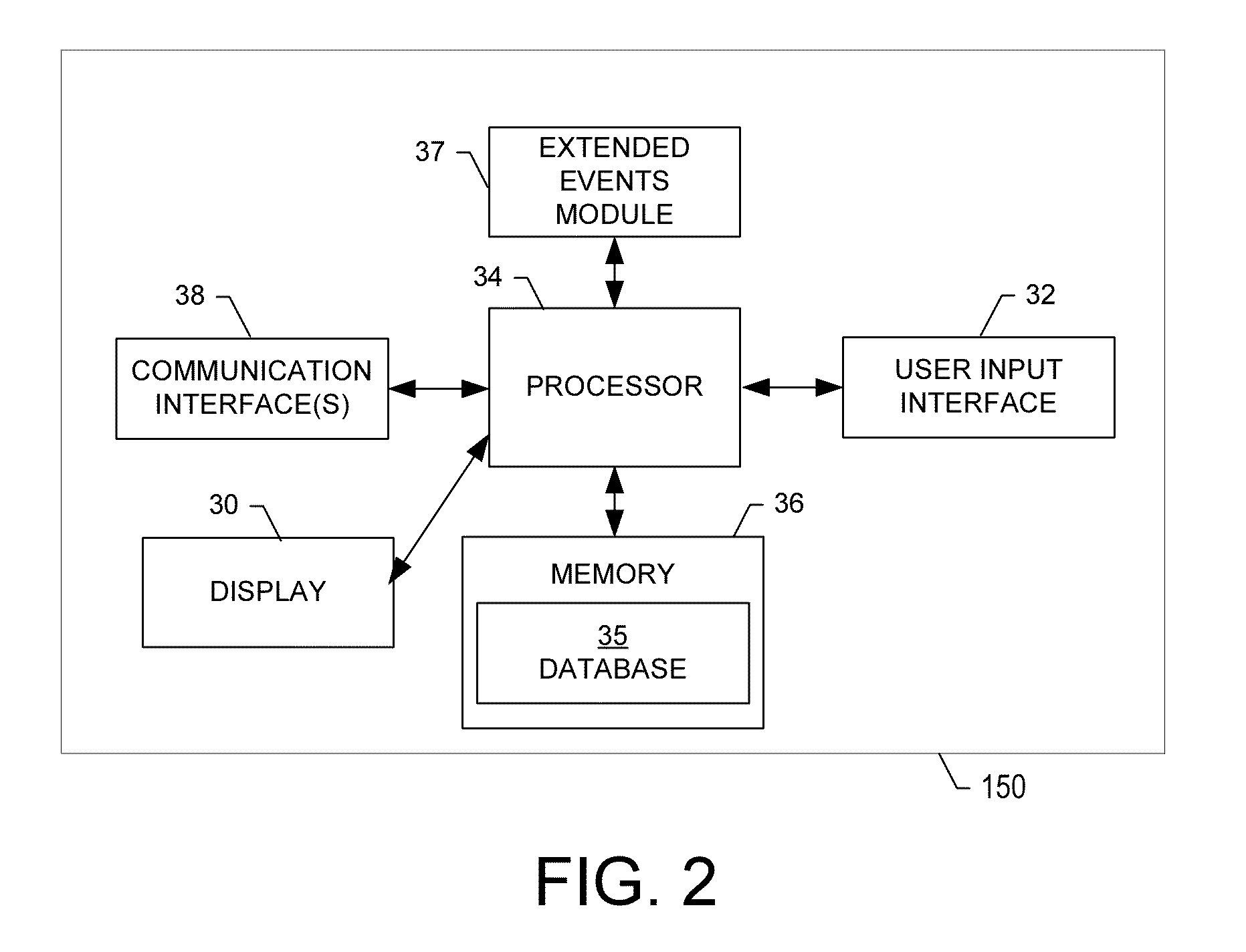
The present invention relates to systems and methods for constructing a regional medical data exchange infrastructure that can provide the aggregation and presentation of personal health data that previously exists in different health care organizations in a segmented fashion. More particularly, the present invention relates to systems and methods for establishing a regional medical data exchange infrastructure, identifying patients across multiple different organizations, creating patient medical data pointers and routing tables, and generating comprehensive medical data sets for an enrolled population. One feature of this present invention permits the regional medical data exchange infrastructure to be built without any protected health information (PHI) being stored in any centralized databases. Another feature of the present invention permits the continuous operation of the regional medical data exchange infrastructure even when the centralized facility experiences downtime. Exemplary embodiments of the present invention permit both local and global logging and tracking of data flows and user activities to satisfy HIPAA compliances. Alternative embodiments of the present invention permit the preservation of the data ownership for the participating organizations.
Owner:WANG HAO +1
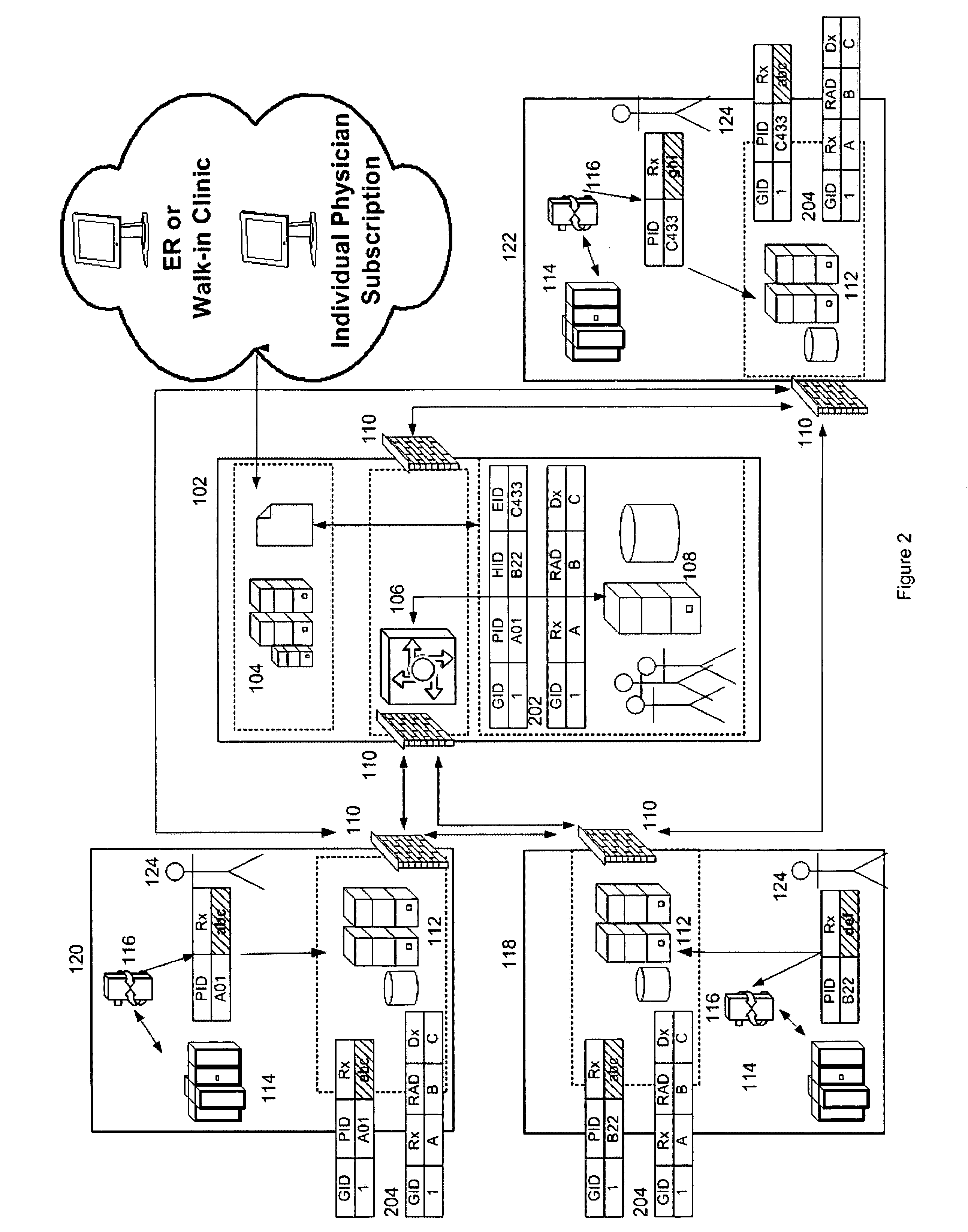
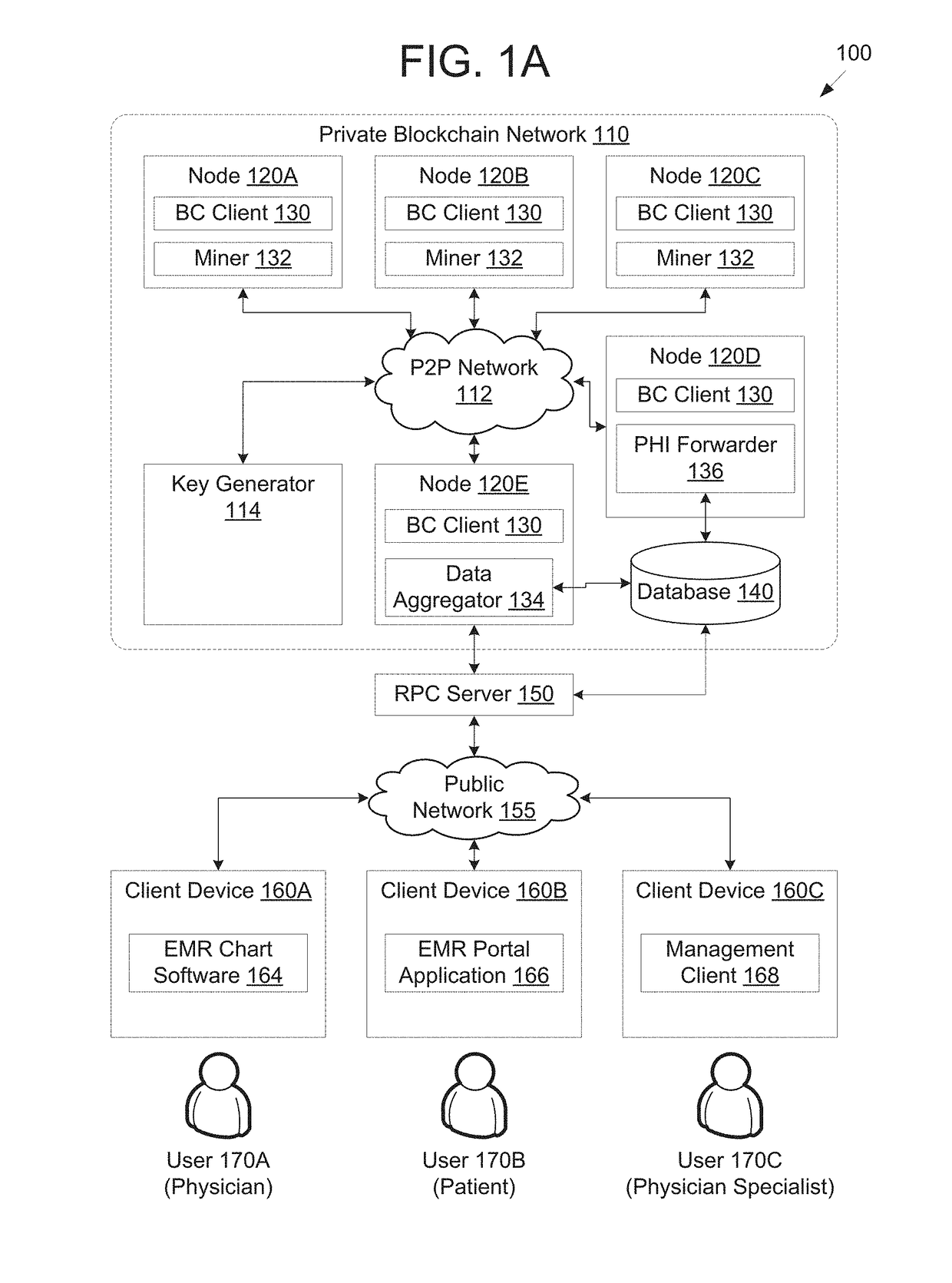
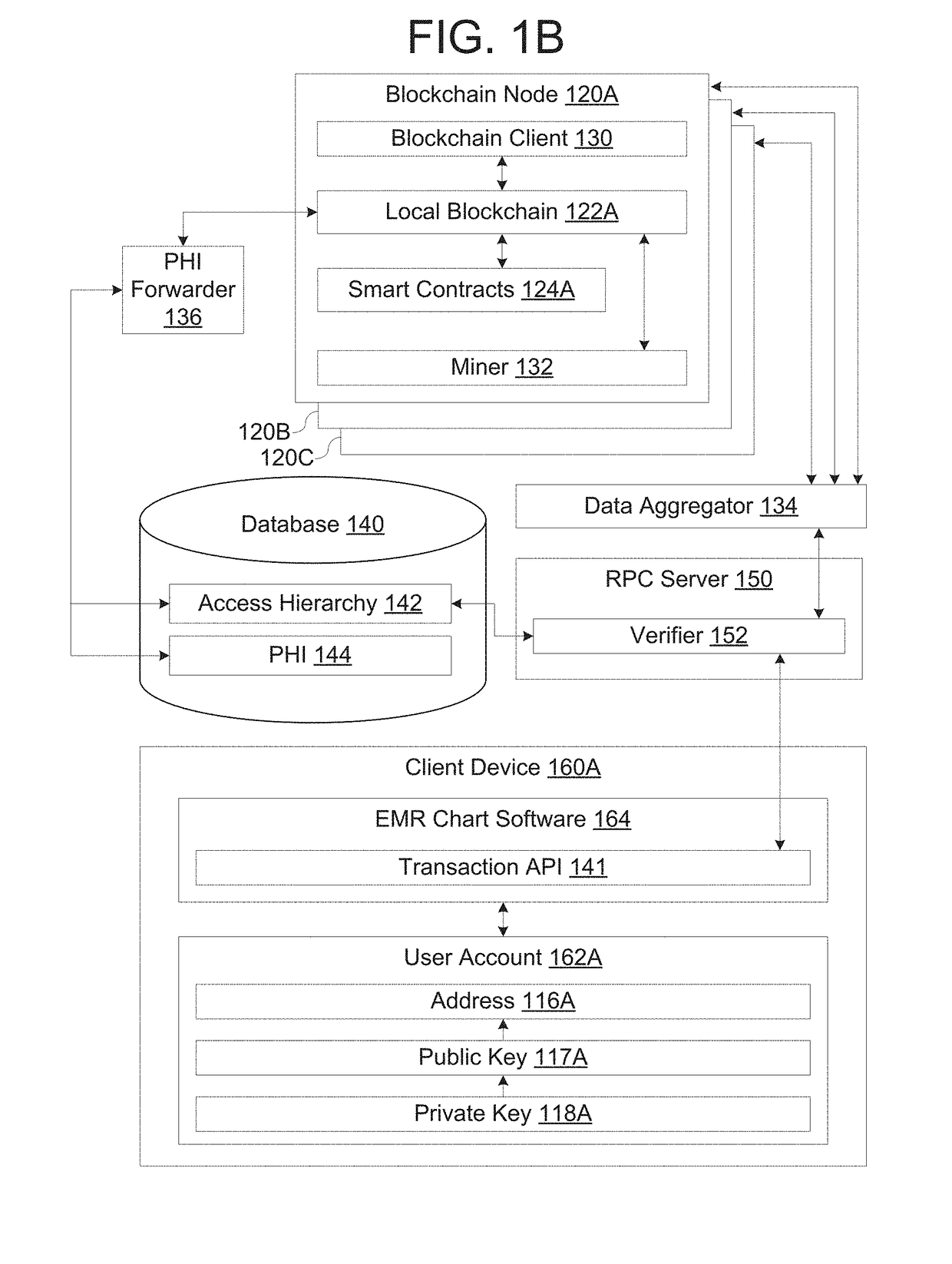
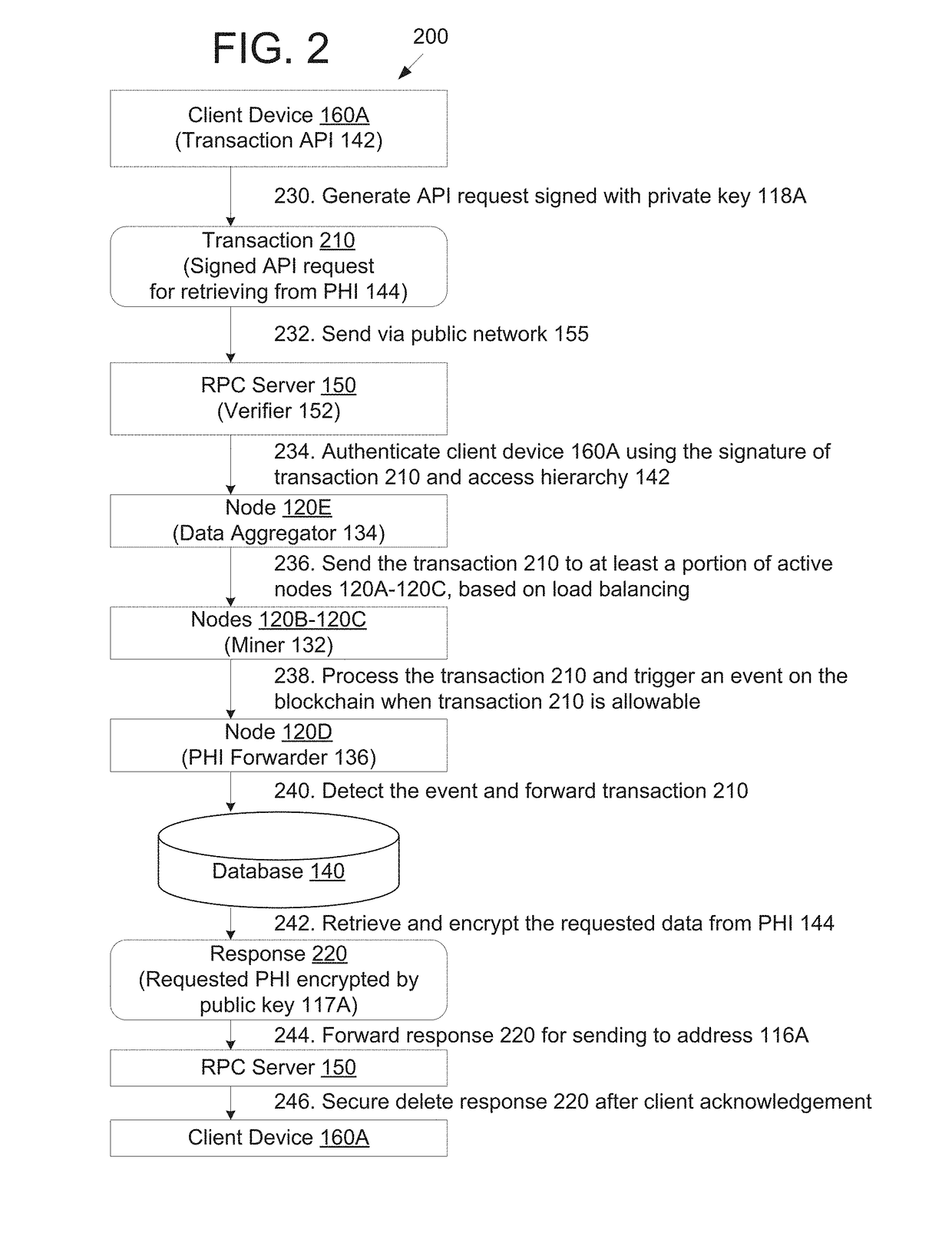
Blockchain network for secure exchange of healthcare information
PendingUS20190027237A1Medical communicationPublic key for secure communicationData aggregatorProtected health information
Disclosed are methods and systems for providing a blockchain network for secure exchange of healthcare information. A system may include a server configured to receive a transaction from a client device via a publicly accessible network, wherein the server authenticates an identity of the client device prior to forwarding the transaction. The system may also include a private blockchain network comprising a data aggregator node configured to receive the transaction forwarded from the server and distribute the transaction to a least a portion of a plurality of processing nodes, wherein each of the plurality of processing nodes executes a respective blockchain client configured to maintain a blockchain having contracts. The private blockchain network may include a forwarder node configured to, in response to detecting an event indicating that the transaction was successfully processed by a respective contract, transact protected health information in a data store separate from the blockchain.
Owner:PATIENTORY INC
Method of maintaining data confidentiality
InactiveUS20060074983A1Avoid accessMaintaining data confidentialityPatient personal data managementSpecial data processing applicationsConfidentialityInternet privacy
A method of maintaining data confidentiality. The method of one embodiment comprises receiving patient data at a medical system. Whether the patient data includes protected health information is determined. If the patient data includes protected health information; the patient data is stored in a secure location. The patient data is annotated for protection if the patient data includes protected health information. Access to the patient data is prevented.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
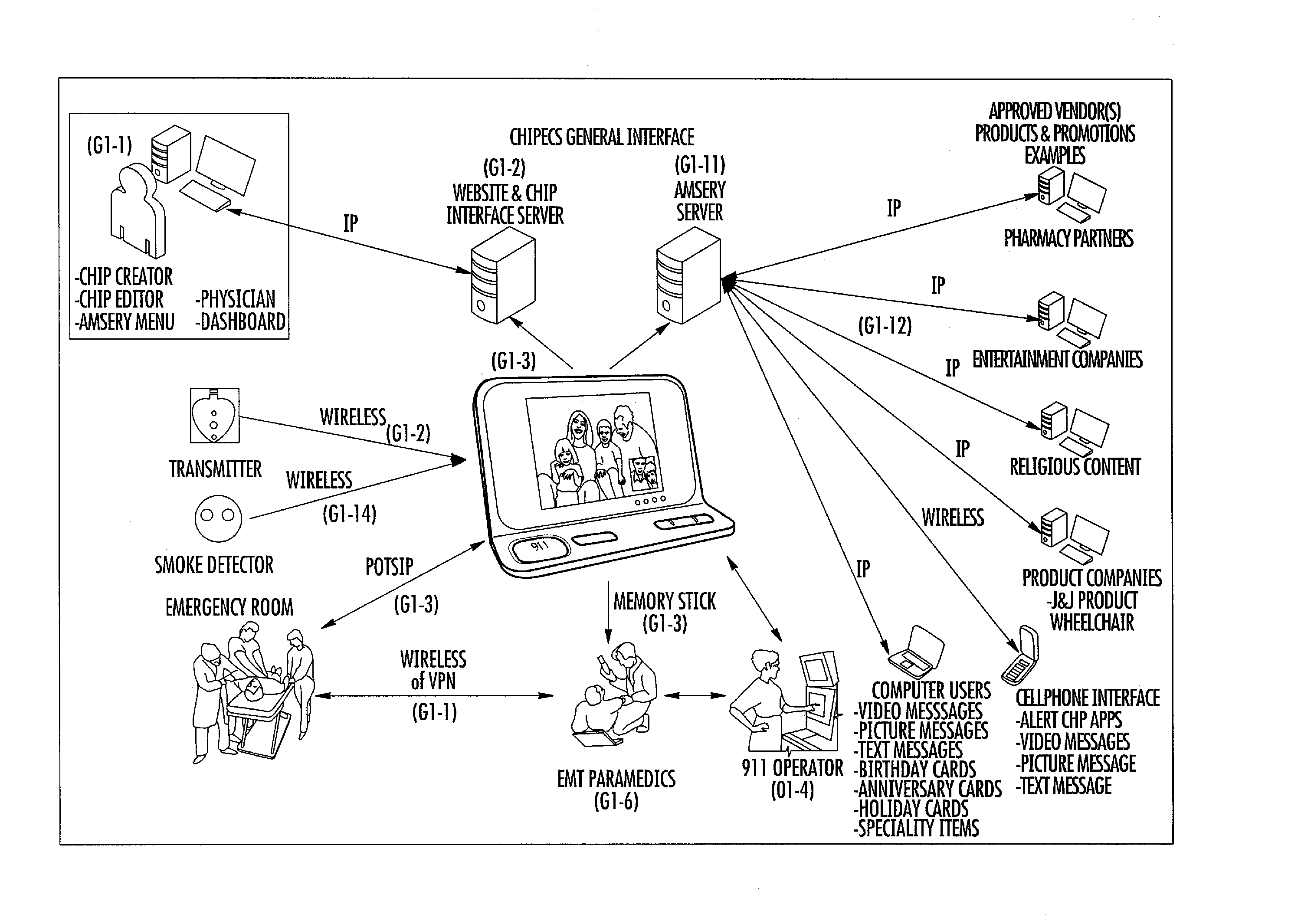
Critical health information profile and emergency communication system
ActiveUS20120088466A1Effectiveness and efficiencyGood serviceTelephonic communicationTelemedicinePoint of careEngineering
A microprocessor-based emergency response communication system used to call and communicate with the 9-1-1 operator and also allows emergency responder's immediate access to a user's Critical Health Information Profile stored in the device at the point and location of crisis. The device is used to create individual Critical Health Information Profiles which is Health Level-7 compliant enabling it to seamlessly communicate with major hospital networks worldwide. This functional capability provides a system that can retrieve and transmit user-stored personal and health information by emergency responders at the point of care. The emergency responder can access the customer's Critical Health Information Profile database, review the data for pertinent information and then transmit that data to a designated receiving hospital or medical center. The device provides an electronic means of dialing and communicating directly with the 9-1-1 operator. A wireless remote transmitter unit can be activated from the wireless transmitter or the base unit to dial and connect with the 9-1-1 operator, broadcast a canned message with or without a personal-recorded message, and personally communicate with the 9-1-1 operator through a two-way speakerphone system. The device contains software enabling the user and medical personnel the ability to input, store, retrieve and analyze the user's vital sign data and other pertinent health information.
Owner:MEDSIGN INT CORP
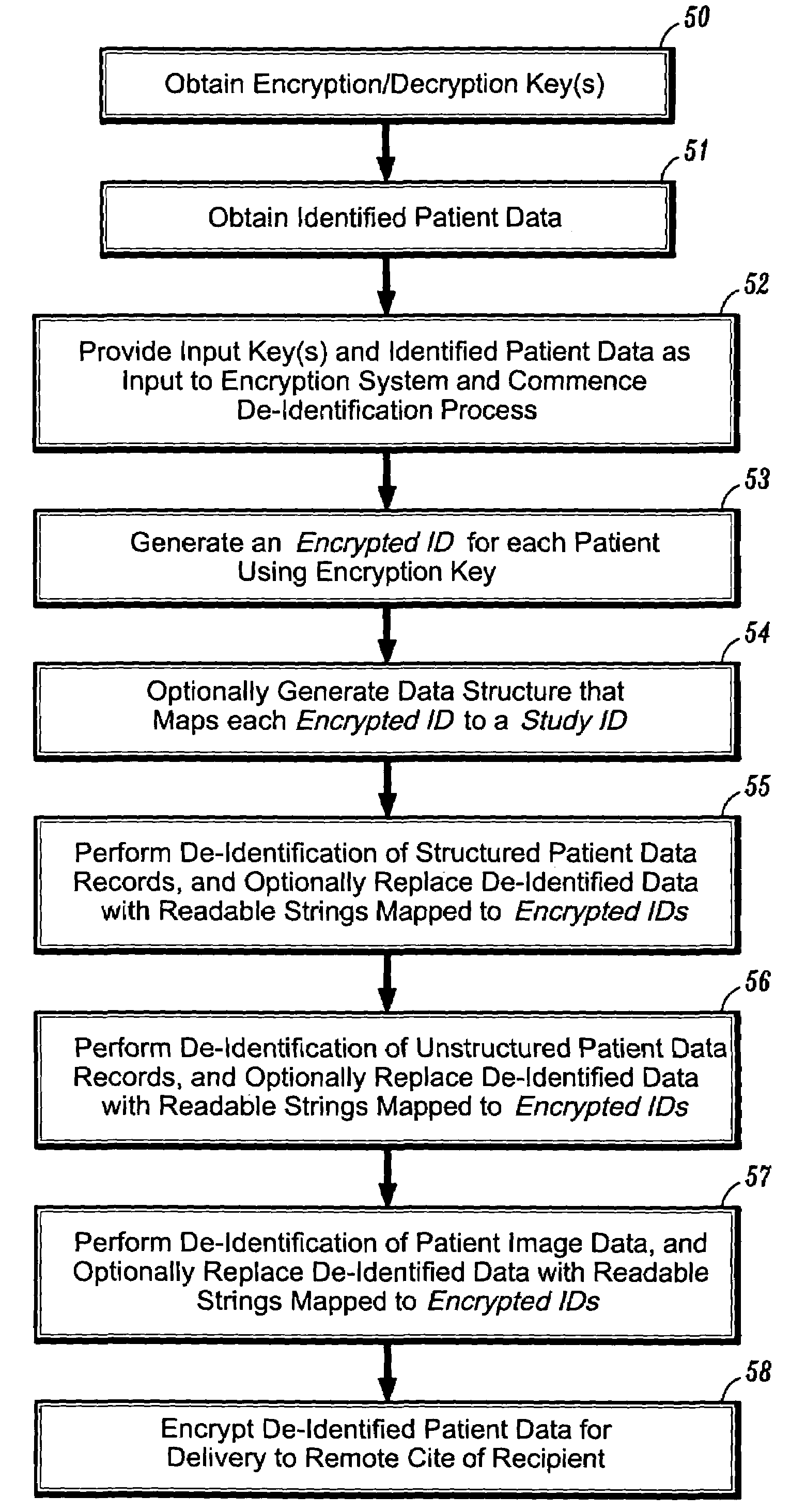
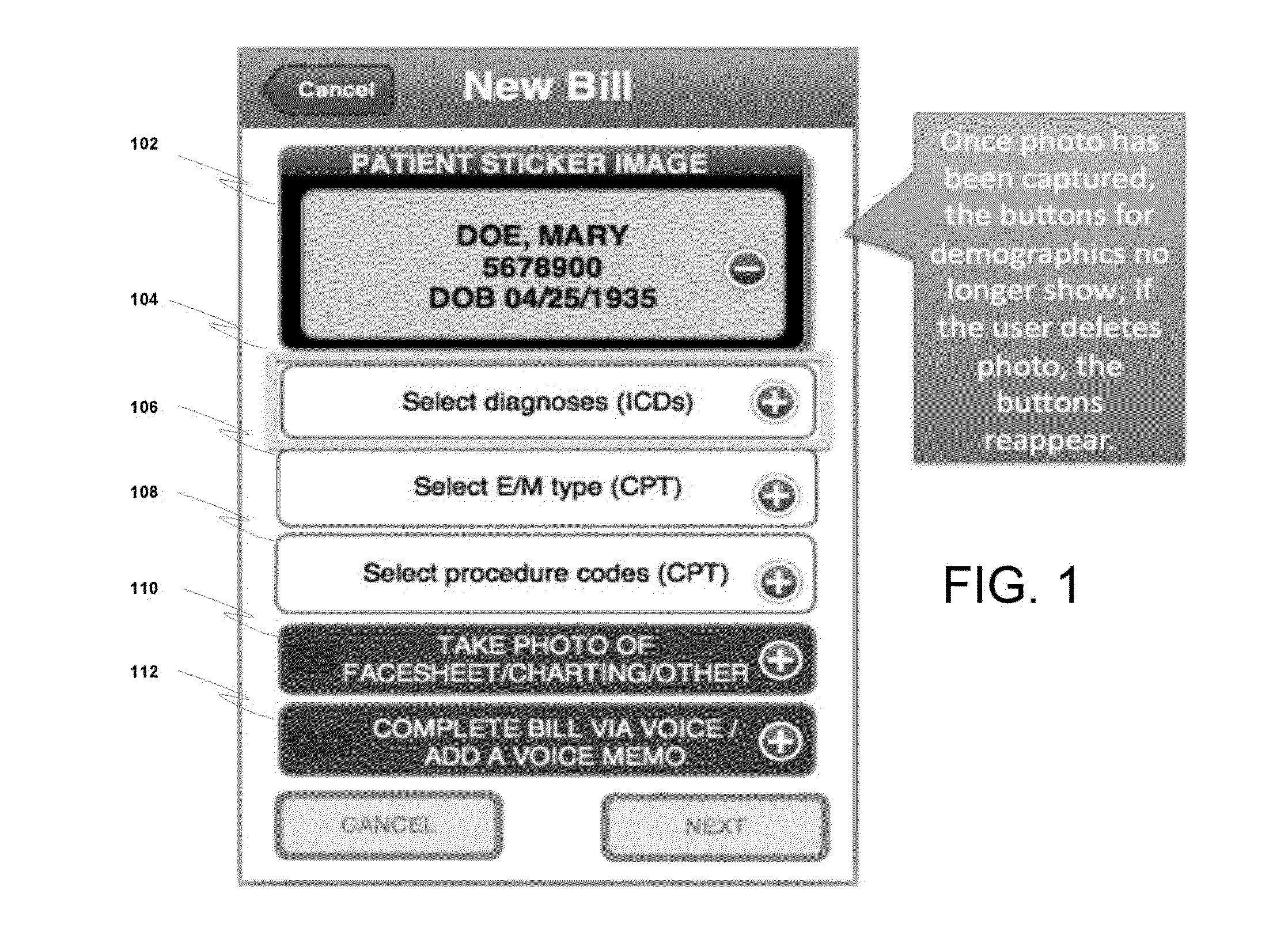
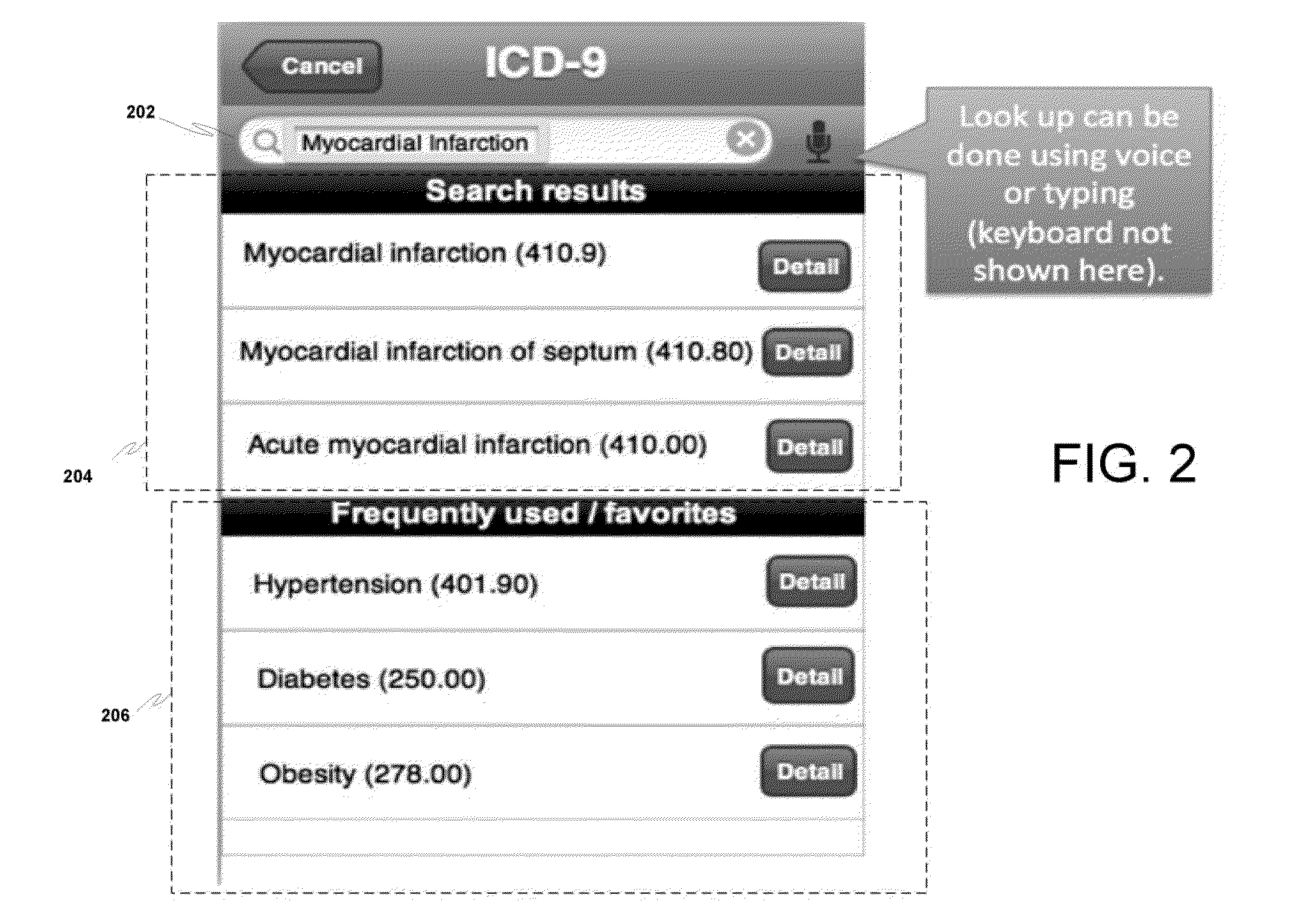
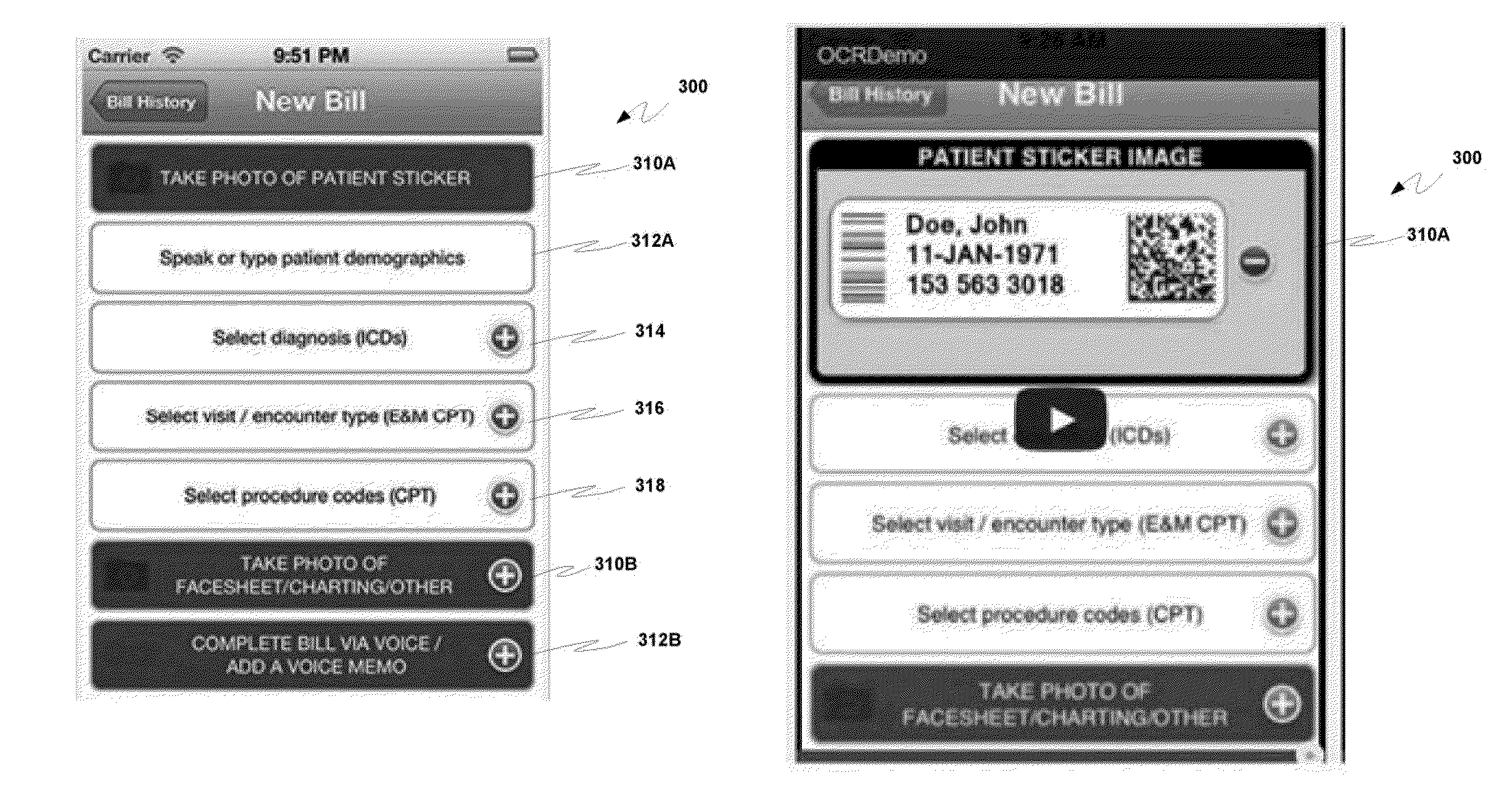
Protected health information image capture, processing and submission from a mobile device
ActiveUS20150281949A1Optimize workflowMore revenueUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet privacyProtected health information
A system and method that permits a user to utilize a means of capturing and managing one or more images containing protected health information (PHI) on a mobile device, as disclosed herein. The user of the system and method may be required to undergo authentication and authorization to access the system and use the method.
Owner:ICONIC DATA
Health information management system based on two-dimension code recognition
InactiveCN104835094AImprove first aid knowledgeAccurate pre-hospital first aidData processing applicationsInformation repositoryMedical knowledge
The present invention relates to a health information management system based on two-dimension code recognition. The health information management system based on the two-dimension code recognition comprises a health information base operated on a network server and used for storing the personal health information containing the personal first aid information of a user, and also comprises a two-dimension code generating module carried by the user, connected with the health information base and used for generating a link pointing to the personal health information of the user in the health information base according to the identity of the user, and an information obtaining module carried by other people, connected with the health information base and the two-dimension code generating module separately and used for the other people to obtain the personal first aid information of the user to thereby be convenient for the pre-hospital first aid of the user when the user has an attack in the open air. Compared with the prior art, and by the two-dimension code generating module of the present invention, other people, especially the passerby can use the information obtaining module to scan a two-dimension code generated by a two-dimension code generator to obtain the personal health information of the user from the health information base, thereby realizing the situation that even the passerby without the medical knowledge can provide the accurate pre-hospital first aid for the user.
Owner:TONGJI UNIV
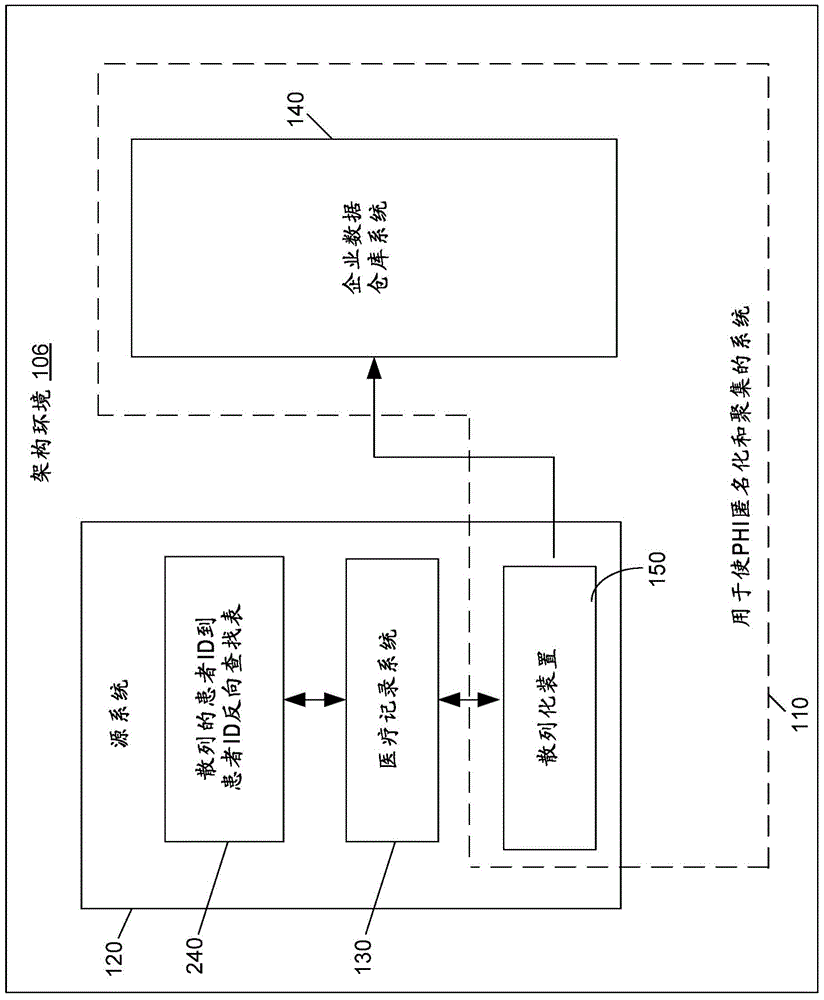
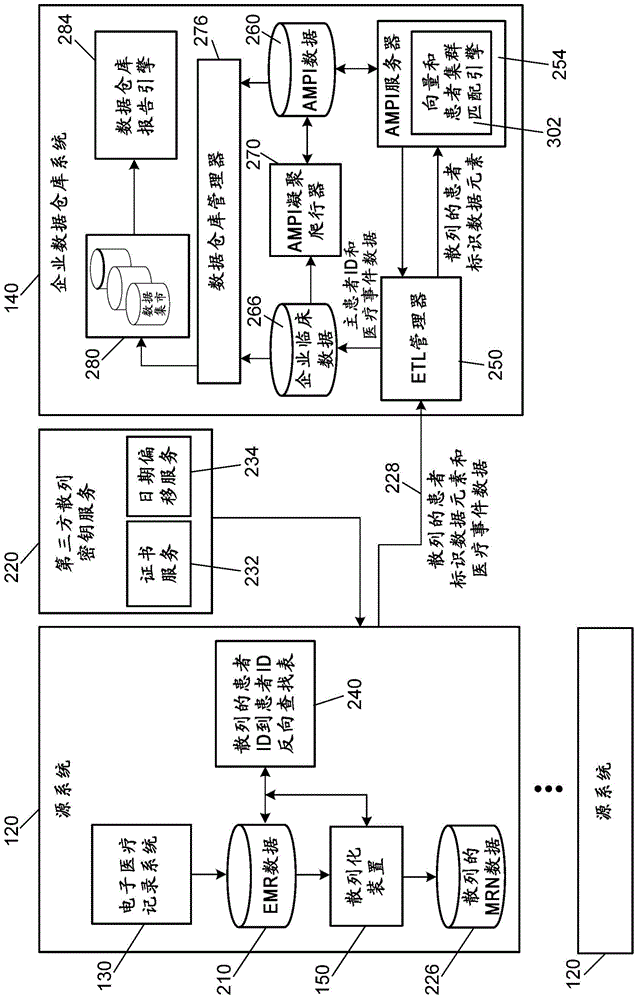
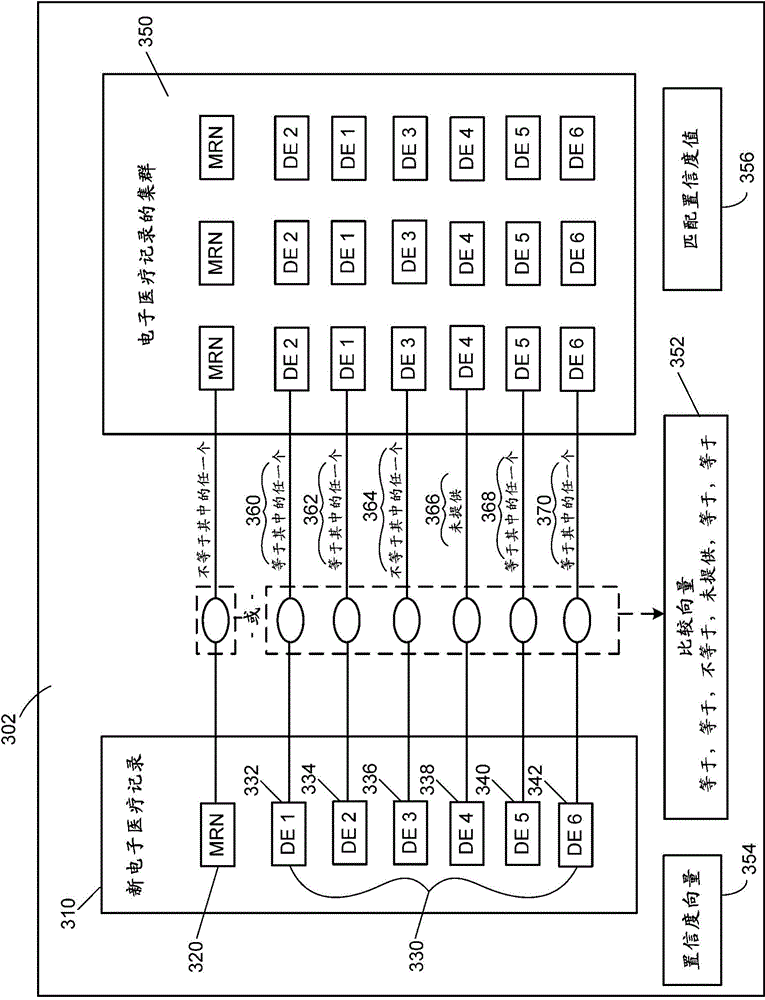
System for anonymizing and aggregating protected health information
ActiveCN104680076AGuaranteed confidentialityComply with HIPAA regulationsData processing applicationsDigital data protectionMedical recordDatasource
A patient anonymizing system includes a plurality of hashing appliances and data sources. Each appliance receives medical records containing at least confidential protected health information (PHI). A salt value is appended to each confidential PHI, and a hash is generated, which replaces the confidential PHI to generate an anonymized record. A master patient index server aggregates the anonymized records. A vector and cluster matching engine determines if the anonymized record matches a unique patient identifier corresponding to a second anonymized record. A comparison vector is generated by comparing hash values of the confidential PHI with hash values in the second anonymized record, and is crossed with a confidence vector having weights based on match conditions. This produces a match confidence level, which is compared to a threshold. If the threshold is met, the anonymized record is mapped to the unique patient identifier associated with the second record.
Owner:ACCENTURE GLOBAL SERVICES LTD
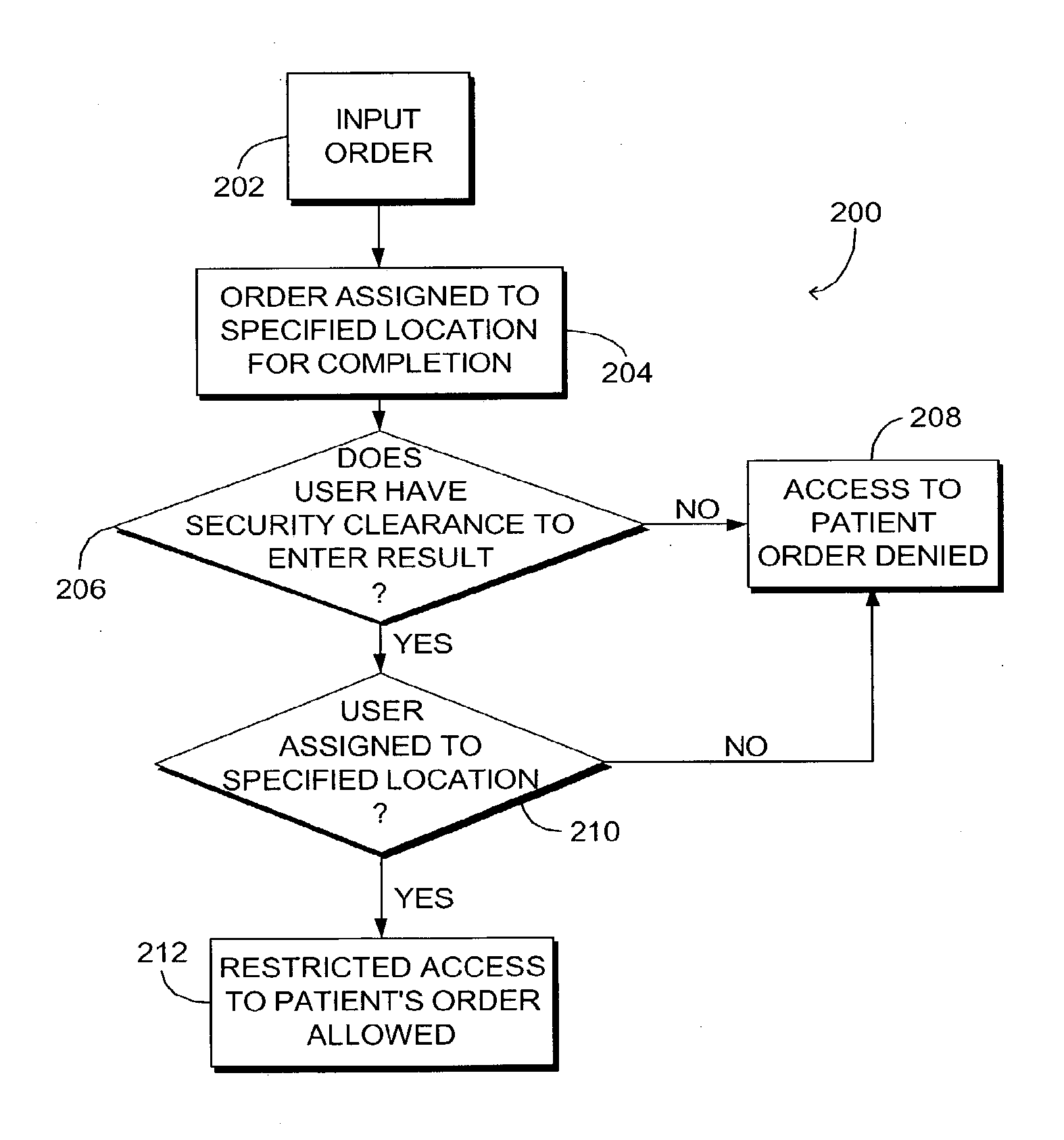
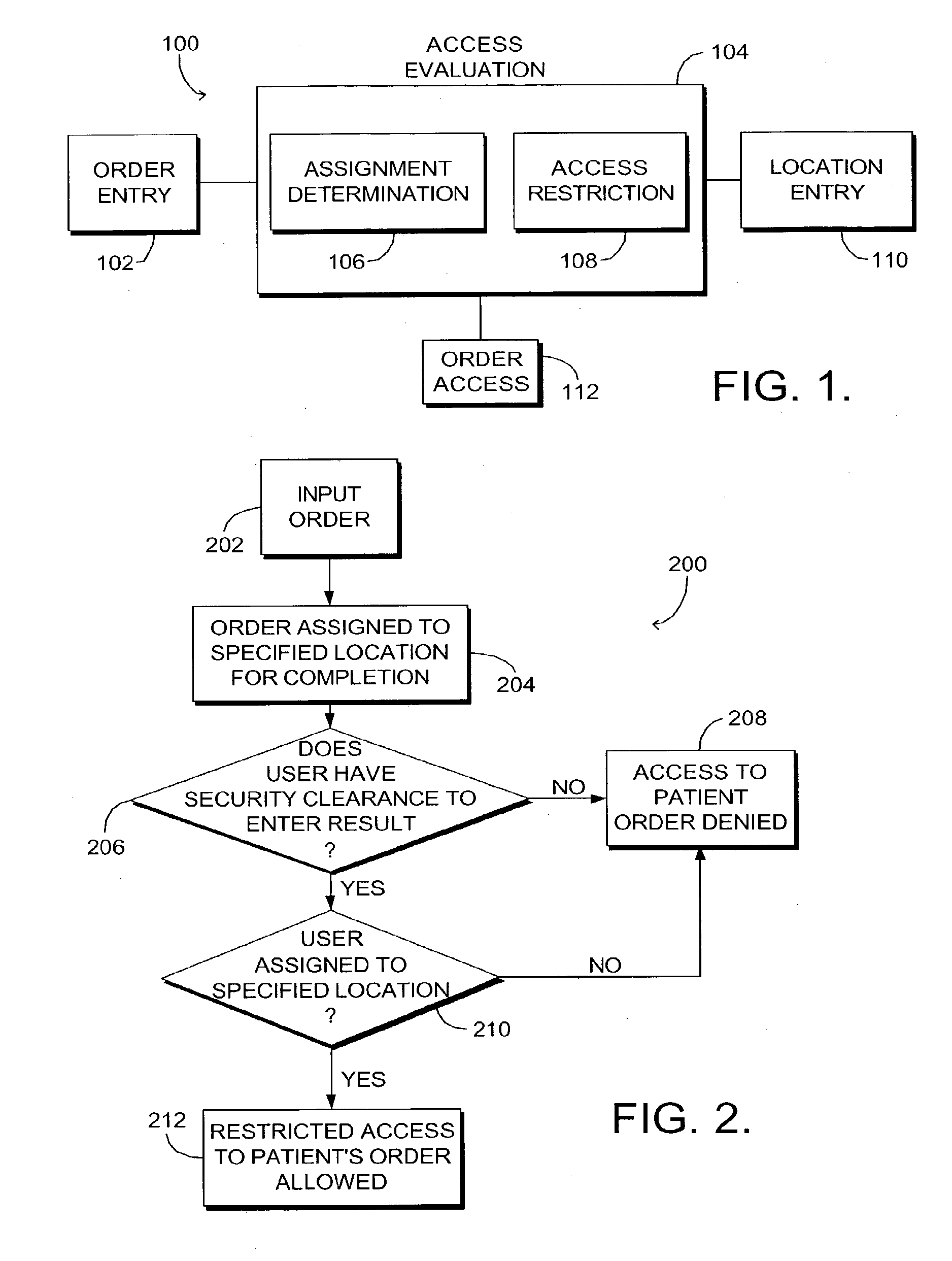
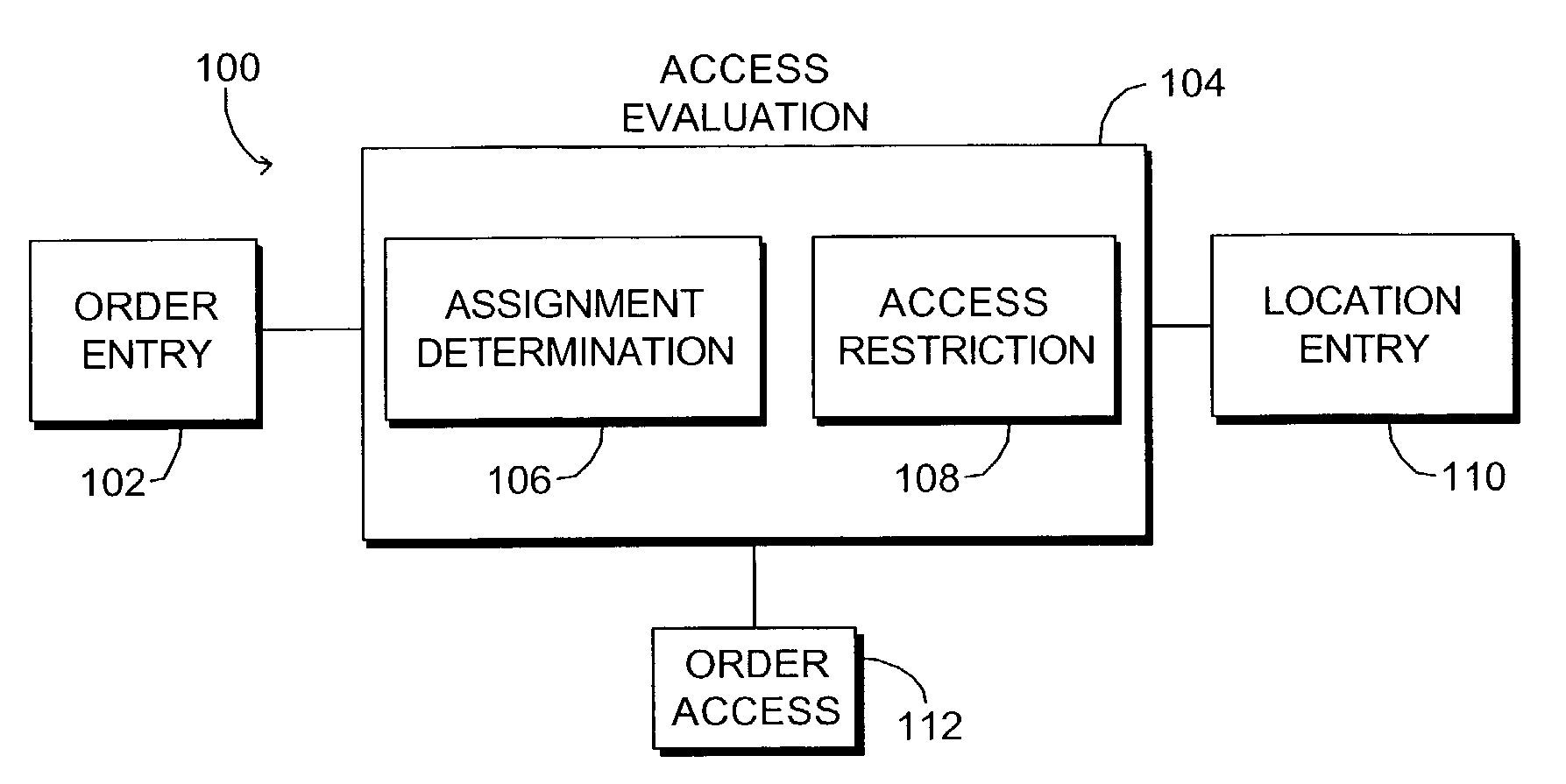
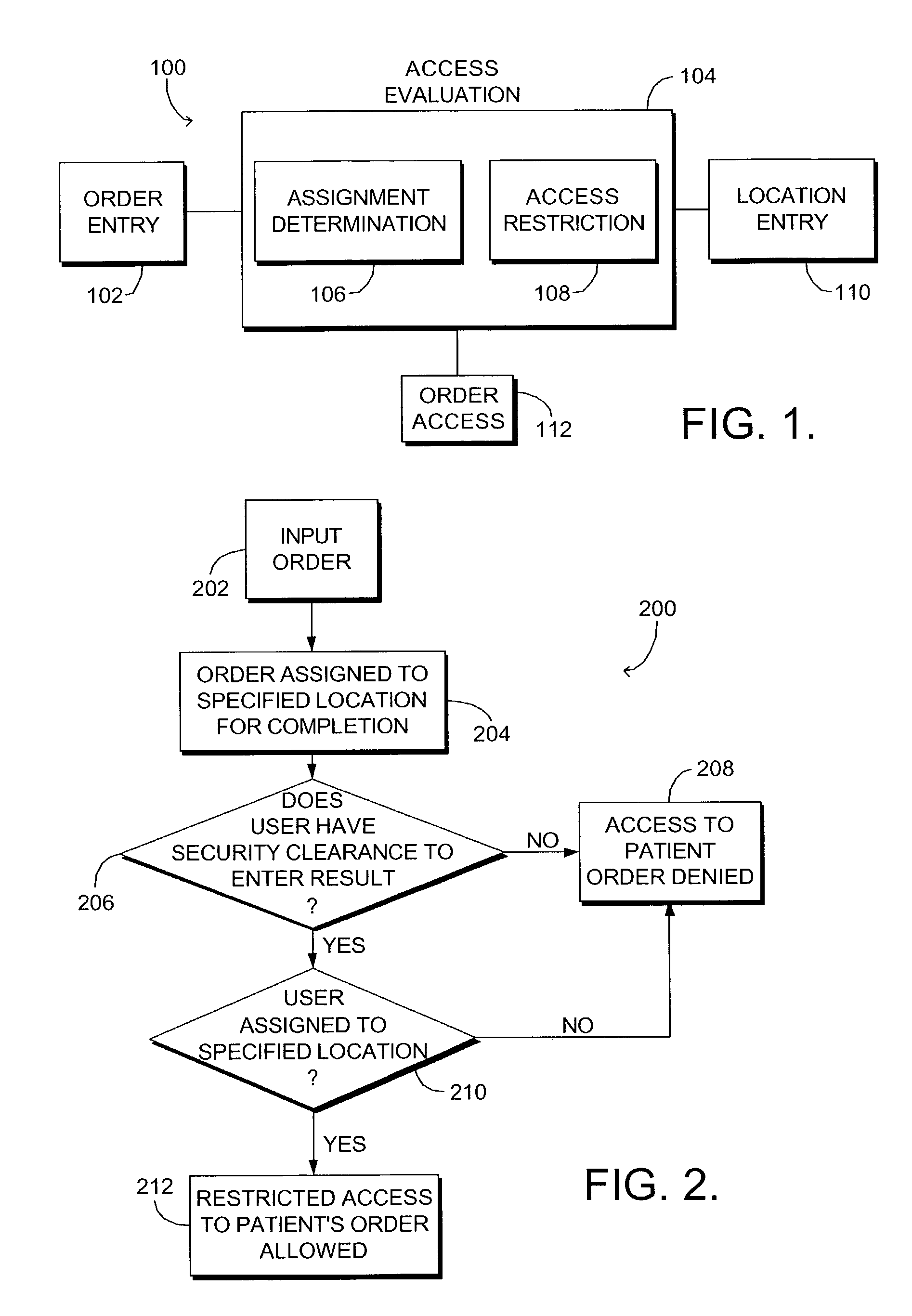
Computerized method and system for restricting access to patient protected health information
ActiveUS7634419B1Prevents unauthorized disclosureImprove securityMechanical/radiation/invasive therapiesDigital data processing detailsComputerized systemComputer module
A computerized system and method for allowing restricted access to patient healthcare information is provided. Upon determining that one or more users are assigned to the location where an order for a patient is to be performed, the method allows one or more users restricted access to the order. The system includes an order entry module, an access evaluation module, a location entry module and a user module. The access evaluation module includes an assignment determination sub-module for determining whether one or more users are assigned to the specified location where an order for a patient is to be performed. The assignment determination module also includes a restricted access sub-module coupled with the assignment determination module and configured to allow restricted access to one or more users assigned to the specified location.
Owner:CERNER INNOVATION
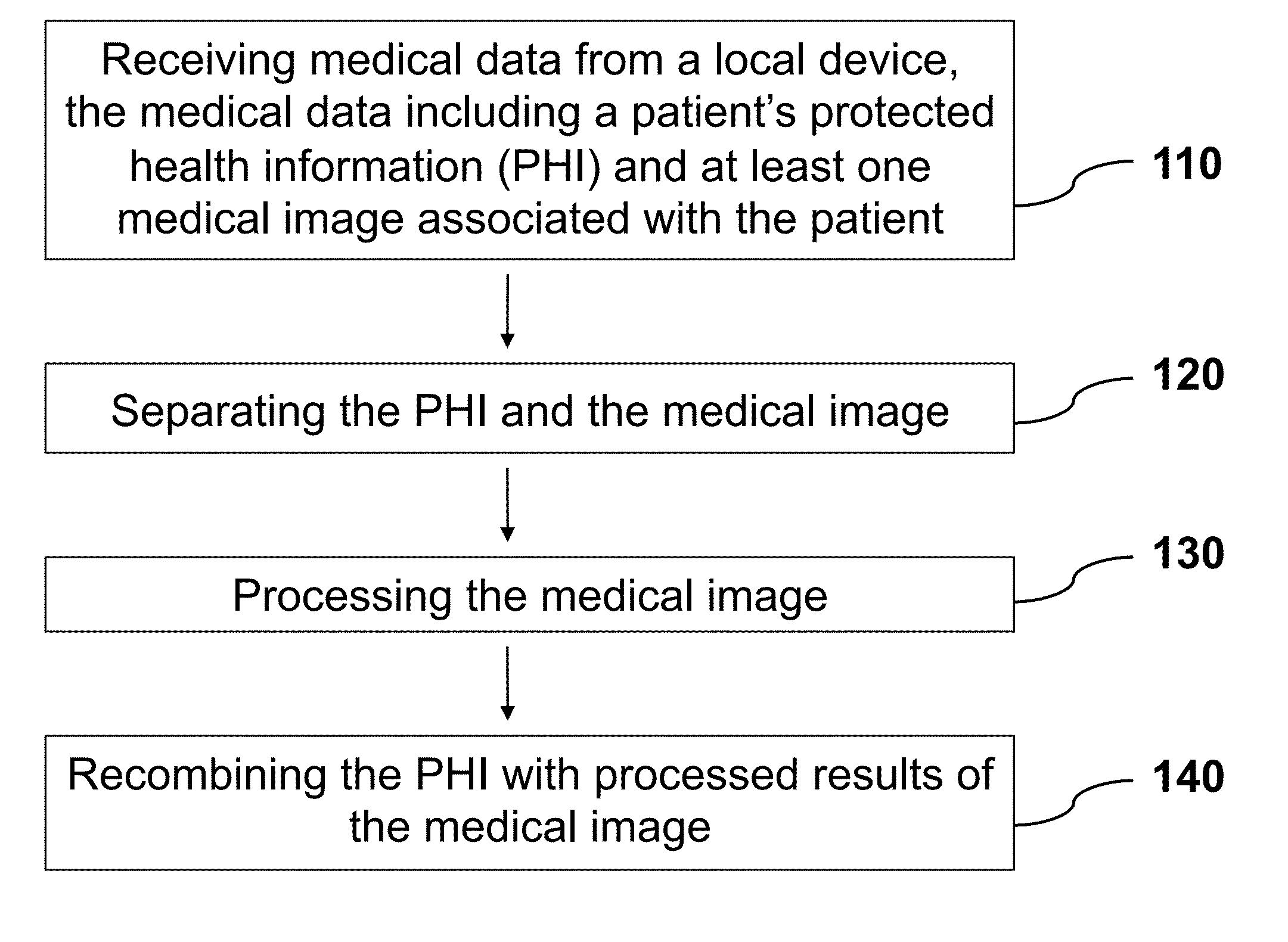
Method and apparatus for anonymized medical data analysis
InactiveUS20160224805A1Risk minimizationGuide and improve medical treatmentDigital data protectionMedical imagesData processing systemImaging processing
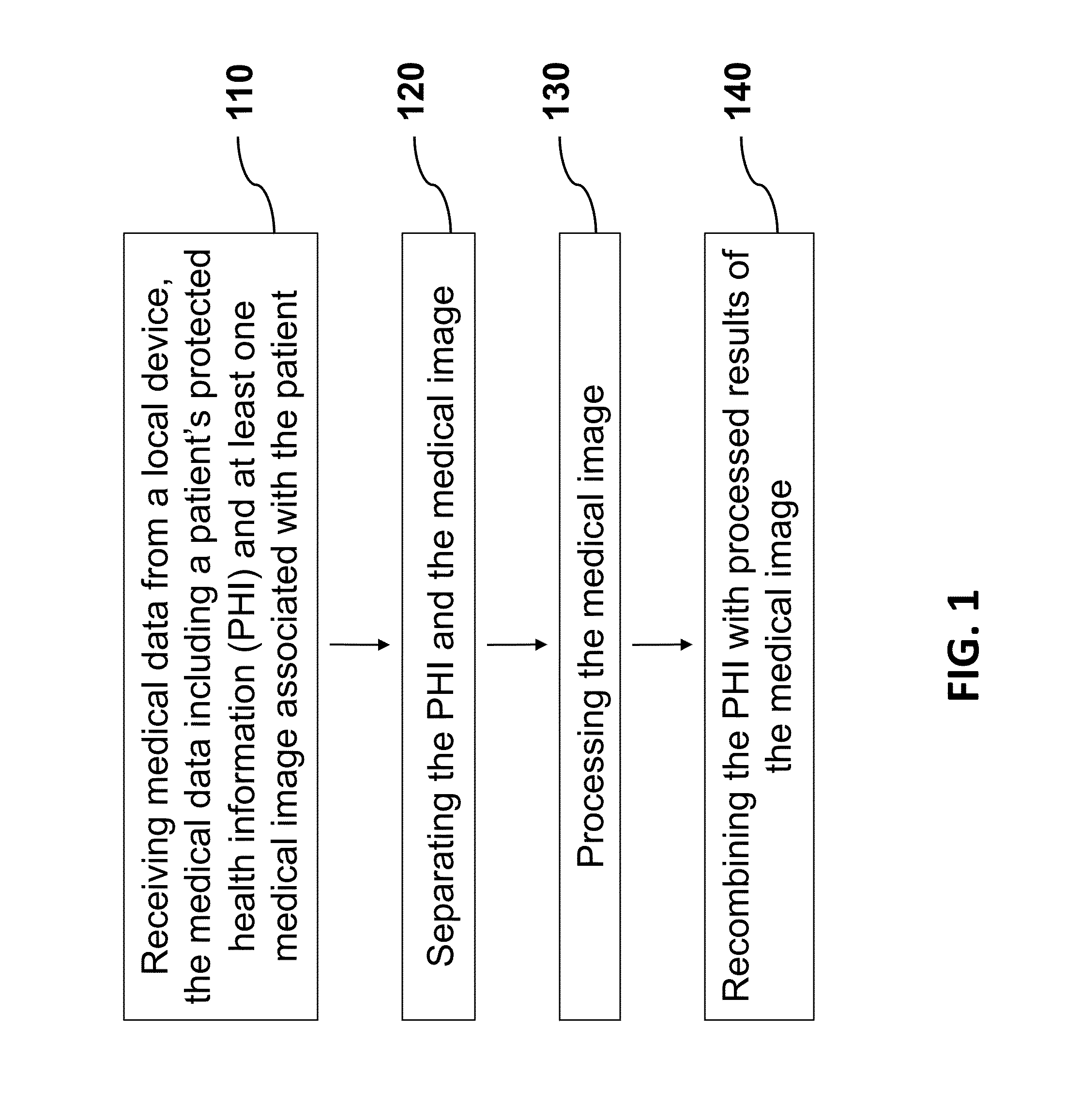
A data processing system may include a local computing device to receive medical data including a patient's protected health information (PHI) and at least one medical image associated with the patient; an anonymizing device to separate the PHI with the medical image; an image processing unit to analyze the medical image; and a processed results managing (PRM) unit configured to recognize and link analyzed results of the medical image to the corresponding patient's PHI, and combine the analyzed results and the patient's PHI to generate an analysis report. The present invention is advantageous because it allows medical images to be analyzed off-site while minimizing the risk of compromising the patient's PHI. Furthermore, the anonymized medical analysis can be used to guide and improve medical treatment especially during a medical procedure.
Owner:PATTI JORDAN
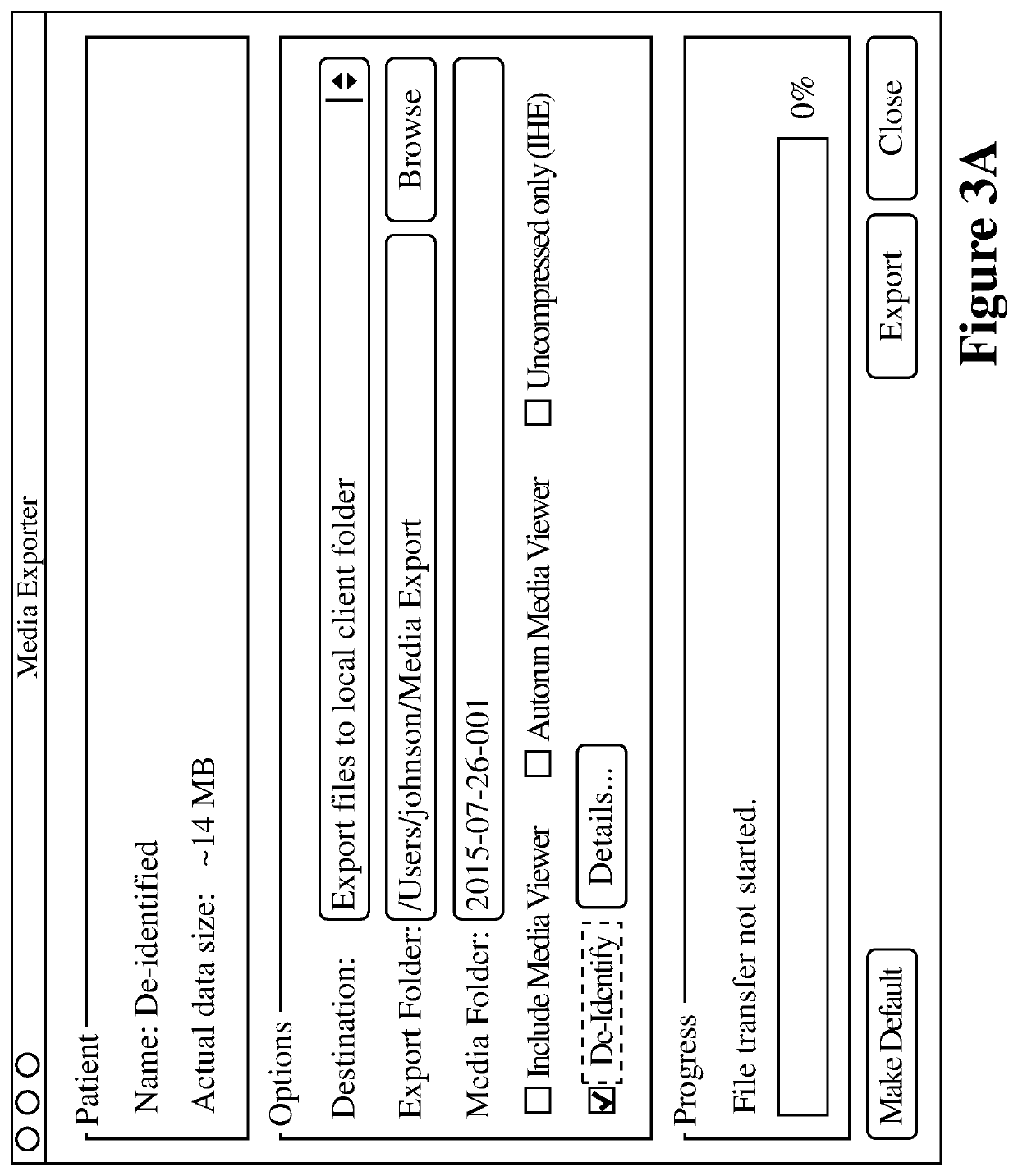
Method and system for rule-based anonymized display and data export
ActiveUS20160342738A1Big amount of dataMedical imagesMedical image data managementProtected health informationWorld Wide Web
The invention provides, in some aspects, a system for implementing a rule derived basis to display anonymized image sets. In various embodiments of the invention, users with the appropriate permission can launch a function inside a system in order to anonymize and export the currently loaded study or studies, or one or more studies identified by a search criteria. The data from the studies that were identified is then anonymized on the system using predefined rules. In an embodiment of the present invention, the data from selected studies is anonymized on a server, and only then transmitted to another network device thus minimizing the risk that protected health information can be inadvertently disclosed. In an alternative embodiment of the present invention, the data from selected studies is anonymized on a server, and only the anonymized data is stored to the hard disk or other media of a user viewing the study.
Owner:PME IP
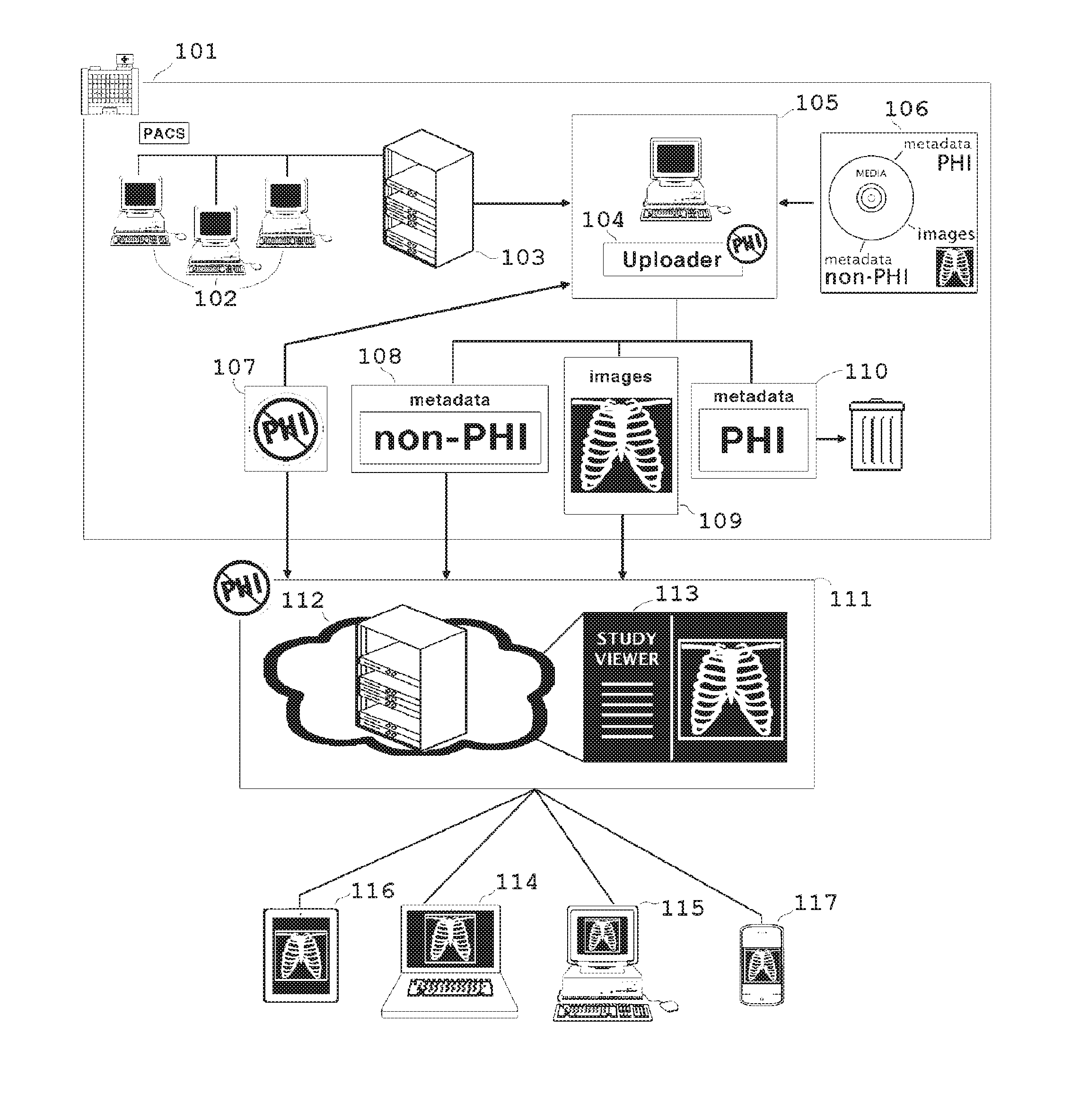
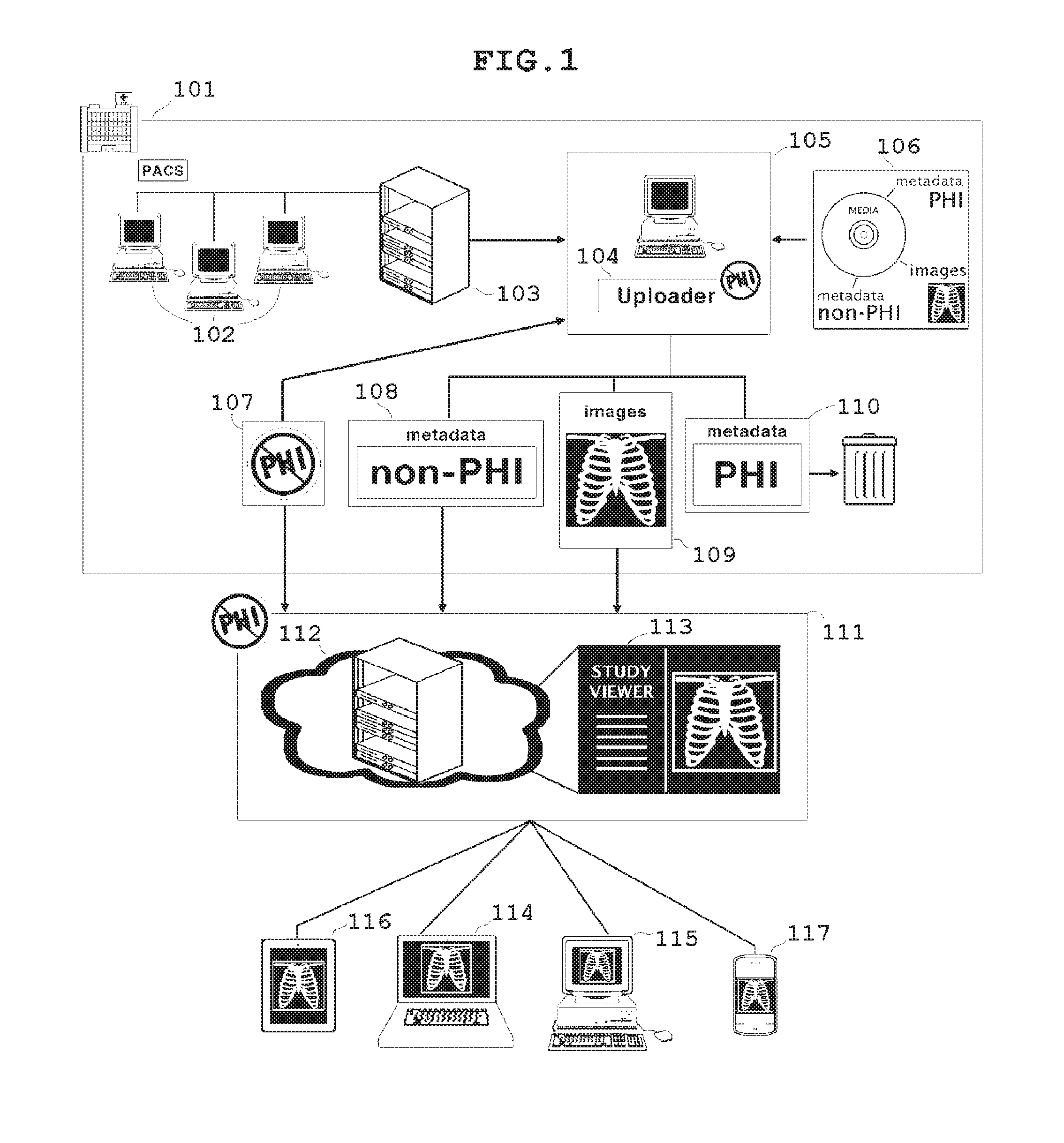
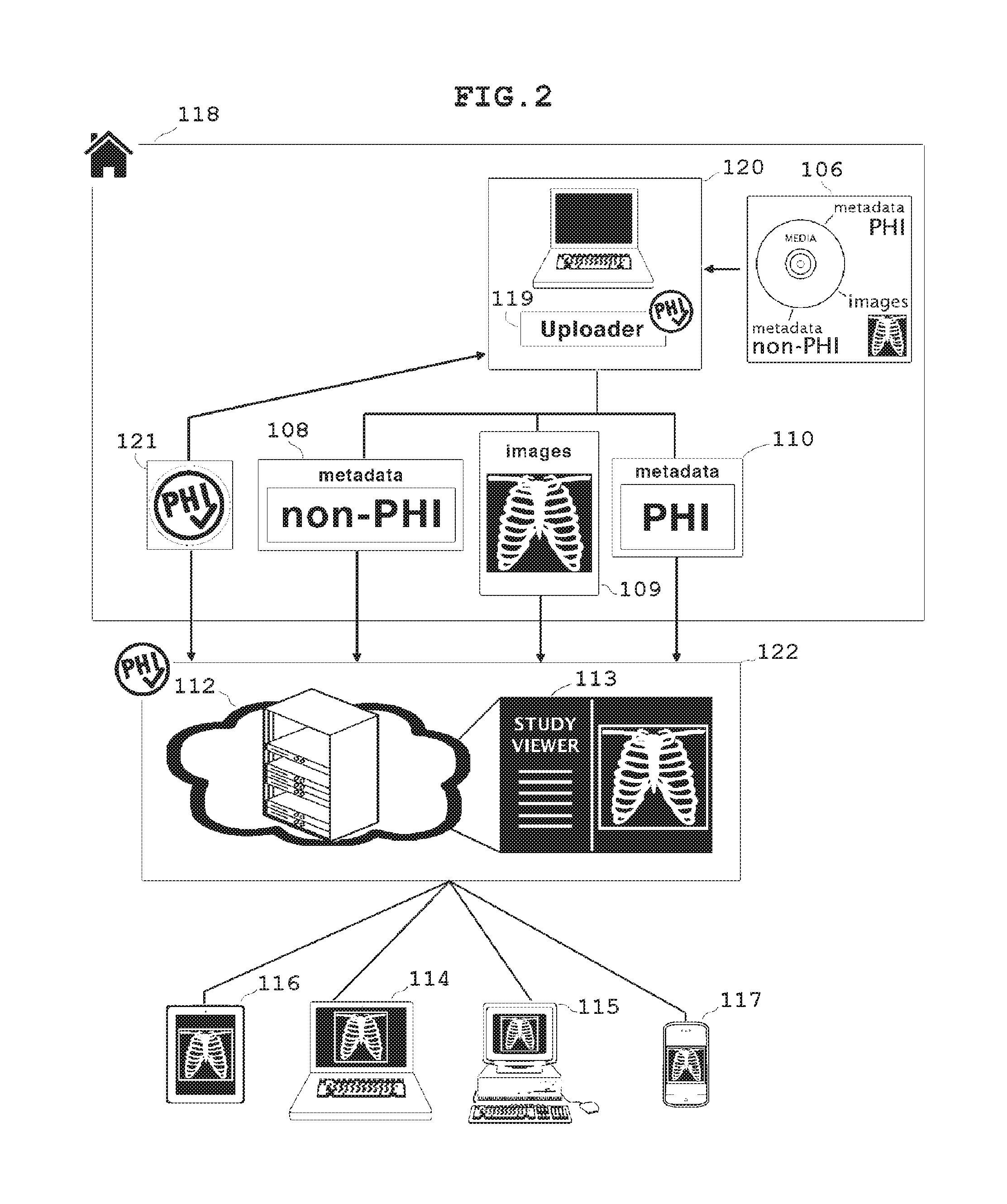
Collaborative cloud-based sharing of medical imaging studies with or without automated removal of protected health information
InactiveUS20160147940A1Easy to watchFinanceDigital data protectionMedical imagingProtected health information
A technique manages medical image data. The technique involves receiving an original medical imaging study that includes a set of medical images and embedded protected patient information. The technique further involves performing a protected patient information removal operation which generates a cloud-storable medical imaging study from the original medical imaging study. The cloud-storable medical imaging study includes the set of medical images but omitting the embedded protected patient information. The technique further involves storing the cloud-storable medical imaging study in a cloud-based medical image repository among other cloud-storable medical image studies. The cloud-based medical image repository is external to the computerized device and public network accessible.
Owner:CITRIX SYST INC
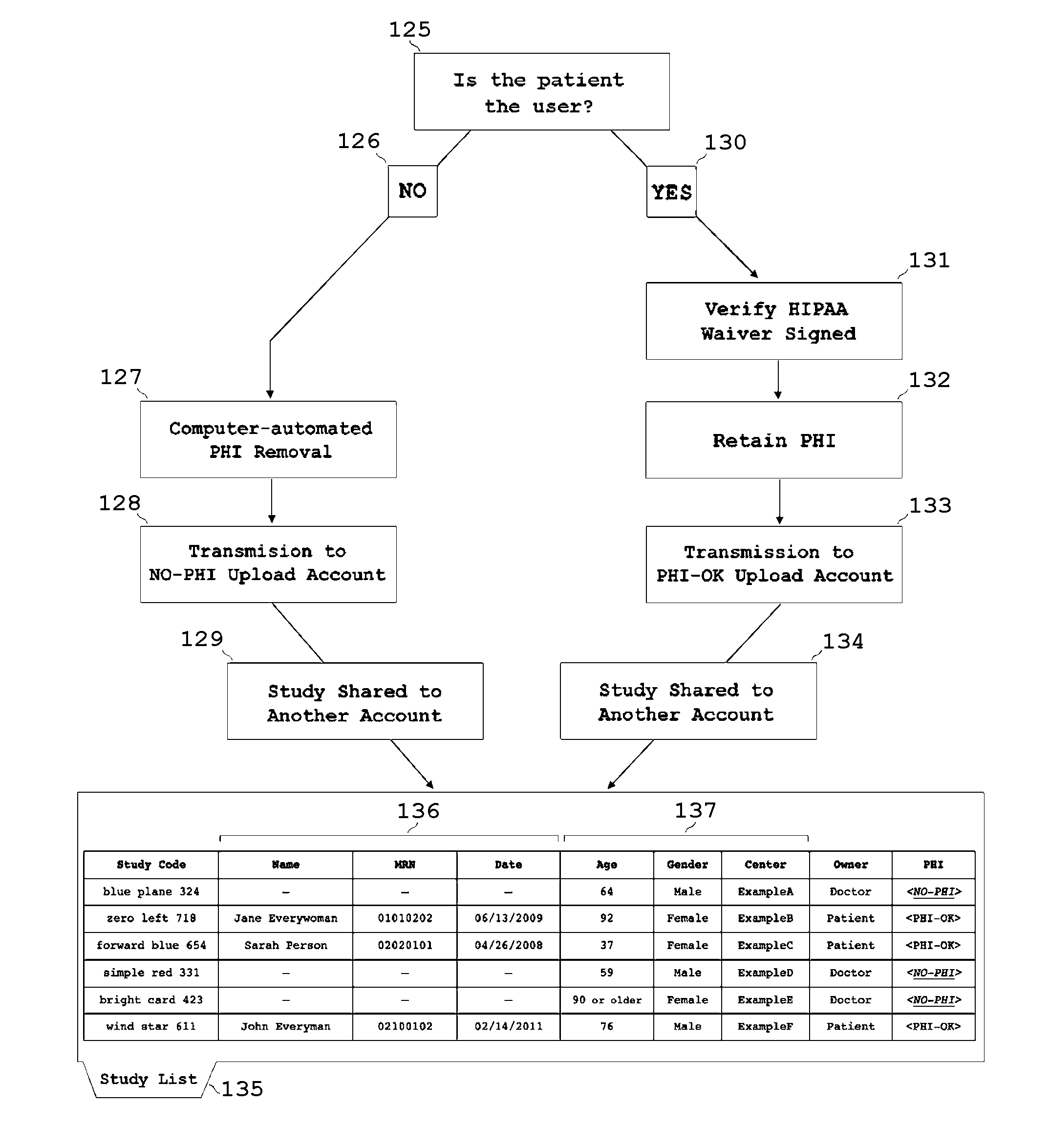
Collaborative cloud-based sharing of medical imaging studies with or without automated removal of protected health information
InactiveUS20140109239A1Facilitate shared study viewingPromote collaborationFinanceDigital data processing detailsThird partyData stream
The present invention teaches a method wherein medical imaging studies are transformed from Identifiable Imaging Studies into Cleared Imaging Studies that can be legally and securely shared, either by automated removal of protected health information (PHI) or by verification that the studies belong to a Patient or Patient's Legal Representative and that a valid effective waiver, such as a HIPAA Waiver, is on file. Cleared Imaging Studies are shared by cloud-based storage and transmission to one or more Third Parties using one or more network-enabled devices. Methods are also provided for one or more users of network-enabled devices to view medical imaging studies simultaneously, with caching of imaging studies in local devices and separation of additional data streams used for collaborative image viewing to ensure that medical images are not degraded.
Owner:CITRIX SYST INC
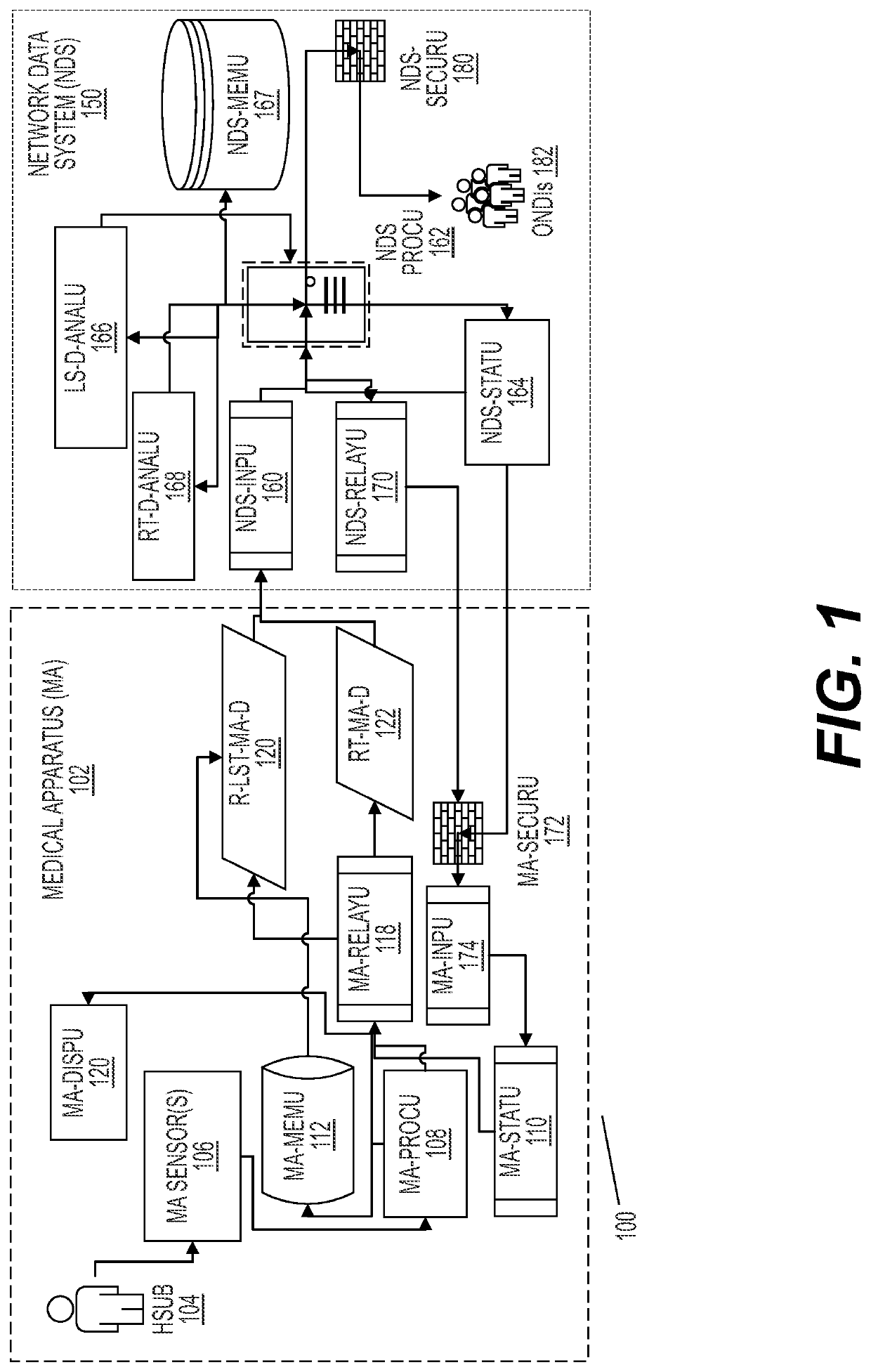
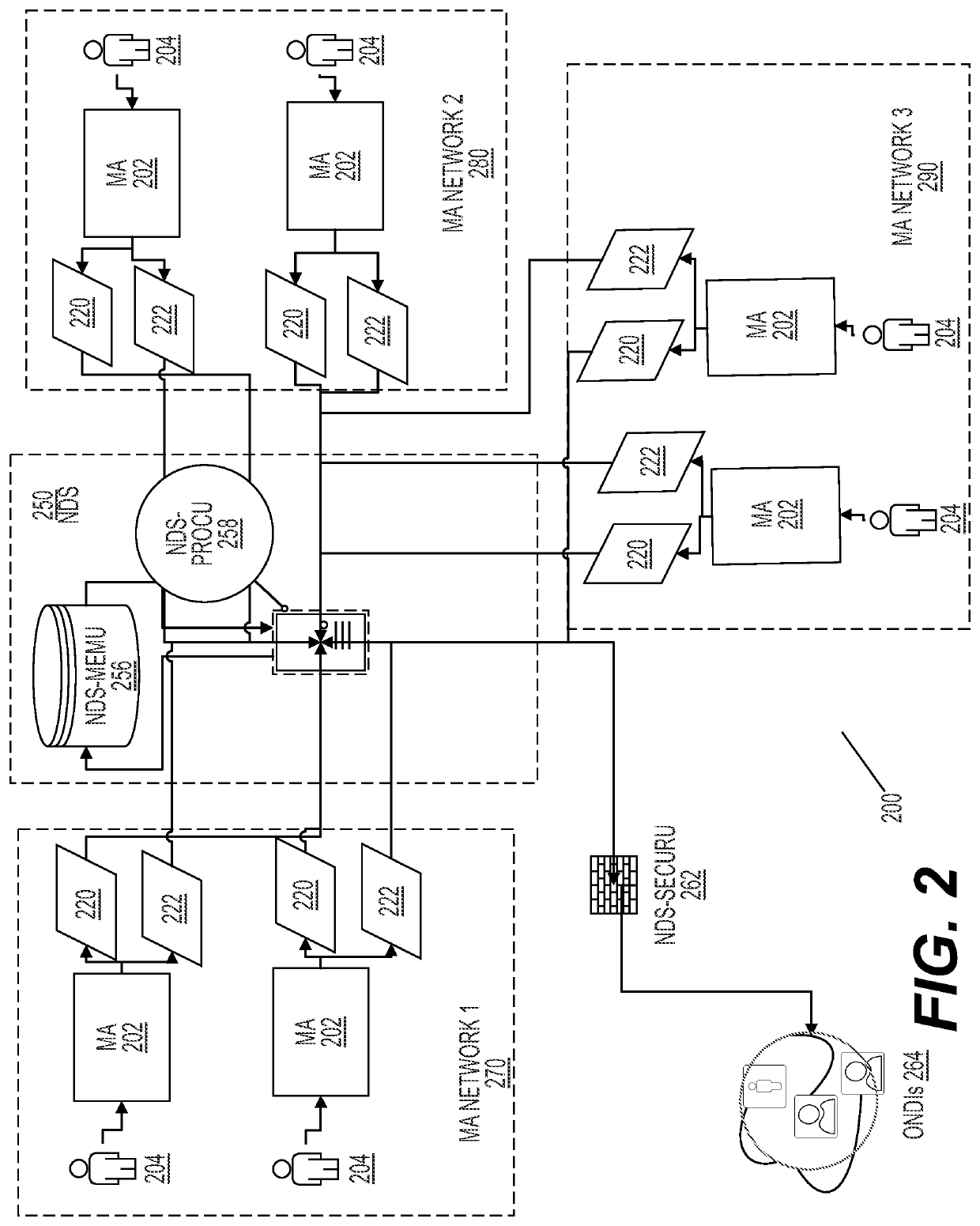
Network-based medical apparatus control and data management systems
InactiveUS20220215948A1Fuzzy logic based systemsMachine learningStreaming dataCustomer relationship management
This invention provides new systems and methods for controlling the operation of medical devices. Devices collect sensor data, relay such data as streaming data via a secure internet connection, but also collect such data locally as cache data. When events occur, such as an offline event, the devices also relay such cache data. Device data is received by a network data system that analyzes the data and controls operation of the devices and other network devices based on such analysis. The medical devices can comprise multiple zones performing different data collection functions and being subject to different data relay rules / processes. The system can segregate protected health information from commercial users that are allowed to access certain analytical data. In aspects, the system interacts with third party databases, e.g., customer relationship management systems, in generating analytical data. In aspects, machine learning processes are employed to improve the operation of such systems.
Owner:ABIOMED
Method and system for rule-based anonymized display and data export
ActiveUS11183292B2Computer security arrangementsMedical imagesEngineeringProtected health information
Owner:PME IP
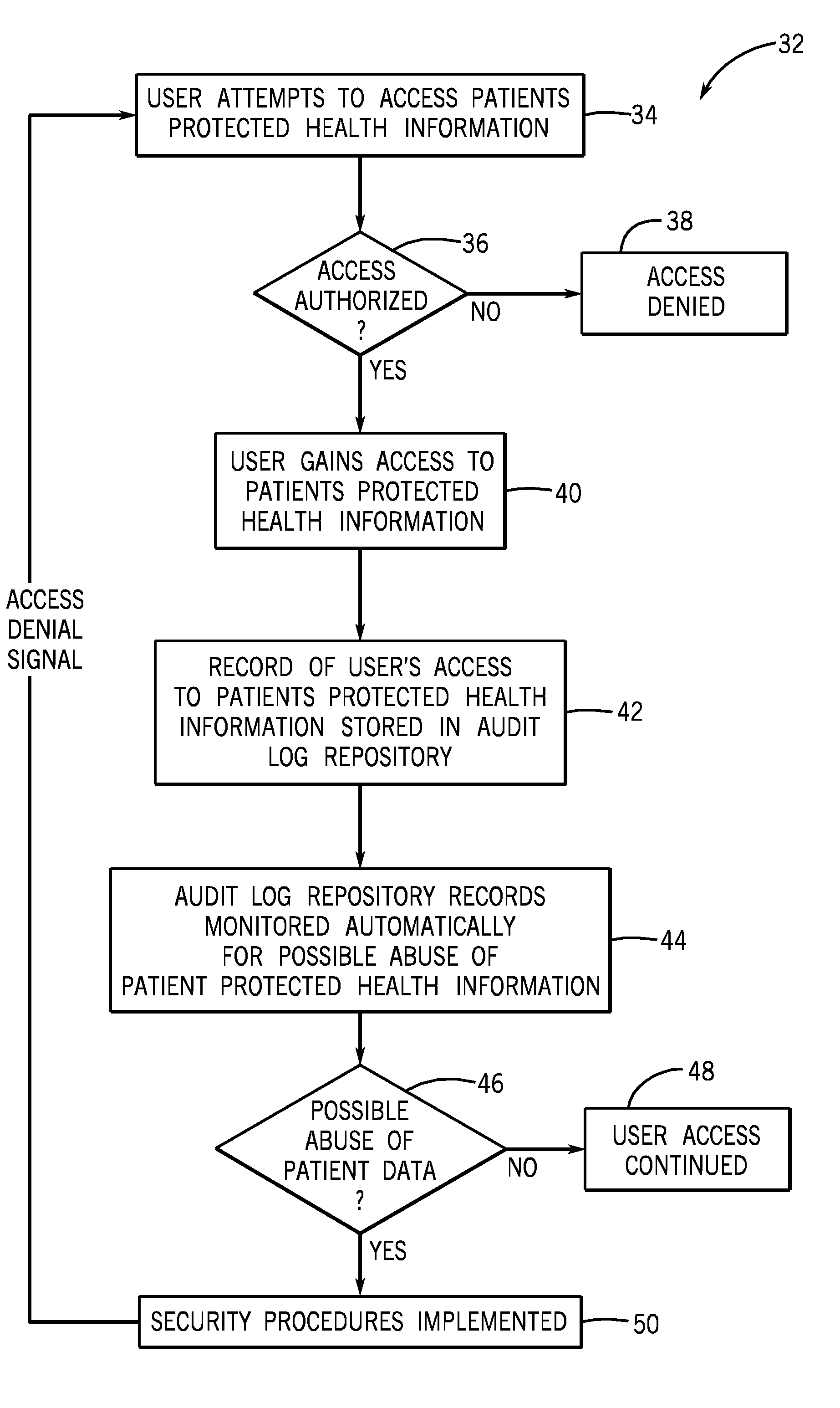
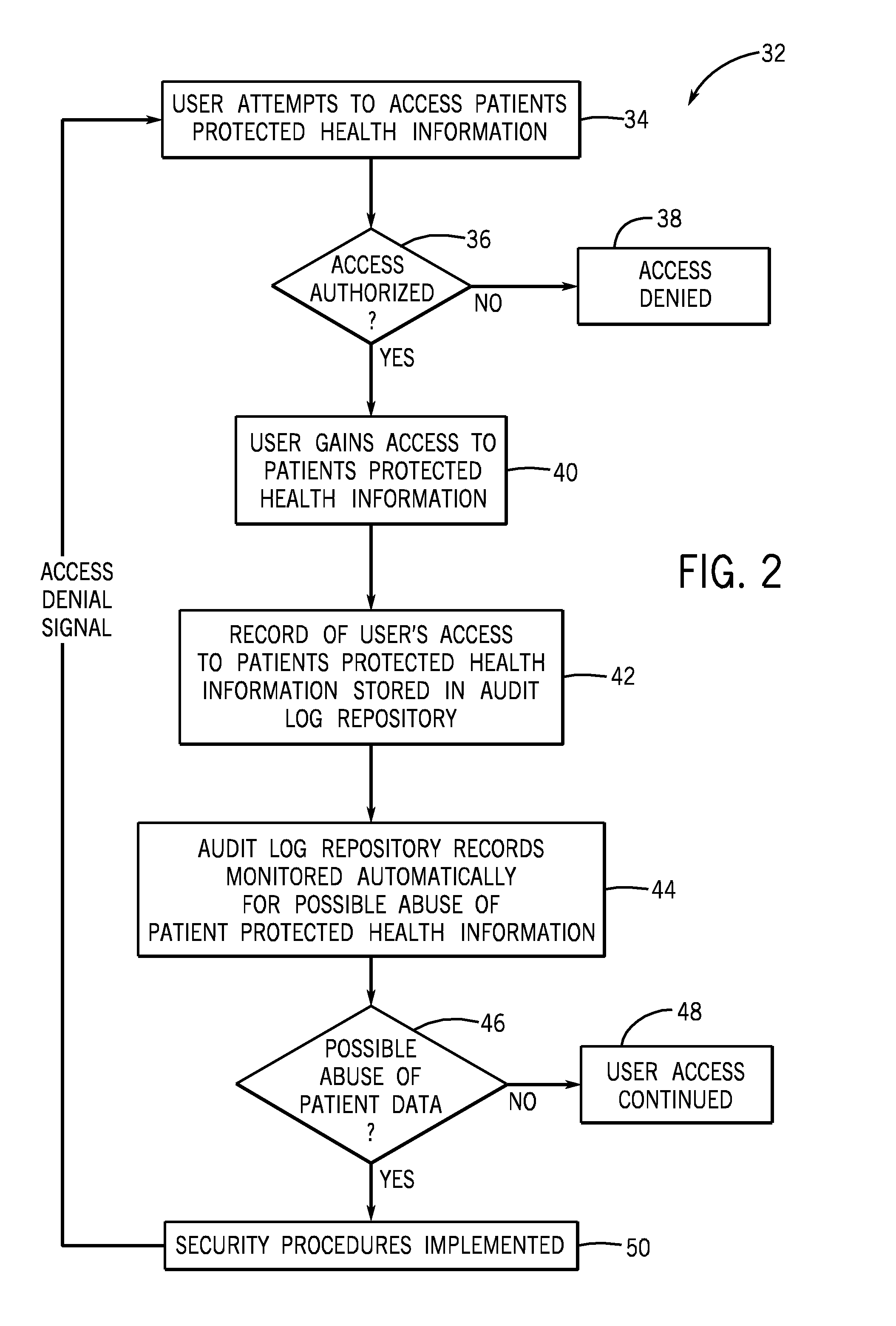
System and method for detection of abuse of patient data
InactiveUS20090089094A1Data processing applicationsComputer security arrangementsInternet privacyPatient data
A technique for detecting abuse of protected health information stored in a medical information system is presented. A record of each user's access to the protected health information is created and stored. The record of the access is configured to provide a basis for determining whether a user's access to the protected health information was for a legitimate reason or was a possible abuse of a patient's protected health information. A data mining program is used to search the records of access to the protected health information and identify possible abuses of patients protected health information. When a possible abuse of a patient's protected health information is identified as a result of the data mining, an alert is sent to notify a responsible authority of a possible abuse of a patient's protected health information.
Owner:GENERAL ELECTRIC CO
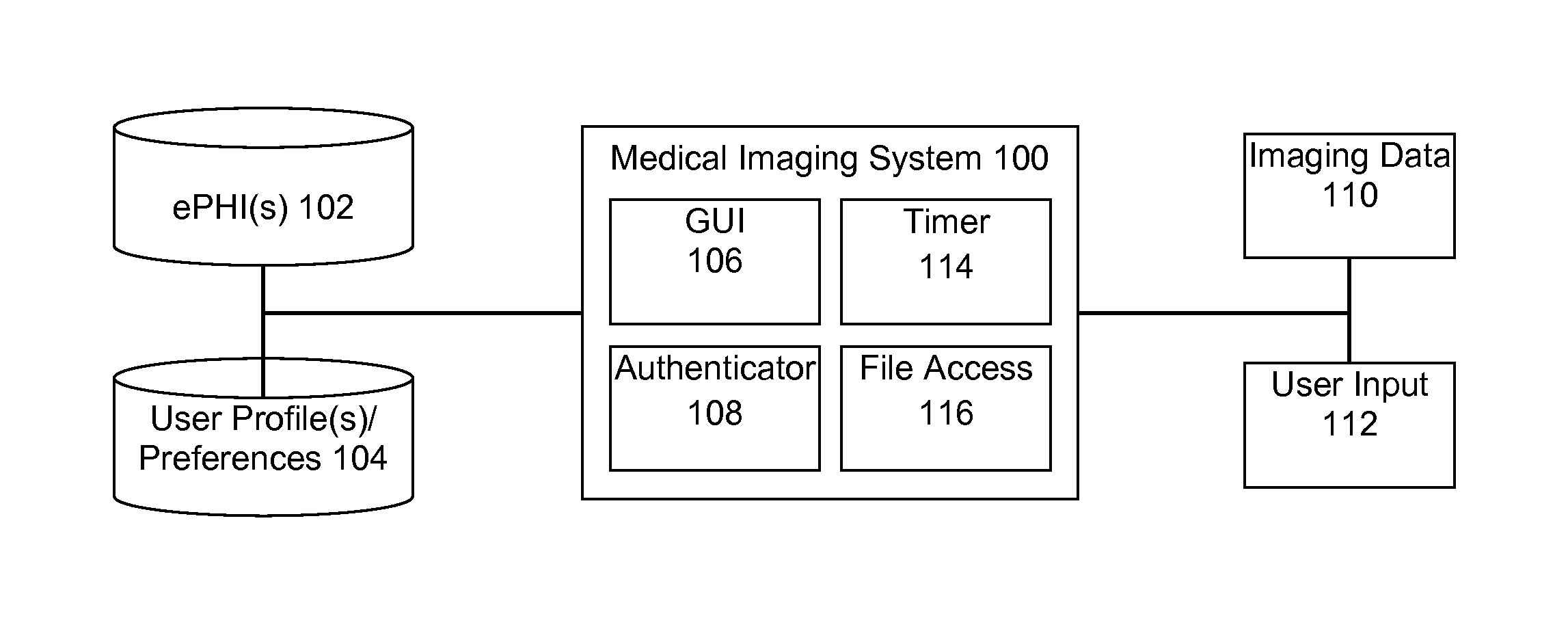
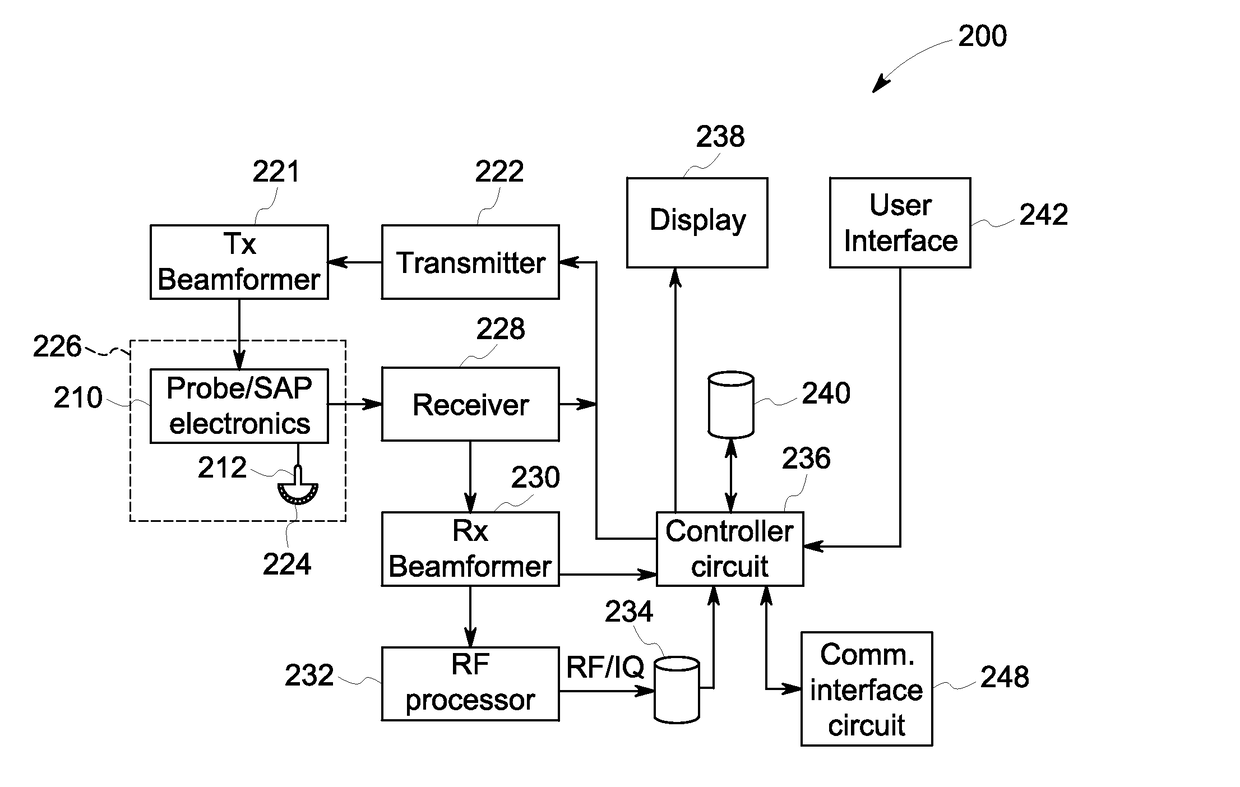
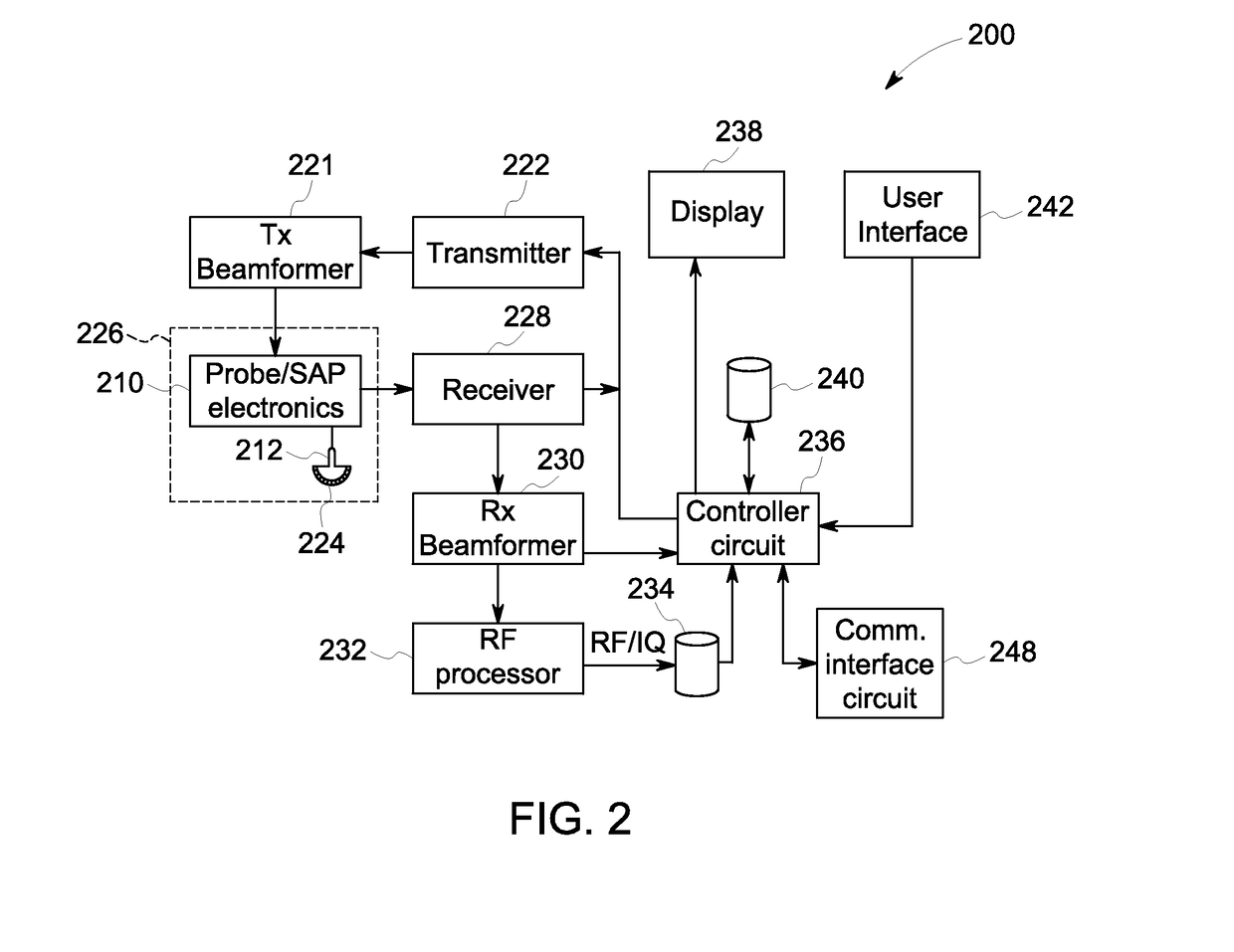
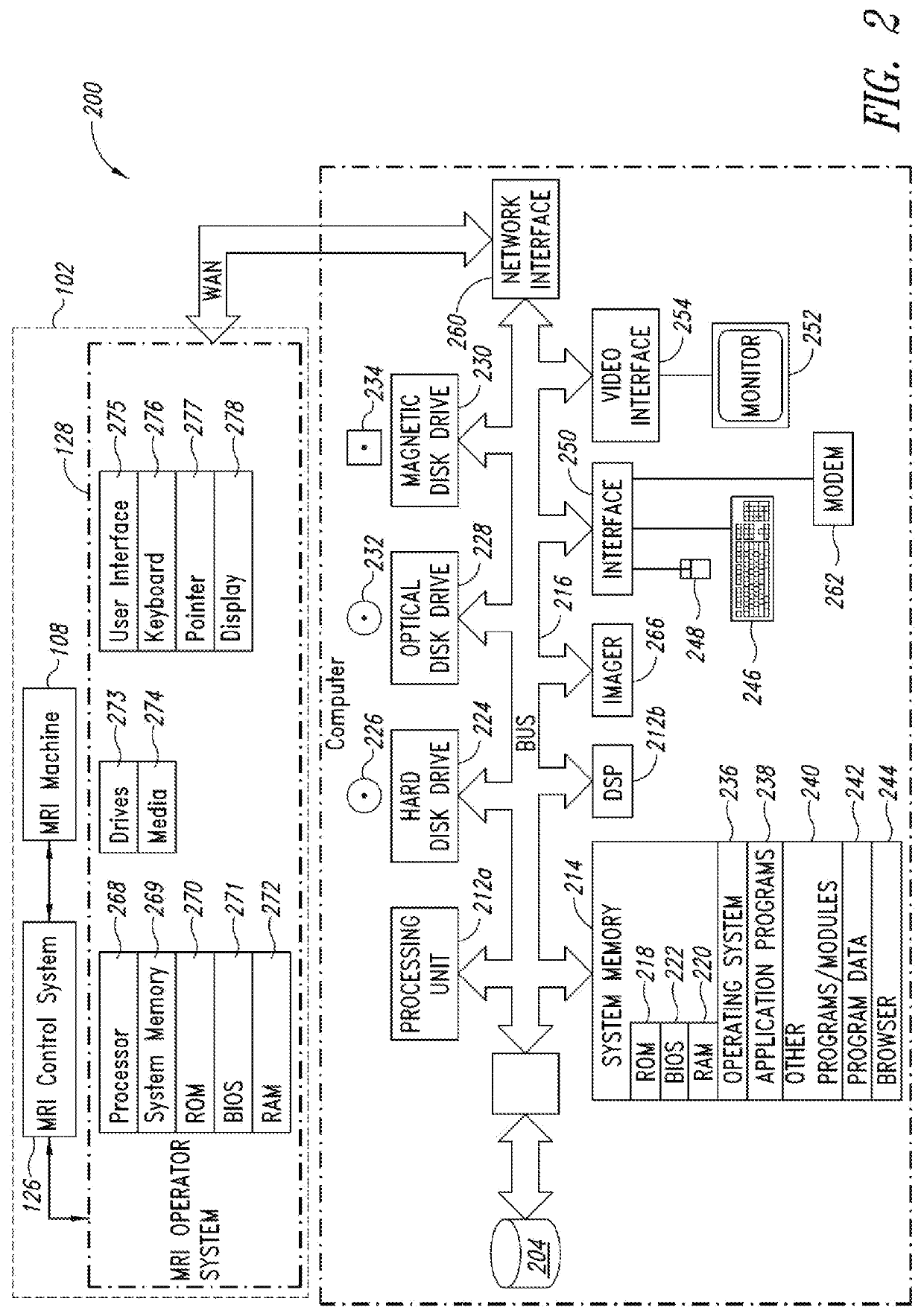
Electronic protected health information security for digital medical treatment room
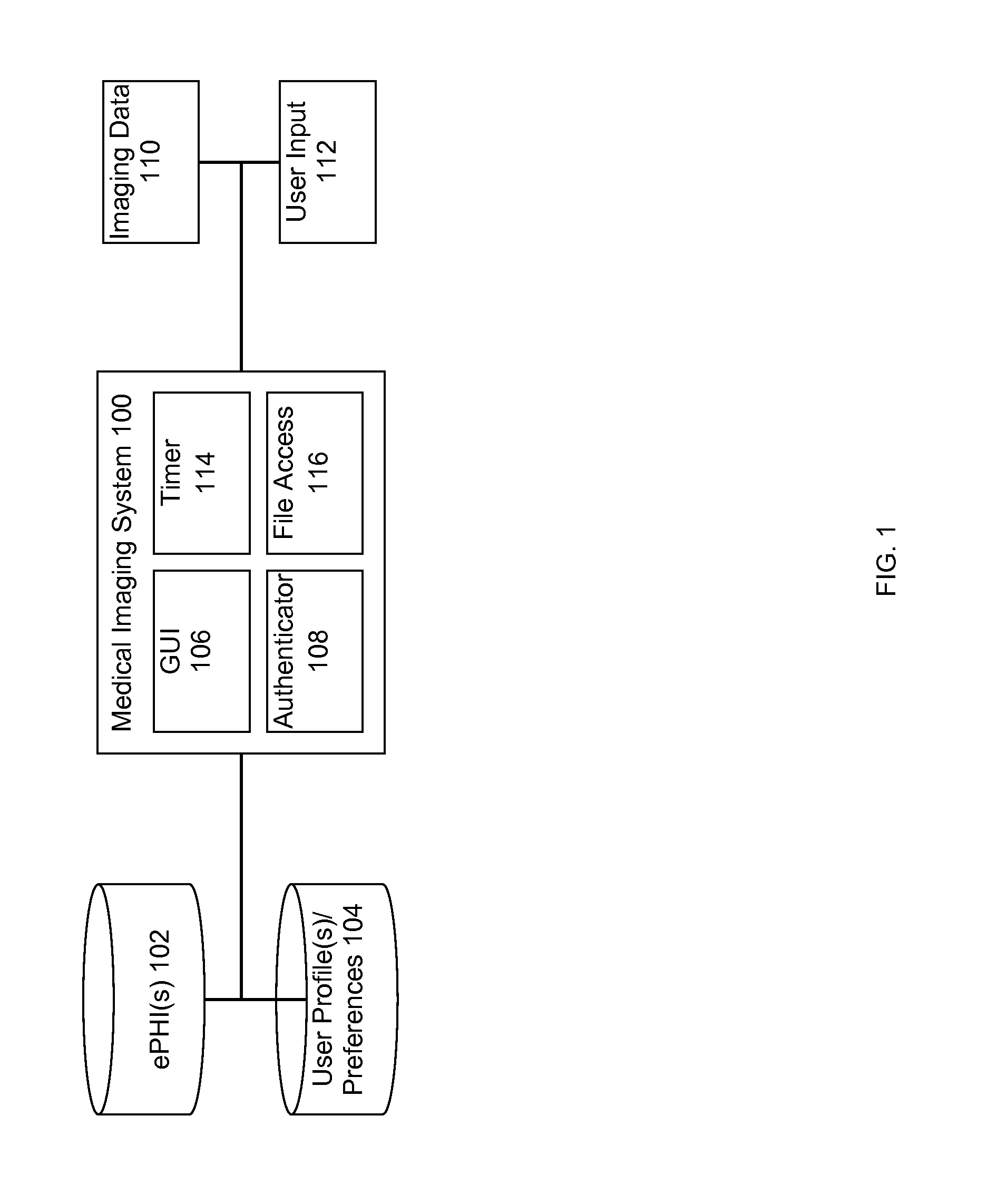
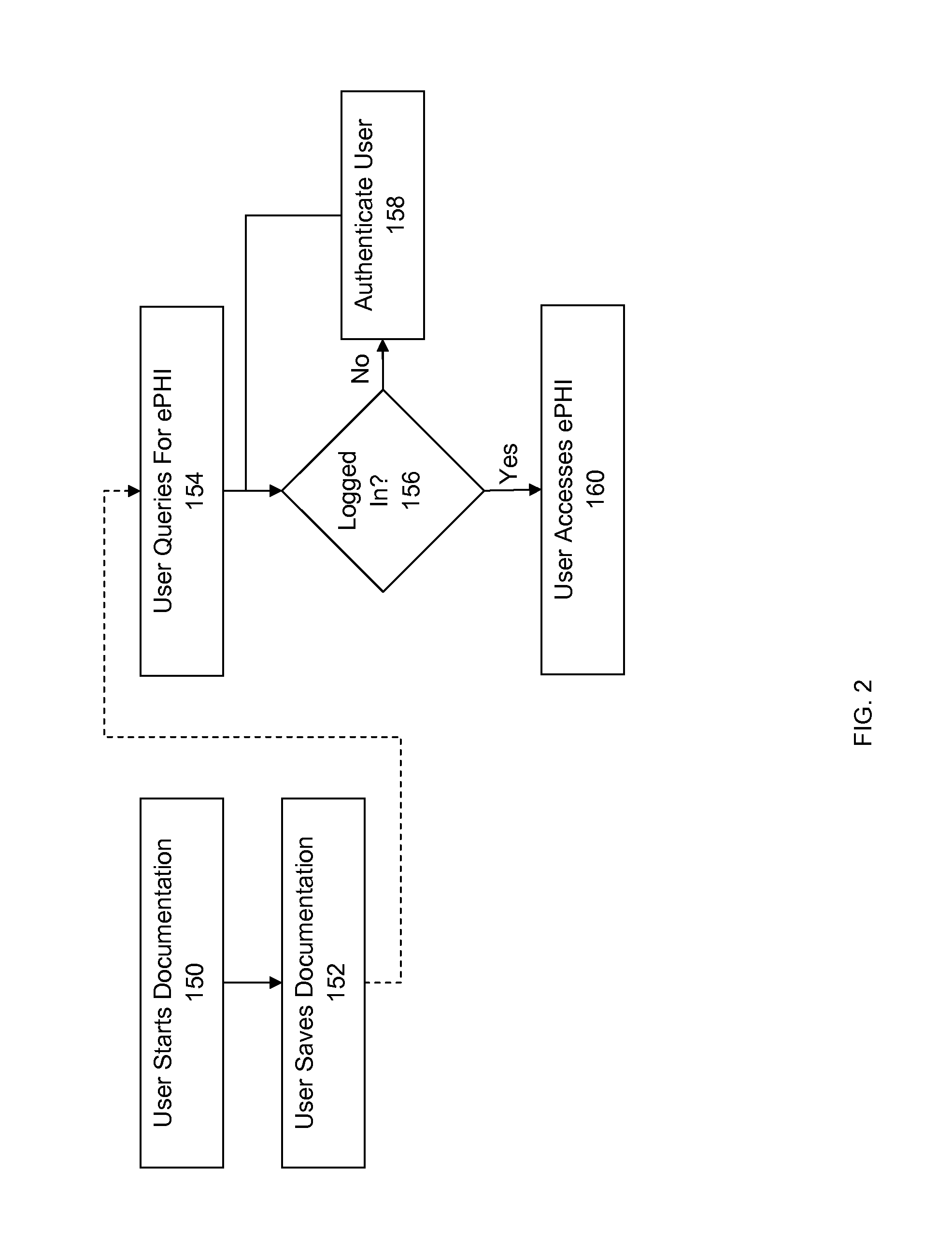
A medical imaging system includes a data store having stored medical imaging data and a computer. The system may be in a medical treatment room and is adapted to receive and display imaging data from a medical procedure. The computer has a graphical user interface that receives authentication credentials. An authenticator alternately prevents or allows a user access by logging the user into the system using the authentication credentials. A file accessor receives received medical imaging data and stores it in the data store, and retrieves the stored medical imaging data and provides it to the graphical user interface for display. Documentation data is received through the graphical user interface and is stored in the data store without requiring the user to provide the authentication credentials or be logged into the system. The user cannot access the stored medical imaging data before providing the authentication credentials and being logged into the system.
Owner:KARL STORZ ENDOSCOPY AMERICA
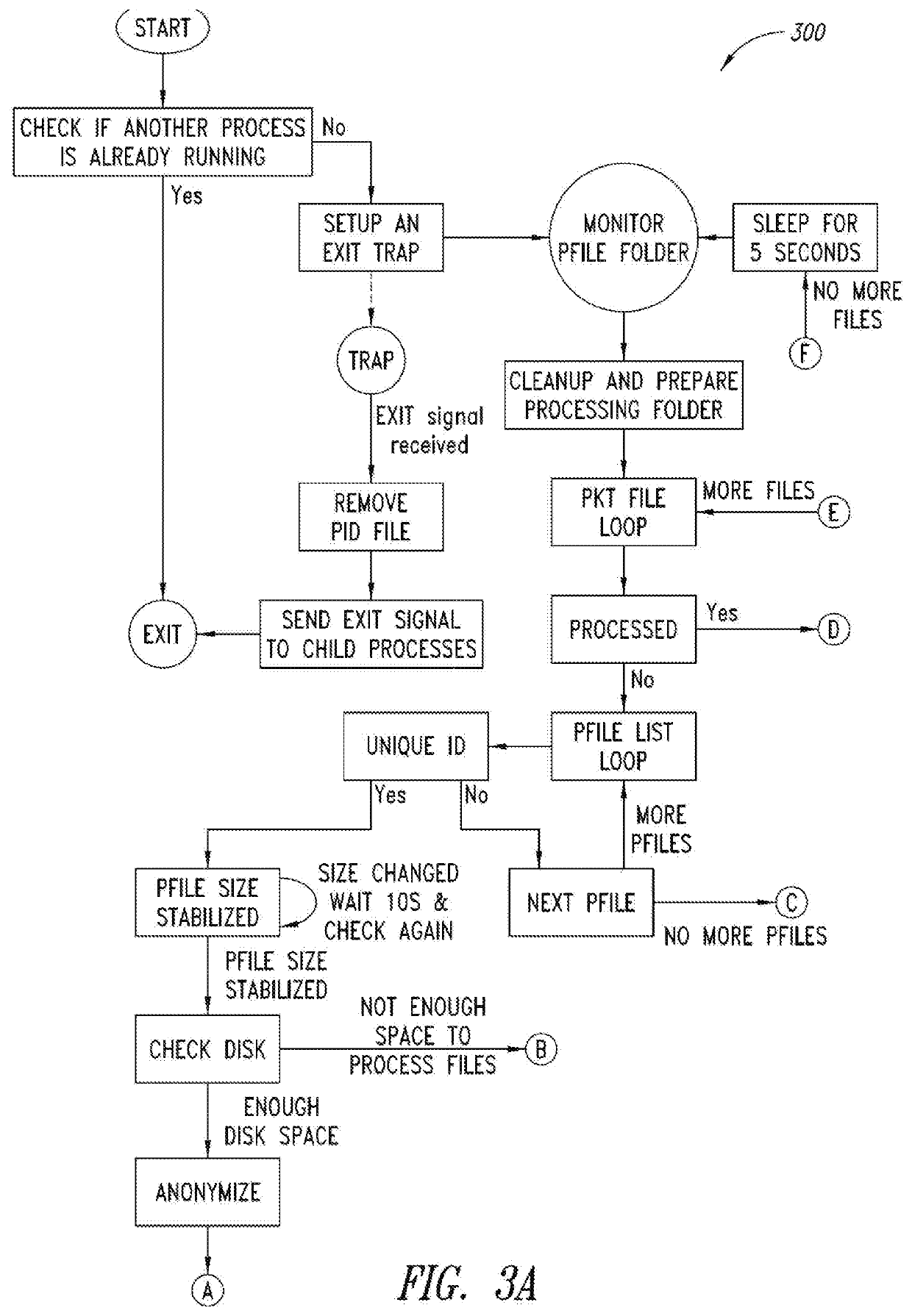
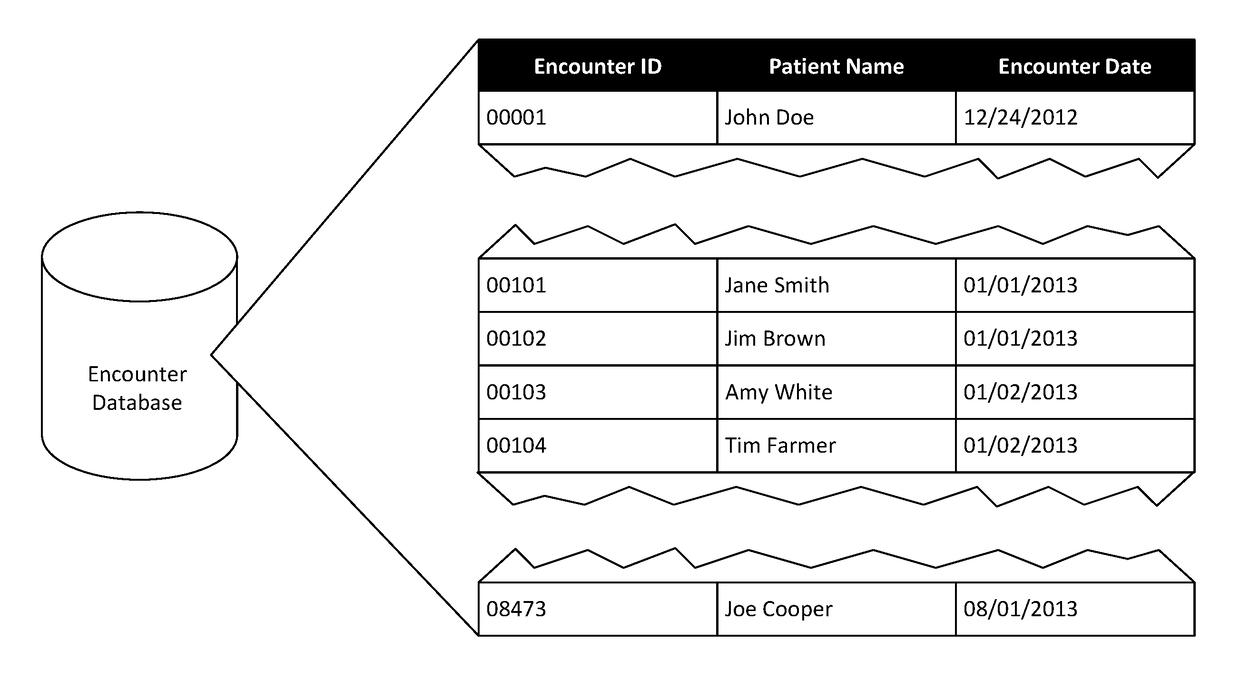
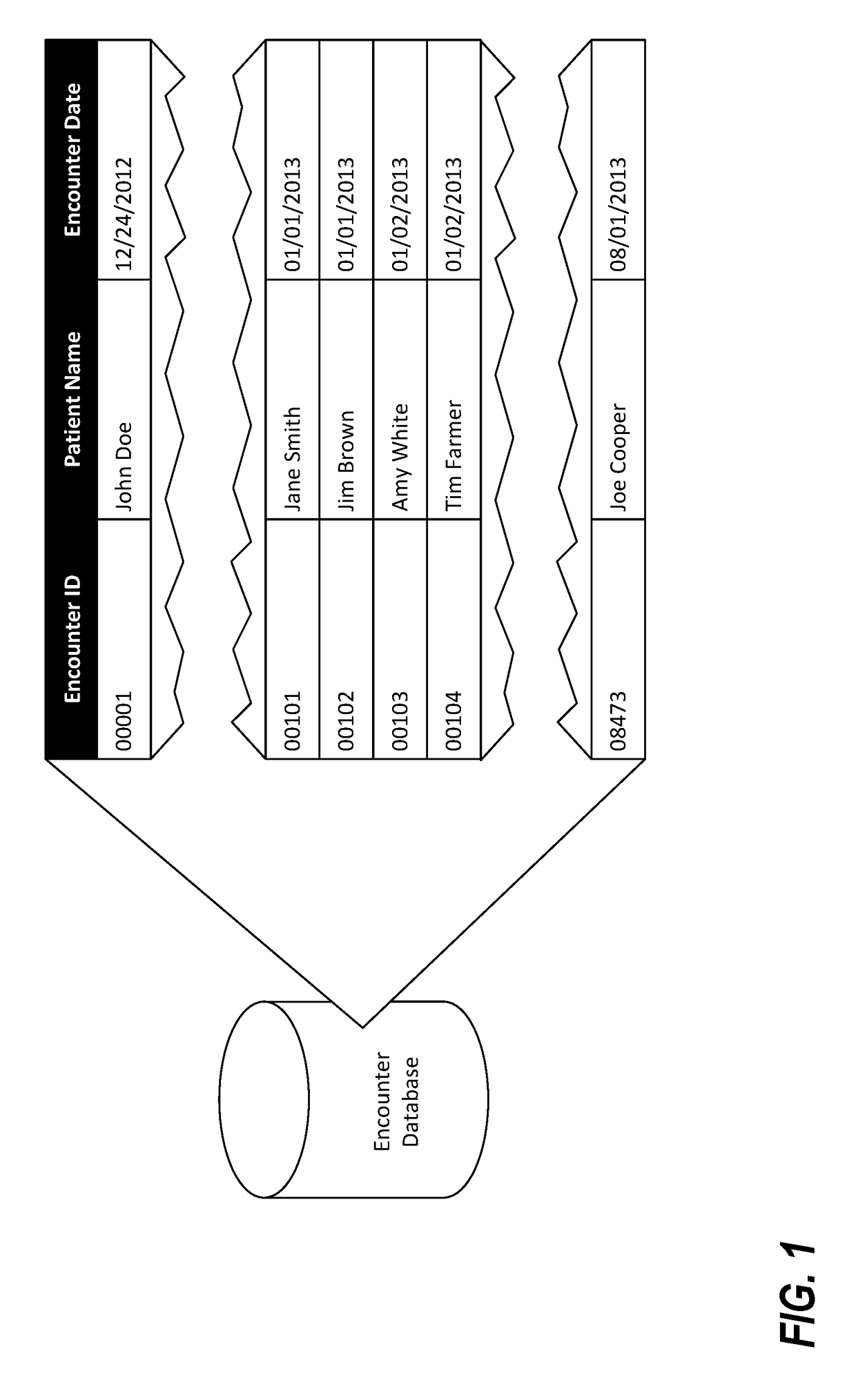
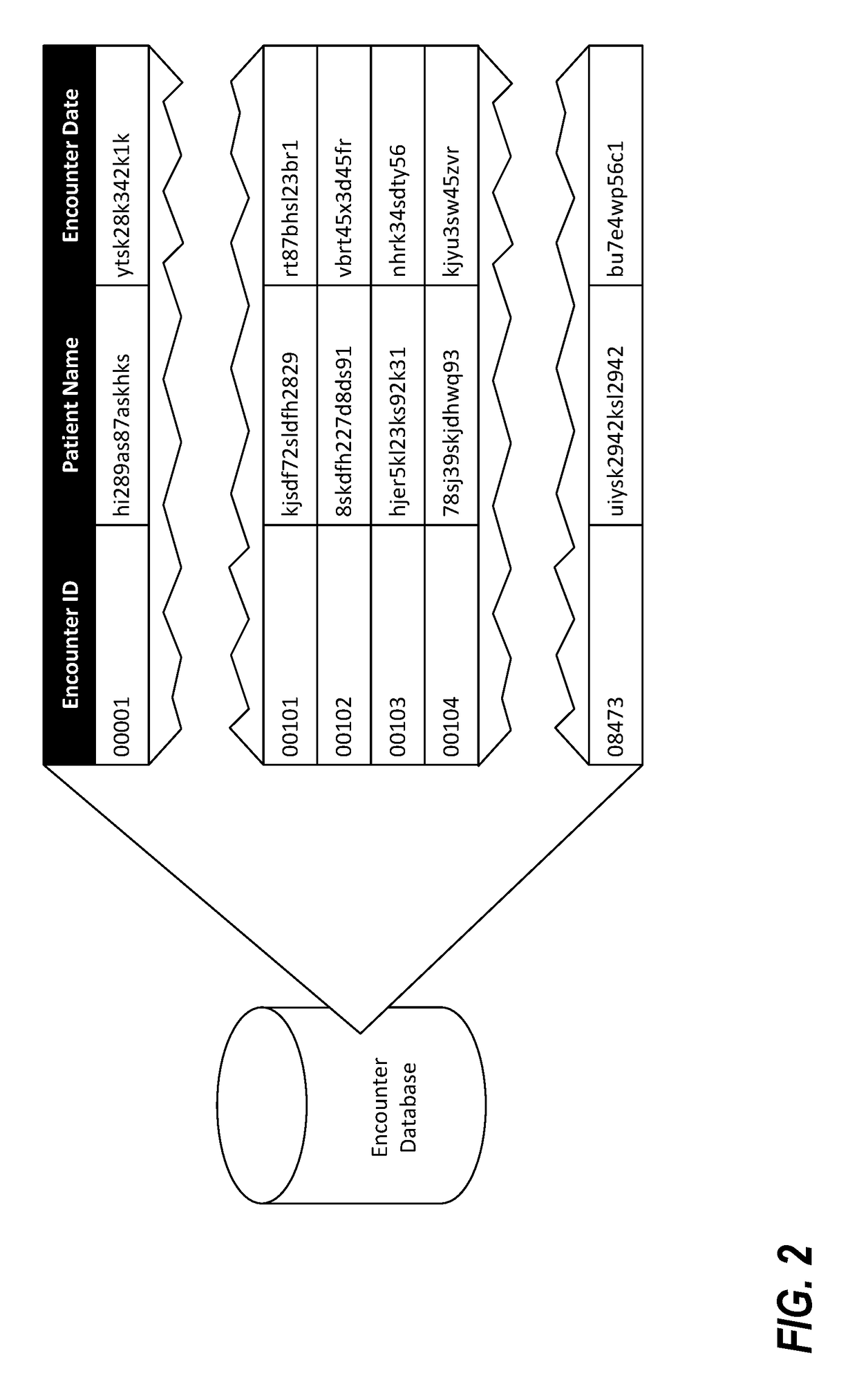
Data de-identification methodologies
ActiveUS10403392B1Office automationPatient-specific dataProtected health informationComputer software
A method includes de-identifying a data table containing protected health information by determining, based on a mappings file, that a first column of the data table is associated with a first data type, accessing each value of the first column, and, for each respective accessed value, automatically generating a de-identified value by applying one or more computer logic instructions associated with de-identification of the first data type to the respective accessed value to result in a respective de-identified value, and saving the respective de-identified value back to the data table in place of the respective accessed value; and utilizing the de-identified data table to test a computer software application.
Owner:ALLSCRIPTS SOFTWARE
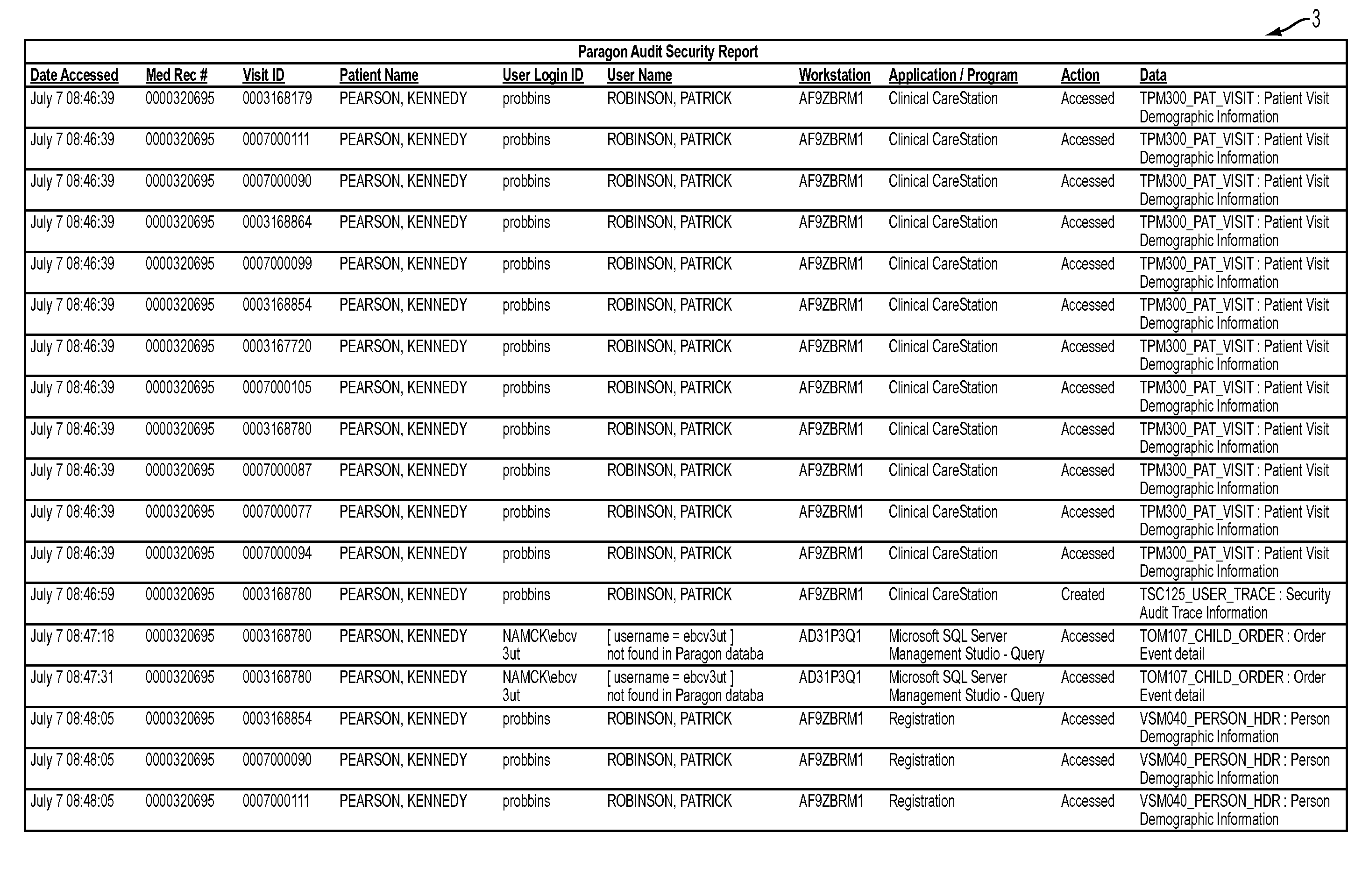
Methods, apparatuses and computer program products for auditing protected health information
ActiveUS20130262503A1Efficient and reliable mechanismEfficient and reliableDigital data processing detailsComputer security arrangementsProtected health informationDatabase
An apparatus is provided for auditing protected health information of one or more patients. The apparatus includes at least one memory and at least one processor configured to detect a query to access information stored in a database including patient-related information. The processor is further configured to save the query in an event file. The processor is further configured to capture query-related information associated with the query and save the query-related information in the event file. The processor is further configured to determine that the query involves protected health information. The processor is further configured to transmit, in response to determining that the query involves protected health information, the query-related information to be used in a reporting table. Corresponding computer program products and methods are also provided.
Owner:HARRIS DAWN HLDG INC
Methods and systems for managing distribution of protected information on a medical display
InactiveUS20170086797A1Organ movement/changes detectionDigital data protectionGraphicsTelecommunications link
Methods and systems managing protected health information (PHI) on a medical display are provided. The systems and methods detect a plurality of communication links between a medical device and a plurality of remote system and display the medical device and the plurality of remote system as corresponding graphical icons on a display. The systems and methods further determine encryption levels for the plurality of communication links and display connection graphics representing the plurality of communication links. Each connection graphic is positioned between the medical device and one of the remote systems having a visual feature corresponding to an encryption level of a communication link between the medical device and the one of the remote systems.
Owner:GENERAL ELECTRIC CO
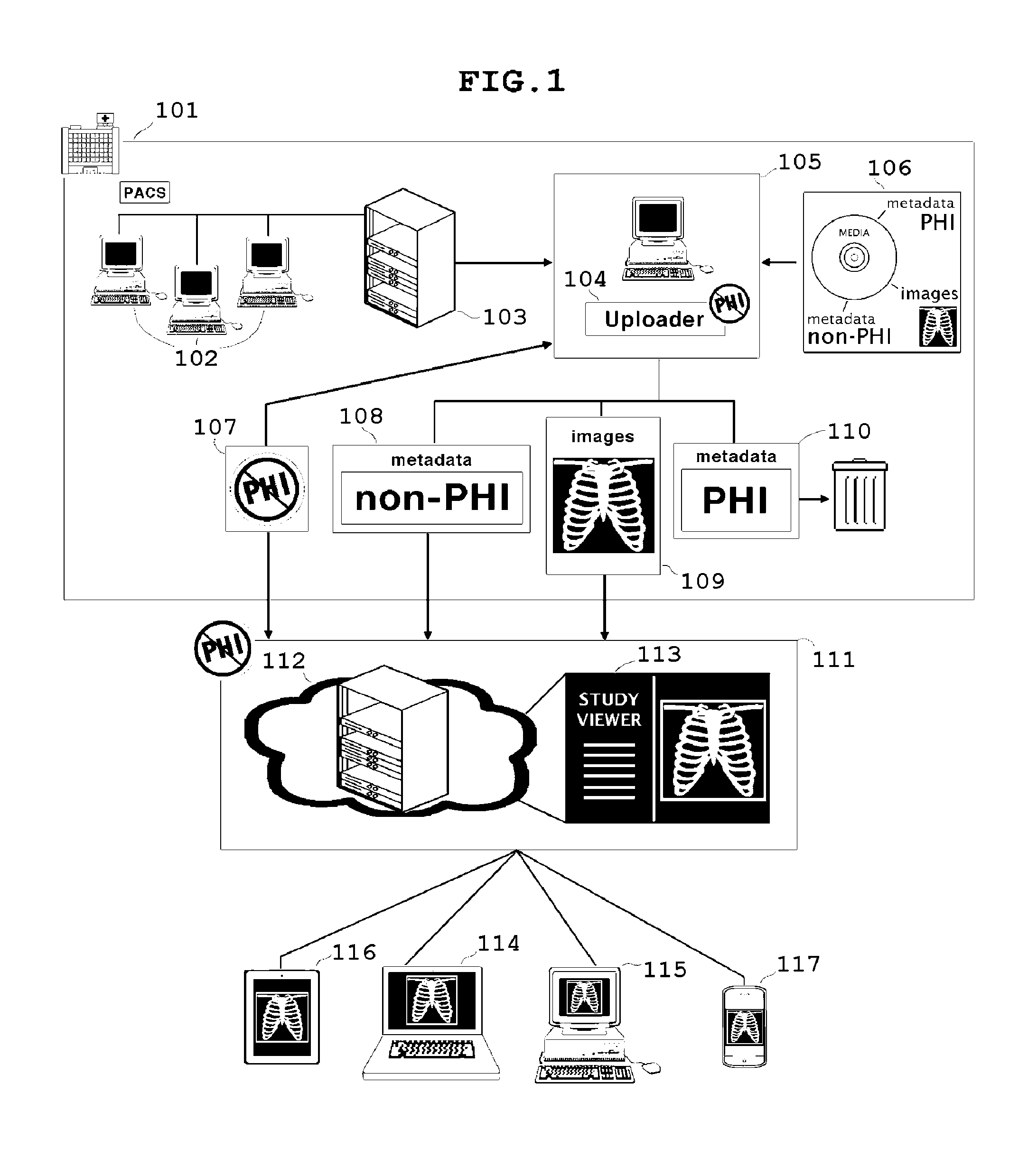
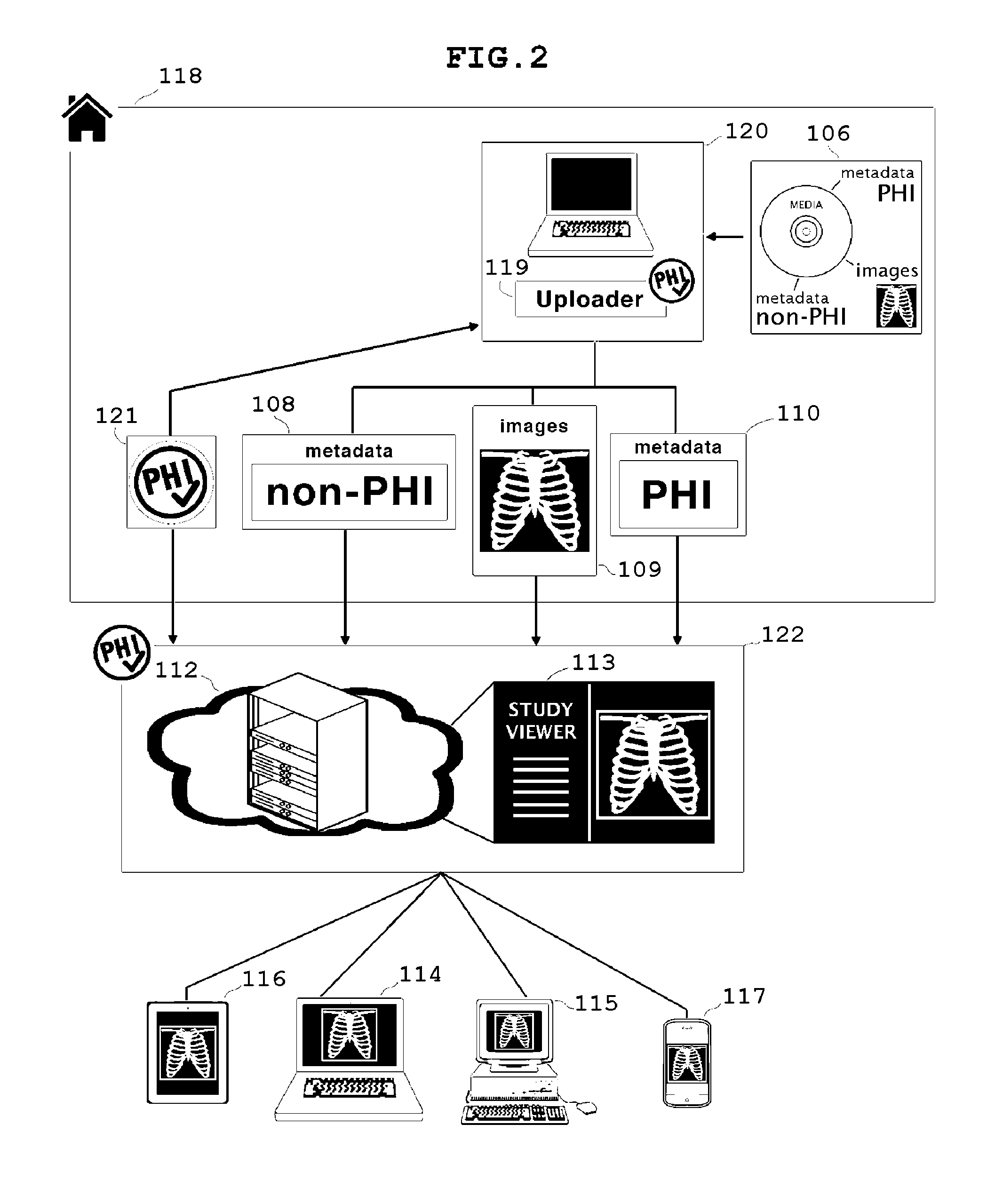
Systems and methods for tracking, accessing and merging protected health information
PendingUS20210391040A1Improve efficiencyIncrease flexibilityMedical communicationMedical automated diagnosisPrivate networkPersonally identifiable information
A protected health information (PHI) service is provided which de-identifies medical study data (e.g., digital imaging and communications in medicine (DICOM) study data) and allows medical providers to control PHI data, and uploads the de-identified data to a remote service system. The PHI service, or an associated service, hosted within an organization performing scans, maintains a database of personally identifiable information, and enables the user to access PHI without having to establish a connection to a virtual private network or WiFi network of the medical service provider. The system also increases the speed, efficiency and flexibility of the technology of medical imaging and analysis over computer networks by correlating unique identifiers in the PHI Service in order to accept DICOM study data over time, and track and retrieve what PHI data has changed regardless of the chronological order in which it was received.
Owner:ARTERYS INC
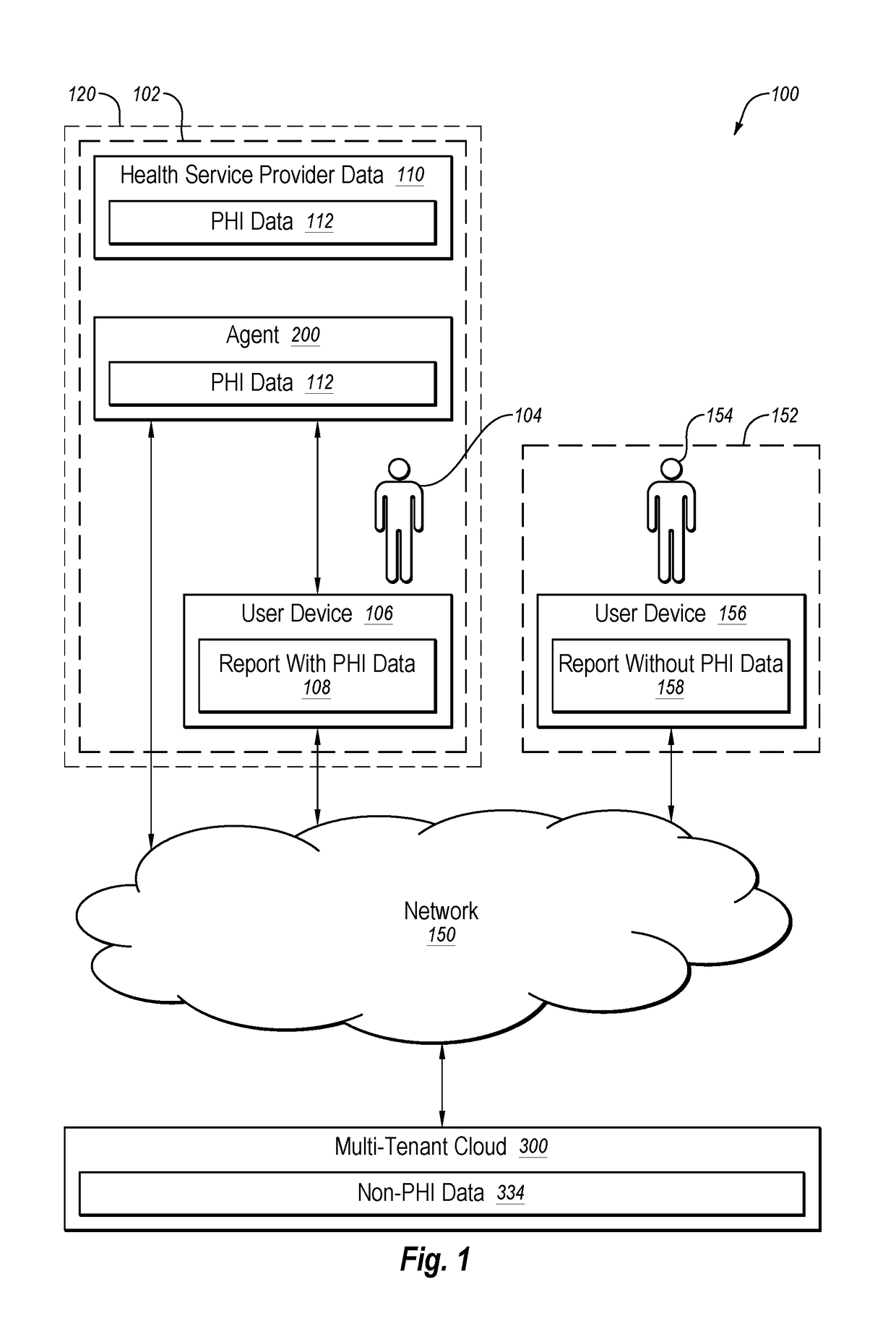
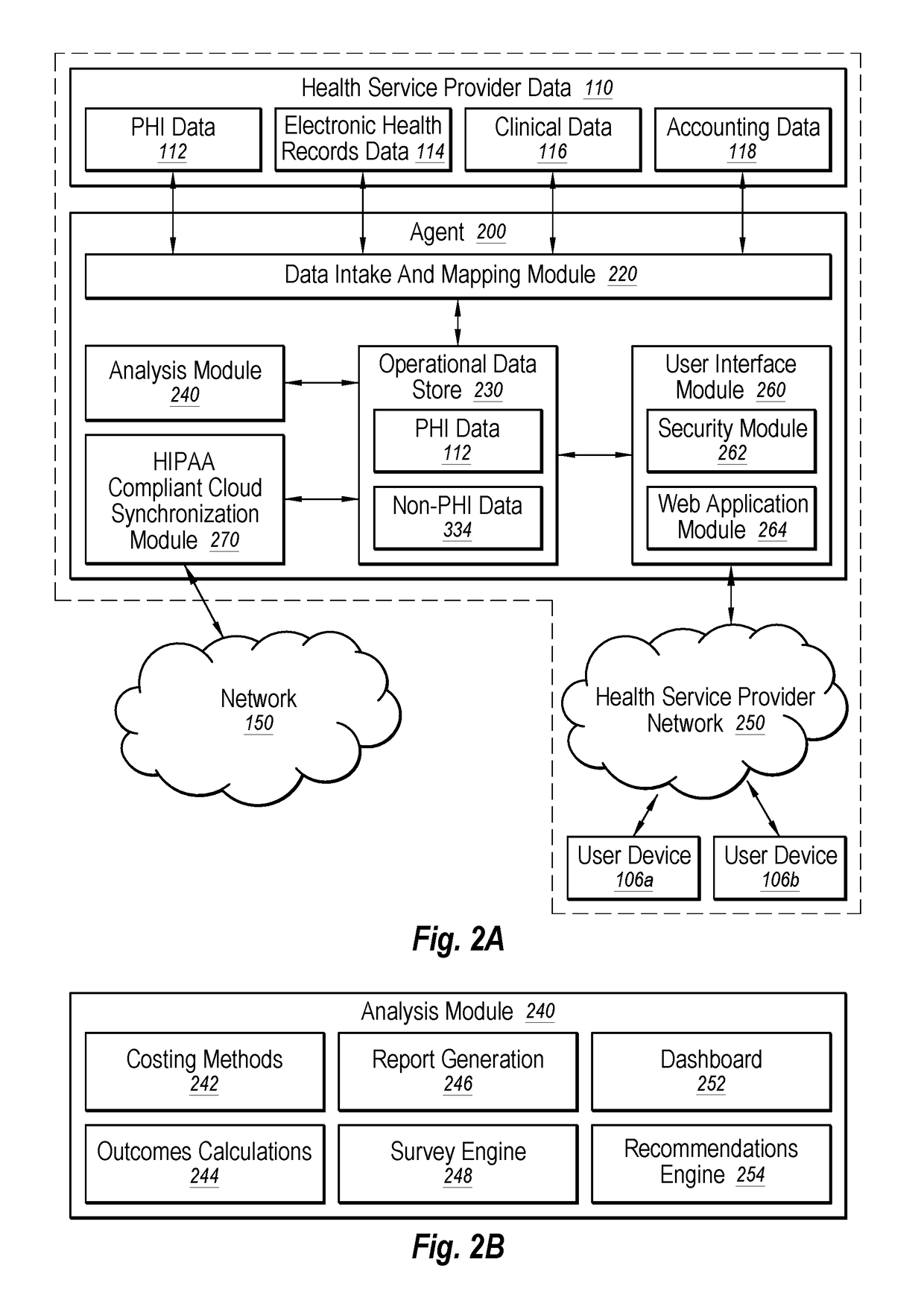
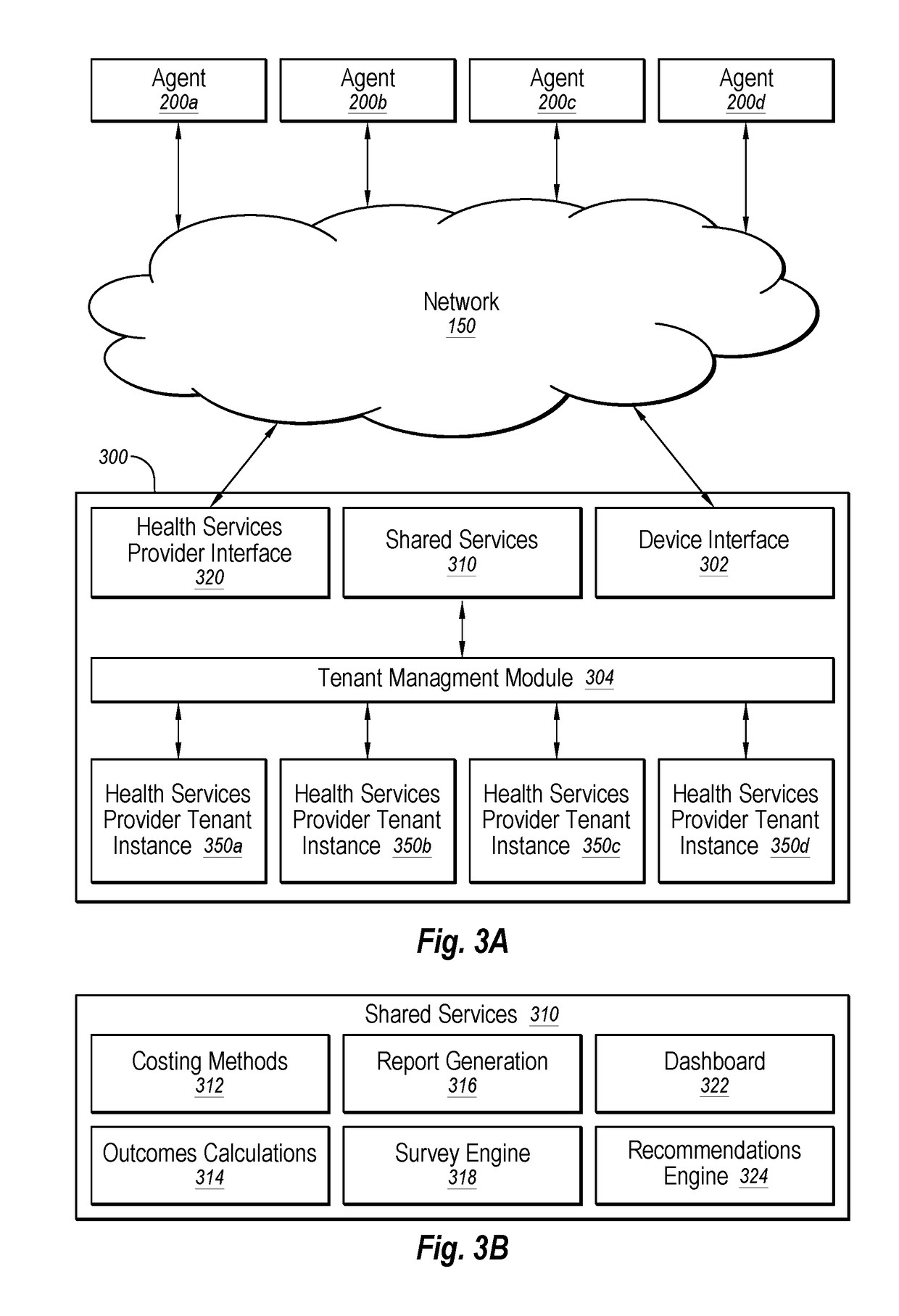
Agent for healthcare data application delivery
InactiveUS20190037019A1Quick implementationIncrease valueLocation information based serviceTransmissionOperational data storeCloud communications
In an example implementation, the method includes automatically determining whether a computer system is located on-premises of a health service provider or on a multi-tenant cloud. The method includes communicatively coupling with health service provider data sources via a local network and extracting health service provider data from them. The health service provider data may include protected health information (PHI) and non-PHI data. The method includes storing the PHI data and the non-PHI data in an on-premises operational data store that is located on-premises of the health service provider. The method includes obtaining data analytics based on the PHI data and the non-PHI data stored in the on-premises operational data store. The method also includes communicatively coupling with a multi-tenant cloud via a global network and synchronizing the non-PHI data in the on-premises operational data store with the multi-tenant cloud via the global network.
Owner:UNIV OF UTAH RES FOUND
Device level security
InactiveUS20190392152A1Platform integrity maintainanceInput/output processes for data processingOperational systemSecurity Measure
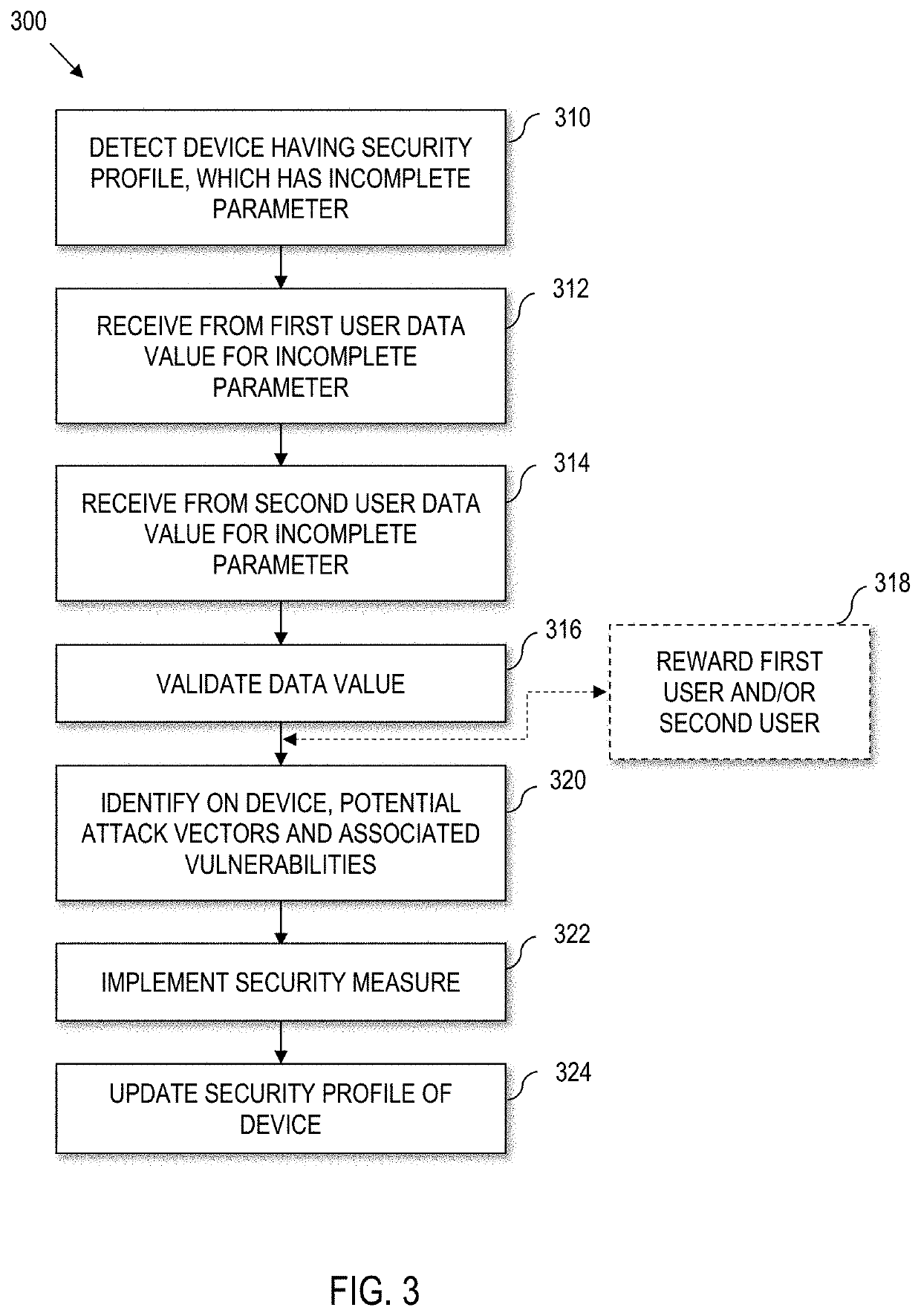
A method for implementing device level security is disclosed. The method involves detecting a device that has a security profile. The security profile has an incomplete parameter (or field) (e.g., make, model, device serial number, FDA class, protected health information, or operating system of the device). The method also includes receiving feedback from a first user to supply a data value for the incomplete parameter. The data value from the first user is validated by a second user (but can require multiple validations). The validated data value is used to identify on the device, potential attack vectors and associated vulnerabilities. The method also includes implementing a security measure based on the identified potential attack vectors and associated vulnerabilities and updating the security profile of the device accordingly.
Owner:MEDITECHSAFE INC
Systems and methods for longitudinally tracking fully de-identified medical studies
InactiveUS20210012883A1Improve performanceCryptography processingUser identity/authority verificationInternet privacyProtected health information
A protected health information (PHI) service is provided which de-identifies medical study data and allows medical providers to control PHI data, and uploads the de-identified data to a remote service system. The PHI service, or an associated service, hosted within an organization performing scans, maintains a database of personally identifiable information, and may generate a cryptographic hash using one or more identifying fields which can then be sent to a service hosting the de-identified data. A cryptographic hash may be further secured by combining the identifying fields with a unique cryptographic key before hashing the value. Matching hashes indicate related studies within the remote service. The service may re-generate and send the cryptographic hashes for each study whenever the configured set of fields changes. This allows all data, historical and new, to be properly linked and related.
Owner:ARTERYS INC
Critical health information profile and emergency communication system
A microprocessor-based emergency response communication system used to call and communicate with the 9-1-1 operator and also allows emergency responder's immediate access to a user's Critical Health Information Profile stored in the device at the point and location of crisis. The device is used to create individual Critical Health Information Profiles which is Health Level-7 compliant enabling it to seamlessly communicate with major hospital networks worldwide. This functional capability provides a system that can retrieve and transmit user-stored personal and health information by emergency responders at the point of care. The emergency responder can access the customer's Critical Health Information Profile database, review the data for pertinent information and then transmit that data to a designated receiving hospital or medical center. The device provides an electronic means of dialing and communicating directly with the 9-1-1 operator. A wireless remote transmitter unit can be activated from the wireless transmitter or the base unit to dial and connect with the 9-1-1 operator, broadcast a canned message with or without a personal-recorded message, and personally communicate with the 9-1-1 operator through a two-way speakerphone system. The device contains software enabling the user and medical personnel the ability to input, store, retrieve and analyze the user's vital sign data and other pertinent health information.
Owner:MEDSIGN INT CORP
Securing date data fields
A method facilitating searching of data containing protected date information includes generating one or more randomly escalating dateID values for each date during a time period and storing such generated dateID values in a lookup table together with an encrypted, associated date value. Such generated dateID values can be stored in a datasource in place of protected dates in order to safeguard protected health information. In one or more preferred implementations, a de-identified date is stored in the lookup table in association with a dateID, and utilized for searching operations.
Owner:ALLSCRIPTS SOFTWARE
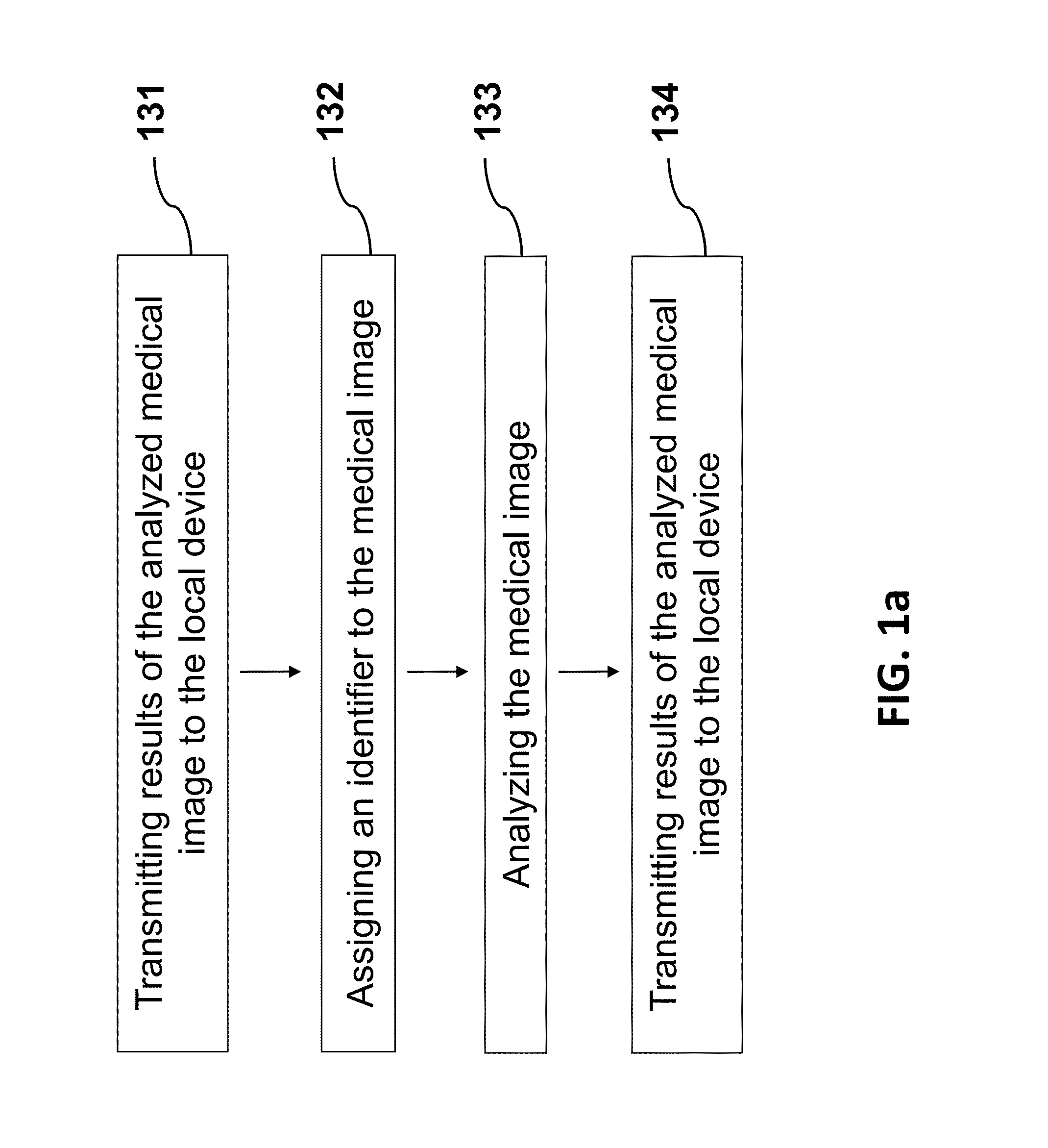
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com