Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
100 results about "Opting out" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
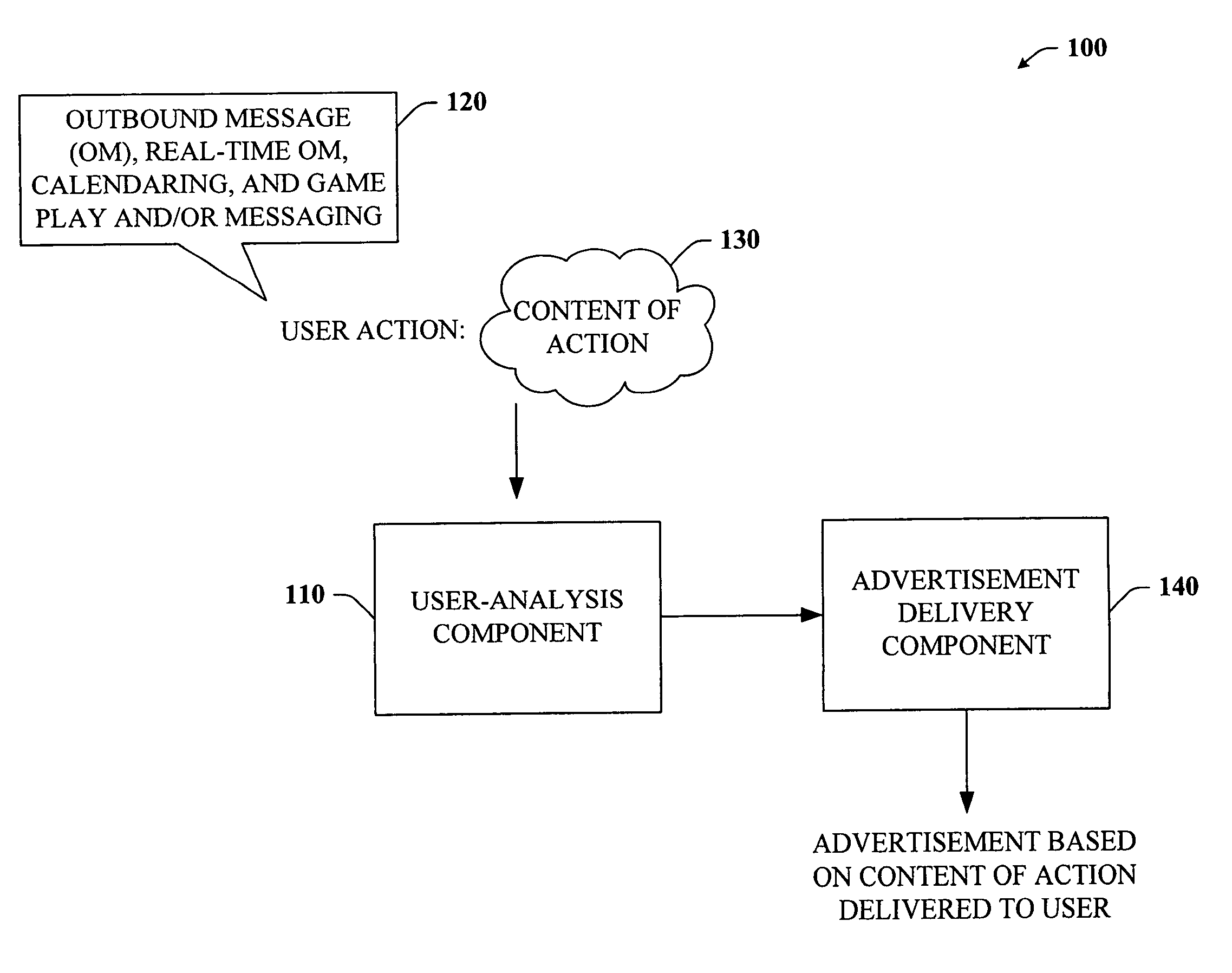
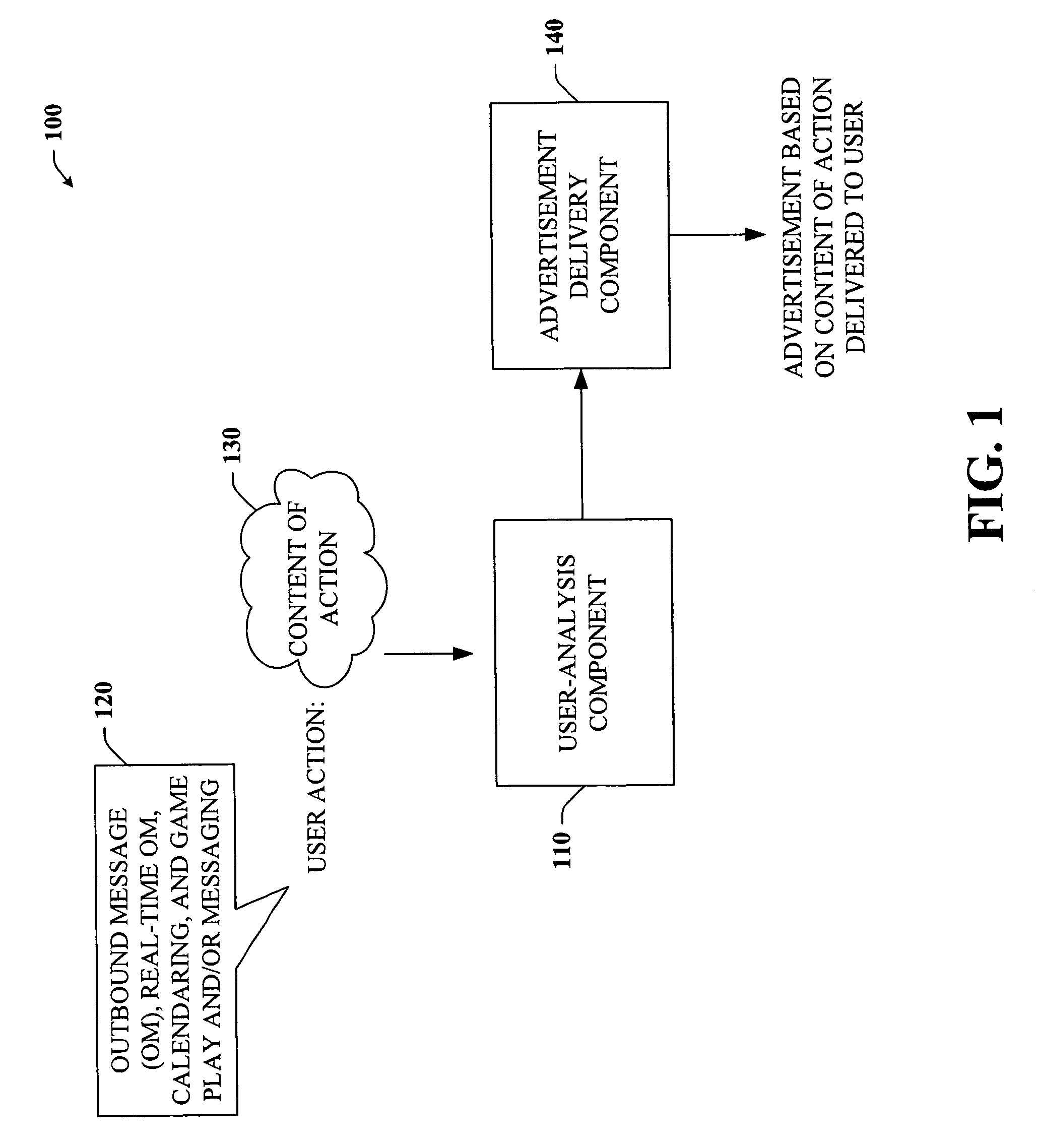
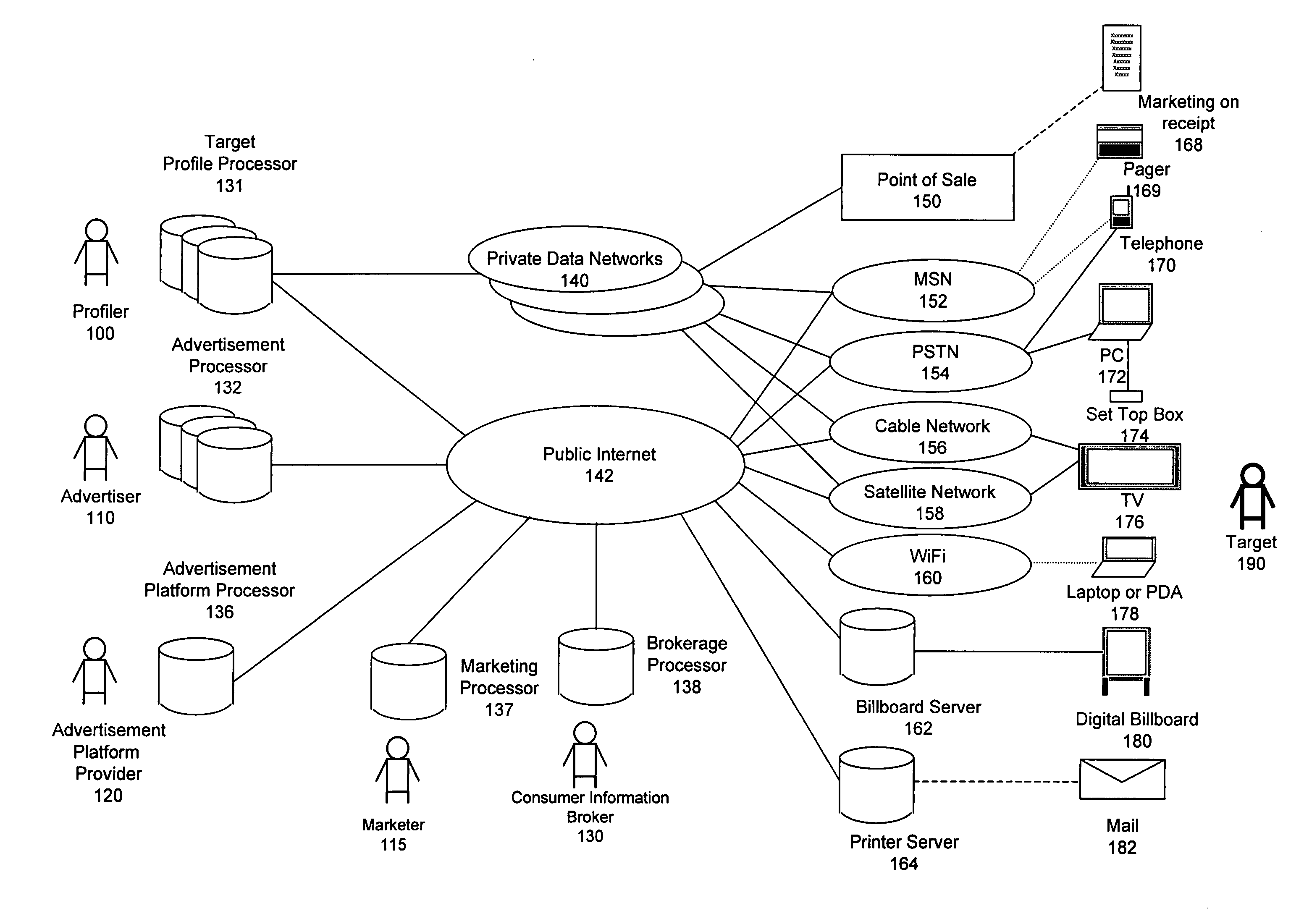
Content-targeted advertising for interactive computer-based applications
InactiveUS20060167747A1Reduce user experienceUser privacy is enhancedMarketingUser privacyContent analytics
The subject invention provides a unique system and method that facilitates providing content-targeted advertising to a user based at least in part on the content of a user action. The user action can be performed in connection with an outbound messaging system, a real-time messaging system such as a chat or instant messaging, a game environment, and / or calendaring system. The system and method analyze at the least the content of an outbound message and then present a content-targeted advertisement based on the content of the message. The same can be done with respect to calendar entries. However, outbound and inbound calendar entries, invitations, and responses to invitations can be analyzed for content and have content-targeted advertisements presented to the sender or receiver of such items. User privacy can be maintained and / or increased by allowing a user to opt out of content-targeting advertisements. Reasons for being targeted can also be provided to the user.
Owner:MICROSOFT TECH LICENSING LLC
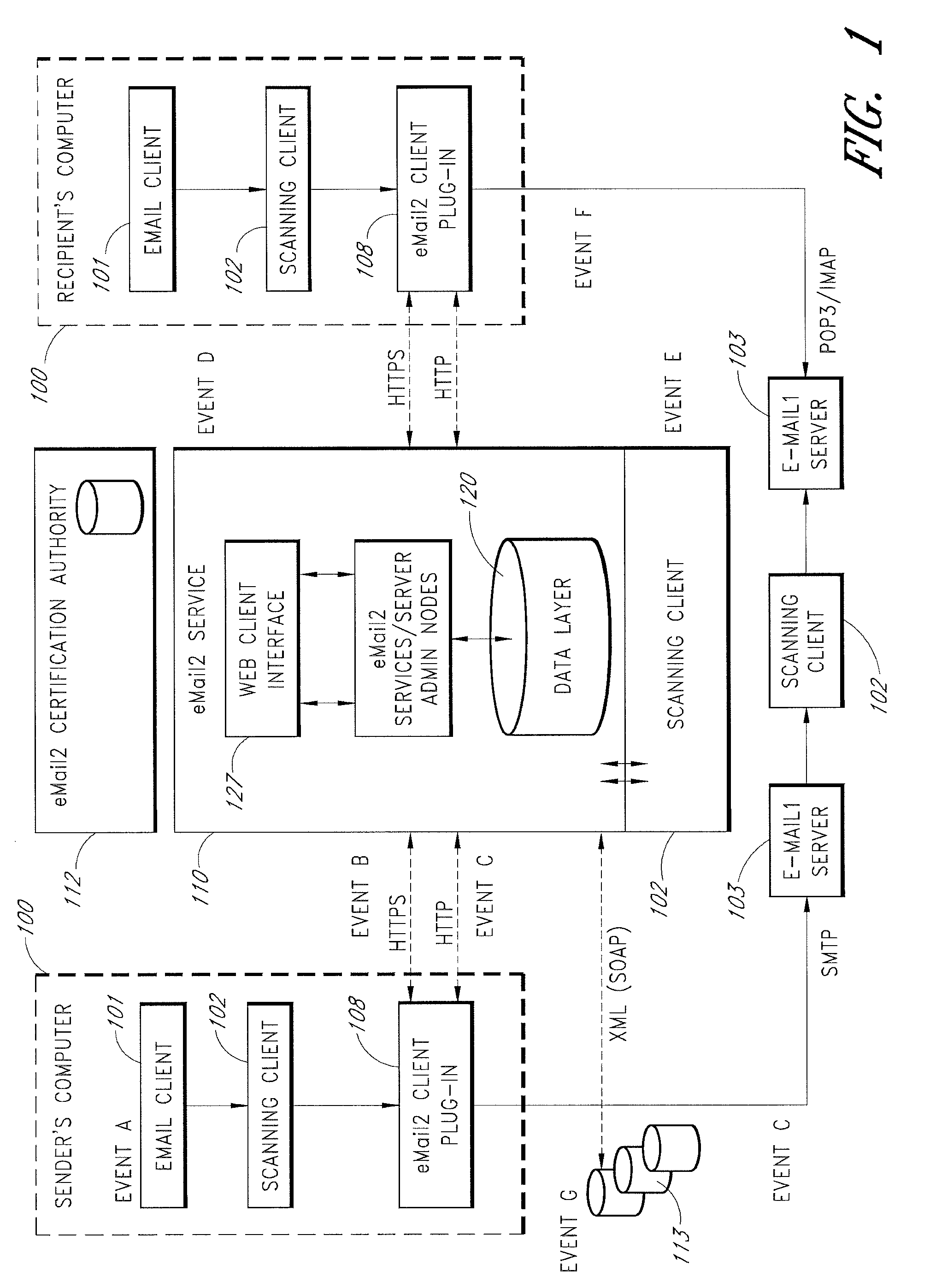
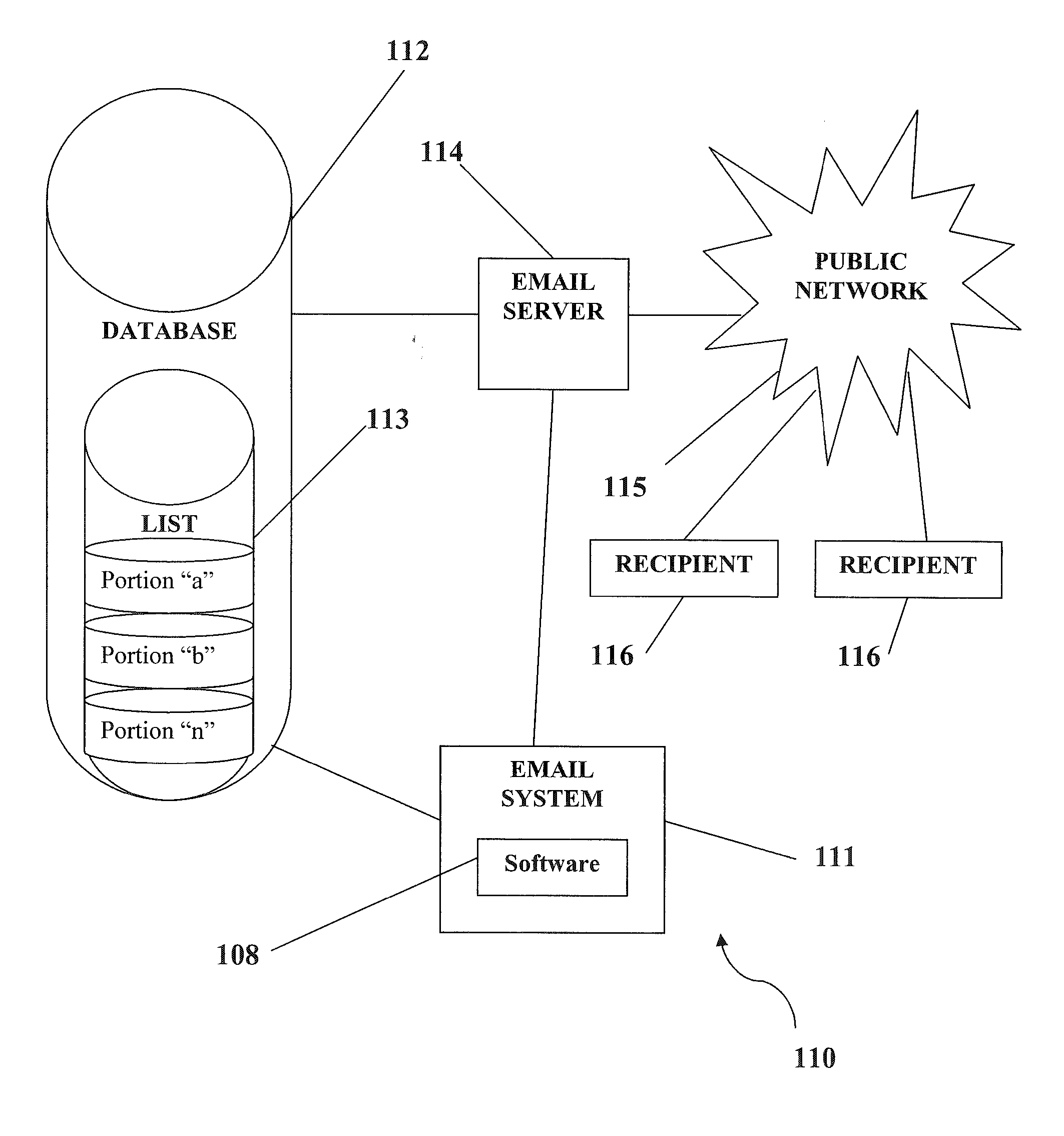
Secure electronic mail system with thread/conversation opt out
ActiveUS9401900B2Easy to watchMultiple digital computer combinationsOffice automationInternet privacyElectronic mail
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. An exemplary method for communicating e-mail messages comprises receiving, at a server system, an original e-mail message associated with a unique message ID that is assigned by the server system. The method further comprises storing a distribution list associated with the unique message ID and a thread participation status indicator for each of the one or more recipients, and, in response to an opt-out request received from one of the recipients, updating the distribution list to thereby produce a modified distribution list that does not include the requesting recipient. The method further comprises receiving a reply e-mail message in the same thread, and sending the reply e-mail message based on the modified distribution list such that the reply e-mail message is not sent to the requesting recipient.
Owner:APPRIVER CANADA ULC
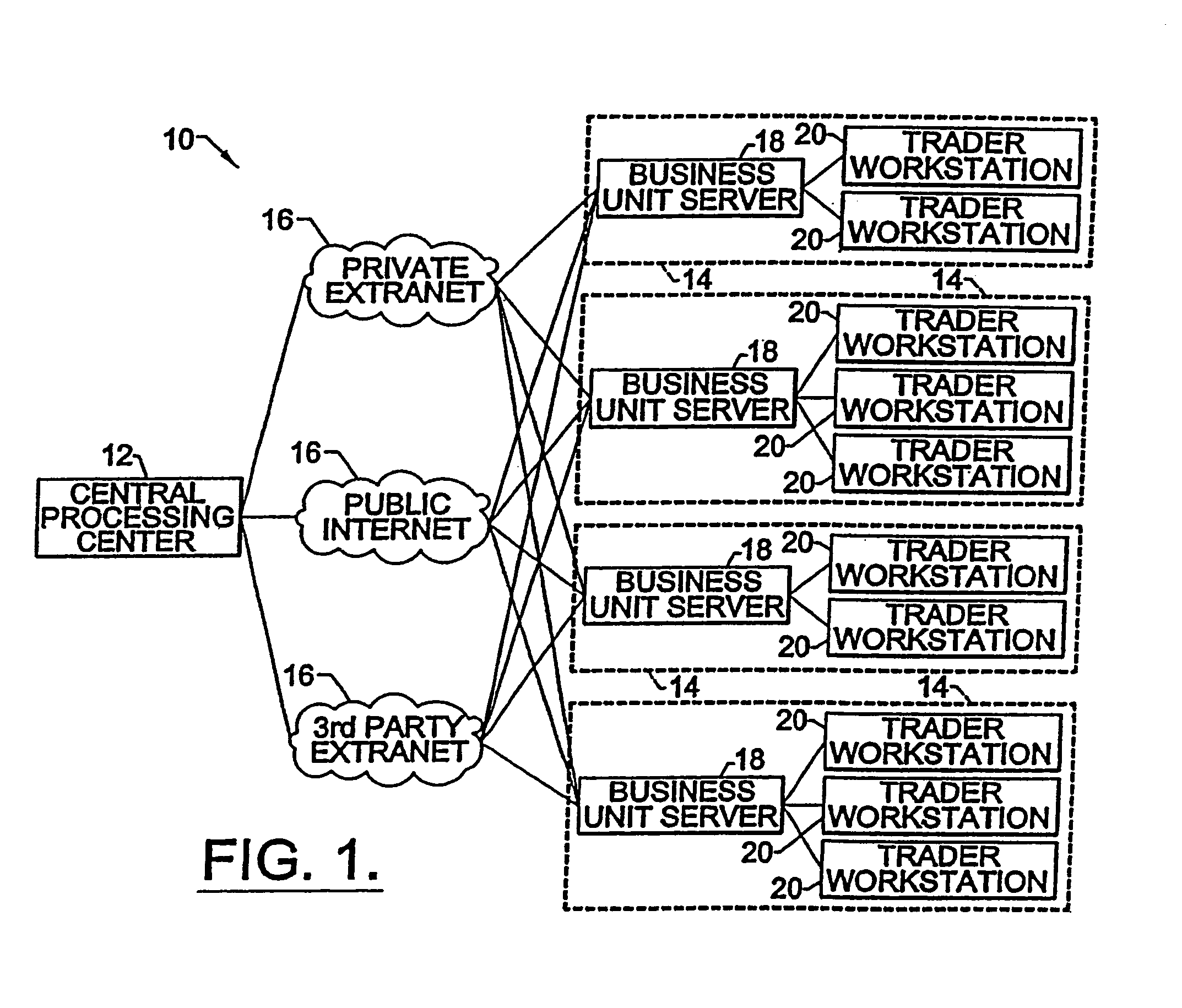
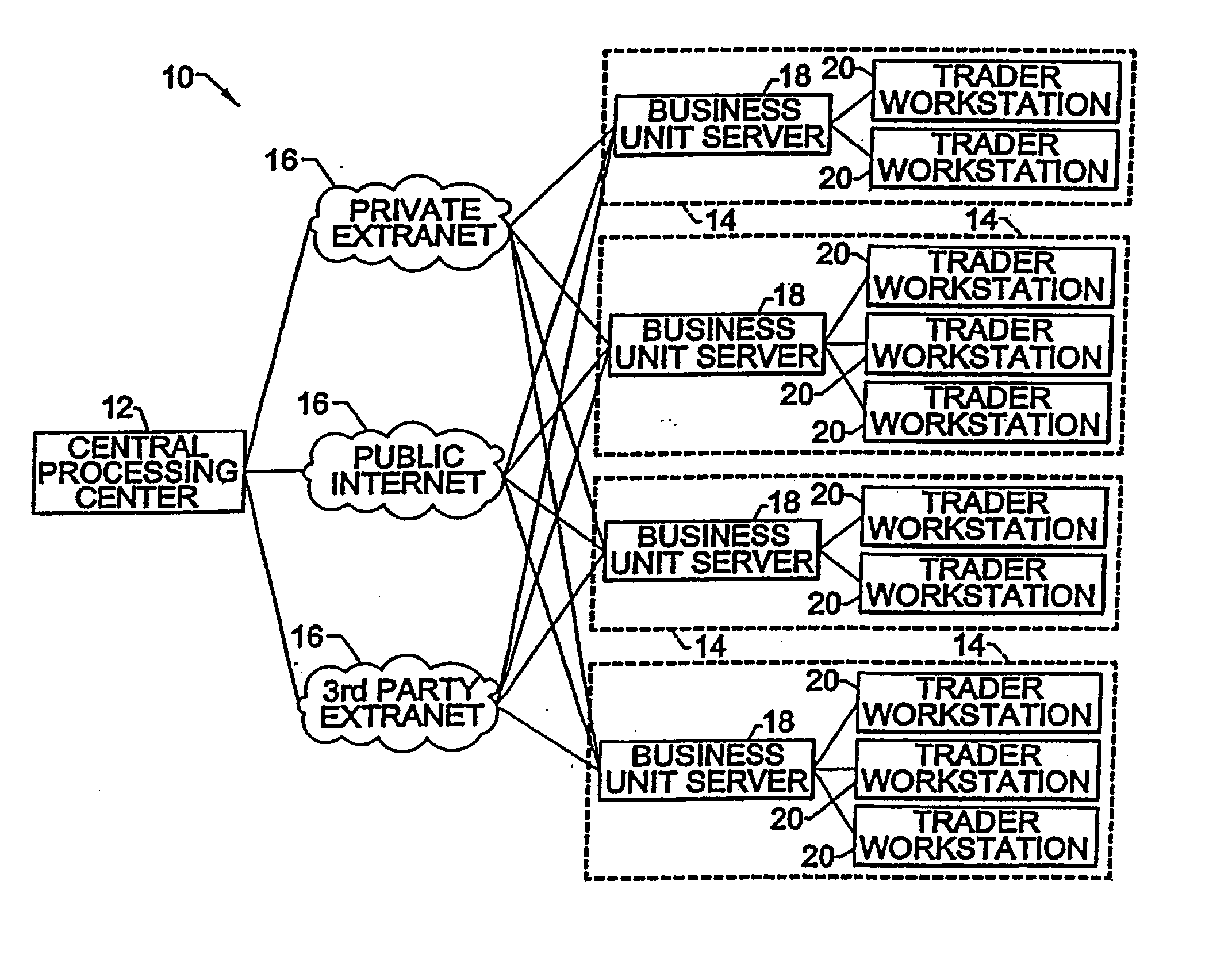
Systems for switch auctions utilizing risk position portfolios of a plurality of traders
A switch engine module receive interest rate risk portfolios from a plurality of traders, and for each prospective trader, provides available switches based on positions in other counterparty portfolios that offset the viewing traders' positions. The offsetting positions are encoded with credit preference information in order to identify eligible trades based on both counterparties credit preferences. In particular, an embodiment provides for a switch auction whereby users can use an auction process to trade for forward rate agreement switches with other counterparties. In the switch auction, the price is predetermined by the system prior to the auction so that parties can opt out of the transaction if desired. The credit preferences of the participating traders are taken in consideration in making matches.
Owner:GFINET INC
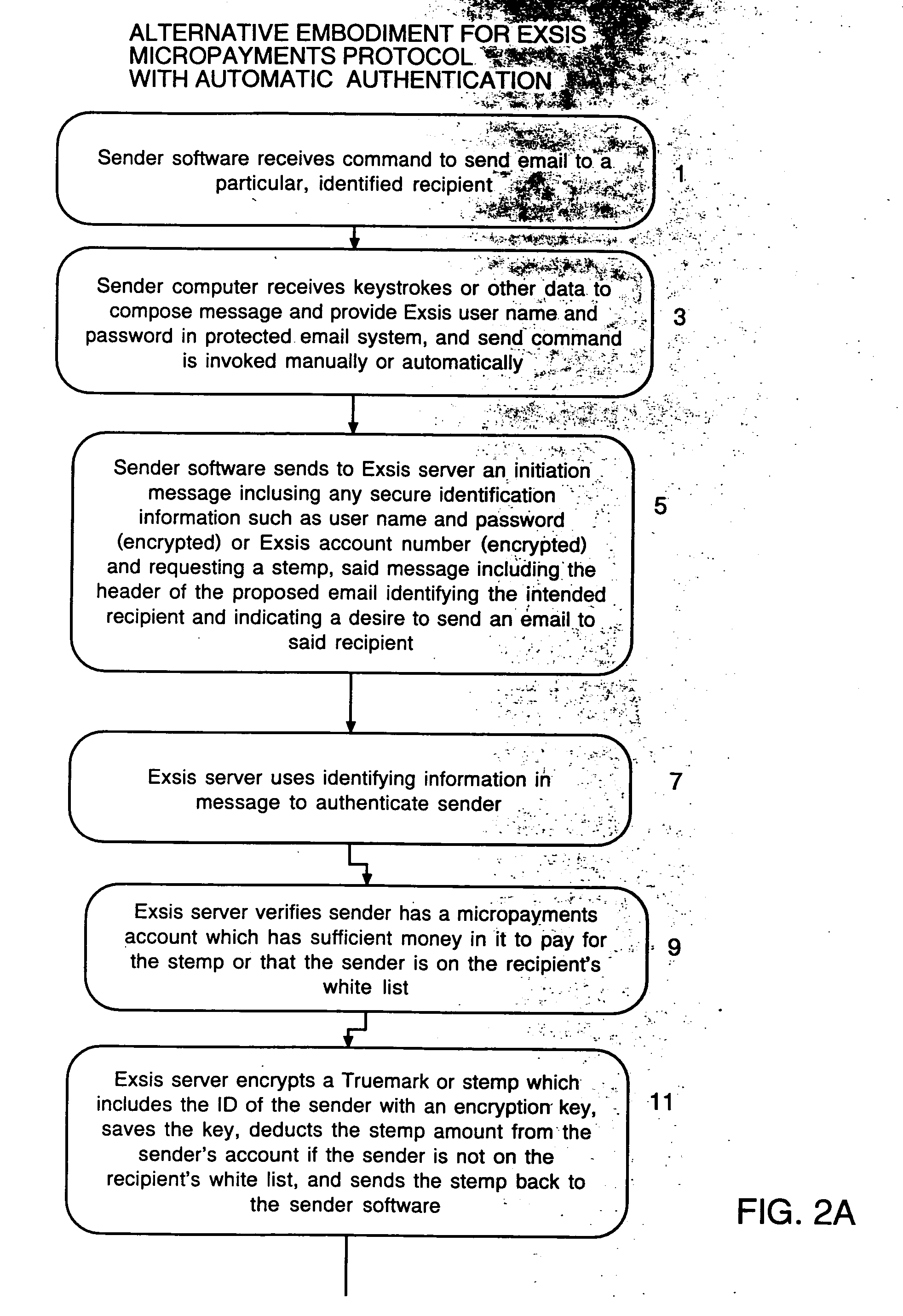
User interface and anti-phishing functions for an anti-spam micropayments system
ActiveUS20060075028A1Control contentEffective controlMultiple digital computer combinationsFlotationTrademarkSpamming
Owner:ICONIX INC
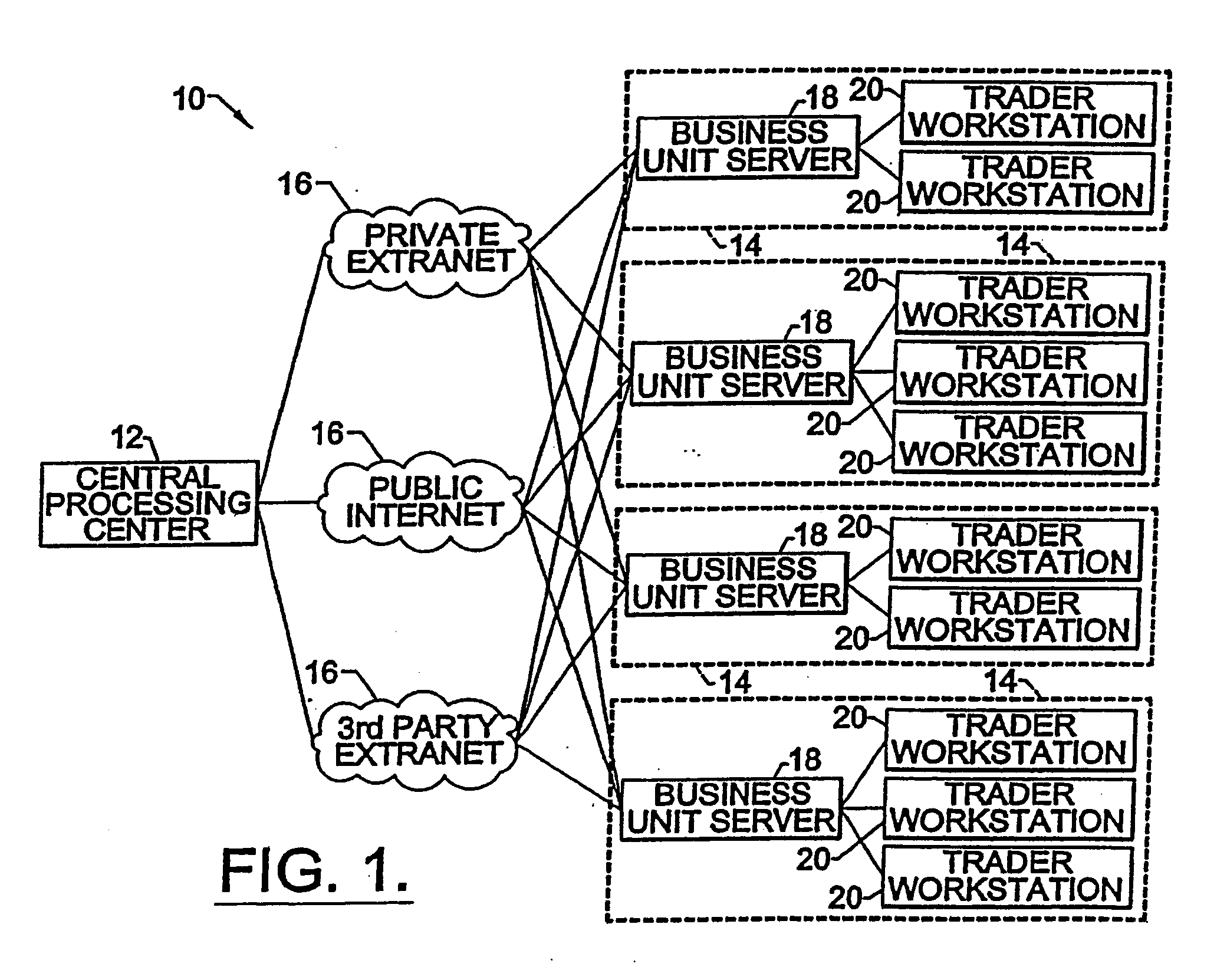
Systems and methods for performing two-way one-to-many and many-to-many auctions for financial instruments
A switch engine module receive interest rate risk portfolios from a plurality of traders, and for each prospective trader, provides available switches based on positions in other counterparty portfolios that offset the viewing traders' positions. The offsetting positions are encoded with credit preference information in order to identify eligible trades based on both counterparties credit preferences. In particular, an embodiment provides for a switch auction whereby users can use an auction process to trade for forward rate agreement switches with other counterparties, for example, in a two-way or many-to-many auction. In the switch auction, the price is predetermined by the system prior to the auction so that parties can opt out of the transaction if desired. The credit preferences of the participating traders are taken in consideration in making matches.
Owner:GFINET INC
System and Method for Sharing Anonymous User Profiles with a Third Party
The invention provides a system and method for sharing anonymous user profiles with a third party. In one aspect of the invention, the system shares user profiles with content servers on a mobile data network so that they may select content responsive to the user's profile. The system provides a store of user profiles for associating profile information with either a source IP address or mobile phone number, where the profile includes information on the user and the user's network usage. The system detects a user's transaction request and inspects it for either an IP address or phone number, which it uses to retrieve the appropriate profile. The system subsequently applies predetermined opt-out policies to determine how much of the user profile may be provided in response to the profile request. The system then returns the profile information such that the user's identity is masked.
Owner:RIBBON COMM SECURITIES CORP
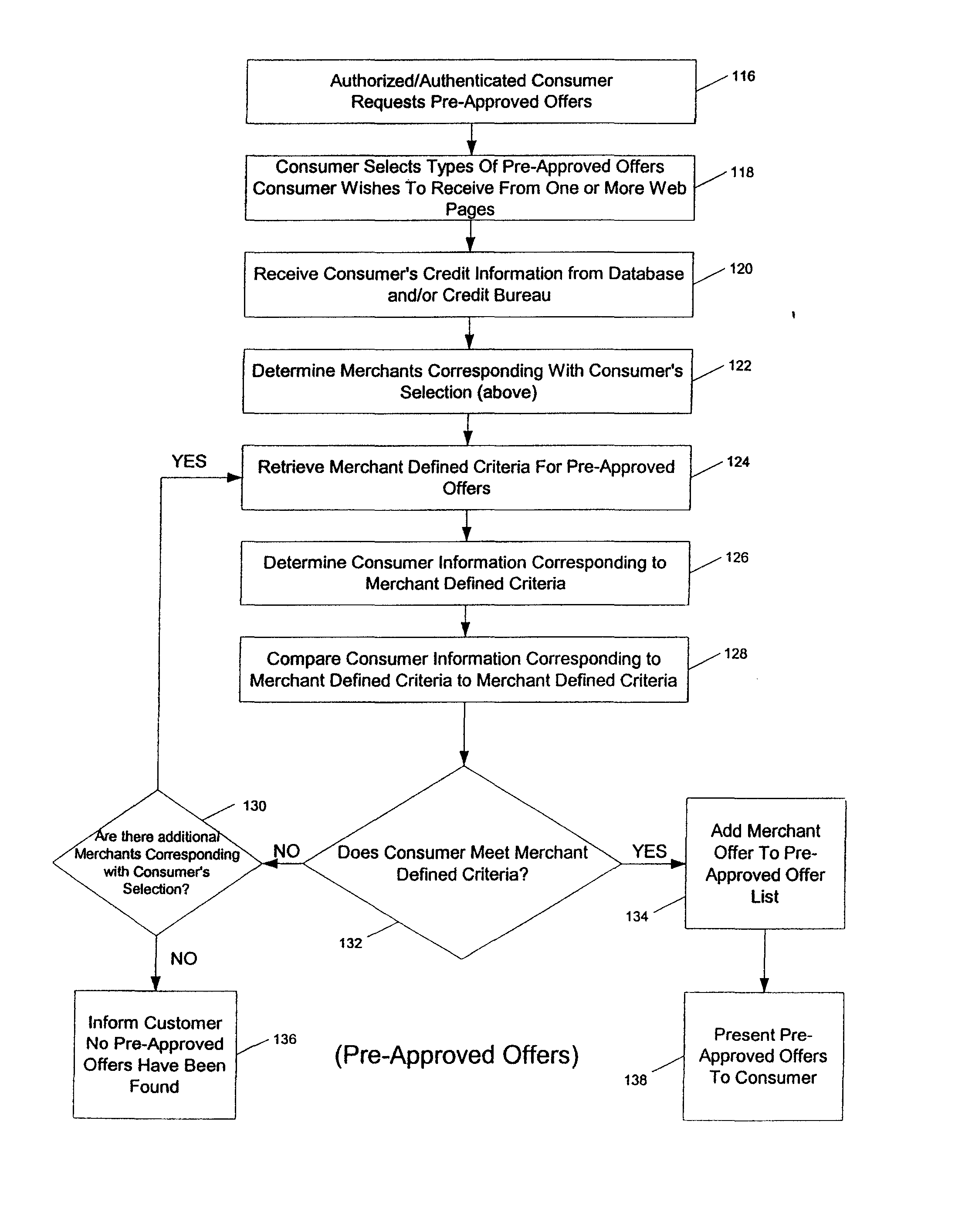
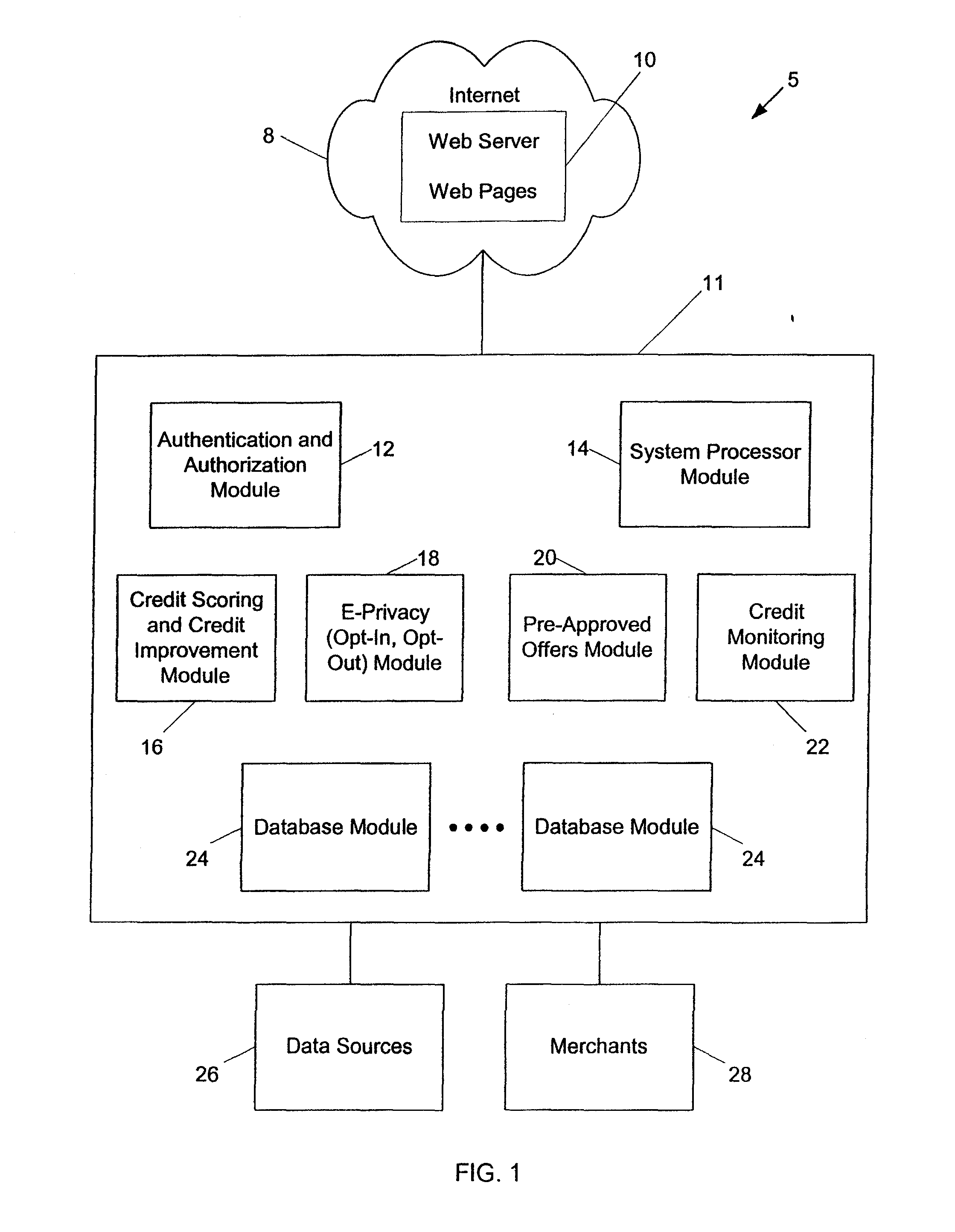
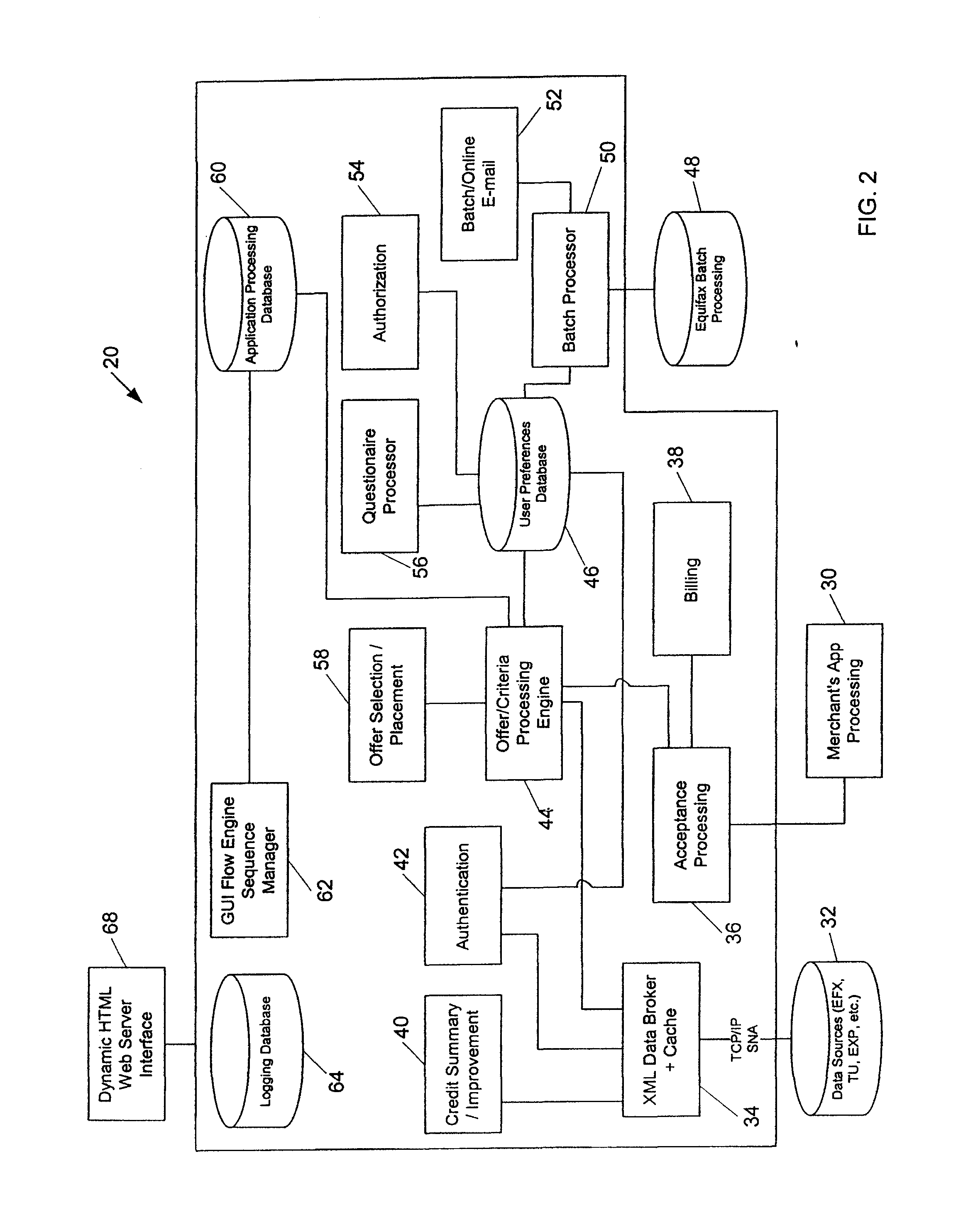
Systems and methods for providing consumers anonymous pre-approved offers from a consumer-selected group or merchants
InactiveUS20070299771A1Increase ratingsFinanceBuying/selling/leasing transactionsThird partyConfidentiality
The system and method of the present invention provides consumers with credit information including information which can help the consumer evaluate the consumer's credit report or credit worthiness. The present invention can also provide consumers with suggestions to help consumers better their credit rating. The system and method of the present invention also provide consumers with pre-approved credit offers from a consumer-selected group of merchants, where the consumers are anonymous to the merchants, and the merchants do not receive copies of the consumer's credit report. Additional functions of the present invention include allowing users to opt-out or opt-into solicitation lists, and enabling users to automatically monitor their credit report. The present invention offers these services through a third party agent of the consumer which can be accessible to the consumer via the Internet. Through this agency relationship, the third party can request consumer information and determine pre-approved offers from a plurality of merchants while protecting the confidentiality of consumer credit information without negative consequences on a consumer's credit.
Owner:BRODY ROBERT M +2
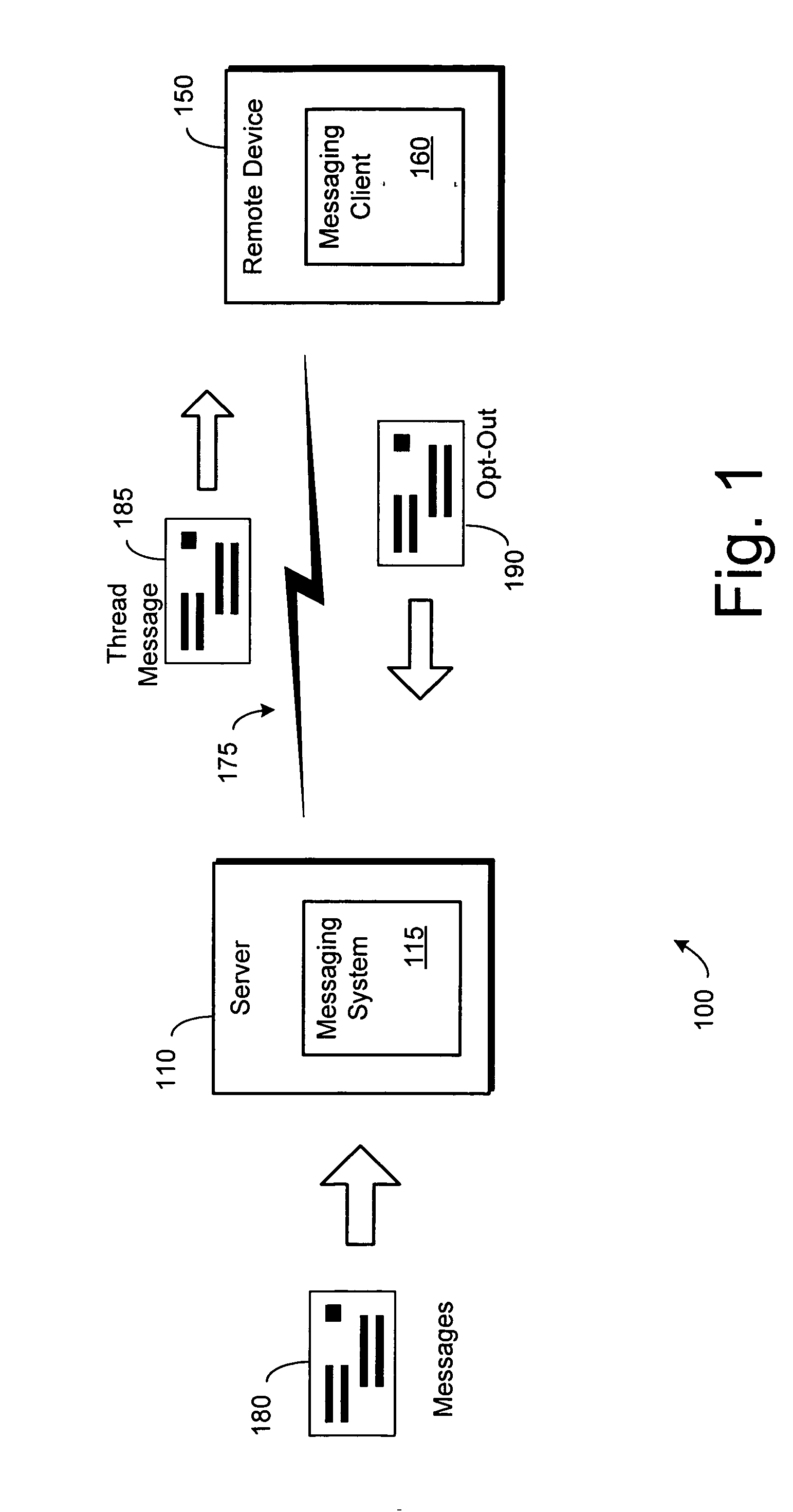
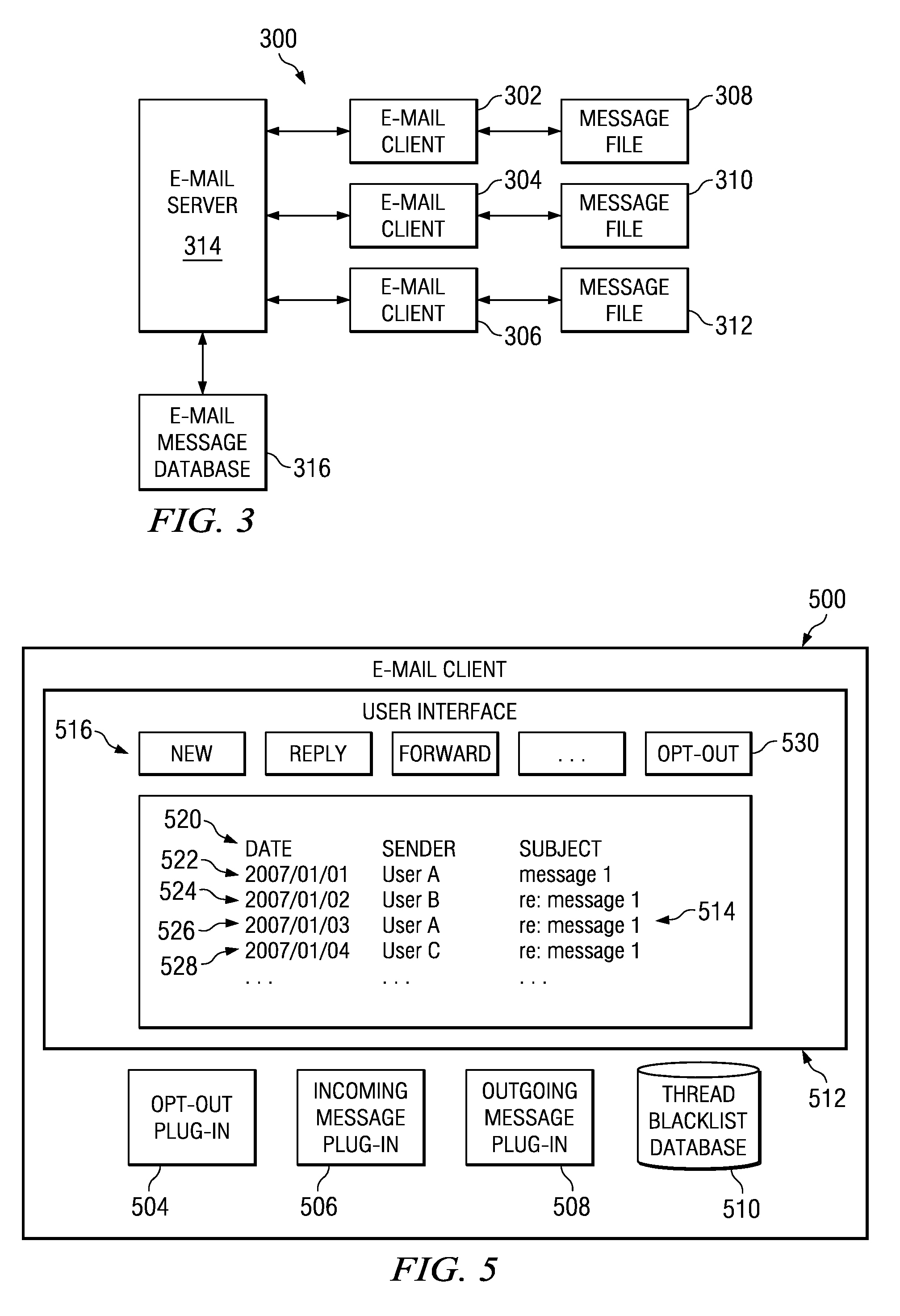
Message thread handling
ActiveUS20060075040A1Automatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsUser interfaceOpting out
Described are techniques and mechanisms for easily allowing a user to unsubscribe (“opt out”) from receiving subsequent messages in a particular message thread. Generally stated, a component maintains information about a message thread that a user has indicated a desire to opt out of. The information includes identifying information about the message thread and an indication that a particular user desires to receive no further messages in the thread. New messages that are identified as belonging to that thread are handled in some fashion that differs from ordinary messages. For example, the messages may simply be deleted, may be held at a message server, may be redirected to a special storage location, or the like. The user indicates the desire to opt out through a user interface mechanism that is available in connection with the user viewing a message in the particular thread. Optionally, the user may have the ability to re-subscribe (“opt in”) to the thread.
Owner:QUALCOMM INC
Method for consumer data brokerage
The present invention provides a method to broker consumer data for the purpose of marketing activities and to compensate consumers for the use of their data. The method provides mechanisms and processes for consumer information brokers to allow providers of real-time advertisement platforms or any static advertisement platform to offer advertisers the opportunity to dynamically bid on individual direct to consumer advertisement opportunities and to adapt individual advertisements according to the profile of each consumer. Furthermore the method allows consumer information brokers to offer marketers targeted direct to consumer marketing measures based on well-defined target profiles. Consumers have the opportunity to allow advertisers to convey advertisements to them and be compensated for viewing them. They may also opt out and forego the opportunity. Furthermore consumers have the opportunity to participate in direct to consumer marketing measures and be compensated for participating. This will lead to significantly improved return on investment for businesses and help them to develop products and services that consumers really want.
Owner:JASCHKE MICHAEL
Systems and methods for providing consumers anonymous pre-approved offers from a consumer-selected group of merchants
ActiveUS7720750B2Increase ratingsFinanceBuying/selling/leasing transactionsThird partyConfidentiality
Owner:EQUIFAX INC
Method and system for providing automated email optimization
InactiveUS20060253537A1Different in contentIncrease the number ofMultiple digital computer combinationsData switching networksEmail marketingSubject matter
A method and system for providing rules-based or algorithms based automated response optimization in the email-marketing environment such that recipient responses during the delivery process of an email campaign influence the delivery parameters and / or message elements of the portions of the campaign yet to be mailed. Responses to an email marketing campaign determine its marketing effectiveness and include delivery statistics, undeliverable statistics, opens, link-clicks, replies, opt-outs, and conversion events. Conversion events are recipient actions that are intended results from the marketing campaign and include marketing or service transactions that are completed online (e.g. purchases, registrations, filling out surveys, etc) and / or offline (e.g. brand awareness, store visits etc.). The system monitors emails as they are being received by recipients during delivery and, based on rules established by the marketer or on default rules established by the system using algorithms, tracks designated response statistics and dynamically alters the email elements, such as subject line and / or other content, including clickable links so that messages that produce the most desirable response statistics is sent to a greater percentage of the remaining recipients. Rather than completing the entire emailing operation using the same content throughout, this invention allows for changing the content for emails remaining to be sent so that the more effective content (in terms of stimulating favorable recipient reactions and purchases) is delivered to as many of the recipients as possible. Additionally, the process may be applied between separately mailed campaigns so that the delivery parameters for subsequent campaigns in a “campaign stream” are automatically modified based on the results of the prior campaigns in the stream and on the rules being applied to the stream.
Owner:EPSILON INTERACTIVE
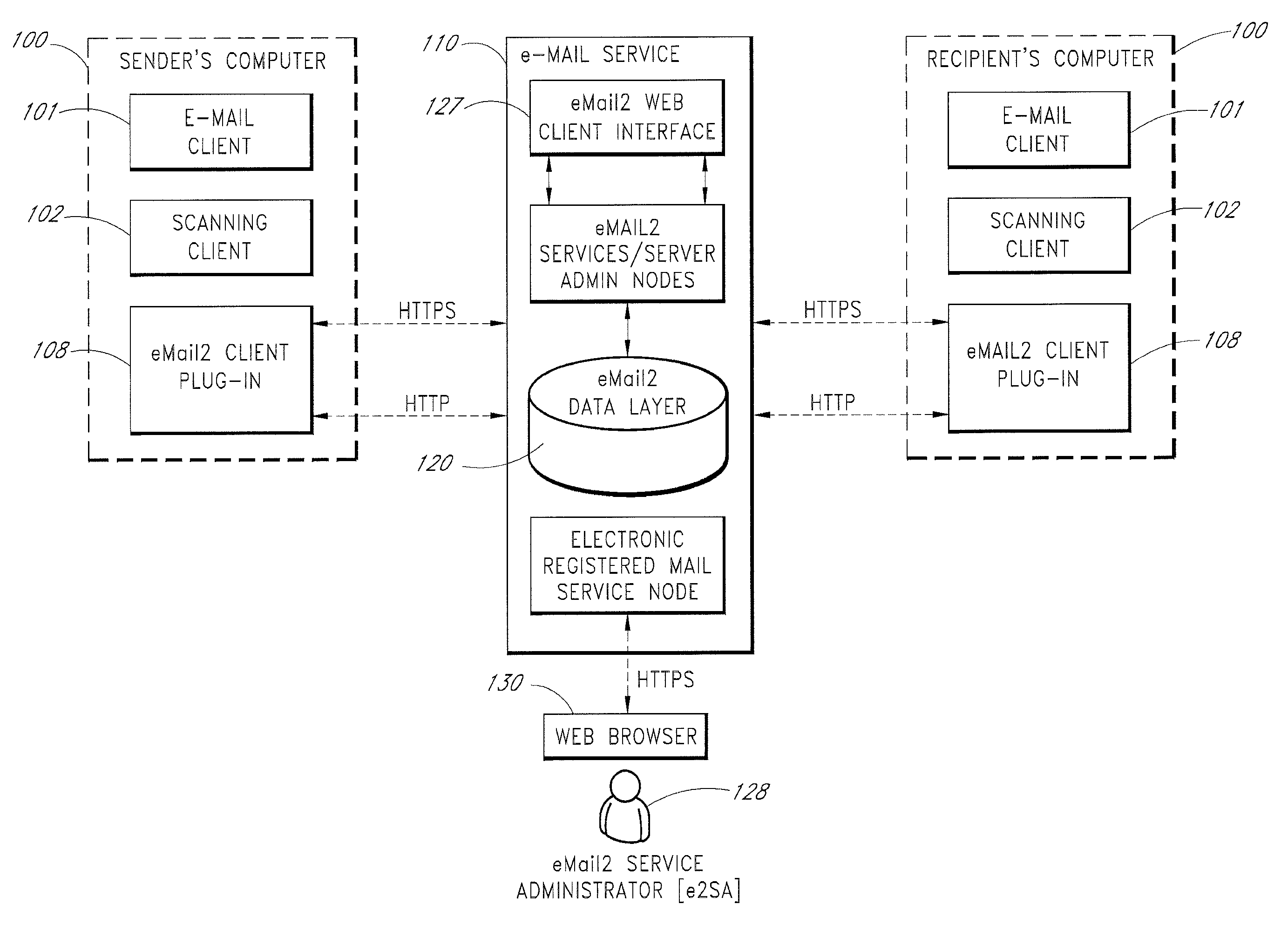
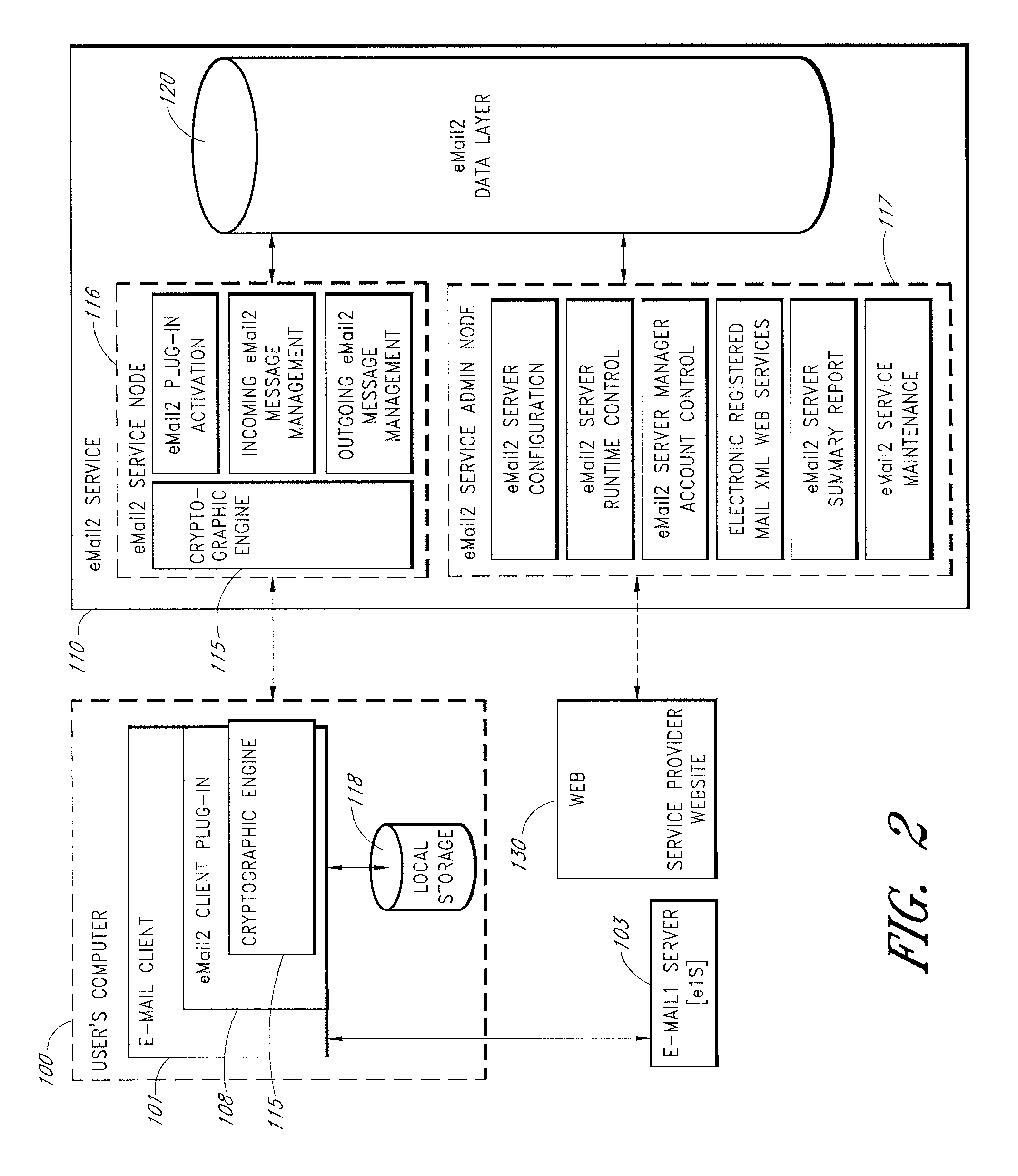
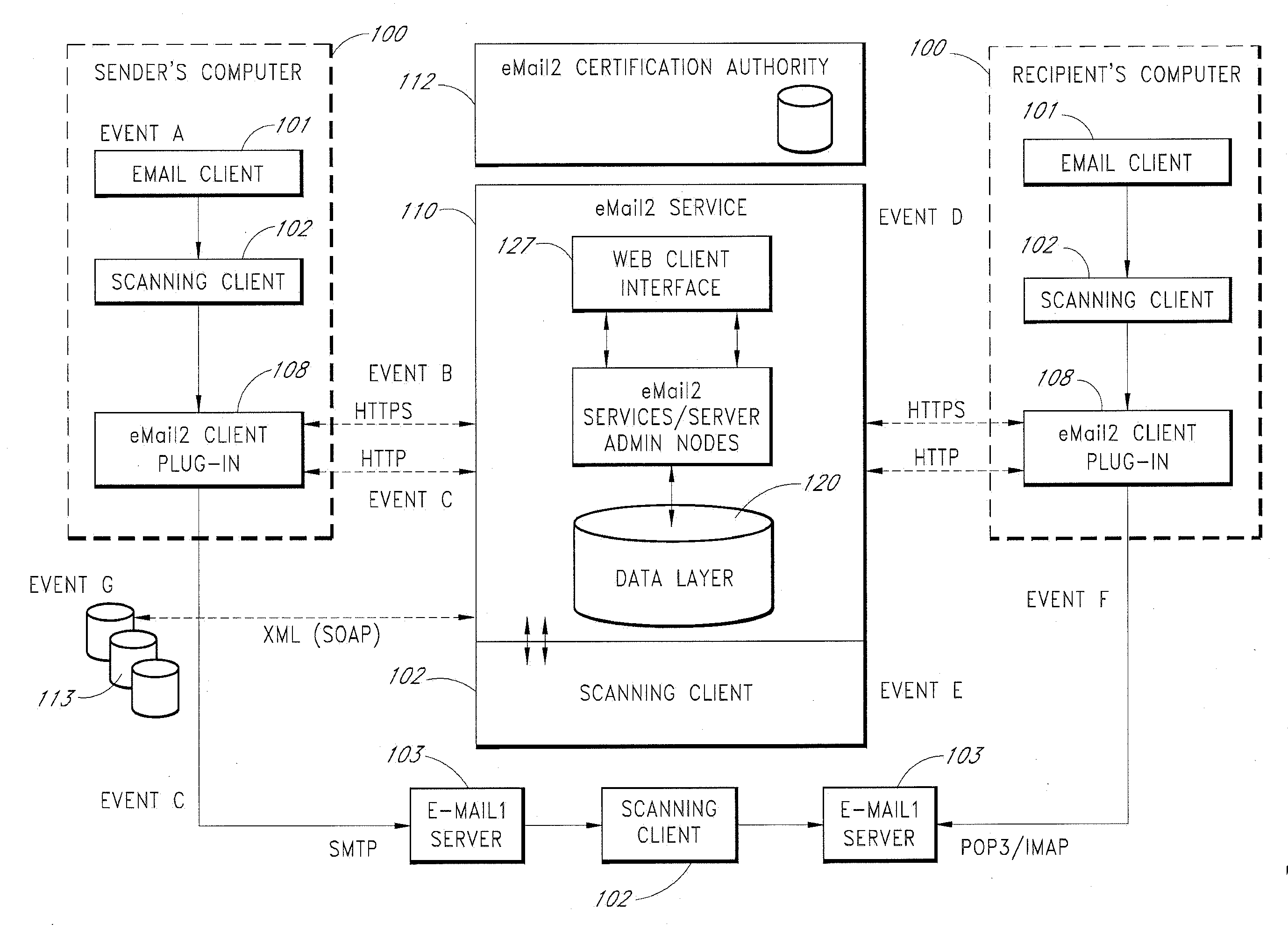
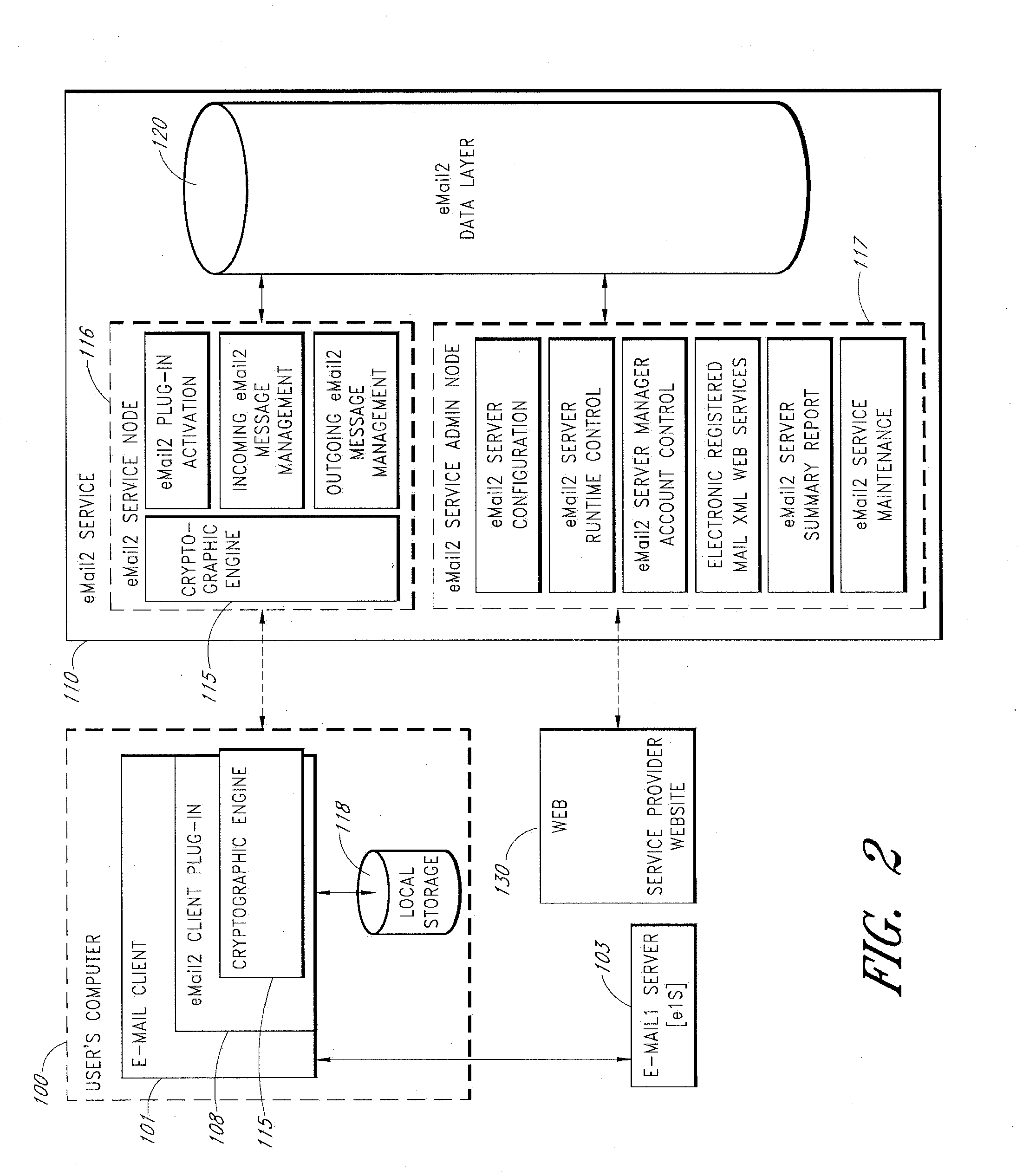
Secure Electronic Mail System
ActiveUS20120198017A1Easy to watchMultiple digital computer combinationsTransmissionInternet privacyElectronic mail
An e-mail system is disclosed that overcomes many deficiencies of, but is backward compatible with, existing e-mail systems. An exemplary method for communicating e-mail messages comprises receiving, at a server system, an original e-mail message associated with a unique message ID that is assigned by the server system. The method further comprises storing a distribution list associated with the unique message ID and a thread participation status indicator for each of the one or more recipients, and, in response to an opt-out request received from one of the recipients, updating the distribution list to thereby produce a modified distribution list that does not include the requesting recipient. The method further comprises receiving a reply e-mail message in the same thread, and sending the reply e-mail message based on the modified distribution list such that the reply e-mail message is not sent to the requesting recipient.
Owner:APPRIVER CANADA ULC
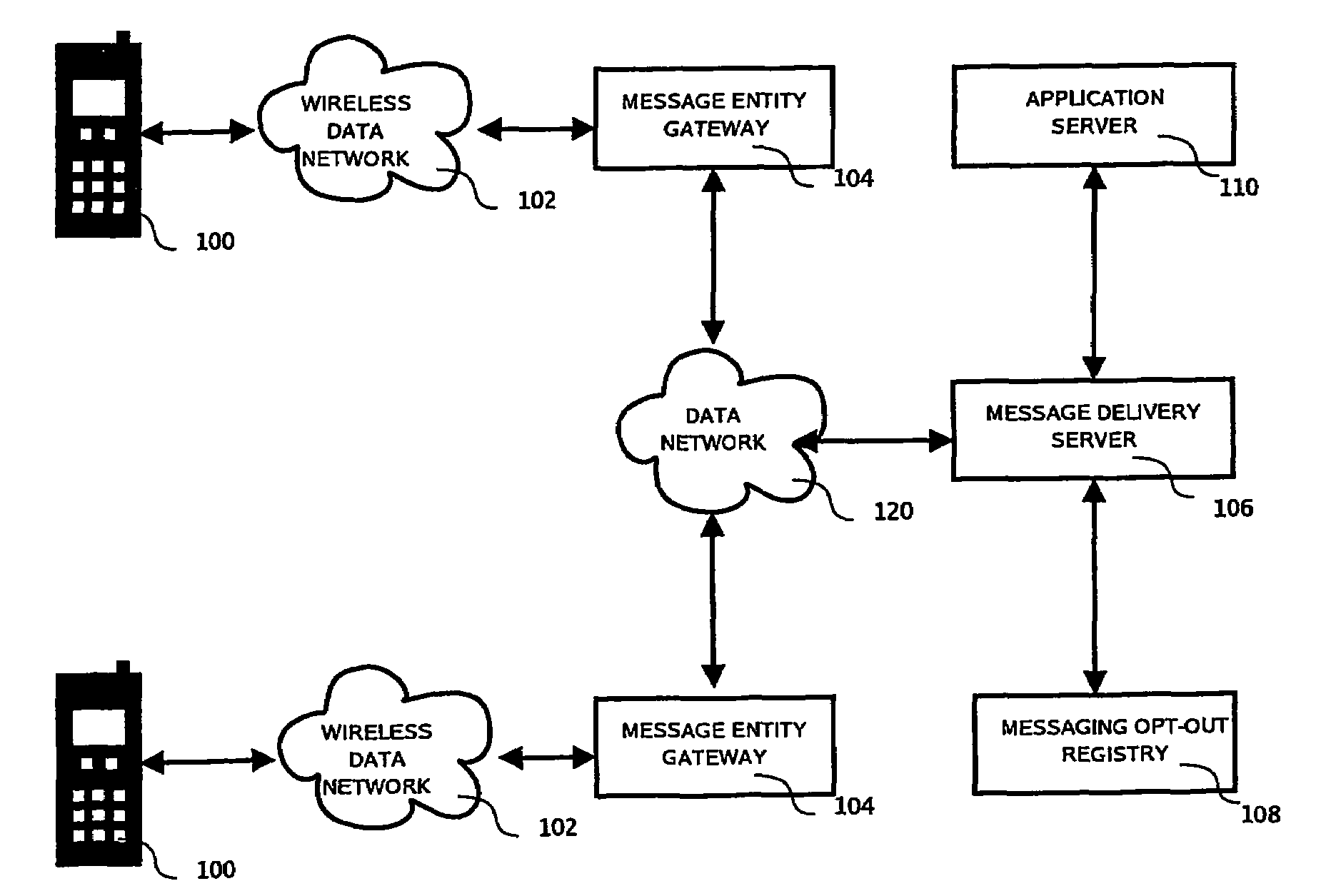
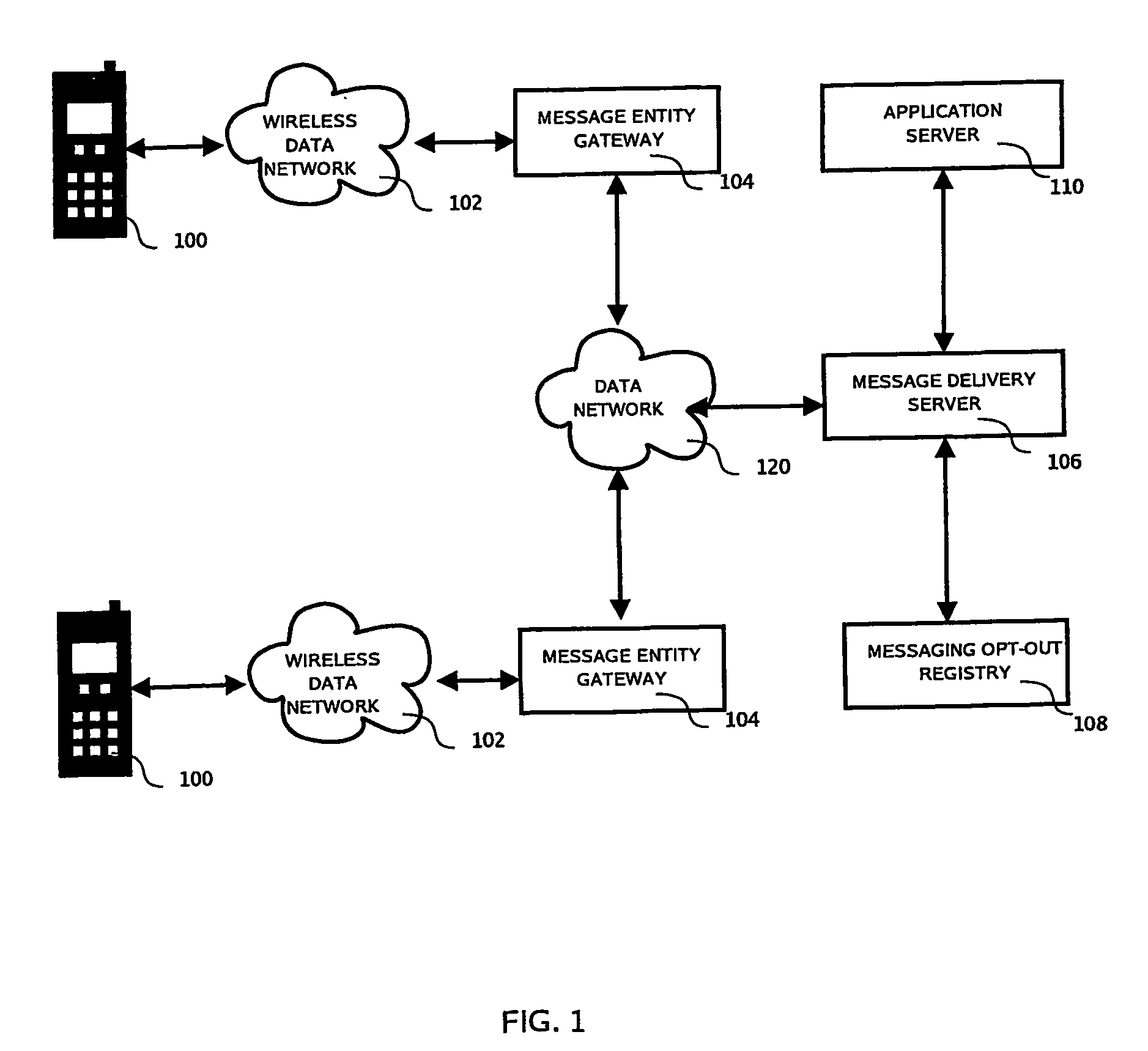
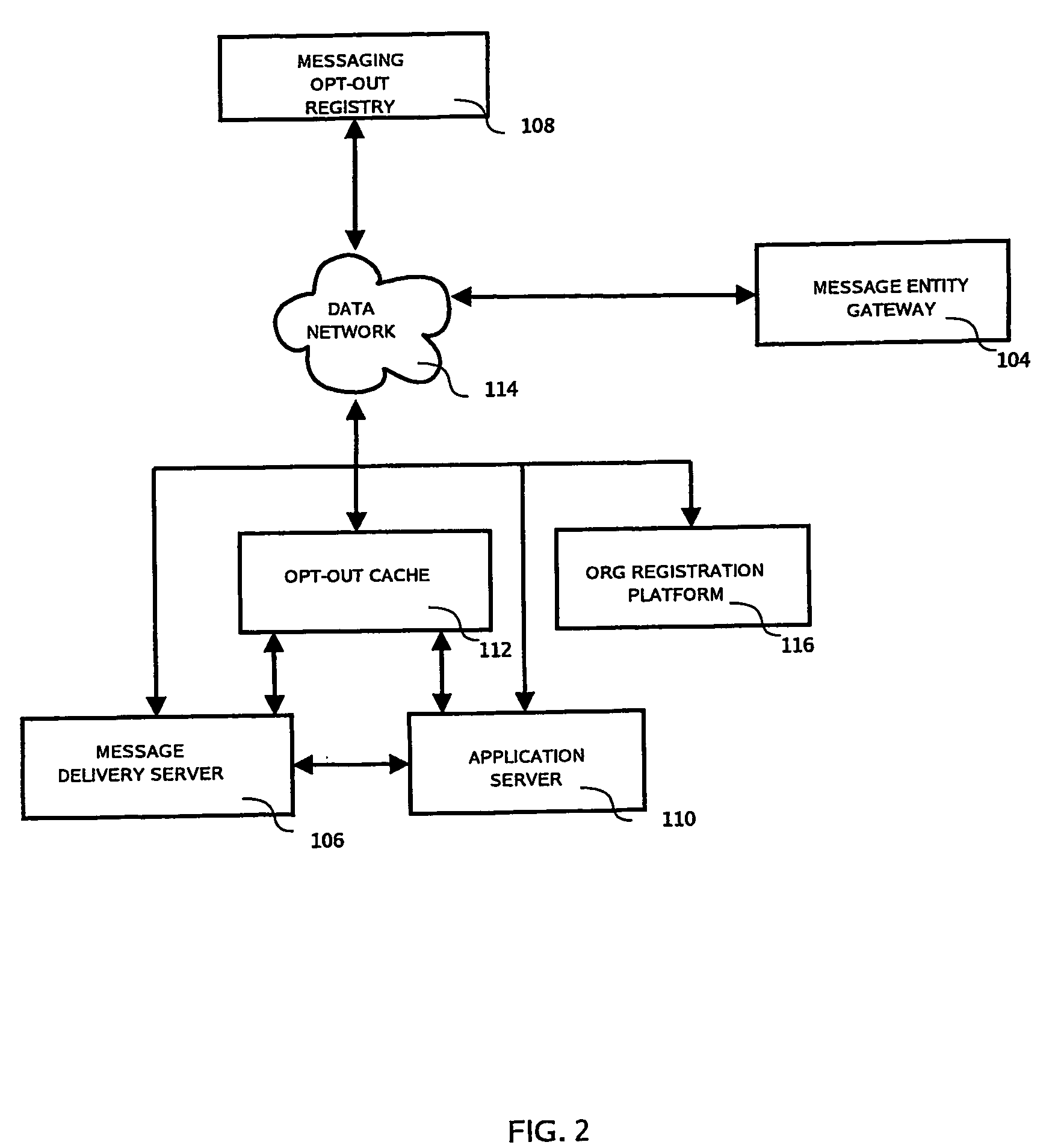
Centralized Mobile and Wireless Messaging Opt-Out Registry System and Method
ActiveUS20080114884A1Avoid receivingAvoid undesirable messagesMultiple digital computer combinationsData switching networksApplication softwareMessage passing
Provided herein is a centralized registry service enabling subscribers to “opt-out” of any or all mobile messaging programs. The registry service supports access to storage medium information by mobile and wireless carriers, companies operating mobile messaging programs, mobile applications or platforms, and most importantly, individual subscribers. The registry service can be used with any message based network, including non mobile networks.
Owner:SYNIVERSE ICX CORP
System and method for dynamically changing the content of an internet web page
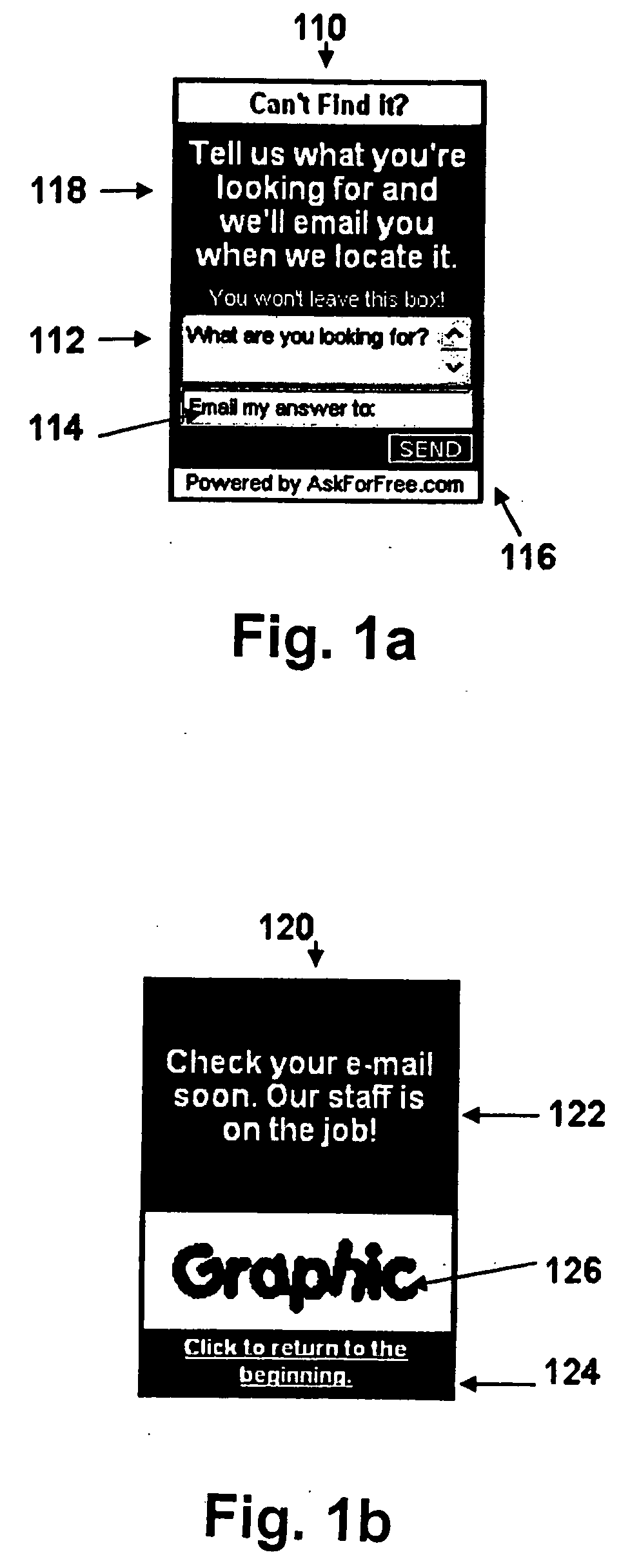
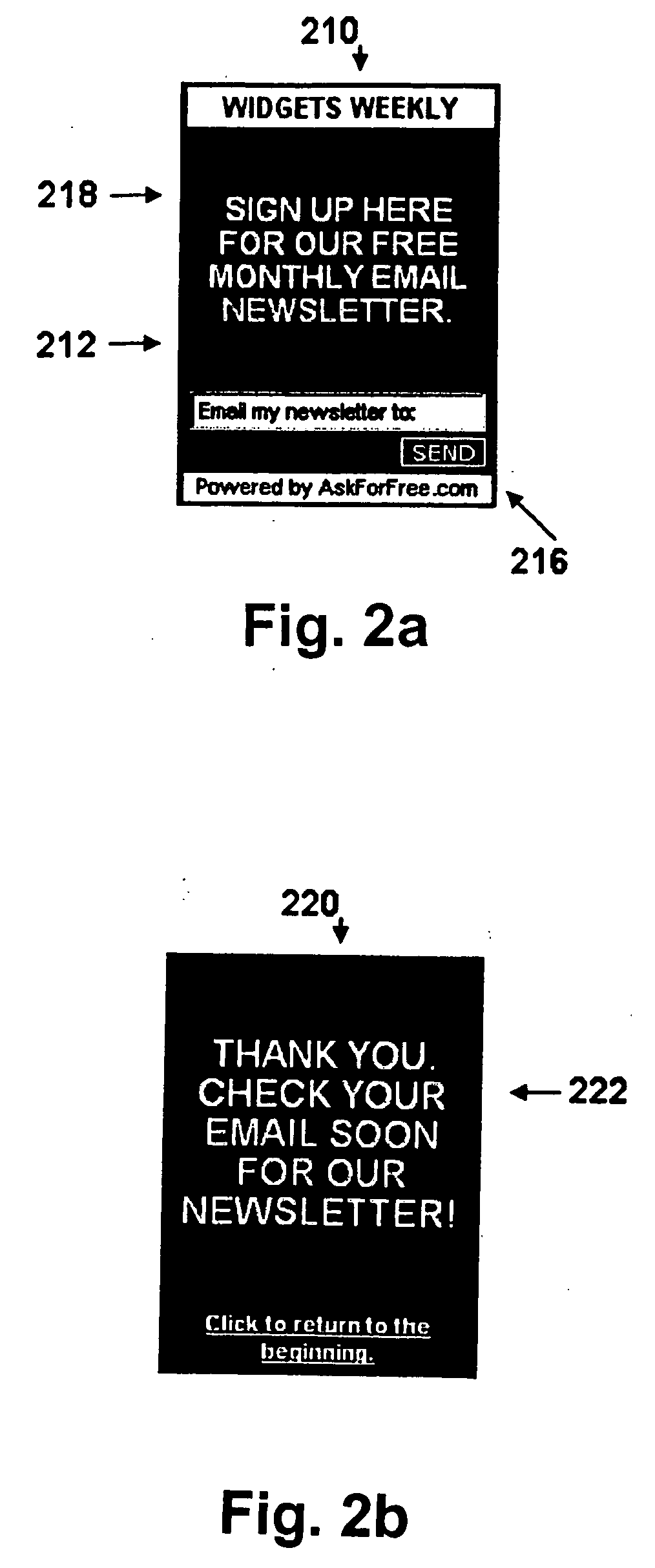
InactiveUS20130117687A1Multiple digital computer combinationsSpecial data processing applicationsInternet usersWeb page
A host Web page includes an evolving interactive dialog box wherein an Internet user may enter user data to be processed. When the user completes entering user data in a first revolution of the interactive dialog box, the first revolution is replaced with a second revolution of the evolving interactive dialog box without disturbing or affecting any other part of the host Web page being displayed. Beneficially, the first and second revolutions may be communicated to a user computer together with and at a same time as the host Web page. Also, the second revolution may include a variety of data which is selected or customized to match the user data submitted in the first revolution. Each revolution of the evolving interactive dialog box may be comprised of any combination of general textual data entry fields, category (pull-down) menus, contact information data entry fields, and opt-in / opt-out buttons.
Owner:PAYPAL INC
Independent class loader for dynamic class loading
InactiveUS6748396B2Data processing applicationsProgram loading/initiatingLoading TechniqueOpting out
Improved techniques are defined for dynamically loading components which have prerequisite relationships more complex than the simple single inheritance chains which are supported with prior art dynamic class loading techniques. Multiple prerequisites are supported in this improved technique, and in preferred embodiments, an arbitrary number of prerequisites may be explicitly specified for a component. Furthermore, techniques are disclosed which enable delaying the loading and initialization of components until such time as a class in the component is actually needed, thereby improving overall efficiency of the system. Optional filtering and export aspects may also be supported to selectively expose classes for use by dependent components and to enable a component to opt out of re-exporting the classes of its prerequisites, respectively.
Owner:IBM CORP
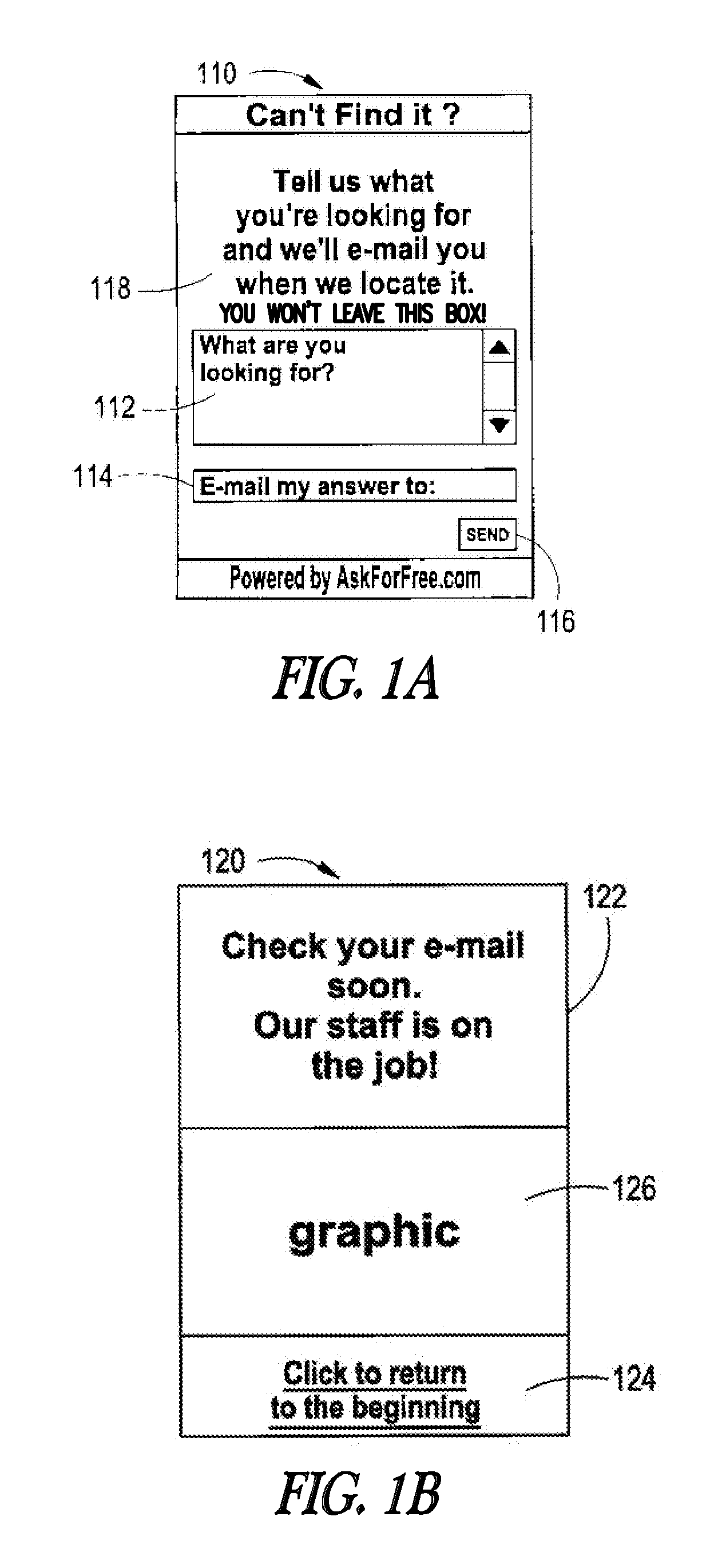
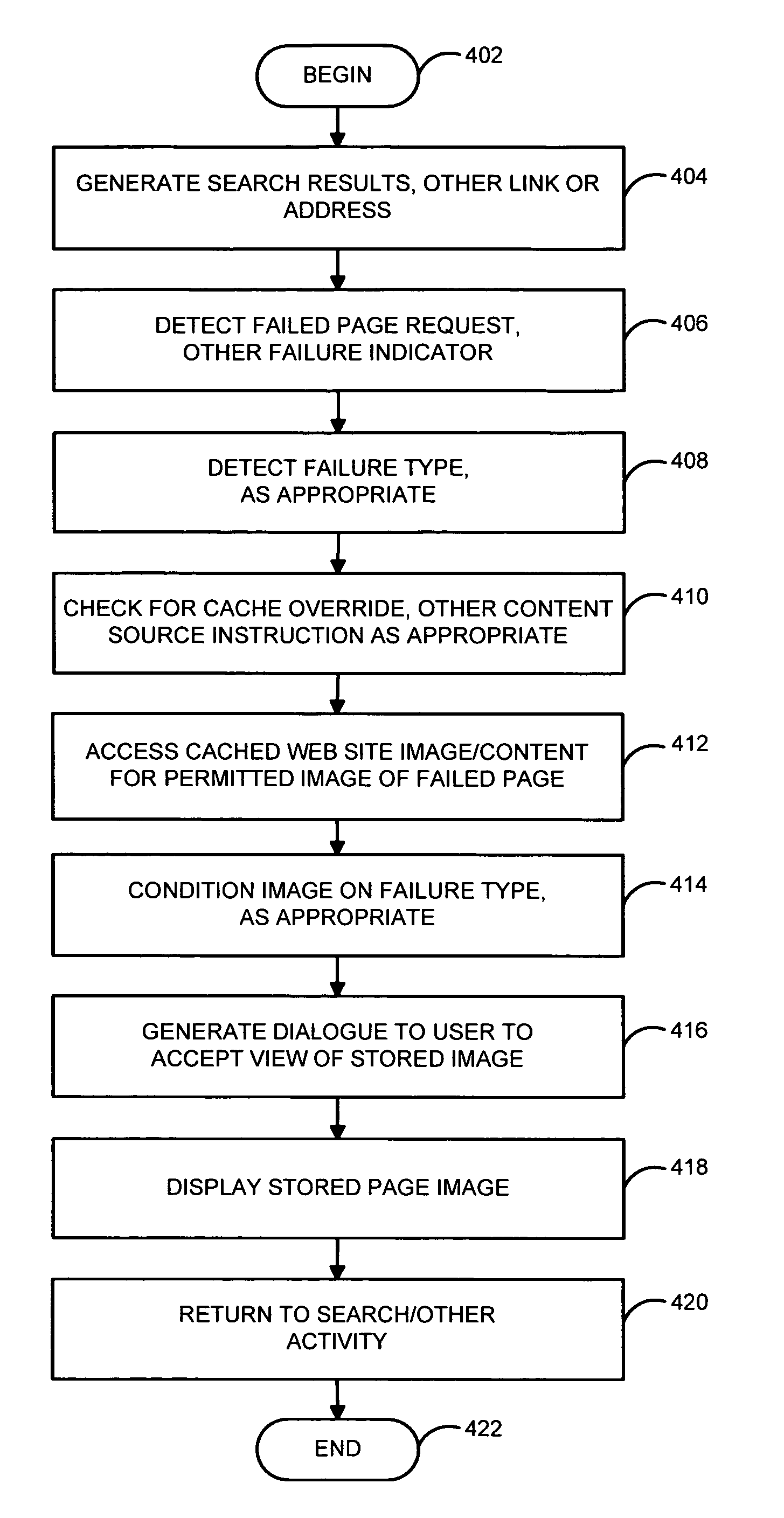
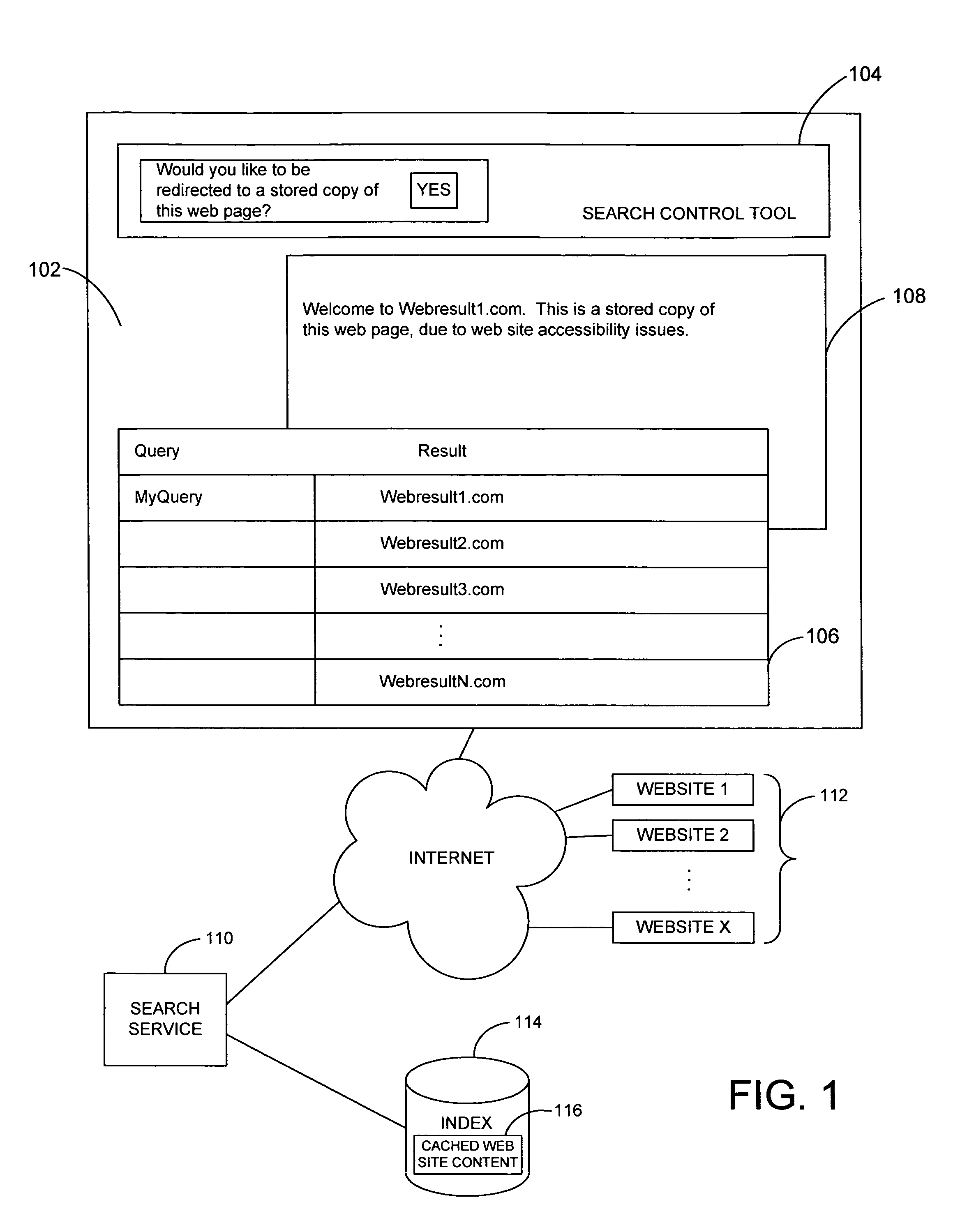
System and method for automatic redirection to stored web resources upon access failure
InactiveUS20060015573A1Lack of responseDigital data information retrievalMultiple digital computer combinationsWeb siteHTTP 404
A system and related techniques monitor a user's attempt to access a Web site or other network site, and detect failed access attempts such as HTTP 404 messages or others. Rather than pass the access failure message directly through to the user, the system may communicate with a search service or other index of stored or cached Web pages or other content images. The user may be given a choice via a dialogue to view a stored version of the site they were attempting to access, so that some or all of the desired information may still be accessed. In embodiments, the user may be directed to differing sources of the identical or similar desired content, via a priority stack. If further embodiments, the operator of the Web site or other content source may choose to apply a cached content override to opt out of making stored content available to searchers or other users, for example for digital rights management purposes.
Owner:MICROSOFT TECH LICENSING LLC
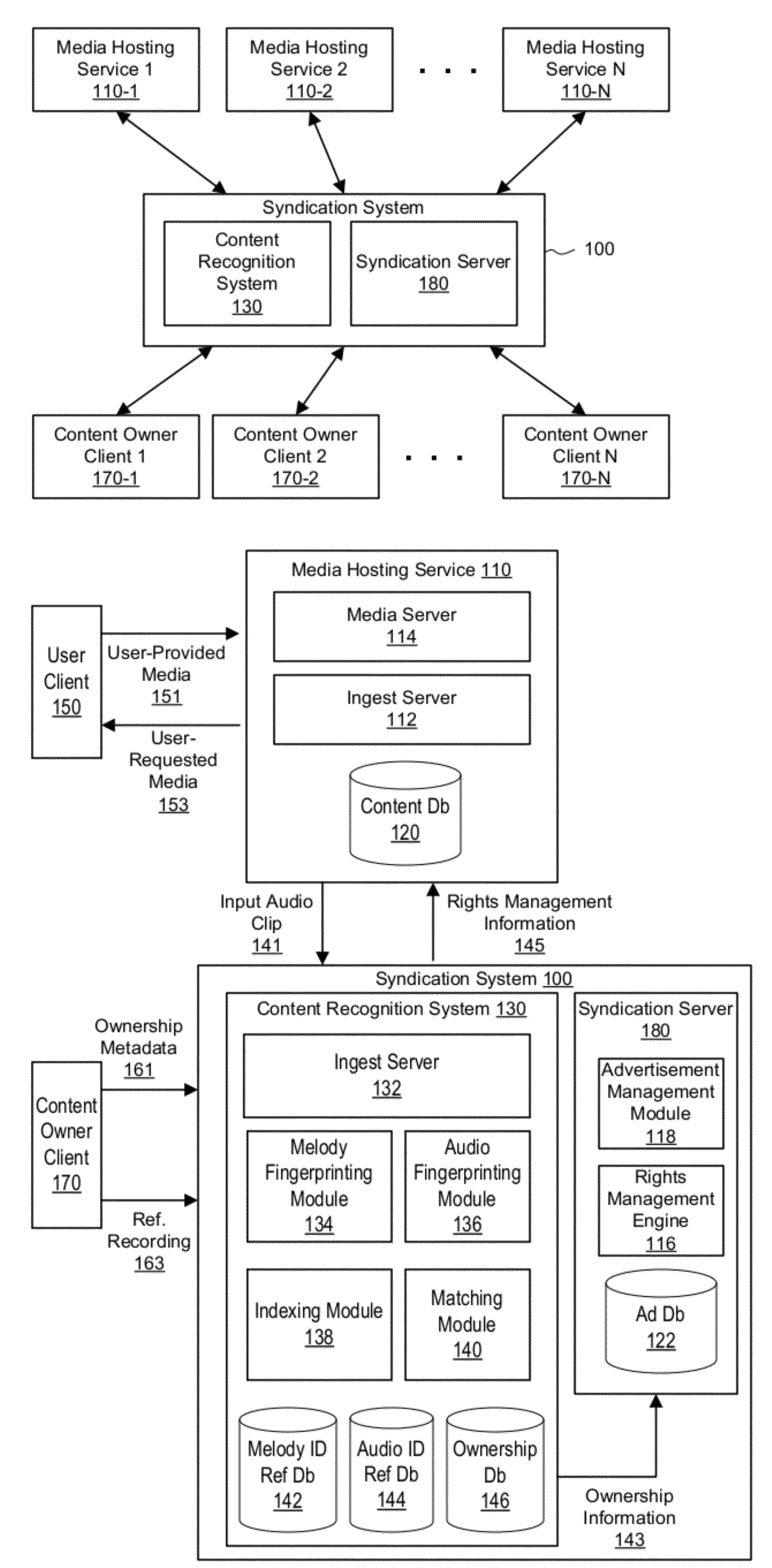
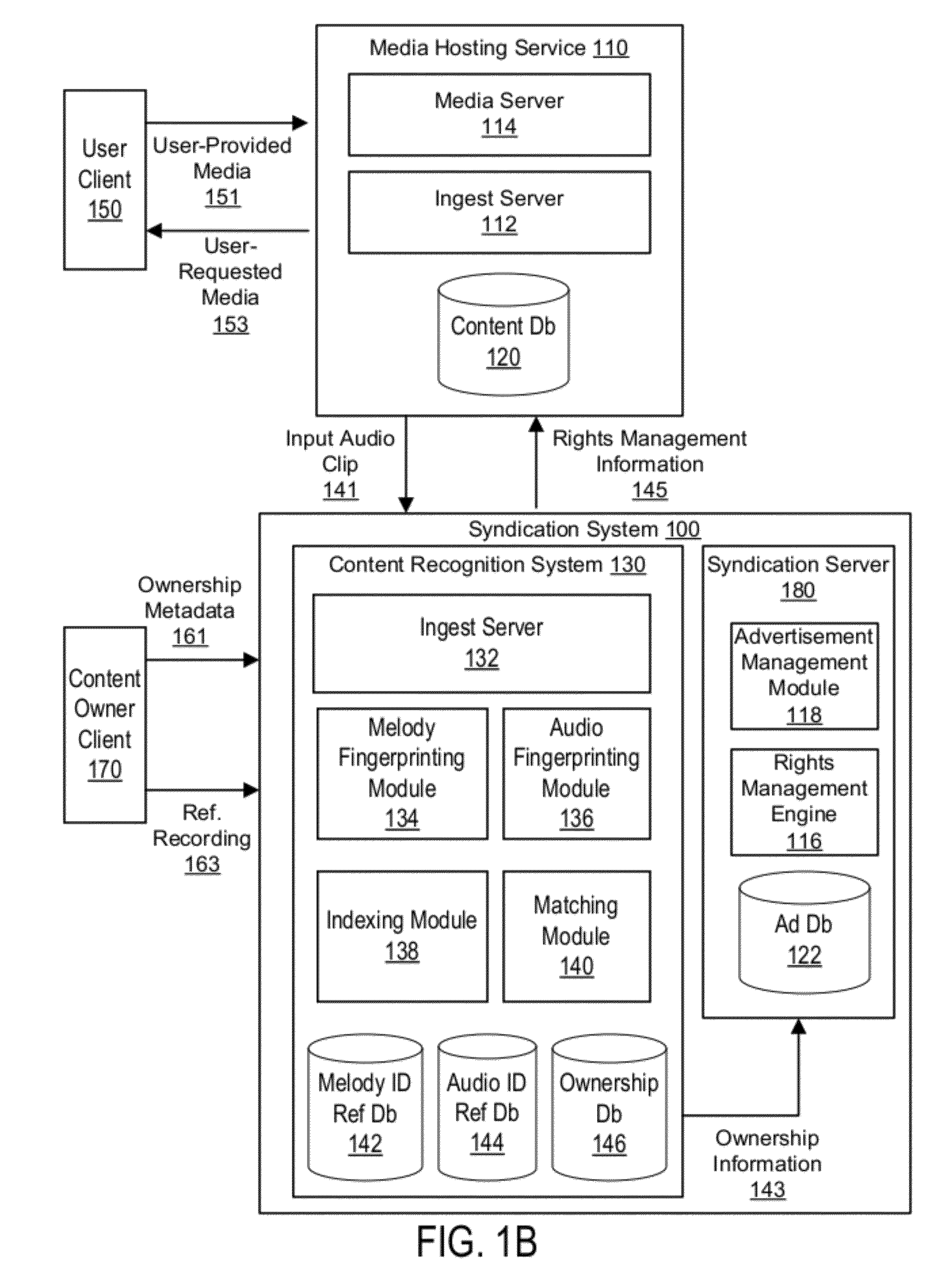
Syndication including melody recognition and opt out
ActiveUS20120124638A1Facilitates right management serviceFacilitates revenue sharingMusical toysUsing detectable carrier informationRights managementOwnership rights
A syndication system facilitates rights management services between media content owners and media hosting services that elect to participate in the syndication system and mutually elect to participate with each other. The syndication system utilizes a content recognition system to identify hosted media content and ownership rights associated with the hosted content. By applying melody recognition, the content recognition system can identify compositions embodied in hosted media content even when these compositions do not precisely match any known sound recording. Thus, the content recognition system is beneficially able to detect, for example, recorded cover performances and recorded live performances embodied in hosted media content. Once identified, ownership information is determined and the syndication system can facilitate rights management policies associated with the content such as monetizing or blocking the protected content.
Owner:GOOGLE LLC
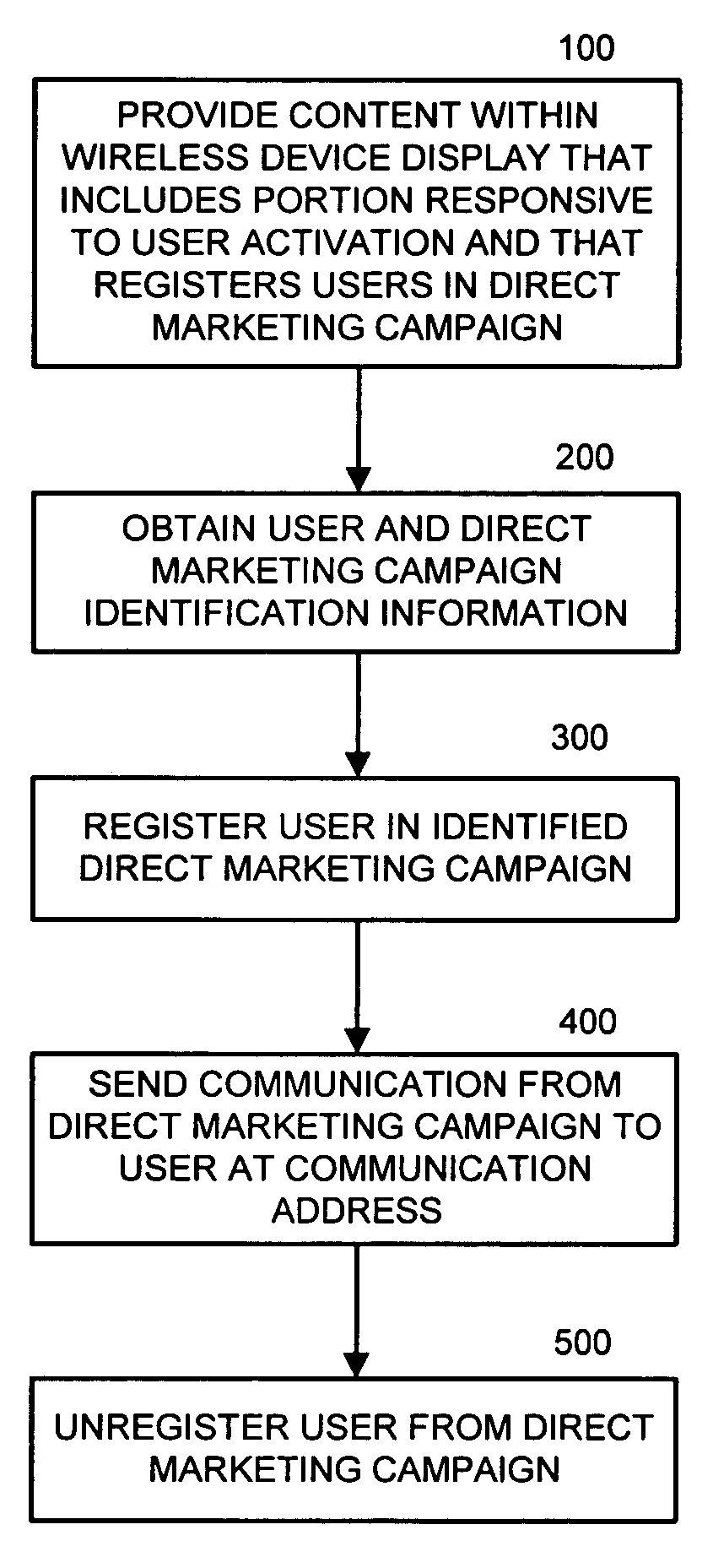
Systems, methods, and computer program products for registering wireless device users in direct marketing campaigns
Systems, methods, and computer program products are provided that allow wireless device users to “opt-in” to a direct marketing campaign by “clicking on” a conventional advertisement displayed within a wireless device and register to receive future promotions via one or more direct marketing channels. Likewise, users can “opt-out” of future direct marketing by “clicking on” content displayed within various promotional content.
Owner:ZAMA INNOVATIONS LLC +1
Changeable display components in an internet Web page
InactiveUS20060184620A1Multiple digital computer combinationsPayment architectureInternet usersWeb page
A host Web page includes an evolving interactive dialog box wherein an Internet user may enter user data to be processed. When the user completes entering user data in a first revolution of the interactive dialog box, the first revolution is replaced with a second revolution of the evolving interactive dialog box without disturbing or affecting any other part of the host Web page being displayed. Beneficially, the first and second revolutions may be communicated to a user computer together with and at a same time as the host Web page. Also, the second revolution may include a variety of data which is selected or customized to match the user data submitted in the first revolution. Each revolution of the evolving interactive dialog box may be comprised of any combination of general textual data entry fields, category (pull-down) menus, contact information data entry fields, and opt-in / opt-out buttons. The evolving interactive dialog box may also include dynamically selectable features, such as font type, font size, font color, box shape, box dimension(s), background colors, foreground colors, etc.
Owner:PAYPAL INC
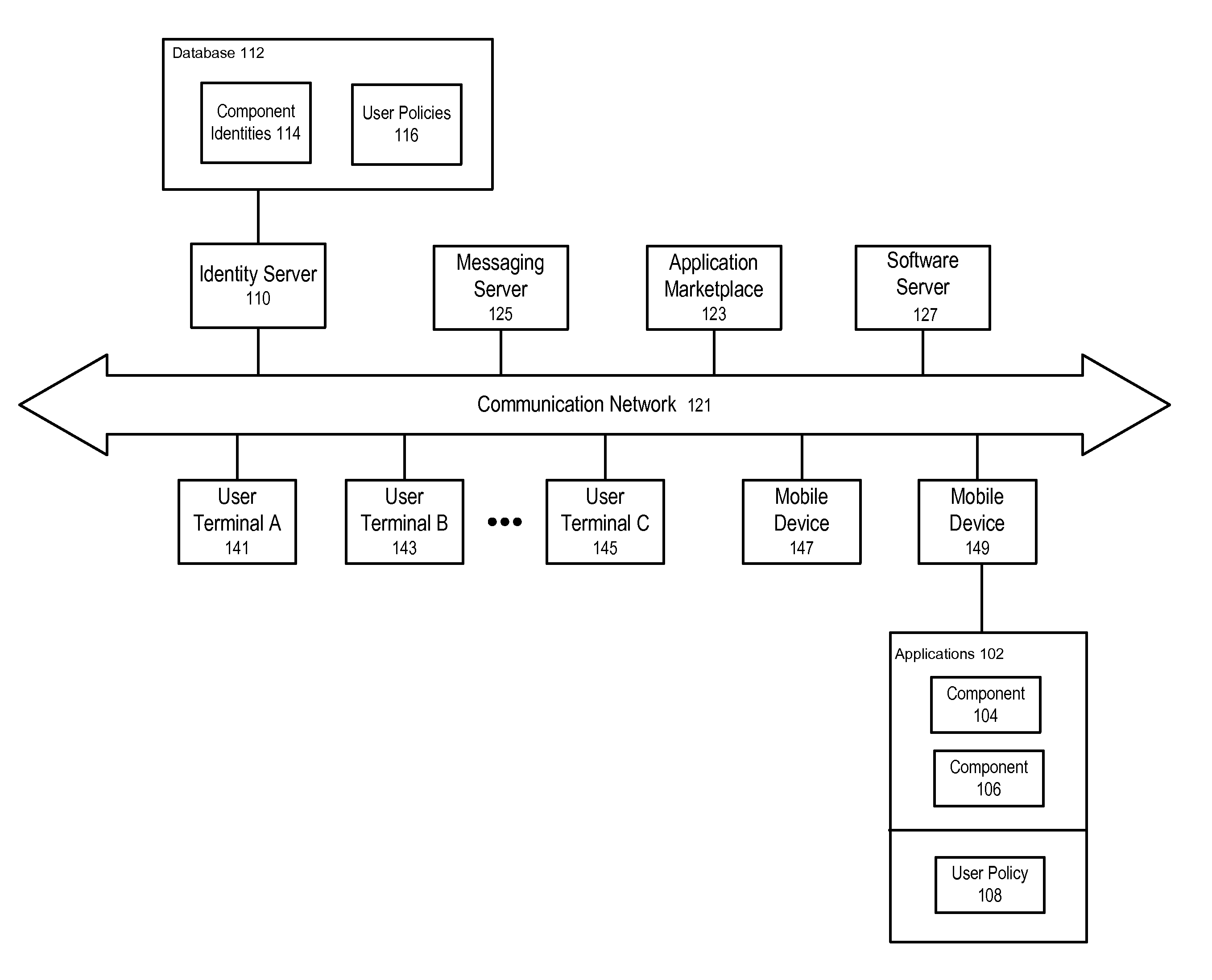
Component analysis of software applications on computing devices
ActiveUS20130326476A1Error detection/correctionSoftware maintainance/managementNetwork communicationApplication software
Detection, identification, and control of application behavior dealing with malware, security risks, data privacy, or resource usage can be difficult in an era of complex, composite software applications composed of multiple components. Software applications are analyzed to determine their components and to identify the behaviors associated with each of the components. Components can also be analyzed with respect to similarity of previously known components. Behaviors can include use of personal identifying information or device information, or any actions that can be taken by applications on the device, including user interface displays, notifications, network communications, and file reading or writing actions. Policies to control or restrict the behavior of applications and their components may be defined and applied. In one embodiment this can include the identification of advertising networks and defining policies to permit various opt-out actions for these advertising networks.
Owner:LOOKOUT MOBILE SECURITY
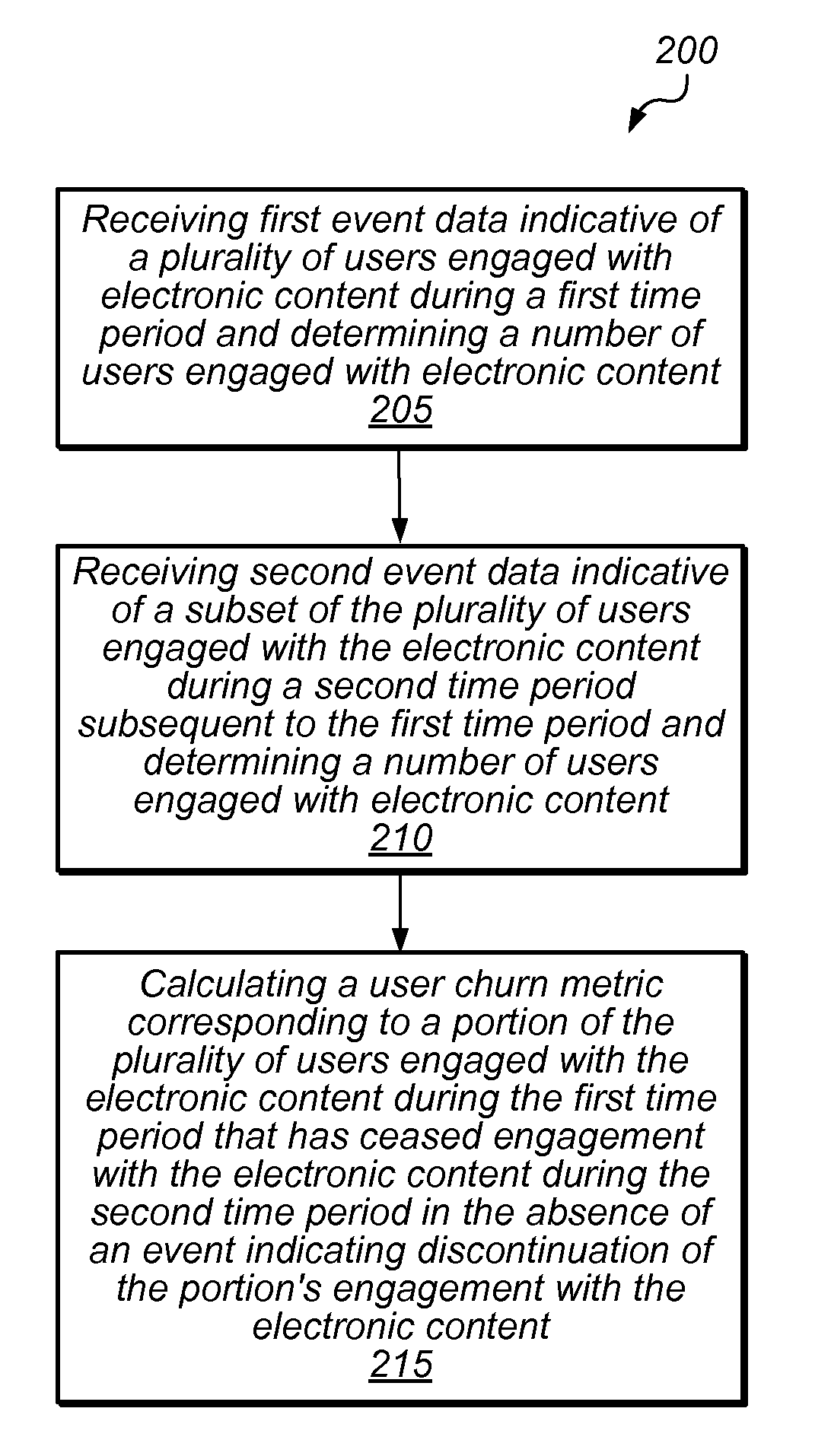
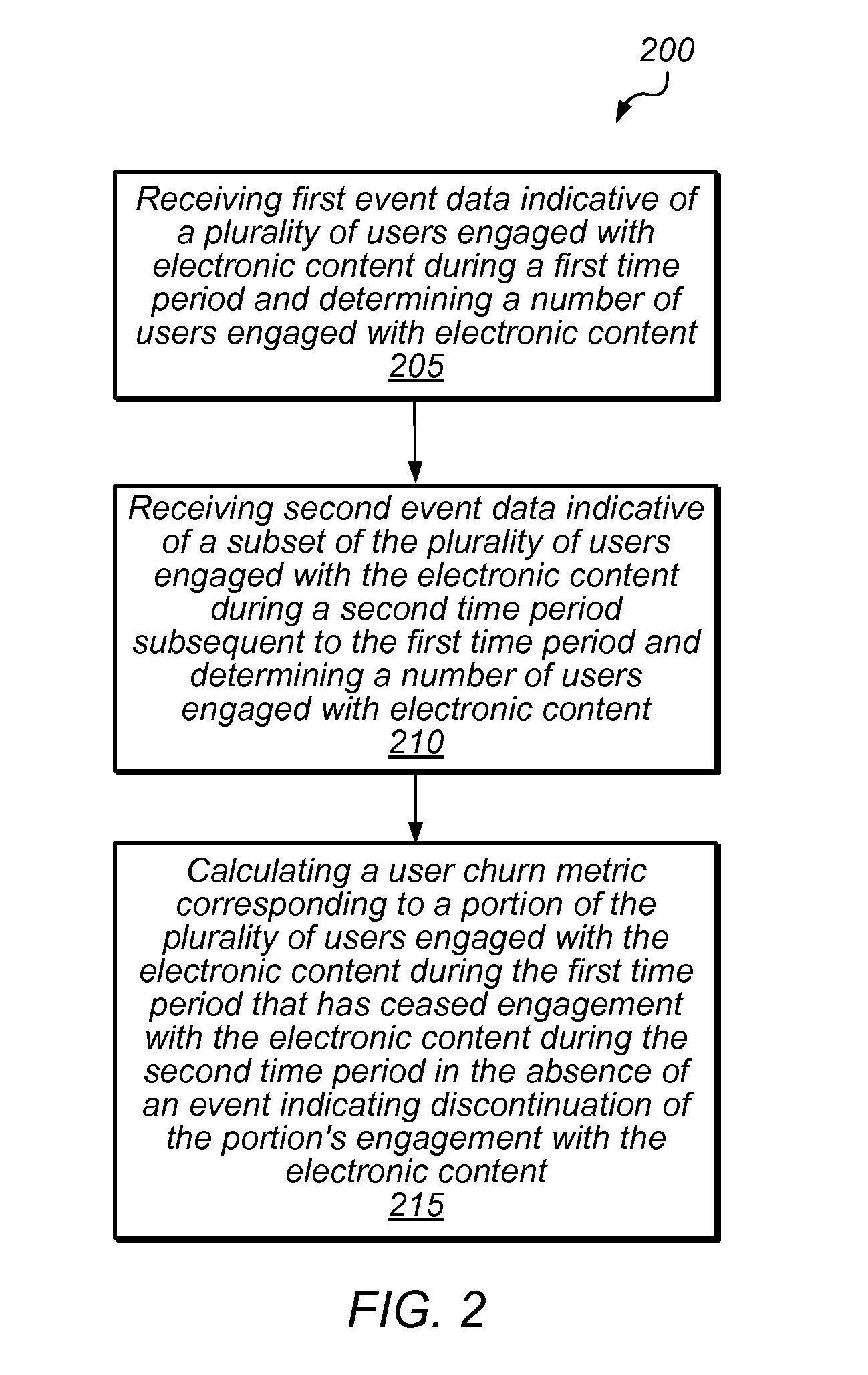
Systems and methods for user churn reporting based on engagement metrics
Methods and systems for user churn reporting based on engagement metrics are disclosed. In some embodiments, methods and systems may provide mechanisms for reporting the number of users or customers that are disengaged from a service or product. These embodiments may be employed, for instance, in cases where there is no “analytic footprint” marking discontinuation of service—e.g., where there is no explicit “subscription cancellation request,”“subscription expiration,”“opt-out,” or the like in connection with a user's disengagement. Other embodiments are applicable to subscription-based models, for example, where users have not “unsubscribed” from the service but should nonetheless no longer be considered engaged. As such, systems and methods disclosed herein may enable assessment and improvement of marketing campaign and retention efforts based on their effectiveness in reducing the number of churned users, re-engagement of users that have abandoned a particular product or service, etc.
Owner:ADOBE INC
Privacy-safe targeted advertising method and system
A method and system for sophisticated consumer deep profile building provided as a service in a certifiably clean, i.e., privacy-safe, manner to advertisers, ad networks, publishers, aggregators and service providers. In an embodiment, an entity provides a tracking and targeting service that acts as a container for sensitive consumer information. The entity preferably implements a stringent policy of transparency and disclosure, deploys sophisticated security and data anonymization technologies, and it offers a simple, centralized consumer service for privacy disclosure, review and deletion of collected profile information, opt-in, opt-out, and the like. In exchange, advertisers, ad networks, publishers, aggregators and service providers (including, without limitation, mobile operators, multiple service providers (MSPs), Internet service providers (ISPs), and the like), receive privacy-safe targeting services without ever having to touch sensitive information.
Owner:SIMEONOV SIMEON S
Method and apparatus for rule triggered mobile advertising
An advertising subsidized communication service is provided that can be utilized by eligible subscribers in instances designated by mobile operators or advertisers. An eligible subscriber that meets certain criteria, such as having a low pre-paid balance, can opt-in to an advertising subsidized service initiated through an SCP proxy for the advertising service platform. The subscriber receives advertising through selected channels, such as voice injection, text messaging or other media, which advertising subsidizes subscriber communication service. The subsidized service may be limited in some regard to number of calls, call duration or incoming calls, as examples. The subscriber may be automatically opted-out of the subsidized service upon payment being applied to a pre-paid for post-paid service account. The opt-in process for subsidized service occurs in real-time and may be prompted through a number of channels, such as voice or text messages.
Owner:XIUS CORP
Opt-in process and nameserver system for IETF DNSSEC
InactiveUS20080260160A1Facilitating DNSSEC deploymentDecreases comprehensivenessSpecial service provision for substationPublic key for secure communicationComputer networkName server
The process of signing and then publishing a DNS zone according to the IETF DNSSEC protocols is improved by the present invention, in order to facilitate the DNSSEC deployment until most of the DNS zones are signed. The prior art situation is that a second-level domain, e.g. example.com, often faces an unwanted status of “DNSSEC island of security,” and a challenging task of “trust anchor key” out-of-band distribution. The invention somehow fixes such broken DNSSEC chains of trust, e.g. it fills the gap between a DNSSEC island of security and its signed grandparent or ancestor. The invention is deemed useful for the introduction of DNS root nameservice substitution for DNSSEC support purposes, and allows opt-in while NSEC3 opt-out is awaiting deployment in large TLDs.
Owner:CONNOTECH EXPERTS CONSEIL
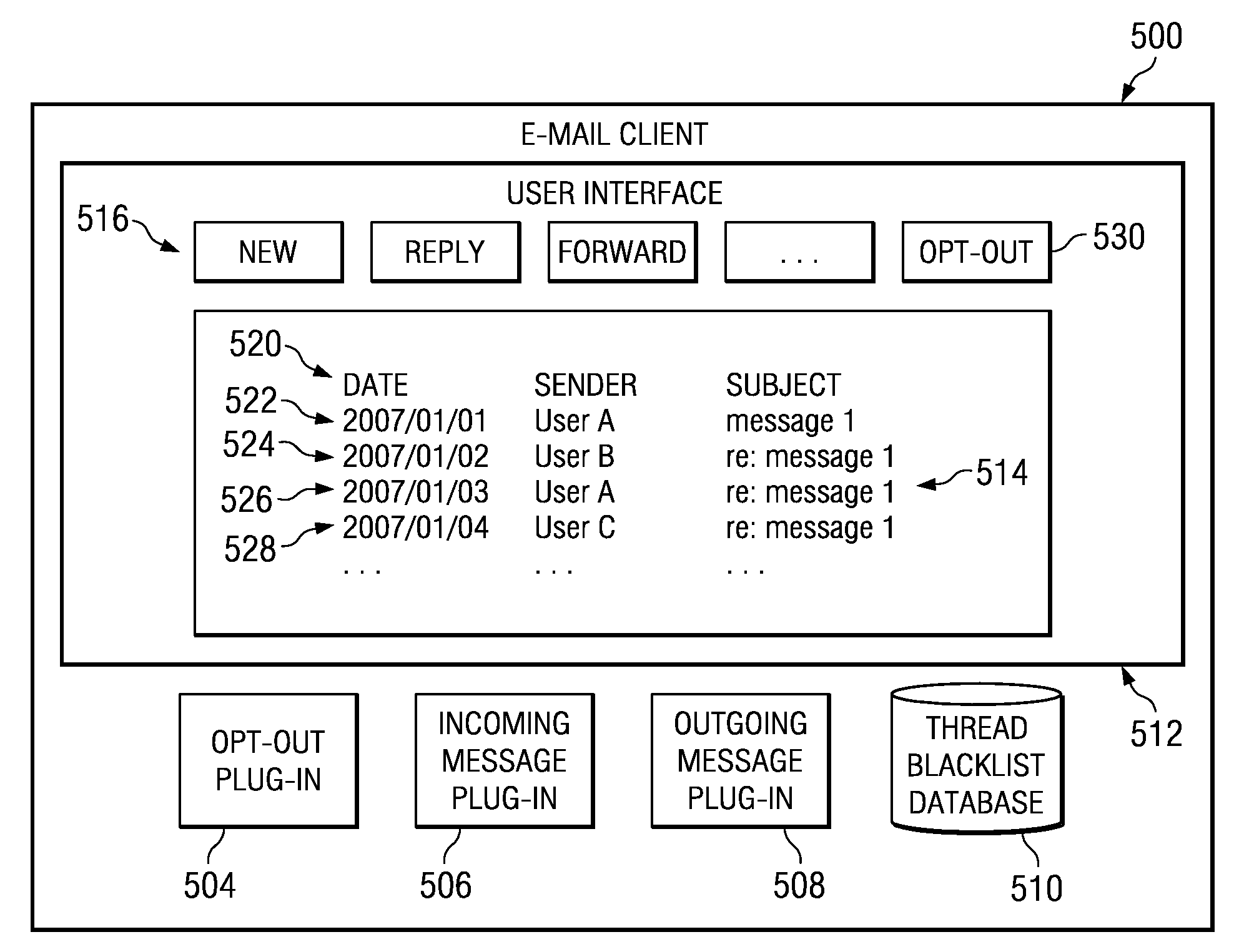
Method and system for removing a person from an e-mail thread
InactiveUS20090132664A1Multiple digital computer combinationsTransmissionEmail addressInternet privacy
A method for automatically removing a user from an e-mail thread is provided. An e-mail client receives a reply e-mail message. Responsive to a determination that the reply e-mail message is a message to opt-out of an e-mail thread, the e-mail address of a sender of the reply e-mail message is associated with the e-mail thread to form a listed e-mail address. The listed e-mail address is stored. When a new e-mail message is generated that is part of the e-mail thread, the listed e-mail address is automatically excluded from a list of recipients of the new e-mail.
Owner:IBM CORP
Expressing intent to control behavior of application components
ActiveUS20130326477A1Error detection/correctionSoftware maintainance/managementNetwork communicationApplication software
Detection, identification, and control of application behavior dealing with malware, security risks, data privacy, or resource usage can be difficult in an era of complex, composite software applications composed of multiple components. Software applications are analyzed to determine their components and to identify the behaviors associated with each of the components. Components can also be analyzed with respect to similarity of previously known components. Behaviors can include use of personal identifying information or device information, or any actions that can be taken by applications on the device, including user interface displays, notifications, network communications, and file reading or writing actions. Policies to control or restrict the behavior of applications and their components may be defined and applied. In one embodiment this can include the identification of advertising networks and defining policies to permit various opt-out actions for these advertising networks.
Owner:LOOKOUT MOBILE SECURITY
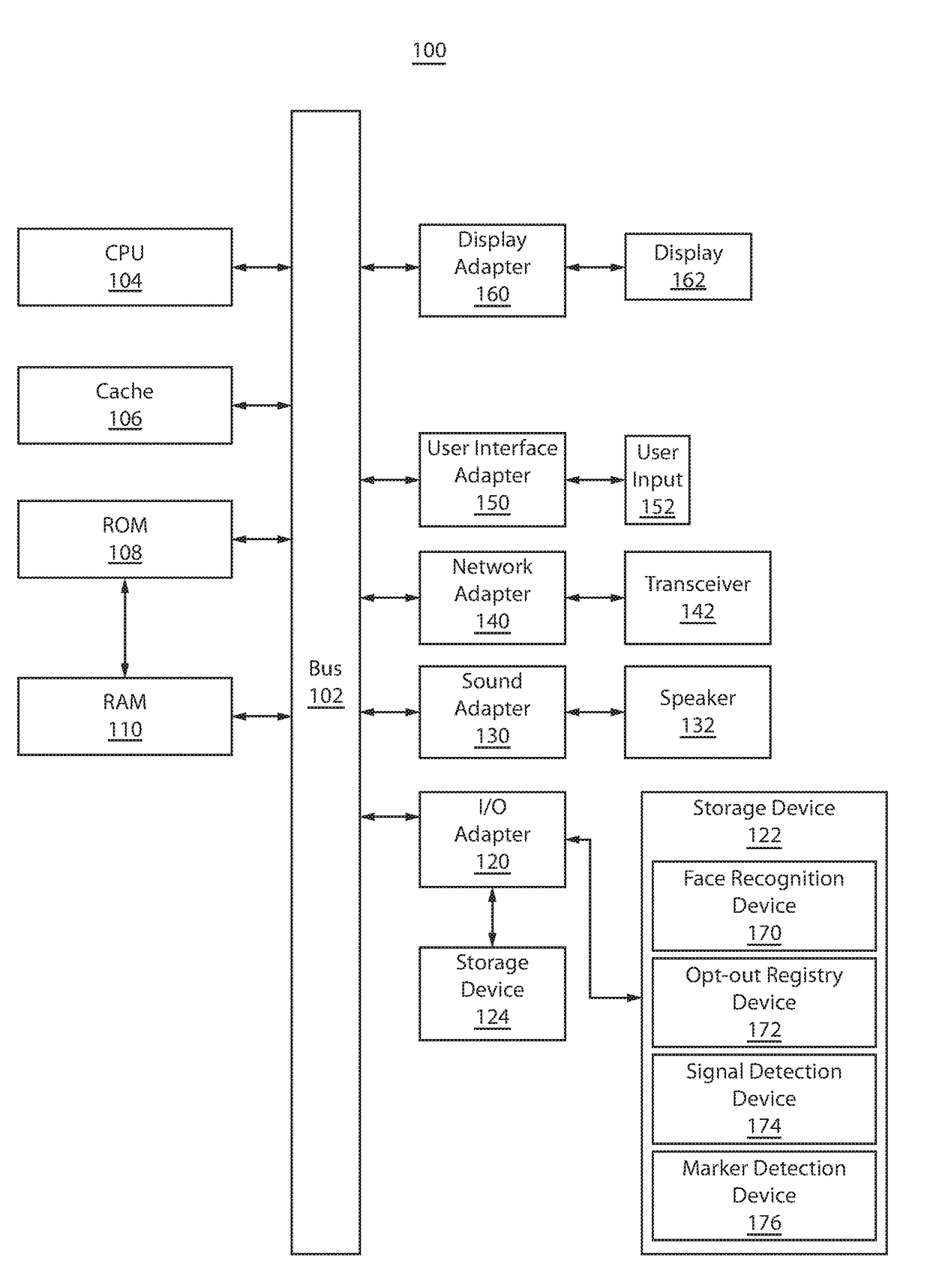
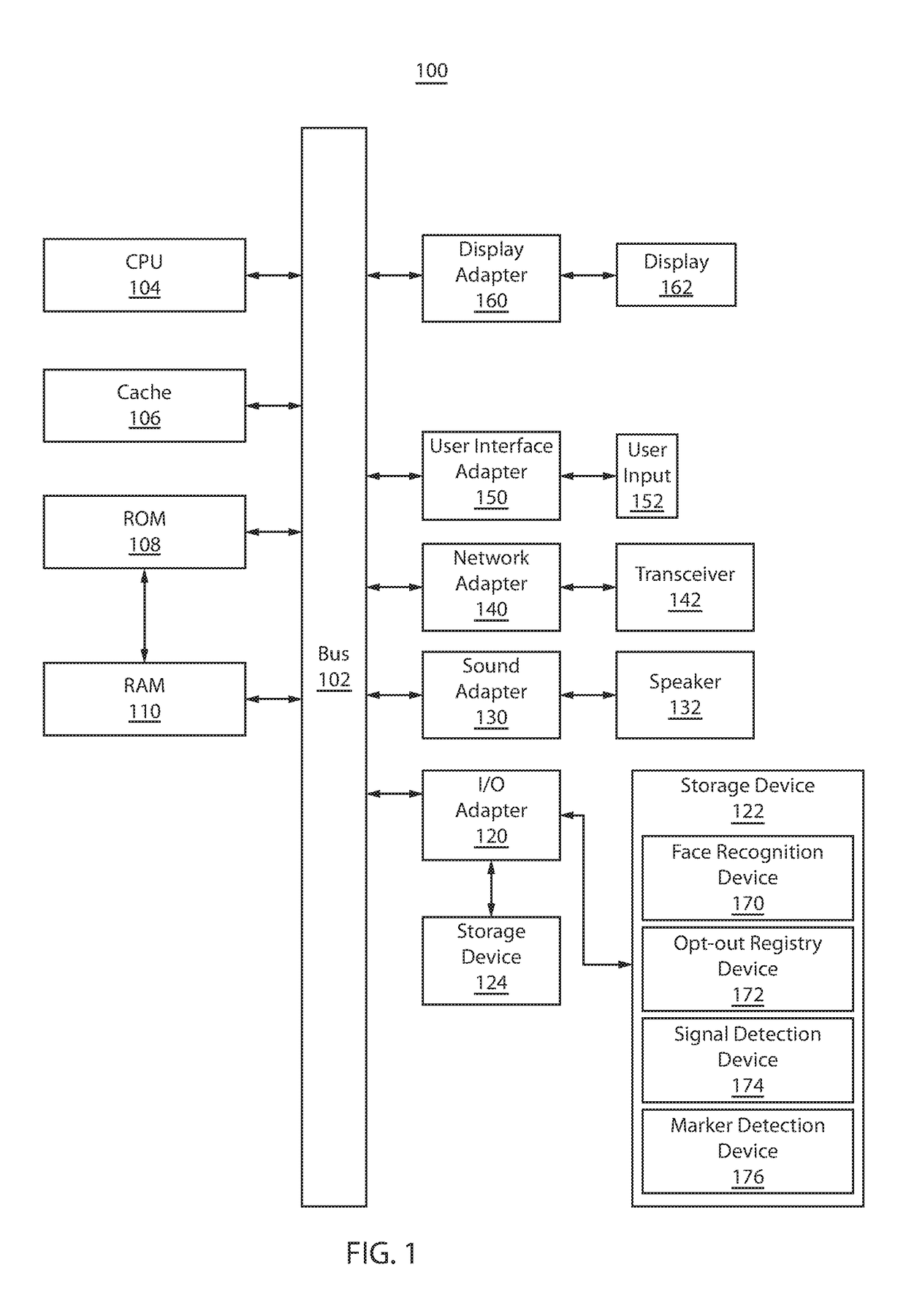
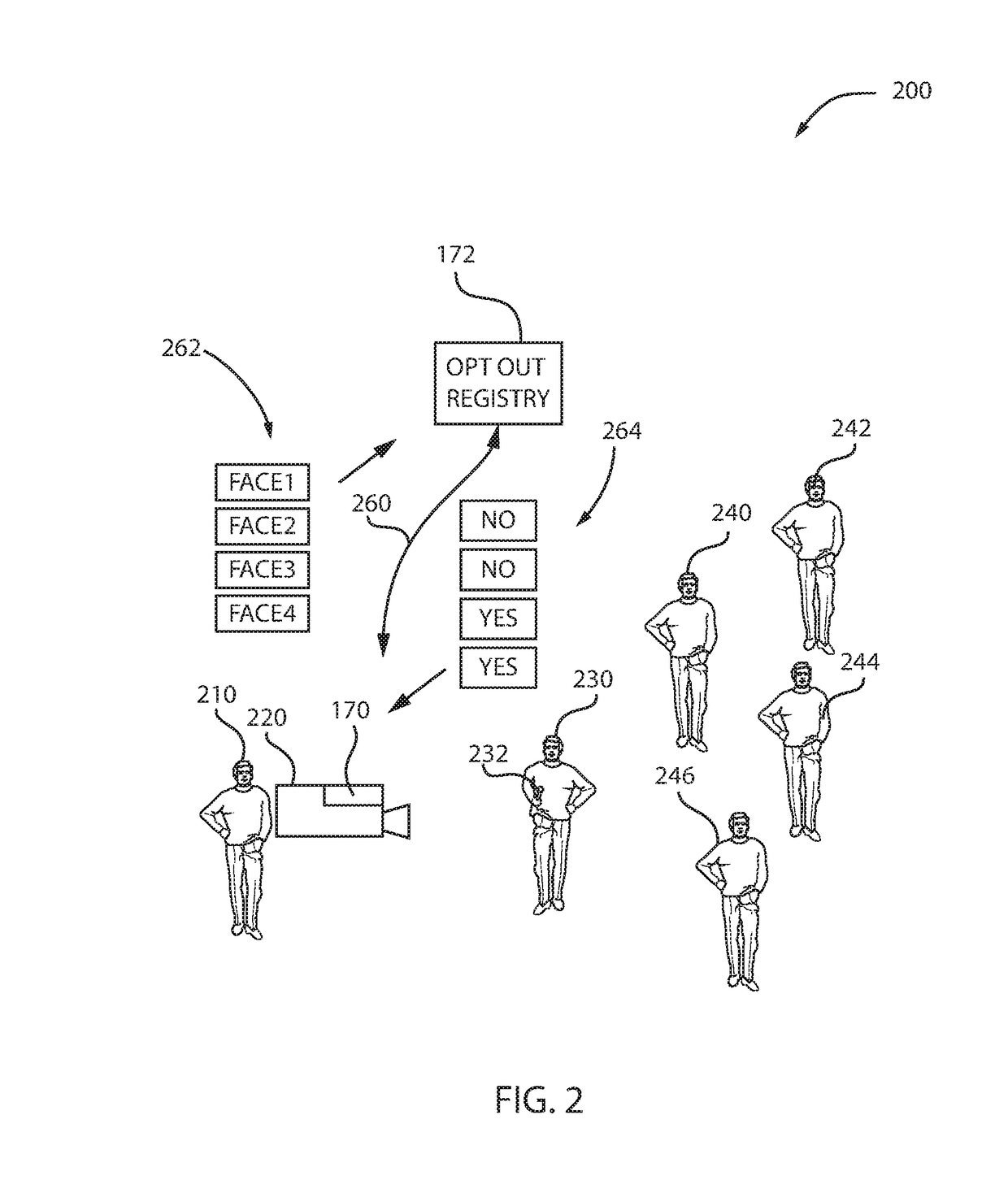
Protecting individuals privacy in public through visual opt-out, signal detection, and marker detection
ActiveUS20180061010A1Enhanced anonymityImage enhancement2D-image generationPattern recognitionAnonymity
A method for protecting anonymity of an individual in public is presented. The computer-implemented method may include registering a plurality of facial features associated with the individual, and, in response to capturing an image of the individual from a video stream, determining whether the facial features associated with the individual are registered. The computer-implemented method may further include, in response to the determination that the facial features associated with the individual are registered, obscuring the facial features of the individual captured from the video stream with an unidentifiable image.
Owner:IBM CORP
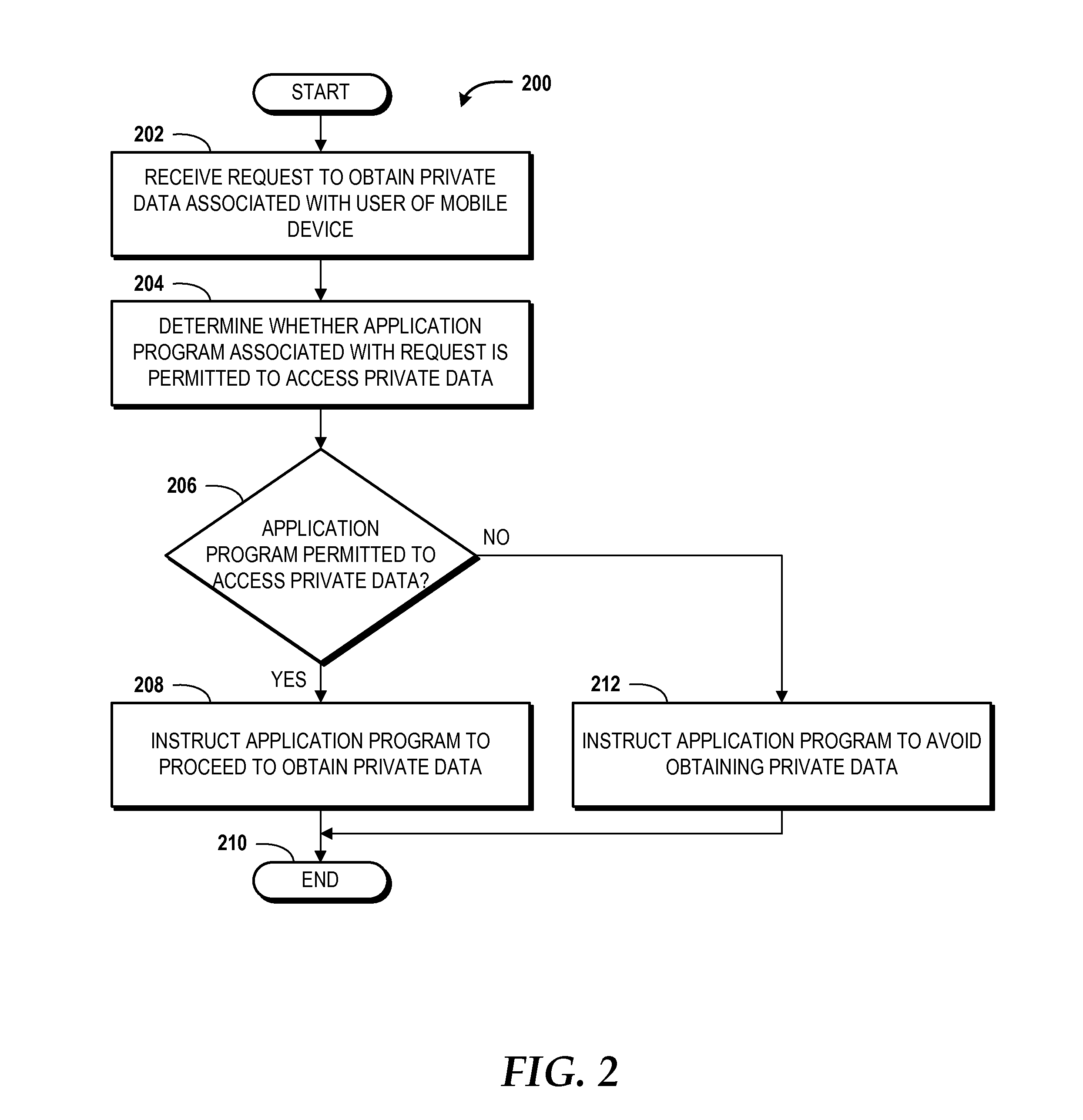
Managing Opt-In and Opt-Out for Private Data Access
ActiveUS20140099920A1Well formedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet privacyData access
Concepts and technologies disclosed herein are for managing opt-in and opt-out for private data access. According to one aspect disclosed herein, a mobile device can receive a request to obtain private data associated with a user of the mobile device and, in response to the request, determine whether an application program associated with the request is permitted to access the private data based upon a rule. The mobile device, in response to determining that the application program is permitted to access the private data based upon the rule, can instruct the application program to proceed to obtain the private data. The mobile device, in response to determining that the application program is not permitted to access the private data based upon the rule, can instruct the application program to avoid obtaining the private data.
Owner:AT&T INTPROP I L P
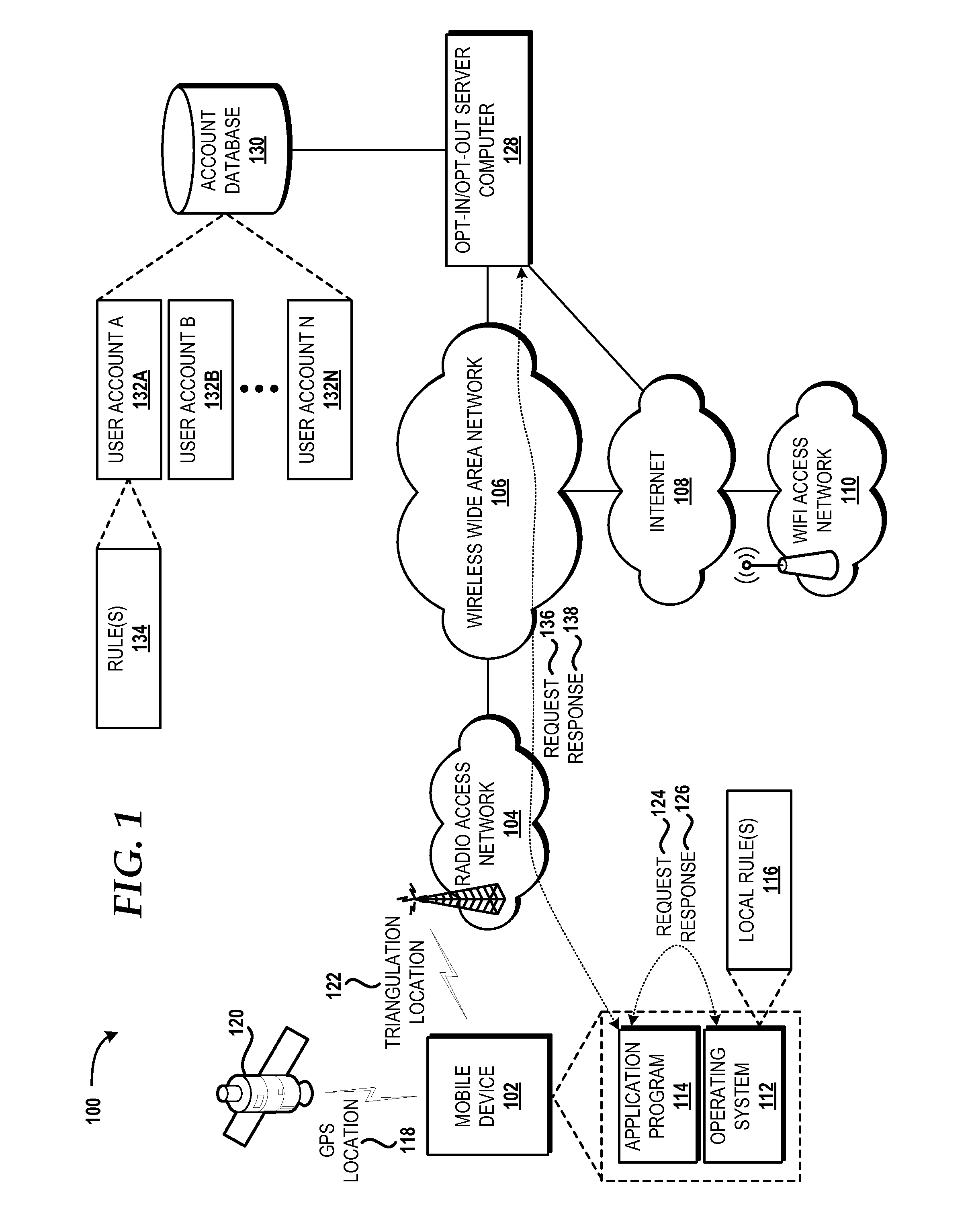
Wireless network communication nodes with opt out capability
ActiveUS20140269272A1Exposure was also limitedError preventionTransmission systemsTelecommunicationsEngineering
Techniques are disclosed herein for providing wireless network communication nodes with opt-out capabilities. Such capabilities may, for example, allow particular customers to opt out of a typical full-scale communication mode such that their associated equipment operates at least temporarily in a limited communication mode. The limited communication mode may limit customer exposure to emissions resulting from RF communications near their homes or other areas, which may be attractive to customers such as those with health or other emission-related concerns.
Owner:ELSTER SOLUTIONS
System and method for controlling targeted advertising
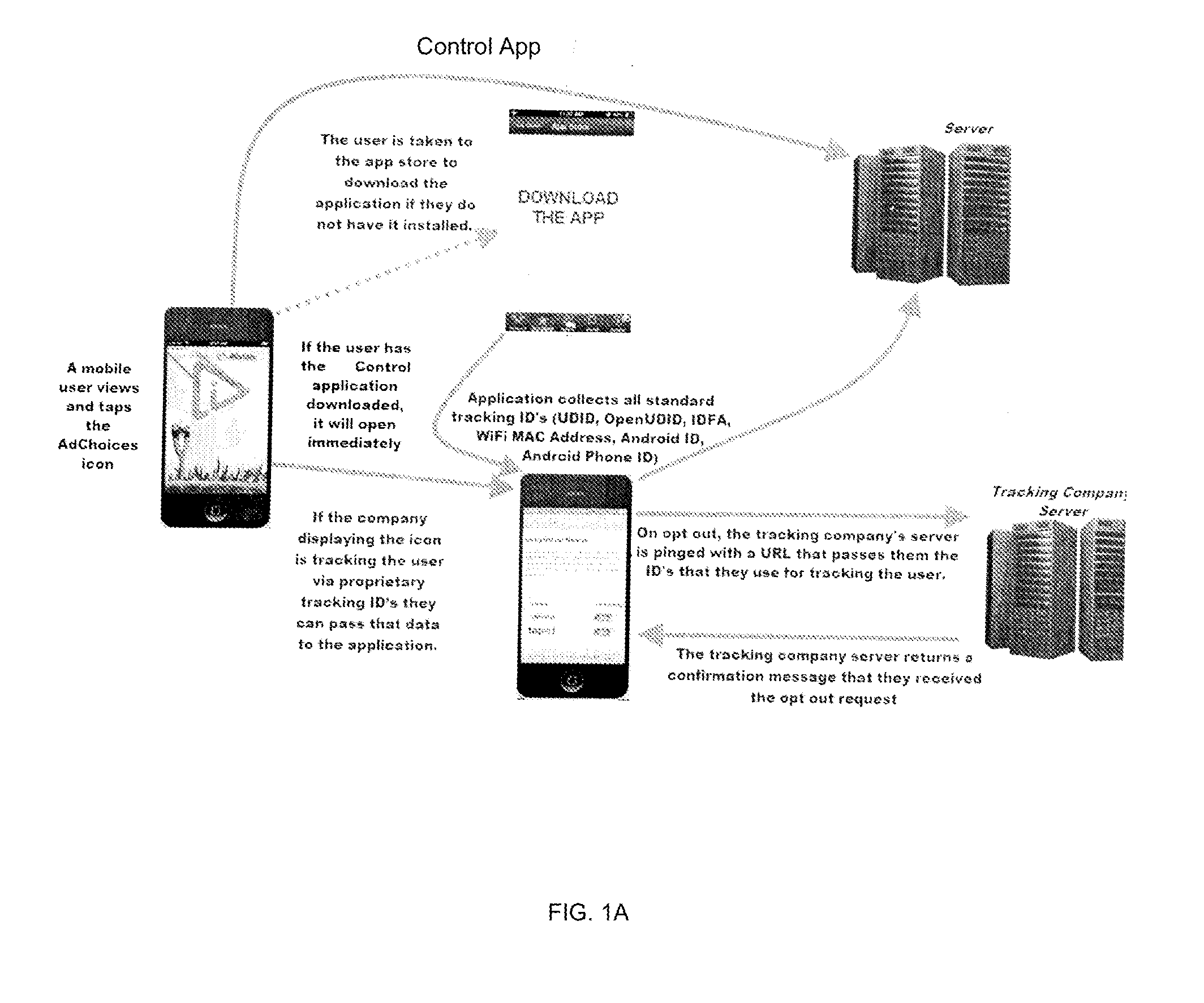
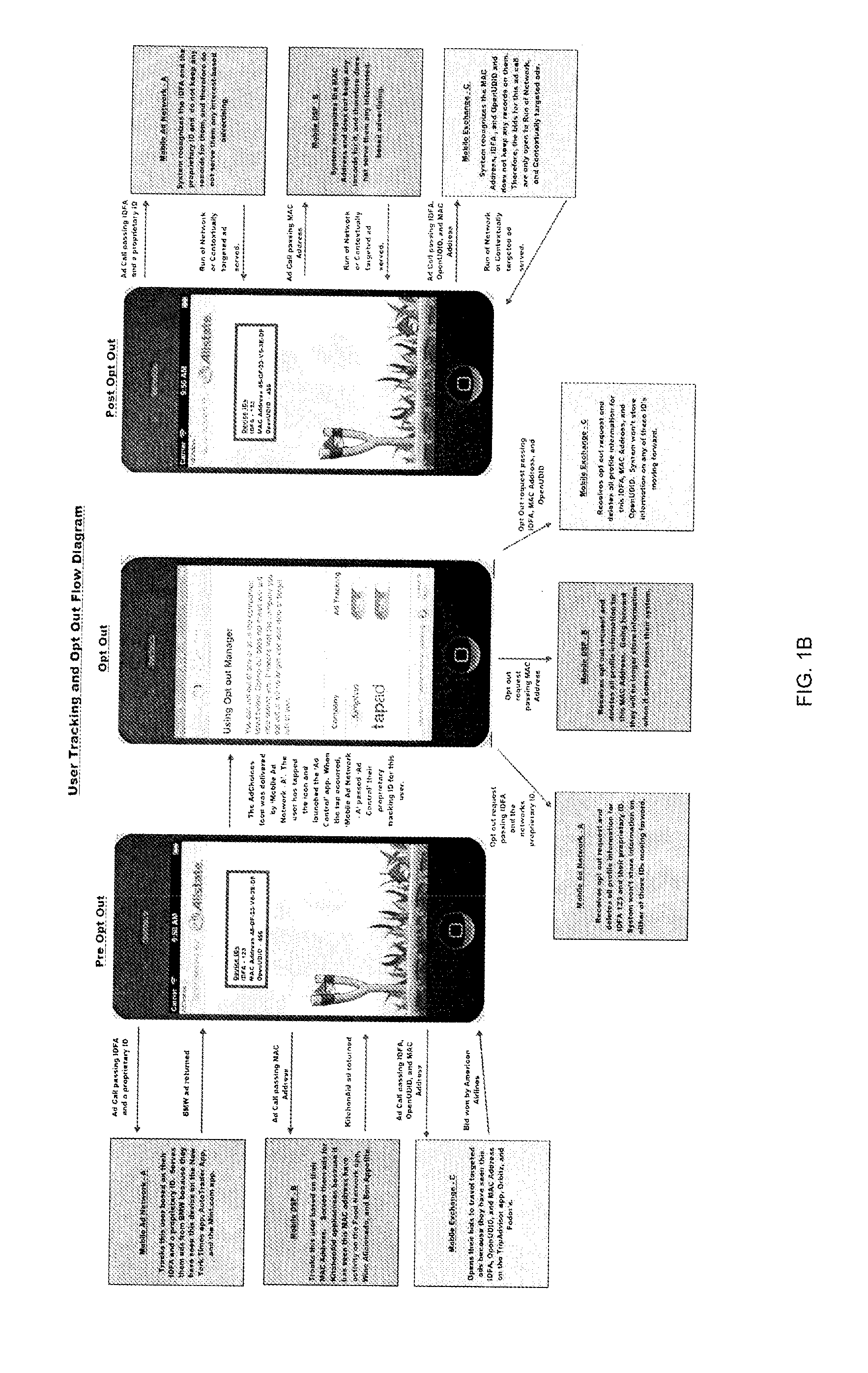
In a system enabling a user to control tracking of online activities of the user on a user device, a list of trackers is presented to the user. For each tracker, an option to opt out of or opt in into tracking by that tracker is also presented. The user's preference for a particular tracker, i.e., opt out or opt in, is transmitted to the tracker via a message that includes the specific ID or IDs used by that particular tracker.
Owner:EVIDON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com