Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Java servlet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
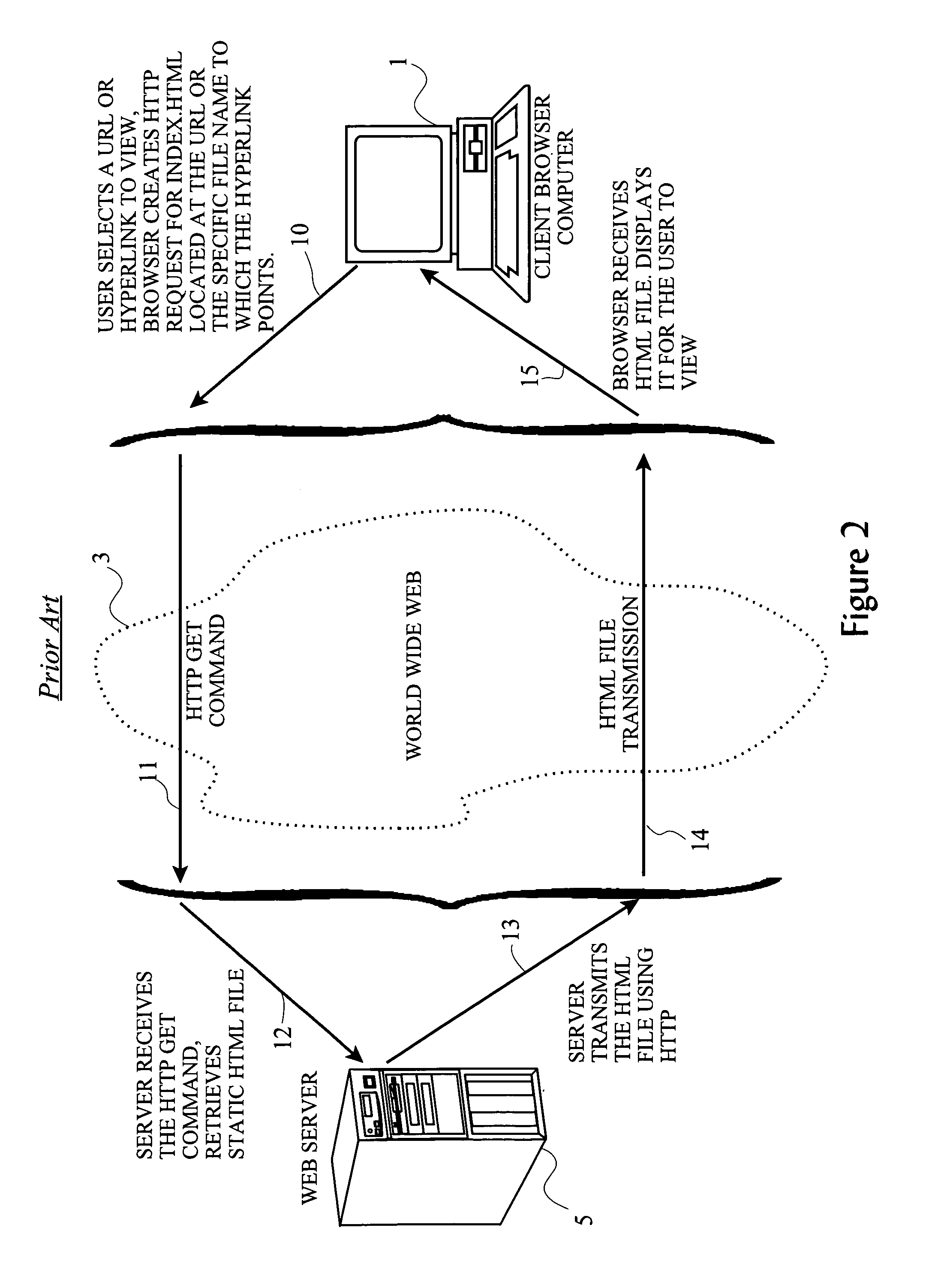
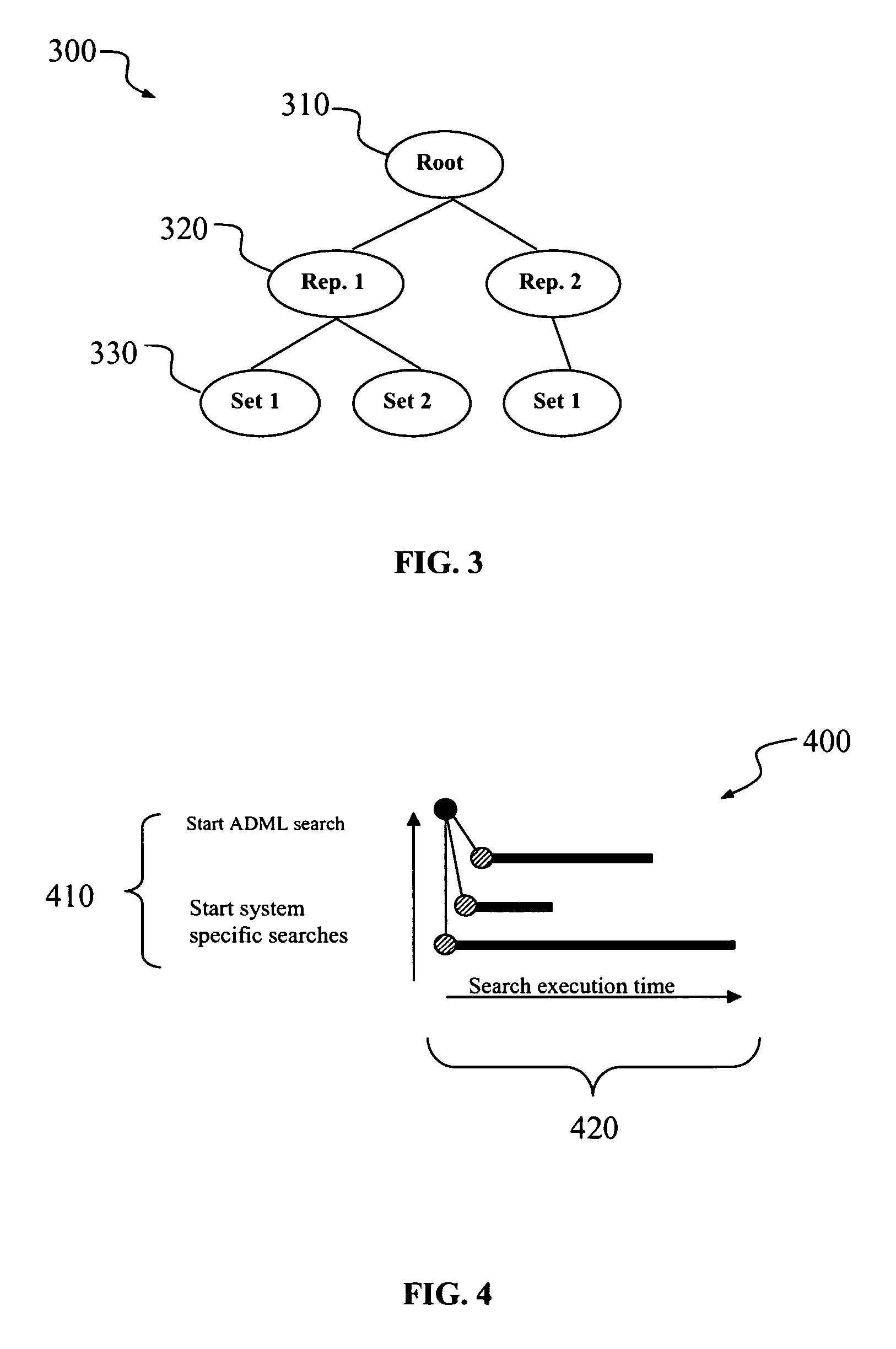
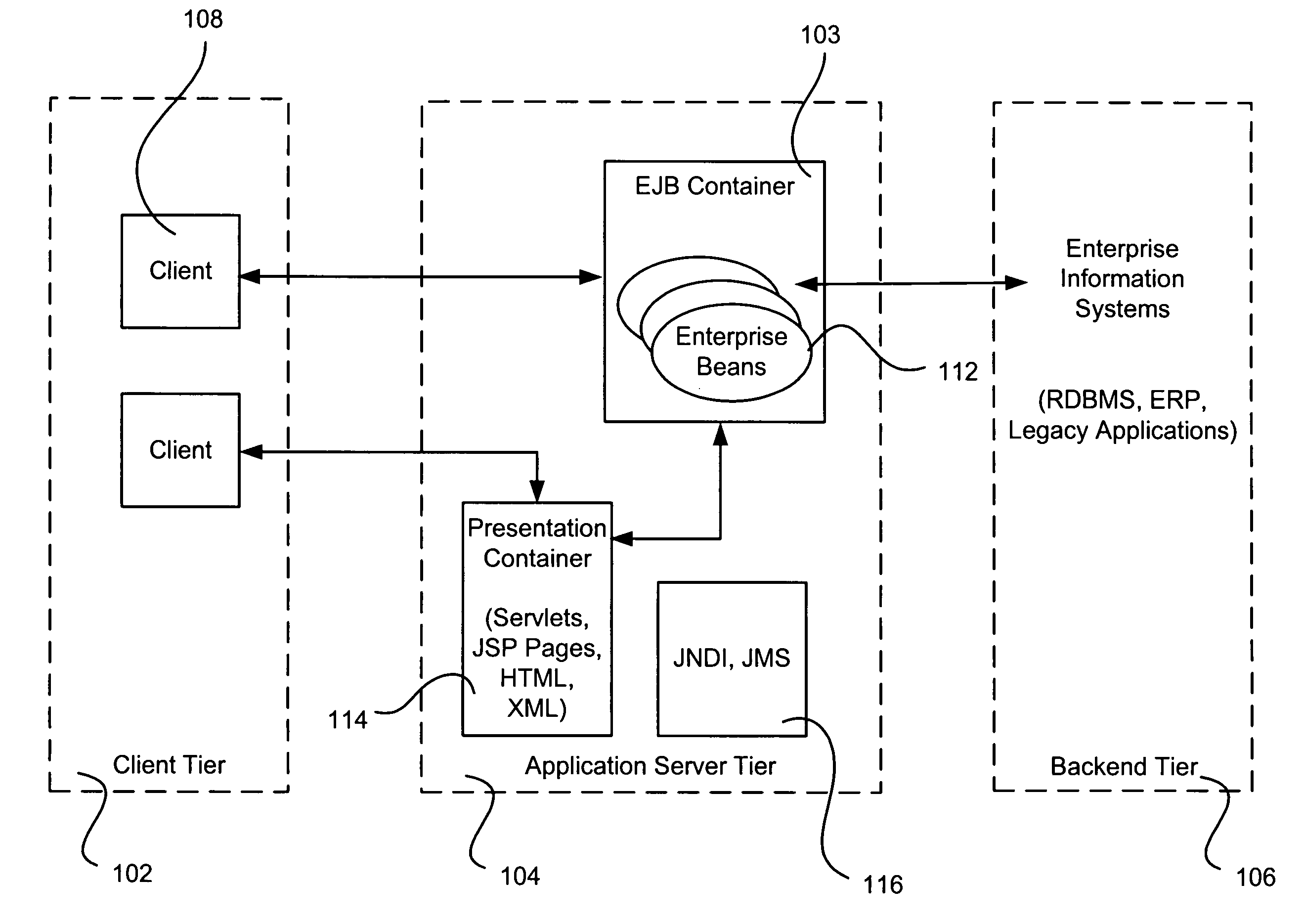
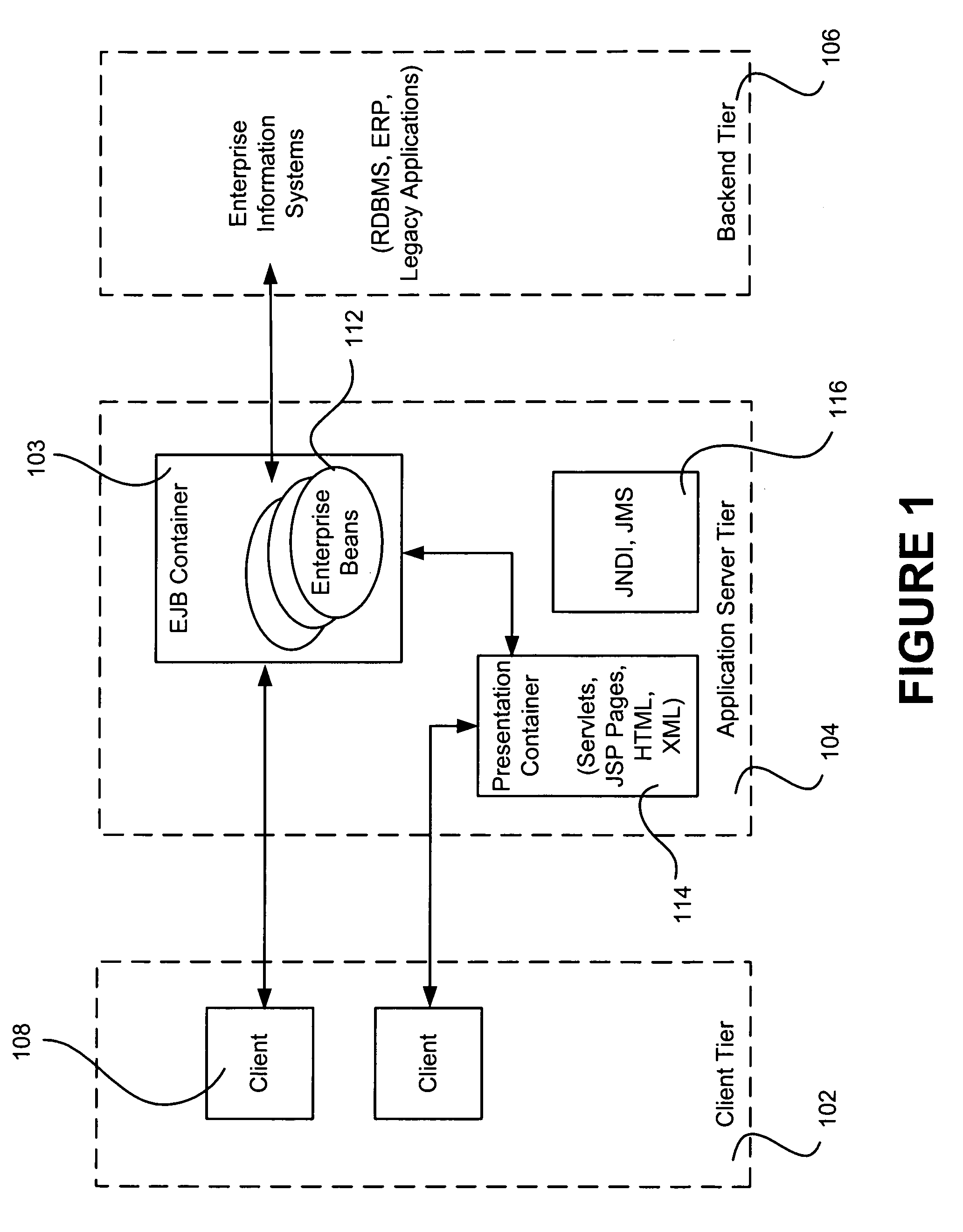
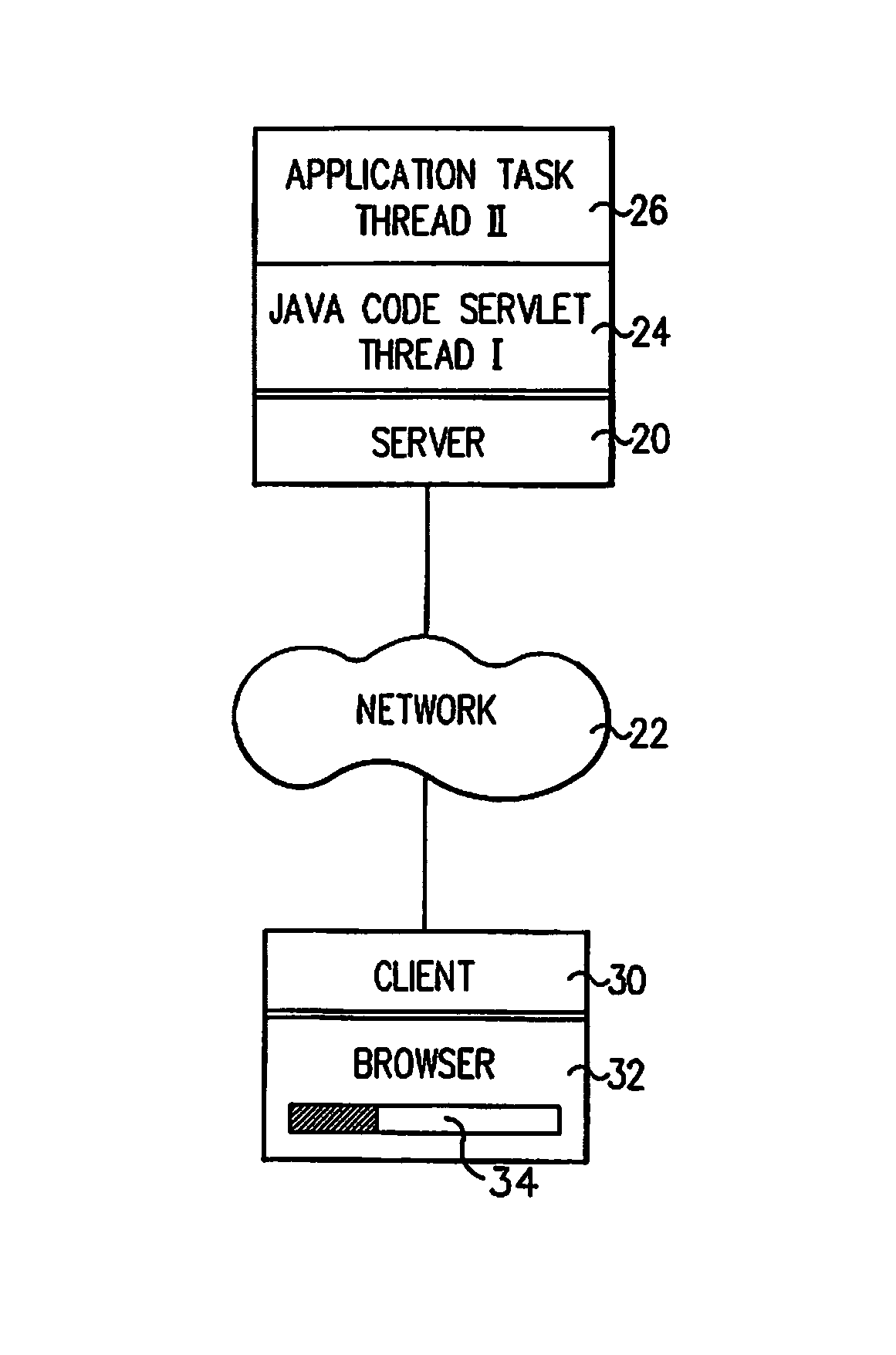
A Java servlet is a Java software component that extends the capabilities of a server. Although servlets can respond to many types of requests, they most commonly implement web containers for hosting web applications on web servers and thus qualify as a server-side servlet web API. Such web servlets are the Java counterpart to other dynamic web content technologies such as PHP and ASP.NET.
Extensible markup language (XML) server pages having custom document object model (DOM) tags
InactiveUS6981212B1Improve performanceMultiple digital computer combinationsWebsite content managementComponent Object ModelExtensible markup
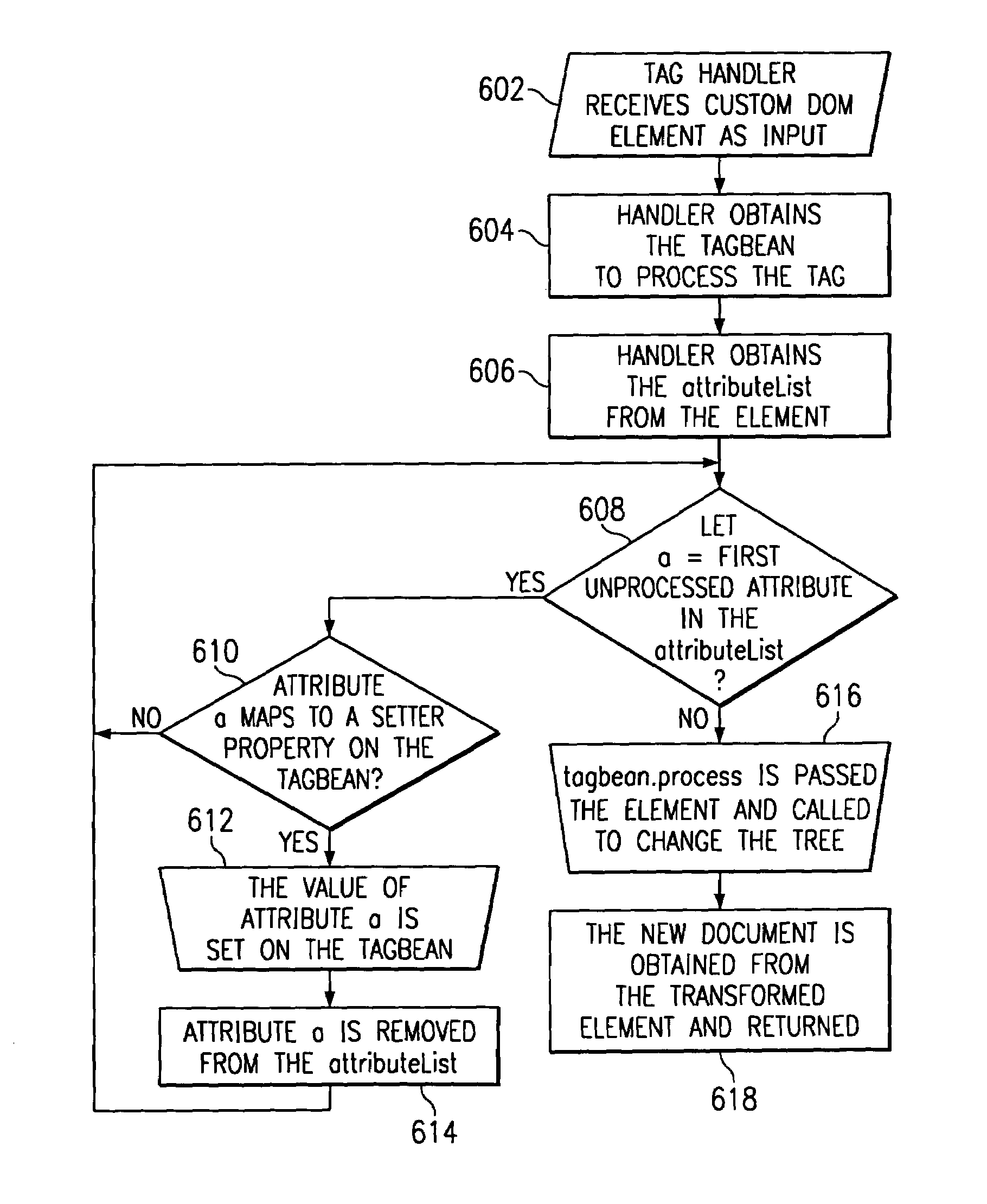
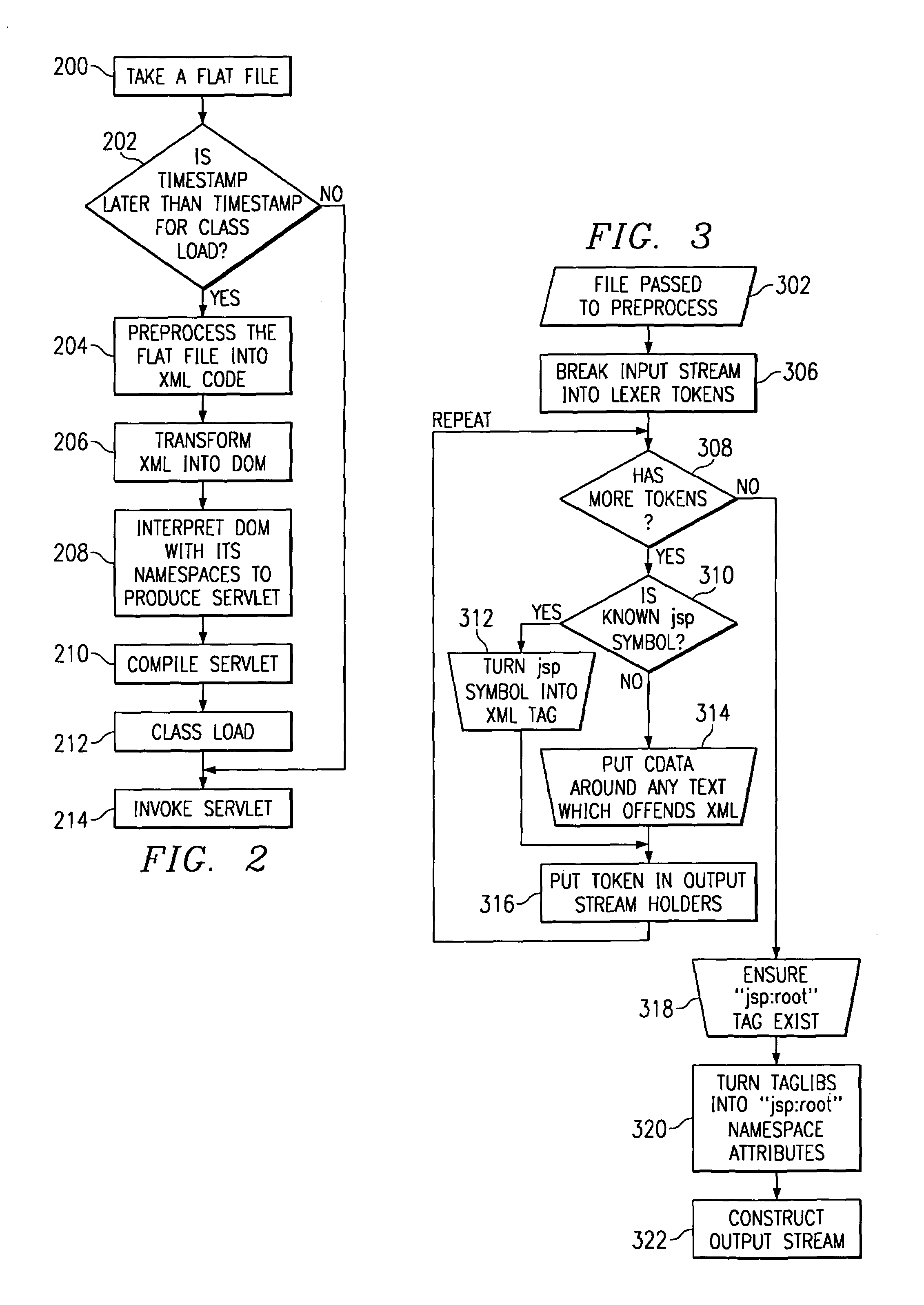
A method for serving a web page uses eXtensible Markup Language (XML) server pages. The first time a page is accessed, a given flat file is parsed into an XML Document Object Model (DOM), and required tag libraries are loaded. The DOM tree is then traversed, preferably in a depth-first, inside-out manner to locate custom tags. Upon locating a custom tag, if the tag is registered as a Java object, the object is loaded. A process method is then called on the object, passing the custom tag's tree node. The Java object then examines the custom tag and replaces it with an object, e.g., script code. Alternatively, if the tag is registered as an XSL stylesheet, the stylesheet is loaded and passed, together with the DOM, to an XSL processor. The processor applies the template to the custom tag and replaces it with given script code. Once all custom tags are reduced to HTML and script code, the DOM is compiled into a Java servlet to service the client request.
Owner:IBM CORP
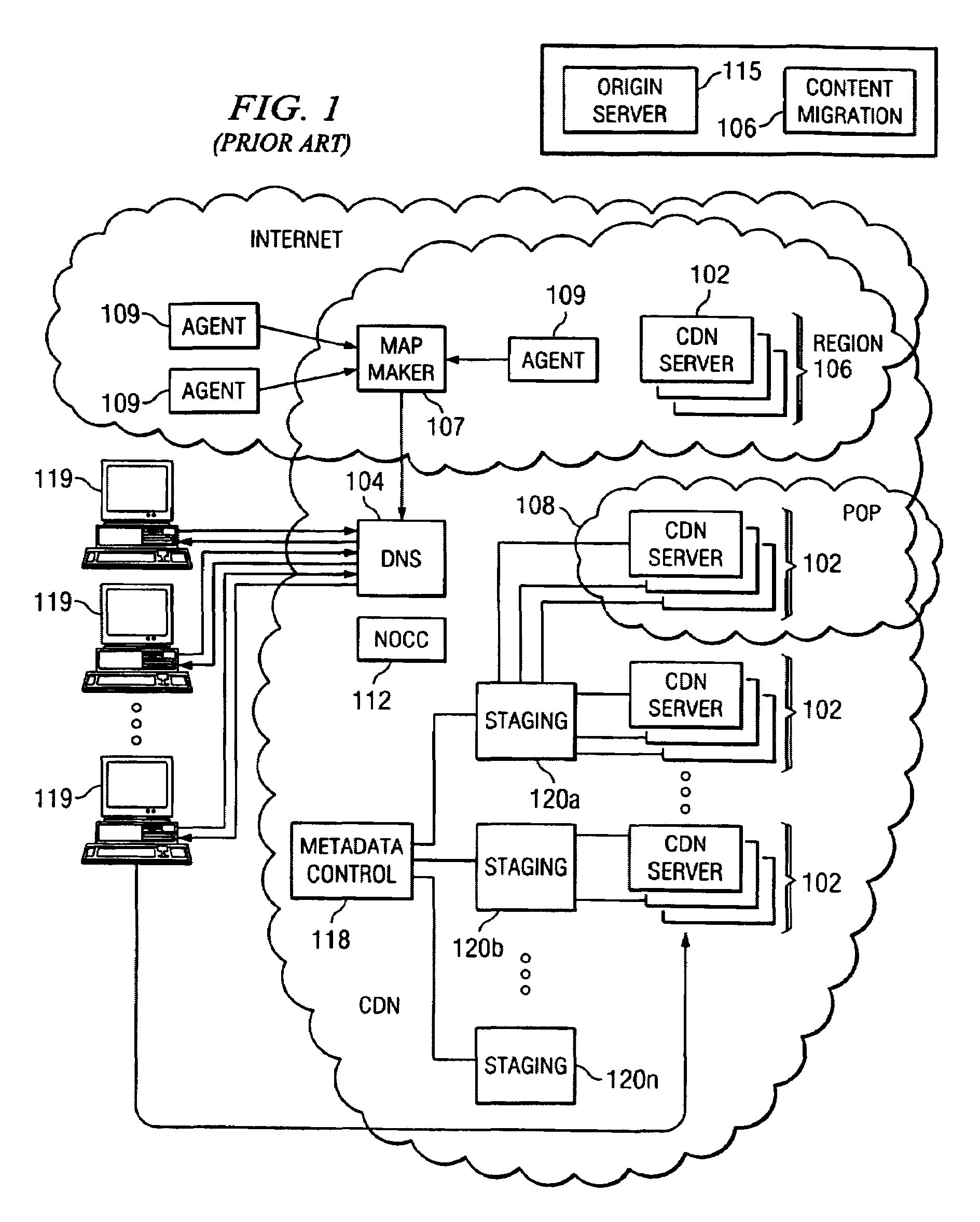
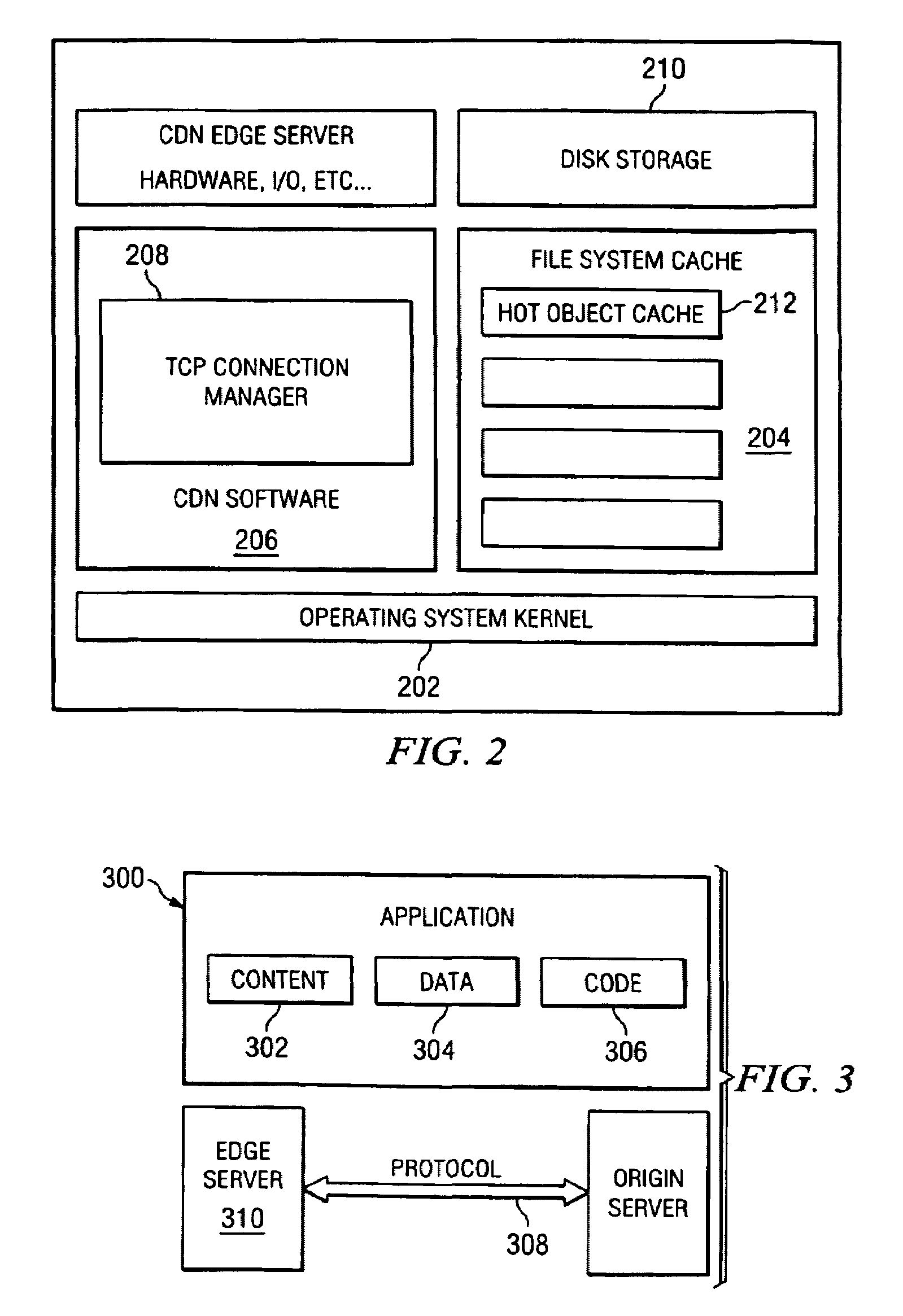
Edge side components and application programming environment for building and delivering highly distributed heterogenous component-based web applications
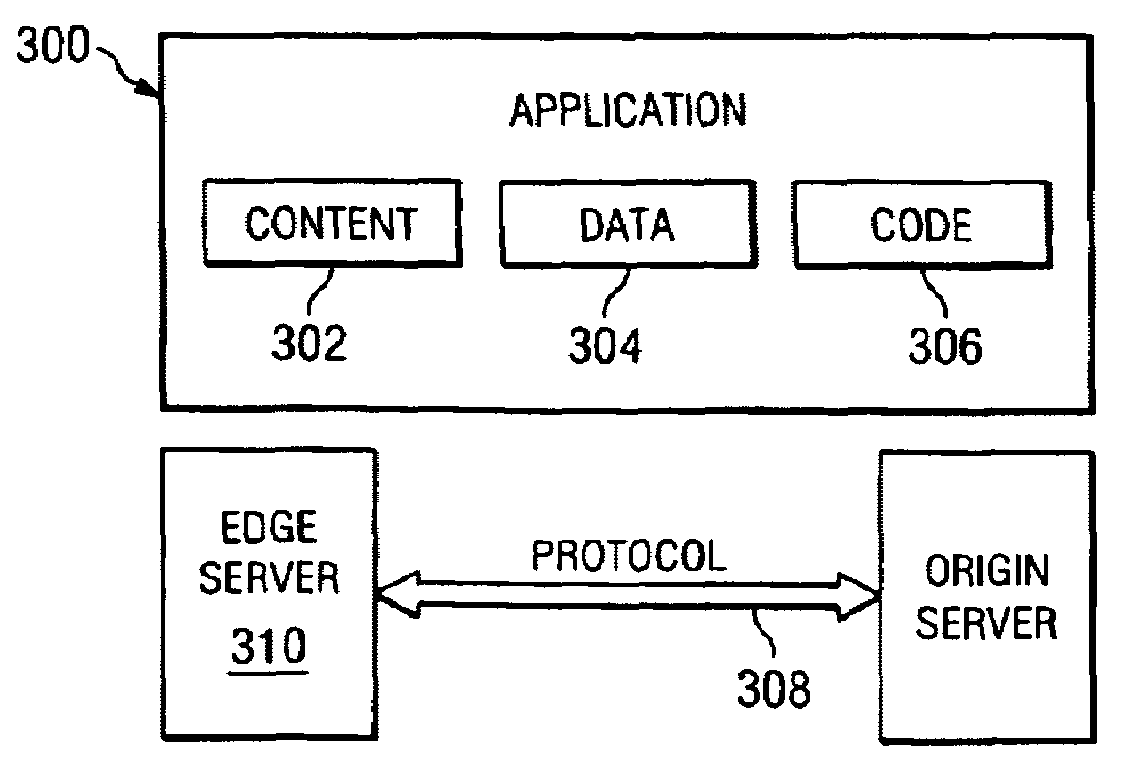
A method is provided for processing an application on an edge server, wherein the application comprises a set of defined presentation, code and data components, each of which are preferably URI-addressable objects. In response to a client request, the presentation, code and data components are processed according to a set of metadata to generate a response, and the response is delivered to the client. The presentation components are typically content such as HTML fragments, WML fragments, or some combination thereof. The code components are typically Java servlets or beans, XSLT style sheets, or some combination thereof. The data components are typically XML files, native database formatted files, and the like. Each of the presentation, code and data components may have a distinct management profile, cacheability profile, deployment profile, invalidation profile, and security profile. These profiles are settable via metadata or other similar means. Using this framework, heterogenous components may be composed into other components and complete applications or services.
Owner:AKAMAI TECH INC
Method and system for producing dynamic web pages
InactiveUS7174506B1Website content managementSpecial data processing applicationsDocument preparationDocumentation
The invention provides systems, computer program products and methods for generating dynamic-content documents suitable for use on and transmission over computer networks, including the World Wide Web and the Internet. The dynamic-content documents are created based upon an extracted layout definition from a static web document with dynamic content mapped into the extracted layout definition. The invention is especially useful for application to Hypertext documents, such as Hyper Text Markup Language documents. The preferred embodiment disclosed is a Java servlet.
Owner:IBM CORP
System for integrating java servlets with asynchronous messages
ActiveUS7003570B2Digital computer detailsMultiprogramming arrangementsApplication serverApplication software
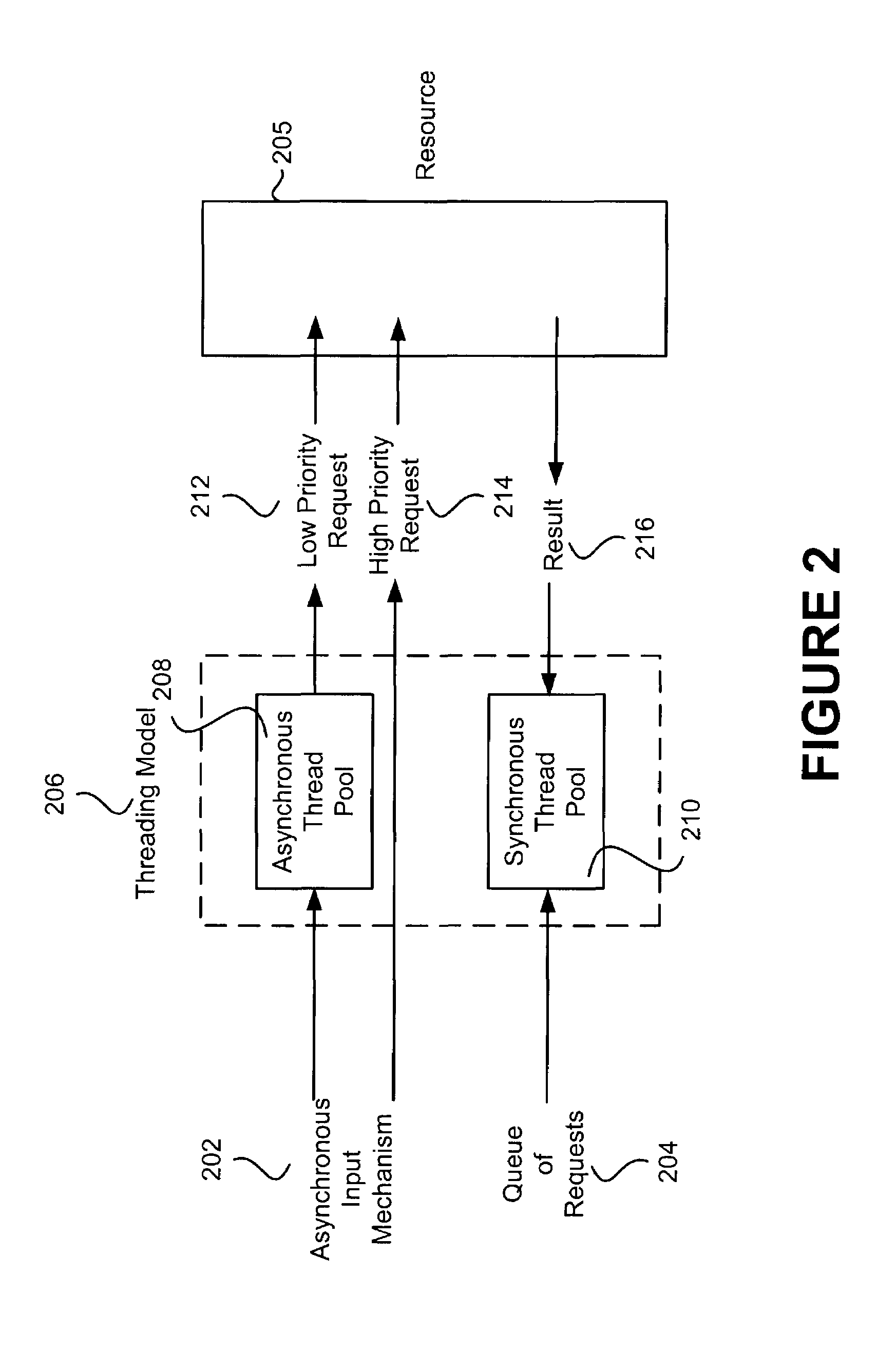
In a traditional application server that uses servlets, when a request is dispatched to a thread the service( ) method of the appropriate servlet is called. When the service( ) method returns the response is sent. This is sub-optimal in the case that an asynchronous event must occur before the response can be sent, because the thread running the servlet must block until the event occurs. The invention provides for asynchronous processing of such requests. In one embodiment, the invention provides an extension to the Servlet API which allows the service( ) method to return (and thus the thread to be freed) before the response is ready to be sent. Then when the asynchronous event later occurs the response may be completed and sent.
Owner:ORACLE INT CORP
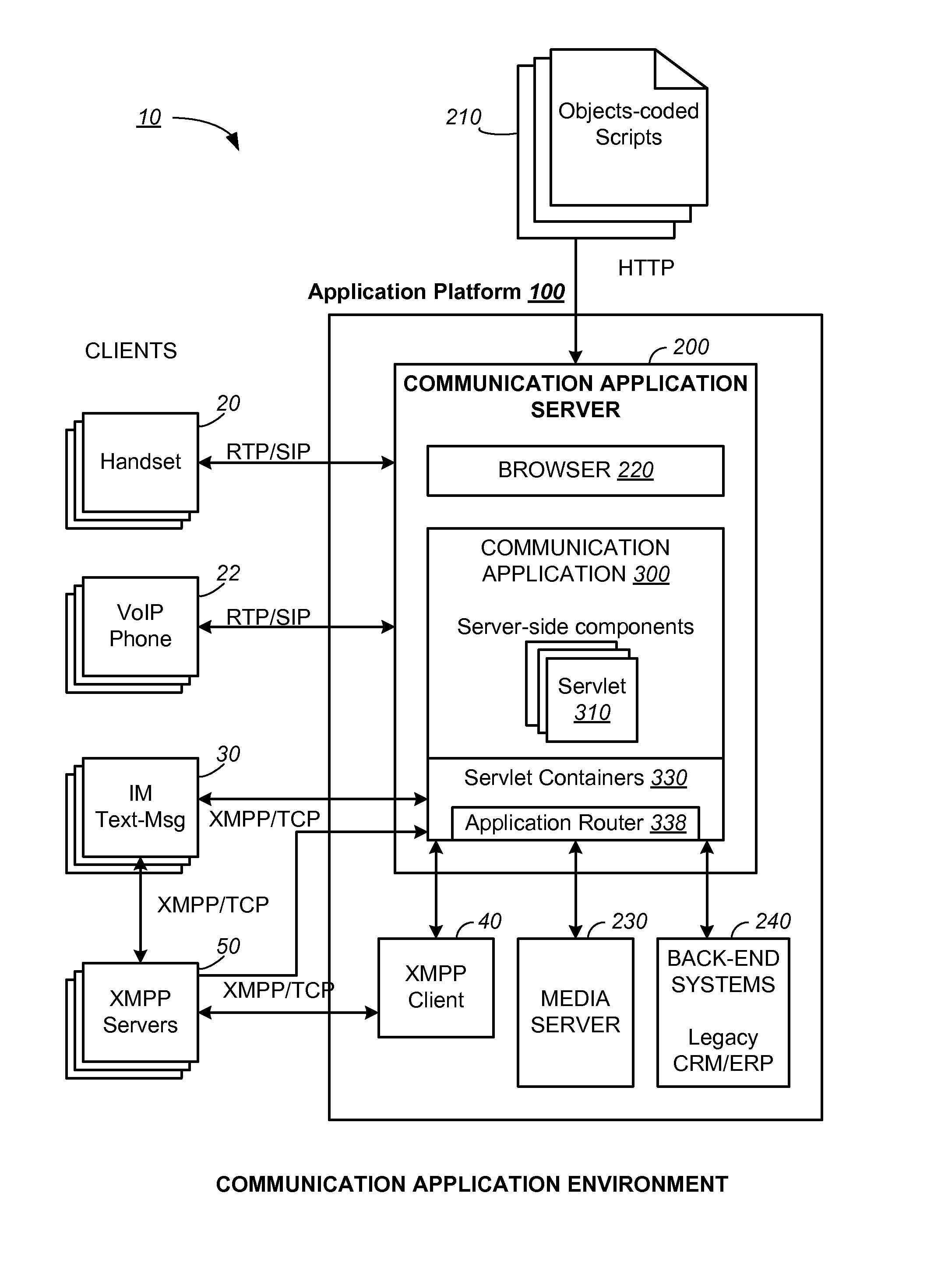
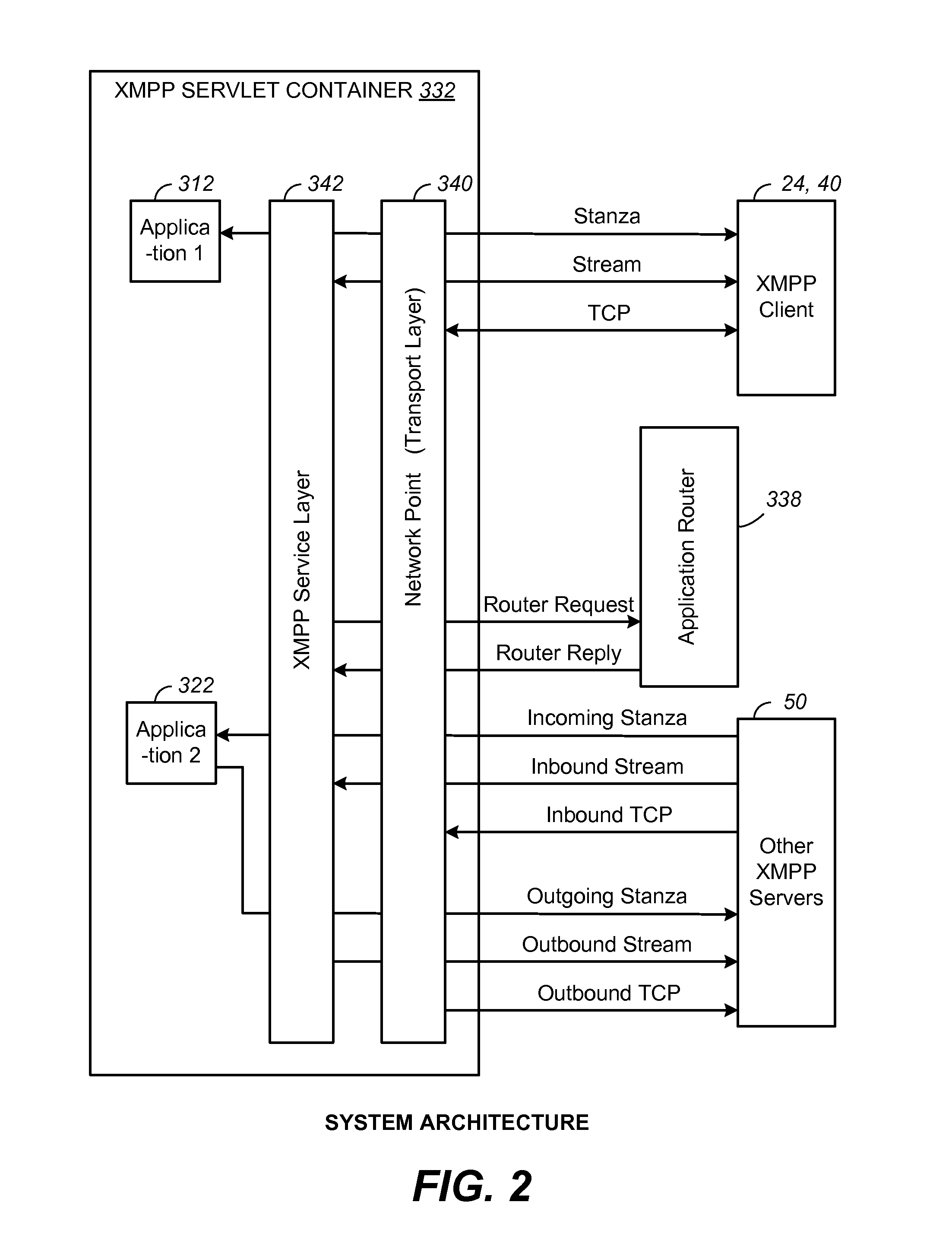
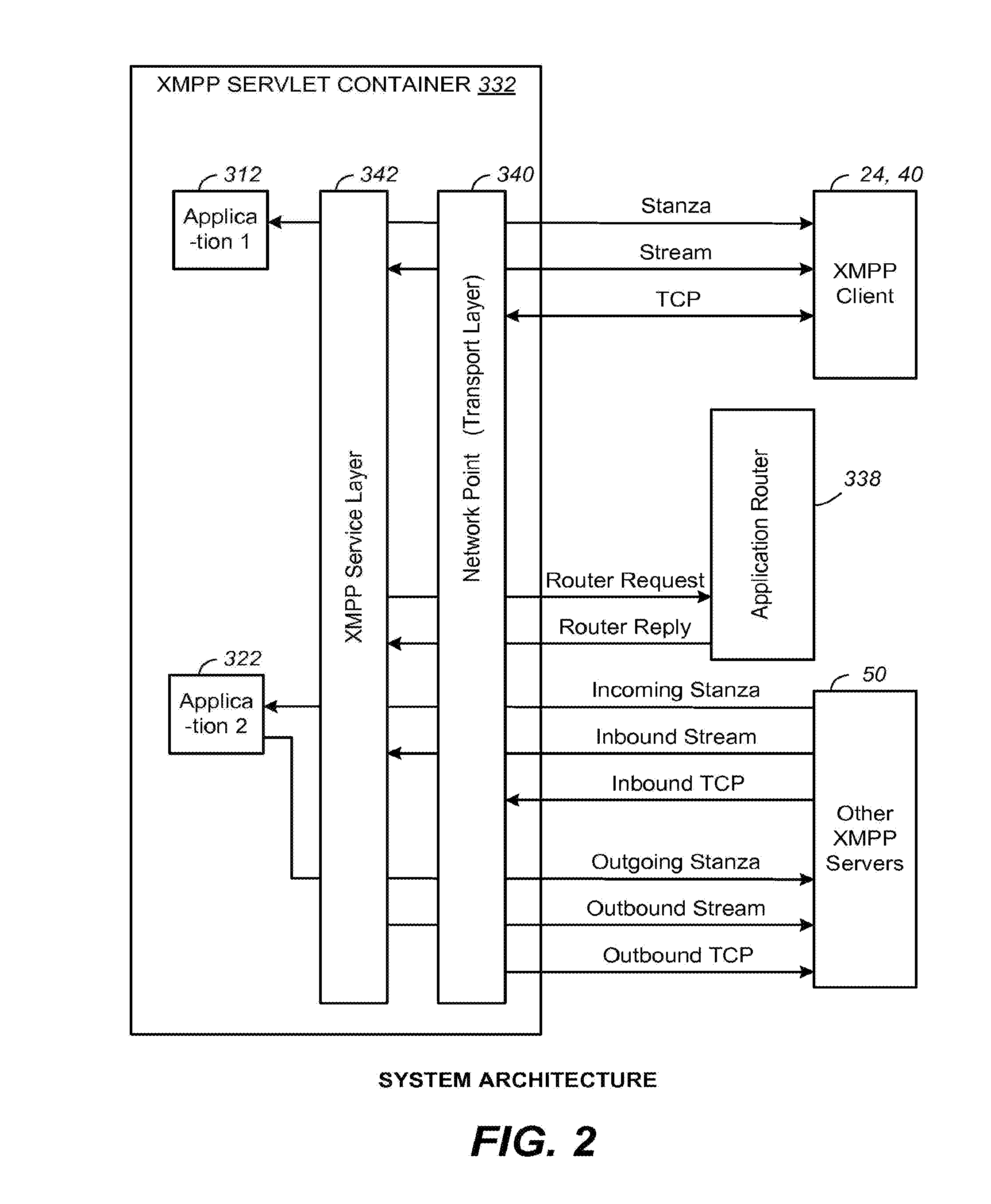
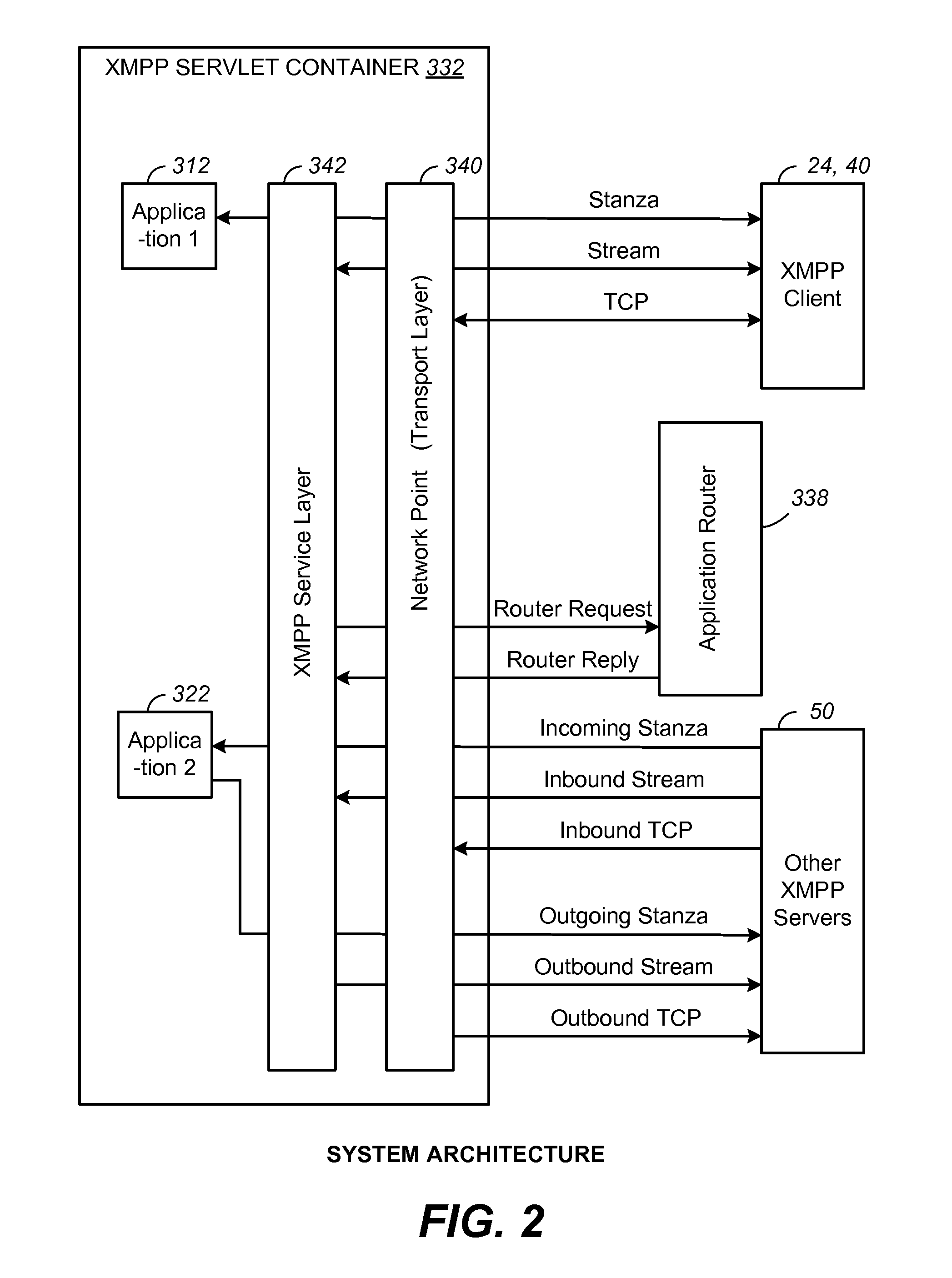
Servlet API and Method for XMPP Protocol
ActiveUS20110258305A1Digital computer detailsData switching networksCommunications systemNetwork connection
A communication system and method include a server hosting an interactive voice response or self-help application in a Java virtual machine. In order to leverage the advantages and facilities of the Java servlet model, a Java XMPP (Extensible Messaging and Presence Protocol) servlet container is provided for the server so that the communication application can be programmed with objects defined by an XMPP servlet API, as well as objects defined by the standards-based Java EE platform such as HTTP and SIP servlets, in order to service an XMPP client. In addition to the generic class objects of the Java servlet model, the API also provides a set of XMPP-specific class objects. The Java XMPP servlet container includes a network point at a transport level for handling network connections, an XMPP service layer for managing XMPP sessions and streams, and an application layer for managing XMPP stanzas.
Owner:CISCO TECH INC
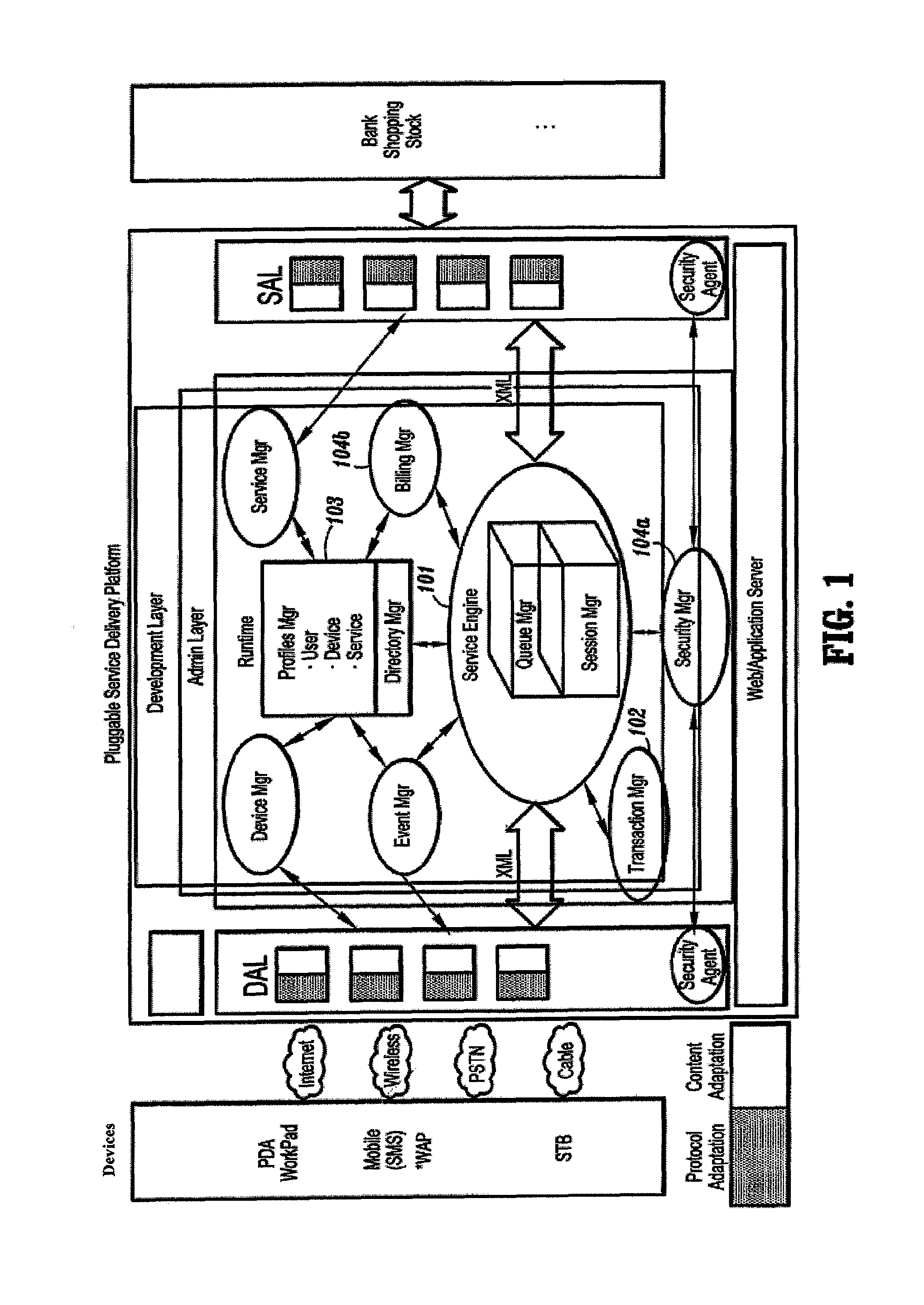
Pluggable service delivery platform
InactiveUS7356615B2Overcomes shortcomingEasy to addMultiple digital computer combinationsTransmissionSoftware engineeringInterface (Java)
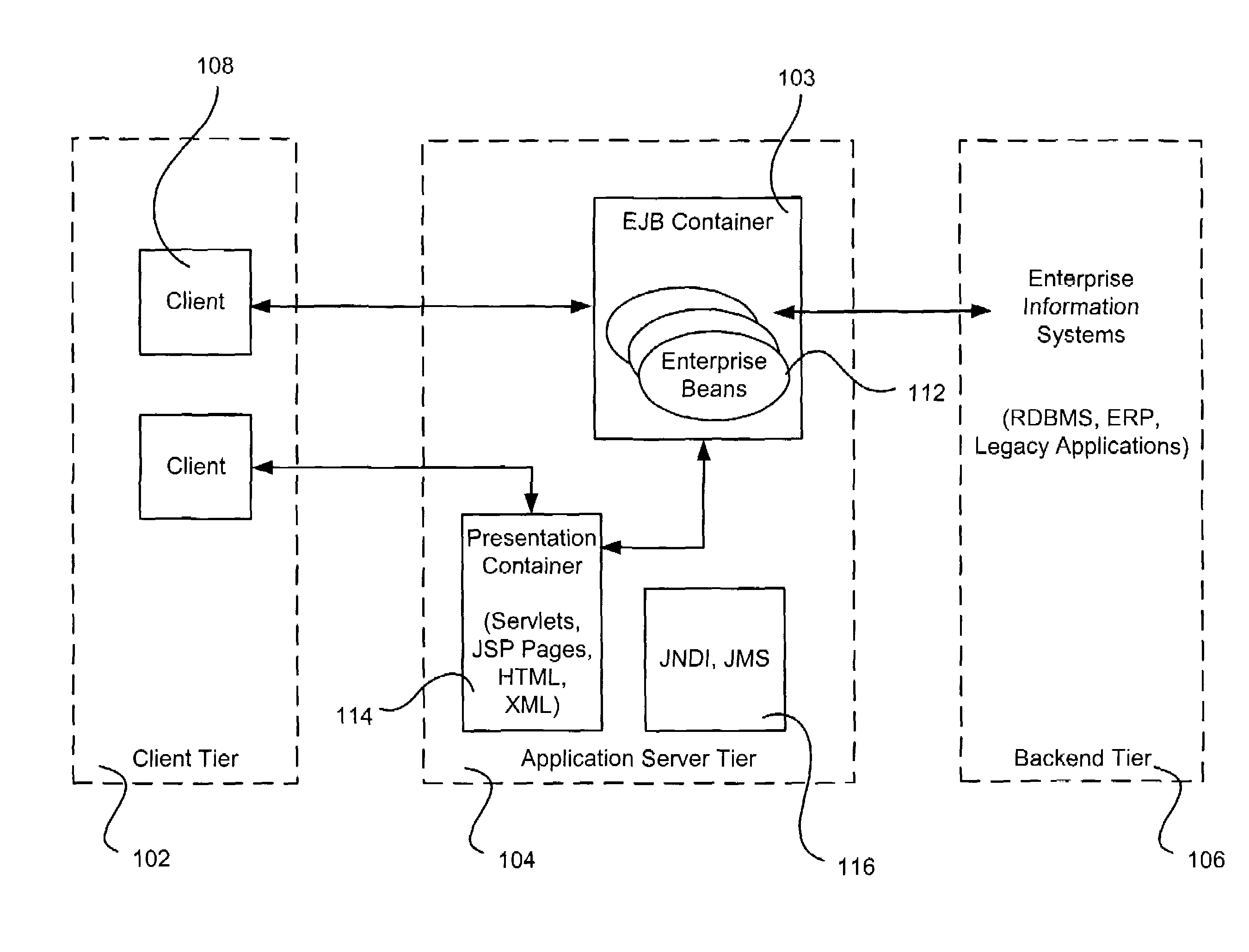
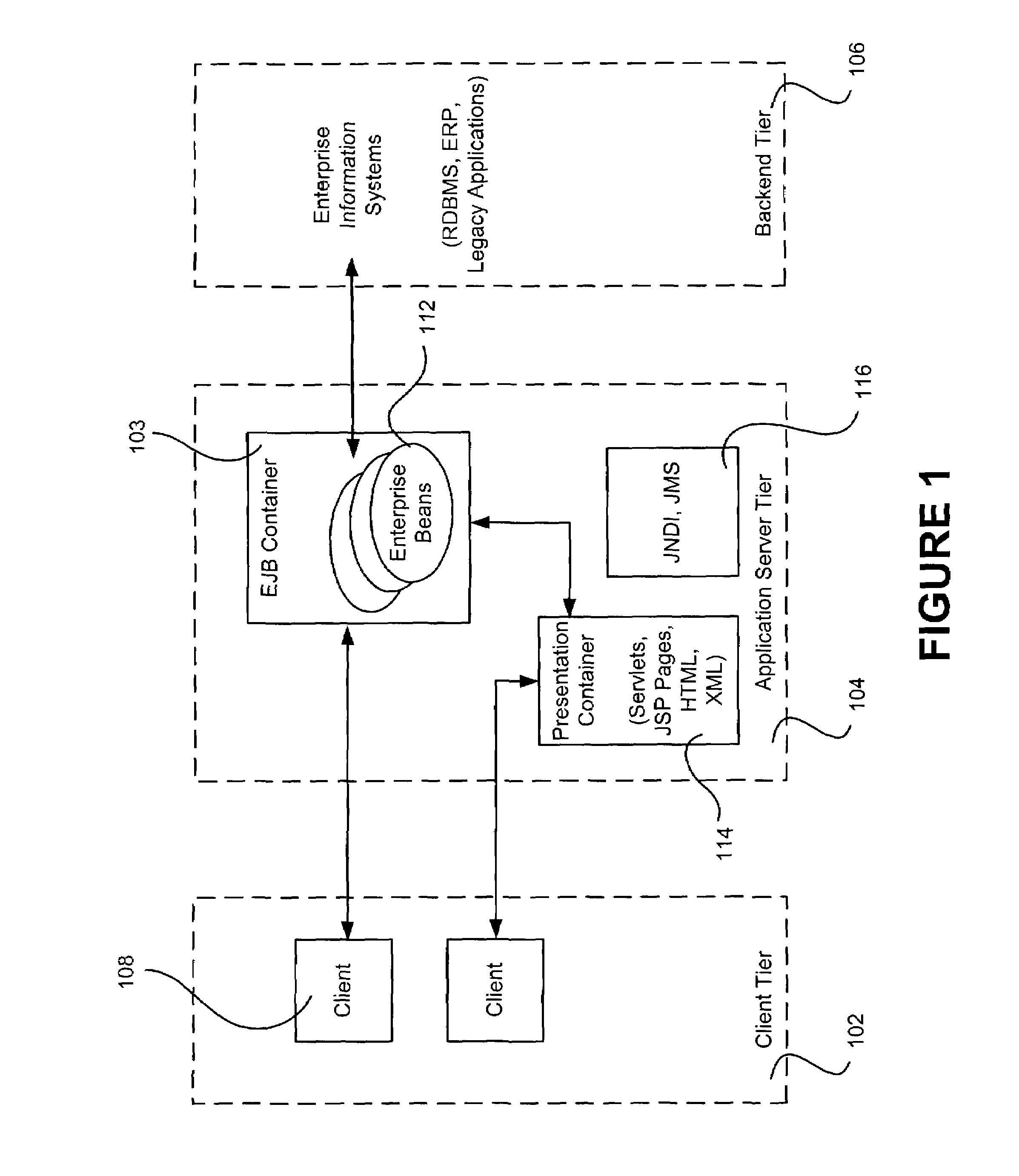
The present invention discloses a pluggable service delivery platform for supporting many devices to many services in an e-business application, comprising a device-platform interface, a service-platform interface and a platform kernel section. The service delivery platform of this invention is a flexible and scalable platform to easily “plug” a new device and a new service, and the different parts of the platform are componentized. Any one of the components can be replaced by a 3rd party's products, providing they abide certain open interface like Java Servlet, LDAP, etc.
Owner:IBM CORP
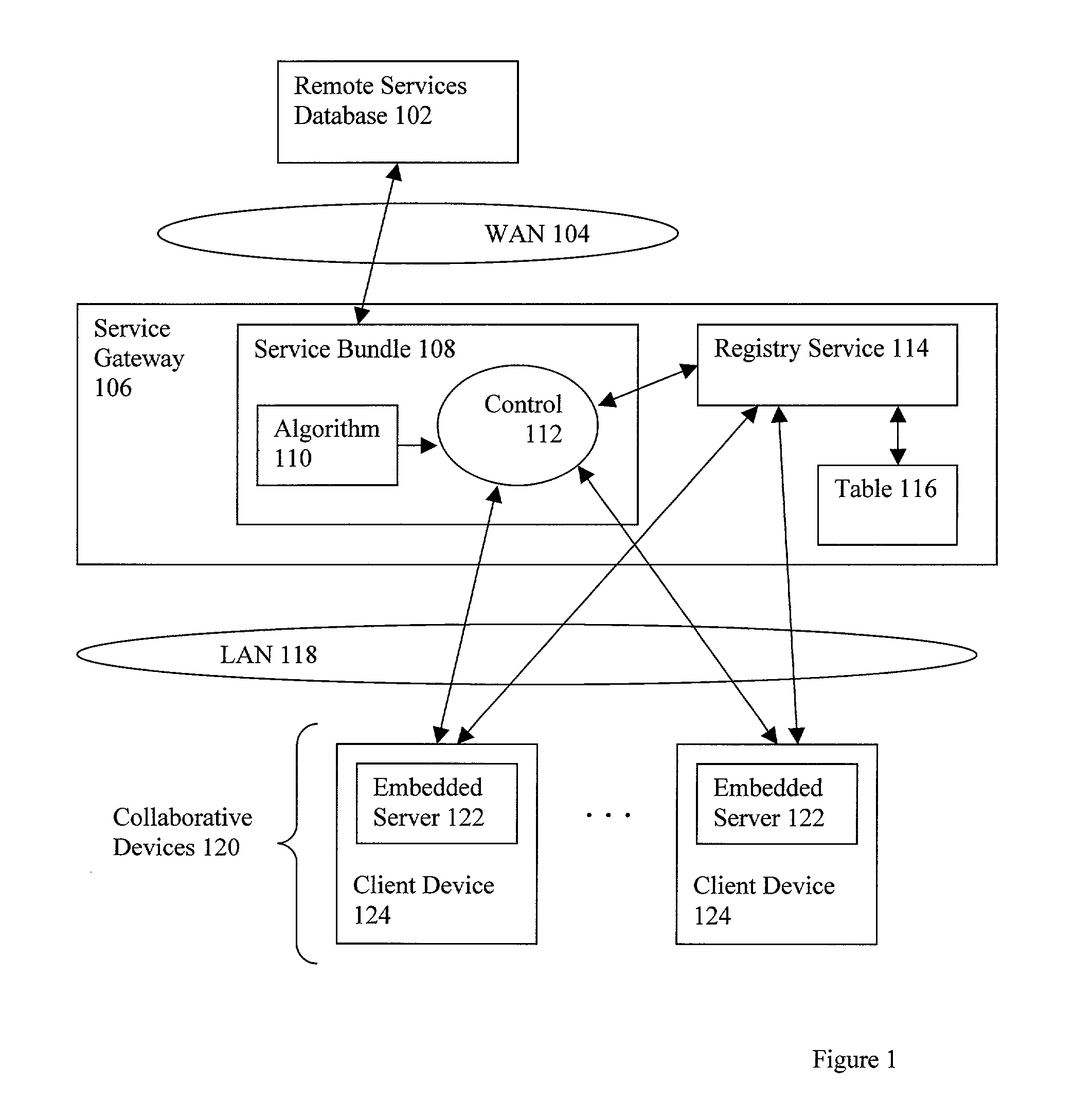
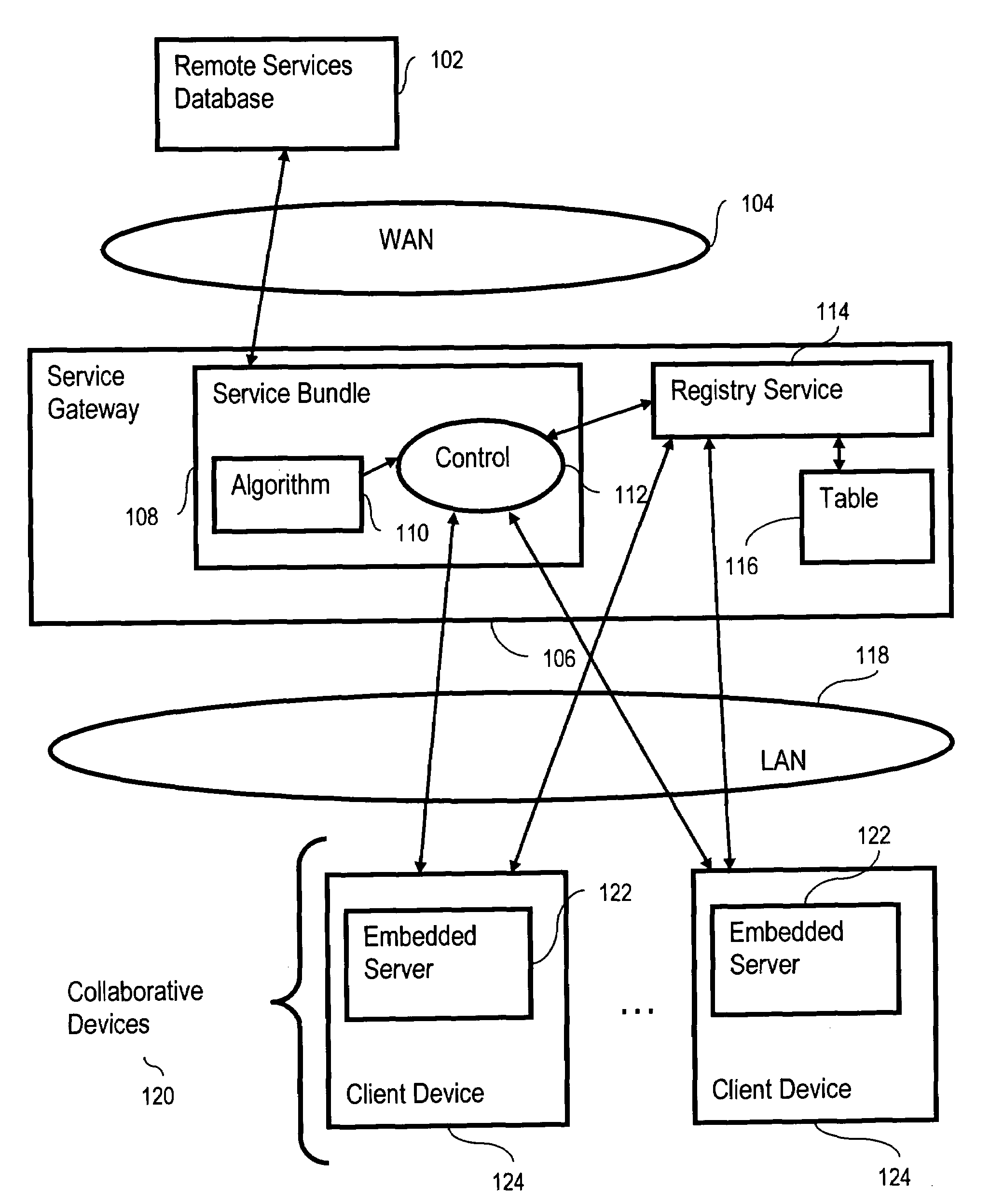
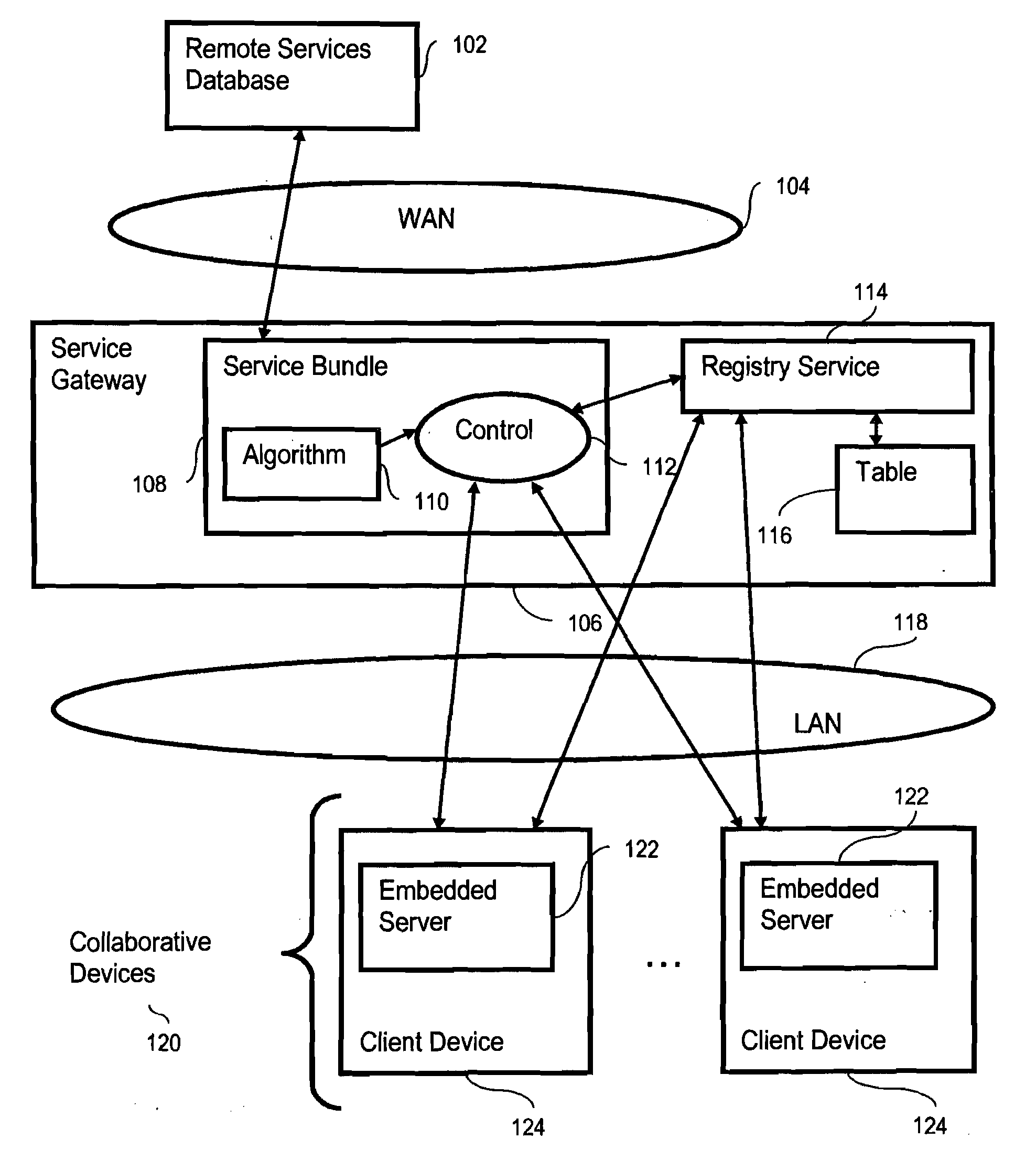
Active control of collaborative devices
InactiveUS20030145053A1Multiple digital computer combinationsSecuring communicationEmbedded JavaClient-side
Control of collaborative devices, including providing at least two collaborative devices, wherein each collaborative device comprises a client device and an embedded Java server, providing a registry service to which the collaborative devices are coupled for data communications, and providing at least one registry table, wherein the registry table includes registry records, wherein the registry records include registry records representing capabilities of collaborative devices, wherein the registry records representing capabilities of collaborative devices include data elements describing, for each collaborative device, capabilities, tertiary relationships, and network connectivities. The method further includes providing a service bundle of OSGI-compliant Java servlets comprising at least one predetermined algorithm for controlling the collaborative devices, and controlling the collaborative devices in accordance with the predetermined algorithm.
Owner:IBM CORP
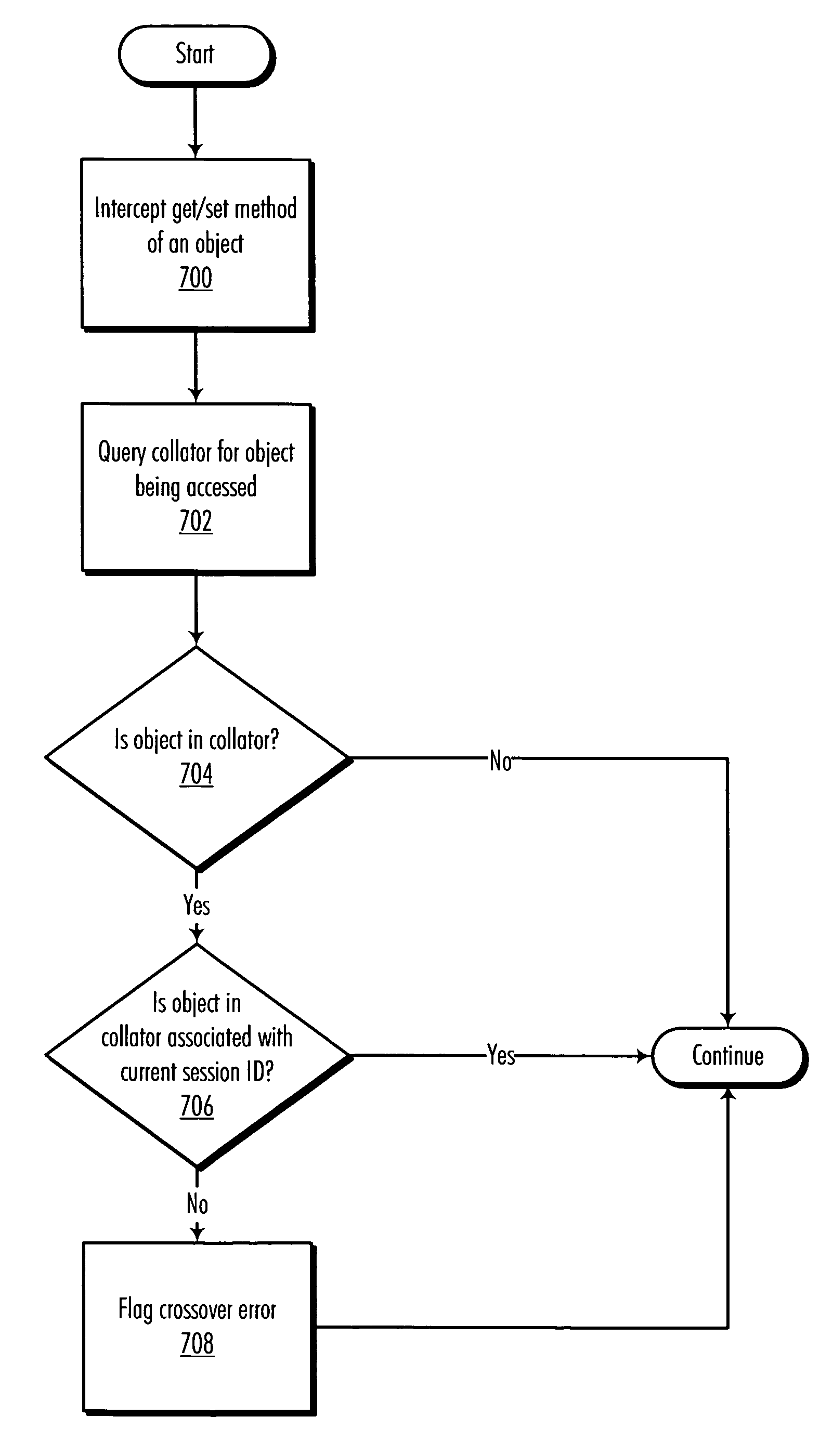
Method and apparatus for protecting HTTP session data from data crossover using aspect-oriented programming
InactiveUS20060288106A1Software engineeringMultiple digital computer combinationsData processing systemPointcut
A method, computer program product, and data processing system for detecting and identifying data crossover errors in servlet code are disclosed. According to a preferred embodiment, techniques of aspect-oriented programming (AOP) are used to instrument JAVA Servlet code to detect potential data crossover errors. Specifically, pointcuts are defined to intercept both the association follow an object with a particular session and the “getting” and “setting” of such objects. Advice code associated with these pointcuts is used to update and / or consult a “collator” data structure, which is used to determine if an object or variable associated with one session is being accessed by a different session. In a preferred embodiment, the AspectJ aspect-oriented programming language / system is used to define the pointcuts and advice code.
Owner:IBM CORP
Edge side components and application programming environment for building and delivering highly distributed heterogenous component-based web applications
InactiveUS20070180099A1Interprogram communicationMultiple digital computer combinationsEdge serverConfigfs
A method is provided for processing an application on an edge server, wherein the application comprises a set of defined presentation, code and data components, each of which are preferably URI-addressable objects. In response to a client request, the presentation, code and data components are processed according to a set of metadata to generate a response, and the response is delivered to the client. The presentation components are typically content such as HTML fragments, WML fragments, or some combination thereof. The code components are typically Java servlets or beans, XSLT style sheets, or some combination thereof. The data components are typically XML files, native database formatted files, and the like. Each of the presentation, code and data components may have a distinct management profile, cacheability profile, deployment profile, invalidation profile, and security profile. These profiles are settable via metadata or other similar means. Using this framework, heterogenous components may be composed into other components and complete applications or services.
Owner:AKAMAI TECH INC
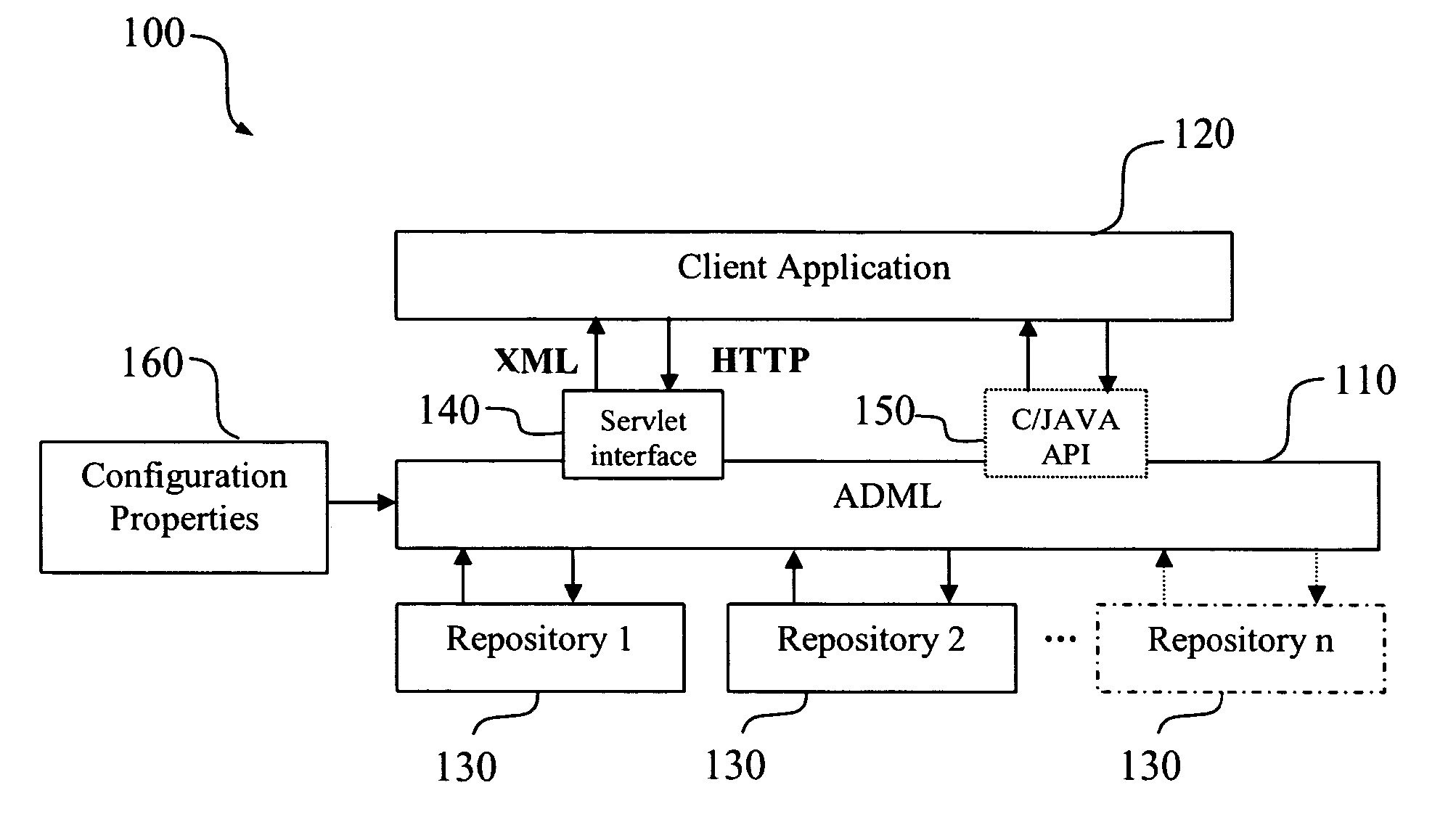
Abstract document management systems and methods
InactiveUS20060041522A1Multiple serviceSpecial data processing applicationsDocument management systemsPaper documentUniform resource locator
An abstract document management layer service (ADML service / module) operating as a single service enabling retrieval, manipulation and management of documents using various specifications. Documents are accessed from a single point of entry. Multiple-document management systems virtually integratale behind ADML. ADML is accessible over a network-enabled interface and provides document access using specification like JAVA, C, CORBA. ADML is Web accessible using JAVA servlet technology. Service requests can be based on HTTP, and ADML responses can be carried out using XML. Access to the contents of a document is URL-based. URLs enable a client application to download documents without additional interaction. URLs can be stored outside of ADML and used to access a specific document. Users can search for a document across repositories based on criteria, retrieve a document, create a document, commit document changes, request additional meta-data, freezes document content prevent changes / deletion, change document states to support workflow, and sets meta-data.
Owner:XEROX CORP
System for integrating java servlets with asynchronous message
InactiveUS20060168139A1Multiprogramming arrangementsMultiple digital computer combinationsApplication serverApplication software
In a traditional application server that uses servlets, when a request is dispatched to a thread the service method of the appropriate servlet is called. When the service method returns the response is sent. This is sub-optimal in the case that an asynchronous event must occur before the response can be sent, because the thread running the servlet must block until the event occurs. The invention provides for asynchronous processing of such requests. In one embodiment, the invention provides an extension to the Servlet API which allows the service method to return (and thus the thread to be freed) before the response is ready to be sent. Then when the asynchronous event later occurs the response may be completed and sent.
Owner:ORACLE INT CORP
System and method for preventing timeout of a client
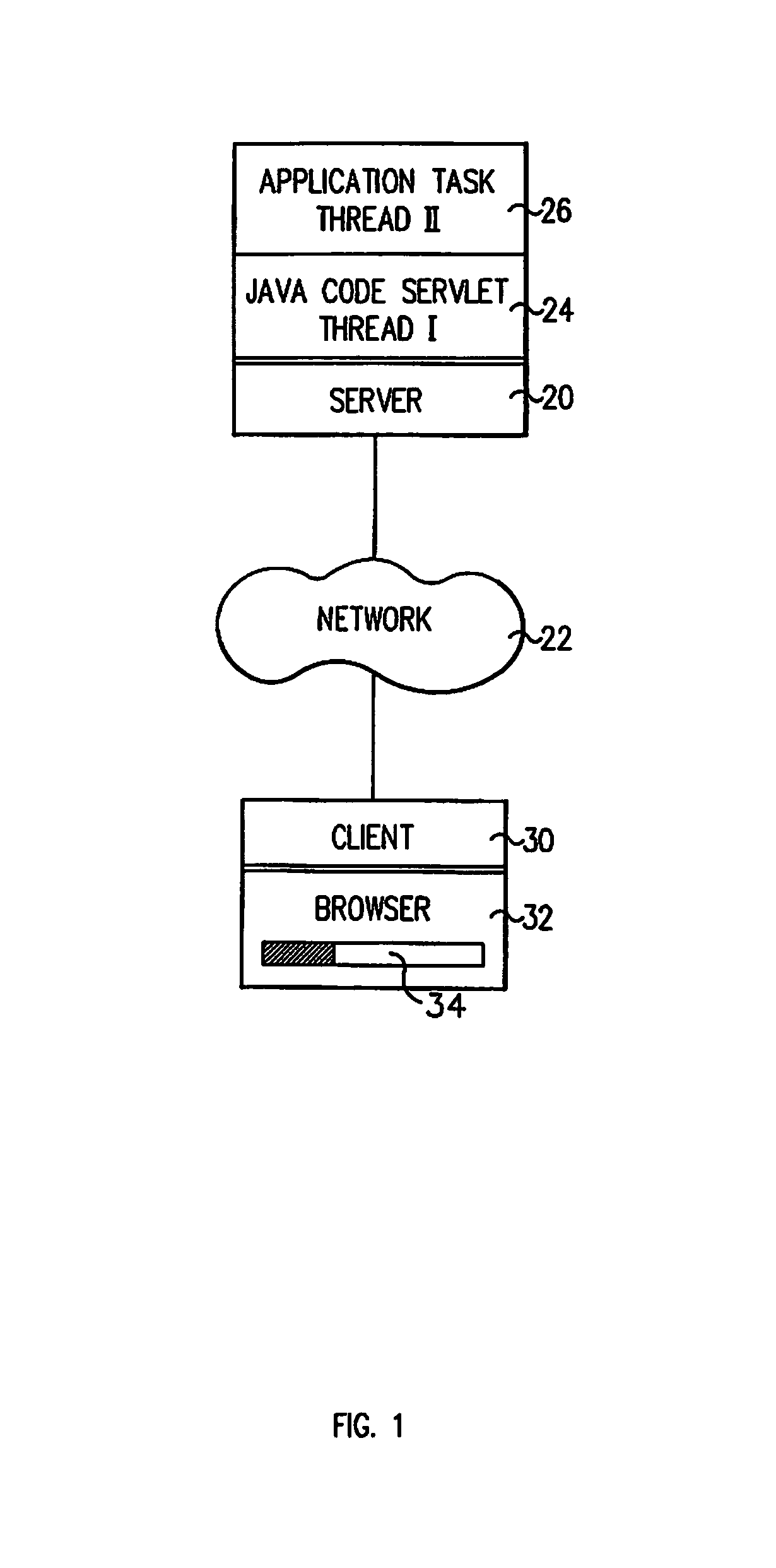
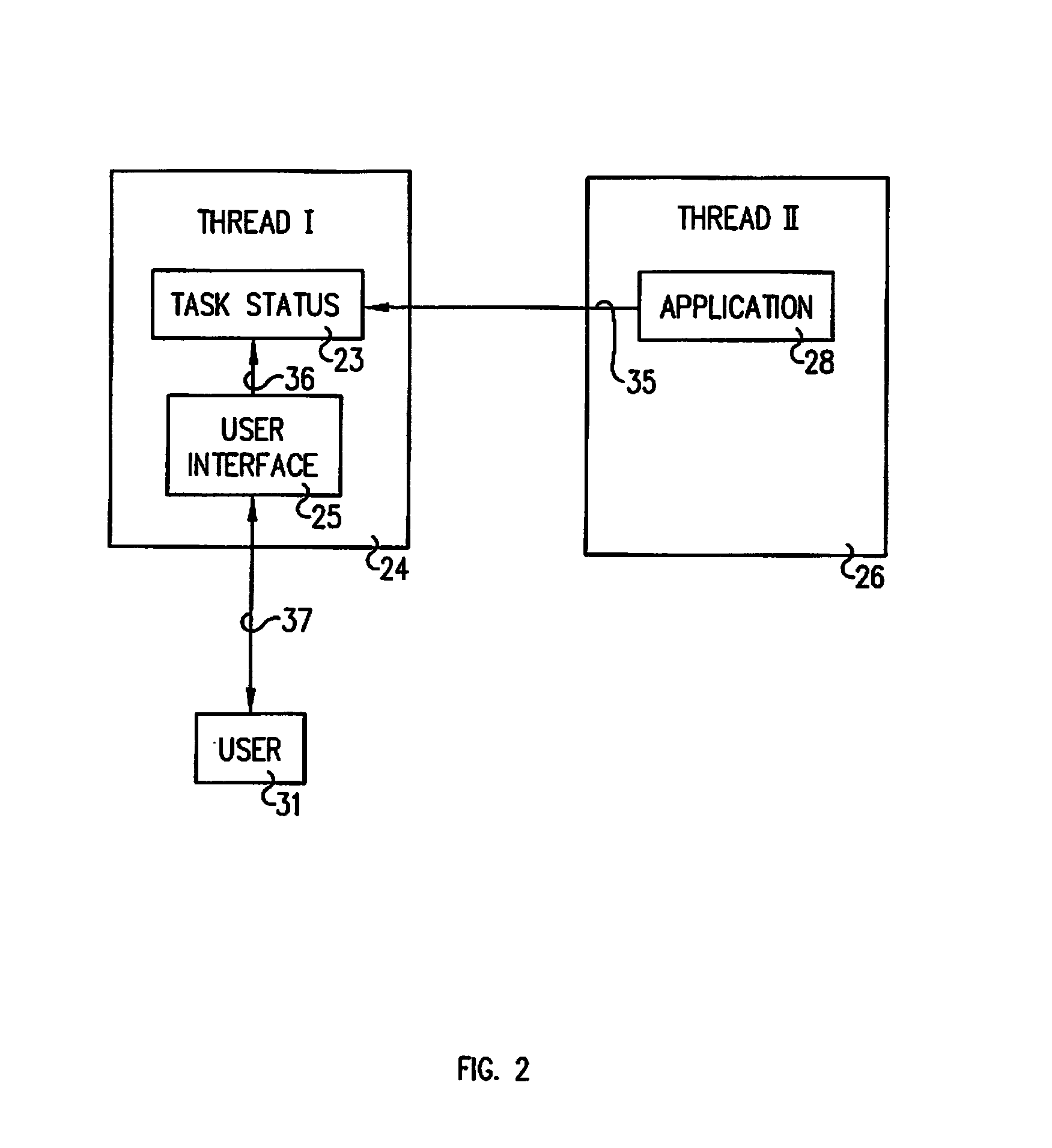
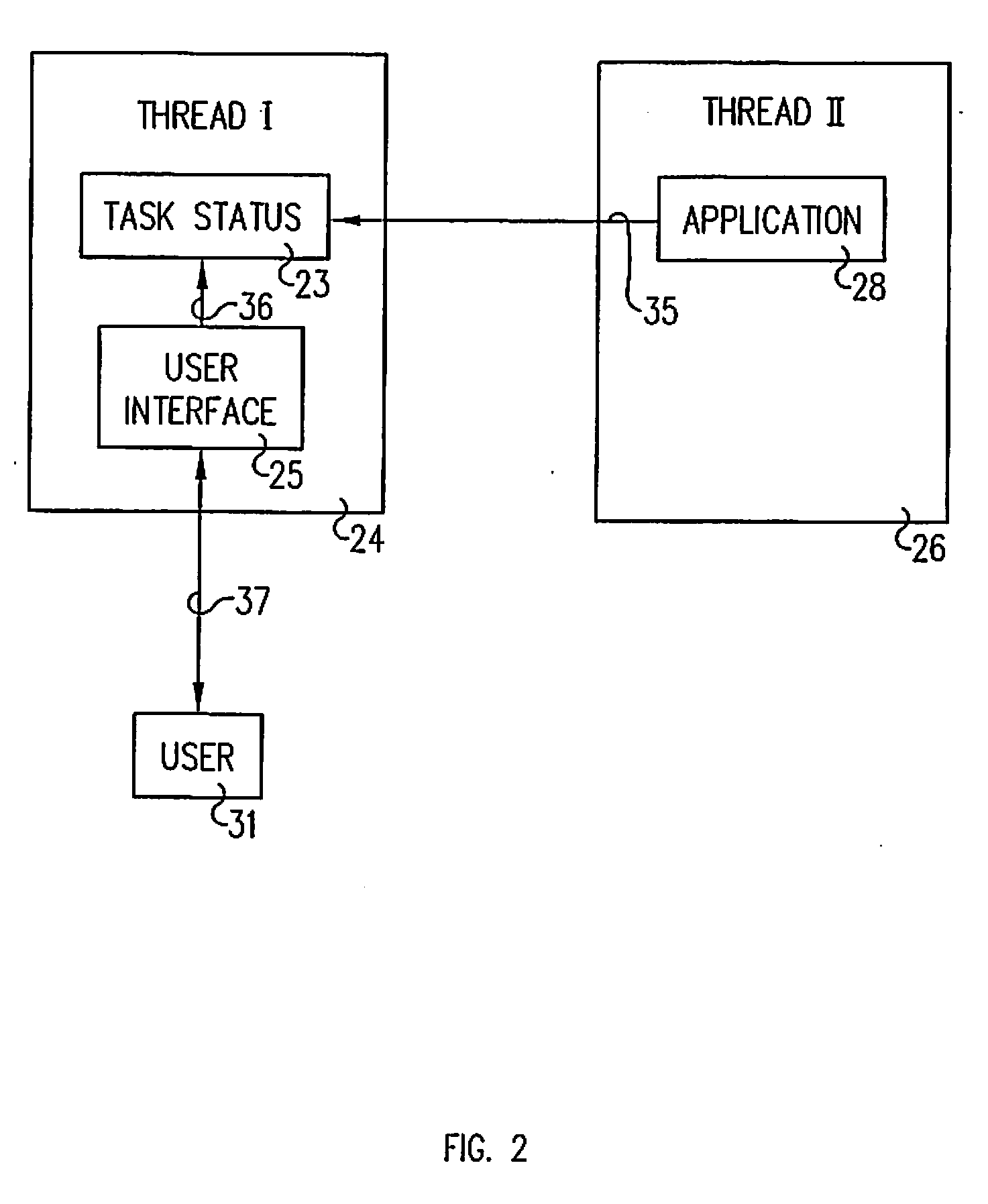
InactiveUS7330894B2Avoid timeoutMultiple digital computer combinationsTransmissionClient-sideApplication software
A system for preventing timeout of a client interface accessing a main Java Servlet executing in a first thread which monitors an application executing in a second thread. A task status object is accessed by the application to post its completion state and by the client interface responsive to a state refresh request to post a state refresh response including the completion state to the client. The state refresh response selectively includes a refresh attribute instructing the client to periodically post the state refresh request. Upon the application going to completion or error state, subsequent state refresh responses do not include the refresh attribute.
Owner:IBM CORP
Computer, computer system, and application execution method
InactiveUS20110107156A1Digital data processing detailsInterprogram communicationComputerized systemParallel computing
A computer receives one or more processing requests from at least one or more clients through a network and executes an application for processing the received processing requests using a Java servlet. The processing requests each contain one or more addresses as the destinations of the processing requests. The computer is connected to a database including the following information: application information in which an identifier that uniquely identifies each application and binary logic for executing the application are brought into correspondence with each other; and adapter information in which the identifier and each of the addresses are brought into correspondence with each other. When the computer receives the processing request, it identifies the binary logic based on an address contained in the received processing request and executes the identified binary logic and thereby executes the application.
Owner:HITACHI LTD
Active control of collaborative devices
InactiveUS7430583B2Multiple digital computer combinationsElectric digital data processingEmbedded JavaClient-side
Control of collaborative devices, including providing at least two collaborative devices, wherein each collaborative device comprises a client device and an embedded Java server, providing a registry service to which the collaborative devices are coupled for data communications, and providing at least one registry table, wherein the registry table includes registry records, wherein the registry records include registry records representing capabilities of collaborative devices, wherein the registry records representing capabilities of collaborative devices include data elements describing, for each collaborative device, capabilities, tertiary relationships, and network connectivities. The method further includes providing a service bundle of OSGI-compliant Java servlets comprising at least one predetermined algorithm for controlling the collaborative devices, and controlling the collaborative devices in accordance with the predetermined algorithm.
Owner:INT BUSINESS MASCH CORP
Edge side components and application programming environment for building and delivering highly distributed heterogenous component-based web applications
InactiveUS7467233B2Interprogram communicationMultiple digital computer combinationsEdge serverConfigfs
Owner:AKAMAI TECH INC
System and method for merging security constraints when using security annotations
ActiveUS20120324528A1Digital data processing detailsAnalogue secracy/subscription systemsApplication serverComputer science
A method is described for merging security constraints associated with an application when using security annotations. The application comprises one or more servlets, such as a Java servlet. During application deployment, a list of role names is generated by merging static security constraints, for example, identified in a deployment descriptor, and in a static security annotation that defines a list containing the names of authorized roles for a servlet. Later, during application runtime in an application server, security constraints are retrieved from a plurality of sources, including both dynamic and static security annotations. Using the list of role names and the security constraints retrieved, a set of merged security constraints having a defined and proper order of precedence is generated. In particular, preferably one or more dynamic security annotations are first merged with one or more static security annotations to generate a set of runtime constraints. The security constraints from the deployment descriptor are then merged with the set of runtime constraints and the list of roles to generate the set of merged security constraints. These merged security constraints are then applied to process a request being handled by the application server.
Owner:IBM CORP
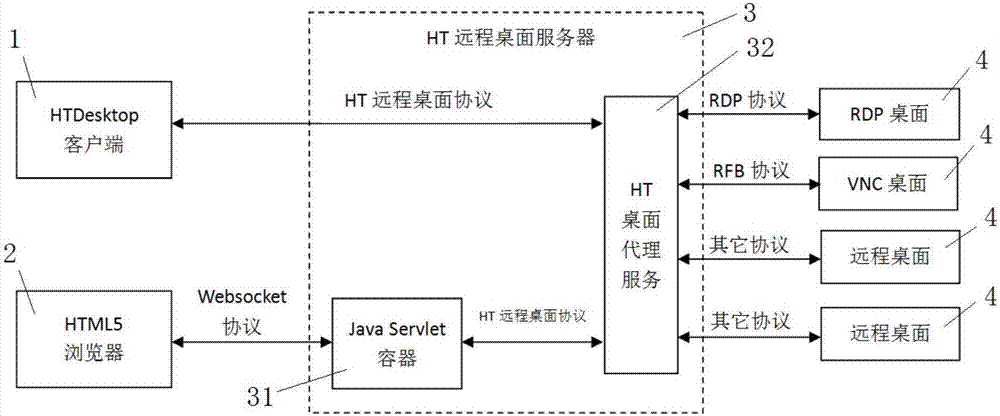
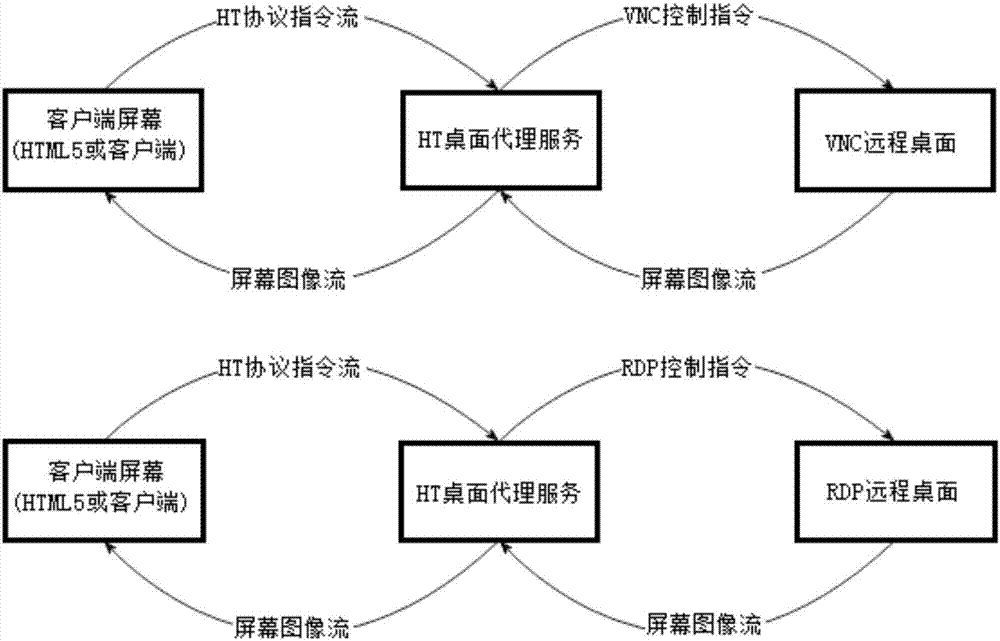
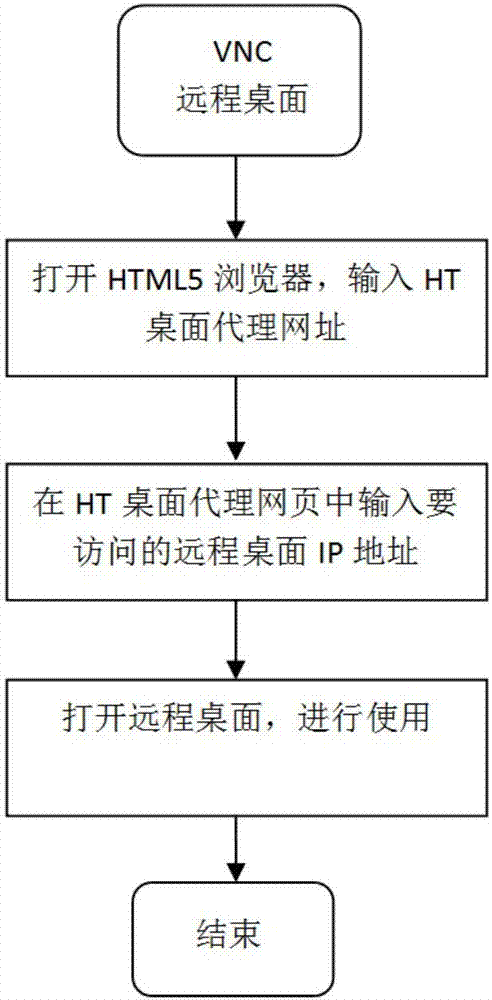
HTML5-based remote desktop access system and remote desktop access method
InactiveCN107124450ANo installation requiredImprove experienceTransmissionSpecific program execution arrangementsHTML5Access method
The invention discloses an HTML5-based remote desktop access system and a remote desktop access method based on the system. The system comprises HTDesktop clients, HTML5 browsers, an HT remote desktop server and remote desktops, wherein the HT remote desktop server comprises Java Servlet containers and HT desktop proxy services, the HTDesktop clients communicate with the remote desktops via the HT desktop proxy services by use of an HT desktop protocol; and the Java Servlet containers communicate with the remote desktops via the HT desktop proxy services by use of the HT desktop protocol. The method comprises the following steps: 1, the HTML5 browsers establish links with the Java Servlet containers, and the Java Servlet containers forward HT desktop protocol instructions from the HTML5 browsers; 2, the HT desktop proxy services, according to information of the remote desktops, convert the HT desktop protocol instructions into instructions corresponding to the remote desktops; and 3, the HT desktop proxy services forward screen data of the remote desktops to the front HTML5 browsers. The system and method provided by the invention have the advantages of convenience in use, good user experience, higher work efficiency, facilitated maintenance of existing remote desktops and the like.
Owner:恒泰艾普(北京)云技术有限公司
Method and apparatus for protecting HTTP session data from data crossover using aspect-oriented programming
A method, computer program product, and data processing system for detecting and identifying data crossover errors in servlet code are disclosed. According to a preferred embodiment, techniques of aspect-oriented programming (AOP) are used to instrument JAVA Servlet code to detect potential data crossover errors. Specifically, pointcuts are defined to intercept both the association follow an object with a particular session and the “getting” and “setting” of such objects. Advice code associated with these pointcuts is used to update and / or consult a “collator” data structure, which is used to determine if an object or variable associated with one session is being accessed by a different session. In a preferred embodiment, the AspectJ aspect-oriented programming language / system is used to define the pointcuts and advice code.
Owner:IBM CORP
Document handling in a web application
InactiveUS7613994B2Efficient solutionAccelerated programComputer security arrangementsSpecial data processing applicationsDocumentation procedureRelational database
A unique document handling facility on the scale of a Lotus Notes document. Preferably, the documents are stored in a relational database and served-up using Java servlets, with provisions for handling document content and group level security. The preferred implementation of the invention provides several specific features: (1) Presentation and control of heterogeneous document content through the service of the Enterprise Application Development Platform, (2) An efficient scheme for group level and user level security, (3) Presentation of heterogeneous document types, (4) Presentation of heterogeneous data types in the document, (5) A method to externalize definition of keyword selections, and (6) The ability to present document fields in any order, regardless of whether they originate in the head or body of the underlying document.
Owner:KYNDRYL INC
Active Control Of Collaborative Devices
InactiveUS20080243987A1Digital data processing detailsMultiple digital computer combinationsEmbedded JavaClient-side
Control of collaborative devices, including providing at least two collaborative devices, wherein each collaborative device comprises a client device and an embedded Java server, providing a registry service to which the collaborative devices are coupled for data communications, and providing at least one registry table, wherein the registry table includes registry records, wherein the registry records include registry records representing capabilities of collaborative devices, wherein the registry records representing capabilities of collaborative devices include data elements describing, for each collaborative device, capabilities, tertiary relationships, and network connectivities. The method further includes providing a service bundle of OSGI-compliant Java servlets comprising at least one predetermined algorithm for controlling the collaborative devices, and controlling the collaborative devices in accordance with the predetermined algorithm.
Owner:INT BUSINESS MASCH CORP
Document handling in a web application
InactiveUS20100049773A1Efficient solutionAccelerated programDigital data processing detailsComputer security arrangementsDocumentation procedureRelational database
Owner:KYNDRYL INC
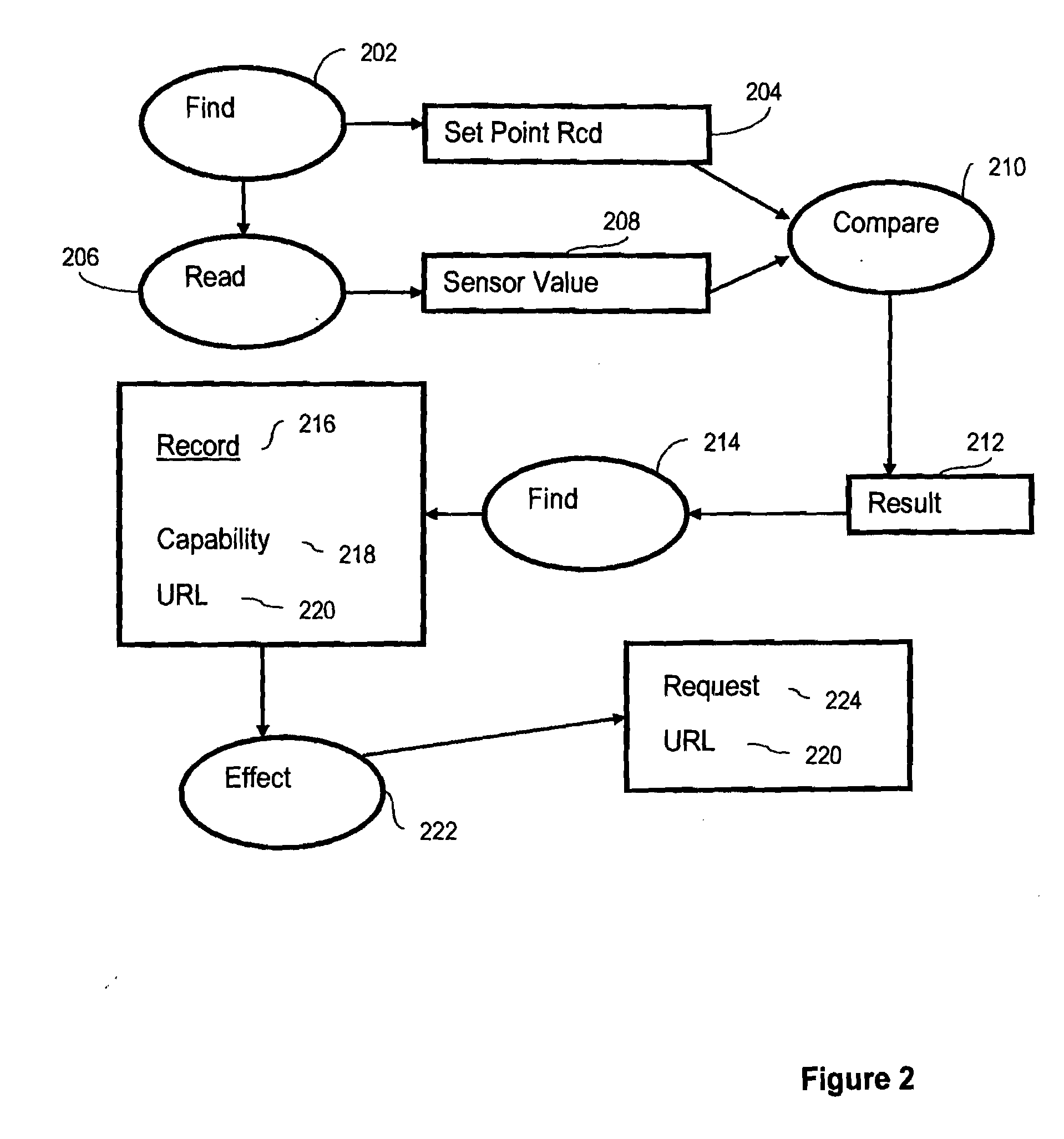
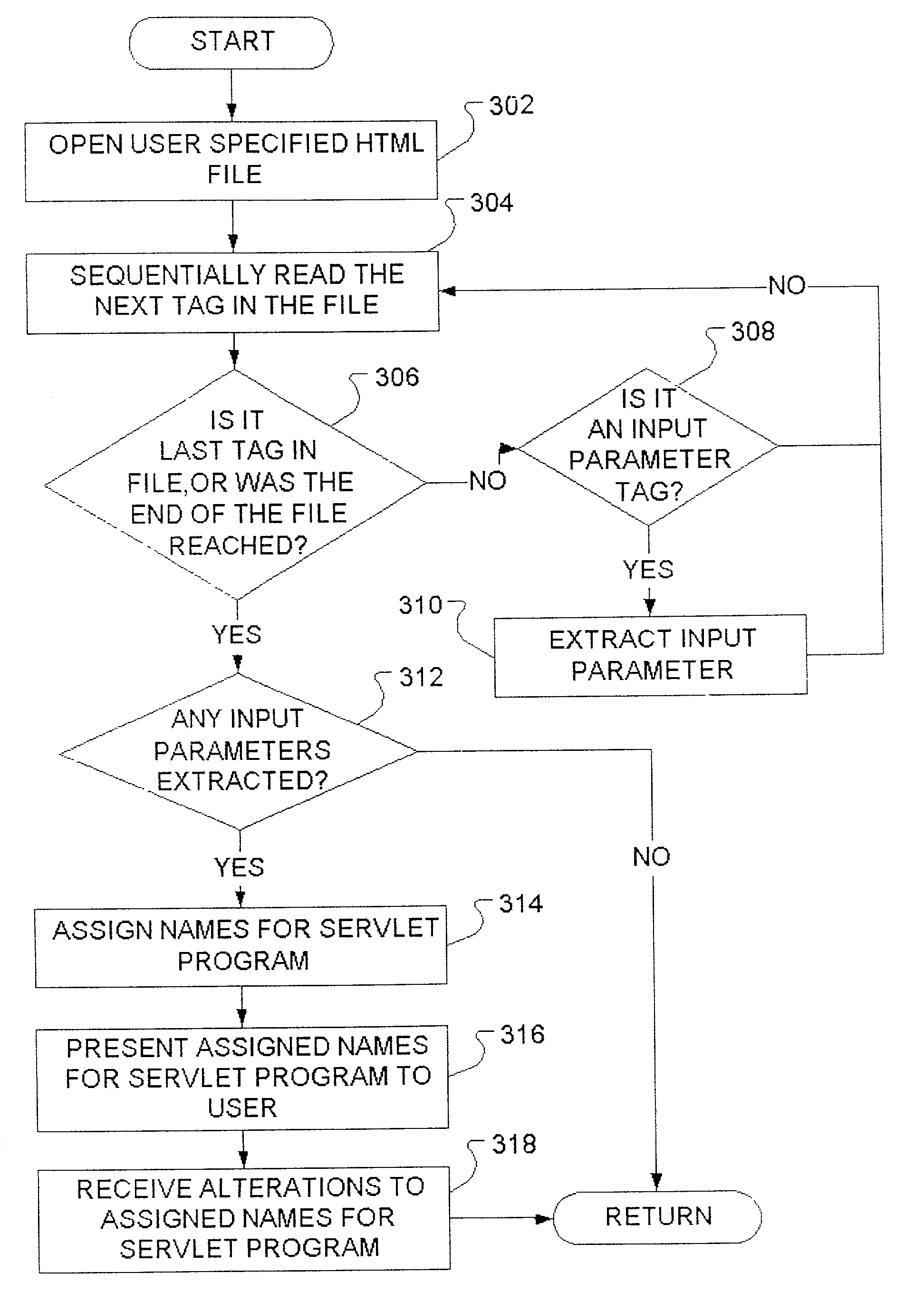
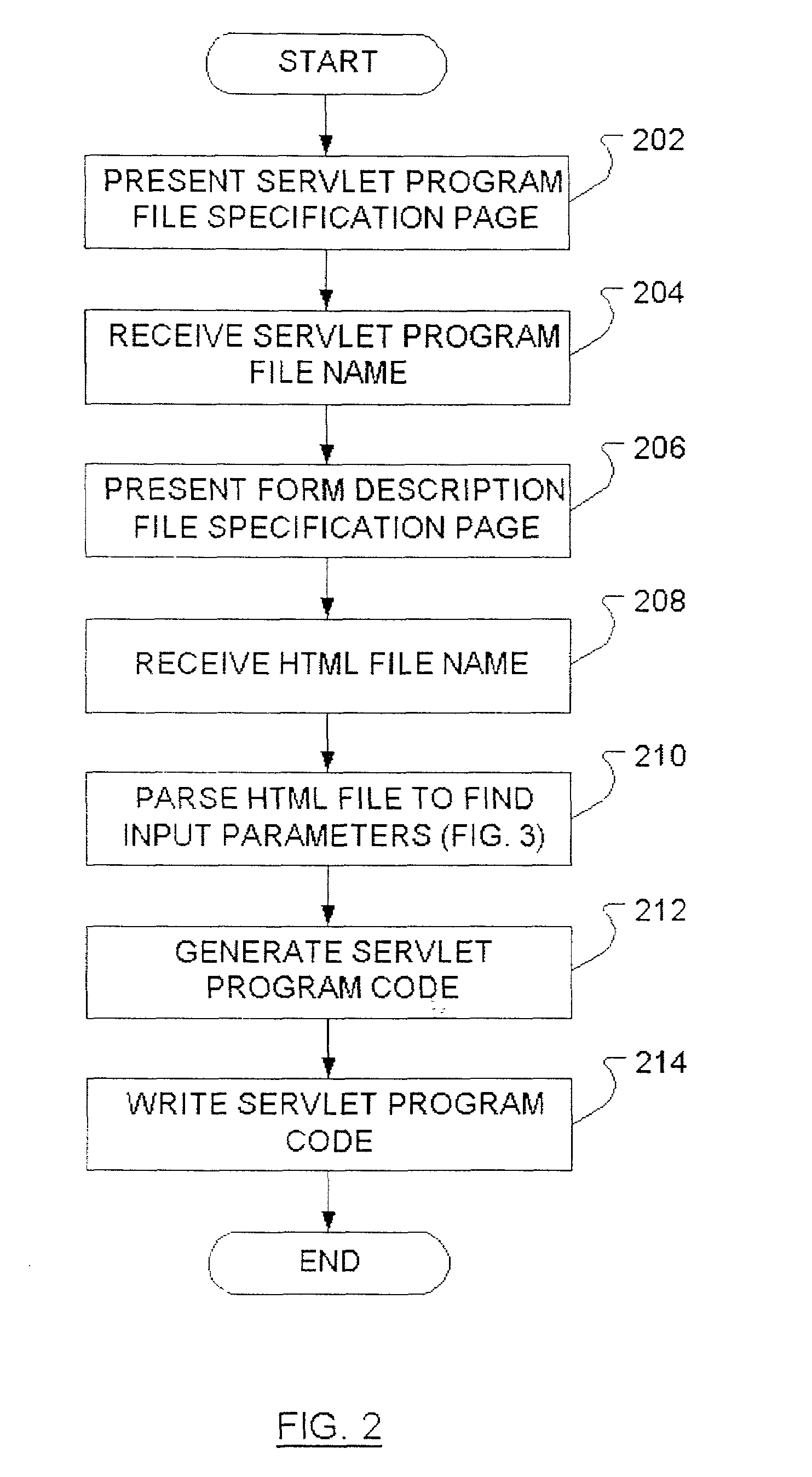
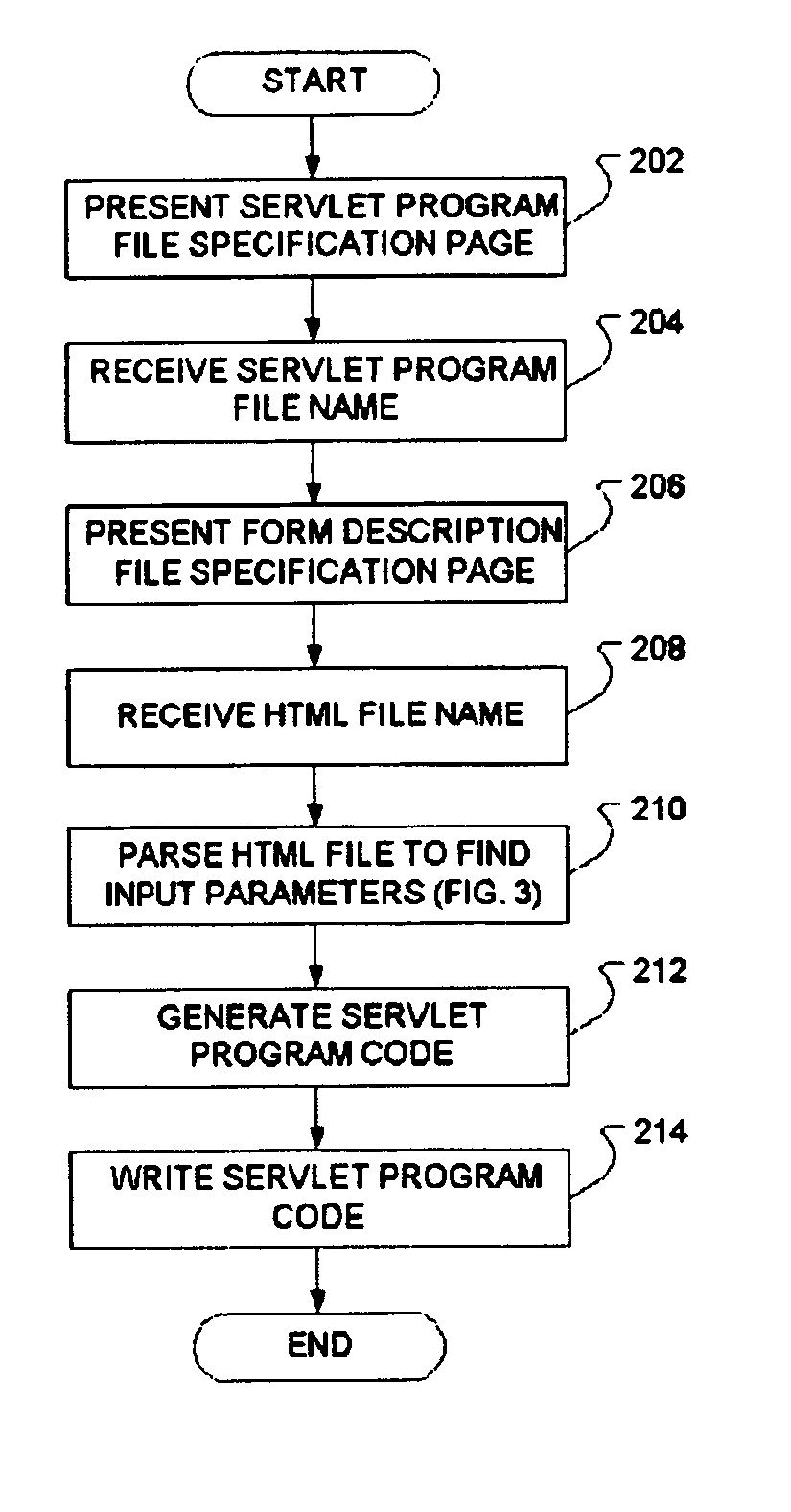
Method to reduce input parameter interface error and inconsistency for servlets
InactiveUS6983284B2Reduce interfaceData processing applicationsDigital data processing detailsProgramming languageUser input
A GUI utility tool running on a web application development environment is presented that acts to eliminate inconsistency between a given HTML user input form description file and a corresponding servlet program file. The tool allows the user to specify an HTML file. The tool may then parse the HTML file to discover input parameters and generate Java servlet program code to receive the input parameters.
Owner:IBM CORP
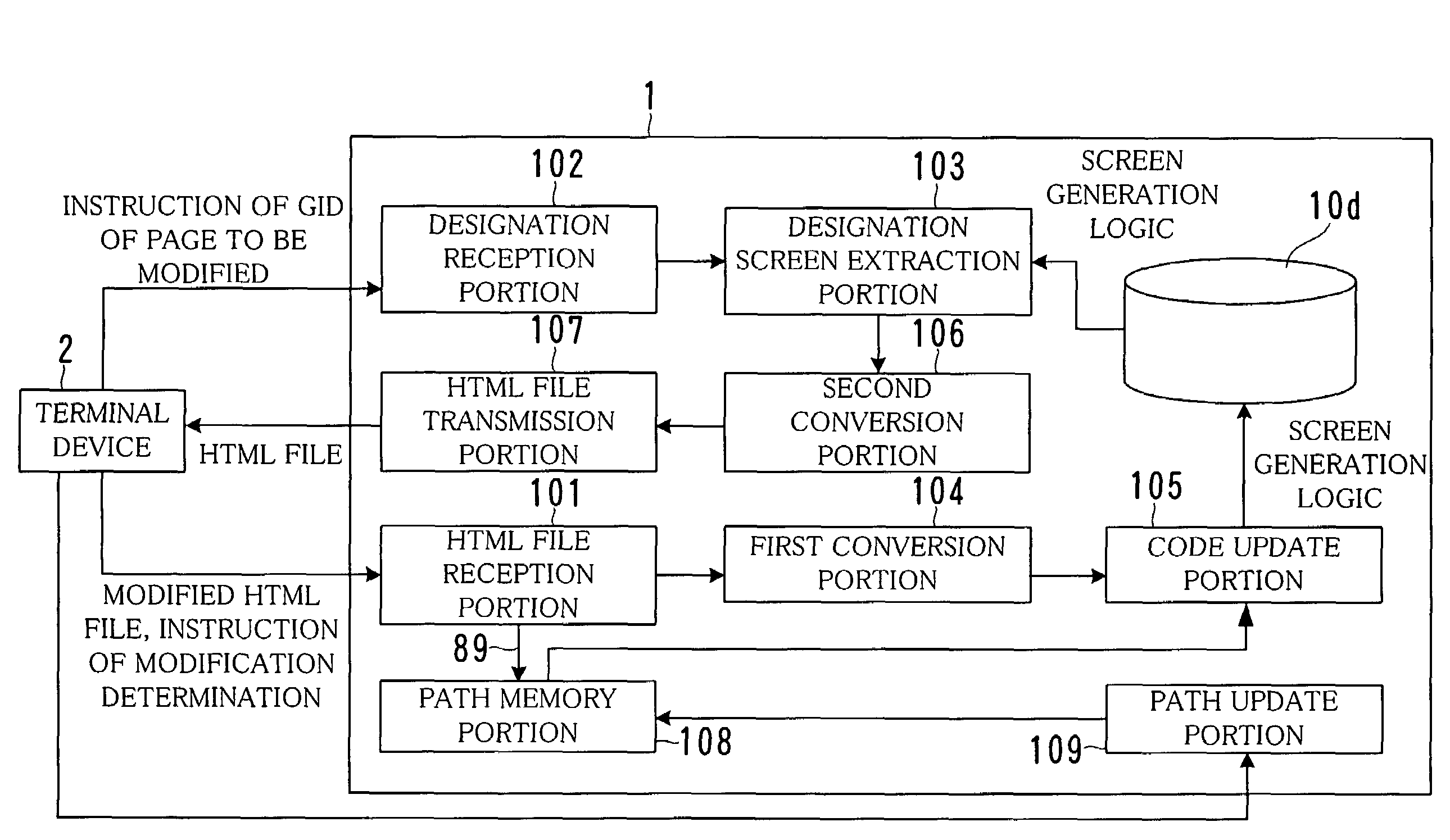
Web server having function of Java servlet, method for updating Java program and computer program
InactiveUS7305657B2Easy to modifyMultiple digital computer combinationsSpecific program execution arrangementsWeb serviceTerminal equipment
A Web server storing a Java program for generating an HTML file of a Web page includes a portion for obtaining an HTML file, a first conversion portion for converting the file into Java codes, a portion for replacing the codes with a part of a Java program related to the Web page structure, the Java program being for generating the HTML file, a portion for extracting Java codes of a part related to a designated Web page structure, a second conversion portion for converting the codes into an HTML file, and a portion for transmitting the file to the terminal device. If the HTML file contains a tag indicating an unmodifiable part, the first conversion portion converts the tag into a Java code indicating an unmodifiable part. The second conversion portion converts the code contained in the Java codes into the tag.
Owner:FUJITSU LTD
Servlet api and method for xmpp protocol
ActiveUS20160204993A1Digital computer detailsData switching networksCommunications systemNetwork connection
A communication system and method include a server hosting an interactive voice response or self-help application in a virtual machine. In order to leverage the advantages and facilities of the servlet model, a XMPP (Extensible Messaging and Presence Protocol) servlet container is provided for the server so that the communication application can be programmed with objects defined by an XMPP servlet API, as well as such as HTTP and SIP servlets, in order to service an XMPP client. In addition to the generic class objects of the Java servlet model, the API also provides a set of XMPP-specific class objects. The XMPP servlet container includes a network point at a transport level for handling network connections, an XMPP service layer for managing XMPP sessions and streams, and an application layer for managing XMPP stanzas.
Owner:CISCO TECH INC
Servlet API and method for XMPP protocol
ActiveUS9215079B2Special service provision for substationDigital computer detailsCommunications systemNetwork connection
A communication system and method include a server hosting an interactive voice response or self-help application in a Java virtual machine. In order to leverage the advantages and facilities of the Java servlet model, a Java XMPP (Extensible Messaging and Presence Protocol) servlet container is provided for the server so that the communication application can be programmed with objects defined by an XMPP servlet API, as well as objects defined by the standards-based Java EE platform such as HTTP and SIP servlets, in order to service an XMPP client. In addition to the generic class objects of the Java servlet model, the API also provides a set of XMPP-specific class objects. The Java XMPP servlet container includes a network point at a transport level for handling network connections, an XMPP service layer for managing XMPP sessions and streams, and an application layer for managing XMPP stanzas.
Owner:CISCO TECH INC
System and method for preventing timeout of a client
Owner:INT BUSINESS MASCH CORP
System and method for merging security constraints when using security annotations
ActiveUS8645679B2Digital data processing detailsAnalogue secracy/subscription systemsApplication serverApplication software
A method is described for merging security constraints associated with an application when using security annotations. The application comprises one or more servlets, such as a Java servlet. During application deployment, a list of role names is generated by merging static security constraints, for example, identified in a deployment descriptor, and in a static security annotation that defines a list containing the names of authorized roles for a servlet. Later, during application runtime in an application server, security constraints are retrieved from a plurality of sources, including both dynamic and static security annotations. Using the list of role names and the security constraints retrieved, a set of merged security constraints having a defined and proper order of precedence is generated. In particular, preferably one or more dynamic security annotations are first merged with one or more static security annotations to generate a set of runtime constraints. The security constraints from the deployment descriptor are then merged with the set of runtime constraints and the list of roles to generate the set of merged security constraints. These merged security constraints are then applied to process a request being handled by the application server.
Owner:INT BUSINESS MASCH CORP
Plug-in service transmission platform
The present invention discloses a pluggable service delivery platform for supporting many devices to many services in an e-business application, comprising a device-platform interface, a service-platform interface and a platform kernel section. The service delivery platform of this invention is a flexible and scalable platform to easily "plug" a new device and a new service, and the different parts of the platform are componentized. Any one of the components can be replaced by a 3rd party's products, providing they abide certain open interface like Java Servlet, LDAP, etc.
Owner:IBM CORP
Method to reduce input parameter interface error and inconsistency for servlets
InactiveUS20050235161A1Reduce input parameter interface errorReduce interfaceData processing applicationsDigital data processing detailsUser inputWeb application development
A GUI utility tool running on a web application development environment is presented that acts to eliminate inconsistency between a given HTML user input form description file and a corresponding servlet program file. The tool allows the user to specify an HTML file. The tool may then parse the HTML file to discover input parameters and generate Java servlet program code to receive the input parameters.
Owner:IBM CORP
Web server, web server having function of Java servlet, and computer readable medium
InactiveUS8533587B2Simple contentDigital computer detailsNatural language data processingWeb serviceTerminal equipment
A Web server for transmitting a Web page to a terminal device of a user via a network includes a dynamic part operation portion for determining contents of a dynamic part of a Web page in accordance with a parameter designated by a user, a dynamic part process portion for performing a process of making a data memory portion store the contents of the dynamic part determined by the dynamic part operation portion in connection with the Web page and the user, a Web page generating portion for generating a Web page in accordance with the determined contents of the dynamic part and a Web page transmission portion for transmitting the generated Web page to the terminal device.
Owner:FUJITSU LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com