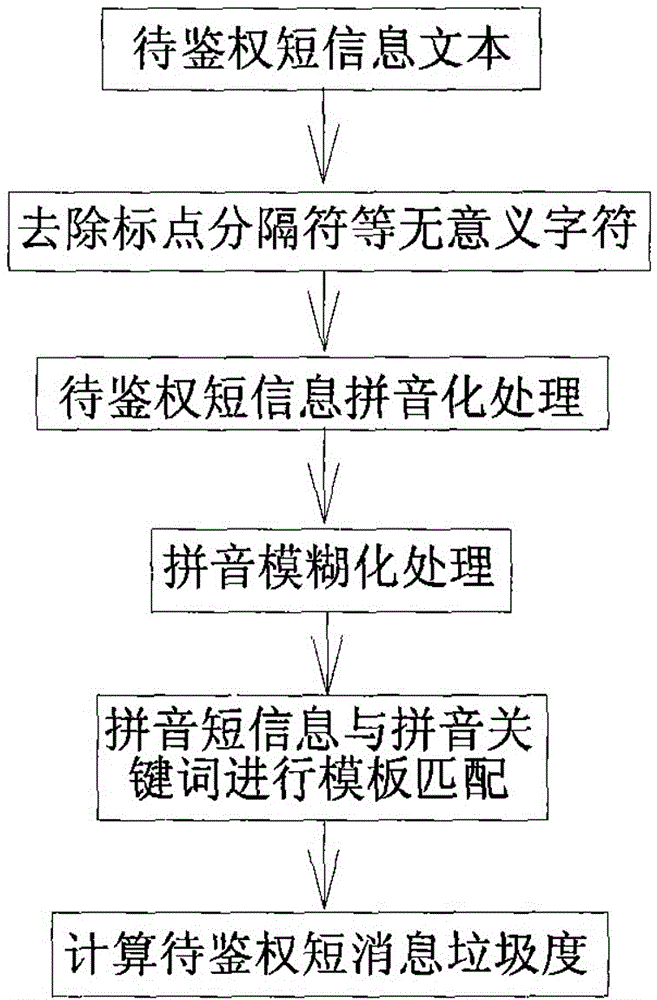
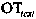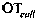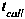Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "User confidence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
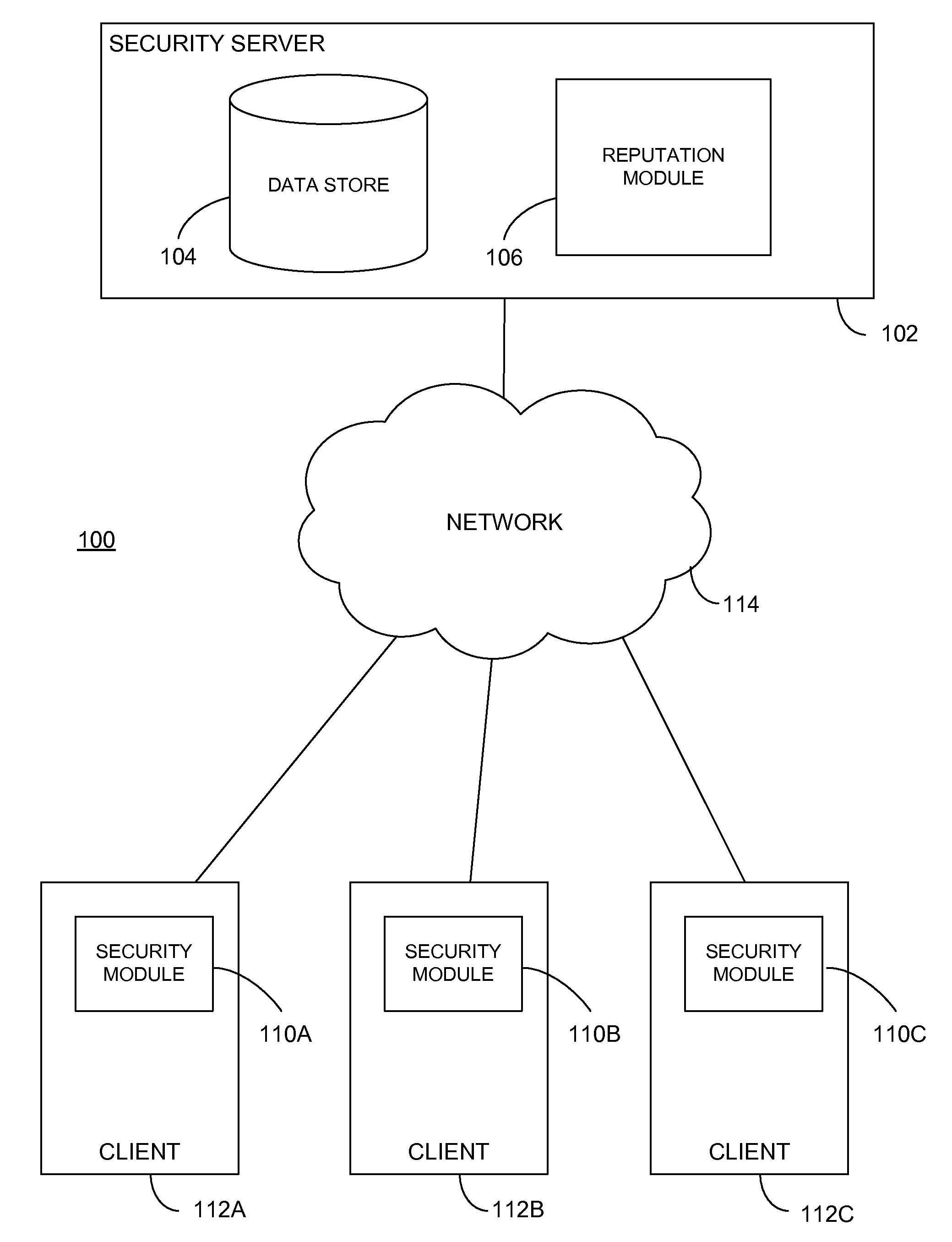
Using Confidence About User Intent In A Reputation System
ActiveUS20110040825A1Multiple digital computer combinationsPlatform integrity maintainanceConfidence metricUser confidence
Reputations of objects are determined by a reputation system using reports from clients identifying the objects. Confidence metrics for the clients are generated using information determined from the reports. Confidence metrics indicate the amounts of confidence in the veracity of the reports. Reputation scores of objects are calculated using the reports from the clients and the confidence metrics for the clients. Confidence metrics and reputation scores are stored in correlation with identifiers for the objects. An object's reputation score is provided to a client in response to a request.
Owner:CA TECH INC
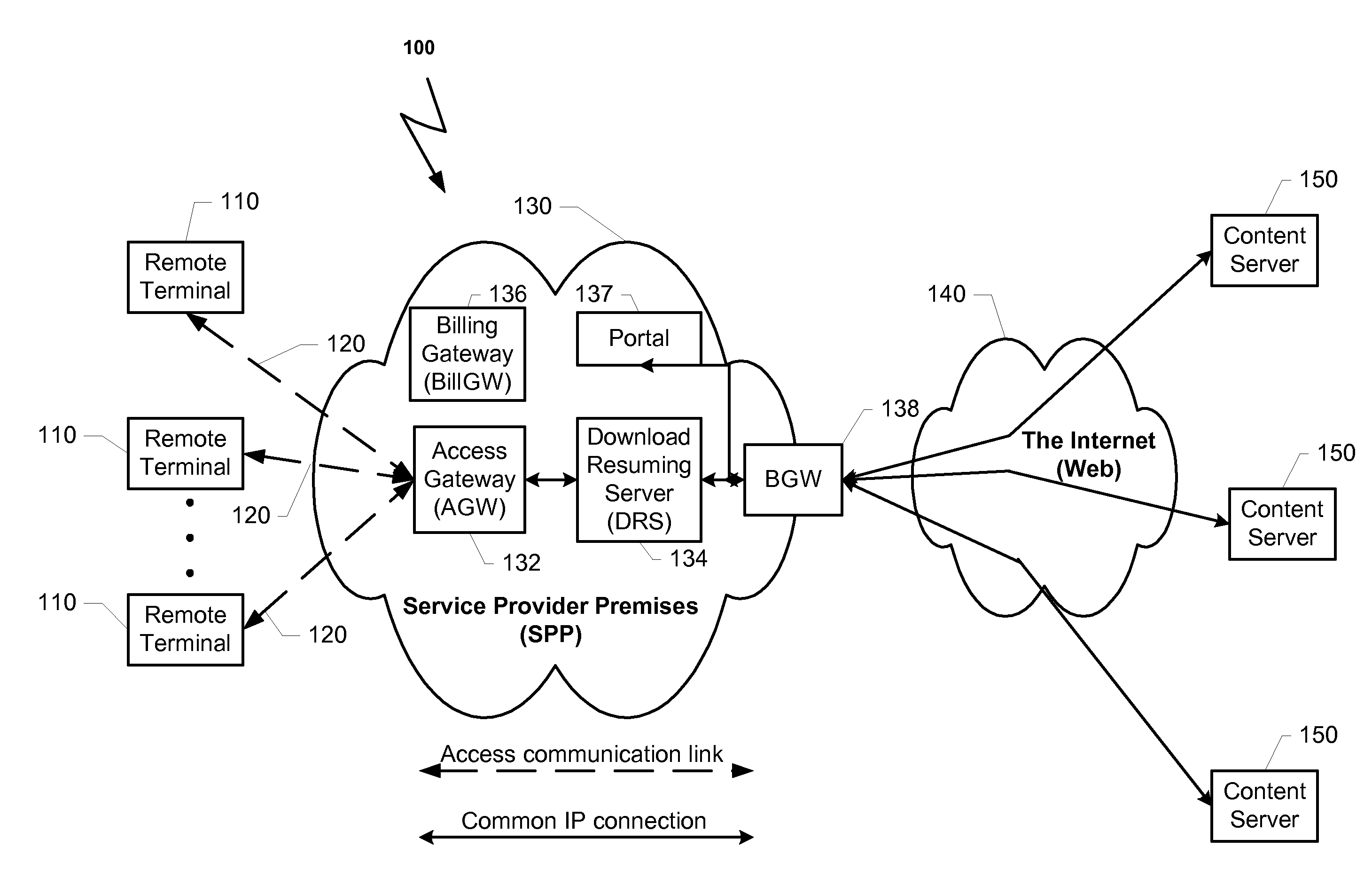
Method and system for improving user confidence and experience in content purchasing via a service provider premises
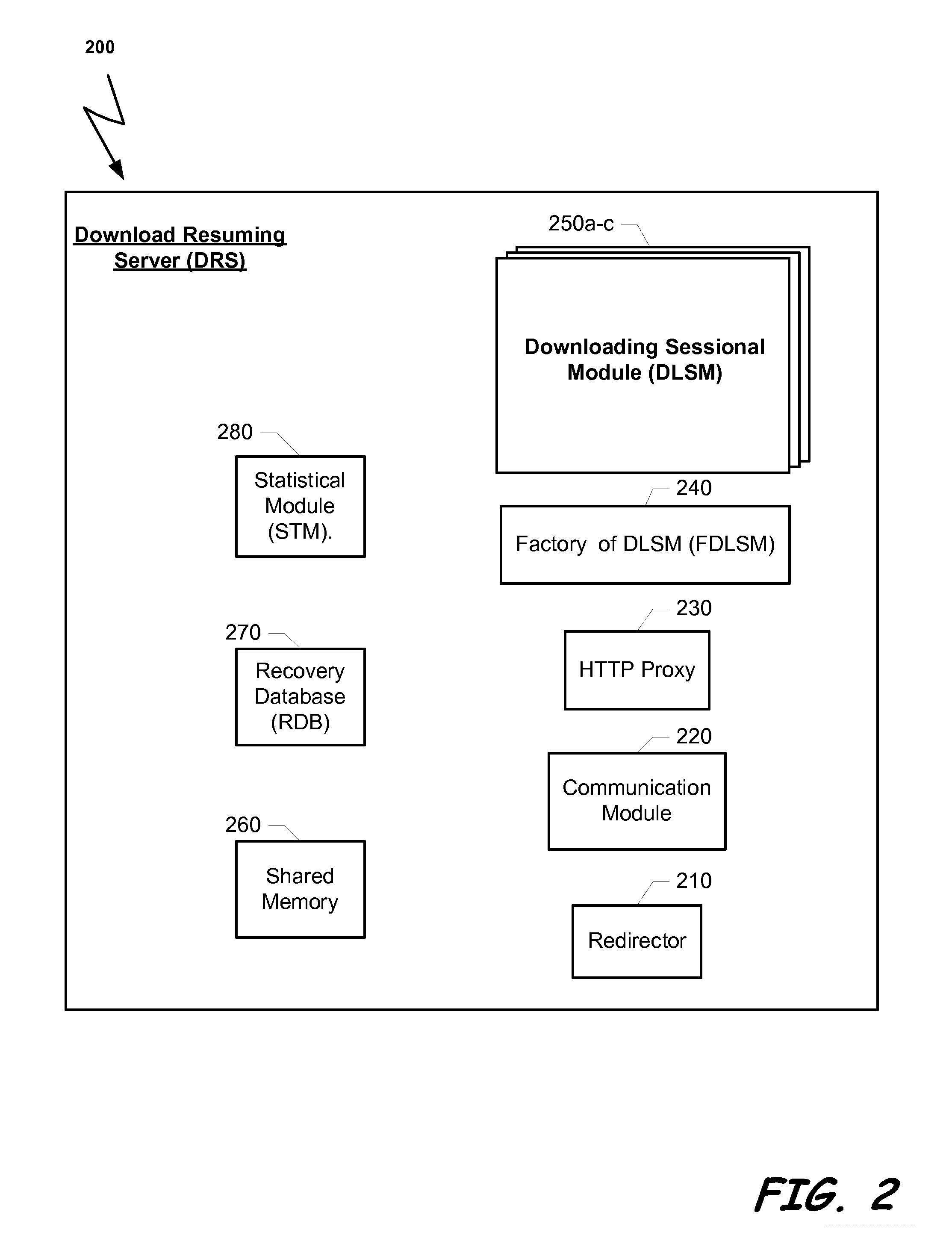
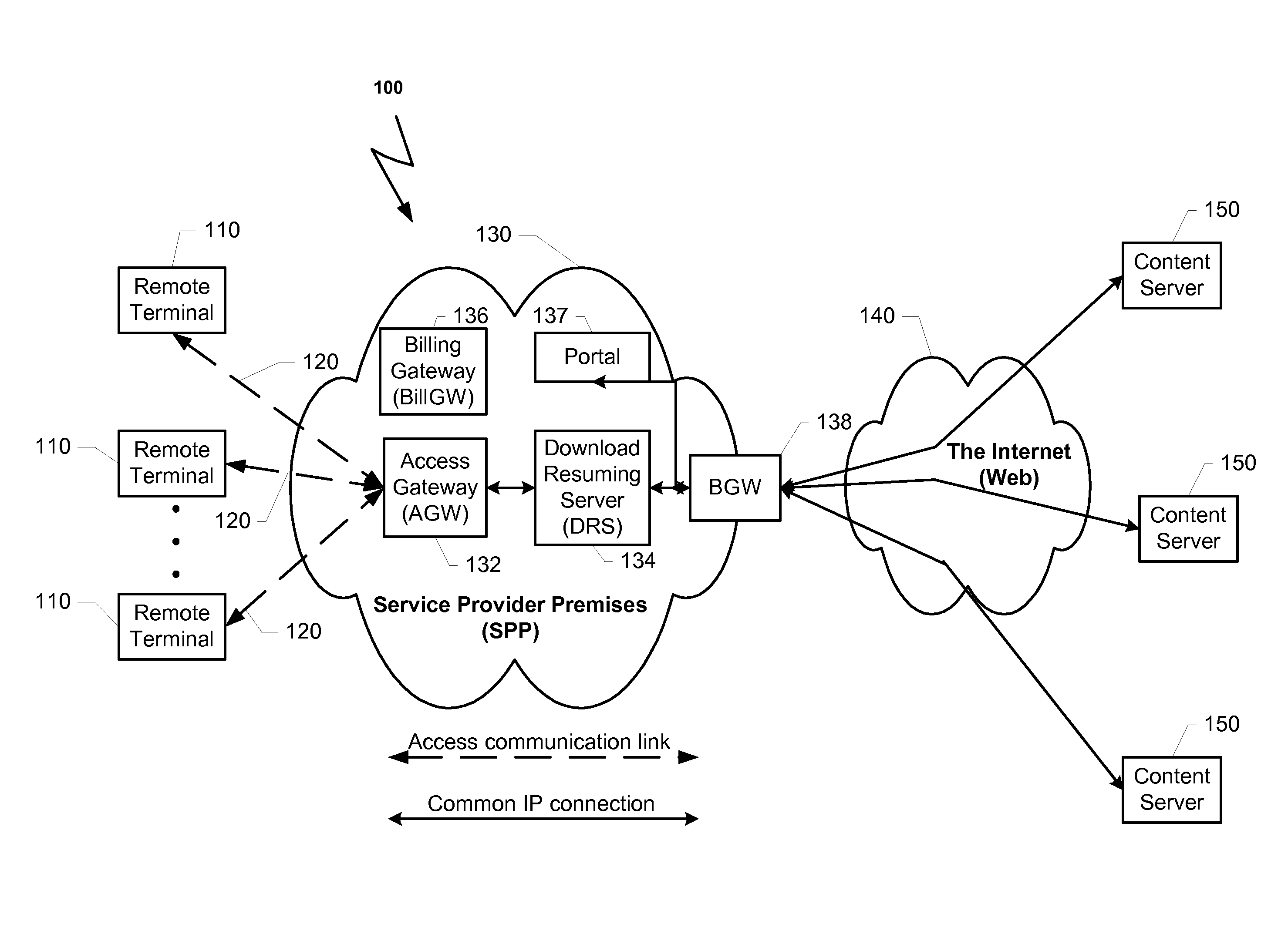
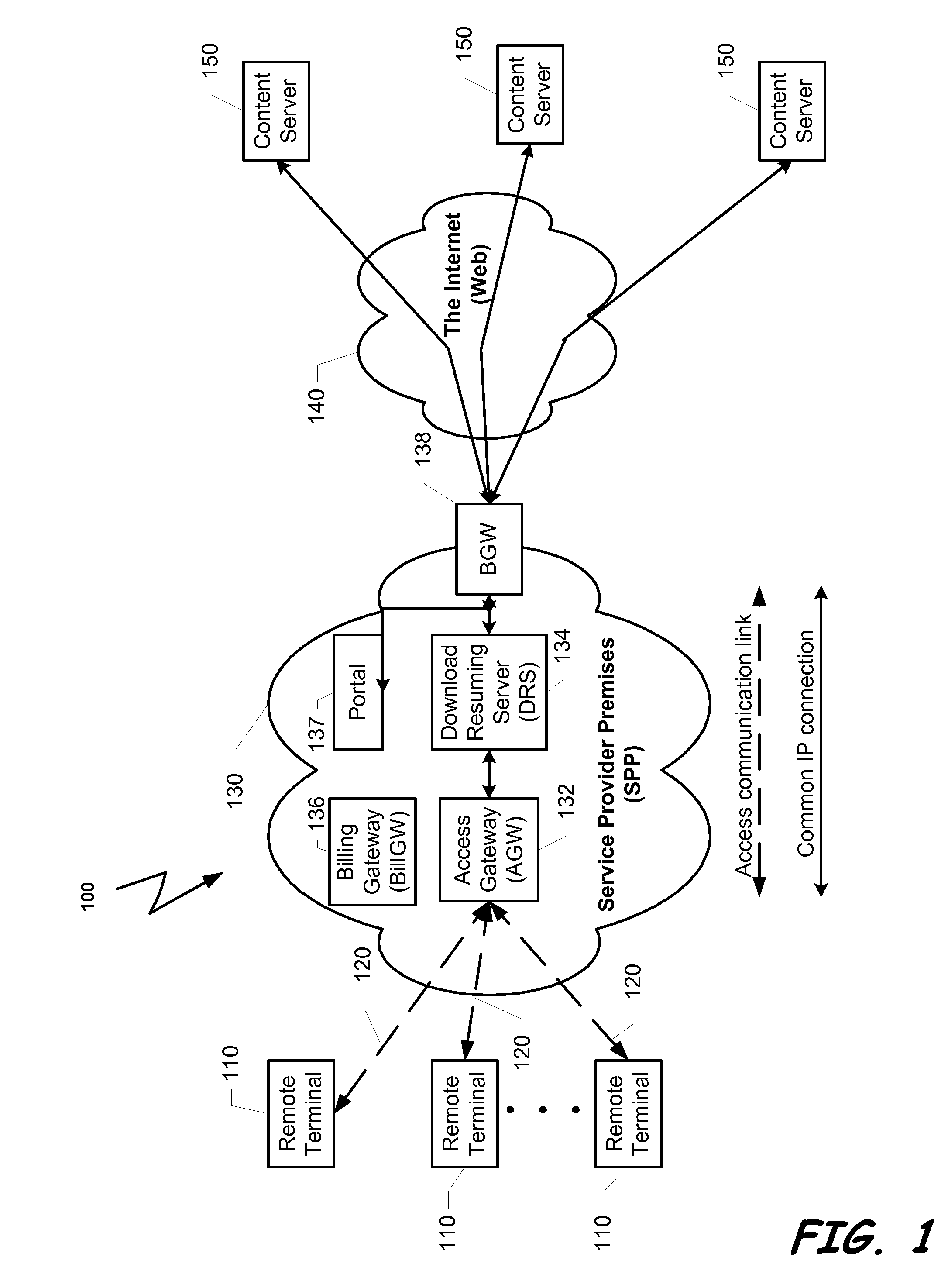
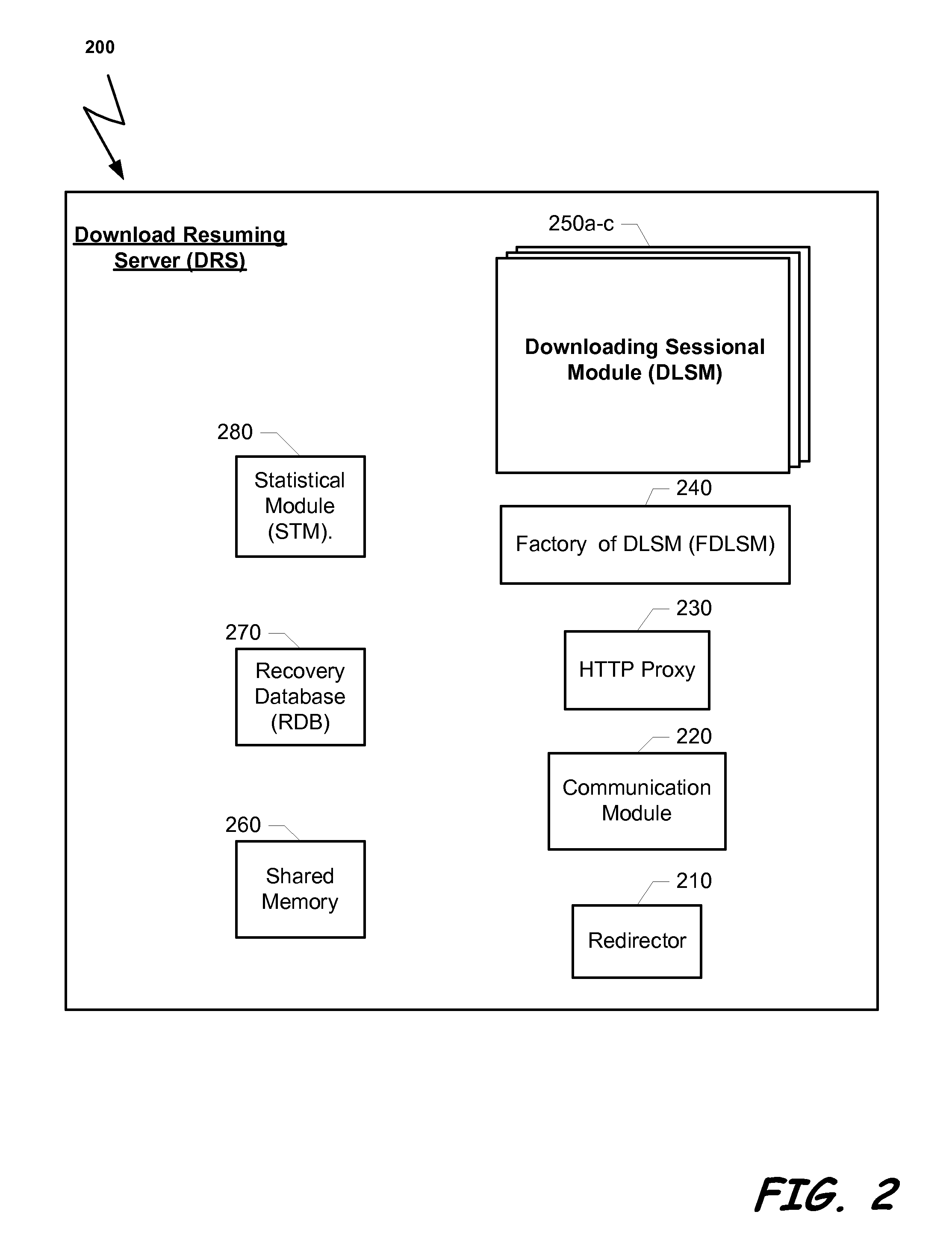
ActiveUS20070127515A1Shorten the timeEasy to identifyStore-and-forward switching systemsLoop networksThe InternetUser confidence
A system that listens to the data traffic running over the Service Provider Premises between the plurality of surfers and the Internet. The system can identify downloading of a content object. The data transportation of each user can be parsed for identifying a connection that is involved in downloading a content object from a content server. When a downloading of a content object is identified, the download process is monitored and resuming information is stored. In case that the download process is incompletely terminated the stored resuming information can be used to accelerate the response to a request to renewal the download process of the same object.
Owner:FLASH NETWORKS
Hybrid collaborative filtering recommendation algorithm based on project attributes
ActiveCN109783734AHigh similarityStrong explainabilityDigital data information retrievalCharacter and pattern recognitionNear neighborRating matrix
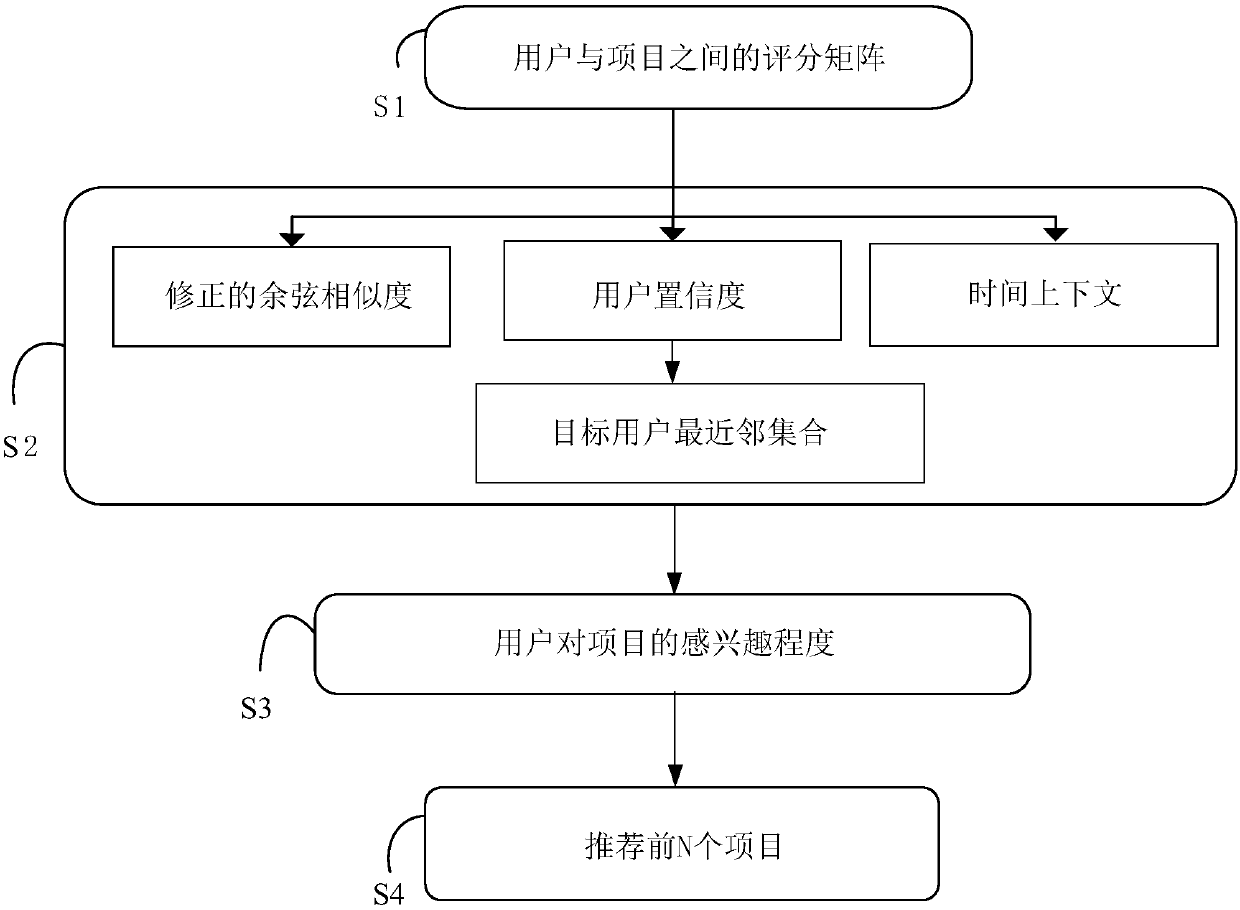
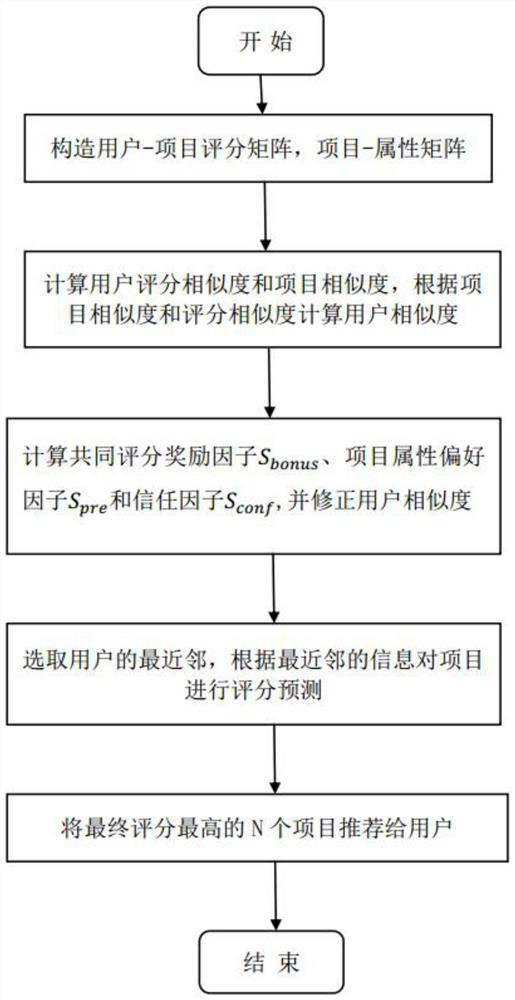
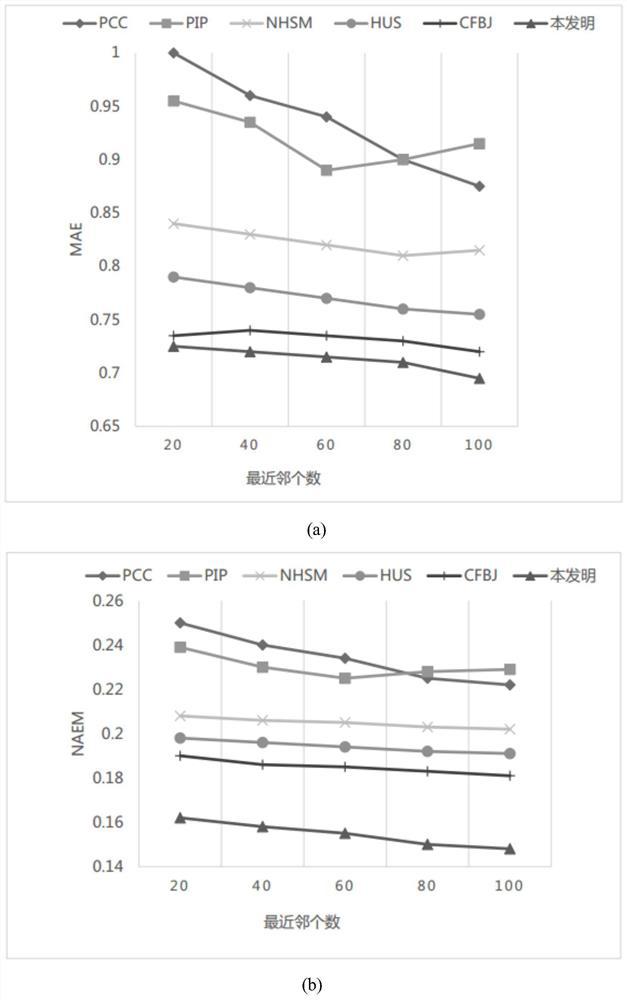
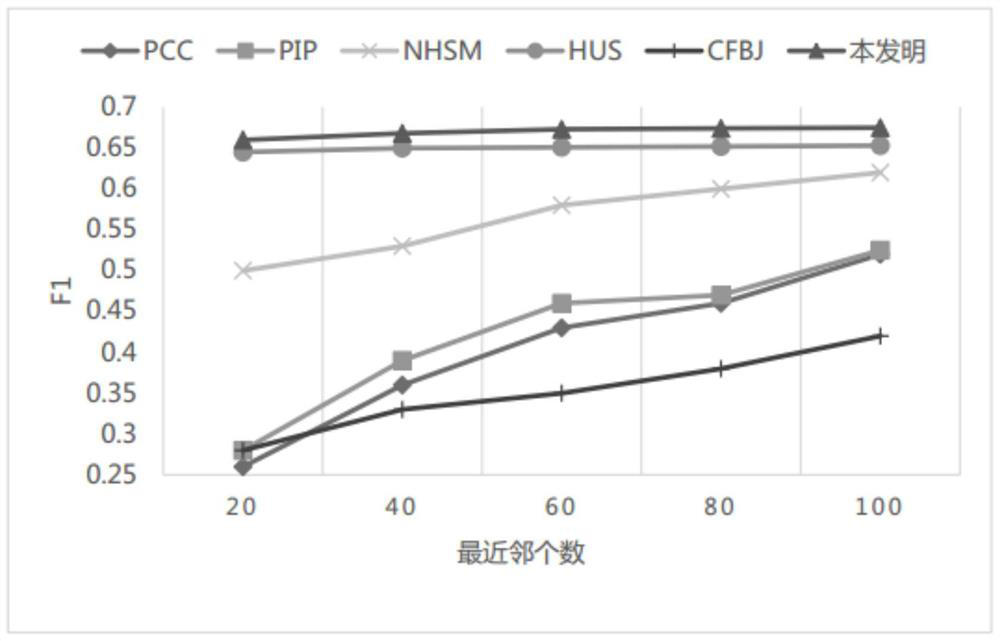
The invention discloses a hybrid collaborative filtering recommendation algorithm based on project attributes. The algorithm comprises the following steps: step 1, generating a user-project scoring matrix and a project-attribute matrix according to user scoring information and project information; step 2, respectively calculating project similarity and user scoring similarity according to the project-attribute matrix and the user-project scoring matrix; step 3, correcting the user score similarity by utilizing the project similarity to calculate the user similarity; step 4, calculating a common score reward factor, a project attribute preference factor and a user confidence coefficient factor to correct user similarity and obtain user final similarity; step 5, selecting the nearest neighbor of the target user according to the final similarity, and predicting the score of the target user on each project based on the score information of all the users in the nearest neighbor; And step 6,recommending the N projects with the highest scores to the target user. The method can be applied to sparse data, and recommendation accuracy can be improved.
Owner:HUNAN UNIV
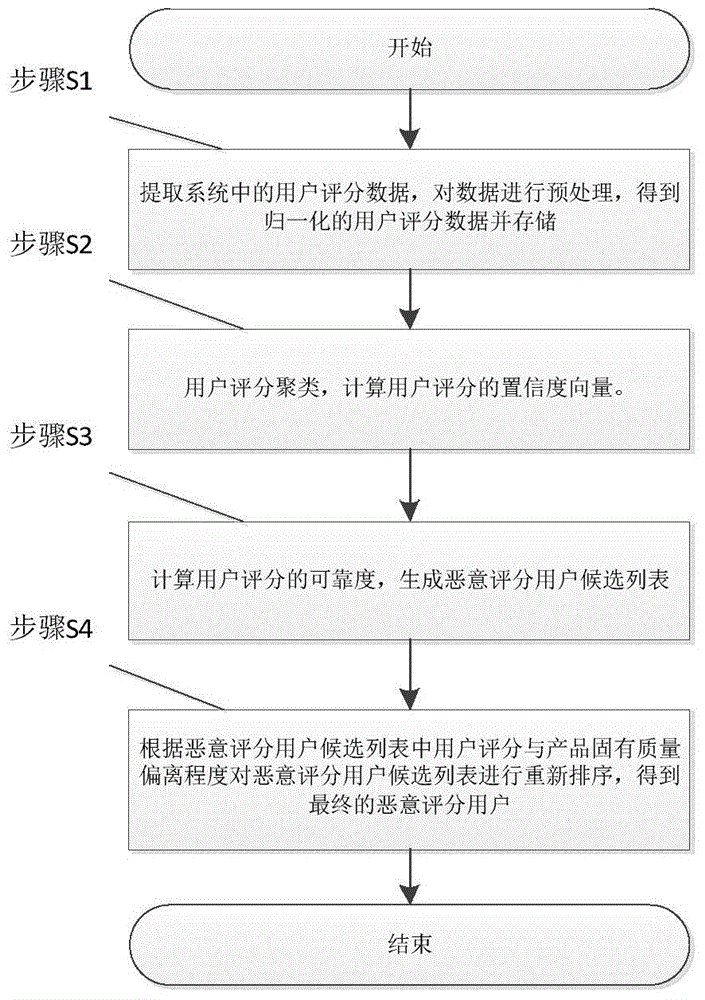
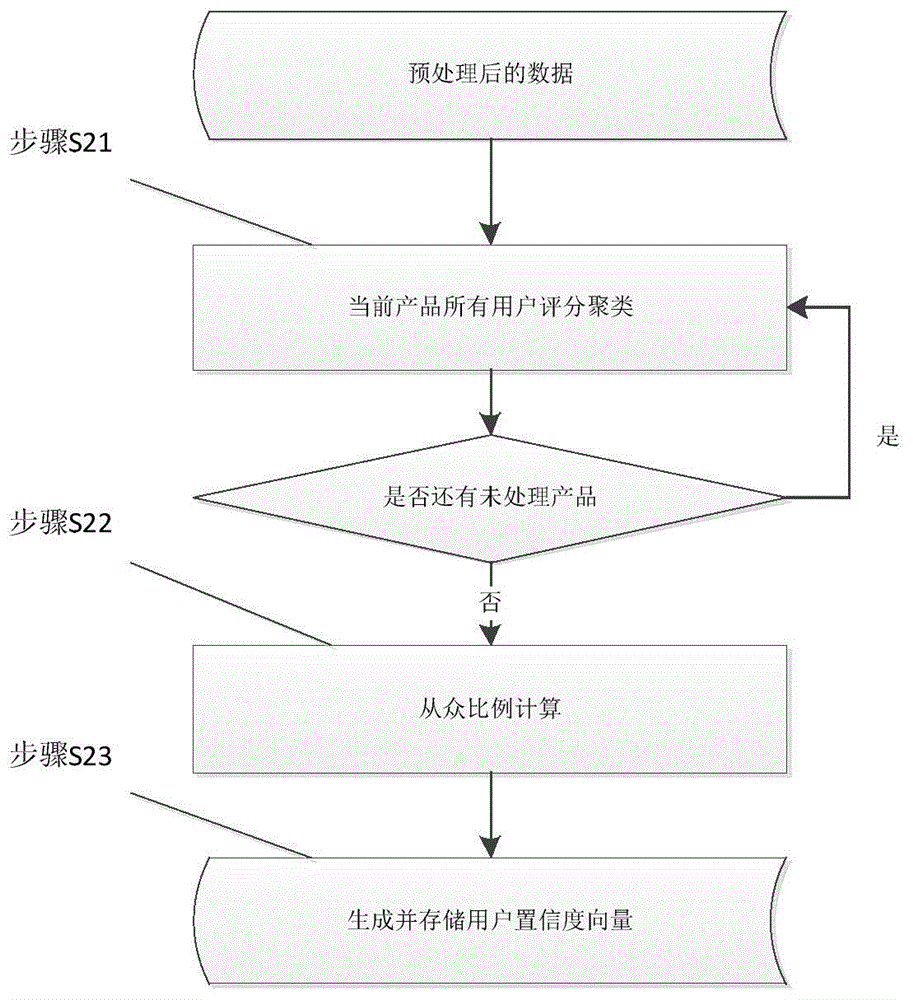
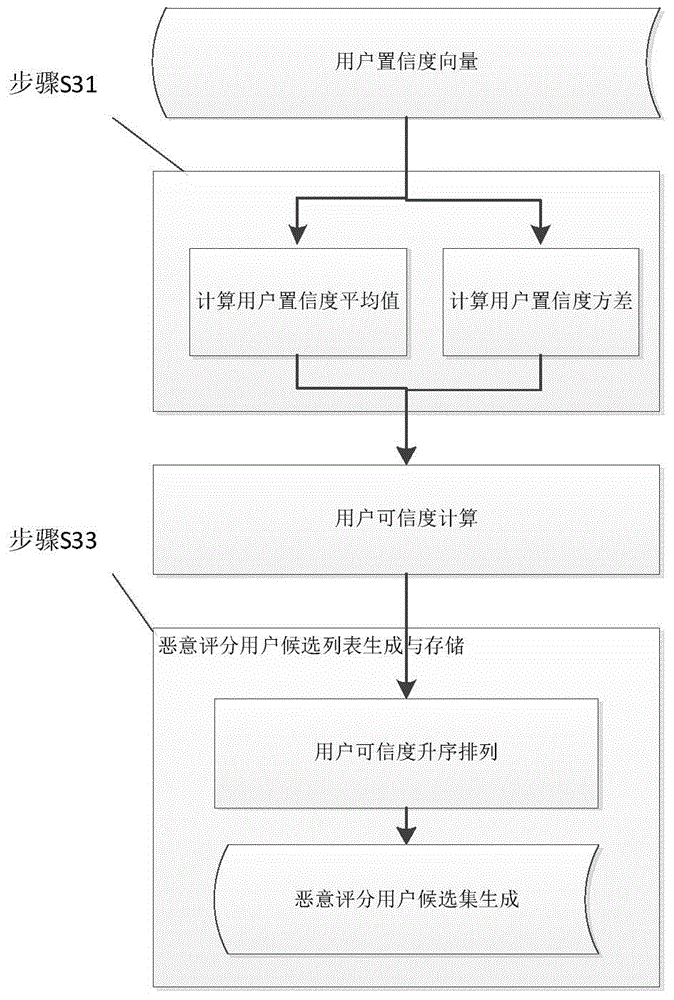
Method for detecting users who score maliciously in online social media system
InactiveCN104463601AReduce processing complexityImprove detection efficiencyCommerceSocial mediaConfidence metric
The invention discloses a method for detecting users who score maliciously in an online social media system. The method for detecting users who score maliciously in the online social media system arms at scoring feedback. Firstly, clustering is conducted according to scores for products by users, and the normalized user confidence degree is calculated; secondly, the reliability degree of user scoring is calculated according to the user confidence degree to obtain a candidate list of the users who score maliciously; finally, candidate users who score maliciously are sorted in combination with the deviation degree of user scoring and product quality to obtain the final list of the users who score maliciously. The method has advantages in the aspects of calculation accuracy and efficiency and can be applied to large-scale online social media websites.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Image Processing Apparatus, Image Processing Method, and Computer Program
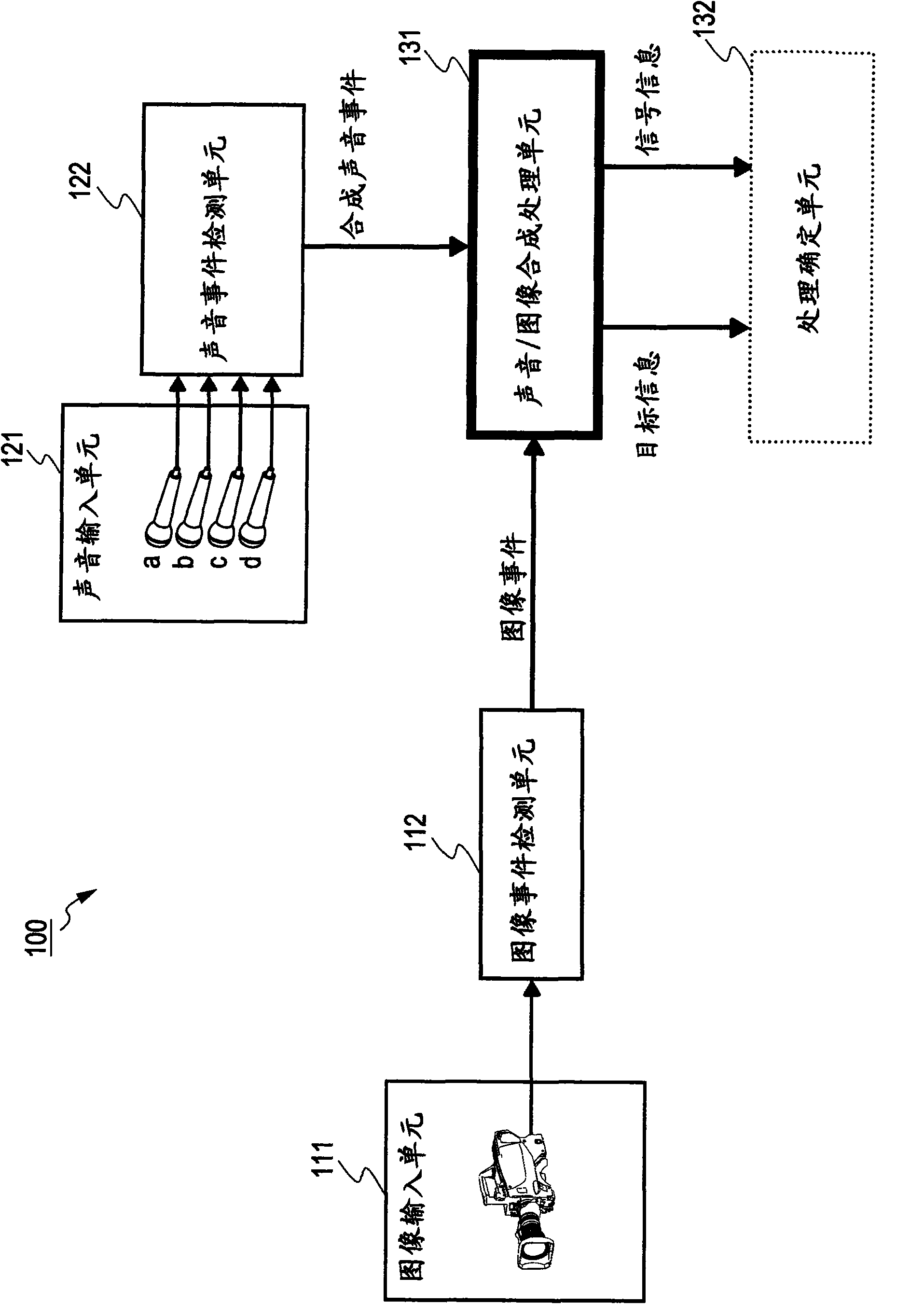
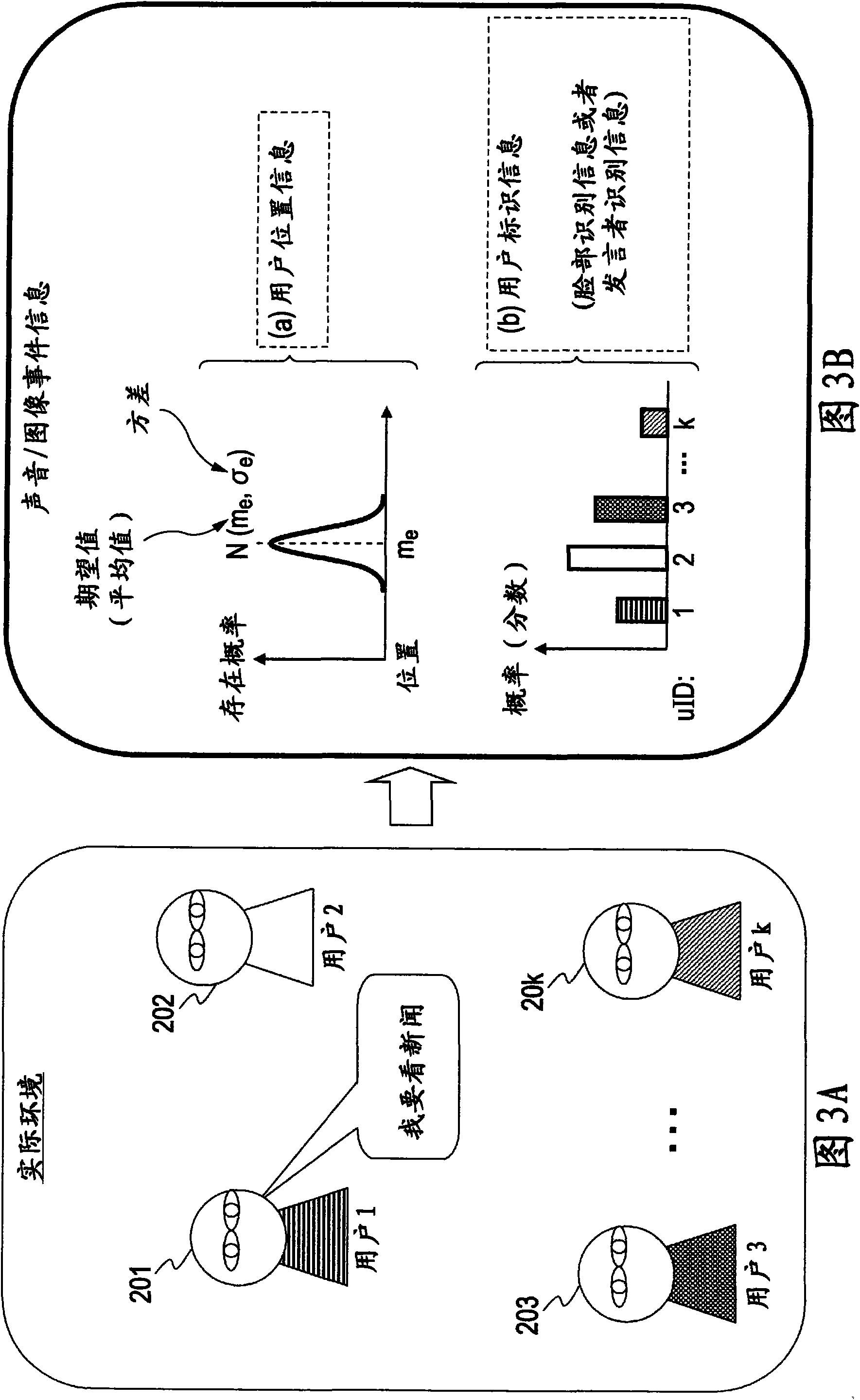
InactiveUS20100036792A1Efficiently execute processingImprove accuracyImage enhancementImage analysisInformation processingData set
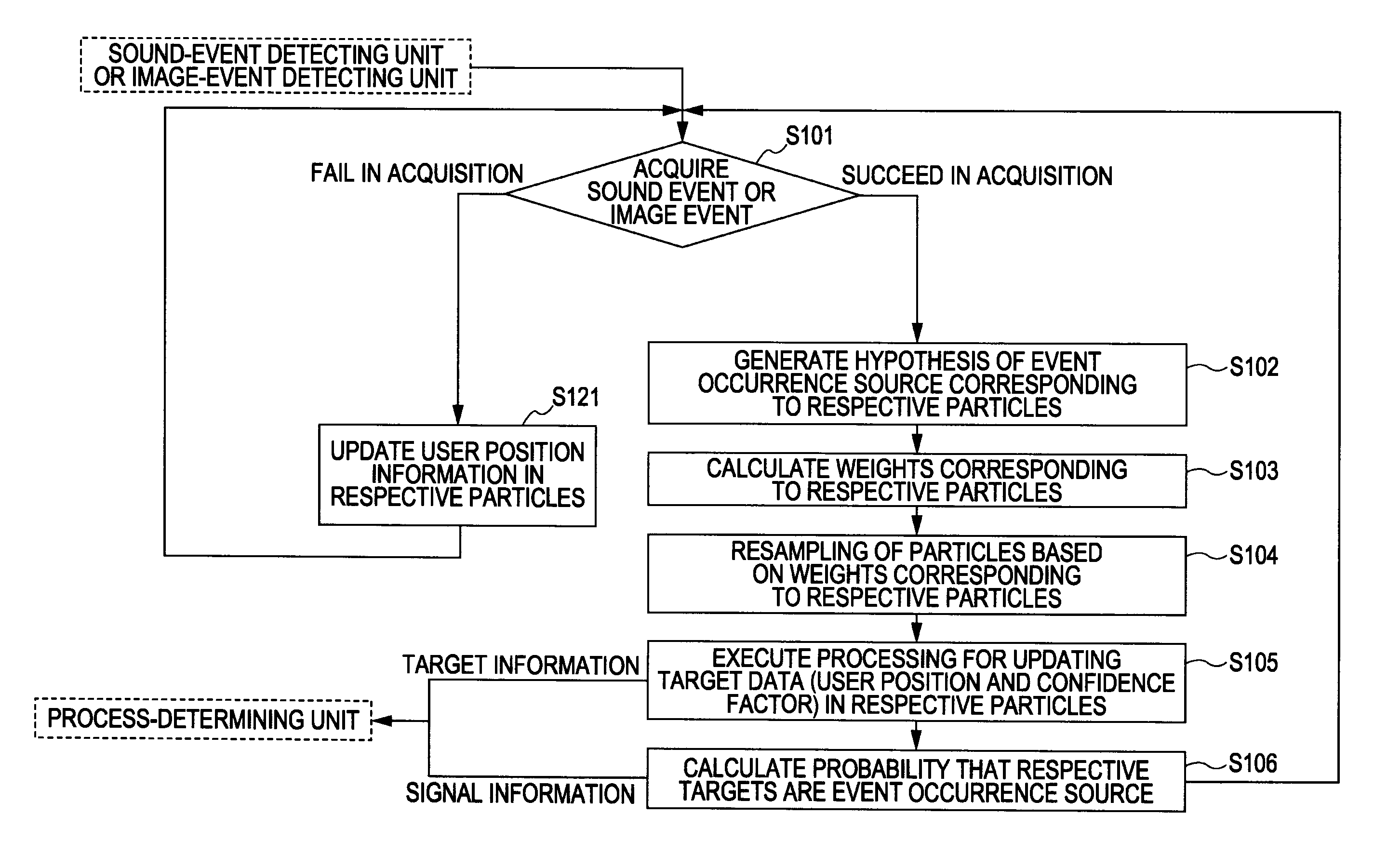
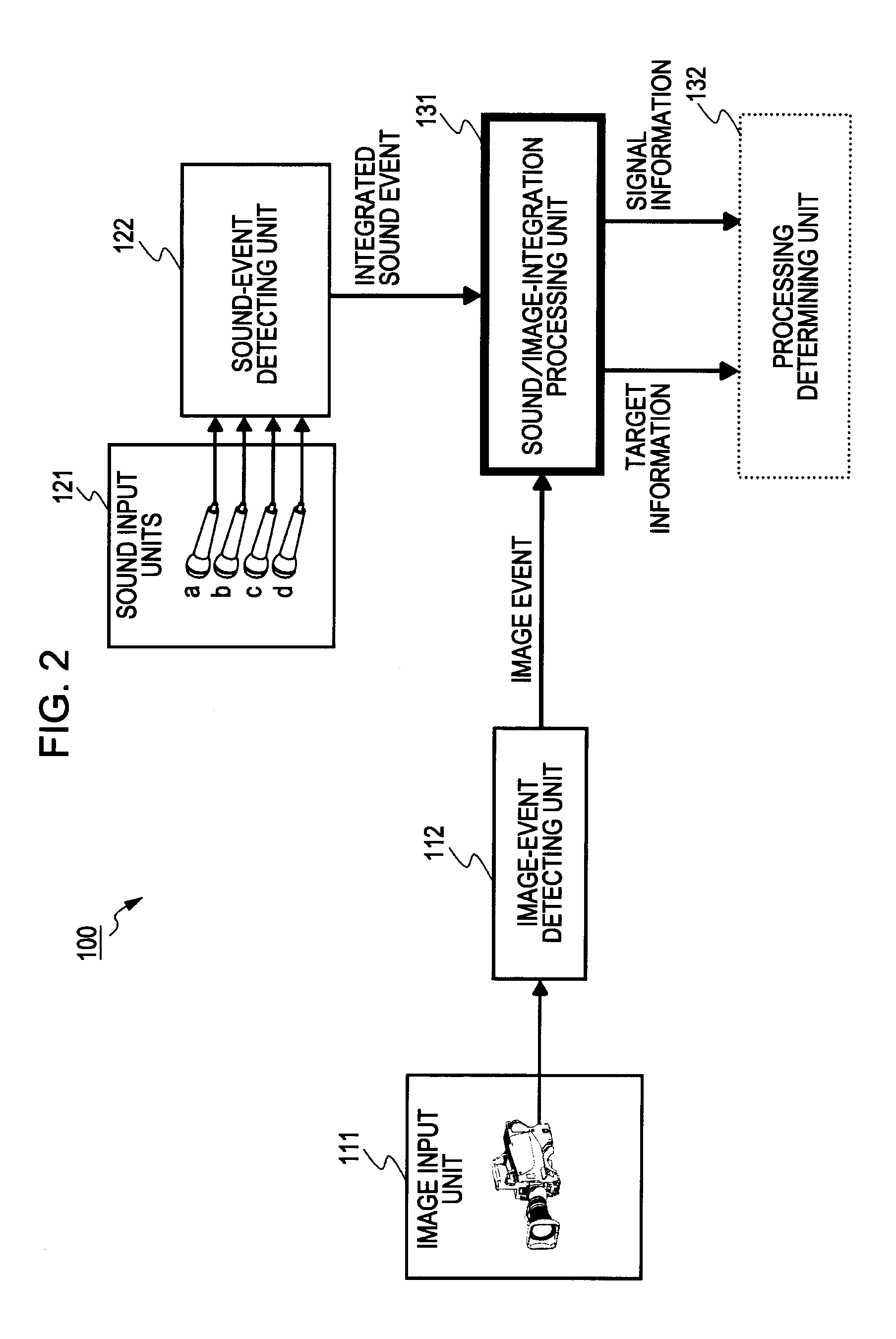
An information processing apparatus includes information input units, an event detecting unit, and an information-integration processing unit. Observed values including user identification data are obtained based on image and sound information from the information input units such as a camera and a microphone. Target data set with plural user confidence factors is updated and user identification is then performed. The user identification information in the observed values is used for updating the simultaneous occurrence probability of candidate data by which targets are corresponded with respective users. The updated value of such probability is used for calculating the user confidence factors corresponding to the targets.
Owner:SONY CORP
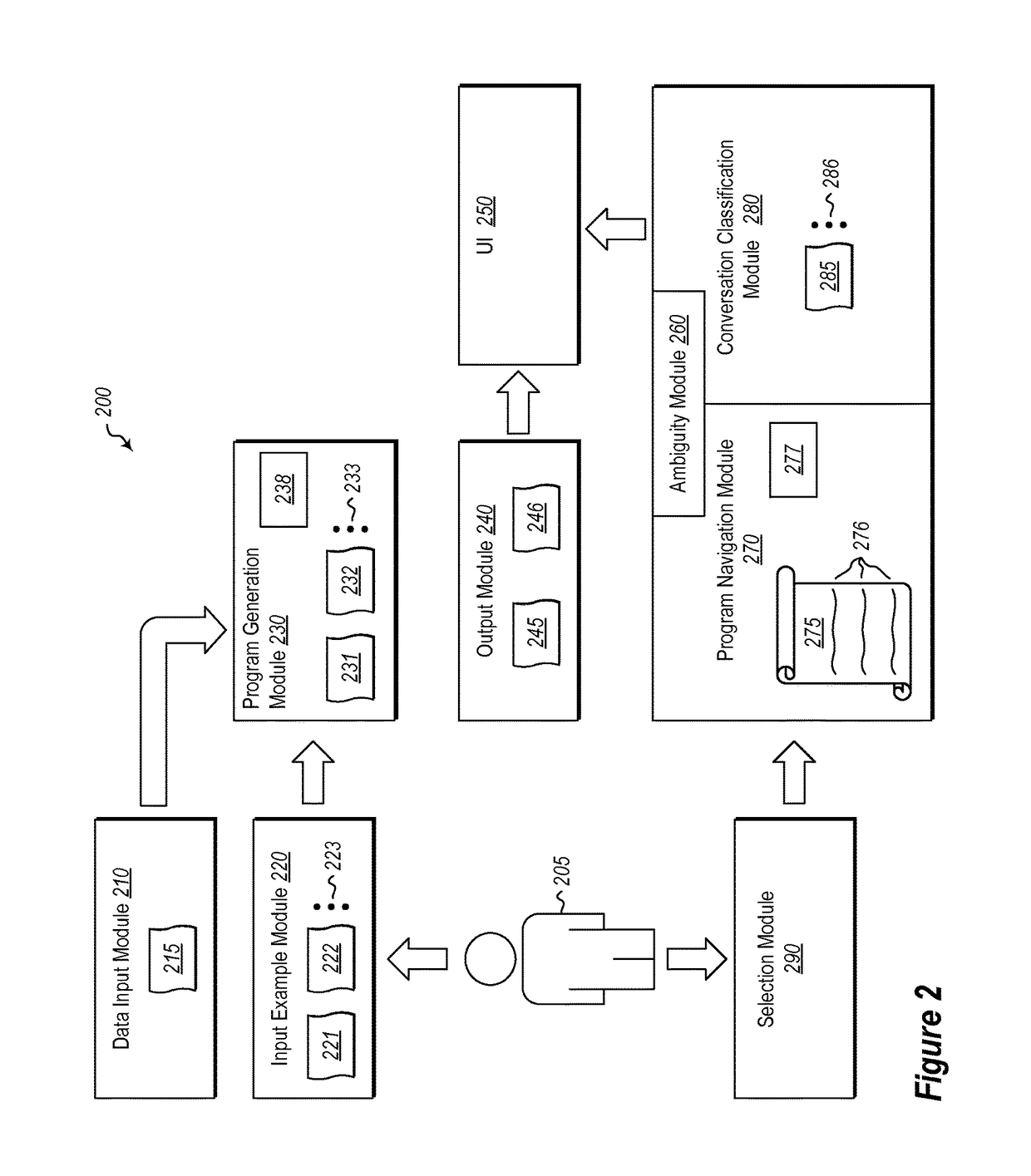
User interaction models for disambiguation in programming-by-example
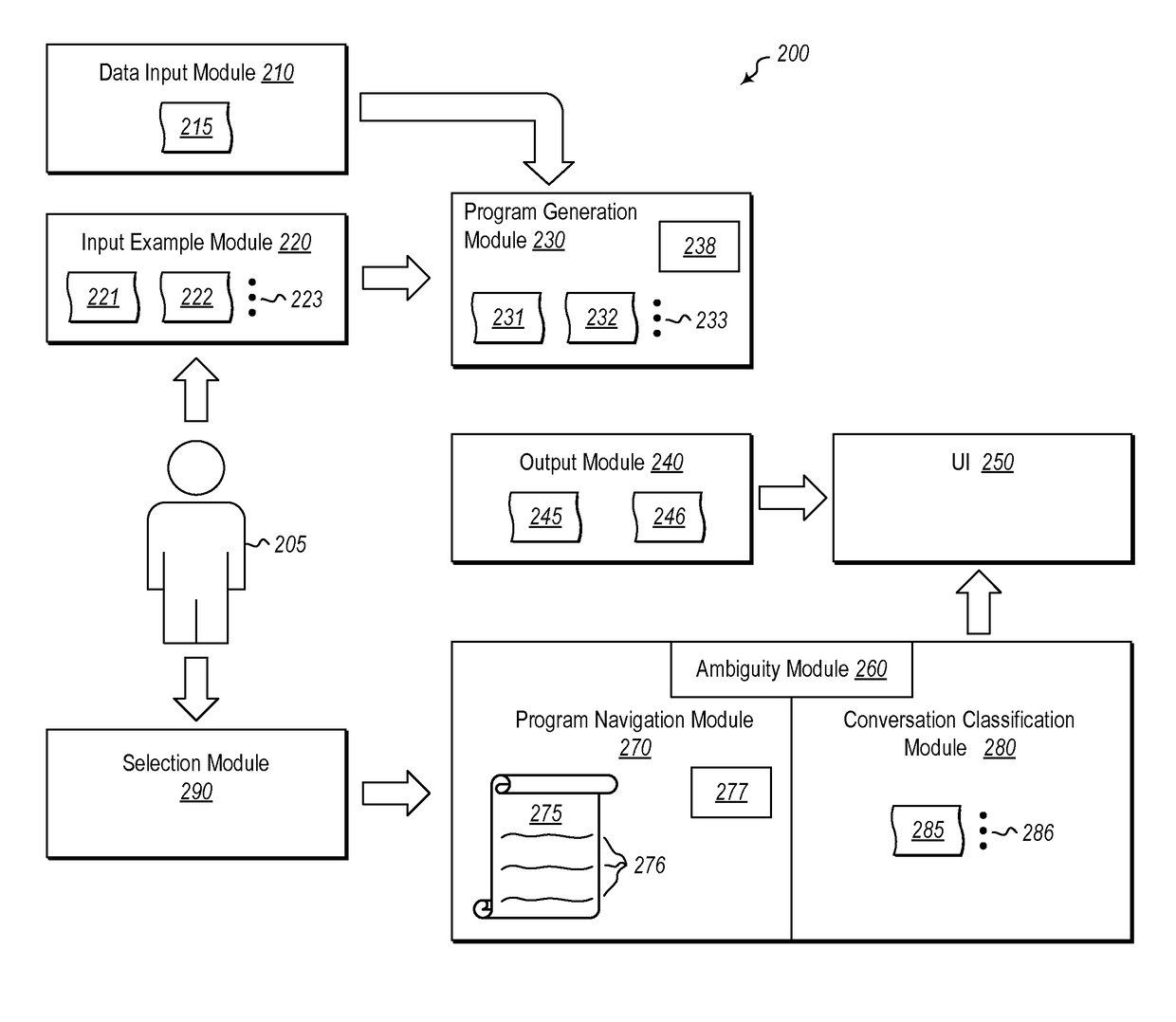
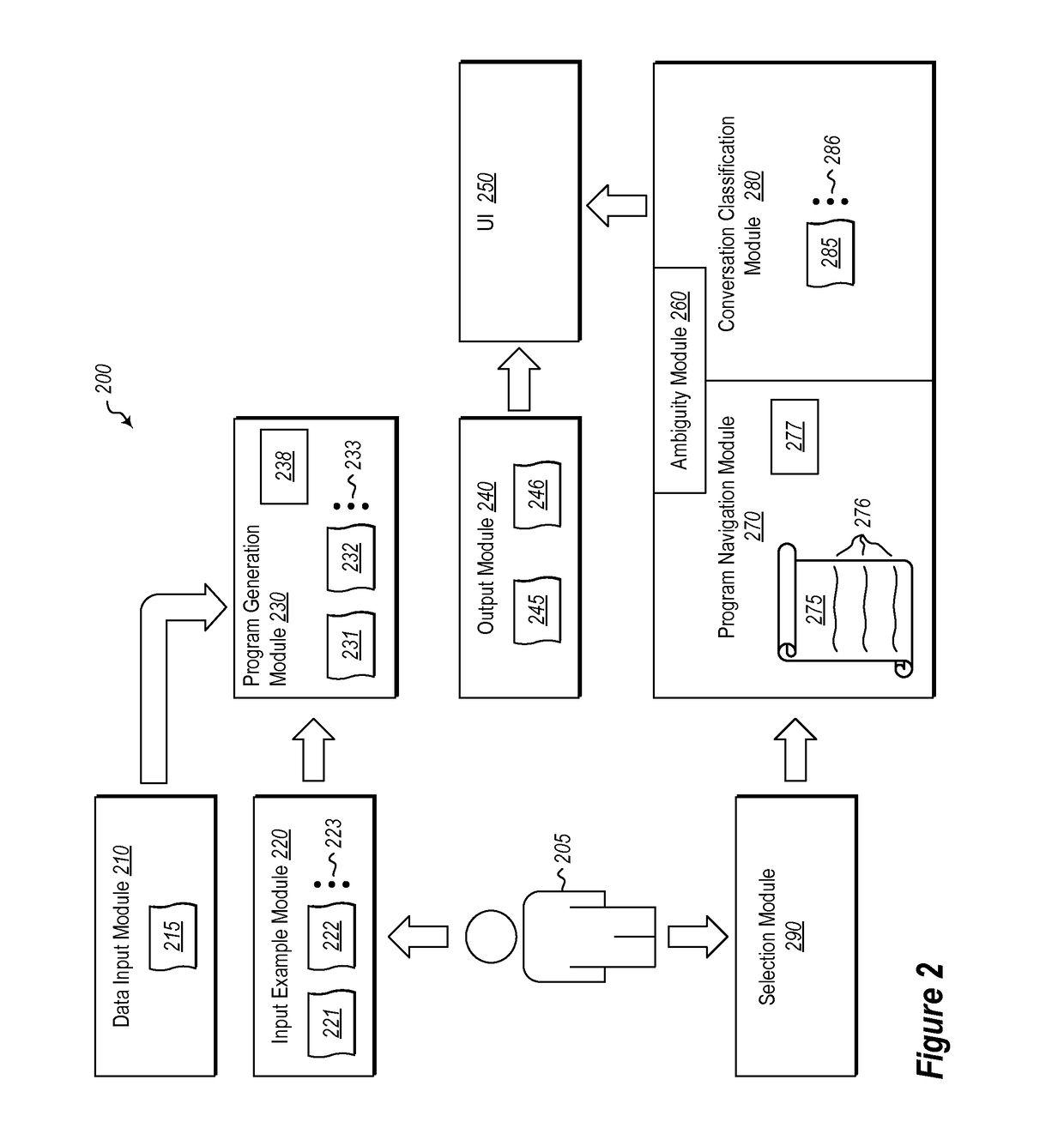
ActiveUS20170075661A1Users' confidence is enhancedConfidenceVersion controlSoftware testing/debuggingUser inputConfidence metric
Systems and methods for increasing user confidence in results that are produced by one or more programs that are generated by an underlying Programming-By-Example (PBE) system based on user input examples. A plurality of generated programs that have been generated using one or more user input examples that are indicative of an output that should be achieved to comply with a user determined result are received. The generated programs are narrowed based on one or more sub-expressions of the programs that are likely to cause the resultant program to comply with the user determined result. The one or more sub-expressions are exposed. Input that selects at least one of the one or more exposed sub-expressions to thereby identify the one of the generated programs that will result in the user determined result is received.
Owner:MICROSOFT TECH LICENSING LLC
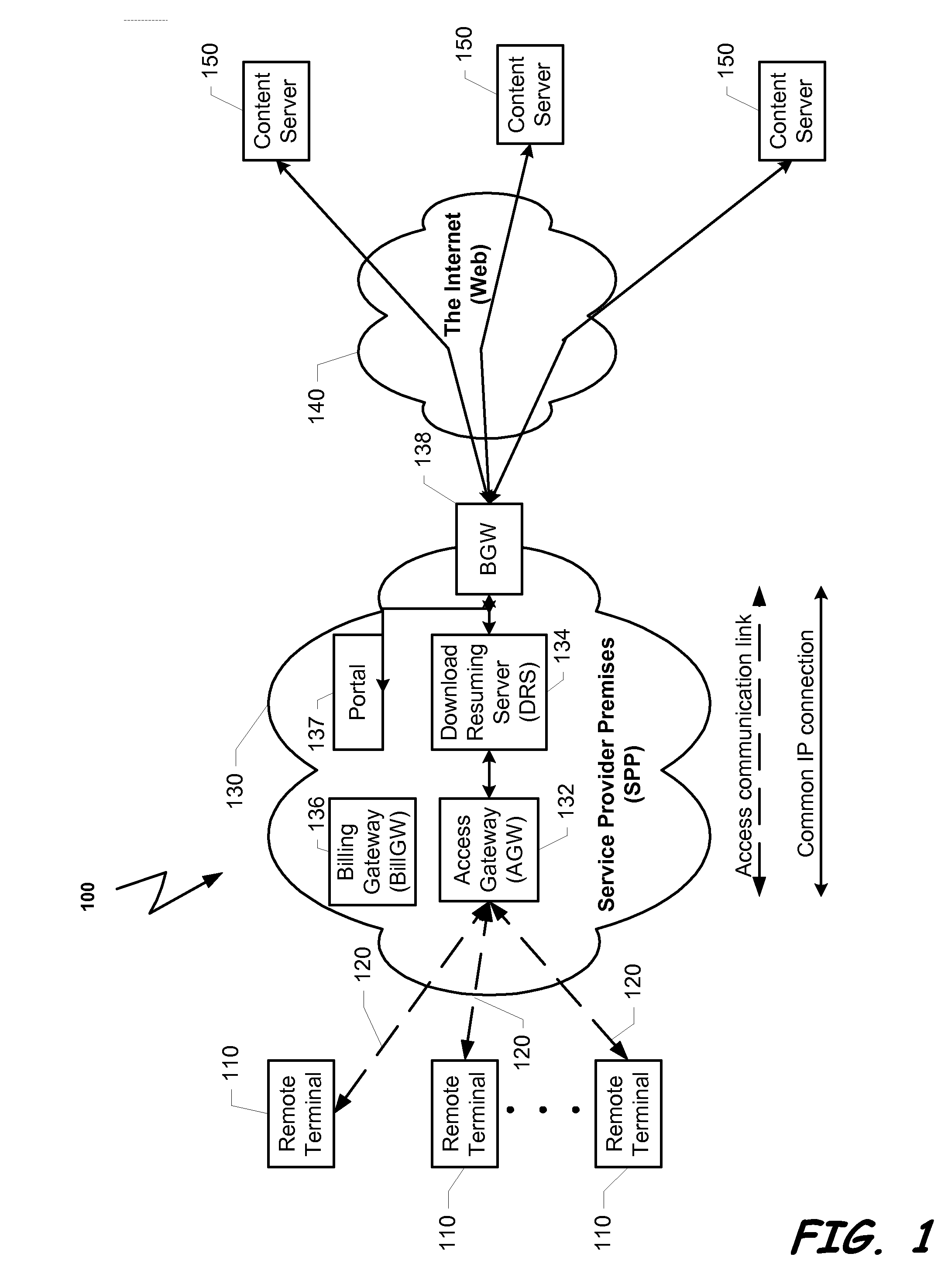
Method and system for improving user confidence and experience in content purchasing via a service provider premises
ActiveUS8214827B2Easy to identifyShorten the time intervalMultiple digital computer combinationsStore-and-forward switching systemsThe InternetUser confidence
A system that listens to the data traffic running over the Service Provider Premises between the plurality of surfers and the Internet. The system can identify downloading of a content object. The data transportation of each user can be parsed for identifying a connection that is involved in downloading a content object from a content server. When a downloading of a content object is identified, the download process is monitored and resuming information is stored. In case that the download process is incompletely terminated the stored resuming information can be used to accelerate the response to a request to renewal the download process of the same object.
Owner:FLASH NETWORKS
Statistical test device and method for verifying safety failure rate of nuclear safety class instrumentation and control platform
The invention discloses a statistical test device for verifying safety failure rate of a nuclear safety class instrumentation and control platform. The device comprises a statistical test unit, a driving unit, an information acquisition unit and a storage unit. The information acquisition unit is connected with the statistical test unit through the driving unit; and the statistical test unit realizes data interaction with the storage unit. According to a statistical test method based on the statistical test device, by carrying out system-level safety failure rate test in the platform development phase, possible defects of refusal of operation and misoperation in actual operation can be found in advance, thereby reducing maintenance cost and preventing safety risks; and meanwhile, actual measurement evidences are provided to check whether the platform meets nuclear power plant safety level instrumentation and control system safety failure rate indexes, and thus user confidence can be improved. Operation refusal rate is tested through a signal value random input method, thereby breaking a fixed input combination mode, and improving defect detection percentage to the maximum degree.
Owner:CHINA TECHENERGY +1
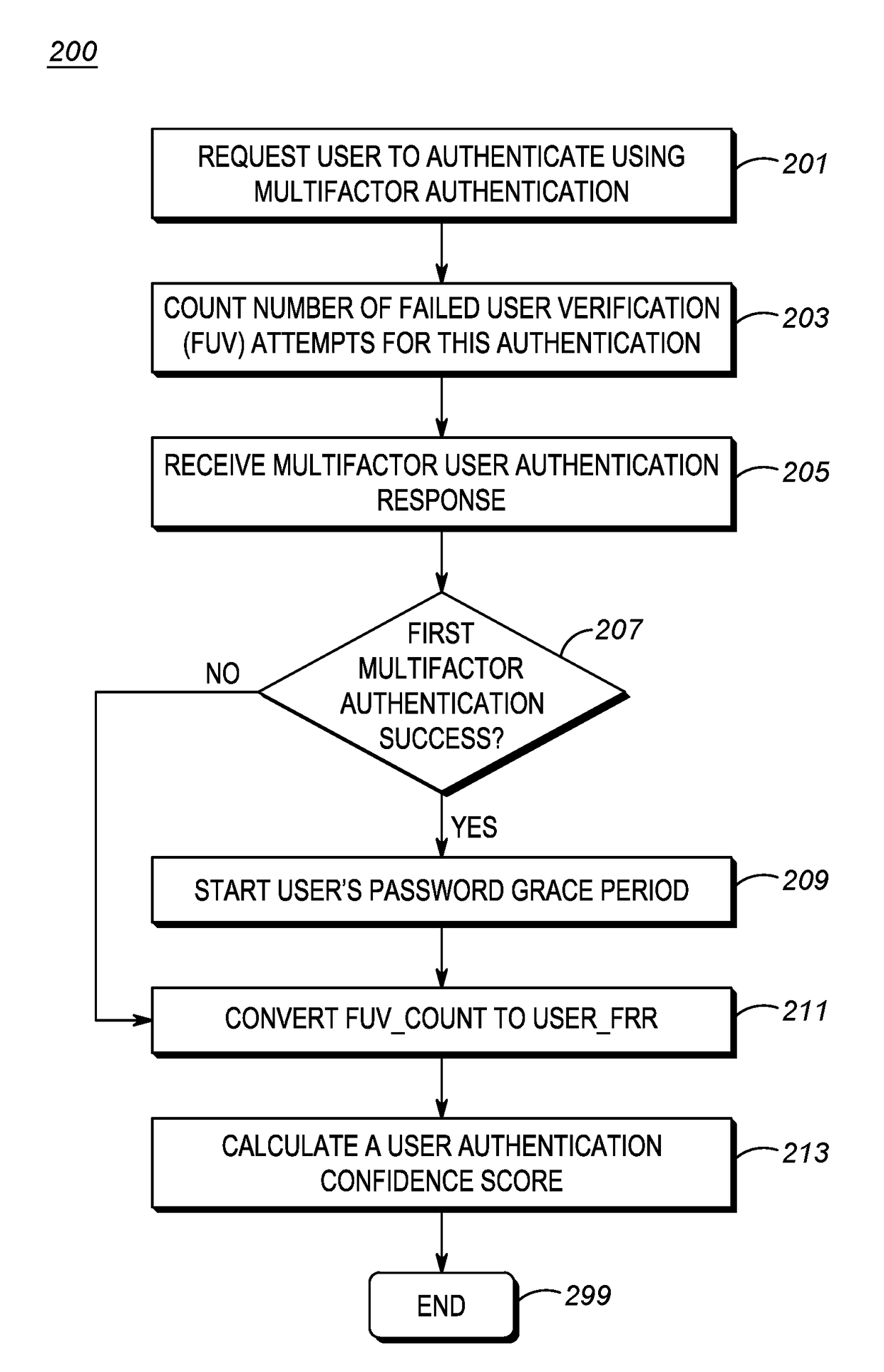
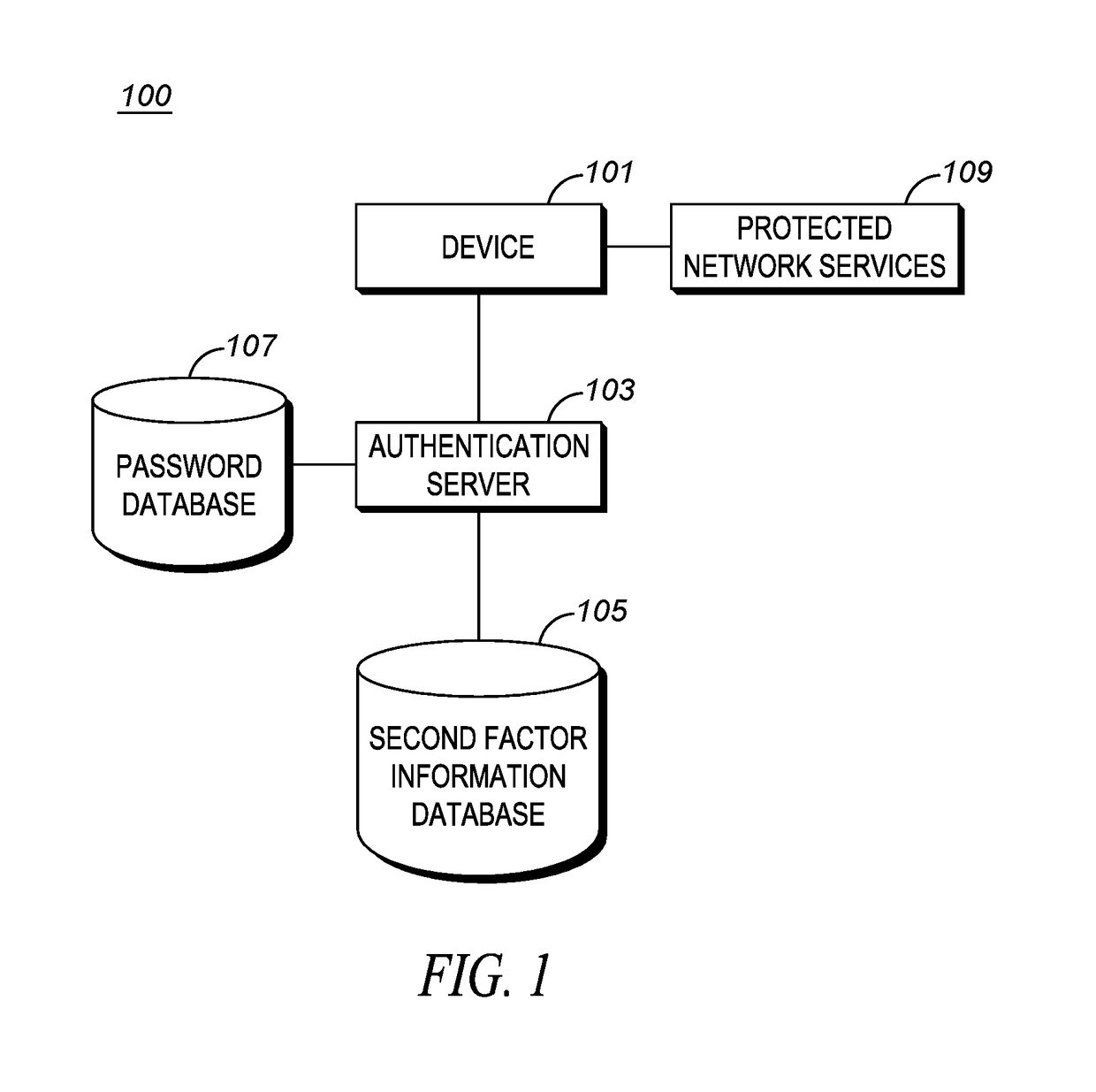
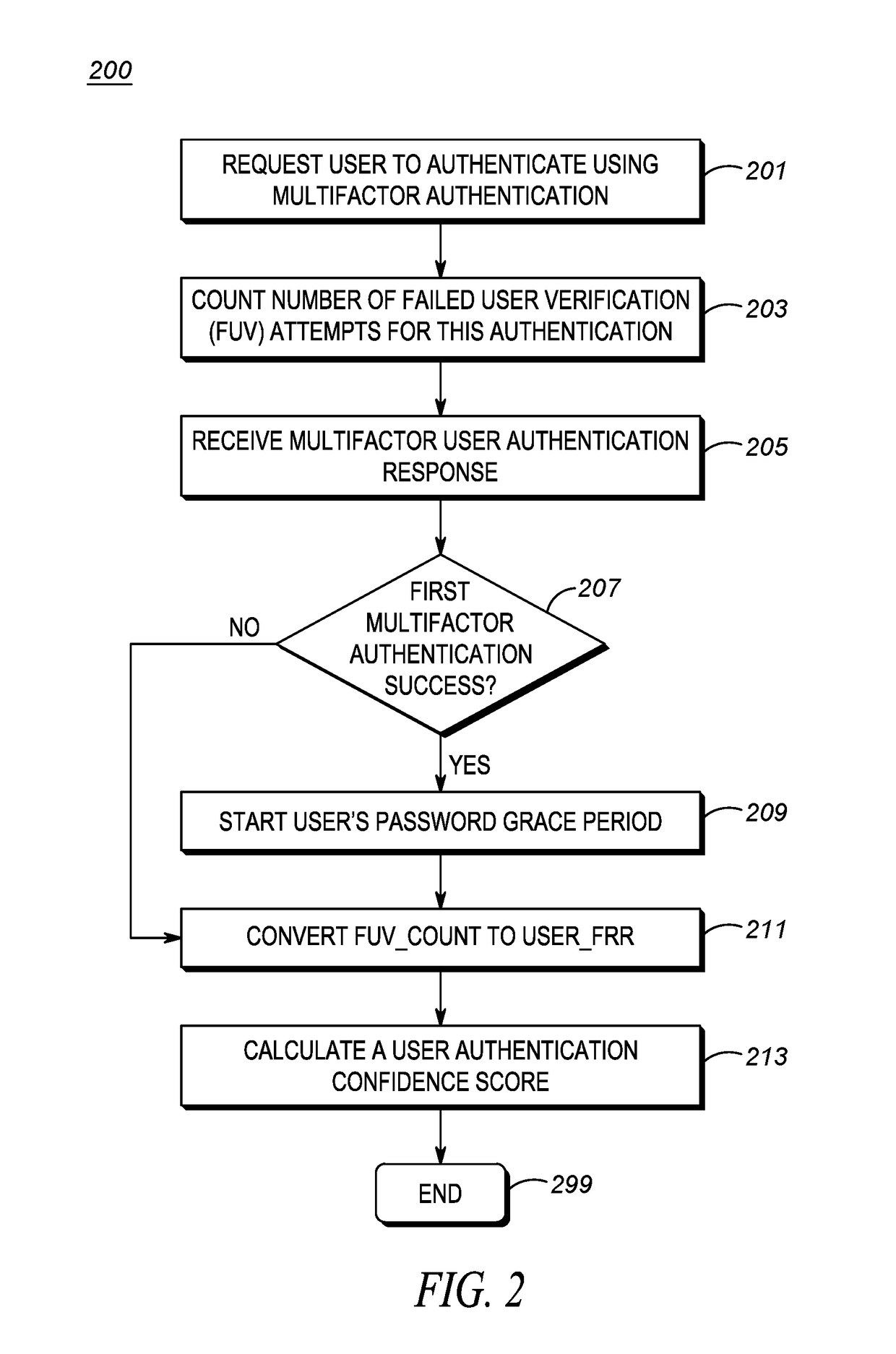
Method for automatically deleting a user password upon successful use of a multi-factor authentication modality
A method is provided for automatically deleting user passwords. Upon receiving a password-less user authentication a password grace period timer is started. Upon expiration of the password grace period timer the password is deleted if a user confidence score associated with the user is greater than a confidence threshold.
Owner:MOTOROLA SOLUTIONS INC
Data mining method and device
InactiveCN106251178AAugmented collectionMarket predictionsBuying/selling/leasing transactionsThe InternetConfidence metric
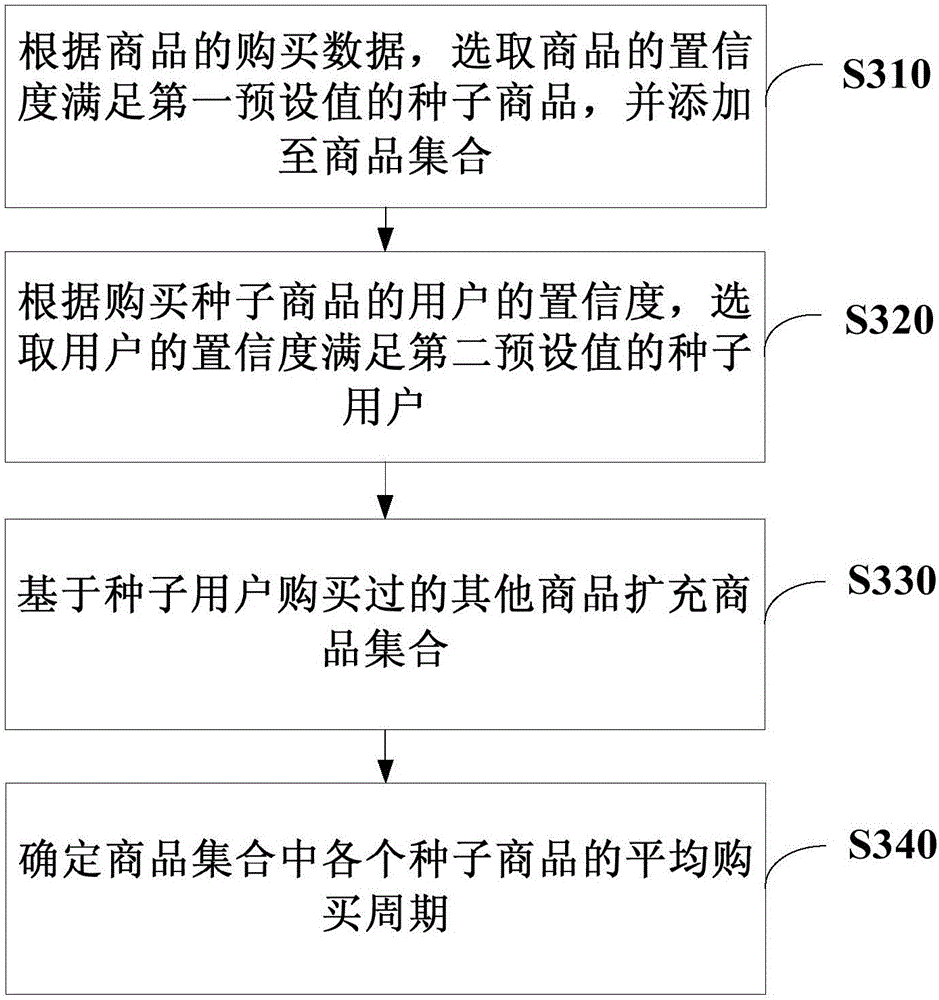
The invention discloses a data mining method and device, and relates to the technical field of Internet data mining. The method of the present invention includes: according to the purchase data of the commodity, selecting a seed commodity whose confidence level meets the first preset value, and adding it to the commodity collection; according to the confidence level of the user who purchased the seed commodity, selecting the user whose confidence level satisfies the first preset value Two preset seed users; expand the product collection based on other products purchased by the seed user; determine the average purchase cycle of each seed product in the product collection. The present invention selects seed commodities through the confidence of commodities, and expands the product collection through other commodities purchased by users who have purchased seed commodities, and combines the reference conditions of the two dimensions of commodity confidence and user confidence and collaborative processing, and finally Select commodities from massive commodity data and determine their purchase cycle.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
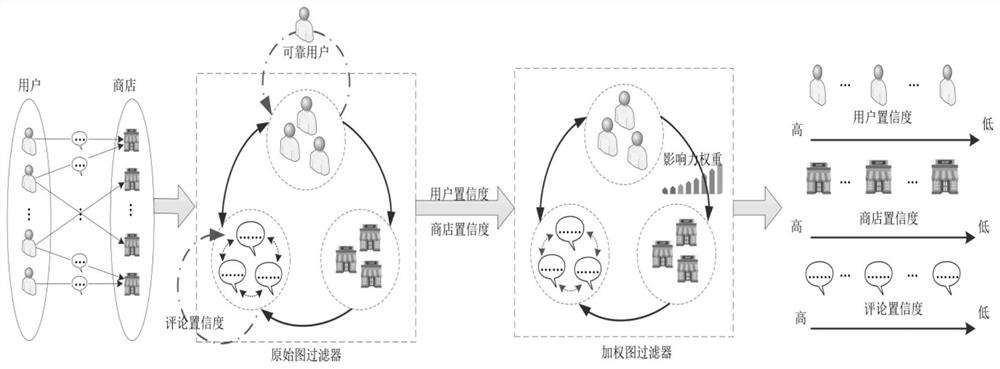
False comment detection method based on bicyclic graph
ActiveCN109344176ATo achieve the detection effectOptimize comment consistencyDigital data information retrievalMarketingUser confidenceCycle graph
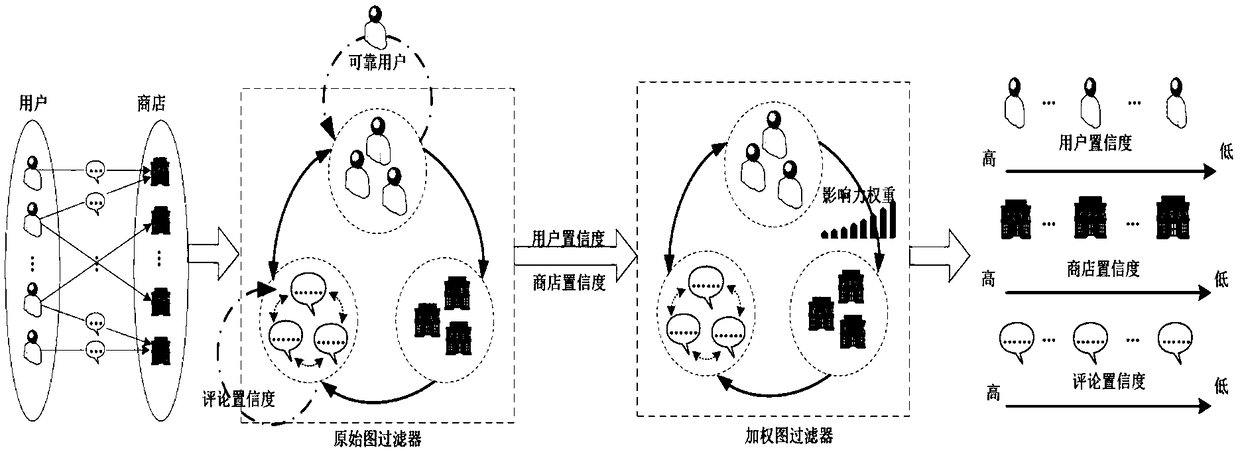
The invention discloses a false comment detection method based on a double-cycle graph, comprising the following steps: (1) using an original graph filter to calculate a comment confidence degree anda user confidence degree of the original comment data, and screening the user confidence degree to obtain a reliable user; (2) calculating the store confidence level of the comment data correspondingto the reliable users by using the original graph filter; (3) updating the comment confidence level in the original graph filter to the comment confidence level obtained in the step (1), and calculating the user confidence level of the original comment data by using the original graph filter; (4) taking the store confidence obtained in the step (2) and the user confidence obtained in the step (3)as initial values to construct a weighted map filter; (5) calculating The store confidence, user confidence and comment confidence of the original comment data by using the weighted graph filter, andthe false comment is obtained by screening according to the comment confidence. This method improves the detection accuracy of false comments.
Owner:ZHEJIANG UNIV OF TECH
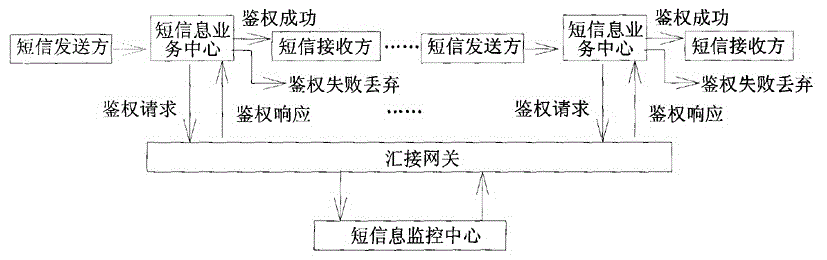
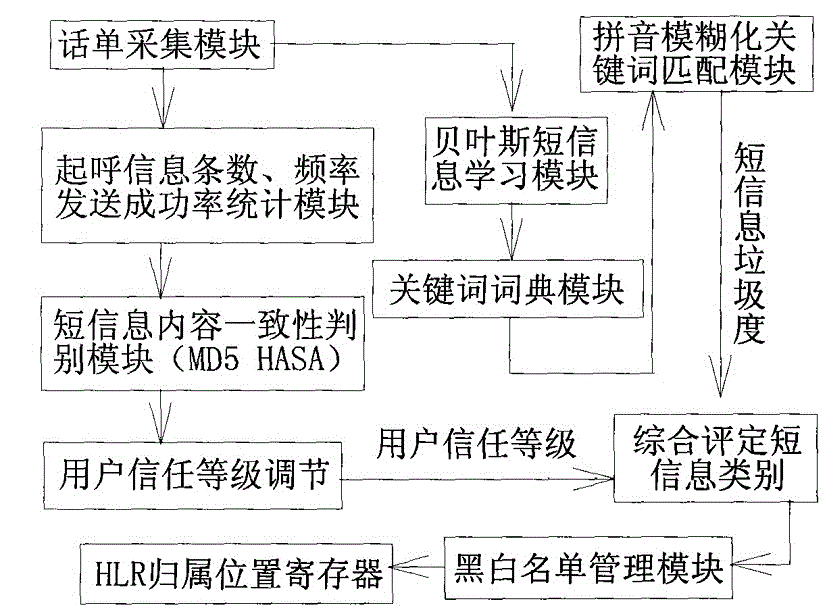
Mobile phone short message monitoring device
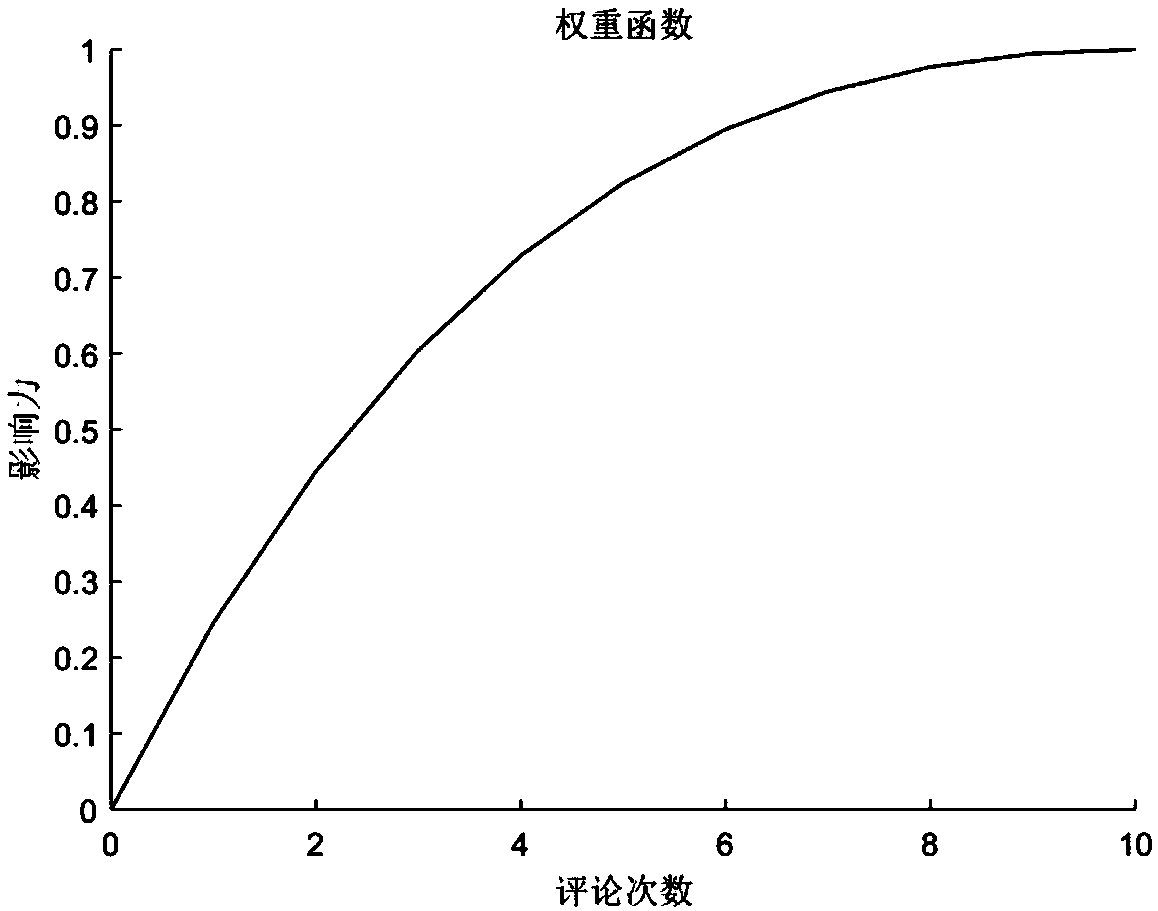
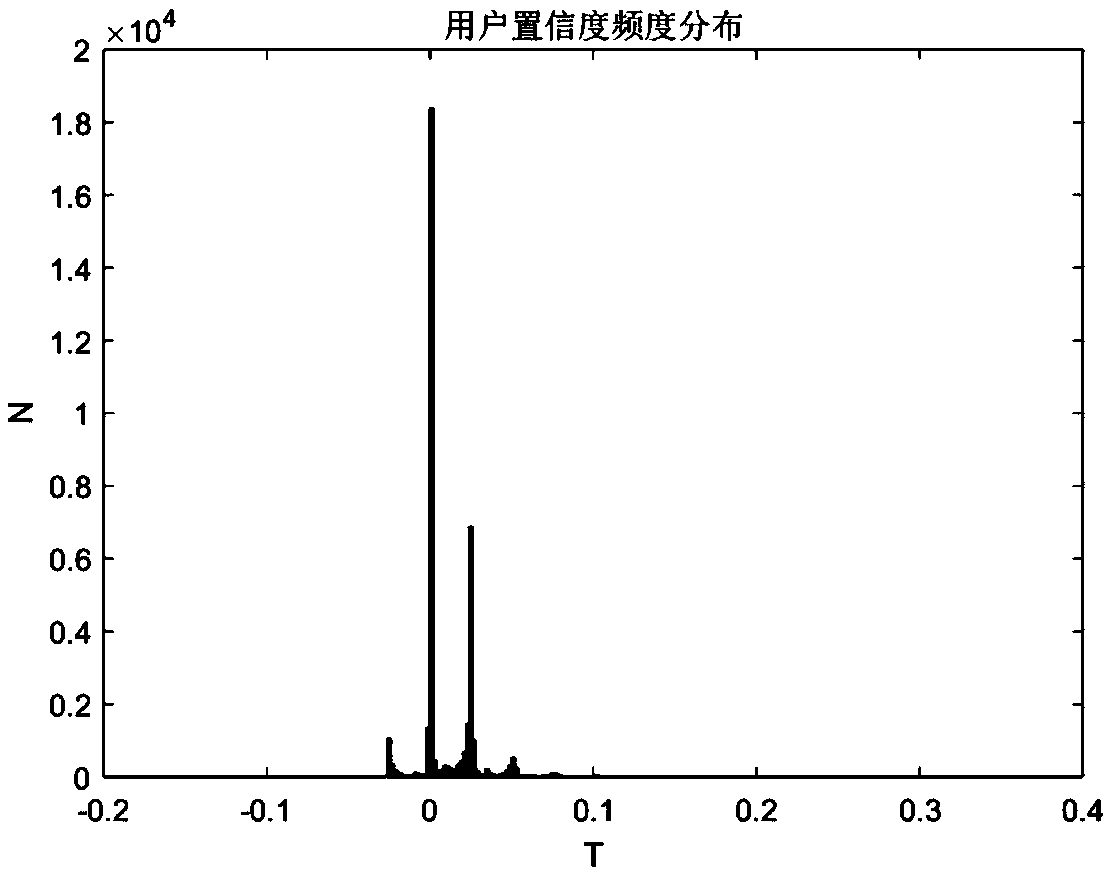
InactiveCN105323751AEliminate distracting informationImprove interception rateAutomatic exchangesMessaging/mailboxes/announcementsUser confidenceBlack list
The invention discloses a mobile phone short message monitoring device. The mobile phone short message monitoring device is characterized in that the short message monitoring device is connected with a short message service center through a tandem gateway, the internal connection relationship of the mobile phone short message monitoring device is that the monitoring device is connected with a call information number, frequency sending success rate counting module, a short message consistency judgment module, a user confidence grade module, a comprehensive assessment short message category module, a black list-white list management module and a home location register module; a telephone bill acquiring module is connected with a Bayes short message learning module, a keyword dictionary module, a spell fussy keyword matching module and the comprehensive assessment short message category module; a mobile phone short message monitoring device hardware platform is an IBMX39508872-7RC multi-core environment. Through the adoption of the device disclosed by the invention, an interference message in the spam short message can be effectively eliminated, the interception rate of the spam short message and the judgment right rate are improved, the influence of the mobile phone short message monitoring device to the processing ability of the short message service center is reduced.
Owner:SHAANXI EYINHE ELECTRONICS
Information processing device, information processing method and computer program
The invention discloses an information processing device, an information processing method and a computer program. The information processing device includes an information input unit, an event detection unit and an information synthesizing and processing unit. An observed value including user identification data is obtained based on image and sound information from the information input unit such as video camera and microphone. Target data, which is equipped with multiple user confidence degrees, is updated, and then user is identified. User identification information in the observed value is used for updating simultaneous probability of target and candidate data corresponding to relevant user. The updating value of the probability is used for calculating the user confidence degree corresponding to the target.
Owner:SONY CORP
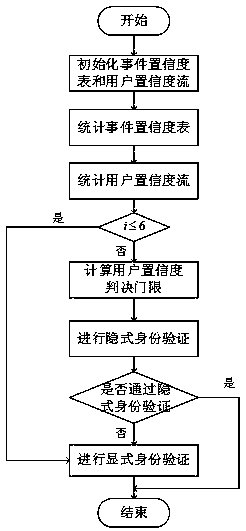
Event trigger implicit identity verification method based on mobile equipment
ActiveCN106170046AConfidence Threshold AccurateEfficient identificationSubstation equipmentSecurity arrangementConfidence metricEvent triggered
The invention discloses an event trigger implicit identity verification method based on mobile equipment. The event trigger implicit identity verification method comprises steps that a type of an implicit trigger event of equipment and a characteristic value of every trigger event are set; when the trigger event occurs, the equipment is used to acquire user confidence by comparing a habit of a current user with a habit of a valid user, and is used to acquire a current decision threshold after calculation by using historical user confidence and a historical decision threshold, and then is used to decide the validity of the current user by comparing the current user confidence with the decision threshold. Problems of a conventional implicit identity verification method such as low efficiency in identifying invalid users and requirement on a lot of user data and learning time are solved.
Owner:陕西尚品信息科技有限公司
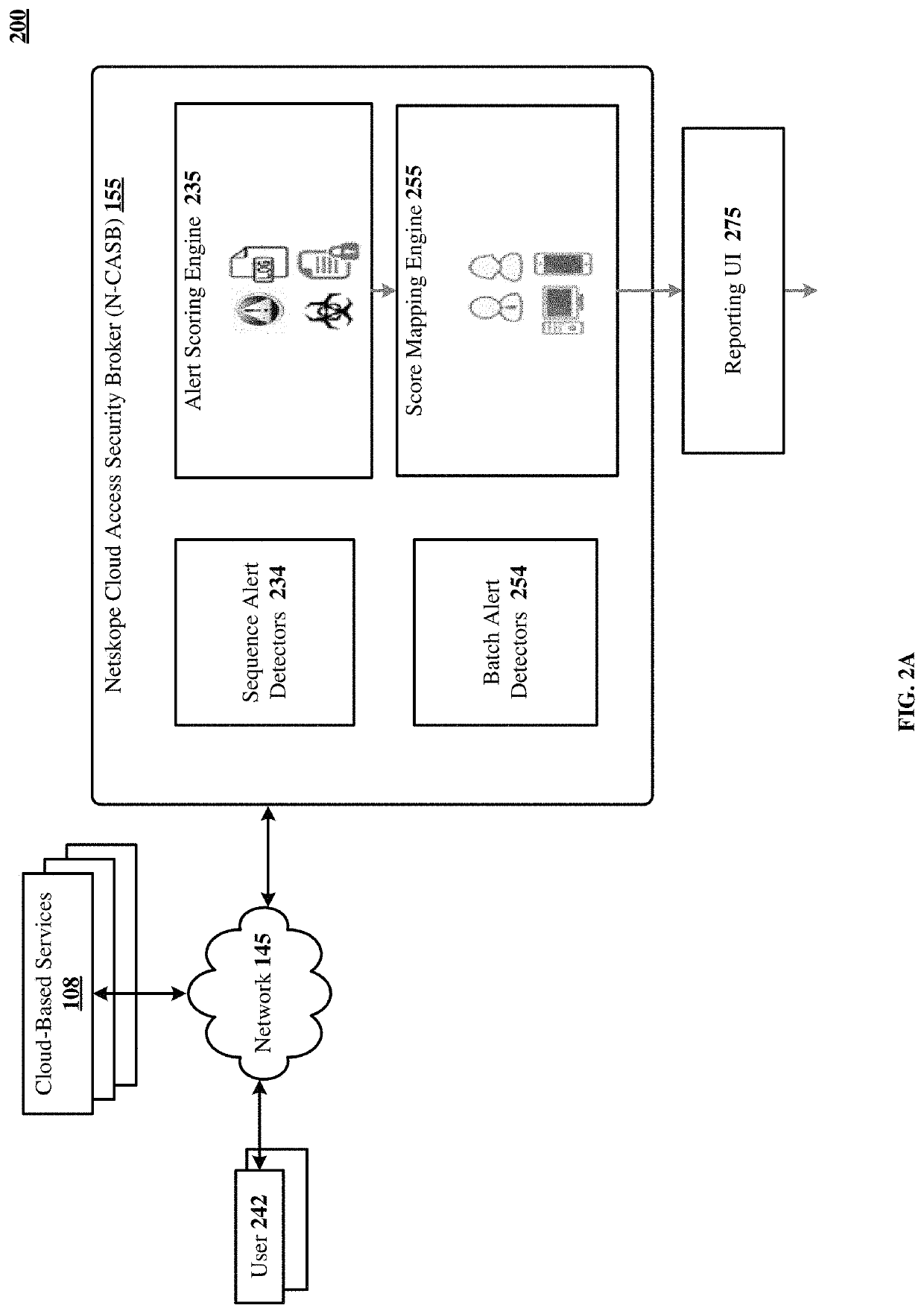
Scoring confidence in user compliance with an organization's security policies
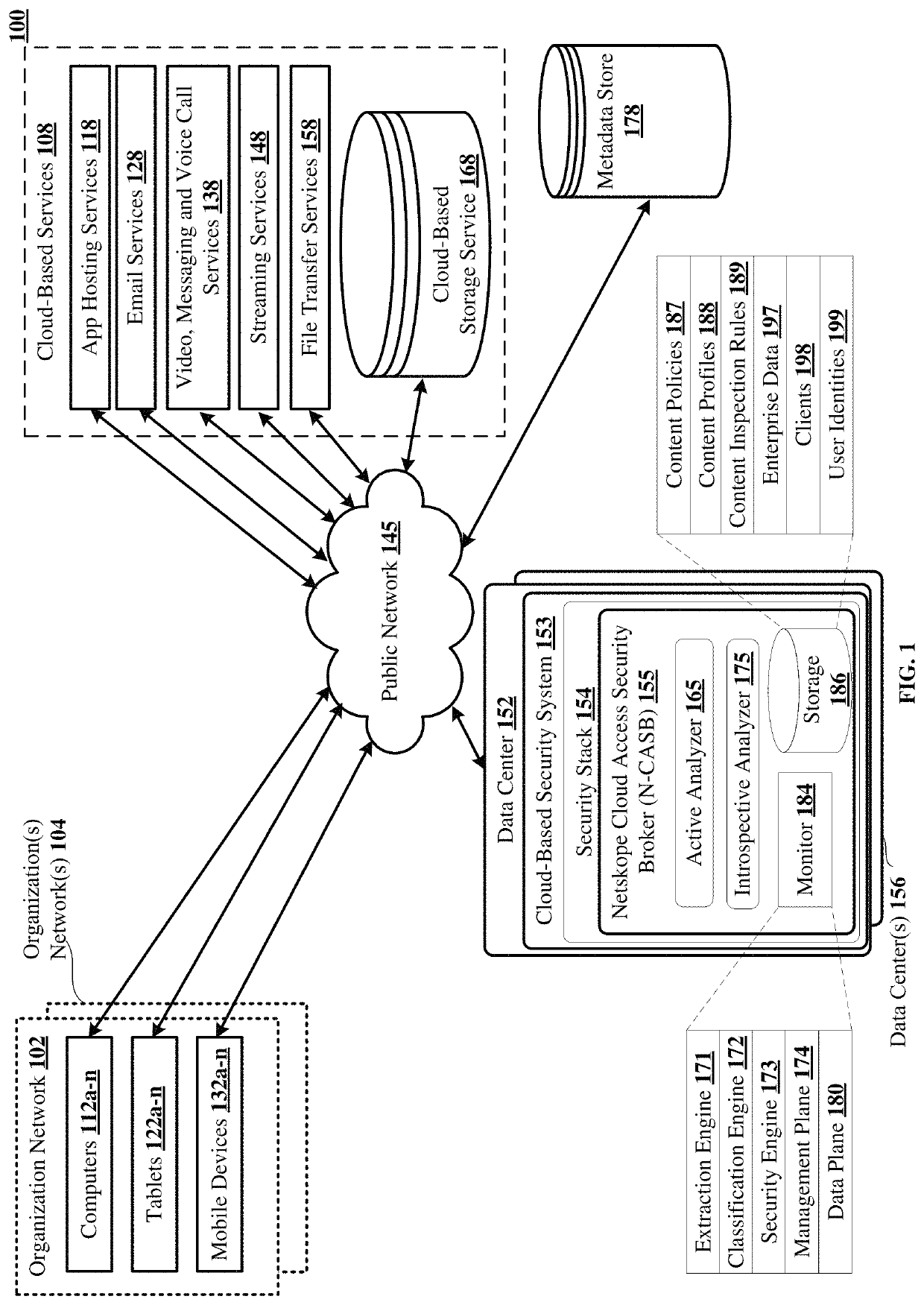
The disclosed technology teaches a method for evaluating user compliance with an organization's security policies, formulating a user confidence or risk score, comprising scoring for each user a sum of alert weights, categorized by severity, and generated over time. Each contribution to an alert weight is generated due to an activity by the user that the organization's security policies treat as risky. Alert weights, over time, are subject to a decay factor that attenuates the alert weights as time passes. Also disclosed is reporting the user confidence score, comprising causing display of a time series of the user confidence or risk scores over a predetermined time and / or a current user confidence or risk score and / or at least some details of the activity by the user that contributed to the alert weights over time.
Owner:NETSKOPE INC
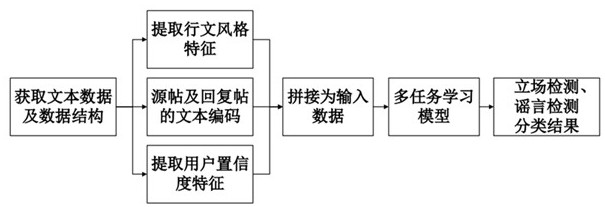
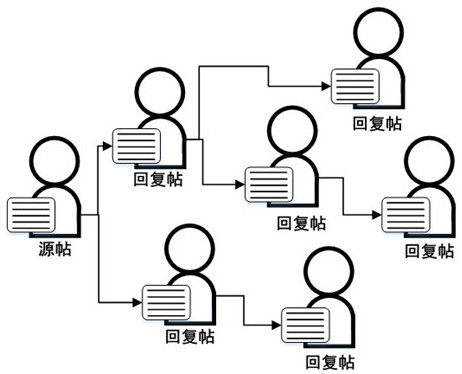
Social media rumor detection method based on multi-task learning
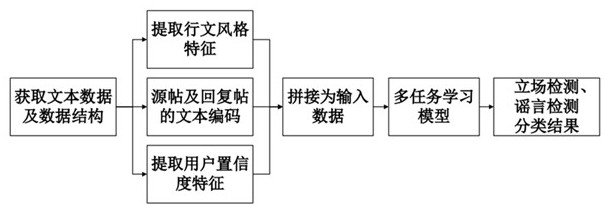
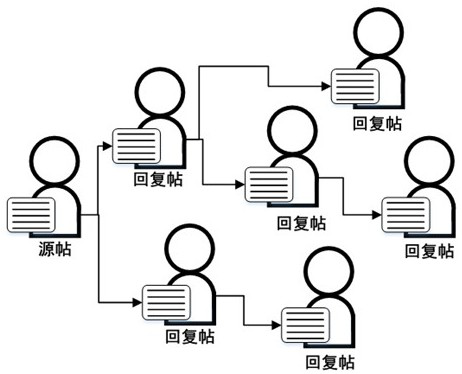
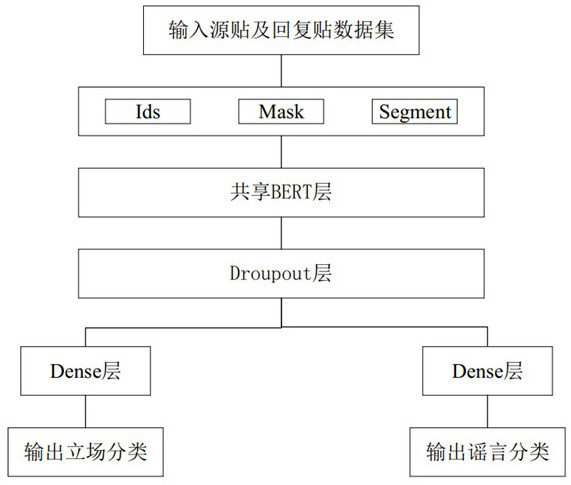
ActiveCN112685541AImprove performanceReduce overfittingData processing applicationsSemantic analysisSocial mediaEngineering
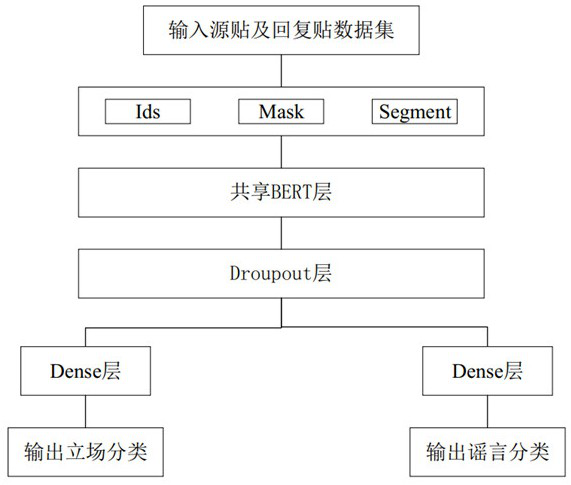
The invention relates to a social media rumor detection method based on multi-task learning, and the method specifically comprises the following steps: S1, carrying out the data extraction and format conversion of a corpus, and obtaining the source, reply and propagation path of a post; s2, extracting features of a line style; s3, extracting features of user confidence; s4, performing text preprocessing on text parts in the source post and the reply post to input subsequent tasks; s5, performing vector splicing on the features extracted in the S2 and the S3 and the text representation in the S4; s6, putting the spliced vector into a shared BERT layer; s7, respectively constructing neural network structures; and S8, inputting the data processed in the S5 into a neural network structure, and outputting standing classification and rumor classification. According to the method, a multi-task joint model can be used for being combined with two highly-related tasks, rumor detection and site classification tasks are improved, and rumor detection performance is improved.
Owner:长沙市智为信息技术有限公司
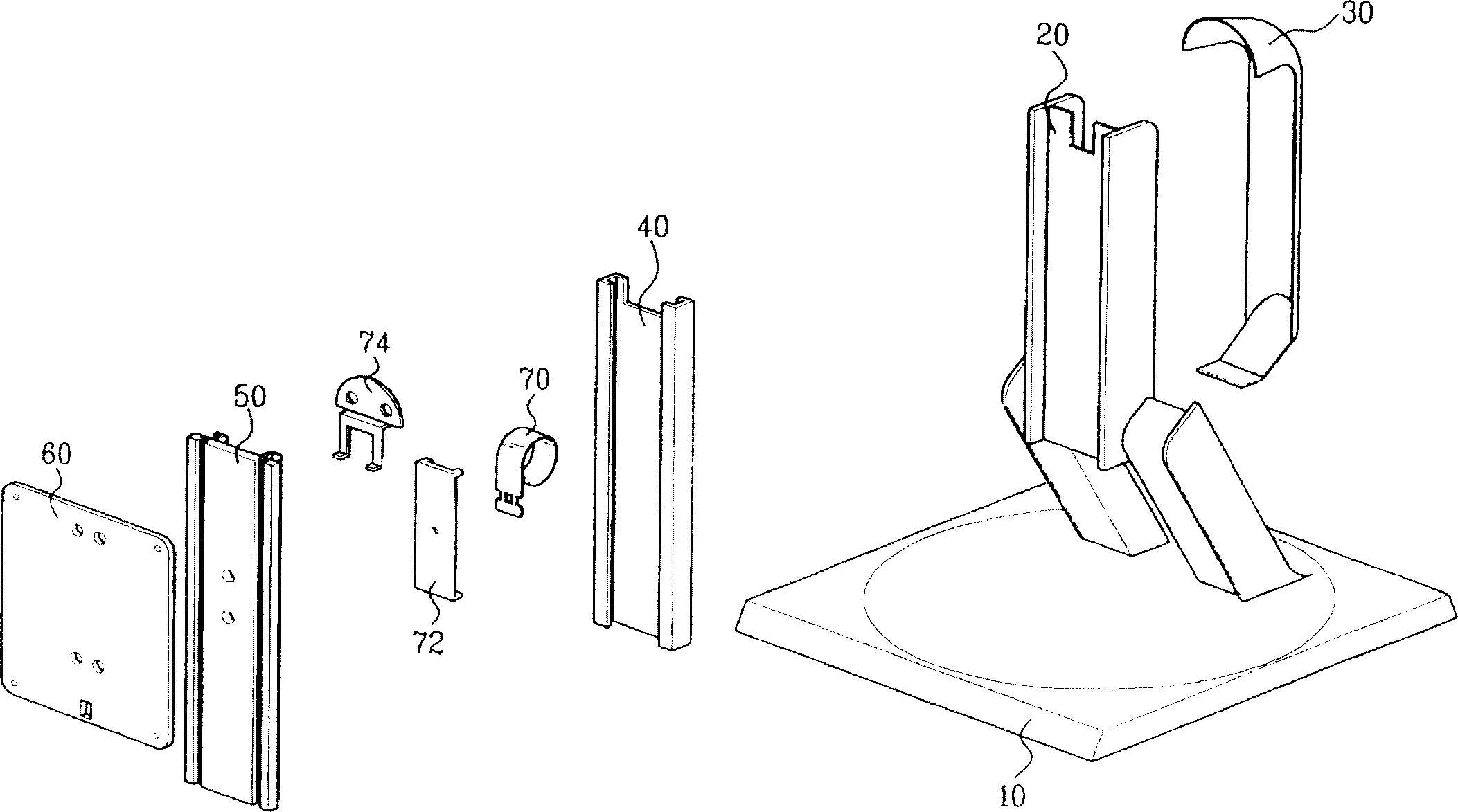
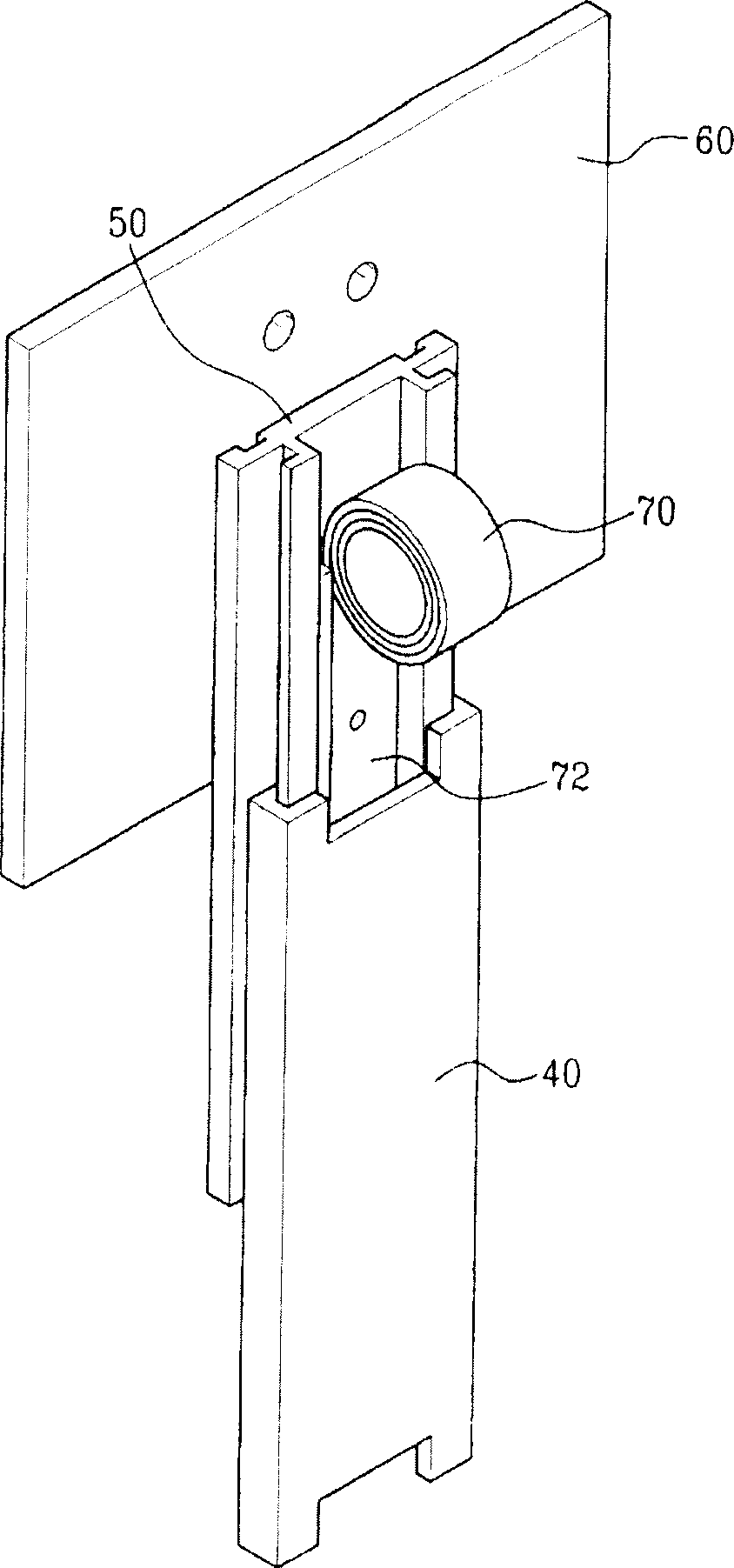
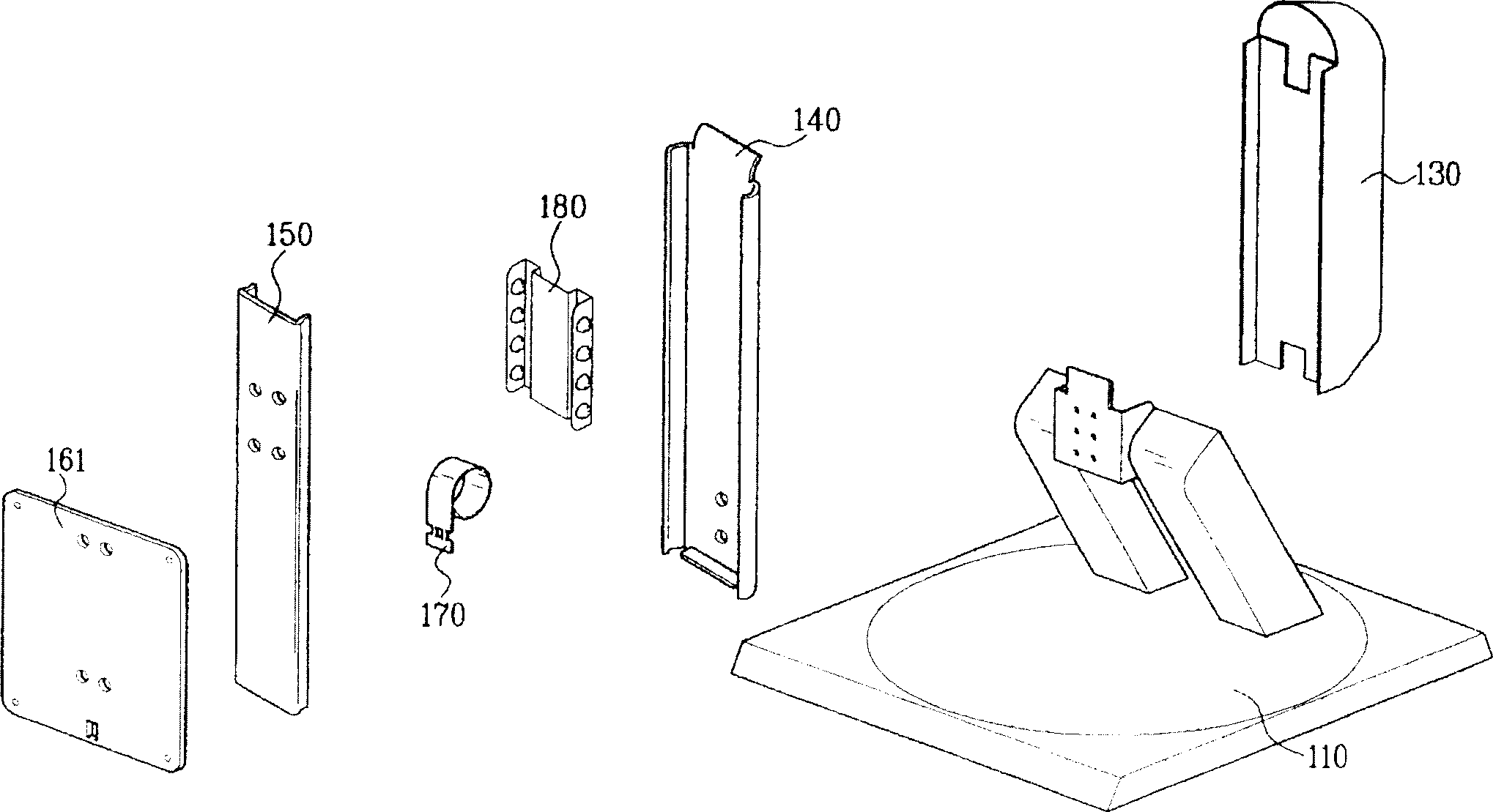
Height adjustment stand of thin type image display device
InactiveCN1764358AImprove performanceSoft and smooth up and down motionCasings/cabinets/drawers detailsRack/frame constructionWork performanceRolling resistance
The invention relates to a height adjustment stand for thin video display device. Wherein, arranging bearing part between fixed guide and slide guide to generate rolling friction, forming spring guide plate on top of fixed guide to separate spiral body and prolongation both of clockwork spring; both the slide guide and clockwork spring have very soft force. This invention improves work performance of display device, and enhances user confidence to the product.
Owner:NANJING LG TONGCHUANG COLOR DISPLAYS SYST CO LTD
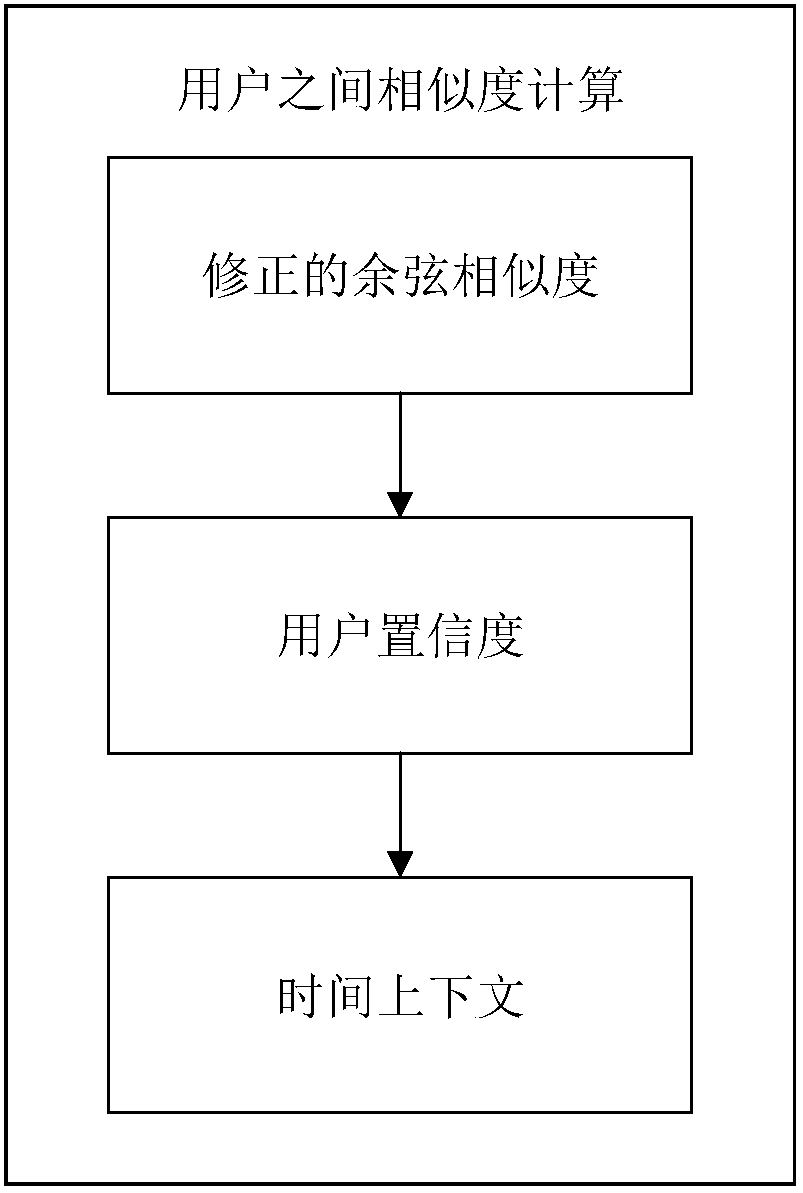
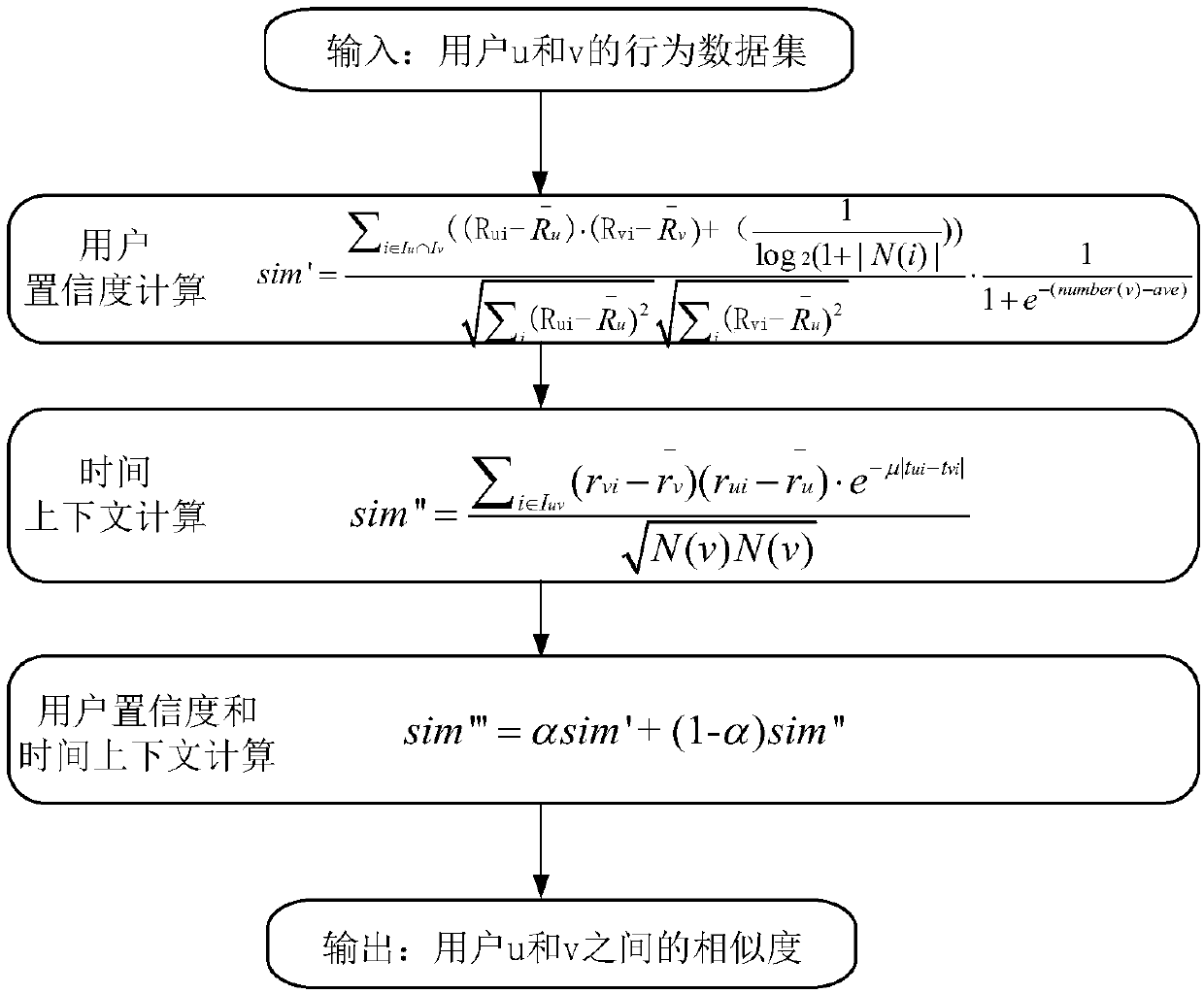
User confidence coefficient and time context-based collaborative filtering recommendation method
InactiveCN108399197AMeets requirementsReduce engagementCommerceSpecial data processing applicationsConfidence metricTemporal context
The invention discloses a user confidence coefficient and time context-based collaborative filtering recommendation method, and relates to calculation of similarities between users in the collaborative filtering recommendation method. Aiming at the deficiency problem of traditional similarity measurement methods and dynamic change conditions of user interests under the condition that user score data is extremely sparse, the method discloses the user confidence coefficient and time context-based collaborative filtering recommendation method. The method comprises the following steps of: constructing a scoring matrix between users and projects; calculating similarities between the users through the user confidence coefficient and time context-based collaborative filtering recommendation method; selecting an optimum adjacent user set according to a sorting result of the similarities between the users, or setting a similarity threshold and selecting the users exceeding the threshold value as neighbors of a target user; and after obtaining nearest neighbor set of the target user, taking the similarities as weights to obtain prediction, for unscored projects, of the target user, so as toform a Top-N list and recommending the Top-N list to the users.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
User interaction models for disambiguation in programming-by-example
Systems and methods for increasing user confidence in results that are produced by one or more programs that are generated by an underlying Programming-By-Example (PBE) system based on user input examples. A plurality of generated programs that have been generated using one or more user input examples that are indicative of an output that should be achieved to comply with a user determined result are received. The generated programs are narrowed based on one or more sub-expressions of the programs that are likely to cause the resultant program to comply with the user determined result. The one or more sub-expressions are exposed. Input that selects at least one of the one or more exposed sub-expressions to thereby identify the one of the generated programs that will result in the user determined result is received.
Owner:MICROSOFT TECH LICENSING LLC
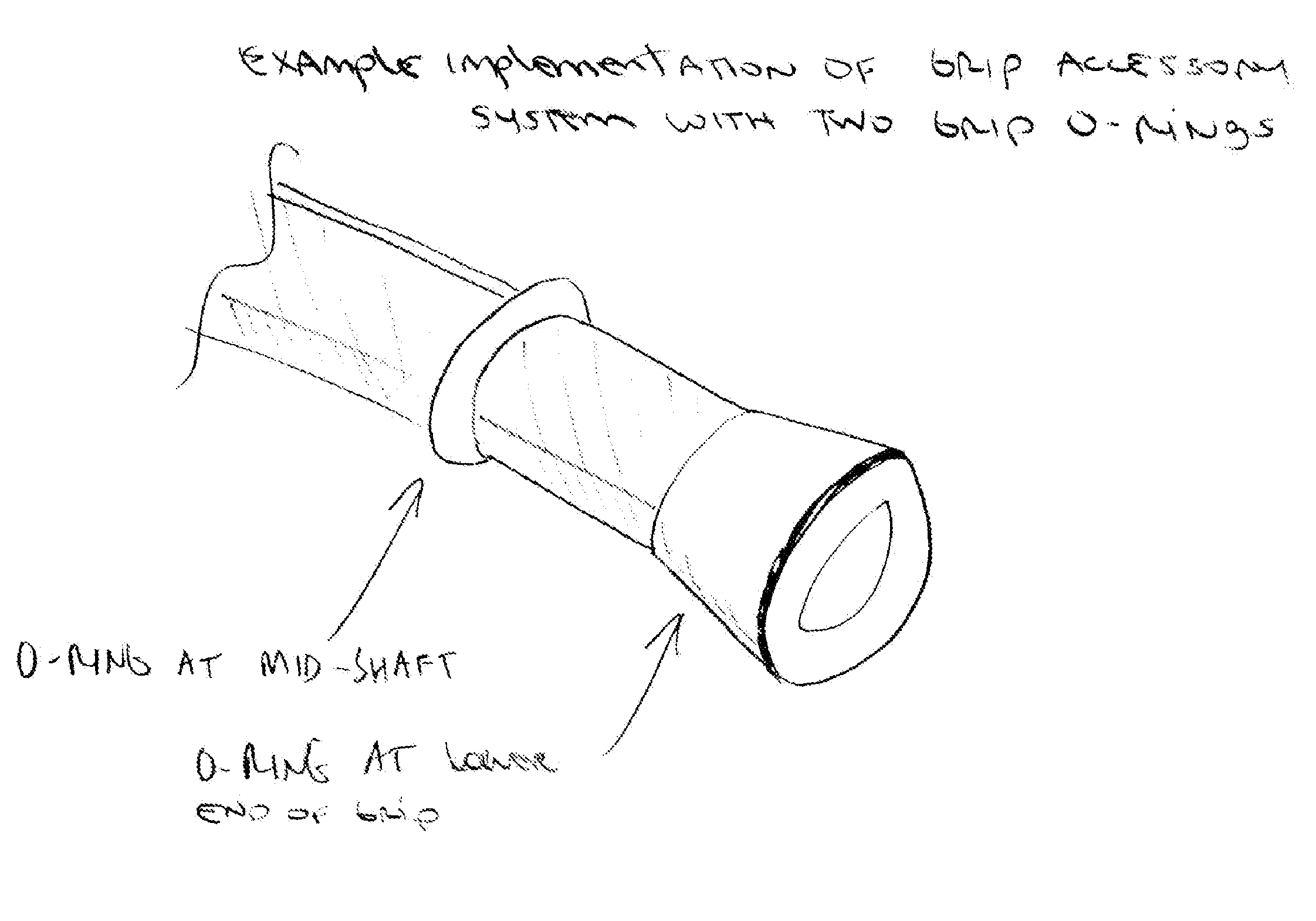
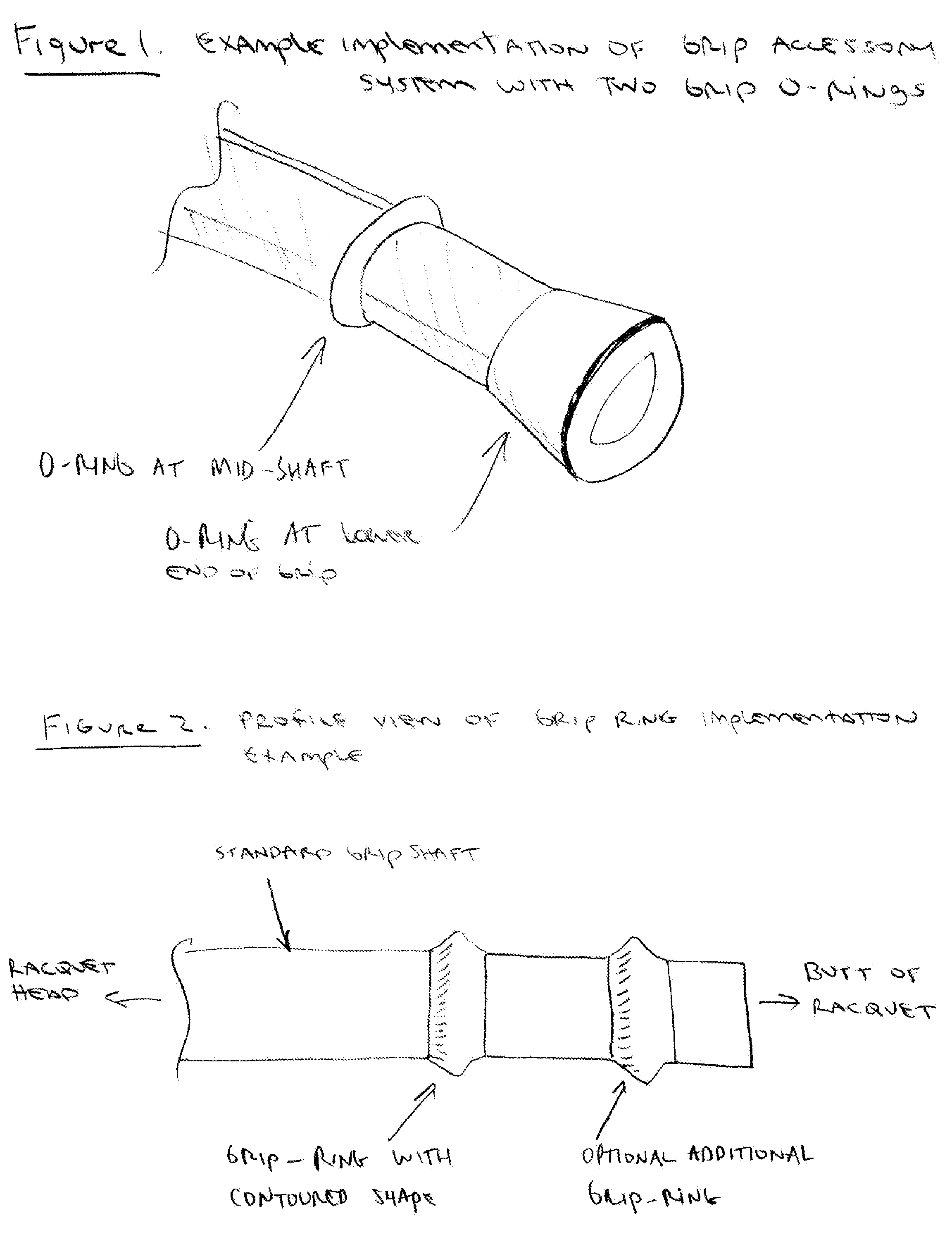
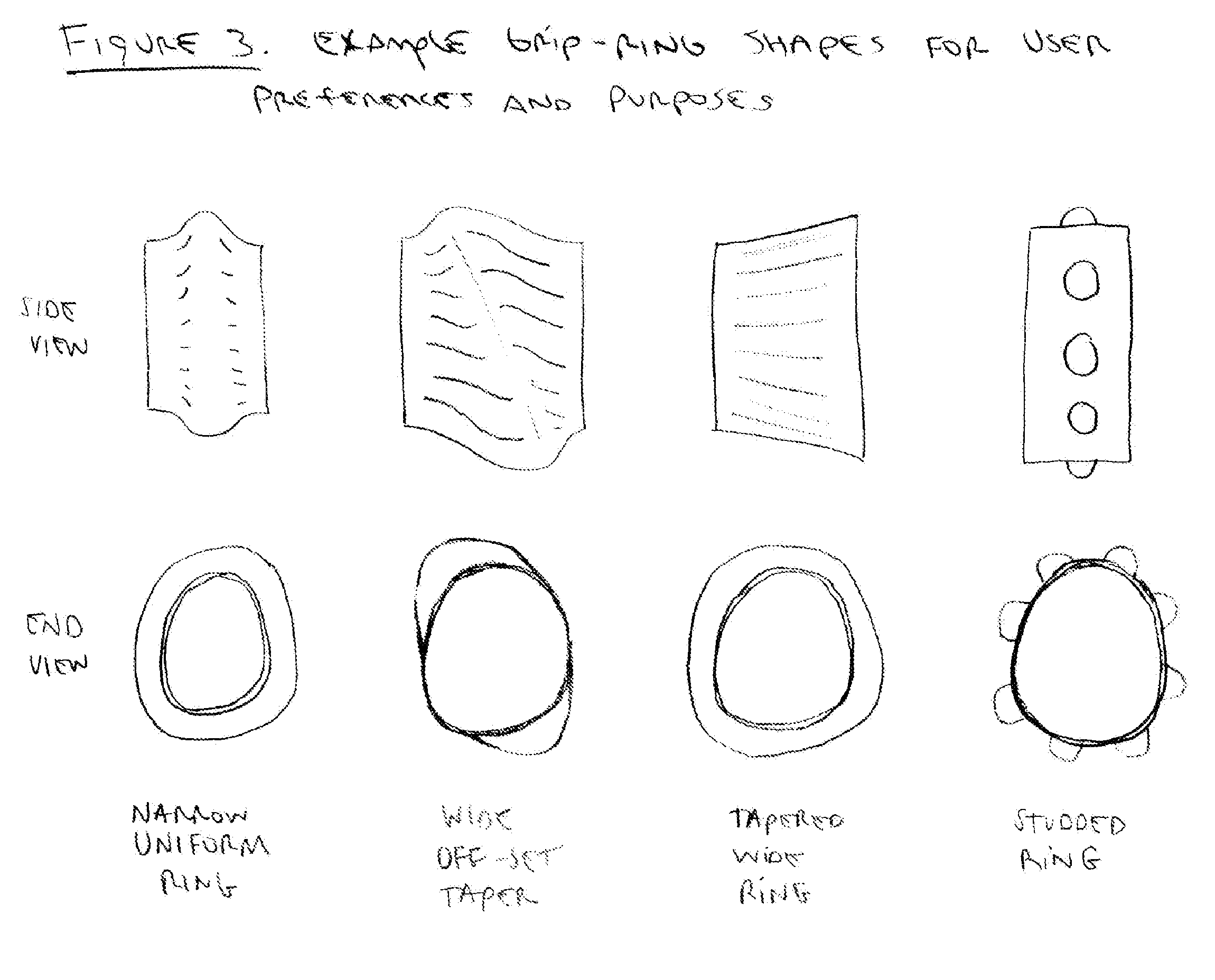
Tennis racquet grip accessory for enhanced grip ergonomics
A tennis racquet grip accessory for adjustable, customizable grip ergonomics is disclosed. This grip accessory system enables the user to precisely tune their grip contours via rings (size, shape, quantity, positioning) for preferred finger and hand traction and leverage. The ring contours provide better personalized fitting in the user's hand and against fingers. The overall system improves user confidence, flexibility, and loose grip for racquet head speed for better shot making: it enables high performance ball speed and spins as well as gentle touch-shots.
Owner:HEACOX EDWIN GRAHAM
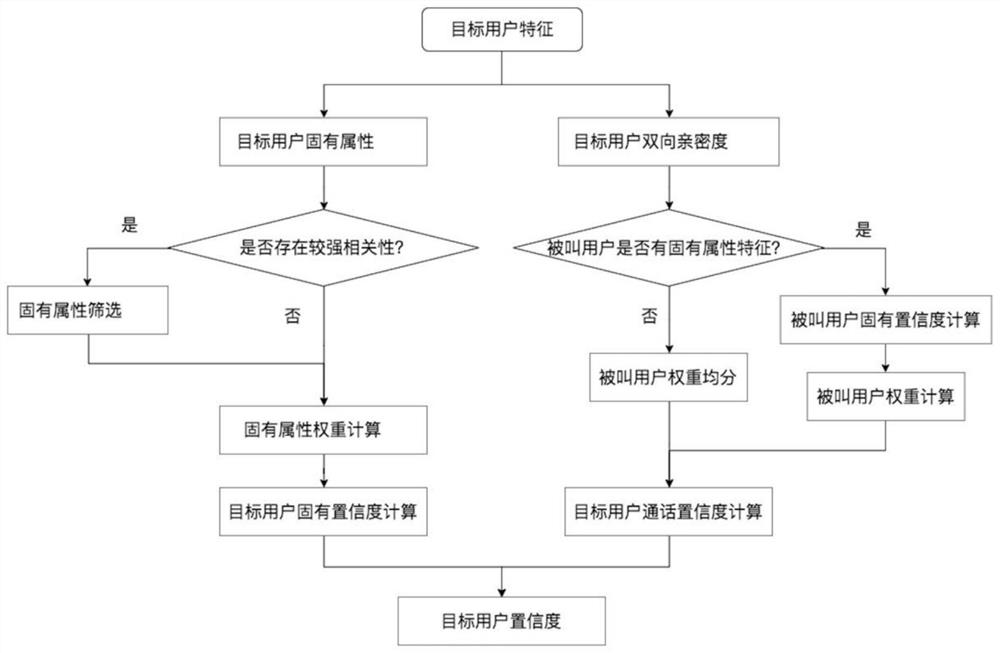
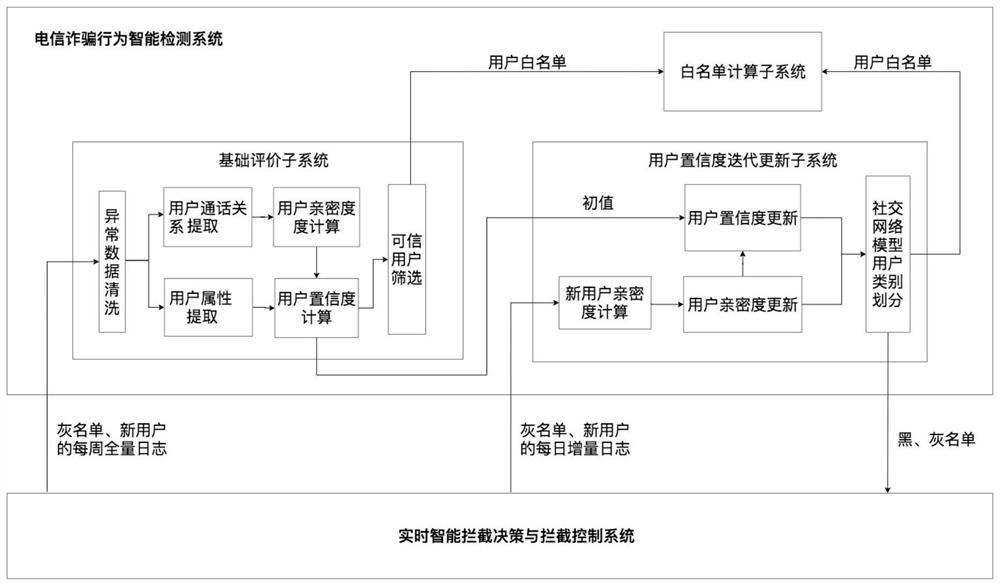
Social network topology model and construction method, user confidence and intimacy calculation method and telecommunication fraud intelligent interception system
ActiveCN111917574AOvercome limitationsReduce baseData switching networksSecurity arrangementUser confidenceData mining
The invention discloses a social network topology model, and the model is a three-layer two-order star-shaped structure constructed by taking each target user as a center and comprises a first-layer node, second-layer nodes and third-layer nodes; the first-layer node is a target user, the second-layer nodes are a direct called user, and the third-layer node is obtained by modularization of neighbor nodes generated by each second-layer node; the node value of the social network topology model is the user confidence, and the edge weight of the social network topology model is the intimacy between users. The invention further discloses a construction method of the social network topology model, a user confidence coefficient and intimacy calculation method and a telecommunication fraud intelligent interception system. The social network topology model does not infinitely increase the data volume over time. According to the telecommunication fraud intelligent interception system, based on user historical data, the infinite increase of the system data size along with time can be avoided, and original and newly-added fraud users can be accurately identified.
Owner:上海阿尔卡特网络支援系统有限公司
Automatic mobile phone communication fee payment machine based on three-dimensional face recognition system
InactiveCN104484961AImprove securitySimple structureComplete banking machinesCharacter and pattern recognitionPattern recognitionConfidentiality
The invention relates to an automatic mobile phone communication fee payment machine based on a three-dimensional face recognition system. The automatic mobile phone communication fee payment machine comprises an automatic mobile phone communication fee payment machine body, wherein a recognition control key, a three-dimensional face recognition device and a fingerprint recognition device are additionally arranged on the automatic mobile phone communication fee payment machine body, the three-dimensional face recognition device and the fingerprint recognition device are located inside the automatic mobile phone communication fee payment machine body, a detection probe of the three-dimensional face recognition device is embedded into the upper surface of the automatic mobile phone communication fee payment machine body, a transparent protection window is arranged at the front end of the detection probe, a detection probe of the fingerprint recognition device is embedded into the upper surface of the automatic mobile phone communication fee payment machine body, and the recognition control key is embedded into the upper surface of the automatic mobile phone communication fee payment machine body. The automatic mobile phone communication fee payment machine is simple in structure, convenient to use and capable of effectively overcoming the defect that frequent input through a keyboard or a touch screen and the like is needed during fee payment. On the one hand, operating steps are simplified, fee payment efficiency is improved, and on the other side, the user confidence confidentiality safety of a fee payment system is also improved greatly.
Owner:SUZHOU FUFENG TECH
A Hybrid Collaborative Filtering Recommendation Algorithm Based on Item Attributes
ActiveCN109783734BRaise the ratioImprove reliabilityDigital data information retrievalCharacter and pattern recognitionAlgorithmNear neighbor
The invention discloses a hybrid collaborative filtering recommendation algorithm based on project attributes. The algorithm comprises the following steps: step 1, generating a user-project scoring matrix and a project-attribute matrix according to user scoring information and project information; step 2, respectively calculating project similarity and user scoring similarity according to the project-attribute matrix and the user-project scoring matrix; step 3, correcting the user score similarity by utilizing the project similarity to calculate the user similarity; step 4, calculating a common score reward factor, a project attribute preference factor and a user confidence coefficient factor to correct user similarity and obtain user final similarity; step 5, selecting the nearest neighbor of the target user according to the final similarity, and predicting the score of the target user on each project based on the score information of all the users in the nearest neighbor; And step 6,recommending the N projects with the highest scores to the target user. The method can be applied to sparse data, and recommendation accuracy can be improved.
Owner:HUNAN UNIV
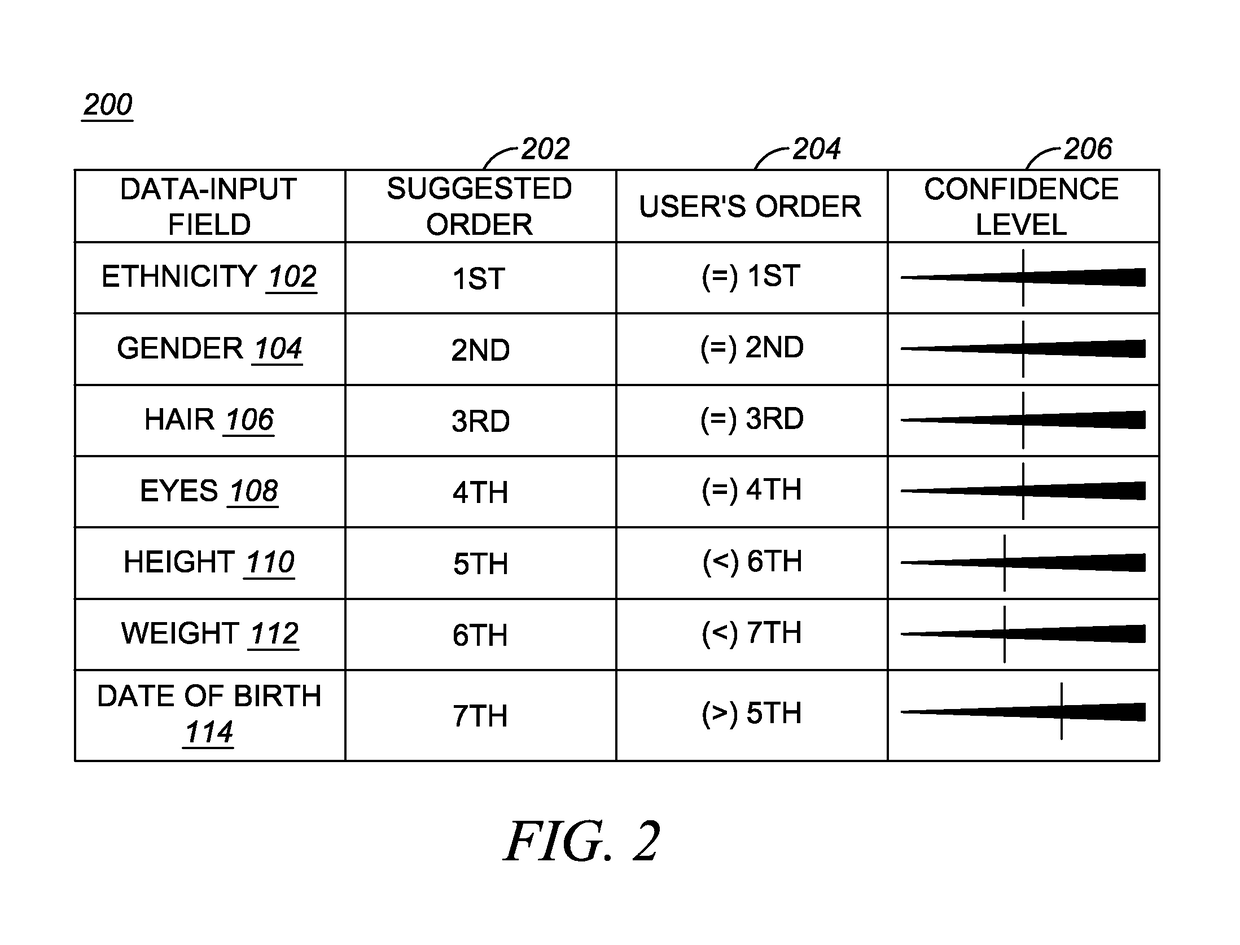
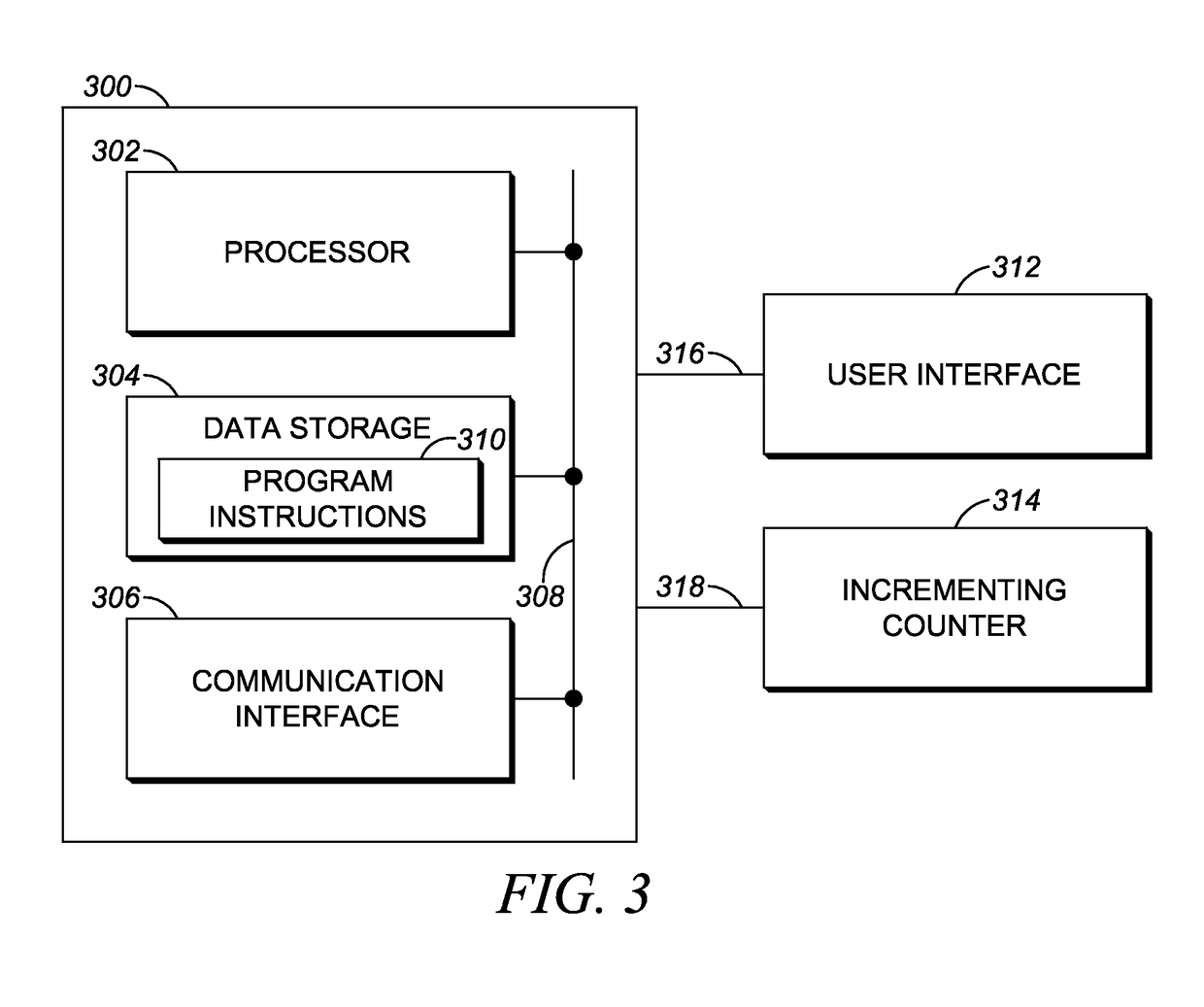
Establishing user-confidence levels of data inputs
ActiveUS10061835B2Relational databasesNatural language data processingConfidence intervalUser confidence
An embodiment takes the form of a method carried out by a computing system comprising a processor and instructions for carrying out the method. The method includes (i) presenting via a user interface a plurality of data-input fields having an associated default order for user entry of respective values in the respective data-input fields, (ii) receiving respective values entered via the user interface in the respective data-input fields, (iii) storing a respective current counter value of an incrementing counter in association with receiving each respective entered value, (iv) establishing a respective user-confidence level for each of one or more of the respective entered values, wherein each established user-confidence level is set based at least in part on a comparison of the associated default order with a set of one or more of the stored counter values, and (v) outputting one or more of the established user-confidence levels.
Owner:MOTOROLA SOLUTIONS INC
A Simple Coding Method for Dirty Paper That Can Approach the Limit of Information Theory
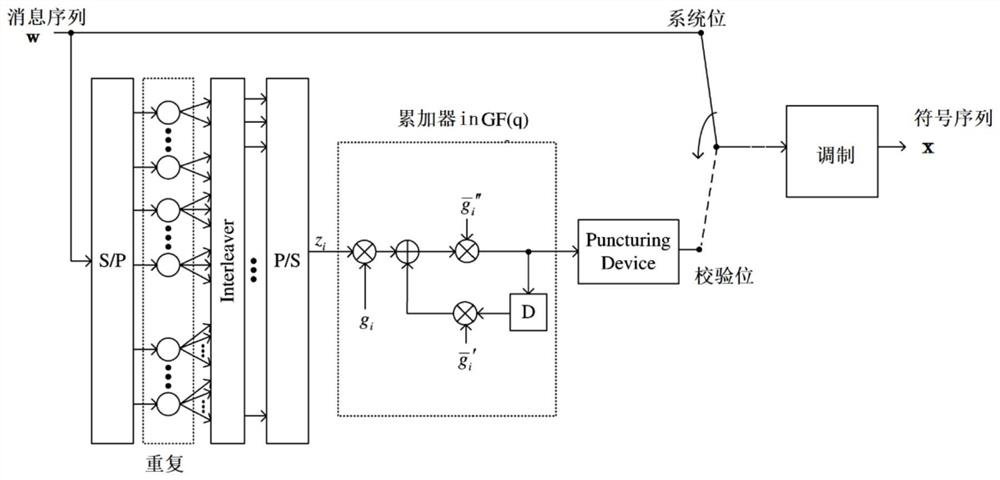
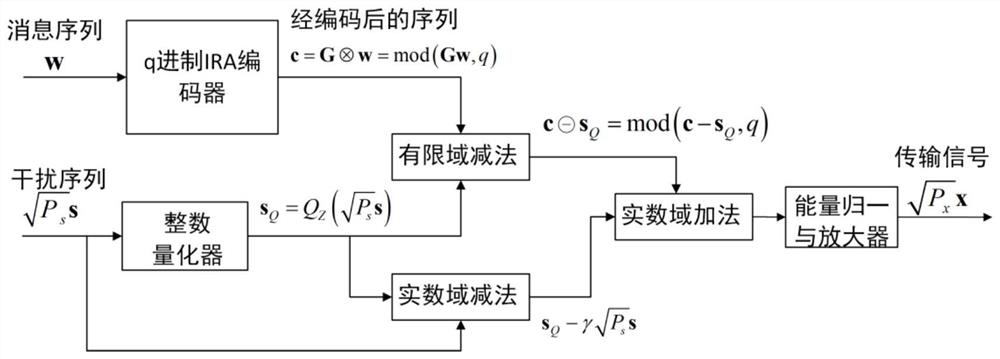
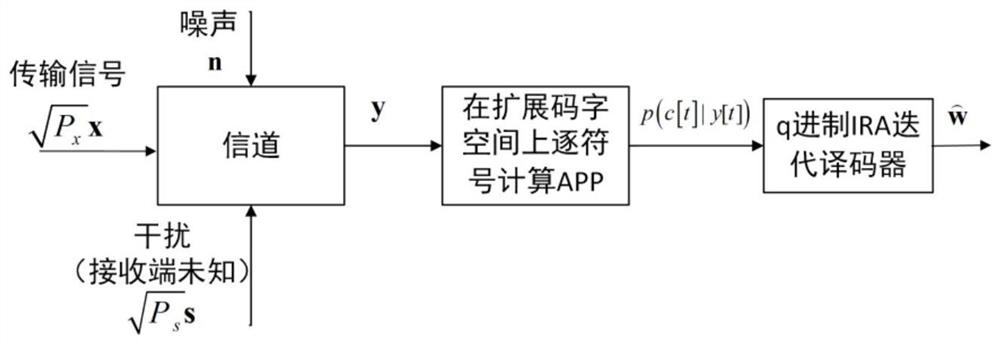
ActiveCN113315553BImprove service qualityConsistent coding complexityTransmission monitoringRadio transmissionSludgeTheoretical computer science
The invention proposes a simple dirty paper encoding method that can approach the limit of information theory. Based on the structural characteristics of q-ary linear modulation codes, that is, multiple codewords fall into the extended codebook of the codebook after being superimposed in the integer field, so that the dirty paper coding in n-dimensional space is simplified to the operation of symbol-by-symbol finite field subtraction , and maintain the optimal performance of dirty paper coding. The coding complexity of this method is basically the same as that of the single-user non-interference system, and dirty paper coding is realized with very low extra overhead. The decoding of this method only needs a symbol-by-symbol soft-value output detector and a single-user belief propagation decoding, and its complexity is basically the same as that of the single-user interference-free system. It has been verified by simulation that this method can approach the information theoretical limit of downlink multi-user channels (the gap is about 1dB), and significantly improve the system throughput and spectral energy efficiency at low cost.
Owner:BEIHANG UNIV
A social media rumor detection method based on multi-task learning
ActiveCN112685541BImprove performanceReduce overfittingData processing applicationsSemantic analysisSocial mediaData extraction
Owner:长沙市智为信息技术有限公司
An event-triggered implicit authentication method based on mobile devices
ActiveCN106170046BConfidence Threshold AccurateEfficient identificationSubstation equipmentSecurity arrangementEvent triggerUser confidence
The invention discloses an event-triggered implicit identity authentication method based on a mobile device. The implementation plan is: set the type of implicit trigger event of the device and the characteristic quantity of each trigger event. When the trigger event occurs, the device obtains the user confidence by comparing the habits of the current user with the habits of legitimate users, and through the history The current judgment threshold is obtained by calculating the user confidence degree and the judgment threshold, and then the legitimacy of the current user is determined by comparing the current user confidence degree and the judgment threshold. The invention solves the problems of inefficient identification of illegal users in the existing implicit identity verification method, requiring a large amount of user data and learning time, and the like.
Owner:陕西尚品信息科技有限公司
False review detection method based on double cycle graph
ActiveCN109344176BTo achieve the detection effectOptimize comment consistencyDigital data information retrievalSpecial data processing applicationsAlgorithmEngineering
The invention discloses a false comment detection method based on a double-cycle graph, comprising the following steps: (1) using an original graph filter to calculate a comment confidence degree anda user confidence degree of the original comment data, and screening the user confidence degree to obtain a reliable user; (2) calculating the store confidence level of the comment data correspondingto the reliable users by using the original graph filter; (3) updating the comment confidence level in the original graph filter to the comment confidence level obtained in the step (1), and calculating the user confidence level of the original comment data by using the original graph filter; (4) taking the store confidence obtained in the step (2) and the user confidence obtained in the step (3)as initial values to construct a weighted map filter; (5) calculating The store confidence, user confidence and comment confidence of the original comment data by using the weighted graph filter, andthe false comment is obtained by screening according to the comment confidence. This method improves the detection accuracy of false comments.
Owner:ZHEJIANG UNIV OF TECH
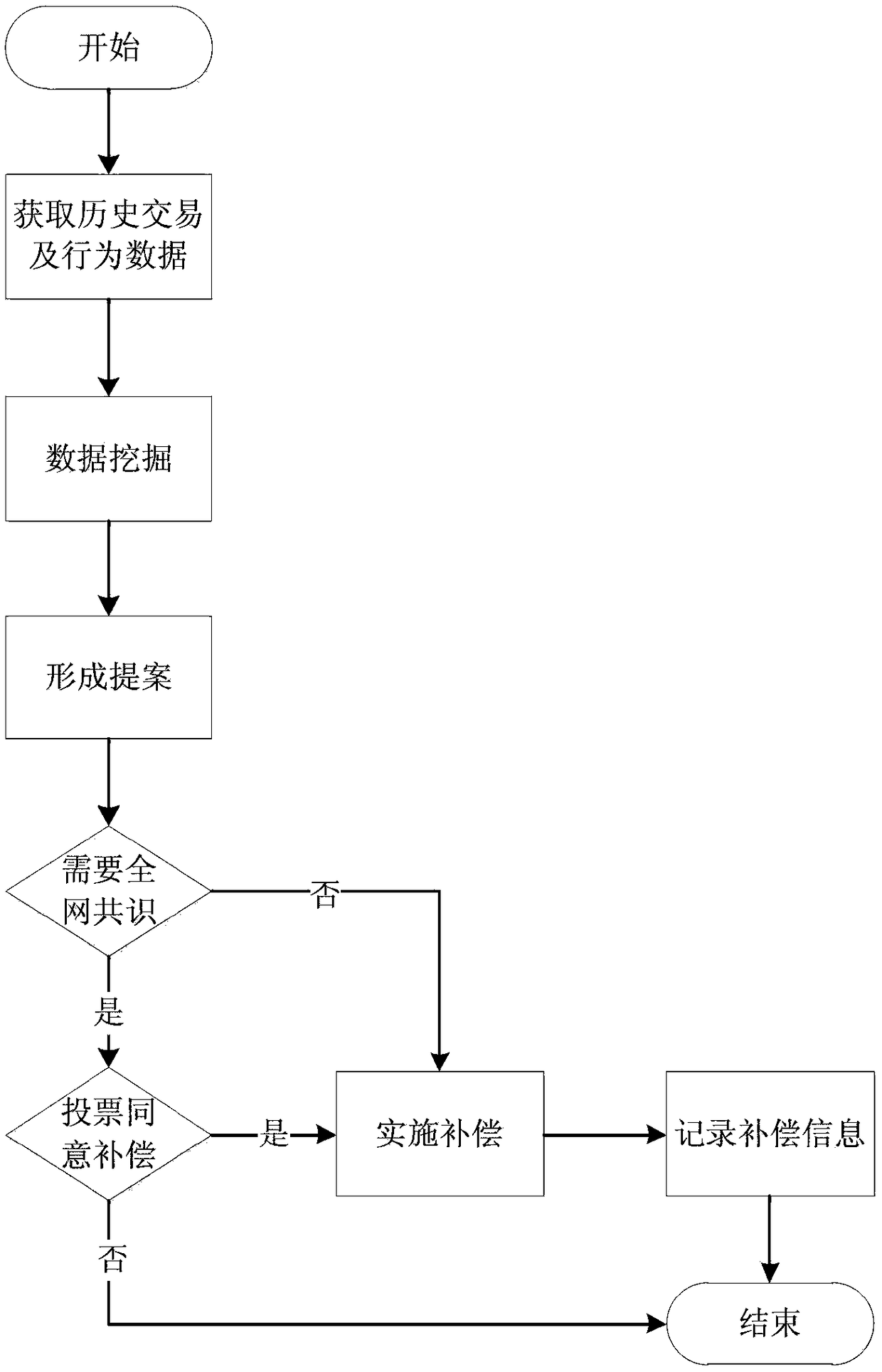
Method and system for no tampering based historical data to compensate exchange losses
PendingCN108711050ALong circulationImprove wealth distributionData miningCurrency conversionUser confidenceAnxiety
The invention provides a method and system for no tampering based historical data to compensate exchange losses. The method includes extracting historical data in a blockchain; performing data excavation according to the data; forming a compensation proposal according to calculation results; voting on proposals that are in need; and implementing compensation and recording. The system includes a historical data extracting module, a data excavation module, a proposal module, a voting module and an implementing module. Blockchain data has the characteristic of no tampering; and subsidies can be performed on users who accord with conditions and the users can be empowered by tracing back to history based on the characteristic of the blockchain. There are no specific constraints on subsidized behavior objects, the time and intensity of the subsidies cannot be known in advance, and thus, moral risks can be avoided, user confidence can be built, buying in or selling out by following the trendcaused by anxiety can be avoided, currency stability can be realized in the long run, and therefore, the ecological balance and sustainable development of blockchain systems can be maintained.
Owner:WUHAN LONGJIN SCI & TECH
An innovative quality assurance and service synergy system applied to the production of plant-derived biological agents
InactiveCN109284923AIncrease convincingIncrease productivityCo-operative working arrangementsResourcesQuality assuranceProduction risk
The invention relates to the field of Internet of things, in particular to an innovative quality assurance and service synergy system applied to the production of plant-derived biological agents, including a quality circulation traceability system, a quality safety inspection system, a support dispatch center, a central integrated processor and an evaluation terminal, the quality flow traceabilitysystem is connected to a central integrate processor. The quality and safety inspection system is connected with the central integrated processor, the guarantee dispatching center is connected with the quality circulation traceability system, the quality and safety inspection system, the evaluation terminal is connected with the integrated processor, the information is interconnected, and the production is managed in a more precise and dynamic way. The main purpose of this system is to realize intelligent identification, tracking, monitoring, sharing and management, improve the production efficiency and reduce the production risk, taking the evaluation of the end-user as the core. Make the industrial chain more transparent, improve the service quality and user confidence; the invention standardizes the industrial production of plant-derived biological preparations and push forward the formation of systems and the process of large-scale industrialization.
Owner:西安绿海生物科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com