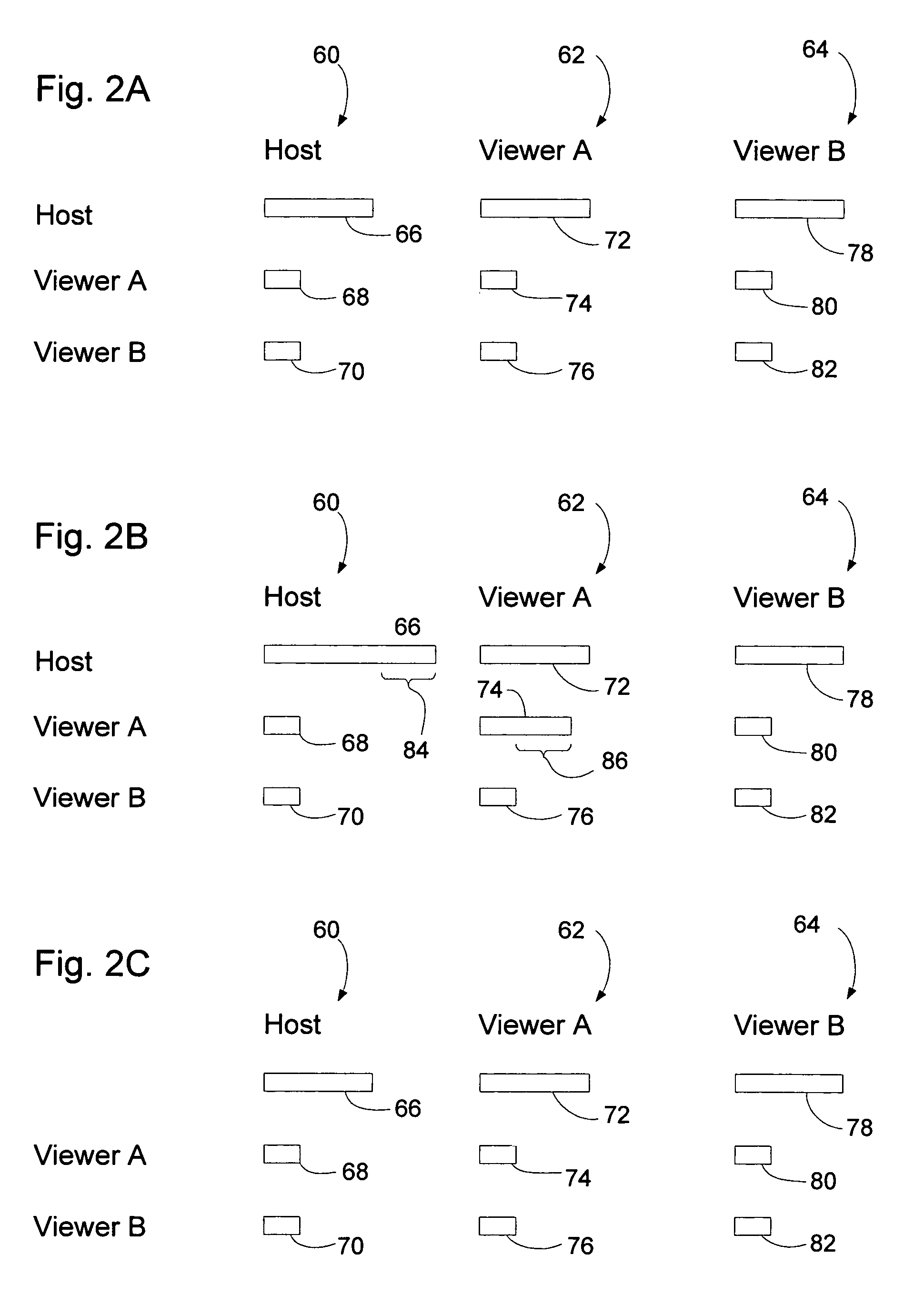
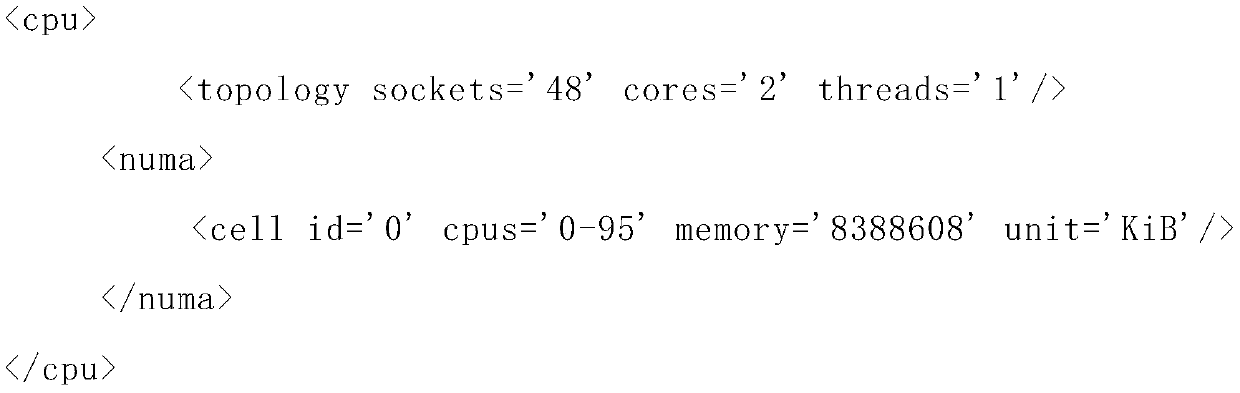Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Host model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networking, a host model is an option of designing the TCP/IP stack of a networking operating system like Microsoft Windows or Linux. When a unicast packet arrives at a host, IP must determine whether the packet is locally destined (its destination matches an address that is assigned to an interface of the host). If the IP stack is implemented with a weak host model, it accepts any locally destined packet regardless of the network interface on which the packet was received. If the IP stack is implemented with a strong host model, it only accepts locally destined packets if the destination IP address in the packet matches an IP address assigned to the network interface on which the packet was received.
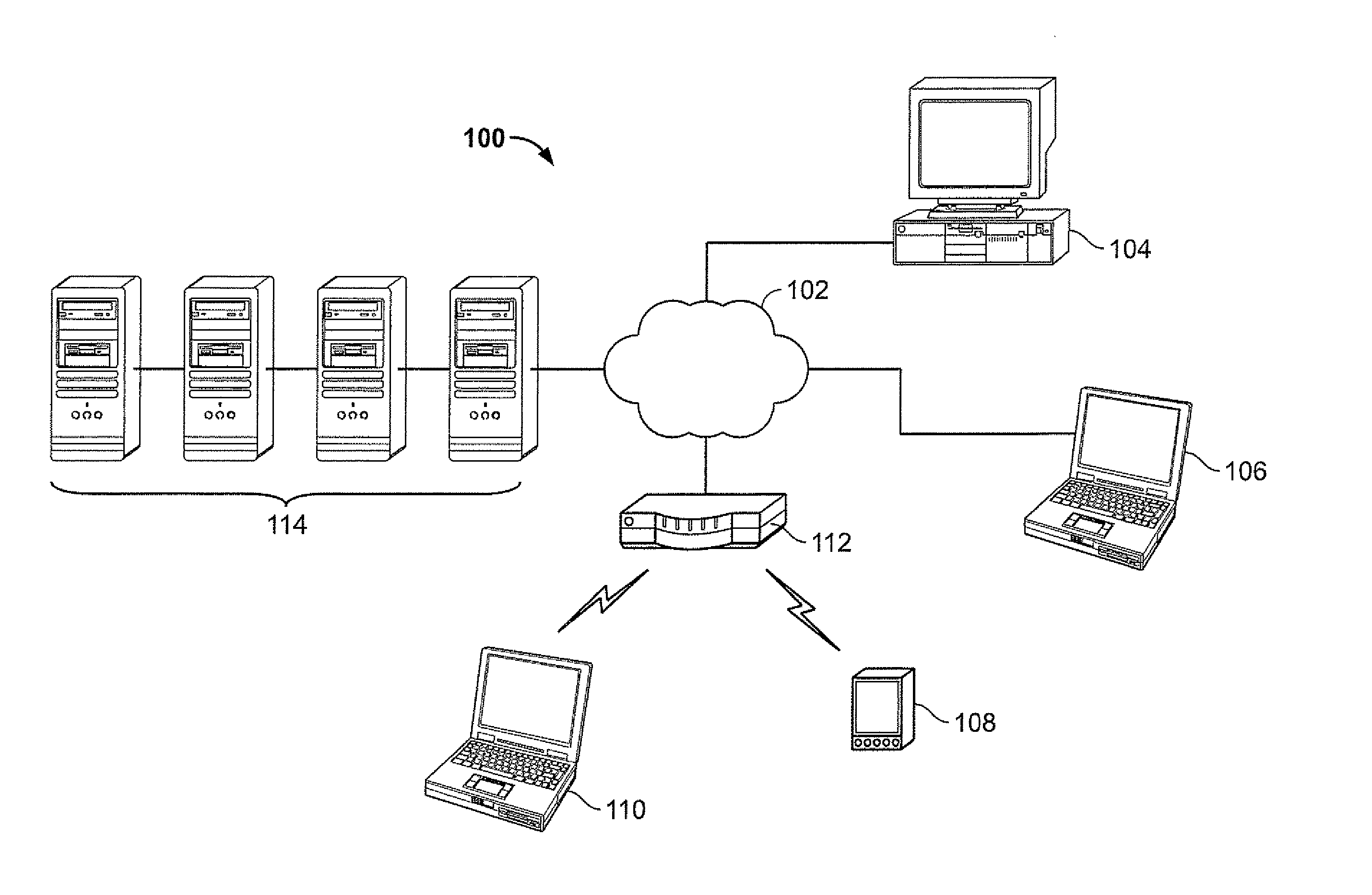
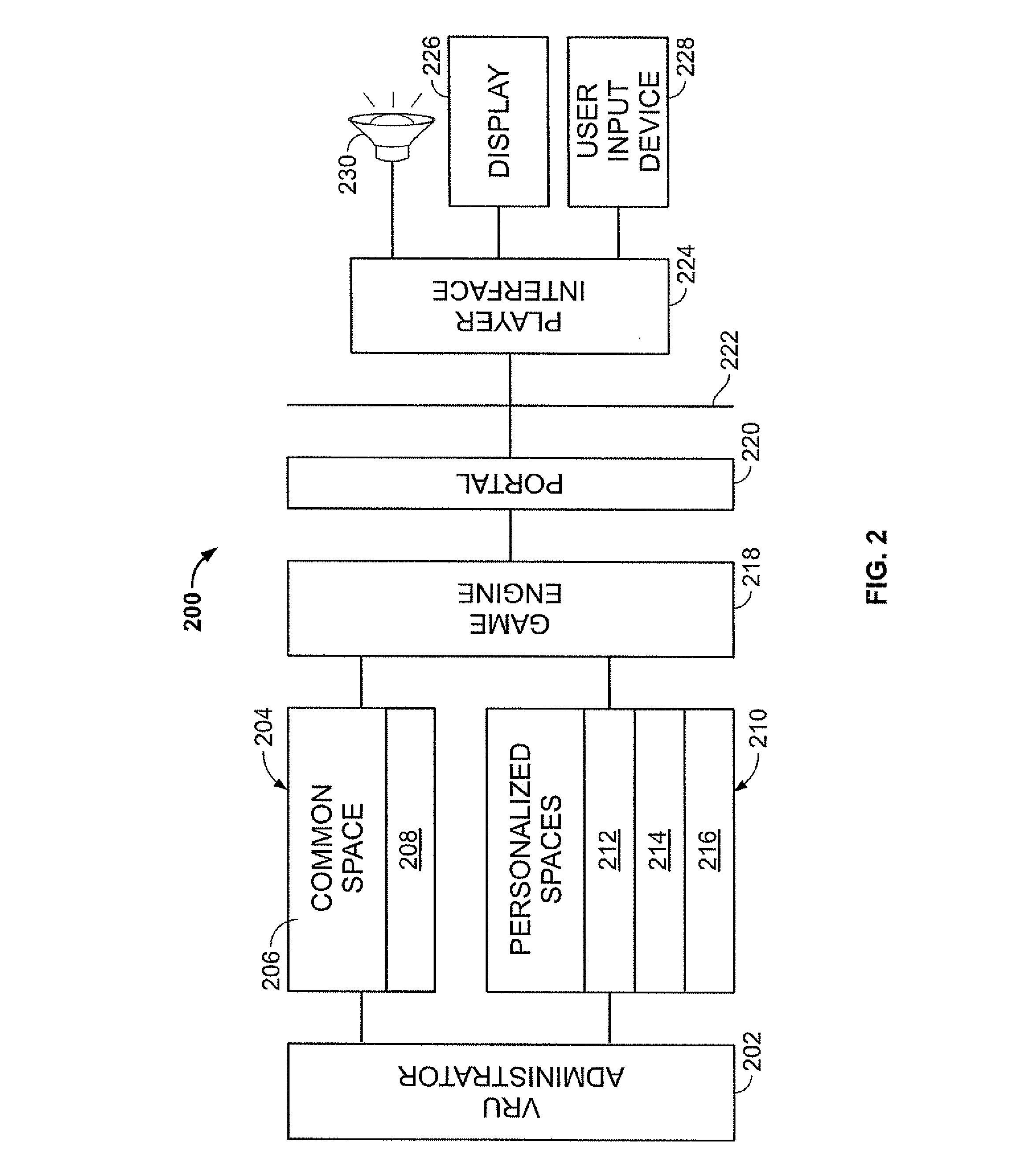
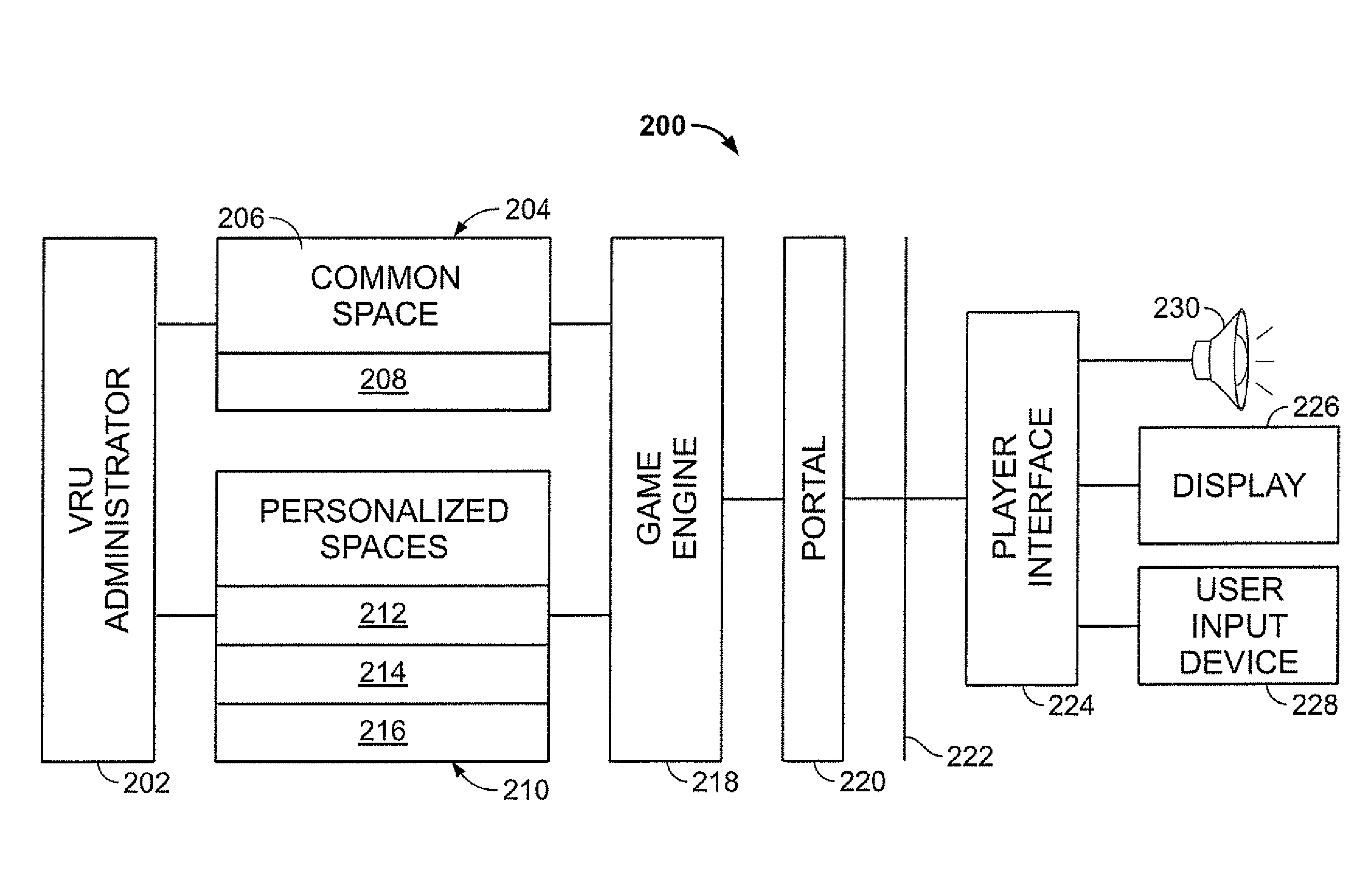
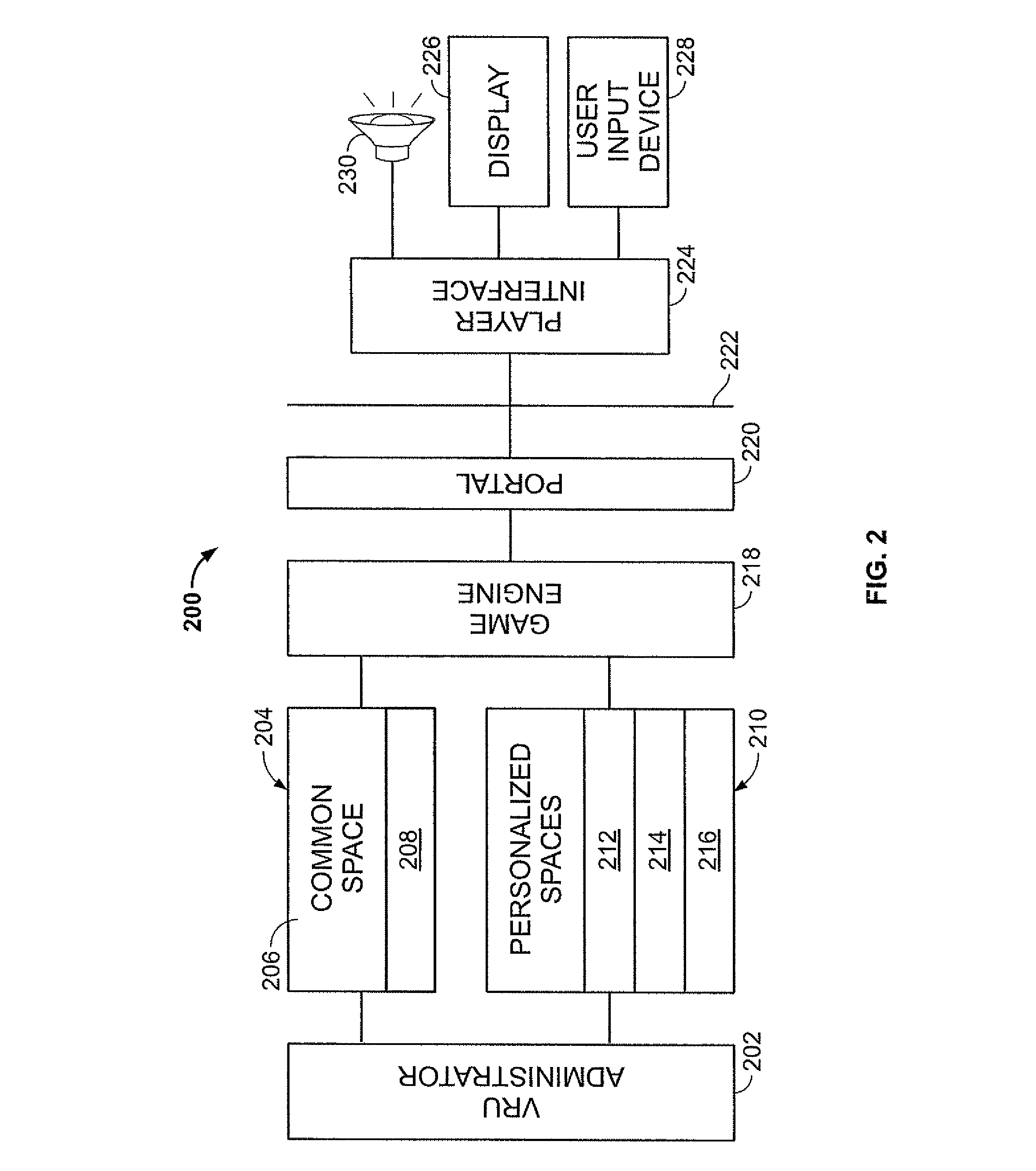
Virtual environment for computer game
A multi-user virtual reality universe (VRU) process receives input from multiple remote clients to manipulate avatars through a modeled 3-D environment. A VRU host models movement of avatars in the VRU environment in response to client input, which each user providing input for control of a corresponding avatar. The modeled VRU data is provided by the host to client workstations for display of a simulated environment visible to all participants. The host maintains personalized data for selected modeled objects or areas that is personalized for specific users in response to client input. The host includes personalized data in modeling the VRU environment. The host may segregate VRU data provided to different clients participating in the same VRU environment according to limit personalized data to authorized users, while all users receive common data.
Owner:PFAQUTRUMA RES LLC
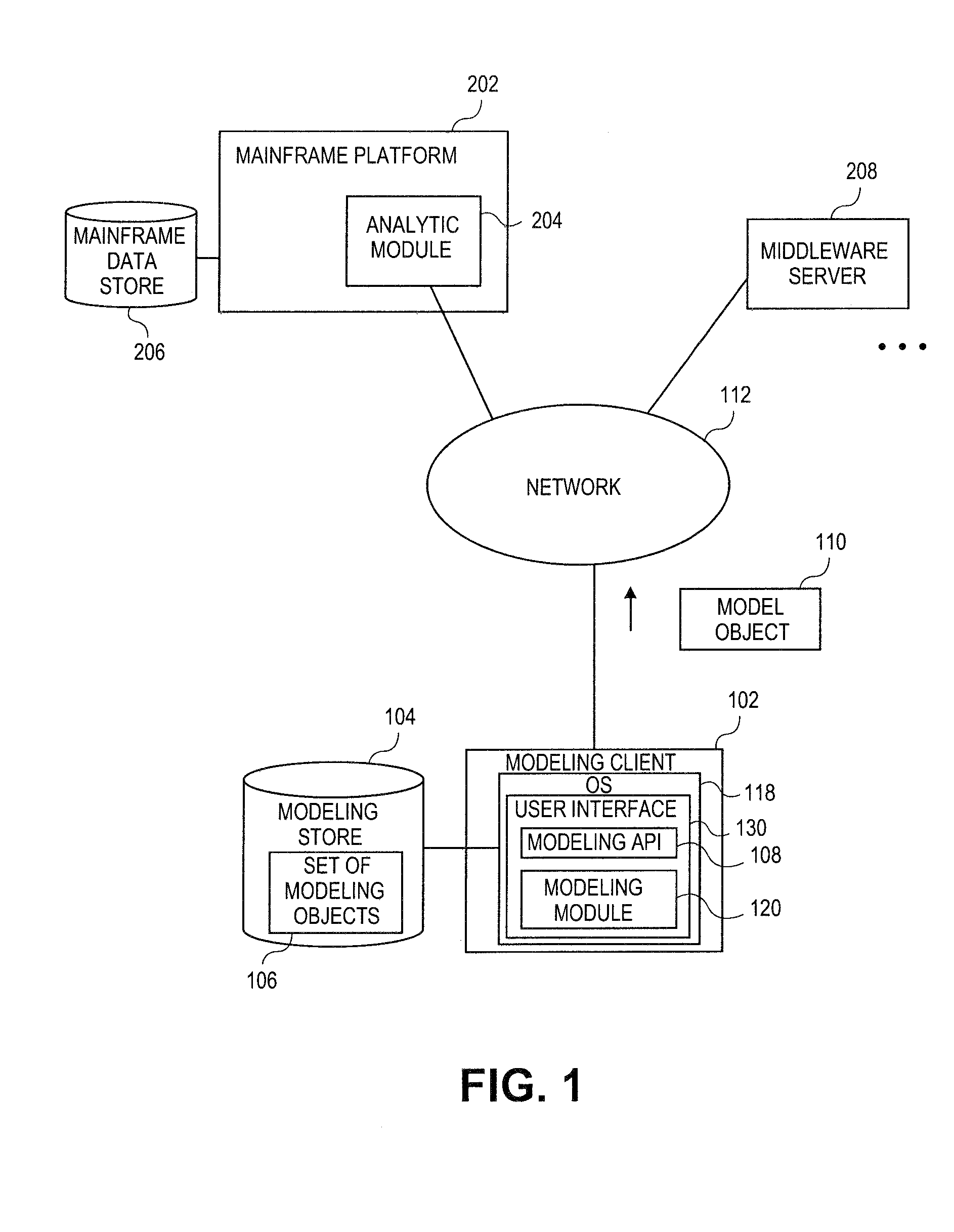
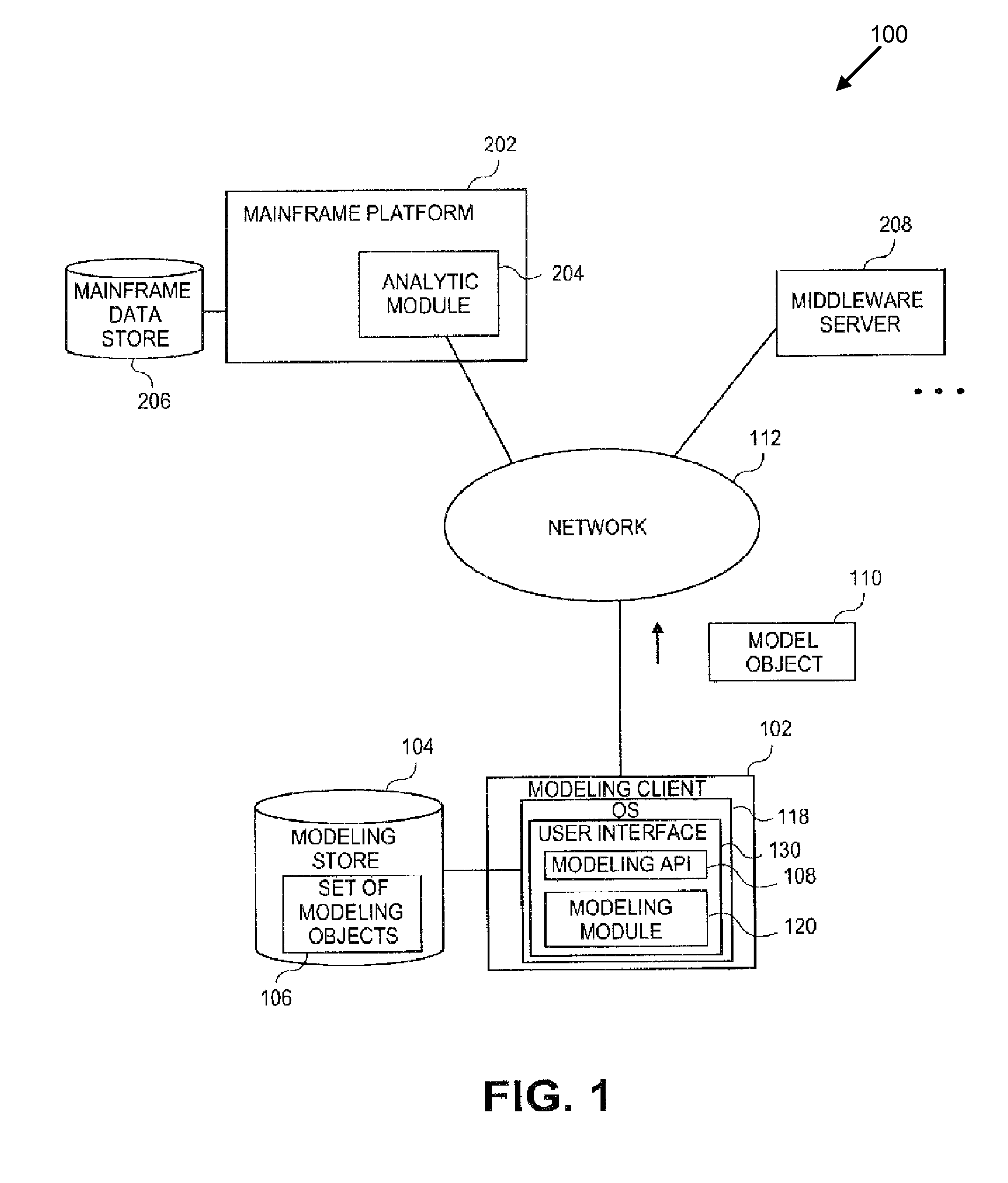
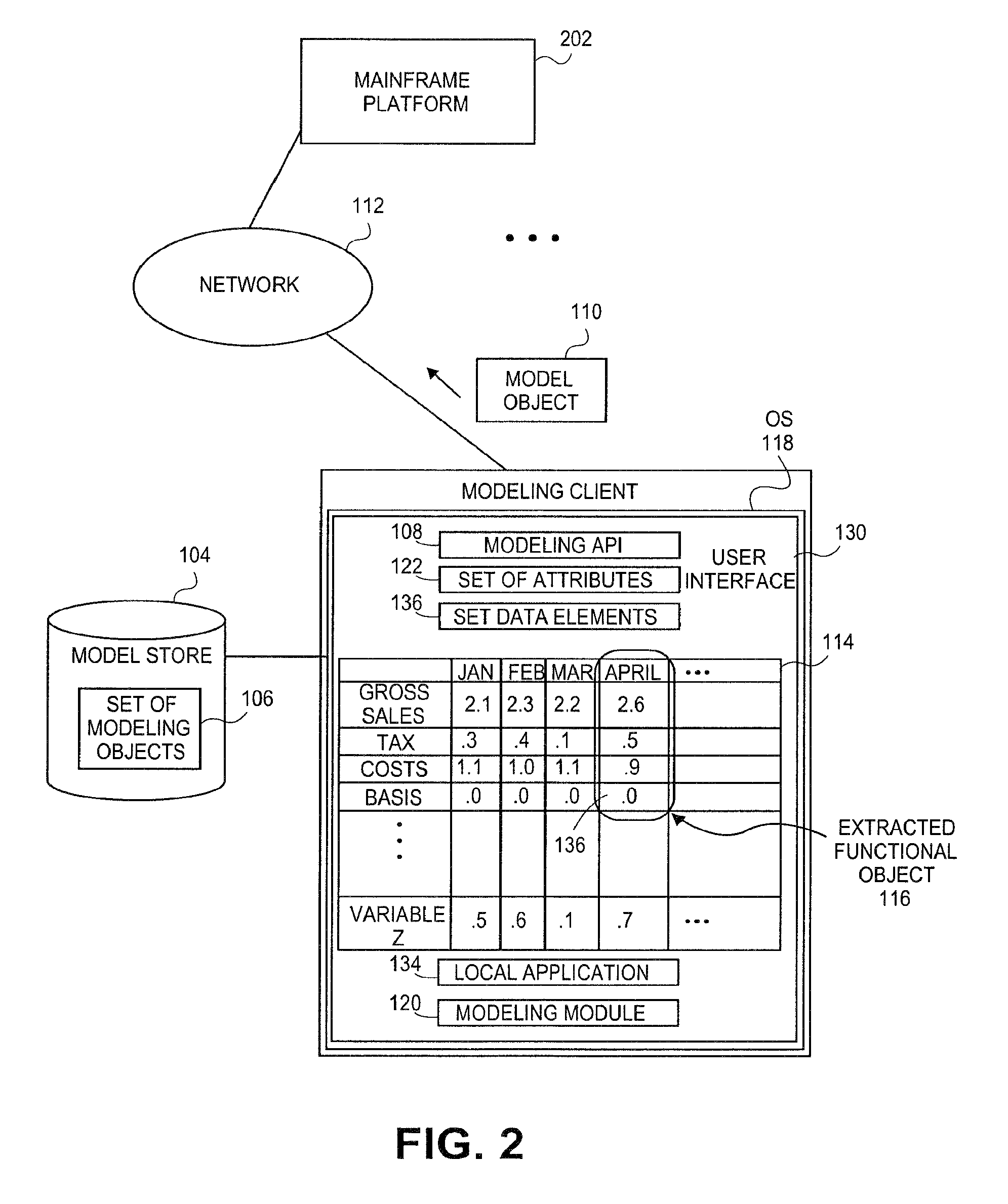
Systems and methods for extracting database dimensions as data modeling object
InactiveUS20100306281A1Software level energy consumption reductionDigital data processing detailsData modelingApplication programming interface
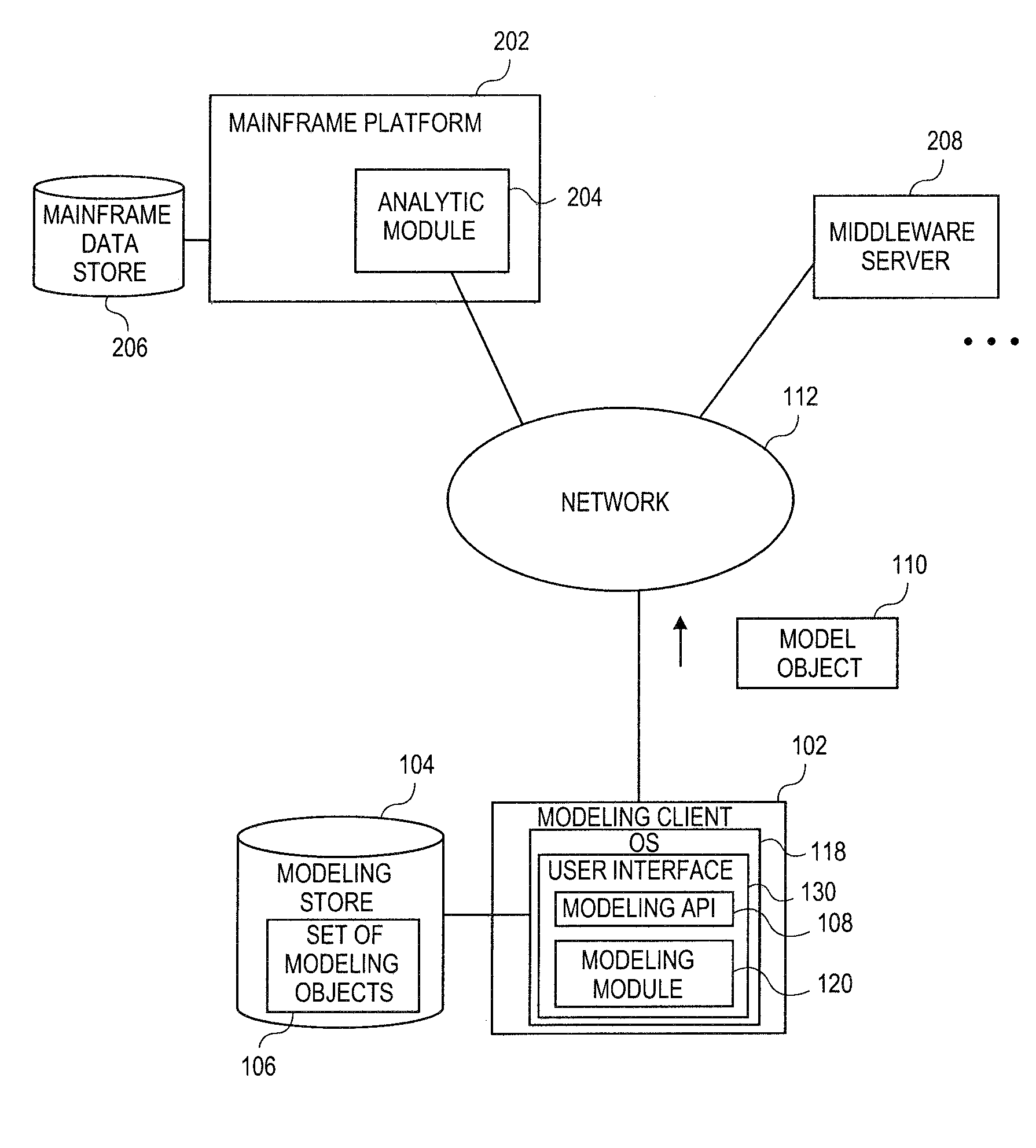
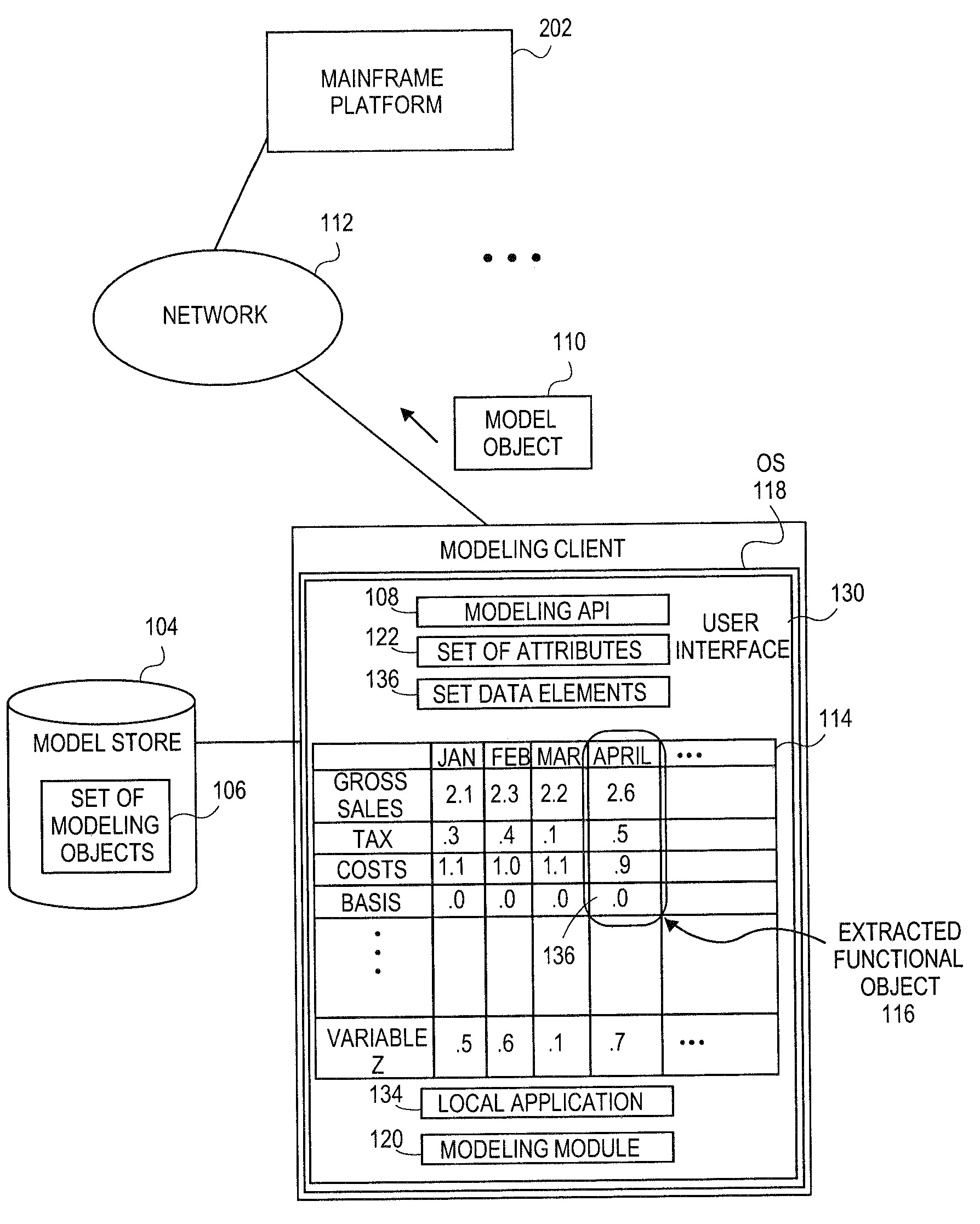
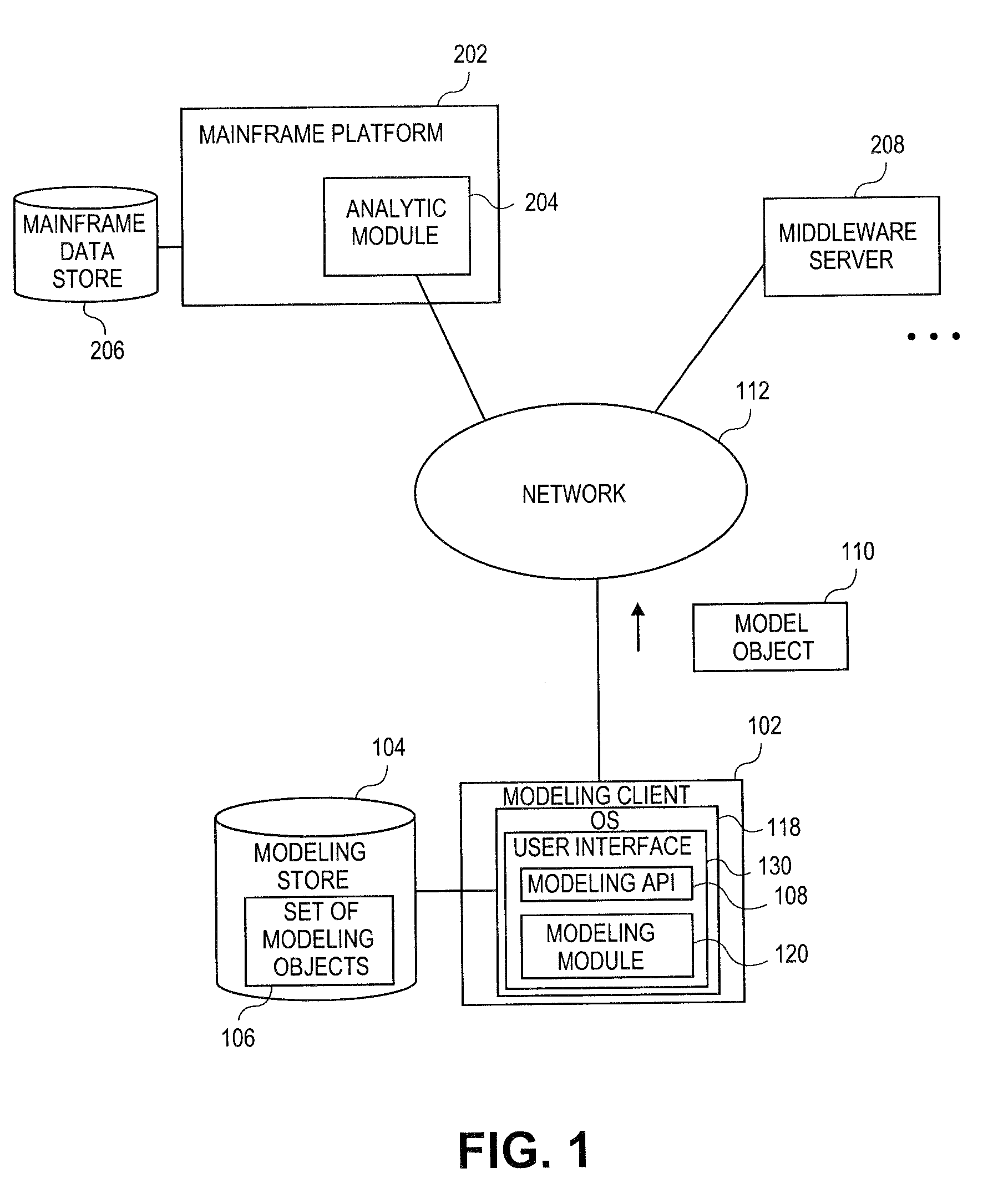
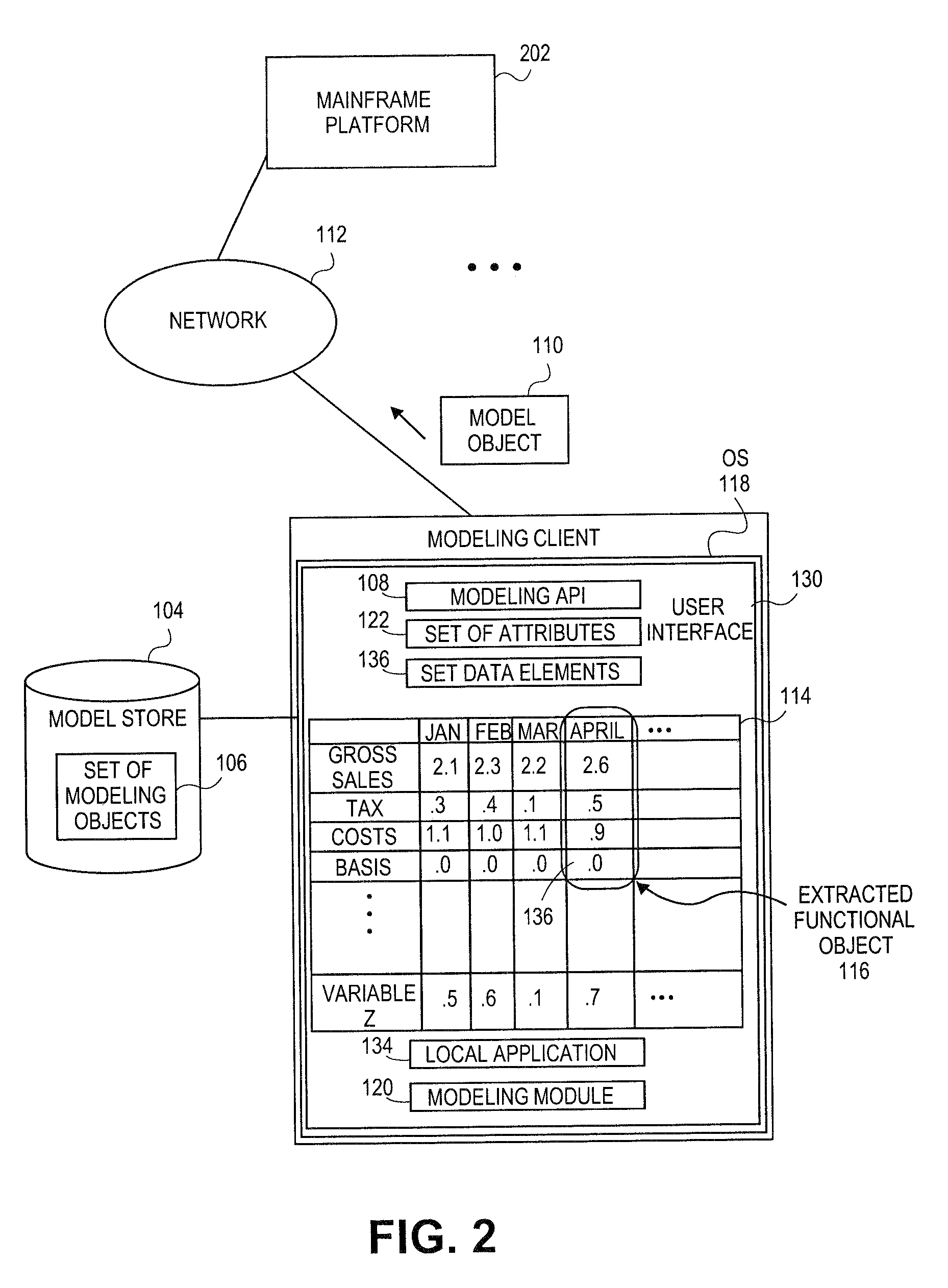
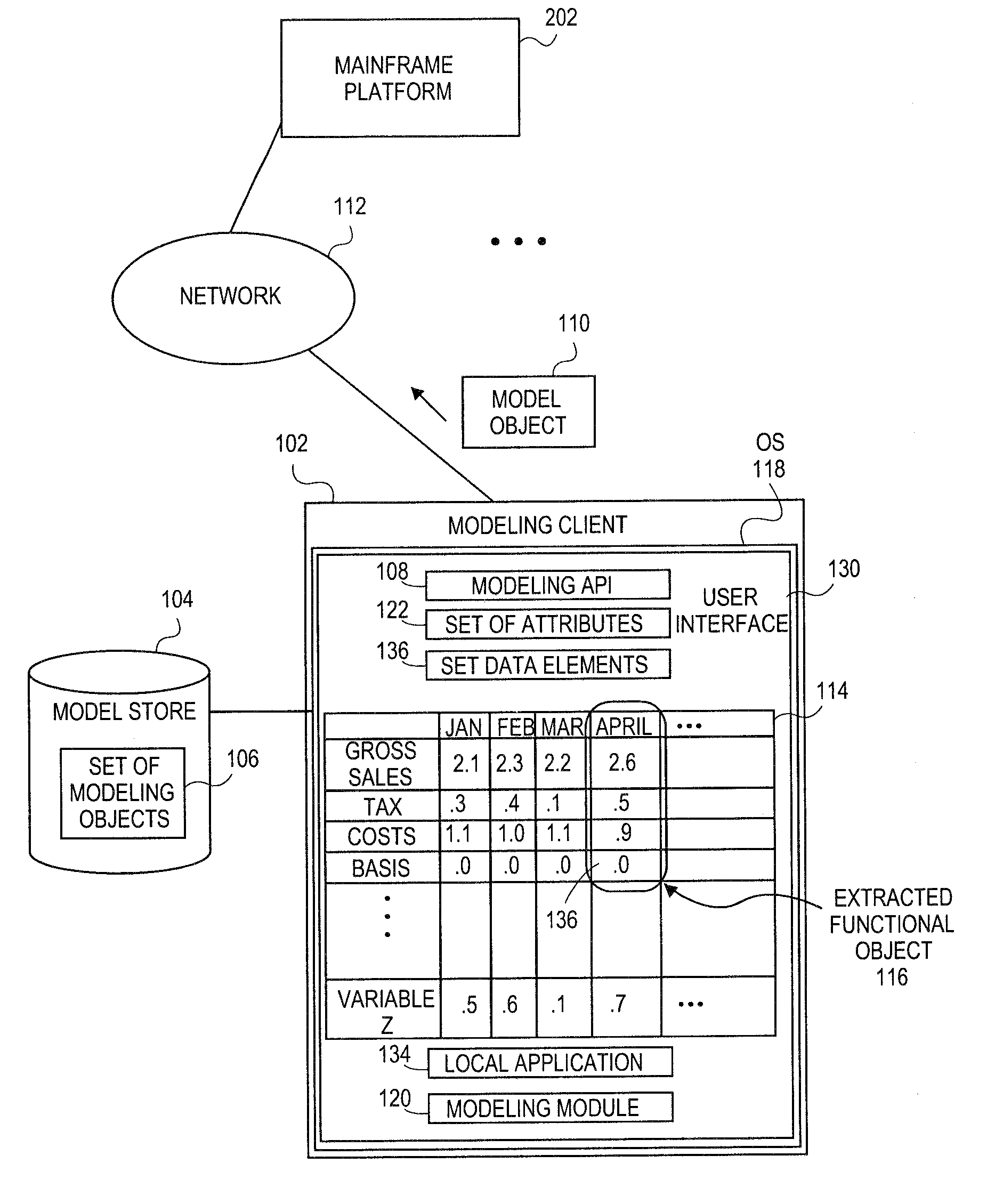
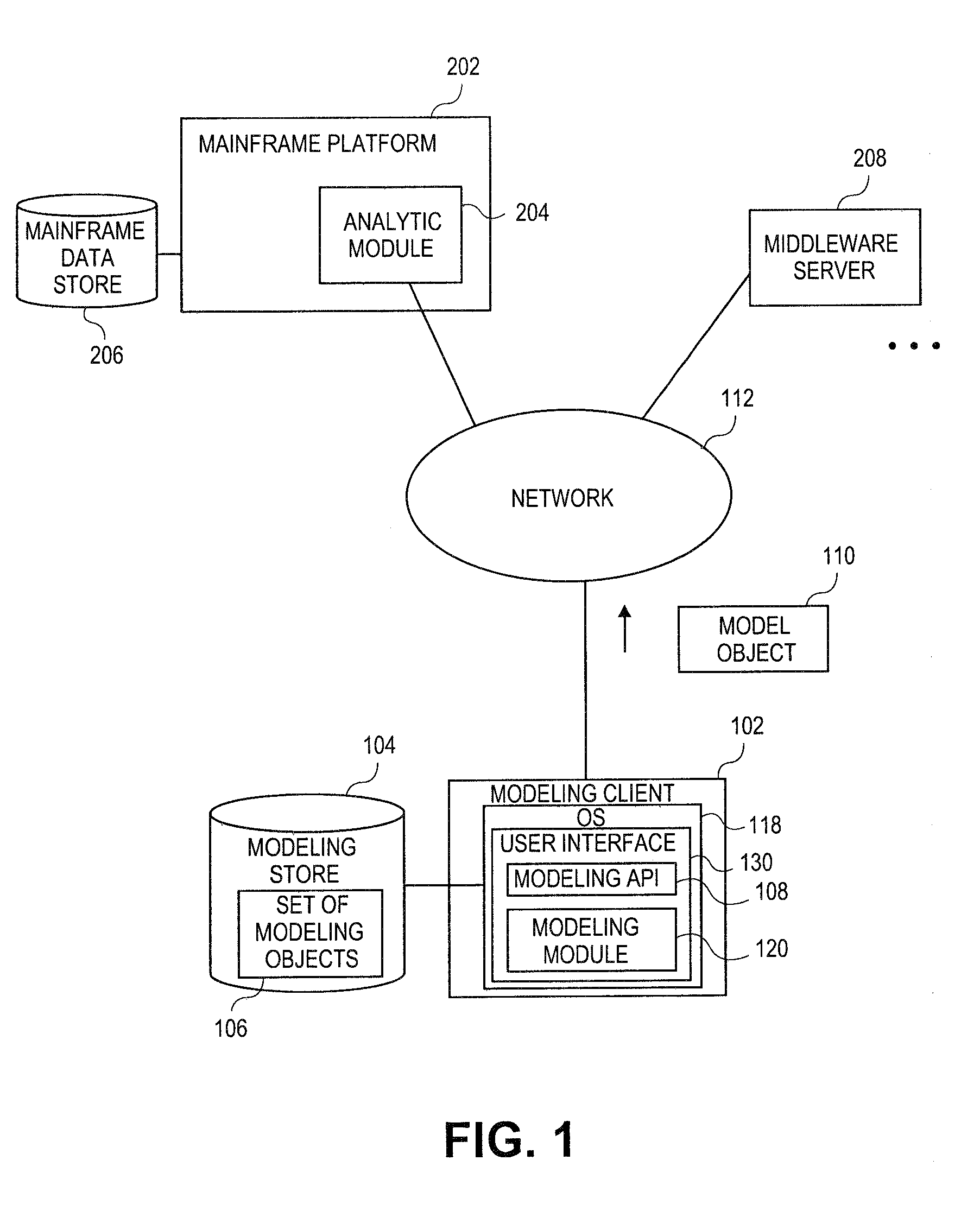
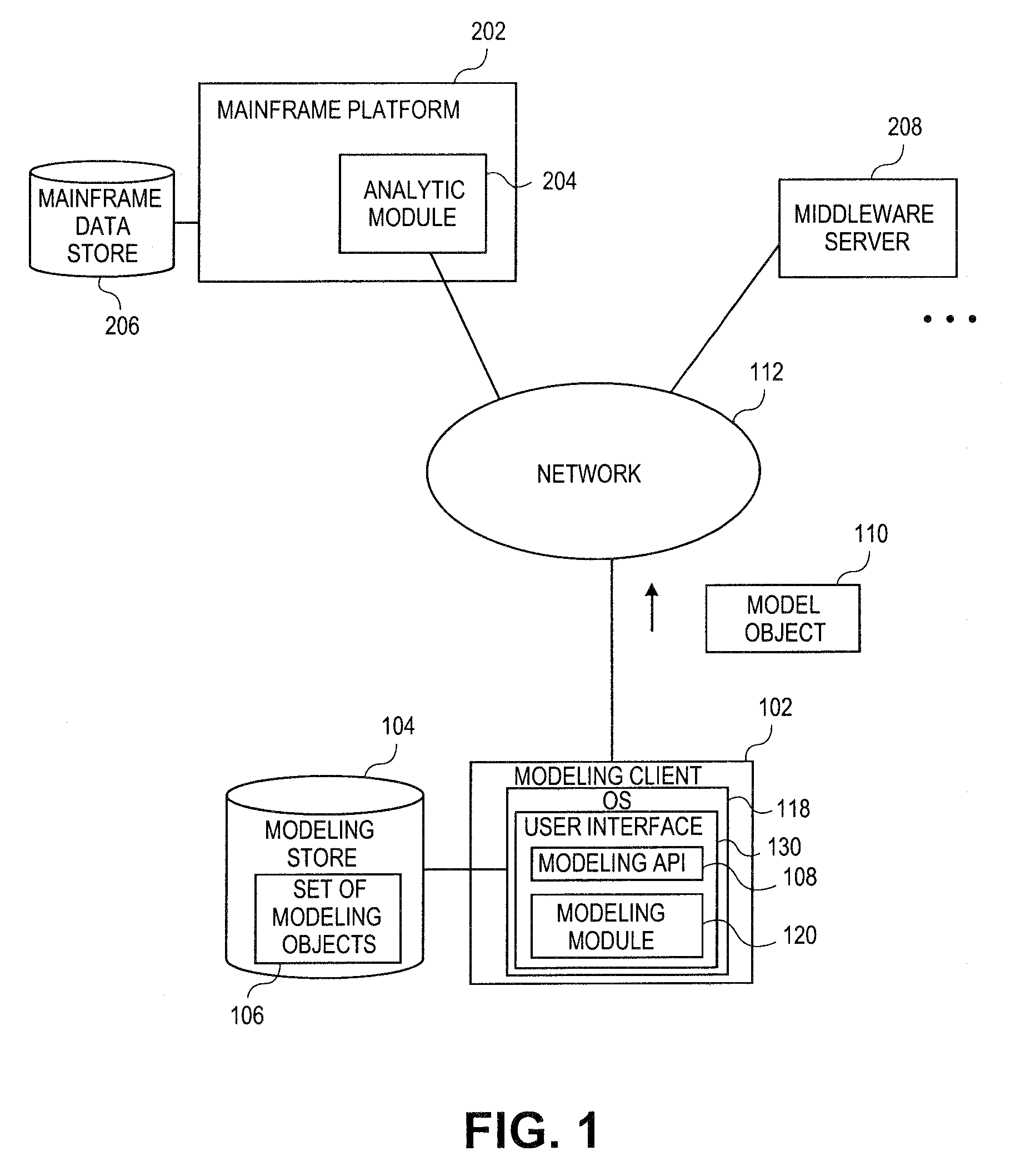
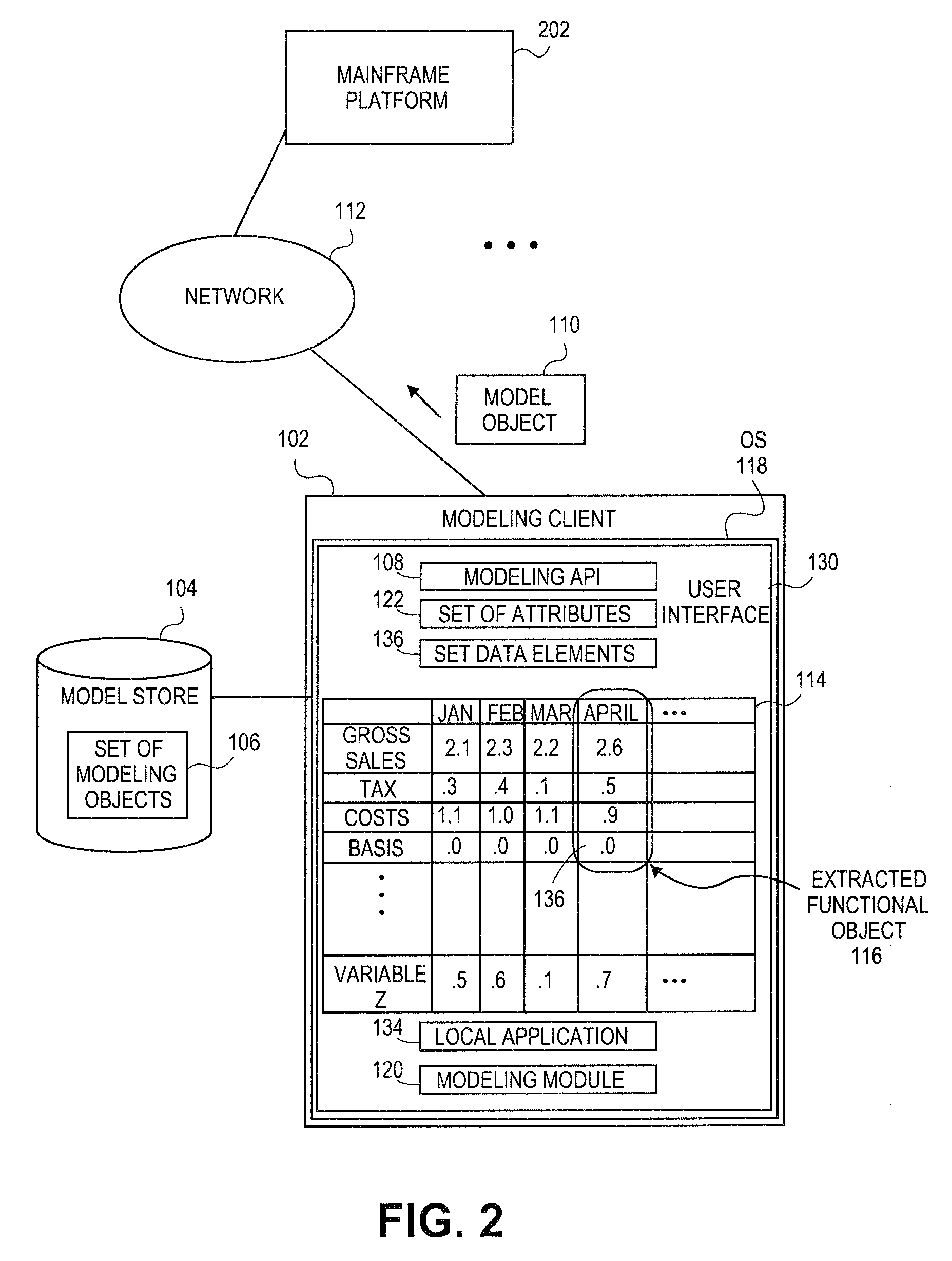
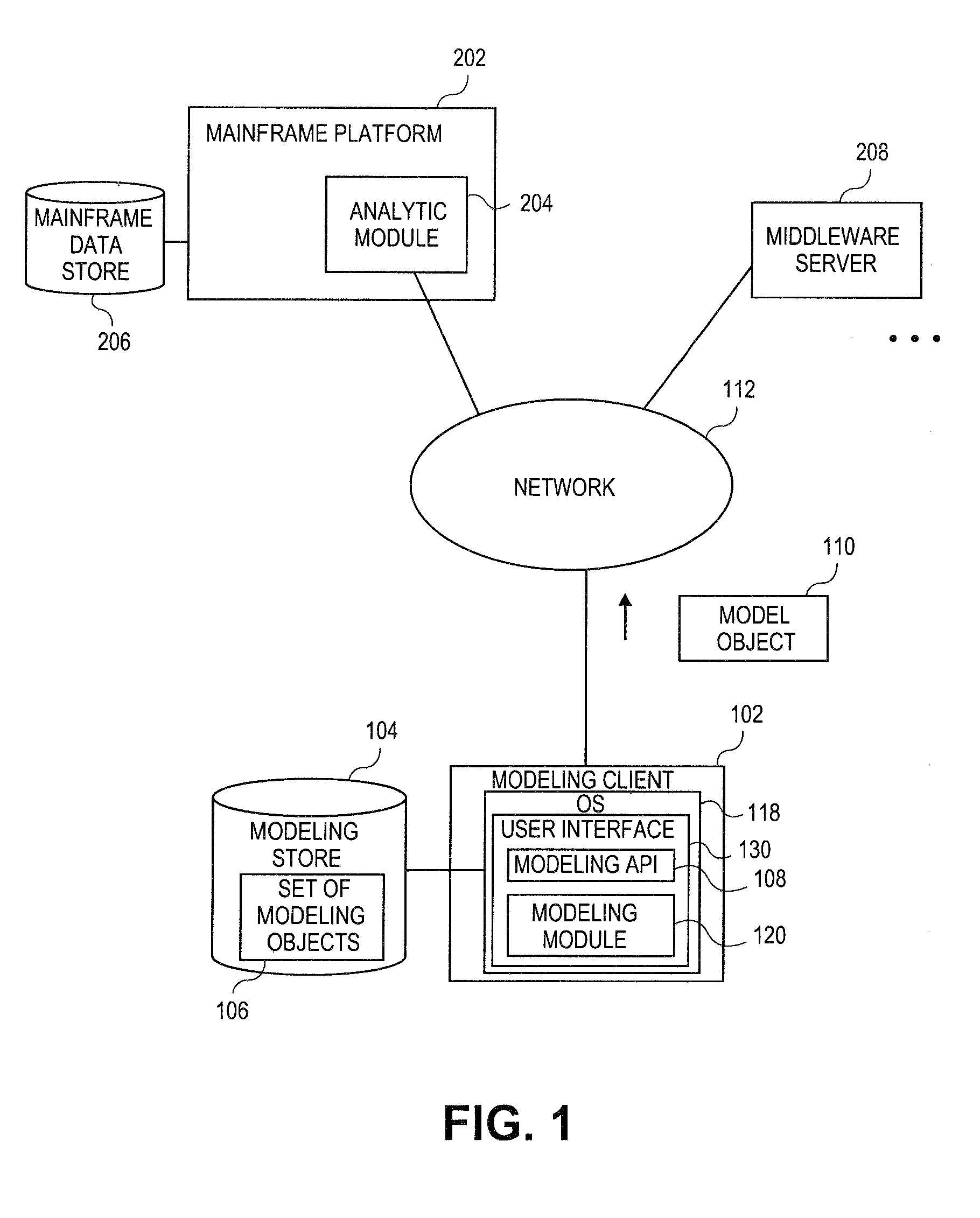
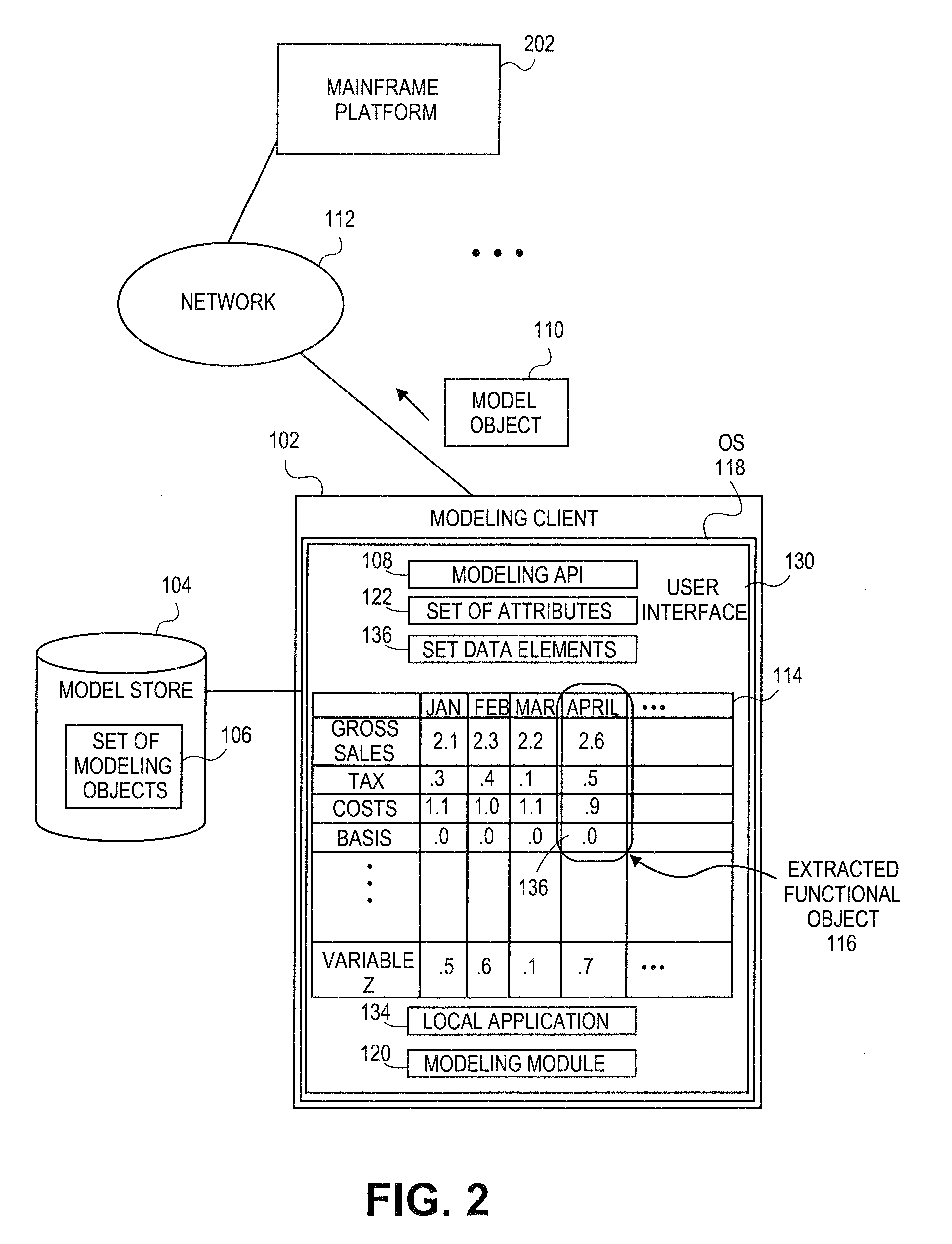
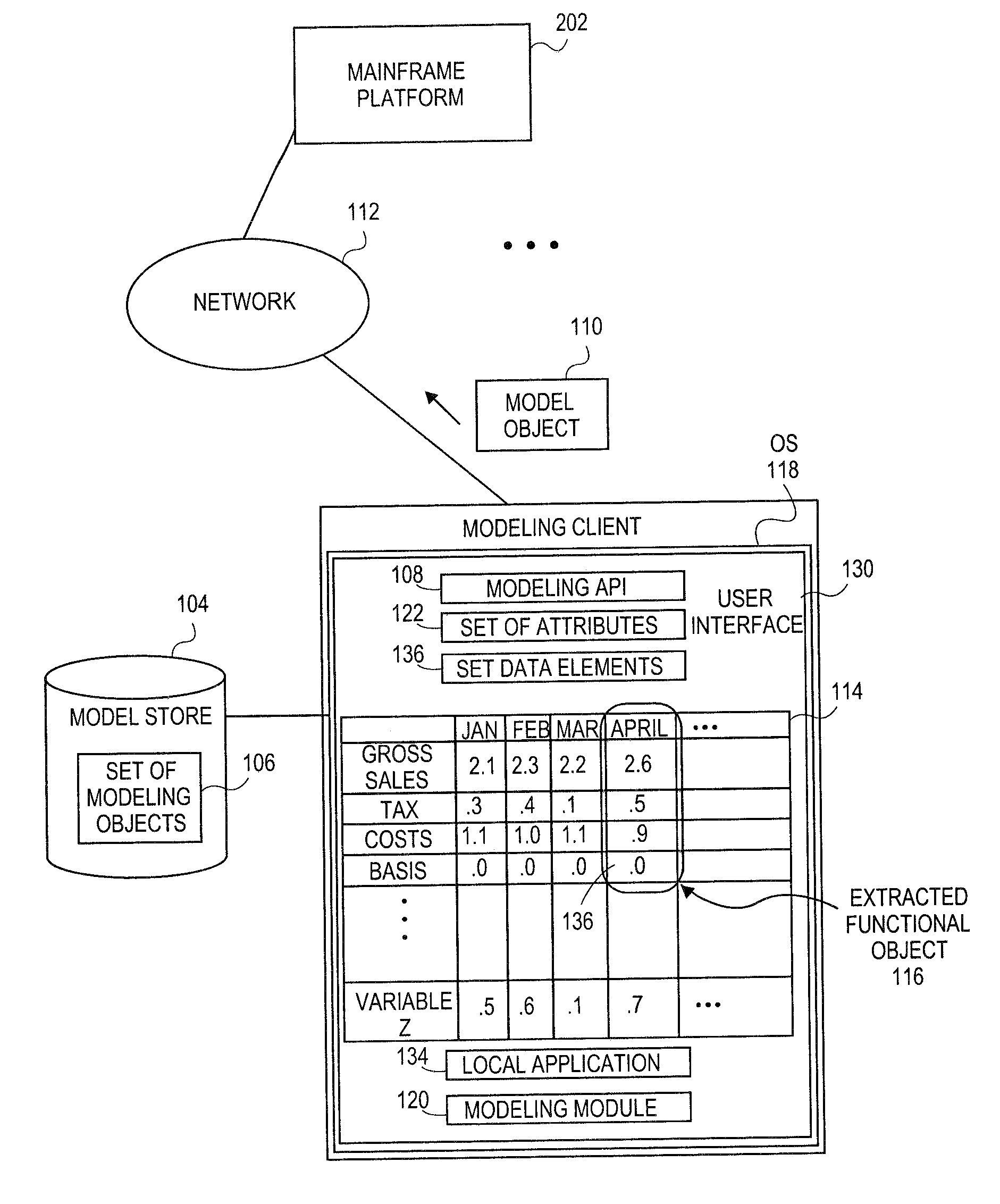
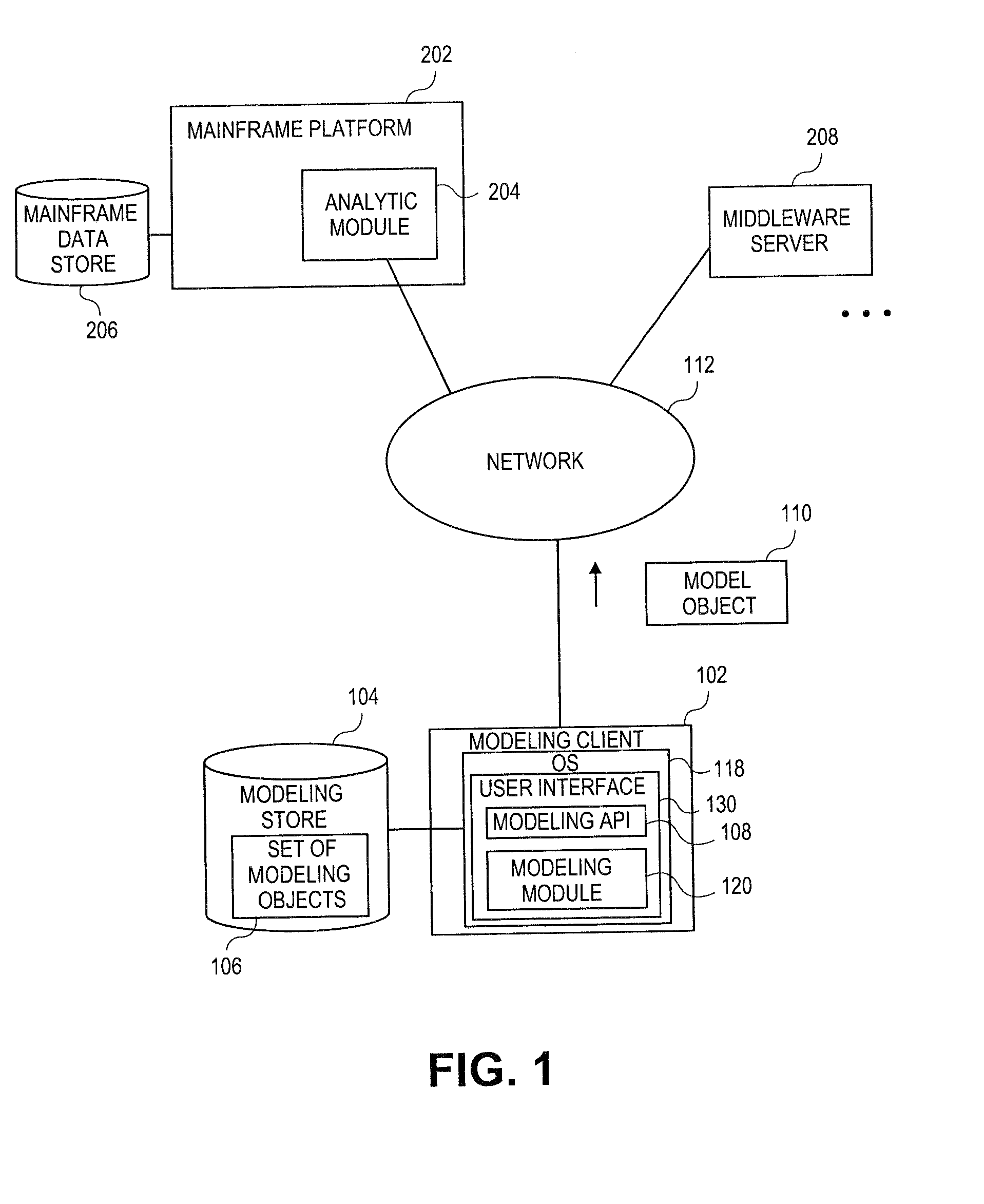
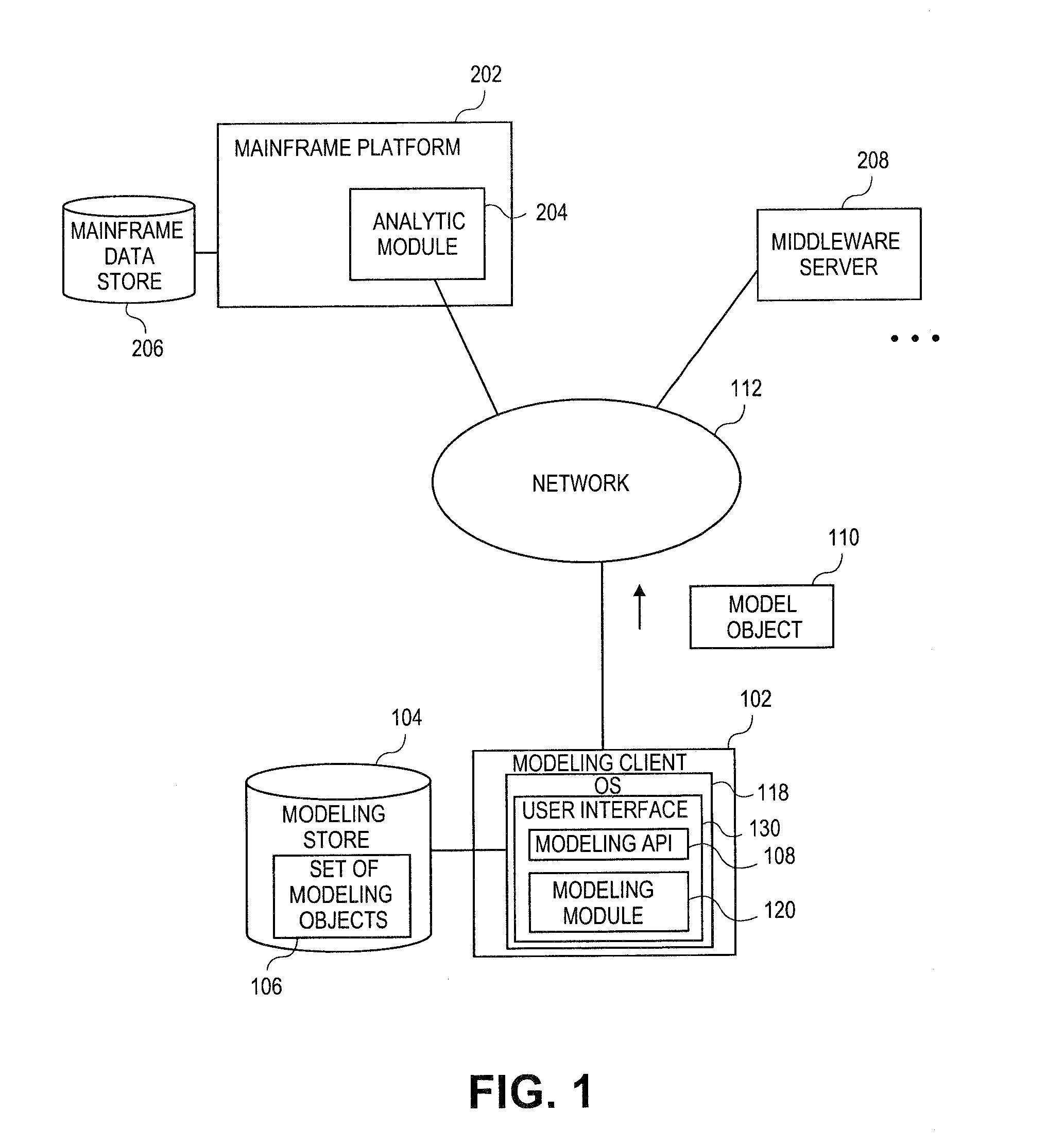
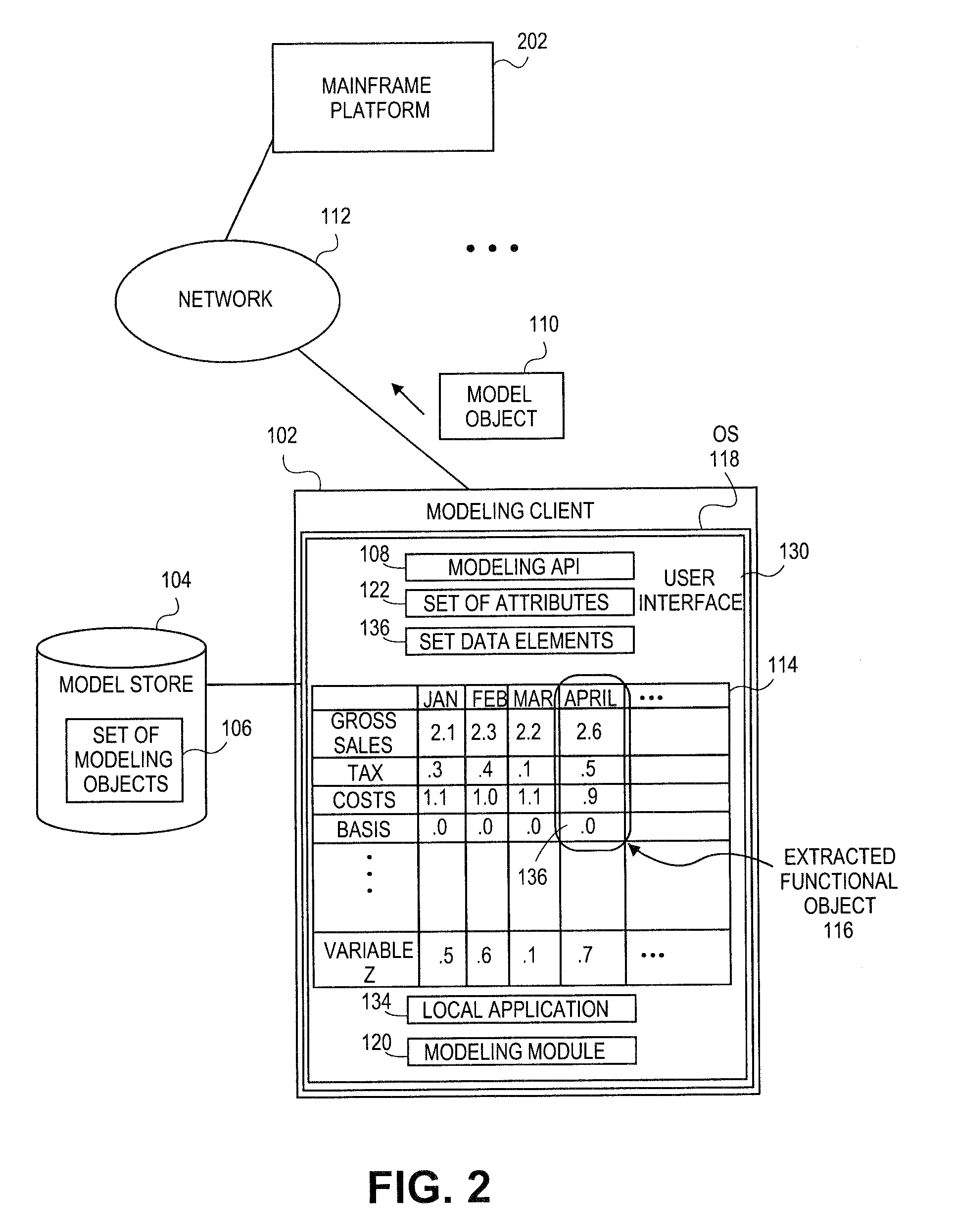
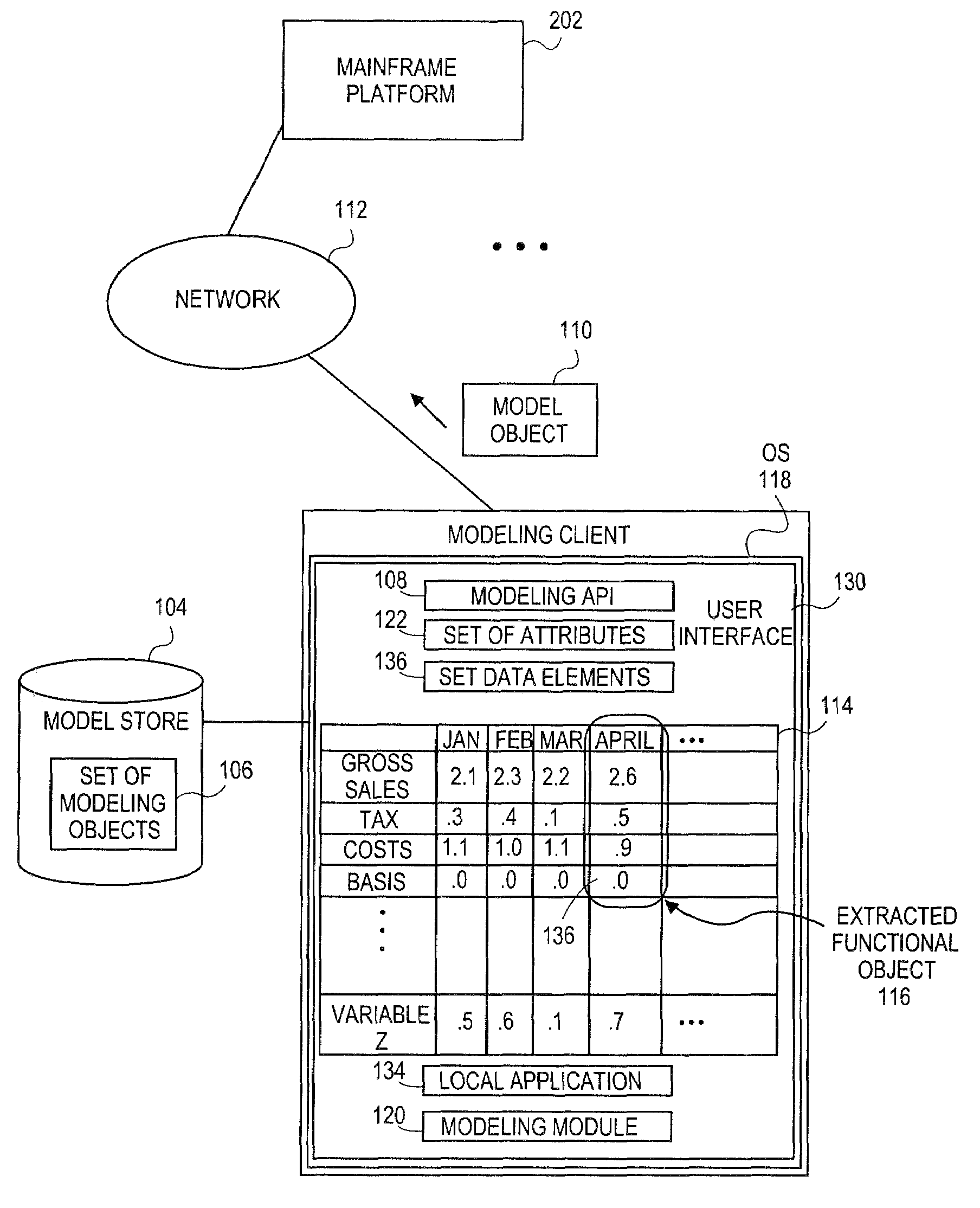
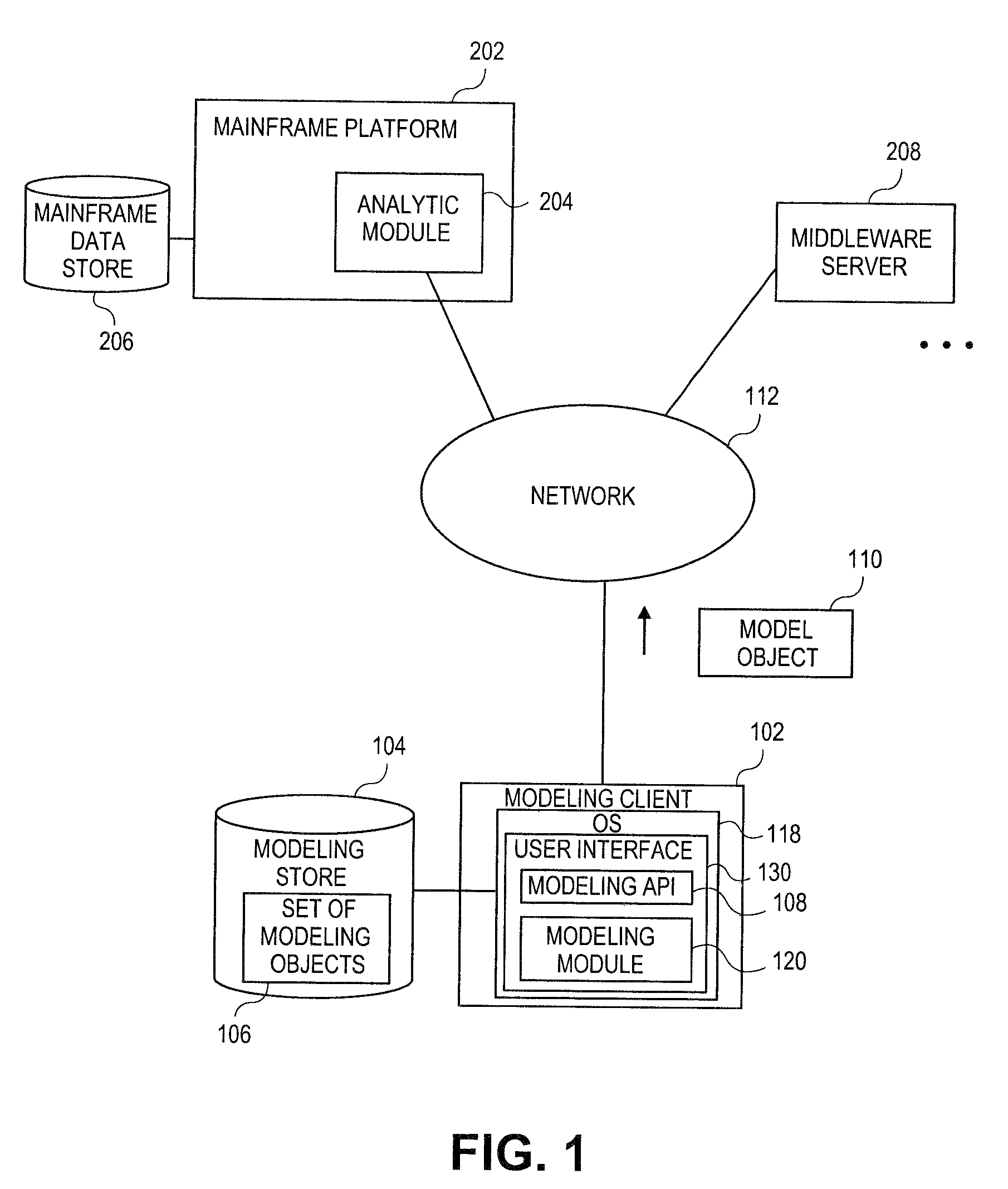
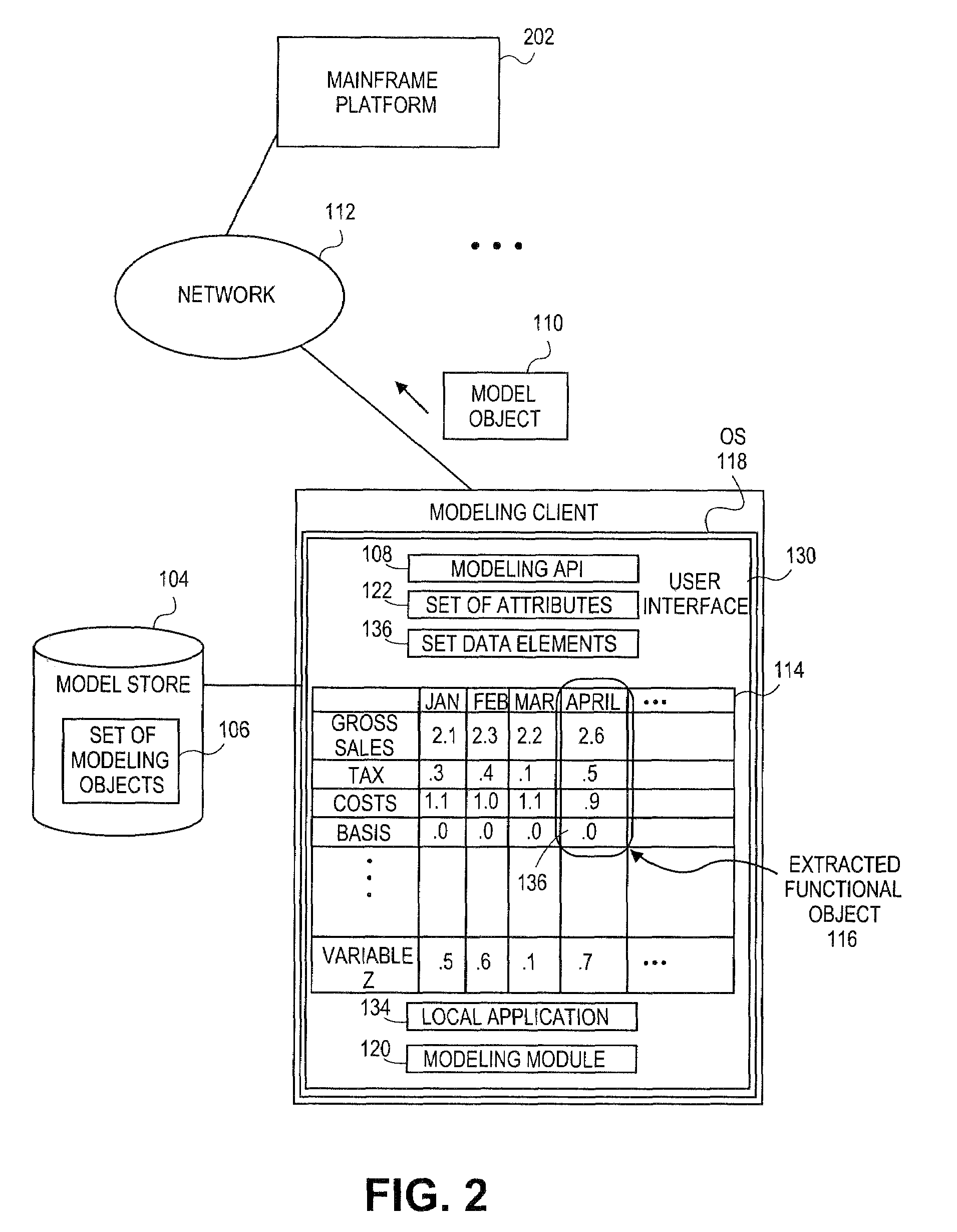
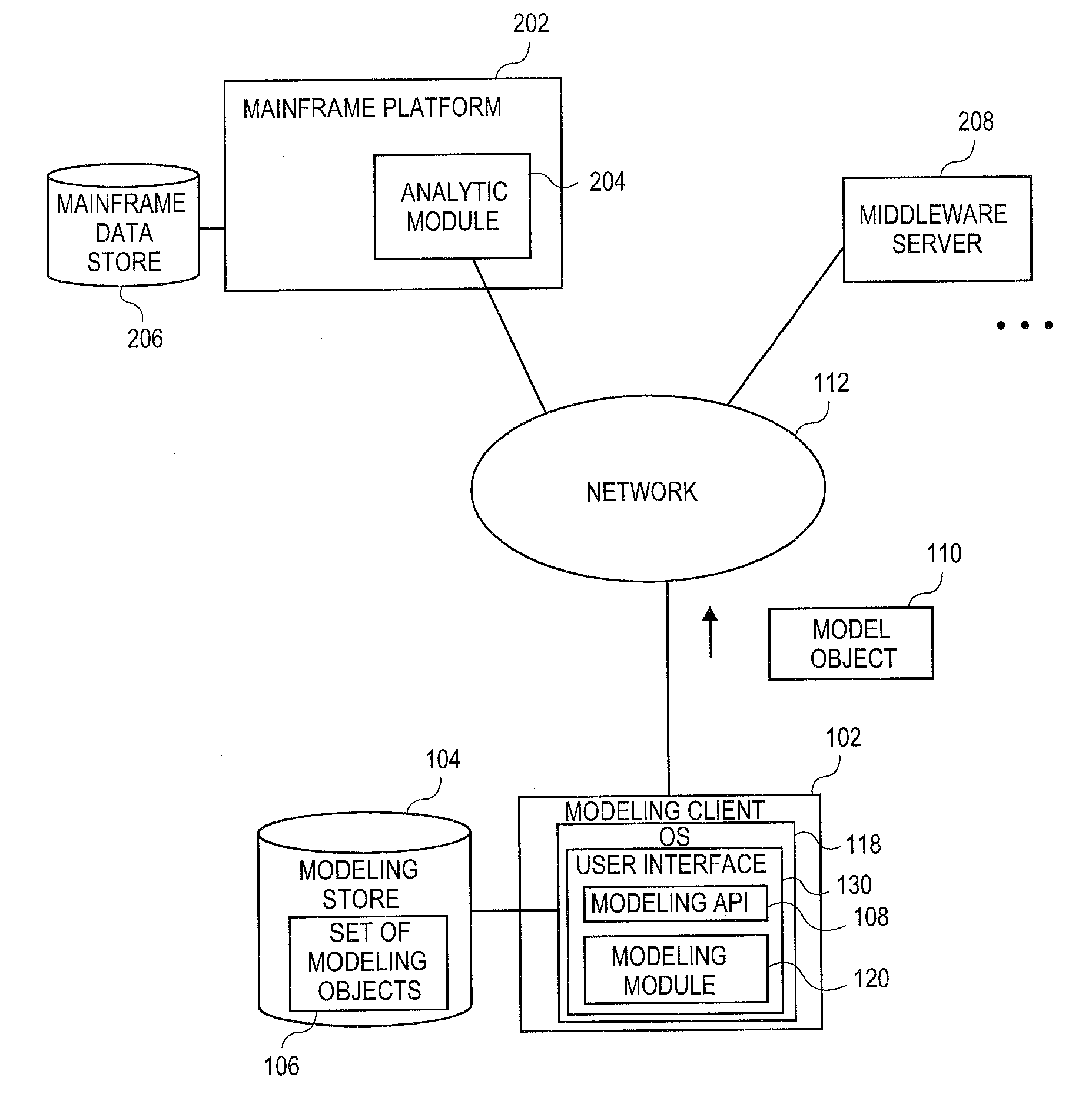
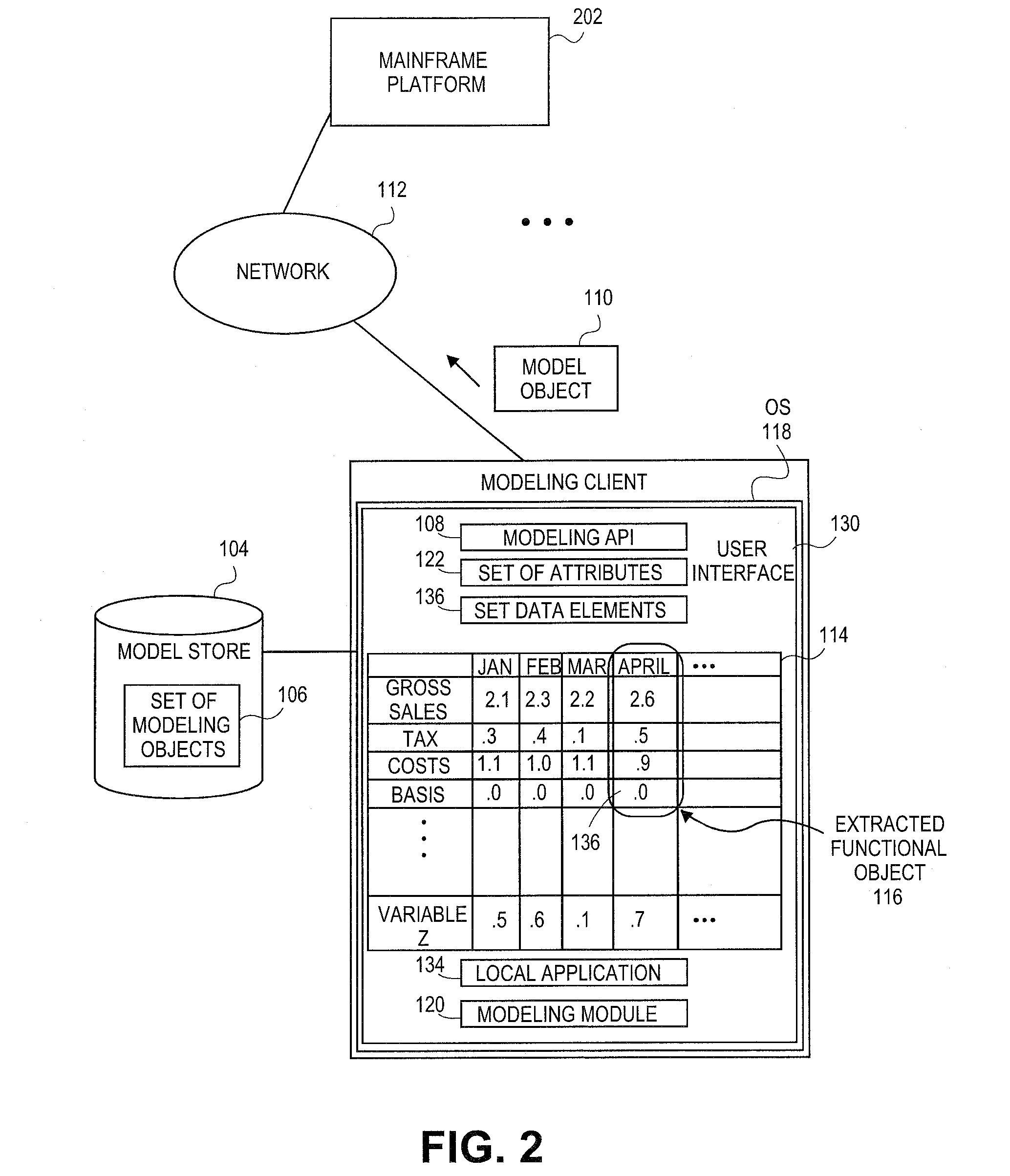
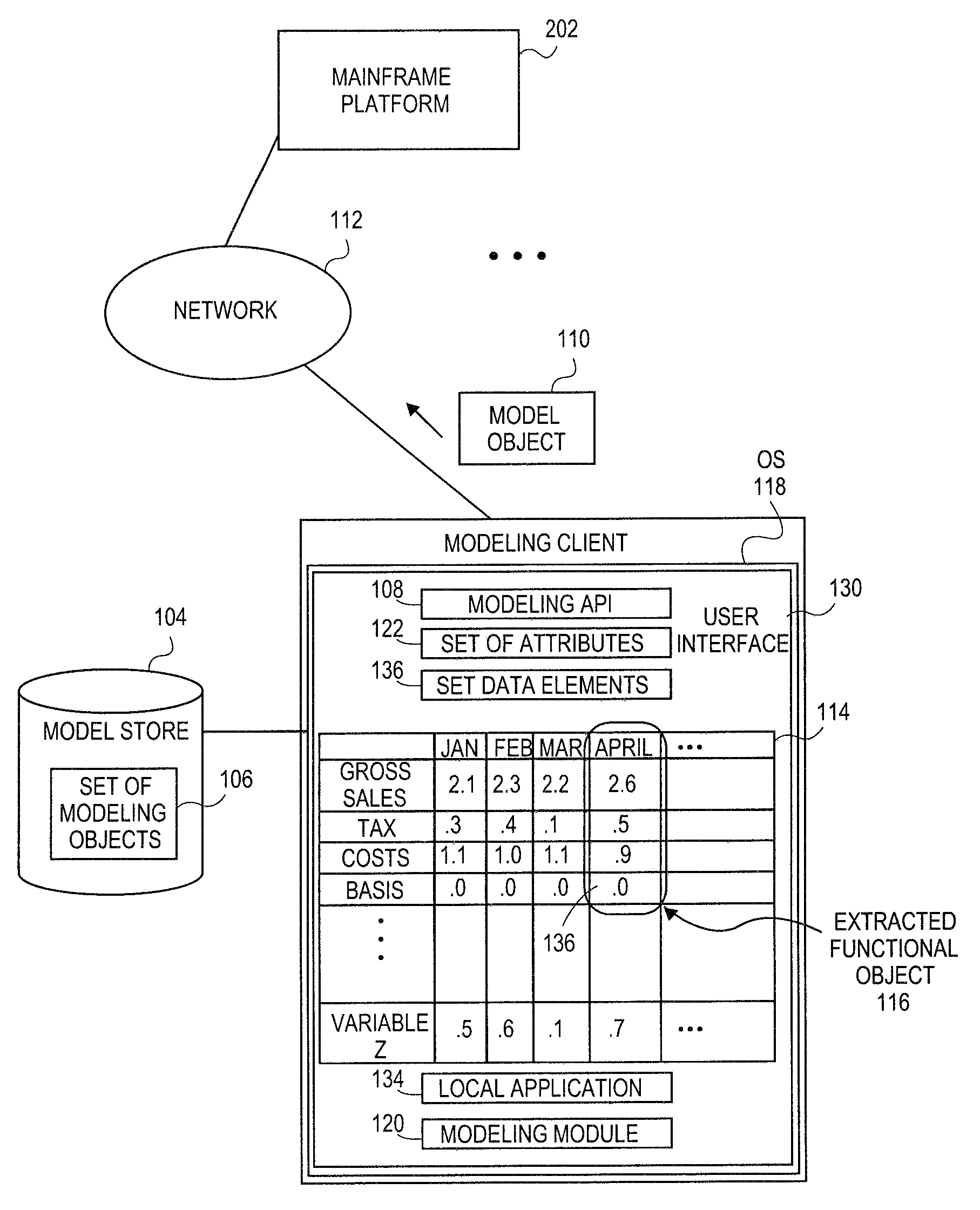
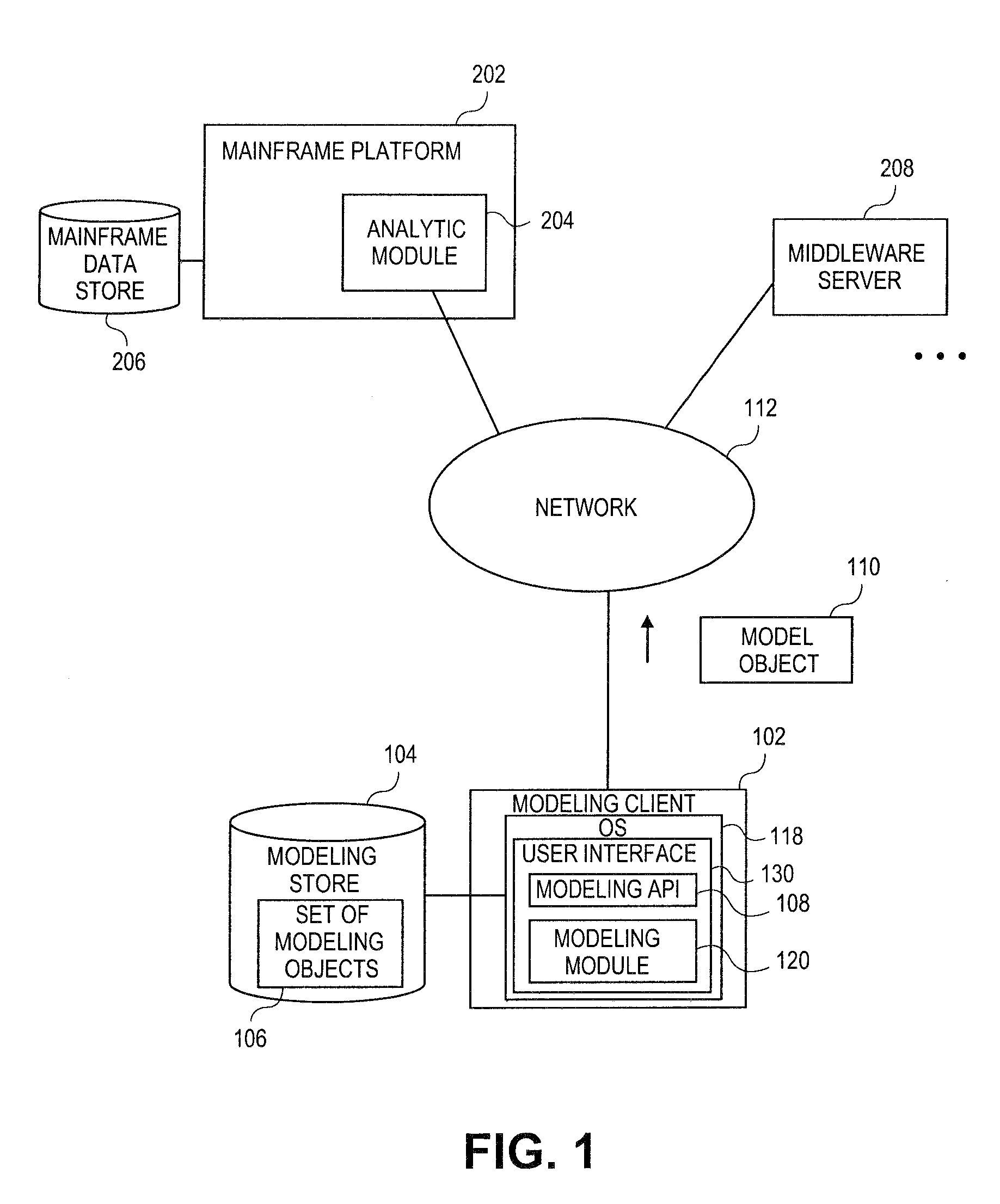
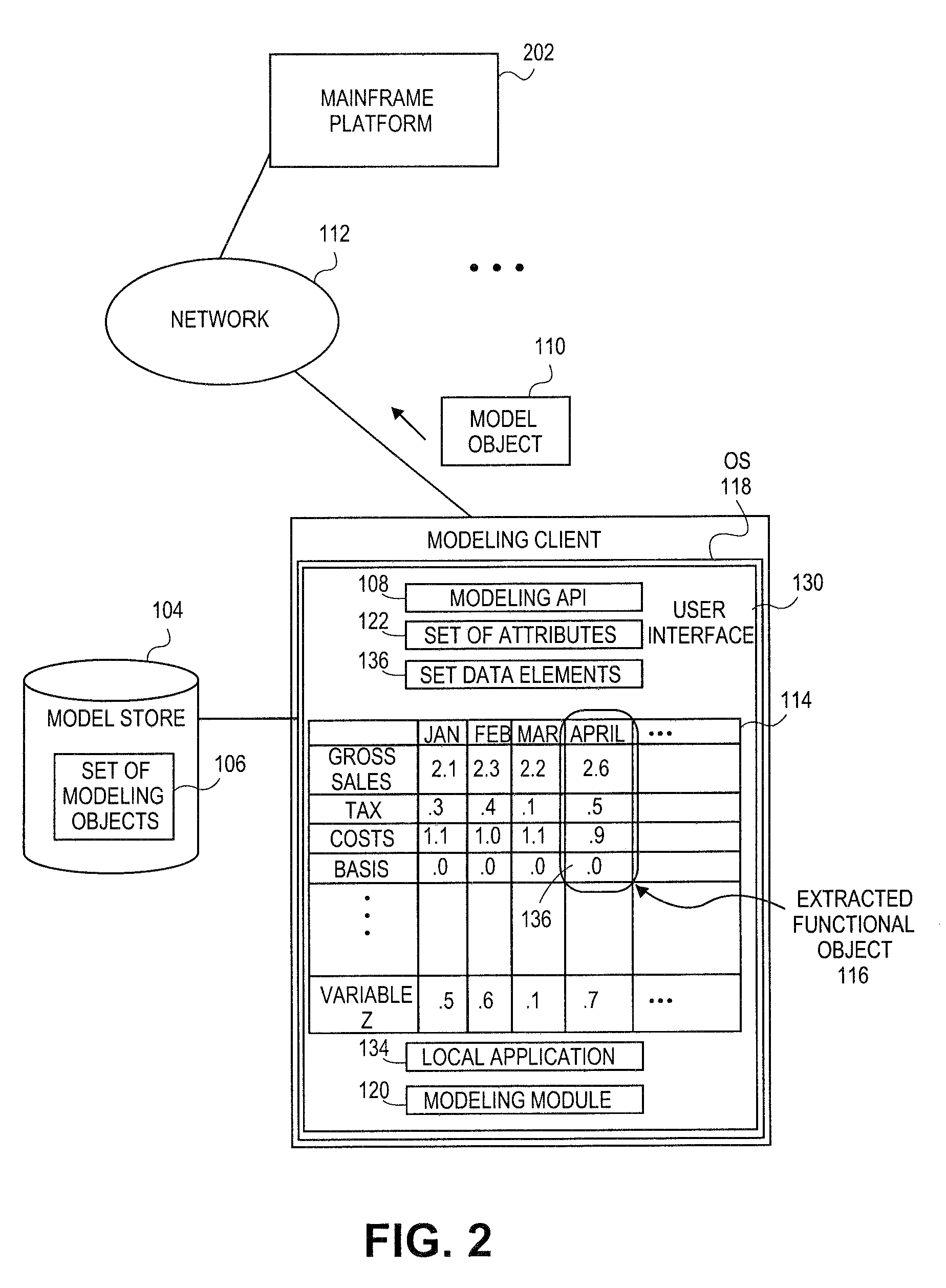
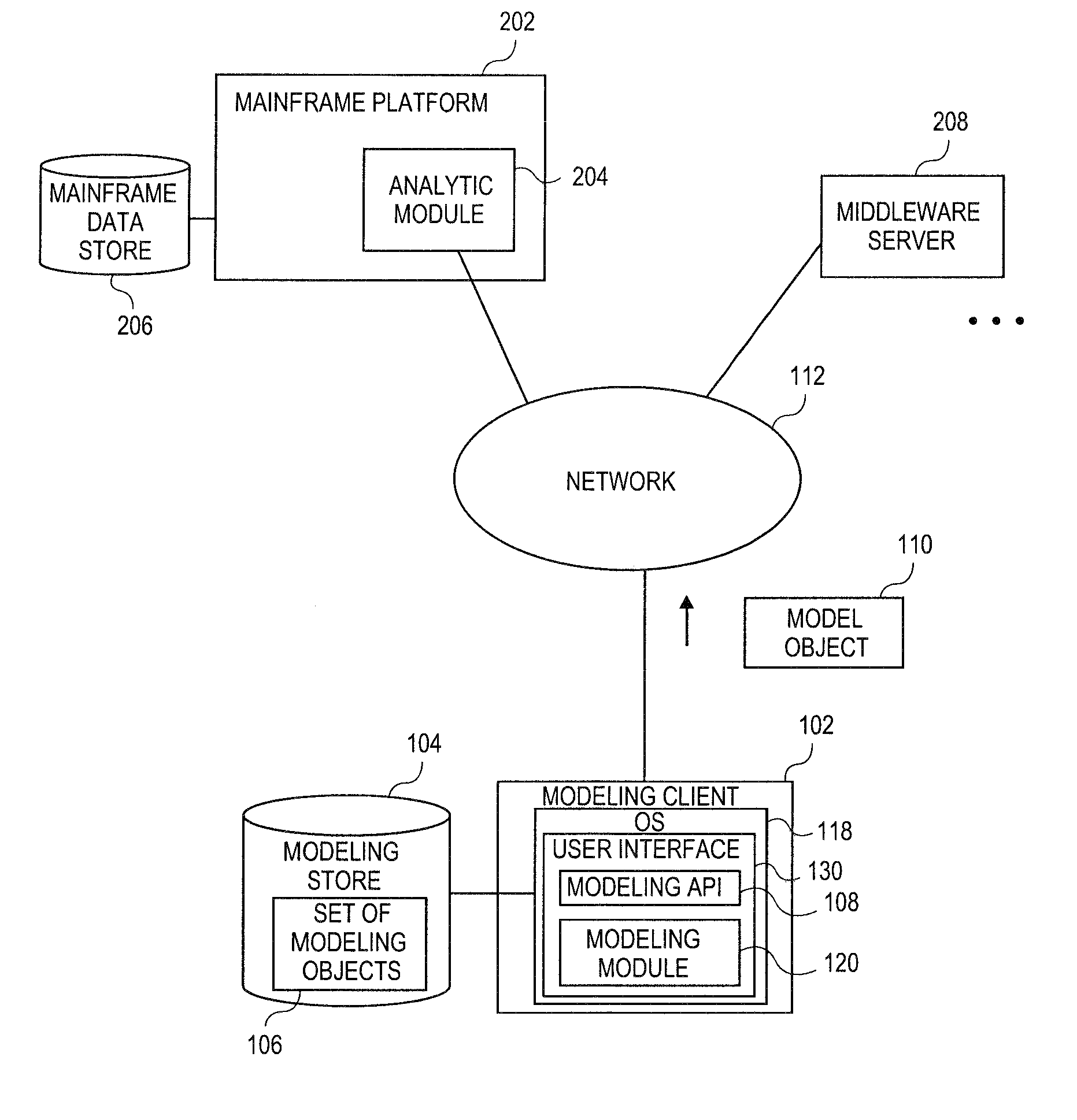
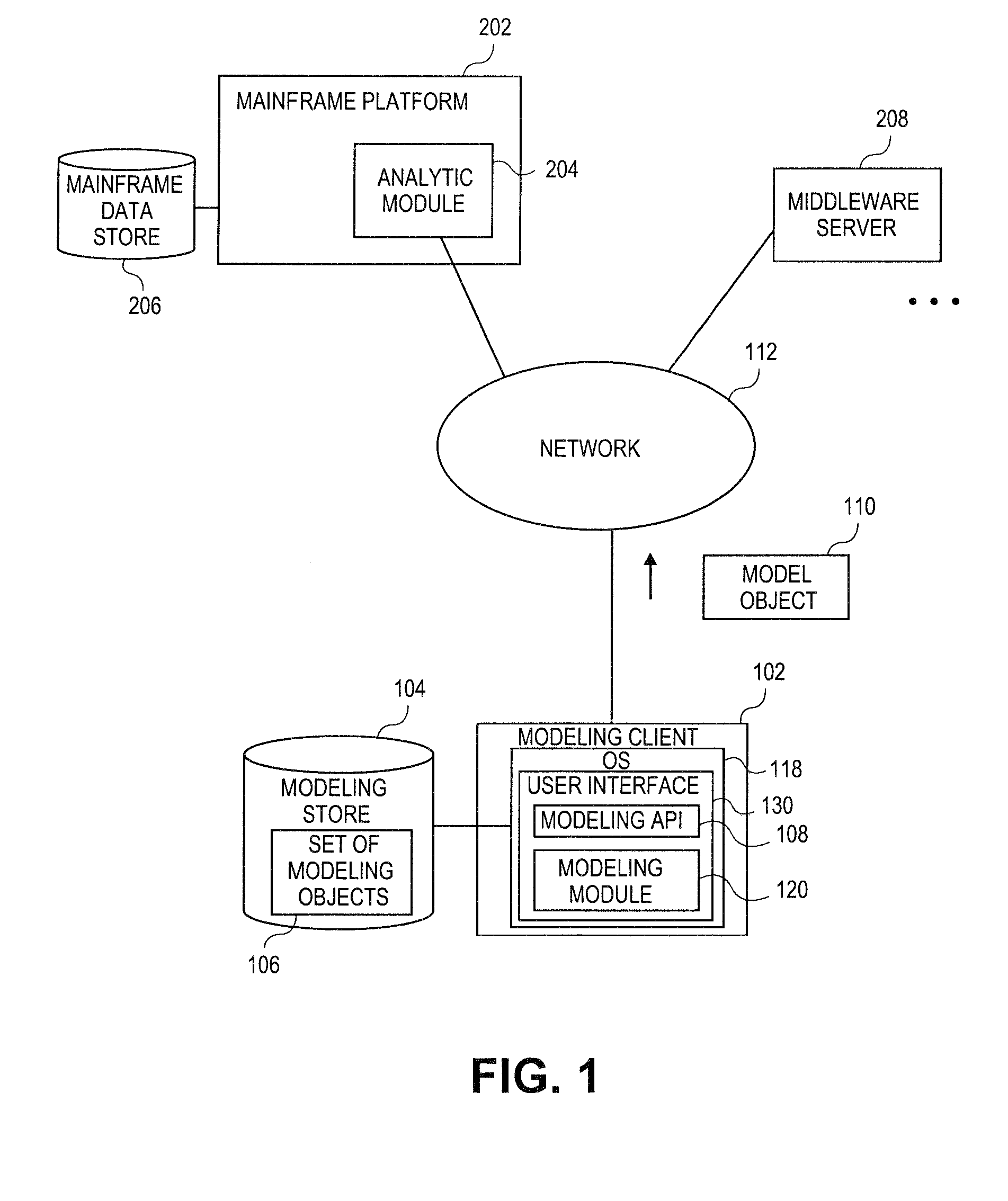
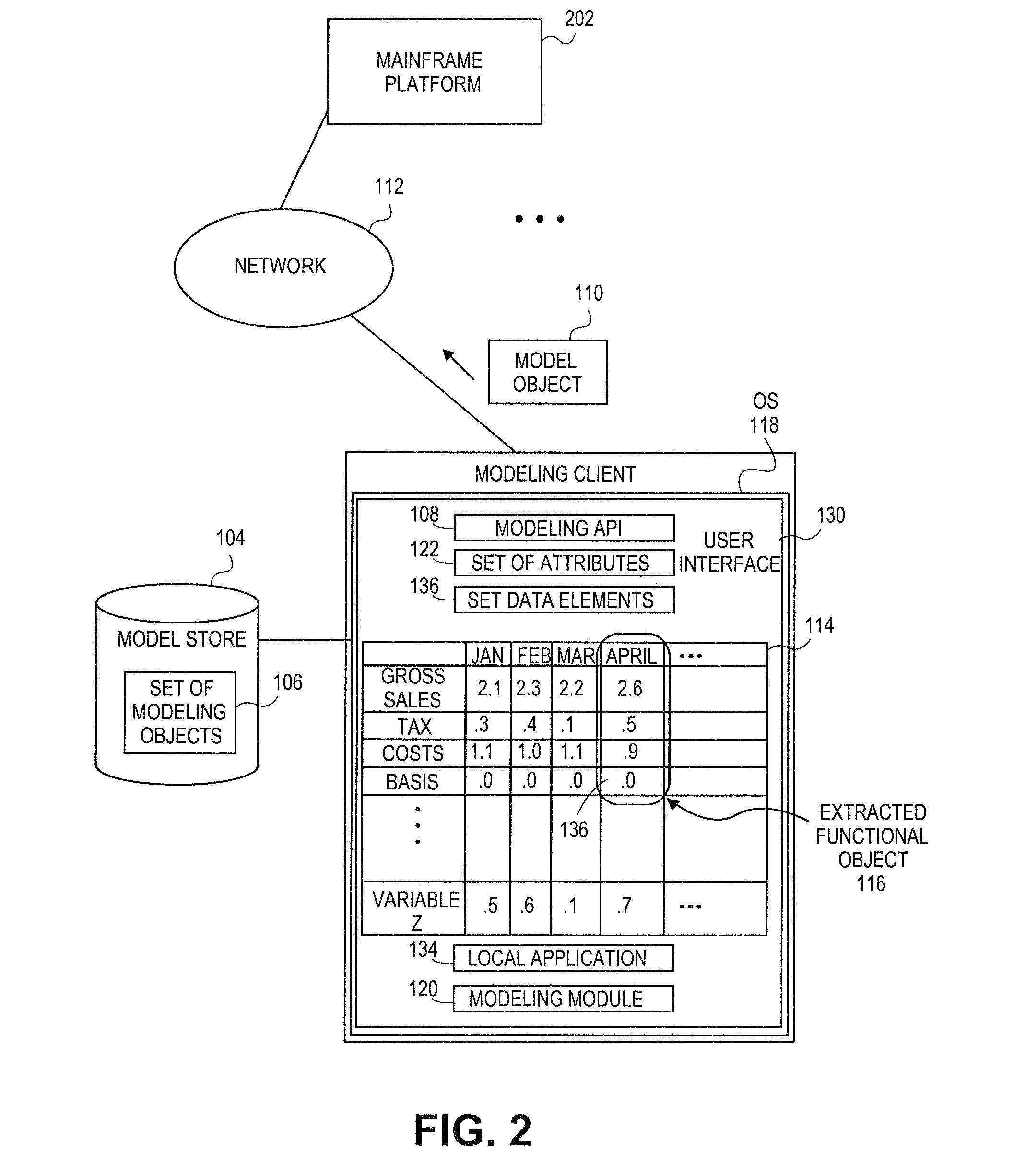
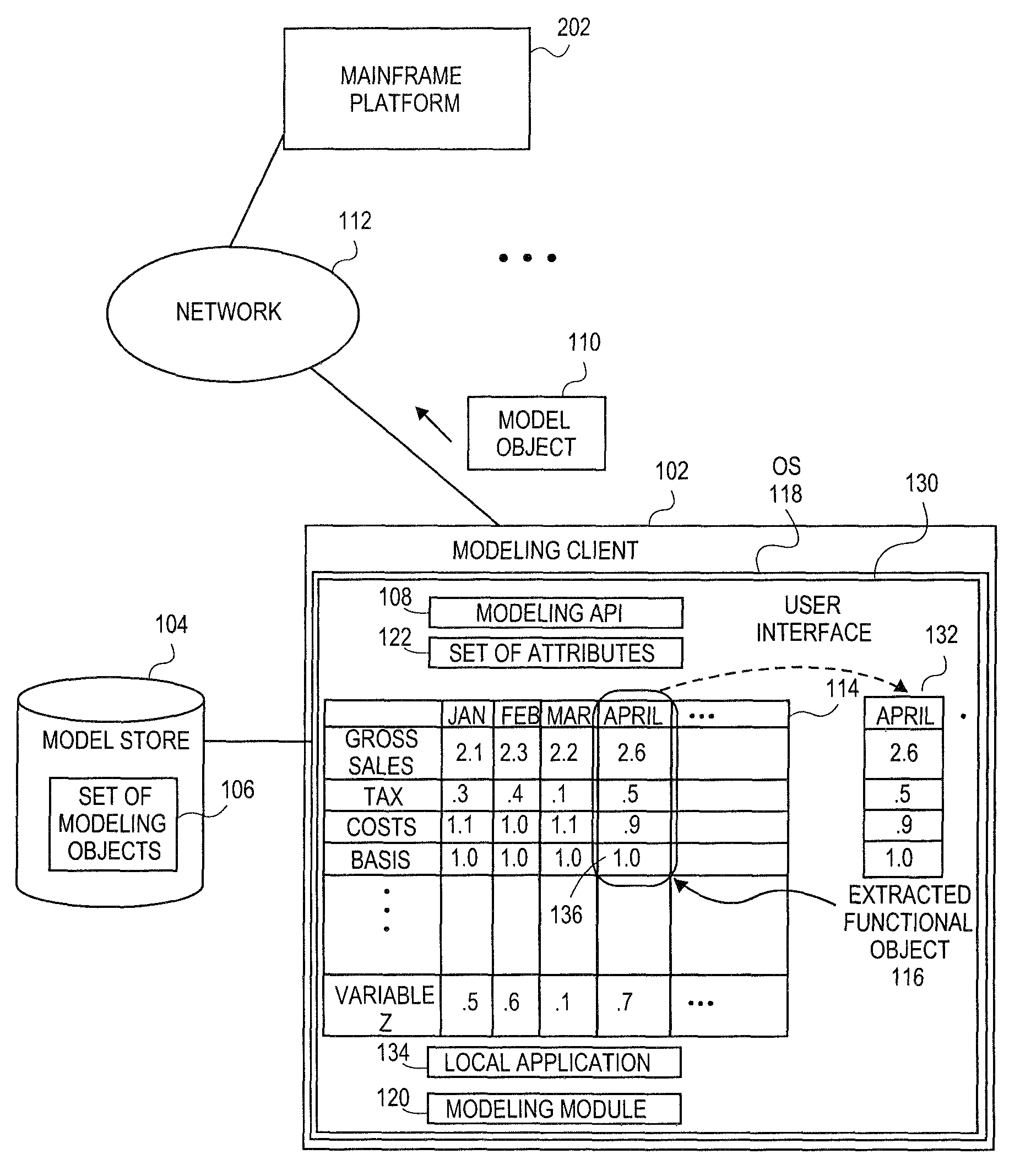
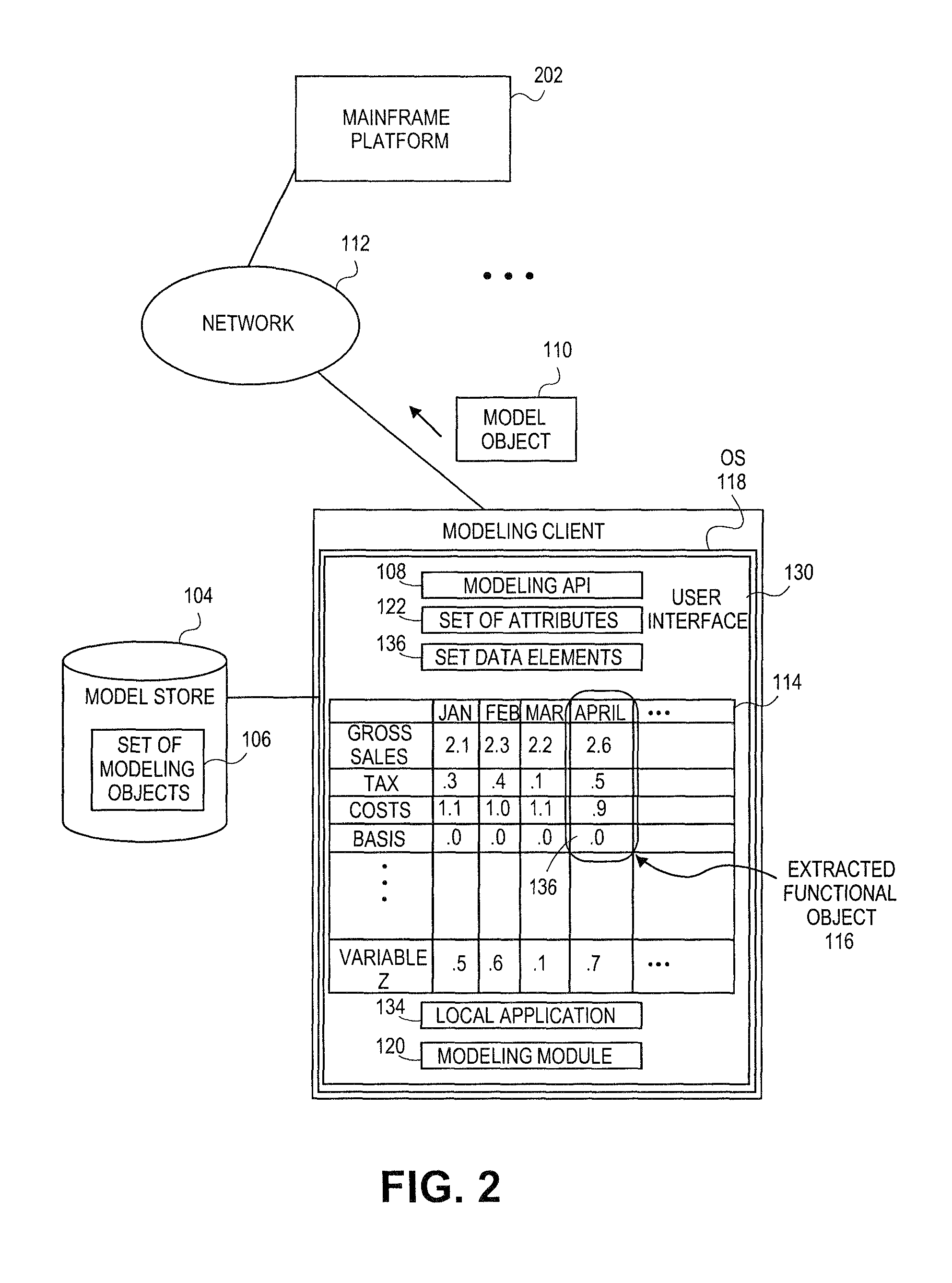
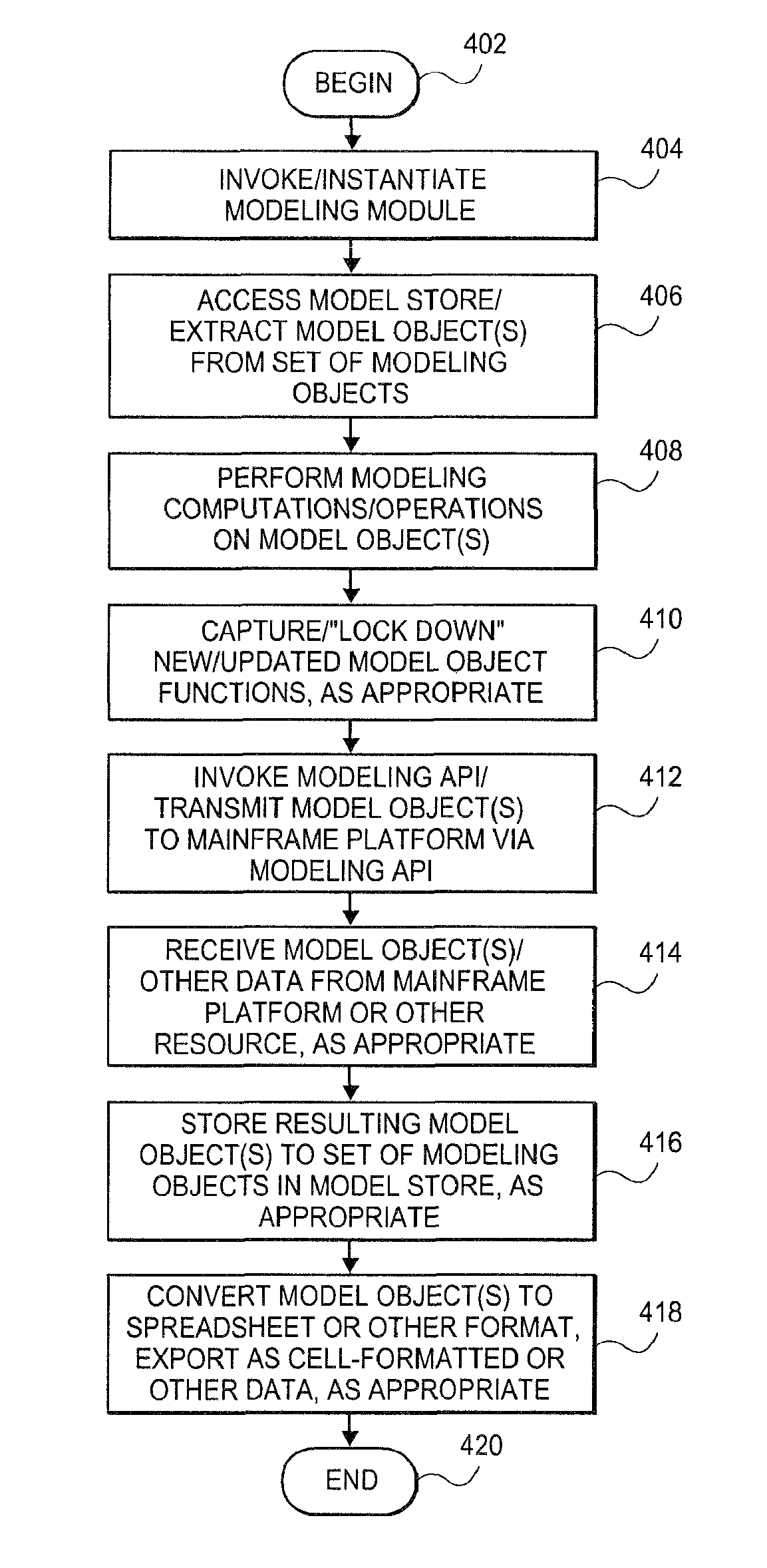
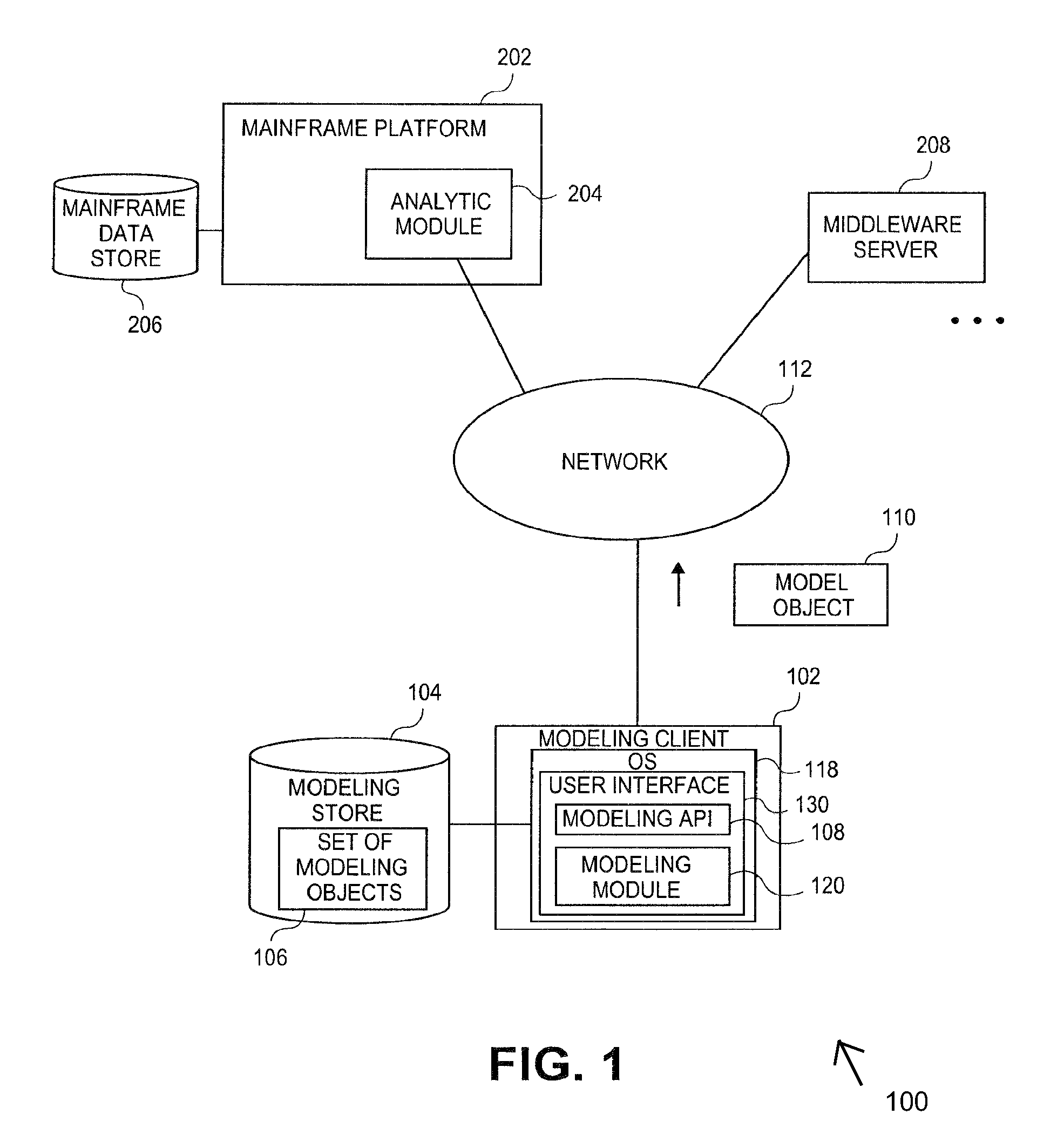
Embodiments relate to systems and methods for extracting a model object from a multi-dimensional source database. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can include consumer or business-level applications, whose database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. The resulting model object can be pivoted along selected dimensions, or otherwise manipulated. The modeling client can exchange one or more modeling object directly with external platforms, such as mainframe modeling platforms, via the application programming interface (API) on a programmatic basis. Costs and maintenance savings over mainframe-based modeling tools can thereby be achieved, while providing greater power than consumer or business-level tools.
Owner:RED HAT
Scalable multiparty conferencing and collaboration system and method of dynamically allocating system resources in same
InactiveUS7167182B2Improve ease of useImprove functionalityMultiplex system selection arrangementsSpecial service provision for substationPrivate communicationCollaboration tool
A networking conferencing and collaboration tool utilizing an enhanced T.128 application sharing protocol. This enhanced protocol is based on a per-host model command, control, and communication structure. This per-host model reduces network traffic, allows greater scalability through dynamic system resource allocation, allows a single host to establish and maintain a share session with no other members present. The per-host model allows private communication between the host and a remote with periodic broadcasts of updates by the host to the entire share group. This per-host model also allows the host to allow, revoke, pause, and invite control of the shared applications. Subsequent passing of control is provided, also with the hosts acceptance. The model contains no fixed limit on the number of participants, and dynamically allocates resources when needed to share or control a shared application. These resources are then freed when no longer needed.
Owner:MICROSOFT TECH LICENSING LLC
Scalable multiparty conferencing and collaboration system and method of dynamically allocating system resources and providing true color support in same
InactiveUS7136062B1Improve functionalityIncrease usageCathode-ray tube indicatorsOffice automationPrivate communicationCollaboration tool
A networking conferencing and collaboration tool utilizing an enhanced T.128 application sharing protocol. This enhanced protocol is based on a per-host model command, control, and communication structure. This per-host model reduces network traffic, allows greater scalability through dynamic system resource allocation, allows a single host to establish and maintain a share session with no other members present, and supports true color graphics. The per-host model allows private communication between the host and a remote with periodic broadcasts of updates by the host to the entire share group. This per-host model also allows the host to allow, revoke, pause, and invite control of the shared applications. Subsequent passing of control is provided, also with the hosts acceptance. The model contains no fixed limit on the number of participants, and dynamically allocates resources when needed to share or control a shared application. These resources are then freed when no longer needed. Calculation of minimum capabilities is conducted by the host as the membership of the share changes. The host then transmits these requirements to the share group.
Owner:MICROSOFT TECH LICENSING LLC
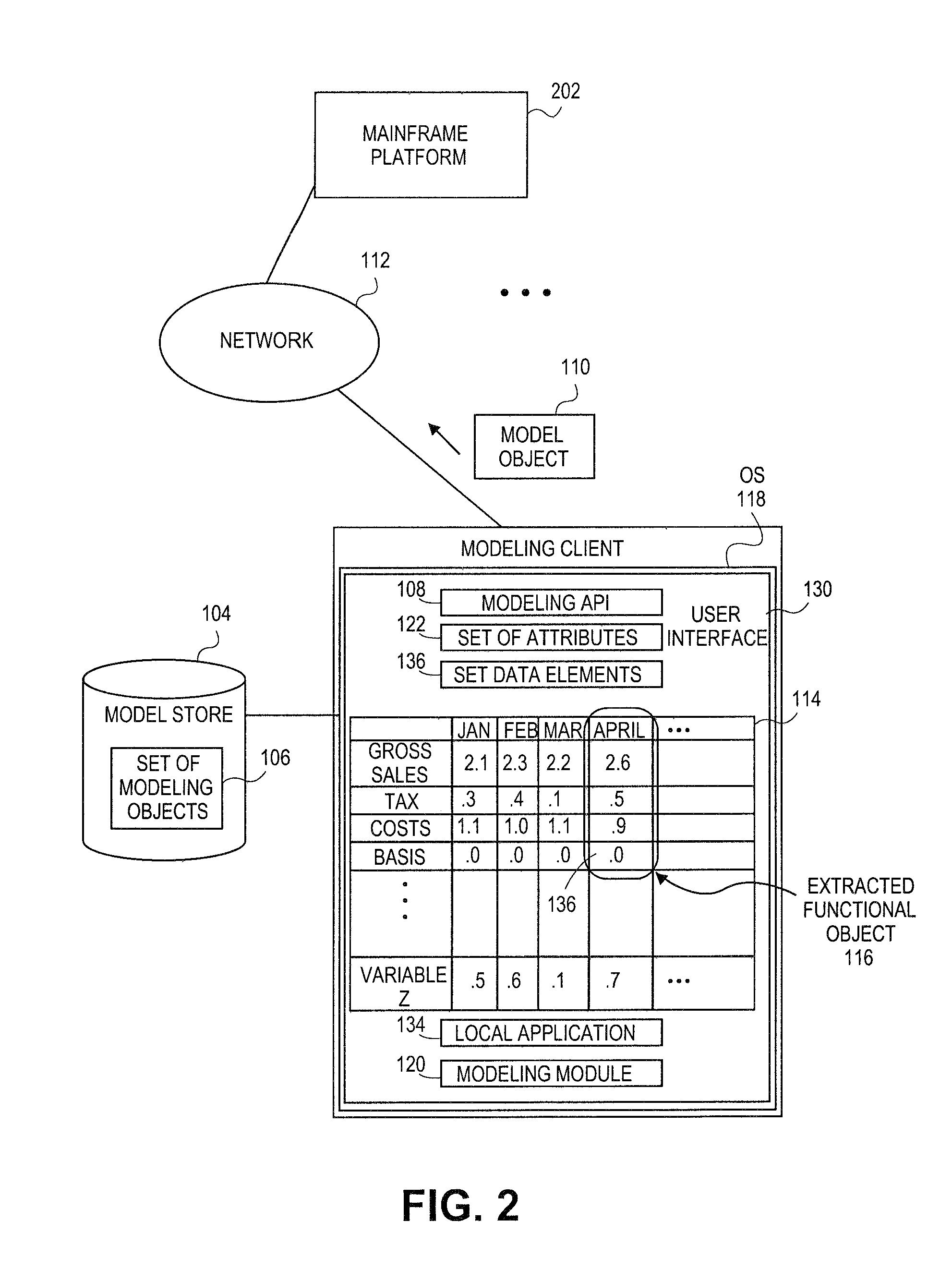
Systems and methods for generating floating desktop representation of extracted model object
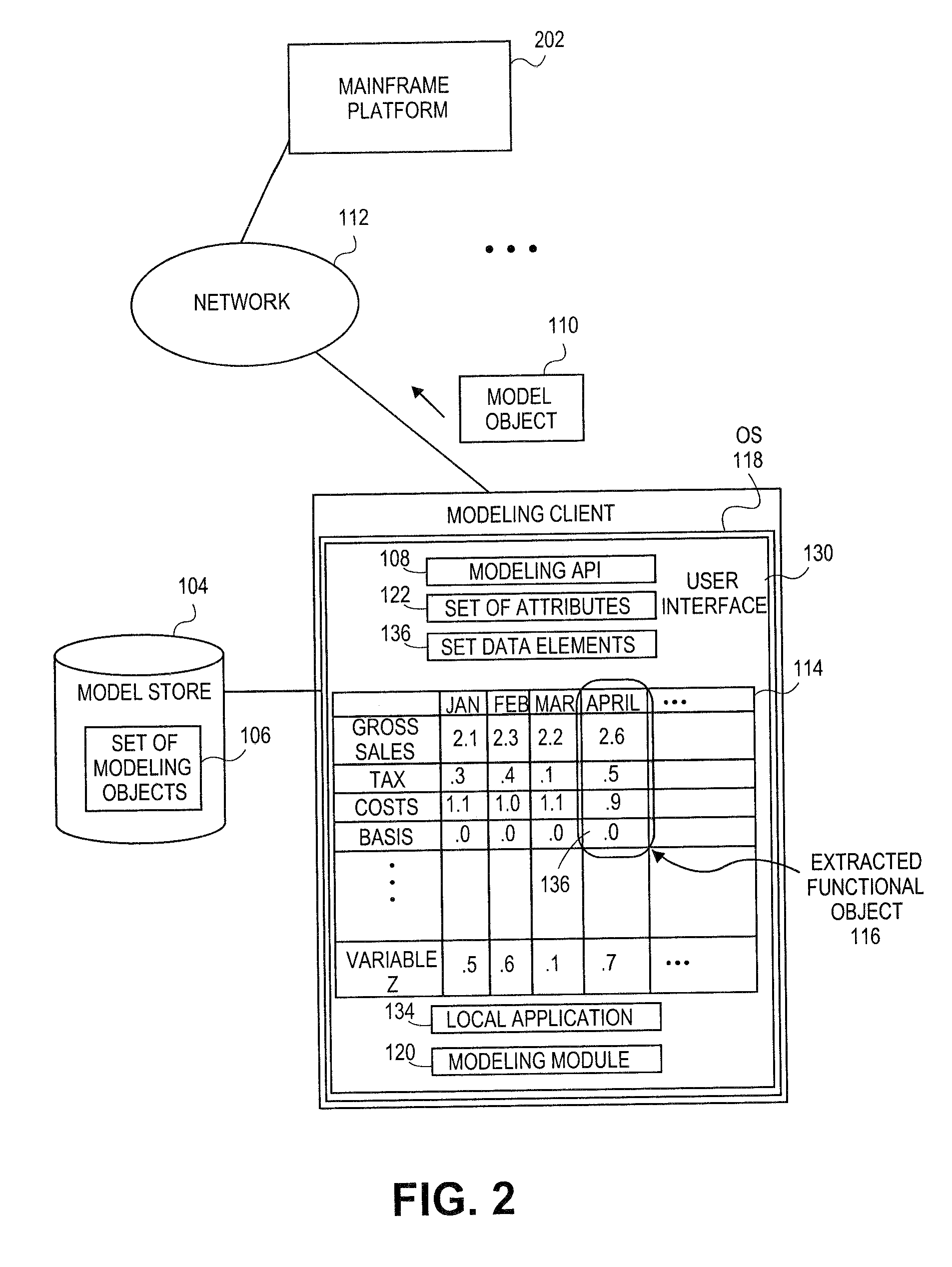
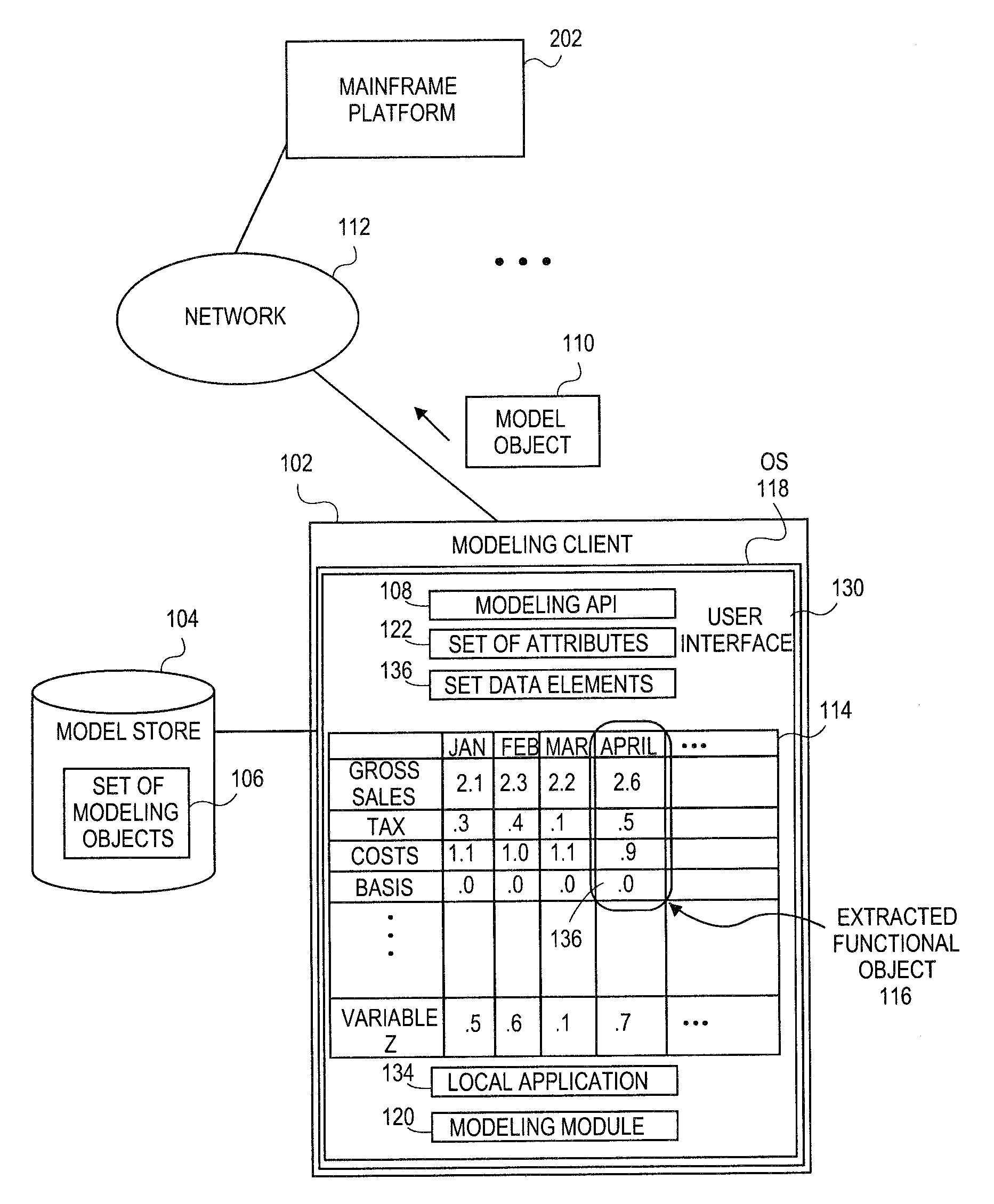
Embodiments relate to systems and methods for generating a floating desktop representation of an extracted model object. Aspects relate to object-based modeling using modeling objects that can be extracted from spreadsheet cells, database entries, or other sources. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data can be accepted into the modeling client from consumer or business-level applications, whose cell, database, or other data content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. An icon or other desktop representation can be generated to present the extracted model object for selection and use in the local environment of the modeling client. The extracted model object can also be exchanged with other applications or platforms.
Owner:RED HAT
Systems and methods for managing sets of model objects via unified management interface
ActiveUS20110055761A1Digital data processing detailsResourcesApplication softwareBiological activation
Embodiments relate to a unified management interface and related resources for managing sets of model objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. The source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. A graphical control application can be used to manage one or more sets of modeling objects from a unified interface, to permit, for instance, the selection and configuration of the connections, activation status, security settings, and / or other attributes of model objects. The management interface can be used to control how the model objects and other resources can exchange outputs, share internal data, and otherwise operate.
Owner:RED HAT
Systems and methods for generating a set of linked rotational views of model objects
ActiveUS20110055680A1Execution for user interfacesSpecial data processing applicationsApplication programming interfaceElectronic form
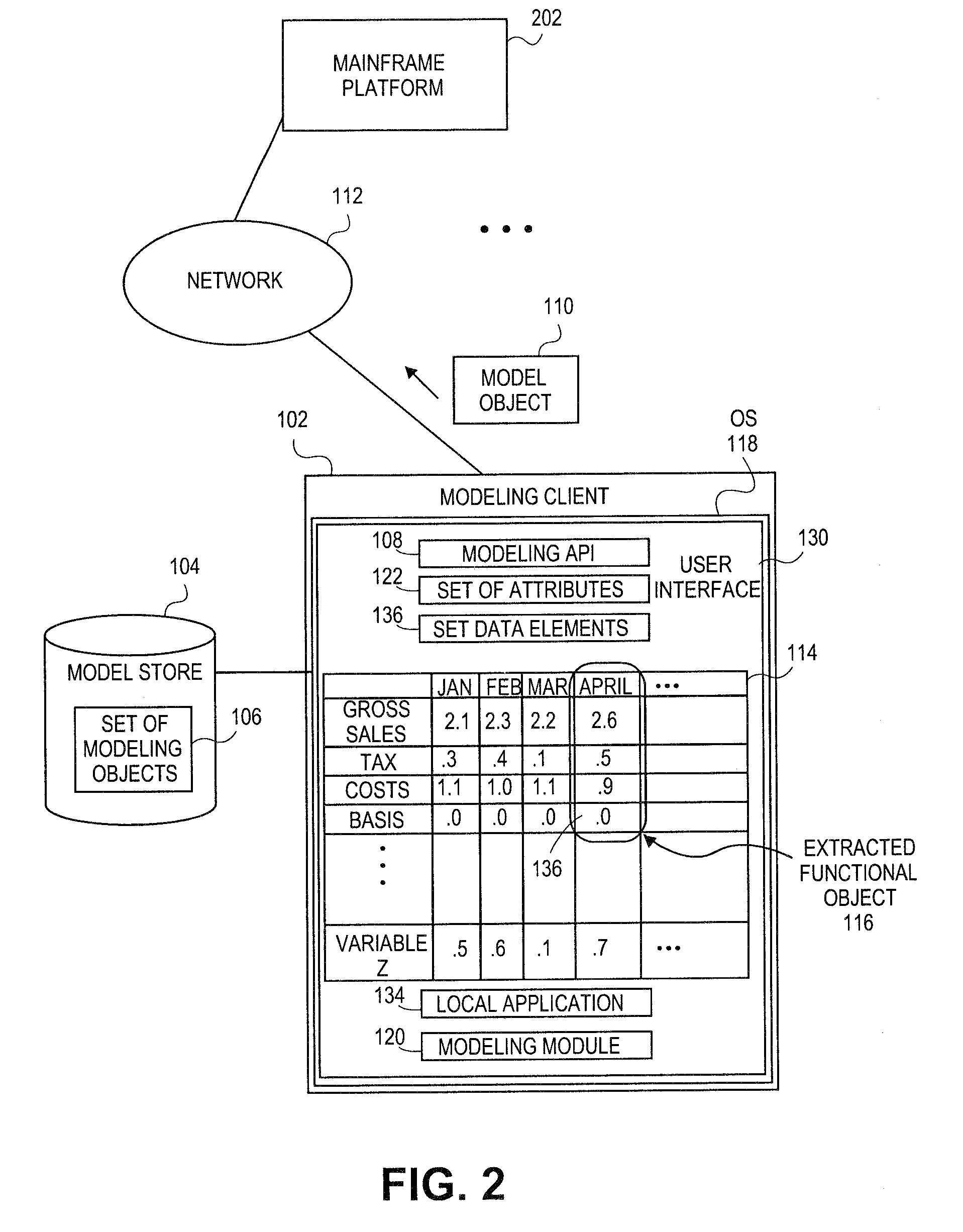
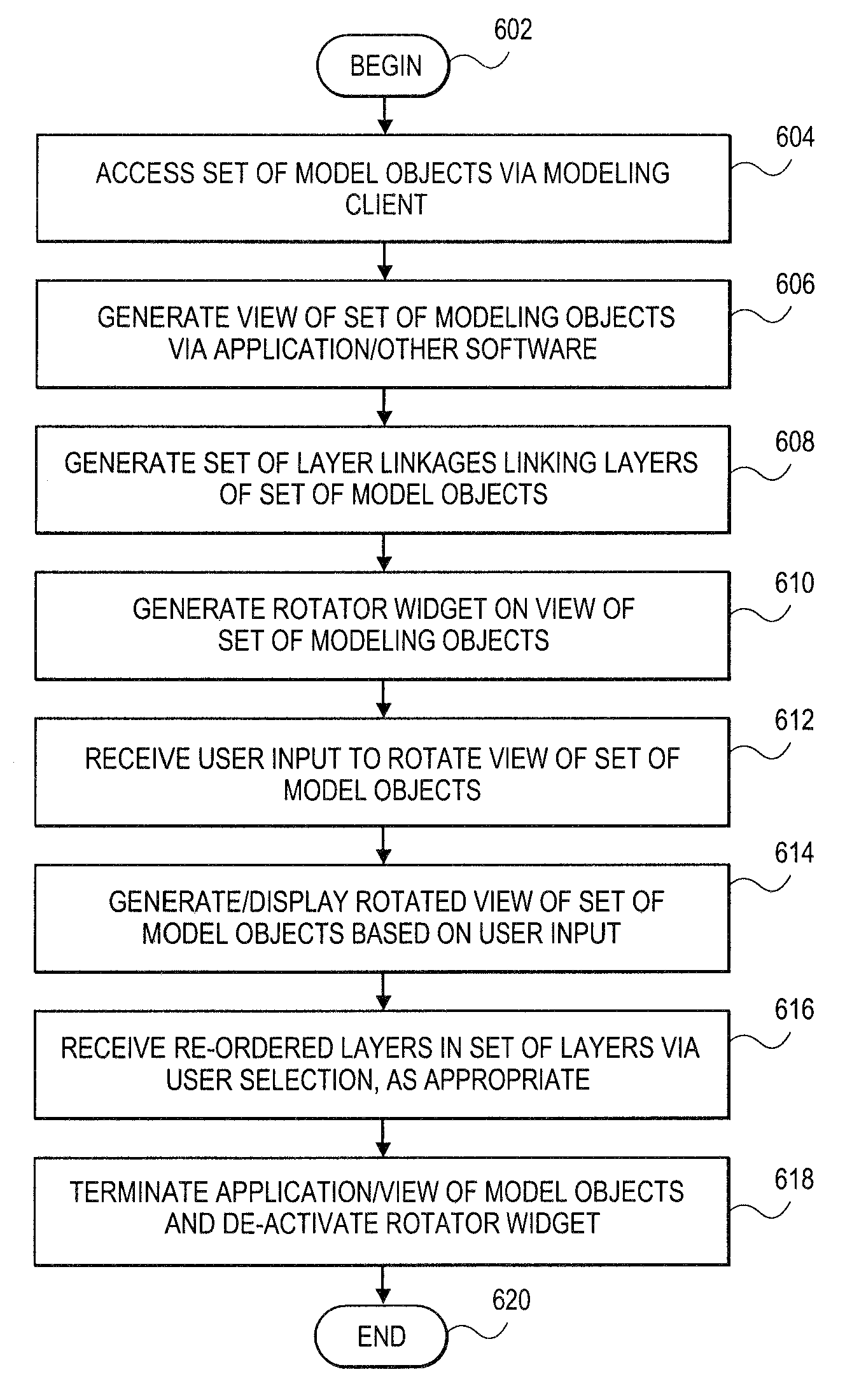
Embodiments relate to systems and methods for generating a set of linked rotational views of a model object. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. The source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. A set of layers of the model objects can be associated via a set of linkages. A rotator widget or other interface object can be presented to allow a user to traverse the linkages and rapidly rotate through layers in a view, without having to switch tabs, planes, database dimensions, or manually operate other dimensional control, enhancing viewing efficiency of large layers.
Owner:RED HAT
Systems and methods for generating rapidly rotatable dimensional view of data objects
ActiveUS20110050728A1Cathode-ray tube indicatorsOffice automationElectronic formApplication programming interface
Embodiments relate to systems and methods for generating generating a rapidly rotatable dimensional view of data objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. The source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. A set of dimensions of each model object can be associated via a set of linkages. A rotator widget or other interface object can be presented to allow a user to traverse the linkages and rapidly rotate through dimensions in a view, without having to manually switch or configure planes or other database dimensions, enhancing viewing efficiency of large layers.
Owner:RED HAT
Systems and methods for object-based modeling using hierarchical model objects
ActiveUS20100306272A1Digital data processing detailsInterprogram communicationObject basedElectronic form
Embodiments relate to systems and methods for object-based modeling using hierarchical model objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in extensible markup language (XML) or other object-oriented format. Various model objects can be extracted from source data, and aggregated into a hierarchical model object encapsulating and preserving the underlying object layers. In aspects, one or more of the model object layers can functionally combine at least two other layers, to relate levels of data in hierarchical fashion. The modeling client can exchange composite or other modeling objects with external platforms on a programmatic basis.
Owner:RED HAT
Systems and methods for generating dimensionally altered model objects
InactiveUS20110054854A12D-image generationComputation using non-denominational number representationElectronic formApplication programming interface
Embodiments relate to a unified management interface and related resources for generating dimensionally altered model objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. The source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. A modeling module can access the modeling objects, decode their row, column, depth, and / or other dimensional attributes, and scale those objects using scaling rules or other logic. In aspects, the dimensionally altered model object(s) can have their number of rows, columns, and / or other dimensions expanded or reduced to conform to dimensions of a destination data object, such as a spreadsheet, database, or other data structure.
Owner:RED HAT
Systems and methods for object-based modeling using composite model object having independently updatable component objects
Embodiments relate to systems and methods for object-based modeling using a composite model object having independently updatable component objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in extensible markup language (XML) or other object-oriented format. Various model objects can be extracted from source data, and aggregated into a composite model object encapsulating the underlying set of component model objects. In aspects, each of the component model objects can be accessed, updated, and stored independently of the other constituent objects. The modeling client can exchange composite or other modeling objects with external platforms on a programmatic basis.
Owner:RED HAT
Systems and methods for generating active links between model objects
ActiveUS20100305922A1Multiple digital computer combinationsSpecial data processing applicationsApplication programming interfaceElectronic form
Embodiments relate to generating active links between model objects. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. The source data accepted into the modeling client can include consumer or business-level applications, whose spreadsheet, database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. Links can be inserted in the resulting model object to link to external resources, such as additional model objects, services, local or remote modeling tools, or other resources. The model object can share, exchange, or combine data from other model object(s), as well as instantiate functions hosted in other model object(s). Multiple links can be inserted to multiple model objects in linked list, node, or other configurations.
Owner:RED HAT
Systems and methods for object-based modeling using model objects exportable to external modeling tools
InactiveUS20100306340A1Multiple digital computer combinationsResourcesObject basedApplication programming interface
Embodiments relate to systems and methods for object-based modeling using modeling objects exportable to external modeling tools. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can be consumer or business-level applications, whose cell, database, or other data content can be extracted and encapsulated in an object-oriented format, such as extensible markup language (XML) format. The modeling client can exchange one or more resulting modeling object directly with external platforms, such as mainframe platforms, middleware databases, and others, via the application programming interface (API) on a programmatic basis. Costs and maintenance savings over mainframe-based modeling tools can thereby be achieved, while providing greater power than consumer or business-level tools.
Owner:RED HAT
Systems and methods for extracting data cell transformable to model object
Embodiments relate to systems and methods for extracting a data cell transformable to a model object. Aspects relate to object-based modeling using modeling objects that can be extracted from spreadsheet cells, database entries, or other sources. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data can be accepted into the modeling client from consumer or business-level applications, whose cell, database, or other data content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. Modeling operations can therefore be performed on or incorporate data that was not originally strictly configured for object-based modeling applications. The extracted model object can also be exchanged with other applications or platforms.
Owner:RED HAT
Systems and methods for extracting database dimensions as data modeling object
InactiveUS8606827B2Energy efficient ICTDigital data processing detailsData modelingApplication programming interface
Embodiments relate to systems and methods for extracting a model object from a multi-dimensional source database. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data accepted into the modeling client can include consumer or business-level applications, whose database or other content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. The resulting model object can be pivoted along selected dimensions, or otherwise manipulated. The modeling client can exchange one or more modeling object directly with external platforms, such as mainframe modeling platforms, via the application programming interface (API) on a programmatic basis. Costs and maintenance savings over mainframe-based modeling tools can thereby be achieved, while providing greater power than consumer or business-level tools.
Owner:RED HAT
Method and System for Testing USB Device
A method for testing a USB (universal serial bus) device includes receiving a USB packet trace output from a USB host, at a USB packet trace converting apparatus, generating at least one token corresponding to the USB packet trace received from the USB host, determining a syntax tree corresponding to the at least one token, and generating a code for a USB host model corresponding to the determined syntax tree.
Owner:SAMSUNG ELECTRONICS CO LTD
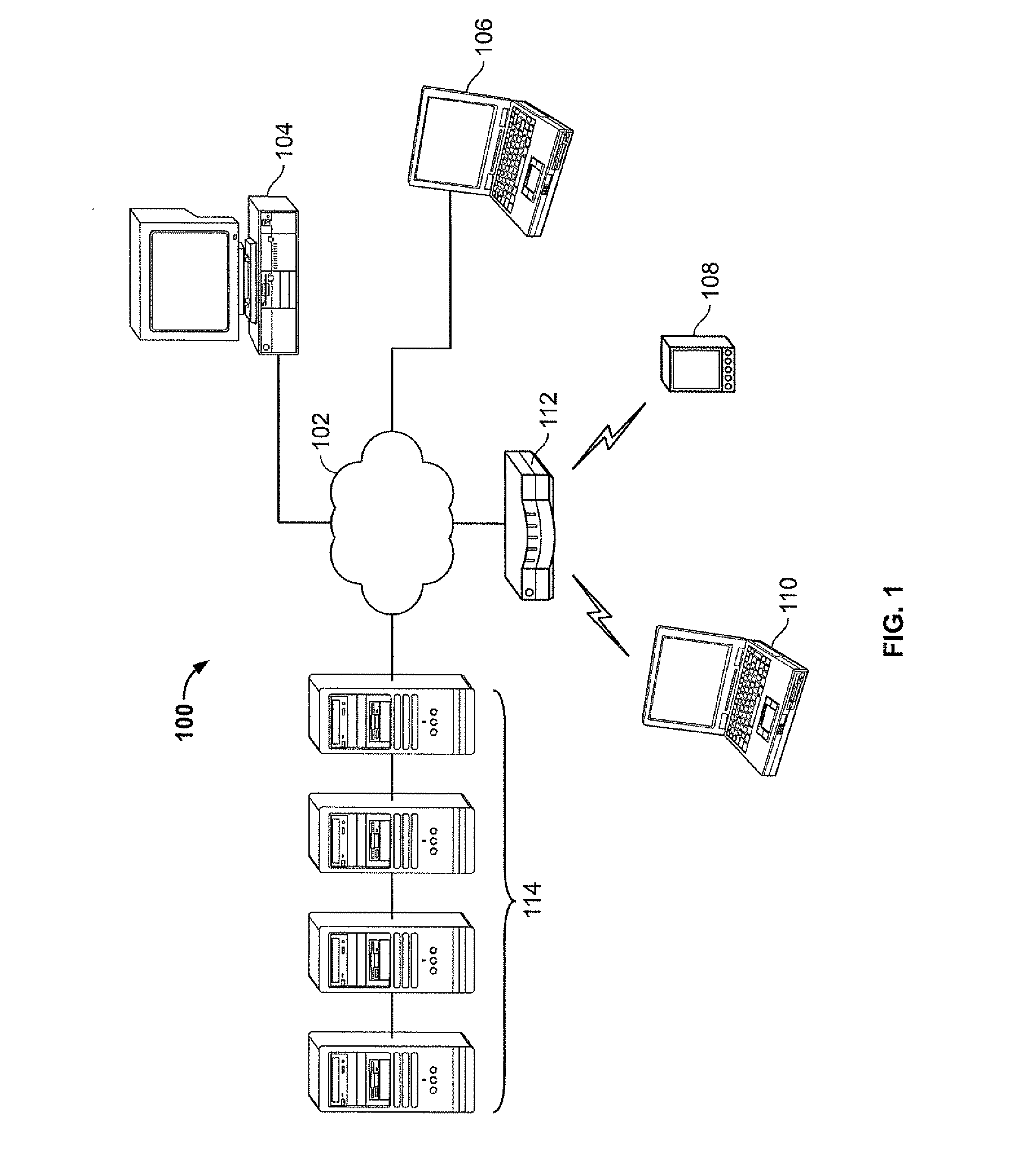
Virtual environment for computer game
A multi-user virtual reality universe (VRU) process receives input from multiple remote clients to manipulate avatars through a modeled 3-D environment. A VRU host models movement of avatars in the VRU environment in response to client input, which each user providing input for control of a corresponding avatar. The modeled VRU data is provided by the host to client workstations for display of a simulated environment visible to all participants. The host maintains personalized data for selected modeled objects or areas that is personalized for specific users in response to client input. The host includes personalized data in modeling the VRU environment. The host may segregate VRU data provided to different clients participating in the same VRU environment according to limit personalized data to authorized users, while all users receive common data.
Owner:PFAQUTRUMA RES LLC
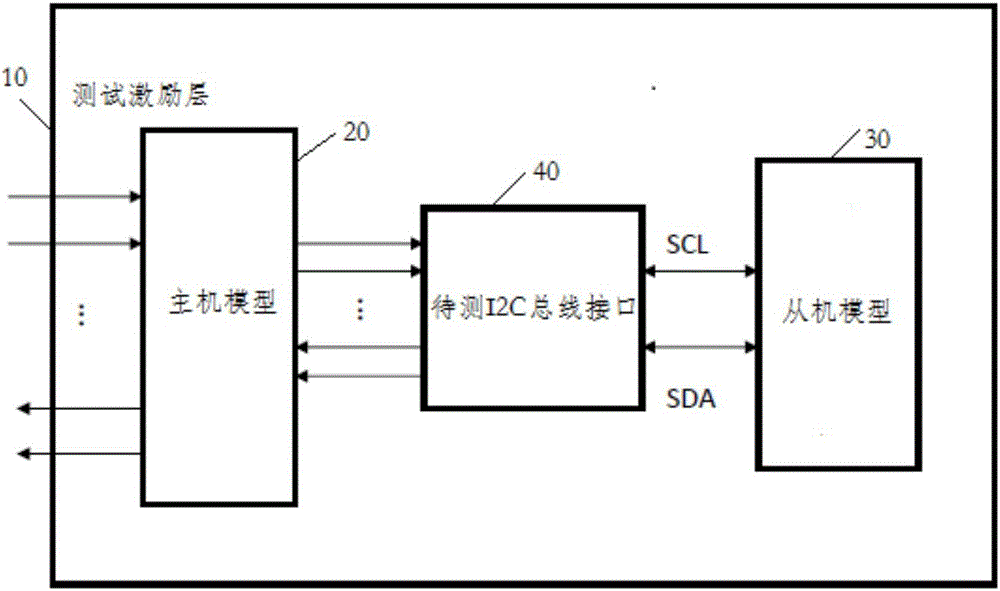
10-bit slave address-based I2C bus verification method and system
ActiveCN106371954AAccurately verify validityAccurately verify boundaryDetecting faulty computer hardwareValidation methodsBus interface
The invention discloses a 10-bit slave address-based I2C bus verification method. The method comprises the steps that a test excitation layer inputs test excitation to an input port of a host model; the host model creates a reading / writing process task to a to-be-tested I2C bus interface according to the test excitation; the to-be-tested I2C bus interface sends the reading / writing process task to a slave model through an SDA line; and the slave model makes a response to the reading / writing process task, the test excitation layer judges whether a response result of the slave model is correct or not, and if the response result is correct, the verification of the to-be-tested I2C bus interface is passed. A verification model is simple in structure; the verification method is concise, good in compatibility and suitable for different kernel buses; an I2C protocol is met; and functional points of reading / writing validity, boundary and the like of an I2C bus can be accurately verified. The invention furthermore discloses a 10-bit slave address-based I2C bus verification system, which has the abovementioned beneficial effects.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Generating floating desktop representation of extracted model object
Embodiments relate to systems and methods for generating a floating desktop representation of an extracted model object. Aspects relate to object-based modeling using modeling objects that can be extracted from spreadsheet cells, database entries, or other sources. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data can be accepted into the modeling client from consumer or business-level applications, whose cell, database, or other data content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. An icon or other desktop representation can be generated to present the extracted model object for selection and use in the local environment of the modeling client. The extracted model object can also be exchanged with other applications or platforms.
Owner:RED HAT
PECI bus verification method and system supporting multiple slaves
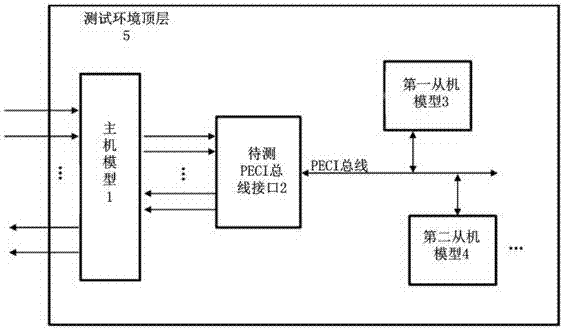
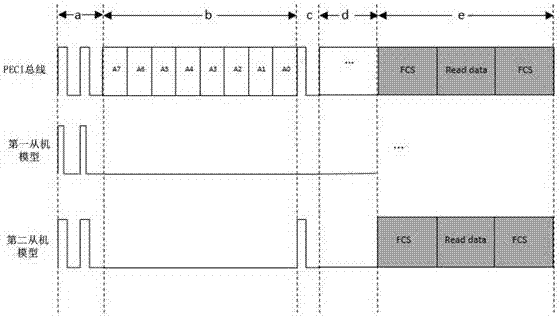
ActiveCN106997318ASimple structureExact orderFunctional testingRedundant data error correctionValidation methodsBus interface
The invention provides a PECI bus verification method and system supporting multiple slaves. The method comprises the steps that 1, models are defined, wherein a host model, a slave model and a test environment top are defined, and the host model comprises a read-write process unit; 2, the test environment top generates test excitation, and the test excitation is input into an input port of the host model; 3, the host model creates a read-write process task to a to-be-tested PECI bus interface according to the test excitation through the read-write process unit; 4, the to-be-tested PECI bus interface sends the read-write process task to the slave model through a PECI bus; 5, the slave model responds to the read-write process task and sends returned data, and the returned data arrives at the host model through the to-be-tested PECI bus interface; 6, the host model outputs the returned data to the test environment top from an output port; and 7, the test environment top judges the correctness of the returned data according to the test excitation, and whether the to-be-tested PECI bus interface has an error is judged.
Owner:GUANGDONG INSPUR BIG DATA RES CO LTD
Method and system for converting USB
A method for testing a USB (universal serial bus) device includes receiving a USB packet trace output from a USB host, at a USB packet trace converting apparatus, generating at least one token corresponding to the USB packet trace received from the USB host, determining a syntax tree corresponding to the at least one token, and generating a code for a USB host model corresponding to the determined syntax tree.
Owner:SAMSUNG ELECTRONICS CO LTD
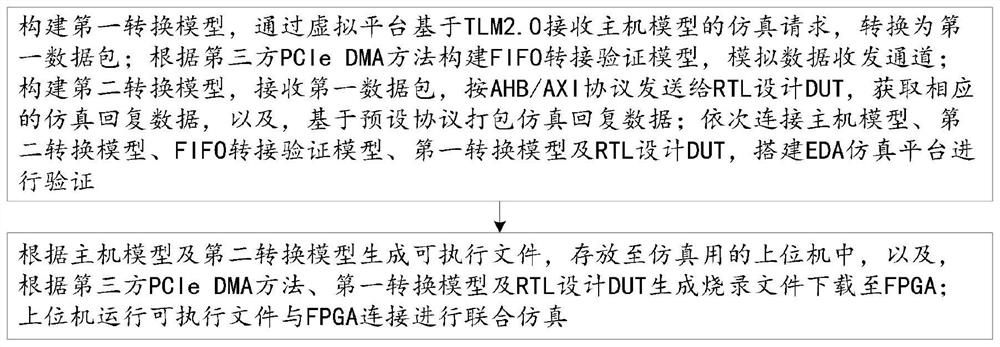
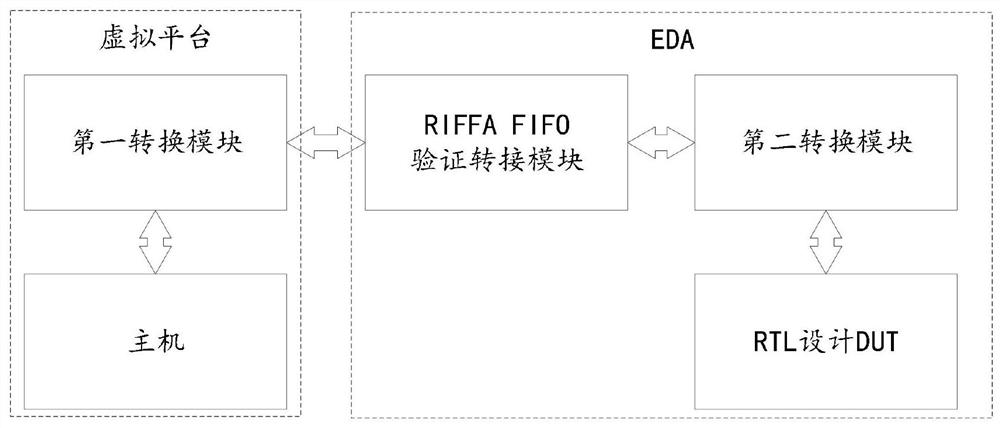
Simulation verification method and system based on combination of virtual platform and FPGA
PendingCN112560377AFlexible modificationReduce economic costsCAD circuit designSpecial data processing applicationsThird partyData pack
The invention discloses a simulation verification method and system based on combination of a virtual platform and an FPGA, and the method comprises a verification step: constructing a first conversion model, receiving a simulation request of a host model through the virtual platform based on TLM2.0, and converting the simulation request into a first data package; constructing an FIFO switching verification model according to a third-party PCIe DMA method, and simulating a data transceiving channel; constructing a second conversion model, receiving the first data packet, performing analysis according to a preset protocol, and sending an analysis result to an RTL design DUT according to an AHB / AXI protocol; and a simulation step: generating an executable file according to the host model andthe second conversion model, storing the executable file in an upper computer for simulation, generating a burning file according to a third-party PCIe DMA method, the first conversion model and RTLdesign DUT, downloading the burning file to the FPGA, and enabling the upper computer to run the executable file to be connected with the FPGA for joint simulation. According to the method and system,the economic cost and the verification cost of simulation are greatly reduced, and a user can conveniently and flexibly optimize and modify according to actual requirements.
Owner:ALLWINNER TECH CO LTD
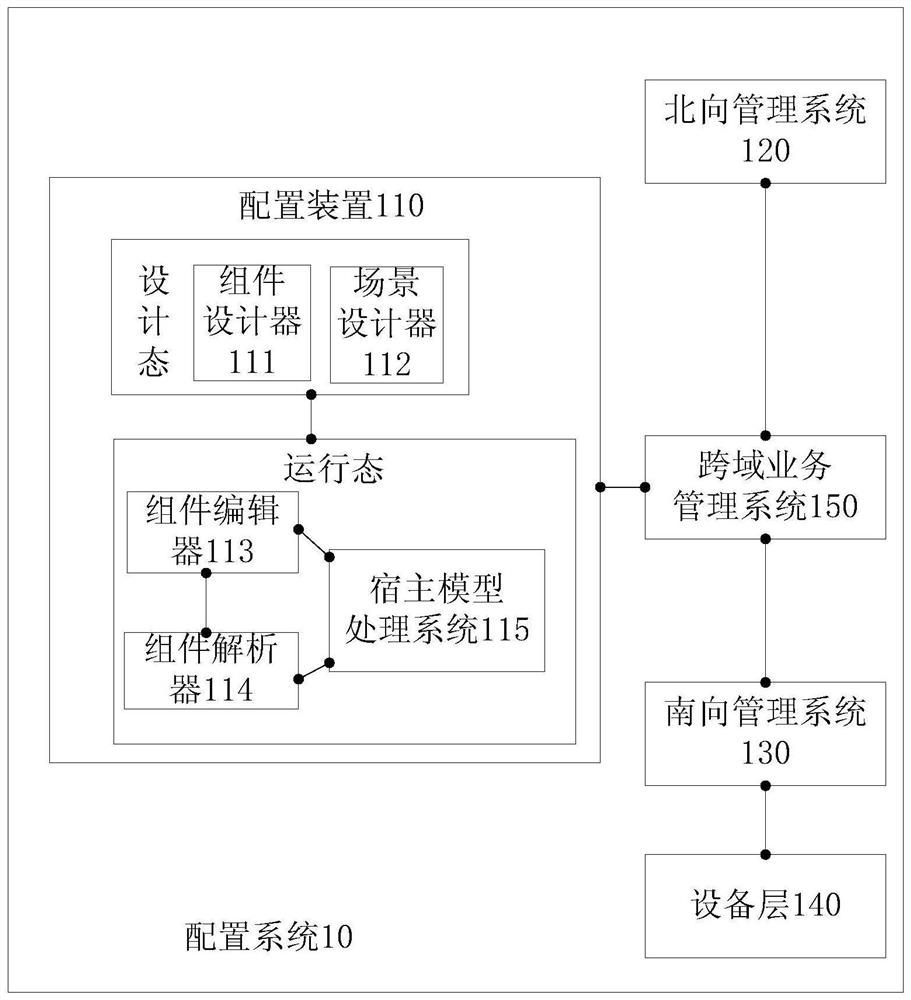
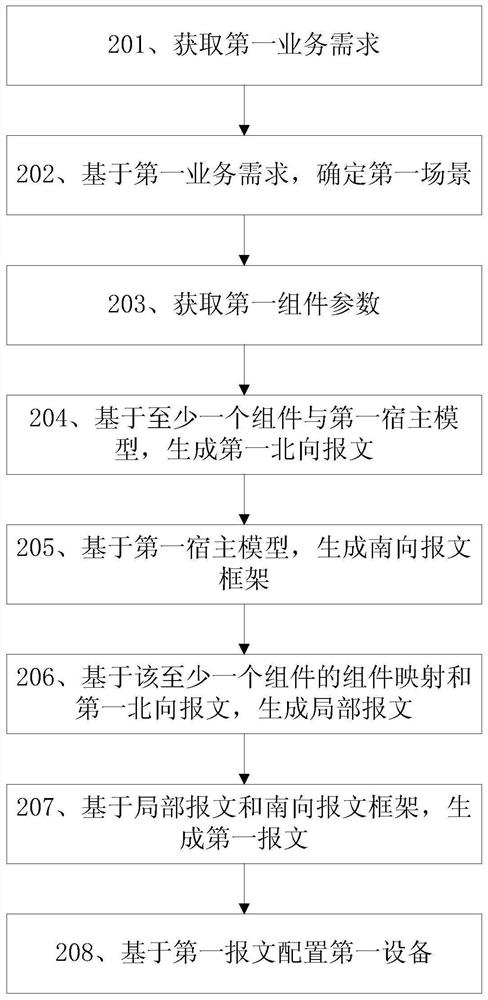
Configuration method, related device and system
PendingCN112737805AReduce difficultyFacilitate subsequent maintenance and upgrade workNetworks interconnectionComputer hardwareOperating system
The embodiment of the invention discloses a configuration method, a related device and a system. The configuration method comprises the following steps: acquiring a first service demand related to first equipment; determining a first host model and at least one component hooked with the first host model based on the first service demand; generating a first message based on the host model and the at least one component; and configuring the first device based on the first message. Because the configuration device can operate independently from the equipment in the service demand, the configuration of the equipment can be completed according to the service demand under the condition that the equipment is not continuously served. By hanging components on the host model, the difficulty in configuration can be effectively reduced.
Owner:HUAWEI TECH CO LTD
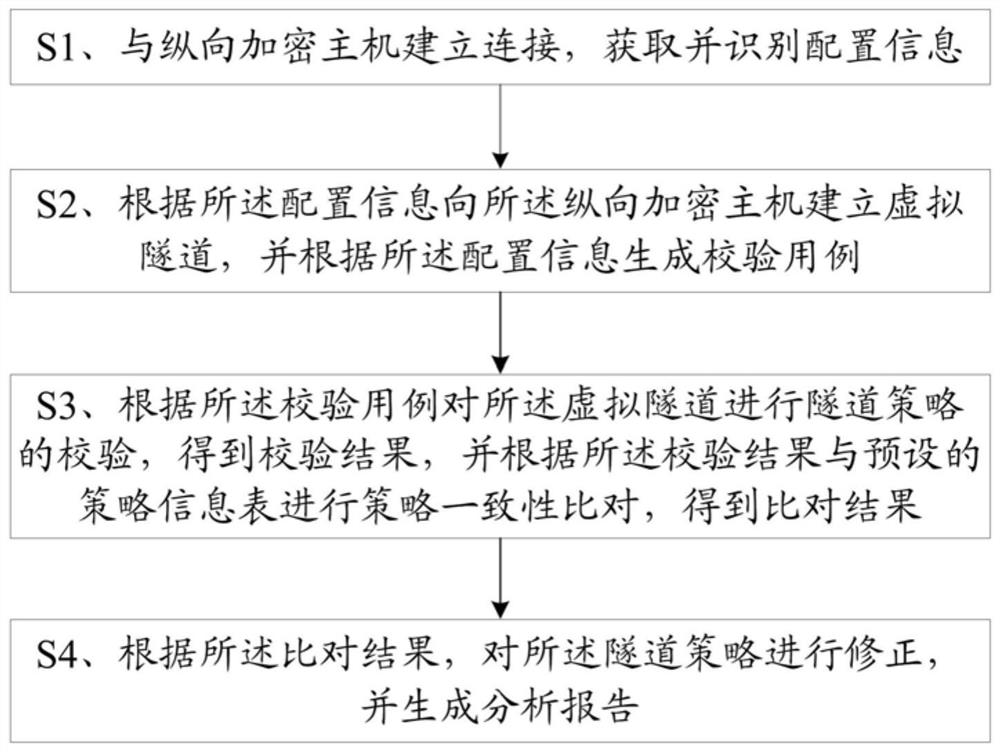
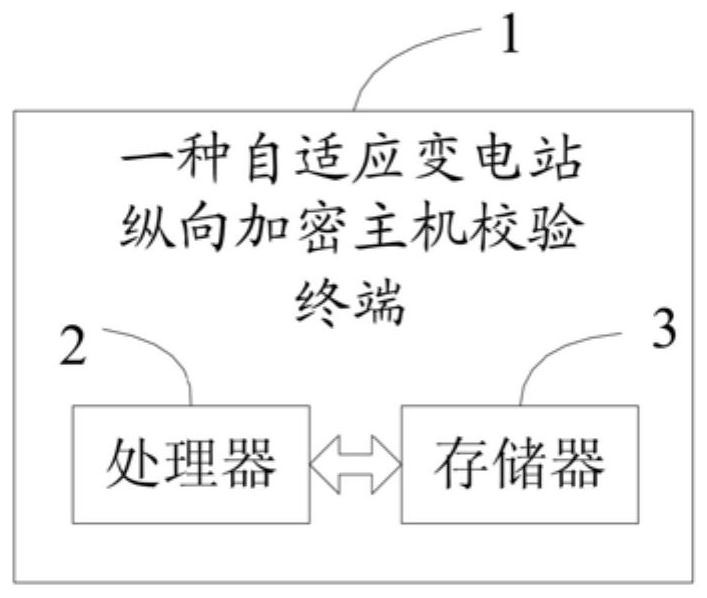
Self-adaptive substation longitudinal encryption host verification method and terminal
ActiveCN113783837ASolve the automatic verification problemImplement Adaptive CalibrationNetworks interconnectionInformation technology support systemComputer hardwareSelf adaptive
The invention discloses a self-adaptive substation longitudinal encryption host verification method and a terminal. The method comprises the following steps: establishing connection with a longitudinal encryption host, and acquiring and identifying configuration information; establishing a virtual tunnel for the longitudinal encryption host according to the configuration information, and generating a verification case according to the configuration information; performing tunnel strategy verification on the virtual tunnel according to the verification case to obtain a verification result, and performing strategy consistency comparison with a preset strategy information table according to the verification result to obtain a comparison result; according to the comparison result, correcting the tunnel strategy, and generating an analysis report. According to the method, the problem of automatic verification of the longitudinal encryption host of the transformer substation is solved, automatic verification of a whole strategy information table covered by multiple channels is realized, adaptive verification and correction of different encryption host models are realized, manual intervention is not needed, and the working efficiency is greatly improved.
Owner:MAINTENANCE BRANCH OF STATE GRID FUJIAN ELECTRIC POWER
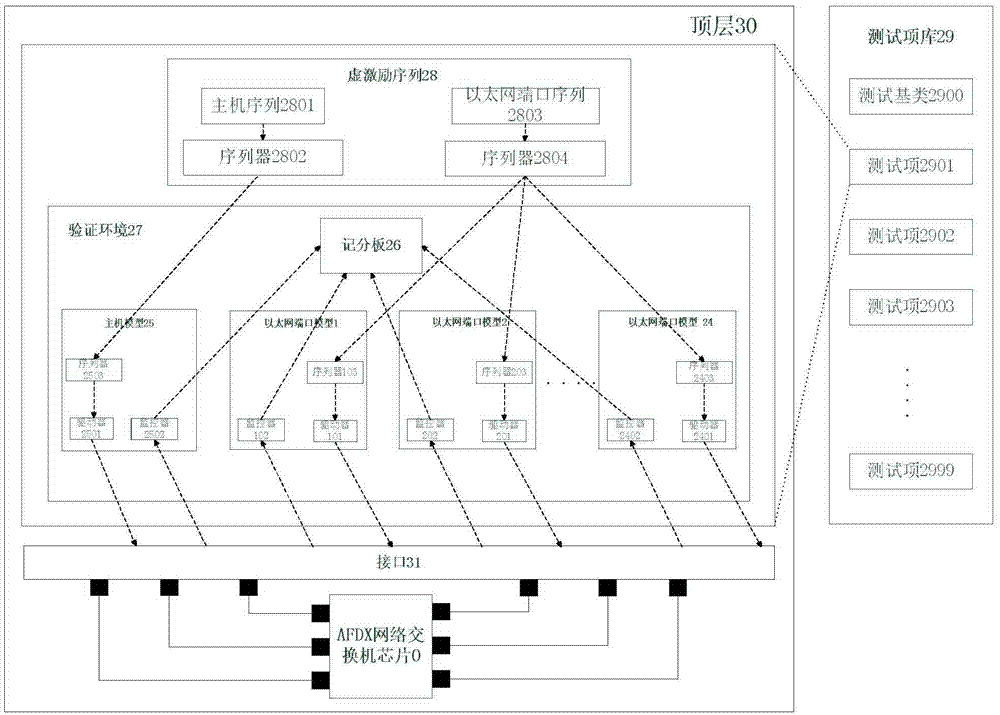
Virtual verification system and method based on AFDX network switch chip
ActiveCN104717052AEliminate competitionImprove developmentData switching networksSecuring communicationNetwork switchVerification system
The invention relates to a virtual verification system and method based on an AFDX network switch chip. The virtual verification system comprises a top level and a test item library, the top level comprises a virtual excitation sequence, a verification environment and interfaces, and the verification environment comprises three or more Ethernet interface modules, a host module and a scoring plate. The virtual verification system and method solve the problem that an existing directional testing virtual verification system and method cannot complete the verification of the AFDX network switch chip, and competition of a design and a model in the simulation process is removed. The read-write operation of an external function model and the read-write operation on a port signal wire are segregated, development and maintenance are easy, and the developing complexity is lowered.
Owner:西安翔腾微电子科技有限公司
Extracting data cell transformable to model object
Embodiments relate to systems and methods for extracting a data cell transformable to a model object. Aspects relate to object-based modeling using modeling objects that can be extracted from spreadsheet cells, database entries, or other sources. A modeling client can host modeling logic and an application programming interface (API) to create, access, manipulate, and import / export modeling objects used in modeling applications, such as engineering, medical, financial, and other modeling platforms. In aspects, the source data can be accepted into the modeling client from consumer or business-level applications, whose cell, database, or other data content can be extracted and encapsulated in object-oriented format, such as extensible markup language (XML) format. Modeling operations can therefore be performed on or incorporate data that was not originally strictly configured for object-based modeling applications. The extracted model object can also be exchanged with other applications or platforms.
Owner:RED HAT
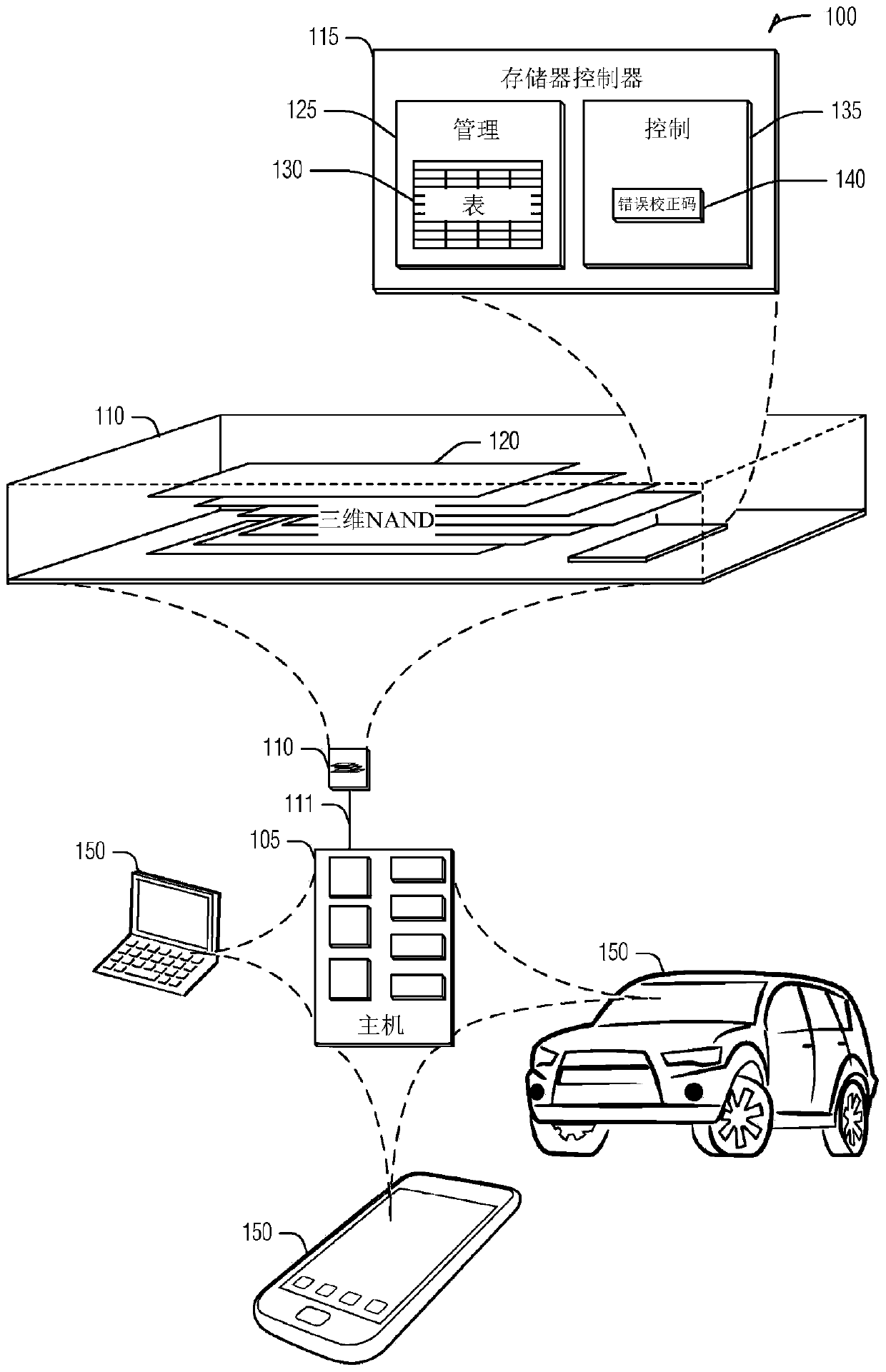
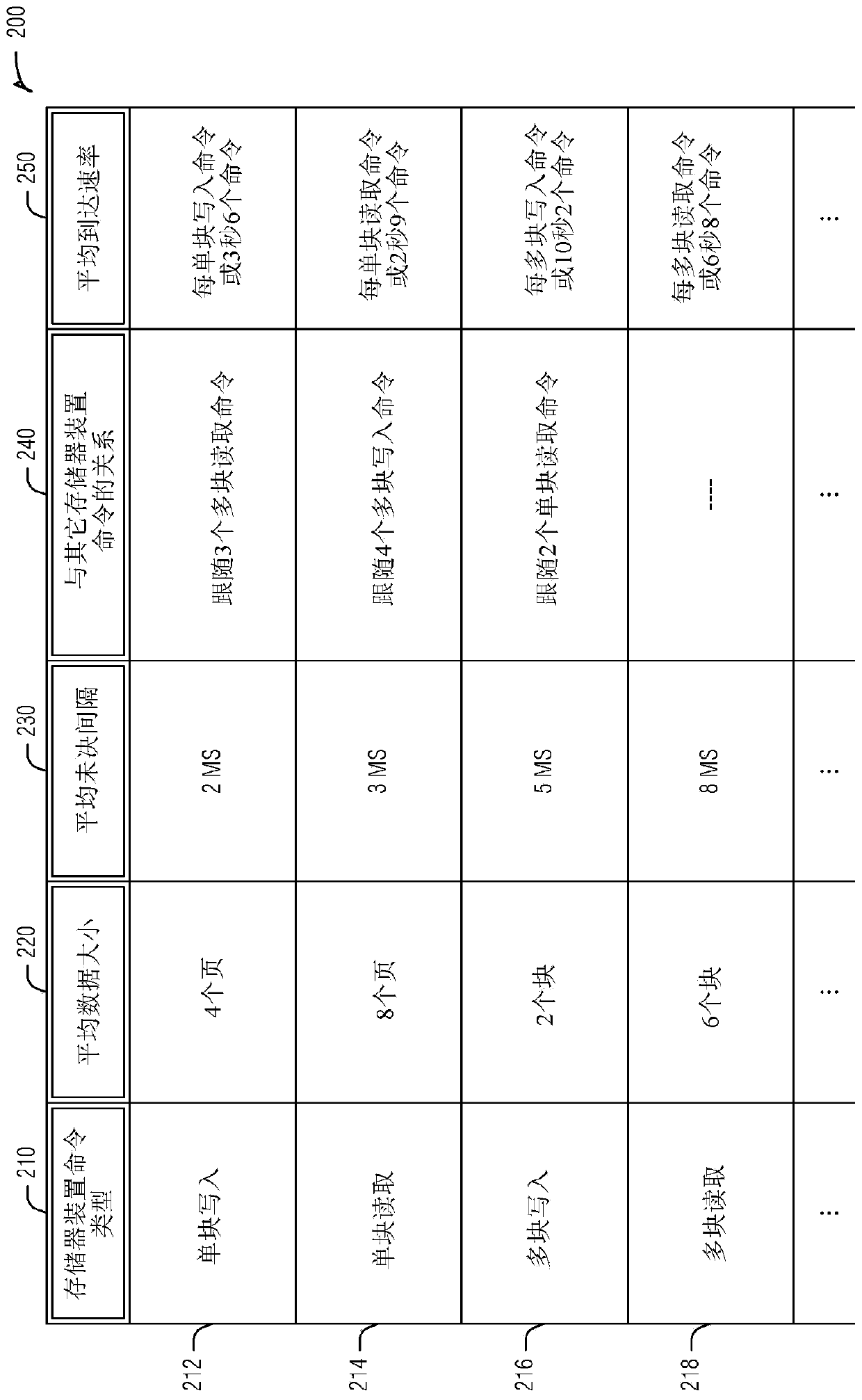
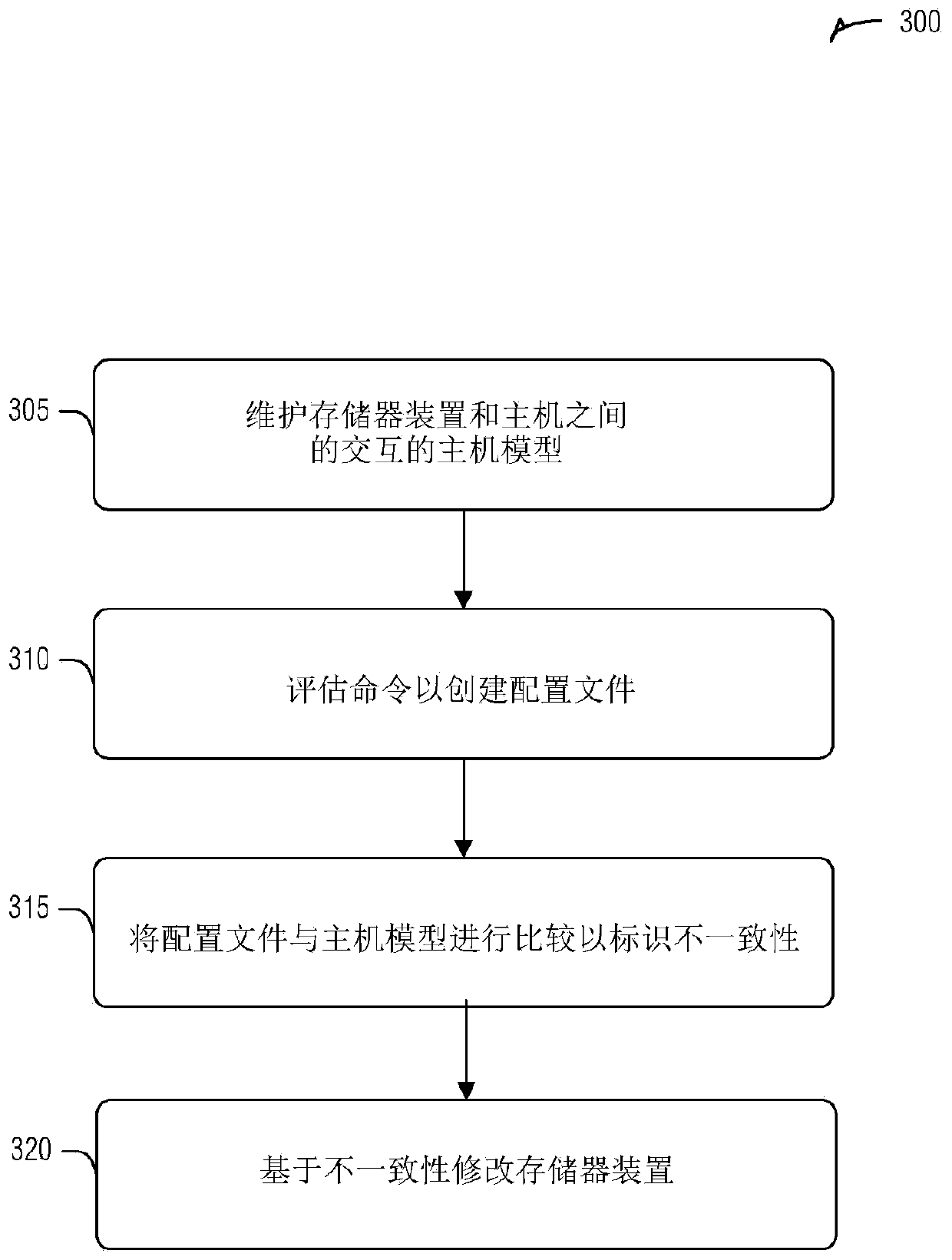
Host adaptive memory device optimization
Devices and techniques for host adaptive memory device optimization are provided. A memory device can maintain a host model of interactions with a host. A set of commands from the host can be evaluated to create a profile of the set of commands. The profile can be compared to the host model to determine an inconsistency between the profile and the host model. An operation of the memory device canthen be modified based on the inconsistency.
Owner:MICRON TECH INC
Method for generating MBD-based mechanical interface control model
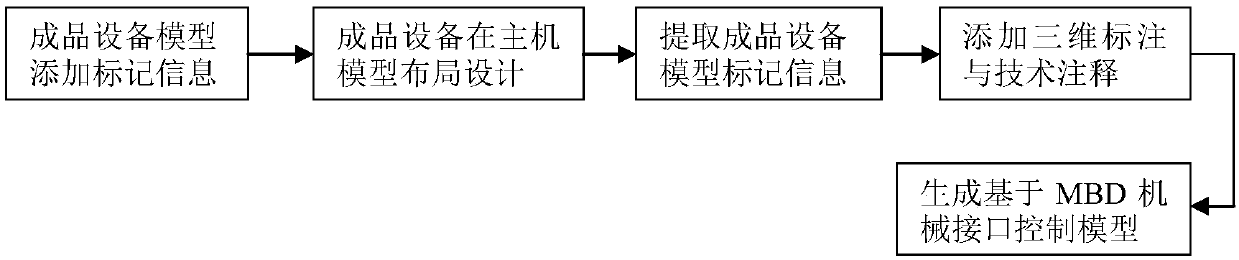
InactiveCN107944171AReduce the number of abstract transitionsImprove R&D efficiencyGeometric CADSpecial data processing applicationsComputer Aided DesignData abstraction
The invention relates to the field of computer aided design, in particular to a method for generating an MBD-based mechanical interface control model. The method comprises the following steps that firstly, marking information is added to a finished product equipment model to be installed on a host through a preset division level; secondly, layout design is conducted on the finished product equipment model on a host model; thirdly, interface information, corresponding to the preset division layer, of the finished product equipment model is extracted on the host model and reconstructed in a newmodel; fourthly, preset standard information is added to a new model file to generate the interface control model. The method for generating the MBD-based mechanical interface control model can quickly generate the MBD-based mechanical interface control model, reduce the frequency of abstract conversion of mechanical interface data and improve the model product development efficiency.
Owner:CHINA HELICOPTER RES & DEV INST
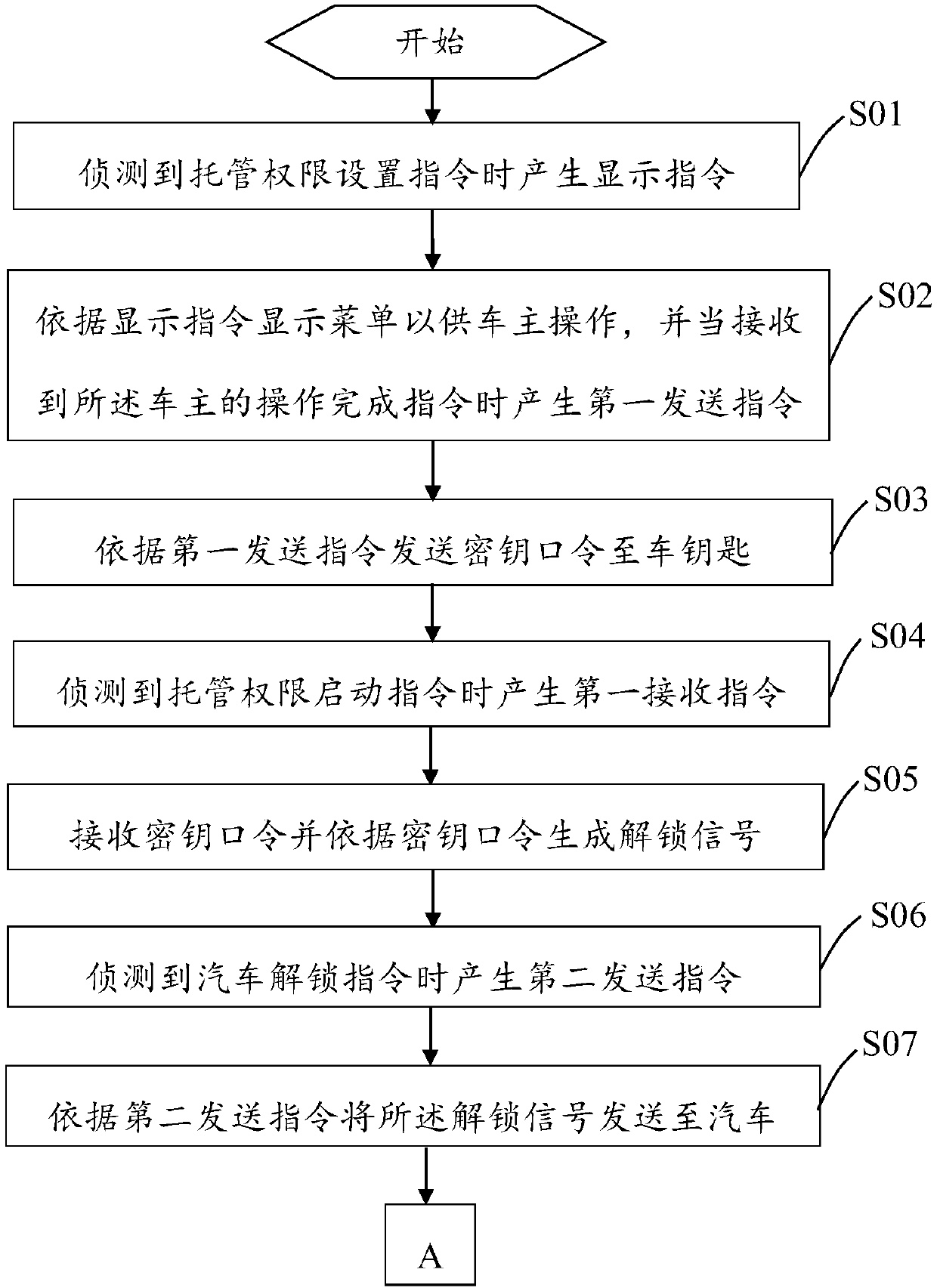
System and method for setting automobile commissioned management permission
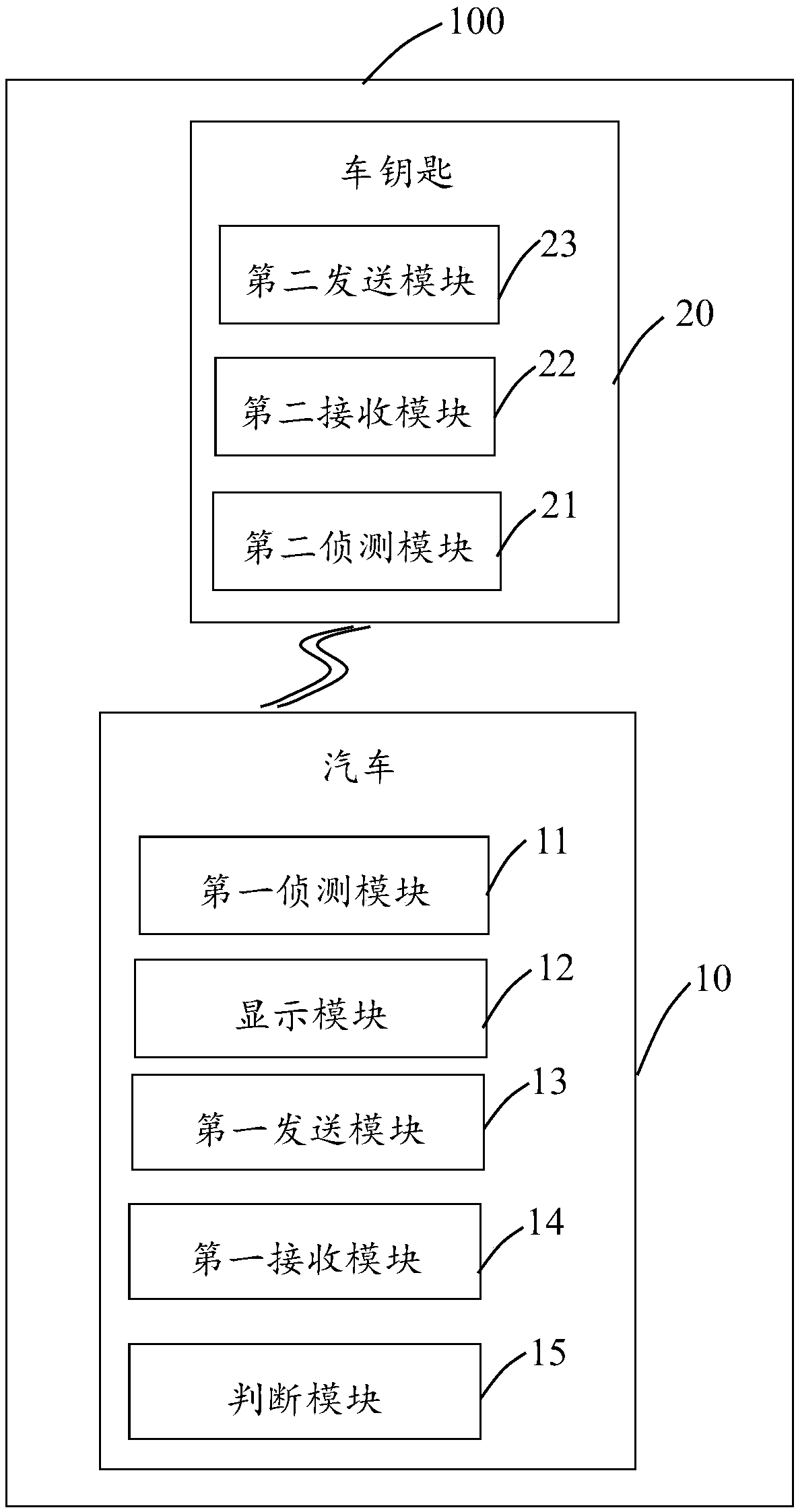
PendingCN107685713AImprove securityAnti-theft devicesIndividual entry/exit registersPasswordEmbedded system
The present invention provides a method for setting the trusteeship authority of an automobile, comprising the following steps: detecting the trusteeship authority setting instruction and generating a display instruction when the trusteeship authority setting instruction is detected; displaying a menu according to the display instruction for the car owner to adjust various parameters of the automobile Set and generate the first sending instruction when receiving the owner’s operation completion instruction; send the key password to the car key according to the first sending instruction; detect the escrow authority start instruction, and generate the second escrow authority start instruction when detecting the escrow authority start instruction A receiving command; receive the key password according to the first receiving command and generate an unlocking signal according to the key password; detect the car unlocking command and generate a second sending command when detecting the car unlocking command; send the unlocking signal according to the second sending command Send to the car to put the car into managed mode. The automobile trusteeship authority setting method provided by the invention improves the safety of the temporary trusteeship of the car. The invention also provides a system for setting the authorization of the car trusteeship.
Owner:OPTIMUM BATTERY CO LTD
Method for testing CPU virtualization performance based on SPECCPU
The invention discloses a method for testing CPU virtualization performance based on an SPECCPU. The method comprises the following steps that S1, the mode of a server cloud host CPU model is modified; and S2, the SPECCPU calls the AVX2 instruction set under the mode of the modified server cloud host CPU model for testing. According to the method, the CPU mode description under the XML file underthe server cloud host is modified into the host-model description, so that the mode of the CPU model of the server cloud host is modified, the SPECCPU is restarted, and the SPECCPU can generate a testreport for the CPU model of the server cloud host.
Owner:UNICLOUD (NANJING) DIGITAL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com