Self-adaptive substation longitudinal encryption host verification method and terminal
A technology of vertical encryption and verification method, applied in the field of vertical encryption host verification of adaptive substation, can solve the problems of inability to achieve large-scale, multi-channel verification, long verification time, dependence on business equipment and personnel skills, etc. Realize the effect of self-adaptive verification and correction to improve work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
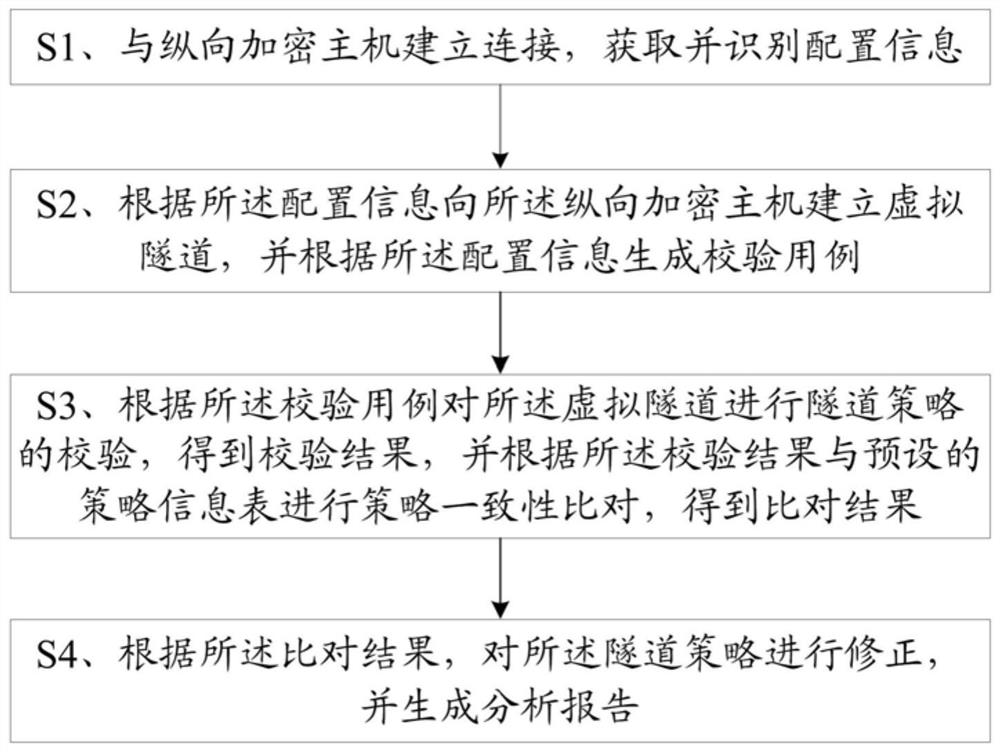
[0079] Please refer to 1 and image 3 , Embodiment 1 of the present invention is:
[0080] An adaptive substation longitudinal encryption host verification method, comprising:
[0081] S1. Establish a connection with the vertical encryption host, acquire and identify configuration information;
[0082] The step S1 is specifically:
[0083] Establishing a connection with the longitudinal encryption host through the configuration port, and obtaining and identifying configuration information through the configuration port, the configuration information includes certificate configuration, tunnel configuration and policy configuration;
[0084] The establishment of a connection with the vertical encryption host through the configuration port is specifically:
[0085] A connection is established with the vertical encryption host through three network ports: a configuration port, an uplink port and a downlink port.
[0086] In this embodiment, we establish a connection with the v...
Embodiment 2
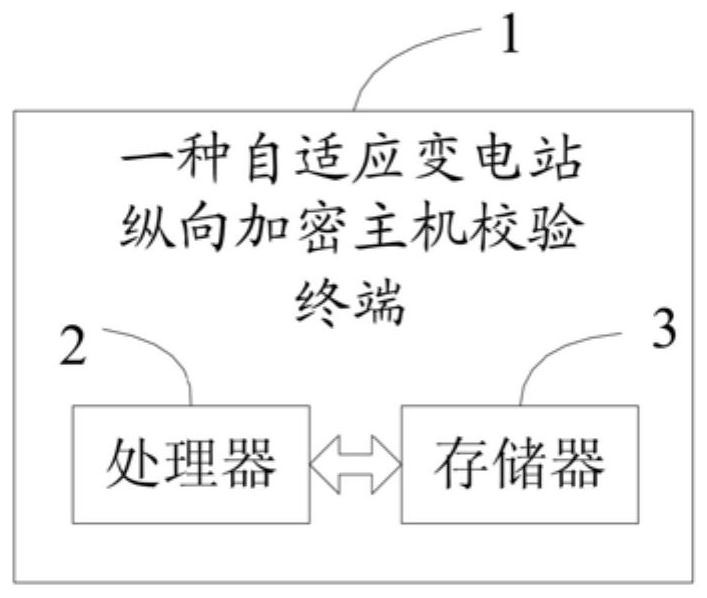
[0104] Please refer to figure 2 , the second embodiment of the present invention is:
[0105] An adaptive substation longitudinal encryption host verification terminal, including a processor, a memory, and a computer program stored on the memory and operable on the processor, when the processor executes the computer program, the above implementations are realized Steps in Example 1.
[0106] To sum up, the invention provided by the present invention obtains the configuration information of the longitudinally encrypted authentication host through the configuration port, automatically identifies the configuration information of different types of hosts, establishes each service tunnel through the acquired configuration information, automatically generates and executes the verification cases The verification program finally generates a verification report and corrects the strategy, solves the problem of automatic verification of the longitudinal encryption host in the substatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com