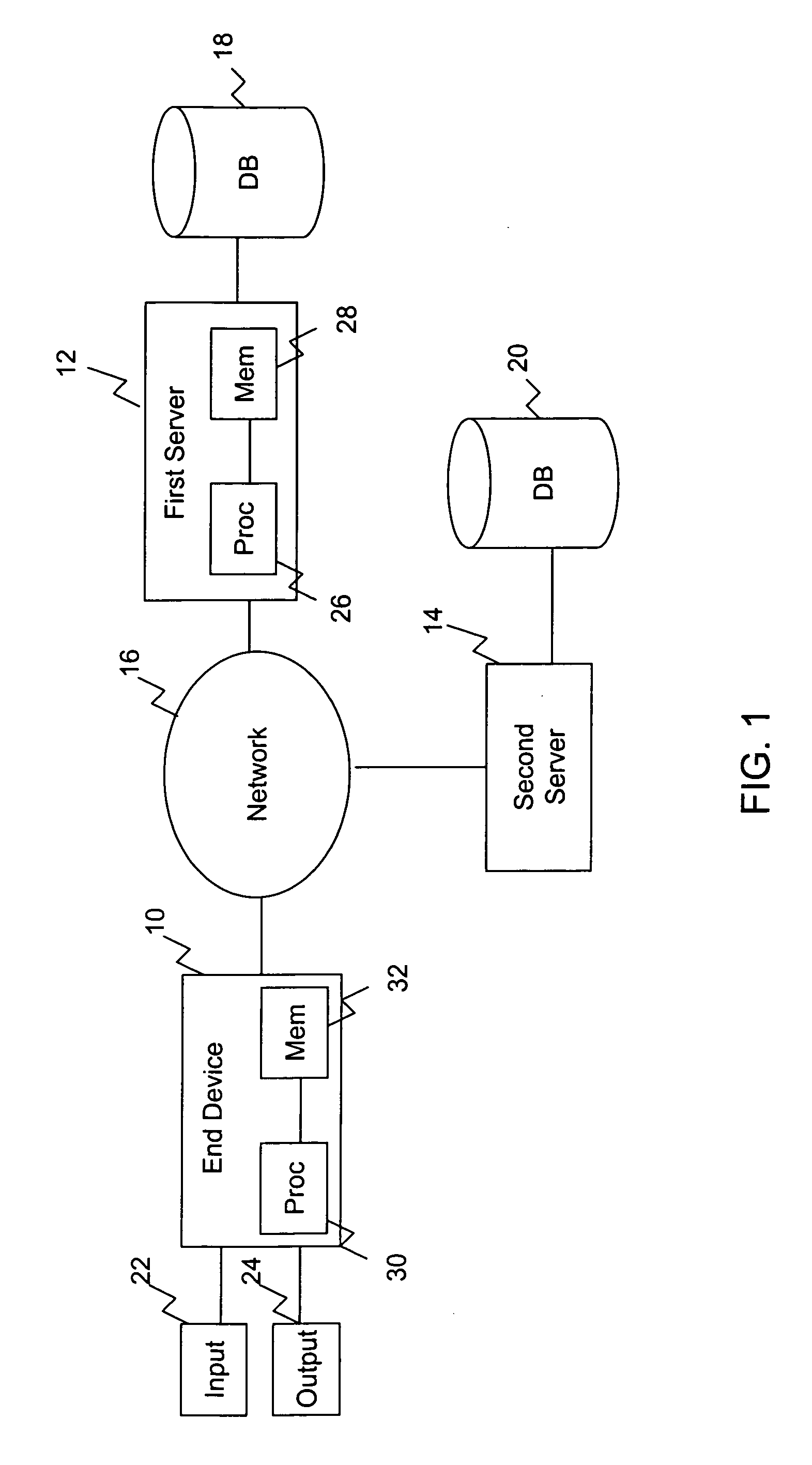
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
130 results about "Potential candidate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
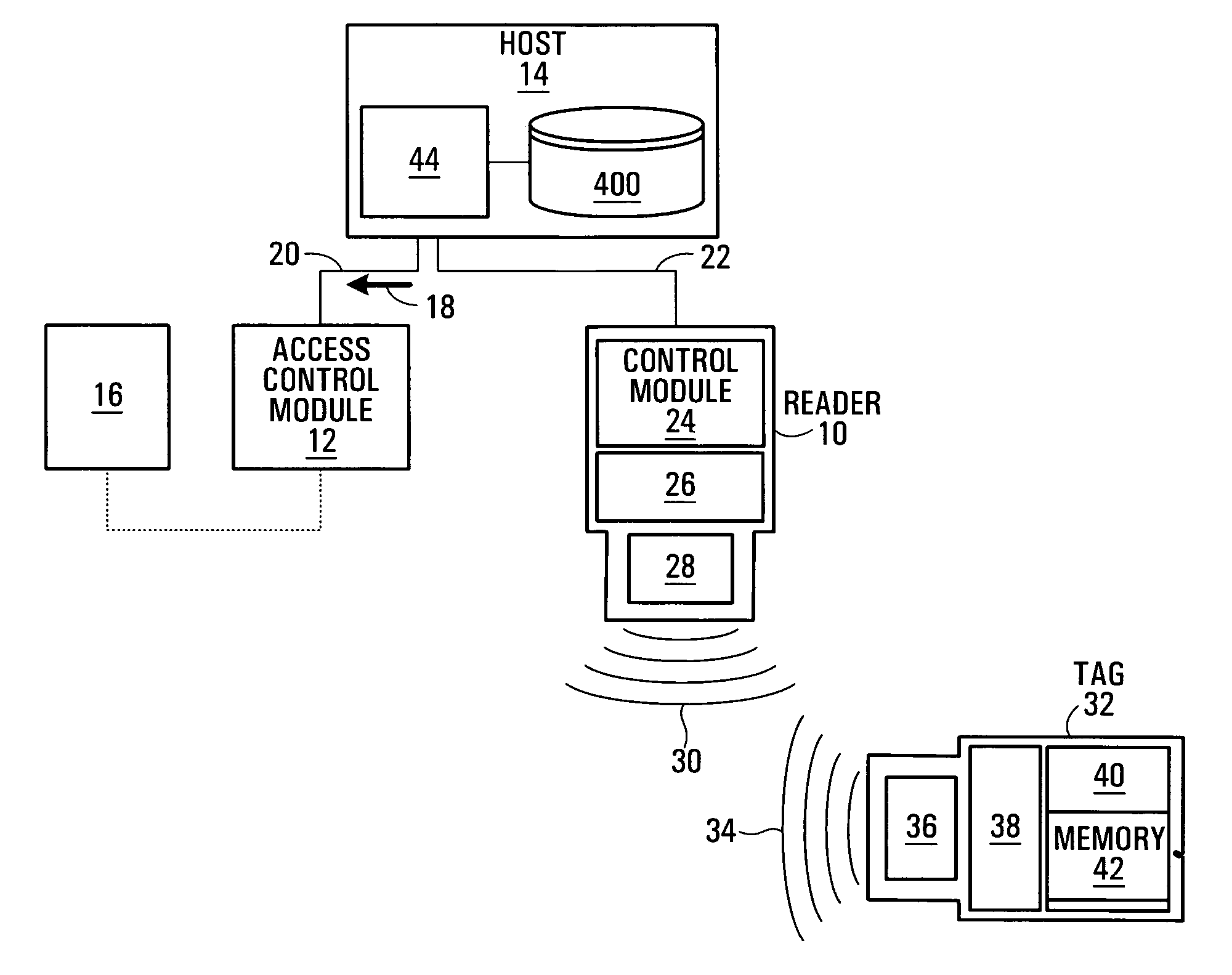
Patent Type
Patent Status
Application Year
Inventor
Potential. A candidate’s potential is determined by their ability and desire to grow and develop within a company. Unlike skills, knowledge, and experience, potential isn’t something that can be learned — it has to be found. The job interview provides a perfect opportunity to get to know candidates and their career aspirations.
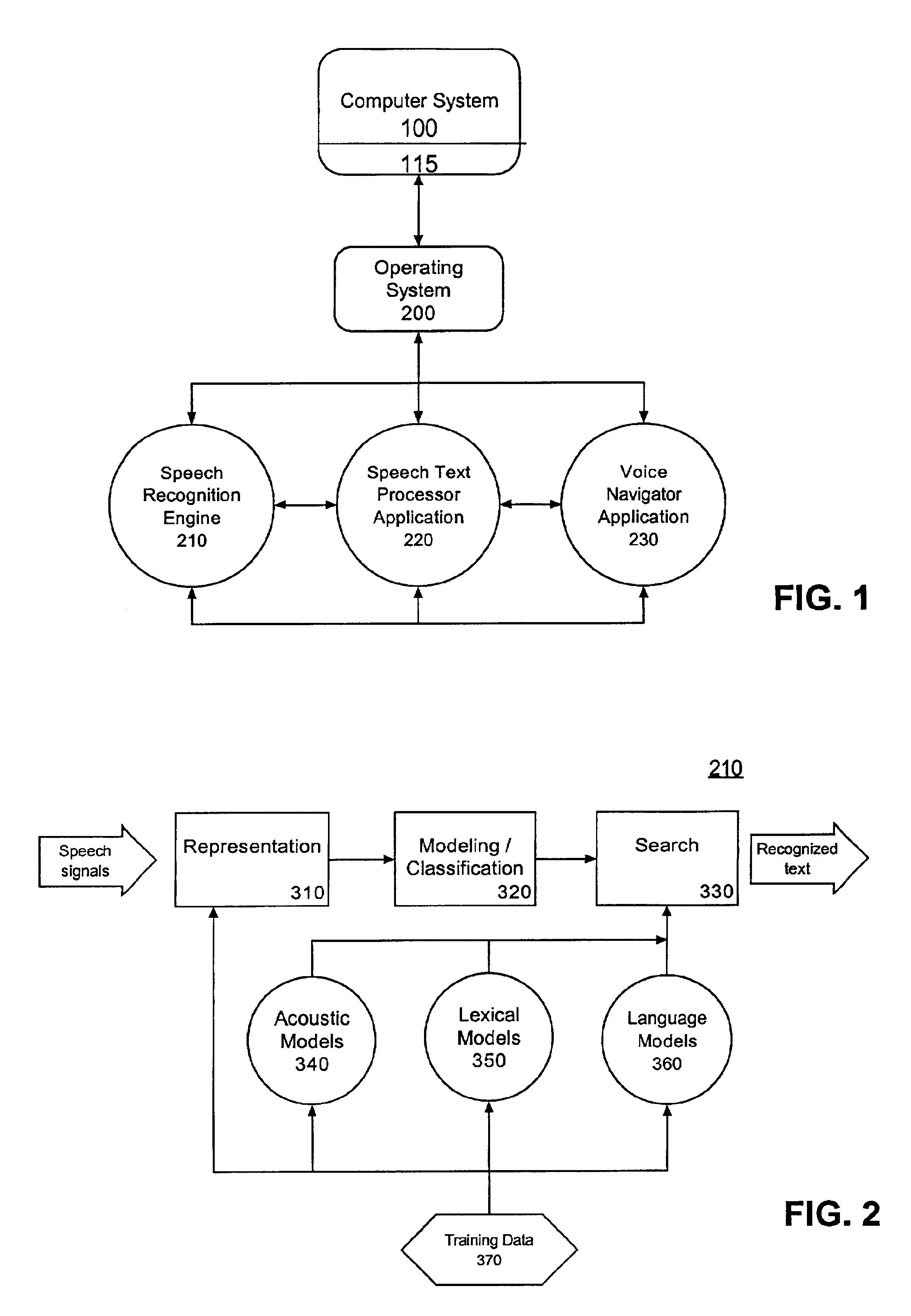
Method of speech recognition by presenting N-best word candidates
A method for performing speech recognition can include receiving user speech and determining a plurality of potential candidates. Each of the candidates can provide a textual interpretation of the speech. Confidence scores can be calculated for the candidates. The confidence scores can be compared to a predetermined threshold. Also, selected ones of the plurality of candidates can be presented to the user as alternative interpretations of the speech when none of the confidence scores is greater than the predetermined threshold. The selected ones of the plurality of candidates can have confidence scores above a predetermined minimum threshold, and thus can have confidence scores within a predetermined range.
Owner:NUANCE COMM INC
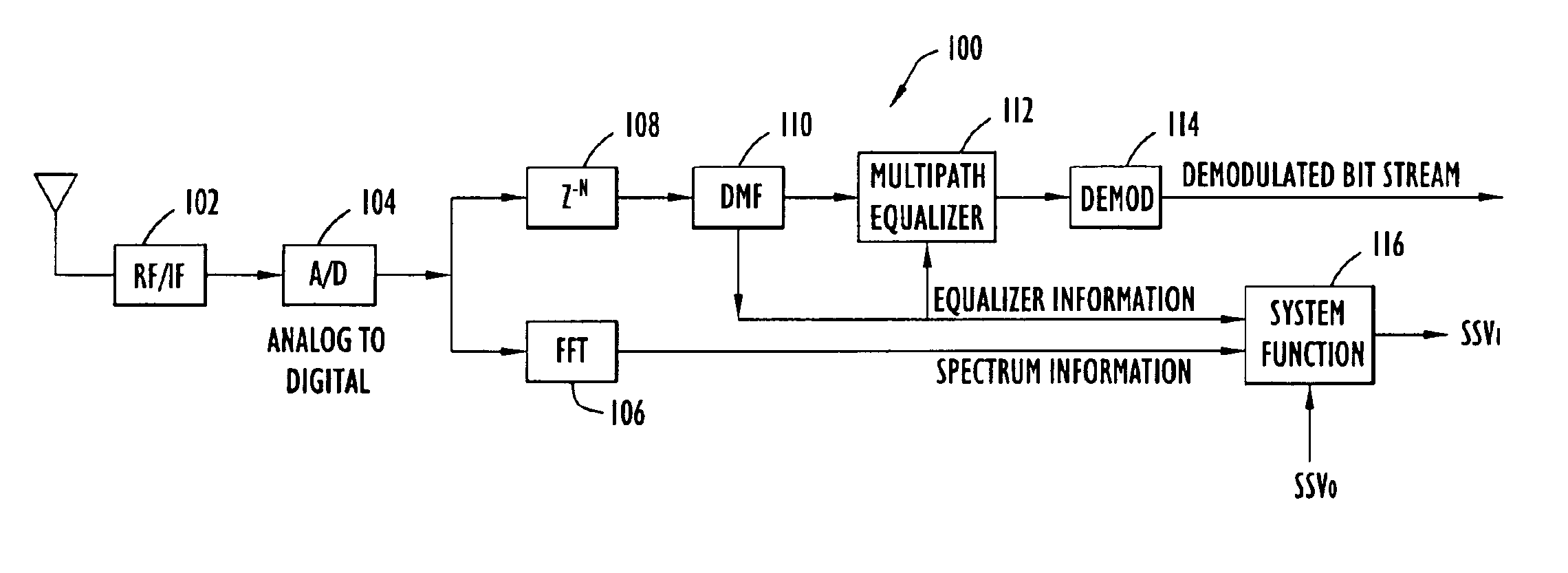
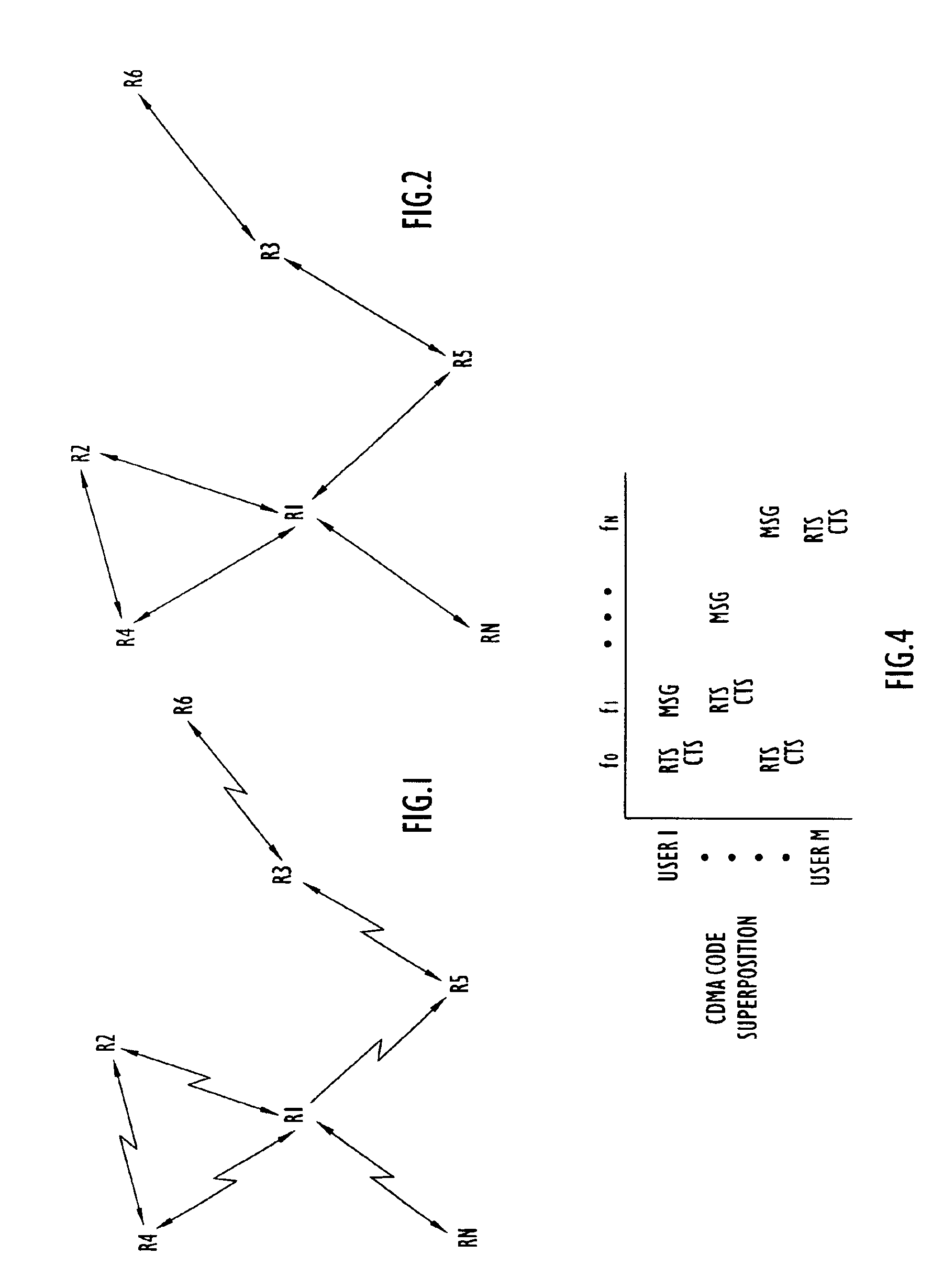
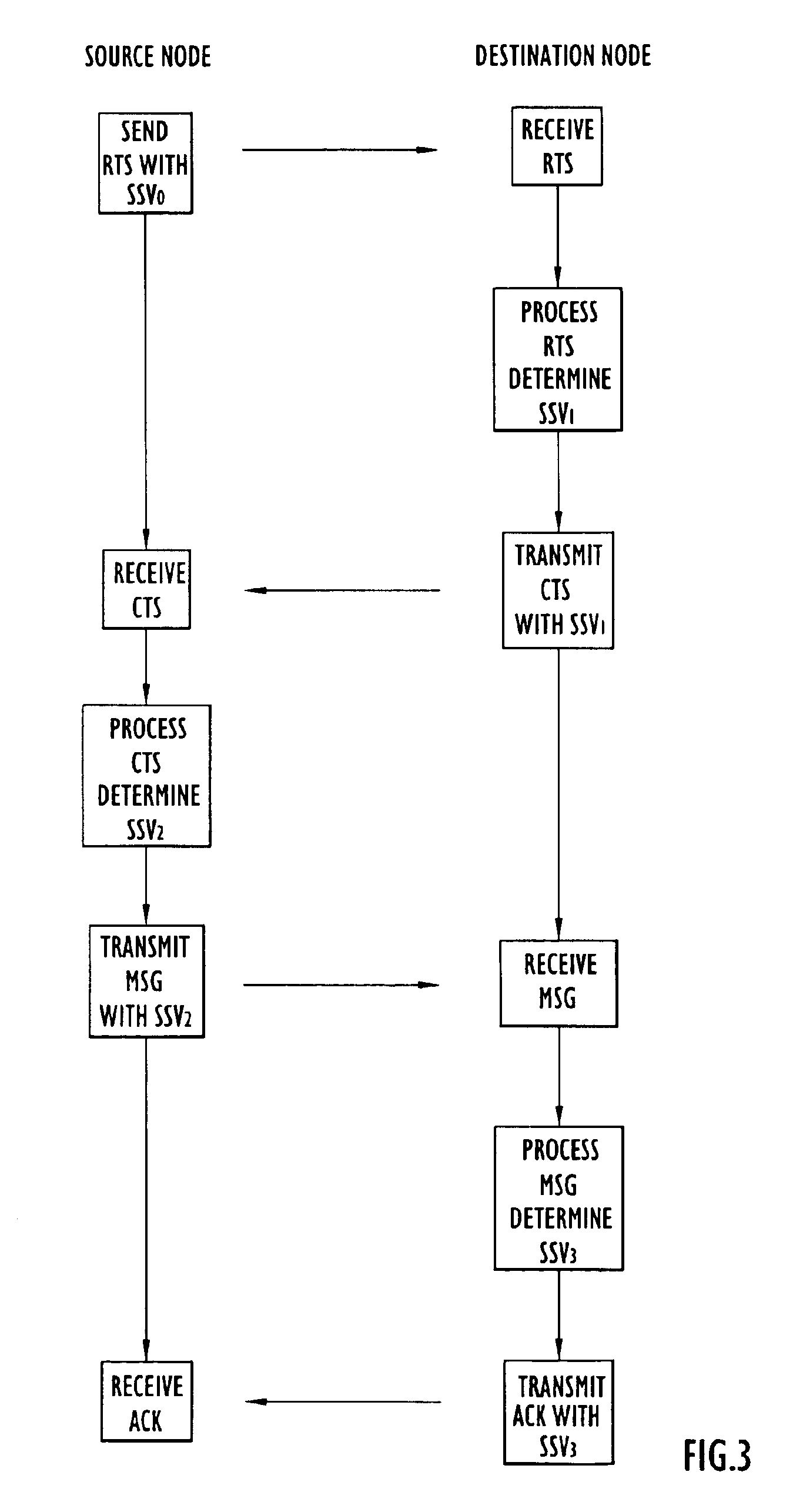
Methods and apparatus for organizing selection of operational parameters in a communication system
InactiveUS6859463B1Expected performanceEliminate needFrequency-division multiplex detailsData switching by path configurationCommunications systemPotential candidate
Operational parameters for transmitting a signal over a communication channel of a network are selected by first determining RF conditions on the communication channel from a received signal transmitted over the communication channel. An initial set of parameter values is selected for transmitting the signal based on RF conditions determined from the received signal. The initial set of parameter values is used to identify other sets of parameter values as other potential candidates for transmitting the signal. The parameter values in the other sets of parameter values differ from parameter values in the initial set of parameter values by less than a predetermined amount. The expected performance of the candidate sets of parameter values is compared to determine which set of parameter values has the best expected performance among the candidate sets of parameter values. The signal is transmitted on the communication channel using the selected set of parameter values.
Owner:STINGRAY IP SOLUTIONS LLC +1
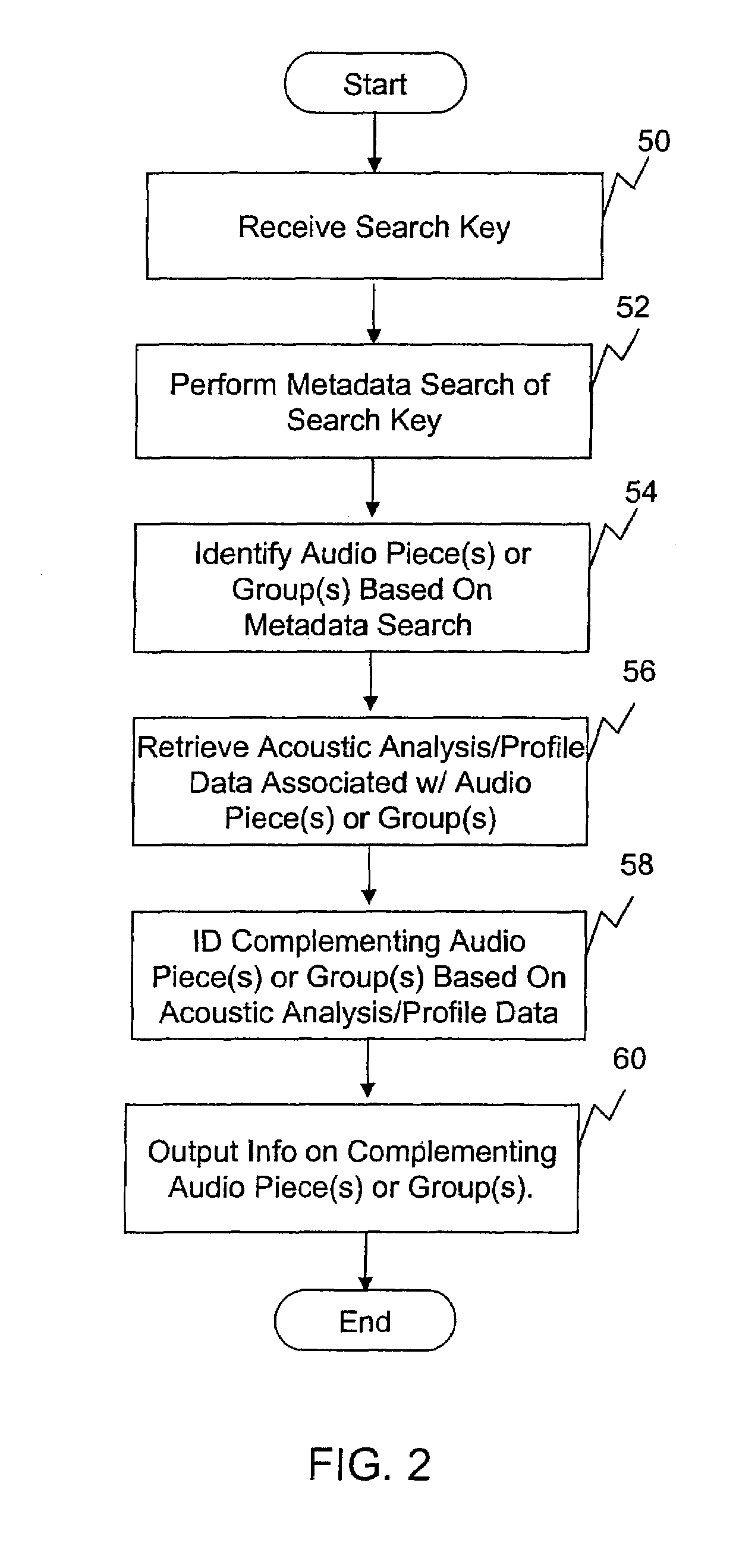
Music searching system and method
InactiveUS20060217828A1Metadata audio data retrievalUsing non-detectable carrier informationAnalysis dataComputer science
A music searching system and method conducting a metadata search of music based on an entered search term. Music identified from the metadata search is used as seed music to identify other acoustically complementing music. Acoustic analysis data of the seed music is compared against acoustic analysis data of potential candidates for determining whether they are acoustically complementing music. The acoustically complementing music is then displayed to the user for listening, downloading, or purchase.
Owner:MUSICIP CORP
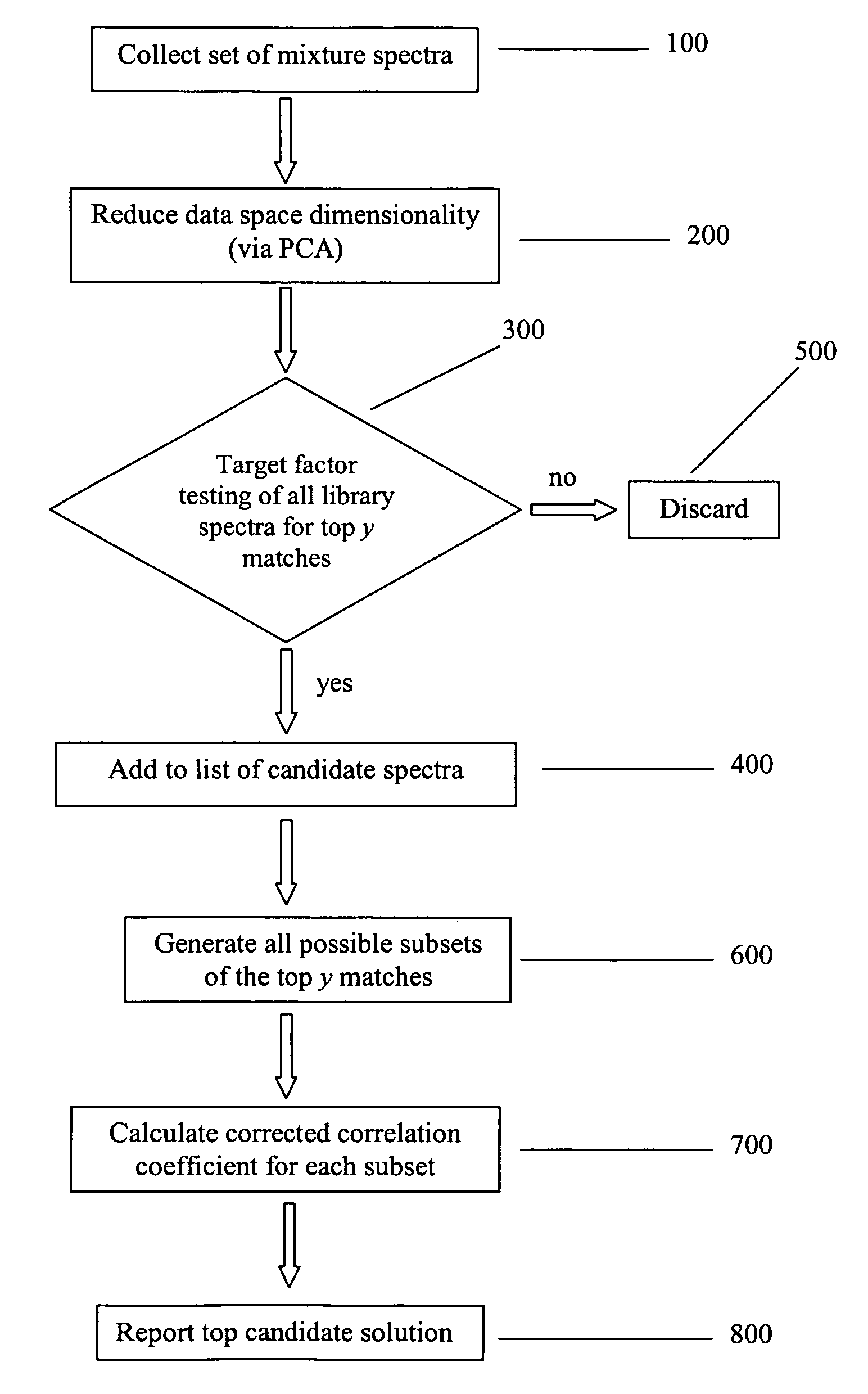
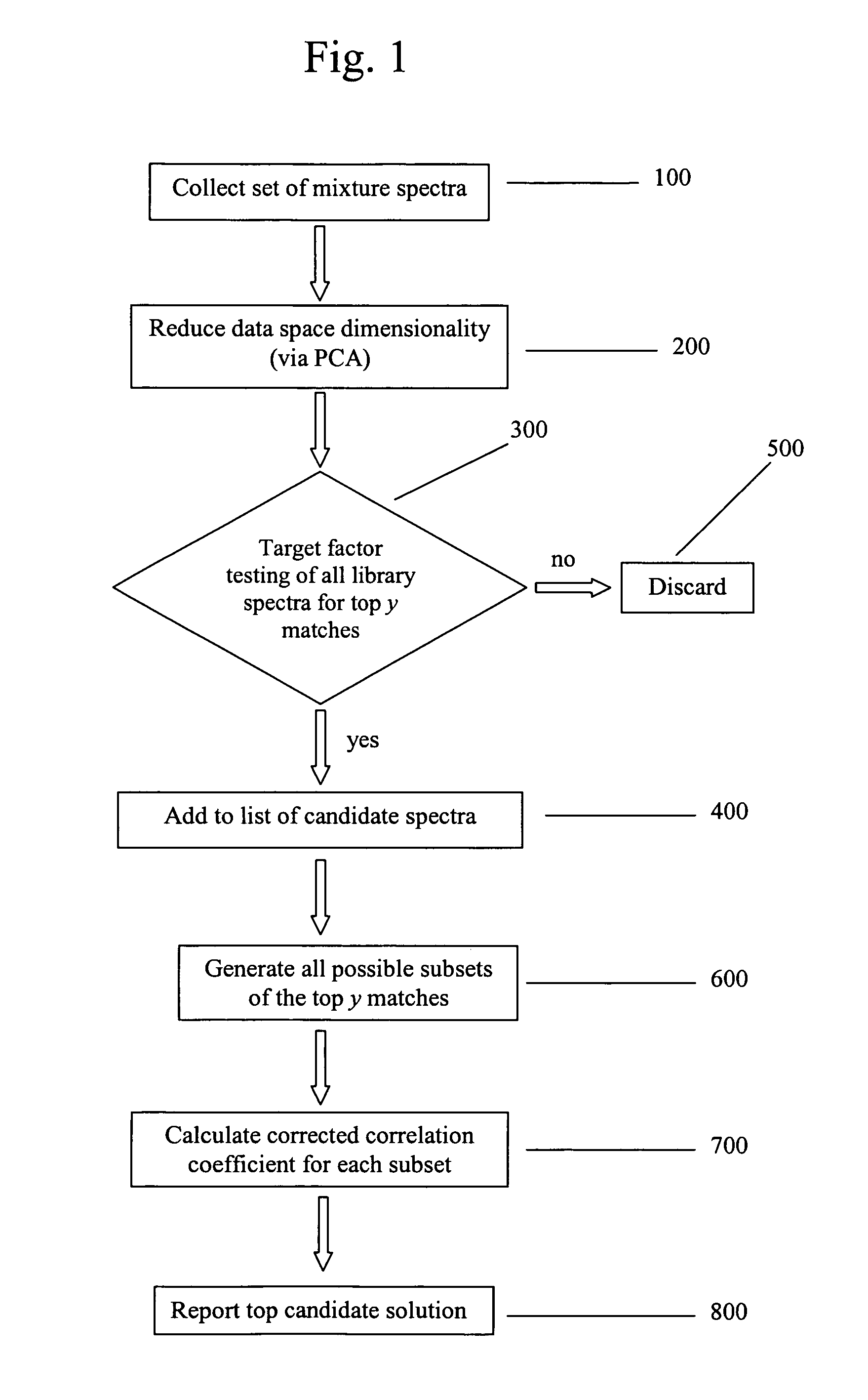
Method for identifying components of a mixture via spectral analysis
ActiveUS7072770B1Easy to detectEasy to identifyMolecular entity identificationSpectrum investigationCorrelation coefficientPresent method
The present invention is directed generally toward the field of spectral analysis and, more particularly, toward an improved method of identifying unknown components of a mixture from a set of spectra collected from the mixture using a spectral library including potential candidates. For example, the present method is directed to identifying components of a mixture by the steps which comprise obtaining a set of spectral data for the mixture that defines a mixture data space; ranking a plurality of library spectra of known elements according to their angle of projection into the mixture data space; calculating a corrected correlation coefficient for each combination of the top y ranked library spectra; and selecting the combination having the highest corrected correlation coefficient, wherein the known elements of the selected combination are identified as the components of the mixture.
Owner:CHEMIMAGE
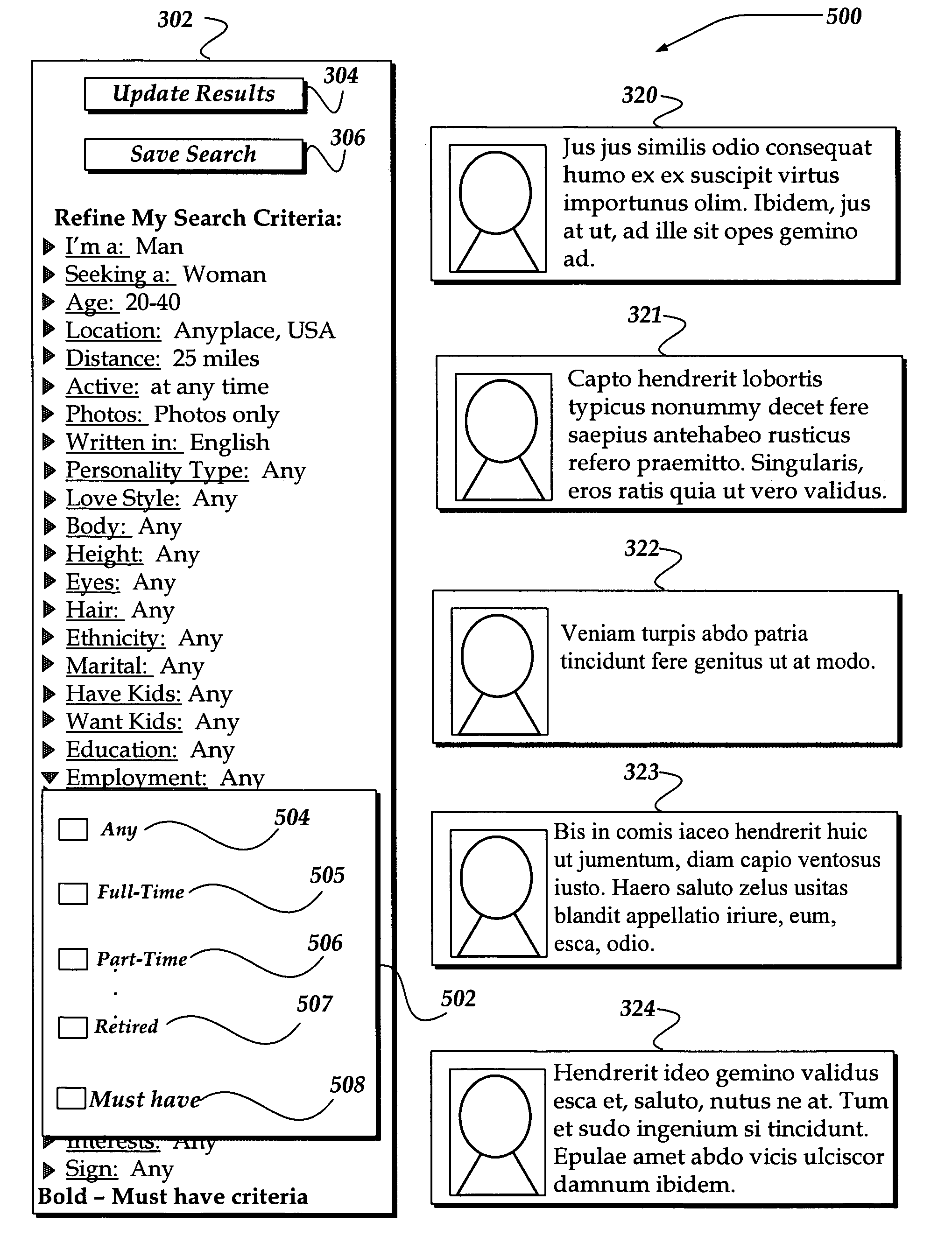
System and method of modifying an on-line dating search using inline editing
InactiveUS20060059142A1CommerceSpecial data processing applicationsPotential candidateInformation retrieval
A method, system, and apparatus are directed towards enabling a subscriber of an online dating service to perform a search for potential candidates to a long-term relationship. Various search criteria may be employed to generate an initial list of candidates. The invention employs the search criteria to identify a potential candidate list for the user. The invention further allows the user to edit inline with a display of the potential candidates various search criteria components using, for example, a drop-down menu to identify an importance of a search criteria component, or to otherwise revise the search criteria. The revised search criteria may then be employed in revising the potential candidate list.
Owner:OATH INC
System and method for resolving decoding ambiguity via dialog
InactiveUS6587818B2Improve accuracyImprove performanceCharacter and pattern recognitionFuzzy logic based systemsAmbiguityPotential candidate
A method of language recognition wherein decoding ambiguities are identified and at least partially resolved intermediate to the language decoding procedures to reduce the subsequent number of final decoding alternatives. The user is questioned about identified decoding ambiguities as they are being decoded. There are two language decoding levels: fast match and detailed match. During the fast match decoding level a large potential candidate list is generated, very quickly. Then, during the more comprehensive (and slower) detailed match decoding level, the fast match candidate list is applied to the ambiguity to reduce the potential selections for final recognition. During the detailed match decoding level a unique candidate is selected for decoding. Decoding may be interactive and, as each ambiguity is encountered, recognition suspended to present questions to the user that will discriminate between potential response classes. Thus, recognition performance and accuracy is improved by interrupting recognition, intermediate to the decoding process, and allowing the user to select appropriate response classes to narrow the number of final decoding alternatives.
Owner:NUANCE COMM INC
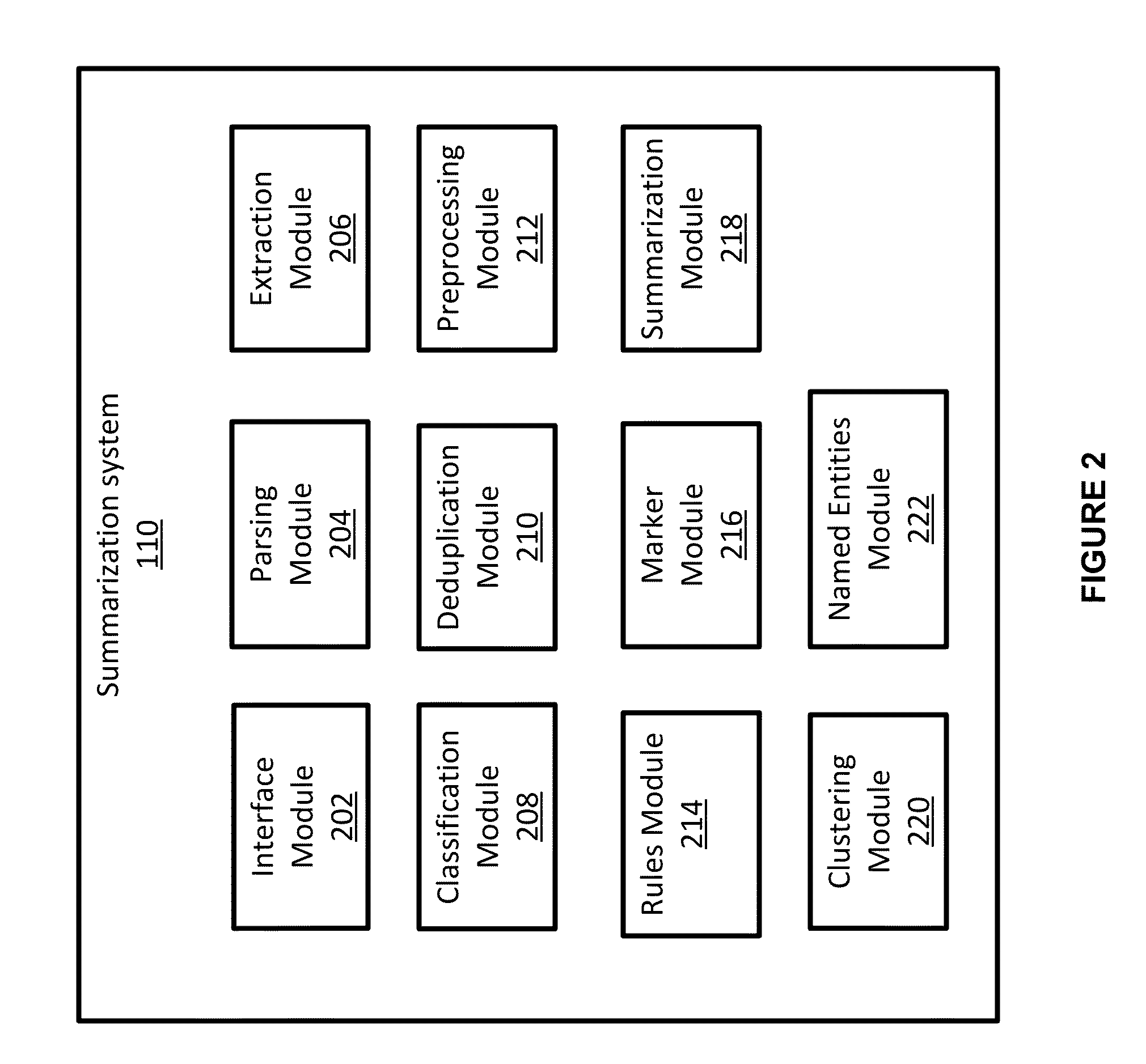
Systems and Methods for Generating Summaries of Documents
ActiveUS20150339288A1Natural language data processingSpecial data processing applicationsDocumentation procedureUser device
Systems and methods for summarizing online articles for consumption on a user device are disclosed herein. The system extracts the main body of an article's text from the HTML code of an online article. The system may then classify the extracted article into one of several different categories and removes duplicate articles. The system breaks down the article into its component sentences, and each sentence is classified into one of three categories: (1) potential candidate sentences that may be included in the generated summary; (2) weakly rejected sentences that will not be included in the summary but may be used to generate the summary; and (3) strongly rejected sentences that are not included in the summary. Finally, the system applies a document summarizer to generate quickly readable article summaries, for viewing on the user device, using relevant sentences from the article while maintaining the coherence of the article.
Owner:CODEQ
System and method for diagnosis and treatment
ActiveUS8658128B2Good curative effectPromote resultsOrganic active ingredientsPeptide/protein ingredientsPhysiologyHydrocortisone
This invention relates to a low cost rapid response diagnostic system to determine cortisol levels in patients selected as potential candidates for GCR (glucocorticoid receptor) antagonist therapy utilizing a GCR antagonist, such as ORG 34517. The rapid, sensitive, and inexpensive test can be used to determine patients who have non-normal cortisol production or disordered circadian rhythms as a method for selecting subjects for GCR antagonist therapy for whom it is likely to have beneficial and / or therapeutic effects, and can also be used to monitor changes in cortisol levels in response to treatment.
Owner:POP TEST ONCOLOGY LIMITED LIABILITY
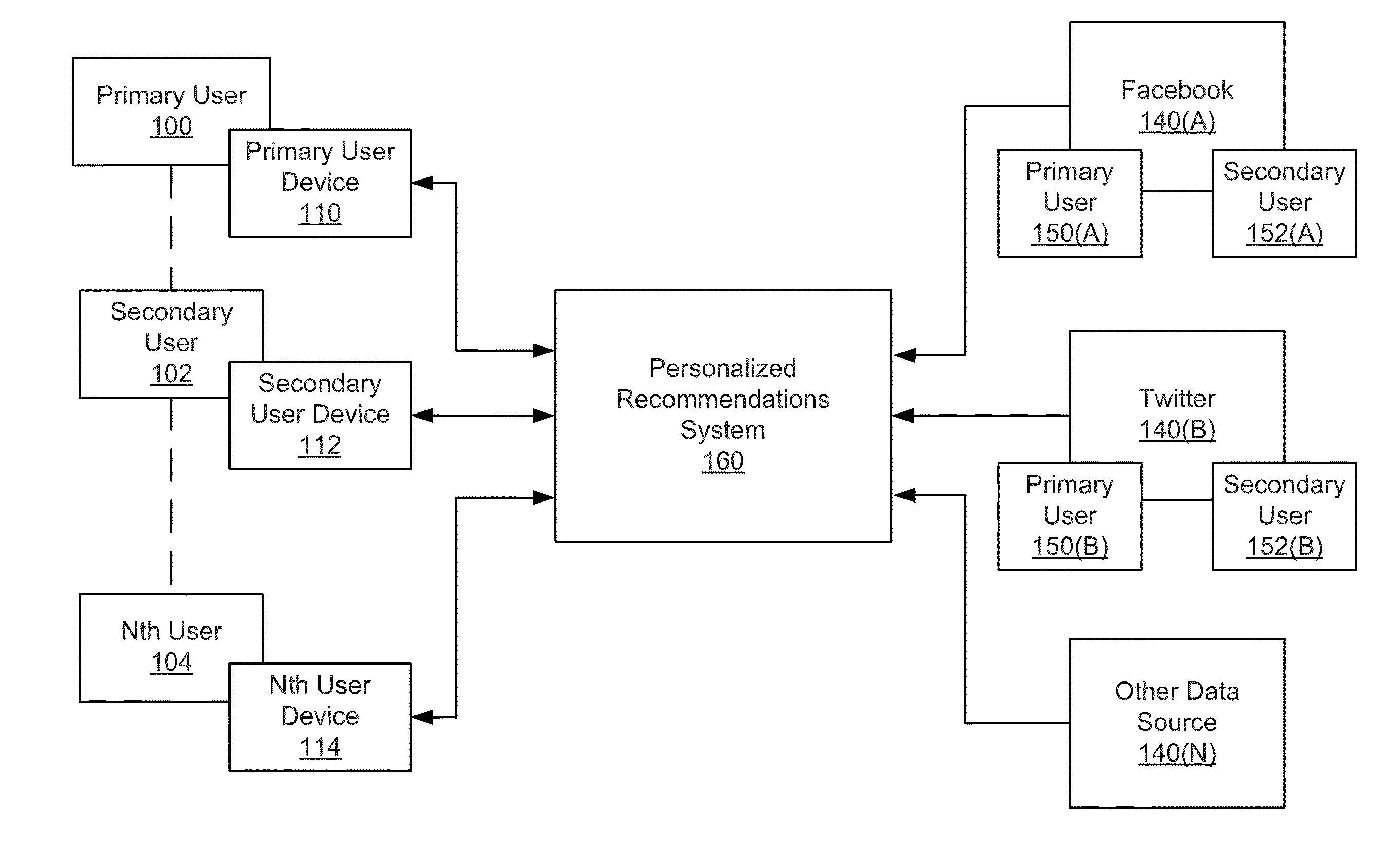
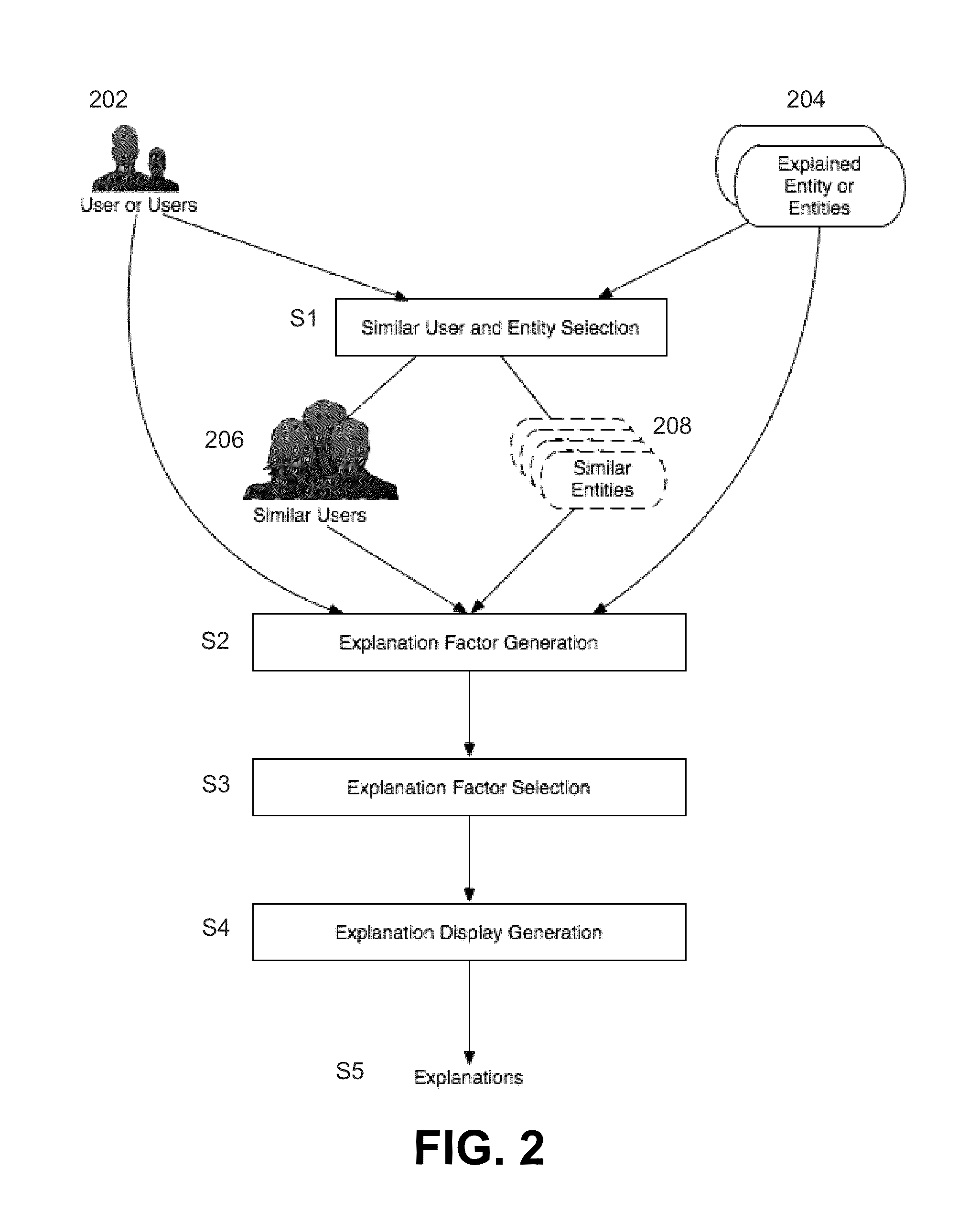
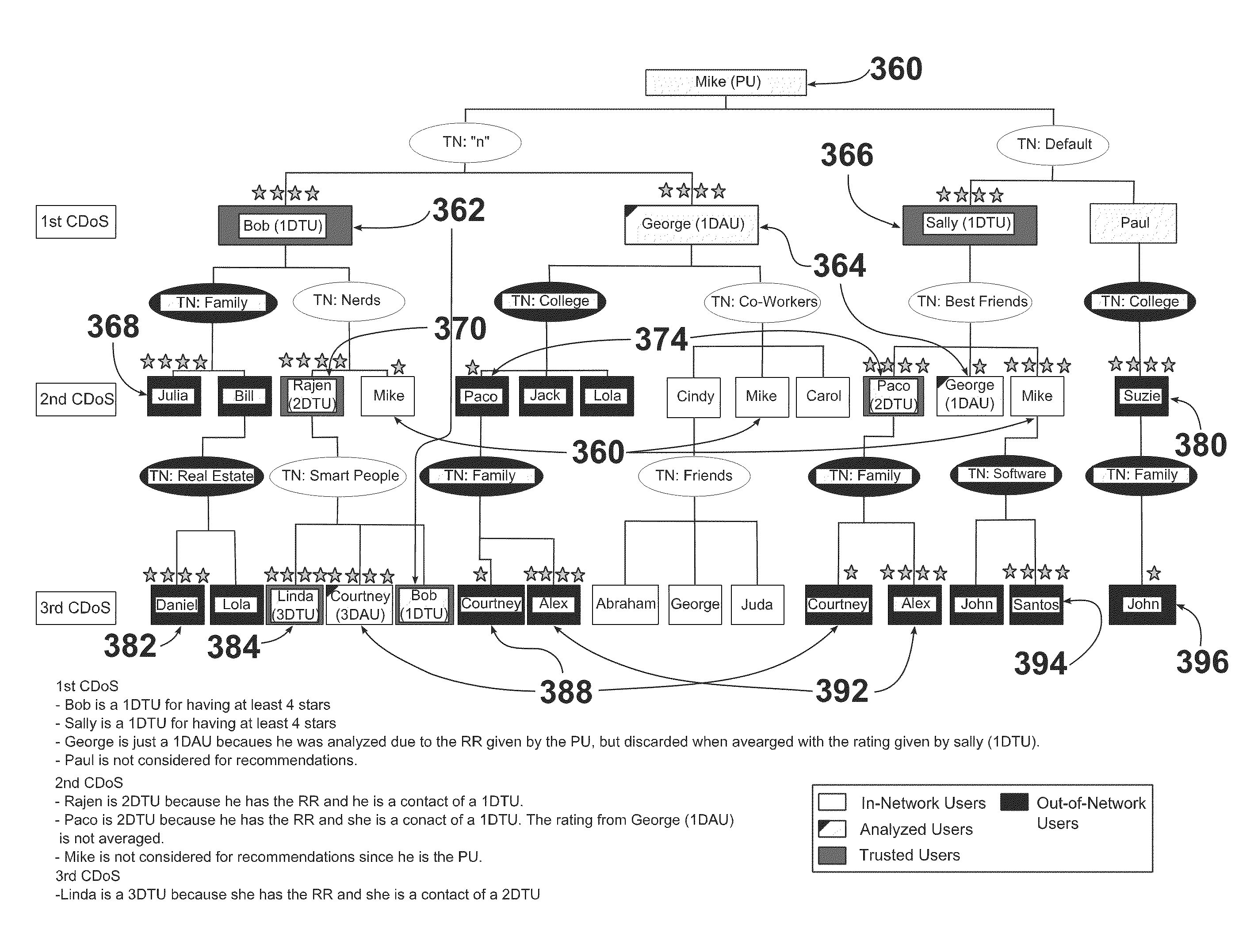
Recommendation engine that processes data including user data to provide recommendations and explanations for the recommendations to a user
InactiveUS20130024464A1Optimize dataWeb data indexingDigital data processing detailsPersonalizationPotential candidate
Embodiments of the invention relate to a computer-implemented method for generating explanatory data from a personalized recommendations process for a primary user based at least on stored data about the primary user. The method comprises a server computer obtaining data related to one or more users who are relevant to the primary user, then determining at least one group of users relevant to the primary user. The server computer also obtains data related to one or more entities, determines one or more entities relevant to the primary user, and associates the at least one relevant group of users with the one or more relevant entities. One or more potential candidate factors are generated. A set of factors are selected from the one or more potential candidate factors, wherein the potential candidate factors are used as explanatory data to determine recommendations to the primary user.
Owner:OPENTABLE
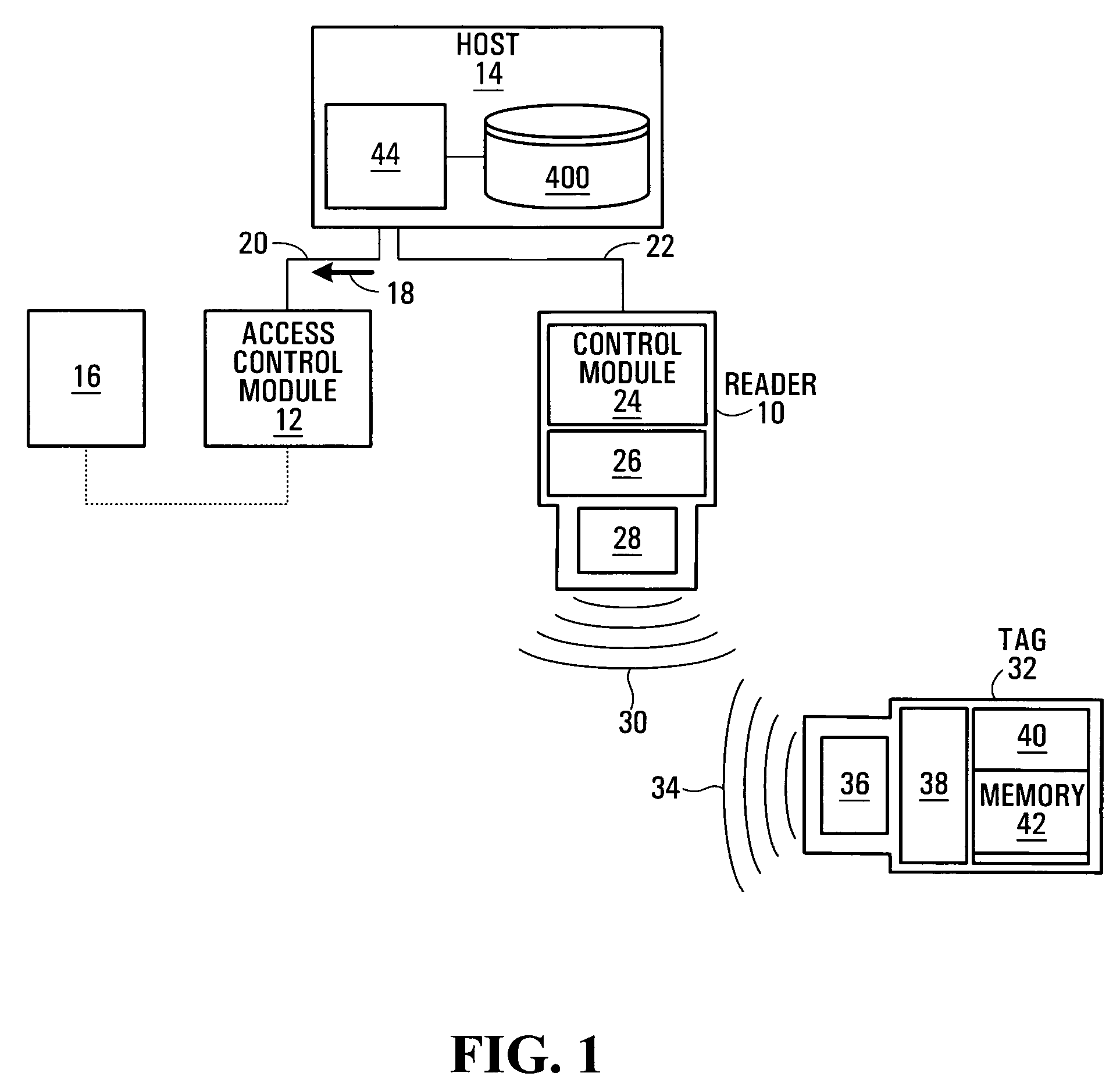
User authentication for contact-less systems
InactiveUS7246744B2Sensing detailsIndividual entry/exit registersUser authenticationComputer science
Owner:BCE
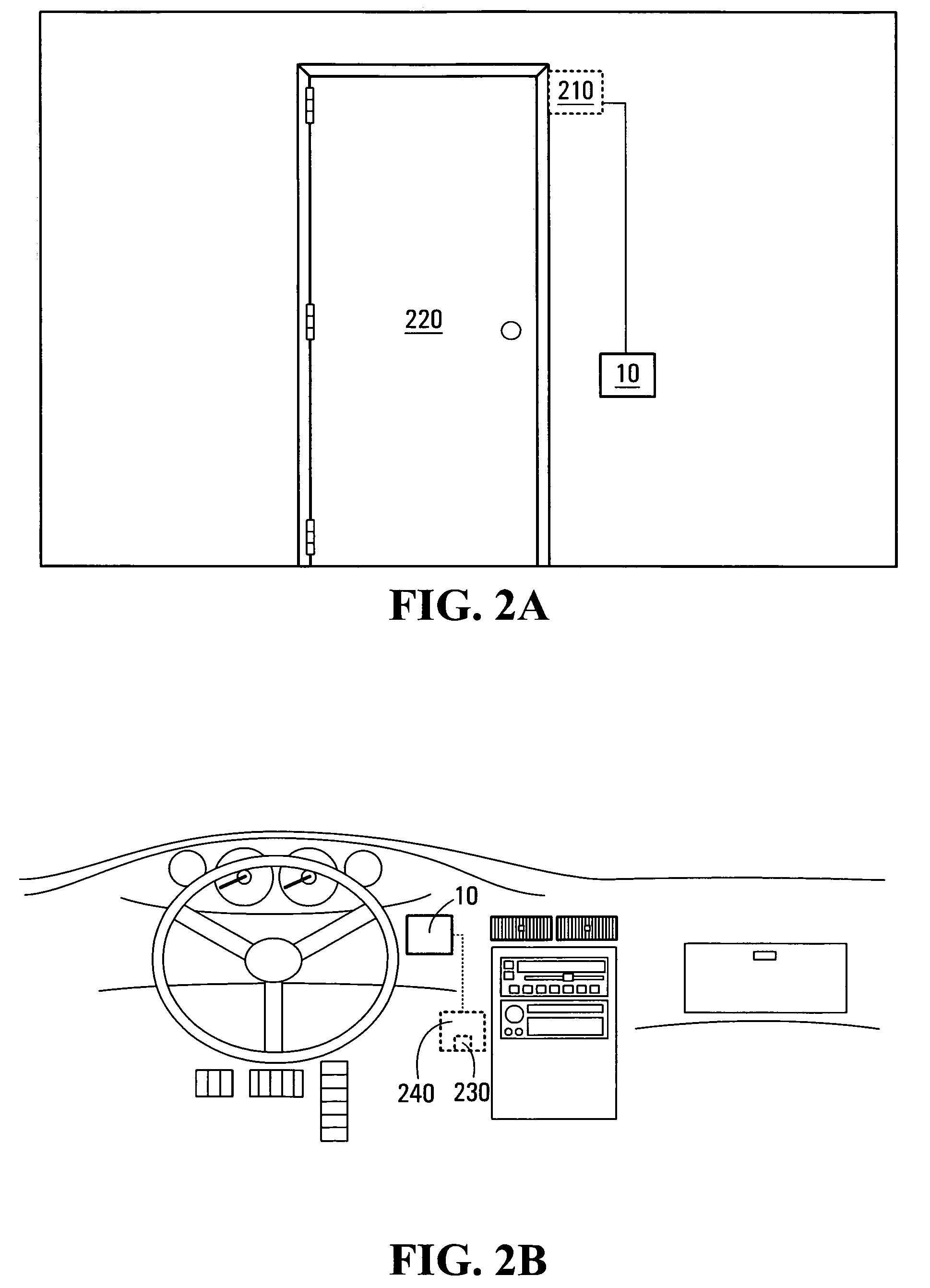
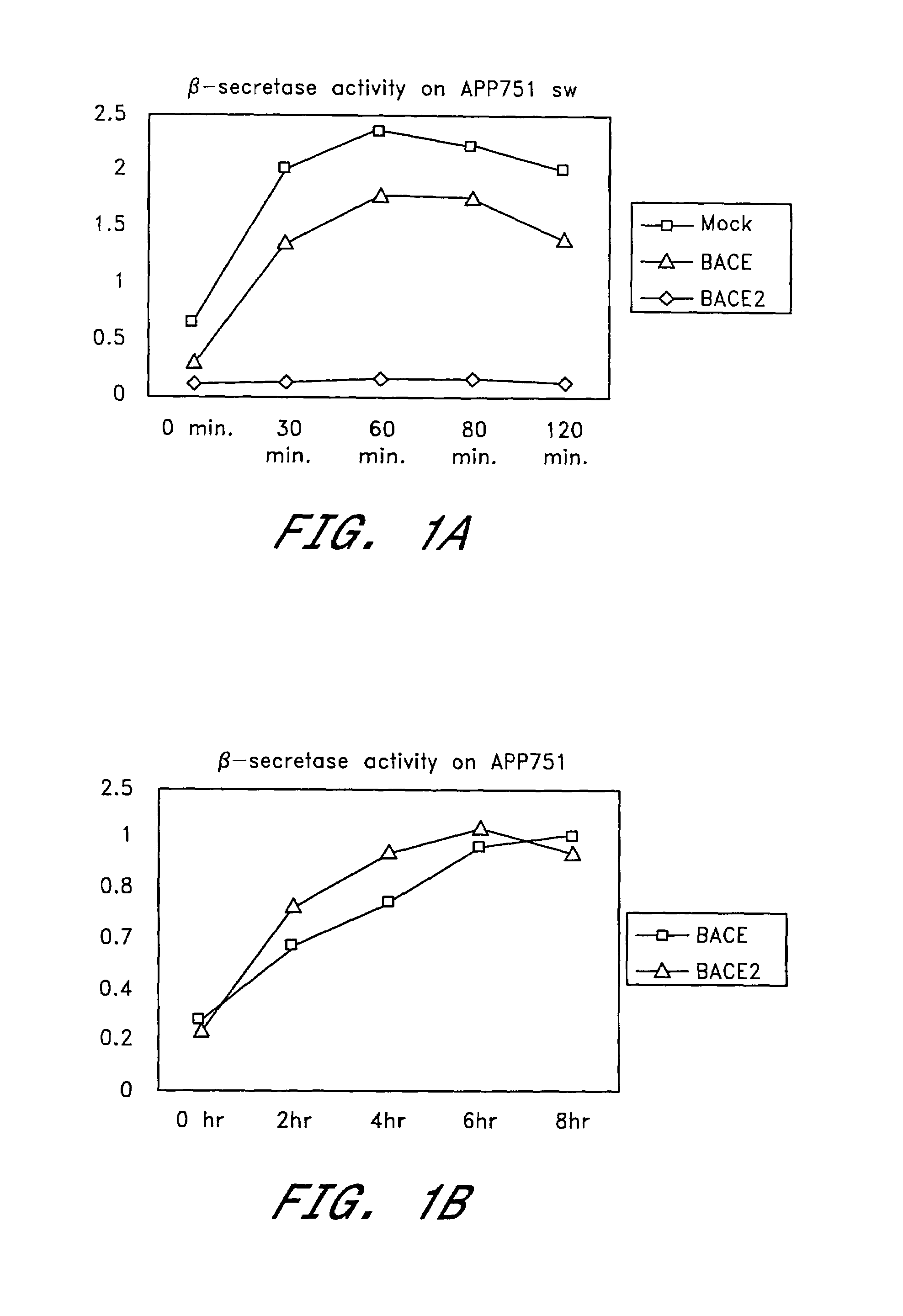
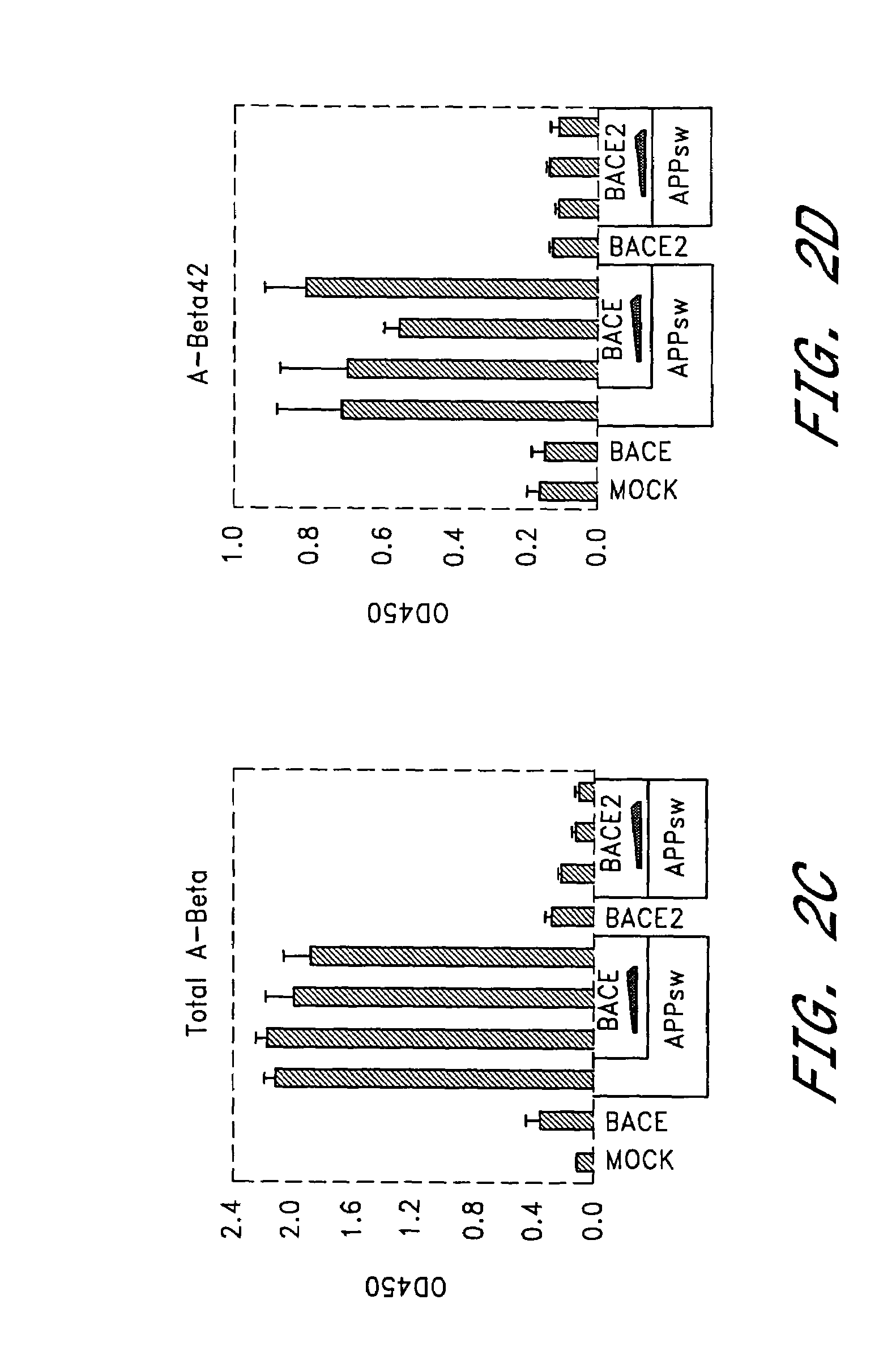
Inhibition of Abeta production by beta-secretase BACE2
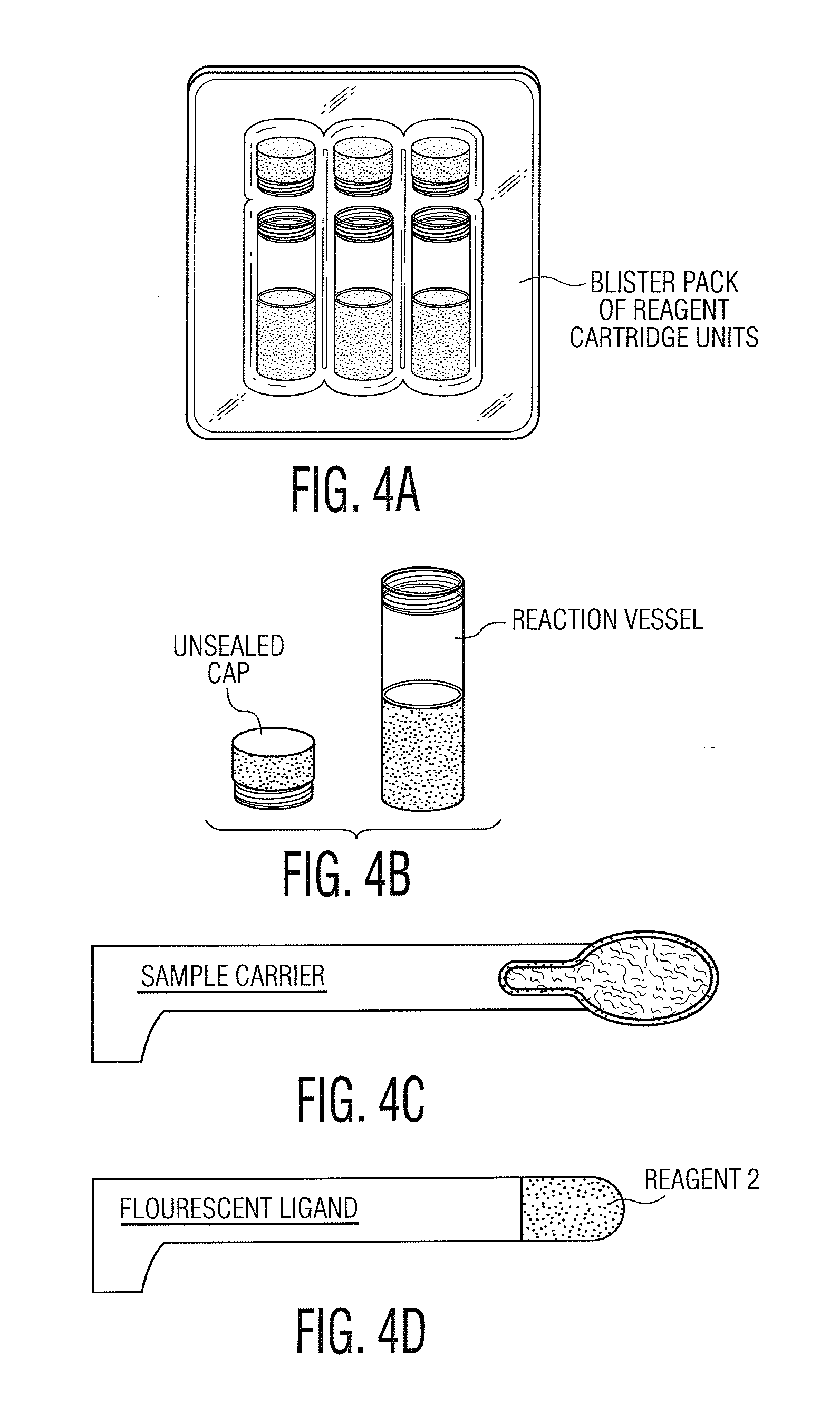
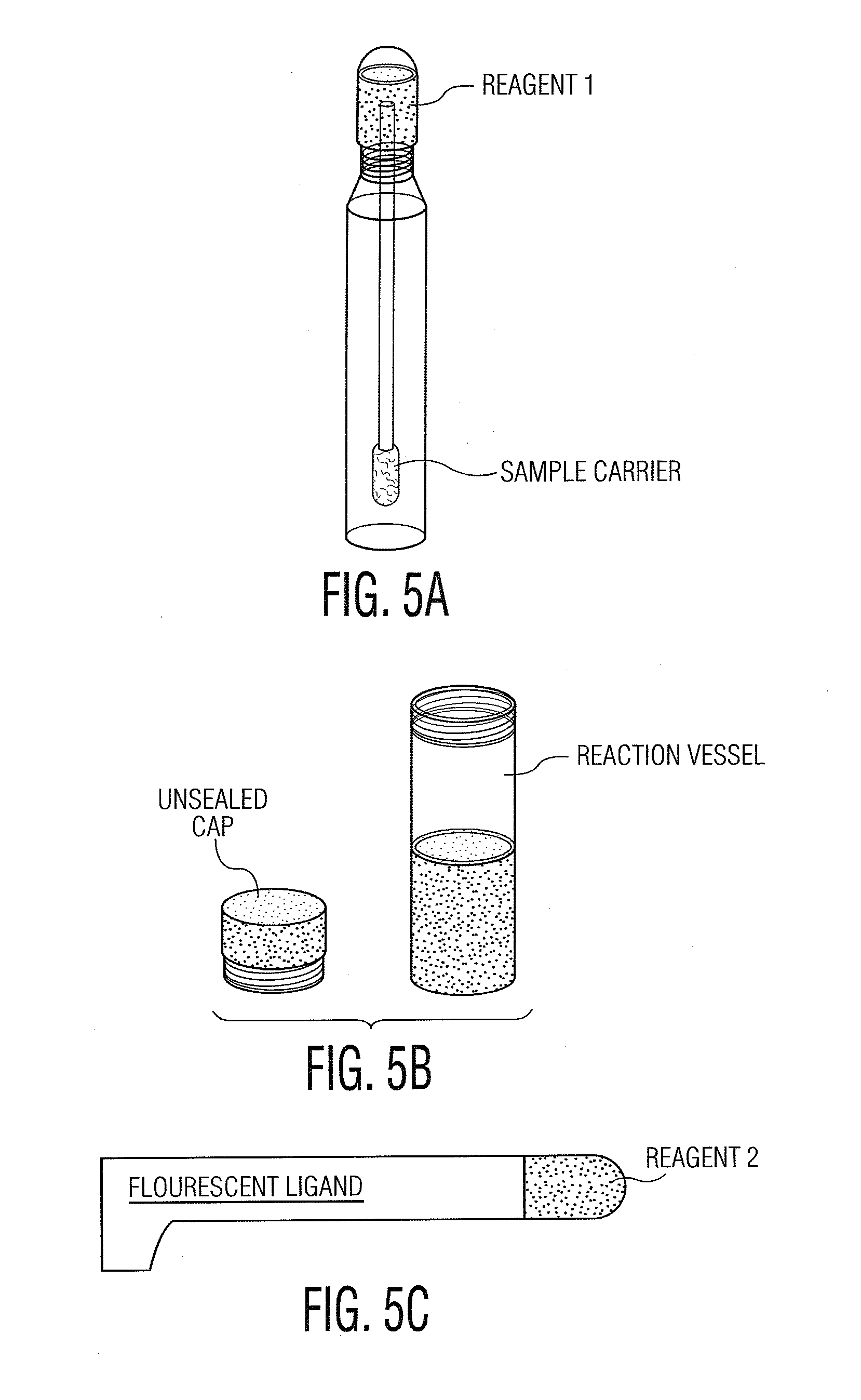
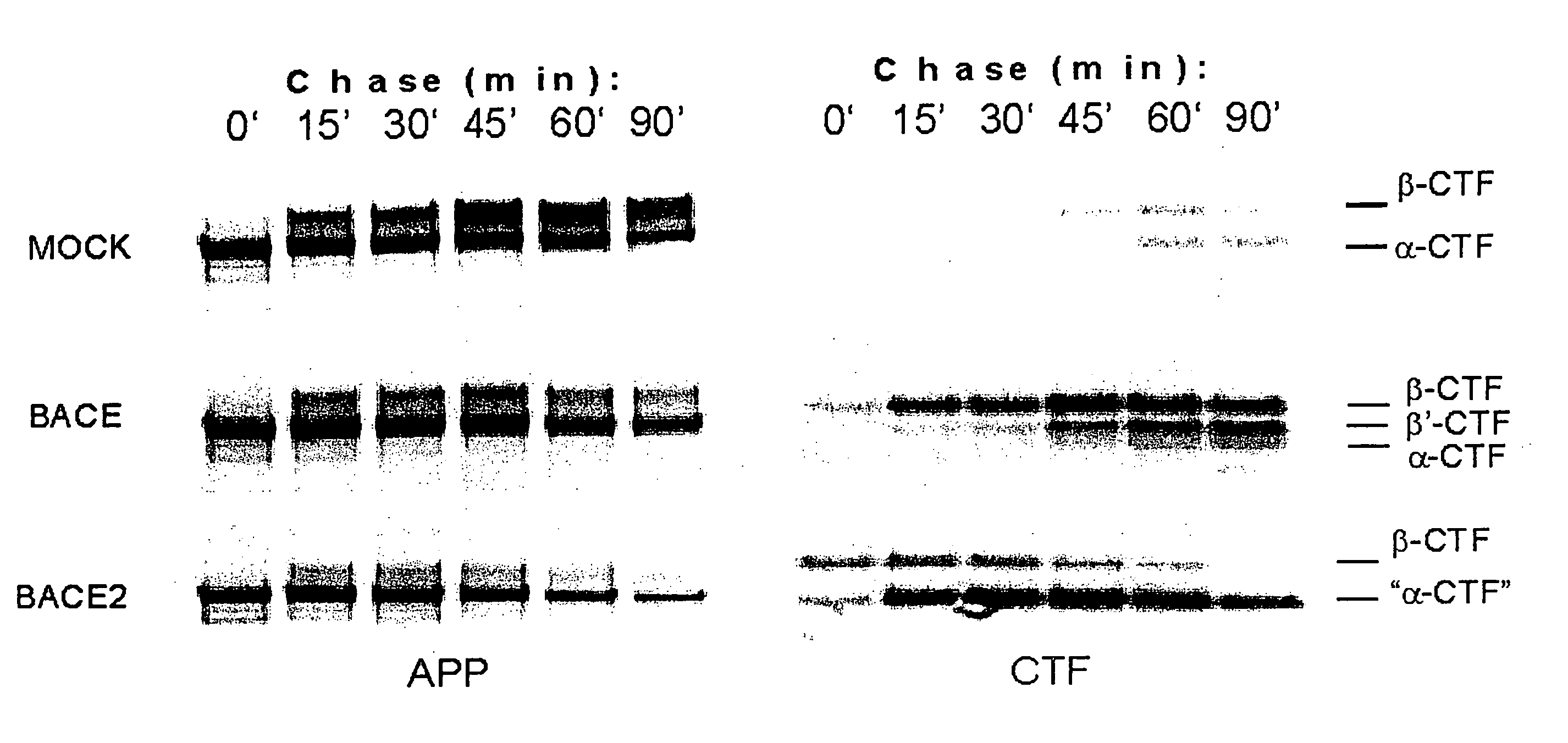
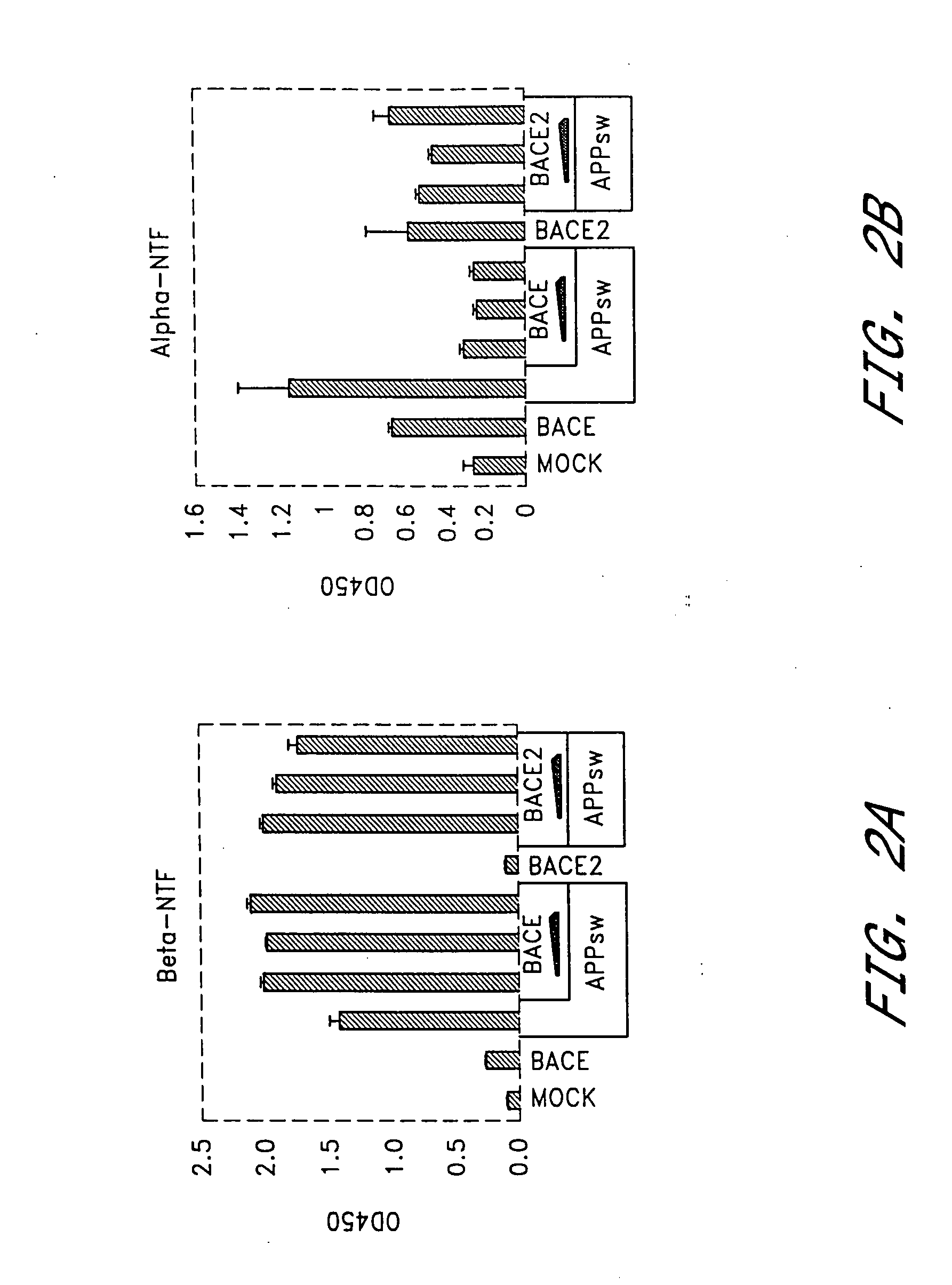
InactiveUS7183070B2Suppressed Aβ productionPromoting alternative non-amyloidogenic APP processing pathwayCompound screeningNervous disorderΒ amyloidAmyloid deposition
The present invention is based on the findings that BACE2, a homolog of β-secretase BACE, is able to stimulate processing of APP in a non-amyloidogenic pathway, thereby suppressing the level of Aβ. Accordingly, the present invention provides methods and means for the identification and use of modulators of this unique activity of BACE2 to suppress Aβ production. The compounds identified using the methods and means provided herein may be used as potential candidates for the treatment of Alzheimer's disease and other neurological diseases by reducing β-amyloid deposit formation.
Owner:SCIOS
Method of, system for, and computer program product for providing automatic identification of a computer program code candidate for web deployment or a stored procedure
InactiveUS6931630B1Good user interfaceImprove usabilitySoftware maintainance/managementSpecific program execution arrangementsTheoretical computer scienceSource code
Computer program code which is a candidate for Web enablement or stored procedures is identified. Source code corresponding to computer program code is scanned and parsed to determine static information concerning the computer program code. The static information is stored in a database. Dynamic information concerning the computer program code during an execution of the computer program code is also collected and stored in the database. Responsive to the static information and dynamic information stored in the database, relationships and dependencies are then developed and stored in the database. The database may then be queried to produce a set of potential candidates of computer program code meeting a constraint of the query. If insufficient candidates are returned by the query, then the query constraint may be relaxed, and the query repeated.
Owner:IBM CORP
Computer algorithm and method for facilitating the networking of individuals
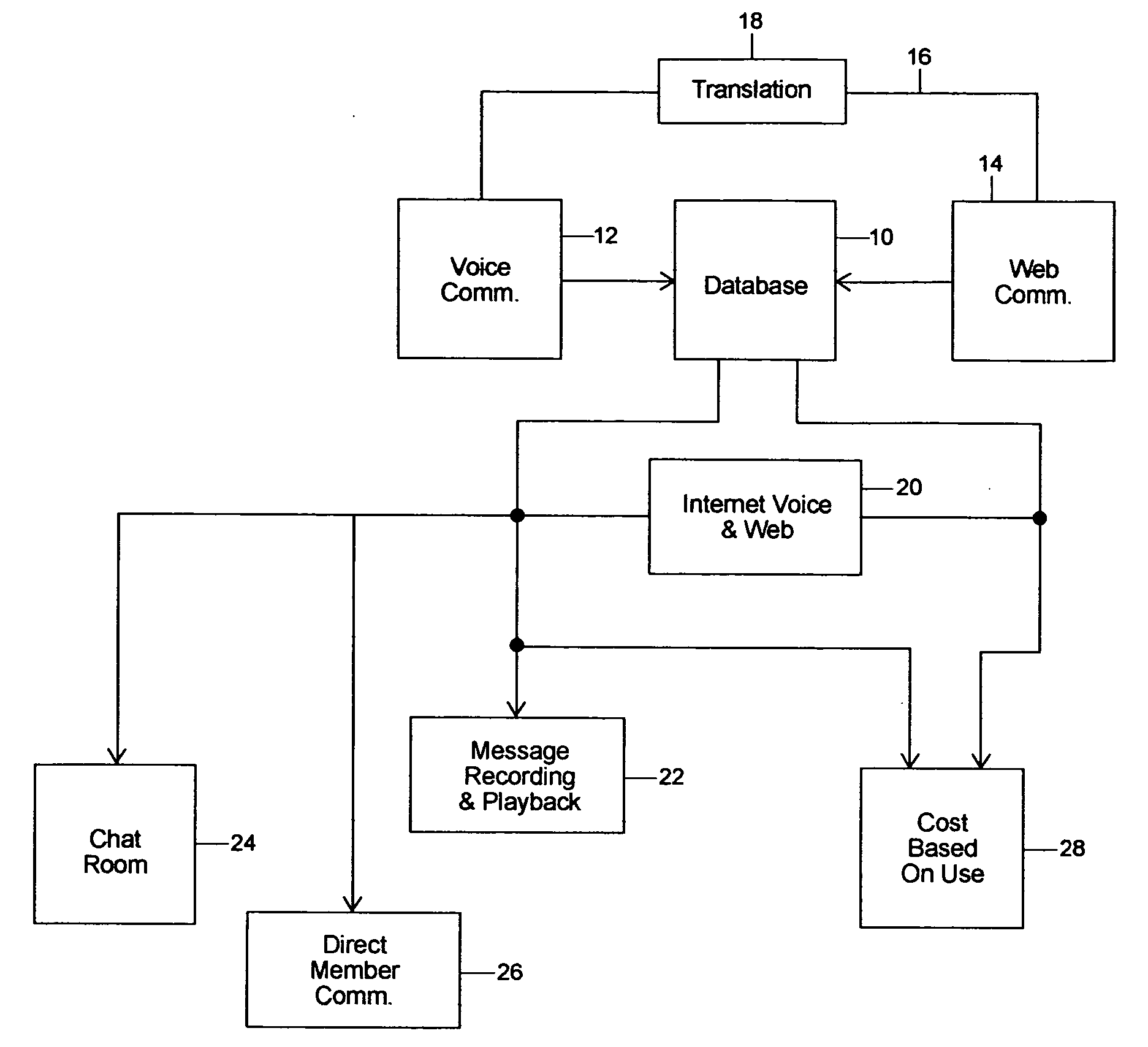
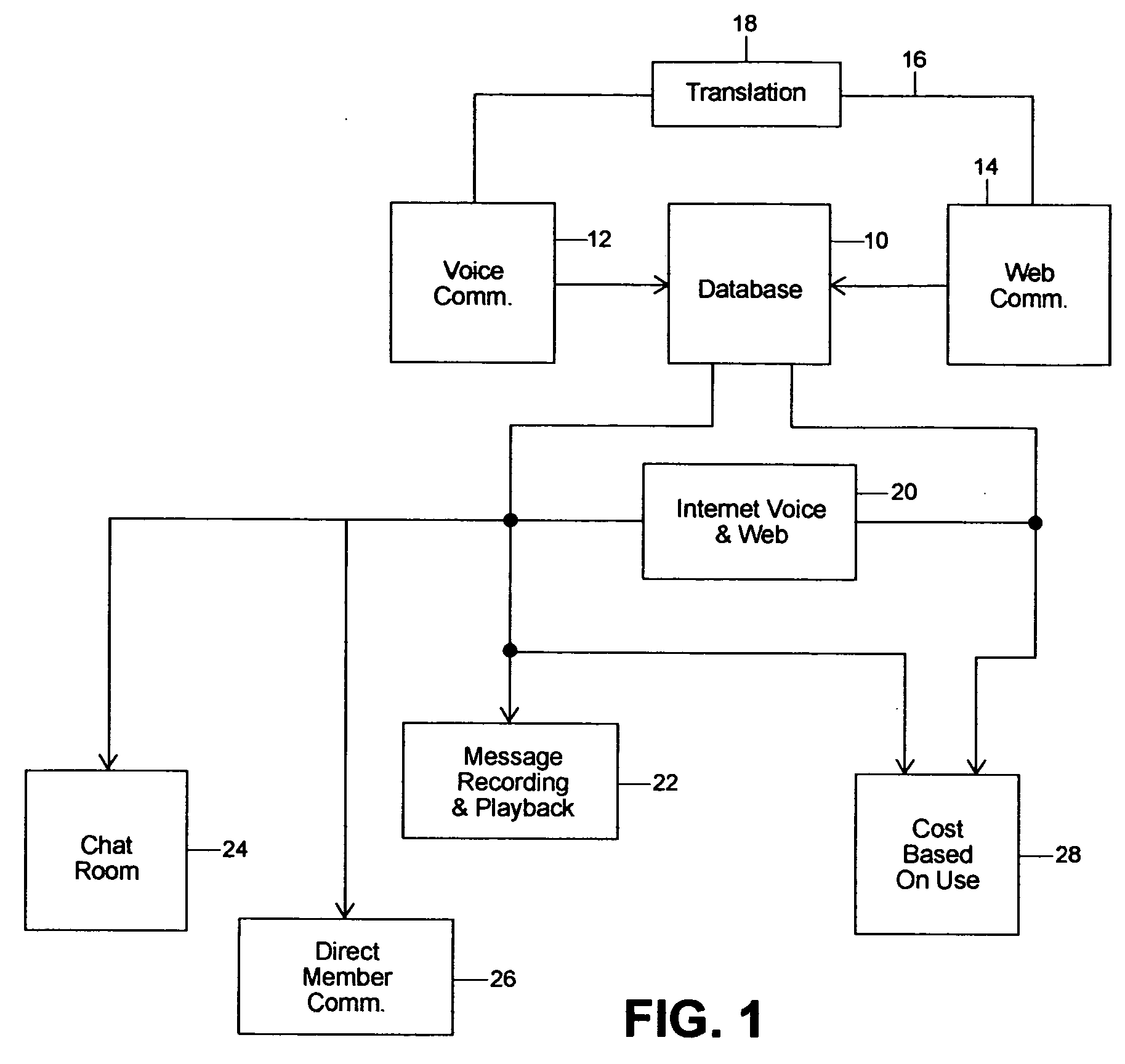
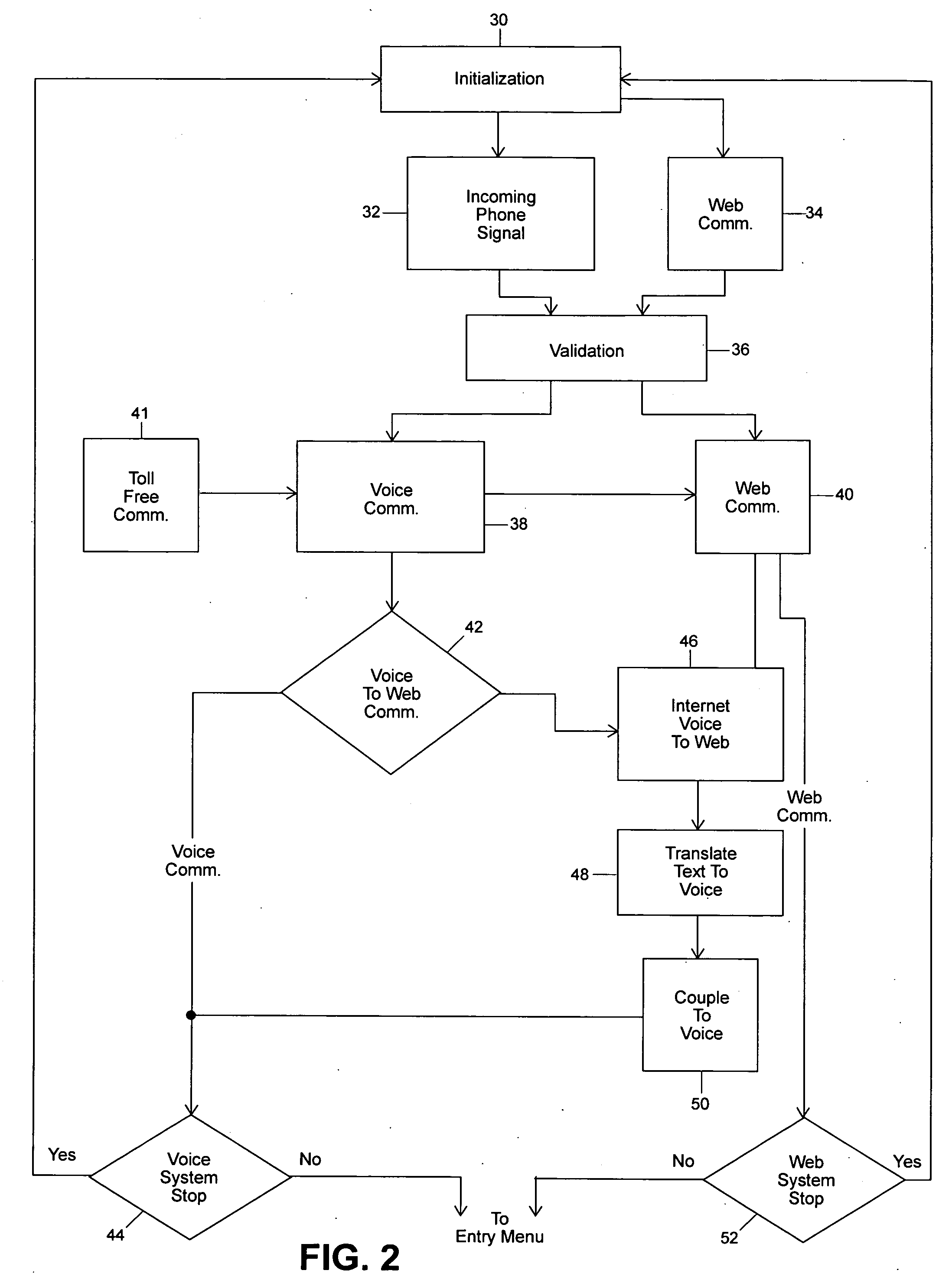
InactiveUS20040184445A1Easy to useSpecial service provision for substationTelephone data network interconnectionsVoice communicationDirect communication
An algorithm and method for using computer services for facilitating the meeting and communication of individuals in a social networking environment. The algorithm and method allow for individuals using differing modes of communication, for example one using voice communication and another using computer communication, to be in direct communication with one another. The algorithm and method also facilitate direct communication when one party locates a potential candidate and is desirous of being in direct communication with that candidate. Message recording and playback are also facilitated as well as other advantages arising from the use of the algorithm and software program derived therefrom as well as the method of the invention.
Owner:BURNE JEFFREY K
Methods for matching metadata from disparate data sources
InactiveUS20100185637A1Well formedDigital data processing detailsSpecial data processing applicationsData sourceMatch rule
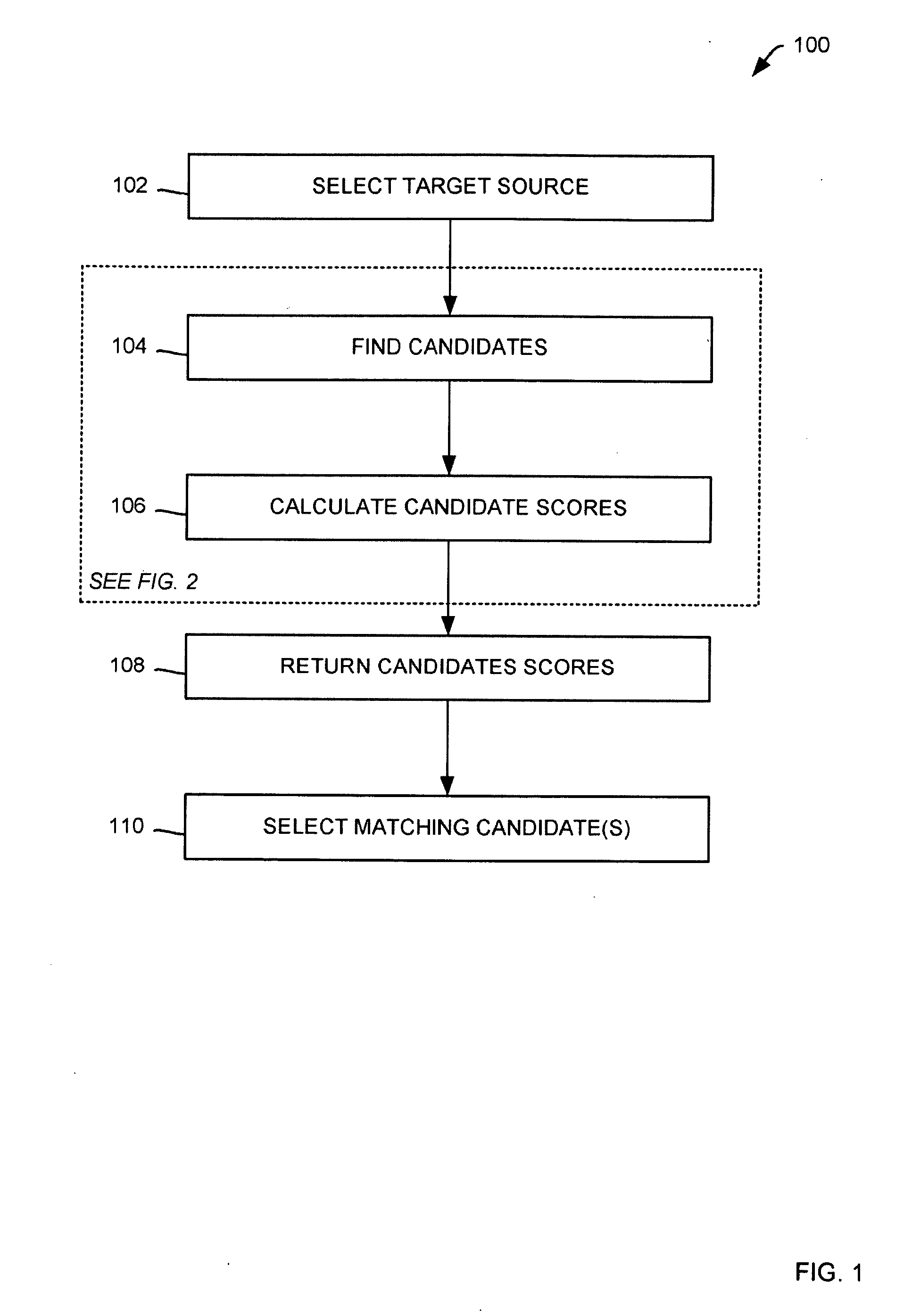
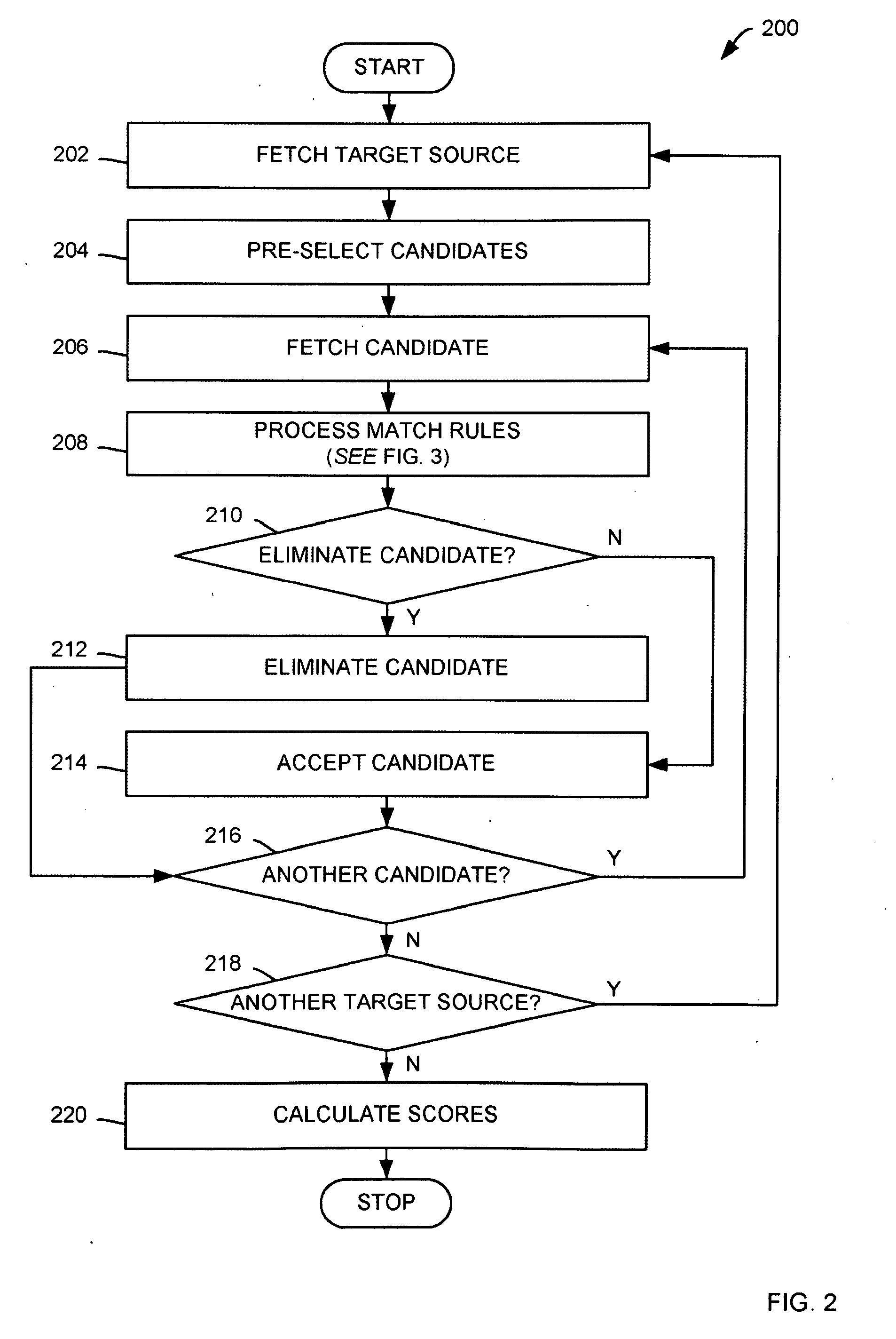
Methods for matching a candidates with a target utilizing extract, transform and load (ETL) metadata utilizing a computer, the candidates originating from a number of secondary data sources are presented including: causing the computer to receive the target from a target data source; causing the computer to fetch the candidates from the number of secondary data sources; causing the computer to process match rules, the match rules configured for determining whether the candidates match with the target, where the ETL metadata provides data for the processing; if the number of match rules determines a potential candidate match, causing the computer to score the potential candidate match utilizing a weighting method, the weighting method corresponding with a degree of importance of the match, where the potential candidate match corresponds with one of candidates; and causing the computer to display the potential candidate match.
Owner:IBM CORP
Automated user chat application that creates chat sessions based on known user credentials and behavioral history
Owner:NUTRASPACE
System and method for providing testing and matching in a network environment
An apparatus for providing a feature in a network environment is provided that includes a central web site operable to interface with one or more end users and to manage information related to one or more of the end users. The central web site offers a test that includes a set of questions for one or more of the end users to complete, whereby the central web site is operable to process answers for the test in order to offer potential candidates for the end users to evaluate.
Owner:MATCH GRP LLC
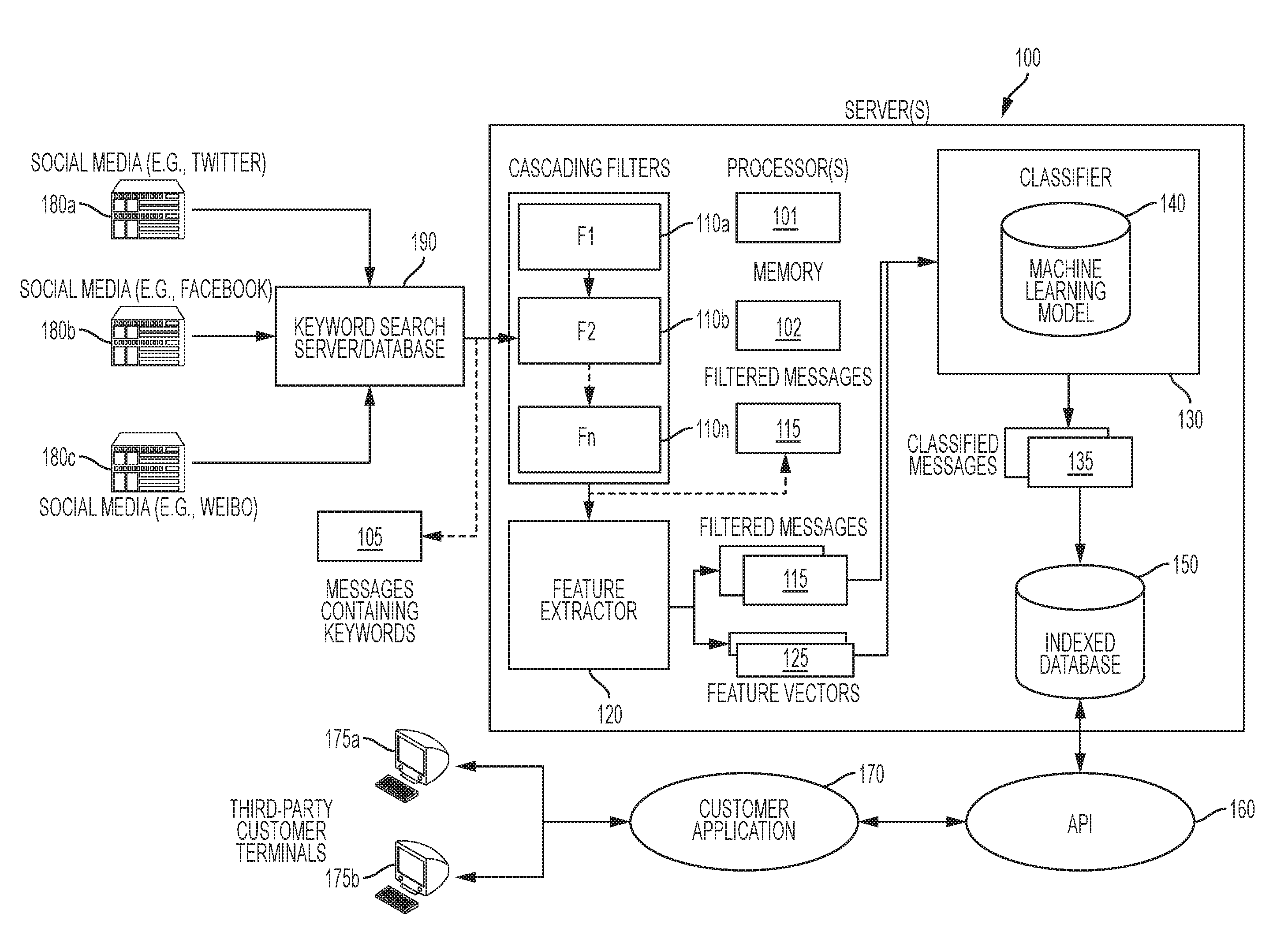
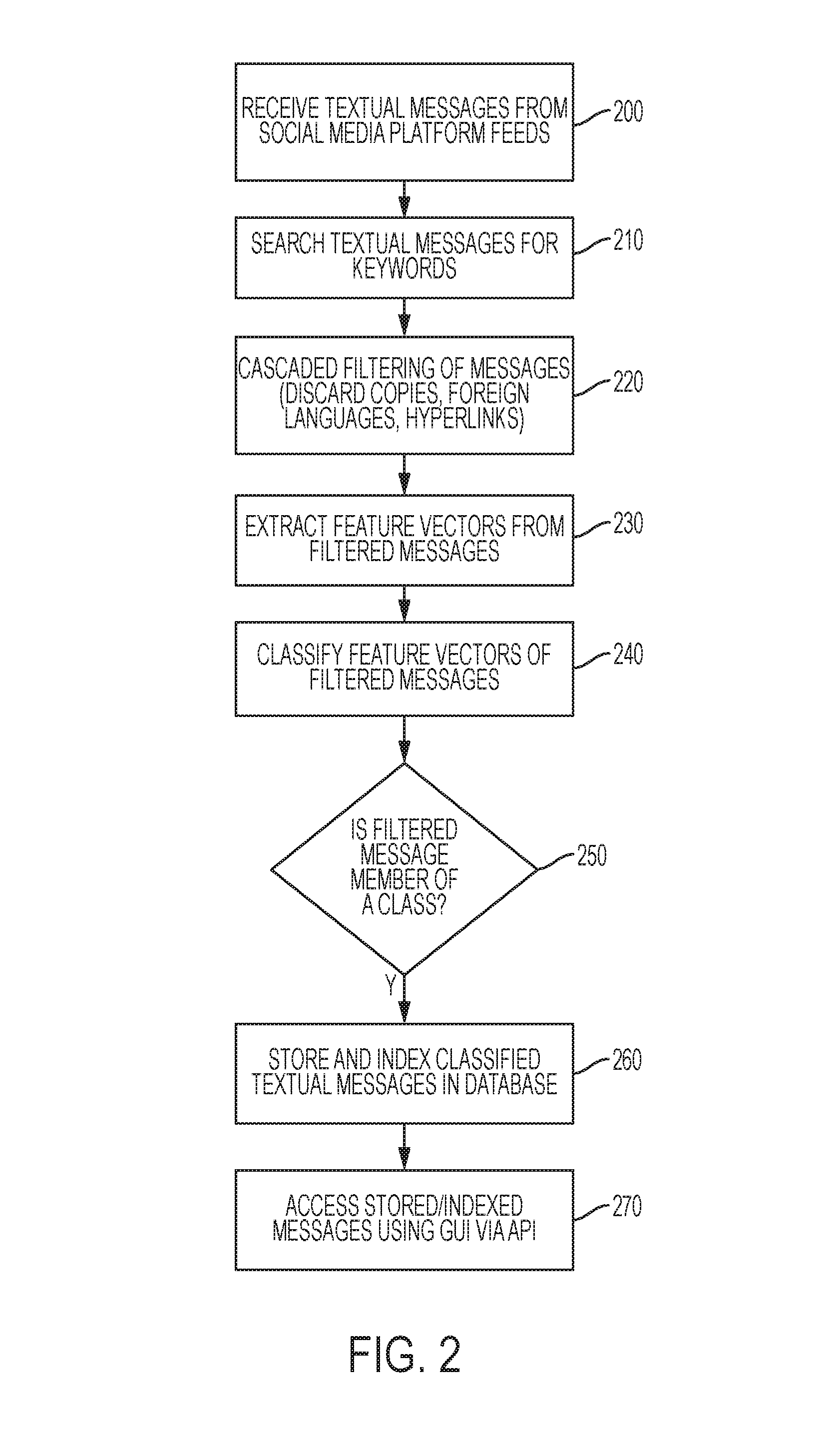
Pharmacovigilance systems and methods utilizing cascading filters and machine learning models to classify and discern pharmaceutical trends from social media posts
InactiveUS20160092793A1Medical communicationDigital data information retrievalSocial mediaSide effect
Systems and methods for utilizing filters to reduce an incoming stream of textual messages to a smaller subset of potentially relevant textual messages, and using trained machine learning models to analyze and classify the content of such textual messages. Analyzed messages that belong to a relevant class as determined by the machine learning model are stored in a database, giving users the ability to determine and analyze trends from the subset of messages, such as adverse side effects caused by pharmaceuticals or the efficacy of pharmaceuticals. Relationships between the side effects caused by different pharmaceuticals can be used to predict potential candidates for drug repositioning.
Owner:THOMSON REUTERS GLOBAL RESOURCES UNLIMITED CO
Music searching system and method
InactiveUS20090254554A1Metadata audio data retrievalUsing non-detectable carrier informationAnalysis dataSearch terms
A music searching system and method conducting a metadata search of music based on an entered search term. Music identified from the metadata search is used as seed music to identify other acoustically complementing music. Acoustic analysis data of the seed music is compared against acoustic analysis data of potential candidates for determining whether they are acoustically complementing music. The acoustically complementing music is then displayed to the user for listening, downloading, or purchase.
Owner:GRACENOTE
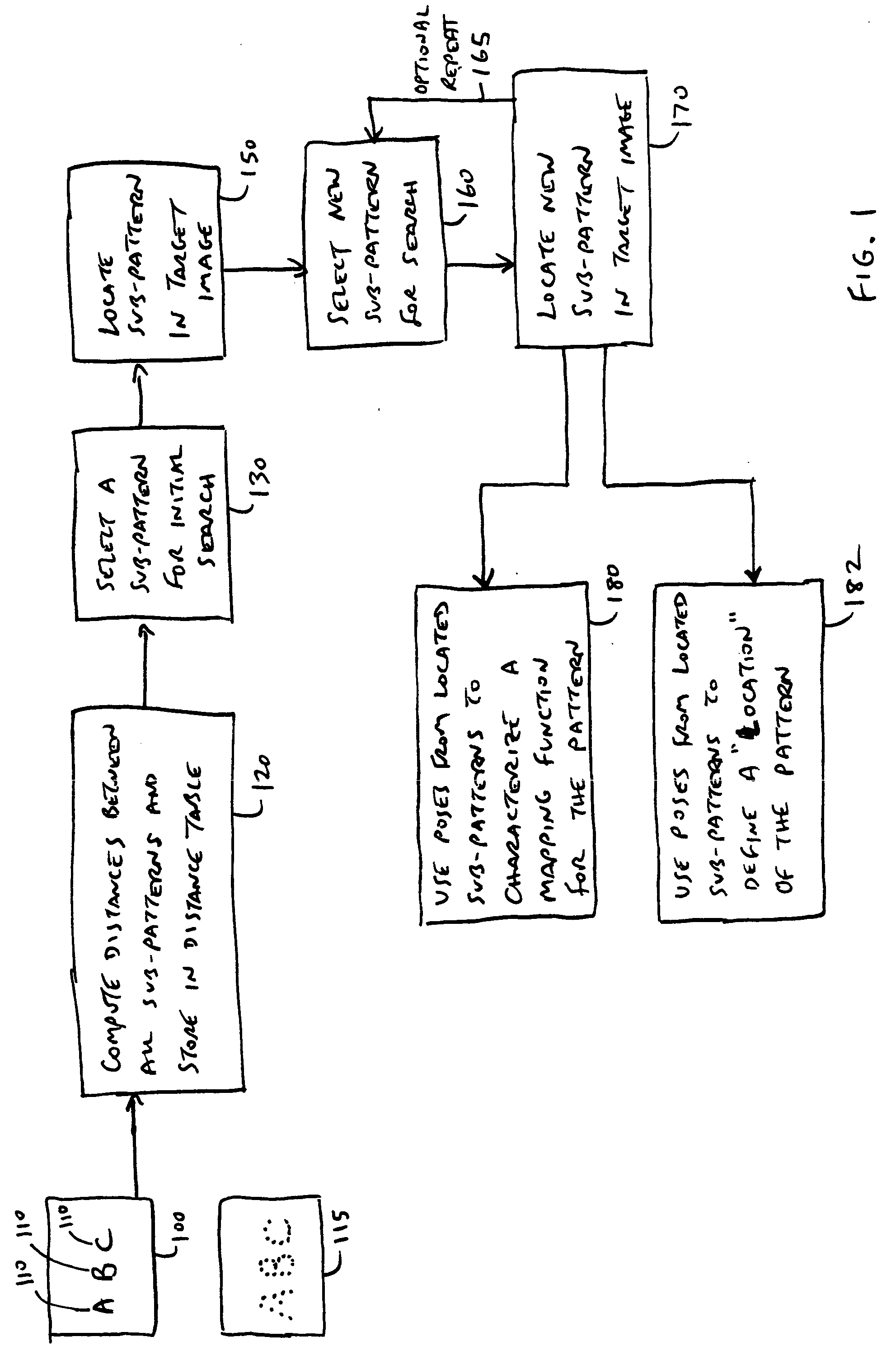
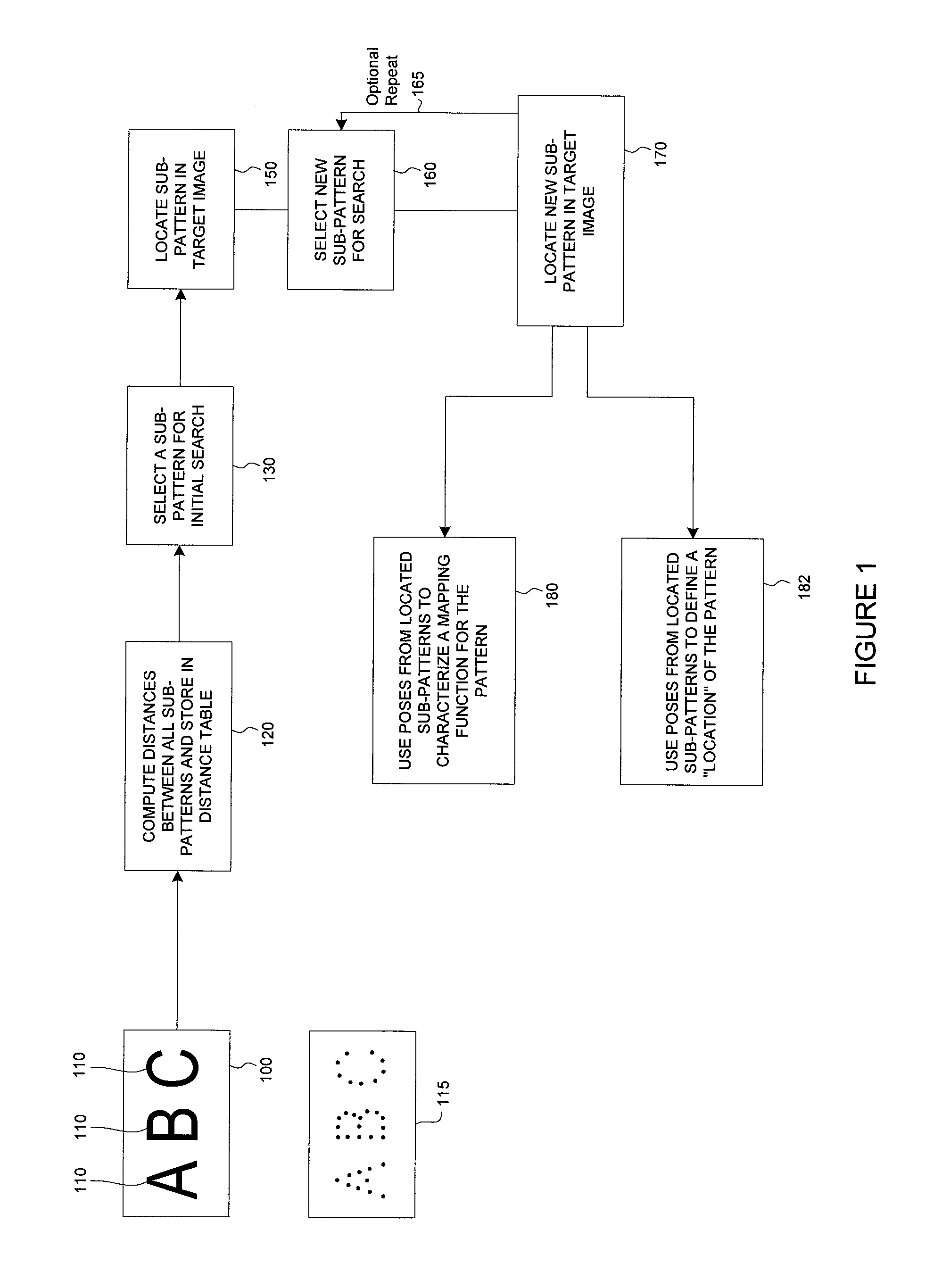
Methods for finding and characterizing a deformed pattern in an image
ActiveUS20050018904A1Reduce in quantityQuick decisionImage analysisCharacter and pattern recognitionPotential candidateFeature based
A method is disclosed for finding a deformed pattern in an image using a plurality of sub-patterns. By advantageously restricting sub-pattern search ranges, search speed is improved, and the incidence of spurious matches is reduced. The method also quickly decides which sub-pattern result, of several potential candidates, is most likely to be the correct match for a deformed sub-pattern. Also, a method is provided for characterizing a deformed pattern in an image by using results from feature-based search tools to create a mapping that models the deformation of the pattern. A transform, selectable by a user, is fit to the results from the search tools to create a global deformation mapping. This transformation is fit only to feature points derived from matches resulting from successful sub-pattern search, without including data from areas of the pattern that were blank, not matched, or otherwise didn't contain information about the pattern's distorted location.
Owner:COGNEX TECH & INVESTMENT
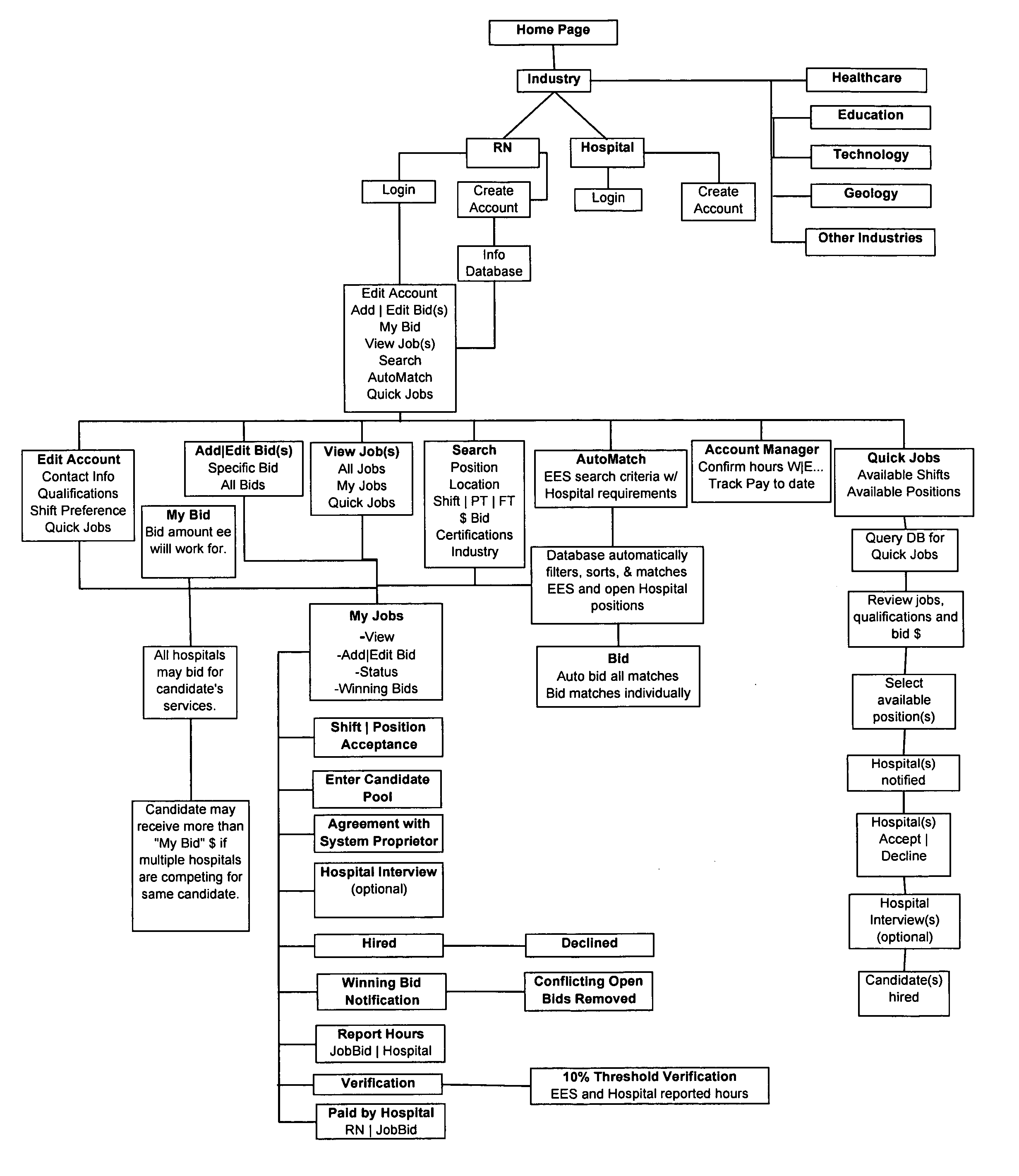
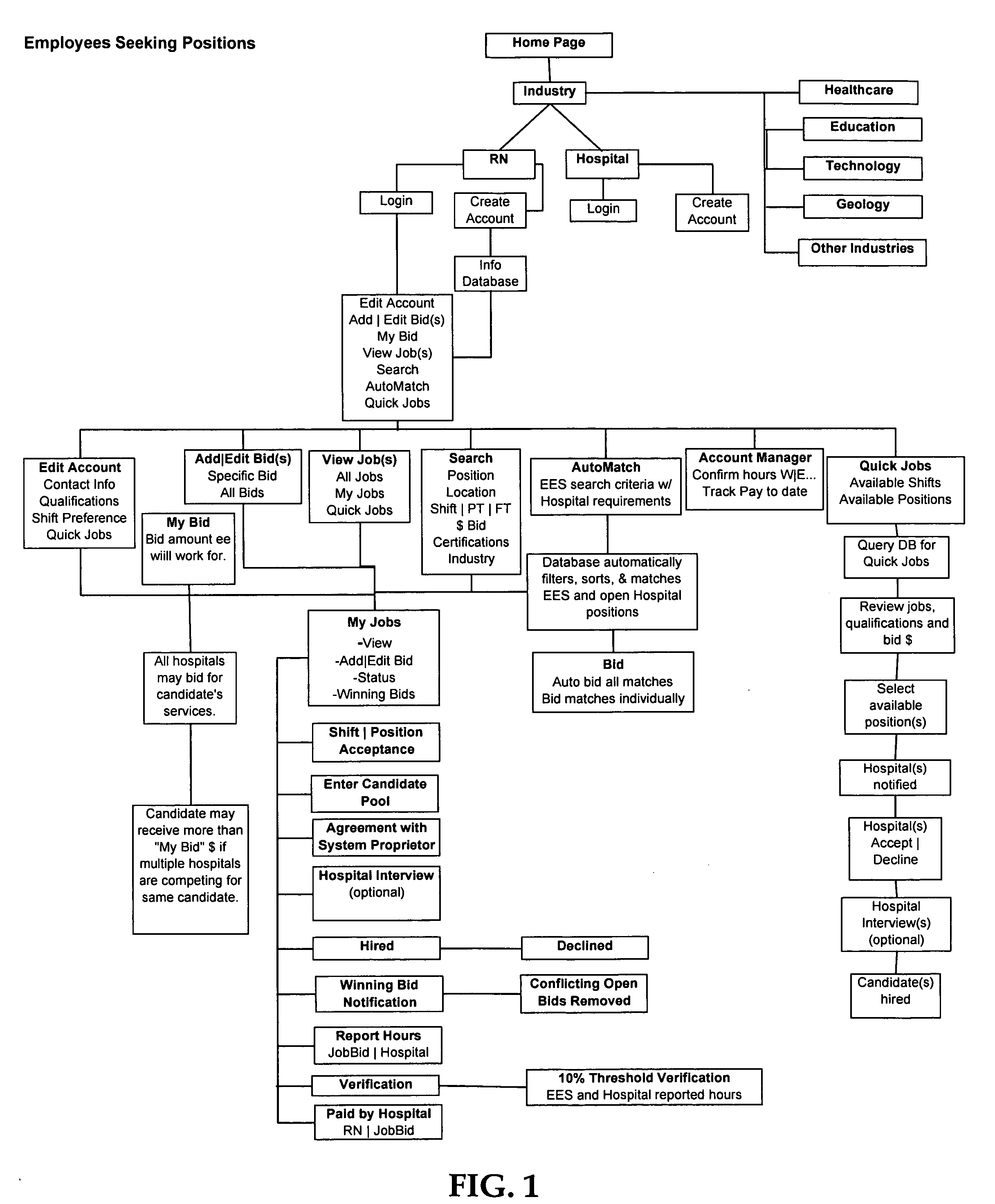
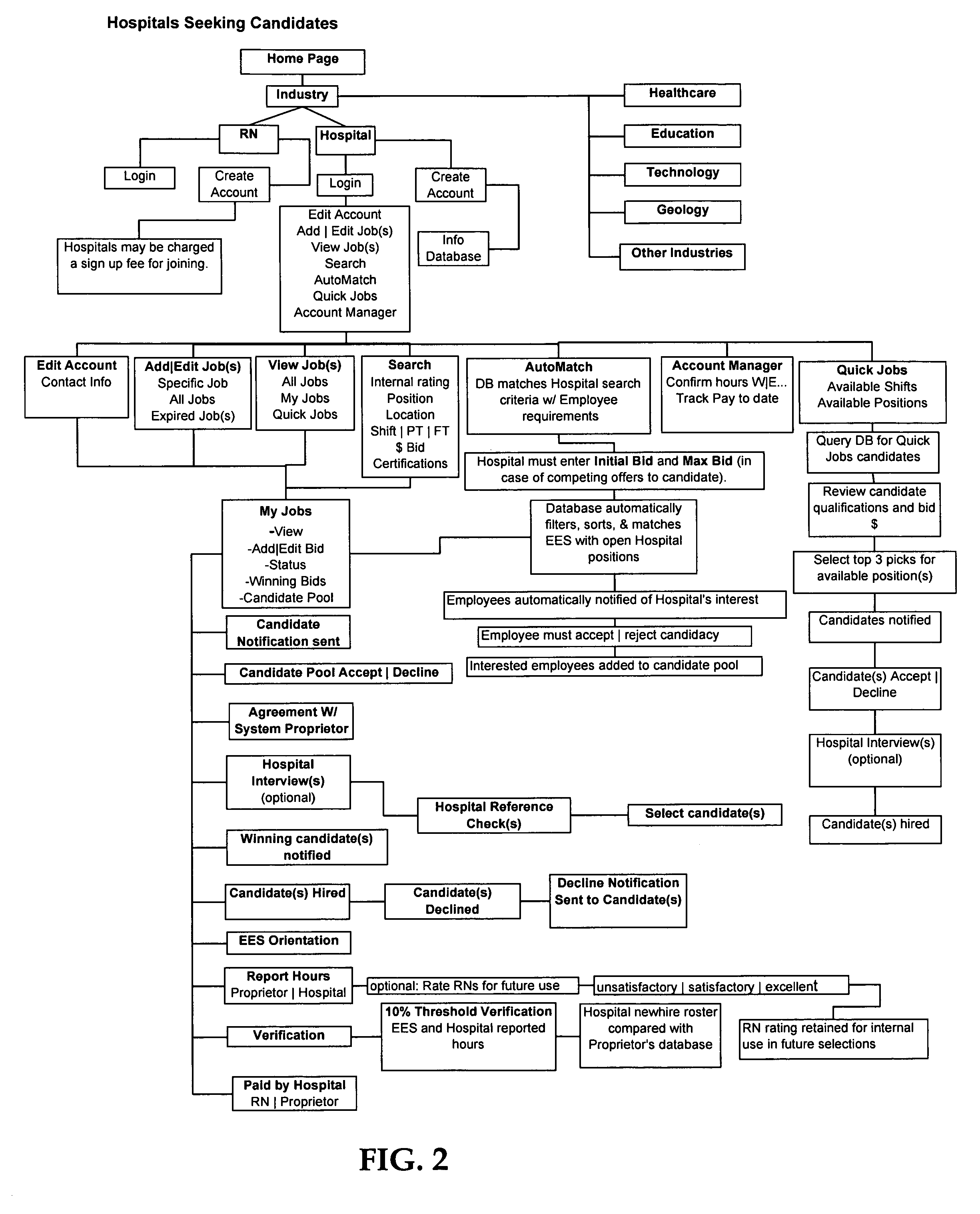
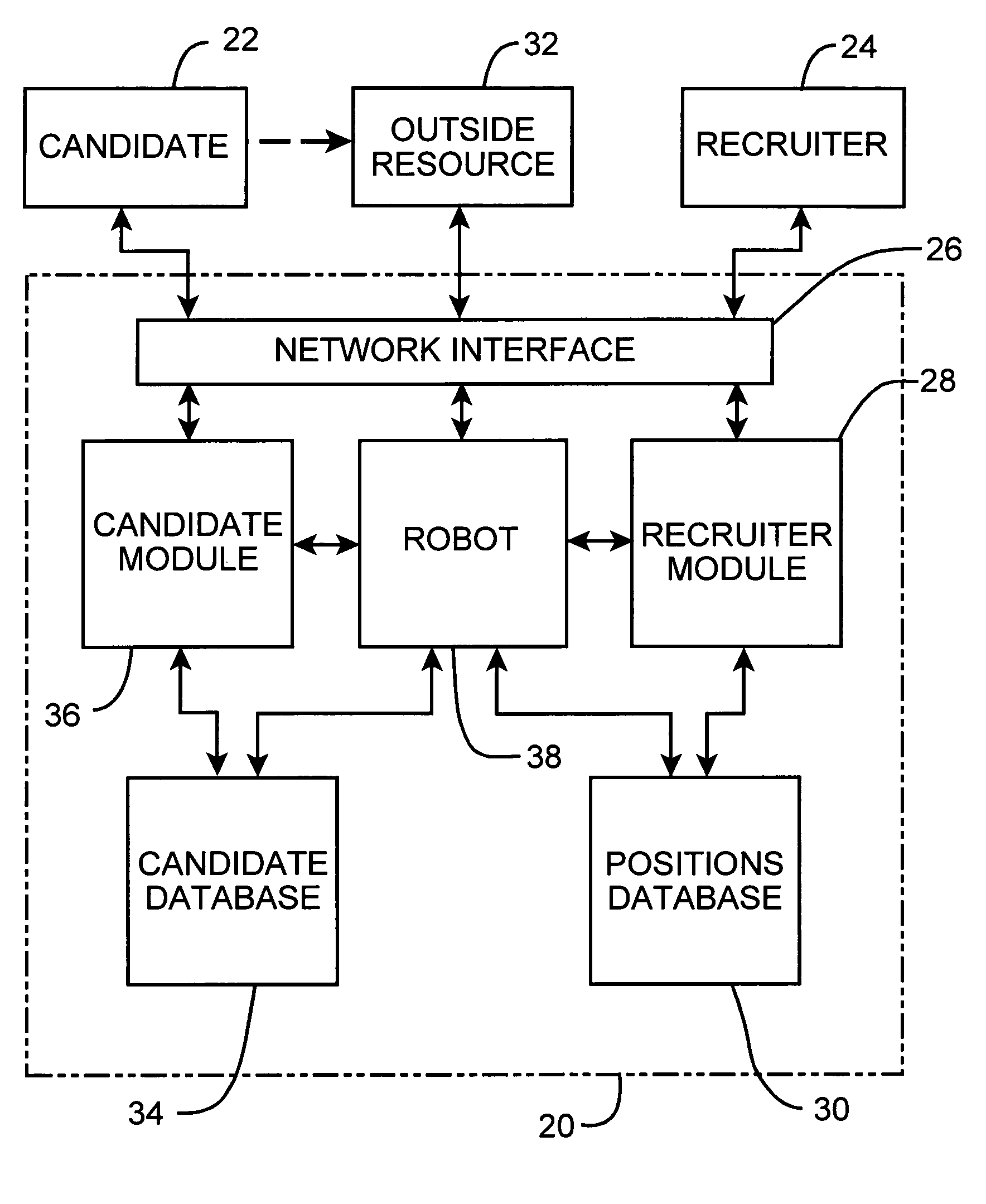
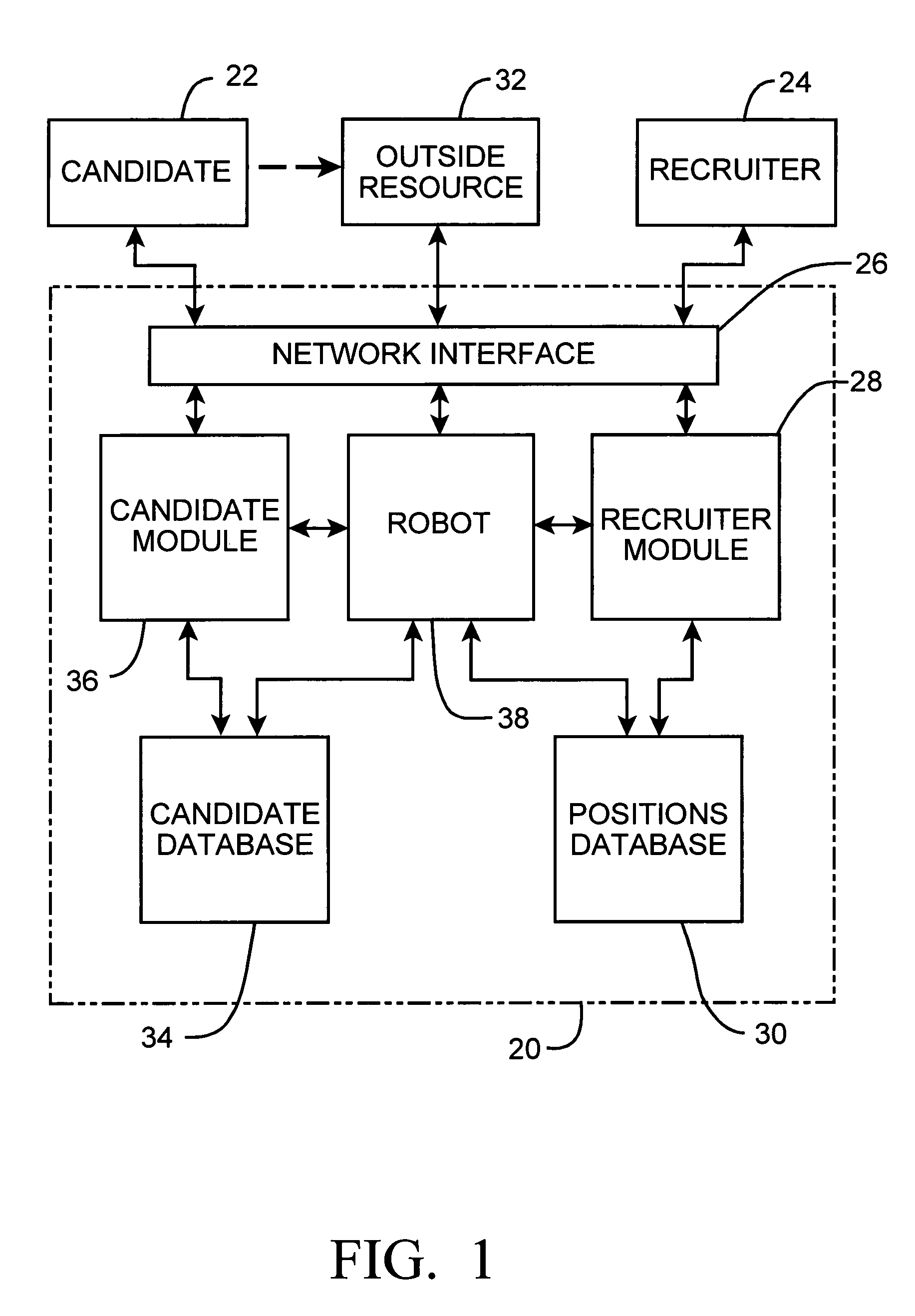
Method and system for recruiting for employee positions and employees bidding for the same
InactiveUS20060155636A1Improve automationImprove efficiencyFinanceCommerceHuman interactionThe Internet
This method and system provides for an organization to electronically post an open position and for potential candidates to bid on those positions through the use of a “blind bid” system. In addition, the system allows organizations to query a database for potential candidates and directly invite them to bid on available positions, or directly request them to fill available positions for a specified hourly wage rate. The system is highly automated and efficient, requiring far less human interaction to recruit potential candidates. The system also utilizes modern technology such as e-mail, text messaging and the Internet to lessen the need to place recruitment advertisements in traditional media. Qualified candidates are able to quickly find positions and place a bid to fill that position. The candidate registers on the system and submits a requested wage rate with the bid such that the organization may compare the candidates' requisite qualifications and wage rates and choose the candidate that is acceptable to the hiring organization.
Owner:SWALLOWS
Methods for finding and characterizing a deformed pattern in an image
ActiveUS7190834B2Reduce in quantityQuick decisionImage analysisCharacter and pattern recognitionPotential candidateFeature based
A method is disclosed for finding a deformed pattern in an image using a plurality of sub-patterns. By advantageously restricting sub-pattern search ranges, search speed is improved, and the incidence of spurious matches is reduced. The method also quickly decides which sub-pattern result, of several potential candidates, is most likely to be the correct match for a deformed sub-pattern. Also, a method is provided for characterizing a deformed pattern in an image by using results from feature-based search tools to create a mapping that models the deformation of the pattern. A transform, selectable by a user, is fit to the results from the search tools to create a global deformation mapping. This transformation is fit only to feature points derived from matches resulting from successful sub-pattern search, without including data from areas of the pattern that were blank, not matched, or otherwise didn't contain information about the pattern's distorted location.
Owner:COGNEX TECH & INVESTMENT
Method and apparatus for performing compiler transformation of software code using fastforward regions and value specialization
InactiveUS7039909B2Software engineeringSpecific program execution arrangementsControl flowComputer science
A method and apparatus for providing compiler transformation of code using regions with simplified data and control flow and value specialization are described. In one embodiment, the method includes identifying in the code a plurality of potential candidates for value specialization, selecting a group of candidates from the plurality of potential candidates based on a value profile associated with each potential candidate, and determining specialized data for each selected candidate using a corresponding value profile. The method further includes forming a plurality of optimized regions based on corresponding specialized data. Each optimized region includes one or more selected candidates.
Owner:INTEL CORP
Method, system, and storage device for job posting, matching, rating, and referral
A job posting method, system, and storage device which allows users to create one or more talent networks each containing one or more connections, create job postings that trickle down to other users according to a set of rules, a referral system for rewarding users who recommend candidates for the job postings, and a recommendation system which allows both job posters and job seekers to have the system recommend potential candidates or jobs, as the case may be.
Owner:VILLASENOR FELIPE
System and Method for Diagnosis and Treatment
ActiveUS20120201747A1Good curative effectPromote resultsOrganic active ingredientsPeptide/protein ingredientsTreatment effectPhysiology
This invention relates to a low cost rapid response diagnostic system to determine cortisol levels in patients selected as potential candidates for GCR (glucocorticoid receptor) antagonist therapy utilizing a GCR antagonist, such as ORG 34517. The rapid, sensitive, and inexpensive test can be used to determine patients who have non-normal cortisol production or disordered circadian rhythms as a method for selecting subjects for GCR antagonist therapy for whom it is likely to have beneficial and / or therapeutic effects, and can also be used to monitor changes in cortisol levels in response to treatment.
Owner:POP TEST ONCOLOGY LIMITED LIABILITY
Employment recruiting system
Recruiting or the process of locating and qualifying potential candidates for employment is largely a manual process consuming significant resources. The employment recruiting system automates many of the services related to employment recruiting. Position advertisements and candidate resumes are stored in computer searchable data bases. A data processing device automatically searches the data base containing candidate resumes in response to a search parameter associated with a position advertisement. The system automatically contacts screens candidates.
Owner:NORTHWEST SOFTWARE
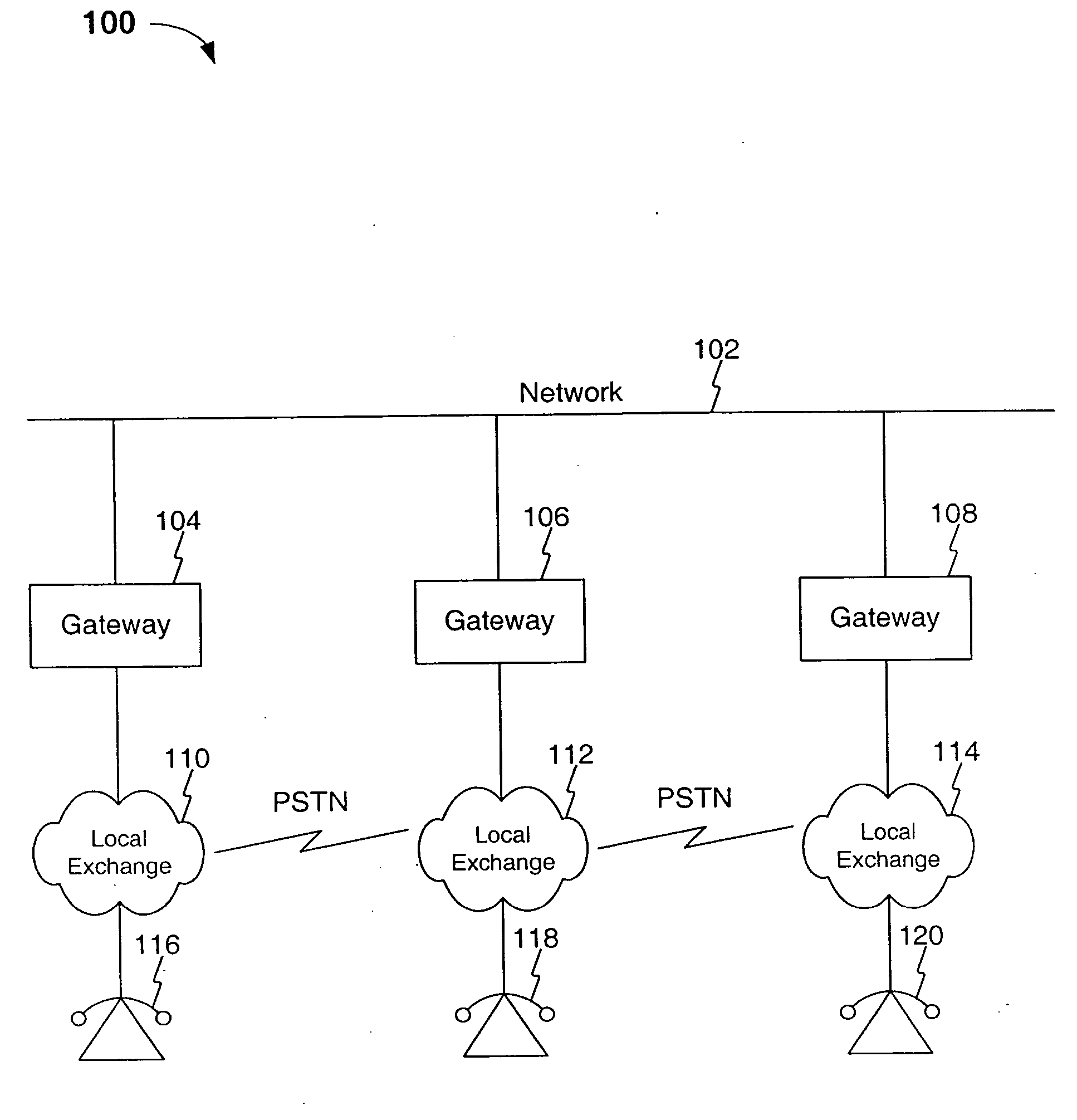
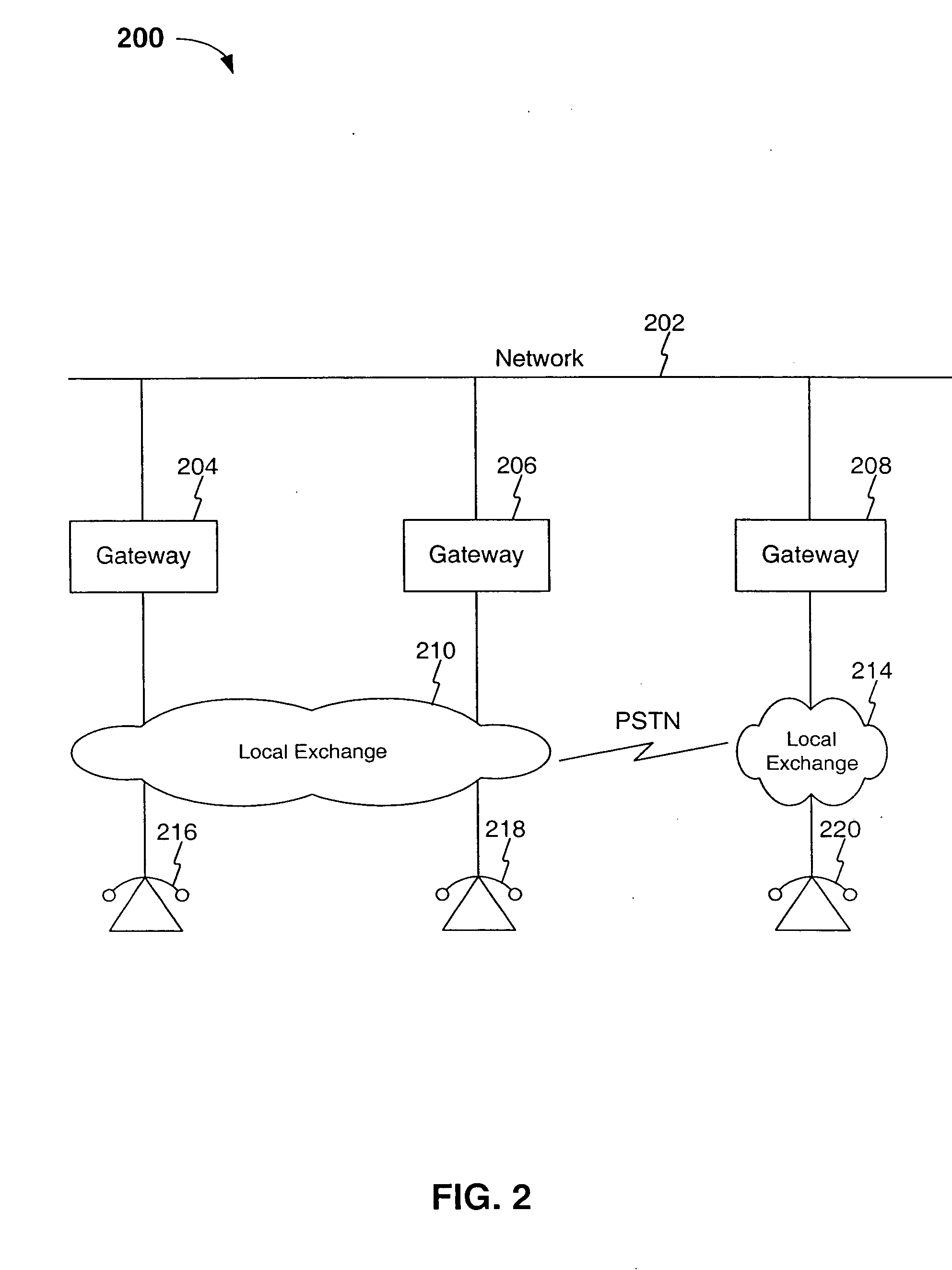
Method, system, and computer program product for route quality checking and management
InactiveUS20050152339A1Easy to routeData switching by path configurationNetwork connectionsVoice over internet protocol voipSpeech sound
A method, system and computer program product for route checking and management is described herein. In a voice over internet protocol environment, the invention allows for the testing of routes among various gateways. In an embodiment, a method for selecting a route for a voice over IP call within a communications network is provided. The method includes receiving a VoIP call request from a user, identifying potential candidate routes, assessing the quality and cost of routes and determining a route based on cost, quality and / or user preferences.
Owner:MIST SILICON LIABILITY
Computer and internet-based performance assessment questionnaire and method of candidate assessment
A computer and / or Internet-based performance assessment and method for candidate assessment, wherein a candidate evaluator utilizes Internet-based, network, or desktop applications to present custom weighted performance assessment questions to candidates, wherein the weighted questions are derived from responses of selected top performers thus enabling a candidate evaluator to evaluate, profile, predict and / or record a potential candidate's performance assessment profile via comparison of the candidate's response with the response of the top performers to predict whether the candidate is likely to be a top performer.
Owner:ROSNER PHILLIP ERNEST +1
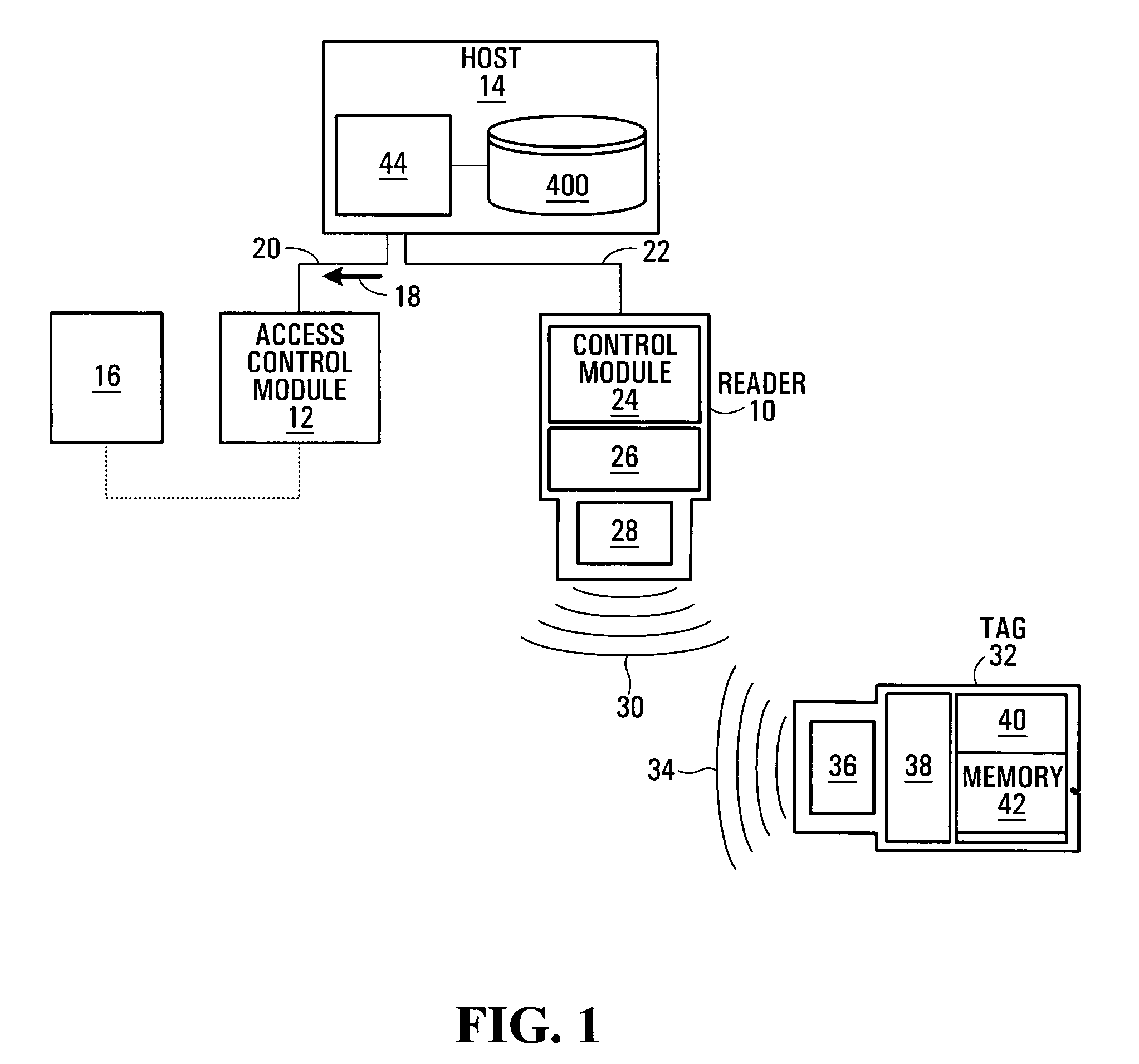
User authentication for contact-less sytems
InactiveUS20060131412A1Sensing detailsIndividual entry/exit registersUser authenticationAuthorization
A validation phase is performed at an RFID reader, in order to ascertain which of a plurality of potential candidates for authentication, are actual candidates for authentication. Once a candidate has been successfully validated, an authentication phase is initiated with a host computer, to determine whether the information presented by the candidate matches expected information about the candidate. If the authentication is considered successful, a final authorization procedure may be performed, or the authenticated candidate may be granted certain predetermined permissions. By performing the validation phase locally at the reader, the need for accessing a host computer is reduced and unnecessary queries to the host computer are avoided.
Owner:BCE
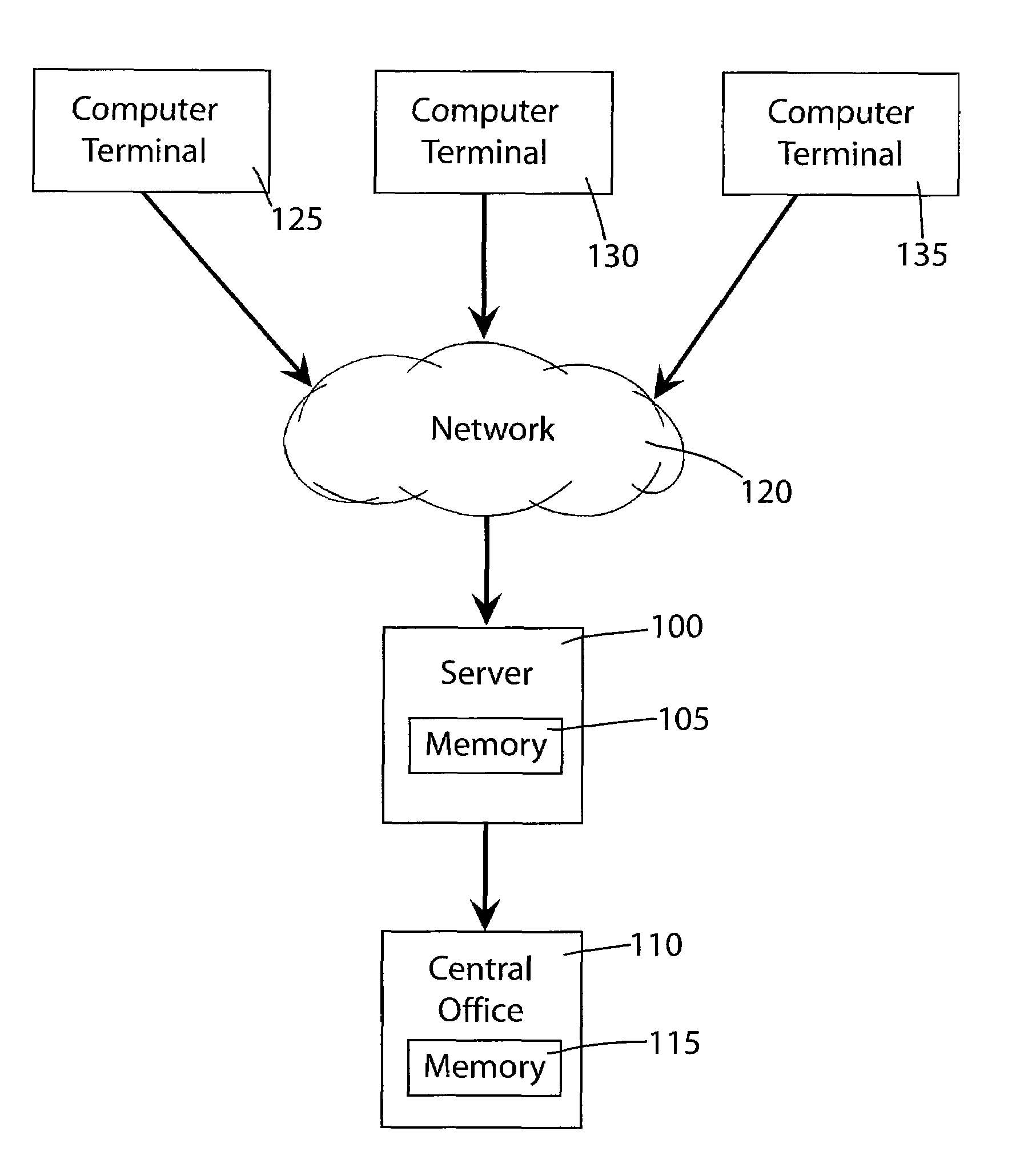
System and method for recruitment of candidates for clinical trials while maintaining security
An on-line click wrap electronic agreement that a user must agree to prior to being registered as a volunteer and considered as a potential candidate in a clinical trial or research study. The agreement authorizes the release of the end user's medical and / or personal information to representatives of the clinical trials and research studies for which the volunteer may be considered as a potential candidate. After receiving the end user's consent to the click wrap agreement an electronic survey form is generated by a secure server and displayed at the end user's computer terminal. Responses by the end user to the survey form are kept secure as much as possible while being transmitted from the computer terminal across the network to the server and while stored and accessed only by authorized personnel at the central office.
Owner:BODY HEALTH RESOURCES CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com