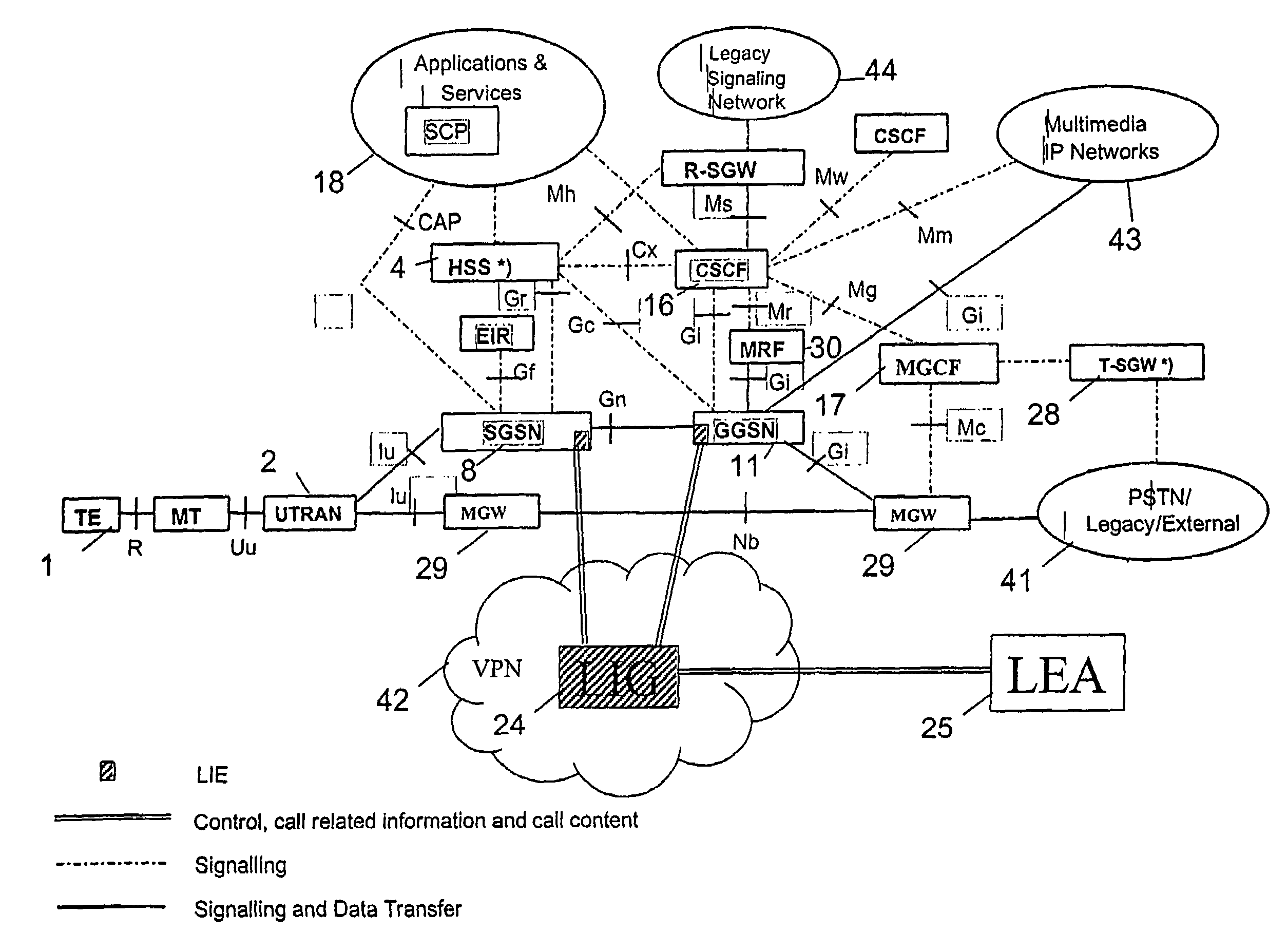
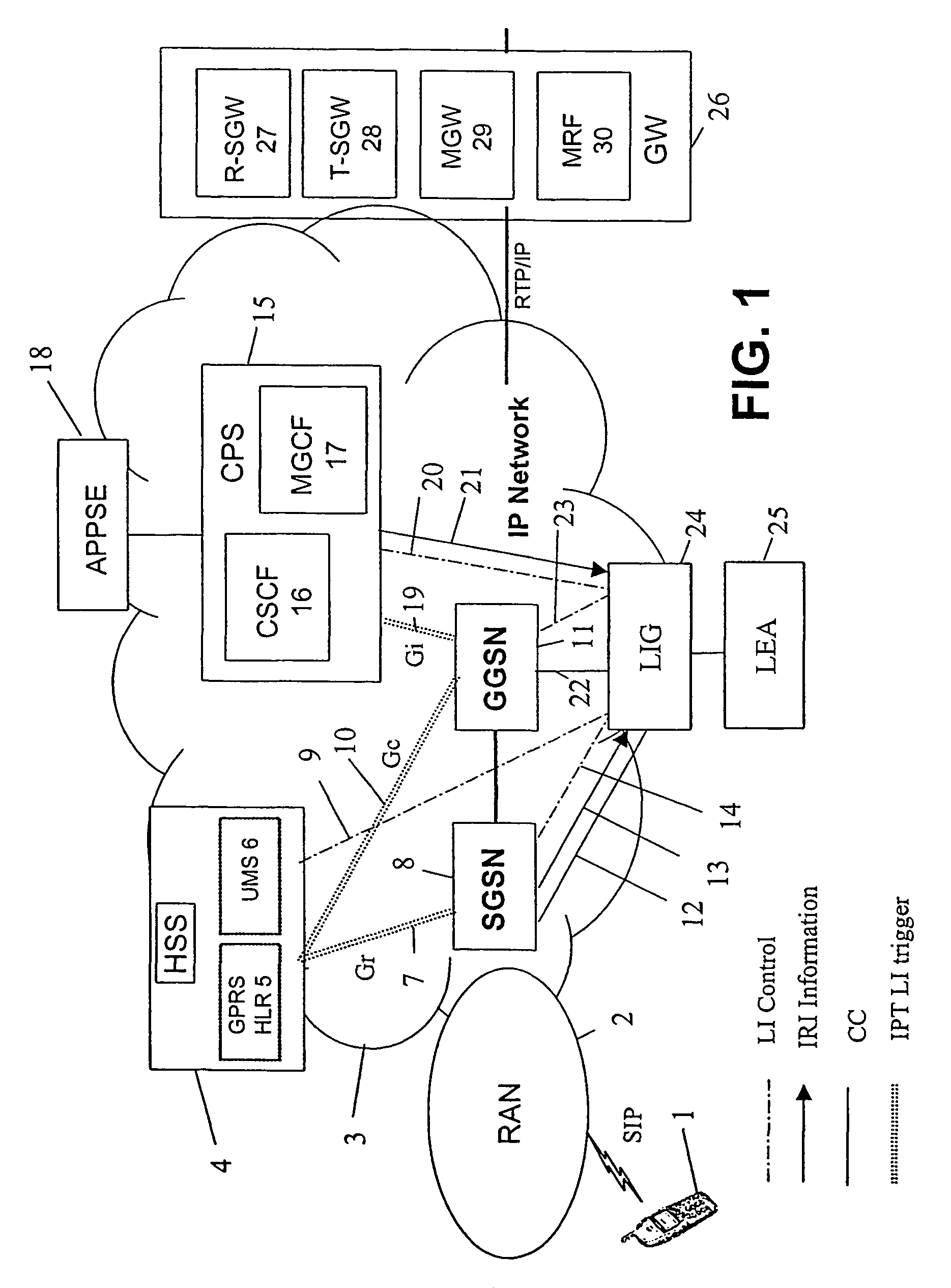
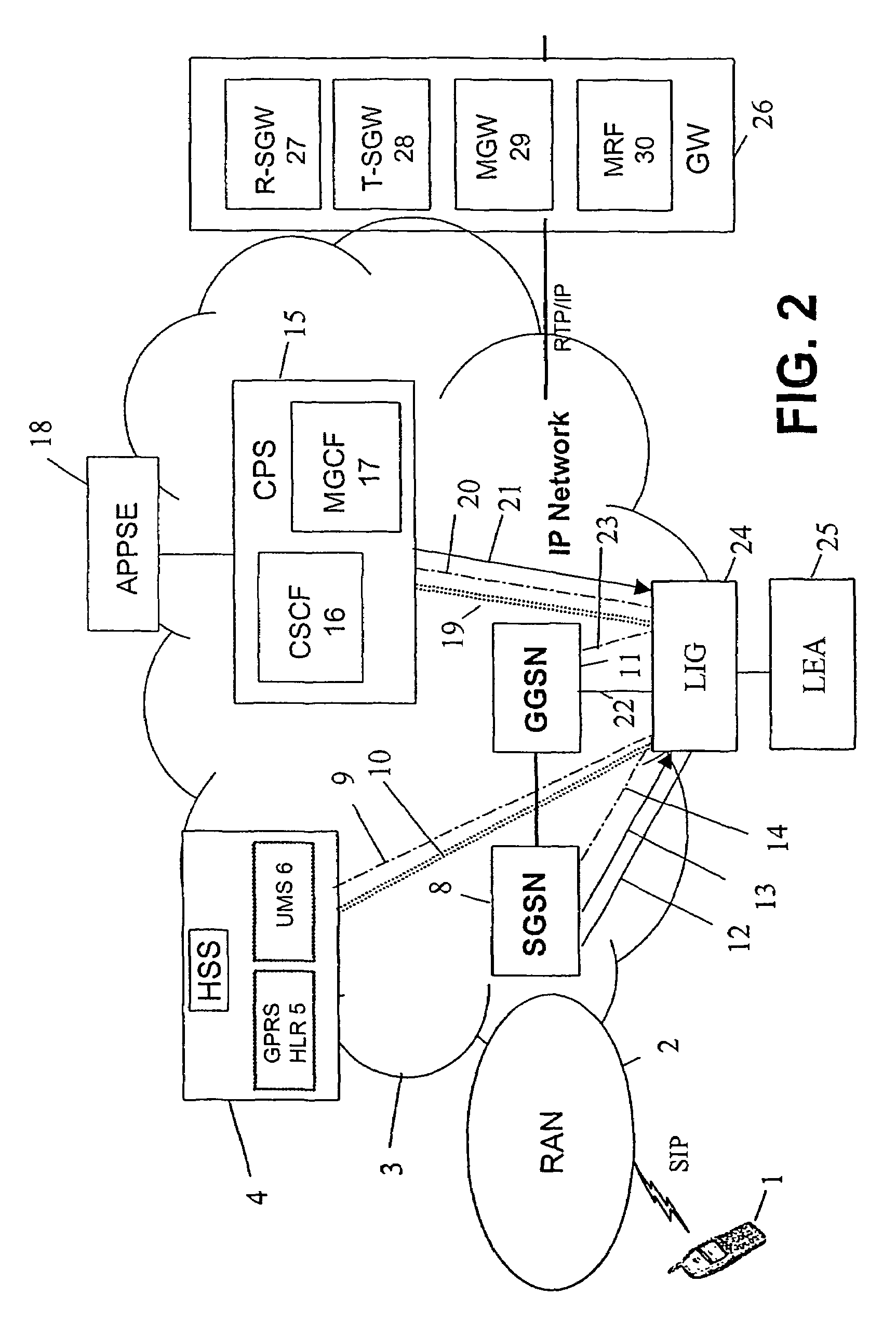
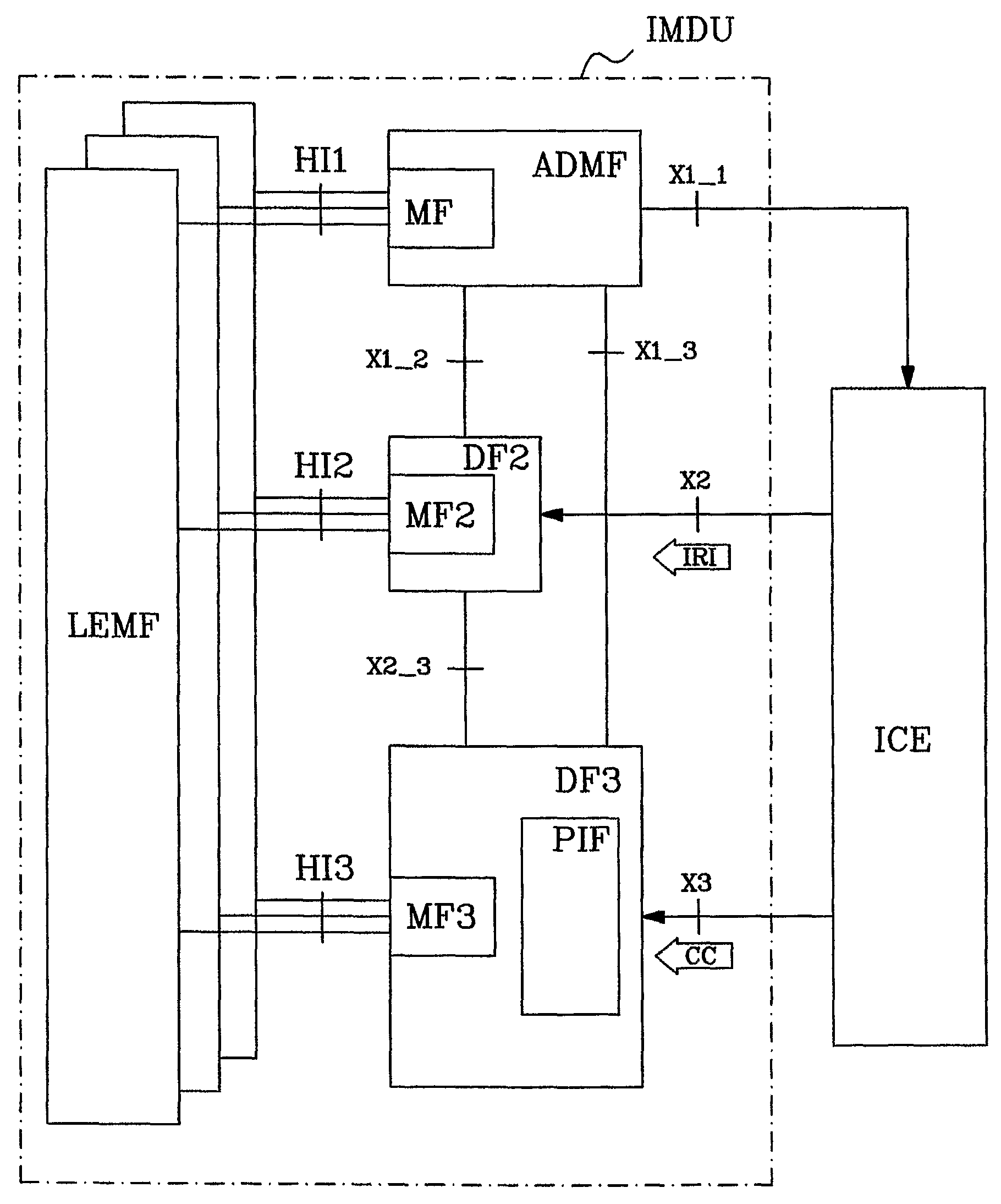
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
167 results about "Lawful interception" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
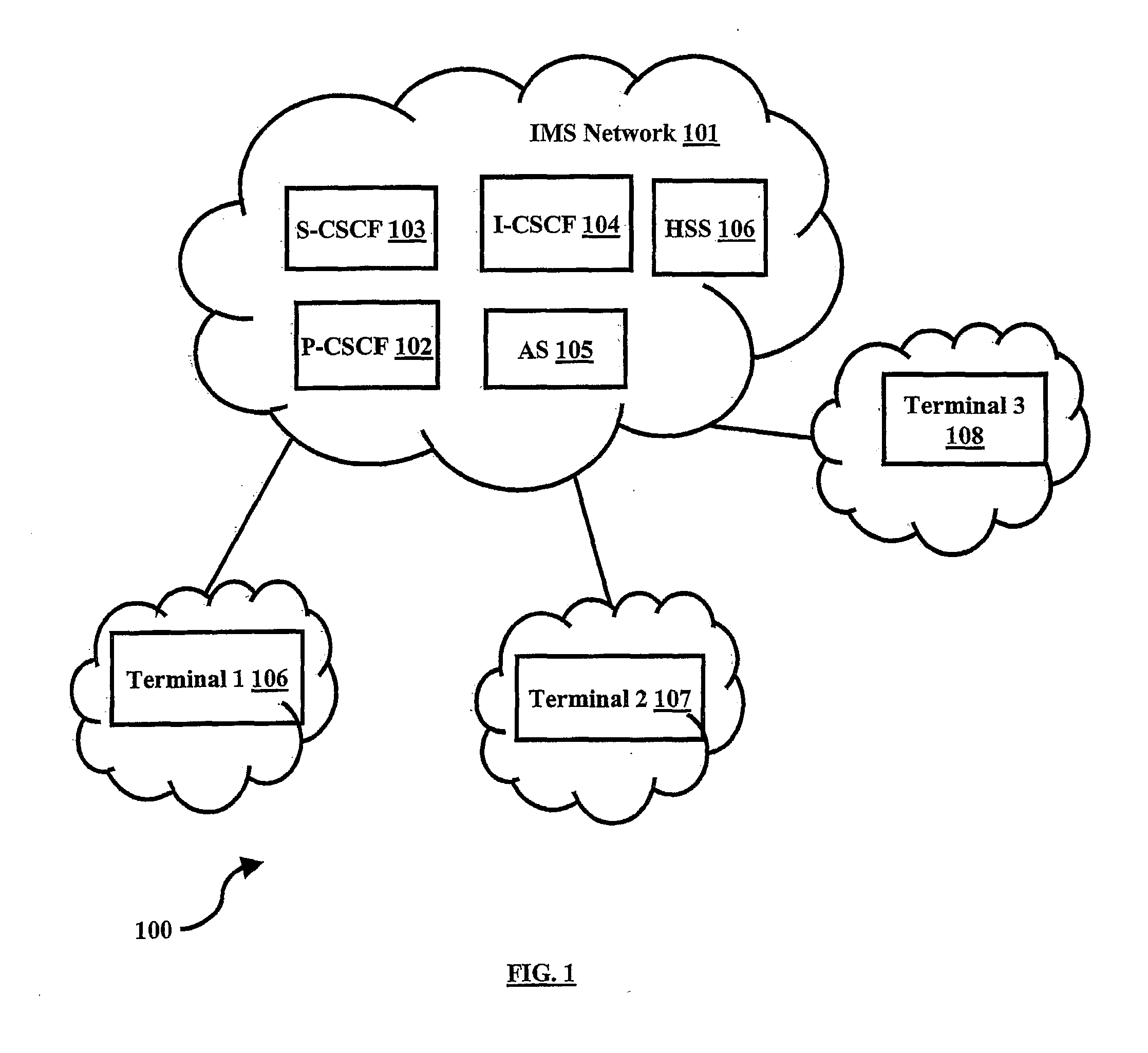
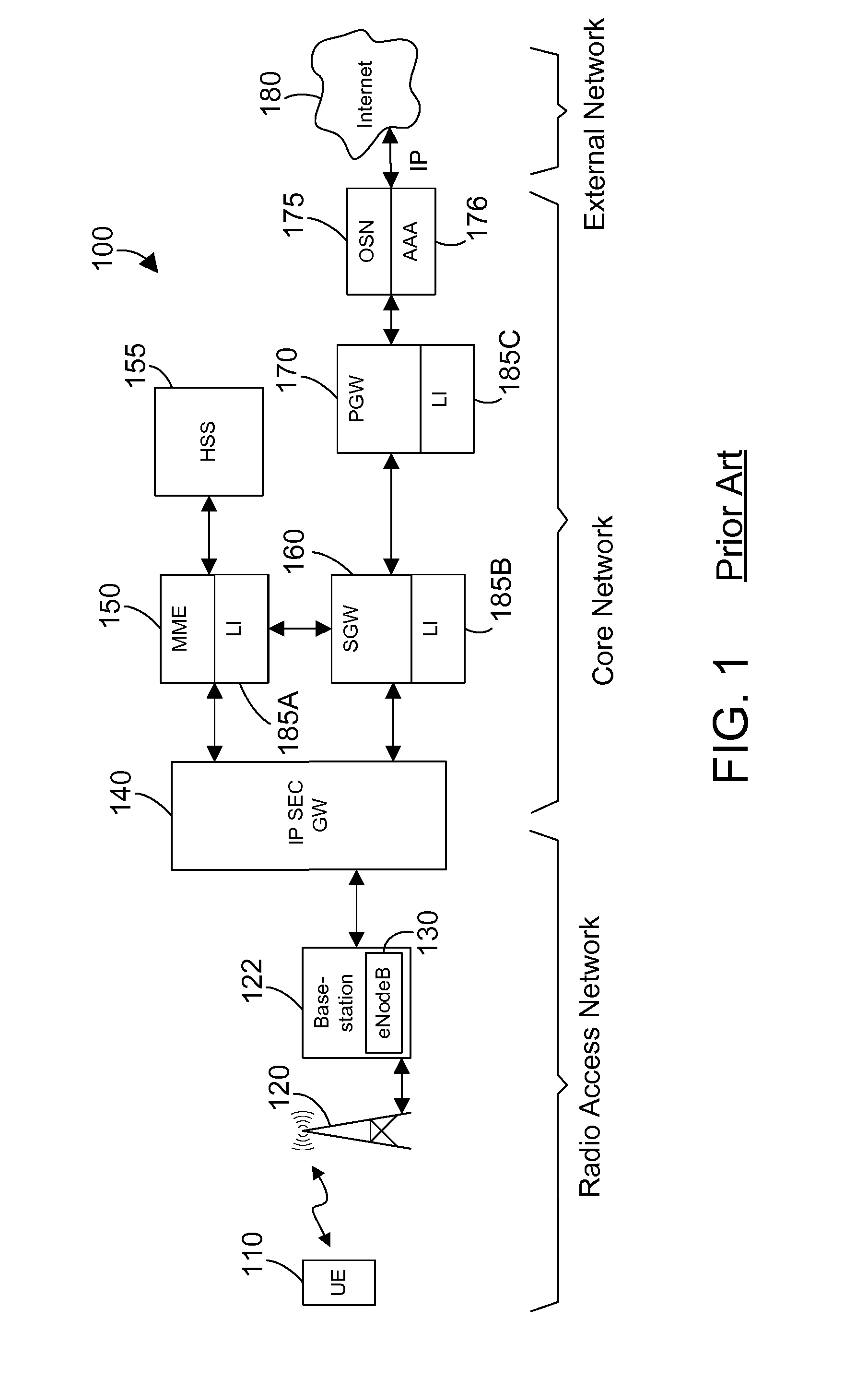
Lawful interception (LI) refers to the facilities in telecommunications and telephone networks that allow law enforcement agencies with court orders or other legal authorization to selectively wiretap individual subscribers. Most countries require licensed telecommunications operators to provide their networks with Legal Interception gateways and nodes for the interception of communications. The interfaces of these gateways have been standardized by telecommunication standardization organizations.
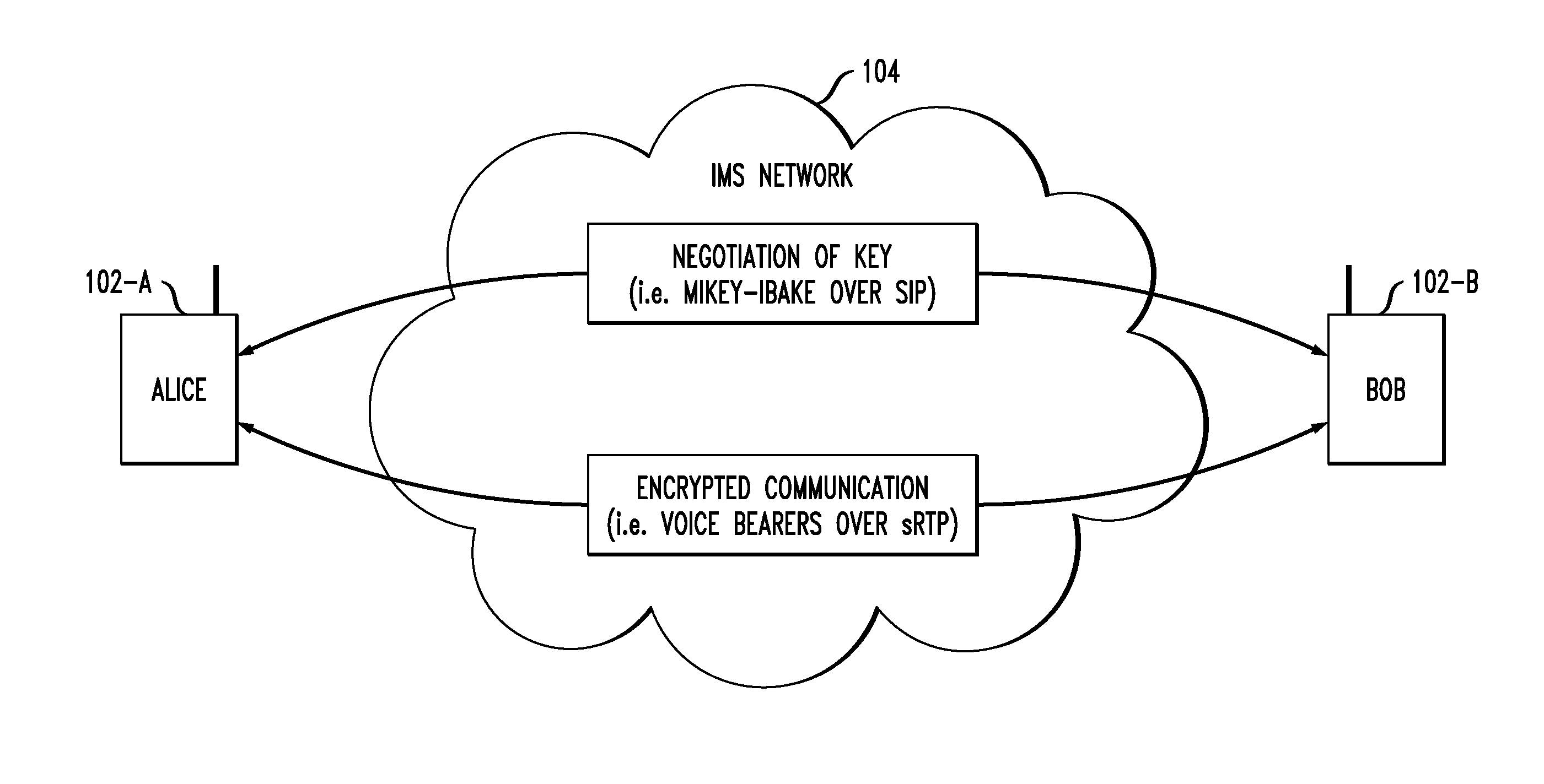
Lawful interception of end-to-end encrypted data traffic
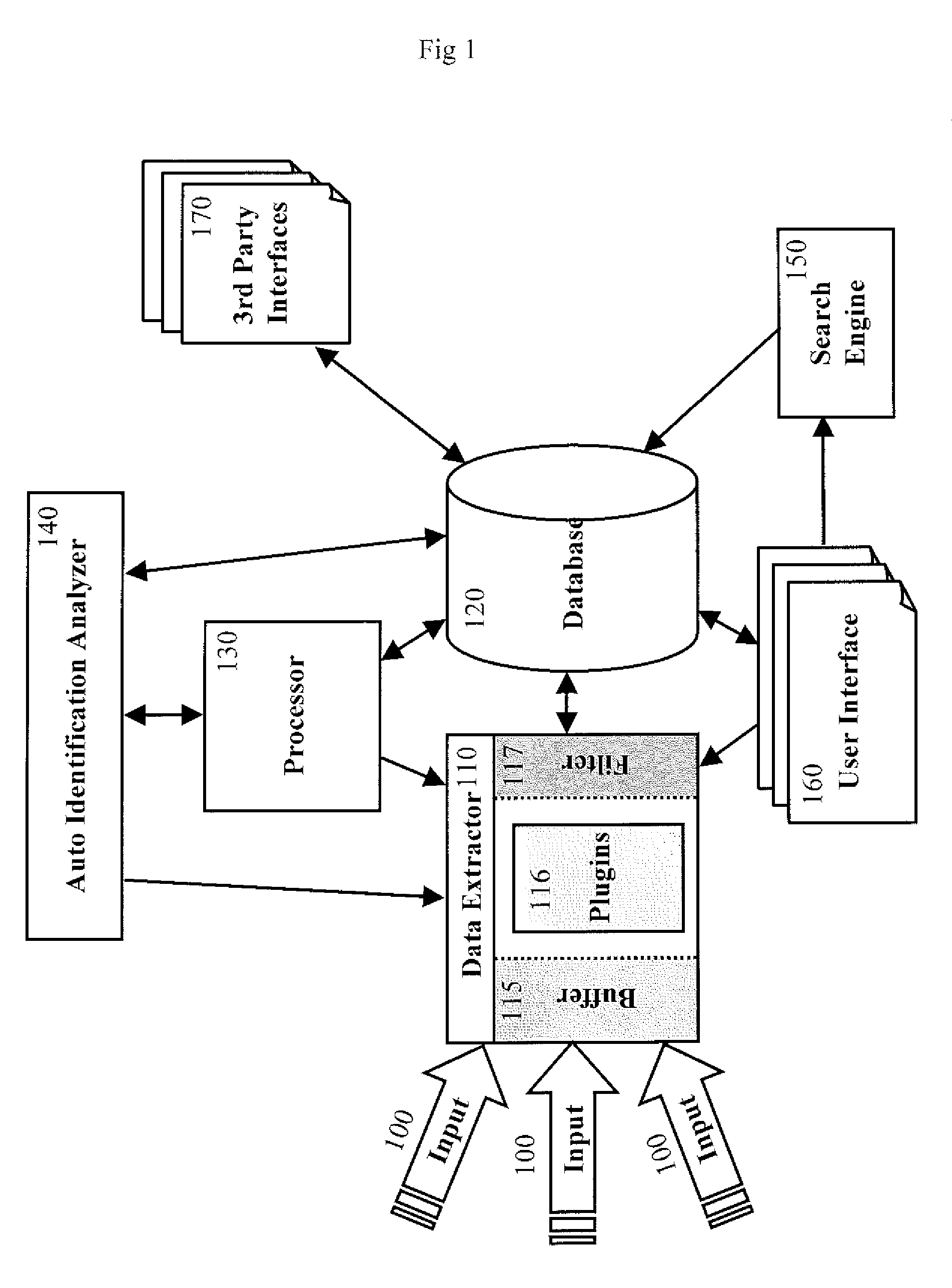
ActiveUS20050063544A1Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
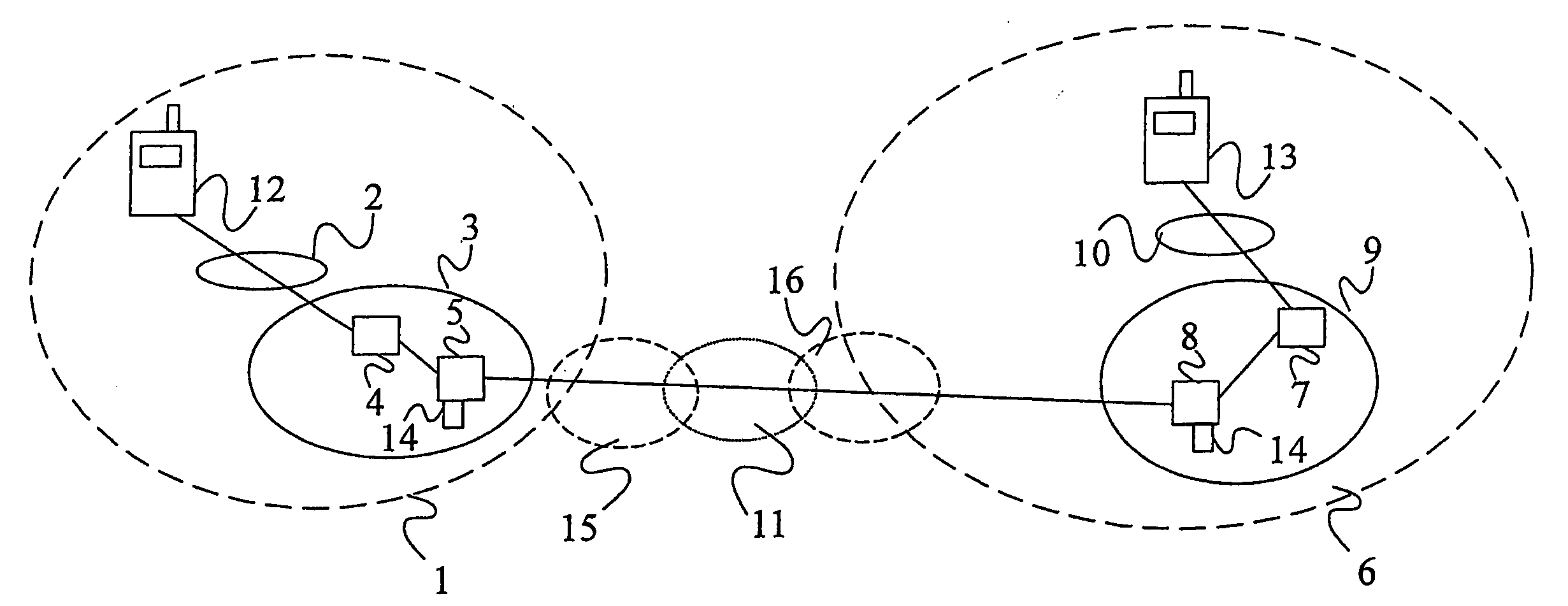
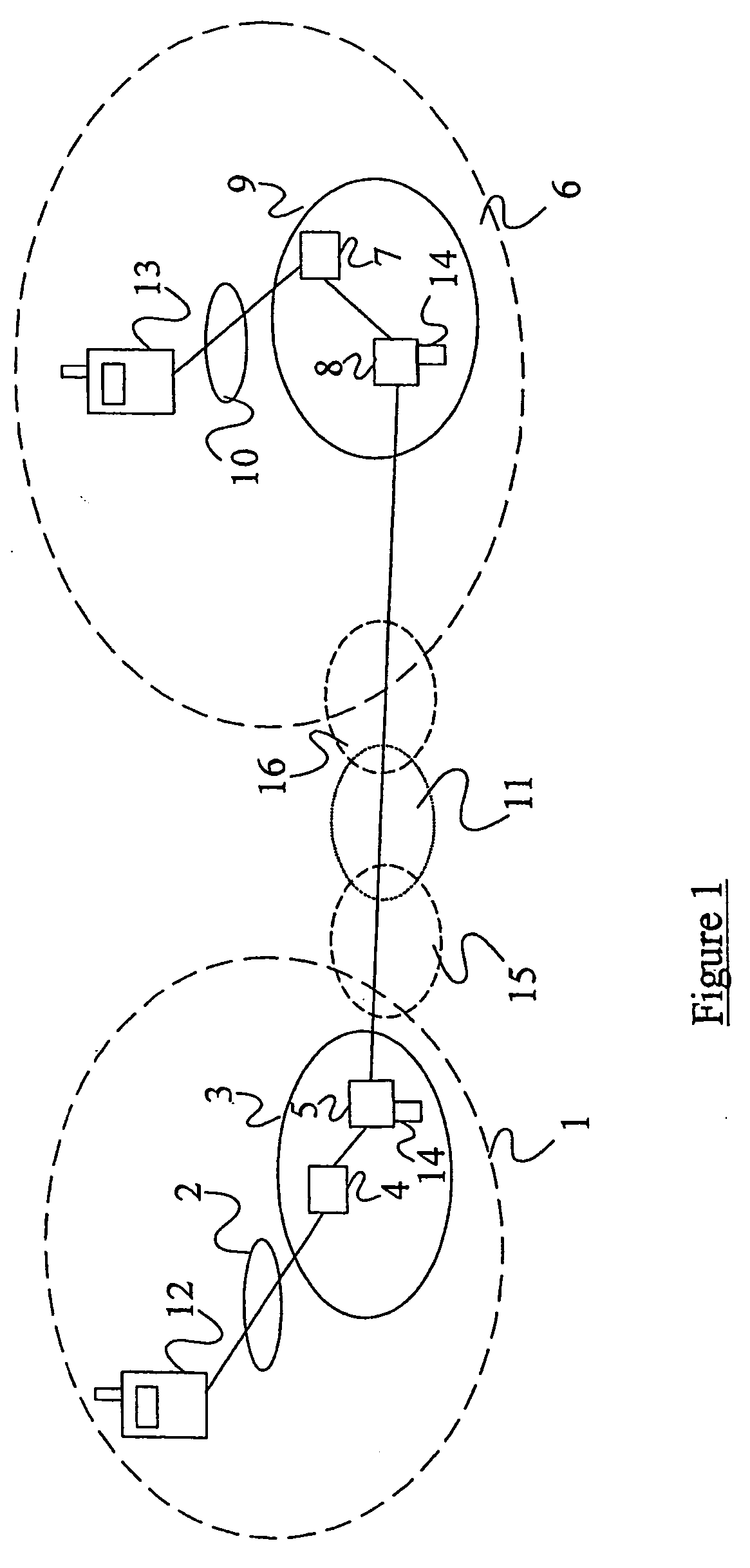
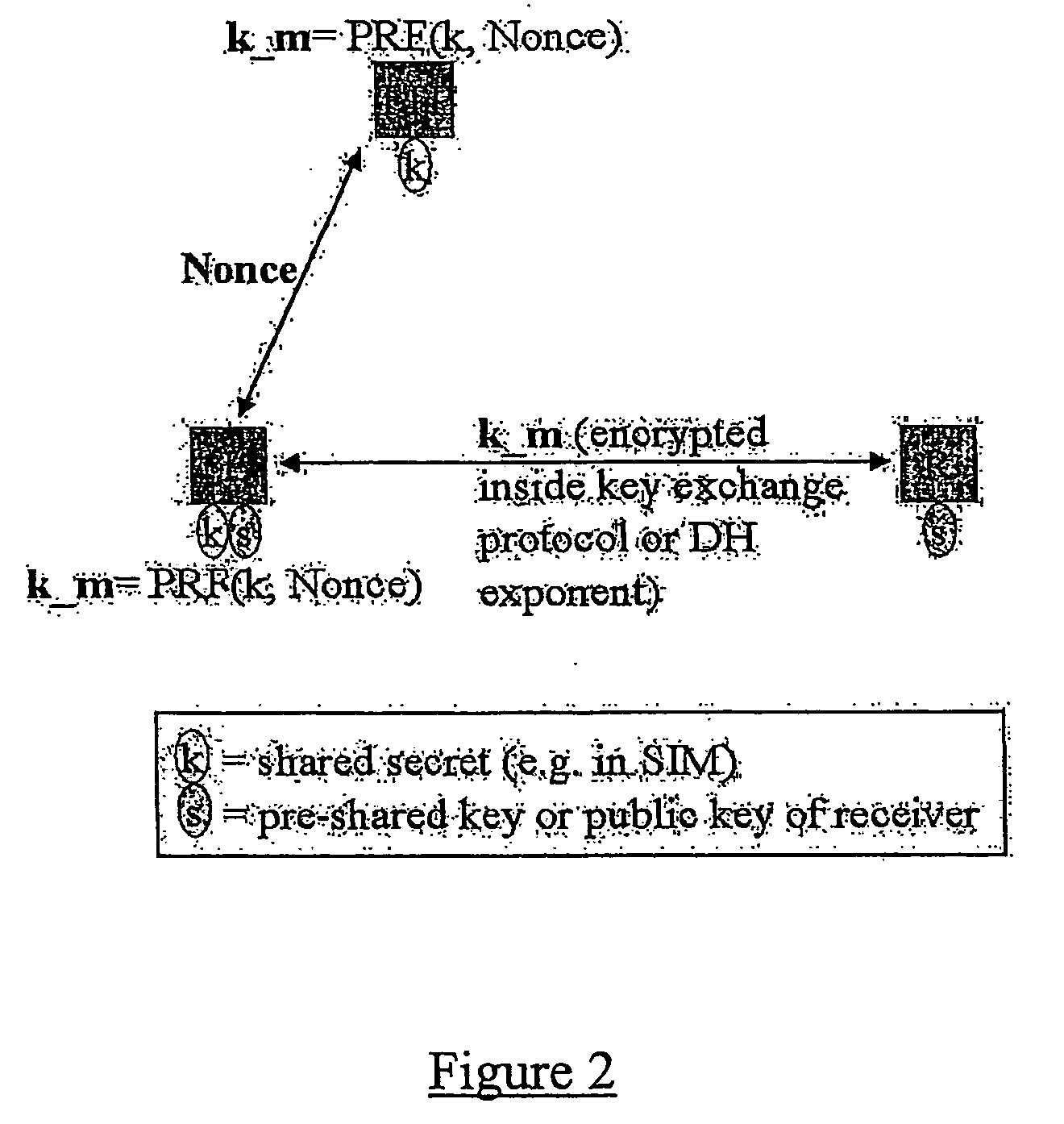
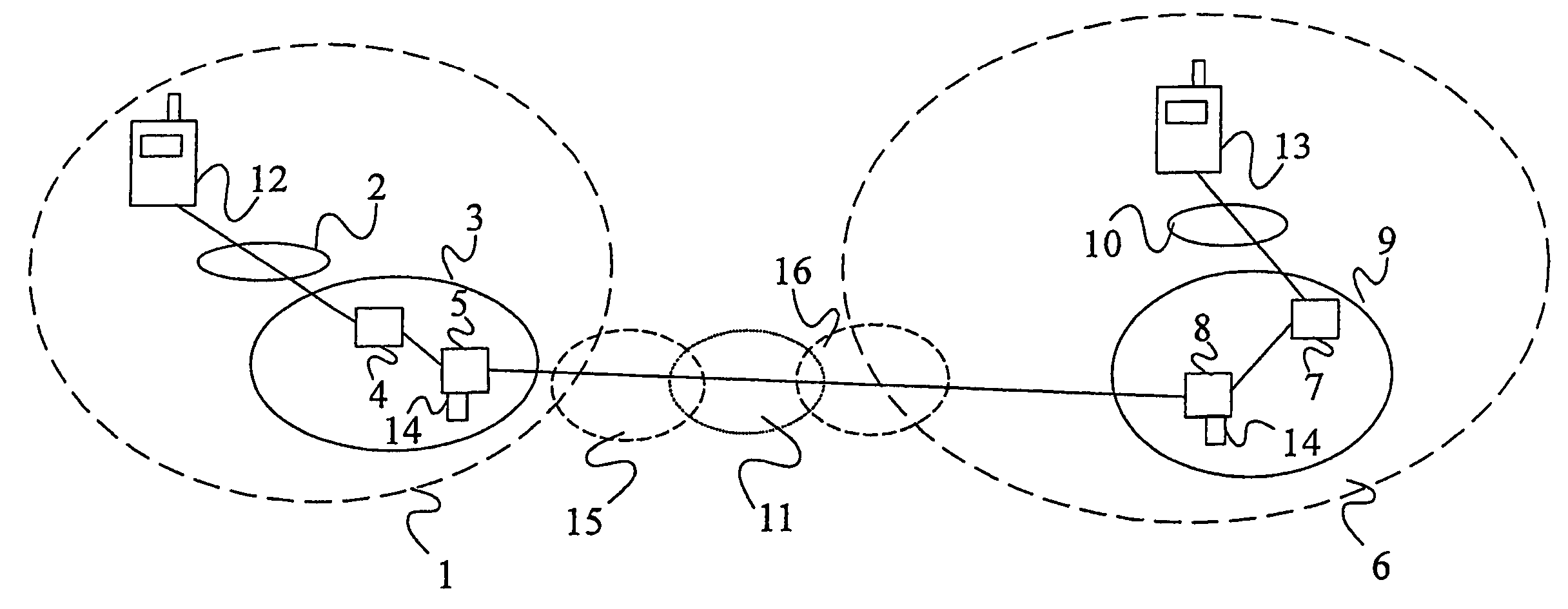
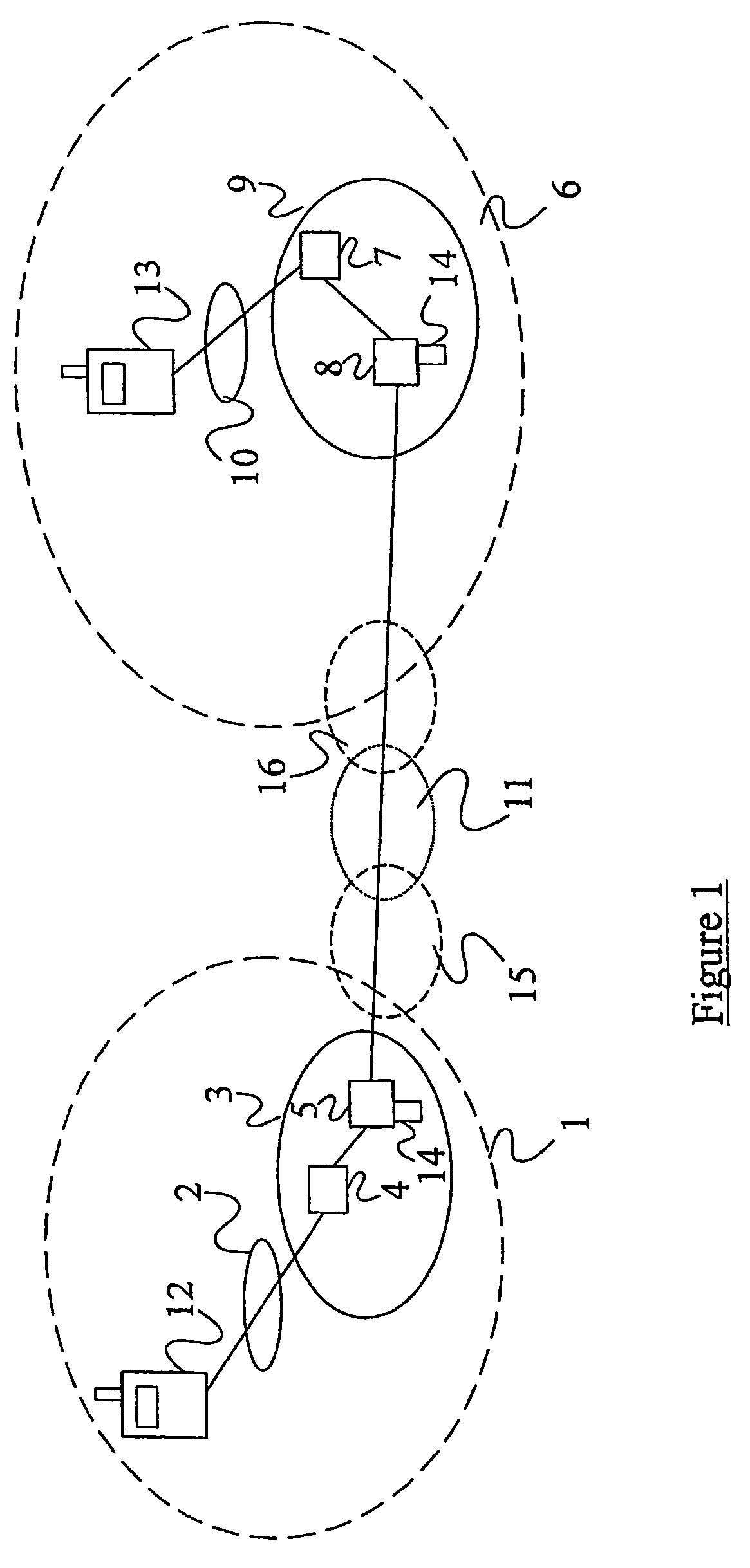
A method of facilitating the lawful interception of an IP session between two or more terminals 12,13, wherein said session uses encryption to secure traffic. The method comprises storing a key allocated to at least one of said terminals 12,13 or to at least one of the subscribers using one of the terminals 12,13, at the terminal 12,13 and at a node 5,8 within a network 1,6 through which said session is conducted, or a node coupled to that network. Prior to the creation of said session, a seed value is exchanged between the terminal 12,13 at which the key is stored and said node 5,8. The key and the seed value are used at both the terminal 12,13 and the node 5,8 to generate a pre-master key. The pre-master key becomes known to each of the terminals 12,13 involved in the IP session and to the network node 5,8. The pre-master key is used, directly or indirectly, to encrypt and decrypt traffic associated with said IP session.
Owner:TELEFON AB LM ERICSSON (PUBL)
Lawful interception of end-to-end encrypted data traffic
ActiveUS7382881B2Facilitate lawful interceptionKey distribution for secure communicationUser identity/authority verificationLawful interceptionMaster key
Owner:TELEFON AB LM ERICSSON (PUBL)
Policy routing-based lawful interception in communication system with end-to-end encryption
Techniques are disclosed for lawfully intercepting information in communication environments with end-to-end encryption. For example, a method for intercepting encrypted communications exchanged between a first computing device and a second computing device in a communication network, wherein the interception is performed by a third computing device in the communication network, comprises the following steps. The third computing device obtains one or more packets having a packet address associated with one of the first computing device and the second computing device. The one or more packets are obtained by the third computing device, in response to at least one interception routing policy being implemented in at least one element in the communication network, such that the one or more obtained packets may be decrypted so as to obtain data contained therein. The third computing device preserves the packet address of the one or more obtained packets. The third computing device forwards the one or more packets toward a packet-destination one of the first computing device and the second computing device such that the packet-destination one of the first computing device and the second computing device is unable to detect from the one or more packets that the one or more packets were intercepted by the third computing device.
Owner:ALCATEL LUCENT SAS
Enhancement to sip forking for improved user services
InactiveUS20110264824A1Convenient for userGood serviceDigital computer detailsTransmissionLawful interceptionThird party
A method of enhancing SIP forking for offering improved call services in a telecommunication network is disclosed. An endpoint of the network is assigned as a Forking Master for providing improved call services for a user in the same Address of Record (AoR) in the presence of forking. The method of assigning a forking master comprises of user provisioning, updating by the user terminal during registration, subsequent declaration by the user terminal, third-party assignment and network-triggered assignment. An endpoint can take up or relinquish the role of Forking Master by specifying the value ‘true’ or false' for the forking-master parameter. The Forking Master can be associated with call completion services, presence-based services, call- forwarding interaction, lawful interception, facilities like PBRT and the like.
Owner:ALCATEL LUCENT SAS
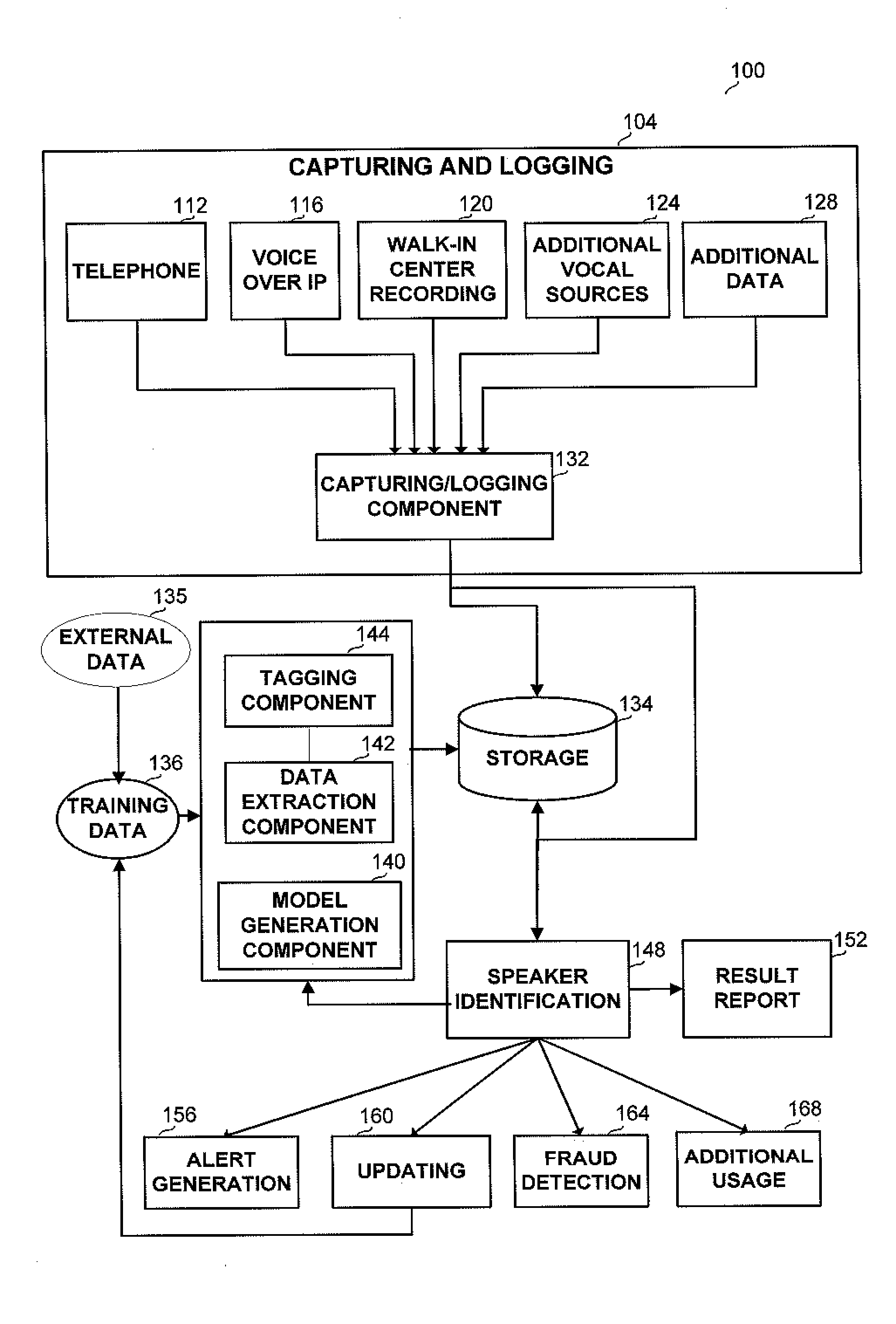
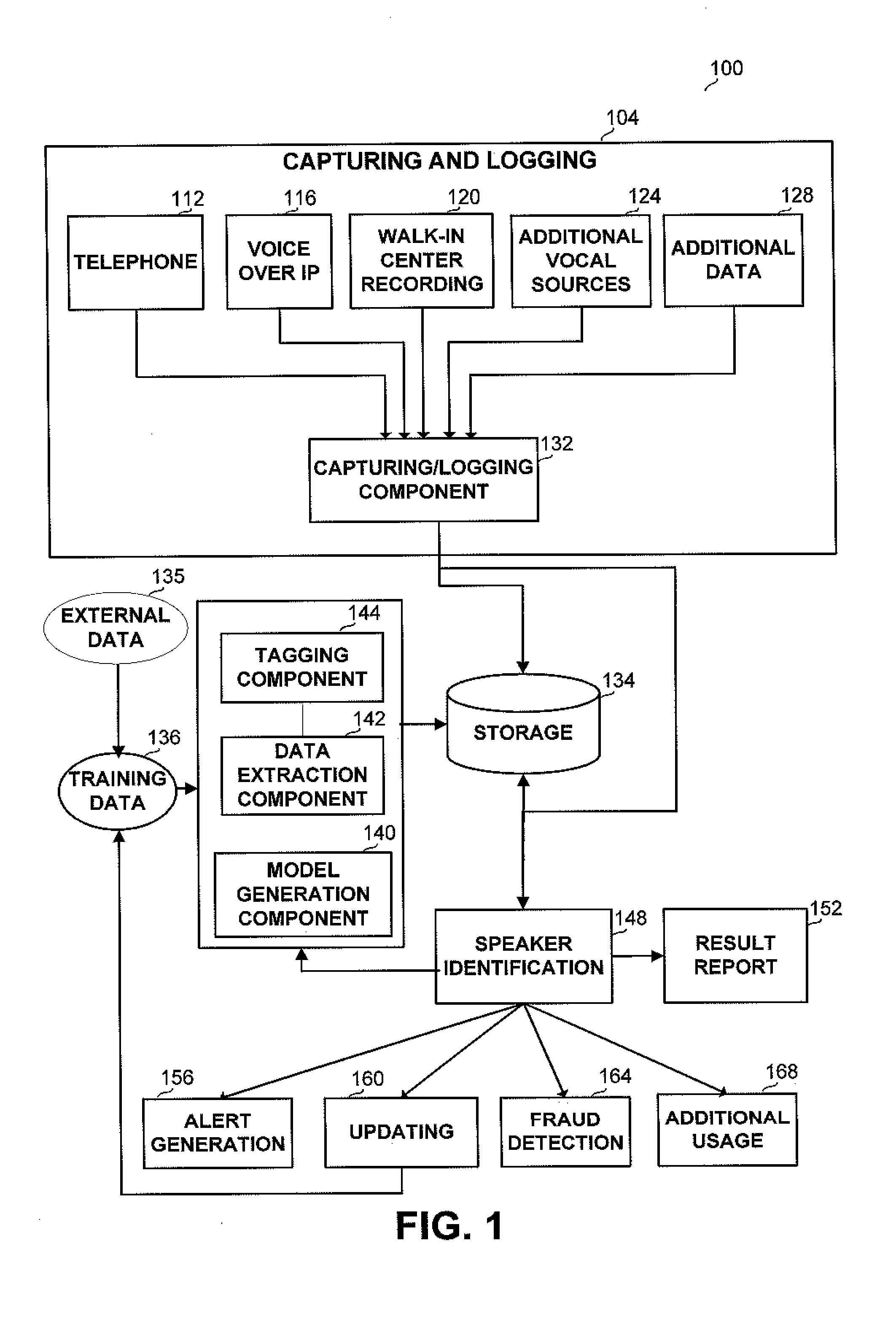
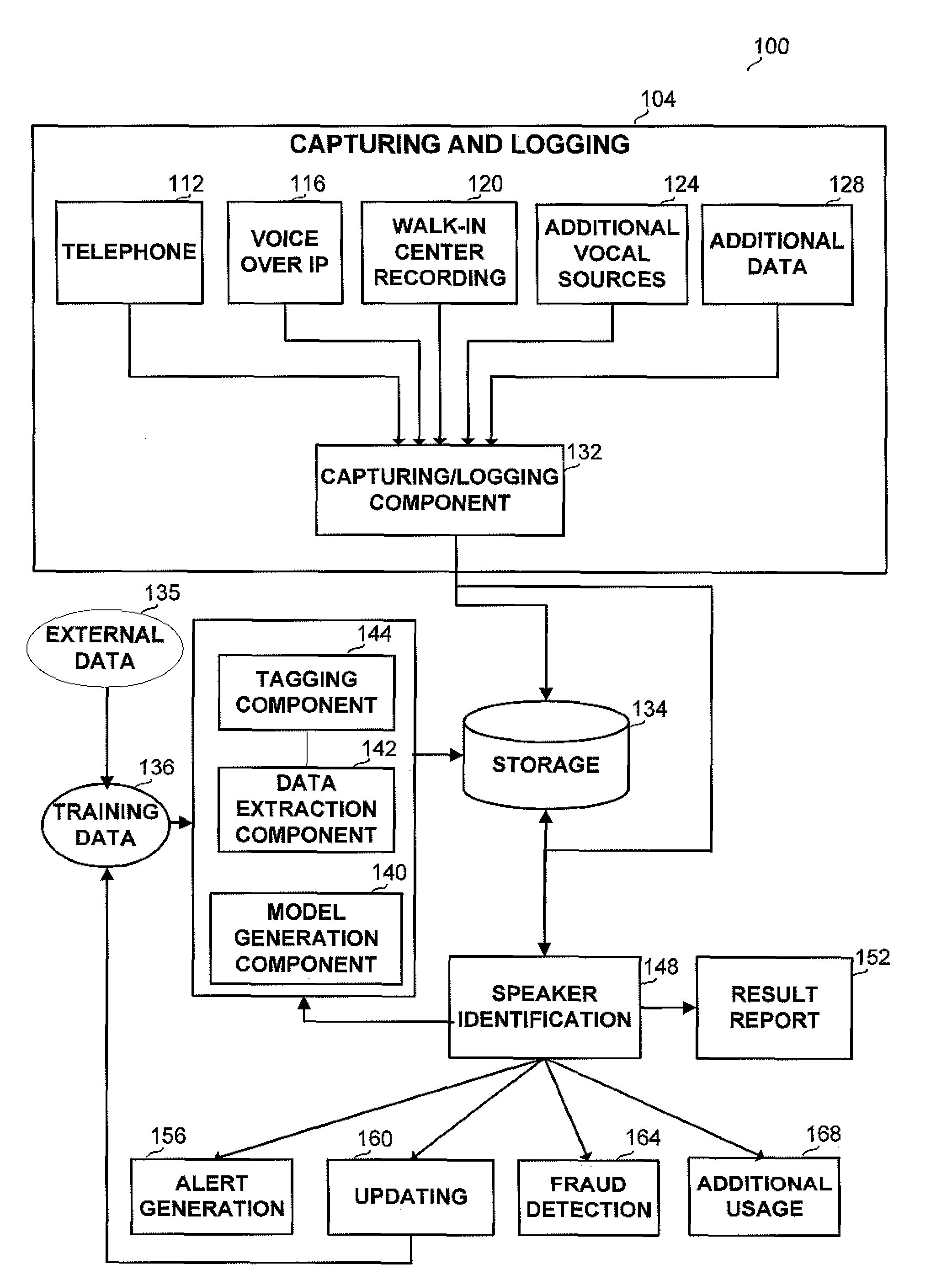
Method and apparatus for recognizing a speaker in lawful interception systems
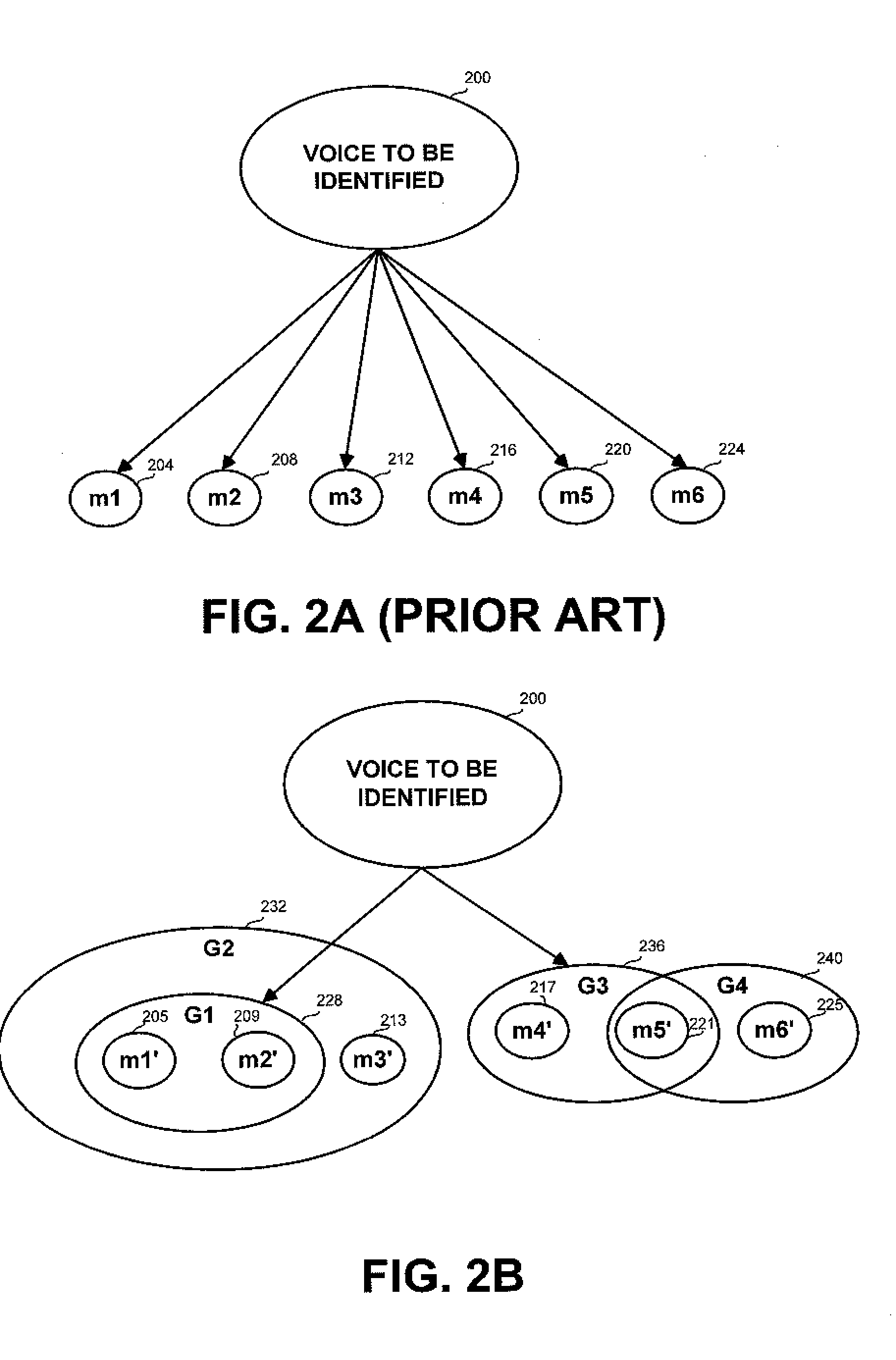
A method and apparatus for identifying a speaker within a captured audio signal from a collection of known speakers. The method and apparatus receive or generate voice representations for each known speakers and tag the representations according to meta data related to the known speaker or to the voice. The representations are grouped into one or more groups according to the indices. When a voice to be recognized is introduced, characteristics are determined according to which the groups are prioritized, so that the representations participating only in part of the groups are matched against the o voice to be identified, thus reducing identification time and improving the statistical significance.
Owner:CYBERBIT
Lawful interception of multimedia calls
ActiveUS20060264200A1Special service provision for substationInterconnection arrangementsLawful interceptionChannel data
A method of performing lawful interception of a multimedia call between two or more terminals. The method comprises detecting the initiation of said call at monitoring equipment located in the call path, and forwarding from the monitoring equipment to a gateway, parameters defining at least one of the forward and reverse channels of said call. At least one multimedia call is set up from said gateway to a monitoring terminal in dependence upon the received parameters. Following the setting up of the first mentioned multimedia call, forward and / or reverse channel data is intercepted at said monitoring equipment, the intercepted data routed to said gateway, and the data transmitted to the monitoring terminal over the forward channel of the or each second mentioned multimedia call.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method for Analyzing Activities Over Information Networks
InactiveUS20080162397A1Knowledge representationData switching networksLawful interceptionInformation networks
The present invention is a method for analyzing large volumes of network information for the purpose of identifying particular patterns of behavior in a plurality of connections. It enables identifying unique digital fingerprints of particular users, be it individuals, groups or organizations, and tracks their activities in large scale information networks such as corporate wide area networks or the public internet despite attempts on the part of the users to hide their identity. By recognizing unique identifiers and distinguishing patterns of behavior the method may differentiate between different users all using a single connection, or identify a single entity across multiple connections. The method may be applicable for tracking hostile entities inside an organizational network. Advertisers may uniquely and anonymously track the activities of users. The method may also be used to track and identify suspicious activities by law enforcement agencies via lawful interception of network data.
Owner:ZALTZMAN ORI
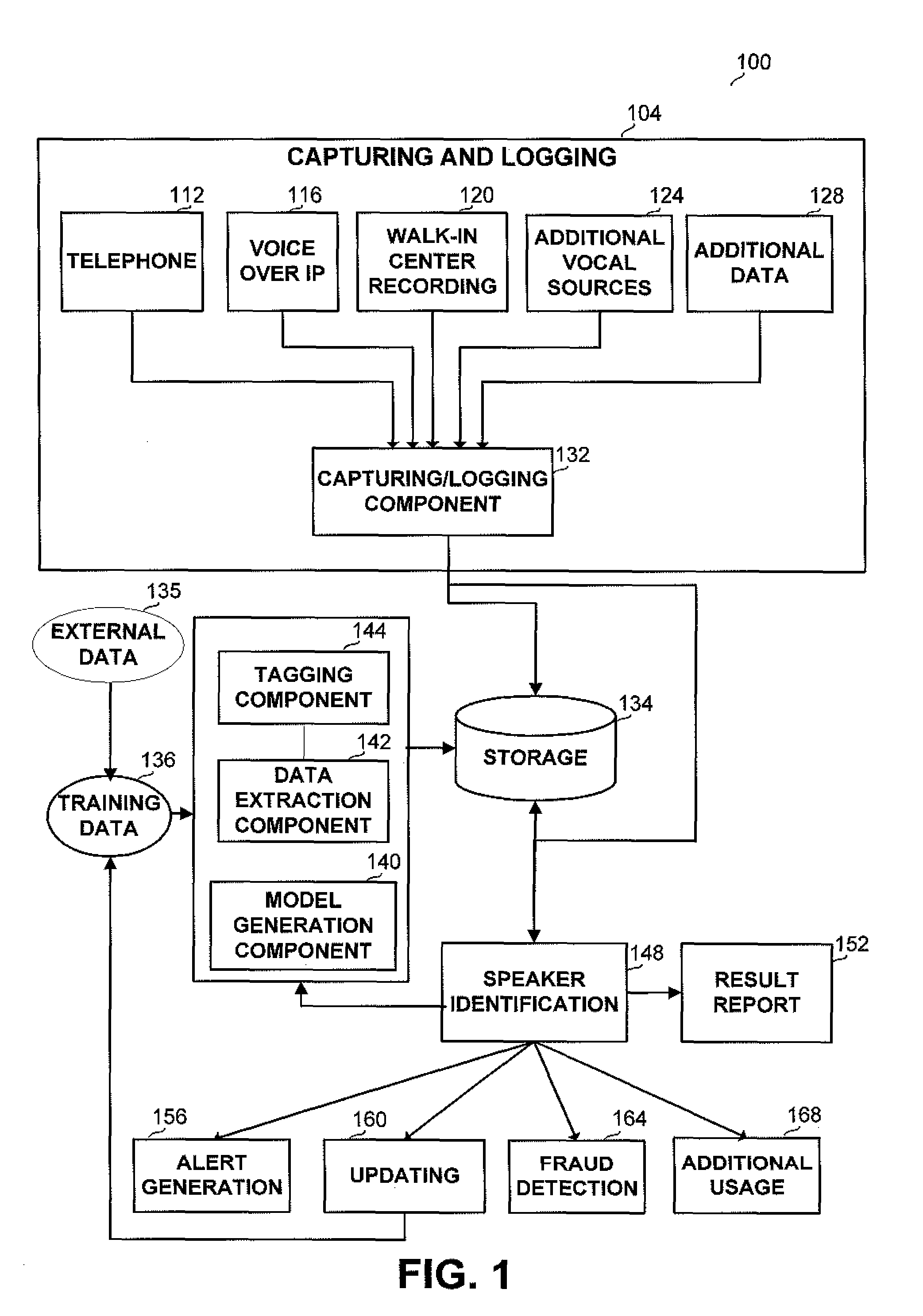
Method and apparatus for recognizing a speaker in lawful interception systems
A method and apparatus for identifying a speaker within a captured audio signal from a collection of known speakers. The method and apparatus receive or generate voice representations for each known speakers and tag the representations according to meta data related to the known speaker or to the voice. The representations are grouped into one or more groups according to the indices. When a voice to be recognized is introduced, characteristics are determined according to which the groups are prioritized, so that the representations participating only in part of the groups are matched against the voice to be identified, thus reducing identification time and improving the statistical significance.
Owner:CYBERBIT
Lawful interception of real time packet data
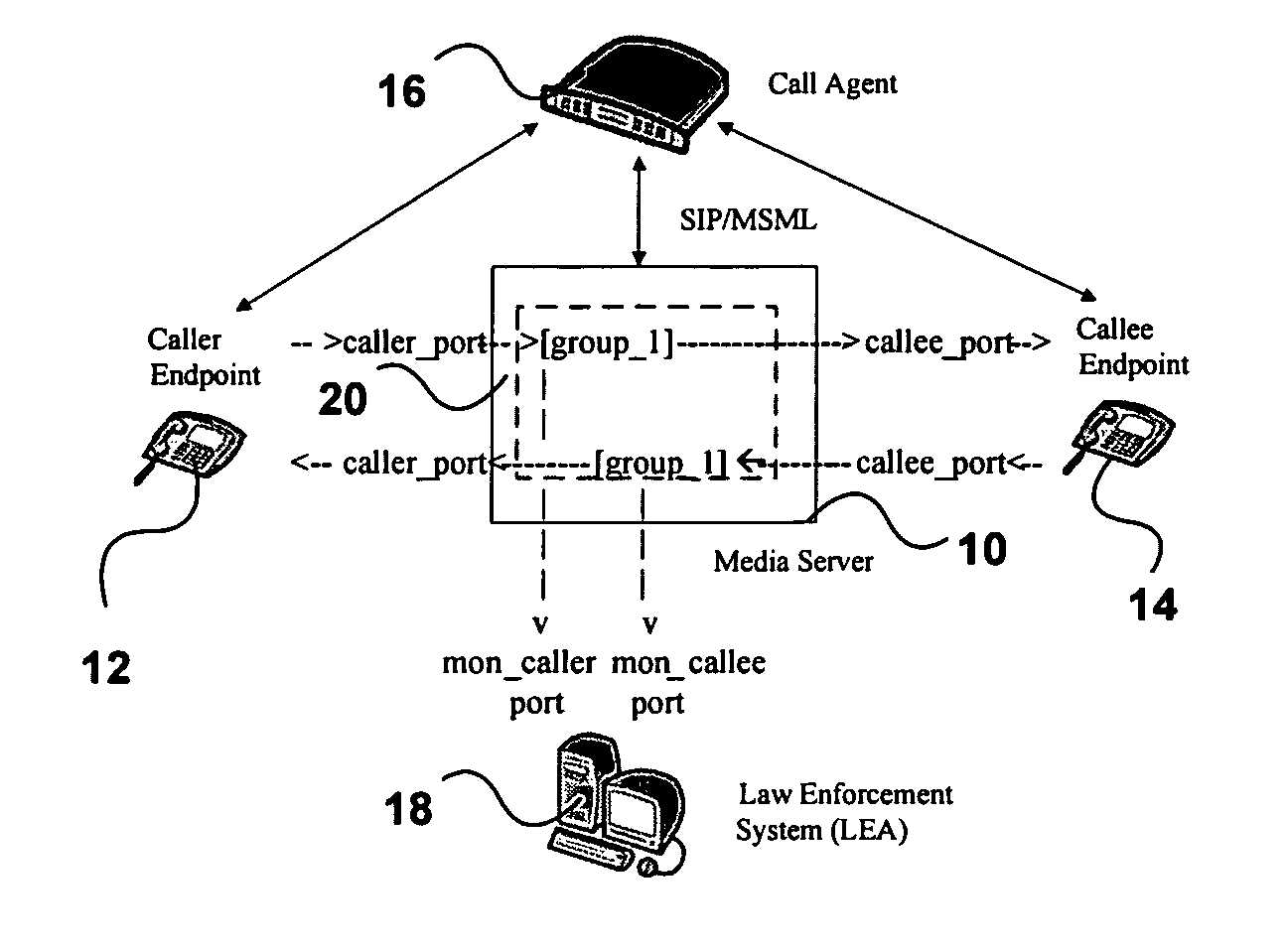
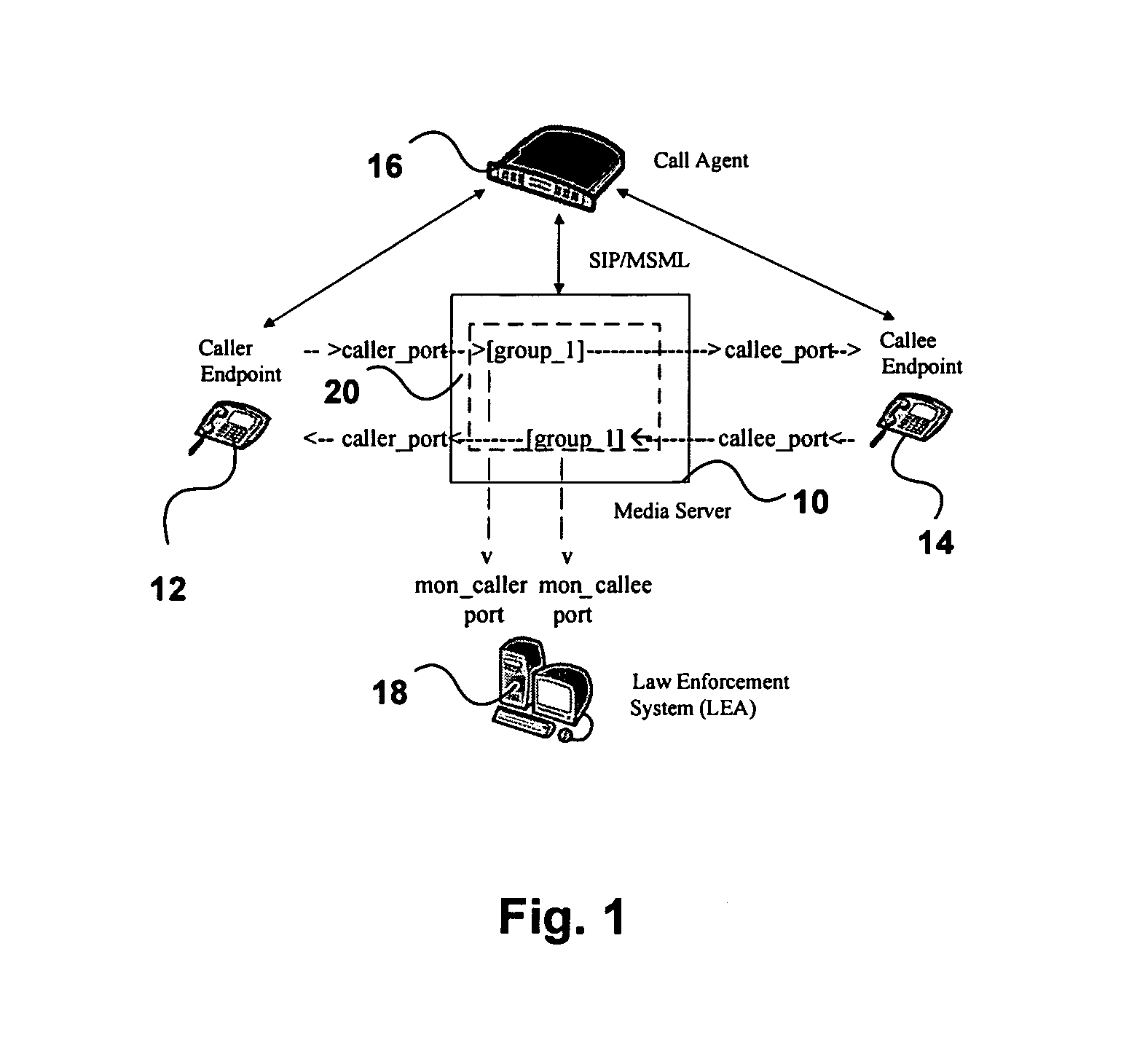
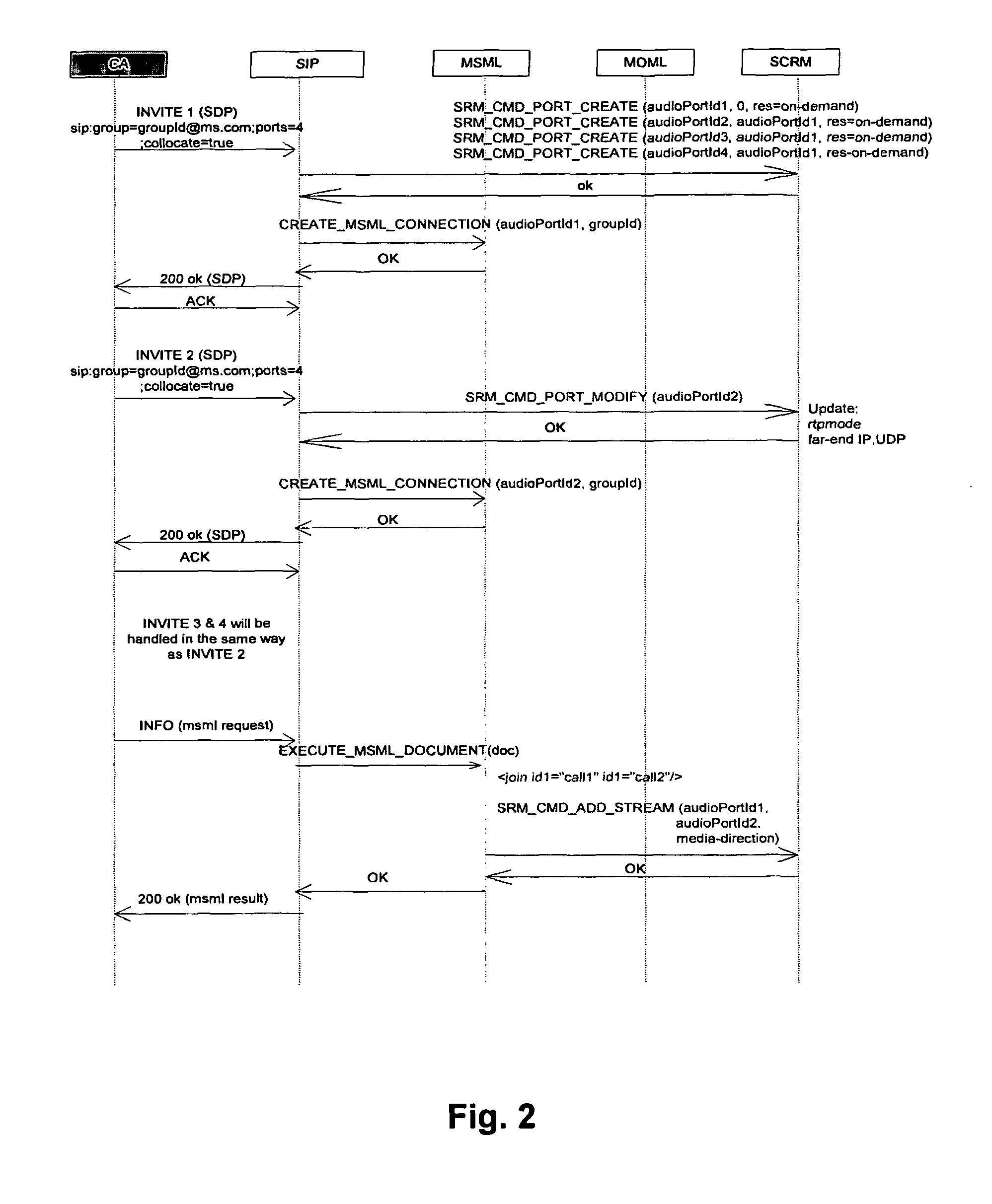
ActiveUS8599747B1Lower latencyLatency delayError preventionTransmission systemsLawful interceptionNetwork packet
A method of conducting a lawful intercept of real time media packet traffic involves redirecting real time media packet streams between a caller and callee through a media server; replicating the media packet streams within the media server; modifying packet headers of the replicated packet streams; and directing the modified packet streams to at least one monitoring port.
Owner:RADISYS CORP
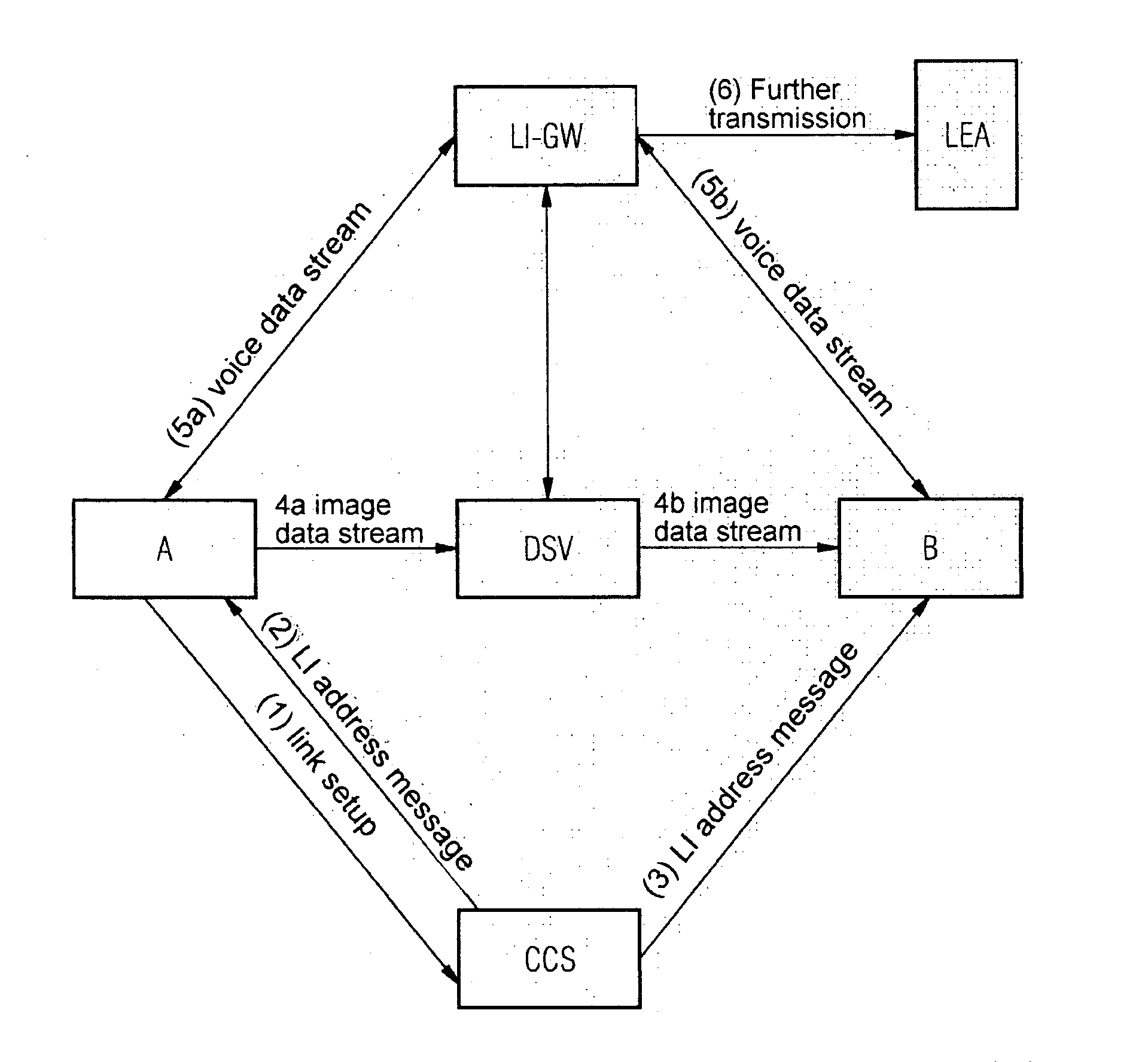
Device For Tapping Useful Data From Multimedia Links In A Packet Network
InactiveUS20080095146A1Active connectionTelevision systemsAutomatic exchangesLawful interceptionData latency
In one aspect, a device for lawful interception of multimedia links in a packet network, over which voice data and image data are transmitted separately is provided. The device includes a receiver unit that receives a image data from a transmit device, and a delay unit that routes the received image data with a delay to a receive device.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
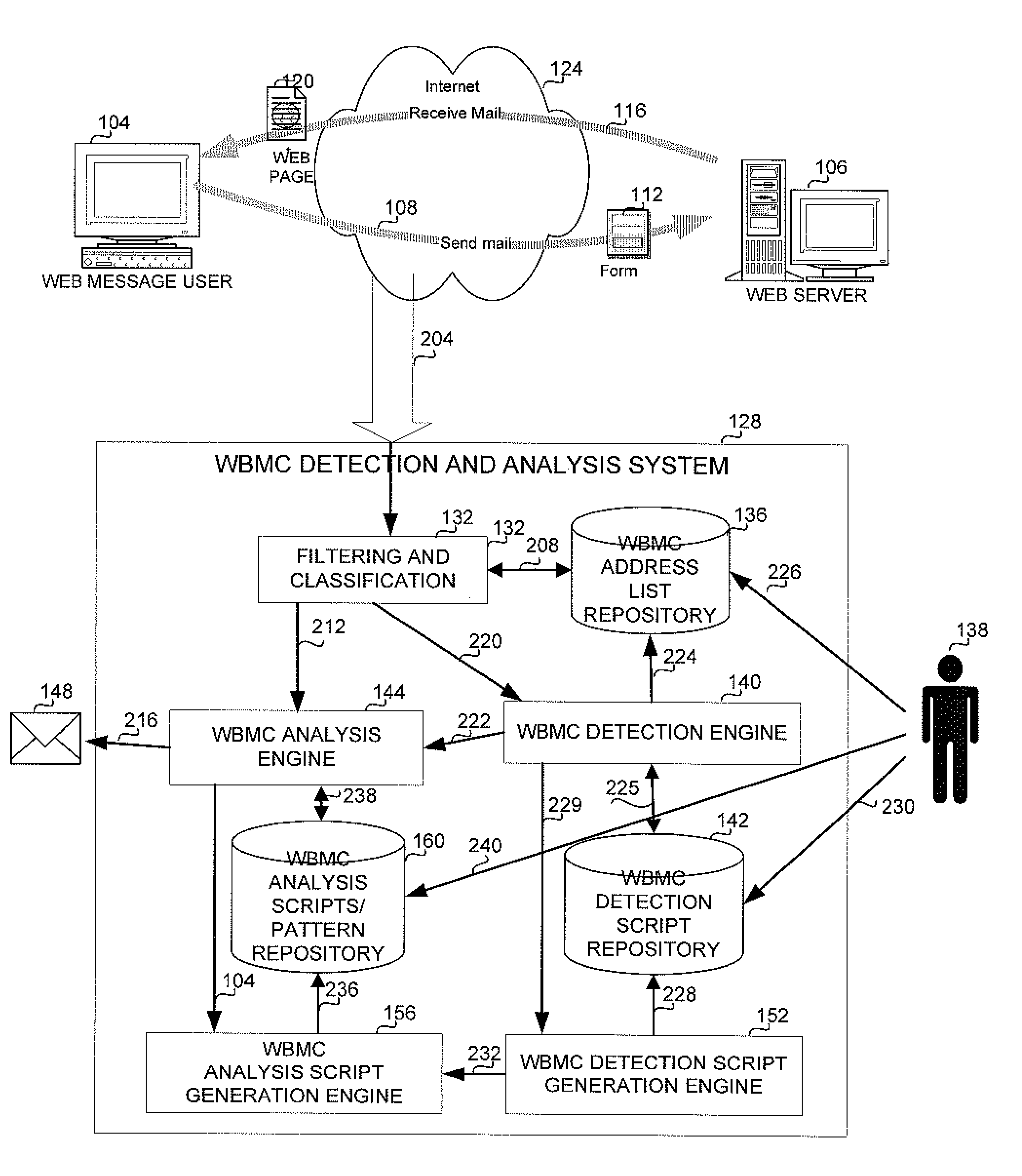
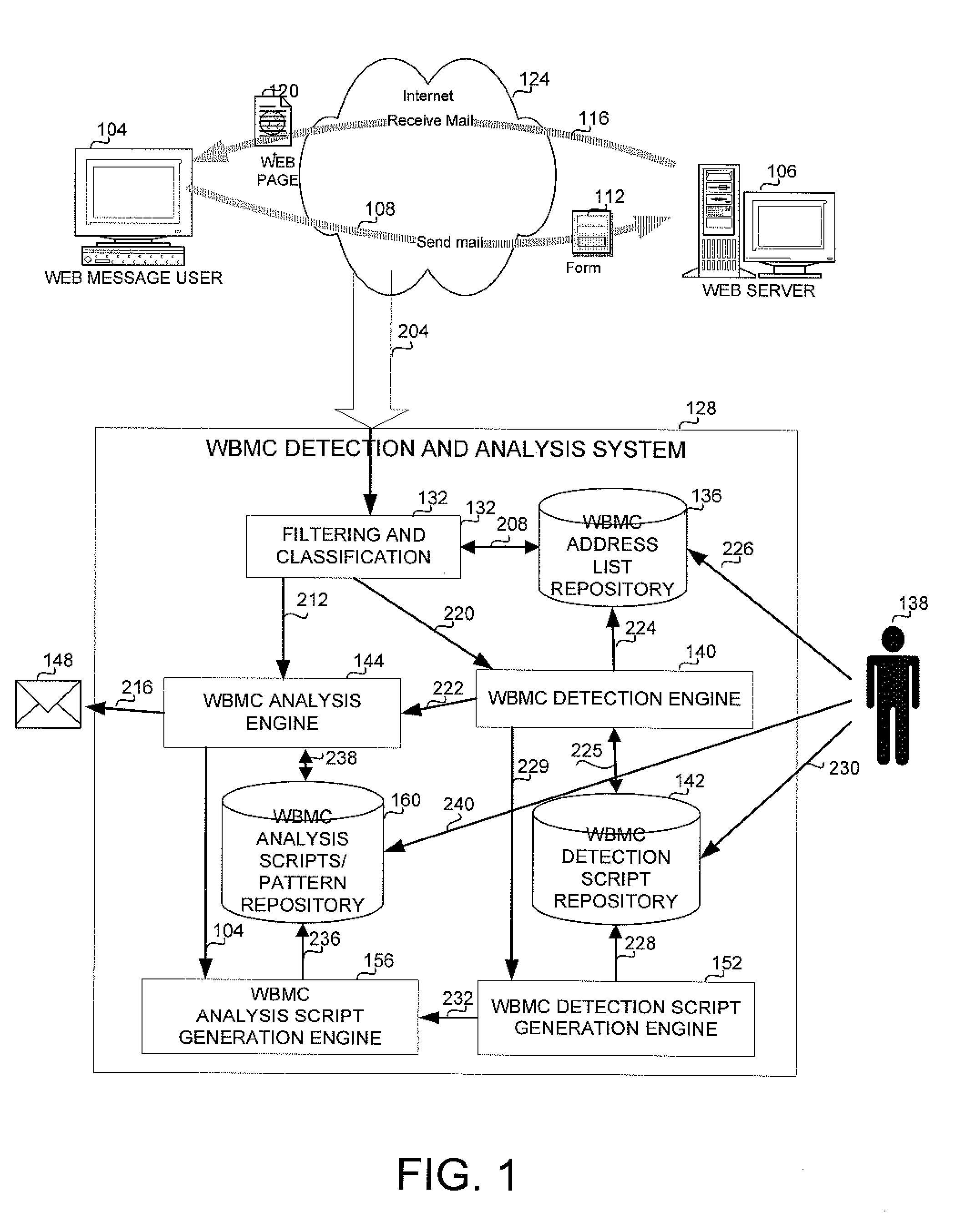
Method and apparatus for lawful interception of web based messaging communication
A method and apparatus for web based mail lawful interception. The method and apparatus enable the detection and automatic analysis of web based mail interactions out of all intercepted web pages. The method and apparatus use and possibly generate scripts for identifying a web page as comprising a web mail message, and scripts for analyzing the web mail messages.
Owner:CYBERBIT
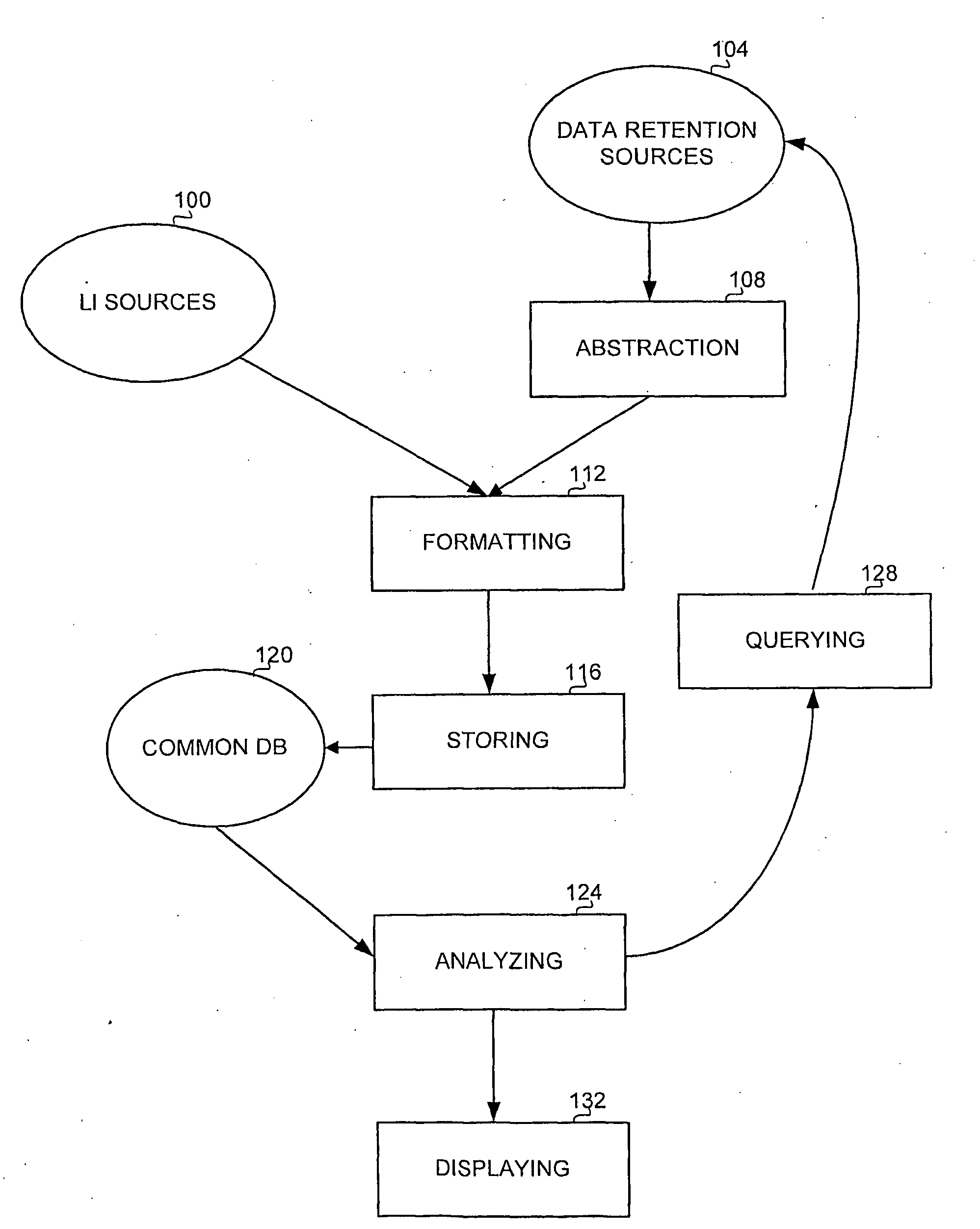
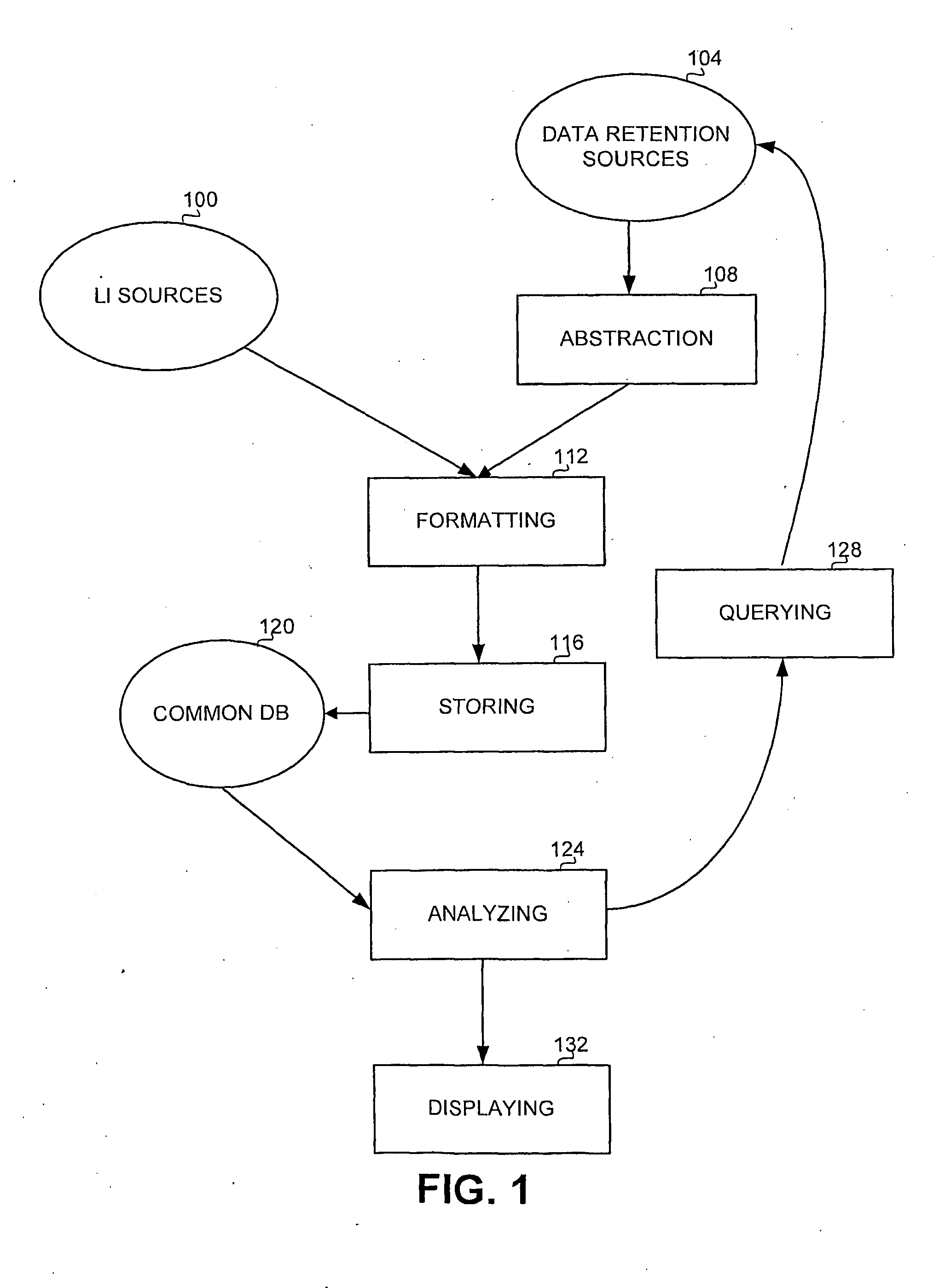
Method and Apparatus for Combining Traffic Analysis and Monitoring Center in Lawful Interception
ActiveUS20090007263A1Memory loss protectionError detection/correctionTraffic capacityLawful interception
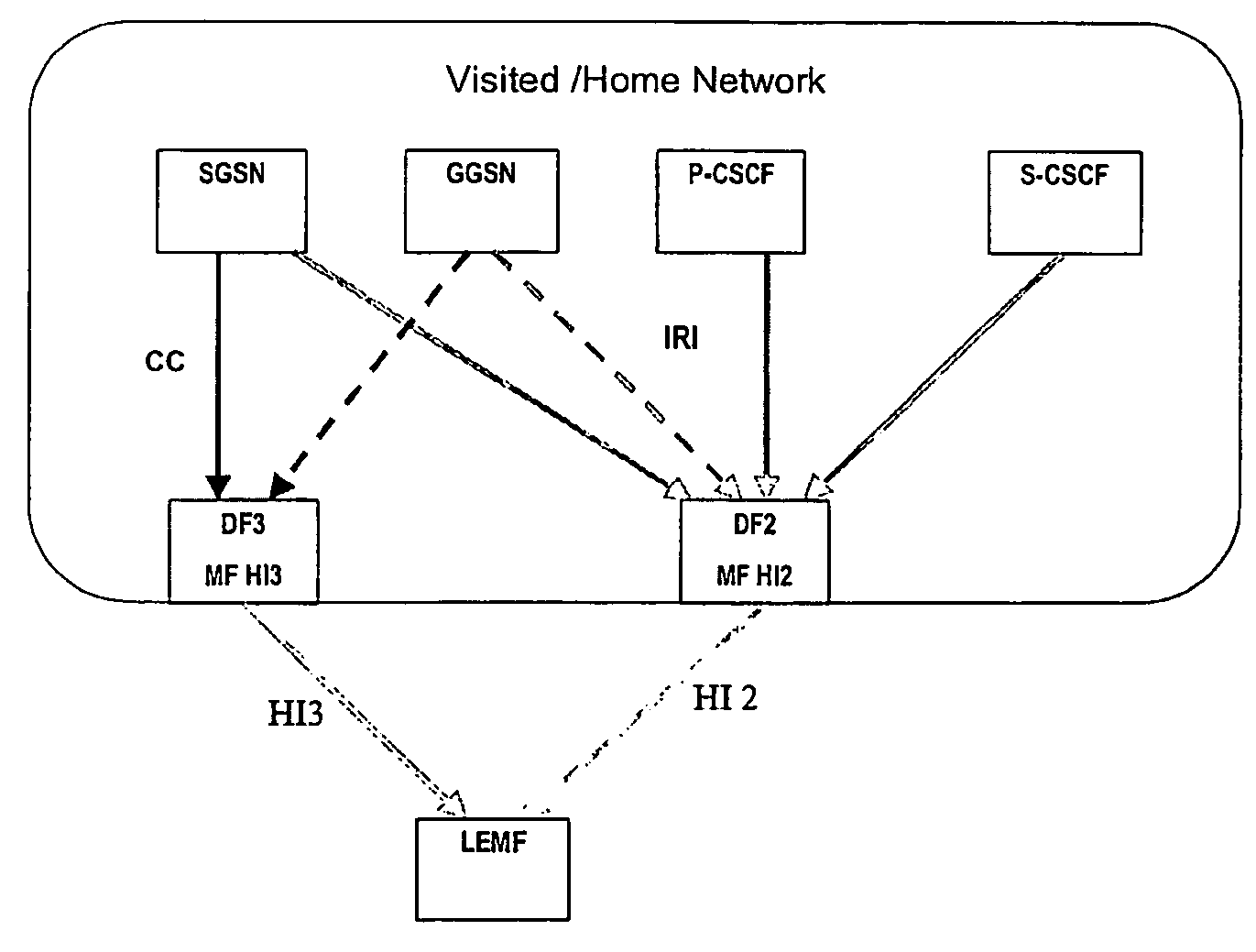
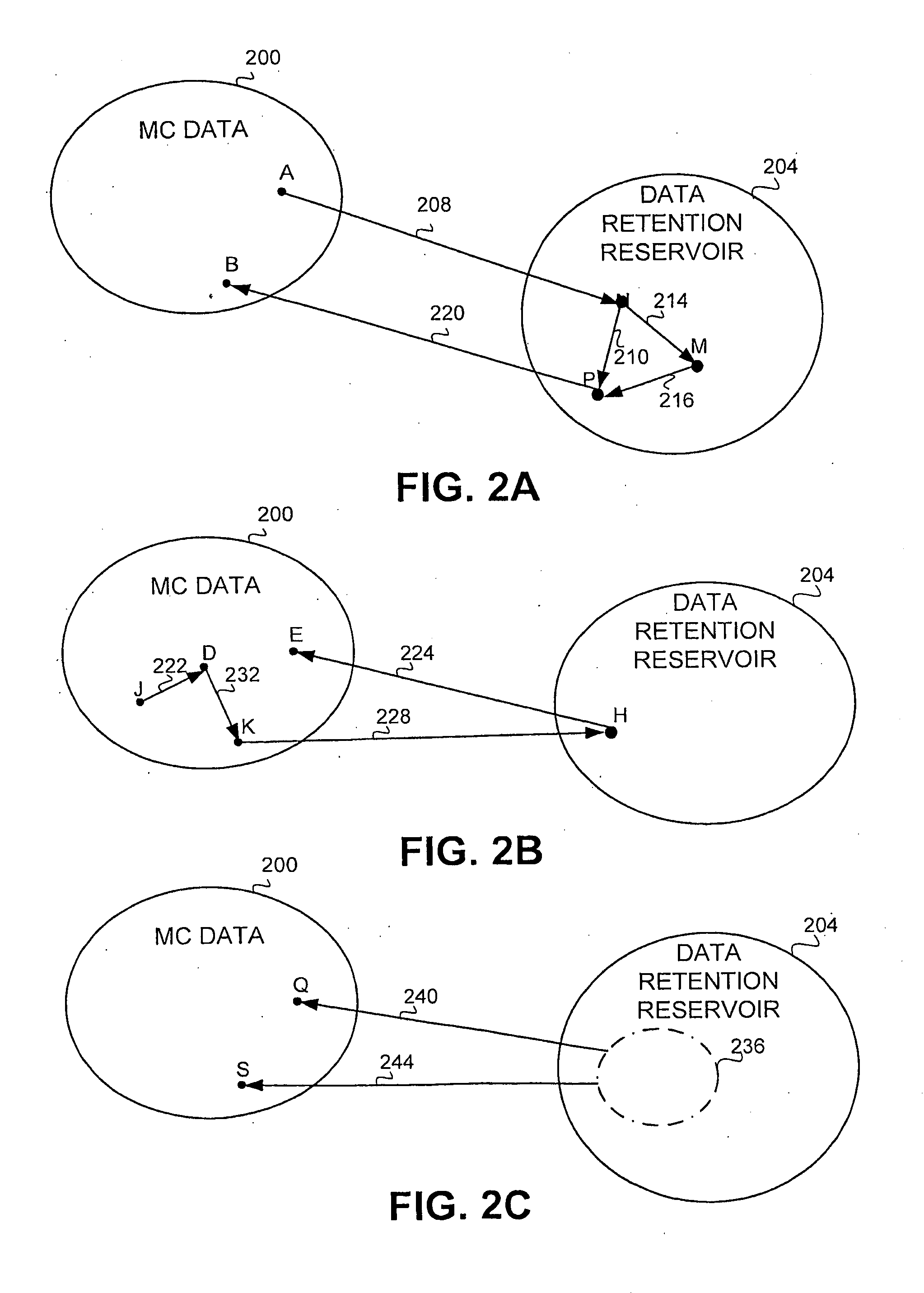
A method and apparatus for integrating intercepted information with information obtained from an at least one data retention source, the method comprising receiving intercepted information from an interception source, receiving information from a data retention source, and analyzing the information received from the data retention source, in association with the intercepted information. The intercepted information can comprise meta data related to the intercepted communications, and / or the contents of the communication themselves. This enables a user such as a law enforcement agency to reveal possibly indirect connections between target entities s wherein the connections involve non-target entities. The method and apparatus combine interception and content analysis methodologies with traffic analysis techniques.
Owner:CYBERBIT
Informing a lawful interception system of the serving system an intercepted target
InactiveUS20060034198A1Special service for subscribersSupervisory/monitoring/testing arrangementsLawful interceptionTelecommunications
The present invention proposes a method for informing a lawful interception system of the serving system serving an intercepted target (MS) roaming within a communication network system, the communication network system comprising at least one serving system each serving system comprising at least one serving system node, (SGSN) serving the intercepted target for communication, the method comprising the steps of first detecting a serving system node change request (1.) from the intercepted target (MS) towards a new serving system node which is currently not serving the target, first processing said serving system node change request at said new serving system node currently not serving the target, wherein said processing comprises the inclusion, to the request, of a serving system address of the new serving system node currently not serving the target, and first forwarding said processed request (2.) to an old serving system node currently serving the target. Also, the present invention proposes a serving system node adapted to be used in such a method.
Owner:NOKIA CORP
Method and system for lawful interception of packet switched network services
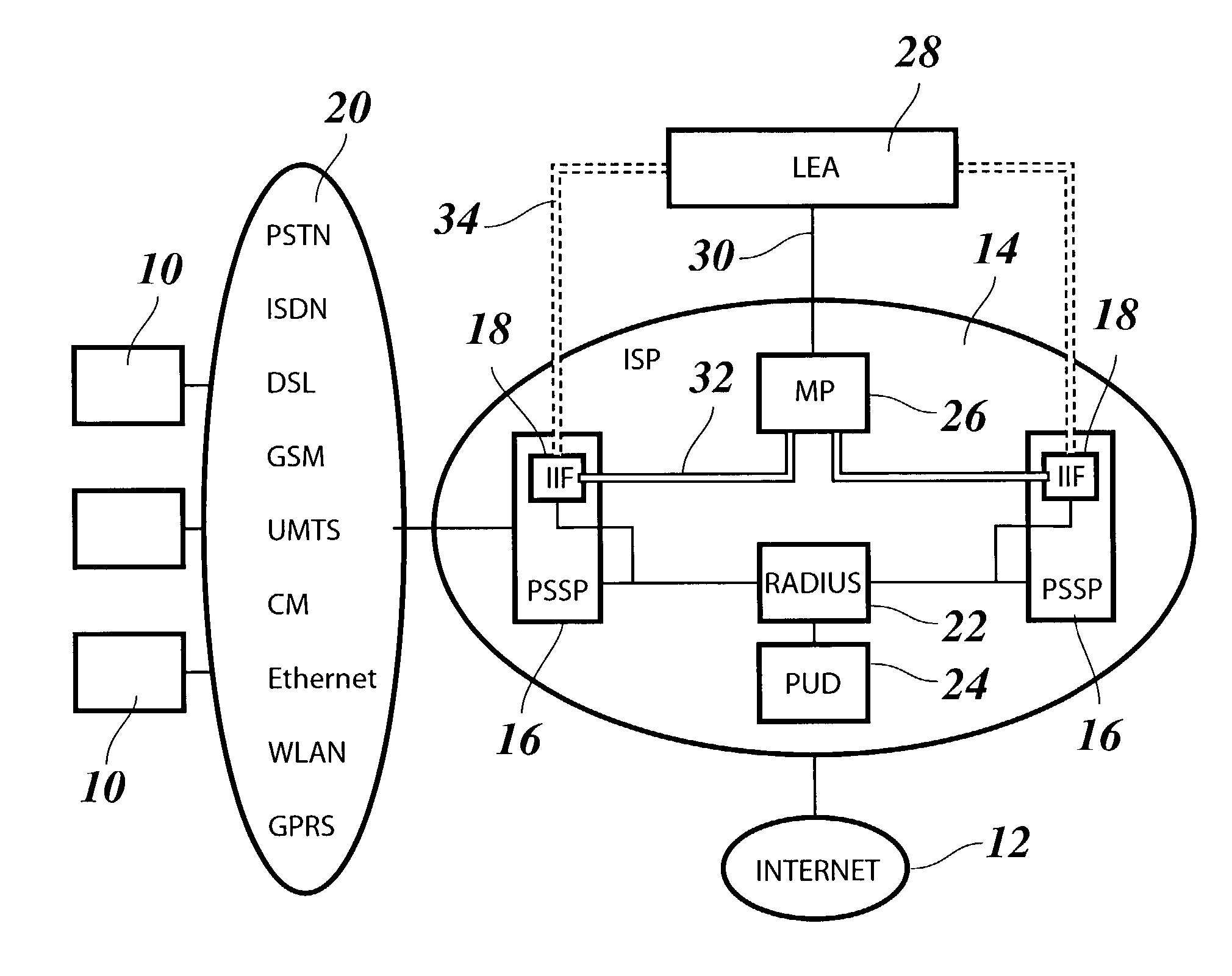
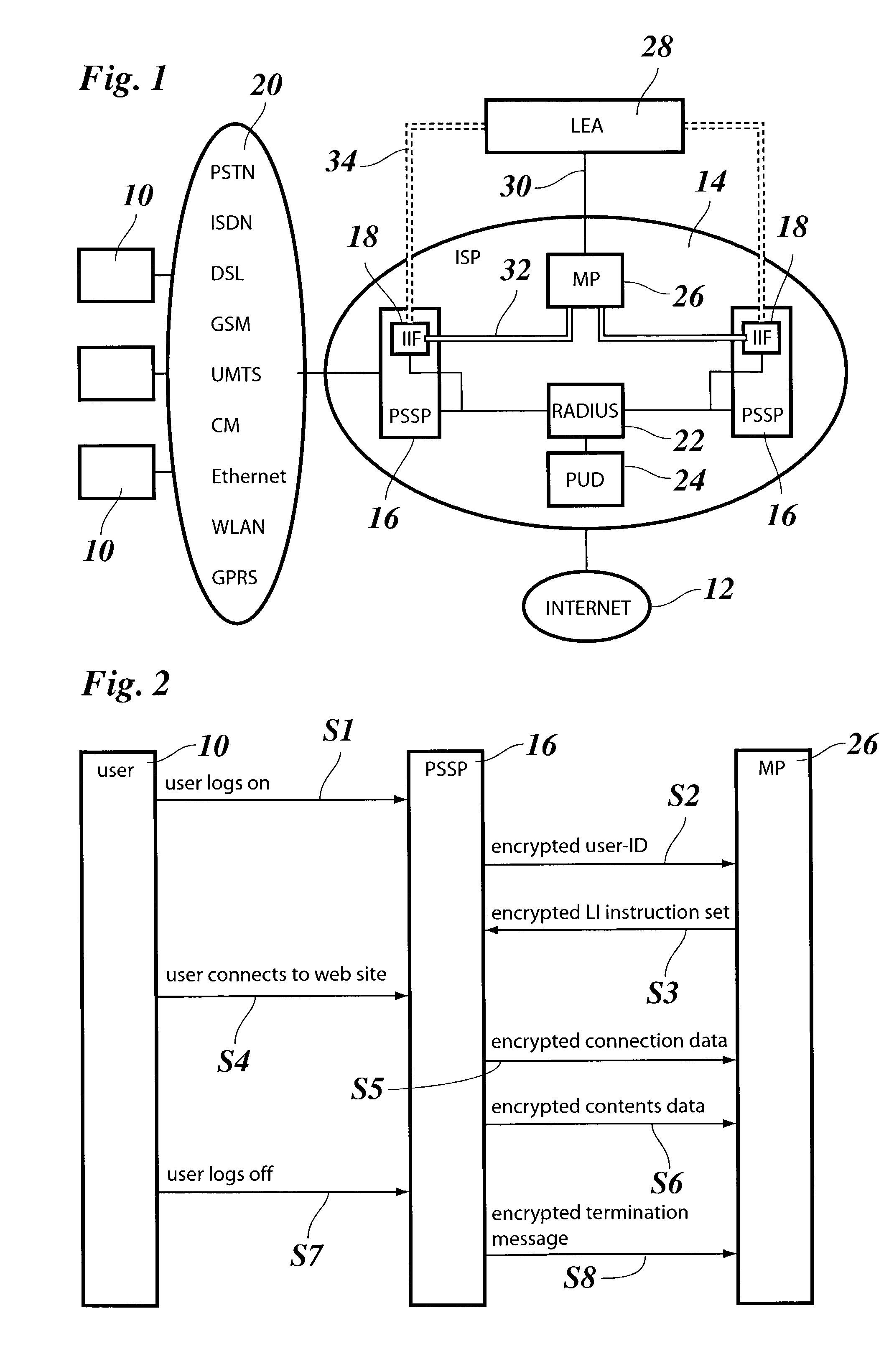
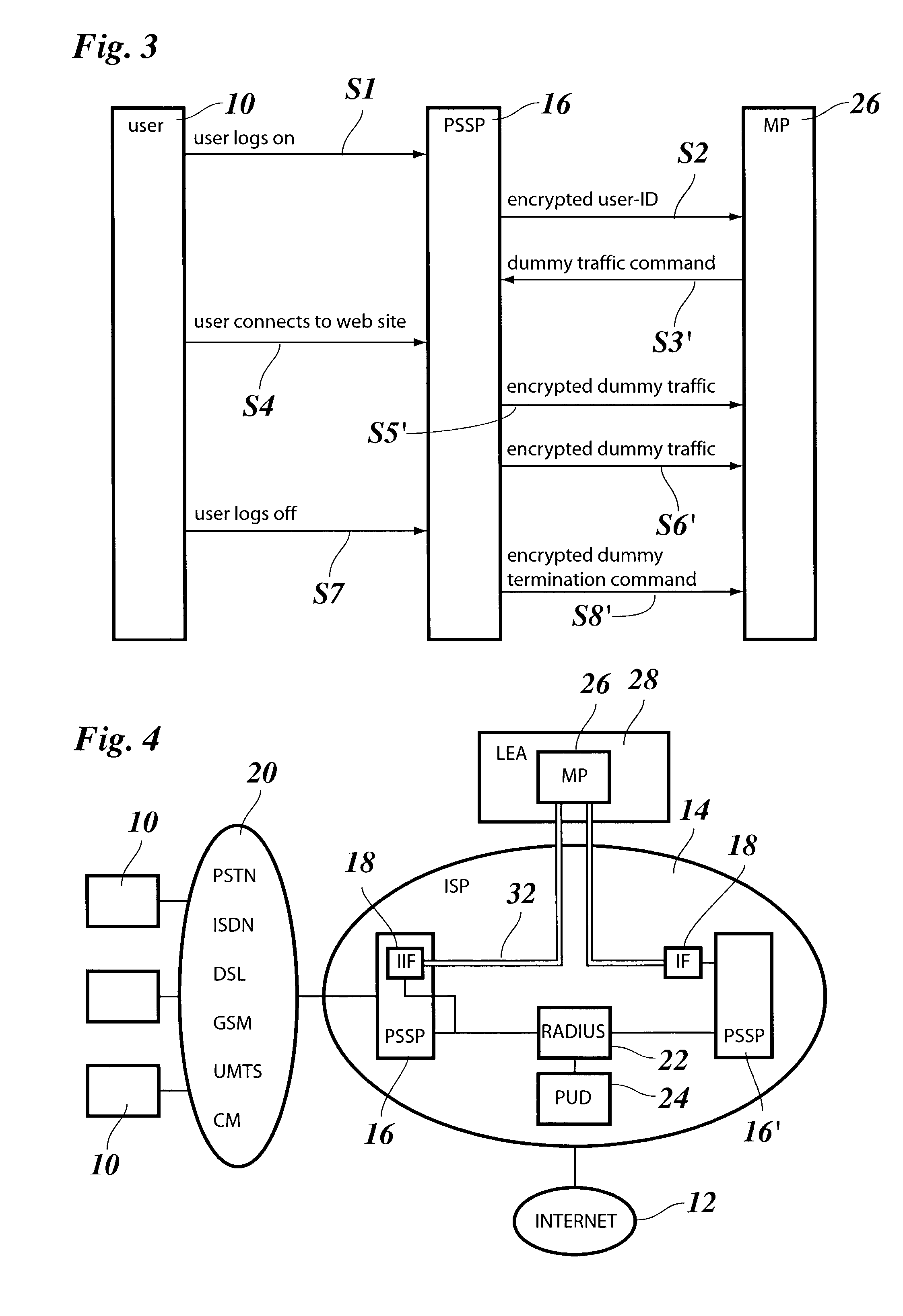
InactiveUS7447909B2Low costImprove securityMemory loss protectionDigital data processing detailsLawful interceptionTraffic capacity
A method for lawful interception of packet switched network services, comprising the steps of:when a user accesses the network and is identified by a target-ID at a primary interception point of the network, sending the target-ID to an interception management center,checking at the interception management center whether the user is a lawful interception target and sending an encrypted interception instruction set to a secondary interception point,decrypting said interception instruction set at the secondary interception point and performing an interception process in accordance with the interception instruction set, said interception process including the transmission of encrypted interception and dummy data to a mediation device, wherein said dummy data are added for obscuring true interception traffic between the secondary interception point and the mediation device.
Owner:RPX CLEARINGHOUSE
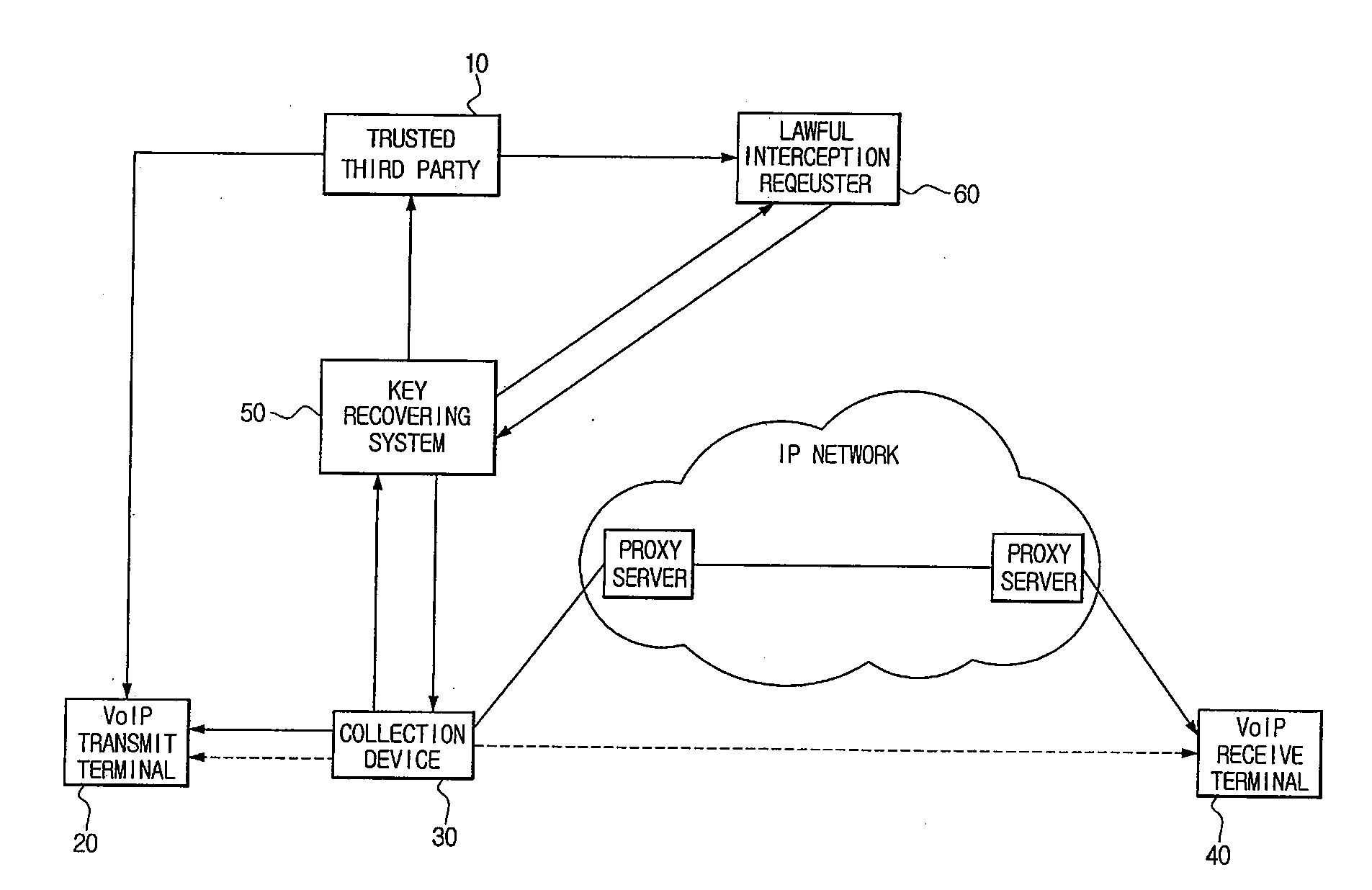
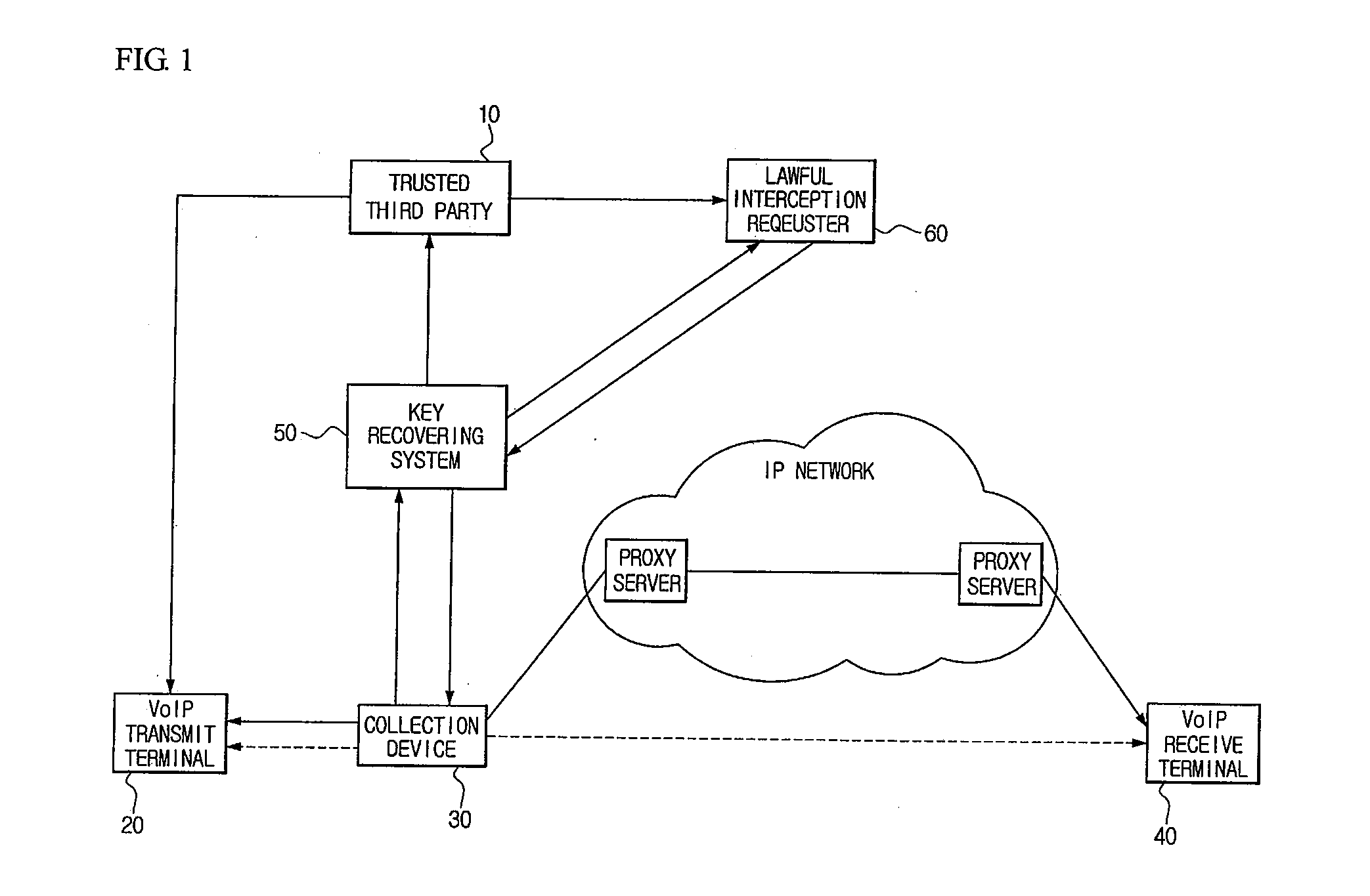
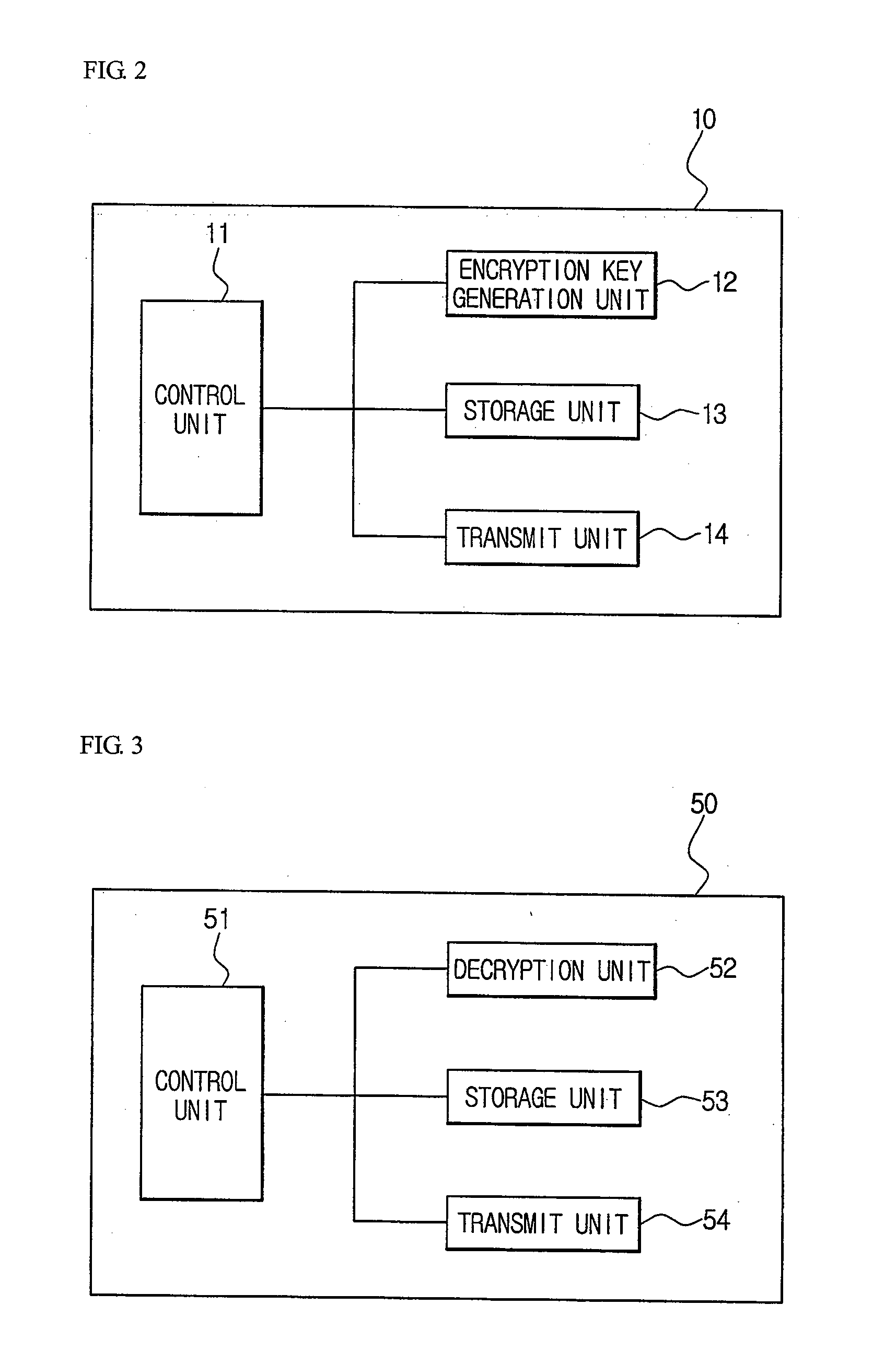
SYSTEM AND METHOD FOR LAWFUL INTERCEPTION USING TRUSTED THIRD PARTIES IN SECURE VoIP COMMUNICATIONS
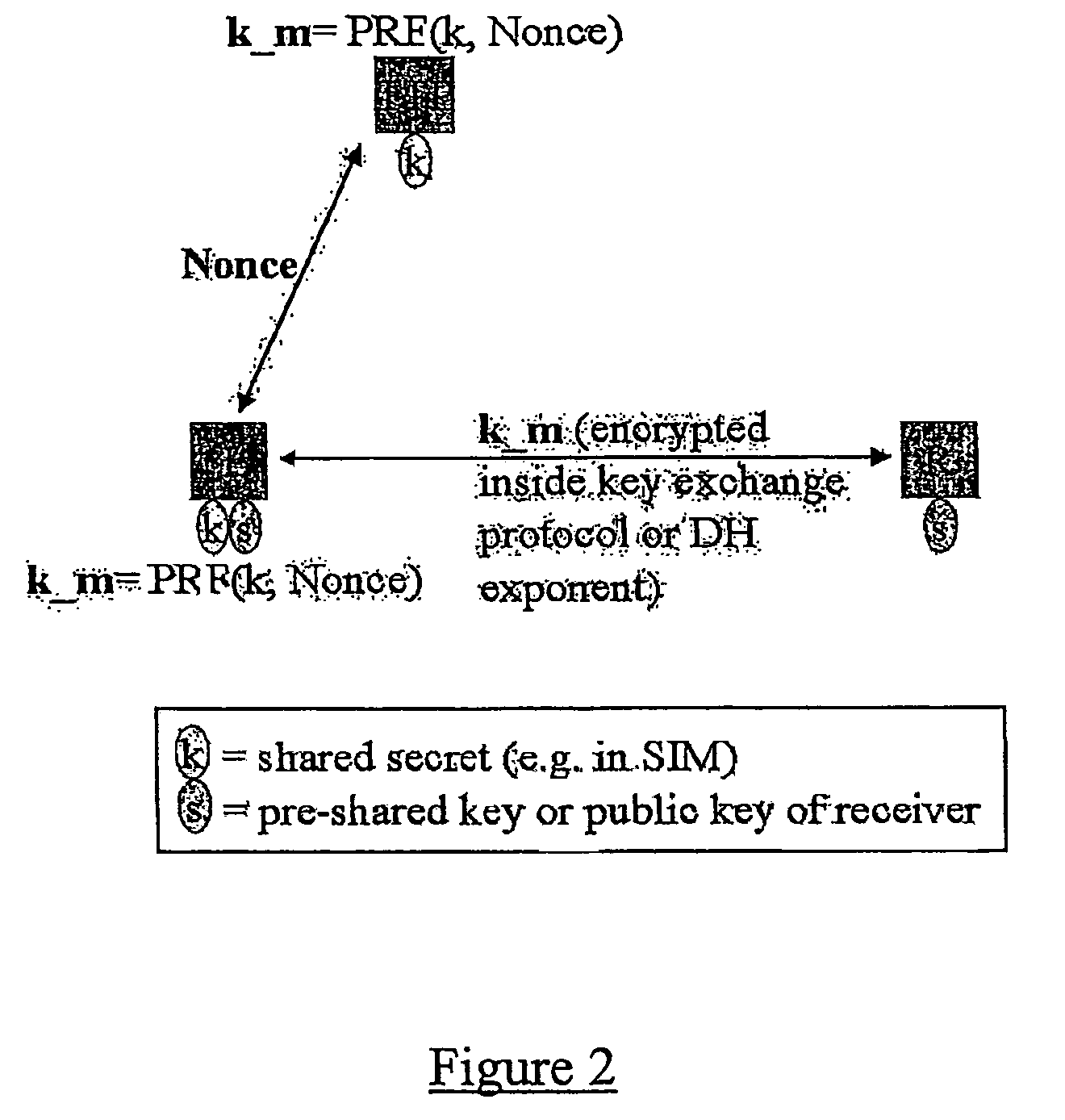
InactiveUS20100002880A1Perfect forward secrecyKey distribution for secure communicationSecret communicationLawful interceptionMaster key
Disclosed is a system for lawful interception using a trusted third party in secure VoIP communication. A VoIP transmit terminal generates a secure packet using a master key received from a trusted third party and then communicates with a VoIP receive terminal. A collection device having received a lawful interception instruction from a key recovering system collects and transmits the secure packet to the key recovering system. The key recovering system decrypts the secure packet using the master key received from the trusted third party and provides the decrypted secure packet to a lawful interception requester or provides the master key received from the trusted third party and the secure packet to the lawful interception requester. It is possible to provide the perfect lawful interception in the secure VoIP communication environment, and to guarantee a perfect forward secrecy since the master key is changed for each call.
Owner:KOREA INTERNET & SECURITY AGENCY
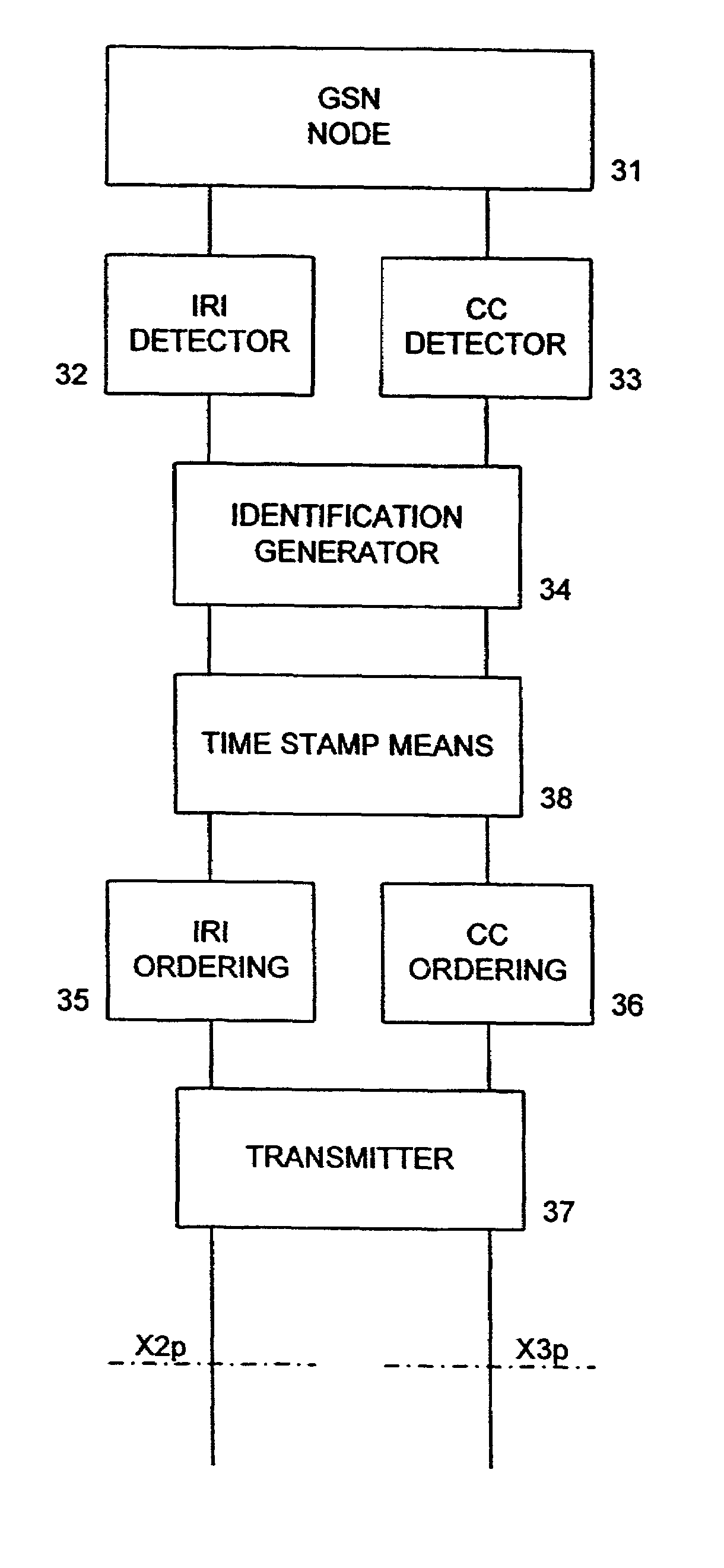
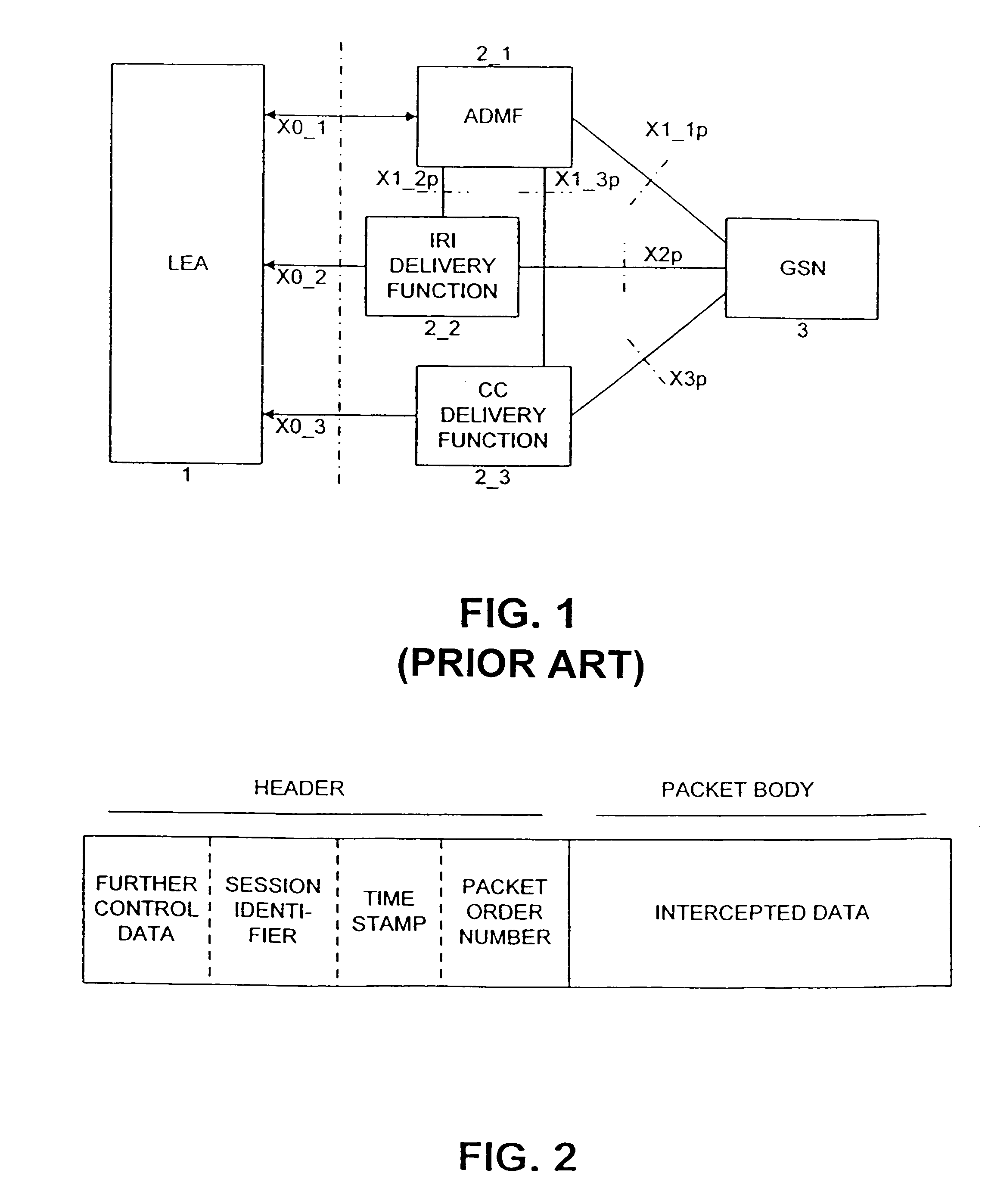
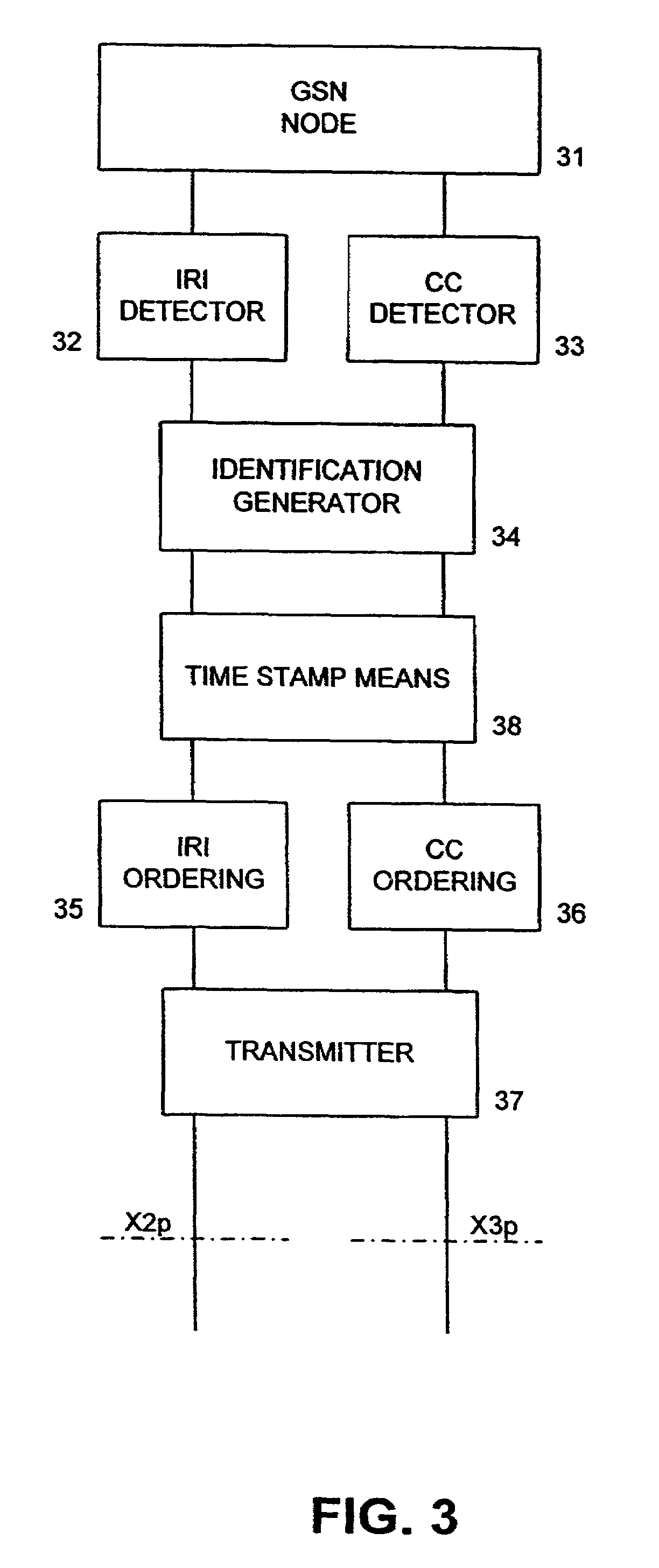
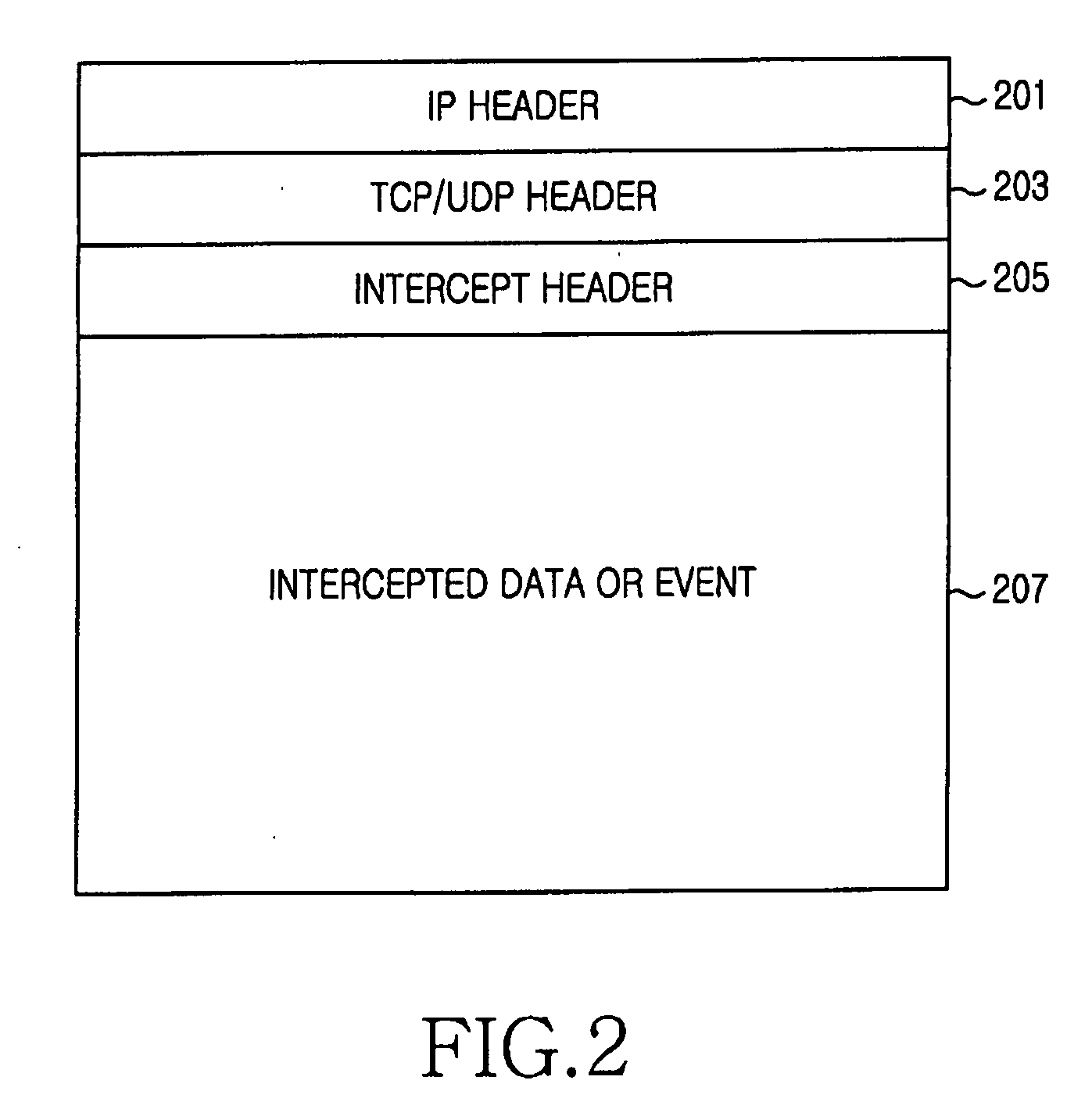
Ordered delivery of intercepted data
InactiveUS7310331B2Inhibition of informationImprove performanceTime-division multiplexSupervisory/monitoring/testing arrangementsLawful interceptionNetwork packet
A method for performing a lawful interception in a packet network comprises the steps of generating (S2) interception related information packets from a communication to be intercepted; generating (S2) communication content packets from a communication to be intercepted; providing (S3) identification data for the interception related information packets and for the communication content packets of one group of communication packets; providing (S5) ordering data for each of the interception related information data packets and for each of the communication content packets; and transmitting (S6) the interception related information packets, the communication packets, the identification data and the ordering data to an interception authority device. By this measure, a missequenced reception of interception related information (IRI) packets and communication content (CC) packets can be avoided. Also, the assembly of IRI packets between corresponding CC packets is possible by a corresponding LEMF of the interception authority.
Owner:NOKIA TECHNOLOGLES OY
Apparatus and method for lawful interception
InactiveUS20120155333A1Special service provision for substationMultiplex system selection arrangementsLawful interceptionSession Initiation Protocol
A lawful interception apparatus activates, invocates, and terminates a lawful interception using a SIP (session initiation protocol) message that is transmitted and received between a terminal to be intercepted and an IP multimedia subsystem.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus, method and computer-readable storage mediums for determining application protocol elements as different types of lawful interception content
ActiveUS20110154181A1Digital data processing detailsAnalogue secracy/subscription systemsLawful interceptionDocumentation
An example apparatus is provided that includes a processor and a memory storing executable instructions that in response to execution by the processor cause the apparatus to at least perform a number of operations. The operations include receiving a communication including an application protocol primitive that itself includes protocol information element(s). The operations also include comparing the application protocol primitive to a protocol document type definition (DTD) including a plurality of elements, and lawful interception attribute(s) for one or more of its elements. The application protocol primitive is compared to the DTD to identify lawful interception attributes of protocol information element(s) of the primitive. The operations also include preparing one or more of the protocol information elements for transmission to an interception monitoring facility according to the lawful interception attributes of the respective protocol information element(s).
Owner:SYNCHRONICA
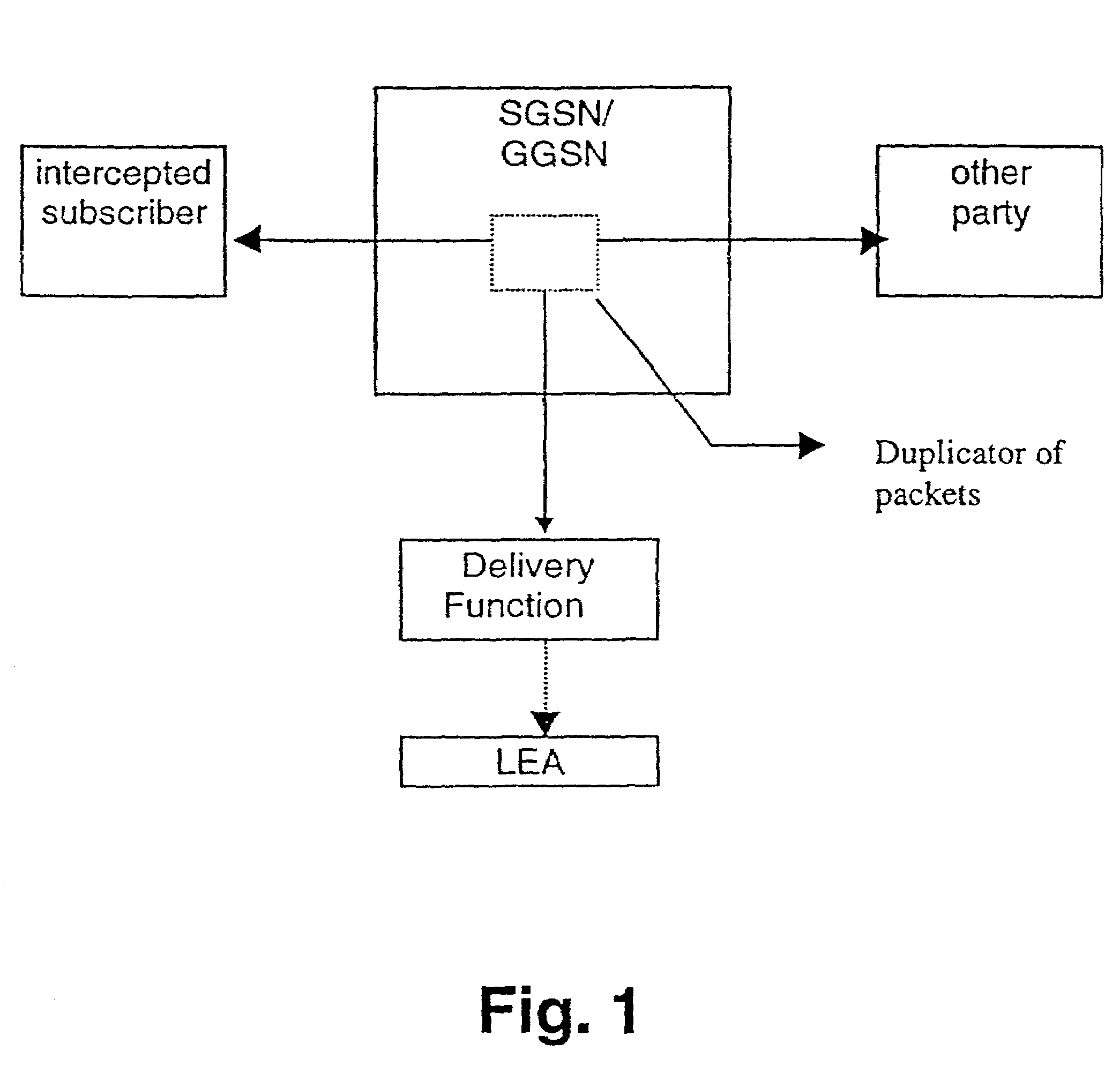
Lawful interception in a mobile data network with data offload at the basestation
ActiveUS20140043980A1Avoid breakoutOut of serviceError preventionTransmission systemsLawful interceptionBiological activation
Lawful interception (LI) is supported on a flat mobile data network with breakout services at the basestation. A first service mechanism at the basestation is prevented from breaking out services for subscribers that are part of LI. A second service mechanism in the core network maintains a subscriber list of subscribers that are subject to LI. In response to a PDP context activation by a subscriber on the list, the second service mechanism does not supply PDP context information to the first service mechanism for data breakout thus preventing breakout for the subscriber subject to lawful interception.
Owner:LENOVO GLOBAL TECH INT LTD
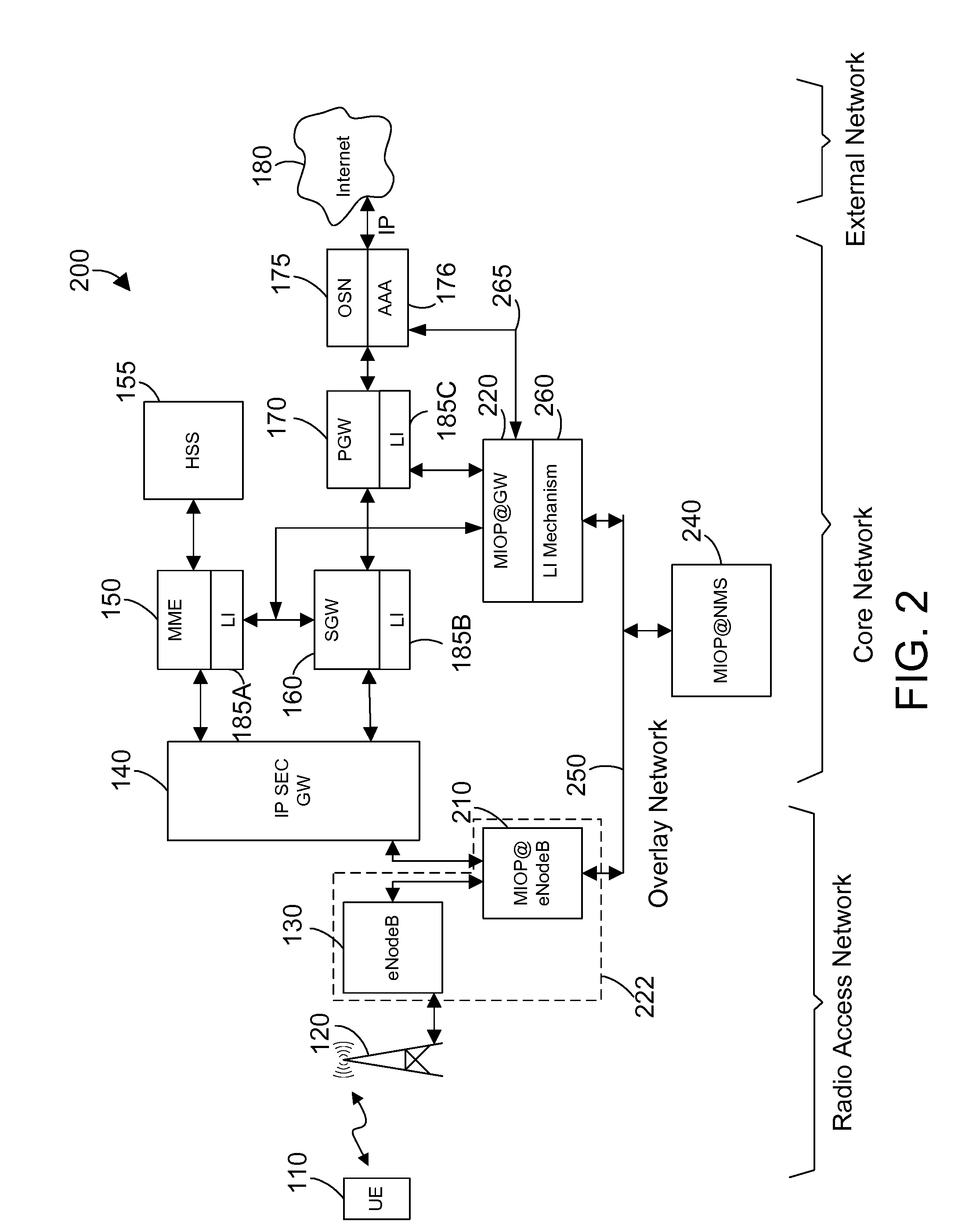
Apparatus and method for intercepting packet data in mobile communication system
InactiveUS20090130984A1Transmission monitoringSecurity arrangementLawful interceptionComputer network
An apparatus and method for intercepting packet data in a mobile communication system is provided. The method includes the steps of: storing intercepted target and interception related information when a target provision request message including the intercepted target and interception related information is received from a Service Provider ADministration Function (SPADF); establishing a data session of the intercepted target according to whether the data session of the intercepted target is established; and intercepting a packet of the intercepted target when the intercepted target starts packet data communication. Accordingly, solutions capable of properly performing Lawful Interception (LI) can be provided while achieving compliance with existing LI on packet data.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system allowing lawful interception of connections such as voice-over-internet protocol calls
InactiveUS7620389B2Raise the possibilityTriggered quicklyError preventionFrequency-division multiplex detailsLawful interceptionCommunications system
The invention relates to a method and communication system allowing interception of a communication or connection of a target to be intercepted. According to preferred embodiments of the invention, interception triggering information is transmitted between the user plane and control plane (e.g. via Gr-, Gc-, Gi-interfaces). The system comprises at least one control means for handling signaling of a connection between a user equipment and another communication device, and a support element for transmitting traffic information between the user equipment and the another communication device. When the connection is to be intercepted, the control means is adapted to generate an interception information for informing the support element or another network element on an identification of the target to be intercepted. The support element is adapted to copy the traffic information to another network element for interception when receiving an interception information from the control means.
Owner:NOKIA CORP
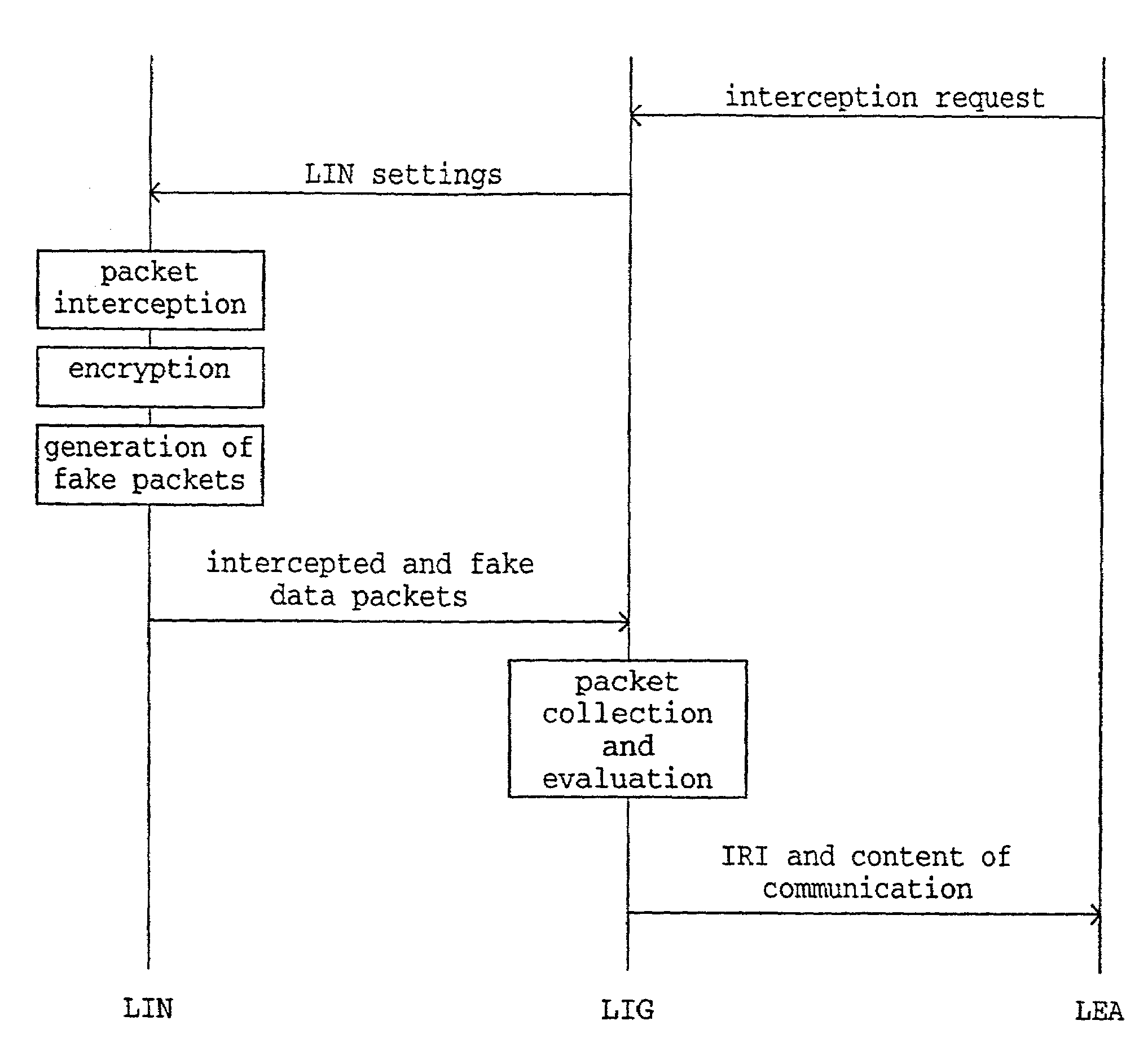
Service based lawful interception
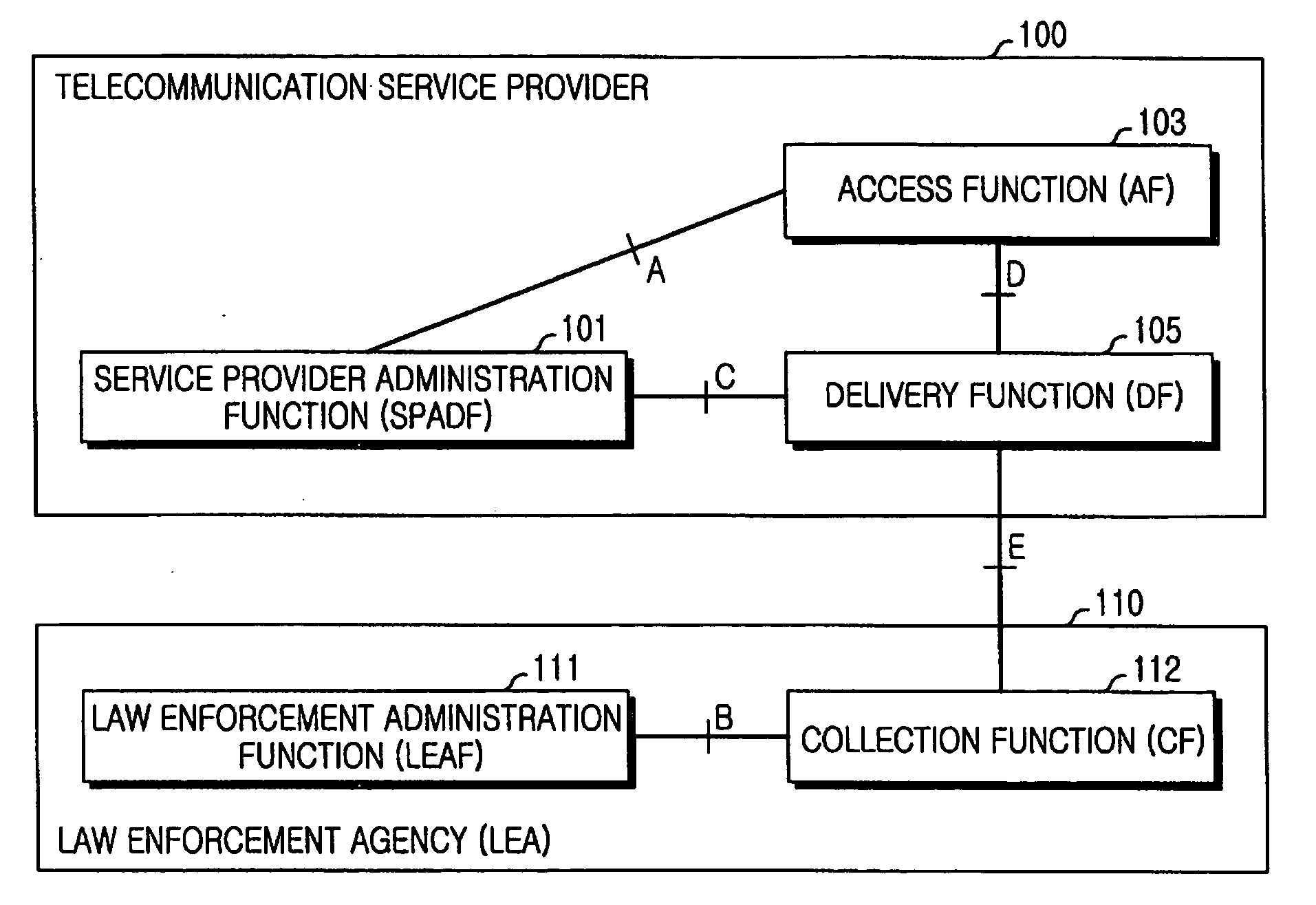
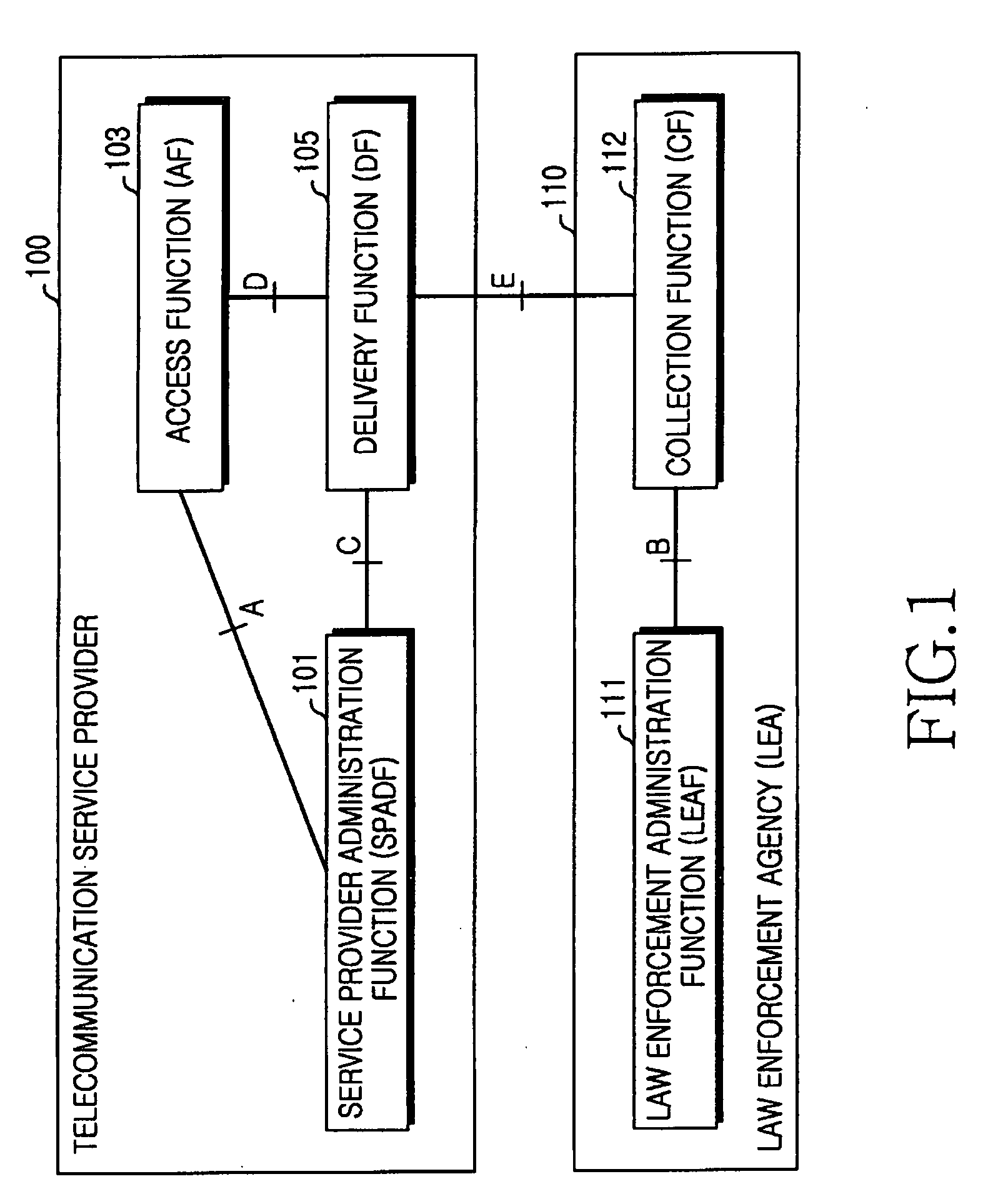
InactiveUS20090207751A1Low costFlexible processInterconnection arrangementsError preventionLawful interceptionComputer network
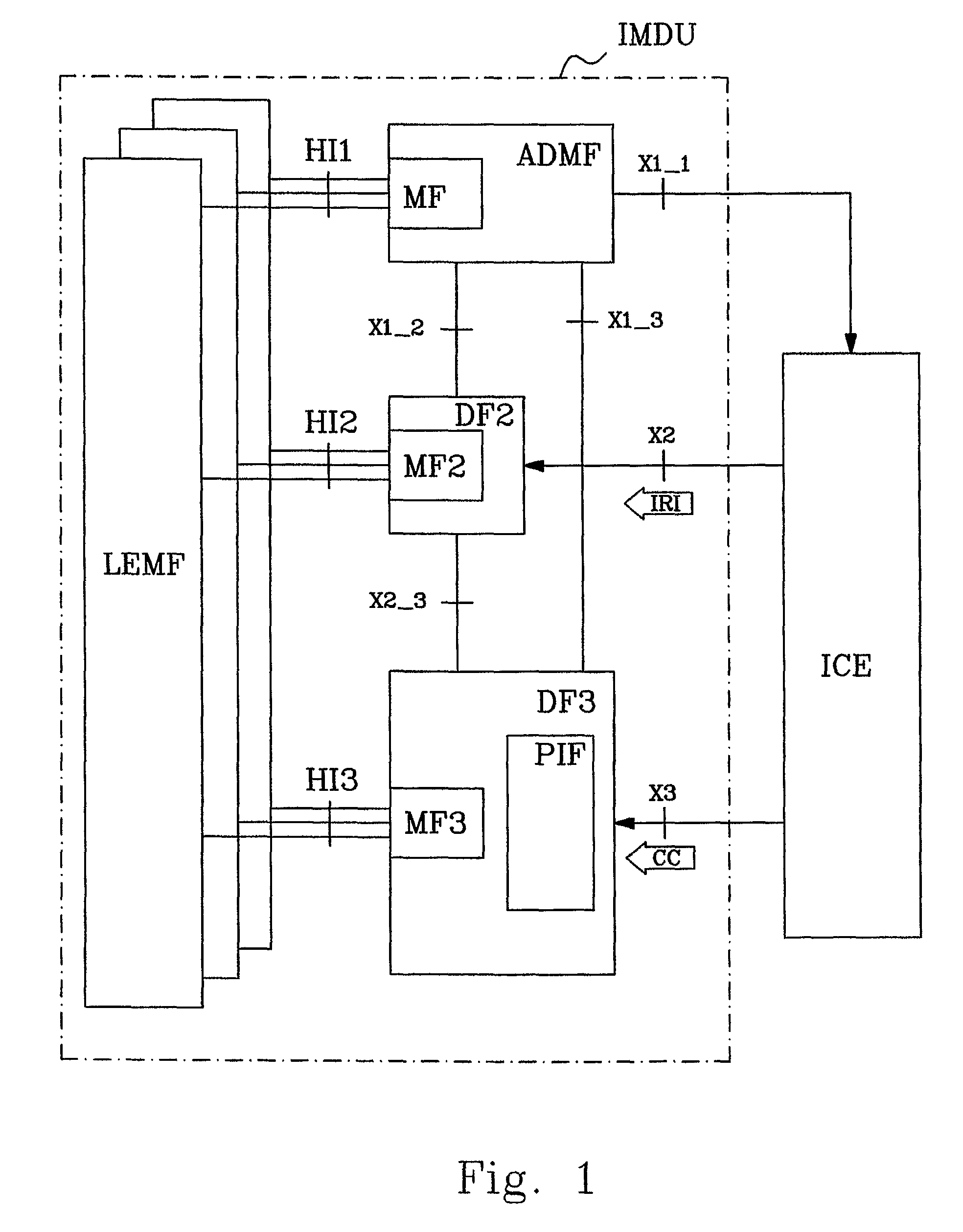
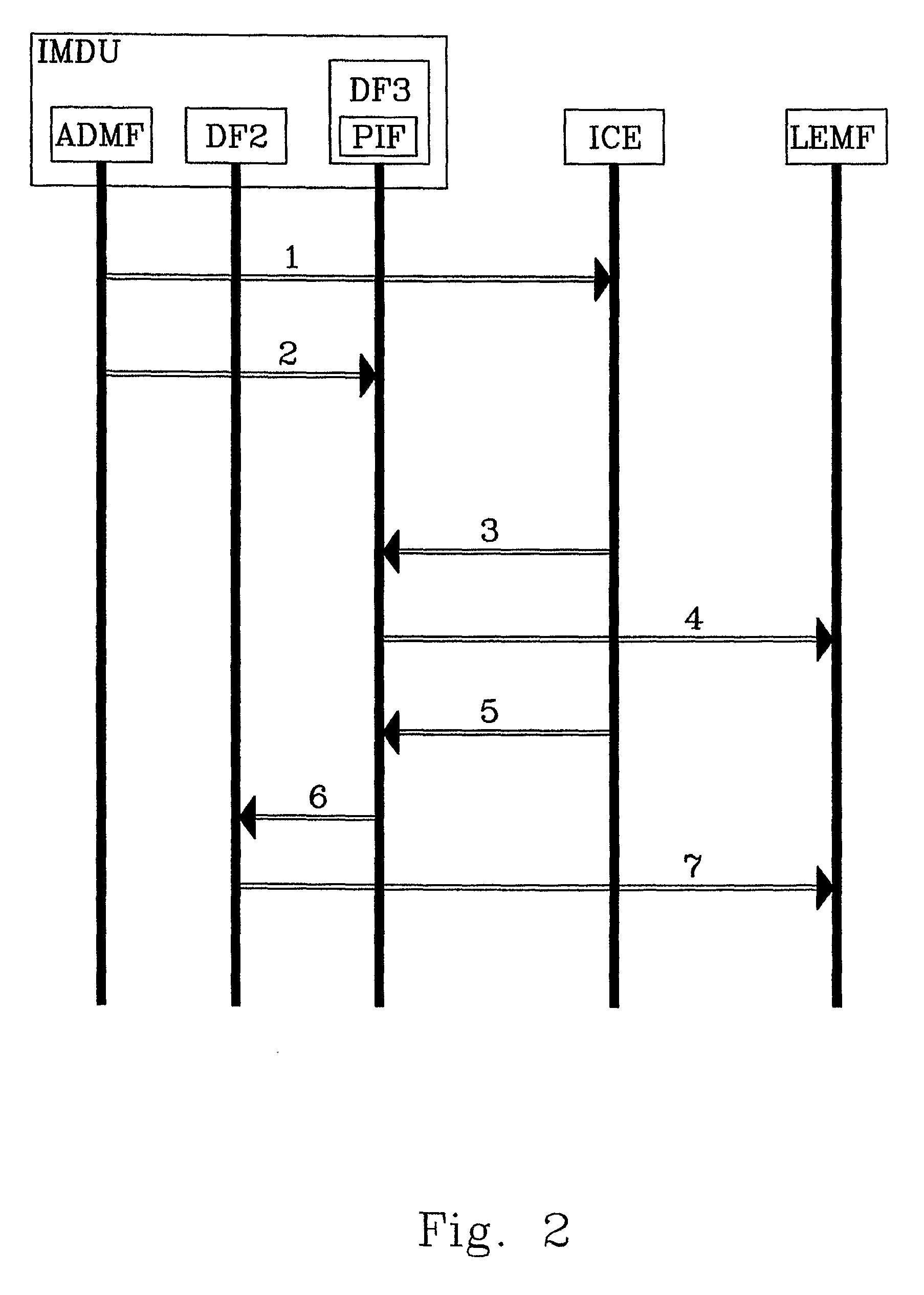
The present invention relates to methods and arrangements in a telecommunication system to monitor information related to specified services in a service unaware node. The node handles Content of Communication associated with services. The system comprises a Delivery Function to which Content of Communication related to a target is received from the node. The method comprises the following steps: Receiving from a requesting entity to the Delivery Function a request to delimit the received Content of Communication according to not desired services. Parsing the received Content of Communication according to not desired services by a Packet Inspection Feature associated with the Delivery Function. Forwarding Control Information related to the not desired services to the requesting entity.
Owner:UNWIRED PLANET
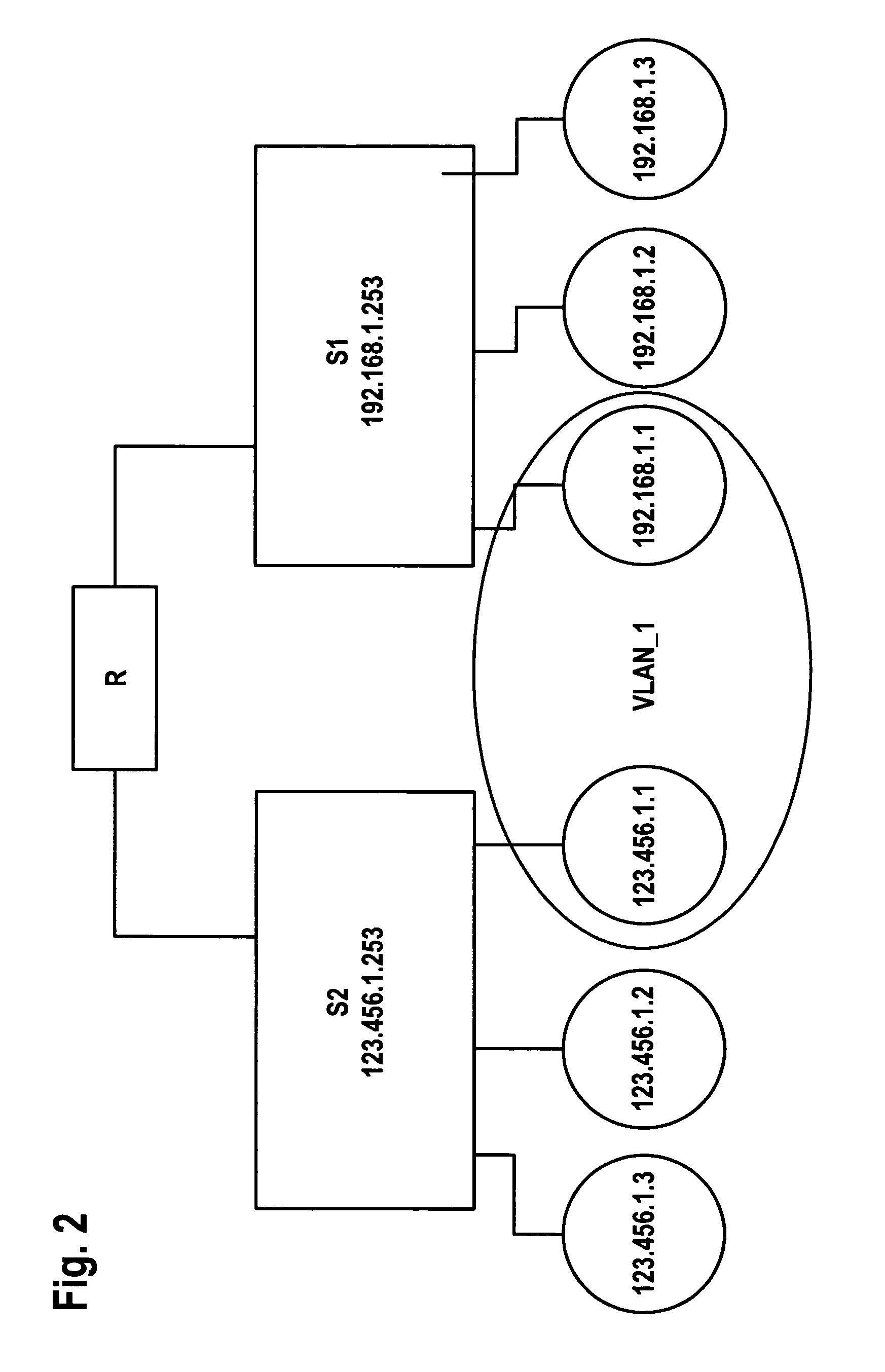
Lawful interception in IP networks
InactiveUS8050273B2Data switching by path configurationWireless commuication servicesLawful interceptionVirtual LAN
Owner:PIECE FUTURE PTE LTD
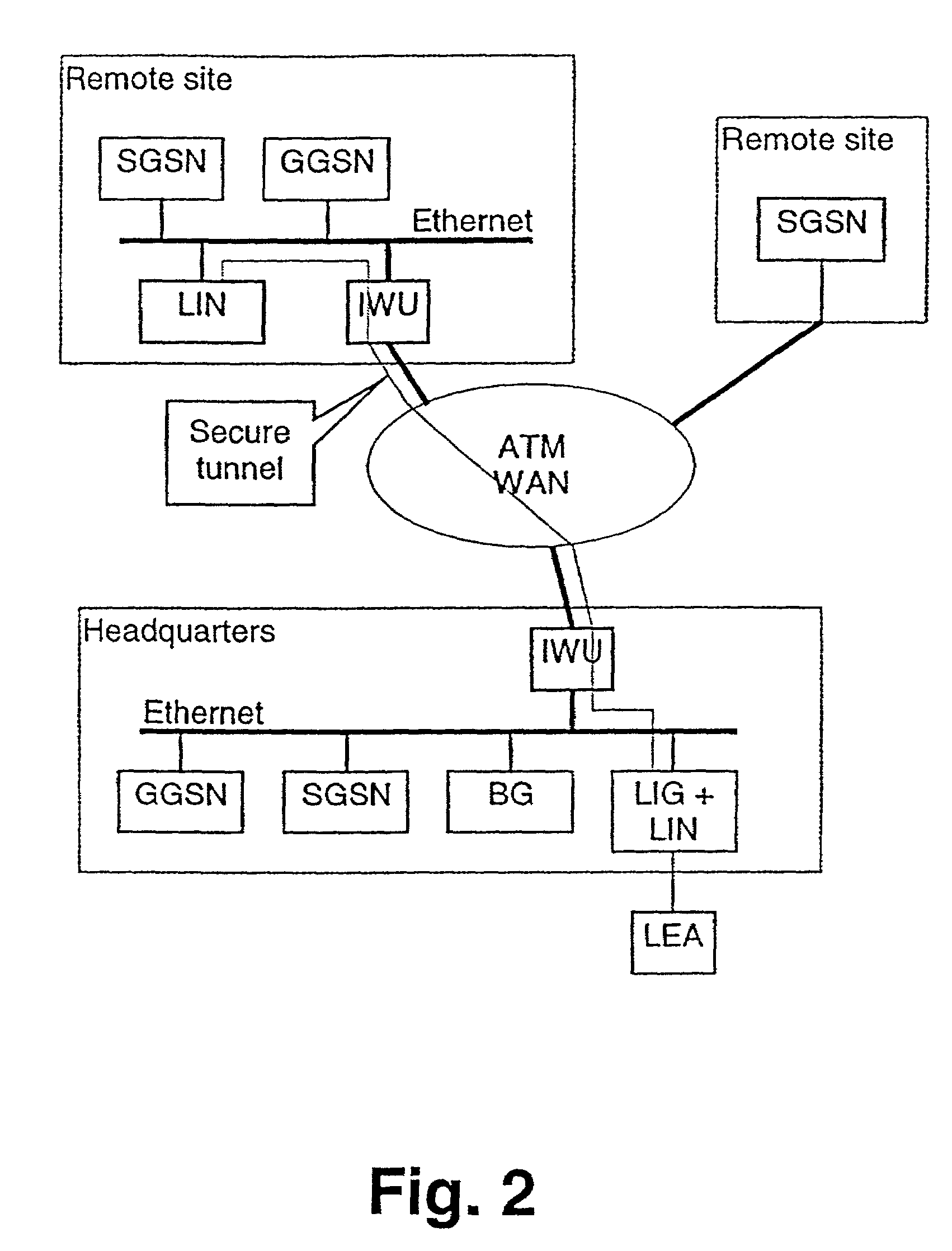
Interception method and system
InactiveUS7302702B2Flexible and scalablePowerful processorMemory loss protectionError detection/correctionLawful interceptionNetwork packet
An interception method and system for performing a lawful interception in a packet network such as the GPRS or UMTS network is described. A first network element having an intercepting function for intercepting data packets is provided, said interception function being controlled by an interception control means implemented in a second network element, wherein an intercepted data packet is transmitted from the first network element via the packet network to an interception gateway element providing an interface to a intercepting authority. The intercepted data packet is transmitted via a secure tunnel provided by an encryption processing. The interception control means and the interception gateway element may both be integrated in the second network element. The interception system has a clear advantage in scalability, no single point of failure, and an adaptation to different authority interfaces can be implemented only in the interception gateway. The network elements can be similar to a high extent for all different authority requirements.
Owner:NOKIA NETWORKS OY
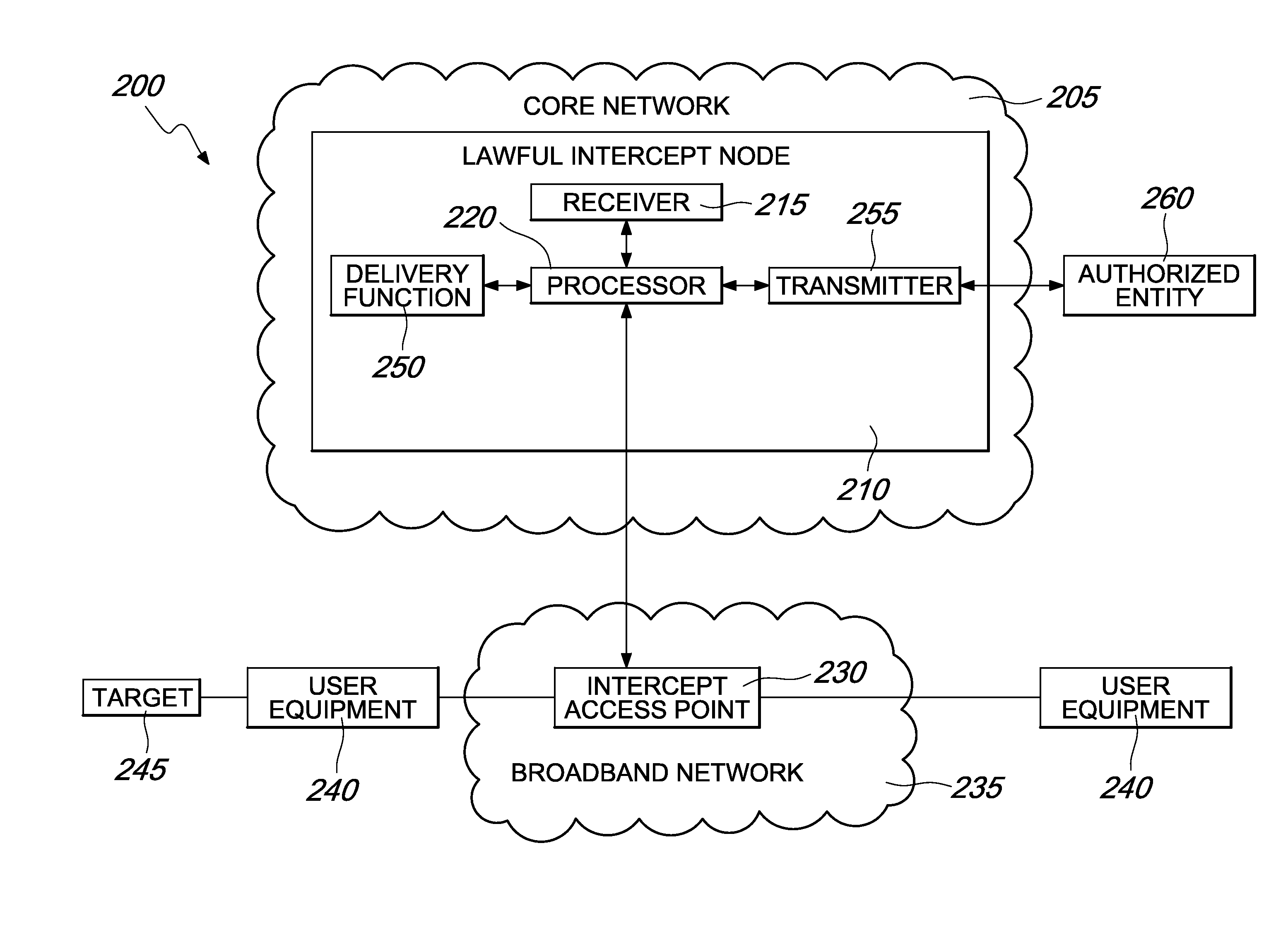
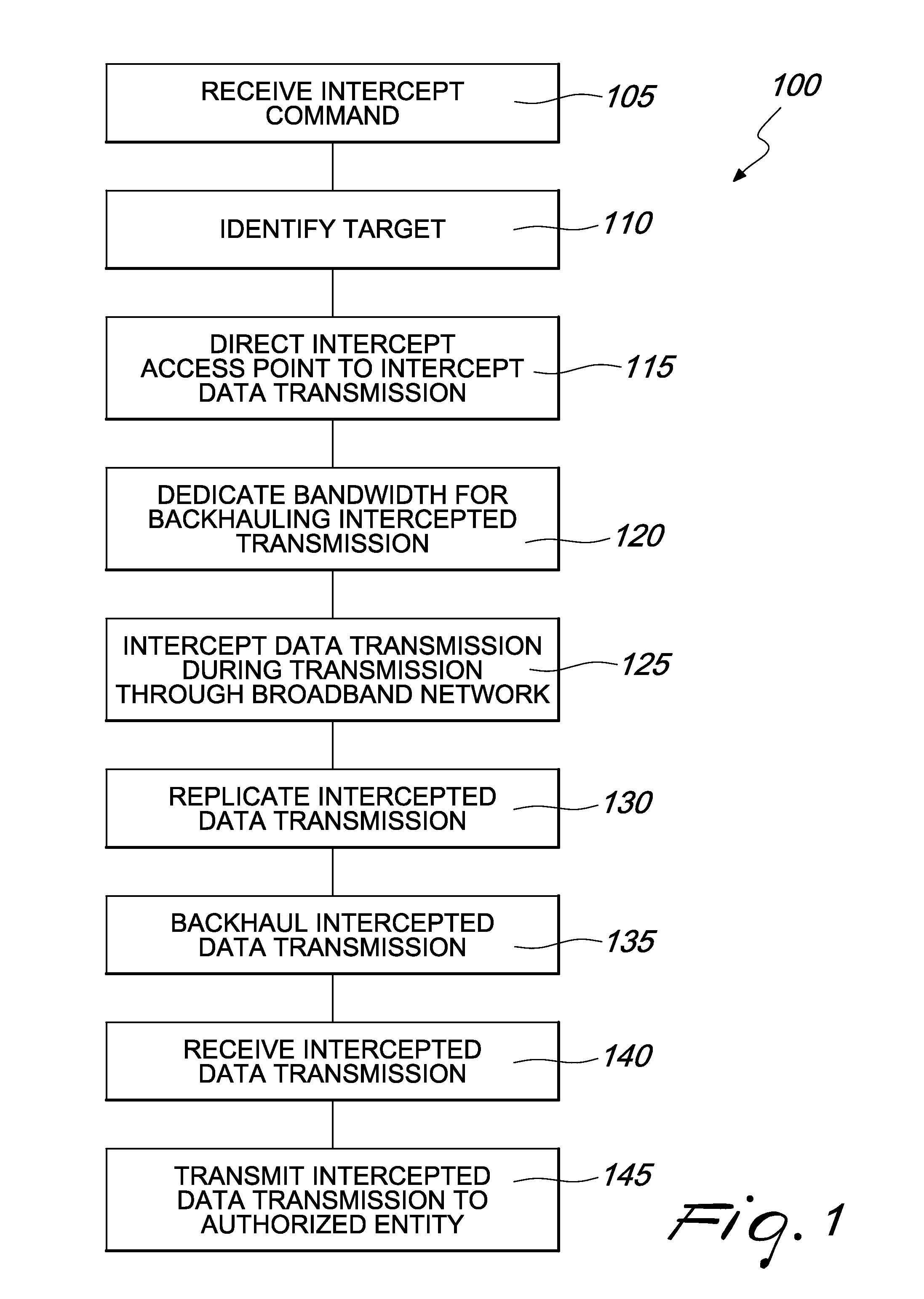
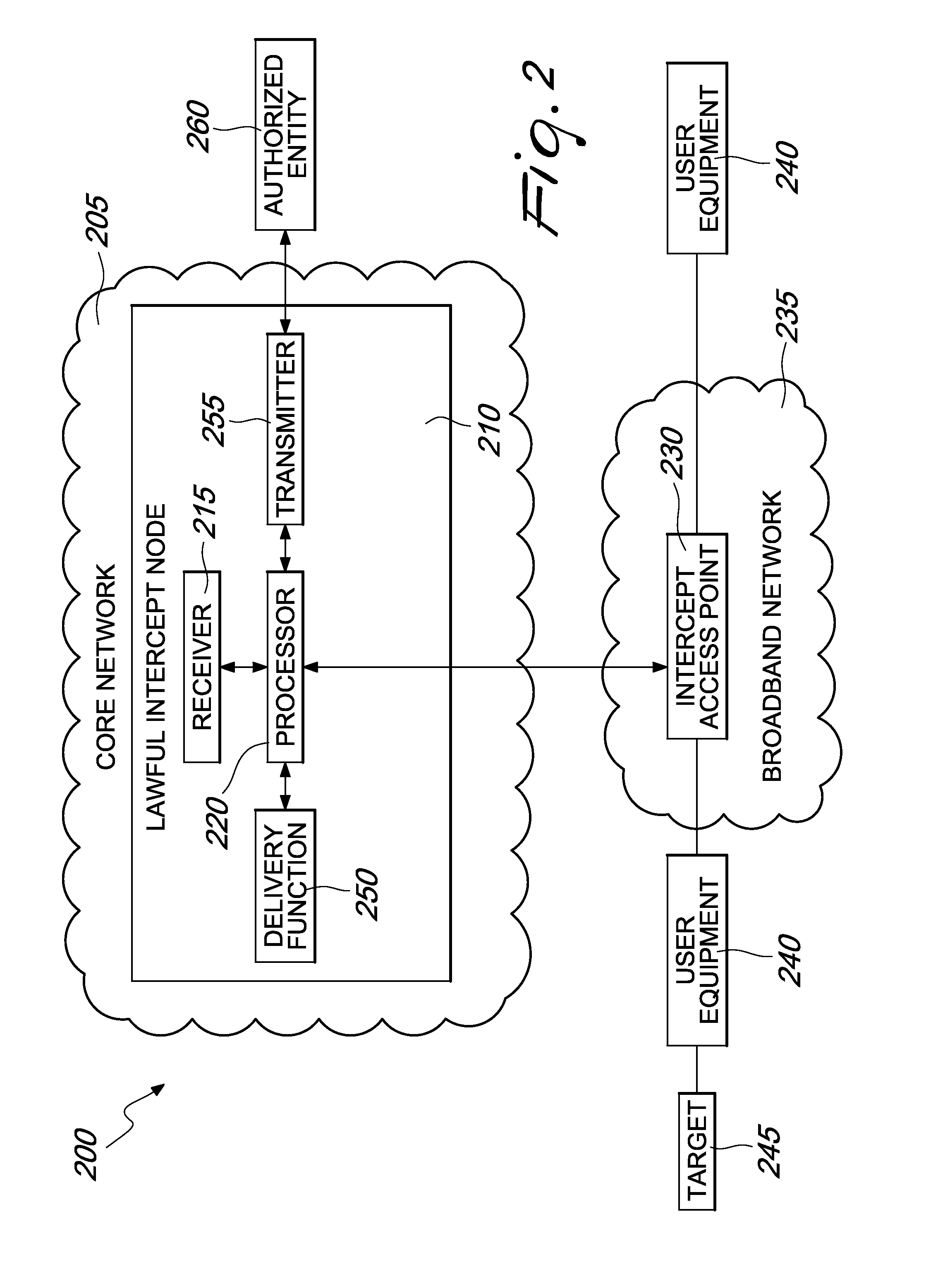
Lawful interception in wireline broadband networks
ActiveUS7969968B2Improve compatibilityImprove efficiencyInterconnection arrangementsTime-division multiplexLawful interceptionHigh bandwidth
Systems and methods are provided for lawful interception of data transmissions through at least one broadband network. Data transmissions, including voice and data services as well as high bandwidth transmissions such as multimedia and video, are intercepted and routed to authorized agencies such as law enforcement monitoring facilities. The systems and methods also enable interception of data transmissions such as peer to peer type data transmissions that pass through broadband networks from source to recipient without passing through centralized core network elements. These transmissions are intercepted at access points distributed throughout the broadband networks and forwarded to lawful intercept node elements for transmission to authorized entities.
Owner:TELEFON AB LM ERICSSON (PUBL)
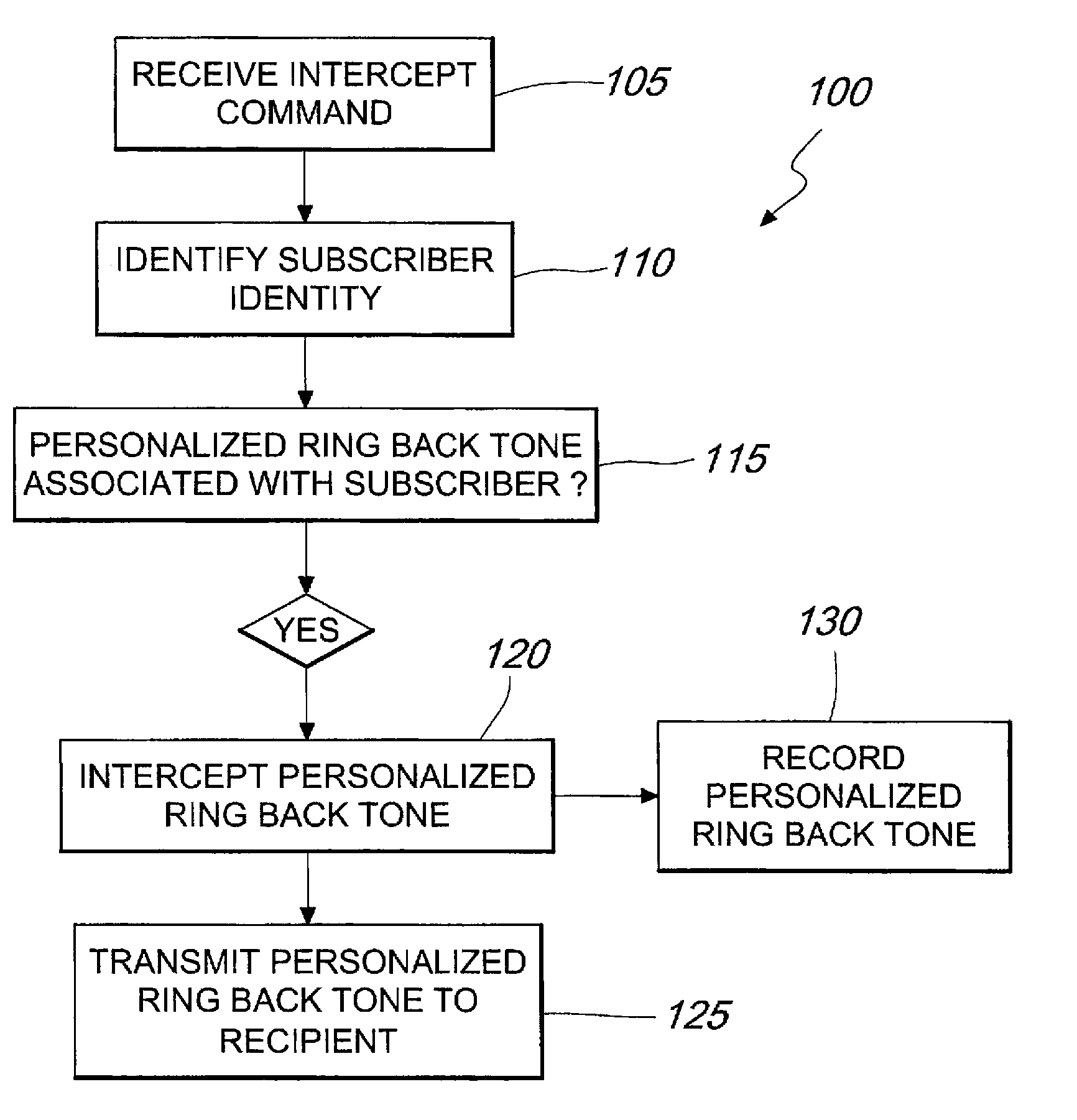
Lawful Interception Of Personalized Ring Back Tones
ActiveUS20080165940A1Improve efficiencyLow costAutomatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsLawful interceptionRing back tone
Systems and methods for legal interception of the transmission of personalized ring back tones as they are sent from a network such as a mobile telephone network associated with a subscriber to a caller in response to a call placed by the caller to the subscriber to allow monitoring of personalized ring back tones and / or their associated call content data. The personalized ring back tone is intercepted at an intercept access point on the network, where the systems and methods of the invention then transmit the intercepted personalized ring back tone to an authorized person or entity, such as a law enforcement agency.
Owner:TELEFON AB LM ERICSSON (PUBL)
SA (security association) negotiation method, device and system
The invention discloses an SA (security association) negotiation method, device and system. The method includes the steps: a key server generates a private key for a communication initiator and a private key for a communication responder; the communication initiator and the communication responder encrypt digital digests of respective messages, to be transmitted, into signatures through the respective private keys, respectively; the signatures are packaged in the messages, to be transmitted, and transmitted to the other parity; the communication initiator and the communication responder determine each other's public keys and use the public keys and the received signatures in the messages to authenticate each other. Through the use of the SA negotiation method, device and system, the problems that an SA negotiation implementation process is complex and communication load is high can be solved; security supervision and lawful interception can be performed on deployment of communication of an IPSec (internet protocol security) protocol network.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and system for lawful interception of value-added service in IP multimedia subsystem
InactiveUS20090097420A1Special service provision for substationMultiplex system selection arrangementsLawful interceptionPresent method
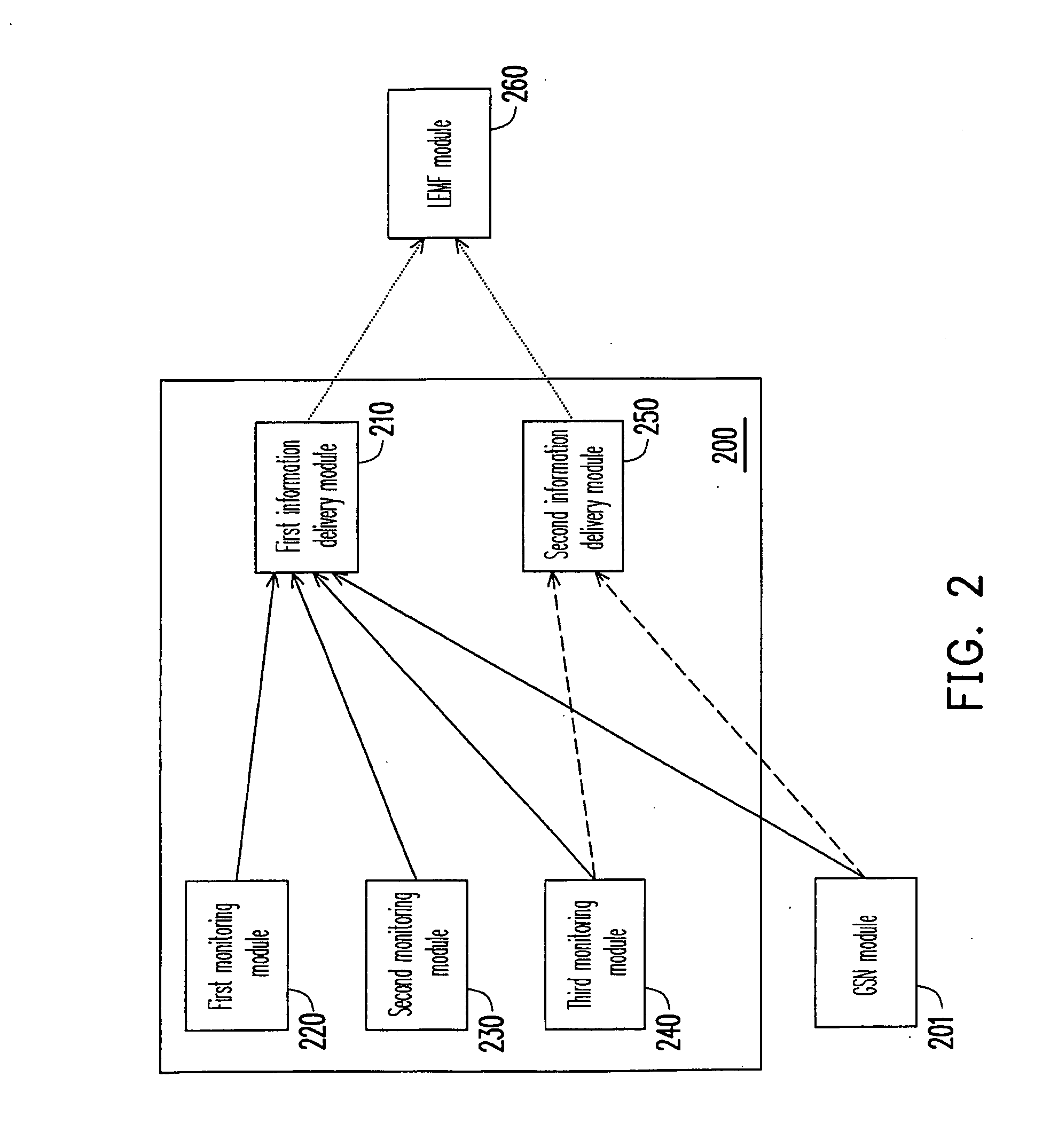
A method and a system for lawfully intercepting a value-added service in an IP multimedia subsystem (IMS) are provided. In the present method, a service subscription information is sent to a first information delivery module when a suspect is registered to an IMS network. A service triggering information is sent to the first information delivery module when the value-added service subscribed by the suspect is triggered. Furthermore, when the value-added service is provided, an intercept related information (IRI) is sent to the first information delivery module according to the characteristics of the value-added service. As a result, the suspect who is using the value-added service in the IMS can be lawfully intercepted according to the information collected by the first information delivery module.
Owner:IND TECH RES INST
Lawful interception in a mobile data network with data offload at the basestation
ActiveUS20140044019A1Avoid breakoutOut of serviceSpecial service provision for substationMultiplex system selection arrangementsLawful interceptionComputer science
Lawful interception (LI) is supported on a flat mobile data network with breakout services at the basestation. A first service mechanism at the basestation is prevented from breaking out services for subscribers that are part of LI. A second service mechanism in the core network maintains a subscriber list of subscribers that are subject to LI. In response to a PDP context activation by a subscriber on the list, the second service mechanism does not supply PDP context information to the first service mechanism for data breakout thus preventing breakout for the subscriber subject to lawful interception.
Owner:LENOVO GLOBAL TECH INT LTD
Lawful interception target apparatus, lawful interception apparatus, lawful interception system and lawful interception method
A lawful interception apparatus, a lawful interception target apparatus and a lawful interception system are provided. If a lawful interception target apparatus accesses a new communication network which has no lawful interception authority, the lawful interception apparatus receives intercept activation information from the lawful interception target apparatus through a communication network which has a lawful interception authority. The lawful interception apparatus performs seamless lawful interception on the lawful interception target apparatus by use of the received intercept activation information.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com