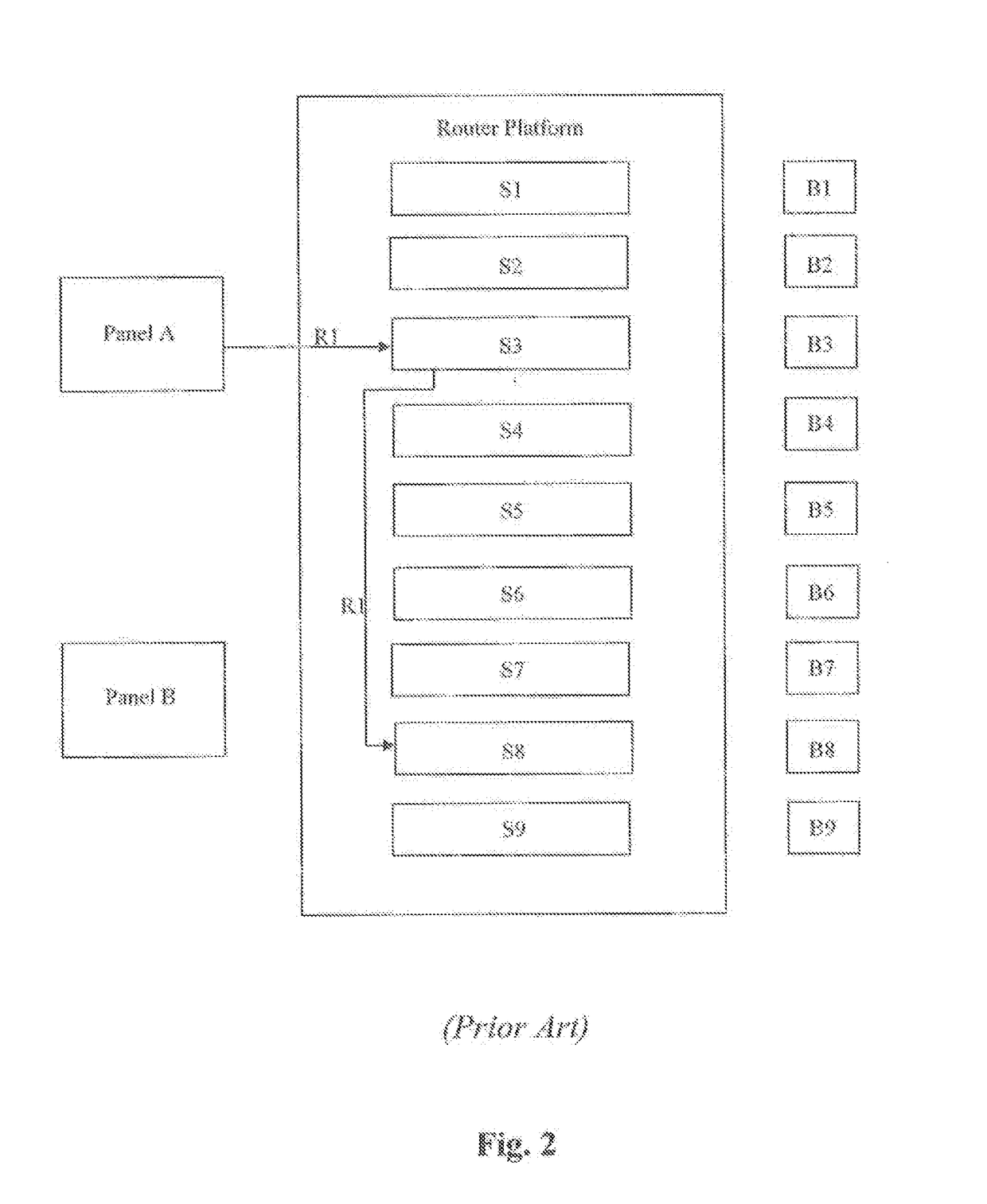
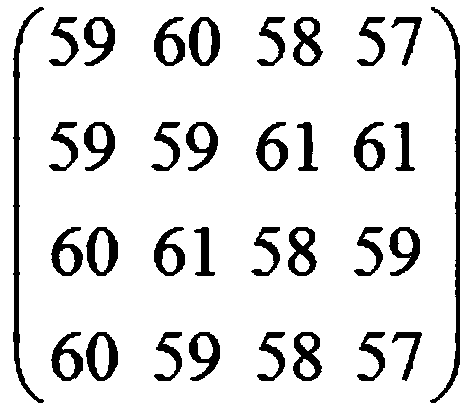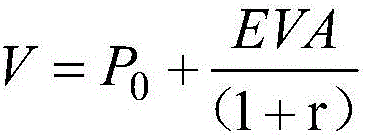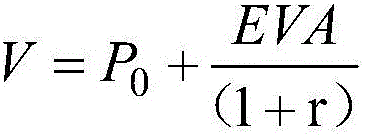Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Embedded value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Embedded Value (EV) of a life insurance company is the present value of future profits plus adjusted net asset value. It is a construct from the field of actuarial science which allows insurance companies to be valued.
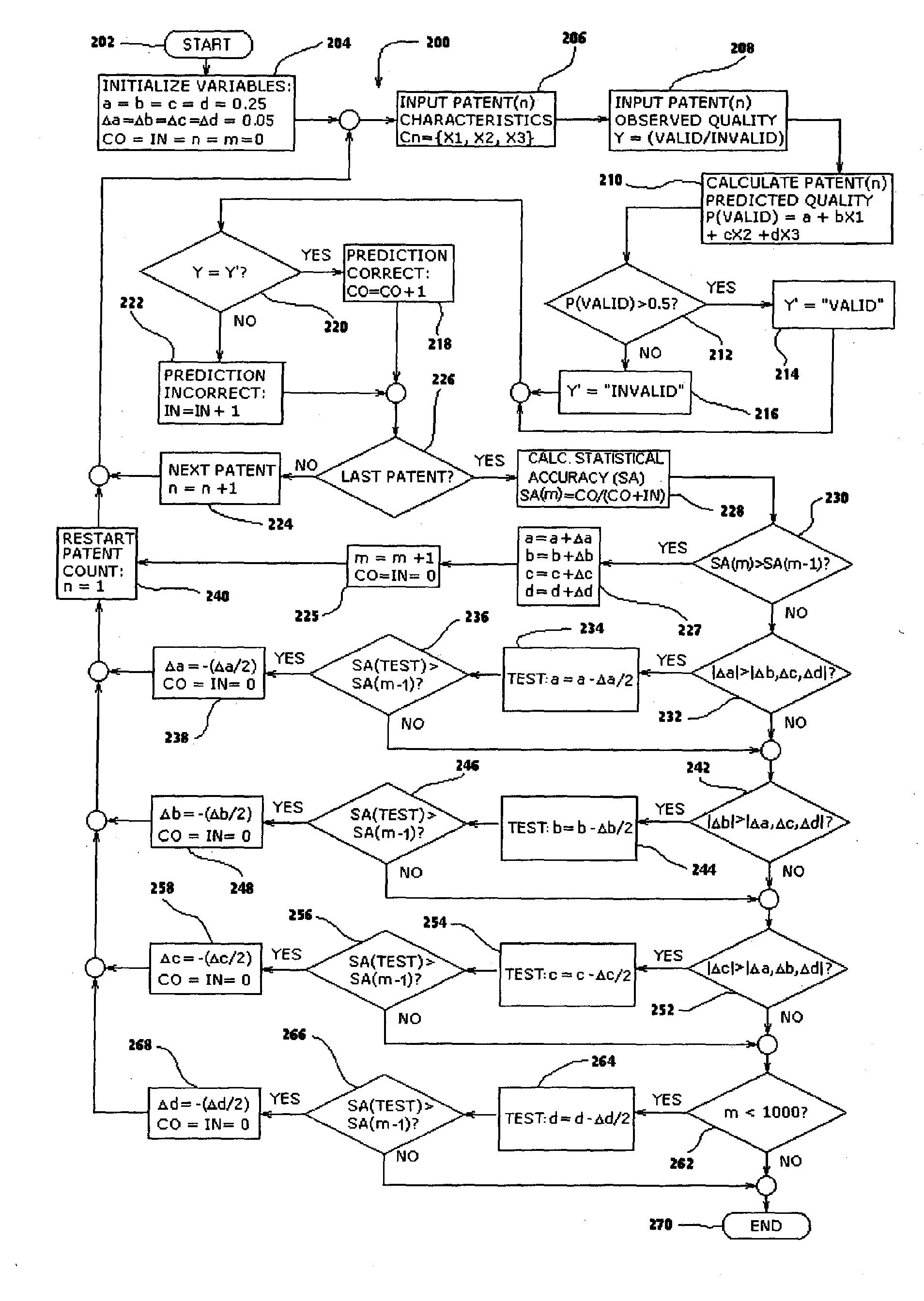
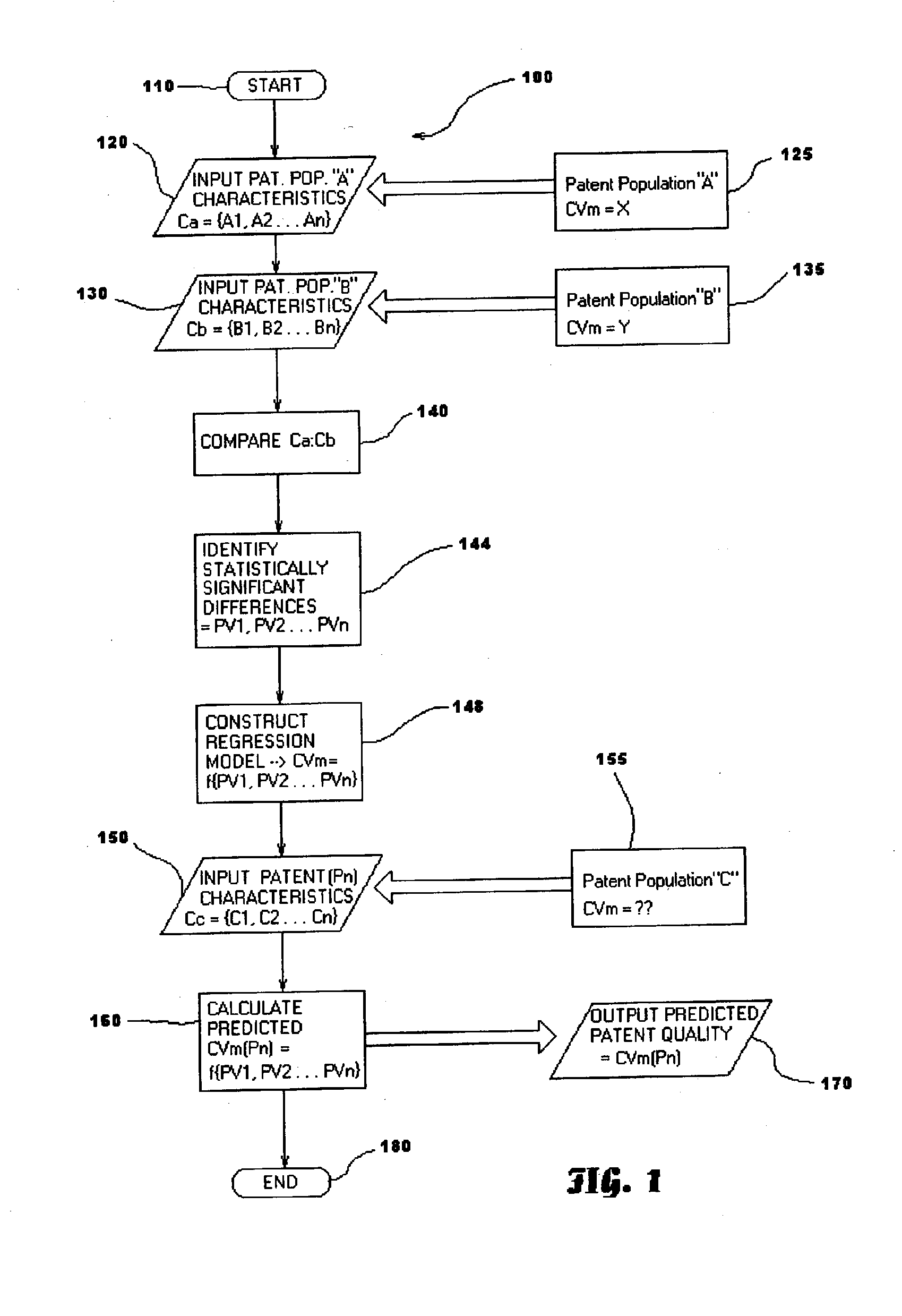
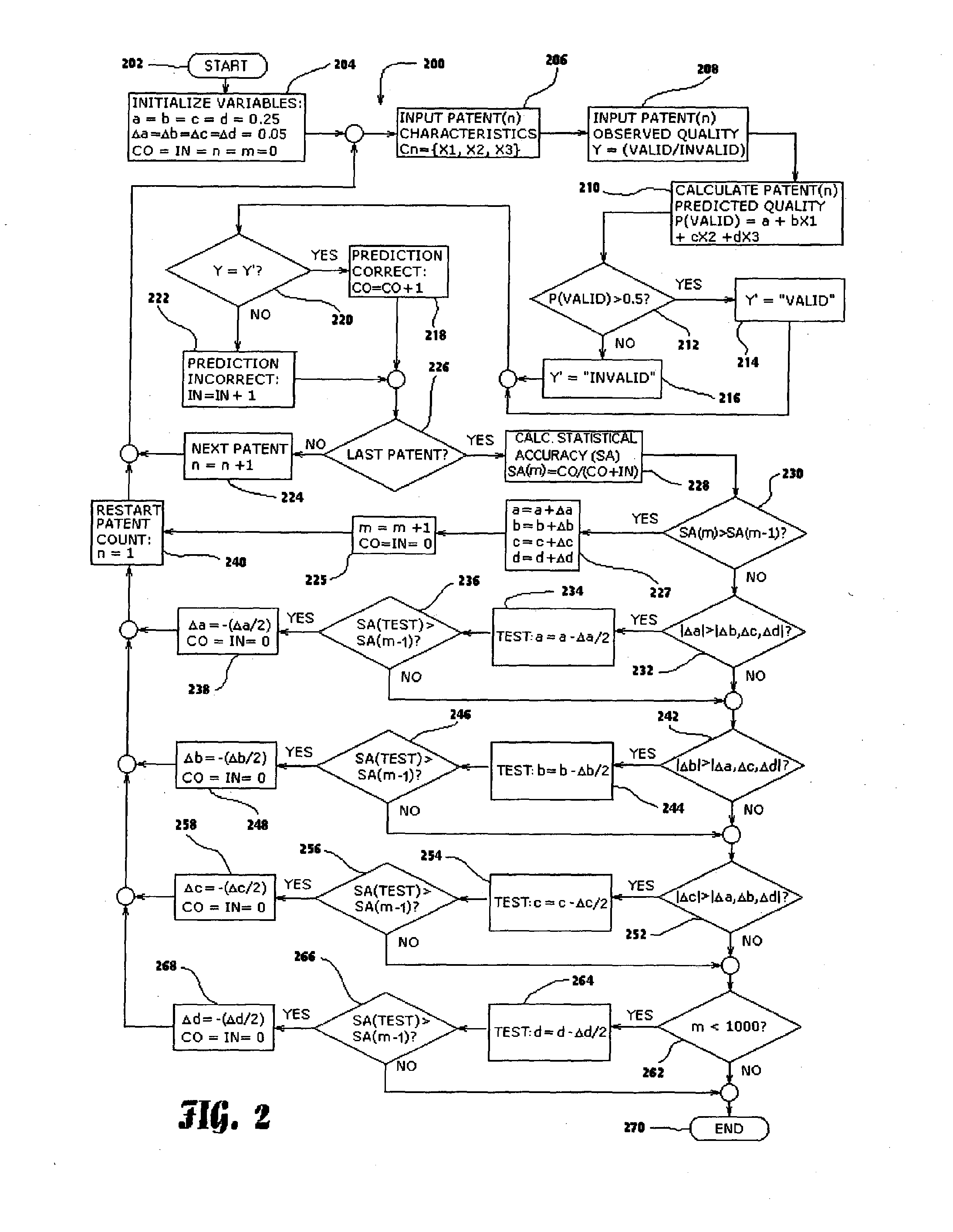
Method and system for rating patents and other intangible assets
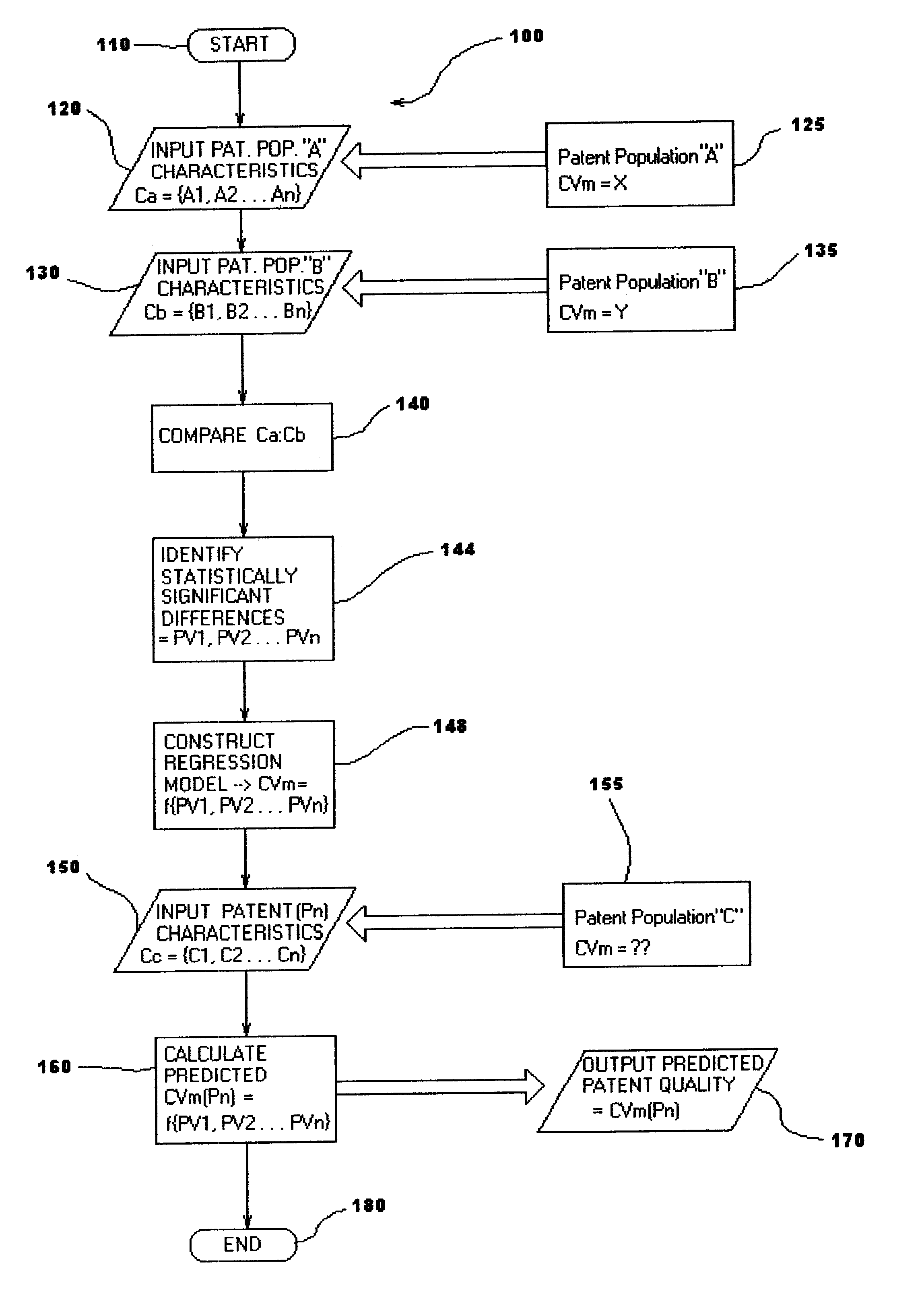
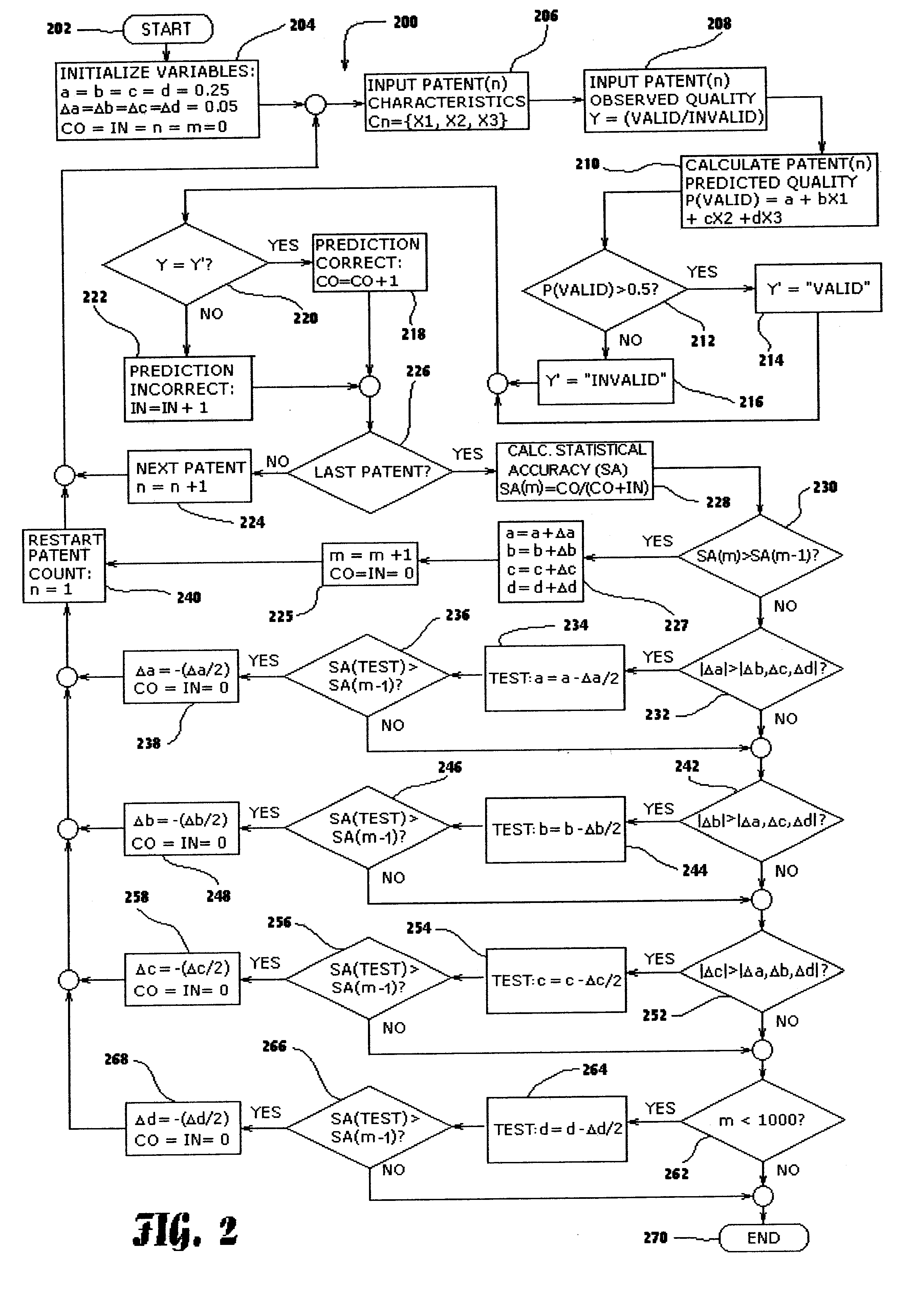
A statistical patent rating method and system is provided for independently assessing the relative breadth ("B"), defensibility ("D") and commercial relevance ("R") of individual patent assets and other intangible intellectual property assets. The invention provides new and valuable information that can be used by patent valuation experts, investment advisors, economists and others to help guide future patent investment decisions, licensing programs, patent appraisals, tax valuations, transfer pricing, economic forecasting and planning, and even mediation and / or settlement of patent litigation lawsuits. In one embodiment the invention provides a statistically-based patent rating method and system whereby relative ratings or rankings are generated using a database of patent information by identifying and comparing various characteristics of each individual patent to a statistically determined distribution of the same characteristics within a given patent population. For example, a first population of patents having a known relatively high intrinsic value or quality (e.g. successfully litigated patents) is compared to a second population of patents having a known relatively low intrinsic value or quality (e.g. unsuccessfully litigated patents). Based on a statistical comparison of the two populations, certain characteristics are identified as being more prevalent or more pronounced in one population group or the other to a statistically significant degree. Multiple such statistical comparisons are used to construct and optimize a computer model or computer algorithm that can then be used to predict and / or provide statistically-accurate probabilities of a desired value or quality being present or a future event occurring, given the identified characteristics of an individual patent or group of patents.
Owner:PATENTRATINGS
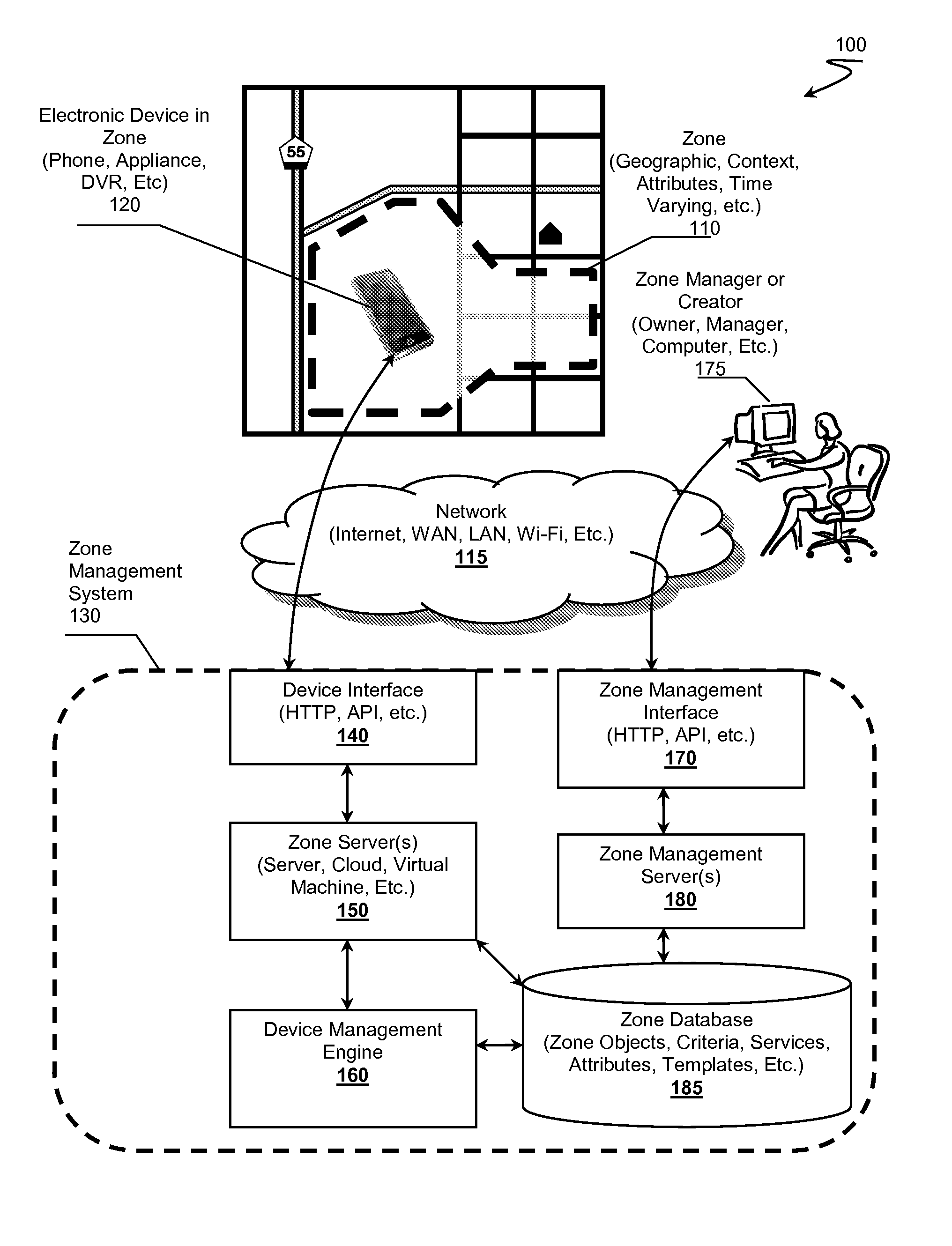
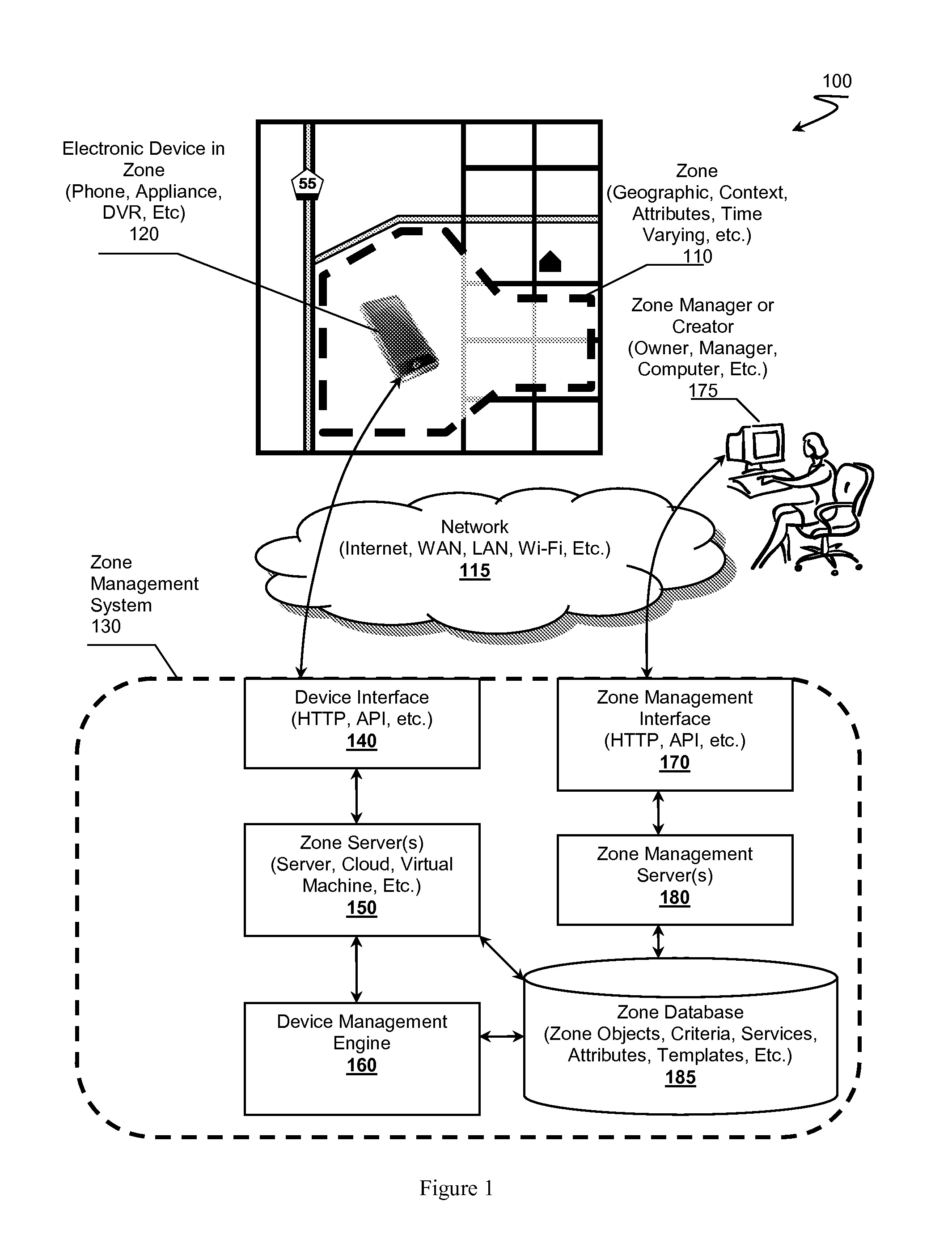
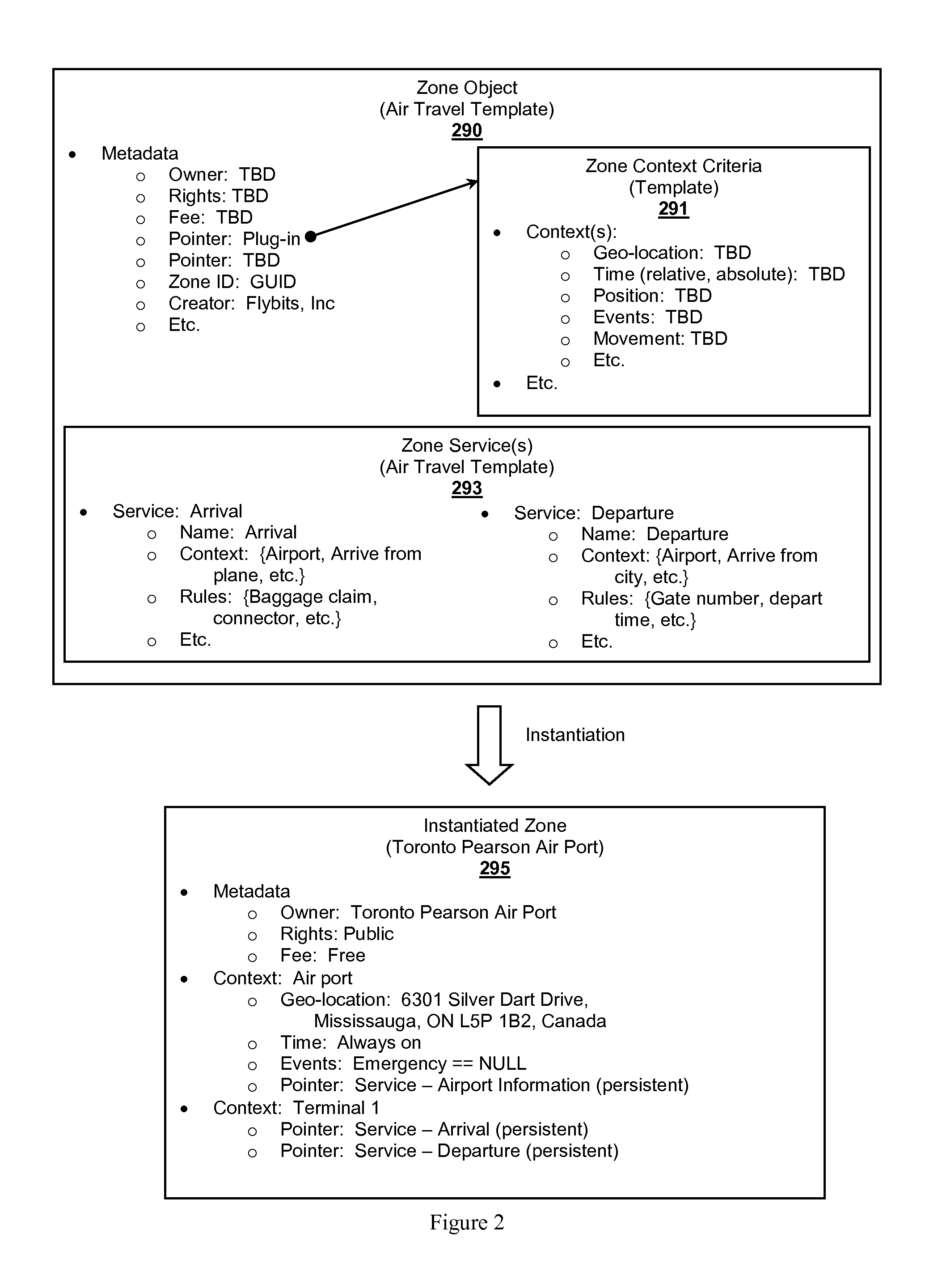
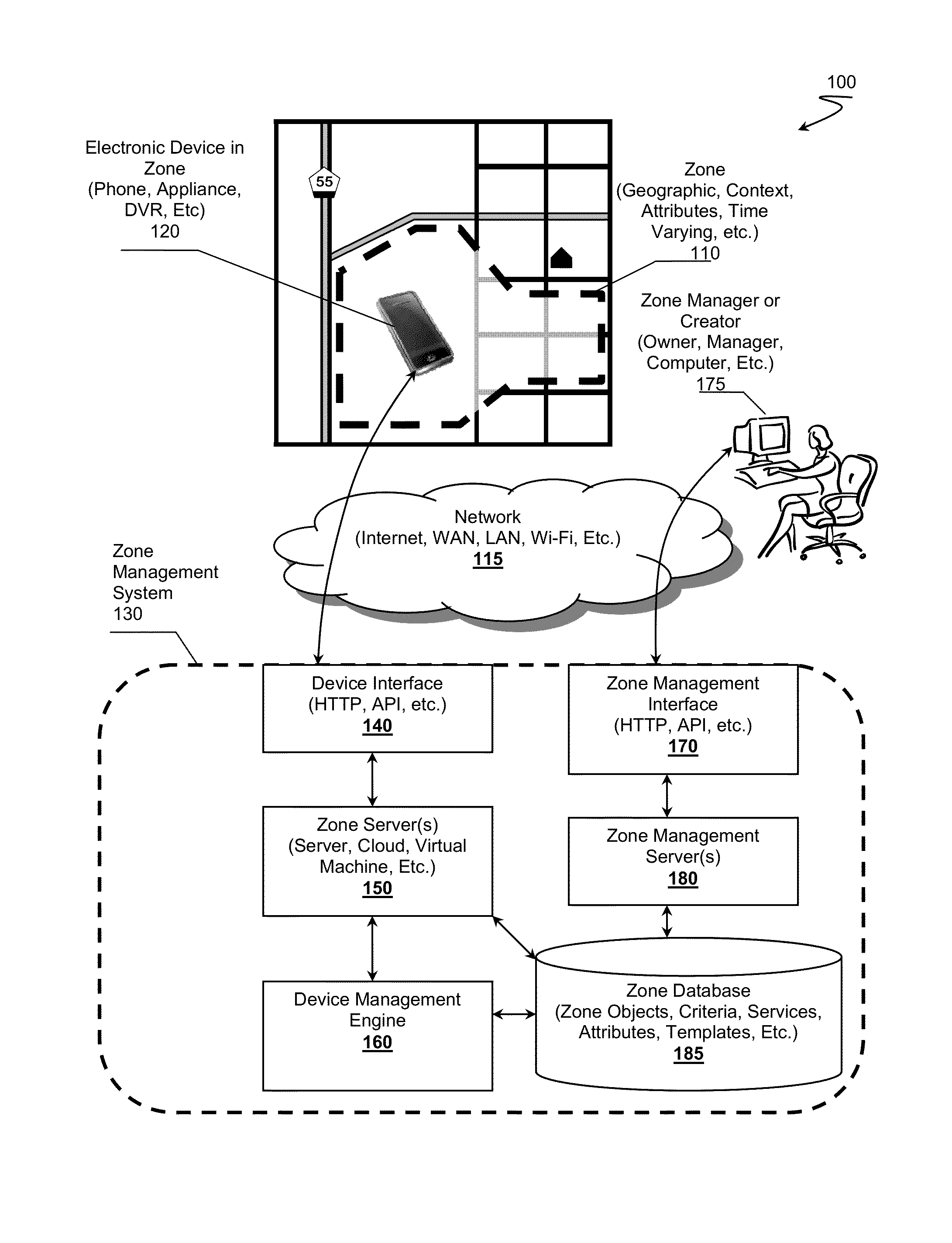
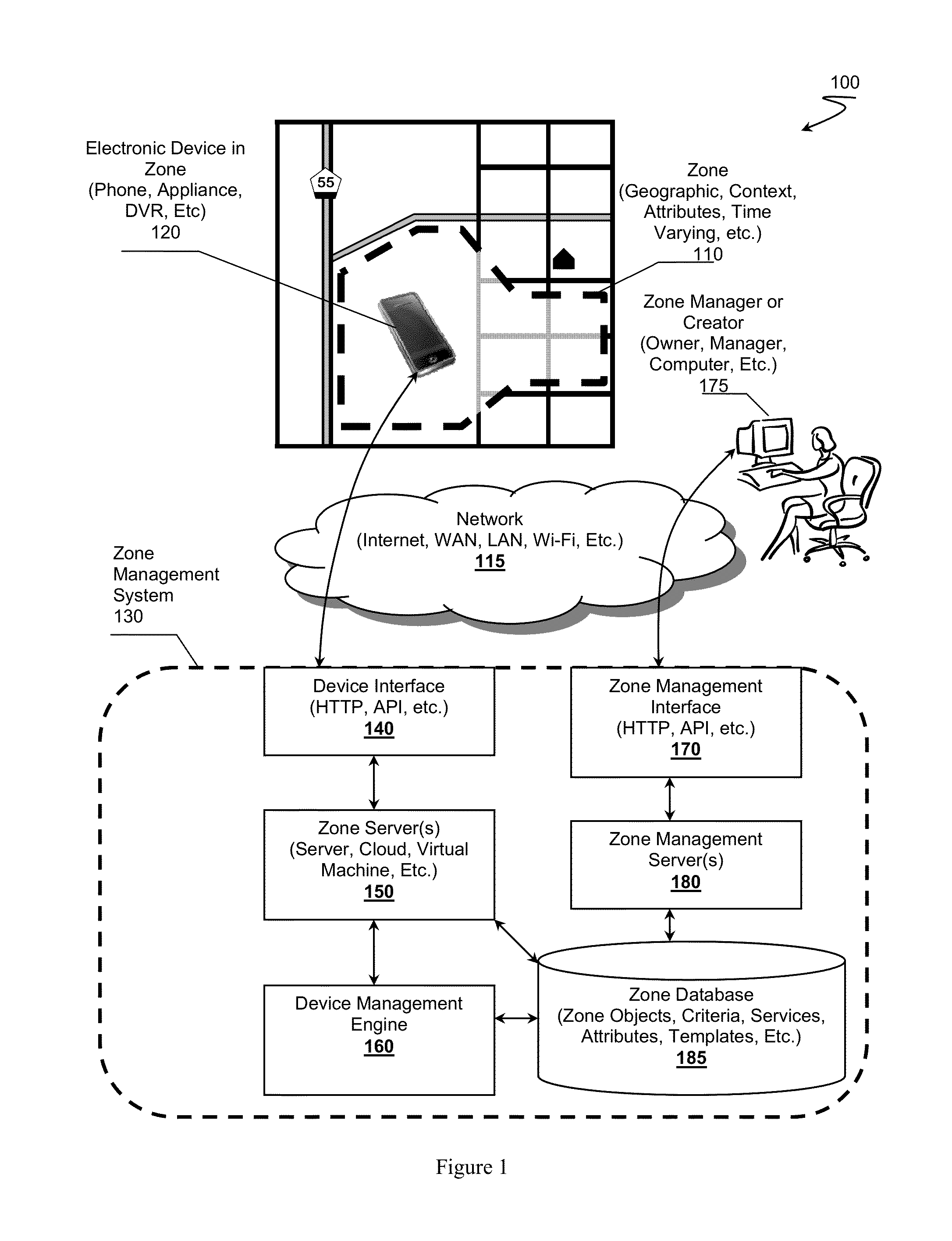
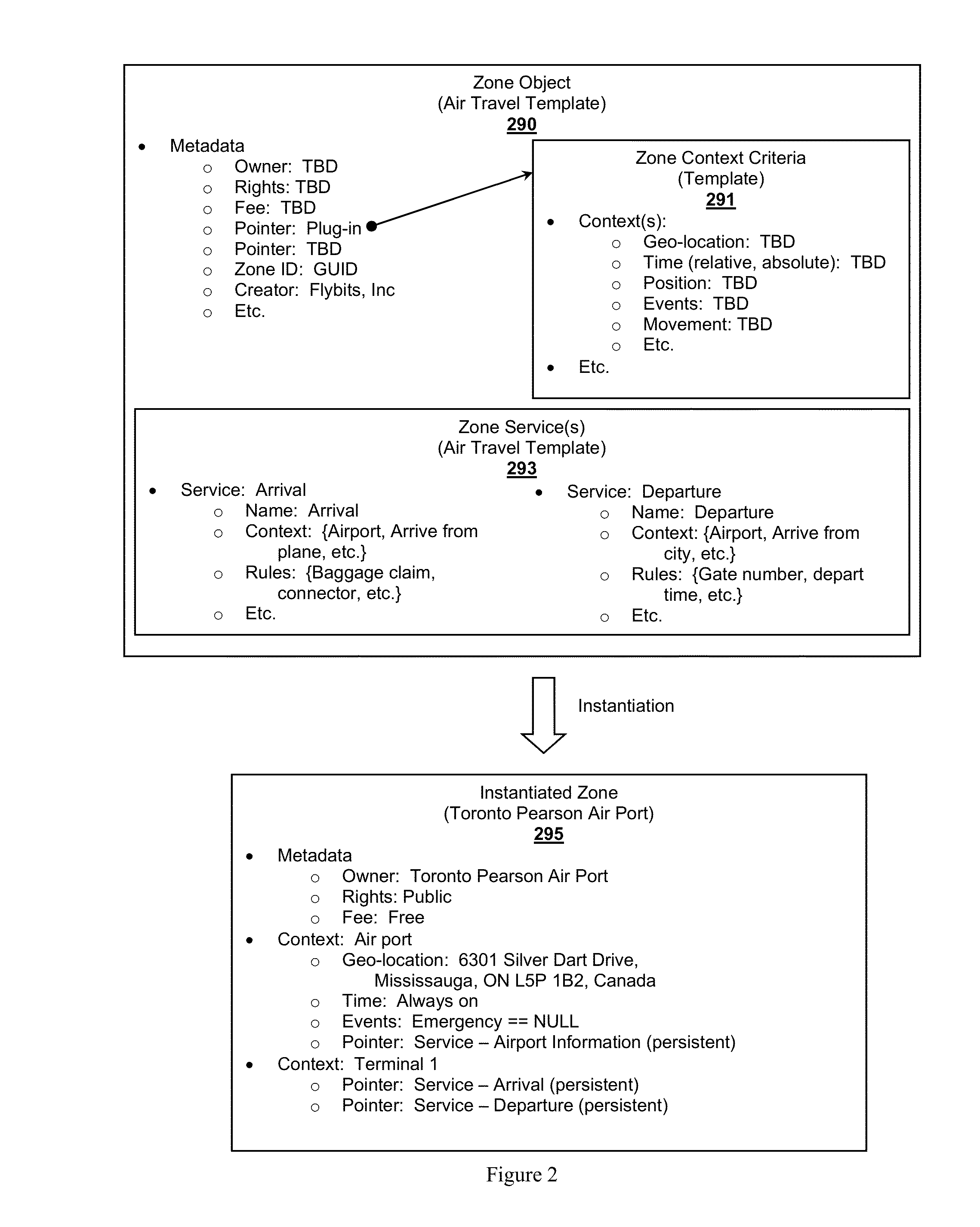
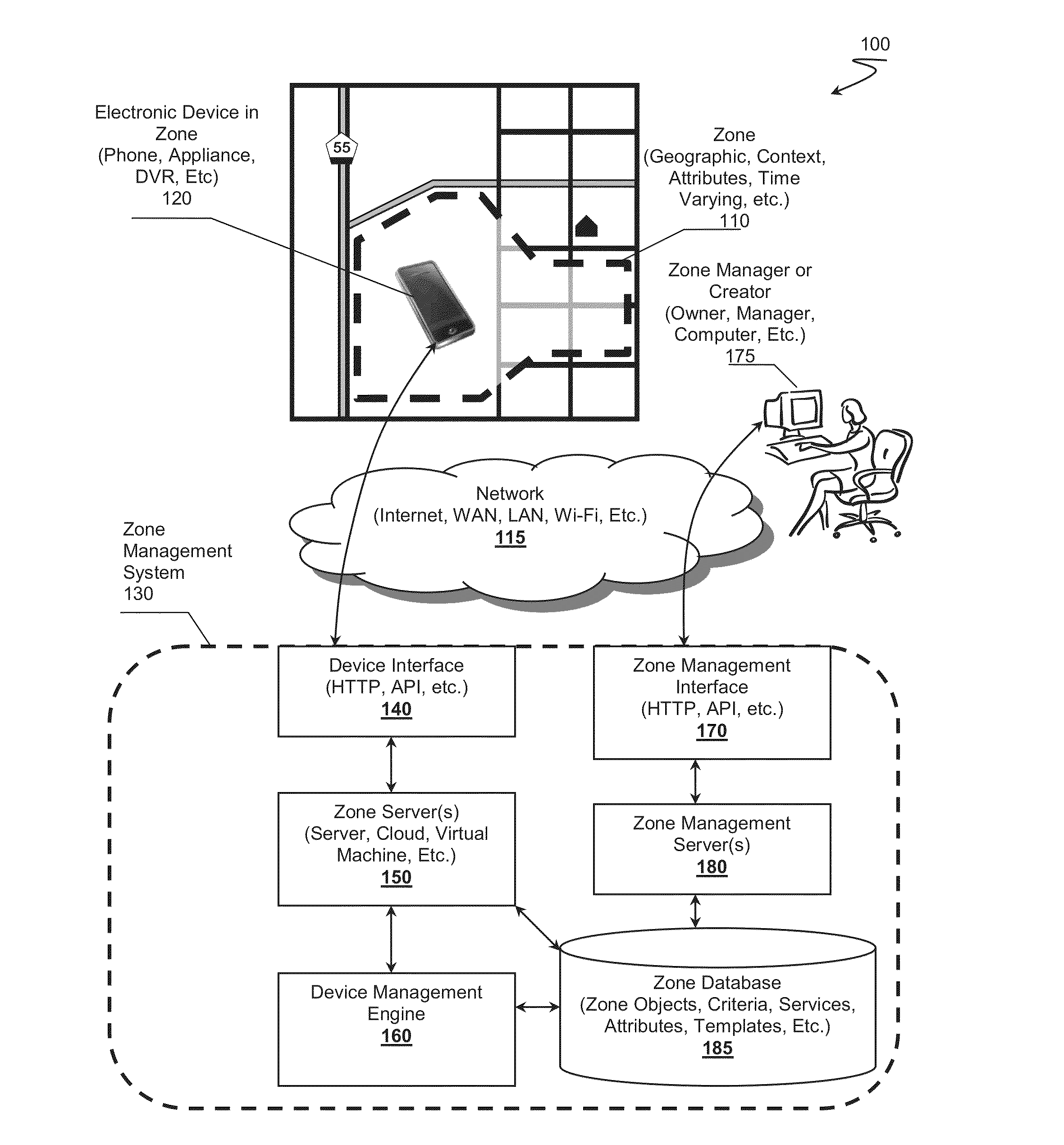
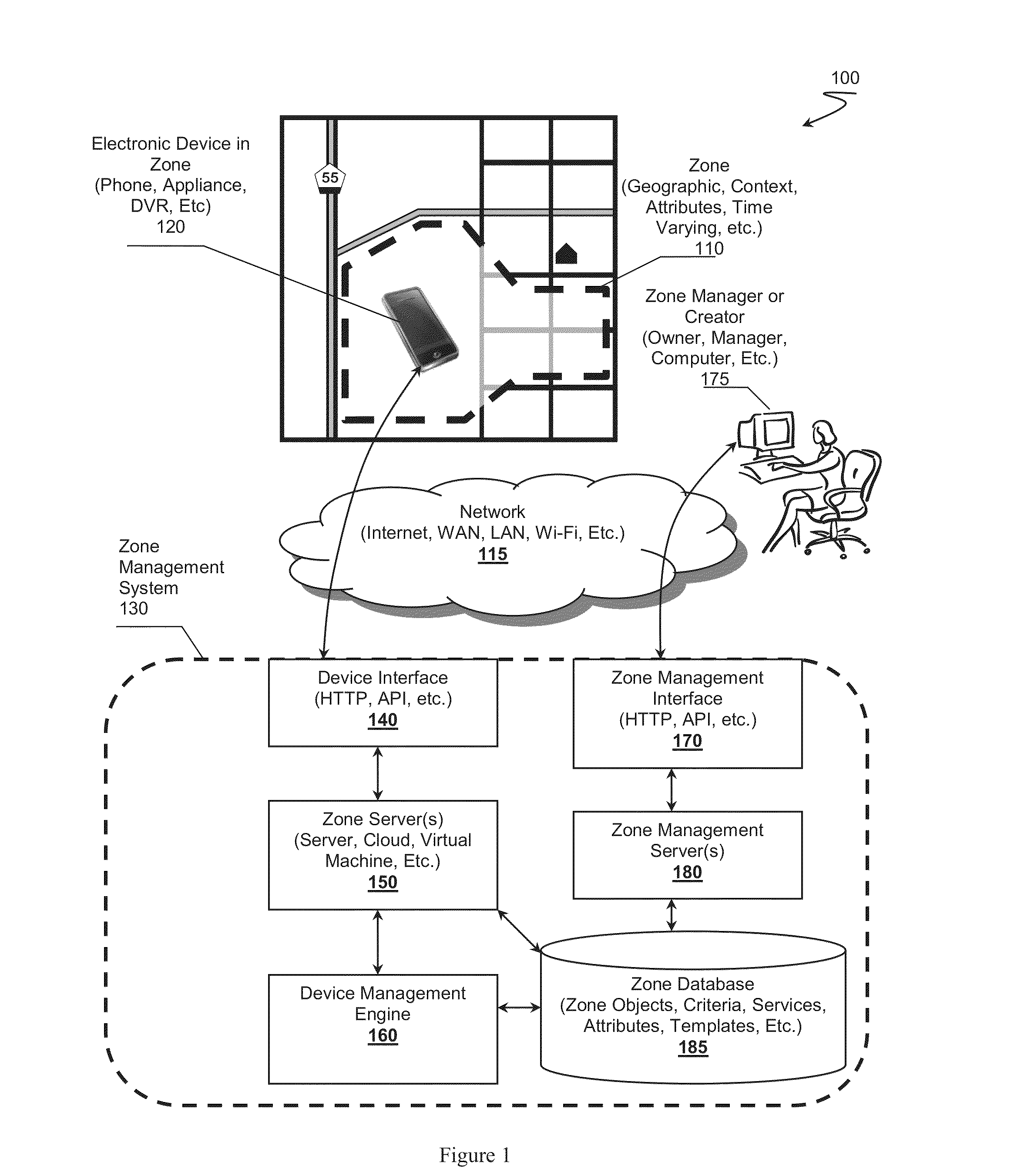
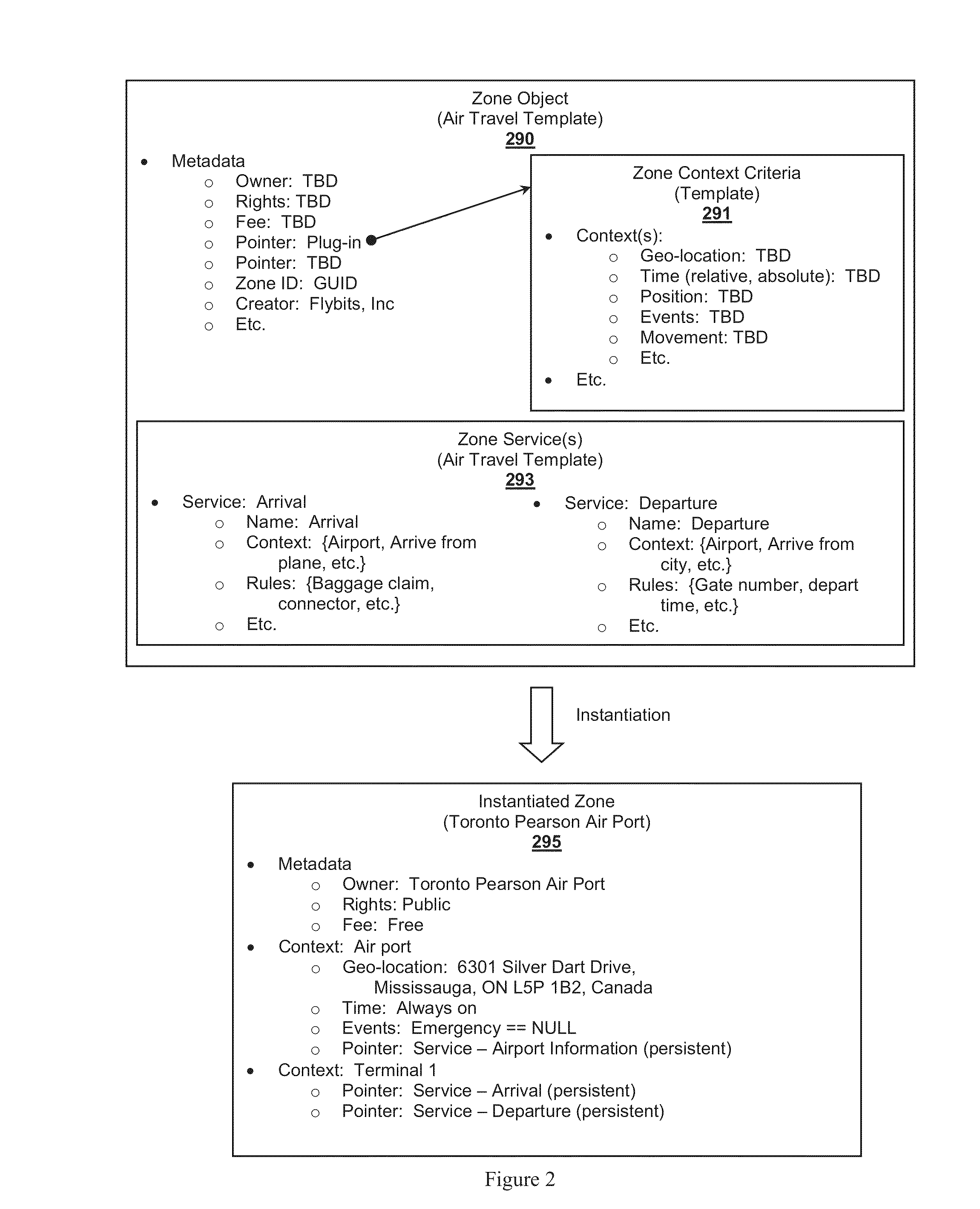
Zone Oriented Applications, Systems and Methods
InactiveUS20130212130A1Reduce development complexityService provisioningDatabase updatingEmbedded valueThird party
Owner:FLYBITS
Method and system for rating patents and other intangible assets
A statistical patent rating method and system is provided for independently assessing the relative breadth (“B”), defensibility (“D”) and commercial relevance (“R”) of individual patent assets and other intangible intellectual property assets. The invention provides new and valuable information that can be used by patent valuation experts, investment advisors, economists and others to help guide future patent investment decisions, licensing programs, patent appraisals, tax valuations, transfer pricing, economic forecasting and planning, and even mediation and / or settlement of patent litigation lawsuits. In one embodiment the invention provides a statistically-based patent rating method and system whereby relative ratings or rankings are generated using a database of patent information by identifying and comparing various characteristics of each individual patent to a statistically determined distribution of the same characteristics within a given patent population. For example, a first population of patents having a known relatively high intrinsic value or quality (e.g. successfully litigated patents) is compared to a second population of patents having a known relatively low intrinsic value or quality (e.g. unsuccessfully litigated patents). Based on a statistical comparison of the two populations, certain characteristics are identified as being more prevalent or more pronounced in one population group or the other to a statistically significant degree. Multiple such statistical comparisons are used to construct and optimize a computer model or computer algorithm that can then be used to predict and / or provide statistically-accurate probabilities of a desired value or quality being present or a future event occurring, given the identified characteristics of an individual patent or group of patents.
Owner:PATENTRATINGS
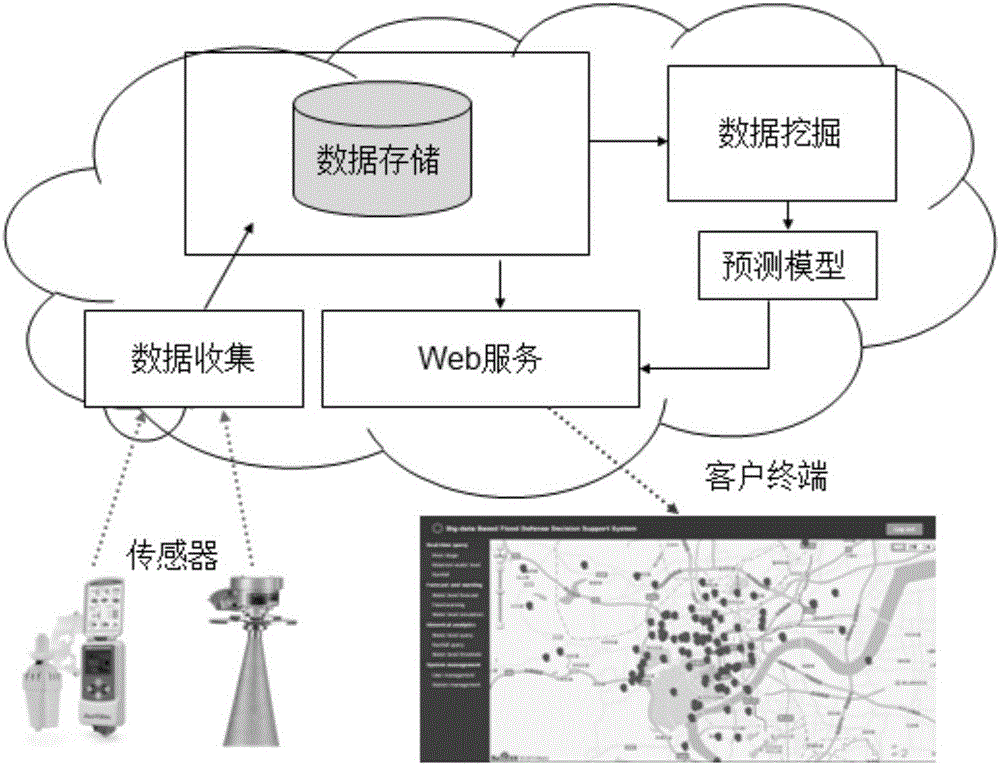
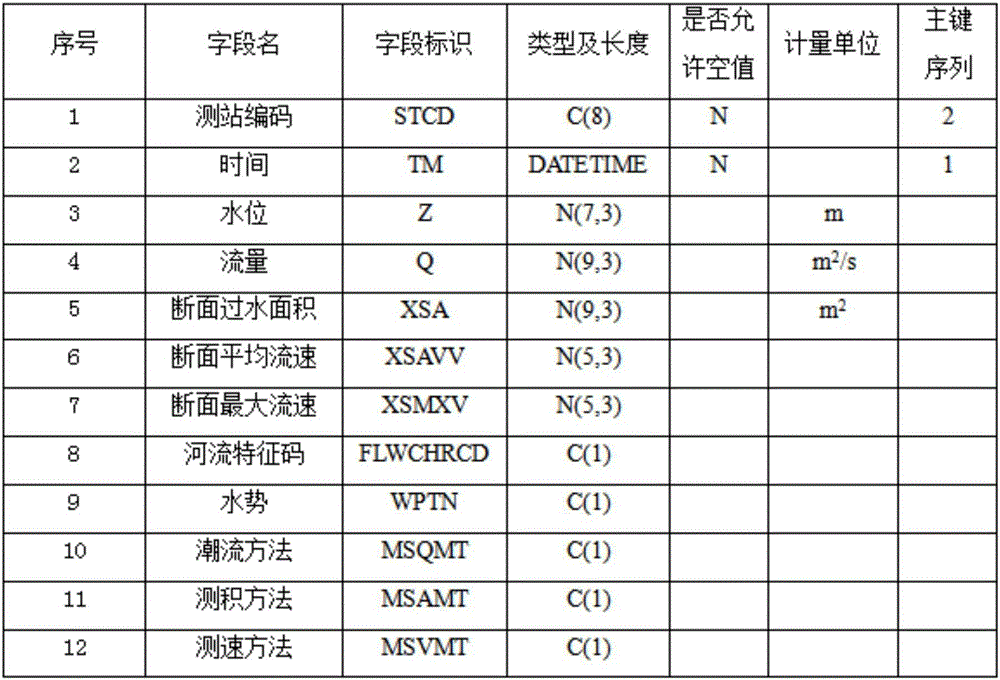
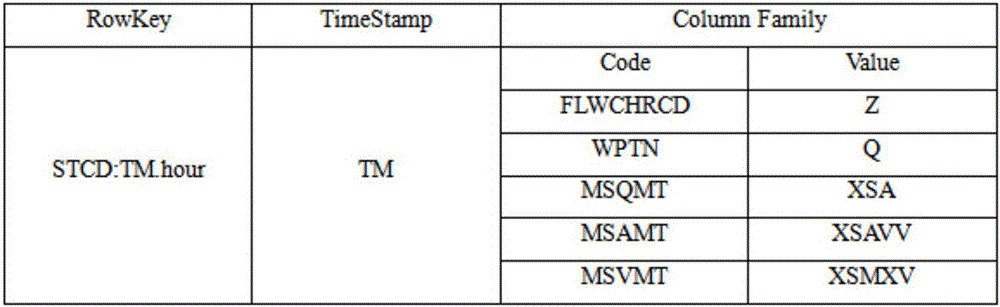
Urban flood prevention decision support system based on big data technique
ActiveCN105843942AEfficient storageEffective predictionClimate change adaptationForecastingRegimenStatistical analysis
The invention discloses an urban flood prevention decision support system based on a big data technique. The urban flood prevention decision support system comprises steps as follows: S1, establishment of a historical water regimen database; S2, acquisition and storage of real-time water regimen data; S3, establishment of a combined water level prediction model; S4, real-time water regimen display and water level prediction; S5, statistical analysis of historical water regimen data. The system has the benefits as follows: the water level in 1-6 hours can be effectively predicted, so that decision support is provided for flood control and disaster reduction work when the urban flood season approaches. The system adopts a distributed database HBase and can effectively store mass water regimen data and cope with rapid growth of data, besides, a big data analysis engine Impala is used for real-time processing and analysis on mass historical water regimen data, intrinsic value of the historical data is explored with a data visualization technology and information guidance is provided for flood prevention work.
Owner:ZHEJIANG UNIV CITY COLLEGE
Comparison based authentication in RTP
InactiveUS20070237145A1Prevent replay attacksSynchronising transmission/receiving encryption devicesData switching by path configurationEmbedded valueDistributed computing
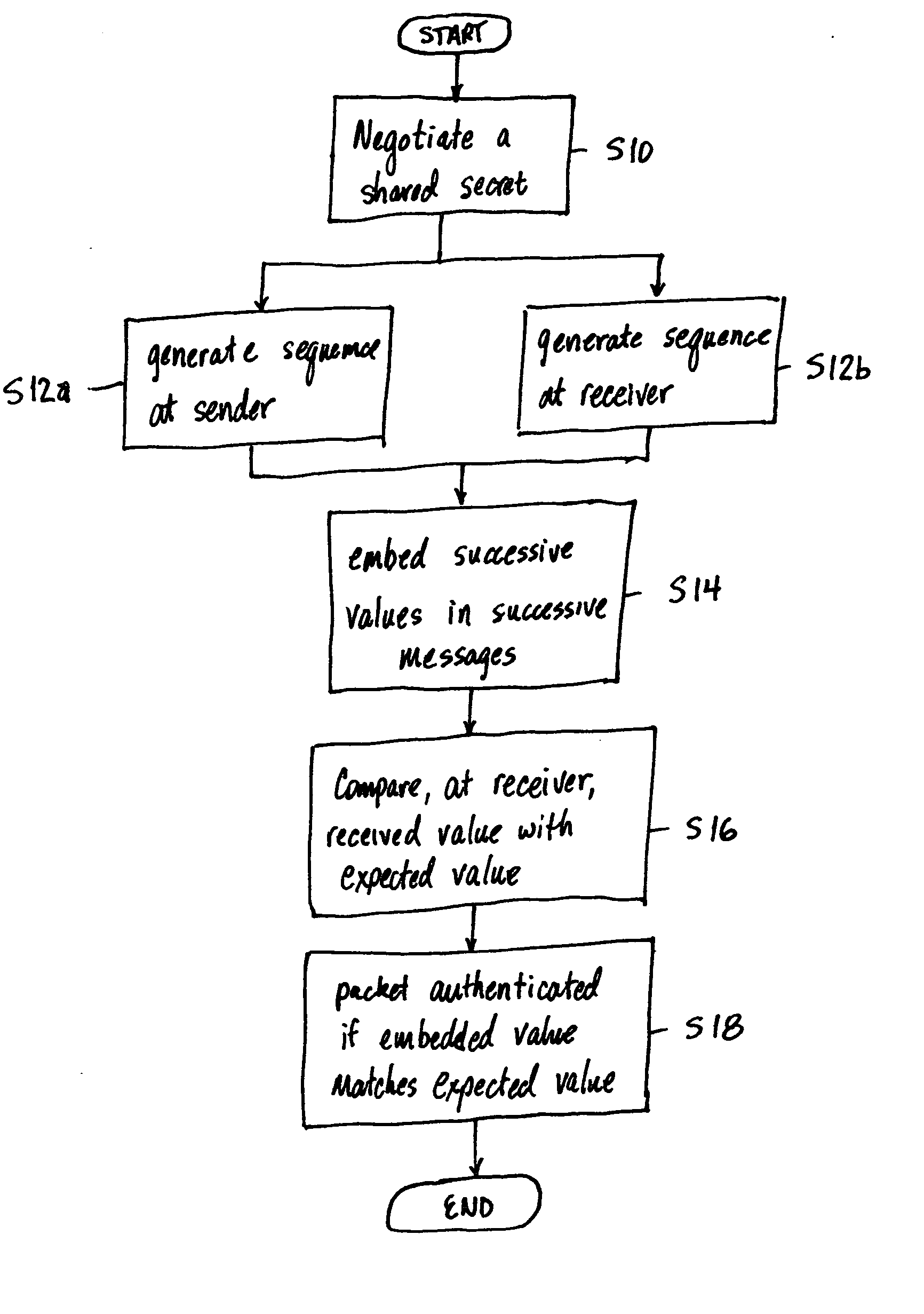
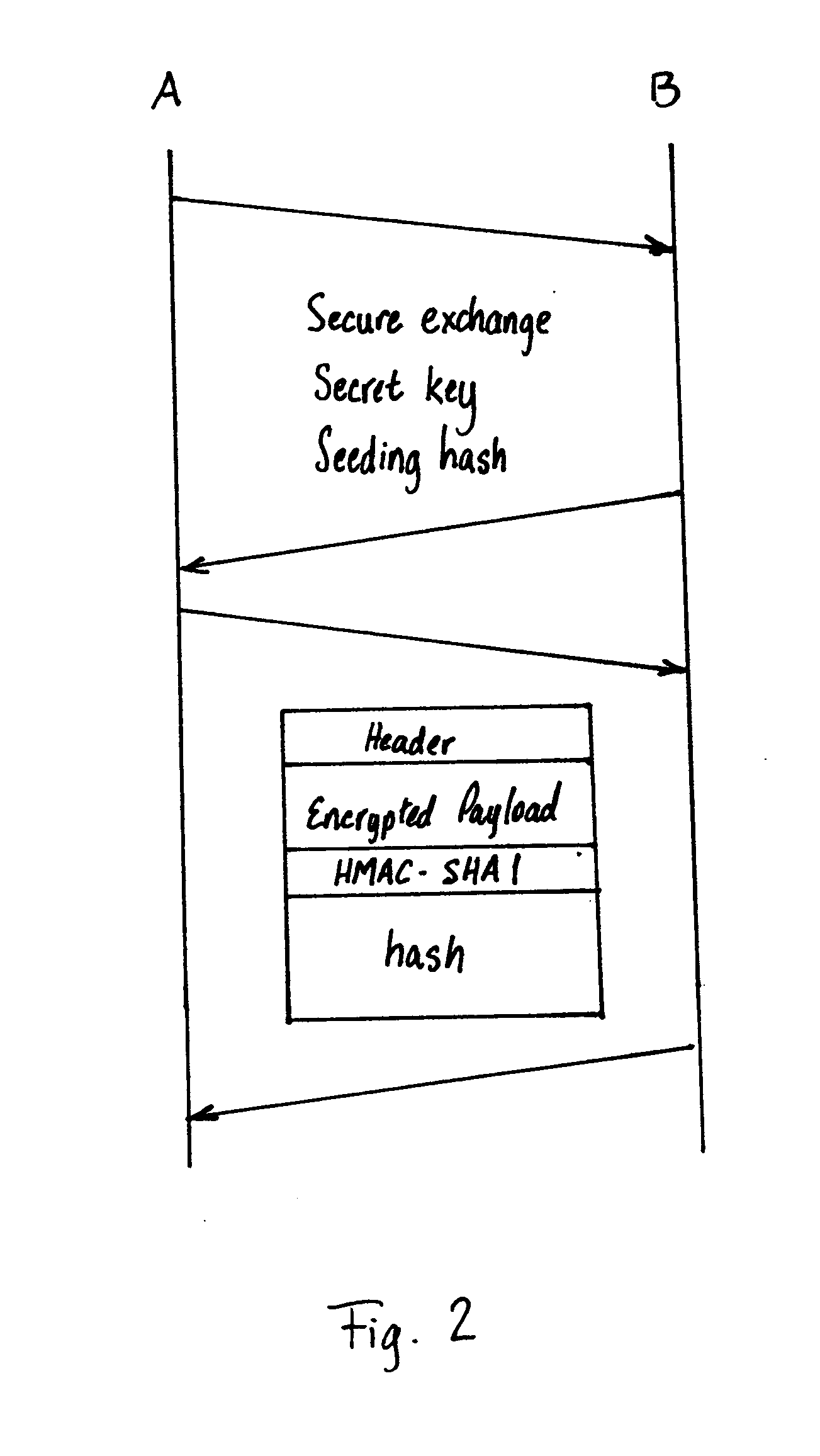
A method of authenticating a communications between a sender and a receiver includes agreeing, by a sender and receiver, on a shared secret, computing a first sequence of numbers at the sender using the shared secret, and computing a second sequence of numbers at the receiver using the shared secret. Successive values of the first sequence are respectively embedded in successive messages by the sender. Upon receiving a message, the receiver compares the embedded value of the first sequence with a list of values including at least one corresponding value from the second sequence and the received message to considered to originate from an authentic sender if the value of the first sequence matches the value of the second sequence. The method value is removed from a list of values in the second sequence for comparing.
Owner:AVAYA INC
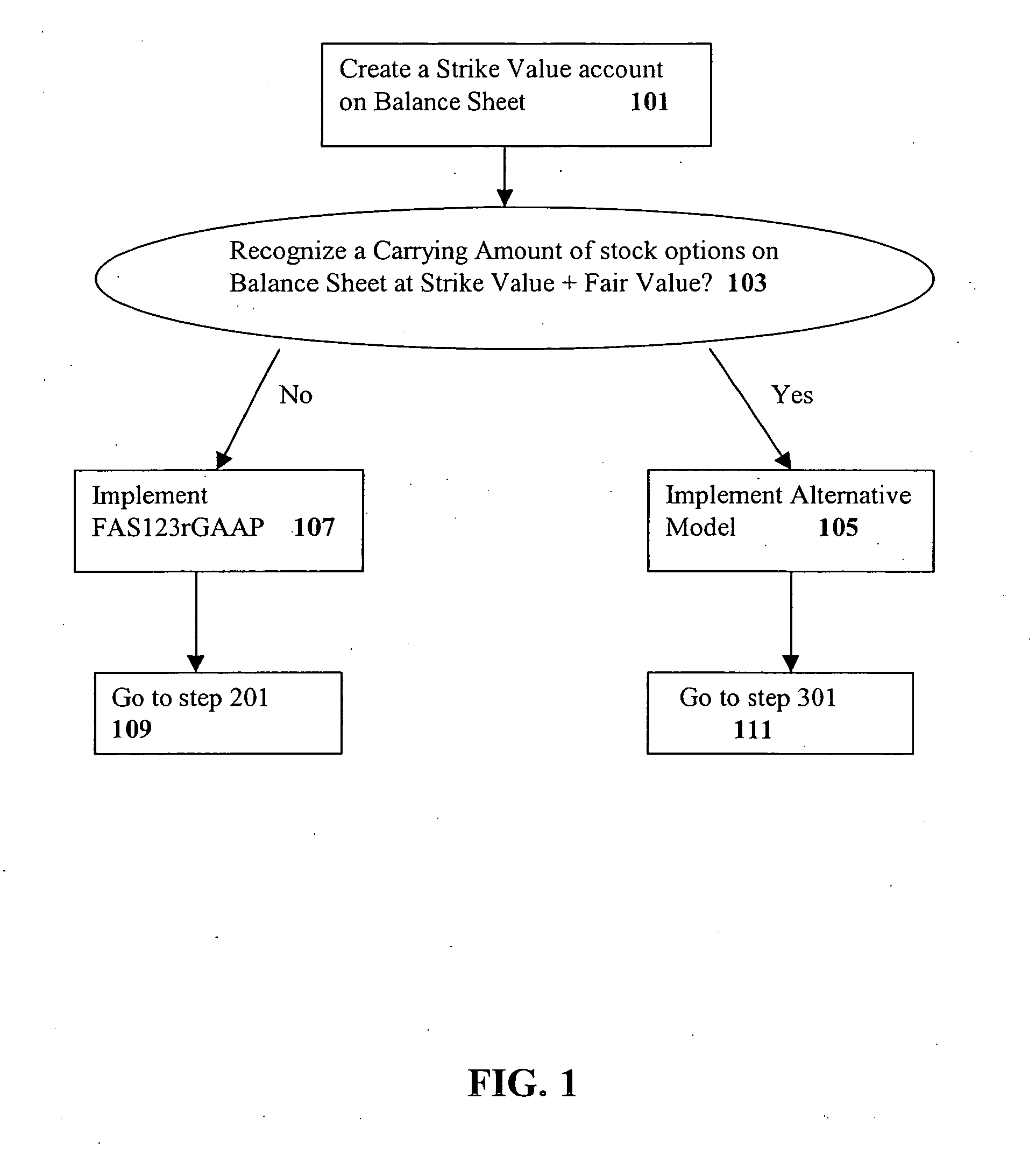
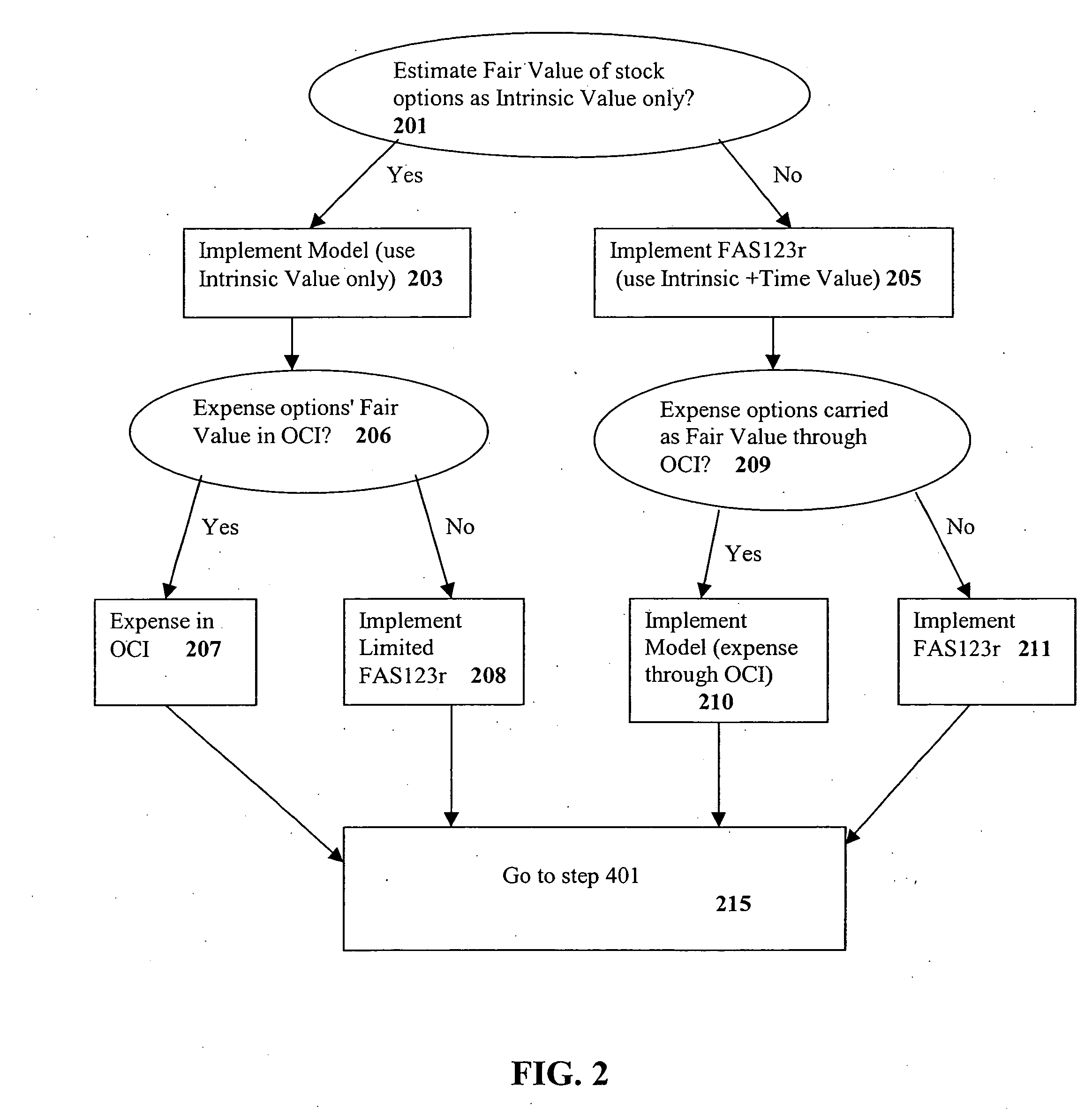
System and method for stock option accounting
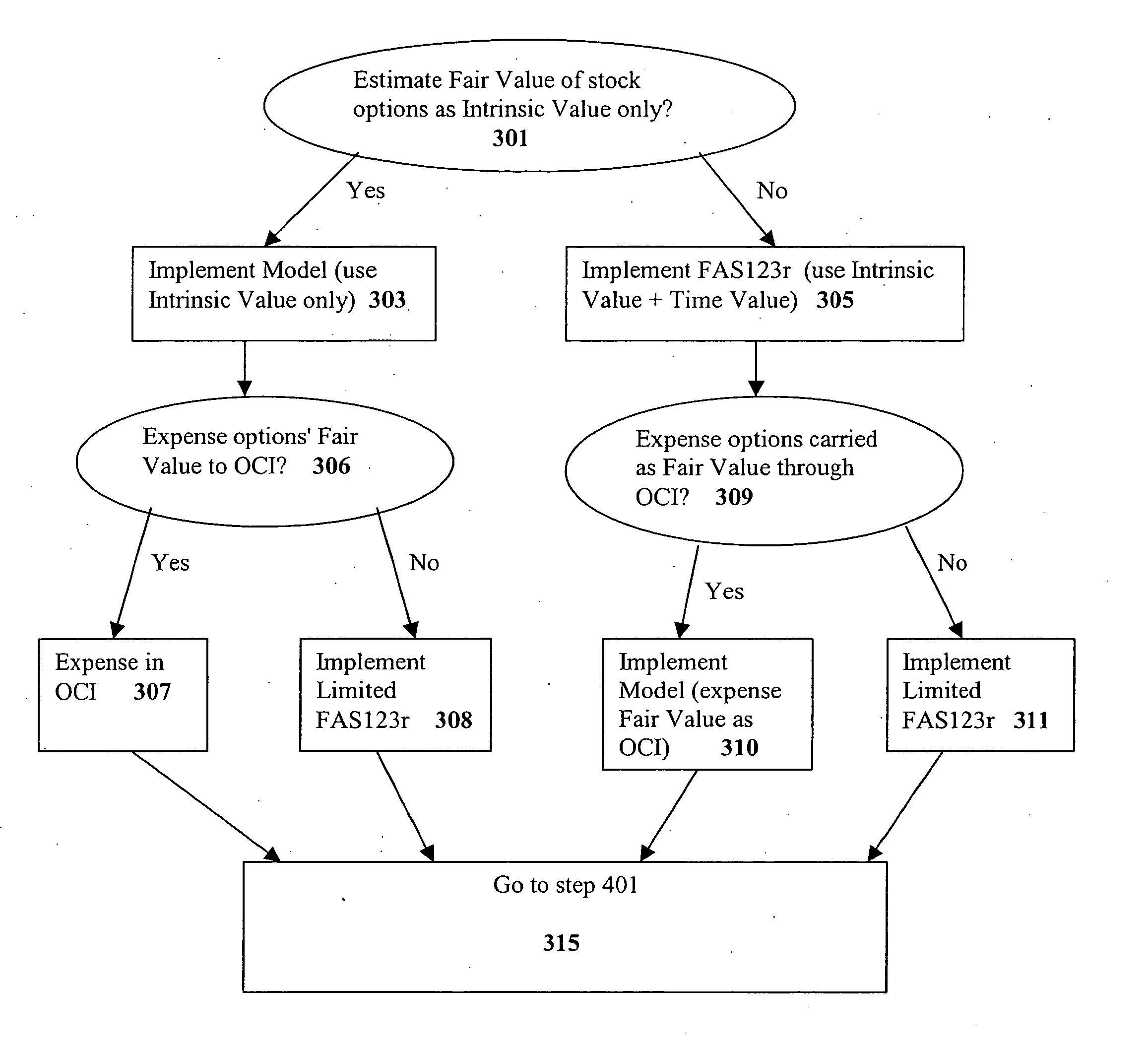
A system and method for providing an alternative model for accounting for stock options. A Strike Value Account is created on a Balance Sheet. User-selectable inputs are provided for indicating whether a Strike Value of the stock option is to be recorded on a balance sheet, whether the Fair Value of the stock options is to be equal to Market Value, whether to update a Carrying Amount of the stock options periodically, whether to keep the Strike Value Account on the Balance Sheet at all times, whether the Intrinsic Value of said options are to be expensed in Earnings, and whether options carried as Fair Value are to be expensed through Earnings. The present invention provides a more accurate assessment of and accounting for stock options via, e.g., the consideration of Strike Values and Intrinsic Values of the stock options.
Owner:LE GUYADER LOUIS P
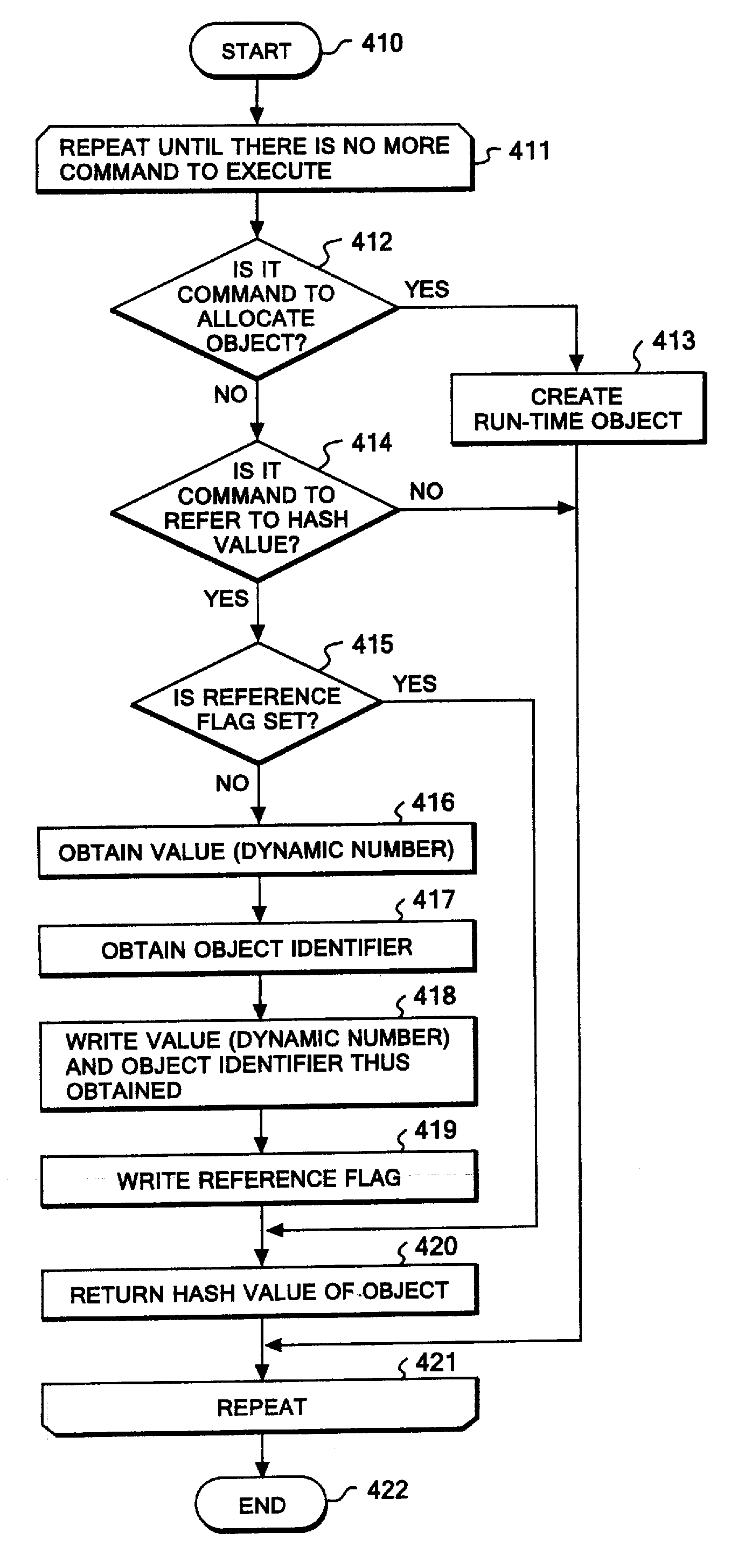
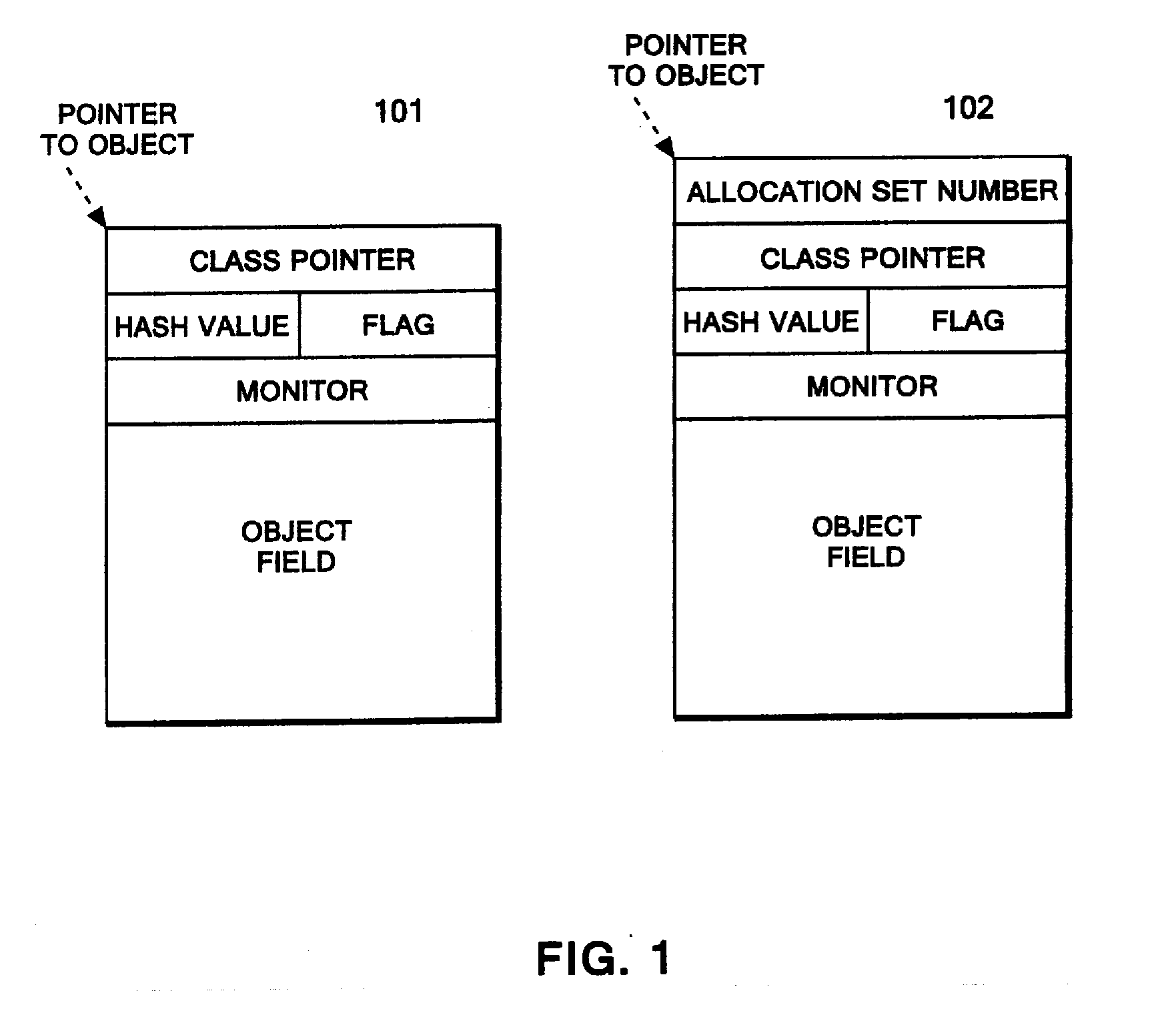
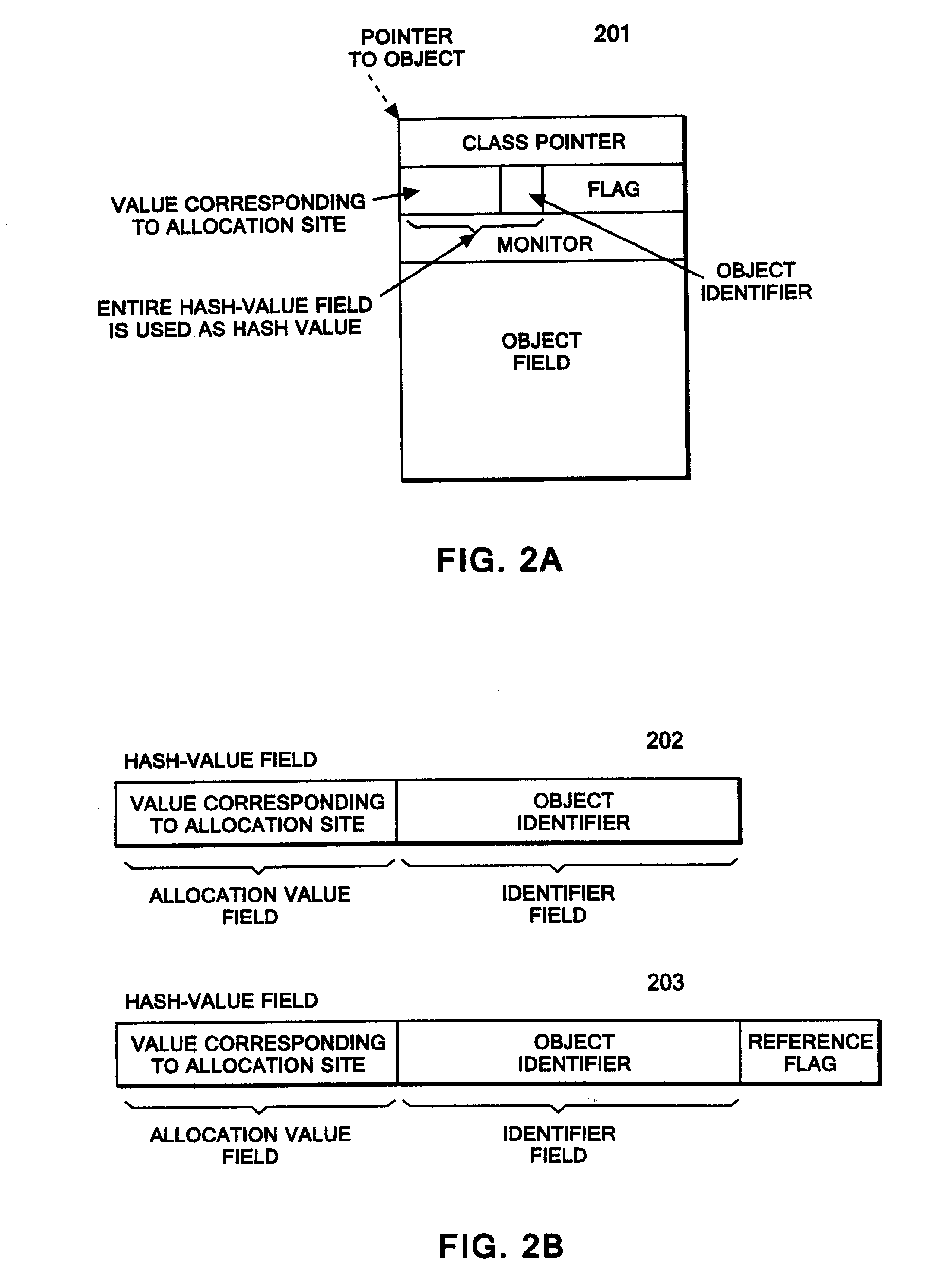
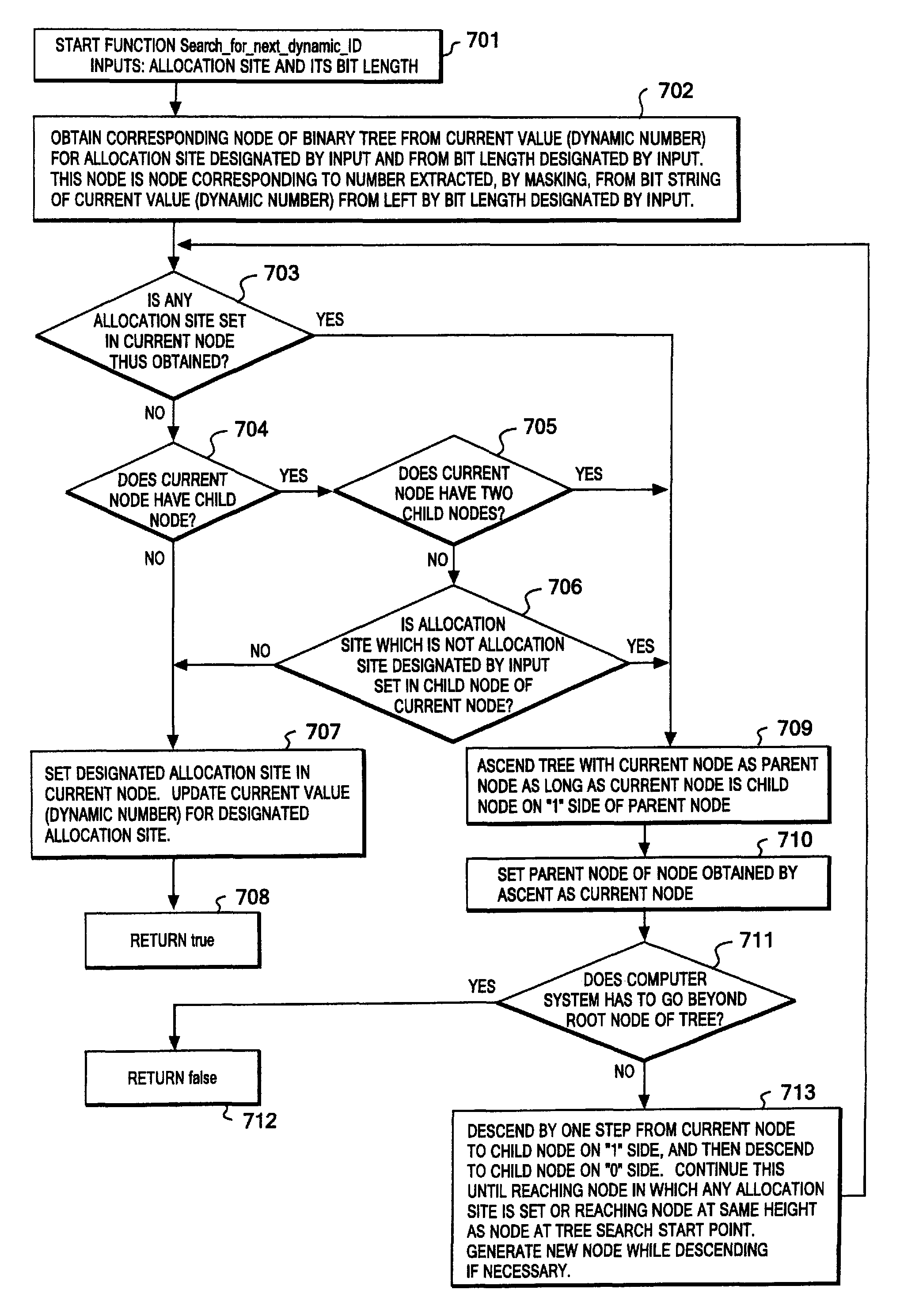
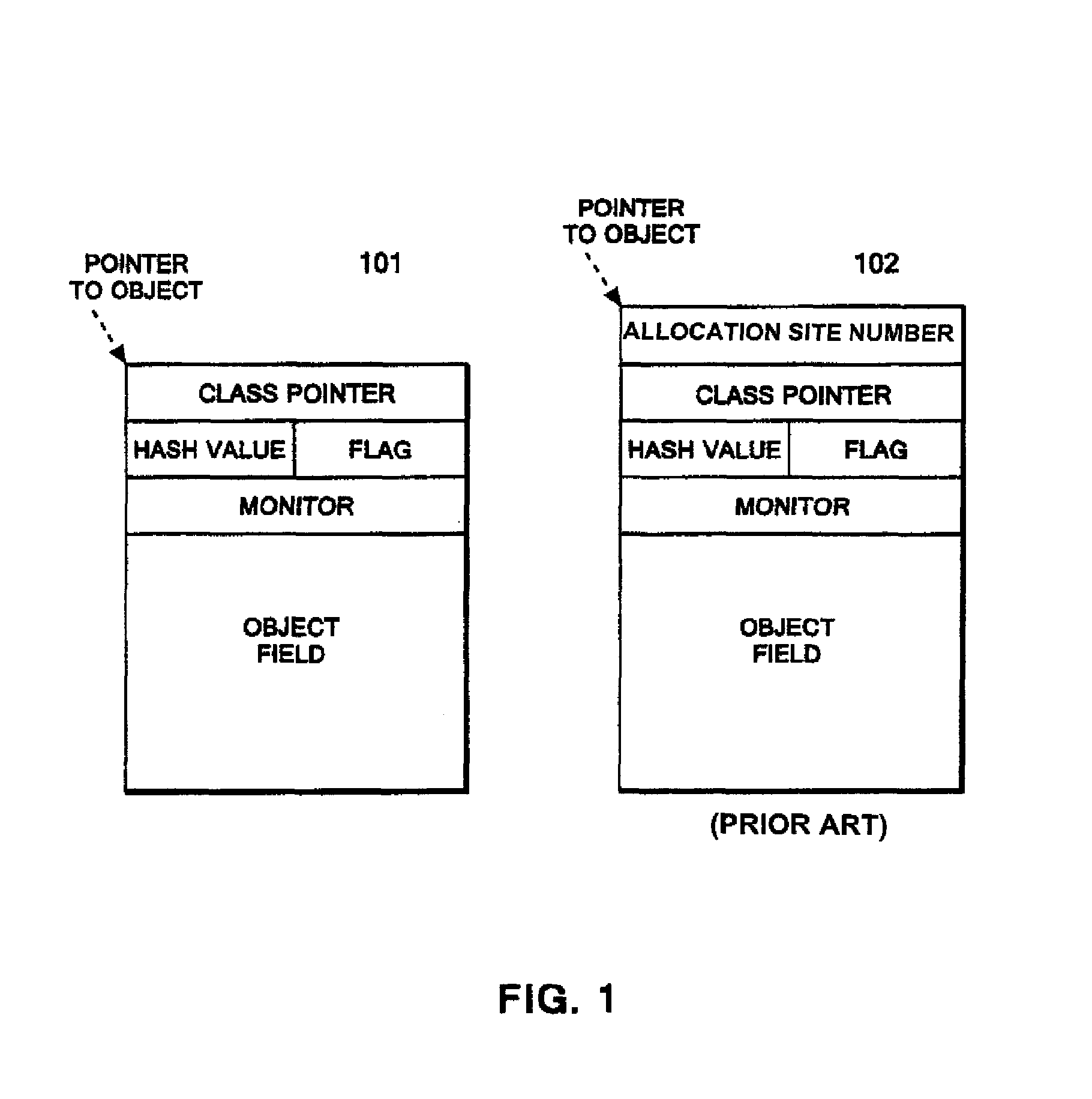
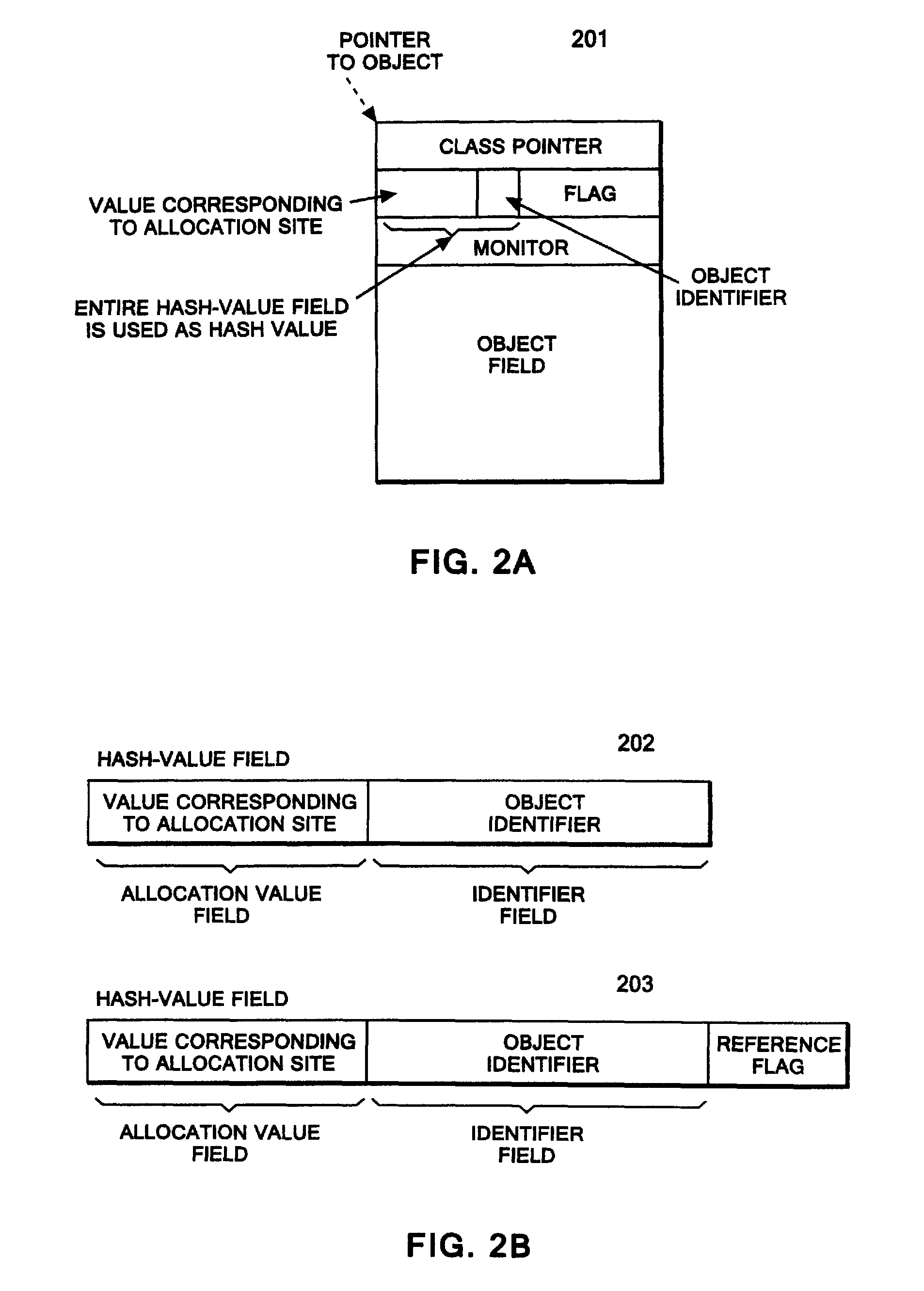
Method of tracing object allocation site in program, as well as computer system and computer program therefor
A data structure of a run-time object having a hash value field. The data structure allows an object allocation site to be traced from the run-time object, the object allocation site being a site in a program allocating the run-time object. A method for allowing an object allocation site to be traced from a run-time object includes embedding a value corresponding to the object allocation site in the program. A hash-value field includes the embedded value and the object identifier, and the tracing is performed by identifying the object allocation site that corresponds to the embedded value. A computer system for tracing an object allocation site includes a memory that stores the run-time object; an acquirer that acquires the value from a hash value field; and an identification unit that identifies the object allocation site that corresponds to the acquired value.
Owner:IBM CORP
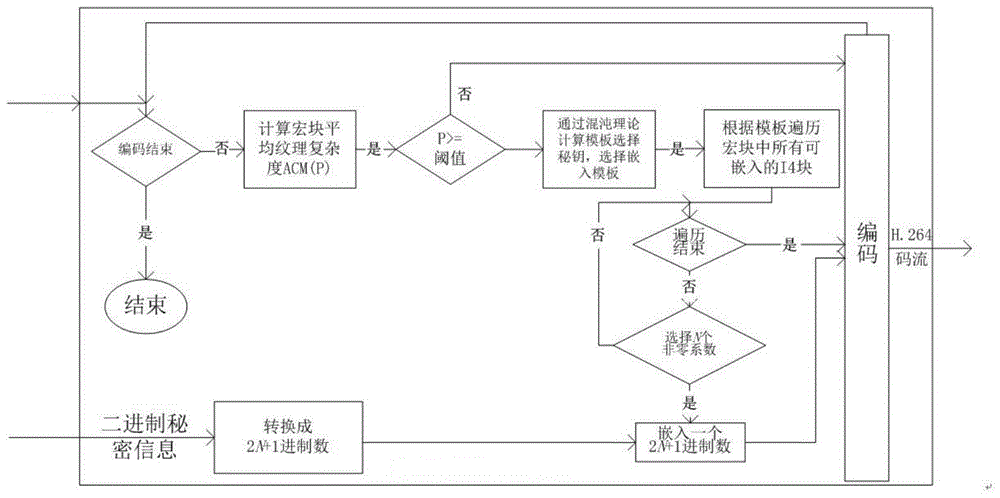
Information hiding and extracting method based on integer DCT (Discrete Cosine Transformation) coefficient modulation
ActiveCN104683811AImprove extraction efficiencyHigh embedding efficiencyDigital video signal modificationEmbedded valueComputation process
The invention provides an information hiding and extracting method based on integer DCT (Discrete Cosine Transformation) coefficient modulation. An N-dimensional 2N+1-order magic cube matrix is constructed, carrier coefficients are respectively mapped in the N-dimensional 2N+1-order magic cube matrix by taking N carrier coefficients as a group, so as to obtain a mapping value, a value of to-be-embedded 2N+1 system number secret information is compared with the mapping value, if the two values are equal, the group of the carrier coefficients do not need to be modified, if the two values are not equal, only one carrier coefficient needs to be modified, so that the mapping value is equal to the to-be-embedded value, one carrier coefficient is modified, so that the embedding of formula bits of the secret information is completed, the embedding efficiency reaches up to formula, and the modification rate of the carrier coefficient is only 1 / N, so that a computing process is simple, and the information hiding and extracting efficiency is improved.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
Comprehensive evaluation method for quality of traditional Chinese medicine
The invention relates to a comprehensive evaluation method for quality of traditional Chinese medicine. According to the method, the comprehensive index of the quality of a sample is taken as a quantitative index for evaluating sample quality, the comprehensive index of the quality is calculated by adopting a triangle area method; first, normalization processing for data is performed by adopting a ratio method, so as to eliminate dimensions, and different evaluation result data are changed to be numerical values from 0 to 1; second, the triangle area method is adopted for carrying out integrated processing on data in three dimensions of experience, chemistry and biology, so as to obtain quality embedded values (triangle area numerical values) of samples in different batches; finally, when the all data in the three dimensions are 1, the triangle area is the maximal, and triangle areas of all samples are used for dividing the maximal triangle area, so as to obtain the comprehensive index of the quality. According to the method in the application, the comprehensive index of the quality embodies the integral view of the traditional Chinese medicine, blends traditional cognition and modern cognition, and connects efficacy and safety.
Owner:THE FIFTH MEDICAL CENT OF CHINESE PLA GENERAL HOSPITAL
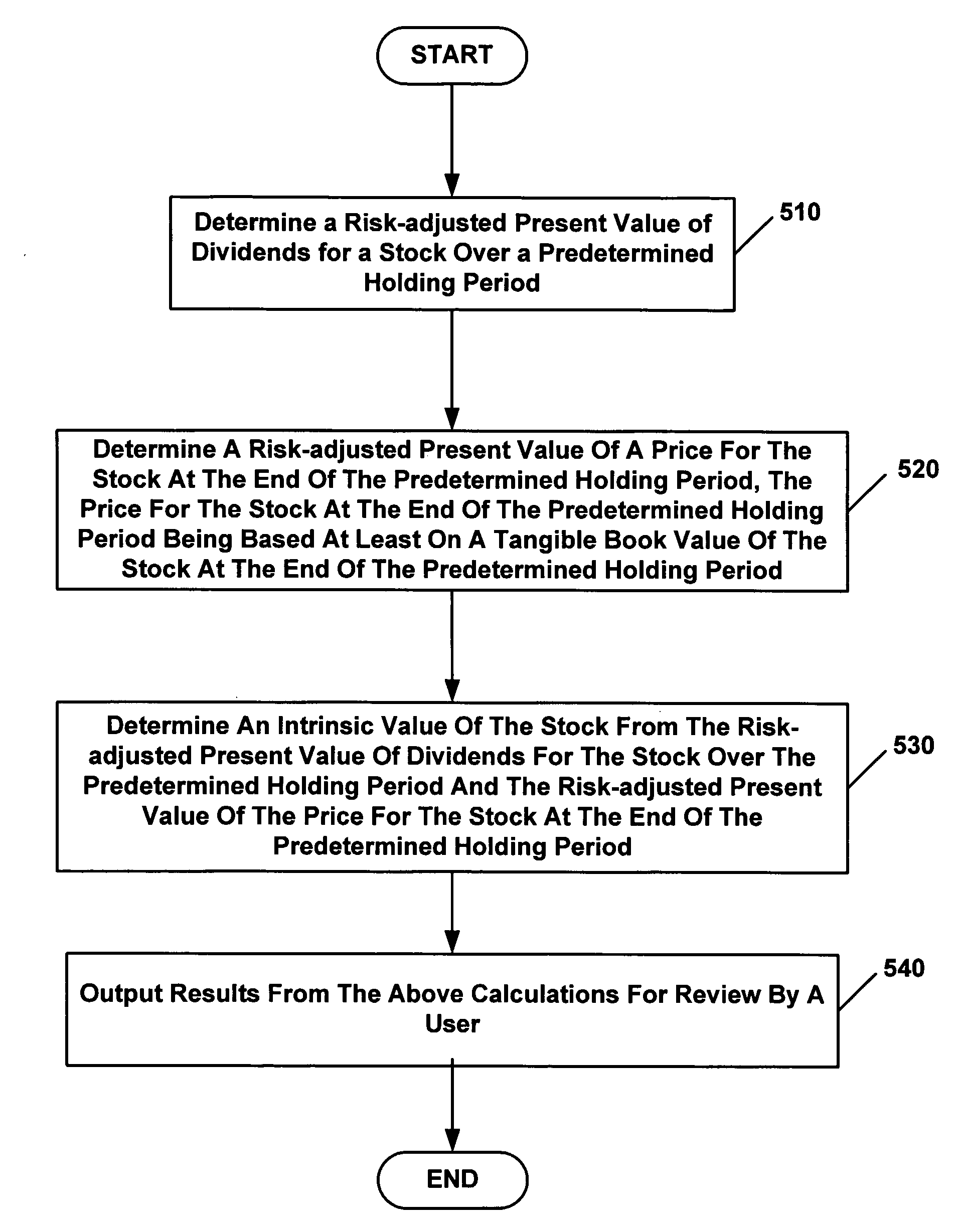
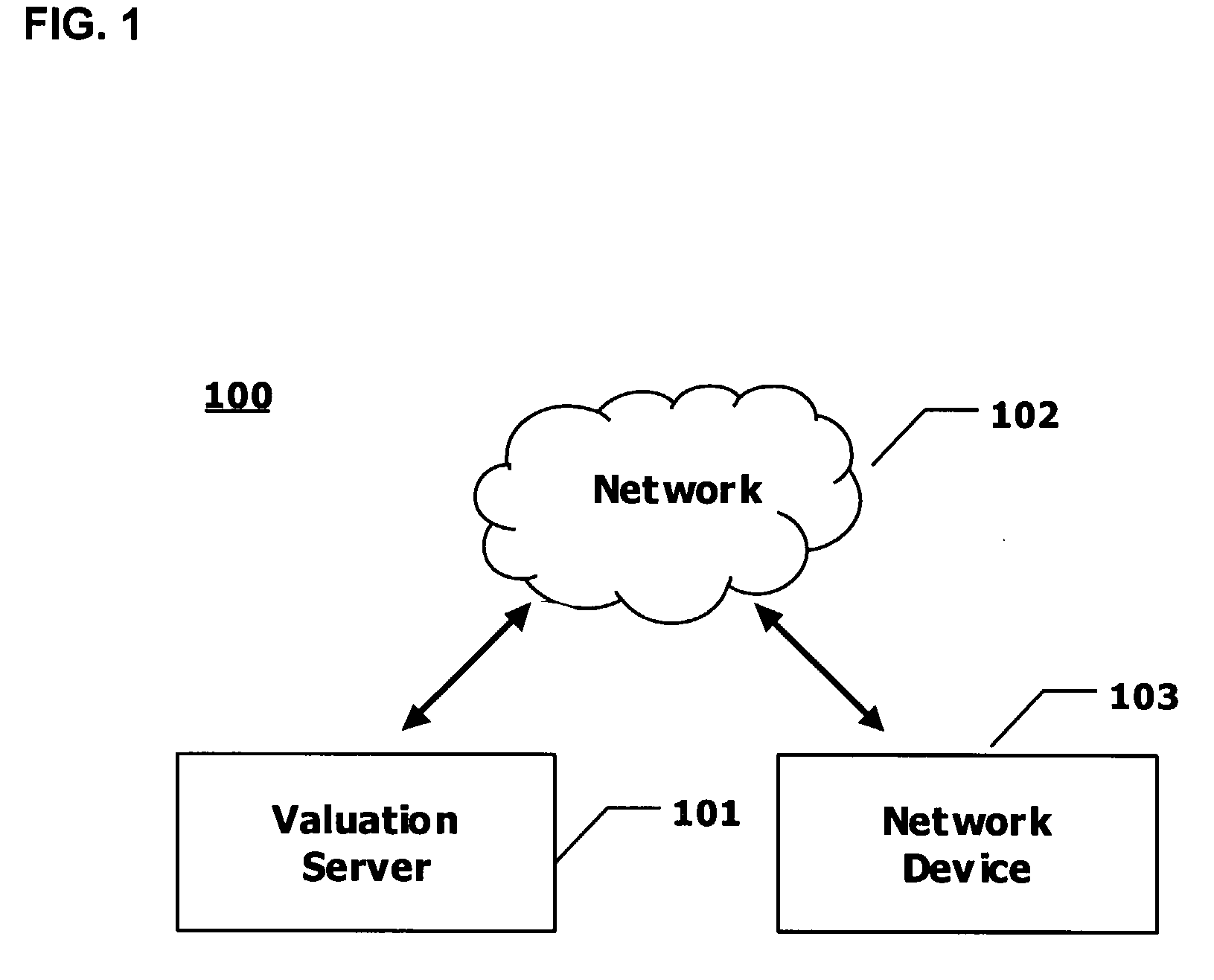
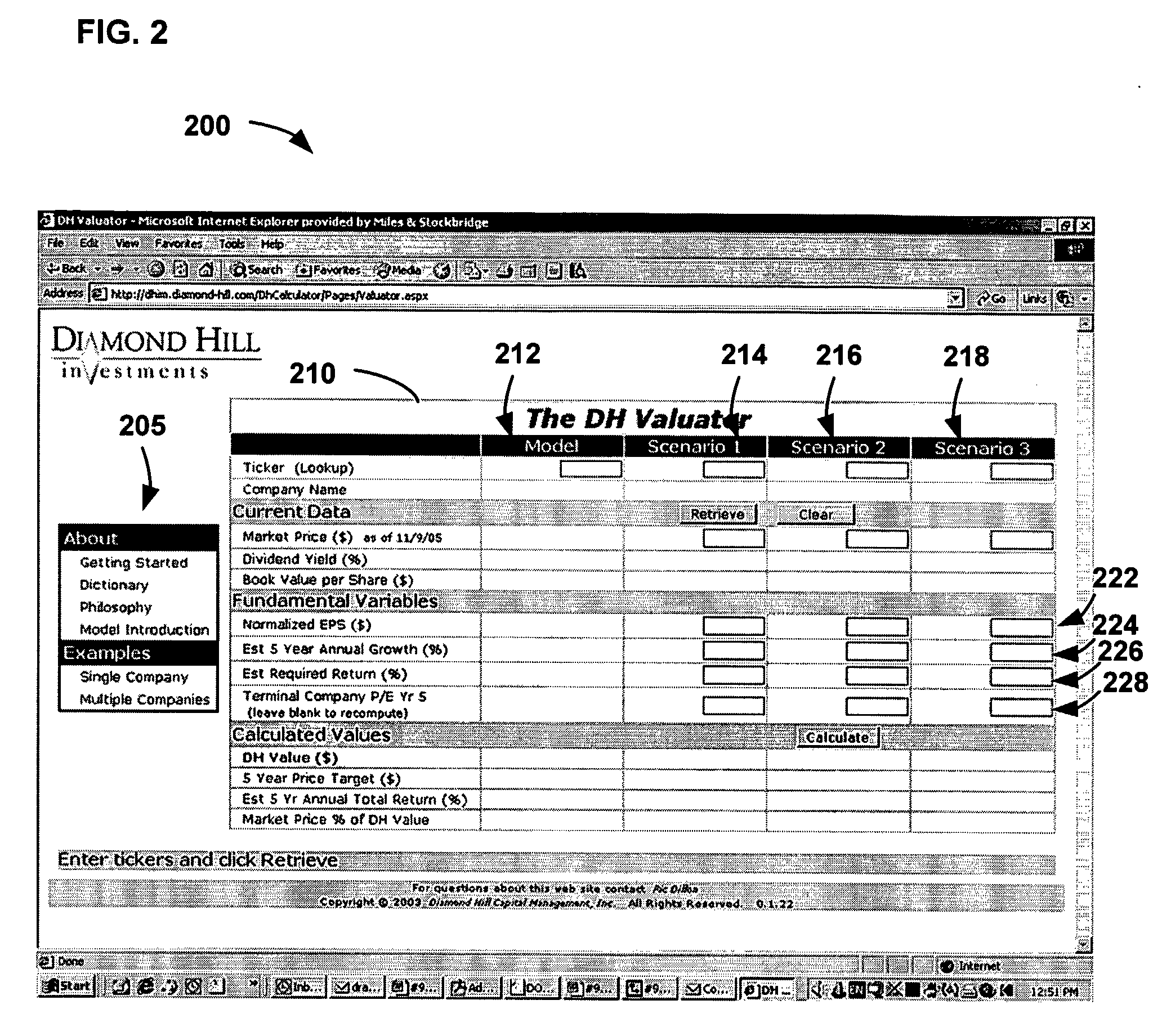
System and Method for Valuing Stocks
A method for valuing stocks includes determining (510) a risk-adjusted present value of dividends for a stock over a predetermined holding period; and determining (520) a risk-adjusted present value of a price for the stock at the end of the predetermined holding period, the price for the stock at the end of the predetermined holding period being based at least on a tangible book value of the stock at the end of the predetermined holding period. The method further includes determining (530) an intrinsic value of the stock from the risk-adjusted present value of dividends for the stock over the predetermined holding period and the risk-adjusted present value of the price for the stock at the end of the predetermined holding period, and displaying (540) the intrinsic value of the stock to a user.
Owner:DILLON RODERICK H
Zone Oriented Applications, Systems and Methods
InactiveUS20140129557A1Reduce development complexityService provisioningDatabase updatingEmbedded valueThird party
Owner:FLYBITS
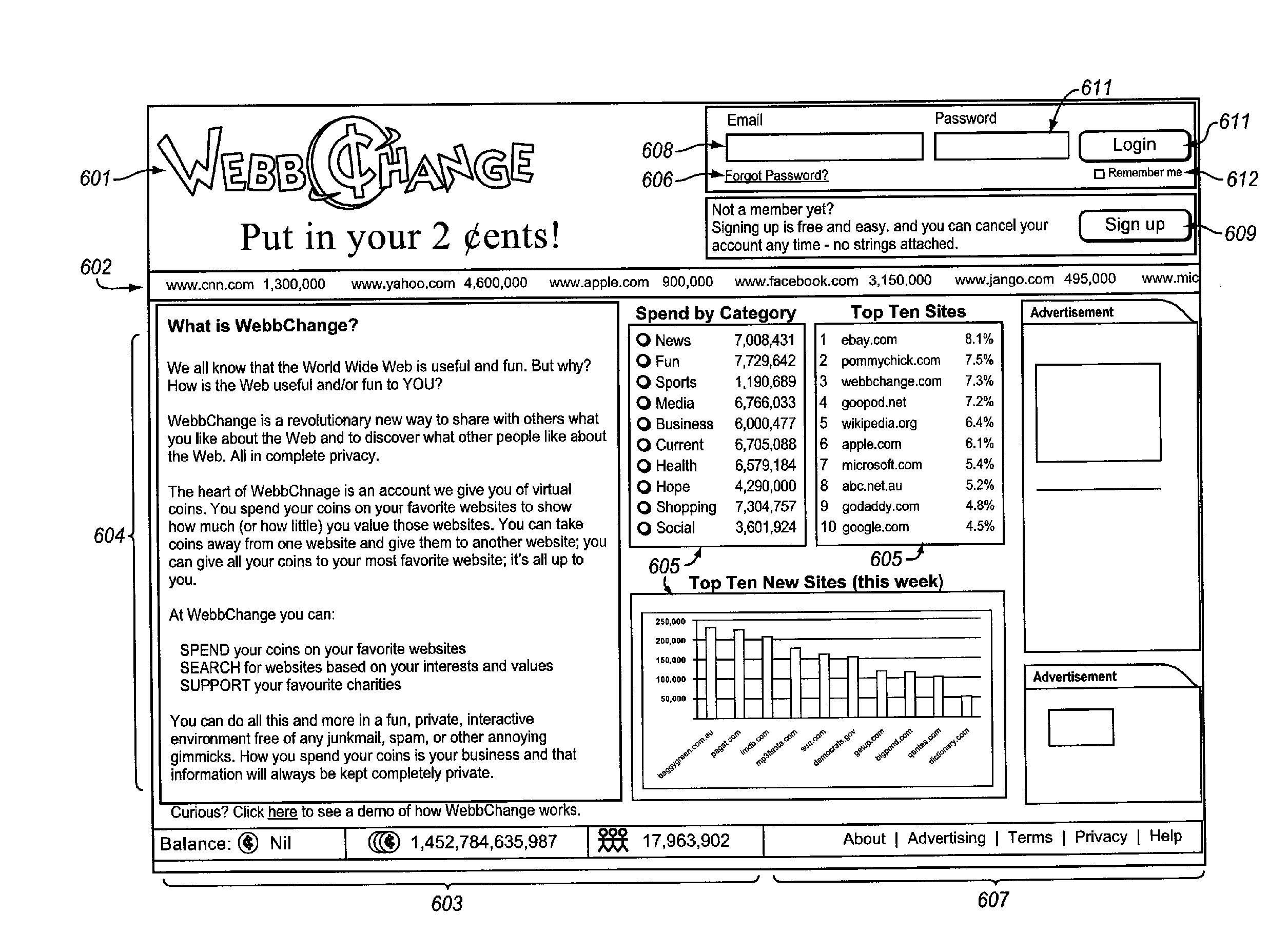
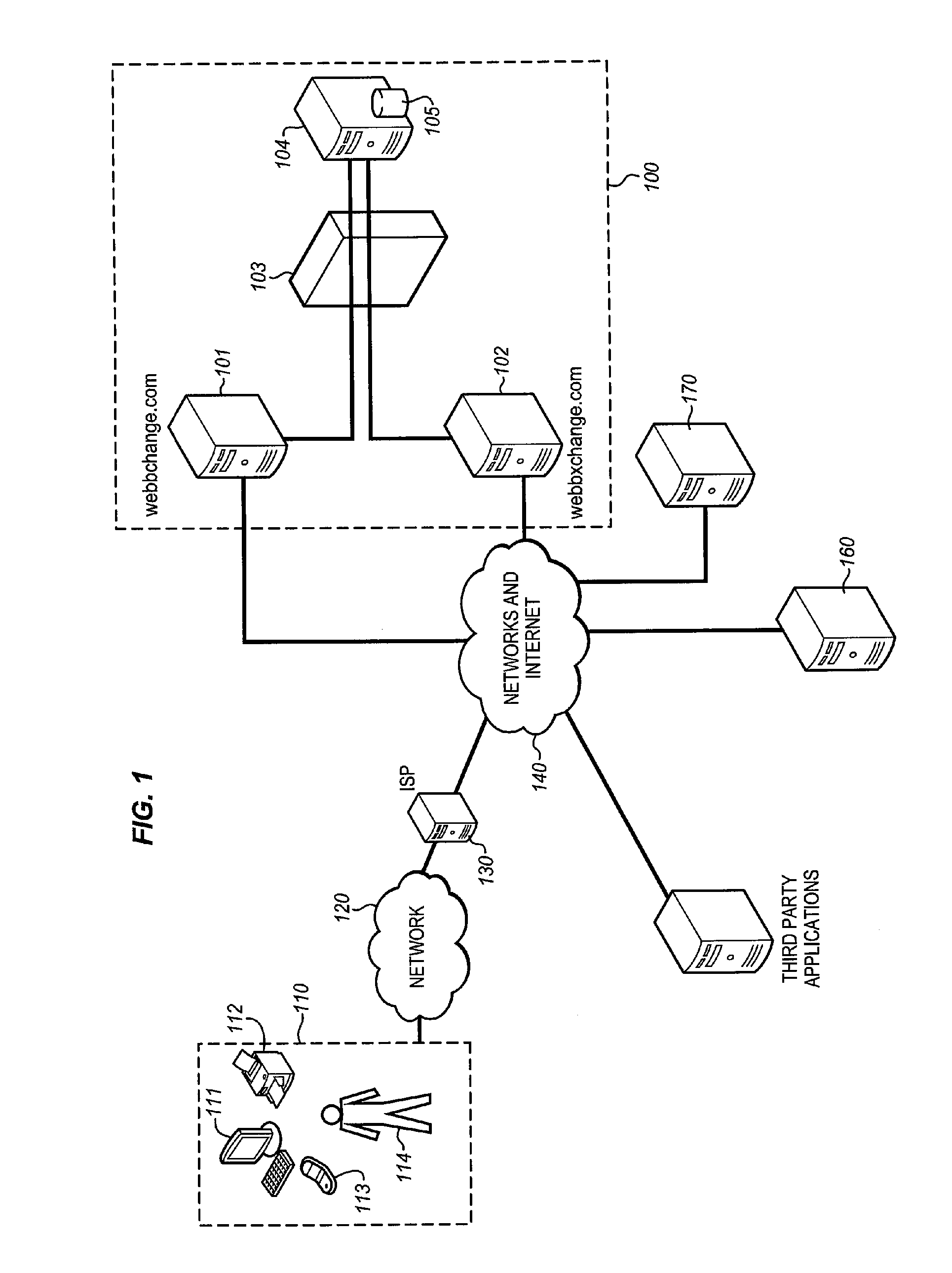
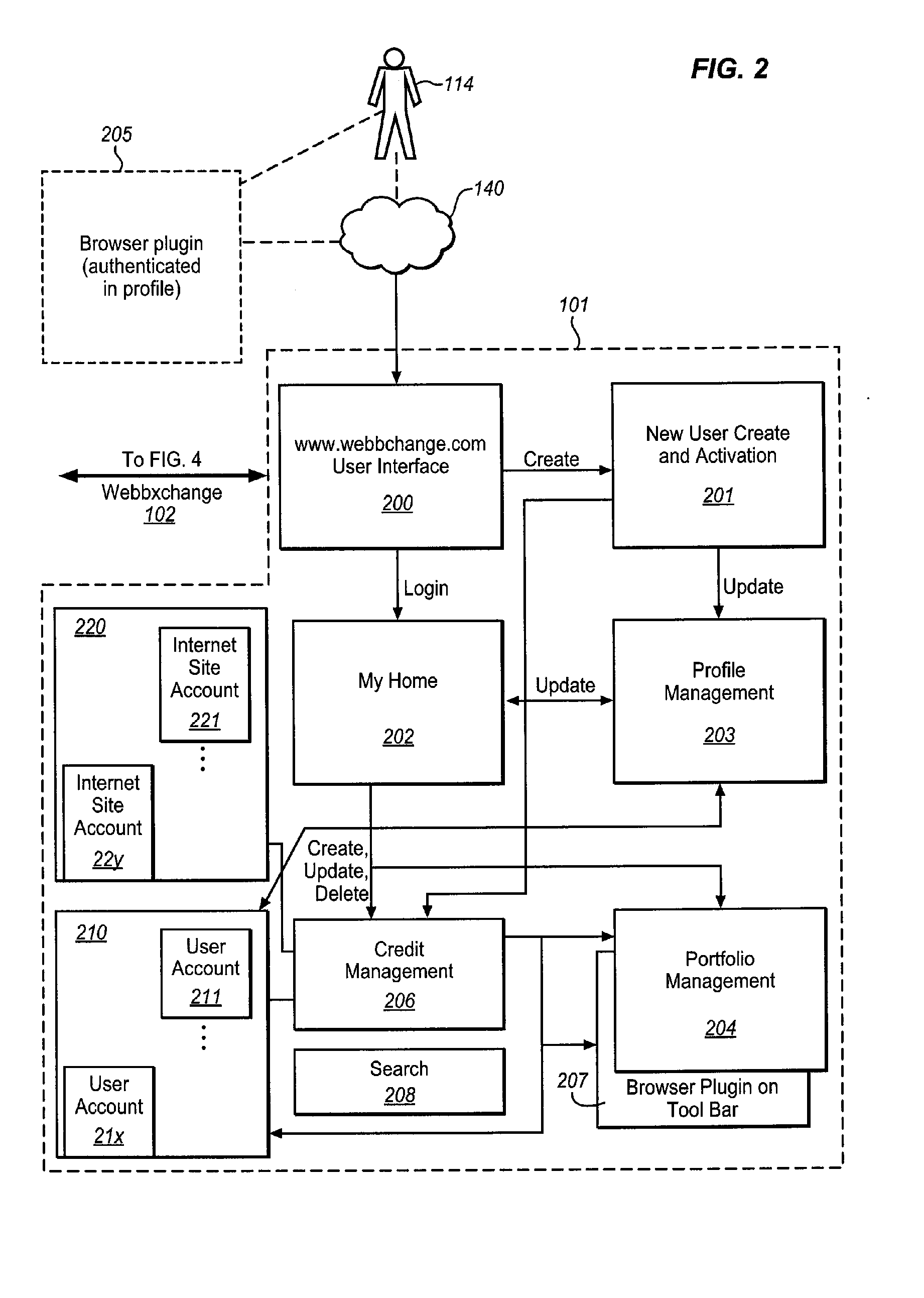
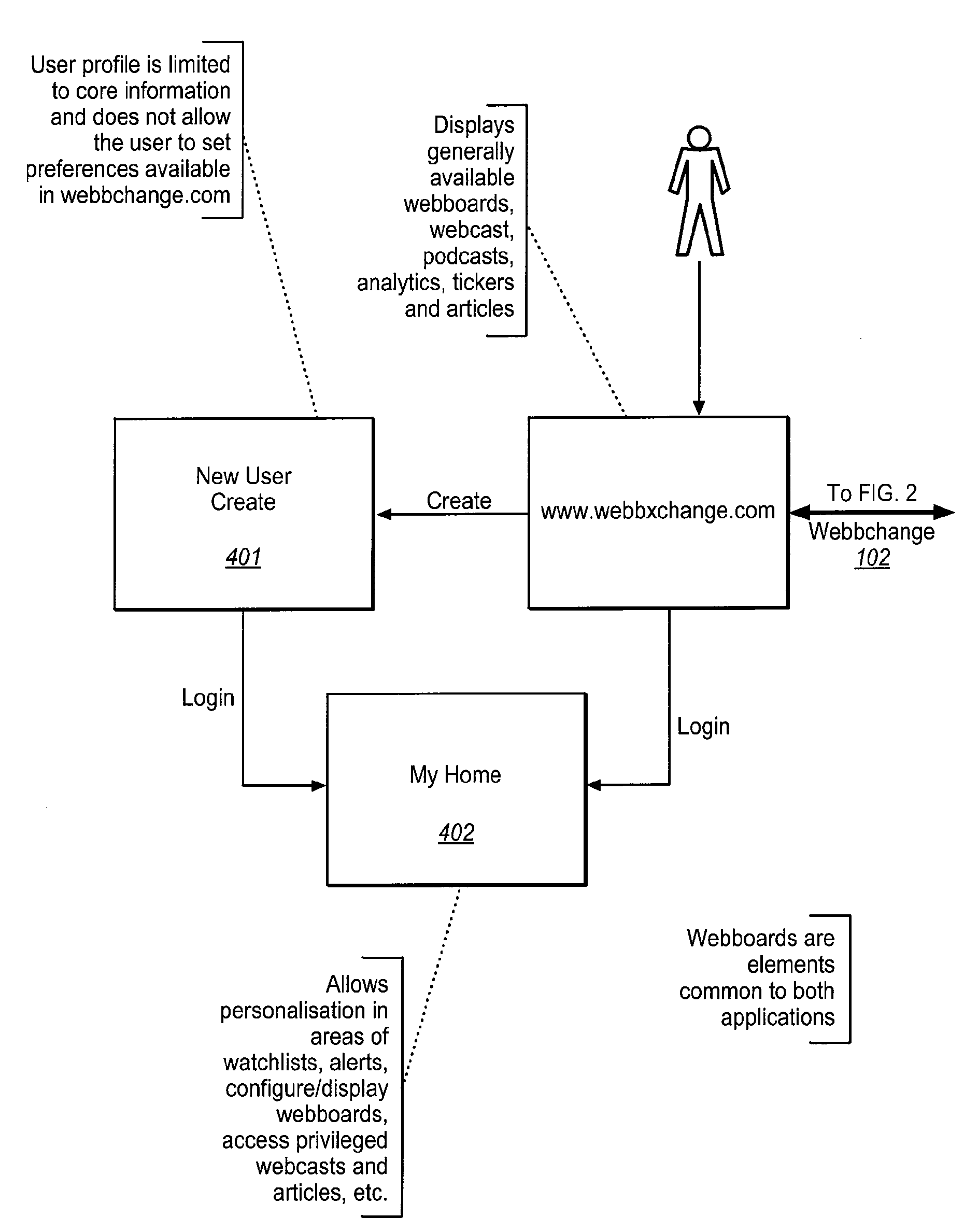
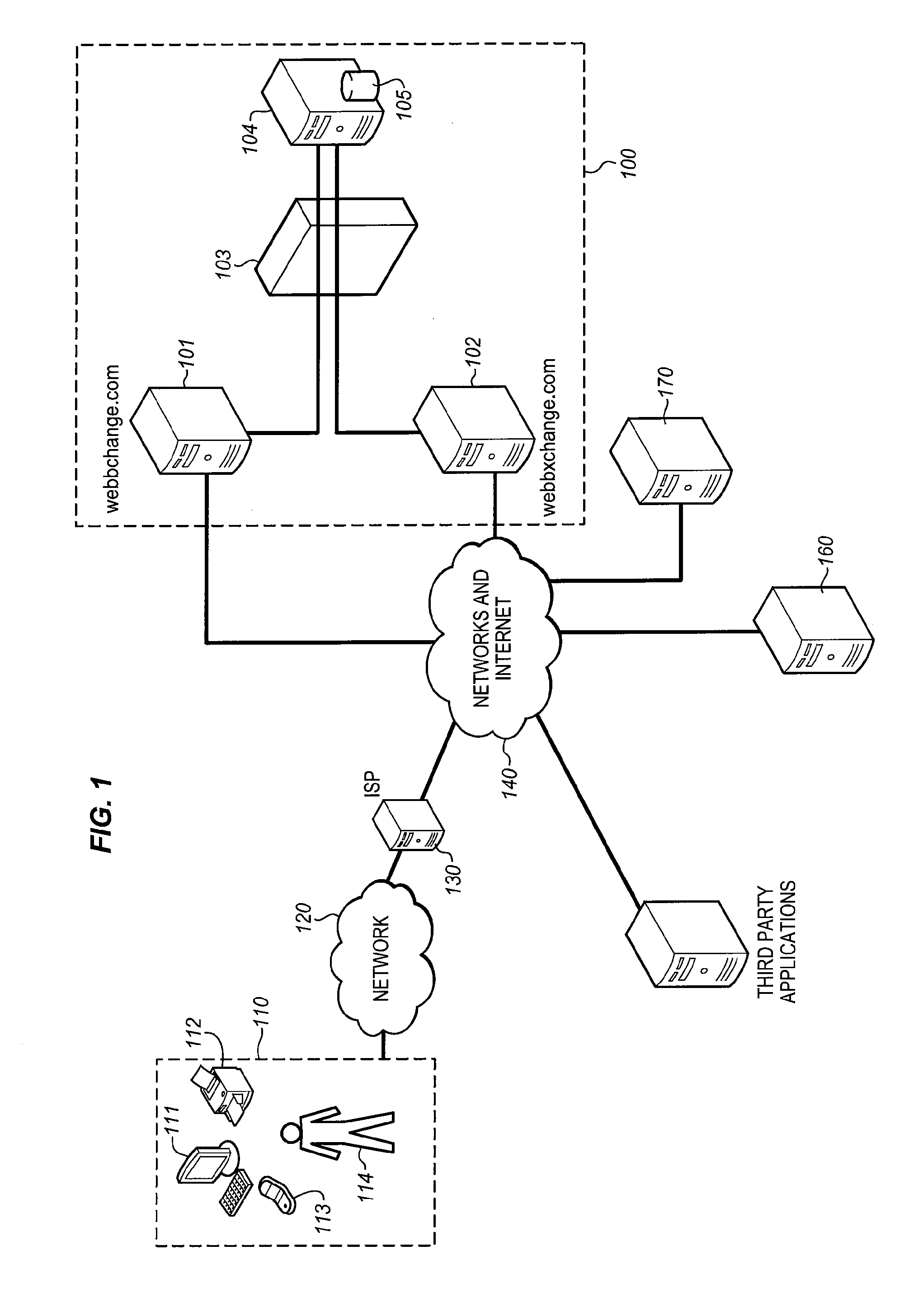
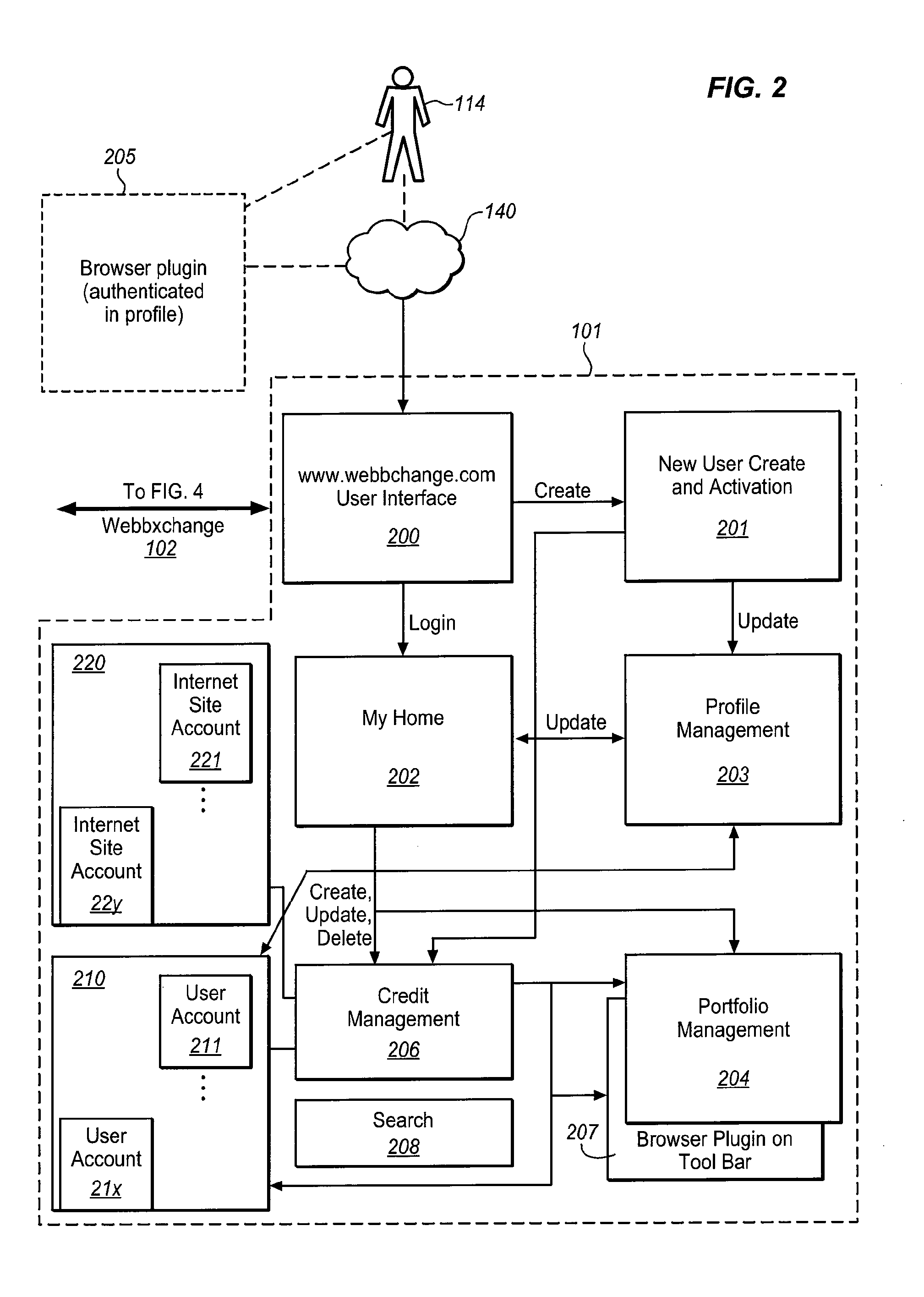
System for determining the intrinsic value provided to internet users by selected web sites
The WEB Site Valuation System identifies each user's personal attribution of value to a selected WEB site. The attribution is constrained by assigning each user a predetermined number of assignable credits / tokens from which the user can draw to “deposit” or “withdraw” previously deposited credits in the “account” of a WEB site. The tally of credits for each WEB site is then a direct indication of the value provided to users. This ultimately creates a token economy for and within the WEB, based upon user opinion of the value of WEB sites. The dynamic mapping and correlation of these value indications with the users' characteristics provides analytical data that can be used to determine the relevance of the WEB site to various socio-demographic populations, as well as the response of the users to changes in the WEB site, market forces, and / or the entire community of WEB sites.
Owner:WEBBCHANGE
System for determining the intrinsic value provided to internet users by selected web sites
The WEB Site Valuation System identifies each user's personal attribution of value to a selected WEB site. The attribution is constrained by assigning each user a predetermined number of assignable credits / tokens from which the user can draw to “deposit” or “withdraw” previously deposited credits in the “account” of a WEB site. The tally of credits for each WEB site is then a direct indication of the value provided to users. This ultimately creates a token economy for and within the WEB, based upon user opinion of the value of WEB sites. The dynamic mapping and correlation of these value indications with the users' characteristics provides analytical data that can be used to determine the relevance of the WEB site to various socio-demographic populations, as well as the response of the users to changes in the WEB site, market forces, and / or the entire community of WEB sites.
Owner:WEBBCHANGE
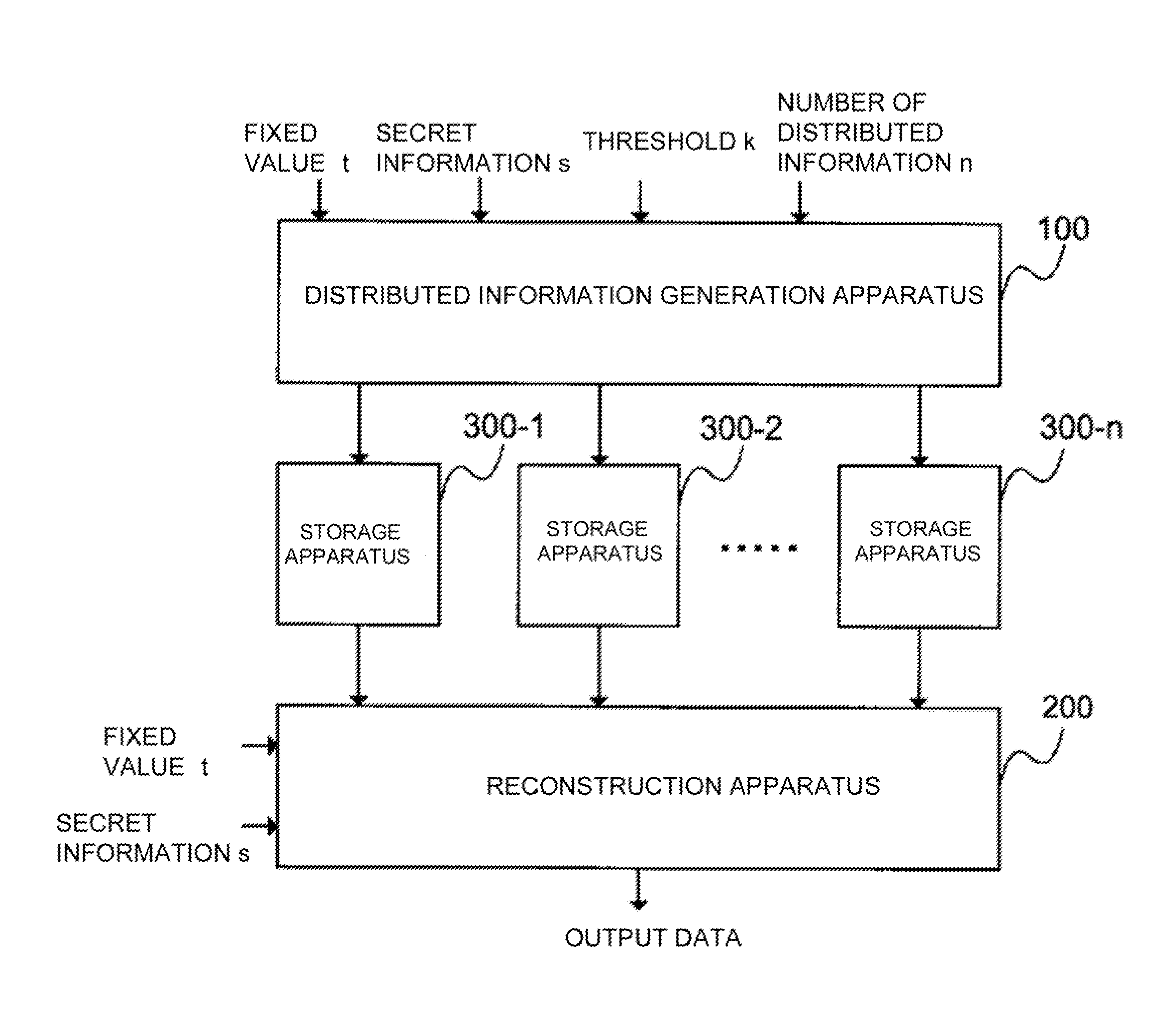
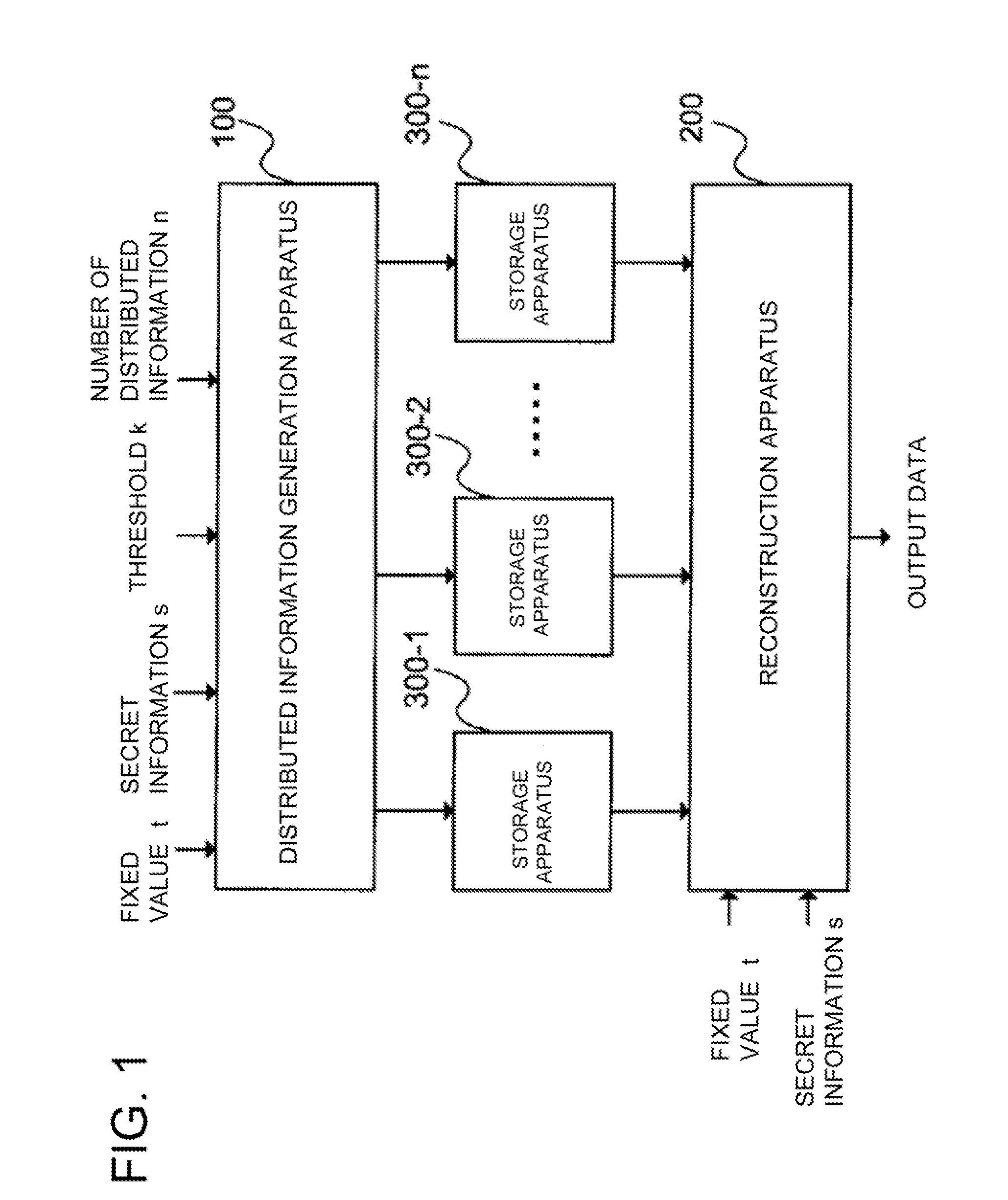
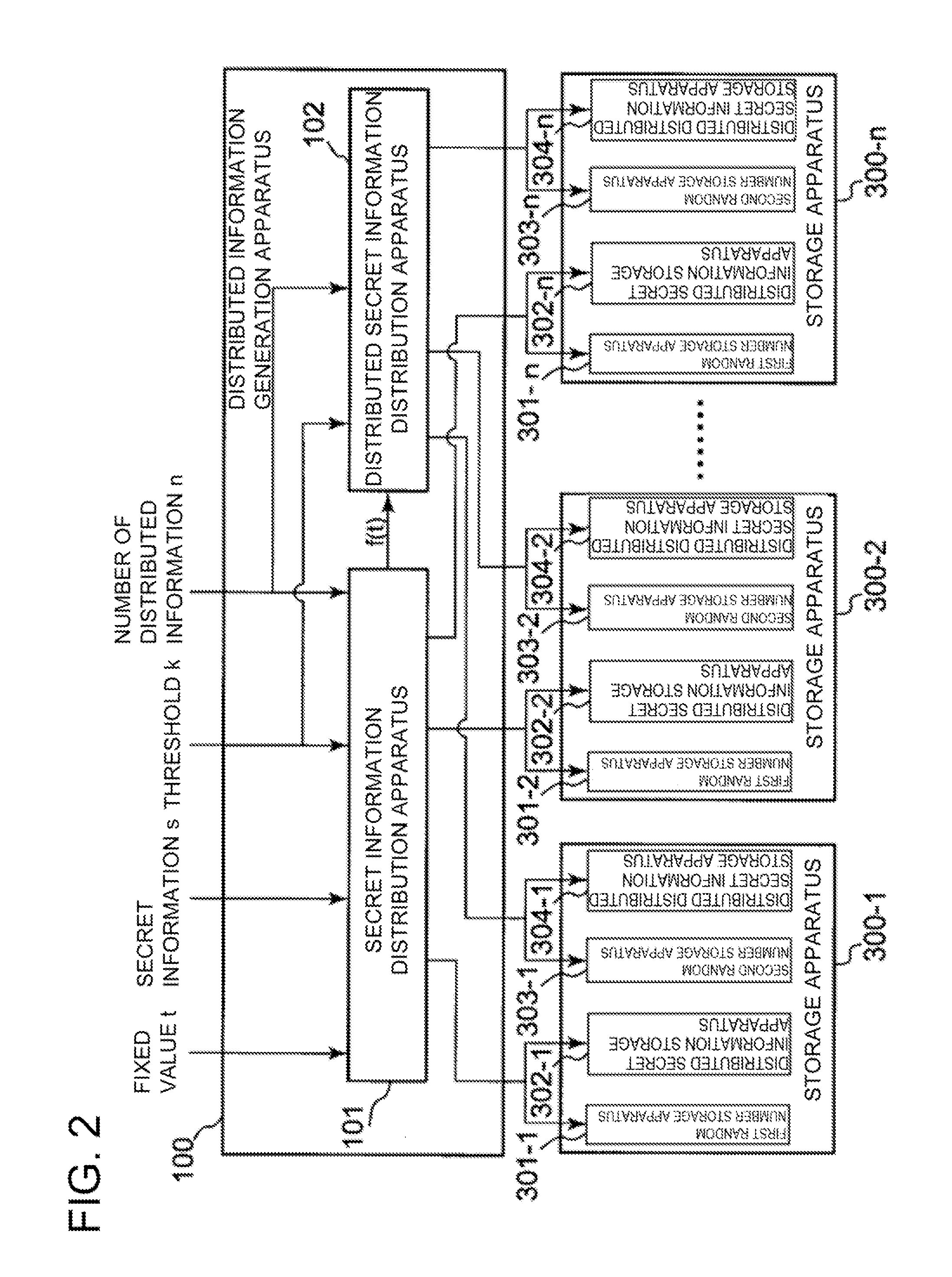
Distributed information generation apparatus, reconstruction apparatus, reconstruction result verification apparatus, and secret information distribution system, method, and program
ActiveUS20100287366A1Improve detection rateSmall sizeKey distribution for secure communicationSecret communicationEmbedded valueHigh probability
A shared information creating device capable of detecting false alteration of shared information with high probability even if a traitor has shares the number of which is above a threshold and creating shared information whose data size is smaller than that of secret information. A recovering device, a recovery result verifying device, and a secret information sharing system, program, and method are also provided. The shared information creating device generates a polynomial F in which secret information s is embedded, outputs a shared secret information, generates a polynomial G in which the output of when a fixed value t is substituted in the polynomial F is embedded as secret information, and creates shared secret information. A recovering device receives k sets of shared secret information to generate a polynomial F′, and receives k sets of shared shared secret information to generate a polynomial G′. When the value embedded as secret information in the polynomial G′ is equal to the output of when the fixed value t is substituted in the polynomial F′, the embedded value is outputted. When they are not equal, information indicating falsification detection is outputted.
Owner:NEC CORP
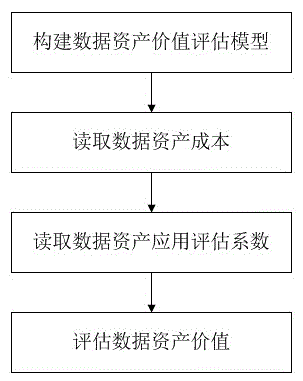
Data asset value evaluation method
InactiveCN105069575AQuantify Intrinsic ValueQuantitative usabilityResourcesEmbedded valueData science
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
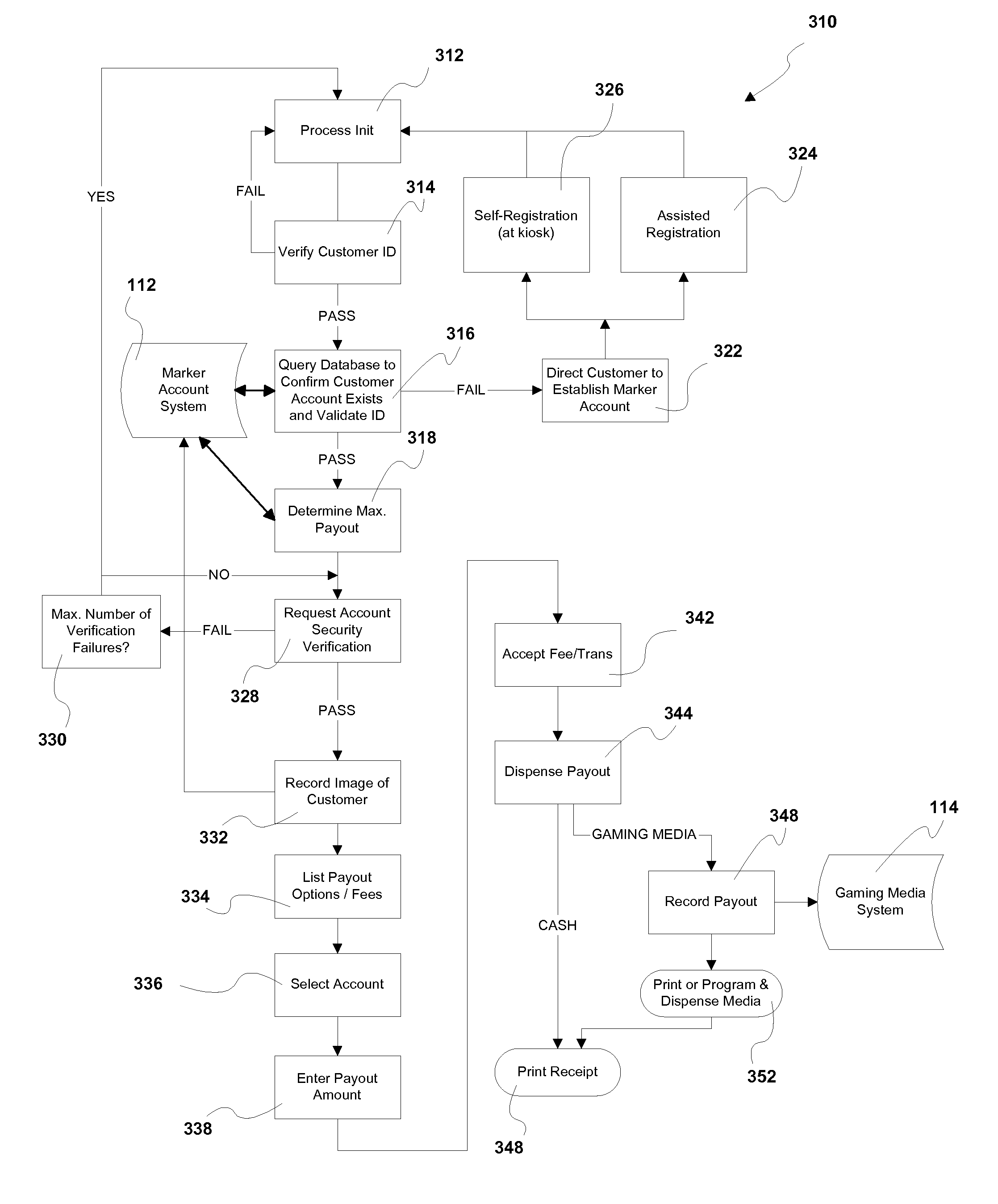
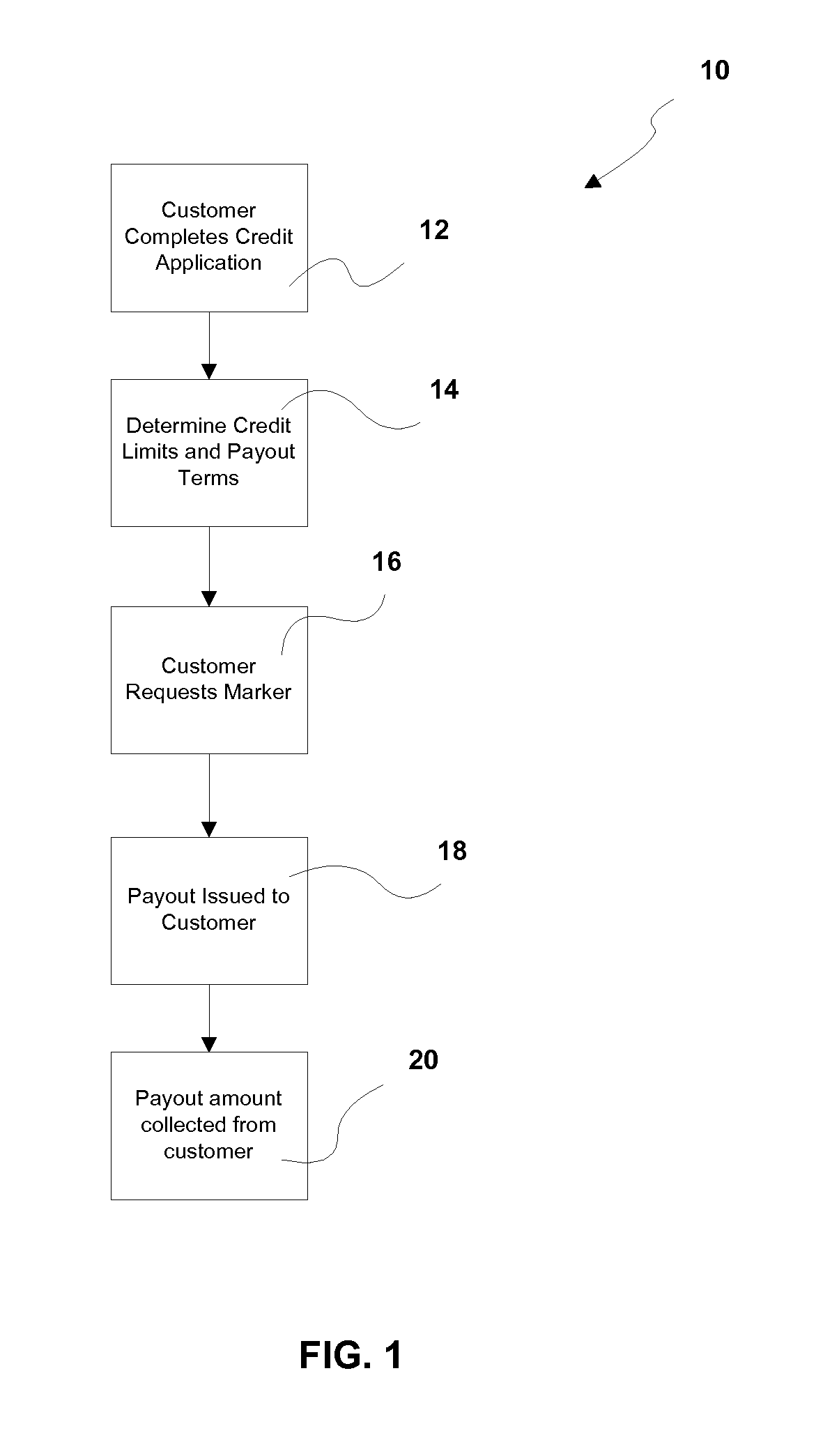
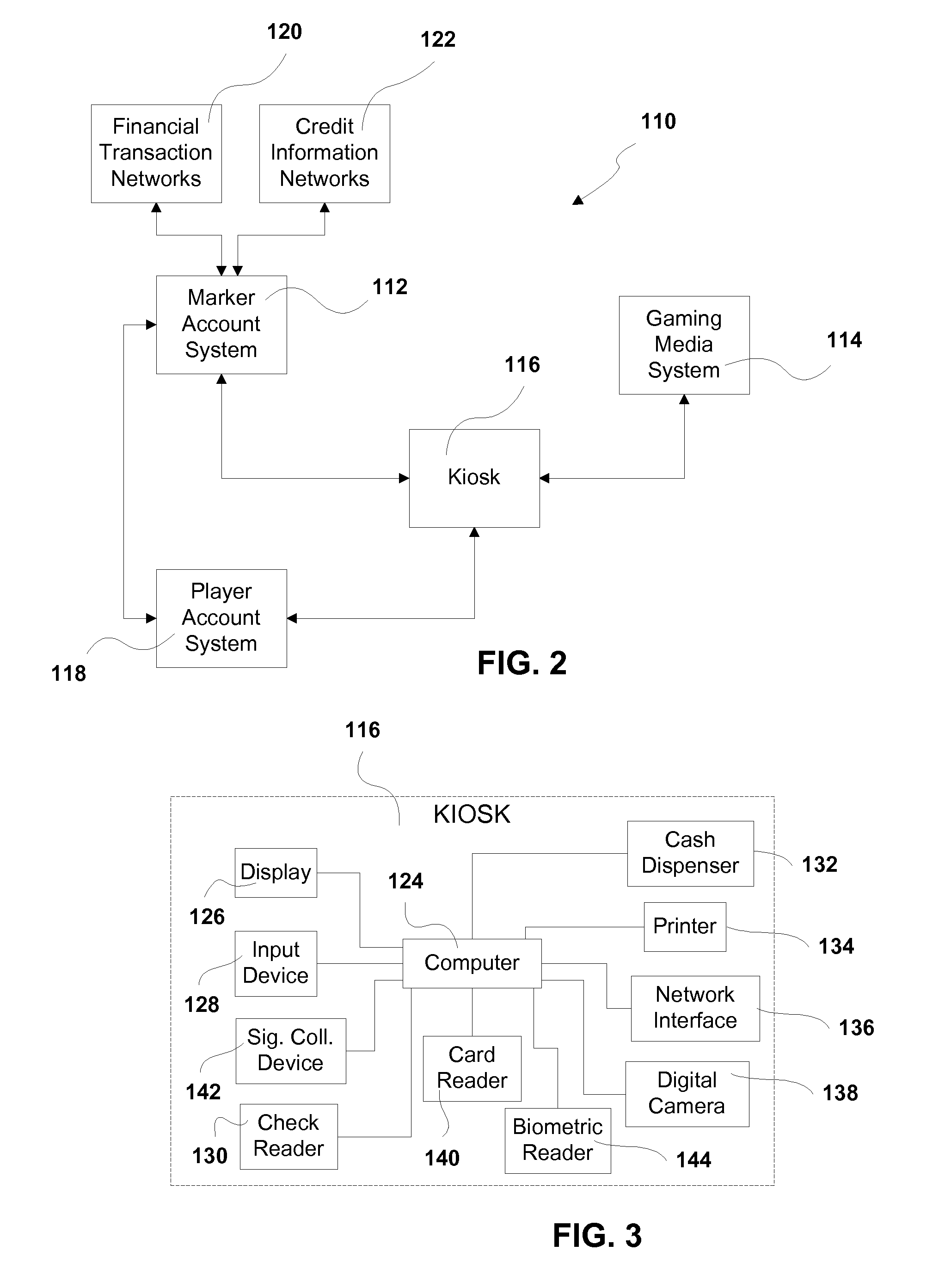
Processing a Marker Transaction at a Gaming Establishment
InactiveUS20120088570A1Apparatus for meter-controlled dispensingVideo gamesEmbedded valueHuman–computer interaction
In one embodiment, a system and method for processing a marker transaction by a customer of a gaming establishment via a kiosk. The customer has a marker account prior to initiating the marker transaction at the kiosk. The kiosk is adapted to communicate with (i) a marker account system to process the transaction and (ii) a gaming media system for marker payouts in the form a gaming media, such as gaming scrips. By providing the customer with gaming scrips having no intrinsic value, the gaming establishment at most assumes a deferred risk and possibly little or no risk at all for having issued the marker to the customer.
Owner:AUTOMATED CURRENCY INSTR
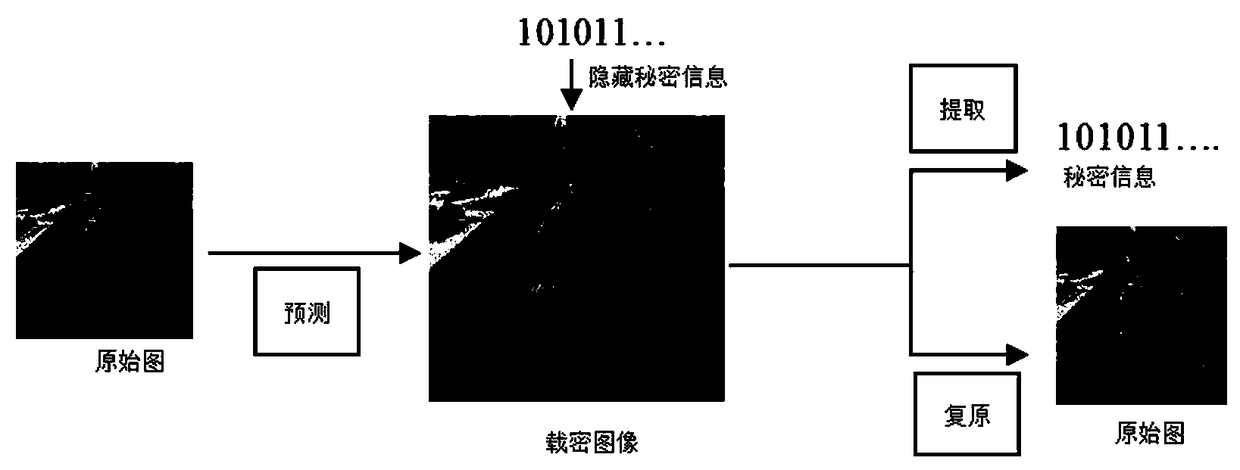
Reversible information hiding method based on dynamic prediction of pixel value
ActiveCN109391819AImprove concealmentSmall distortionDigital video signal modificationPattern recognitionEmbedded value
The invention discloses a reversible information hiding method based on dynamic prediction of pixel values. The method is characterized by comprising the following steps: 1) dynamically predicting pixel values; 2) embedding secret information; 3) extracting the secret information and recovering images. The method is high in hiding capacity, and precision of the predicted pixel value is high through dynamically predicting the pixel value, and an optimal embedded value is adjusted according to hidden information capacity, so that image distortion after hiding the information is small, and hidingeffect is good.
Owner:GUANGXI NORMAL UNIV
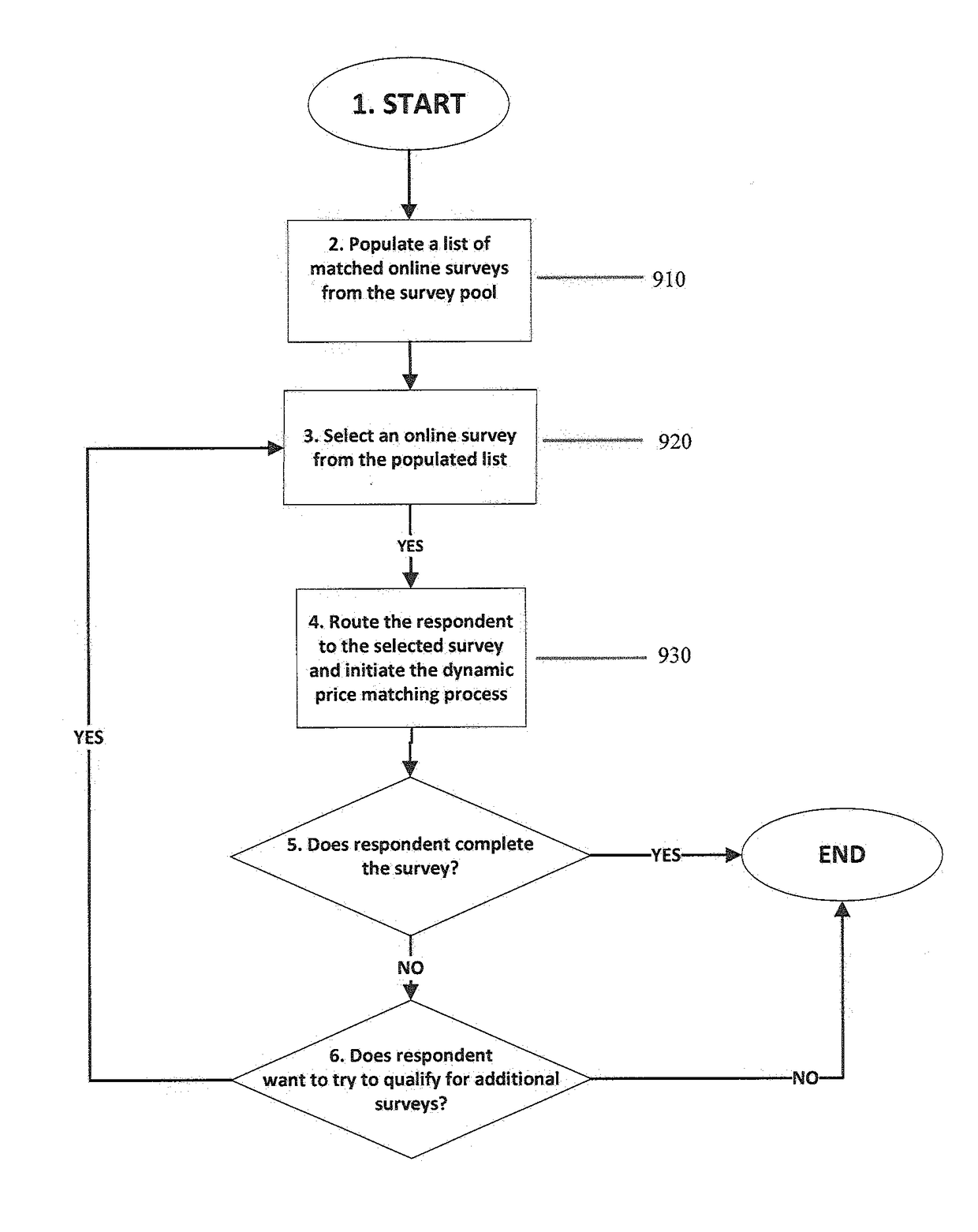
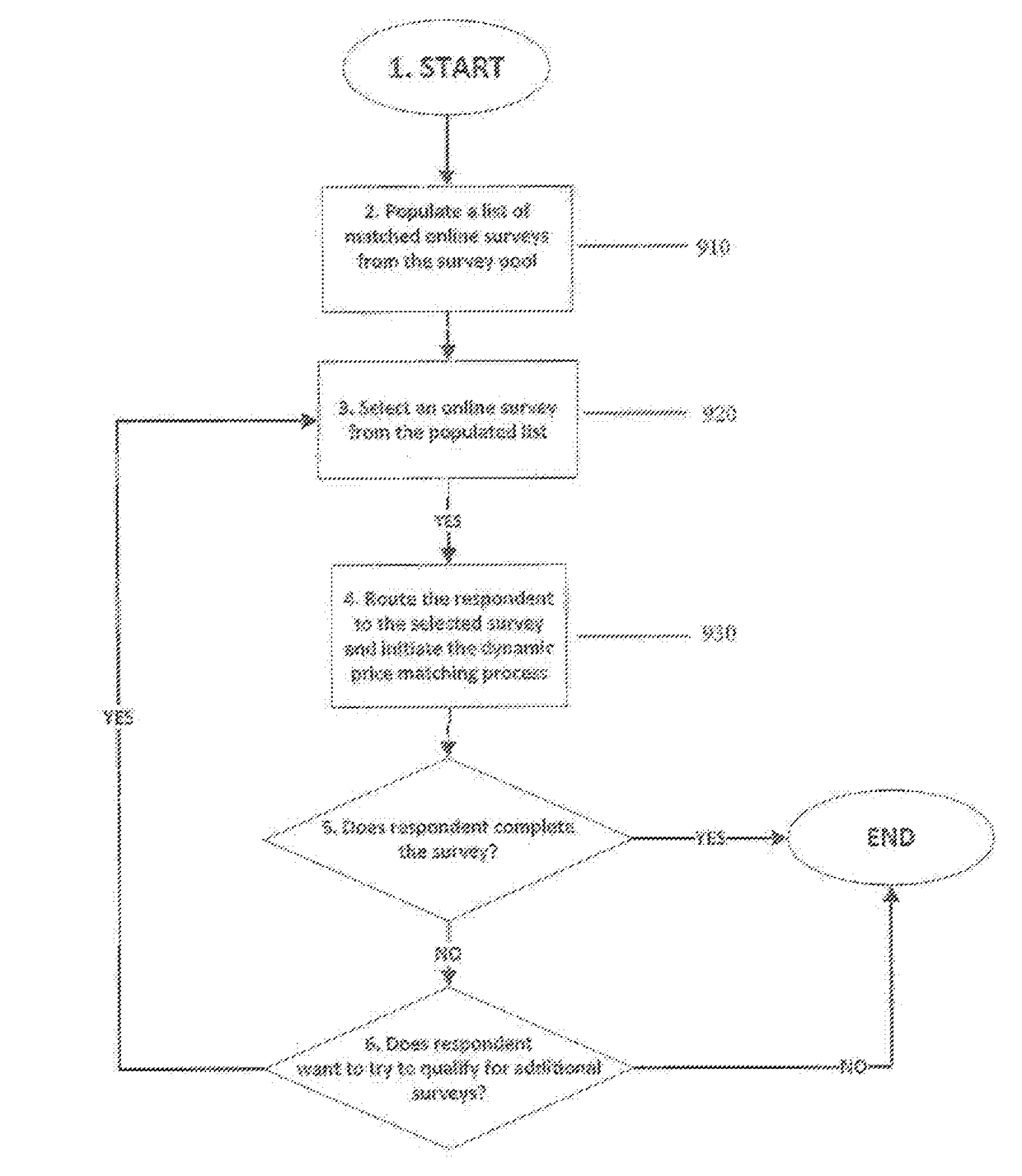
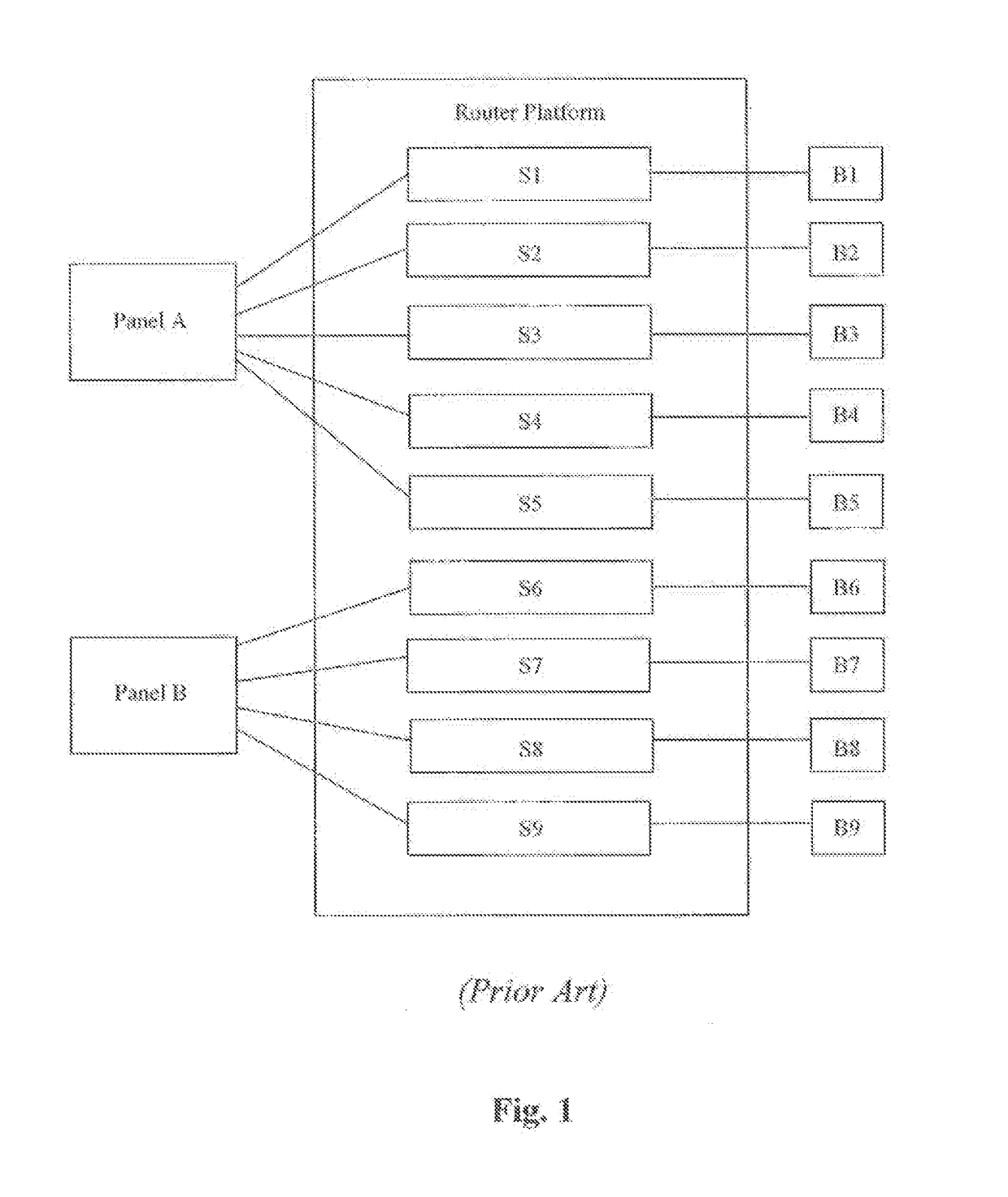
Method of correlating bid price to intrinsic value in a survey platform
An online survey platform and process for correlating the bid price offered by a supplier for the completion of an out-of-network survey hosted on the survey platform to one or more intrinsic value indicators of the survey. If the supplier's bid price is less than or equal to the survey budget price set by the buyer, then the routing platform of the present invention will route the supplier's respondent(s) to the survey.
Owner:LUCID HLDG LLC
Zone Oriented Applications, Systems and Methods
InactiveUS20140129693A1Reduce development complexityService provisioningDatabase updatingThird partyEmbedded value
Owner:FLYBITS
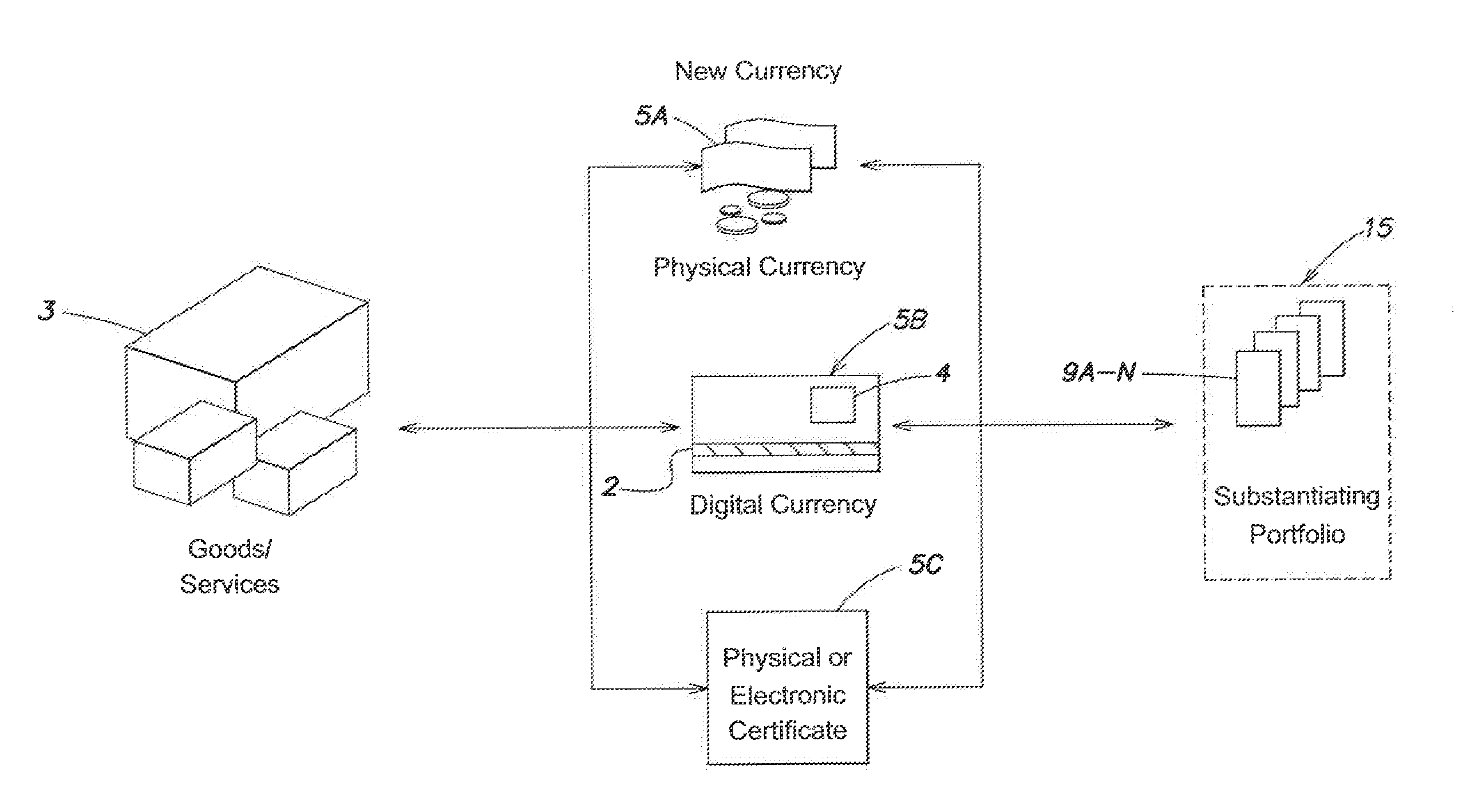
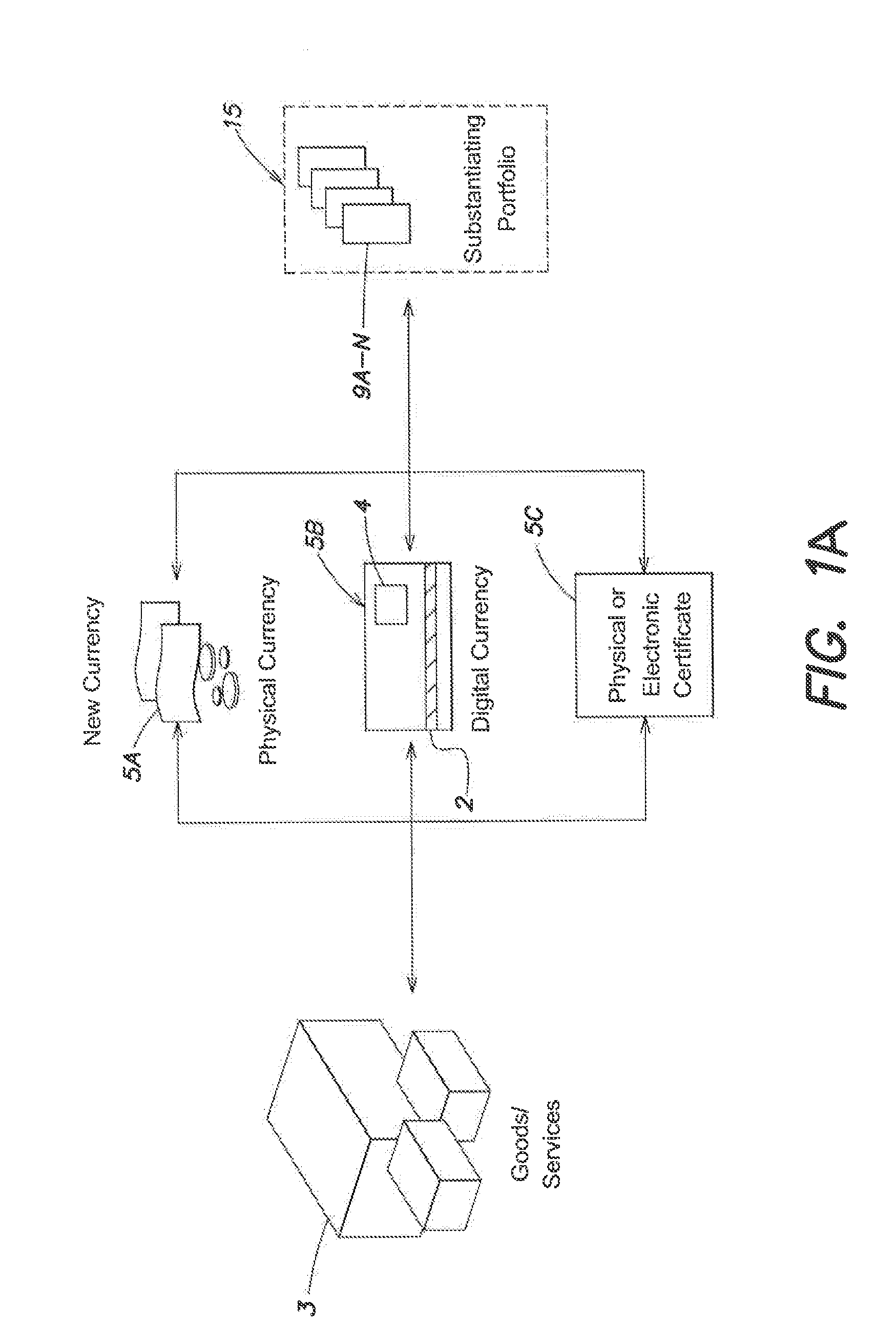
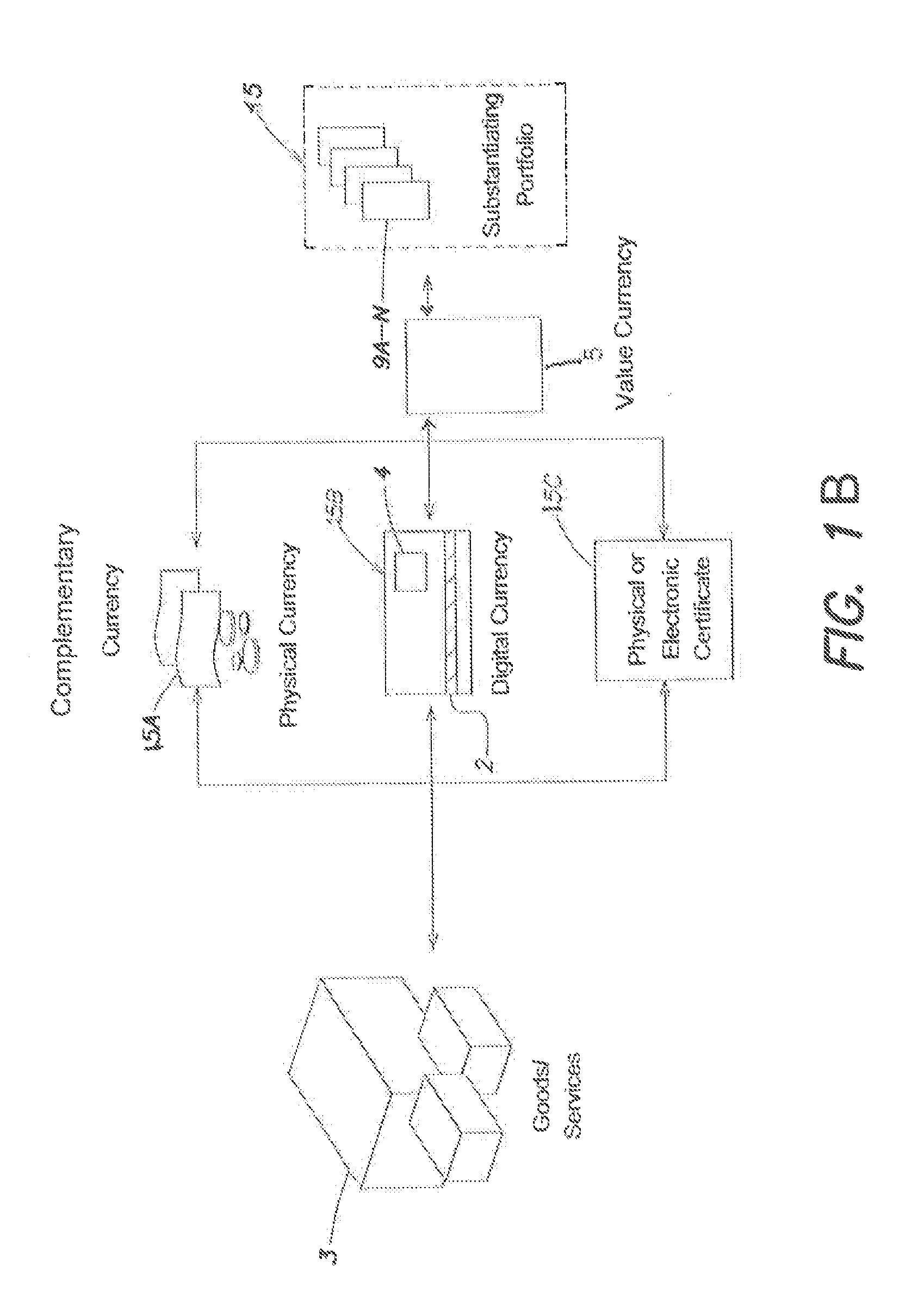
Targeted objective complementary currency
InactiveUS20140074679A1Reduce the valueReducing debtFinanceFinancial managementEmbedded valueComputer science
Owner:VAN COPPENOLLE BART P E +1
Big data tracing method and system based on digital watermarking
PendingCN110069907AImprove robustnessStrong anti-deletion attackDigital data protectionImage data processing detailsEmbedded valueNumeric data
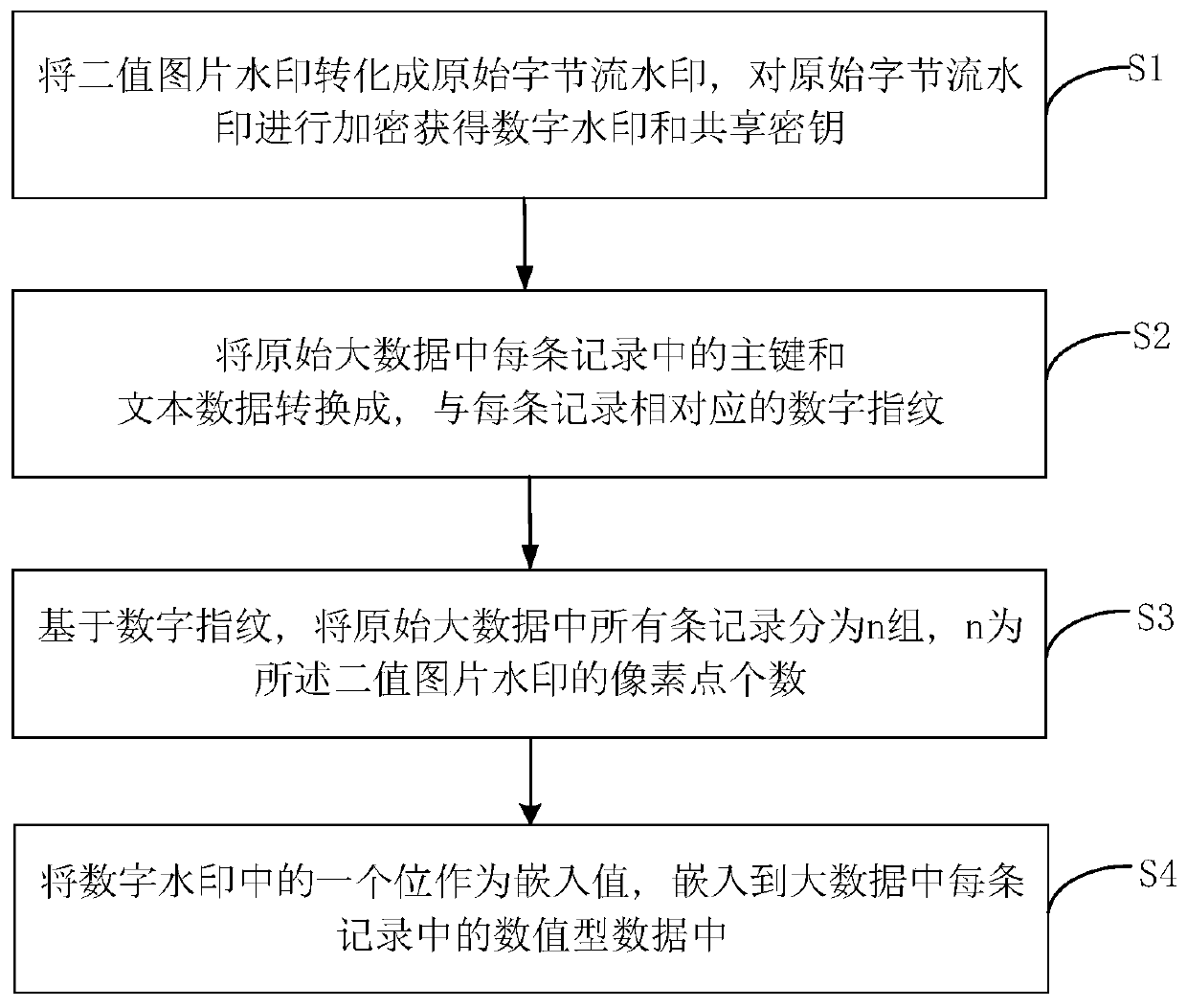
The embodiment of the invention provides a big data tracing method and system, and the method comprises the steps: enabling a binary image watermark to be converted into an original byte flow watermark, and carrying out the encryption of the original byte flow watermark, and obtaining a digital watermark and a shared key; converting the primary key and the text data in each record in the originalbig data into digital fingerprints corresponding to each record; dividing all records in the original big data into n groups based on the digital fingerprint, n being the number of pixel points of thebinary image watermark, wherein each record and the digital fingerprint corresponding to each record correspond to one pixel in the binary image watermark, namely one bit in the digital watermark; and taking one bit in the digital watermark as an embedded value, and embedding the embedded value into numeric data in each record in the big data. The embodiment of the invention has the following advantages: the problems of poor algorithm robustness, poor deletion attack resistance, poor increase attack resistance and the like in the prior art are solved.
Owner:刘忠平 +2
Method of tracing object allocation site in program, as well as computer system and computer program therefor
Owner:INT BUSINESS MASCH CORP
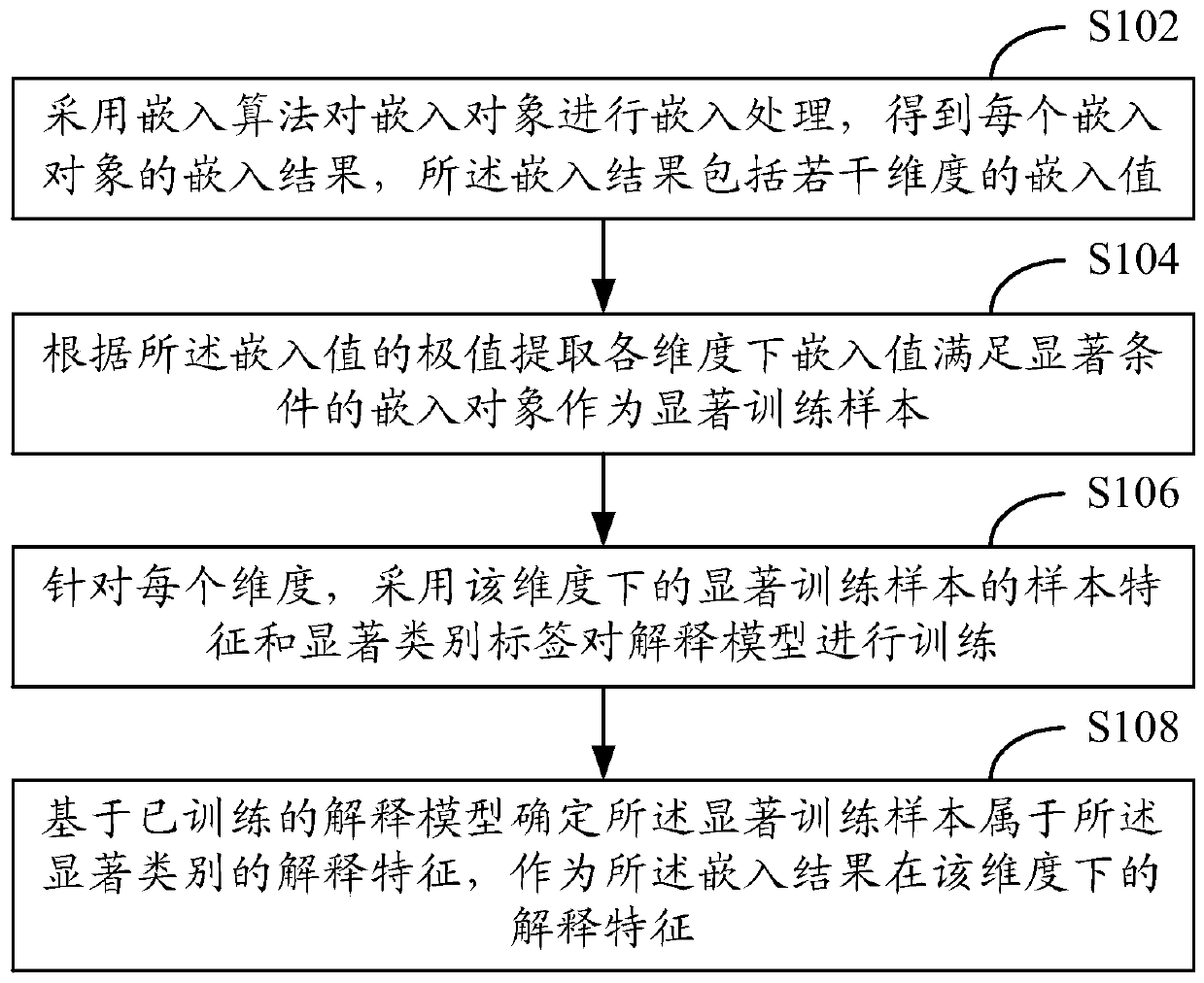
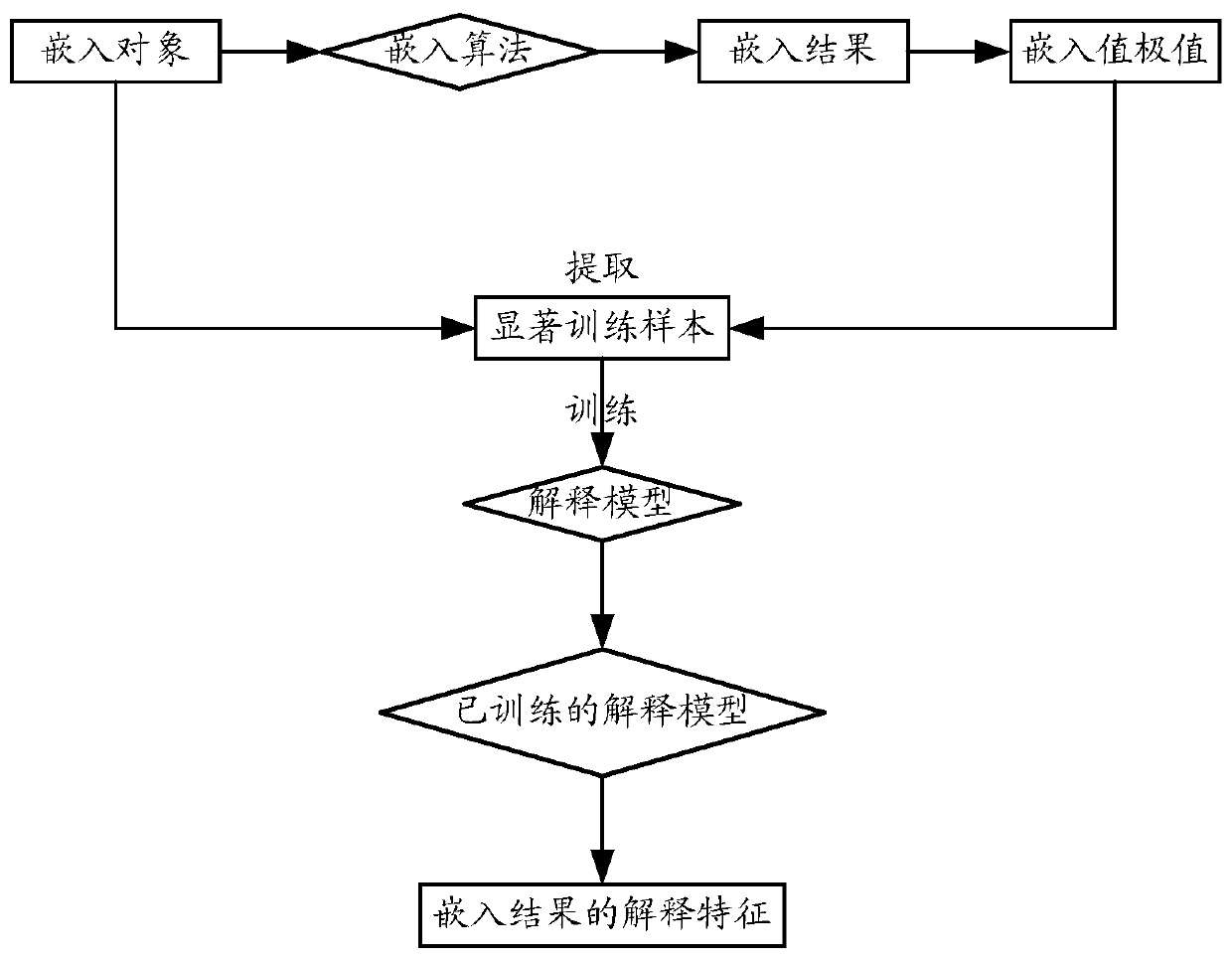
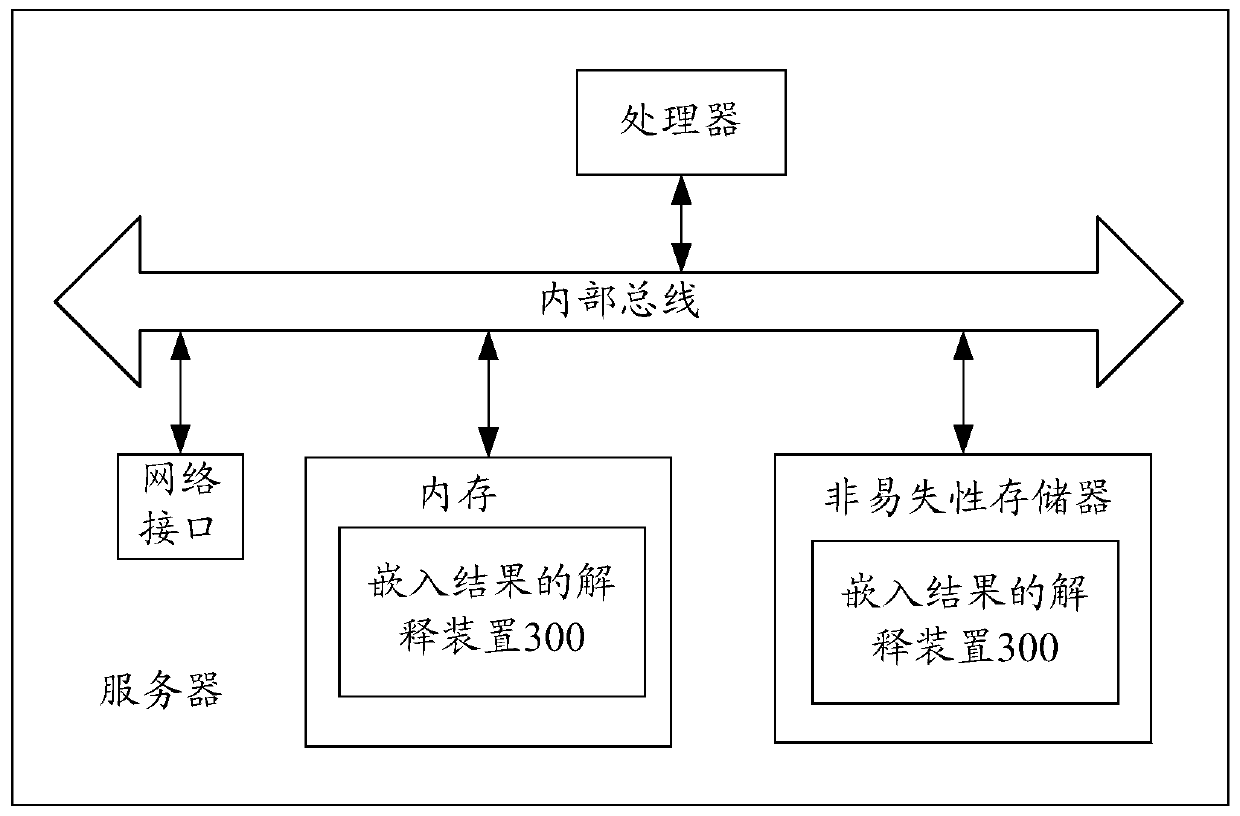
An interpretation method and device for an embedding result
ActiveCN109902167AImprove generalization abilityImprove performanceCharacter and pattern recognitionSpecial data processing applicationsEmbedded valueAlgorithm
The invention discloses an interpretation method and device of an embedding result. The method comprises: adopting an embedding algorithm to carry out embedding processing on embedded objects, obtaining an embedding result of each embedded object, wherein the embedding result comprises a plurality of dimensions of embedding values; According to the extreme value of the embedded value, extracting an embedded object with the embedded value meeting a significant condition under each dimension as a significant training sample; For each dimension, training an interpretation model by adopting the sample characteristics of the significant training samples under the dimension and the significant category tags; And based on a trained explanation model, determining the explanation characteristics ofthe significant training sample belonging to the significant category, and taking the explanation characteristics as the explanation characteristics of the embedding result under the dimension.
Owner:ADVANCED NEW TECH CO LTD
Multi-head intelligent mutual mobile cropping control method based on embedded-type typesetting
ActiveCN103170749AIncrease profitUniform configurationLaser beam welding apparatusEmbedded valueMachining process
The invention discloses a multi-head intelligent mutual mobile cropping control method based on embedded-type typesetting and relates to the raw material cutting field of stuffed toys and the shoemaking industry. The control method comprises the steps of establishing a template target, a line standardization target and a row standardization target which are needed by typesetting, respectively acquiring coordinates and template target parameters, and calculating line embedded value and row embedded value in the embedded-type typesetting; combining template target coordinates, the line embedded value and the row embedded value to calculate the coordinates of a copy template target and conduct the embedded-type typesetting; calculating the coordinates of respective starting cutting points of multiple heads, and controlling the multiple heads to move to the respective starting cutting points; and calculating the number of multiple head template targets to be cut, controlling the multiple heads to start cutting simultaneously, and respectively controlling light opening operation and light closing operation of laser. The multi-head intelligent mutual mobile cropping control method greatly improves the fabric utilization rate and cropping efficiency of raw materials, and brings convenient to control of the whole processing process by customers.
Owner:WUHAN GOLDEN LASER
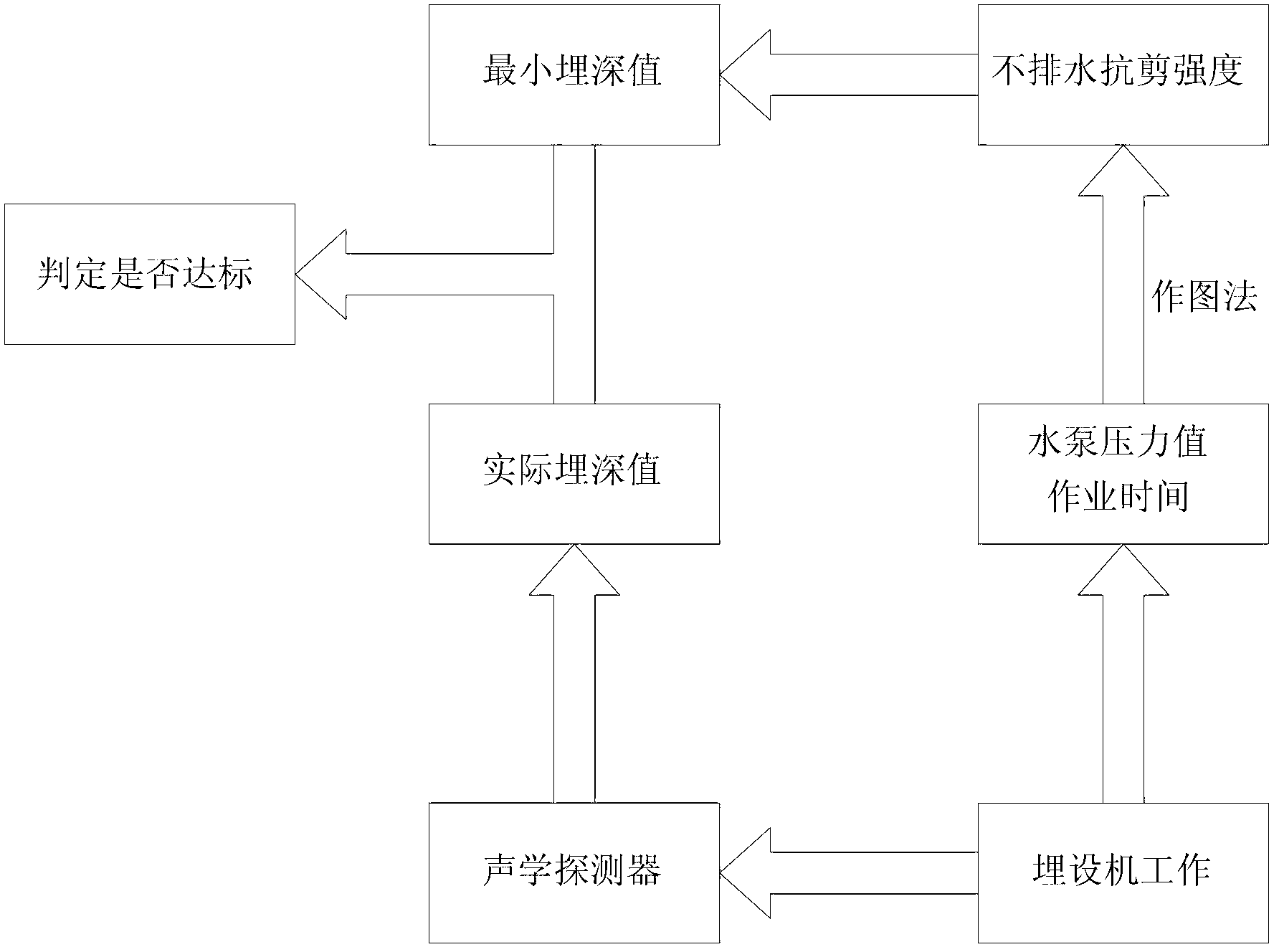
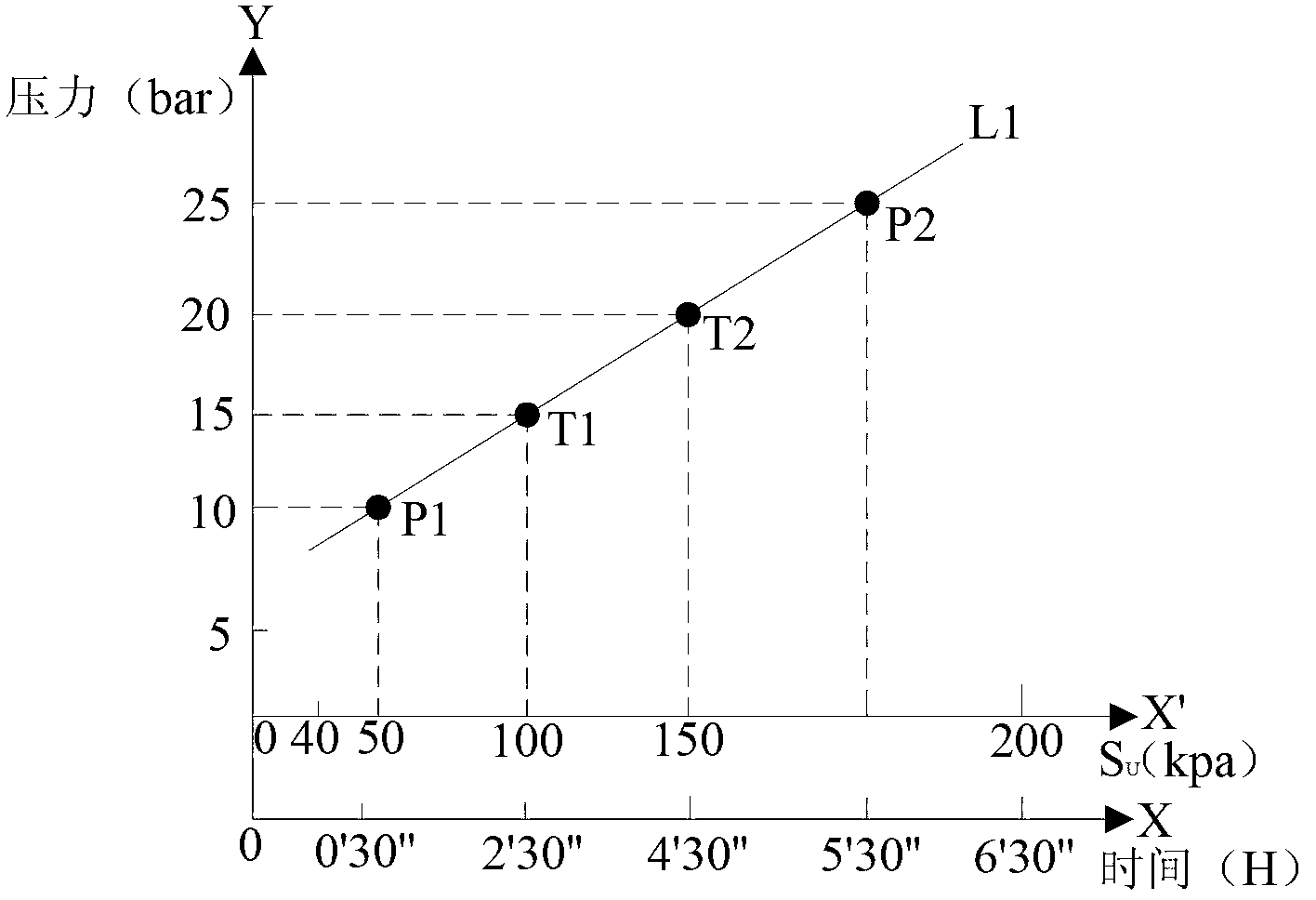
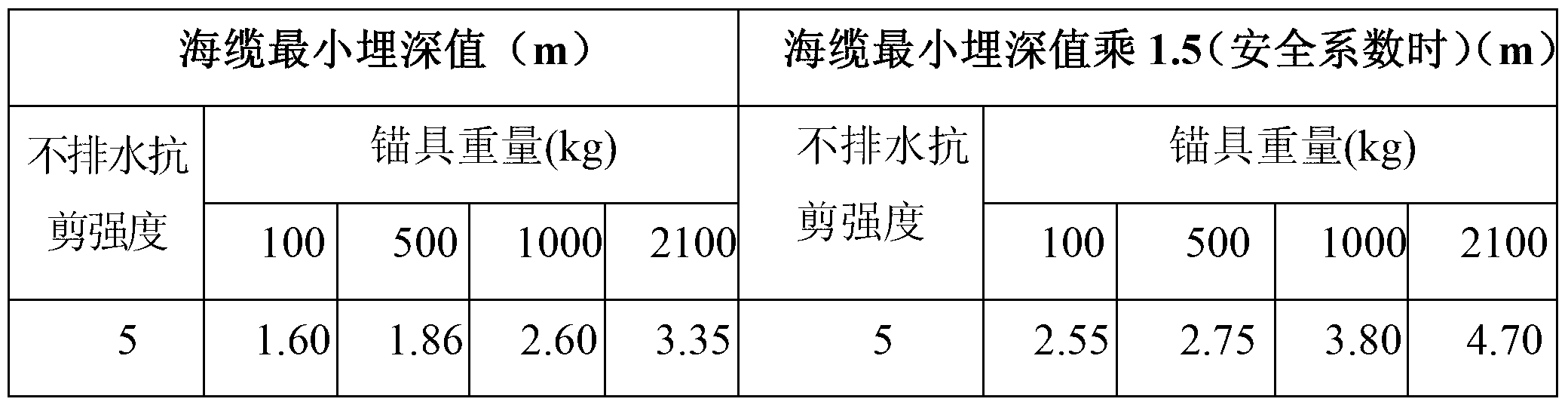
Submarine cable embedding protecting judging method based on undrained shear strength
The invention discloses a submarine cable embedding protecting judging method based on the undrained shear strength. The method includes the following steps that 1 a submarine cable is led into a seabed cut groove cut by a high-pressure water pump; 2 the actual embedded value of the submarine cable is detected; 3 the current undrained shear strength of the seabed geological soil is obtained; 4 the minimum embedded value corresponding to the current undrained shear strength of the seabed geological soil is calculated; and 5 the minimum embedded value is compared with the actual embedded value, and a submarine cable embedding protecting project is evaluated. During embedding, by comparing the actual embedded value with the minimum embedded value corresponding to the undrained shear strength of the seabed geological soil, whether the embedding protecting project reaches the standard is judged, overall detection of the whole project is not required after construction is finished, and a large quantity of labor and financial resources are saved.
Owner:CSG EHV POWER TRANSMISSION
Method of correlating bid price to intrinsic value in a survey platform
An online survey platform and process for correlating the bid price offered by a supplier for the completion of an out-of-network survey hosted on the survey platform to one or more intrinsic value indicators of the survey. If the supplier's bid price is less than or equal to the survey budget price set by the buyer, then the routing platform of the present invention will route the supplier's respondent(s) to the survey.
Owner:LUCID HLDG LLC
Digital audio signal processing method
The invention provides a digital audio signal processing method, and the method comprises the specific steps: selecting frame 0 as an embedded audio frame based on an MP3 frame structure; selecting apredetermined embedded bit, and setting the predetermined embedded bit as a to-be-embedded value, wherein the scaling factor value of the frame edge information of the predetermined embedded bit is 0,and the predetermined embedded bit is located in the scaling factor of a predetermined band in a non-short window of an audio frame. The invention also provides a digital audio signal processing method, and the former frame 0 reads the value of the predetermined embedded bit of the scaling factor. The method can achieve the data embedding and reading of the former audio files or data after compression and coding.
Owner:李庆成 +1
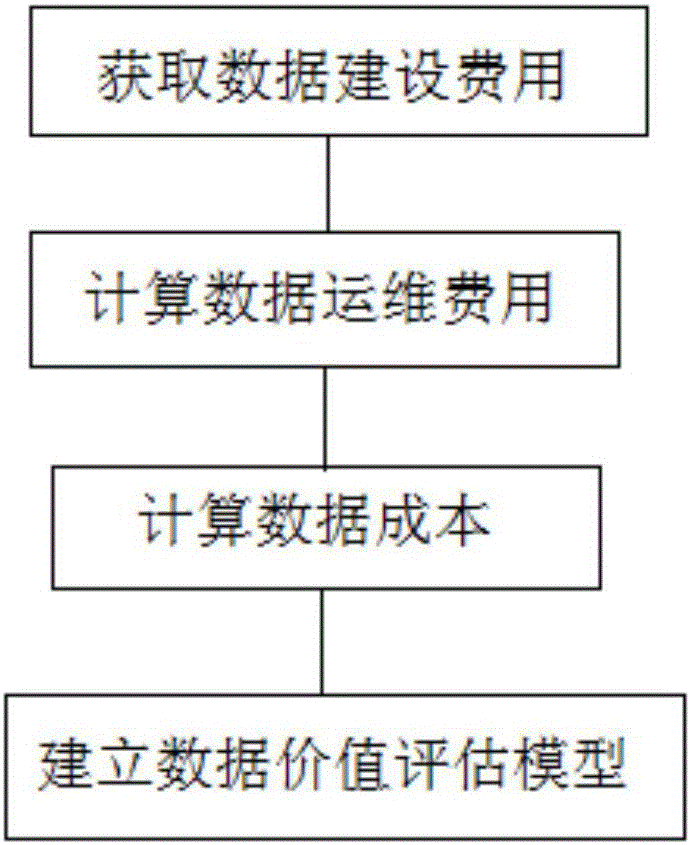
EVA (economic value added)-based modeling method of data value evaluation model
InactiveCN106529785ARealize multi-angle value evaluationEasy data managementResourcesEmbedded valueData operations
The invention relates to an EVA (economic value added)-based modeling method of a data value evaluation model. The method includes the following steps that: (1) data construction cost J is obtained, and data operation cost Y is calculated; (2) data cost P0 is calculated according to the data construction cost J and the data operation cost Y based on a formula that P0=J+Y; (3) an economic value added (EVA) is calculated according to a formula that EVA=W0-J, wherein EVA represents the economic value added, W0 represents data application economic benefits, and J represents the data construction cost; and (4) the data value valuation model is constructed. With the EVA (economic value added)-based modeling method of the data value evaluation model of the invention adopted, the internal value and use value of data can be expressed as quantitative indexes, multi-angle value evaluation on the data can be realized, the quantitative representation of the data value of an information system can be achieved, and the optimization of the data management of the information system can be promoted.
Owner:国网甘肃省电力公司信息通信公司 +2
Multi-head Intelligent Mutual Shift Cutting Control Method Based on Embedded Typesetting
ActiveCN103170749BIncrease profitUniform configurationSpecial data processing applicationsLaser beam welding apparatusEmbedded valueCross cut
The invention discloses a multi-head intelligent mutual mobile cropping control method based on embedded-type typesetting and relates to the raw material cutting field of stuffed toys and the shoemaking industry. The control method comprises the steps of establishing a template target, a line standardization target and a row standardization target which are needed by typesetting, respectively acquiring coordinates and template target parameters, and calculating line embedded value and row embedded value in the embedded-type typesetting; combining template target coordinates, the line embedded value and the row embedded value to calculate the coordinates of a copy template target and conduct the embedded-type typesetting; calculating the coordinates of respective starting cutting points of multiple heads, and controlling the multiple heads to move to the respective starting cutting points; and calculating the number of multiple head template targets to be cut, controlling the multiple heads to start cutting simultaneously, and respectively controlling light opening operation and light closing operation of laser. The multi-head intelligent mutual mobile cropping control method greatly improves the fabric utilization rate and cropping efficiency of raw materials, and brings convenient to control of the whole processing process by customers.
Owner:WUHAN GOLDEN LASER
Systems, devices, and methods for determining value of an entity based on stock price and financial data
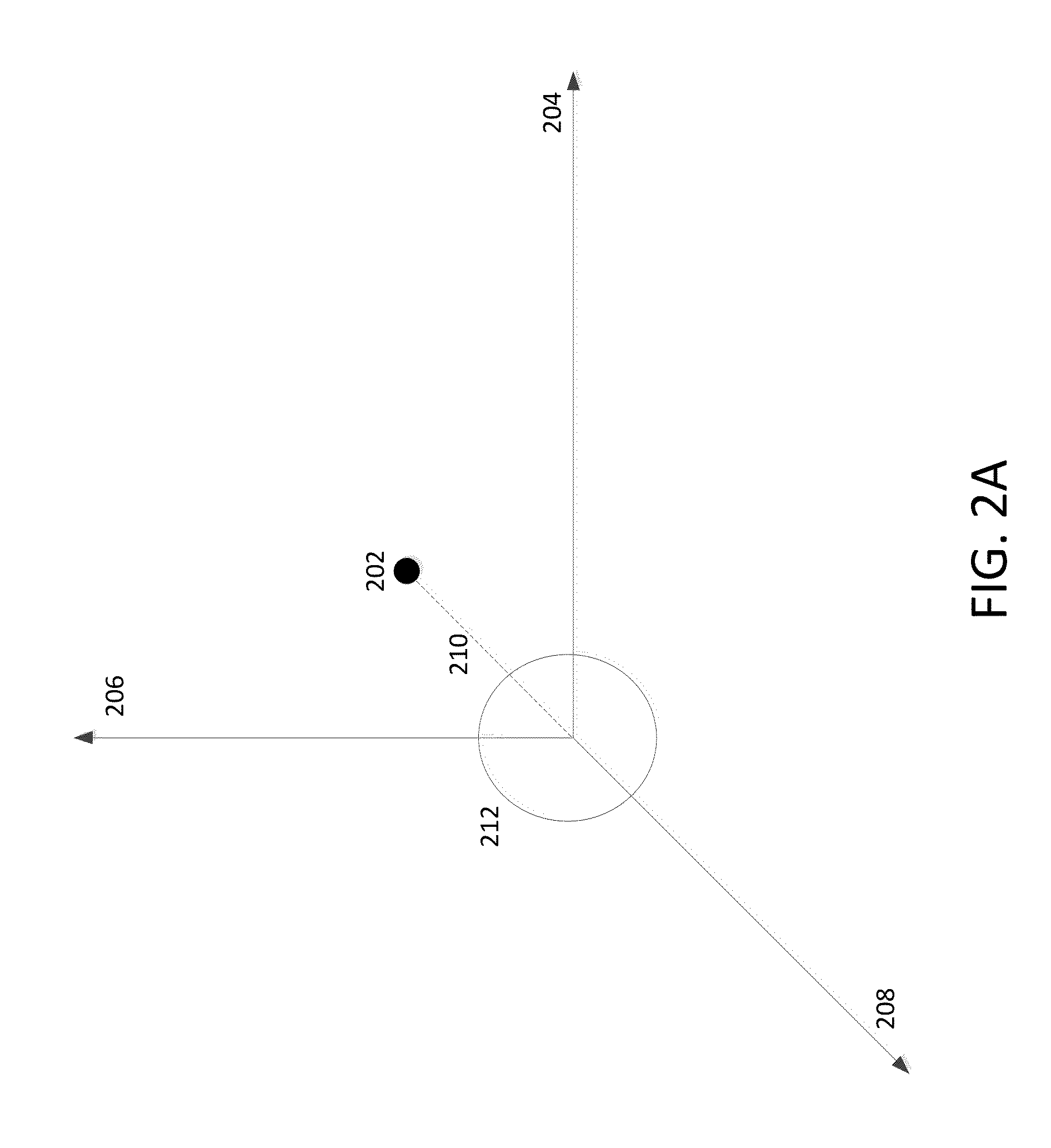
Embodiments of the present disclosure include a communication network and a financial data computer server coupled to a user computing device through the communication network. The financial data computer server stores and processes financial data information. The user computing device may request and receive, from the financial data computer server, a market price for a primary entity and three variables based on financial data information of the primary entity. Further, the user computing device may render a primary point in a three-dimensional scatter plot of the market price of the primary entity based on the three variables and calculate a spherical distance of the primary point to the origin to determine and compare market price to the intrinsic value of the primary entity based on the spherical distance and a predetermined threshold.
Owner:WERNHER MARKET APPL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com