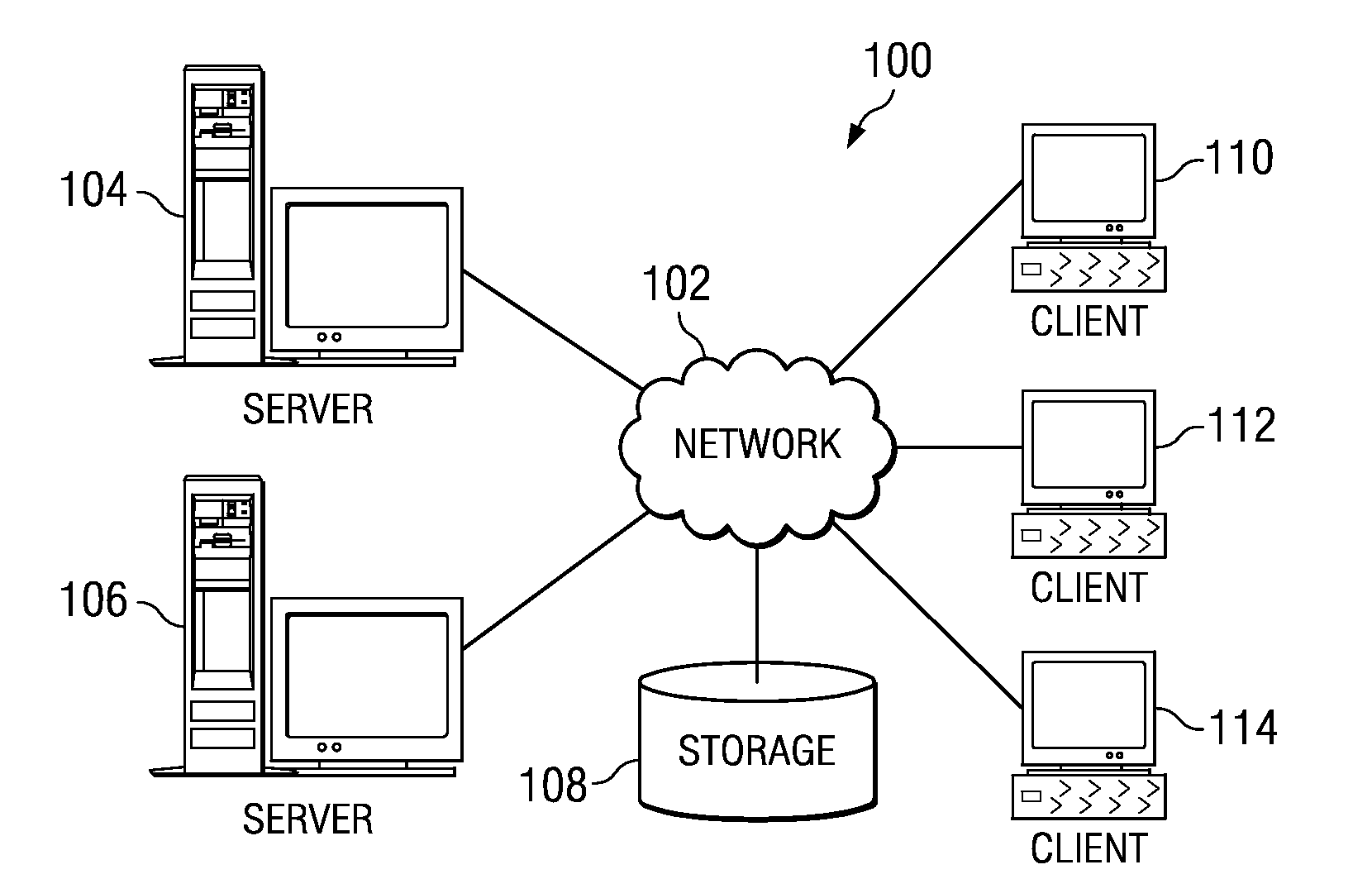
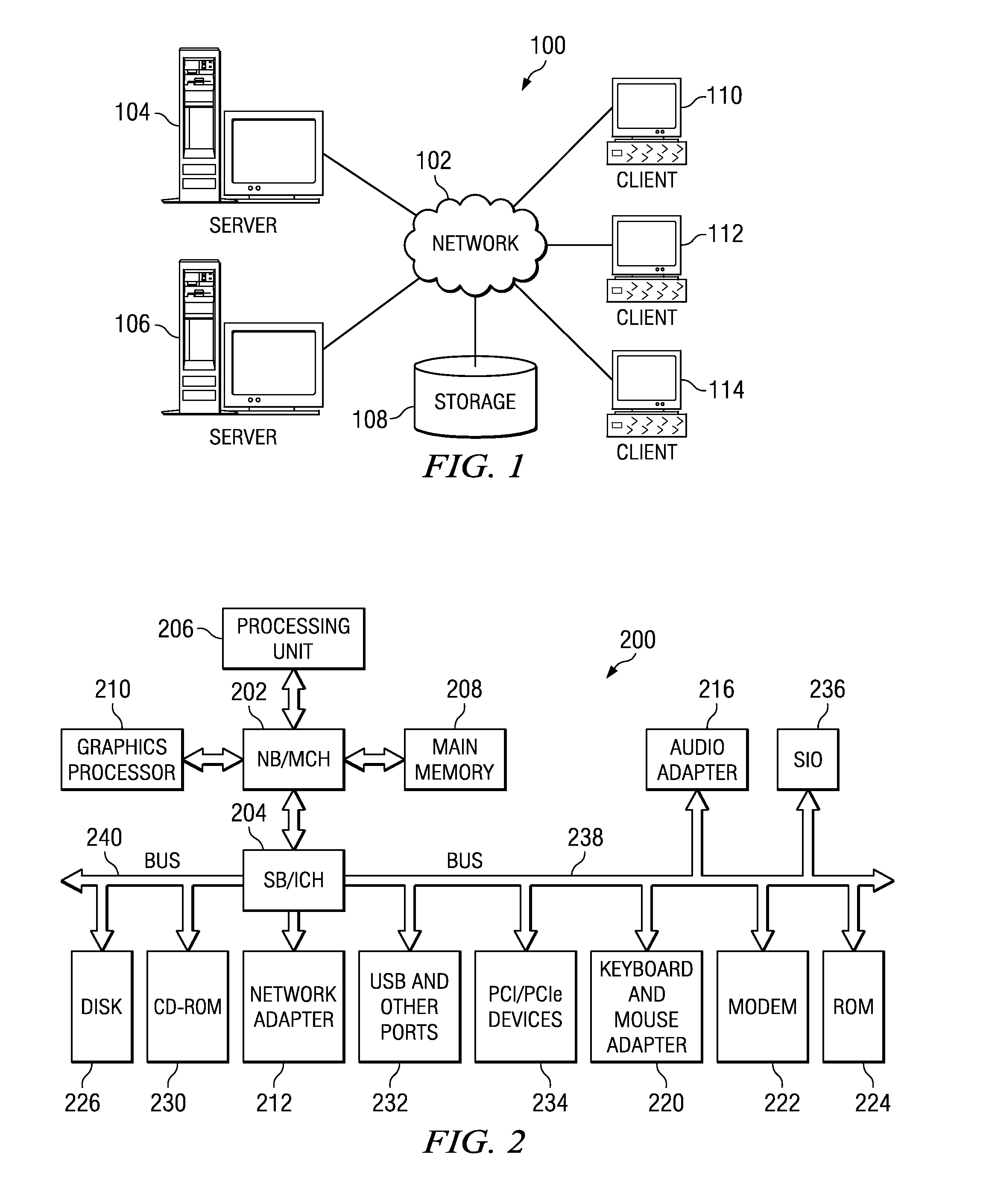
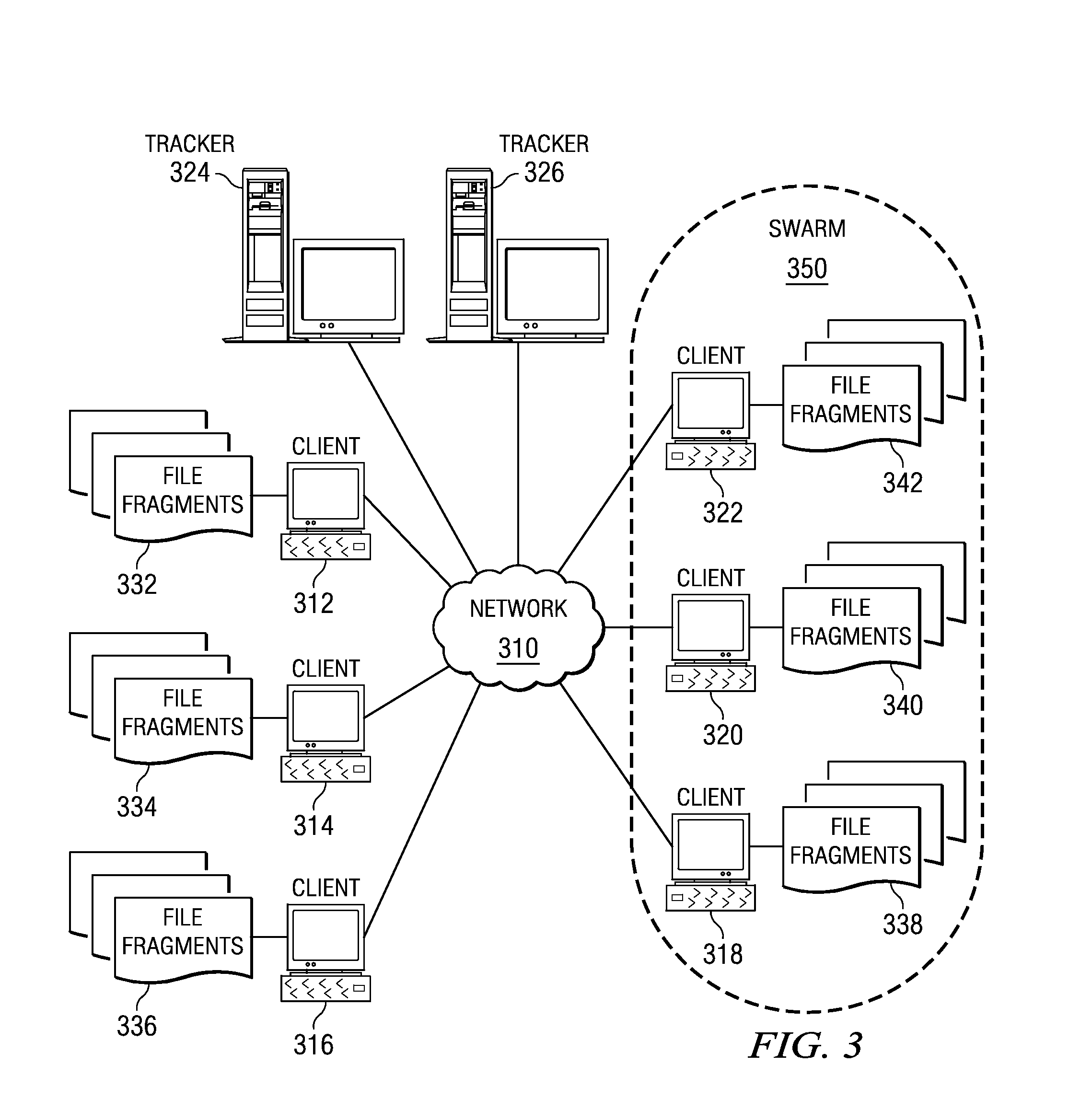
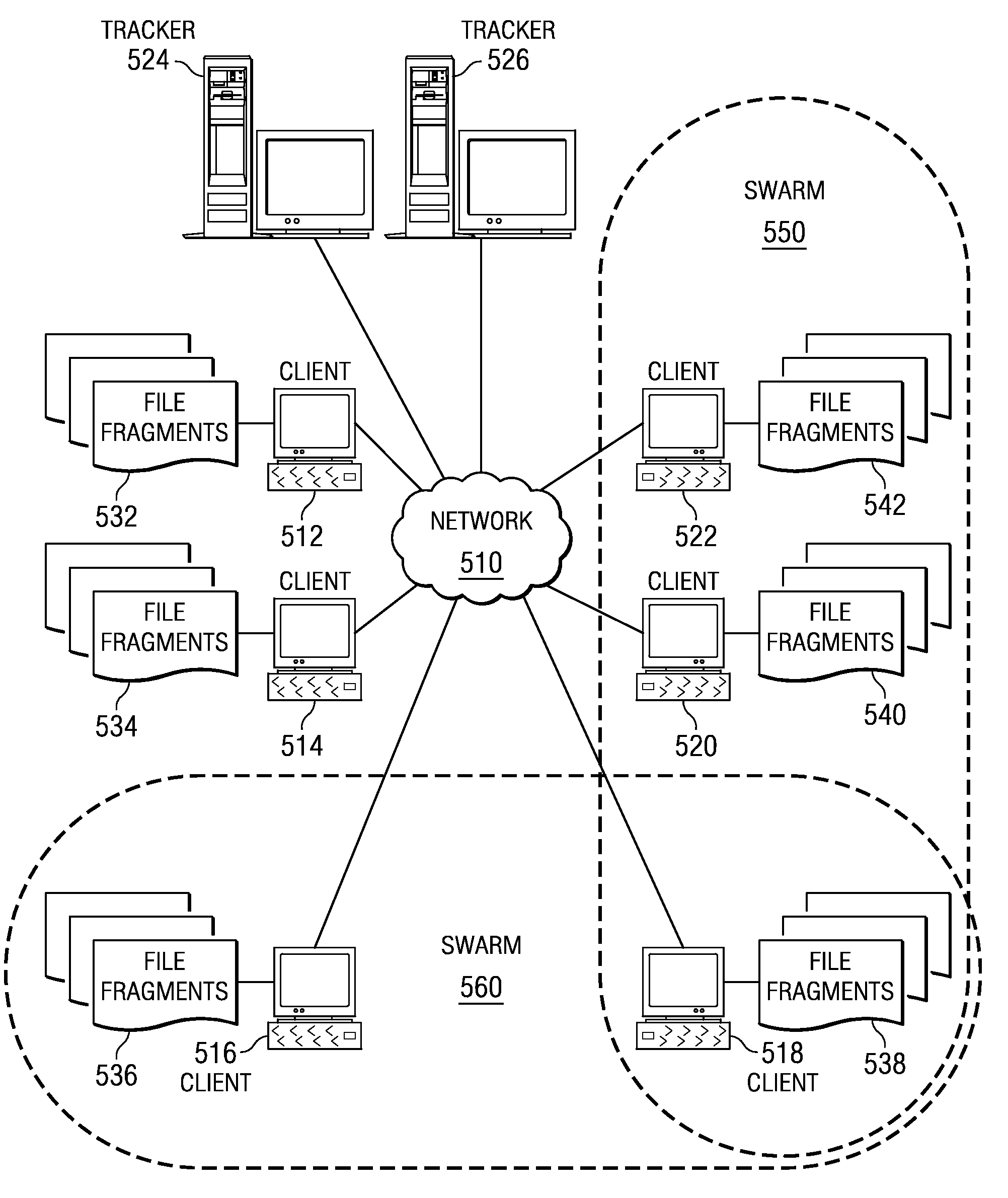
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38 results about "Peer to peer file sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
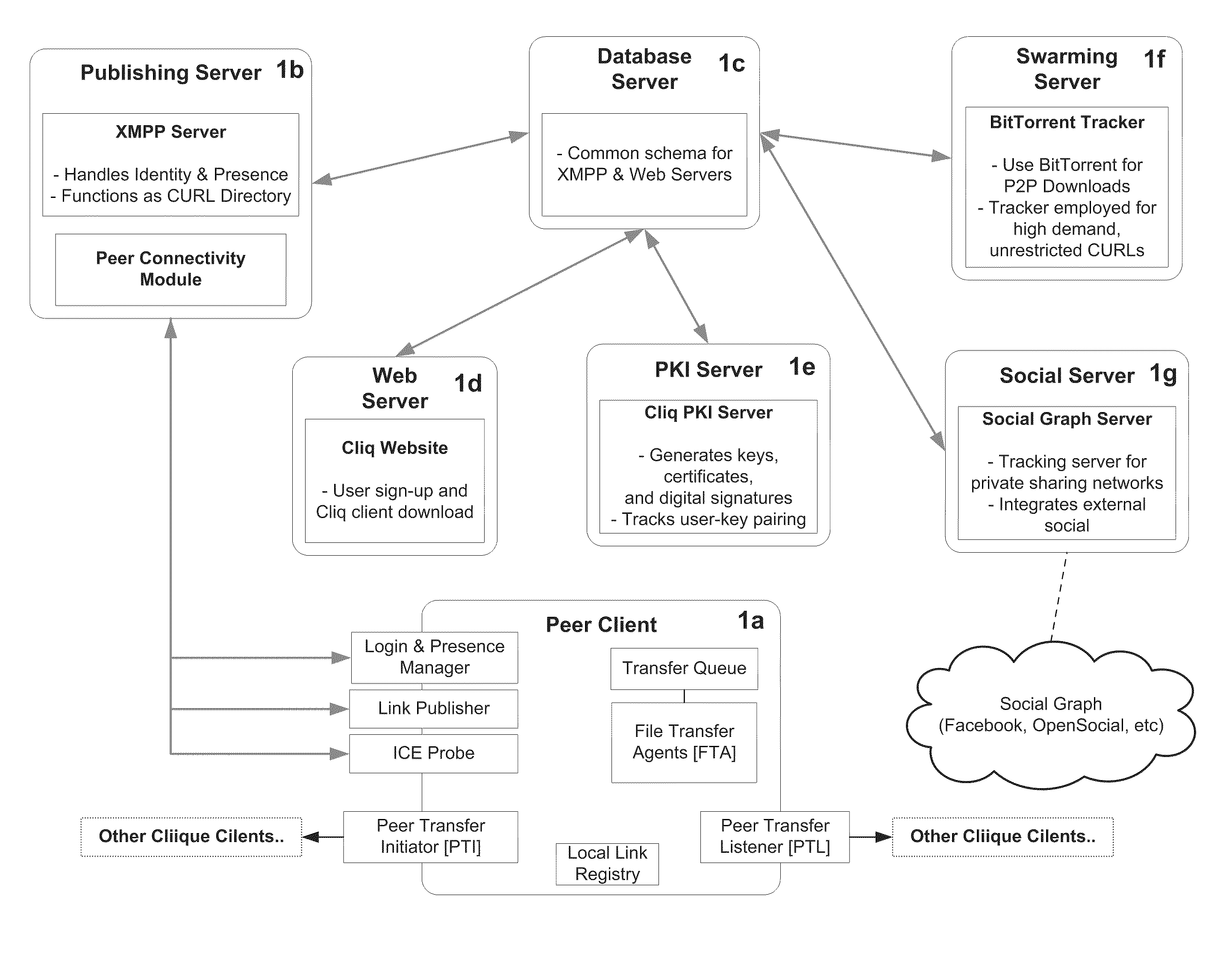
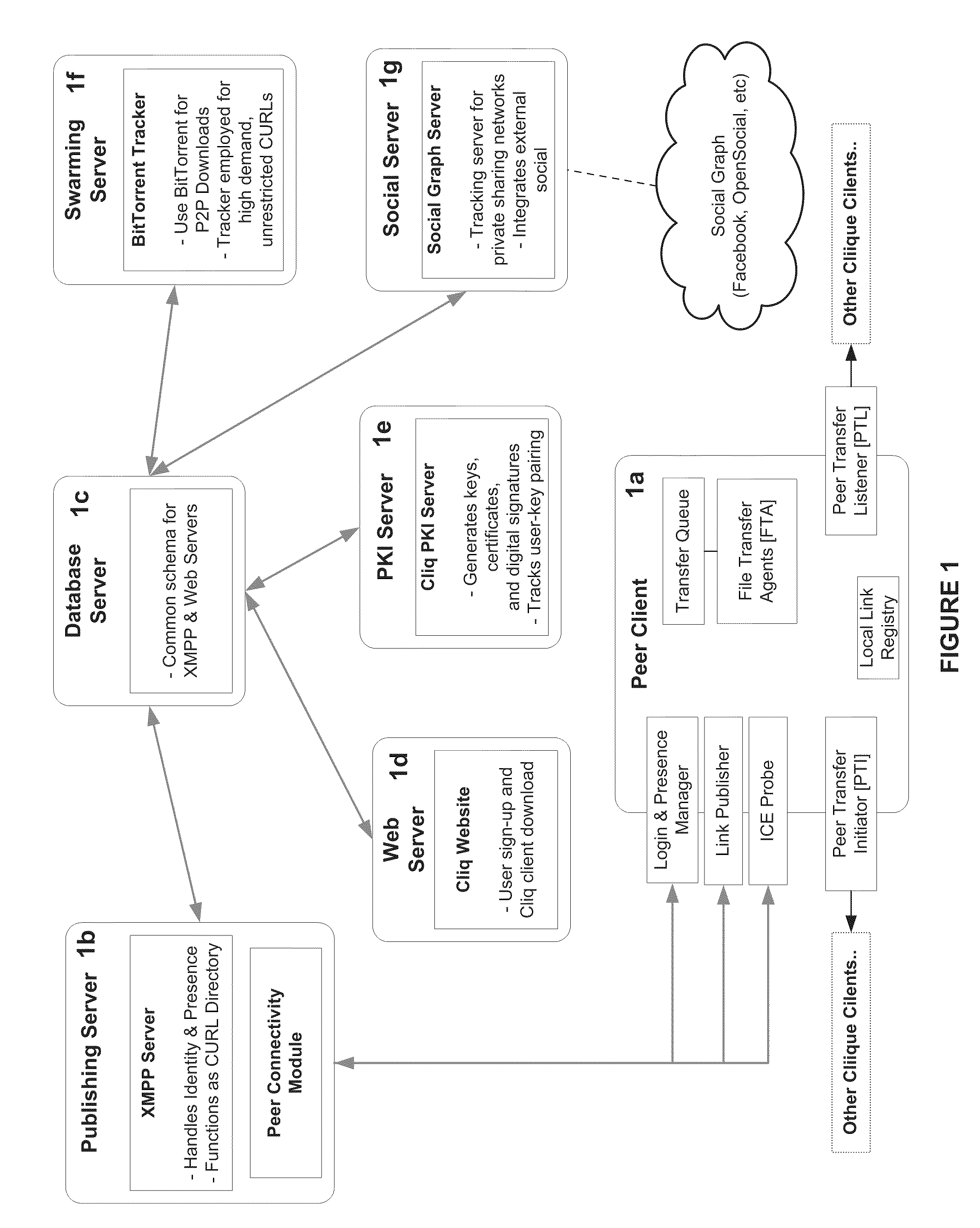
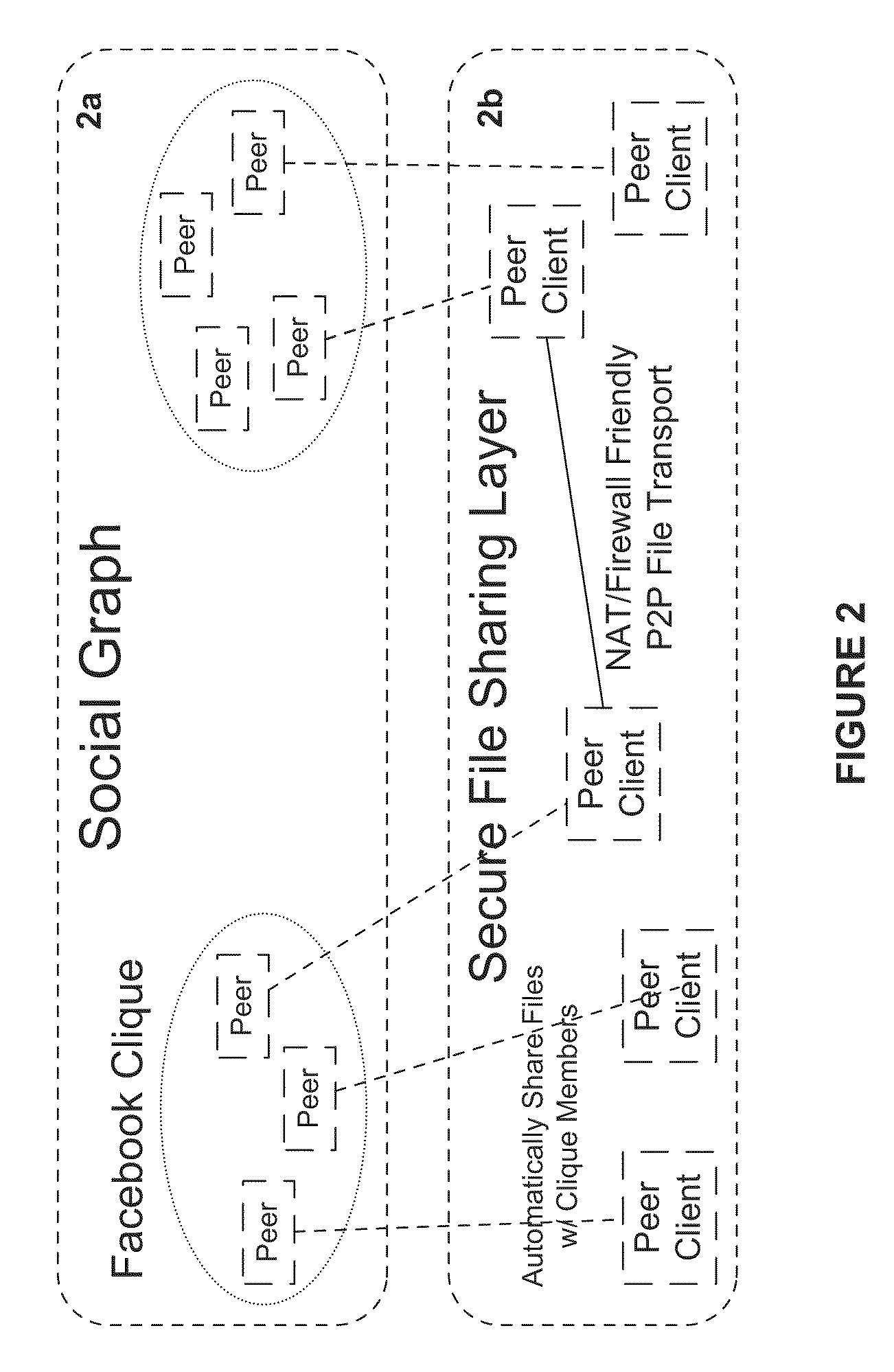
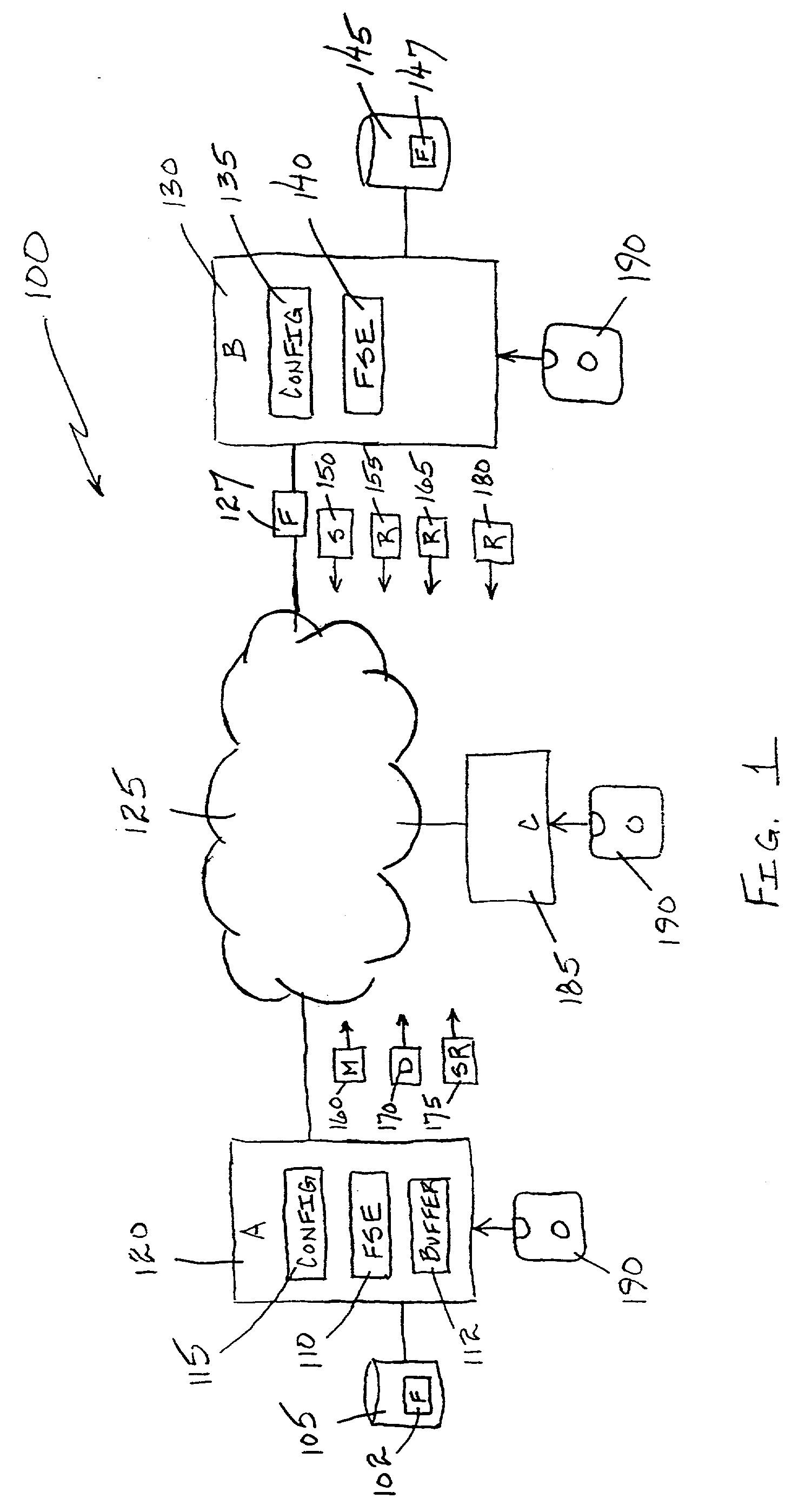
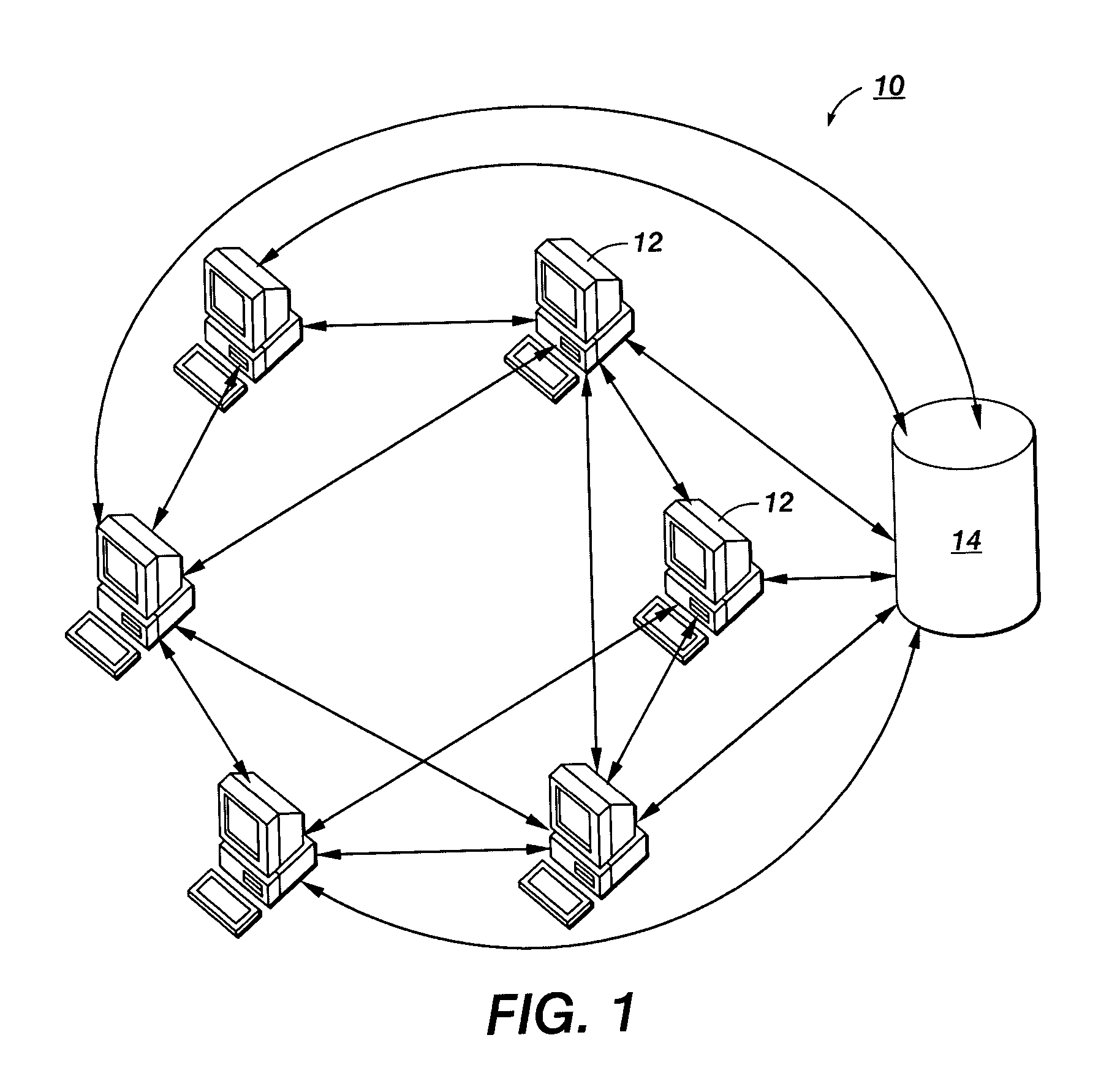
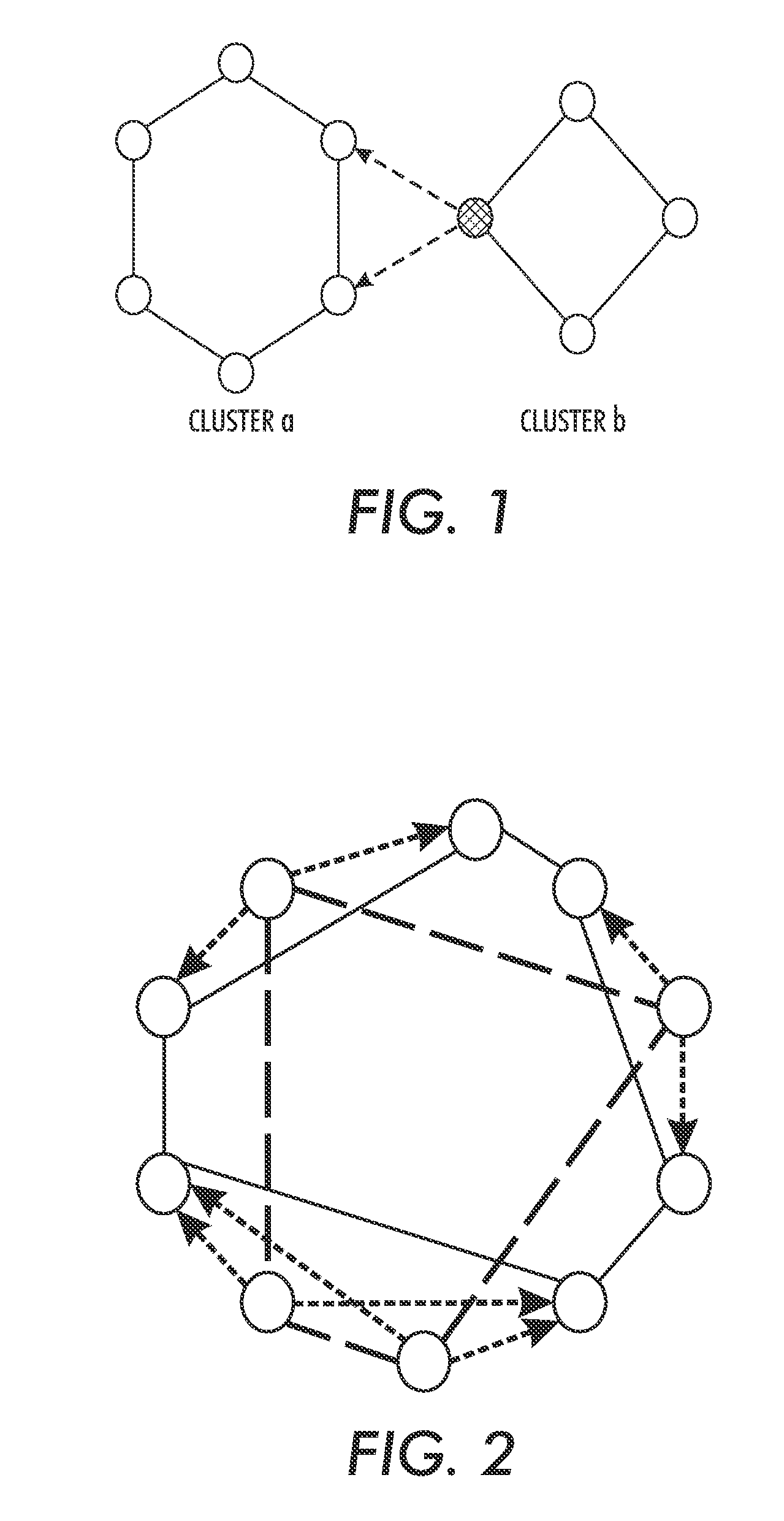
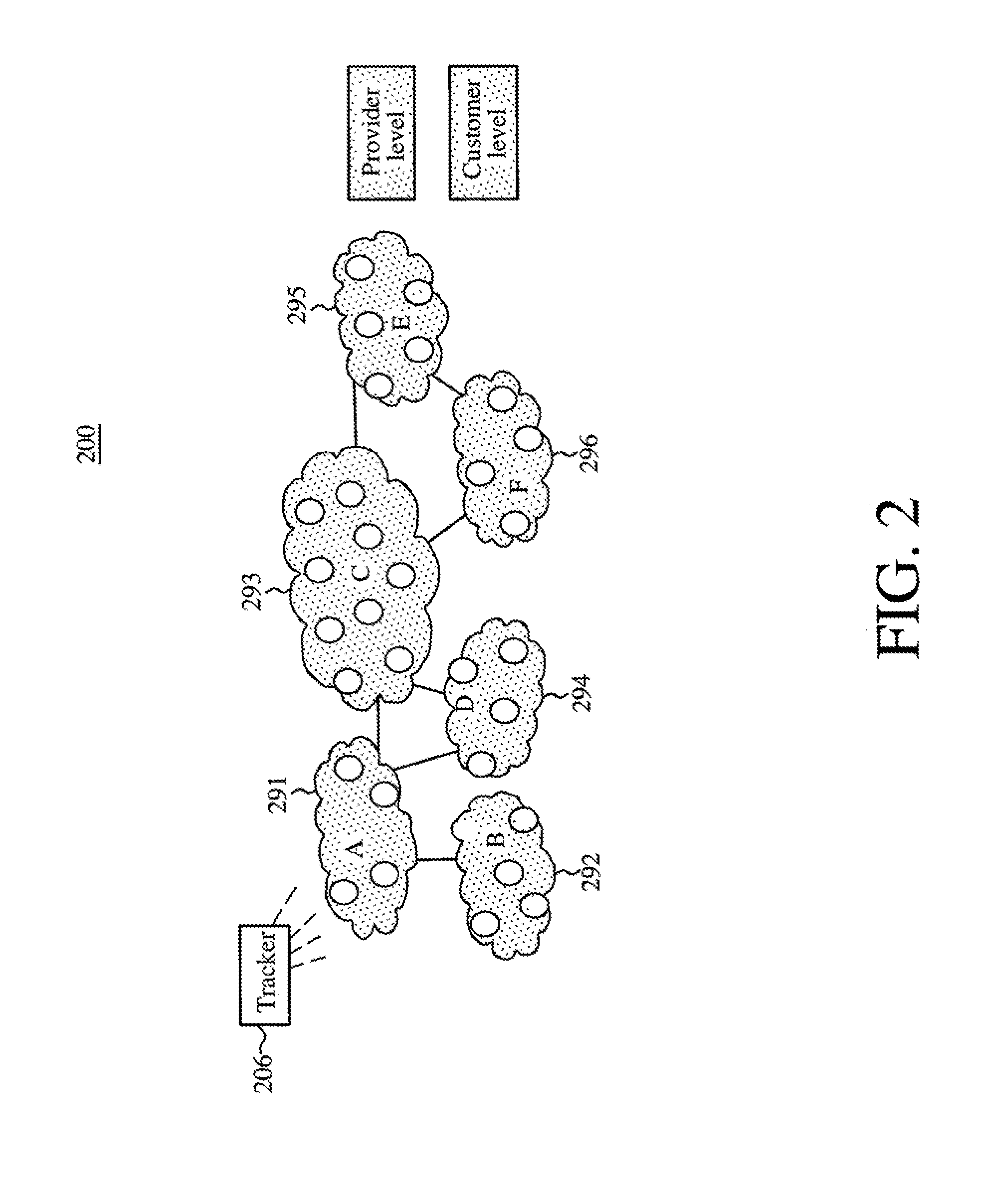
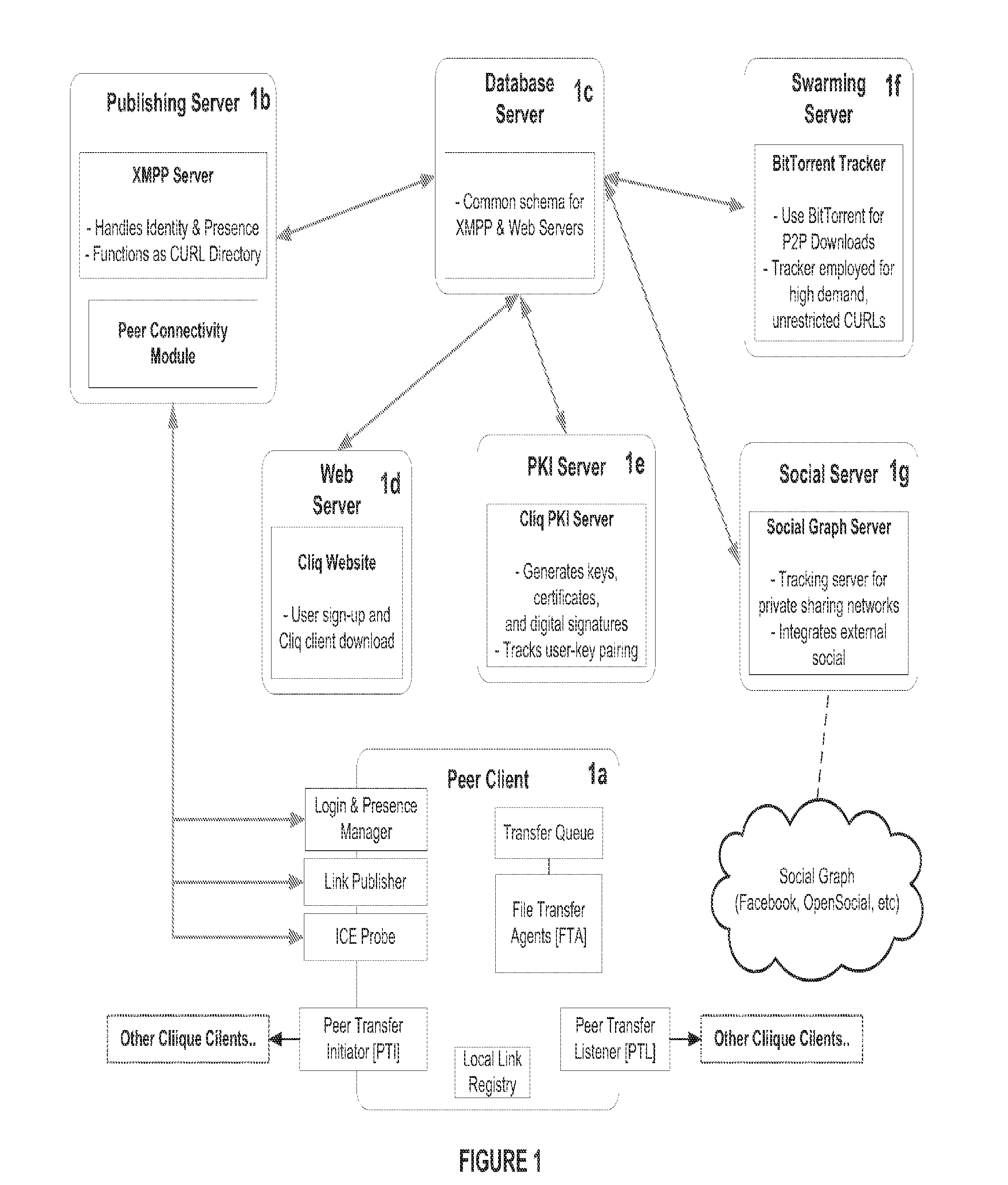
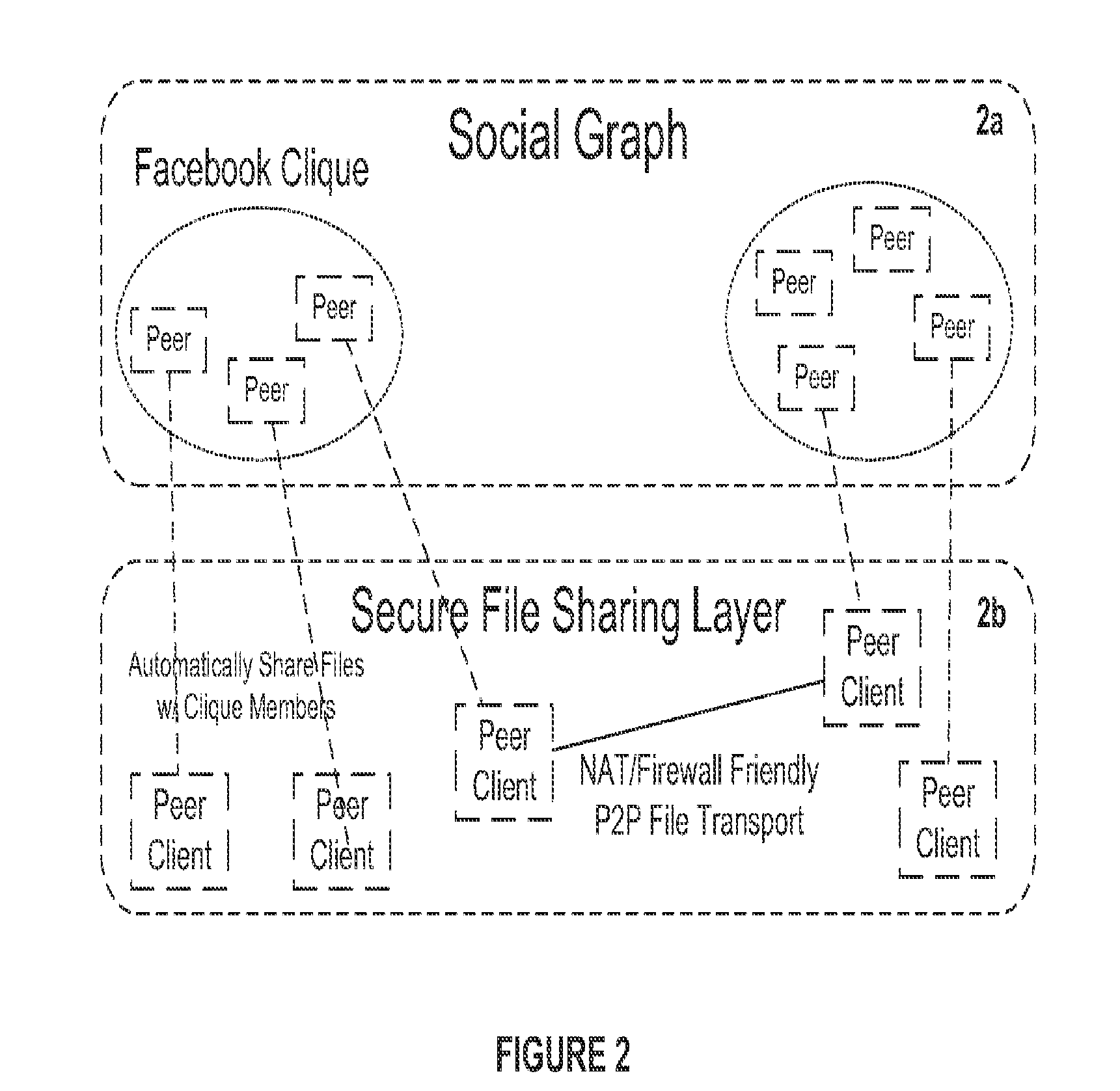
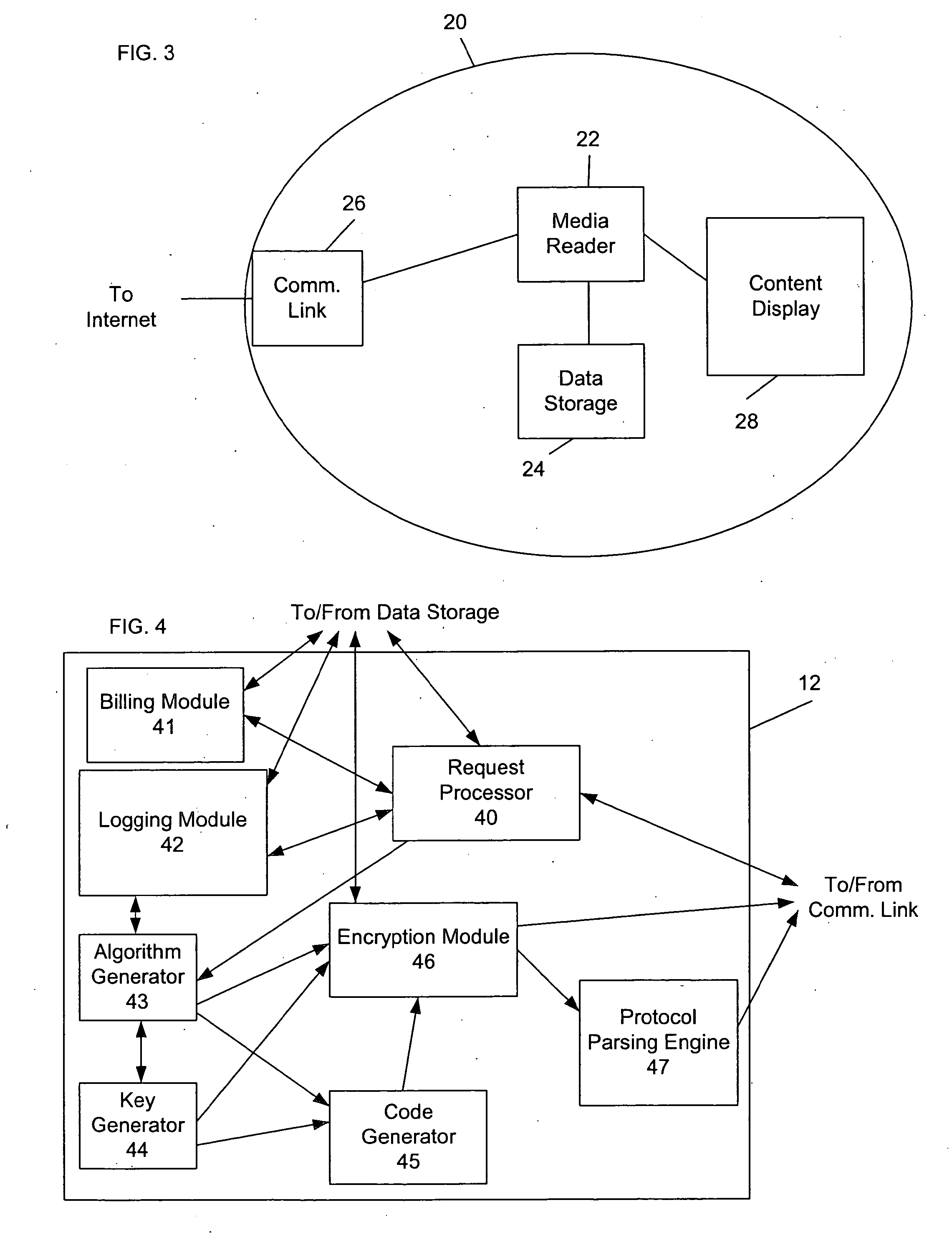
System and Method for Anonymous Addressing of Content on Network Peers and for Private Peer-to-Peer File Sharing
ActiveUS20110035503A1Efficient and privateEfficient and private peer-to-peer file sharingMultiple digital computer combinationsTransmissionPeer to peer file sharingPeer-to-peer
A system and method for efficient and private peer-to-peer file sharing consists of ascribing a uniquely identified and anonymous link (an“edgelink”) to any file or set of files on a peer computer. The link is registered with a publishing server along with continuously updated connectivity information about the peer without registering any identifying information about the file. A peer recipient is able to access the link, receive connectivity information about the publishing peer from the server, and then receive the file from the publishing peer without file content passing through the server, mediating any intermediary NAT devices without requiring any manual or automatic device reconfiguration.
Owner:ZAID SAM
Peer to peer file sharing system using common protocols
There is provided a method for exchanging data between a first device and a second device via a network. The method includes (a) communicating a request for the data from the second device to the first device, (b) communicating an identifier for the data from the first device to the second device, (c) communicating the identifier from the second device back to the first device, and (d) communicating the data from the first device to the second device, after the communication of the identifier from the second device back to the first device. The request, the identifier, and the data are formatted in accordance with a protocol that is common to both of the first device and the second device. There is also provided a system for a first device to exchange data with a second device via a network.
Owner:IBM CORP
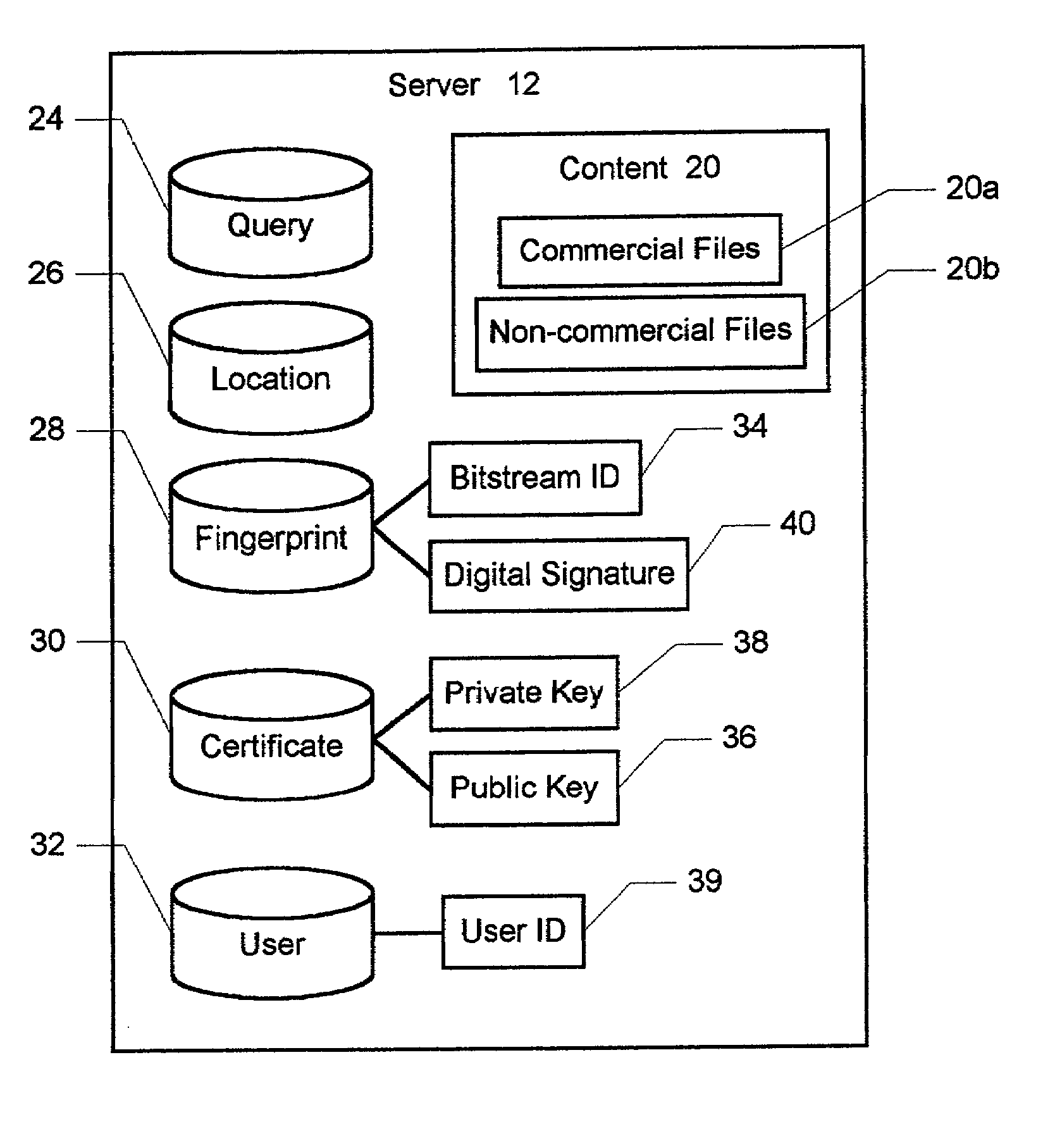
Method and system for providing a secure peer-to-peer file delivery network
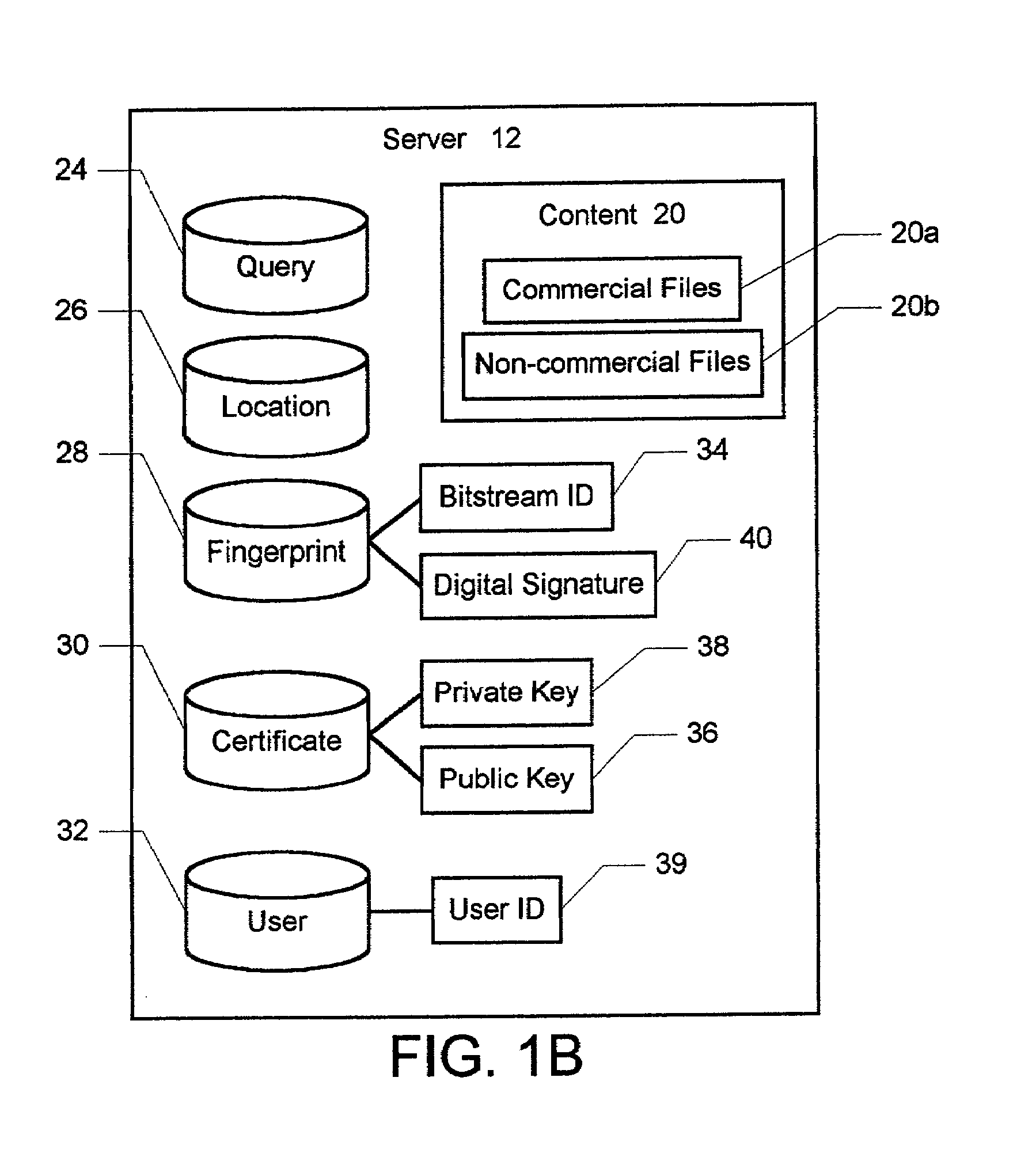
InactiveUS7047406B2Utilizes bandwidth efficientlyEffective bandwidthUser identity/authority verificationUnauthorized memory use protectionPublic networkClient-side
A method and system for electronically delivering files over a public network is disclosed. The network includes a plurality of computers including at least one server node and multiple client nodes. In a first aspect of the present invention, the method and system enable secure and reliable peer-to-peer file sharing between two client nodes. First, a digital fingerprint is generated and associated with a file in response to the file being selected for publication on a first client node. An entry for the file is then added to a searchable index of shared files on the server node, and the fingerprint for the file is also stored on the server. In response to a second client selecting the file from the search list on the server node, the file is automatically transferred from the first client node directly to the second client node. The second client node then generates a new fingerprint for the file and compares with the new fingerprint with the fingerprint from the server node, thereby verifying the authenticity of the file and publisher. In a second aspect of the present invention, the method and system also enable subscription-based decentralized file downloads to the client nodes. First, the client nodes are allowed to subscribe with the server node to periodically receive copies of one of the files. To provide a current subscribing client node with the file, the geographically closest client node containing the file is located, and the file is transferred from the closest node directly to the current subscribing node, thereby efficiently utilizing bandwidth.
Owner:QURIO HLDG
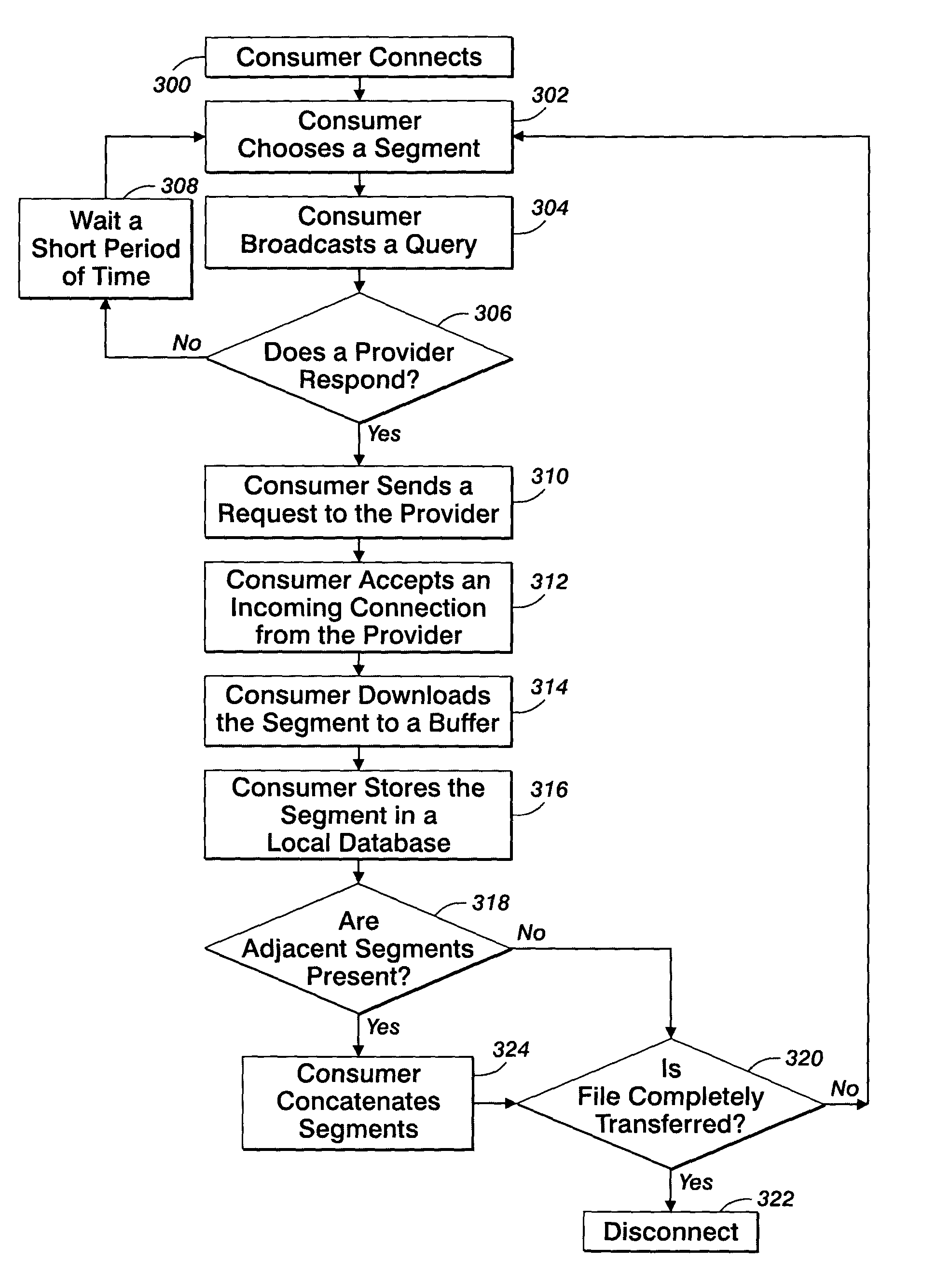
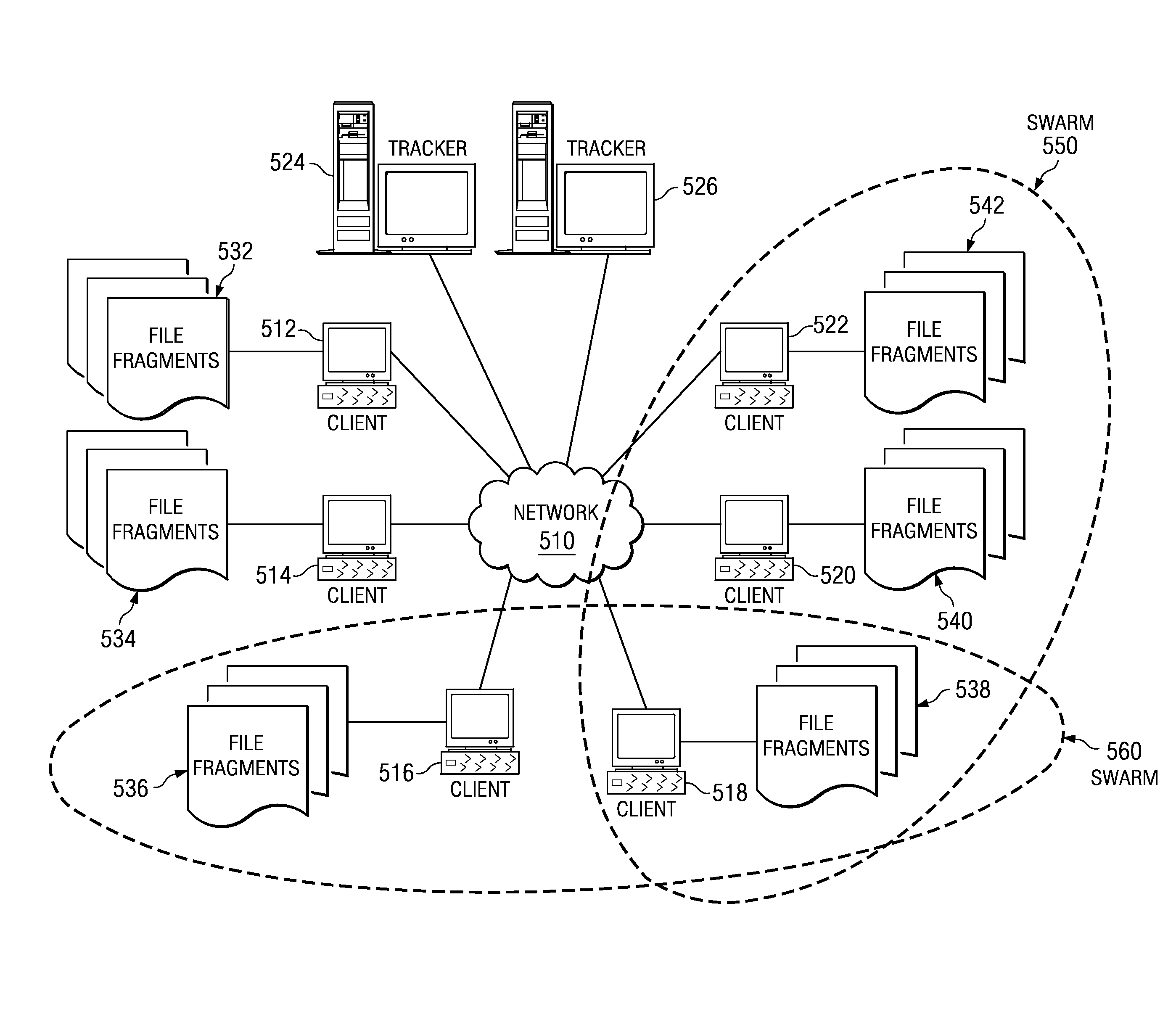
Peer-to-peer file sharing system and method using downloadable data segments
InactiveUS7970835B2Multiple digital computer combinationsTransmissionData segmentDistributed computing
A peer-to-peer filing sharing system and method are provided which allow peers in a P2P network system to download segments of a large file in indeterminate order, storing them in a database and making those segments available to other peers in the P2P network system. Given the possibility that only a few peers in the P2P network system may have a complete copy of the file at any given time, the potentially many peers each having a different subset of segments from the total file, can immediately make the segments available to other peers. Given a sufficient number of peers, and a reasonable amount of time, it is highly likely that a complete copy of the file will exist and be distributed throughout the P2P network system, even if the original provider disconnects from the P2P network system or by some other reason becomes unavailable.
Owner:XEROX CORP
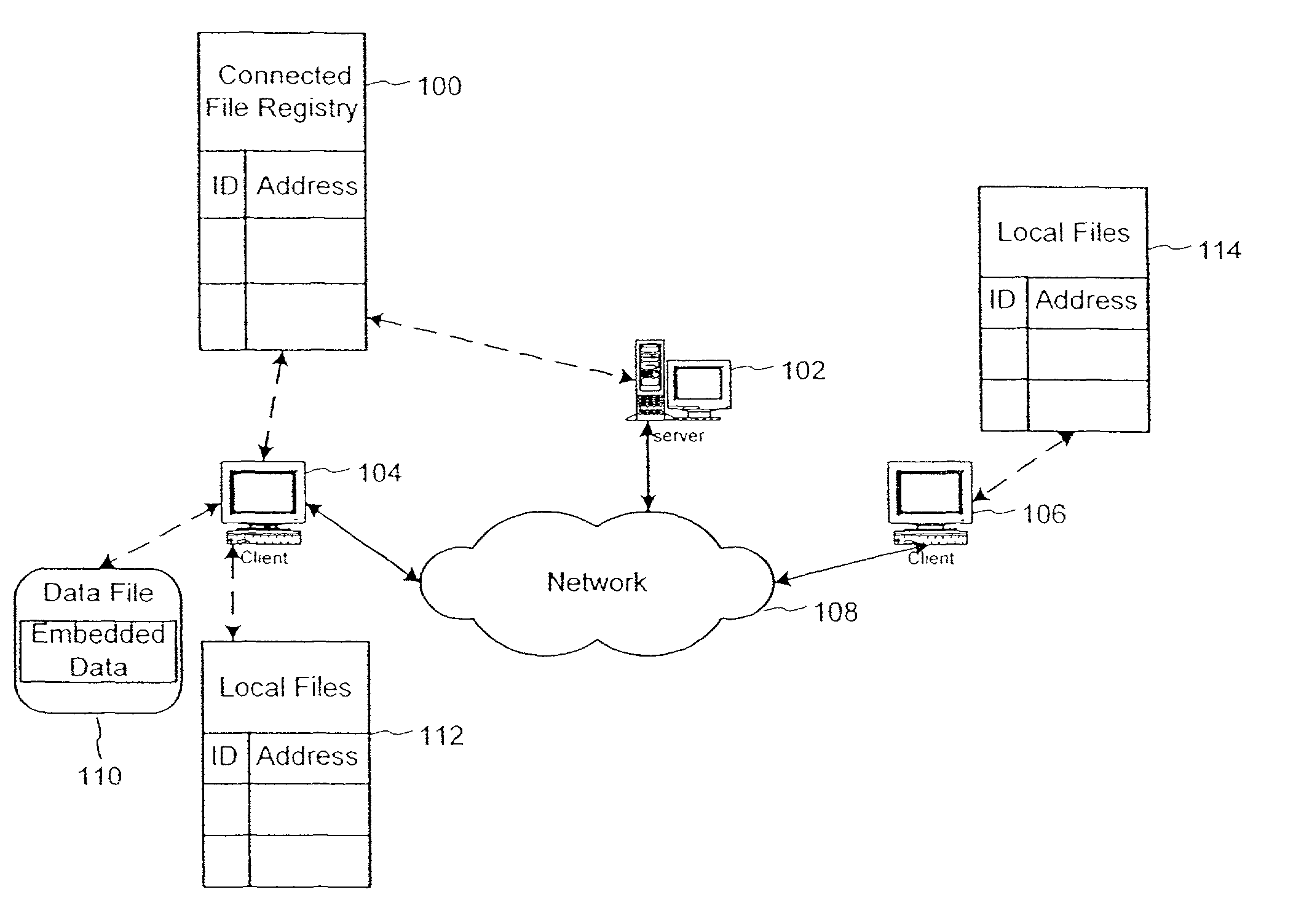
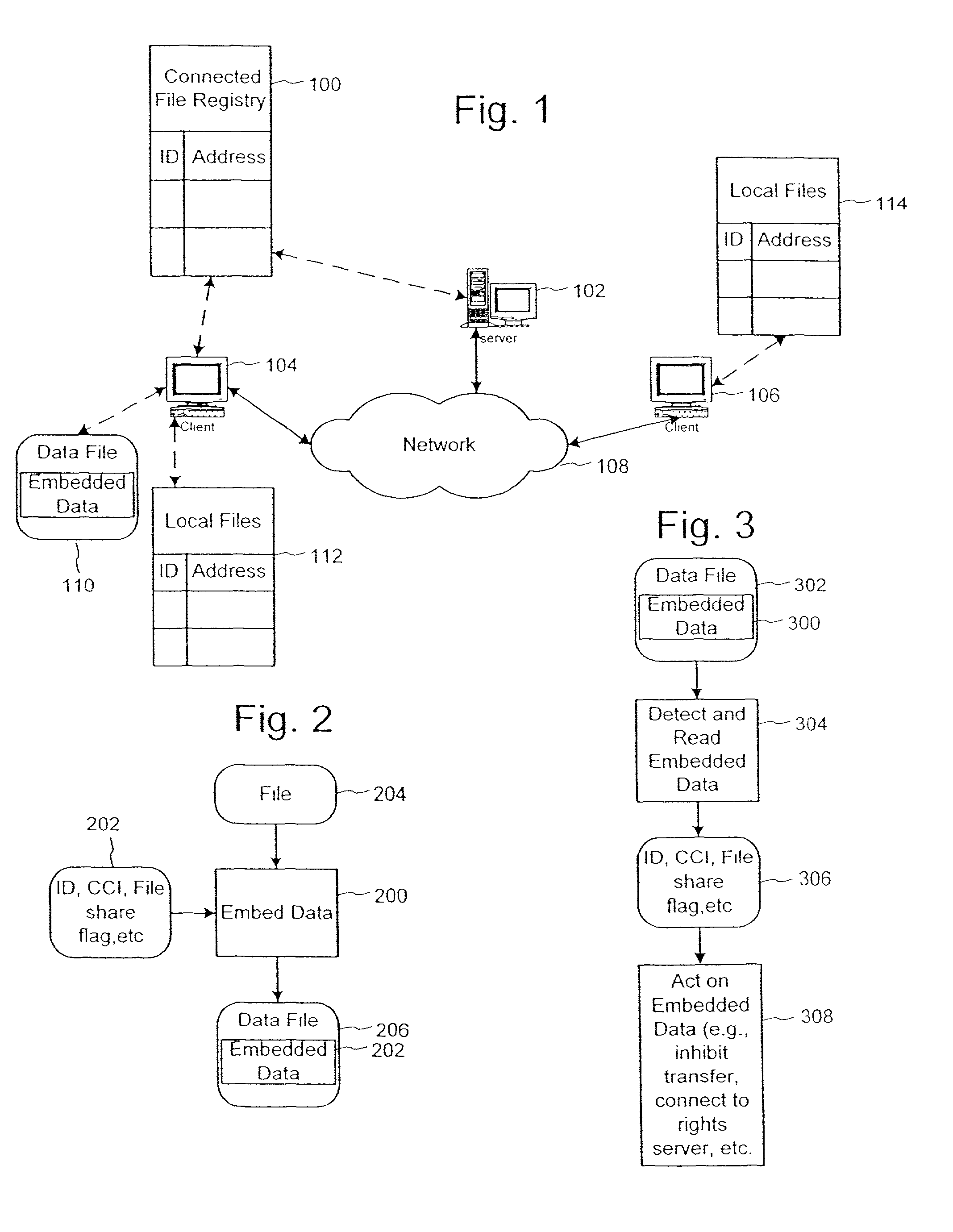
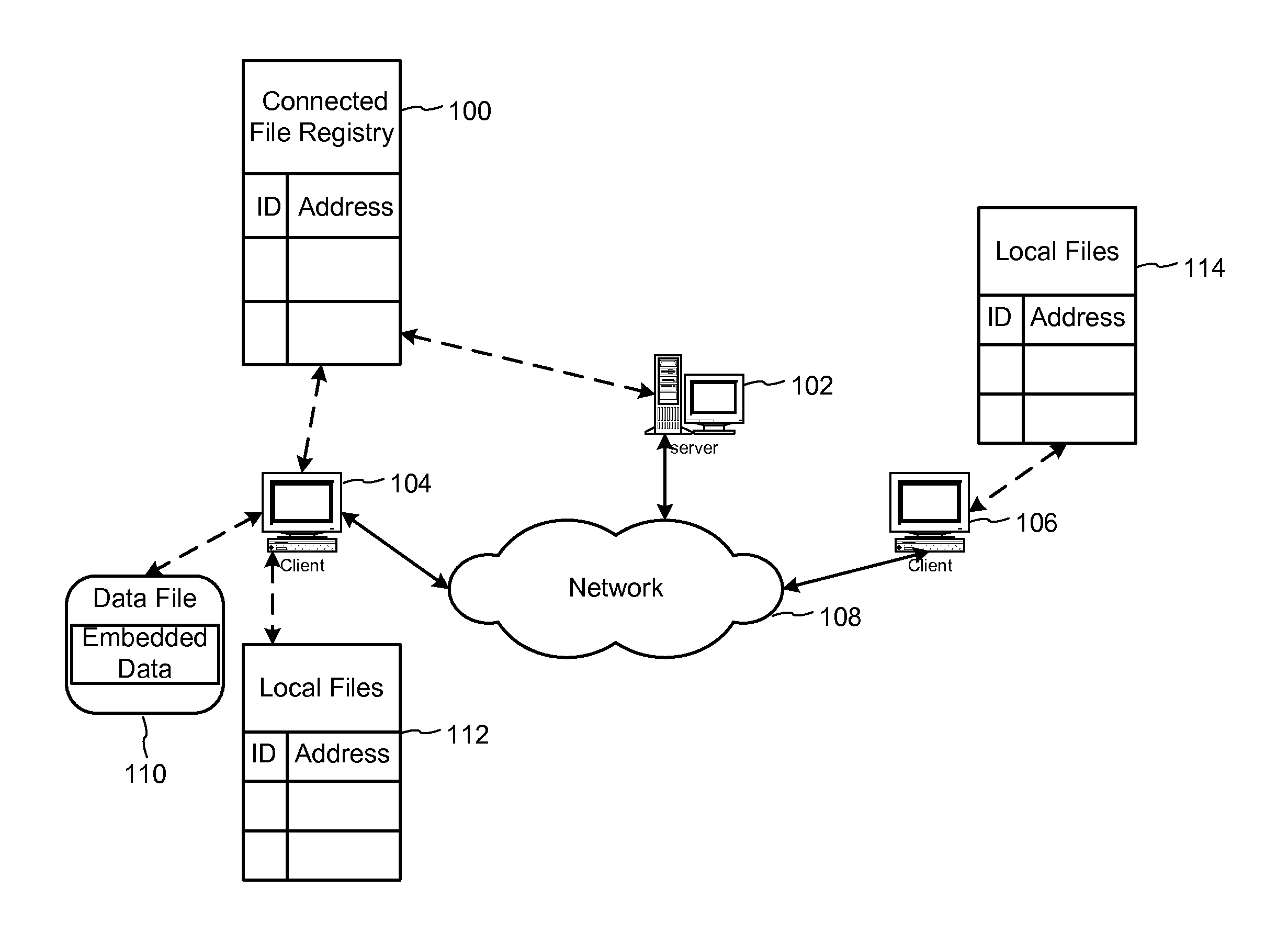
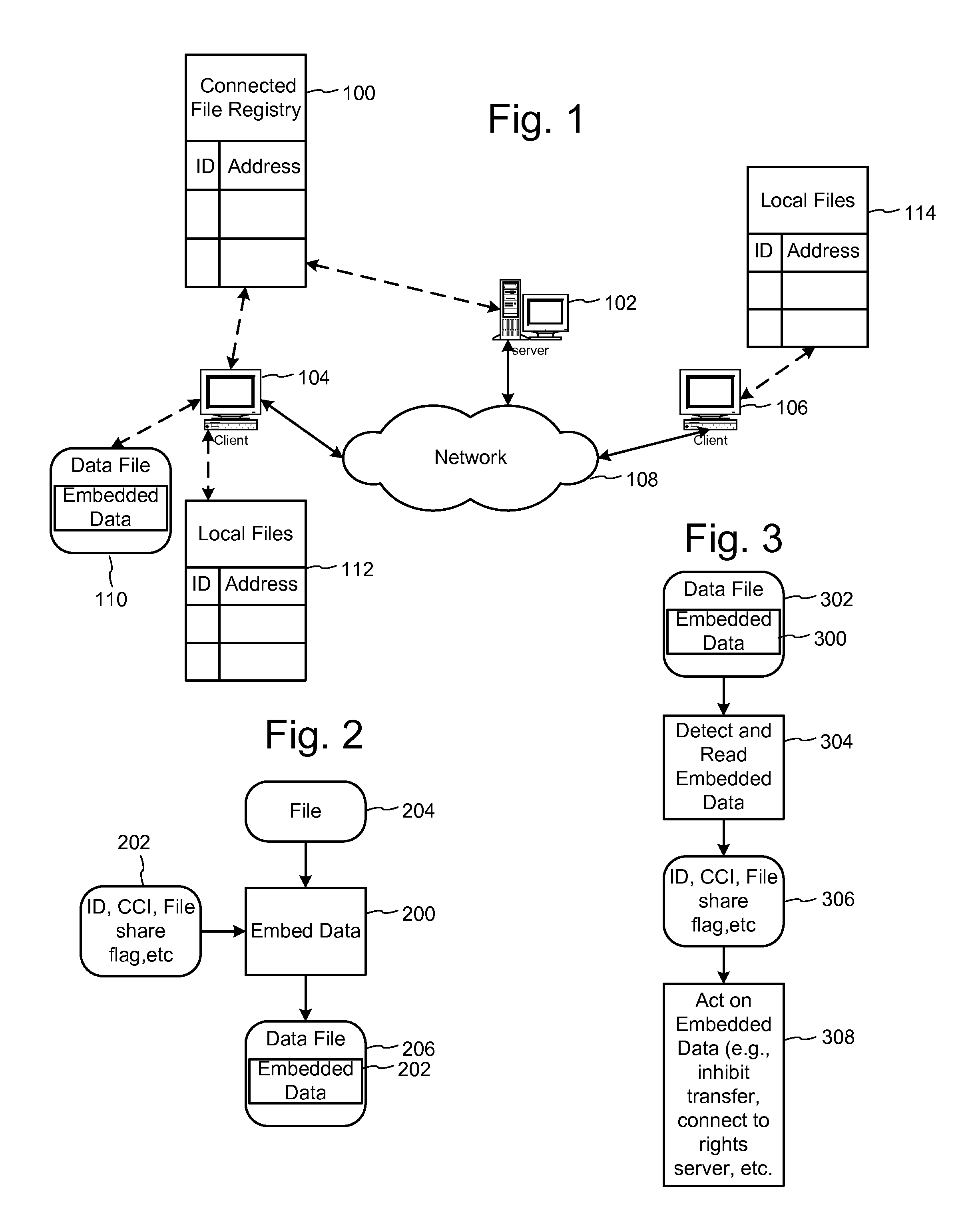
Using embedded data with file sharing
InactiveUS7756892B2Easy to liftFacilitates and enhances authorized file sharingDigital data processing detailsUser identity/authority verificationReplica managementManagement system
Owner:DIGIMARC CORP
Method and System of Administrating a Peer-to-Peer File Sharing Network
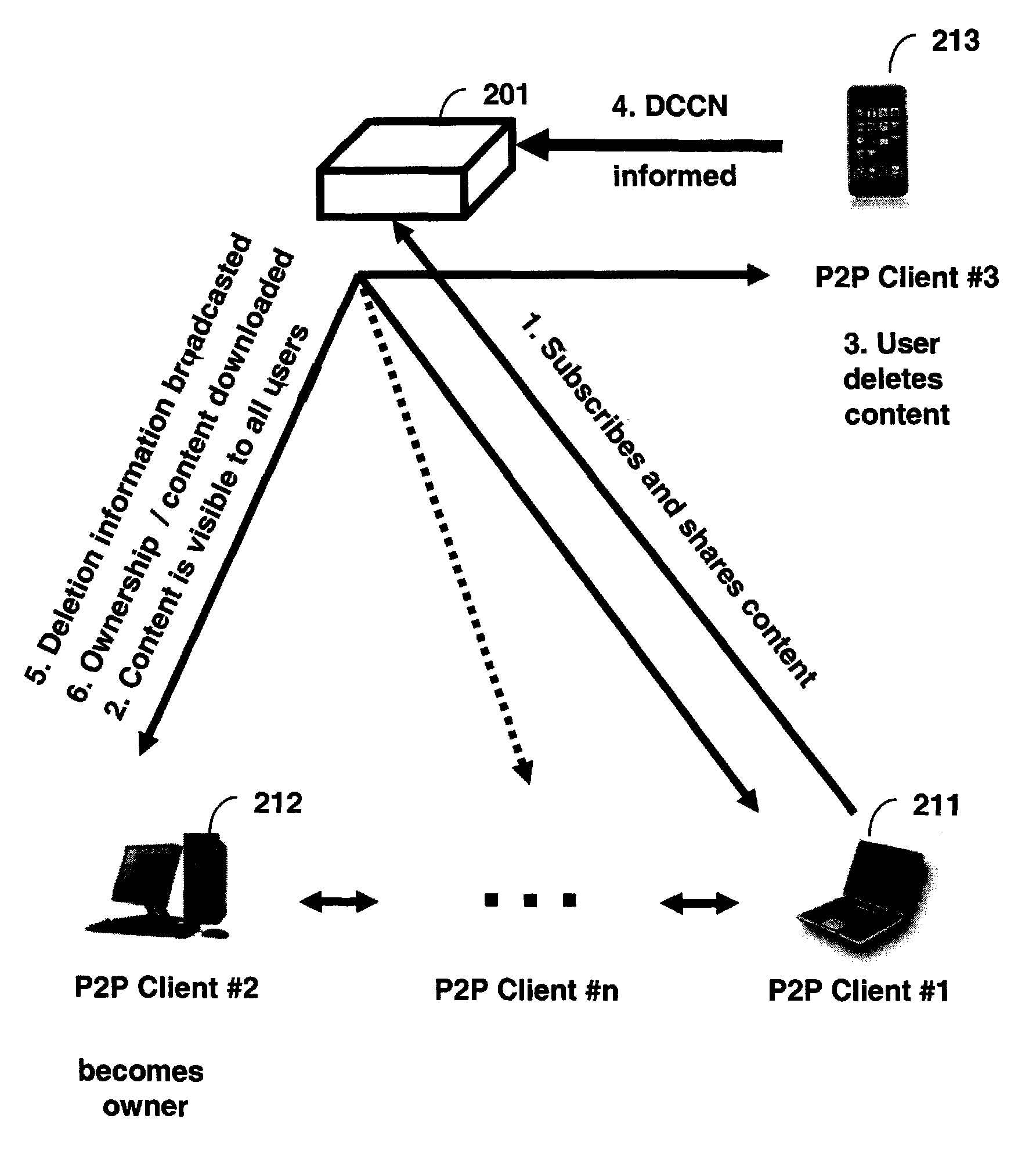
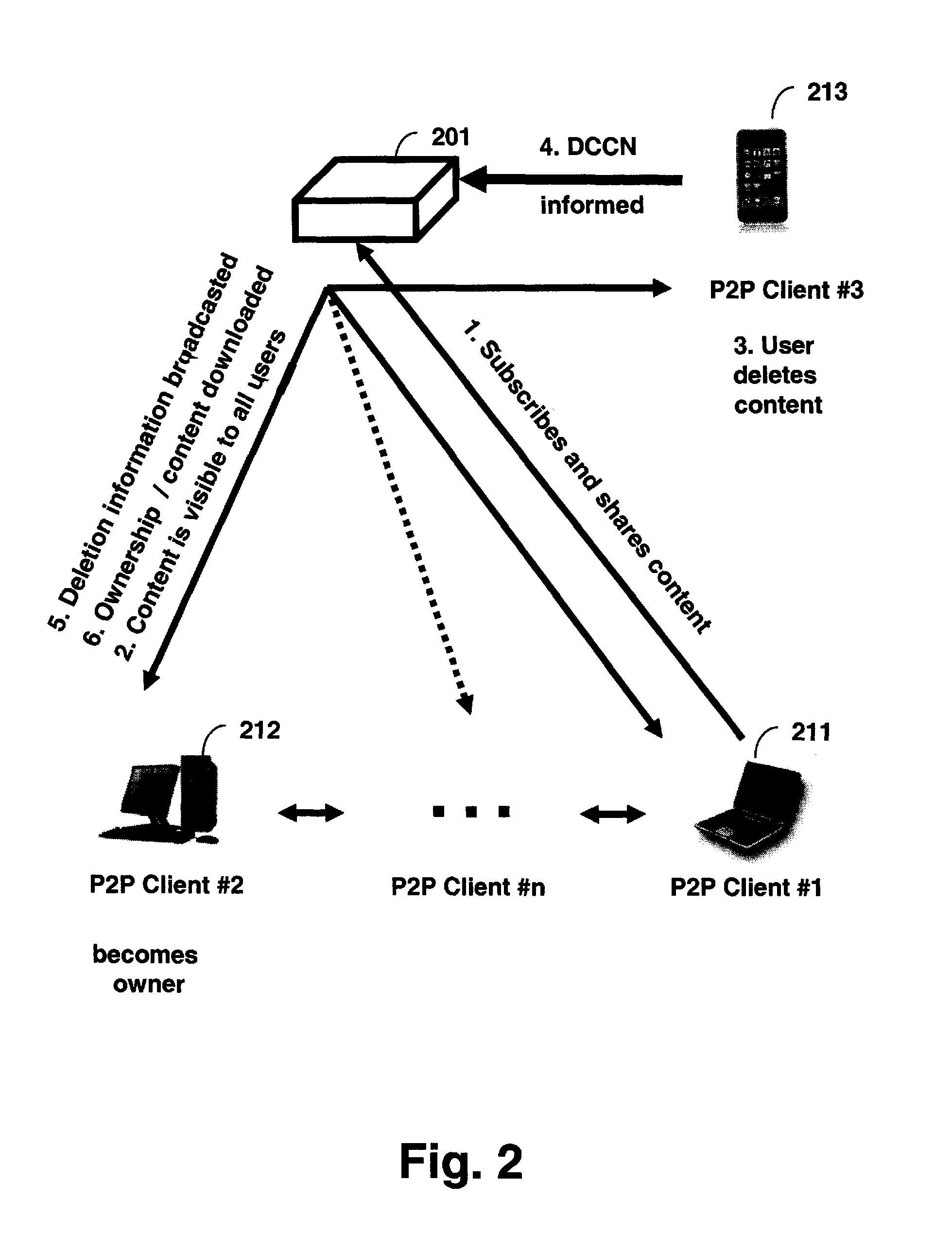
A computer-implemented method, system, and computer program product for administering a peer-to-peer file sharing computer network. The method includes: maintaining a reference associating a particular shared file with a seeder in a community of peers and a number of seeders in the community; and registering a second peer as a second seeder of the particular shared file, if a first seeder in the community of peers has informed the peers of a termination of the availability of a file seeding of the particular shared file. The system includes means for performing the steps of the method. The computer program product includes computer program instructions for carrying out the steps of the method.
Owner:IBM CORP
Using embedded data with file sharing
InactiveUS7689532B1Easy to liftDigital data processing detailsUser identity/authority verificationExtensibilityManagement system
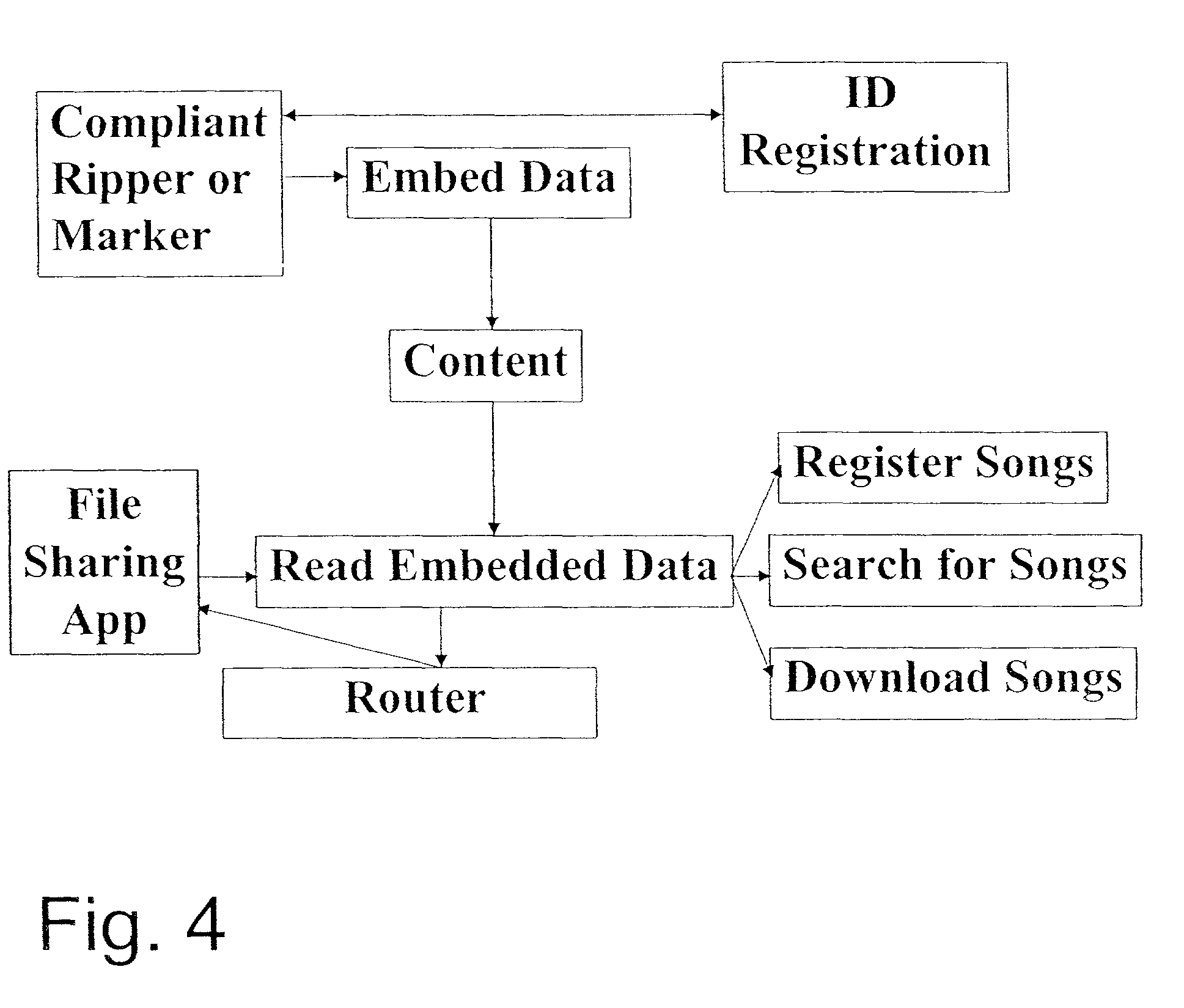
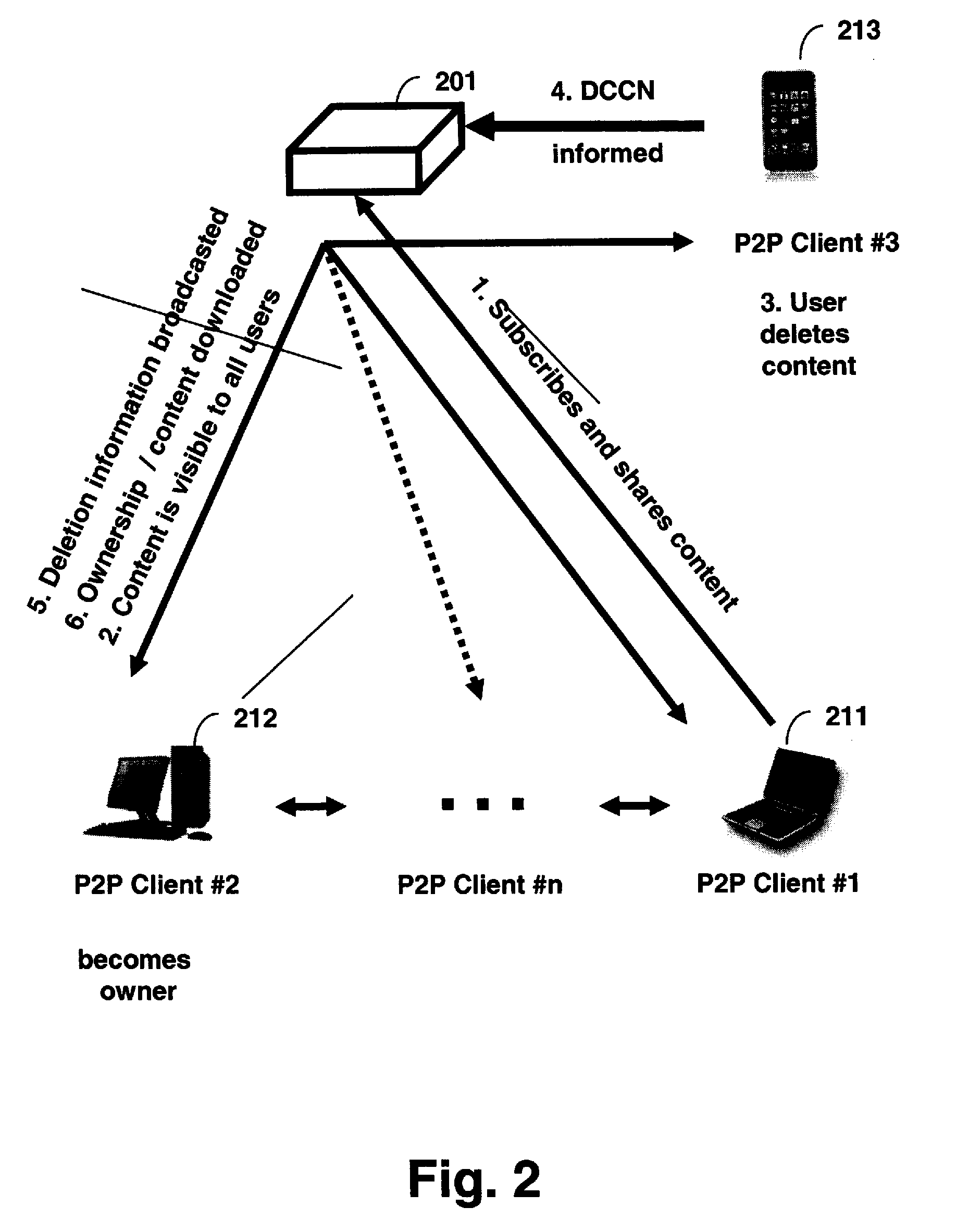
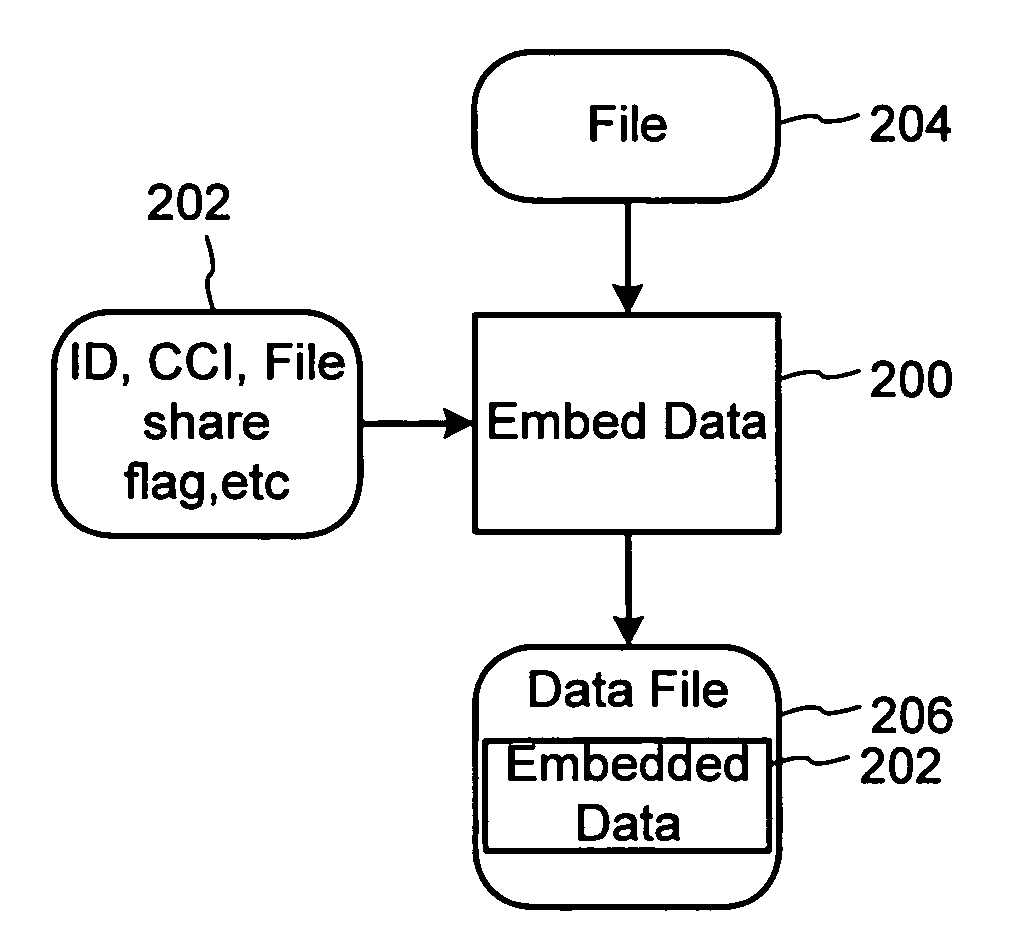
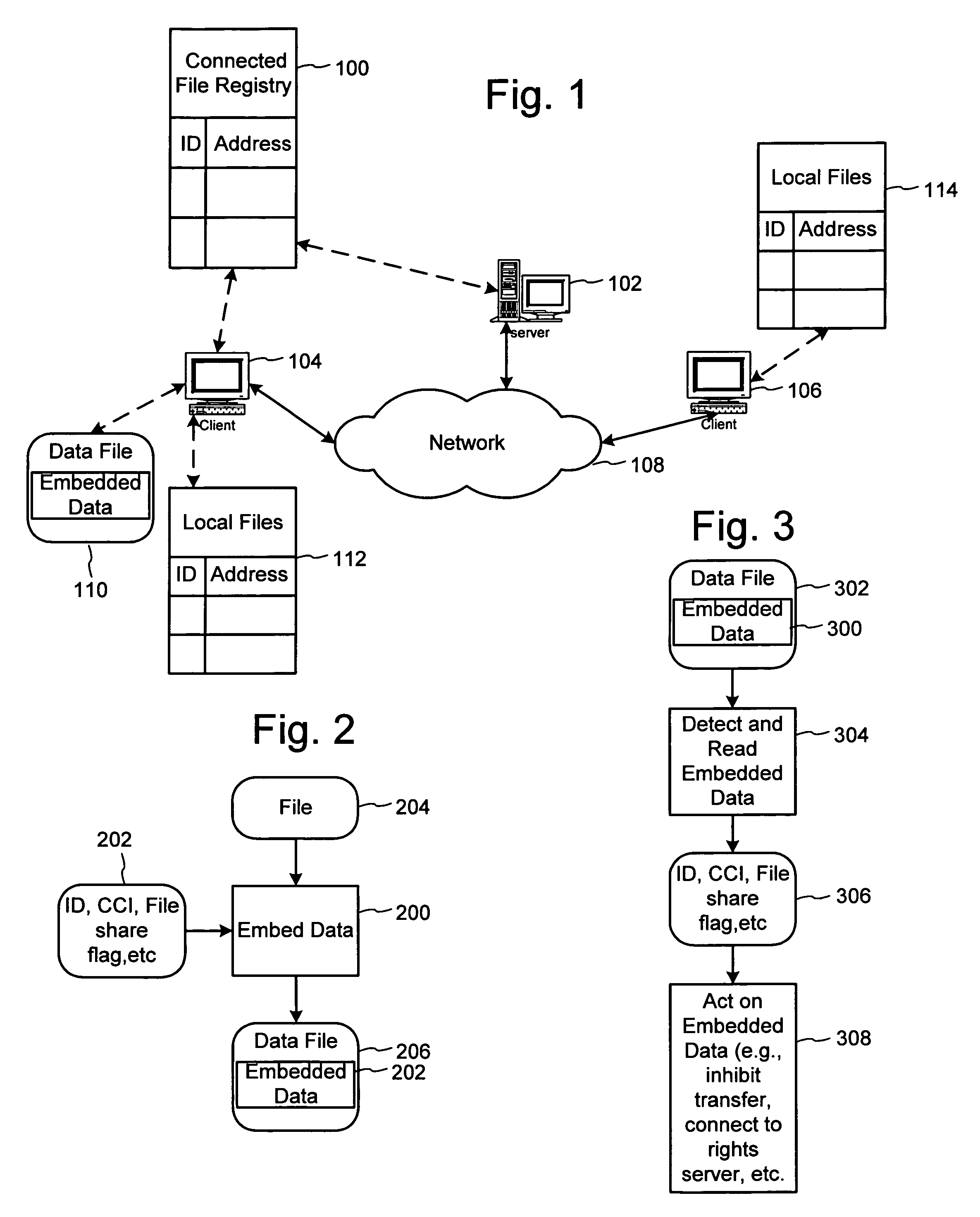
Peer-to-peer file sharing is increasing in popularity on the Internet, faster than any product known in history. Although file-sharing can enable massive piracy, it has many advantages for distribution of information including scalability. Alternatively, file-sharing can be sabotaged with falsified files and used to distribute viruses. To this end, a solution that maintains the scalability of file-sharing and promotes reliability is proposed. The solution involves embedding data within the file or content and using the data to identify the content, demonstrate its completeness and lack of viruses, and verify the file can be shared. The embedded data can be checked when the file is registered with the database for sharing, and before or while the file is being uploaded and / or downloaded. Ideally, the embedded data is added at the time of creation for the file. The embedded data may include a watermark and be linked to other copy management systems, such as those proposed in DVD and SDMI. Finally, the embedded data can be used to enable purchases of files that owners do not have rights to share.
Owner:ROVI TECH CORP
Background file sharing in a segmented peer-to-peer file sharing network
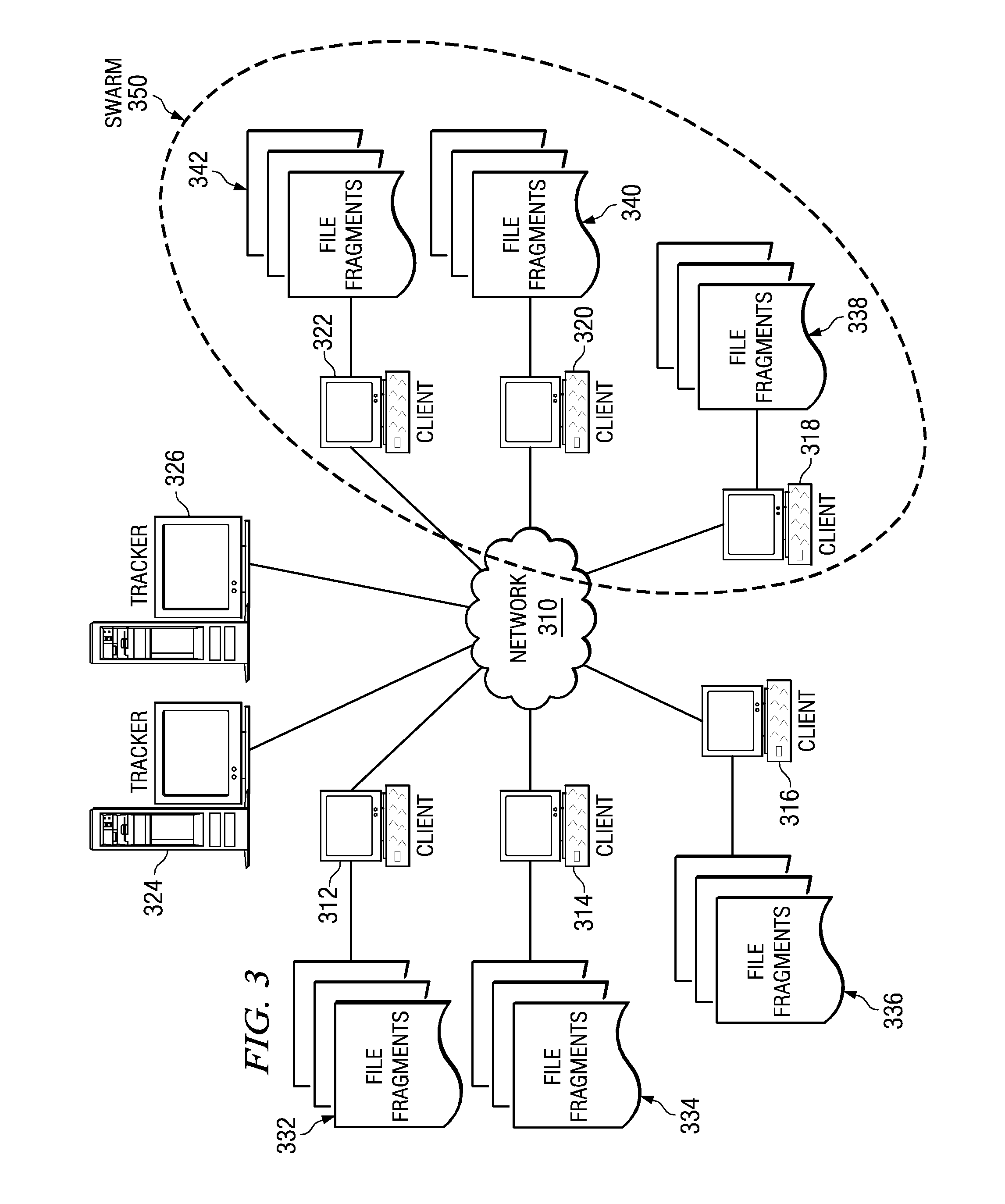
ActiveUS20080133538A1Increase speedDigital data processing detailsMultiple digital computer combinationsFile area networkClient-side
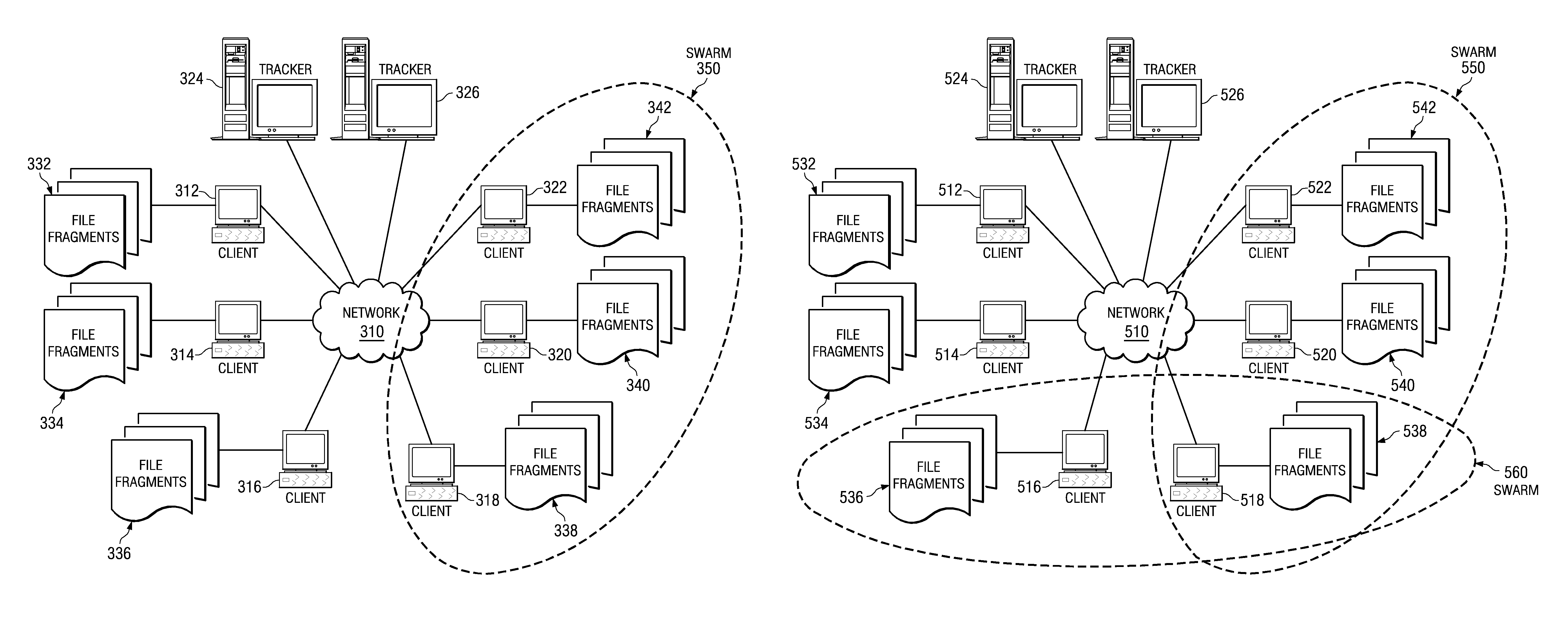
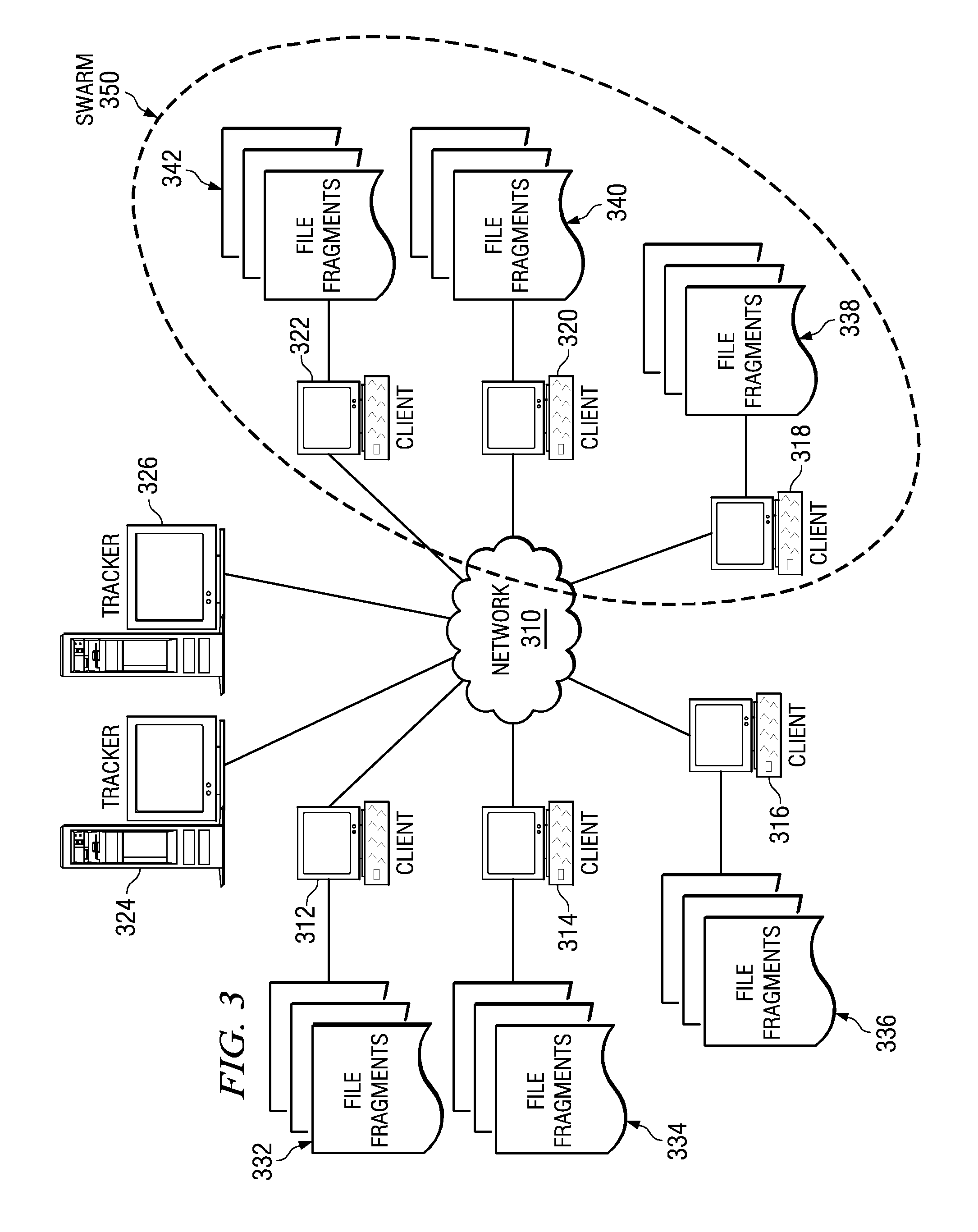
A peer-to-peer file sharing client with background file sharing is provided in a segmented peer-to-peer file sharing network. Each file sharing participant may designate an amount of bandwidth and / or storage space for background file sharing. Peer-to-peer file sharing clients then share file data and content in the background automatically. The client may participate in additional swarms, in the background, to generally increase the number of peers in file sharing networks, thus increasing the speed of downloading desired files for other users.
Owner:DROPBOX
Content identification and management in content distribution networks
InactiveUS20100306257A1Easy to liftFacilitates and enhances authorized file sharingDigital data processing detailsMultiple digital computer combinationsContent distributionMetadata management
Peer-to-peer file sharing and uploading of content to content server systems is increasing in popularity on the Internet. Content signals can be edited and combined with other content programming, and or altered in ways that make it difficult to identify using conventional techniques. Content identification based on content fingerprints is used to retrieve related metadata, which in turn, is used to manage use of the content signal in content distribution systems. The content signal is uploaded to a computer within a network of computers in the content distribution system. A content fingerprint of the content signal is computed and sent to a database to look up related metadata. The metadata is received and used to manage use of the content signal in the content distribution system based on the metadata. This can include blocking uploading or rendering of audio or video, controlling streaming of audio or video, linking to a licensing server, which provides usage control rules, etc.
Owner:DIGIMARC CORP
Two-level structured overlay design for cluster management in a peer-to-peer network
InactiveUS20080177767A1Multiple digital computer combinationsData switching networksFile replicationLevel structure
A method and system for designing file replication schemes in file sharing systems consider node storage constraints and node up / down statistics, file storage costs, and file transfer costs among the nodes, user request rates for the files, and user specified file availability requirements. Based on these considerations, a systematic method for designing file replication schemes can be implemented. The method first determines the number of copies of the files to be stored in the system to achieve the desired goal (e.g., to satisfy file availability requirements, or to maximize the system hit rate), and then selects the nodes at which to store the file copies to minimize the total expected cost. The file replication scheme for a peer-to-peer file sharing system in a distributed and adaptive manner can scale to a large number of nodes and files and can handle changes in the user request pattern over time.
Owner:XEROX CORP
Price-aware neighborhood selection for peer-to-peer networks
A method and apparatus for peer-to-peer file sharing is provided. In some embodiments, the method includes receiving a request for a list of neighbor peers, where the request is made by a requesting peer device, and where the requesting peer device has a local internet service provider (ISP). The method may also include employing a server device to rank each neighbor peer in a plurality of neighbor peers based on whether the respective neighbor peer is external to the local ISP, and if the respective neighbor peer is external to the ISP, further based on a cost metric associated with a next ISP hop from the requesting peer device to the respective neighbor peer. The method may also include generating the list of neighbor peers based on the ranking of the neighbor peers, and enabling transmission of the list of neighbor peers to the requesting peer device.
Owner:DEUTSCHE TELEKOM AG
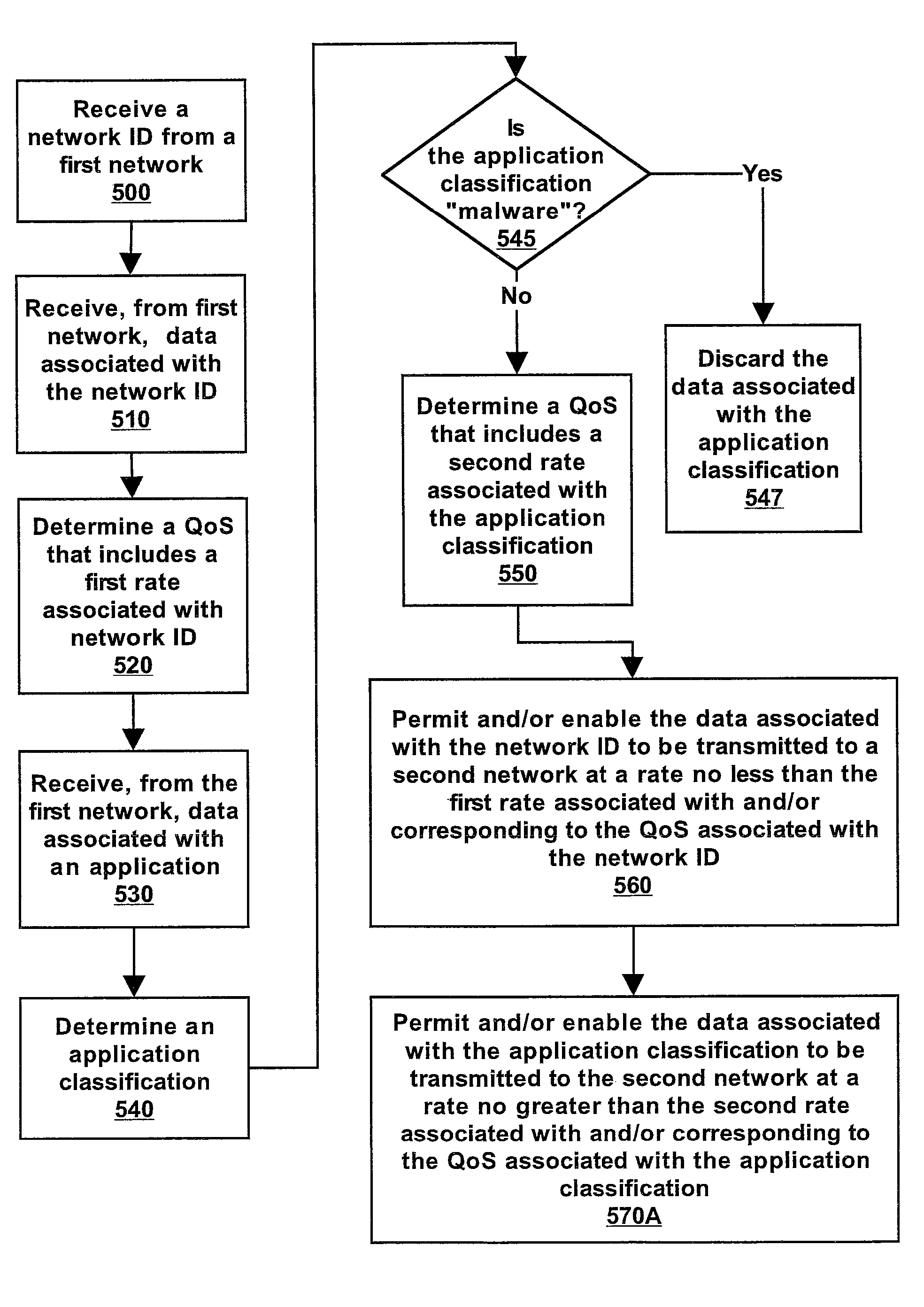
System and Method for Providing Application Categorization and Quality of Service in a Network With Multiple Users
InactiveUS20080281979A1Memory loss protectionError detection/correctionQuality of serviceCredit card
Internet protocol (IP) data service providers may provide several services over a single communications channel and / or circuit. For example, the provider may deliver public services such as Wi-Fi, content, gaming, etc. as well as business-critical “back-office” services such as credit card processing, VoIP, streaming video, video conferencing, etc. Some applications can very demanding from a quality of service standpoint, whereas other applications are unwanted or unauthorized on the network such as worms, viruses, denial of service attacks and / or certain types of peer-to-peer file sharing applications. Applications sharing the communication channel may be classified into one or more application classifications. The available bandwidth over the communications channel and / or circuit may then be managed via a prioritization system that can be parameterized based on the available bandwidth and / or the desired application behavior for given characterized applications. Many of the above unwanted applications can be suppressed, after being classified.
Owner:WAYPORT
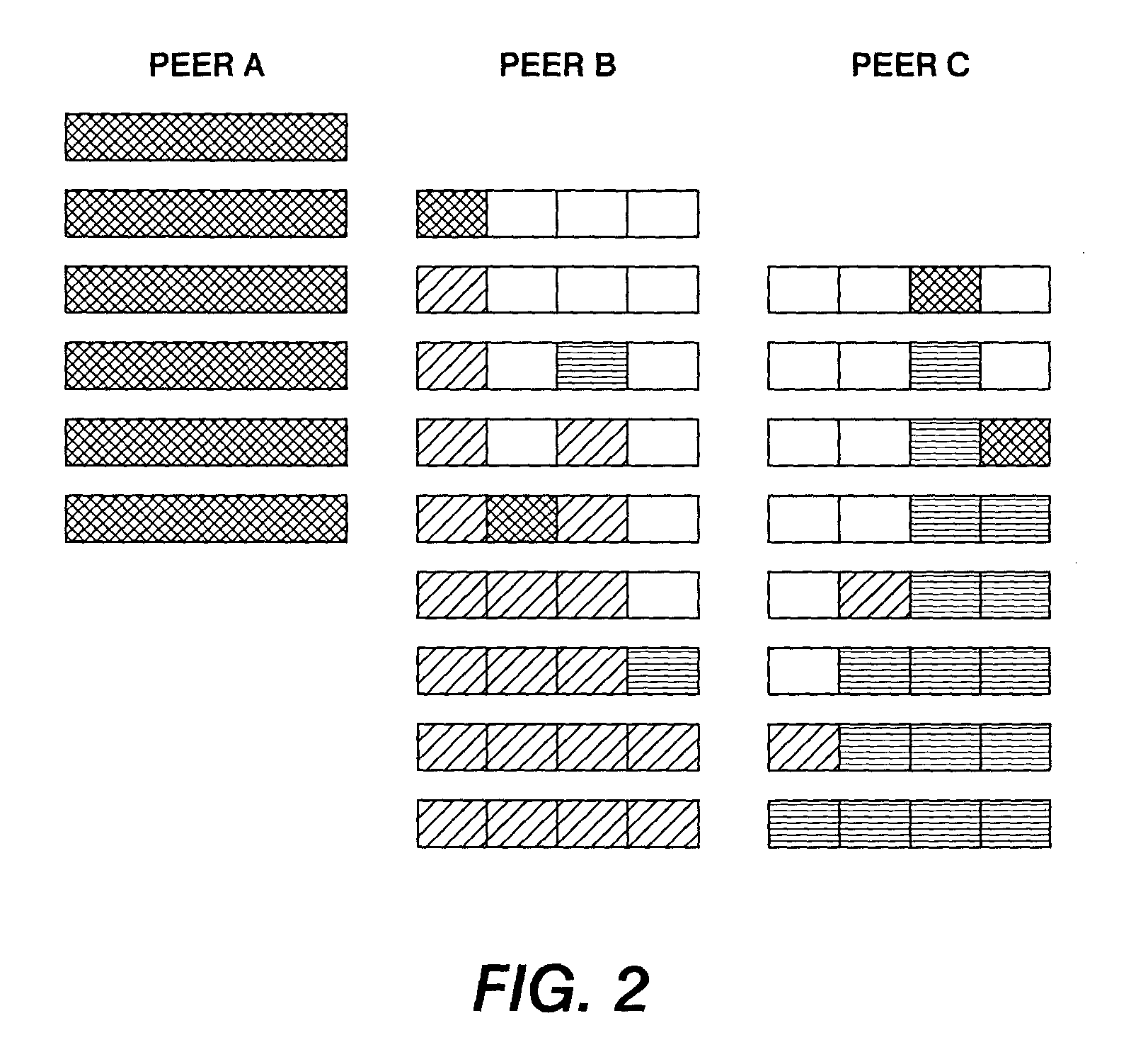
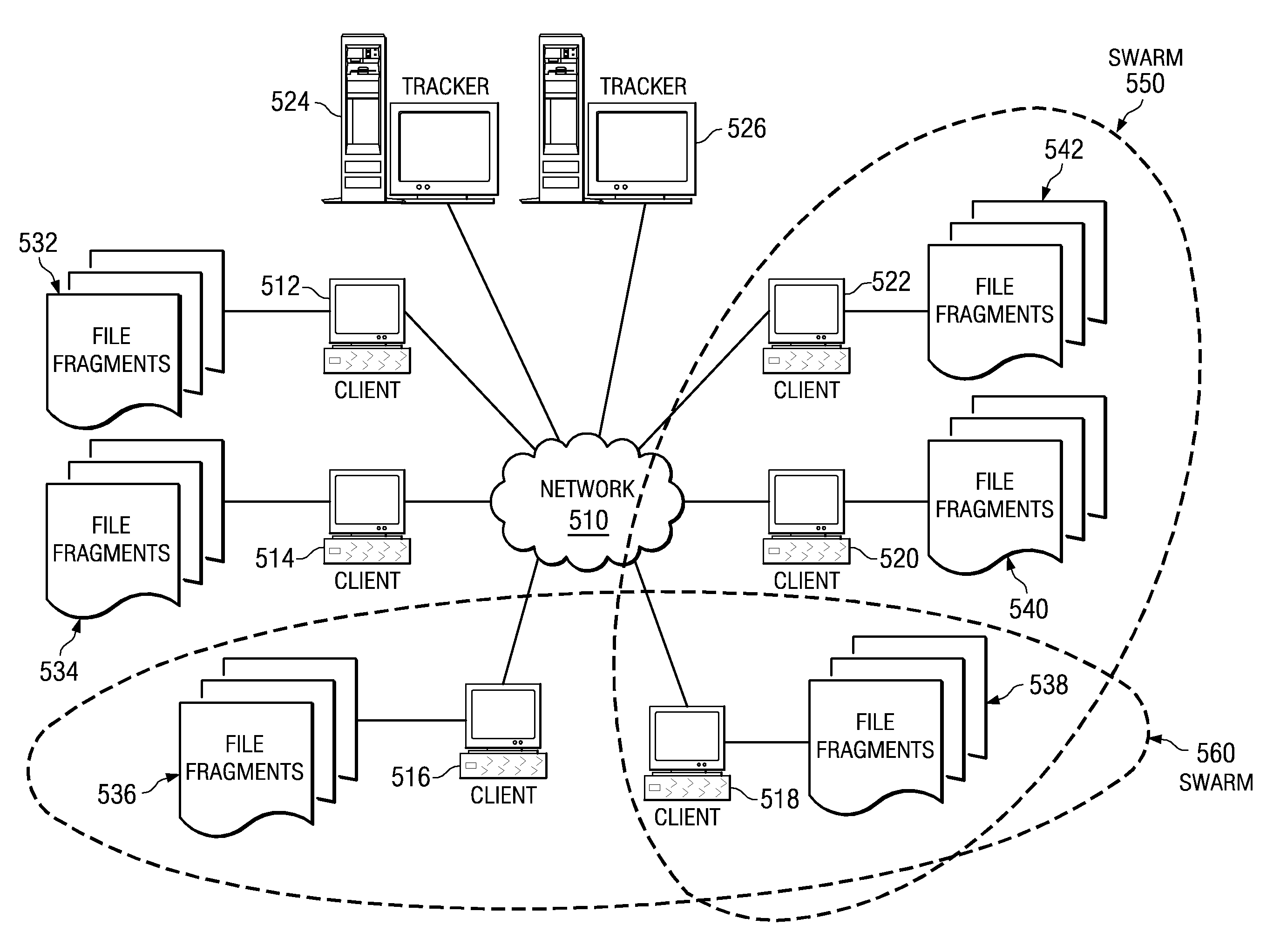
File Fragment Trading Based on Rarity Values in a Segmented File Sharing System
ActiveUS20080133698A1Increase speedMultiple digital computer combinationsTransmissionClient-sideDistributed computing
Peer-to-peer file sharing clients share file fragments in the background based on rarity values. When a first peer offers a fragment to a second peer to be shared in the background, the second peer checks the rarity of the fragment and identifies one or more fragments from its swarm that is approximately as rare as the fragment being offered. The second peer then offers the one or more fragments in exchange for the originally offered fragment. The first peer may then offer the one or more fragments to other peers in its swarm to be shared in the background.
Owner:DROPBOX
File fragment trading based on rarity values in a segmented file sharing system
ActiveUS7814146B2Increase speedMultiple digital computer combinationsTransmissionClient-sideDistributed computing
Peer-to-peer file sharing clients share file fragments in the background based on rarity values. When a first peer offers a fragment to a second peer to be shared in the background, the second peer checks the rarity of the fragment and identifies one or more fragments from its swarm that is approximately as rare as the fragment being offered. The second peer then offers the one or more fragments in exchange for the originally offered fragment. The first peer may then offer the one or more fragments to other peers in its swarm to be shared in the background.
Owner:DROPBOX
Security protocols for hybrid peer-to-peer file sharing networks
ActiveUS20090259847A1User identity/authority verificationMultiple digital computer combinationsComputer networkDigital signature
In a hybrid peer-to-peer file sharing network including a receiver peer and a provider peer, the receiver sends the provider a ticket [710] obtained from a server authorizing the receiver to obtain a data object O. The receiver obtains a root value of a hash tree for the object, verifies its digital signature, and sends the provider peer a request for a block of data object O and a request for a corresponding set of hash tree of hash values from the hash tree [714]. The receiver receives from the provider peer the block of O and the corresponding set of hash values of the hash tree [716] that do not contain any hash value in the local hash tree. The receiver sends the provider an acknowledgement of receipt [718], obtains a block key from the provider [720], decrypts the block, verifies the integrity of the block using the subset of hash values and the local hash tree for O, and updates the local hash tree by adding the subset of hash values to the local hash tree, as well as any newly calculated hash values [722]. The provider may submit to a server the acknowledgements as proof of its service to the receiver.
Owner:OREGON HEALTH & SCI UNIV
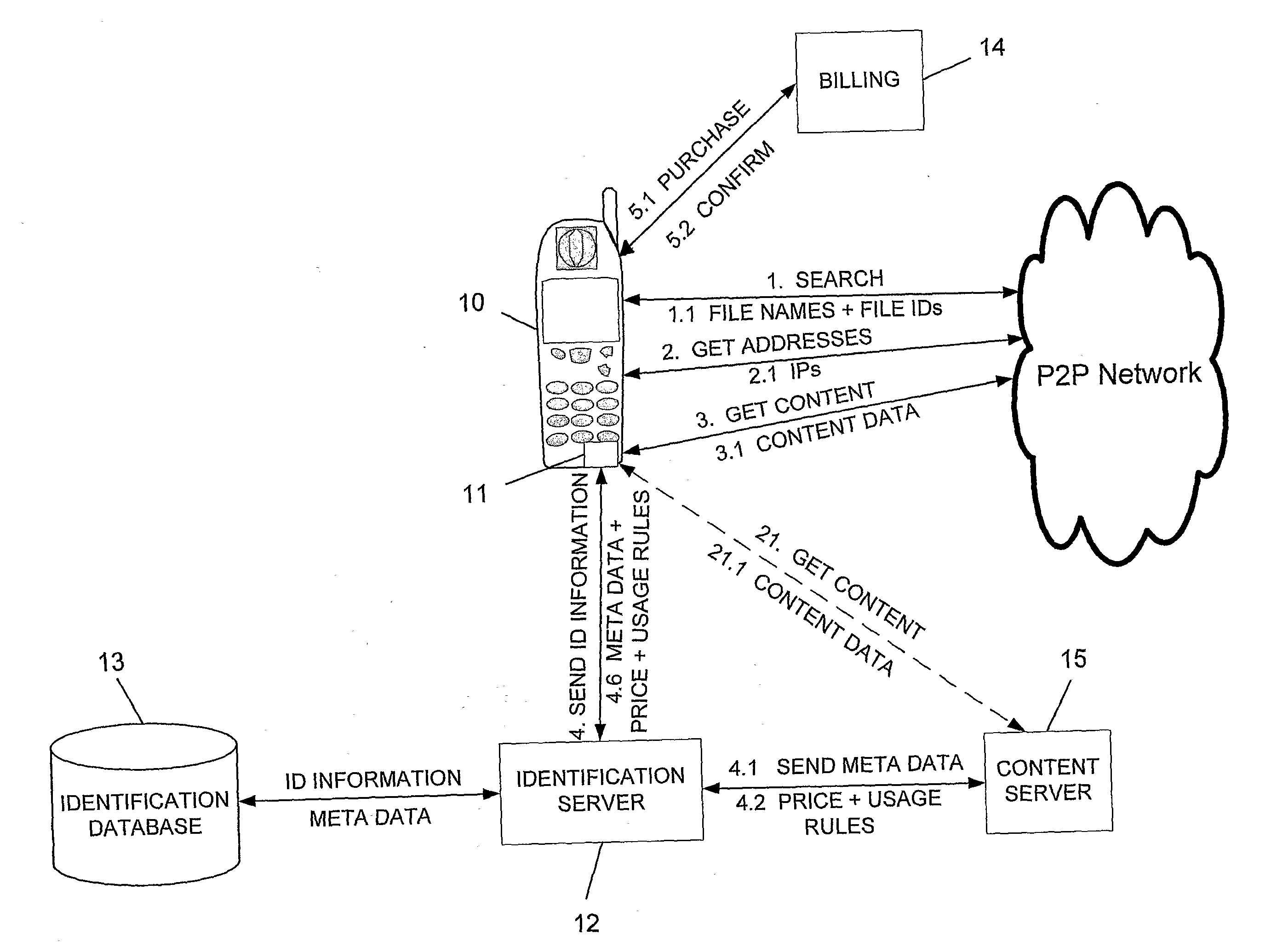
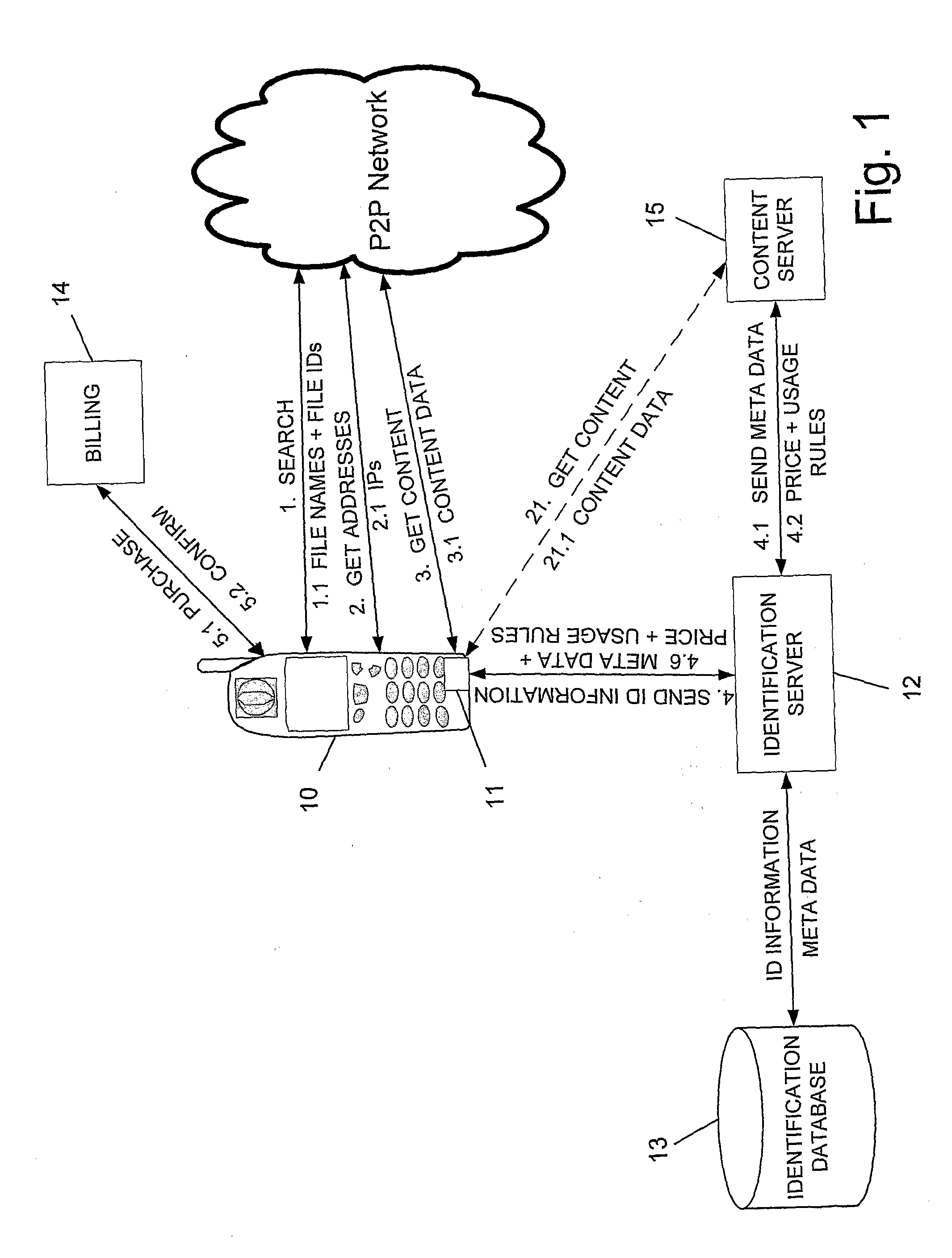
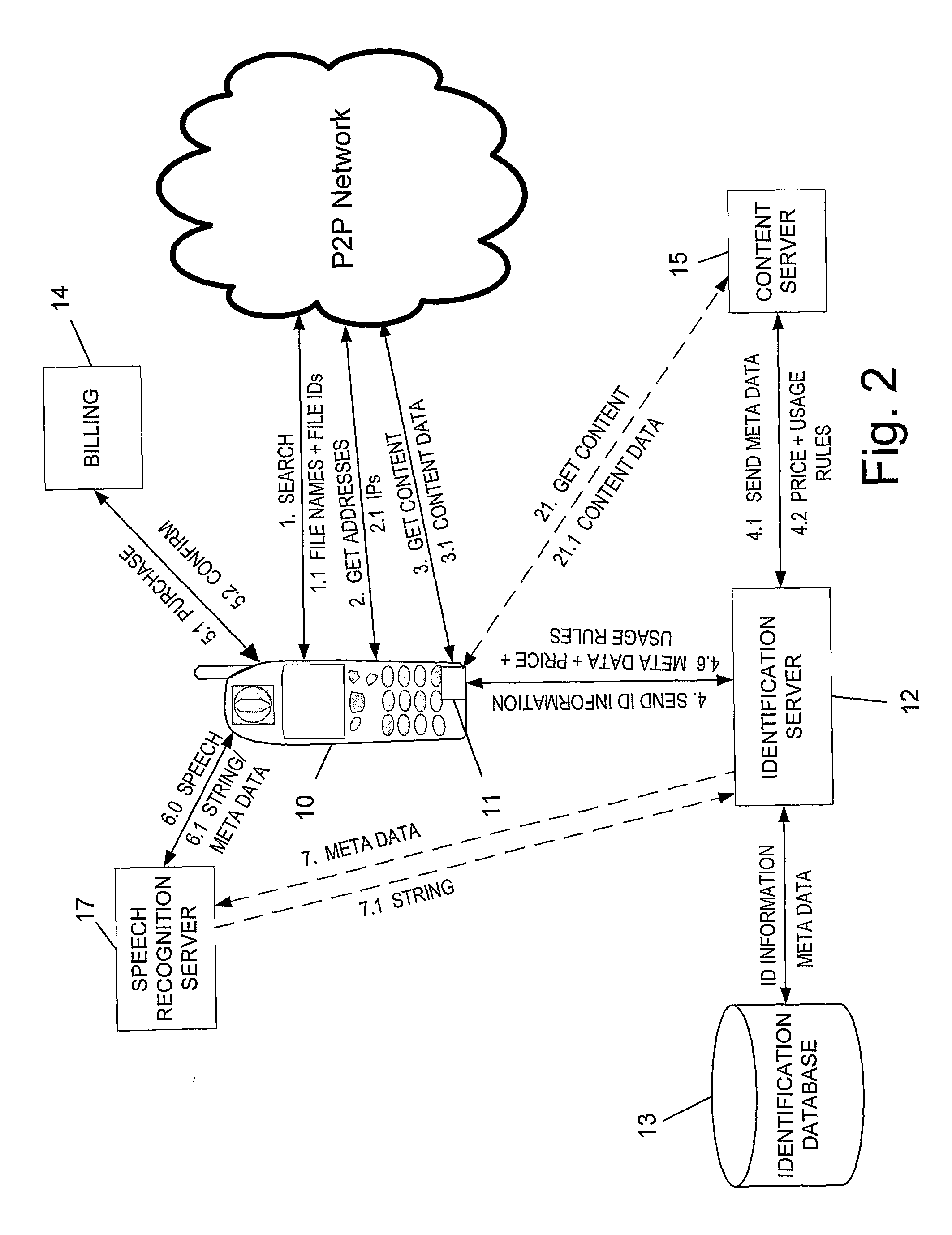
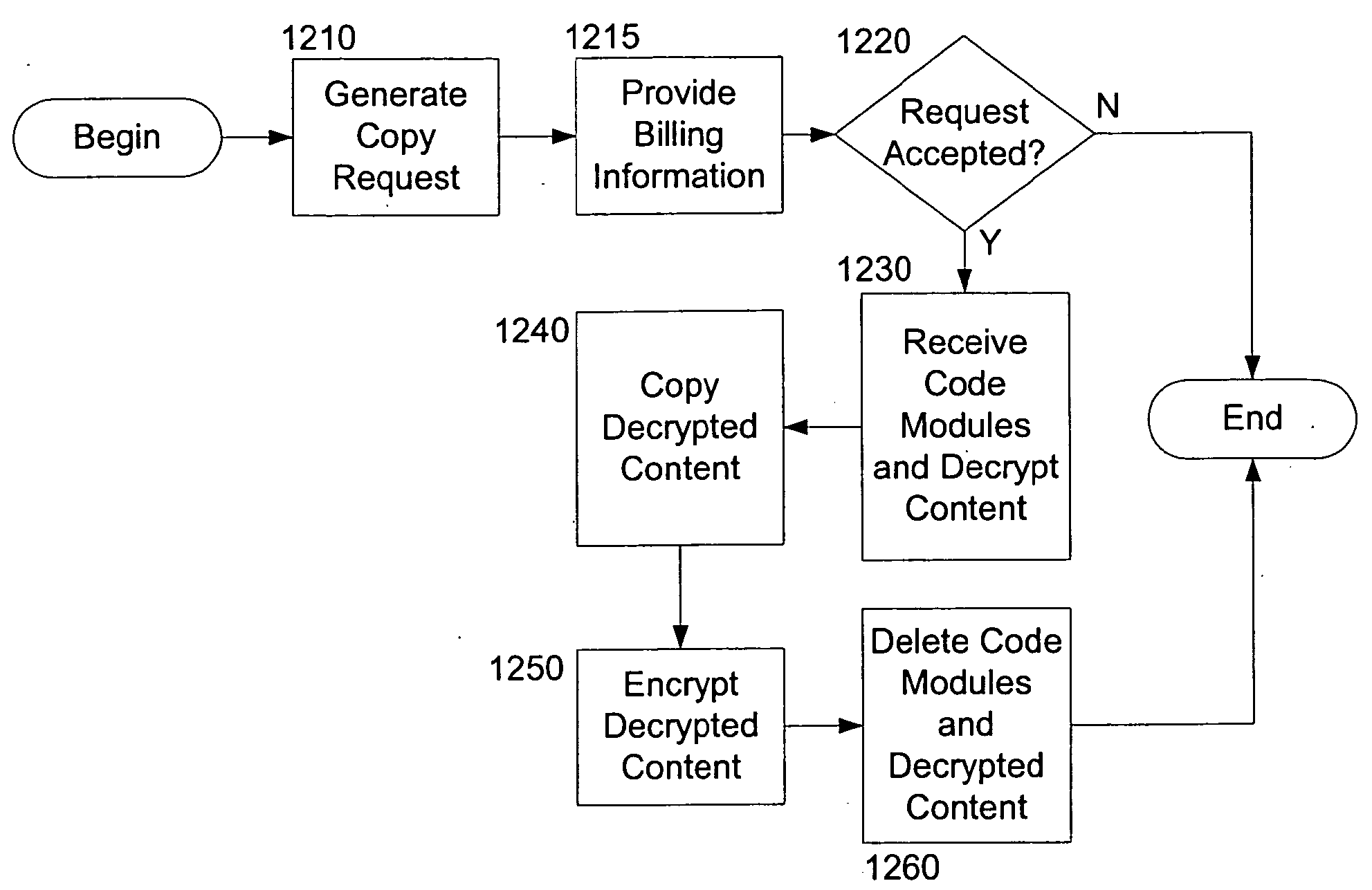
Peer to Peer File Sharing Mobile System with Copyright Protection
InactiveUS20090006256A1High usage priorityBuying/selling/leasing transactionsProgram/content distribution protectionPaymentMobile device
The present invention relates a peer to peer system for enabling a mobile device user to legally search and only legally download content items by his mobile device, comprising: (a) a user software having a user interface at the mobile device for connecting to a peer to peer network, searching for a content item according to a user query, introducing the results to the user, and enabling a conditional downloading only upon ensuring payment for items that are found to be copyright protected; (b) an identification server for receiving identification information relating to a selected right protected item from said user software, searching for at least meta data and price corresponding to said item, and forwarding the found meta data and price to the user software; (c) a module within said user software for, upon receipt of said meta data and price, suspending the conditional downloading, prompting the user to appropriately pay at a billing server if the item is copyright protected, and resuming the download only upon clearing said payment; and (d) billing server for receiving payment from the user, and upon completion of same, sending payment clearance to said user software, which in turn resumes downloading of the item.
Owner:NETBARRAGE
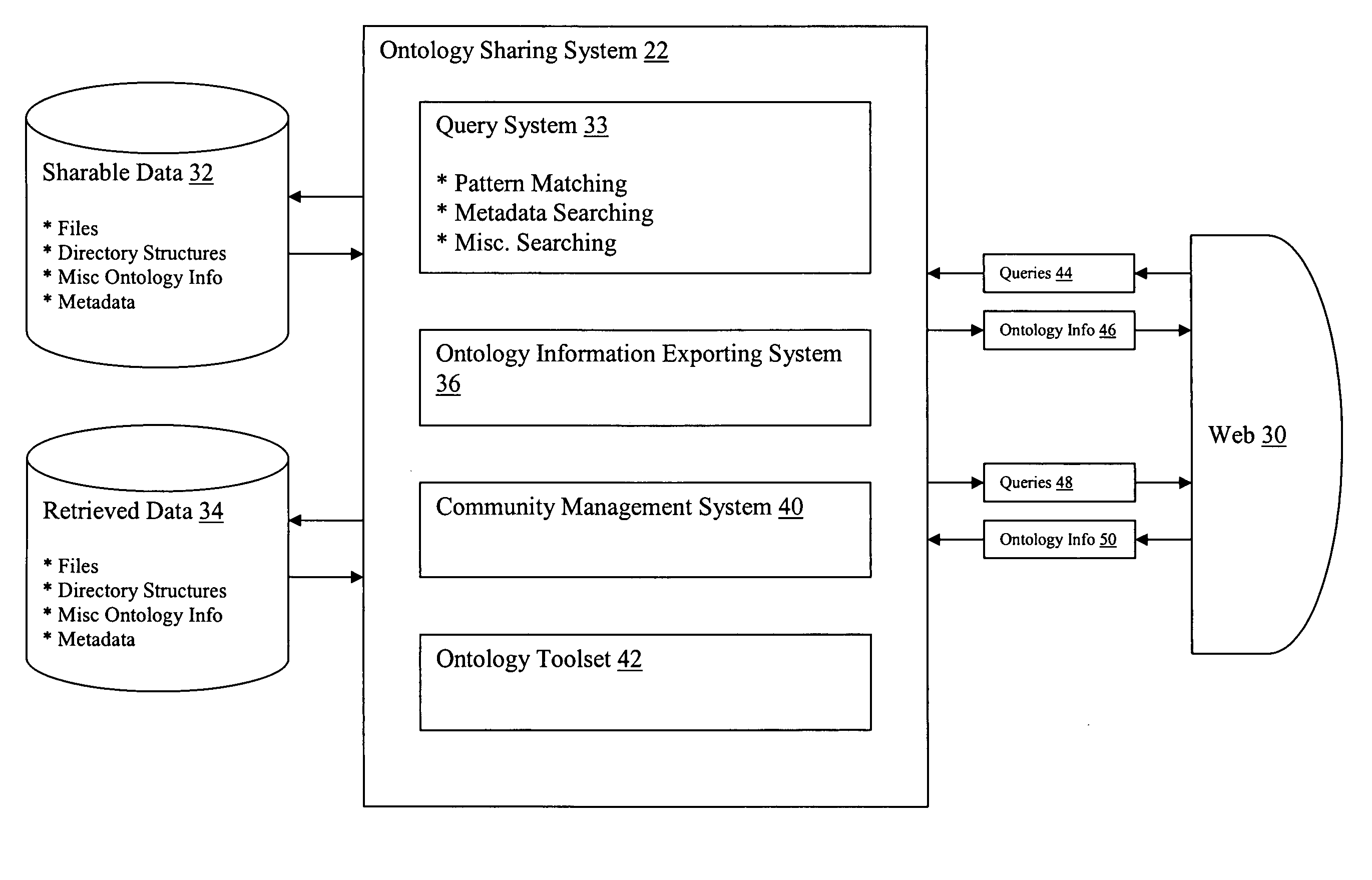
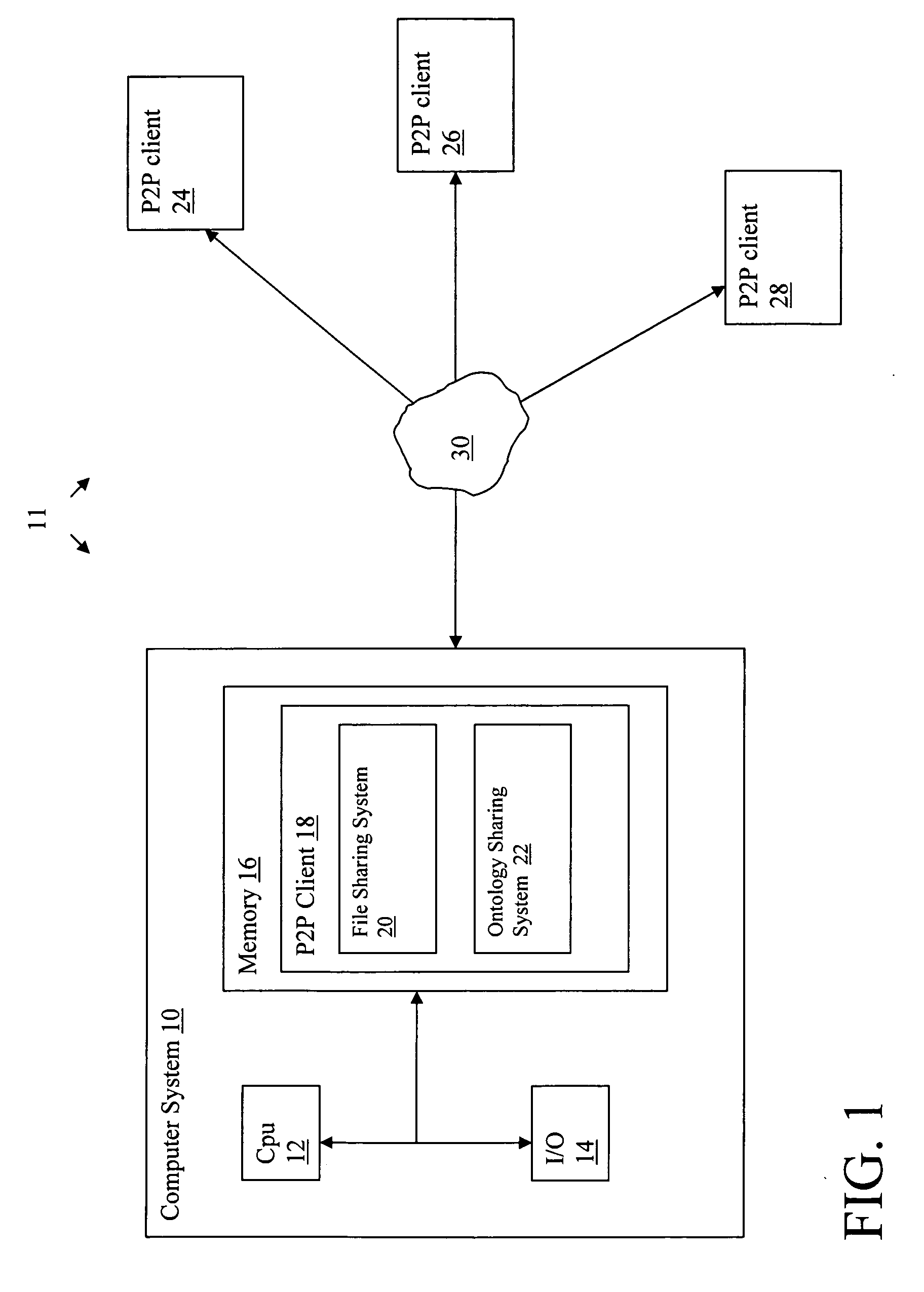
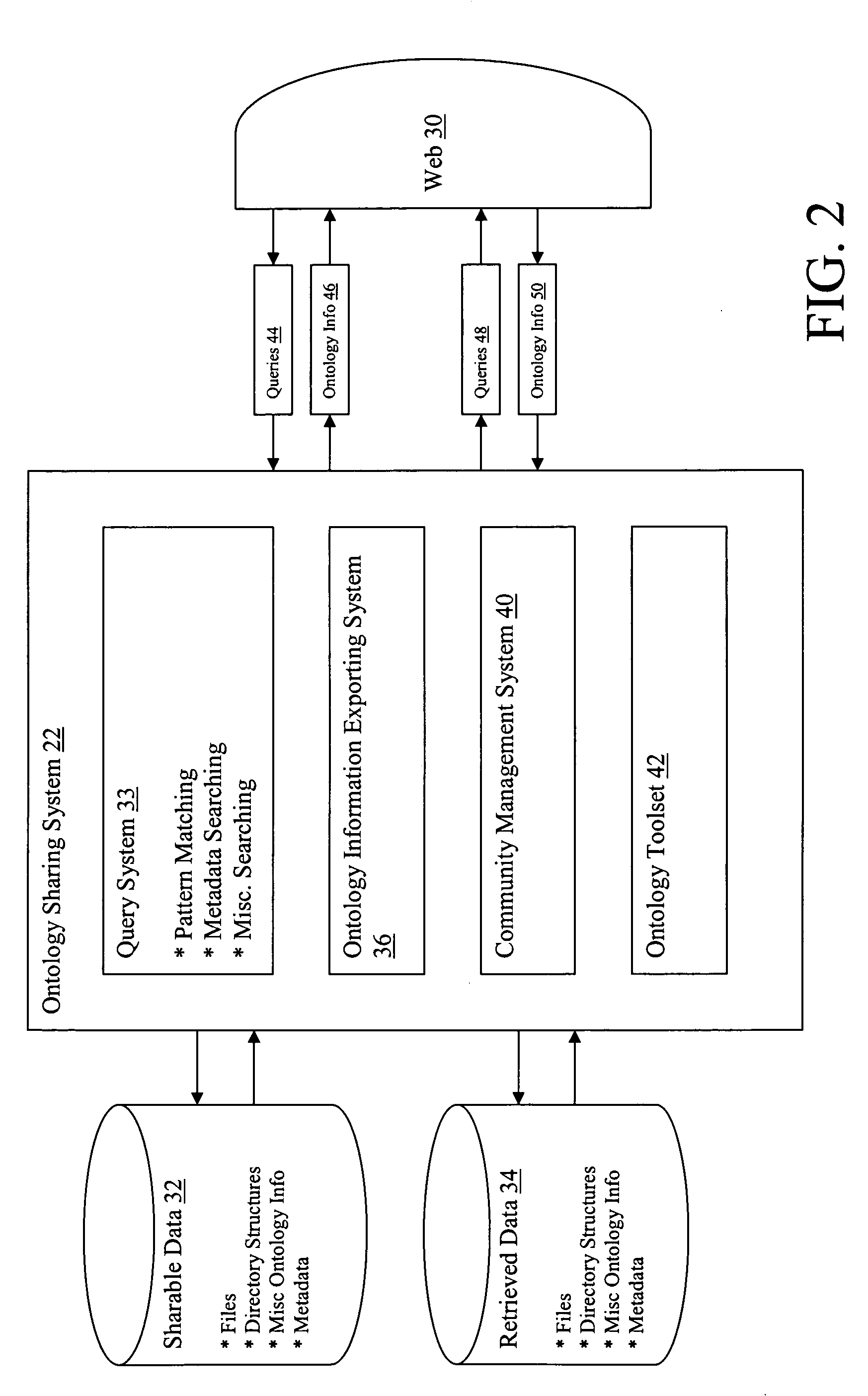
System for sharing ontology information in a peer-to-peer network
InactiveUS20060031386A1Multiple digital computer combinationsTransmissionClient-sideDistributed computing
A system and program product for sharing ontology information in a computer network. The system comprises a peer-to-peer file sharing system that is implemented by a plurality of clients within a network, wherein each client includes: a file sharing system that allows each client to access files from other clients in the network; and an ontology sharing system that allows each client to access ontology information from other clients in the network.
Owner:IBM CORP
Background file sharing in a segmented peer-to-peer file sharing network
ActiveUS8131673B2Digital data processing detailsMultiple digital computer combinationsClient-sidePeer-to-peer
A peer-to-peer file sharing client with background file sharing is provided in a segmented peer-to-peer file sharing network. Each file sharing participant may designate an amount of bandwidth and / or storage space for background file sharing. Peer-to-peer file sharing clients then share file data and content in the background automatically. The client may participate in additional swarms, in the background, to generally increase the number of peers in file sharing networks, thus increasing the speed of downloading desired files for other users.
Owner:DROPBOX
System and method for anonymous addressing of content on network peers and for prvate peer-to-peer file sharing
InactiveUS20160191608A1Efficient and private peer-to-peer file sharingImprove privacyTransmissionPeer to peer file sharingPeer-to-peer
Owner:ZAID SAM
Systems and methods for prevention of peer-to-peer file sharing
InactiveUS20090063846A1Multiple keys/algorithms usageUnauthorized memory use protectionDigital contentSystem usage
Owner:NB NETWORKS
Method, apparatus and system for flow control of point-to-point file sharing
ActiveCN101202700AEnsure fairnessAvoid long-term occupationSpecial service provision for substationTraffic capacityDistributed computing
The invention relates to a method, a device and a system used for controlling the flow of point to point document sharing in the technical field of communication. The device includes a strategy module used for providing a flow control implement strategy for sharing document; a packet filtering module receives a data packet transmitted by a Router, extracts the connection control information to form an information packet and filters the data packet and / or information packet according to the flow control implement strategy; a flow control module used for carrying through flow control on the document sharing according to the analyzed result. The invention provides a flexible control mechanism for the operation business to carry through adjusting on the document sharing part of the total flow for one side and the other side ensures the equity for a user to use a flow bandwidth to prevent some users from occupying massive bandwidth for a long time at the other side by carrying through dynamic control on the flow of the document sharing action of the user.
Owner:泰州市海通资产管理有限公司
Mapping file fragments to file information and tagging in a segmented file sharing system
ActiveUS8775562B2Increase speedMultiple digital computer combinationsTransmissionRelational databaseClient-side
Owner:DROPBOX
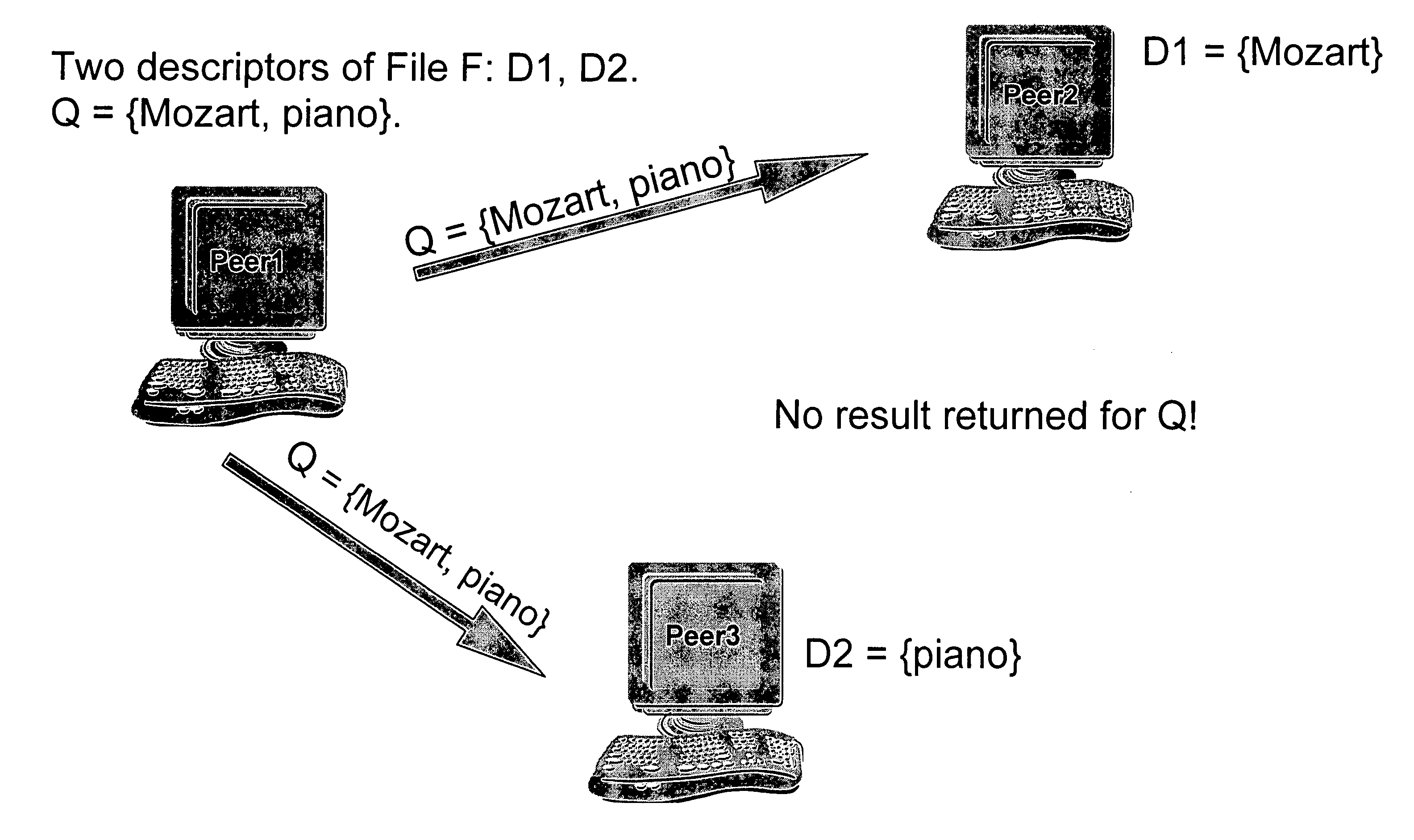
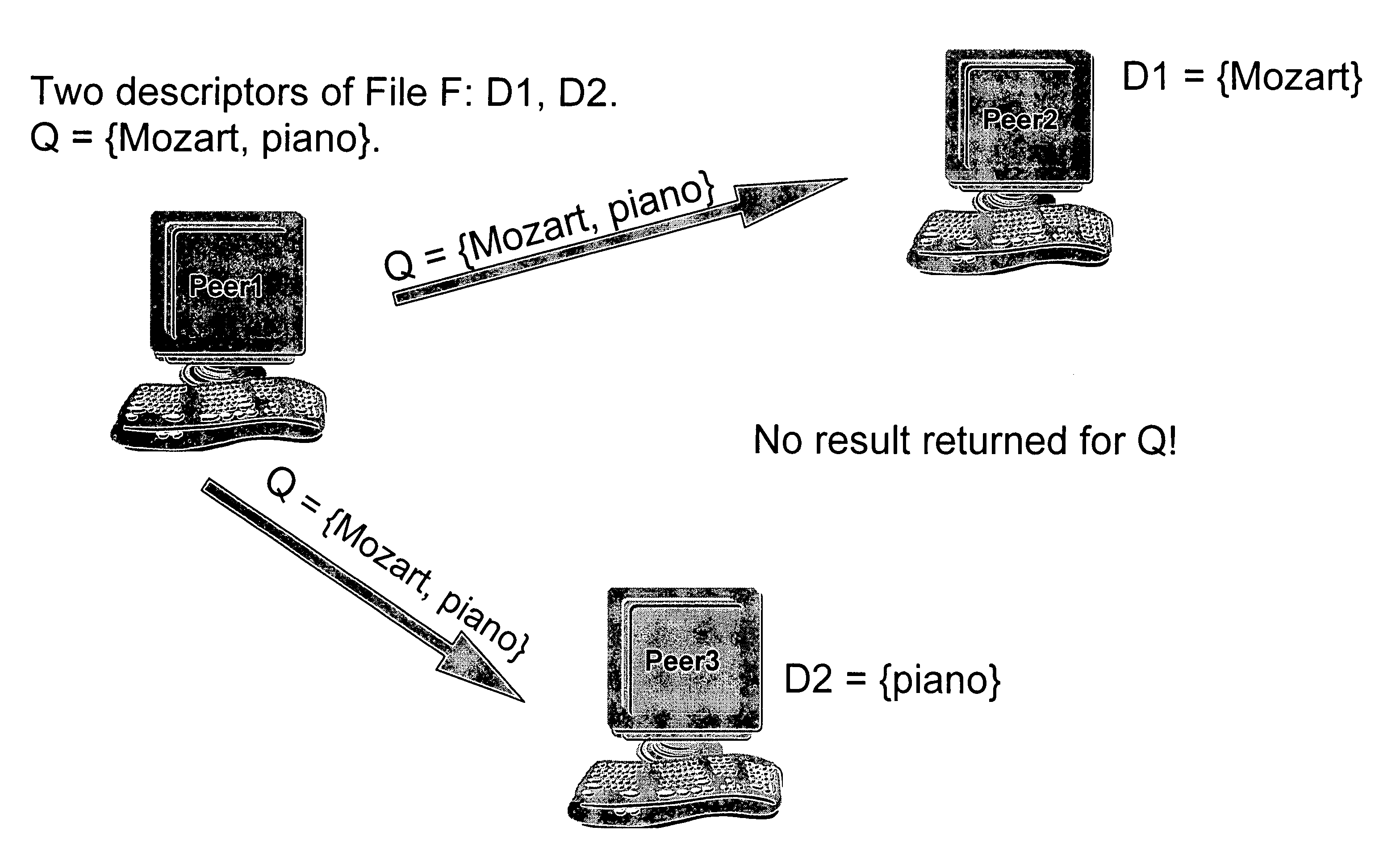
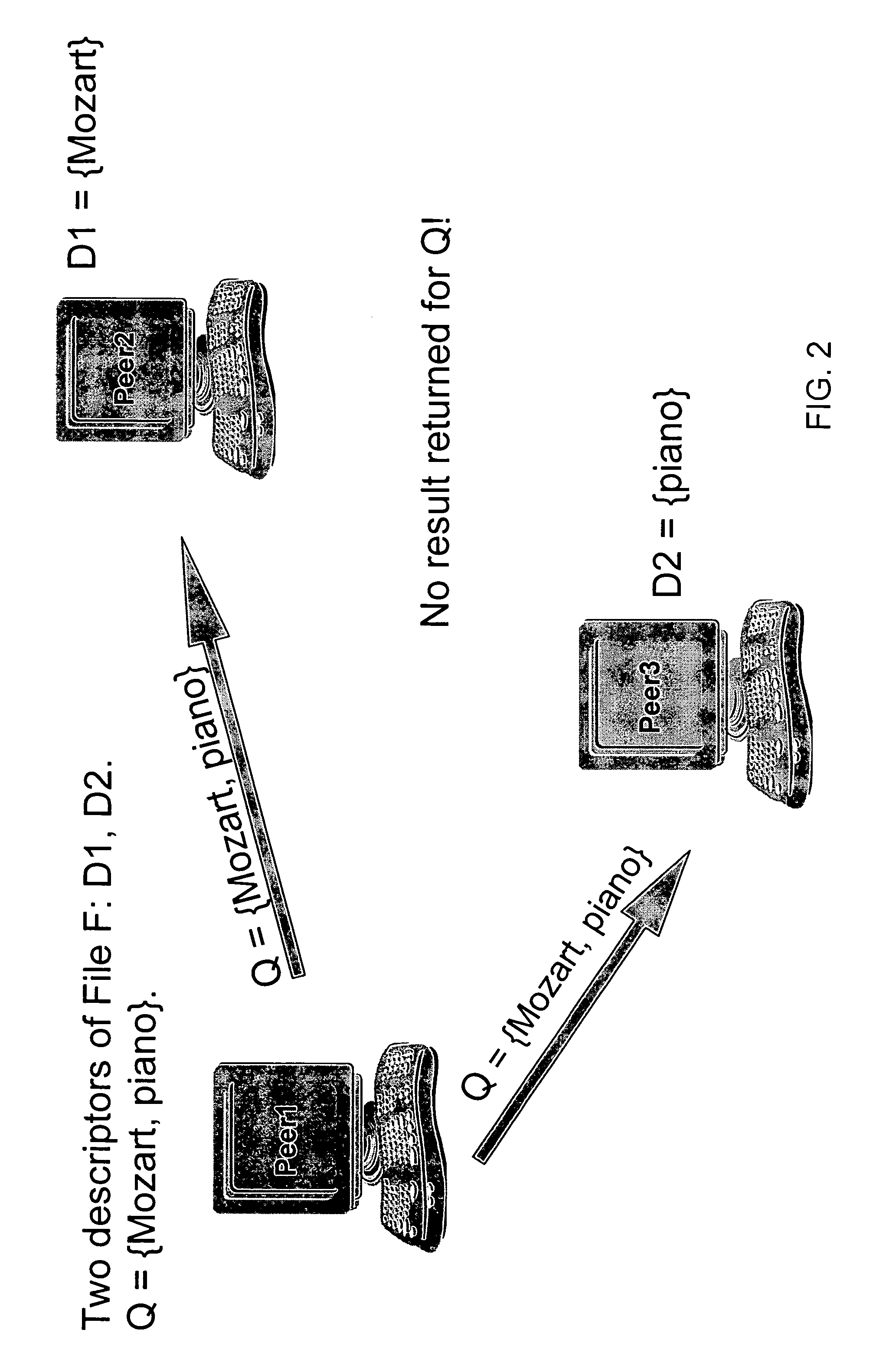
Method for improving local descriptors in peer-to-peer file sharing
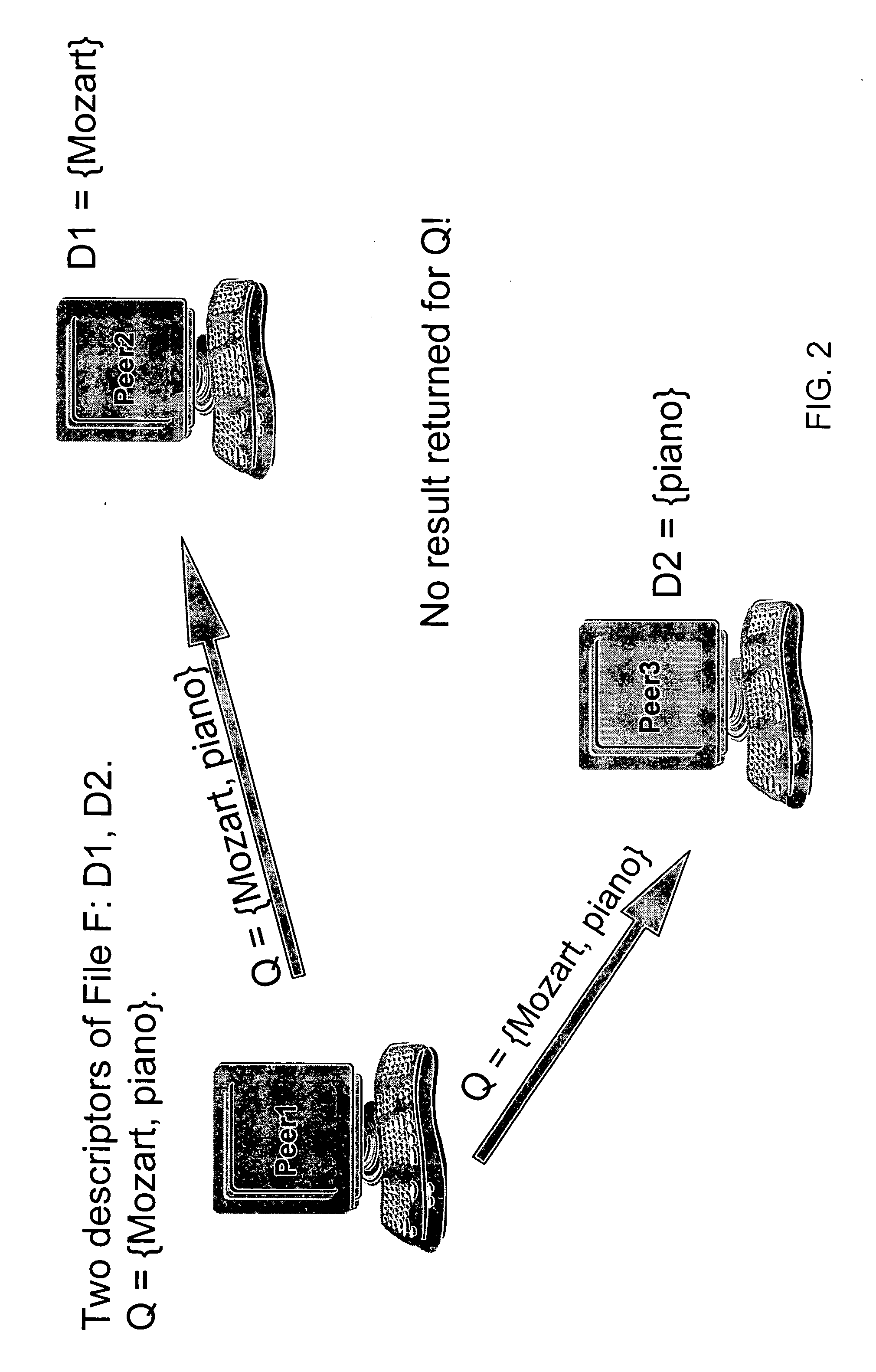
InactiveUS20080120295A1Improving and enhancingIncrease the difficultyDigital data information retrievalData processing applicationsDatabasePeer-to-peer
A method for improving searches in a peer-to-peer (P2P) file sharing system that includes a plurality of server computers. A content file, identified by a descriptor including at least one metadata term and a mathematical identifier that uniquely identifies the content file in one of the server computers, is selected for searching. Other server computers are searched to find one or more matching content files; one that has a descriptor with a mathematical identifier matching the mathematical identifier of the first content file. The descriptors of the matching content files are returned to the searching server computer and used to expand the local descriptor.
Owner:FRIEDER OPHIR +1
System and method for providing application categorization and quality of service in a network with multiple users
InactiveUS7958256B2Multiple digital computer combinationsData switching networksCredit cardQuality of service
Internet protocol (IP) data service providers may provide several services over a single communications channel and / or circuit. For example, the provider may deliver public services such as Wi-Fi, content, gaming, etc. as well as business-critical “back-office” services such as credit card processing, VoIP, streaming video, video conferencing, etc. Some applications can very demanding from a quality of service standpoint, whereas other applications are unwanted or unauthorized on the network such as worms, viruses, denial of service attacks and / or certain types of peer-to-peer file sharing applications. Applications sharing the communication channel may be classified into one or more application classifications. The available bandwidth over the communications channel and / or circuit may then be managed via a prioritization system that can be parameterized based on the available bandwidth and / or the desired application behavior for given characterized applications. Many of the above unwanted applications can be suppressed, after being classified.
Owner:WAYPORT
Method and system of administrating a peer-to-peer file sharing network
InactiveUS8924460B2Multiple digital computer combinationsTransmissionDistributed computingPeer to peer file sharing
A computer-implemented method, system, and computer program product for administering a peer-to-peer file sharing computer network. The method includes: maintaining a reference associating a particular shared file with a seeder in a community of peers and a number of seeders in the community; and registering a second peer as a second seeder of the particular shared file, if a first seeder in the community of peers has informed the peers of a termination of the availability of a file seeding of the particular shared file. The system includes means for performing the steps of the method. The computer program product includes computer program instructions for carrying out the steps of the method.
Owner:IBM CORP
Peer-to-peer file sharing system and method
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Method for improving local descriptors in peer-to-peer file sharing
InactiveUS7558789B2Improving P2P searchingImprove and enhanceDigital data information retrievalData processing applicationsDatabasePeer-to-peer
A method for improving searches in a peer-to-peer (P2P) file sharing system that includes a plurality of server computers. A content file, identified by a descriptor including at least one metadata term and a mathematical identifier that uniquely identifies the content file in one of the server computers, is selected for searching. Other server computers are searched to find one or more matching content files; one that has a descriptor with a mathematical identifier matching the mathematical identifier of the first content file. The descriptors of the matching content files are returned to the searching server computer and used to expand the local descriptor.
Owner:FRIEDER OPHIR +1
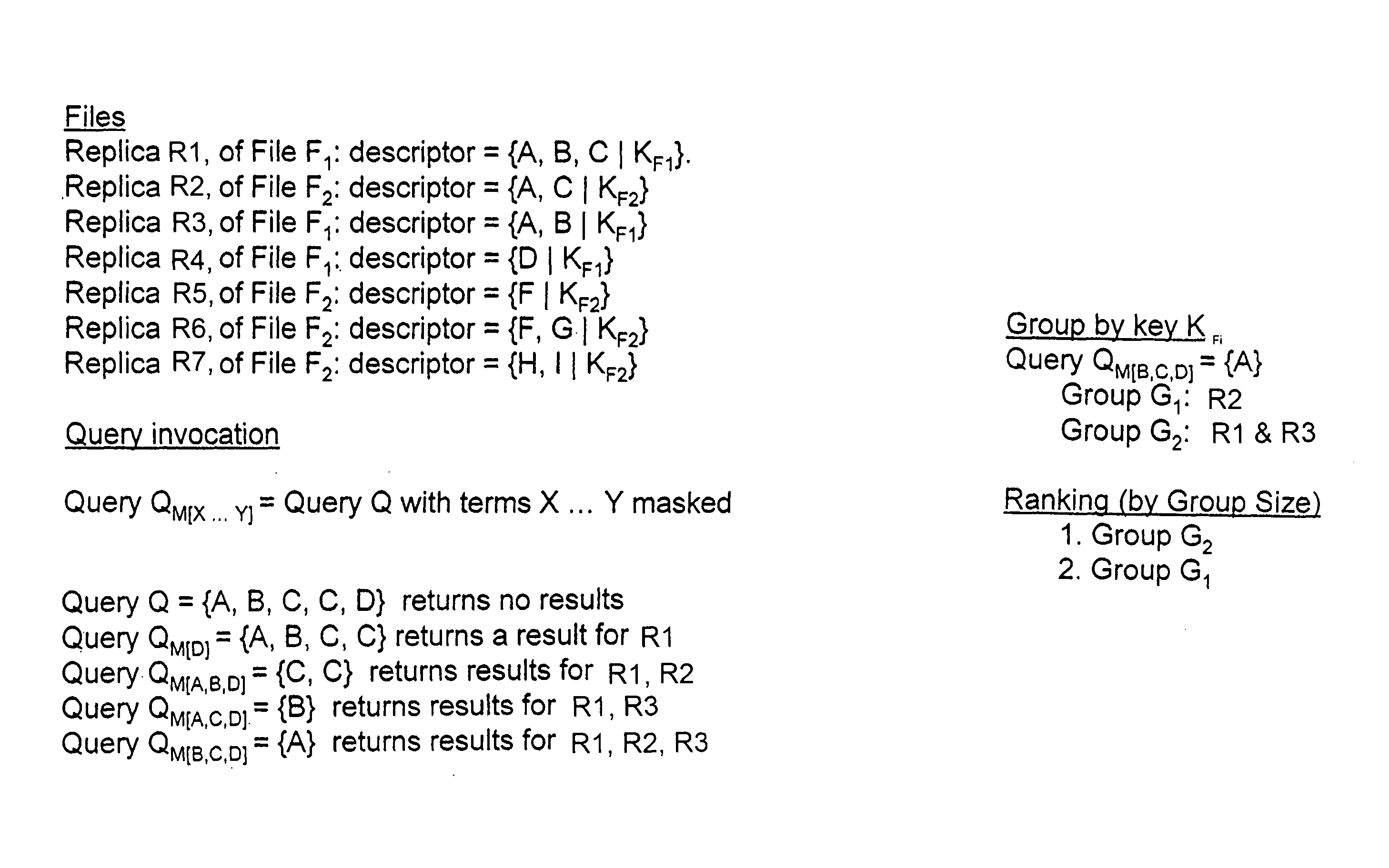
Peer-to-peer file sharing
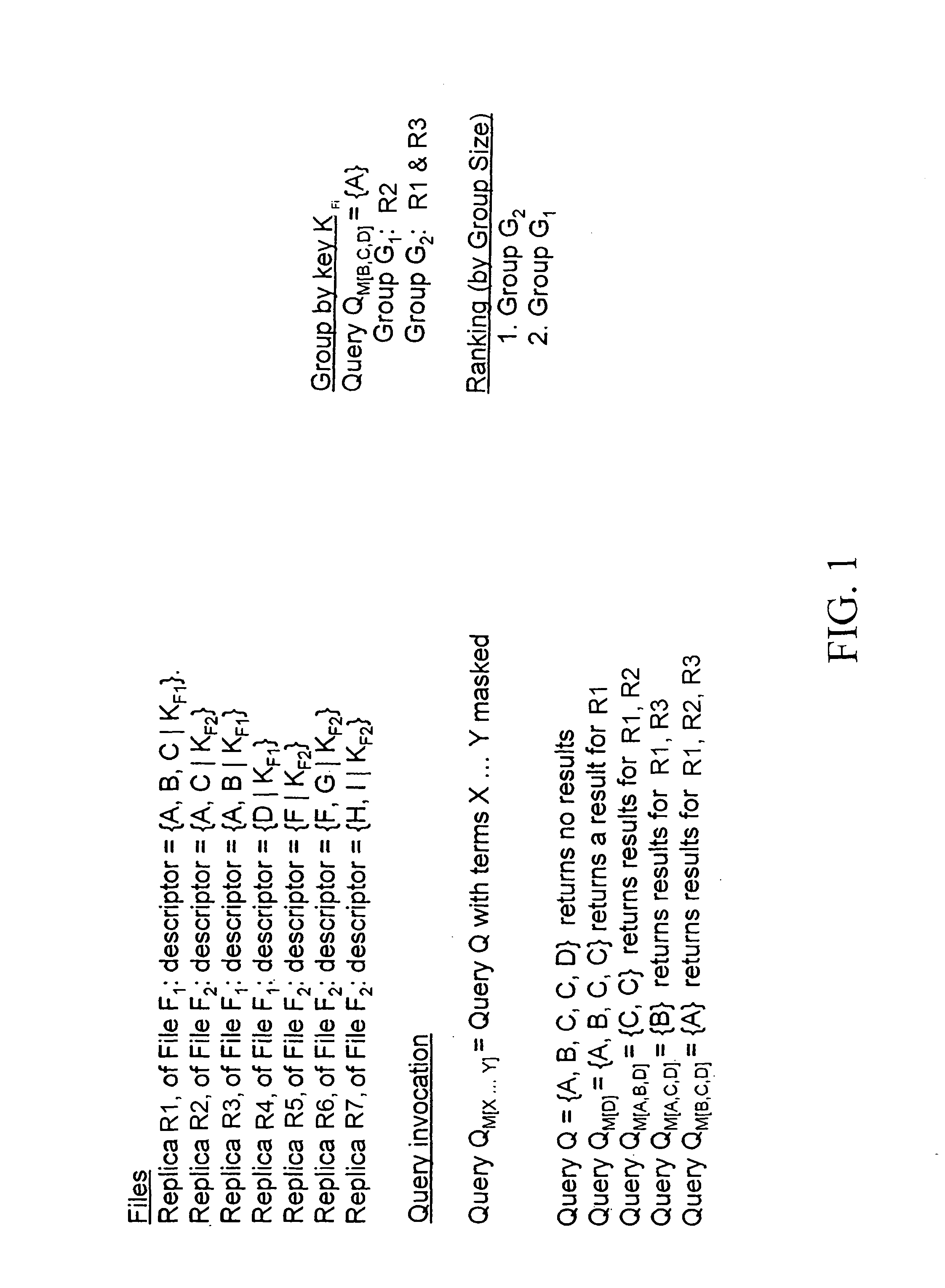
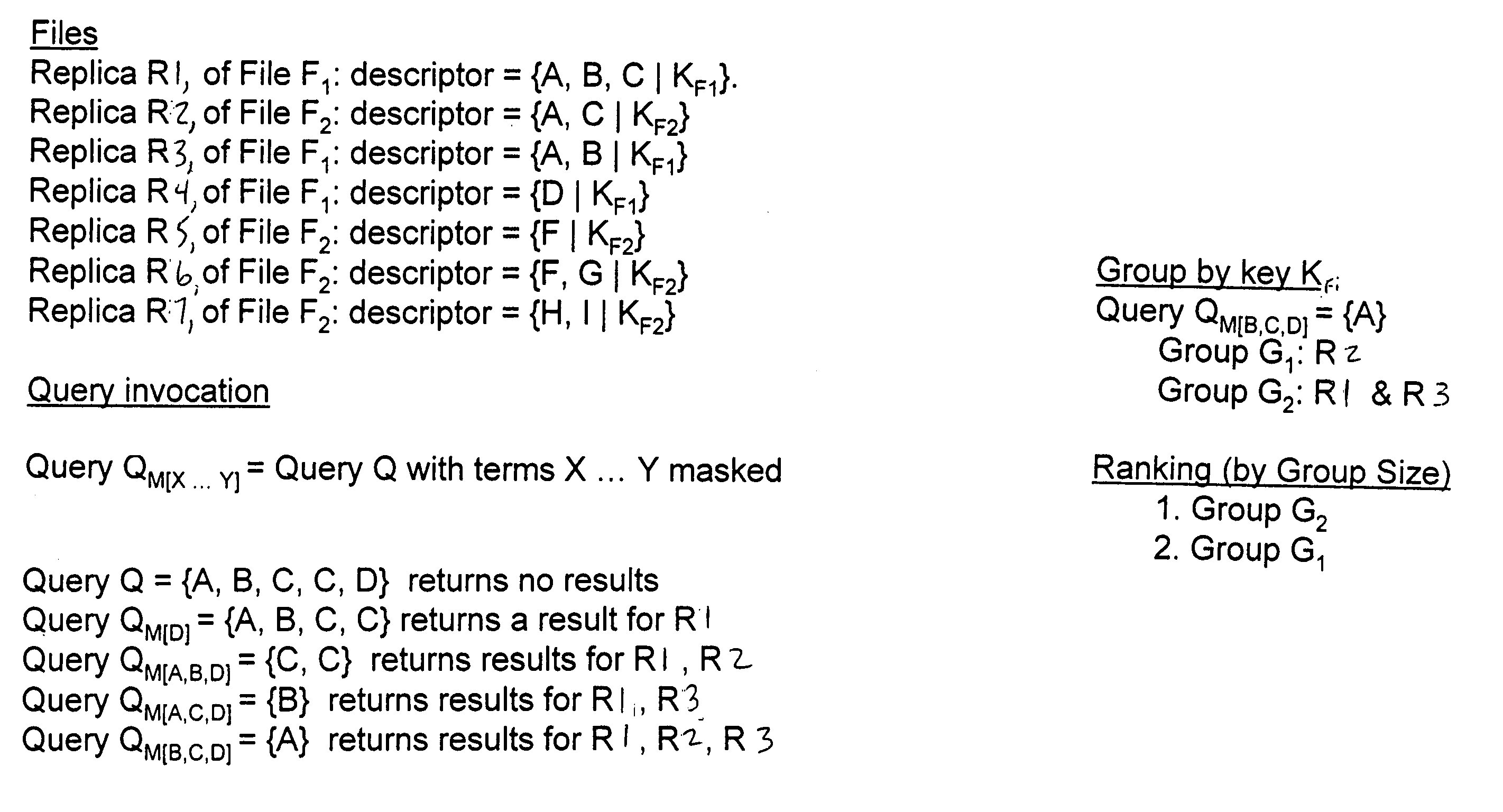
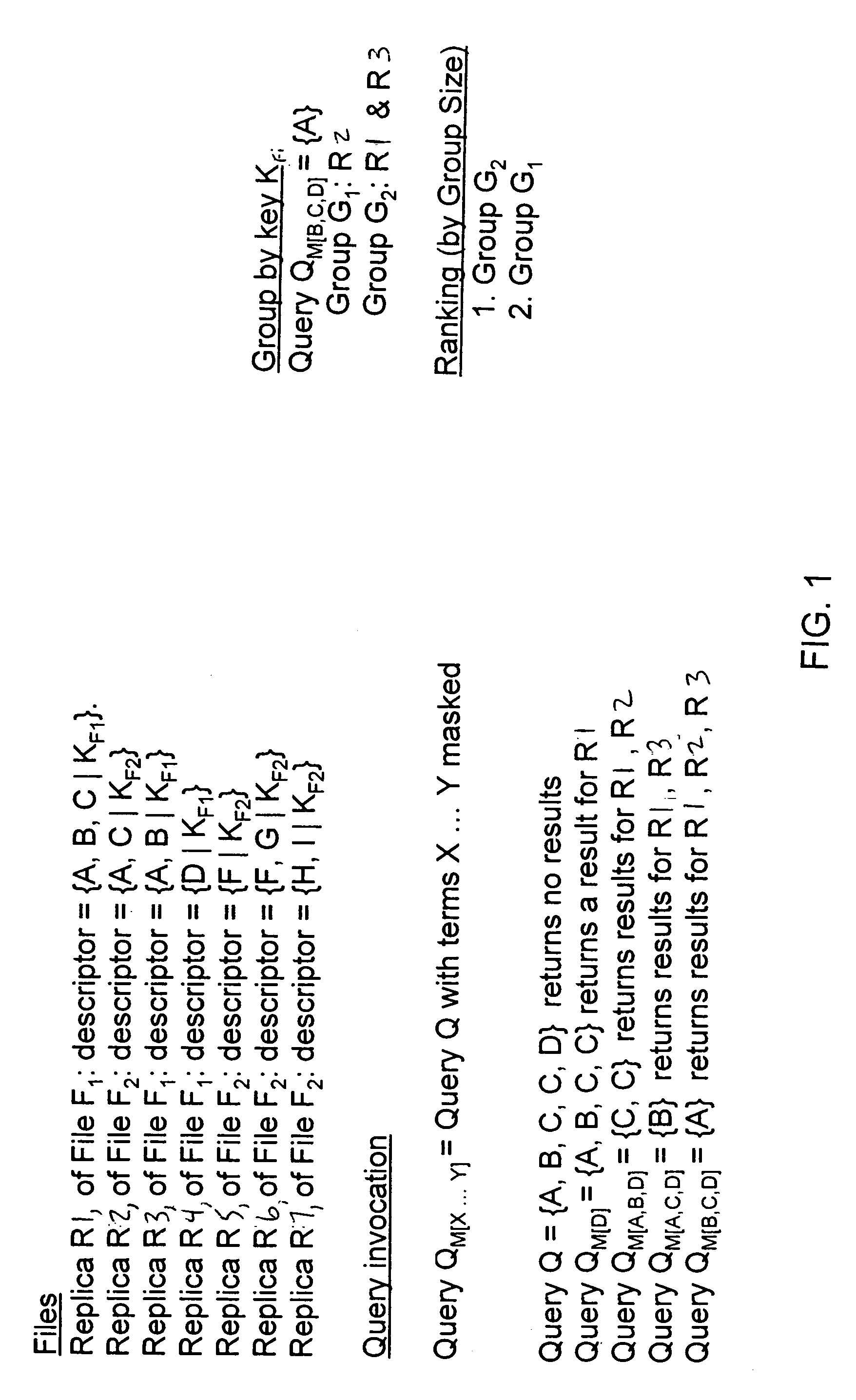
InactiveUS7860876B2Improve search accuracyImprove accuracyData processing applicationsDigital data information retrievalFile descriptorClient-side
A peer-to-peer (P2P) file sharing system is provided with an enhanced search method for a client computer therein. The method includes masking at least one term in a multi-term query entered into a client computer of the P2P system to obtain a masked query and routing the masked query to a plurality of server computers. The masked query is compared to a file descriptor of server files in each of the plurality of server computers to identify a plurality of matching server files. The server computers return to the client computer as search results the file descriptor and a mathematical identifier for each of the plurality of matching server files. The server computer may return to the client computer only a subset of the plurality of the matching server files. Enhanced P2P file searching accuracy is provided.
Owner:ILLINOIS INSTITUTE OF TECHNOLOGY
Peer-to-peer file sharing system and method
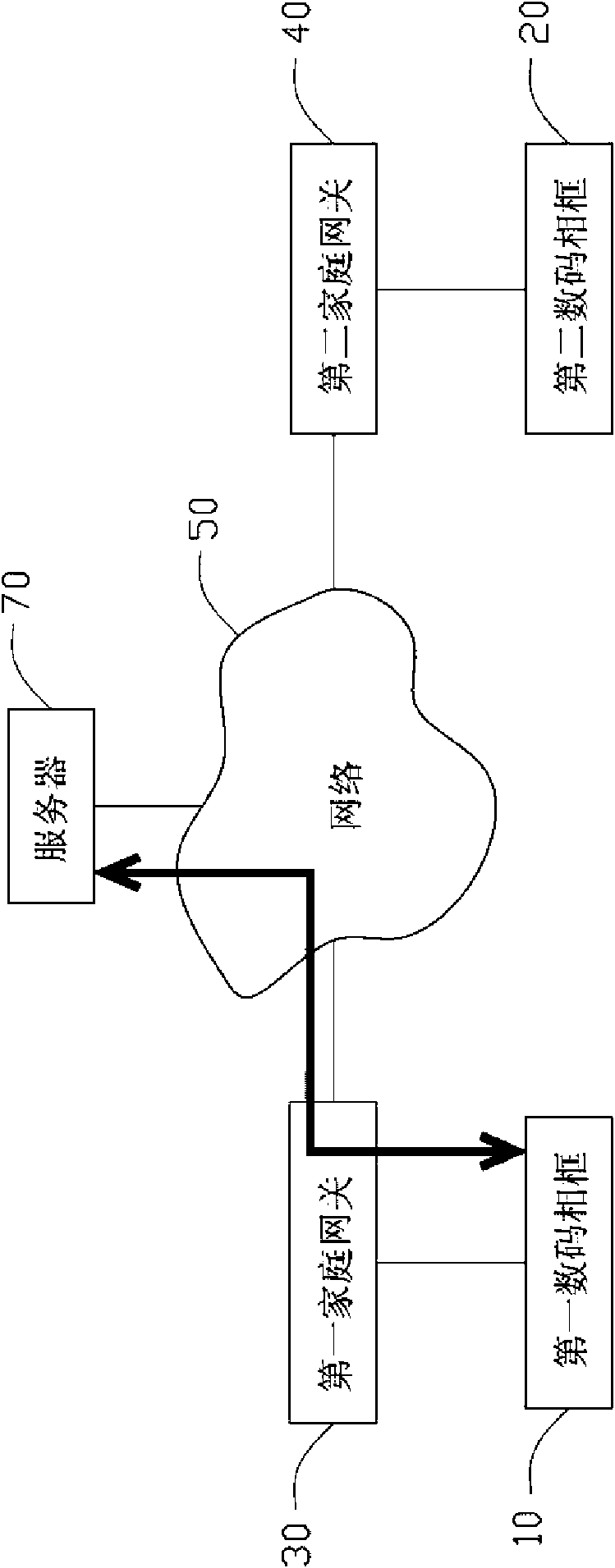
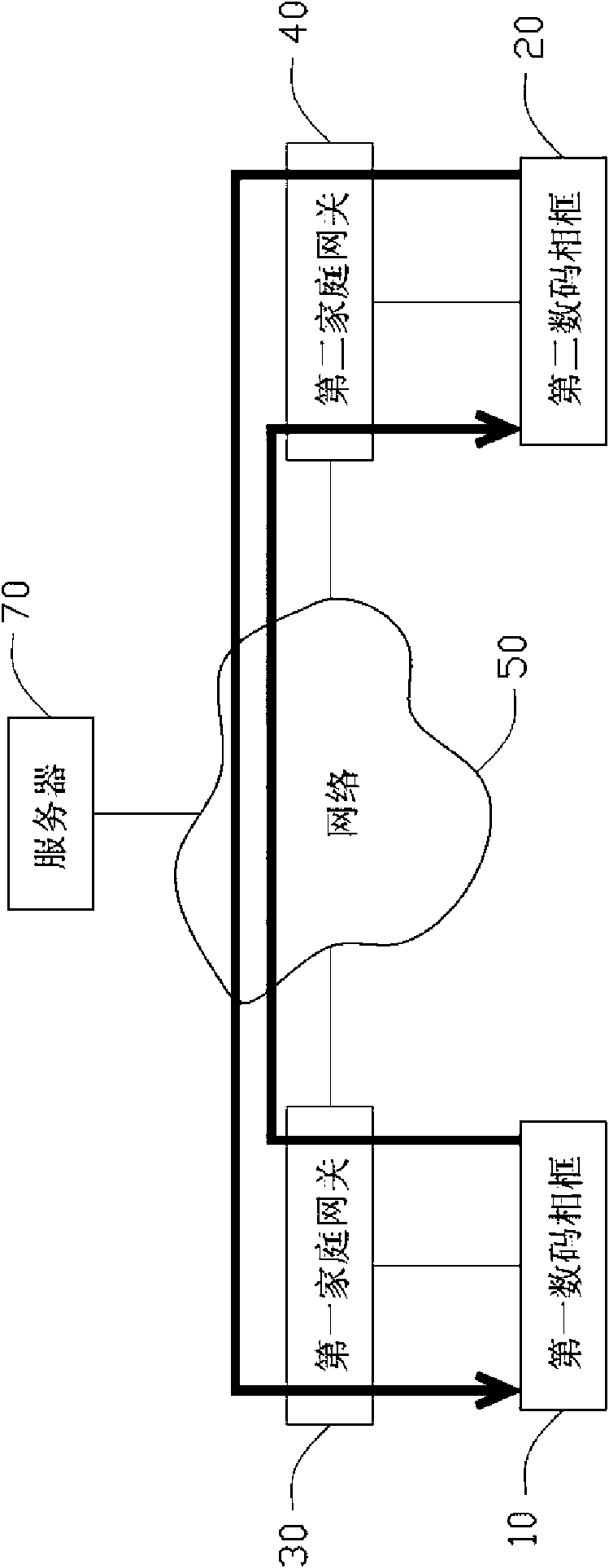
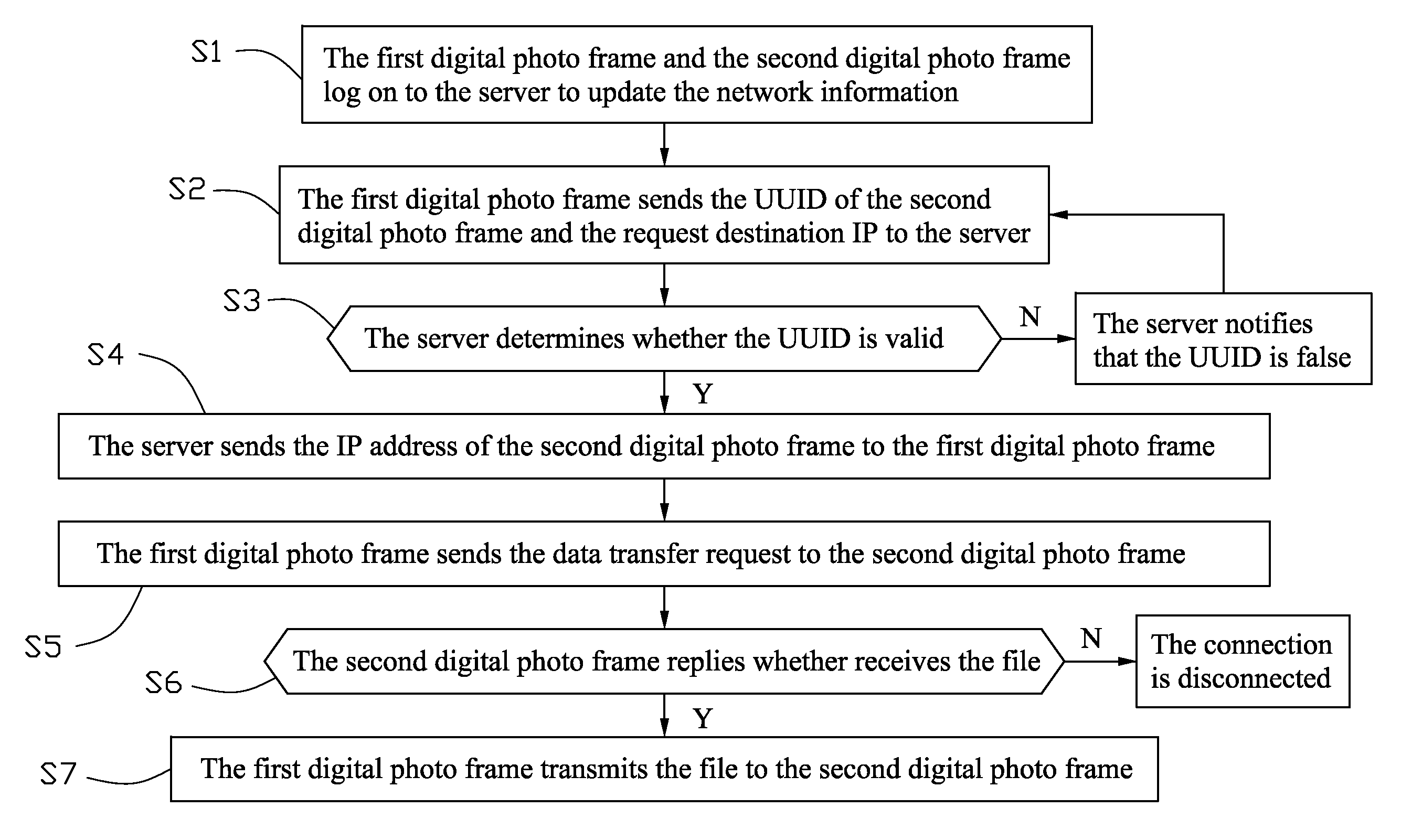
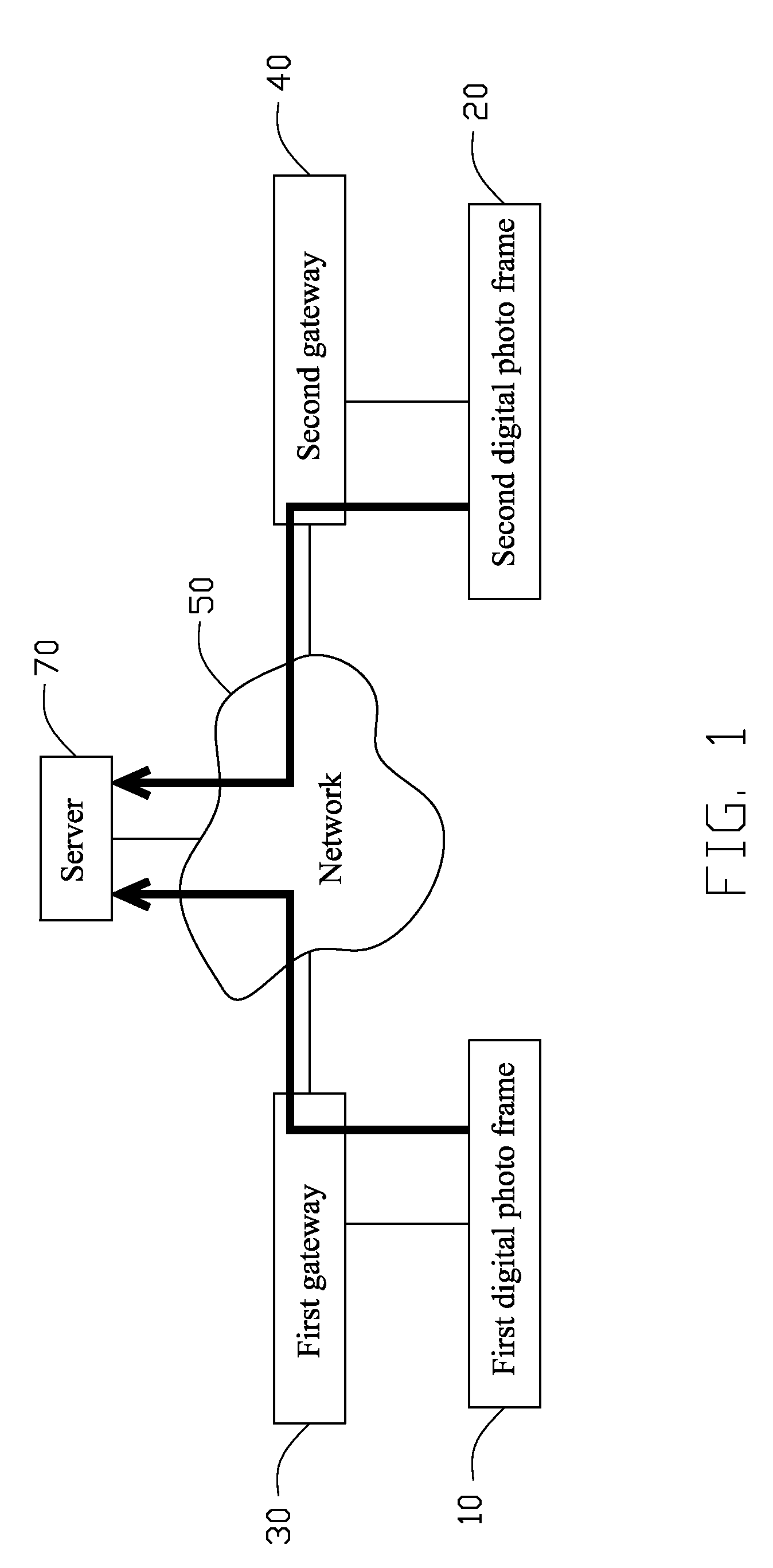
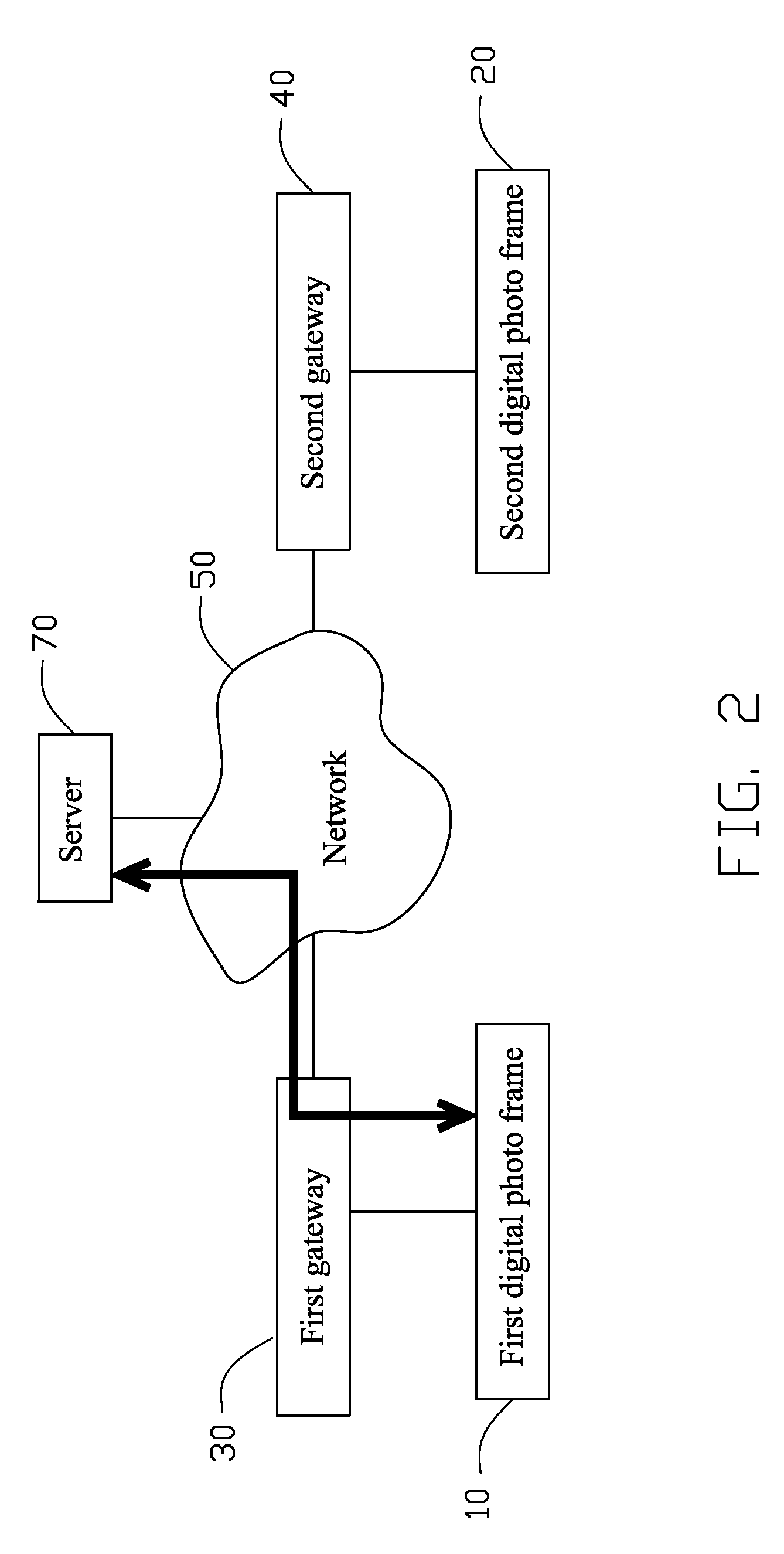
InactiveUS20100254631A1Character and pattern recognitionMultiple digital computer combinationsPeer to peer file sharingPeer-to-peer
A peer-to-peer file sharing system includes a first digital photo frame connected to a network, a second digital photo frame connected to the network, and a server connected to the network. A plurality of files is stored in the first digital photo frame. An address information of the second digital photo frame is stored in the server. The first digital photo frame is capable of acquiring the address information of the second digital photo frame from the server, and transmitting the files to the second digital photo frame directly based on the address information.
Owner:HON HAI PRECISION IND CO LTD
Peer-to-peer file sharing
InactiveUS20070294257A1Improve search accuracyDegree improved search accuracyDigital data information retrievalSpecial data processing applicationsFile descriptorClient-side
A peer-to-peer (P2P) file sharing system is provided with an enhanced search method for a client computer therein. The method includes masking at least one term in a multi-term query entered into a client computer of the P2P system to obtain a masked query and routing the masked query to a plurality of server computers. The masked query is compared to a file descriptor of server files in each of the plurality of server computers to identify a plurality of matching server files. The server computers return to the client computer as search results the file descriptor and a mathematical identifier for each of the plurality of matching server files. The server computer may return to the client computer only a subset of the plurality of the matching server files. Enhanced P2P file searching accuracy is provided.
Owner:ILLINOIS INSTITUTE OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com